Method and device for hiding information based on word2007 text segmentation
A word2007, information hiding technology, applied in the field of information hiding based on word2007 text segmentation, can solve the problems of seizure, increase of file suspiciousness, increase in size, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] In order to make the purpose and technical solution of the present invention clearer, the information embedding and extraction process proposed by the embodiment of the present invention will be described in detail below in conjunction with the accompanying drawings.
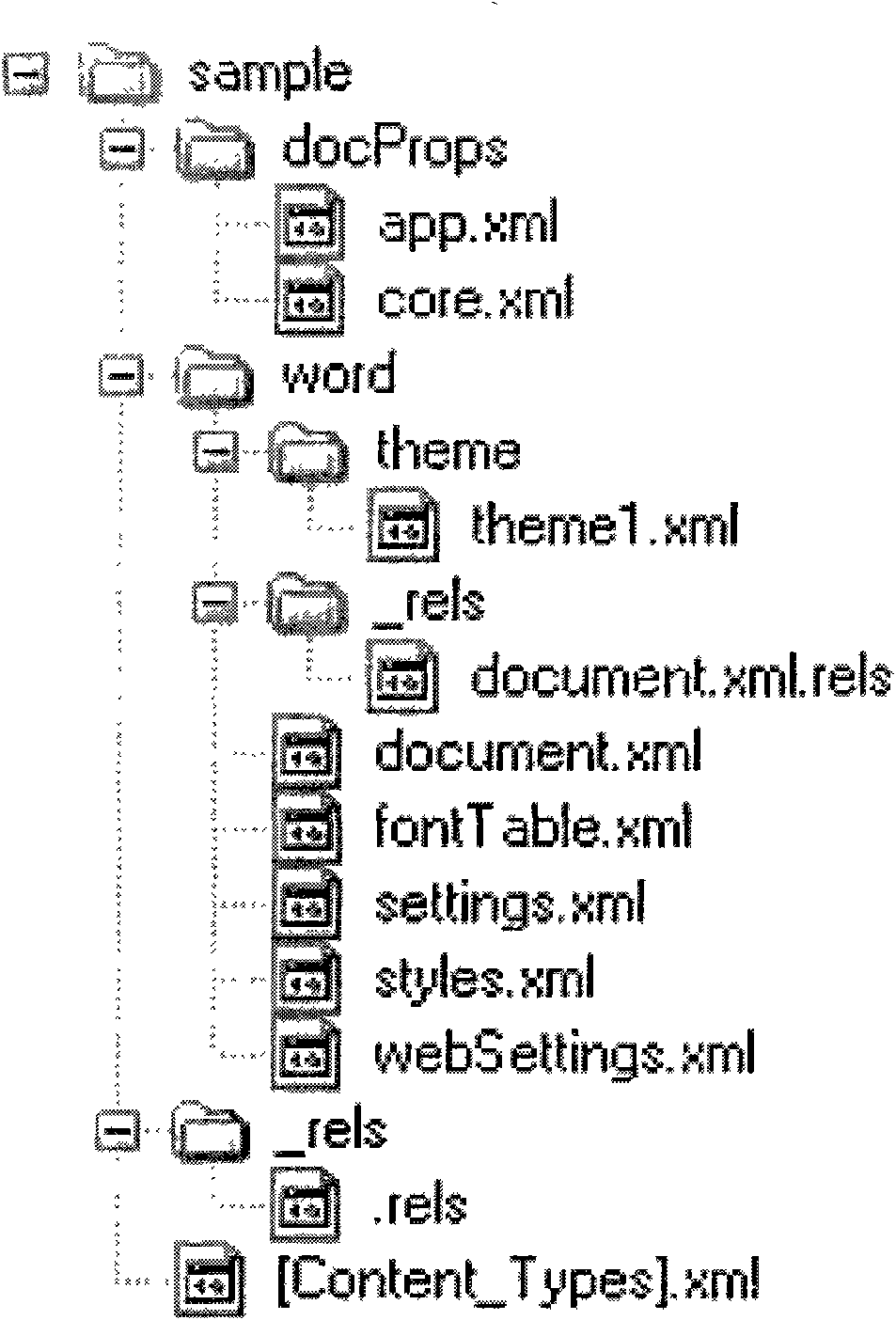
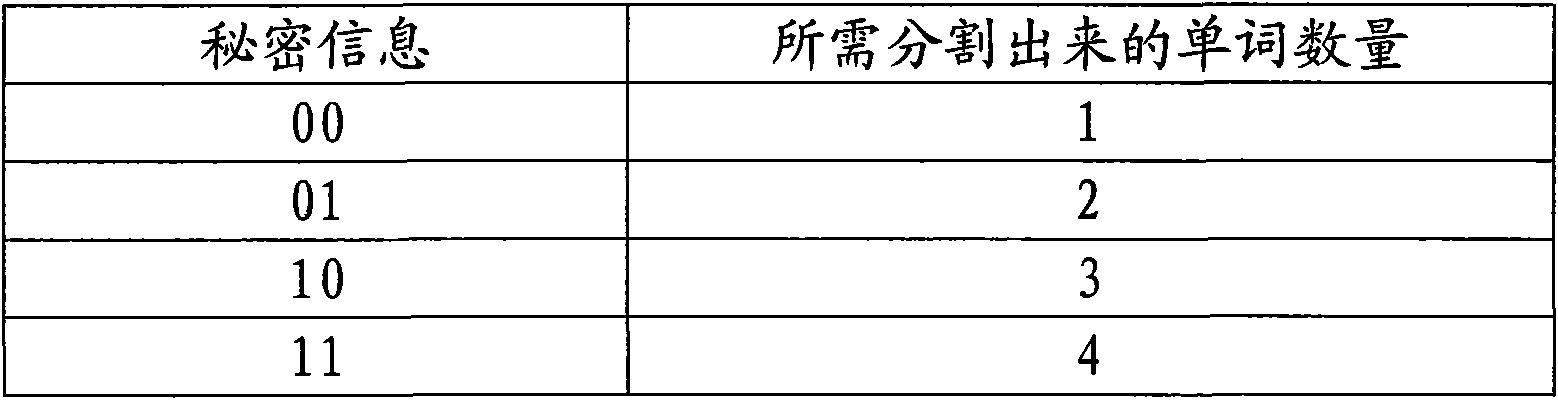
