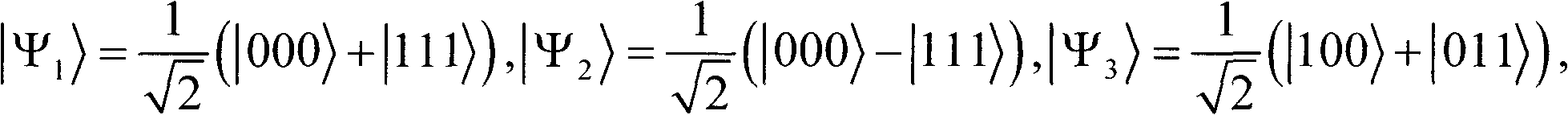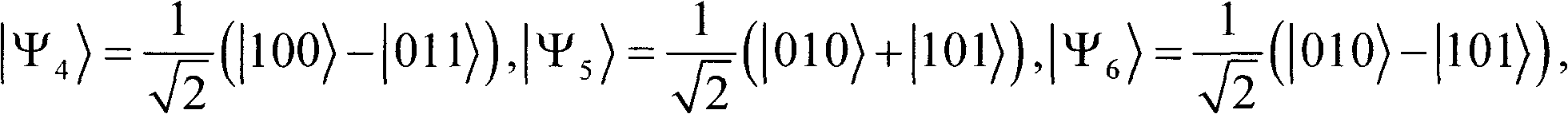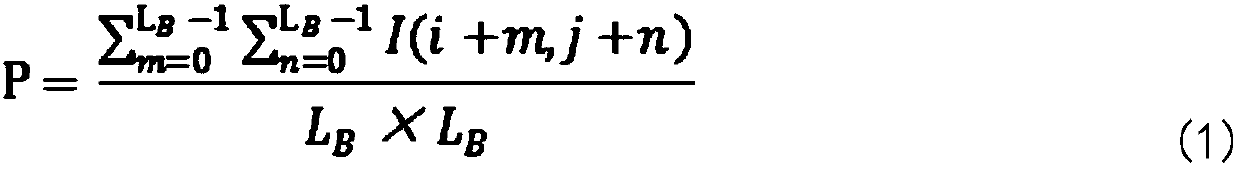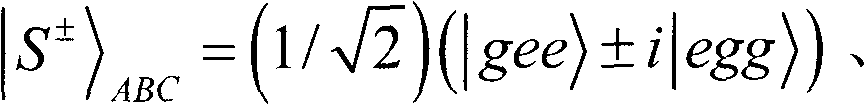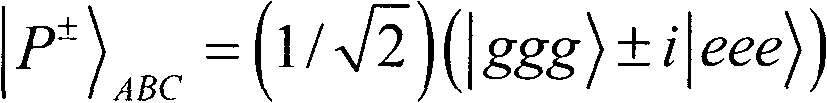Patents
Literature
246 results about "Covert communication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Overt communication is the evident meaning of words exchanged. Covert communication is the murky world of implications, inferences, and attributions of motive. Covert communication includes the subtleties of meaning that are attached to the more obvious.
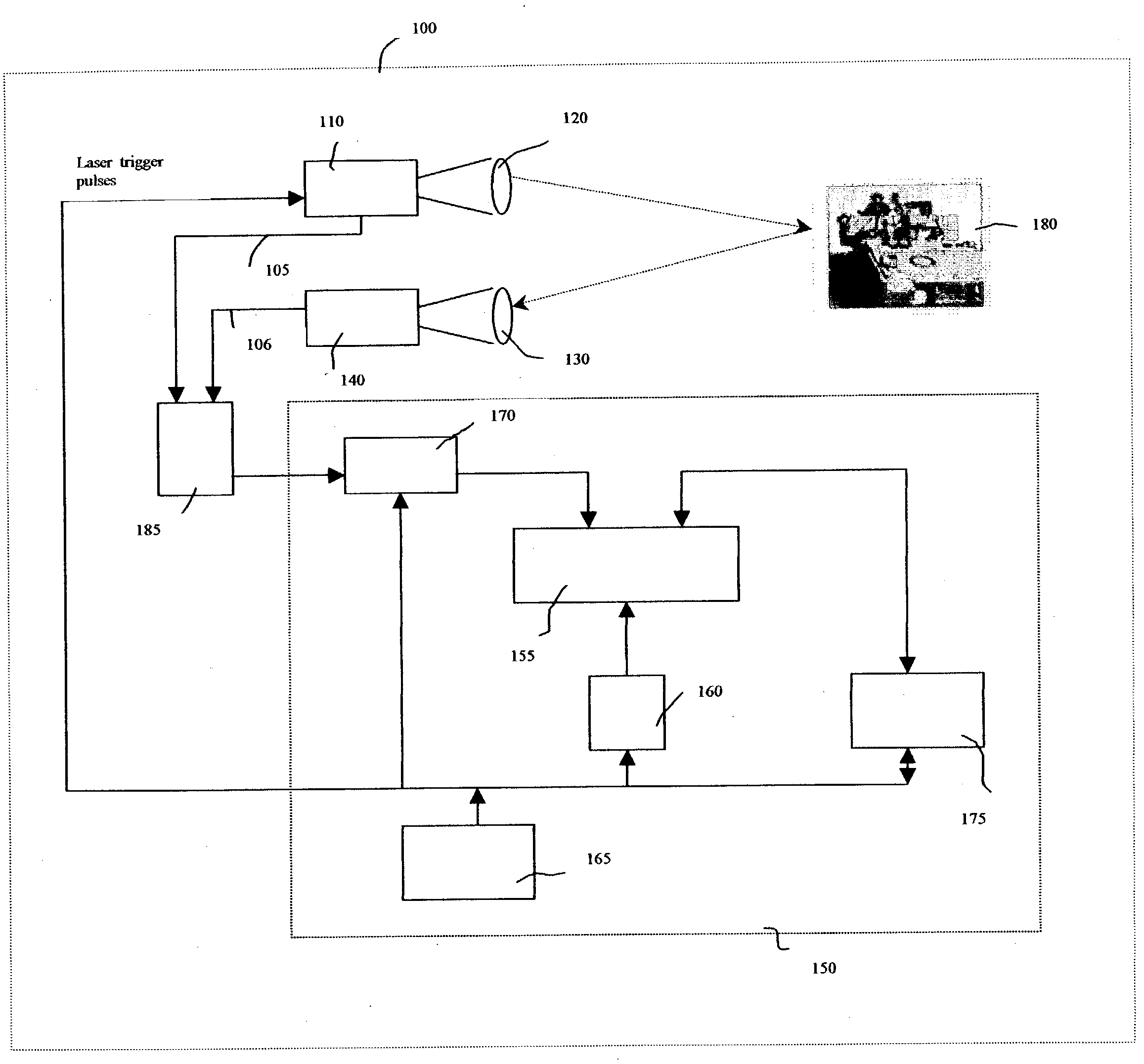
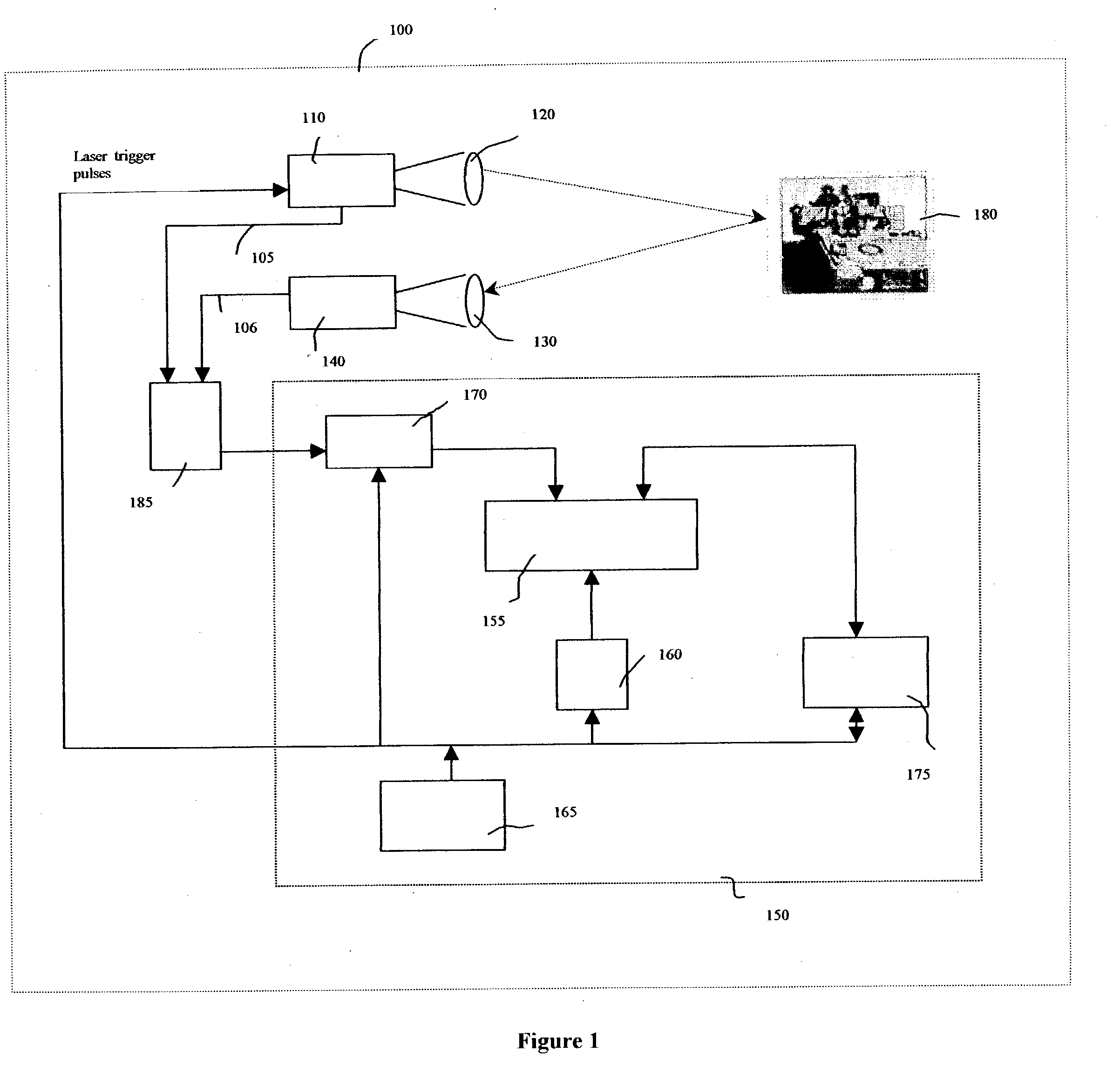
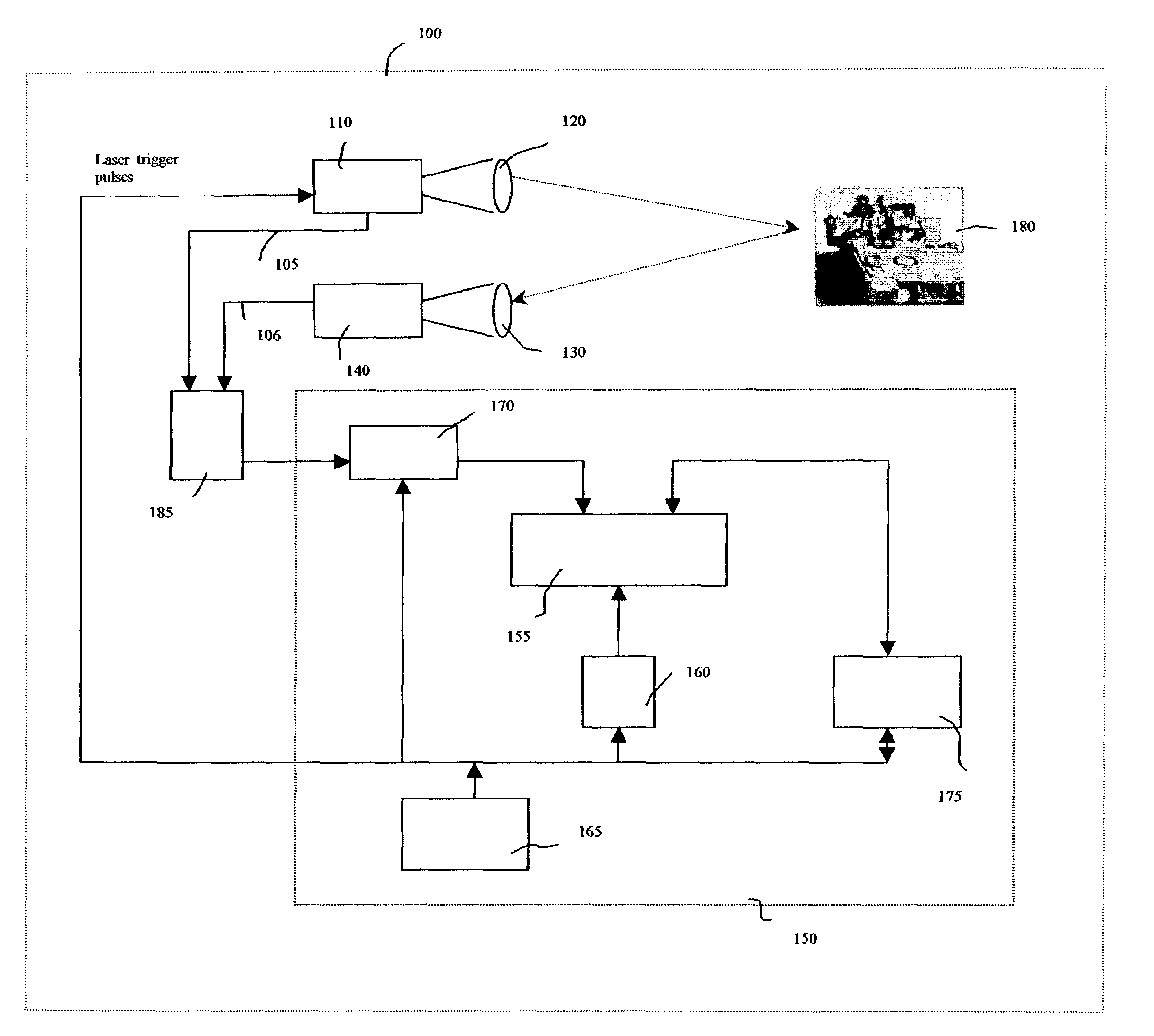
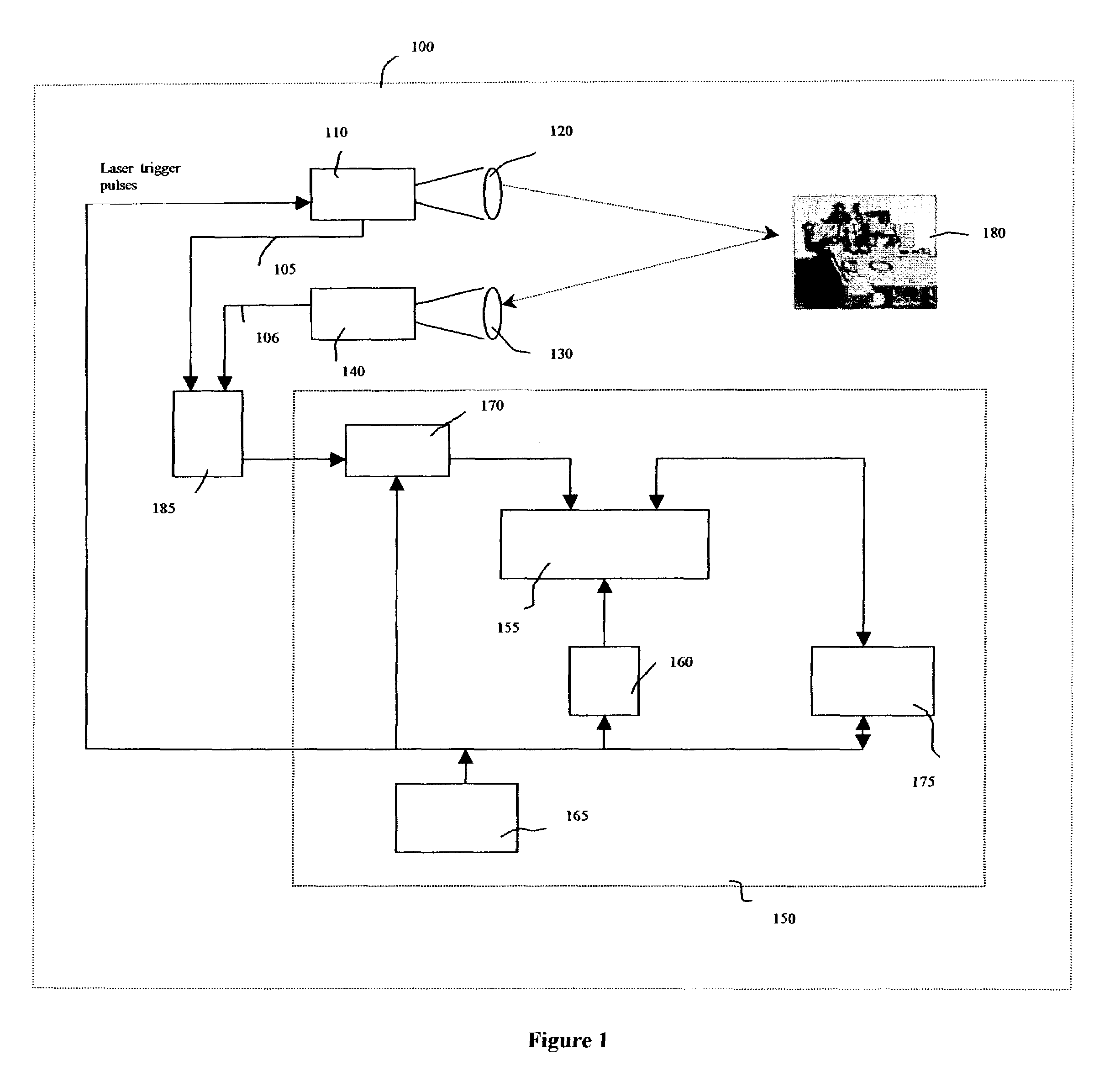
Integrated optical communication and range finding system and applications thereof
InactiveUS20090010644A1Transmission monitoringTransmission monitoring/testing/fault-measurement systemsLaser rangingCovert communication
The present invention is directed toward systems for conducting laser range and enabling optical communication between a plurality of entities and to the application of such systems in a secure covert combat identification system. In one embodiment, the present invention uses a novel laser system that generates high pulse rates, as required for optical communications, while concurrently generating sufficiently high power levels, as required by laser range finding operations. One application of the present invention is in enabling secure covert communications between a plurality of parties. Another application of the present invention is in tracking and identifying the movement of objects.
Owner:CUBIC CORPORATION
Integrated optical communication and range finding system and applications thereof
InactiveUS7489865B2Transmission monitoringTransmission monitoring/testing/fault-measurement systemsLaser rangingCovert communication
The present invention is directed toward systems for conducting laser range and enabling optical communication between a plurality of entities and to the application of such systems in a secure covert combat identification system. In one embodiment, the present invention uses a novel laser system that generates high pulse rates, as required for optical communications, while concurrently generating sufficiently high power levels, as required by laser range finding operations. One application of the present invention is in enabling secure covert communications between a plurality of parties. Another application of the present invention is in tracking and identifying the movement of objects.
Owner:CUBIC CORP
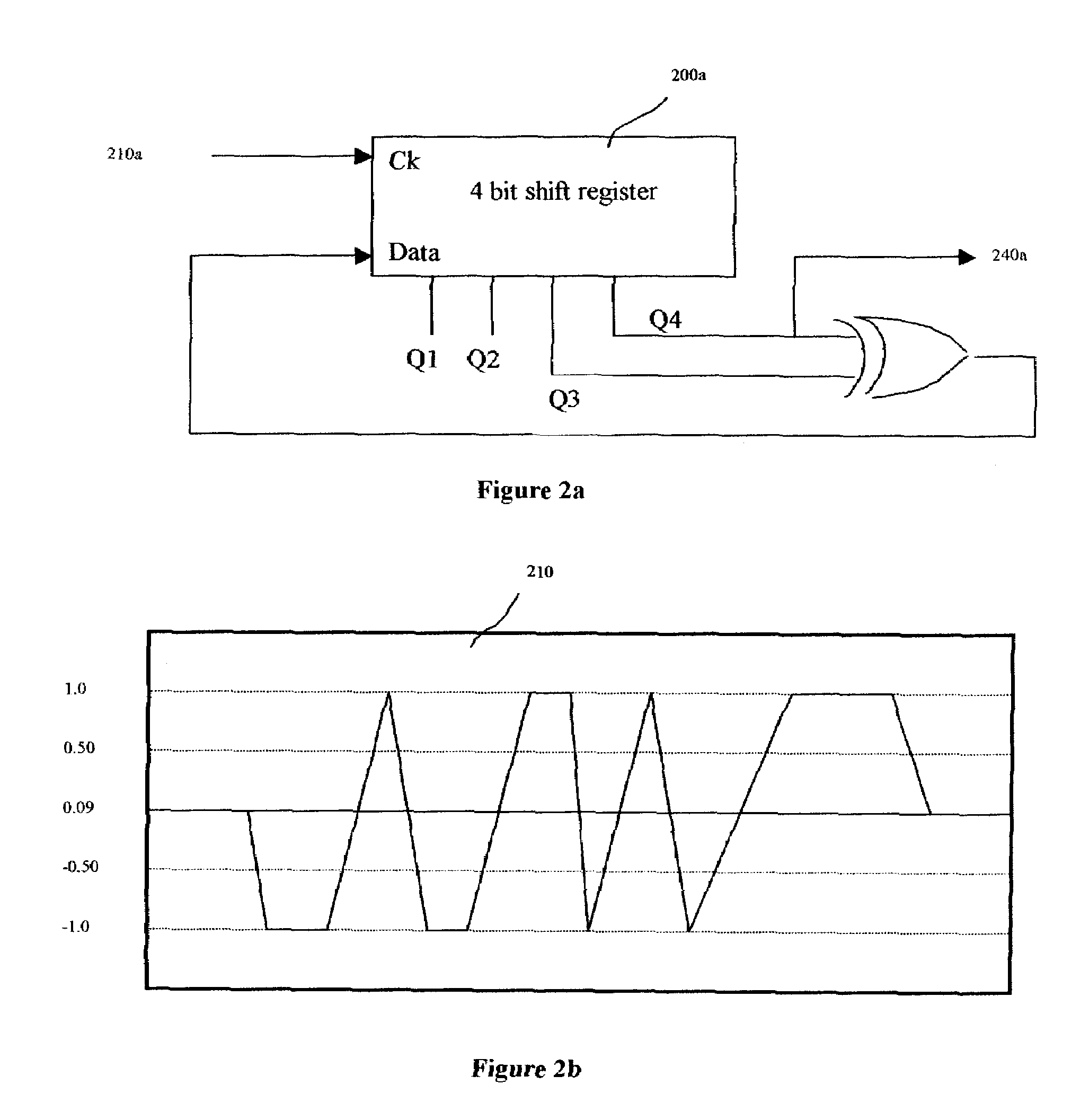
