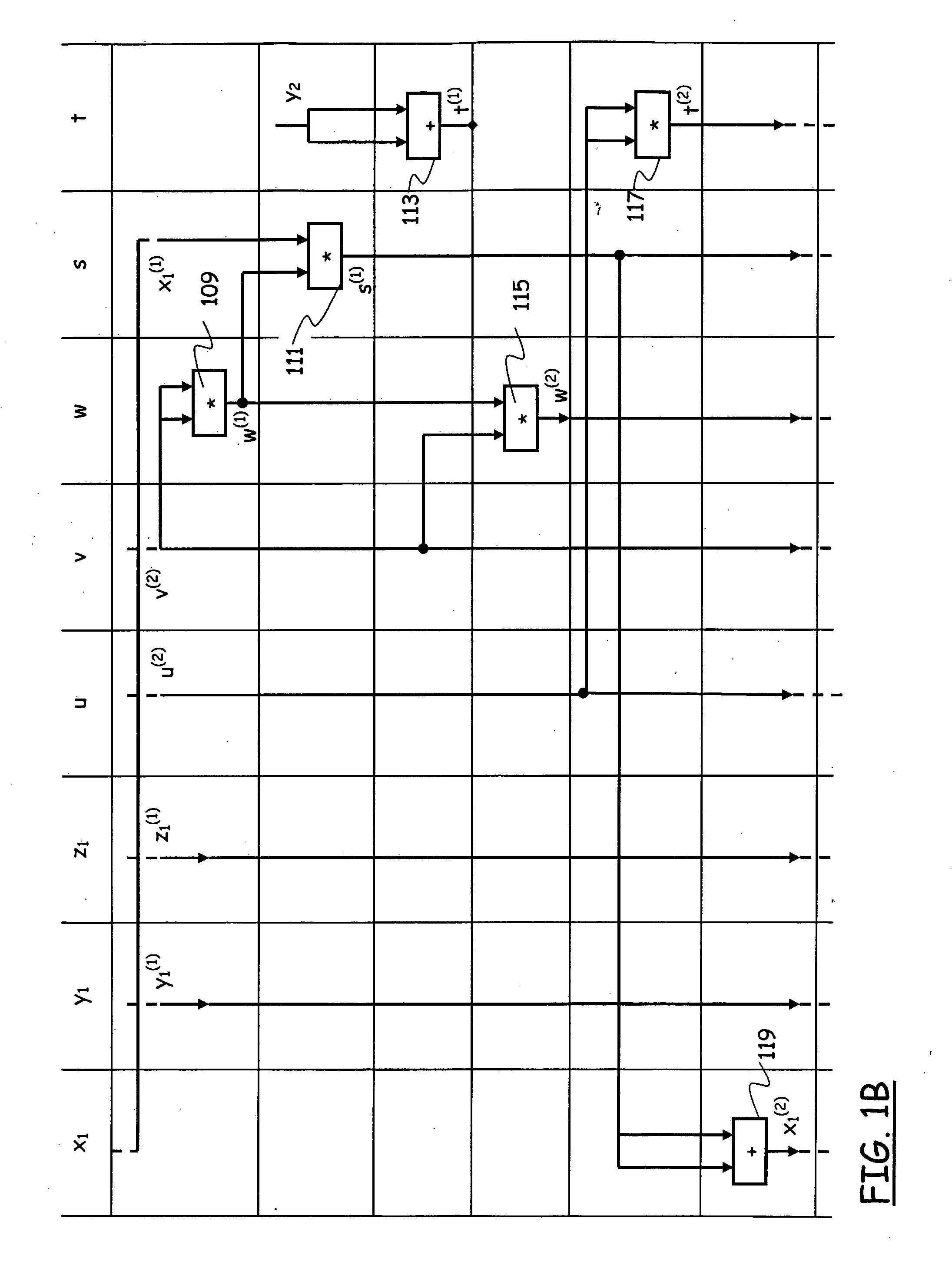
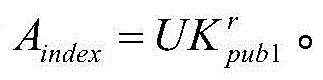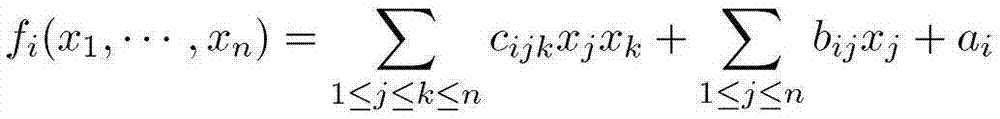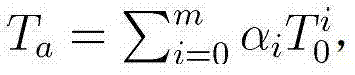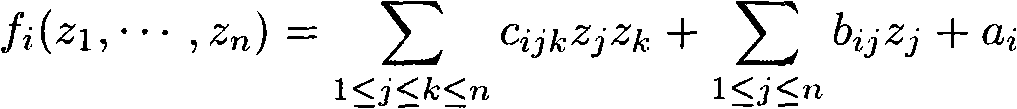Patents
Literature
733results about How to "Resist attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
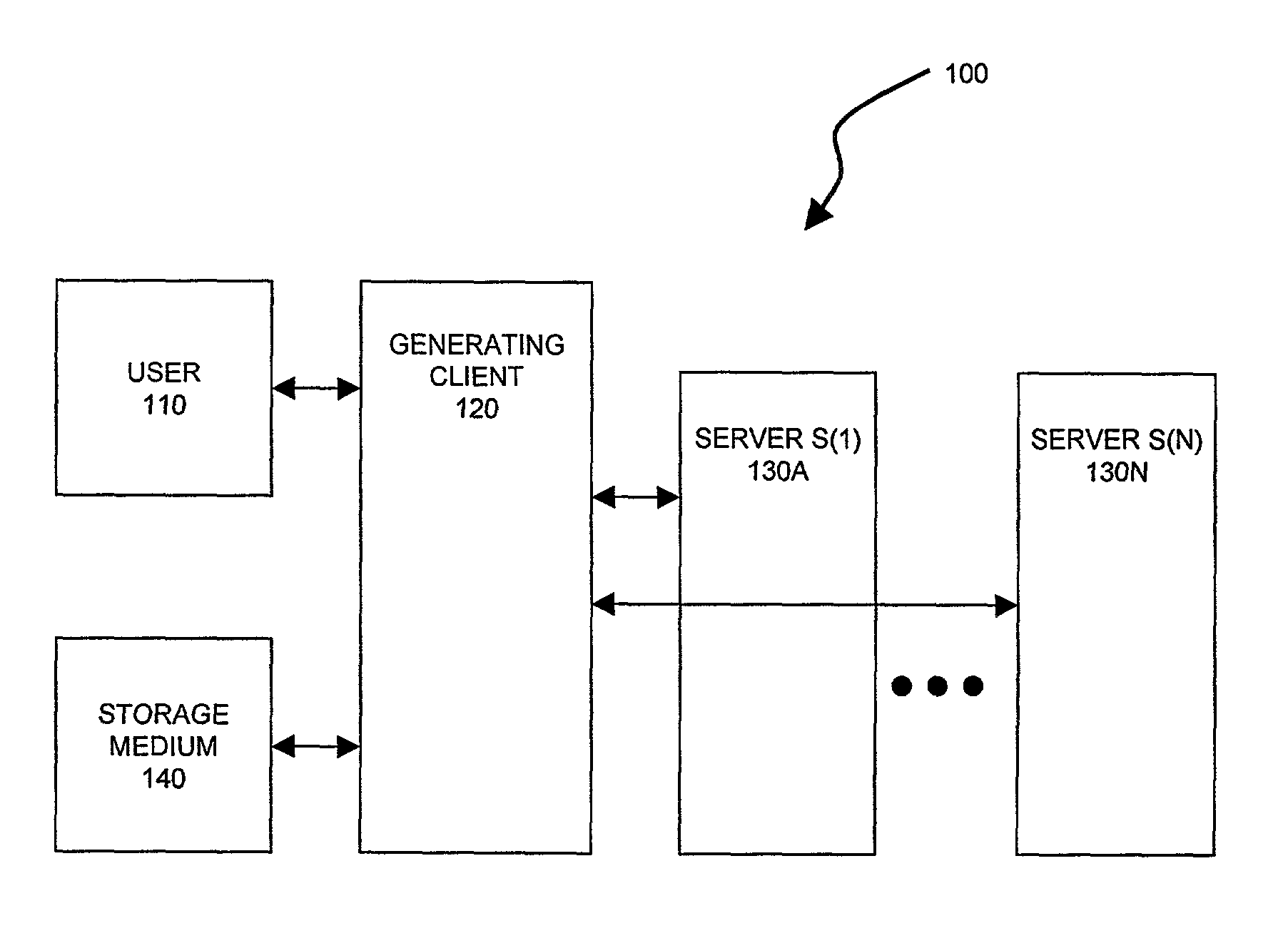
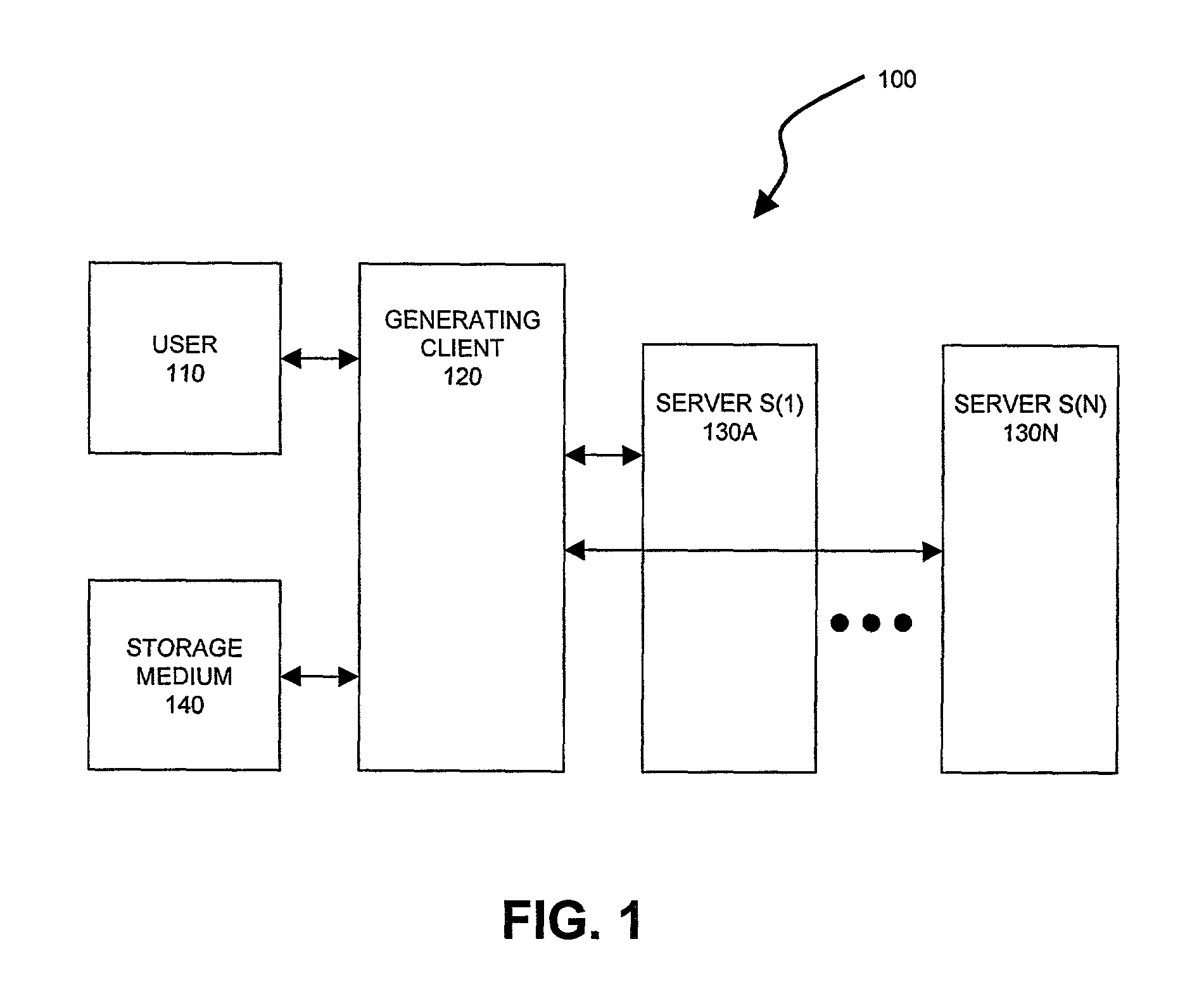
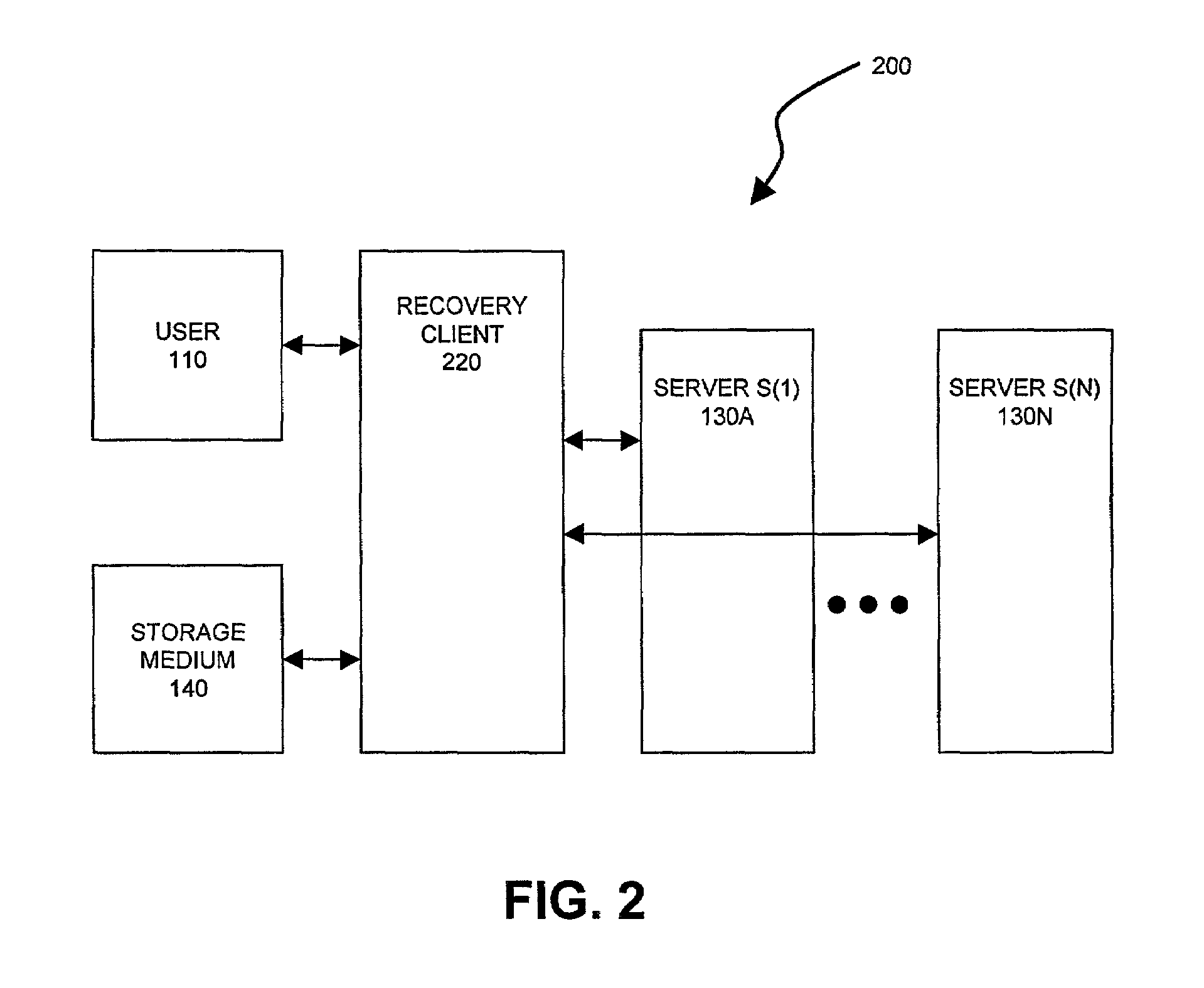
Server-assisted regeneration of a strong secret from a weak secret
InactiveUS7359507B2Resist attackKey distribution for secure communicationPublic key for secure communicationPasswordCipher
Methods for regenerating a strong secret for a user, based on input of a weak secret, such as a password, are assisted by communications exchanges with a set of independent servers. Each server holds a distinct secret value (i.e., server secret data). The strong secret is a function of the user's weak secret and of the server secret data, and a would-be attacker cannot feasibly compute the strong secret without access to both the user's weak secret and the server secret data. Any attacker has only a limited opportunity to guess the weak secret, even if he has access to all messages transmitted in the generation and regeneration processes plus a subset (but not all) of the server secret data.
