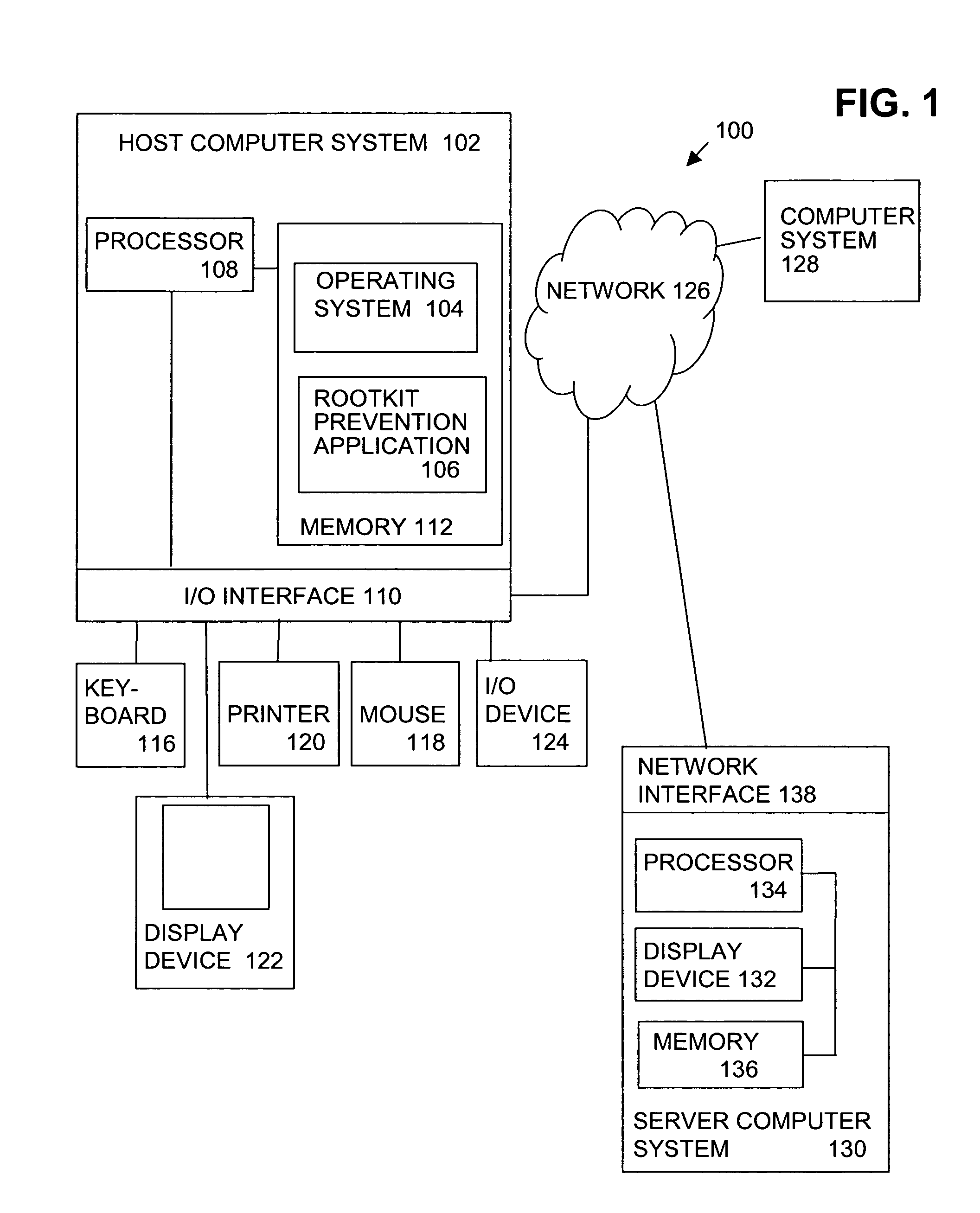
Patents
Literature
84 results about "Rootkit" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A rootkit is a collection of computer software, typically malicious, designed to enable access to a computer or an area of its software that is not otherwise allowed (for example, to an unauthorized user) and often masks its existence or the existence of other software. The term rootkit is a concatenation of "root" (the traditional name of the privileged account on Unix-like operating systems) and the word "kit" (which refers to the software components that implement the tool). The term "rootkit" has negative connotations through its association with malware.
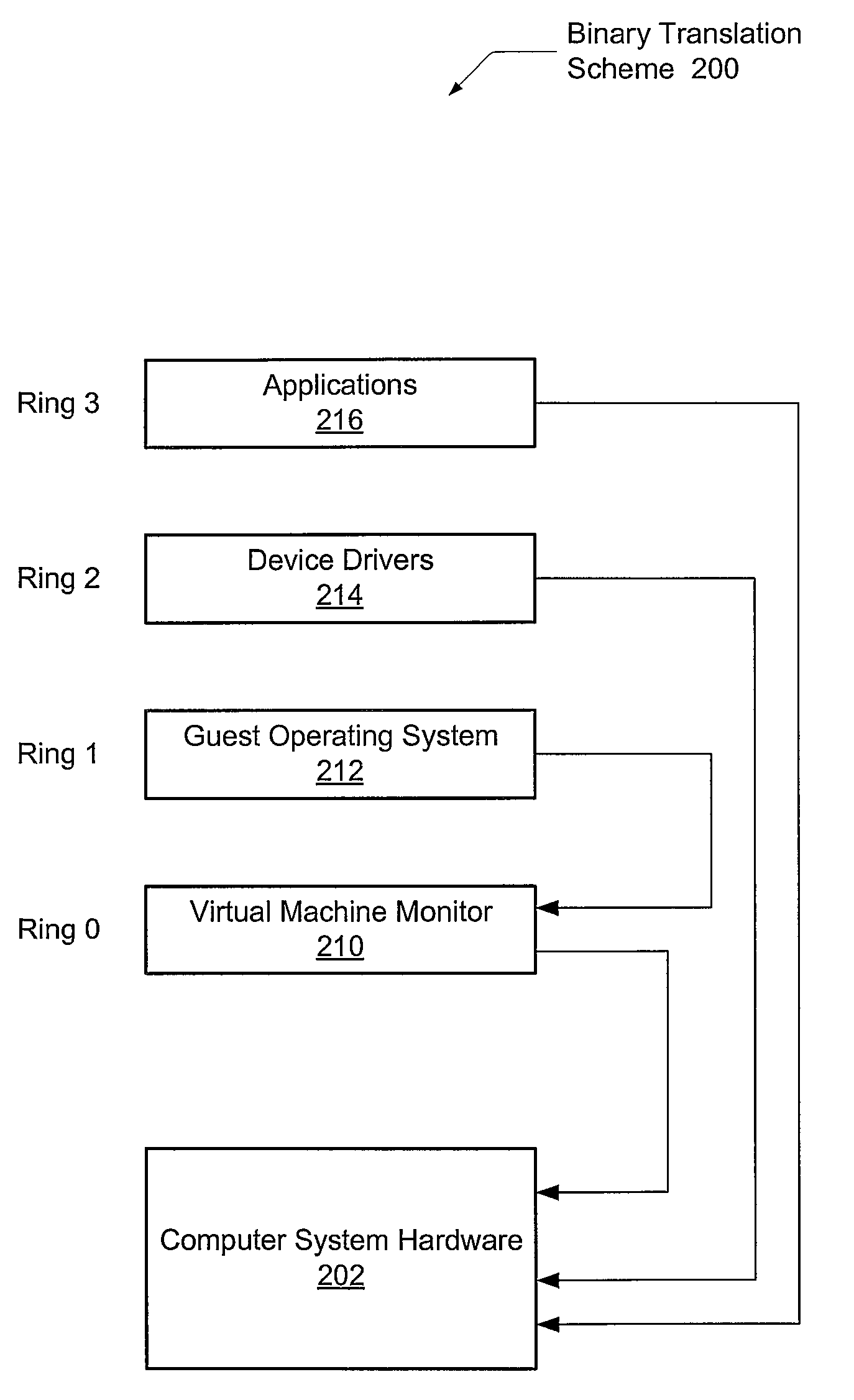
Security driver for hypervisors and operating systems of virtualized datacenters
A system and method for efficient security protocols in a virtualized datacenter environment are contemplated. In one embodiment, a system is provided comprising a hypervisor coupled to one or more protected virtual machines (VMs) and a security VM. Within a private communication channel, a split kernel loader provides an end-to-end communication between a paravirtualized security device driver, or symbiont, and the security VM. The symbiont monitors kernel-level activities of a corresponding guest OS, and conveys kernel-level metadata to the security VM via the private communication channel. Therefore, the well-known semantic gap problem is solved. The security VM is able to read all of the memory of a protected VM, detect locations of memory compromised by a malicious rootkit, and remediate any detected problems.
Owner:CA TECH INC
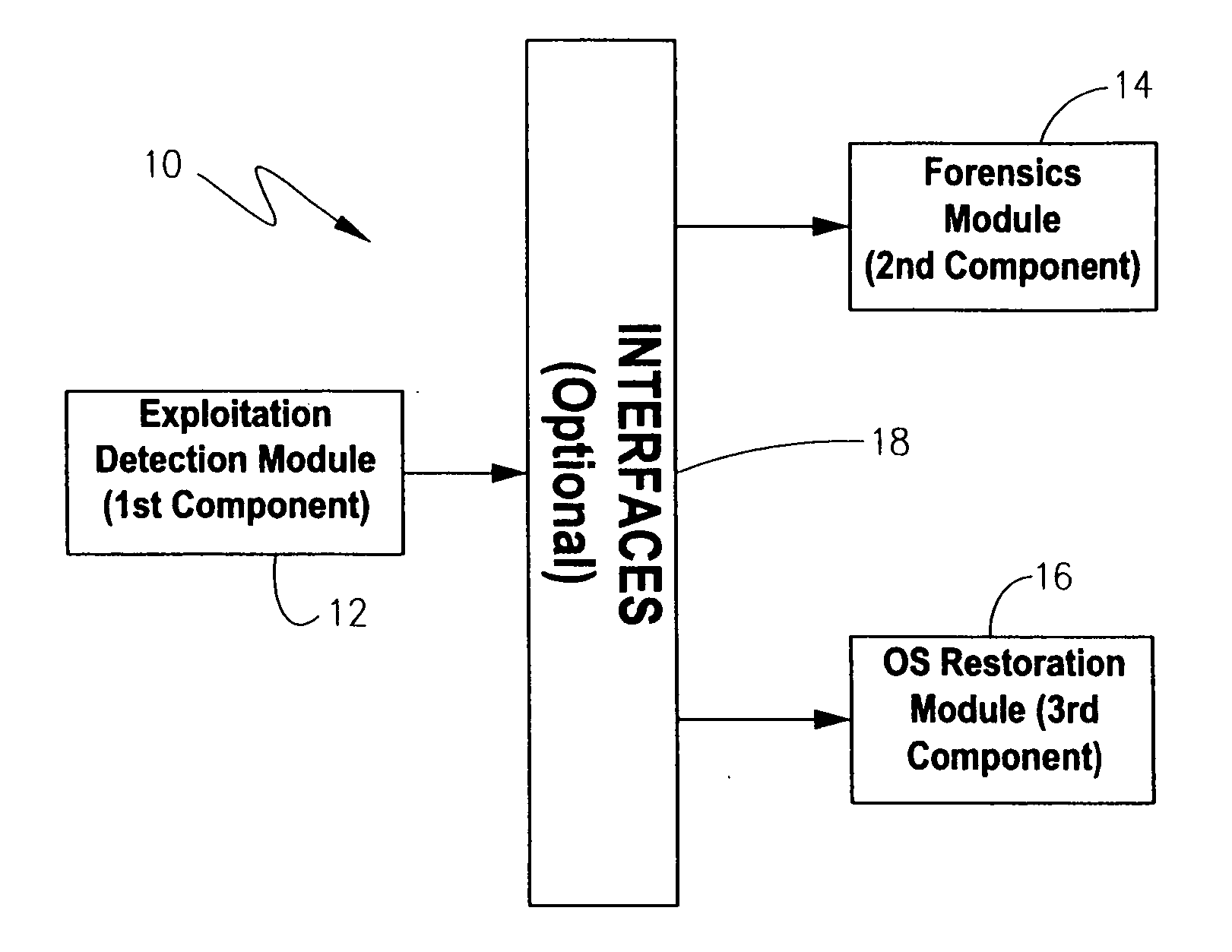
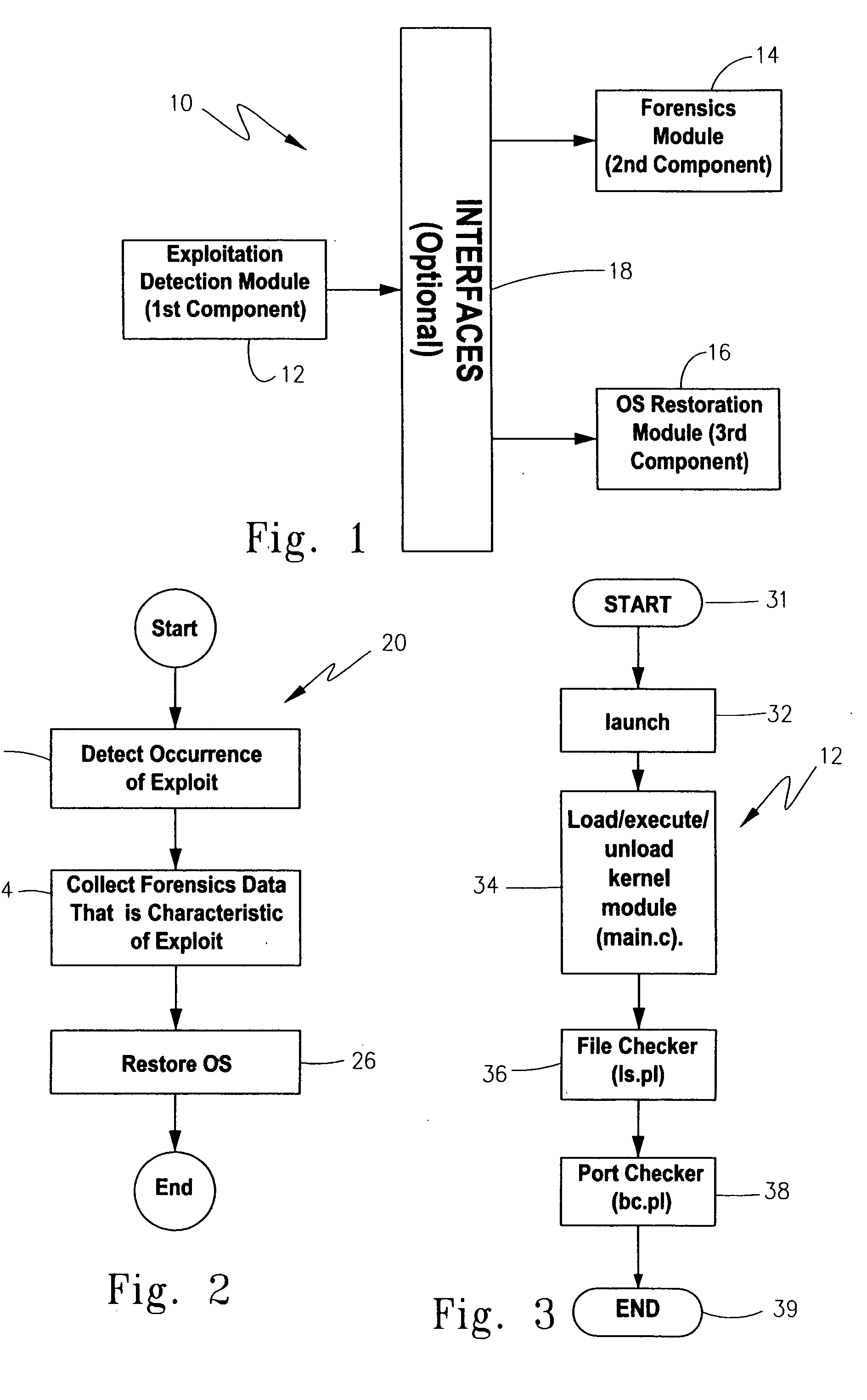
Methodology, system, and computer readable medium for detecting operating system exploitations
InactiveUS20050204205A1Error detection/correctionUnauthorized memory use protectionOperational systemOperating system
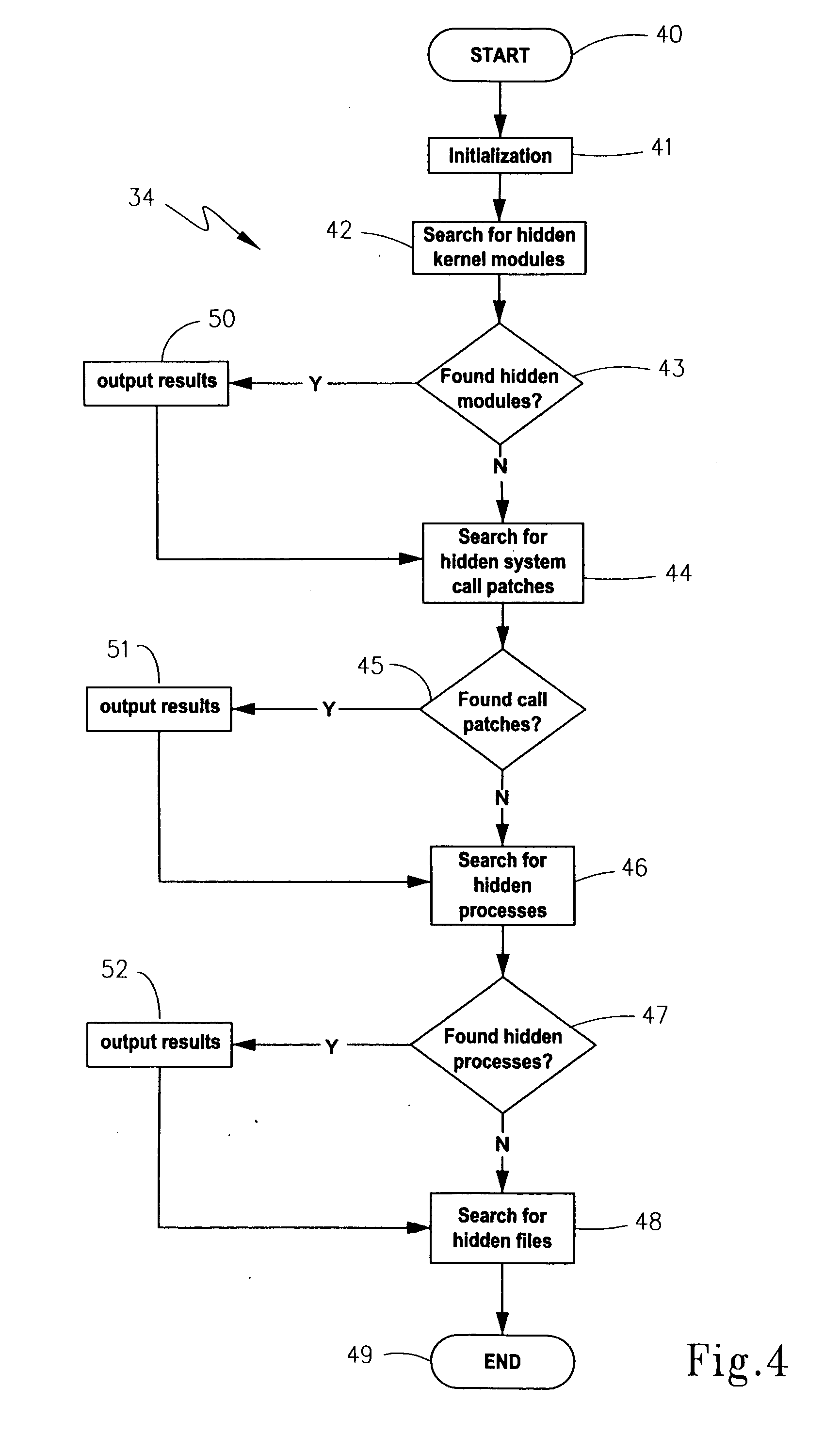
A system, computerized method and computer-readable medium are provided for the detection of an operating system exploitation, such as a rootkit install. The operating system is monitored to ascertain an occurrence of anomalous activity resulting from operating system behavior which deviates from any one of a set of pre-determined operating system parameters. Each parameter corresponds to a dynamic characteristic associated with an unexploited operating system. Output can then be generated to indicate any anomalous activity that is ascertained. The computer-readable medium may comprise a loadable kernel module for detecting hidden patches, processes, files or other kernel modules.
Owner:RING SANDRA E +1
Method and apparatus for detecting and removing kernel rootkits
ActiveUS7802300B1Image interferenceMemory loss protectionDigital data processing detailsOperational systemComputer module
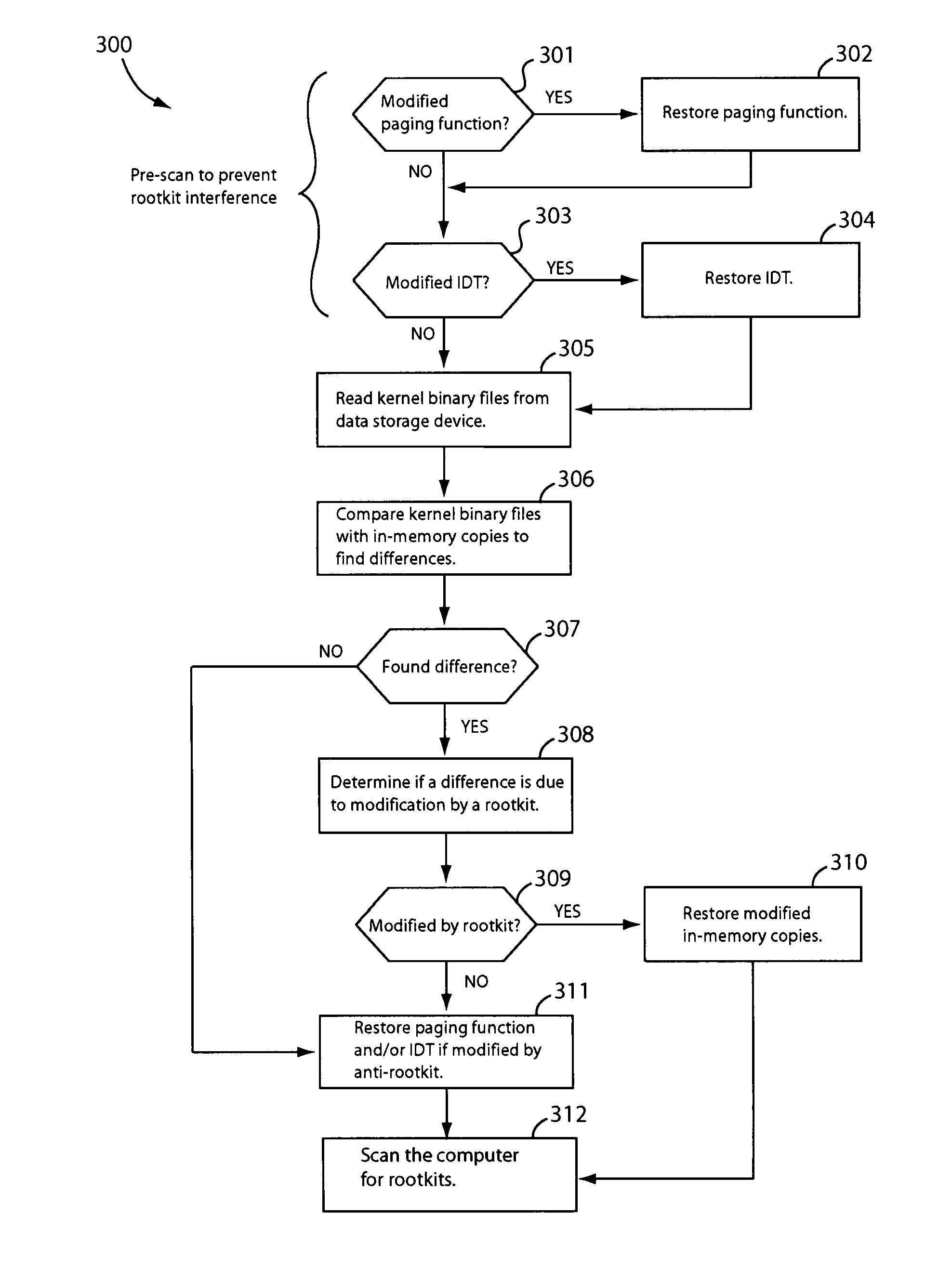
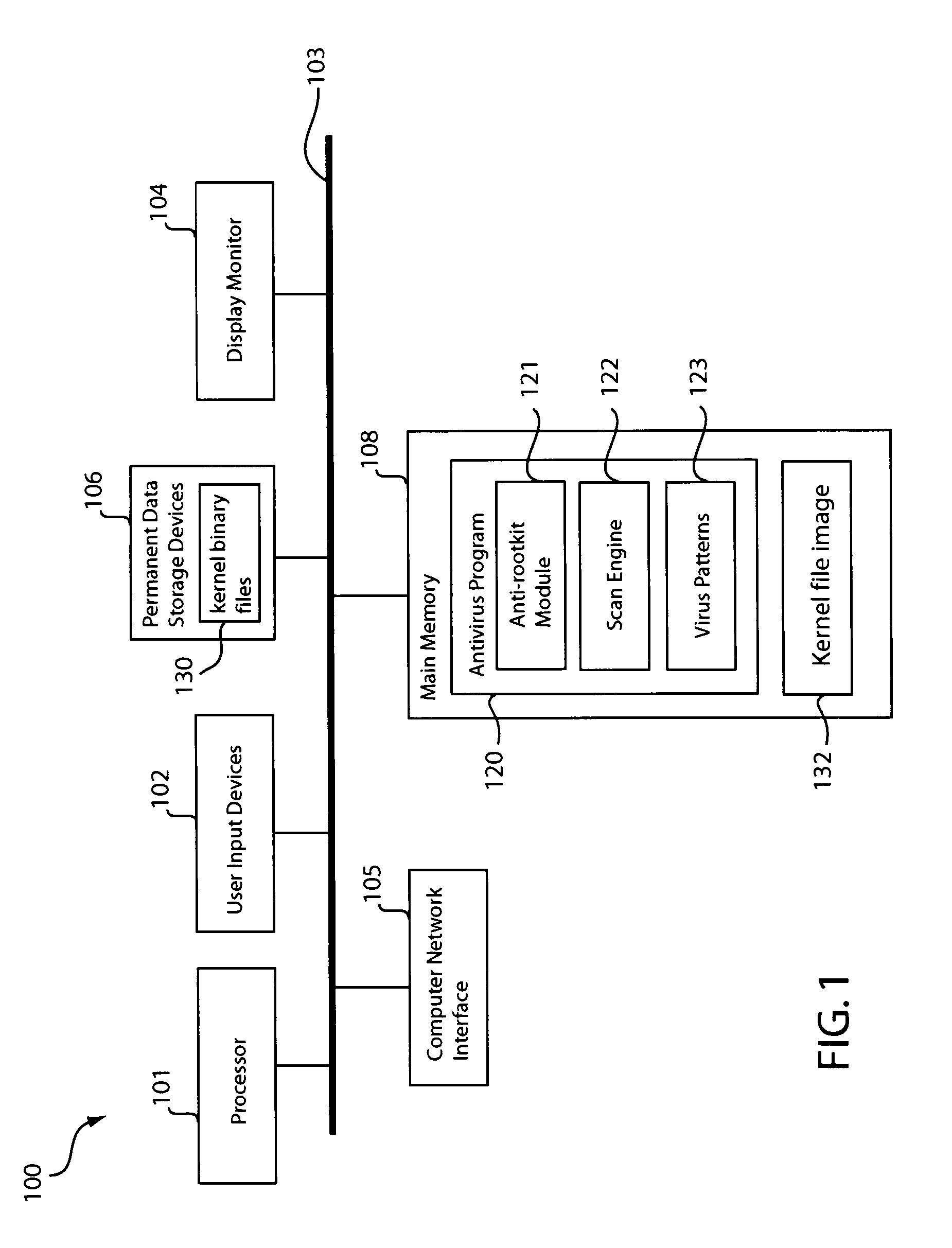
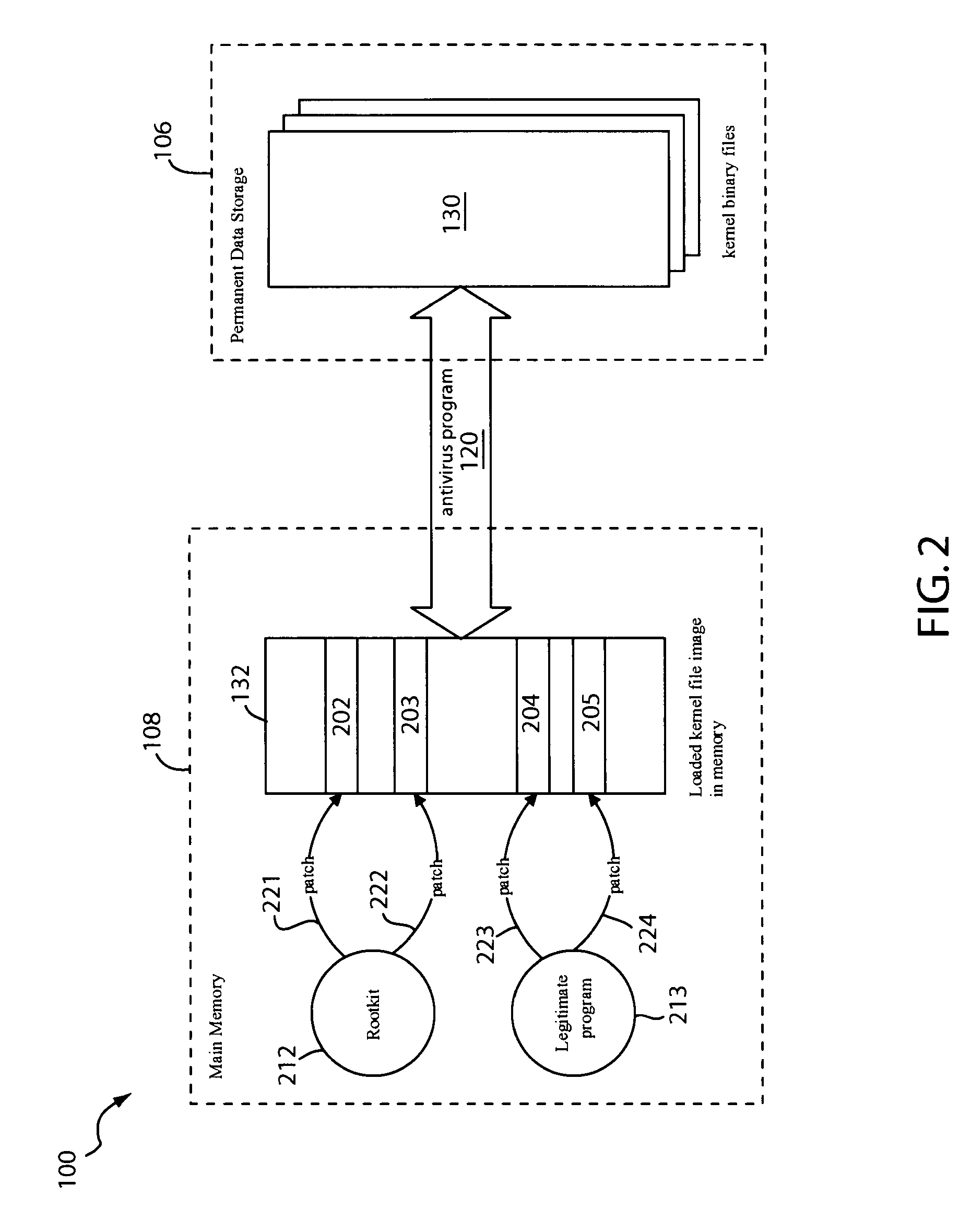
In one embodiment, an anti-rootkit module compares operating system kernel binary files to their loaded kernel file image in memory to find a difference between them. The difference may be scanned for telltale signs of rootkit modification. To prevent rootkits from interfering with memory access of the kernel file image, a pre-scan may be performed to ensure that paging functions and the interrupt dispatch table are in known good condition. If the difference is due to a rootkit modification, the kernel file image may be restored to a known good condition to disable the rootkit. A subsequent virus scan may be performed to remove remaining traces of the rootkit and other malicious codes from the computer.
