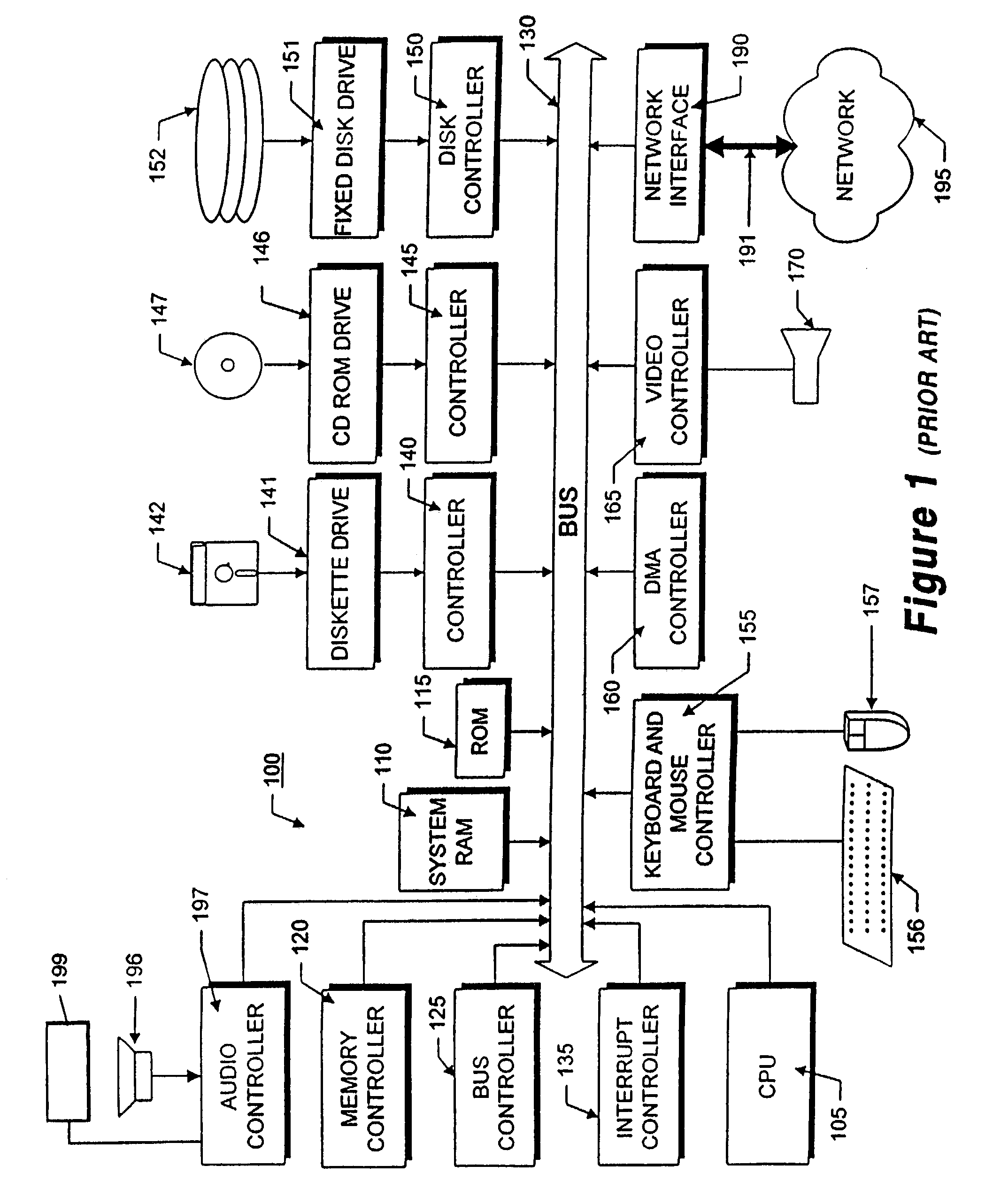
Patents
Literature
74 results about "TRADACOMS" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
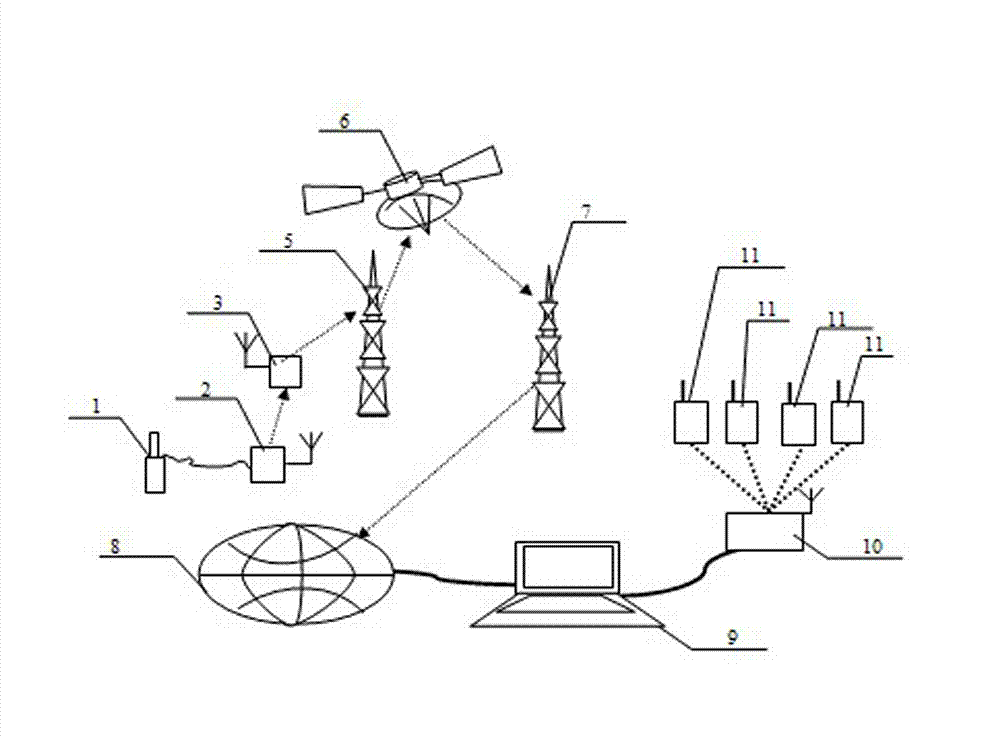
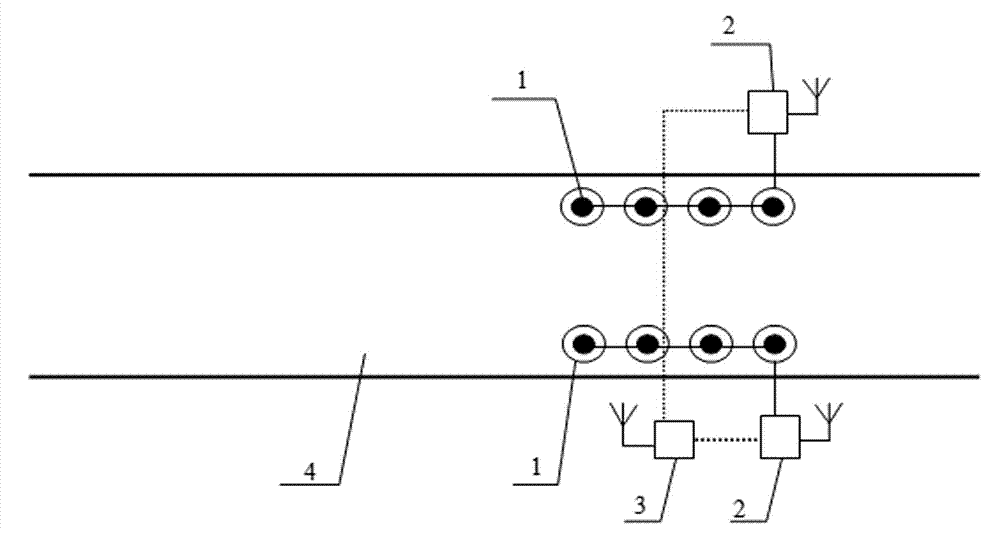
Tradacoms is an early standard for EDI (Electronic Data Interchange) primarily used in the UK retail sector. It was introduced in 1982 as an implementation of the UN/GTDI syntax, one of the precursors of EDIFACT, and was maintained and extended by the UK Article Numbering Association (now called GS1 UK).
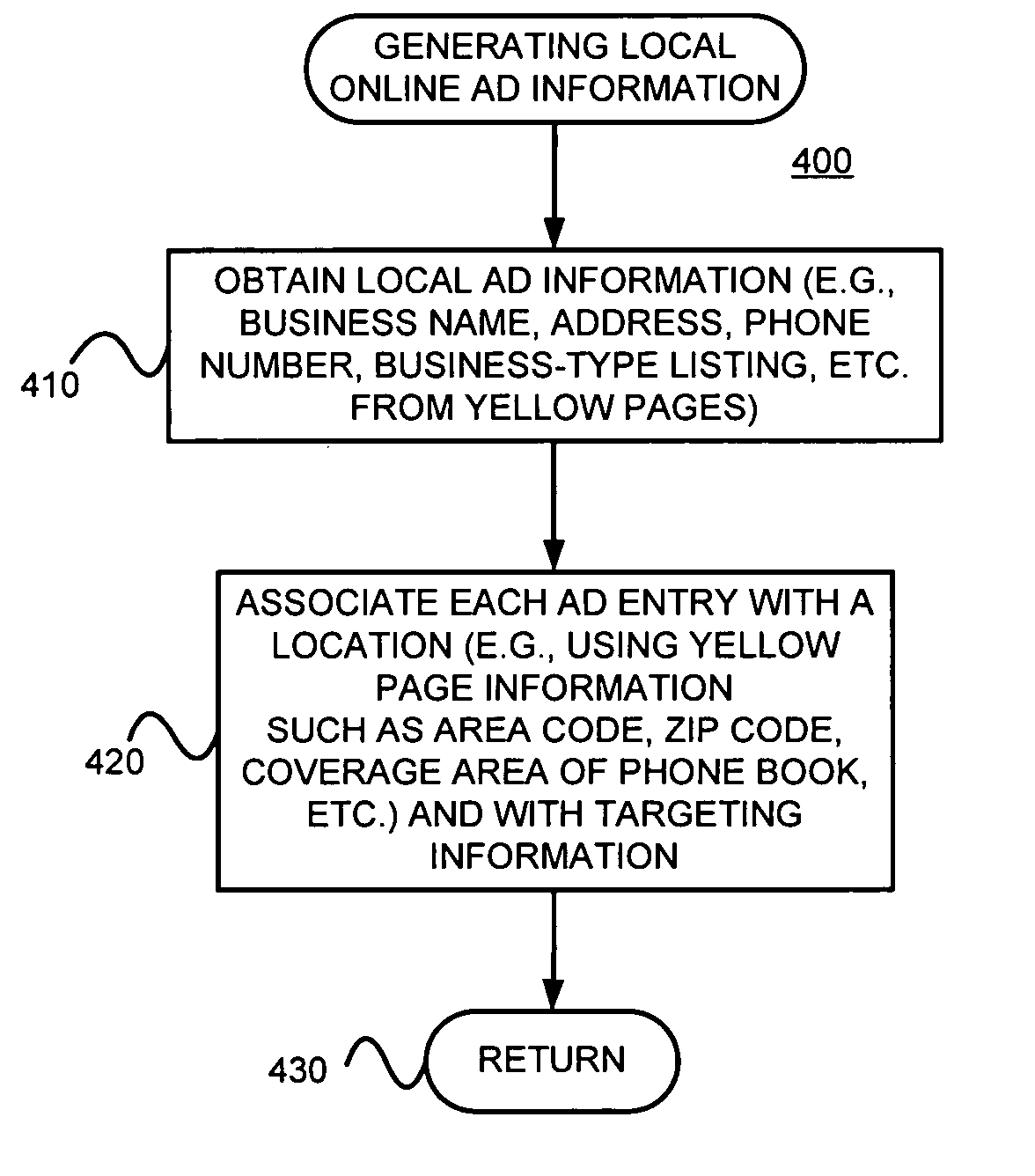
Generating and/or serving local area advertisements, such as advertisements for devices with call functionality
Sets of local, (e.g., online) ads may be generated by obtaining sets of information about (e.g., local) establishments, each set including a business address information and / or a telephone number, (b) determining, for each of the sets, a location using at least one of at least a portion of the business address information and at least a portion of the telephone number, and (c) generating, for each of the sets, an ad that includes targeting information that targets the serving of the ad to queries related to the determined location. A query, including information about a location of a client device, may be accepted and at least one of the generated ads that includes targeting information that targets the location of the client device may be determined.
Owner:GOOGLE LLC
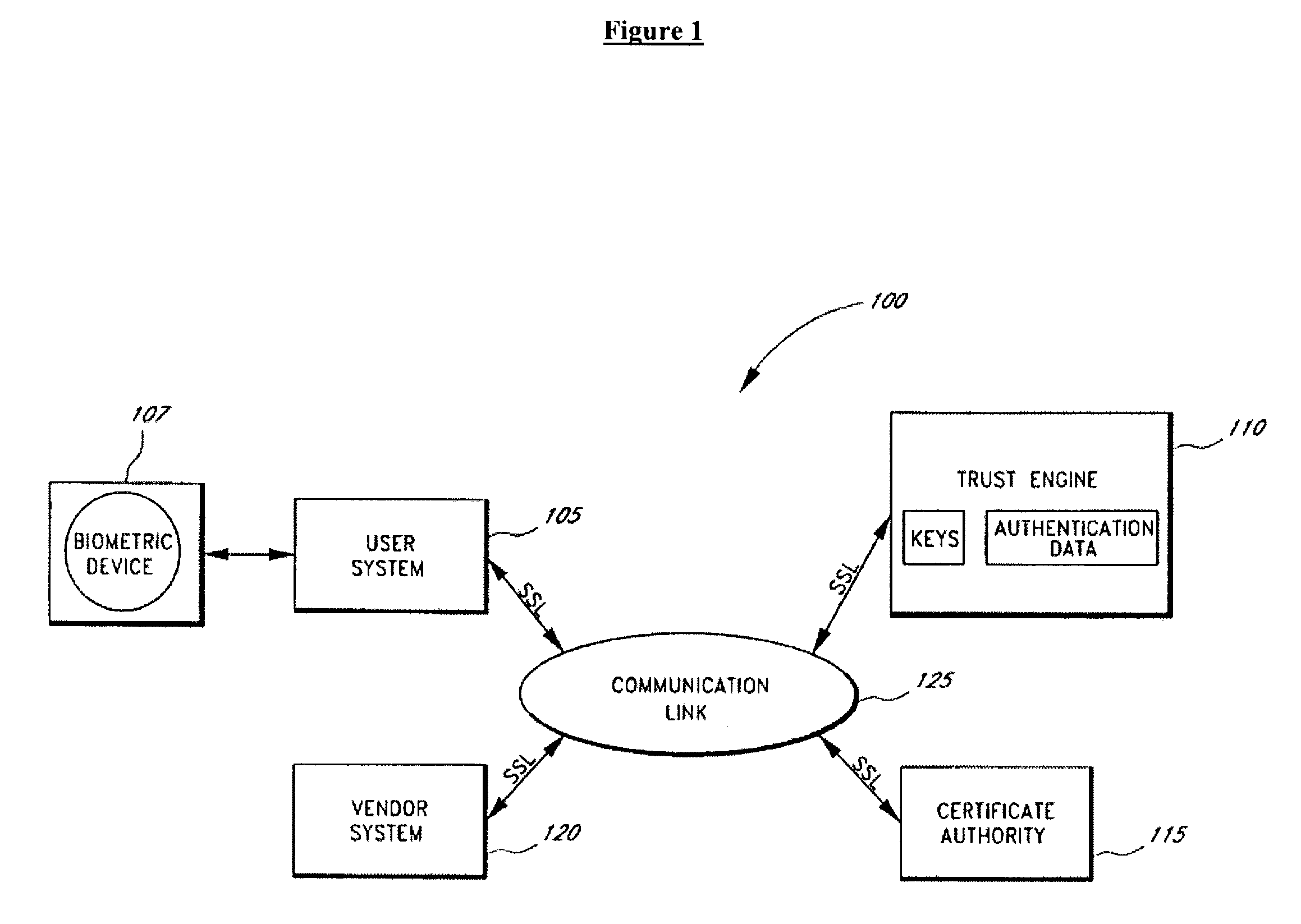
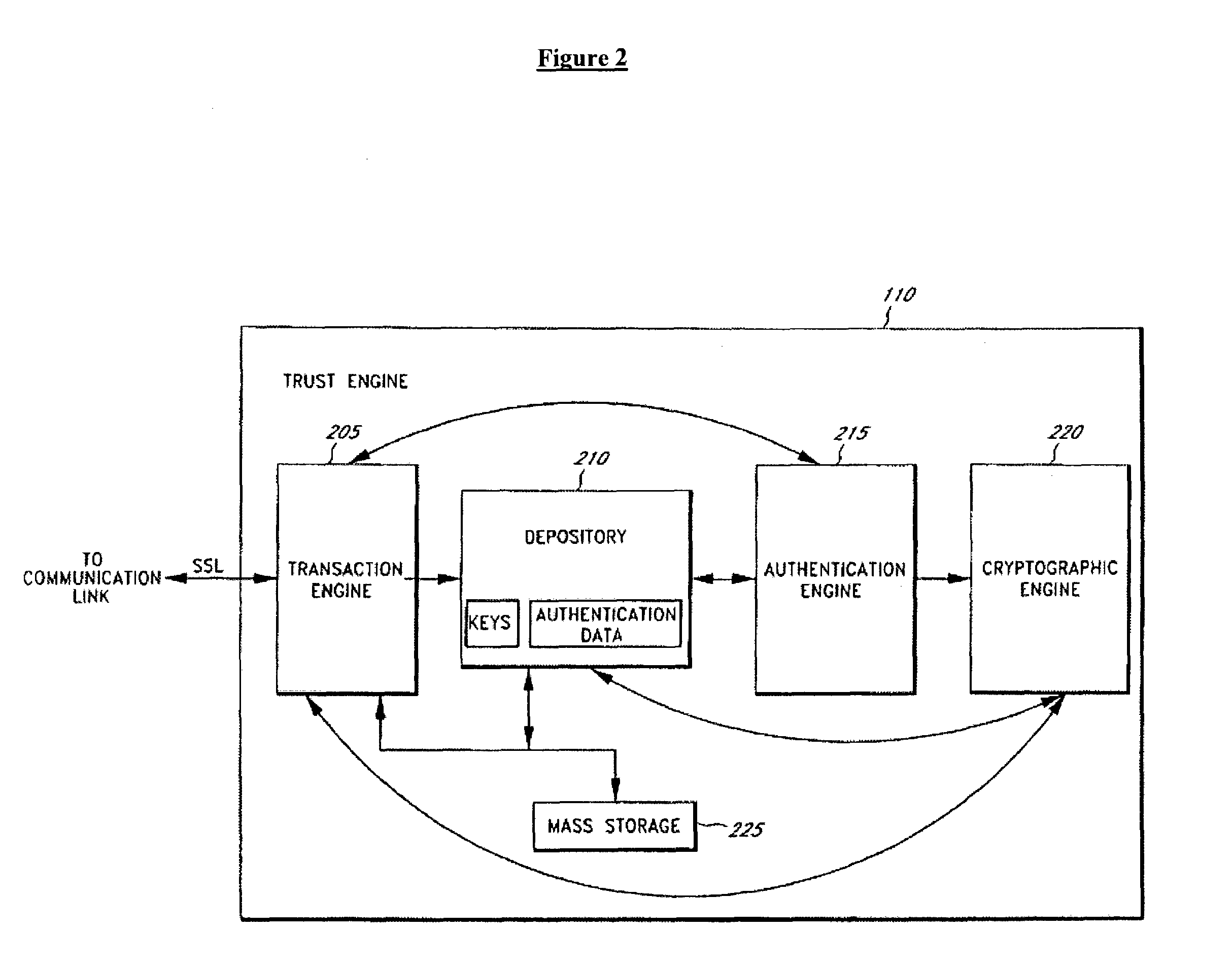
Secure data parser method and system
InactiveUS7391865B2Minimal compute resourceAvoid the needDigital data processing detailsUser identity/authority verificationGovernmental agencyVariospora
The present invention provides a method and system for securing sensitive data from unauthorized access or use. The method and system of the present invention is useful in a wide variety of settings, including commercial settings generally available to the public which may be extremely large or small with respect to the number of users. The method and system of the present invention is also useful in a more private setting, such as with a corporation or governmental agency, as well as between corporation, governmental agencies or any other entity.
Owner:SECURITY FIRST INNOVATIONS LLC
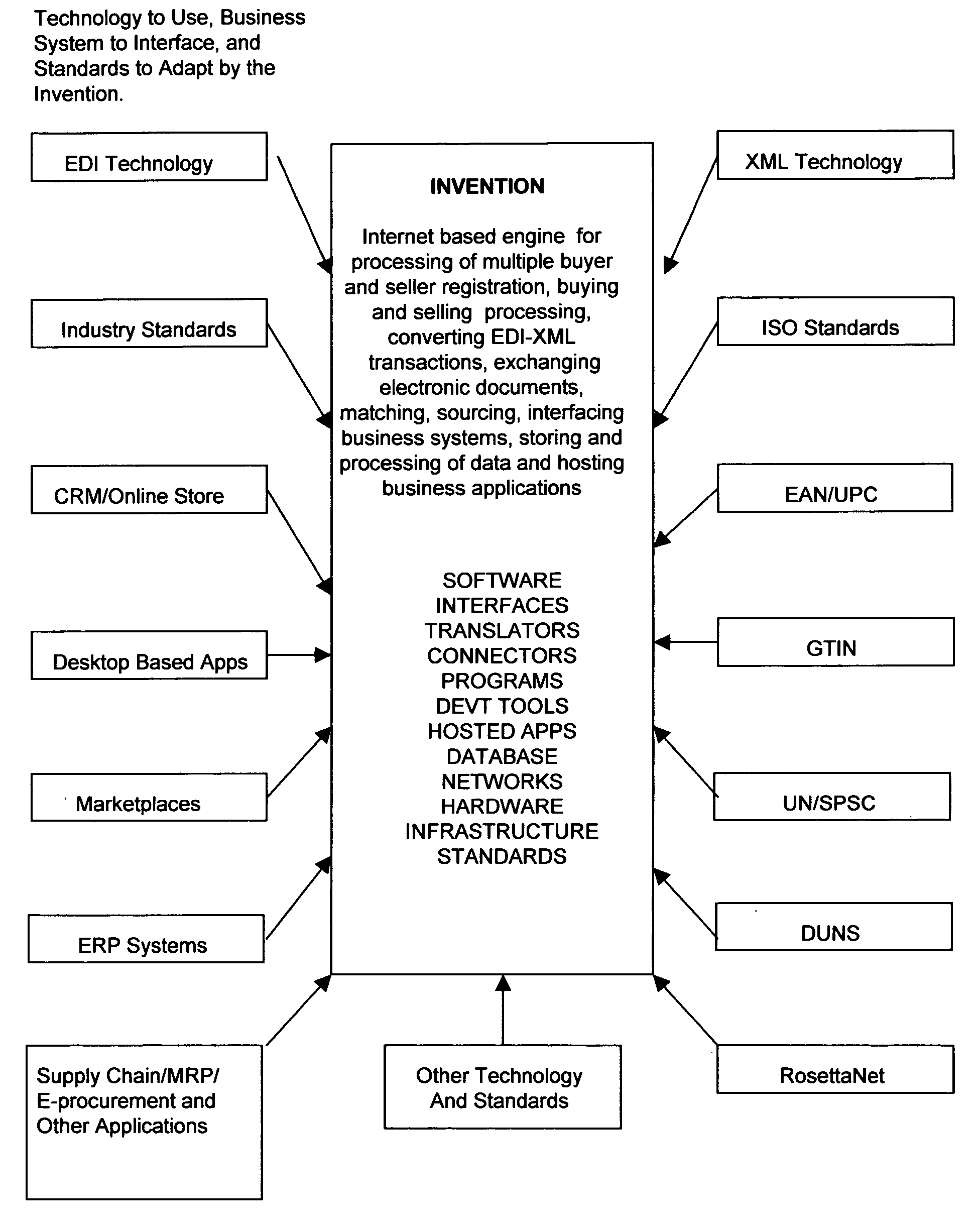
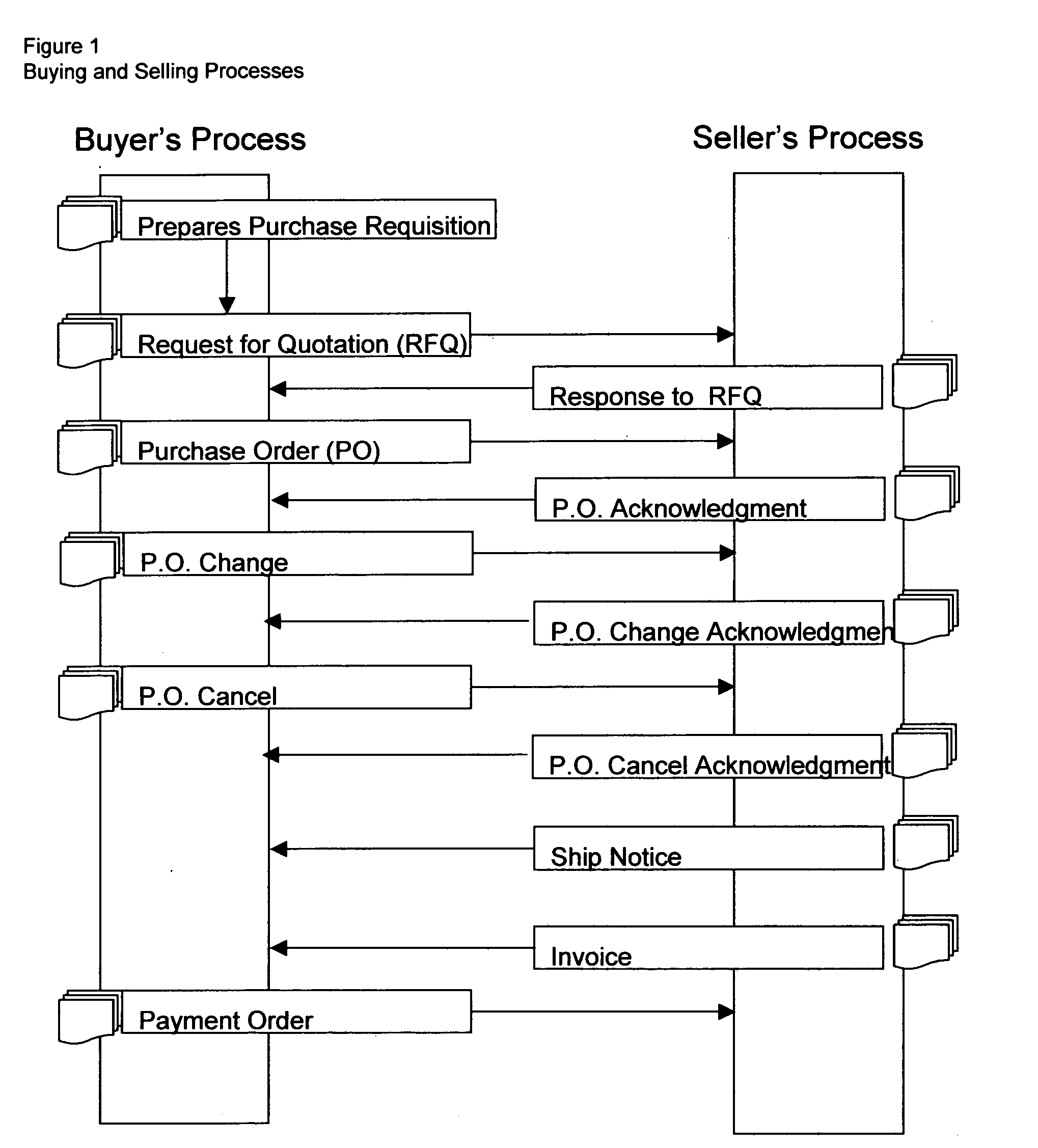
System and method for business-to-business buying, selling, sourcing and matching of proudcts and services across multiple business partners over the internet
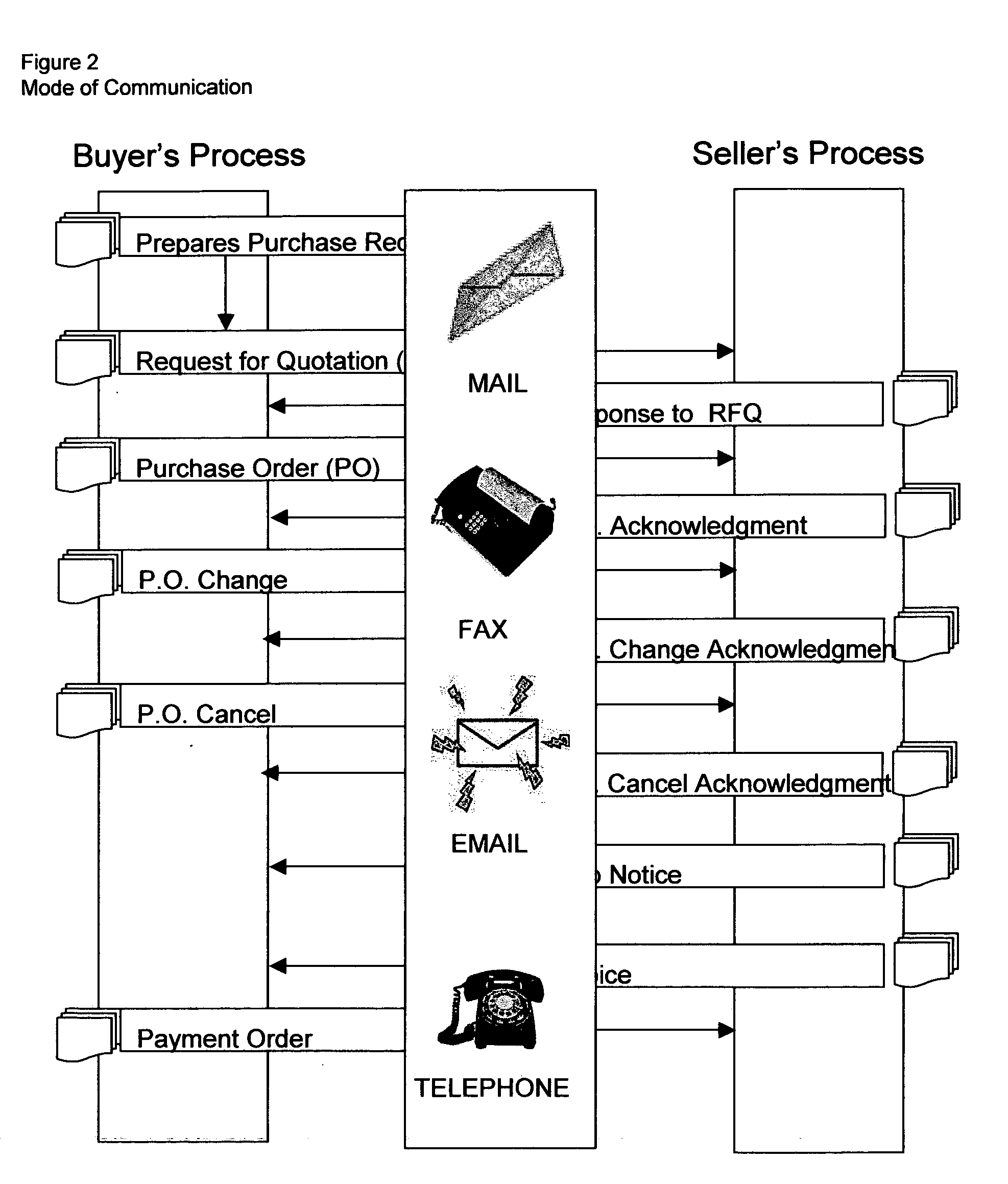
This invention relates in general to a system and method for business-to-business buying, selling, sourcing and matching of products and services across multiple business partners over the Internet. The invention covers an internet based solution comprise of: 1) business partner registration, 2) buying and selling processing, 3) matching of codes, 4) conversion of EDI transactions, 5) sourcing / offering of products / services and 6) electronic documents processing. The invention provides: 1) support on EDI technology conversion into Rosettanet technology, 2) enhancements to Rosettanet technology so that code matching is possible for companies with or without support on GTIN, DUNS, ISO, UN / SPSC and other globally set codes, 3) an intermediary infrastructure for consolidation and standardization of business data across multiple electronic business applications (EBAs) and platforms with or without manufacturer part number (MPN) and customer part number (CPN) support, 4) a conversion mechanism where internet published auctions and reverse auctions are converted into sales quotations (SQs) and request for quotations (RFQ) respectively, 5) a solution to extract data from various EBAs, interface, update, match and store codes such as company codes, product / service codes, currency code, unit of measure code, country code and class code from globally defined codes and business partner defined codes and 7) a sourcing / offering mechanism where it detects potential suppliers and buyers based on the calculation logic described on FIGS. 21 and 22.
