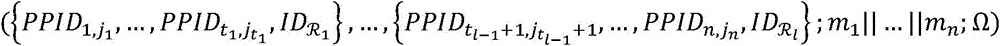Patents
Literature
344 results about "Private communication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
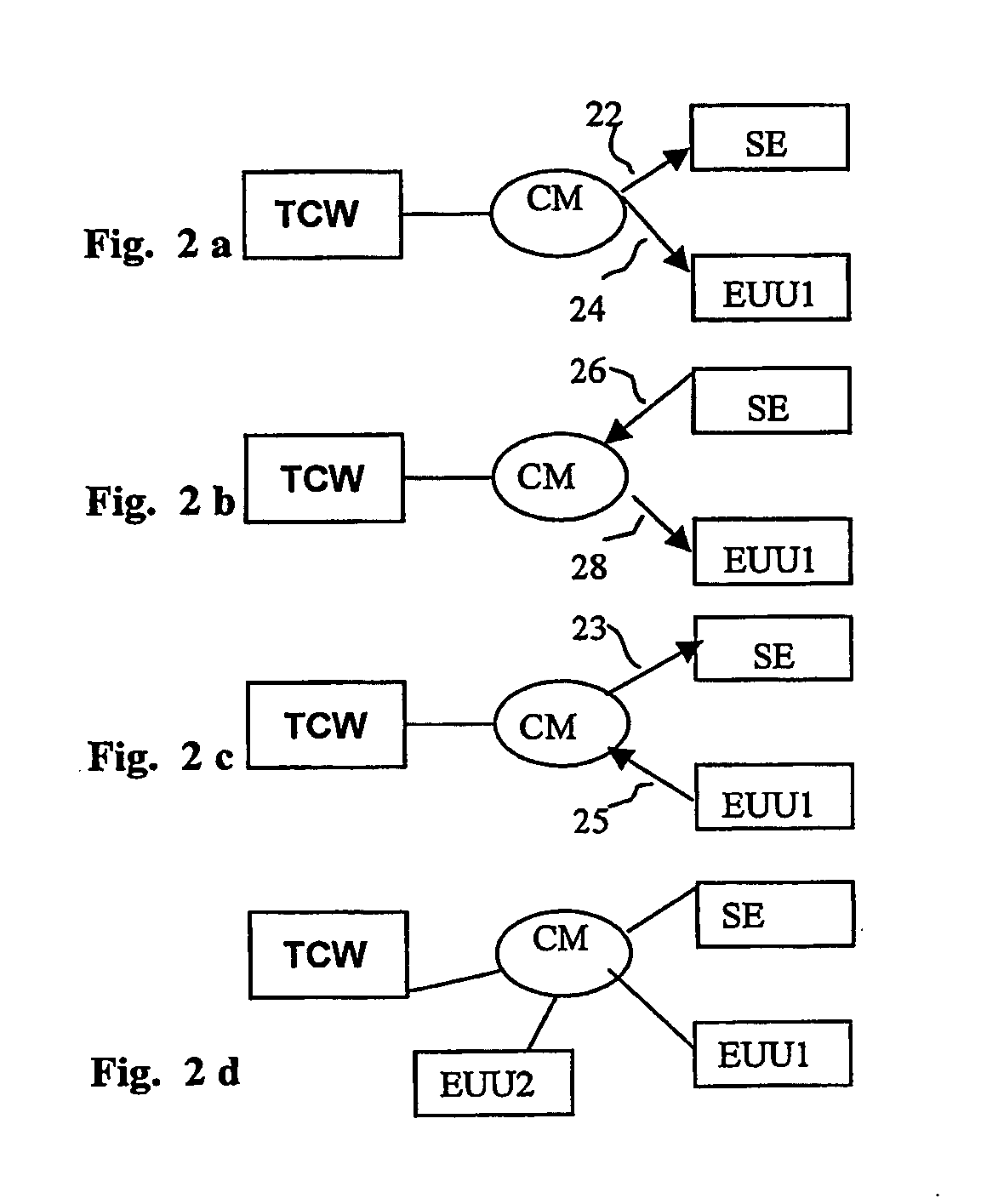
Managed peer-to-peer applications, systems and methods for distributed data access and storage
InactiveUS20050114711A1Digital data processing detailsUser identity/authority verificationPrivate communicationDisplay device
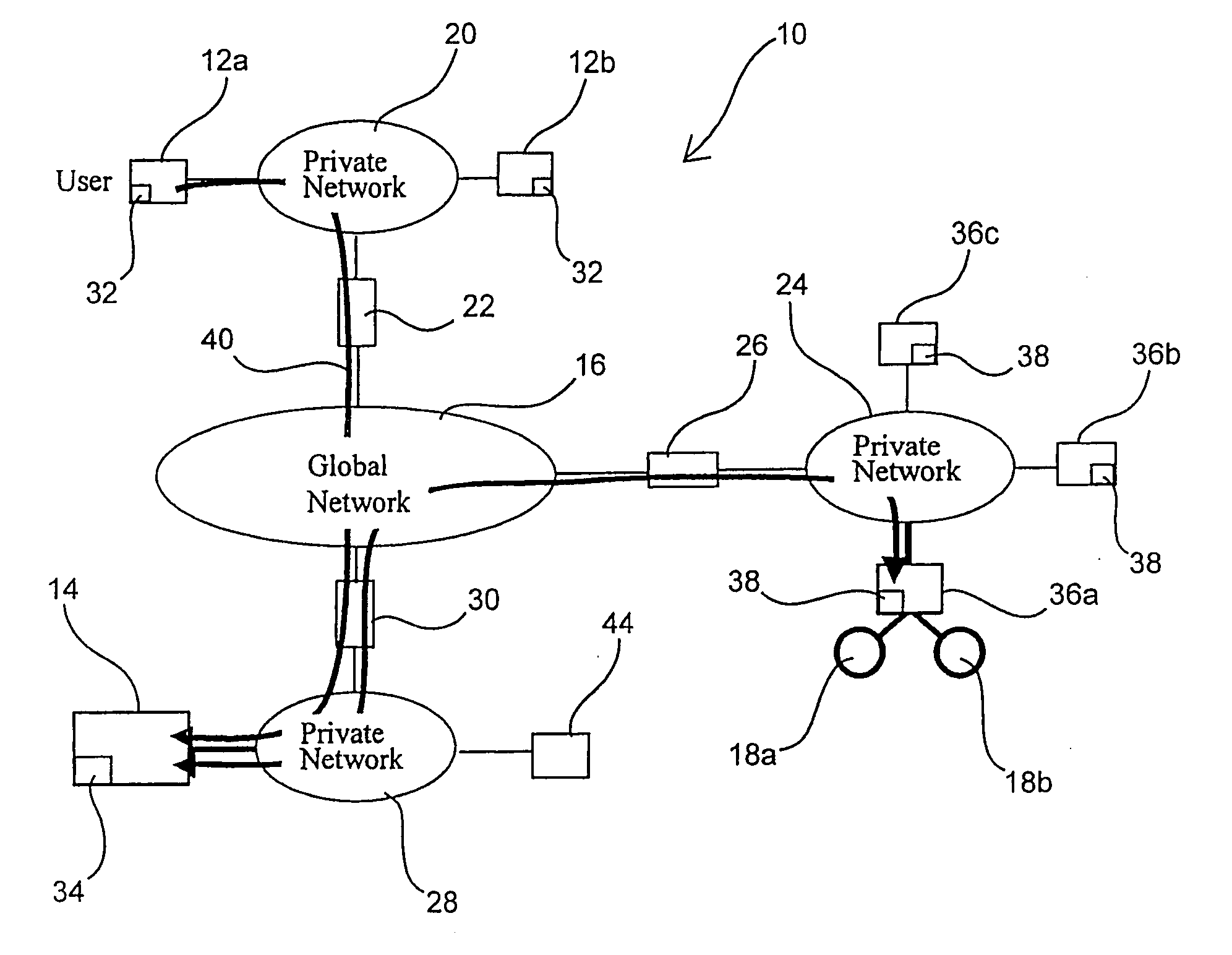
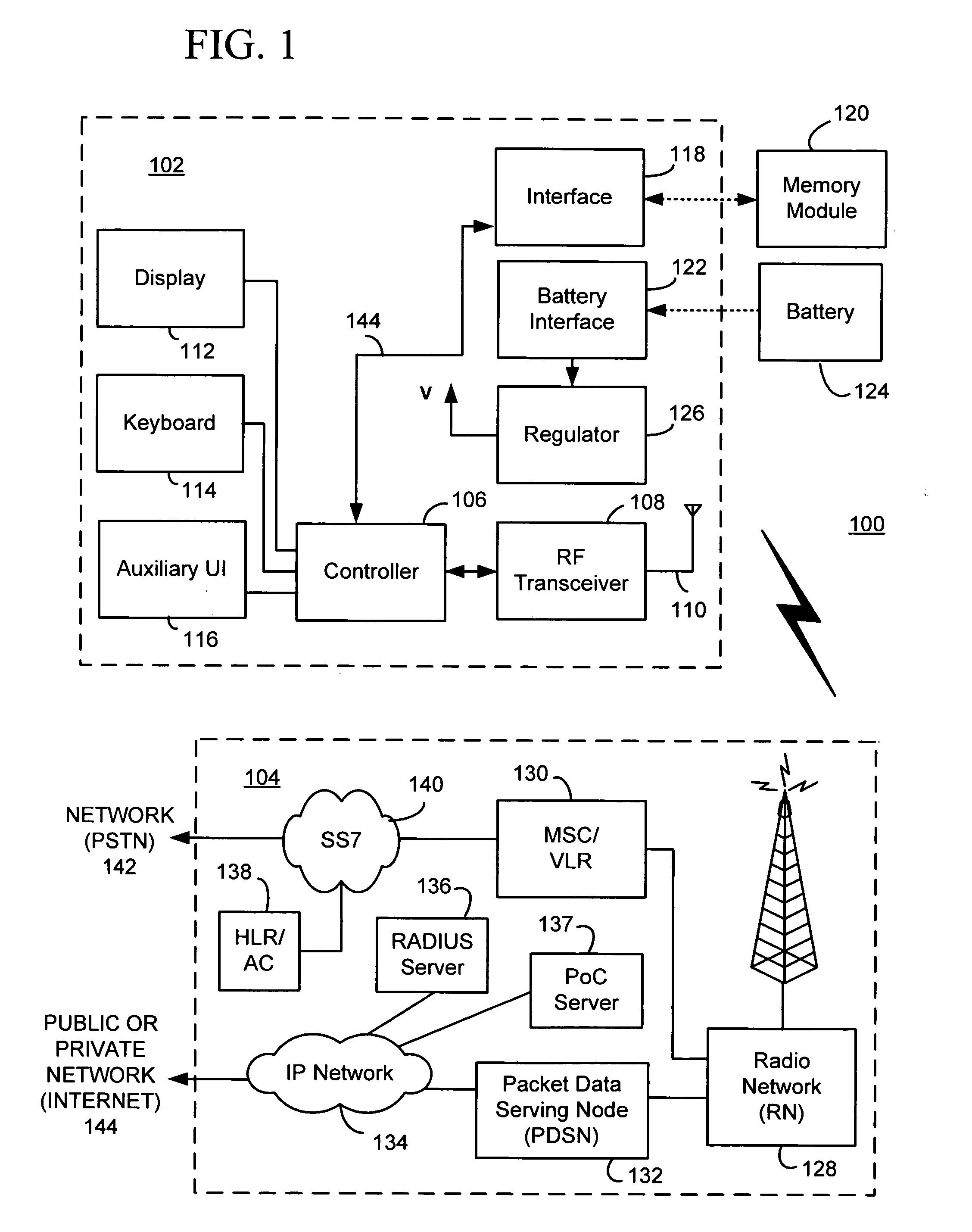
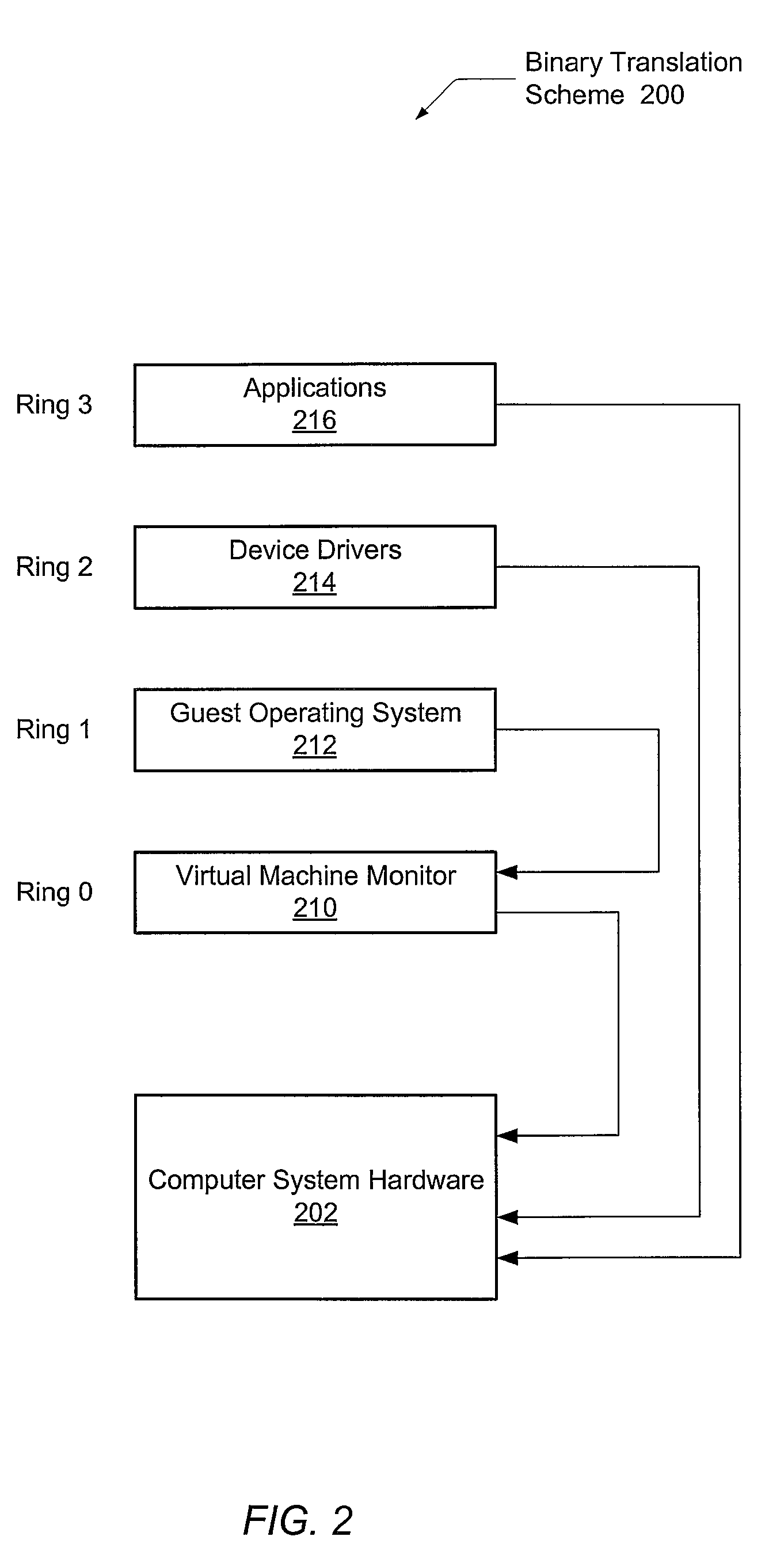
Applications, systems and methods for securely and remotely operating a remote computer from a local computer over a network while providing seamless, firewall-compliant connectivity. Secure and remote operation includes authenticating at least one remote computer for connection to at least one computer over the network and / or at least one local computer for connection to at least one remote computer over the network; establishing a secure connection between the at least one local computer and the at least one remote computer over the network; and integrating a desktop of at least one remote computer on a display of at least one local computer. The connections may be made over a public network, as well as through multiple firewalls without loss of functionality. A method of accessing and using at least one remote computer from a local computer over a public network may include centrally authenticating, at a location having a public address, a first computer having a first, firewall protected private address; creating a first firewall compliant connection between a publicly addressed connection server and the first computer upon authentication of the first computer; establishing a second firewall compliant connection between the publicly addressed connection server and a second computer having a second firewall protected private address; establishing a private-to-public-to-private communications tunnel, wherein the connection server routes communications from the first computer through the first firewall compliant connection and the second firewall compliant connection to the second computer, and from the second computer through the second firewall compliant connection and the first firewall compliant connection to the first computer; and performing at least one further step selected from the group consisting of: integrating a file structure of accessible files accessed at the second or first computer, into a file structure contained at the first or second computer, respectively; at least one of integrating a desktop of the second computer on a display of the first computer and integrating a desktop of the first computer on a display of the second computer; and directly operating the second computer from the first computer or the first computer from the second computer, wherein the computer that is directly operated is selected from the group consisting of: home appliances, video equipment, audio equipment, printers, fax machines, office equipment, medical devices, vehicles, cameras, RFID equipment, laboratory equipment, manufacturing machinery, GPS equipment, and devices having one or more embedded microprocessors.
Owner:WESTERN DIGITAL TECH INC
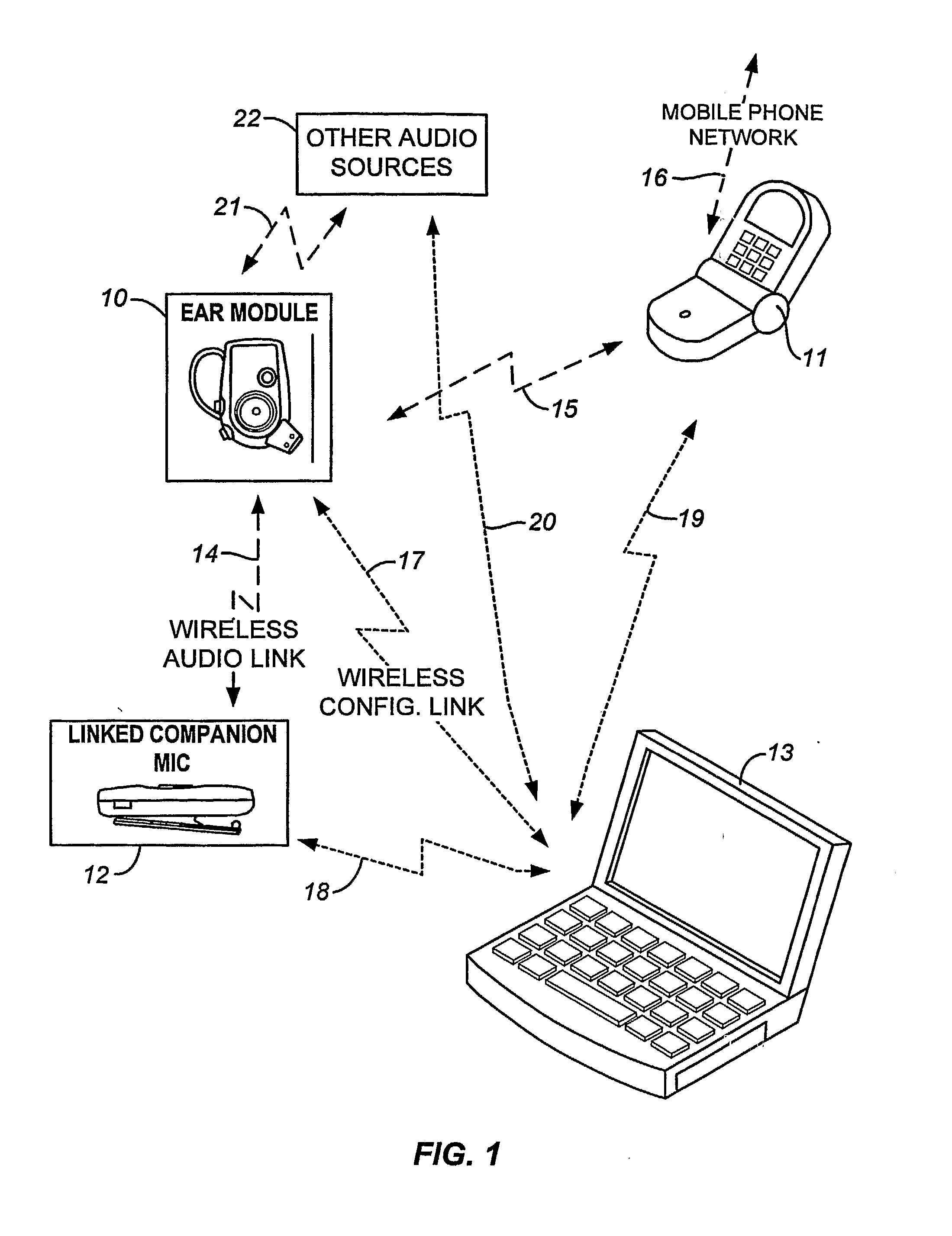
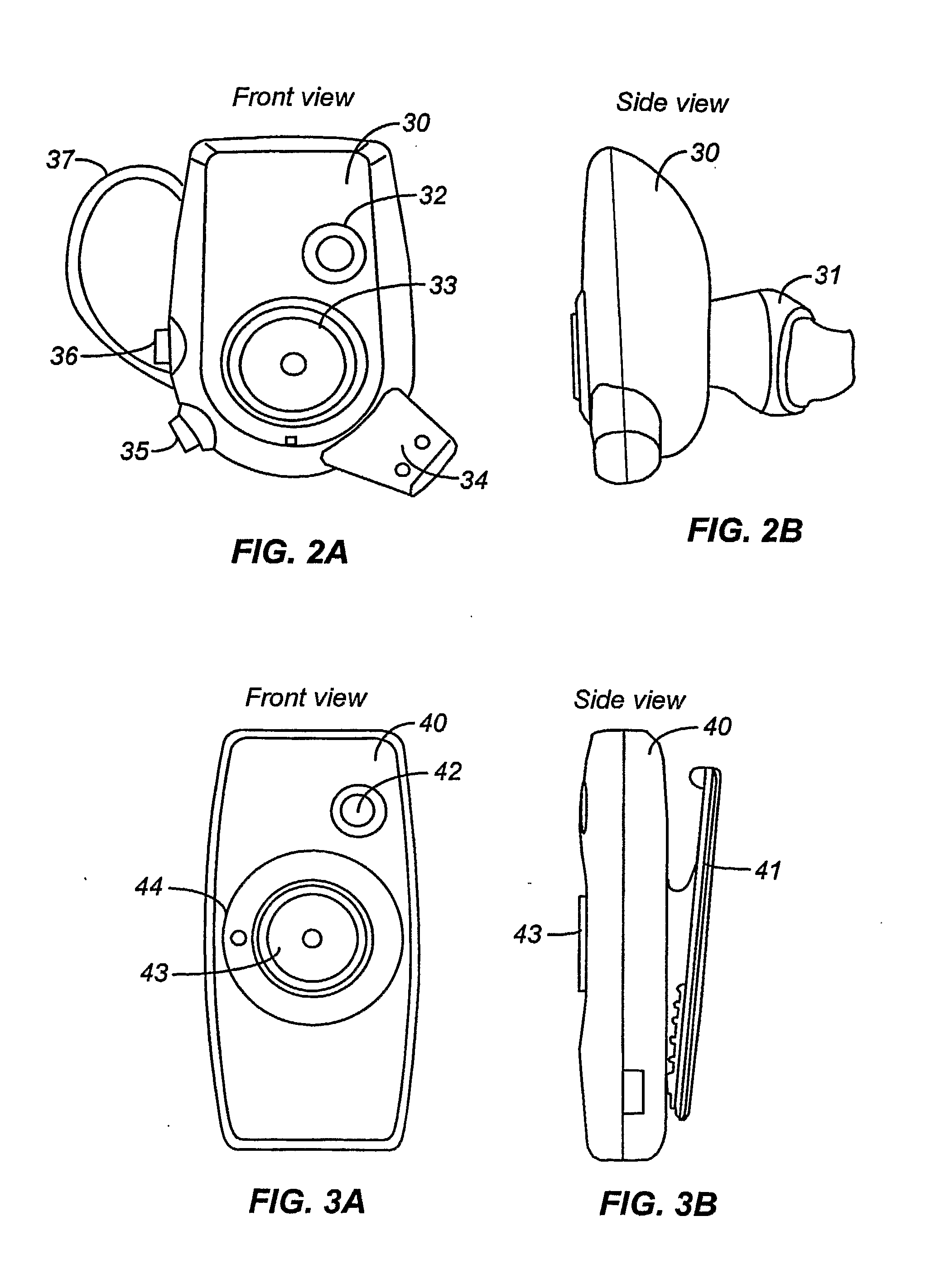
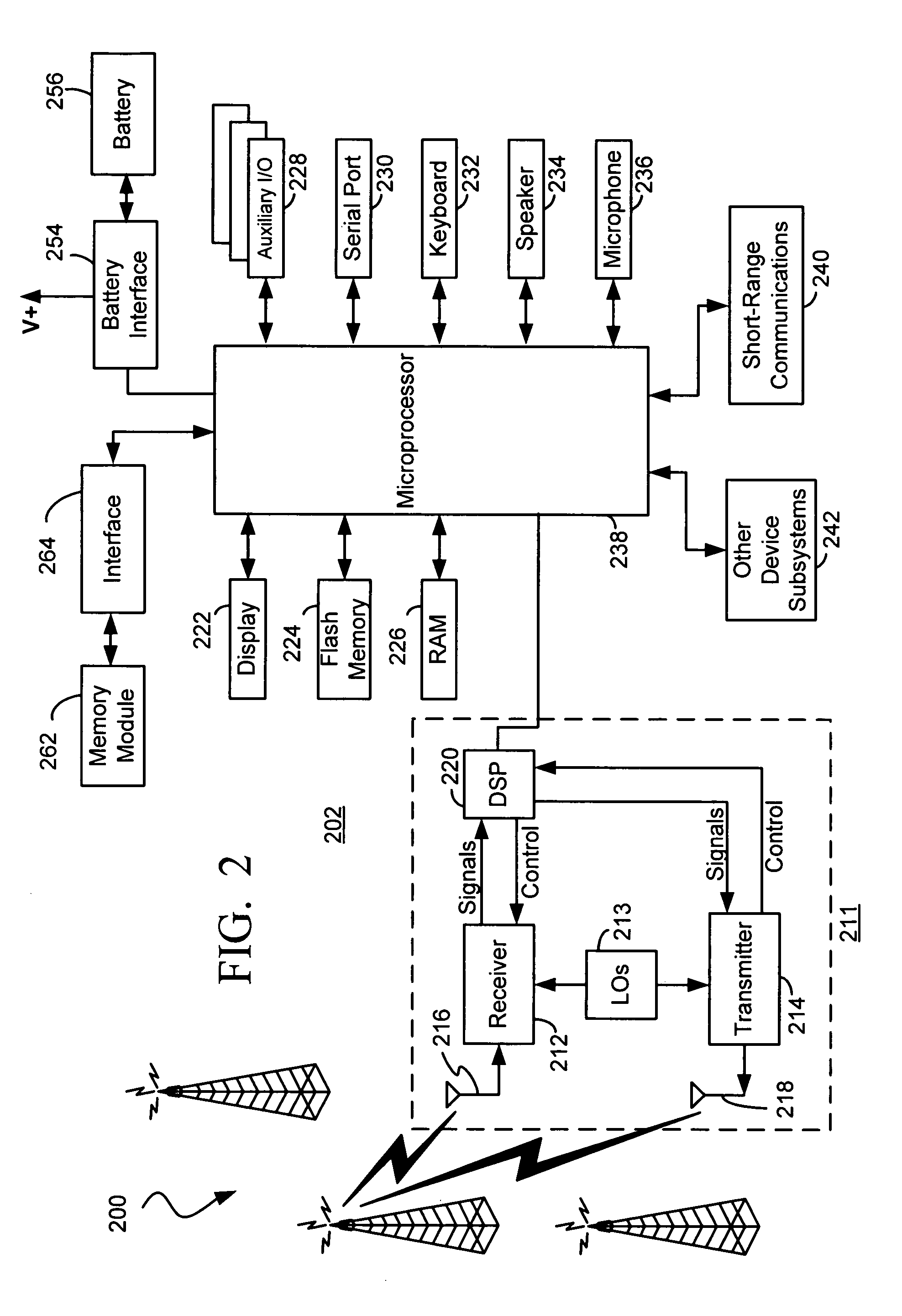
Personal Sound System Including Multi-Mode Ear Level Module with Priority Logic
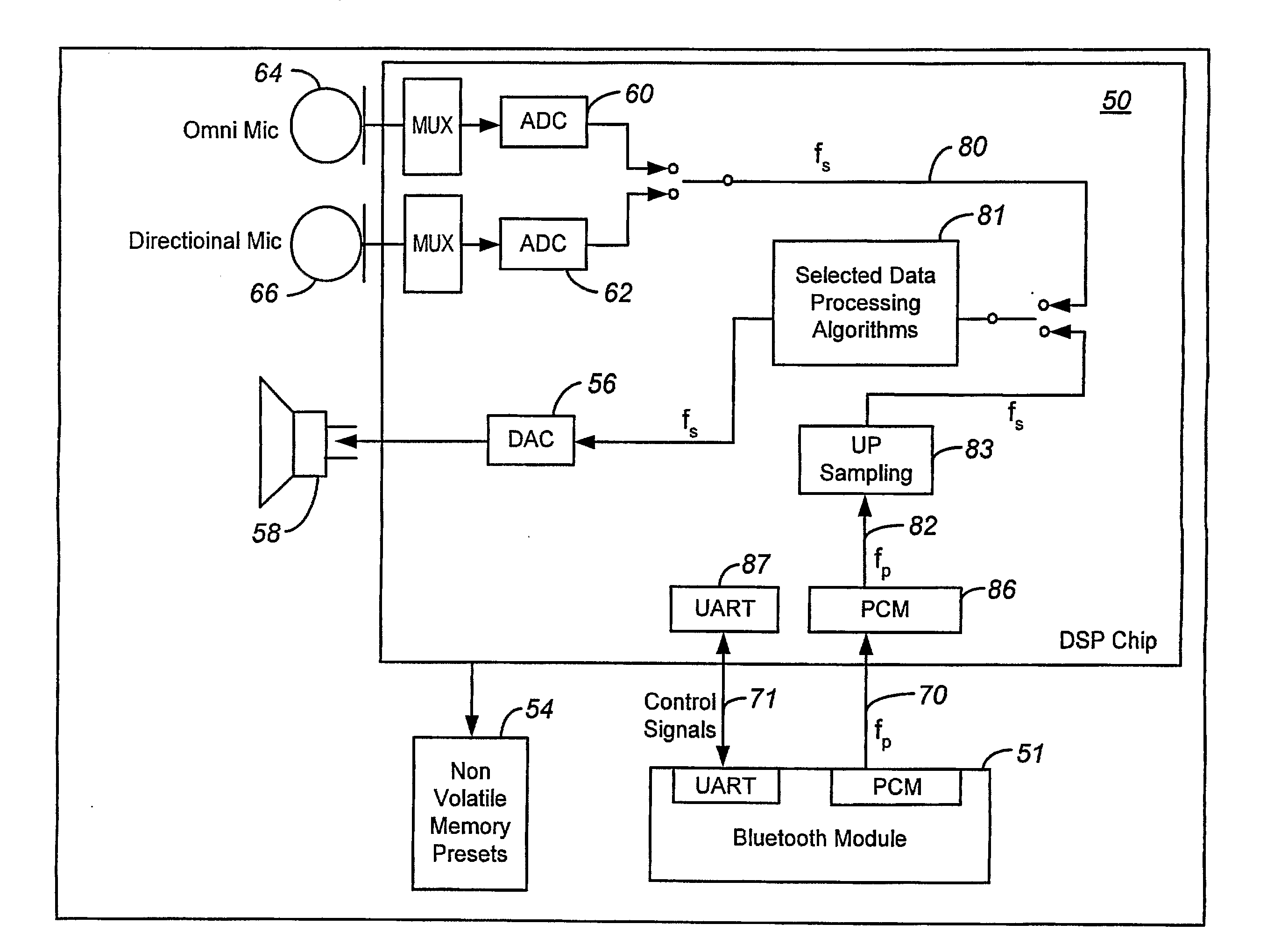
ActiveUS20070255435A1Securing the ear module in the ear comfortably and easilyMicrophonesHearing device energy consumption reductionPrivate communicationData source
A personal sound system is described that includes a wireless network supporting an ear-level module, a companion module and a phone. Other audio sources are supported as well. A configuration processor configures the ear-level module and the companion module for private communications, and configures the ear-level module for a plurality of signal processing modes, including a hearing aid mode, for a corresponding plurality of sources of audio data. The ear module is configured to handle variant audio sources, and control switching among them.