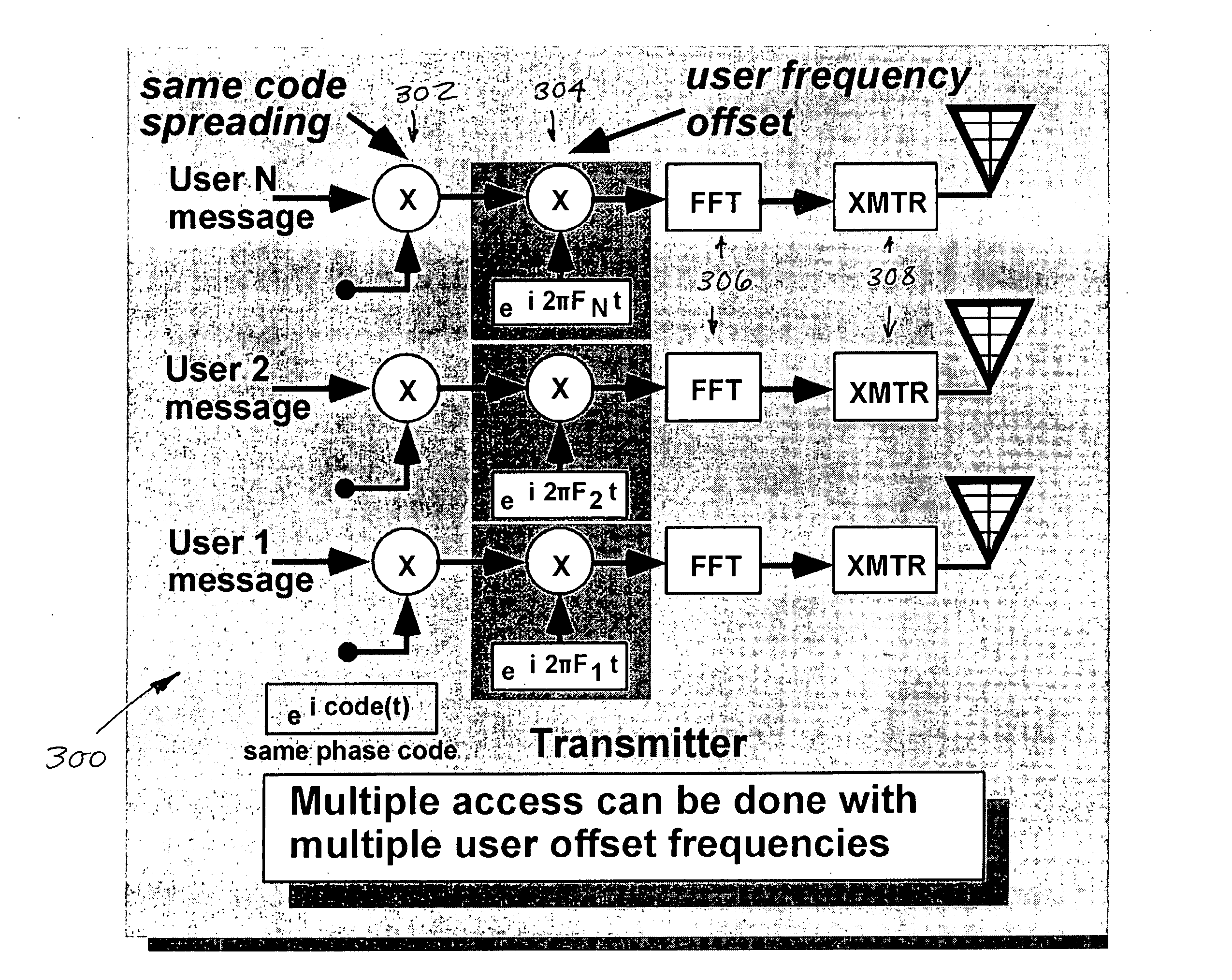
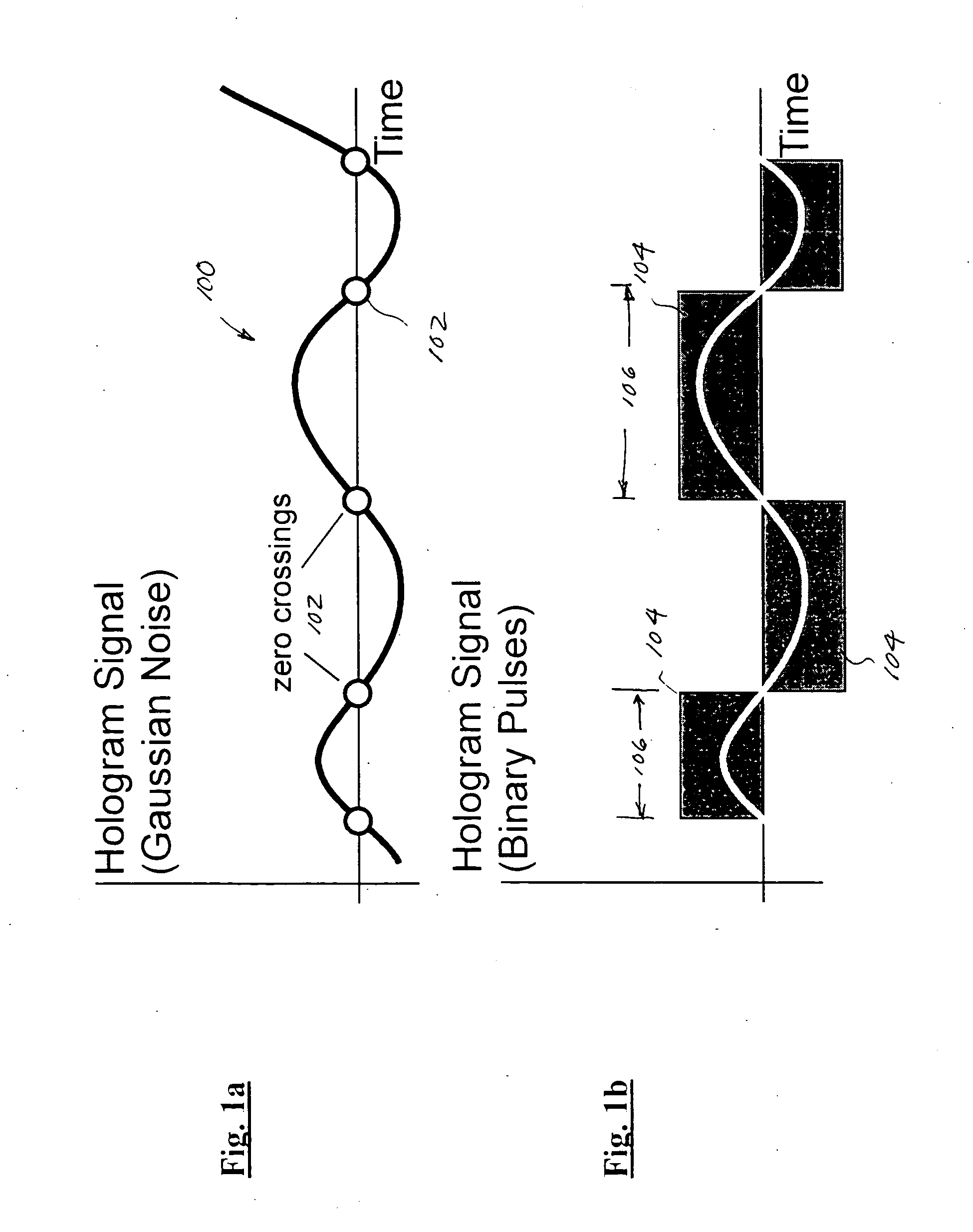
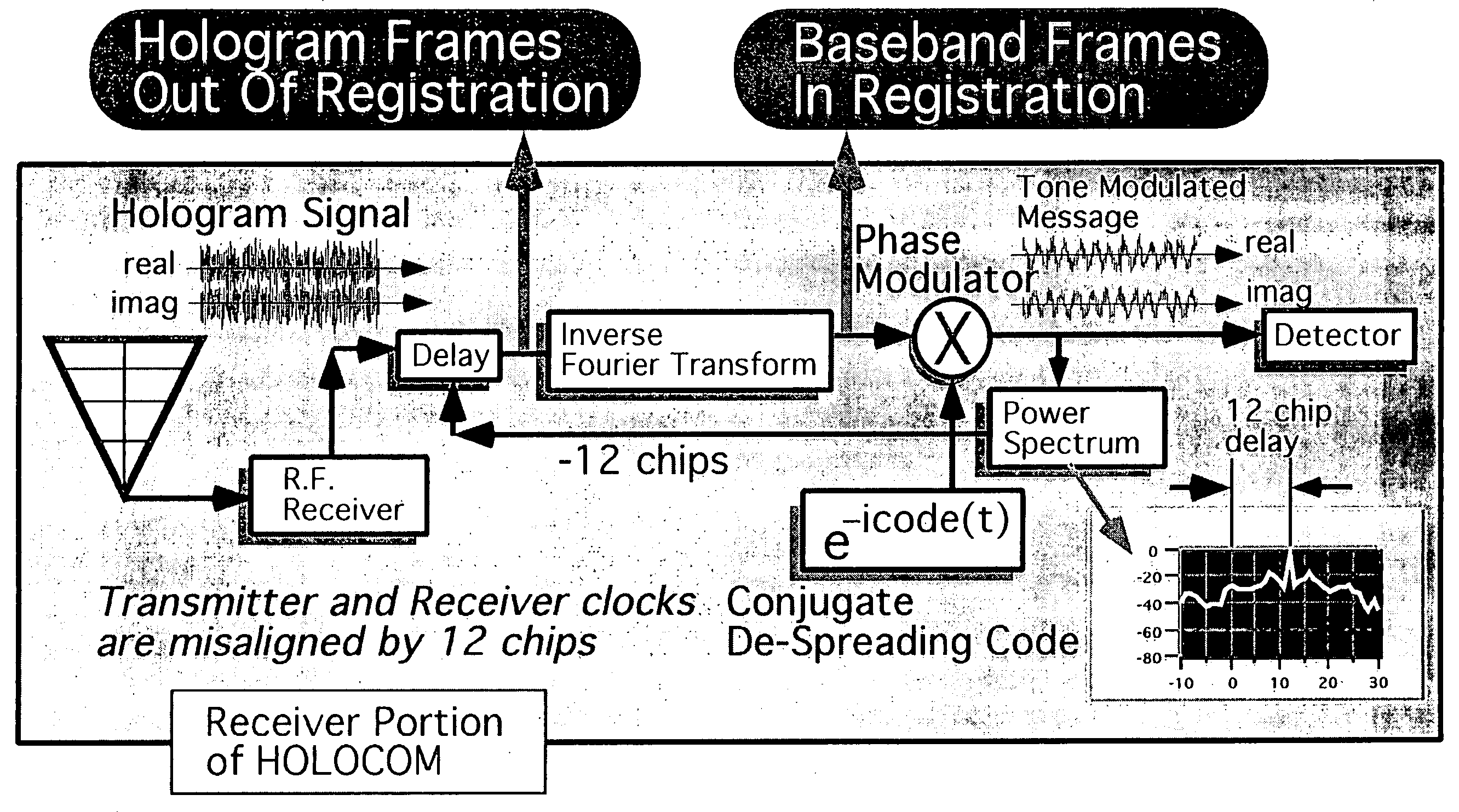
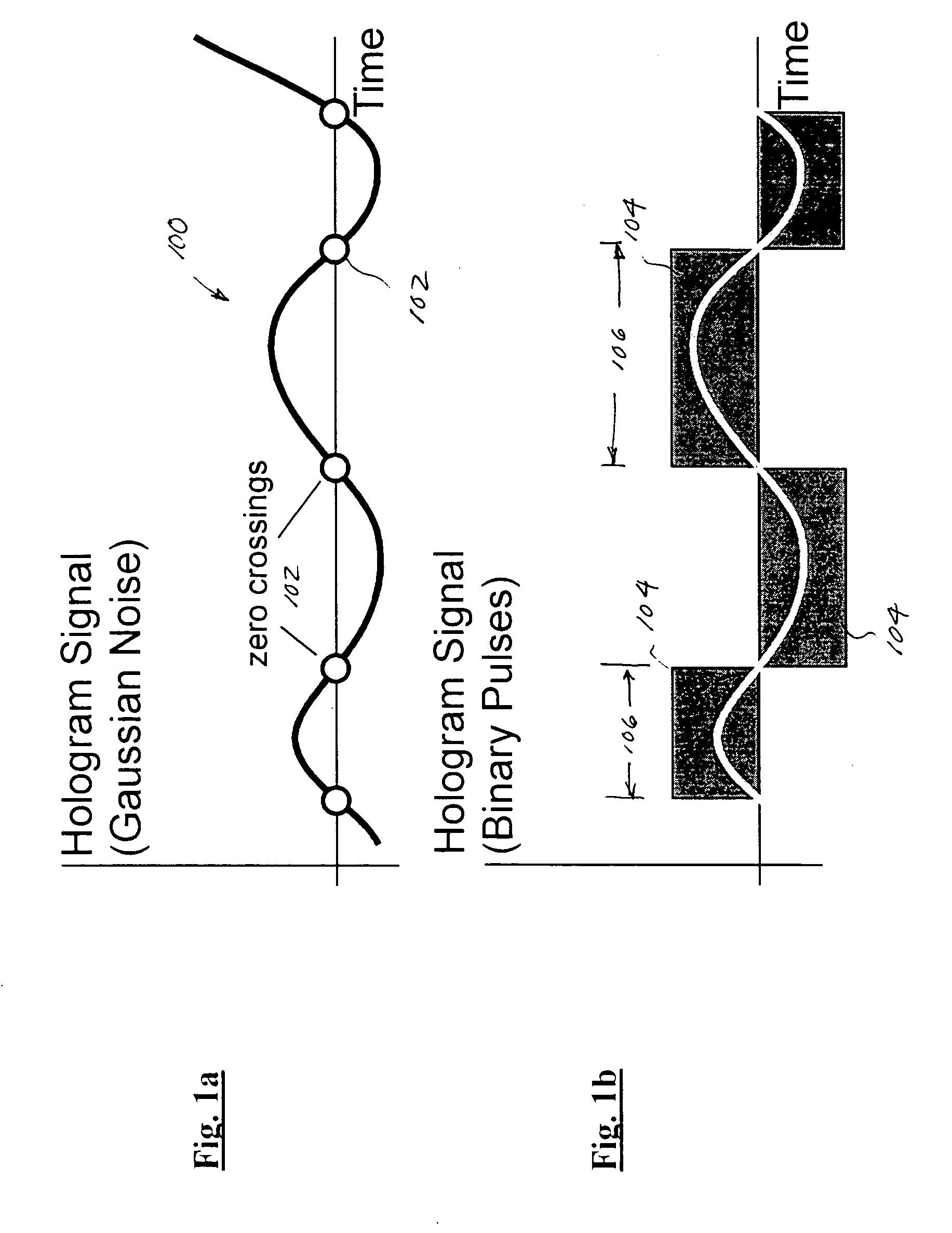
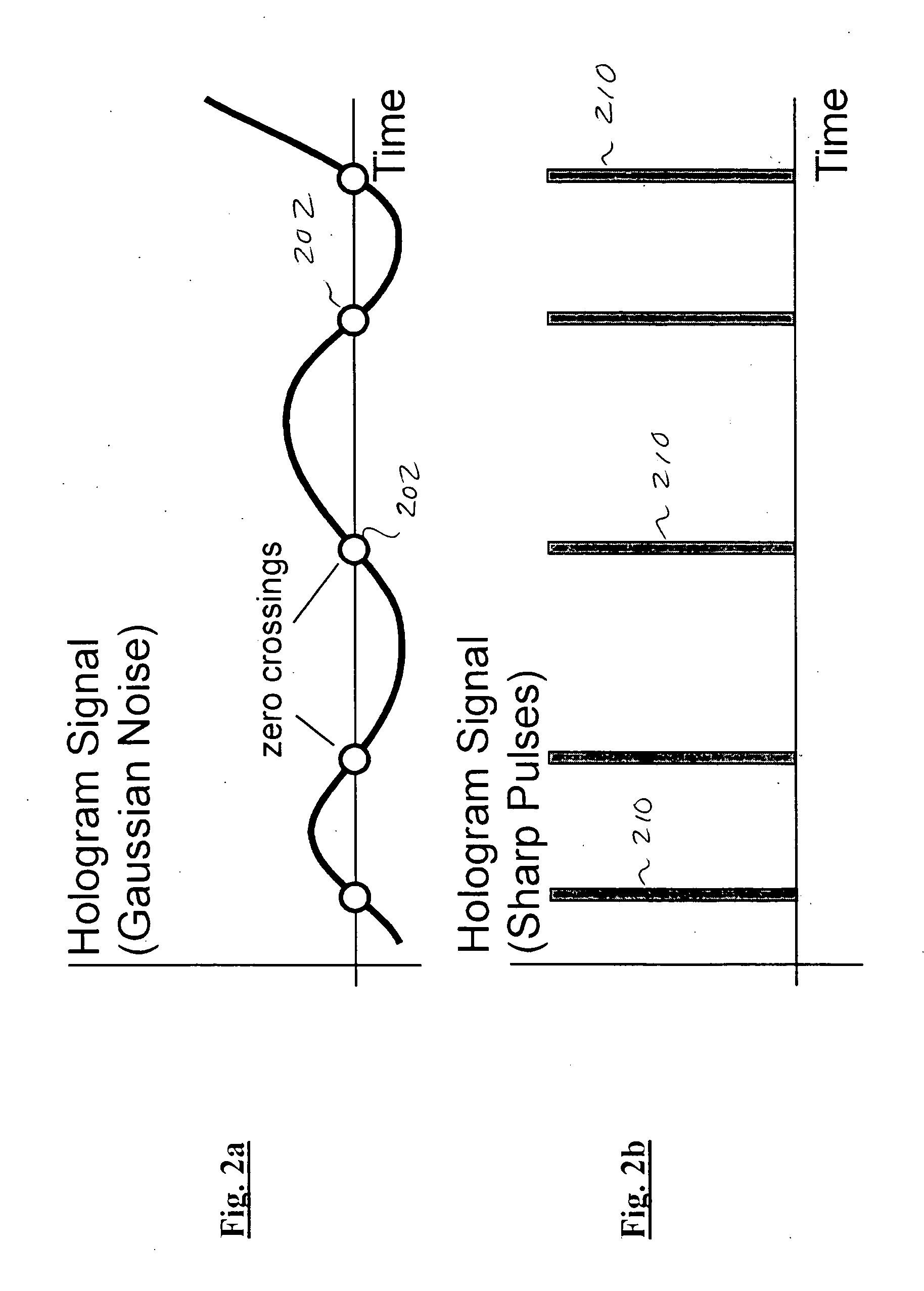
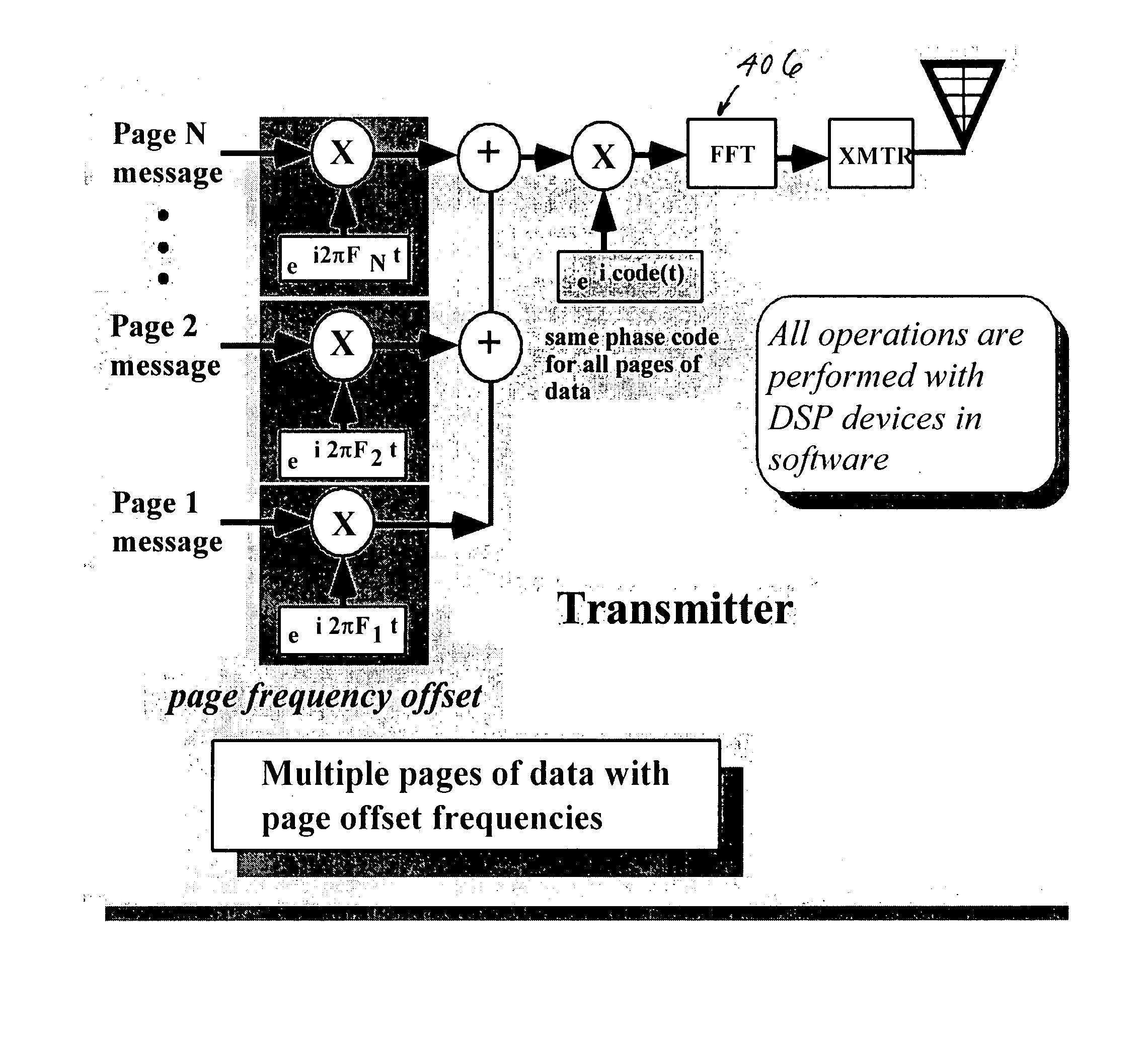
Multiple access holographic communications apparatus and methods
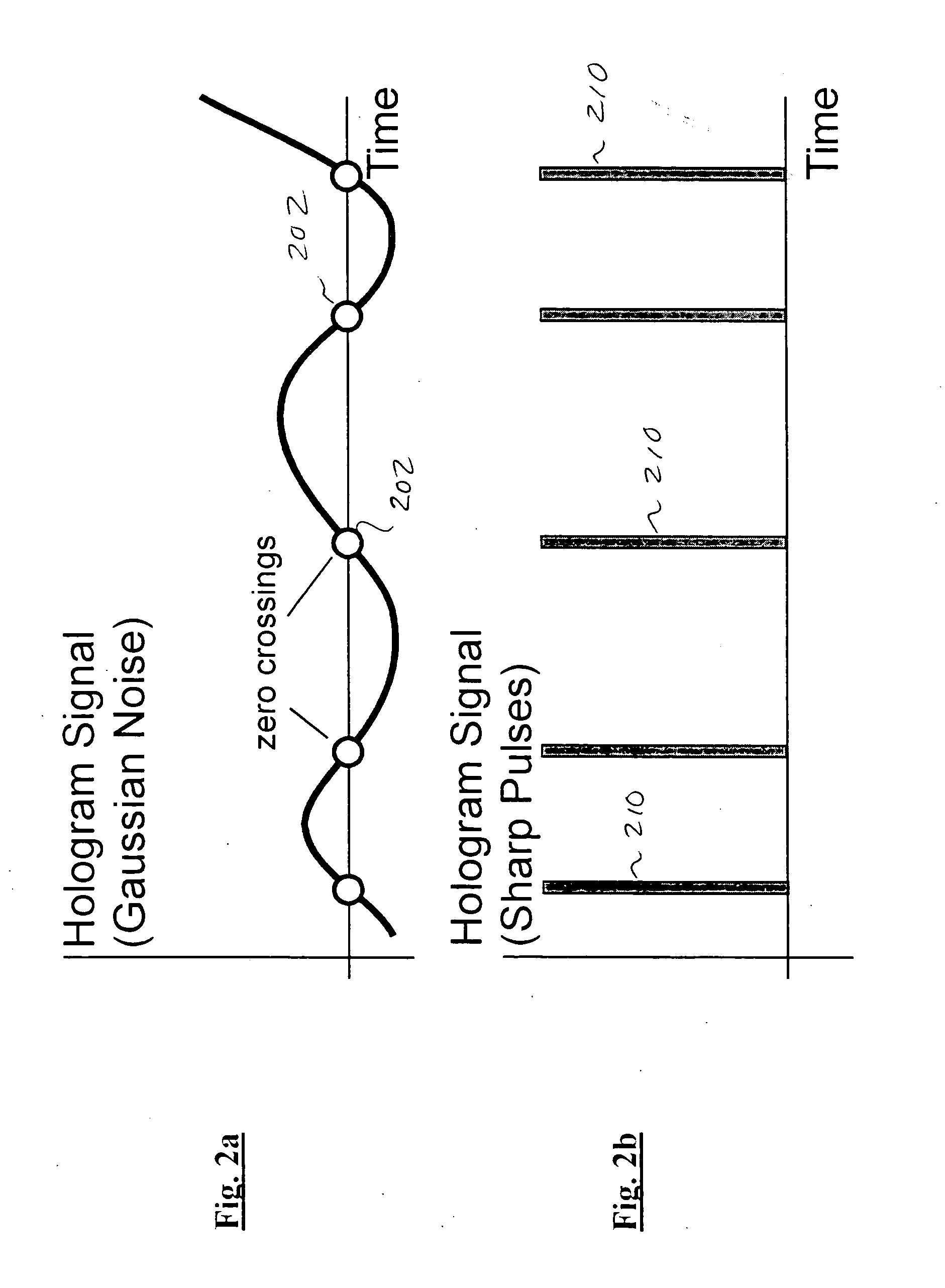
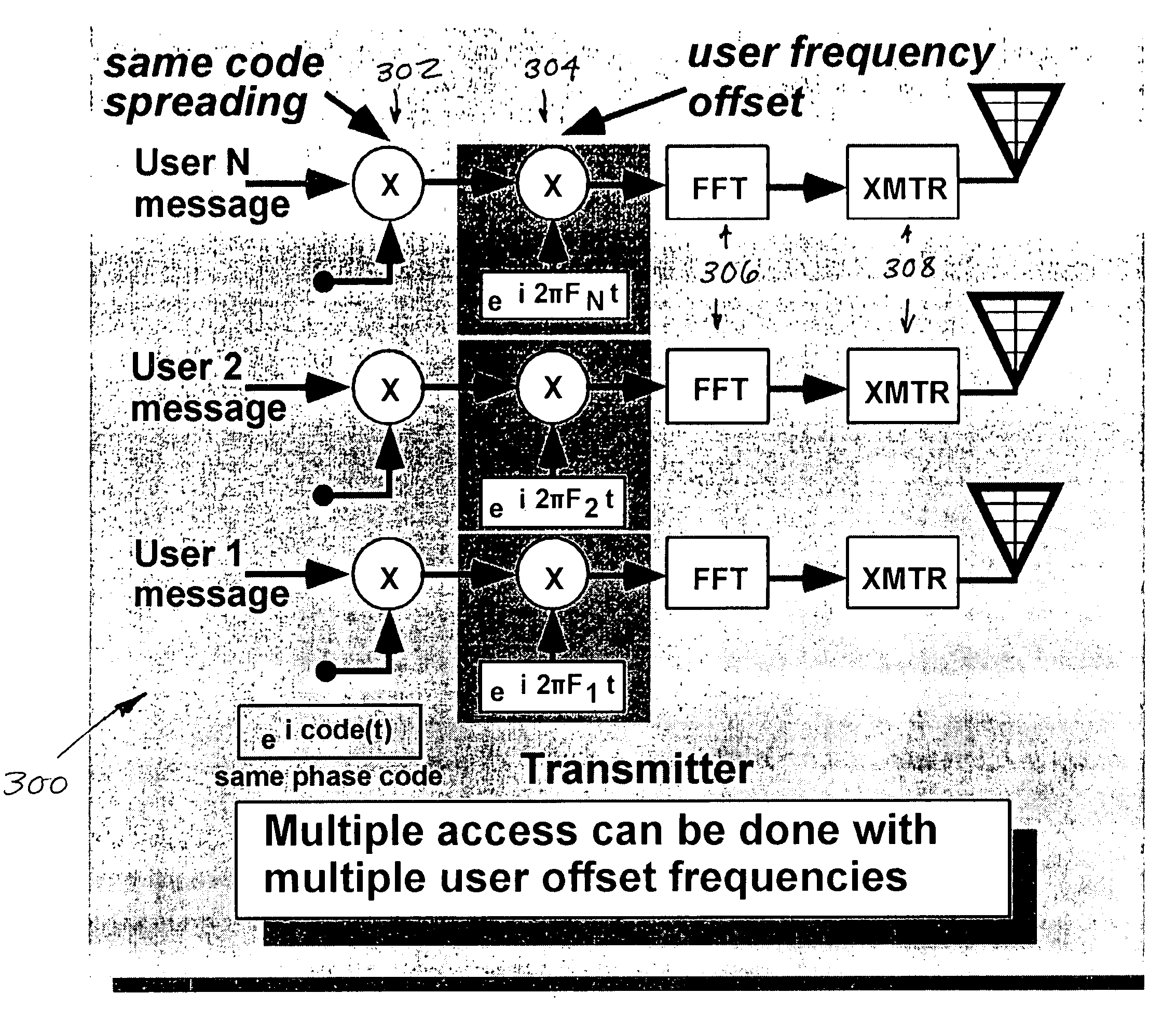
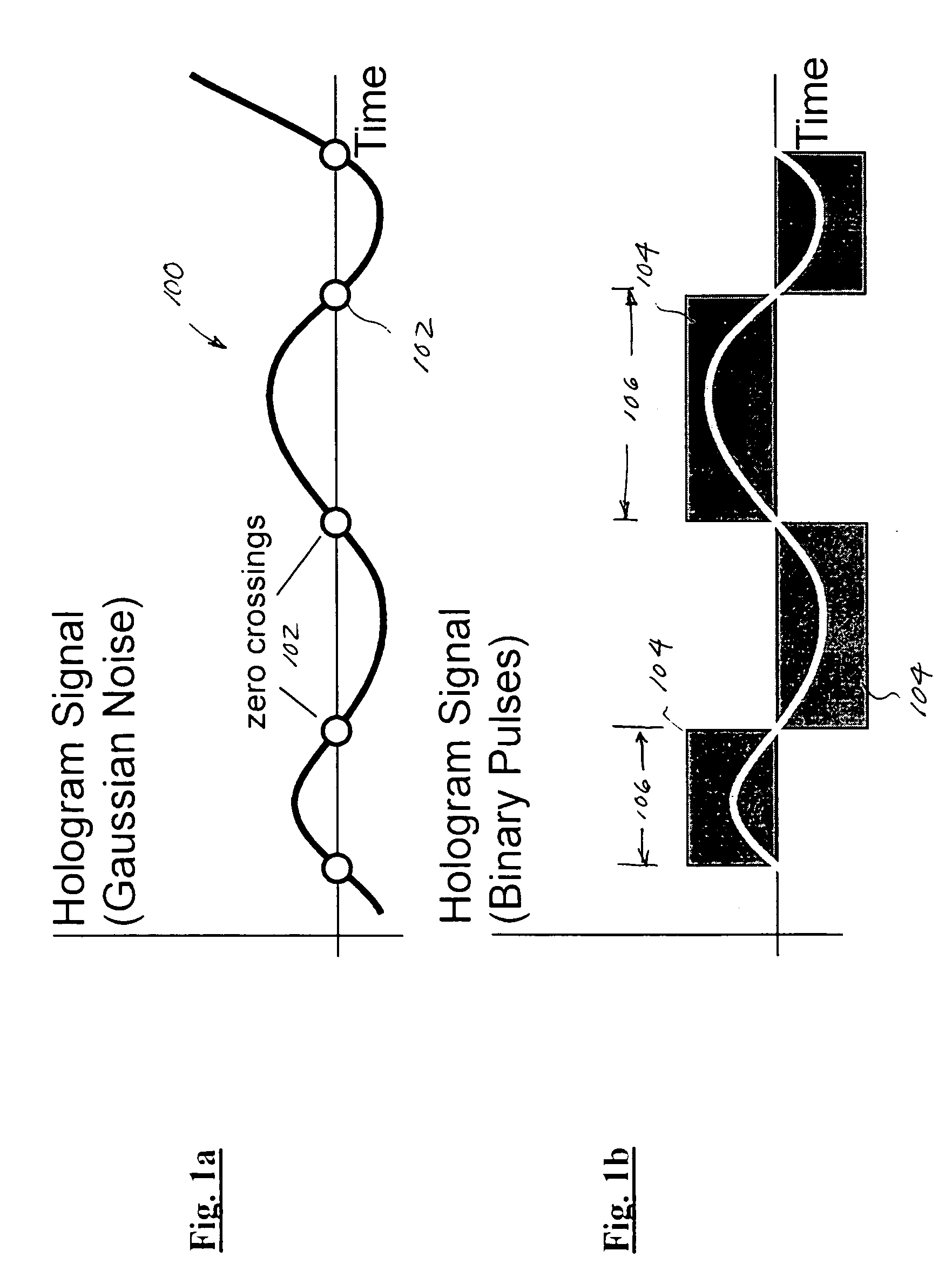
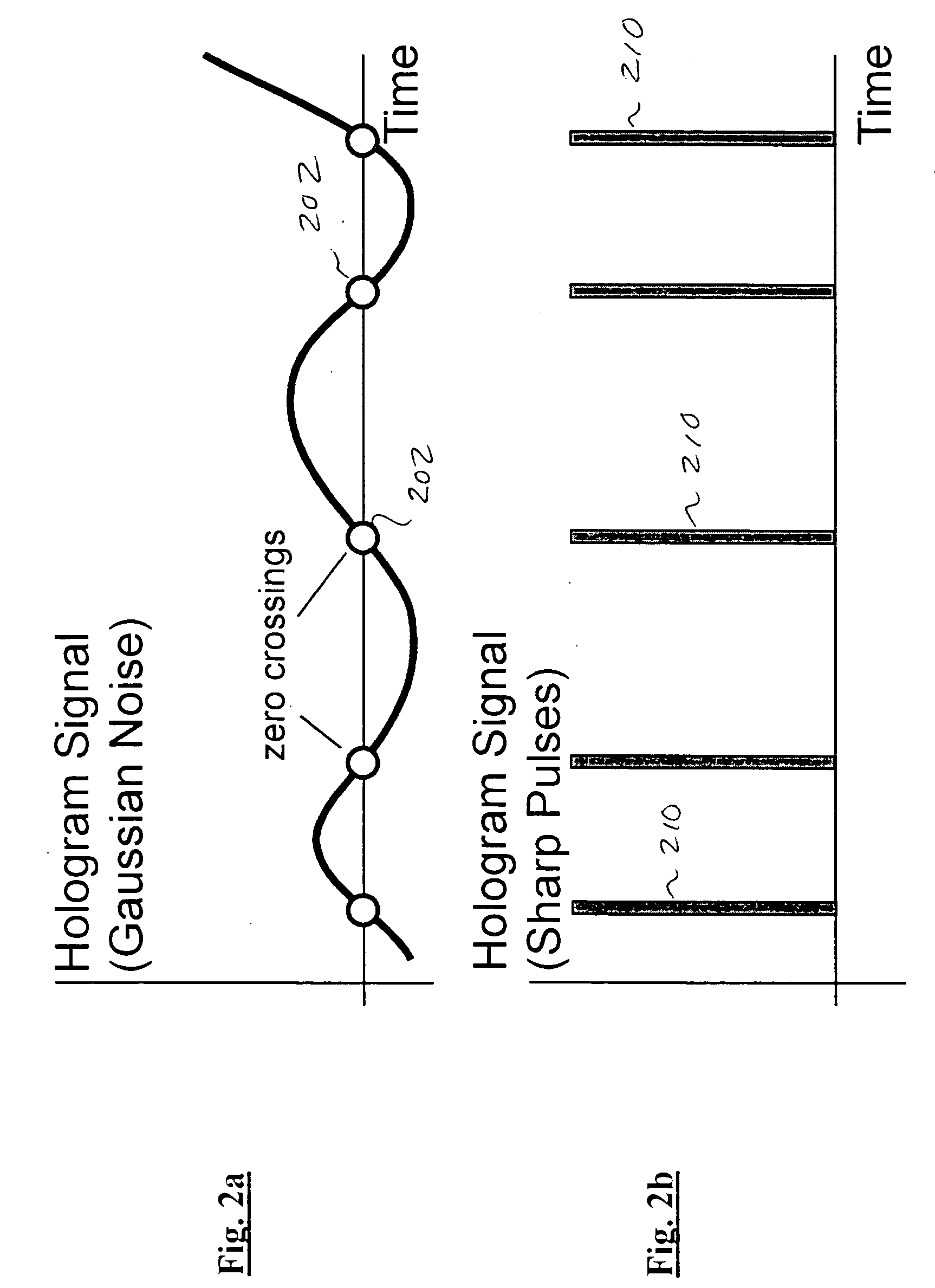
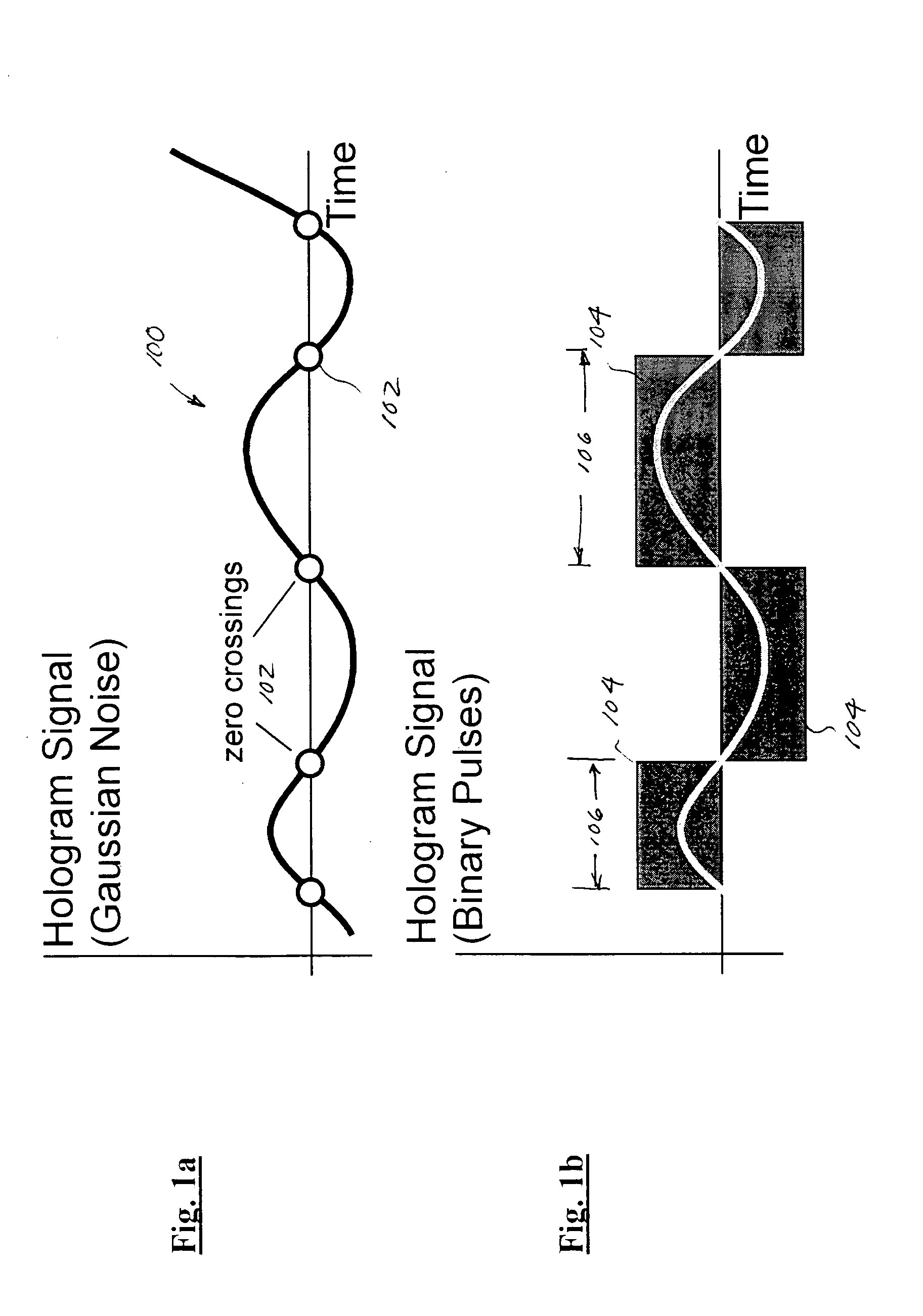
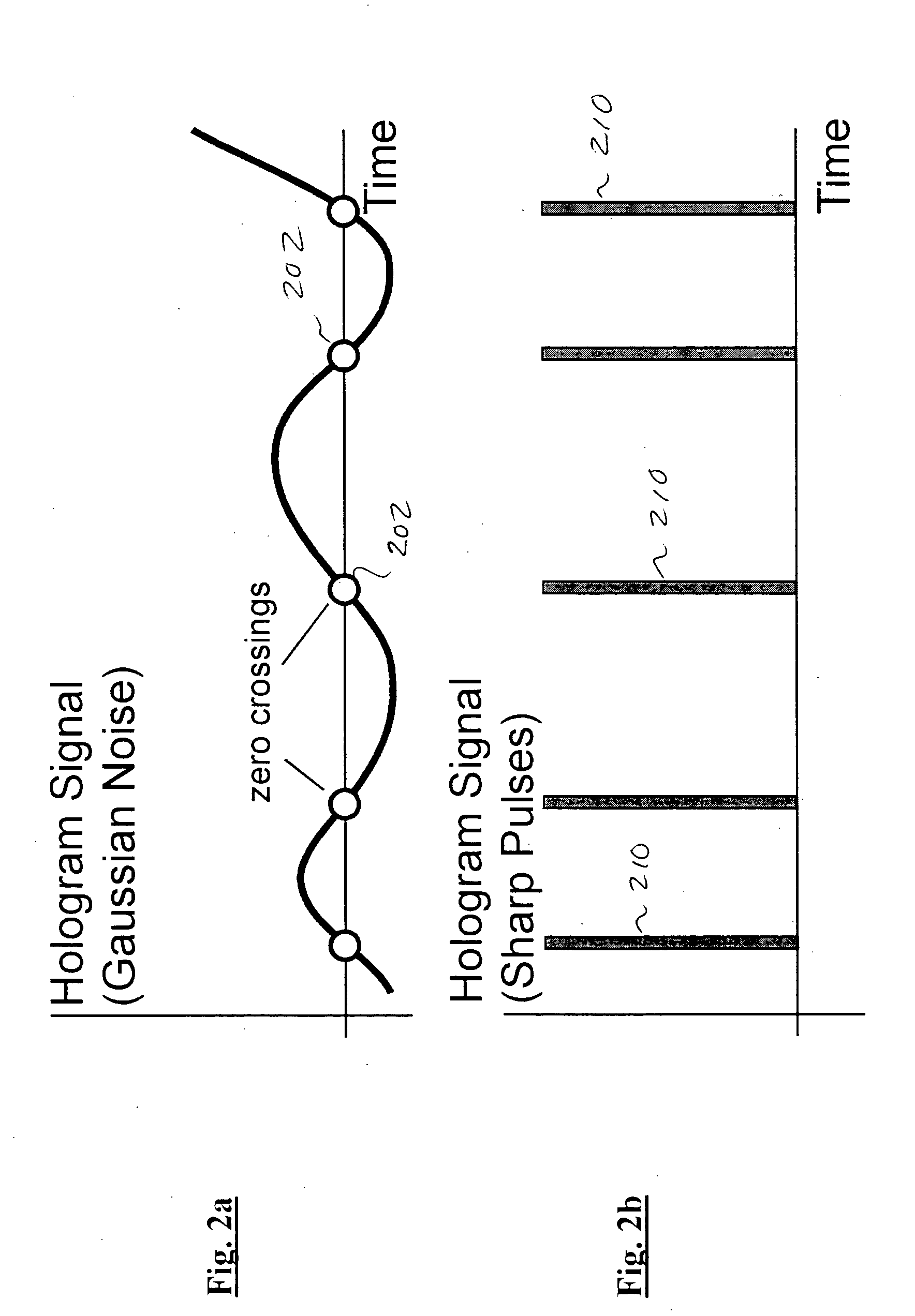
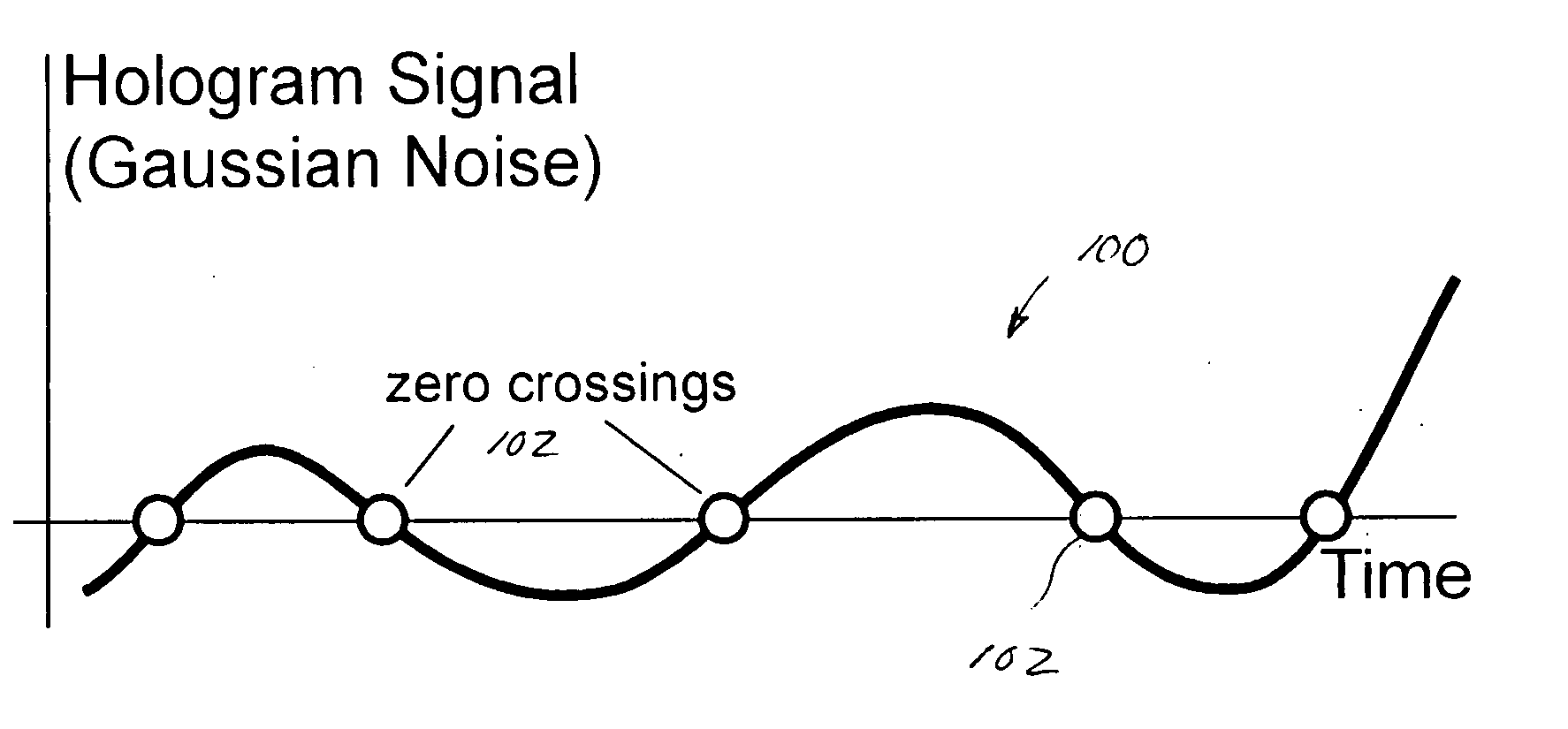
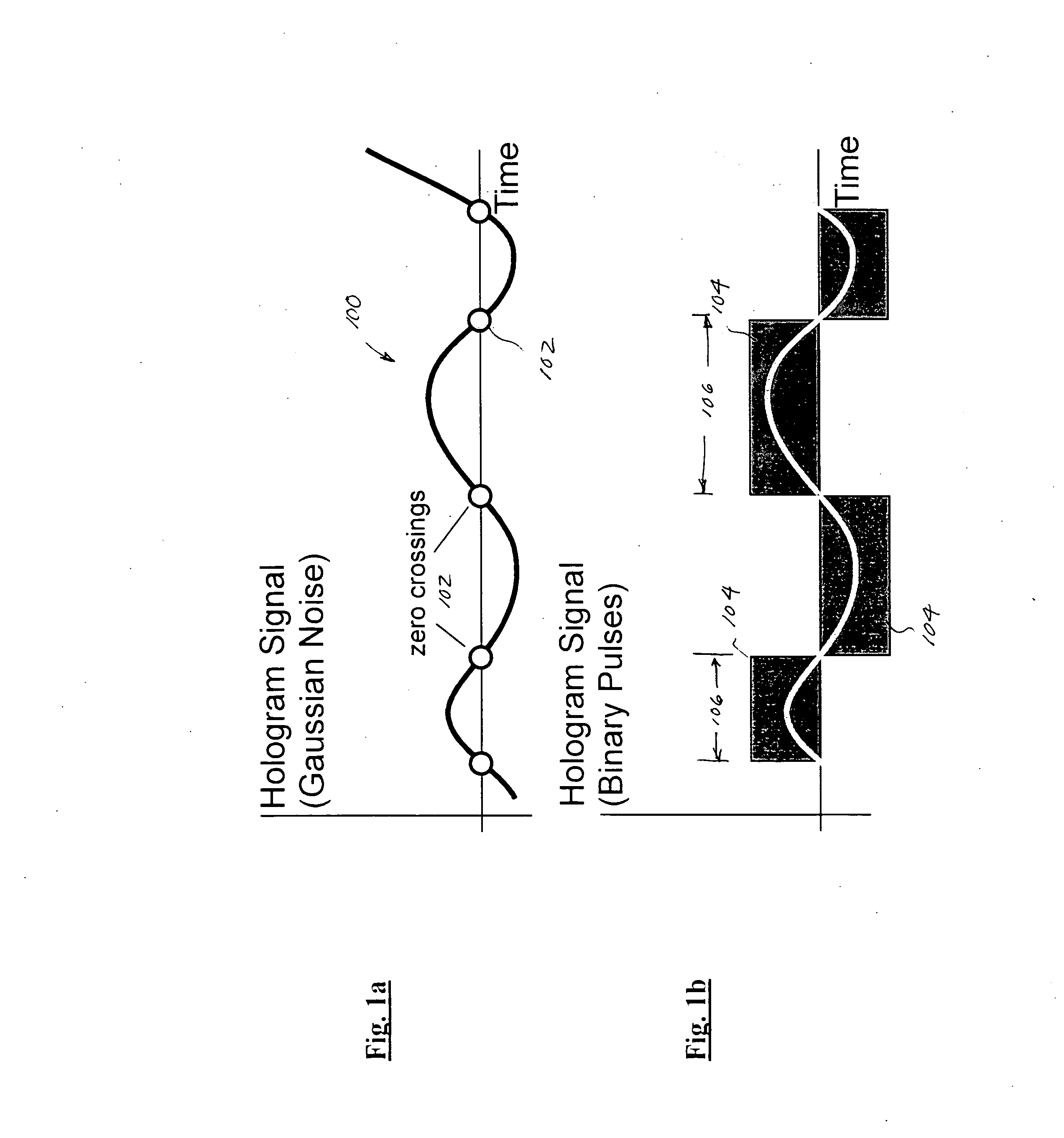
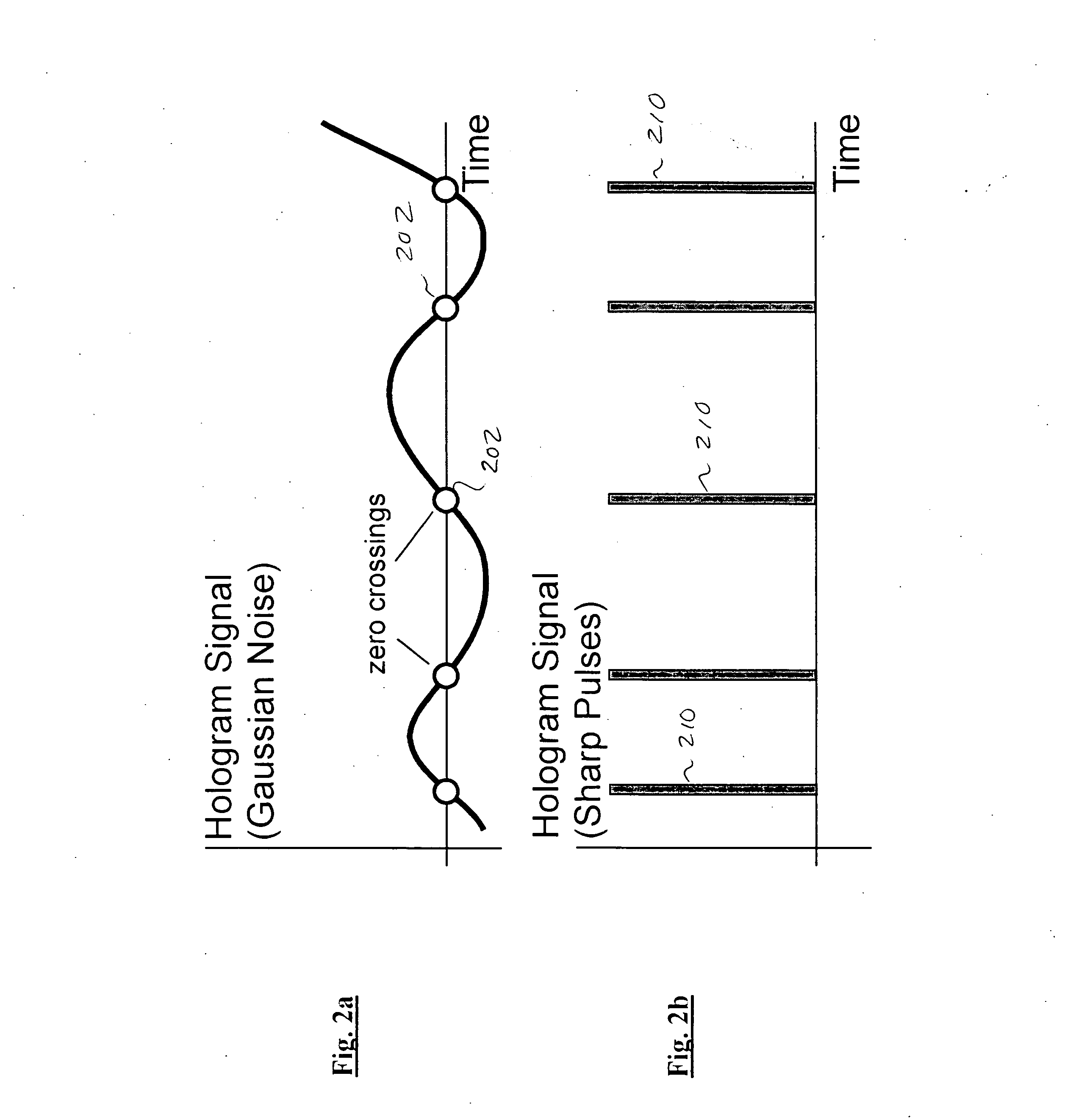
Improved apparatus and methods for utilizing holographic waveforms for a variety of purposes including communication, ranging, and detection. In one exemplary embodiment, the holographic waveforms are transmitted over an RF bearer medium to provide, inter alia, highly covert communications, radar systems, and microwave data links. The bearer (i.e., carrier) is optionally frequency-hopped, and various pulse modulation techniques applied in order to further increase communications efficiency and covertness. Methods of providing multiple access including multiple data “pages”, and high bandwidth data transmission, are also disclosed. Improved apparatus utilizing these features; e.g., a wireless miniature covert transceiver / locator, are also disclosed.
Owner:HOLOWAVE
Epoch-variant holographic communications apparatus and methods
Improved apparatus and methods for utilizing holographic waveforms for a variety of purposes including communication, ranging, and detection. In one exemplary embodiment, the holographic waveforms are transmitted over an RF bearer medium to provide, inter alia, highly covert communications, radar systems, and microwave data links. The bearer (i.e., carrier) is optionally frequency-hopped, and various pulse modulation techniques (including variation of the phase-coding clock epoch) applied in order to further increase communications efficiency and covertness. Methods of providing multiple access and high bandwidth data transmission are also disclosed. Improved apparatus utilizing these features; e.g., a wireless miniature covert transceiver / locator, are also disclosed.
Owner:HOLOWAVE
Integrated optical communication and range finding system and application thereof
InactiveUS20090142053A1Transmission monitoringTransmission monitoring/testing/fault-measurement systemsLaser rangingCovert communication