Owner:PADILLA RAYMUND MARCOS
Descriptive-profile mercantile method
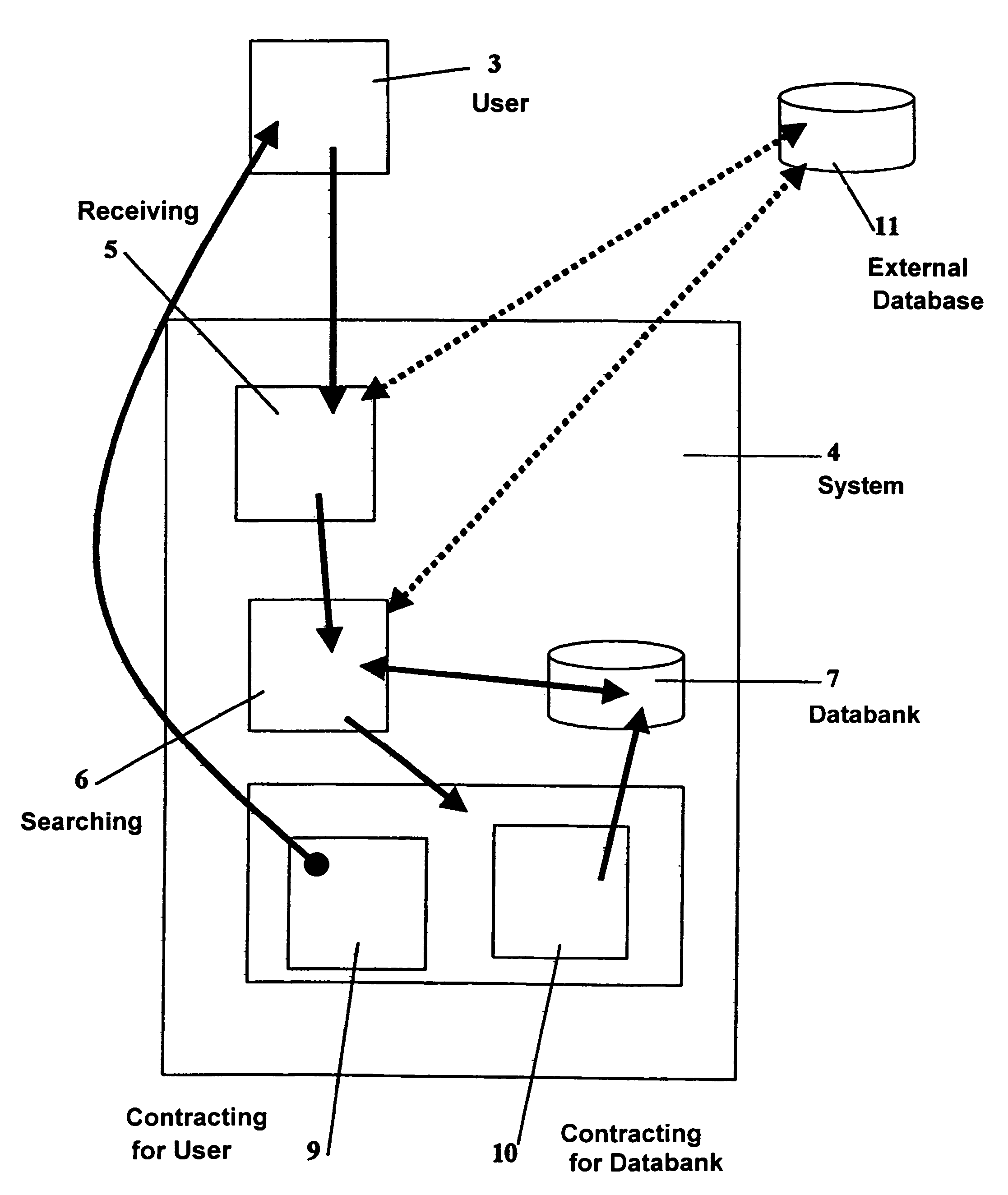
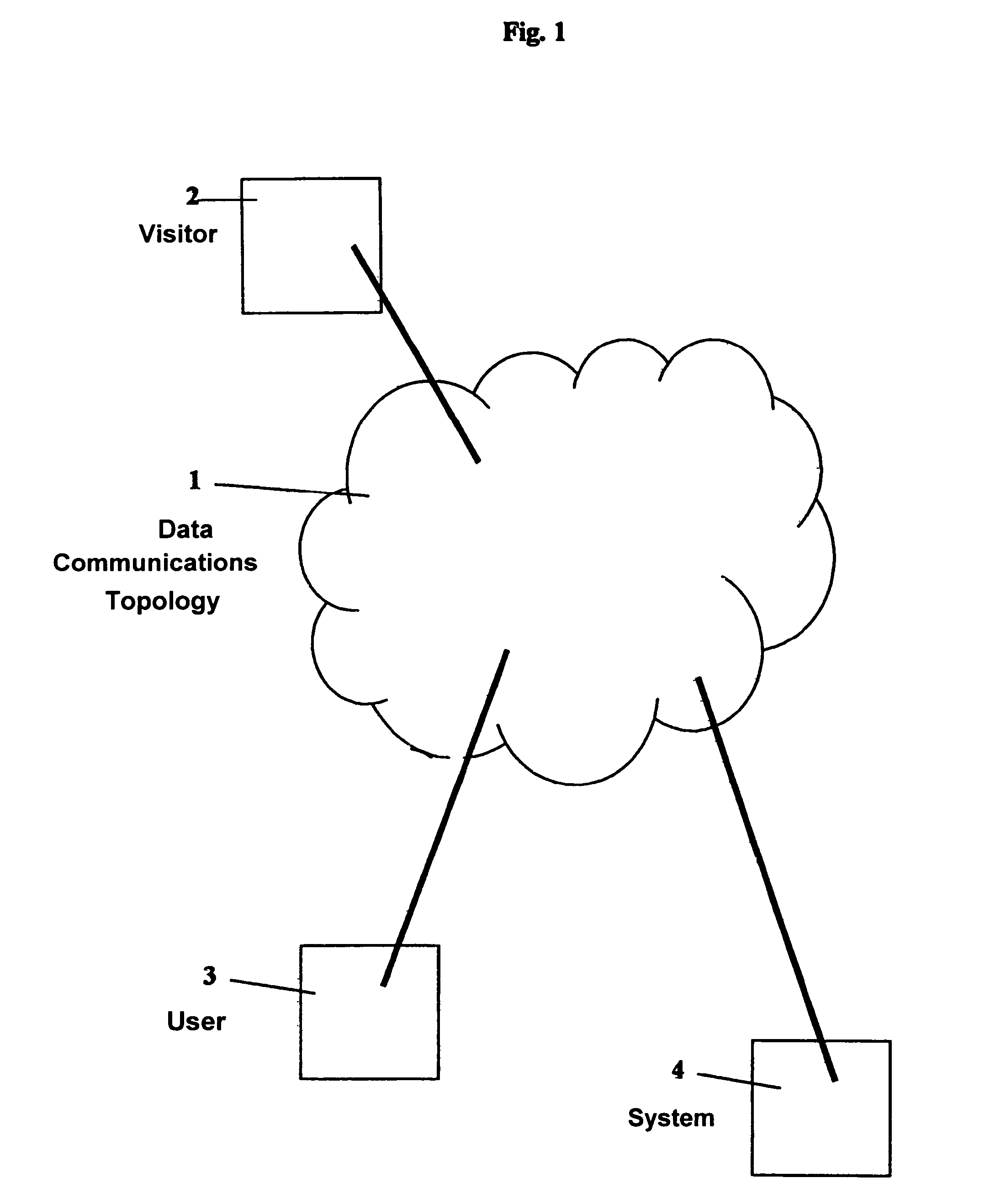
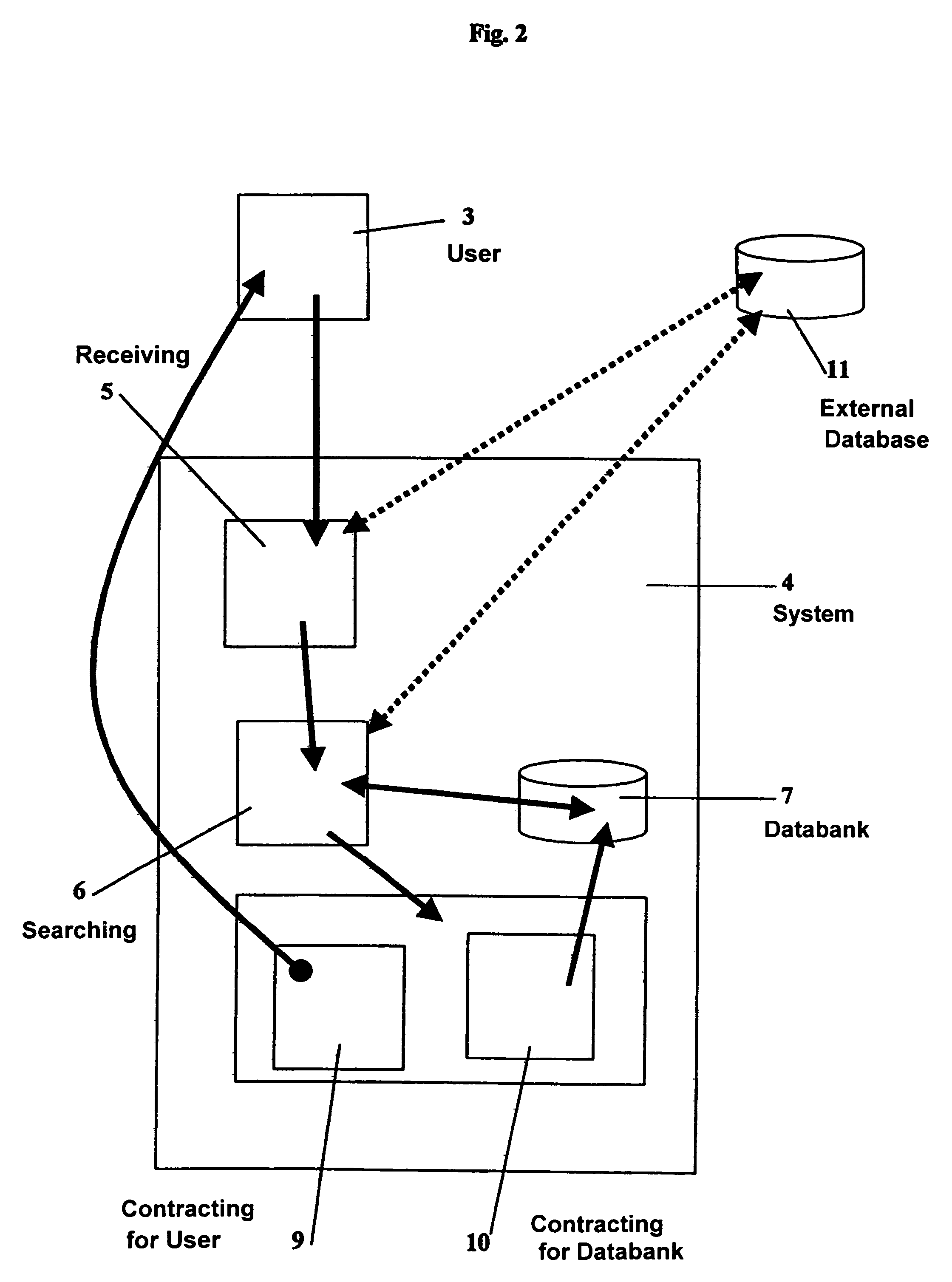
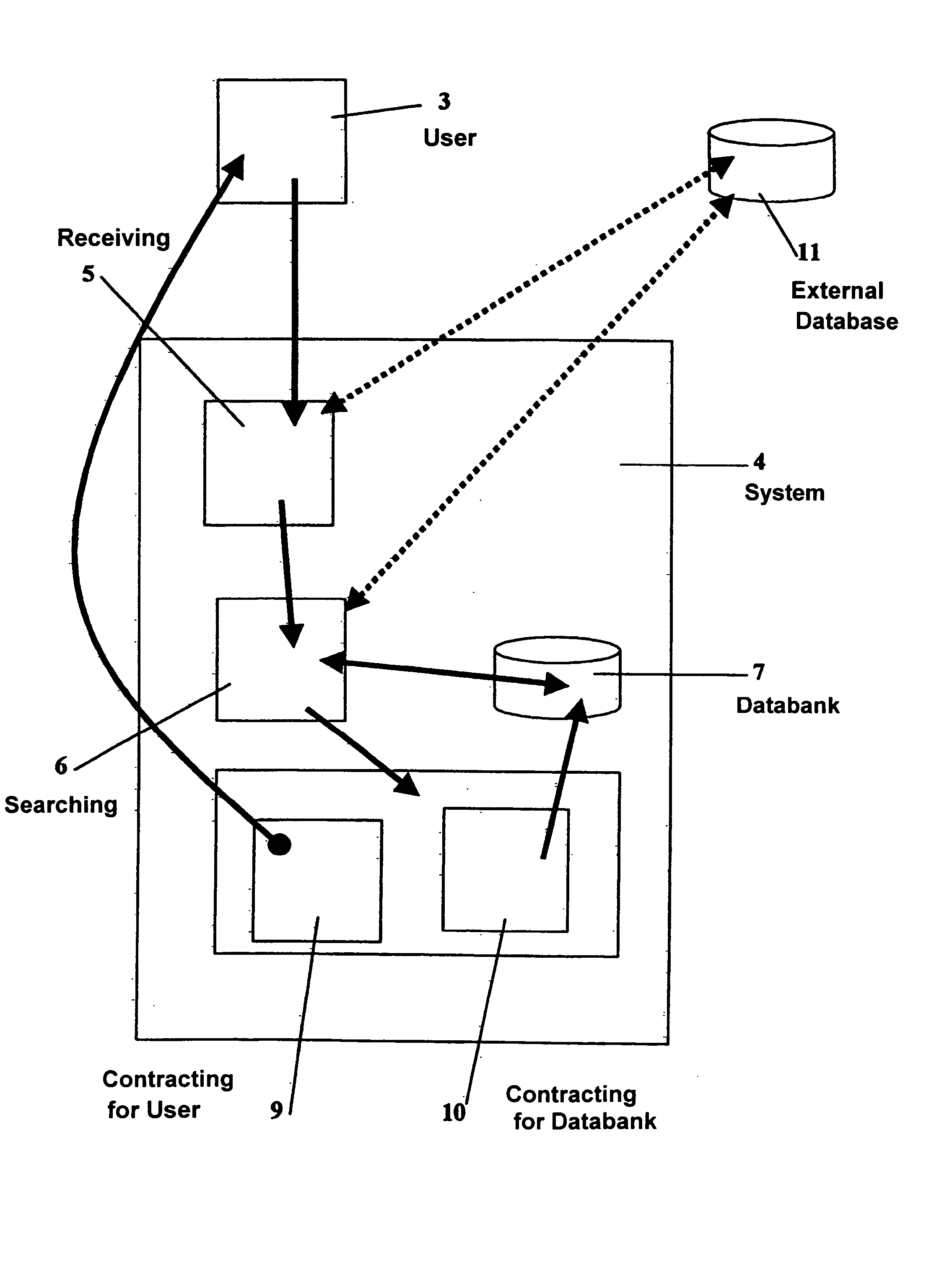
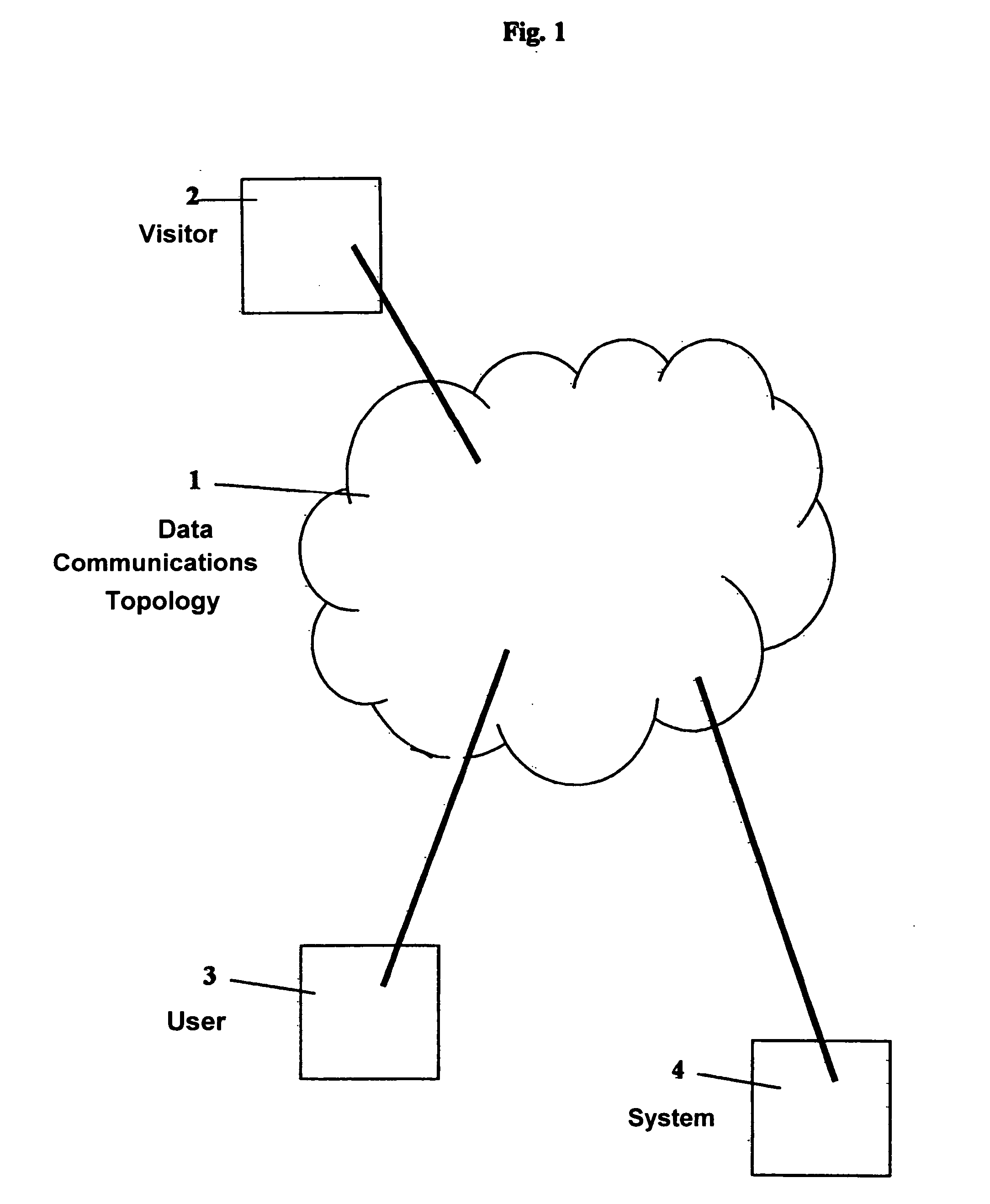
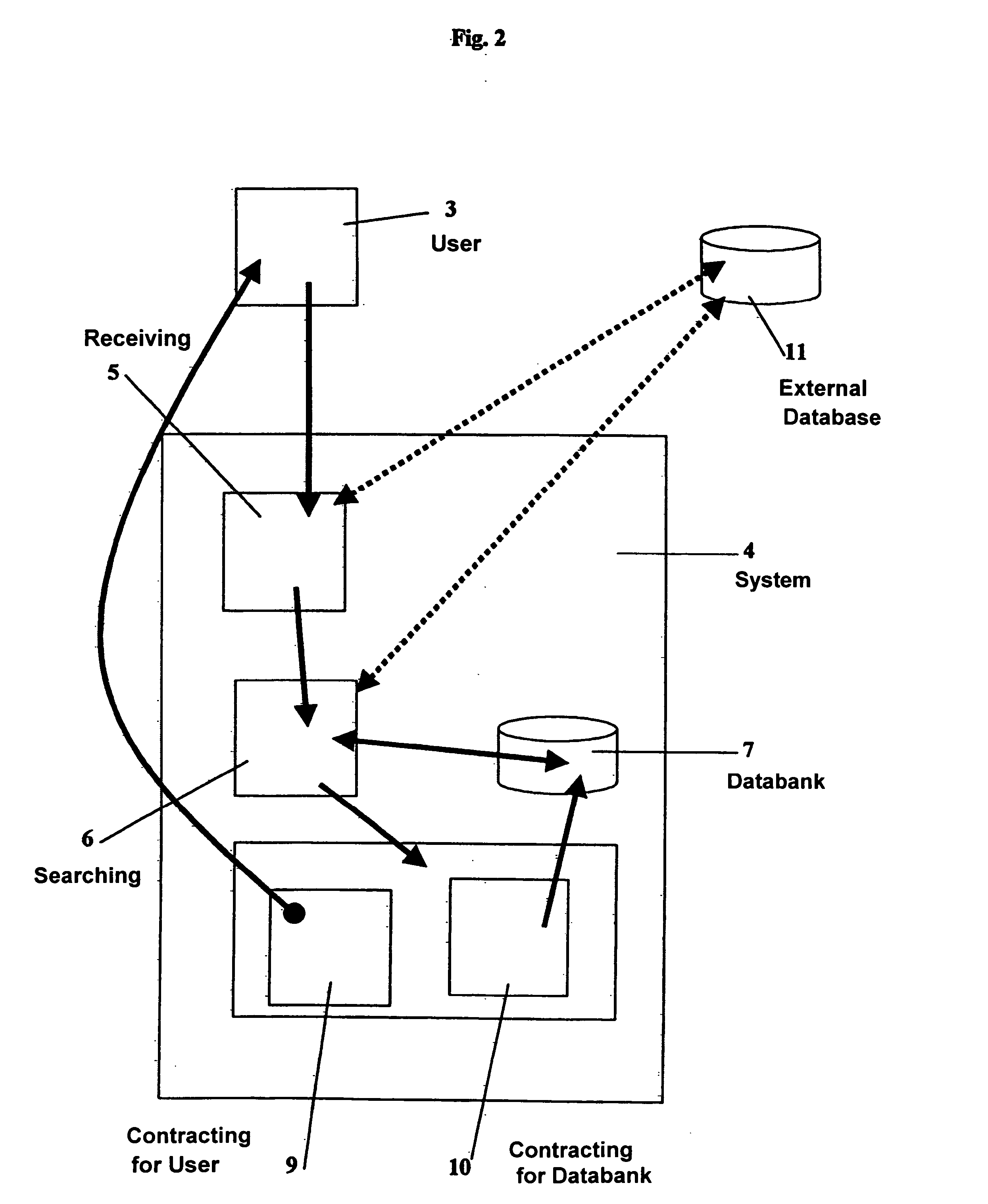
A descriptive-profile mercantile method, for use at a juncture in a data-communications topology having associated therewith a maintained databank of partial profiles, is disclosed. The method includes the steps of: from a user, receiving a transaction having therein a first partial profile; using the first partial profile, searching a databank having a plurality of second partial profiles, wherein is included in said databank at least one null profile so that said searching will always yield at least one proximate second partial profile to the first partial profile; and between the user and the databank, contracting: (I) for the databank to own or represent a right to a first mutually agreed portion of the first partial profile, and substantially thereafter said databank incorporating the agreed portion of the first profile into at least one second partial profile; or (II) for the user to own or represent a right to a second mutually agreed portion of at least one said proximate second partial profile, and substantially thereafter the databank transmitting to the user the second mutually agreed portion of the second profile. The present invention operates best on a brokerage representation model; and thereby provides a means for making viable the economic commerce in information attributes.
