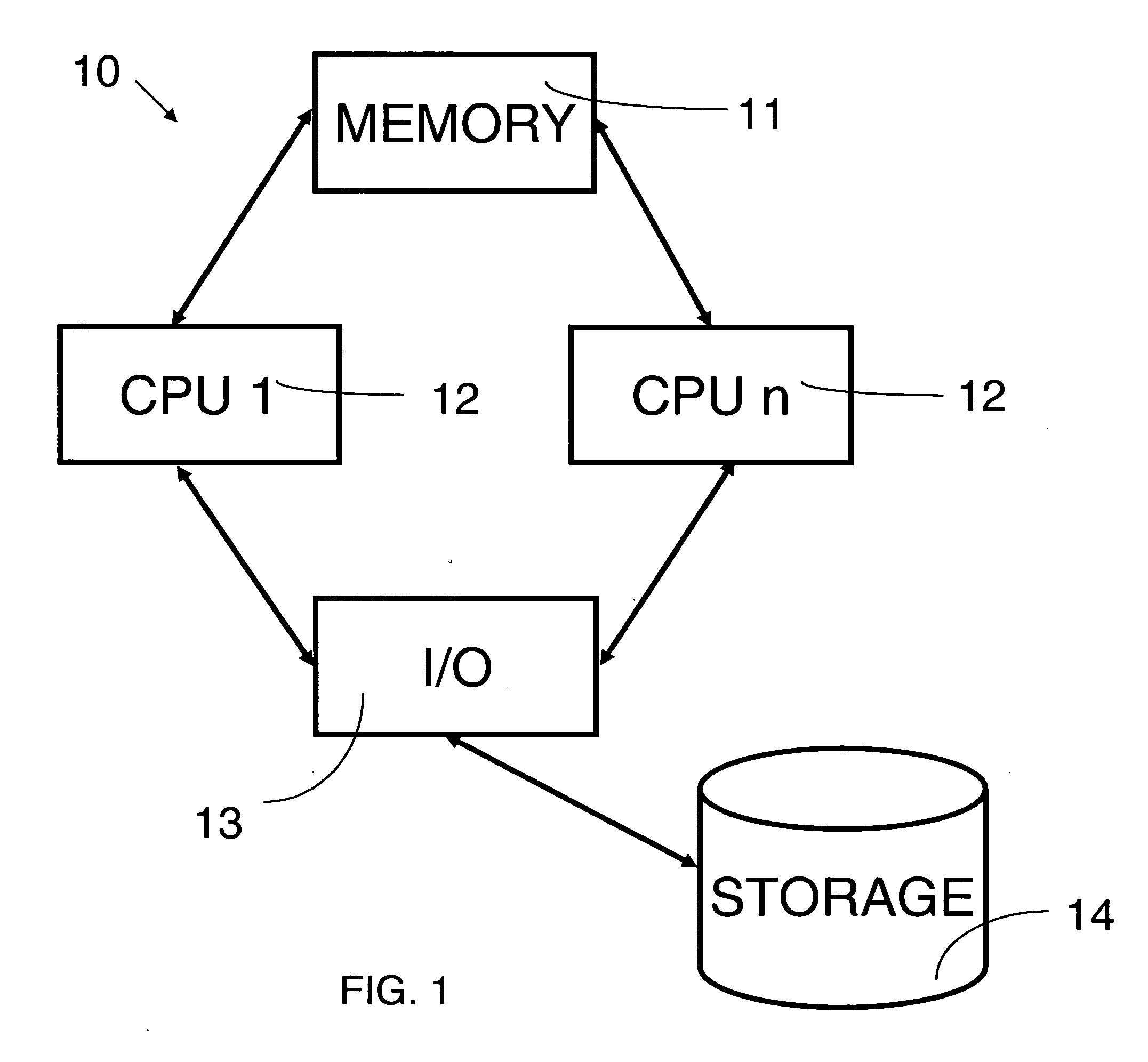
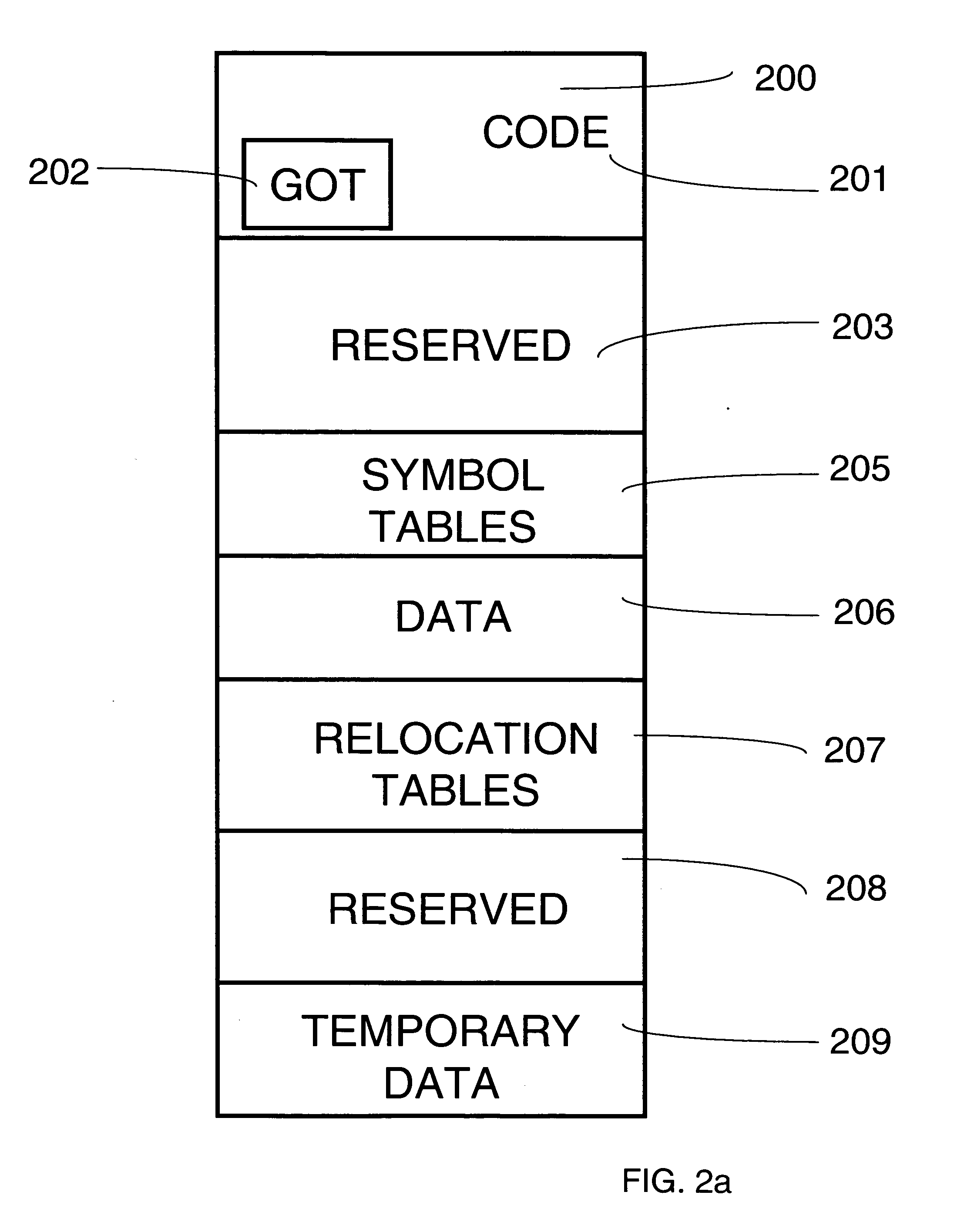
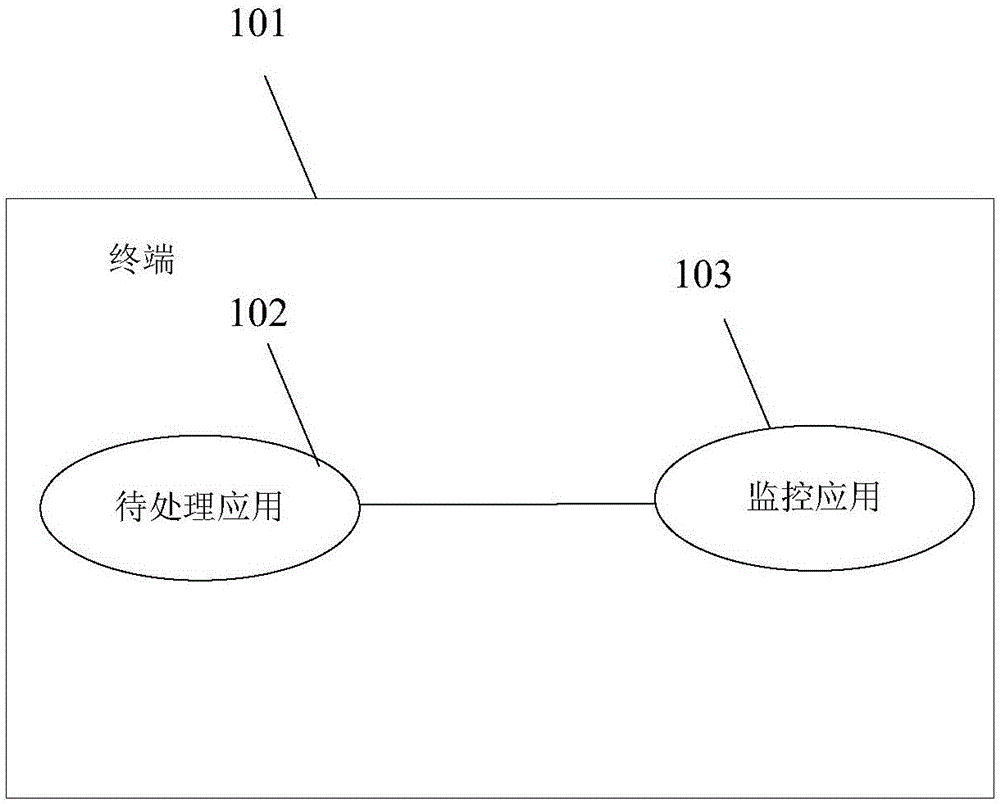
Patents
Literature
152 results about "Function pointer" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A function pointer, also called a subroutine pointer or procedure pointer, is a pointer that points to a function. As opposed to referencing a data value, a function pointer points to executable code within memory. Dereferencing the function pointer yields the referenced function, which can be invoked and passed arguments just as in a normal function call. Such an invocation is also known as an "indirect" call, because the function is being invoked indirectly through a variable instead of directly through a fixed identifier or address.
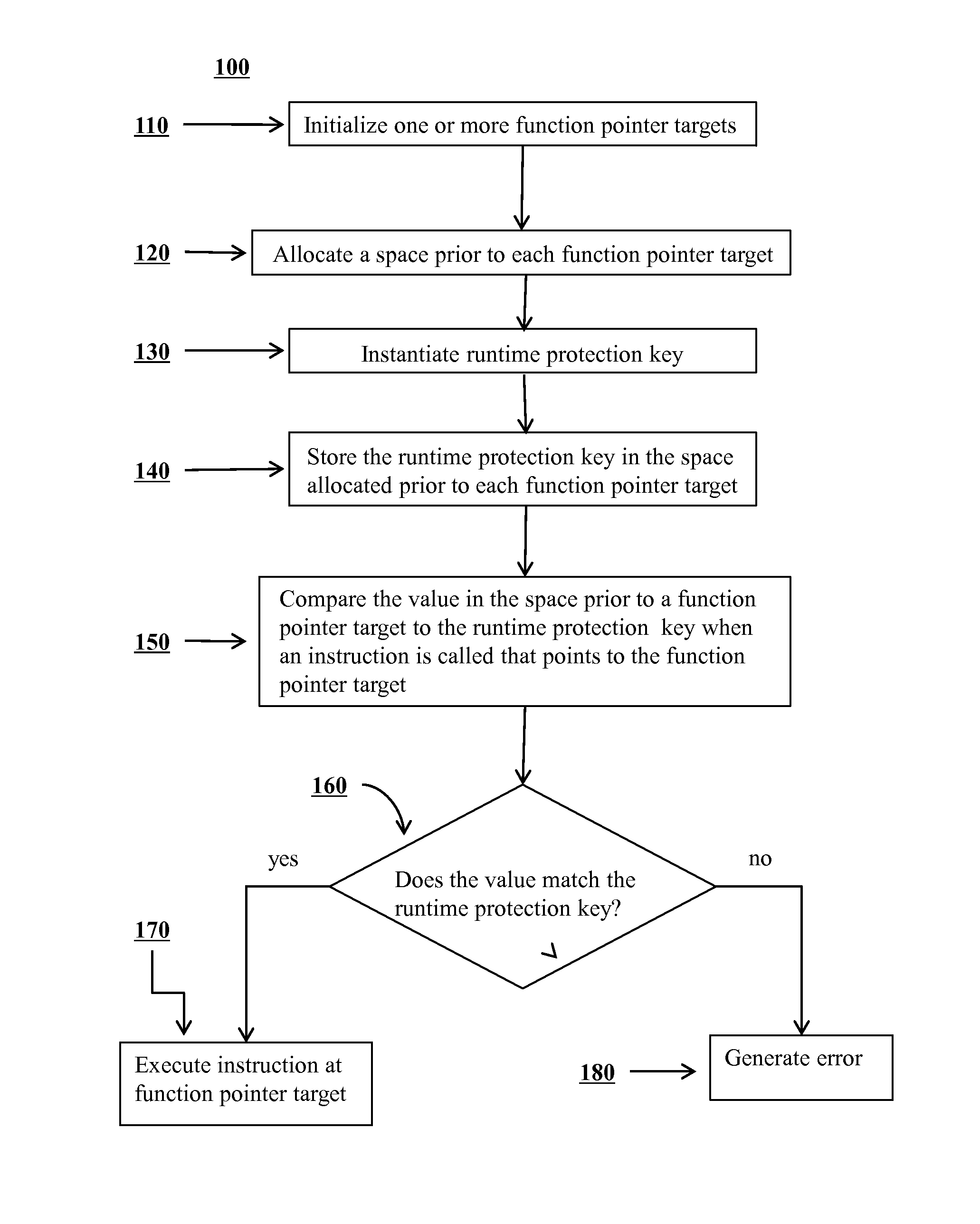
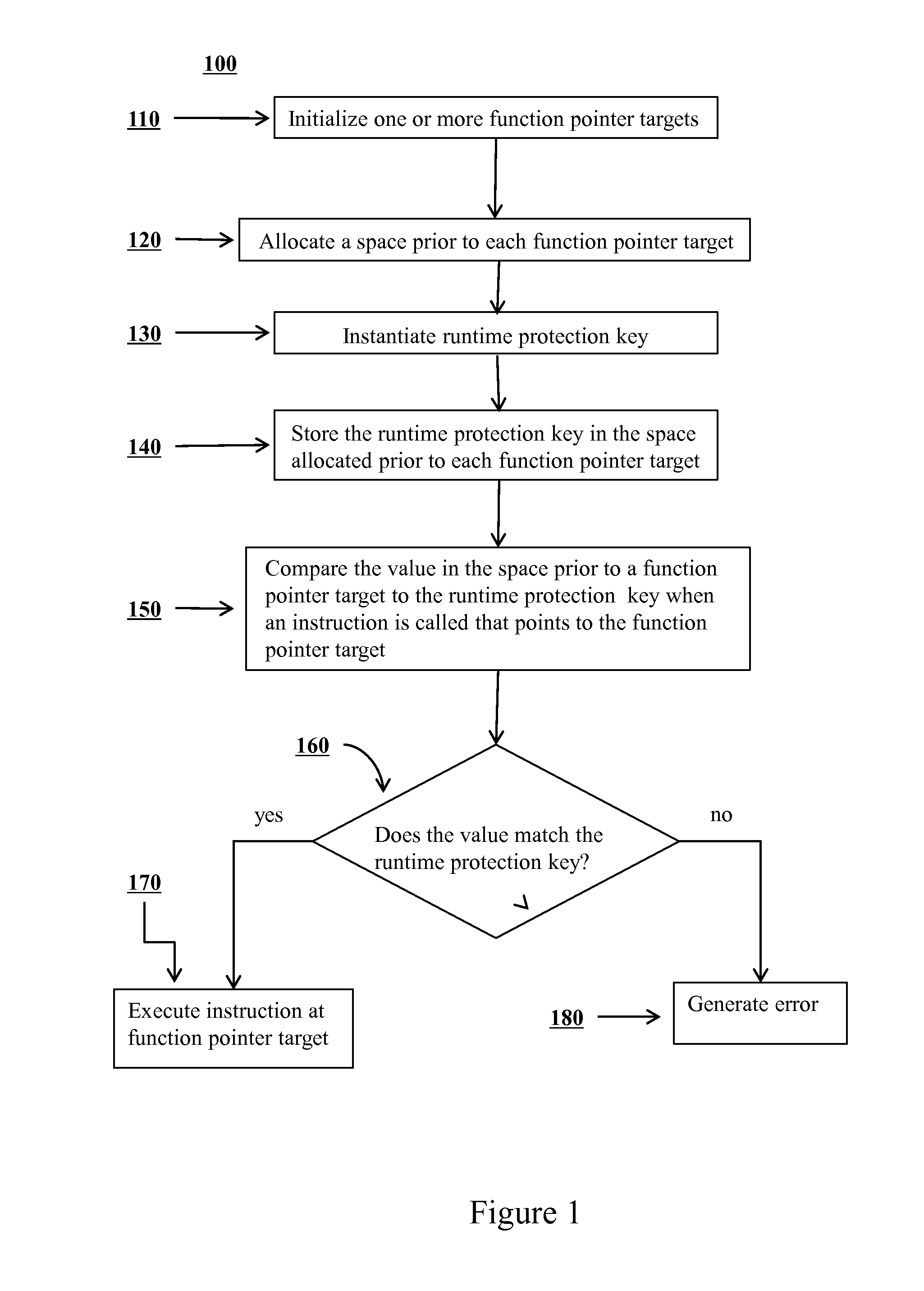
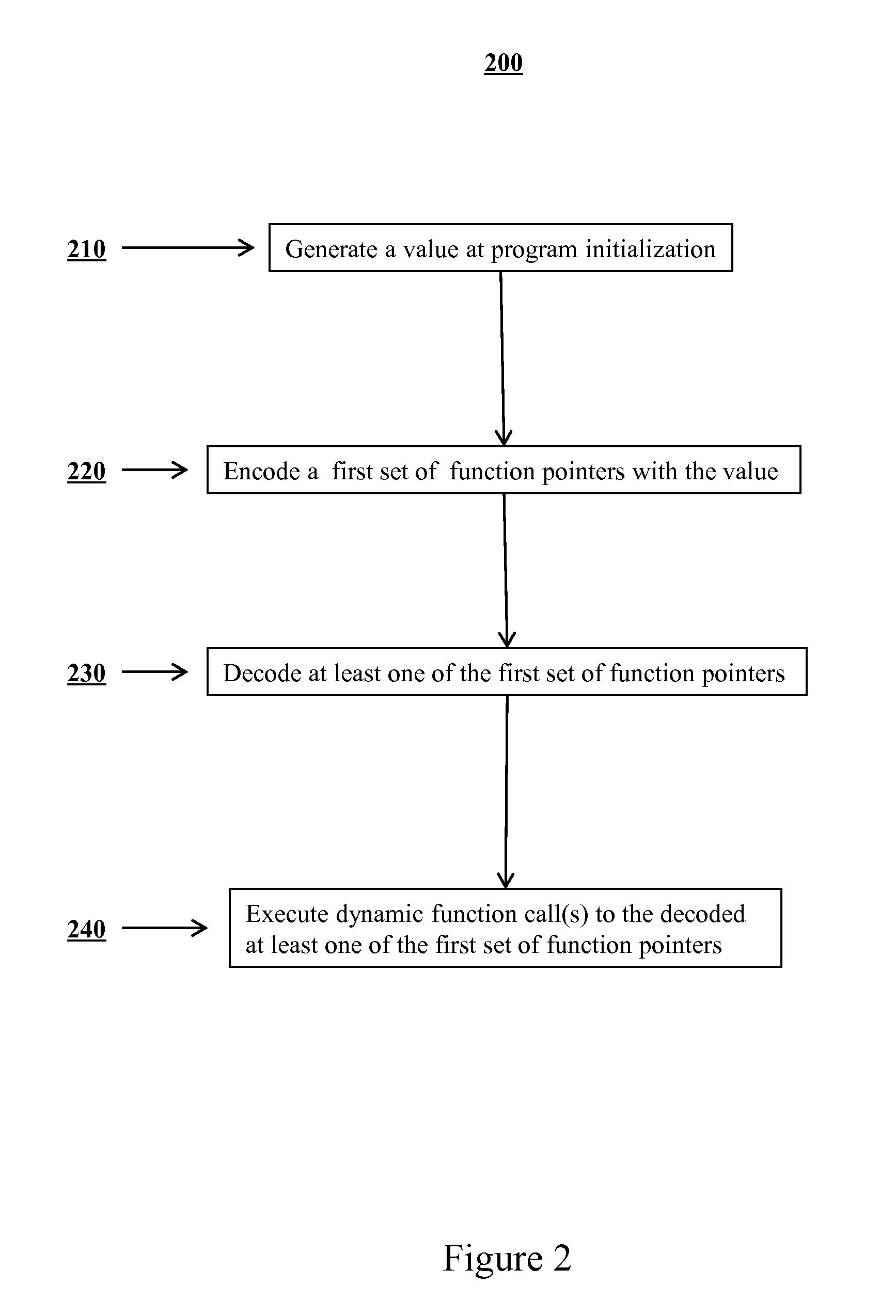
Mitigation of function pointer overwrite attacks
ActiveUS20140020092A1Reduce attackMitigating function pointer overwrite attackMemory loss protectionError detection/correctionFunction pointerExecution control
Methods are disclosed for improving security of computer software and preventing potential attackers from gaining control of computer software via function pointer overwrite attacks. One or more additional layers of complexity may be imposed that would have to be circumvented in order to gain execution control over portions of software. One or more function pointers can be encoded using a value that may be generated on program initialization and decoded before any dynamic function call occurs. In the event of memory corruption that affects an encoded function pointer, the value will cause the destination of the function pointer to decode to an invalid and random address and will induce an error. An application may be prevented from calling an attacker corrupted function pointer by introducing various checks around the call point at compile time that check the validity of the destination to which the function pointer points.
