Patents
Literature
126 results about "Kernel level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A kernel is the lowest level of easily replaceable software that interfaces with the hardware in your computer.
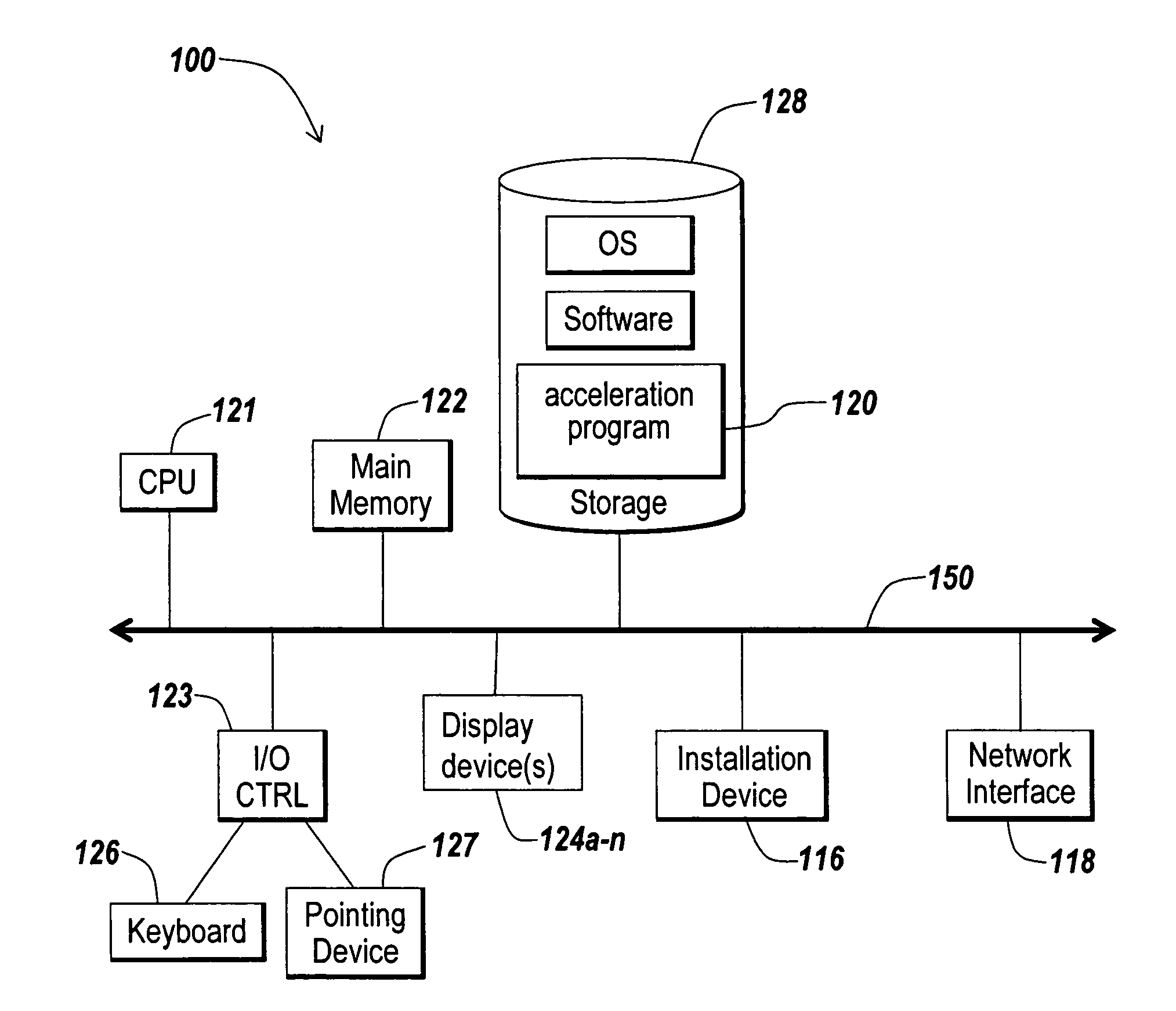
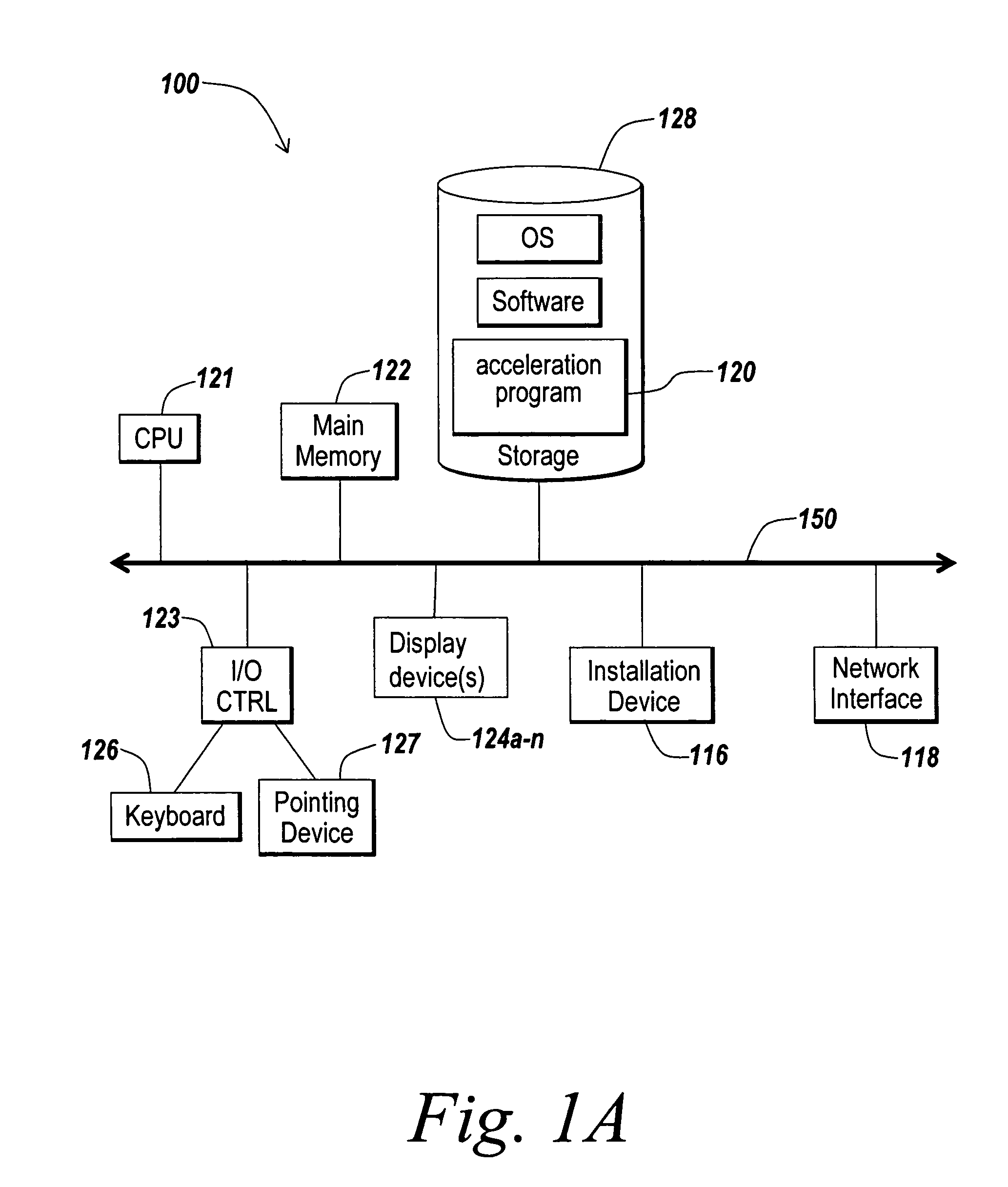
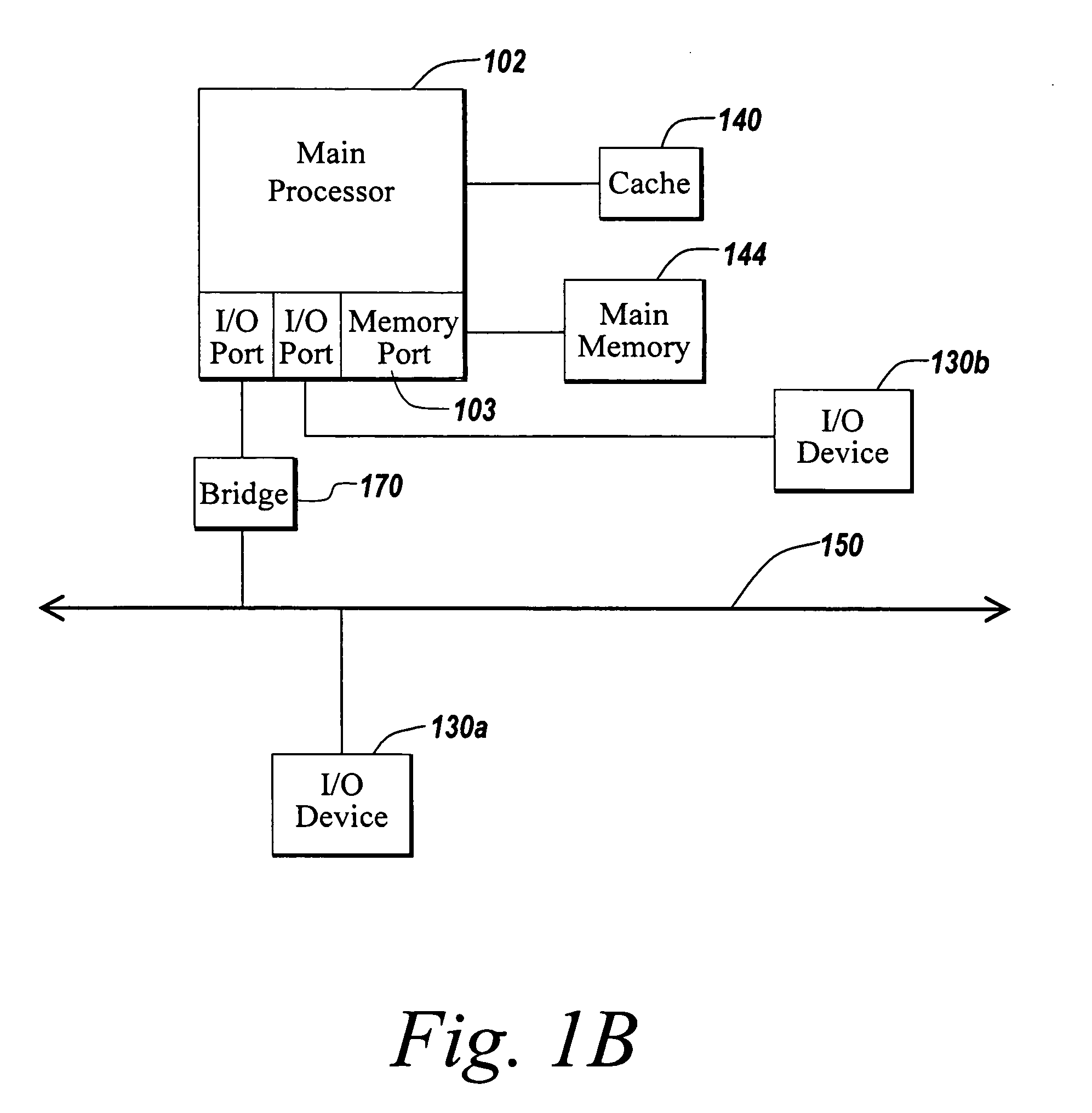
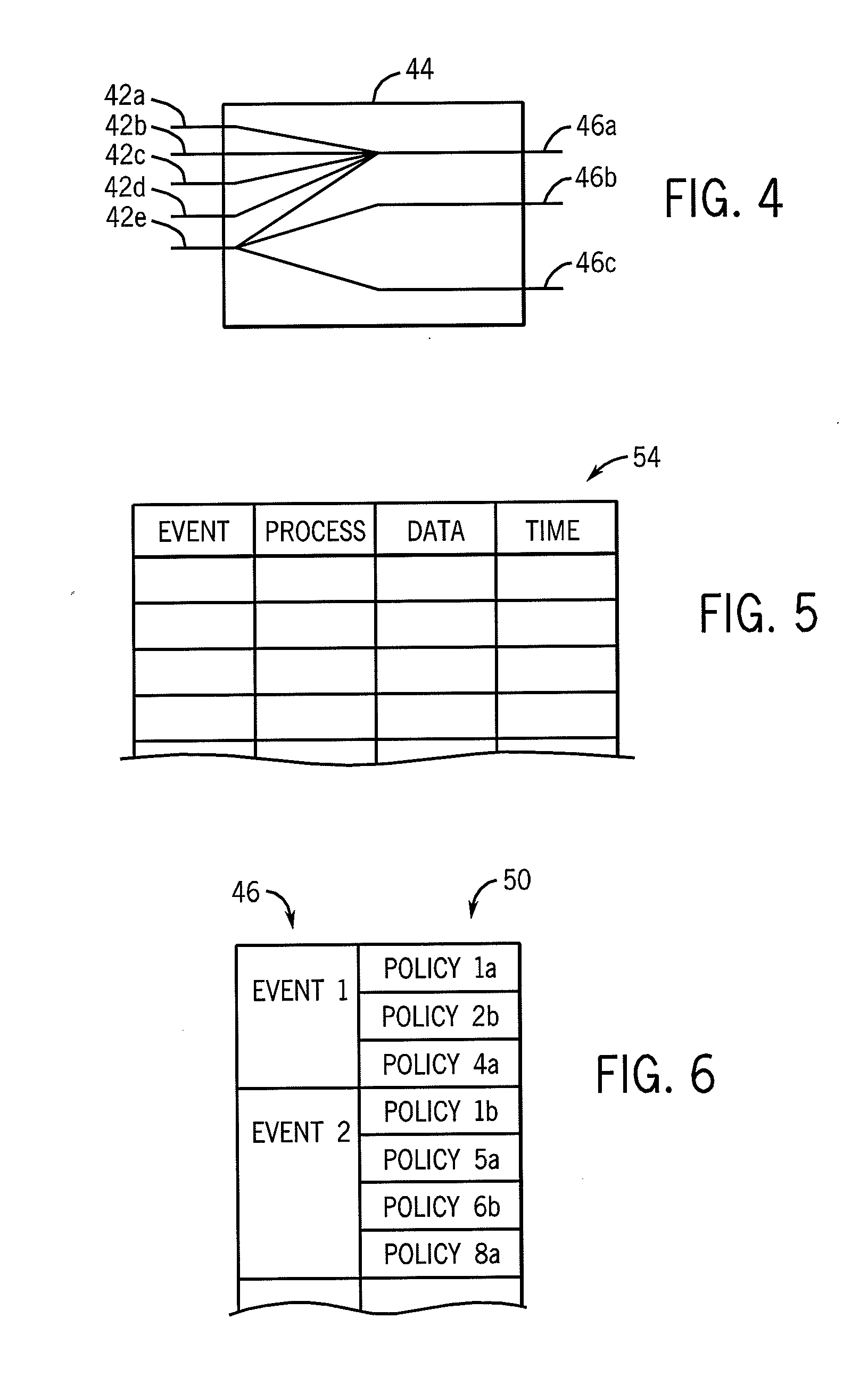
Systems and methods for providing integrated client-side acceleration techniques to access remote applications
InactiveUS20060253605A1Improve performanceReduce deliveryDigital computer detailsTransmissionTransport control protocolInterface point
The present invention is directed towards systems and methods for dynamically deploying and executing acceleration functionality on a client to improve the performance and delivery of remotely accessed applications. In one embodiment. The client-side acceleration functionality is provided by an acceleration program that performs a plurality of the following acceleration techniques in an integrated and efficient manner: 1) multi-protocol compression 2) transport control protocol pooling, 3) transport control protocol multiplexing 4) transport control protocol buffering, and 5) caching. The acceleration program establishes a transport layer connection between the client and server, and intercepts network packets at the transport layer. The acceleration program uses a kernel-level data structure to access the network packet intercepted at the transport layer, and performs subsequently one or more of the acceleration techniques on the intercepted network packet at one interface point or point of execution of the acceleration program.
Owner:CITRIX SYST INC
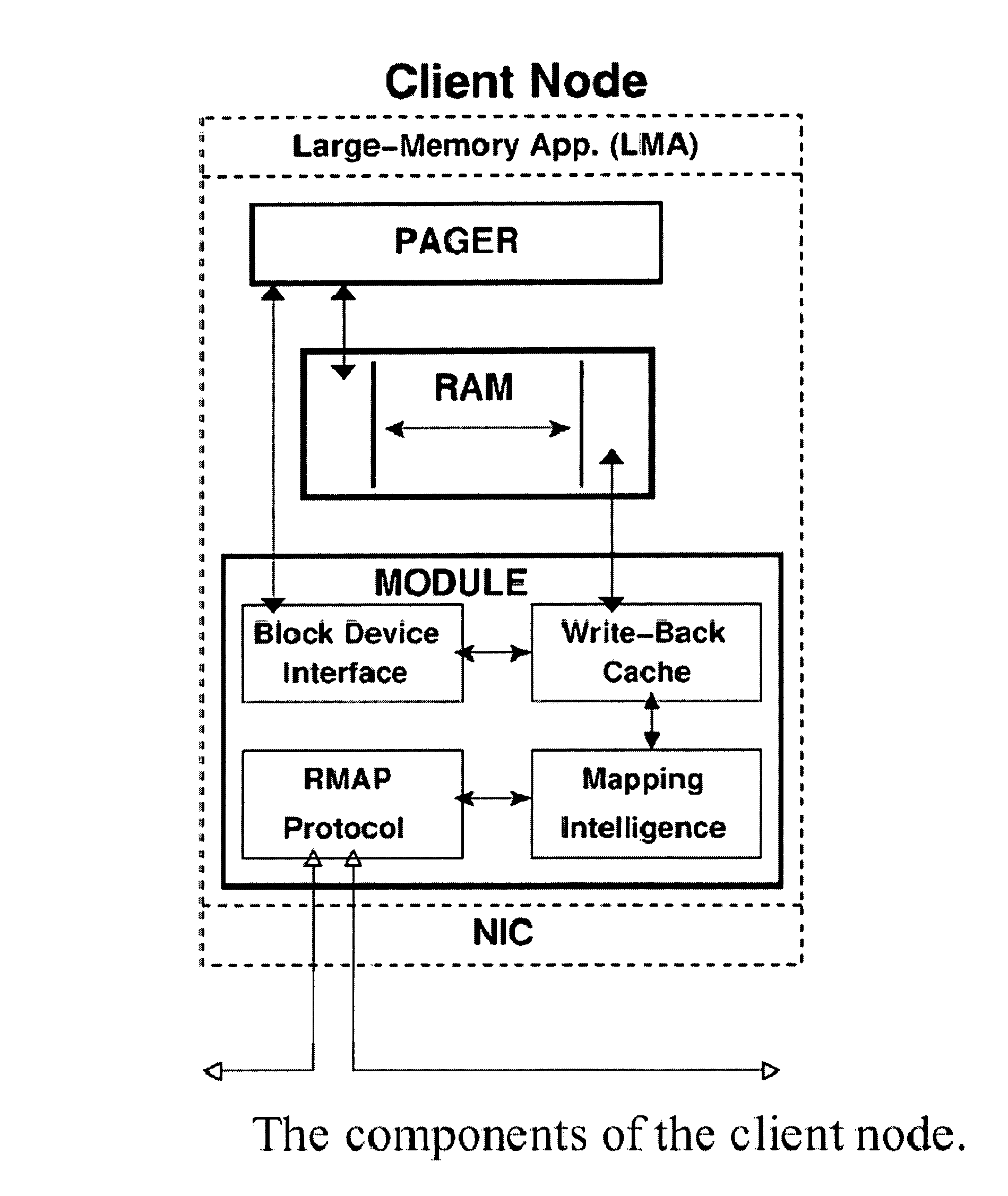
Distributed adaptive network memory engine
ActiveUS7917599B1Processing speedLower latencyMultiple digital computer combinationsTransmissionMass storageOperational system
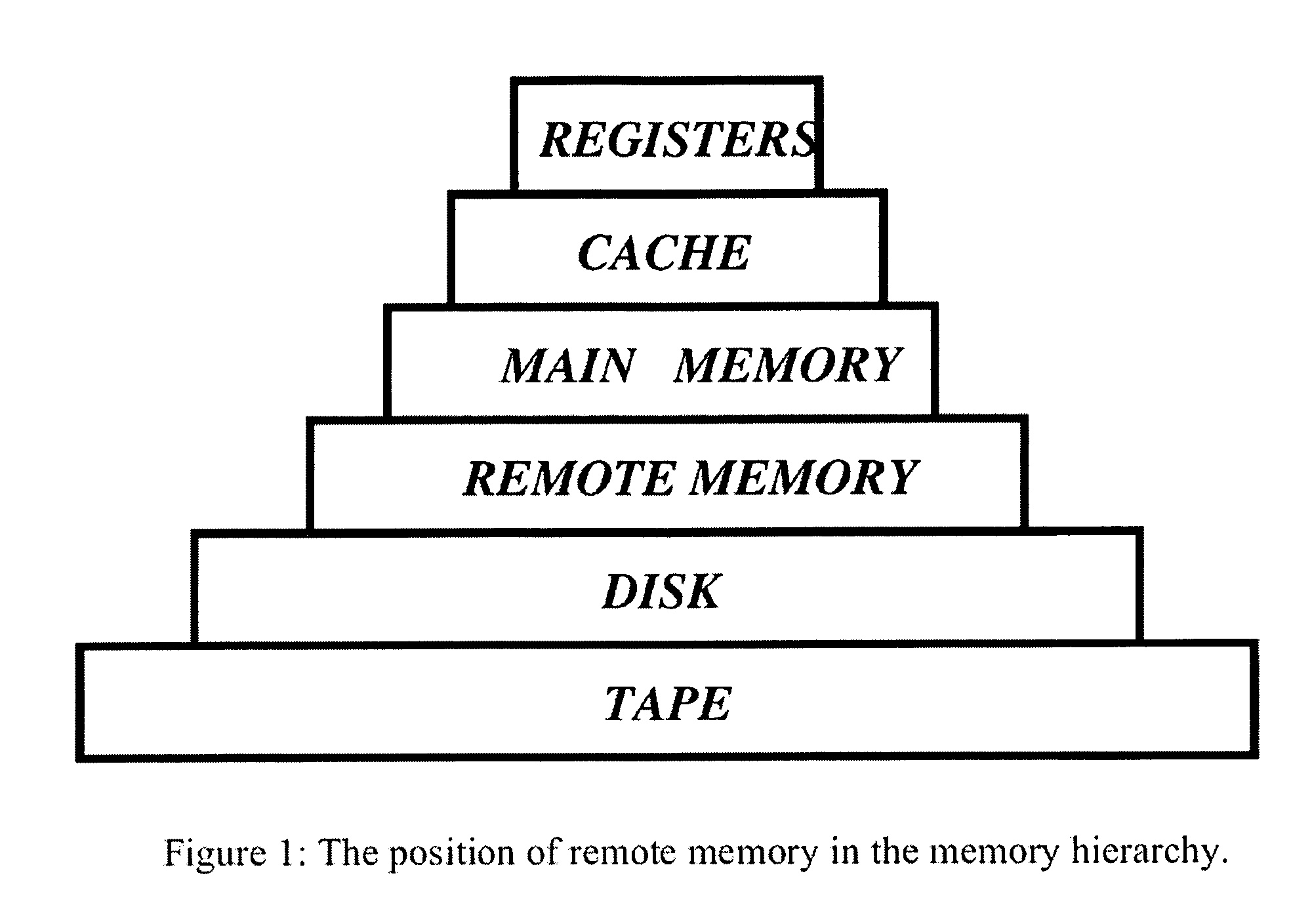
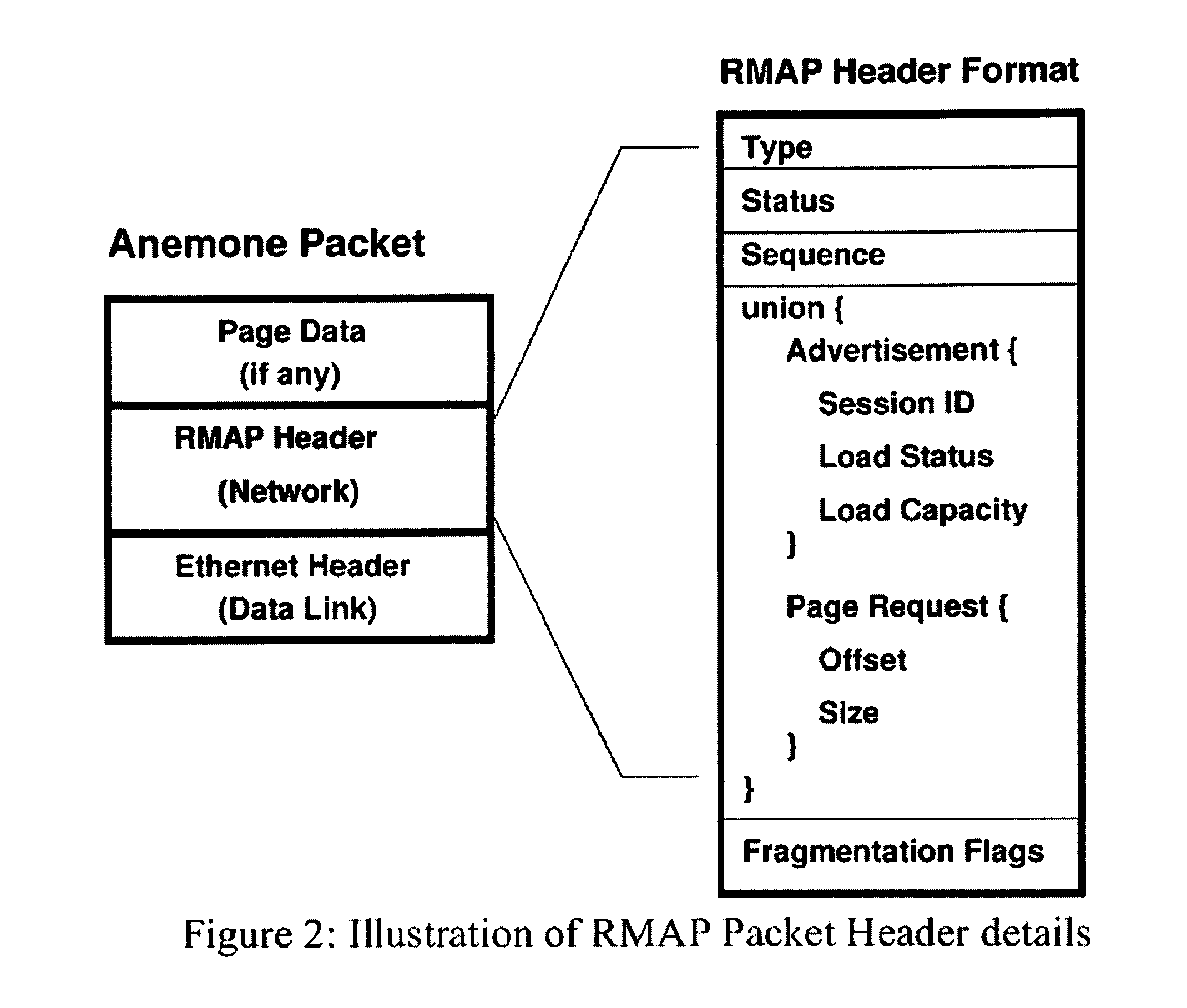
Memory demands of large-memory applications continue to remain one step ahead of the improvements in DRAM capacities of commodity systems. Performance of such applications degrades rapidly once the system hits the physical memory limit and starts paging to the local disk. A distributed network-based virtual memory scheme is provided which treats remote memory as another level in the memory hierarchy between very fast local memory and very slow local disks. Performance over gigabit Ethernet shows significant performance gains over local disk. Large memory applications may access potentially unlimited network memory resources without requiring any application or operating system code modifications, relinkling or recompilation. A preferred embodiment employs kernel-level driver software.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
Malware prevention system monitoring kernel events
ActiveUS20090070878A1Reduce overheadAvoid choiceMemory loss protectionError detection/correctionOperational systemKernel level
A malware prevention system monitors kernel level events of the operating system and applies user programmable or preprepared policies to those events to detect and block malware.
Owner:WISCONSIN ALUMNI RES FOUND
Security driver for hypervisors and operating systems of virtualized datacenters
A system and method for efficient security protocols in a virtualized datacenter environment are contemplated. In one embodiment, a system is provided comprising a hypervisor coupled to one or more protected virtual machines (VMs) and a security VM. Within a private communication channel, a split kernel loader provides an end-to-end communication between a paravirtualized security device driver, or symbiont, and the security VM. The symbiont monitors kernel-level activities of a corresponding guest OS, and conveys kernel-level metadata to the security VM via the private communication channel. Therefore, the well-known semantic gap problem is solved. The security VM is able to read all of the memory of a protected VM, detect locations of memory compromised by a malicious rootkit, and remediate any detected problems.