Owner:HIMPP
Communications web site
InactiveUS20050182824A1Overcome disadvantagesMultiplex system selection arrangementsMultiple digital computer combinationsPrivate communicationWeb site
A web site for providing communications a web page associated with a specific entity and a processing device. The web page is configured to accept an inputting of data and the processing device is configured to provide private communications between an end user unit and the specific entity using the inputting of data.
Owner:COMBOTS PRODUCT GMBH & CO KG
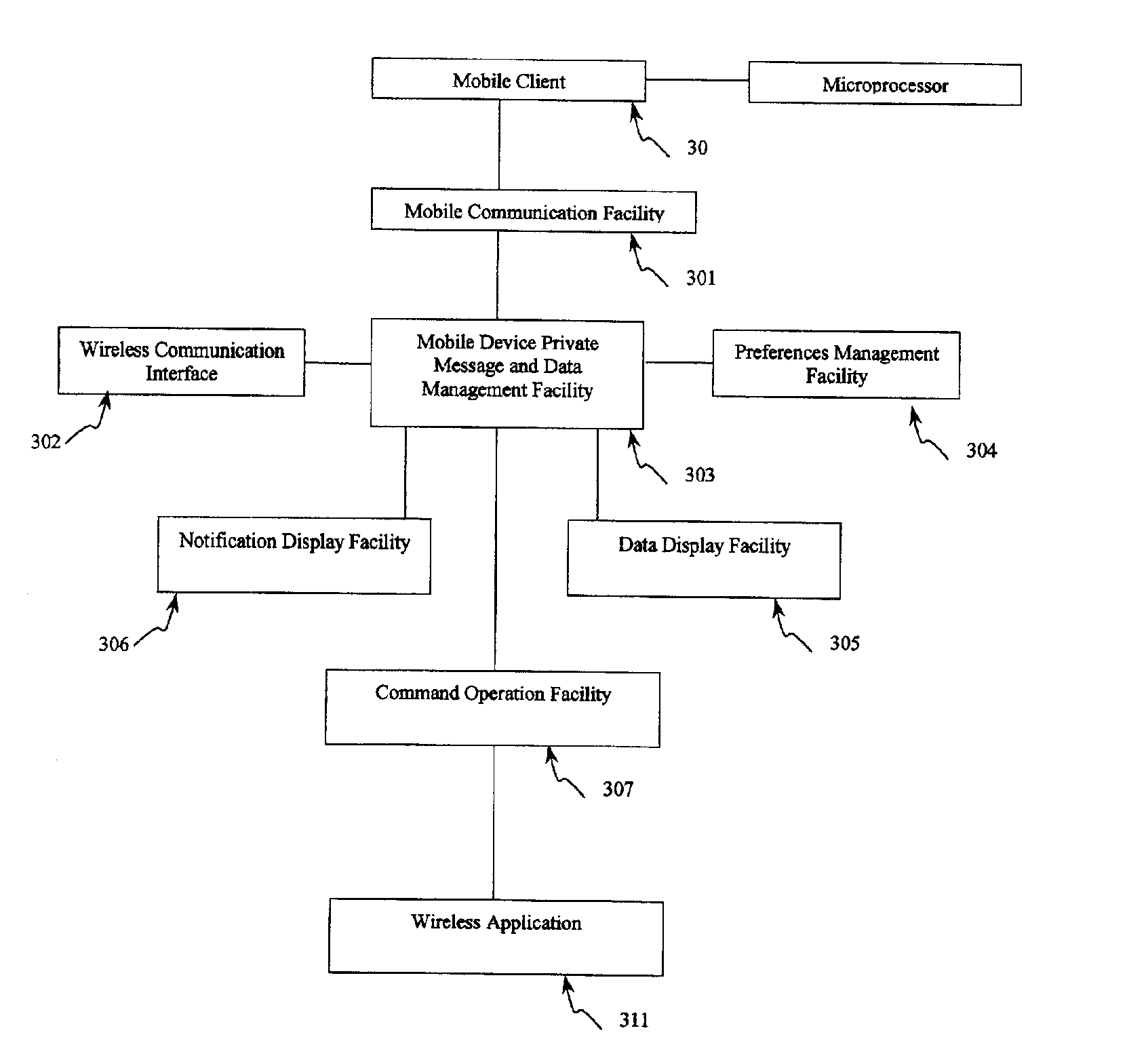
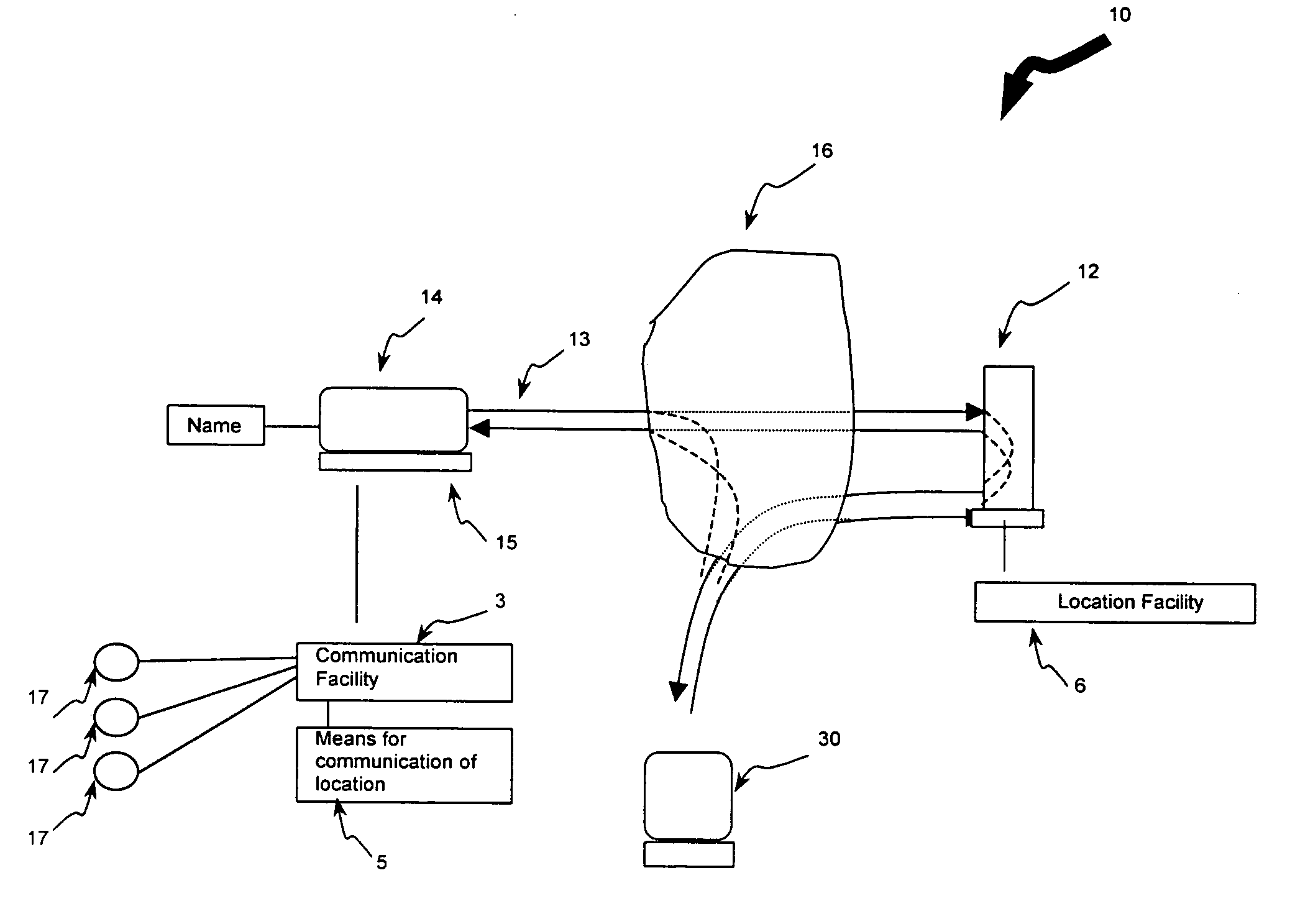
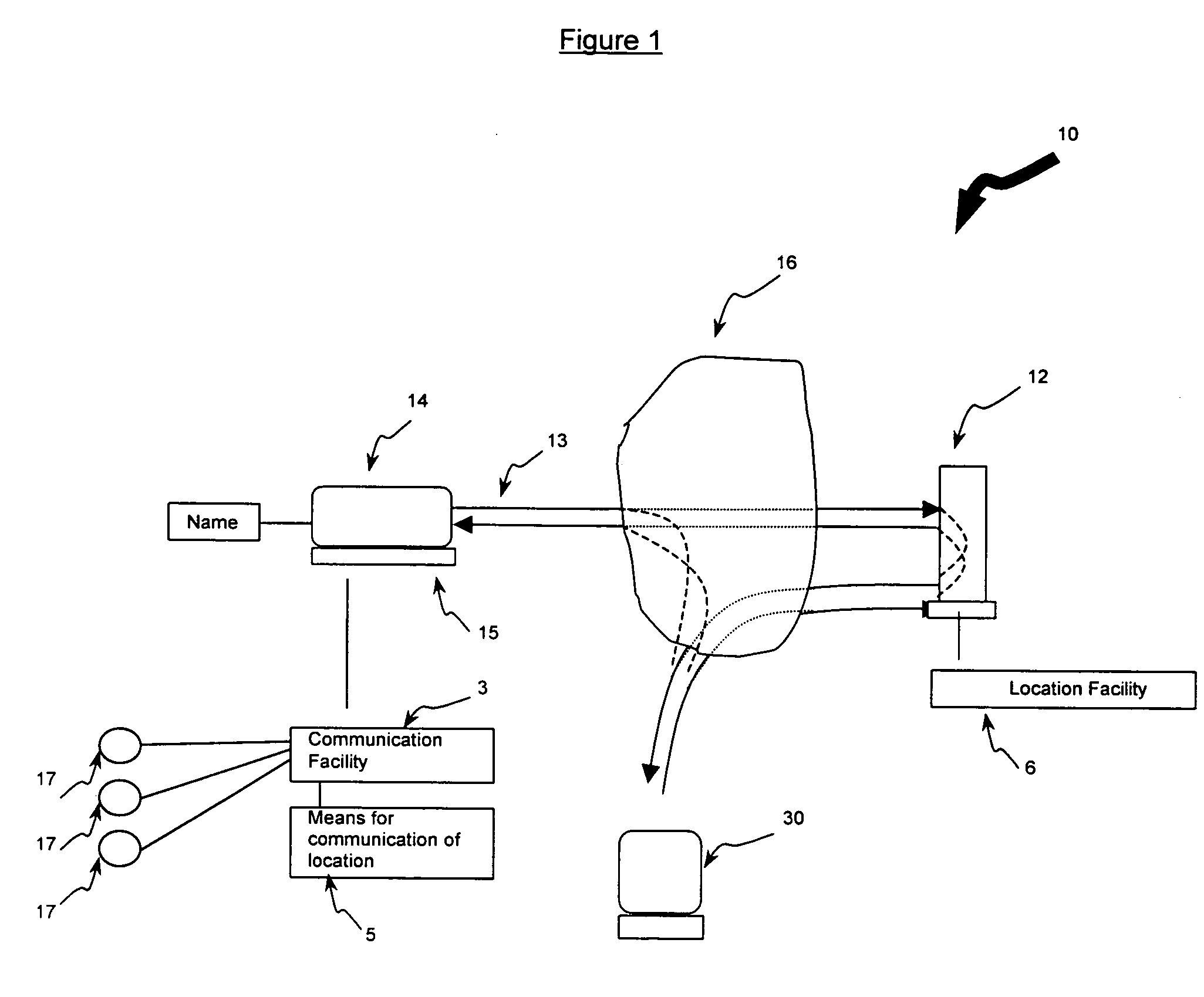
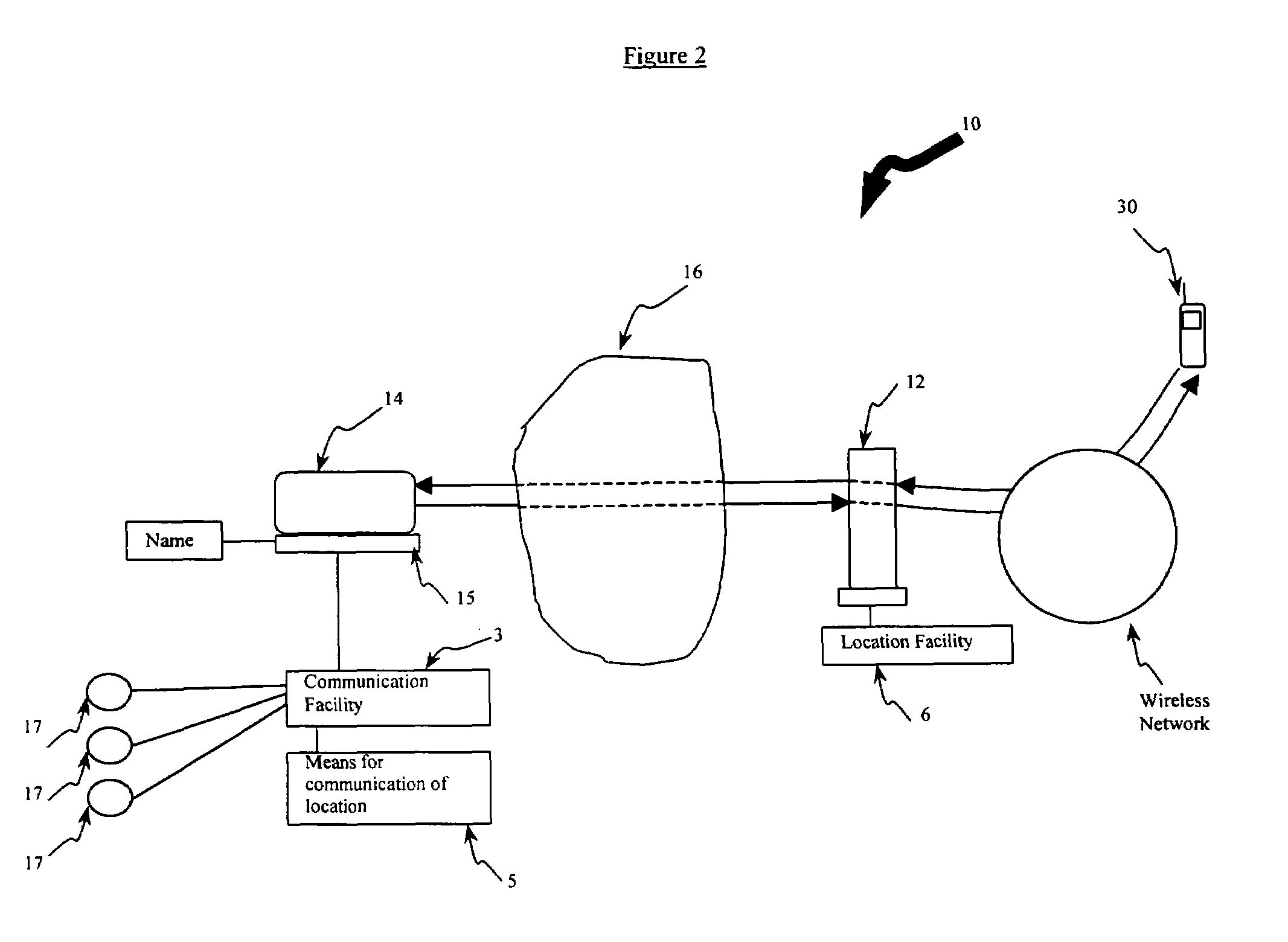
System, computer product and method for interfacing with a private communication portal from a wireless device
InactiveUS6938076B2Data switching by path configurationMultiple digital computer combinationsPrivate communicationThe Internet
A system for providing provisioning and operation at a wireless device comprising a first computer comprising a communication facility adapted to communicate information to remote computers and the wireless device; a second computer comprising a locating facility for locating the first computer; and a wireless device comprising a microprocessor and a mobile communication facility; wherein the first computer, the second computer and the wireless device are connected to the Internet; wherein the locating facility is adapted to facilitate communication between the first computer and the wireless device; and wherein the first computer and the wireless device are adapted to permit a user of the wireless device to access information at the first computer from the wireless device.
Owner:01 COMMUNIQUE LAB INC
Method and apparatus for remotely monitoring the condition of a patient
InactiveUS7448996B2Improve functionalityFunction increaseSurgeryPerson identificationPrivate communicationTelecommunications link
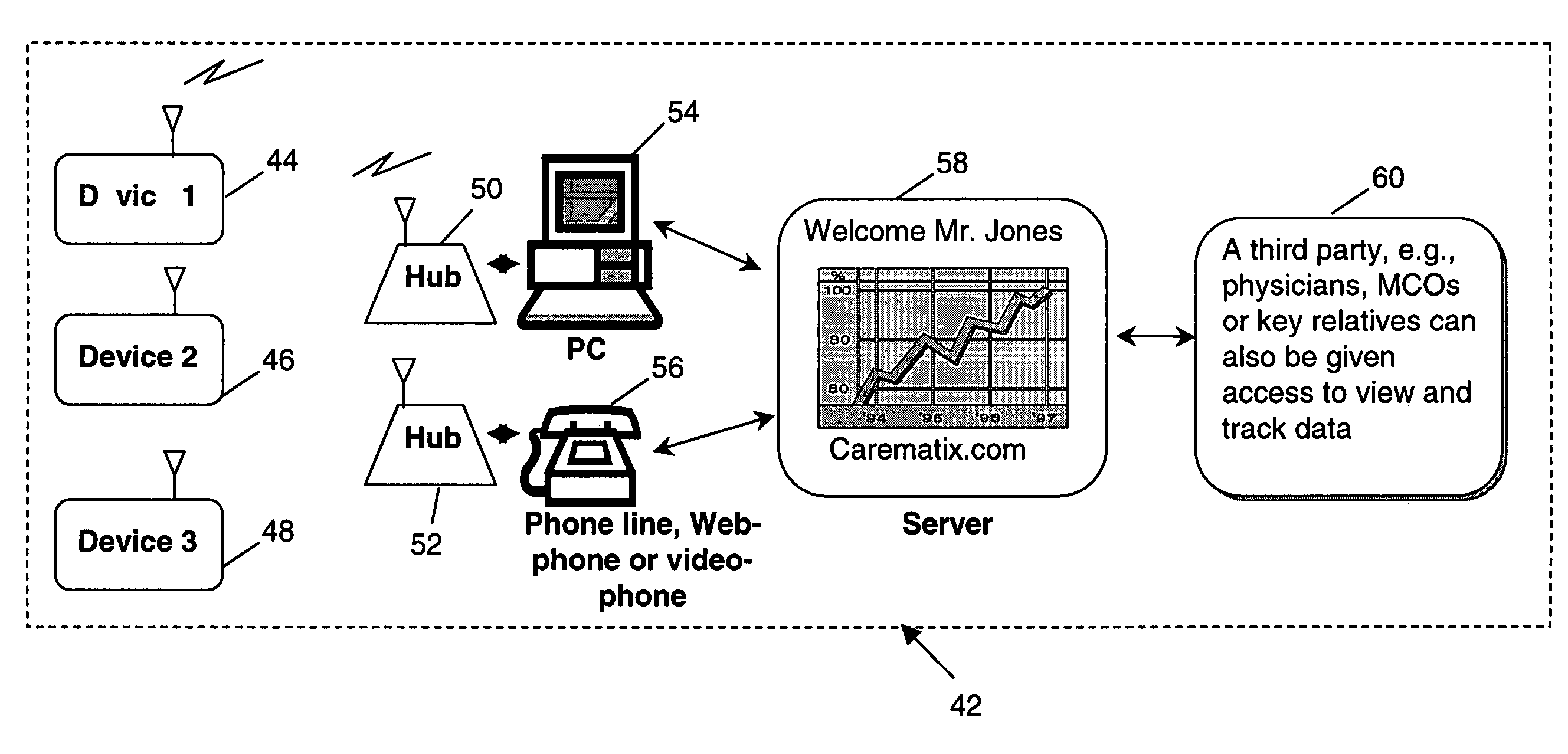
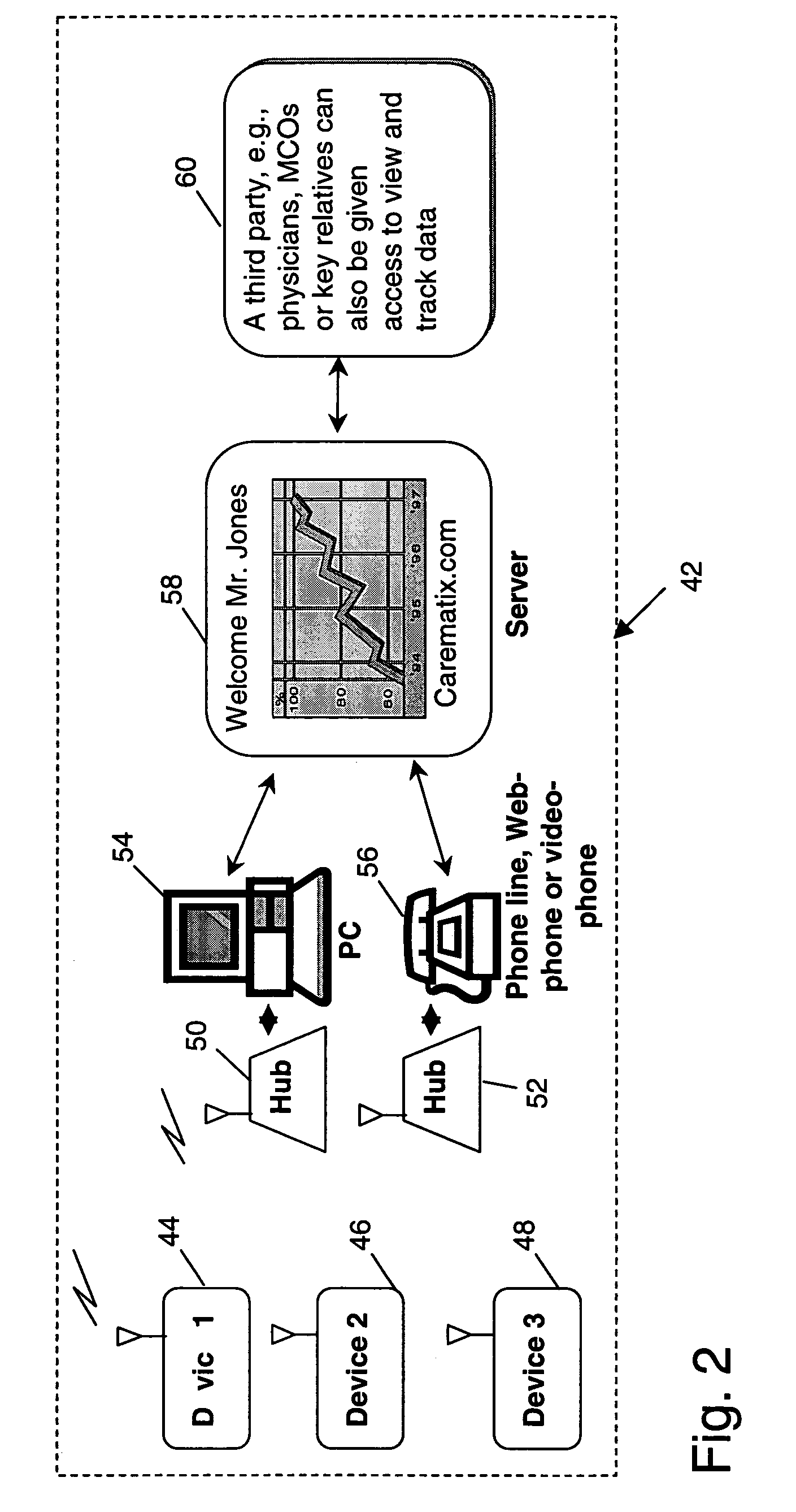
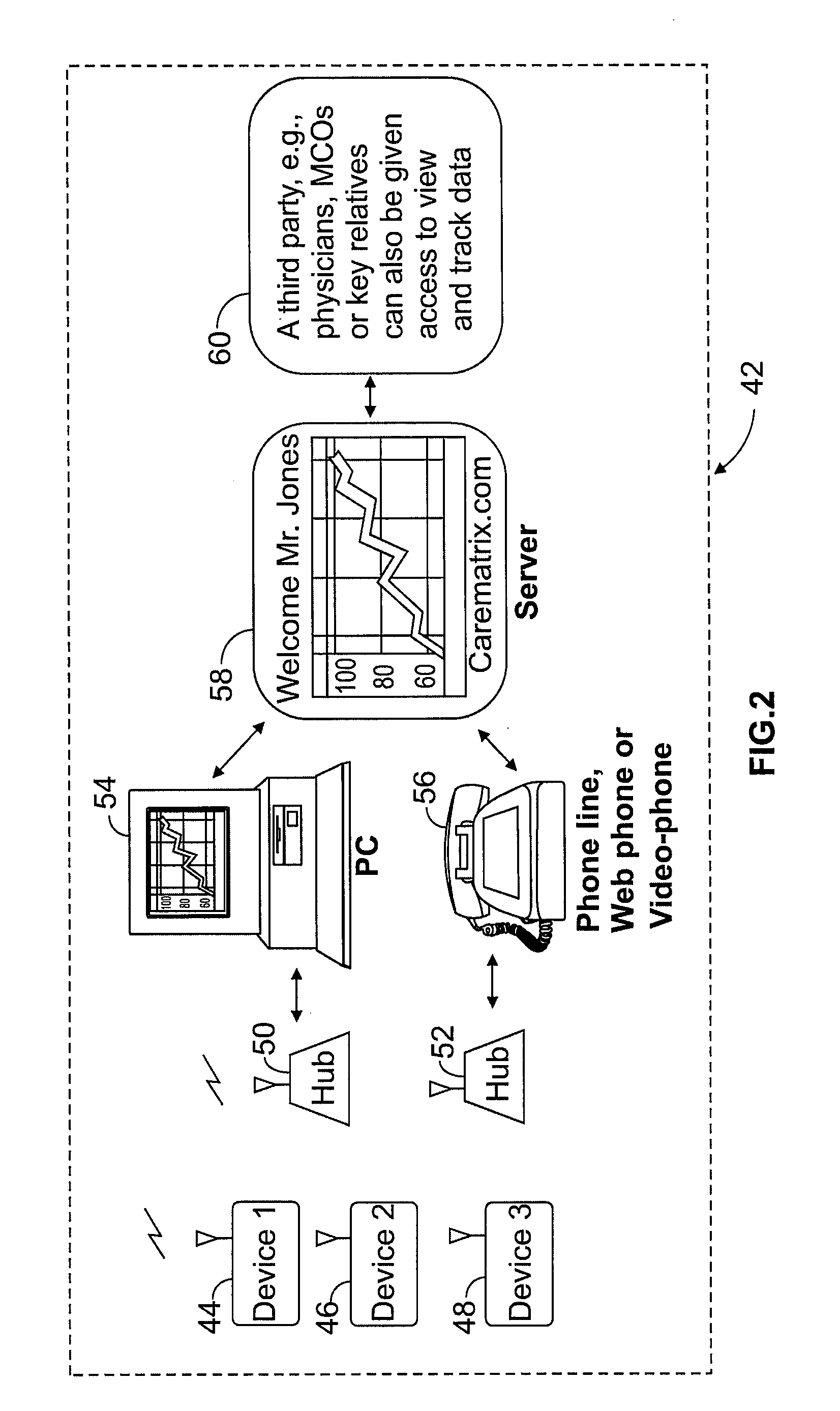
A patient monitoring system provides enhanced functional capability relative to known systems and provides a wireless communication link between a patient monitoring device, worn by a patient, and a local hub. The patient monitoring system is adapted to monitor various patient physiological characteristics, such as blood pressure, pulse rate, blood glucose, weight, pulse oximetry and others. The data from the patient monitoring device is wirelessly transmitted to a local hub, which, in turn, is configured to automatically transfer the data to a remote server, for example, over a public or private communications network. In one embodiment of the invention, the server is configured as a web portal to selectively allow access to such patient physiological data by designated third parties, such as physicians, clinicians, relatives and the patient themselves.