Owner:LEVIATHAN SECURITY GRP
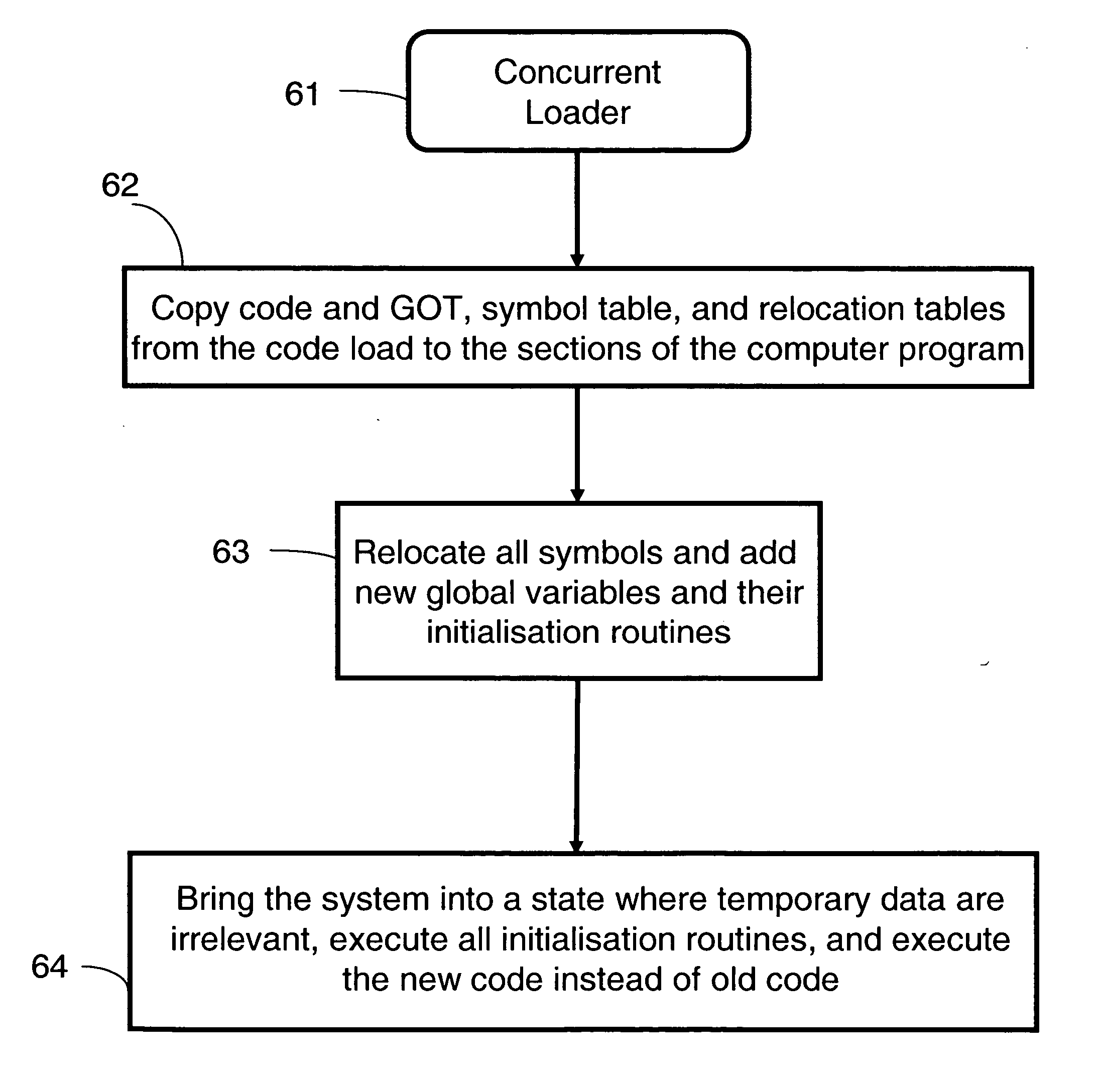
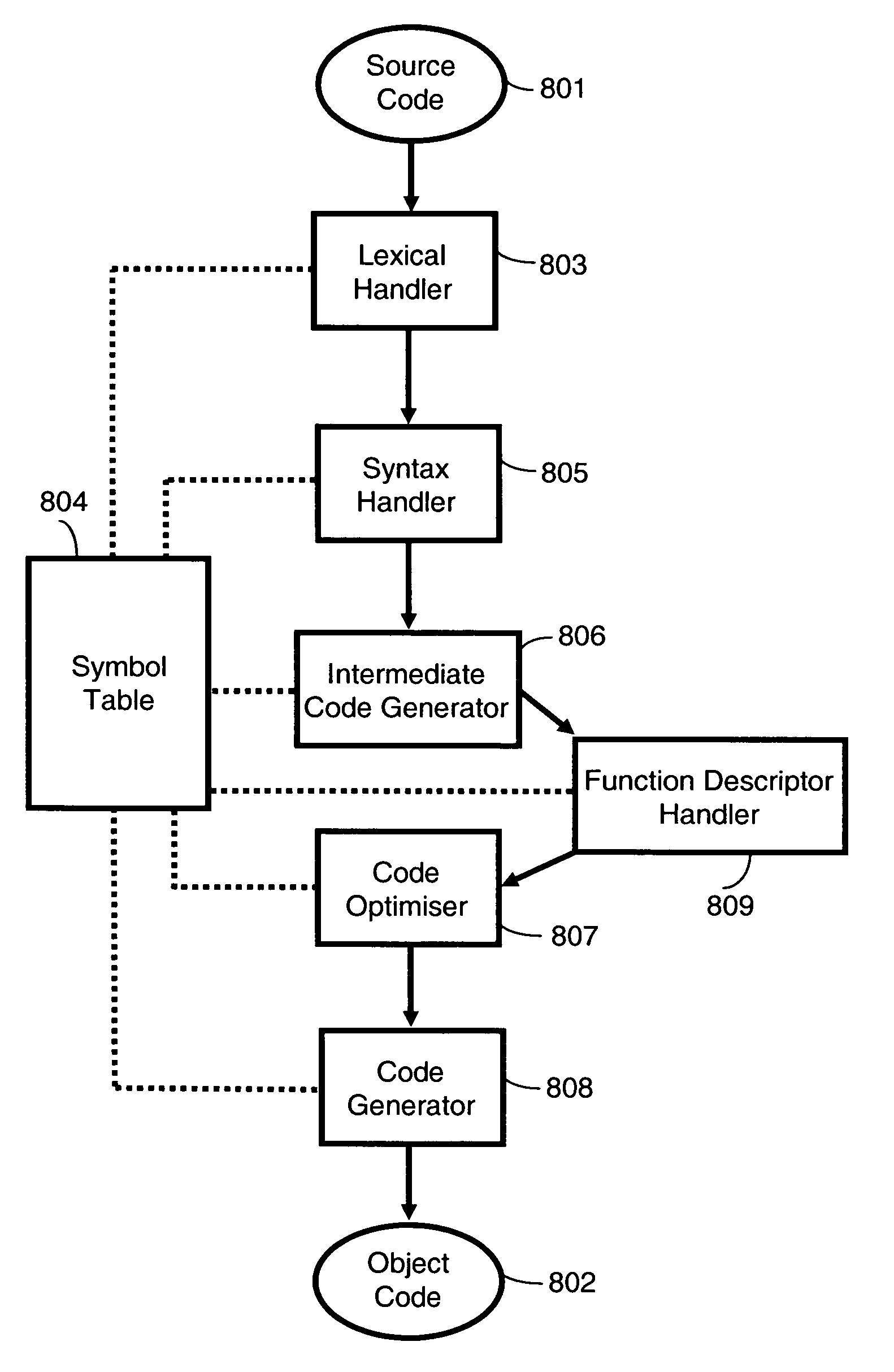
Method and system for generating and applying patches to a computer program concurrently with its execution
InactiveUS20070006201A1Improve executionSoftware engineeringSpecific program execution arrangementsFunction pointerComputer program
A method, a computer program product, and a system for generating and applying patches to a computer program concurrently with its execution. It provides full support for function pointers, transparent to the programmer and nearly transparent to the concurrent loader. A reference to a function pointer is translated into a sequence of processor instructions called function descriptor instead of translating it into an address. The purpose of the function descriptor is to jump to the memory location of the sequence of instructions generated by the compiler for the procedure referenced by the function pointer. The function descriptor is masked as a static data variable and therefore preserved during the application of a concurrent patch. The address for the jump to the procedure is updated by the regular relocation process during the application of a concurrent patch.
Owner:IBM CORP
Method for determining dynamic function call relation based on register transfer languages
The invention discloses a method for determining a dynamic function call relation based on register transfer languages, mainly aiming to solve the problems in design that a call relation of a function pointer and a loadable module function cannot be analyzed through a static function call relation. The method includes: detecting function call executing events during system operation, if call instructions are detected, analyzing function names corresponding to function entry addresses called through the instructions, performing statistics on number of the instructions and outputting the function names, call occurrence time, subordinate process numbers, subordinate threading numbers, subordinate stack top pointers and module numbers prior to storing to a trace data file; if the detected instructions are return instructions, outputting time, the subordinate process numbers, the subordinate threading numbers and the subordinate stack top pointers to the track data file; processing the track data file to acquire the data format with predetermined standard, transmitting the track data file to a static function call relation generating device so as to generate a dynamic function call graph describing the function call relation.
Owner:TSINGHUA UNIV
Function call method and device
ActiveCN106502745AFlexible callIncrease flexibilitySoftware testing/debuggingProgram loading/initiatingFunction pointerObject function
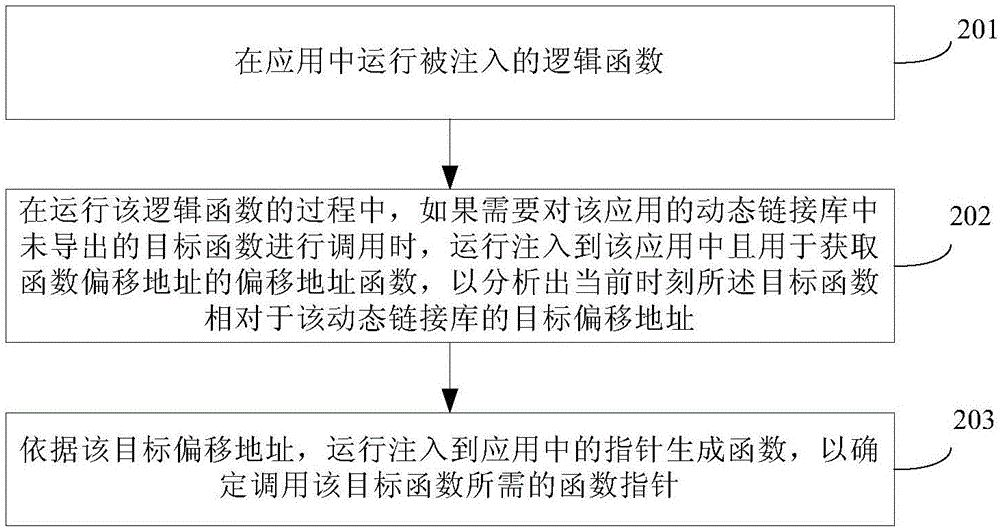
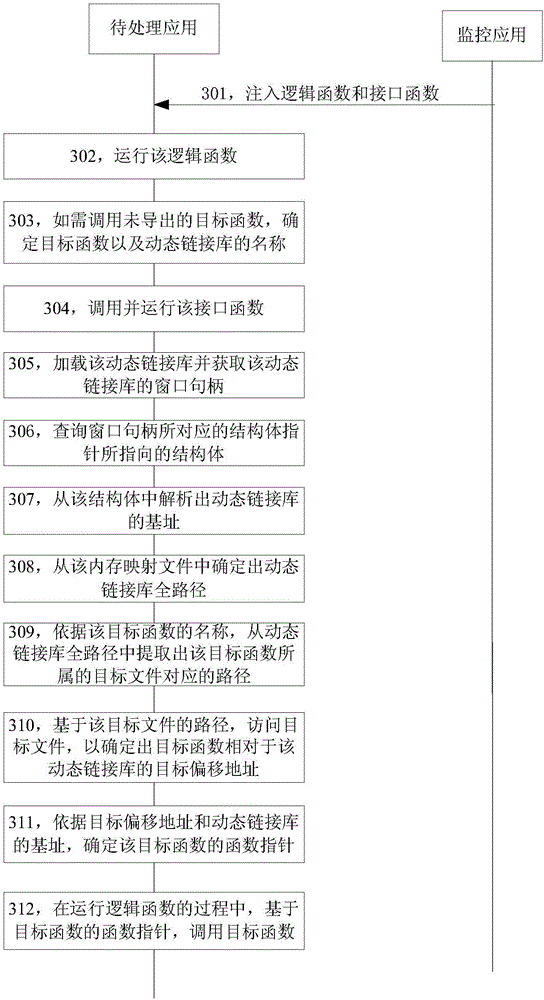
The invention discloses a function call method and device. The method comprises the steps of running an injected logical function in an application for testing or secondary development of the application. In the process of running the logical function, if it is necessary to call an objective function not derived in the dynamic link library of the application, operation is injected into the application to obtain an offset address function which is address offset, so as to analyze the objective offset address of the objective function relative to the dynamic link library at the current moment; according to the objective offset address, the operation is injected into a pointer generation function in the application to determine the function pointer required to call the objective function. The scheme can reduce the complexity of calling underived functions and improve convenience and flexibility of calling the underived functions in the process of performance test or secondary development of an application.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method for capturing function for resulting in memory rewriting by wild pointer
ActiveCN100517249CSoftware testing/debuggingRedundant operation error correctionFunction pointerEmbedded system
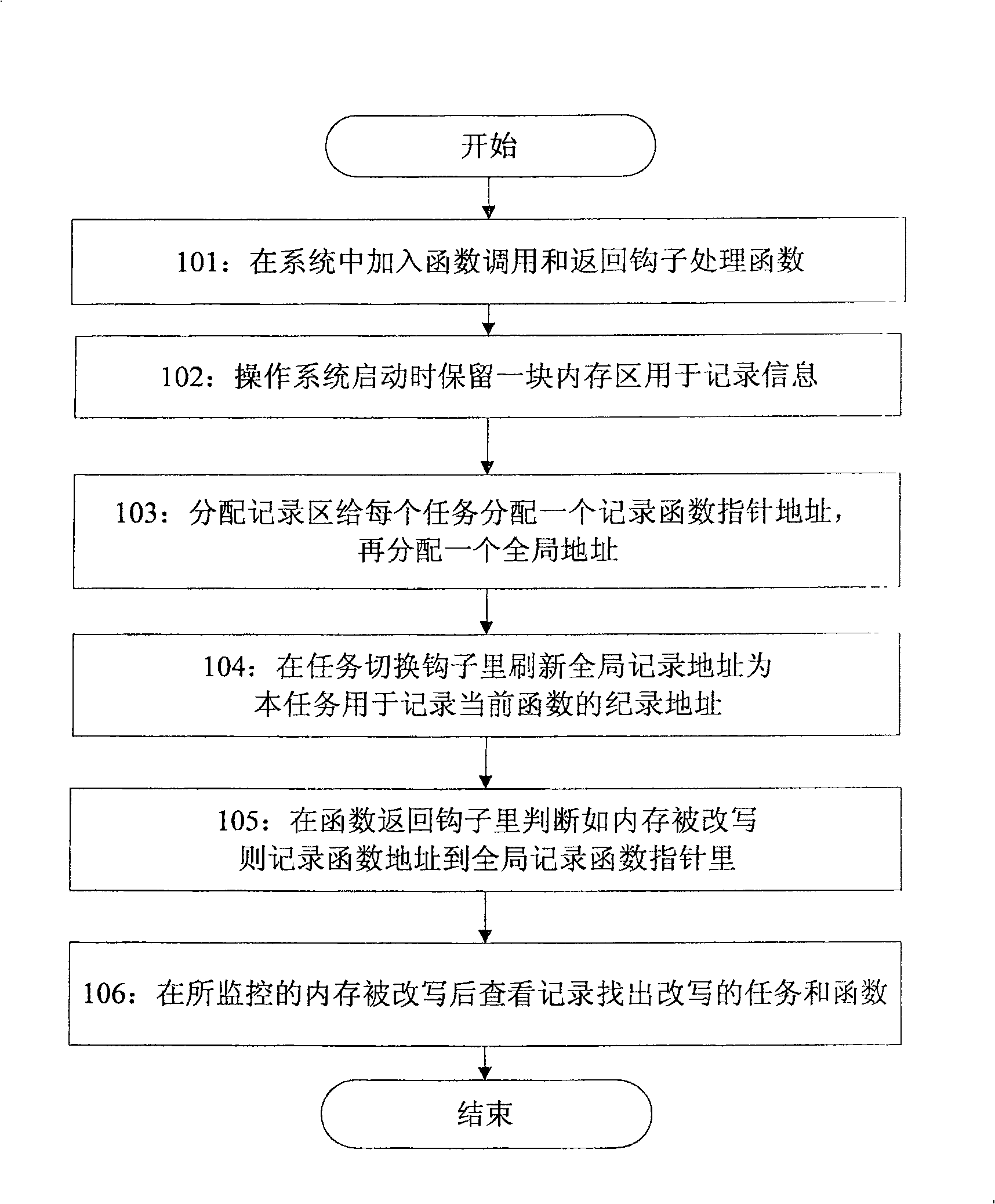
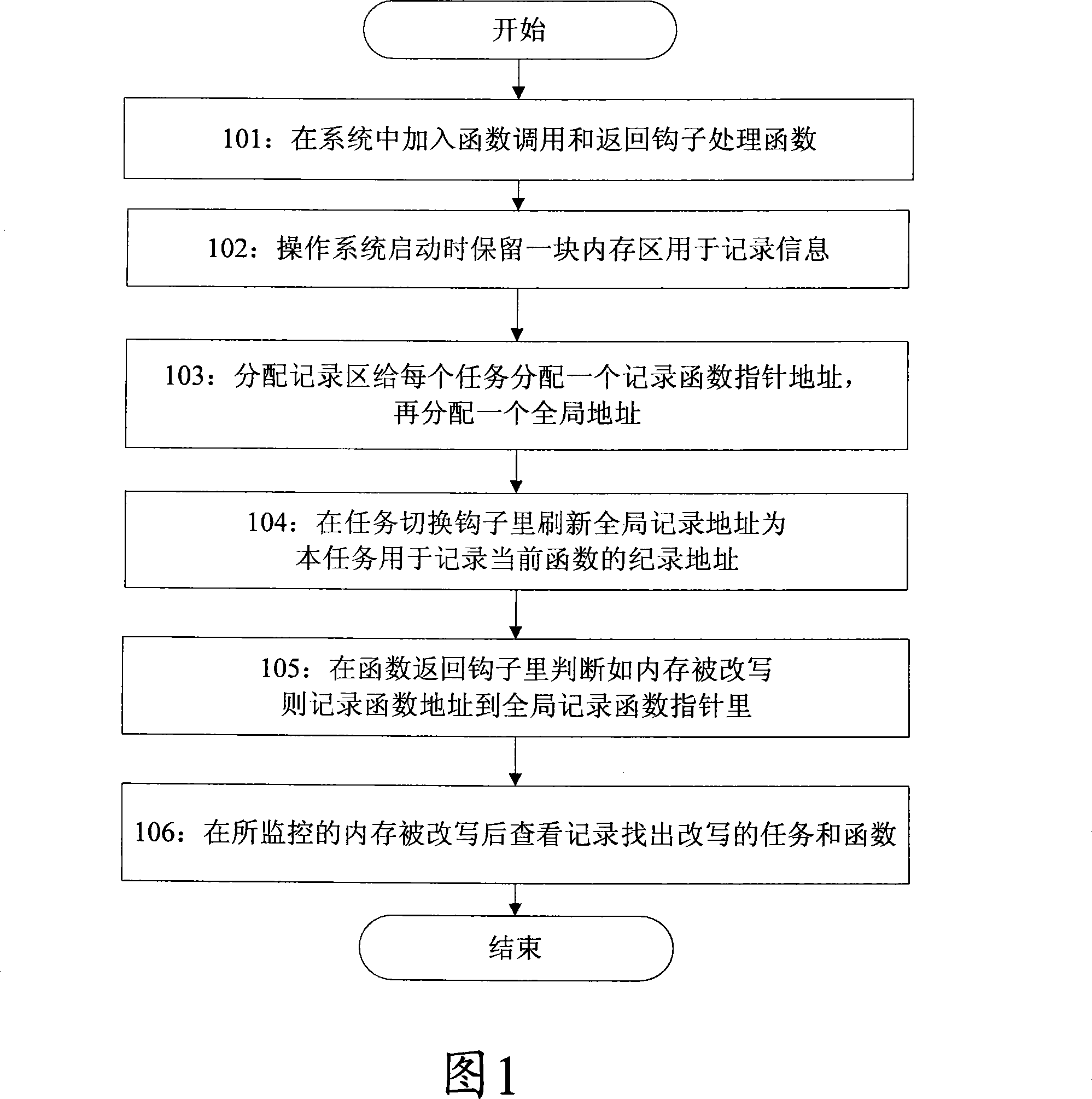
The invention discloses a method for capturing functions that cause memory to be rewritten by wild pointers, comprising the following steps: adding a function call and return hook function in the system, and configuring a global function pointer; when the system is running, in the function call hook function Record the value of the monitored memory. In the function return hook function, compare the memory value recorded by the function call hook function with the current memory value. If they are inconsistent, record the address of the currently running function to the global in the function pointer. Further, when the task is switched, the global function pointer is assigned as the address of the recorded function pointer in the memory area corresponding to the switched-in task. By applying the capture method of the present invention, the function that causes the memory to be rewritten by the wild pointer can be captured and recorded in real time, and furthermore, the task that calls the function can also be located.