Owner:CA TECH INC
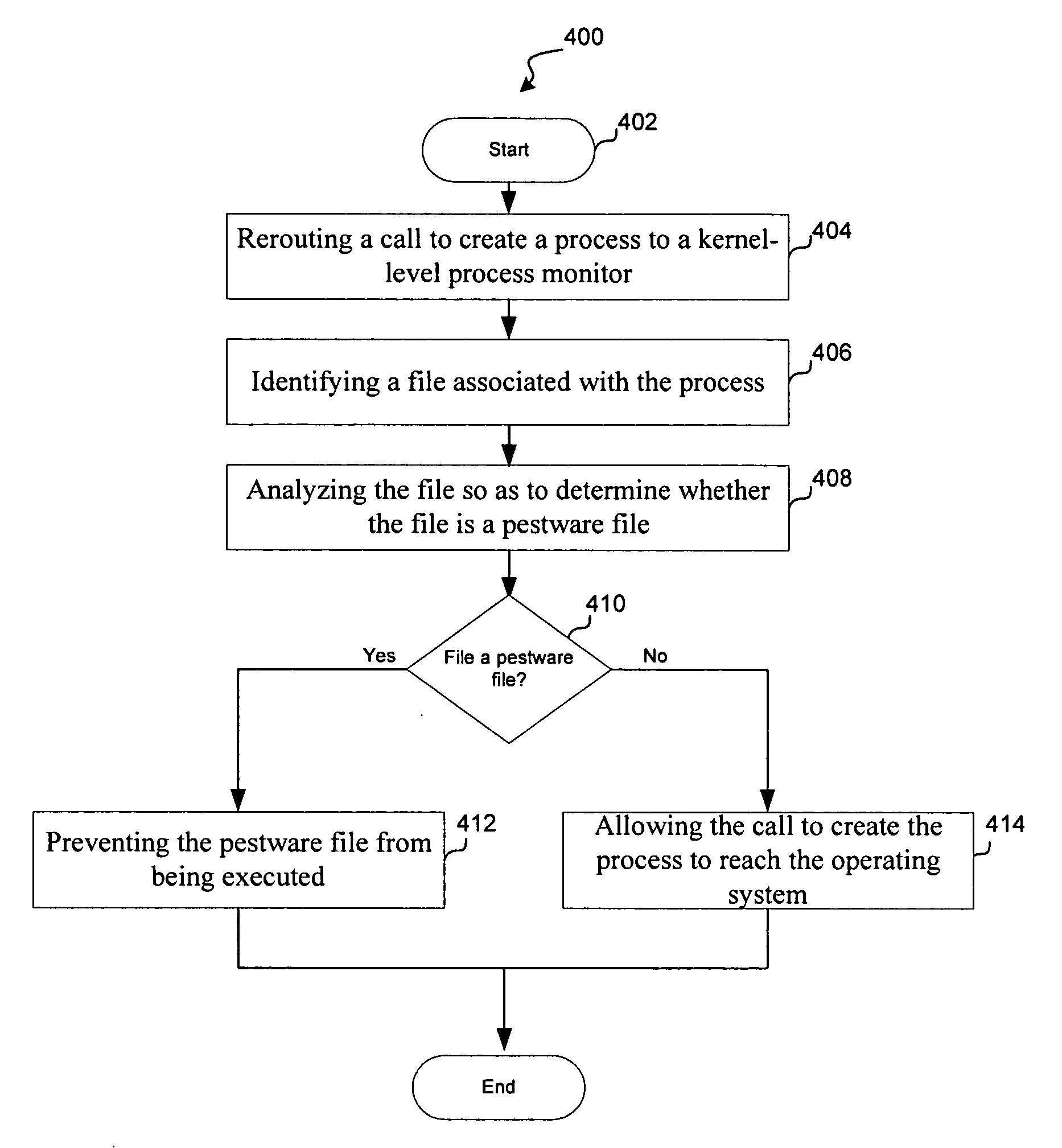
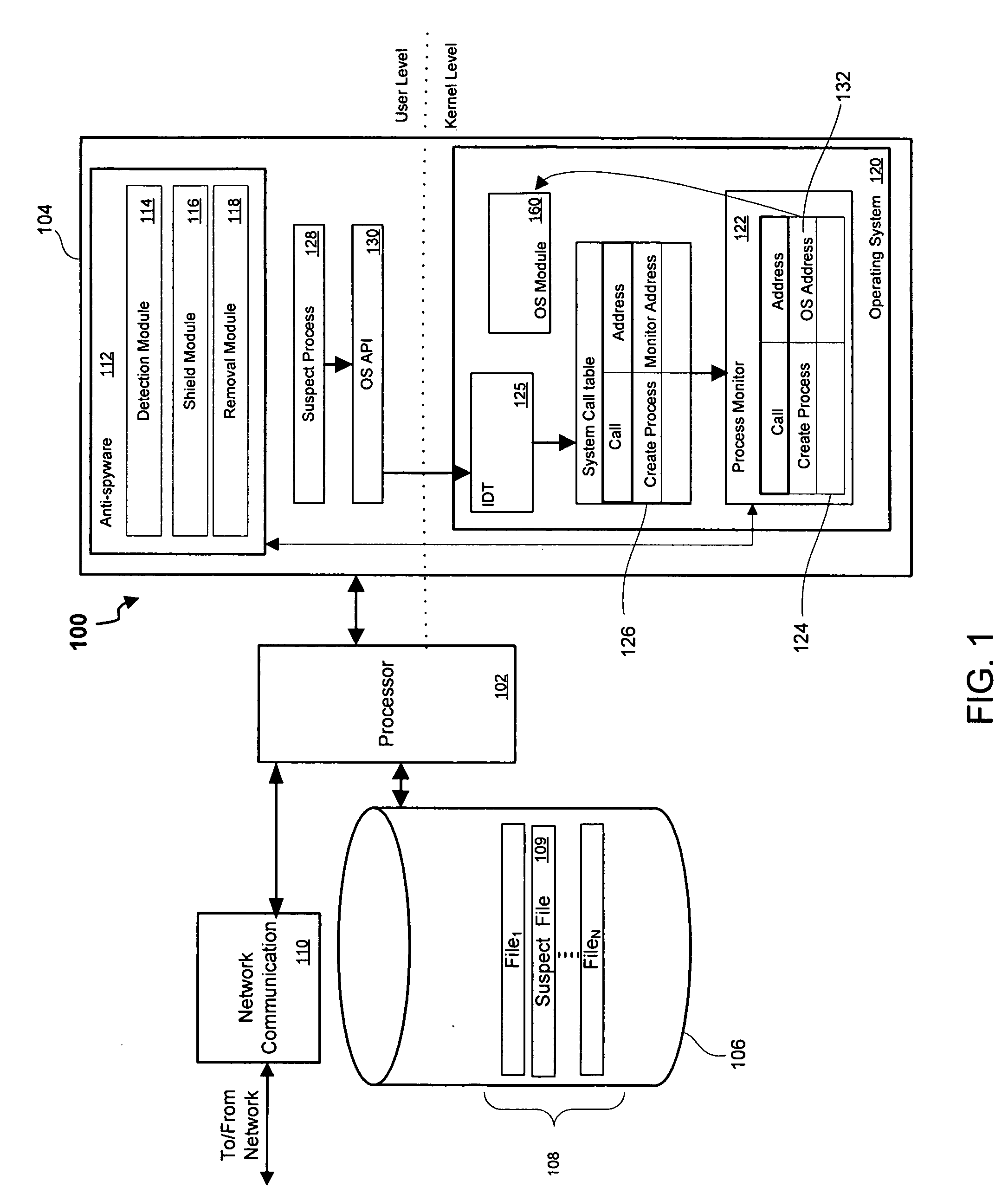
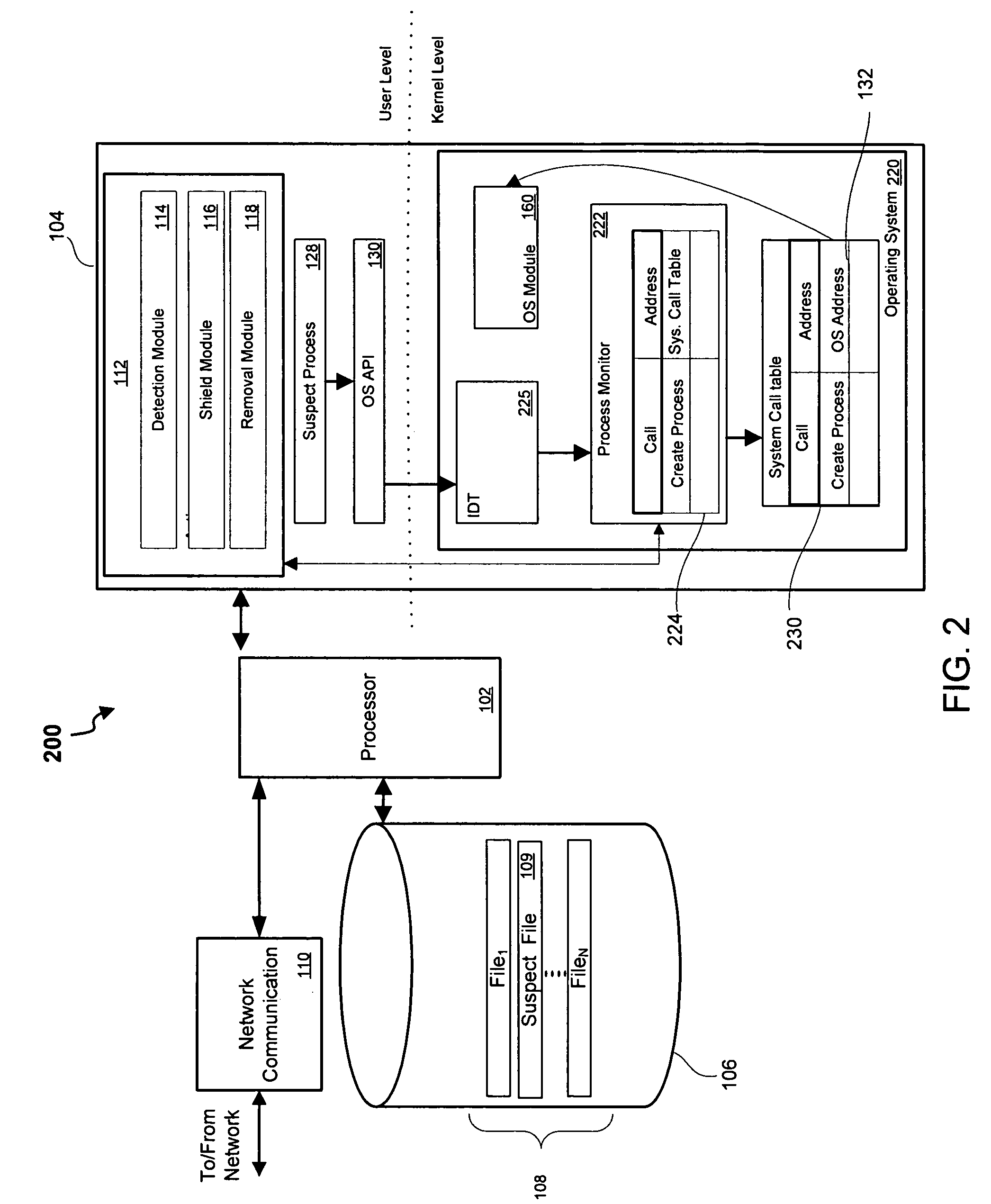
System and method for kernel-level pestware management
InactiveUS20070094496A1Avoid creatingComputer security arrangementsSecuring communicationKernel levelManagement system
Owner:WEBROOT SOFTWARE INCORPORATED
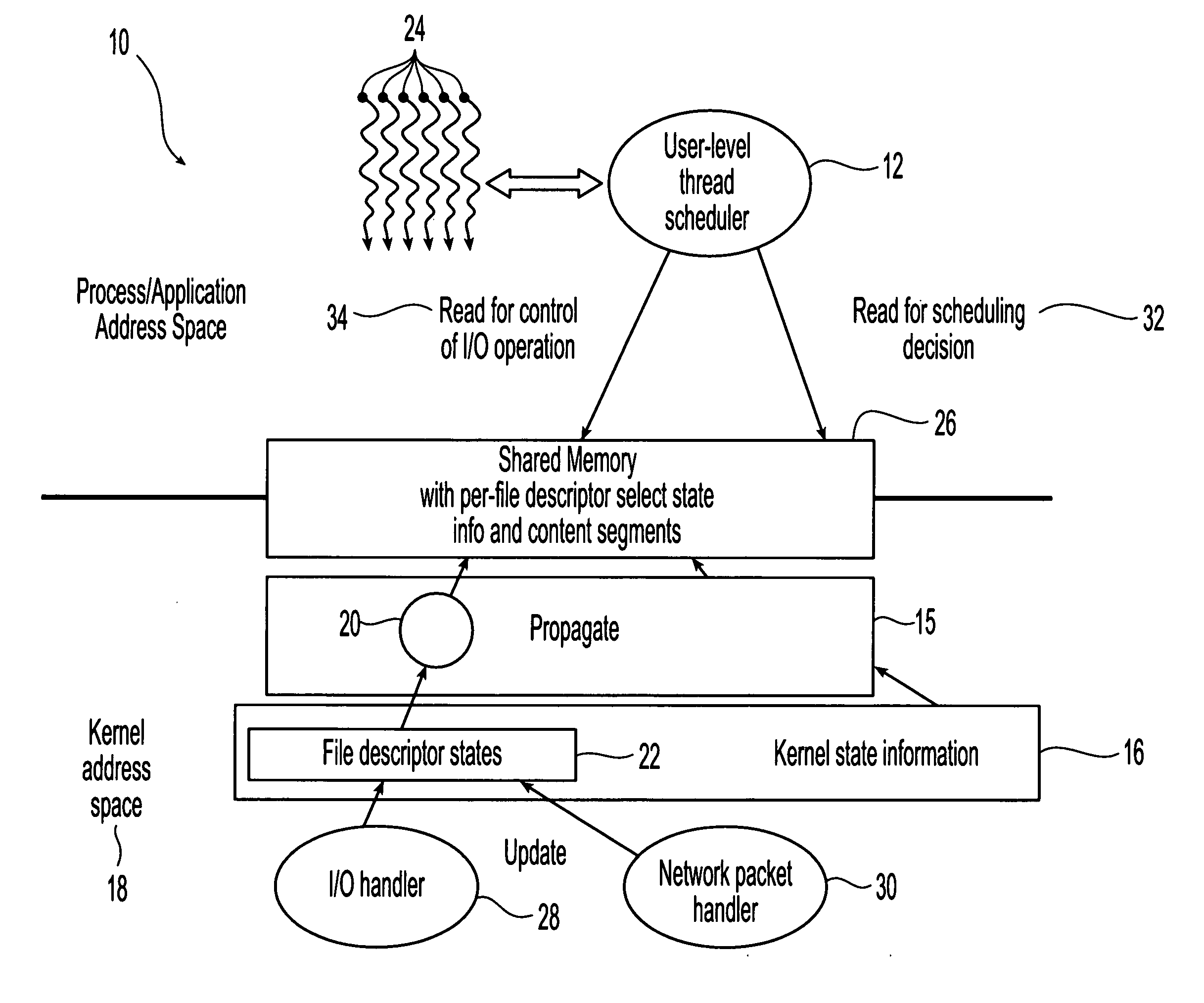
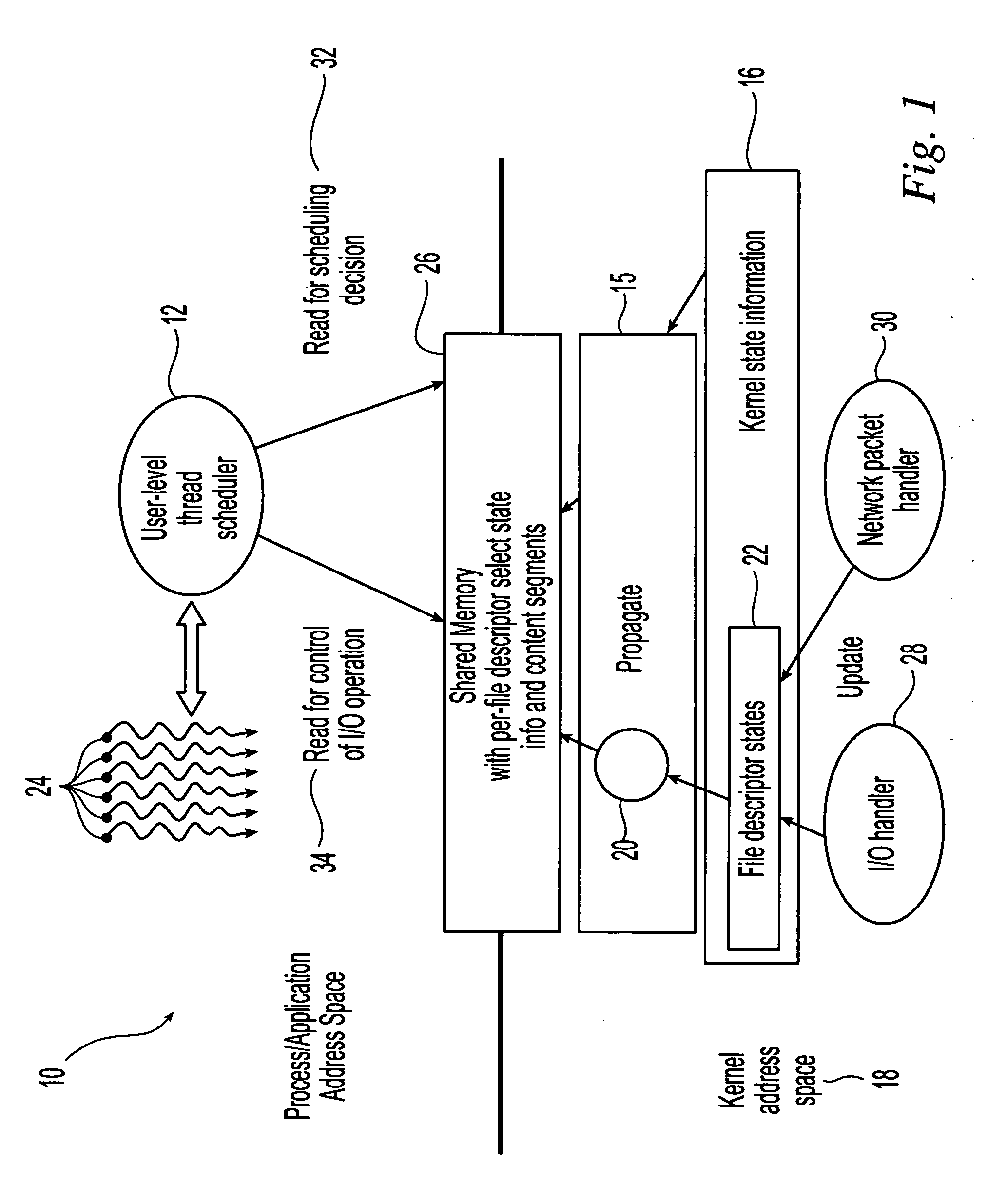
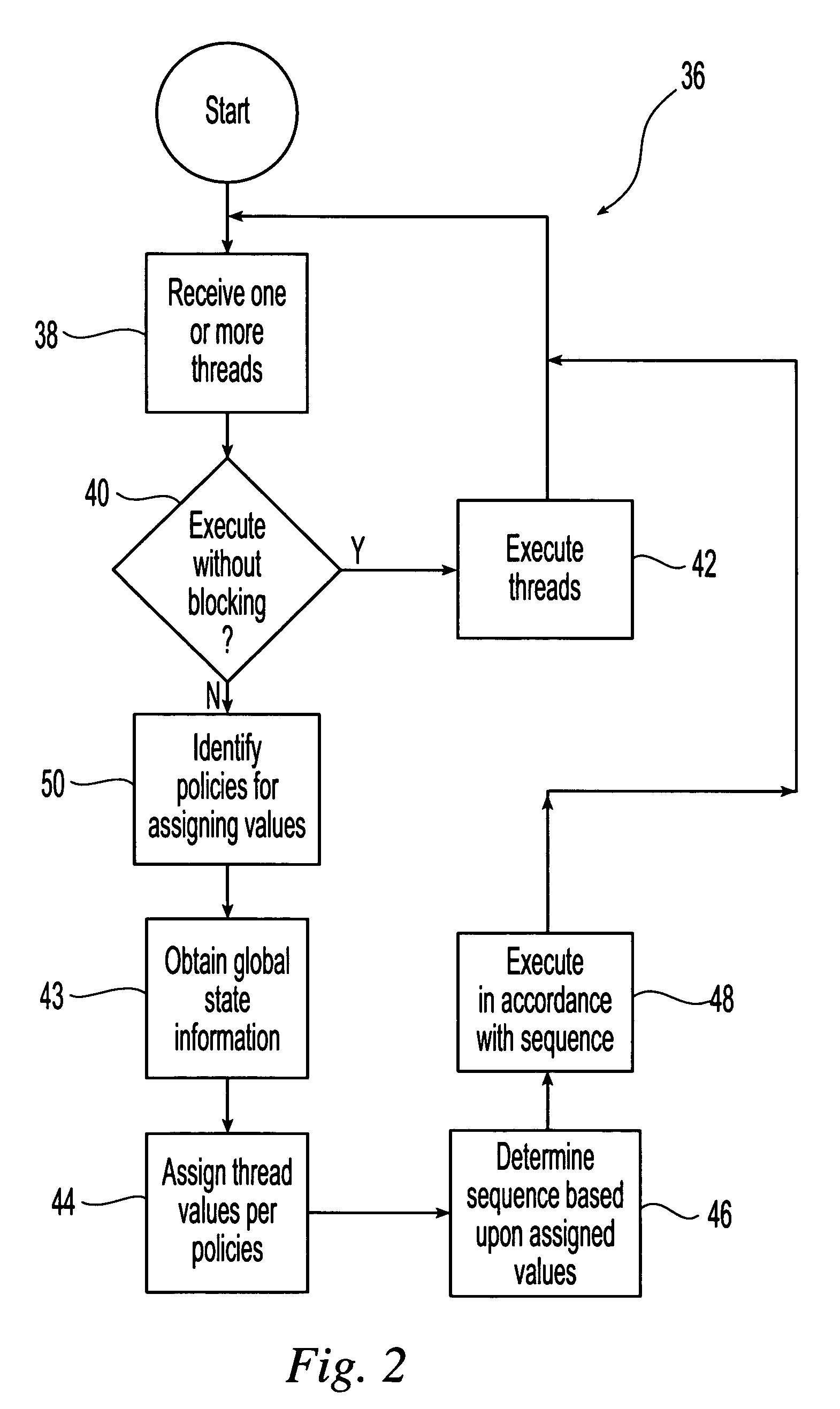
Method and system for scheduling user-level I/O threads
InactiveUS20060075404A1Efficiently determineReduce in quantityMultiprogramming arrangementsMemory systemsThread schedulingKernel level
The present invention is directed to a user-level thread scheduler that employs a service that propagates at the user level, continuously as it gets updated in the kernel, the kernel-level state necessary to determine if an I / O operation would block or not. In addition, the user-level thread schedulers used systems that propagate at the user level other types of information related to the state and content of active file descriptors. Using this information, the user-level thread package determines when I / O requests can be satisfied without blocking and implements pre-defined scheduling policies.
Owner:IBM CORP
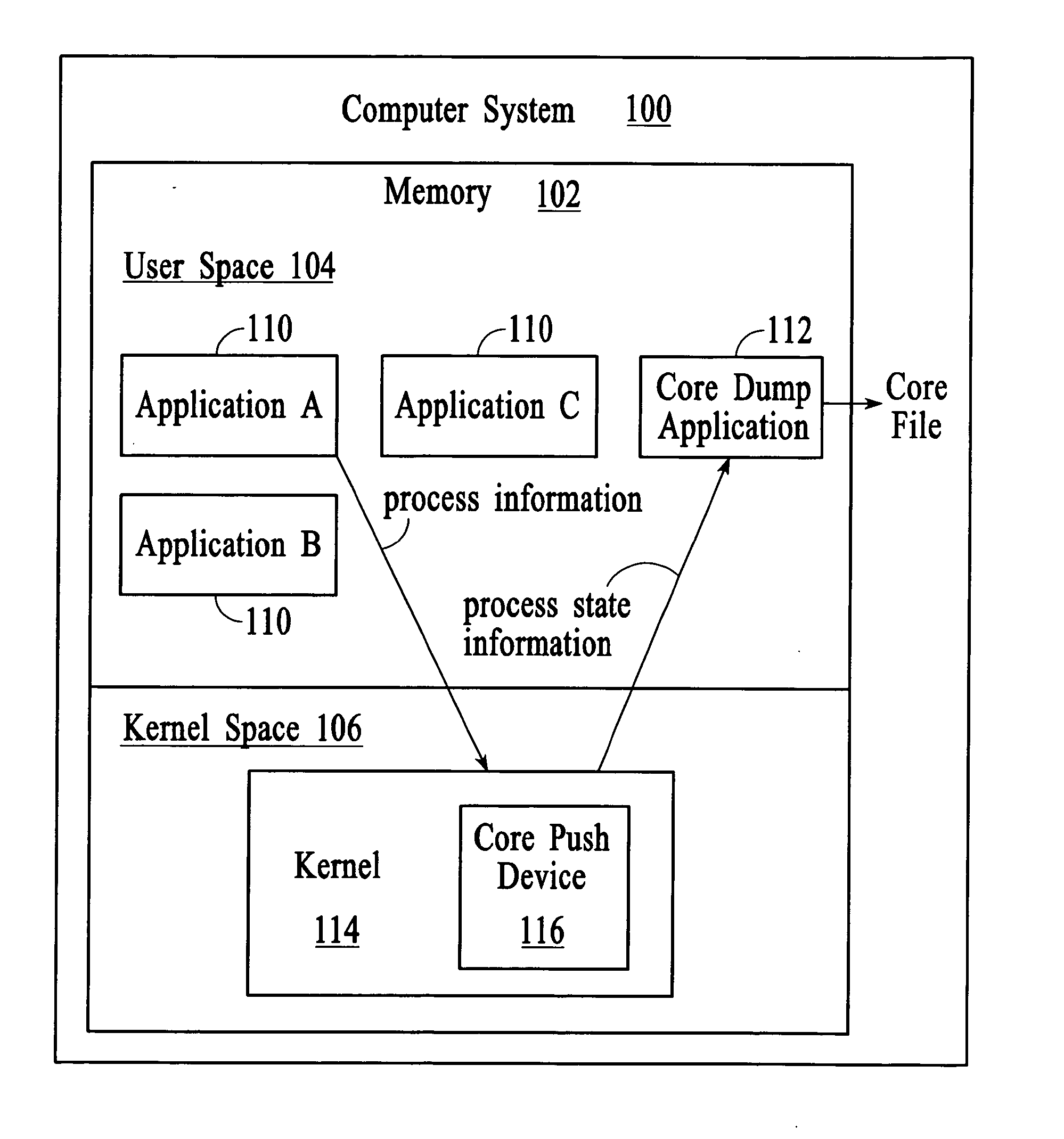
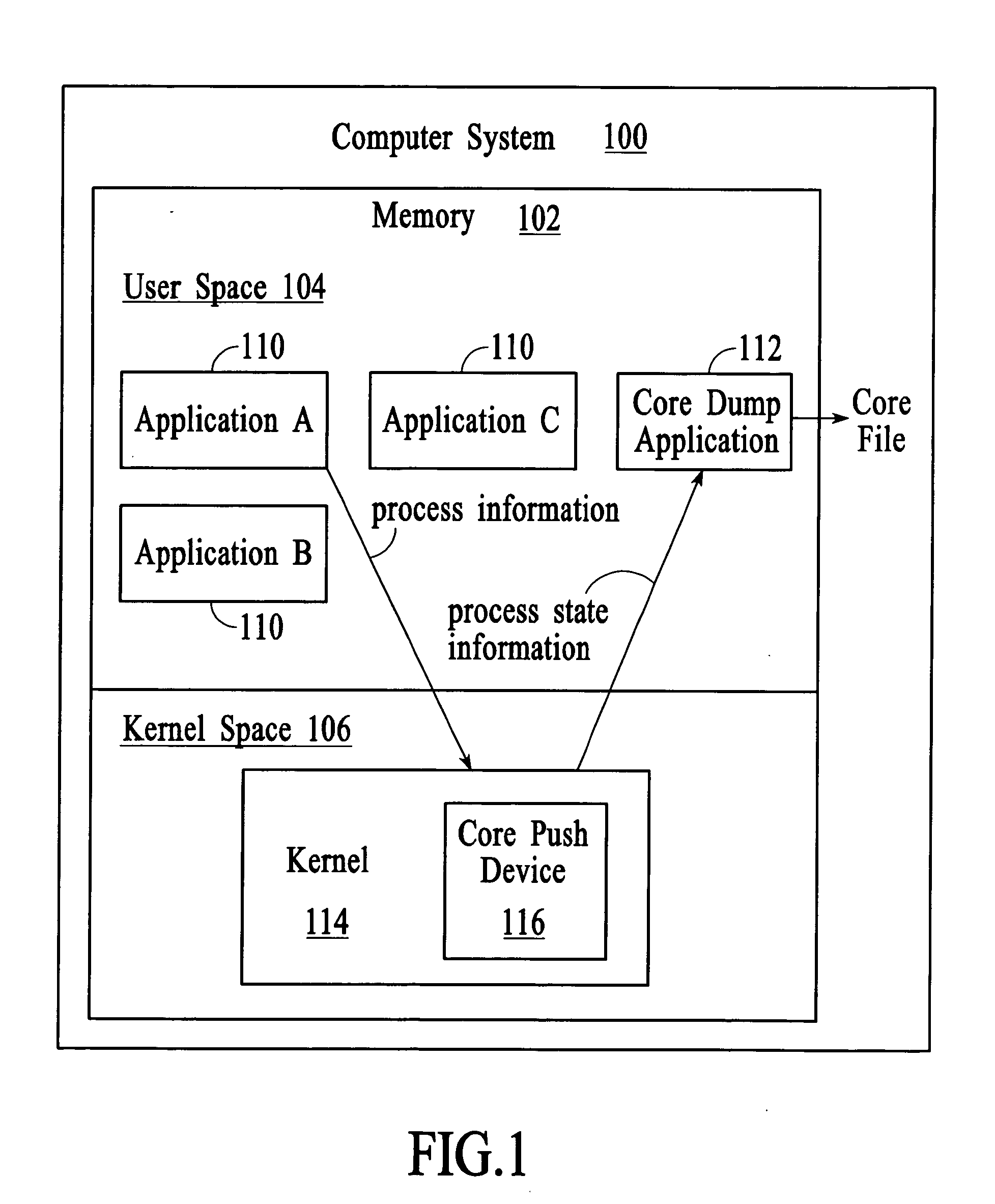
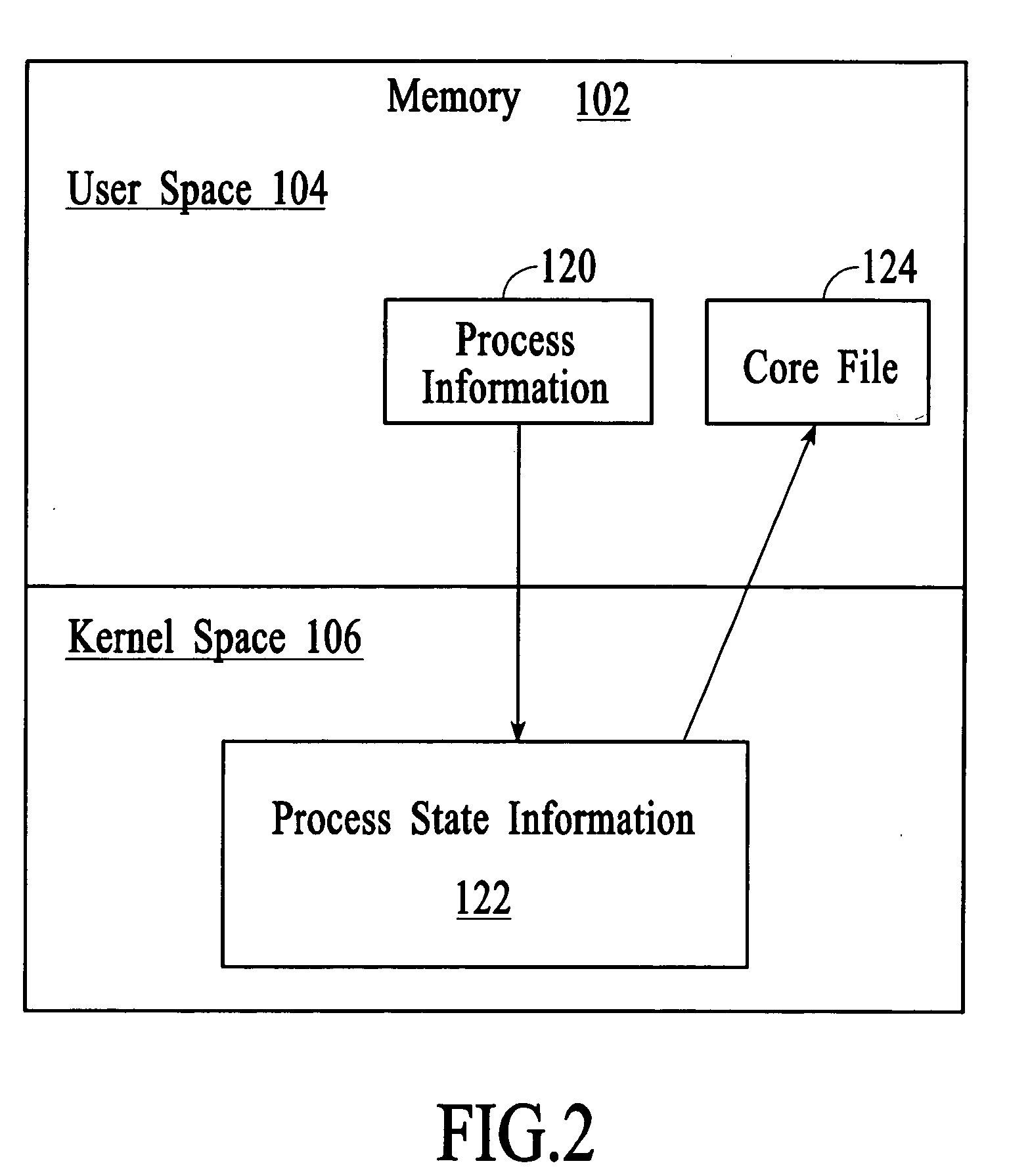
Managing process state information in an operating system environment
InactiveUS20050210077A1Excessively generatedNon-redundant fault processingProgram controlCore dumpOperational system
A technique for managing process state information involves pushing process state information from the kernel space to the user space in the event of an application crash and generating a core file at the user level instead of at the kernel level. Handling the process state information at the user level instead of at the kernel level provides more flexibility in the generation and management of a core file as compared to systems that use kernel code to generate and manage the core file. A core dump application at the user level can be programmed to forward the core file to another system that has permanent storage capacity available. Additionally, the core dump application can be programmed to compress the process state information and / or to extract only certain information from the process state information while generating the core file.