Owner:RSA
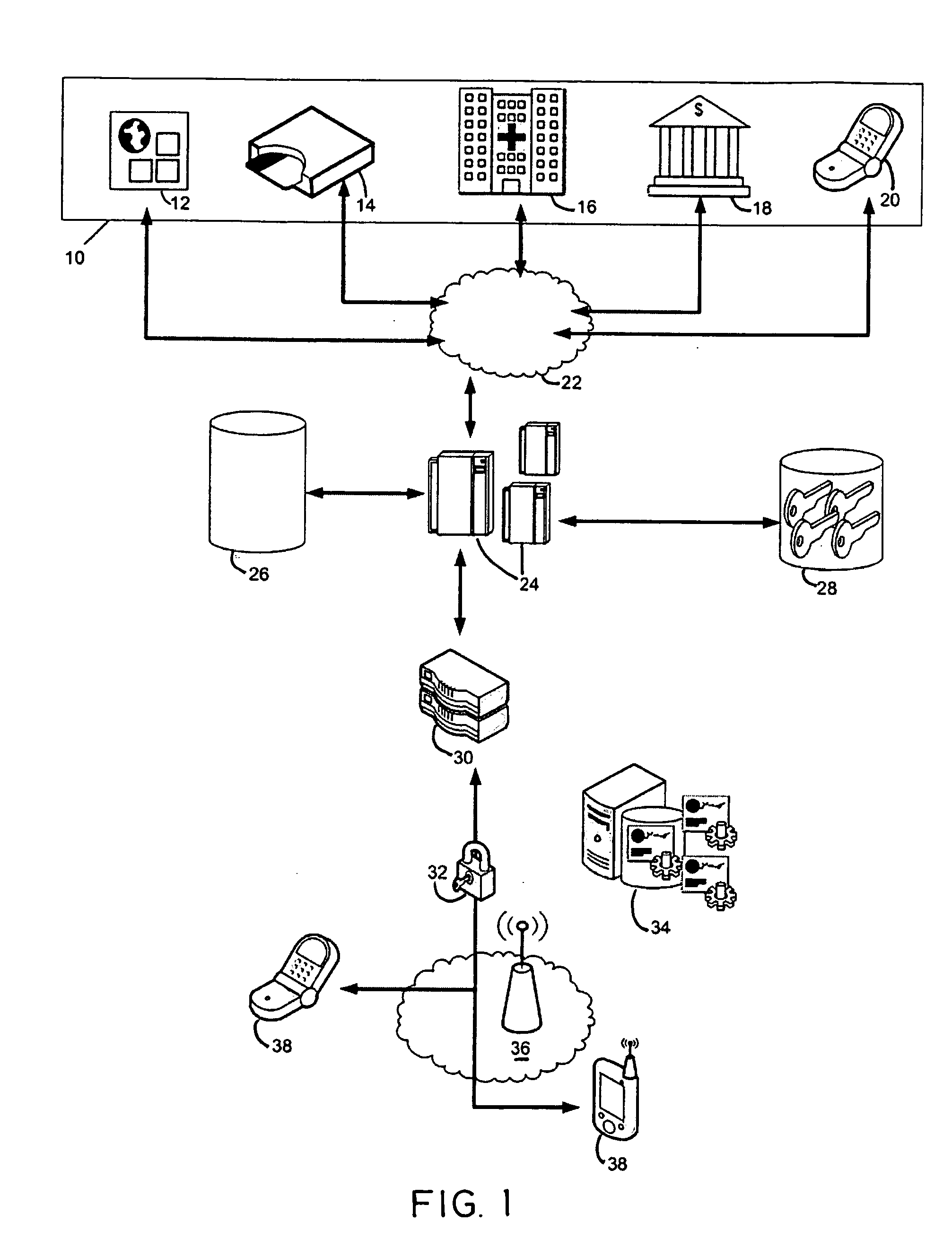
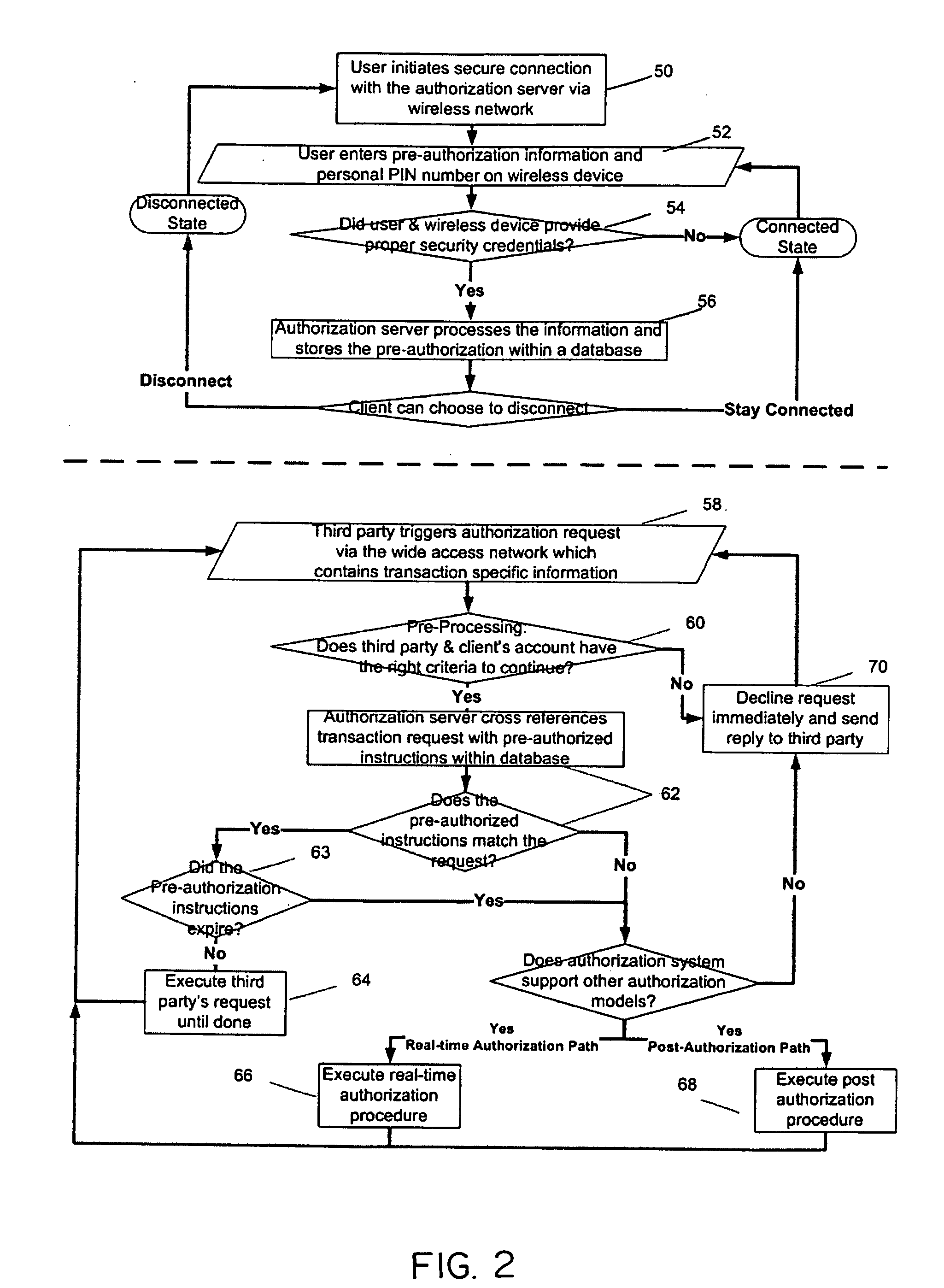
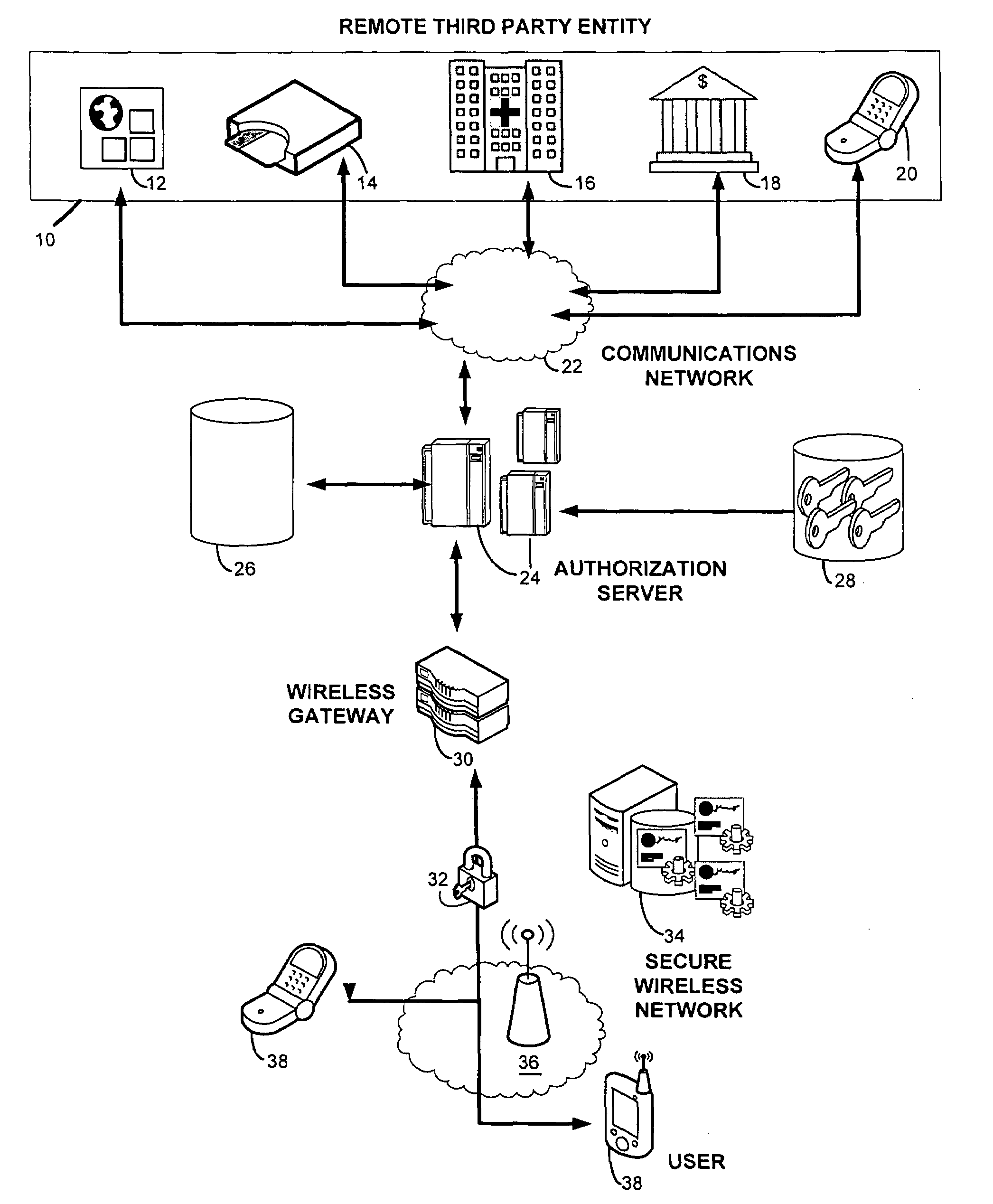
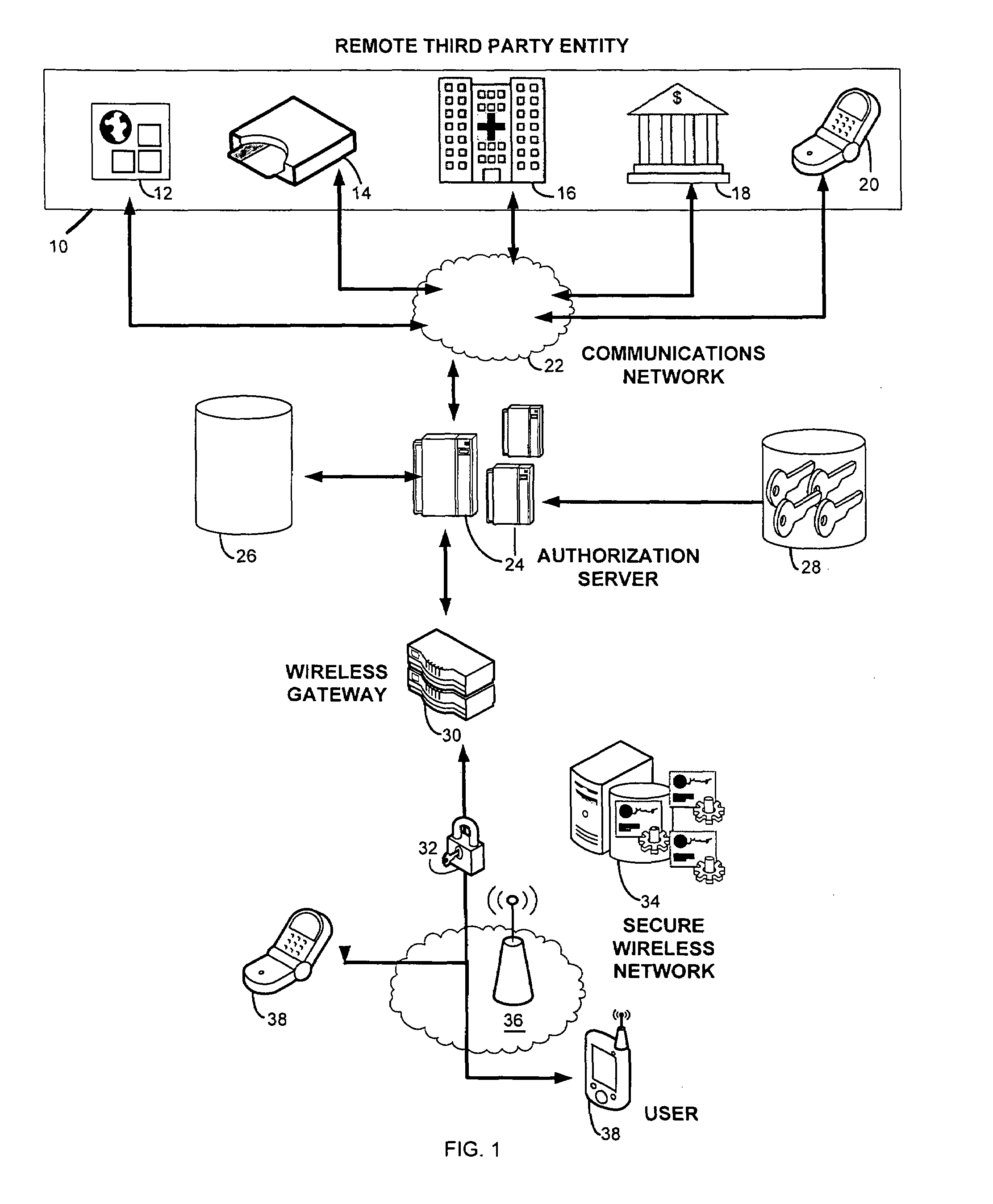
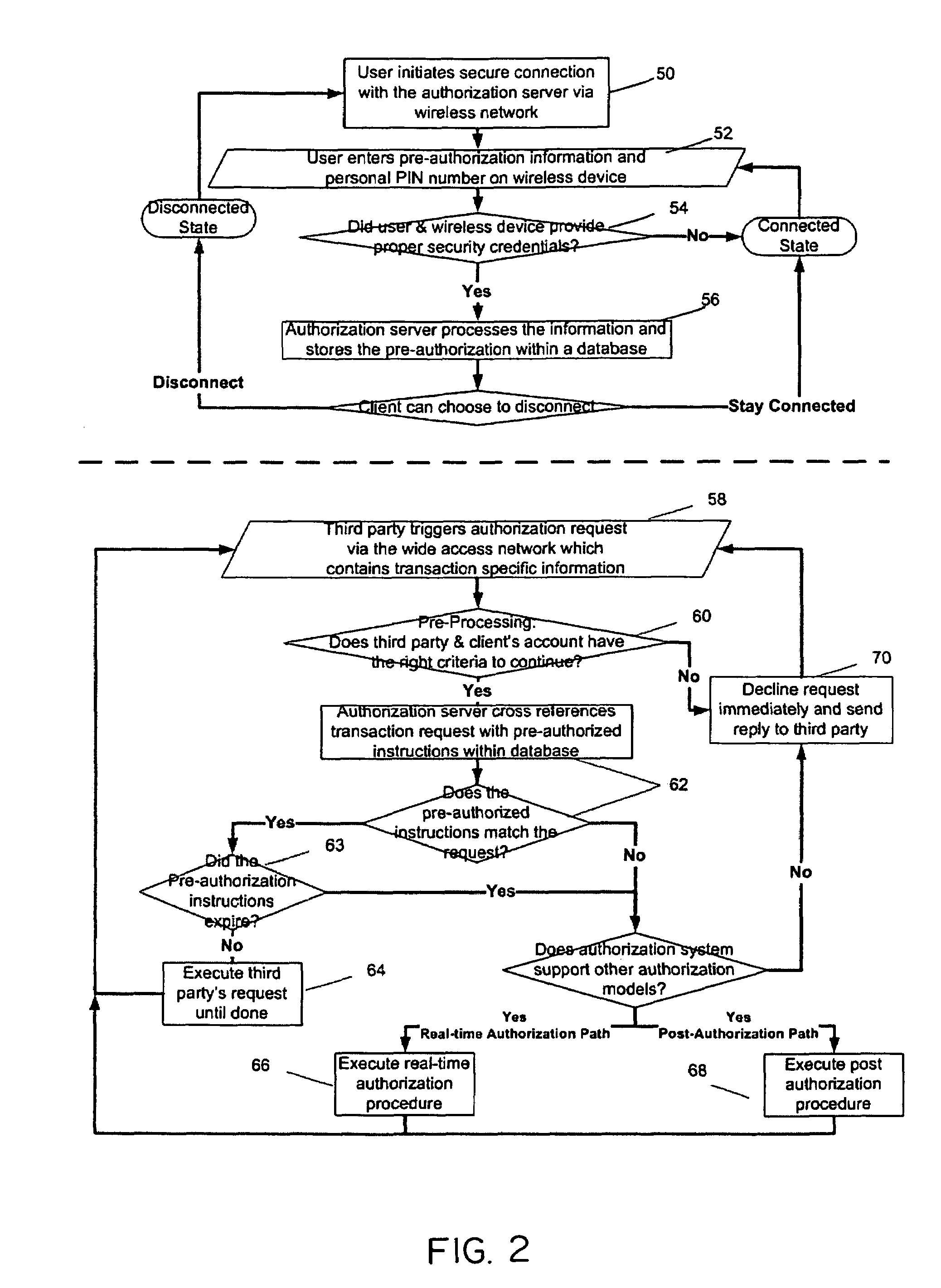
Secure wireless authorization system
ActiveUS20050184145A1Minimize the possibilityReduce financial costsFinanceUnauthorised/fraudulent call preventionThird partyAuthorization
The invention relates to a secure wireless authorization system by which a user can employ a wireless device to authorize a request that is initiated by a remote third party and transmitted to the user by an authorization server. The system includes the authorization server that is linked to the third party by way of a communications connection and a wireless device that is adapted to securely store an encryption scheme and create a secure authorization from the user in response to the third party request and has the ability to establish a secure wireless connection over which the secure authorization is transmitted from the user's wireless device to the authorization server. Pre-authorization, real-time authorization and post-authorization methods are disclosed by which user authorized transactions can be completed by way of the authorization system of this invention.