The present invention is directed toward systems for conducting laser range and enabling optical communication between a plurality of entities and to the application of such systems in a secure covert combat identification system. In one embodiment, the present invention uses a novel laser system that generates high pulse rates, as required for optical communications, while concurrently generating sufficiently high power levels, as required by laser range finding operations. One application of the present invention is in enabling secure covert communications between a plurality of parties. Another application of the present invention is in tracking and identifying the movement of objects.
Owner:CUBIC CORP
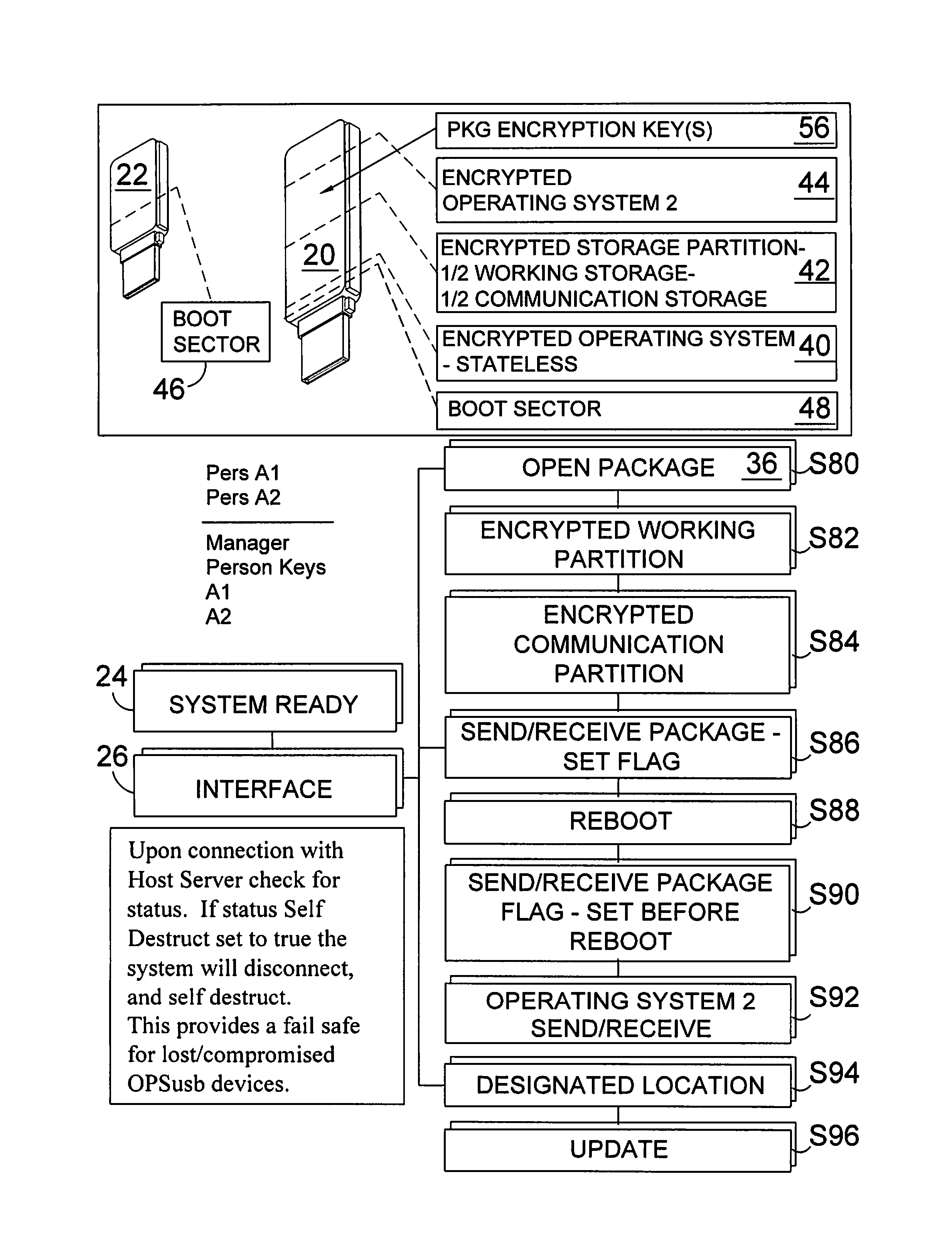
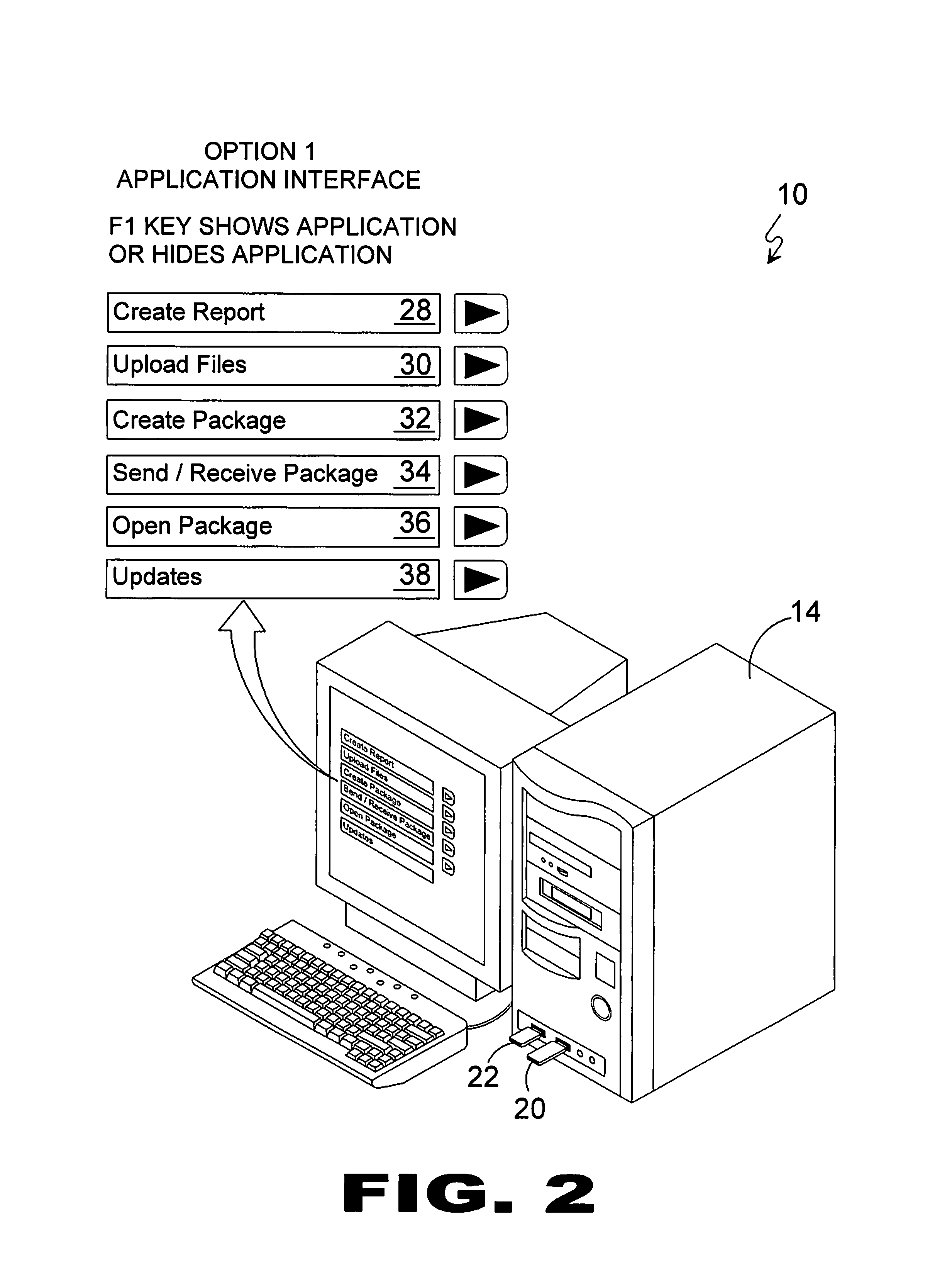
Bootable covert communications module
InactiveUS8868898B1Memory loss protectionDigital data processing detailsCommunications systemCovert communication
A method for a covert communication system comprising a pair of flash memory devices having encrypted boot instructions and communication software thereon whereby the flash memory devices once plugged into a computer's USB ports and the computer is powered on, the flash memory boot load tests for the presence of a flash memory device dongle having an encrypted key that that once validated starts the encrypted communication software designed to create, edit, send and receive a report comprising data files forming a data package, which can only be transmitted by restarting the computer.
Owner:VAN HOOF ROBERT
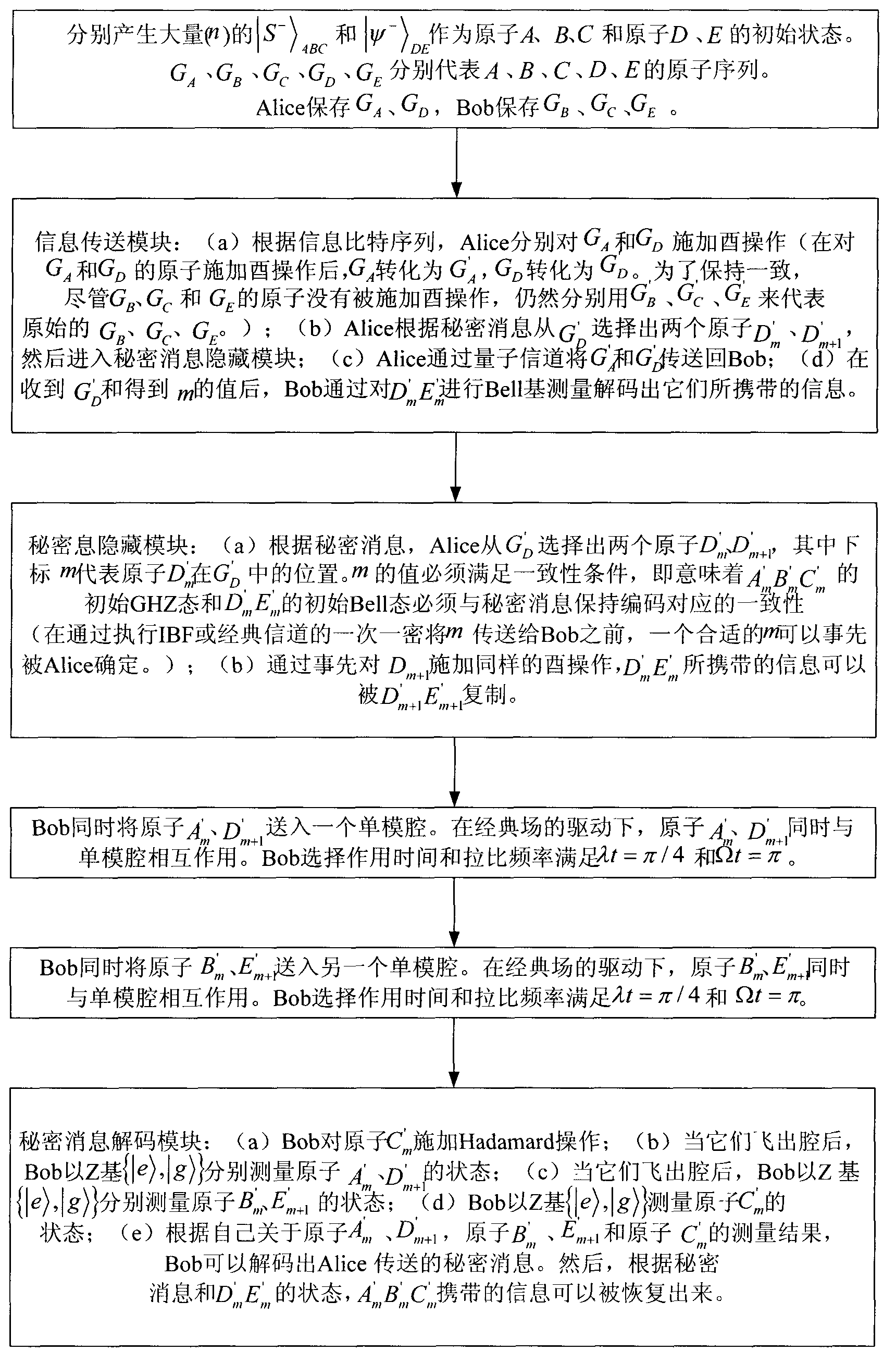
Quantum steganography protocol based on gigahertz (GHZ) state dense coding and entanglement exchange
InactiveCN102801518AIncrease imperceptibilityImprove securityError preventionSecuring communicationSecure communicationClassified information
According to quantum steganography, the classical steganography and quantum secure communication are combined together, and the quantum steganography is popularized in the field of quanta. The quantum steganography aims to realize secret transmission of classified information by utilizing a quantum hidden channel. The invention provides a quantum steganography protocol based on gigahertz (GHZ) state dense coding and entanglement exchange. A hyper-quantum channel of the protocol is formed by establishing the hidden channel on a quantum secure direct communication (QSDC) protocol. The classified information is transmitted by combining the GHZ state dense coding and GHZ state entanglement exchange based on the original QSDC. The capacity of the hyper-quantum channel of the protocol reaches 6-bit per round in covert communication. In addition, the protocol has high imperceptibility and high safety.