Owner:LUCENT TECH INC
Lossless recovery for computer systems with remotely dependent data recovery
InactiveUS20050289414A1Well formedElectronic circuit testingRedundant hardware error correctionDistributed File SystemKernel level
An architecture and implementation for losslessly restarting subsystems in a distributed file system is described. By partitioning functionality and logging appropriately across the kernel and user-level boundaries on a client, the user-level subsystem may be made losslessly restartable. Practical mechanisms for supporting state-based recovery in replicated state machines and like replica are described. In particular, each client daemon may include an operations log and an applied log sequence number. Each client driver may include a potentially different operations log. Each client daemon may be configured to request logged operations associated with log sequence numbers in one or more ranges specified by a specification that includes the applied log sequence number. The requested logged operations may reside in the operations log maintained by a client driver. Each client daemon may operate in accordance with user-level constraints and each client driver may operate in accordance with kernel-level constraints.
Owner:MICROSOFT TECH LICENSING LLC
System and method for the managed security control of processes on a computer system
InactiveUS7565549B2Minimizing interruptionFast and efficient securityMemory loss protectionDigital data processing detailsOperational systemKernel level
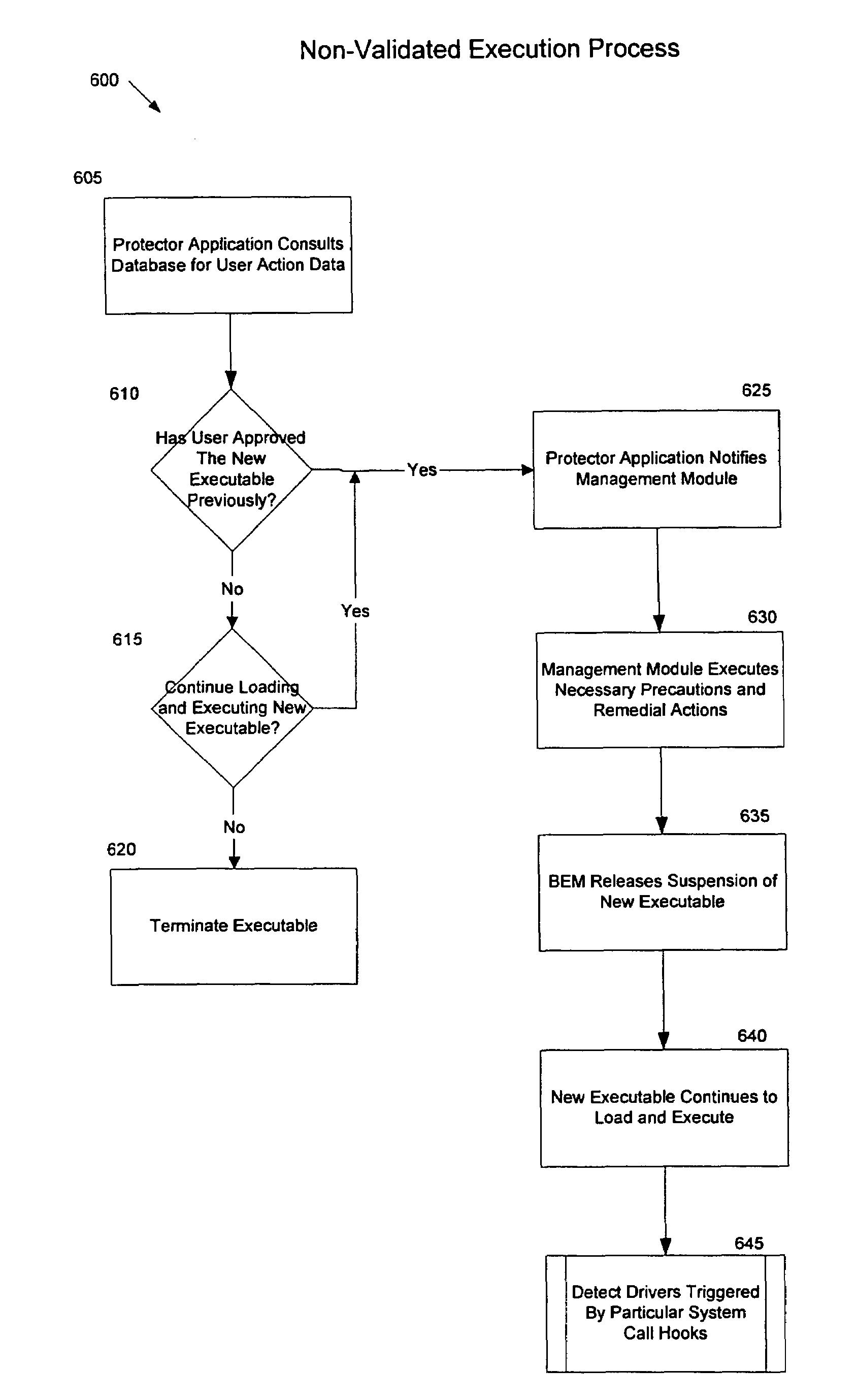
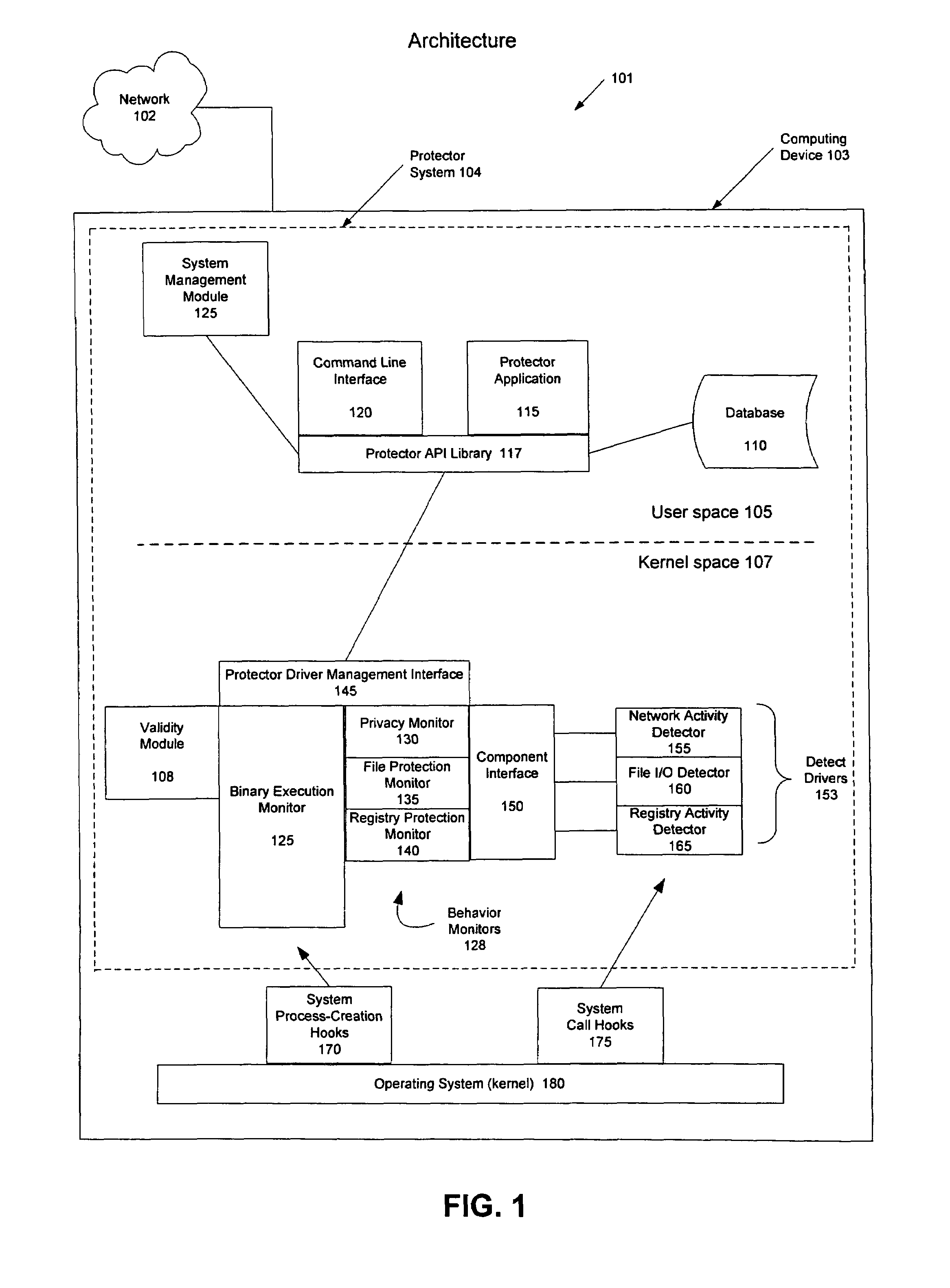
Managing and controlling the execution of software programs with a computing device to protect the computing device from malicious activities. A protector system implements a two-step process to ensure that software programs do not perform malicious activities which may damage the computing device or other computing resources to which the device is coupled. In the first phase, the protector system determines whether a software program has been previously approved and validates that the software program has not been altered. If the software program is validated during the first phase, this will minimize or eliminate security monitoring operations while the software program is executing during the second phase. If the software program cannot be validated, the protector system enters the second phase and detects and observes executing activities at the kernel level of the operating system so that suspicious actions can be anticipated and addressed before they are able to do harm to the computing device.
Owner:TAASERA LICENSING LLC
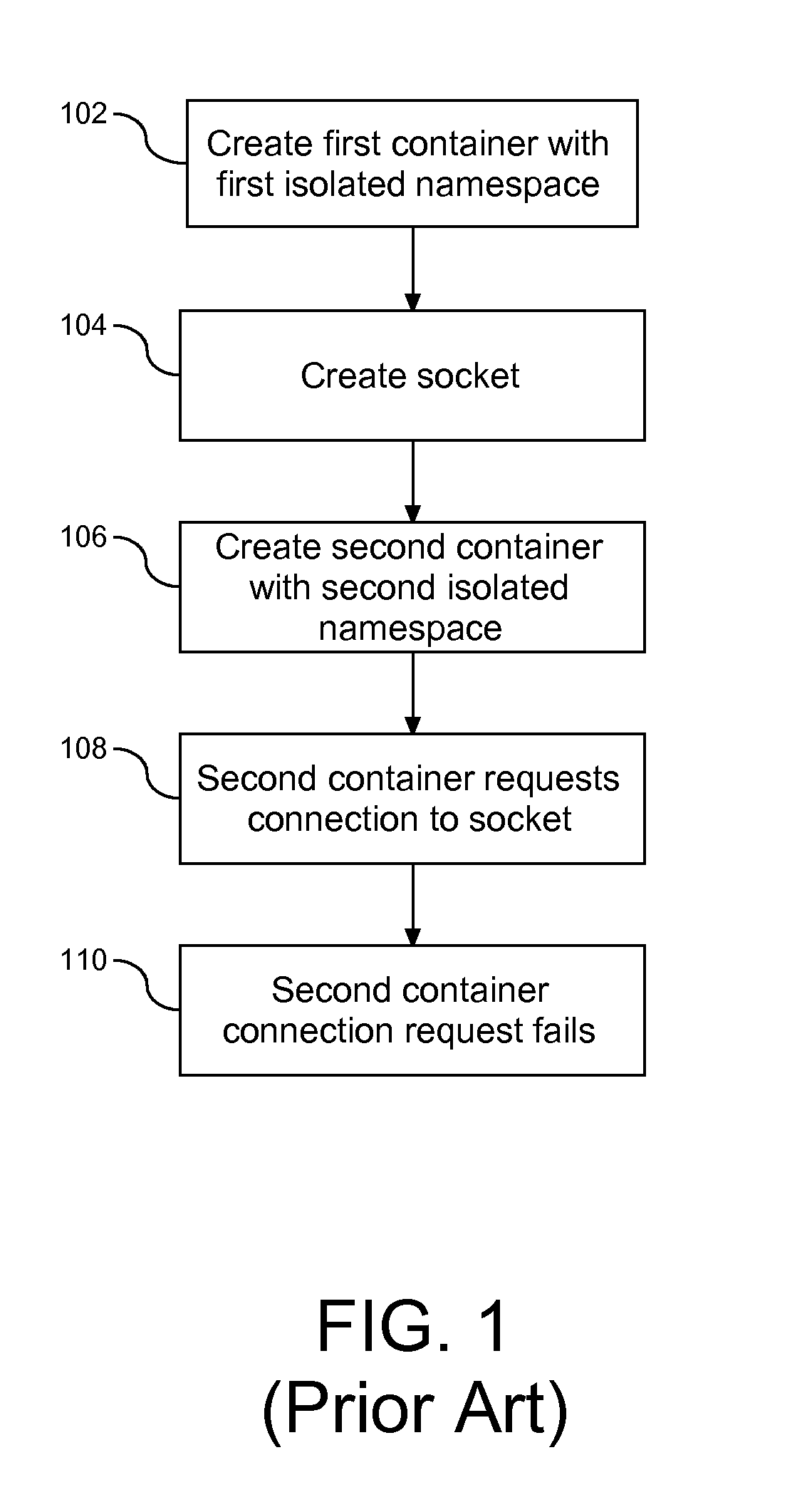
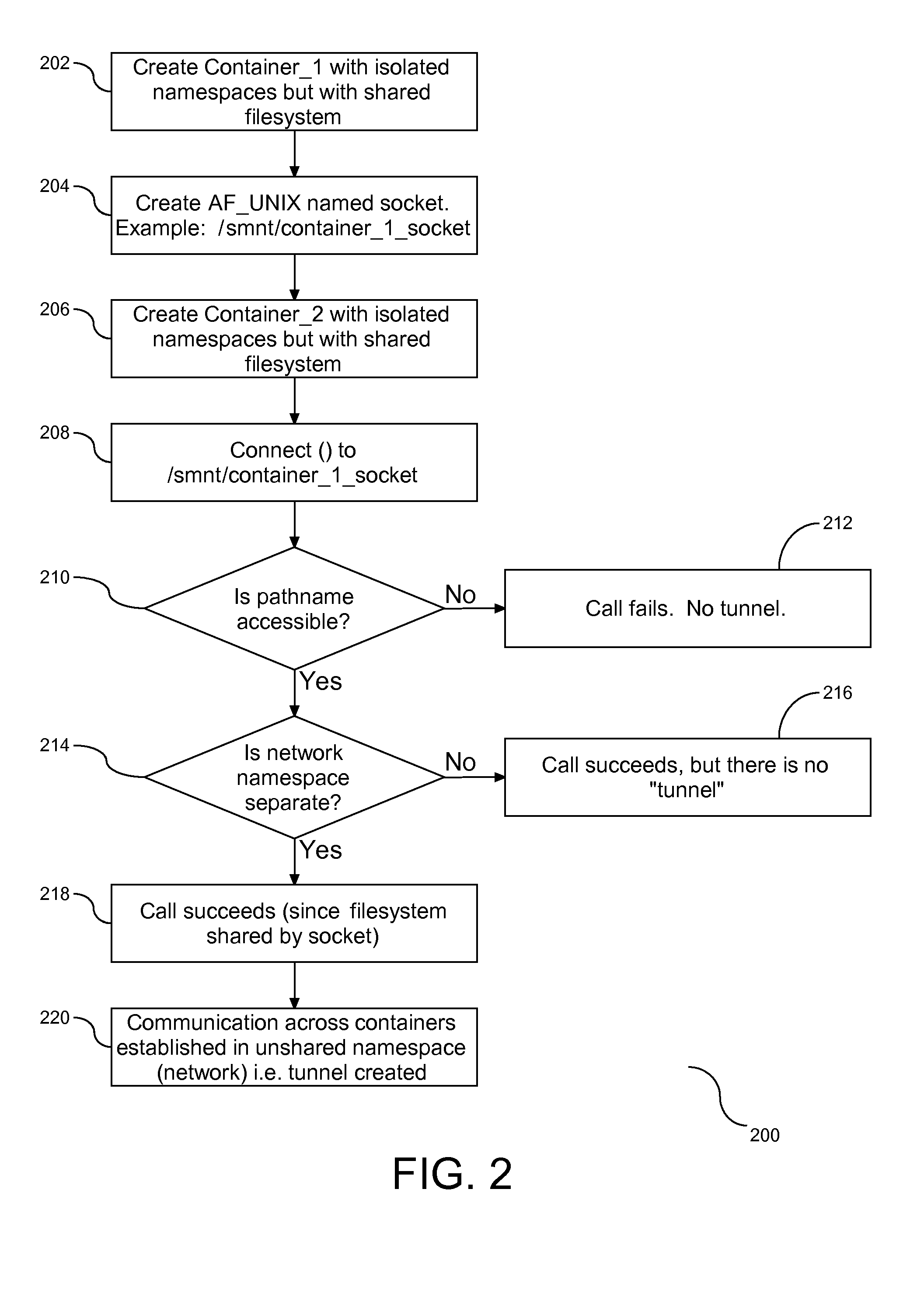
Pipeline Across Isolated Computing Environments
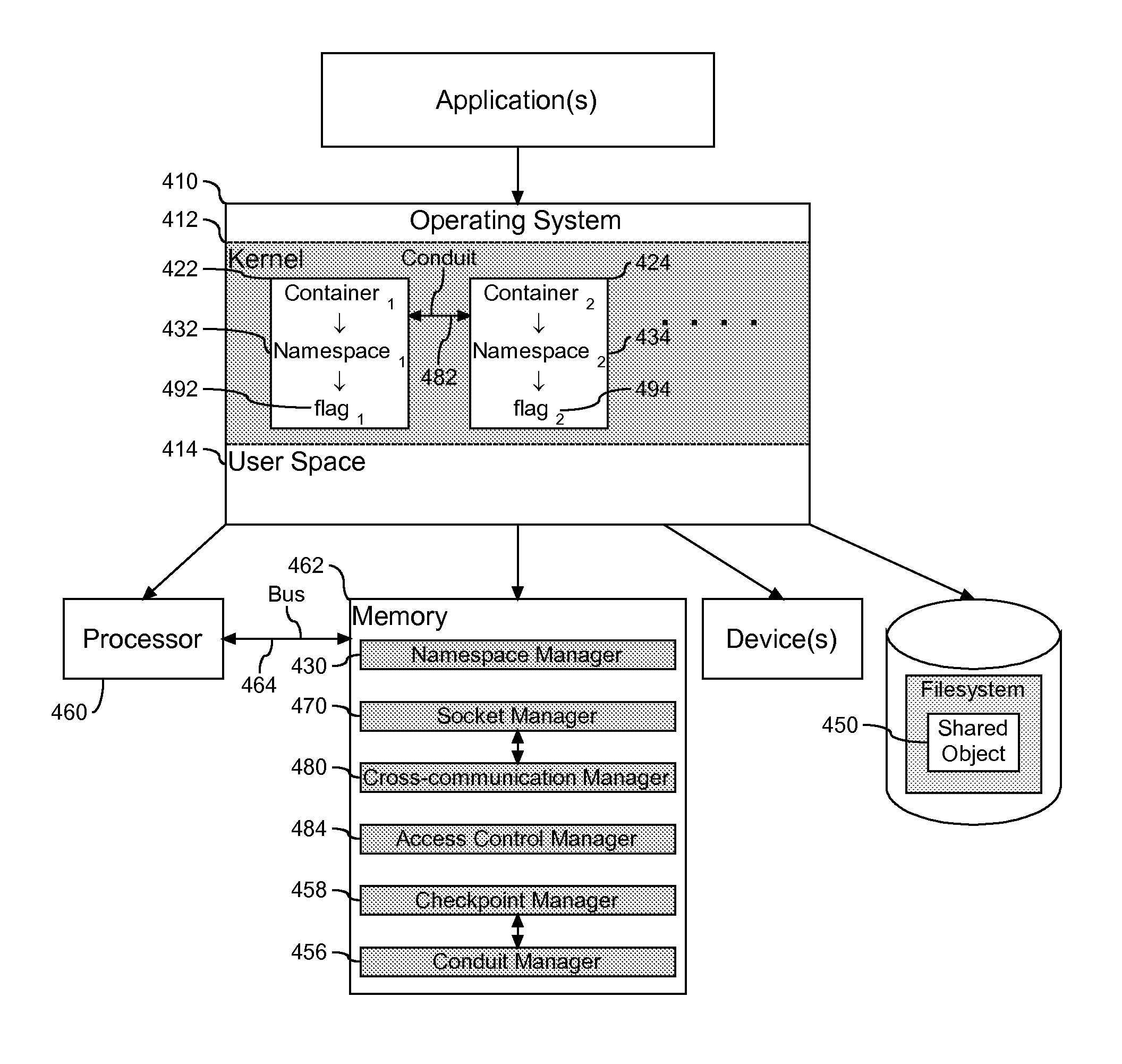
InactiveUS20110161988A1Program controlInput/output processes for data processingComputerized systemKernel level
A method, system, and article to support sharing resources in a computer system. An operating system within the computer system, the operating system having a kernel level and a user level, with the kernel level configured with a first container and a second container. The first container is assigned to a first namespace and the second container is assigned to a second namespace. Both the first and second namespaces are isolated from each other and at the same time in communication with at least one shared object. Communication across the containers is created through a socket in the namespace of the shared object of one or both of the containers. In addition, a conduit is formed between the containers by connecting the container absent the created socket to the container with the socket.
Owner:IBM CORP
Malware prevention system monitoring kernel events
ActiveUS8065728B2Reduce overheadPreventing executionMemory loss protectionError detection/correctionKernel levelMalware
A malware prevention system monitors kernel level events of the operating system and applies user programmable or preprepared policies to those events to detect and block malware.
