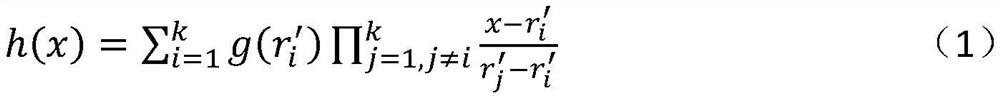Data hidden transmission method based on block chain multi-transaction splitting
A transmission method and data concealment technology, which is applied in the direction of digital transmission system, transmission system, data processing application, etc., can solve the problems of application failure and data concealment transmission application security threats, etc., achieve strong practicability, improve concealment, and concealment high effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
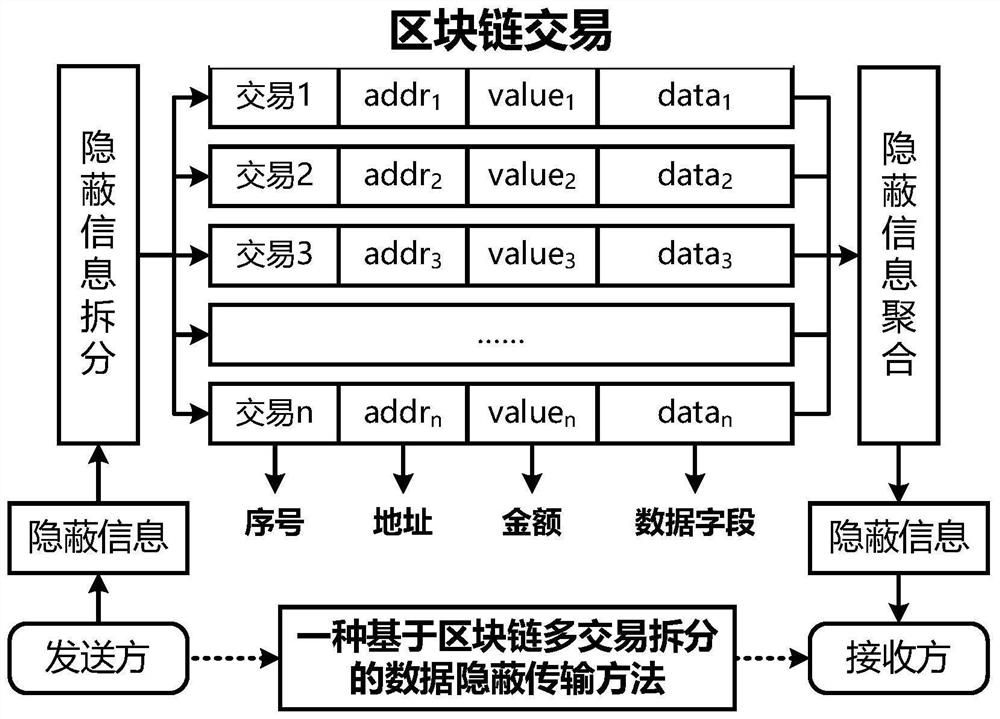
[0032] This embodiment proposes an information splitting method based on XOR. The sender splits the concealed information into n parts, and the receiver needs to aggregate all n parts of the split information to recover the hidden information.
[0033] Such as figure 1 As shown, a data covert transmission method based on blockchain multi-transaction splitting includes the following process:
[0034] Step 1: Off-chain negotiation.
[0035] Before carrying out the covert transmission of blockchain data, the sender and the receiver first negotiate the address set A used through the off-chain channel, A={A 1 ,...,A m}, where A includes m blockchain addresses, all of which are generated by the sender. At the same time, the sender and the receiver negotiate the number n of splitting the hidden information, n
Embodiment 2
[0048] Embodiment 2 proposes an information splitting method based on secret sharing. The sender splits the hidden information into n parts, and the receiver only needs to aggregate the split information of t parts to recover the hidden information. t≤n.
[0049] Such as figure 1 As shown, a data covert transmission method based on blockchain multi-transaction splitting includes the following process:
[0050] Step 1: Off-chain negotiation.
[0051] Before carrying out the covert transmission of blockchain data, the sender and the receiver need to pre-negotiate the address set A={A 1 ,...,A m}, which includes m blockchain addresses, all of which are generated by the sender. In addition, the sender and receiver negotiate the number of splits n of the concealed information, where n (wherein N is a 256-bit prime number), and an embedding / extracting method of hidden information. The concealed information embedding / extracting method here can be implemented using existing techn...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com