Owner:唐山安生纸制品制造有限公司
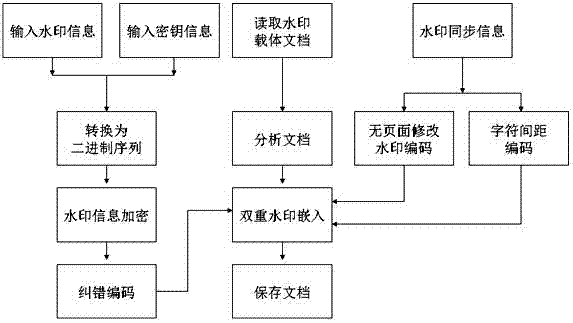
Character pitch encoding-based dual-watermark embedded text watermarking method
InactiveCN103049682AImprove robustnessRealize portabilityProgram/content distribution protectionSpecial data processing applicationsData integrityCovert communication
The invention relates to a character pitch encoding-based dual-watermark embedded text watermarking method, comprising the following steps of: converting watermark information M and a key D, which are required to be hidden, into a binary sequence, circularly executing modulus to get an encrypted binary sequence, adding error-correcting codes for the to-be-embedded watermark information, and finally embedding dual watermarks and synchronization information of the watermarks by encoding the attribute of a text object without page modification and encoding a character pitch. With the method, the text content cannot be changed, the watermark information is hidden well, and the method has the characteristics of high robustness and high capacity. By extracting the embedded watermark information, transmission and modification of a document can be controlled effectively, and whether the document is modified can be judged, and finally, the aims of digital copyright protection, data integrity authentication and safe covert communication for the text document are achieved.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
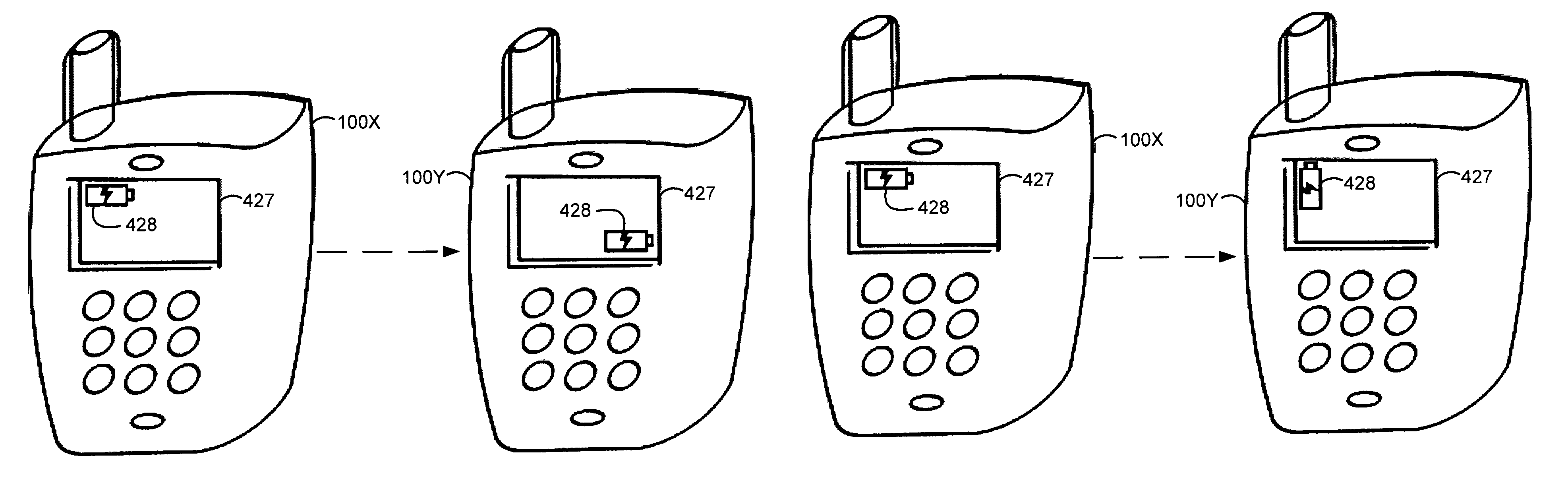
Covert and non-covert mode communication
ActiveUS8190128B1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsCovert communicationUser interface
A method and system are described for operating a source communication device. The source communication device receives a first request from a user through a user interface requesting a first communication session with a target communication device. The source communication device transfers a first signal to a network requesting the first communication session with the target communication device, wherein the target communication device provides an overt communication alert for the first communication session. The source communication device receives a second request from the user requesting a second communication session requesting that the target communication device provide a covert communication alert for the second communication session. The source communication device transfers a second signal to the network requesting the second communication session with the target communication device and indicating the request for the covert communication alert, wherein the target communication device provides the covert communication alert for the second communication session.
Owner:T MOBILE INNOVATIONS LLC
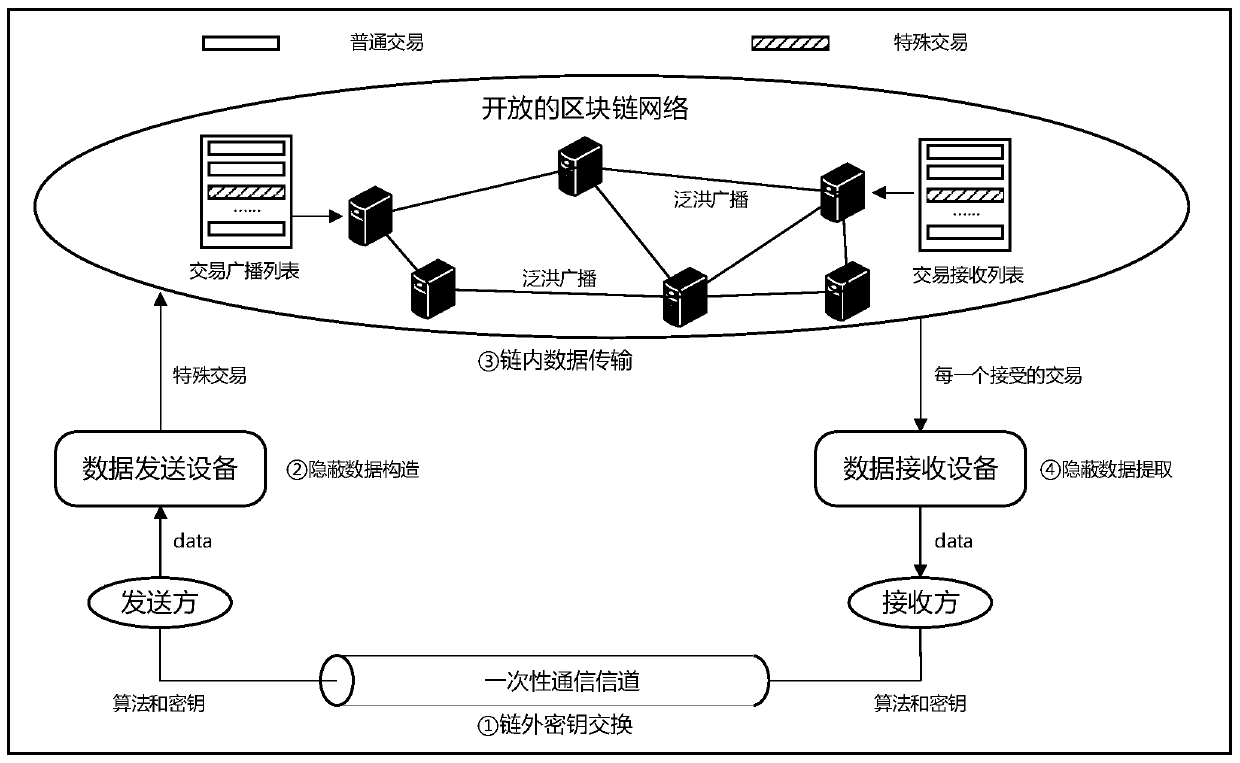
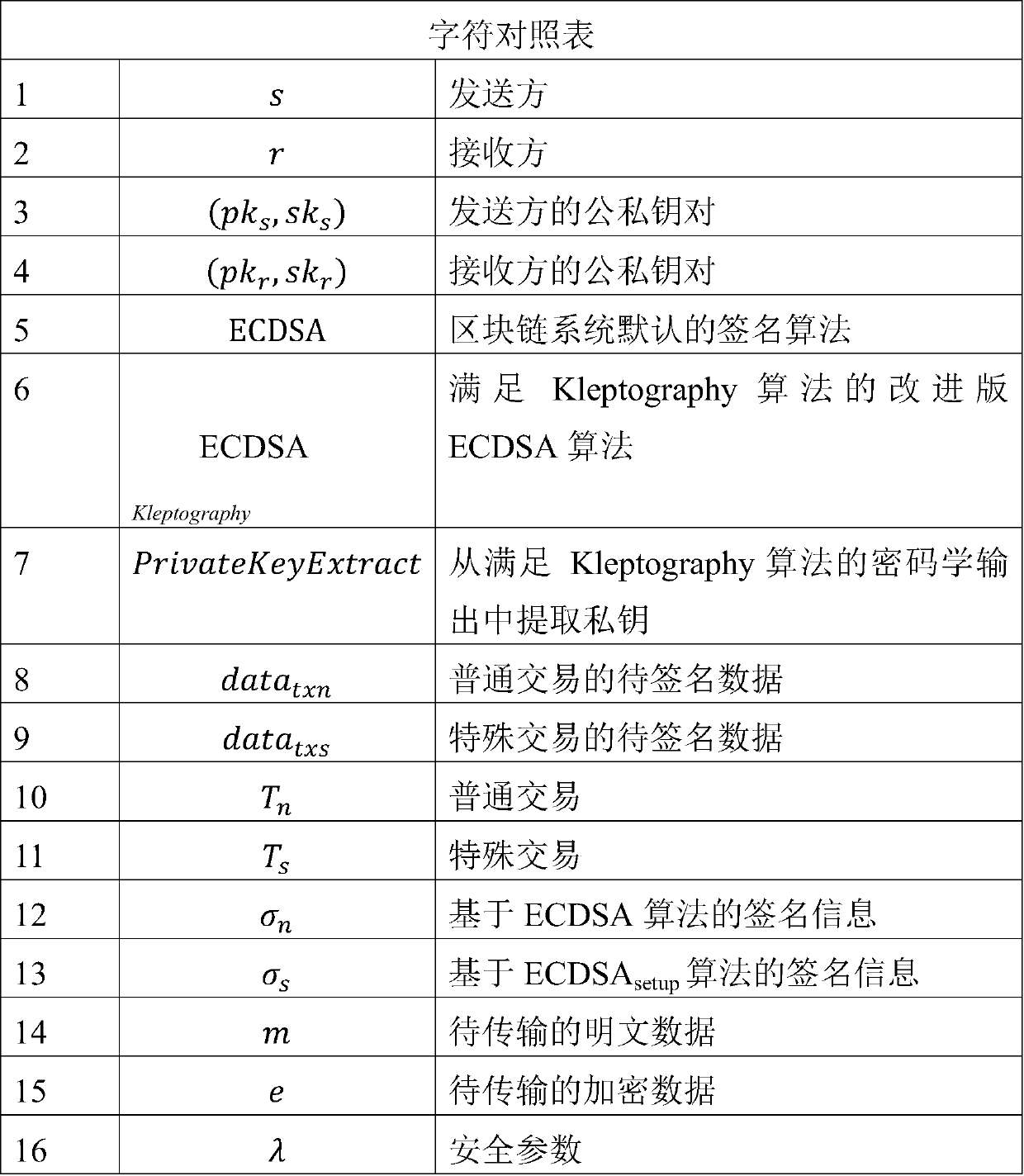
Data covert transmission method based on block chain network
ActiveCN110225016AImprove concealmentAvoid Statistical LawsFinanceMultiple keys/algorithms usageKey exchangeCovert communication
The invention relates to a data covert transmission method based on a block chain network, and belongs to the technical field of data covert transmission. According to the method, a public key servingas a certificate of covert communication is exchanged through an out-of-chain key exchange stage; then constructing a special transaction which contains a message encrypted by a sender private key and can leak signature information of the sender private key and is generated by using a Kleptography technology through a covert data construction stage; then, the special transaction is propagated through an in-chain data transmission stage; and finally, reading and detecting each block chain transaction propagated in the block chain network one by one by a receiver in a hidden data extraction stage, and if the signature data in the transaction can extract a private key by using a Kleptograpy technology, indicating that the transaction is a special transaction carrying encrypted data. And thereceiver decrypts the original text by using the extracted private key. Compared with the prior art, the method has the characteristic of high concealment, and an enemy cannot identify a concealed channel according to account characteristics.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
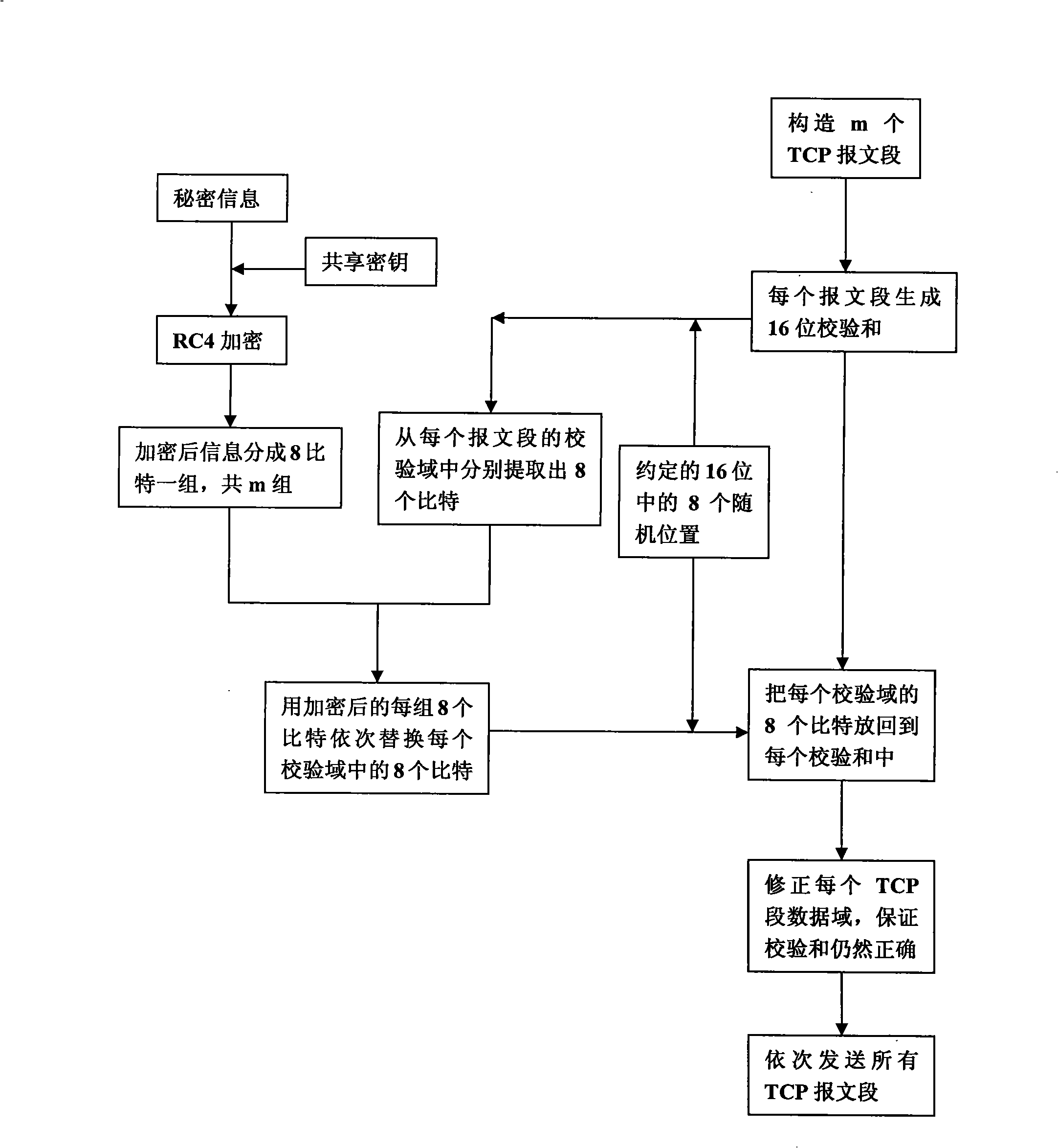
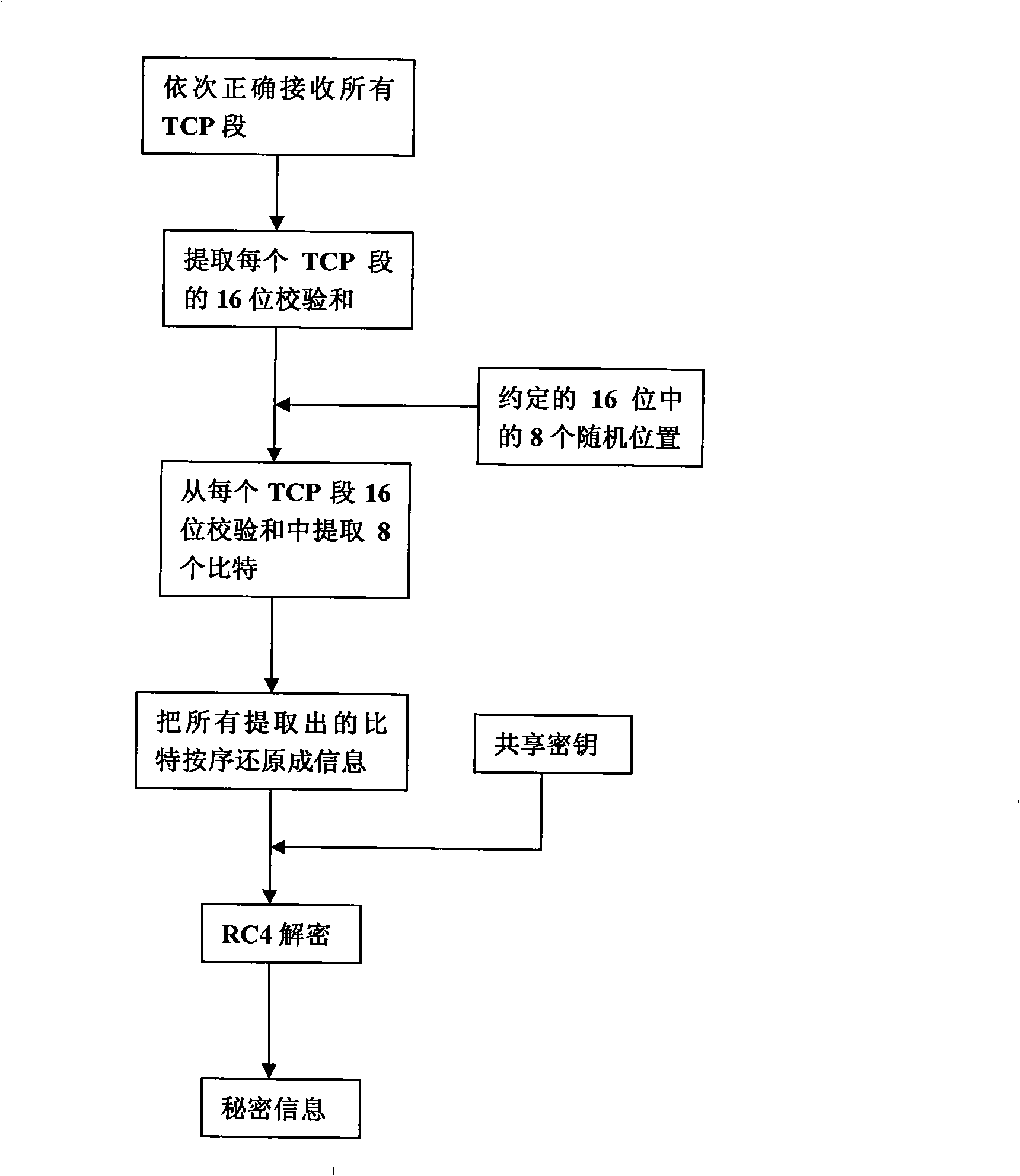
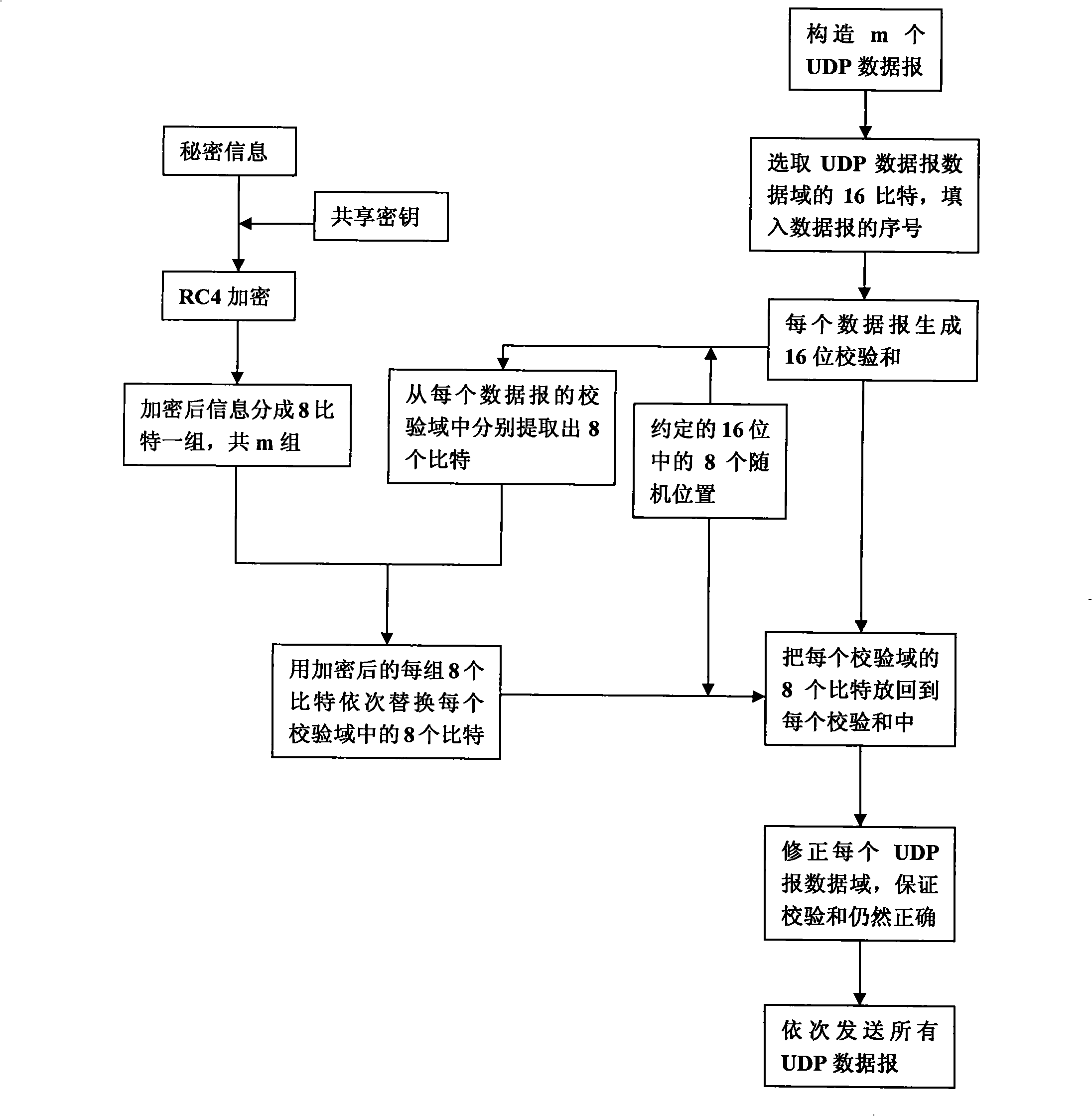
Transmitting/receiving method for secret communication
InactiveCN101277194AImprove concealmentGood secrecySecuring communicationNetworking protocolConfidentiality
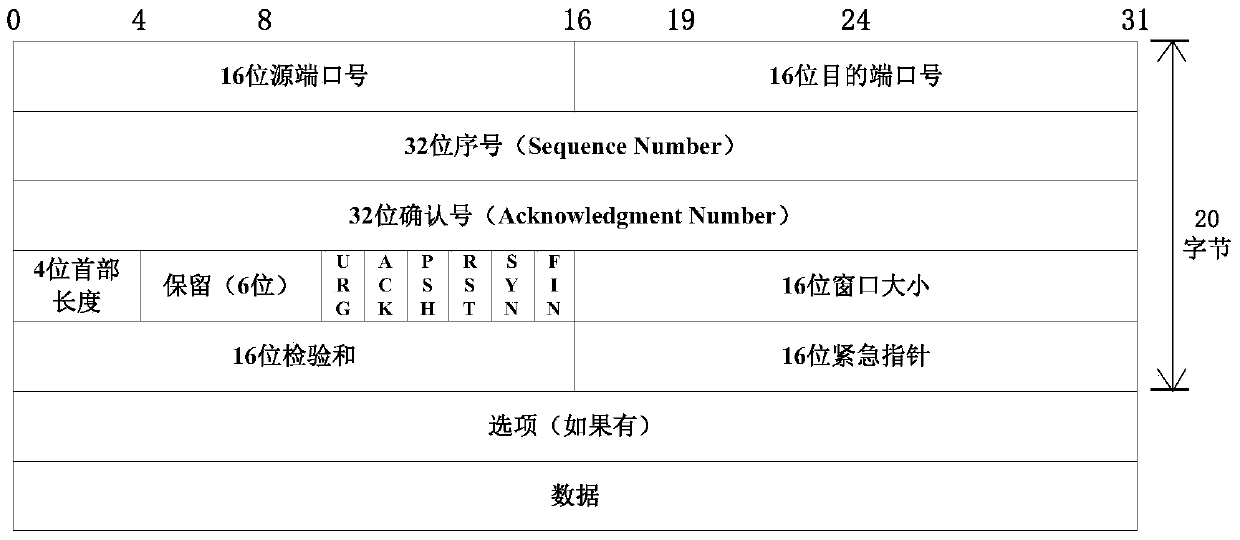
The invention discloses a transmitting / receiving method of covert communication. The method conceals important information waiting convey into a carrier in computer network environment, and important information is unware. When a transmitter transmits network date, a secret information is random embedded into a check field of network protocol date unit (TCP section or UDP) header, and date field is corrected for ensuring check sum right after the secret information is embedded; a receiver extracts the secret information after receiving network protocol date unit from network. The method has better confidentiality and anti-attack by using check and covert information of protocol date unit, and is safely and reliable. The method is especially suitable for convert communication of important information with less date quantity.
Owner:JIANGSU UNIV OF SCI & TECH
Multipath-adapted holographic communications apparatus and methods
InactiveUS20050100077A1Simultaneous amplitude and angle modulationModulation with suppressed carrierTransceiverRadar systems
Improved apparatus and methods for utilizing holographic waveforms for a variety of purposes including communication, ranging, and detection. In one exemplary embodiment, the holographic waveforms are transmitted over an RF bearer medium to provide, inter alia, highly covert communications, radar systems, and microwave data links. Multipath propagation is compensated for by either filtering the multipath signals in the decoded baseband, or alternatively adding the various signals, using a power spectrum. Methods of providing multiple access and high bandwidth data transmission are also disclosed. Improved apparatus utilizing these features; e.g., a wireless miniature covert transceiver / locator, are also disclosed.
