Covert communication system based on random noise modulation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
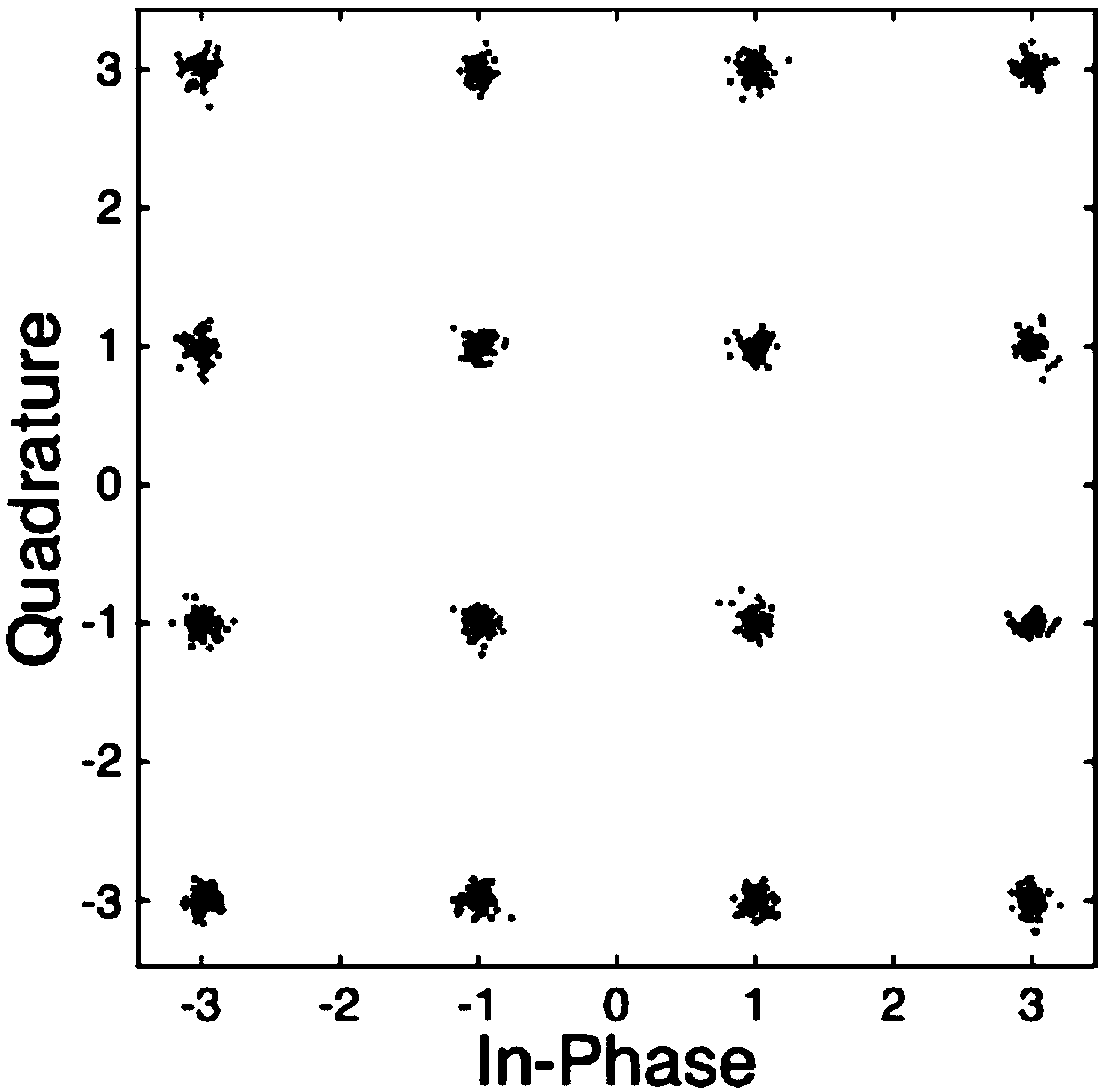