Owner:ZTE CORP
Profile-guided data layout
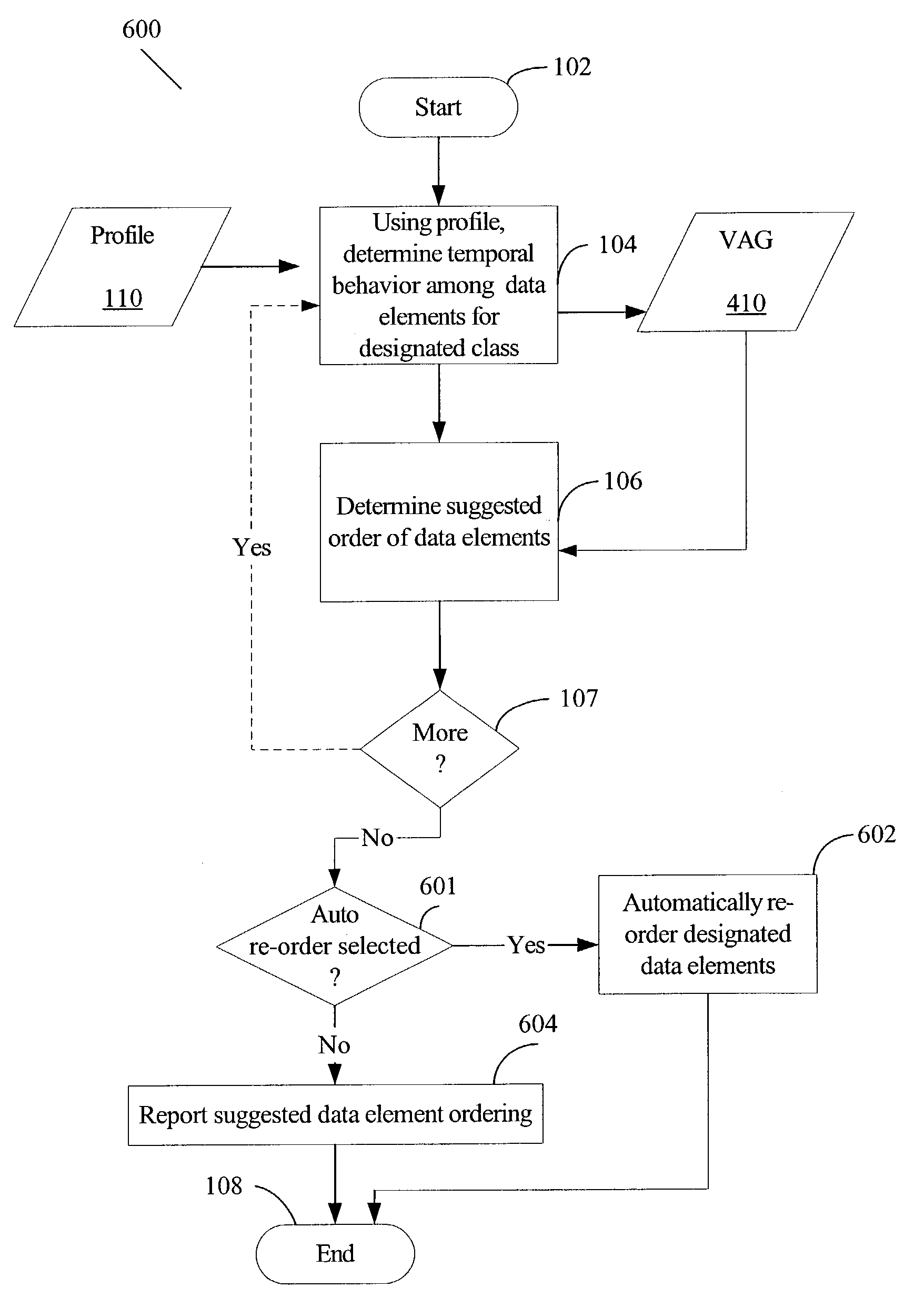
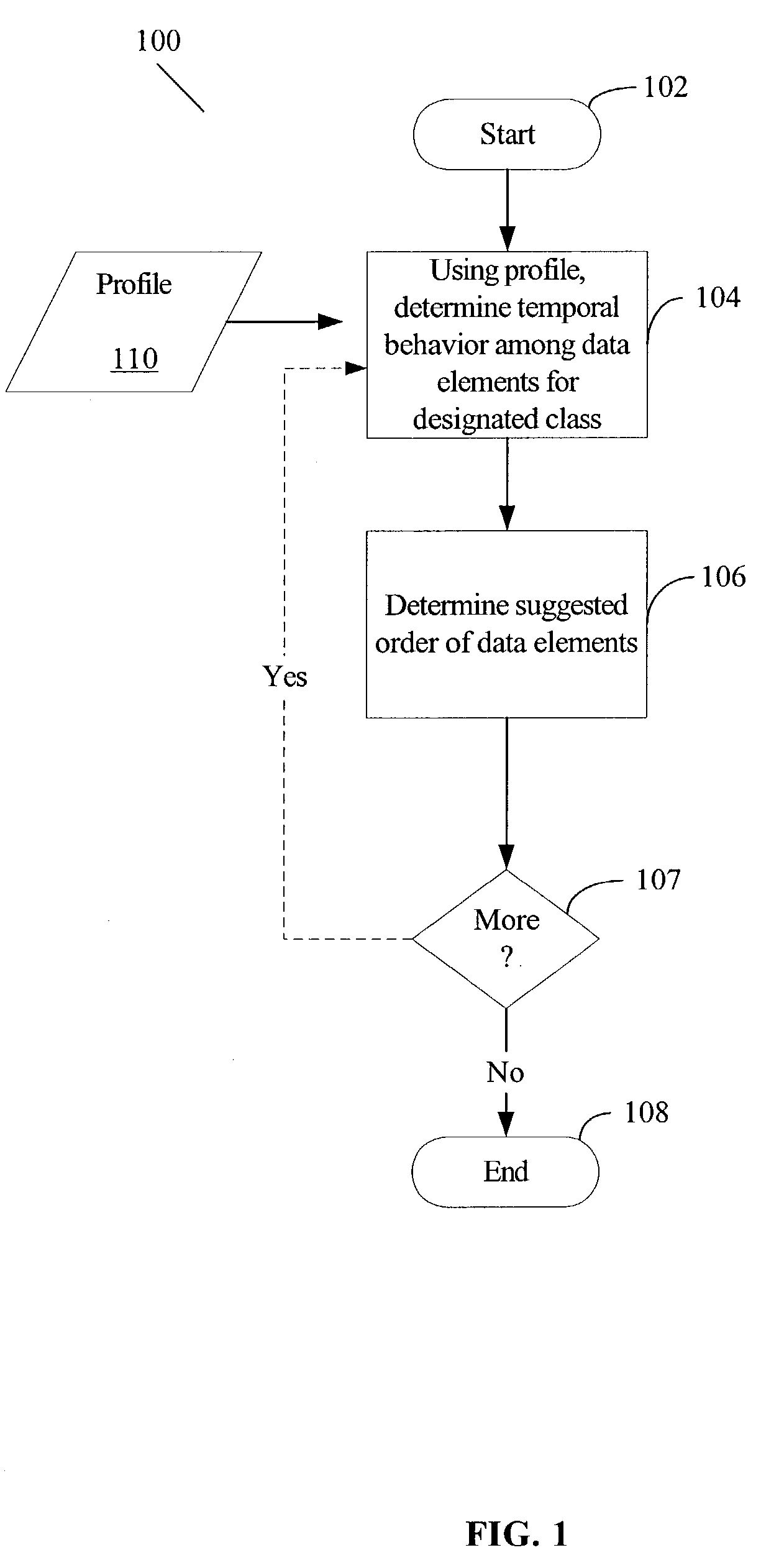
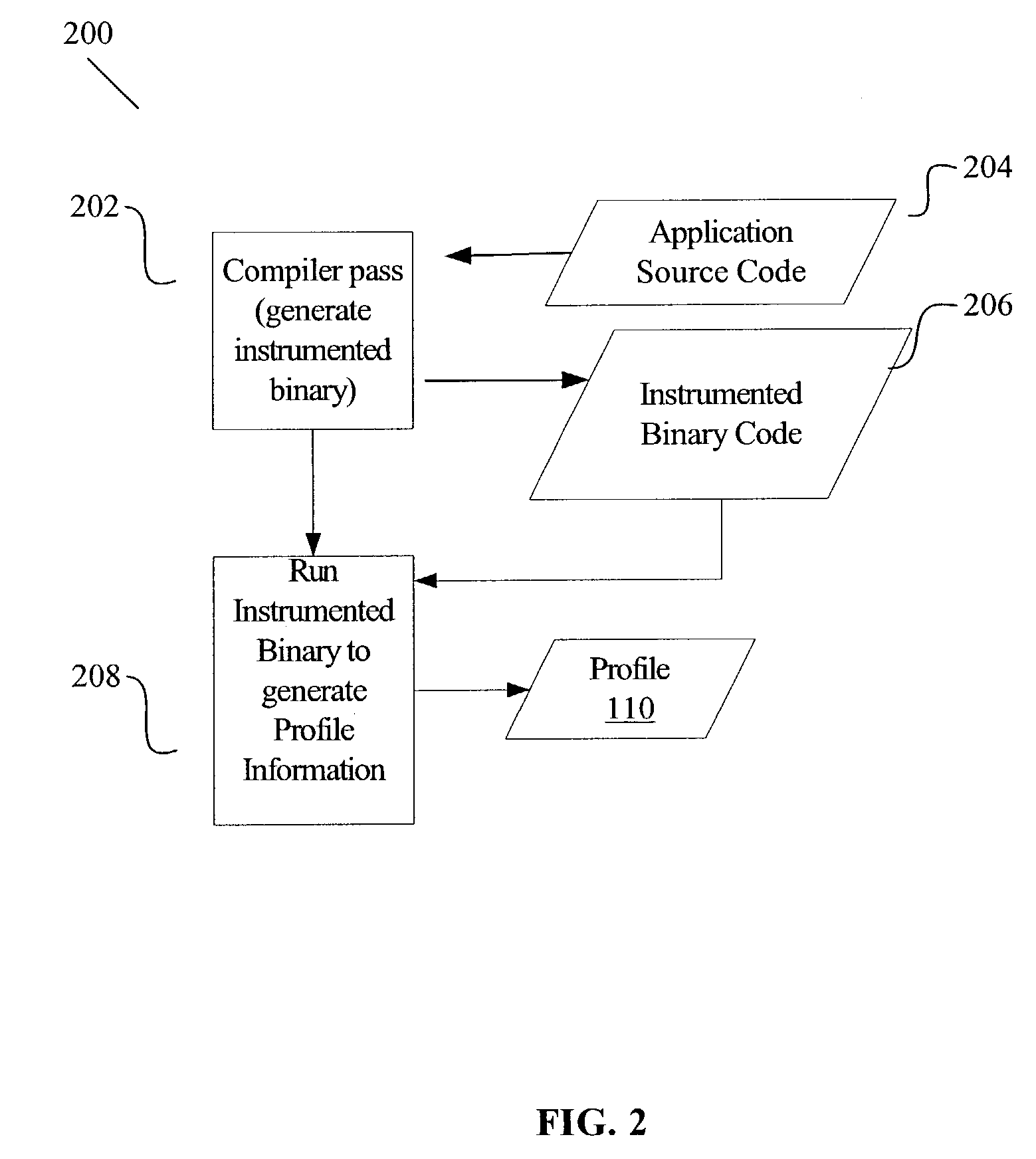
A method for optimizing (re-structuring) data layout for 1) local or global variables and / or 2) fields of a structure or object and / or 3) function pointers in a virtual function table in a compiled program is based on profile feedback. A user, such as a software programmer, identifies one or more classes of data elements in an application that the user wishes to optimize. A method, which may be implemented in a software program such as a compiler, analyzes the profile for the designated data elements to determine, based on the application's temporal behavior, how to order the designated data elements in order to optimize data cache performance.
Owner:INTEL CORP
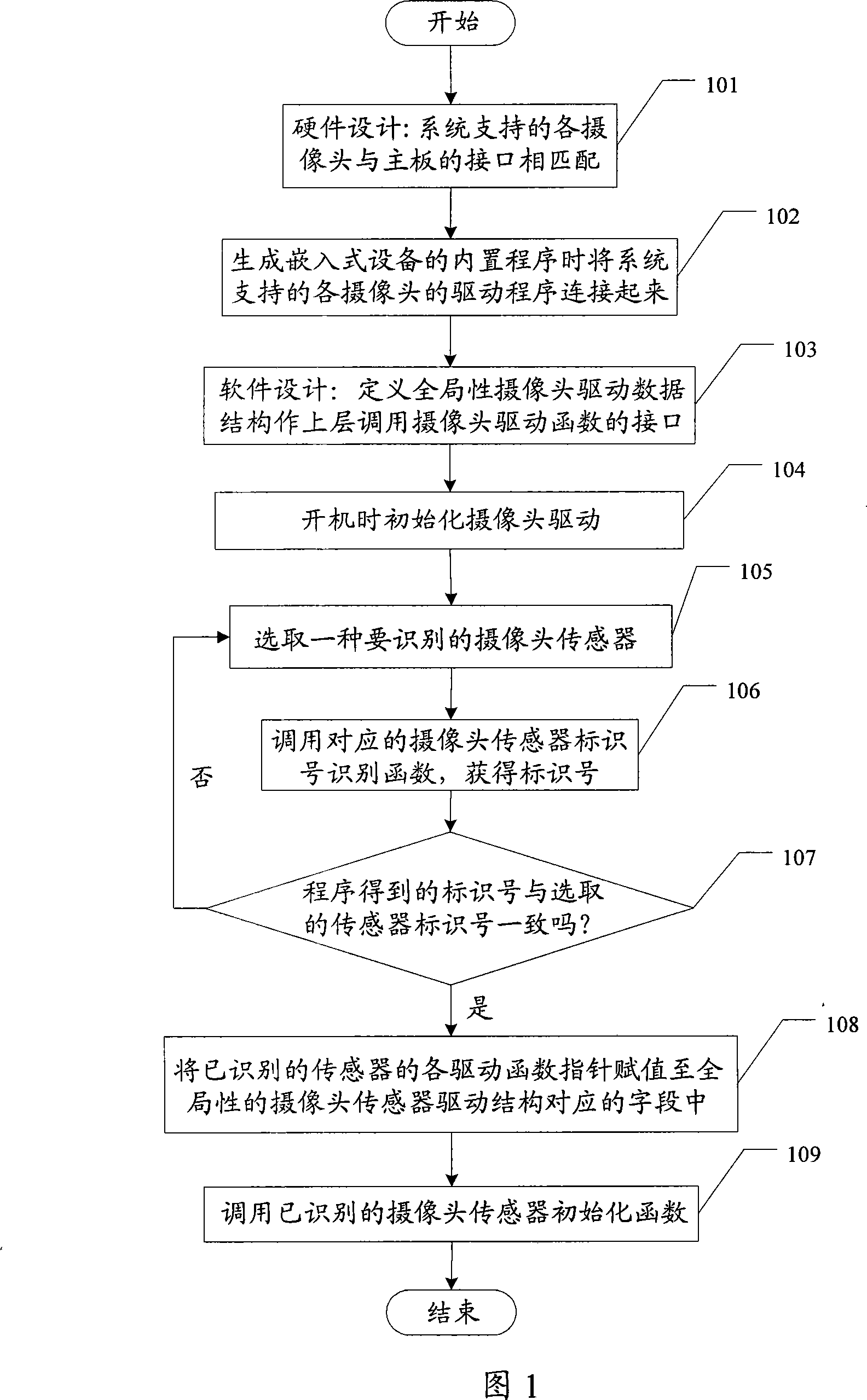
Embedded equipment camera software dynamic recognizing method
InactiveCN101159814APromote research and developmentEasy to manufactureTelevision system detailsColor television detailsFunction pointerService efficiency
The invention discloses a method for dynamically identifying embedded equipment camera software. The invention comprises that: a), a camera drive is initialized when the system is in start-up state; b), a camera sensor to be identified is selected and a corresponding sensor identification number is called to identify function and gain the identification number. The identification number obtained by the program is judged whether it is consistent with that of the selected sensor or not. If yes, then each driven function pointer of the identified camera sensor is valued in a corresponding field of the overall camera driven structure; otherwise, go back to Step b); c), the identified camera sensor initialization function is called. The embedded equipment camera software dynamic identification method of the invention enhances the research and development, manufacture and after-sales service efficiency of the embedded device with the camera, and lowers the product cost of each step.
Owner:KONKA GROUP
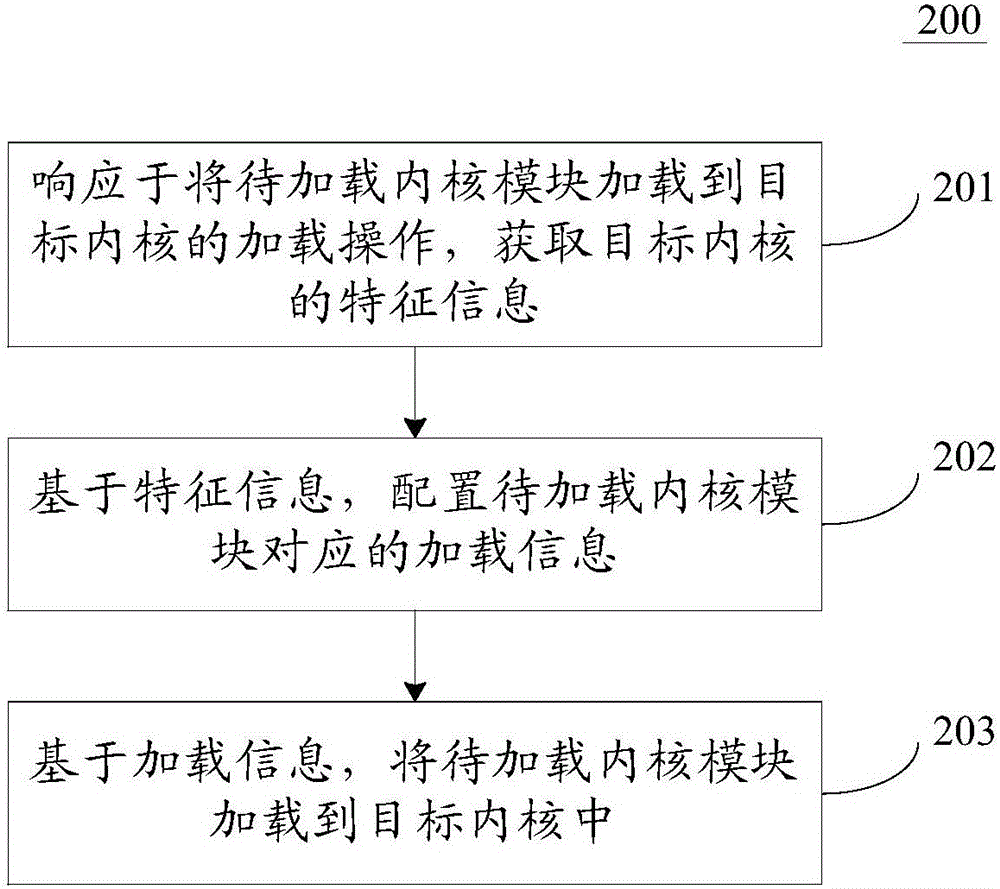
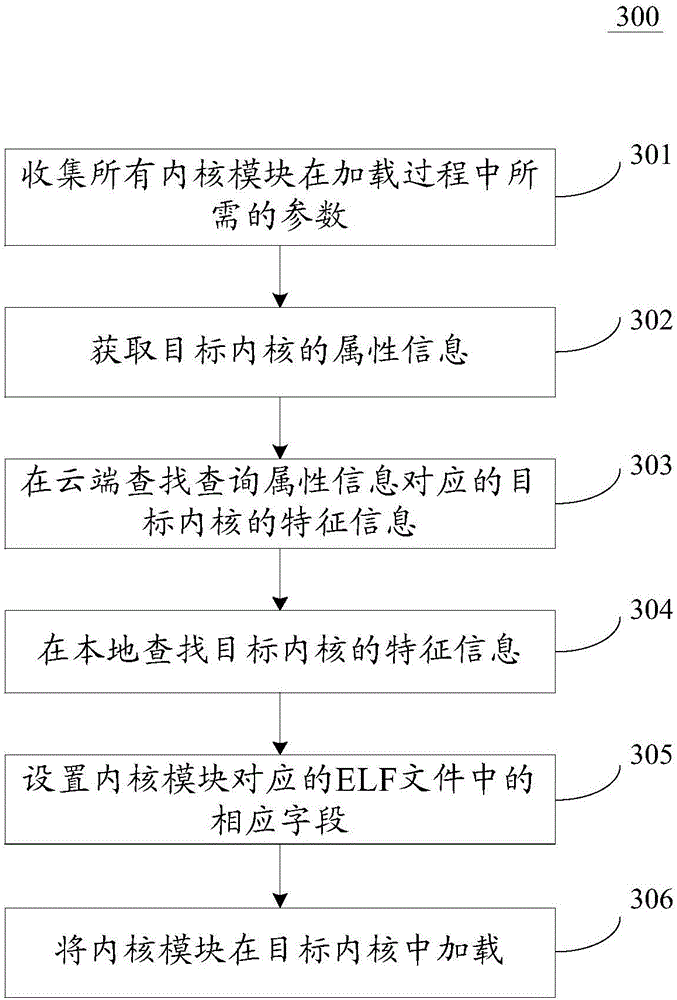
Method and device for loading kernel module
InactiveCN105893085AImprove applicabilityReduce development costsProgram loading/initiatingFunction pointerOperating system
The invention discloses a method and device for loading a kernel module. The method comprises the specific steps that a response to a loading operation for loading the kernel module to be loaded to a target kernel is made, and feature information of the target kernel is acquired; based on the feature information, loading information corresponding to the kernel module to be loaded is configured; based on the loading information, the kernel module to be loaded is loaded into the target kernel. When the kernel module needs to be loaded to the target kernel, kernel version parameters, kernel symbol verifying parameters, kernel module loading function pointers, kernel module unloading function pointers and other loading information in an ELF file corresponding to the kernel module are directly modified, the loading information is suitable for verification of the target kernel, and the kernel module can be loaded into the target kernel. Under the condition that the kernel module does not need to be recompiled, the kernel modules are loaded into kernels of different versions, the applicability of the kernel module is enhanced, and the development cost is reduced.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Defense method for kernel-level return-oriented rootkits
InactiveCN102375957AFree from harmAchieve the purpose of the attackPlatform integrity maintainanceOperational systemControl data
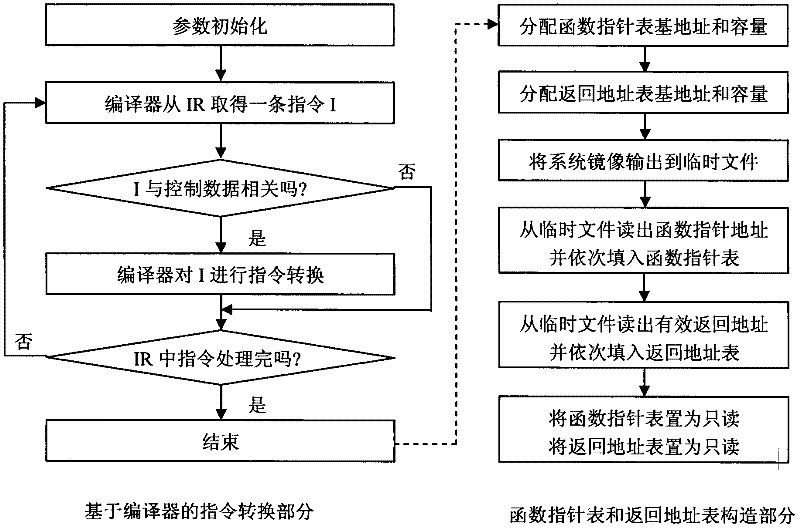
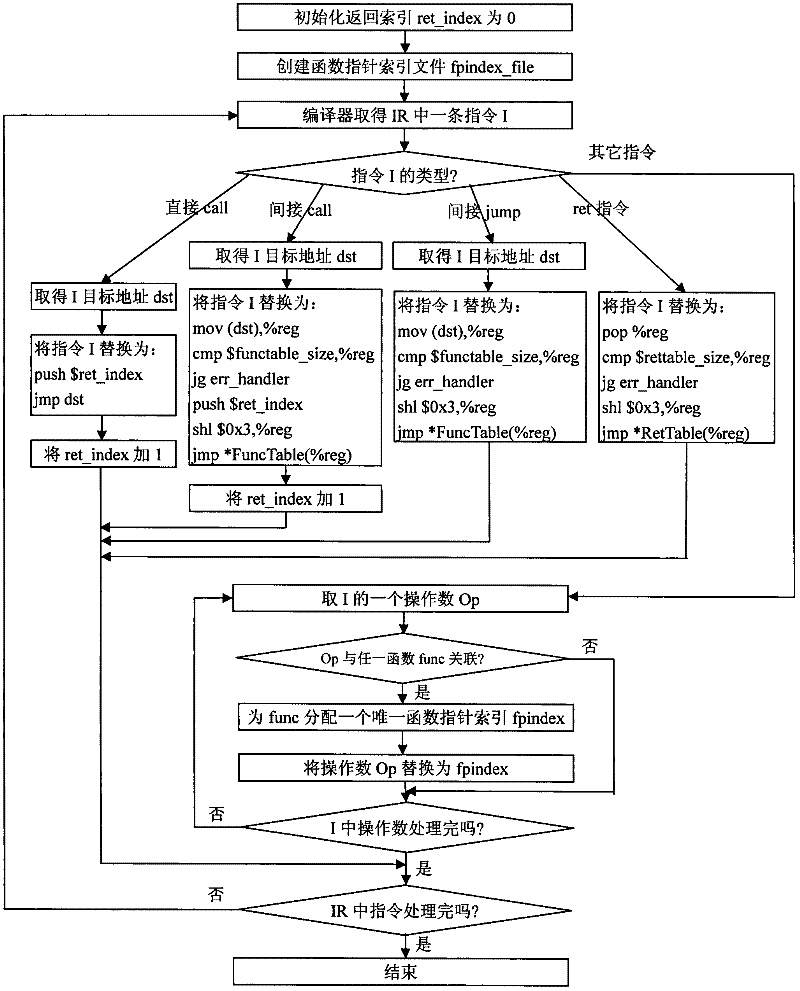
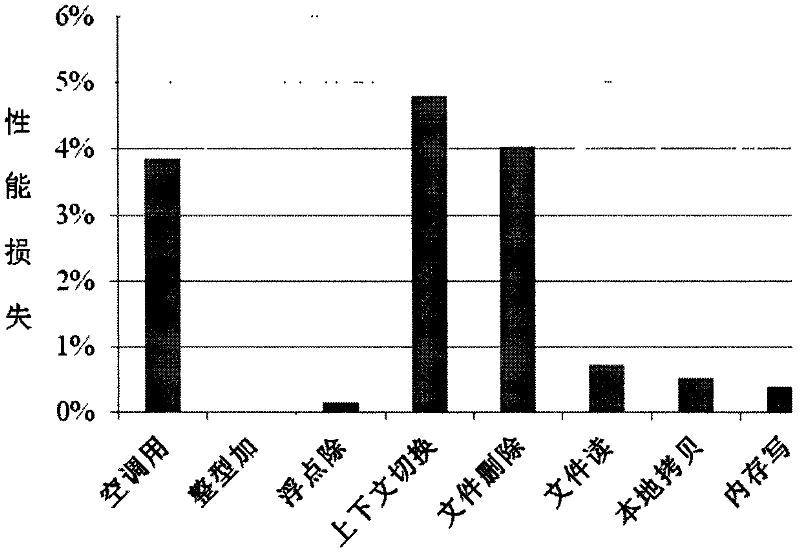
The invention discloses a defense method for kernel-level return-oriented rootkits, which mainly solves the problem of incapability of defending the latest kernel-level return-oriented rootkits attack in the prior art. The method comprises the following implementation steps of: distributing an index for each piece of control data by a compiler and converting a related instruction so as not to directly use the control data during program skip but search a certain skip table by using the index distributed by the compiler to obtain a really effective skip address to indirectly perform; and then collecting all effective skip addresses, namely control data, in a system to a function pointer table and returning to an address table for protection. By adopting the method, a second step of conducting attack cannot be finished by the kernel-level return-oriented rootkits, namely the original execution flow of the system is required to be changed by rewriting a certain piece of control data, and the method can be used for protecting safety of an operating system.
