Patents
Literature
12252 results about "Business enterprise" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
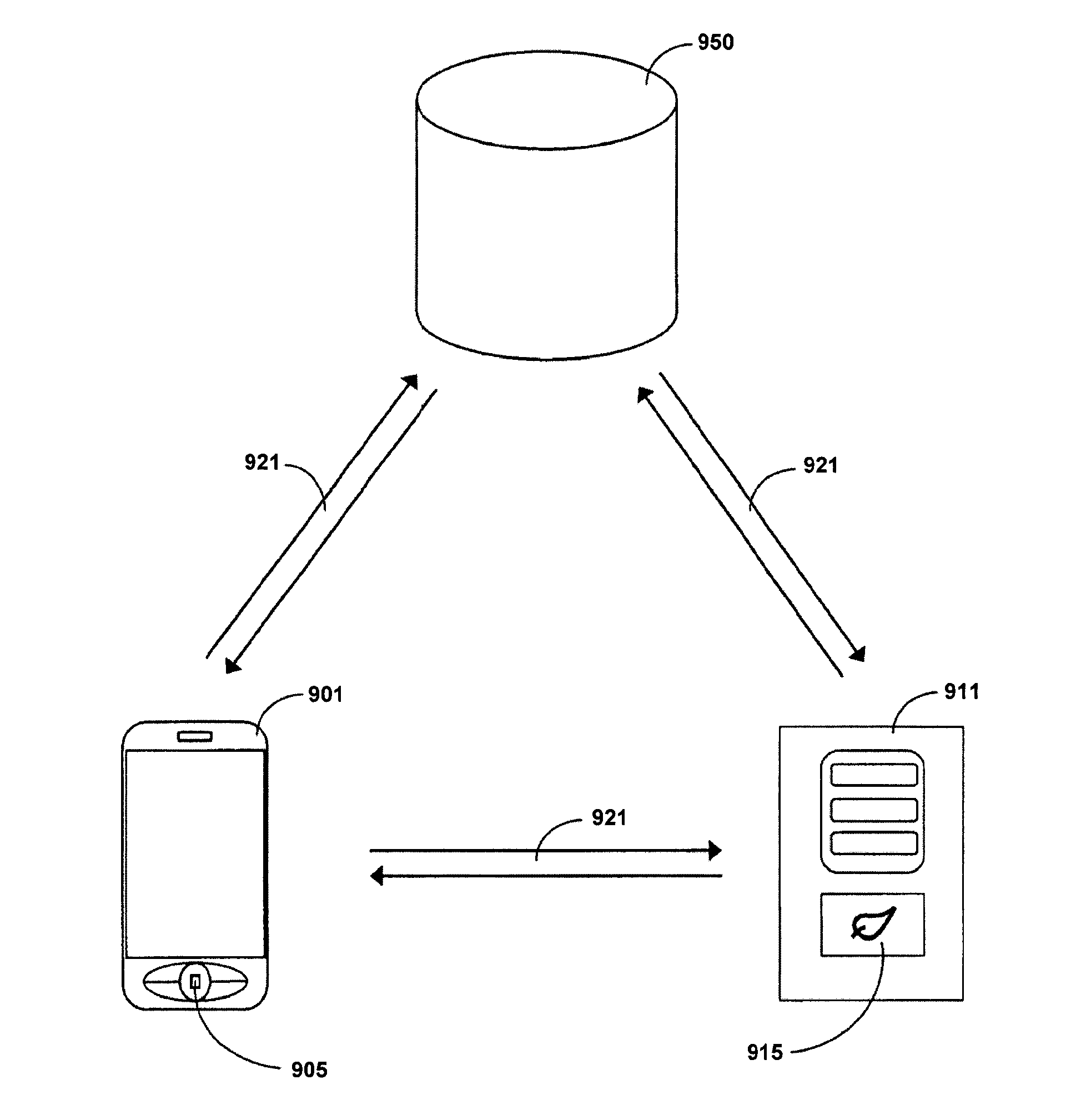
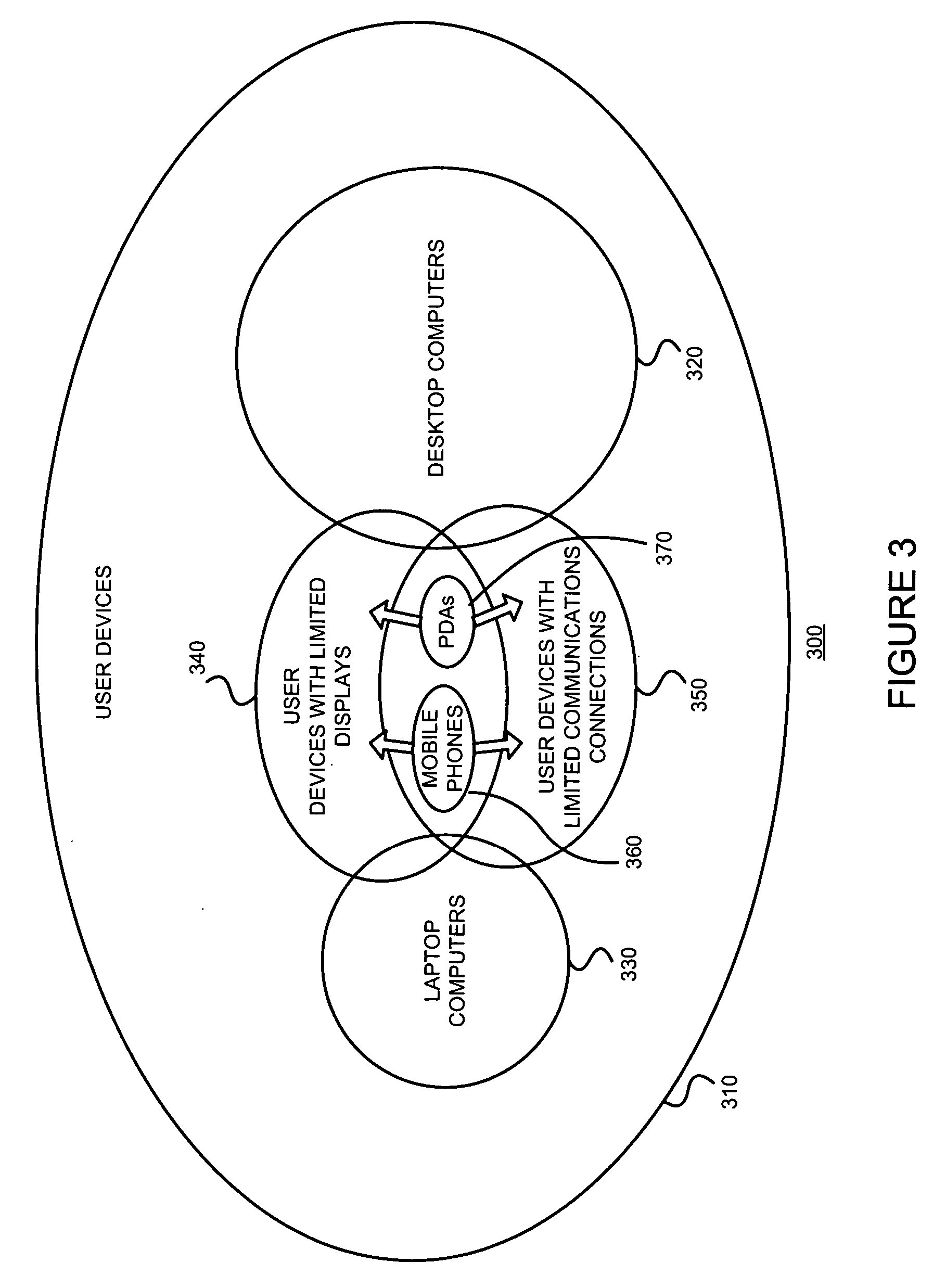
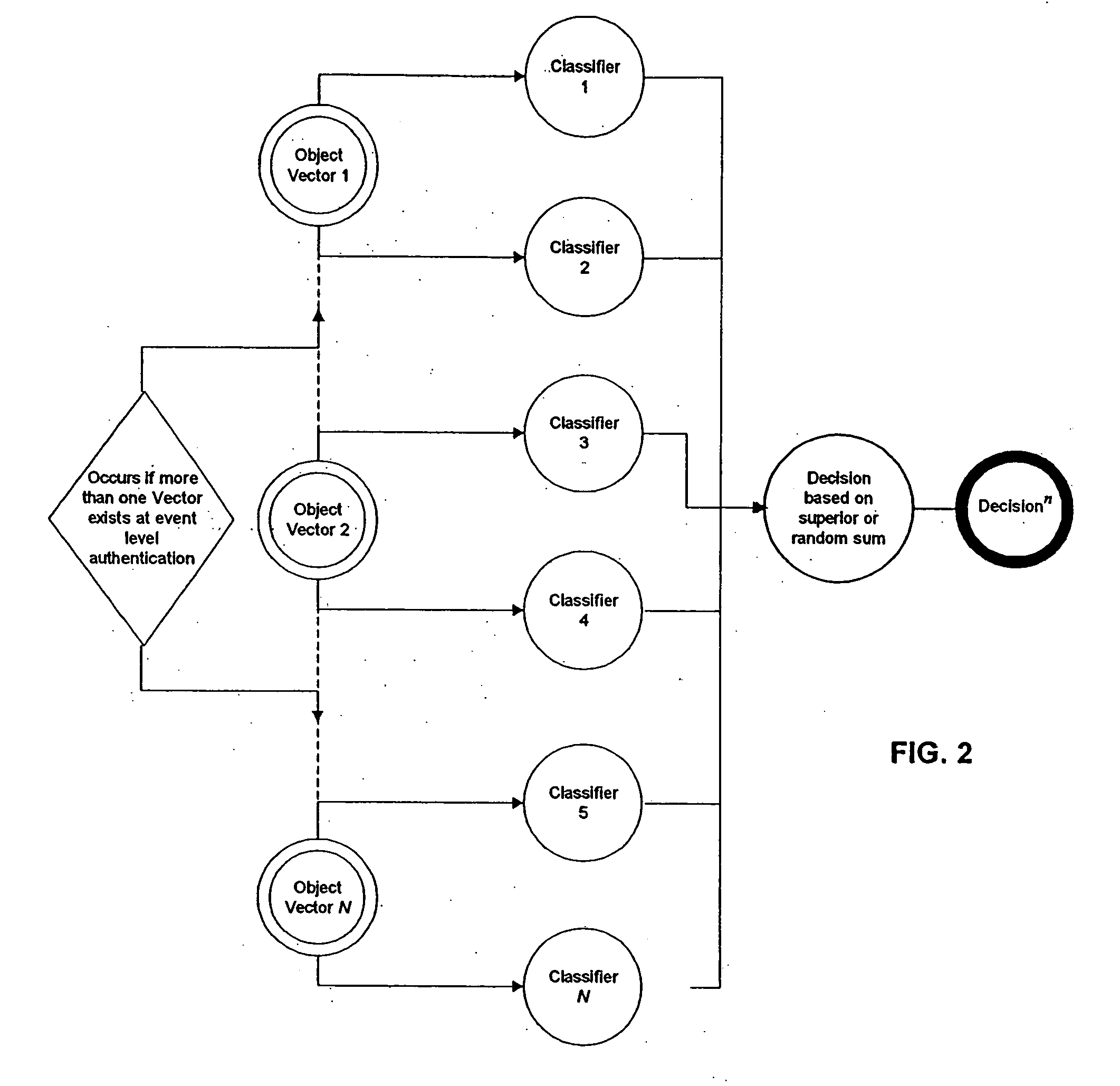
Methods and systems for sharing risk responses between collections of mobile communications devices
Methods are provided for determining an enterprise risk level, for sharing security risk information between enterprises by identifying a security response by a first enterprise and then sharing the security response to a second enterprise when a relationship database profile for the first collection indicates the security response may be shared. Methods are also provided for determining whether to allow a request from an originating device where the request may have been initiated by a remote device.
Owner:LOOKOUT MOBILE SECURITY
Methods and/or systems for an online and/or mobile privacy and/or security encryption technologies used in cloud computing with the combination of data mining and/or encryption of user's personal data and/or location data for marketing of internet posted promotions, social messaging or offers using multiple devices, browsers, operating systems, networks, fiber optic communications, multichannel platforms
InactiveUS20130268357A1Data can be securedDigital data processing detailsAnalogue secracy/subscription systemsOperational systemMessage delivery
A method, apparatus, computer readable medium, computer system, wireless or wired network, or system to provide an online and / or mobile security of a user's privacy and / or security method of internet or mobile access or system, apparatus, computer readable medium, or system using encryption technologies and / or filters to access data, encrypt and / or decrypt data, sync data, secure data storage and / or process data using cloud technology across many different networks and / or fiber optic communications from an endpoint accessed through multiple devices, browsers, operating systems, networks, servers, storage, software, applications or services integrated in a public cloud or a private cloud within an enterprise, a social network, big data analytics or electronic surveillance tracking or some mashup of two or more to prevent the unauthorized collecting, tracking and / or analysis of a user's personal data by a third party and / or for generating relevant advertising, mobile, internet social messaging, internet posted promotions or offers for products and / or services.
Owner:HEATH STEPHAN
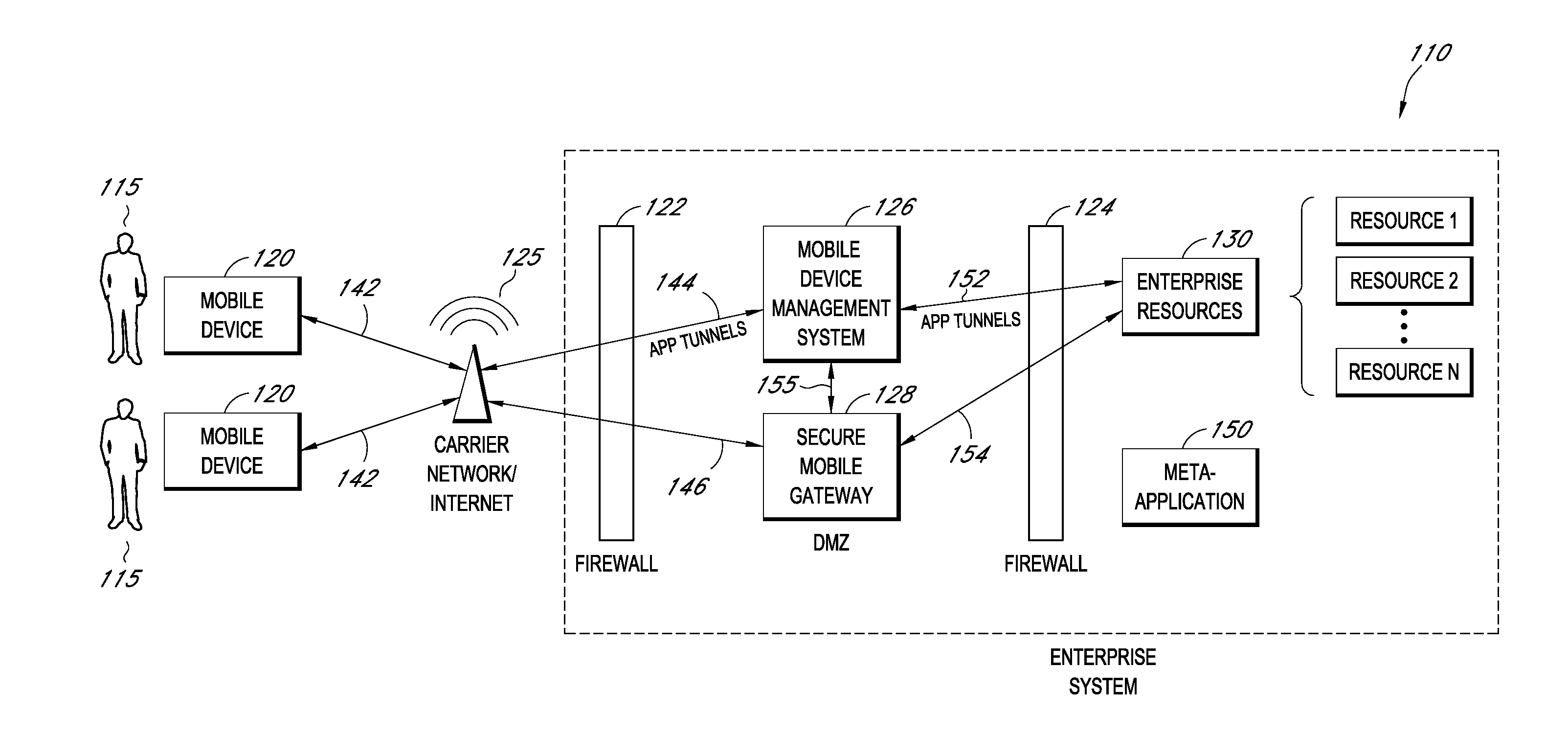
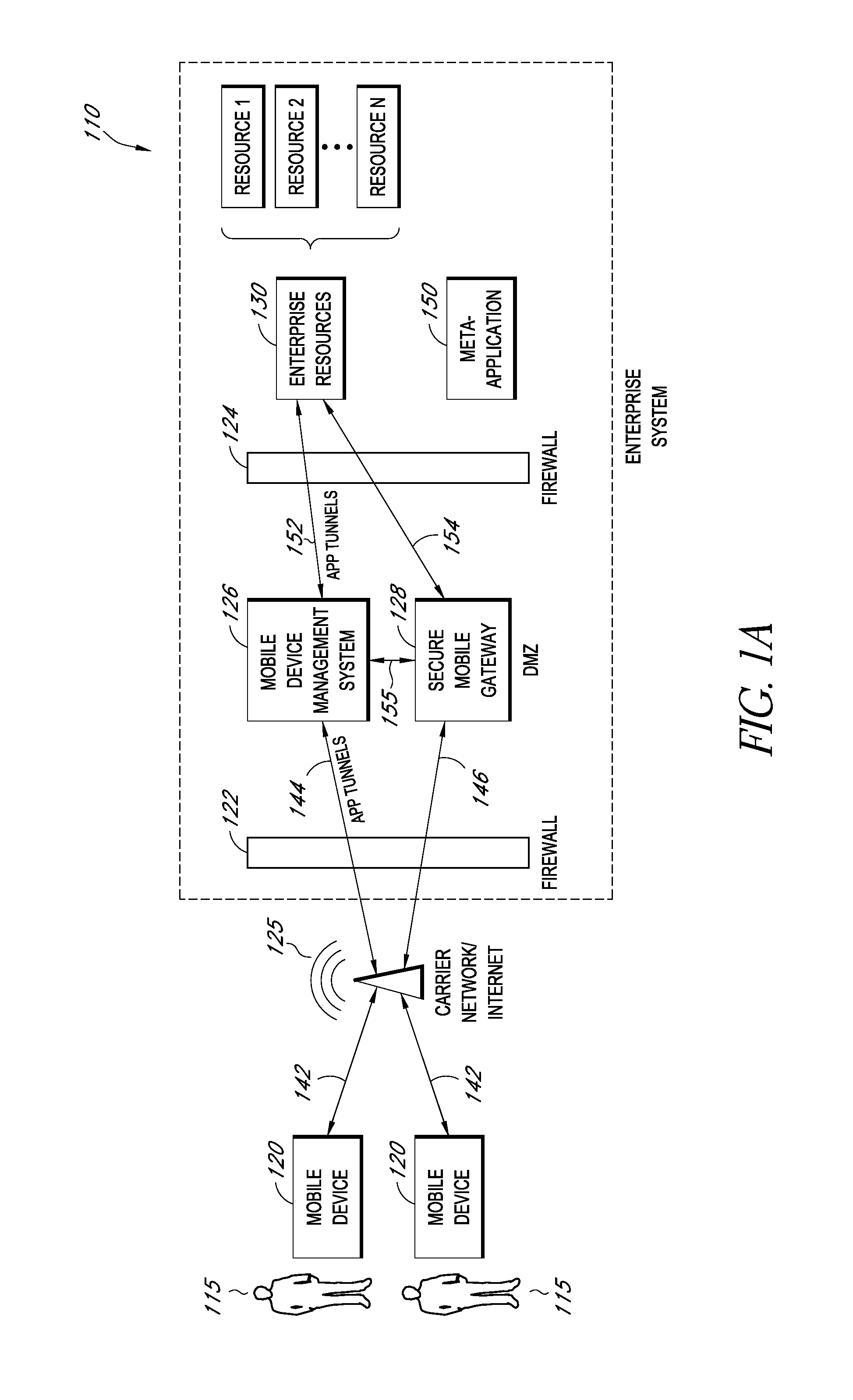
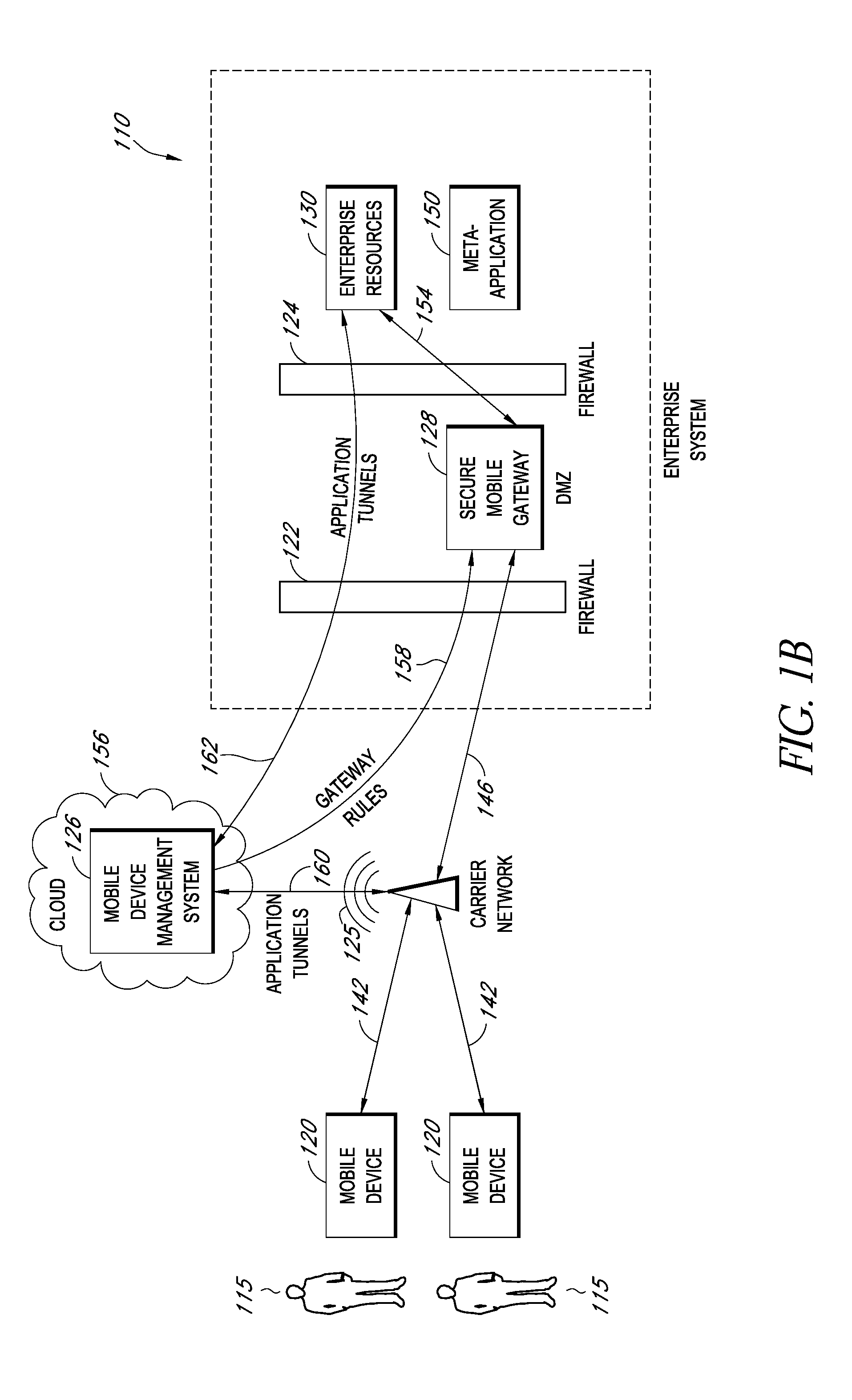
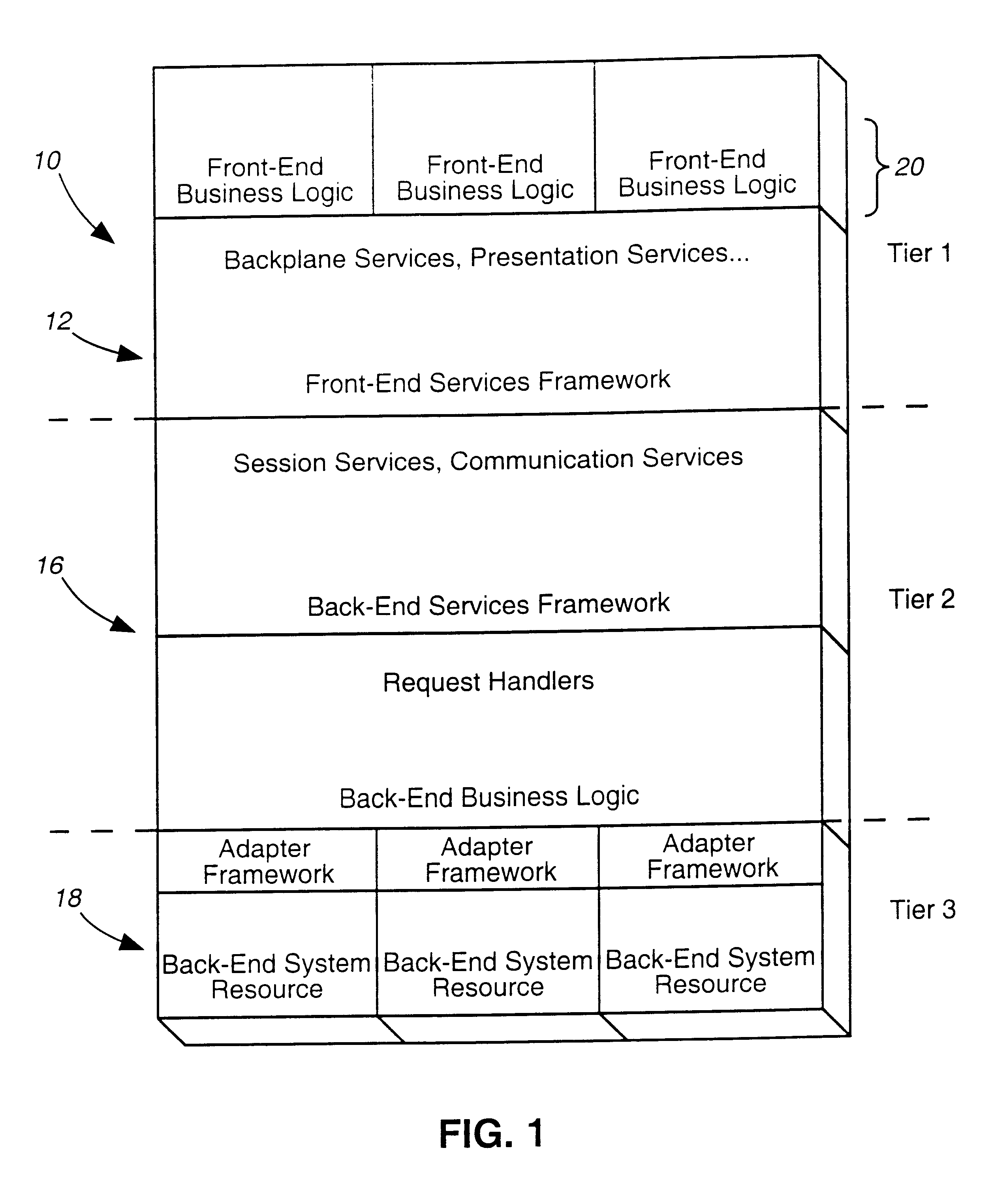
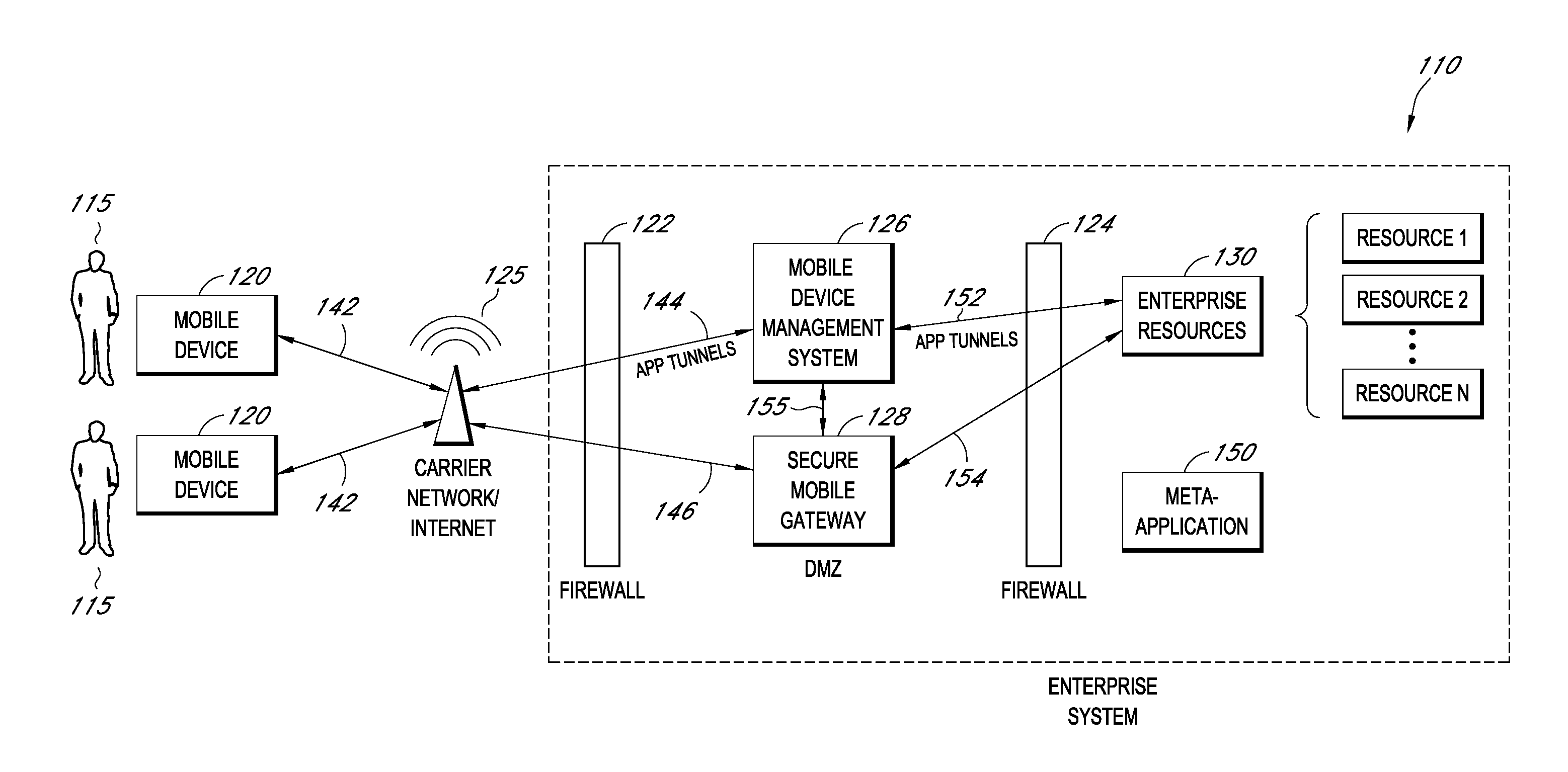
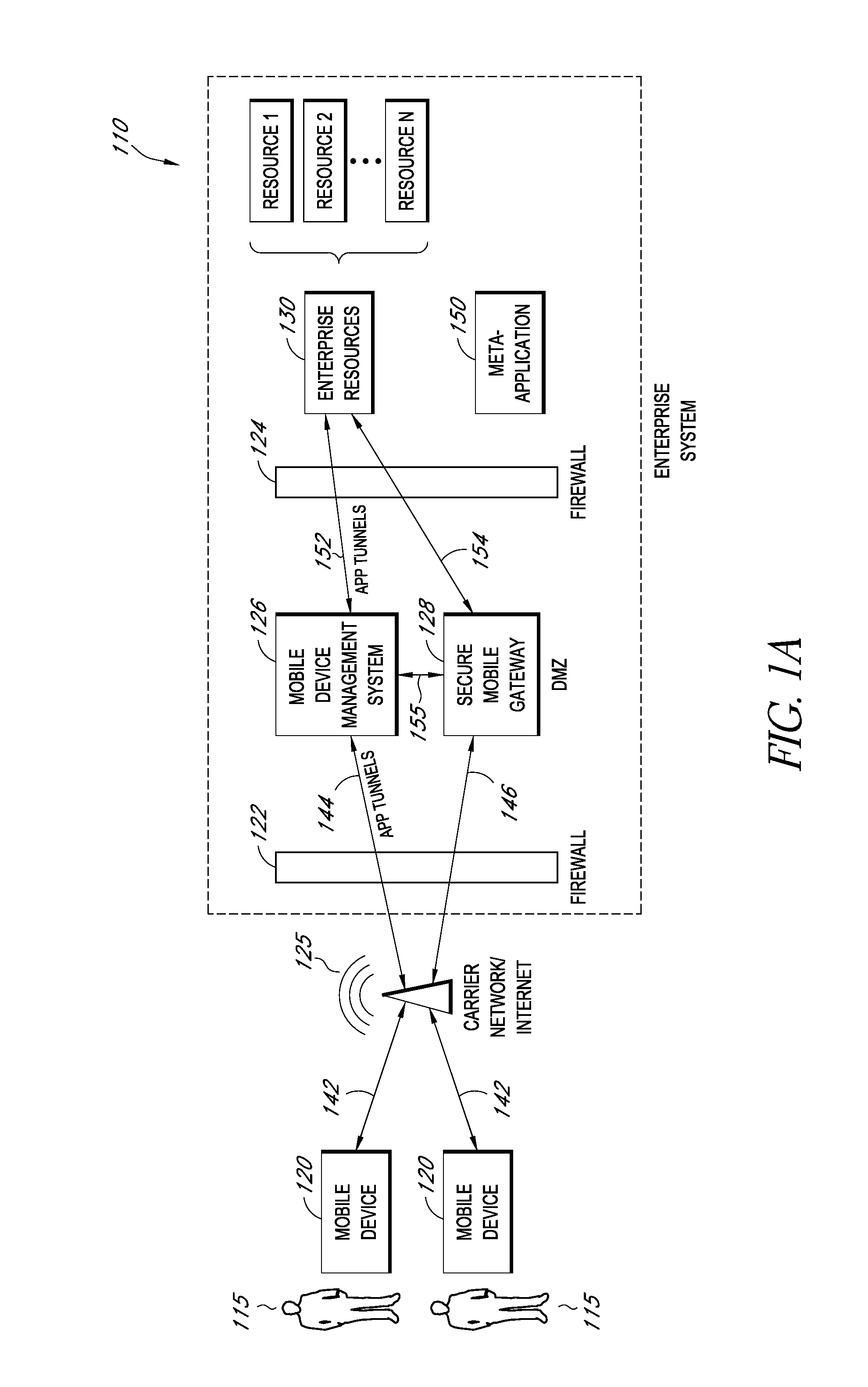
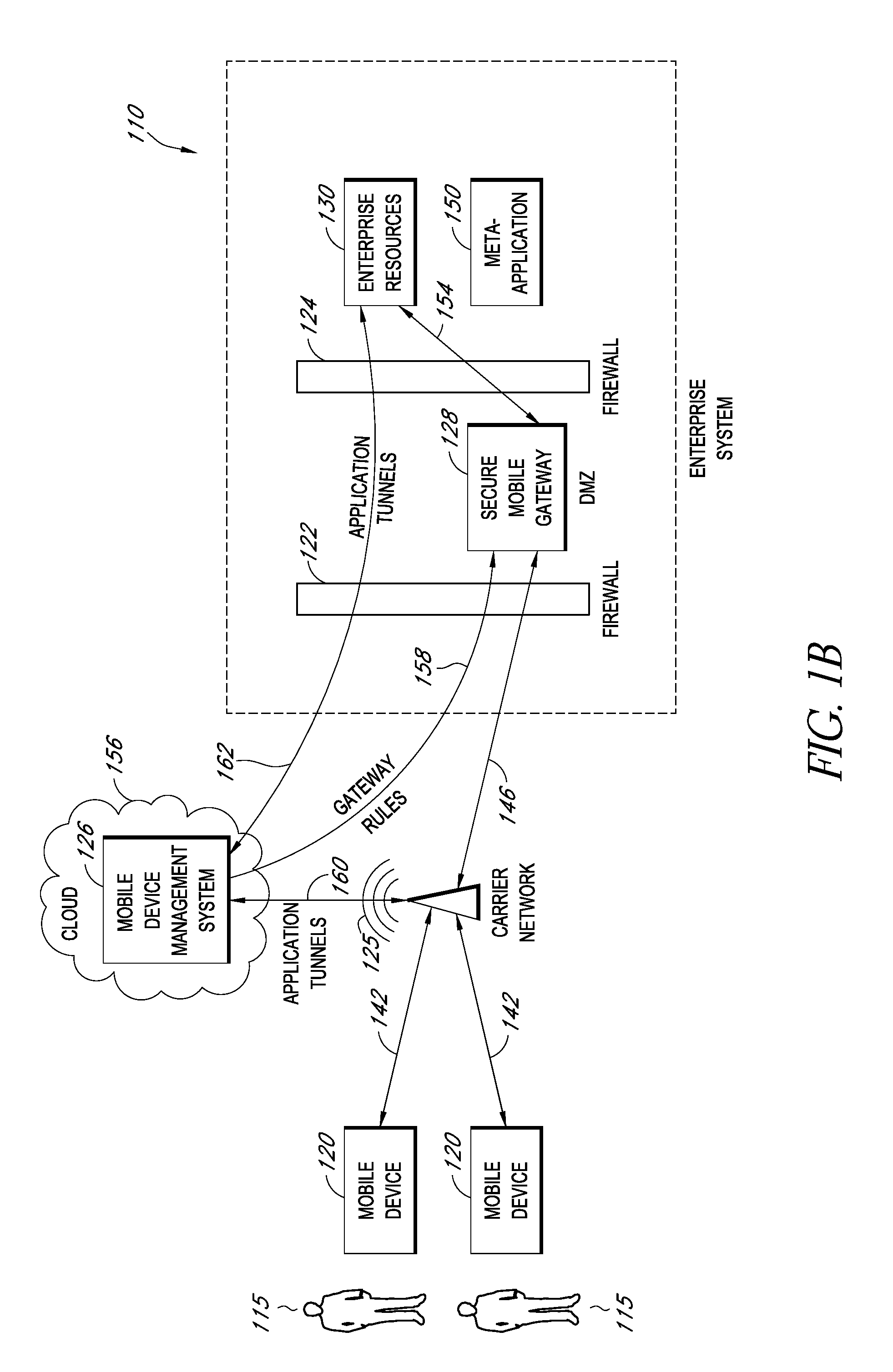
Secure execution of enterprise applications on mobile devices
ActiveUS20140007222A1Decompilation/disassemblyDigital data processing detailsClient-sideApplication server
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
Customer centric revenue management
InactiveUS20090234710A1Improve recommendationsImprove definitionMarket predictionsSpecial data processing applicationsCustomer centricSoftware
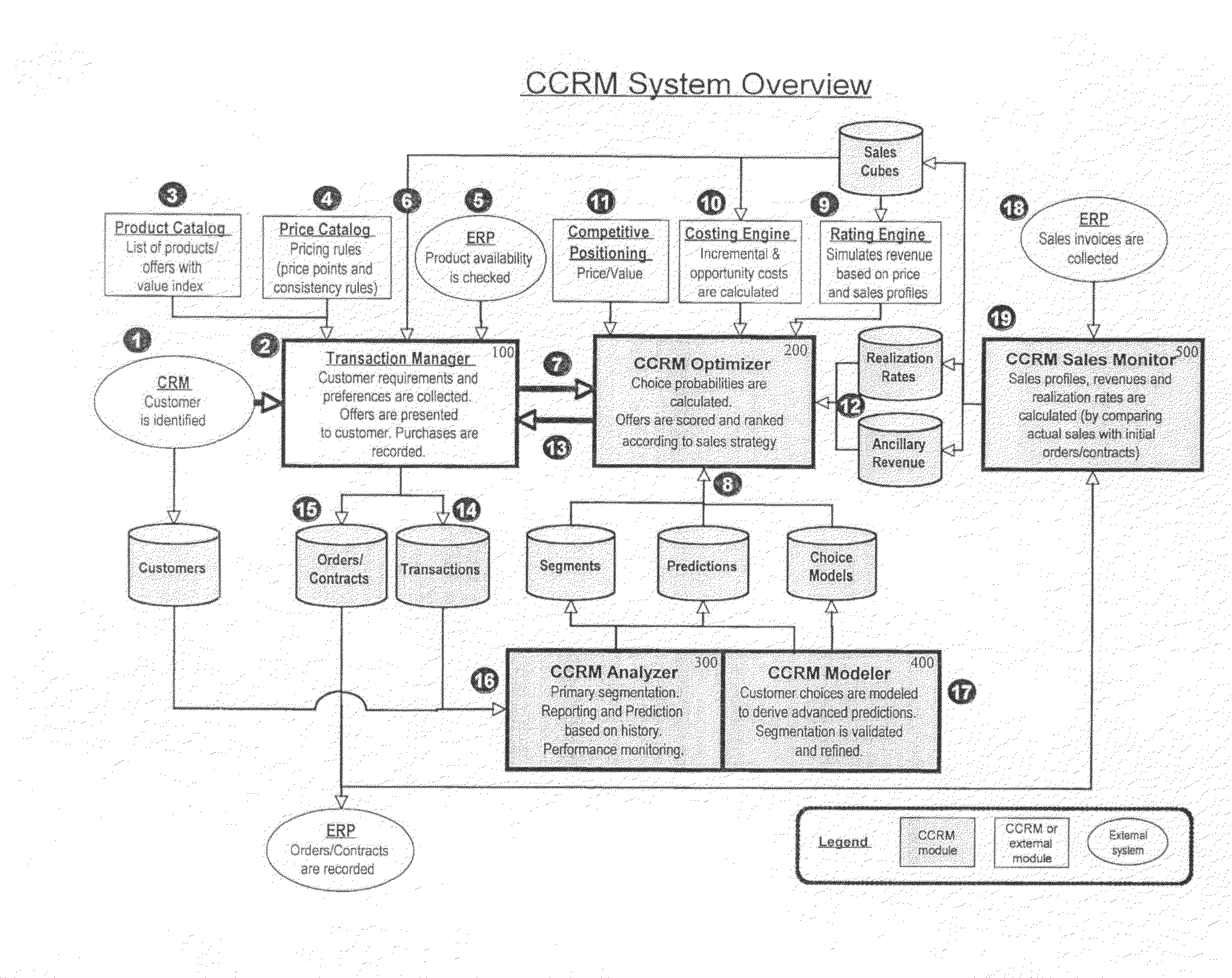
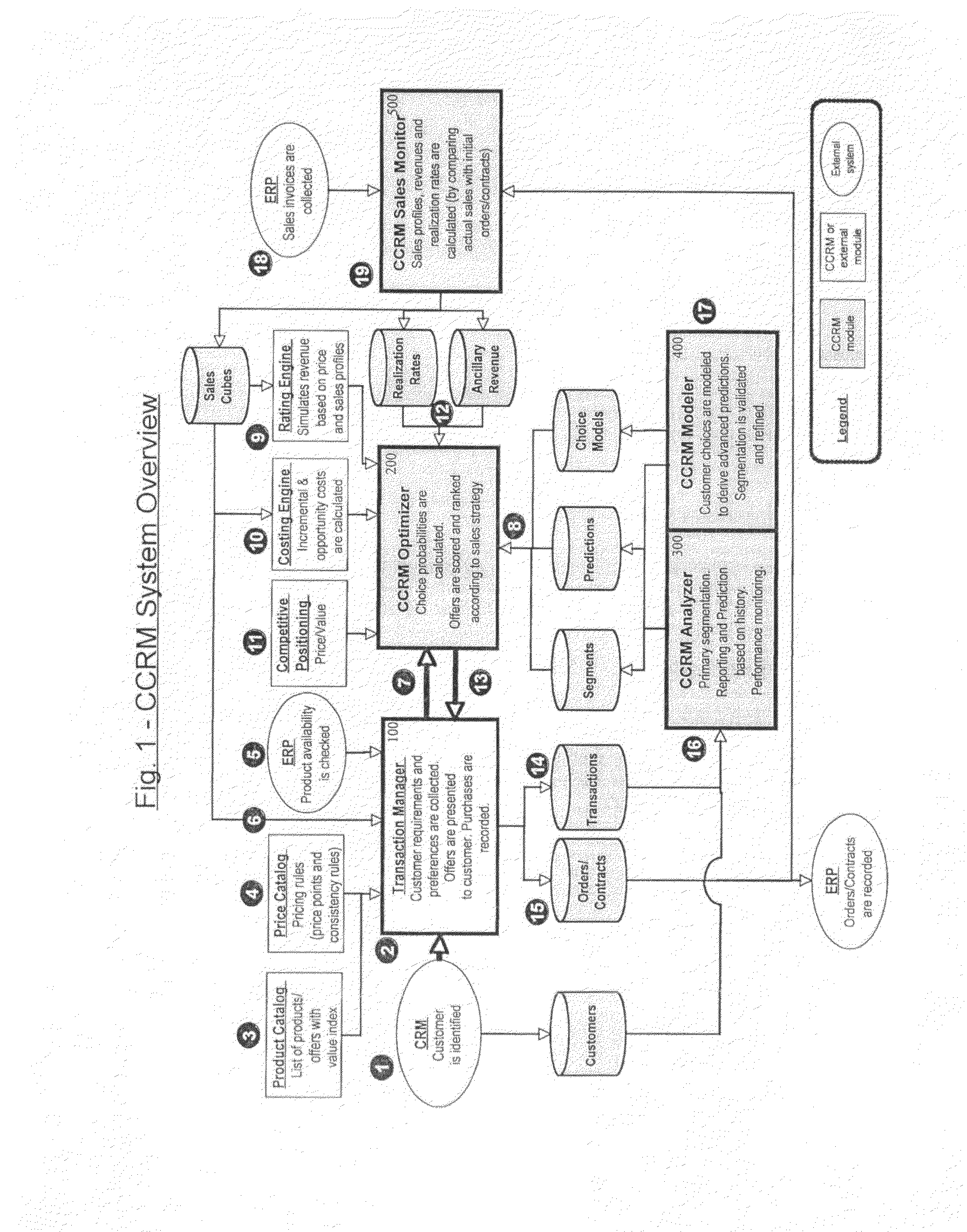
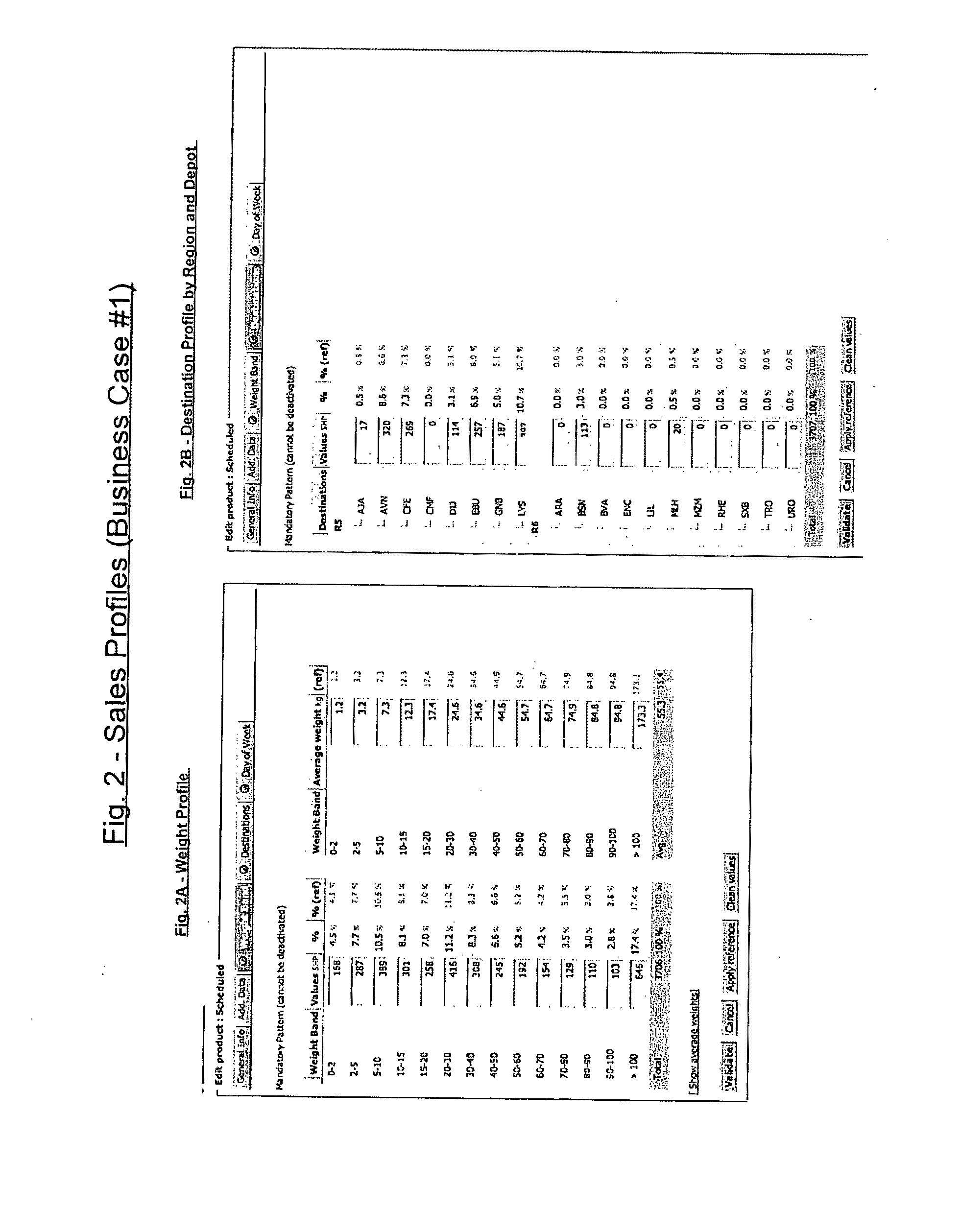
CCRM is a business method and computer software system, to be used by Enterprises selling portfolios of products / services, aiming to optimize the expected value of transactions (or contracts) with consumers or business customers. At a transaction level, CCRM estimates the probability of choice of potential offers by the customer. These offers may be presented alone with possible variation of their attributes (such as price), or in combinations / sets, or in sequences. CCRM calculates the probability of consequent conversion and realization of the sale. Probabilities of choice and conversion are forecasted based on a disaggregated customer choice model, taking into account customer characteristics and stated preferences as well as product / service attributes such as price. Offers are then scored and ranked by expected value based on their revenue, cost and choice probability. Finally, CCRM recommends which offer(s) to present to the customer, at which price(s) and in which display / sequence order, to maximize a business objective function such as the expected value of the transaction / contract.
Owner:OPEN PRICER
Authentication and authorization methods for cloud computing security
ActiveUS8769622B2Retain controlKey distribution for secure communicationDigital data processing detailsResource poolThird party
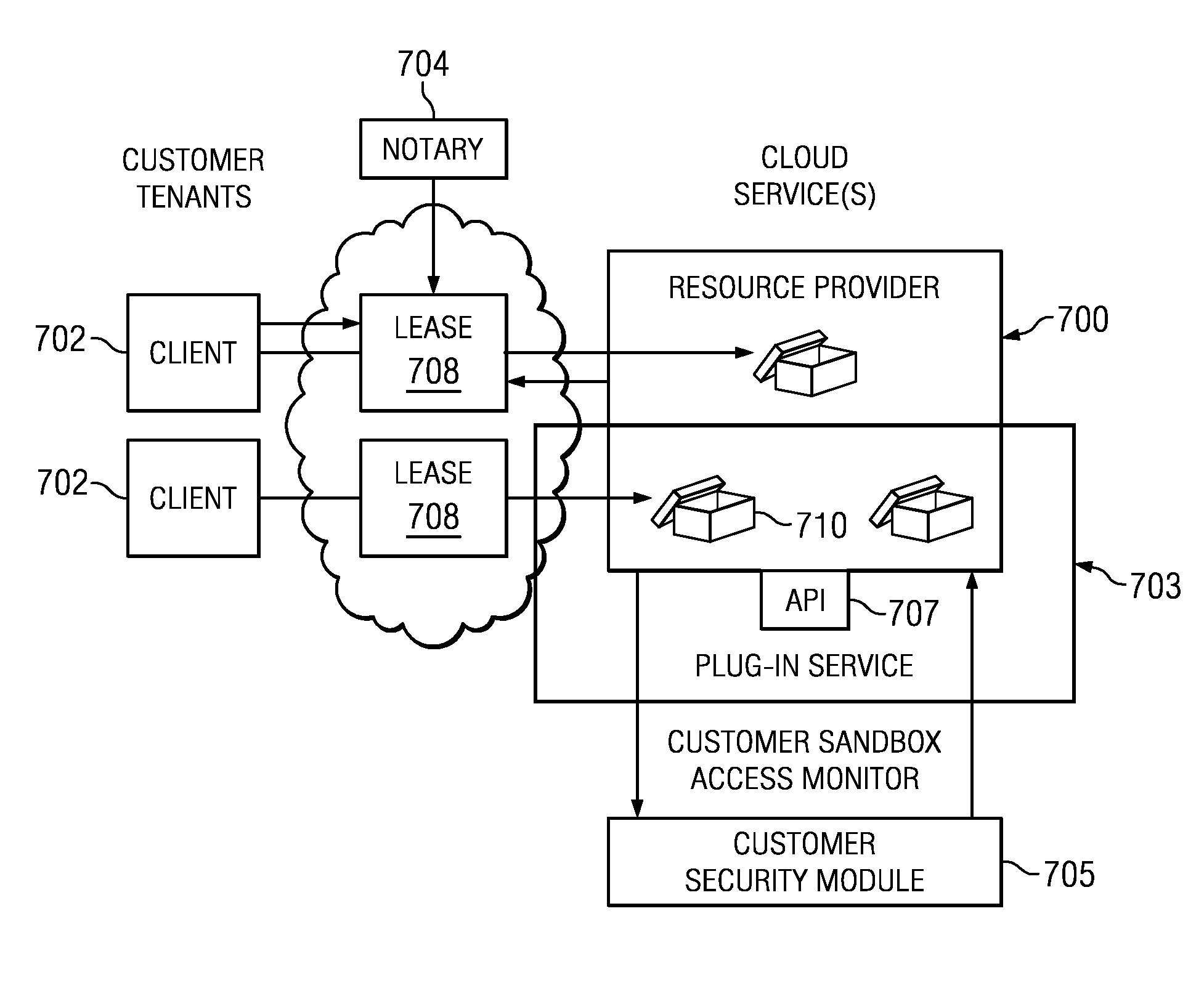