Owner:CAREMATIX
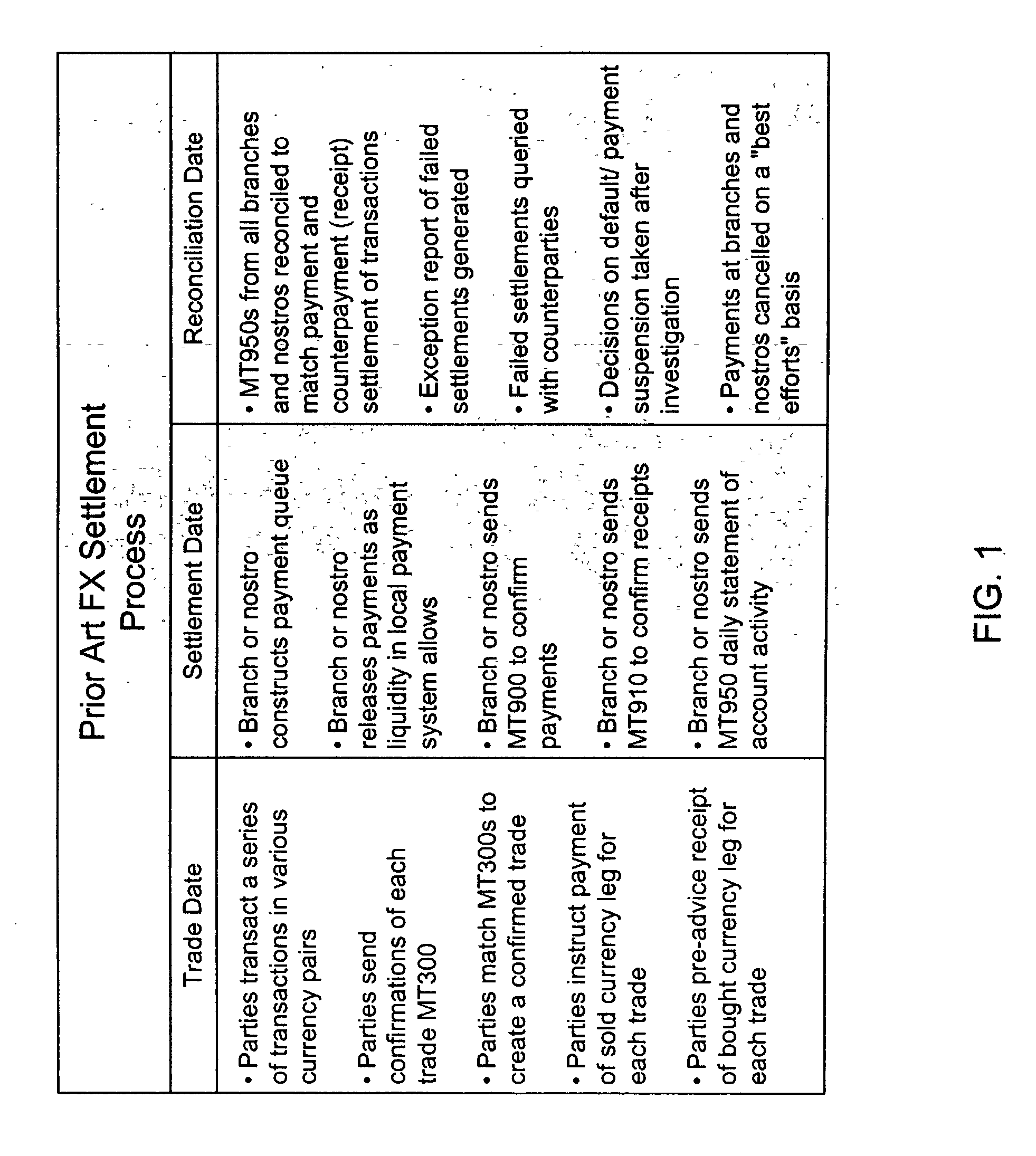
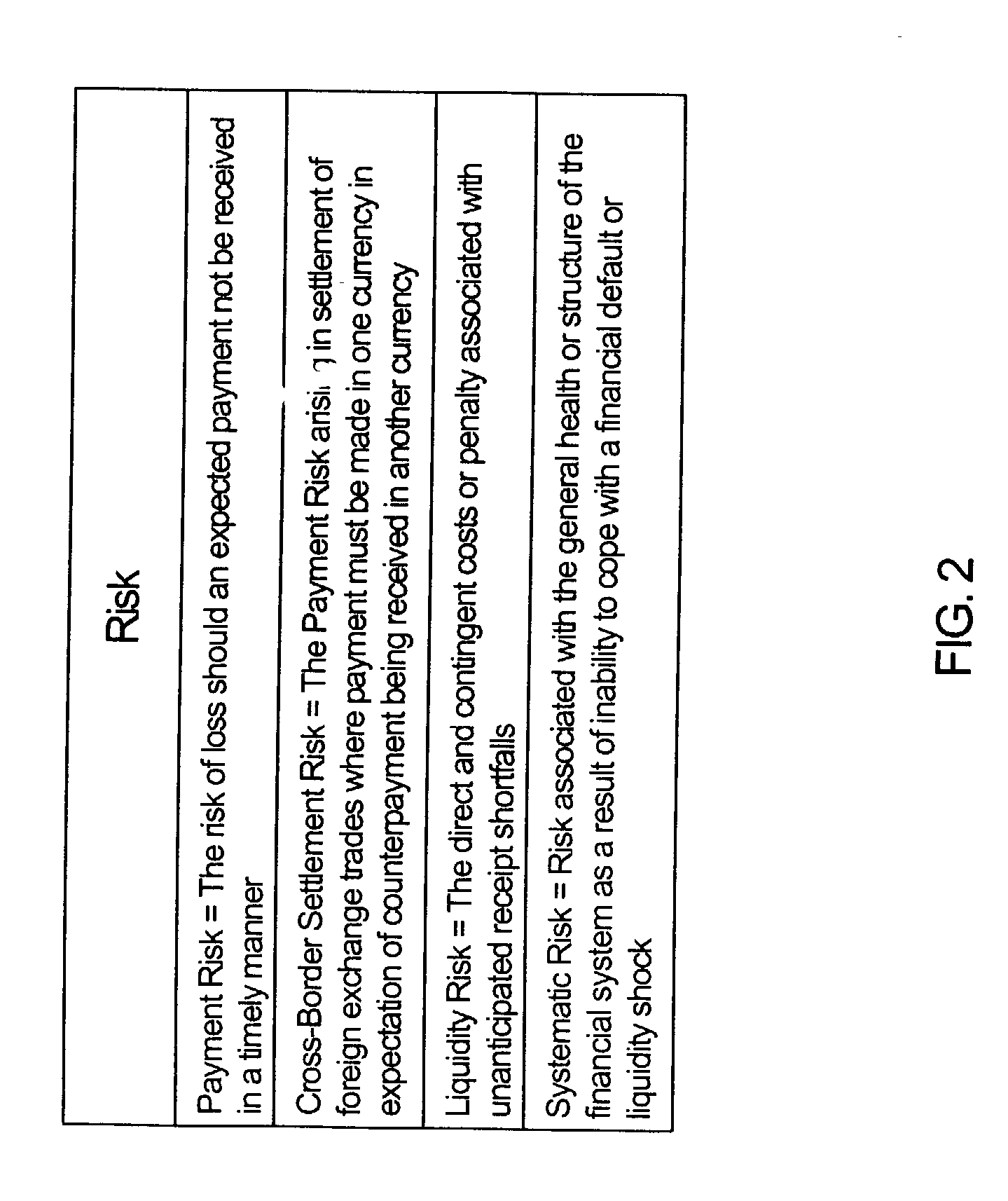
Method of and system for mitigating risk associated with settling of foreign exchange and other payments-based transactions
InactiveUS20020152156A1Improve liquidityFacilitates broad range of communicationFinanceBilling/invoicingPrivate communicationThird party
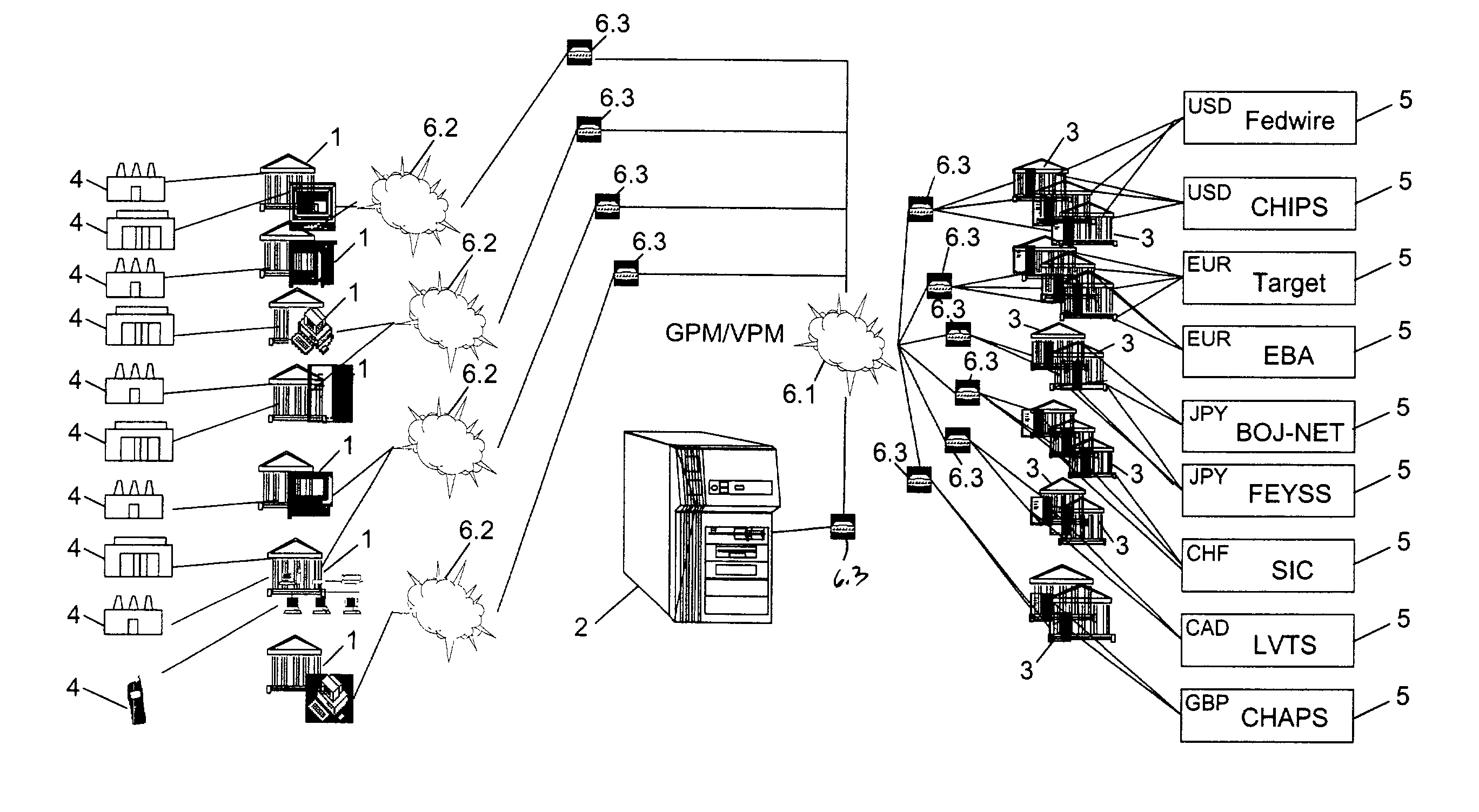
A real-time, global system and method for controlling payments risk, liquidity risk and systemic risk arising between financial counterparties active in payments-based transactions. The system comprises: a plurality of User Host Applications for use by plurality of Users; a plurality of Third Party Host Applications for use by plurality of Third Parties; and a plurality of Payment Bank Host Applications for use by a plurality of Payment Banks operating a plurality of domestic payment systems. All host applications communicate via cryptographically secure sessions via private communications networks and / or the Internet global computer network. User and Payment Bank access is secured by digital certification. Each Payment Bank Host Application has a mechanism for processing payment messages, including payments instructions to be carried out in its domestic payments system on behalf of a plurality of account holders (including bank correspondents). In addition, each Payment Bank Host Application includes a filter process module for processing payments instructions, prior to being carried out by the domestic payment system. In the event of a counterparty payment failure or insolvency, the Filter Process Module enables instantaneous, automated suspension of all further payments to the counterparty in a multiplicity of chosen currencies on instruction from a Third Party, User or Payment Bank. The filter process module can also be instructed to override risk control parameters to enable payments to proceed regardless for identified transactions, counterparties or intermediaries. All applications improve the availability and timeliness of payments information. The reduction in payments risk and liquidity risk to predetermined tolerances reduces the likelihood of contingent defaults in the event of payment failure due to bank insolvency or other unforeseen event, and thereby reduces systemic risk to the global financial system.
Owner:MIND FUSION LLC
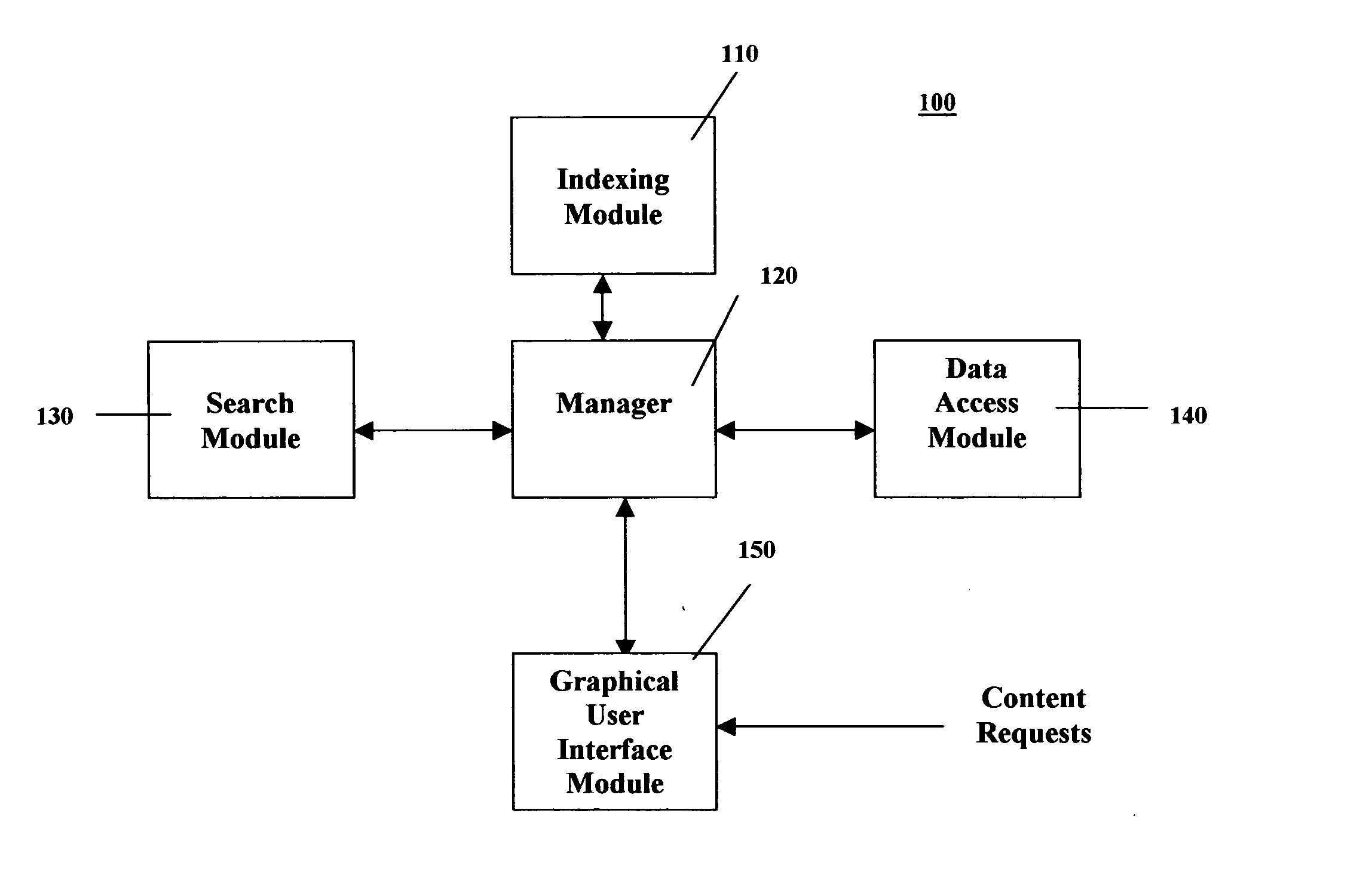
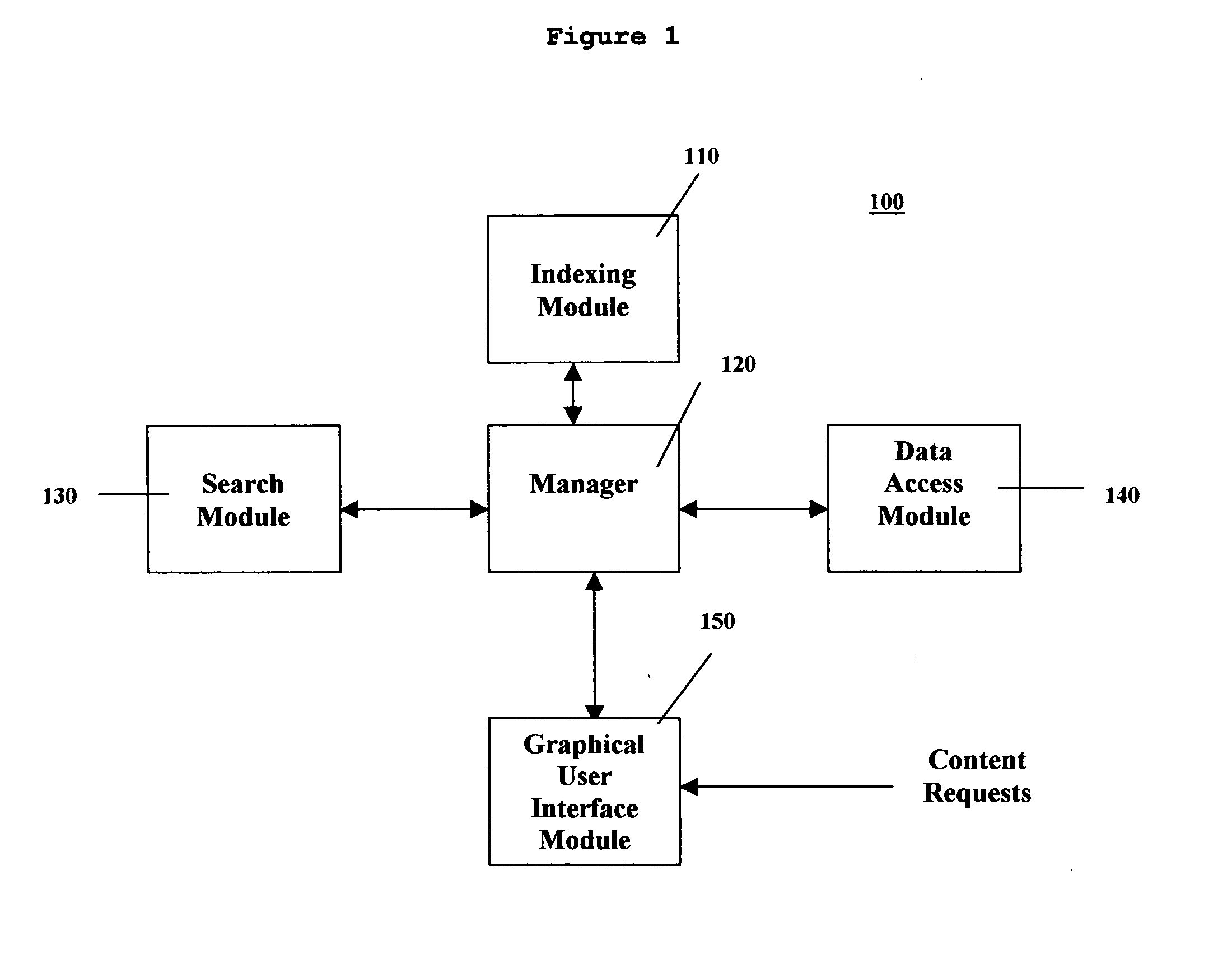
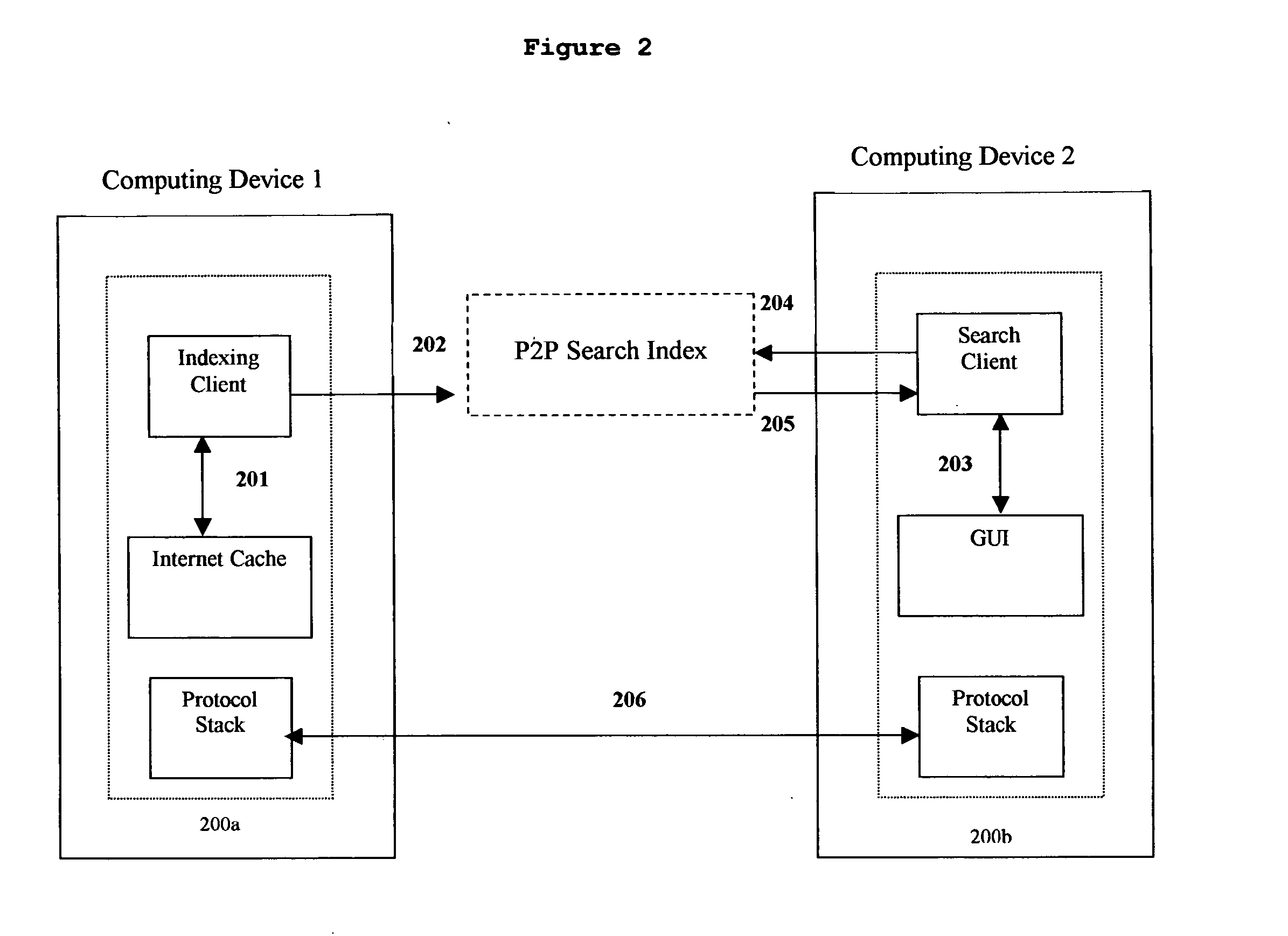
Methods and systems for searching content in distributed computing networks
ActiveUS20050050028A1Efficient access to dataEfficient accessWeb data indexingDigital data processing detailsPrivate communicationImproved method
The present invention discloses an improved method and system for indexing and searching content in a distributed computing network. The present invention also enables users to search for content on a distributed computing network, as well as on the web, via a unified interface. In one embodiment, the present invention is directed toward a method for searching content on a distributed computing network having an index of available data. The method comprises scanning cached network files in a computer that is in data communication with a network wherein said network files are generated in the course of a user's access of public or private communication networks, indexing the cached network files to generate index data, and supplying index data to the index of available data on the distributed computing network.