Owner:HOLOWAVE
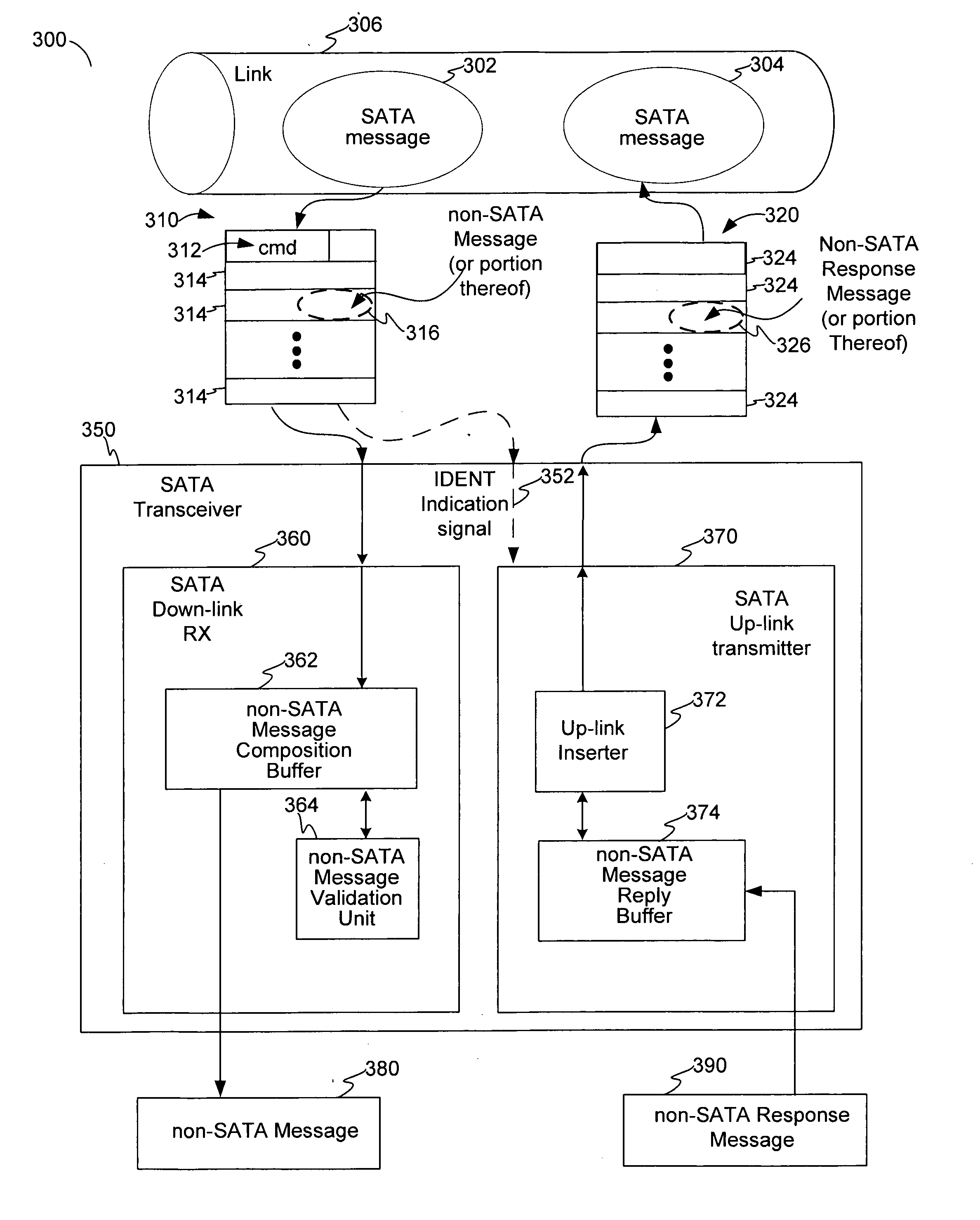
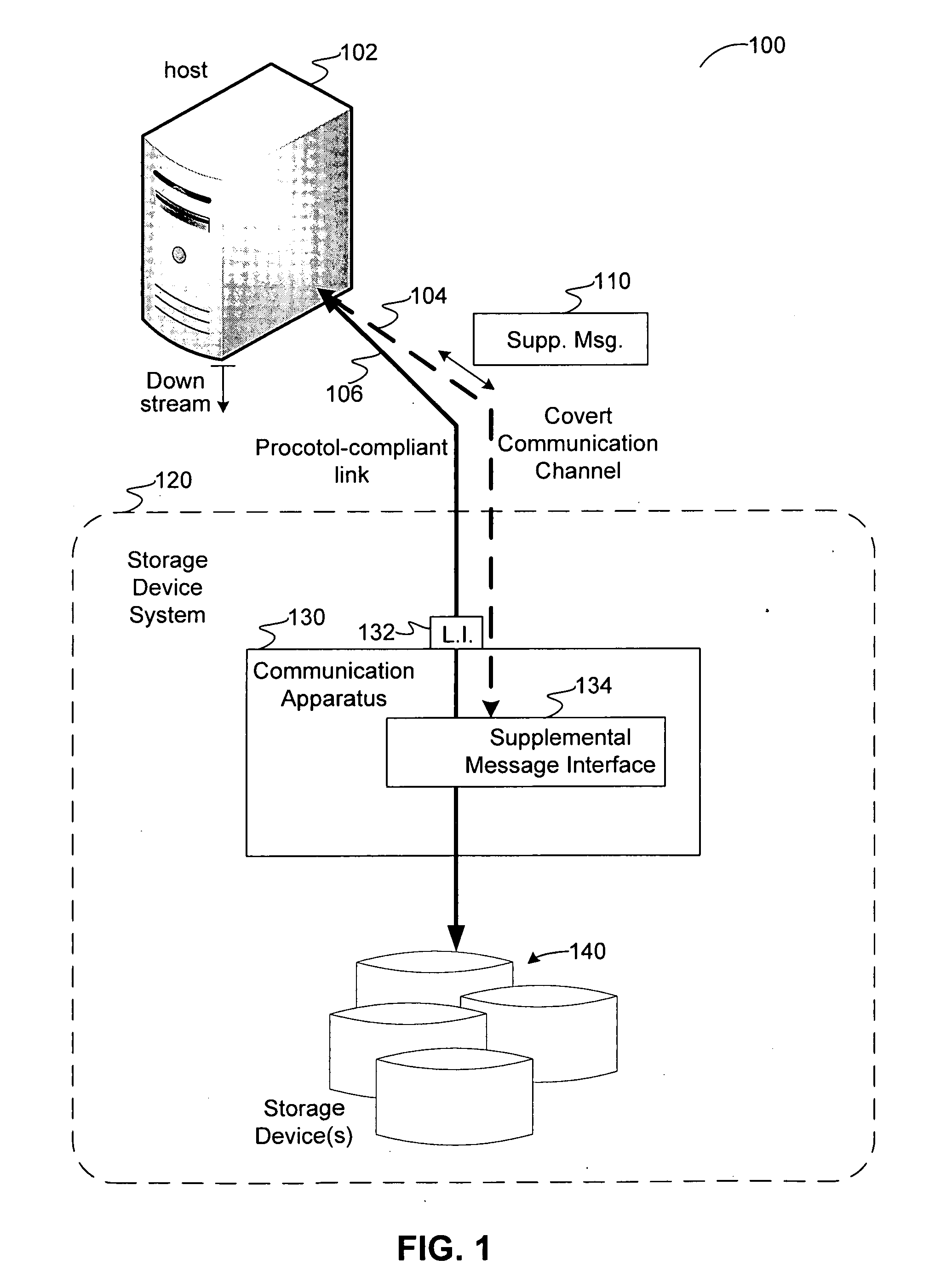
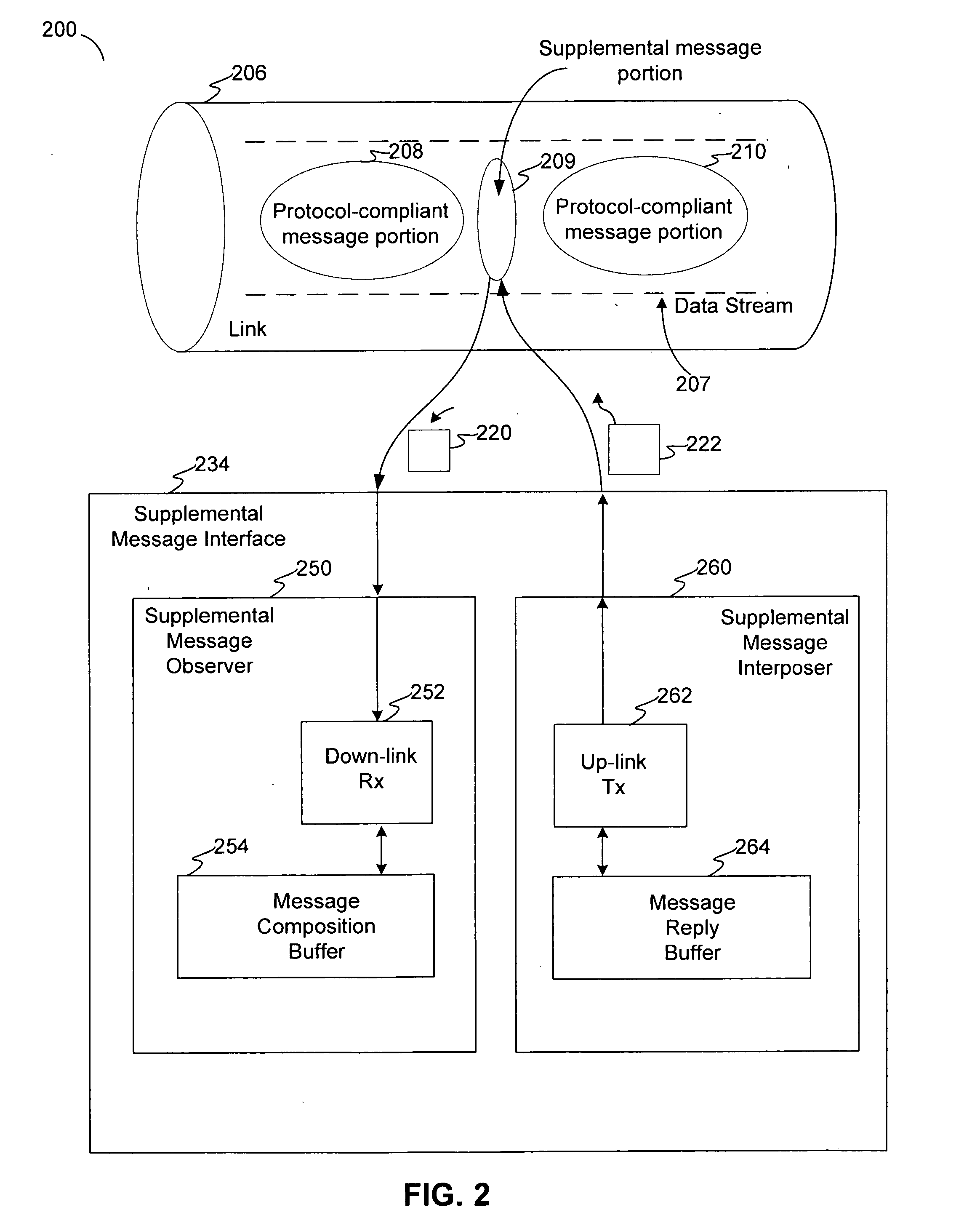
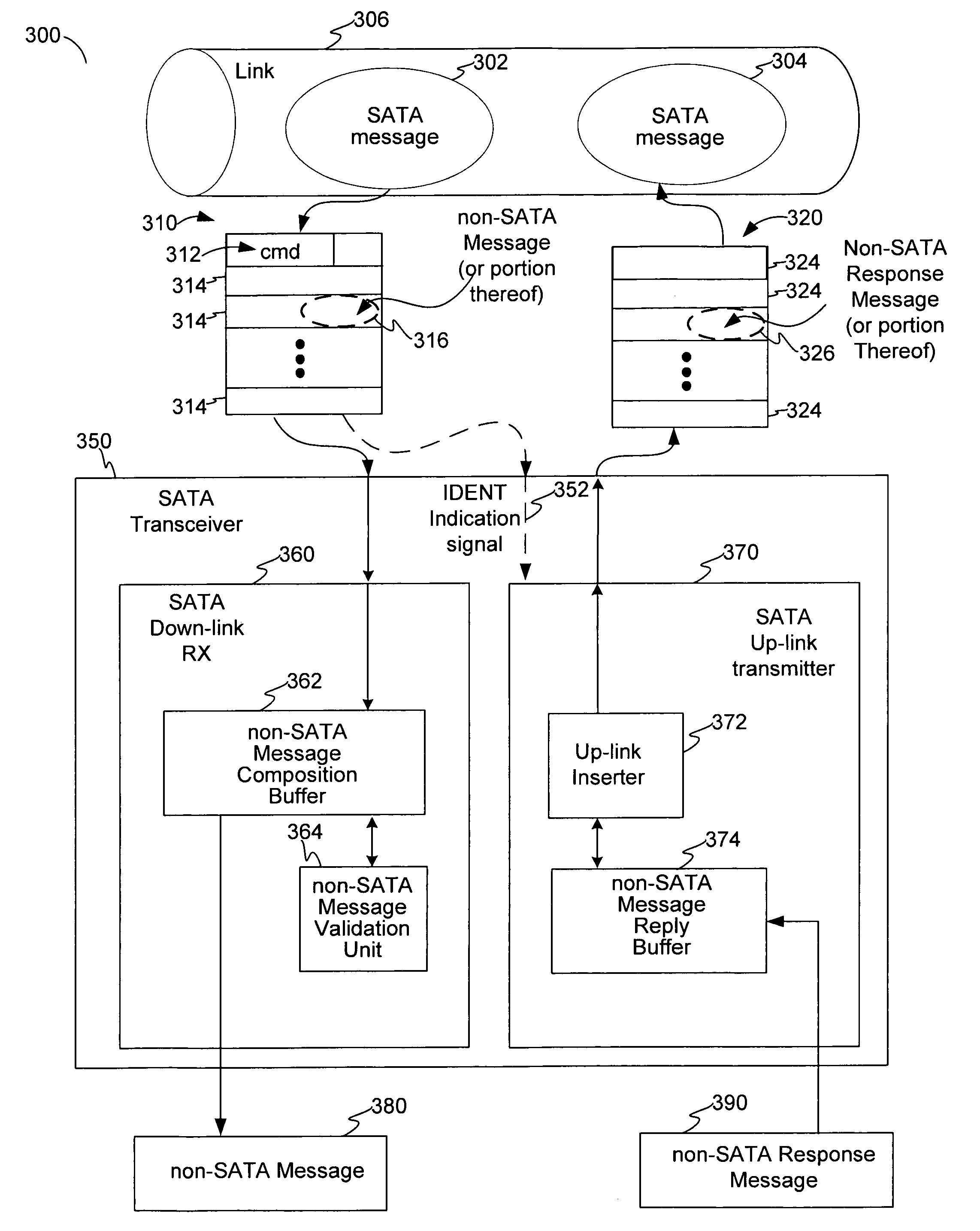
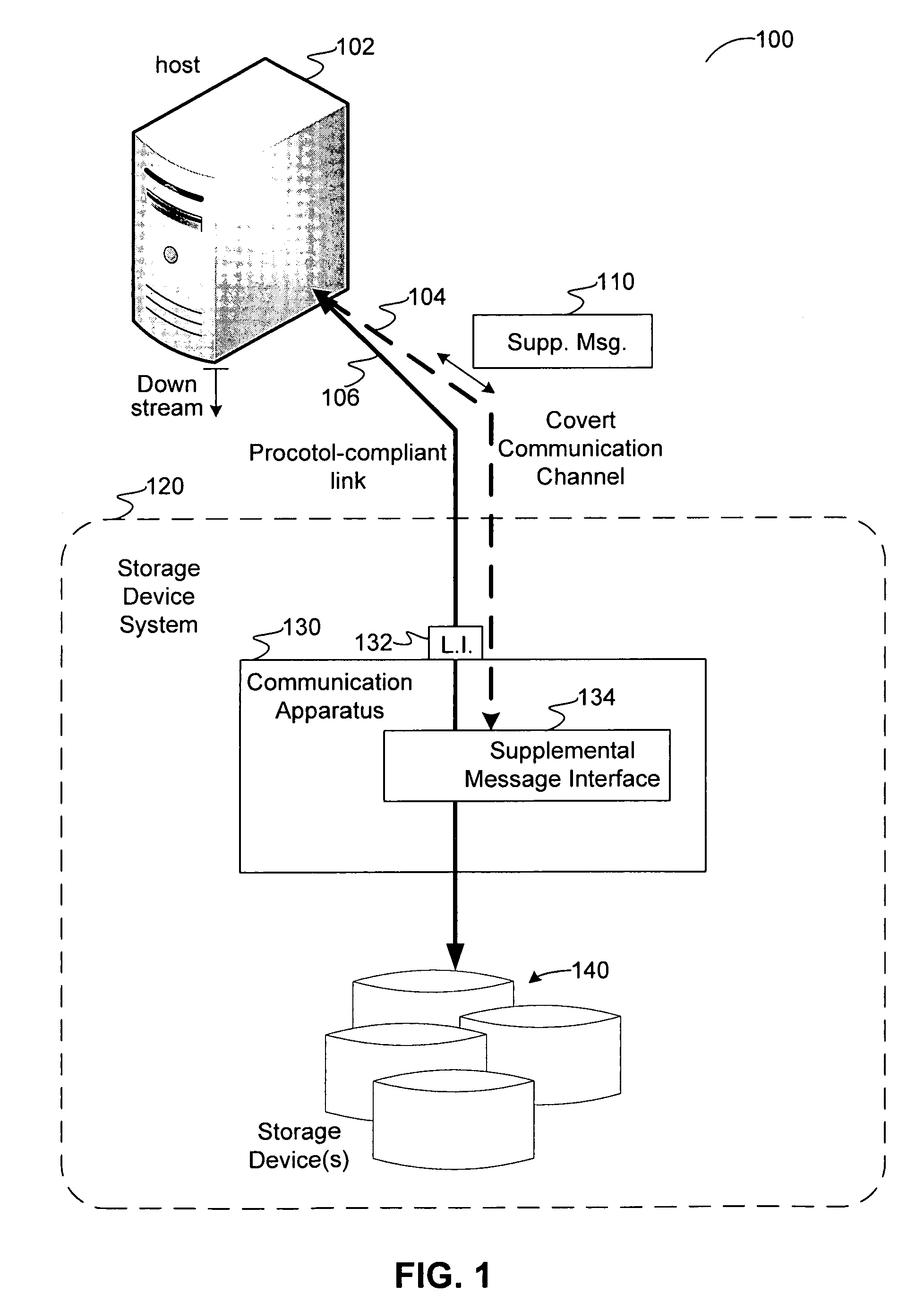
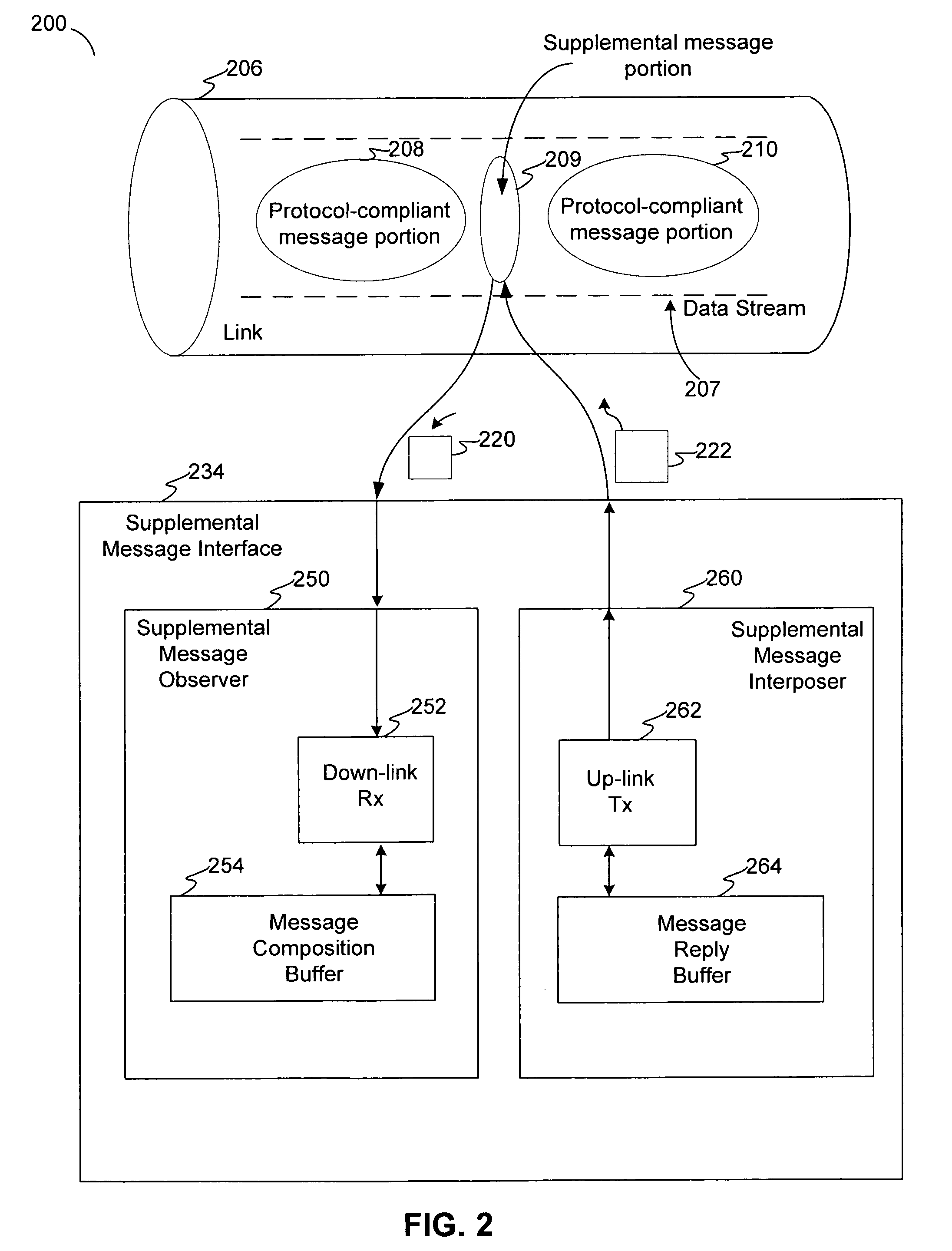
Covert channel for conveying supplemental messages in a protocol-defined link for a system of storage devices
ActiveUS20070180172A1Function increasePreserve computational resources of a host computing deviceCorrect operation testingData taking preventionPort multiplierData stream
Disclosed are communication apparatus, a SATA communication device, a system, an enhanced port multiplier and a method for, among other things, establishing a covert communication channel in a protocol-compliant link. In one embodiment, a communication apparatus includes a link interface and a supplemental message interface. The link interface is configured to communicatively couple the communication apparatus to the link for accessing a data stream passing through the link in accordance with a standardized protocol. The supplemental message interface is configured to exchange a supplemental message within the data stream to establish a covert communication channel in the link. The supplemental message supplements the standardized protocol without violating the protocol.
Owner:LATTICE SEMICON CORP
Covert communication method under cloud computing environment
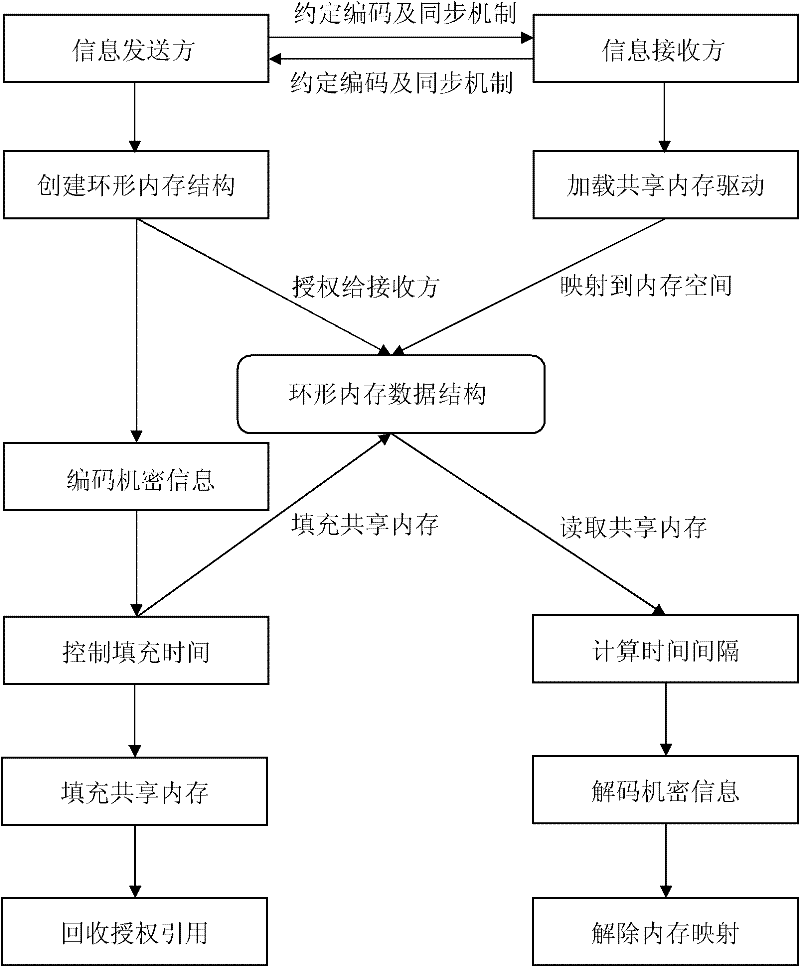
InactiveCN102244682AAchieving covert transmissionBreak integrityTransmissionMemory addressCovert communication
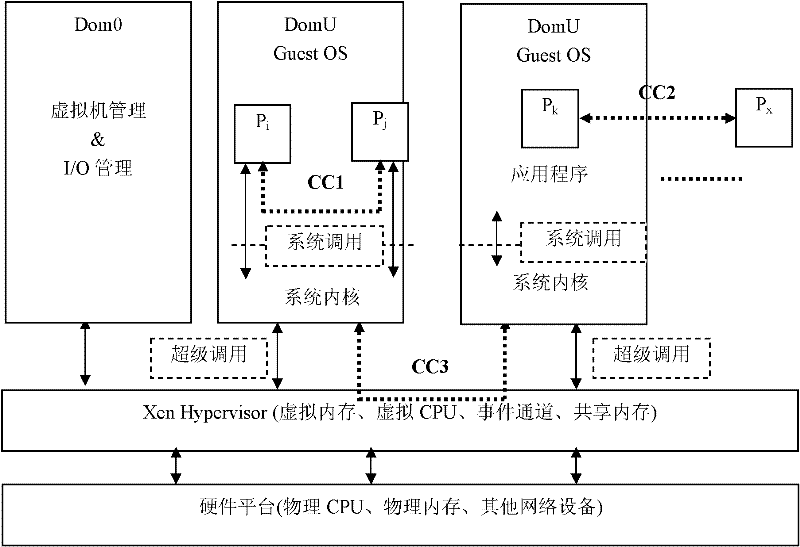
The invention discloses a covert communication method under a cloud computing environment. The method comprises the following steps: 1) a sender and a receiver agree on a coding and decoding method of confidential information, wherein the coding and decoding method means that the confidential information is coded into interval time in a normal data transmission; 2) the sender establishes a annular shared memory data structure and sends an authorization reference to the receiver, and the sender and the receiver load an annular shared memory control driver as a form of a kernel module to a client virtual machine core; 3) the receiver maps the shared memory to memory address space of the sender; 4) the sender and the receiver write and read normal data containing the confidential information in and from the shared memory as a mode of a producer / a consumer; 5) the receiver acquires an interval time sequence which represents the confidential information, decodes the interval time sequence and turns the interval time sequence into the confidential information; 6) the receiver removes the shared memory mapping, and the receiver recovers the authorization reference. By using the method of the invention, current integrity and safety mechanism of the virtual machine system can be broken through and covert information transmissions between the virtual machines can be realized.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Self-adaption covert communication method based on satellite channel coding
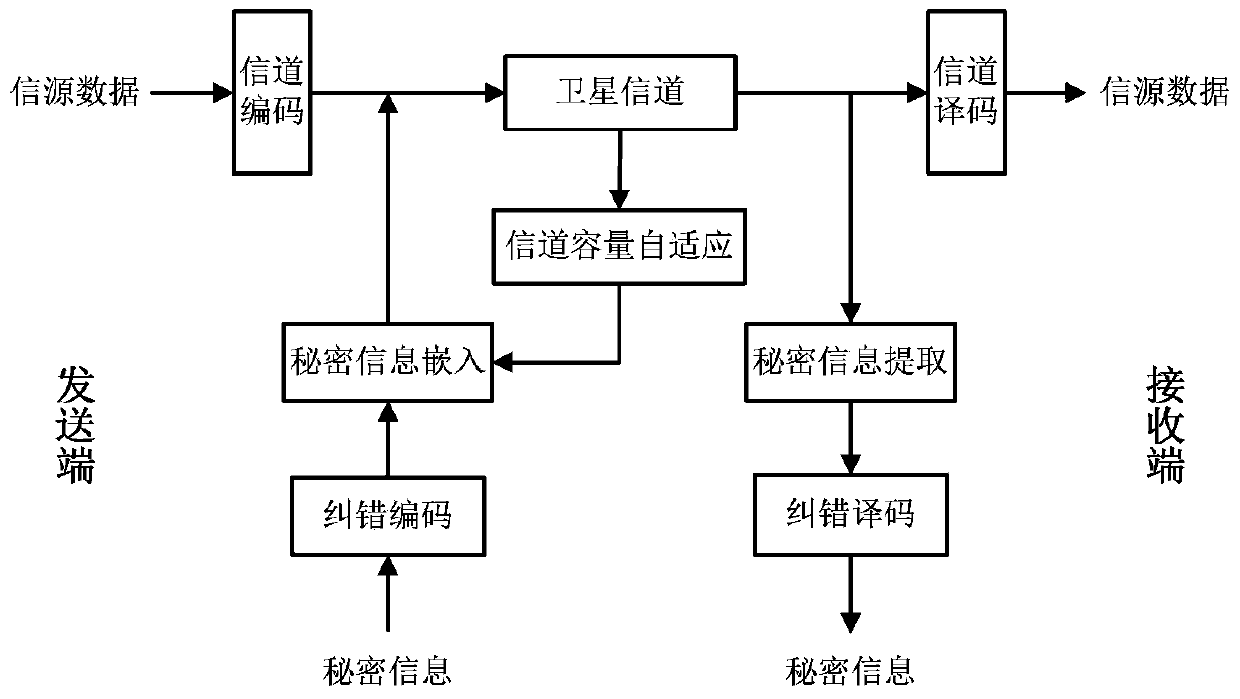
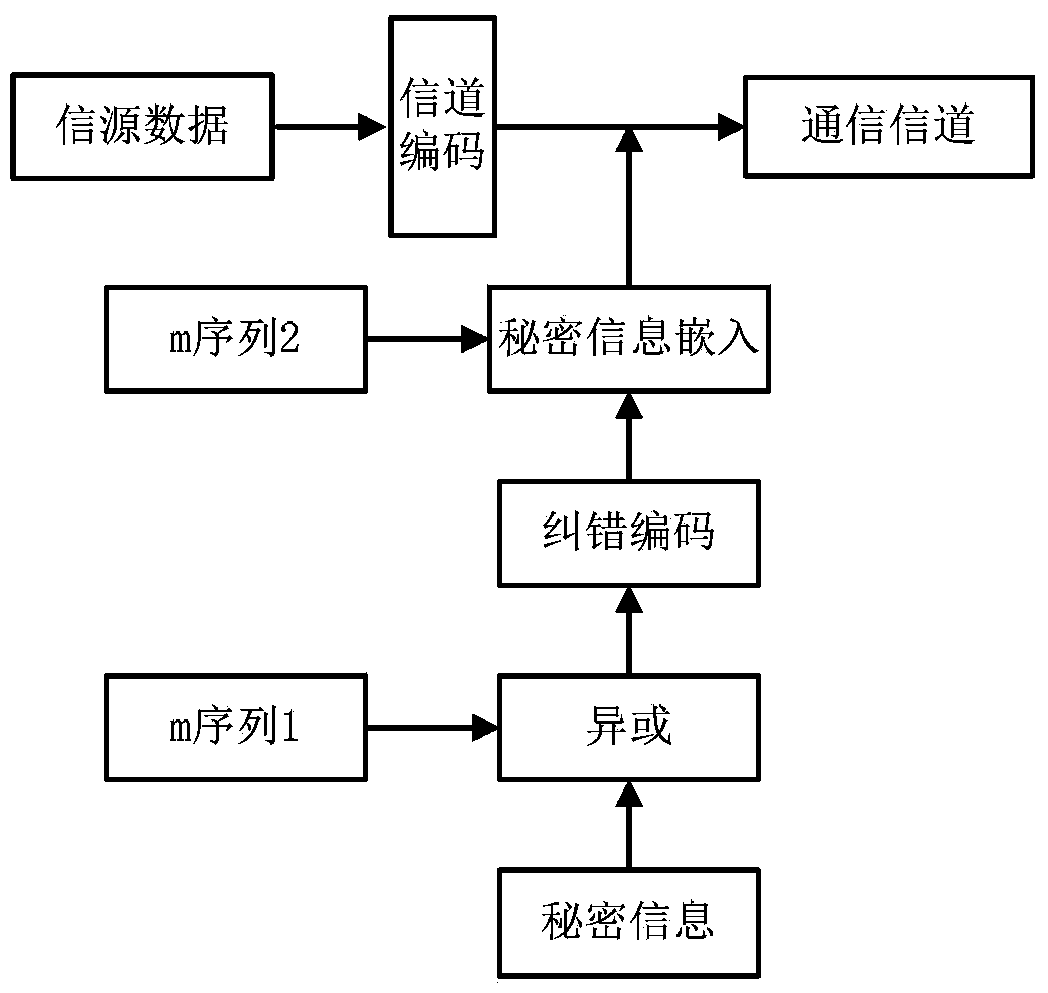
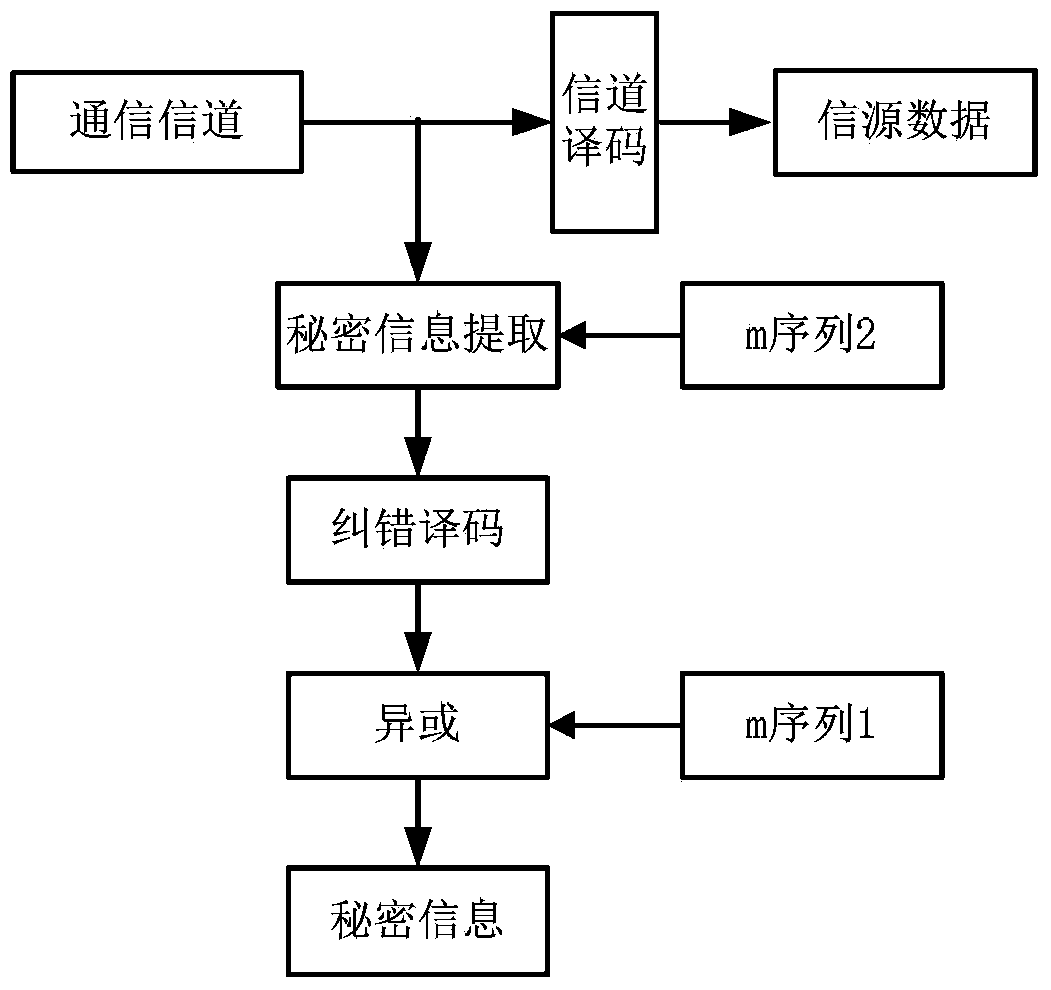
InactiveCN103476026AAvoid bit errorsImprove securityError preventionSecurity arrangementBlock codeCovert communication
The invention provides a self-adaption covert communication method based on satellite channel coding, and directing at different channel encoding algorithms of block codes, RS codes, convolutional codes, serial concatenated code and the like, provides a capacity self-adaption method for secrete information embedding; further provides a channel encoding information embedding and extracting algorithm based on m sequences. By the utilization of the self-adaption covert communication method, the capacity of covert channels can be determined in a self-adaption mode according to different used channel encoding algorithms and different used communication environments; normal use of carriers containing secretes is not influenced, and main steganalysis attacks such as chi-square analysis attacks and RS analysis attacks can be resisted; under the condition that the satellite channel bit error rate is 10-3-10-5, quasi error-free transmission of secrete information can be realized.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Adaptive spatial steganographic method based on adjacent pixel difference
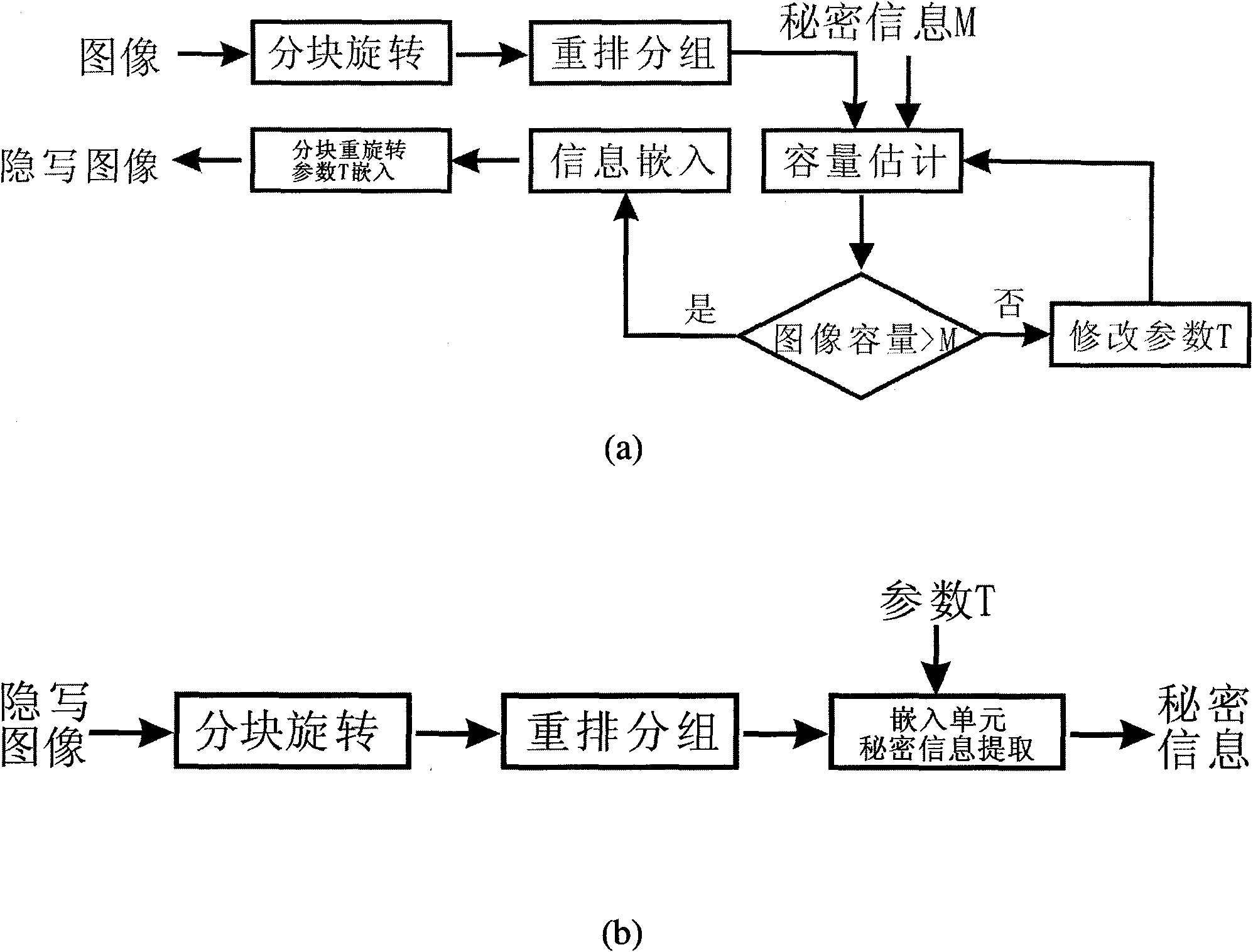
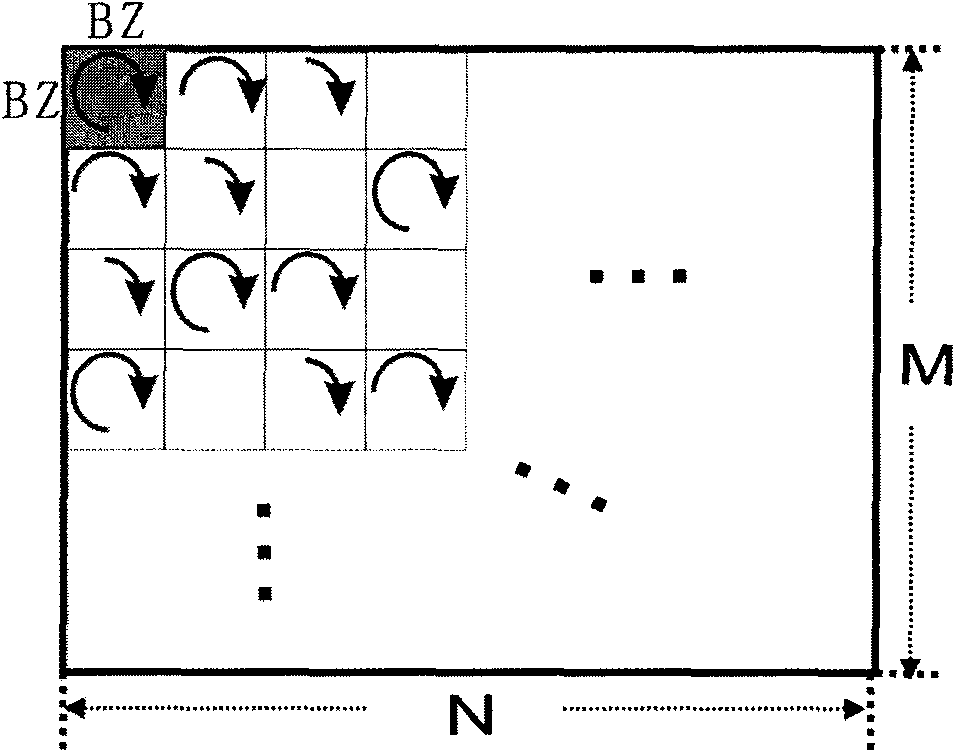
InactiveCN101582157AImprove securityImplement embeddingImage data processing detailsPattern recognitionCovert communication
The invention provides an adaptive spatial steganographic method based on adjacent pixel difference. The method comprises the following two steps: embedding secret information and extracting the secret information. The method takes three continuous adjacent pixels in an image as an embedding unit and reaches the goal of hiding information by changing the value of the middle pixel in each unit. During information embedding, a steganographic algorithm always mains the size relationship of each pixel in the embedding unit, and adaptively adjusts the capacity of embedding information through a parameter according to the content of the image. Experiments show that the adaptive spatial steganographic method has higher safety and adaptive ability compared with the prior steganographic method based on pixel difference. Therefore, the adaptive spatial steganographic method has great practical significance to application fields such as covert communication and the like.