Owner:XIDIAN UNIV
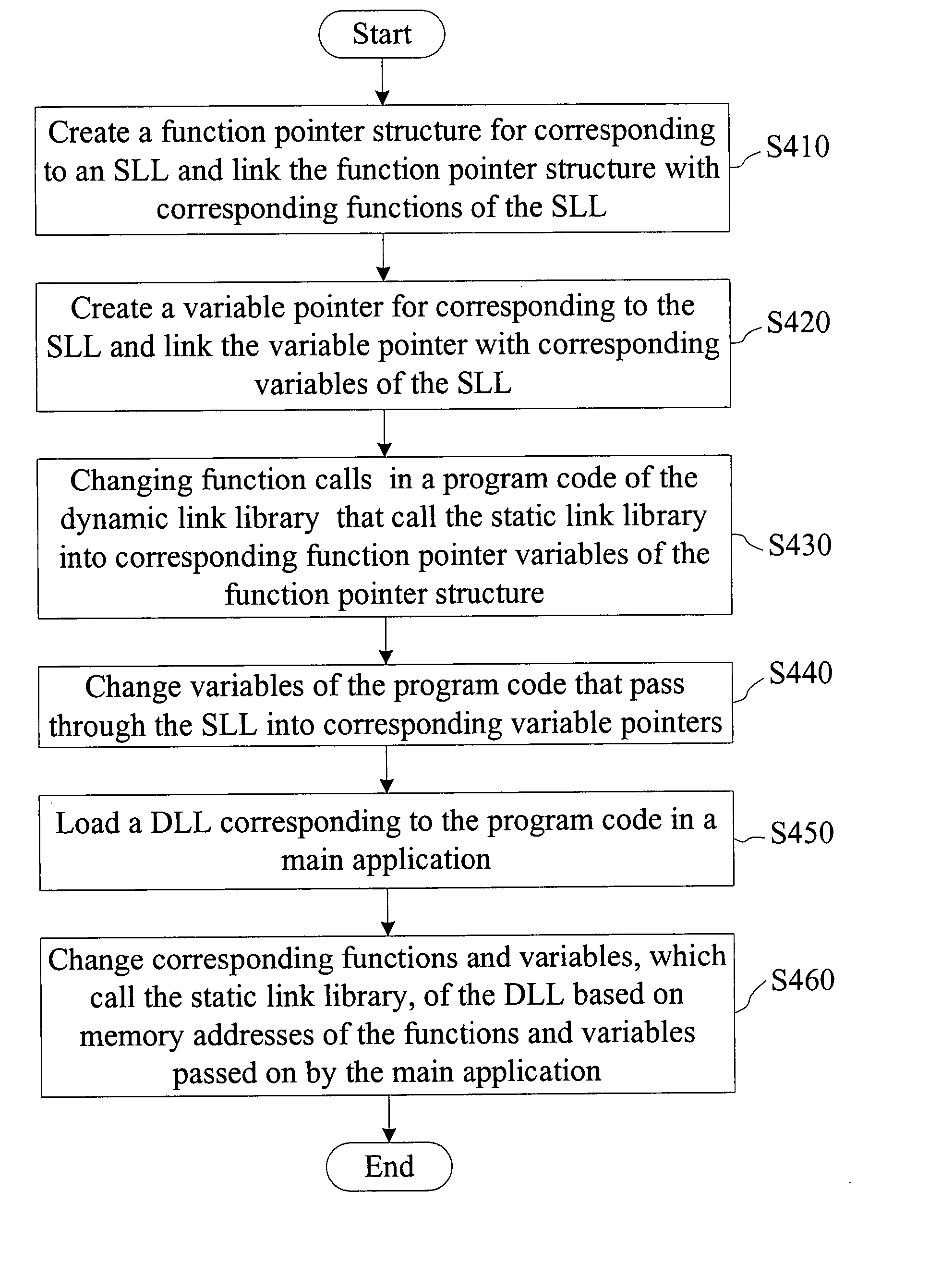
Method for dynamic linking function library sharing static linking function library with primary application
InactiveCN101131635AReduce memory requirementsReduce complexitySpecific program execution arrangementsProgramming languageCorrelation function
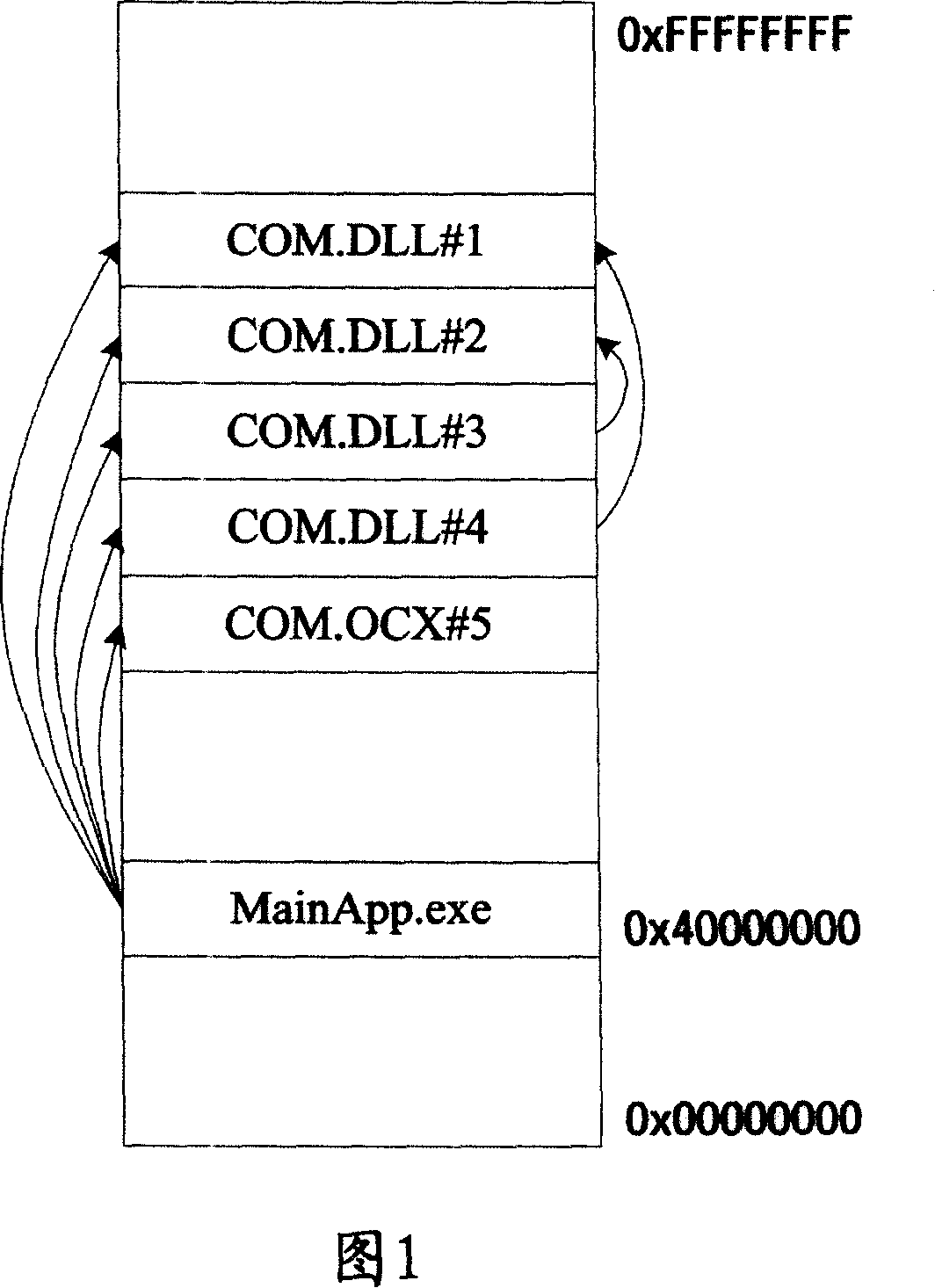
A kind of method of the dynamic chain joint function library sharing the static chain joint function with the main application program and the main application program chains a static chain function library and then establish a function pointer variable and a variable pointer variable of the static chain function library by the dynamic chain joint function library; and then transfer the function section calling from the static chain function library in the dynamic chain joint function library program code into the function pointer variable; then transfer the variable section calling from the static chain function library in the dynamic chain joint function library program code into the variable pointer variable; at last compile the main application program and the dynamic chain joint program code to the function library individually among them the related function of dynamic chain joint function library and the variable has been replaced by the way of pointer and then load the dynamic chain joint function library in the main application program at the same time deliver the storage location of function and variable to the dynamic chain joint function library which makes the function and variable section called to the static chain joint function library form the dynamic chain joint function library could share the static chain joint function library connected by the main application program.
Owner:SUNPLUS TECH CO LTD
System and method for registering native libraries with non-native enterprise program code
ActiveUS20060129989A1Specific program execution arrangementsMemory systemsProgramming languageApplication server
A system and method are described for implementing native methods within a Java environment. The native methods may be used, for example, as part of a startup framework for a cluster of Java application servers. In one embodiment, a class object for a the class containing the native methods is instantiated in a memory. After the class object is loaded, one or more function pointers are inserted within the class object. The function pointers include identification information identifying an implementation of the native methods.
Owner:SAP AG
Method for mobile phone to be compatible to different display part
InactiveCN101127978AImprove R&D efficiencyIncrease productivitySubstation equipmentRadio/inductive link selection arrangementsElectricityLiquid-crystal display
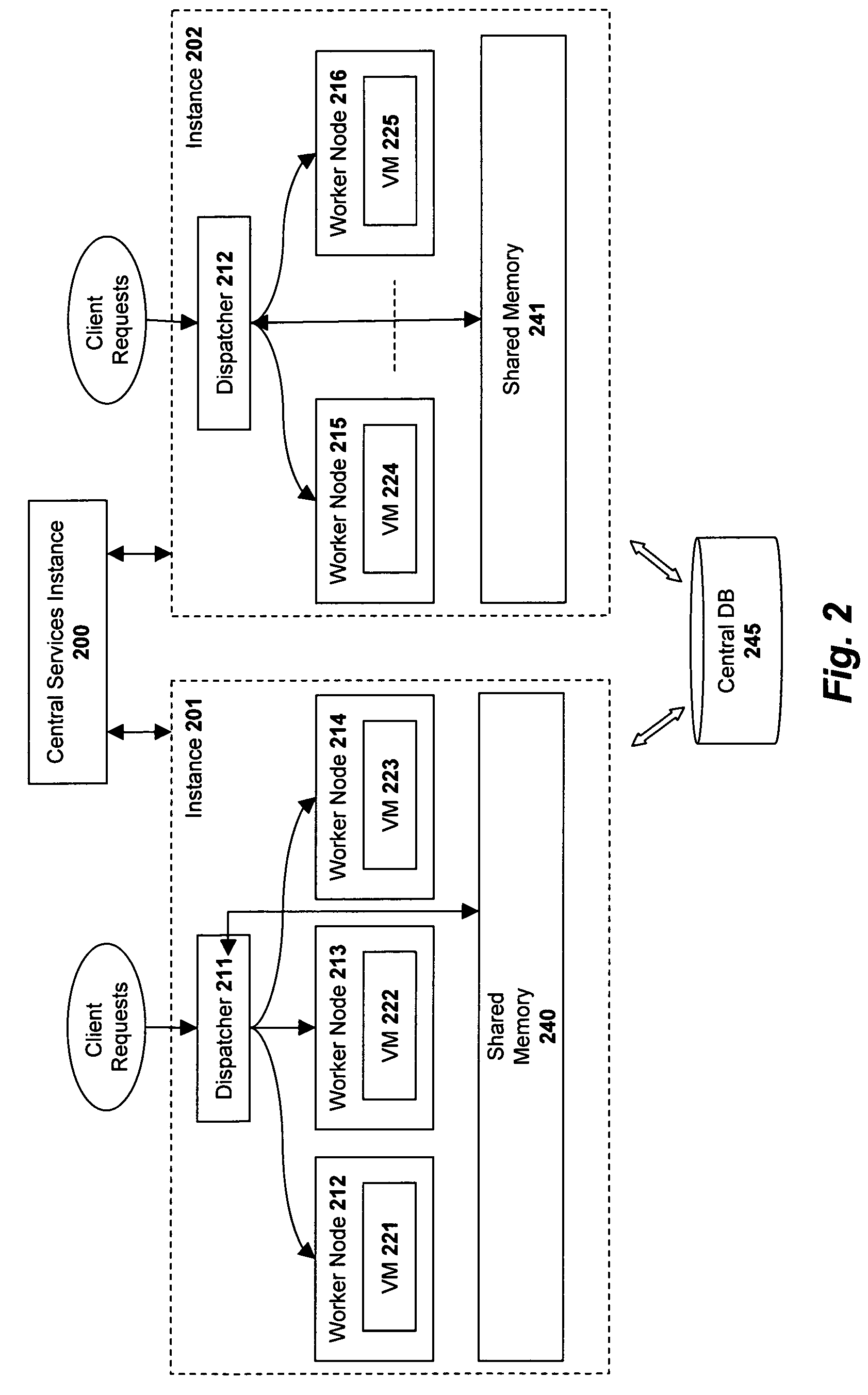
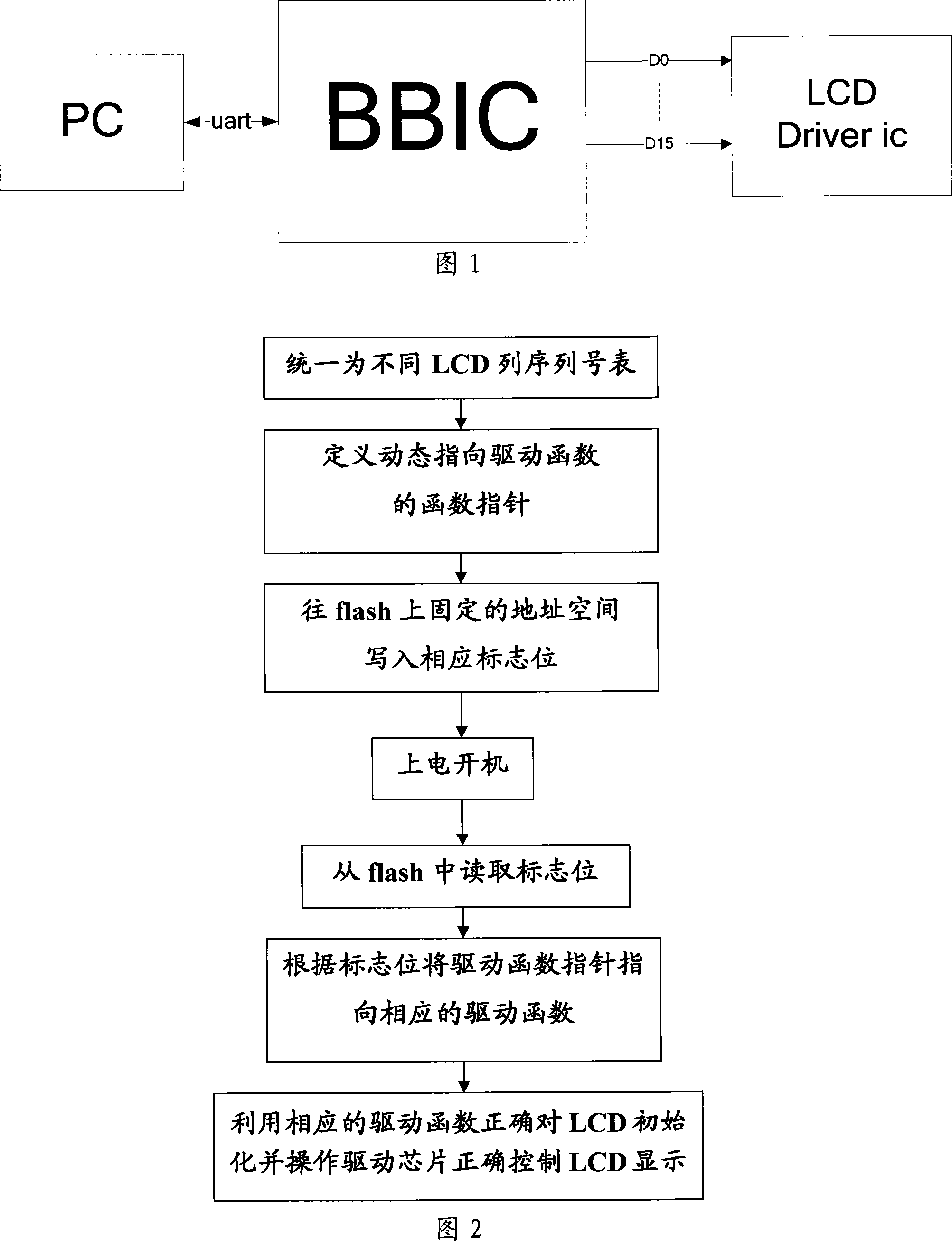
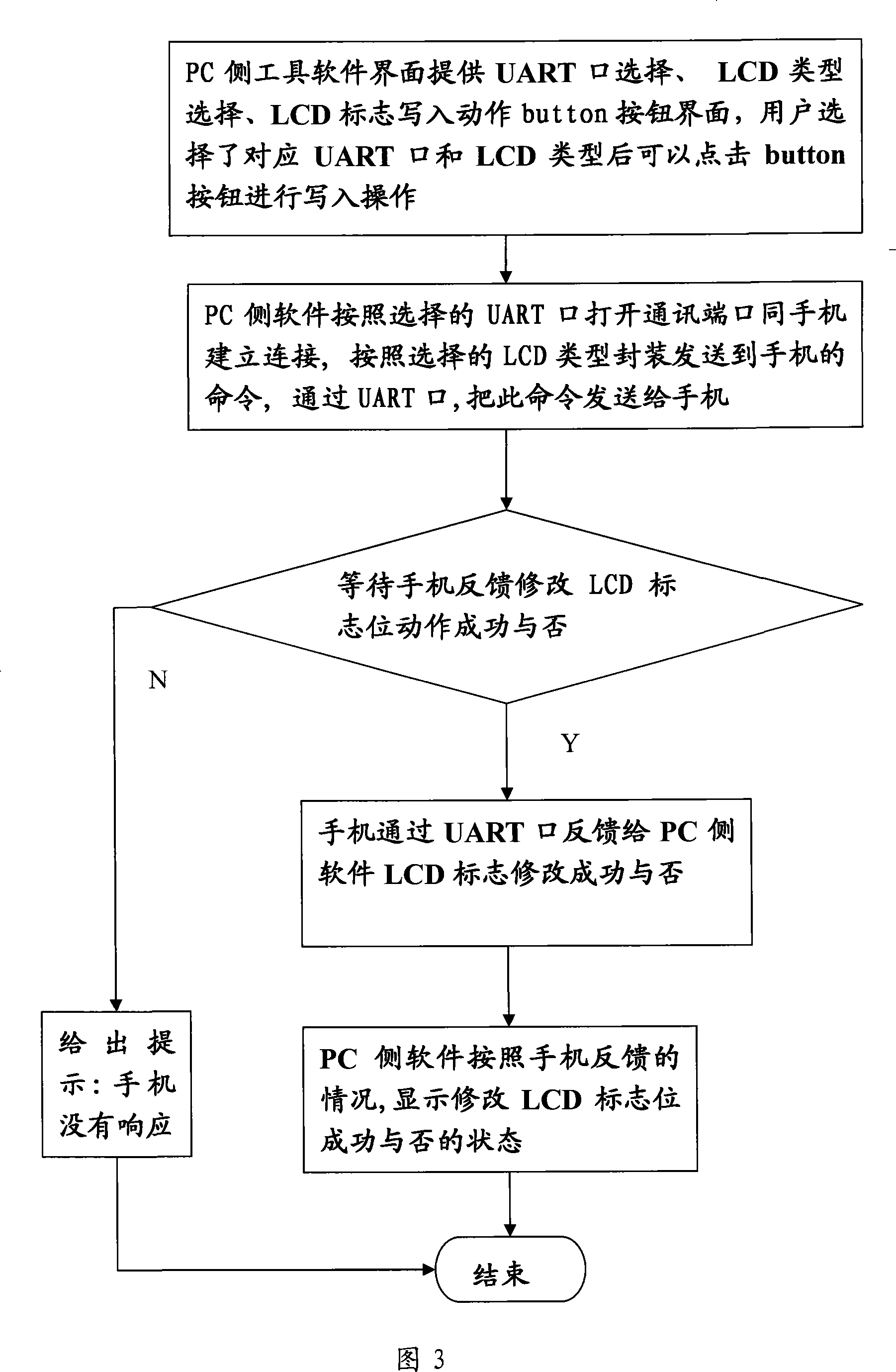
The utility model relates to a method that a mobile phone is compatible with different display devices, which comprises the following steps: Step 1. a standard series number list is compiled for a LCD device; Step 2. relevant driving motions of LCD are defined to be a uniform dynamic function pointer; Step 3. a space is cultivated inside the flash disk of the mobile phone to store condition codes; Step 4. a condition code is written into the fixed storage space inside the flash disk of the mobile phone; Step 5. after the mobile is equipped with batteries and switched on, a condition code is released from the fixed location inside the flash disk that is cultivated in Step 3; by matching with the standard series number list, a corresponding LCD device driving function can be found and the function pointer points to the corresponding driving function; Step 6. the LCD device is initialized by the driving function and displaying of the LCD device is controlled properly by operation of the driving core of the LCD device. The utility model has the advantages that the method can download fixed program into the mobile phones, which improves efficiency of development and production for mobile phones largely and saves cost as well as time.