Owner:ALMONDNET
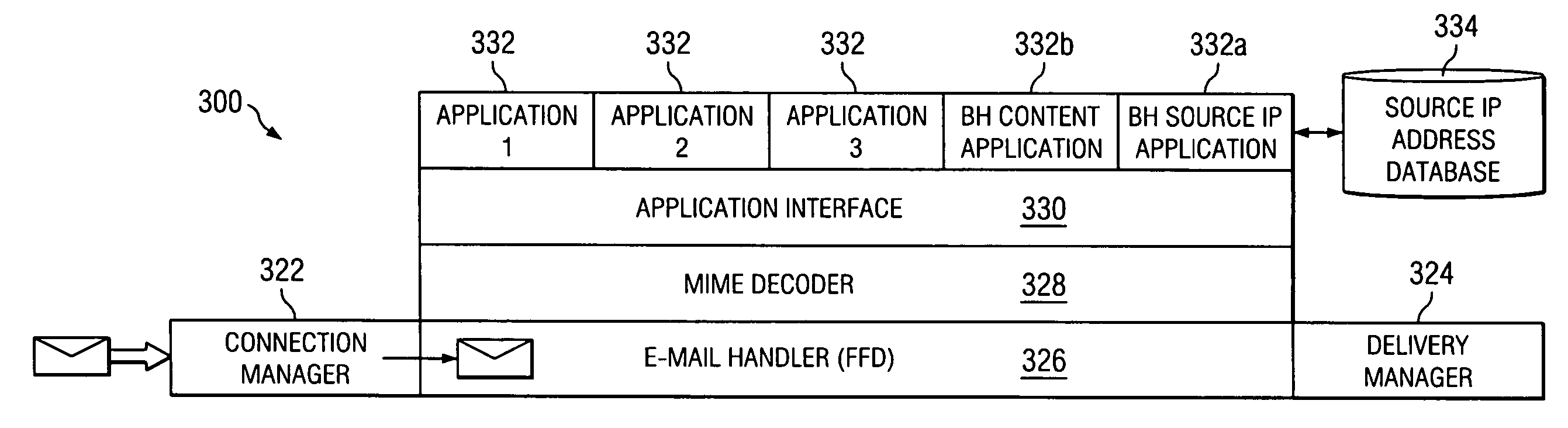
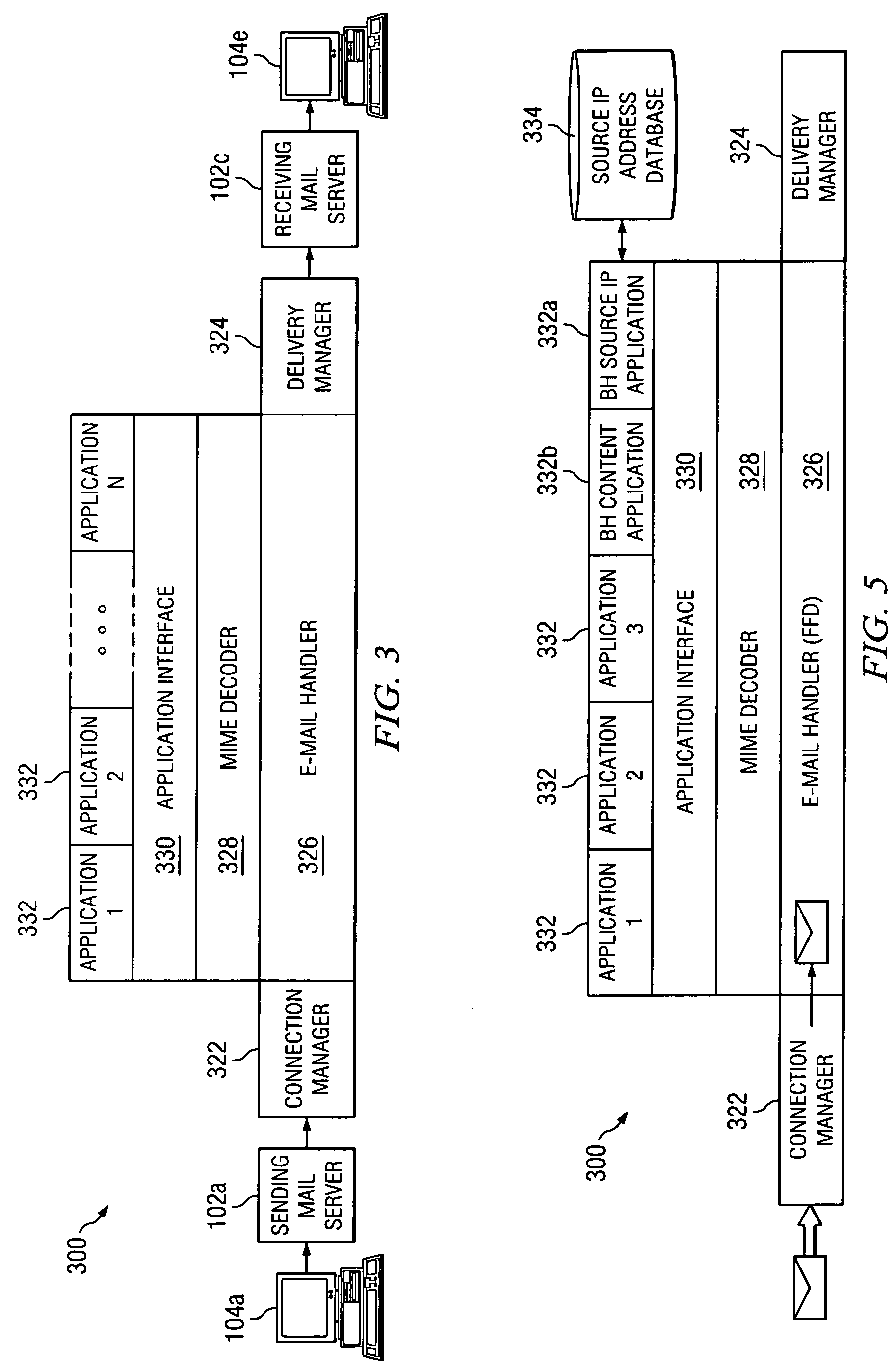
System and method for filtering electronic messages using business heuristics
Disclosed are systems and methods for use in filtering electronic messages using business heuristics. In one aspect, a method includes determining whether the electronic message is associated with a desirable business, and adjusting the likelihood of delivering the electronic message to an intended recipient of the message if the electronic message is determined to be associated with the desirable business. In a more specific embodiment, the method further includes assigning a spam-score to the electronic message based on a likelihood that the electronic message is not unwanted by the intended recipient, blocking delivery of the electronic message to the intended recipient when the spam-score does not cross an overall threshold, and delivering the electronic message to the intended recipient based on the adjusted likelihood when the electronic message is determined to be associated with the desirable business.
Owner:GOOGLE LLC
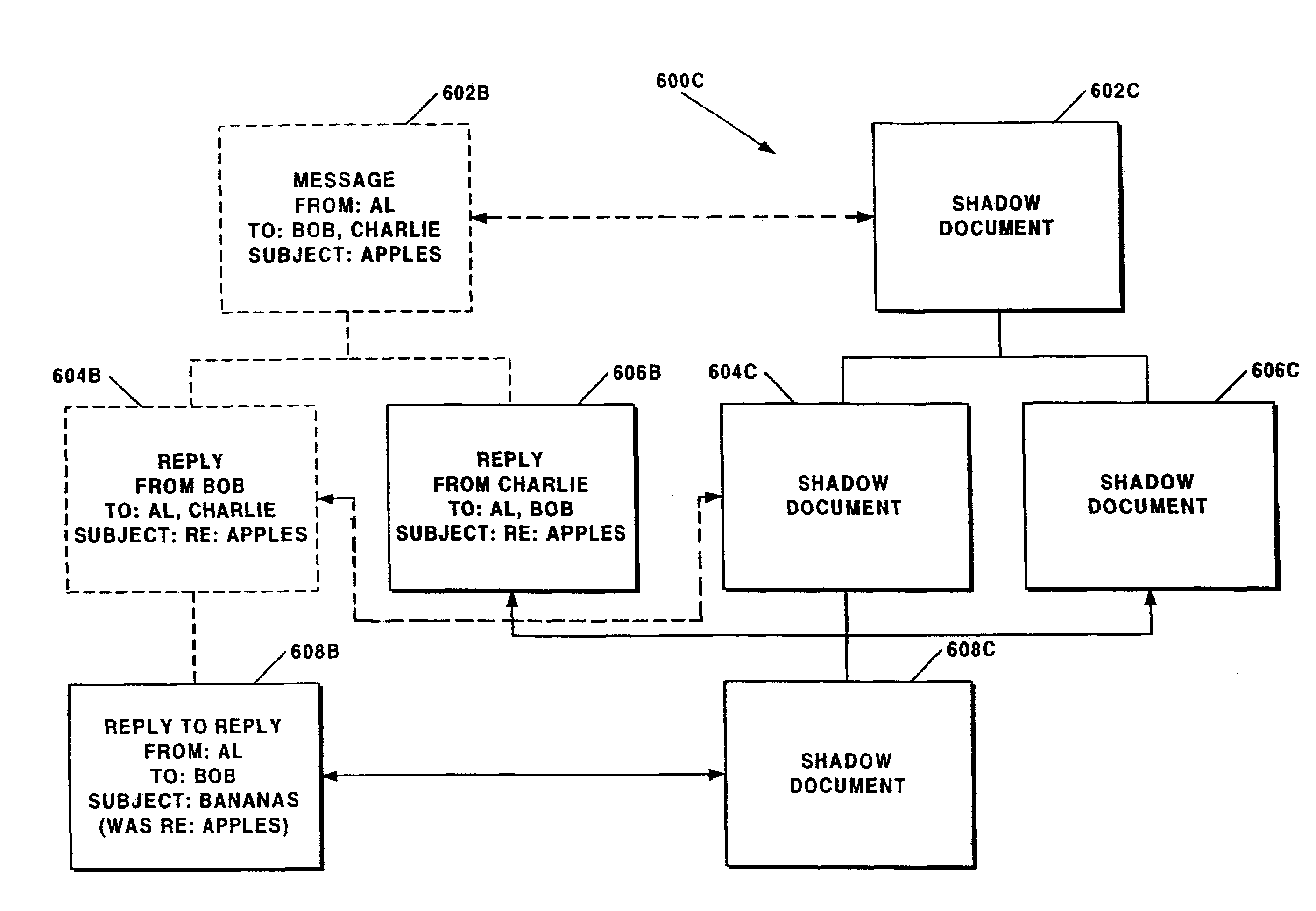
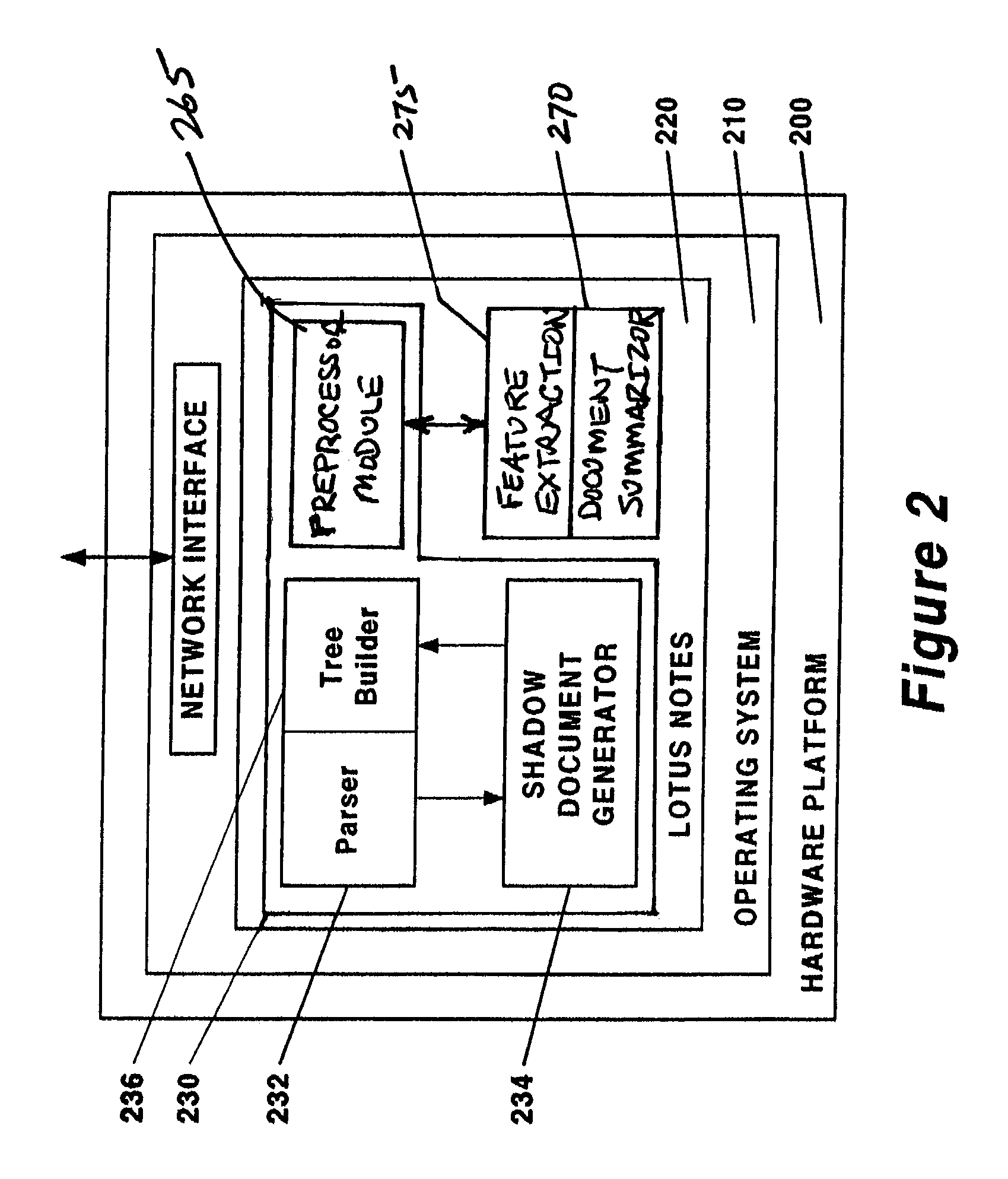
Method for summarization of threads in electronic mail
ActiveUS7392280B2Better summaryConvenience to workMultiple digital computer combinationsSpecial data processing applicationsDocument summarizationDocument preparation
The present invention discloses a pre-processing summarization technique that makes use of knowledge specific to the electronic mail domain to pre-process an electronic mail message so that commercially-available document summarization software can subsequently generate a more useful summary from the message. The summarization technique removes extraneous headers, quoted text, forward information, and electronic signatures, leaving more useful text to be summarized. If an enclosing electronic mail thread exists, the summarization technique uses the electronic mail message's ancestors to provide additional context for summarizing the electronic mail message. The disclosed system can be used with IBM Lotus Notes and Domino infrastructure, along with existing single-document summarizer software, to generate a summary of the discourse activity in an electronic mail thread dynamically. The summary may be further augmented to list any names, dates, and names of companies that are present in the electronic mail message being summarized.
Owner:META PLATFORMS INC
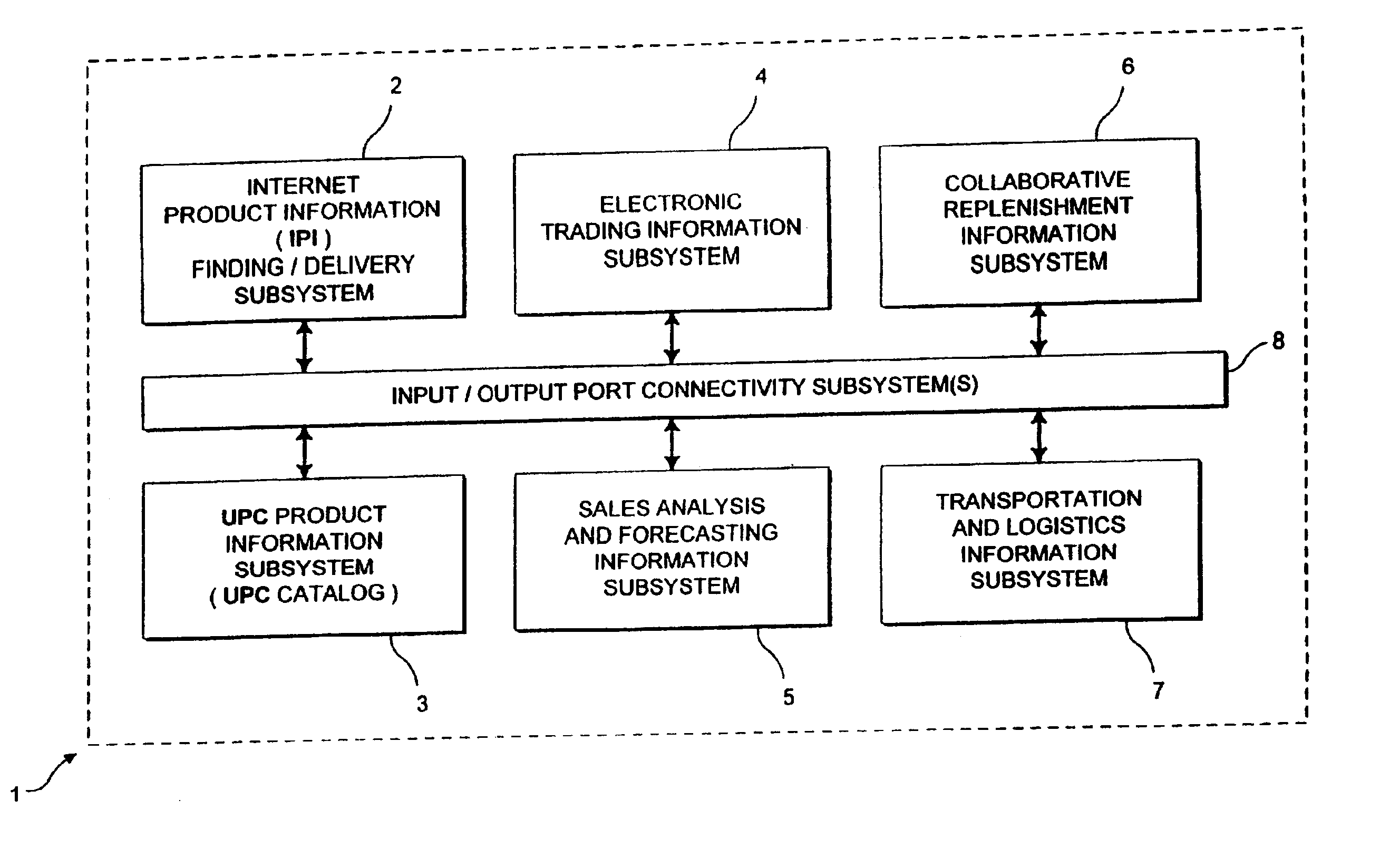
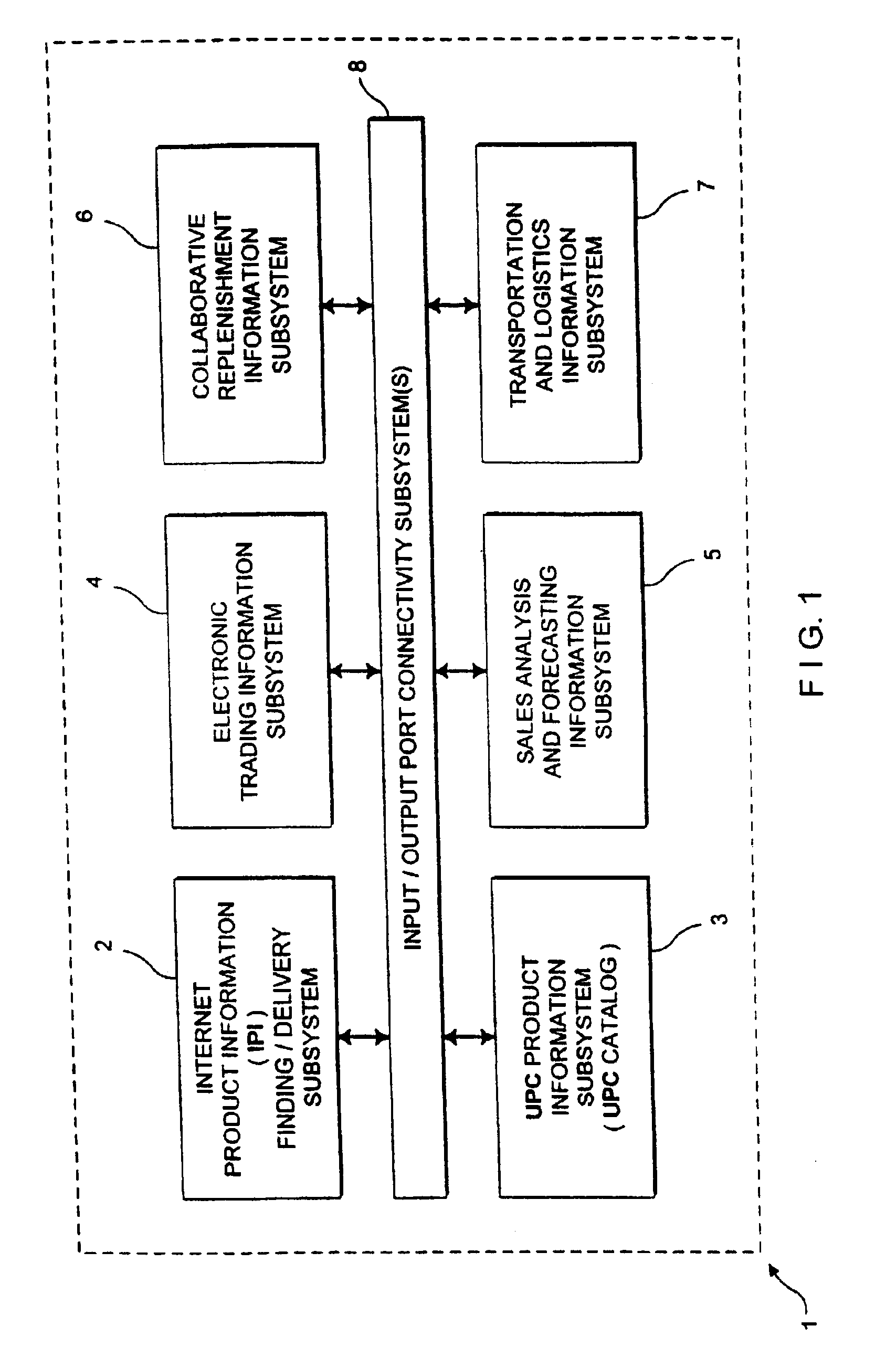
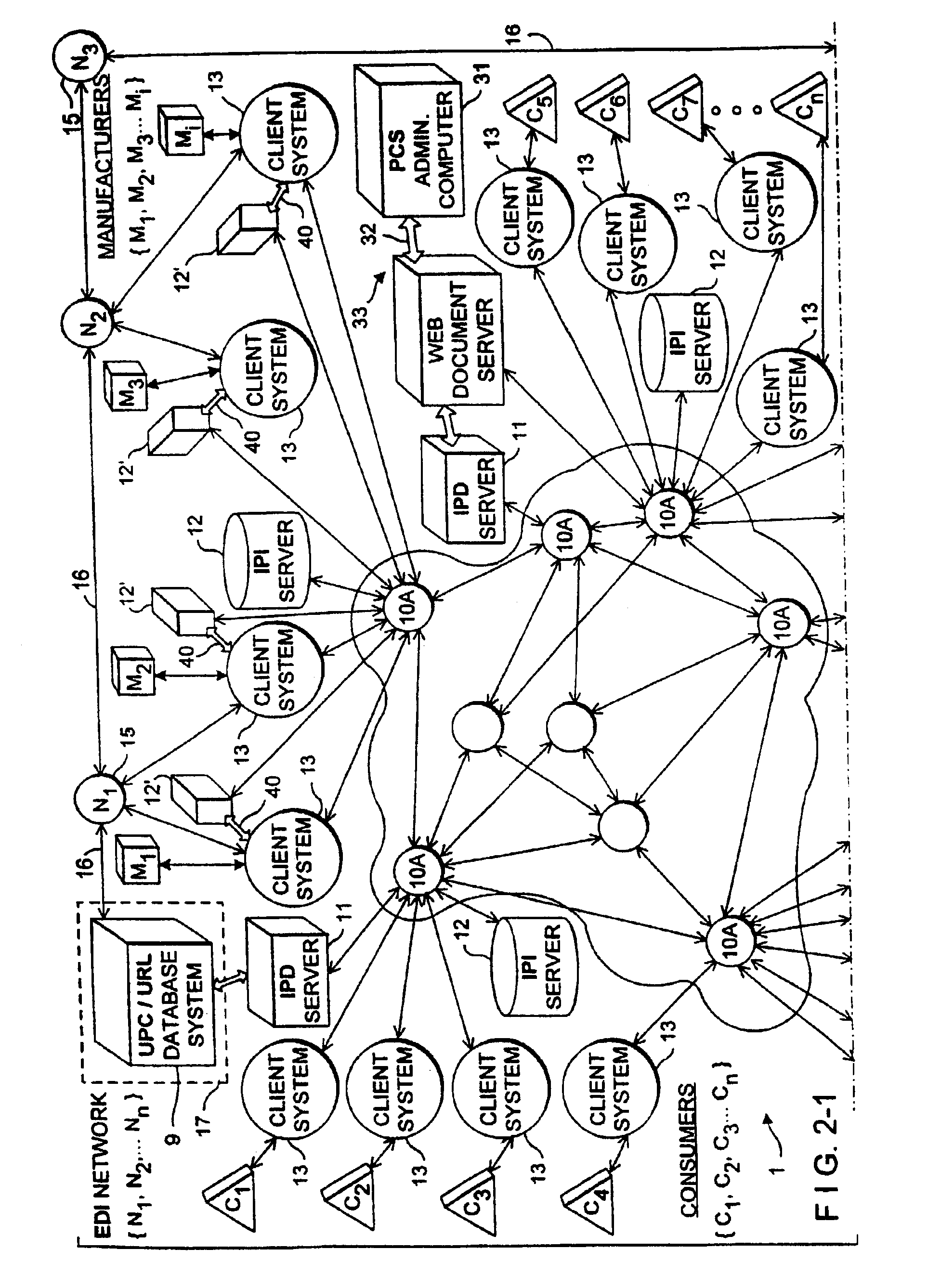
Internet-based method of and system for enabling communication of consumer product information between vendors and consumers in a stream of commerce, using vendor created and managed upn/tm/pd/url data links
InactiveUS6961713B2High acceptanceEasy to disassembleApparatus for meter-controlled dispensingBuying/selling/leasing transactionsGraphical user interfaceInternet privacy
An Internet-based method of and system for enabling communication of consumer product information between a vendor and a consumer in a stream of commerce. The Internet-enabled system comprises an Internet-enabled database server operably connected to the Internet, for storing a plurality of UPN / TM / PD / URL links for each consumer product registered with the Internet-enabled database server and offered for sale by the vendor in the stream of commerce. A first http-enabled information server enables the vendor and / or its agents to create and manage the UPN / TM / PD / URL links stored in the Internet-based information server. A second http-enabled information server publishes an HTML-encoded graphical user interface (GUI) which functions as a consumer product information (CPI) search screen. An http-enabled client enables the consumer to (i) access and display the published HTML-encoded GUI, and (ii) provide, as search keys, one or more UPN, TM and / or PD data elements to the Internet-enabled database server, by way of the published HTML-encoded GUI, and access and display a plurality of URLs associated with the entered UPN, TM and / or PD data elements. By virtue of the present invention, the consumer can access and display one or more displayed URLs on the Internet, and thereby enable communication of consumer product information between the vendor and the consumer in the stream of commerce using the vendor created and managed UPN / TM / PD / URL data links.