Owner:SUN YAT SEN UNIV
Covert channel for conveying supplemental messages in a protocol-defined link for a system of storage devices
ActiveUS7571269B2Function increasePreserve computational resources of a host computing deviceCorrect operation testingData taking preventionPort multiplierData stream
Disclosed are communication apparatus, a SATA communication device, a system, an enhanced port multiplier and a method for, among other things, establishing a covert communication channel in a protocol-compliant link. In one embodiment, a communication apparatus includes a link interface and a supplemental message interface. The link interface is configured to communicatively couple the communication apparatus to the link for accessing a data stream passing through the link in accordance with a standardized protocol. The supplemental message interface is configured to exchange a supplemental message within the data stream to establish a covert communication channel in the link. The supplemental message supplements the standardized protocol without violating the protocol.
Owner:LATTICE SEMICON CORP
Adaptive steganography algorithm based on binary image
ActiveCN108537049AReduce quality impactHigh resistance to detectionImage analysisDigital data protectionPattern recognitionCovert communication
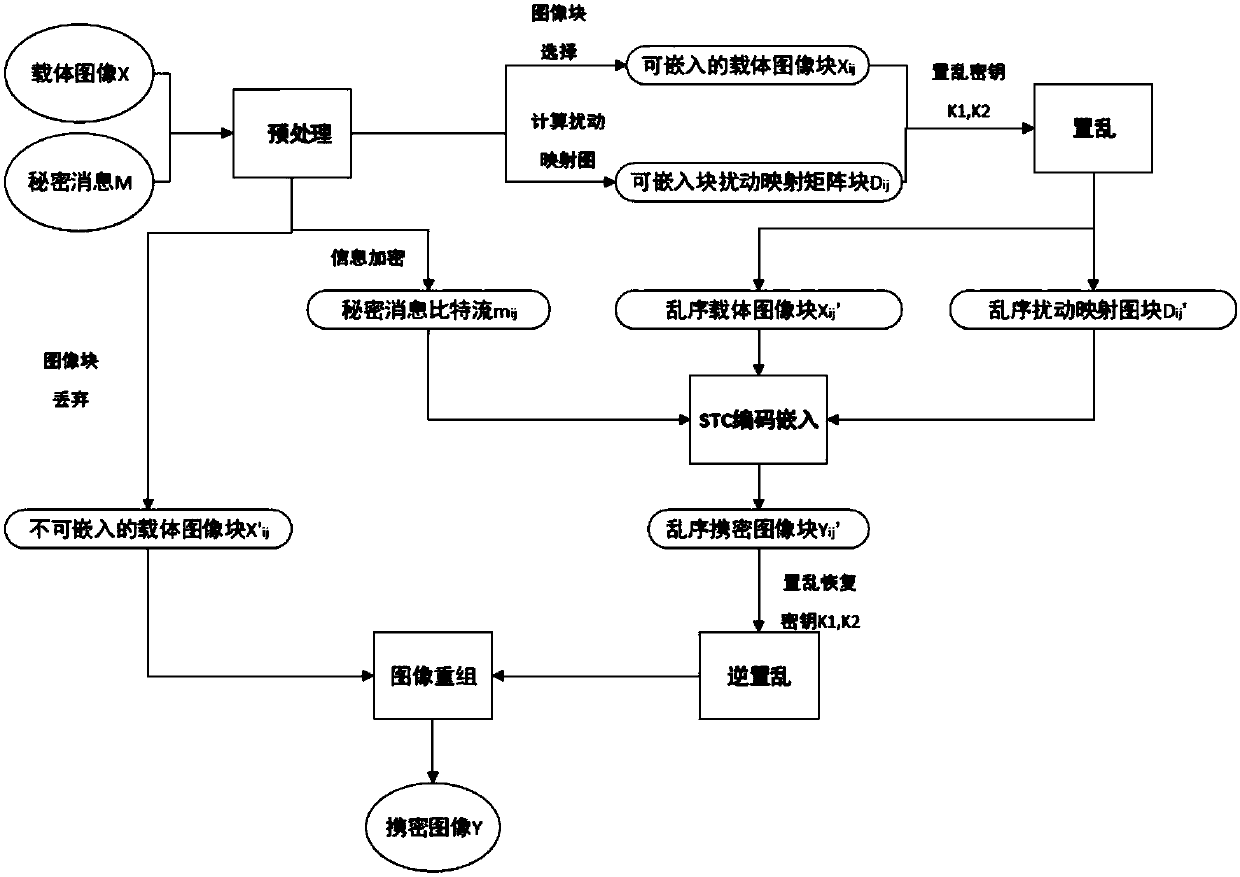
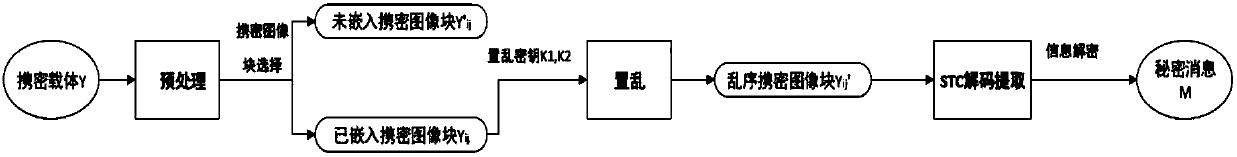
The invention discloses an adaptive steganography algorithm based on a binary image. The adaptive steganography algorithm based on the binary image comprises the following steps: calculating perturbation of a carrier image according to image texture features, dividing the carrier image into blocks, scrambling image blocks, encrypting secret information, performing STC encoding embedding, reverselyscrambling the encrypted image blocks, and restoring the encrypted image to obtain the encrypted image having the complete texture and the embedded secret information. According to the invention, a novel carrier scrambling algorithm having high security performance and capable of effectively resisting exhaustion cracking is used; through combination of a high-detection resistance measurement method and STC encoding, a designed binary image information hiding method has very high security performance and detection resistance and plays a very important role in secure covert communication.
Owner:SUN YAT SEN UNIV
Method and apparauts for quantum measurement via mode matched photon conversion
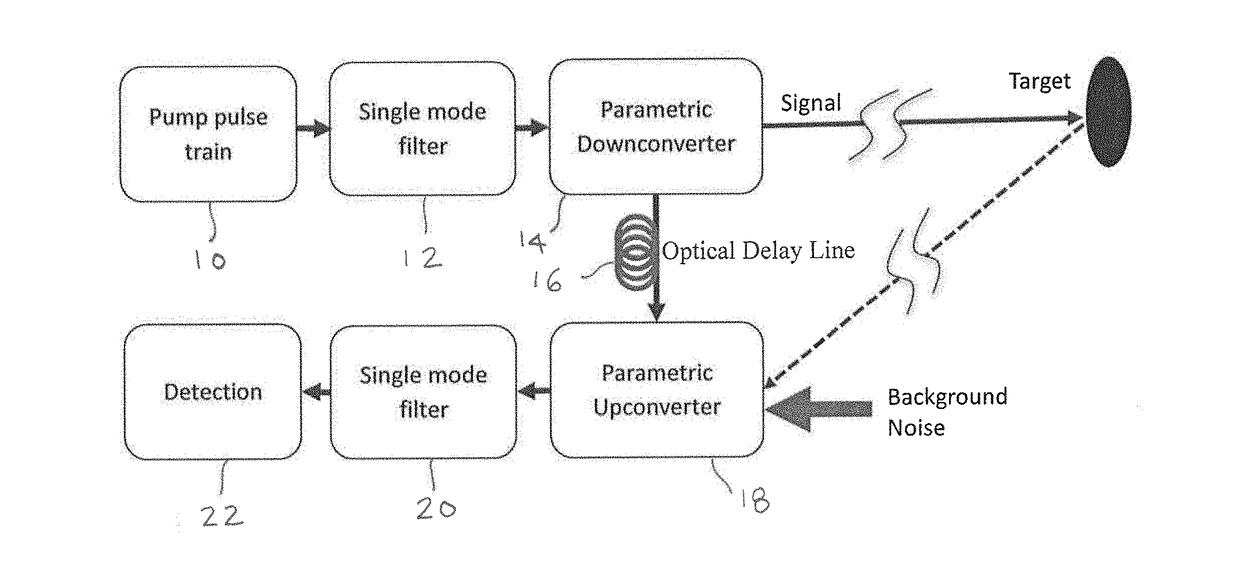
ActiveUS20180149476A1Increase heightImprove system performanceOptical rangefindersNanoopticsNonlinear opticsCovert communication
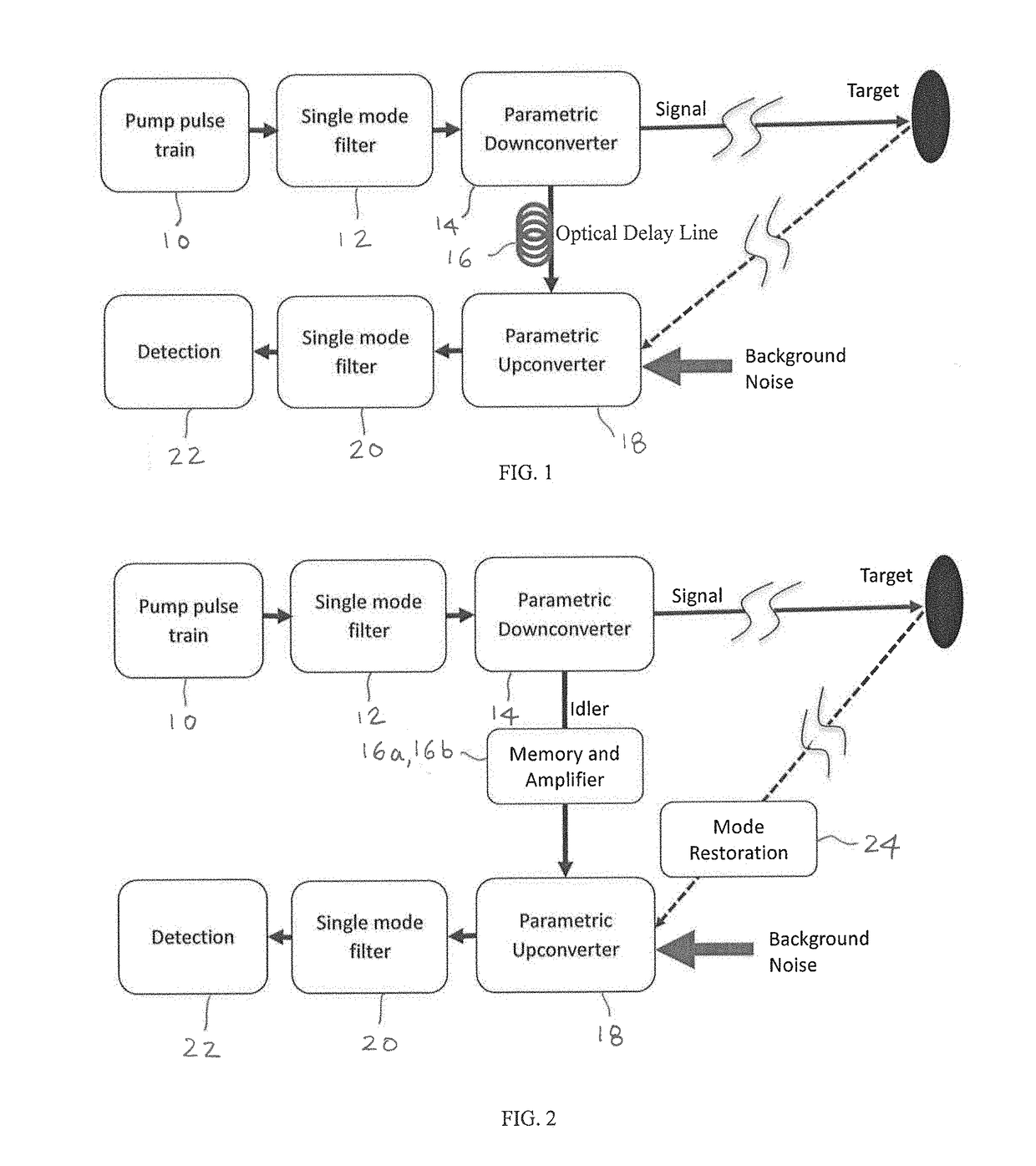
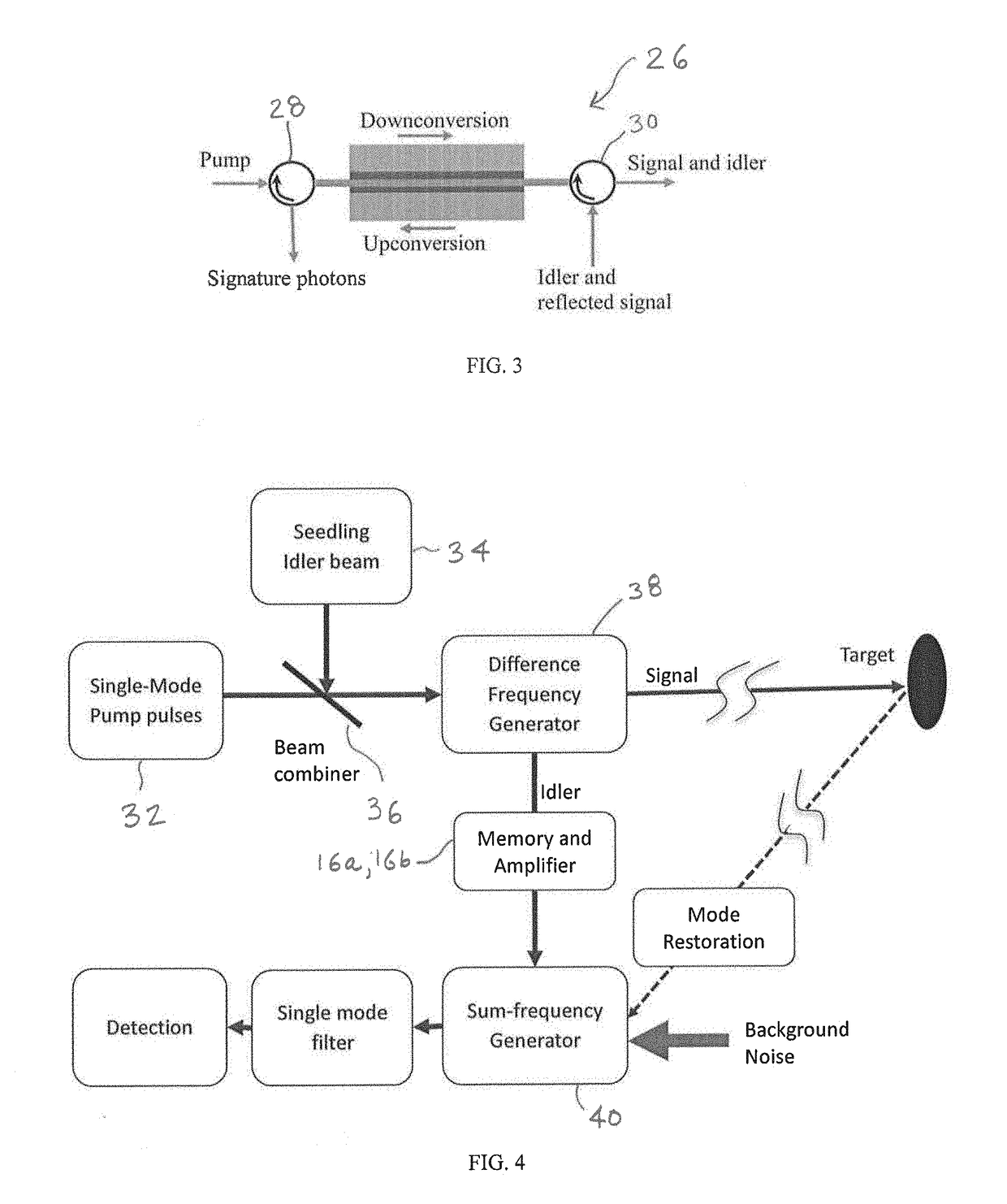
The present disclosure relates to a generally-applicable measurement technique based on coherent quantum enhancement effects and provides embodiments with nonlinear optics. The technique utilizes parametric nonlinear processes where the information-carrying electromagnetic quanta in a number of electromagnetic modes are converted phase coherently to signature quanta in a single mode or a few modes. The phase coherence means that while the quanta before conversion may have unequal or uncertain phase values across the modes, the signature quanta converted from those different modes have the (near) uniform phase. This can lead to significant increase in the signal to noise ratio in detecting weak signal buried in strong background noise. Applications can be found in remote sensing, ranging, biological imaging, field imaging, target detection and identification, covert communications, and other fields that can benefit from improved signal to noise ratios by using the phase coherent effect.
Owner:STEVENS INSTITUTE OF TECHNOLOGY
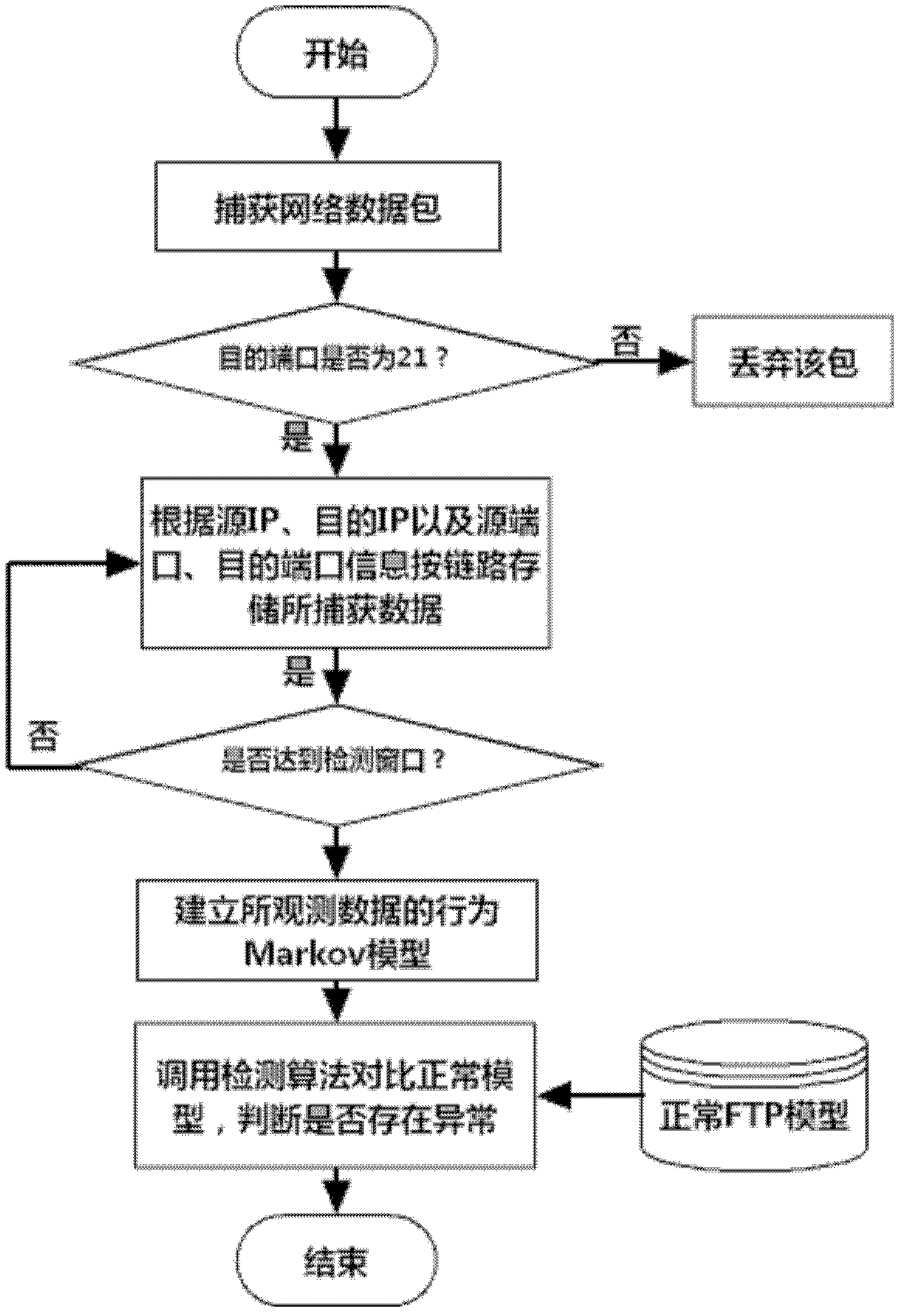
Network covert channel detecting method
InactiveCN102594619AReliable detectionOvercome the disadvantages of only targeting specific covert channelsData switching networksData streamCovert communication
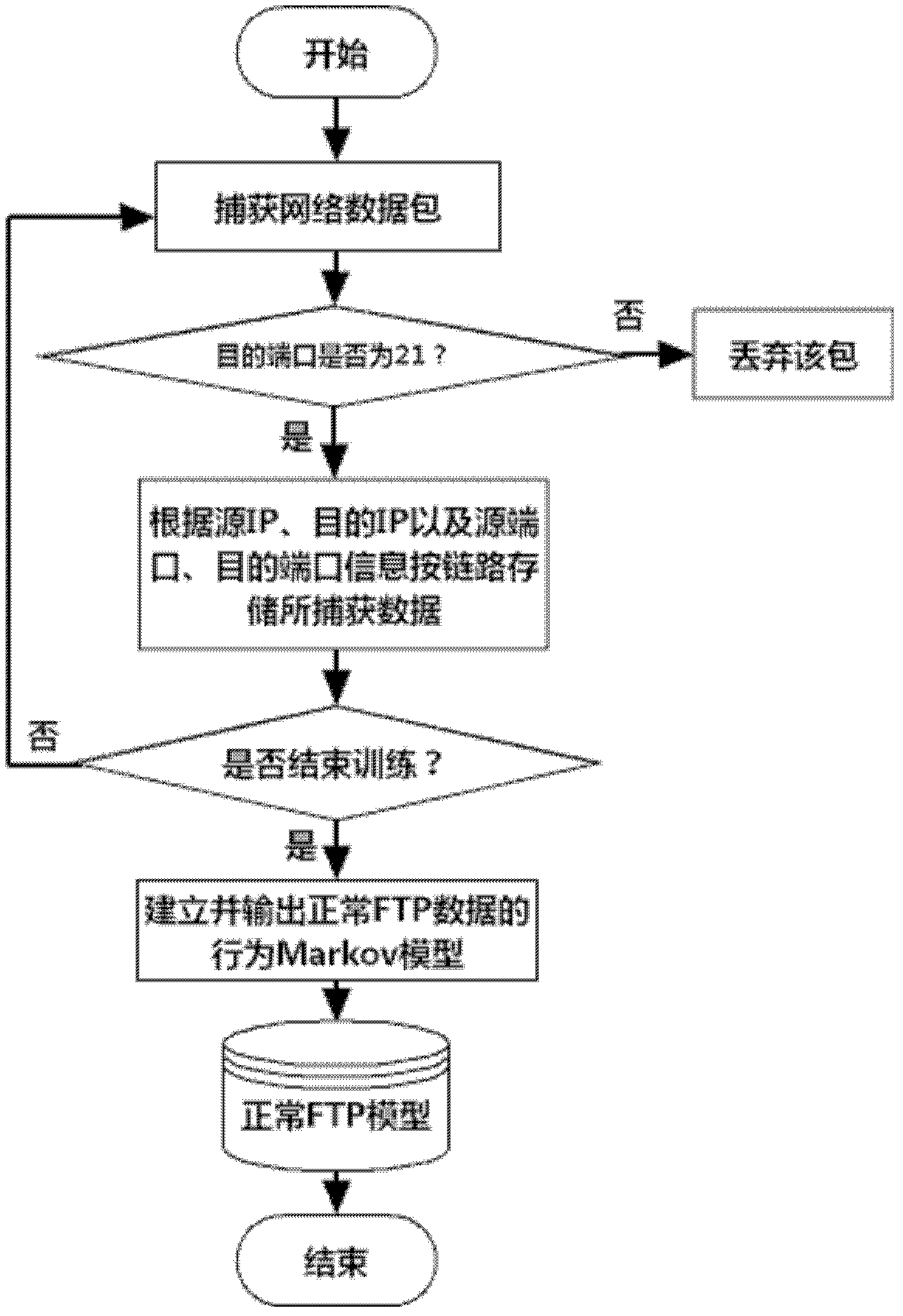
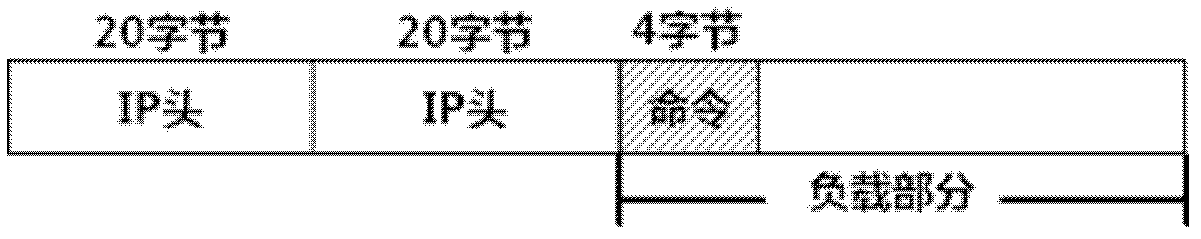
An FTP (File Transfer Protocol) command-sequence-coding network covert channel (FTP-NCC) is a covert communication mode that a transmitting end embeds covert information into a normal FTP application by a certain coding mode. The invention discloses a network covert channel detecting method for the FTP command sequence coding on the basis of a Markov model. The network covert channel detecting method comprises two steps of training and detection, wherein the training step is used for acquiring the Markov model of a normal FTP communication command data stream; the detection step is used for performing FTP-NCC detection by using a maximum posterior probability method according to the model obtained by the training step. The method can realize reliable detection for the FTP-NCC.