Owner:7611544 CANADA
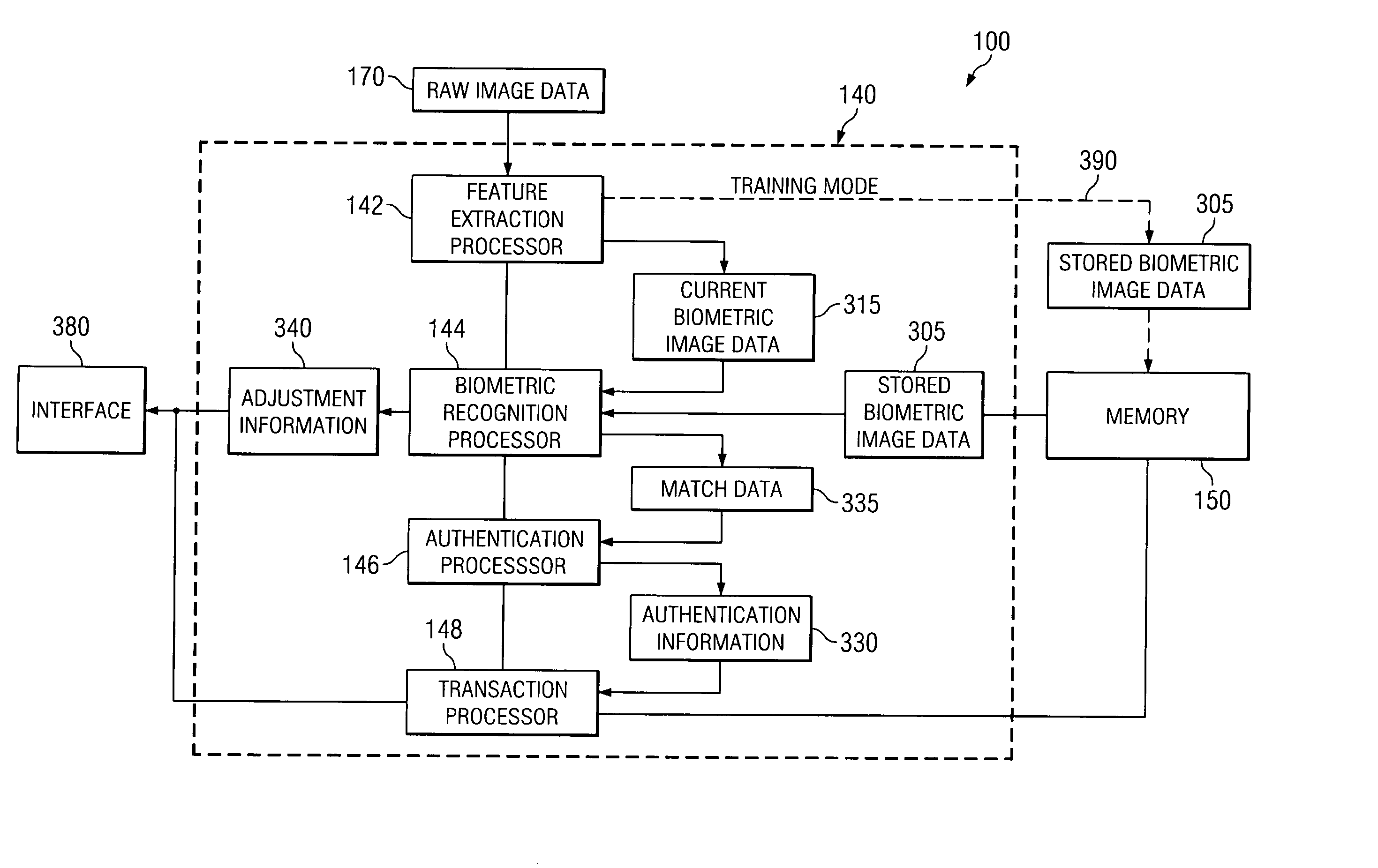
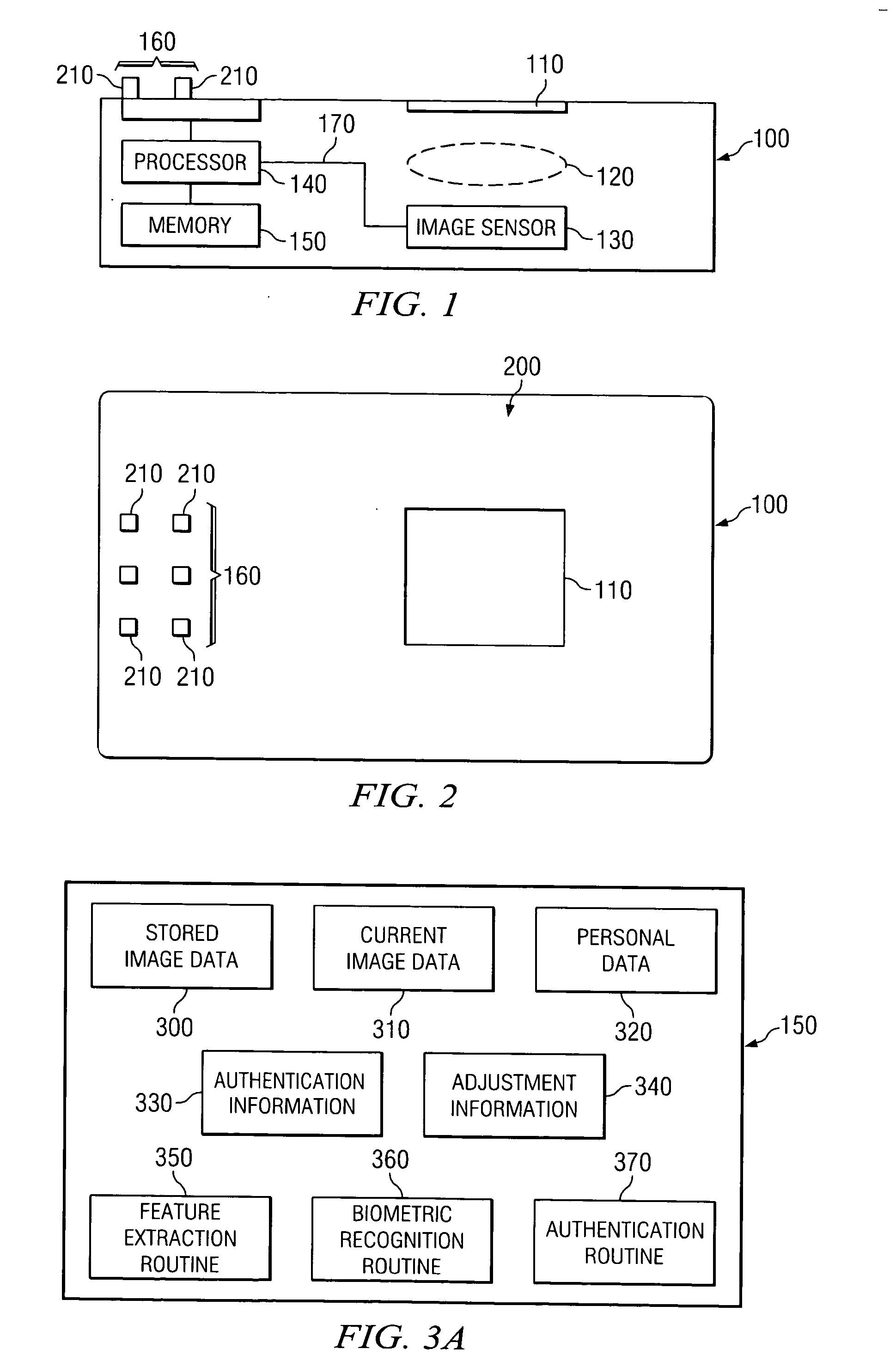
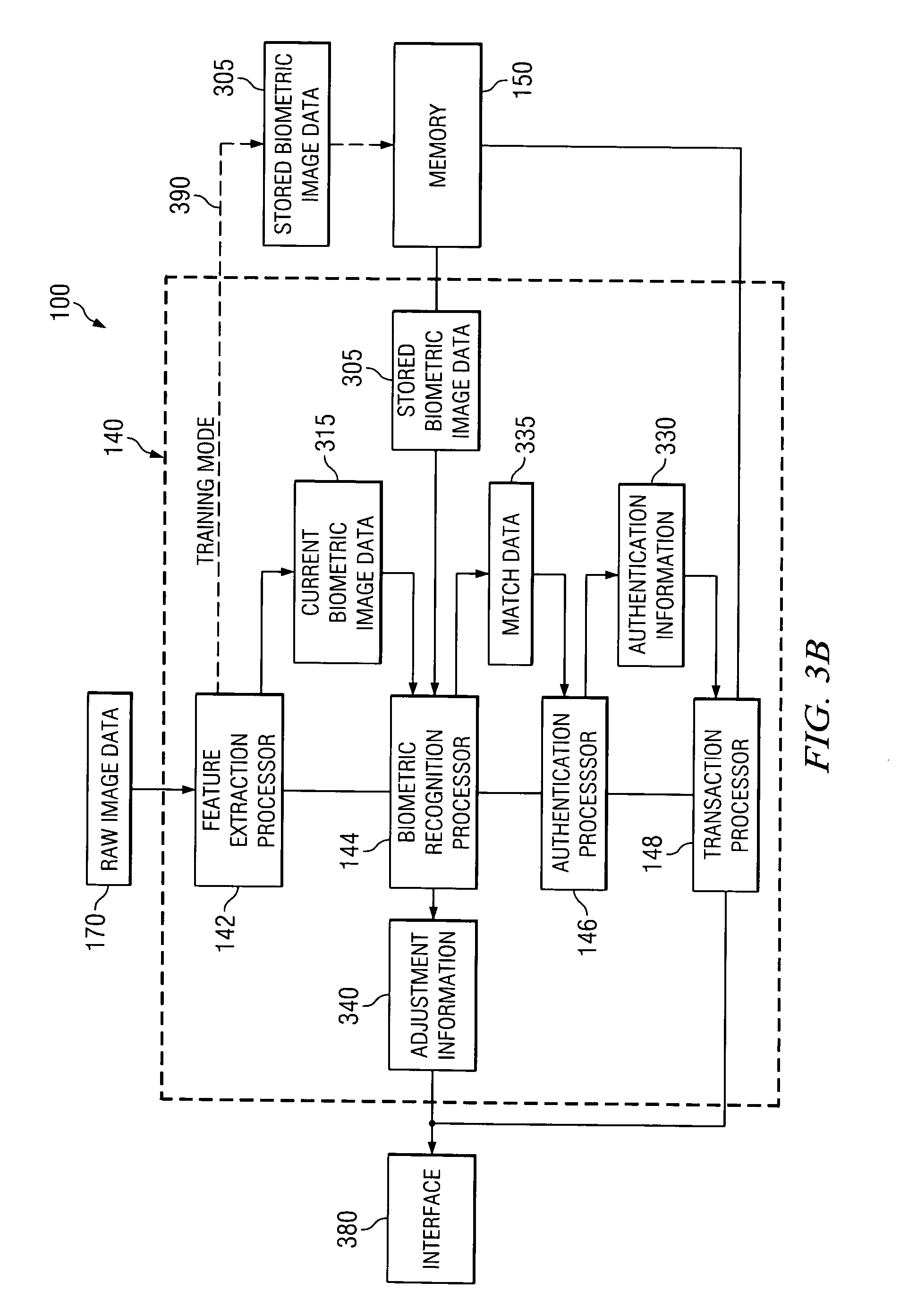
Biometric data card and authentication method
InactiveUS20050232471A1Accurate authenticationResist attackImage analysisBathroom accessoriesComputer hardwareBiometric data
A biometric data card includes an image sensor for capturing an image of a biometric feature of a user of the biometric data card and producing first image data representing the image. The biometric data card compares the first image data to second image data stored within the biometric data card to authenticate the user. The biometric data card is usable with a terminal including a slot for receiving the biometric data card. The terminal can further include an optical element optically coupled to direct the image onto the image sensor of the biometric data card.
Owner:AGILENT TECH INC
Secure wireless authorization system
ActiveUS7447494B2Theft is not still reducedEnsure safetyFinanceUnauthorised/fraudulent call preventionThird partyAuthorization
The invention relates to a secure wireless authorization system by which a user can employ a wireless device to authorize a request that is initiated by a remote third party and transmitted to the user by an authorization server. The system includes the authorization server that is linked to the third party by way of a communications connection and a wireless device that is adapted to securely store an encryption scheme and create a secure authorization from the user in response to the third party request and has the ability to establish a secure wireless connection over which the secure authorization is transmitted from the user's wireless device to the authorization server. Pre-authorization, real-time authorization and post-authorization methods are disclosed by which user authorized transactions can be completed by way of the authorization system of this invention.
Owner:7611544 CANADA
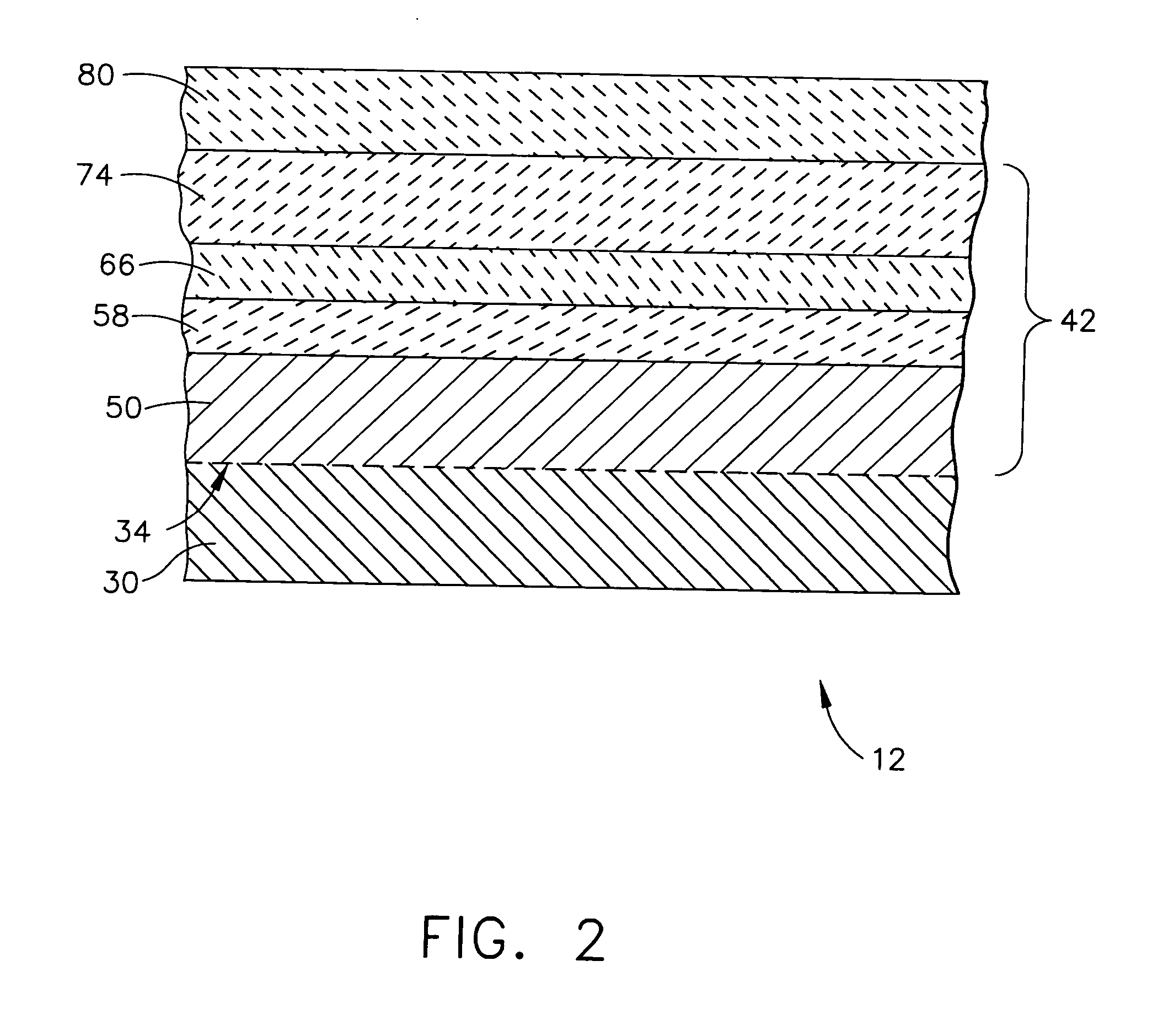
Corrosion resistant sealant for outer EBL of silicon-containing substrate and processes for preparing same
InactiveUS20060280954A1More resistant to environmental attackResist attackMolten spray coatingBlade accessoriesAluminateMetallurgy
An article comprising a silicon-containing substrate, an environmental barrier coating (EBC) overlying the substrate, wherein the EBC comprises a higher metal silicate-containing outer barrier layer; and a corrosion resistant alumina / aluminate sealant for the higher metal silicate-containing outer barrier layer. A process is also provided for forming a corrosion resistant alumina / aluminate sealant layer over the higher metal silicate-containing outer barrier layer. Also provided is an alternative process for treating a porous higher metal silicate-containing outer barrier layer with a liquid composition comprising an corrosion resistant alumina / aluminate sealant precursor to infiltrate the porous higher metal silicate-containing outer barrier layer with the alumina / aluminate sealant precursor in an amount sufficient to provide, when converted to the corrosion resistant alumina / aluminate sealant, protection of the environmental barrier coating against environmental attack; and converting the infiltrated alumina / aluminate sealant precursor within the porous higher metal silicate-containing outer barrier layer to the corrosion resistant alumina / aluminate sealant.