Owner:PERKOWSKI THOMAS J
Transaction system and methodology with inter-party communications capability
InactiveUS20050144121A1Maintain confidentialityAvoid the needFinanceAdvertisementsEmail addressComputer science
In a preferred embodiment of the present invention, although not necessarily limited thereto, the system of the present invention may function in the context of an internet based commercial real estate brokering system. In such a system, potential buyers, sellers, lessors and lessees list and respond to offerings having characteristics as described in connection with the listings. For example, a potential landlord may, through interaction with the system of the present invention, list one or more buildings for lease. Communication and interaction may occur on an anonymous basis such that the potential landlord is unaware of the actual identity of the prospective tenant and vice versa until such time as one or the other or both decide to reveal their identity. It is also possible to avoid the need to reveal any contact information associated with either party (including, for example, email addresses, phone numbers, addresses, etc.) until such time as a party wishes to disclose such information. Another aspect of the system of the present invention provides users of the transaction system as well as the operator thereof with the ability to conveniently and accurately track orders and renewals of listings. All that is necessary from the advertiser's point of view is to select and activate the “reply” button on, for example, the advertiser's email application screen. Once this is done, a reply email is sent to and received by the system of the present invention and, based upon the specific “reply to address”, the system processes the reply and carries out the automated billing process.
Owner:MAYO ANTHONY PAUL
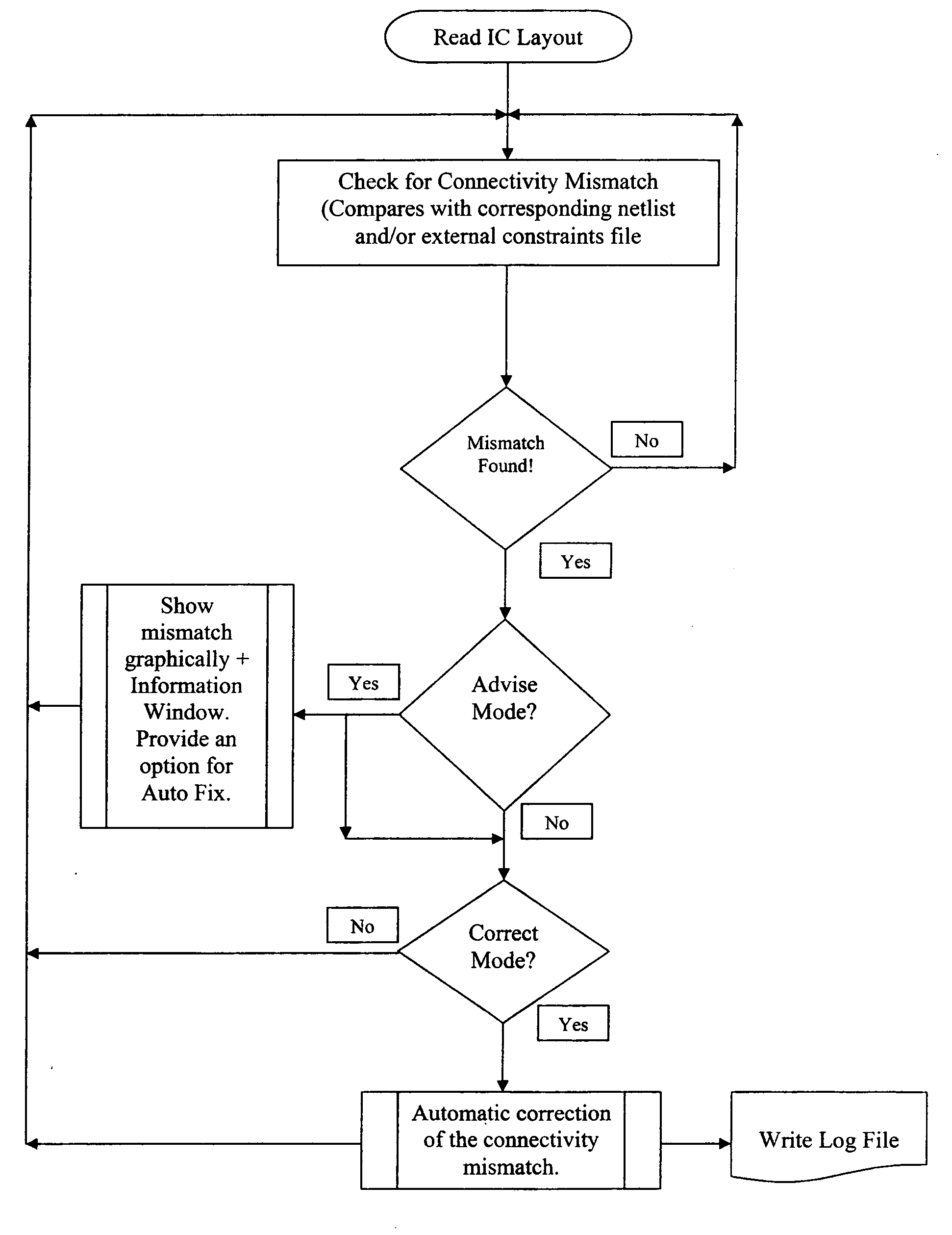
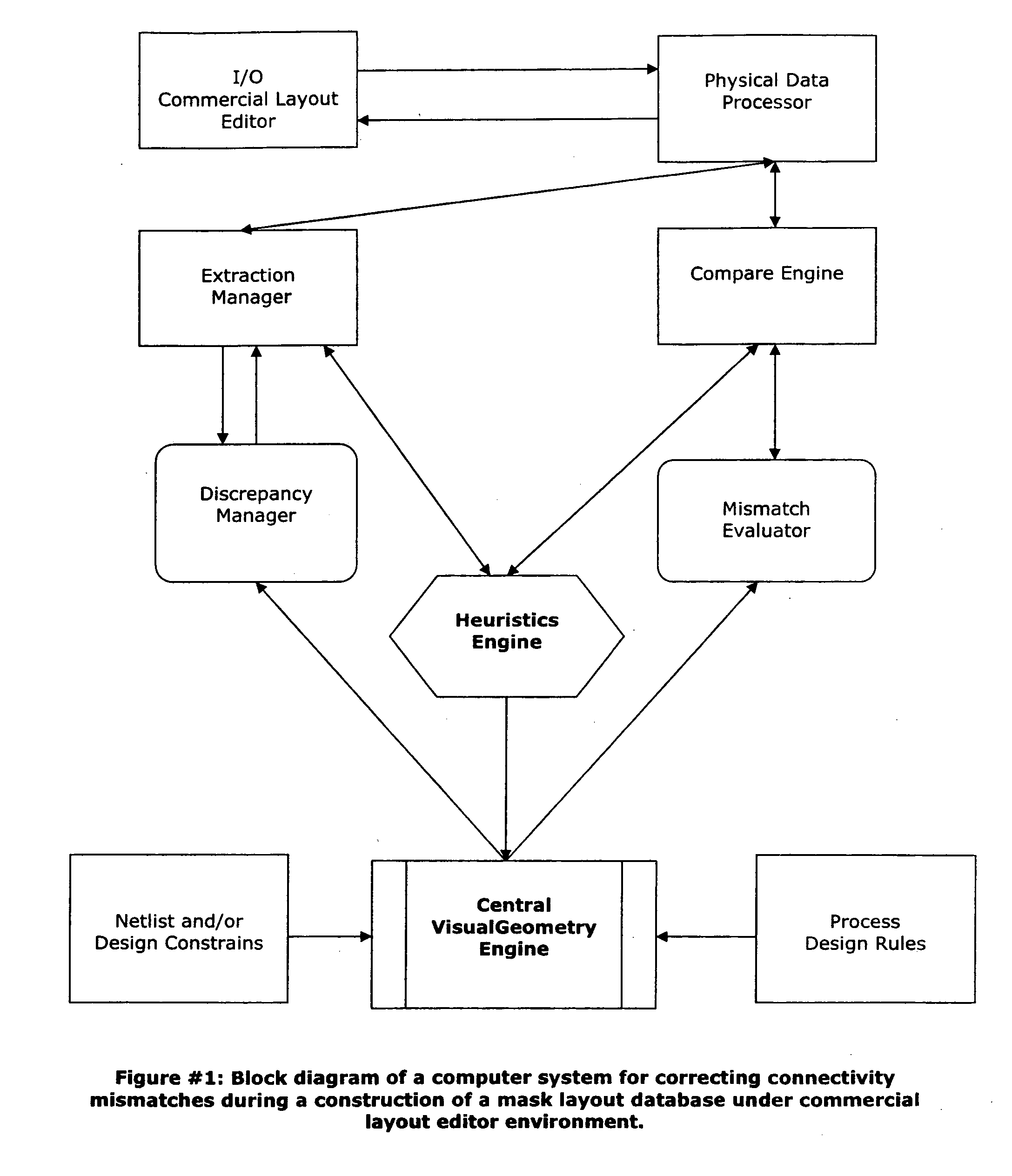
System and method for automatic elimination of connectivity mismatches during construction of a mask layout block, maintaining process design rule correctness
InactiveUS20080115102A1Eliminate the problemCorrecting connectivityCAD circuit designSpecial data processing applicationsGraphicsParallel computing
A system and method for automatic elimination of connectivity mismatches during construction of a mask layout block, maintaining the process design rules (DRC Clean) and layout connectivity (LVS Clean) correctness are disclosed. The method includes analyzing a selected polygon or net for connectivity, in a mask layout block and comparing it to a netlist that is associated with the polygon or net. The method includes comparing a physical connection in a mask layout database within a commercial layout editor to a corresponding connection in a schematic netlist and / or external constraints file. A connectivity mismatch is identified if the physical connection in the commercial layout editor database does not match the same connection in the netlist and / or external constraints file. When a mismatch is identified the connectivity error is graphically presented in the mask layout database within commercial layout editor. The method and system also provides an option to automatically correct the connectivity mismatch during the construction of the mask layout block within commercial layout editor using the editor's commands and functions.
Owner:MICROLOGIC DESIGN AUTOMATION
Descriptive-profile mercantile method
A descriptive-profile mercantile method, for use at a juncture in a data-communications topology having associated therewith a maintained databank of partial profiles, is disclosed. The method includes the steps of: from a user, receiving a transaction having therein a first partial profile; using the first partial profile, searching a databank having a plurality of second partial profiles, wherein is included in said databank at least one null profile so that said searching will always yield at least one proximate second partial profile to the first partial profile; and between the user and the databank, contracting: (I) for the databank to own or represent a right to a first mutually agreed portion of the first partial profile, and substantially thereafter said databank incorporating the agreed portion of the first profile into at least one second partial profile; or (II) for the user to own or represent a right to a second mutually agreed portion of at least one said proximate second partial profile, and substantially thereafter the databank transmitting to the user the second mutually agreed portion of the second profile. The present invention operates best on a brokerage representation model; and thereby provides a means for making viable the economic commerce in information attributes.
Owner:ALMONDNET
Method and device for hiding information based on word2007 text segmentation
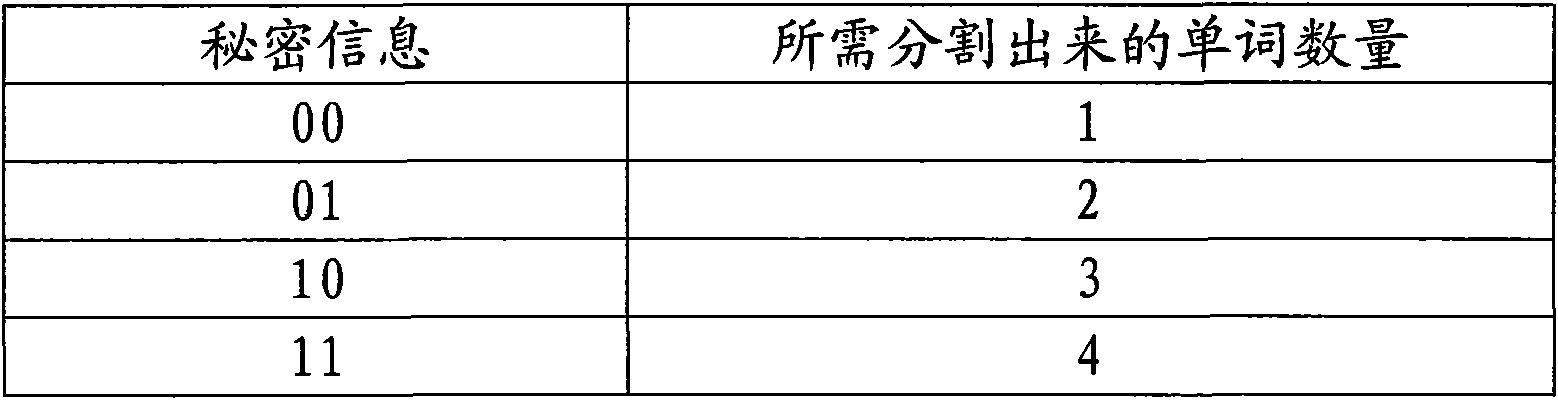
InactiveCN102096787AWill not affect the displayStrong concealmentDigital data protectionSpecial data processing applicationsExtensible markupMicrosoft Office
The invention relates to a method and a device for hiding information based on word2007 text segmentation. An Office Open extensible markup language (XML) file format is a new file format which is adopted by Microsoft office 2007 and later versions thereof. In the method for hiding secret information, the secret information is converted into a numerical value so as to be embedded into run number of each paragraph according to the coding requirement of the secret information to be transmitted based on the paragraph serving as a unit by segmenting the number of run elements in each paragraph. Meanwhile, the robustness of the hiding method is improved by adding robust marks into the segmented run elements. The extraction process of the secret information is a reverse embedding process. In the method, any displayed content of an electronic document is not changed; the method has extremely strong concealment; the robustness of hidden information is enhanced by adding the robust marks; and the method can be applied to hidden transmission of confidential information such as national defense, politics, commerce and the like.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
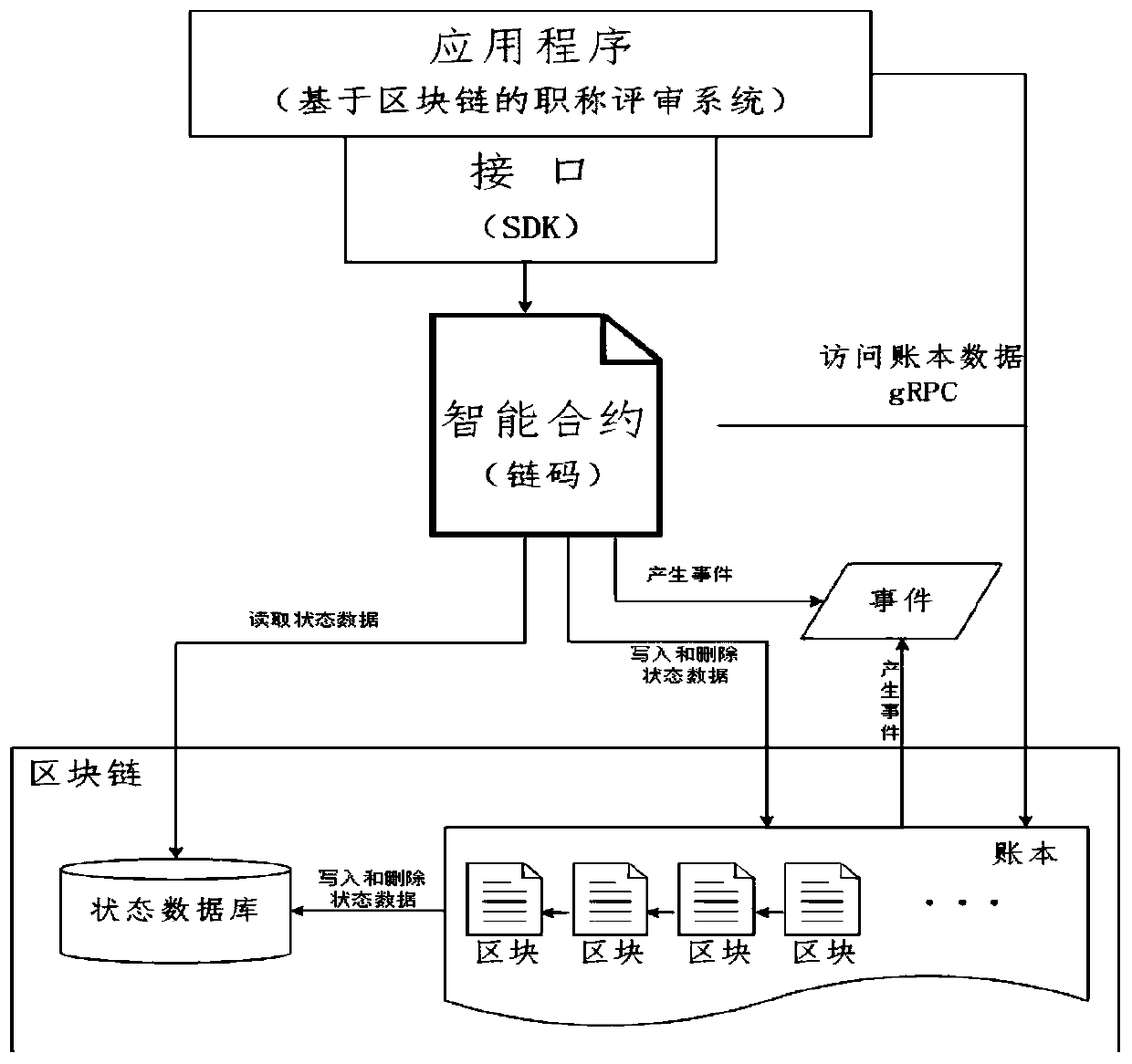
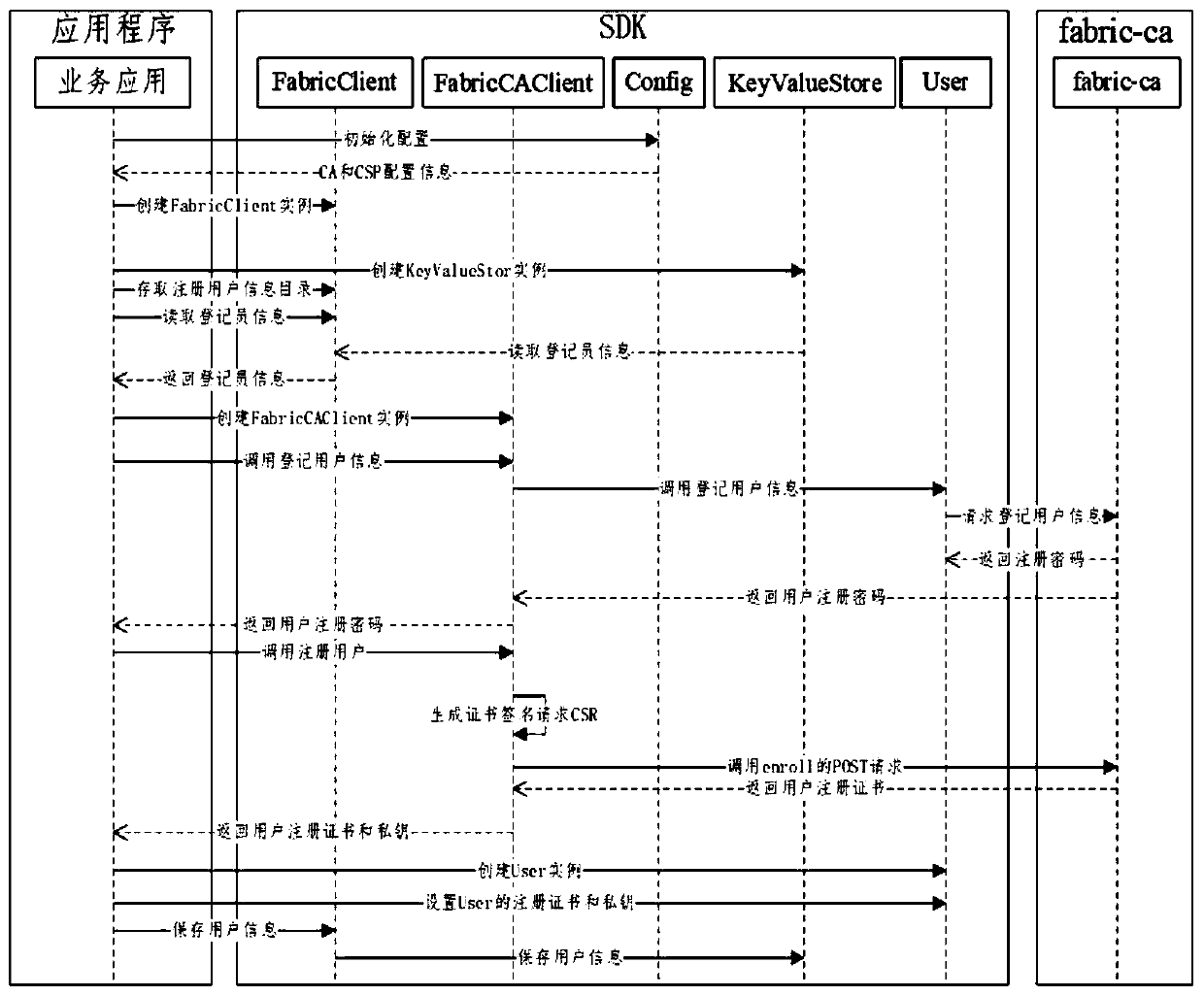
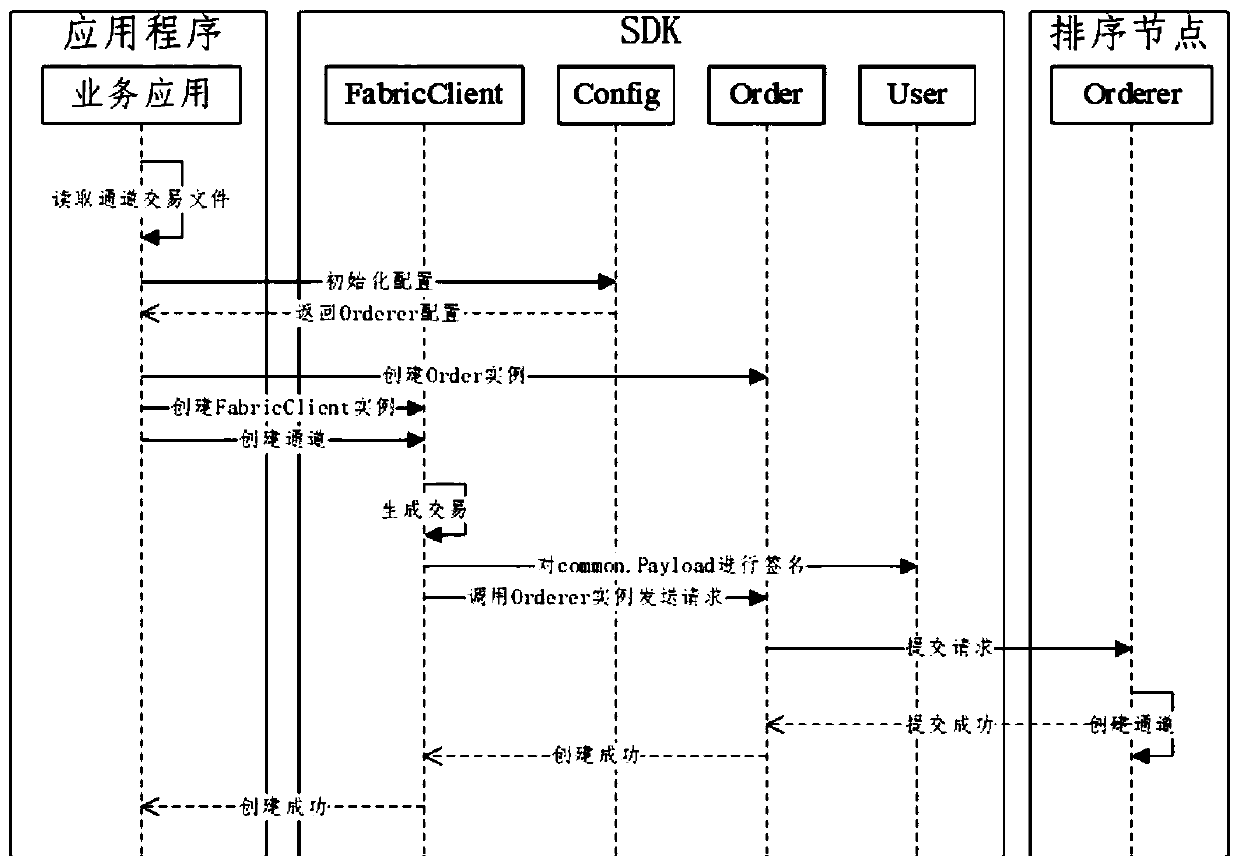
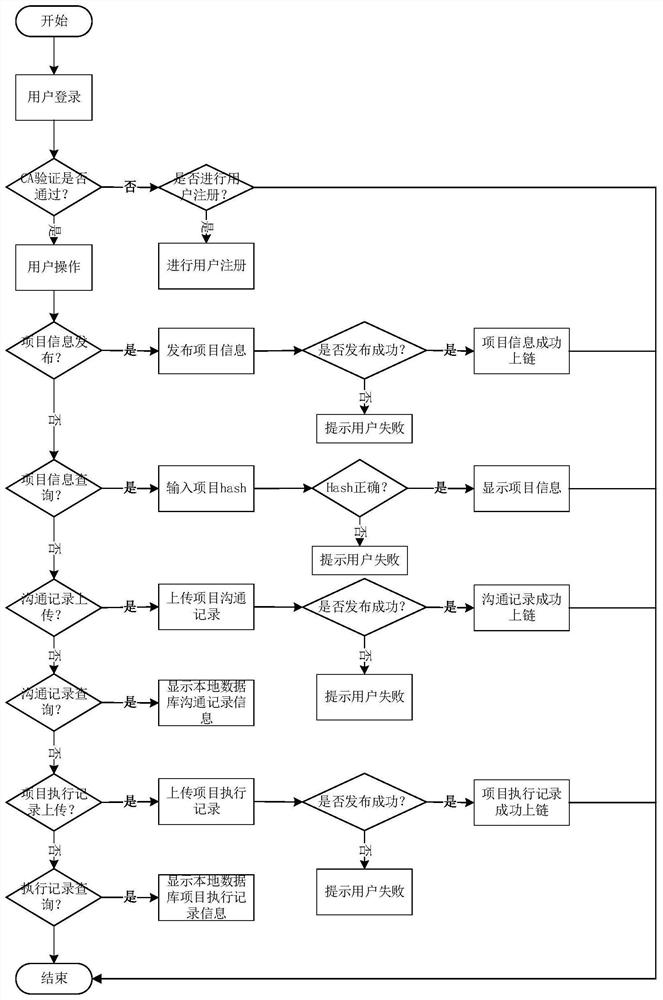
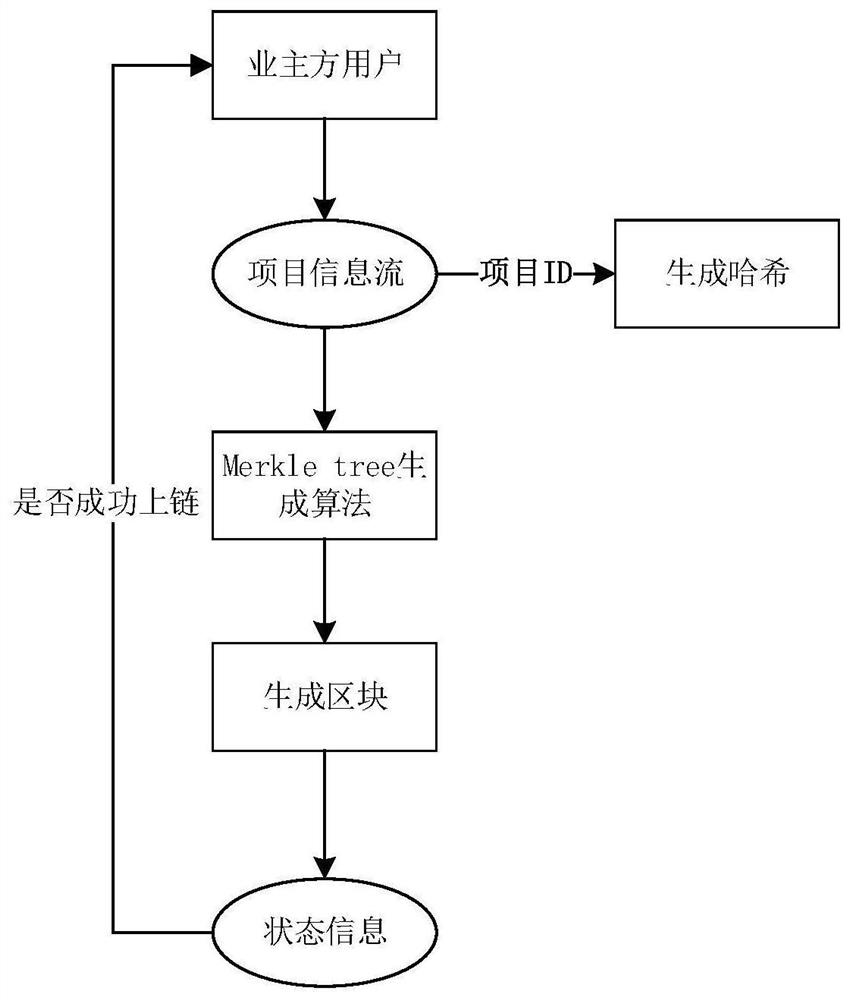
Professional title evaluation method and system based on blockchain
PendingCN111476548ASolve the centralized storage of dataSolve human interference in the review processDigital data protectionOffice automationEvaluation resultData set
The invention discloses a professional title evaluation method and a professional title evaluation system based on a blockchain. The professional title evaluation method comprises the steps of: generating a block for received professional title evaluation data, and storing the block into a blockchain network according to a sorting service; accessing an evaluation node according to evaluation authority, and sequentially evaluating the professional title evaluation data by calling an intelligent contract; and encrypting the evaluation result, and broadcasting the encrypted evaluation result to the blockchain network. The problems of centralized data storage, human intervention in the evaluation process, lack of impartiality of publicity information and the like of an existing commercial professional title evaluation system are solved. On the basis of a decentralized blockchain platform, blocks are generated for received professional title evaluation data, and the professional title evaluation data is evaluated in sequence by calling the intelligent contract, so that decentralization is realized, the evaluation process is traceable, the data cannot be tampered, and publicity is credible.
