Kernel-level code reuse type attack detection method based on QEMU
A technology for code reuse and attack detection, applied in the field of computer science and technology, to achieve the effects of strong scalability, low cost, and high performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] Below in conjunction with accompanying drawing and embodiment the present invention is described in further detail:
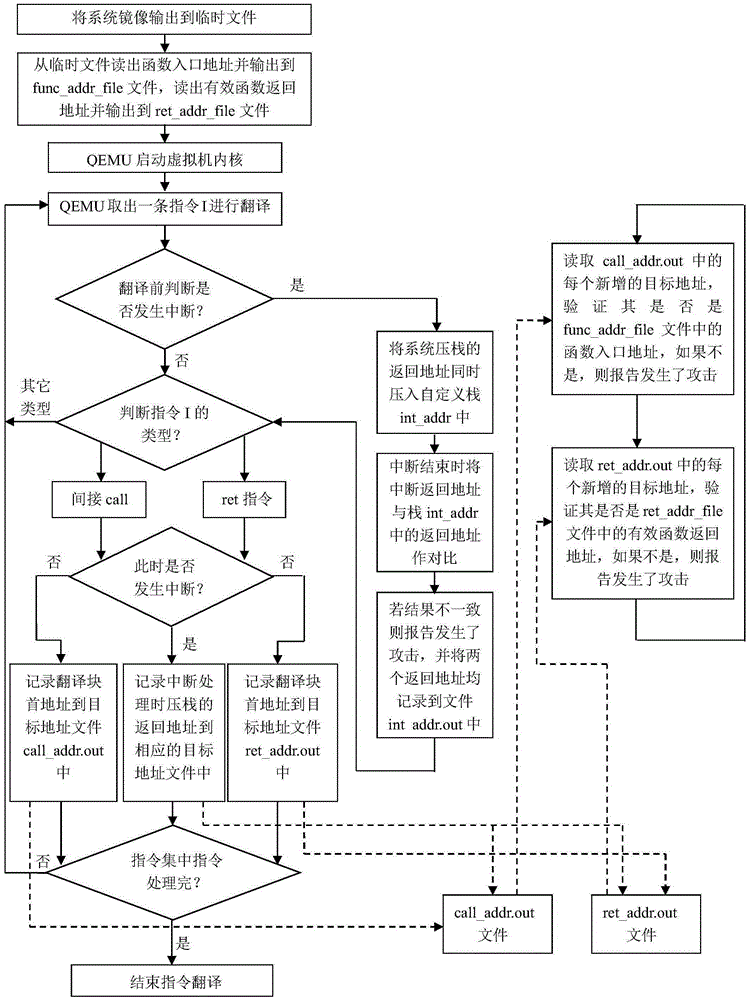
[0052] refer to figure 1 , the present invention includes preprocessing and QEMU-based record of jump instruction target address and interrupt process verification, and legality verification of jump instruction target address. Among them, the jump instructions related to the control flow include indirect call instructions and ret instructions. By recording their jump target addresses, and then comparing these target addresses with the target addresses in the normal system execution process, it is detected whether the system is running normally. be attacked.
[0053] The present invention is proposed based on such an observation: no matter what type of code reuse attack, if they want to implement the attack, they must change the original execution flow (or control flow) of the system and jump to the attacker's selected The first instruction fragment is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com