Owner:TREND MICRO INC
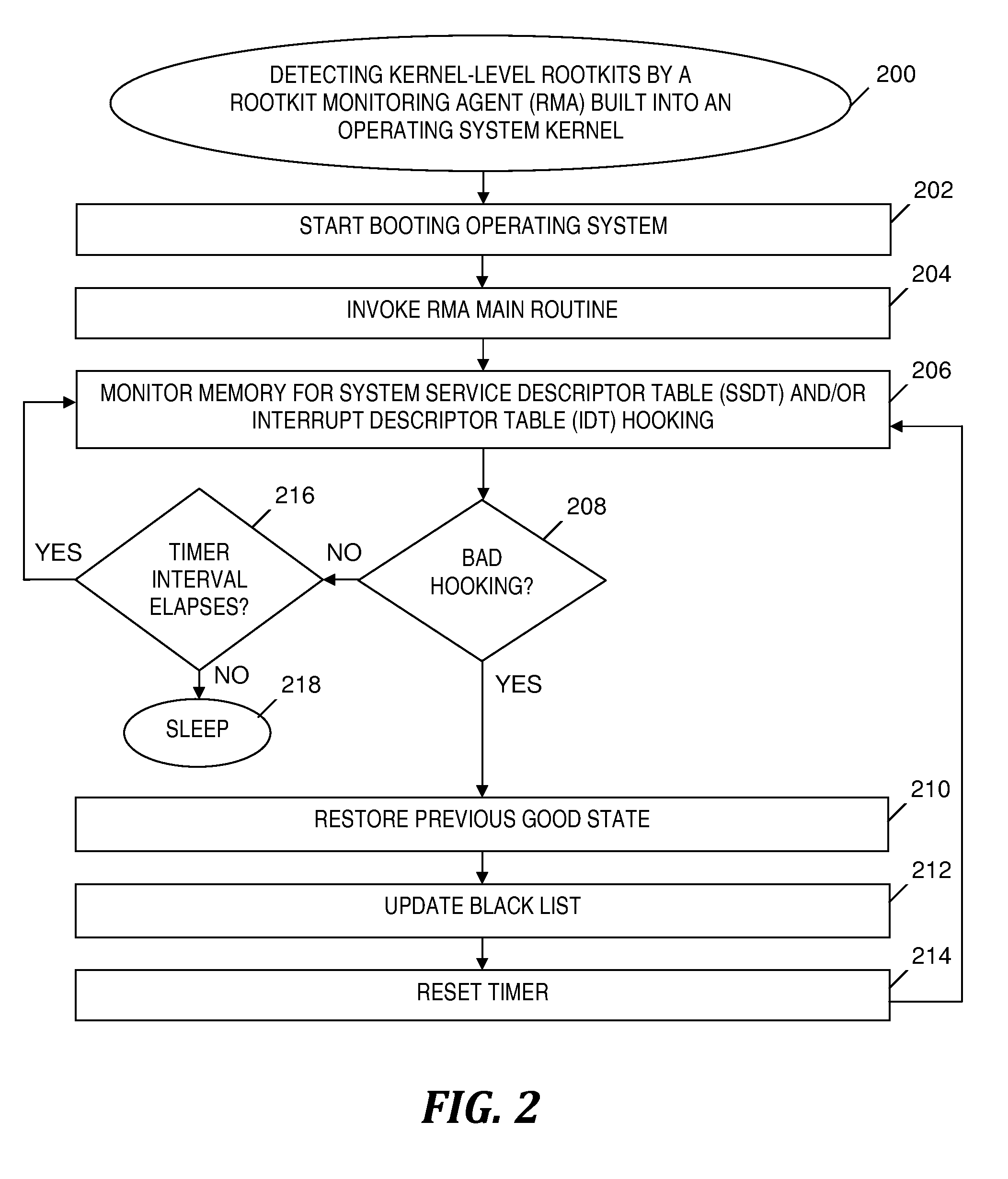
Rootkit monitoring agent built into an operating system kernel
InactiveUS20120054868A1Avoid negative effectsMemory loss protectionUnauthorized memory use protectionWhitelistRootkit
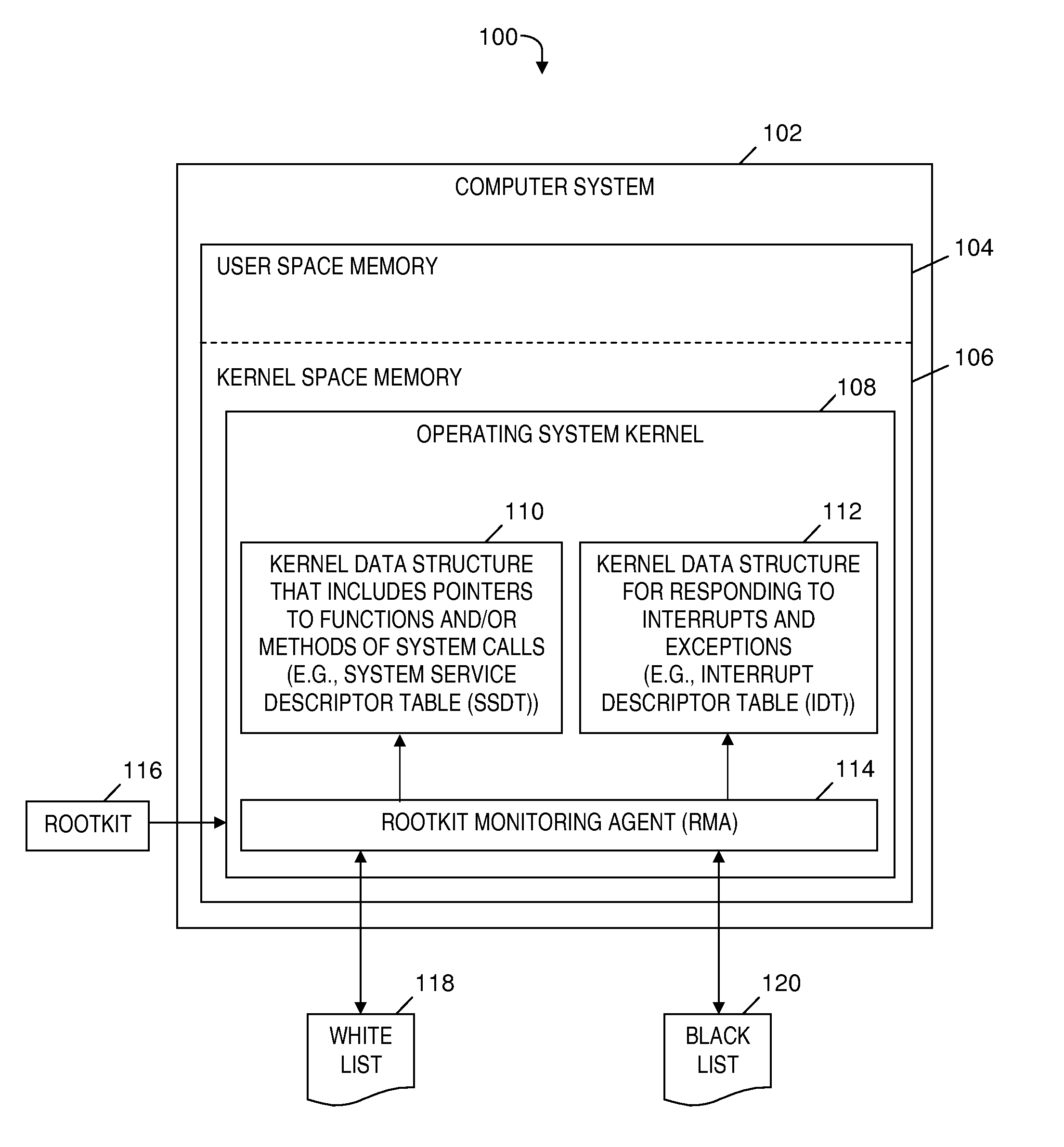
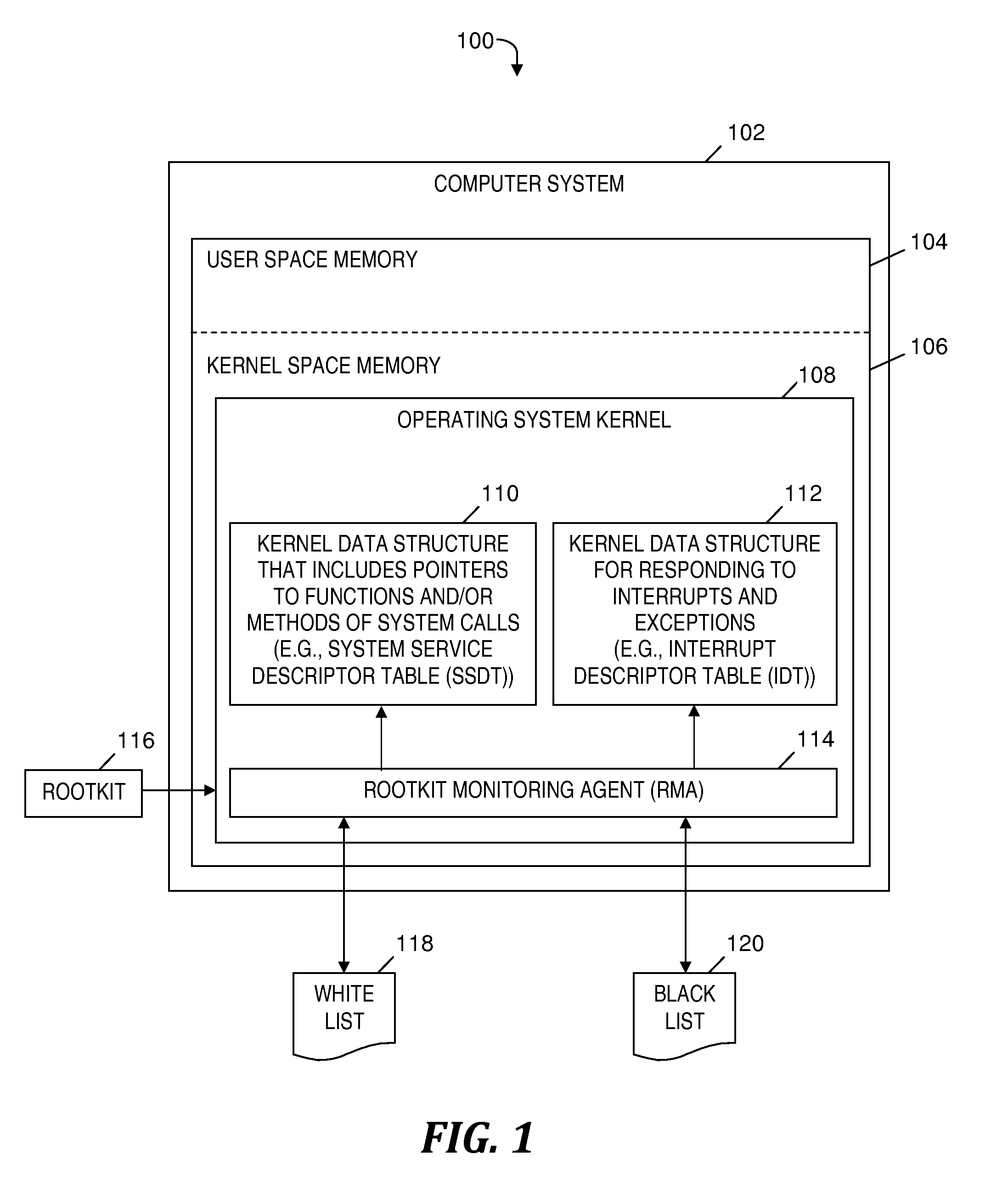
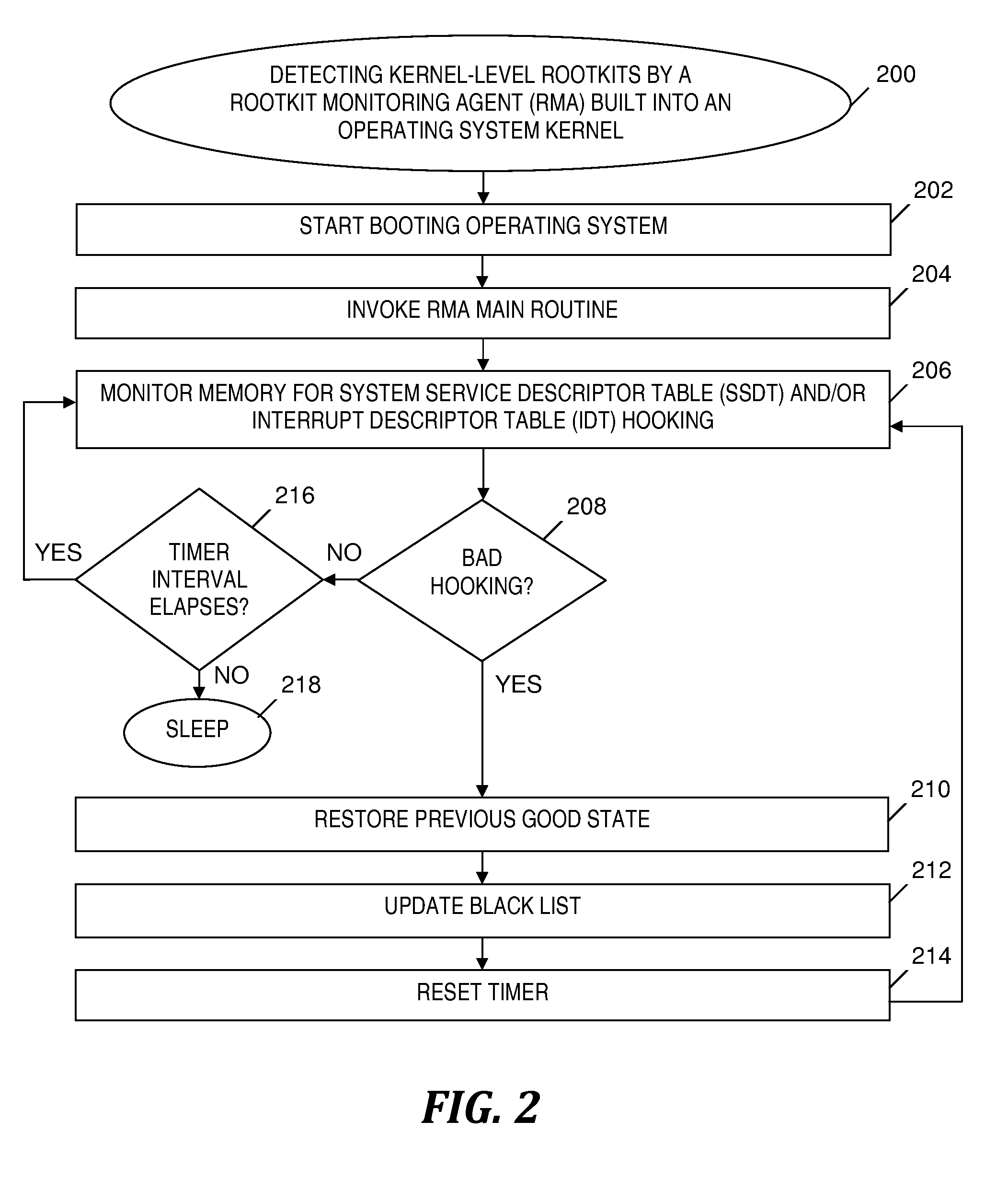
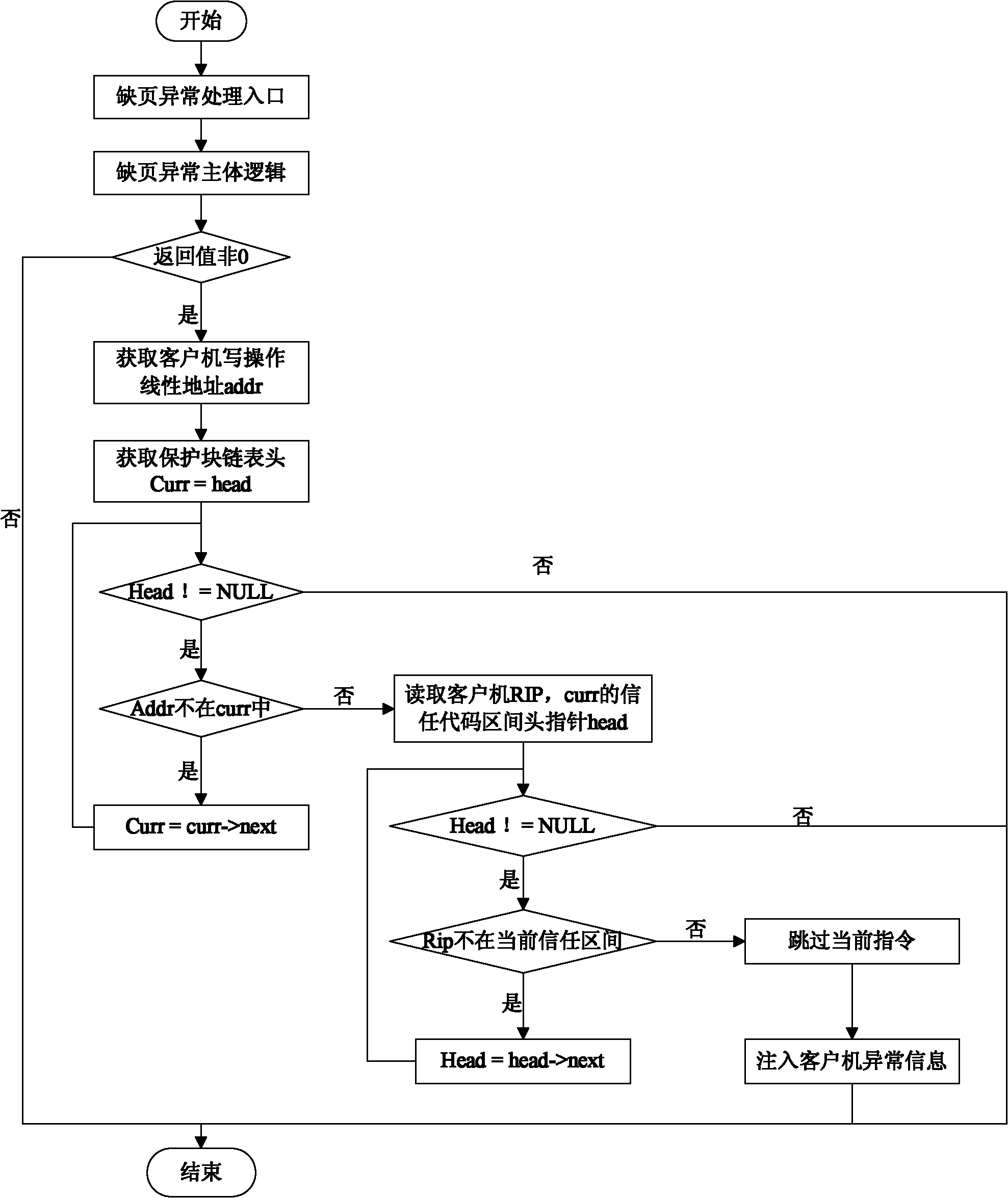
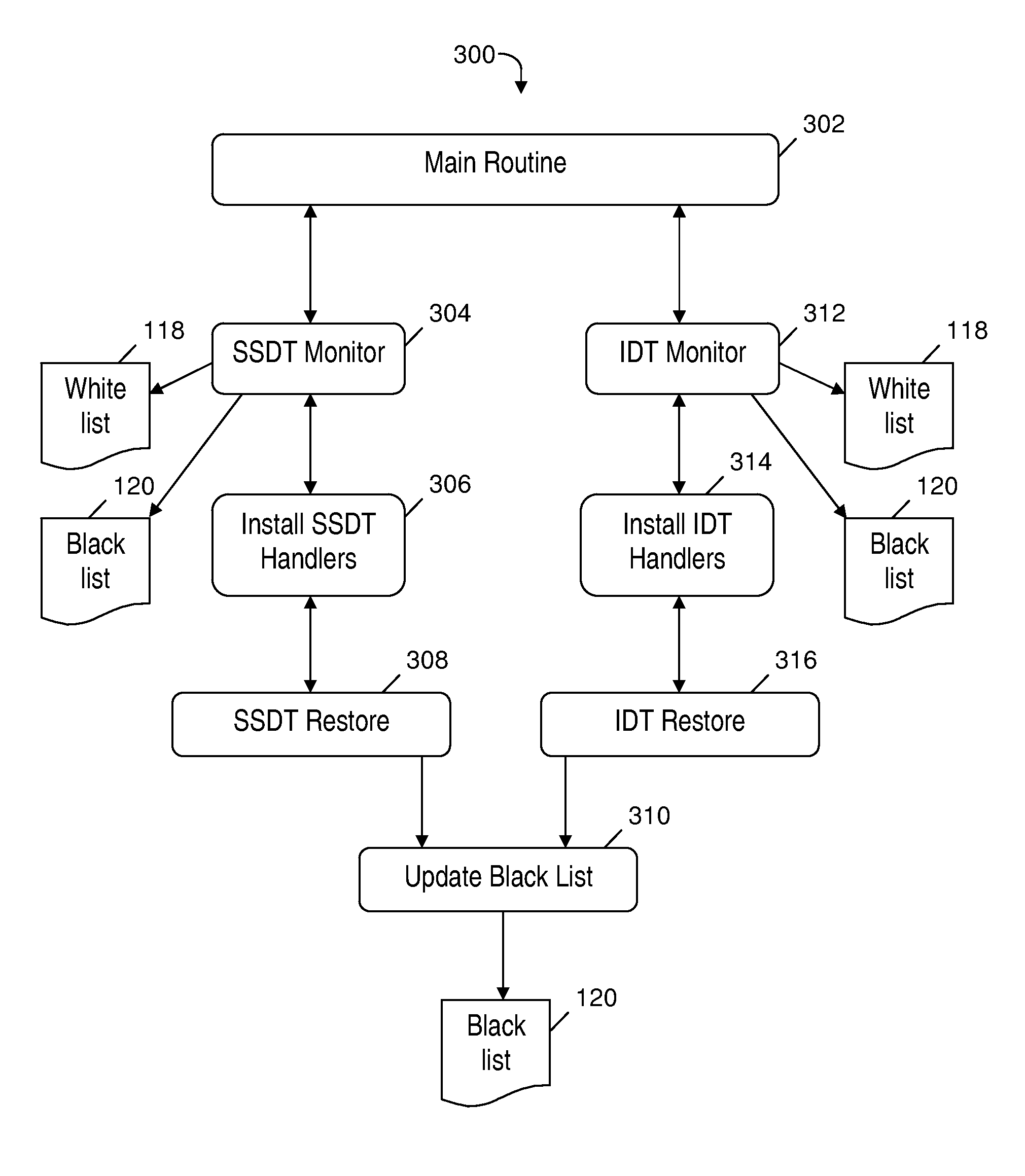
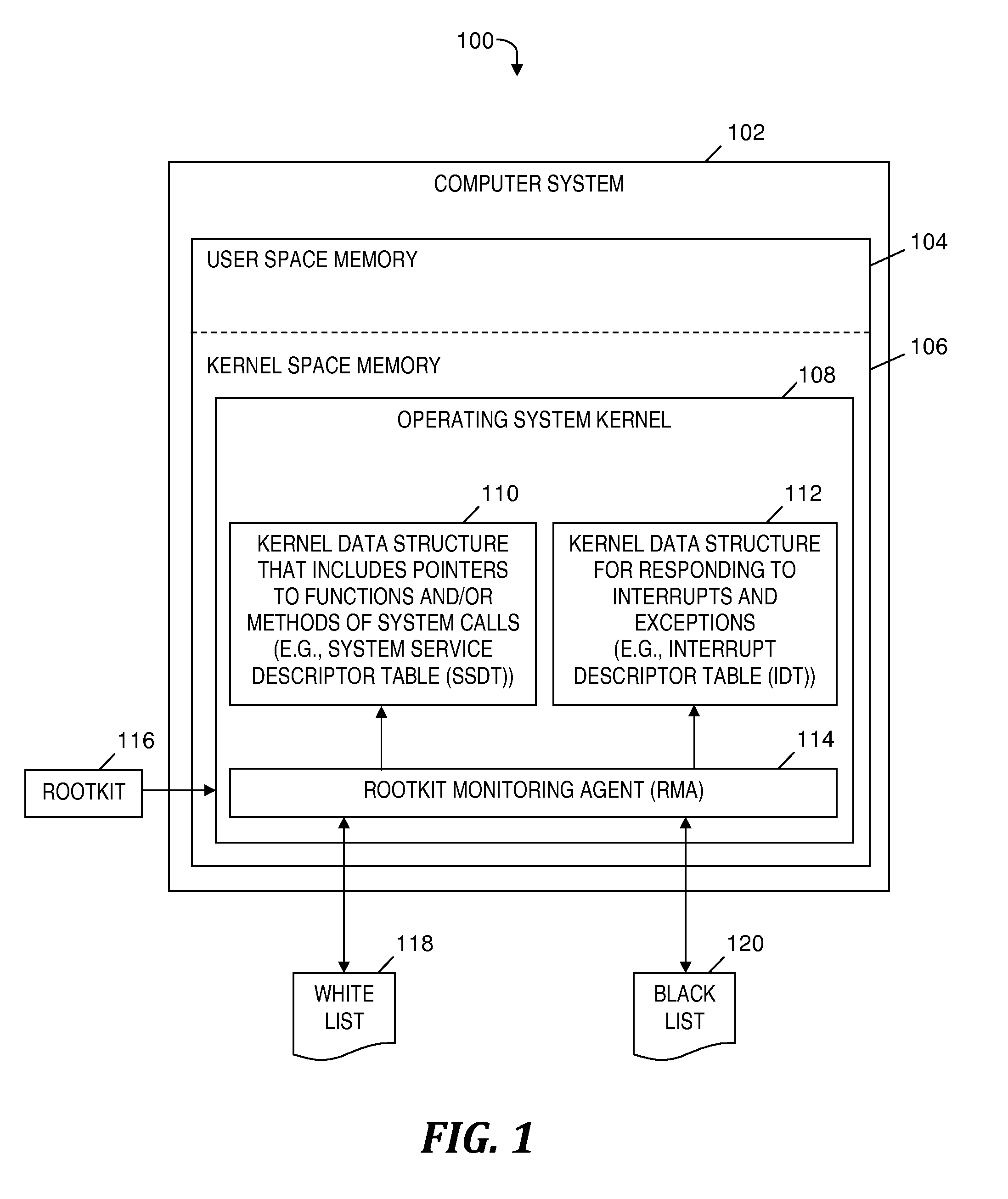
A rootkit monitoring agent (RMA) built into an operating system (OS) kernel for detecting a kernel-based rootkit and preventing subsequent effects of the rootkit. The RMA is activated as a kernel process subsequent to the OS initialization and stores a good state of OS kernel data structures including the System Service Descriptor Table (SSDT) and Interrupt Descriptor Table (IDT). The RMA monitors the SSDT and IDT and detects that a hook previously stored in the good state is changed by an installation of suspect software. The RMA determines the suspect software is a kernel-based rootkit by determining a whitelist does not indicate the changed hook. The RMA restores the changed hook to its good state. The RMA updates a blacklist to reference the changed hook.
Owner:IBM CORP
System and method for hypervisor-based security
ActiveUS20160224789A1Platform integrity maintainanceSoftware simulation/interpretation/emulationInternet privacyReference image
Aspects of the present invention include hypervisor based security using a hypervisor to monitor a VM. In embodiments of the present invention, the information gathered by the hypervisor in the monitoring is compared against a reference image to determine if there are possible rootkits present on the VM. If there are potential rootkits, the VM can be quarantined.