Owner:SHANDONG NORMAL UNIV
Method and system for managing interactive communications campaigns
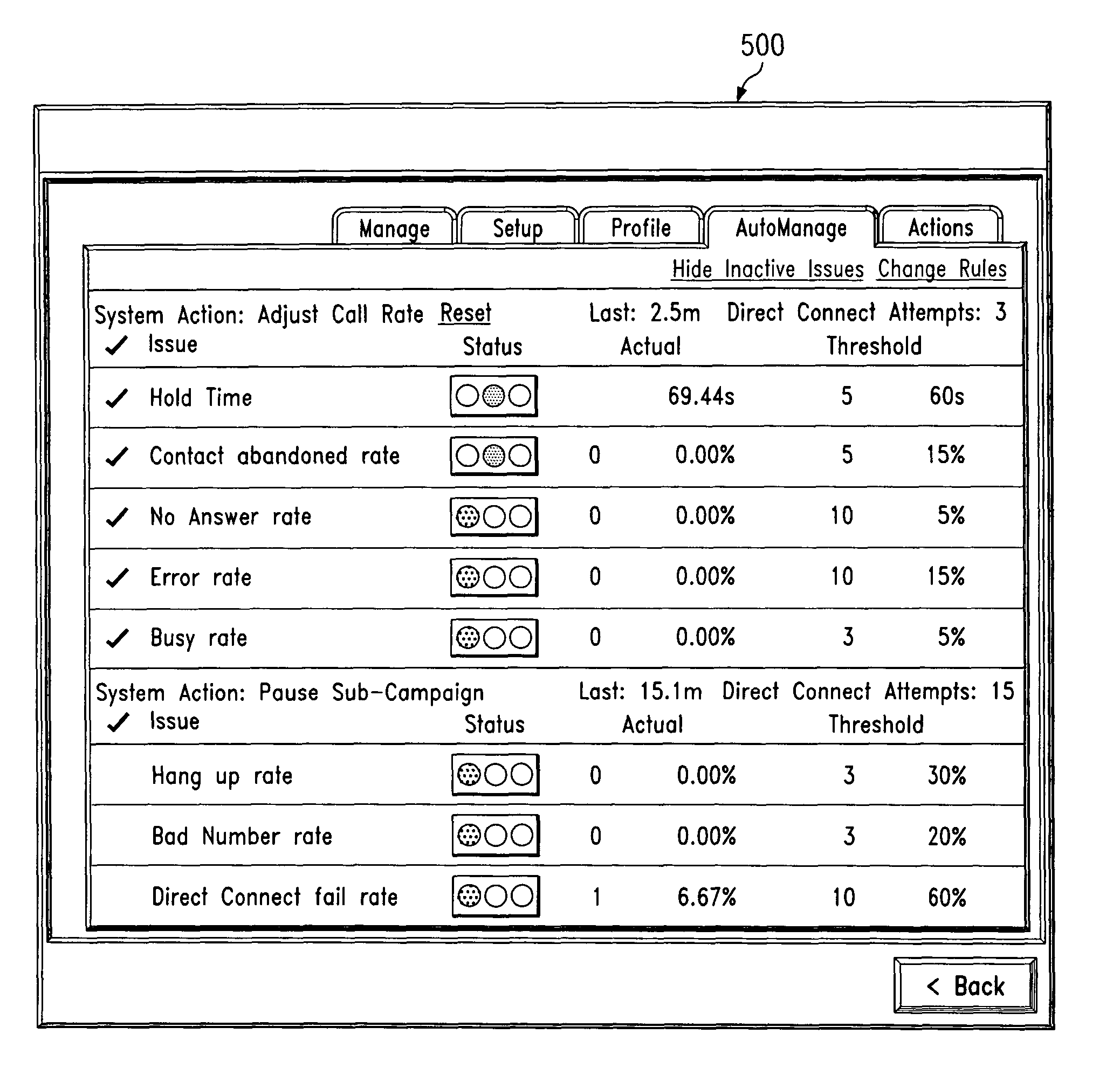
A web-based hosted solution through which business entities create and manage communications campaigns, such as interactive campaigns that afford target recipients an opportunity to be connected to a third party call center. A web interface is provided to enable a business entity customer to create a set of one or more rules that, when triggered during the campaign, cause the hosted solution to take certain control actions in real-time, based on campaign performance. Preferably, this “campaign performance” is measured indirectly, i.e. without requiring a direct connection to an on-premises call center ACD. Rather, preferably all information about the call center's performance during the campaign is derived from information (gathered by the hosted solution) about calls delivered, or attempted to be delivered, to the call center. In effect, the call center performance is inferred, and this performance is then exposed to the business entity customer through a web-based interface. In particular, the interface provides the business entity customer with a convenient and easy-to-use display that identifies any rule that has been (or may be getting ready to be) triggered, together with a then current status of the campaign. The system is programmed to take a given control action (e.g., campaign suspension, adjusting an outbound call rate, or the like) when a customer-configurable rule is triggered.
Owner:GENESYS TELECOMMUNICATIONS LABORATORIES INC
Remote intelligent three-dimensional digital early warning method and system for subgrade surface settlement
ActiveCN102829759AImprove driving safetyImprove traffic safetyTransmission systemsHeight/levelling measurementSoftware systemSMARAD
According to the invention,a subgrade surface settlement value model is established according to subgrage design parameters and construction filling record data by using the FLAC three-dimensional technology; and is based on a three-dimensional visualized safety early warning platform established by a VTK business software system; the invention is characterized in that a real time monitoring data of subgrade surface settlement is collected through a hydrostatic level arranged on the subgrade, and the real time monitoring data is transmitted to an user remote computer, the actual measured deformation value of the subgrade surface settlement obtained by the subgrade settlement value model is compared with the subgrade settlement threshold value and then an analysis is carried out, the graded prealarming is carried out on the stability of the subgrade surface settlement, and is displayed through the three-dimensional visualized safety early warning platform, and all the early warning information is send to a cellphone of relative management staff by a short message mode through a short message module connected to the computer, and the remote intelligent three-dimensional digital early warning for the subgrade surface settlement can be completed. The prevention measurements can be timely adopted according to the early warning information by the relative management staff in the railway and road departments; and the driving and traffic security can be enhanced.
Owner:CHINA RAILWAY 21TH BUREAU GROUP
Systems and methods to capture prioritize and visualize tacit and collective knowledge of business strategies
The invention relates to a method and system for including tacit and collective information on the strategic value of new business opportunities and corporate decisions, which can be added to firmware, software or other instructions that can be processed in a computer and / or stored in a computer-readable medium. Said addition can include code which can be executed in a web-based application which, when executed on a business intelligence or customer relationship management system, makes a data-processing device provide a graphical representation of the reported value of new business opportunities and corporate decisions. The graphic representation can include a plurality of fields which are grouped together in a bubble chart with prioritization criteria. The invention provides a method for capturing statistical data regarding tacit knowledge of the business strategy and decisions in an organization by means of a business intelligence (BI) or customer relationship management (CRM) system over the internet.
Owner:ELECTRONICSOSONLINE COM S A DE
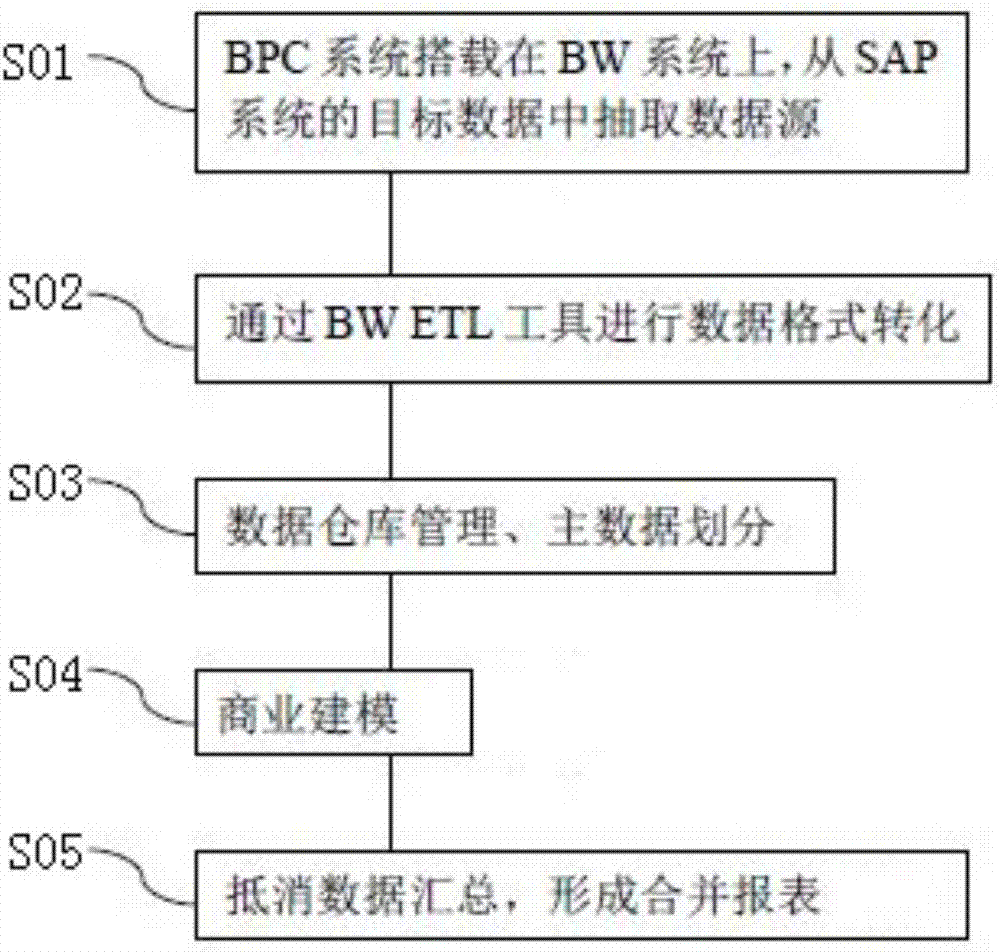
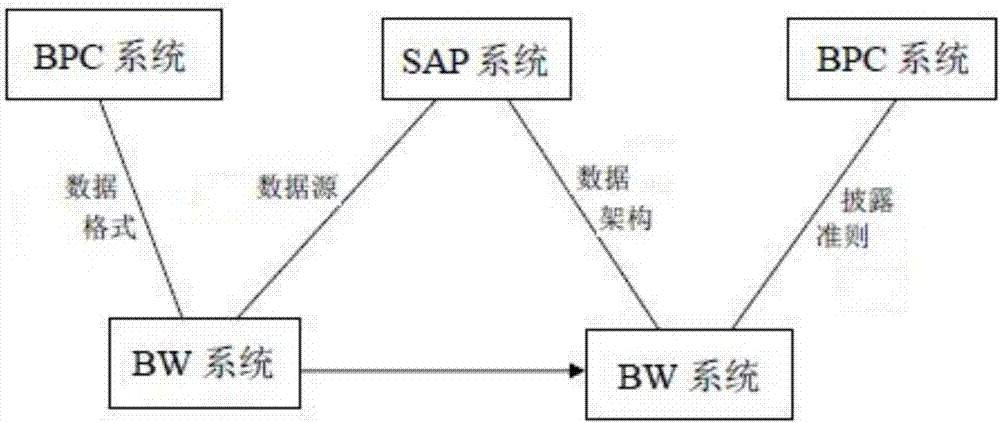
SAP and BPC data exchange method and system
InactiveCN107153992AEasy to handleEasy data collectionFinanceSpecial data processing applicationsData warehouseData source
The invention discloses an SAP and BPC data exchange method, and the method comprises the steps: enabling a BPC system to be installed on a BW system, building a BPC merging system on a BW multi-dimensional data model, and employing a BW ETL tool and an SAP commercial suite for data exchange. The invention also discloses an SAP and BPC data exchange system corresponding to the method, and the system comprises a data source storage module, a data conversion module, a data warehouse management module, a commercial modeling module, and a merging processing control monitor. The method and system are advantageous in that the method and system greatly optimize a data collection process of a consolidated statement system, meet the demands of dual-rule checking and statement revealing brought by different operation modes of the SAP system and a non-SAP system, optimize the processing of data reclassification of dual-rule statement data, optimize the maintenance process of main data, and enable the data analysis process to be more flexible.
Owner:上海世茂物联网科技有限公司
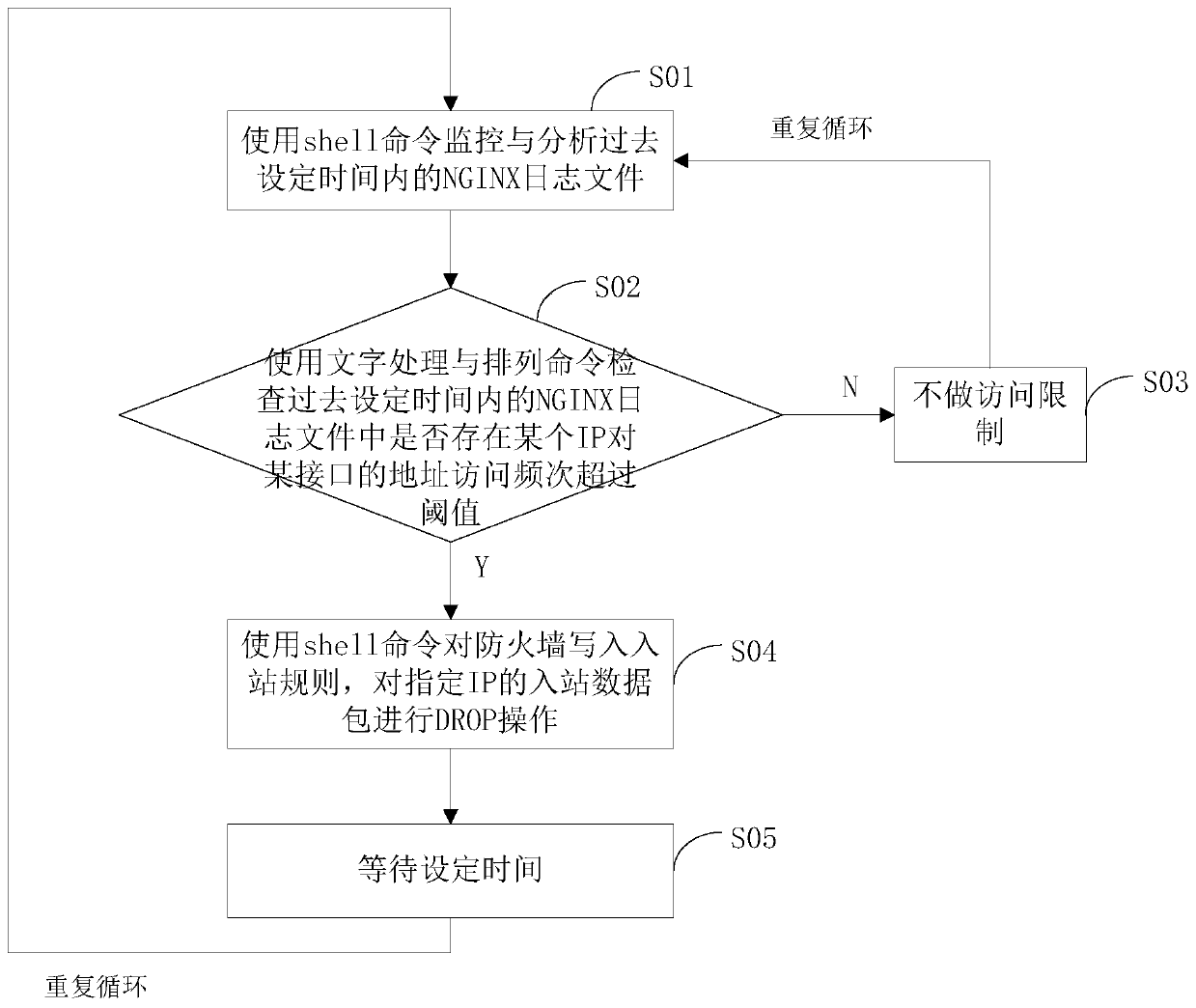
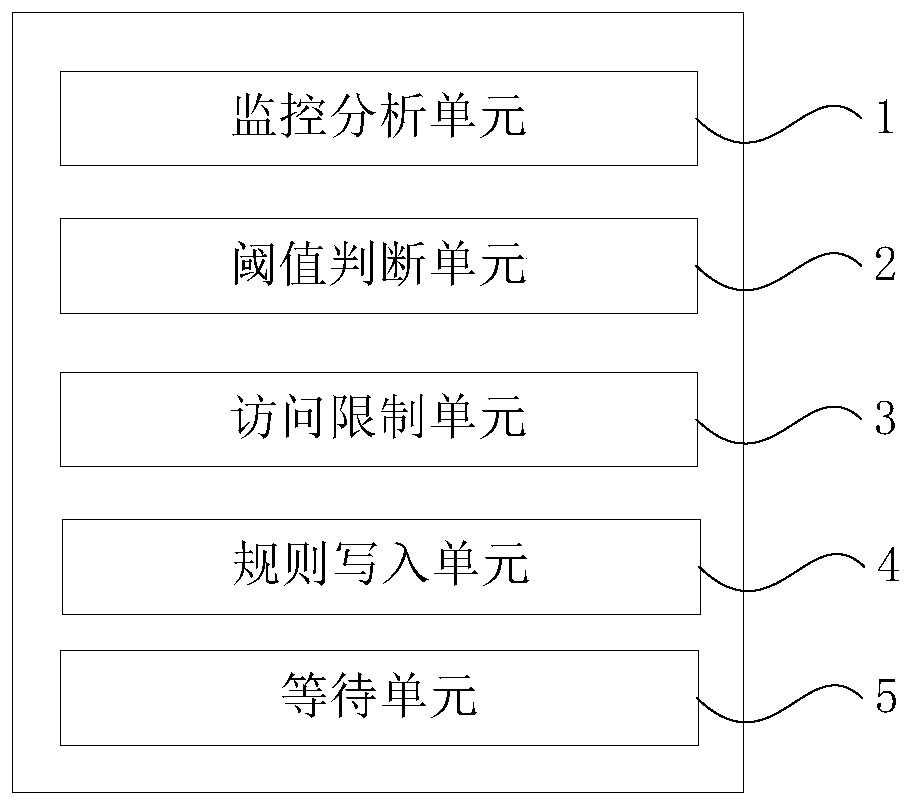
Malicious network CC attack prevention method and device
InactiveCN110401664ASolve the irresistible shortcomingsAvoid the tediousness of adding rules manuallyData switching networksNetwork packetAccess frequency
The invention discloses a malicious network CC attack prevention method and device. The method comprises the following steps: A) monitoring and analyzing an NGINX log file in past set time by using ashell command; B) checking whether the access frequency of a certain IP to an address of a certain interface exceeds a threshold value or not in the NGINX log file in the past set time by using a textprocessing and arrangement command, and if so, executing the step D); otherwise, executing the step C); C) not realizing access limit, returning to the step B); D) writing an inbound rule into the firewall by using the shell command, and performing DROP operation on the inbound data packet of the specified IP; E) waiting for a set time, and returning to the step A. The method can solve the problem that a traditional firewall is difficult to resist CC attacks, can also avoid the tedious operation of manually and repeatedly adding rules, can transparently present a working principle of a completely self-compiled script, can also be customized at will according to needs, and does not need to buy commercial protection services at a high price at the same time.
Owner:广东分利宝金服科技有限公司
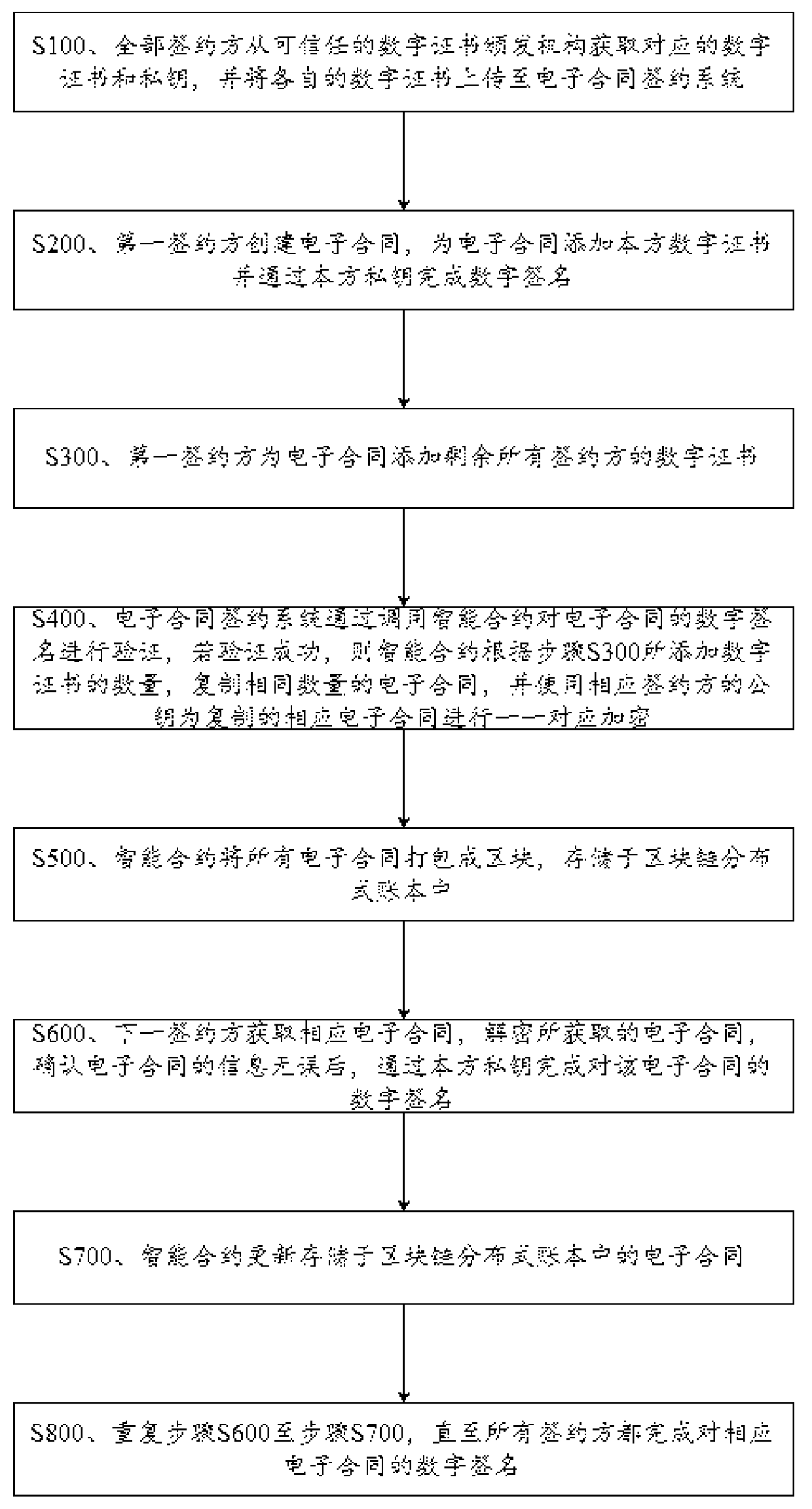
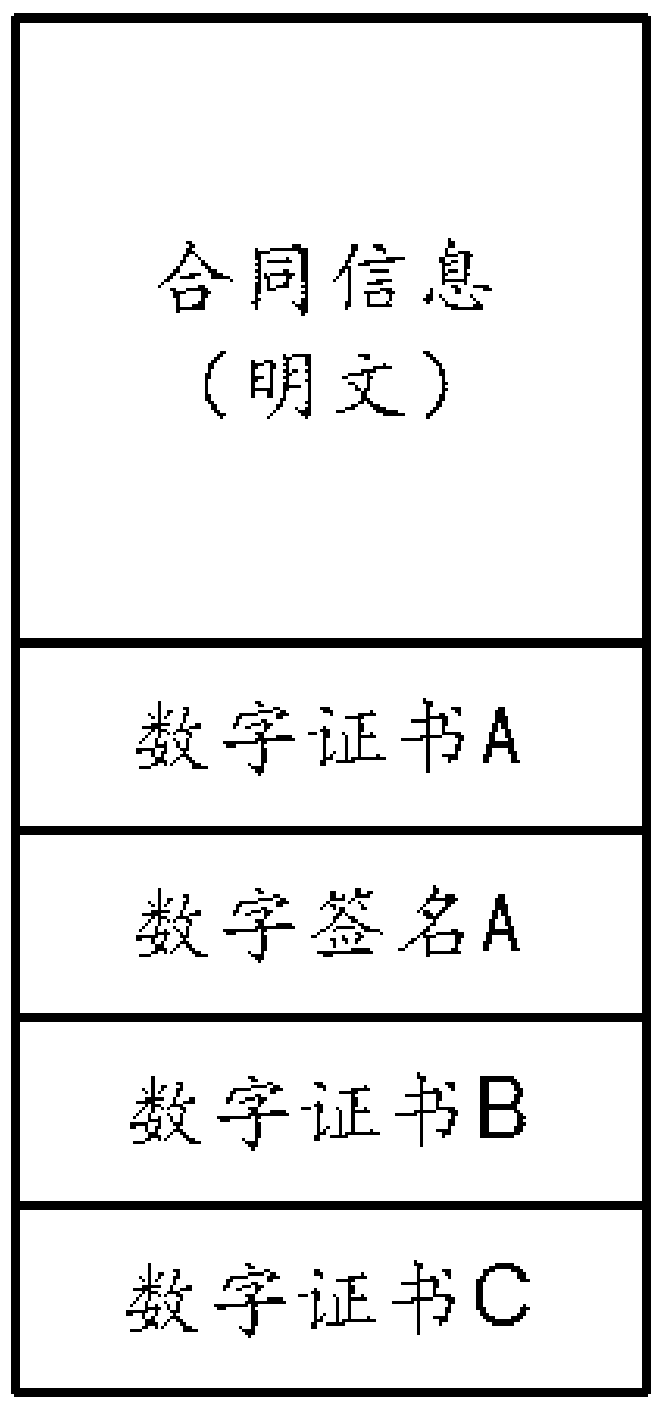
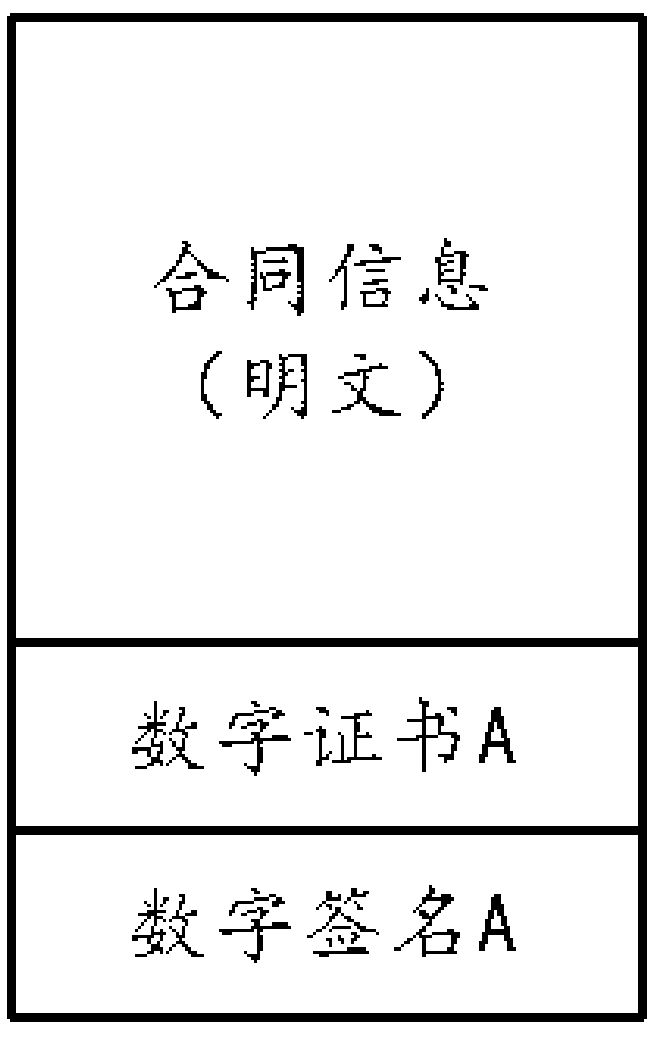
Signing method and equipment for realizing encrypted electronic contract based on blockchain intelligent contract
PendingCN112307125AGuaranteed confidentialityEnsure objectivityDatabase updatingFinanceElectronic contractsDigital signature
The invention discloses a signing method and equipment for realizing an encrypted electronic contract based on a blockchain intelligent contract. The signing method comprises the following steps: uploading a digital certificate to an electronic contract signing system by a signing party; creating a target electronic contract and performing digital signature by a first signing party; adding digitalcertificates of other signing parties to the target electronic contract by the first signing party; verifying the digital signature of the first signing party by an intelligent contract; enabling theintelligent contract to encrypt the target electronic contract; and letting other signing parties to complete digital signatures. The electronic contract is stored in a distributed account book through a decentralized block chain technology, the intelligent contract is used for processing the electronic contract, it is ensured that rules are transparent, dark box operation is effectively prevented, the asymmetric encryption technology is ingeniously used for encrypting the contract, all other people except the contract signing party cannot check contract information, and undesirable phenomenalike commercial confidential leakage are avoided. In conclusion, the method effectively ensures the confidentiality, objectivity, legality and authenticity of the contract.