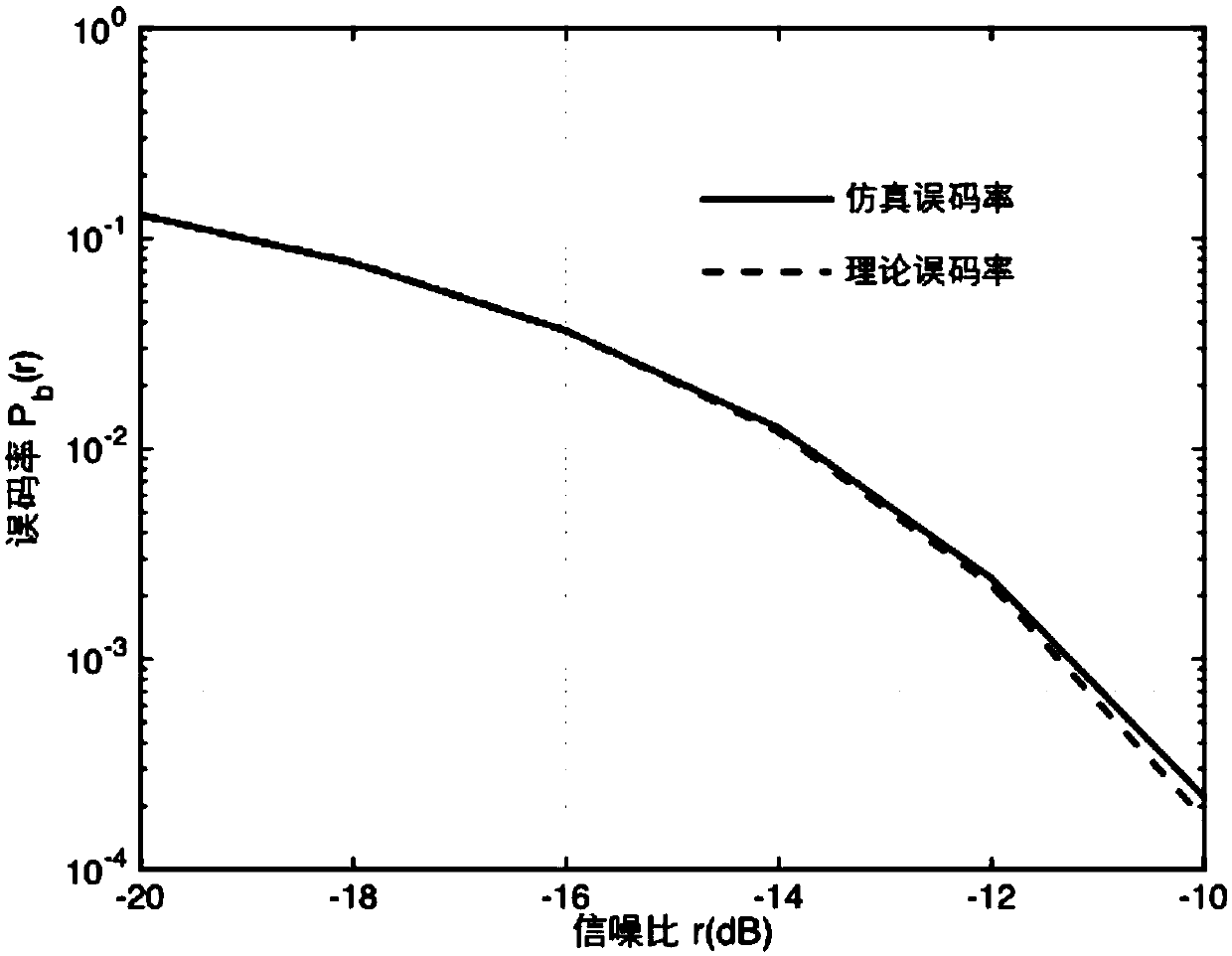
Image
Examples
Embodiment Construction
[0039] The present invention will be further described below in conjunction with the accompanying drawings.