Owner:VMWARE INC
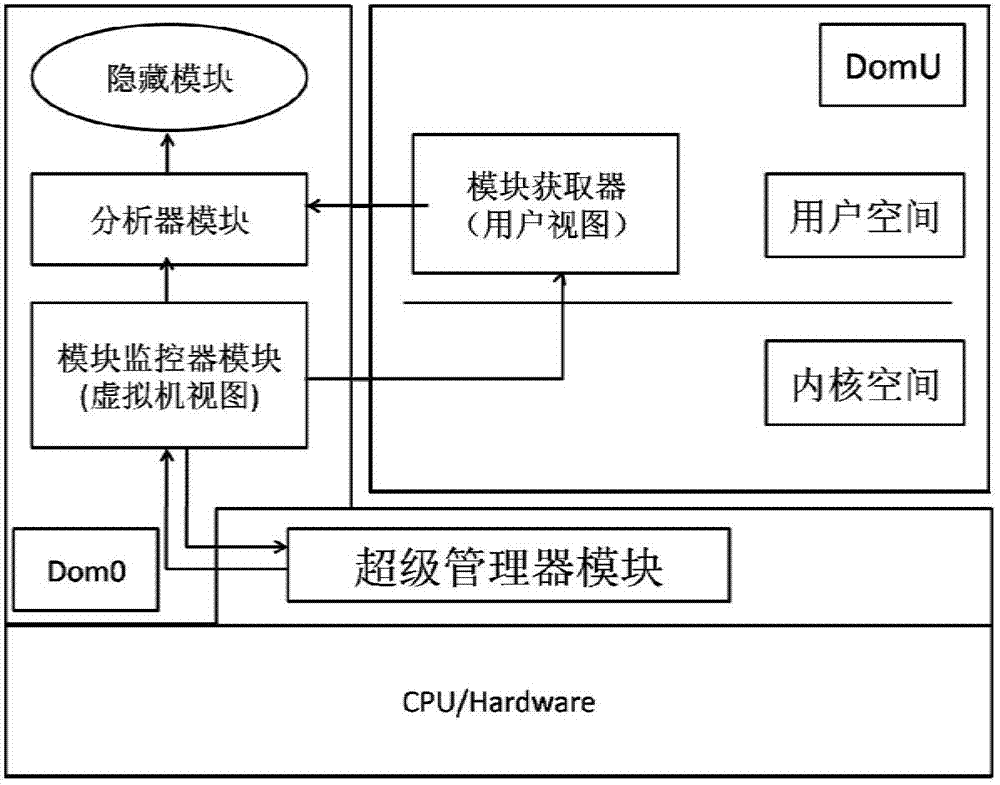
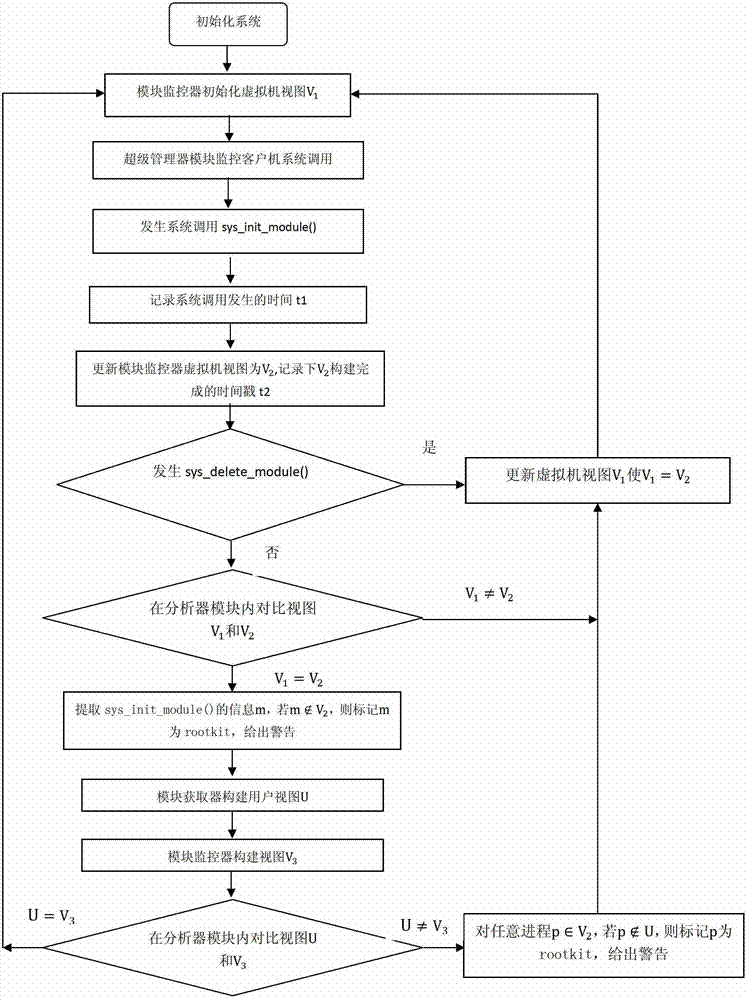
Rootkit detection mechanism and detection method based on kernel-based virtual machine
InactiveCN102194080ARealize isolation preservationEasy to detectPlatform integrity maintainanceData segmentClient machine
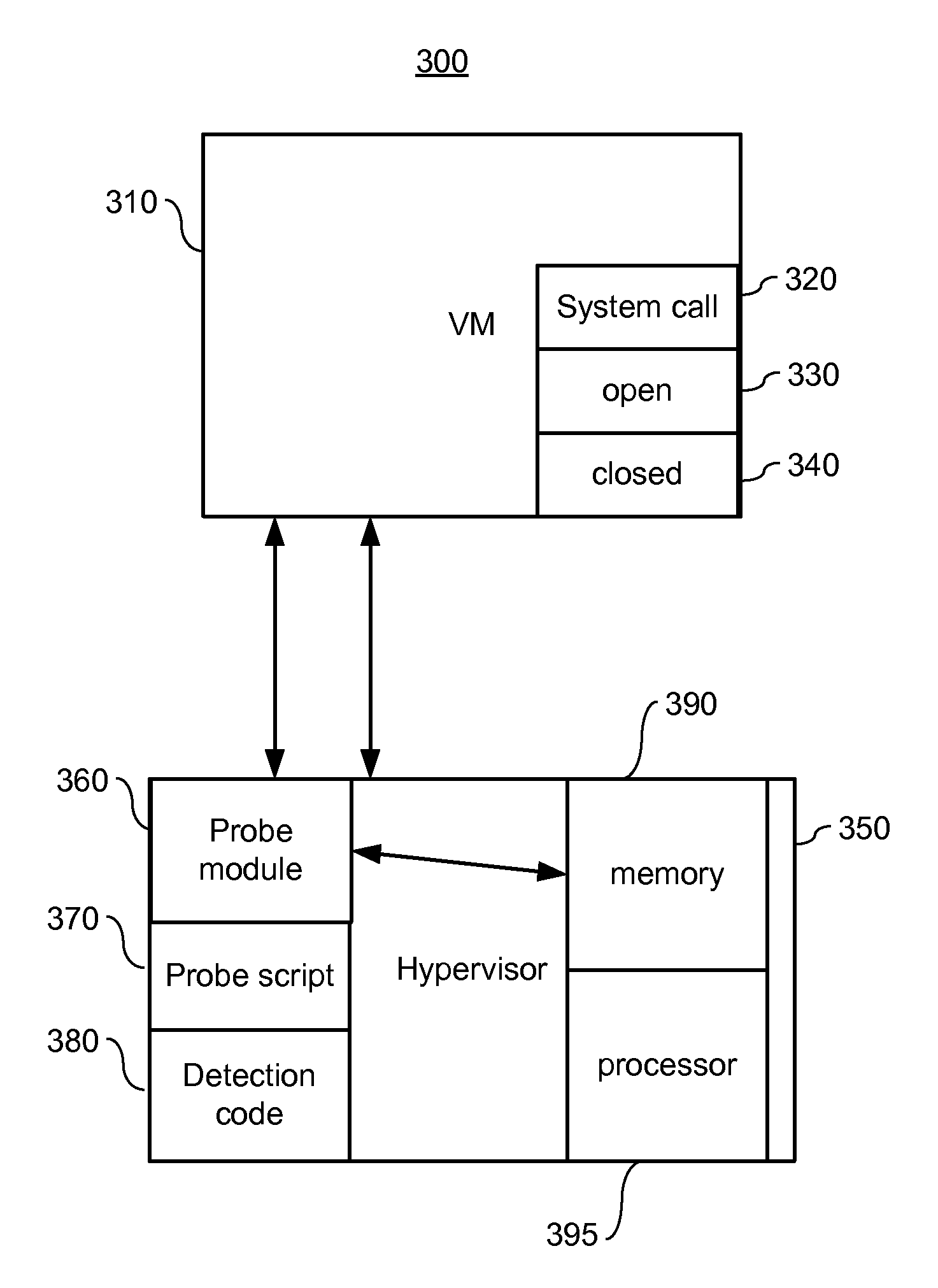
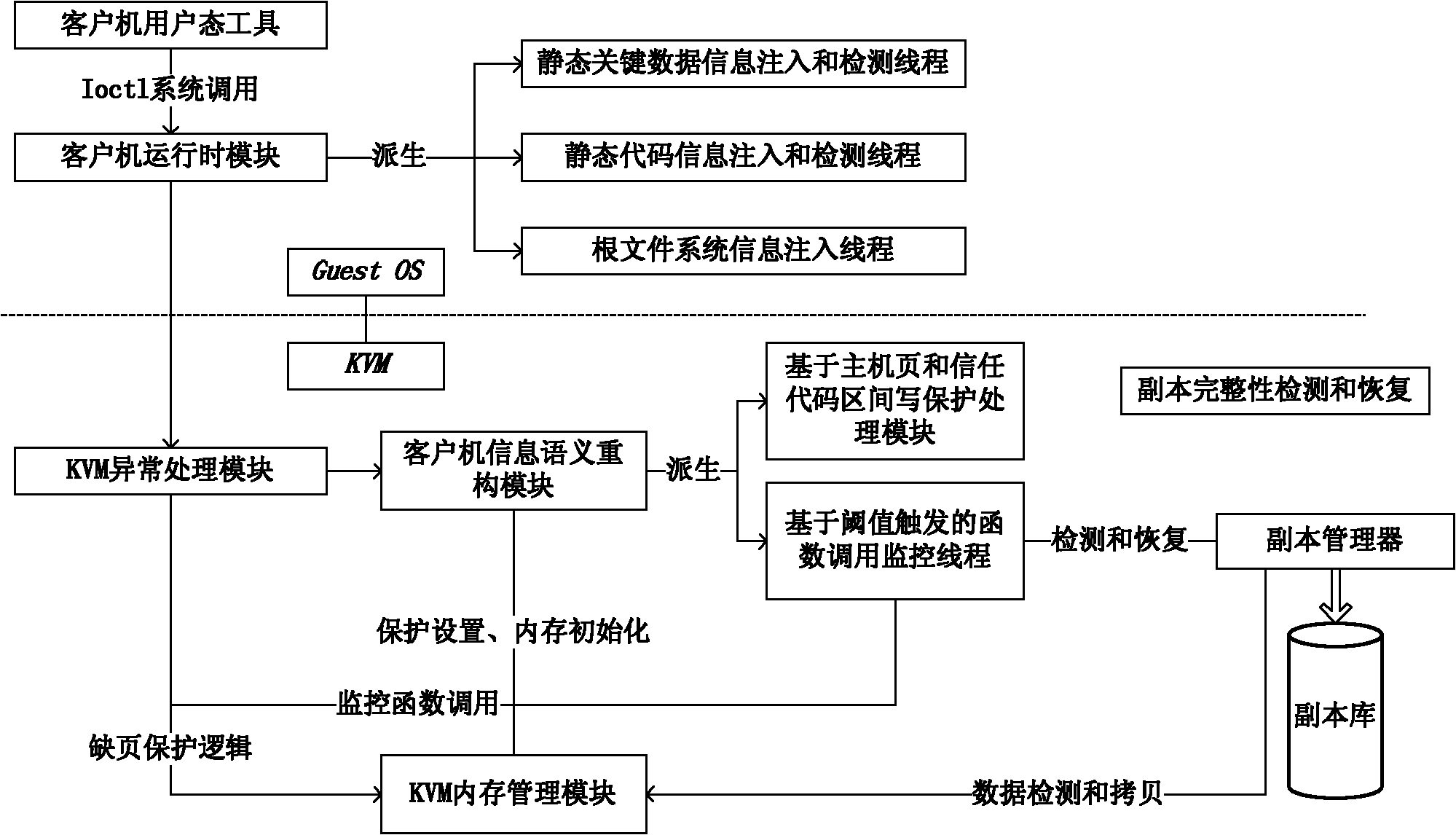
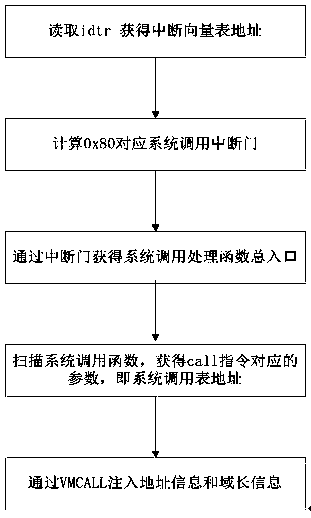
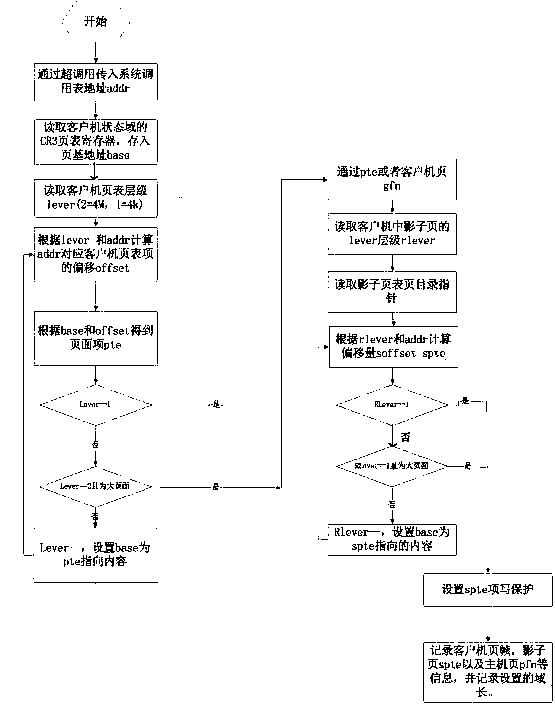
The invention provides a rootkit detection method based on a kernel-based virtual machine. By adopting the rootkit detection method, the types of objects attacked by rootkit are subjected to abstract classification into static code segment, static data segment, dynamic distribution function and heap space data, and different protection and detection mechanisms are provided specific to different types; while specific rootkit sensitive information is obtained through a runtime module operating in a client machine, information interaction between the kernel-based virtual machine and the client machine is realized by adding a semantic processing pathway, and by extending a corresponding page-fault exception handler and a vmcall active trap-in mechanism, the normal execution of the client machine is guaranteed under the rootkit detection mechanism. The rootkit detection mechanism and detection method, provided by the invention, can be used for effectively preventing the attack specific to static codes and data segments, and realizing isolated storage, detection and recovery of dynamic information at very low cost under a secure environment.
Owner:XI AN JIAOTONG UNIV +1
Rootkit monitoring agent built into an operating system kernel
InactiveUS8539584B2Avoid negative effectsMemory loss protectionUnauthorized memory use protectionOperational systemWhitelist
A rootkit monitoring agent (RMA) built into an operating system (OS) kernel for detecting a kernel-based rootkit and preventing subsequent effects of the rootkit. The RMA is activated as a kernel process subsequent to the OS initialization and stores a good state of OS kernel data structures including the System Service Descriptor Table (SSDT) and Interrupt Descriptor Table (IDT). The RMA monitors the SSDT and IDT and detects that a hook previously stored in the good state is changed by an installation of suspect software. The RMA determines the suspect software is a kernel-based rootkit by determining a whitelist does not indicate the changed hook. The RMA restores the changed hook to its good state. The RMA updates a blacklist to reference the changed hook.
Owner:INT BUSINESS MASCH CORP
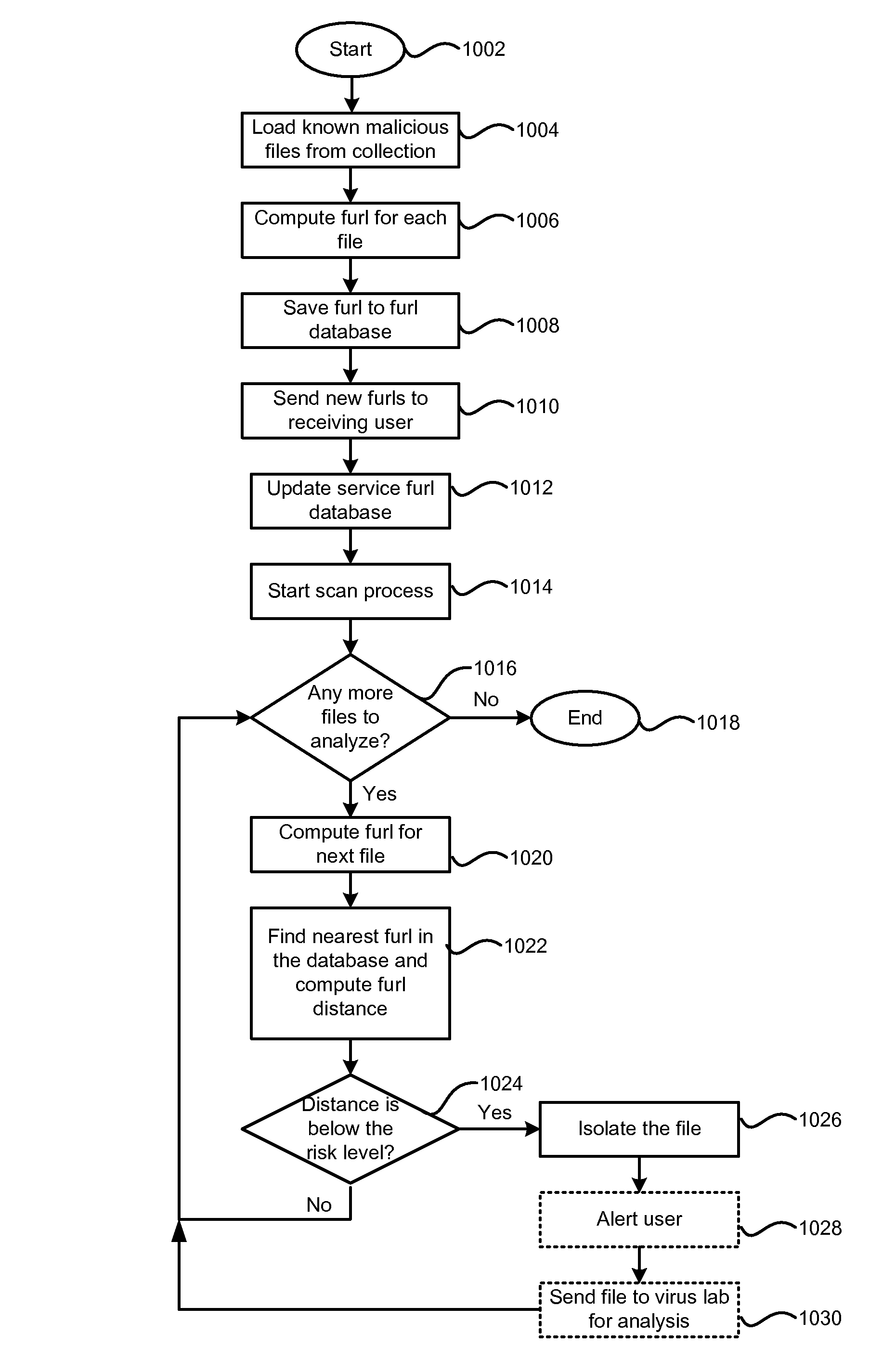
Rapid heuristic method and system for recognition of similarity between malware variants
ActiveUS8250655B1Memory loss protectionUnauthorized memory use protectionPattern recognitionCorrelation coefficient
A system, method and computer program product for identifying new variants of certain data objects, for example, malware-carrying files, including (a) dividing a file into a plurality of N pieces; (b) for each of the N pieces, calculating an average value of bytes in that piece; (c) generating a furl of length N elements, wherein each element of the furl has a value that represents the average value of its corresponding file piece; (d) calculating the distance between the furl and a second furl that corresponds to the file known to contain malware; and (e) based on the distance, determining whether the file is likely to carry a malicious object. The malicious object is, for example, a trojan, a virus, a rootkit or a worm. The second furl can be selected by comparing file size, and taking into account whether the file is packed. The furl elements are bytes, words, half words, etc. The distance is calculated based on, e.g., the sum of absolute value differences, root mean square difference and a correlation coefficient. The average value is an arithmetic average and a geometric average.
Owner:AO KASPERSKY LAB
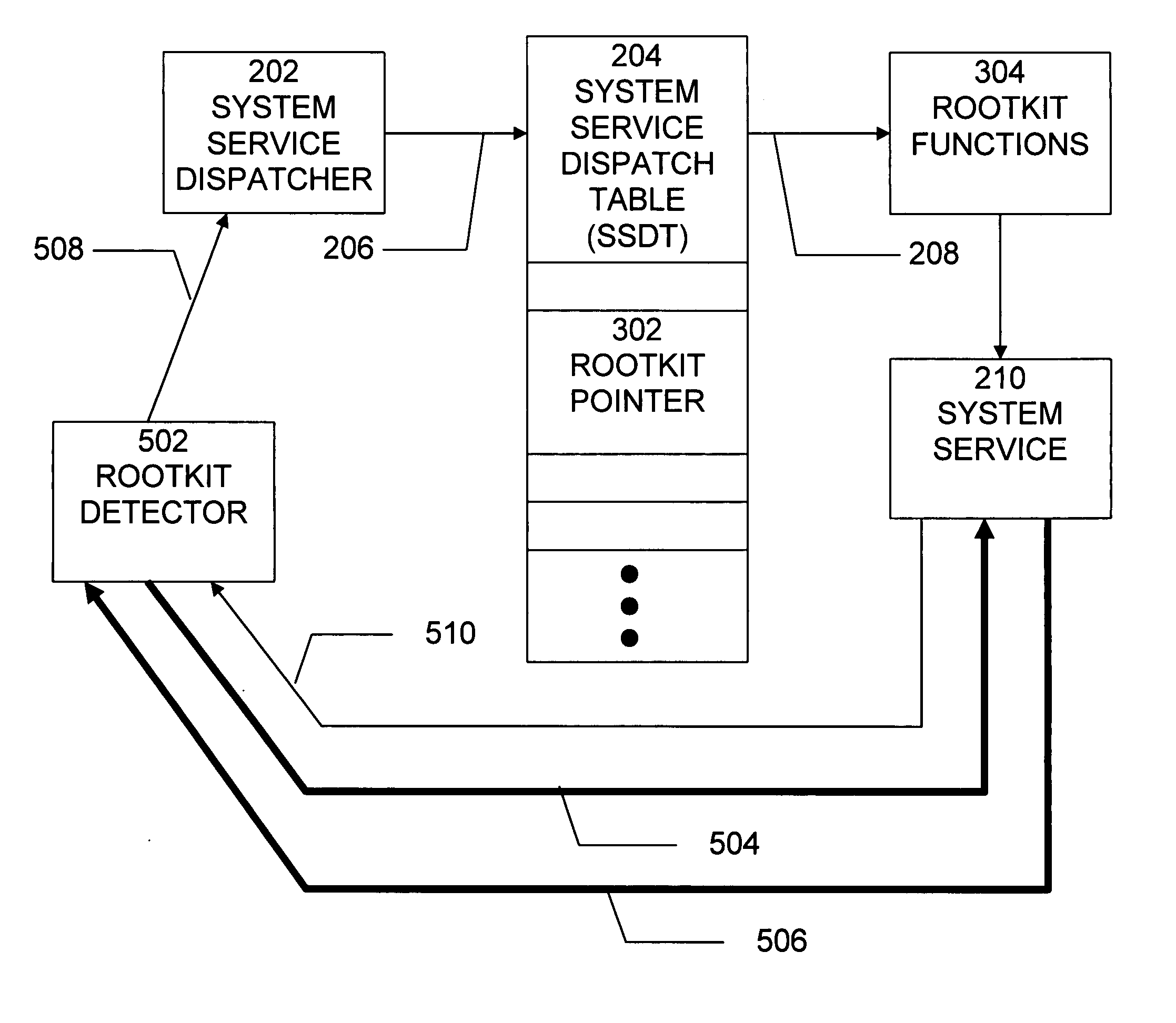
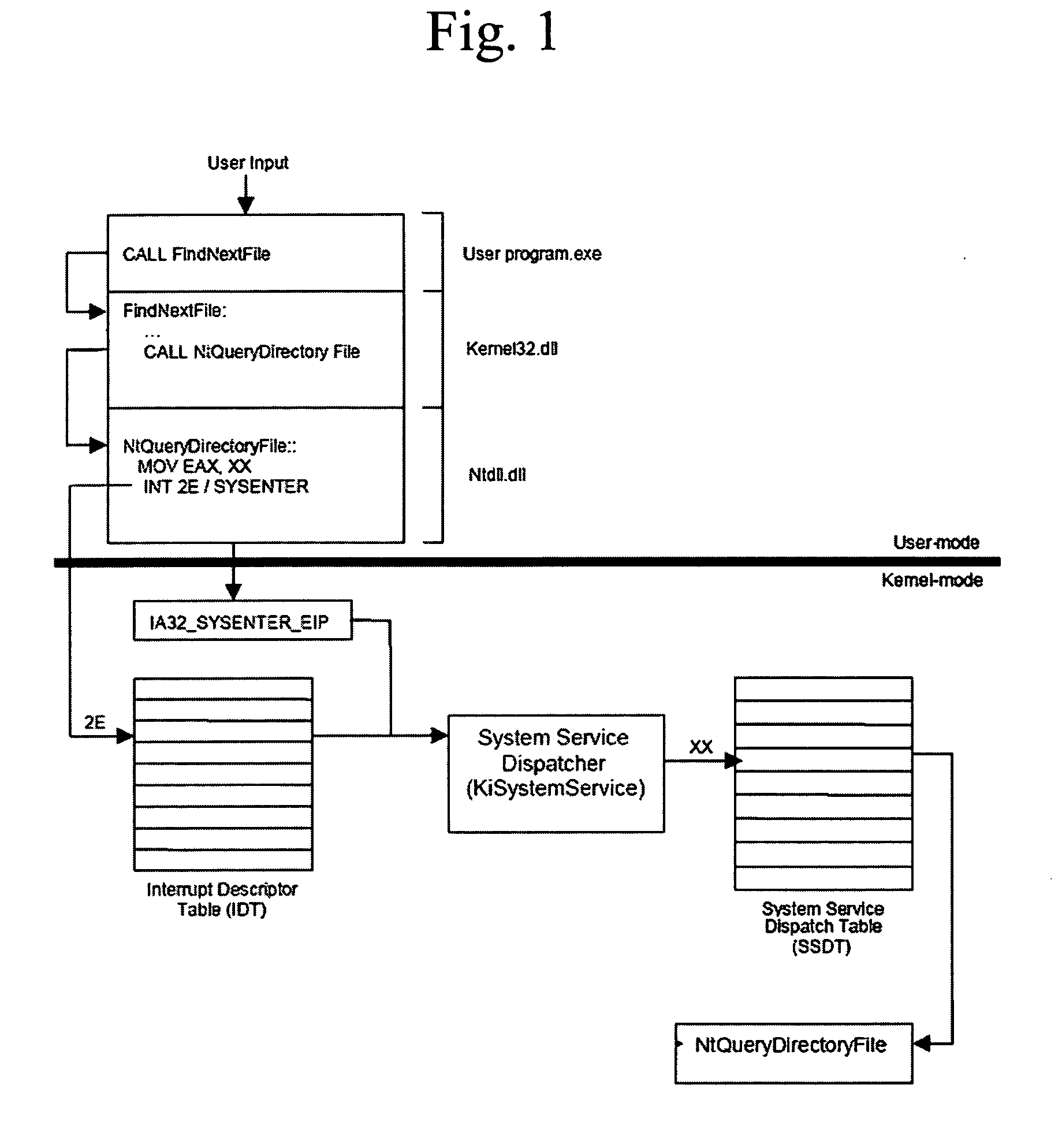
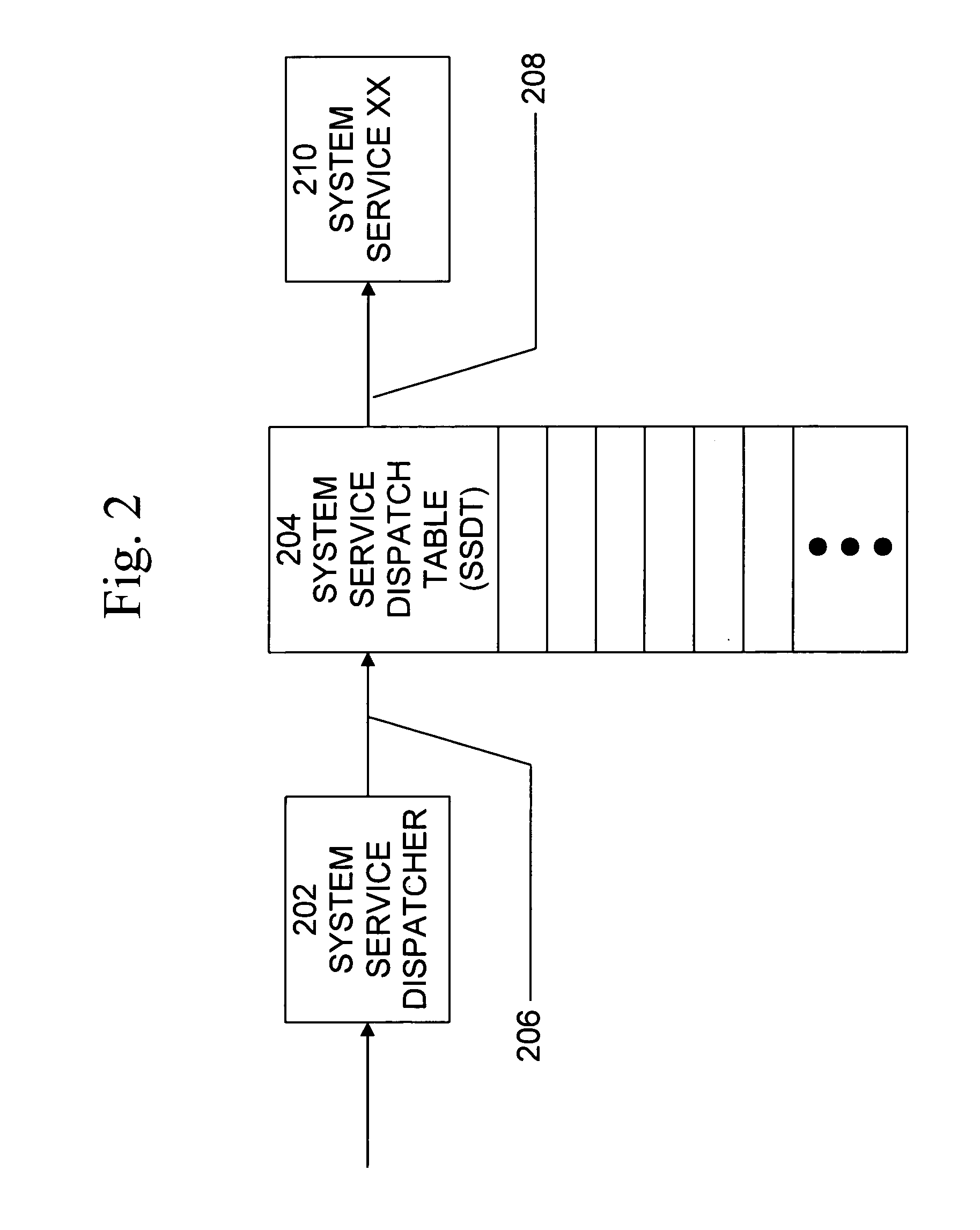
Method and system for detecting windows rootkit that modifies the kernel mode system service dispatch table
ActiveUS20080127344A1Memory loss protectionError detection/correctionSoftware engineeringApplication software
A method, system, and computer program product for detecting a kernel-mode rootkit that hooks the System Service Dispatch Table (SSDT) is secure, avoids false positives, and does not disable security applications. A method for detecting a rootkit comprises the steps of calling a function that accesses a system service directly, receiving results from calling the function that accesses the system service directly, calling a function that accesses the system service indirectly, receiving results from calling the function that accesses the system service indirectly, and comparing the received results from calling the function that accesses the system service directly and the received results from calling the function that accesses the system service indirectly to determine presence of a rootkit.