Owner:WINGTECH COMM
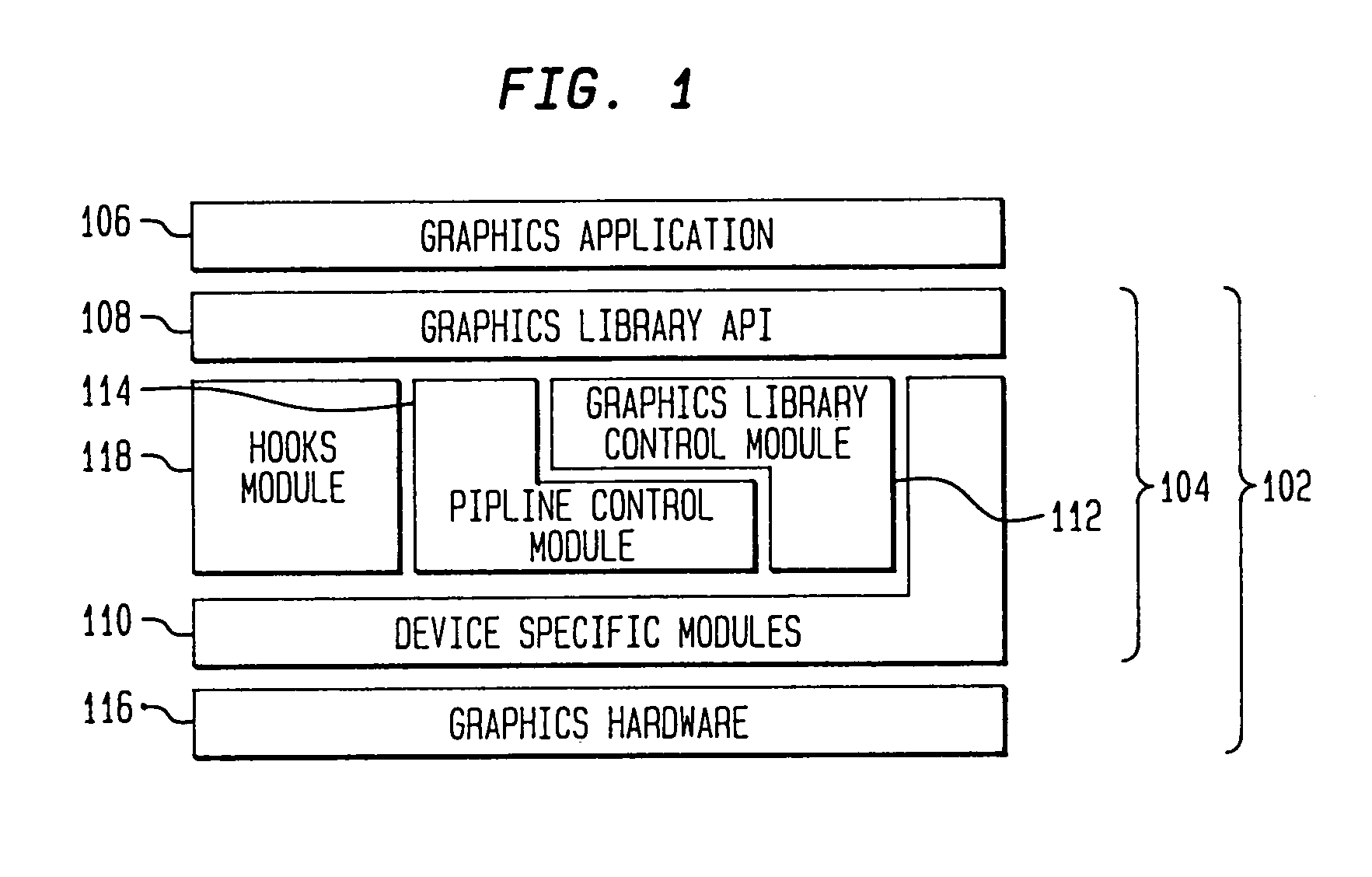
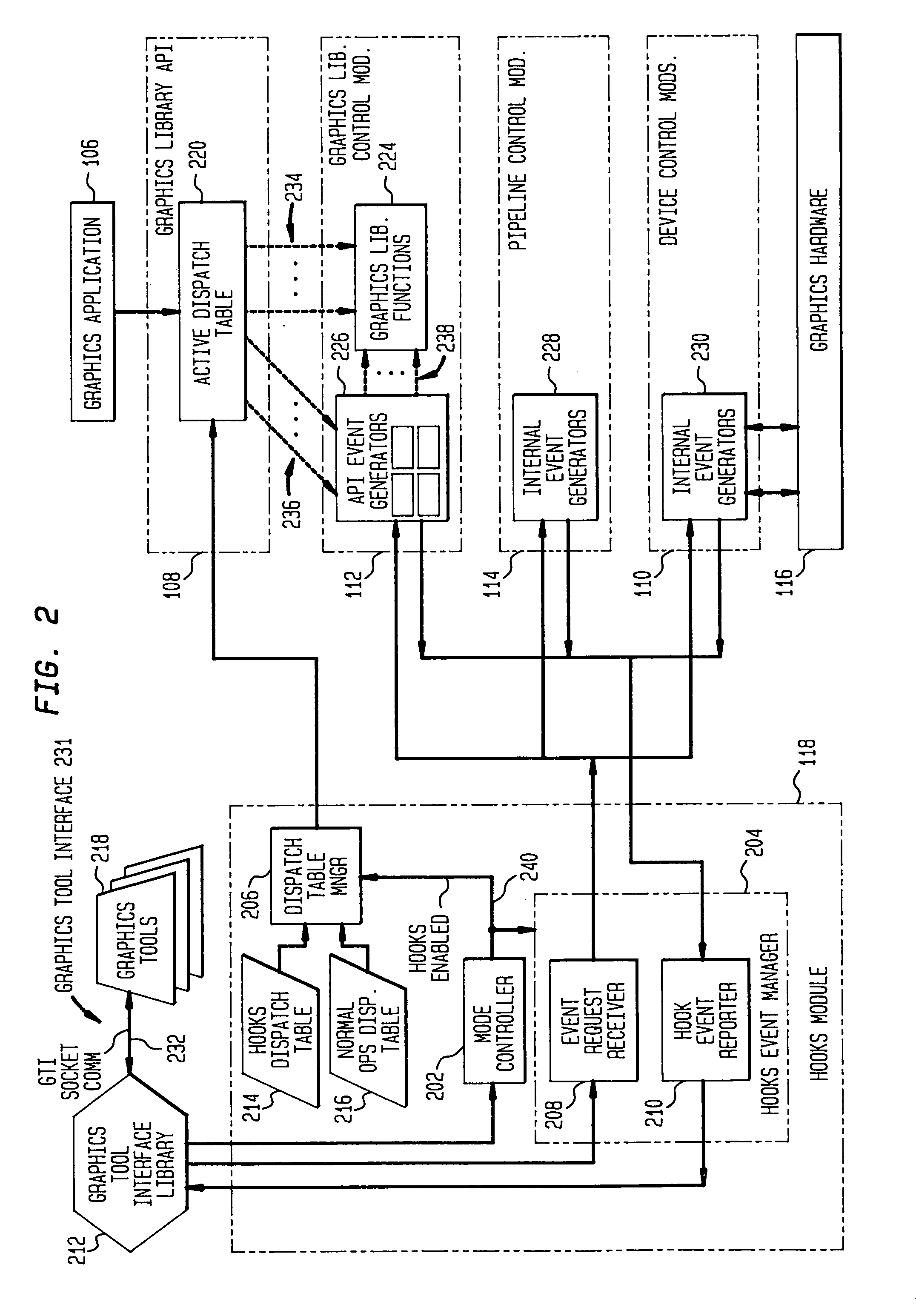
Accessing a graphics system for graphics application evaluation and control
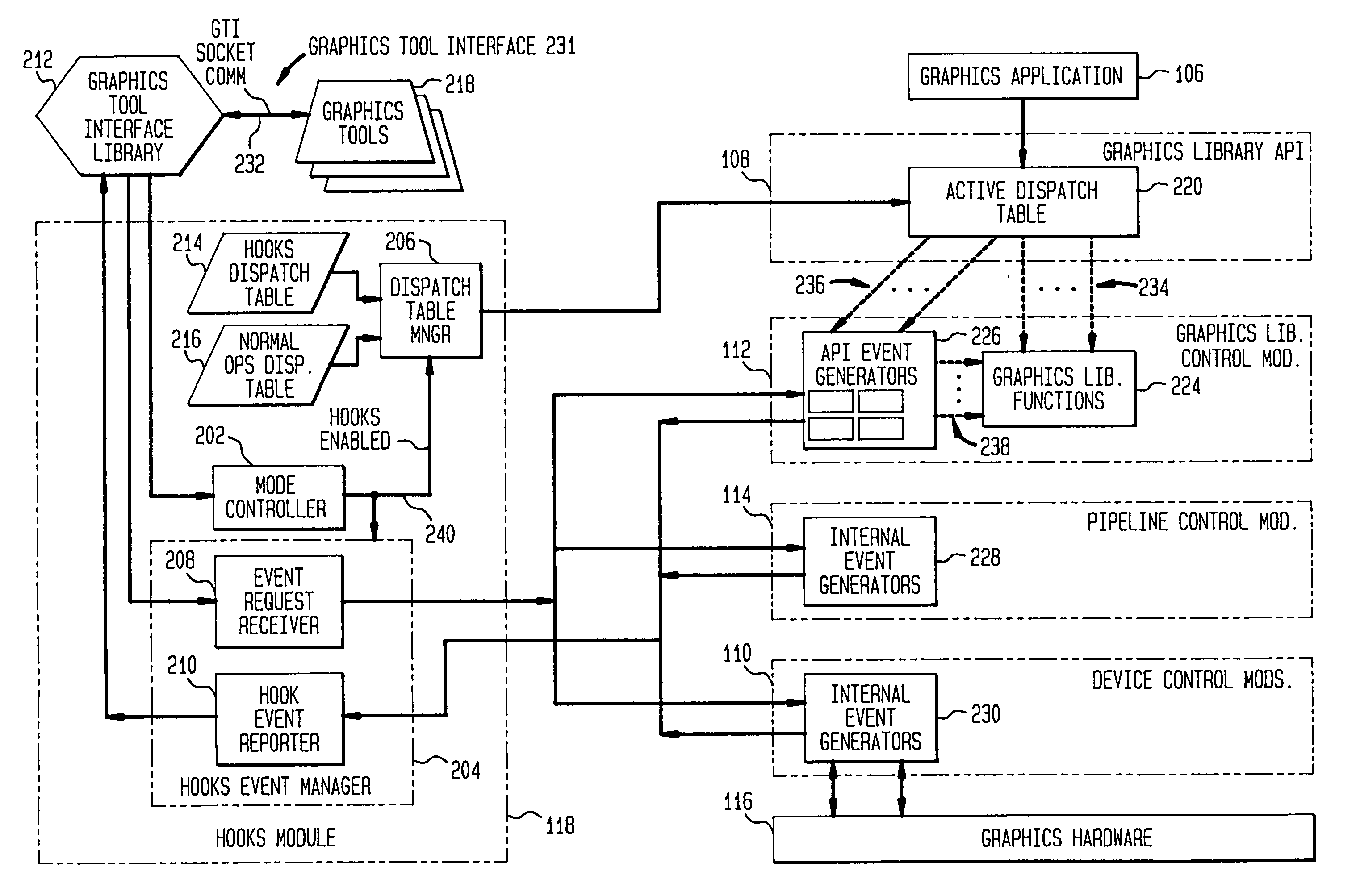
InactiveUS7028309B2Significant informationMore informationInterprogram communicationMemory systemsGraphic systemFunction pointer
A system for providing a graphics tool access to a computer graphics system to evaluate and control a graphics application executing on the computer graphics system. The system includes application program interface (API) event generators for performing predetermined operations relating to a graphics library function call and for generating a hook event containing results of the predetermined operations; dispatch table manger for selecting an active dispatch table from a normal operations dispatch table having function pointer to the graphics library functions and a hooks dispatch table having pointer to the API event generators; and hook event manager for enabling and configuring selected ones of the API event generators in response to a graphics tool event request. The system further includes internal event generators, integrated along various locations of a graphics pipeline managed by the graphics library, for performing predetermined diagnostic operations in the graphics system. In this embodiment the hook event manager also enables and configures selected ones of the internal event generators.
Owner:HEWLETT PACKARD DEV CO LP
Method and system for generating and applying patches to a computer program concurrently with its execution
InactiveUS7913243B2Software engineeringSpecific program execution arrangementsFunction pointerTerm memory
A method, a computer program product, and a system for generating and applying patches to a computer program concurrently with its execution. It provides full support for function pointers, transparent to the programmer and nearly transparent to the concurrent loader. A reference to a function pointer is translated into a sequence of processor instructions called function descriptor instead of translating it into an address. The purpose of the function descriptor is to jump to the memory location of the sequence of instructions generated by the compiler for the procedure referenced by the function pointer. The function descriptor is masked as a static data variable and therefore preserved during the application of a concurrent patch. The address for the jump to the procedure is updated by the regular relocation process during the application of a concurrent patch.
Owner:INT BUSINESS MASCH CORP
Covering film intelligent card with extended functions
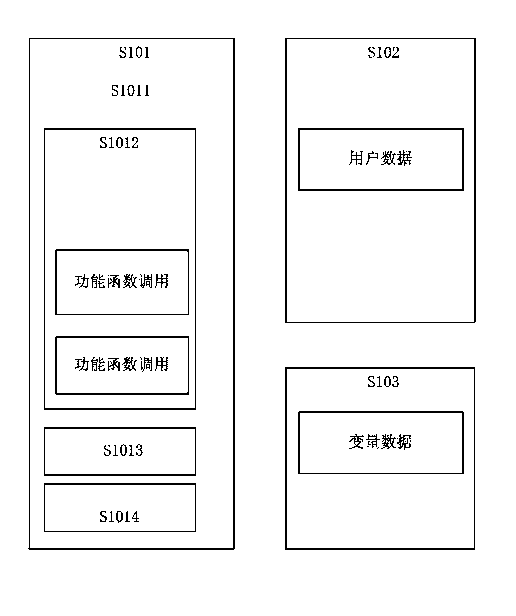
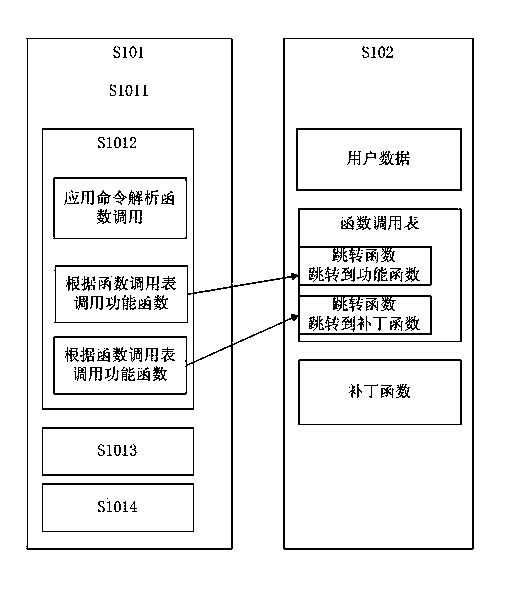
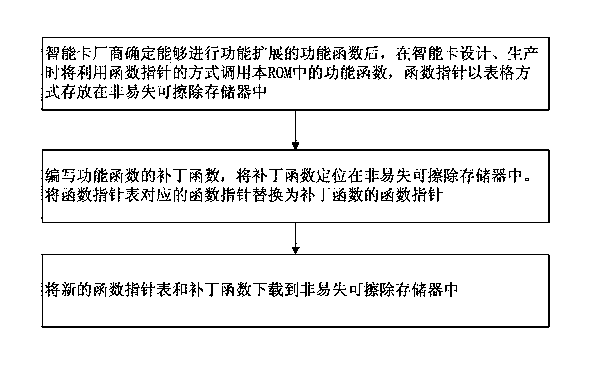
ActiveCN103632185AReduce manufacturing costNo additional call time overheadRecord carriers used with machinesPerformance functionRandom access memory
The invention provides a covering film intelligent card with extended functions, and relates to the technical field of an intelligent card. The covering film intelligent card comprises a read-only memory, a random access memory and a nonvolatile erasable memory. An operating system of the read-only memory comprises a main process, an application command processing unit and a performance function unit. The random access memory comprises variable data. The nonvolatile erasable memory comprises modifiable user data. Structural characteristics of the covering film intelligent card are that the nonvolatile erasable memory also comprises a performance function pointer table, an application command function pointer table, a patch function unit, an additionally arranged command function pointer table and an additionally arranged application command function unit. The operating system of the read-only memory acquires a function pointer via inquiring the performance function pointer table, the application command function pointer table and the additionally arranged command function pointer table, and a function is scheduled in a function pointer mode so that functions of the intelligent card are realized. The covering film intelligent card can be applied to function restoration and expansion of new functions of the intelligent card after film covering so that the covering film intelligent card has characteristics of being simple in structure, small in space occupation and high in execution speed.
Owner:北京紫光青藤微系统有限公司
Method and device for acquiring webpage address
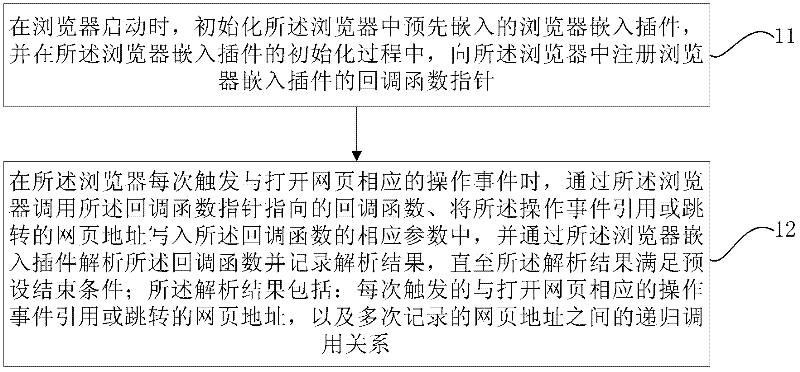
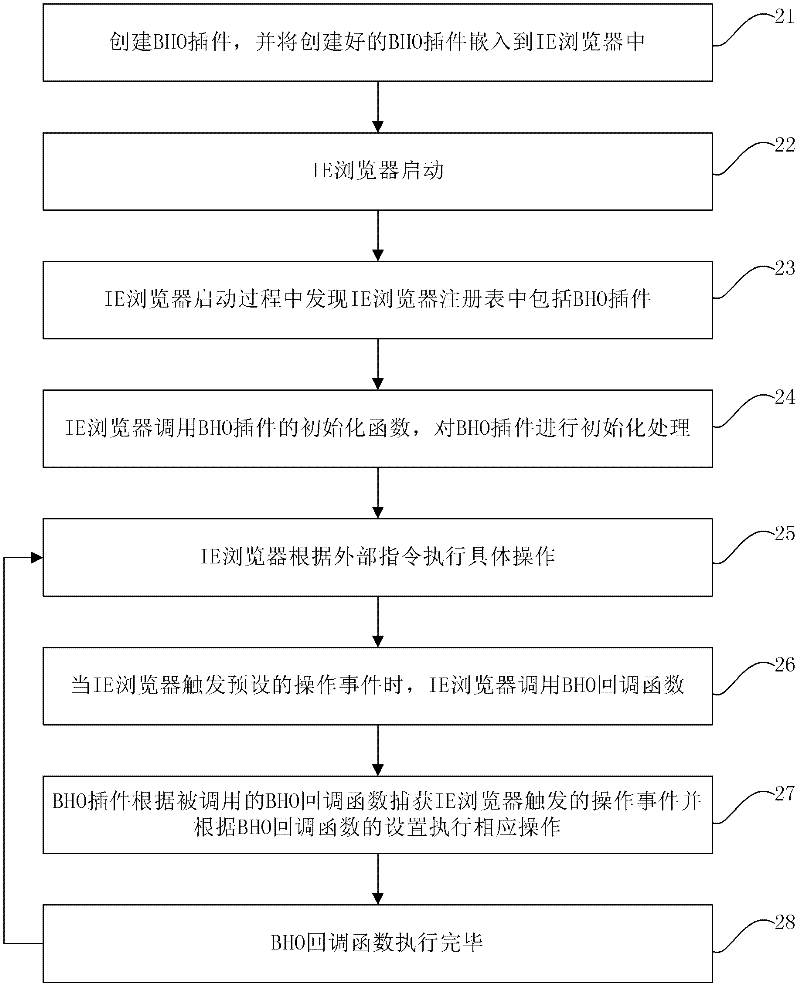
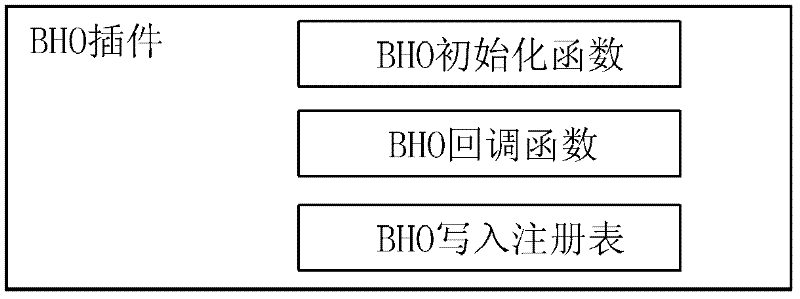
ActiveCN102346780AIncrease success rateImprove acquisition efficiencySpecial data processing applicationsFunction pointerFunction point
The invention discloses a method and device for acquiring a webpage address. The method comprises the following steps of: initializing a browser embedded insert preliminarily embedded in a browser, and registering a callback function pointer of the browser embedded insert in the browser in the process of initializing the browser embedded insert; when the browser triggers an operation event corresponding to an opened webpage every time, writing a webpage address quoted or skipped by the operation event into a corresponding parameter of a callback function through calling the callback function pointed by the callback function pointer by the browser, and analyzing the callback function through the browser embedded insert and recording an analysis result until the analysis result meets a preset ending condition, wherein the analysis result comprises the webpage address triggered every time and quoted or skipped by the operation event corresponding to the opened webpage and a recursion call relationship among webpage addresses recorded many times. By using the method and device for acquiring the webpage address in the invention, the cost for acquiring the webpage address is reduced, and the efficiency of acquiring the webpage address is increased.