An authentication and authorization plug-in model for a cloud computing environment enables cloud customers to retain control over their enterprise information when their applications are deployed in the cloud. The cloud service provider provides a pluggable interface for customer security modules. When a customer deploys an application, the cloud environment administrator allocates a resource group (e.g., processors, storage, and memory) for the customer's application and data. The customer registers its own authentication and authorization security module with the cloud security service, and that security module is then used to control what persons or entities can access information associated with the deployed application. The cloud environment administrator, however, typically is not registered (as a permitted user) within the customer's security module; thus, the cloud environment administrator is not able to access (or release to others, or to the cloud's general resource pool) the resources assigned to the cloud customer (even though the administrator itself assigned those resources) or the associated business information. To further balance the rights of the various parties, a third party notary service protects the privacy and the access right of the customer when its application and information are deployed in the cloud.
Owner:IBM CORP
Broad and alternative category clustering of the same, similar or different categories in social/geo/promo link promotional data sets for end user display of interactive ad links, promotions and sale of products, goods and services integrated with 3D spatial geomapping and social networking
InactiveUS20130073400A1Efficient and economicalCheaply obtain dataInput/output for user-computer interactionMultiple digital computer combinationsWeb siteData set
A technique, method, apparatus, and system to provide related and integrated social networking, real time geospatial mapping, geo-target location and multiple points of interest, receiving current location of user's electronic or mobile device and multiple points of interest, cloud-type configuration storing and handling user data across multiple enterprises, generating user behavior data and ad links, promotions (“social / geo / promo”) links on a website for any product, good or service, including social / geo / promo data sets for user customized visual displays showing 3D map presentations with correlated or related broad or alternative categories of social / geo / promo links to be displayed with web page content for view by an end user.
Owner:HEATH STEPHAN
System and method for providing educational related social/geo/promo link promotional data sets for end user display of interactive ad links, promotions and sale of products, goods, and/or services integrated with 3D spatial geomapping, company and local information for selected worldwide locations and social networking
InactiveUS20130073387A1Exceptional educational toolEfficient and economicalMarketingLocal information systemsData set
A technique, method, apparatus, and system to provide educational related, integrated social networking, real time geospatial mapping, geo-target location based technologies including GPS and GIS and multiple points of interest, receiving current location of user's electronic or mobile device and multiple points of interest, cloud-type configuration storing and handling user data across multiple enterprises, generating user behavior data and ad links, promotions (“social / geo / promo”) links on a website for educational related products, goods, and / or services, including educational related social / geo / promo data sets for user customized visual displays showing 3D map presentations with correlated or related broad or alternative categories of social / geo / promo links to be displayed with web page content for view and interaction by an end user.
Owner:HEATH STEPHAN
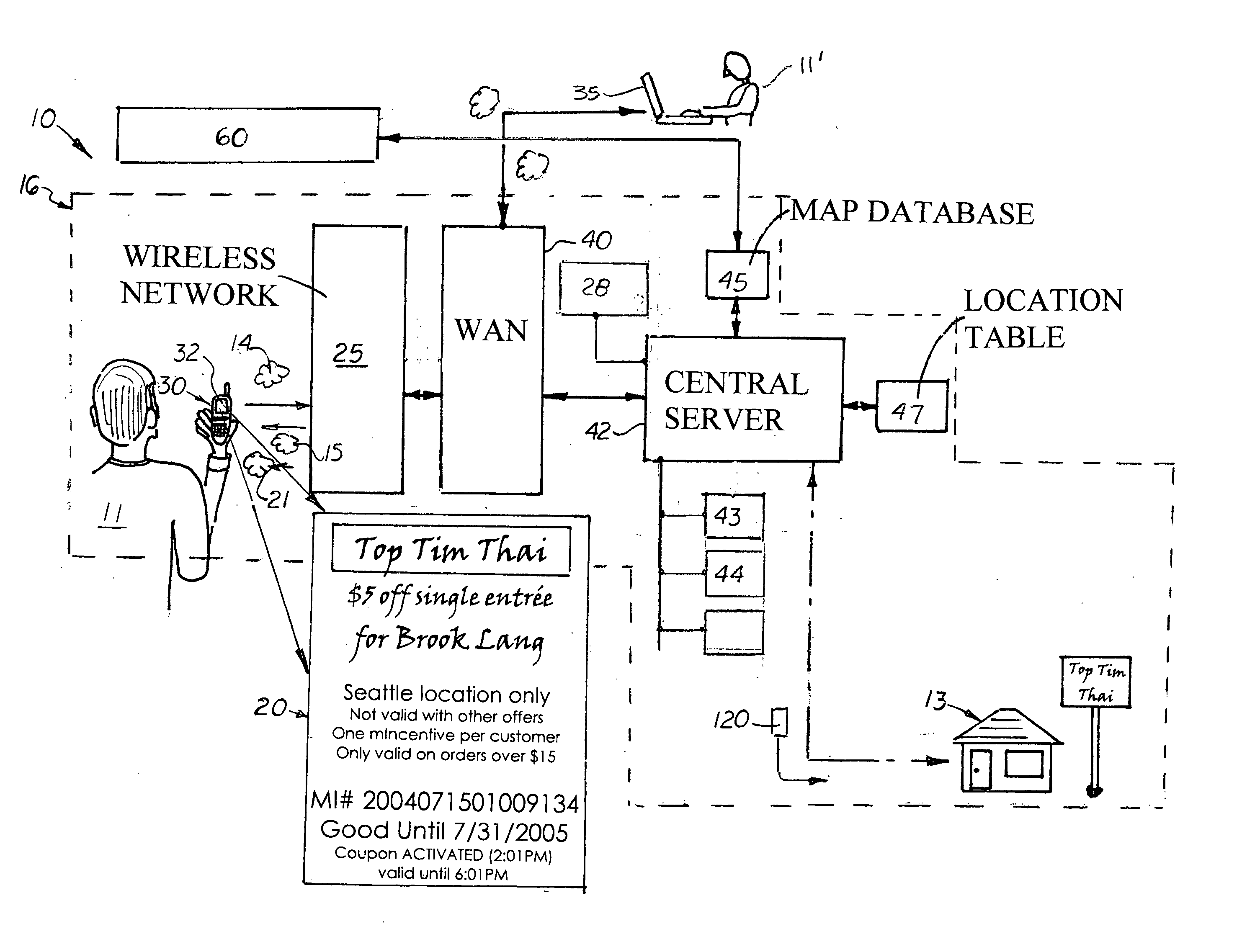
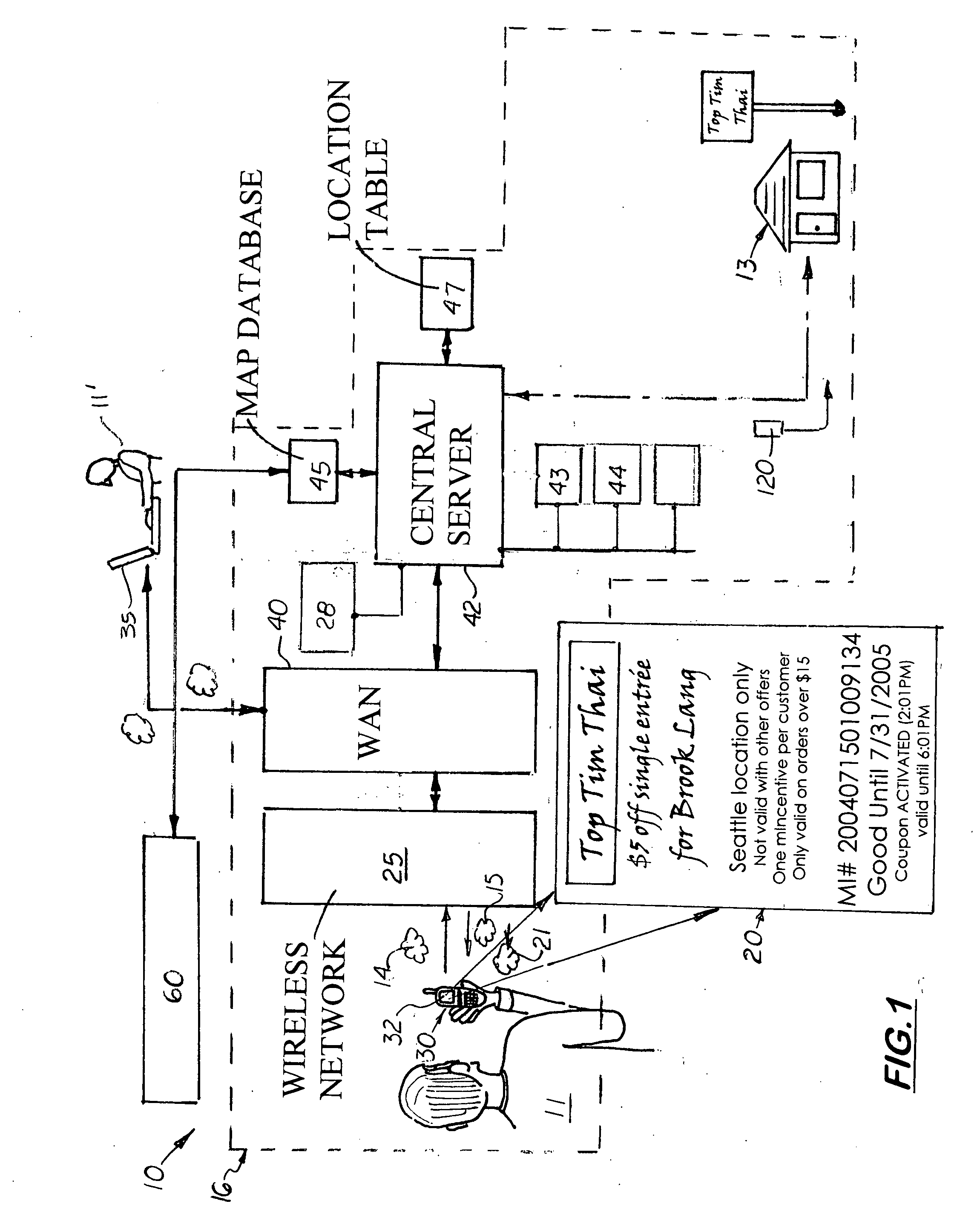
Method and distribution system for location based wireless presentation of electronic coupons
A method and system for distributing electronic coupons offered by businesses via the wireless devices operated by potential customers in a region. The invention includes a wireless communication device and a central server capable of communicating via a wireless communication network The central server is connected to a search engine, a business database containing the names and locations of businesses located in the region offering discounted coupons for goods and services to its potential customers. Connected to the central server is a discount coupon database and a map database that contains coupon information, a graphic file of the coupon, and the businesses location information. When the potential customer desires a discount coupon for a particular service or goods in the region, the potential customer contacts the central server, which instructs the search engine to conduct a search based on the criteria submitted by the potential customer. The search engine produces a list of businesses currently offering discount coupons that is then transmitted to the potential customer.