Owner:WISCONSIN ALUMNI RES FOUND
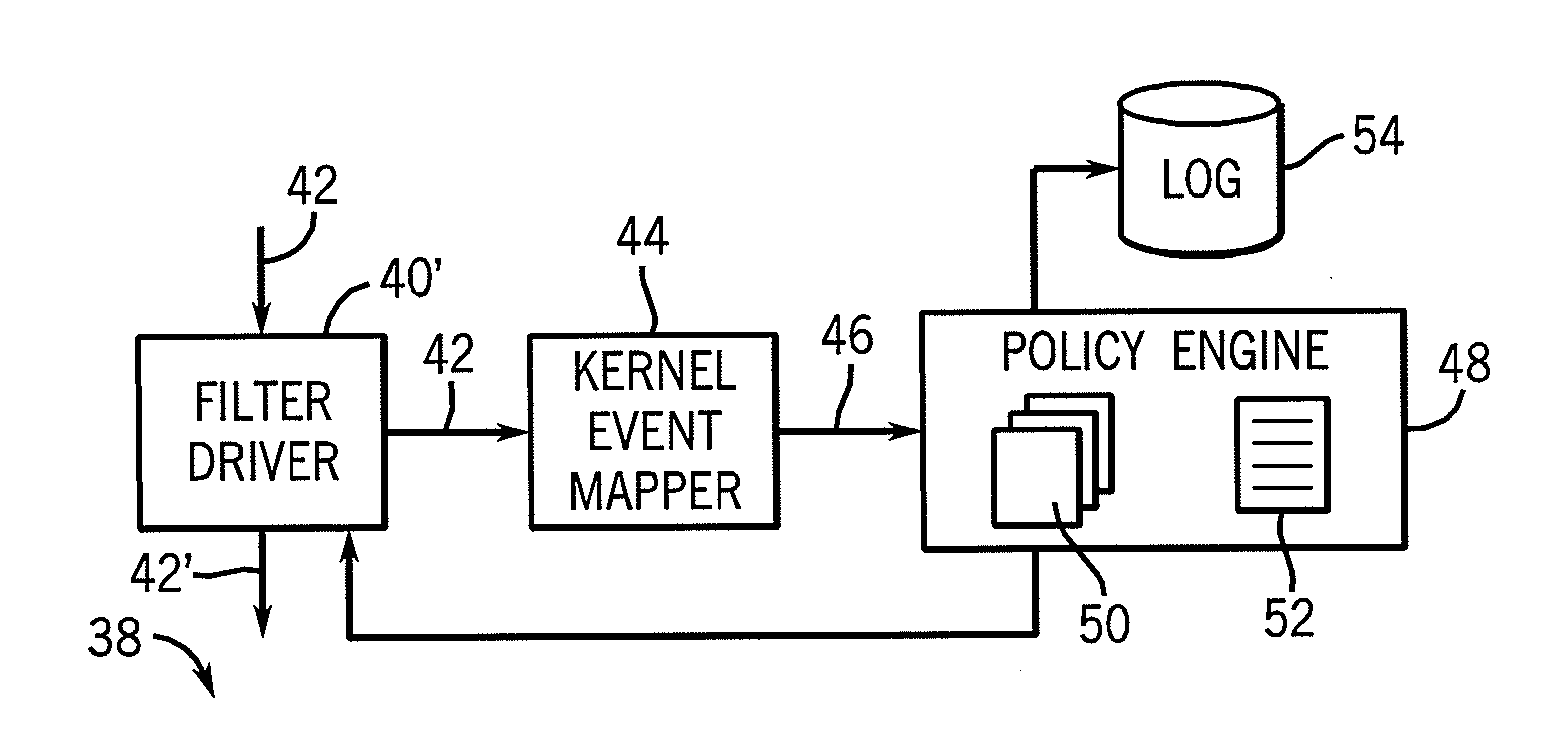
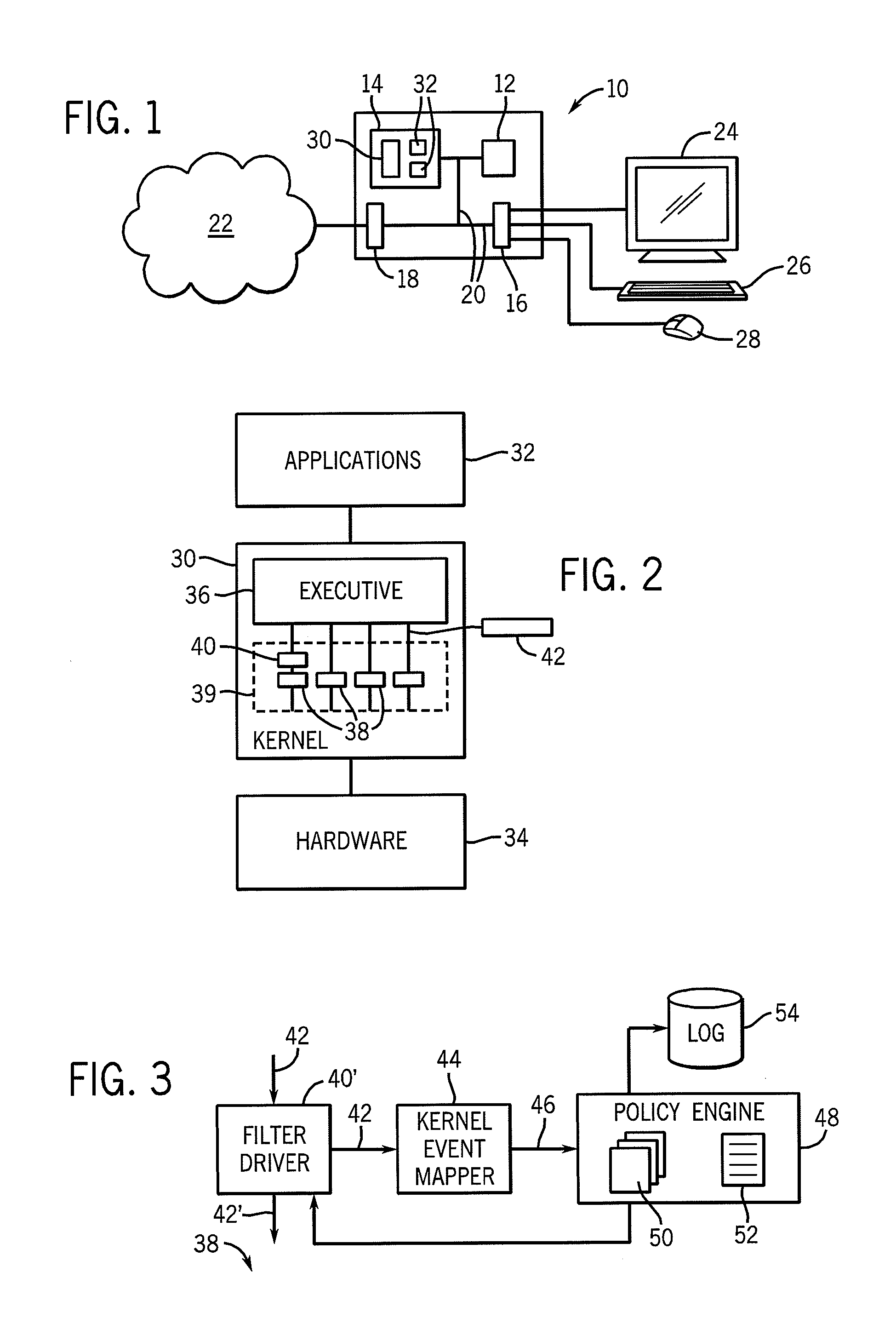
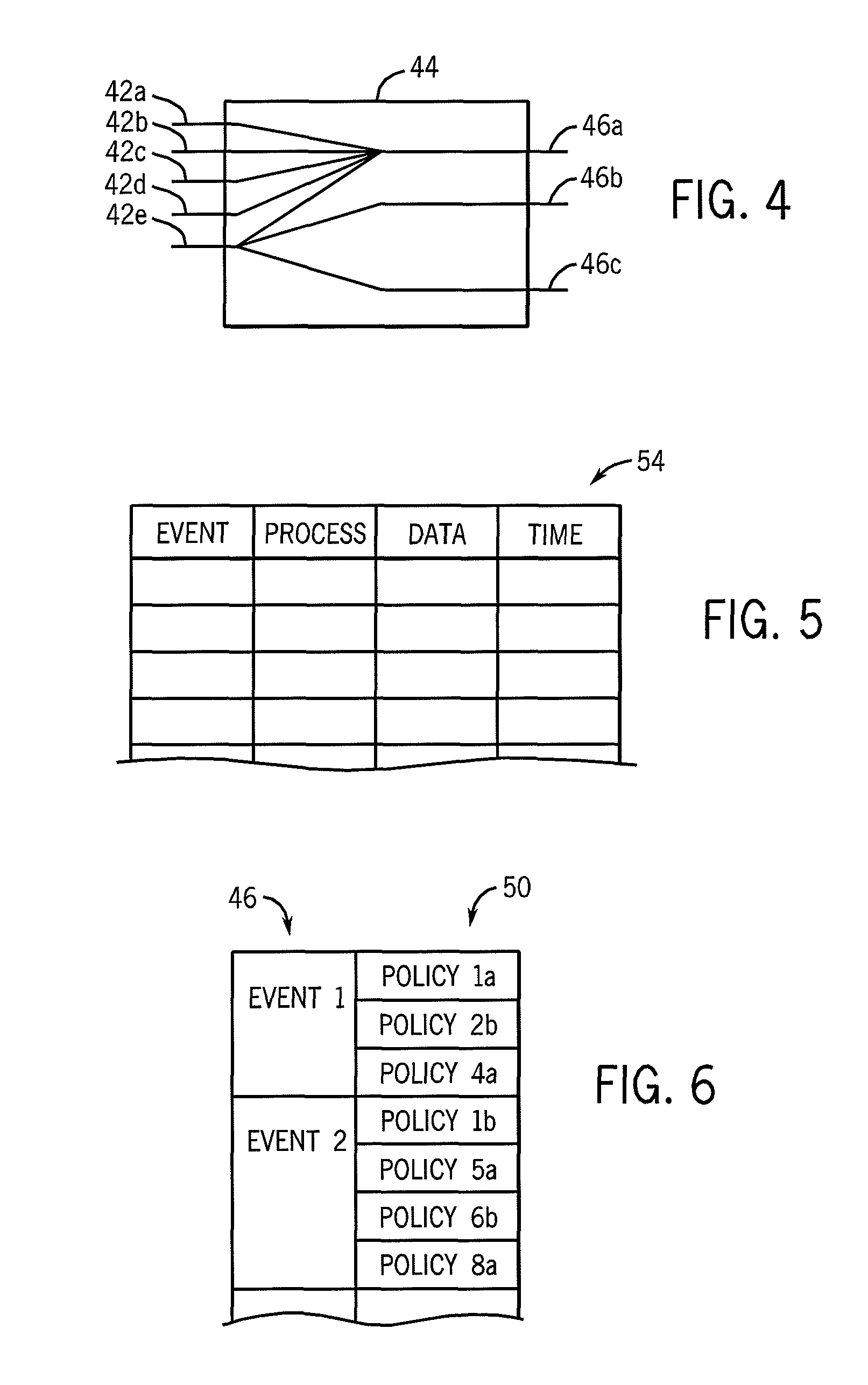
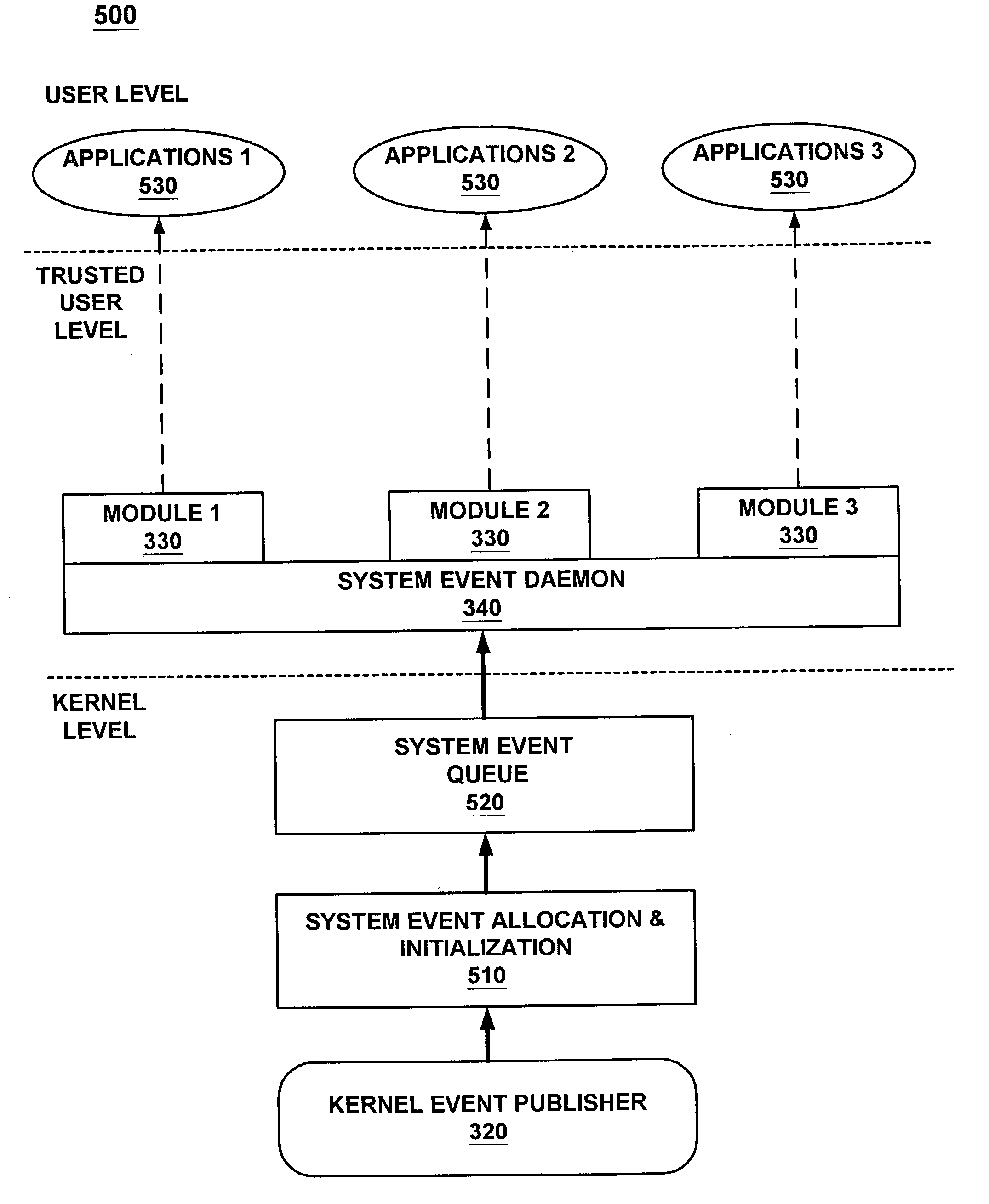
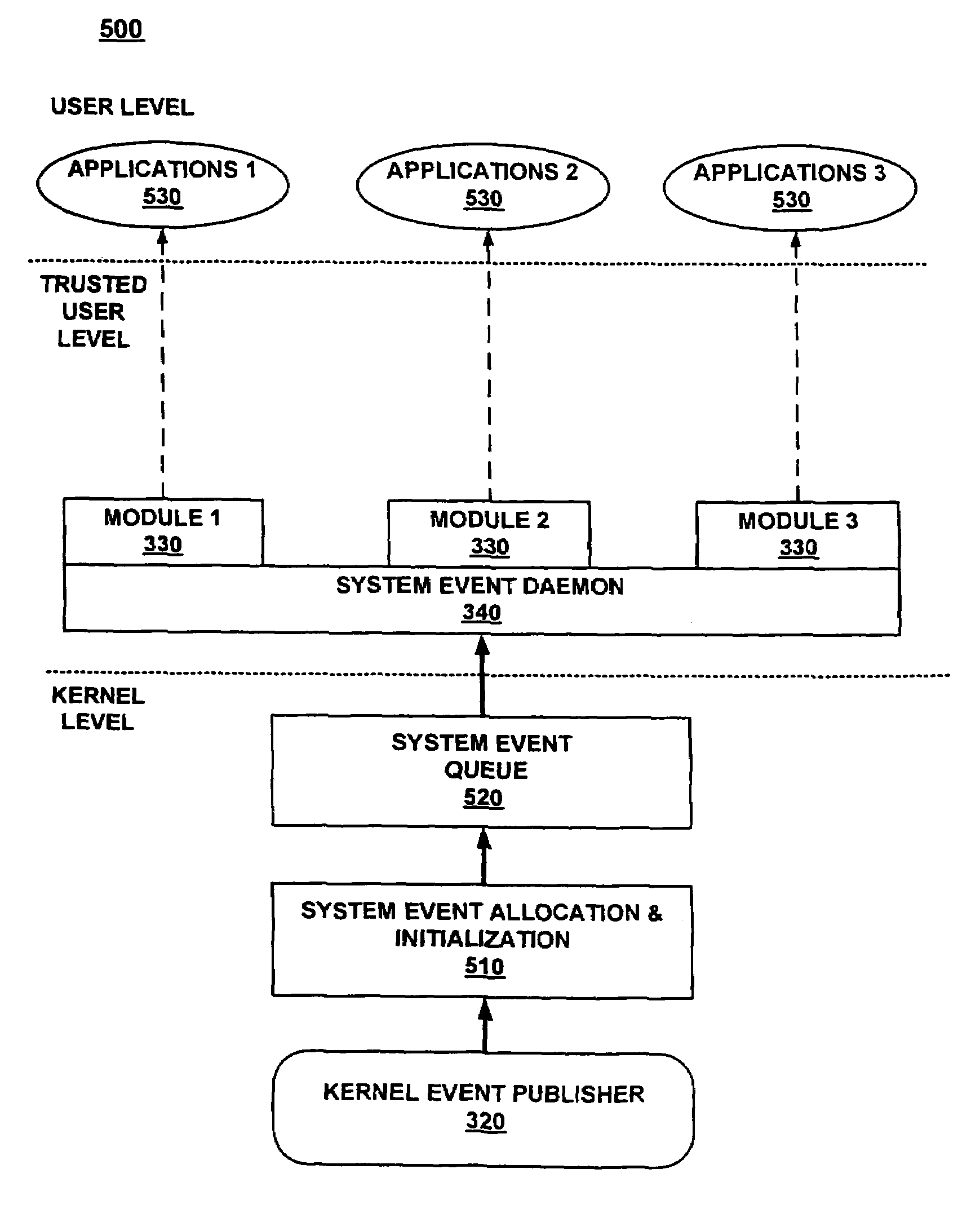
Kernel event subscription and publication system and method
ActiveUS7028229B2Minimize the numberLess costlyError detection/correctionMultiprogramming arrangementsKernel levelApplication software
An event subscription and publication system for dynamically notifying user level applications of kernel level events. The kernel level events may include hardware and software events as well as system level errors that occur in the kernel. User level applications that need information on these kernel level events subscribe to the event monitoring and publication framework of the present invention and are notified of these kernel level events when they occur. Upon notification of an event, the user application also is provided with specific information classifying the nature and details of the event. The kernel event monitoring and publication system of the present invention allows user level applications to be dynamically notified of kernel level events without requiring the user level application to interrupt the normal processing states to identify these events when the events occur.
Owner:ORACLE INT CORP
Distributed dynamic network security protecting system
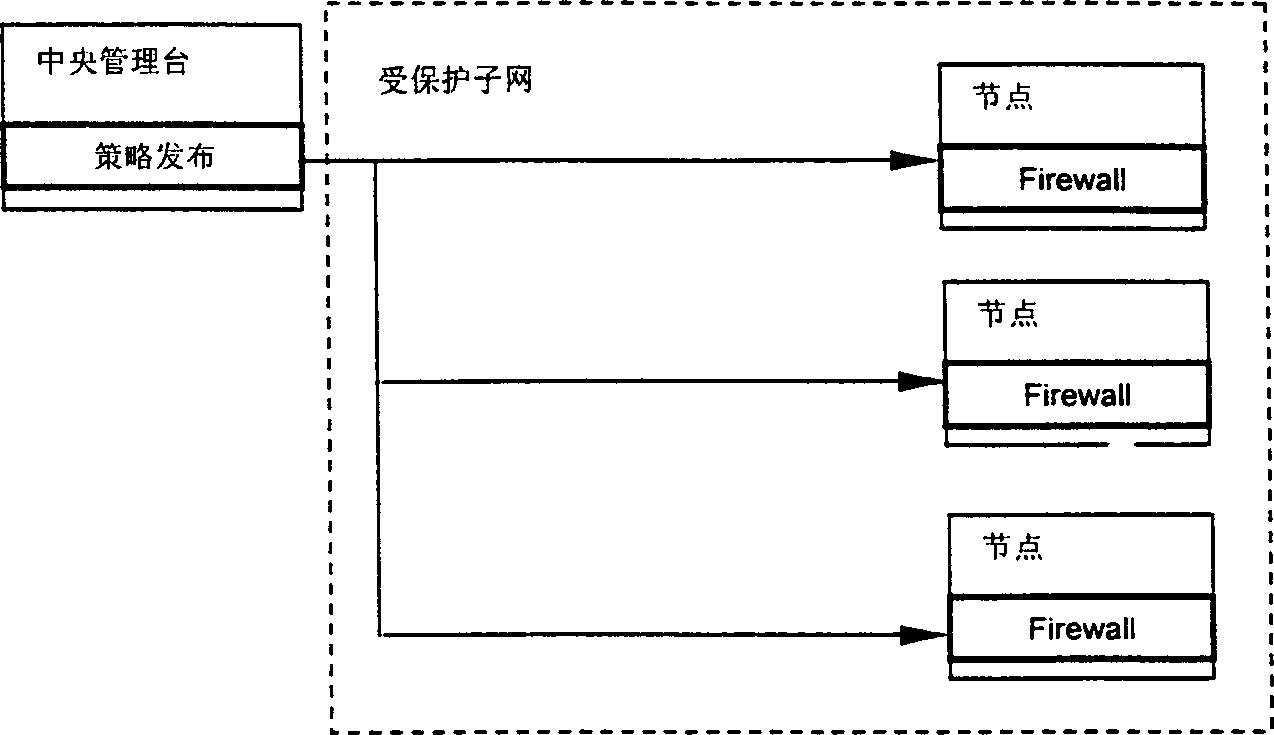
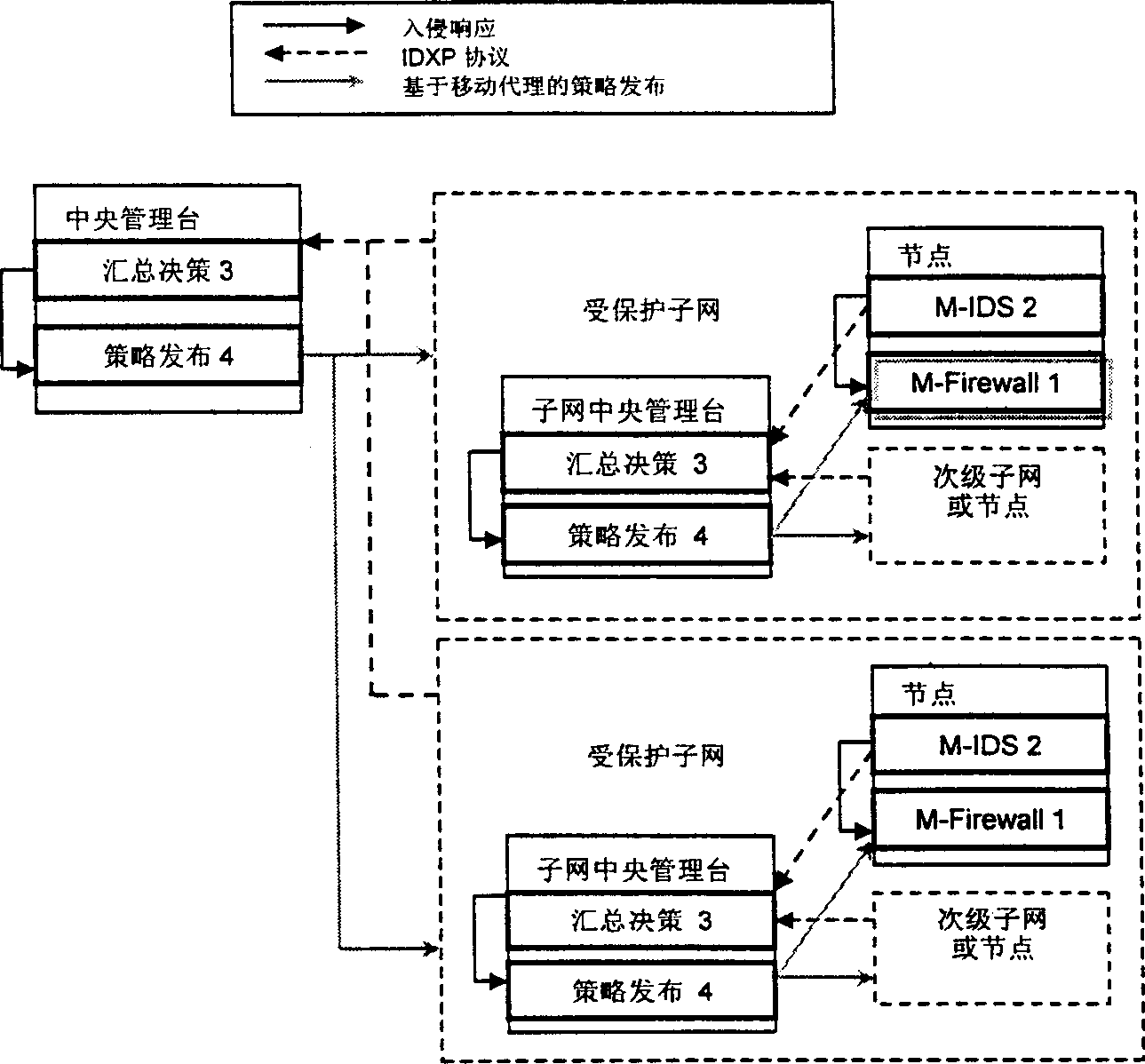
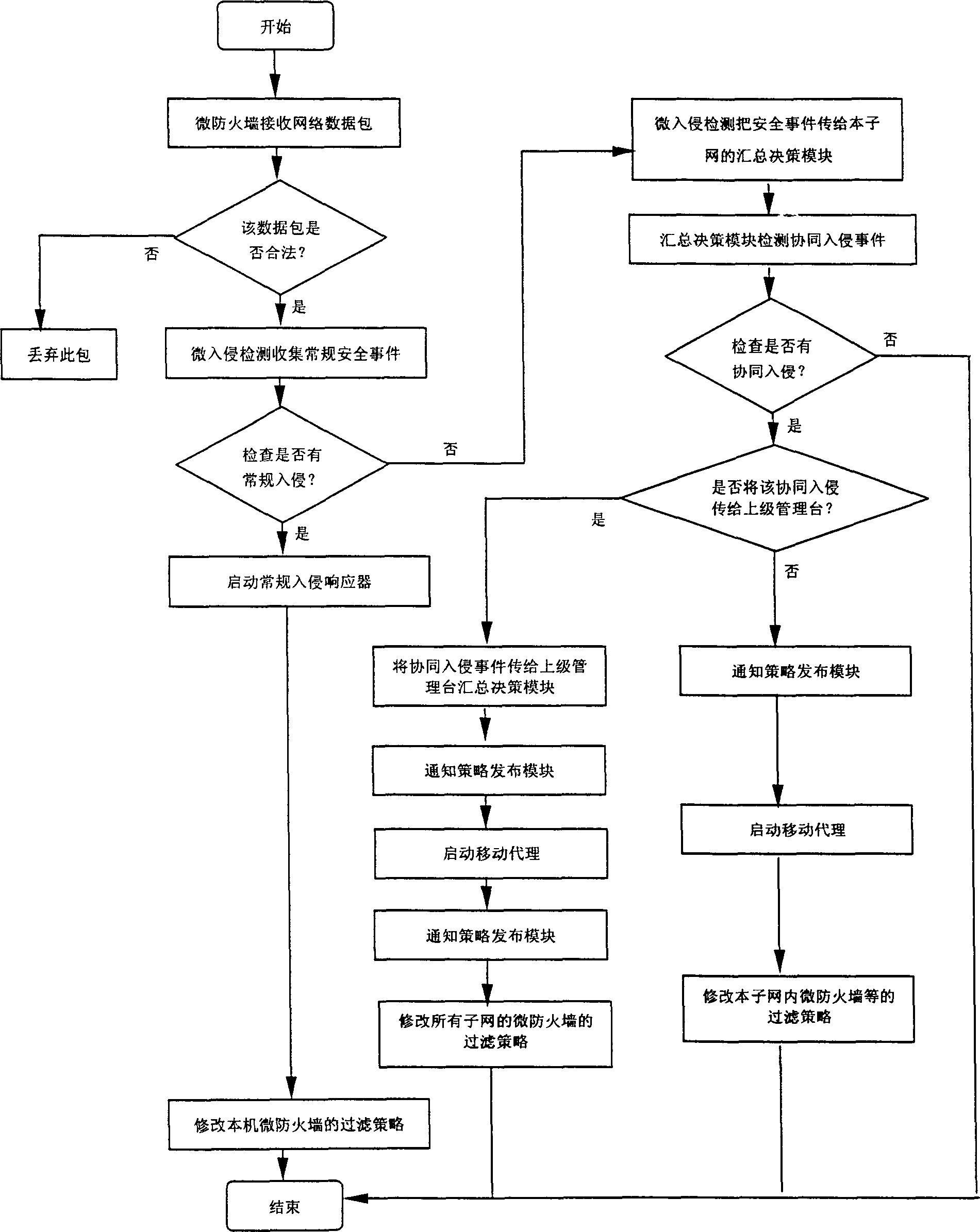
InactiveCN1384639ADouble safety protectionEliminate single points of failureSecuring communicationExtensibilityStructure of Management Information
The distributed dynamic network security protecting system has central network administration station provided with summarizing decision module and policy releasing module. The network is divided into N subnetworks in tree structure, and each subnetwork administration station is provided with summarizing decision module and policy releasing module. Each node in the subnetwork has micro invasion detecting module and micro fire wall module installed. In the policy releasing module, mobile agency technology is adopted. The distributed micro invasion detecting module provides security protection in application layer while the distributed micro fire wall module provides security protection in kernel level. The double security protection makes the system capable of preventing outer and inner attack, preventing cooperative invasion and providing dynamic immunity.
Owner:HUAZHONG UNIV OF SCI & TECH
Method and system for event publication and subscription with an event channel from user level and kernel level
A method and system for event publication and subscription with an event channel from user level and kernel level are disclosed. The system comprises an event channel. The event channel includes an event queue for an event sent by a publisher. Additionally, the event channel has a plurality of subscriber-based queues each corresponding to a subscriber. If the corresponding subscriber has subscribed to receive delivery of the event, the subscriber-based queue includes the event. Moreover, the event channel further comprises a dispatcher for dispatching based on filtering criteria the event to the subscriber-based queue if the corresponding subscriber has subscribed to receive delivery of the event, and a delivery mechanism for delivering the event from the subscriber-based queue to the corresponding subscriber. The publisher can be a user level publisher or a kernel level publisher. The subscriber can be a user level subscriber or a kernel level subscriber.
Owner:ORACLE INT CORP
Storage I/O path partitioning to eliminate I/O interference in consolidated servers
ActiveUS20140310473A1Eliminate distractionsError detection/correctionMemory adressing/allocation/relocationFile systemKernel level
A method for storage input / output (I / O) path configuration in a system that includes at least one storage device in network communication with at least one computer processor; the method comprising providing in the I / O path into at least: (a) a block-based kernel-level filesystem, (b) an I / O cache module controlling an I / O cache implemented on a first computer readable medium, (c) a journaling module, and (d) a storage cache module controlling a storage cache implemented on a second computer readable medium, the second computer readable medium having a lower read / write speed than the first computer readable medium. Furthermore, the steps of translating by the filesystem, based on computer executable instructions executed by the at least one processor, a file I / O request made by an application executed by the at least one computer processor into a block I / O request and fulfilling by the at least one processor the block I / O request from one of the I / O cache and the storage cache complete the I / O operation.