Owner:MCAFEE LLC
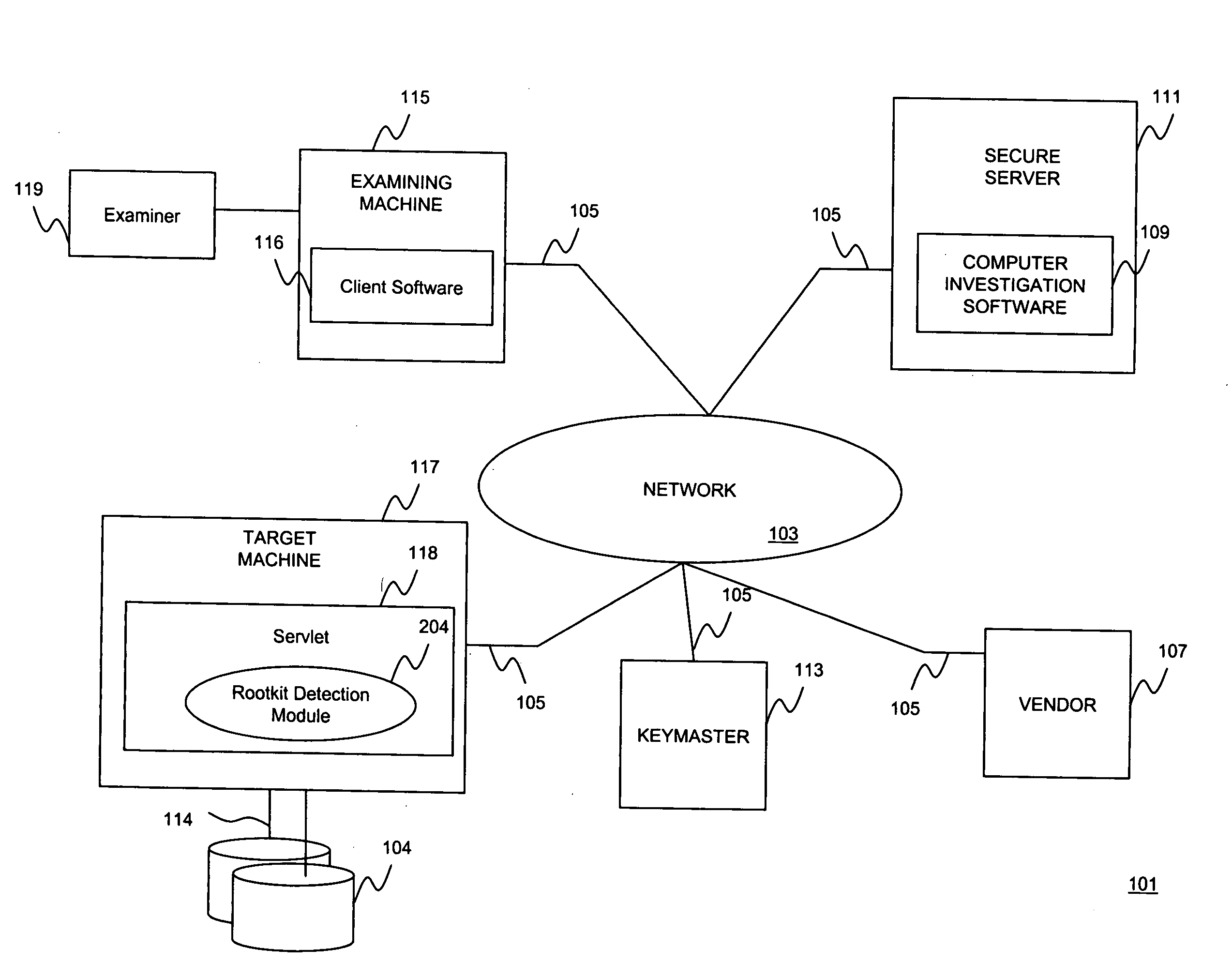
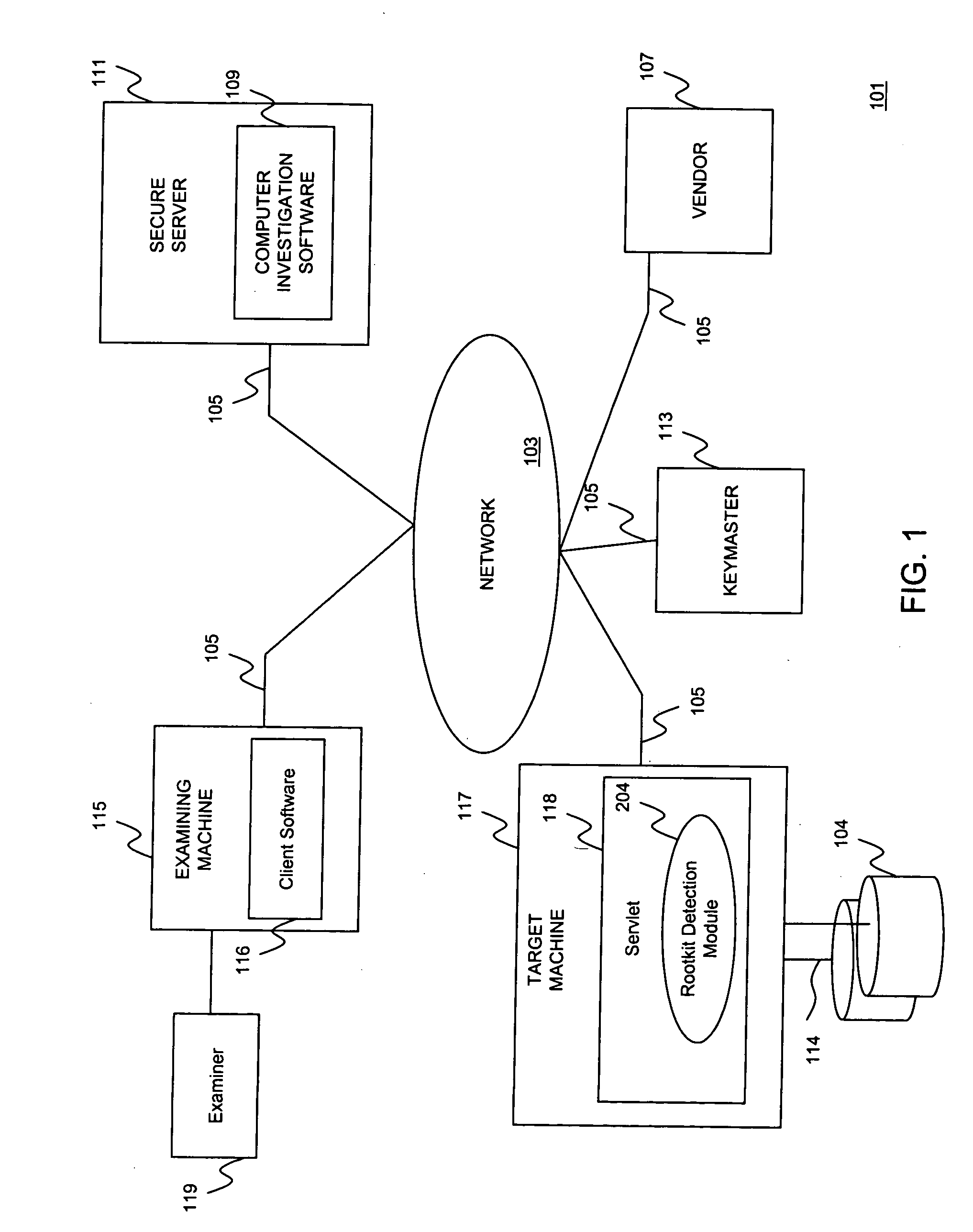
Rootkit detection system and method
InactiveUS20080016571A1Memory loss protectionUser identity/authority verificationOperational systemRootkit
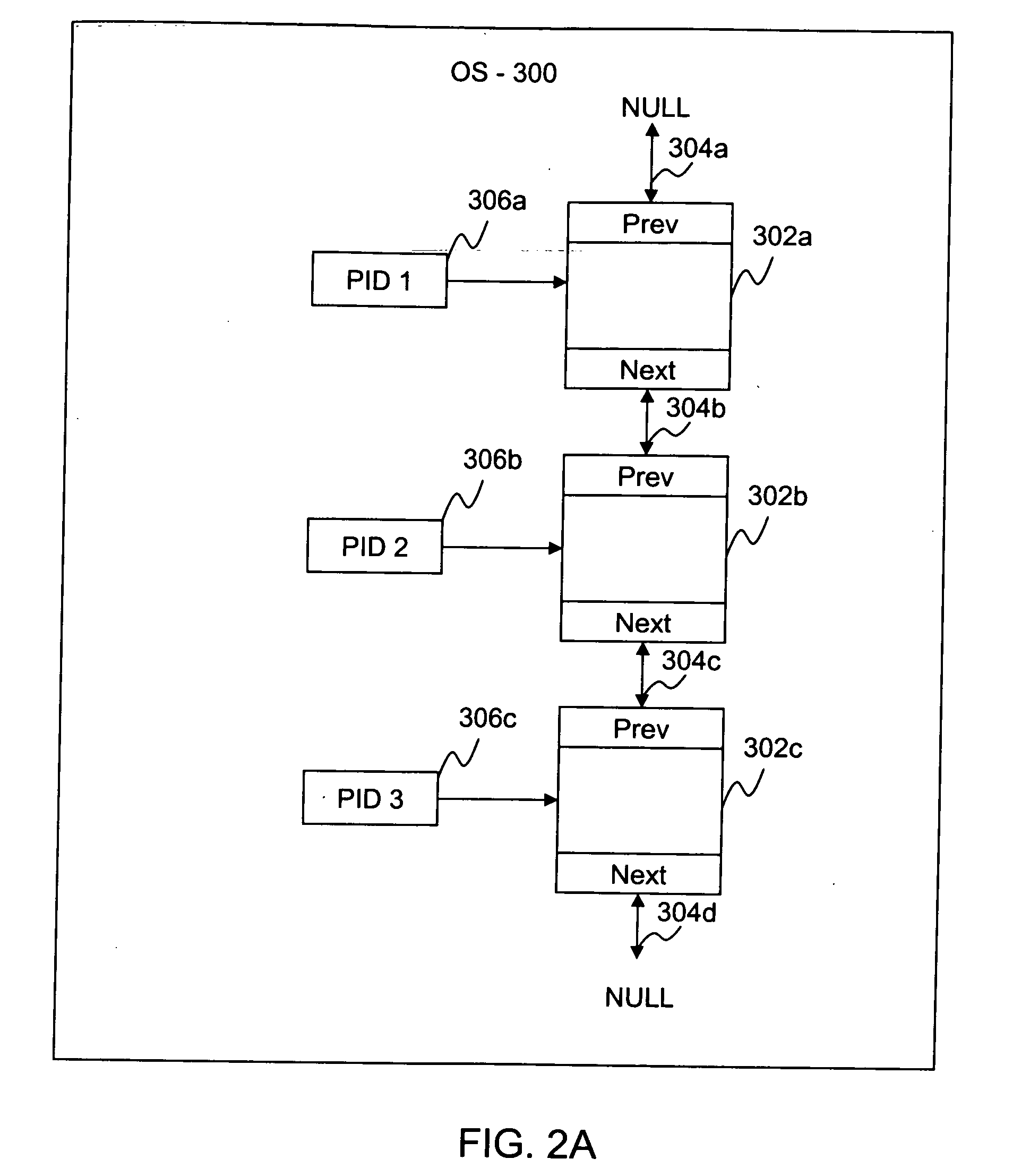
A system and method is provided for detecting operating system compromises due to inconspicuous rootkit installations. A rootkit detection module identifies hidden processes running on top of the operating system. Processes operating in an uncompromised environment expose their process identifiers (PIDs) to the operating system. Thus, if a hidden process is discovered, this is an indication that a rootkit program may have compromised the operating system. The rootkit detection mechanism according embodiments of the present invention detect hidden processes by identifying a range of all possible PIDs and identifying PIDs that are not being reported by the operating system. Specifically, the rootkit detection mechanism according to one embodiment of the invention tests each PID in the range via lower level function calls that do not rely on published operating system APIs, and examines the memory location referenced by the PID for determining if a hidden process exists.
Owner:GUIDANCE SOFTWARE
Kernel level rootkit detection method and system in Andriod system
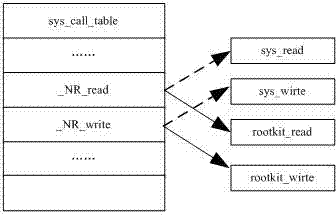
InactiveCN104598823AImprove securityImprove reliabilityPlatform integrity maintainanceKernel levelSystem call
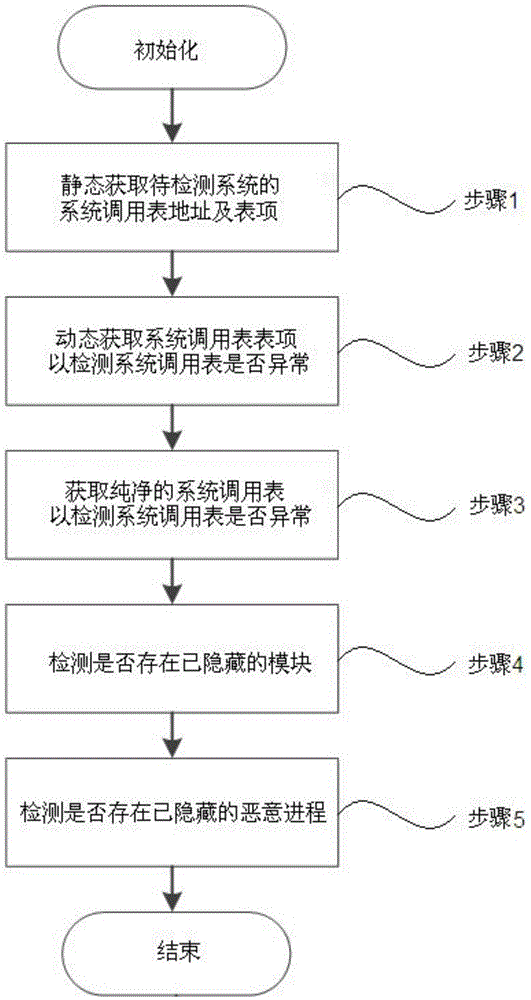
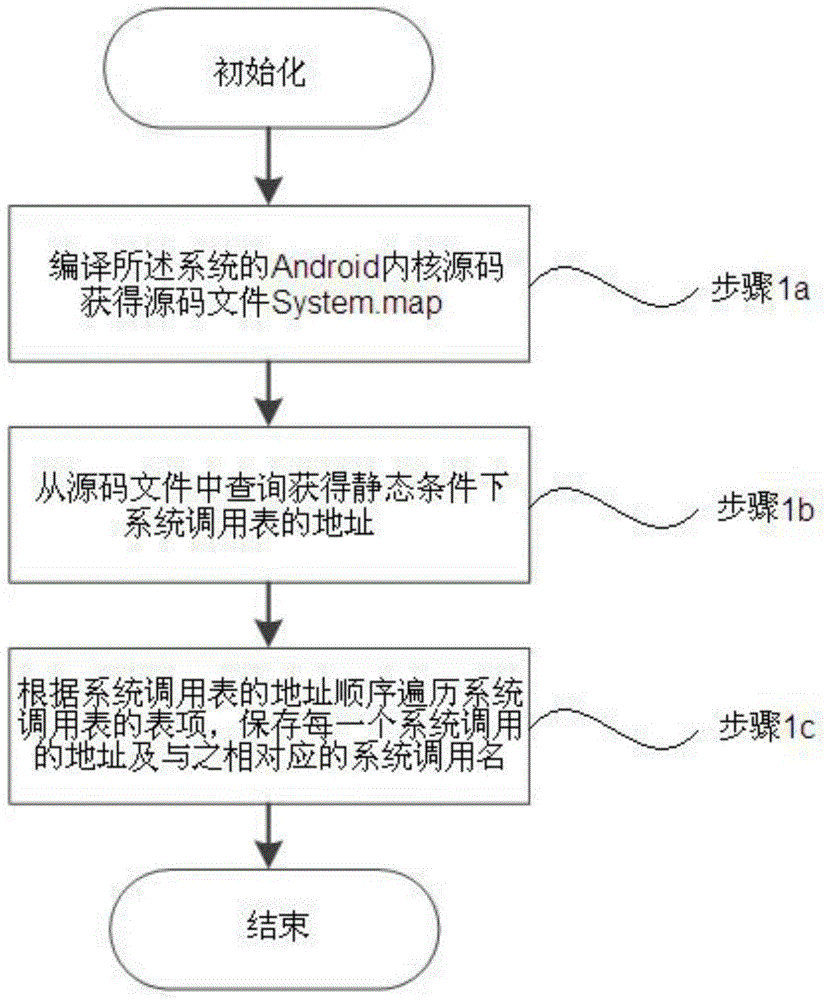
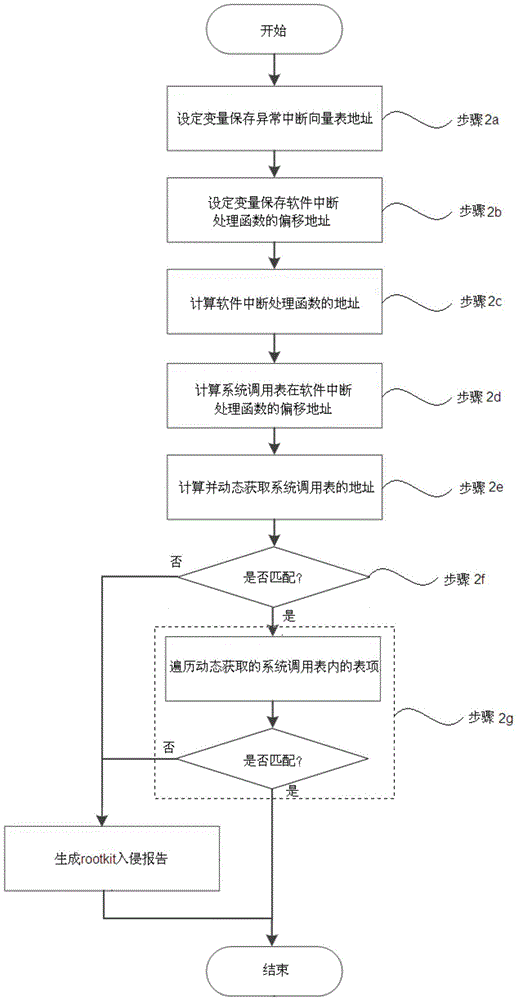
The invention discloses a kernel level rootkit detection method in an Andriod system, comprising the following steps of statically obtaining an address and a table entry of a system call table; entering into a kernel mode from a user mode; dynamically obtaining the address of the system call table; if the addresses are not matched, then generating an intrusion reporting; obtaining a pure address of the system call table; if the system call table is not matched, then generating the intrusion reporting and restoring; intercepting a module name called by a module loading function, retrieving the dynamically loaded module name, if the name is not matched, then deleting the hidden module, and generating the intrusion reporting; obtaining all the progress information actually loaded by a system to be detected, and obtaining all the progress information by using a command query, if the progress information is not matched, then eliminating the malicious processes and generating the intrusion reporting. The invention also discloses a rootkit detection system, which can detect the intruded rootkit and delete the rootkit with an illegal act, so as to improve the safety and reliability of the system.
Owner:EAST CHINA NORMAL UNIV
Detecting and removing rootkits from within an infected computing system
InactiveUS7631357B1Efficient and quick removalMemory loss protectionError detection/correctionFile systemRootkit
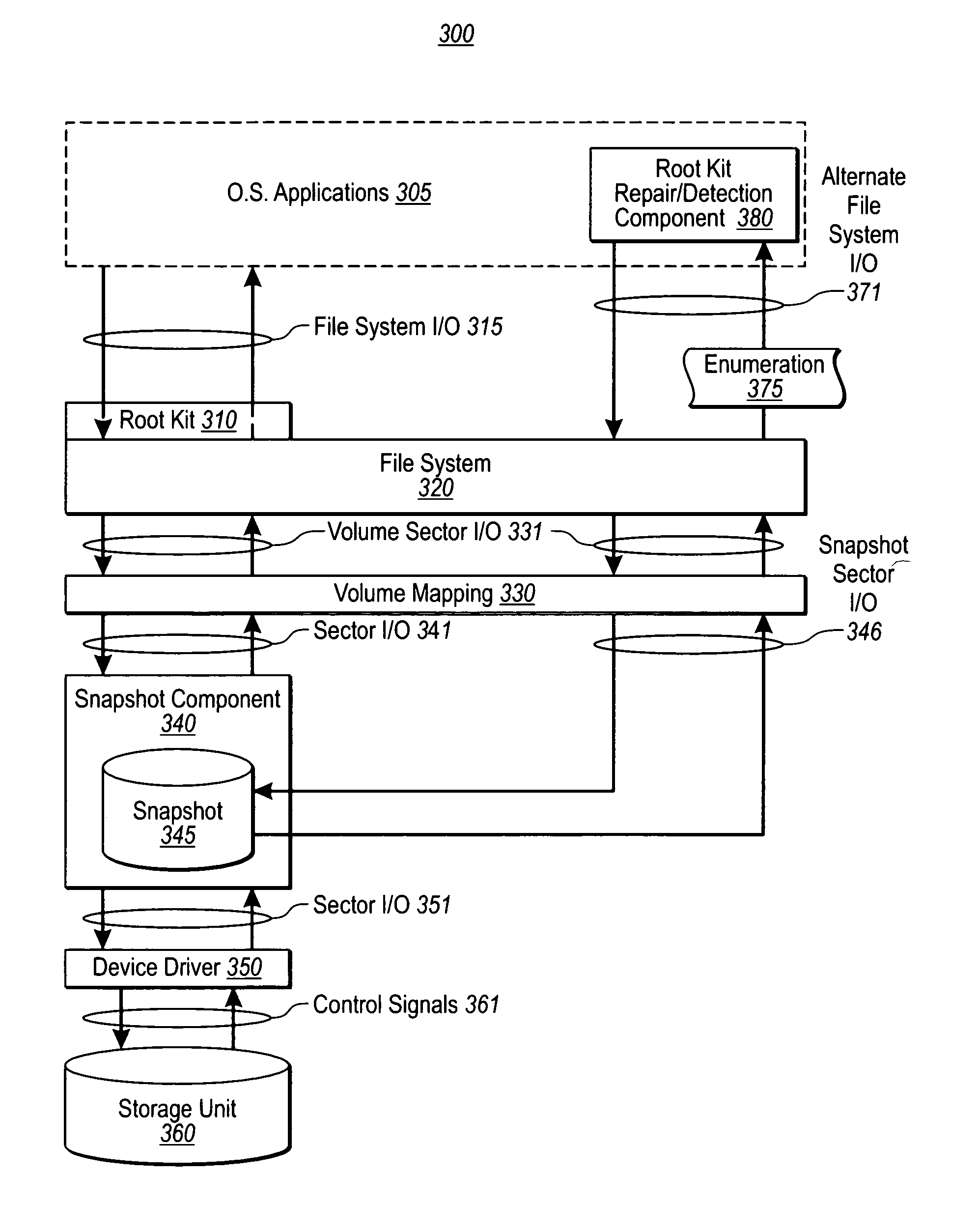
A computing system configured to detect and / or remove a rootkit. For detection, a snapshot component takes a snapshot of a storage unit. A rootkit detection component accesses an enumeration of individual files stored on the storage unit using an alternative file system I / O to detect the presence of a rootkit. For removal, the location of a rootkit is identified and a computing system shutdown is initiated. A snapshot component pauses the shutdown operation prior to the completion of the shut down and takes a snapshot of a file storage unit. A rootkit repair component accesses the identified location of the portion of the file storage unit containing the rootkit and modifies the portion of the snapshot of the file storage unit so as remove the rootkit.
Owner:CA TECH INC
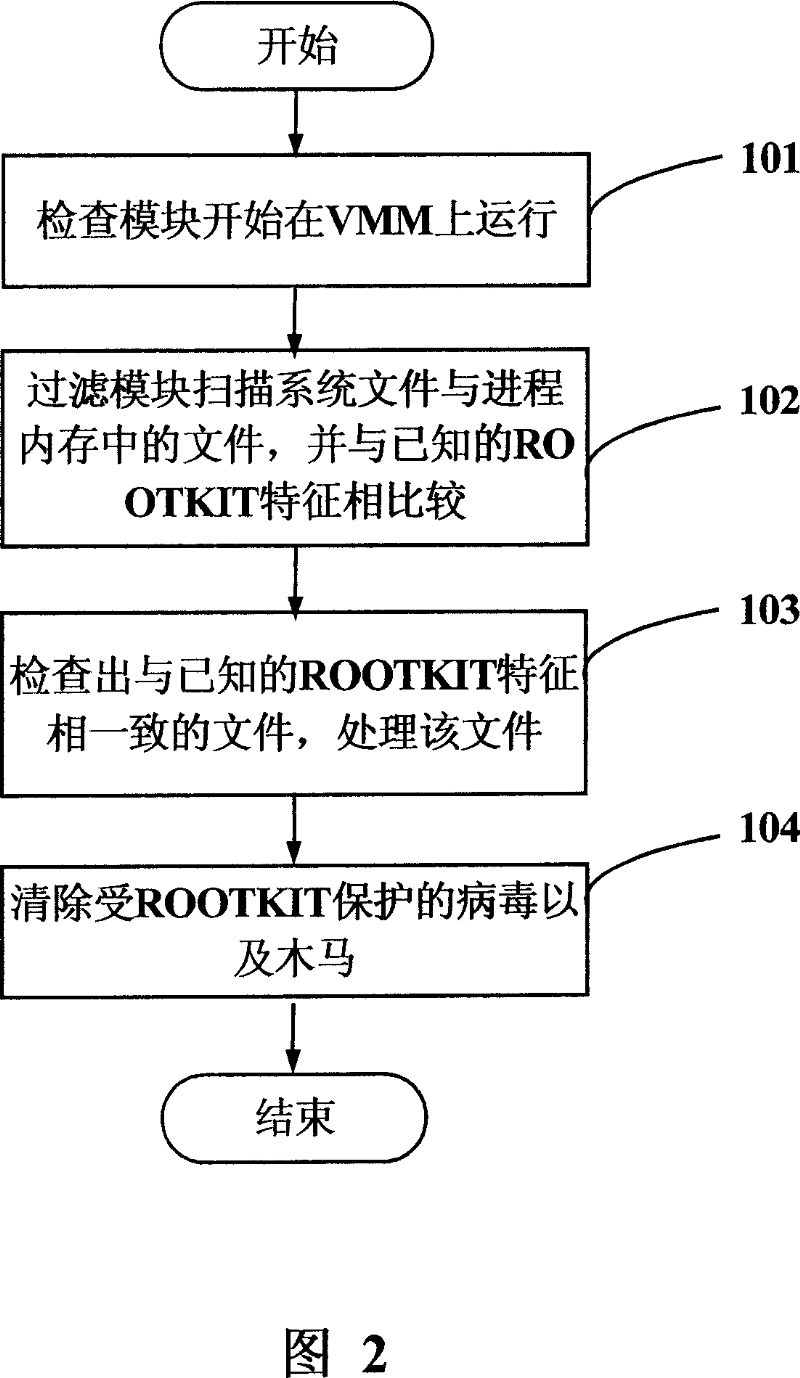
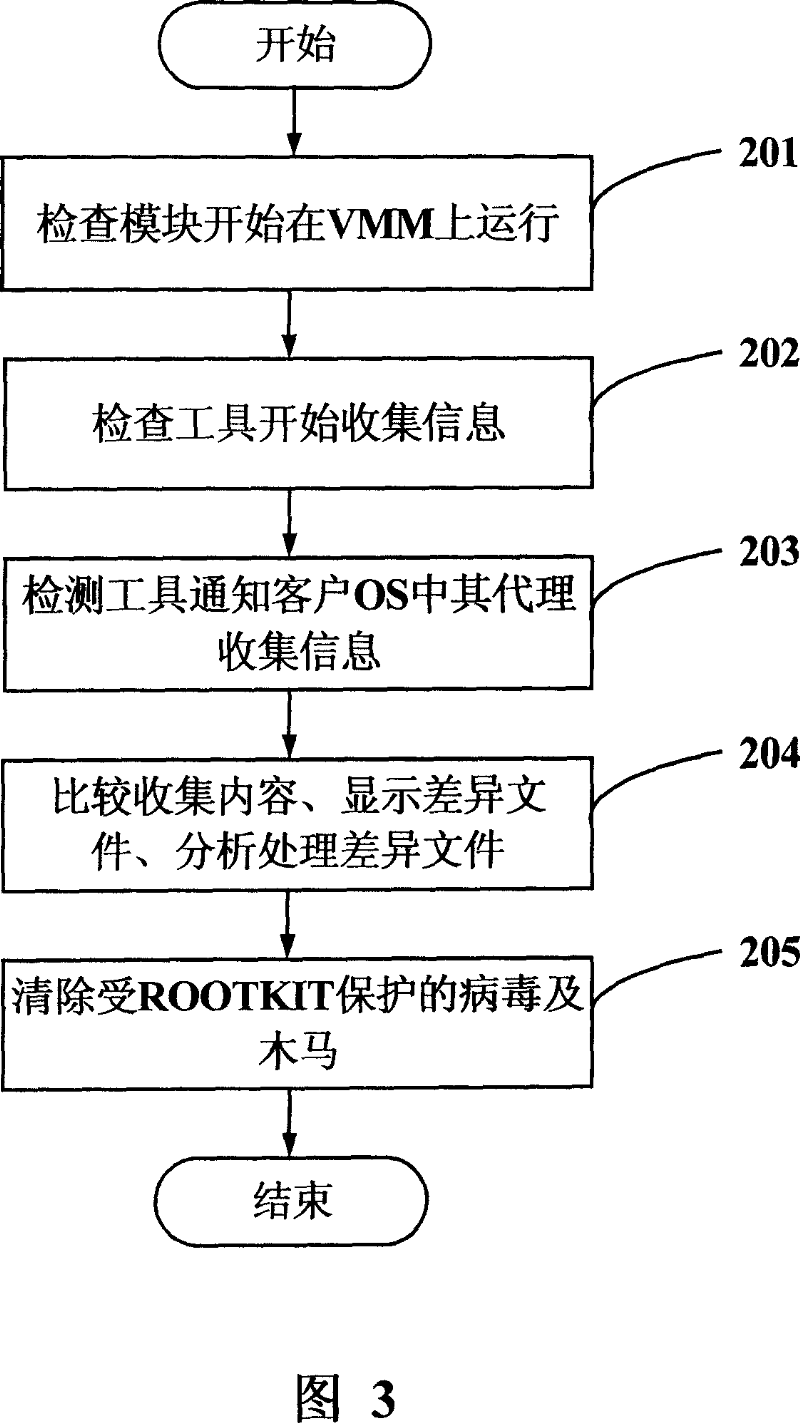
System and method for killing ROOTKIT
InactiveCN101042719AReliable killingAttack will notDigital data processing detailsPlatform integrity maintainanceOperational systemVirus
This invention discloses one virus killing ROOTKIT system and method, wherein, the system comprises virtual machine monitor, service operation system in virtual monitor and at least one customer operation system; the service operation system comprises test module to check whether there is ROOTKIT in the operation system and to find alarm. This invention system and method can check ROOTKIT in reliable operation inside the memory area besides operation system.
