Internet asset exposure information checking method
An asset information and Internet technology, applied in the field of Internet asset exposure information investigation, can solve problems such as inaccuracy, excessive Internet assets, and incomplete accounts
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
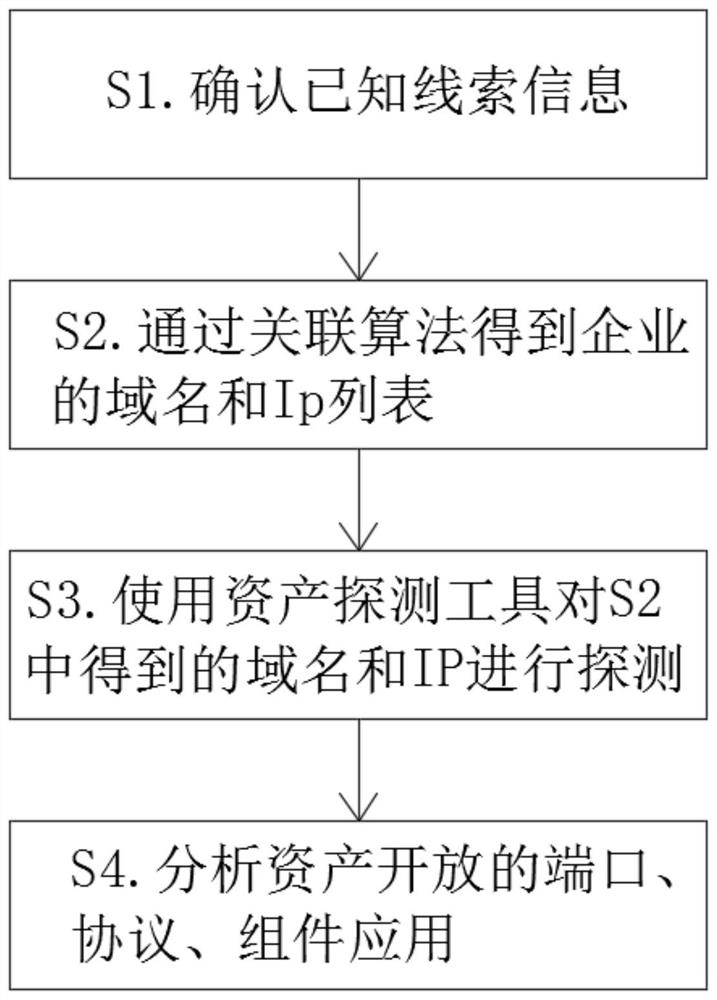
[0029] see figure 1 , the present invention provides a technical solution: a method for checking Internet asset exposure information, comprising the following steps:
[0030] S1. Confirm known clue information;
[0031] S2. Obtain the domain name and Ip list of the enterprise through the association algorithm;
[0032] S3. Use the asset detection tool to detect the domain name and IP obtained in S2;
[0033] S4. Analyze the ports, protocols, and component applications opened by assets.
[0034] In this embodiment, preferably, the known clues of S1 include enterprise domain name, IP and enterprise information keywords.
[0035] In this embodiment, preferably, the association algorithm in S2 includes certificates, sub-domain name blasting, traffic analysis, ICP information, domain name registration information, enterprise name, app and WeChat applet.
[0036] In this embodiment, preferably, the S1 further includes asset identification, the asset identification is used to ide...
Embodiment 2
[0048] see figure 1 , the present invention provides a technical solution: a method for checking Internet asset exposure information, comprising the following steps:
[0049] S1. Confirm known clue information;
[0050] S2. Obtain the domain name and Ip list of the enterprise through the association algorithm;
[0051] S3. Use the asset detection tool to detect the domain name and IP obtained in S2;
[0052] S4. Analyze the ports, protocols, and component applications opened by assets.
[0053] In this embodiment, preferably, the known clues of S1 include enterprise domain name, IP and enterprise information keywords.
[0054]In this embodiment, preferably, the association algorithm in S2 includes certificates, sub-domain name blasting, traffic analysis, ICP information, domain name registration information, enterprise name, app and WeChat applet.
[0055] In this embodiment, preferably, the S1 further includes asset identification, the asset identification is used to iden...
Embodiment 3
[0066] see figure 1 , the present invention provides a technical solution: a method for checking Internet asset exposure information, comprising the following steps:
[0067] S1. Confirm known clue information;
[0068] S2. Obtain the domain name and Ip list of the enterprise through the association algorithm;
[0069] S3. Use the asset detection tool to detect the domain name and IP obtained in S2;
[0070] S4. Analyze the ports, protocols, and component applications opened by assets.
[0071] In this embodiment, preferably, the known clues of S1 include enterprise domain name, IP and enterprise information keywords.
[0072] In this embodiment, preferably, the association algorithm in S2 includes certificates, sub-domain name blasting, traffic analysis, ICP information, domain name registration information, enterprise name, app and WeChat applet.
[0073] In this embodiment, preferably, the S1 further includes asset identification, the asset identification is used to ide...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com