Owner:BRILLIANT DIGITAL ENTERTAINMENT
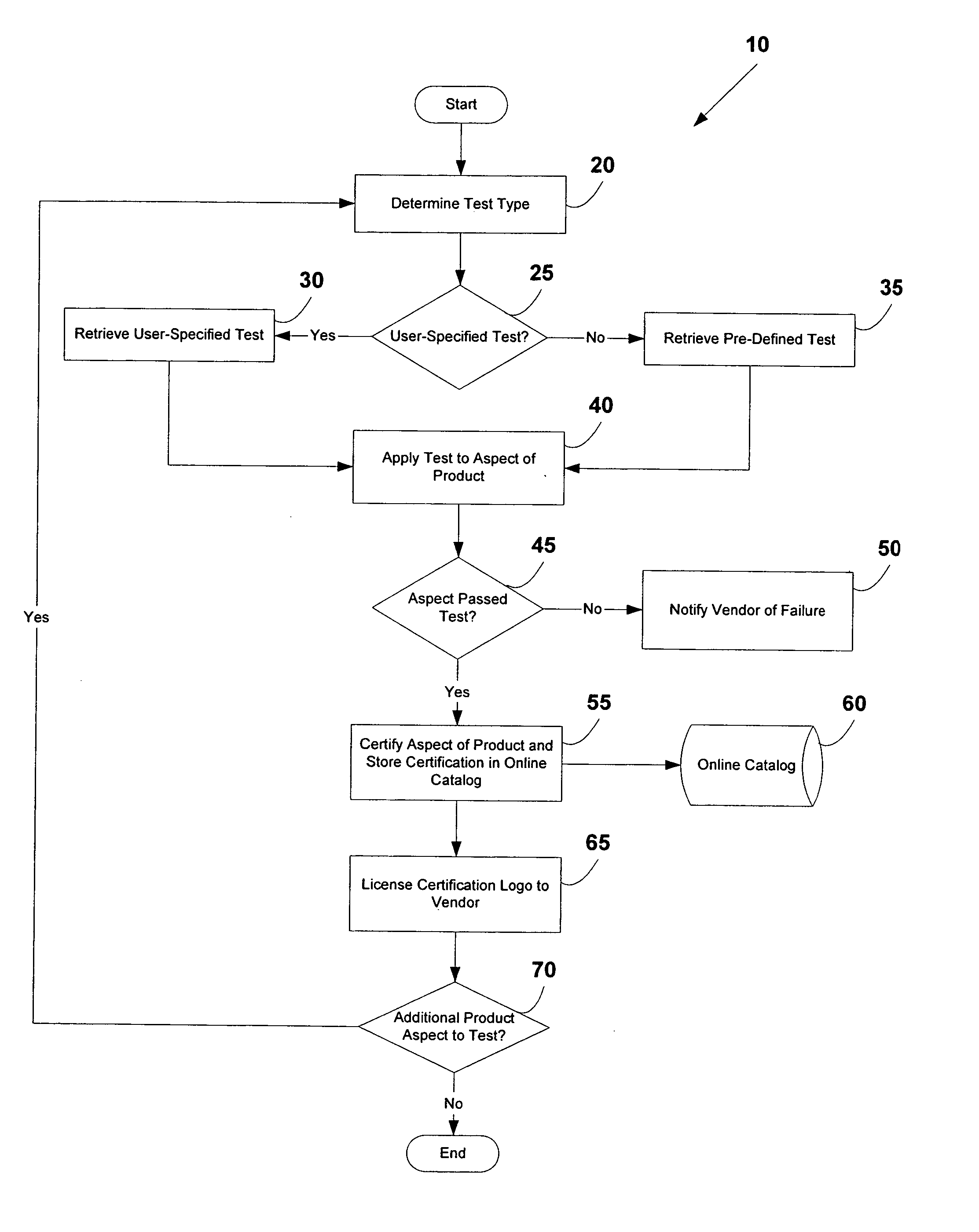
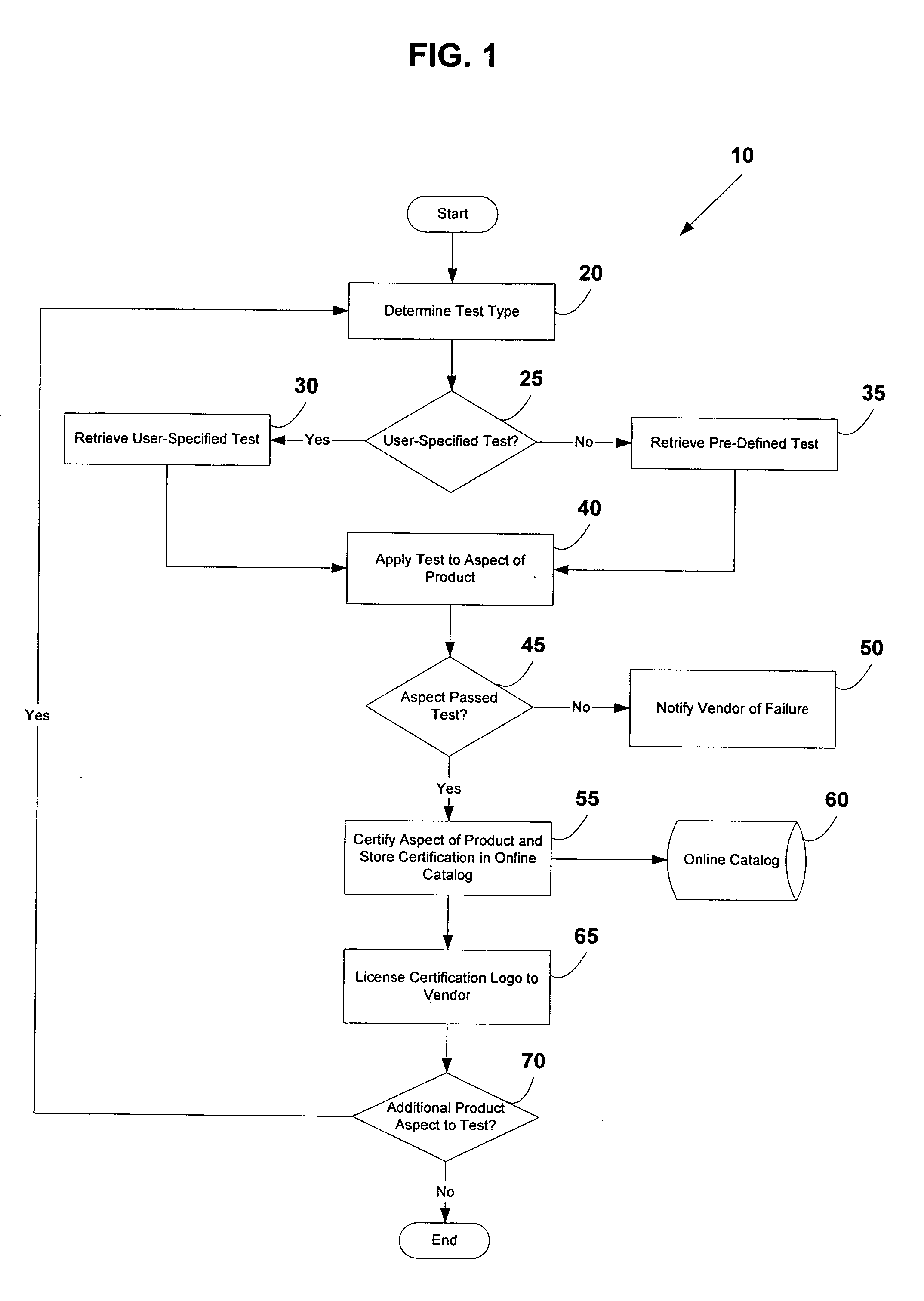
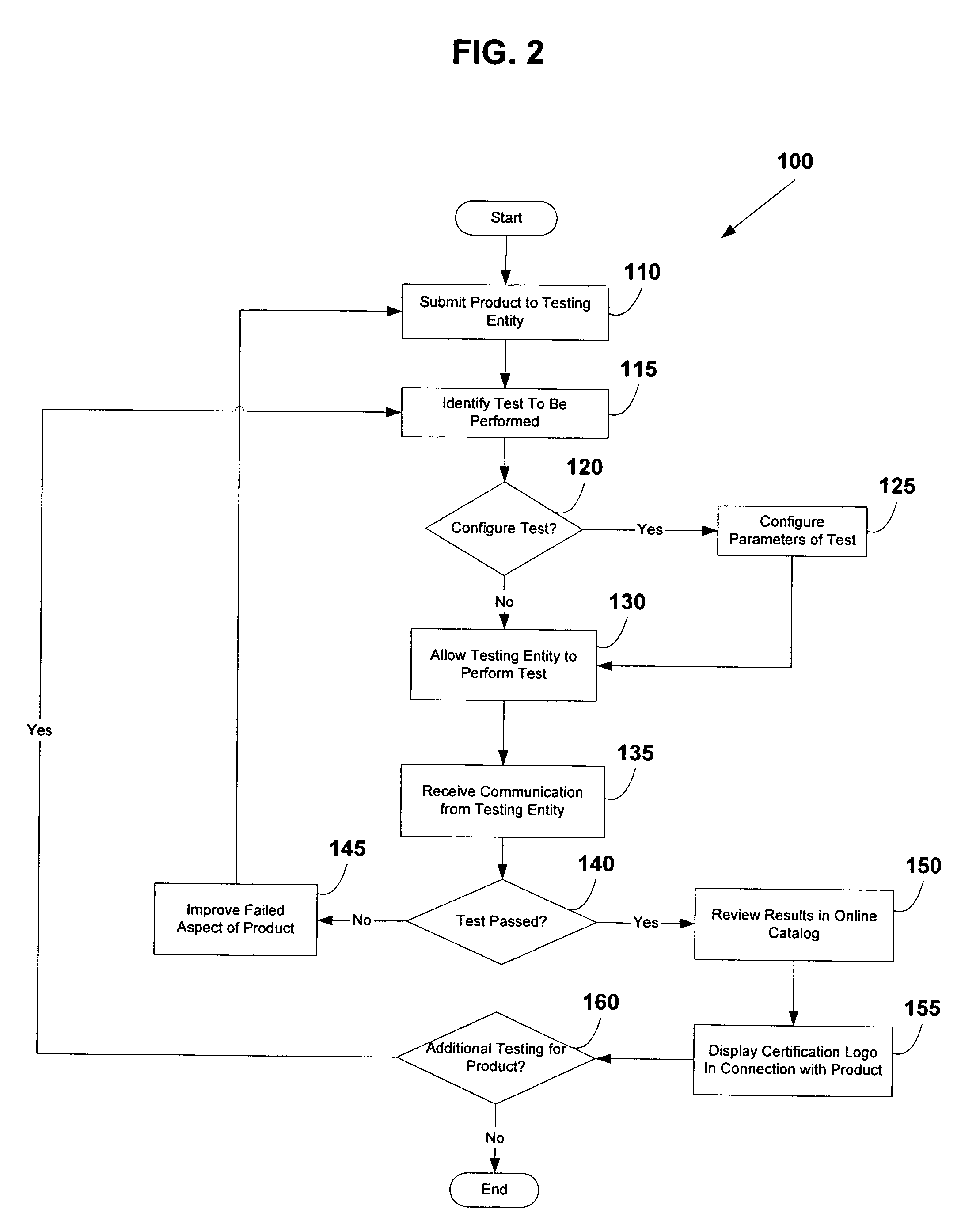
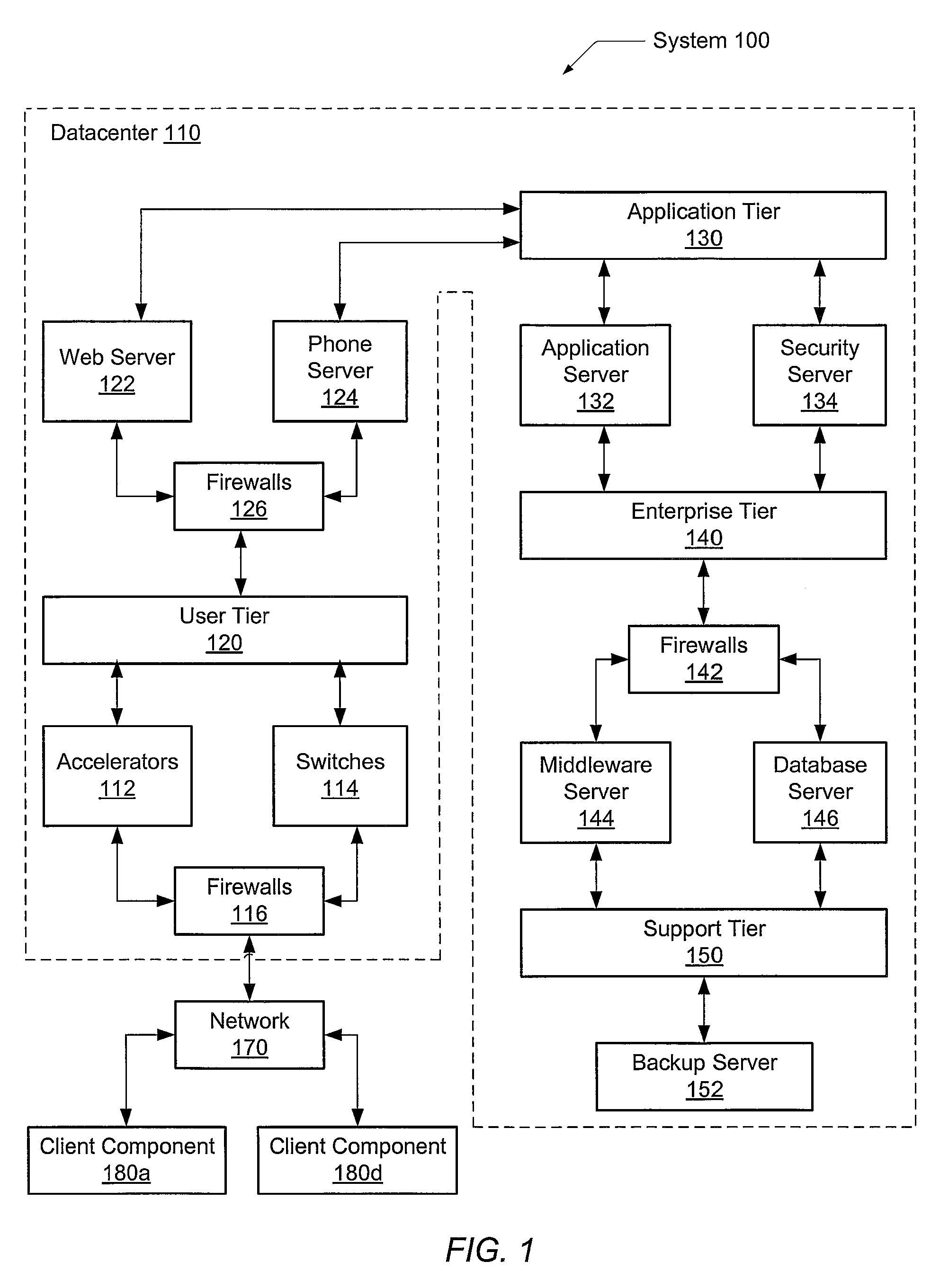
System and method for testing and certifying products
The present invention provides a system and method for testing and certifying one or more aspects of a device, such as a network, telecommunications, or computing device. One or more pre-defined or user-specified tests are identified by a user and applied by a testing entity to an aspect of the device. The results of the test are gathered and compared to one or more pre-determined standards. If the product passes the test, the device is certified by the testing entity and the results are published in an online catalog accessible via the Internet. Additionally, the product vendor is granted a license to use a certification logo in connection with the product. If the product fails the test, a private communication is sent from the testing entity to the product vendor indicating the failure. Any desired test can be applied to one or more aspects of a product, such as Voice-over-IP (VoIP) capabilities and other desired features of the product.
Owner:TOLLY KEVIN
Multi-protocol label switching virtual private networks
InactiveUS7039687B1Digital computer detailsData switching by path configurationPrivate communicationPrivate network
A virtual private network enables private communications over a shared MPLS network between two or more private networks. The virtual private networks include a first router connected to the shared MPLS network and configured to dynamically distribute first router VPN information across the shared MPLS network. The first router VPN information includes a VPN identifier which is assigned to the first router. The VPN also includes a second router connected to the shared MPLS network and and configured to dynamically distribute second router VPN information across the shared MPLS network. The second router VPN information includes a VPN identifier which is assigned to the second router and which is identical to the VPN identifier assigned to the first router. The first and second routers are also configured to establish label switched paths therebetween. A method of automatically configuring virtual private networks over a shared MPLS network includes creating a link between a private network router and a shared network router. It also includes assigning a VPN identifier to the shared network router, assigning the same VPN identifier to at least one other shared network router, determining all shared network routers which are assigned the same VPN identifier, and creating at least two label switched paths between the shared network router and the other shared network routers.
Owner:RPX CLEARINGHOUSE
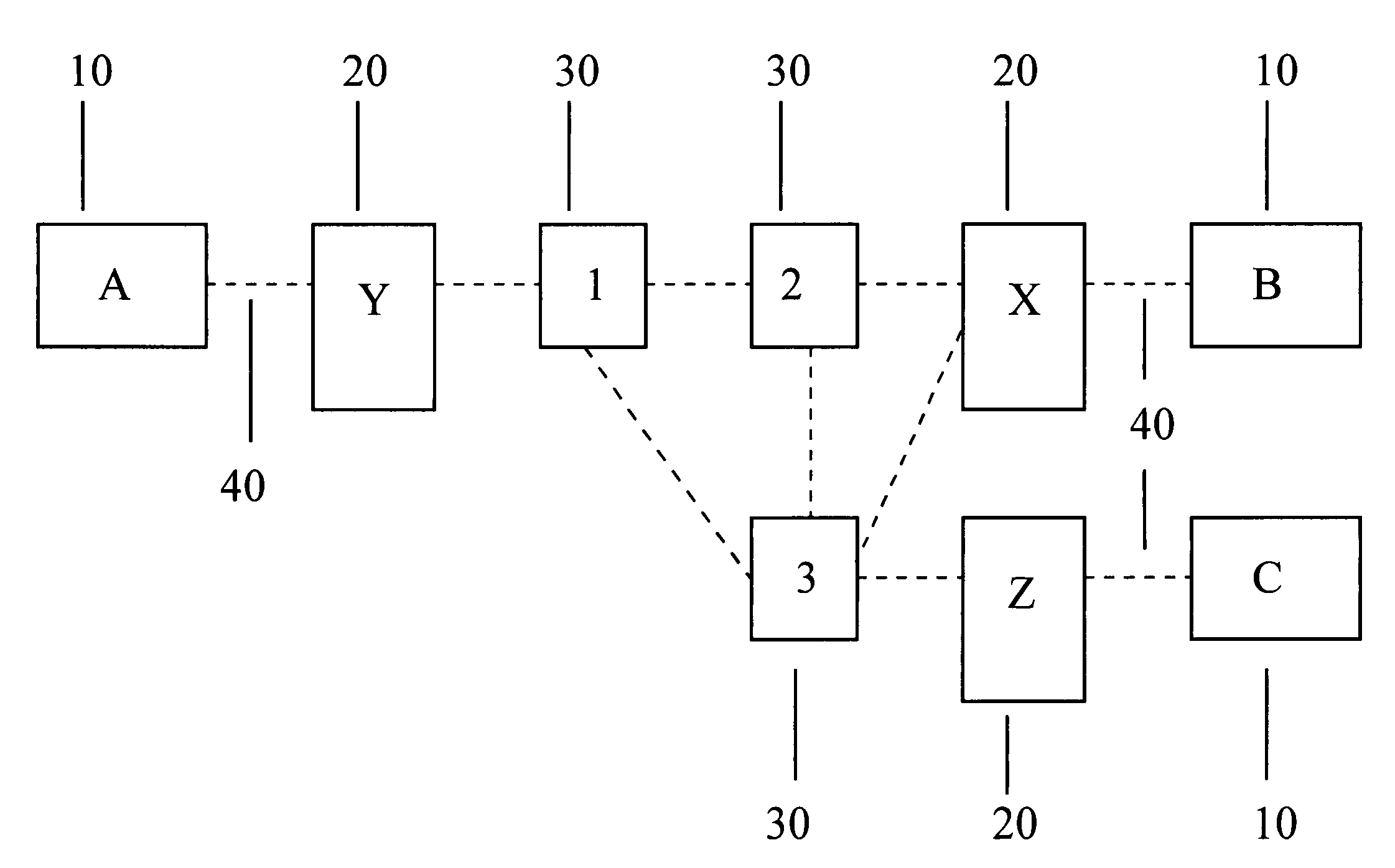
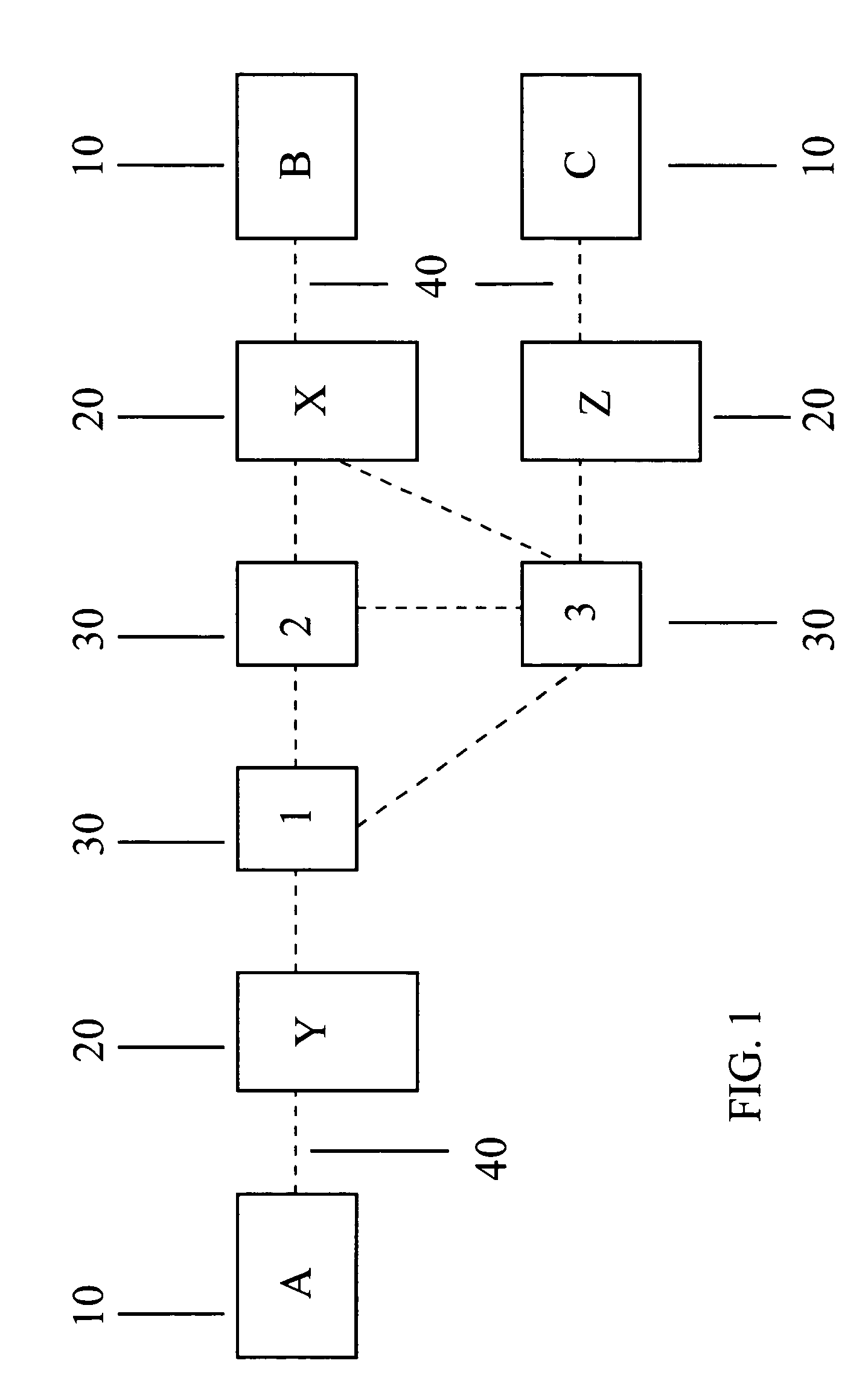
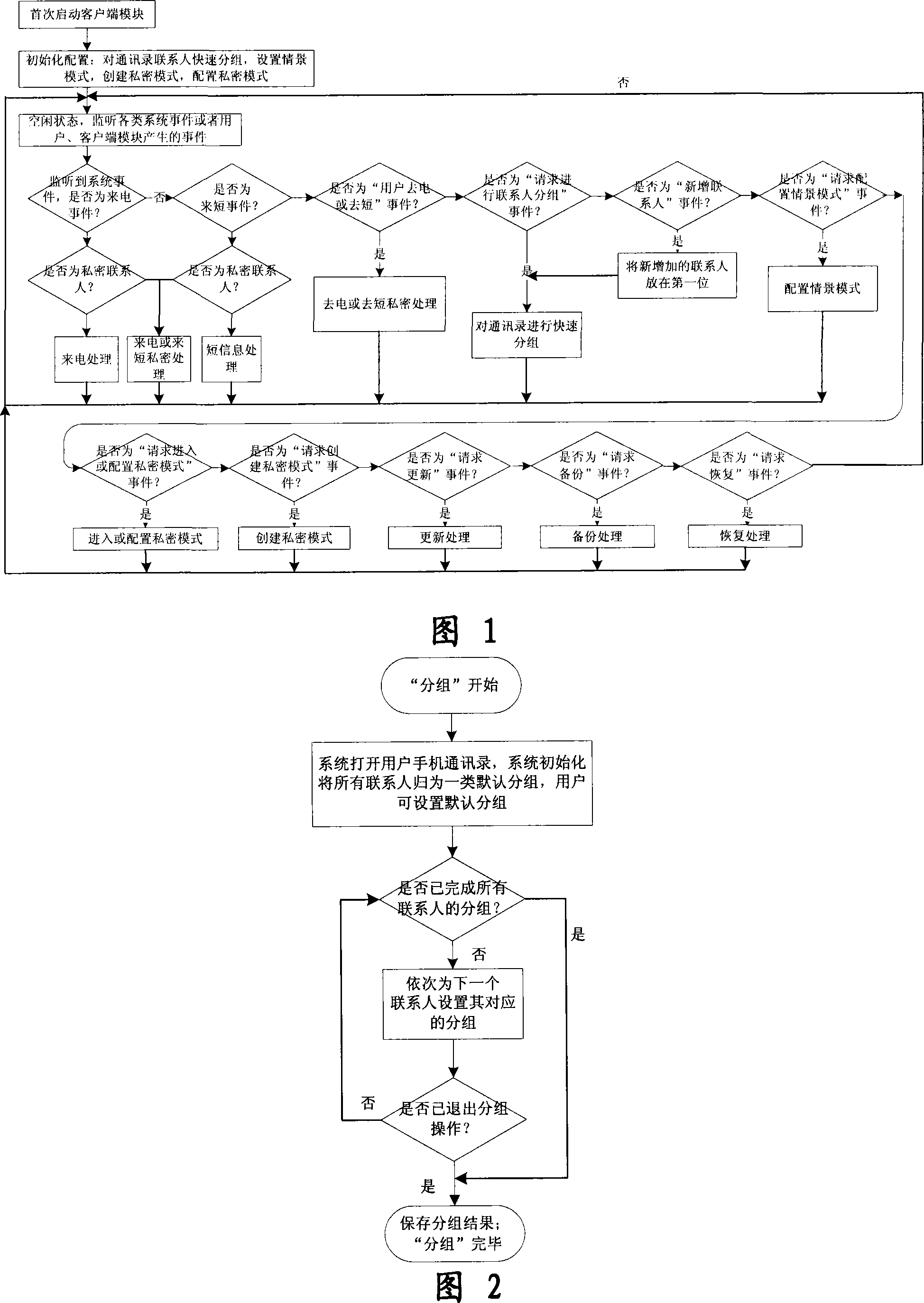
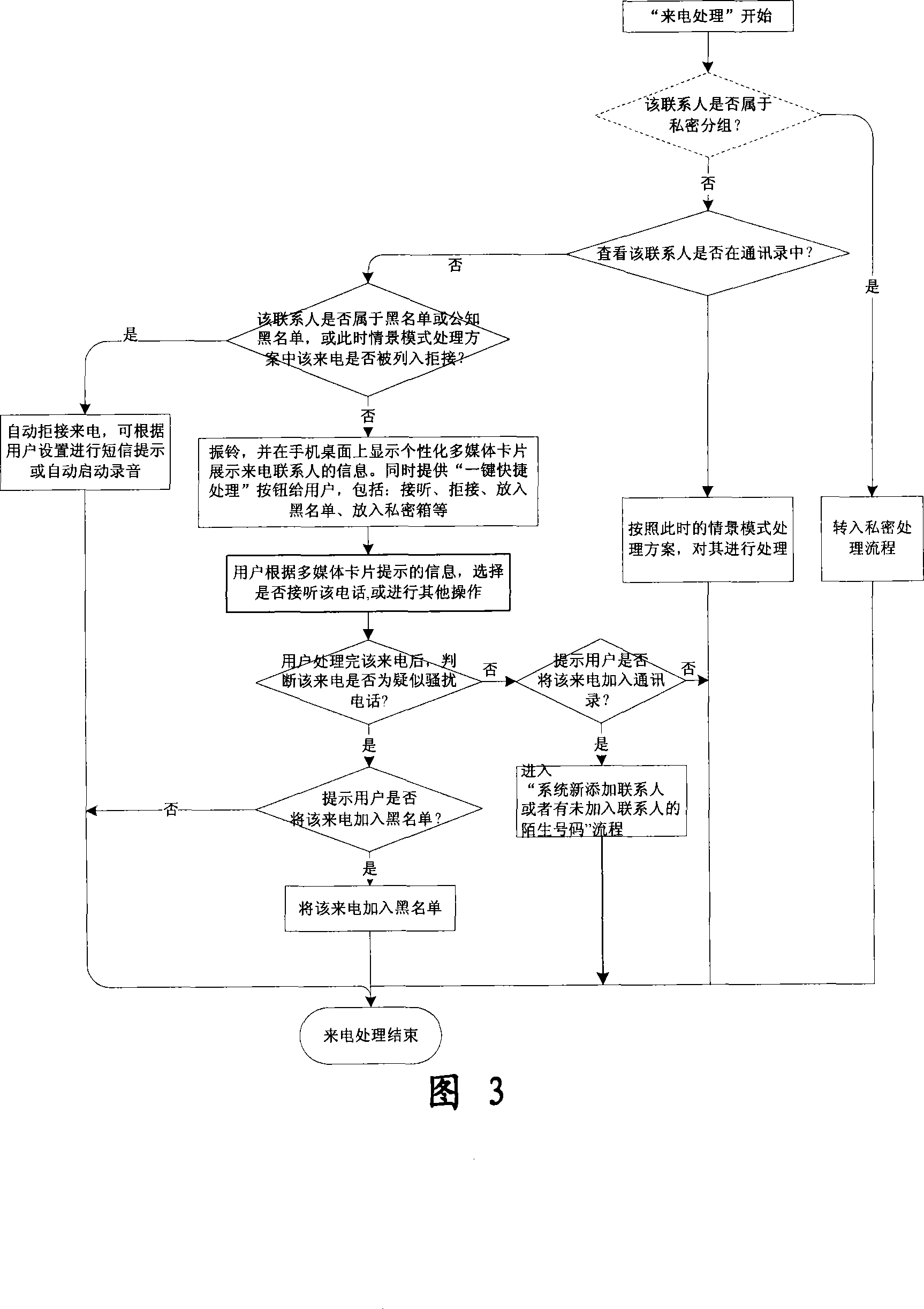
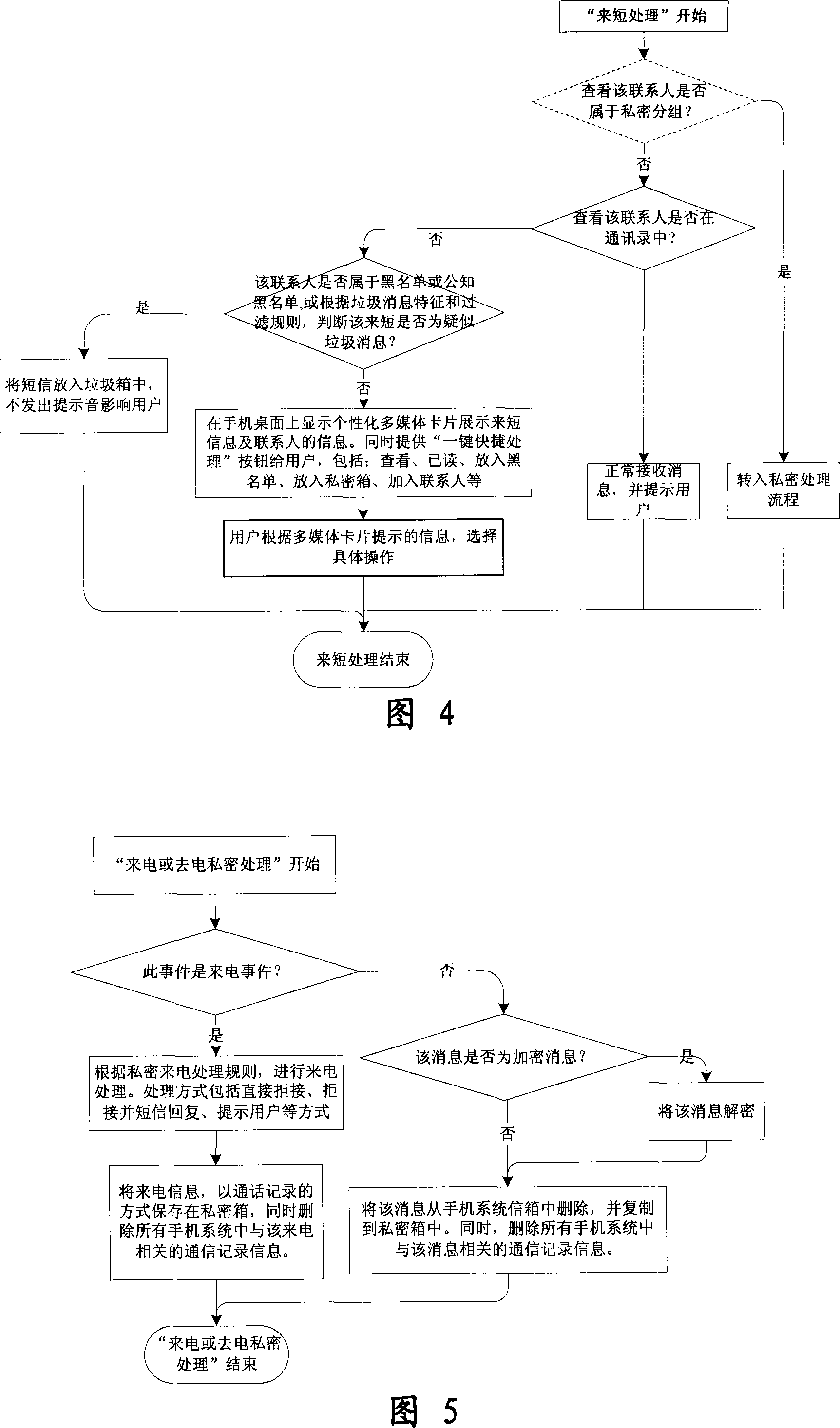
Mobile phone telephone and message anti-disturbance and private communication method and system
InactiveCN101184264AImprove filtering effectOptimize the effect of anti-harassmentRadio/inductive link selection arrangementsSubstation equipmentPrivate communicationSocial statistics
The invention relates to a processing method and the system of anti-harassment of mobile phone calls and messages and private communication, which is as follow: when grouping the contacts in the mobile phone address list according to different classes, a private group of private communicating contacts is added, and different scene modes of the user are set; when receiving a mobile phone call or a message (text message, multimedia message), depending on the grouping sort of the contact of the incoming call or the message or the multimedia message, and the current scene of the user, together with the behavior characteristics of the harassing call and the spam message with the database information of the public harassing message issued by the authoritative institution or obtained from social statistics, the corresponding process to the call, the message and the multimedia message of the mobile phone is executed to reduce harassment; meanwhile the communication records of incoming, dialed calls and message, multimedia message with the contacts in the private grouping are encrypted and preserved to protect the personal privacy of the user. The invention has the advantages of adopting the operating steps of uniform process, and resolving synthetically the harassment of calls, messages and multimedia messages for the mobile phone and the private protection.