Owner:LENOVO (BEIJING) CO LTD
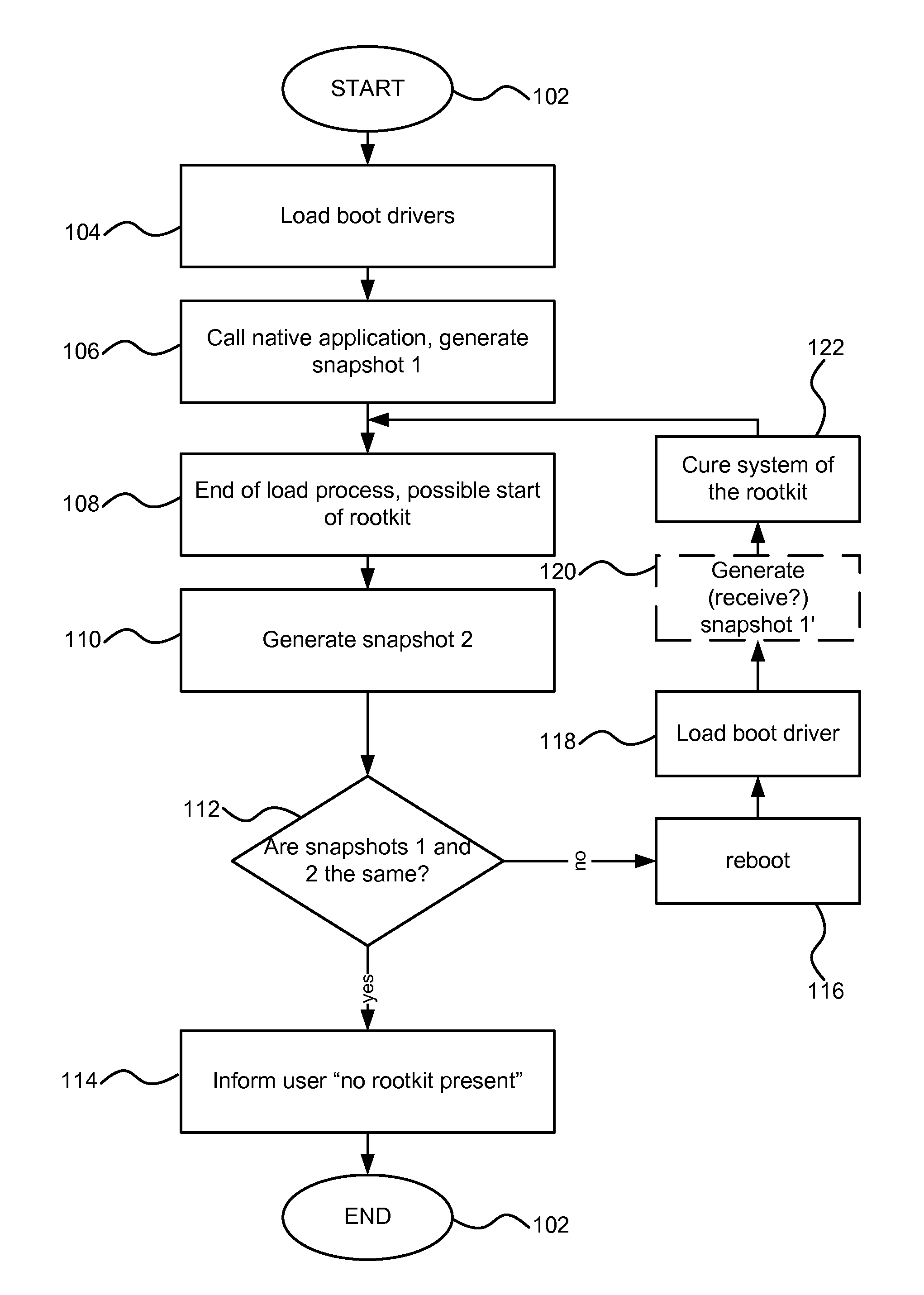
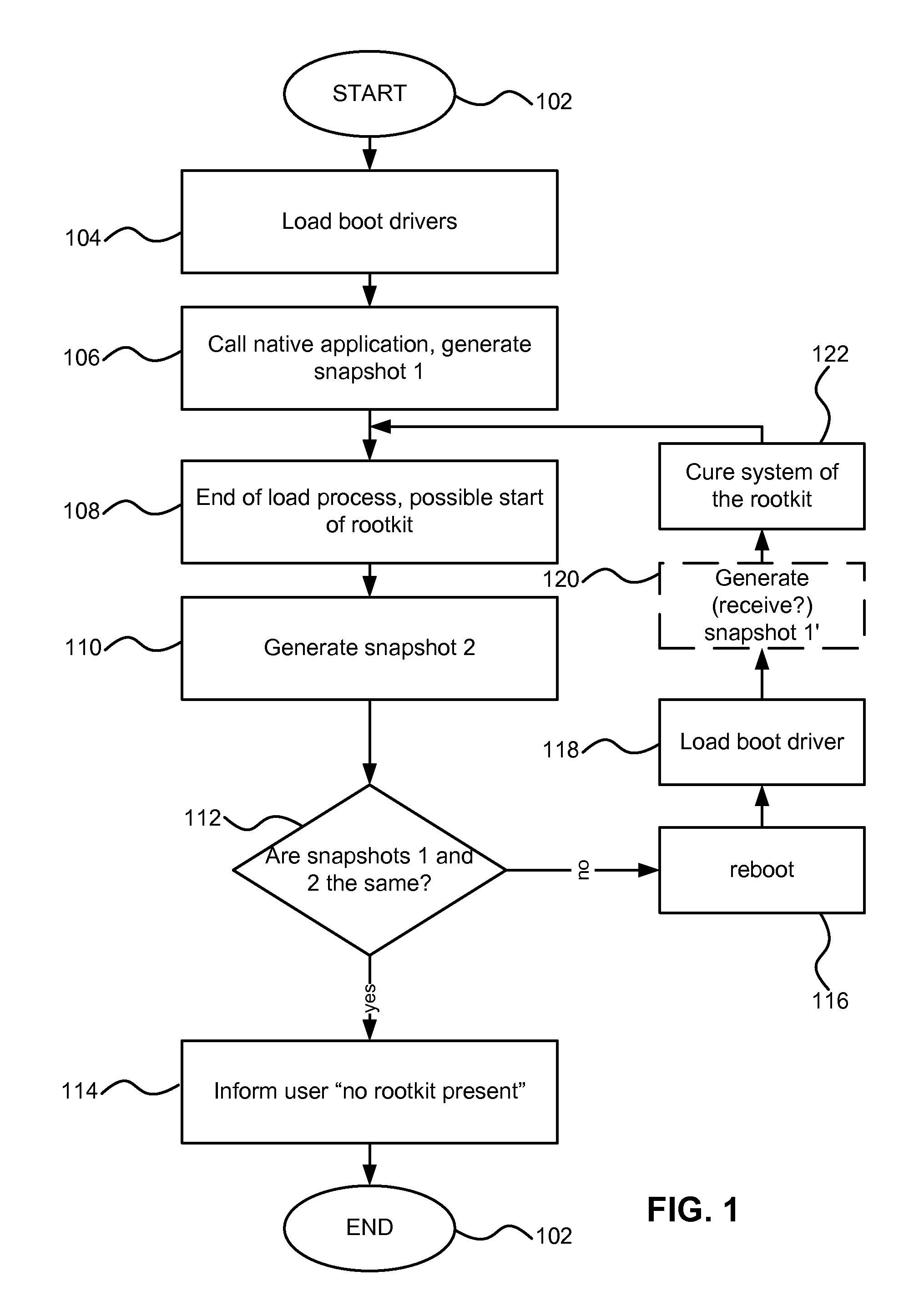
System and method for rootkit detection and cure
InactiveUS7921461B1Eliminate disadvantagesMemory loss protectionError detection/correctionOperational systemApplication software
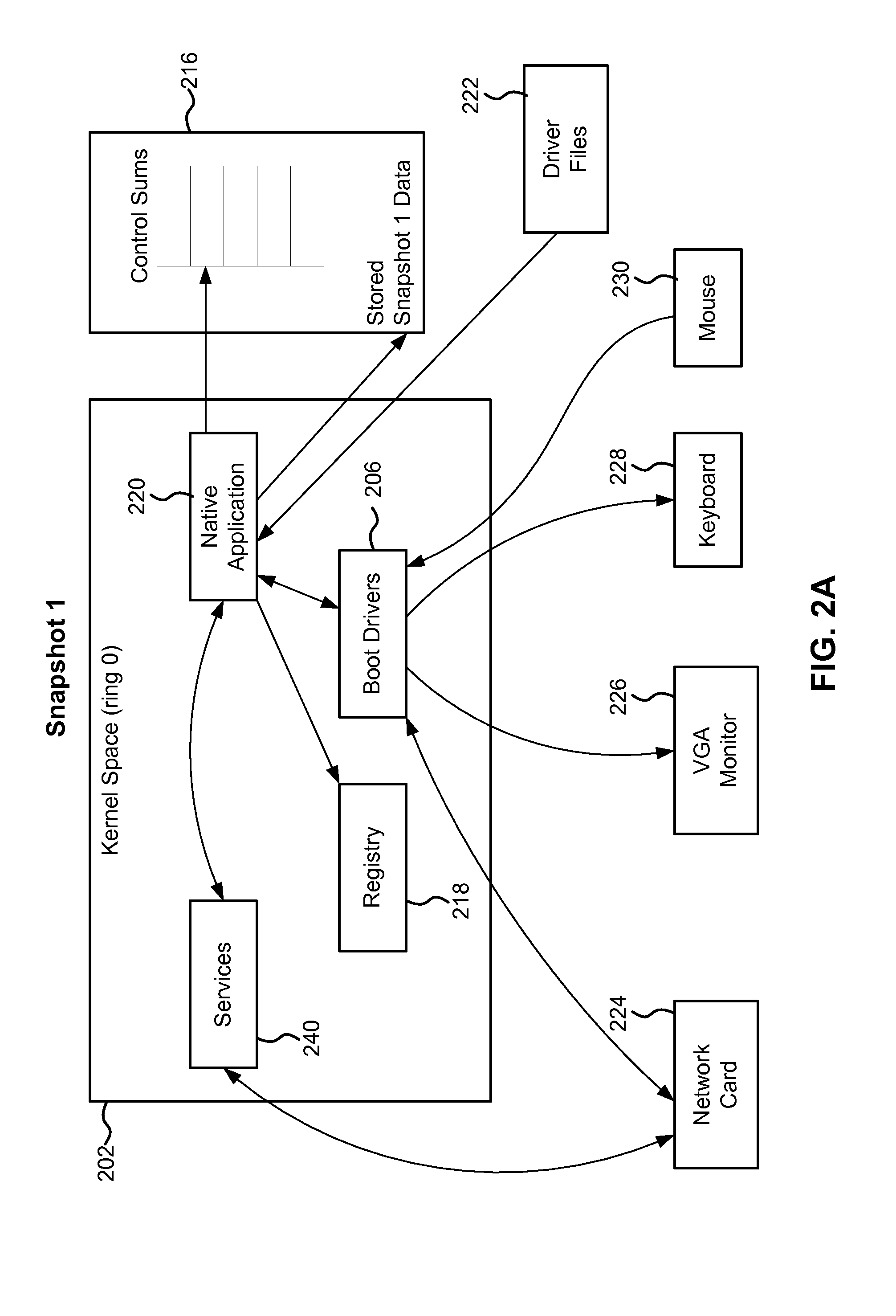
A system, method and computer program product for system for detecting a rootkit on a computer having an operating system, including a native application in ring 0 which, when the operating system is in a trusted state upon a reboot of the computer, after loading of the boot drivers but before loading of non-boot drivers, generates a first snapshot for selected files of the operating system and for a registry; the first snapshot being stored on a persistent storage medium of the computer; a second snapshot for the selected files and for the registry generated by the ordinary application after the loading of the non-boot drivers, generating; means for comparing the second snapshot with the first snapshot; and upon detecting, in the comparing step, one of a masked file and a masked registry branch, means for informing a user of possible rootkit presence on the computer.
Owner:KASPERSKY LAB ZAO
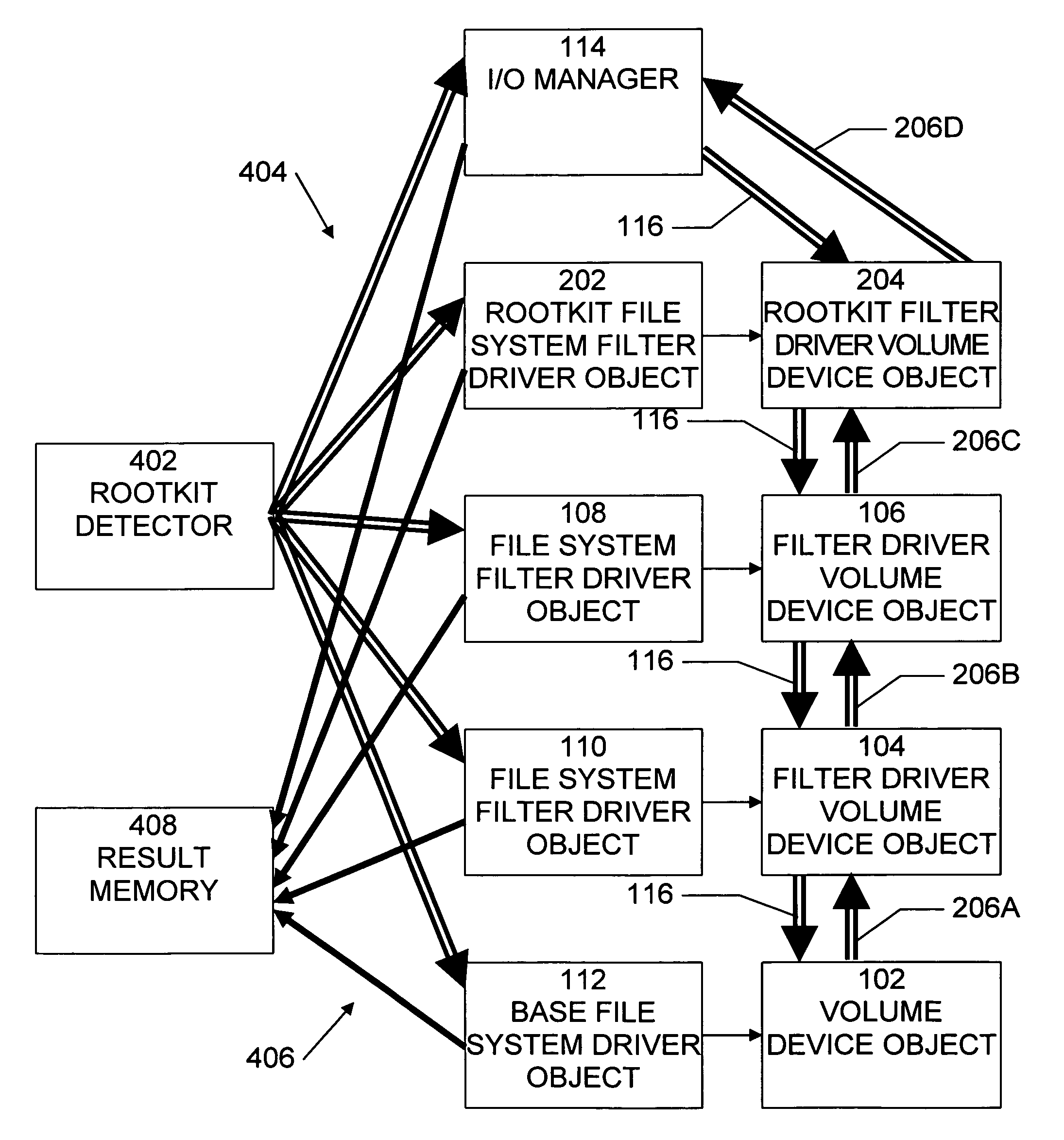
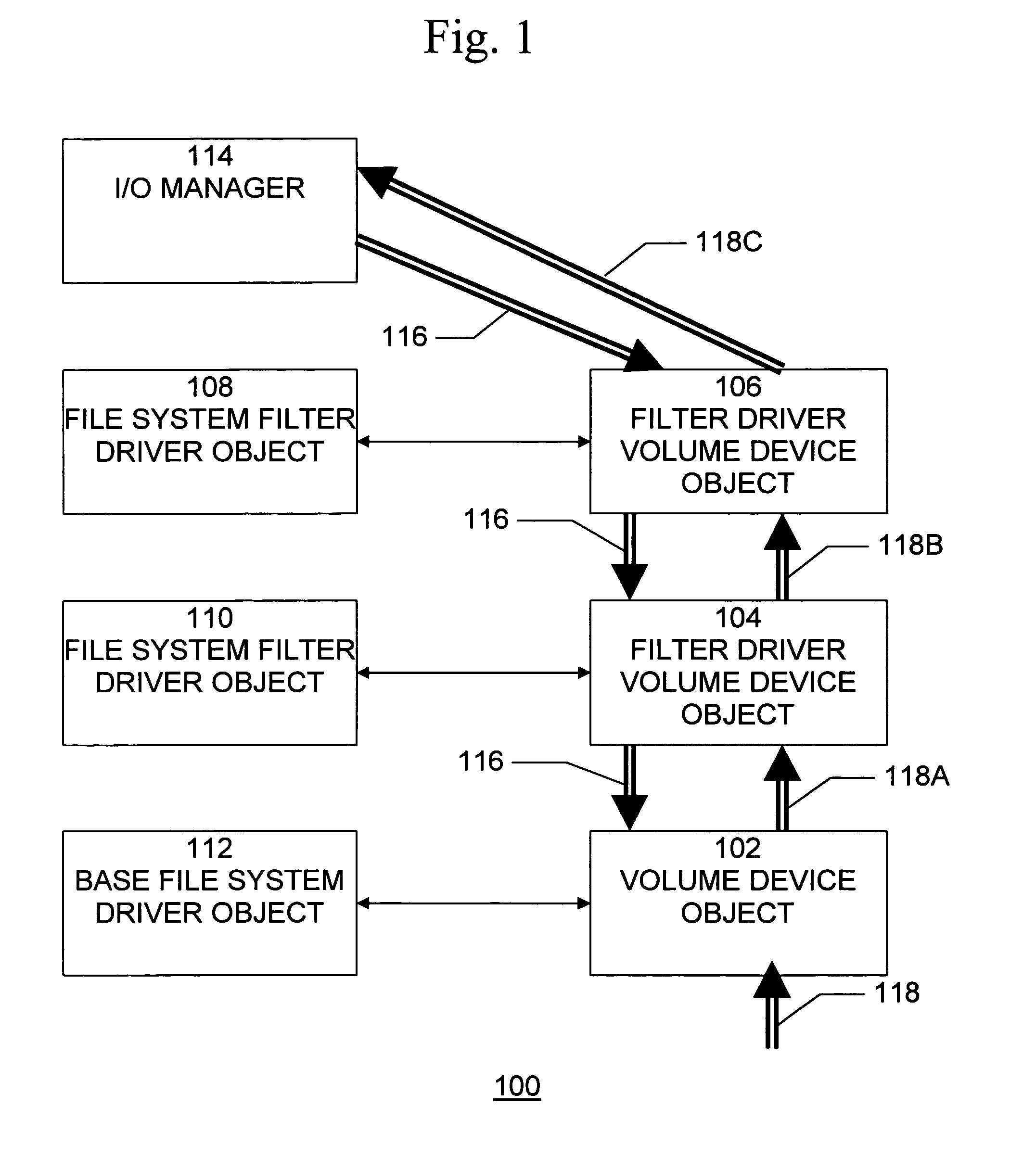
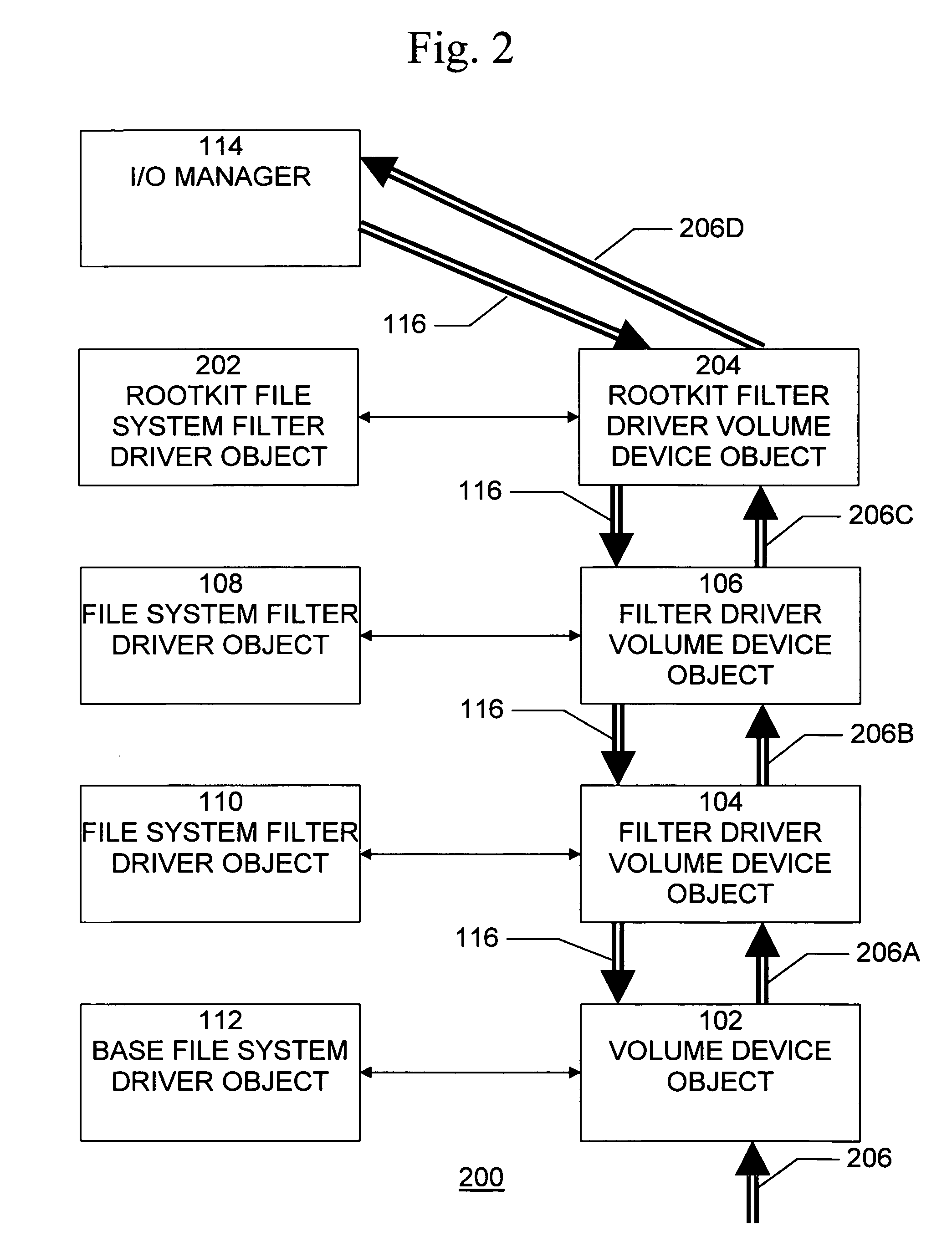
Method and system for the detection of file system filter driver based rootkits
ActiveUS20080109906A1Suitable for detectionMemory loss protectionError detection/correctionRootkitWork systems
A method, system, and computer program product for detecting hidden files and folders that may be installed by or as part of a rootkit provides the capability to identify the method that is used to hide the files and folders, will continue working even if the operating system is modified, and is suitable for real-time detection of hidden files and folders. A method for detecting a rootkit comprises the steps of generating a plurality of query input / output request packets, each query input / output request packet requesting information relating to a file system directory folder, transmitting a generated query input / output request packet to each file system driver object, receiving a result including the requested information relating to a file system directory folder from each file system driver object, and determining differences among each result, to determine information relating to a file system directory folder that is removed by at least one file system driver object.
Owner:MCAFEE LLC
Bootstrap OS protection and recovery
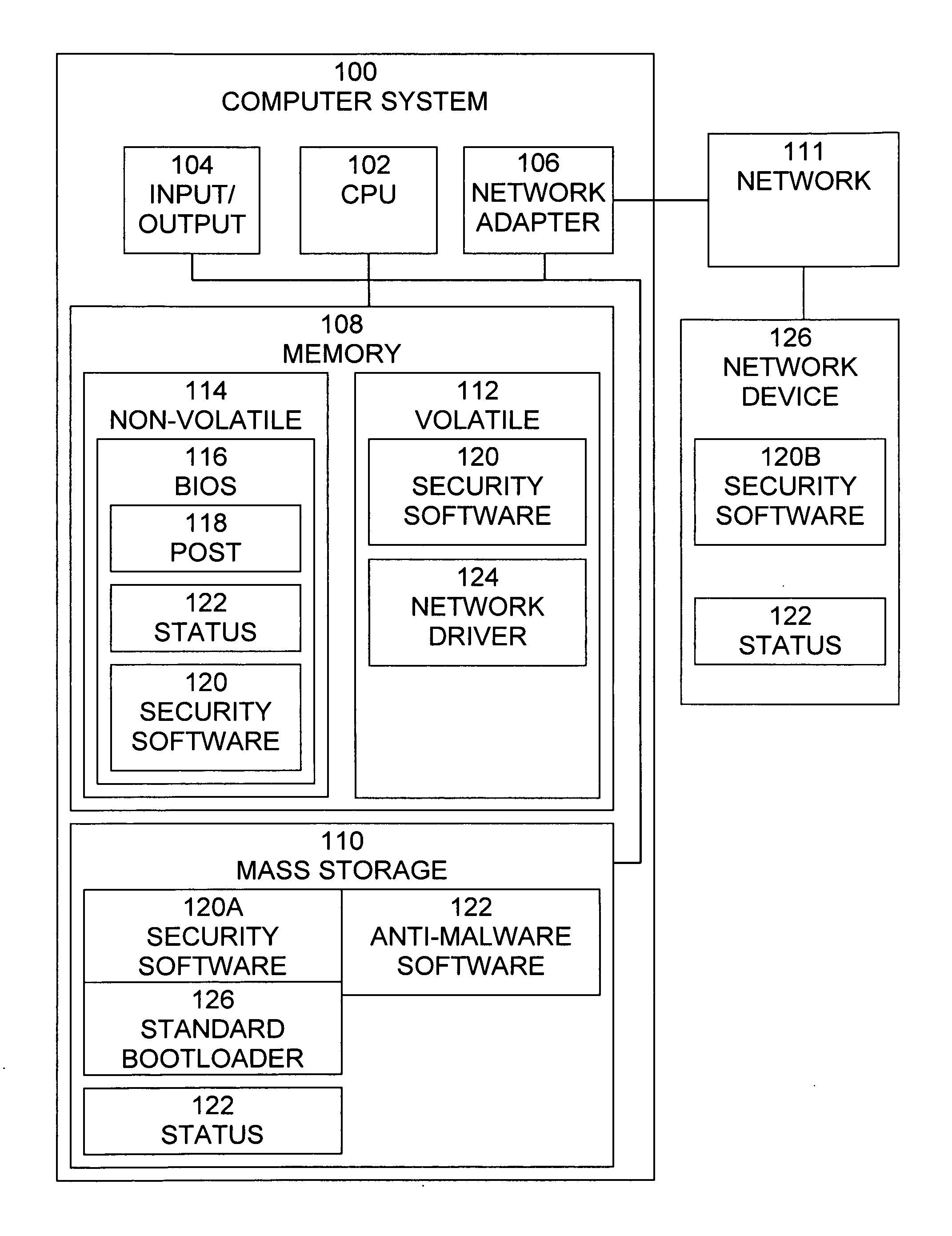
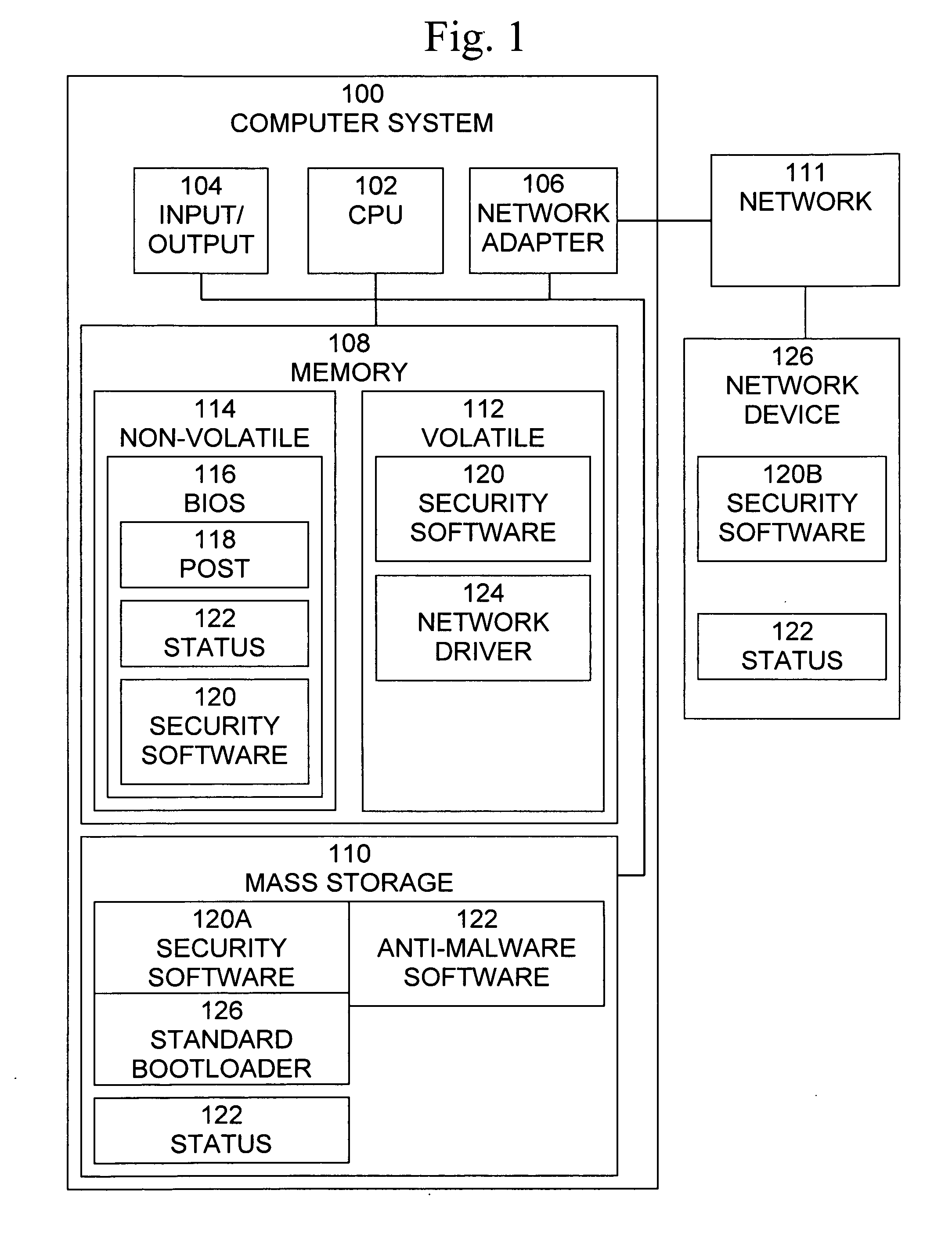
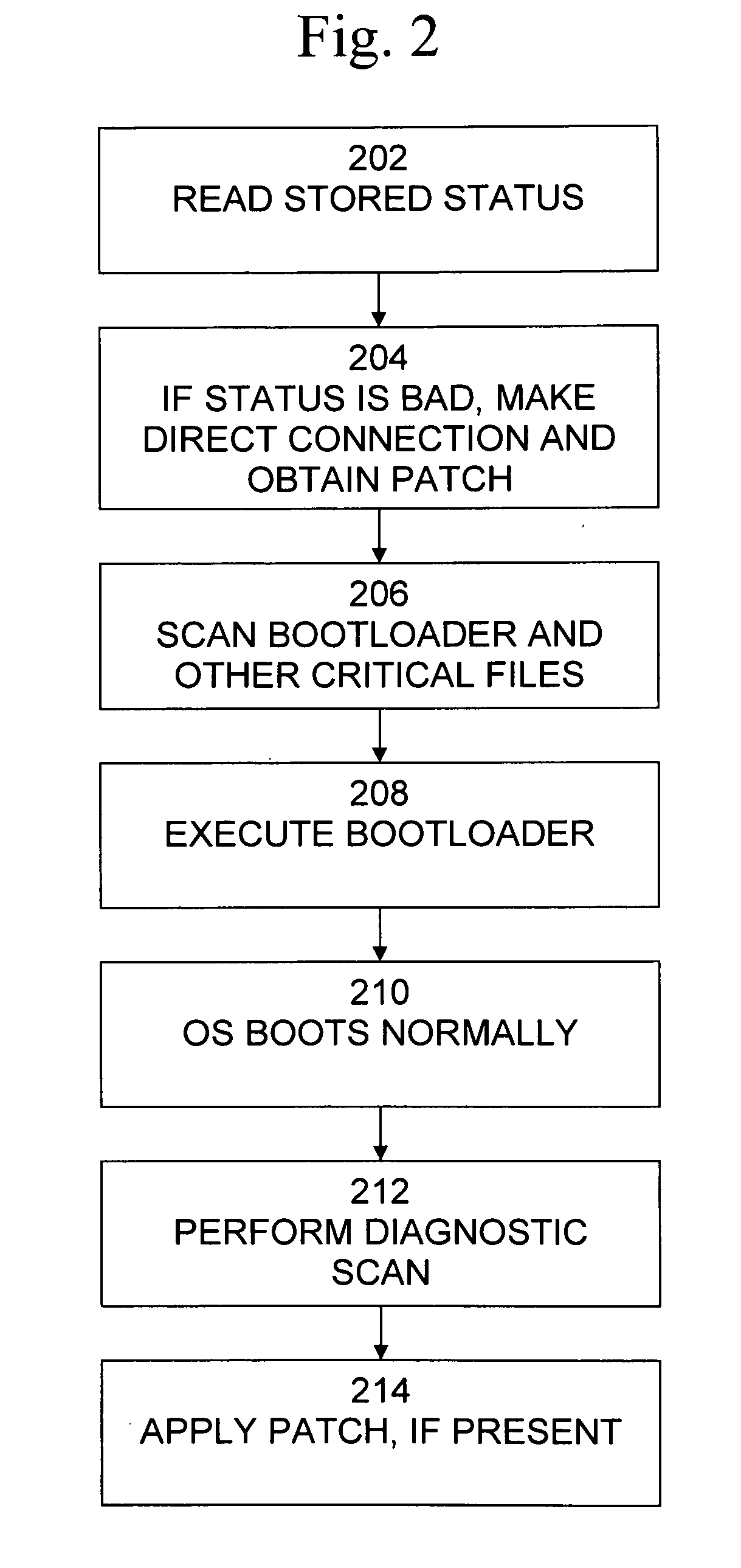
ActiveUS20090205045A1Provide capabilityMemory loss protectionError detection/correctionOperational systemThe Internet
A method, system, and computer program product for protecting a computer system provides bootstrap operating system detection and recovery and provides the capability to detect malware, such as rootkits, before the operating system has been loaded and provides the capability to patch malfunctions that block the ability of the computer system to access the Internet. A method for protecting a computer system includes reading stored status information indicating whether network connectivity was available the last time an operating system of the computer system was operational, when the stored status information indicates that network connectivity was not available, obtaining a software patch, and executing and applying the software patch.