Owner:北龙中网(北京)科技有限责任公司
A priority packet scheduling method and system utilizing data topological information
ActiveCN105528243AAchieve reuseOptimizing Cache ReuseProgram initiation/switchingFunction pointerTask mapping
The invention provides a priority packet scheduling method and system utilizing data topological information. The method comprises the steps of obtaining an original grid space of data topological information, setting the size and the floating point precision of a grid sheet of the original grid space and generating a new grid space; according to the stencil format of the new grid space and a parallel zone, establishing a condensed task graph (four-dimensional time-space domain) and calculating a priority packet serial number of each task therein; obtaining a data piece visited by the current task, determining whether neighbor data dependence is involved through format abstract or function pointer and actual parameters , generating a corresponding mark, and identifying a cycle involving the neighbor data dependence according to the mark, wherein the cycle is effective time steps; mapping the task on the cycle to some task of the condensed task graph according to the current effective time steps, calculating the priority serial number of the current task according to the priority serial number of the latter. The priority packet scheduling of tasks is supported.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
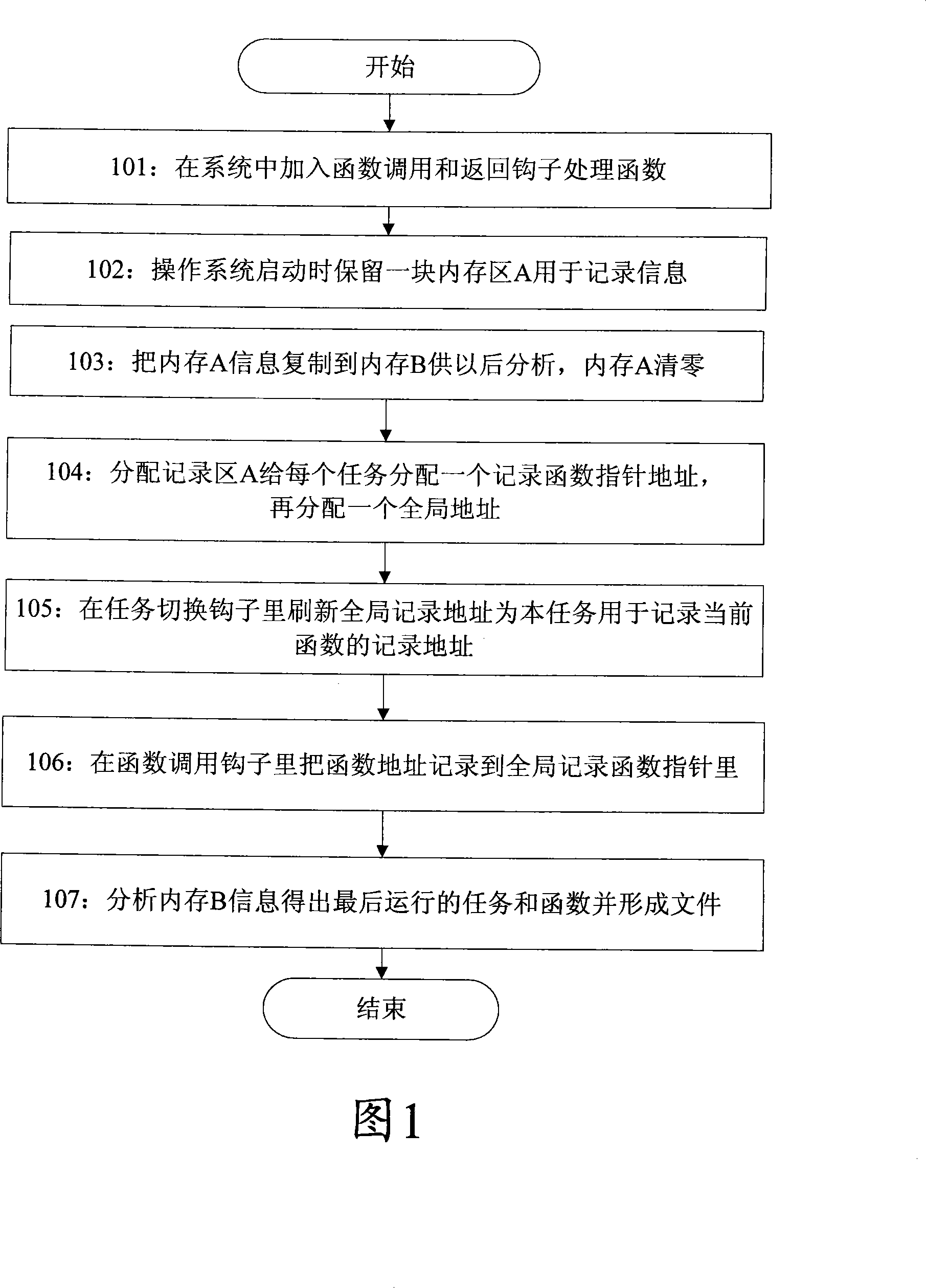
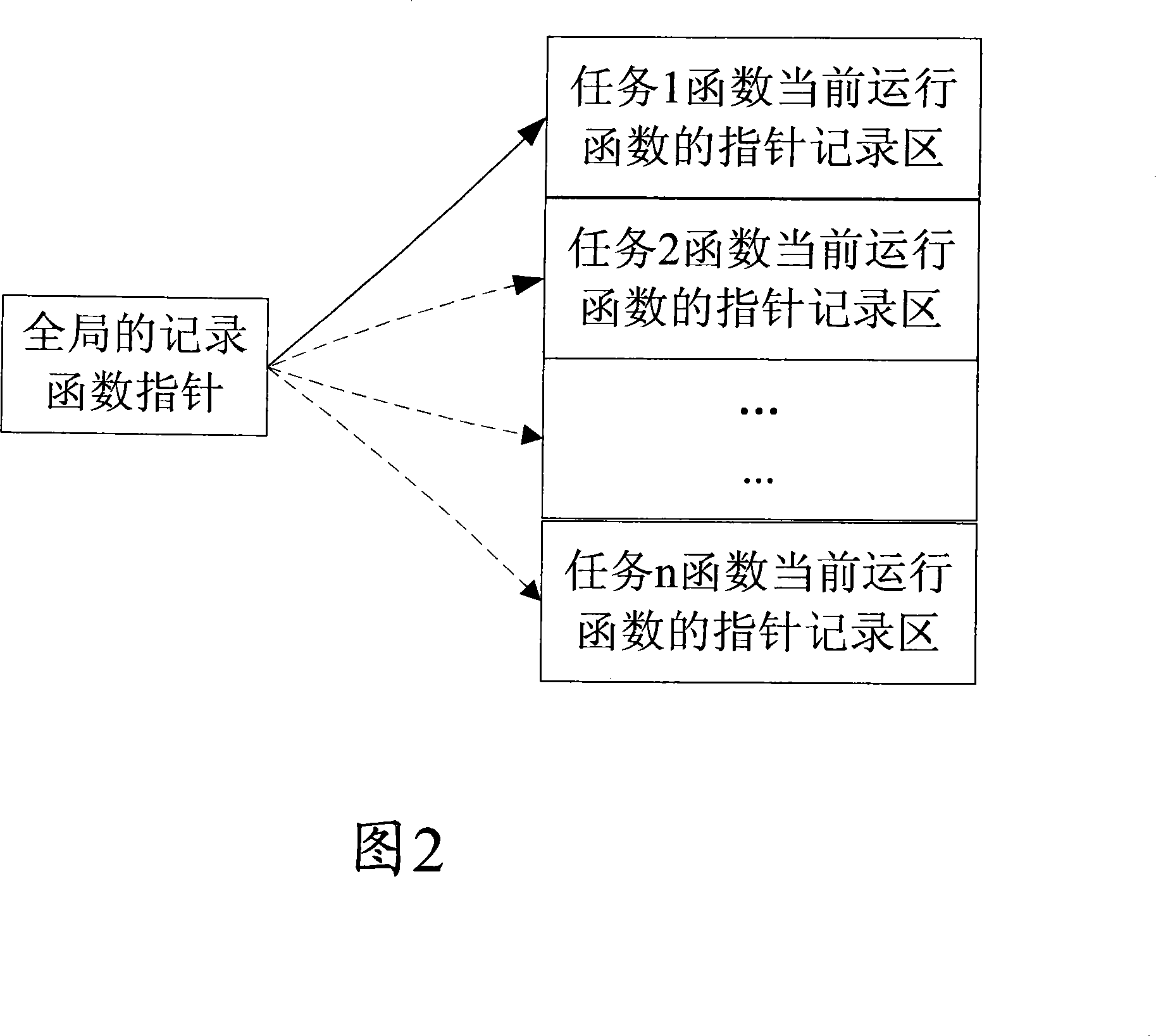
Method for recording function for leading to system abnormity
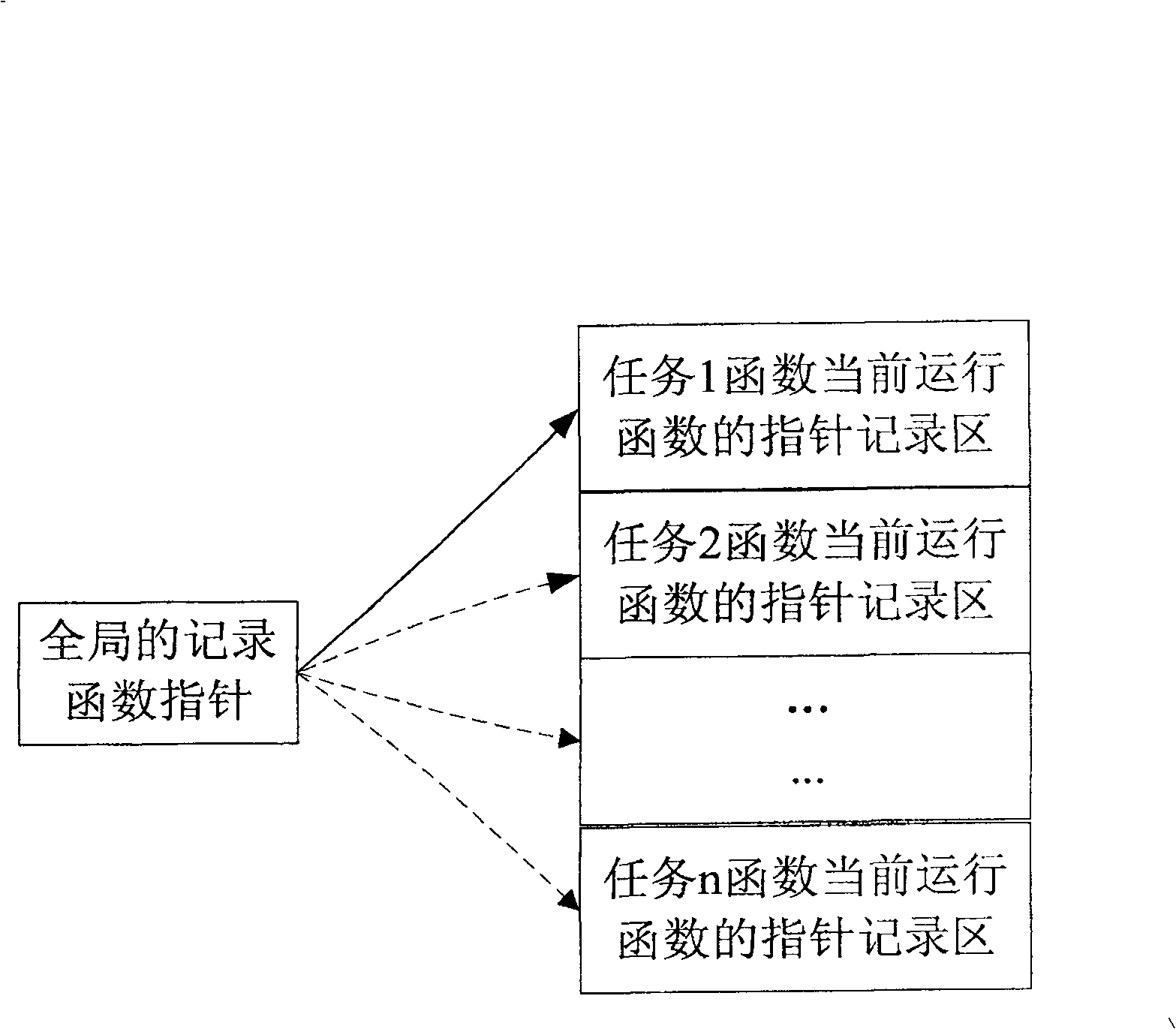
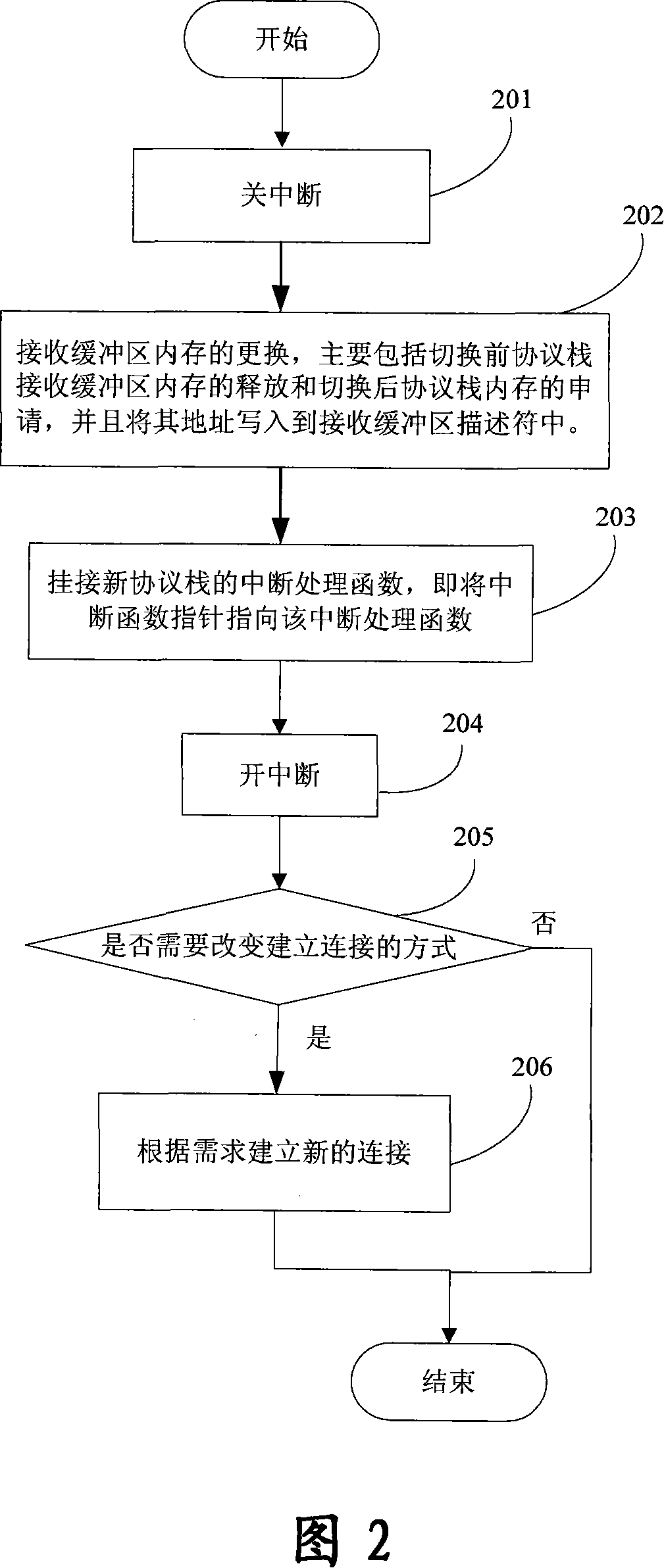
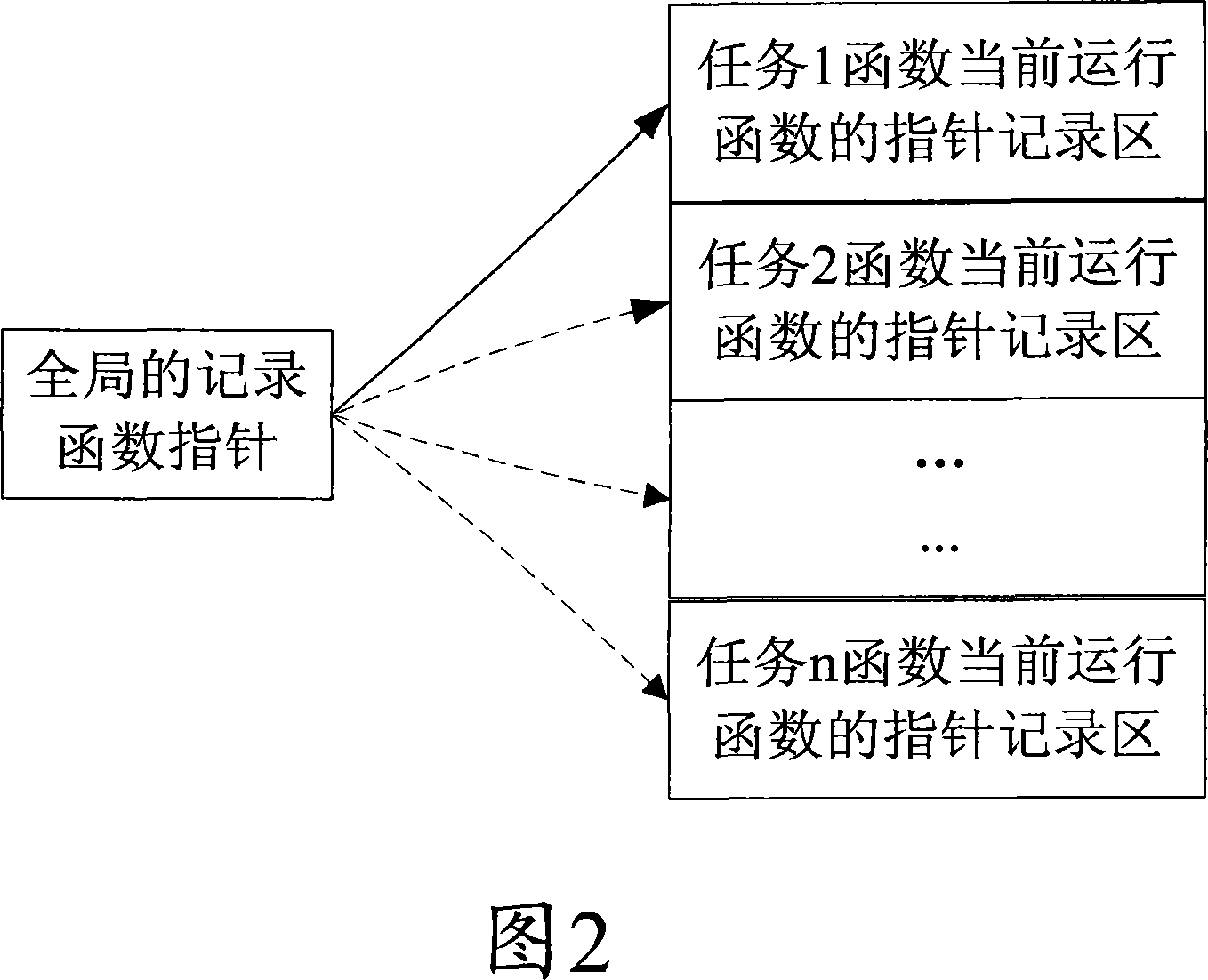
ActiveCN101169753AEffective record informationNarrow down the scope of fault findingSoftware testing/debuggingRedundant operation error correctionArray data structureFunction pointer
The invention discloses a method for recording a function causing a system to halt or reset. The method comprises firstly allocating a function pointer array element for recording a function address for each task in a memory recording area, defining a global function pointer for tracking the currently operating task, and adding a hook function calling function in a file to be operated by the system; when switching a task, assigning the global function pointer to the address of the function pointer array element corresponding to the newly switched task in a task switch hook function; and recording the address of the currently called function in the current task in the global function pointer in the hook function calling function. The invention can capture the function causing system to halt or reset and capture the task operating the function, so as to provide effective recorded information for locating system failure afterwards, and shorten trouble shooting range, thereby facilitating to locate the system.
Owner:ZTE CORP
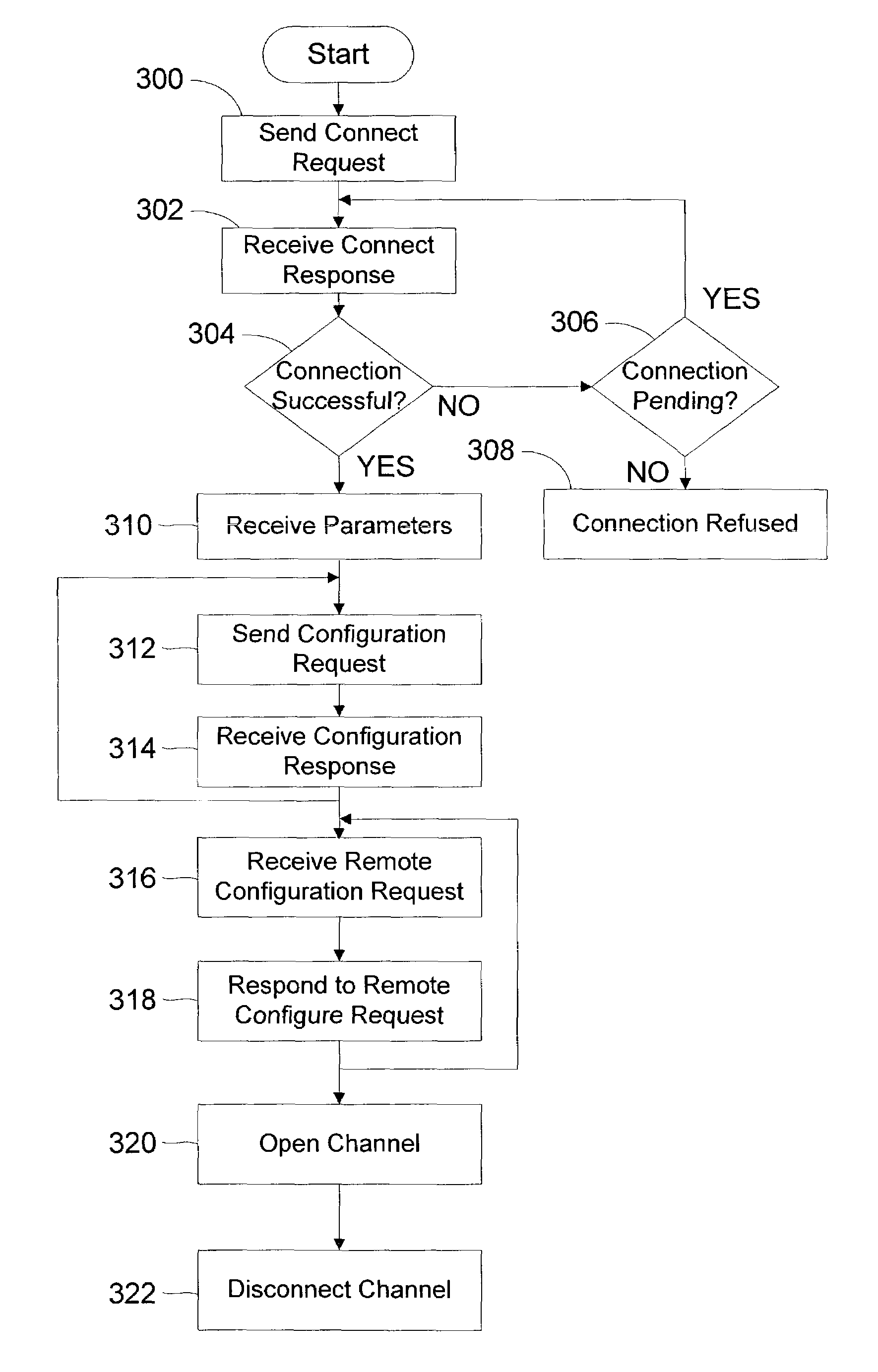
Method to configure a bluetooth logical link control and adaptation protocol channel
InactiveUS7082461B2Network traffic/resource managementNetwork topologiesThree levelTelecommunications
A technique to simplify L2CAP channel creation / configuration for a node is presented. The method enables a node to determine how involved it is in the L2CAP channel connection creation and management process. There are three levels of participation that the node may specify. The three levels are no involvement at all, minimal involvement, and total involvement. In no involvement, the channel is dropped if a remote node does not accept all node specified parameters. In minimal involvement, the channel is dropped if a remote node does not accept all node specified parameters and the node is notified when the connection has been disconnected by a remote disconnect or HCI link loss. In the total involvement level, the node is fully involved in the channel creation / configuration. The node provides a function pointer that is called to confirm or reject parameters. If a parameter is unacceptable, the connection is disconnected.