Owner:GENERAL ELECTRIC CO
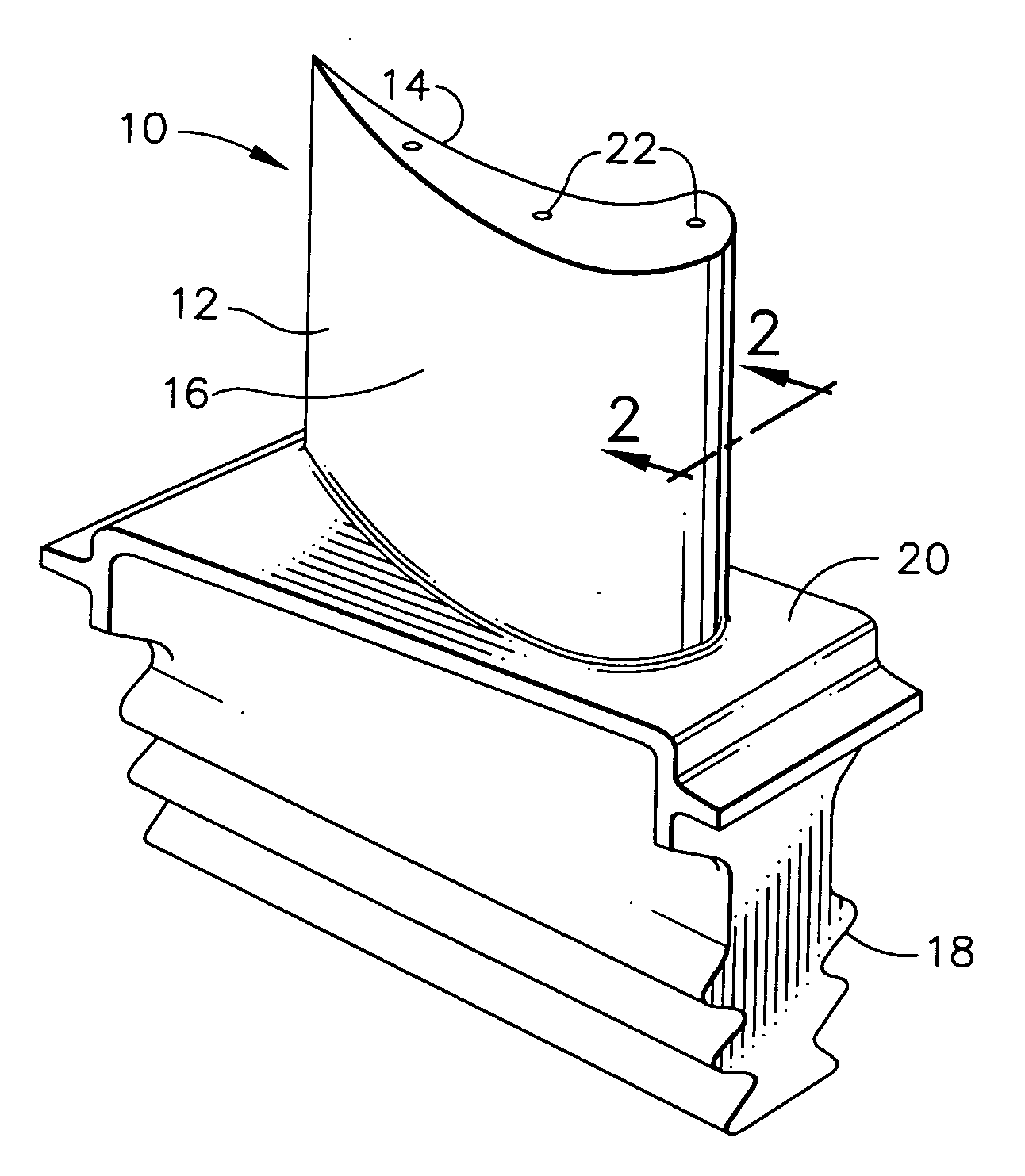
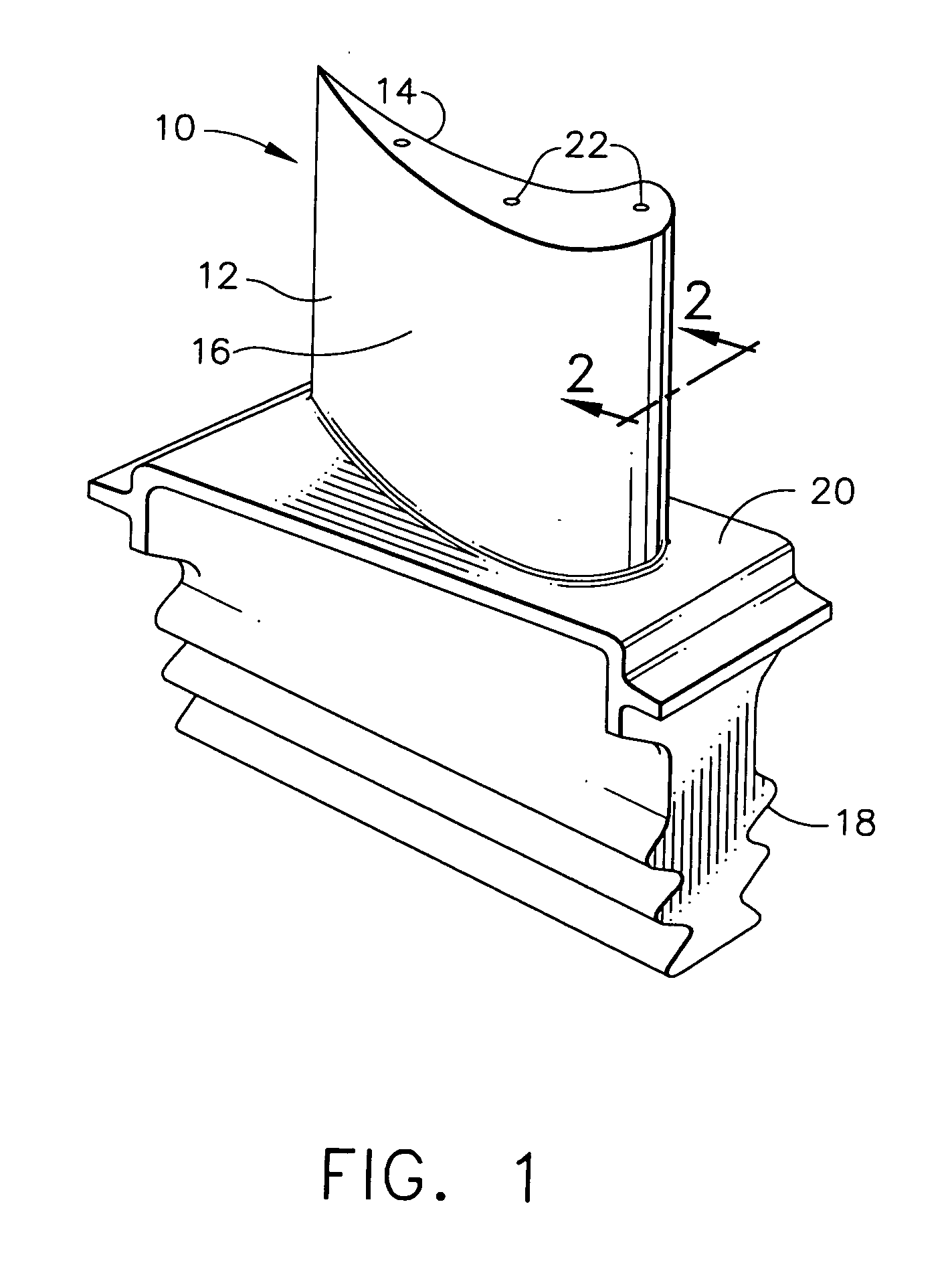
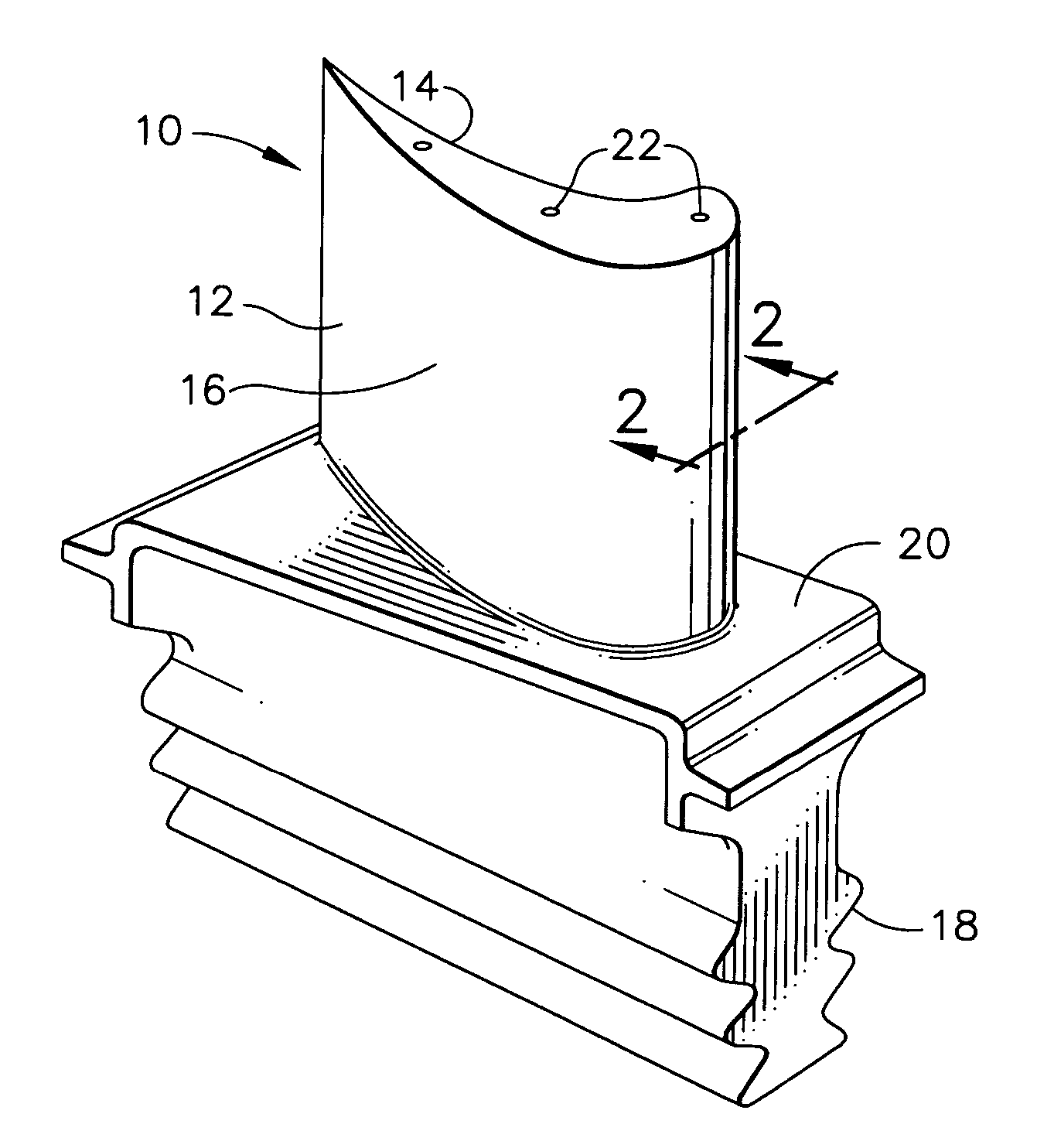
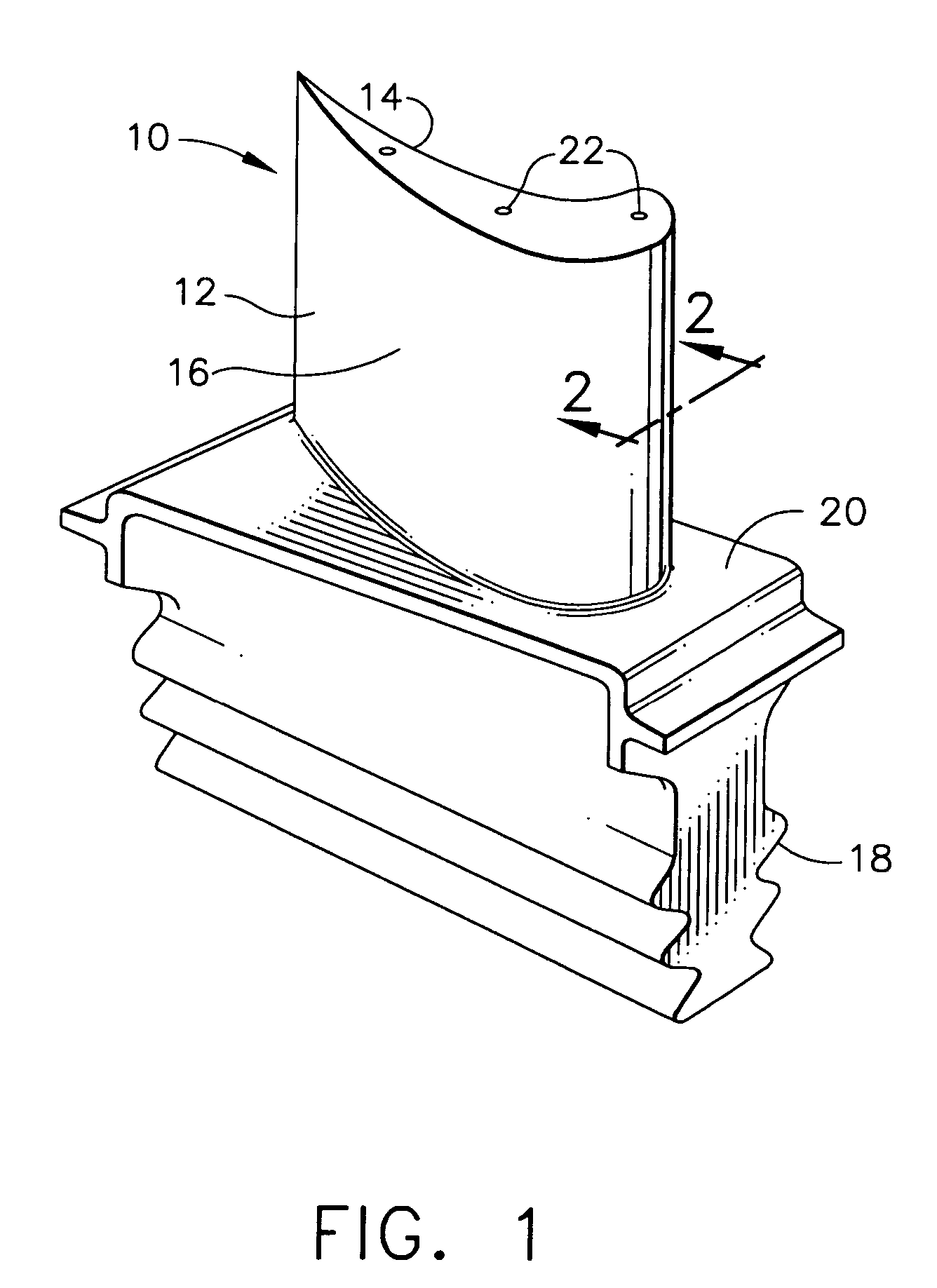
Lightweight ballistic resistant rigid structural panel
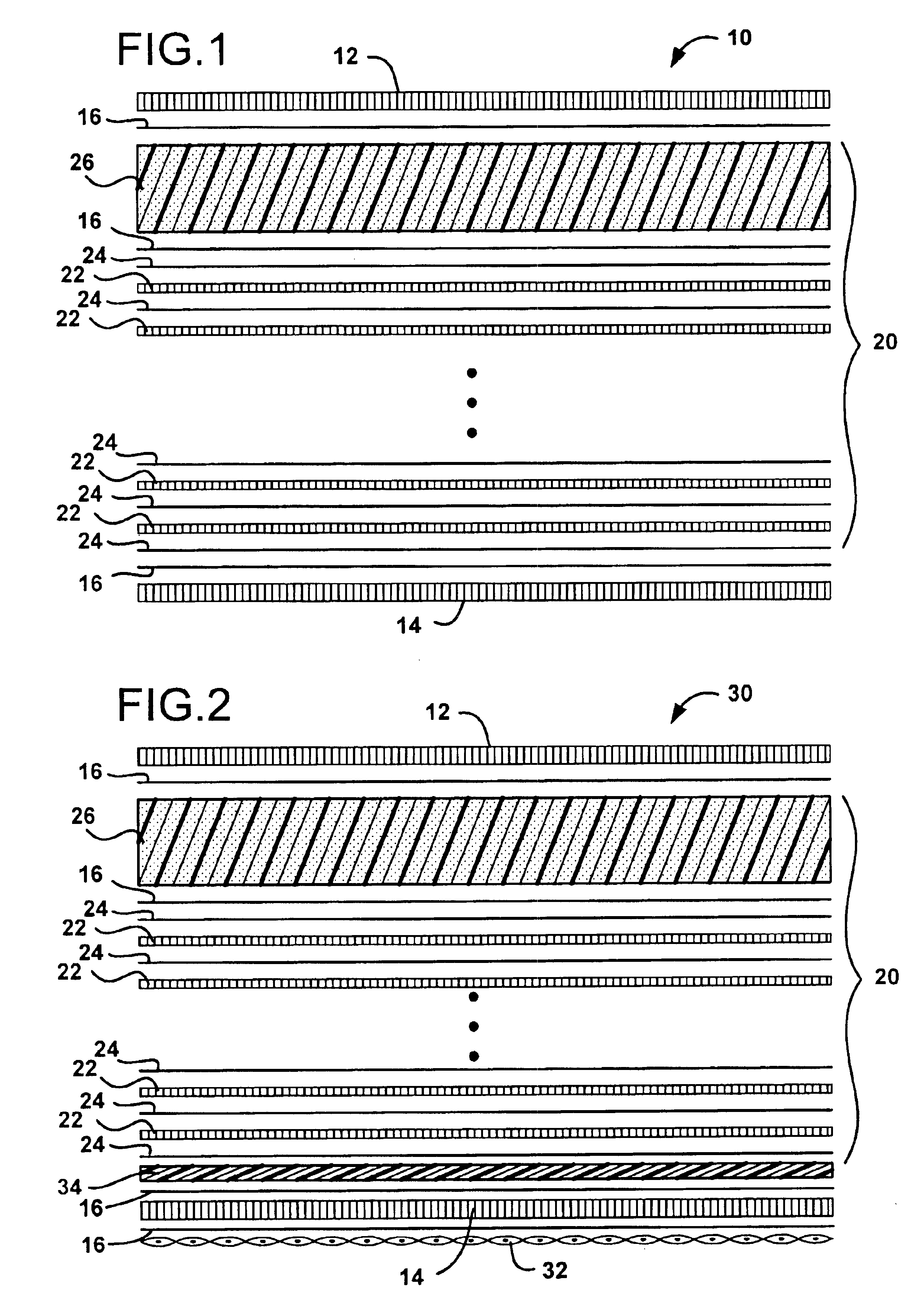
InactiveUS6825137B2Without sacrificing ballistic resistanceImprove fatigueFuselage framesFuselage bulkheadsAdhesiveEngineering
A lightweight ballistic resistant rigid structural panel especially for use in aircraft interiors is disclosed. The rigid structural panel is made up of a core layer including a plurality of sheets of flexible, high-tensile strength fabric interleaved with a plurality of sheets of a thermal-fusible film adhesive, and a sheet of cushioning material adhered to the plurality of sheets of flexible, high-tensile strength fabric. Fiber-reinforced face skins are adhered to exterior surfaces of the panel core for structural strength and rigidity. The rigid structural panel is capable of resisting ballistic attack from handguns and like weapons, while maintaining a high degree of strength and rigidity.