Owner:MCAFEE LLC
System rogue program detecting method and device
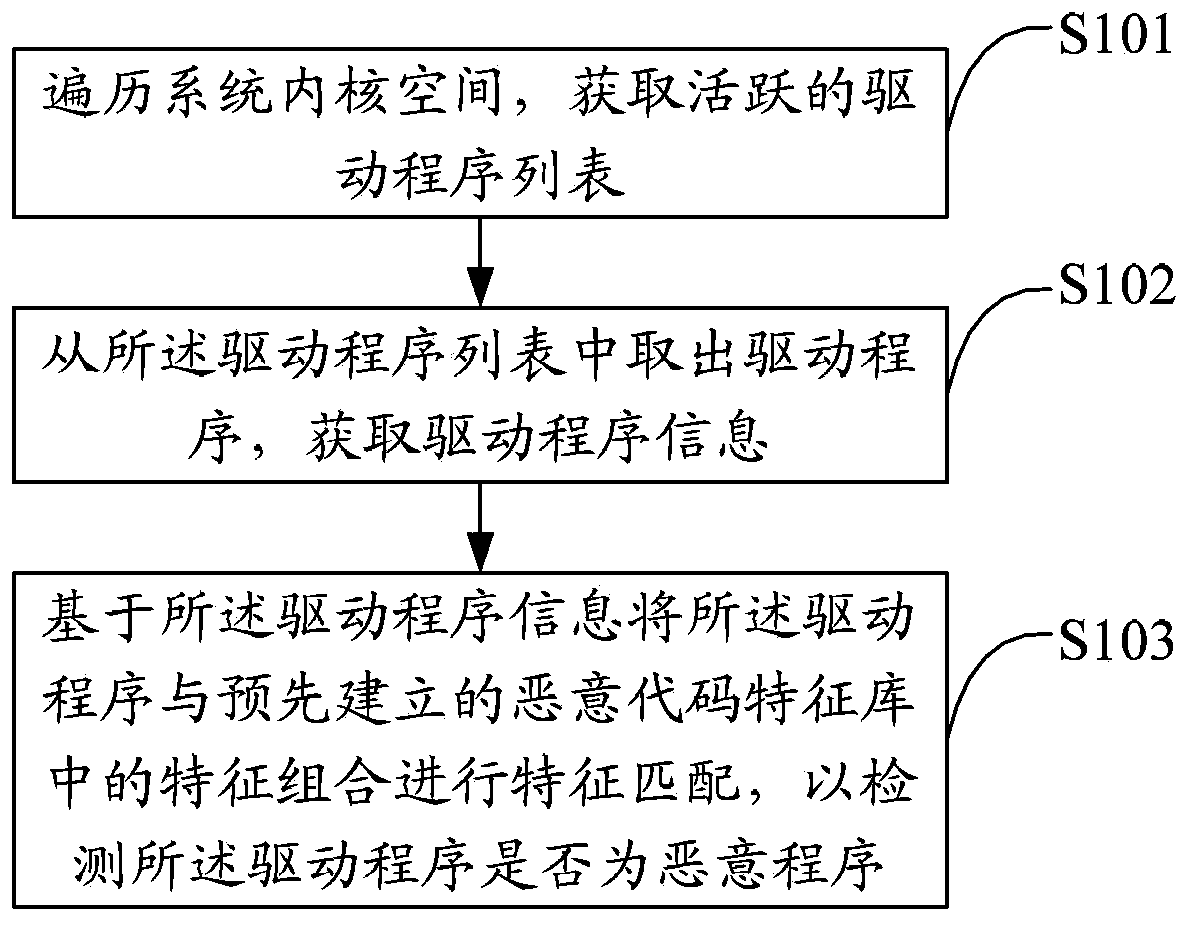
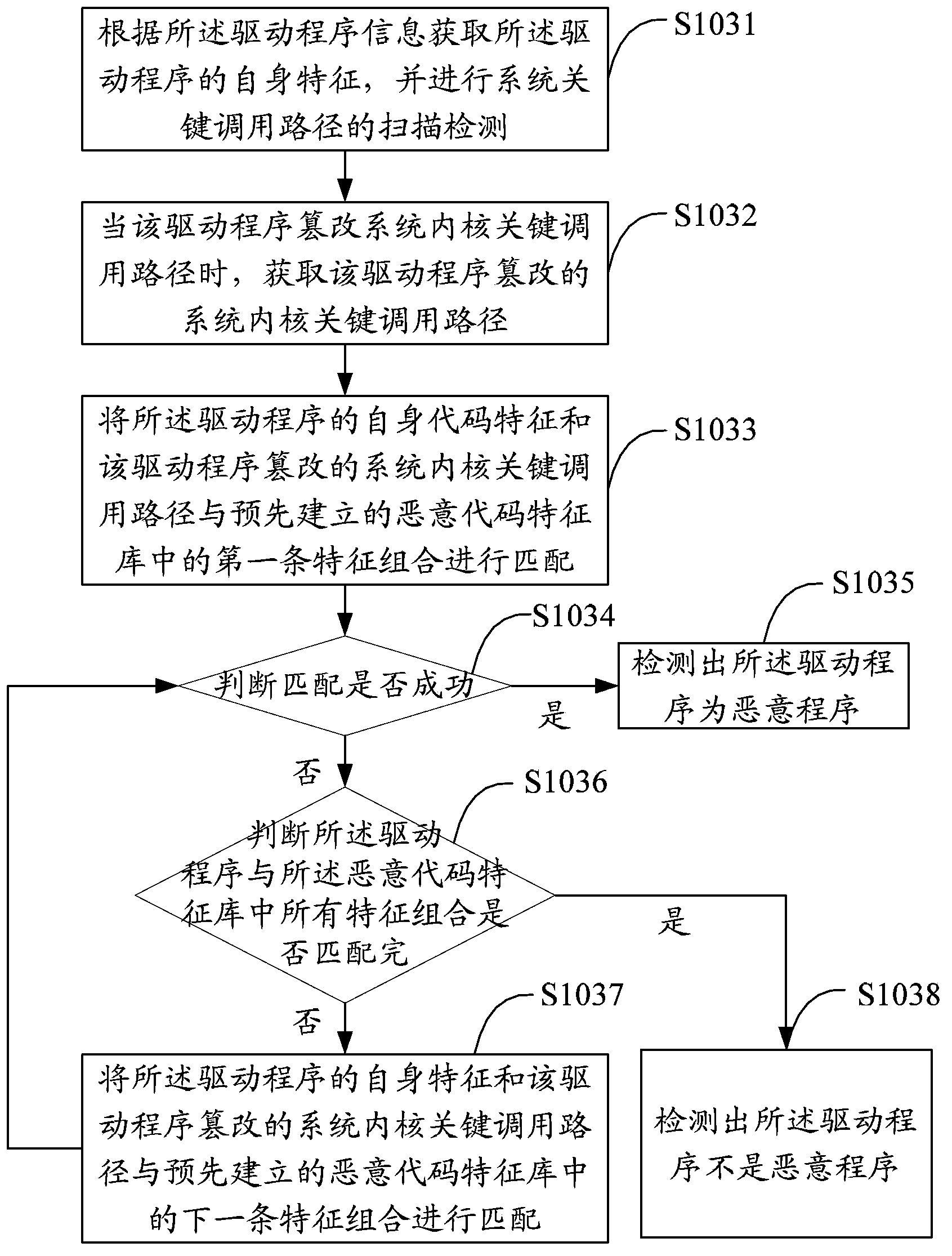
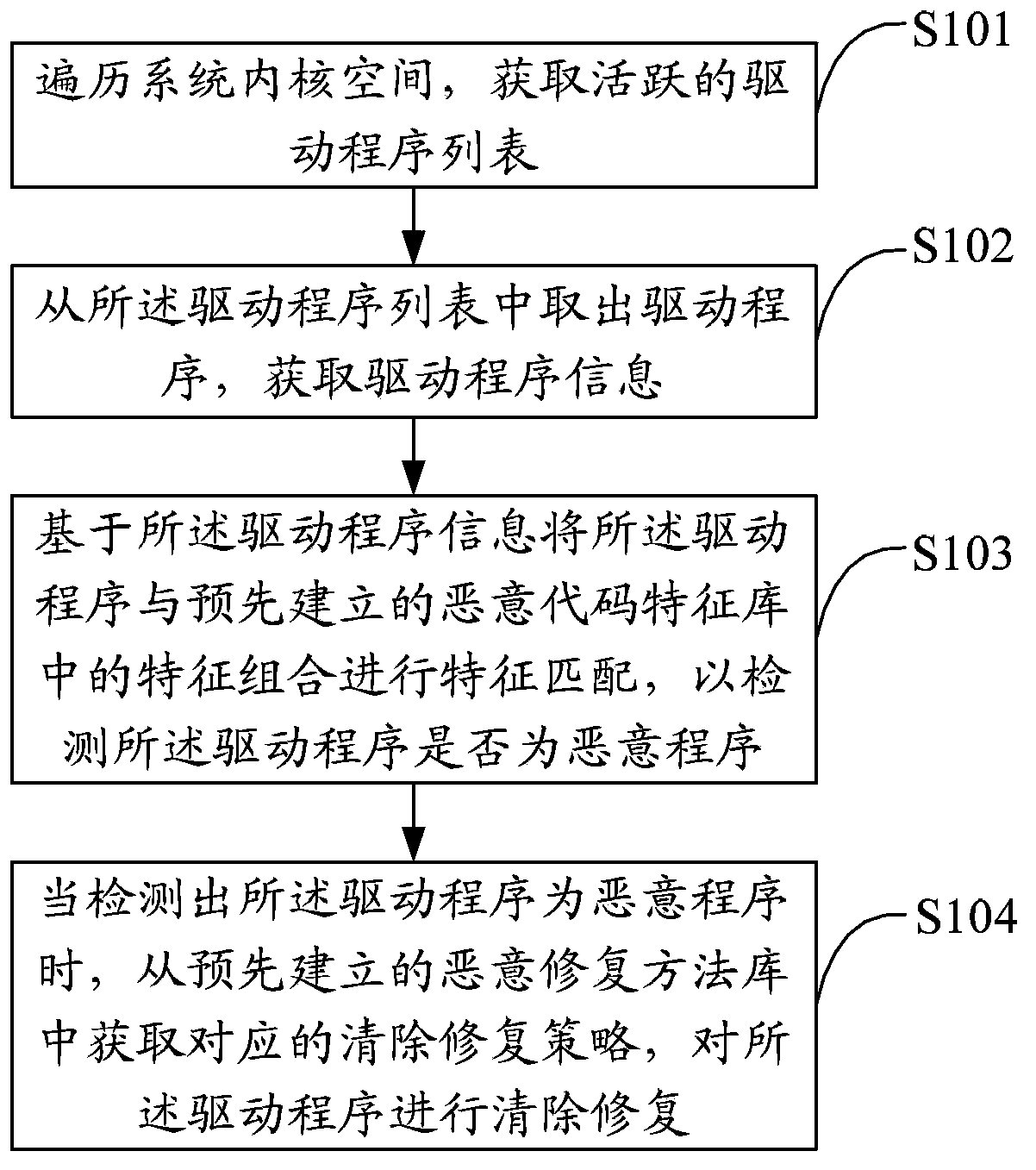
ActiveCN103679013AImprove detection accuracyImprove securityPlatform integrity maintainanceSoftware engineeringFalse alarm
The invention discloses a system rogue program detecting method and device. The method comprises the steps of traversing system kernel space to obtain an active drive program list, taking the drive programs from the drive program list so as to obtain drive program information, matching the drive programs with the characteristic combinations in a preset malicious code characteristic base in characteristic on the basis of the drive program information so as to detect whether the drive programs are rogue programs. According to the system rogue program detecting method and device, the safety condition of the system kernel is checked in the drive level, whether key calling paths of a system is tampered and destroyed by stubborn rogue programs is checked, and corresponding elimination repair strategies are selected for rogue programs such as Rootkit Trojan programs to eliminate the rogue programs and repair the system. The system rogue program detecting method and device are strong in pertinency, low in false alarm rate, accurate in repair, and capable of preventing repeated infection, can thoroughly eliminate Rootkit type Trojan, ensure normal utilization of a user system, and greatly improve the safety of the system.
Owner:TENCENT TECH (SHENZHEN) CO LTD
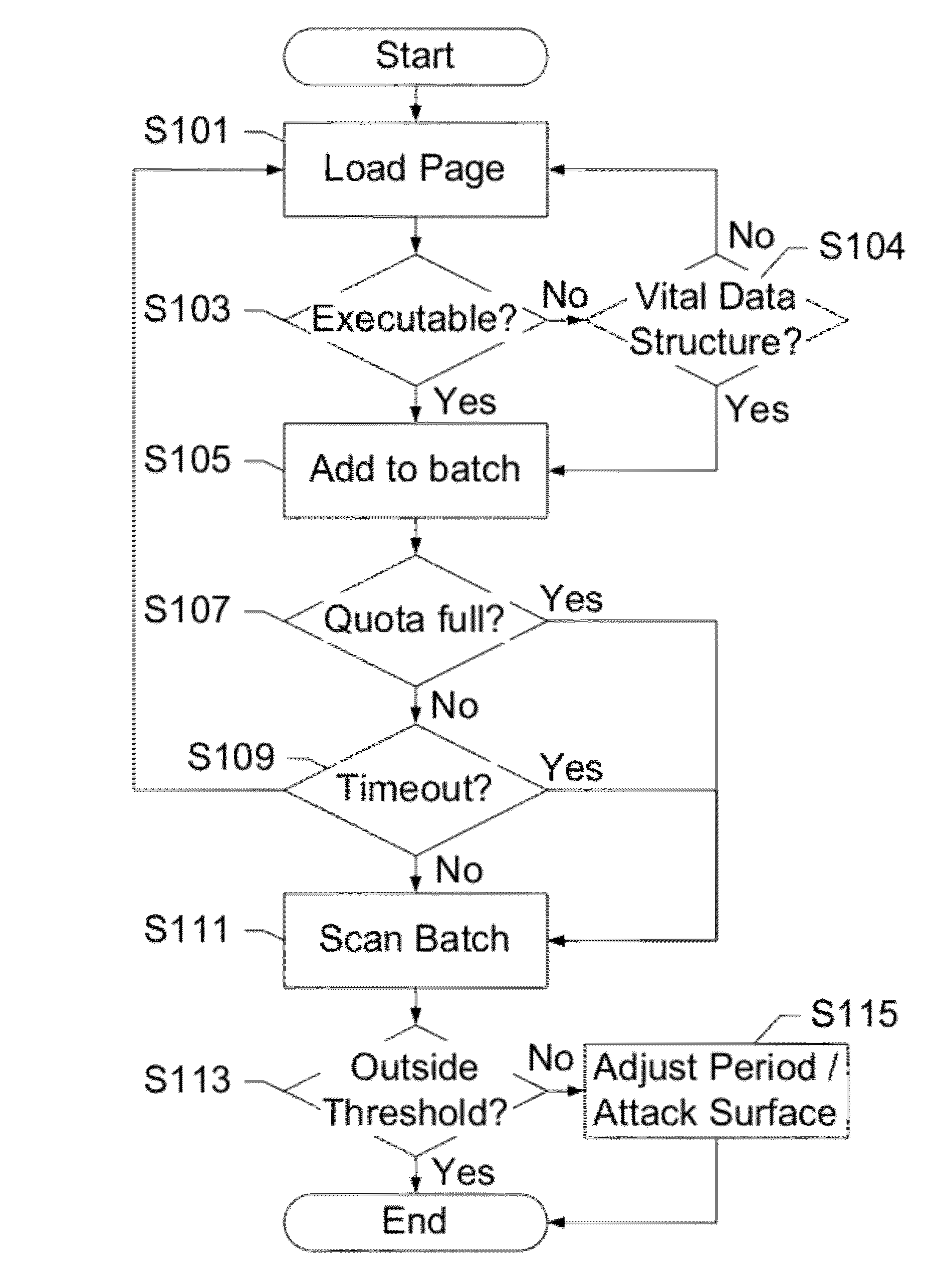
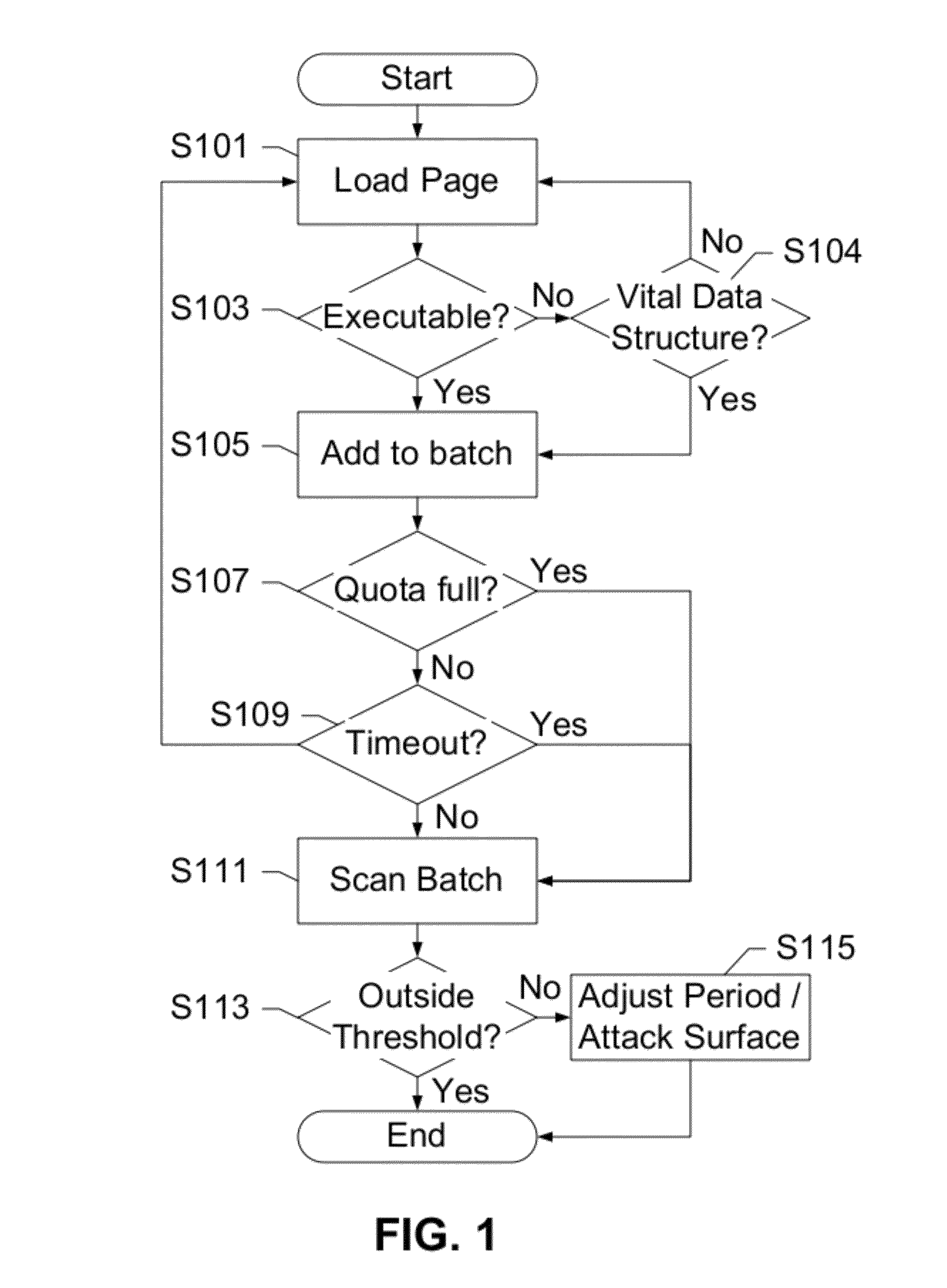
Balancing Malware Rootkit Detection with Power Consumption on Mobile Devices
InactiveUS20120291126A1Improve compromiseMemory loss protectionError detection/correctionOperational systemEnergy expenditure
The subject disclosure presents a novel technique for balancing the tradeoff between security monitoring and energy consumption on mobile devices. Security / energy tradeoffs for host-based detectors focusing on rootkits are analyzed along two axes: a scanning frequency, and a surface of attack. Experimental results are applied to a hypervisor-based framework, and a sweet spot is identified to minimize both energy consumption and a window of vulnerability for critical operating system objects such as code pages and kernel data.
Owner:AT&T INTPROP I L P +1
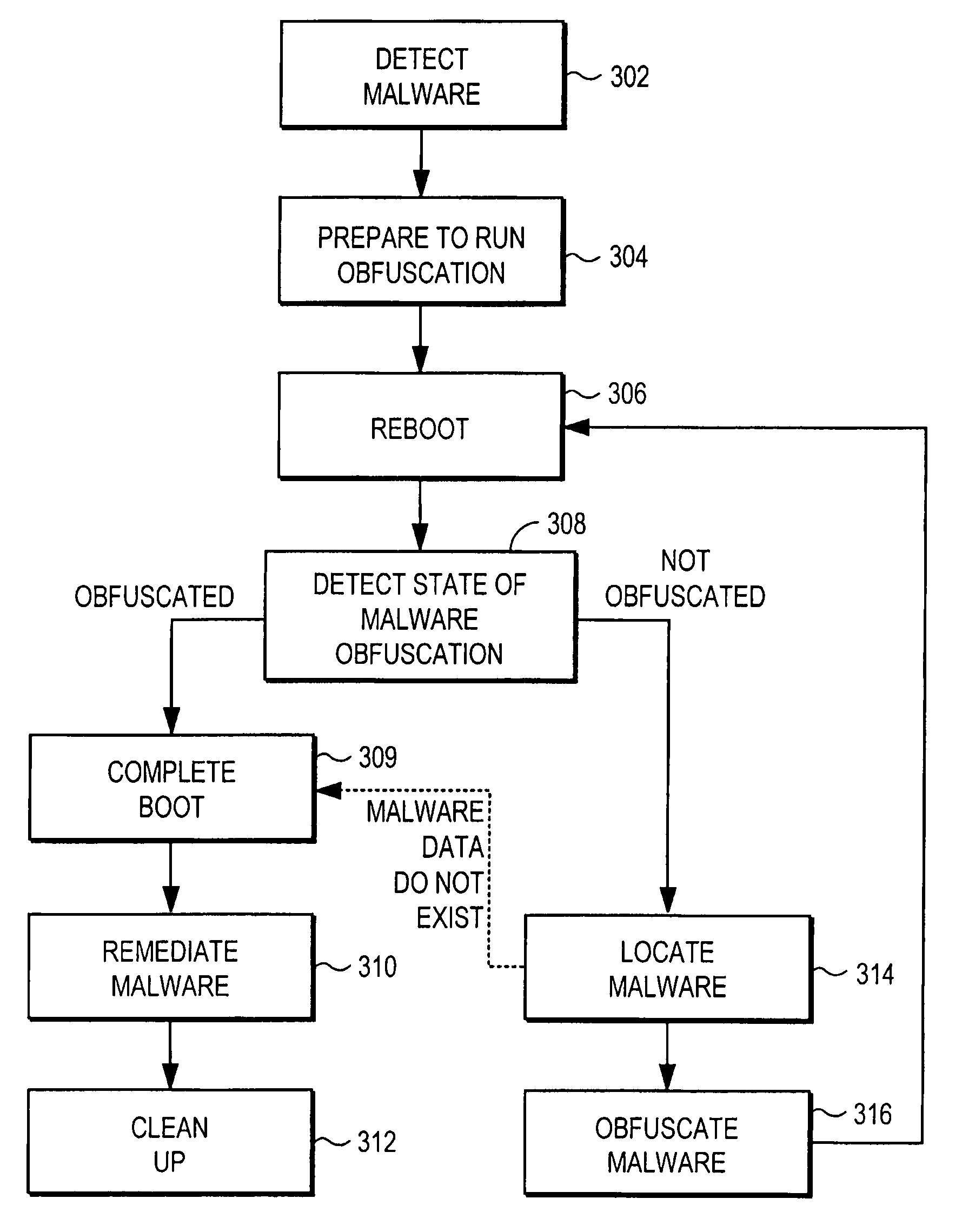
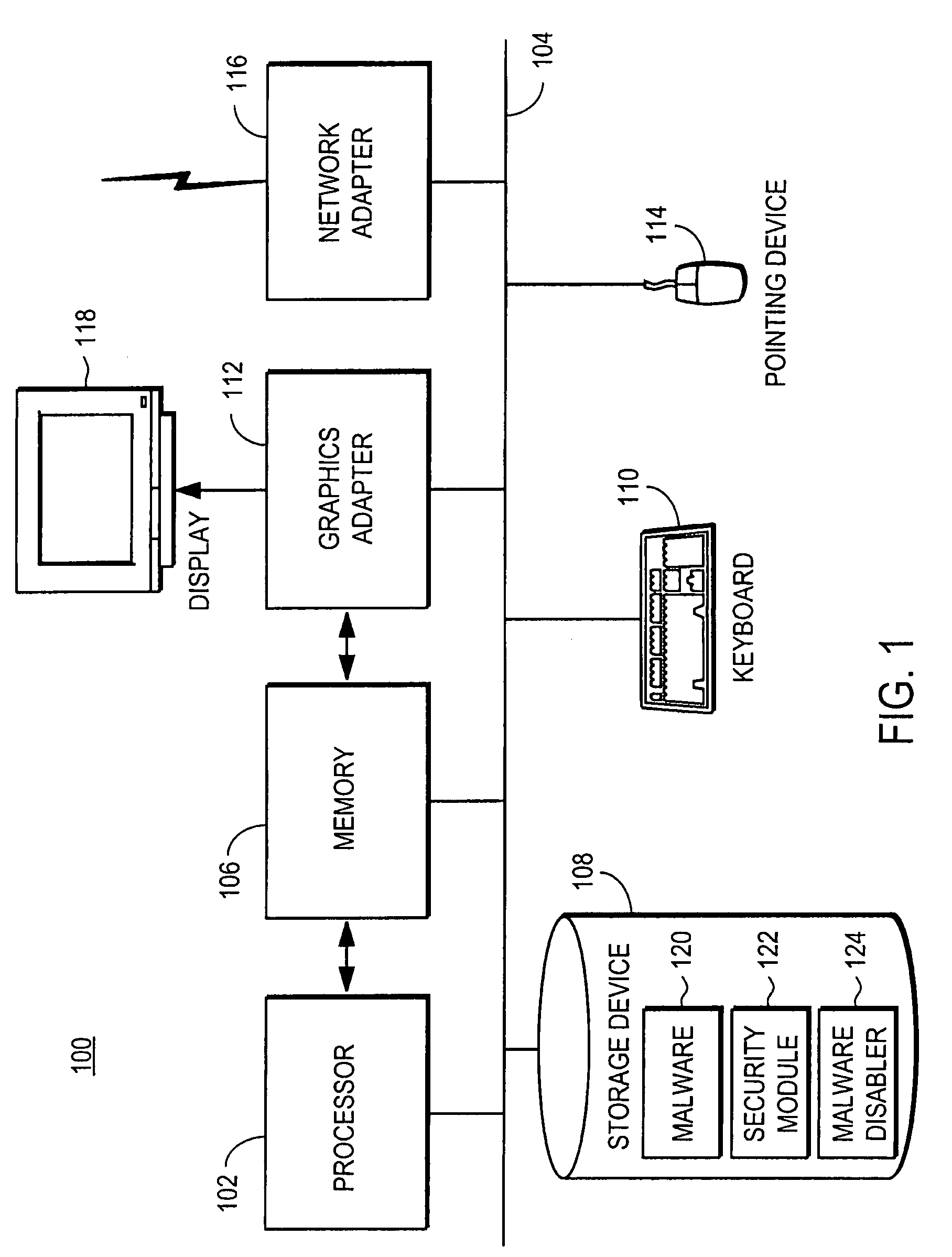
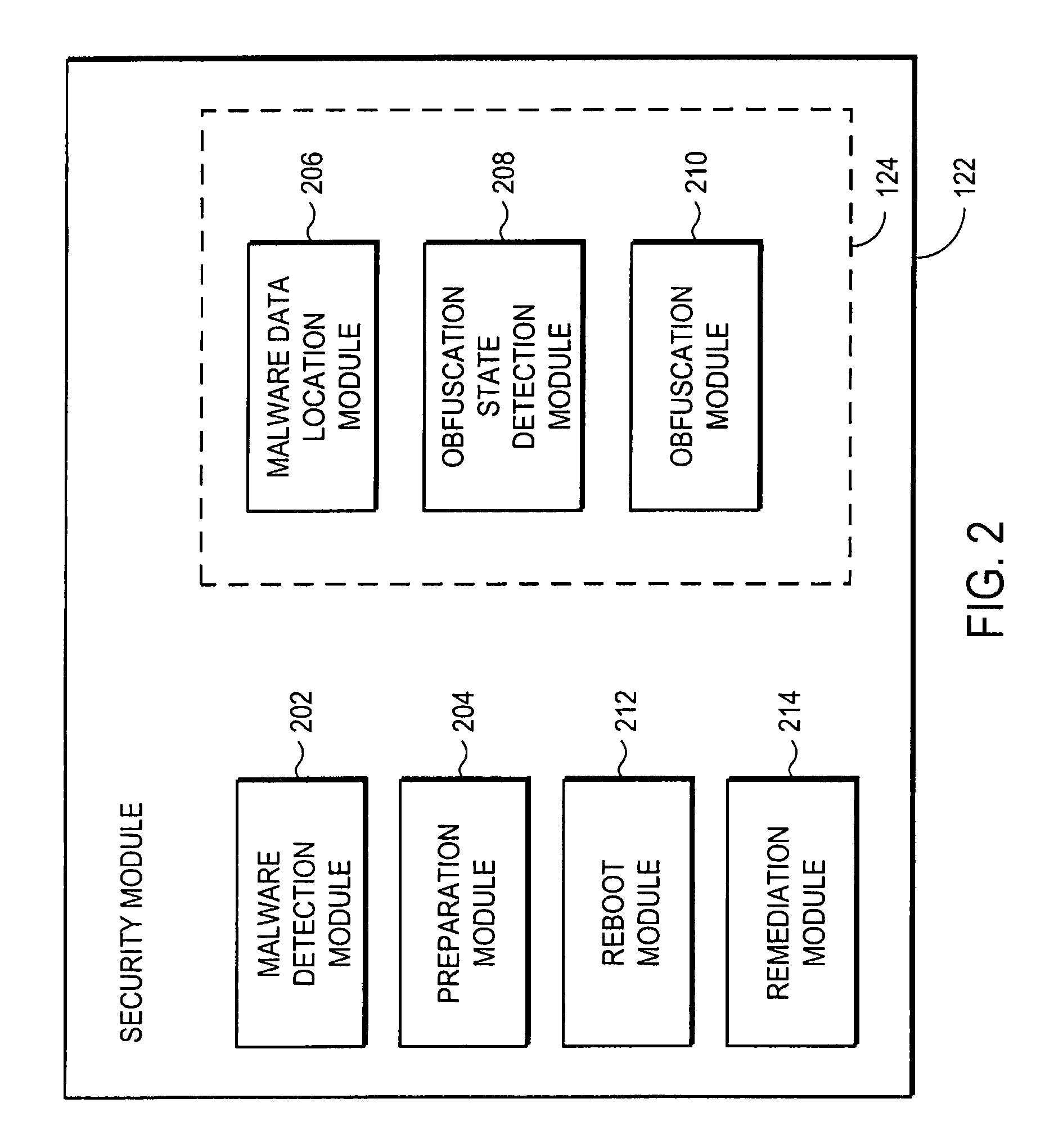
Remediating malware infections through obfuscation
A computer has a storage device that is infected with malicious software (malware). The malware uses stealth or rootkit techniques to hide itself in the storage device. A security module within the storage device detects the malware by comparing the files read from the storage device to those reported by the operating system. Upon detecting the malware, the security module prepares the computer for malware obfuscation by storing information describing the location of the malware, deploying an executable file, and configuring it to run on reboot. The executable file executes upon reboot and locates the data on the storage device associated with the malware. The executable file obfuscates the data so that the malware no longer loads at boot time, thereby disabling the rootkit technique. The computer reboots and the security module remediates the malware infection.