Owner:MICROSOFT TECH LICENSING LLC
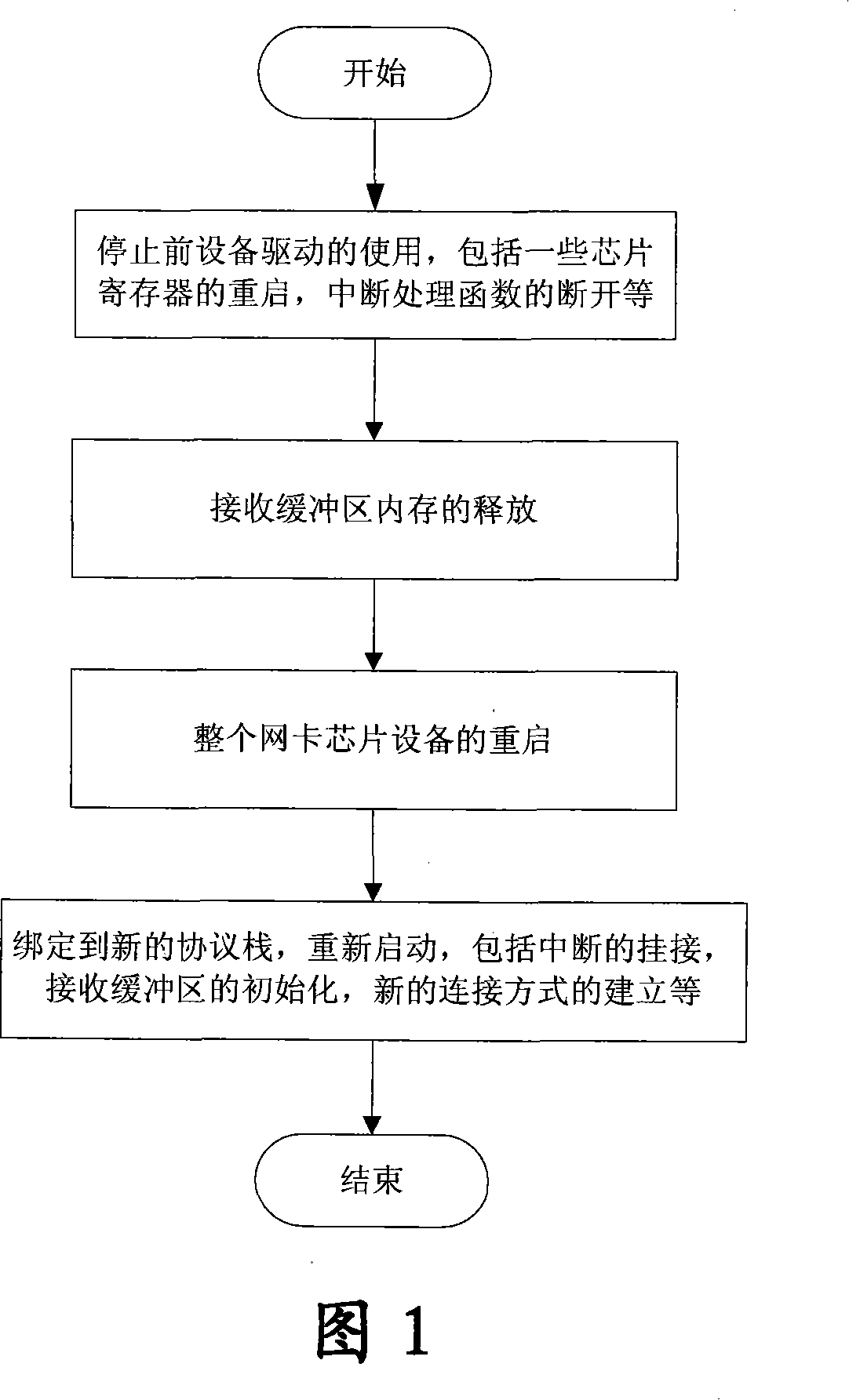
A method for realizing dual-protocol stack switching based on network card
InactiveCN101150412AShorten the timeNo packet lossData switching detailsProcess mechanismProcess function
This invention relats to a method for realizing switch of double-protocol stack by a network card including: 1, interruption process means to alter an interrupt function pointer to be connected to the interrupt process function of a new protocol stack, 2, distribution and releasing of EMS memory is to exchange memory in a buffer region including release of memory of a received buffer region of a protocol stack before switch and application for distribution of memory of the protocol stack after switch and writes the address into a descriptor of the received buffer region, 3, mode of connection is to judge if the current set-up mode of connection satisfies communication of the switched protocol stack when switching, if so, the current mode is kept, if not, new connection is set up again, thus, only different points in the switch key points are switched in each time of switch.
Owner:ZTE CORP
Method for capturing function for resulting in memory rewriting by wild pointer
ActiveCN101169752ASoftware testing/debuggingRedundant operation error correctionReturn functionMemory bank
The invention discloses a method for capturing a function causing memory to be rewritten by a stray pointer. The method comprises adding a hook function calling function and a hook function returning function in a system and allocating a global function pointer; when the system is running, recording a monitored memory value in the hook function calling function and comparing the recorded memory value by the hook function calling function with the current memory value in the hook function returning function, and in case of inconsistency, recording the address of the currently operating function to the global function pointer; and further, when switching a task, assigning the global function point to the corresponding recorded function pointer address of the switched task in the memory bank. The inventive capturing method can capture and record the function causing memory to be rewritten by the stray pointer in real time and further can locate the take calling the function.
Owner:ZTE CORP
Method and device for implementing undo and/or redo
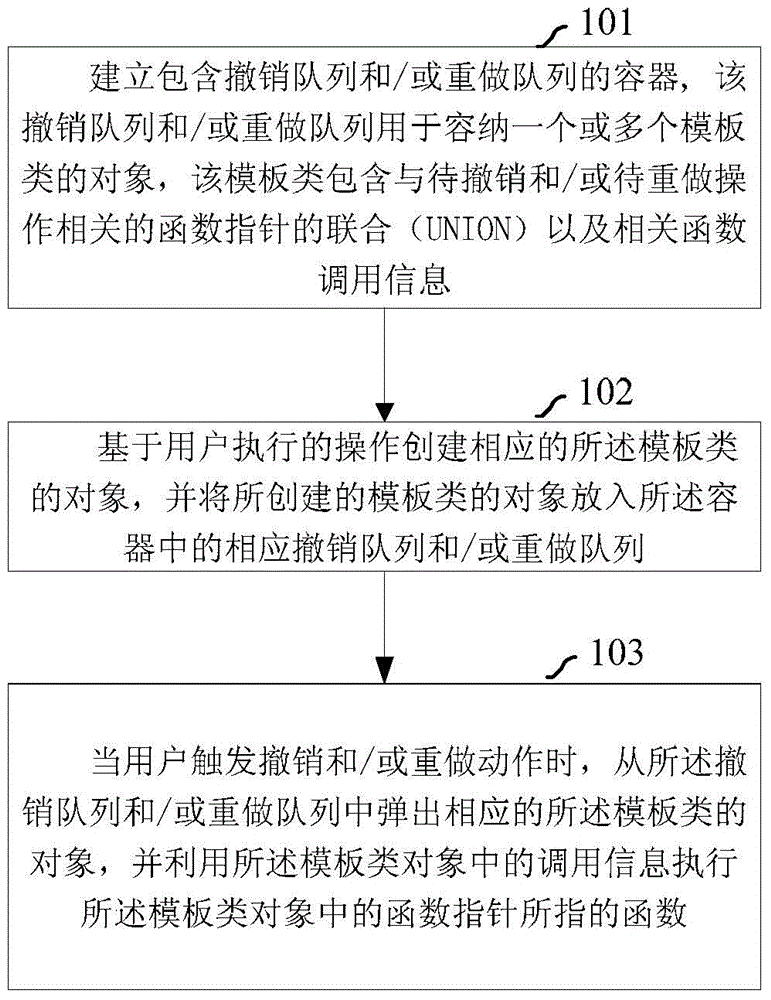
ActiveCN104572034AShorten design timeReduce occupancySpecific program execution arrangementsData operationsFunction pointer
The embodiment of the invention discloses a method and device for implementing undo and / or redo. The method comprises the following steps: establishing a container containing an undo queue and / or a redo queue, wherein the undo queue and / or the redo queue are / is used for accommodating one or more objects of a template class, and the template class contains the UNION of functional pointers related to operation to be undone and / or to be redid and related function call information; establishing the corresponding object of the template class based on the operation executed by a user, and putting the established object of the template class in the corresponding undo queue and / or redo queue in the container; when the user triggers an undo action and / or an redo action, popping the corresponding object of the template class from the undo queue and / or the redo queue, and utilizing the call information in the object of the template class to execute functions of the functional pointers in the object of the template class. By adoption of the template class as an operator of undo and / or redo, various types of classes can be accommodated, and data operation is not involved, so that the method is suitable for various application environments.
Owner:BEIJING SIEMENS CERBERUS ELECTRONICS
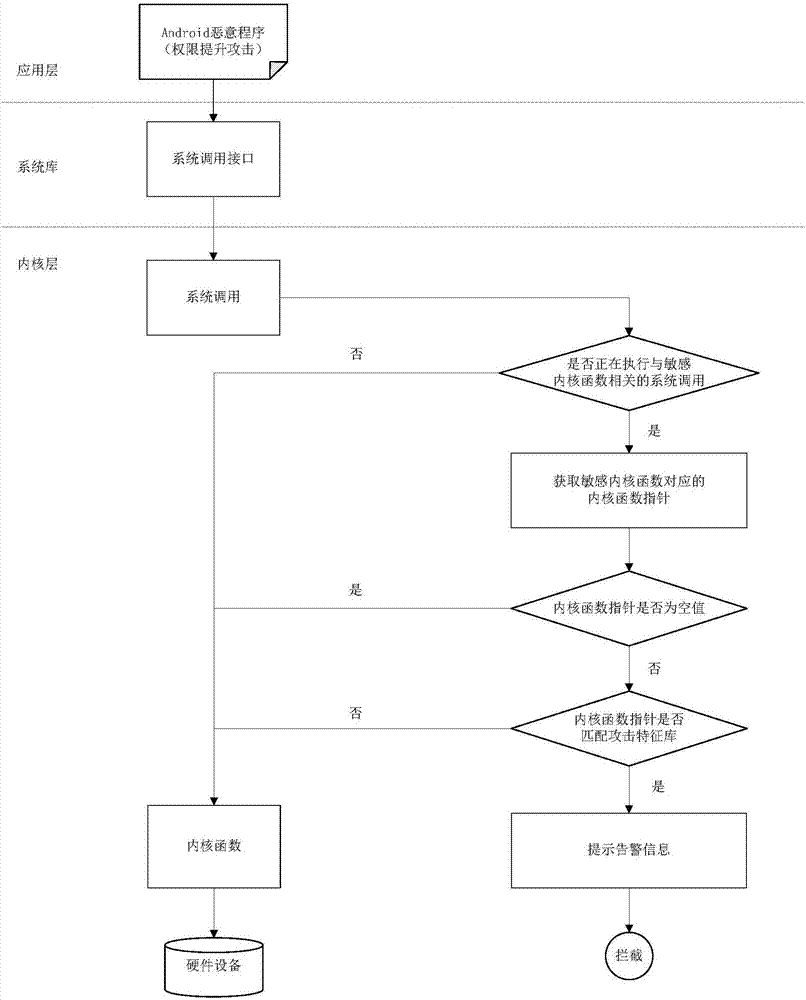
Security defense method and device of Android privilege escalation attack based on integrity verification
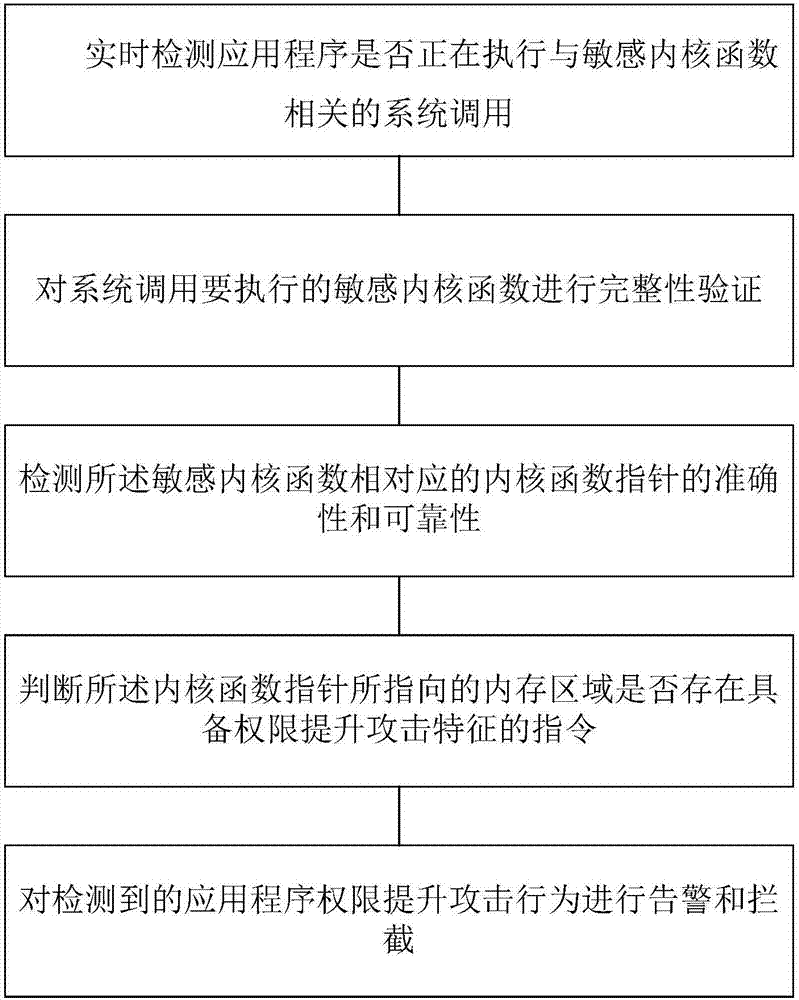
ActiveCN107016283AAvoid destructionReduce security threatsPlatform integrity maintainanceFunction pointerSystem call
The invention relates to a security defense method and device of the Android privilege escalation attacks based on integrity verifications. The method comprises the steps that the case that whether or not an application program is executing the system calls associated with sensitive kernel functions is detected in real time; integrity verifications are conducted on the sensitive kernel functions to be executed by the system calls; the accuracy and reliability of the kernel function pointer corresponding to the sensitive kernel functions are examined; the case that whether or not the internal storage pointed by the kernel function pointers has the commands for the privilege escalation attack features is evaluated; the detected application privilege escalation attacks are given warnings and blocked. According to the security defense method and device of the Android privilege escalation attacks based on integrity verifications, the privilege escalation attack behaviors of malicious programs are detected in real time and are given warnings and blocked, and the damages caused by attacks on the Android system are prevented, and the securities of the application and data are effectively protected. The security defense method and device of the Android privilege escalation attacks based on integrity verifications reduce security threats brought to the Android system by the privilege escalation vulnerabilities, and enhance the security of the Android system.
Owner:INST OF INFORMATION ENG CAS
Method for sharing static link code by software components in DLL and main program
InactiveUS20070288913A1Reduce complexityReduce memory requirementsLink editingVersion controlMemory addressFunction pointer
A method for sharing static link codes by software components in a dynamic link library (DLL) and a main program. First, the main program links to a static link library (SLL) and creates function pointers and variable pointers in the DLLs corresponding to the SLL. Next, the functions of a DLL program code associated with calling the SLL are changed into corresponding function pointers. Next, the variables of the DLL program code associated with calling the SLL are changed into corresponding variable pointers. Finally, the main program and the DLLs are compiled into the respective program codes, wherein the functions and variables associated with a DLL are obtained via the pointers. When the DLL is loaded in the main program, the memory addresses of the functions and variables for calling and corresponding to the SLL are passed to the DLL to share the static link codes with the main program.
Owner:SUNPLUS TECH CO LTD
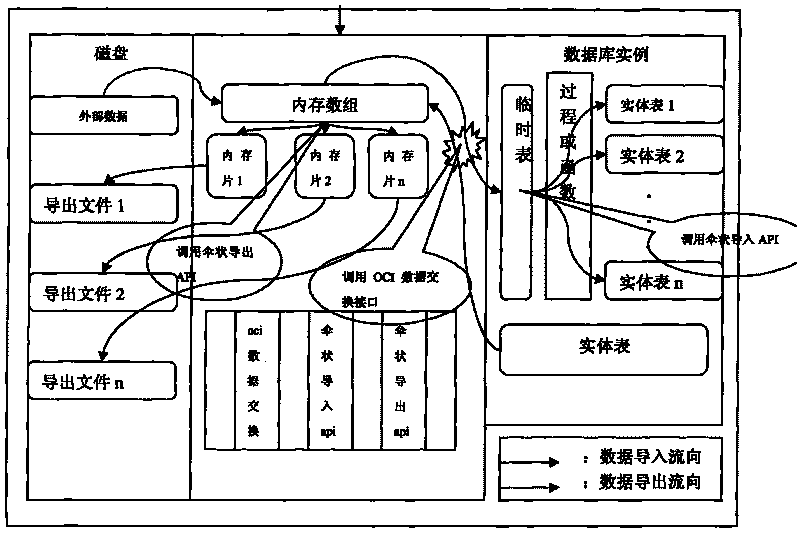
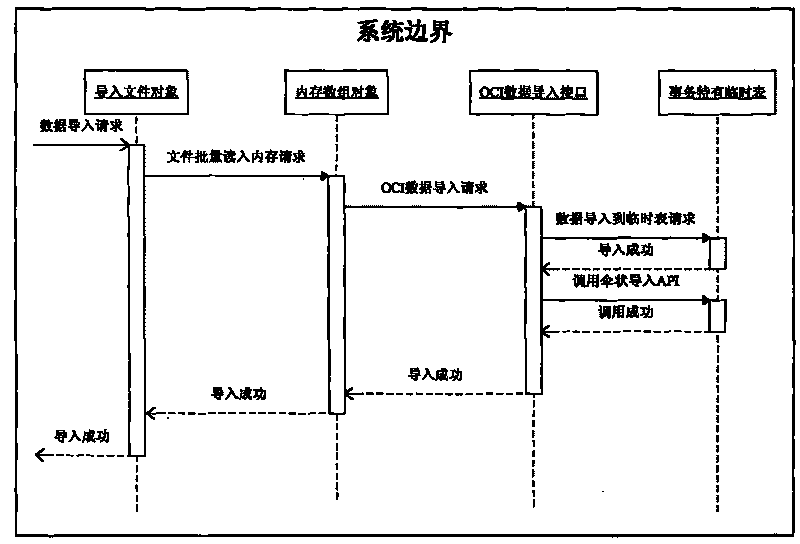
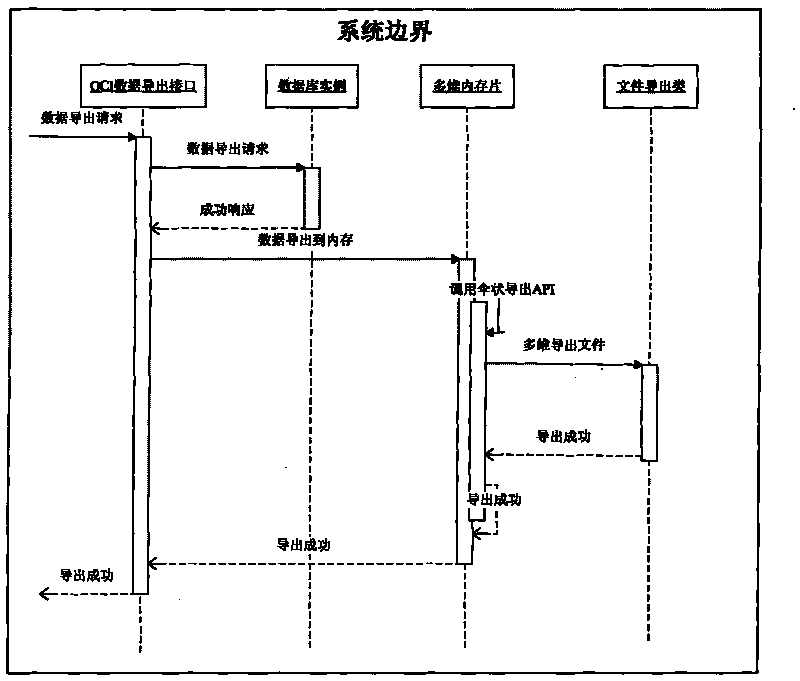
ORACLE-based umbrella data import/export method
ActiveCN101706779AReduce parsingReduce the number of executionsMulti-dimensional databasesSpecial data processing applicationsMemory chipArray data structure
Owner:LINKAGE SYST INTEGRATION
Monitoring method and system for time consumption of IOS application method and time consumption of view loading
ActiveCN108197004AImplement call time-consuming monitoringEasy to controlHardware monitoringFunction pointerComputer engineering
The invention discloses a monitoring method and system for the time consumption of an IOS application method and the time consumption of view loading, and relates to the technical field of IOS applications. The method comprises the steps that an objc_msgSend function pointer is set as a hook function; when an IOS application calls any method in a main thread, the hook function is called through the objc_msgSend function pointer, and the time consumption of calling an objc_msgSend function when the IOS application calls the method in the main thread is calculated through the hook function; thetime consumption of calling the objc_msgSend function when the IOS application calls each method in the main thread can be obtained by calling the hook function separately, since calling of each method in the main thread can correspond to calling of the objc_msgSend function, the time consumption of calling the objc_msgSend function is that of calling the method in the main thread, and therefore the time consumption of calling each method in the main thread when the IOS application runs is monitored.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
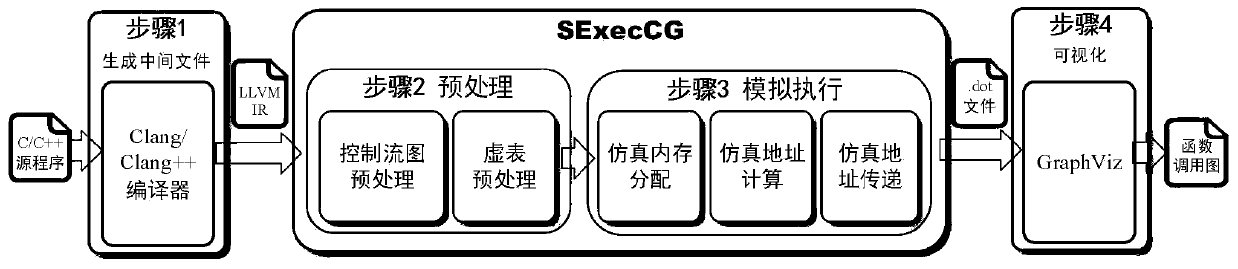
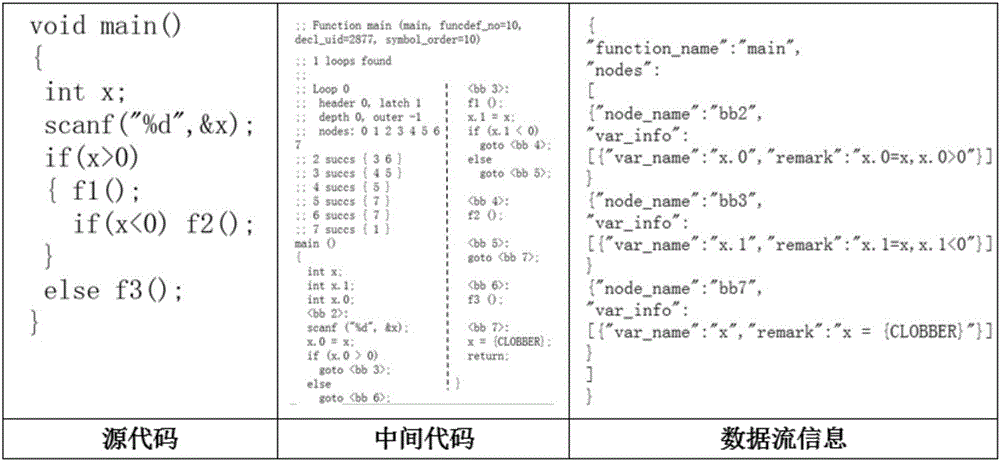
The Static function call graph construction method suitable for virtual function and function pointermethod is suitable for constructing static function call graph of virtual function and function pointer
ActiveCN110187988AThe analysis result is accurateAccurate analysisInterprogram communicationCall graphFunction pointer
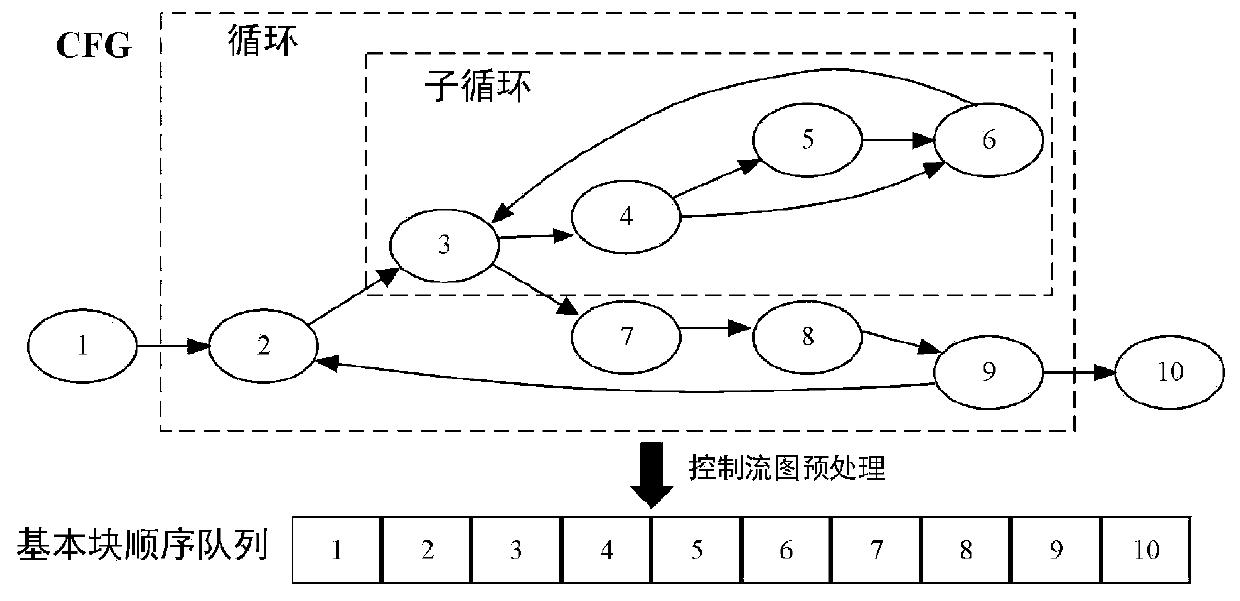
The invention discloses a static function call graph construction method suitable for a virtual function and a function pointer. The static function call graph construction method comprises the following steps: 1, obtaining an intermediate code of a source program; 2, obtaining key information in the intermediate code, wherein the key information comprises a basic block sequence queue and virtualfunction related information; 3, performing simulation execution on the intermediate code based on the key information, analyzing an actual function called by a function calling instruction in the intermediate code, and recording a function calling relation; and 4, constructing a static function call graph according to the function call relationship. According to the method, the virtual function,the function pointer calling and the thread creation relationship can be comprehensively analyzed, and the complex function pointer calling can be accurately analyzed, so that program developers can be better helped to understand programs, and meanwhile, the accuracy of a static analysis method depending on a function calling graph is improved.