Owner:湖南慧途科技有限公司
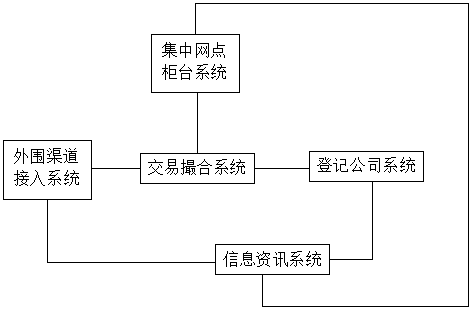
OTC network transaction system
The invention discloses an OTC network transaction system. The OTC network transaction system comprises a transaction matching system, a company registering system, a network counter concentrating system, a plurality of peripheral channel access systems and an information system. Material submission and audit between an enterprise and an exchange are finished through a network, an objection is raised in time for submitted problematical files or submitted unqualified files, enterprise personnel can effectively correct the files through the network in time, workers can finish related operation just by sitting before computers, the enterprise personnel do not need to repeatedly travel to and fro between the enterprise and the exchange, the time of the workers of the enterprise is greatly saved, a great number of materials are not combed manually any more, and the workload of the workers is greatly reduced to a certain extent; the system is simple in overall structure, convenient to operate and capable of effectively achieving efficient, fast and convenient transactions and meets the requirement of modern commercial transactions developing at a high speed.
Owner:TSINGHUA SWIFT BEIJING INVESTMENT MANAGEMENT CO LTD
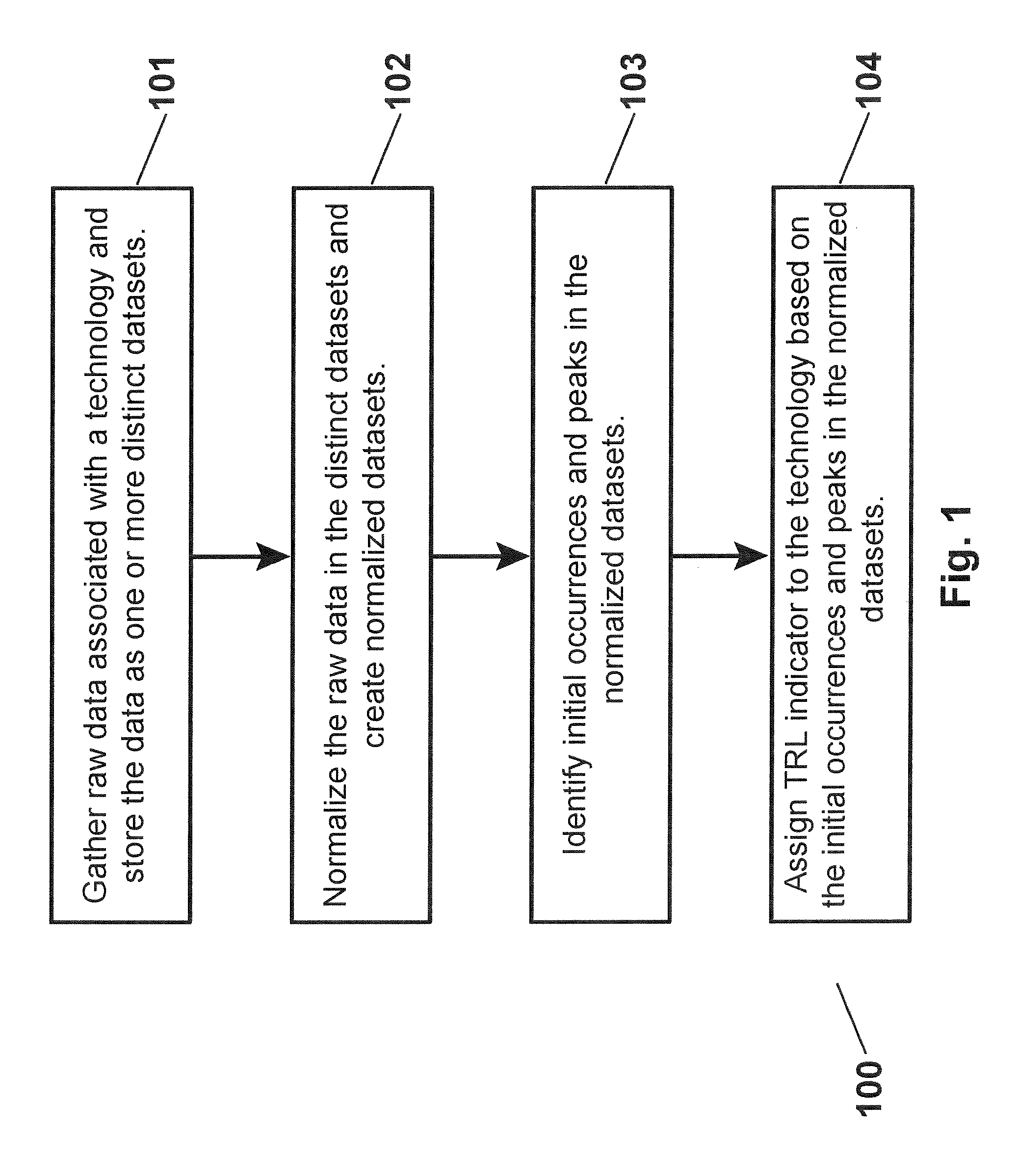
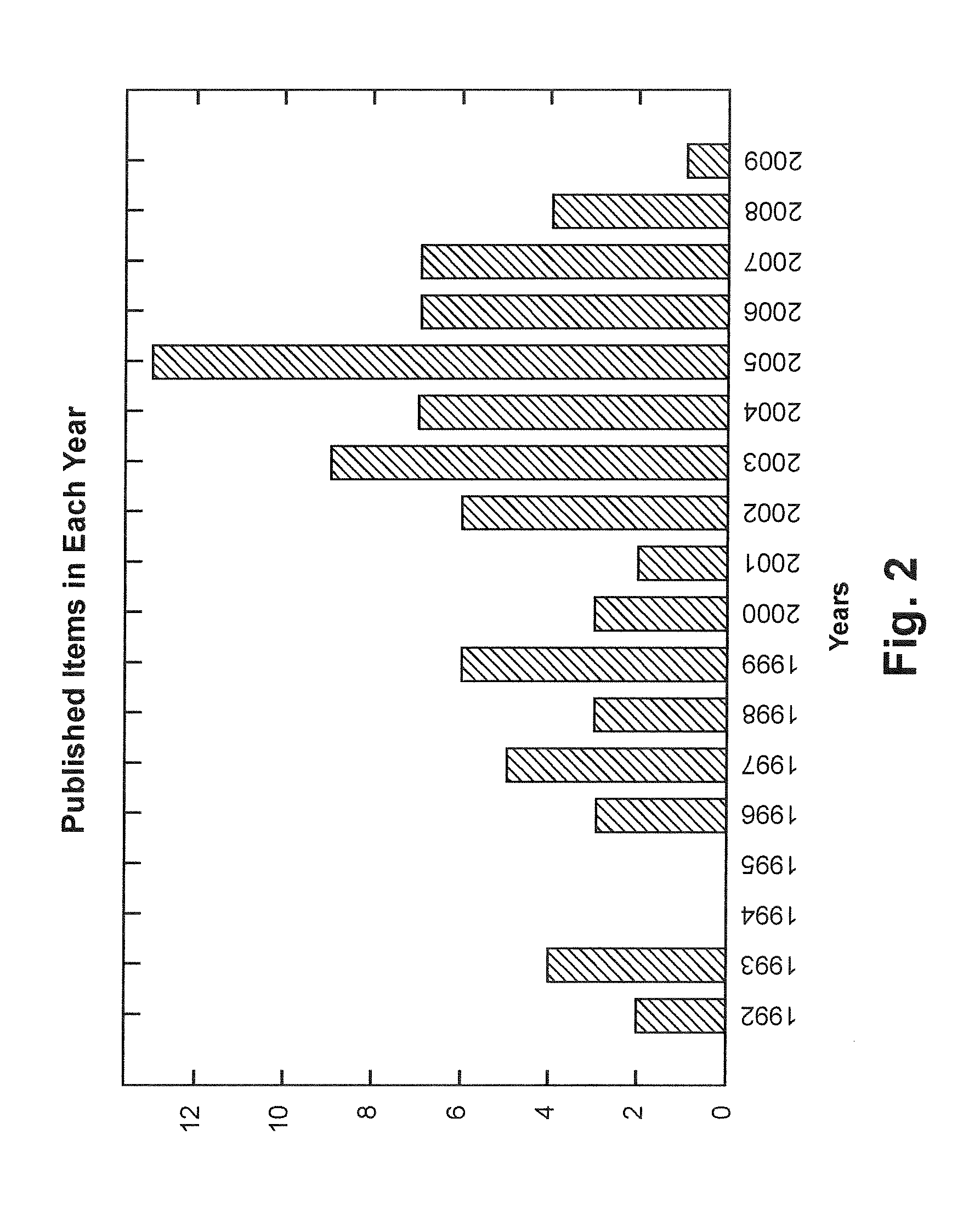
Scientometric methods for identifying emerging technologies
Provided is a method of generating a scientometric model that tracks the emergence of an identified technology from initial discovery (via original scientific and conference literature), through critical discoveries (via original scientific, conference literature and patents), transitioning through Technology Readiness Levels (TRLs) and ultimately on to commercial application. During the period of innovation and technology transfer, the impact of scholarly works, patents and on-line web news sources are identified. As trends develop, currency of citations, collaboration indicators, and on-line news patterns are identified. The combinations of four distinct and separate searchable on-line networked sources (i.e., scholarly publications and citation, worldwide patents, news archives, and on-line mapping networks) are assembled to become one collective network (a dataset for analysis of relations). This established network becomes the basis from which to quickly analyze the temporal flow of activity (searchable events) for the example subject domain.
Owner:UT BATTELLE LLC
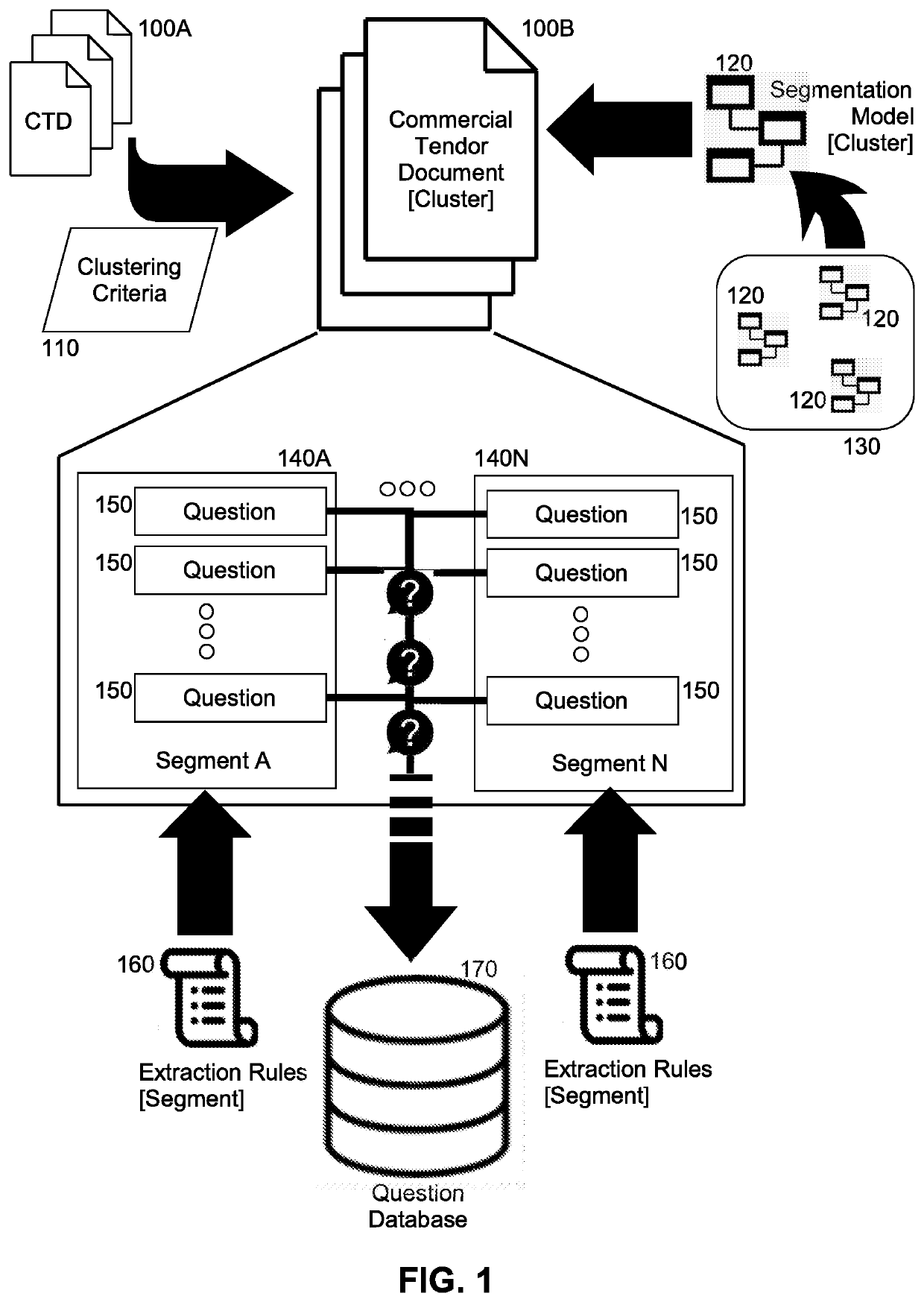
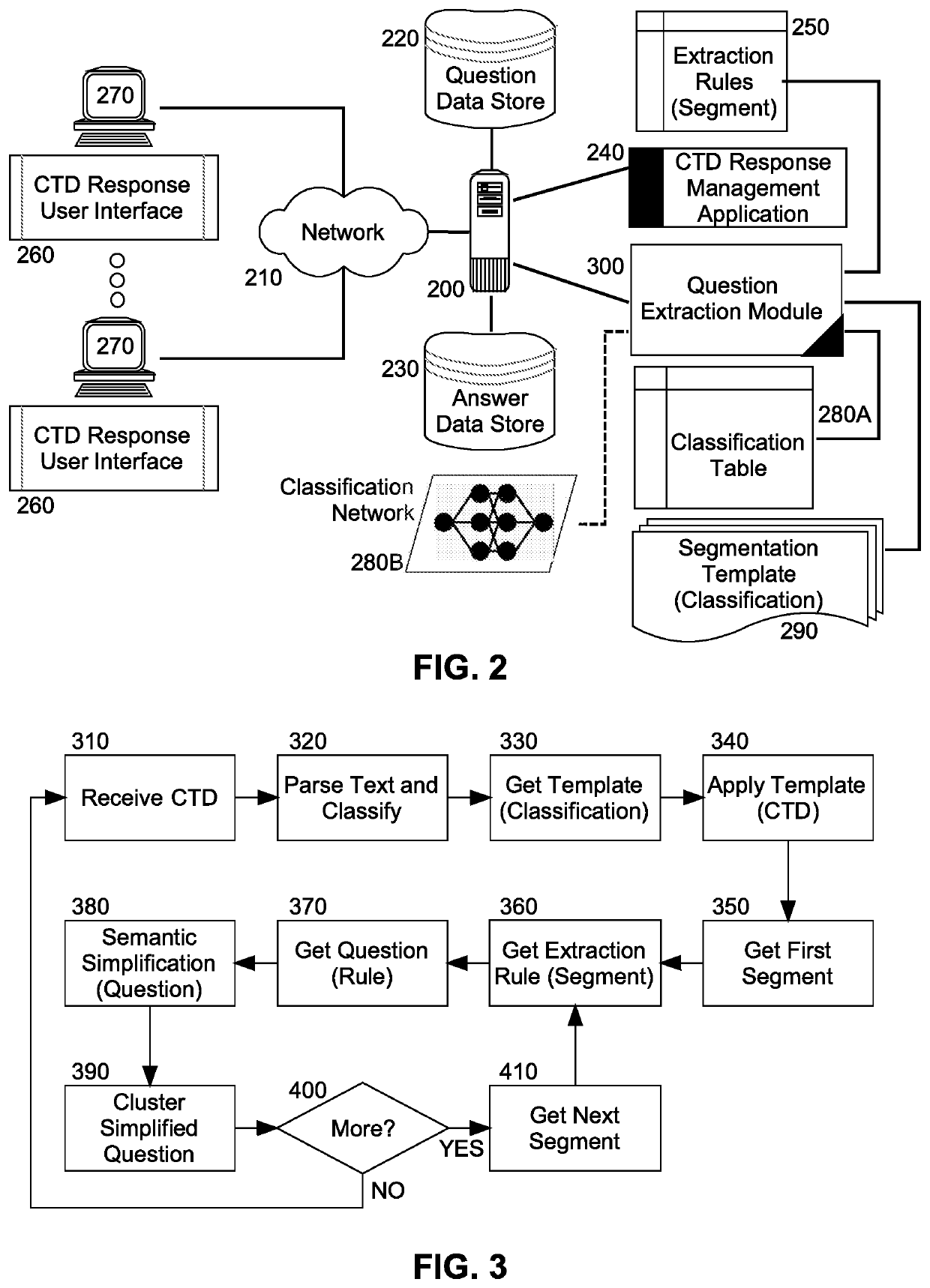
Computer driven question identification and understanding within a commerical tender document for automated bid processing for rapid bid submission and win rate enhancement
In a method for computer driven question identification and understanding within a commercial tender document (CTD), different CTDs from different individuals are uploaded into fixed storage of a computer. Then, different ones of the CTDs are loaded into memory and clustered into different clusters according to at least one clustering criteria. For each one of the CTDs, a corresponding one of the clusters is identified, and a segmentation model selected for the identified one of the clusters. Thereafter, segmentation is performed upon the CTD utilizing the selected segmentation model to produce a set of segmented portions of the CTD. Finally, for each one of the segmented portions, a set of extraction rules mapped to the one of the segmented portions is retrieved, at least one question extracted from the one of the segmented portions utilizing the set of extraction rules and each extracted question stored in a crowd-sourced database of questions for CTDs.
Owner:BIDIFY LTD
Automated service level management in financial terms
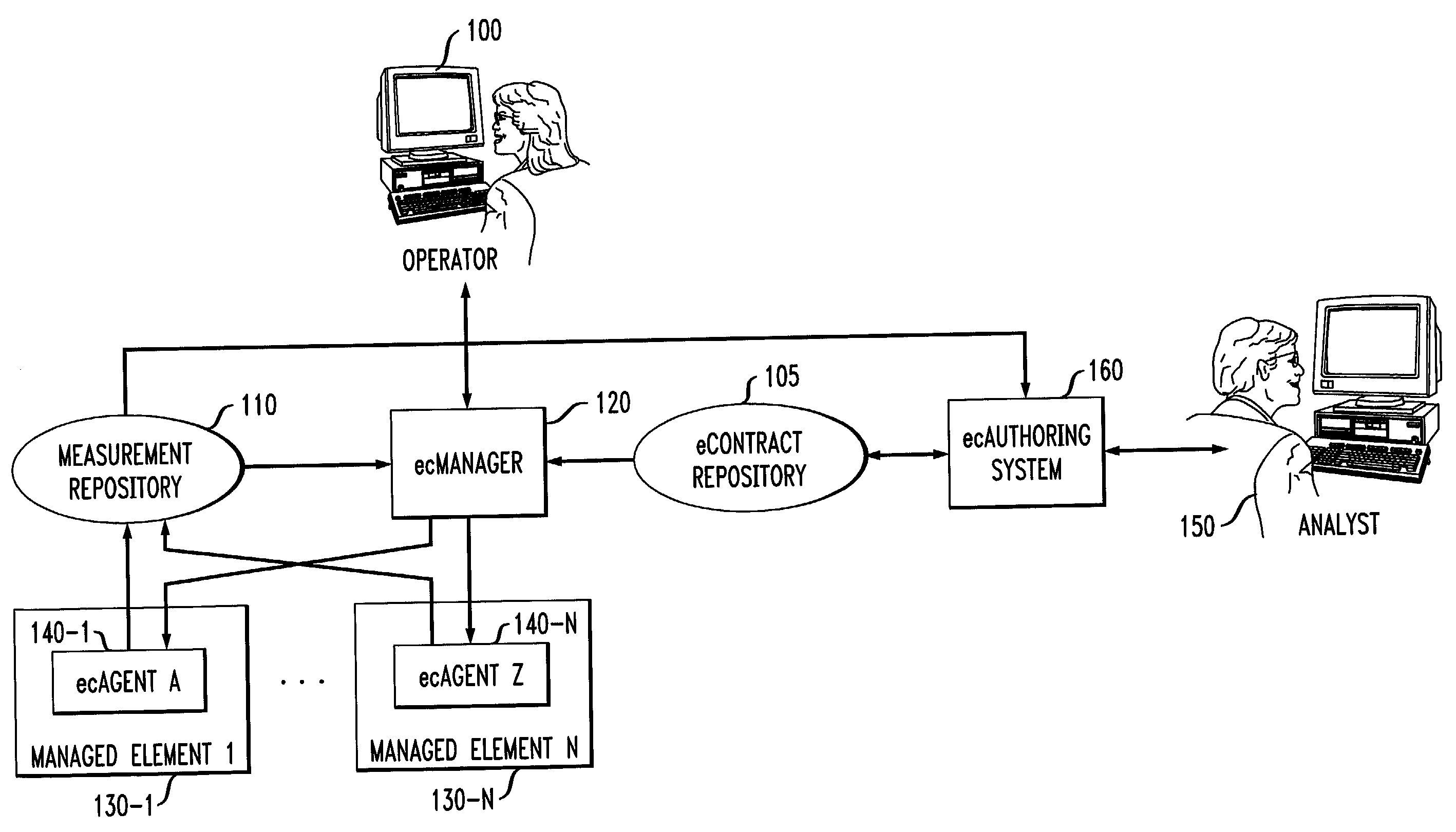
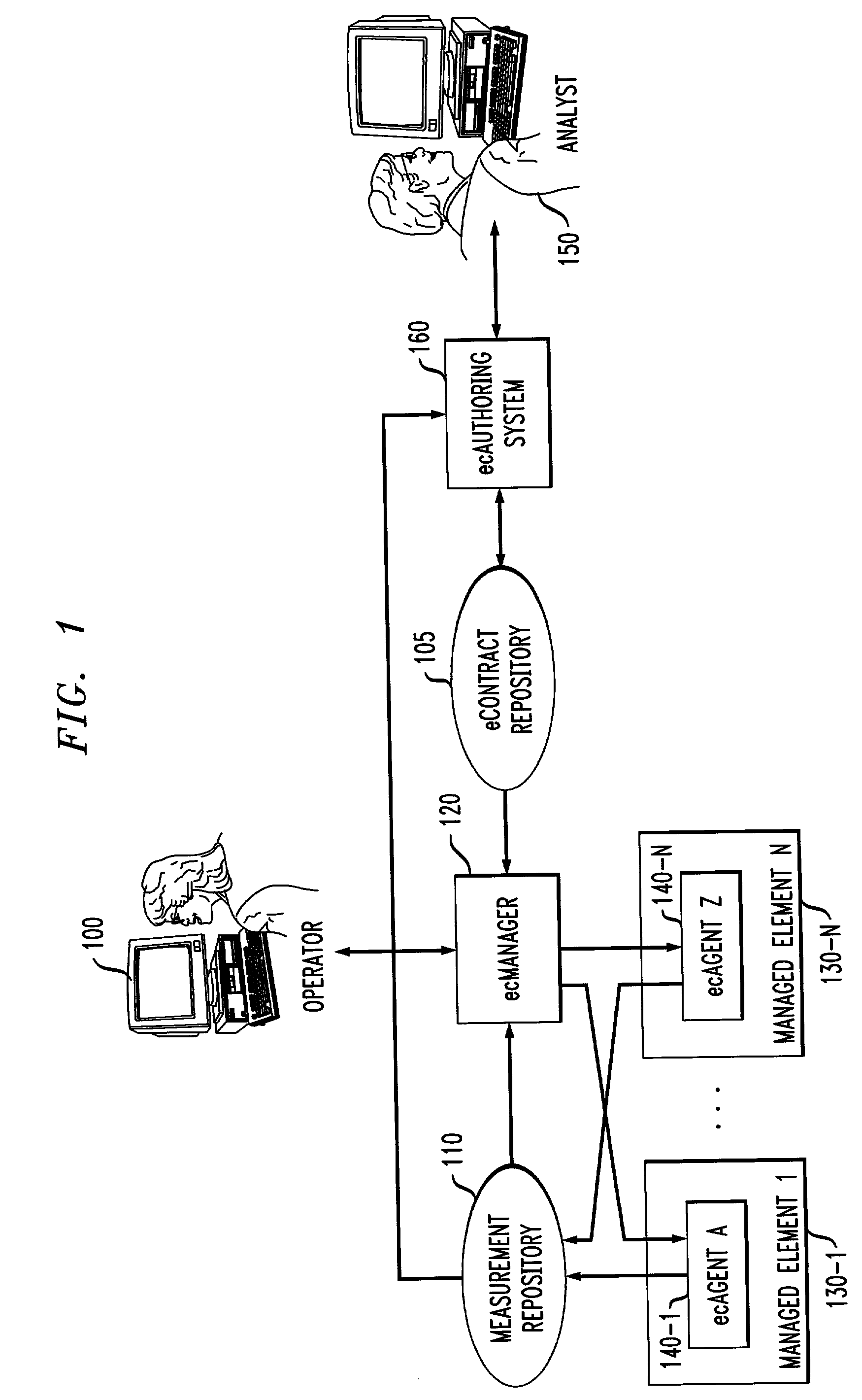
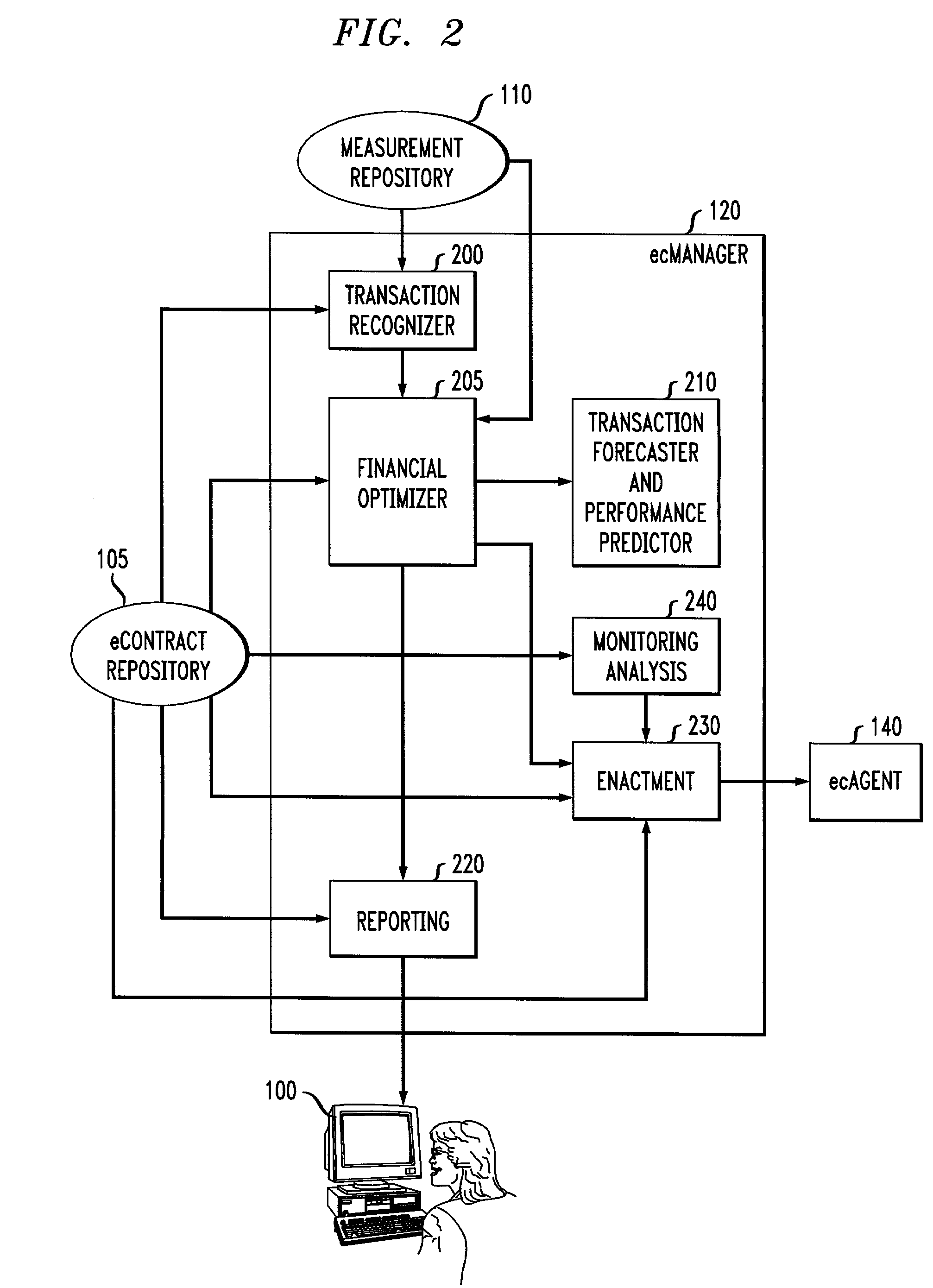
InactiveUS7610228B2Present inventionFinanceDigital computer detailsService-level agreementElectronic contracts
Electronic contracts or “eContracts” for representing service level agreements are provided. In one illustrative embodiment, the eContract may comprise information pertaining to: (a) descriptions of business transactions in IT terms; (b) financial implications of business transaction service levels; and (c) reporting to be done in business terms. Of course, the eContract may comprise other terms and conditions. In an illustrative aspect of the invention, a system for managing IT resources in terms of business financials comprises an electronic contract authoring system or “ecAuthoring system,” an electronic contract manager module or “ecManager,” and one or more electronic contract agent modules or “ecAgents” that may run on IT elements (e.g., components of the network) that are being managed. Analysts interact with the ecAuthoring system to construct eContracts. An eContract is input to an ecManager that interprets the contract to report on and optimize IT resources based on business financials. The ecManager collaborates with ecAgents to monitor, report, and enforce contracts expressed in such business terms.