Owner:NORDISK AVIATION PRODS A S
Porcine circovirus 2 type inactivated vaccine
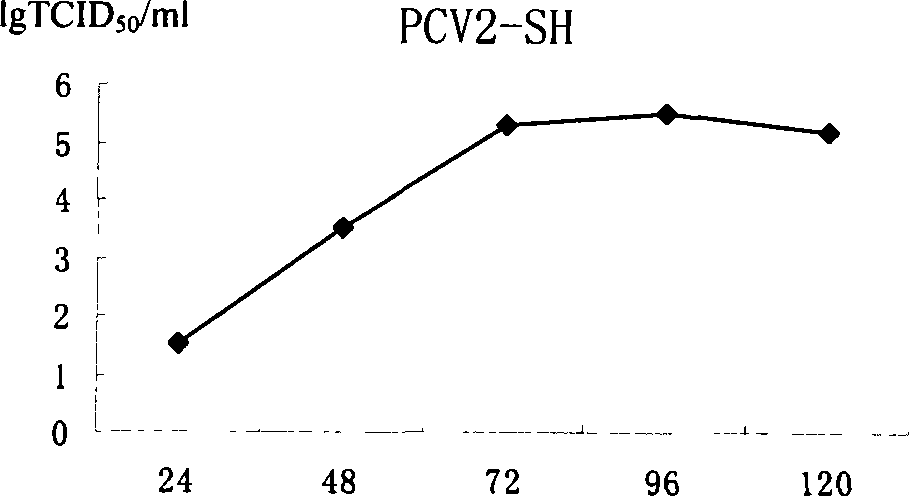
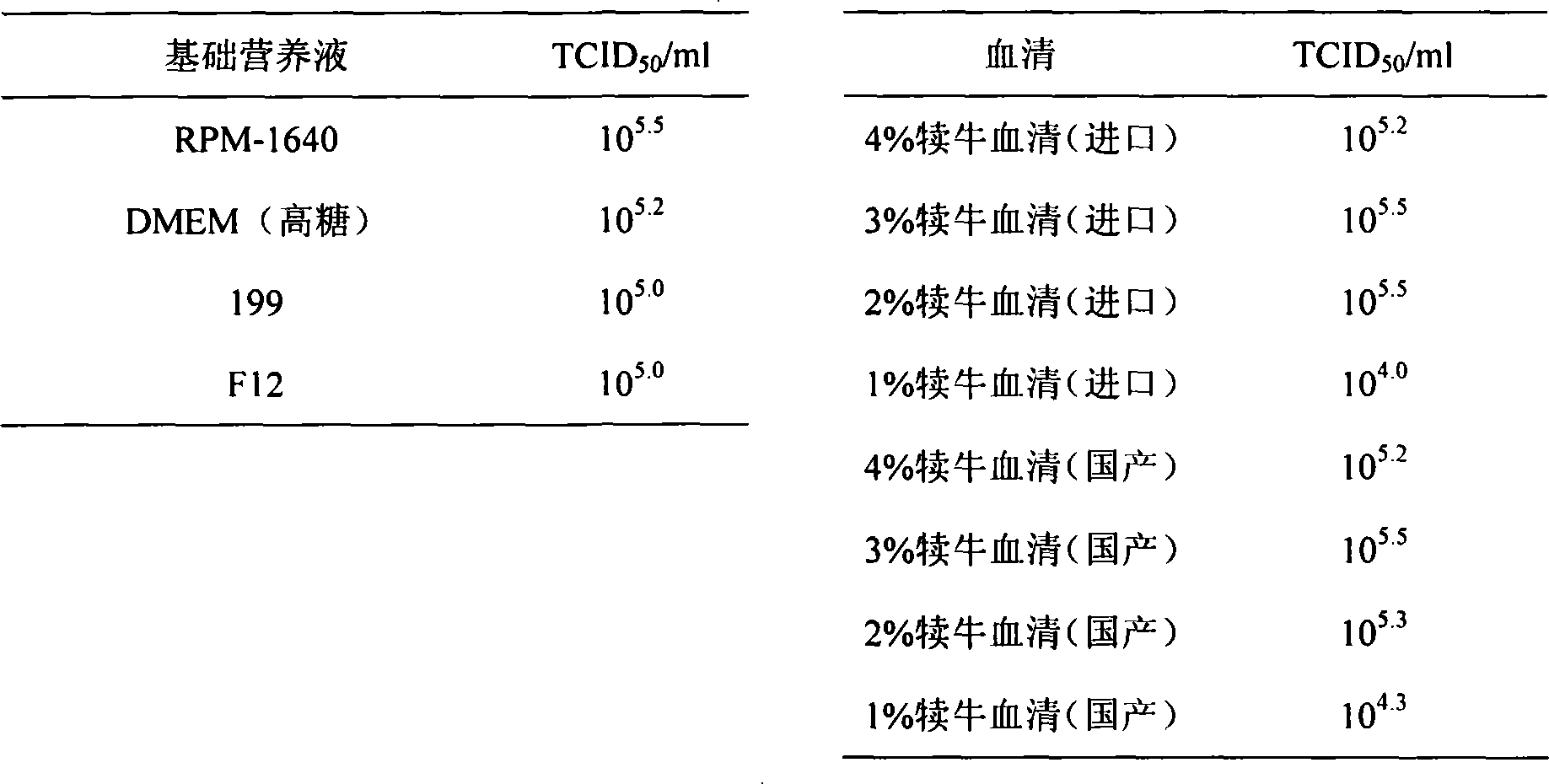
InactiveCN101240264ASimple processEasy to operateViral antigen ingredientsMicroorganism based processesAdjuvantVaccine Production
The pig circular ring virus 2 type (PVC2) inactivated vaccine (SH individual plant) of the invention belongs to biotechnology field. The pig circular ring virus 2 type poisonous individual plant SH belongs to circular ring virus section circular ring virus genus which has been preserved in Wuhan institute of virology, Chinese academy of sciences. The shanghai separated individual plant SH of purified PCV2 virus is obtained by gathering raw material from hogpen which happened bad weaning piglet multisystem exhaustion failure syndrome in Shanghai in 2002 year, separating, appraising and purifying virus. The PCV2-SH plant is proliferated in mass in PK-15 cell, inactivated through methyl aldehyde and emulsified with liquid paraffine adjuvant to prepare conventional liquid paraffin(e) adjuvant immunomodulators for vaccines. The laboratory has trial-manufactured five lots vaccines successfully which are good safety and also can induce pig bring immune protection effect, made out a draft rules for vaccines production and testing. The inactivated vaccine proved by every aspects experiment has met state biological products standard completely.
Owner:NANJING AGRICULTURAL UNIVERSITY
Searchable encryption method based on Chinese in cloud environment
ActiveCN105681280ASearchable implementationSearchable encryption implementationTransmissionSpecial data processing applicationsDocument preparationSearch function
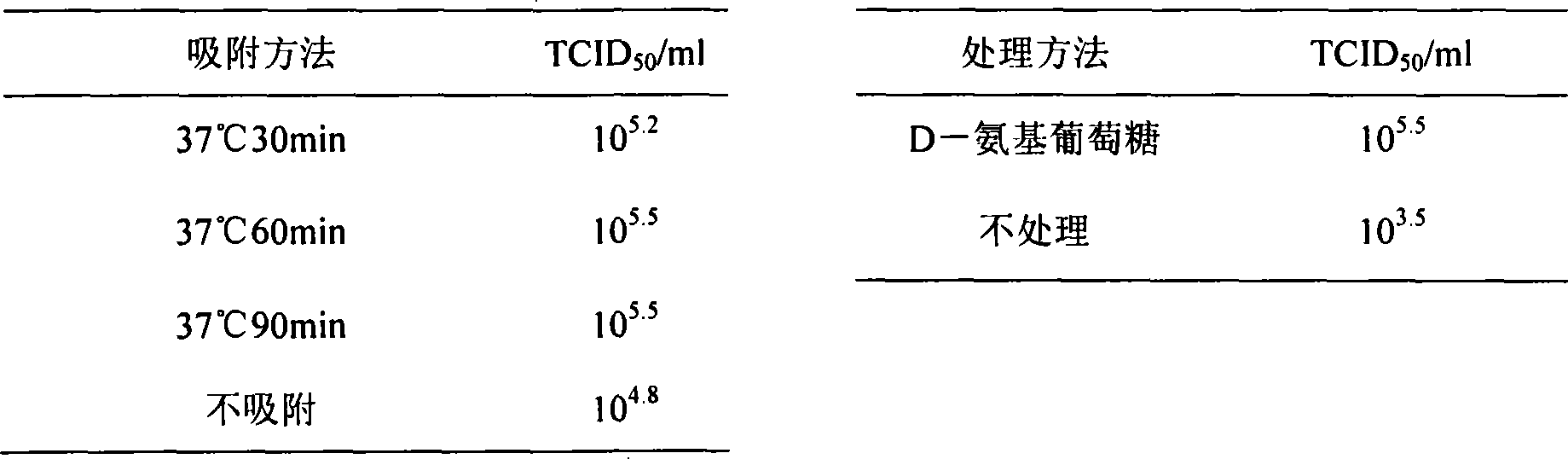
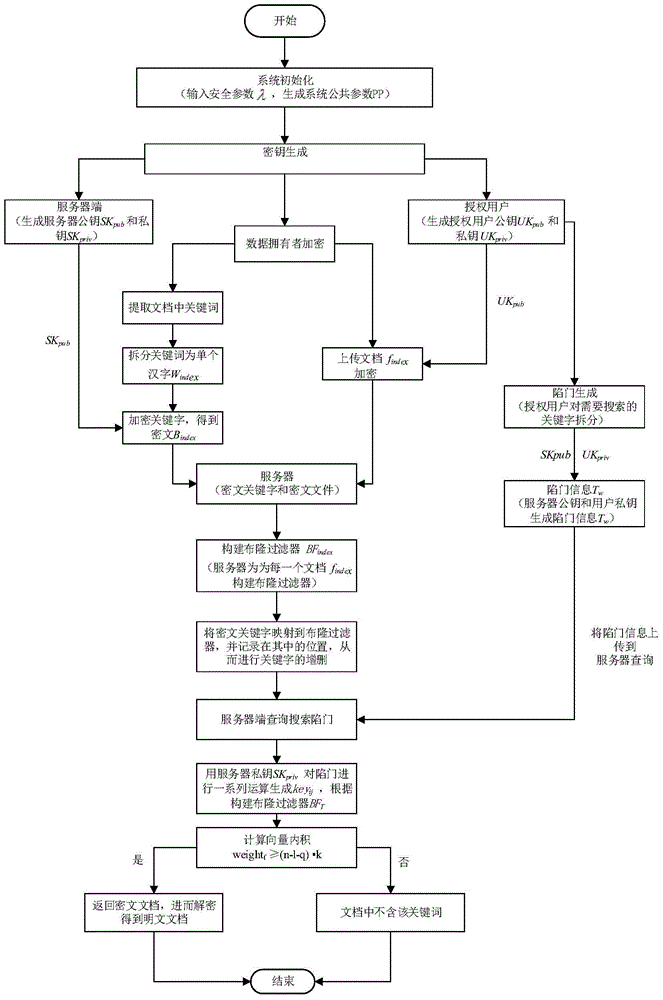
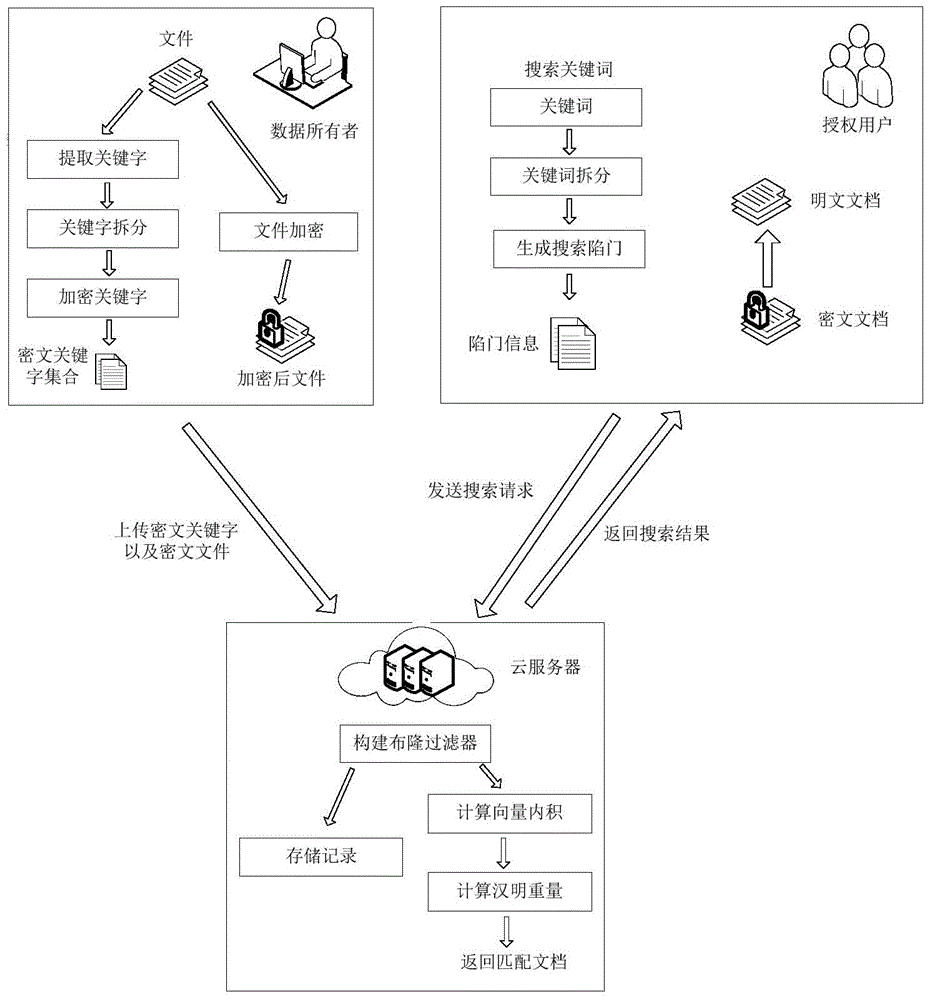
The invention discloses a searchable encryption method based on Chinese in a cloud environment. A dynamic searchable encryption scheme is finished based on the features of a PEKS scheme and a Bloom filter; a ciphertext search function is finished in an insecure channel; fuzzy keyword search based on a public key searchable encryption scheme is supported; multi-keyword search of the Chinese is supported; the keywords in a document are dynamically added or deleted; according to the method provided by the invention, an inner product operation is carried out through constructing a search vector and a file vector so as to finish a fuzzy search matching function; the similarity weight of the keywords in the document and the keywords of a search trap door is calculated through importing the vectors; the ciphertext search function and the fuzzy keyword search function are realized; the ciphertext keywords can be securely transmitted on a public channel in adoption of a server and user double-key pair mode; in application of a hash function and a pseudo-random function, through the scheme, the keyword selection attack can be resisted effectively; and the ciphertext is searched under a condition that the cloud server is semi-trusted.
Owner:XIDIAN UNIV
Watermarking and fingerprinting digital content using alternative blocks to embed information
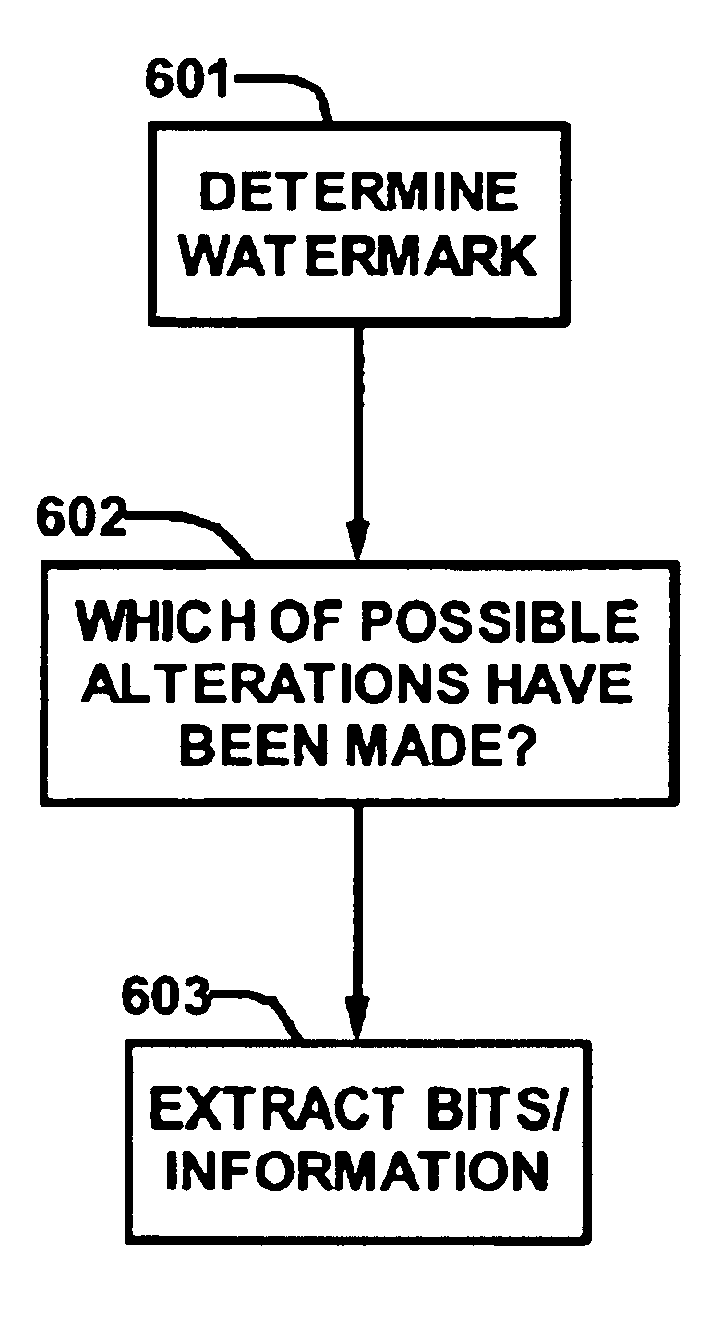
InactiveUS7003131B2Resist attackSimple to implementOther printing matterCharacter and pattern recognitionFingerprintDigital content
A method of embedding information in digital content representing media streams. The method includes (1) selecting a set of locations within that digital content reprensenting the media stream to embed information, (2) selecting a set of possible alterations to make at those locations, and (3) making a subset of the possible alterations. The set of locations and possible alterations is herein sometimes called a “watermark.” The subset of actual alterations that are made is herein sometimes called a “fingerprint.” The method determines a set of locations at which there are alternative versions of digital content representing the same media stream, such as one being the original and one being an alternative version of the same digital content, herein sometimes called the “original movie” and the “alt-movie,” or herein sometimes called the “original block” and the “alt-block” for a particular block in the digital content representing the media stream.