Owner:UNIV OF SCI & TECH OF CHINA
Inaccessible function call path detection method in complex system
InactiveCN106021116AAccurate detectionEfficient analysisSoftware testing/debuggingControl flowCoding block
The invention provides an inaccessible function call path detection method in a complex system. The method comprises the steps that 1, function pointer processing is carried out for a source code to distinguish declaration, evaluation and use of a function pointer; 2, the source code processed through the function pointer generates an intermediate code of the source code, wherein the intermediate code comprises multiple function units, each function unit uses a function as a basic processing unit, each function unit comprises at least one basic code block, and data flow information in each basic code block and control flow information among the basic code blocks are extracted and stored in a json file; 3, whether a branch node in the control flow information has the certain direction or not is judged so as to carry out inaccessible control flow detection.
Owner:BEIJING INFORMATION SCI & TECH UNIV +1
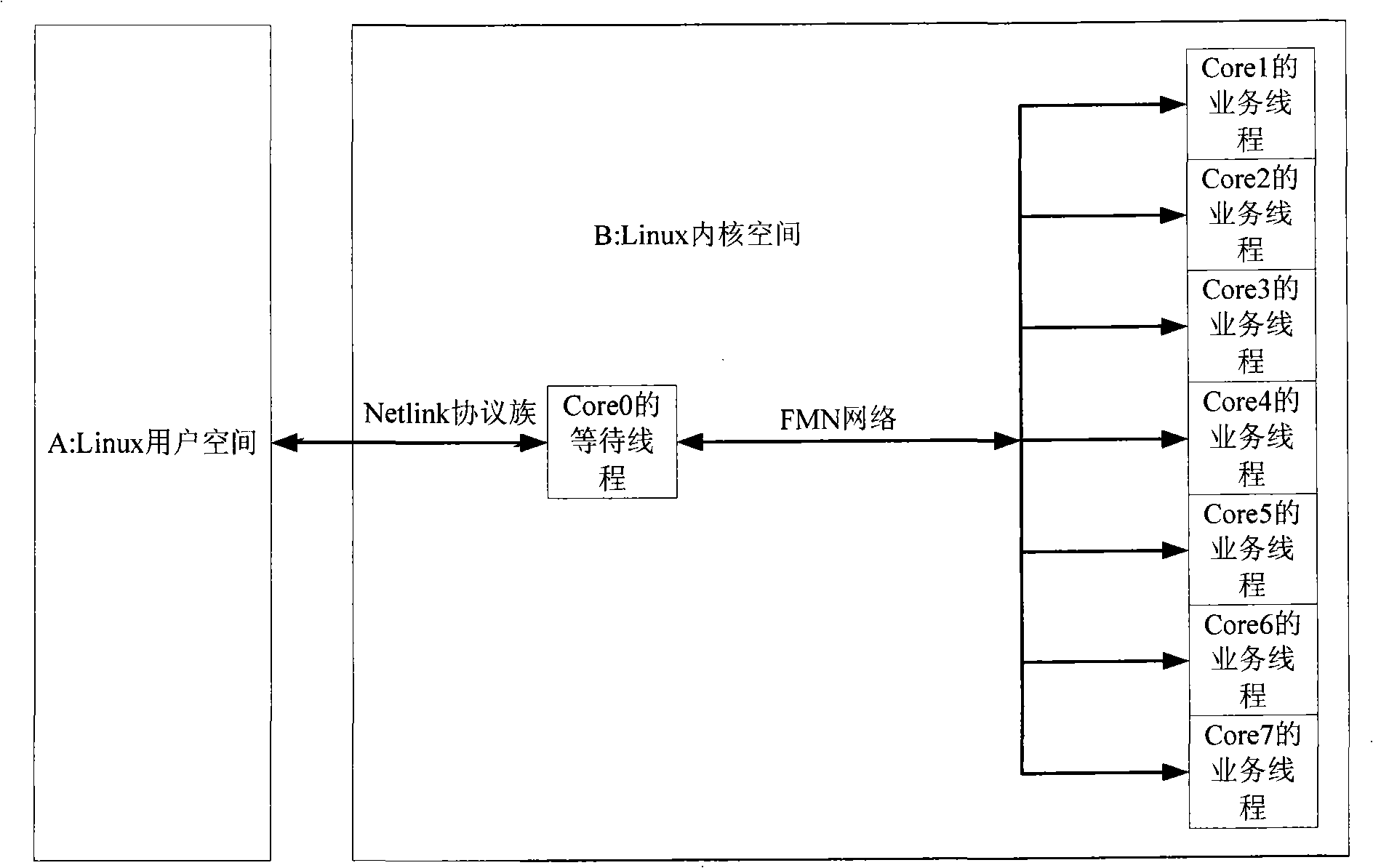
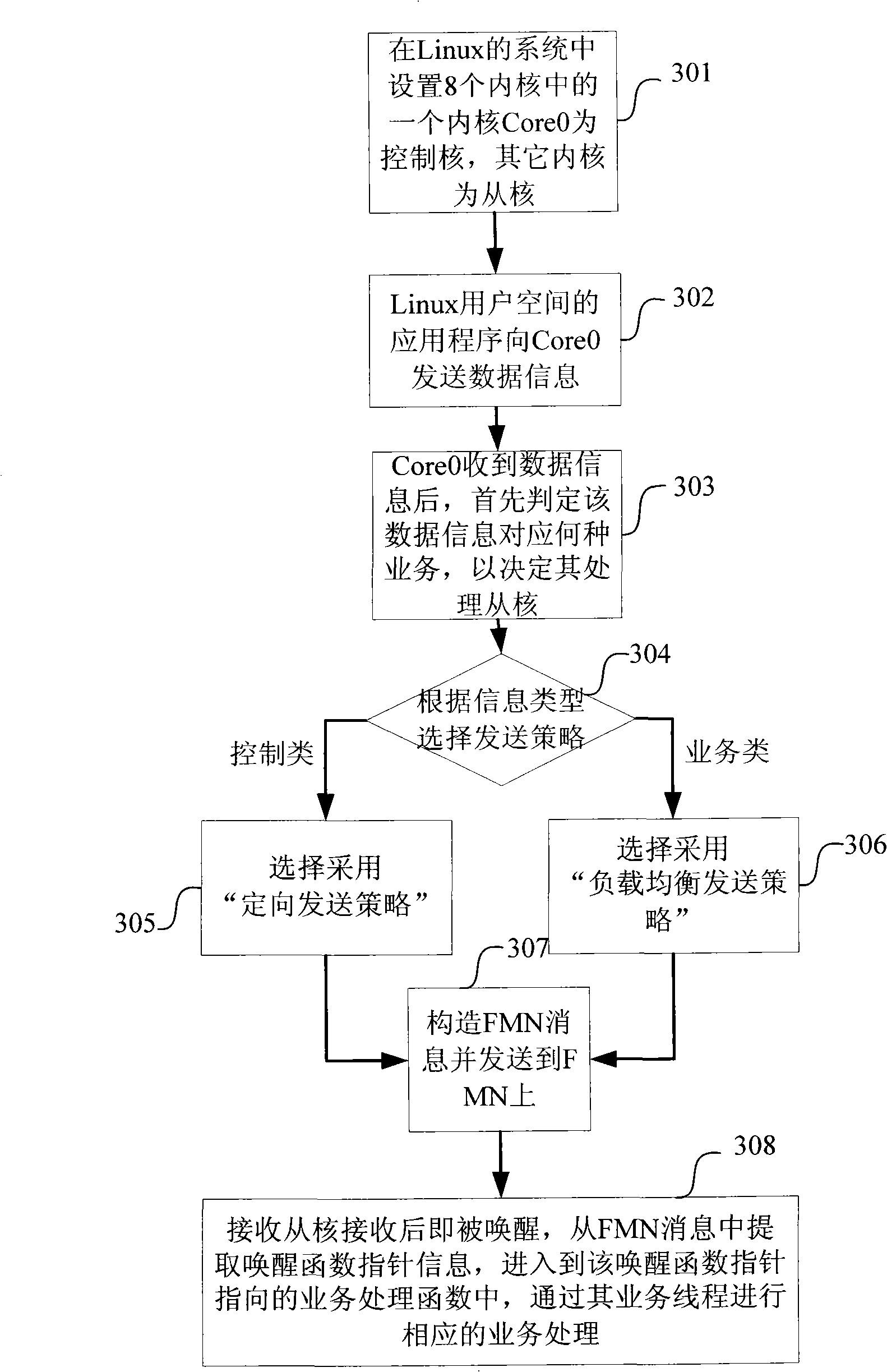
Method for user and multi-inner core to perform communication in Linux system
InactiveCN101276289AReduce development costsImprove business processing performanceMultiprogramming arrangementsData switching networksGNU/LinuxFunction pointer
The present invention provides a communication method of users with a multi-kernel in a Linux system, including: (1) a kernel of the multi-kernel in the Linux system is provided as a control kernel, other kernels are provided as accompanied kernels; (2)After receiving the data message transmitted by the application program in the Linux user space, Linux control kernel transmits an arousing function pointer message containing arousing receiving accompanied kernels and message of the receiving accompanied kernels to FMN according to the type selection transmission strategy of the data message; (3) Linux is aroused by receiving the message of FMN received by the accompanied kernels, extracting the arousing function pointer message from the FMN message, entering in the service processing function pointed by the arousing function pointer, processing service process by the service line program. The invention achieves the progress that the communication between user and kernel is from single kernel to multiple-kernel, achieving effect of realizing communication between user and multiple-kernel in Linux system.
Owner:江苏三农乐购电子商务有限公司
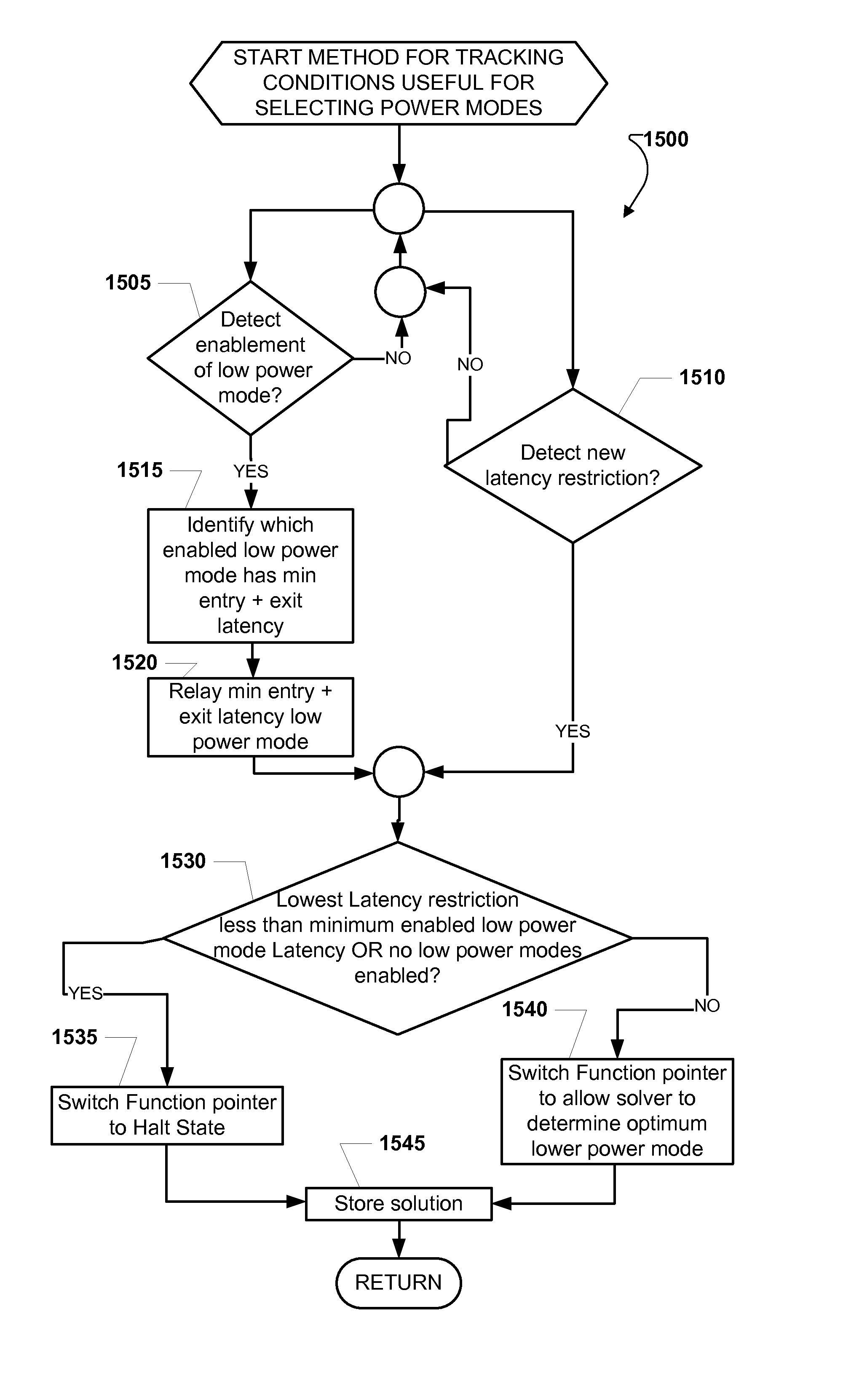
Method and System for Tracking and Selecting Optimal Power Conserving Modes of a PCD
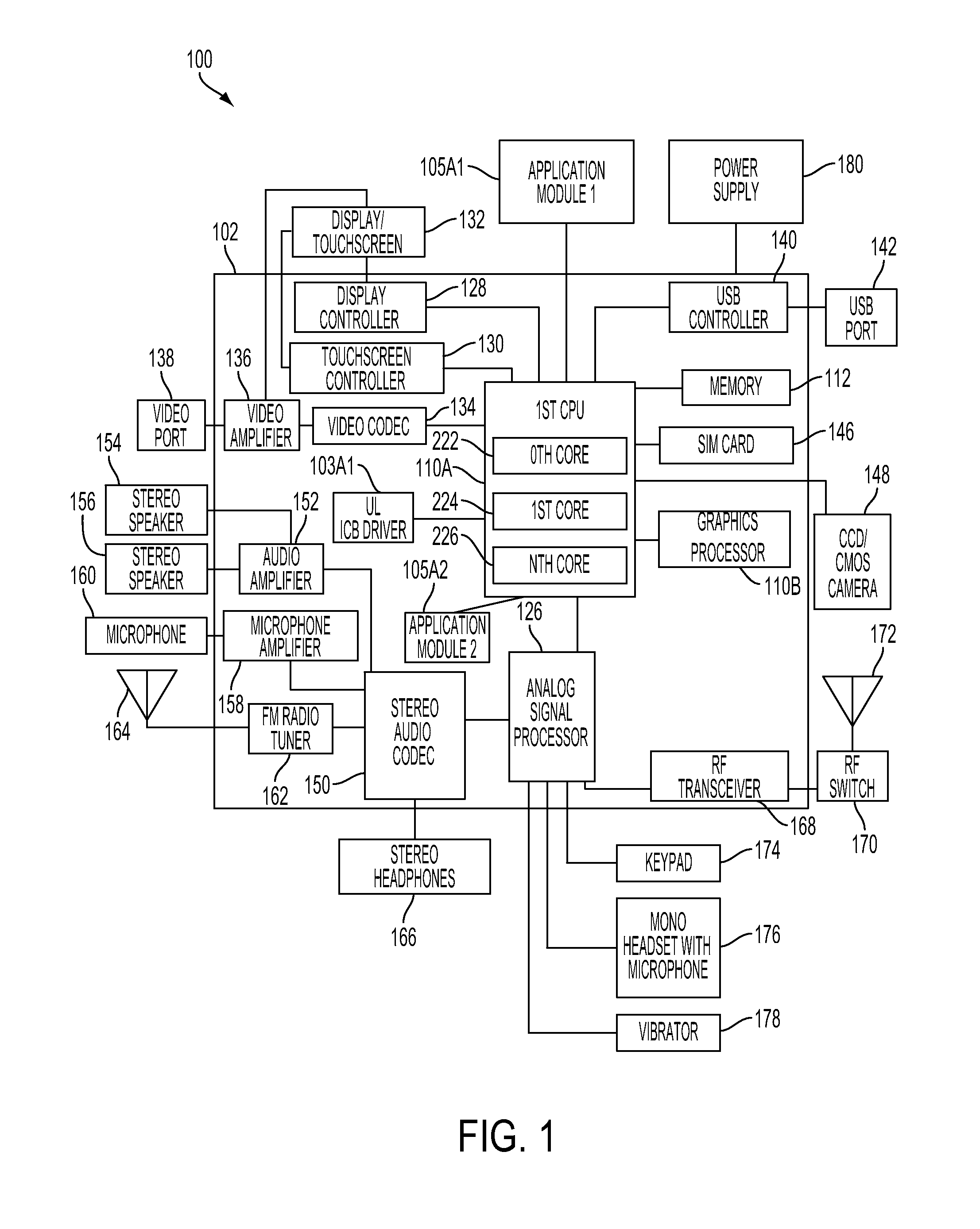
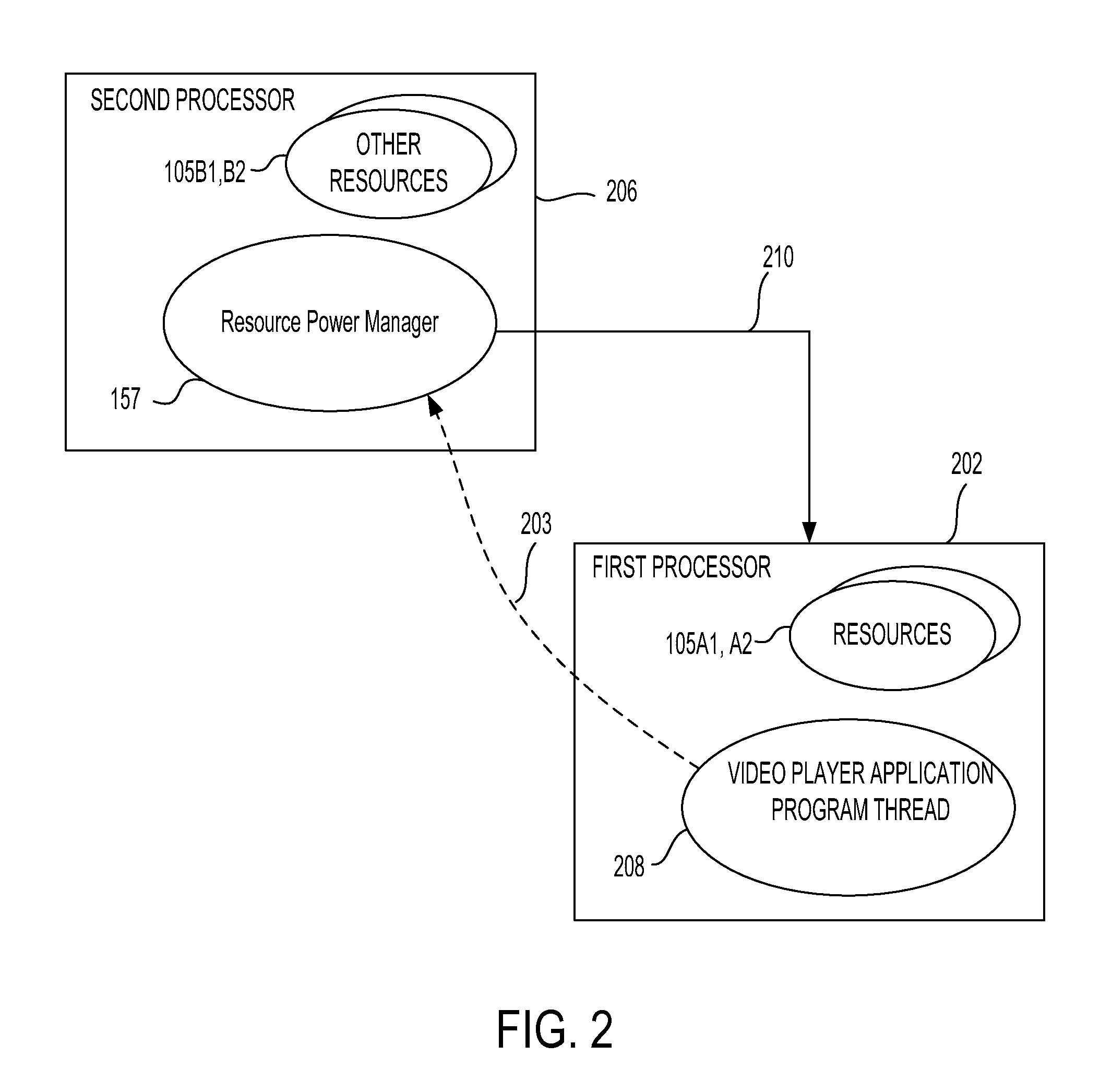
InactiveUS20130275791A1Optimum power conservationEnergy efficient ICTPower supply for data processingPower modeLatency (engineering)
A method and system for tracking and selecting optimal power conserving modes of a PCD includes detecting enablement or disablement of a reduced power mode and detecting one of a new and a change in a latency restriction. Next, a low power mode which has a minimum entry and exit latency may be identified. Then, it may be determined if a lowest latency restriction is less than the minimum entry and exit latency. A function pointer may be adjusted based on the output of the determining step. The function pointer may reference a halt state and a reduced power state for the PCD. Then, conditions favorable for at least one of an idle state and a reduced power mode of the PCD may be assessed. If conditions are favorable for an idle state or a reduced power mode for the PCD, then status of the function pointer may be read.
Owner:QUALCOMM INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com