[0048] The original covert carrier document is a word electronic document in Open Office XML format, and its ZIP package document structure is as attached figure 1 shown. The secret information to be hidden is encoded and converted into 8-bit binary data: 00101101. The correspondence between the secret information to be hidden and the number of words required is as follows figure 2 shown. Then the steps to hide the secret information in the word2007 electronic document are:
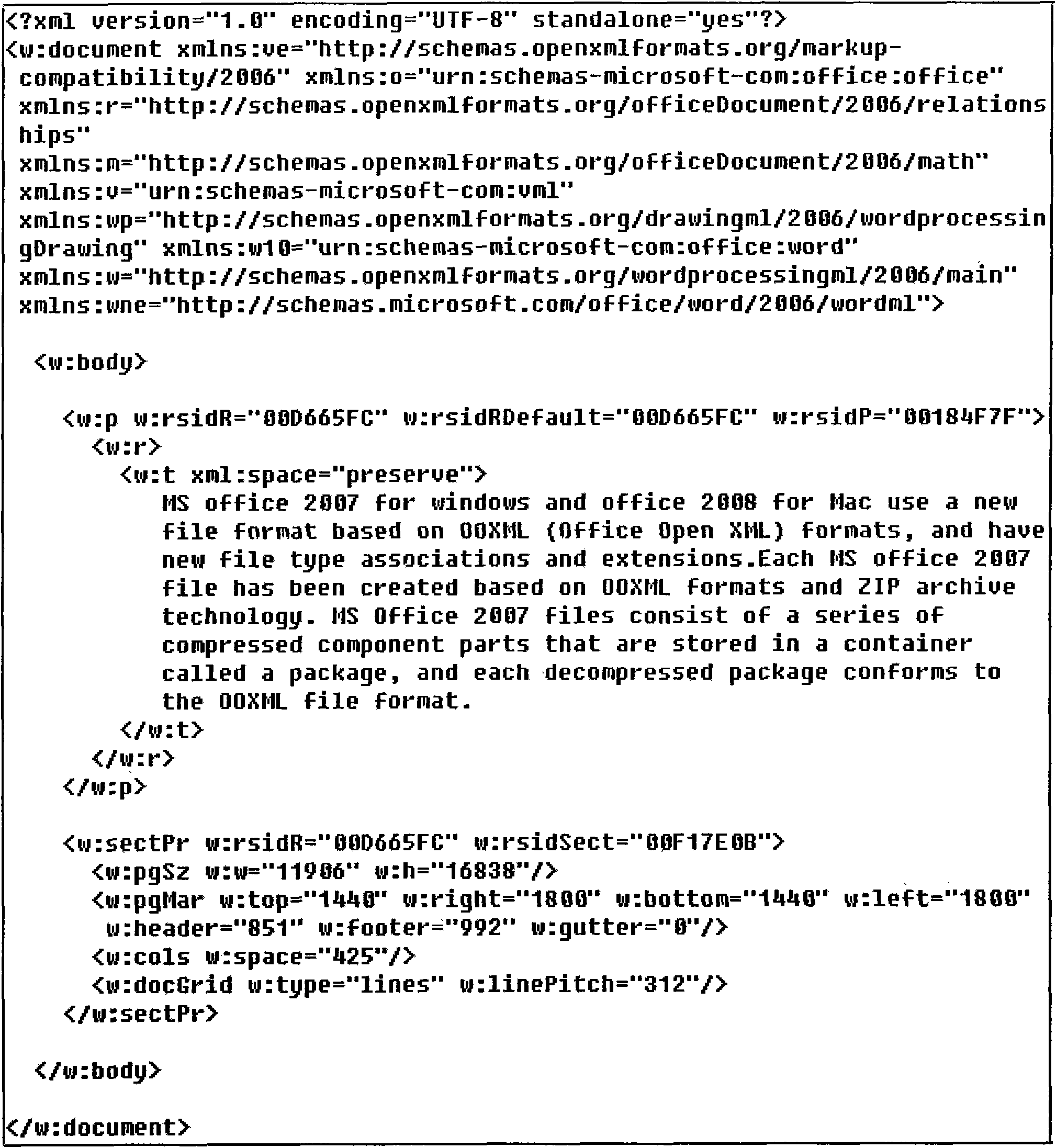
[0049] The first step is to read the main component document.xml file in the hidden carrier word2007 document package, and extract the root node (document), container (body), paragraph (paragraph), text and its attribute set (run...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com