Owner:LANG BROOK W
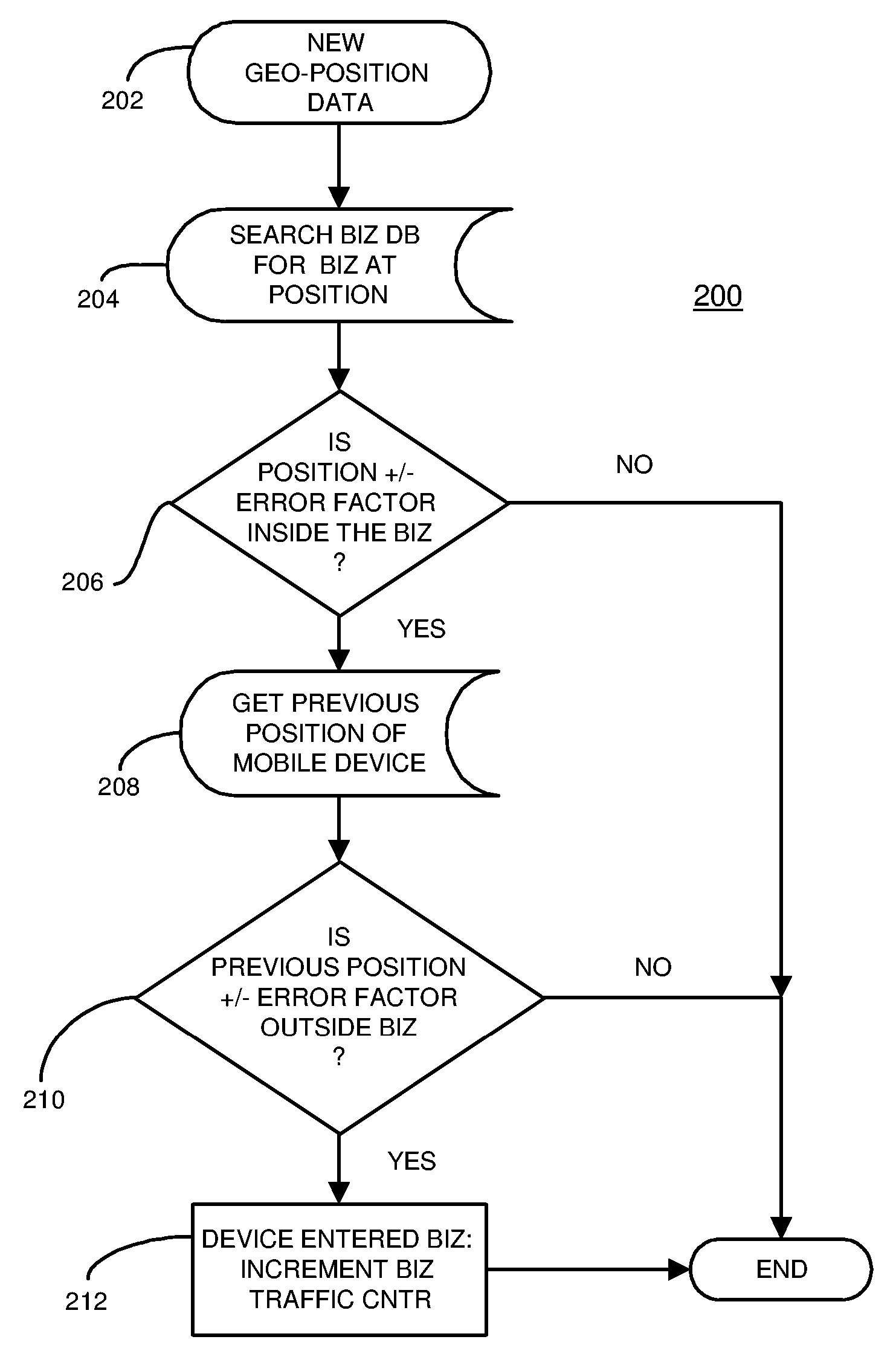
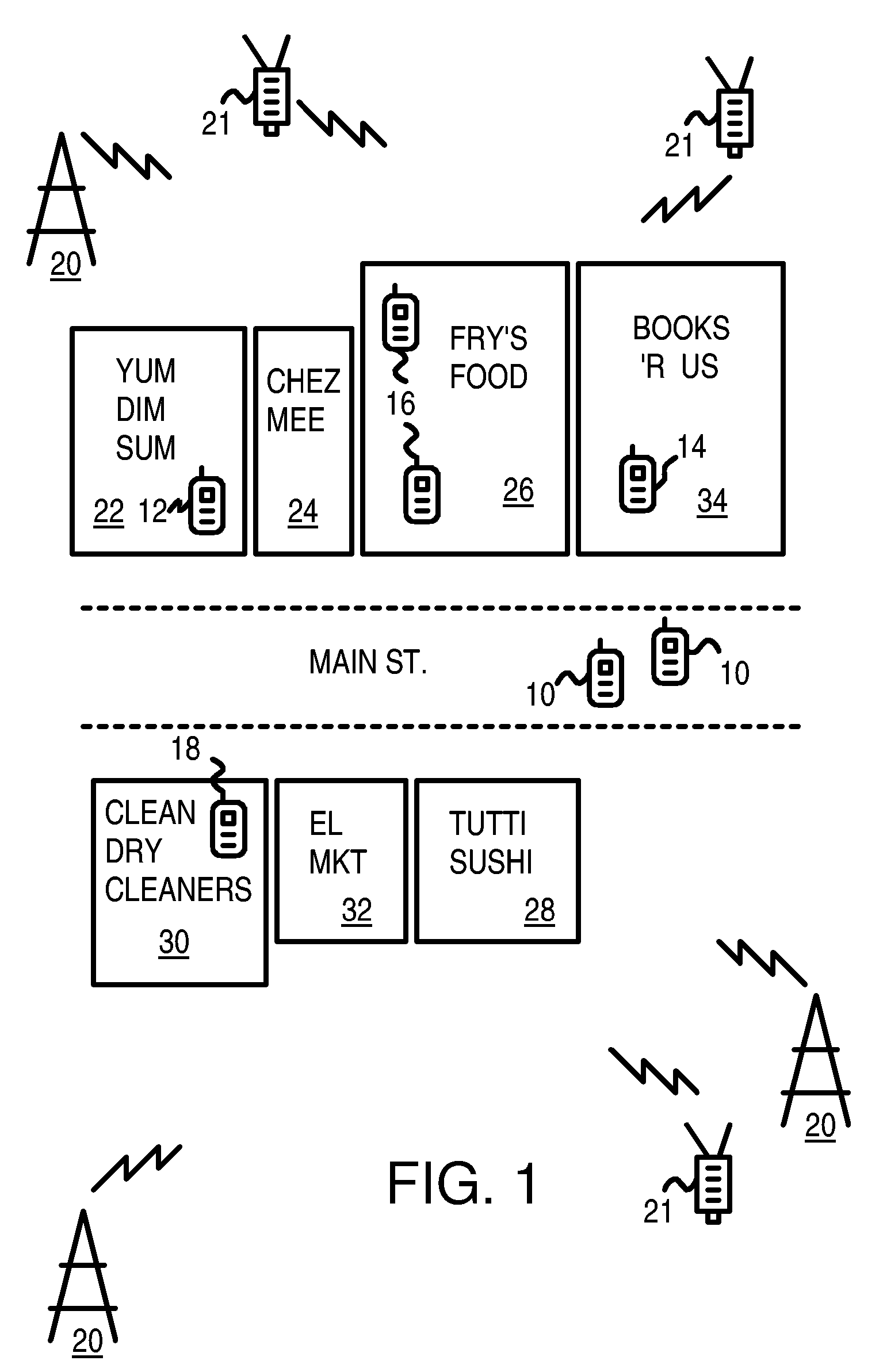
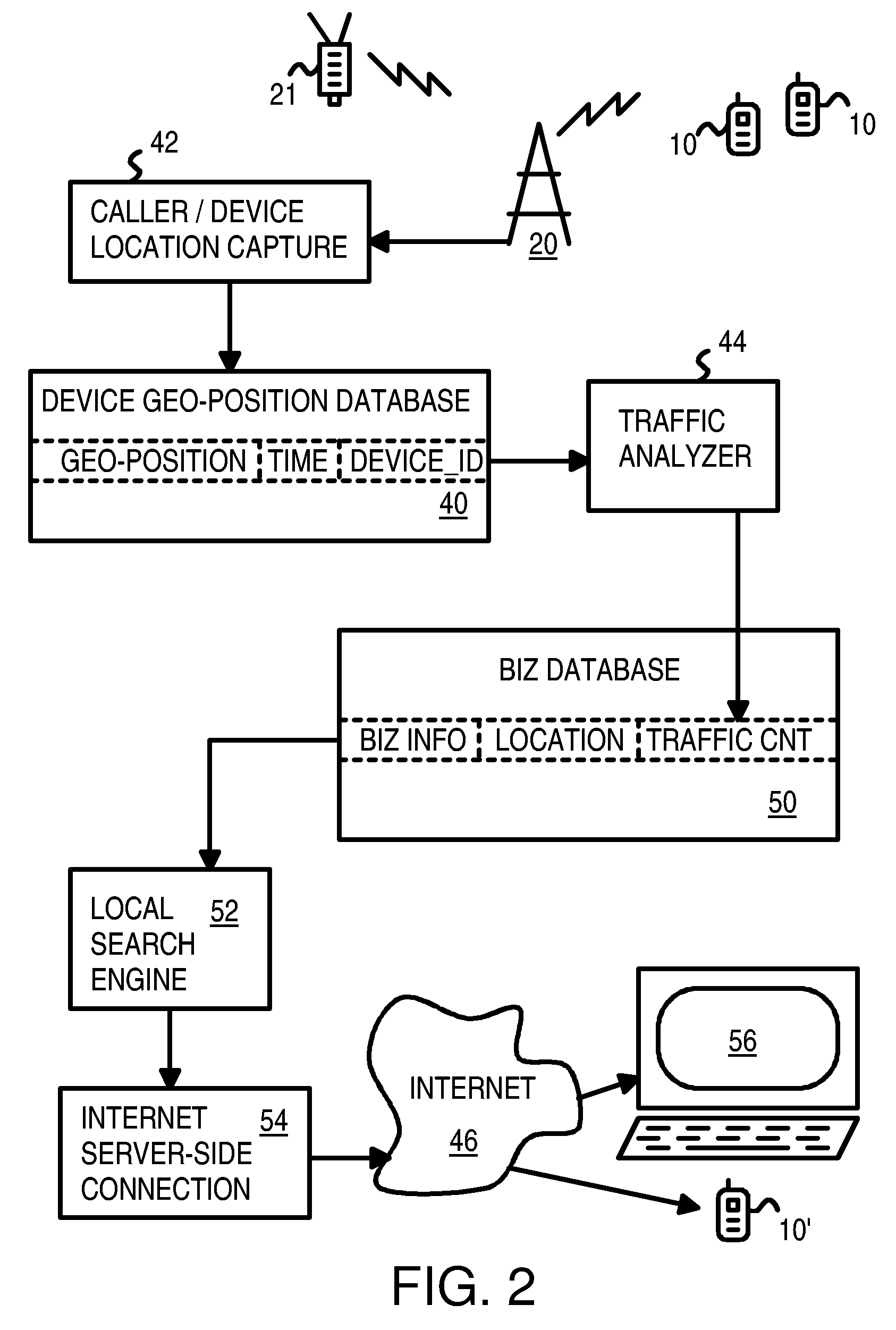
Ranking Internet Search Results Based on Number of Mobile Device Visits to Physical Locations Related to the Search Results
An Internet search engine ranks search results based on popularity with mobile-device users. Geo-position data from cell phones and other mobile devices are collected into a device geo-position database. The geo-position data is compared to locations of businesses in a business database. When a mobile device's geo-position moves inside a business location, a traffic counter for that business location in the business database is updated. When an Internet user performs a local search, the result set is sorted based on a rank that is at least partially determined by the traffic counters. The popularity-ranked search results indicate which businesses received the most mobile-device visits, an indication of the business's overall popularity. The popularity ranking may be adjusted for business size by dividing the traffic counter by the square footage of the business and sorting the result set based on the mobile-device visits, or repeat visits, per square foot.
Owner:NG DAVID WAY
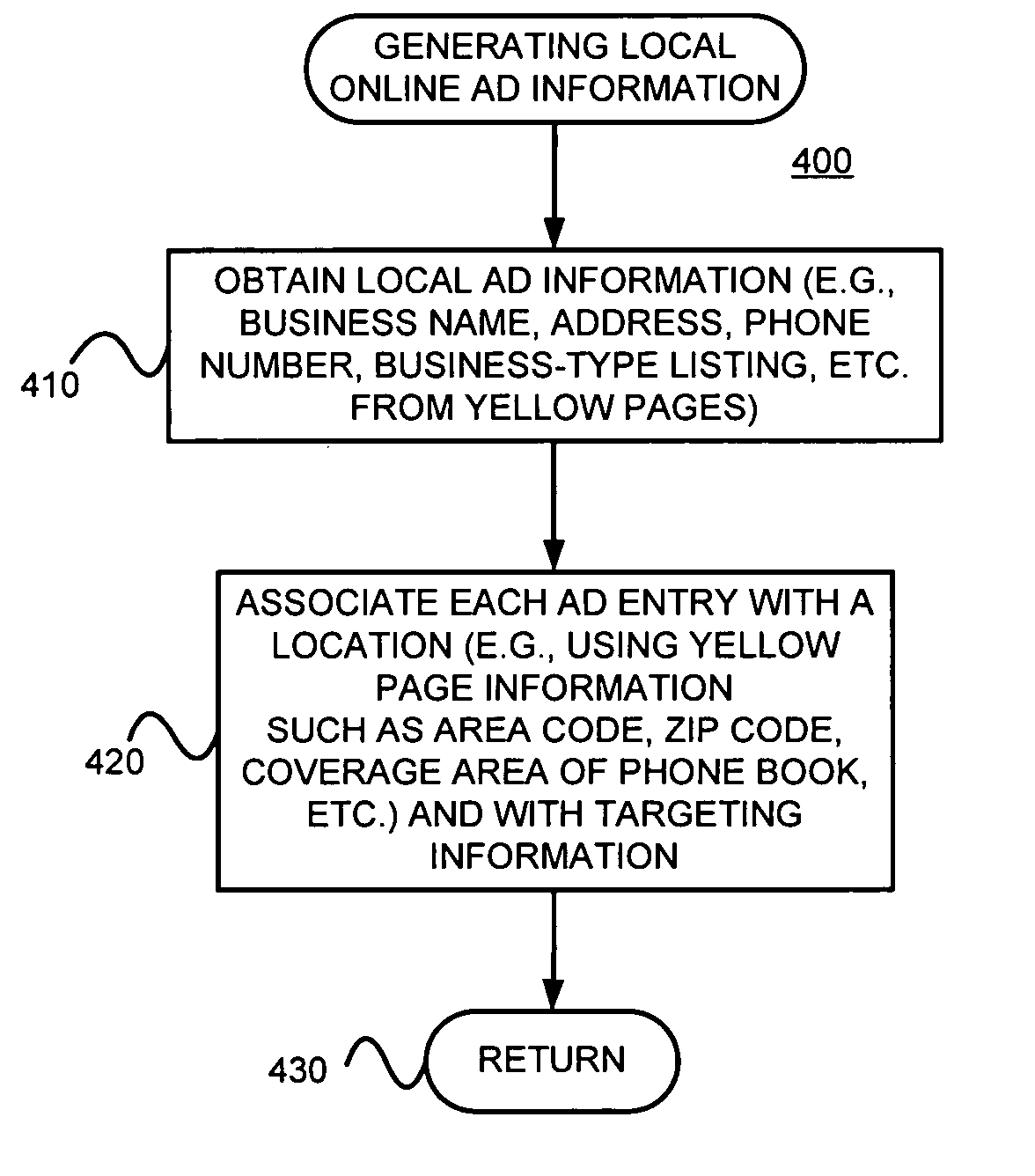
Generating and/or serving local area advertisements, such as advertisements for devices with call functionality
Sets of local, (e.g., online) ads may be generated by obtaining sets of information about (e.g., local) establishments, each set including a business address information and / or a telephone number, (b) determining, for each of the sets, a location using at least one of at least a portion of the business address information and at least a portion of the telephone number, and (c) generating, for each of the sets, an ad that includes targeting information that targets the serving of the ad to queries related to the determined location. A query, including information about a location of a client device, may be accepted and at least one of the generated ads that includes targeting information that targets the location of the client device may be determined.
Owner:GOOGLE LLC
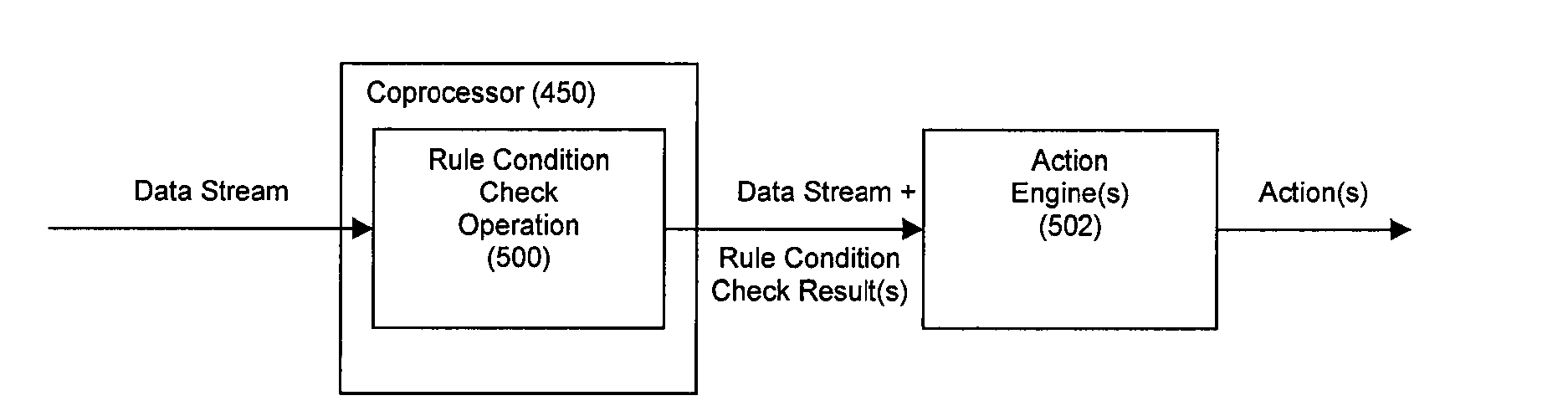
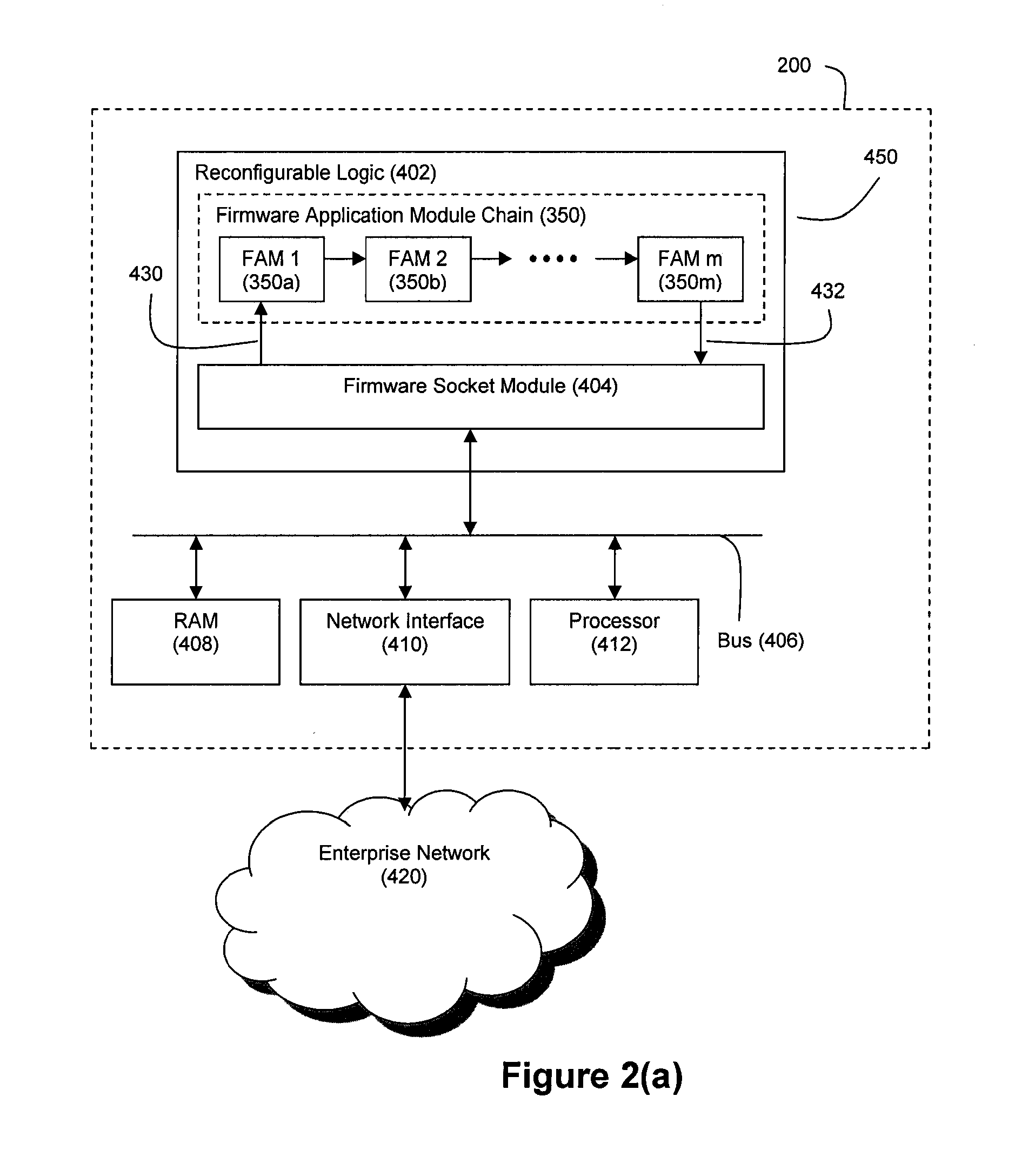
Method and System for Accelerated Stream Processing
ActiveUS20090287628A1Lower latencyImprove latencyDigital computer detailsCode conversionBusiness ruleEvent stream
Disclosed herein is a method and system for hardware-accelerating various data processing operations in a rule-based decision-making system such as a business rules engine, an event stream processor, and a complex event stream processor. Preferably, incoming data streams are checked against a plurality of rule conditions. Among the data processing operations that are hardware-accelerated include rule condition check operations, filtering operations, and path merging operations. The rule condition check operations generate rule condition check results for the processed data streams, wherein the rule condition check results are indicative of any rule conditions which have been satisfied by the data streams. The generation of such results with a low degree of latency provides enterprises with the ability to perform timely decision-making based on the data present in received data streams.