Owner:INST OF COMP SCI ICS OF THE FOUND FOR RES & TECH HELLAS FORTH
Method and equipment for detecting course
ActiveCN101206692AEfficient detectionGuaranteed accuracyMultiprogramming arrangementsPlatform integrity maintainanceOperational systemDynamic monitoring
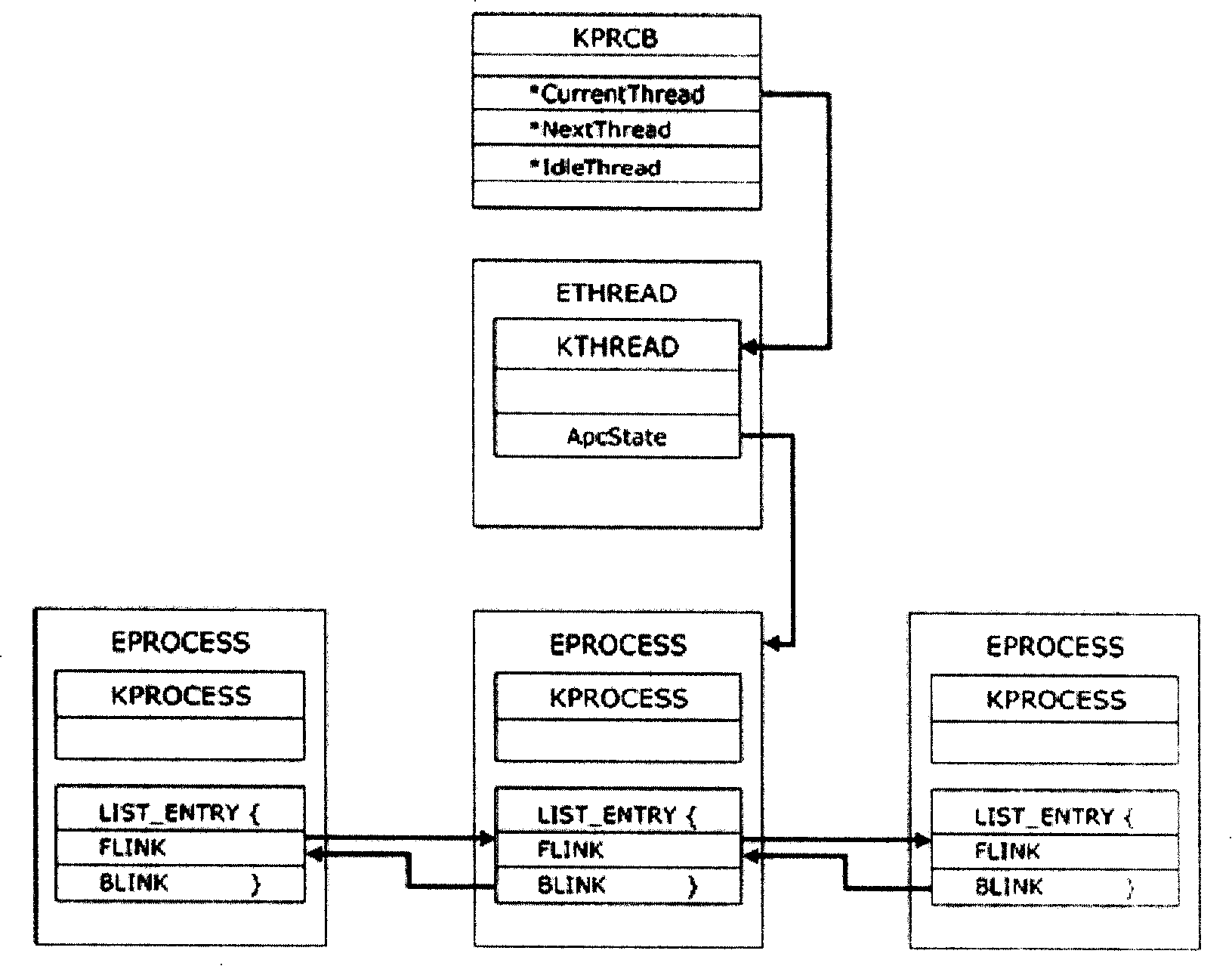
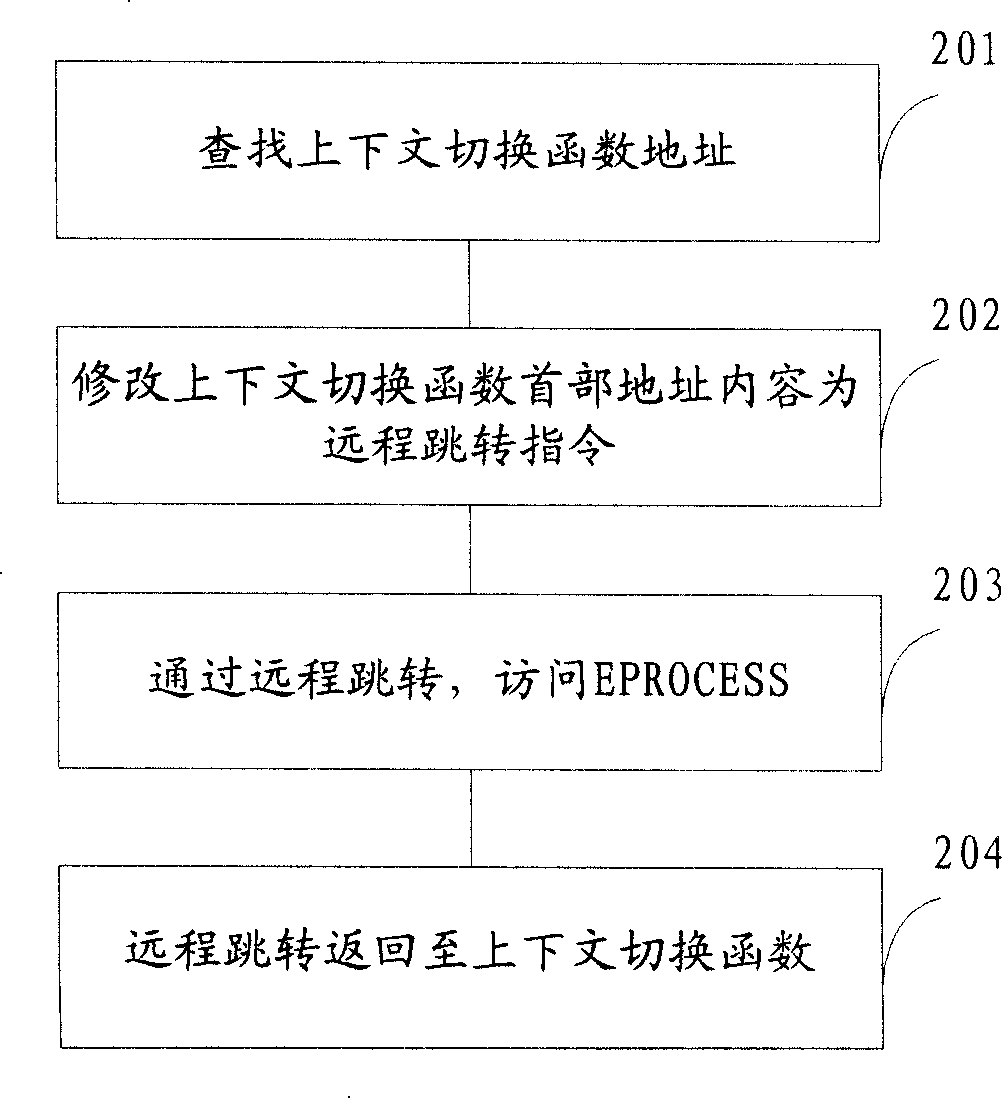
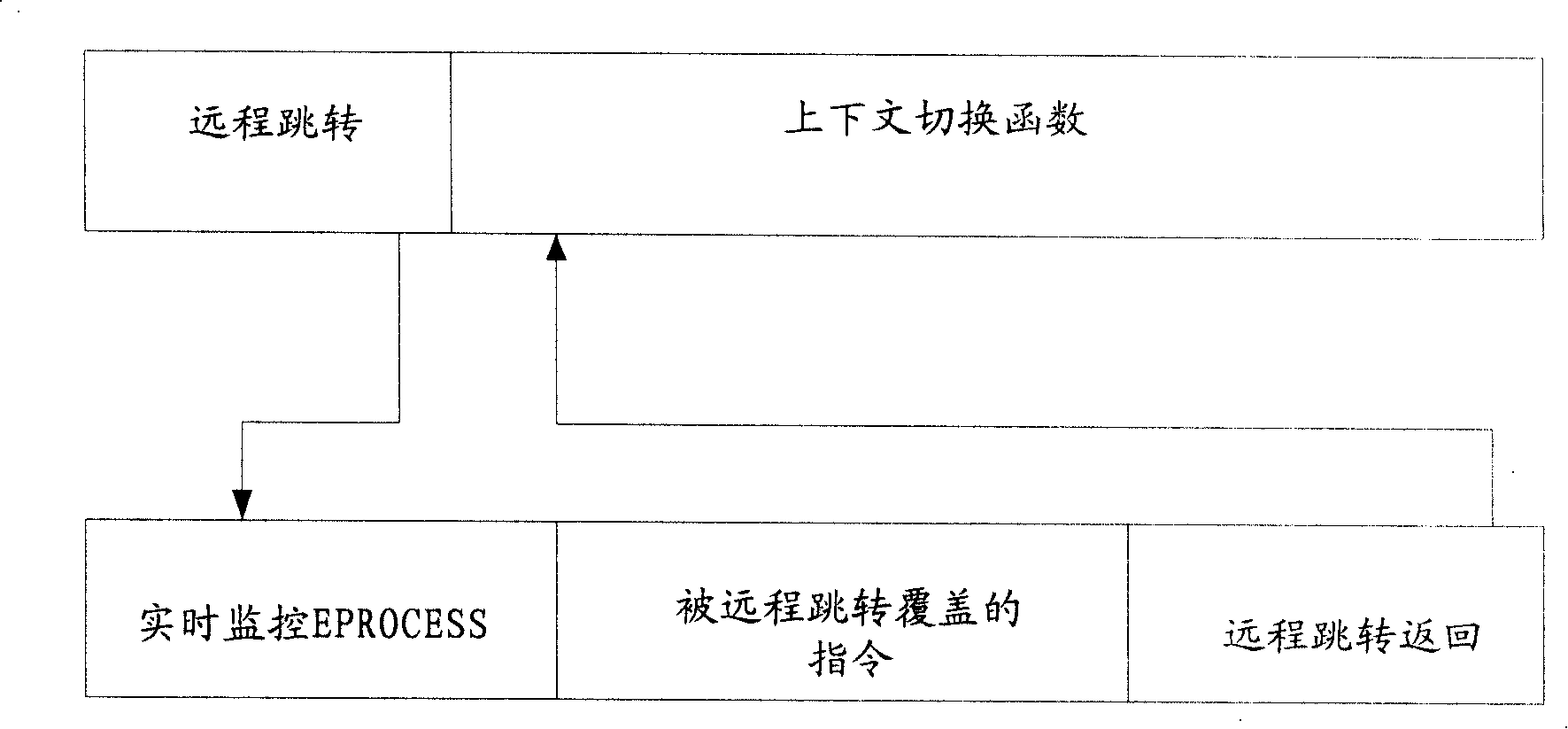
The invention discloses a detection method for processes, which particularly aims at detecting kernel level hidden processes and comprises the following steps: address spaces of operating system kernels are searched, and addresses of a context switch function are obtained; a header address content of the context switch function is modified as a long-distance jump instruction, and process information is acquired by accessing process struct through long-distance jump. Because the invention starts off from the context switch function of a thread which is arranged at the bottom most of an operating system, realest kernel object information can be acquired; the detection method can be in common use in various operating systems and can effectively detect DKOM hidden processes; moreover, detection accuracy of the hidden processes is guaranteed through dynamic monitoring and update of the header address content of the context switch function and alarm journals. The invention also discloses a detection device for the processes.
Owner:LENOVO (BEIJING) CO LTD
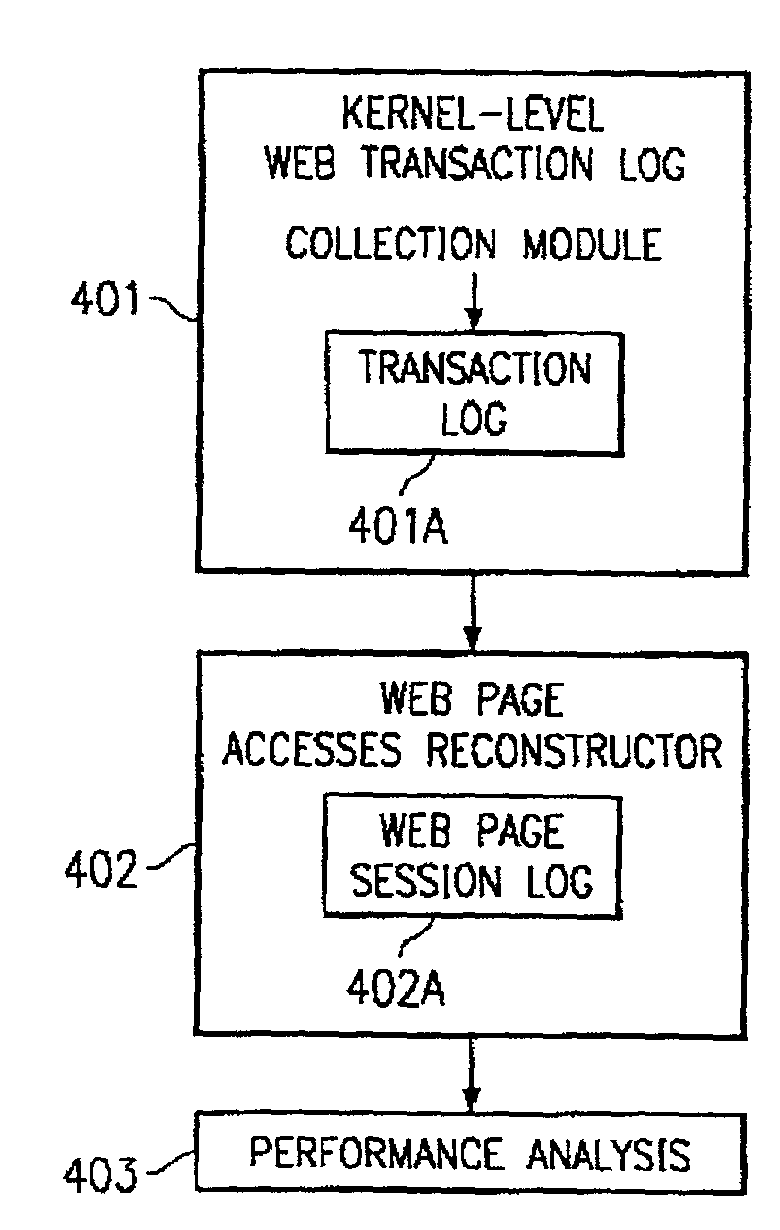
System and method for collecting desired information for network transactions at the kernel level
According to one embodiment of the present invention, a method for compiling desired information for network transactions is provided. The method comprises capturing network-level information in a kernel-level module of a processor-based device arranged on the server-side of a client-server communication network, and using the captured network-level information to compile, in the kernel-level module, desired information for at least one network transaction conducted between a client and a server via the client-server communication network. Another embodiment of the present invention provides a method for compiling desired information for network transactions that comprises implementing a kernel-level module in a STREAMS-based network stack of a server, wherein the kernel-level module is operable to monitor a network connection to the server to compile desired information for network transactions conducted through the network connection.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
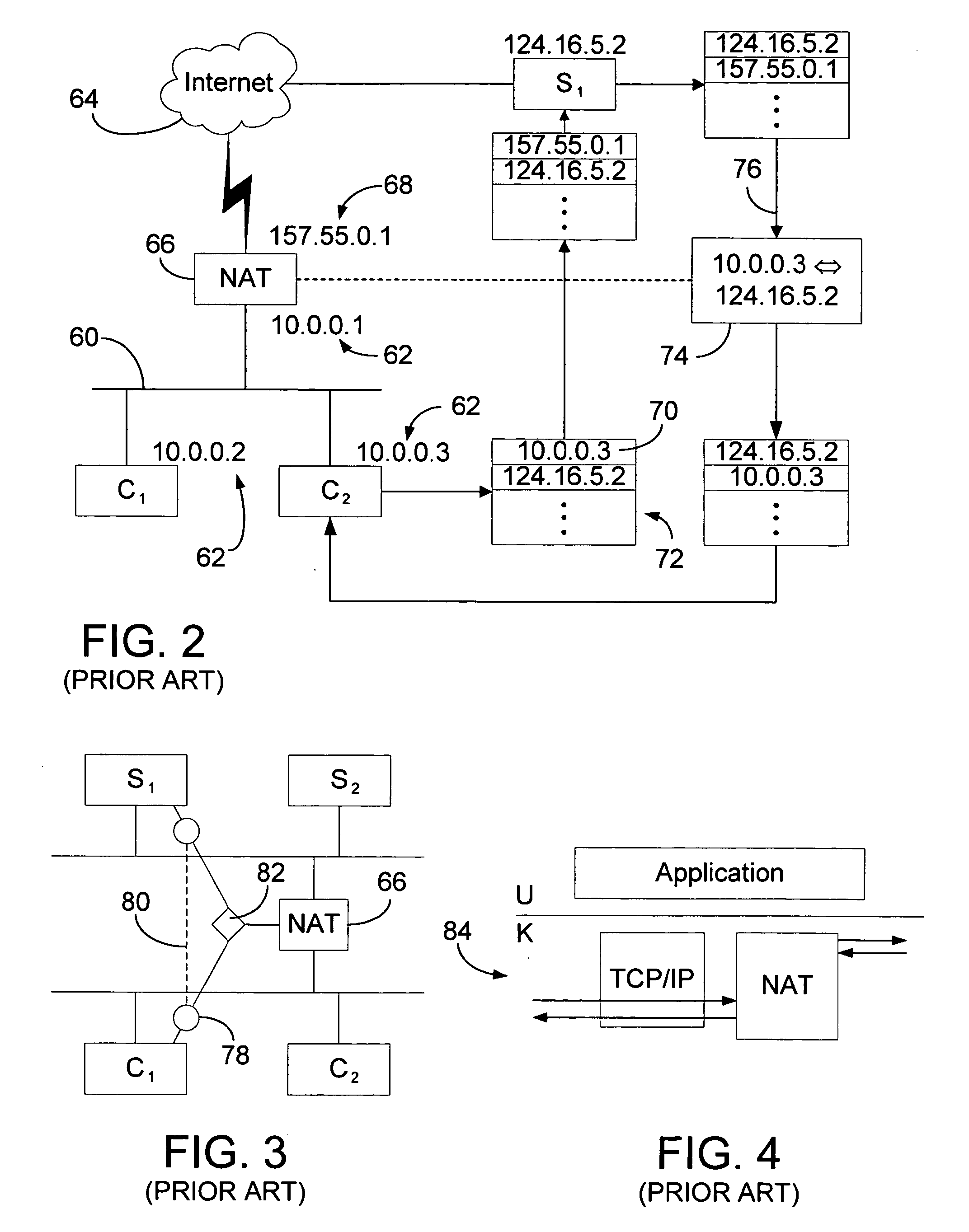
Application programming interface and generalized network address translation for translation of transport layer sessions
InactiveUS20080071915A1Increase speedSpeed up the flowMultiple digital computer combinationsTransmissionData packTransport layer
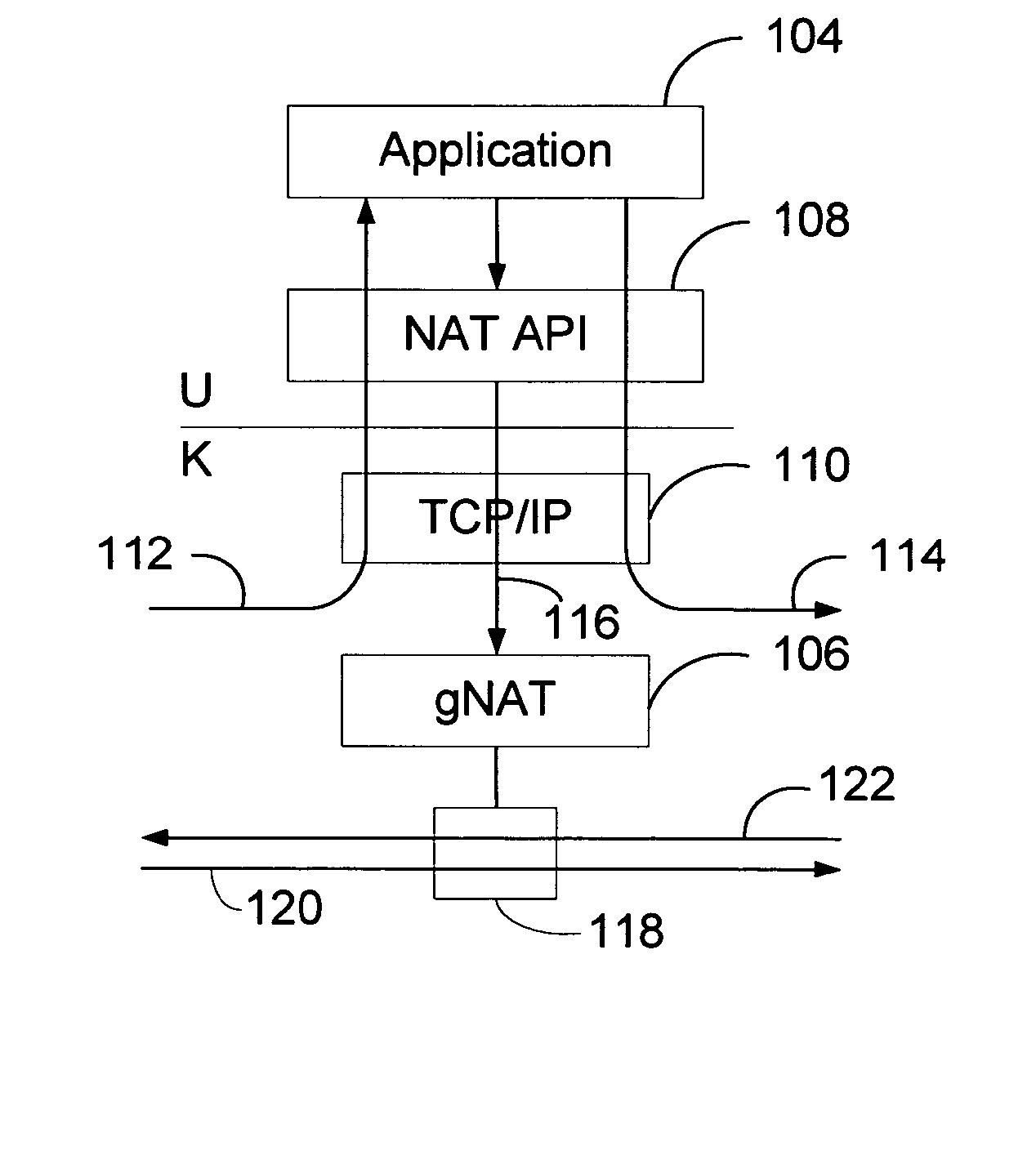
An application programming interface for translation of transport-layer sessions is presented. The system includes kernel-mode support for application-controlled network address translation and user-mode implementation of the redirect API routines. An application process may request that a network gateway modify the source and / or destination of a given network session in a manner transparent to the original source host and / or the replacement destination host. With the generalized NAT (gNAT) of the instant invention and its associated API, both the source and the destination addresses of message packets may be changed. The address changes are mapped in the gNAT, and may result in apparent sessions between different clients and servers. Depending on the protocol in use (e.g. TCP or UDP), the address translation may be made dynamically by the gNAT, under the command of the application, and take place at the kernel level.
Owner:MICROSOFT TECH LICENSING LLC
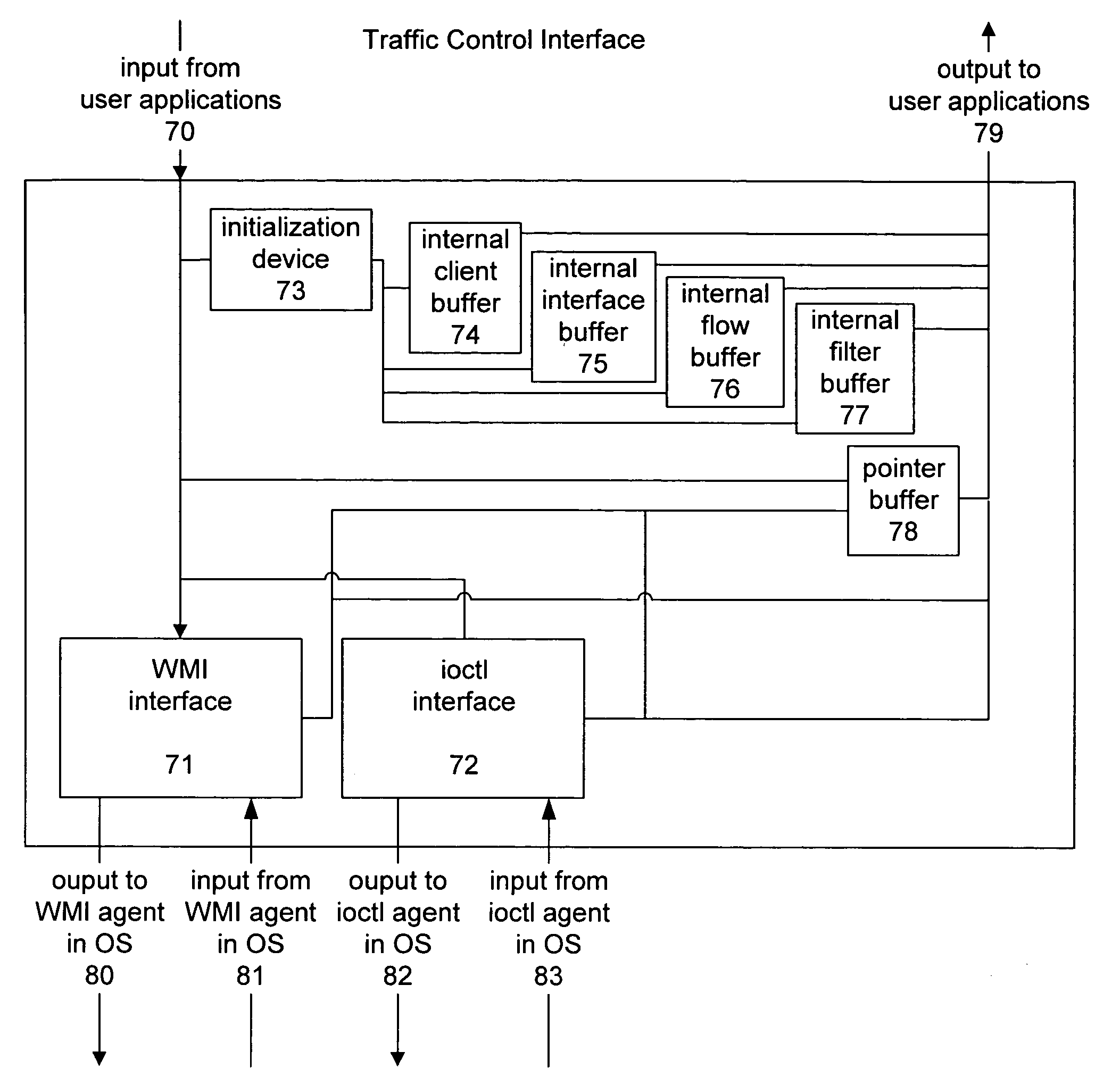
Method and system of a traffic control application programming interface for abstracting the use of kernel-level traffic control components
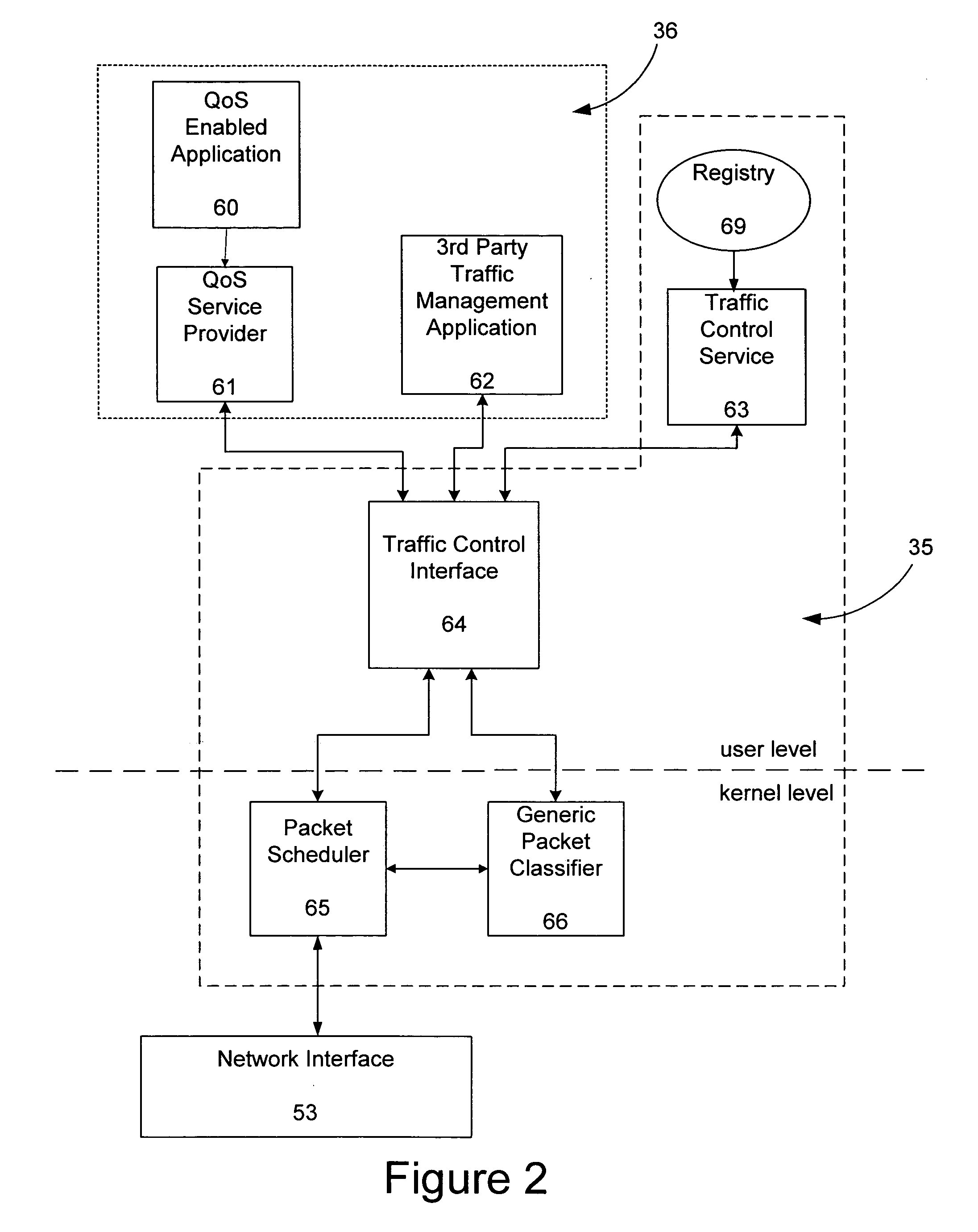
InactiveUS7168078B2Convenient verificationConvenient queryMultiple digital computer combinationsData switching networksQuality of serviceTraffic capacity
A traffic control application programming interface for abstracting the use of traffic control components to client applications to provide quality of service. The traffic control interface accepts input from a client application and based on that input, communicates with the operating system to control kernel level traffic control components. The client can register with the traffic control interface, and it can open and close interfaces, add, modify, and delete flows on those interfaces, and attach or delete filters on the flows. The client can also obtain data on any currently active interface, flow, or filter. The traffic control interface will send the appropriate message to the operating system, directing that the necessary tasks be performed by either a packet scheduler or a packet classifier. Those kernel level components then return through the operating system the results of the operations requested, and that return data will be passed back to the client application.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for obfuscation of computer program execution flow to increase computer program security
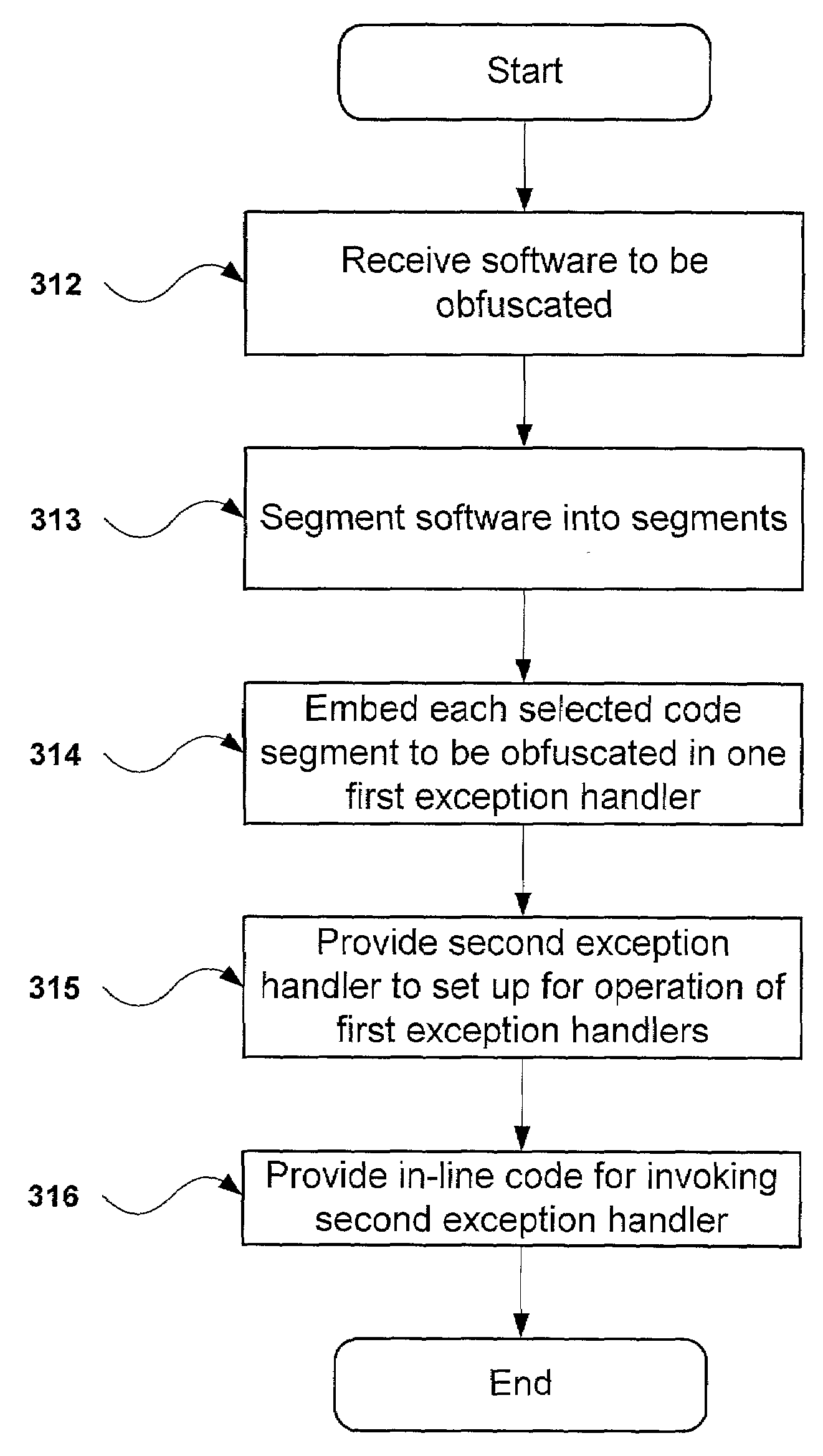
ActiveUS7243340B2Improve securityIncrease the reverse difficultyUnauthorized memory use protectionHardware monitoringObfuscationKernel level
A method and system for increasing security of a software program by obfuscation of program execution flow is disclosed, wherein the software program is executed on a computer system that includes a user-level protected mode and a kernel-level unprotected mode. The method and system include first identifying critical code segments to be hidden in the software program. The non-critical portions of the software program are then executed in the user-level protected mode, while the critical code segments are executed within respective exception handlers, thereby hiding execution of the critical code segments from a debugger program.