Owner:KALEIDESCAPE
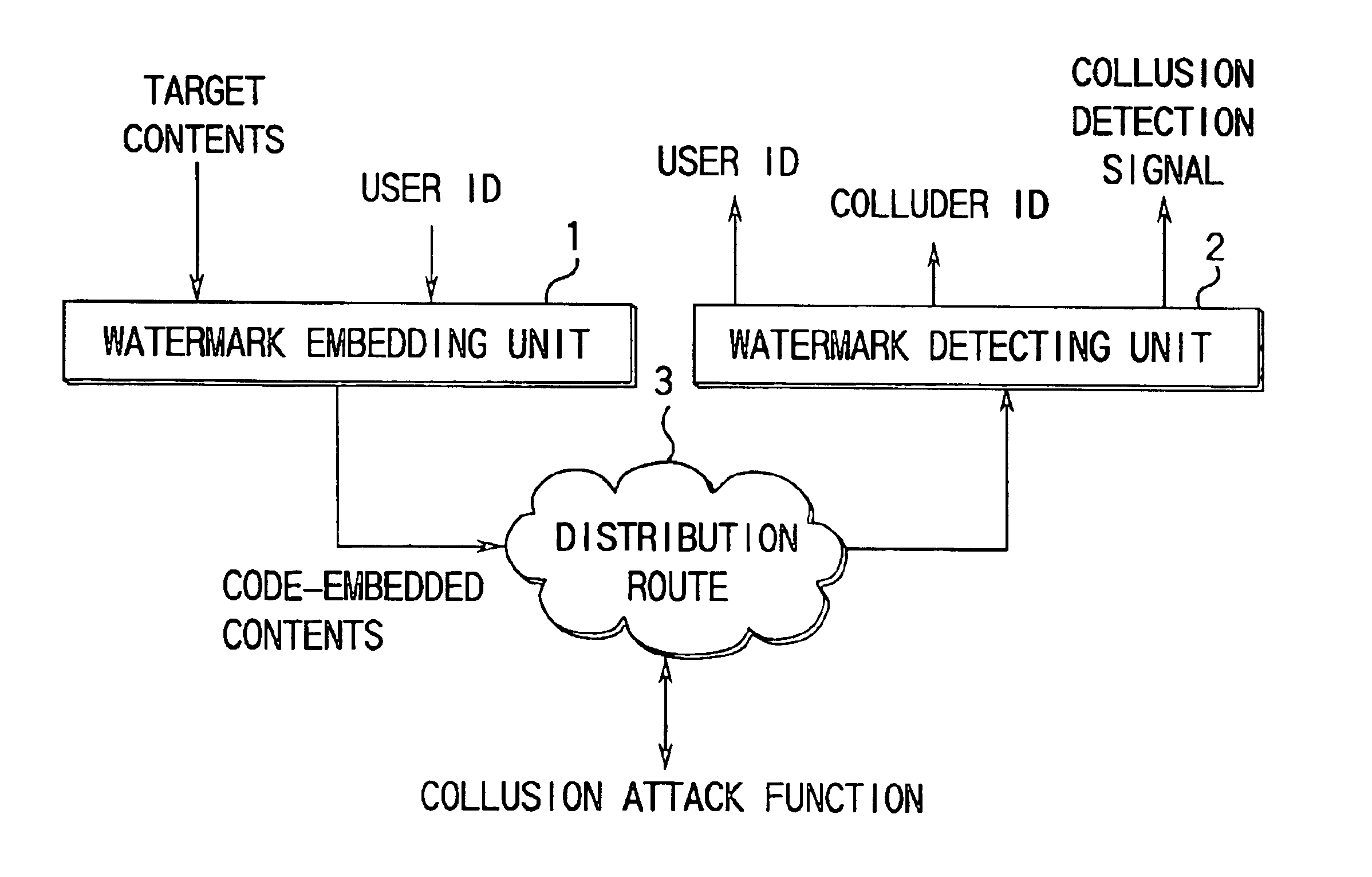
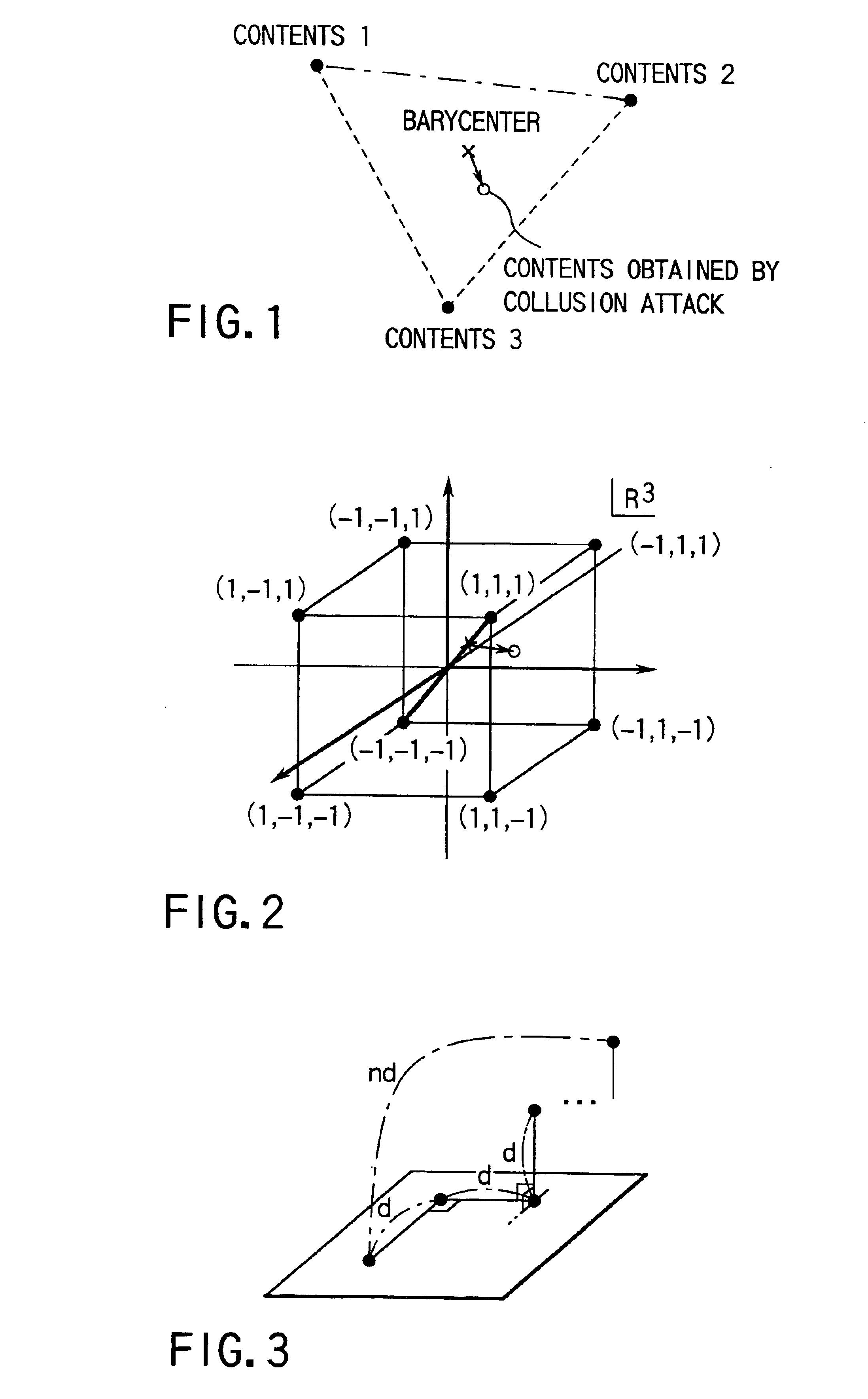
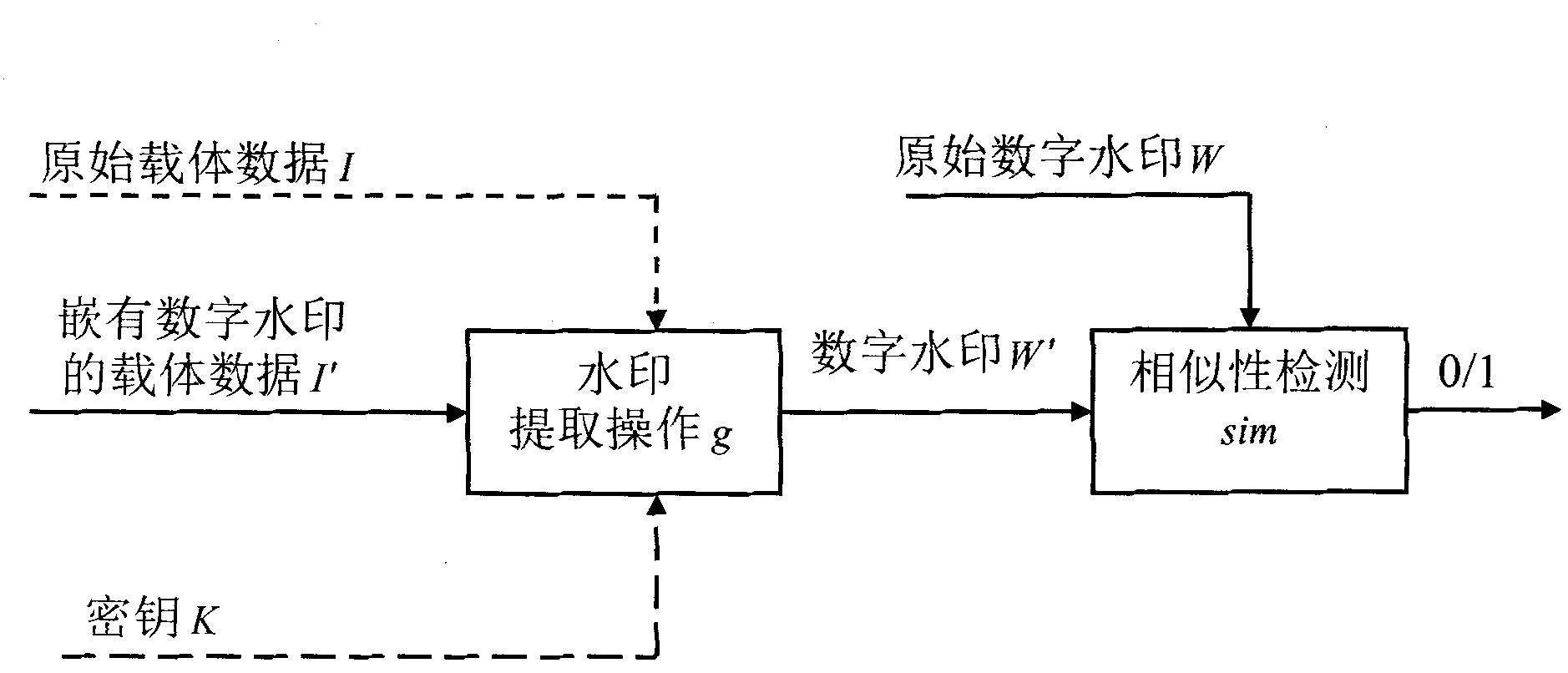
Code generating method and unit thereof, code detecting method and unit thereof, and watermark embedding unit and watermark detecting unit
InactiveUS6901515B1Deterioration can be suppressedResist attackPulse modulation television signal transmissionDigital data processing detailsComputer architectureUser identifier
Residue calculating sections respectively obtain residues which take a plurality of integers as modulus, with respect to a user ID. The plurality of integers are stored in modulus storage sections and are prime to each other. Based on these residues and parameters stored in a coding parameter storage section, component codes constructed by continuous sequences of 1 and 0 using a predetermined number of bits as a unit are respectively generated by component code generating sections. These component codes are concatenated by a concatenating section, thereby to obtain a code to be embedded, which constructs watermark information.
Owner:KK TOSHIBA
System and method for perennial distributed back up
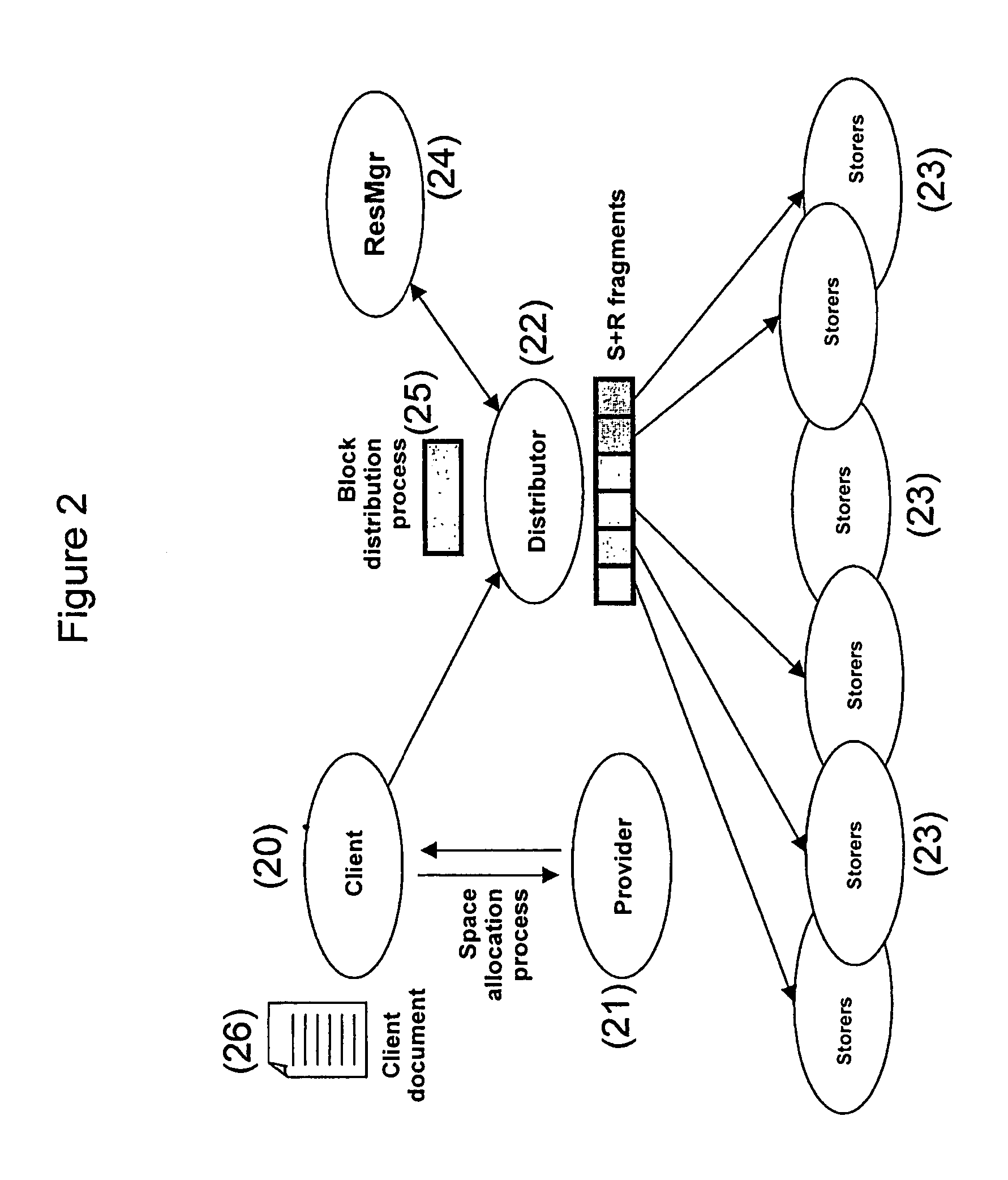
InactiveUS20080005334A1Resist attackImprove networkingError detection/correctionData switching by path configurationDistributed hash tableDigital data
The invention relates to computer networks and to a digital data protection thereon, in particular to a method for the distributed backup of a digital data block (B) in an computer network comprising a DHT distributed hash table and at least one node NO, wherein said NO nodes are connected to said network. The inventive method consists in dividing said block B into digital data r fragments F, in storing the fragment F in the NOF resource memories, in recording couples (block B, node NOF) and (node NOF, fragment F) in the DHT parts contained in at least two nodes and in a centralised server when no operation on the DHT or storage operation is carried out during said process.