Owner:IP RESERVOIR
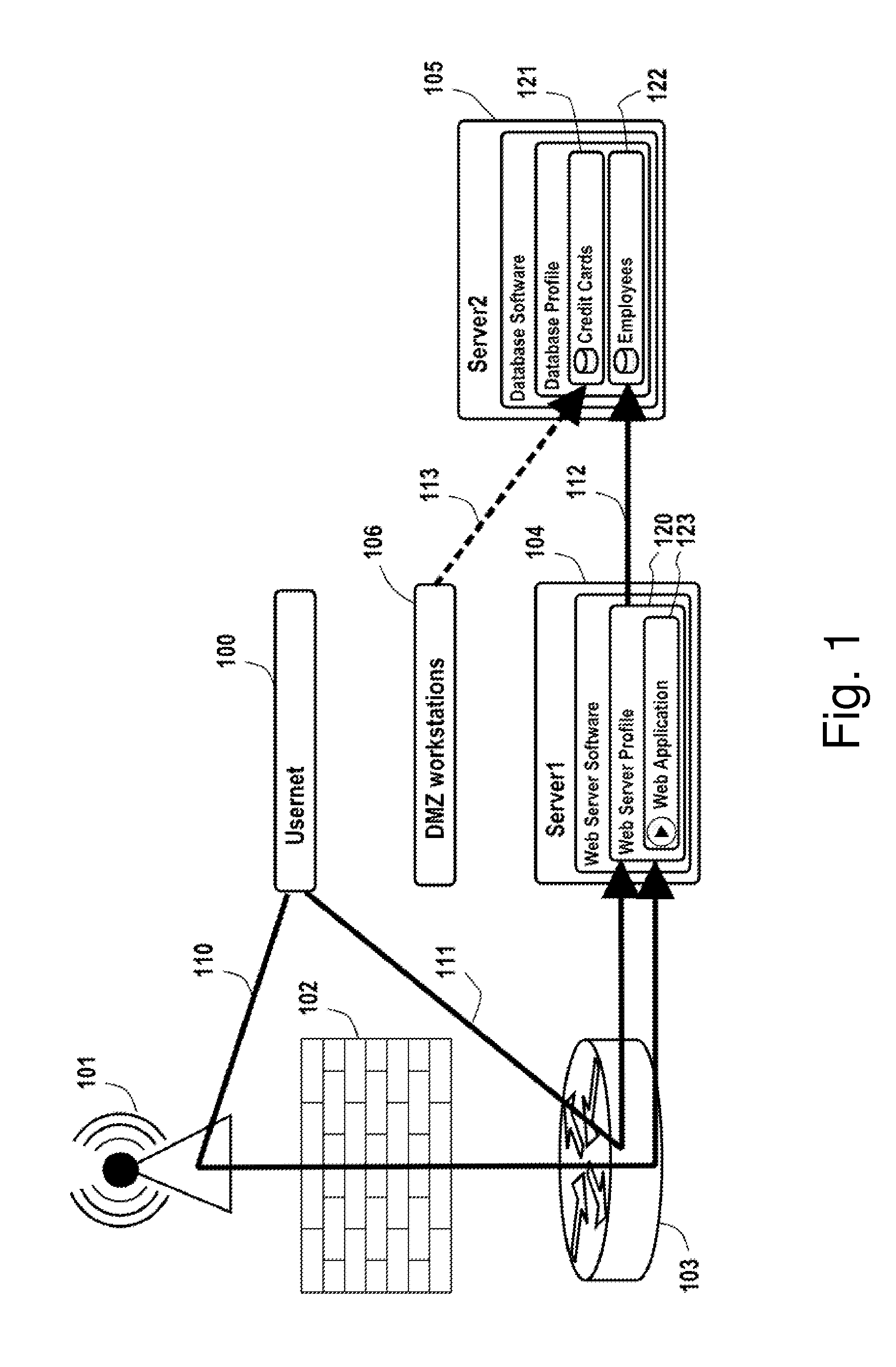
Integrated customer web station for web based call management
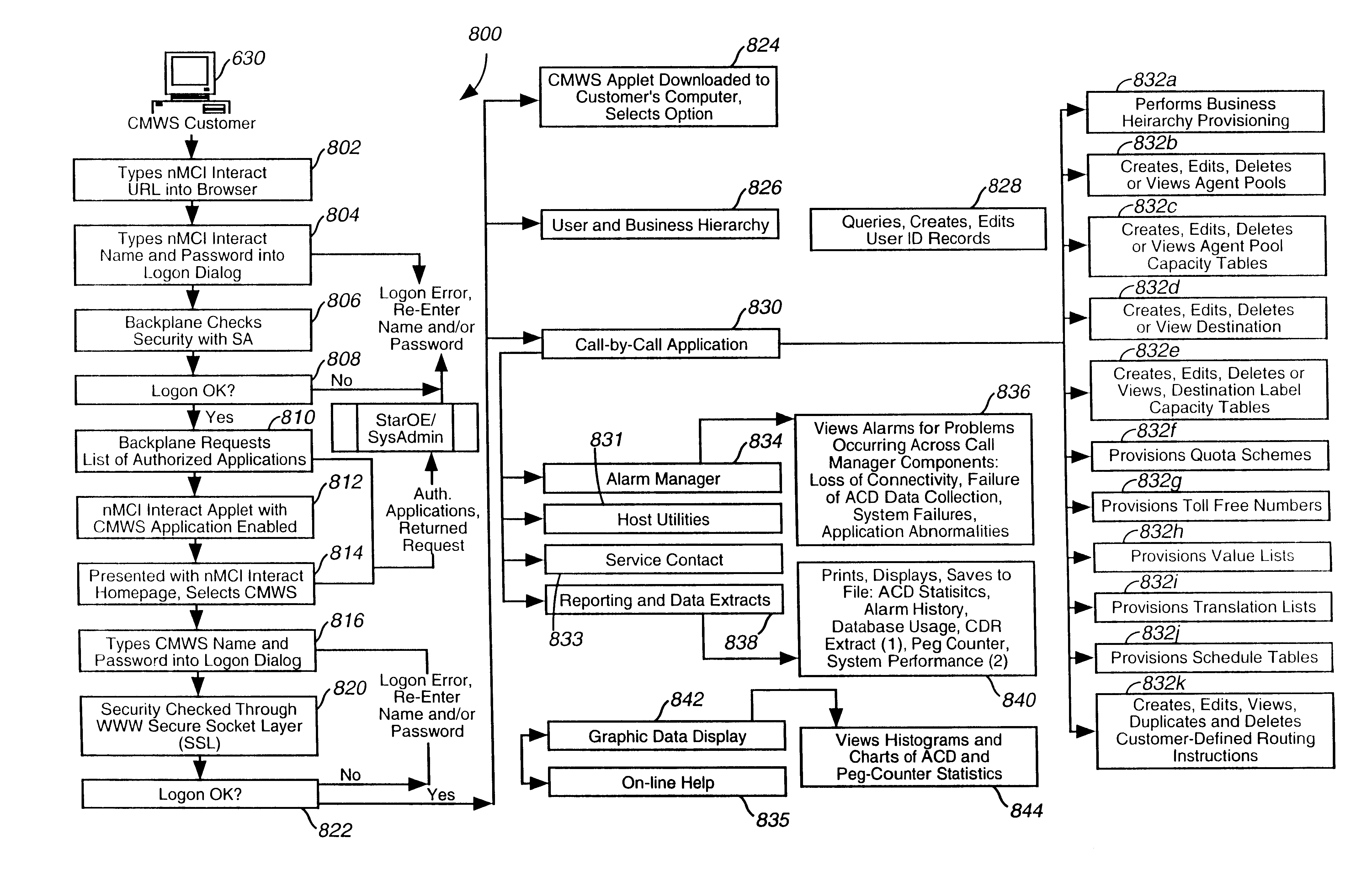
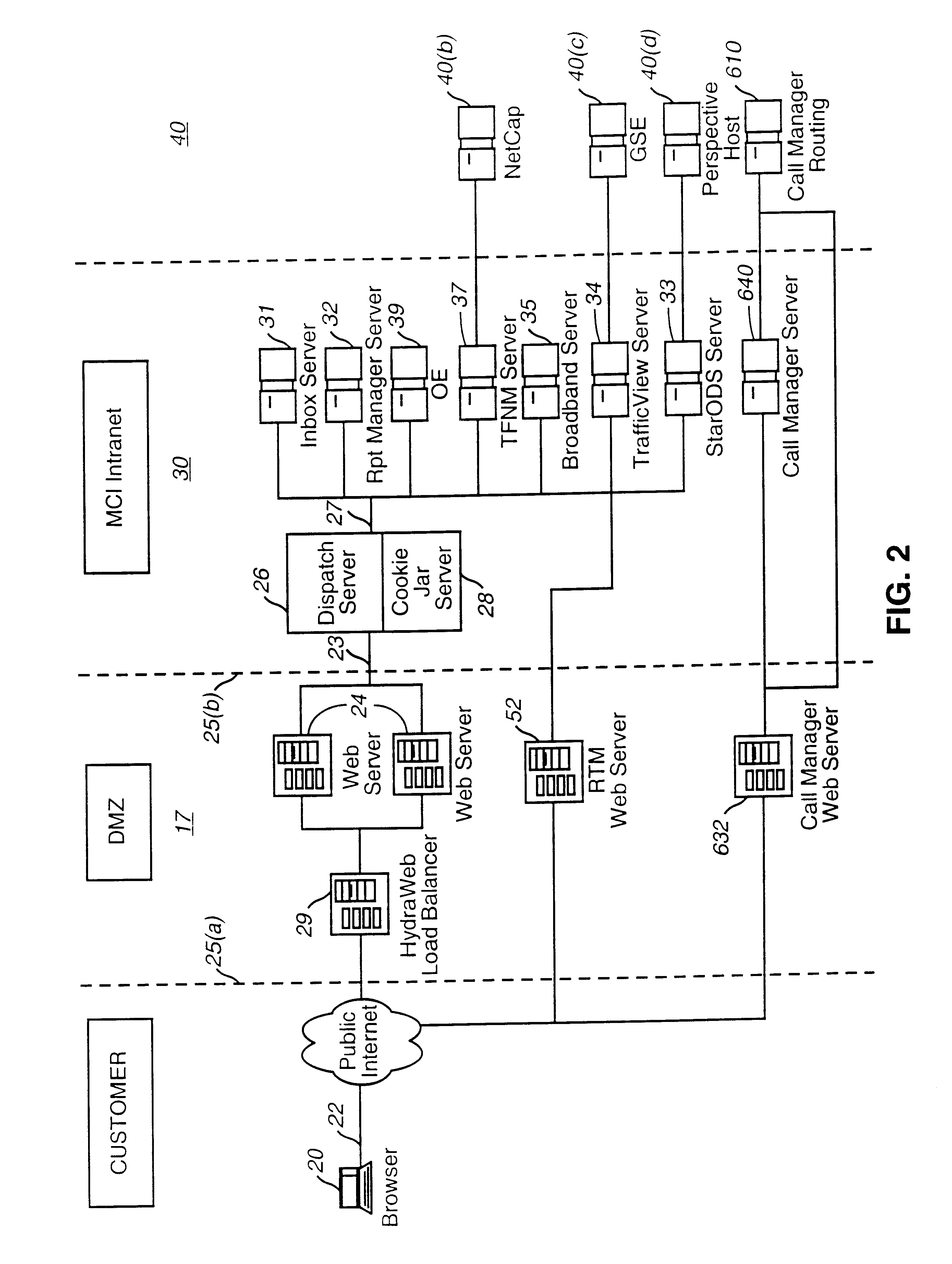
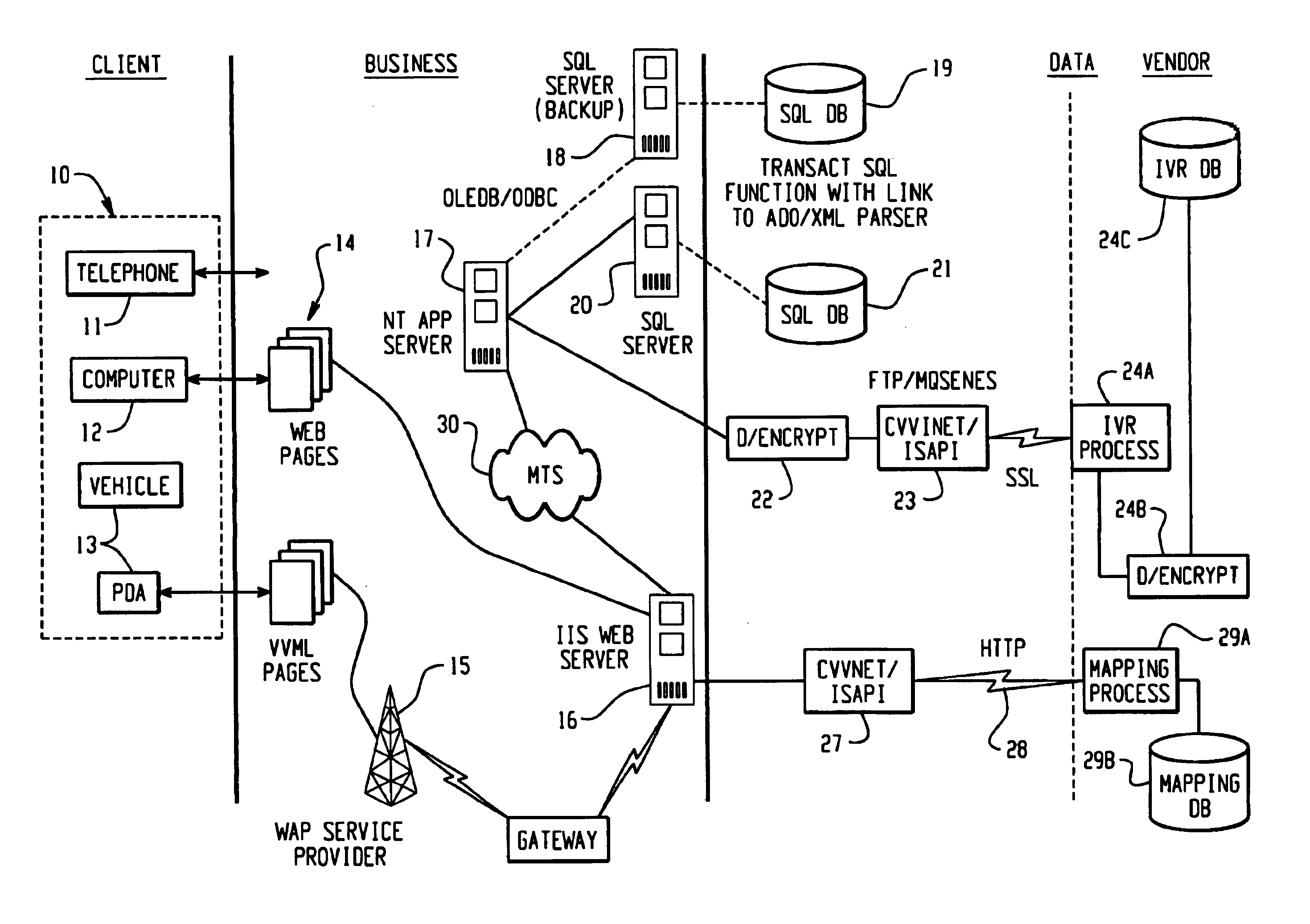
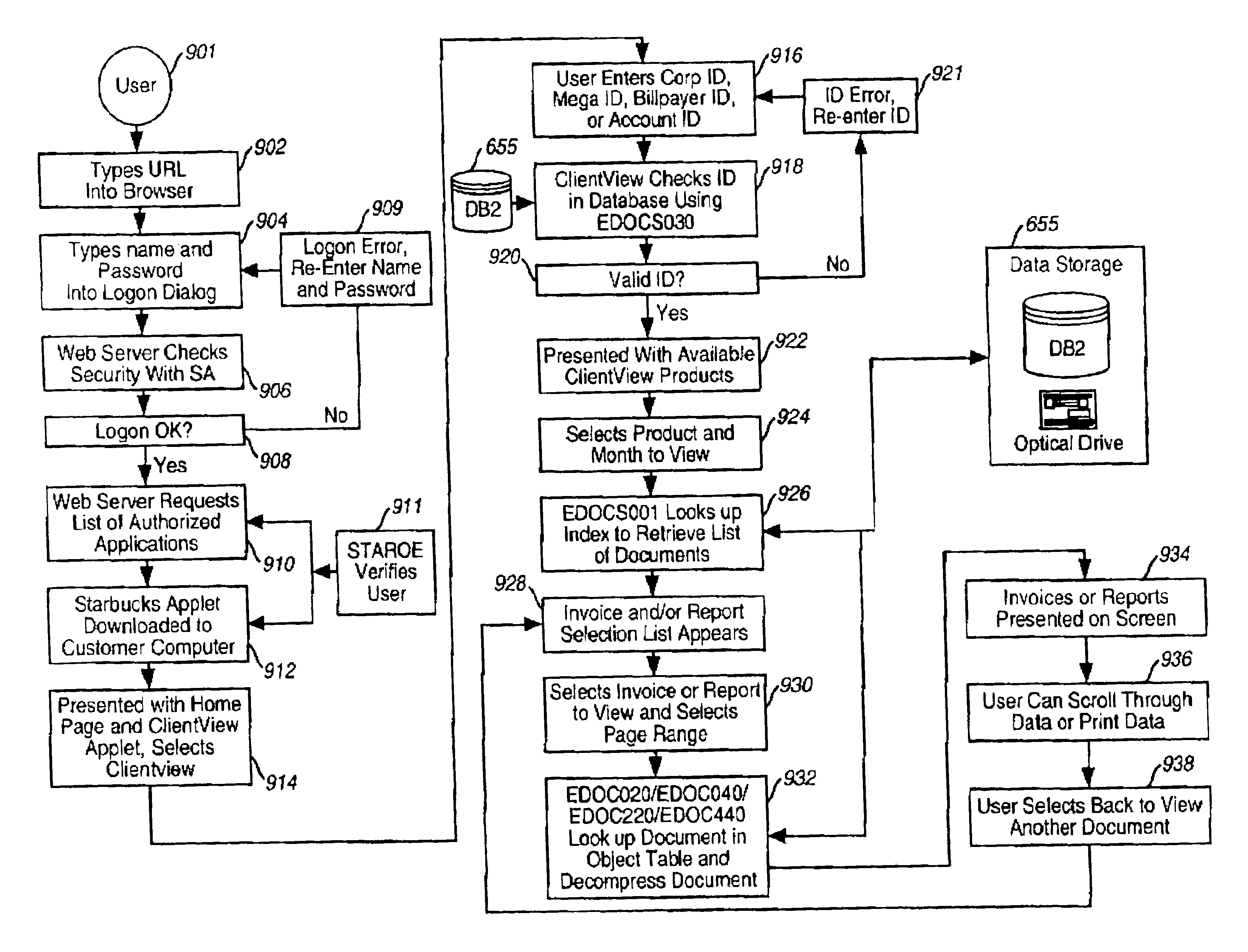
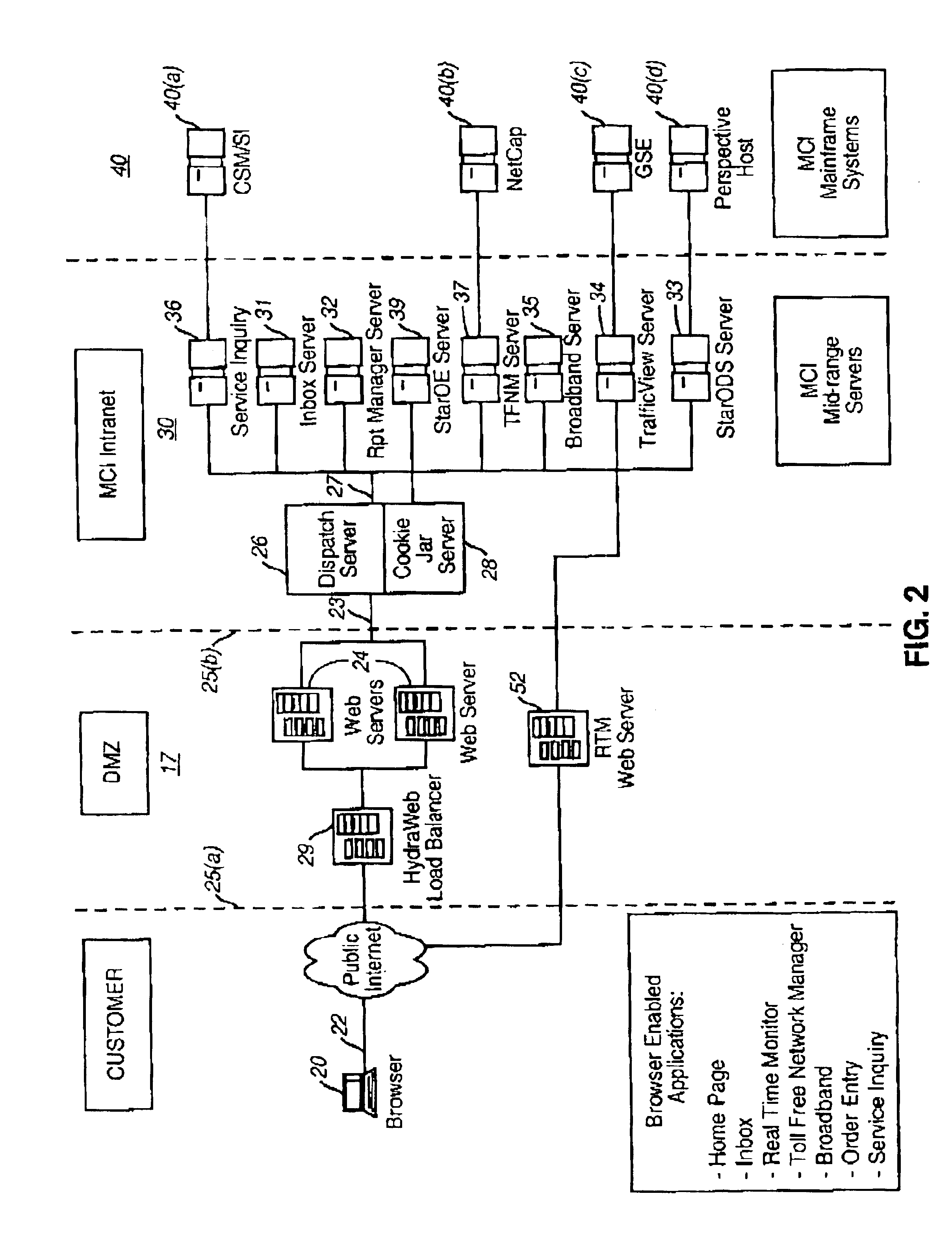
A Web-based call routing management workstation application which allows authorized customers to control toll free routing and monitor call center status. An architecture including one or more web servers located in a firewalled demilitarized zone (DMZ) as communications medium between the customer workstations at the customer sites and the enterprise back-end applications providing the call routing management services, provides a secure infrastructure for accessing the enterprise applications via the otherwise insecure public Internet. The present invention enables creation and management of call by call routing rules by a customer with a workstation having an Internet access and a supported Web browser. The customized rules may be tested and / or debugged via the Web-enabled workstation, using a debugger / tester which runs the routing rules under a simulated environment. In addition, customers may provision hierarchies for their business; create, modify or delete agent pools; manipulate capacity tables; and define quota schemes, value lists and schedule tables, all at the customer site via the Web-enabled workstation. The present invention also enables the customers to view near real-time displays of call center ACD statistics and peg counts based on routing rules, as well as, run provisioning and statistical reports on provisioning and statistical data and also to extract the data for further analysis. Additionally, the present invention supports foreign language and branding features on a graphical user interface. An infrastructure is provided which enables secure initiation, acquisition, and presentation of the call manager functionalities to customers from any computer workstation having a web browser and located anywhere in the world.
Owner:VERIZON PATENT & LICENSING INC
Secure container for protecting enterprise data on a mobile device
ActiveUS20140006347A1Digital data information retrievalDecompilation/disassemblyDocumentation procedureApplication server
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
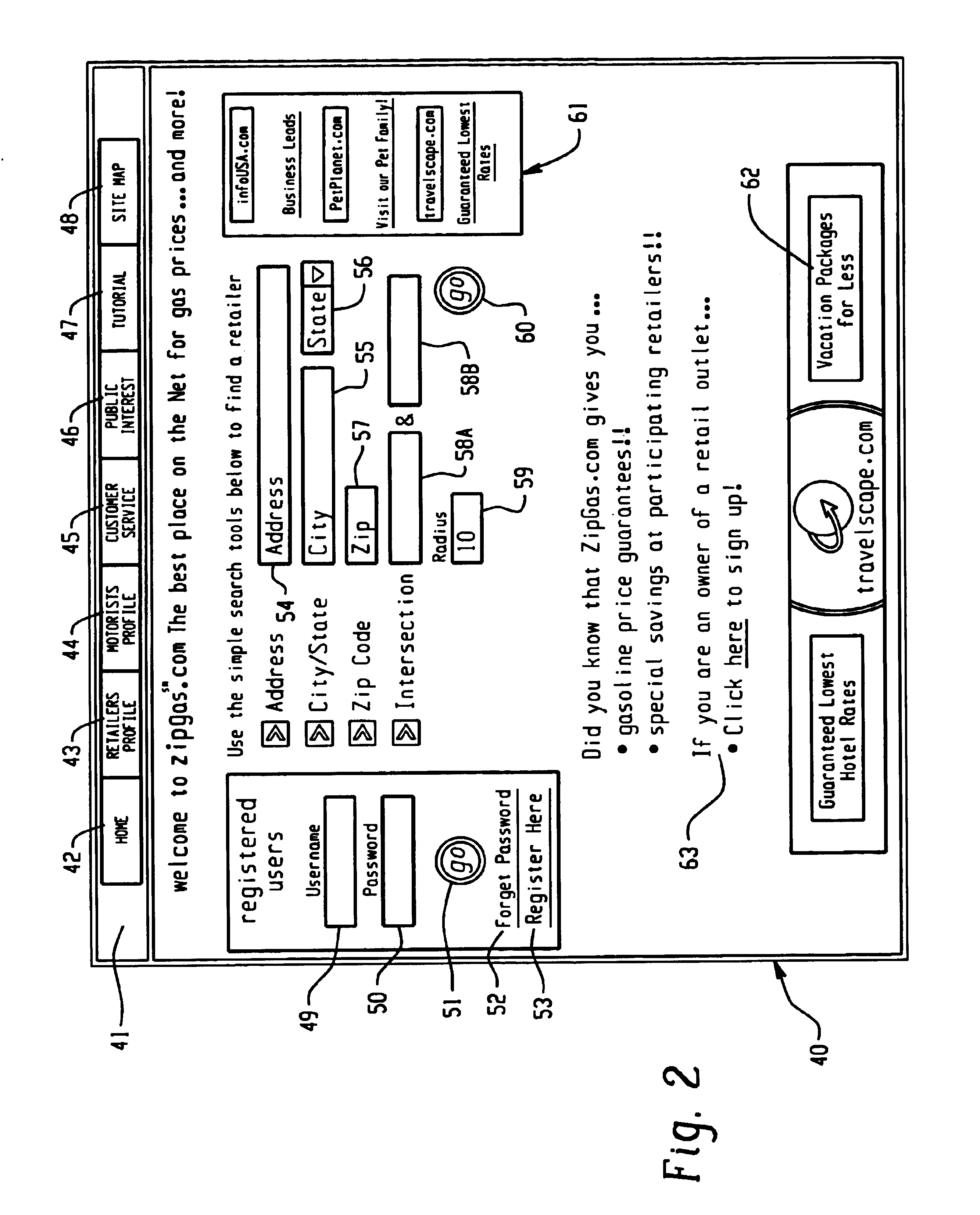
Systems, methods and computer program products for facilitating the sale of commodity-like goods/services
InactiveUS6965872B1Facilitating the sale of goods/servicesPrice fluctuationAdvertisementsBuying/selling/leasing transactionsComputer scienceEnd user
The invention provides systems and methods for facilitating the sale of commodity-like goods / services. The commodity-like goods / services at which the invention is directed, are of a type that are relatively indistinguishable from one brand, identity and / or outlet to another in end-use functionality and features. These types of goods / services are many times sold at retail under various brands or identities at multiple locations, to the final end user. Such goods / services may also or separately be of a type that are repeatedly purchased at intervals, and / or for which the price varies between purchases, from outlet to outlet or brand to brand. The goods / services may also be of a character such that they are not deliverable to the consumer, but require the consumer to travel to the retailer outlet. The system and methods also provide information relating to the consumers and competitors of a retailer of such goods / services. The invention establishes methods and procedures to define, organize, collect, distribute, and maintain information that can be used by the owner of a business selling commodity-like goods / services as well as by its customers. This information may include, but is not limited to, name brand of the product, location of the retailer, price of the product, other related goods / services available and their prices, and promotions. These processes may be performed and implemented on a computer network that is accessible in real time via a suitable communication device, such as a computer, wireless communication device, telephone or the like. A database of such information is created, allowing the consumer and other retailers to query the database using various search criteria. The consumer has the opportunity to obtain information about retailers of commodity-like goods / services that meet the consumer's requirements, and pricing may be guaranteed by the retailer.
Owner:GRDINA JEROME M
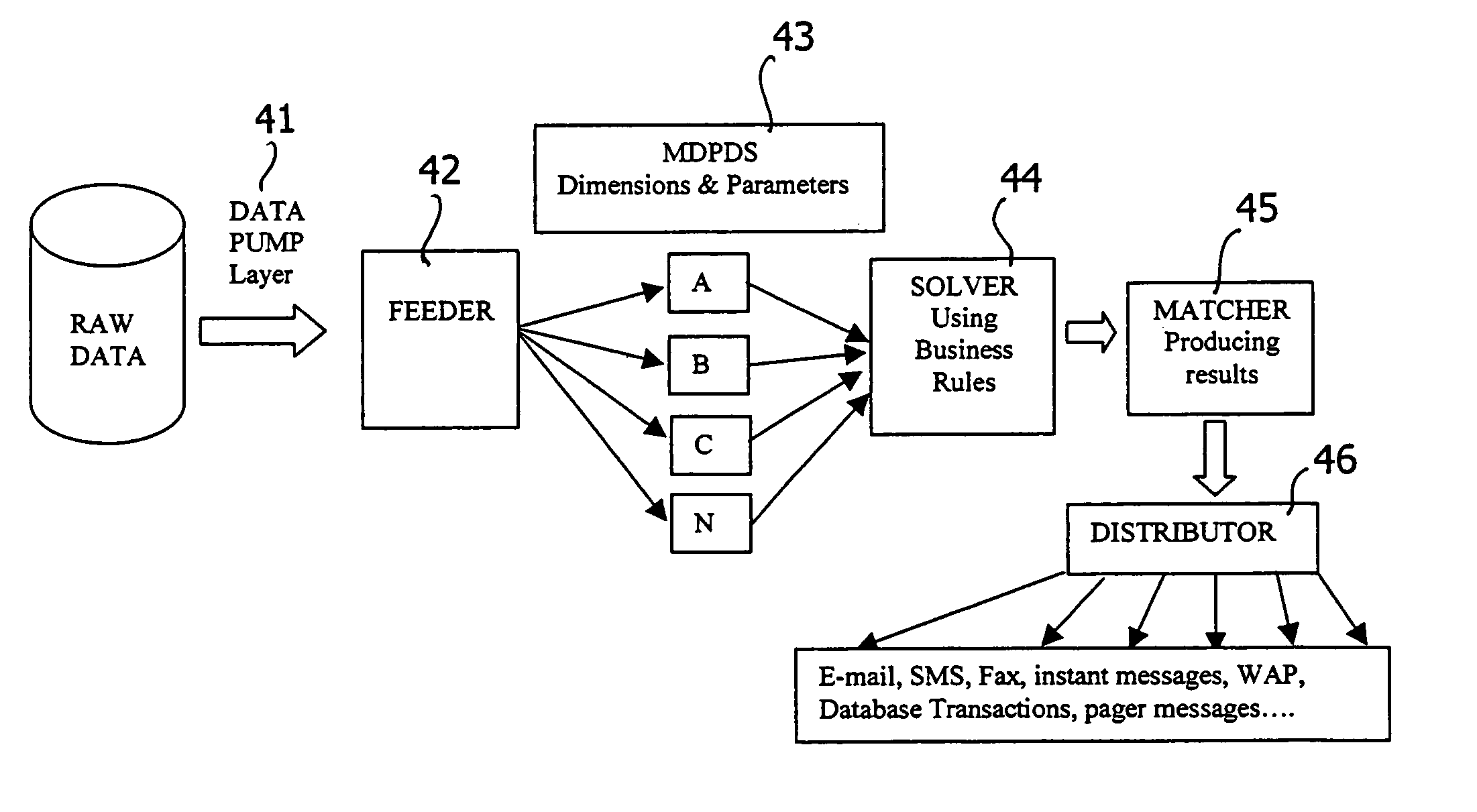
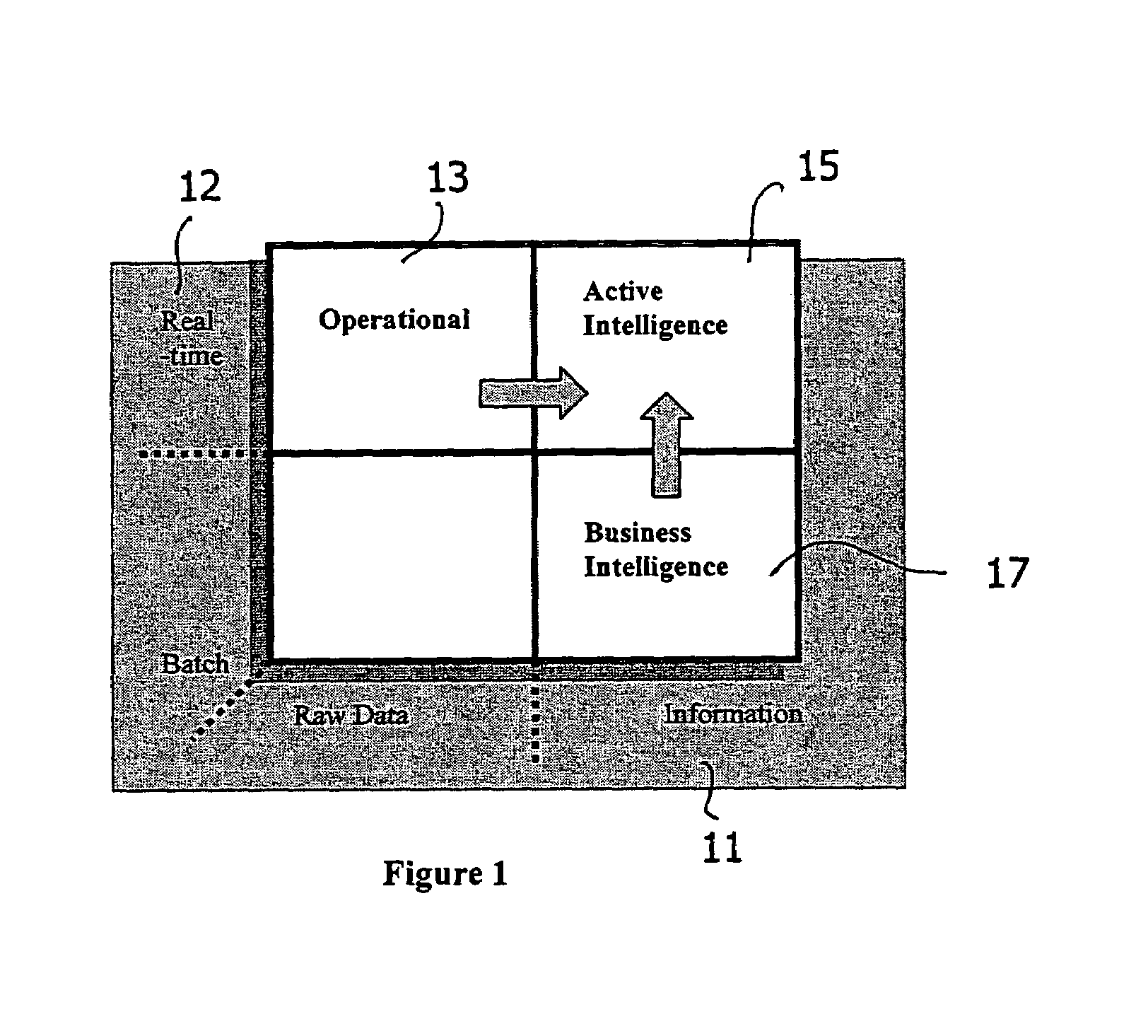
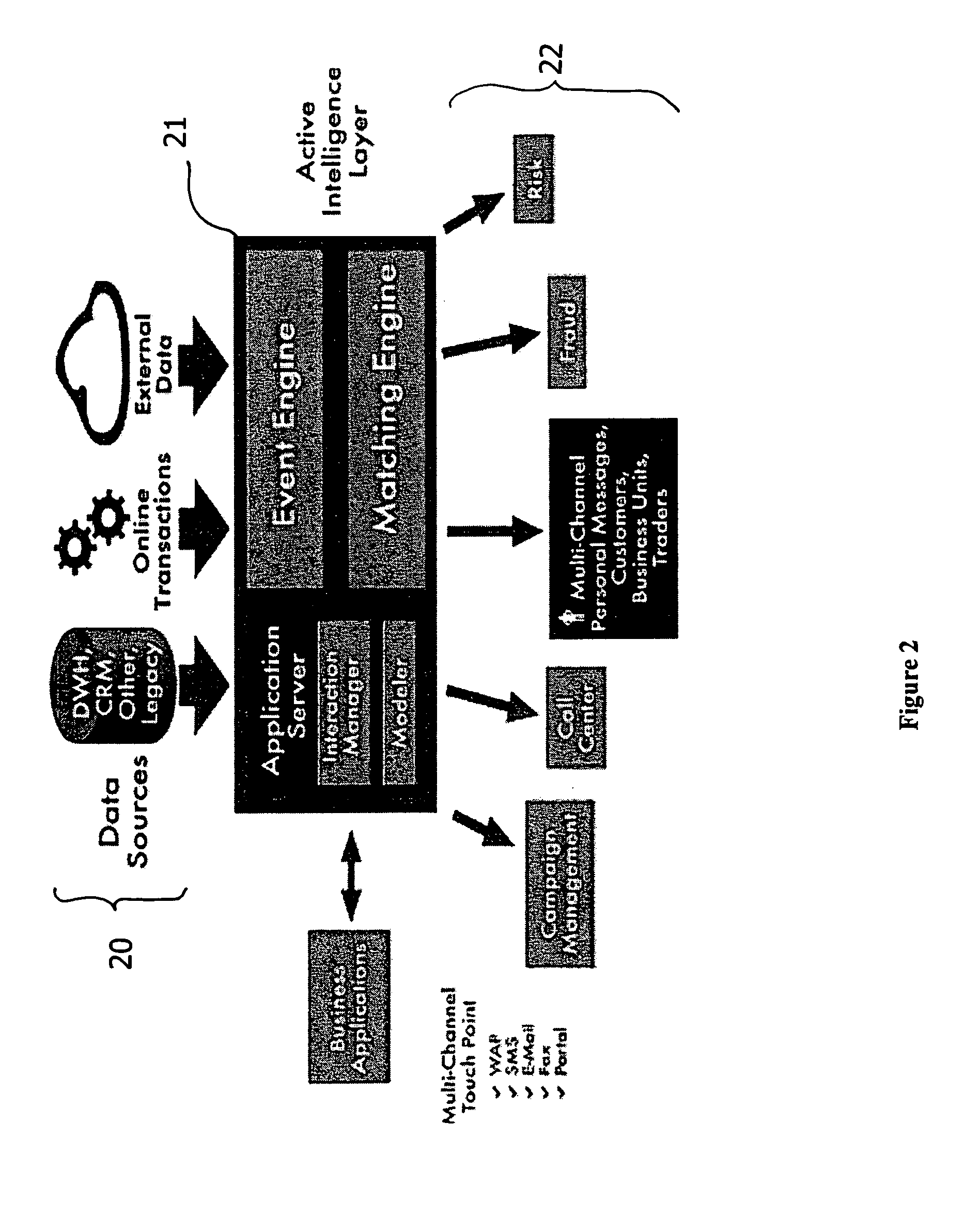
System and method for analyzing and utilizing data, by executing complex analytical models in real time
InactiveUS6965886B2Efficiently distributedIncrease opportunitiesDigital computer detailsOffice automationOperational systemReal-time data
A system and method for collecting, filtering, analyzing, distributing and effectively utilizing highly relevant events (such as key business events) in real time, from huge quantities of data. The present invention analyzes both historic and real-time data stemming from operational activity, by interfacing with internal data repositories (such as Enterprise Resource Planning (ERP) and Customer Relationship Management (CRM)), external data sources (such as suppliers and clients), and real time operational systems in order to create an Active Intelligence Platform. This Active Intelligence Platform is positioned as a layer between the organization's data sources and its applications, monitoring inputs and relaying only the important data items to the relevant individuals and / or systems. This allows individuals and systems to respond immediately and effectively to key events.