Owner:PACE ANTI PIRACY
Collaborative file access management system
InactiveUS7725490B2Digital data processing detailsProgram/content distribution protectionNetwork management applicationKernel level
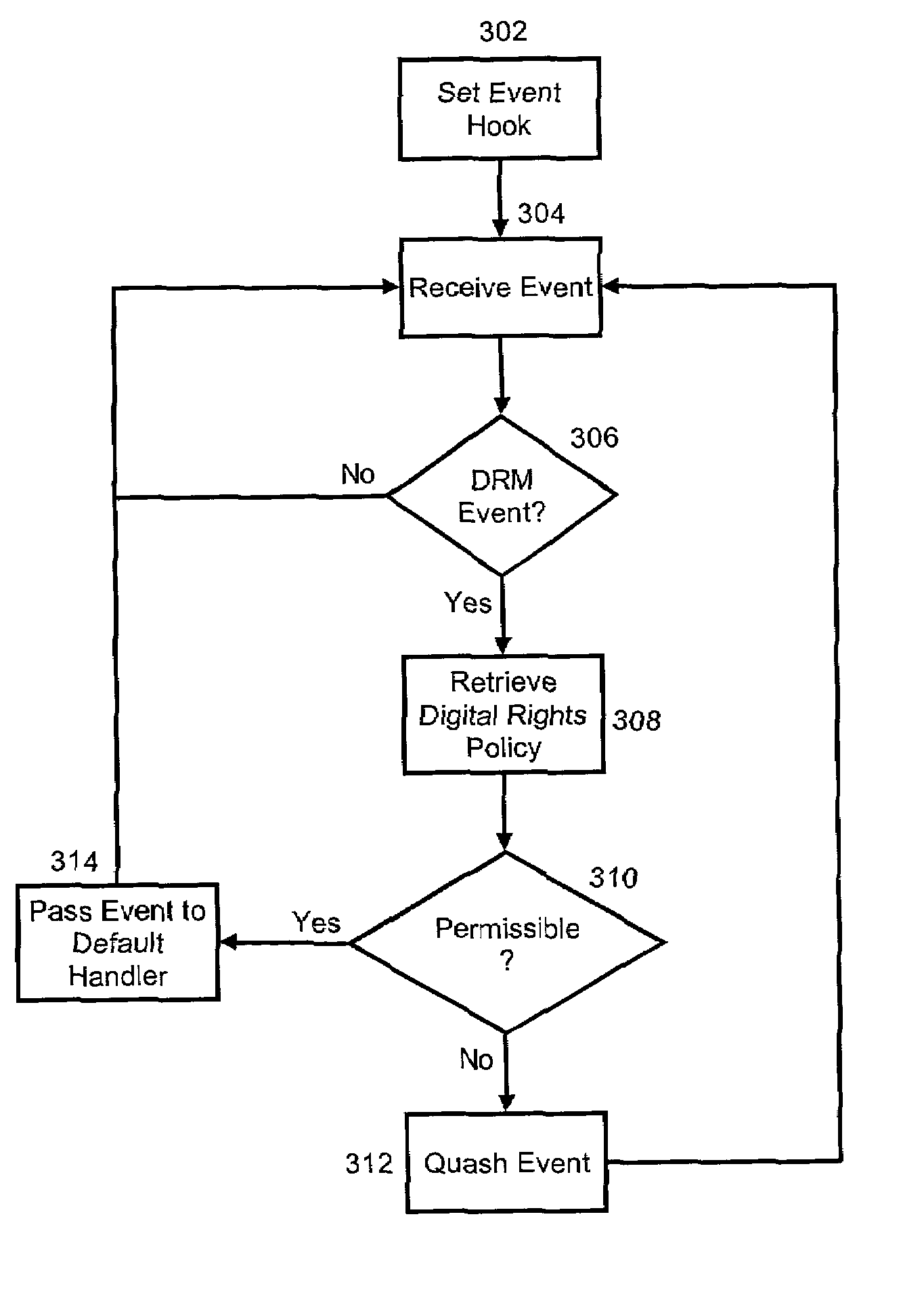
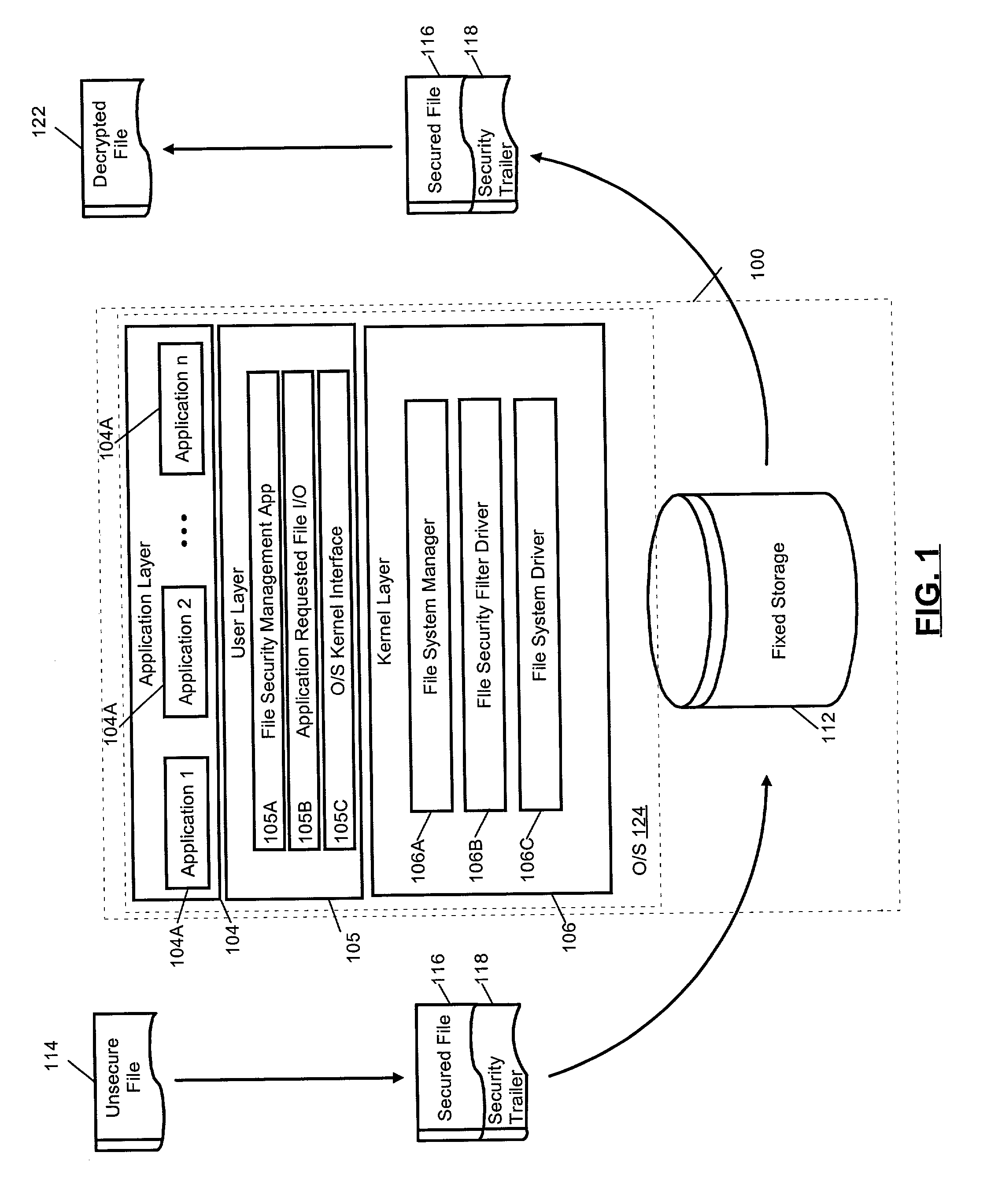
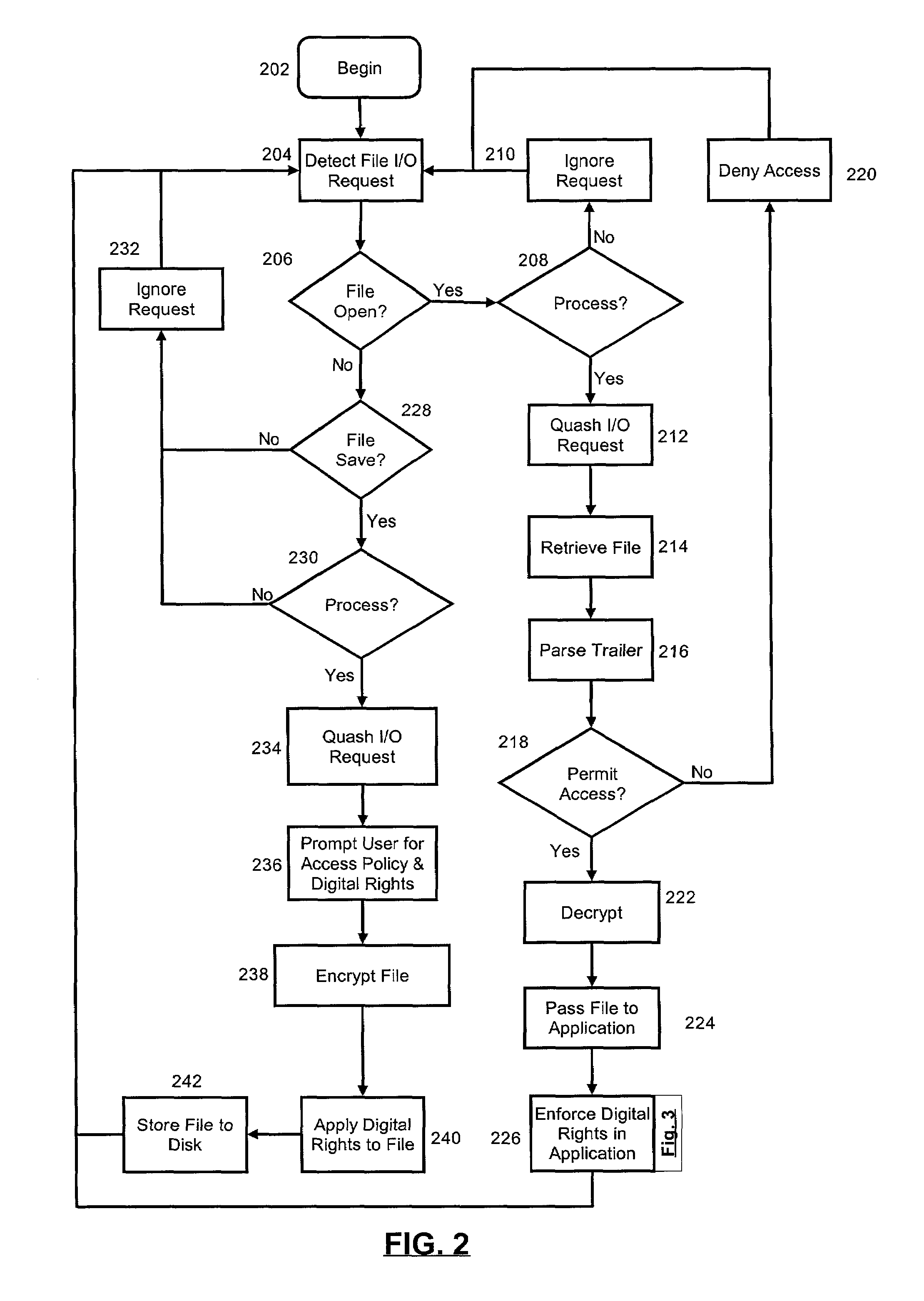
A collaborative file access management system. The system can include one or more secure, collaborative files, each secure, collaborative file including a security trailer specifying at least one of an access policy and associated digital rights. The system also can include a user-layer file management application configured to limit access to the secure, collaborative file based upon the access policy. Finally, the system can include a kernel-layer file security service configured both to detect kernel-level requests to access the secure, collaborative files, and also, responsive to the detected kernel-level requests, to invoke the file management application.
Owner:CRUCIAN GLOBAL SERVICES
Server monitoring framework
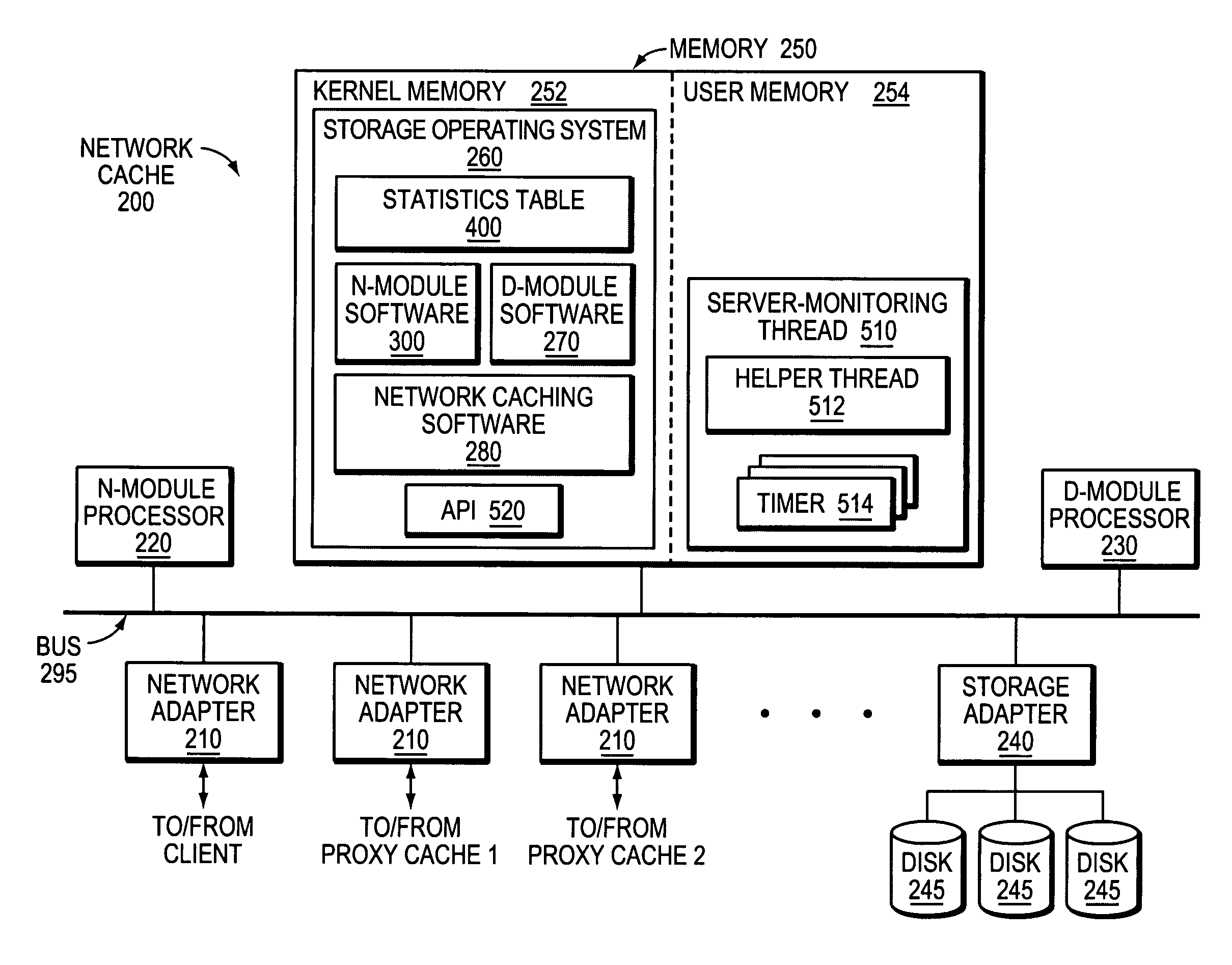
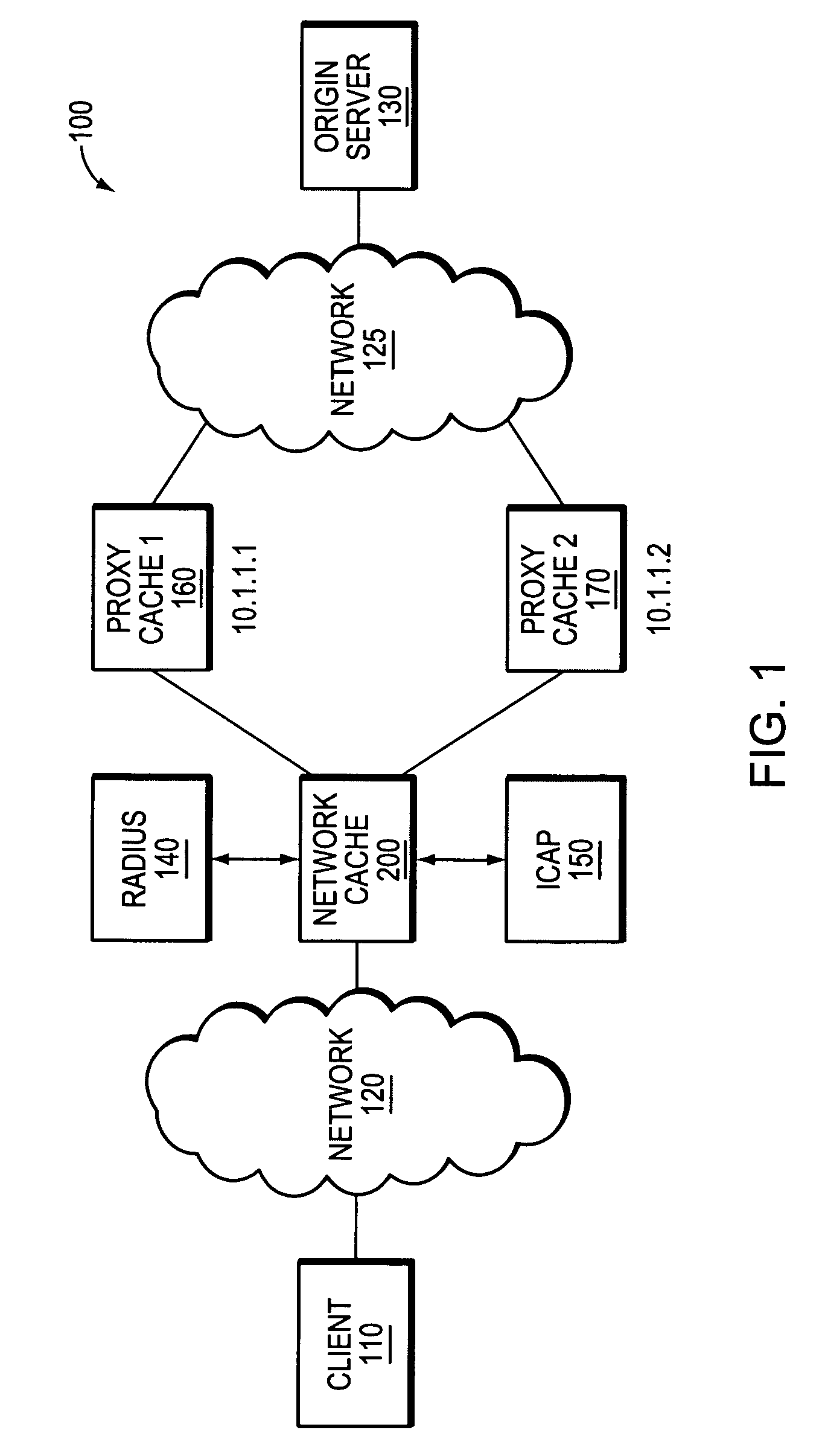
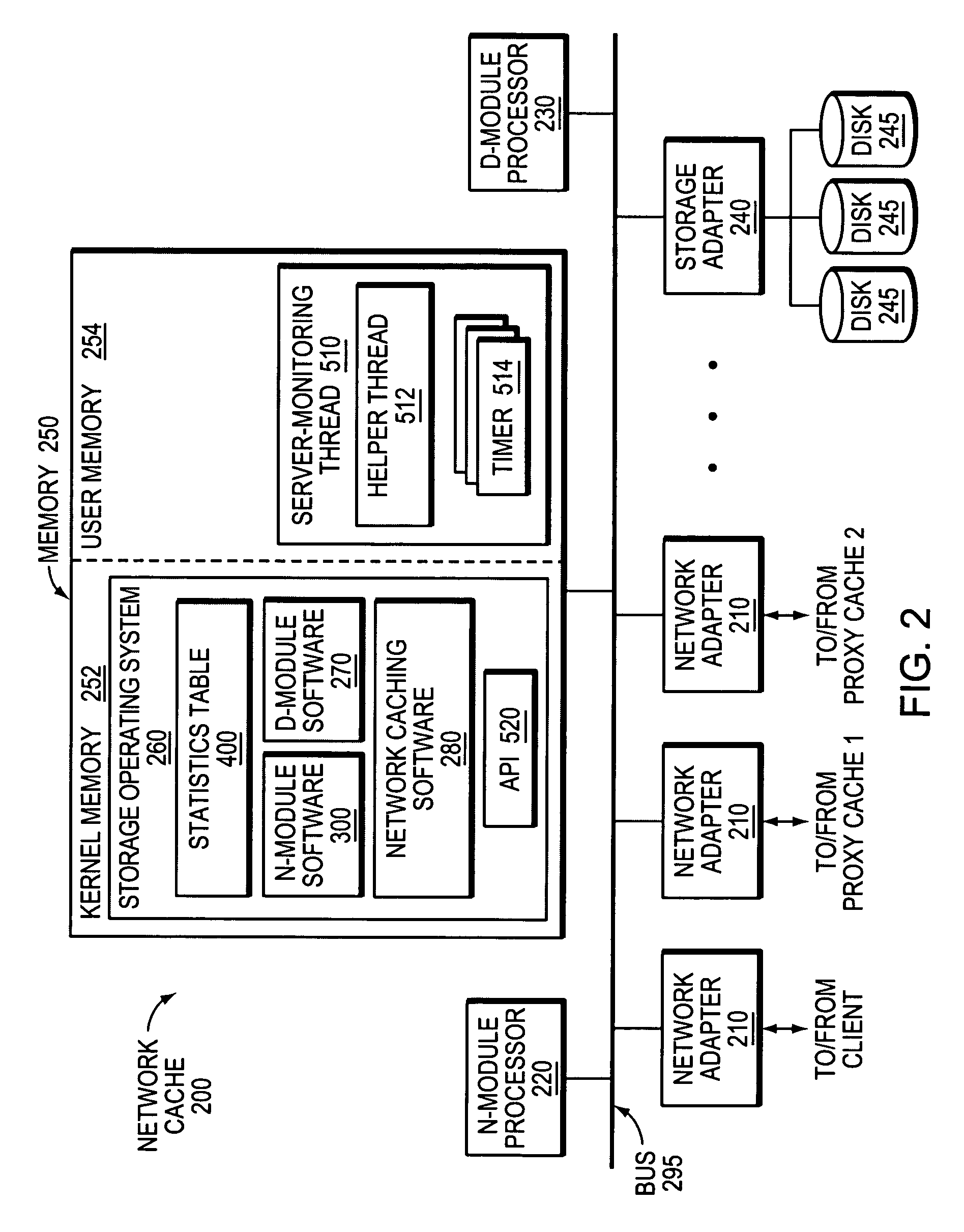
ActiveUS7653722B1Efficient use of resourcesSimplified code managementDigital data information retrievalMultiple digital computer combinationsKernel levelAuthentication server
A novel software framework monitors server statistics for a plurality of software modules and makes its collected statistics available to those modules. Unlike prior implementations, the framework provides shared server-monitoring code through which the plurality of software modules can monitor various types of servers, such as authentication servers, ICAP servers, origin servers, hierarchical proxy servers and so forth. Because the same server-monitoring code is accessed by each of the software modules, the overall amount of code that is written, compiled and executed may be reduced. Moreover, the shared server-monitoring code is not protocol-dependant and therefore may be coded outside of the kernel-level protocol engines. Preferably, the shared server-monitoring code is implemented as a user-level thread or process.