Owner:UGLOO +1
IP address jump safety communication method based on SDN framework
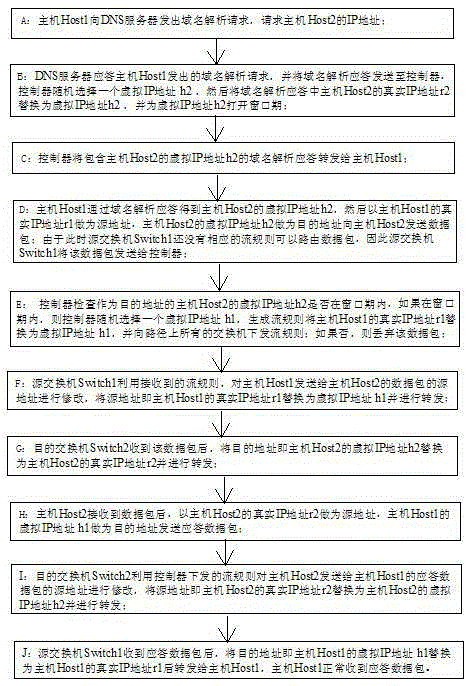
InactiveCN105429957AIncrease attack difficultyRealize IP hoppingData switching networksDomain nameSafety Communications
The invention discloses an IP address jump safety communication method based on an SDN framework. The method comprises steps that A, an IP address of a Host2 is requested by a Host1; B, a real IP address r2 of the Host2 is replaced by a virtual IP address h2 through a controller; C, a domain analysis response is forwarded by the controller to the Host1; D, an r1 is taken as a source address and the h2 is taken as a target address by the Host1 to send a data packet to the Host2; E, a flow rule is generated by the controller to replace the r1 by a virtual IP address h1, and the flow rule is issued; F, the r1 is replaced by the h1 through the source switch, and forwarding is carried out; G, the h2 is replaced by the r2 through the target switch, and forwarding is carried out; H, the r2 is taken as a source address and the h1 is taken as a target address by the Host2 to send a response data packet; I, the r2 is replaced by the h2 through the target switch, and forwarding is carried out; J, the h1 is replaced by the r1 through the source switch, and forwarding to the Host1 is carried out. Through the method, jump IPs can be dynamically distributed to a host computer in the IPH network, one-time one-change access to the host computer IP is transparently realized, attack based on scanning and DDoS attach can be effectively fought against.
Owner:芦斌
Corrosion resistant sealant for EBC of silicon-containing substrate and processes for preparing same
InactiveUS20060280955A1More resistant to environmental attackResist attackMolten spray coatingBlade accessoriesAluminateSealant
An article comprising a silicon-containing substrate, an environmental barrier coating (EBC) overlying the substrate, wherein the EBC comprises an outer alkaline earth aluminosilicate barrier layer; and a corrosion resistant alumina / aluminate sealant for the outer barrier layer. A process is also provided for forming a corrosion resistant alumina / aluminate sealant layer over the outer barrier layer of the EBC. Also provided is an alternative process for treating a porous outer barrier layer with a liquid composition comprising an corrosion resistant alumina / aluminate sealant precursor to infiltrate the porous outer barrier layer with the alumina / aluminate sealant precursor in an amount sufficient to provide, when converted to the corrosion resistant alumina / aluminate sealant, protection of the environmental barrier coating against environmental attack; and converting the infiltrated alumina / aluminate sealant precursor within the porous outer barrier layer to the corrosion resistant alumina / aluminate sealant.
Owner:GENERAL ELECTRIC CO
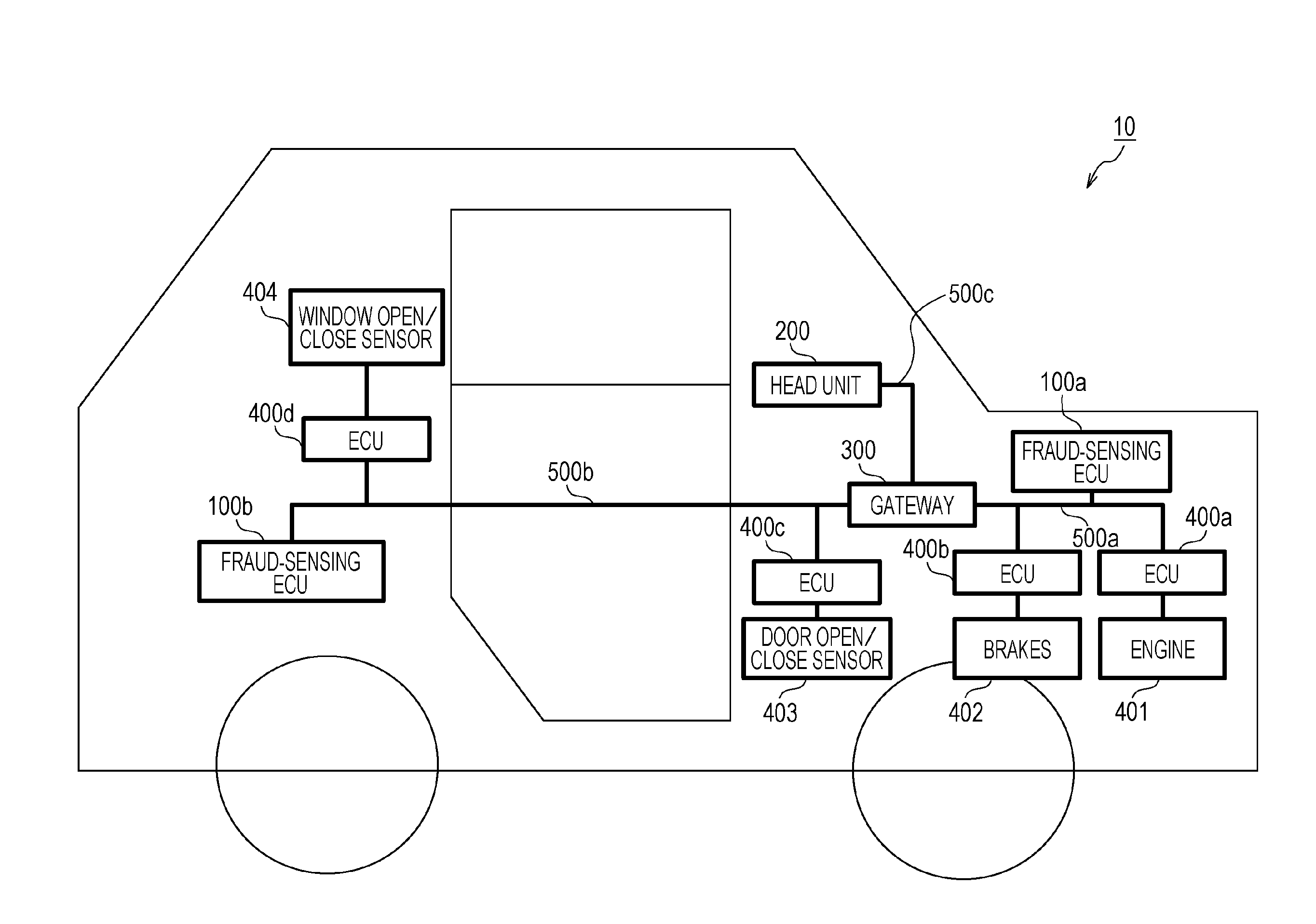
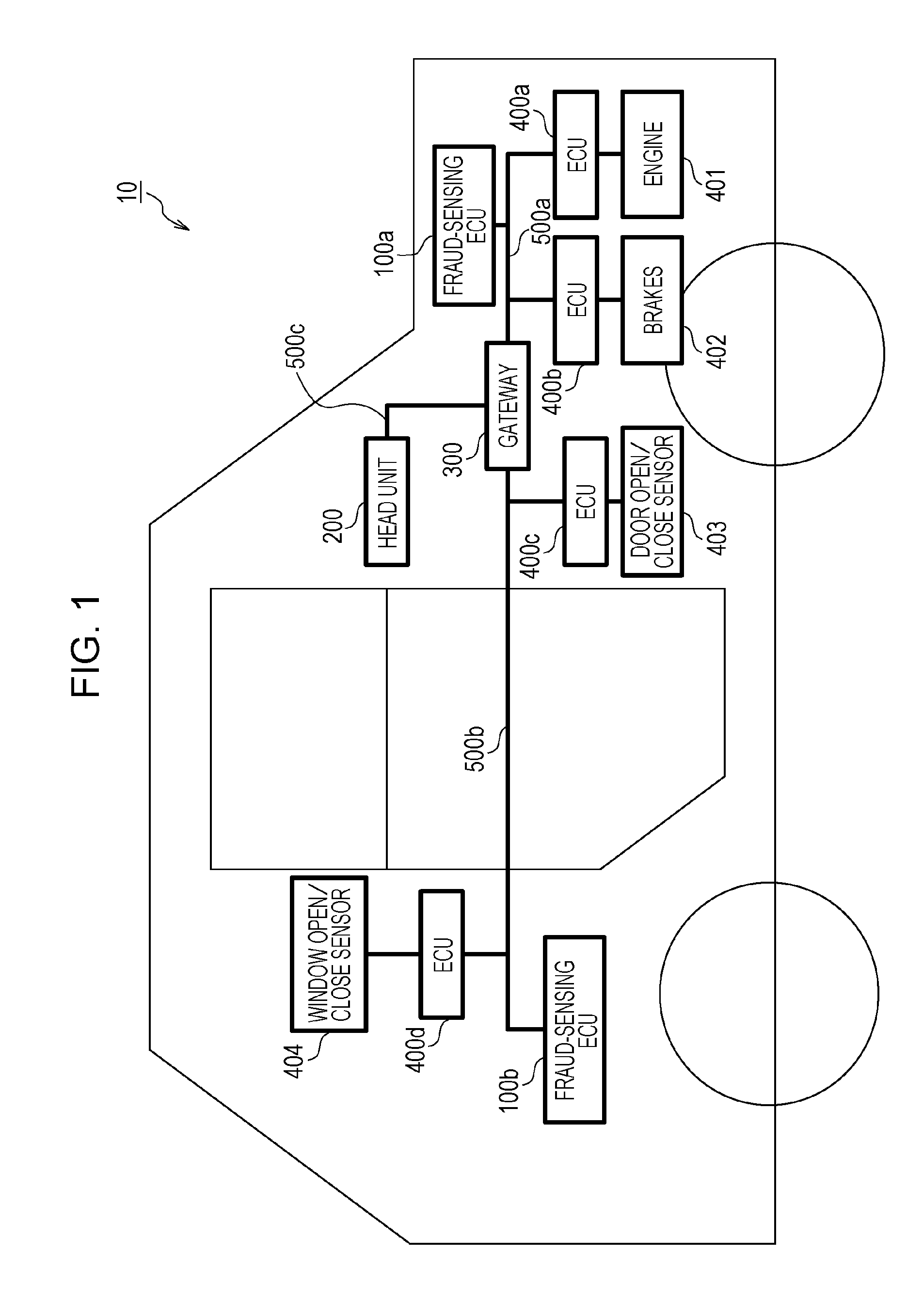
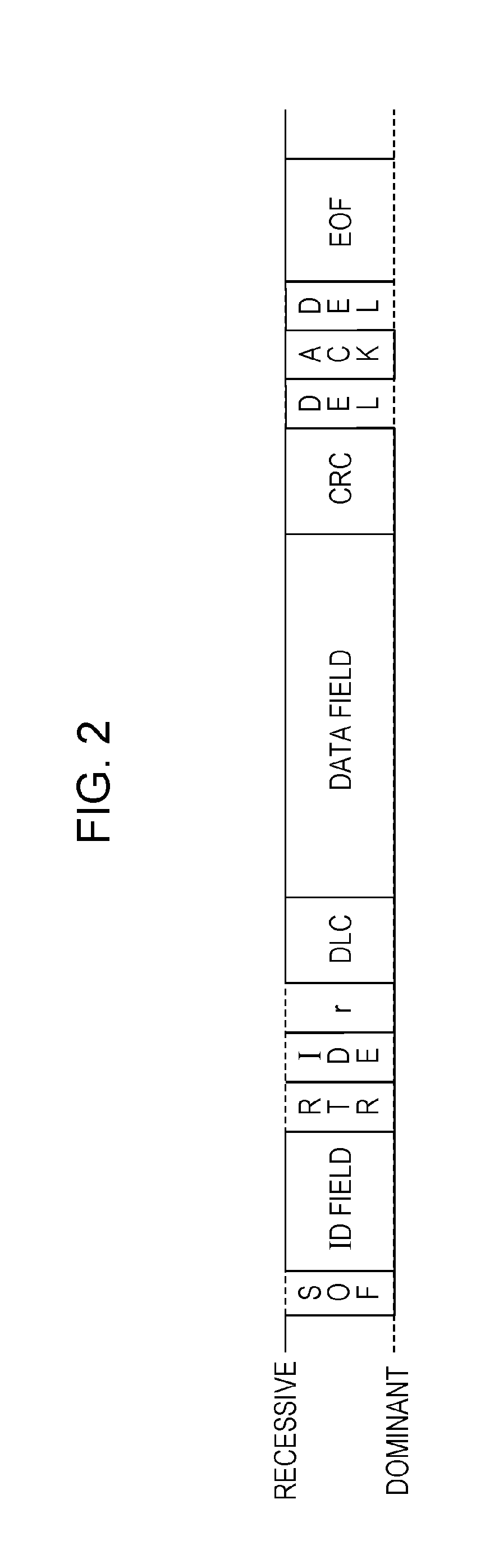
Method for handling transmission of fraudulent frames within in-vehicle network
ActiveUS20160297401A1Improve the immunityAccurate processingAnti-theft devicesSecuring communicationIn vehicleMessage authentication code
An anti-fraud method for use in an in-vehicle network system including a plurality of electronic control units that exchange data frames, each having added thereto a message authentication code (MAC), via at least one bus includes: receiving a data frame transmitted on the bus; generating a first MAC by using a MAC key and a value of a counter that counts the number of times a data frame having added thereto a MAC is transmitted; in a case where the verification has failed, (i) generating as second MAC by using an old MAC key; (ii) re-verifying that the received data frame has added thereto the generated second MAC; transmitting, in a case where the re-verification has succeeded, via the bus a key-update frame indicating a request for updating the MAC key; and updating the MAC key in response to the transmission of the key-update frame.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
Apparatus and method for inputting user password
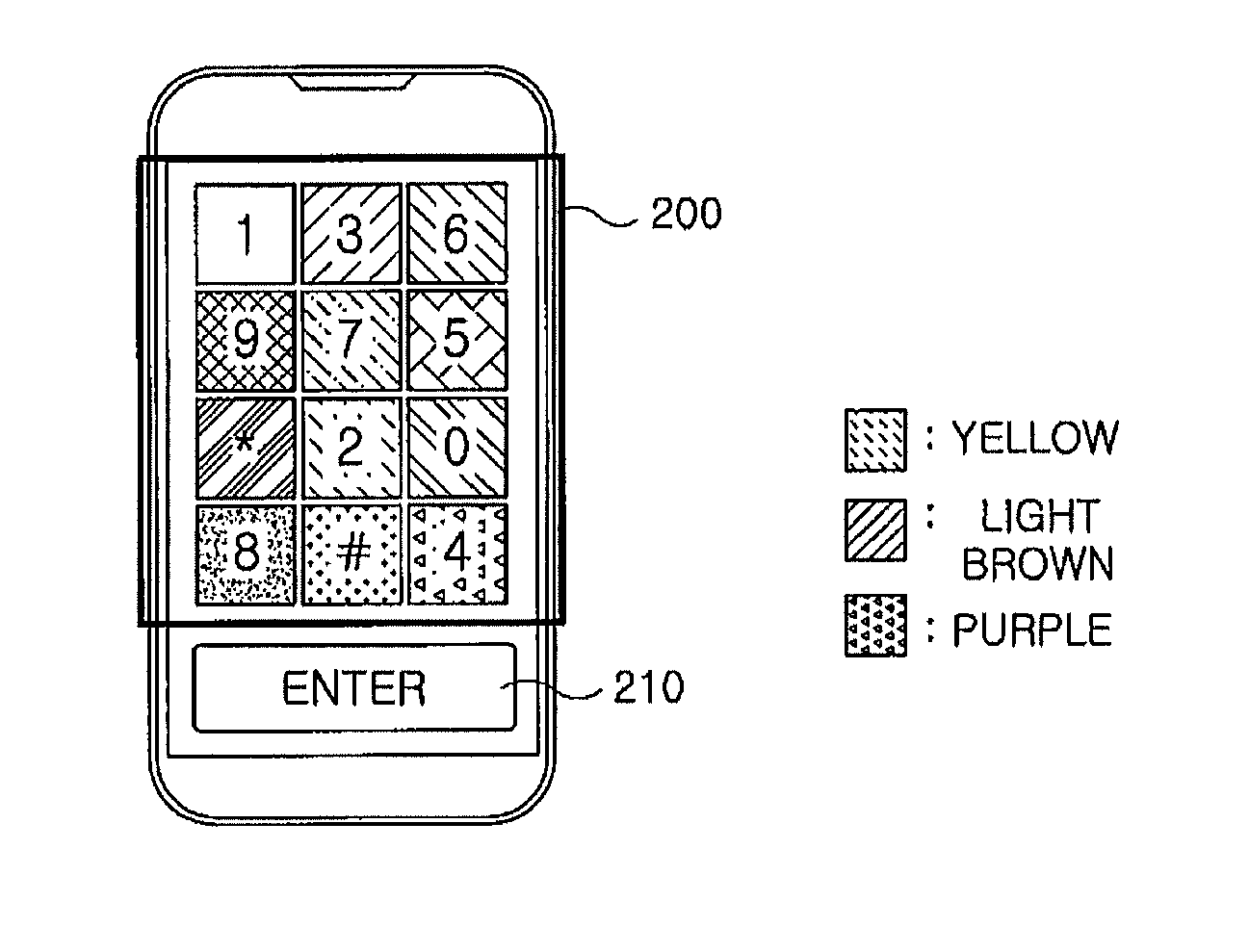
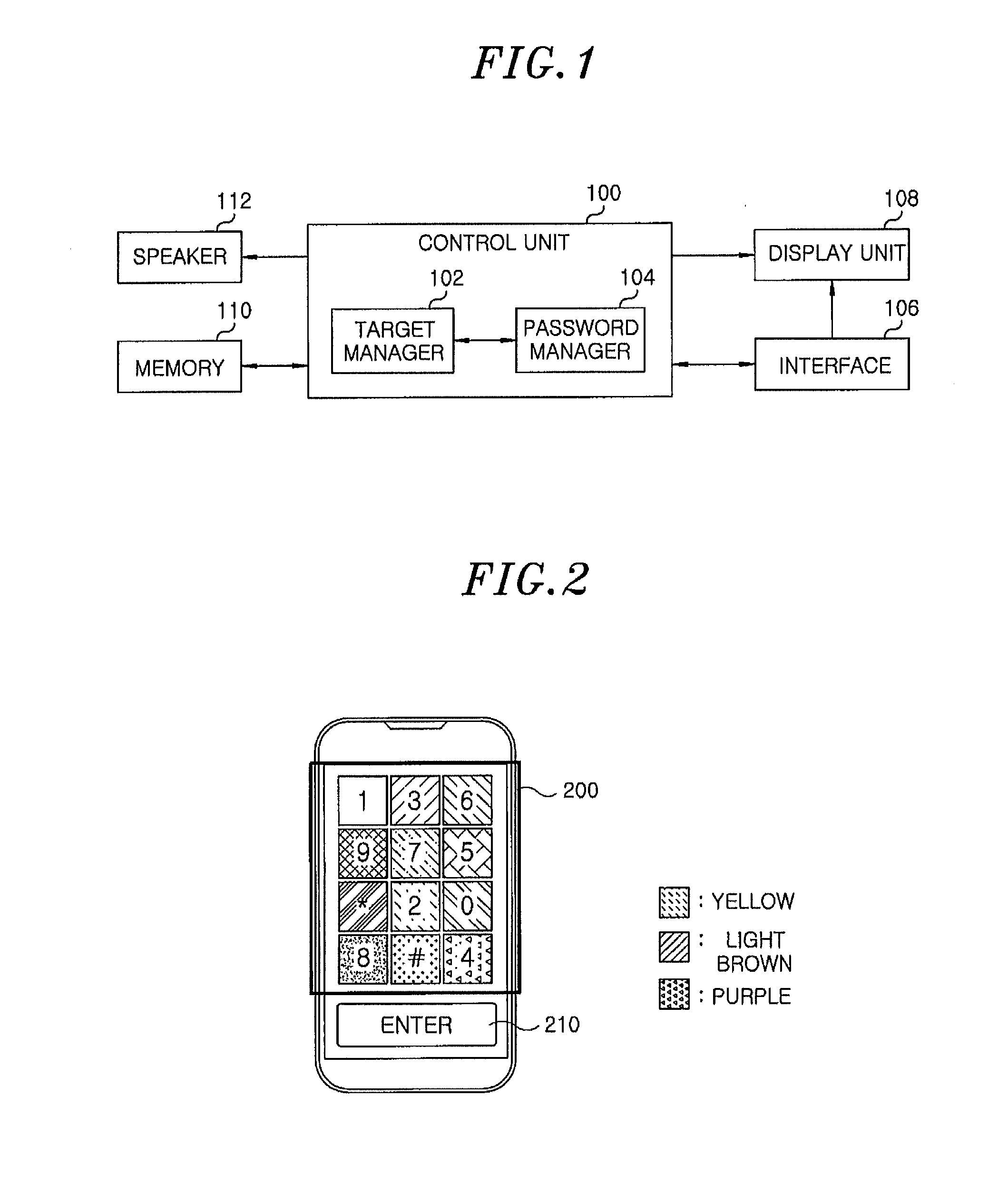
InactiveUS20120110663A1Broaden applicationResist attackDigital data processing detailsUnauthorized memory use protectionPasswordAuthentication
An apparatus for inputting a user password, includes an interface receiving a command. Further, the apparatus for inputting the user password includes a control unit setting a target based on the command from the interface, receiving and storing a password character, and determining that authentication is successes only when the set target and the password character are positioned at a same coordinate on a skin image. Furthermore, the apparatus for inputting the user password includes a display unit connected to the interface to display the skin image of the interface that is transmitted from the control unit.