Owner:CA TECH INC
Method and device of detection processing of core-level rootkit
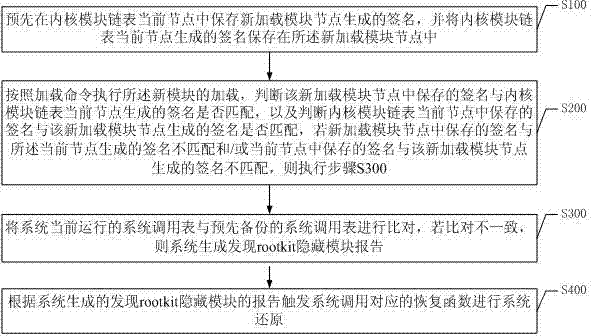
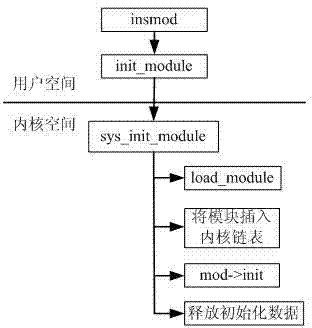
InactiveCN103699839AImprove reliabilityGuaranteed safe operationPlatform integrity maintainanceComputer hardwareOperational system
The invention discloses a method and a device of detection processing of a core-level rootkit. The method comprises the following steps of A, pre-storing a new loading module node signature at a current node of a core module chain table, and storing a current node signature into a new loading module node; B, loading a new module, judging whether the signature stored in the new loading module node is matched with the current node signature or not, judging whether the signature stored in the current node is matched with the new loading module node signature or not, if one is not matched, preforming the step C; C, comparing a currently operational system call table with a spare system call table, if not consistent, generating a report of discovering a hidden module. According to the method and the device, invasion of the rootkit is detected by setting a mutually matching mechanism of the new loading module and the current node signature of the chain table, and the report is further affirmed through comparing the system call table with a spare reference file, so that the reliability of a detection result is improved, and meanwhile, through setting a system recovery method, safety operation of the system is ensured.
Owner:TCL CORPORATION
Method and apparatus for preventing rootkit installation
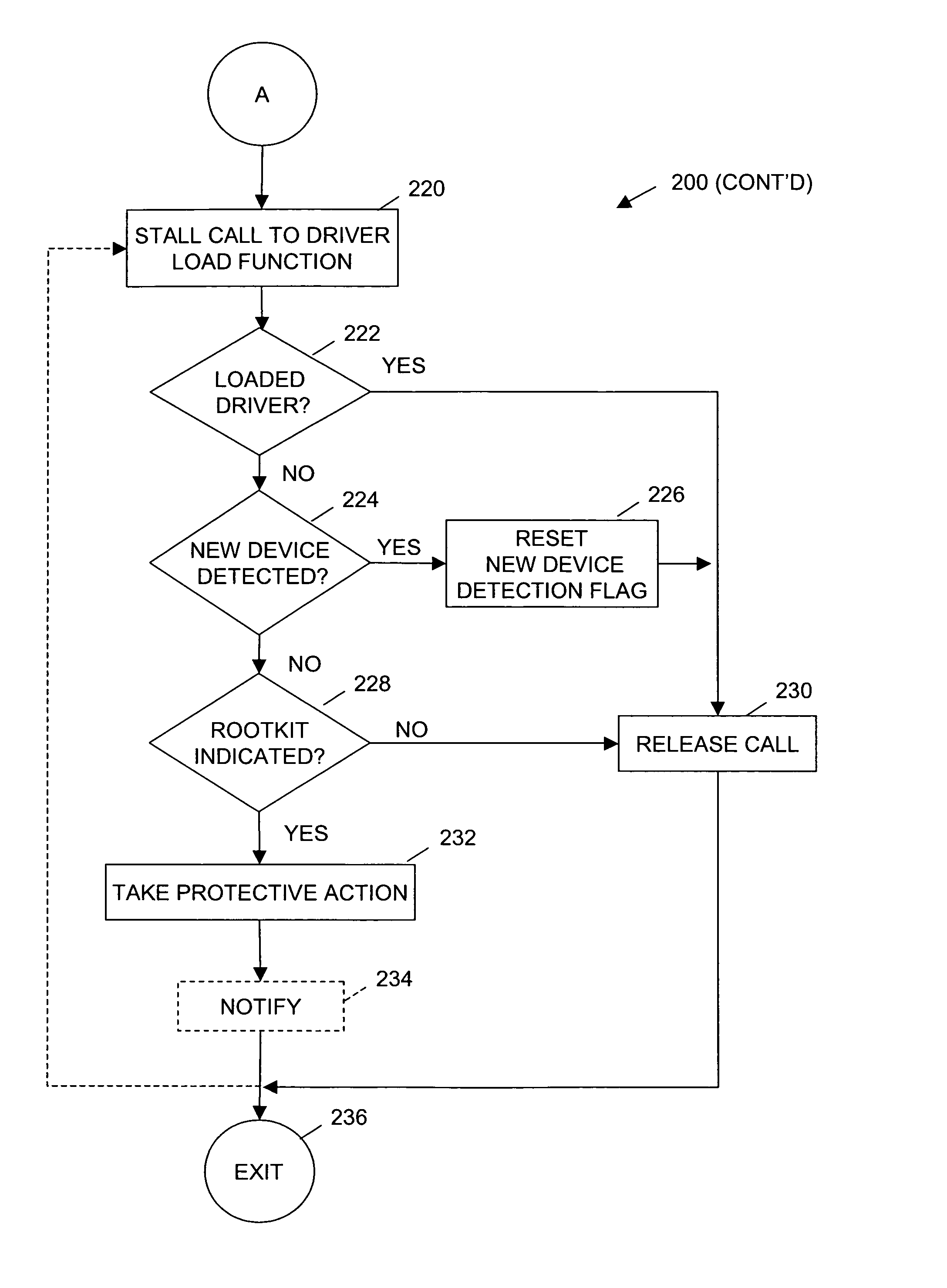
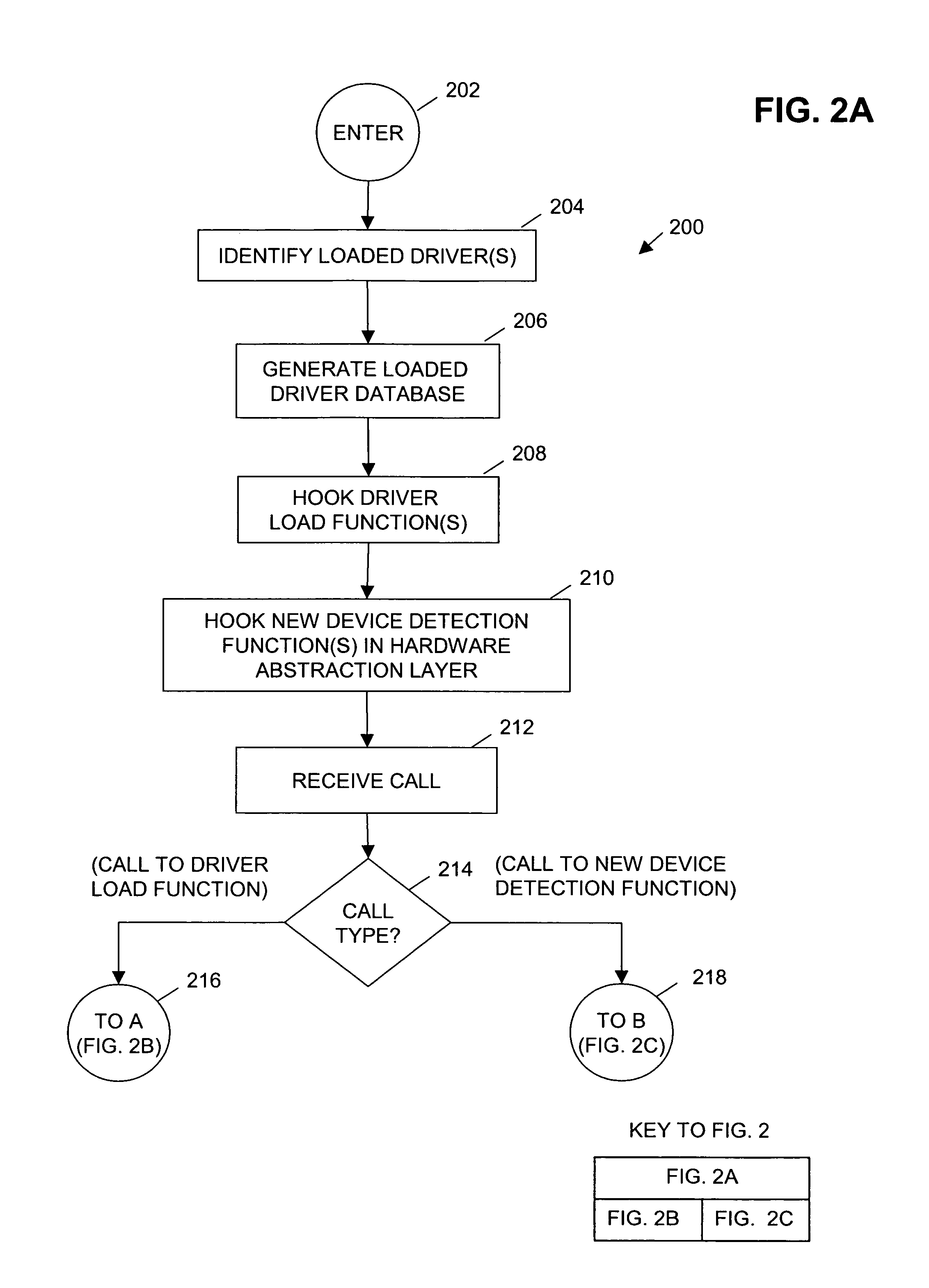
InactiveUS7607173B1Preventing possible unauthorized access and other compromisePrevented from installingMemory loss protectionUnauthorized memory use protectionComputerized systemEngineering
Call to driver load functions, including associated driver objects to be loaded, are stalled and evaluated for indications of a rootkit. When a rootkit is indicated, protective action is taken, and optionally a user or system administrator are notified. Calls not indicative of a rootkit are released and allowed to load. In one embodiment, calls to currently loaded drivers and calls related to installation of new hardware, are excluded from the evaluation for indications of a rootkit. In additional embodiments, sensitive structures and calls to sensitive structures of a computer system are also evaluated for indications of a rootkit.
Owner:CA TECH INC
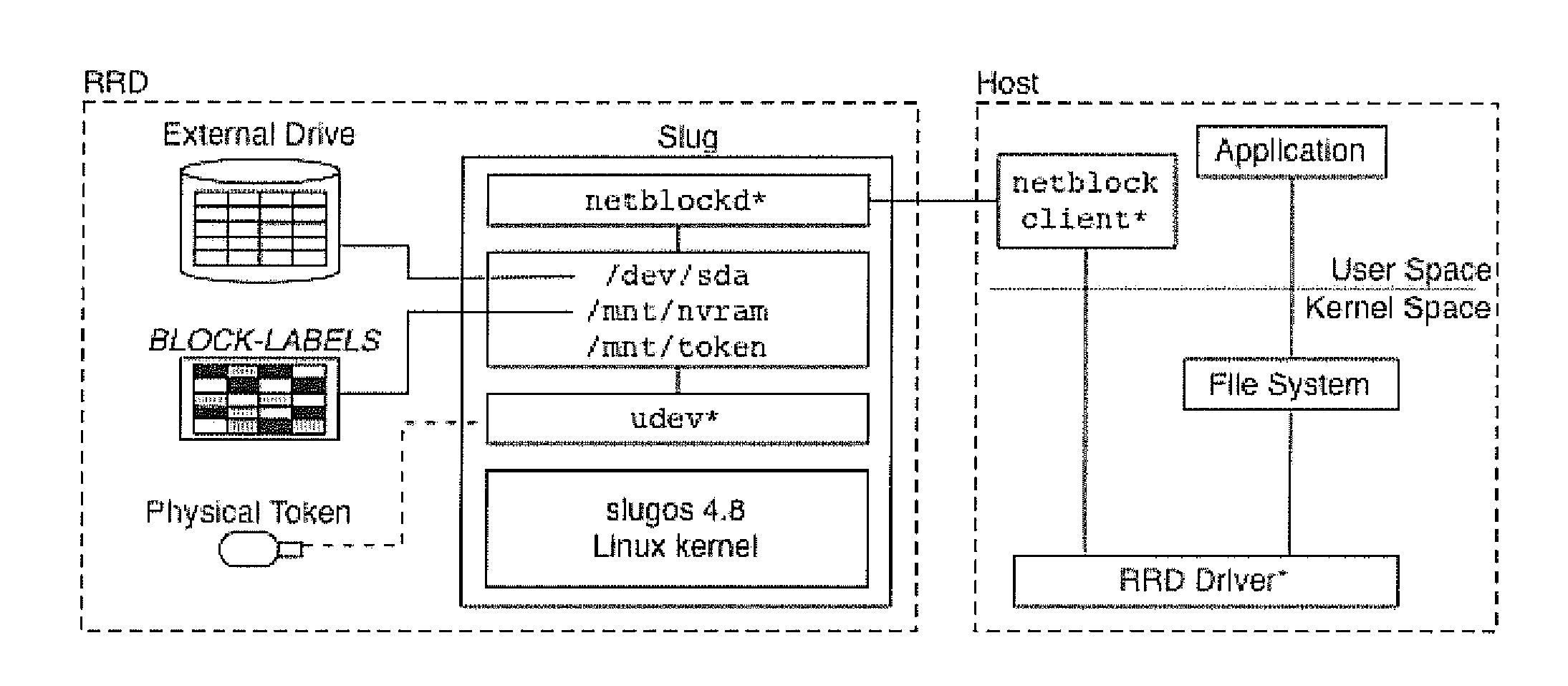
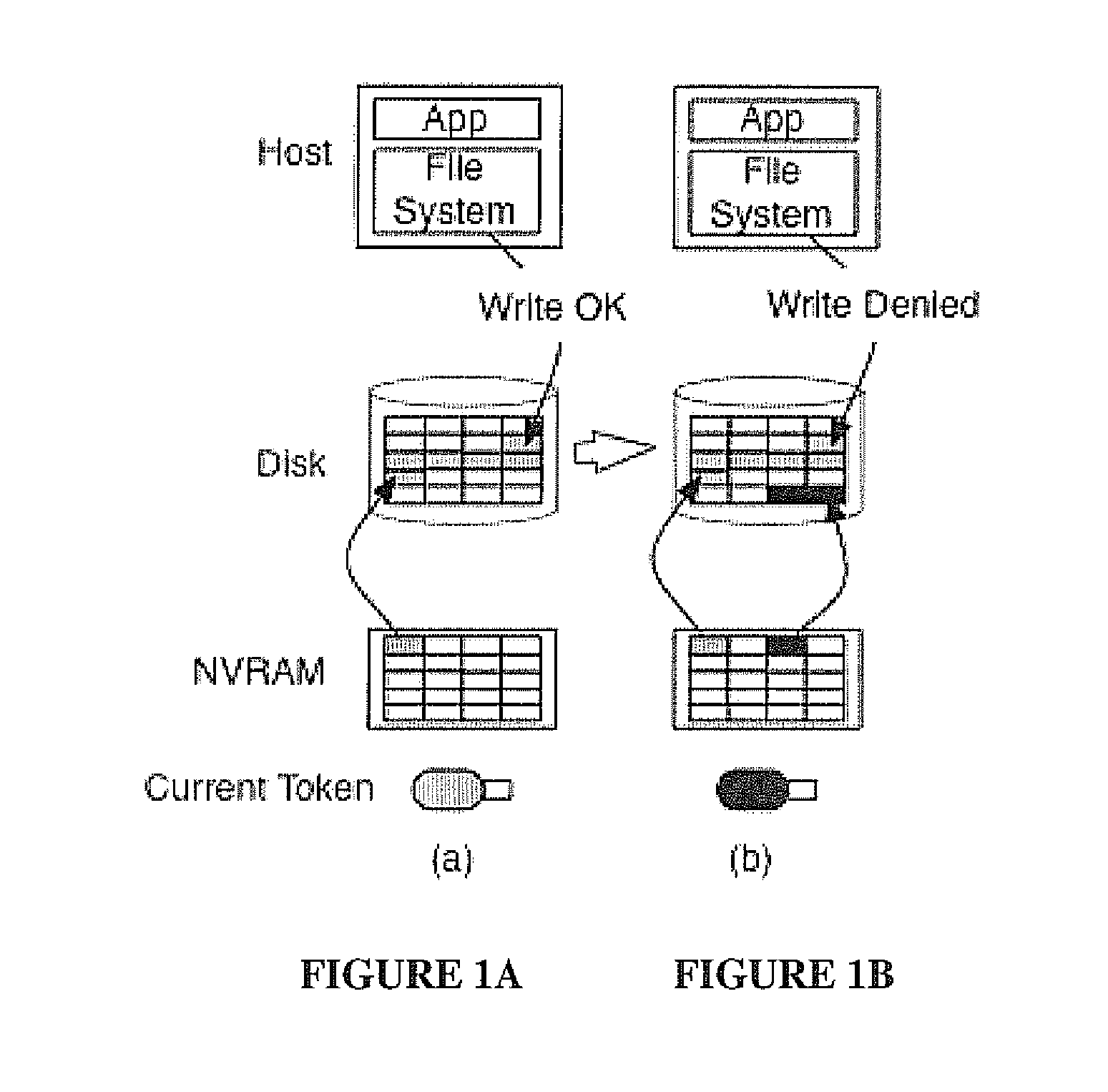
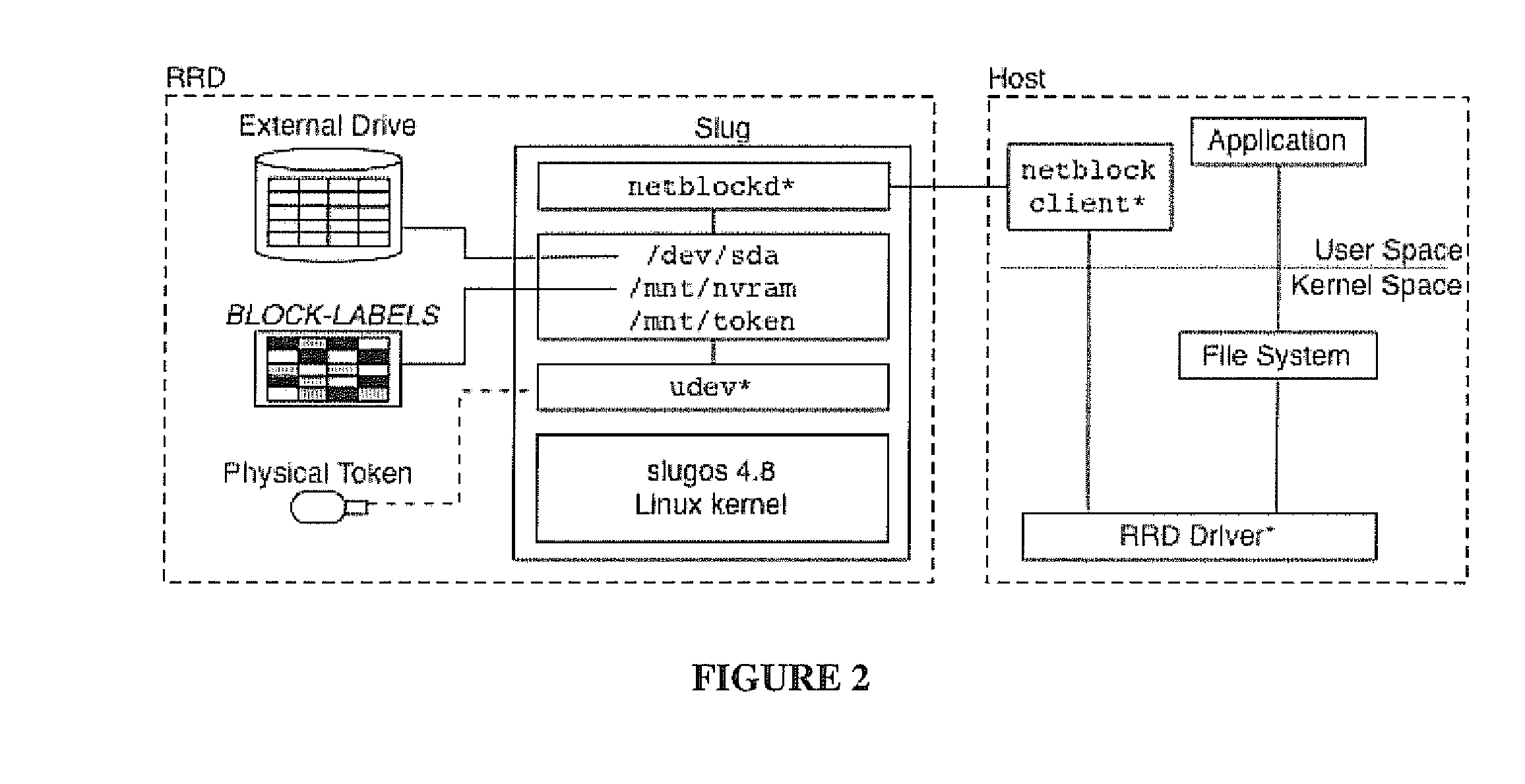
Rootkit-resistant storage disks
InactiveUS20110035808A1Cutting costsDigital data processing detailsAnalogue secracy/subscription systemsOperational systemDisk controller
Rootkit-resistant disks (RRD) label all immutable system binaries and configuration files at installation time. During normal operation, the disk controller inspects all write operations received from the host operating system and denies those made for labeled blocks. To upgrade, the host is booted into a safe state and system blocks can only be modified if a security token is attached to the disk controller. By enforcing immutability at the disk controller, a compromised operating system is prevented from infecting its on-disk image.
Owner:PENN STATE RES FOUND
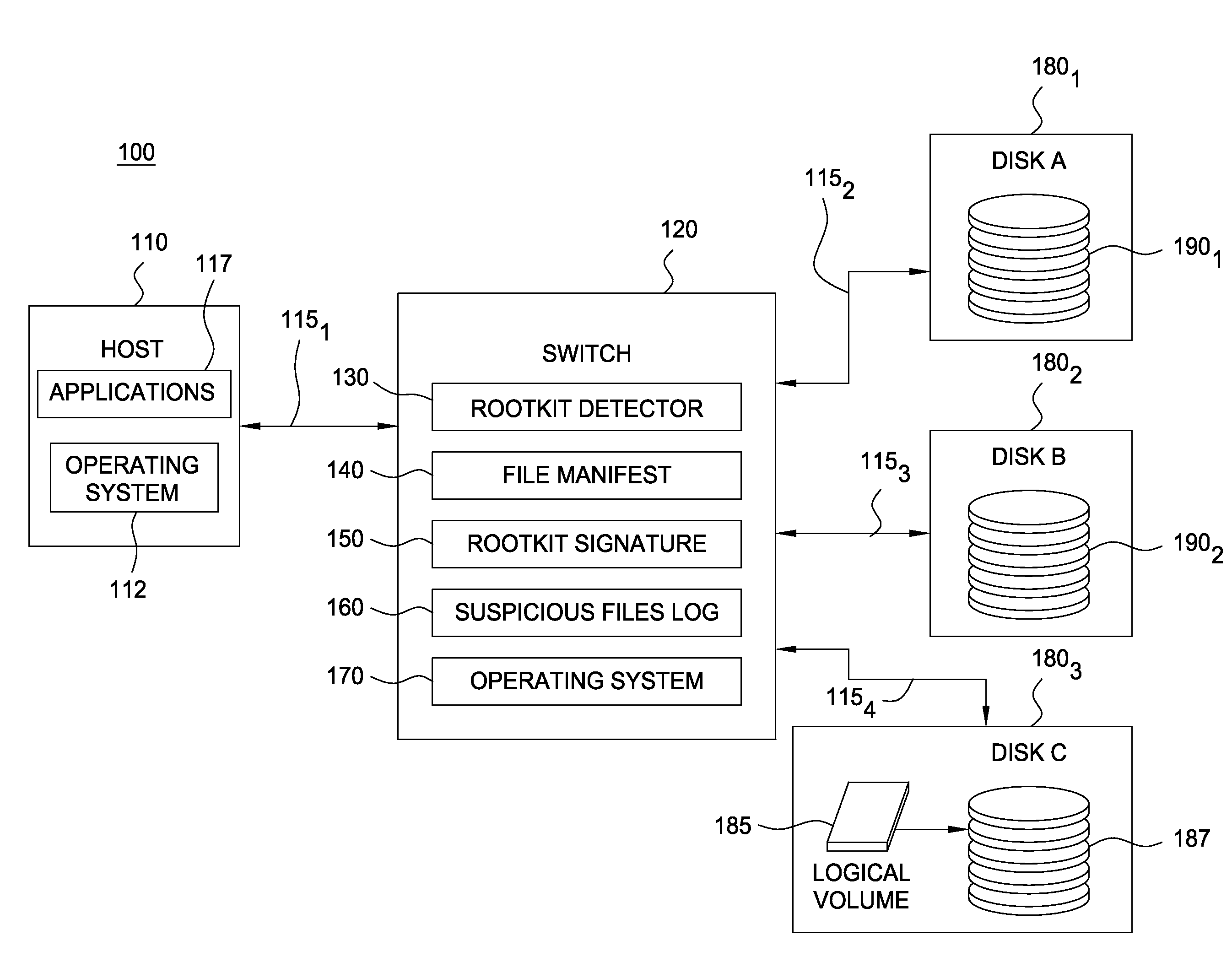
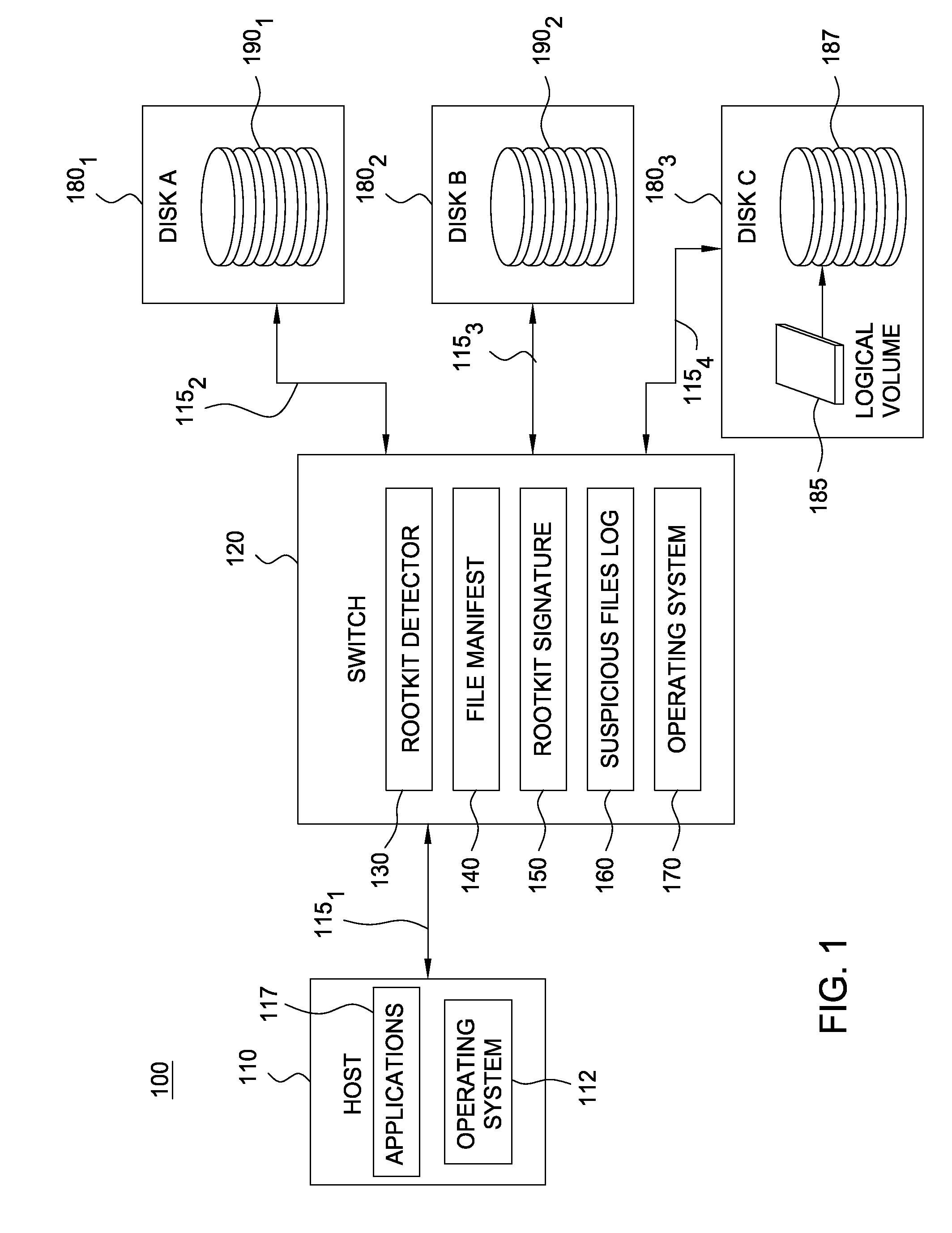
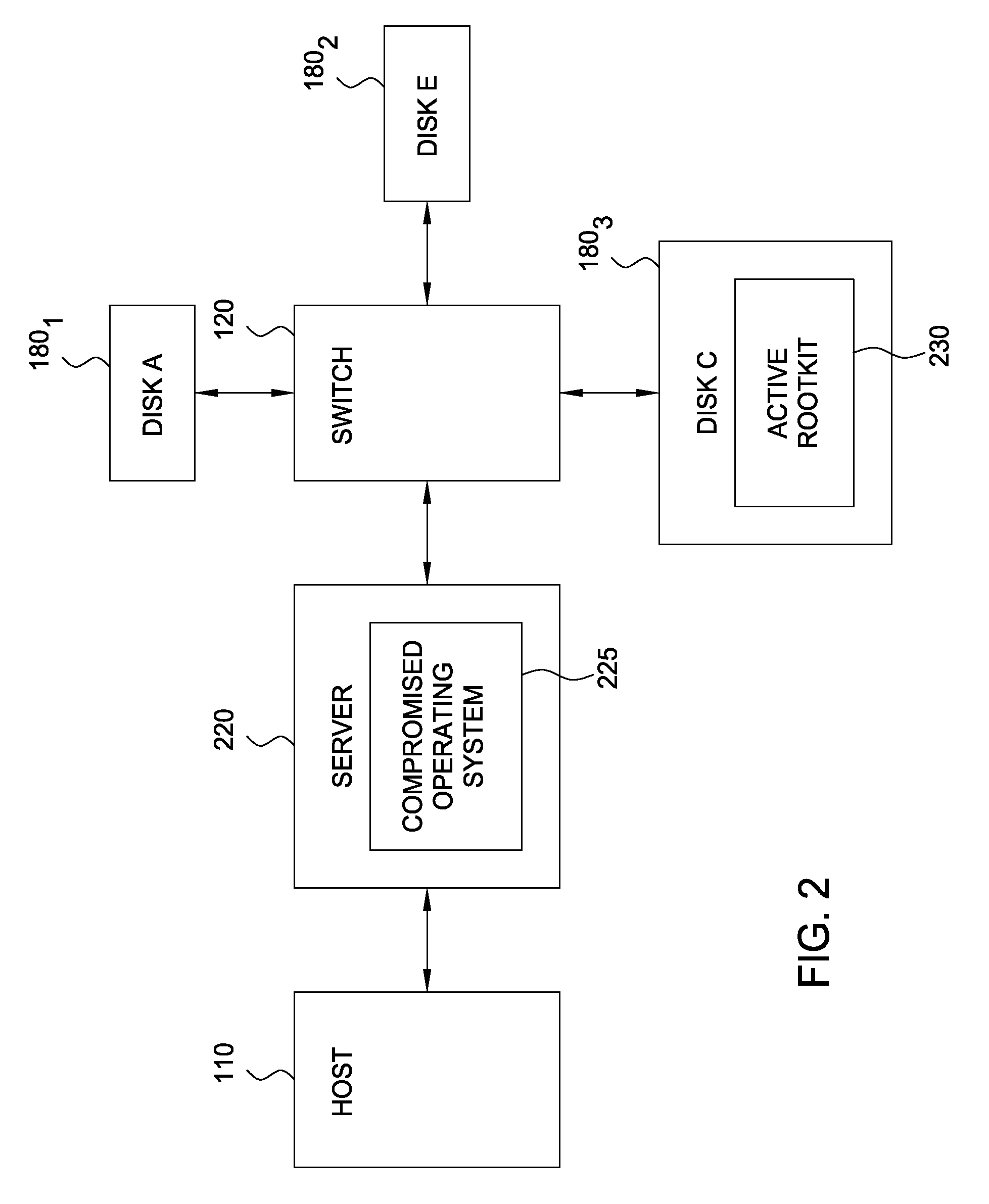
Detecting rootkits over a storage area network
ActiveUS20090172816A1Memory loss protectionUnauthorized memory use protectionStorage area networkApplication software
Embodiments of the invention improve the detection of malicious software applications, such as a rootkit, on hosts configured to access storage volumes over a storage area network (SAN). A rootkit detection program running on a switch may be configured to detect rootkits present on the storage volumes of the SAN. Because the switch may mount and access storage volumes independently from the (possibly comprised) hosts, the rootkit is not able to conceal itself from the rootkit detection program running on the switch.