Owner:NETWORK APPLIANCE INC
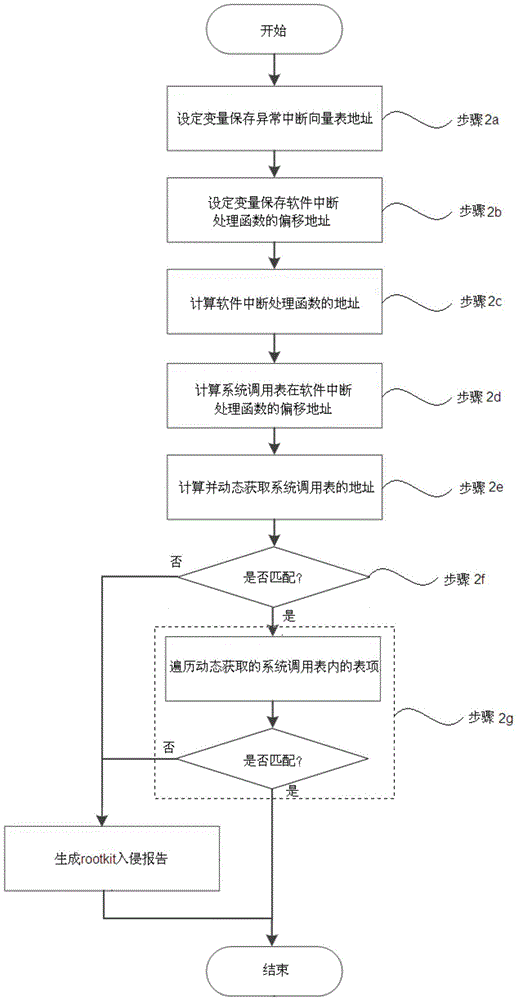
Kernel level rootkit detection method and system in Andriod system
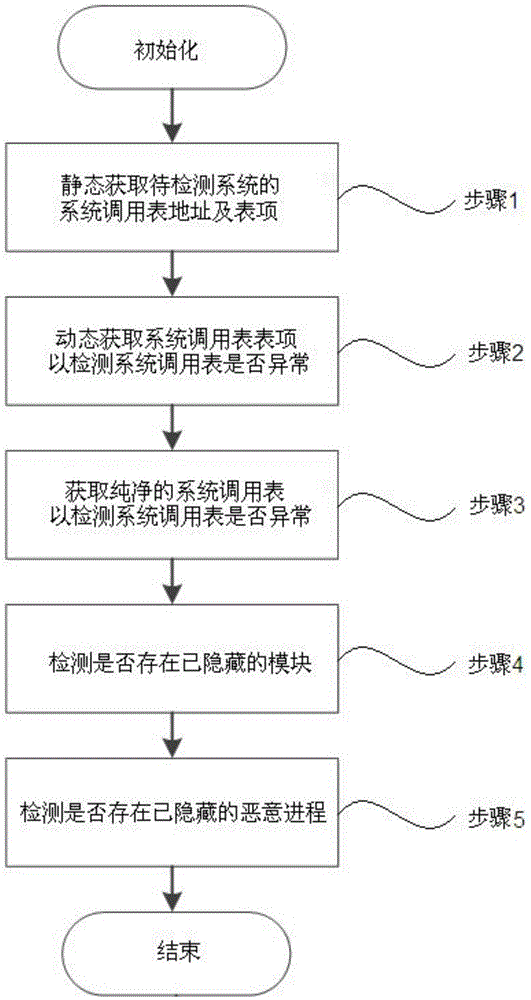
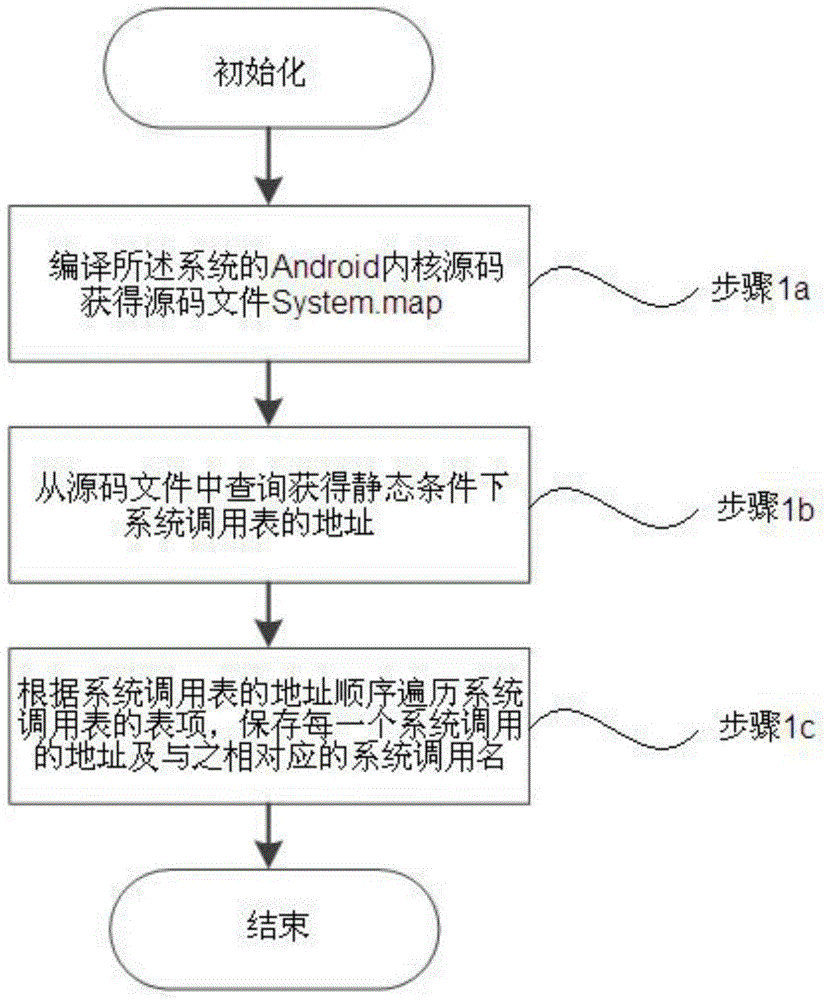
InactiveCN104598823AImprove securityImprove reliabilityPlatform integrity maintainanceKernel levelSystem call
The invention discloses a kernel level rootkit detection method in an Andriod system, comprising the following steps of statically obtaining an address and a table entry of a system call table; entering into a kernel mode from a user mode; dynamically obtaining the address of the system call table; if the addresses are not matched, then generating an intrusion reporting; obtaining a pure address of the system call table; if the system call table is not matched, then generating the intrusion reporting and restoring; intercepting a module name called by a module loading function, retrieving the dynamically loaded module name, if the name is not matched, then deleting the hidden module, and generating the intrusion reporting; obtaining all the progress information actually loaded by a system to be detected, and obtaining all the progress information by using a command query, if the progress information is not matched, then eliminating the malicious processes and generating the intrusion reporting. The invention also discloses a rootkit detection system, which can detect the intruded rootkit and delete the rootkit with an illegal act, so as to improve the safety and reliability of the system.
Owner:EAST CHINA NORMAL UNIV
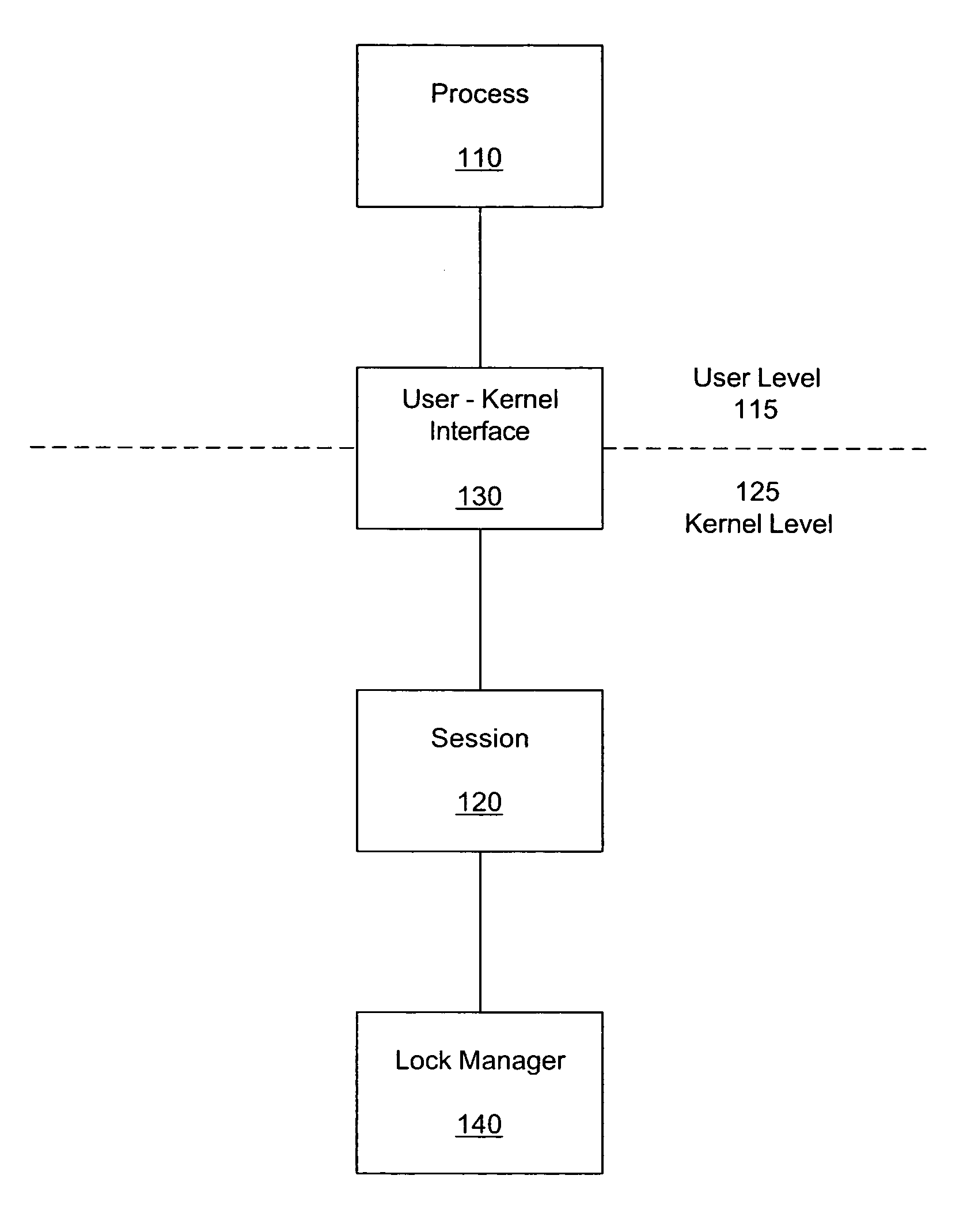
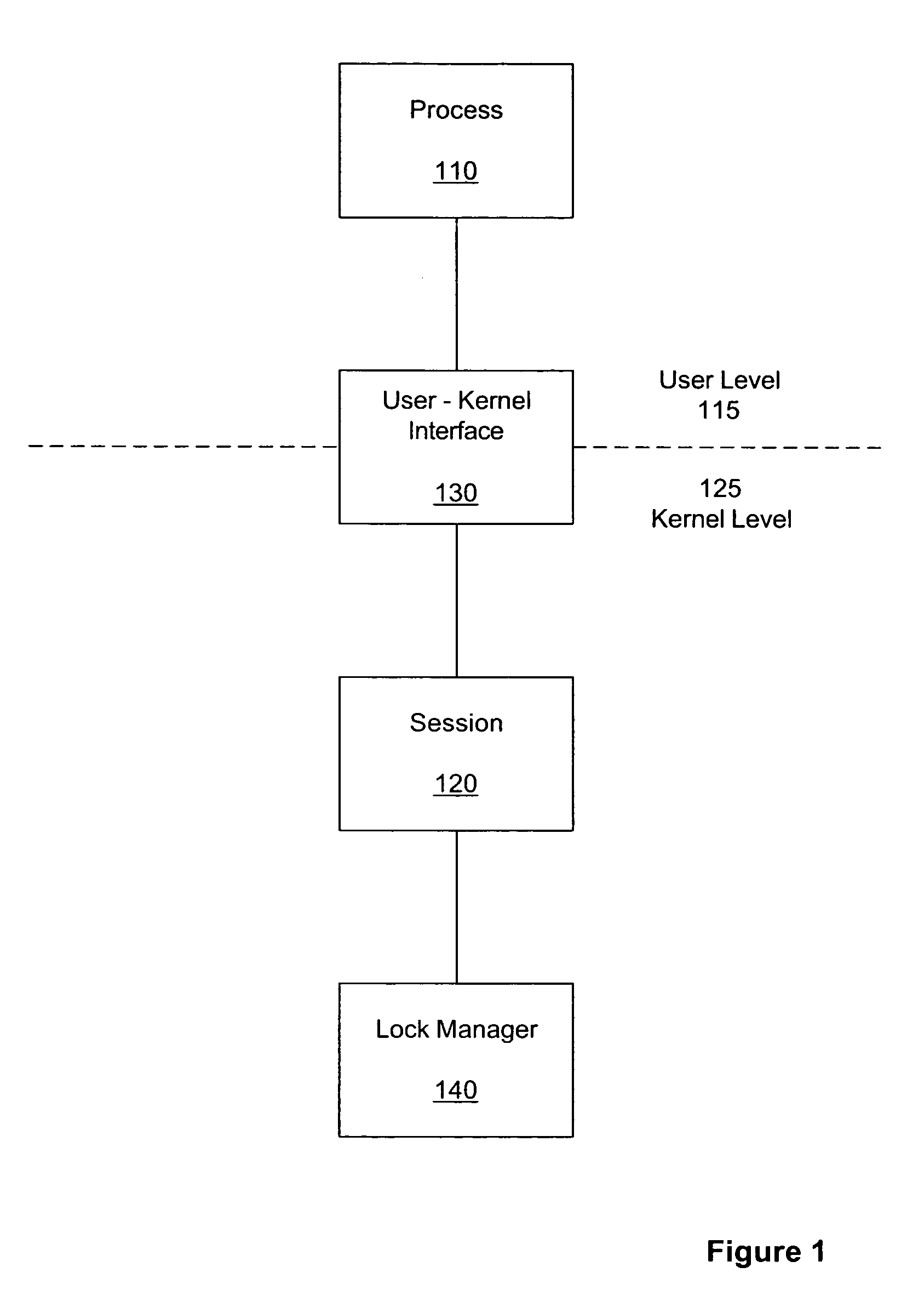
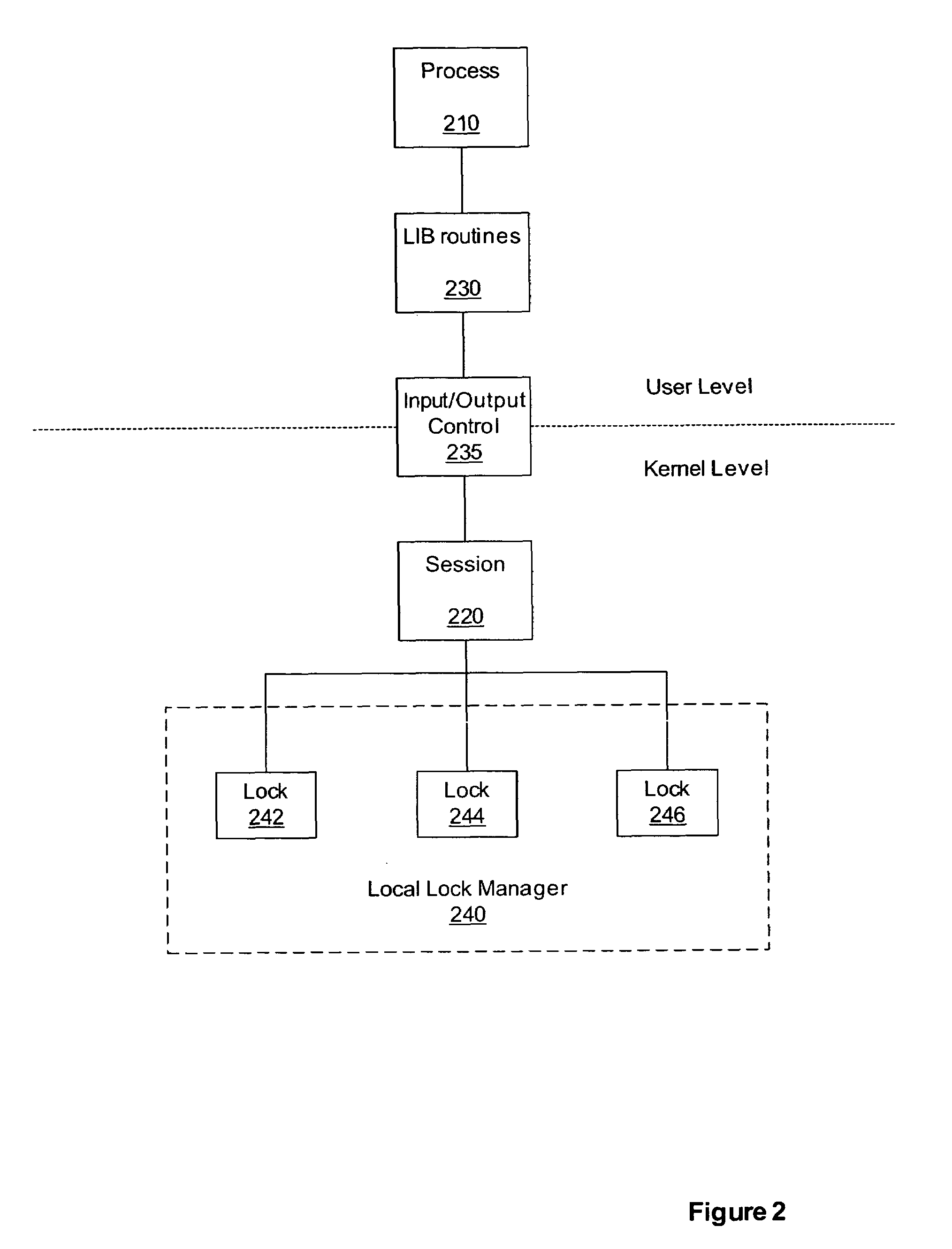
Method and system for persistent, recoverable user-level locks
InactiveUS7698708B1Guaranteed to workMultiprogramming arrangementsMemory systemsKernel levelRecovery mechanism
Methods, systems, and apparatus can provide a means for a user-level process to acquire locks on resources at the kernel level through the use of a session that persists after the termination of the user-level process. A session recovery mechanism can be provided so that a newly started process can query an existing kernel-level lock session to discover which locks were held by a previously terminated process. This is accomplished, in part, through associating the kernel session with a token, rather than by associating the locks with a user-level process ID. Such a mechanism provides the ability for the new process to perform appropriate lock cleanup or to continue the work of the previous process under protection of the surviving locks.
Owner:SYMANTEC OPERATING CORP
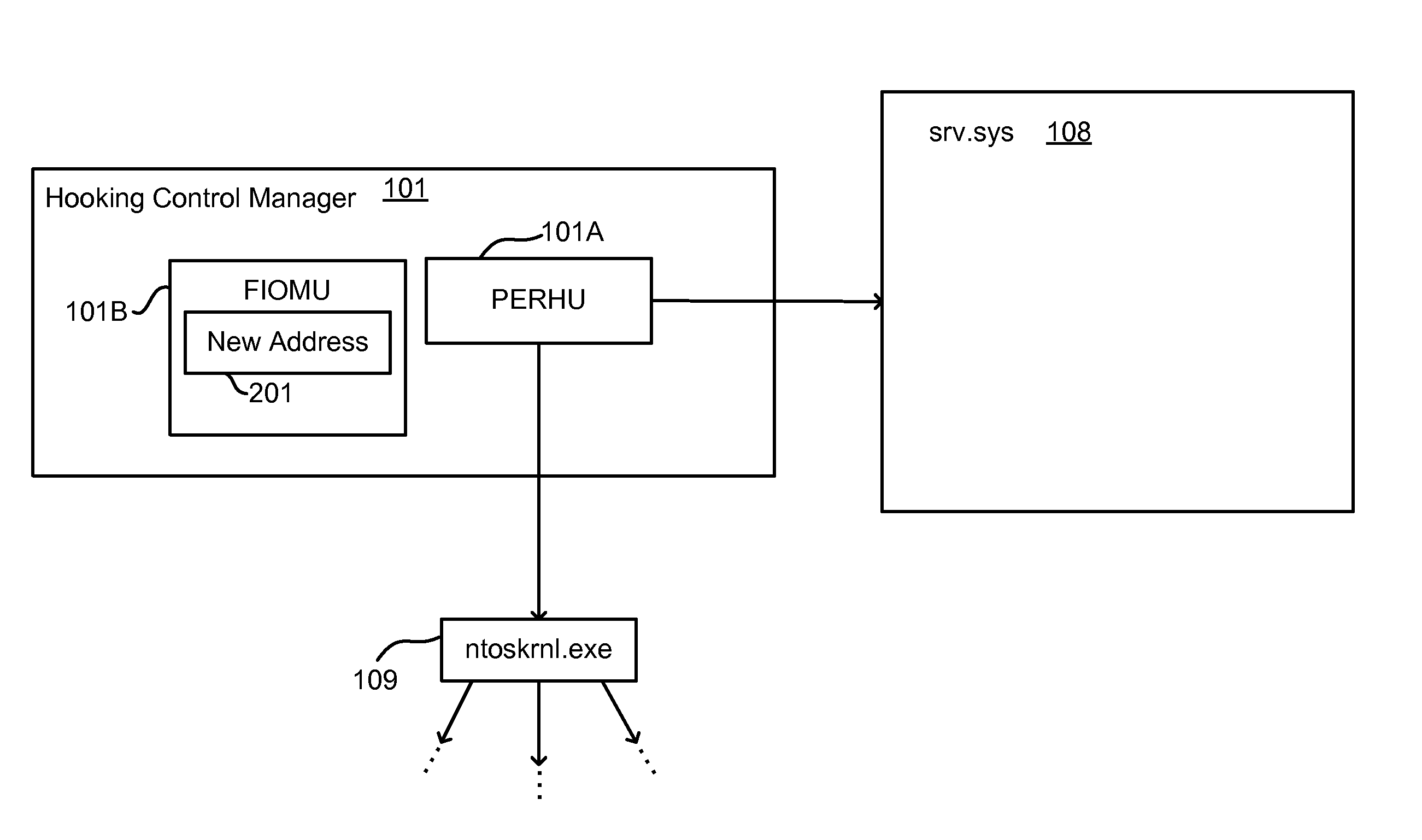
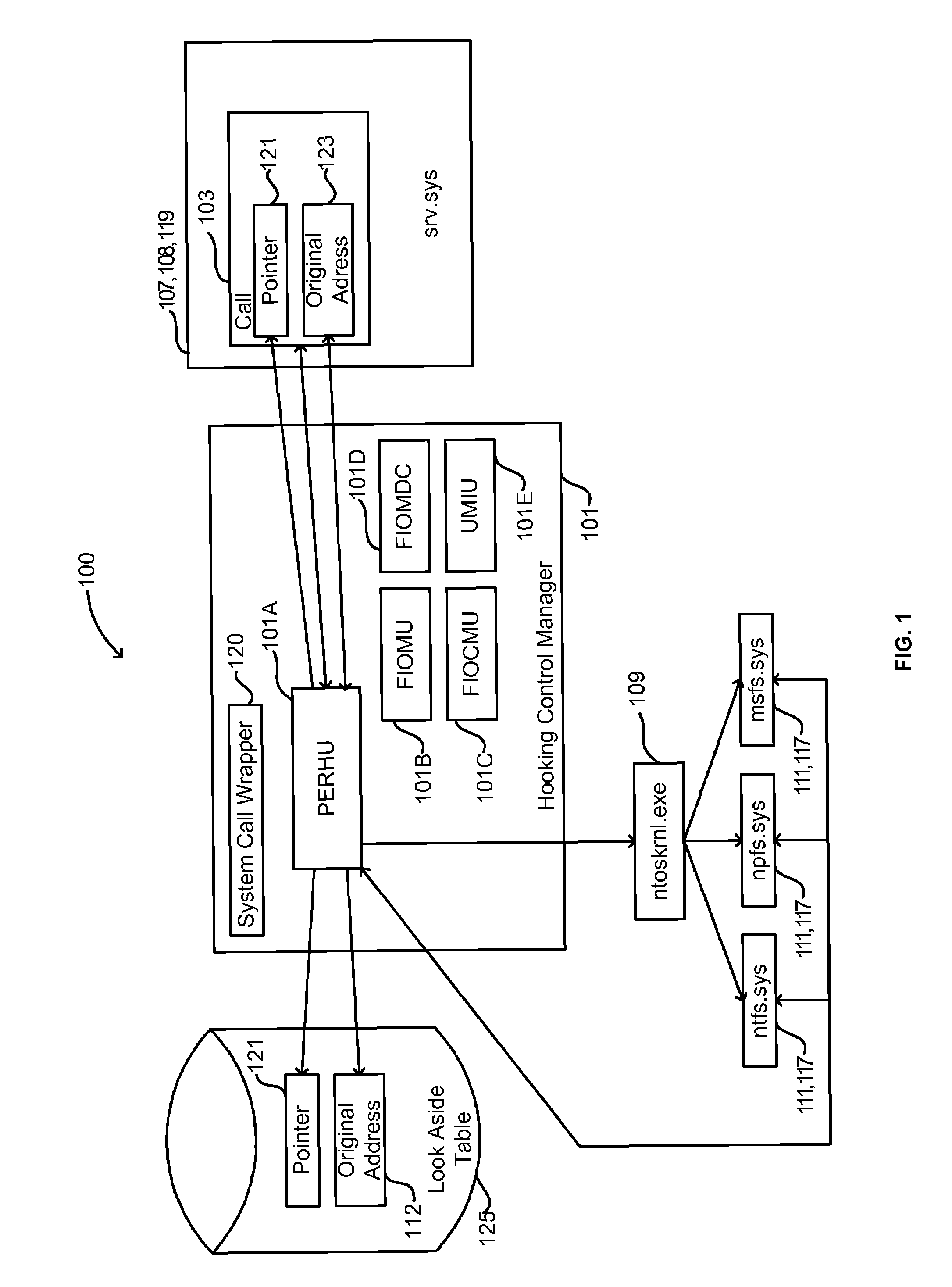
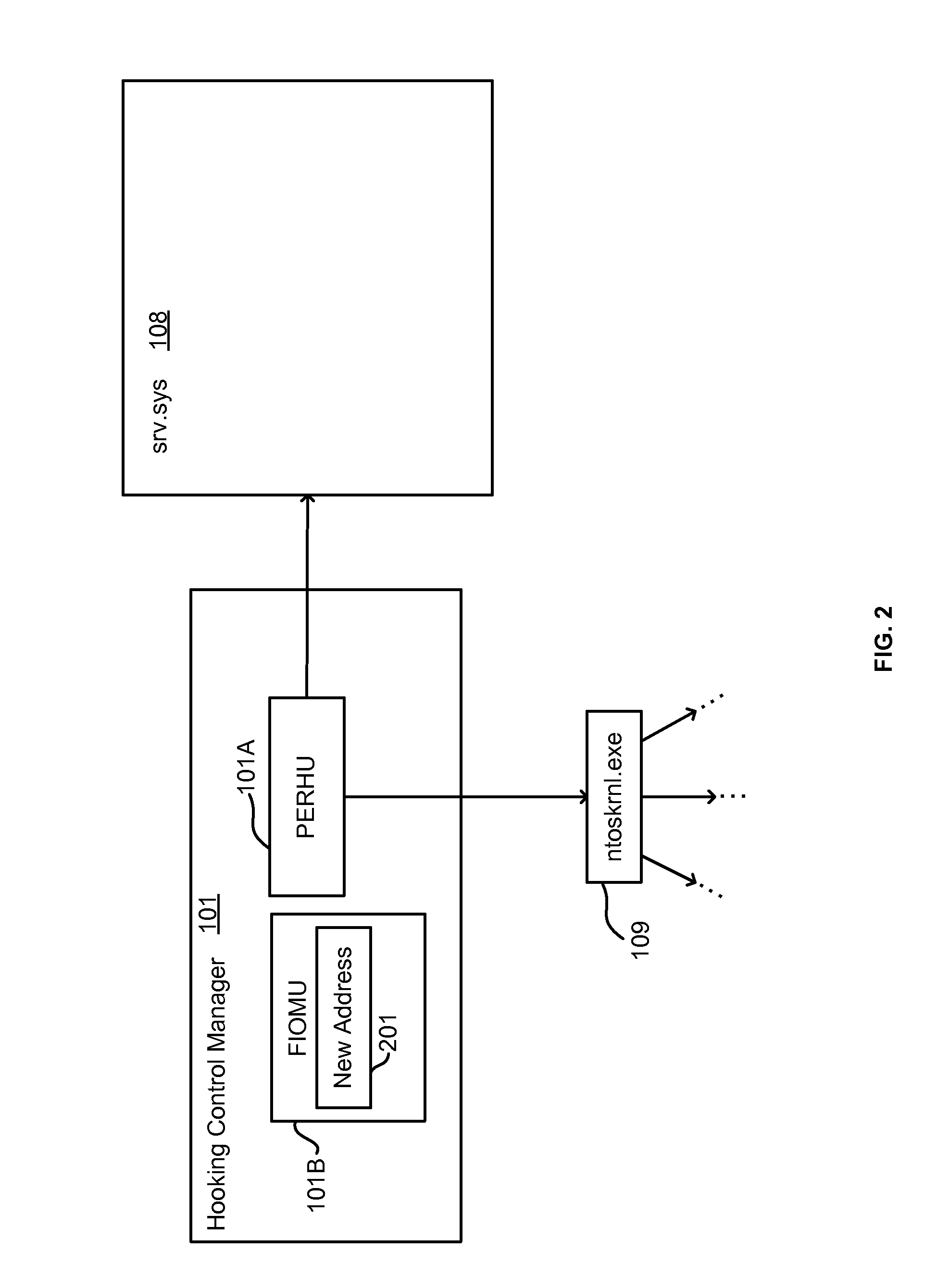
Lightweight hooking mechanism for kernel level operations
A hooking control manager hooks kernel level operations. The kernel level hooking control manager identifies a kernel level component for which to filter outgoing kernel level system calls. For each of a select set of outgoing kernel level system calls imported by the kernel level component, the kernel level hooking control manager locates the address of the system call in the kernel level component, stores the address, and patches the kernel level component with an address of alternative code to execute when the kernel level component makes the outgoing system call. Upon the unloading of the kernel level hooking control manager, for each call of the select set, the kernel level hooking control manager locates the address of the system call in the kernel level component, and patches the kernel level component so as to restore the stored address.