Owner:BEIJING NETQIN TECH
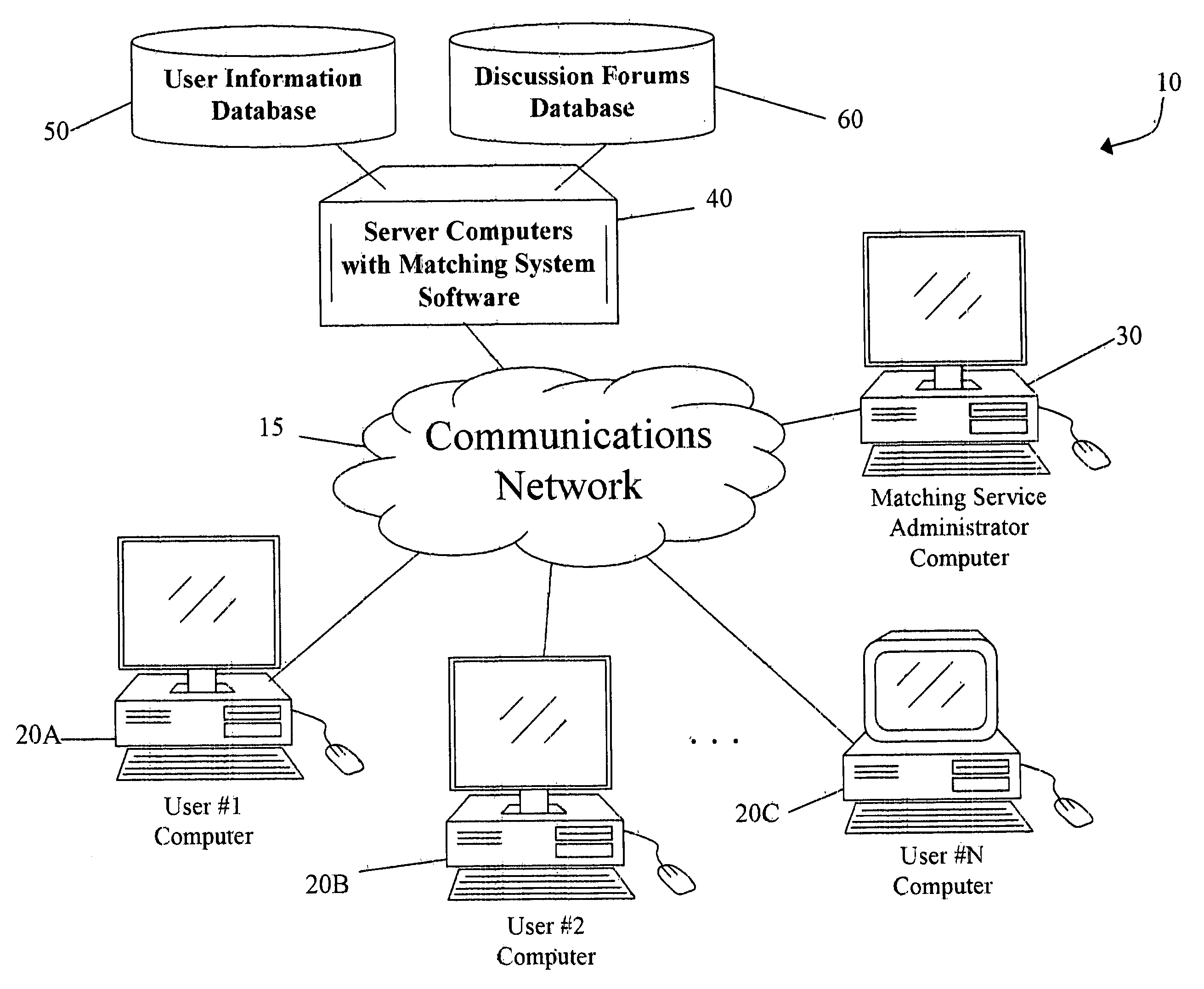
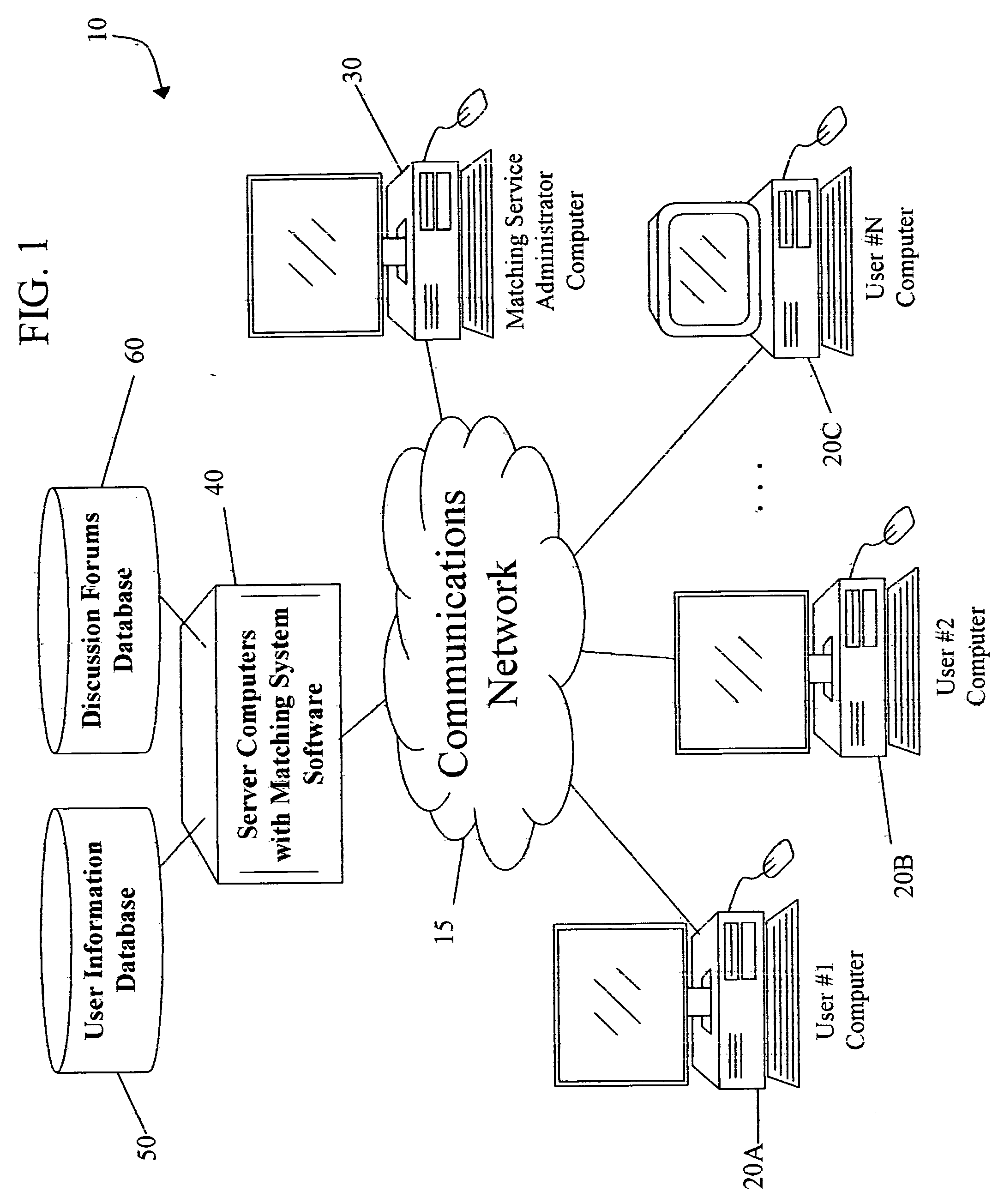
Method and system for matching users for relationships using a discussion based approach
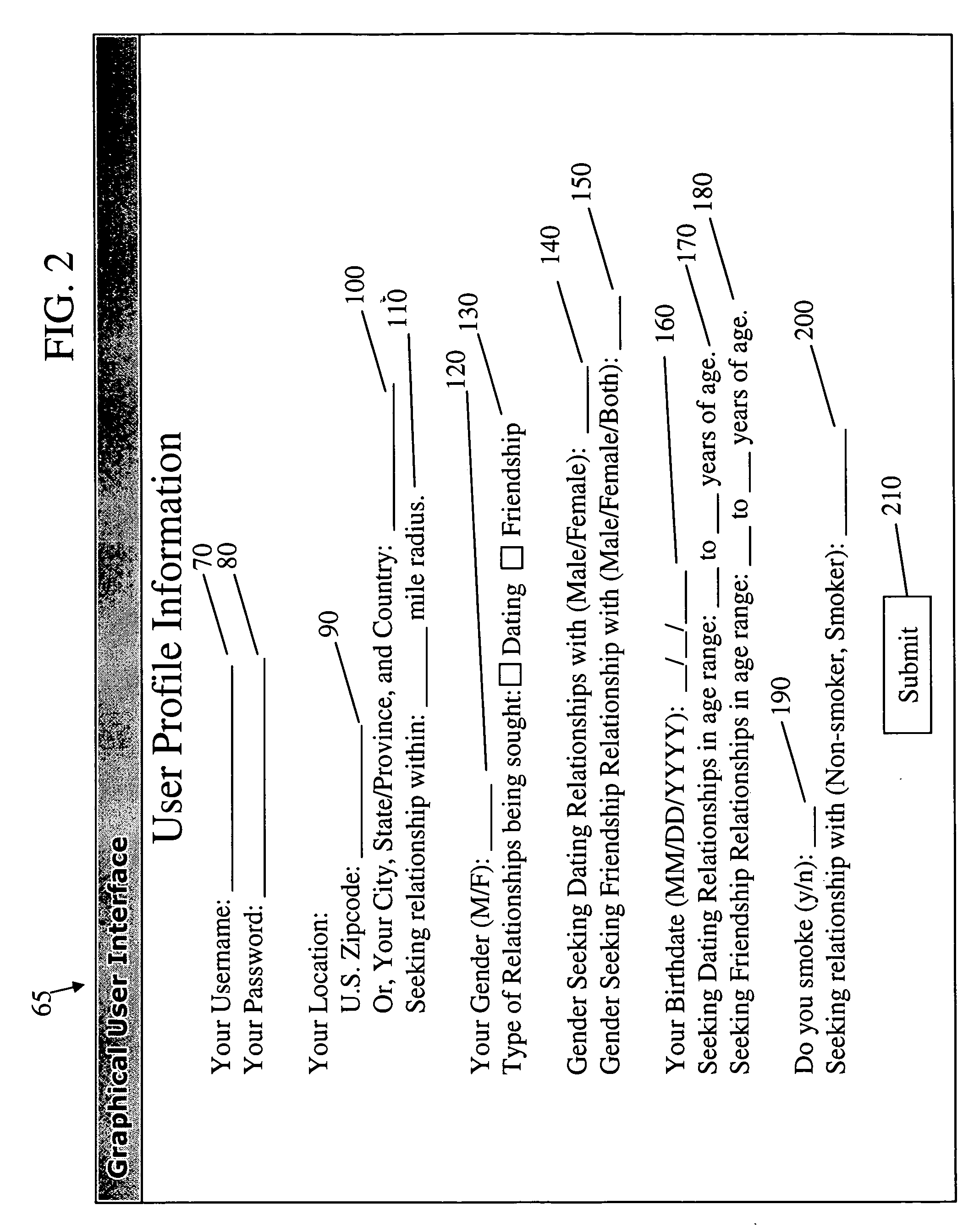
InactiveUS20060282426A1Data processing applicationsDigital data information retrievalPrivate communicationPersonal details
A system of matching users for relationships based upon both user provided profile information, and preferences they develop as they participate in discussion forums. User profile information can be used to determine the universe of users who have mutually compatible relationship criteria, but not necessarily the actual pairs of users who have the best chance of a successful relationship. The invention introduces the concept of discussion-based matching, wherein users interact in online forums to discuss topics of interest to them. The system informs users about which other users in the discussion are potential matches. As they interact, they begin to narrow down the universe of compatible matches to a smaller set of users who they have observed or interacted with in the discussion forum. This eases the transition to private communication, which is necessary for a personal relationship to begin, and results in more successful relationships. The system also regulates abusive or rude users in the online forums by allowing other users to report such behavior. The system records these reports and can automatically take punitive action against offending users, such as displaying a list of offending users, displaying special icons next to those user's usernames, and ultimately blocking a user from accessing the system.
Owner:SPEARS MINE
Secure key distribution for private communication in an unsecured communication channel
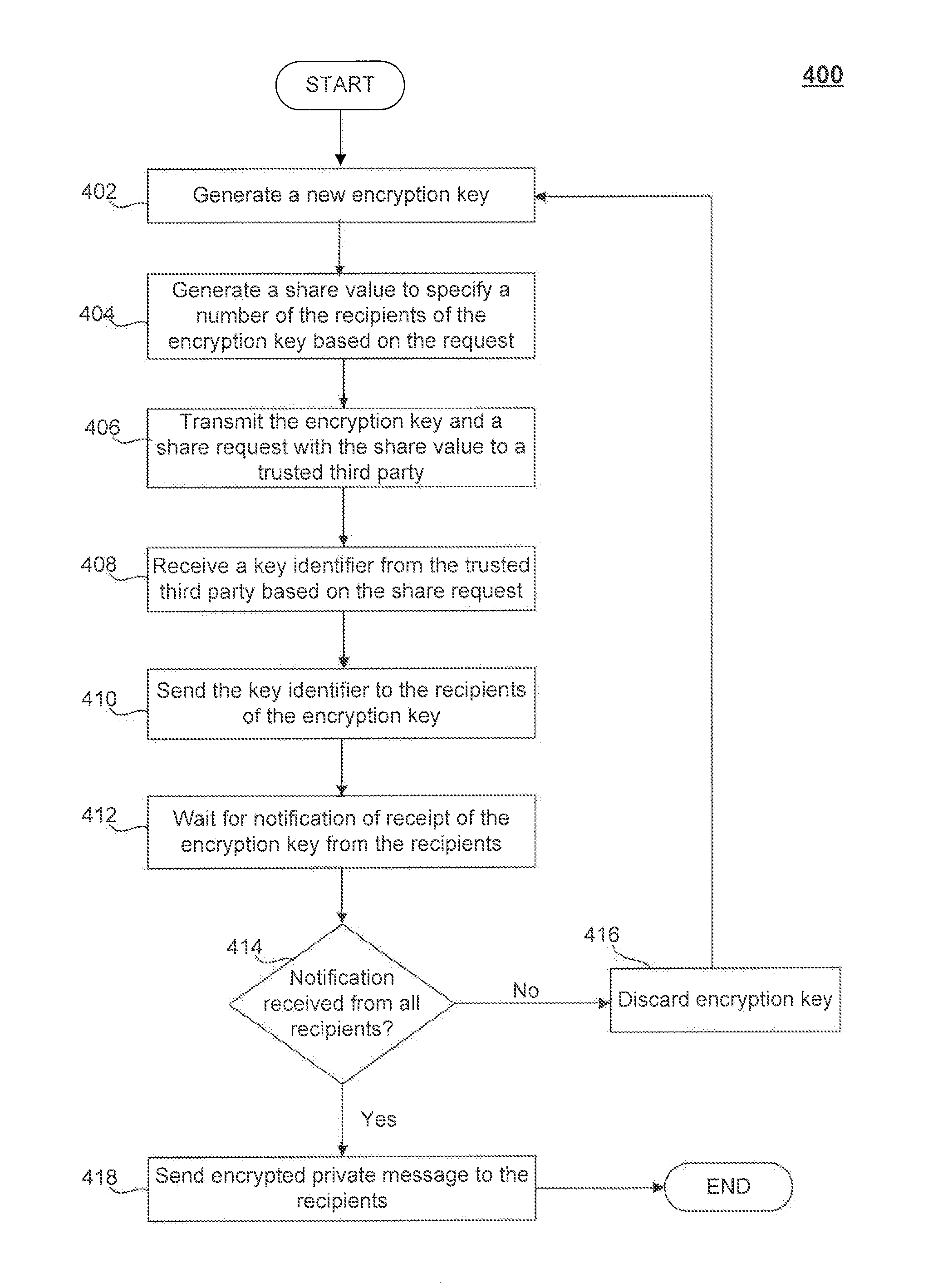
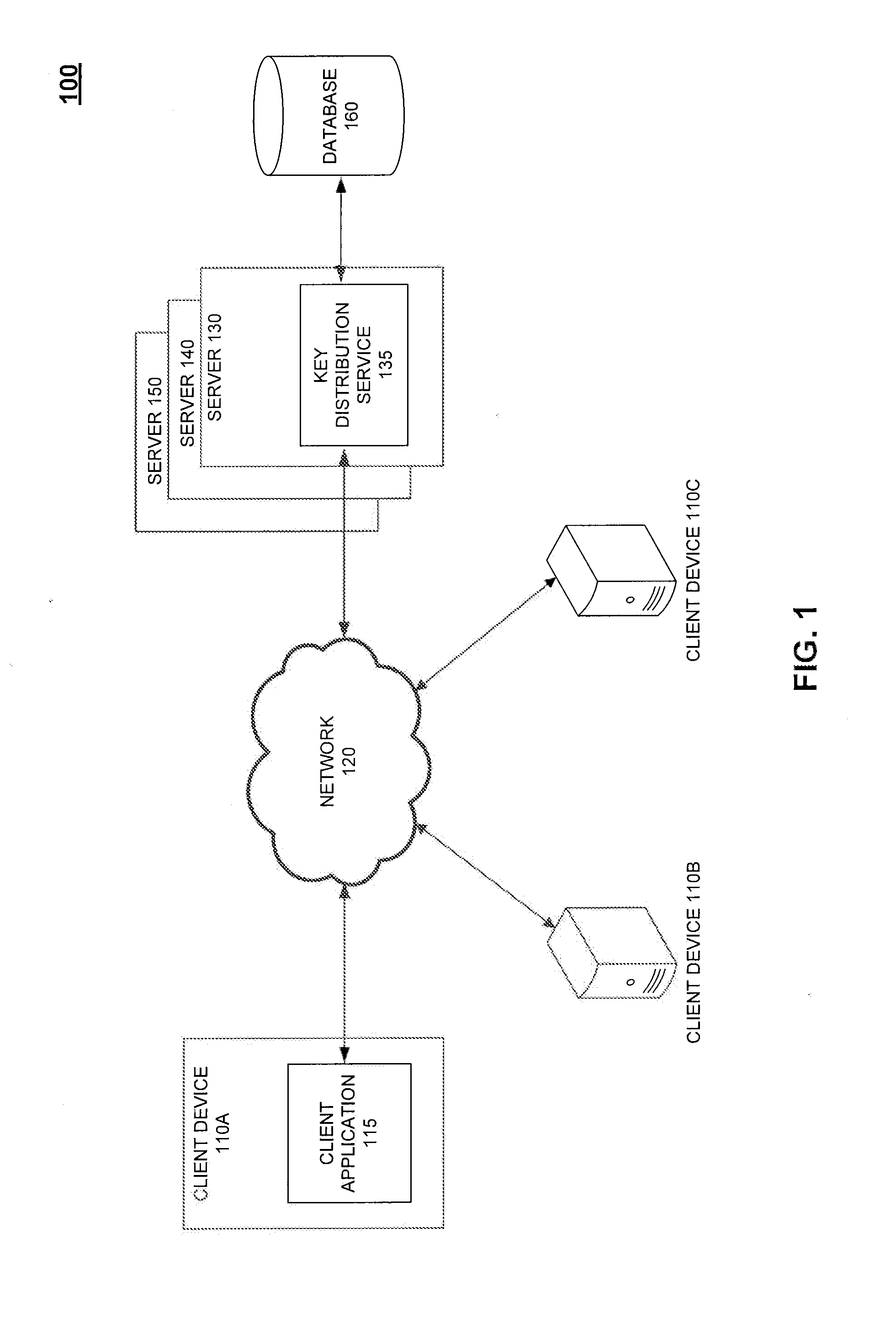
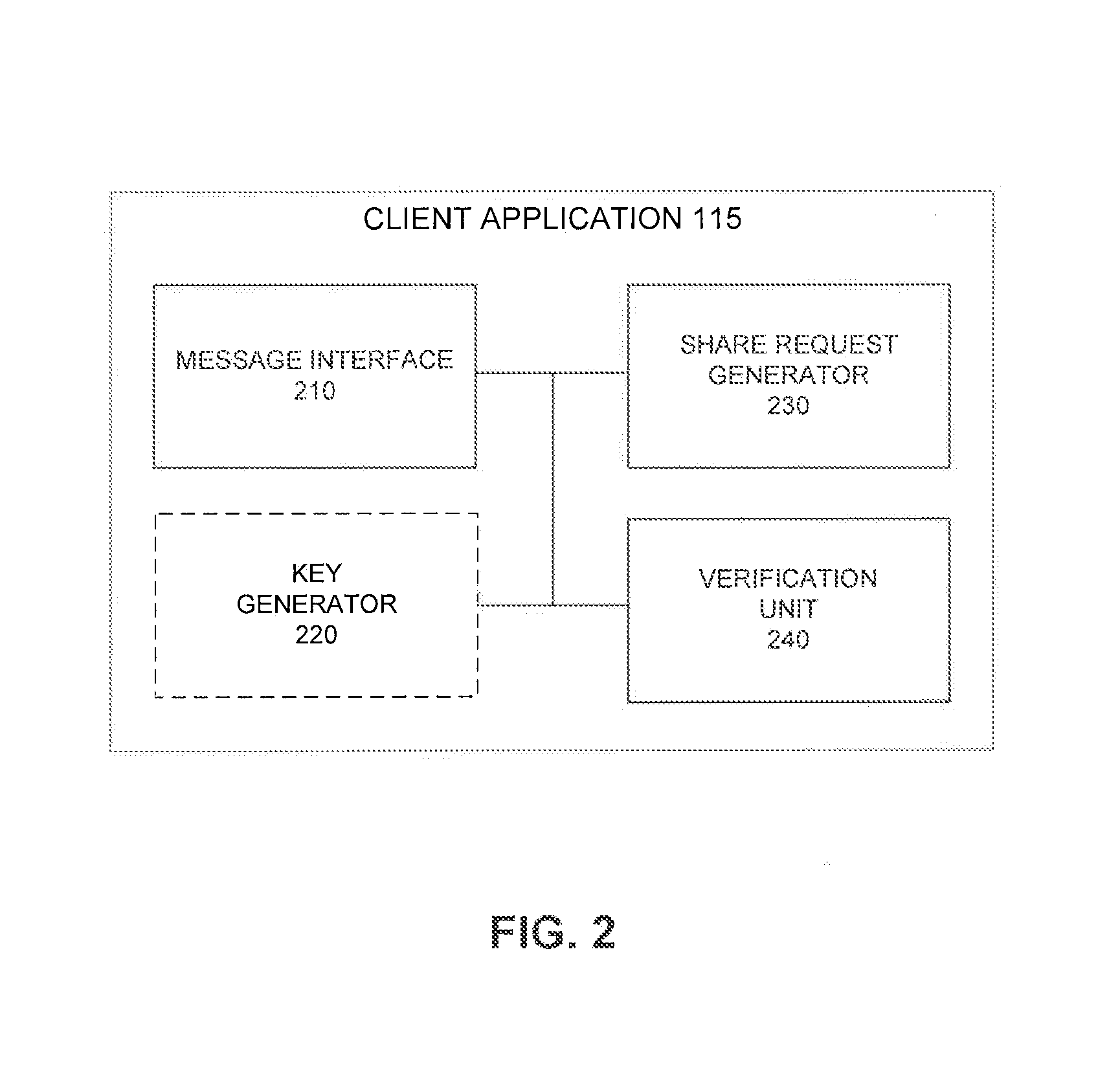
ActiveUS8379857B1Secure distributionMitigate or preclude any loss of confidential information during communicationKey distribution for secure communicationSecret communicationSecure communicationPrivate communication
A method to enable the secure distribution of encryption keys so as to facilitate private communication between users in an unsecured communication network is provided. Such a method may also provide a way to detect an unauthorized access of an encryption key so as to mitigate or prevent any loss of confidential information during communication.
Owner:GOOGLE LLC
System and method for operating a private wireless communications system
InactiveUS20070010245A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsPrivate communicationCommunications system
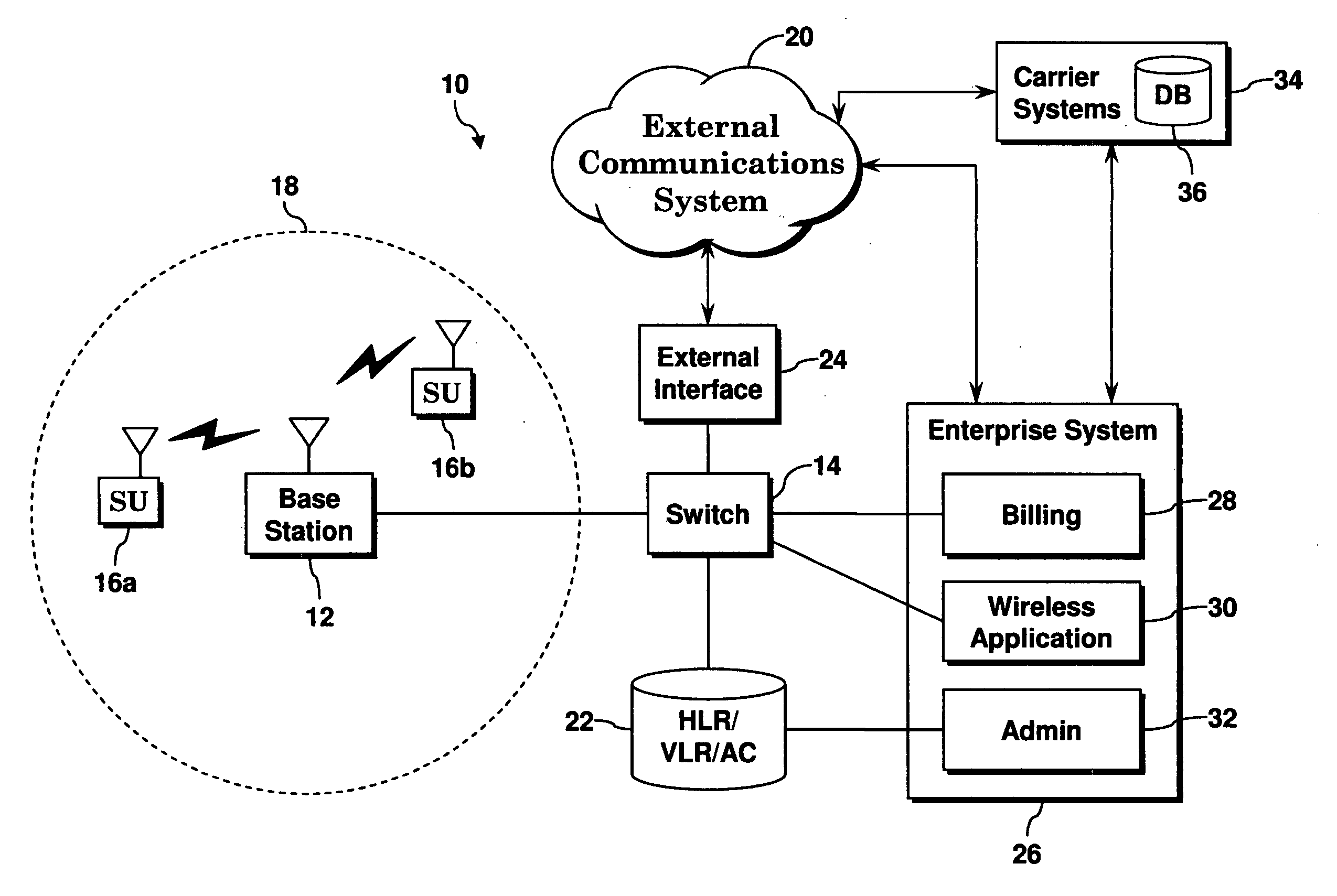
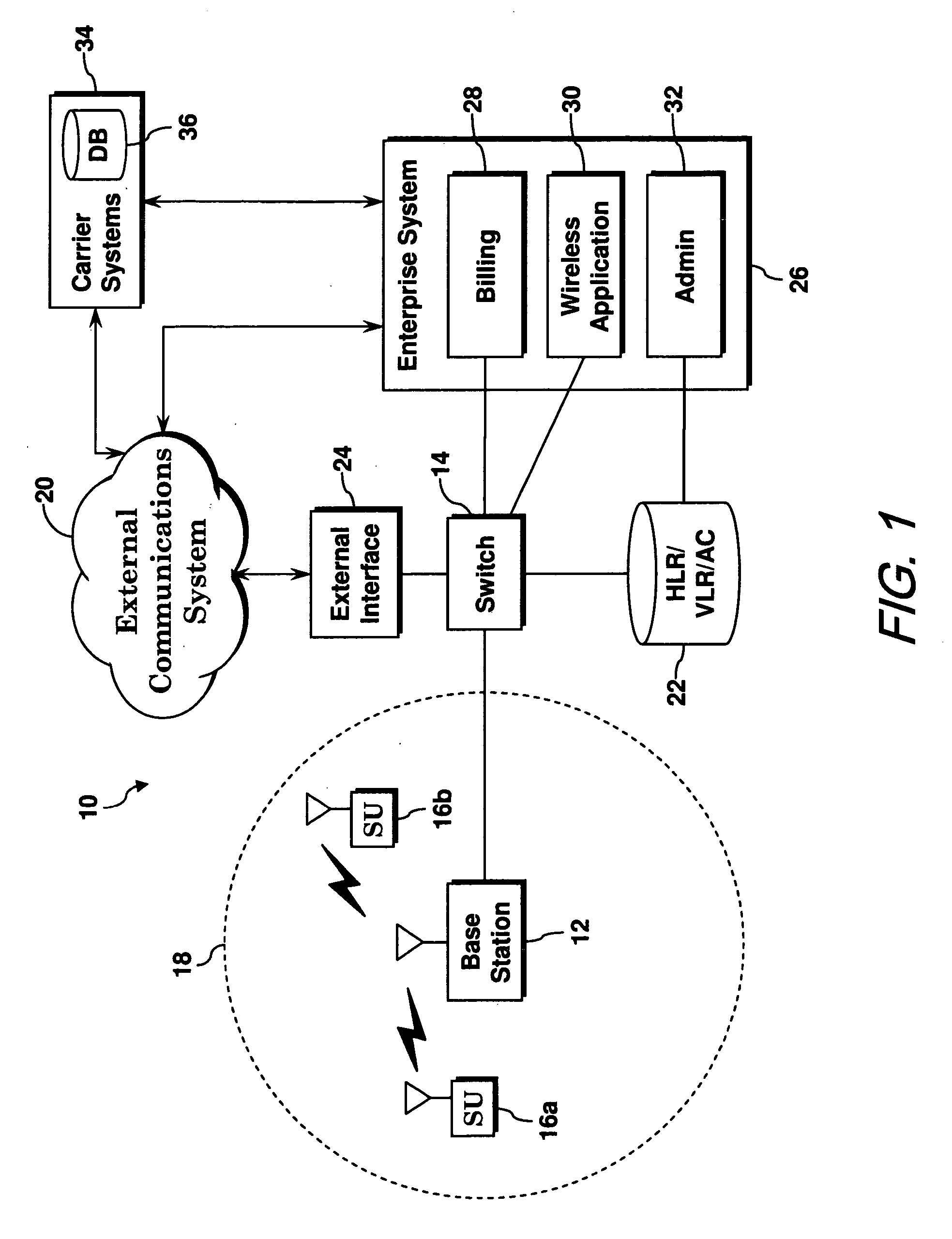
A private communications system includes a base station, a switch and an interface to an external network. The base station provides a radio link between the private communications system and a subscriber unit. The subscriber unit has an associated mini-subscription providing the subscriber unit with temporary access to the private communications system. The switch is connected to the base station and provides the subscriber unit with access to the private communications system when the mini-subscription is active. The interface is connected to the switch. In operation, the mini-subscription information is automatically transmitted to the external wireless network, via the interface, when the mini-subscription is terminated.