Owner:ACTIMIZE
Web based integrated customer interface for invoice reporting
InactiveUS6745229B1Metering/charging/biilling arrangementsMultiple digital computer combinationsGraphical user interfaceCustomer interface
A Web-based invoice viewing system and method for enabling a customer to generate invoices relating to various network services provided to the customer by an enterprise. A Web enabled invoice viewing system provides billing and invoice information to remote customers having a workstation with a Web browser and an Internet access. A graphical user interface system at the customer workstation presents a list of invoice documents organized into products and date ranges applicable to the customer for the customer to select and view. Various displays presented at the customer workstation may be printed, faxed, or queued for batch printing at the enterprise remotely. The customer is enabled to view dynamically summed results of numerical figures displayed on the invoice documents by highlighting the numbers in the document directly on the display.
Owner:VERIZON PATENT & LICENSING INC
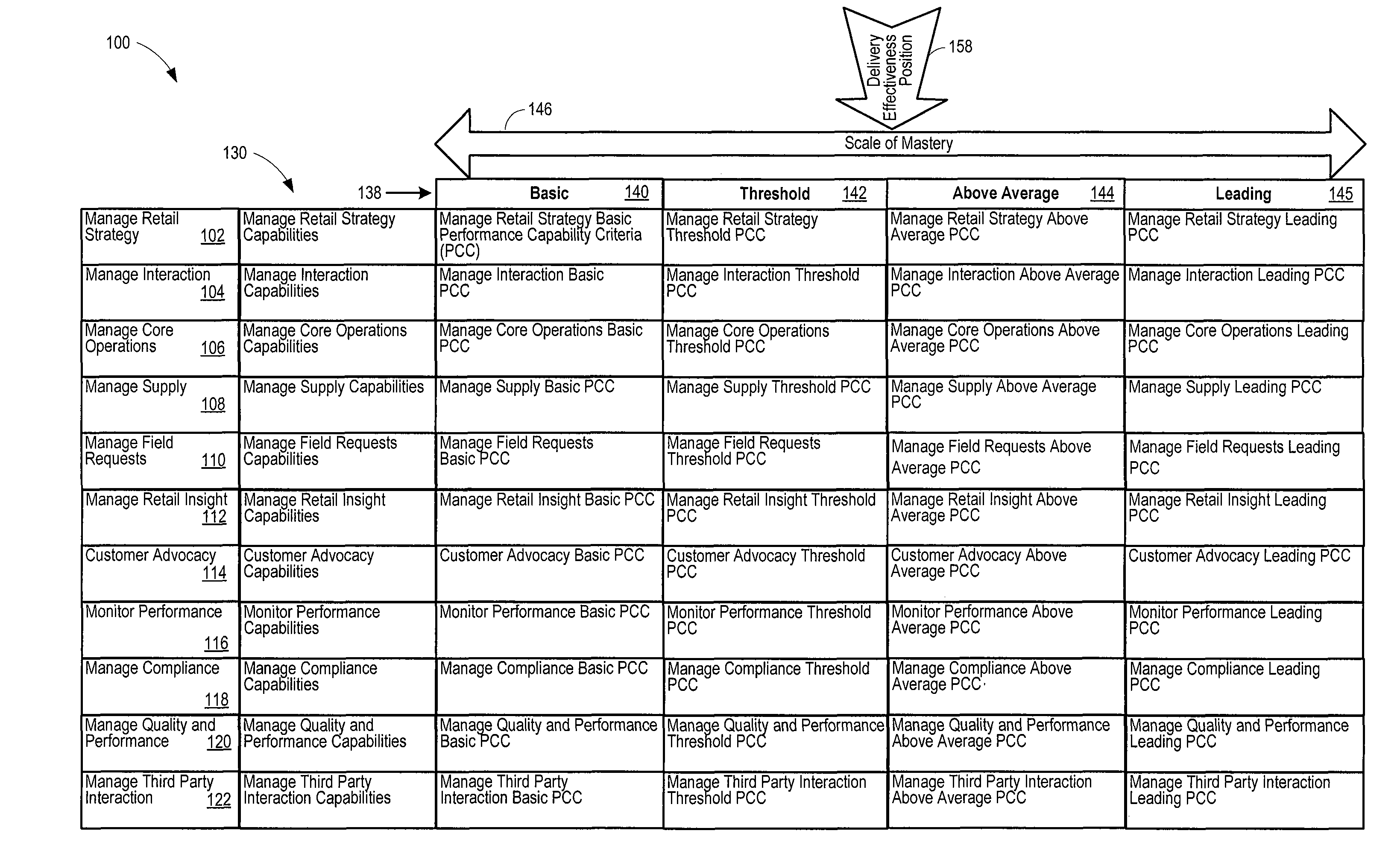
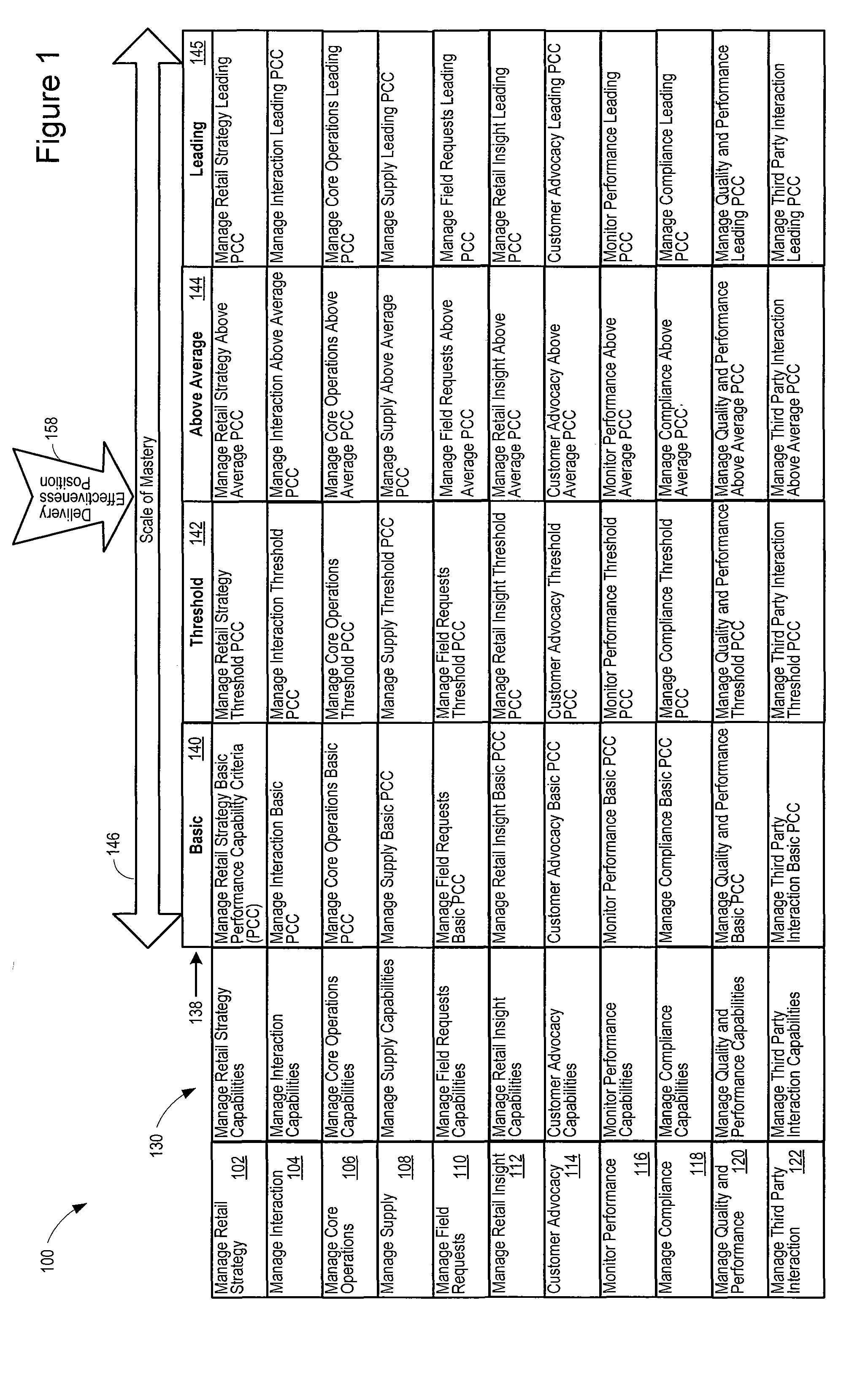
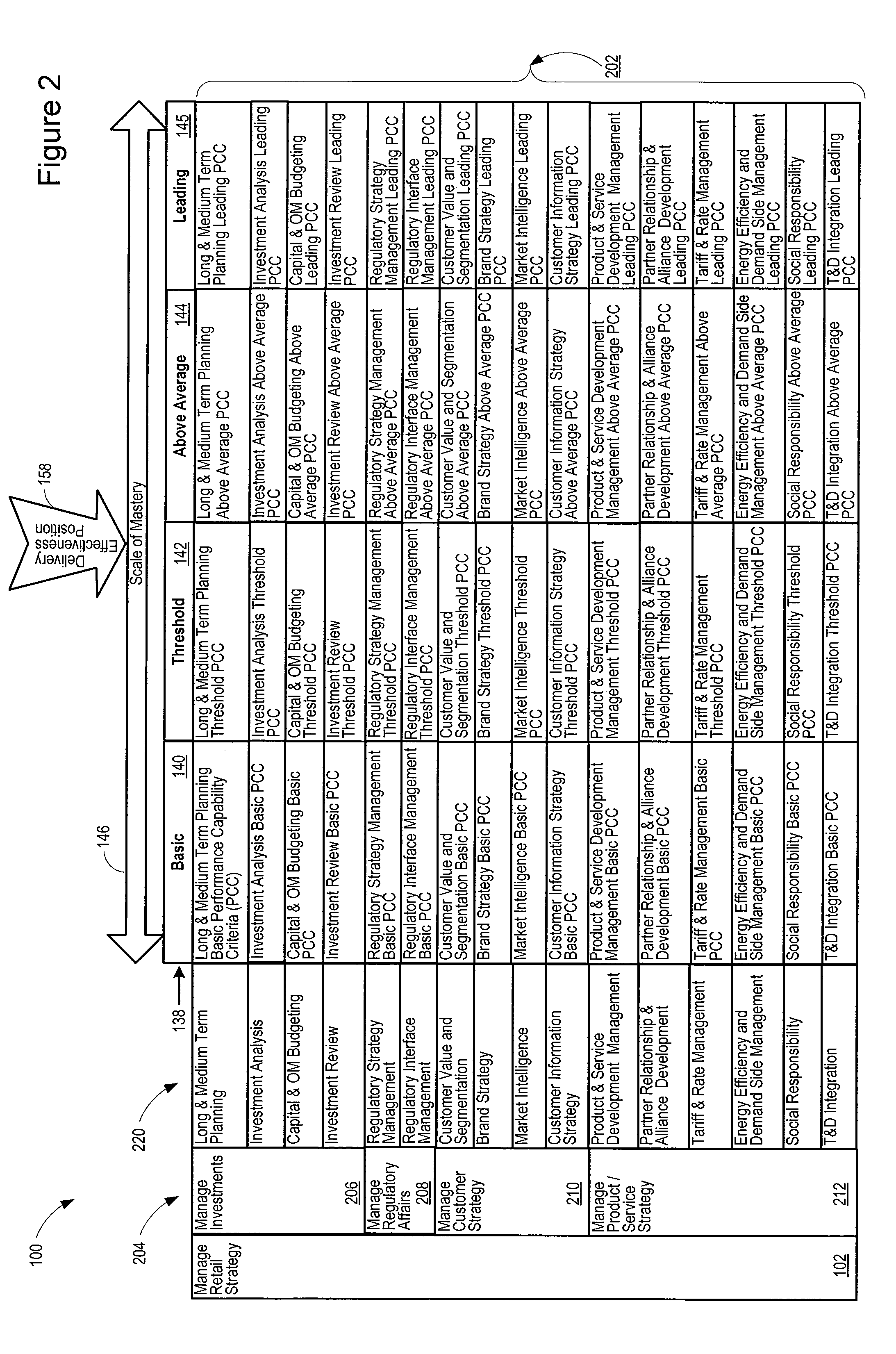
Utility high performance capability assessment
ActiveUS8311863B1High performance capabilityEasy to findCommerceCapacity assessmentProcess complexity
A high performance capability assessment model helps a utility industry business meet the challenges of the global marketplace. As a result, the utility industry business can achieve the clarity, consistency, and well-defined execution of core processes that reduce inefficiencies and waste that result from unnecessary process complexity and exceptions. In addition, the high performance capability assessment model helps the utility industry business to identify specific areas in which improvements may be made and understand how to make the improvements, and establishes levels of capability along the way to reaching an ultimate capability goal.
Owner:ACCENTURE GLOBAL SERVICES GMBH
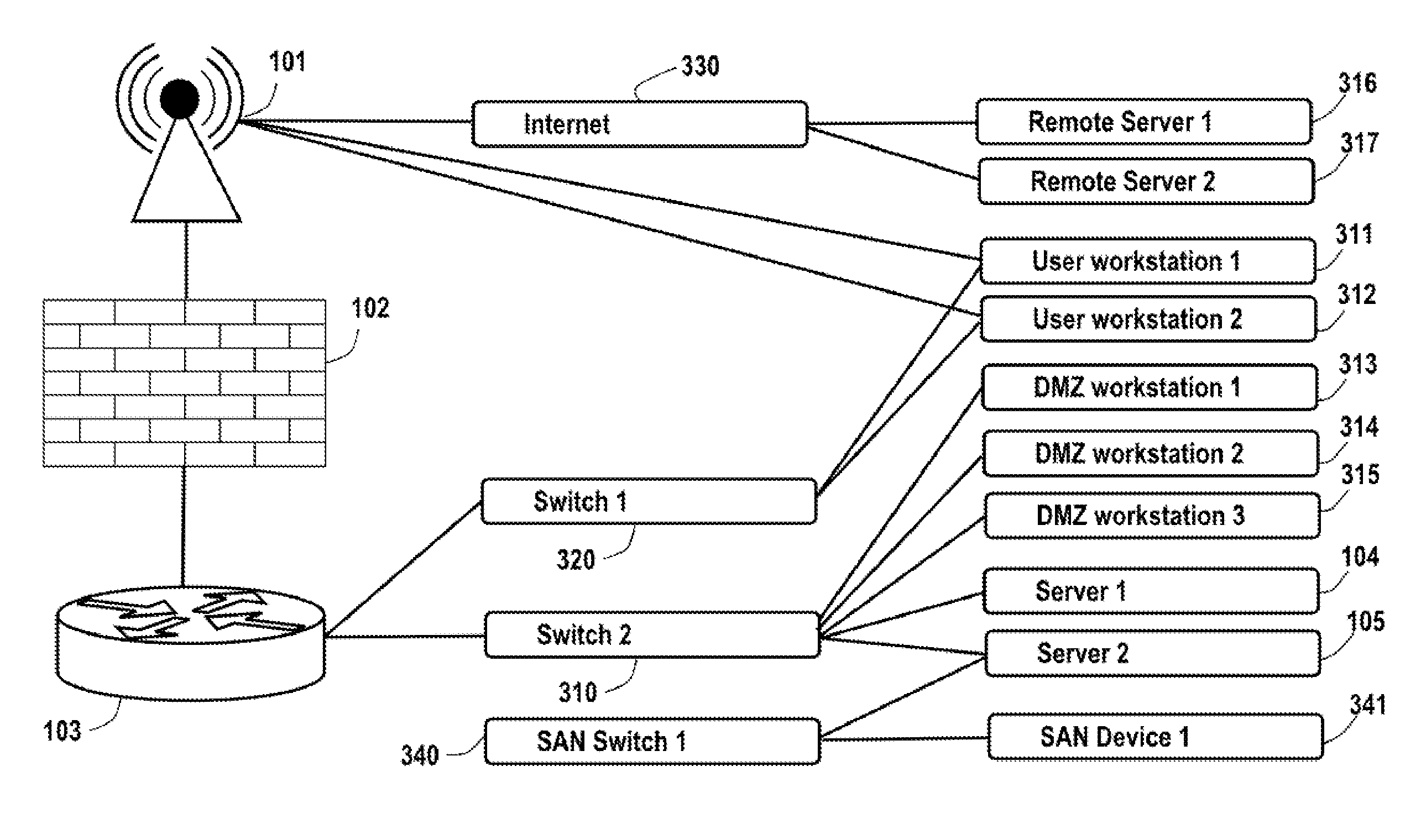
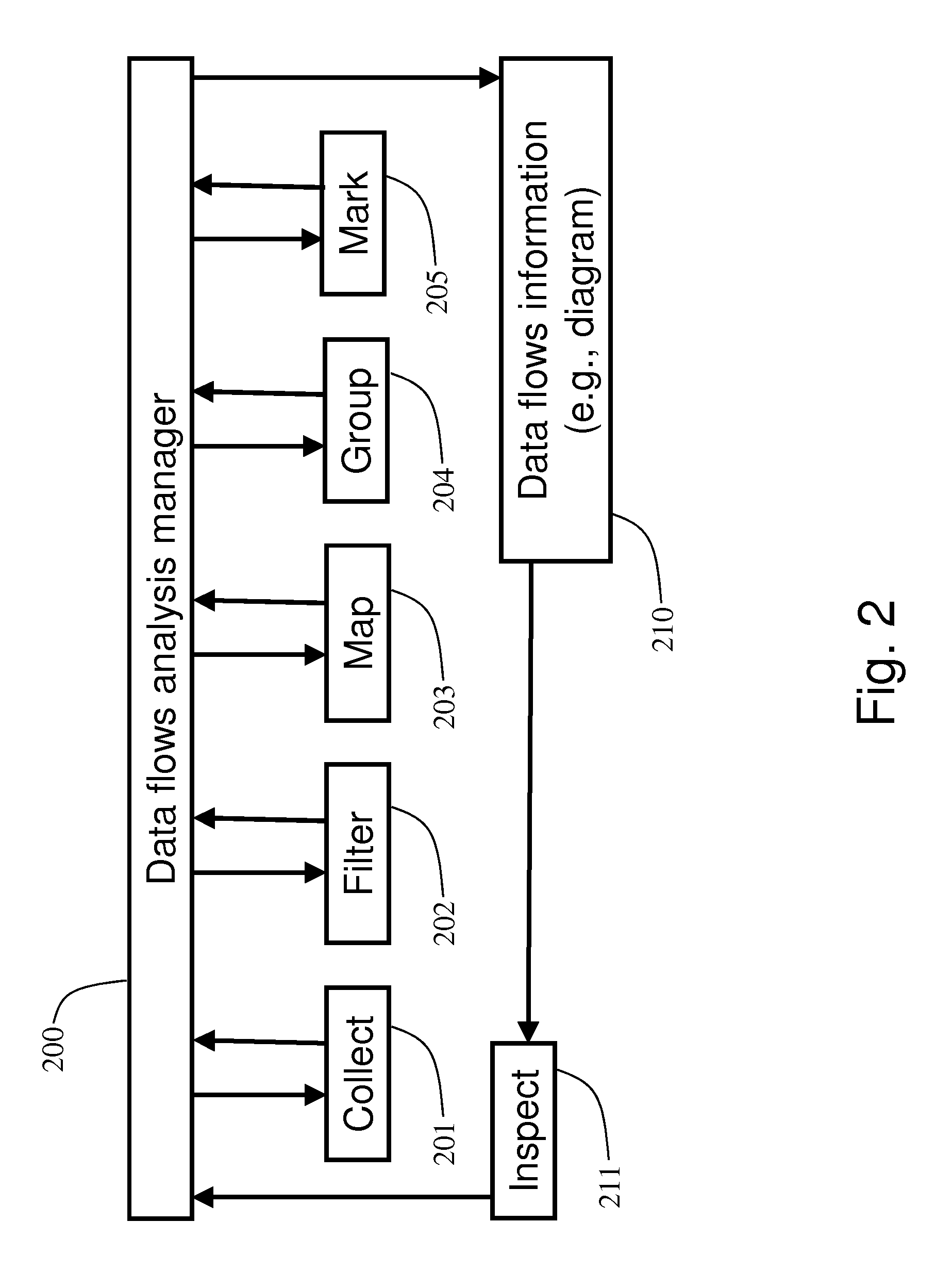
Analysis of data flows in complex enterprise it environments
The present technology enables identification, visualization, and analysis of data flows via network components in complex enterprise IT environments including but not limited to servers, workstations, switches, routers, wireless access points, traffic shapers, firewalls, storage systems and SAN systems. The technology is based on a combination of information collection, information filtering, mapping, grouping, marking, report generation, and verification.
Owner:MODELIZEIT INC
Workflow system and method
A network-enabled workflow system is used in conjunction with a rules-based search engine to provide an easy-to-use interface to build workflow processes that facilitate the support for electronic business applications as well as business-to-business relationships. The system allows workflow services to be rendered to external organizations such as partners, suppliers, distributors and customers. Workflow services are preferably represented by roles that can be used to represent workflow actors in the workflow routing rules. These roles are preferably evaluated at run-time to best match recipients (via the MORSE algorithm) depending on the organization context from which the routing request is made. Furthermore, the network-enabled workflow system provides for the analysis of workflow processes in real time.
Owner:GINEGAR LLC
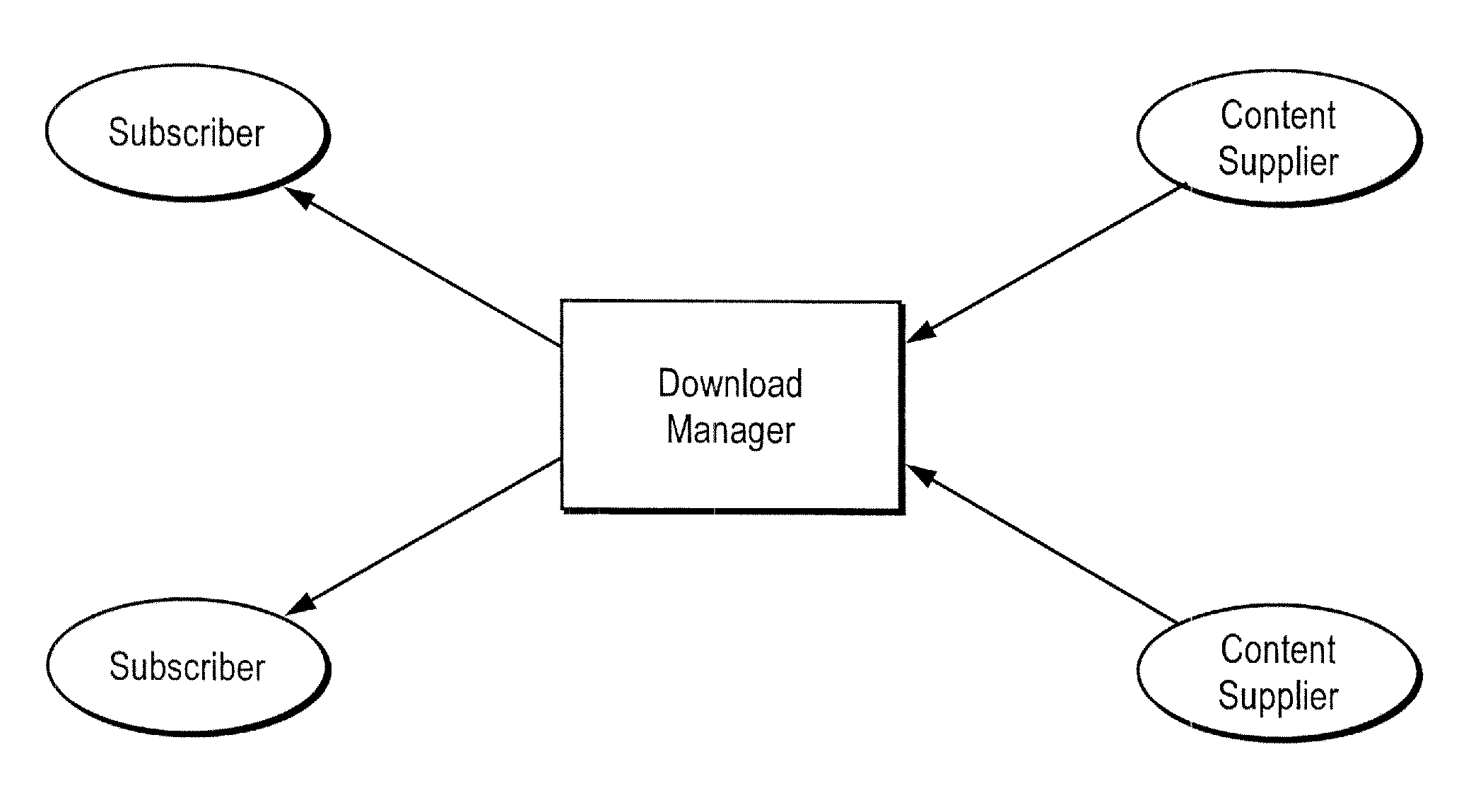
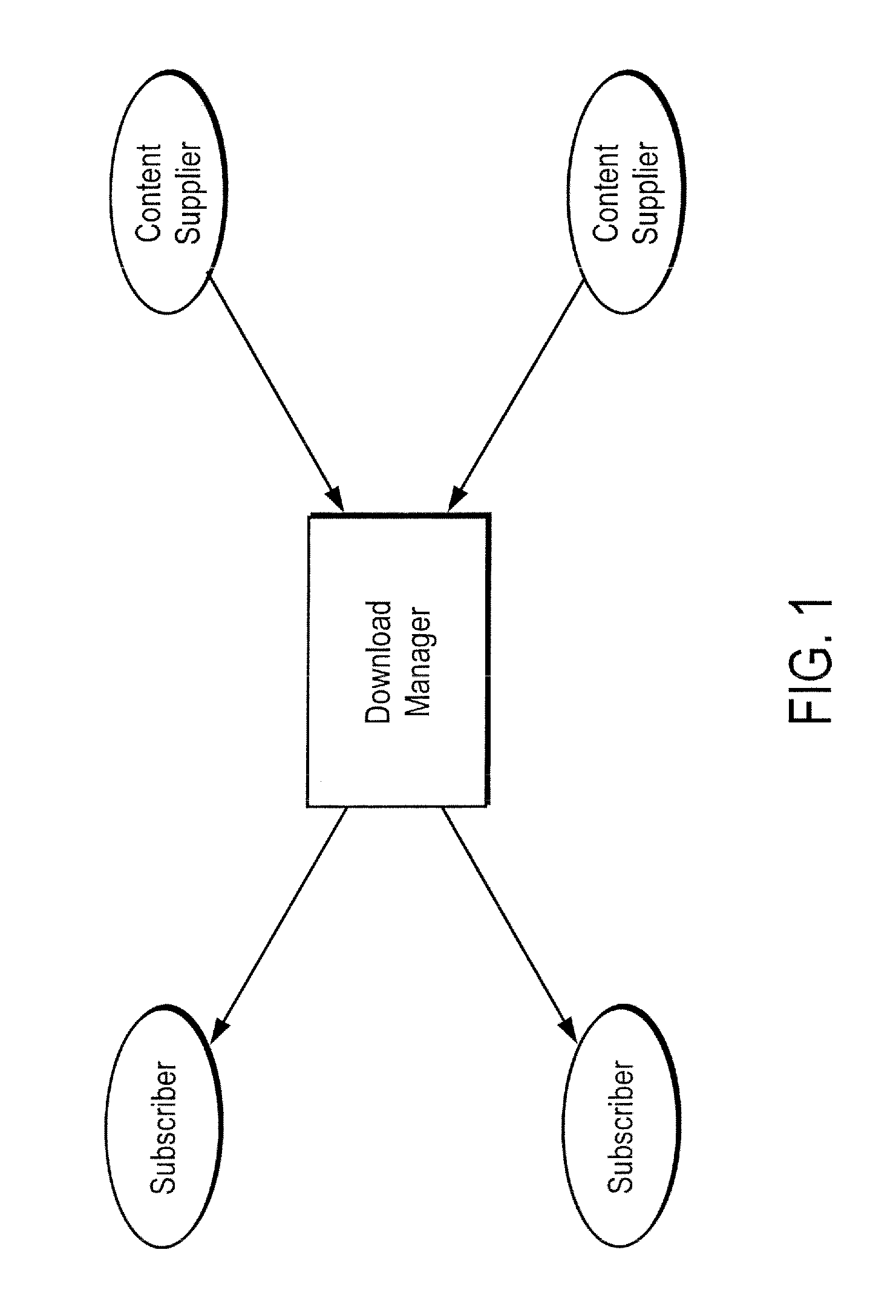
Domain-based management of distribution of digital content from multiple suppliers to multiple wireless services subscribers
ActiveUS7299033B2Digital data information retrievalSpecial service for subscribersDigital contentBusiness enterprise
A network server system includes a download manager that manages the publication, purchase and delivery of digital content from multiple content suppliers to wireless services subscribers in multiple domains. Each domain is defined as a different grouping of subscribers, such as a wireless carrier or subsidiary thereof, a business enterprise, or other defined group of subscribers. The download manager maintains data defining the multiple domains and associations between the domains and wireless services subscribers. Digital content suppliers can publish and manage their products on the server system via a computer network and make their products available to the subscribers for purchase or licensing. The subscribers in each of the domains can access the server remotely to purchase rights to download and use the digital content on associated wireless communication devices.