Owner:CHANGSHU RES INSTITUE OF NANJING UNIV OF SCI & TECH
Frequency-hopped holographic communications apparatus and methods
InactiveUS20050041757A1Simultaneous amplitude and angle modulationModulation with suppressed carrierTransceiverRadar systems
Improved apparatus and methods for utilizing holographic waveforms for a variety of purposes including communication, ranging, and detection. In one exemplary embodiment, the holographic waveforms are transmitted over an RF bearer medium to provide, inter alia, highly covert communications, radar systems, and microwave data links. The bearer (i.e., carrier) is optionally frequency-hopped, and various pulse modulation techniques applied in order to further increase communications efficiency and covertness. Methods of providing multiple access and high bandwidth data transmission are also disclosed. Improved apparatus utilizing these features; e.g., a wireless miniature covert transceiver / locator, are also disclosed.
Owner:HOLOWAVE
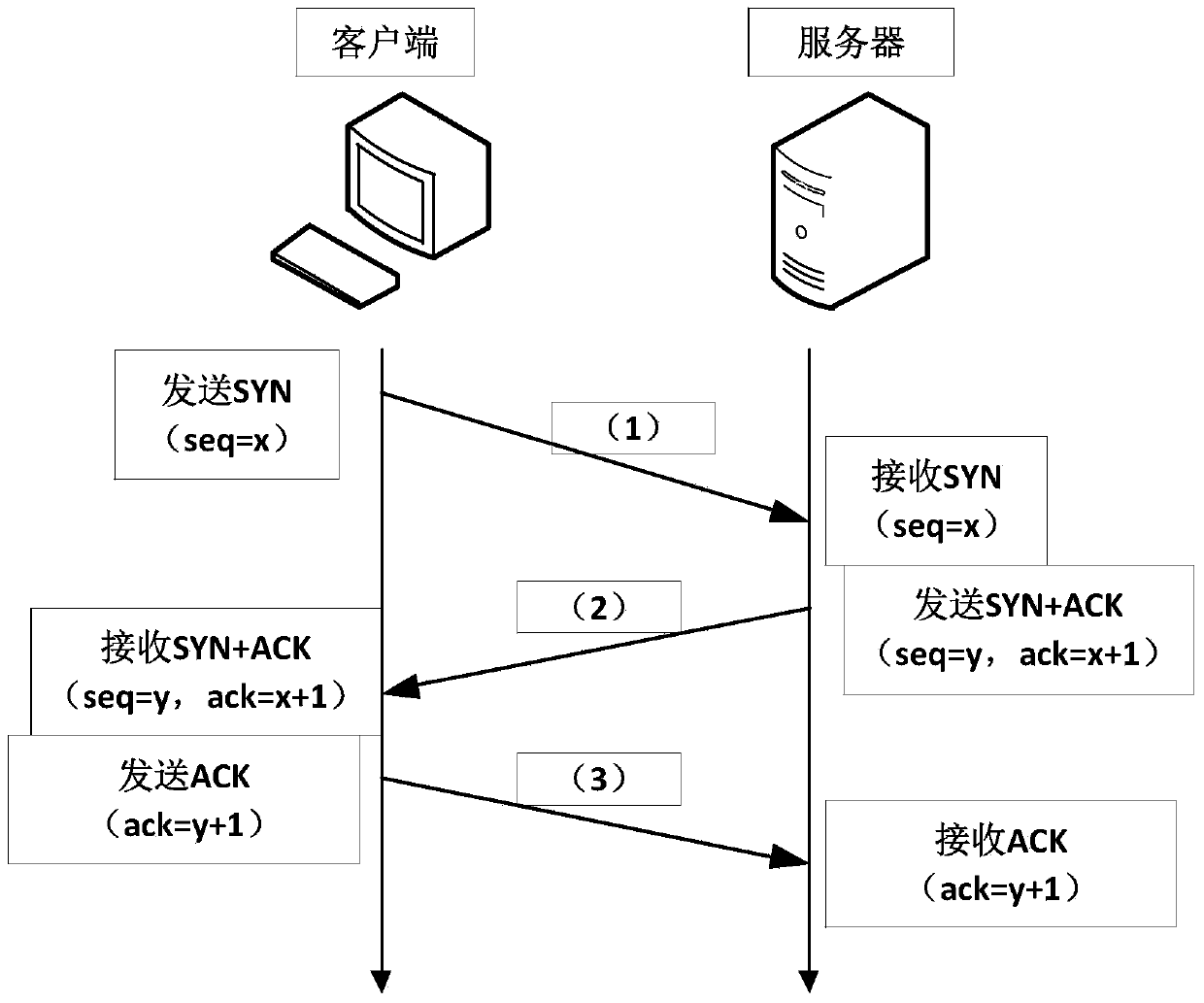
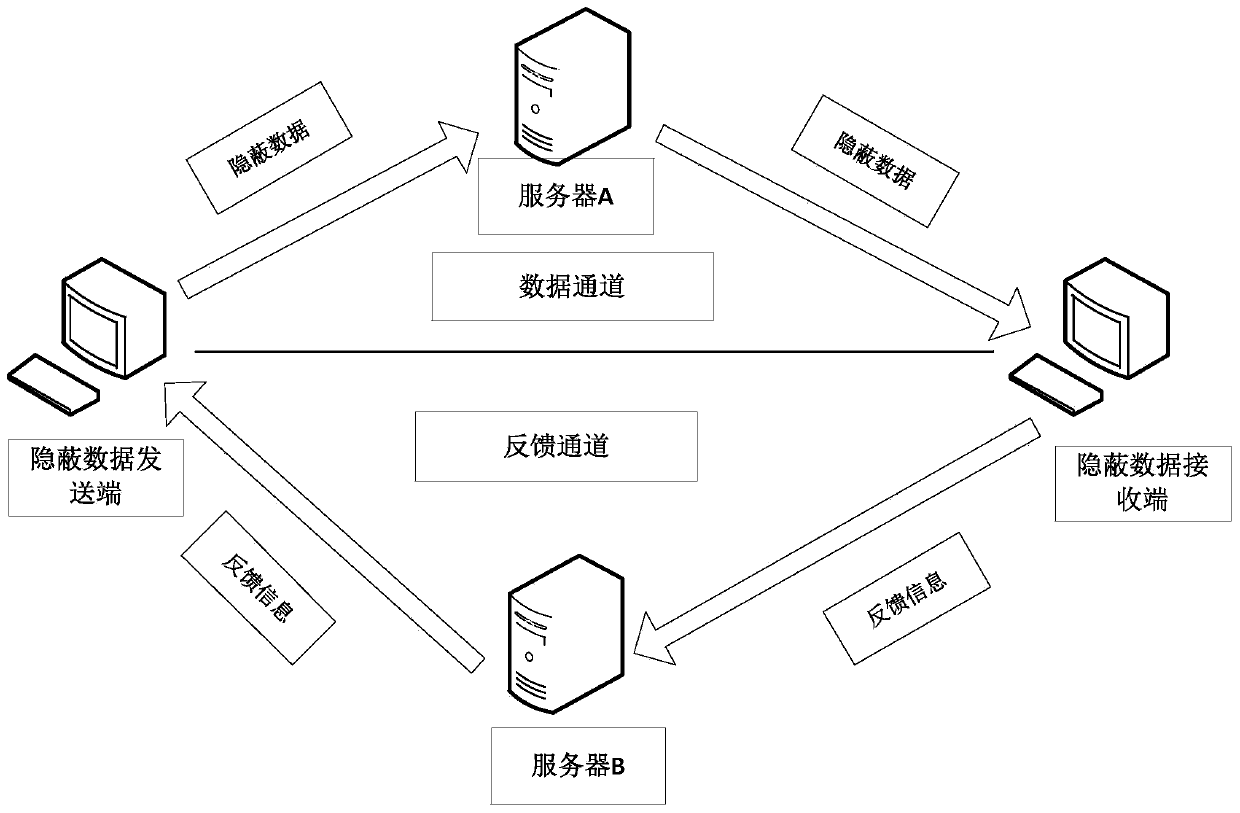
Counterfeit TCP covert communication method based on SYN-ACK dual-server rebound pattern
InactiveCN103475706AMany optionsImprove concealmentError prevention/detection by using return channelIp addressCovert communication
The invention discloses a counterfeit TCP covert communication method based on an SYN-ACK dual-server rebound pattern. A covert information sending end is in communication with a covert information receiving end through a rebound server A or a rebound server B. A three-way handshake principle of connection is set up through a TCP, and covert information is embedded into a sequence number domain of the TCP and an acknowledgement number domain through a counterfeit source IP address and sent to a target end through rebound of the rebound server A. Meanwhile, the covert information feeds information back to the covert information sending end according to the modification operation of a sequence number and the modification operation of an acknowledge number and through the rebound server B, and the loss detection of the target end and the retransmission timeout of the target end are achieved.
Owner:SUZHOU INST FOR ADVANCED STUDY USTC
Holographic ranging apparatus and methods
InactiveUS20050041758A1Simultaneous amplitude and angle modulationModulation with suppressed carrierRadar systemsCovert communication
Improved apparatus and methods for utilizing holographic waveforms for a variety of purposes including communication, ranging, and detection. In one exemplary embodiment, the holographic waveforms are transmitted over an RF bearer medium to provide, inter alia, highly covert communications, ranging, radar systems, and microwave data links. The bearer (i.e., carrier) is optionally frequency-hopped, and various pulse modulation techniques applied in order to further increase communications efficiency and covertness. Methods and apparatus for ranging (as well as determining relative velocity and acceleration) using inherent characteristics of the holographic waveforms are also disclosed.
Owner:HOLOWAVE
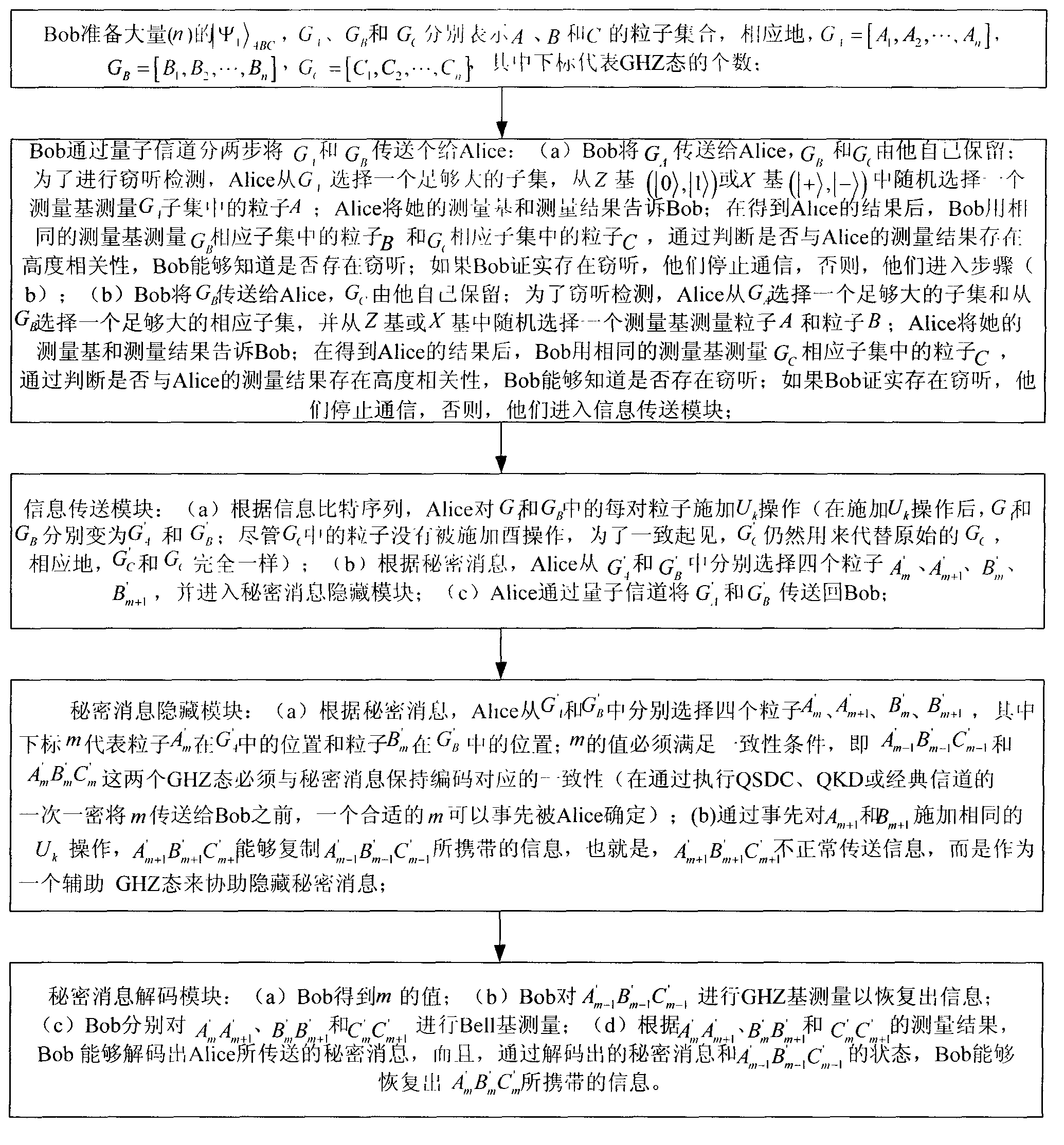
Quantum steganography protocol based on quantum electrodynamics (QED)
The quantum steganography aims to realize covert communication of classified information through a quantum hidden channel. The quantum steganography has important applications in multiple aspects, such as covert communication and quantum identity authentication. The invention provides a quantum steganography protocol based on quantum electrodynamics (QED). The quantum steganography protocol is not influenced by cavity leakage and thermal cavity field. The classified information is secretly transmitted through the entanglement exchange between a GHZ state and a Bell state and Hadamard operation in the cavity QED. When the quantum steganography decodes the 2-bit classified information, only local independent measurement is required to be performed; and moreover, the capacity of the hidden channel can be improved to 4 bits.
Owner:唐山安生纸制品制造有限公司
Miniaturized holographic communications apparatus and methods
InactiveUS20050041805A1Simultaneous amplitude and angle modulationModulation with suppressed carrierTransceiverRadar systems
Improved apparatus and methods for utilizing holographic waveforms for a variety of purposes including communication, ranging, and detection. In one exemplary embodiment, the holographic waveforms are transmitted over an RF bearer medium to provide, inter alia, highly covert communications, radar systems, and microwave data links. A wireless miniature covert holographic transceiver / locator having optional features including pre-stored messages, LPI burst mode, low-power “sleep” mode, and GPS positioning is also disclosed. In one variant, the device comprises a JTRS software-controlled radio.
Owner:HOLOWAVE
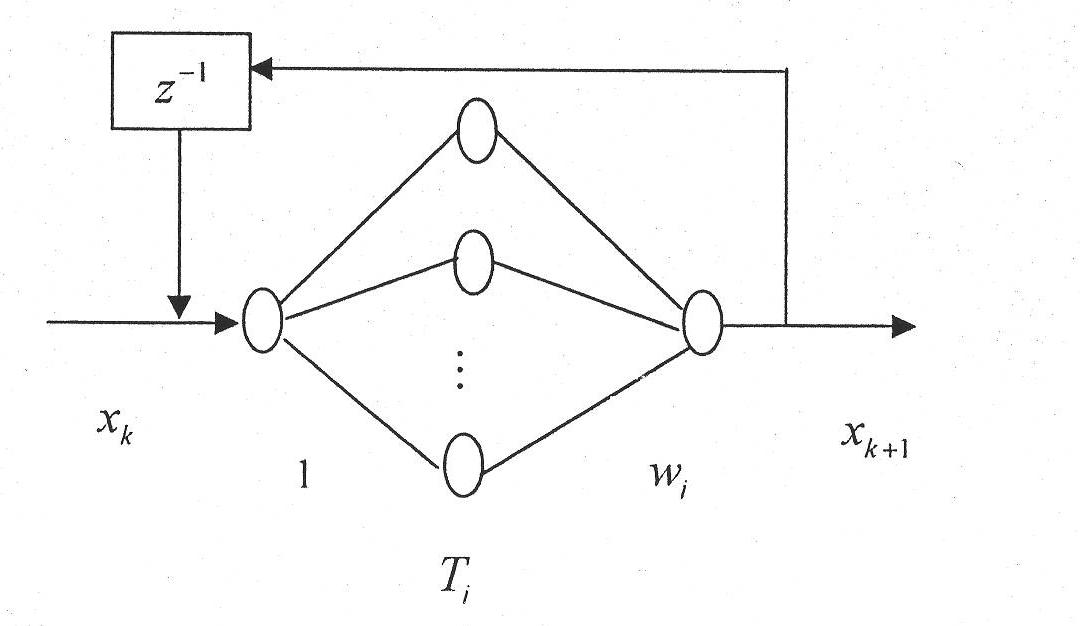
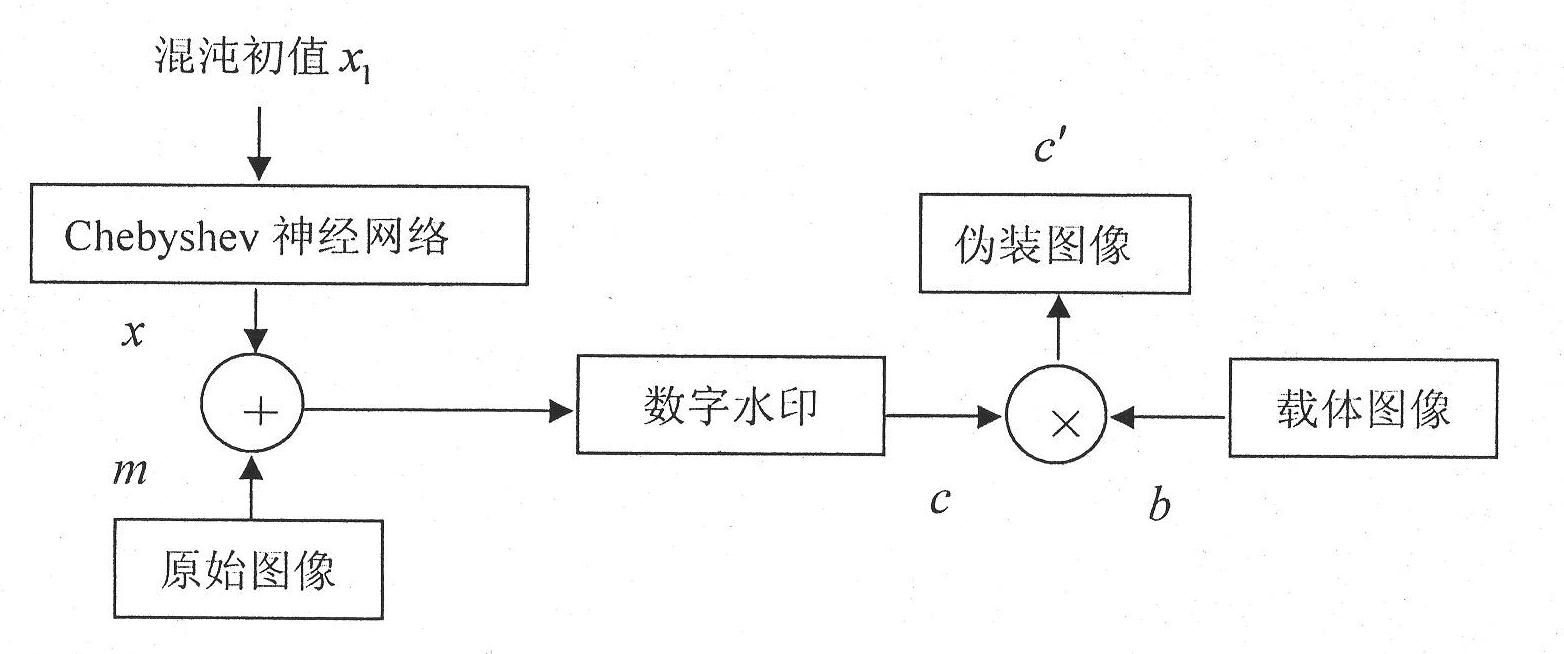
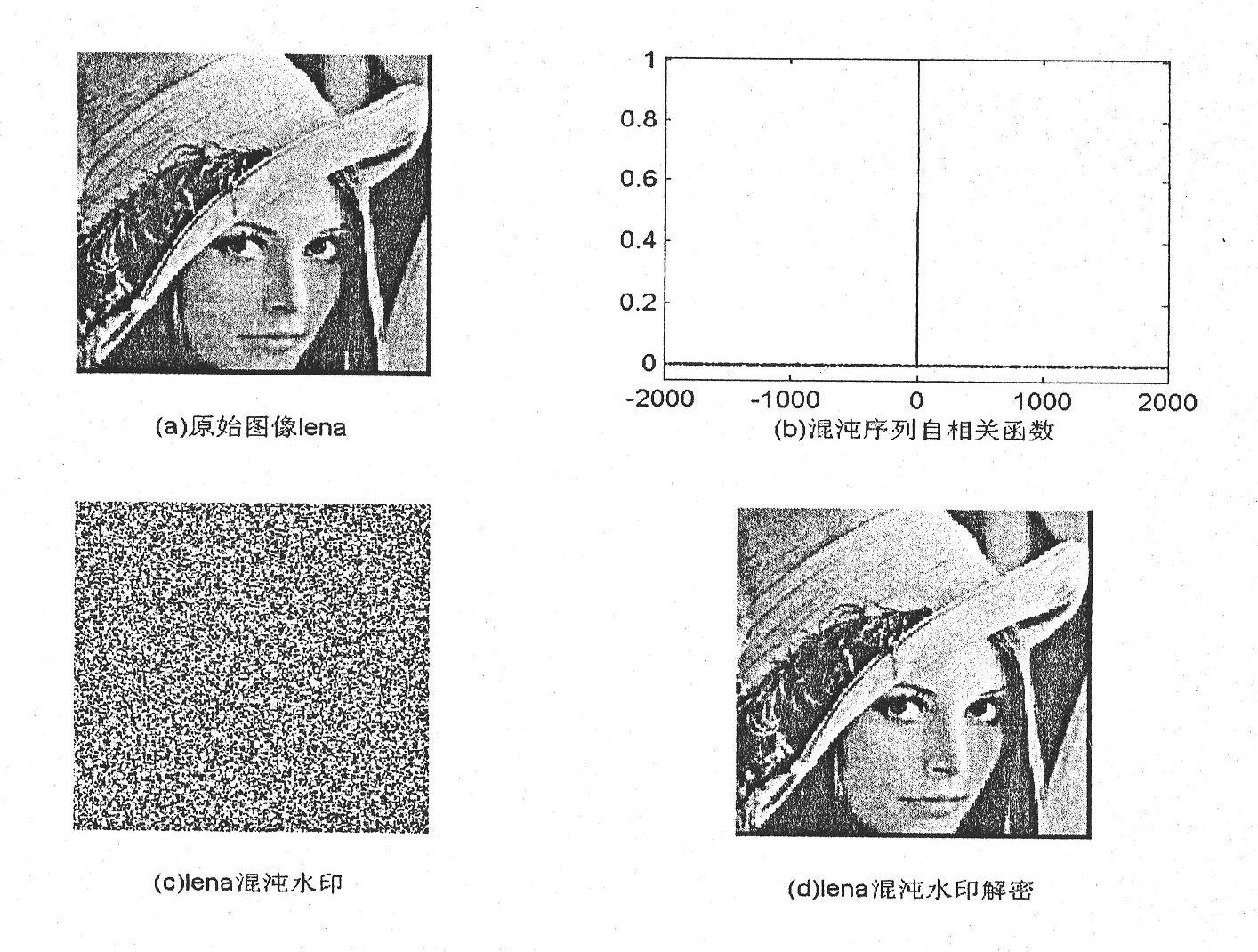
Method for hiding Chebyshev neural network chaotic digital watermark information
InactiveCN101882296AIncrease the difficultyEasy to detectBiological neural network modelsImage data processing detailsData integrityCovert communication
The invention discloses a method for hiding Chebyshev neural network chaotic digital watermark information. The method comprises the following steps: utilizing a neural network to generate a chaotic sequence; carrying out XOR encryption on digital image secret information needing to be hidden to generate chaotic digital watermark; embedding the digital watermark into a carrier image; under the condition of basically not changing the external character and the use value of the carrier image, ensuring that the sense organs of people can not sense the existence of hardly-sensing digital watermark on the appearance of a stego-image, thereby escaping the attention and attacks of illegal users to achieve the covert transfer of secret information as well as achieve the purpose of covert communication. The invention can be widely used in covert communication, data non-repudiation, digital copyright protection, antifalsification and data integrity.
Owner:GUANGDONG OCEAN UNIVERSITY
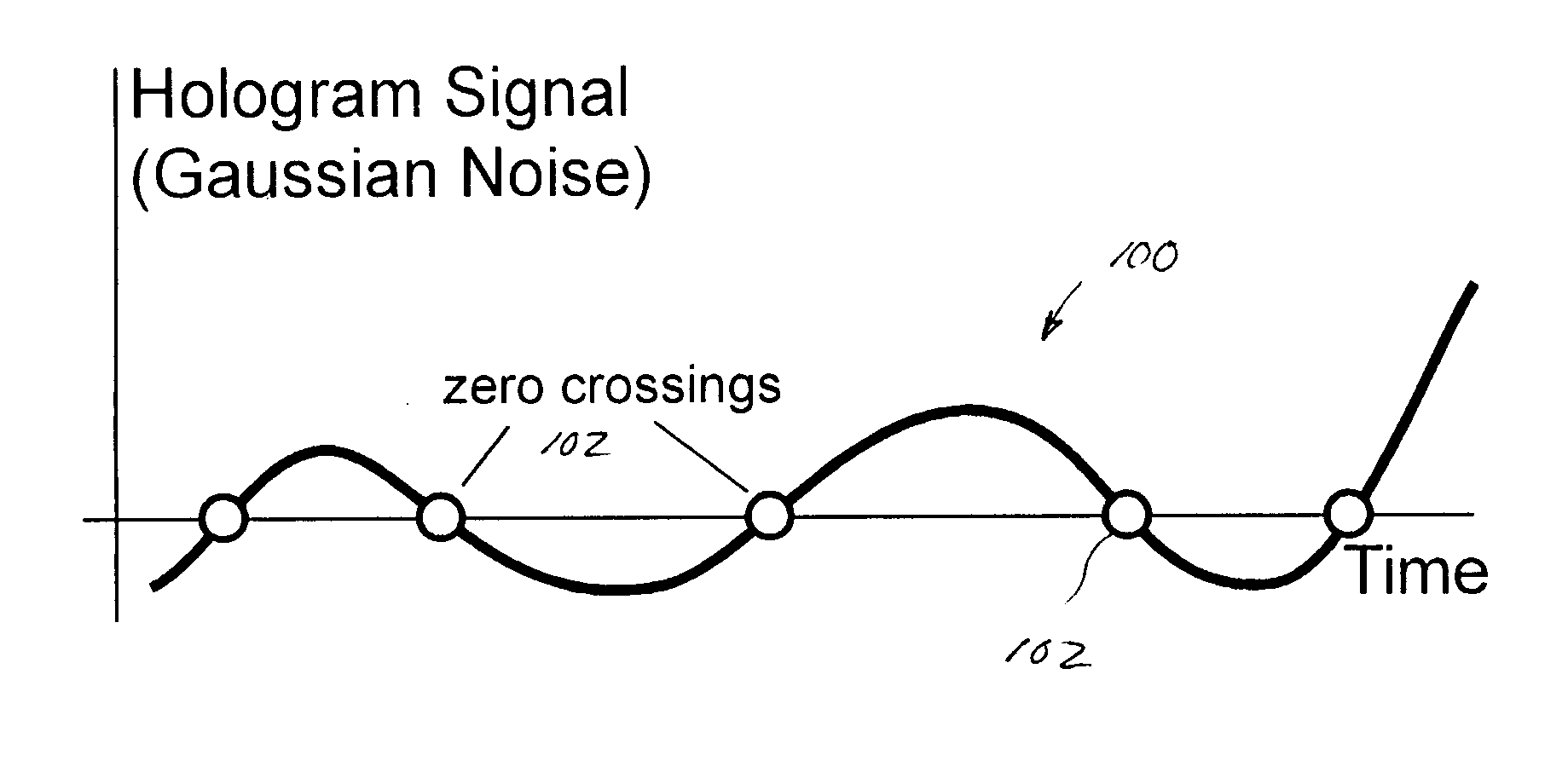
Covert communication system based on random noise modulation
ActiveCN108632255AAchieving covert transmissionError detection/prevention using signal quality detectorChannel estimationCorrelation coefficientCommunications system
The invention discloses a covert communication system based on random noise modulation. At a transmitter, host data is taken as a seed of a Gaussian noise generator, a correlation coefficient of jointnormal distribution noise is modulated by a covert bit, and the joint normal distribution noise carrying the covert bit is linearly overlapped with output of a host transmitter digital modulator; andat a receiver, Gaussian noise the same as the transmitter is generated by taking the host data as the seed, then the Gaussian noise and the estimation of the joint normal distribution noise are correlated, and the covert bit can be restored through hard decision, so the covert transmission of the information is realized. The system has relatively high covert performance.