Owner:NEXTEL COMMUNICATIONS
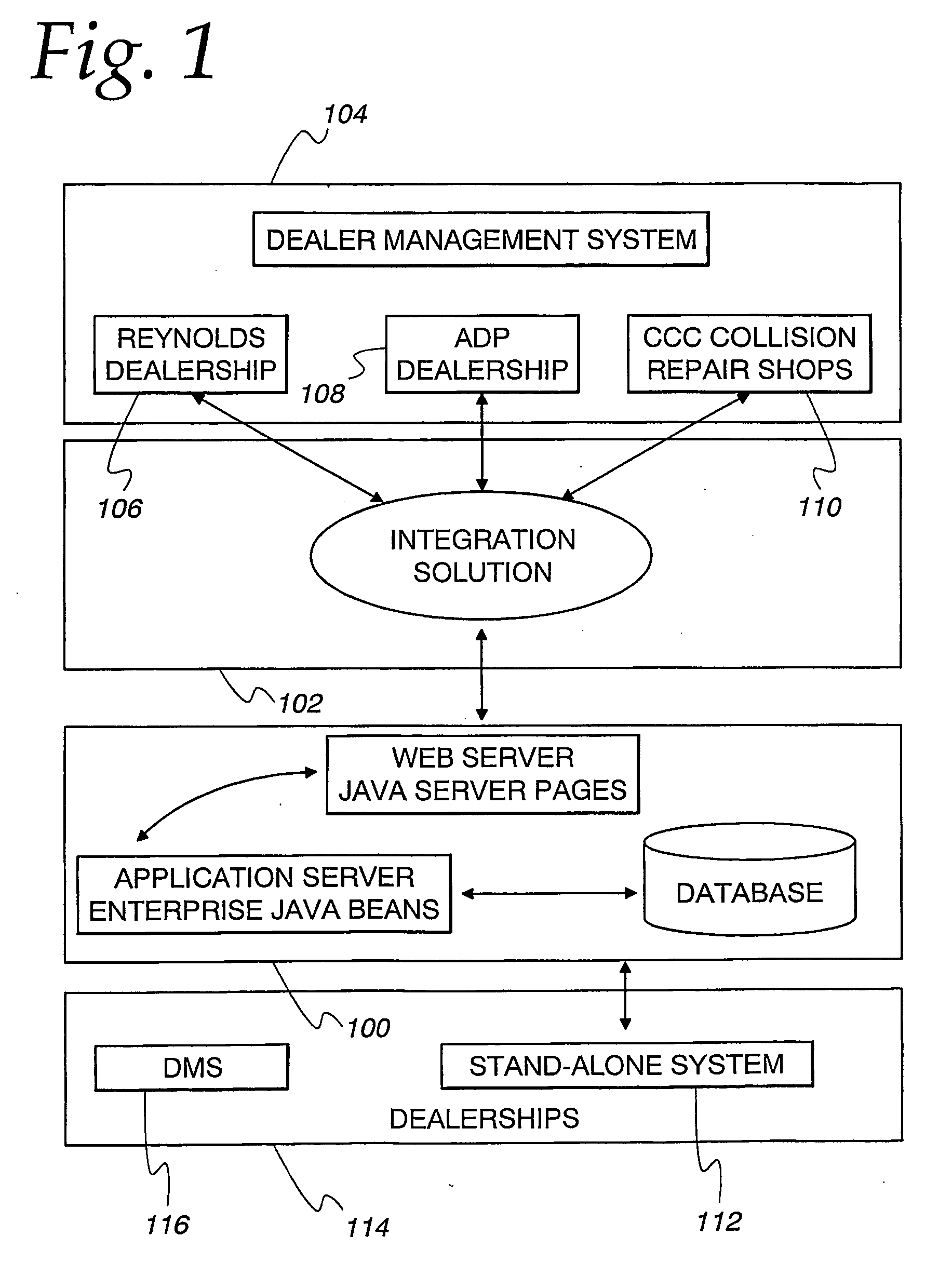
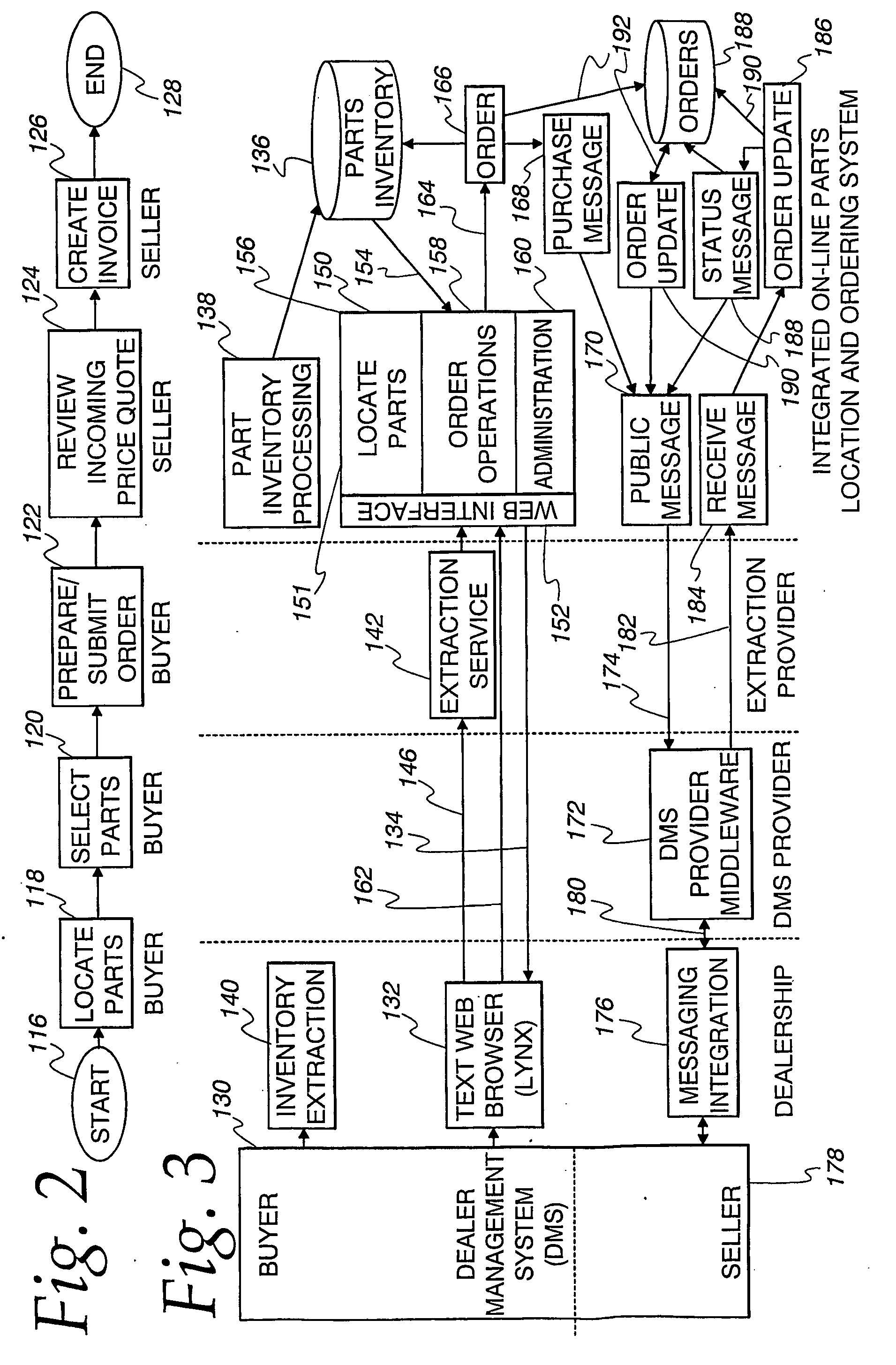
On-line parts location and transaction system
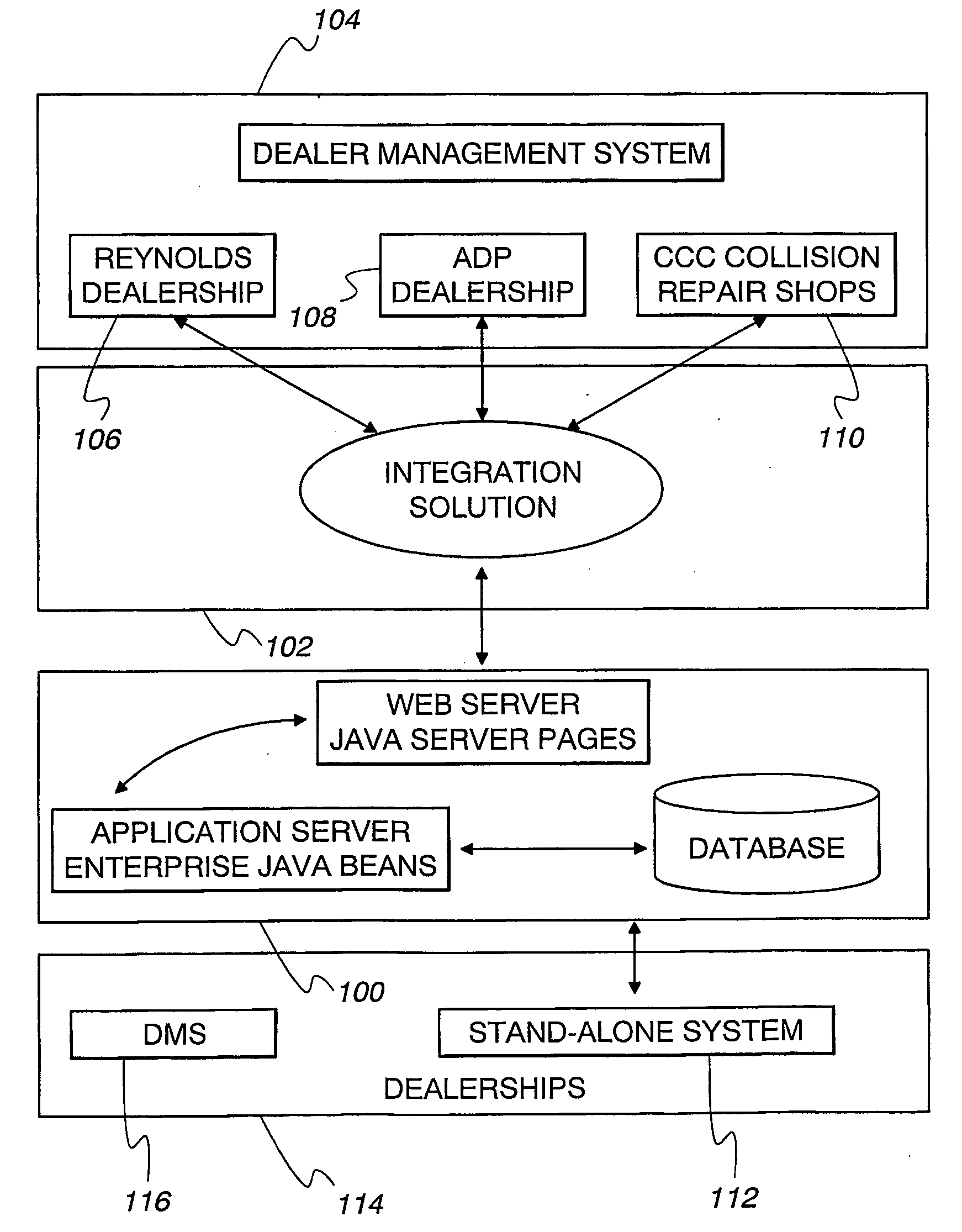
InactiveUS20050187834A1Easily and quickly locateBuying/selling/leasing transactionsLogisticsRepair shopPrivate communication
An integrated parts location and transaction system for original equipment manufacturer (OEM), non-OEM as well as aftermarket automobile parts is adapted to be integrated with business management computer system (BMS) software, currently used by automobile dealerships (210) as well as repair shops. All participating parts suppliers, including dealerships (210), and repair shops are networked together, for example, over a combination of public and private communication networks to enable participating parts suppliers and potential buyers (for example, dealers and repair shops) to easily and quickly locate as well as buy and sell parts from each other.
Owner:CHOICEPARTS
Scalable multiparty conferencing and collaboration system and method of dynamically allocating system resources in same
InactiveUS7167182B2Improve ease of useImprove functionalityMultiplex system selection arrangementsSpecial service provision for substationPrivate communicationCollaboration tool
A networking conferencing and collaboration tool utilizing an enhanced T.128 application sharing protocol. This enhanced protocol is based on a per-host model command, control, and communication structure. This per-host model reduces network traffic, allows greater scalability through dynamic system resource allocation, allows a single host to establish and maintain a share session with no other members present. The per-host model allows private communication between the host and a remote with periodic broadcasts of updates by the host to the entire share group. This per-host model also allows the host to allow, revoke, pause, and invite control of the shared applications. Subsequent passing of control is provided, also with the hosts acceptance. The model contains no fixed limit on the number of participants, and dynamically allocates resources when needed to share or control a shared application. These resources are then freed when no longer needed.
Owner:MICROSOFT TECH LICENSING LLC
System for providing session-based network privacy, private, persistent storage, and discretionary access control for sharing private data
InactiveUS20040143738A1Public key for secure communicationDigital data processing detailsPrivate communicationPrivate network
The invention provides secure and private communication over a network, as well as persistent private storage and private access control to the stored information, which is accomplished by imposing mechanisms that separate a user's actions from their identity. The system provides (i) anonymous network browsing, in which event the anonymity system is unaware of both the user's identity and browsing activities, (ii) private network storage and retrieval of data such as passwords, profiles and files in a manner such that the data can be stored into the system and later retrieved without the system knowing the contents or owners of the data, and (iii) the ability of the user to control and manage access to the remotely stored data without the system knowing the contents, owners, or accessors of the data.
Owner:PONOI CORP
Video conference system providing private and attorney-client privileged communications
A conference system includes a first conference station generating at least one of audio and video signals from at least an attorney and a second conference station generating at least one of audio and video signals from the attorney's client, the attorney and the attorney's client having a relationship protected by the attorney-client privilege. The system also includes at least one communications link connecting the first and second conference stations that carries the audio and / or video signals between the first and second conference stations. A signal processor is disposed within the communications link between the first and second conference stations to route signals between the first and second conference stations. At least one control panel communicates with the signal processor and provides control over audio and / or video signals so that the attorney and the attorney's client are permitted to engage in a private communication without vitiating the attorney-client privilege.
Owner:COMBINED PUBLIC COMM LLC
Methods and apparatus for increasing security and control of voice communication sessions using digital certificates
InactiveUS20070150723A1Security arrangementSecuring communicationPrivate communicationVoice communication
Methods and apparatus for increasing security and control of voice communication sessions, such as Push-To-Talk (PTT) over Cellular (PoC) sessions, using digital certificates are disclosed. A certificate control mechanism of a private communication network is used to help facilitate secure PoC sessions for mobile communication devices associated with the private network. The certificate control mechanism of includes a certificate controller which is adapted to communicate with a Certificate Authority (CA) component which produces and stores a plurality of digital certificates for the mobile devices. The certificate controller is further adapted to communicate with one of a PoC server and a PoC group list server through a public communication network (e.g. the Internet) so as to provide the plurality of digital certificates for secure PoC communication sessions for chat groups which include the plurality of mobile communication devices. In one illustrative technique, a request message for participation in a PoC session is received by an authentication component of a PoC server from a mobile device. The request message is signed with use of a private key of a digital certificate which may be associated with the mobile device, an end user of the mobile device, or a chat group which includes the mobile device. An authentication procedure is performed on the request message by the authentication component. The authentication procedure includes retrieving a public key associated with the digital certificate and attempting to validate the signature with use of the public key. Processing for the PoC communication session is permitted for the mobile communication device if the authentication is successful, and otherwise denied. Several other techniques and variations are described.
Owner:BLACKBERRY LTD
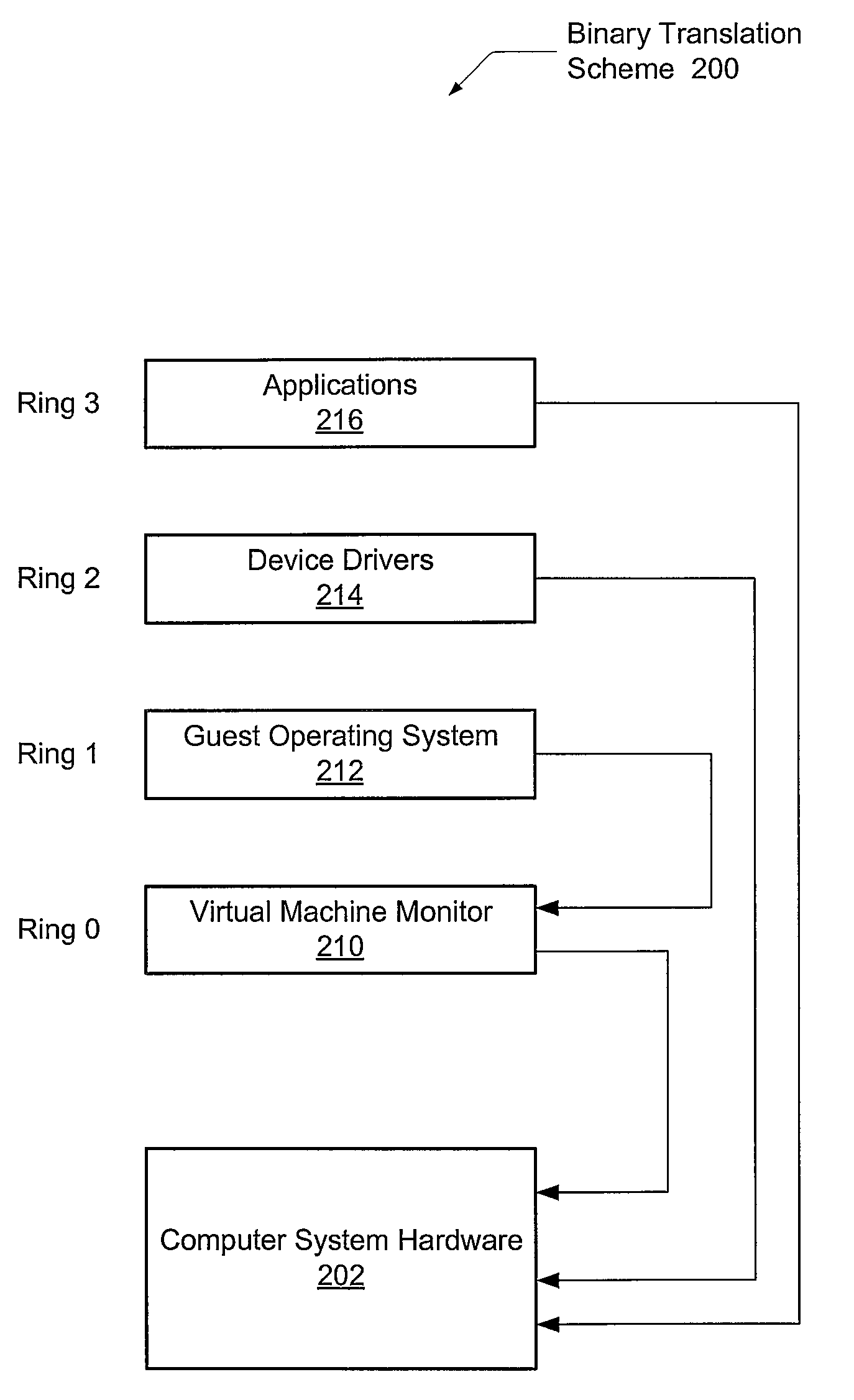
Security driver for hypervisors and operating systems of virtualized datacenters
A system and method for efficient security protocols in a virtualized datacenter environment are contemplated. In one embodiment, a system is provided comprising a hypervisor coupled to one or more protected virtual machines (VMs) and a security VM. Within a private communication channel, a split kernel loader provides an end-to-end communication between a paravirtualized security device driver, or symbiont, and the security VM. The symbiont monitors kernel-level activities of a corresponding guest OS, and conveys kernel-level metadata to the security VM via the private communication channel. Therefore, the well-known semantic gap problem is solved. The security VM is able to read all of the memory of a protected VM, detect locations of memory compromised by a malicious rootkit, and remediate any detected problems.
Owner:CA TECH INC
Scalable multiparty conferencing and collaboration system and method of dynamically allocating system resources and providing true color support in same
InactiveUS7136062B1Improve functionalityIncrease usageCathode-ray tube indicatorsOffice automationPrivate communicationCollaboration tool
A networking conferencing and collaboration tool utilizing an enhanced T.128 application sharing protocol. This enhanced protocol is based on a per-host model command, control, and communication structure. This per-host model reduces network traffic, allows greater scalability through dynamic system resource allocation, allows a single host to establish and maintain a share session with no other members present, and supports true color graphics. The per-host model allows private communication between the host and a remote with periodic broadcasts of updates by the host to the entire share group. This per-host model also allows the host to allow, revoke, pause, and invite control of the shared applications. Subsequent passing of control is provided, also with the hosts acceptance. The model contains no fixed limit on the number of participants, and dynamically allocates resources when needed to share or control a shared application. These resources are then freed when no longer needed. Calculation of minimum capabilities is conducted by the host as the membership of the share changes. The host then transmits these requirements to the share group.
Owner:MICROSOFT TECH LICENSING LLC
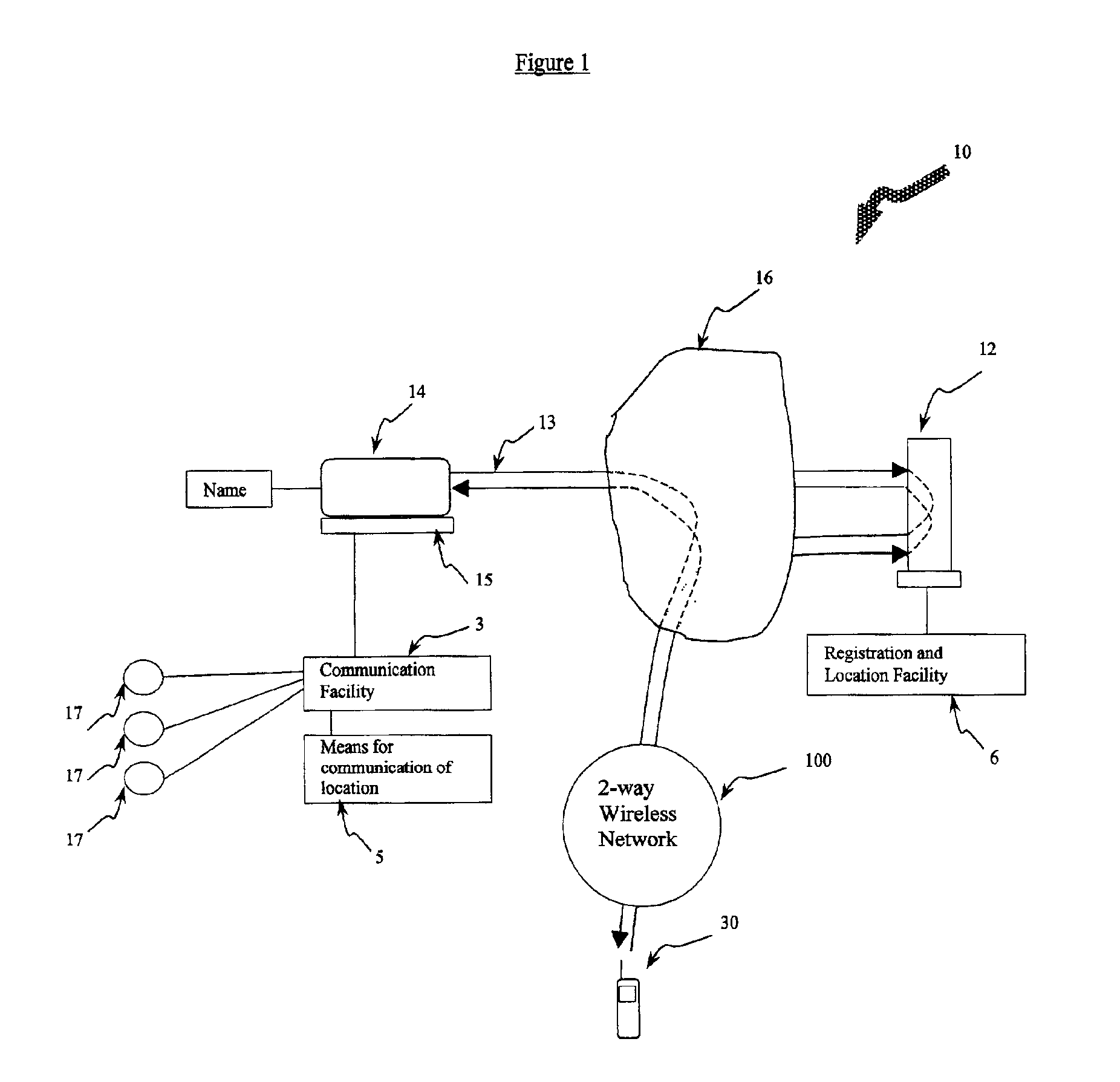
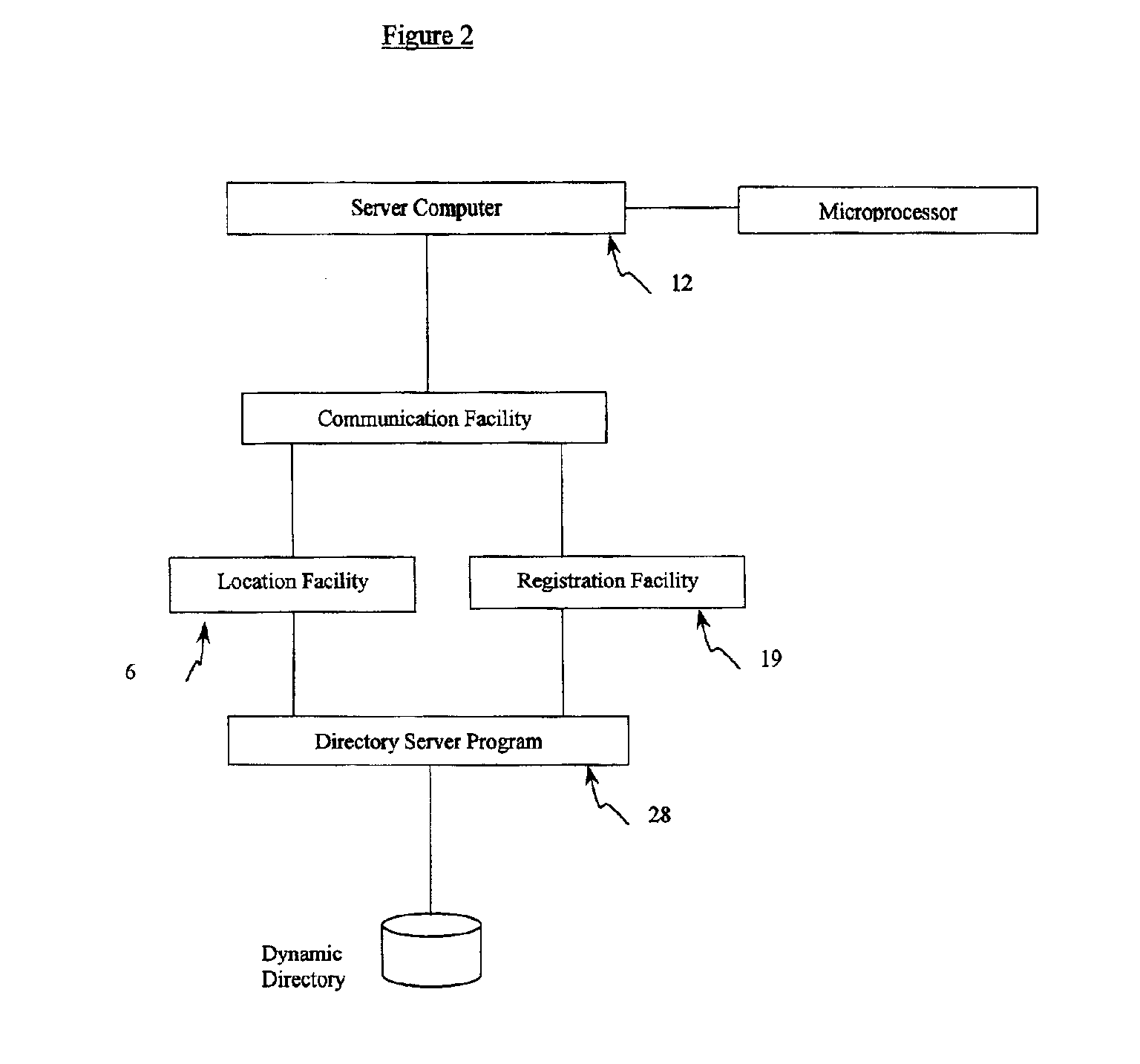
System computer product and method for providing a private communication portal
InactiveUS6928479B1Easy remote accessLow feesMultiple digital computer combinationsTransmissionPrivate communicationDistributed computing
A system, computer product and method for providing a private communication portal at a first computer connected to a network of computers includes a communication facility resident at the first computer, and a second computer including a locating facility for locating the current location of the first computer on the network, where the second computer facilitates communication between the first computer and a third computer by authenticating the third computer for communication with the first computer and providing the location of the first computer for communication with the third computer.