Owner:CISCO TECH INC
Security verification method during kernel operation of operation system
InactiveCN103473508AEnsure consistencySecurity is comprehensive and thoroughPlatform integrity maintainanceOperational systemSecurity software
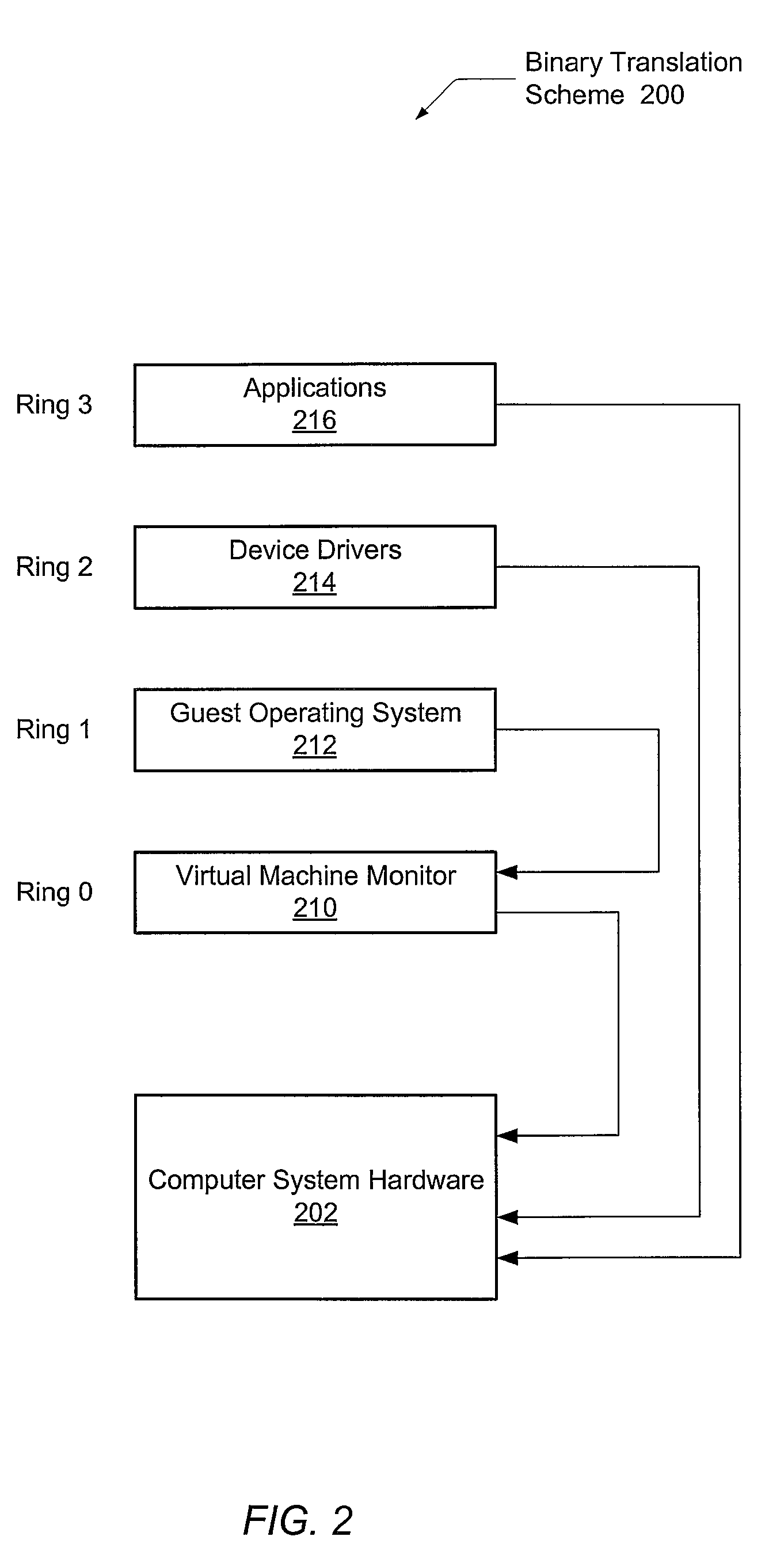
The invention provides a security verification method during kernel operation of an operation system. The security verification method comprises the following steps that the validity of all kernel module files of a target operation system is confirmed, the validity of loaded modules in a kernel is verified, the validity verification is carried out on a new kernel module loaded at any time, all entrances switched from the user grade to the privilege grade in a processor are set again, each instruction to be translated required by the binary translation is checked, and the like. The method can be used for computer security software and can be used for fundamentally detecting the computer operation system in the operation for detecting kernel viruses existing in the computer operation system, in addition, the precaution can be carried out on the existing operation system for finding the kernel viruses tried to invade a computer, and in addition, viruses are conditionally cleared. The method belongs to a measure for thoroughly solving the problem of rootkit.
Owner:肖楠
Defense method for kernel-level return-oriented rootkits
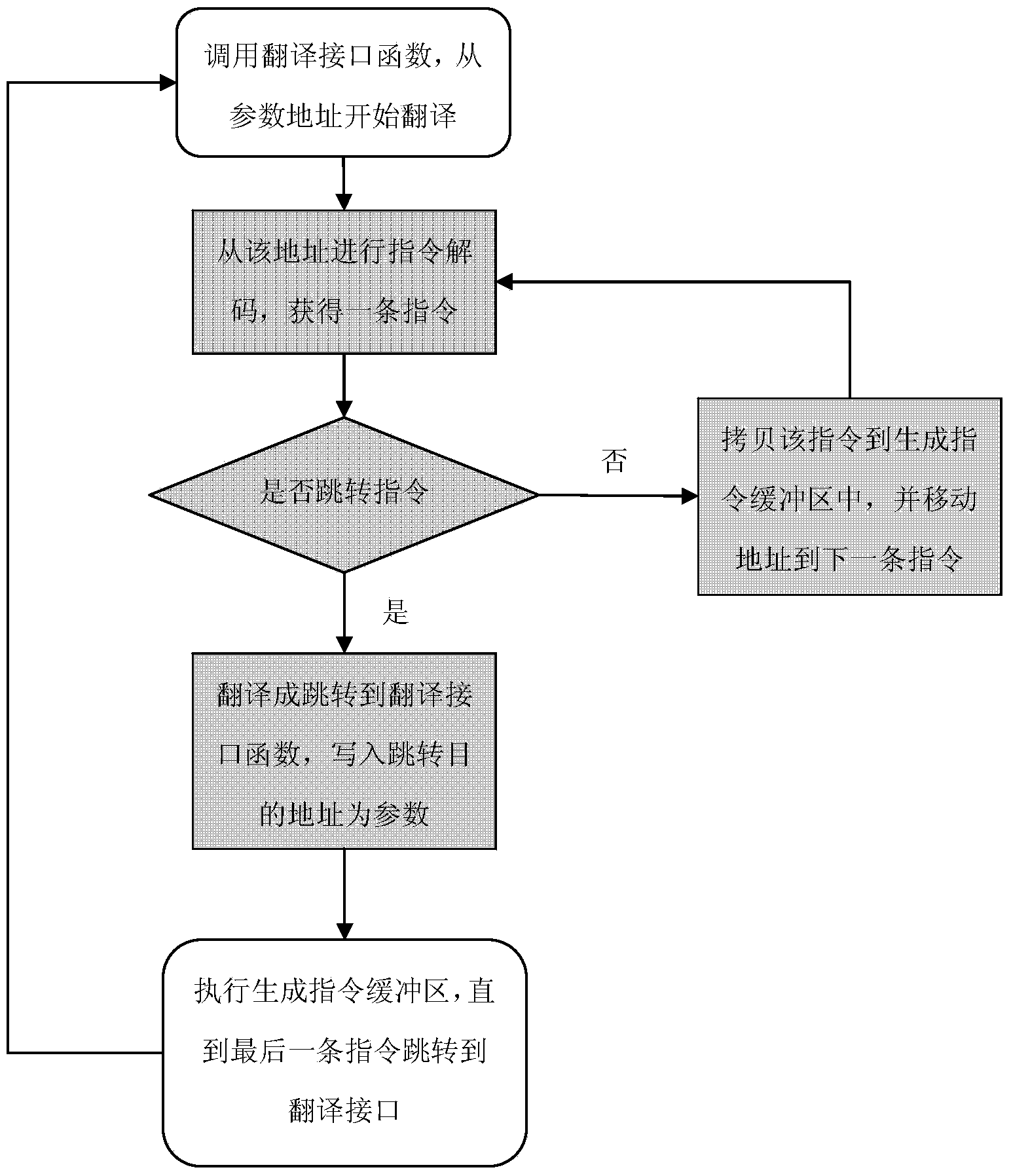
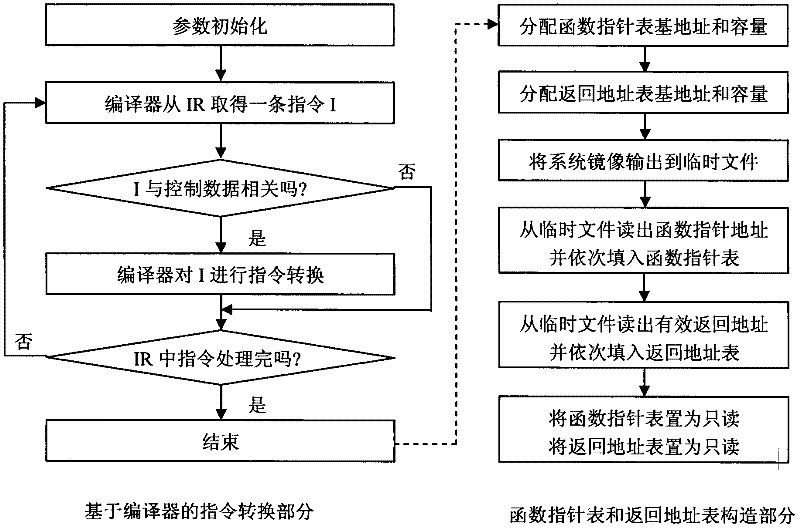
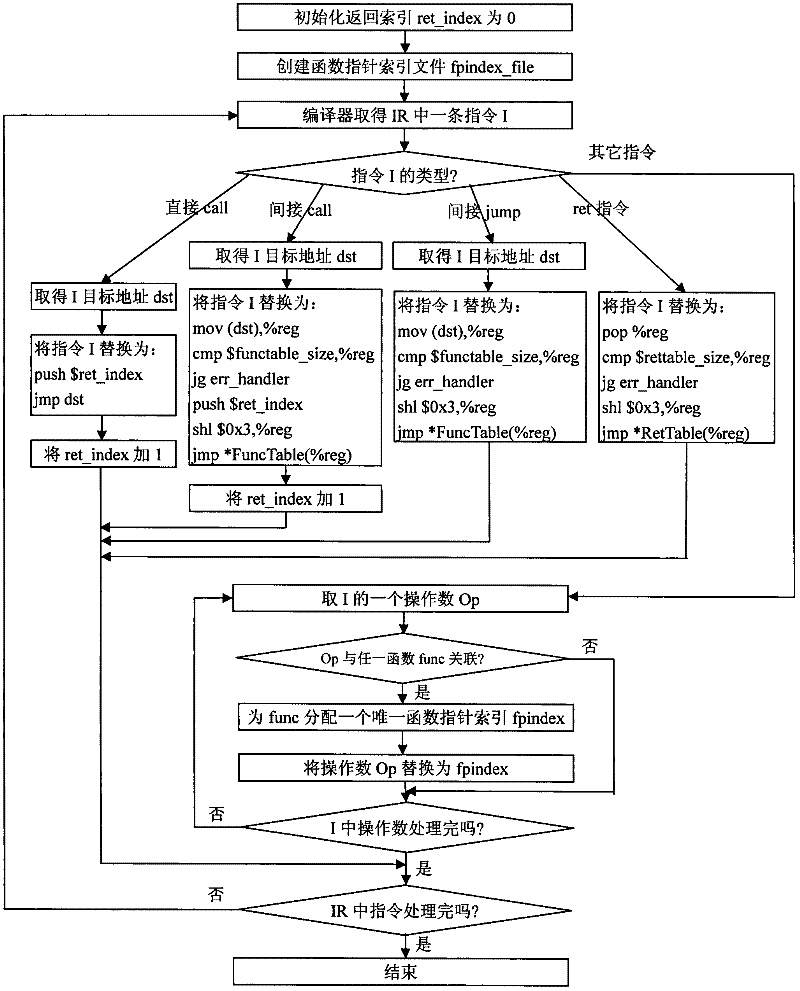
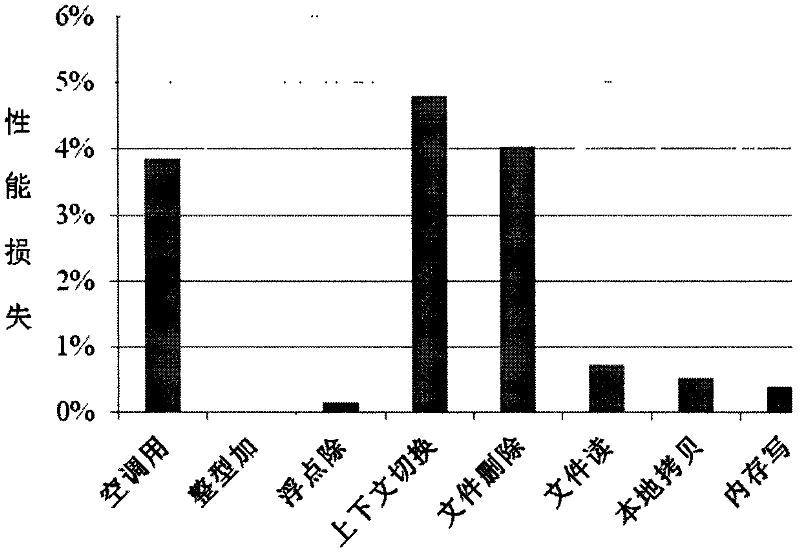
InactiveCN102375957AFree from harmAchieve the purpose of the attackPlatform integrity maintainanceOperational systemControl data
The invention discloses a defense method for kernel-level return-oriented rootkits, which mainly solves the problem of incapability of defending the latest kernel-level return-oriented rootkits attack in the prior art. The method comprises the following implementation steps of: distributing an index for each piece of control data by a compiler and converting a related instruction so as not to directly use the control data during program skip but search a certain skip table by using the index distributed by the compiler to obtain a really effective skip address to indirectly perform; and then collecting all effective skip addresses, namely control data, in a system to a function pointer table and returning to an address table for protection. By adopting the method, a second step of conducting attack cannot be finished by the kernel-level return-oriented rootkits, namely the original execution flow of the system is required to be changed by rewriting a certain piece of control data, and the method can be used for protecting safety of an operating system.
Owner:XIDIAN UNIV
Kernel mode Rootkit detection method based on system virtualization technology
ActiveCN103310152AAvoid attackGuarantee authenticityPlatform integrity maintainanceVirtualizationSystem call
The invention provides a kernel mode Rootkit detection method based on system virtualization technology. A Rootkit principle, system calling and an LKM (Loadable Kernel Module) are analyzed deeply to obtain the behavior characteristic of hiding of own module information of kernel mode Rootkit. Specific to the characteristic, the Rootkit detection method based on cross view validation is designed. A Xen kernel is changed to intercept system calling, so that a credible view is constructed. An infected view is constructed by using a user mode tool of a target client. Hidden modules are found by comparing the credible view with the infected view.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
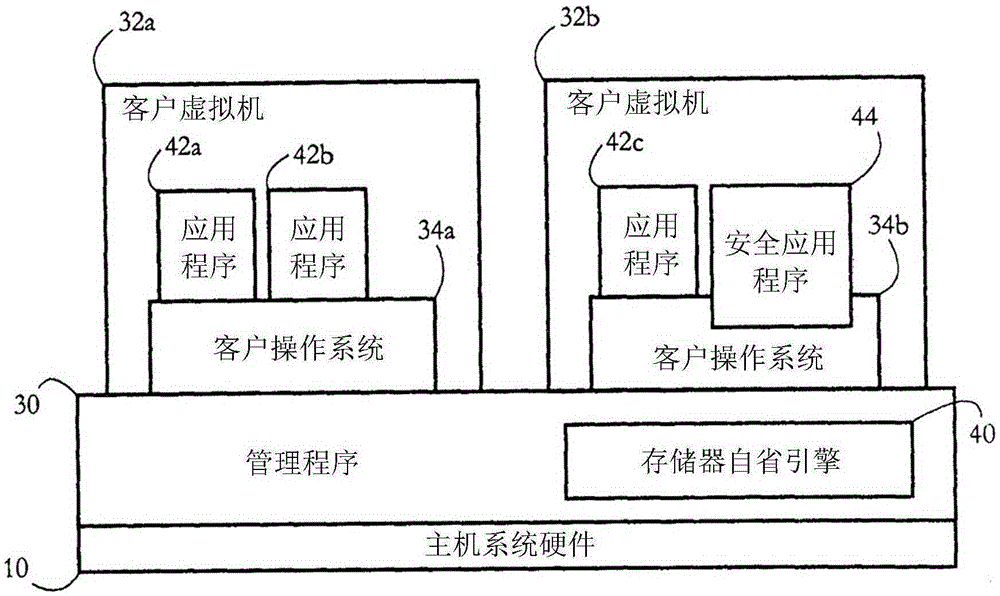
Process evaluation for malware detection in virtual machines
Described systems and methods allow protecting a computer system from malware, such as viruses and rootkits. An anti-malware component executes within a virtual machine (VM) exposed by a hypervisor executing on the computer system. A memory introspection engine executes outside the virtual machine, at the processor privilege level of the hypervisor, and protects a process executing within the virtual machine by write-protecting a memory page of the respective process. By combining anti-malware components executing inside and outside the respective VM, some embodiments of the present invention may use the abundance of behavioral data that inside- VM components have access to, while protecting the integrity of such components from outside the respective VM.
Owner:BITDEFENDER IPR MANAGEMENT
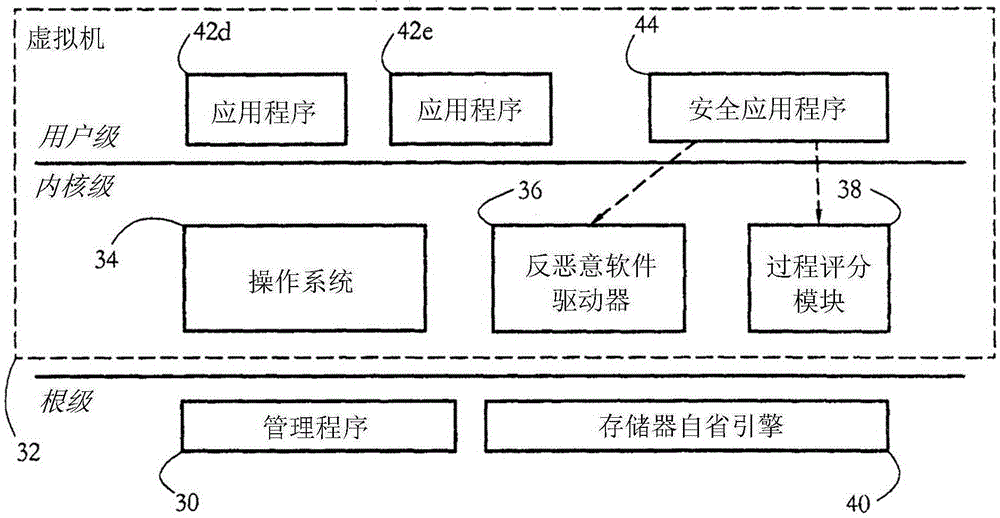
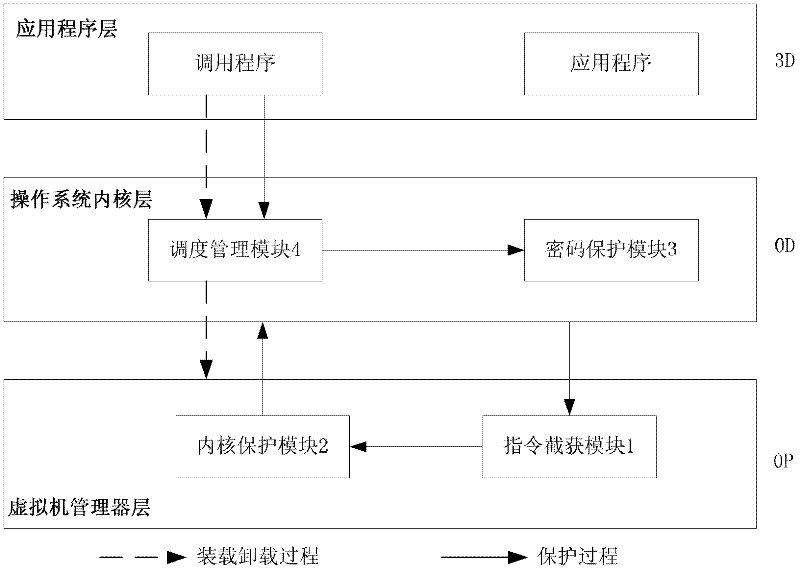
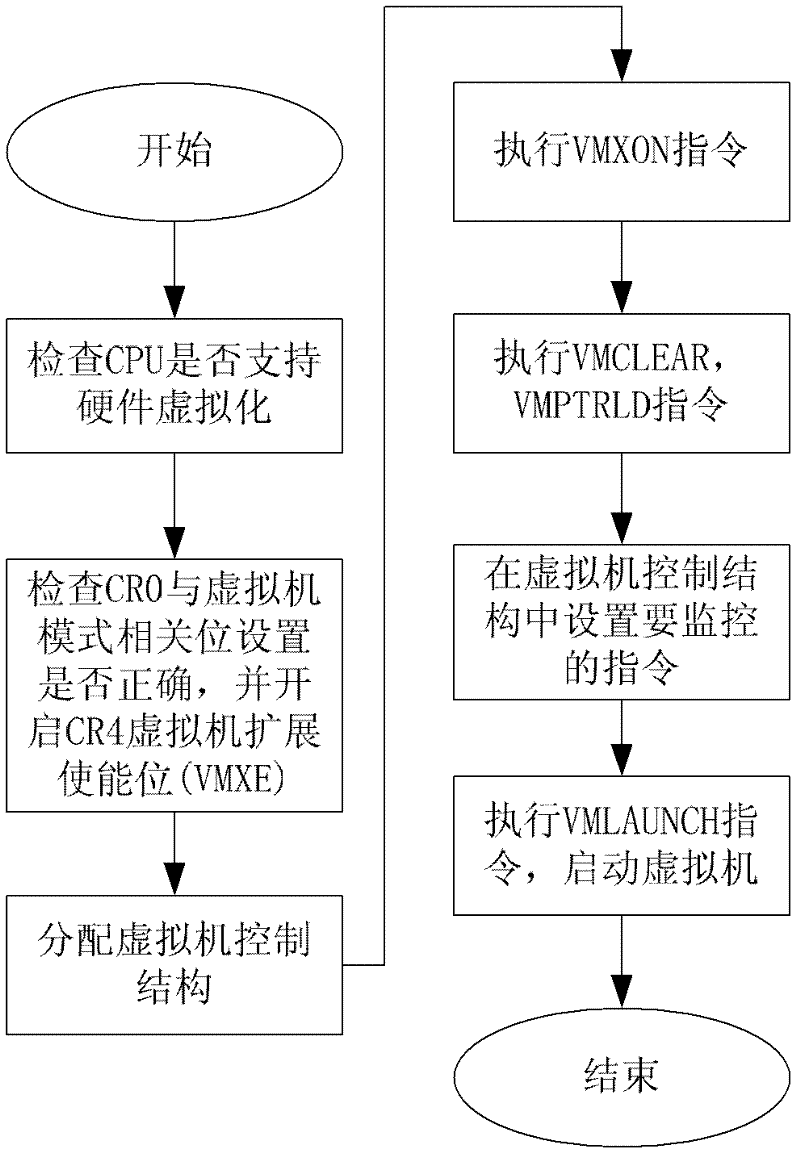
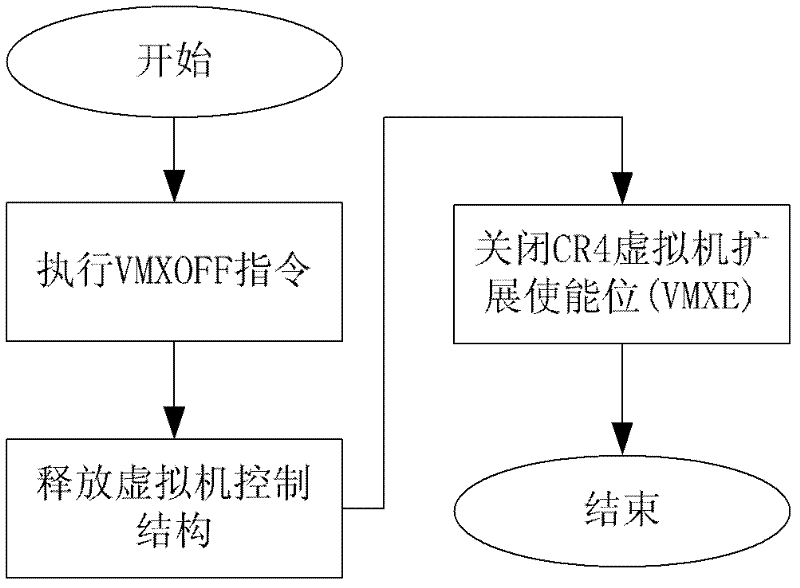
Password protection system based on hardware virtualization
InactiveCN102521531AImprove securityIncrease flexibilityDigital data authenticationOperational systemTrusted Computing
The invention provides a password protection system based on hardware virtualization, which aims at the current situation that a traditional password protection system cannot defend an inner nuclear layer rootkit. The password protection system based on hardware virtualization deploys a password protection module and a scheduling management module in an inner nuclear layer of an operation system, provides a safe input environment and an interactive interface, and simultaneously deploys an instruction intercepting module and an inner core protection module in a manager layer of a virtual machine. The instruction intercepting module is used for intercepting privileged instructions, and transmitting the current privileged instruction information to the inner core protection module so as to lead an execution flow path to enter a manger of the virtual machine from the inner nuclear layer of the operation system. The inner core protection module prevents the rootkit from randomly modifying nuclear data and service in the operation system, and guarantees password protection in the inner nuclear layer of the operation system. The password protection system based on hardware virtualization moves a trusted computing base (TCB) from the inner nuclear layer of the operation system to the manager layer of the virtual machine, thereby achieving lower level and higher safety.
Owner:HUAZHONG UNIV OF SCI & TECH
Balancing malware rootkit detection with power consumption on mobile devices
InactiveUS8566935B2Improve compromiseMemory loss protectionError detection/correctionOperational systemEnergy expenditure
Owner:AT&T INTPROP I LP +1
Highly-available system design method based on virtualization
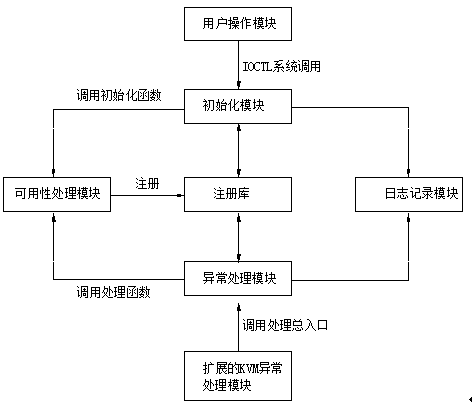
ActiveCN103996004AAvoid attackImprove usabilityPlatform integrity maintainanceVirtualizationSystems design
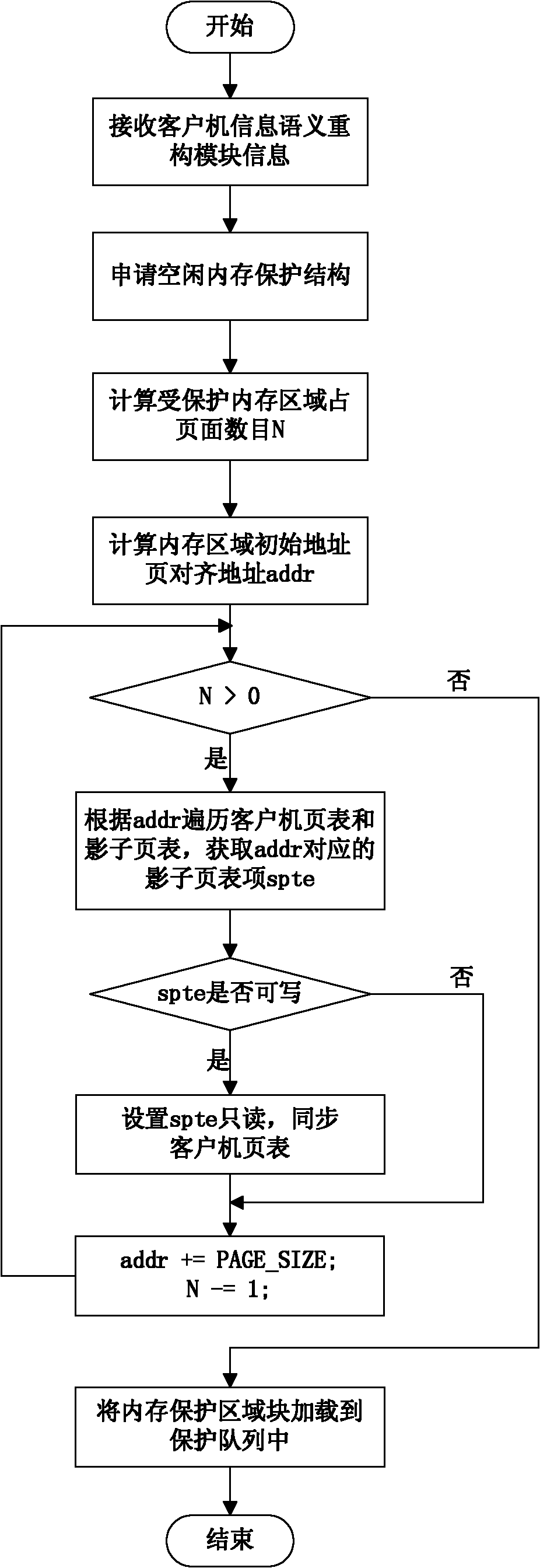
The invention discloses a highly-available system design method based on virtualization. The strategy of protecting a kernel key data structure is achieved on the basis of the virtualization technology by mainly relying on a shadow page table management mechanism, a hypercall mechanism and correct and effect execution of exception handling logic; a highly-available system based on client abnormity processing is put forward, wherein an overall system frame of the system is mainly composed of a user operation module and a kernel module. By means of the highly-available system design method, the kernel key data structure is protected based on the virtualization technology and through client authority downgrading and resource management measures, the process of tampering kernel key data to obtain the control authority through a malicious program is avoided, availability of a kernel of the operation system is effectively improved, attack from rootkit is effectively avoided, performance loss is small, no hardware framework is relied on, and the highly-available system design method is transparent for applications and users.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com