Defense method for kernel-level return-oriented rootkits
A kernel-level, instruction-based technology, applied in computer science and malware protection fields, can solve problems such as difficult to deal with, and achieve high performance and protection from infringement.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
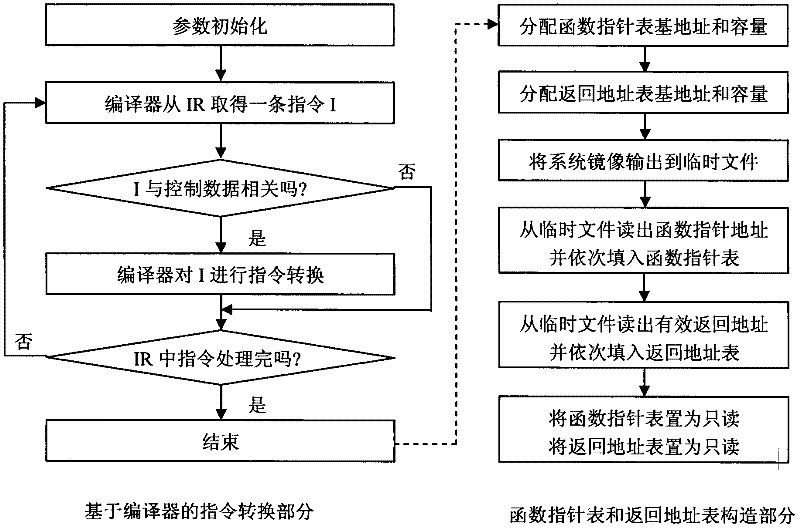
[0062] refer to figure 1 , the present invention includes two parts: instruction conversion based on compiler and construction of function pointer table and return address table. Among them, the instruction conversion based on the compiler mainly includes parameter initialization and conversion of instructions related to control data. After the instruction conversion is completed, the function pointer table and the return address table are constructed.
[0063] 1. Compiler-based instruction conversion
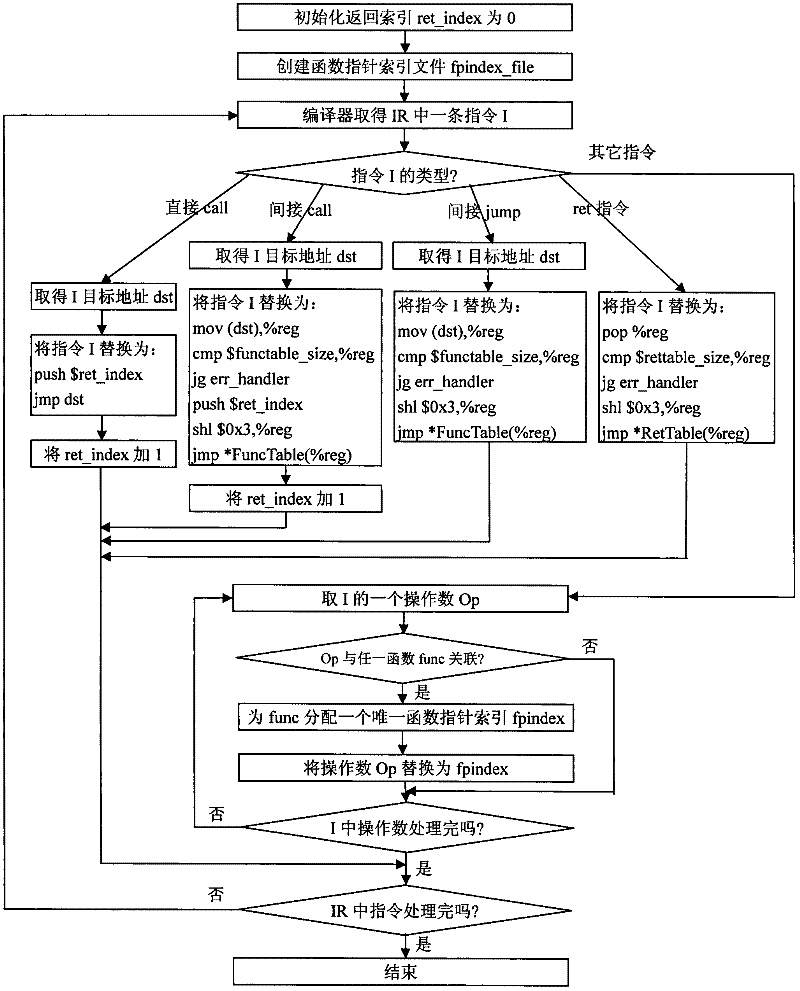
[0064] refer to figure 2 , the specific implementation of this part is as follows:
[0065] Step 1, initialize the return index ret_index to 0.
[0066] The present invention allocates a unique return index ret_index for each return address, and the ret_index starts counting from 0 and adds 1 every time it is allocated.
[0067] Step 2, create an empty function pointer index file fpindex_file.
[0068] The present invention generates an empty function pointer index file f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com