Owner:ZHEJIANG POLICE COLLEGE
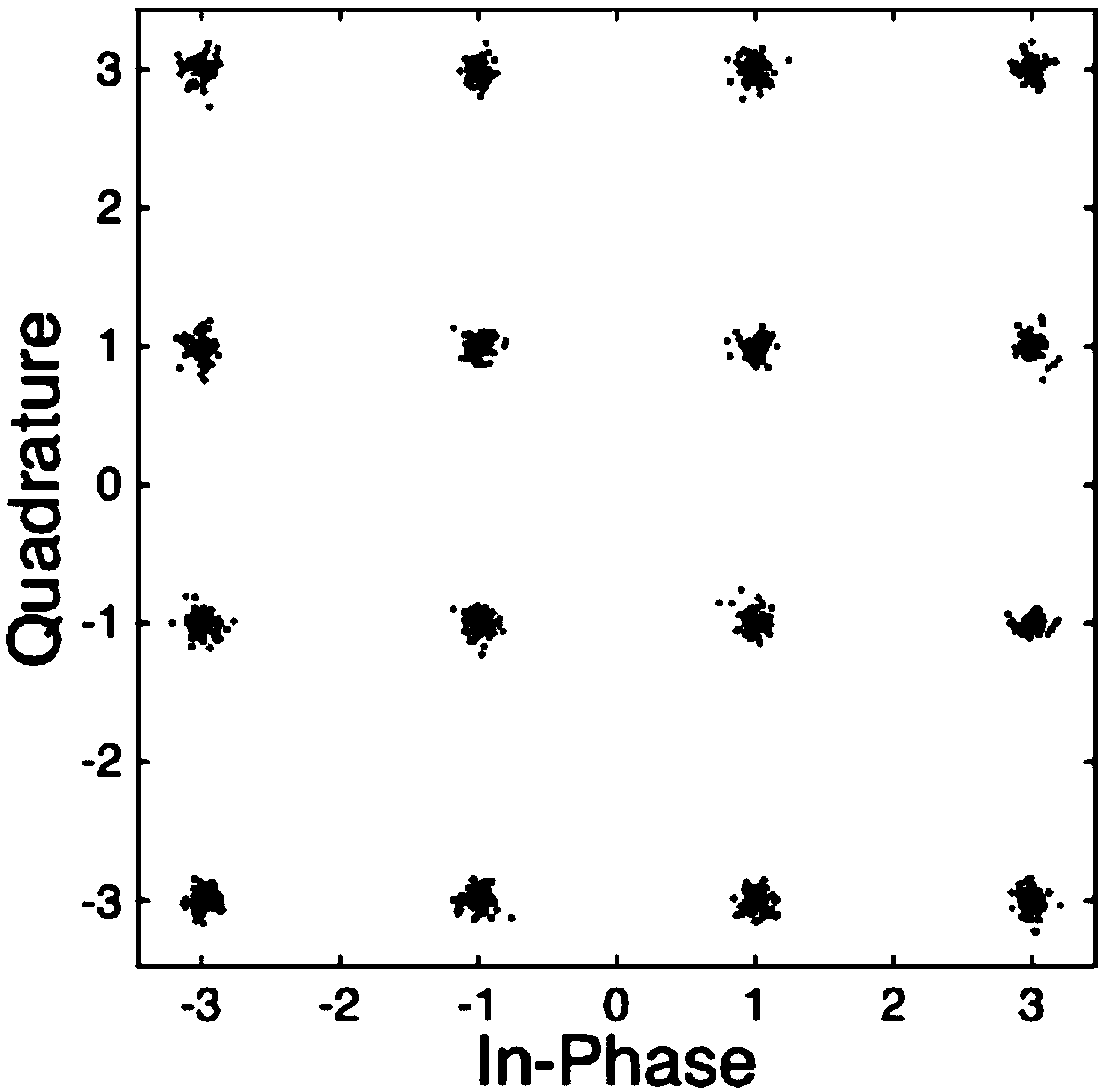
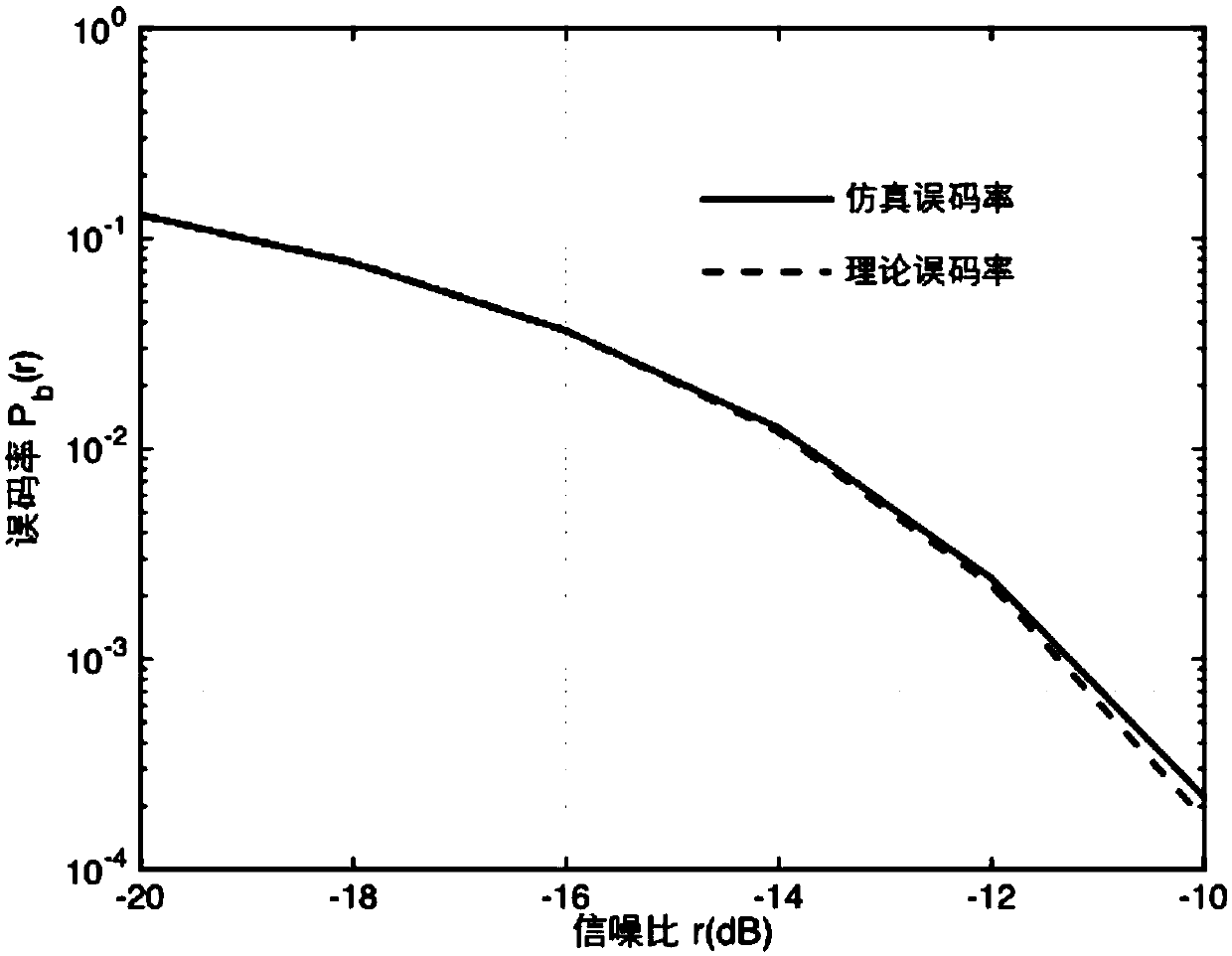
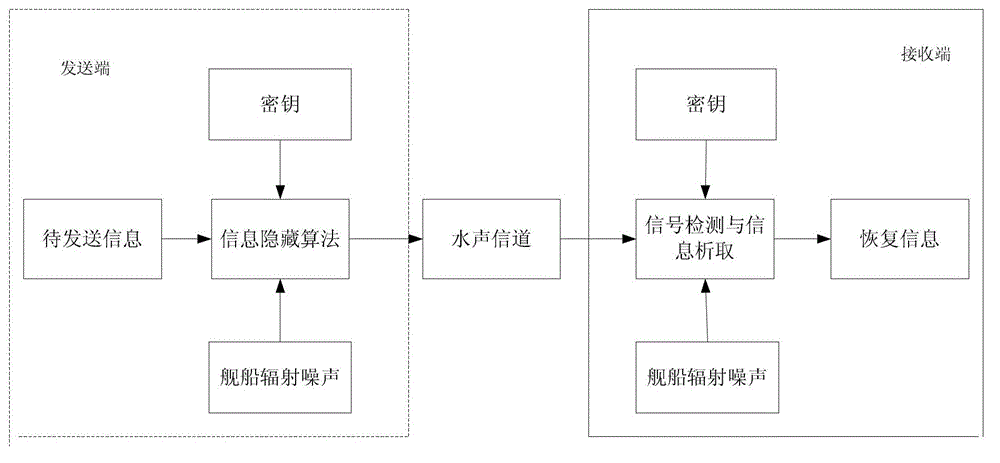
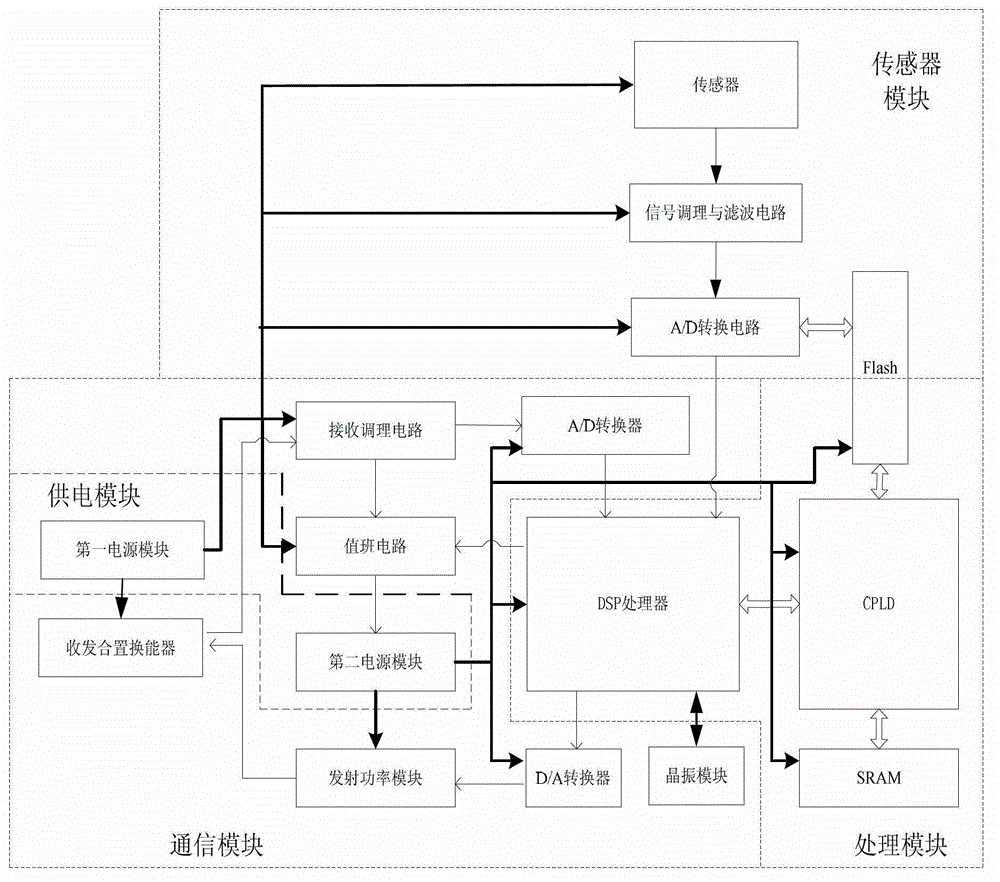
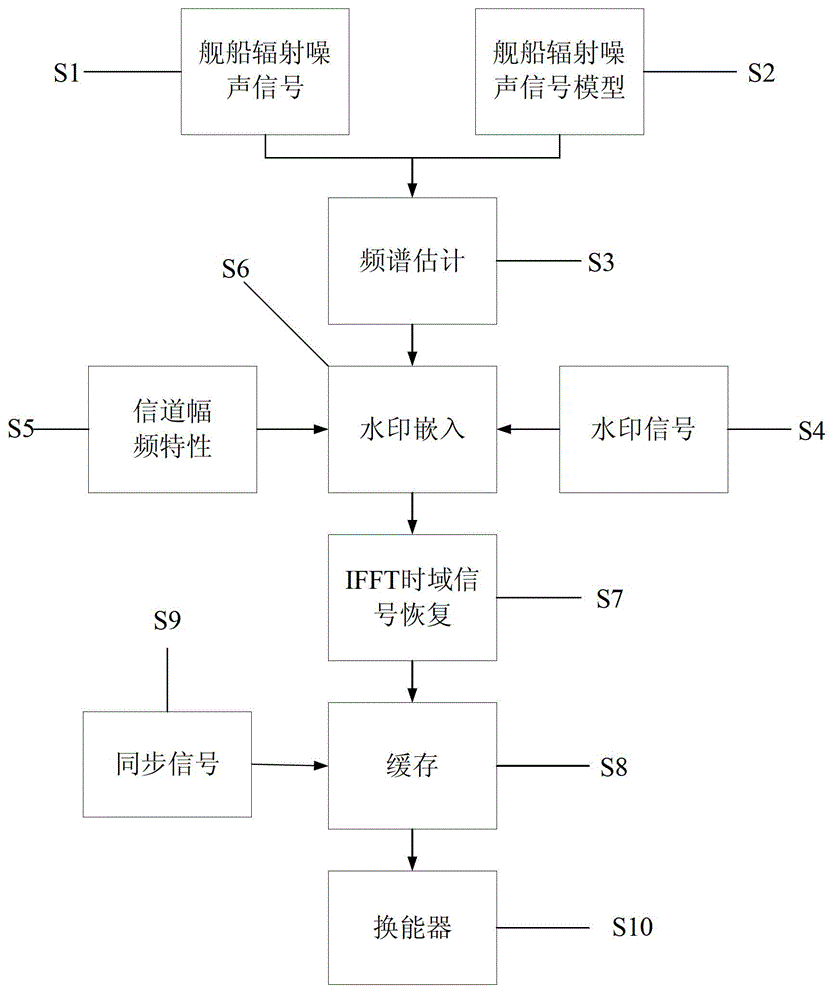
Underwater sound covert communication method and system based on ship radiation noise
InactiveCN102916750ASecure transmissionSpeech analysisTransmissionFrequency spectrumCovert communication
The invention discloses an underwater sound covert communication method based on ship radiation noise. The underwater sound covert communication method comprises the following steps of: on a sending end, carrying out spectral analysis on a carrier signal, realizing information embedding in a frequency domain, carrying out amplitude-frequency modifying on an embedded frequency domain signal, obtaining a time domain signal by carrying out inverse transformation on the frequency domain, constructing a final emitting signal by adding a synchronizing signal in front of a time domain communication signal embedded with the information, and carrying out power amplifying on the signal and outputting the signal to a low-frequency energy converter to realize emitting; on a receiving end, converting an induced acoustic signal into an electric signal, detecting whether a communication signal exits by the synchronizing signal known in advance, if the communication signal exits, obtaining an encrypted message by an inverse operation mapped with the sending end, and finally, restoring the original message or information required to sent through a decipherment algorithm by a secret key. According to communication method, not only the information can be safely and reliably transmitted, but also the communication process has hidden property. The invention further discloses an underwater sound covert communication system based on the ship radiation noise.
Owner:JIANGSU UNIV OF SCI & TECH
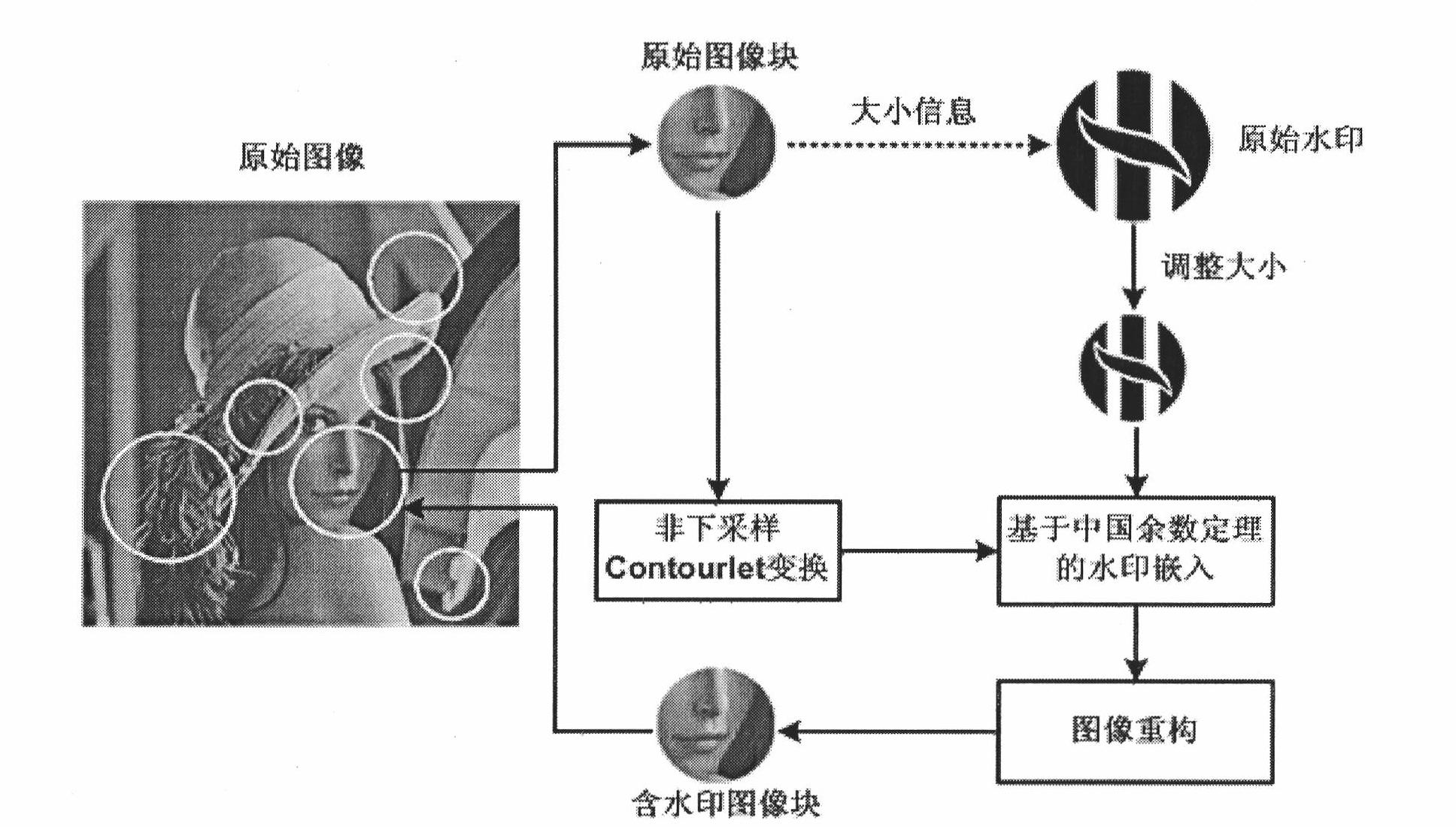
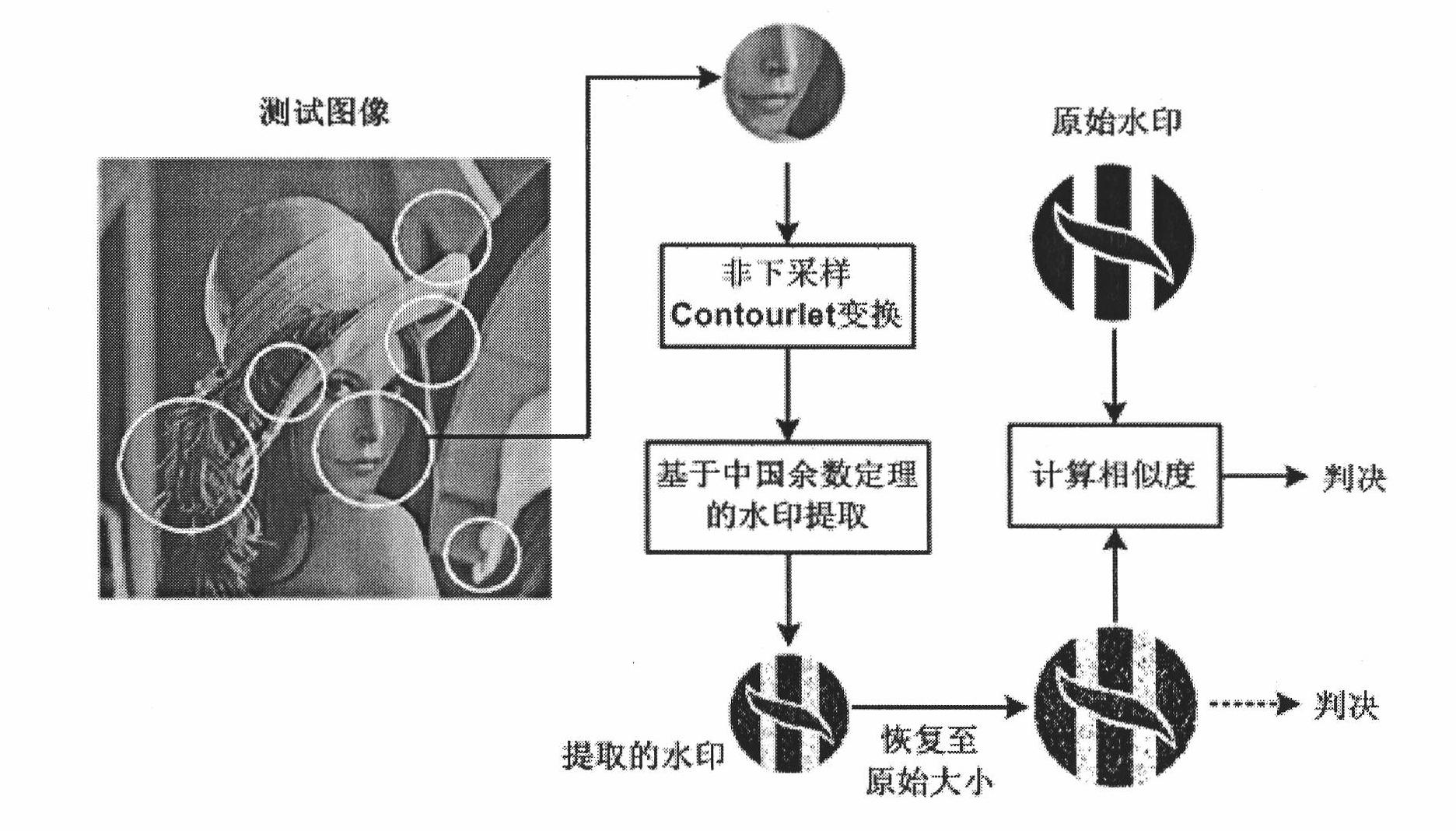
High-capacity digital watermarking method combining multi-scale characteristics and Chinese remainder theorem
InactiveCN102044055AImmutableEffective Watermark ExtractionImage data processing detailsPattern recognitionImaging processing
The invention discloses a high-capacity digital watermarking method combining multi-scale characteristics and a Chinese remainder theorem, which is a high-capacity digital watermarking method used for covert communication and digital images. The method is used for determining positions for embedding and extracting watermarks by using multi-scale characteristic points with multiple-invariance, and embedding binary watermark images in a non-subsampled profile wave domain by using the Chinese remainder theorem. Before embedding, the watermark images are adjusted correspondingly according to an embedding region to ensure that watermark signals are adaptive to the embedding region. During extracting, a region containing watermarks is positioned by using a same method first, and the watermarks are extracted in the non-subsampled profile wave domain according to the Chinese remainder theorem. In the method, while high-capacity watermark signals are embedded, images containing the watermarks can obtain very high quality; and the extracted watermarks can resist conventional image processing operations and geometric transformations such as rotation, zooming, translation and the like, and the geometric transformations of the extracted watermarks and images are kept consistent for protecting the copyrights of the convert communication and the digital images.
Owner:CHINA UNIV OF MINING & TECH
Long-range control method and system
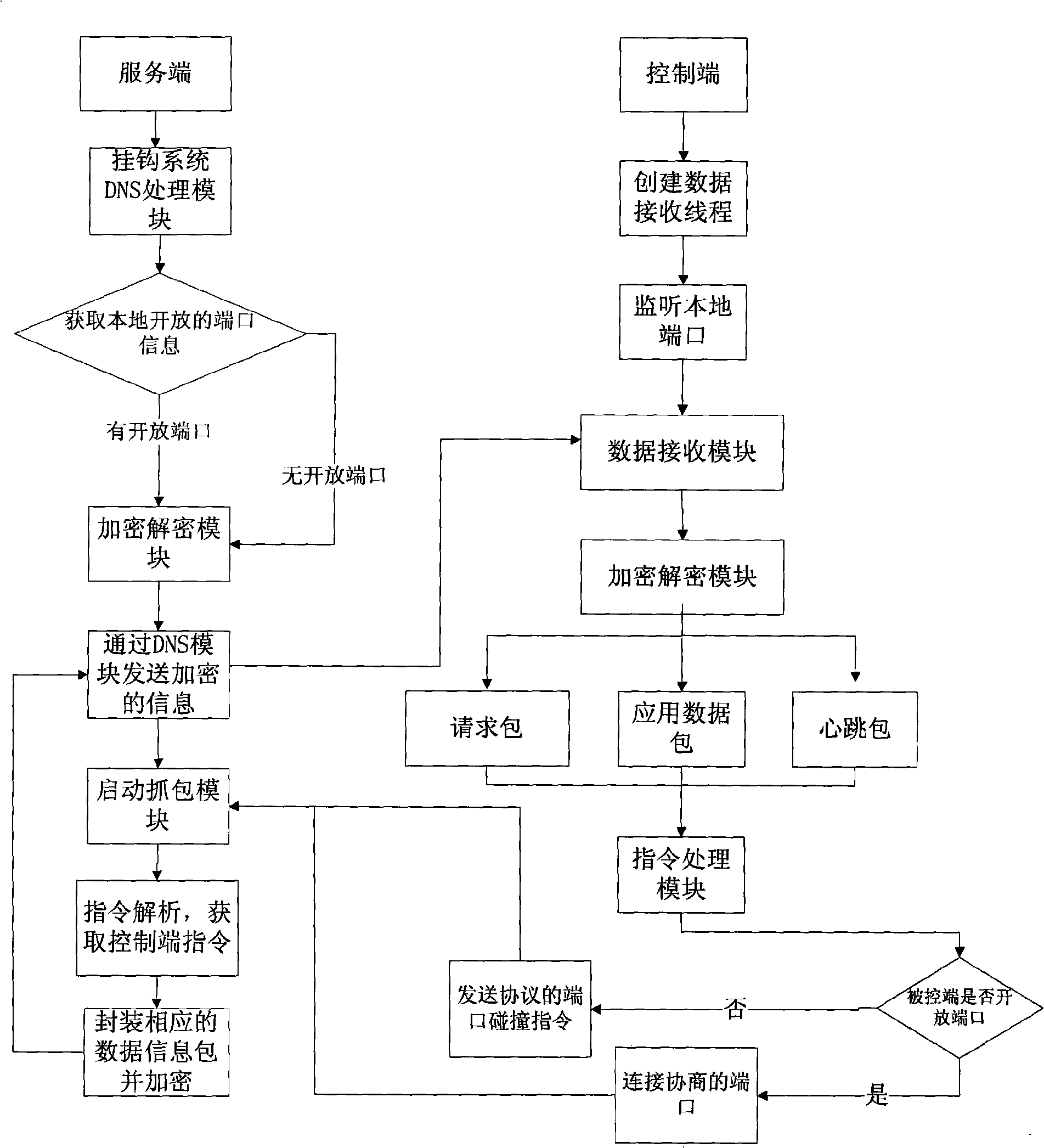
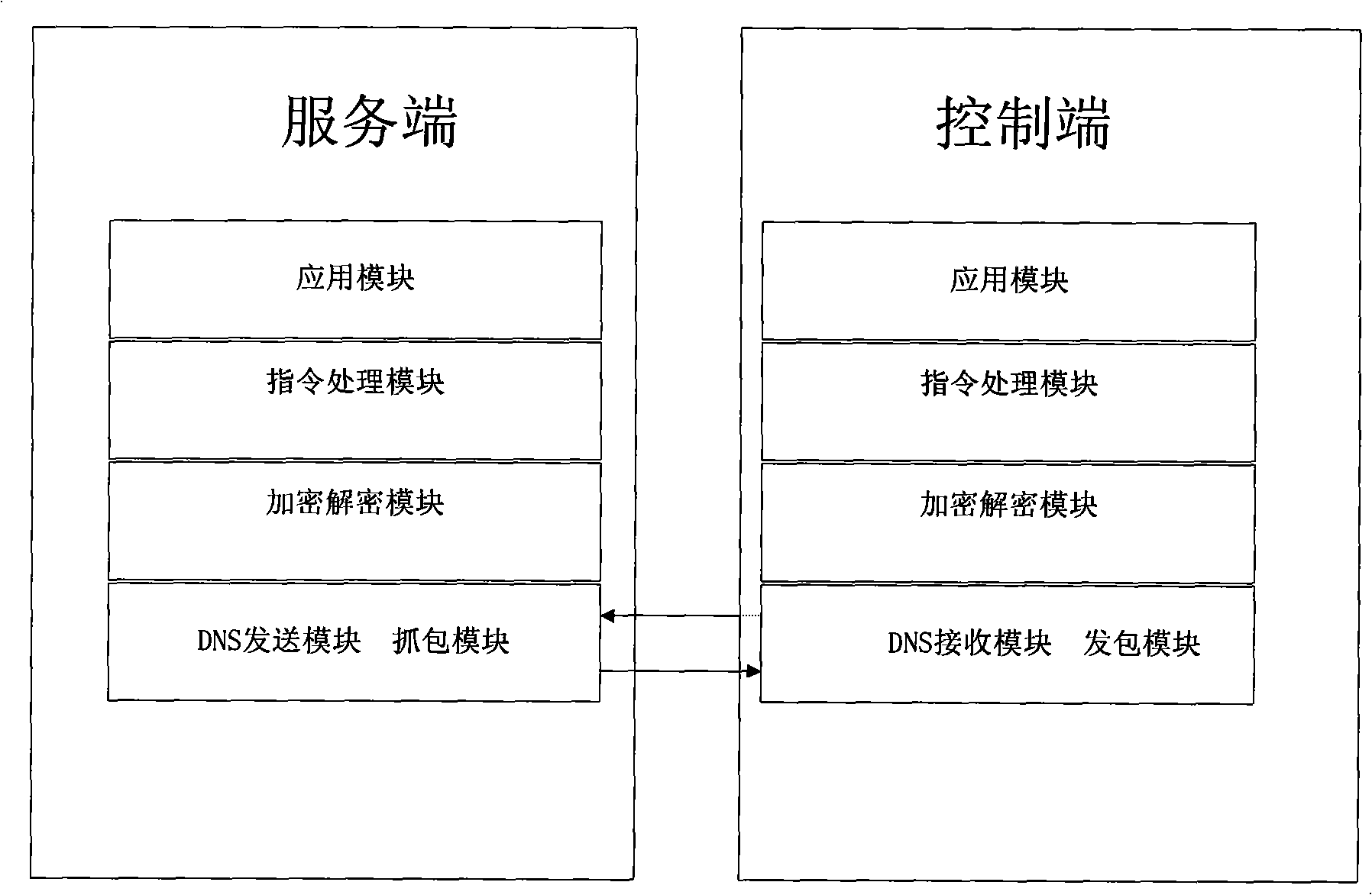
InactiveCN101286995AStrong Covert Communication CapabilityStrong communication securityTransmissionControl systemRemote control
The invention pertains to the field of network communication security, which particularly relates to a remote control method and remote control system. The invention adds modules into a service end and a control end; the service end is arranged in a computer to be controlled and initiatively connected with the control end; improvement is carried out according to the mechanism of firewall or intrusion detection systems; the firewall or the intrusion detection systems are penetrated initiatively, thus easily traversing interception and realizing the purpose of covert communication.
Owner:RUN TECH CO LTD BEIJING
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com