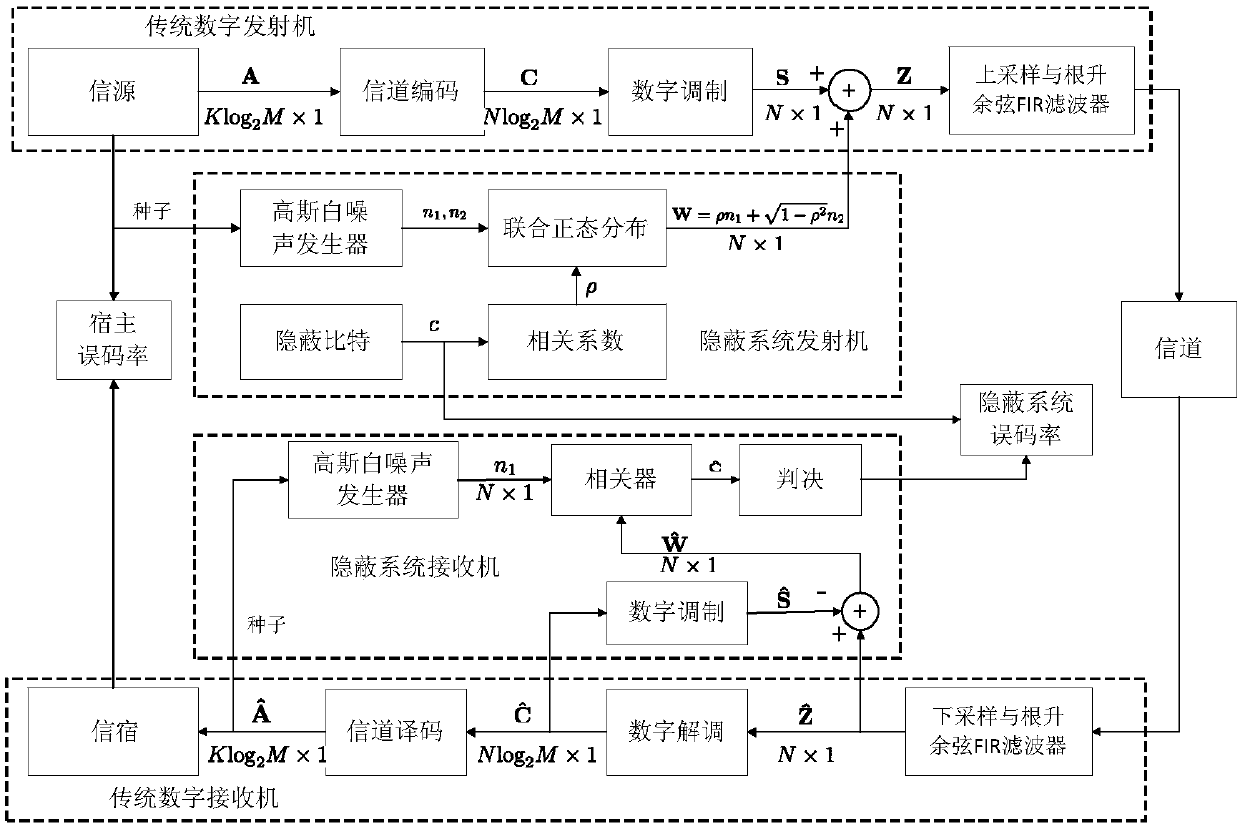
[0040] refer to Figure 1 ~ Figure 3 , a covert communication system based on random noise modulation, comprising:
[0041] A covert transmitter for generating a Gaussian white noise generator in a covert system using host communication data as a seed to generate a noise sequence n 1 , n 2 ; n 1 , n 2 Constitute the joint normal distribution noise w, whose correlation coefficient is hidden bit c to modulate; the random noise w is superimposed on the digitally modulated output of the traditional digital transmitter, enters the up-sampling and root-raised cosine filter, and then transmits to the channel;
[0042]The covert receiver is used for the synchronization, channel estimation and recovery of random noise w at the receiving end of the covert system, all of which are completed with the help of the host system; the data of the host system is used as the seed of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com