Owner:UNWIRED PLANET
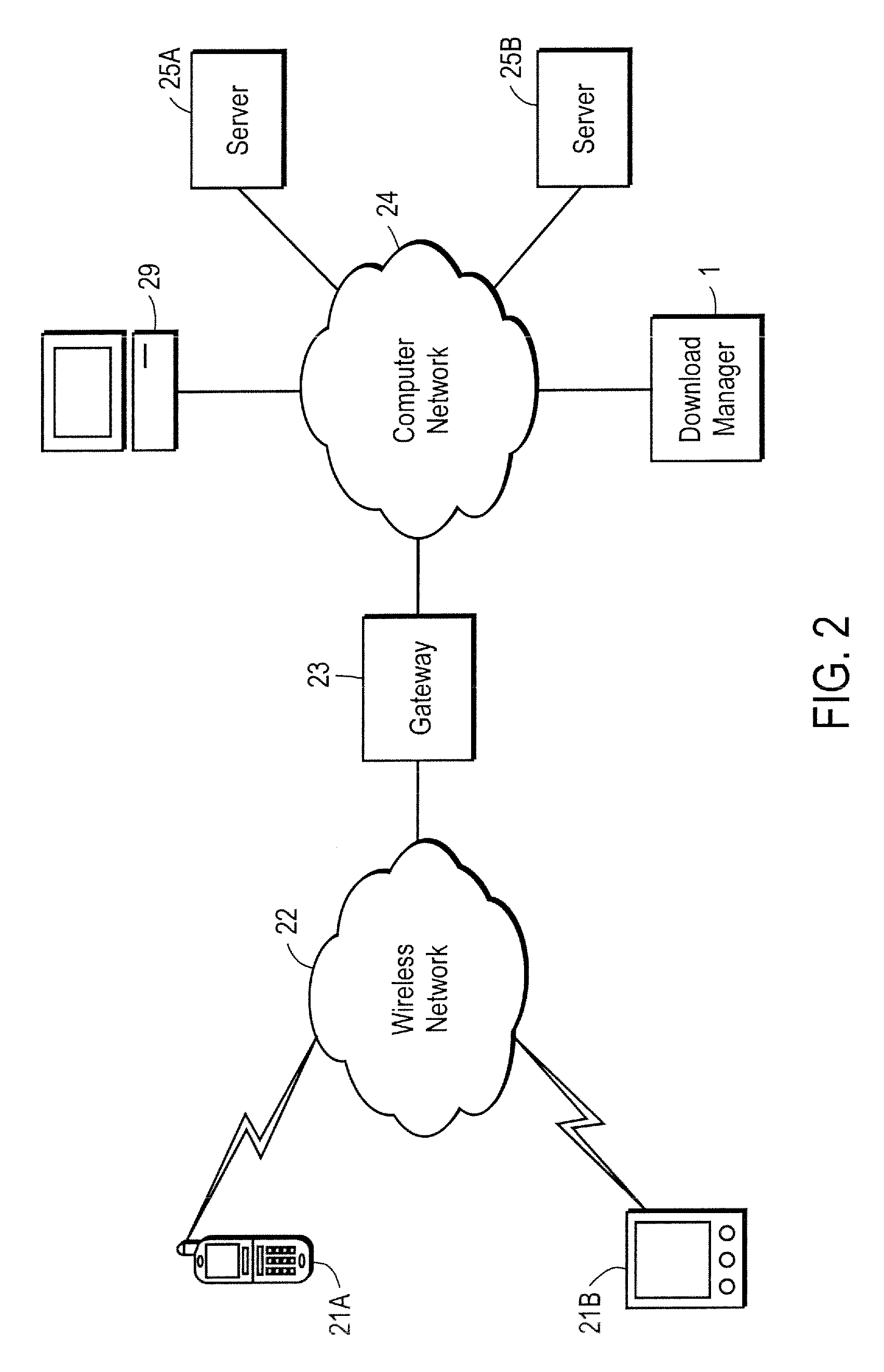
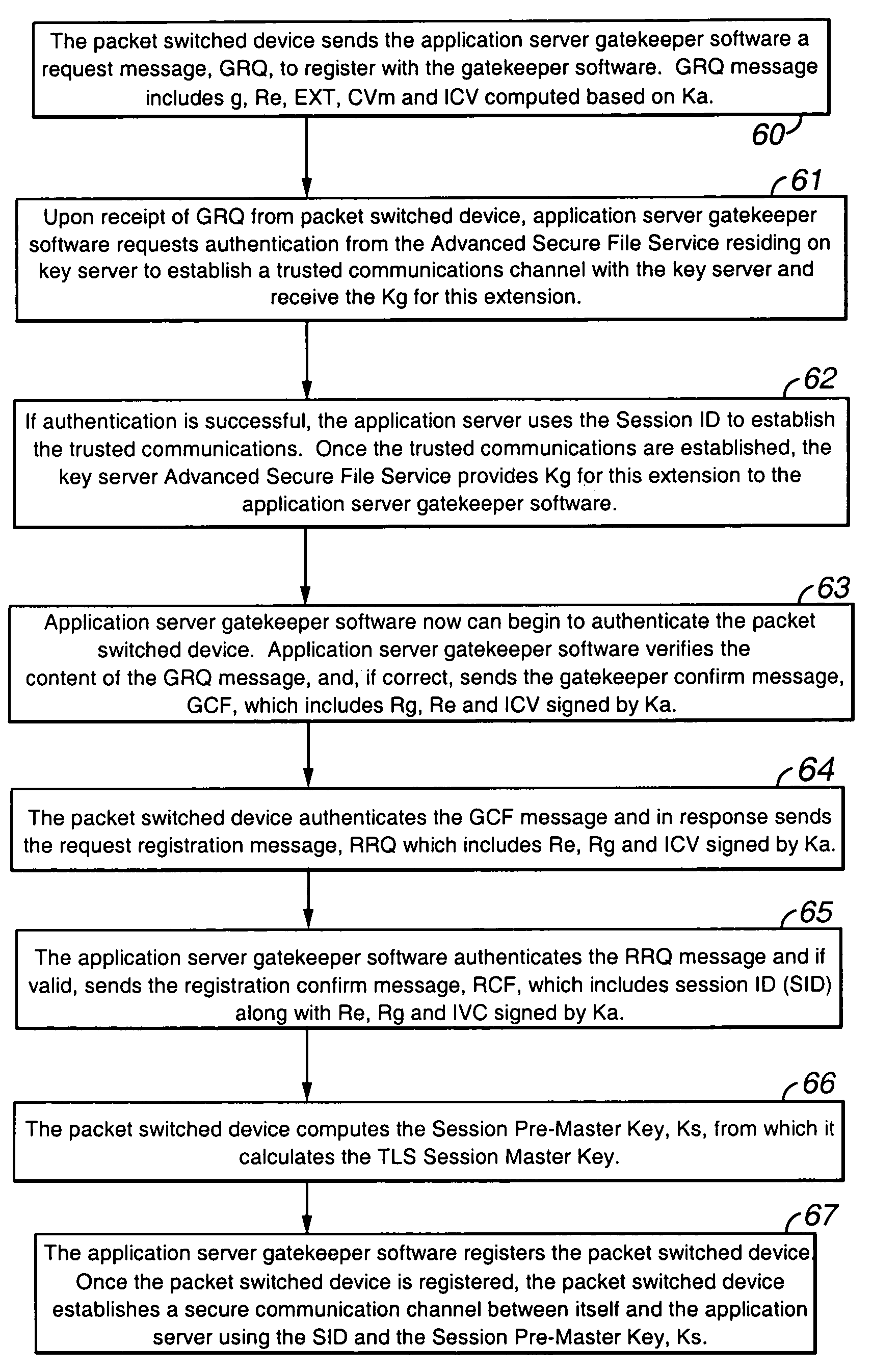
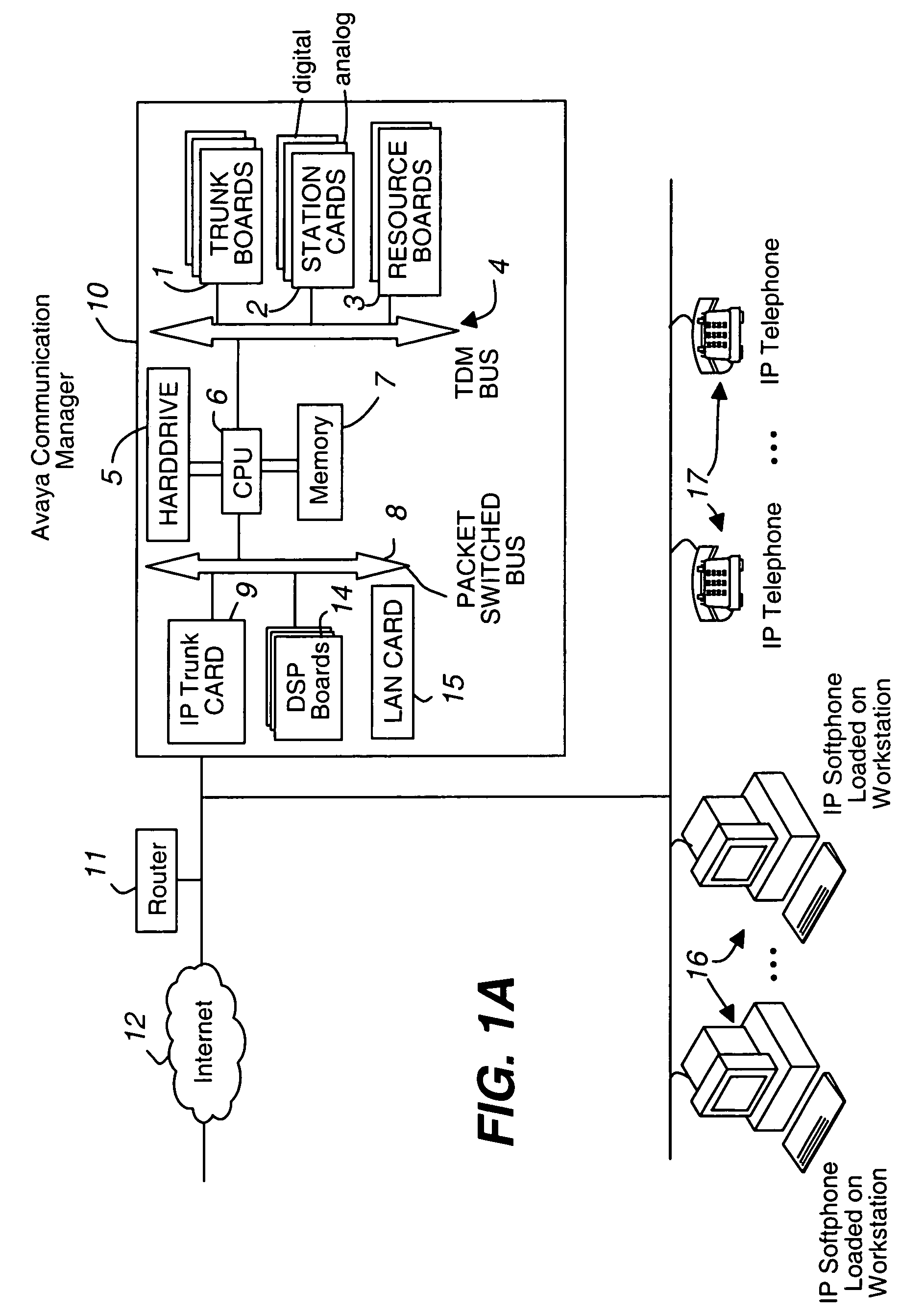
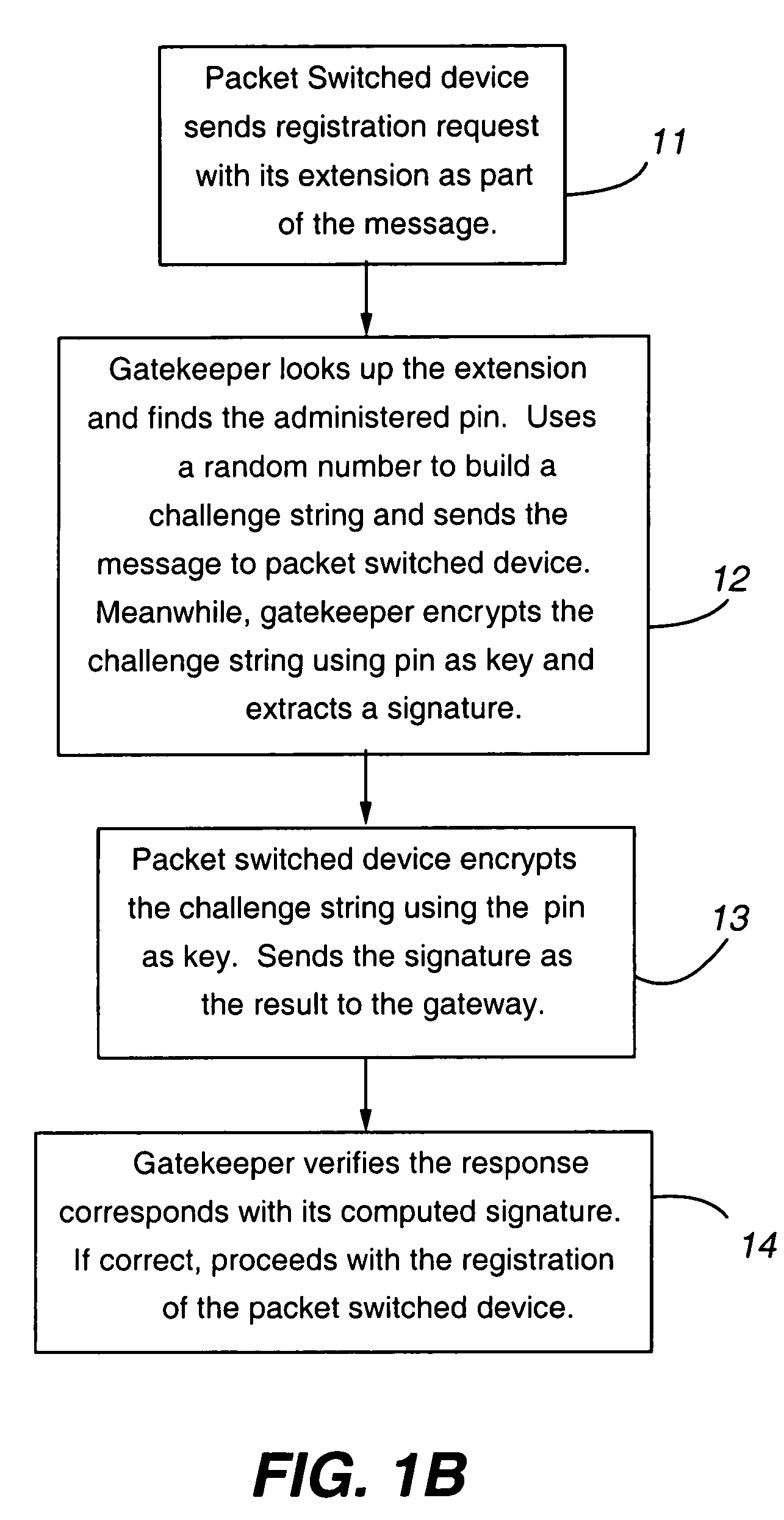
Key server for securing IP telephony registration, control, and maintenance
A packet-switched communications device in an enterprise network is provided. The packet-switched communications device has a corresponding unique identifier, such as an address or extension. The device includes a processor operable to (a) establish a secure communications session with a key generating agent in the enterprise network; (b) provide, to the key generating agent through the session, the unique identifier of the communications device; and (c) receive, from the key generating agent through the session, a secret key and a key identifier. An application server authenticates the packet switched device using the secret key. After authentication is successful, secure communications is established between the packet switched device and the application server.
Owner:AVAYA INC
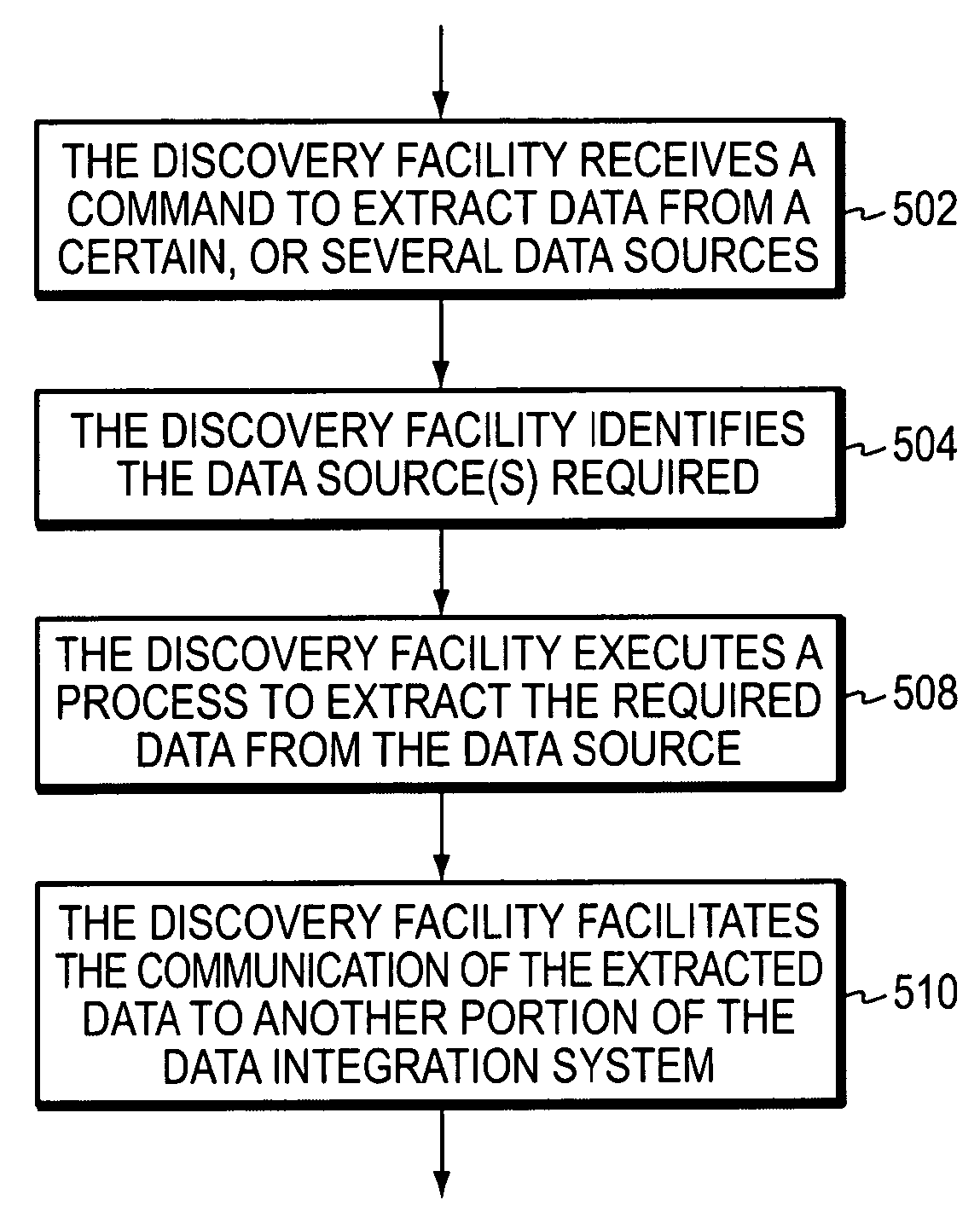
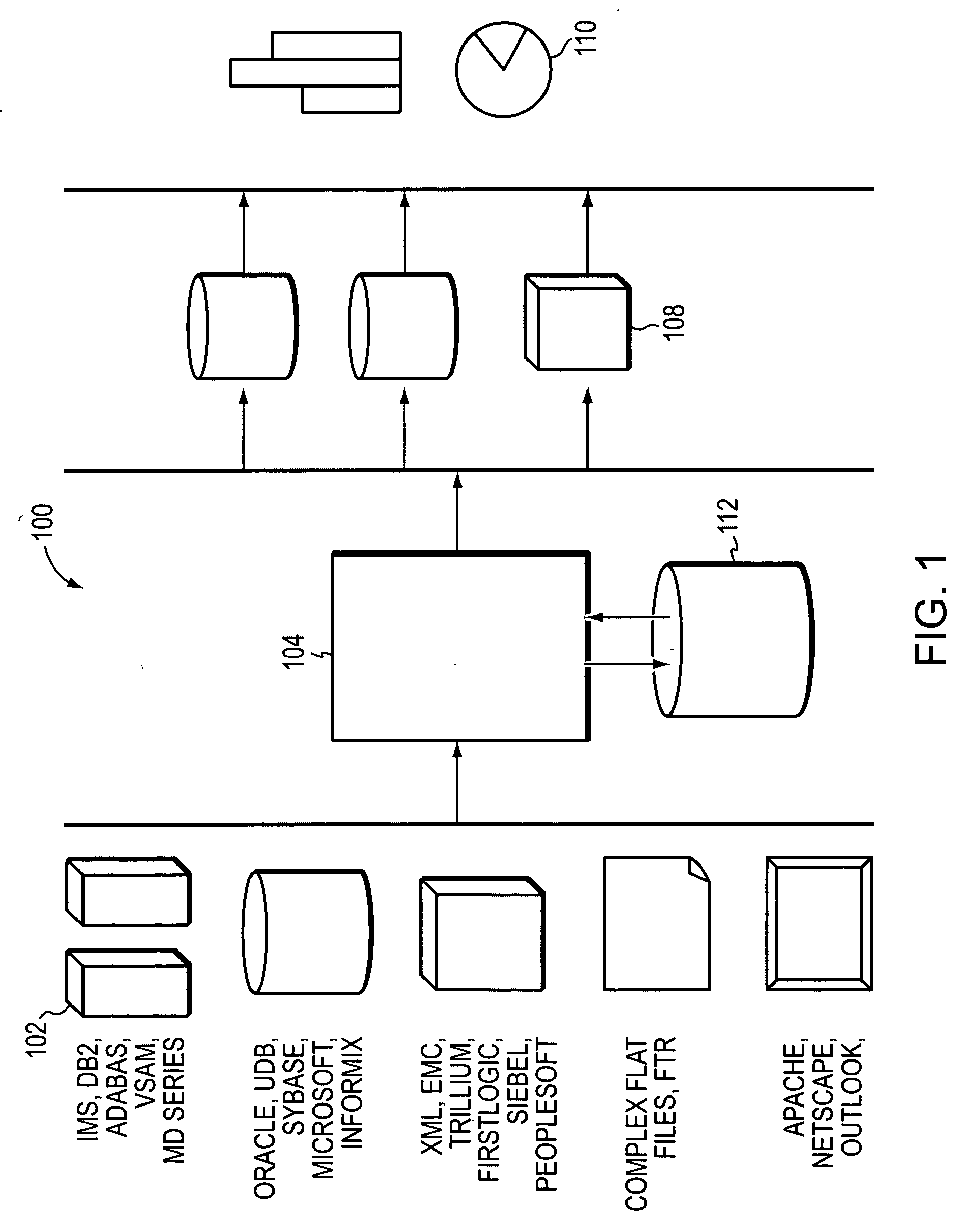
Methods and systems for real time integration services
ActiveUS20050086360A1Digital data information retrievalMultiple digital computer combinationsGraphicsGraphical user interface
Methods and systems for enterprise data integration are described. The methods and systems take elements of a data integration process typically operating in a batch-mode, transform the elements in real time, and expose the results as a service that can be accessed by a business enterprise in real time, and optionally also in batch mode. The service can be accessed through a graphical user interface, providing automatic data integration in real time without additional coding. The service can also operate with mobile devices.