Owner:01 COMMUNIQUE LAB INC
Private communications network with wildcard dialing
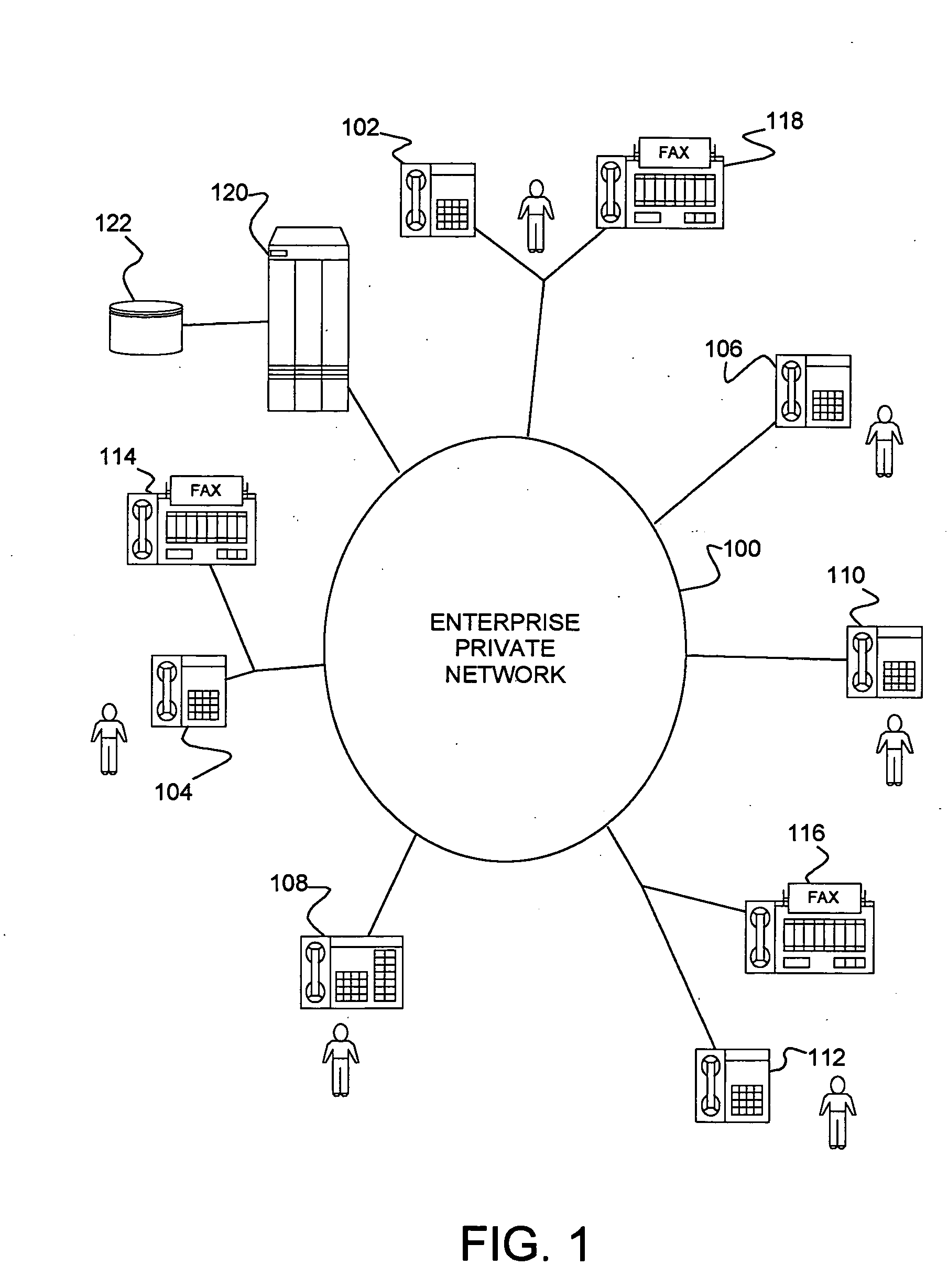
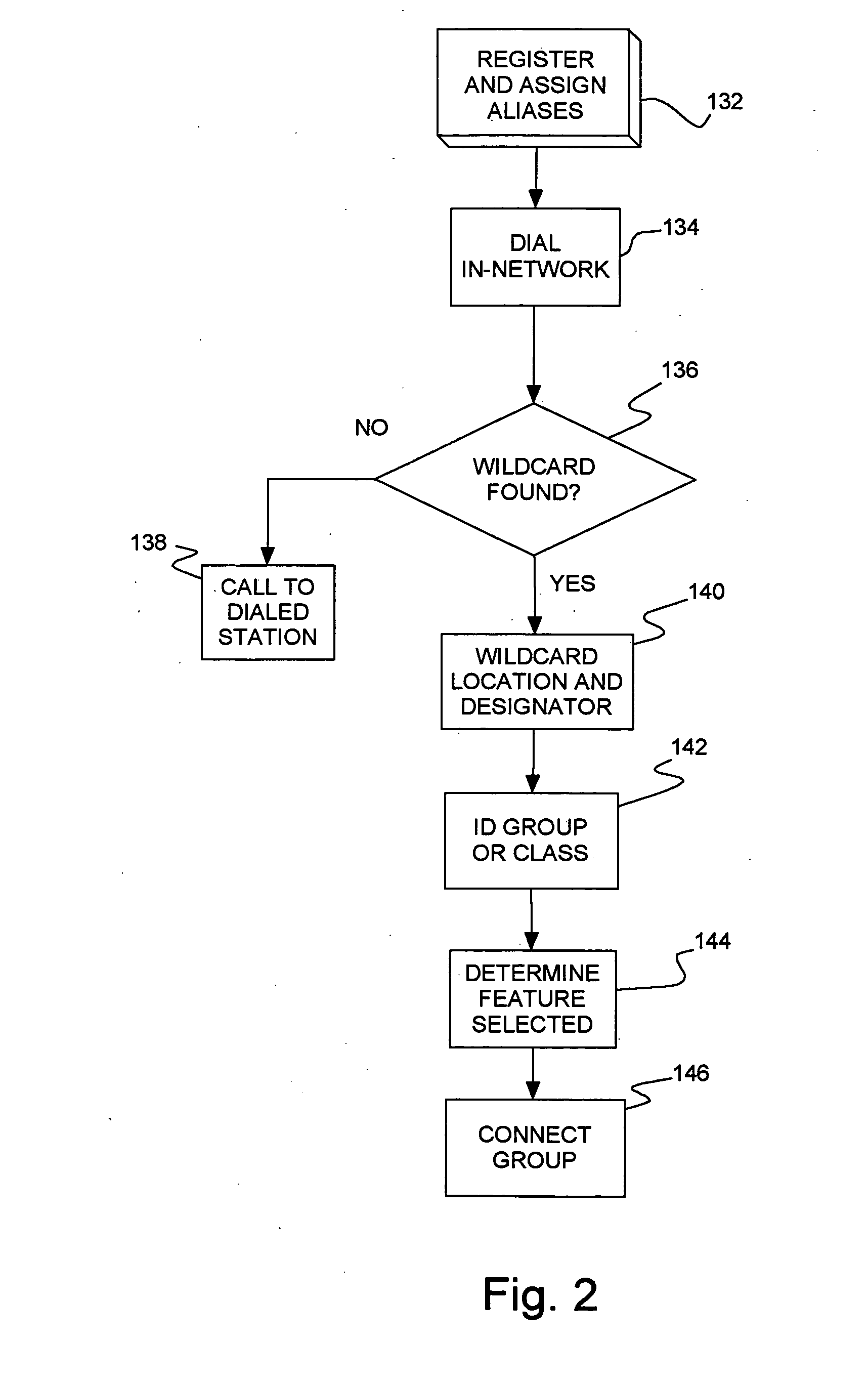
InactiveUS20080043972A1Simplify usingSpecial service for subscribersPrivate communicationConference call
A private communications network and method of managing calls in a private communications network. Connected communications devices register with the network and are assigned aliases, with aliases for groups of registered devices sharing one or more common digits. Dialing strings for in-network calls are monitored for inclusion of a wildcard (e.g., *) which are treated as a “don't care.” The wildcard invokes group features, such as placing a conference call, invoking a hunting feature and invoking a pickup feature. The call is distributed / connected to the group corresponding to the remaining digits.
Owner:UNIFY INC
Speakerphone with detachable ear bud
This invention is a wireless, speakerphone accessory that allows the user to be in either public or private communication with a remote electronic device like a mobile telephone. The accessory includes a detachable ear bud that can be worn in a user's ear so that only the user hears the audio signal being received. When the ear bud is coupled to the speakerphone accessory, the circuitry in the ear bud is used to control a loudspeaker and other components in the accessory so as to convert the combined device in to a speakerphone that may be heard by the user and others in his immediate vicinity. The speakerphone accessory optionally includes pockets for receiving rechargeable batteries, as well as utility pockets for holding spare components like ear sleeves. The invention not only offers the dual functionality of private and public operating modes, but serves as a self-retaining case to greatly reduce the chances that any of the components become lost.
Owner:MOTOROLA INC
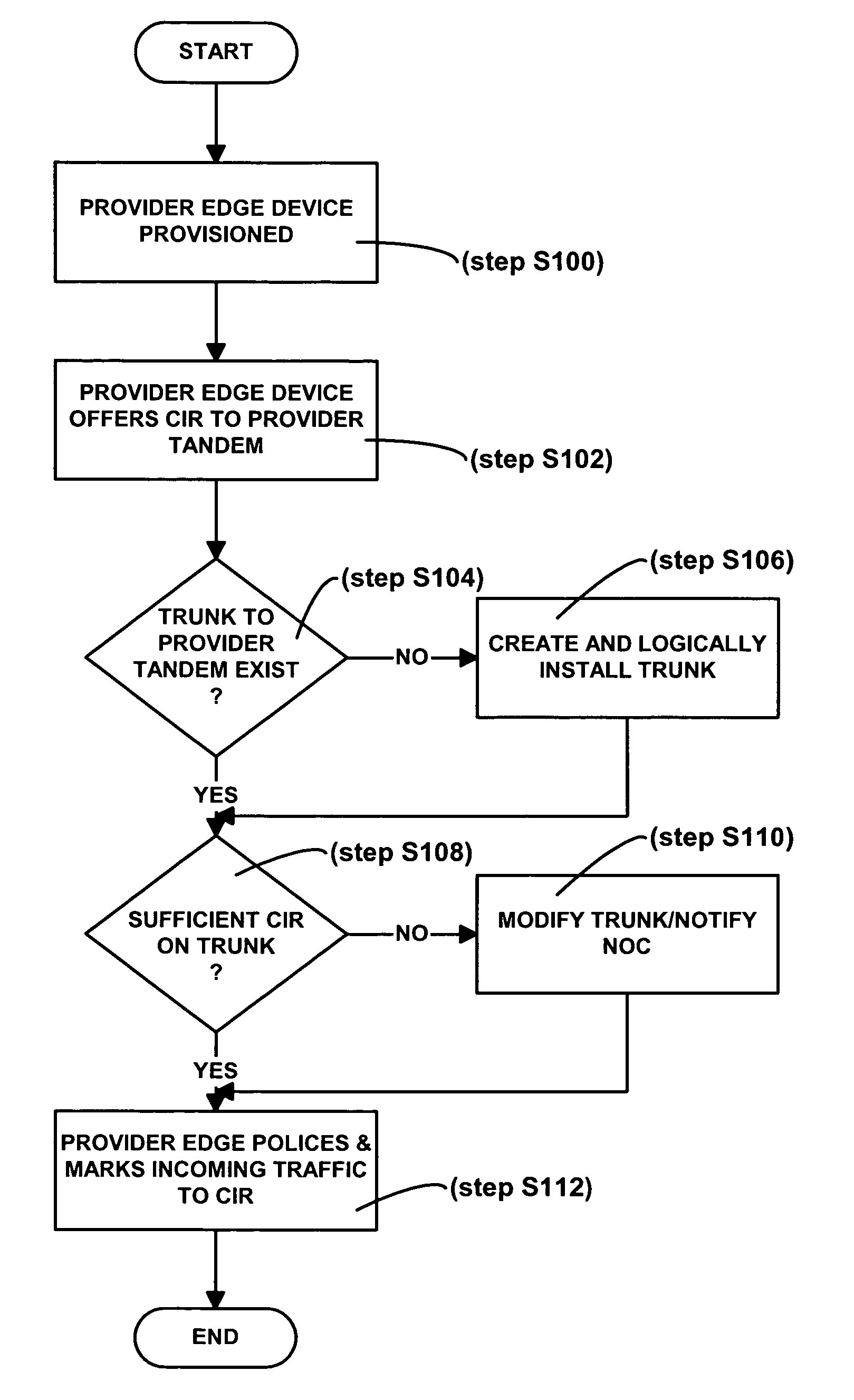
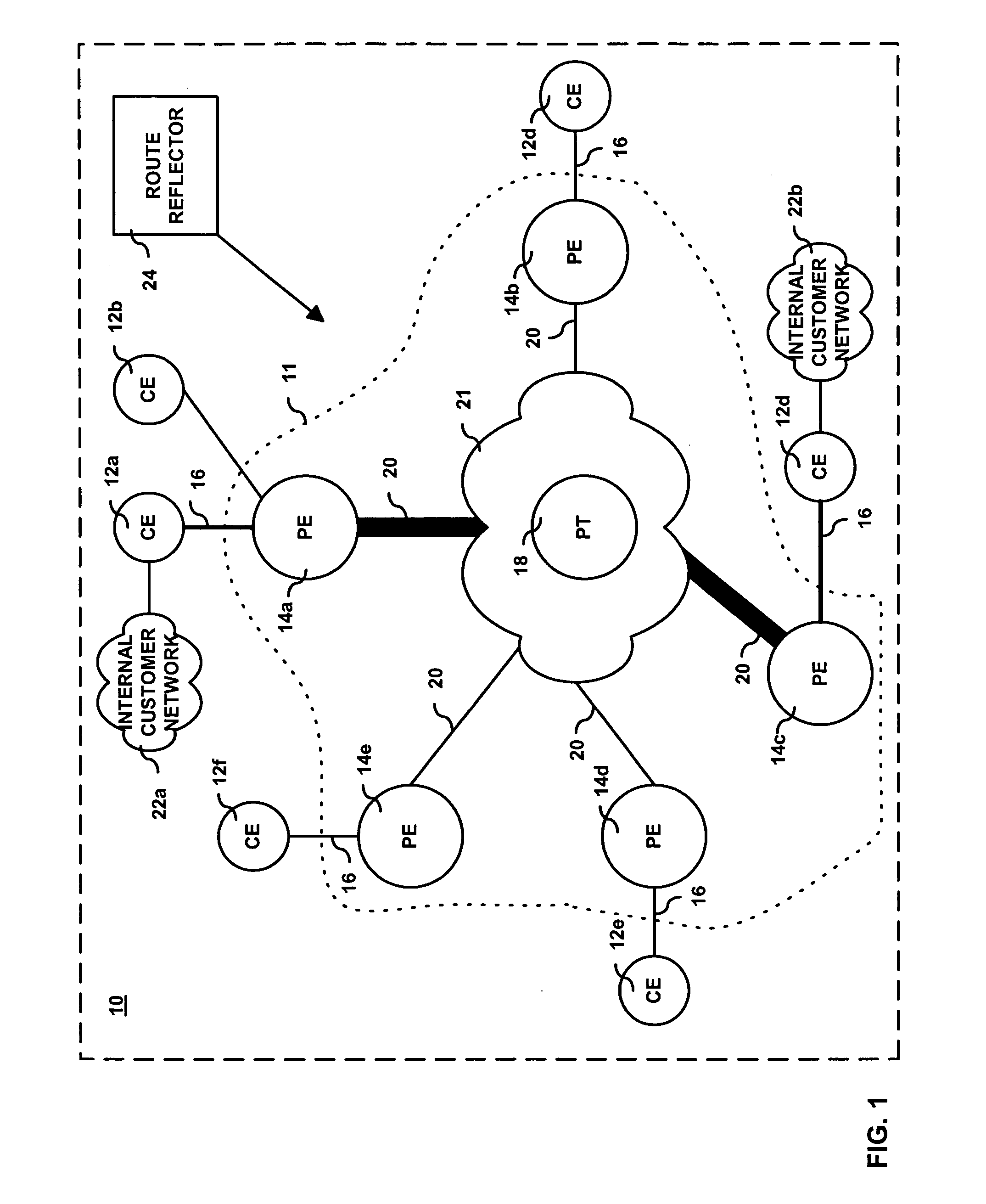
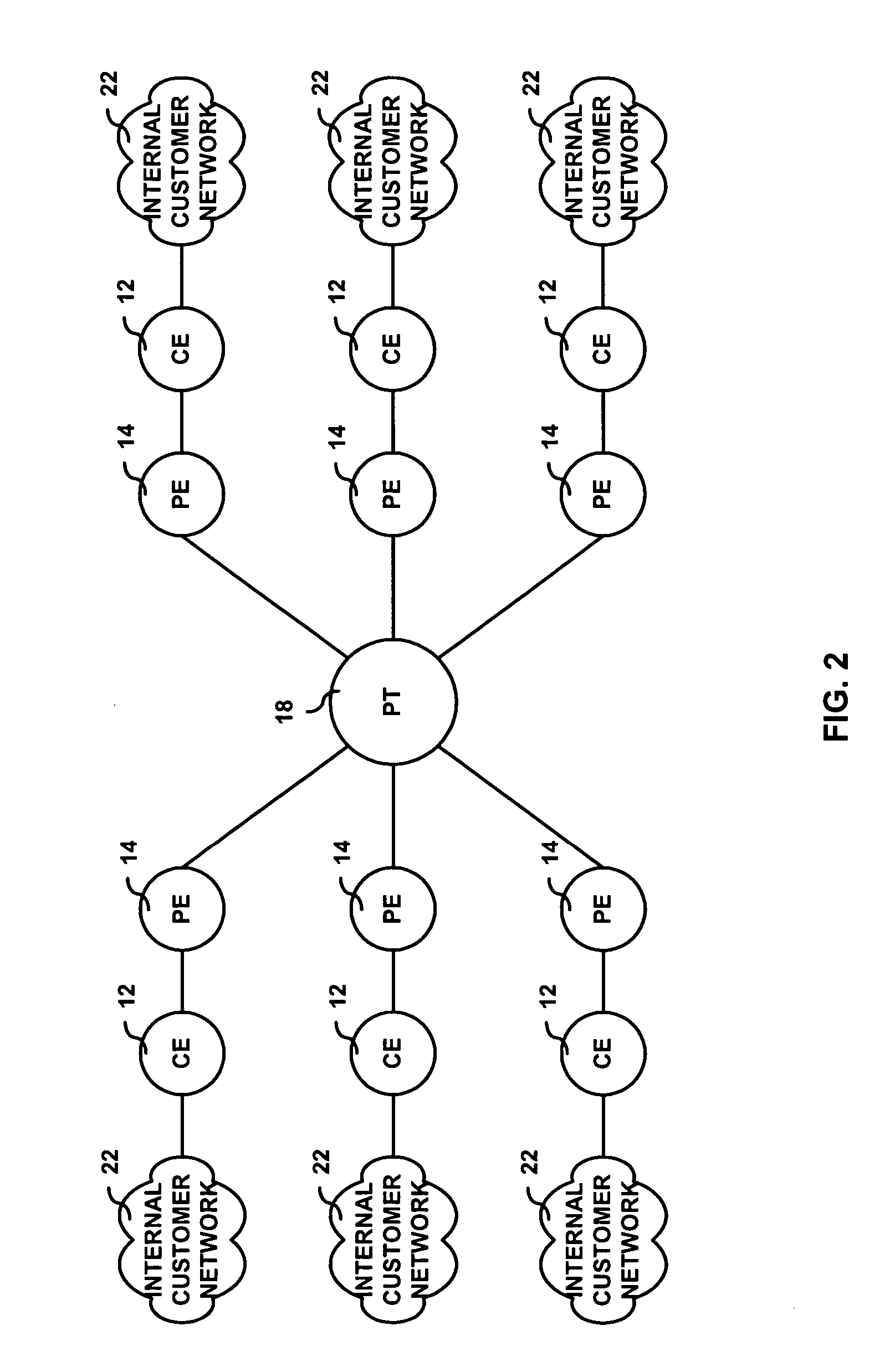
System and method for hub and spoke virtual private network
InactiveUS20060029032A1Data switching by path configurationPrivate communicationCommitted information rate
A method and system for providing a virtual private communication network to transport customer data between a set of customer devices coupled to a provider network. A committed information rate is advertised to a provider tandem. The provider tandem determines whether sufficient network resources exist to successfully transport to a destination customer device all offered data from the set of customer devices.
Owner:RPX CLEARINGHOUSE
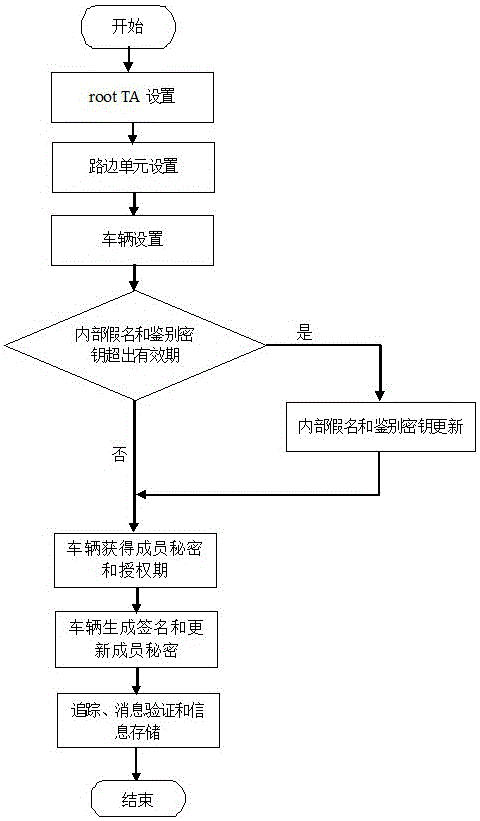
Distributed aggregation authentication method having privacy protection function for vehicle-mounted self-organizing network
InactiveCN105763558ASatisfy unlinkable privacyKey distribution for secure communicationSecurity arrangementPrivate communicationPrivacy protection
The invention discloses a distributed aggregation authentication method having a privacy protection function for a vehicle-mounted self-organizing network. The method comprises the following steps: a step of trusted root mechanism arrangement, a step of road side unit arrangement, a step of vehicle arrangement, a step of internal pseudonym and authentication key updating, a step of a vehicle obtaining secrets of members and authorization terms, a step of the vehicle generating signatures and updating the secrets of the members, a step of tracking and a step of message verification and information storage. The distributed aggregation authentication method is characterized in that conditional privacy is not associable, the method is independent of an ideal and strict anti osmosis device, and no secret key trusteeship problem can be caused. Safe and private communication of a the vehicle-mounted self-organizing network can be realized through the distributed aggregation authentication method.