Owner:INT BUSINESS MASCH CORP
Big data recommendation method, system and device for insurance industry
ActiveCN111506908ADigital data information retrievalFinanceRecommendation modelConcurrent computation
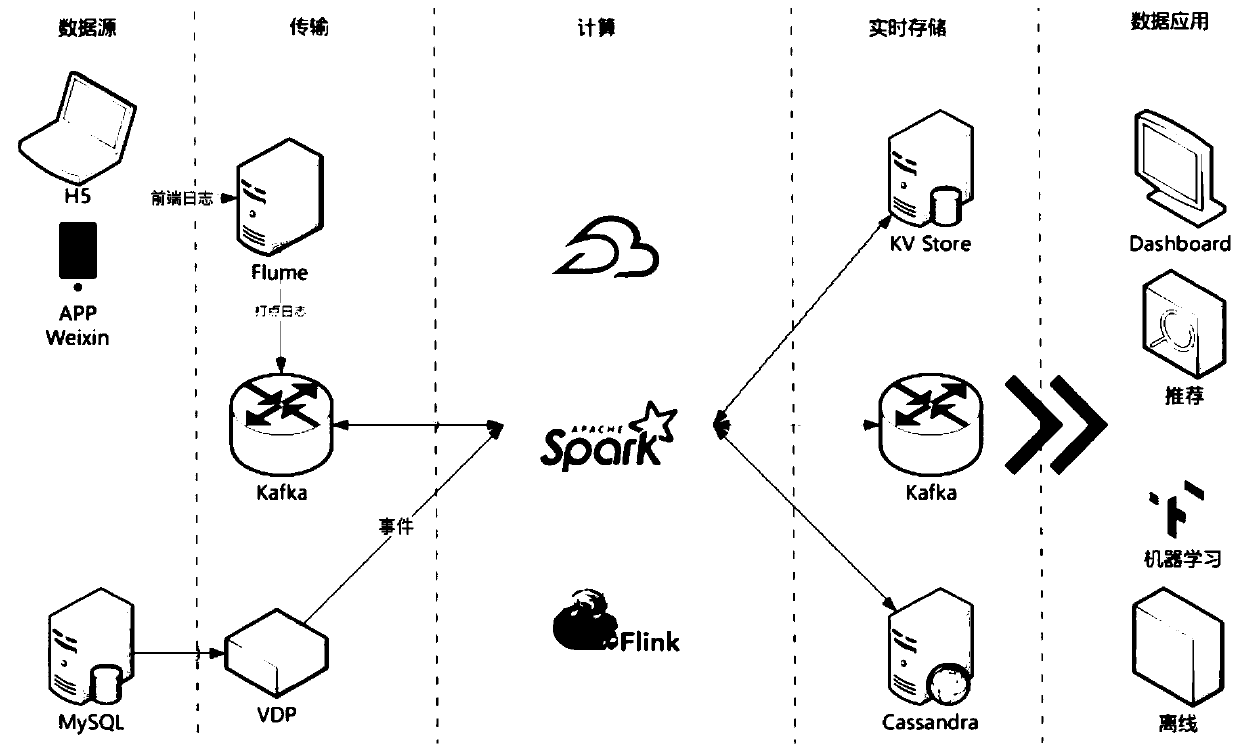
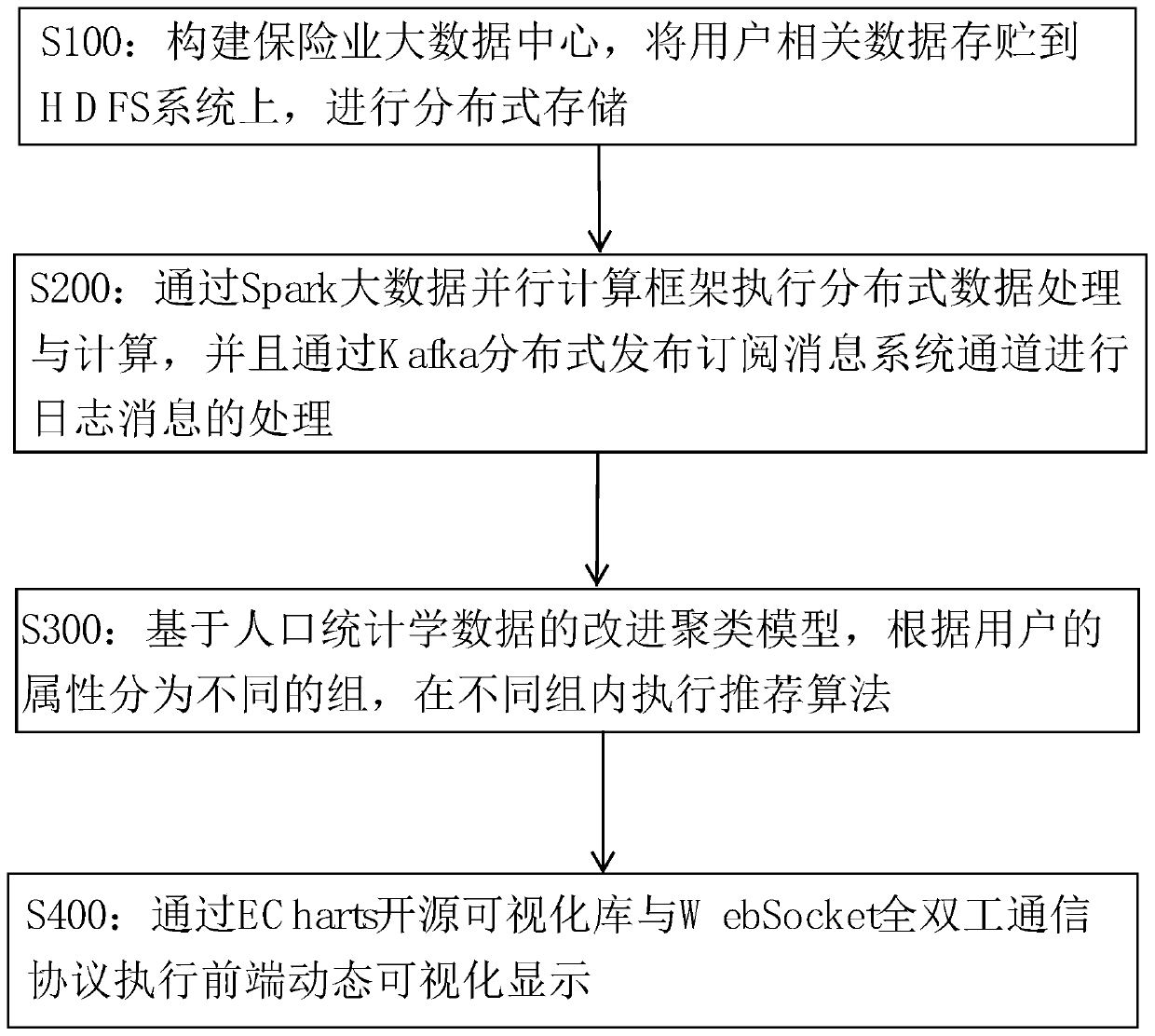
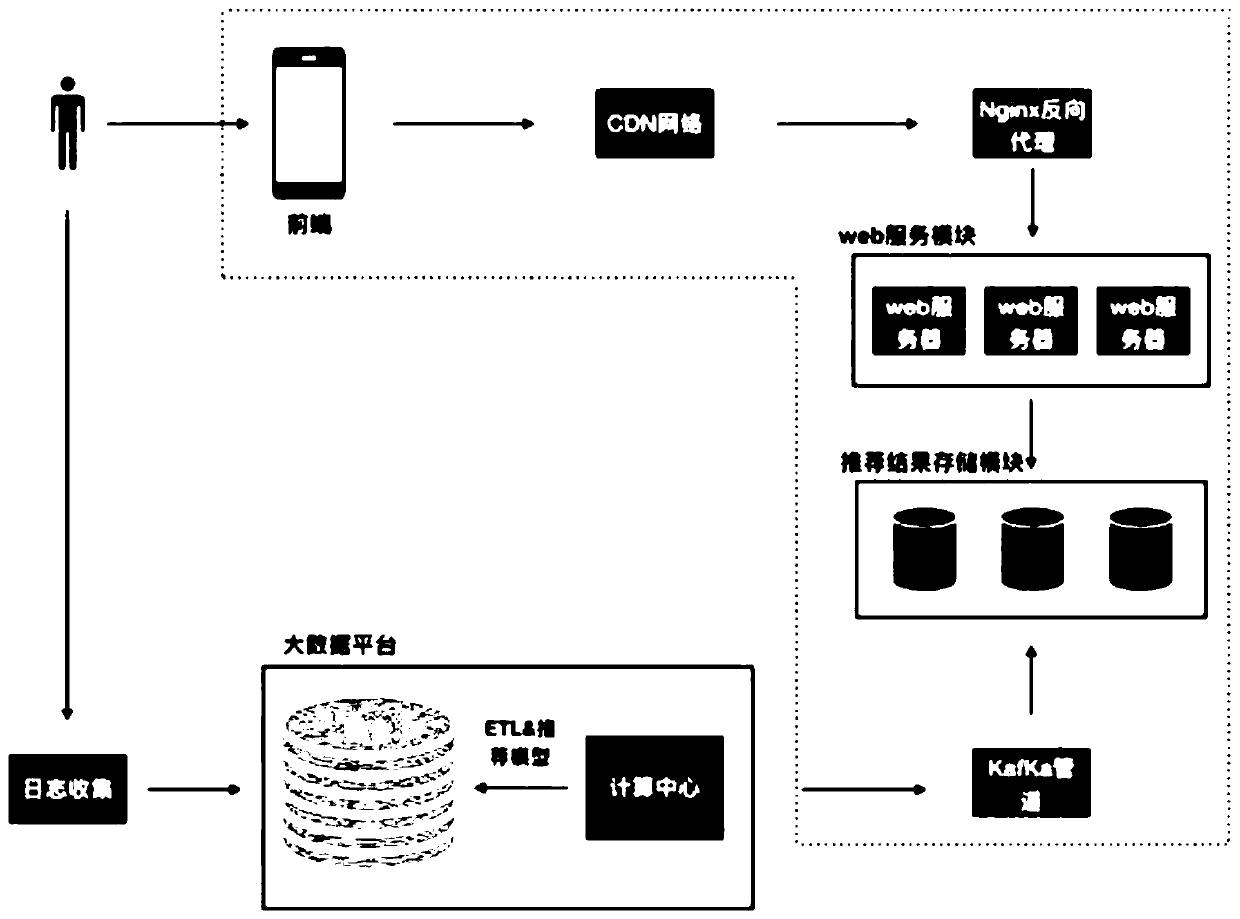
The invention provides a big data recommendation method, system and device for the insurance industry, and the method comprises the following steps: (A) constructing an insurance industry big data center, storing the related data of a user in an HDFS system, and carrying out the distributed storage; (B) executing distributed data processing and computing through a Spark big data parallel computingframework, and processing log messages through a Kafka distributed message publishing and subscribing system channel; (C) dividing the users into different groups according to the attributes of the users based on an improved clustering model of demographic data, and executing a recommendation algorithm in different groups; and (D) executing front-end dynamic visual display through the ECharts open source visual library and the WebSocket full duplex communication protocol. The method can assist the insurance industry in commercial decision making, provides an insurance industry recommendationmodel, and guarantees the data safety.
Owner:深圳新致软件有限公司
Path verification method and related equipment
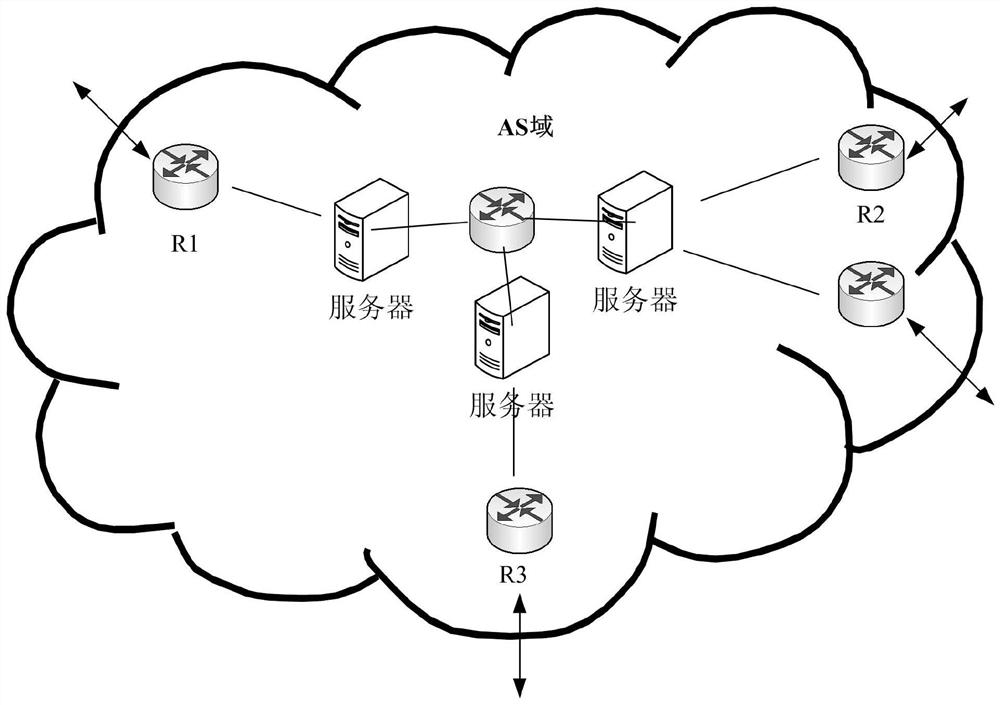
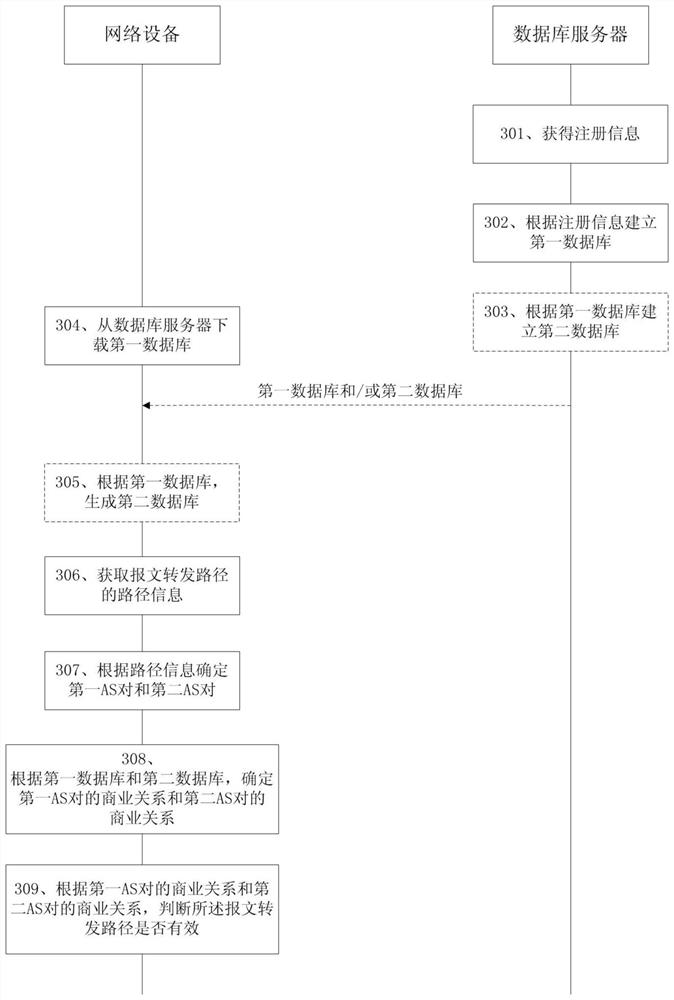
InactiveCN113132228AAccurate CalibrationThe verification result is credibleData switching networksPathPingTRADACOMS
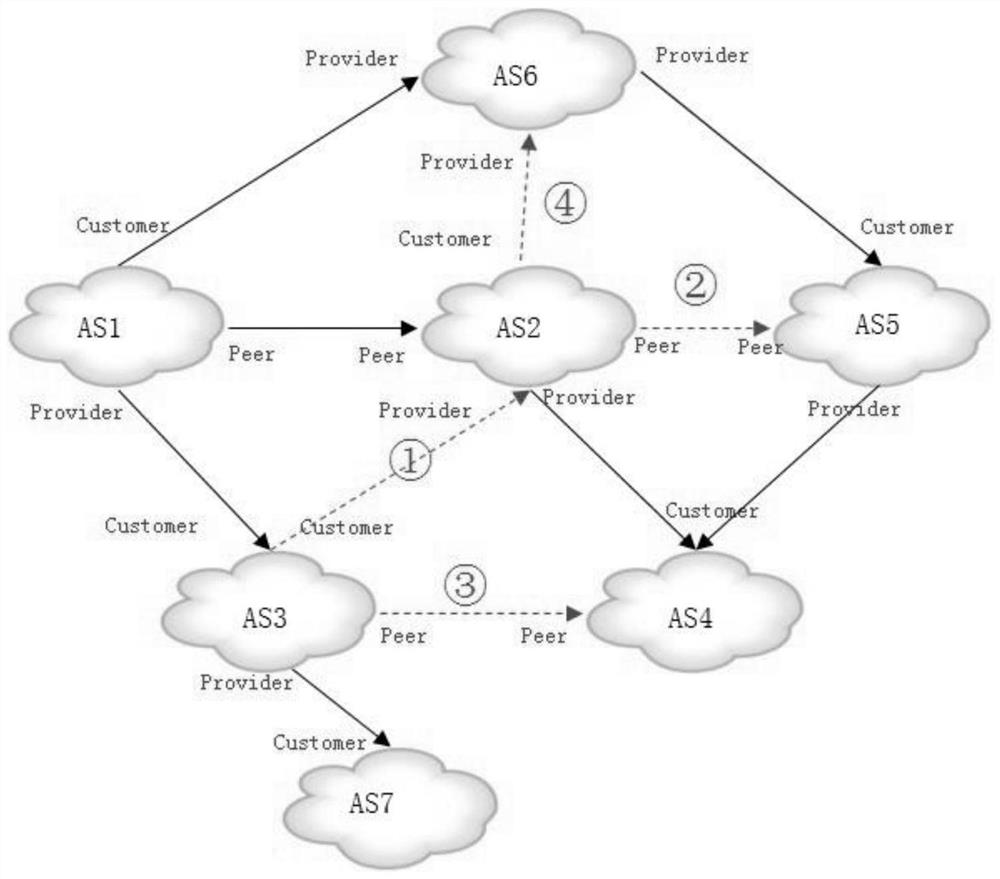
A path verification method and related equipment are used in the technical field of communication. The method comprises the following steps: network equipment obtains path information of a message forwarding path, the message forwarding path passes through a third autonomous domain AS, a second AS and a first AS in sequence, and the third AS, the second AS and the first AS are adjacent in sequence; the network equipment determines a business relationship of a first AS pair and a business relationship of a second AS pair, the first AS pair comprises a first AS and a second AS which are arranged in sequence, and the second AS pair comprises a second AS and a third AS which are arranged in sequence; the network equipment judges whether the message forwarding path is valid or not according to the business relationship of the first AS pair and the business relationship of the second AS pair; and according to the embodiment of the invention, whether the path is valid or not needs to be determined according to the business relationship between the adjacent AS pairs, so that the P2P routing information leakage condition can be verified more accurately, and the verification result is more credible.