Owner:IBM CORP
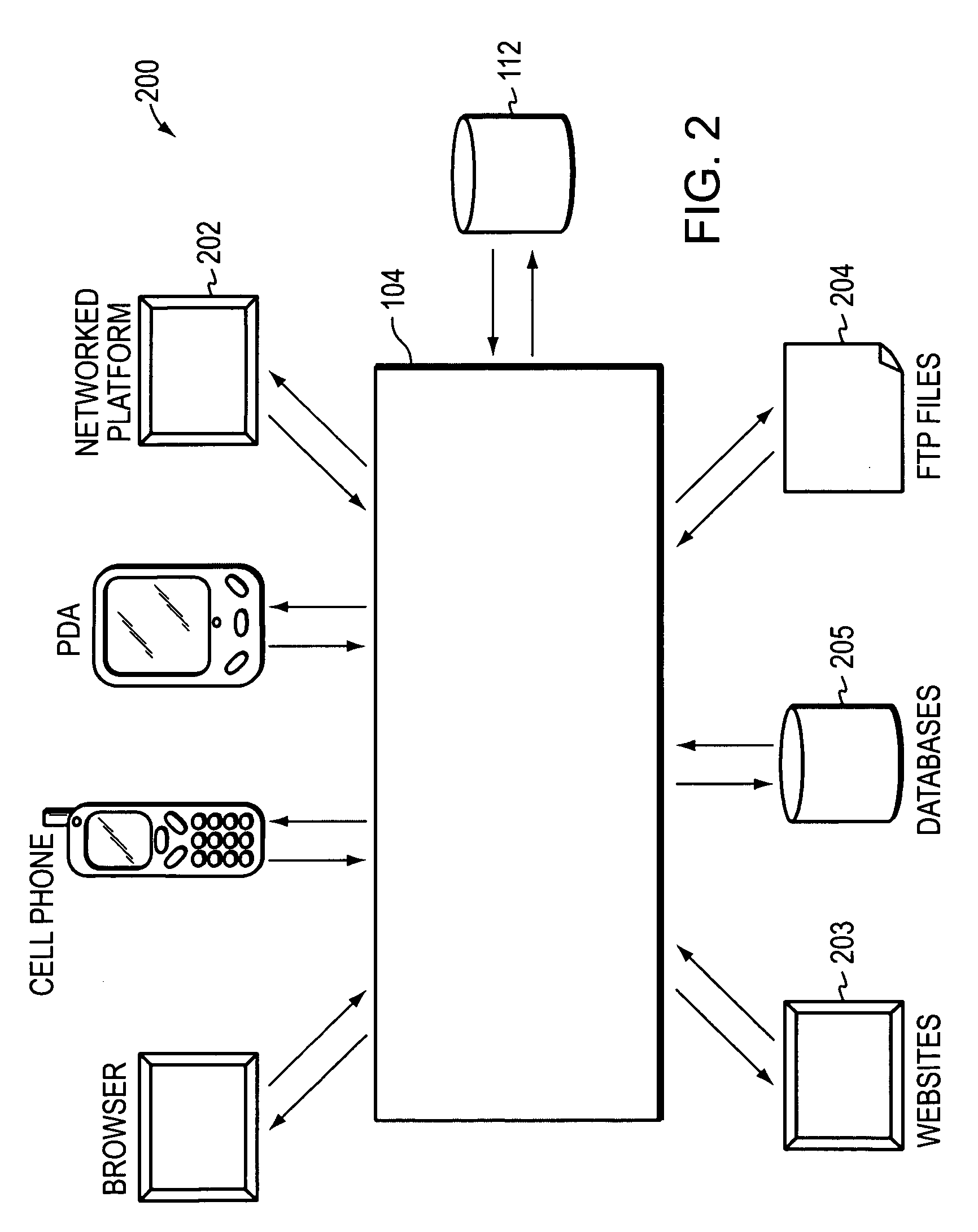
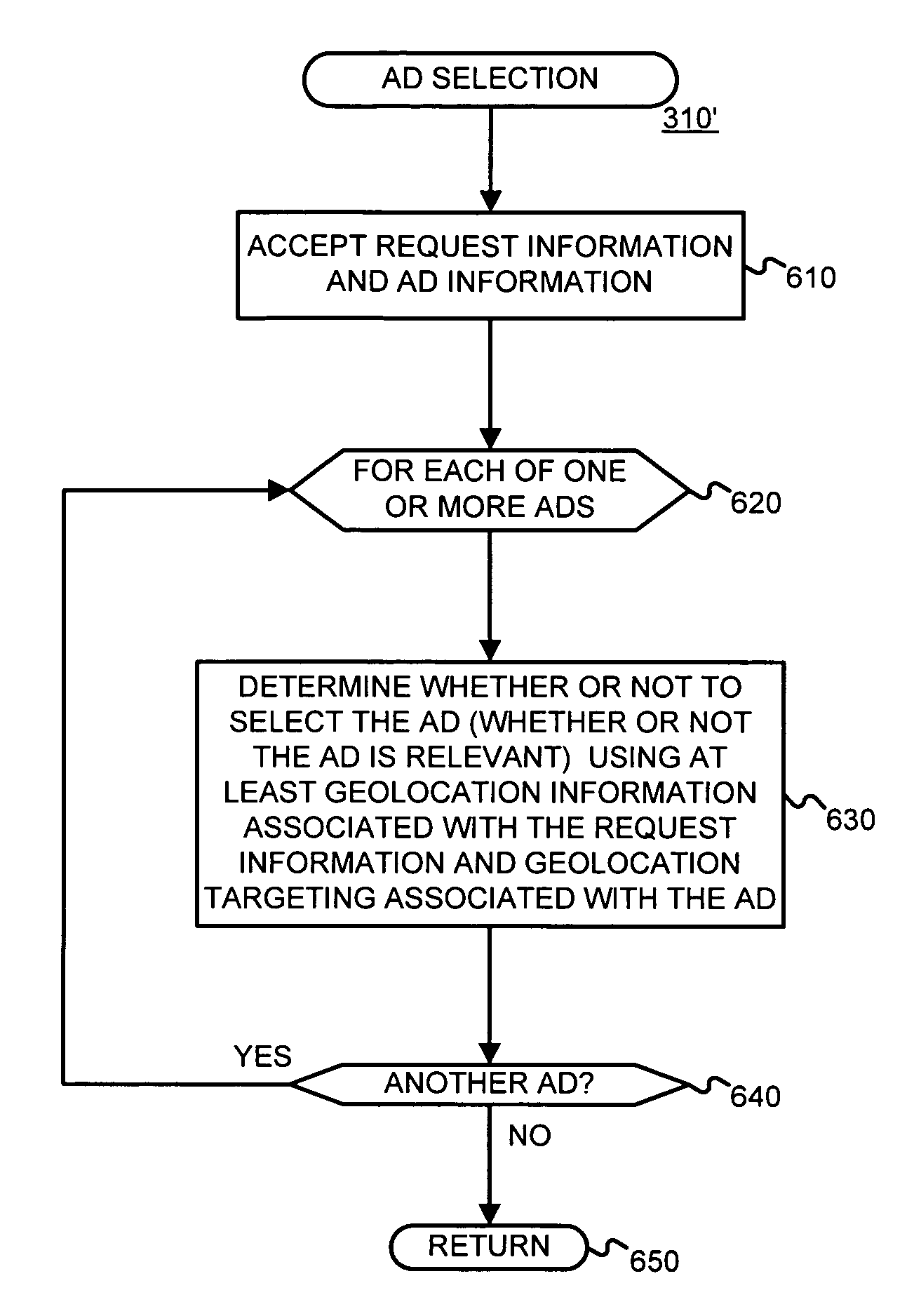
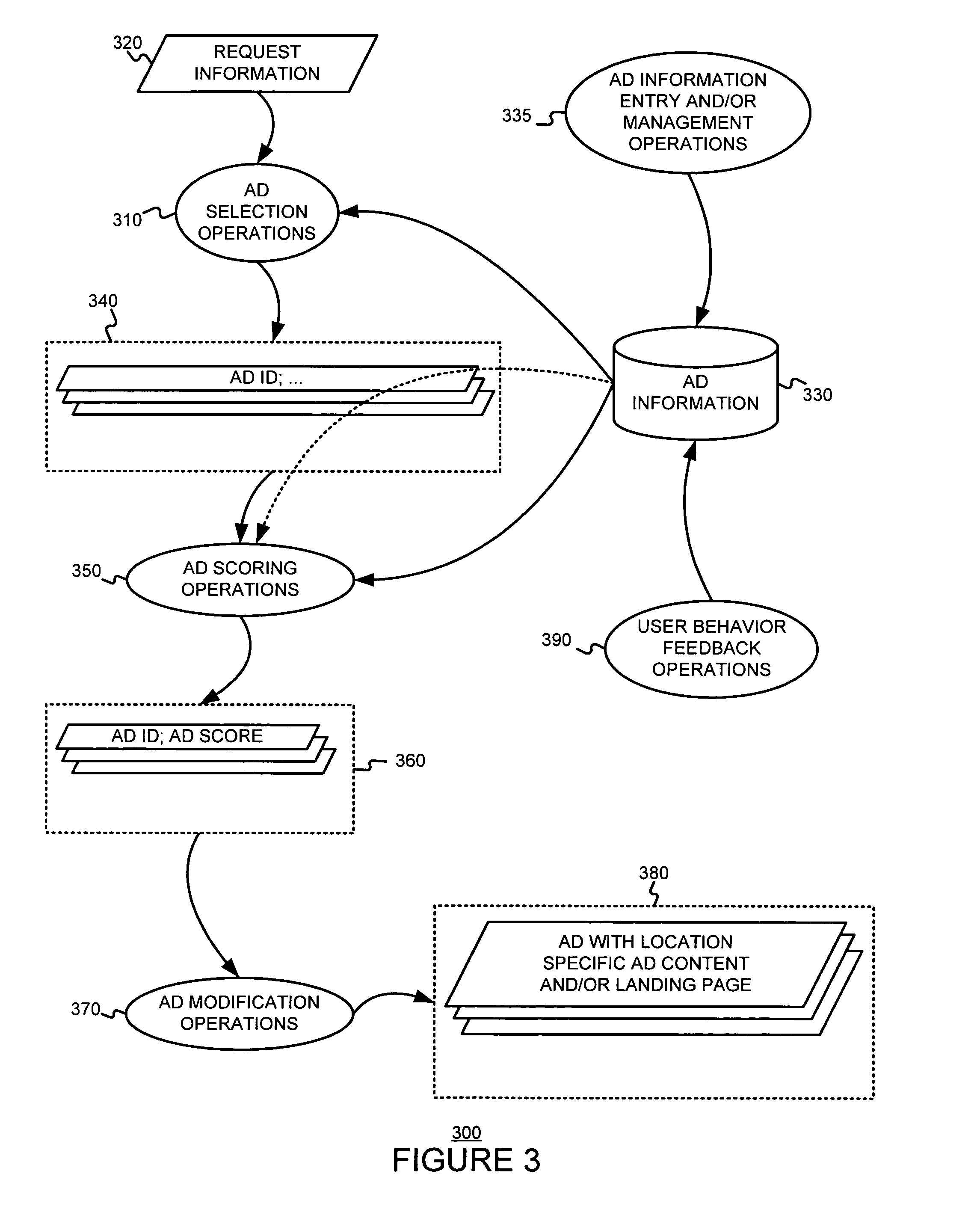
Determining and/or using location information in an ad system
ActiveUS7668832B2Improve performanceImprove the usefulnessDigital data information retrievalDigital data processing detailsEllipseLongitude
The usefulness, and consequently the performance, of advertisements are improved by allowing businesses to better target their ads to a responsive audience. Location information is determined (or simply accepted) and used. For example, location information may be used in a relevancy determination of an ad. As another example, location information may be used in an attribute (e.g., position) arbitration. Such location information may be associated with price information, such as a maximum price bid. Such location information may be associated with ad performance information. Ad performance information may be tracked on the basis of location information. The content of an ad creative, and / or of a landing page may be selected and / or modified using location information. Finally, tools, such as user interfaces, may be provided to allow a business to enter and / or modify location information, such as location information used for targeting and location-dependent price information. The location information used to target and / or score ads may be, include, or define an area. The area may be defined by at least one geographic reference point (e.g., defined by latitude and longitude coordinates) and perhaps additional information. Thus, the area may be a circle defined by a geographic reference point and a radius, an ellipse defined by two geographic reference points and a distance sum, or a polygon defined by three or more geographic reference points, for example.
Owner:GOOGLE LLC
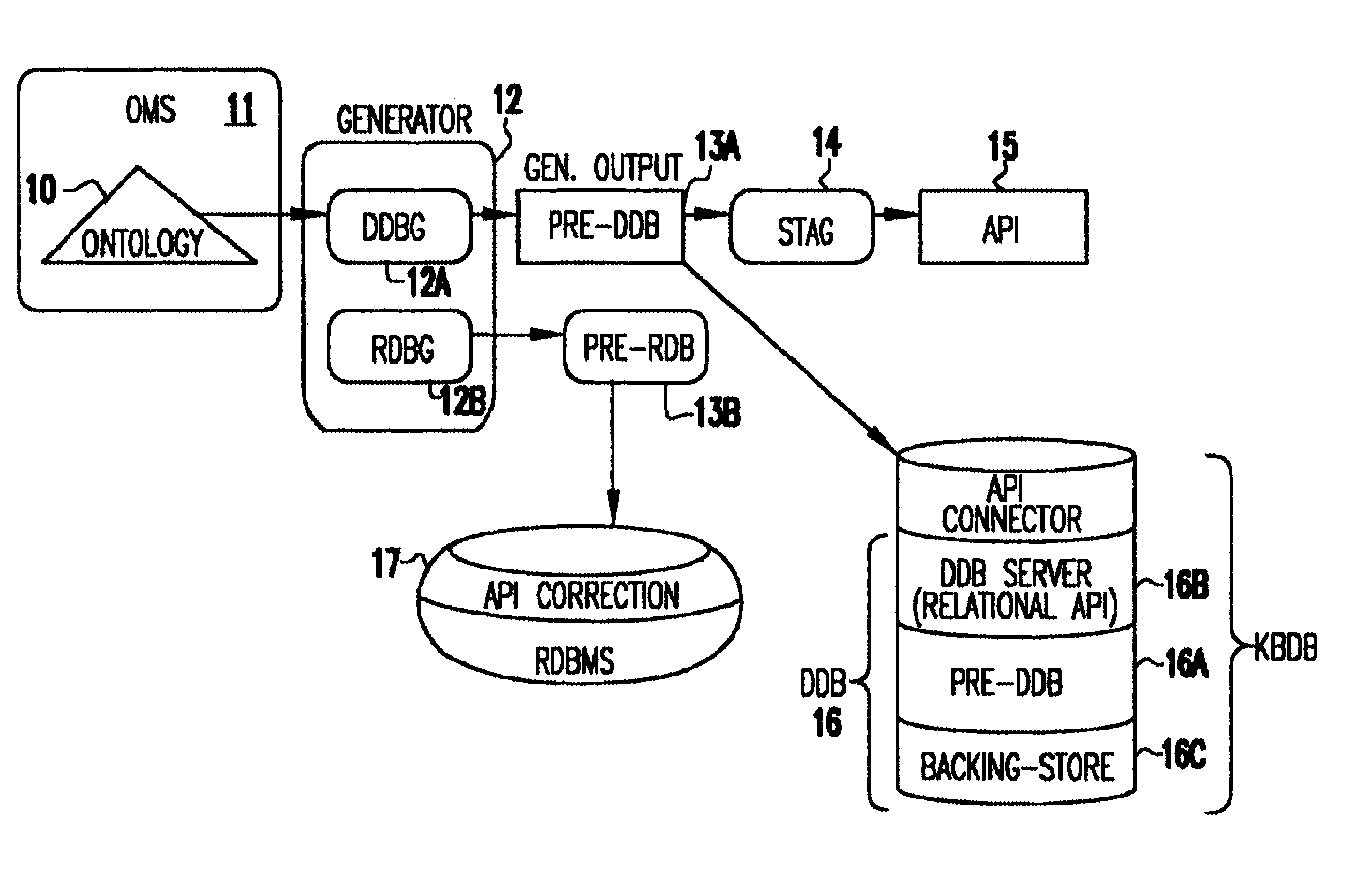
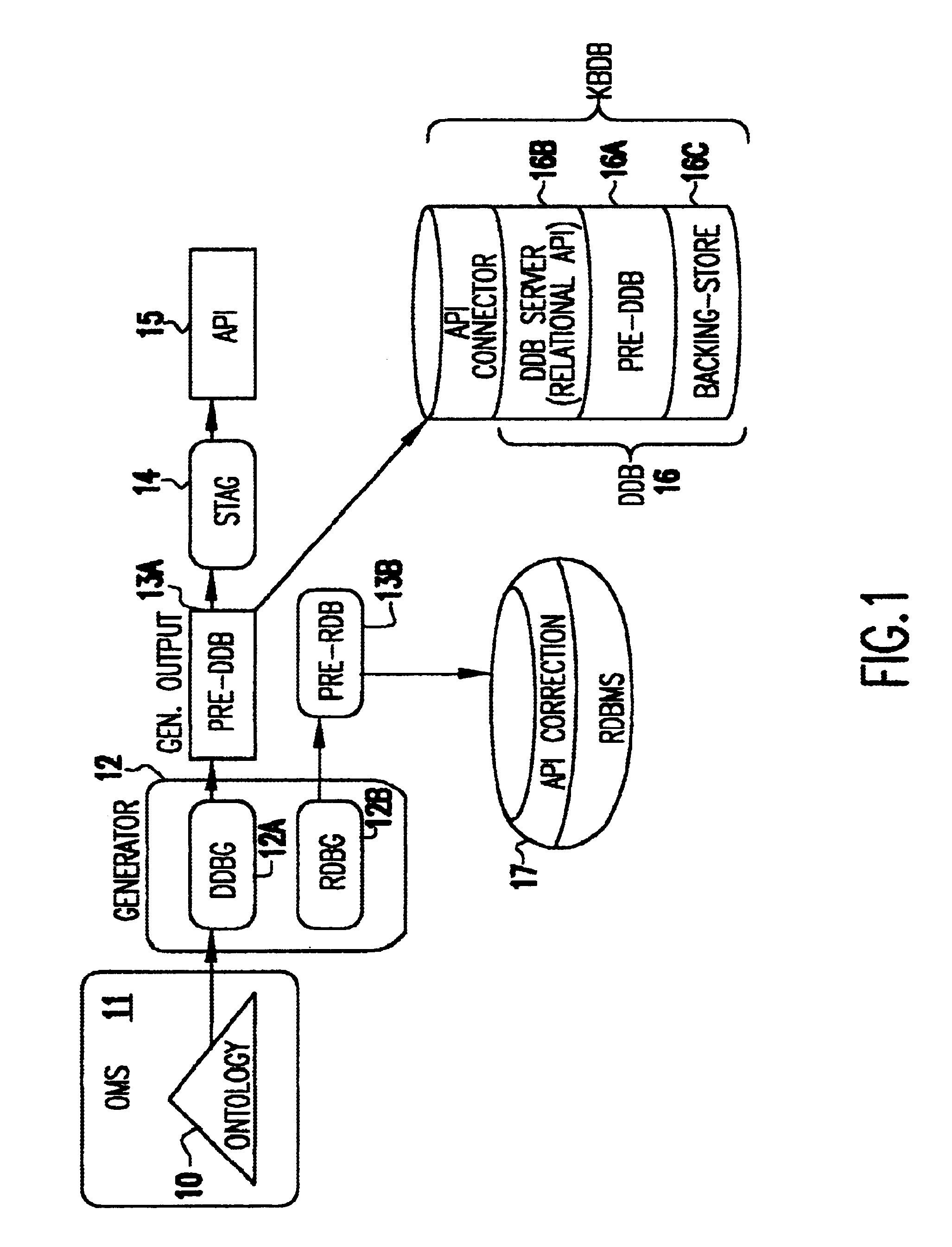
Ontology for database design and application development
InactiveUS6640231B1Improve fidelityImprove efficiencyData processing applicationsDigital data processing detailsEntity typeMaintainability
A system and method lets a user create or import ontologies and create databases and related application software. These databases can be specially tuned to suit a particular need, and each comes with the same error-detection rules to keep the data clean. Such databases may be searched based on meaning, rather than on words-that-begin-with-something. And multiple databases, if generated from the same basic ontology can communicate with each other without any additional effort. Ontology management and generation tools enable enterprises to create databases that use ontologies to improve data integration, maintainability, quality, and flexibility. Only the relevant aspects of the ontology are targeted, extracting out a sub-model that has the power of the full ontology restricted to objects of interest for the application domain. To increase performance and add desired database characteristics, this sub-model is translated into a database system. Java-based object-oriented and relational application program interfaces (APIs) are then generated from this translation, providing application developers with an API that exactly reflects the entity types and relations (classes and methods) that are represented by the database. This generation approach essentially turns the ontology into a set of integrated and efficient databases.
Owner:KYNDI
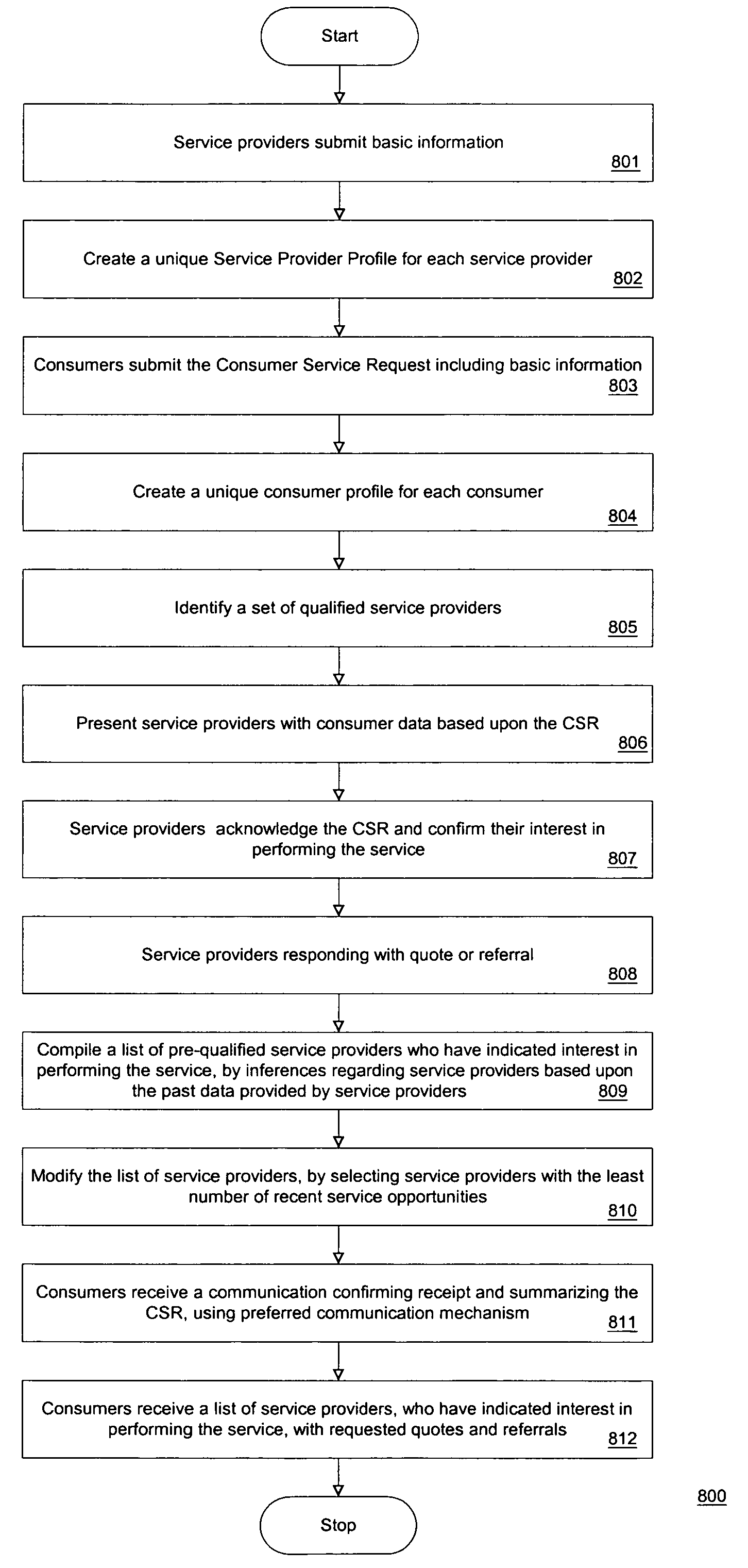
Facilitating commerce among consumers and service providers by matching ready-to-act consumers and pre-qualified service providers
A method and apparatus are provided for matching ready-to-act consumers and pre-qualified service providers. According to one aspect of the present invention, the Internet is used to attempt to solve communications problems and to achieve efficiency in Consumer-to-Business commerce transactions. Initially, a database of pre-qualified service providers is established. Then, a description of the consumer's needs may be extracted from a consumer using decision trees appropriate for the desired task. Subsequently, the consumer needs are packaged and presented to multiple service providers that meet a set of predetermined qualifications. The consumer needs may be presented, for example, by way of a set of heterogeneous communication devices depending upon preferences supplied by the service providers. For example, the set of heterogeneous communication devices may include facsimile, pager, mobile phone, home phone, office phone, Interactive Voice Response (IVR) unit, email, etc. The service providers may choose to submit a response for the consumer's needs or reject the task. After a sufficient number of responses have been received from the pre-qualified service providers, they are presented to the consumer. The consumer may then select from the pre-qualified service providers based upon one or more objective and / or subjective factors associated with the pre-qualified service providers. For example, objective service provider qualification information may be presented to the consumer along with the service provider responses. In addition, a database of consumer-generated service provider ratings and / or reviews may be maintained and made available for consumer queries.
Owner:SERVICEMAGIC
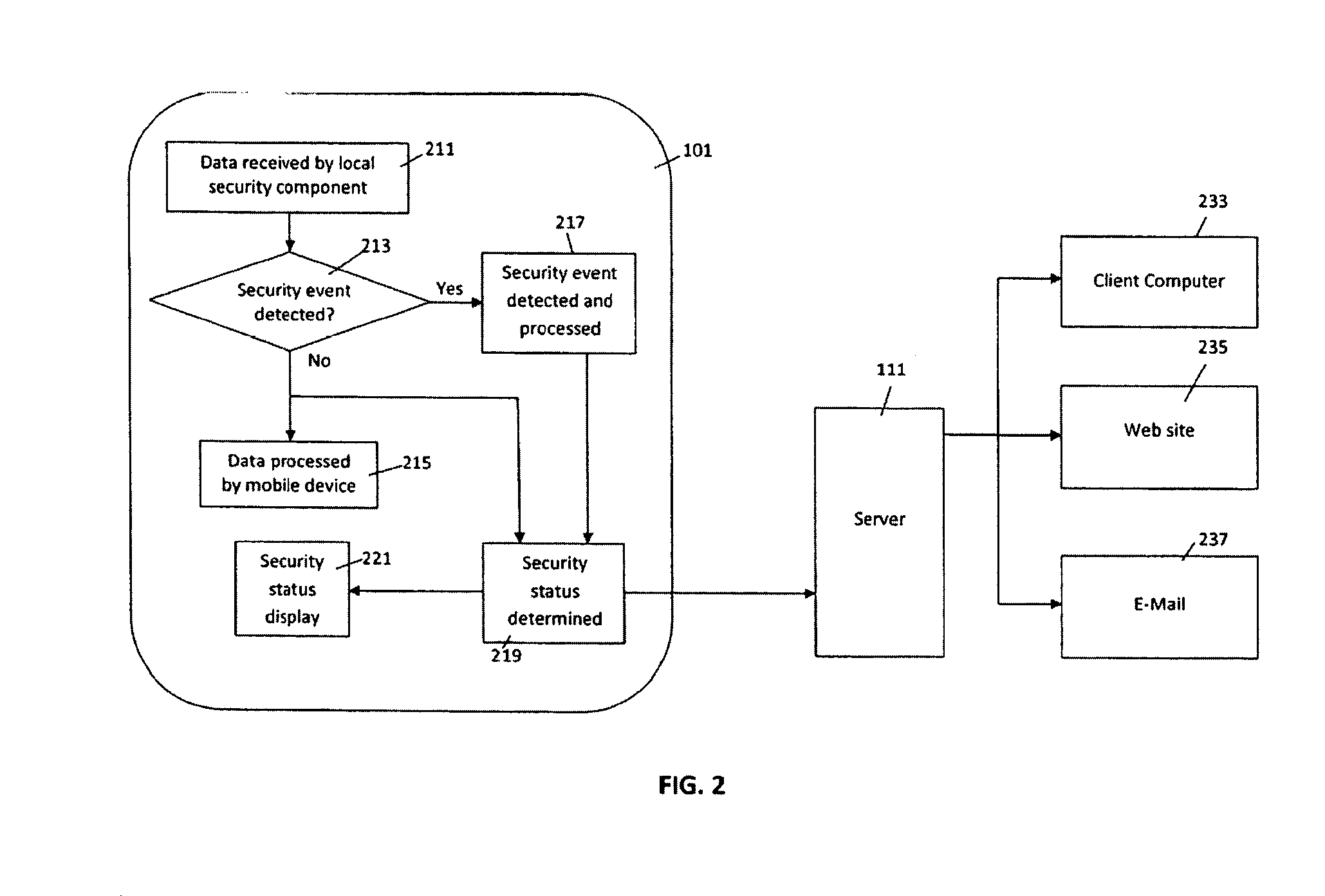
Pervasive, user-centric network security enabled by dynamic datagram switch and an on-demand authentication and encryption scheme through mobile intelligent data carriers
InactiveUS20040221163A1Improve reliabilityIncrease flexibilityKey distribution for secure communicationUnauthorised/fraudulent call preventionNetwork connectionEngineering
Methods and systems are provided for improving access control, administrative monitoring, reliability, as well as flexibility of data transmission and remote application sharing over a network. Secure, stable network connections and efficient network transactions among multiple users are supported by an open and distributed client-server architecture. A datagram schema is adapted to enable dynamic datagram switching in support of a multitude of applications and network services. Mobile intelligent data carriers are provided that allow for the implementation of an authentication and encryption scheme. The intelligent data carriers are adapted to target deliver applications to authorized users, thereby achieving access control to not only data but also applications. The authentication and encryption scheme in one embodiment is based on physical or performance biometrics. The methods and systems of this disclosure may be advantageously deployed in an enterprise network environment to support a wide spectrum of business, research, and administrative operations.