Owner:CA TECH INC
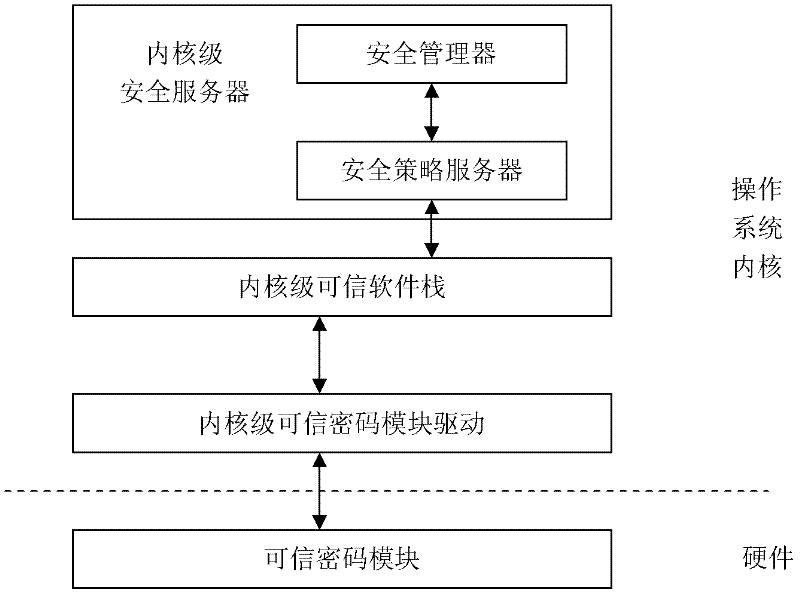
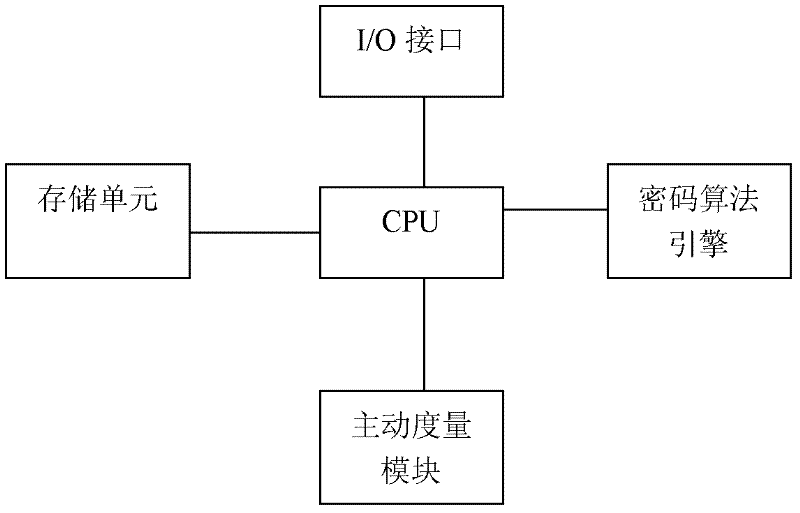
A Trusted Software Base for Proactive Security Services
InactiveCN102270287APrevent unauthorized operationsPrevent unauthorized modificationPlatform integrity maintainanceActive safetyBIOS
The invention discloses a trusted software base providing an active security service, comprising a trusted password module and an operating system kernel. The operating system kernel is provided with a kernel-level trusted password module driver, a kernel-level trusted software stack and a kernel-level security service module; a security manager and a security strategy server are arranged in the kernel-level security service module; the trusted password module provides a hardware engine for encryption operation and hash operation, and verifies integrity of a trusted BIOS (Basic Input / Output System); the trusted BIOS is used for verifies the integrity of PC hardware devices and an MBR (Master Boot Record); the MBR is used for guiding an OS (Operating system) Loader, and verifies the integrity of the OS Loader; and the kernel-level security service module captures security related information at a key security control point in a kernel layer of the operating system, and performs access control and least privilege control. The trusted software base effectively prevents unauthorized operations and rogue programs from performing unauthorized modification on application codes and configurations, and prevents secret disclosure of application resources, thereby guaranteeing the privacy and the integrity of an application environment.
Owner:中国人民解放军海军计算技术研究所
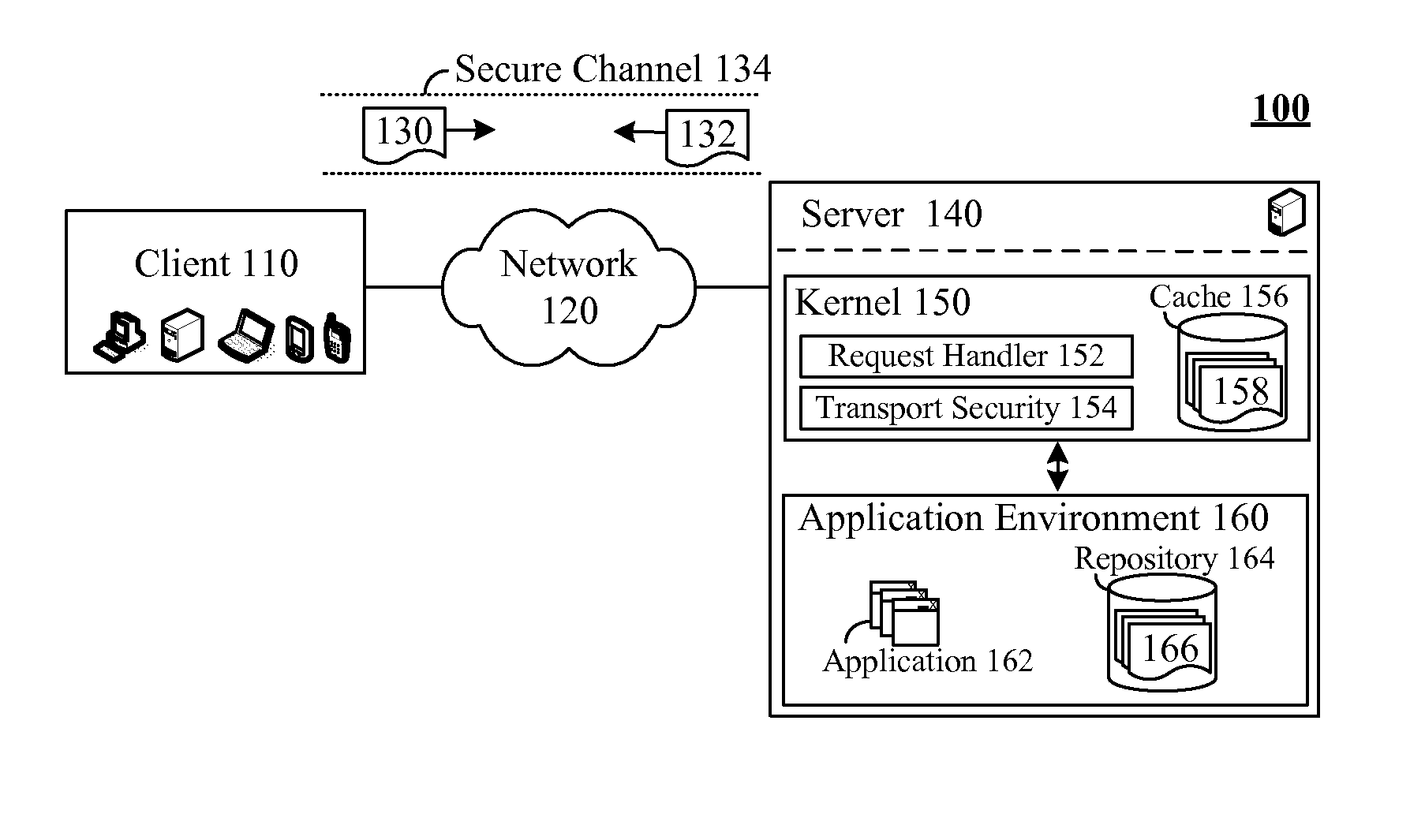
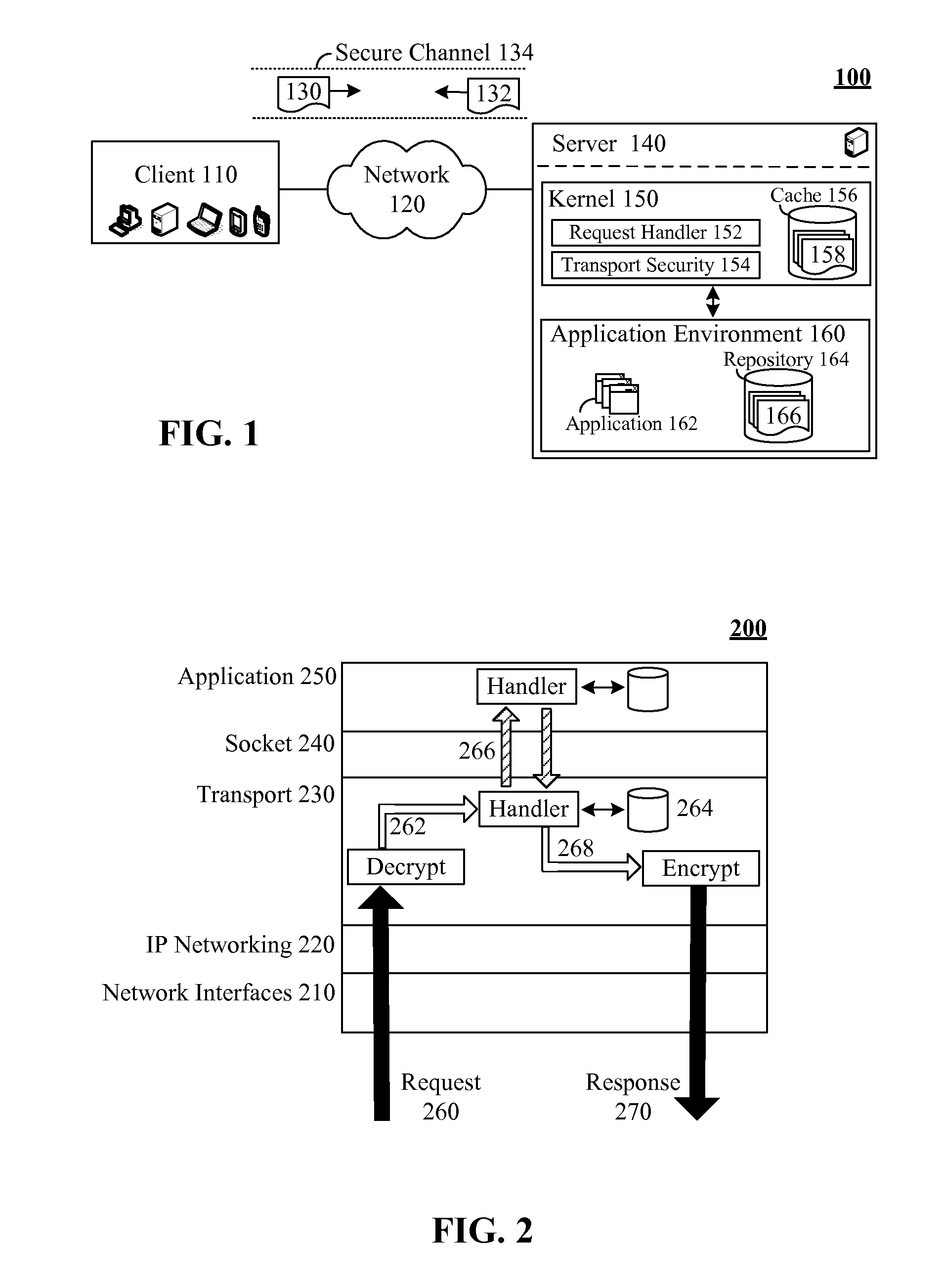
Secure request handling using a kernel level cache
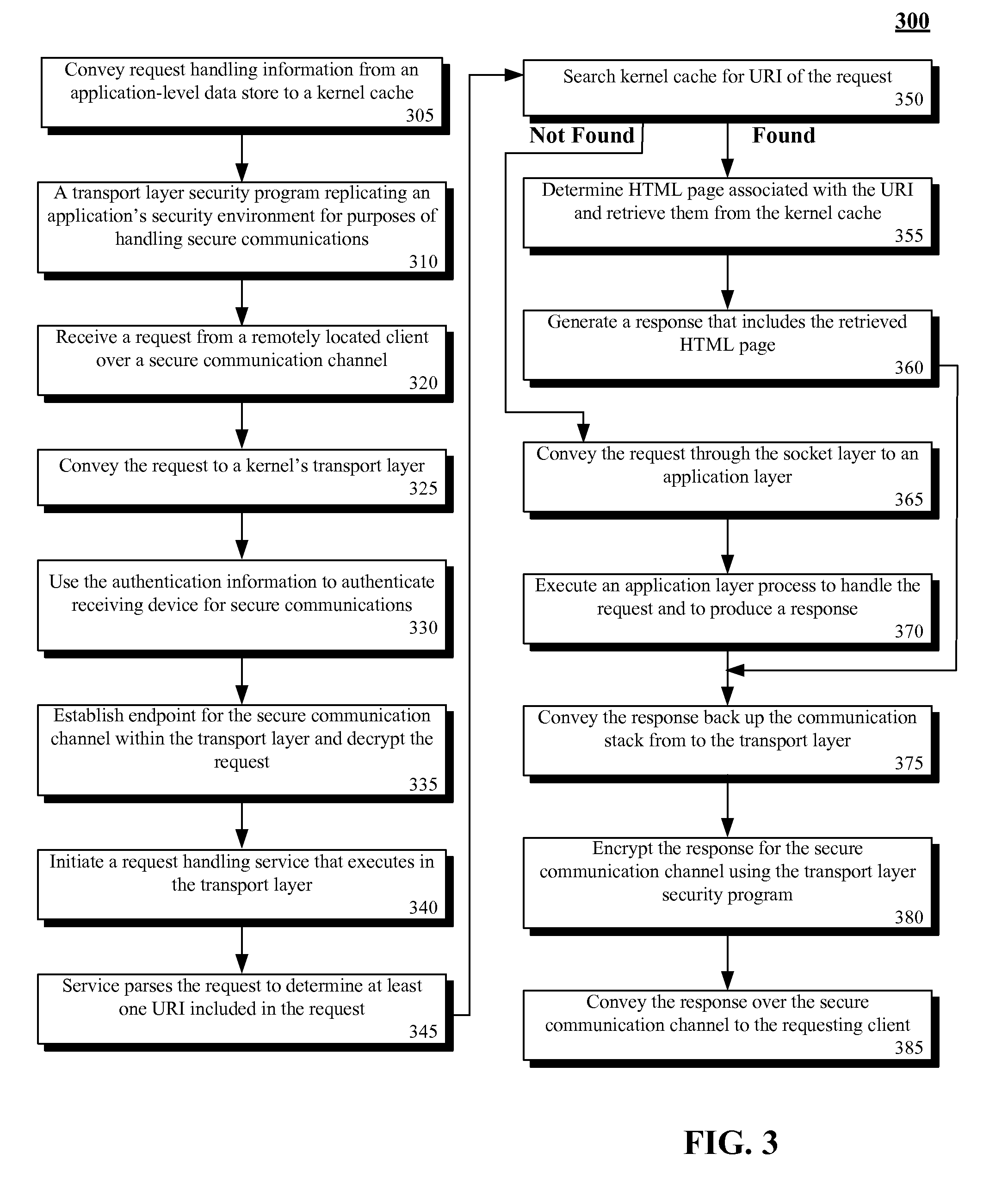
ActiveUS8335916B2Digital data processing detailsAnalogue secracy/subscription systemsTransport layerKernel level
The present invention discloses a system, method, apparatus, and computer usable product code for handling requests. The invention can include a kernel level cache, a request handling service, and a transport layer security service. The kernel level cache can store request handling data. The request handling service can handle secure requests at a transport layer of a kernel when request handling data is present in the kernel level cache. The transport layer security service can handle encryption / decryption operations for the secure requests and request responses at the transport layer.
Owner:INT BUSINESS MASCH CORP
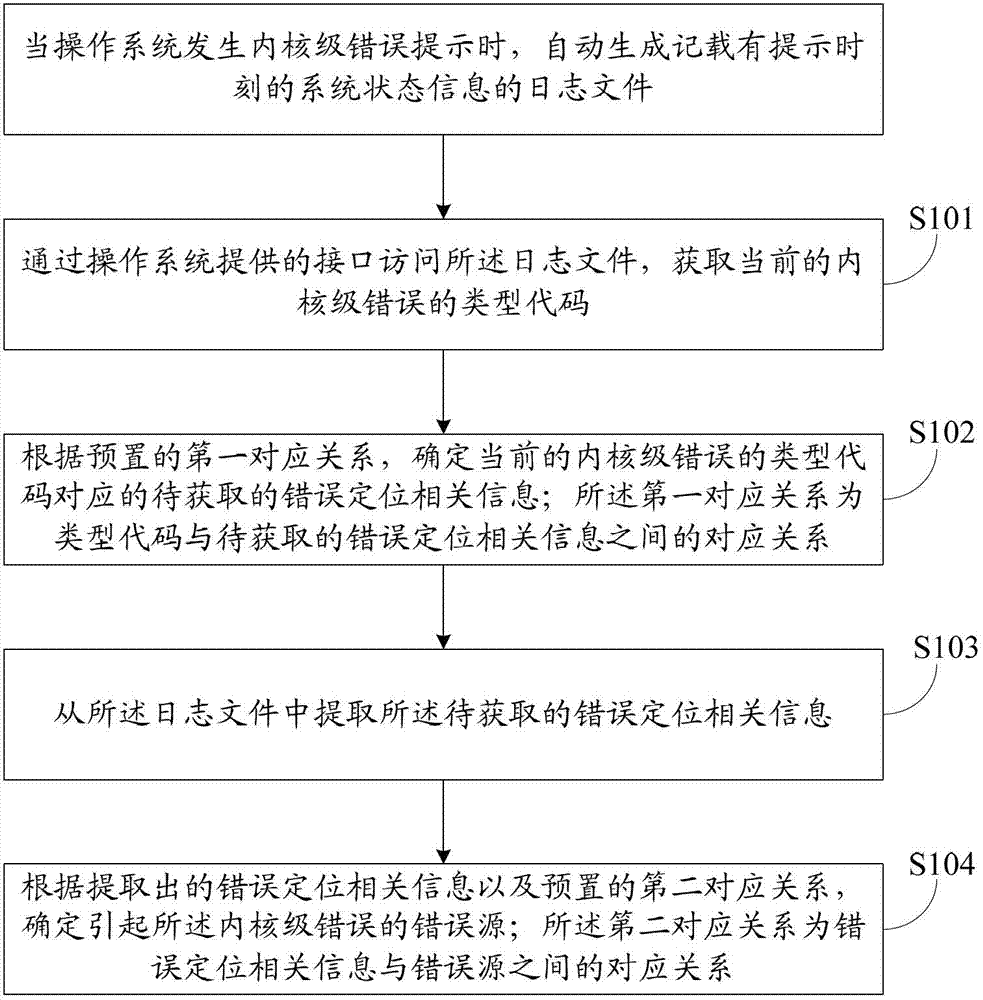
Operating system kernel-level error positioning method and device
The invention discloses an operating system kernel-level error positioning method and an operating system kernel-level error positioning device. When an operating system generates a kernel-level error prompt, a log file recording the system state information at the prompting moment is automatically generated. The method comprises the following steps that the log file is accessed through an interface provided by the operating system, and the type code of the current kernel-level error is obtained; error positioning related information to be obtained corresponding to the type code of the current kernel-level error is determined according to the preset first corresponding relationship; the first corresponding relationship is the corresponding relationship between the type code and the error positioning related information to be obtained; the error positioning related information to be obtained is extracted from the log file; an error source causing the kernel-level error is determined according to the extracted error positioning related information and the preset second corresponding relationship; and the second corresponding relationship is the corresponding relationship between the error positioning related information and the error source. Through the method and the device provided by the invention, the error source causing the kernel-level error can be automatically positioned.
Owner:三六零数字安全科技集团有限公司
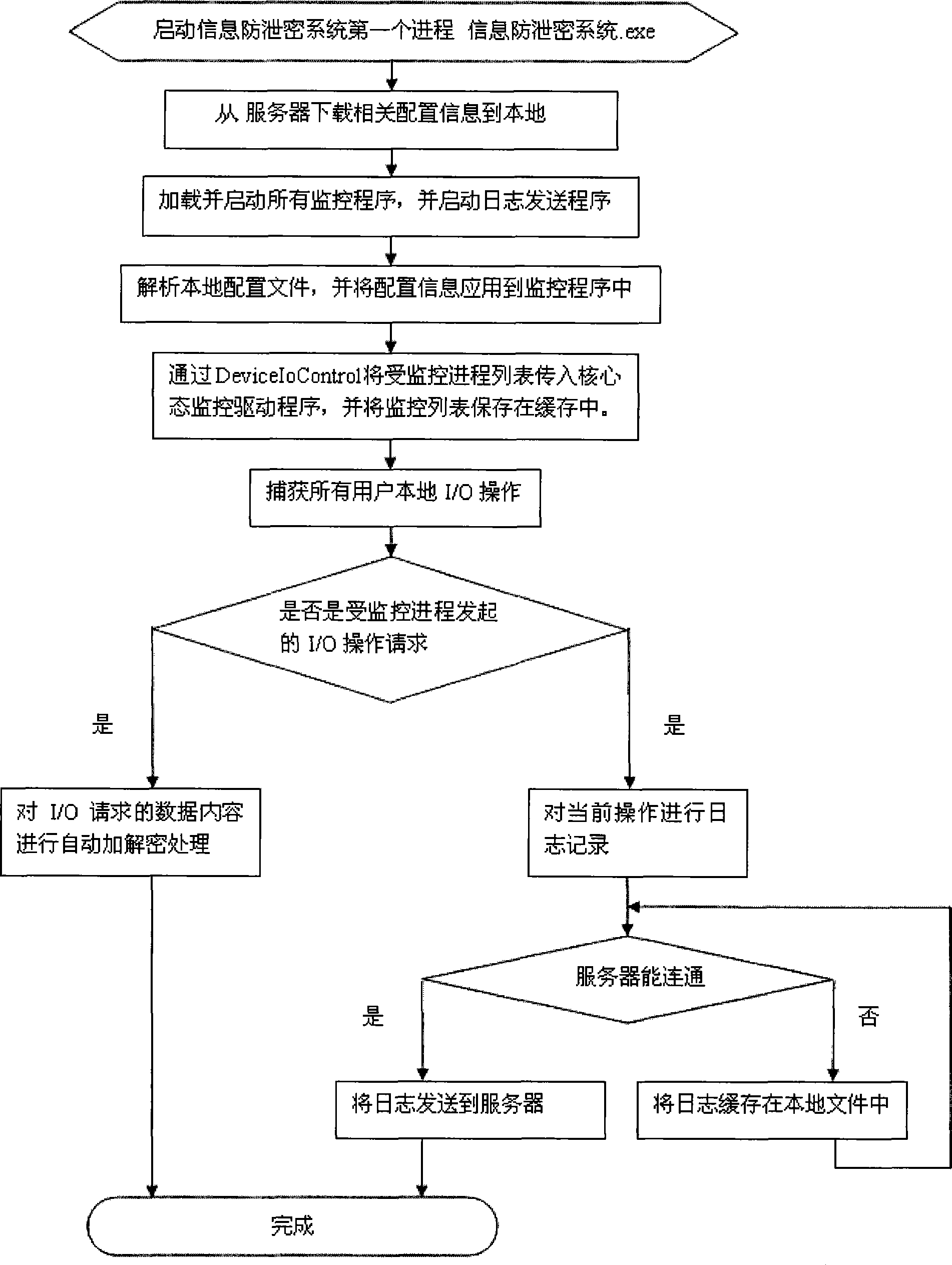
Information leakage prevention system
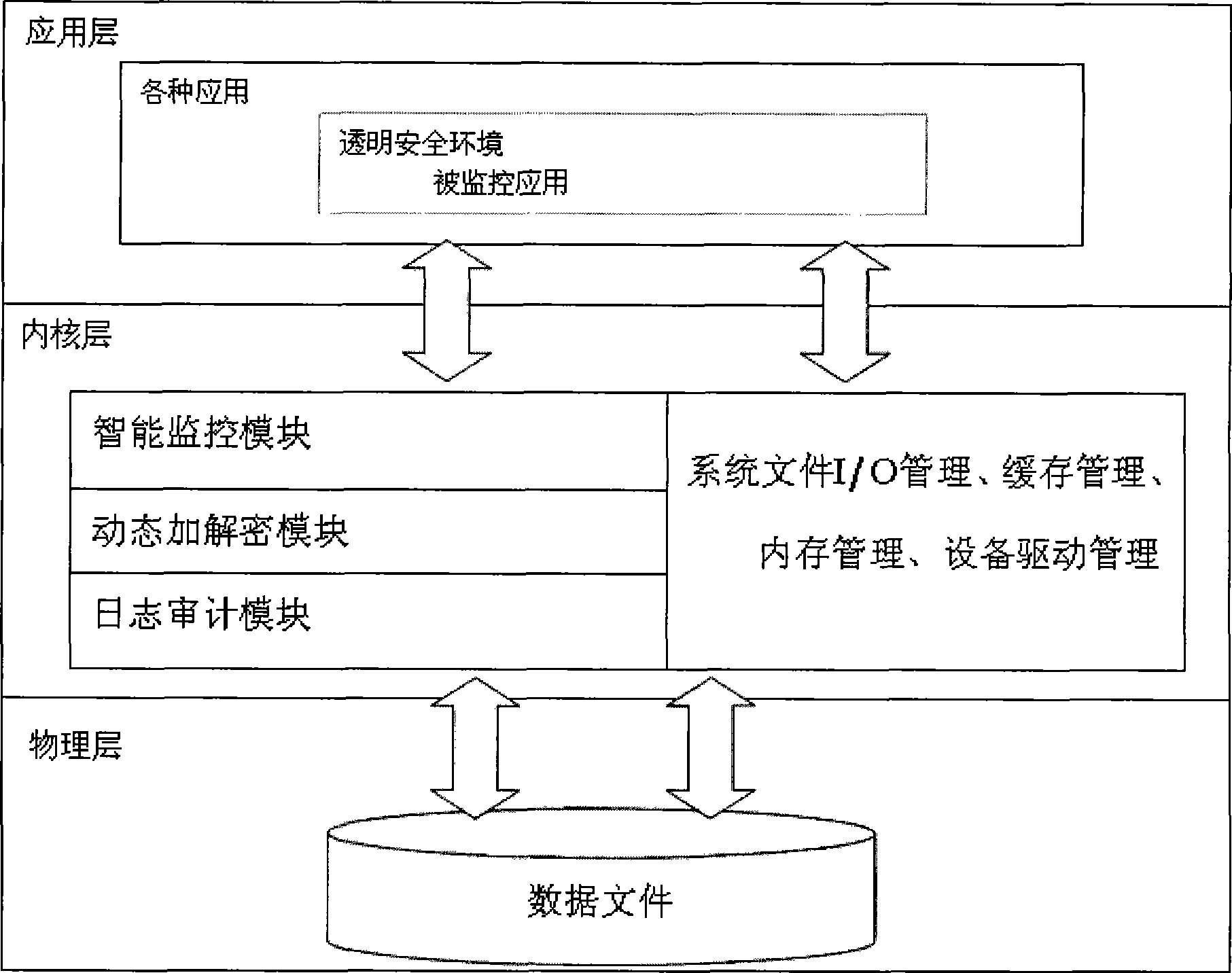
InactiveCN101453327AImprove safety and reliabilityUser identity/authority verificationOperational systemKernel level
The invention discloses a safe and reliable information anti-leakage system capable of enciphering in real time, which comprises a server and a client, wherein an operating system kernel of the client comprises an intelligent monitoring module, a dynamic enciphering and deciphering module and a log auditing module; the client enters a local safety environment after verified by the server; and the intelligent monitoring module comprises a text / binary discrimination submodule, a local file I / O monitoring submodule, a network I / O monitoring submodule, a clipboard monitoring submodule, a drag monitoring submodule and a printing monitoring submodule. The information anti-leakage system constructs a transparent use environment for users, wherein all file I / O and the all network I / O of the users in the transparent environment are automatically monitored, and all local text file I / O in the environment is automatically enciphered and deciphered. The information anti-leakage system monitors various applications and possible risks at the kernel level of the system, and has higher safety and reliability.
Owner:北京鼎信高科信息技术有限公司
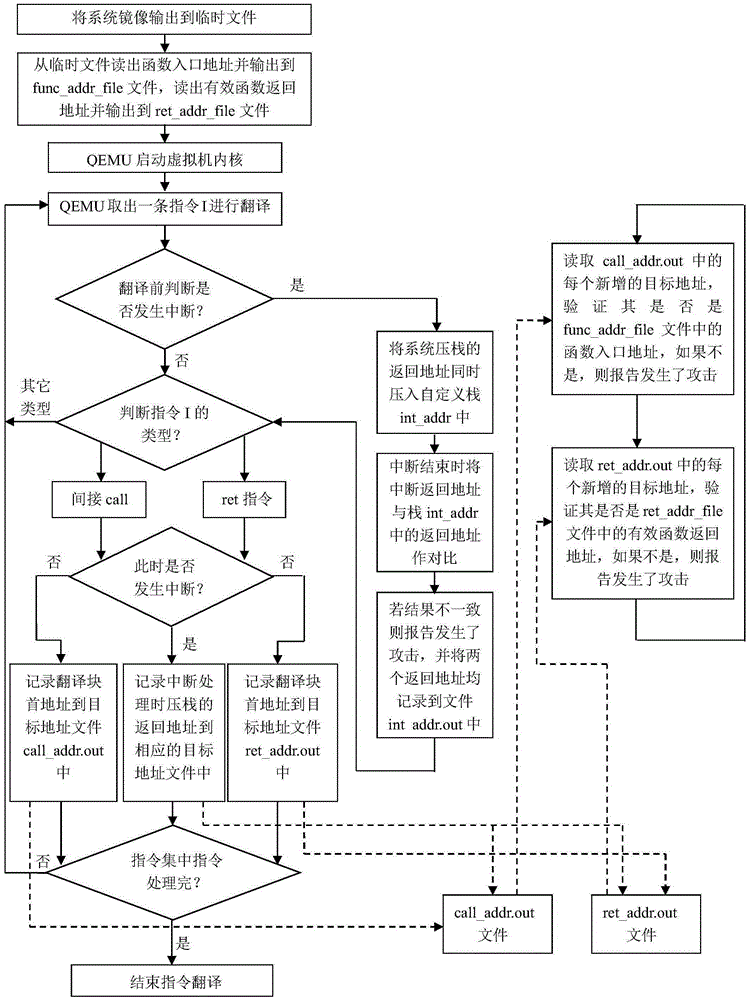
Kernel-level code reuse type attack detection method based on QEMU
ActiveCN105260659AProtection securityLow costPlatform integrity maintainanceControl flowOperational system
The invention discloses a kernel-level code reuse type attack detection method based on QEMU. The method mainly solves the problem of relying on hardware or need of modifying kernel source code in the prior art. According to the method, a function module of a QEMU virtual machine manager is expanded; each instruction which operates on the function module and in an operating system kernel is traversed and detected; jumping instructions relevant to the control flow process are recognized from the instructions, wherein the jumping instructions include ret and indirect call instructions; the jumping target addresses of the instructions are recorded; then, the target addresses are compared with legal target addresses in the system normal execution flow process for detecting whether a system is normally executed or not; and meanwhile, the interruption return addresses pushed into a stack during the interruption occurrence and the return addresses used during interruption actual return are subjected to comparison verification, so that whether attack occurs or not is judged. The kernel-level code reuse type attack detection method has the advantages that by aiming at the characteristic that the system original execution flow process needs to be changed for the code reuse type attack, the attack can be effectively discovered by monitoring the kernel execution flow process change instructions (and positions), and the kernel-level code reuse type attack detection method can be used for protecting the security of an operating system.
Owner:XIDIAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com