Owner:HUAWEI TECH CO LTD
Interconnecting enhanced and diversified communications with commercial applications
InactiveUS20150242873A9Easy to createFacilitate communicationNatural language translationSpecial data processing applicationsPersonalizationTRADACOMS
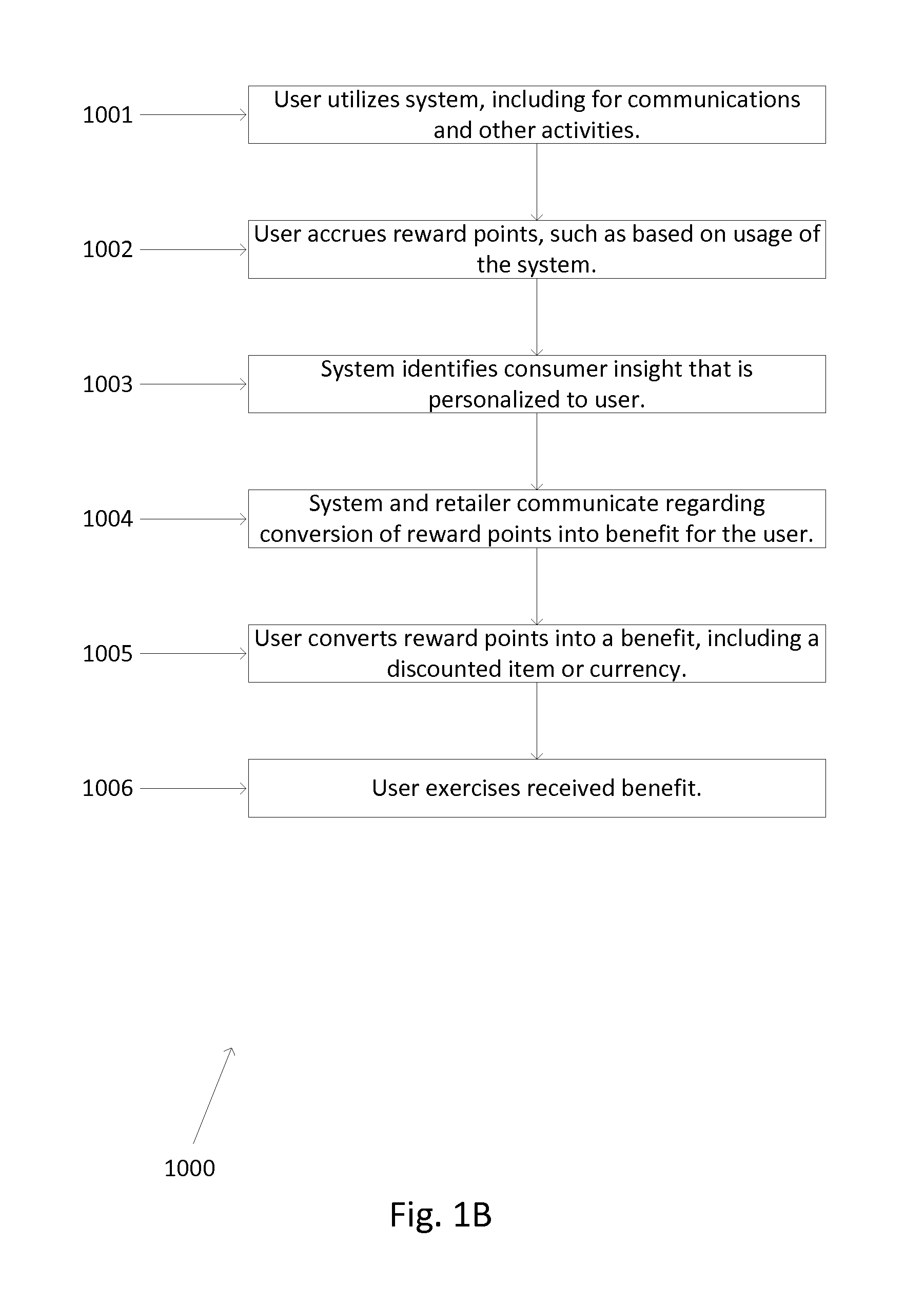
A system for interconnecting enhanced and diversified communications with commercial applications using efficient and user-friendly features and methods by which users can create, share, and proliferate symbols, use translations, message contractions, message expansions, hidden messages, scrolling or bill-boarding messages, timed messages, Morse messages, and inter-language translations, all using various forms of formatting and presentation configurations. Such system and communications are used and made amongst various social groupings, providing benefits and incentives for usage of the system, and personalized consumer insight that links to commercial applications
Owner:ILYNGO
Method and system for identifying and intercepting crawlers based on business data
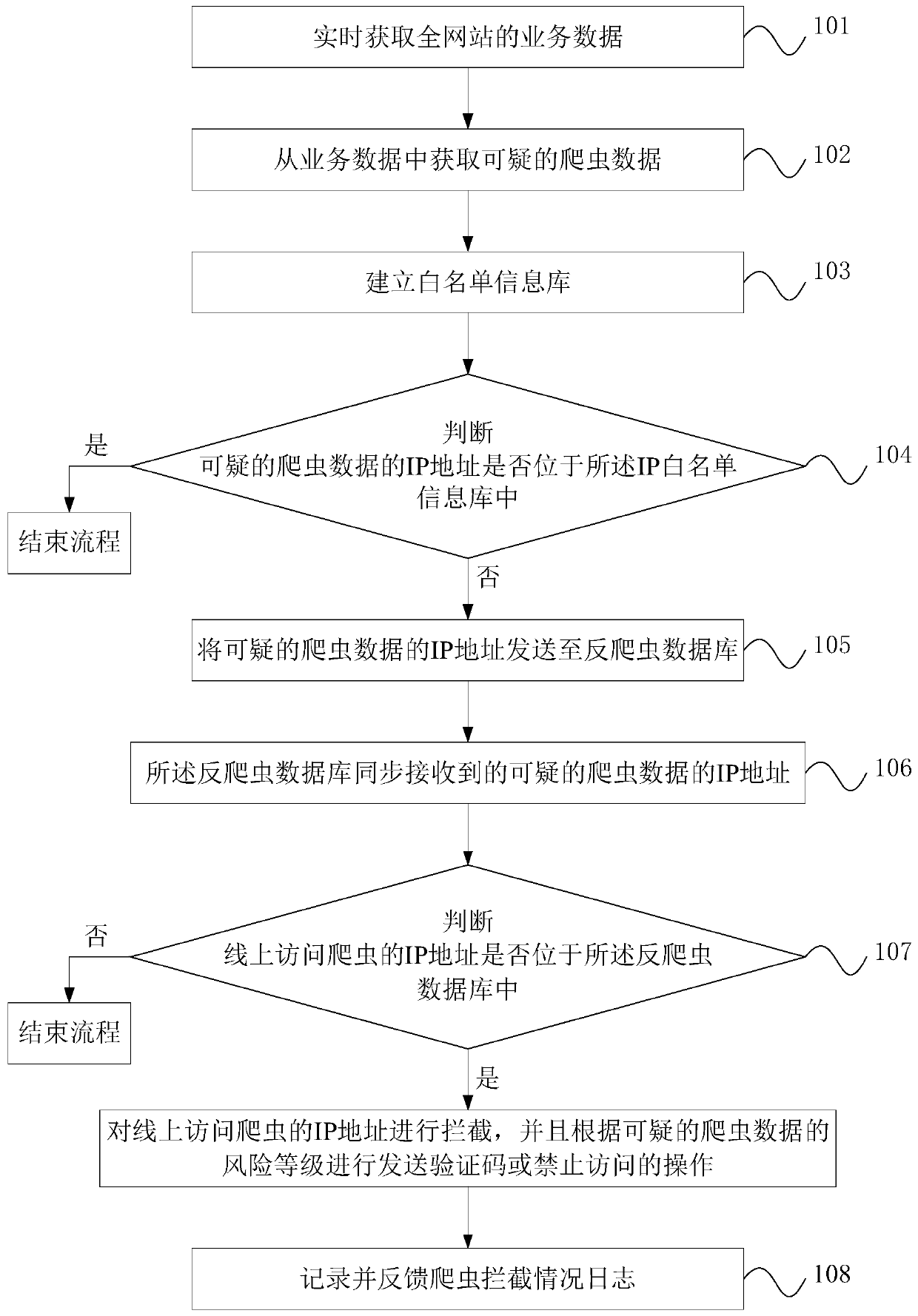
ActiveCN106790105BReal-time interceptionReal-time monitoring of crawlersTransmissionInformation repositoryWeb site
The invention discloses a crawler identification and interception method and system based on service data. The crawler identification and interception method and system based on service data comprises the following steps: S1, obtaining the service data of a whole website in real time; S2, obtaining suspicious crawler data from the service data; S3, establishing an IP white list information library, wherein effective IP addresses allowed to access the website are recorded in the IP white list information library; S4, judging whether the IP address of the suspicious crawler data is in the IP white list information library, and if not, executing S5; S5, sending the IP address of the suspicious crawler data to an anti-crawler database; S6, synchronously receiving the IP address of the suspicious crawler data by the anti-crawler database; and S7, judging whether the IP address of an online access crawler is in the anti-crawler database, and if so, intercepting the IP address of the online access crawler. By adoption of the crawler identification and interception method and system disclosed by the invention, the IP address of the crawler can be intercepted in real time, thereby reducing the possibility that commercial pricing systems of companies are stolen by the crawler on the service.
Owner:CTRIP TRAVEL NETWORK TECH SHANGHAI0
Highway engineering project information collaboration method and system based on Fabric alliance chain
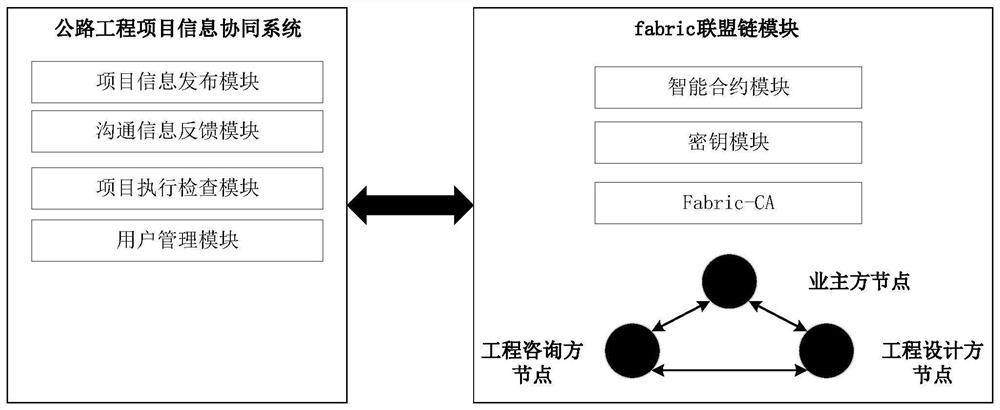
PendingCN112001702ASolve data security issuesFix security issuesOffice automationTransmissionTRADACOMSBusiness data
The invention discloses a highway engineering project information collaboration method and system based on a Fabric alliance chain, and the method enables each transaction marked according to time tobe copied to a block chain and not to be tampered. All participants can store a large amount of same data at the same time, a data distributed network is formed, and a series of problems of commercialdata monopoly, data security and the like are solved; according to the invention, each collaboration party can easily verify the information source, human errors can be prevented, the risk of information asymmetry is greatly reduced, the cost is reduced, each link can better understand the information of the project, and the collaboration efficiency of each collaboration party is improved.
Owner:陕西交建云数据科技有限公司
Auto-generation or auto-execution of web service description language call flow implementation
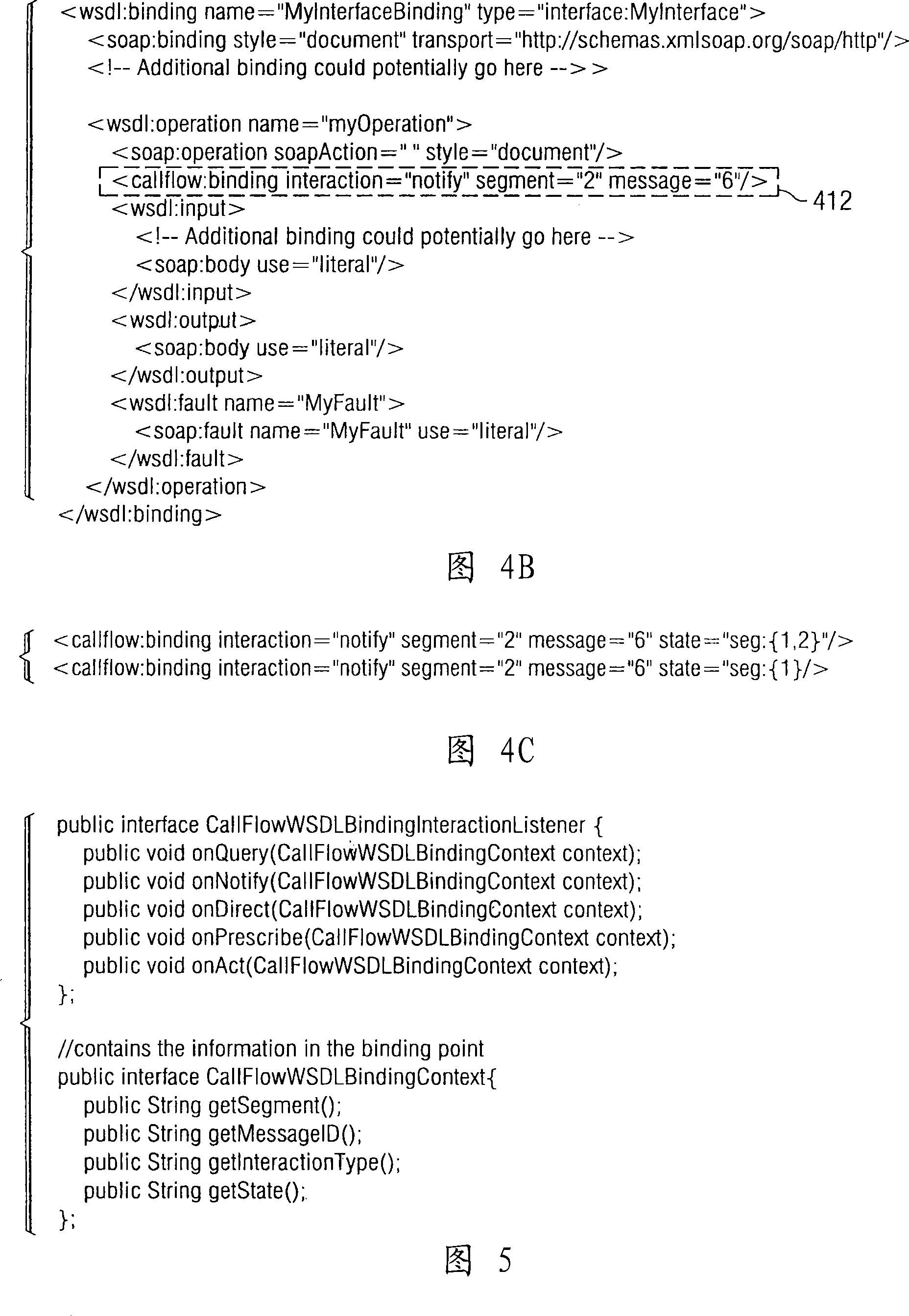
Development tooling receives the extended Web services description language with call flow interactions. The development tooling allows the user to select trivial message exchanges in the call flow. The development tooling may generate servlets for the selected message exchanges automatically to form a template form of the application that will execute in the converged application engine. Alternatively, the development tooling may generate a template form of the application that may be interpreted in an interpretive engine. The user may then drop in higher level business logic. The automatically generated servlets, or template form of the application to be interpreted, are configured to pass to the Web services information, including the last message contents.
Owner:IBM CORP
System and method for sharing confidential data on blockchain
PendingCN111858519AAvoid lossKey distribution for secure communicationMultiple keys/algorithms usageData providerTRADACOMS
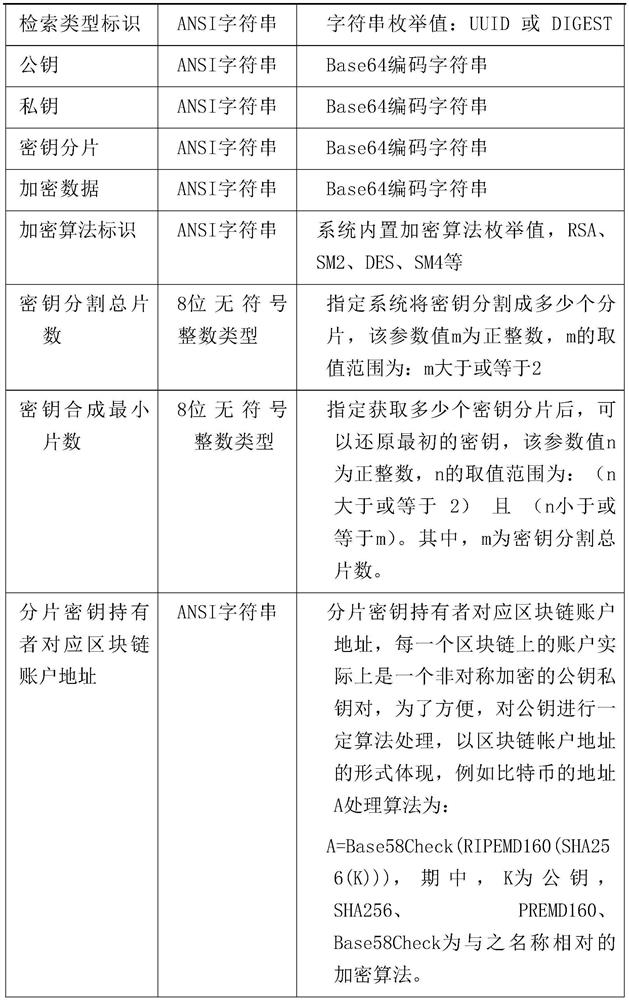
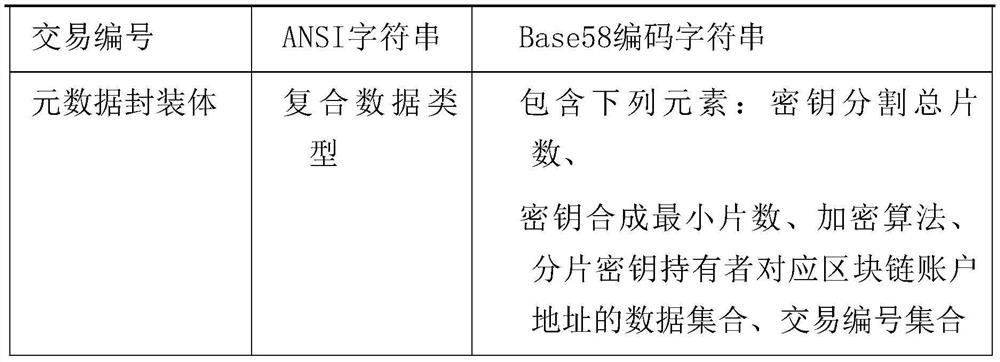
The invention discloses a system and a method for sharing confidential data on a blockchain. The system comprises a data encryption subsystem, a key distribution subsystem, a metadata directory subsystem, a key collection subsystem, a data decryption subsystem and a confidential data storage subsystem. The invention belongs to the technical field of blockchains. The invention relates to a system and a method for sharing confidential data on a blockchain. After the key is segmented, the key is stored on blockchain and is prevented from being lost, an innovative data use and supervision mechanism is provided; after the data provider encrypts the data, the key fragments are distributed to each holder, and each key fragment holder is a data stakeholder or a data supervision mechanism; when a user wants to win the encrypted data, the user needs to obtain approval of each holder; and, through the mechanism, it can be clearly recorded that the data is provided, supervised and used by who, andall historical records cannot be changed, and reasonable and legal exchange and use of the data in the digital economy era, business and personal data can be effectively guaranteed.
Owner:北京远景视点科技有限公司
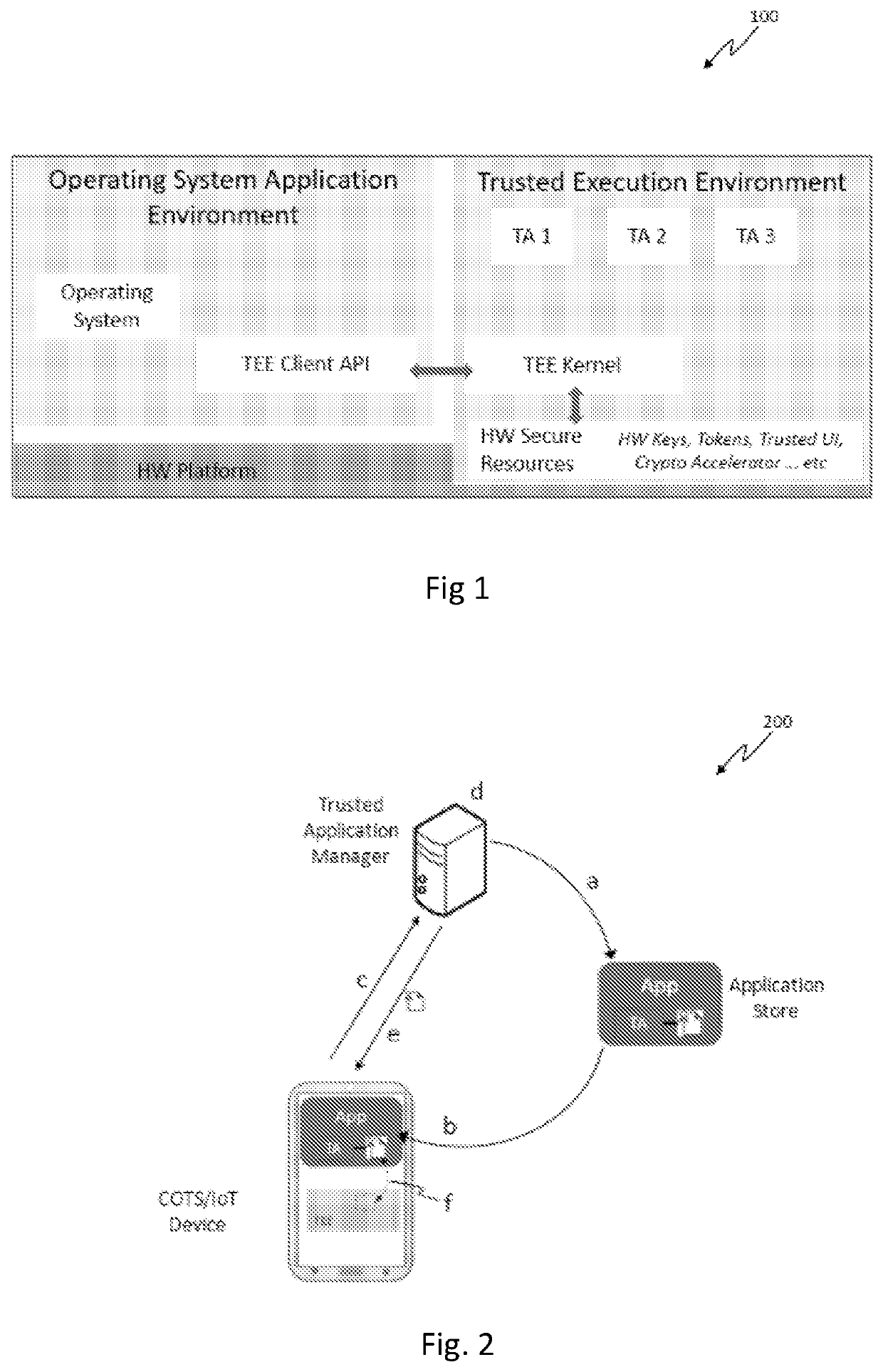
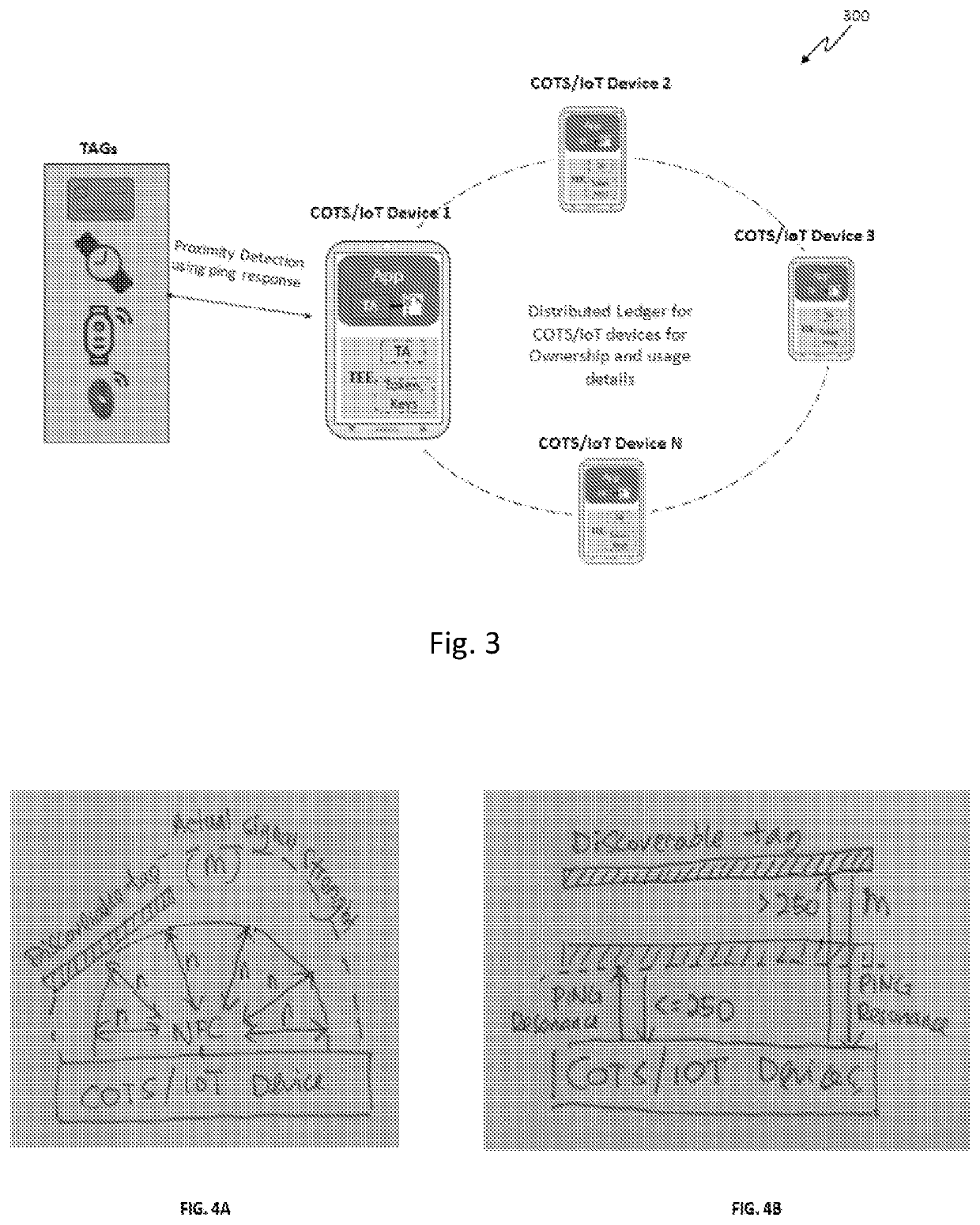
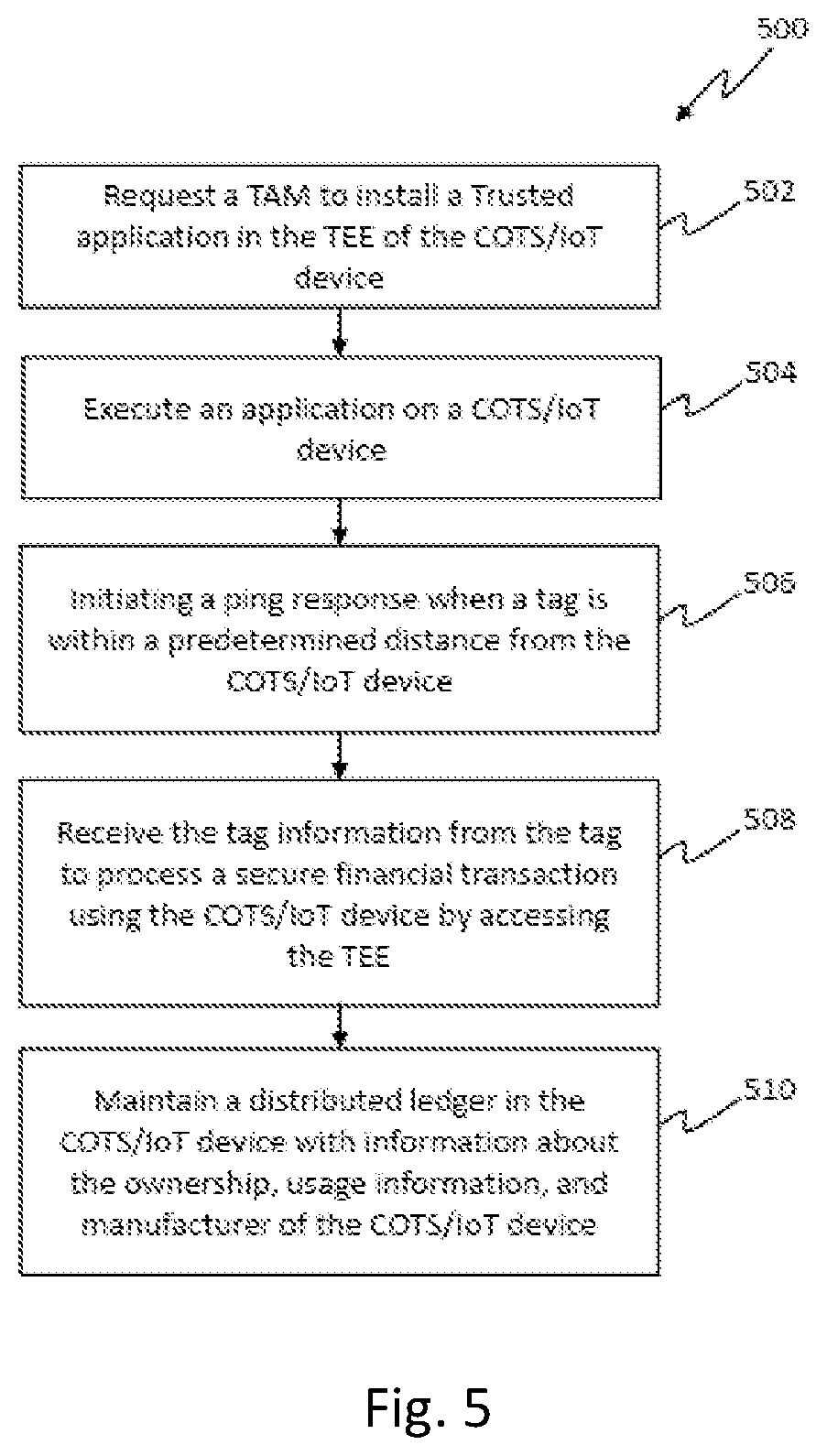
Method for processing a secure financial transaction using a commercial off-the-shelf or an internet of things device
PendingUS20210209579A1Cryptography processingUser identity/authority verificationTRADACOMSEngineering
A system and method for processing a secure financial transaction using a Commercial off-the-shelf (COTS) or Internet of Things (IoT) device is provided. The method comprises requesting a Trusted Application Manager (TAM) to verify the COTS / IoT device identity and executing an application on a COTS / IoT device. Upon verification, TAM installs a Trusted Application (TA) in a Trusted Execution Environment (TEE) of the COTS / IoT Device. Further, initiating a resonance response when a tag is within a predetermined distance from the COTS / IoT device with TA installed, and receive the tag information from the tag. Finally, processing a secure financial transaction using the COTS / IoT device based on the received tag information by accessing the TEE. The COTS / IoT device includes a distributed ledger, and which comprises information corresponding to at least one of COTS / IoT device ownership, manufacture, and usage information.
Owner:LEONG CHRISTOPHER YEW CHONG +3
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com