Owner:EAST CHINA NORMAL UNIV
Secure entry of a user-identifier in a publicly positioned device
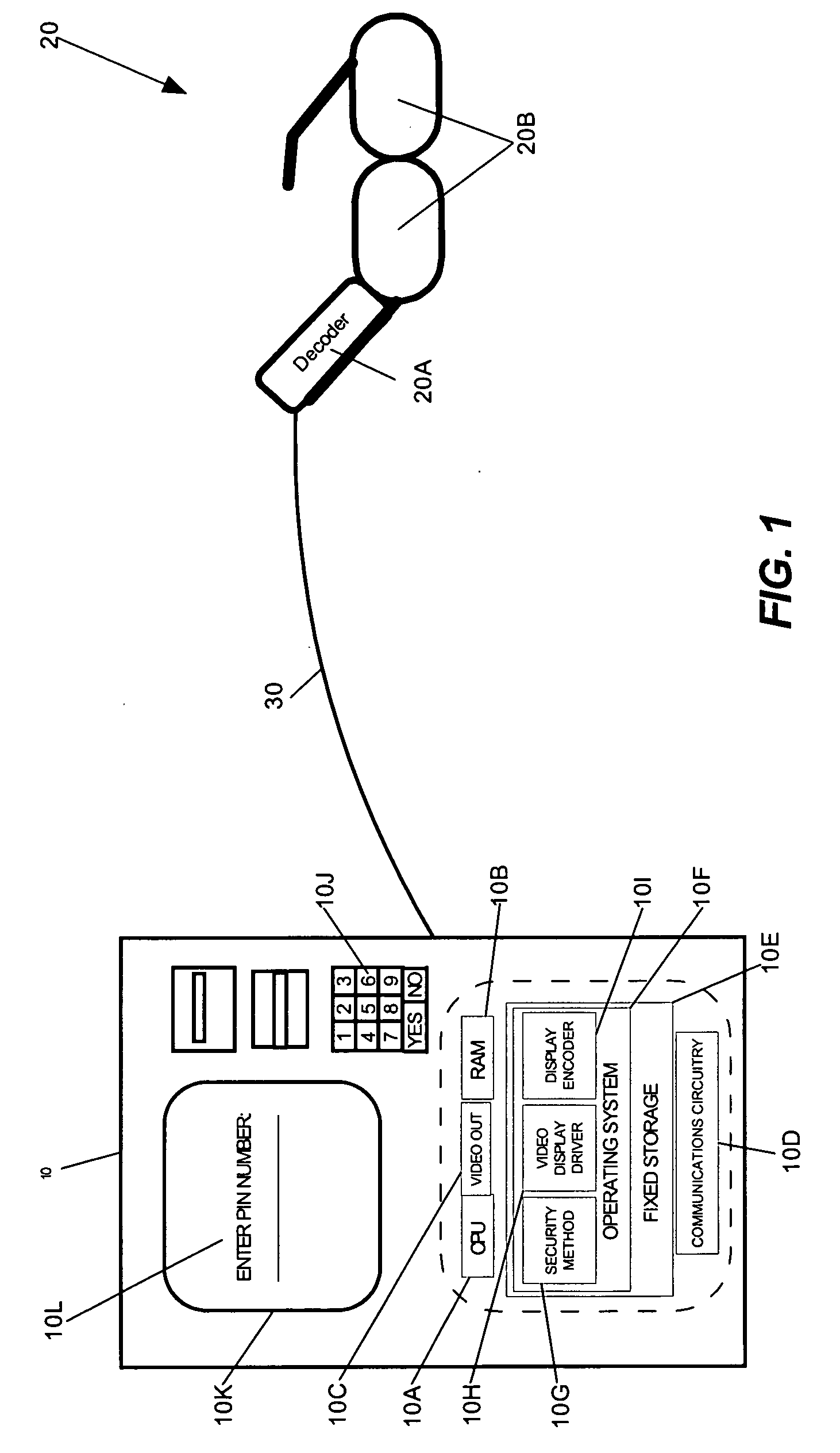
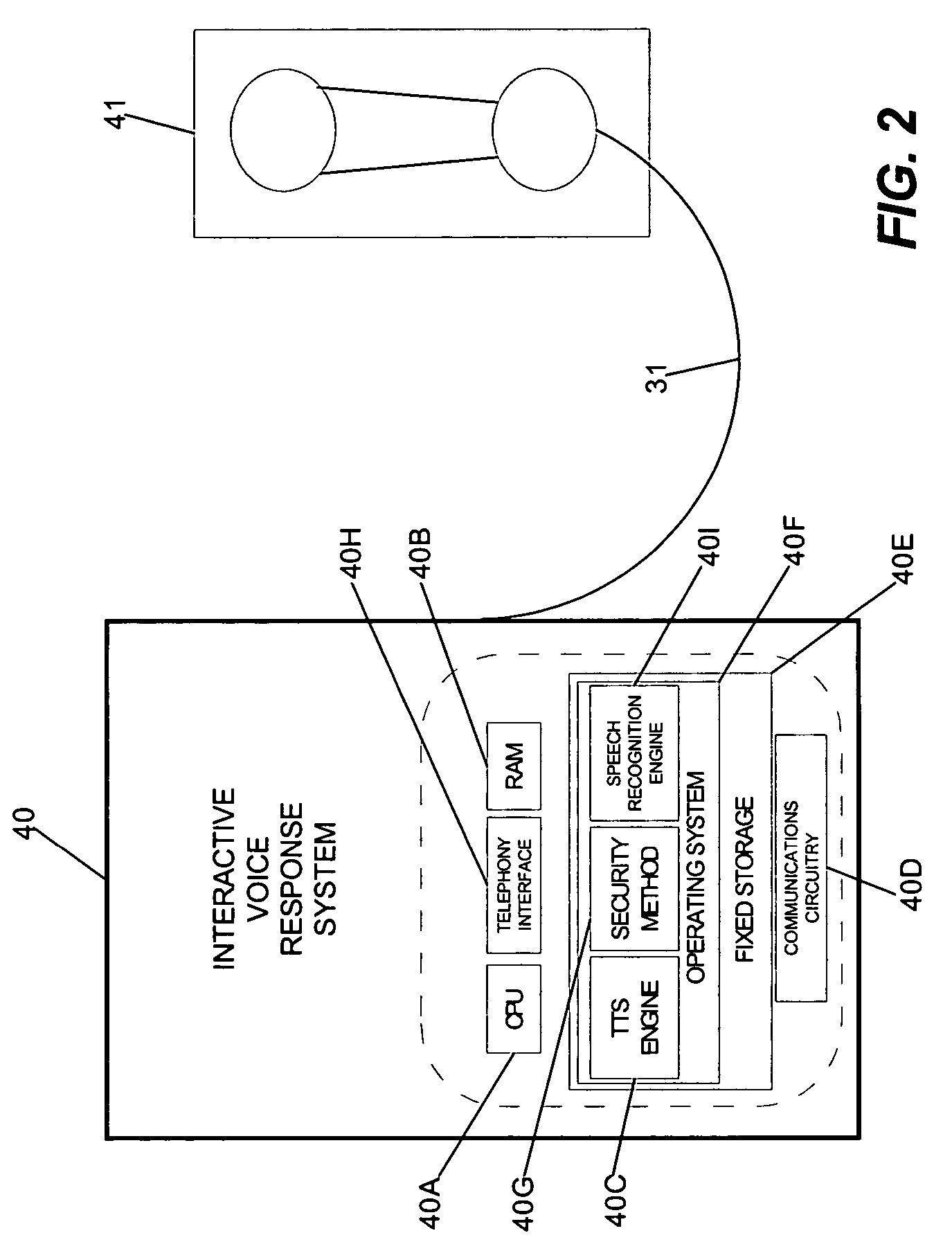
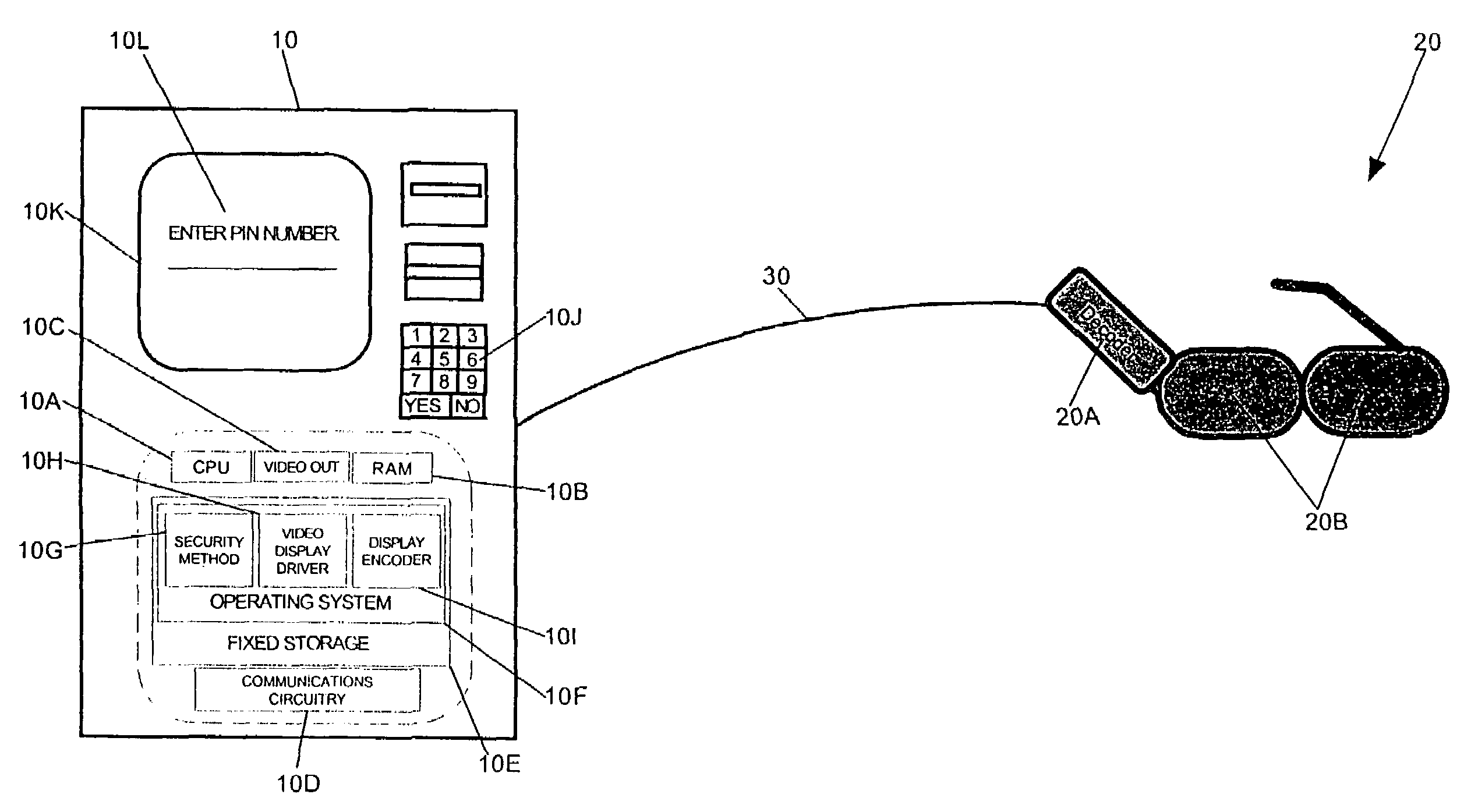
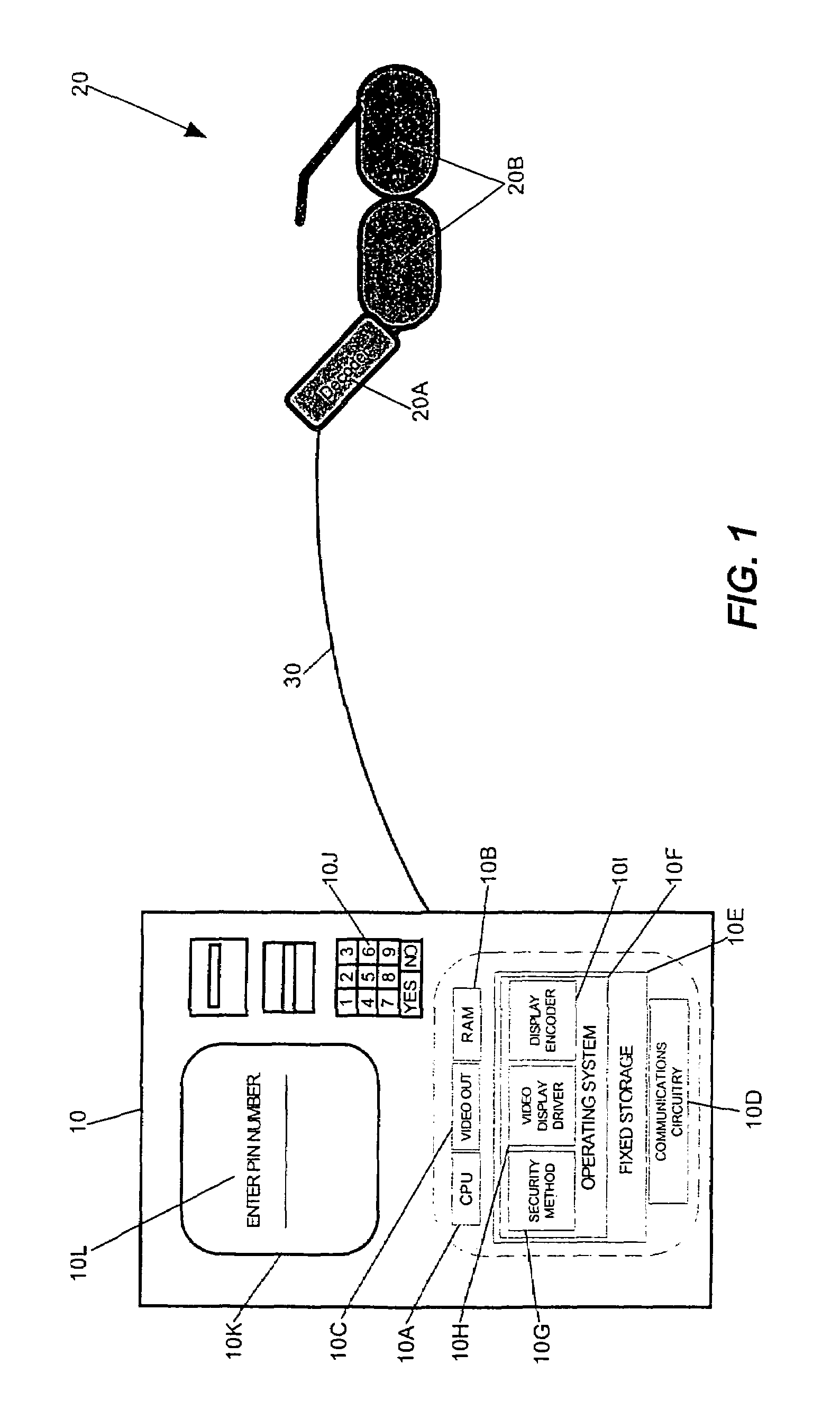
InactiveUS20060041758A1Cathode-ray tube indicatorsComputer security arrangementsPrivate communicationTelecommunications link
Owner:INT BUSINESS MASCH CORP
Method and Apparatus for Remotely Monitoring the Condition of a Patient
InactiveUS20090118596A1Improve functionalityFunction increaseSurgeryPerson identificationPrivate communicationTelecommunications link
A patient monitoring system provides enhanced functional capability relative to known systems and provides a wireless communication link between a patient monitoring device, worn by a patient, and a local hub. The patient monitoring system is adapted to monitor various patient physiological characteristics, such as blood pressure, pulse rate, blood glucose, weight, pulse oximetry and others. The data from the patient monitoring device is wirelessly transmitted to a local hub, which, in turn, is configured to automatically transfer the data to a remote server, for example, over a public or private communications network. In one embodiment of the invention, the server is configured as a web portal to selectively allow access to such patient physiological data by designated third parties, such as physicians, clinicians, relatives and the patient themselves.
Owner:CAREMATIX
Video conference system providing private and attorney-client privileged communications
A conference system includes a first conference station generating at least one of audio and video signals from at least an attorney and a second conference station generating at least one of audio and video signals from the attorney's client, the attorney and the attorney's client having a relationship protected by the attorney-client privilege. The system also includes at least one communications link connecting the first and second conference stations that carries the audio and / or video signals between the first and second conference stations. A signal processor is disposed within the communications link between the first and second conference stations to route signals between the first and second conference stations. At least one control panel communicates with the signal processor and provides control over audio and / or video signals so that the attorney and the attorney's client are permitted to engage in a private communication without vitiating the attorney-client privilege.
Owner:COMBINED PUBLIC COMM LLC
Secure entry of a user-identifier in a publicly positioned device
InactiveUS6959389B1Electric signal transmission systemsMultiple keys/algorithms usagePrivate communicationTelecommunications link
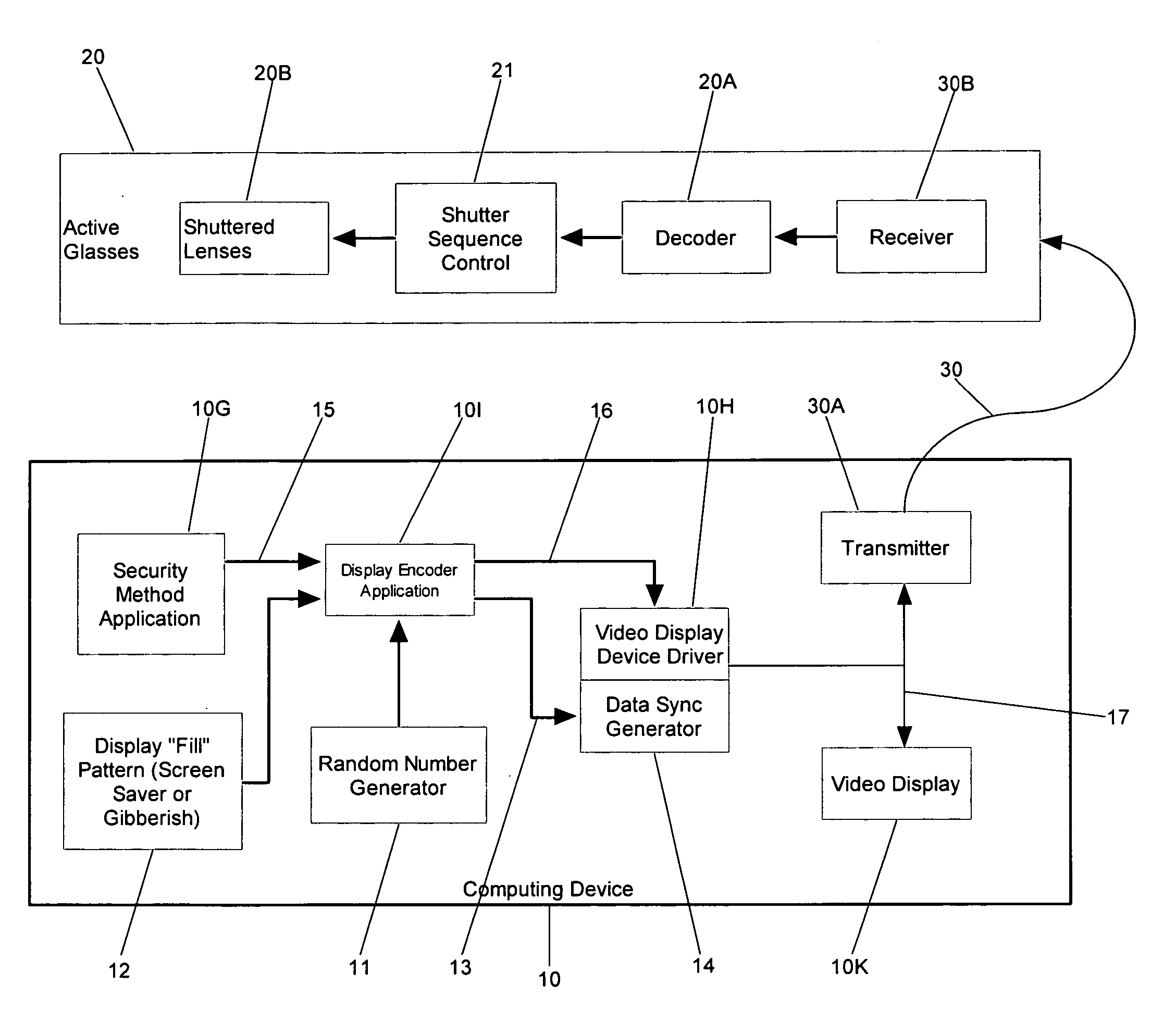
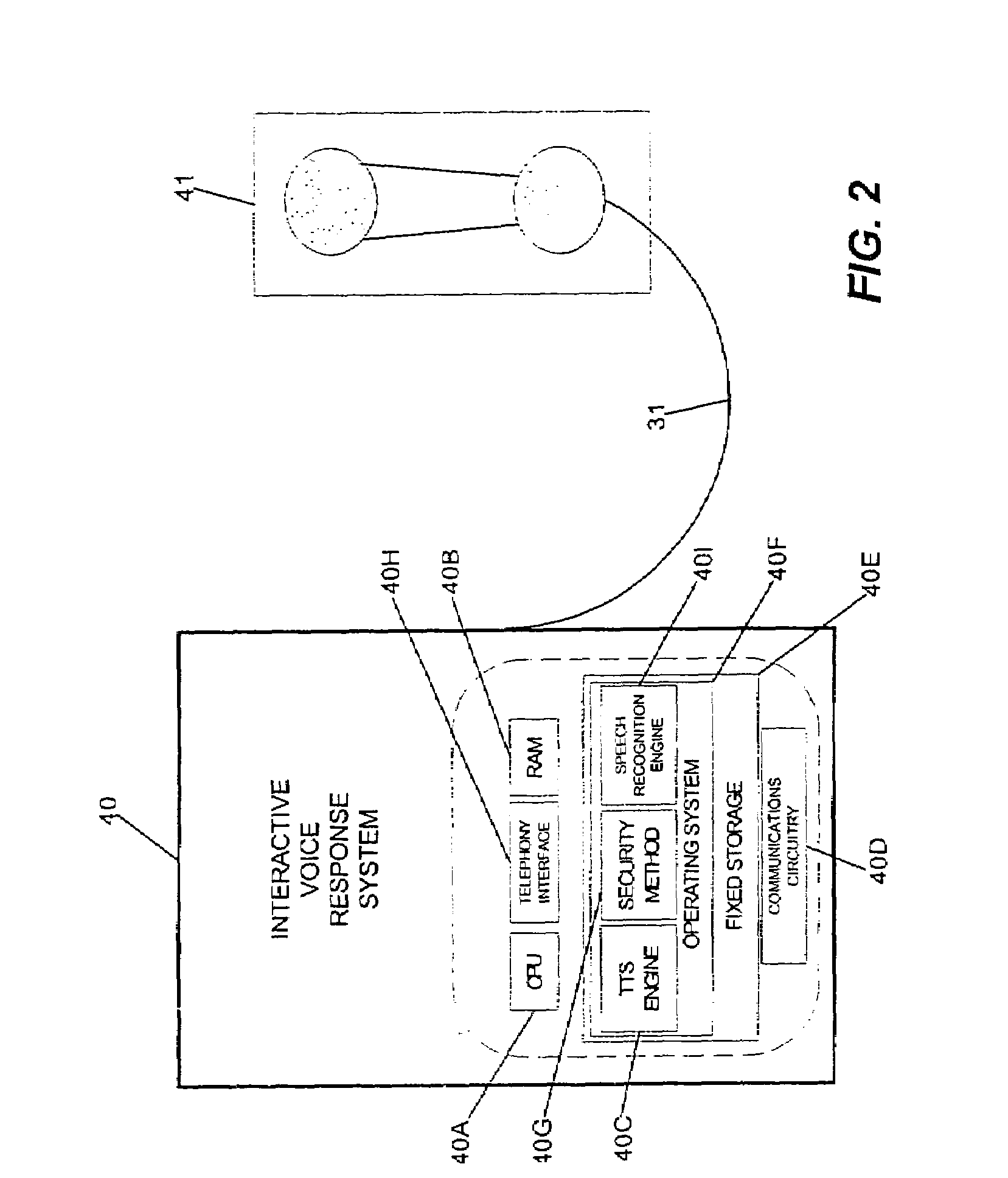
A method for secure entry of a user-identifier in a publicly positioned device can include establishing a private communications link between a user and the publicly positioned device; dividing the user-identifier into at least two portions; separately prompting the user for each portion of the user-identifier; prompting the user for a combination of random data and the user-identifier; and, discarding the random data from the combination. In the preferred embodiments, the publicly positioned device can have a visual interface through which the user can be visually prompted for the random data and the user-identifier. Alternatively, the publicly positioned device can have a telephone interface through which the user can be audibly prompted for the random data and the user-identifier. In the case of a visual display, the private communications link can be established by linking the publicly positioned device to active glasses having a shuttered display. The opening and closing of the shuttered display can be synchronized with the display of the prompts in the visual interface such that only the wearer of the active glasses can view the prompts. In the case of a telephone interface, an telephone operator system, for example an Interactive Voice Response system or a human operator, can provide the prompts audibly through the telephone interface.
Owner:IBM CORP
Mobile phone private communication management system and method
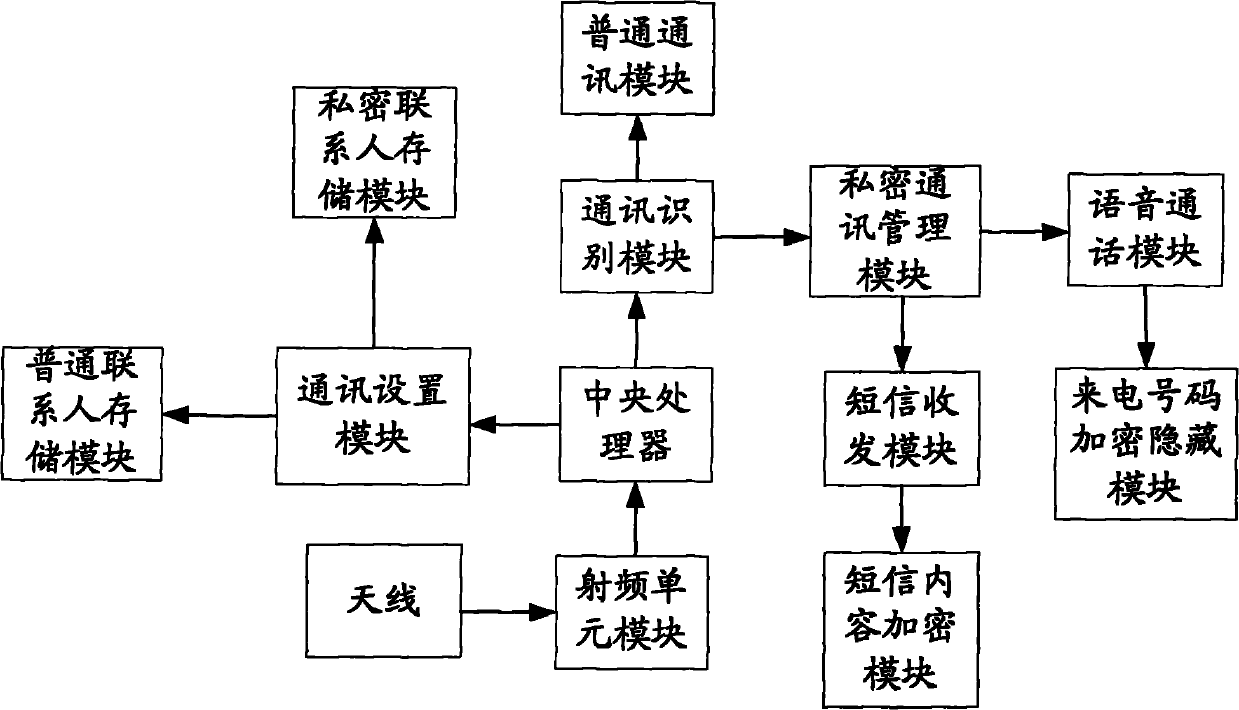
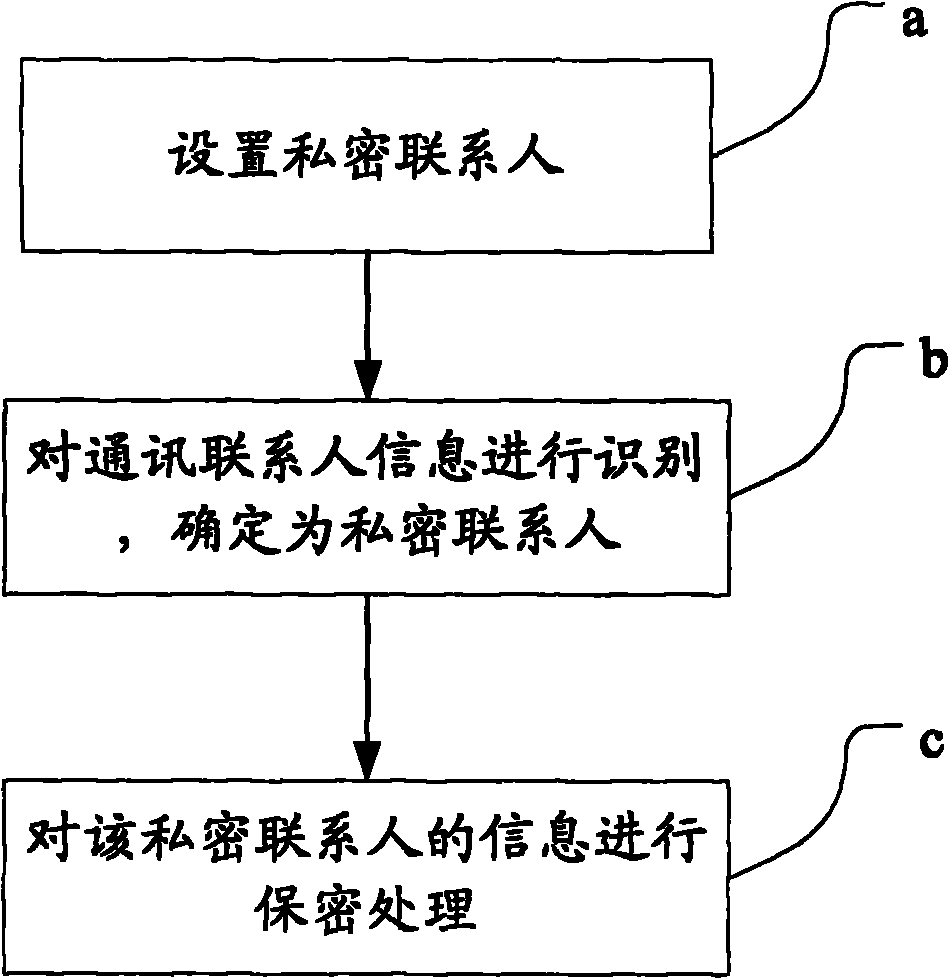
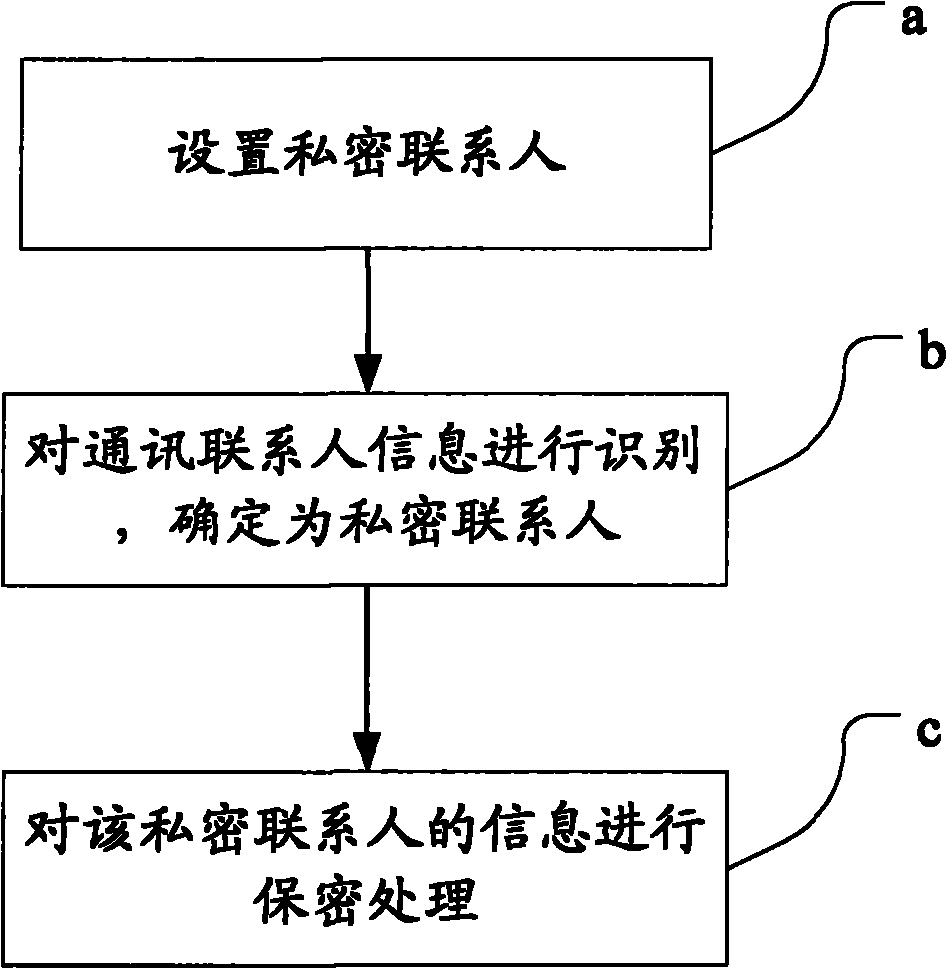
InactiveCN102006358AImprove securityPrevent leakageSubstation equipmentSecurity arrangementPrivate communicationMobile phone
The invention discloses a mobile phone private communication management system and a mobile phone private communication management method. The method comprises the following steps of: a, setting private contacts; b, identifying communication contact information, and determining that the communication contact is the private contact; and c, performing confidential processing on the information of the private contact. By setting the private contacts, storing the private contacts and common contacts separately, managing the contacts through a private communication management module, reediting the names of the contacts in advance, concealing the telephone numbers and encrypting short message contents, all information can be concealed or encrypted according to the presetting when the contact is an incoming call user or a short message sending user. Compared with the prior art, the system and the method realize private management of incoming call information and received short message of the mobile phone of the user by presetting, improve the security of the mobile phone information and avoid the possibility of private information divulgence of the mobile phone.
Owner:SHENZHEN GIONEE COMM EQUIP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com