Owner:GIRITECH APS
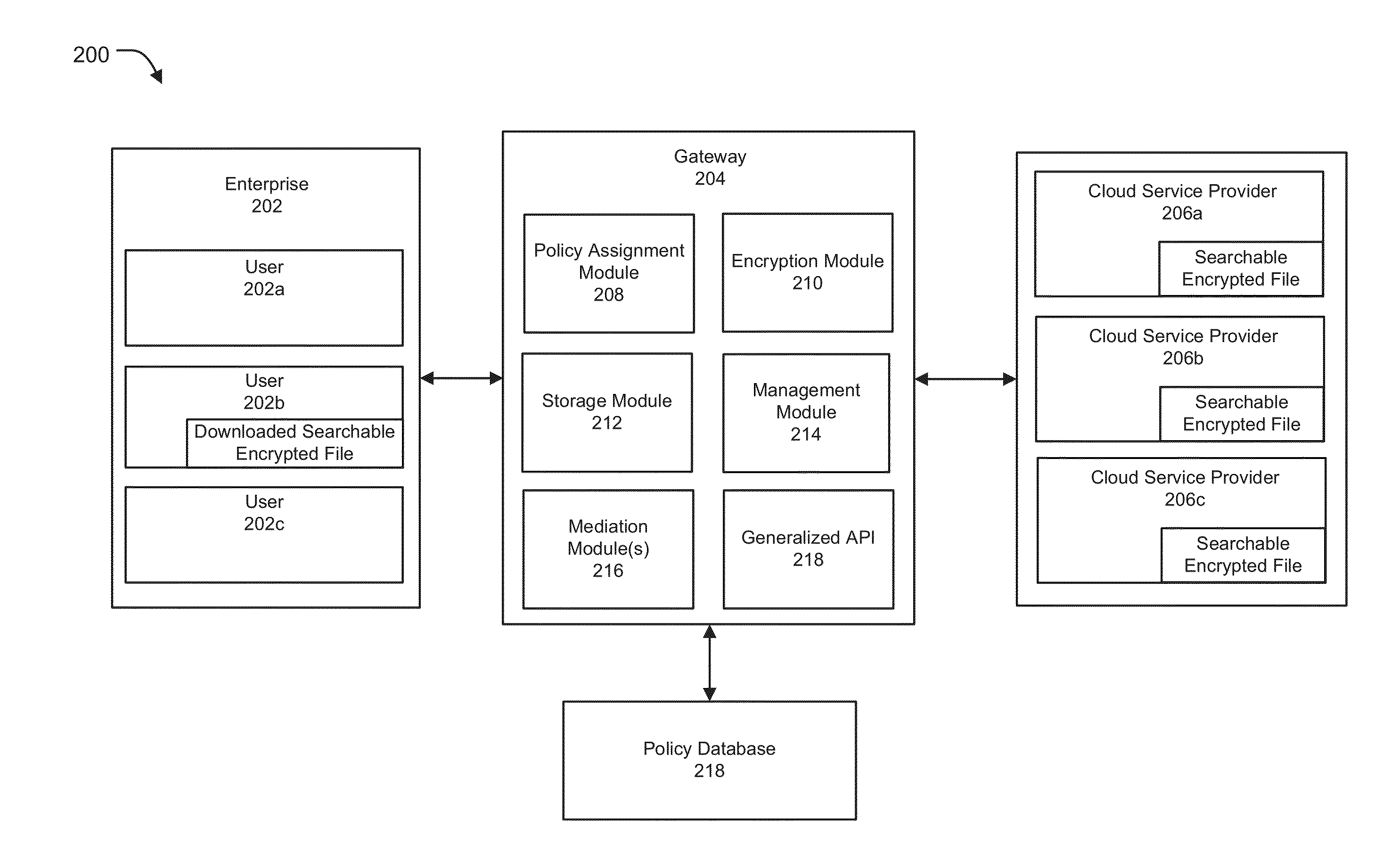
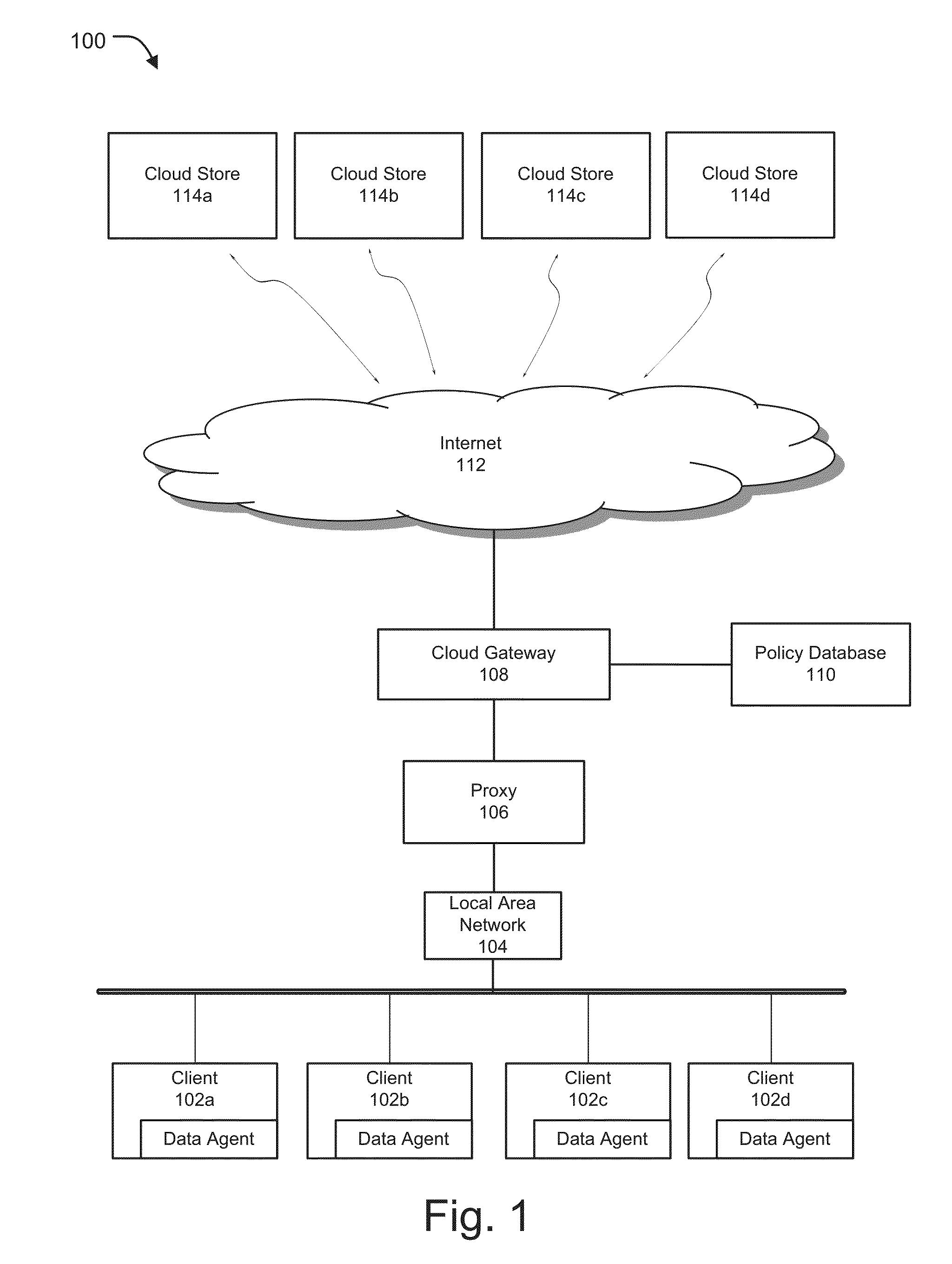
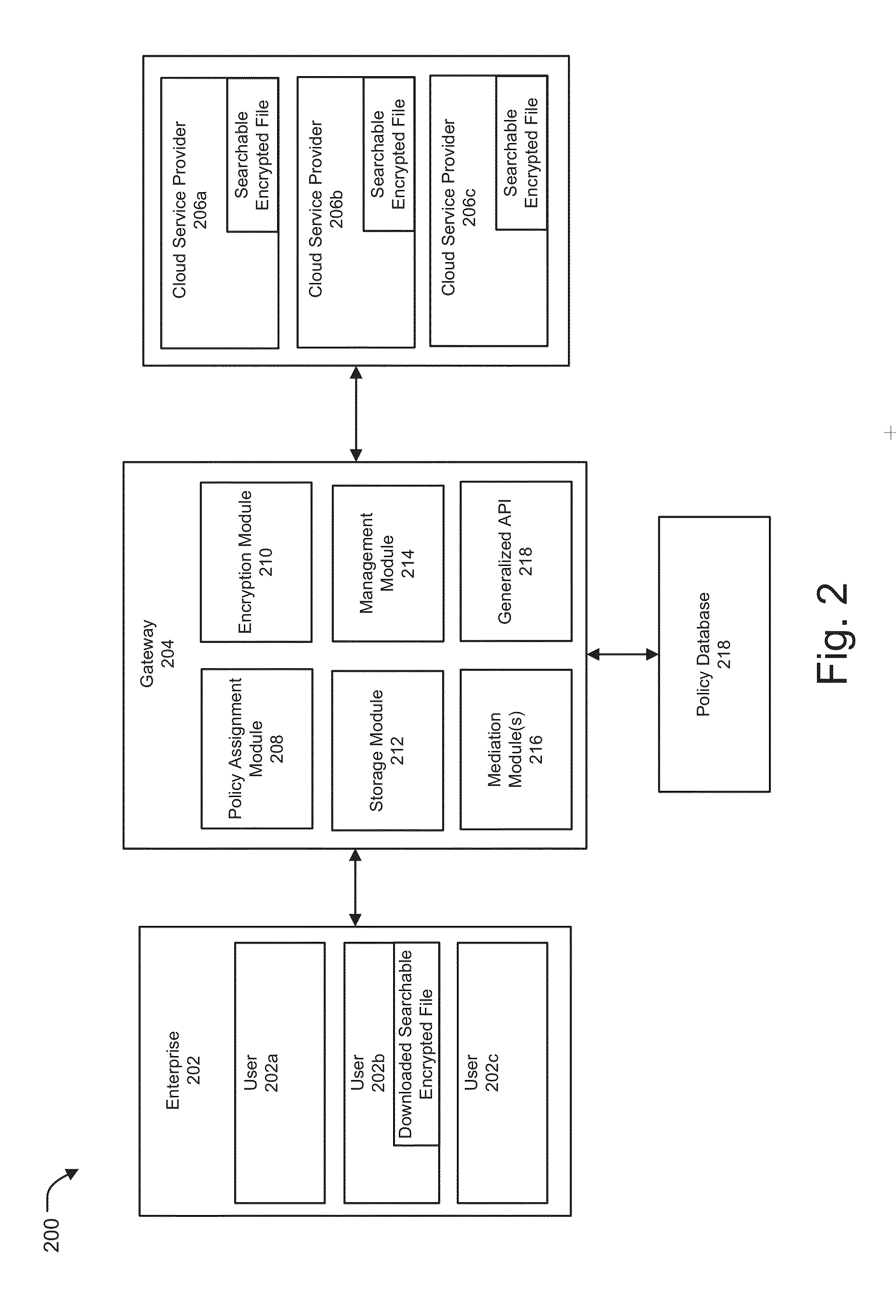
Secure cloud storage distribution and aggregation
ActiveUS20150154418A1Easy to storeDigital data protectionSpecial data processing applicationsThird partyApplication programming interface
Methods and systems for vendor independent and secure cloud storage distribution and aggregation are provided. According to one embodiment, an application programming interface (API) is provided by a cloud storage gateway device logically interposed between third-party cloud storage platforms and users of an enterprise. The API facilitates storing of files, issuing of search requests against the files and retrieval of content of the files. A file storage policy is assigned to each user, which defines access rights, storage diversity requirements and a type of encryption to be applied to files. Responsive to receiving a request to store a file, (i) searchable encrypted data is created relating to content and / or metadata of the file based on the assigned file storage policy; and (ii) the searchable encrypted data is distributed among the third-party cloud storage platforms based on the storage diversity requirements defined by the assigned file storage policy.
Owner:FORTINET
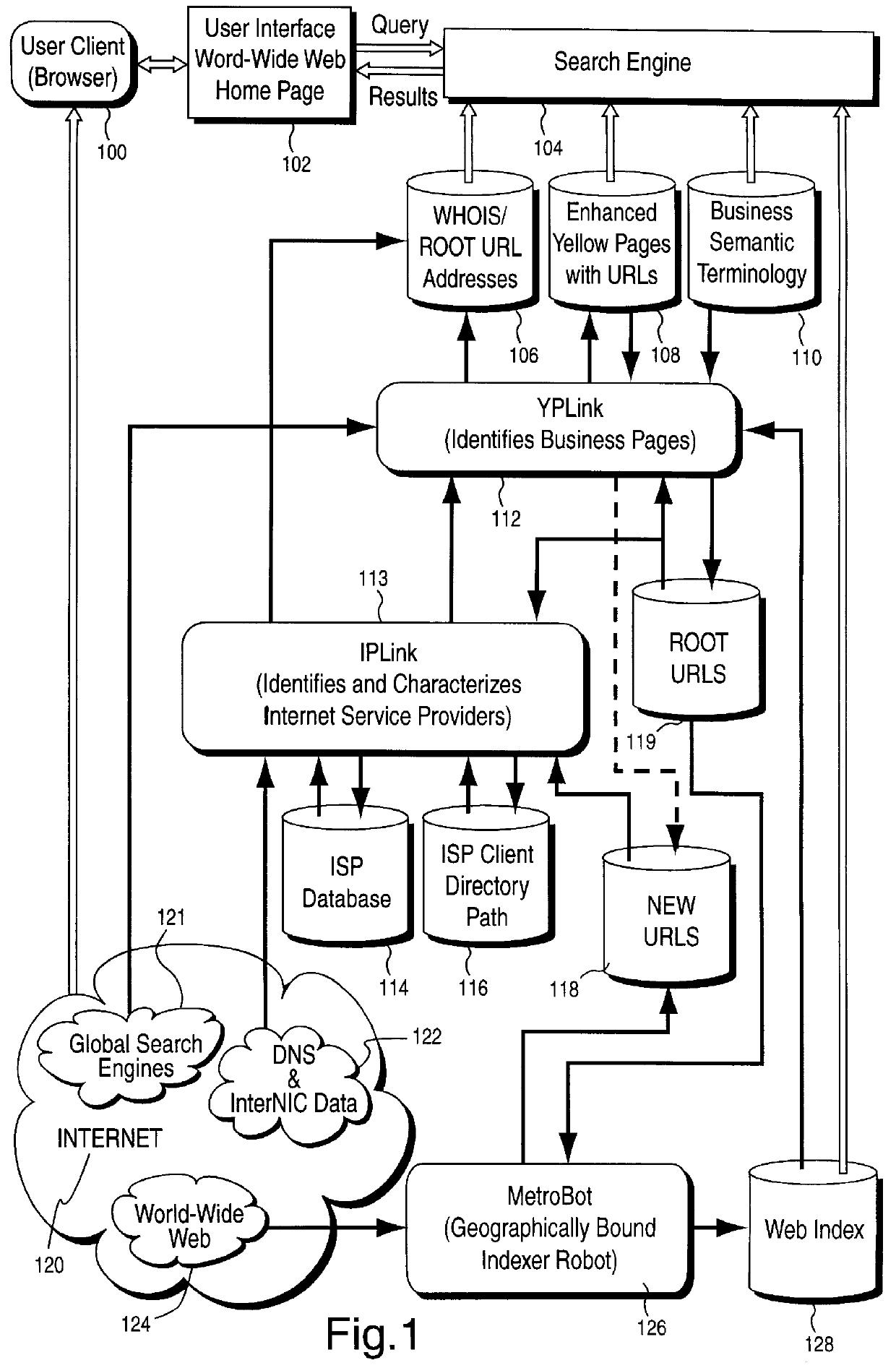
System and method for geographically organizing and classifying businesses on the world-wide web
InactiveUS6148289AWeb data indexingBuying/selling/leasing transactionsData matchingDocumentation procedure
A method and search engine for classifying a source publishing a document on a portion of a network, includes steps of electronically receiving a document, based on the document, determining a source which published the document, and assigning a code to the document based on whether data associated with the document published by the source matches with data contained in a database. An intelligent geographic- and business topic-specific resource discovery system facilitates local commerce on the World-Wide Web and also reduces search time by accurately isolating information for end-users. Distinguishing and classifying business pages on the Web by business categories using Standard Industrial Classification (SIC) codes is achieved through an automatic iterative process.
Owner:META PLATFORMS INC
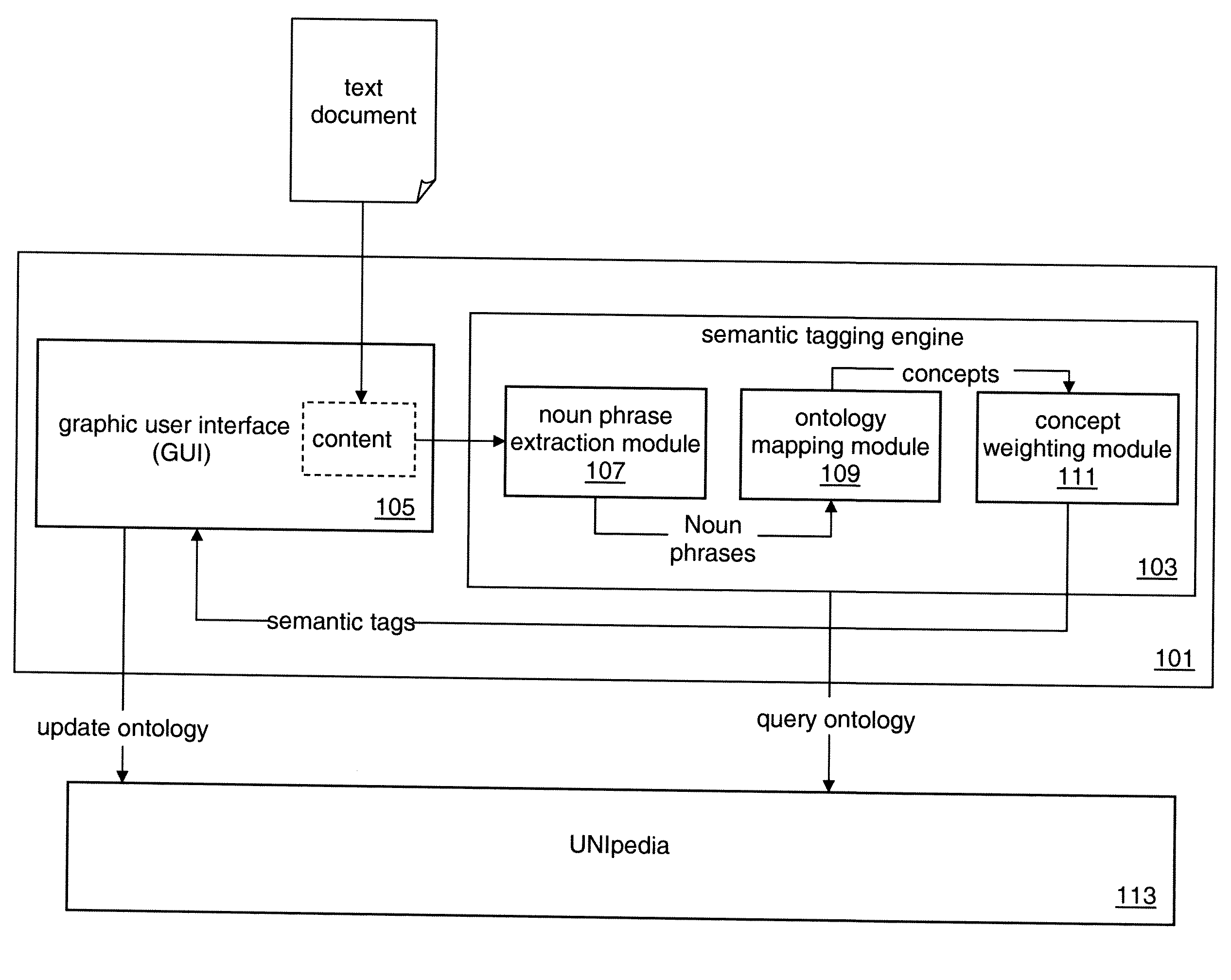
Indexing content at semantic level
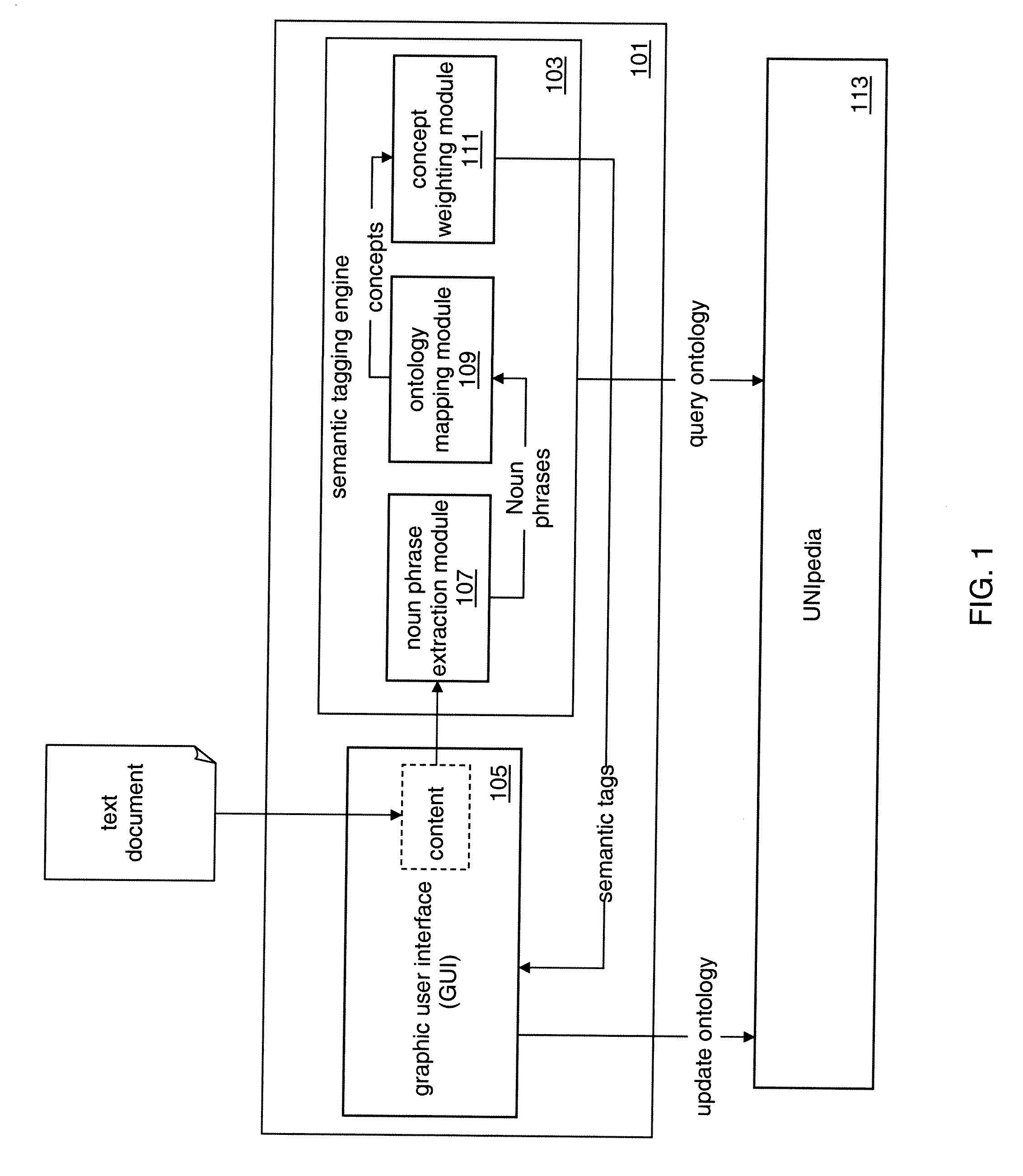
InactiveUS20110196670A1Semantic analysisSpecial data processing applicationsBusiness enterpriseEnterprise content management
Systems and methods are disclosed that perform automated semantic tagging. Automated semantic tagging produces semantically linked tags for a given text content. Embodiments provide ontology mapping algorithms and concept weighting algorithms that create accurate semantic tags that can be used to improve enterprise content management, and search for better knowledge management and collaboration.
Owner:SIEMENS AG
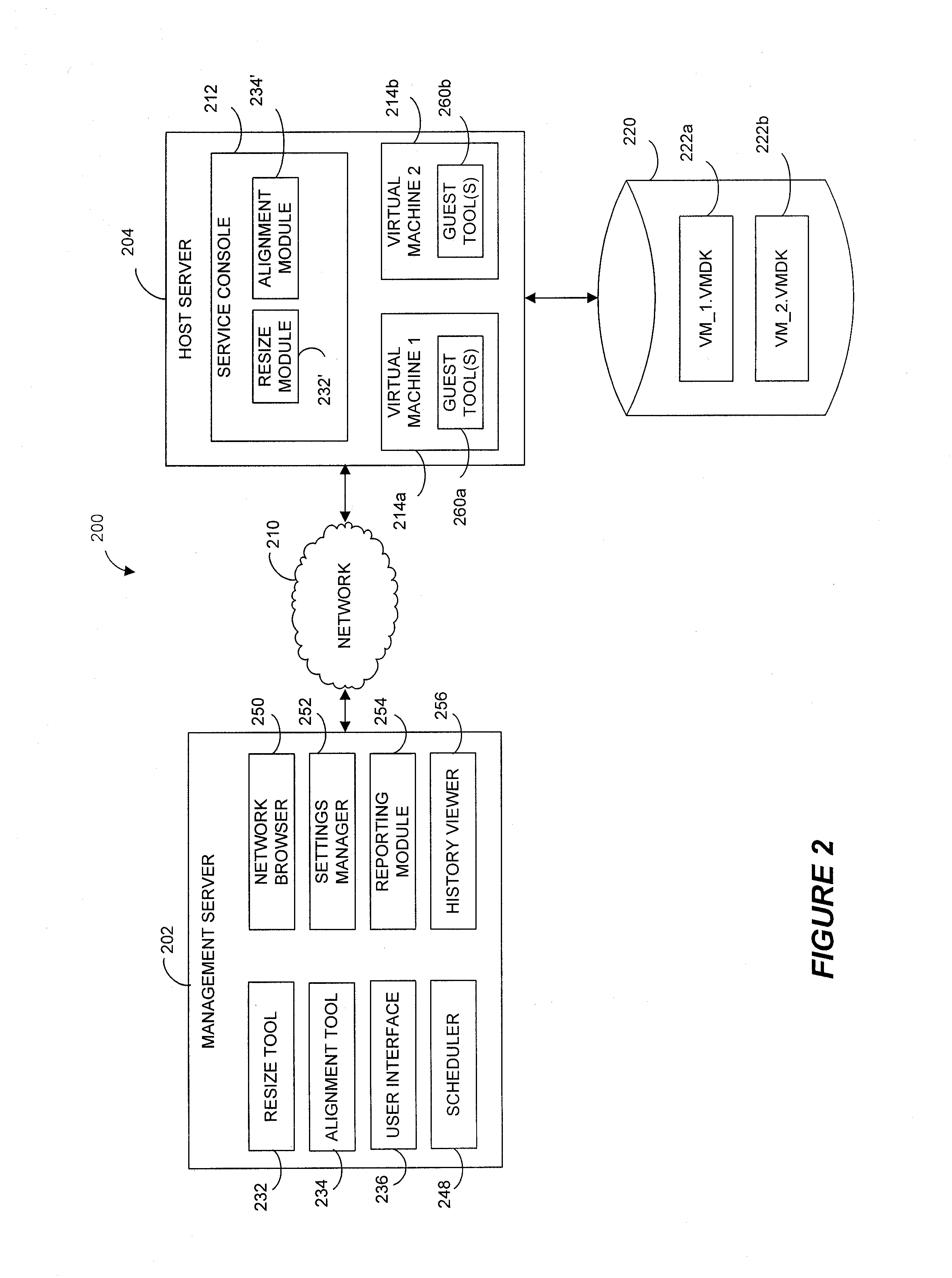
Systems and methods for improving virtual machine performance
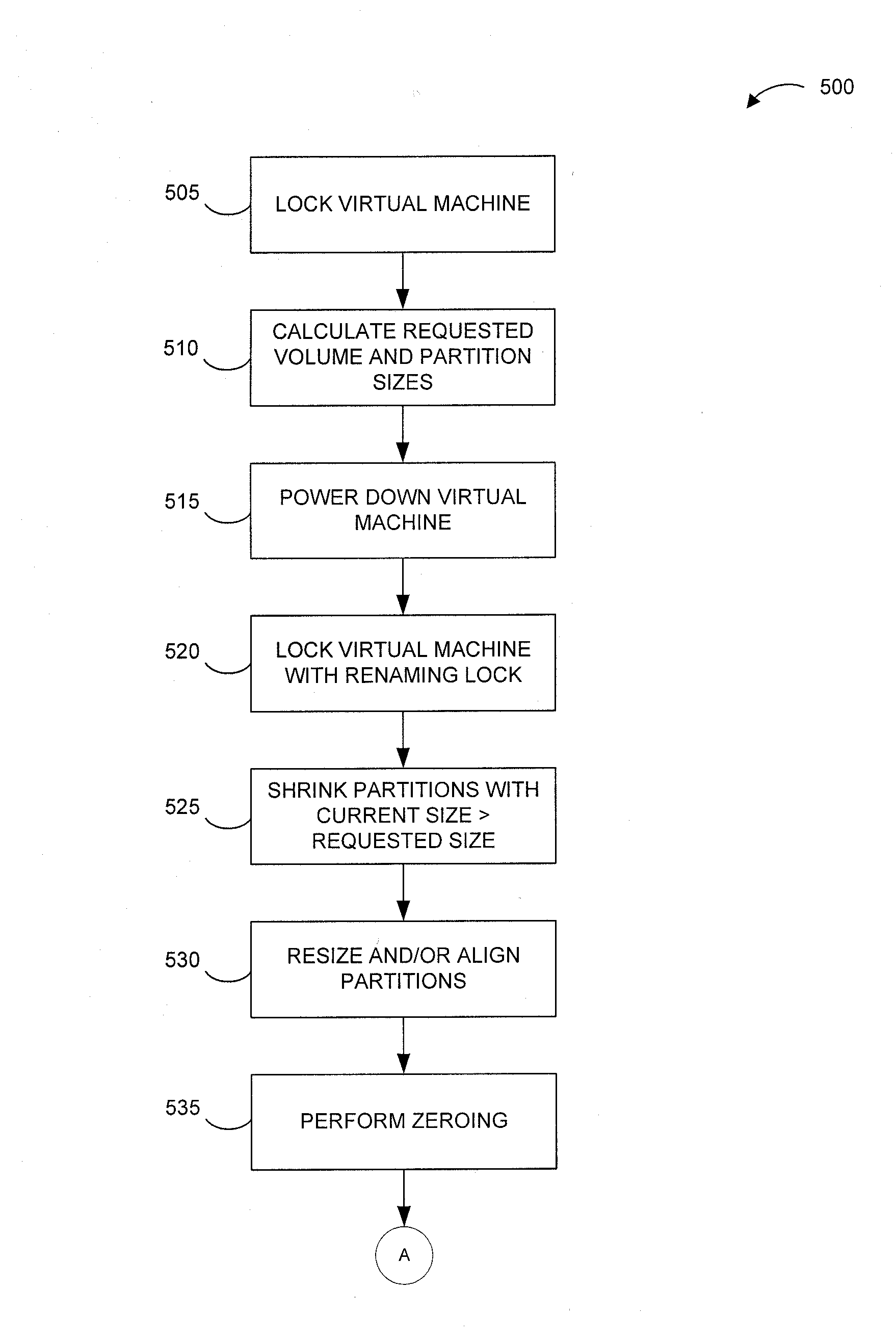
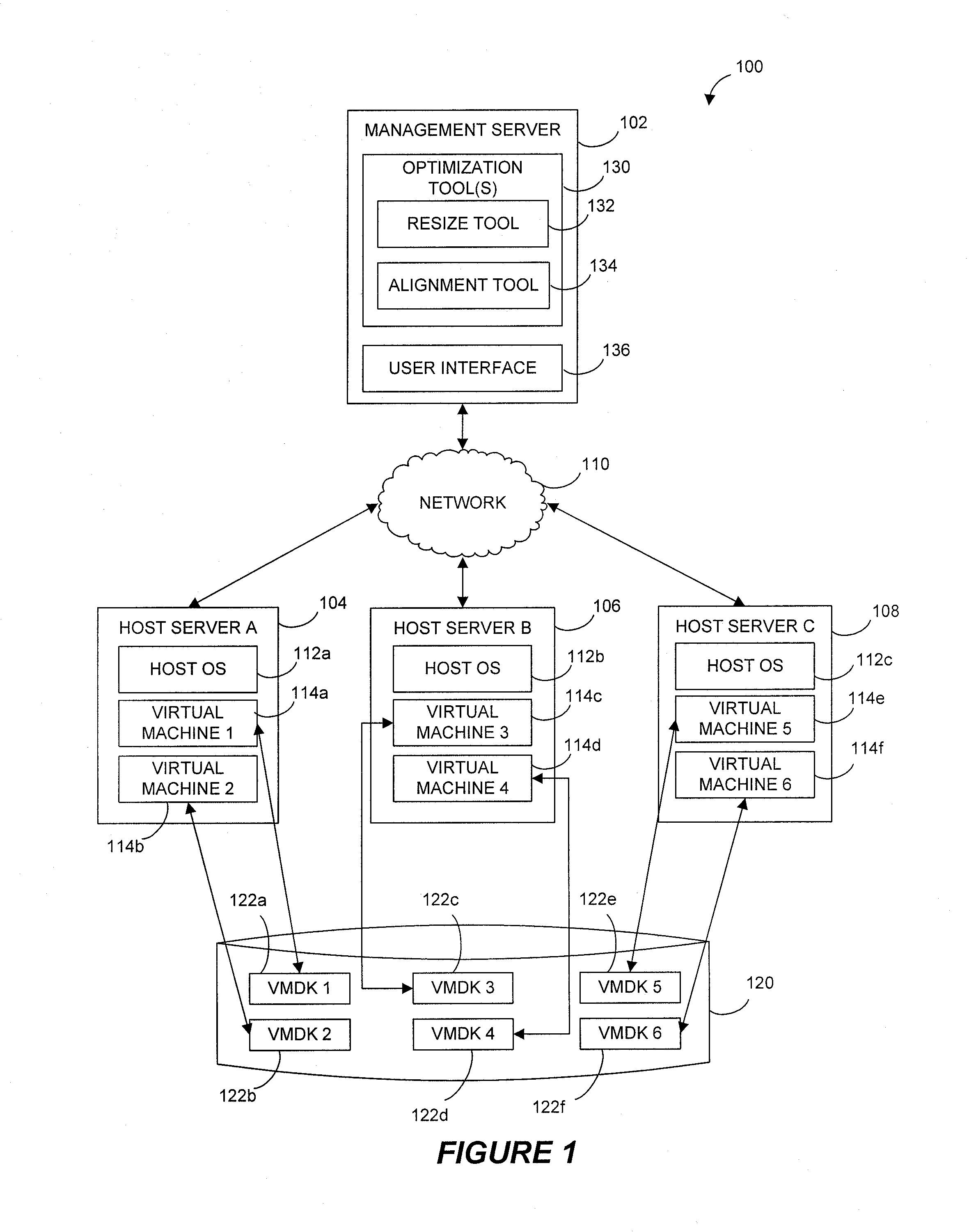
ActiveUS8332571B1Improve machine performanceEffectively preventing painful and costly virtual machine outagesComputer security arrangementsProgram controlContent replicationBusiness enterprise
Virtual machine optimization and / or storage reclamation solutions are disclosed that manage virtual machine sprawl and / or growing enterprise storage costs. For instance, certain solutions receive recommendations based on one or more rules, policies and / or user preferences that identify storage and / or alignment criteria for virtual machine disk (VMDK) partition(s). In certain examples, a resize tool that operates within a host operating system of a host server dynamically resizes and / or aligns one or more VMDK partitions of a powered-down virtual machine. For instance, the resize tool can be injected to the host server from a remote management server and can resize and / or align the VMDK partitions without requiring contents of the VMDK to be copied to another VMDK. By reallocating storage and / or aligning the VMDK partitions, embodiments of the invention can increase virtual machine performance and improve storage management.
Owner:QUEST SOFTWARE INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com