Owner:ELECTRONICS & TELECOMM RES INST
Lightweight ballistic resistant rigid structural panel
InactiveUS20030114064A1Without sacrificing ballistic resistanceImprove fatigueFuselage framesFuselage bulkheadsAdhesiveEngineering
A lightweight ballistic resistant rigid structural panel especially for use in aircraft interiors is disclosed. The rigid structural panel is made up of a core layer including a plurality of sheets of flexible, high-tensile strength fabric interleaved with a plurality of sheets of a thermal-fusible film adhesive, and a sheet of cushioning material adhered to the plurality of sheets of flexible, high-tensile strength fabric. Fiber-reinforced face skins are adhered to exterior surfaces of the panel core for structural strength and rigidity. The rigid structural panel is capable of resisting ballistic attack from handguns and like weapons, while maintaining a high degree of strength and rigidity.
Owner:NORDISK AVIATION PRODS A S
Network safety isolating and information exchanging system and method based on proxy mapping
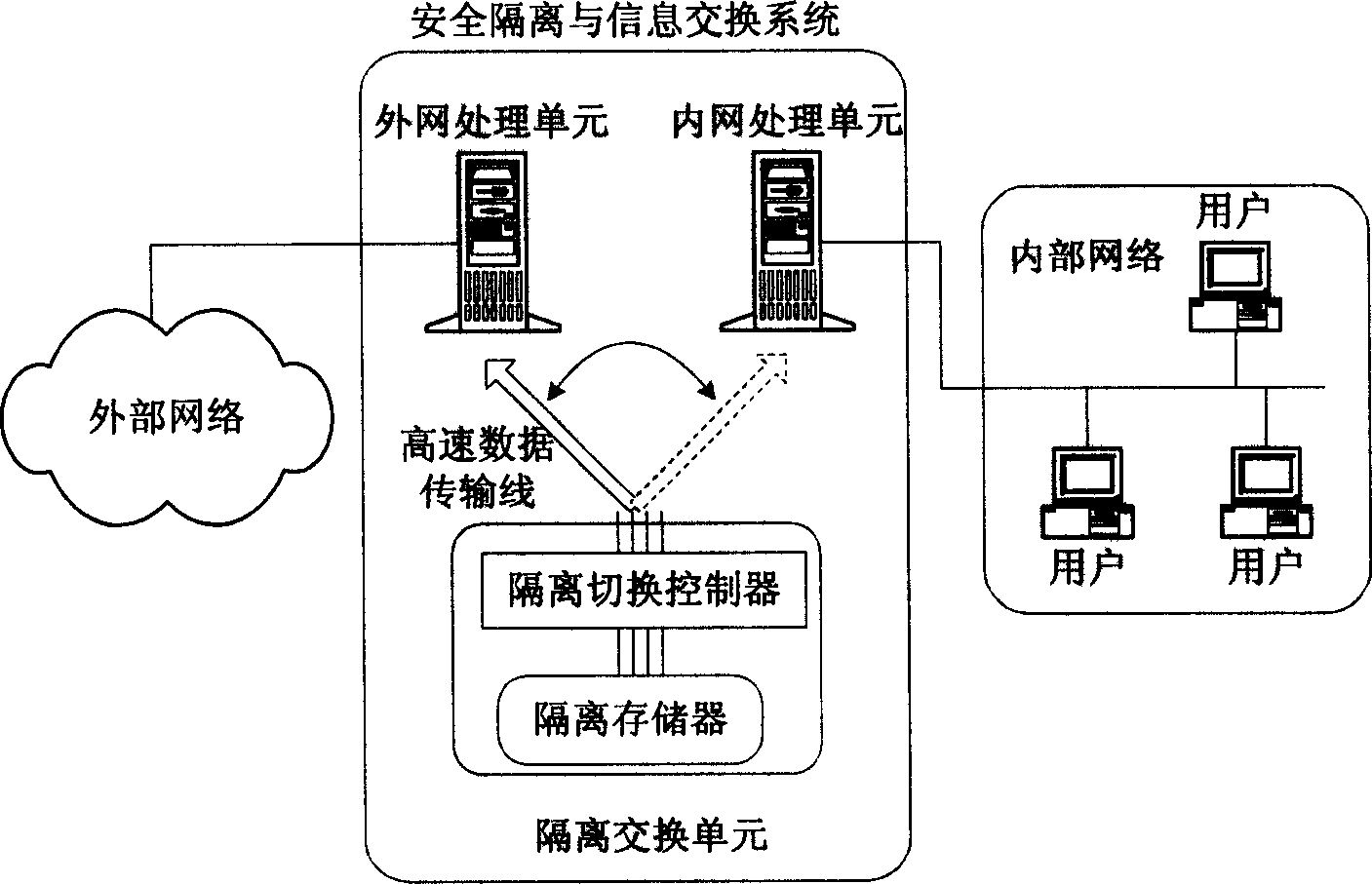
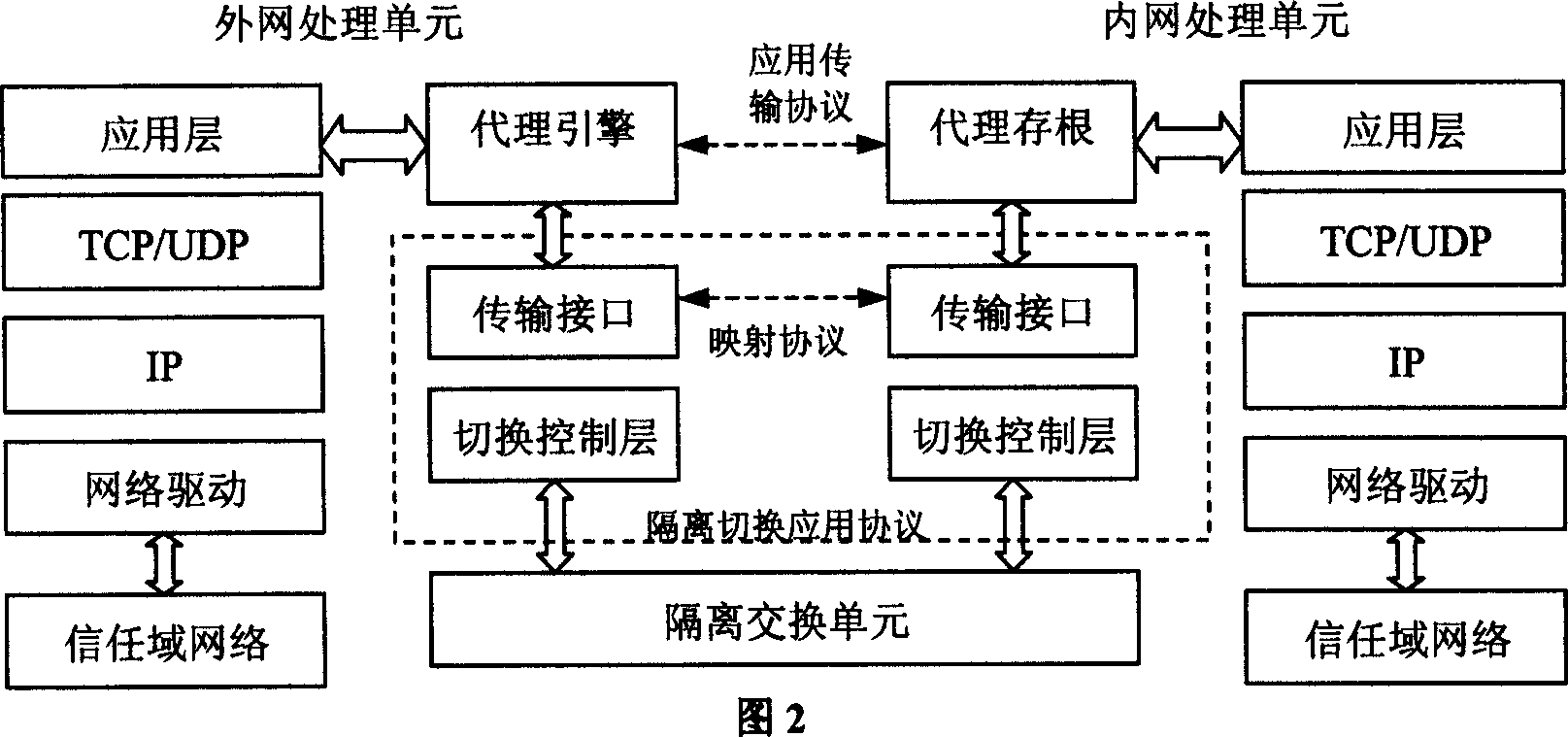
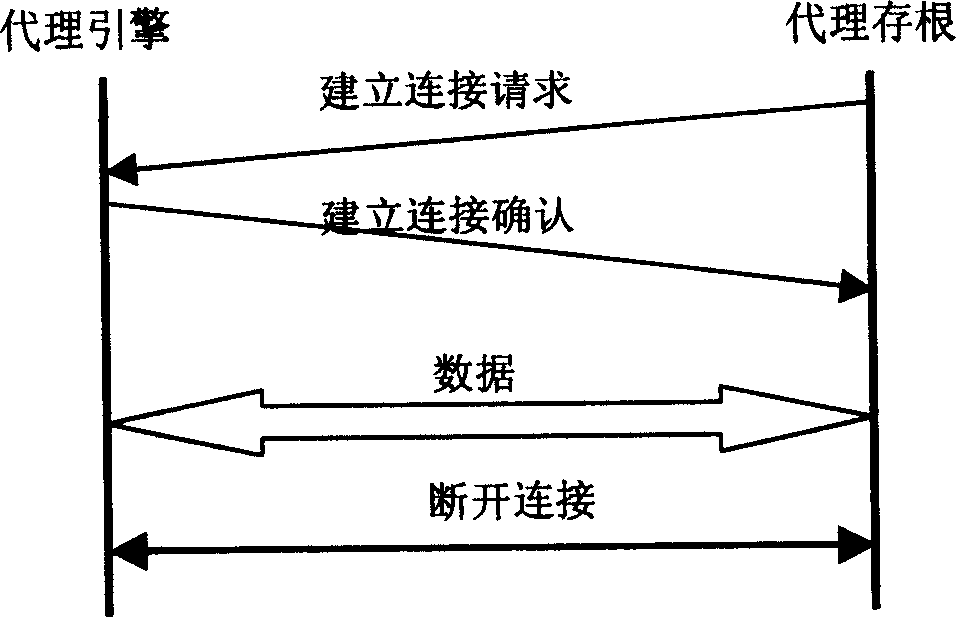
InactiveCN1571398AResist attackProtection securitySubstation remote connection/disconnectionStore-and-forward switching systemsClient-sideNetwork data
The invention relates to network security isolation based on agent mapping and information exchanging system and its method. It uses in information exchanging field and network data exchanging field. The in-out net processing units are each connected to the inner net and the outer net in the system. Isolation exchanging unit includes isolation switching controller and isolation storage. The in-out net processing units are connected to the isolation switching controller through high speed data transmission line. The isolation switching controller is connected to the isolation storage. Only one of the in-out net processing units can assess the isolation storage. The in-out net processing units exchange the information through the isolation exchanging unit. The inner net processing unit includes an agent stub and the outer net processing unit includes an agent engine. The method of the invention is that the inner defined transmission interface is called by the agent stub and the agent engine, and the date is exchanged between the in-out net processing units by isolation exchanging unit. So this can construct an information exchanging channel between the inner net client end and the outer net server in the form of agent mapping.
Owner:SHANGHAI JIAO TONG UNIV
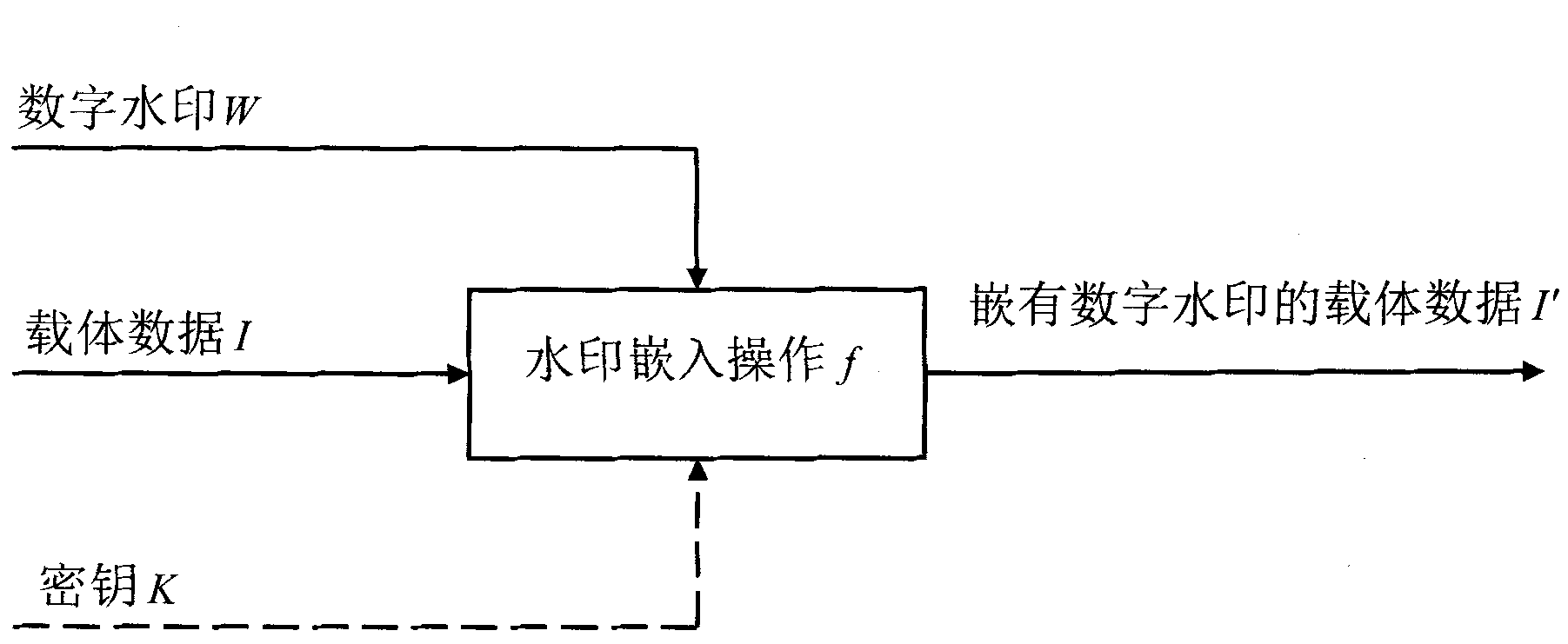
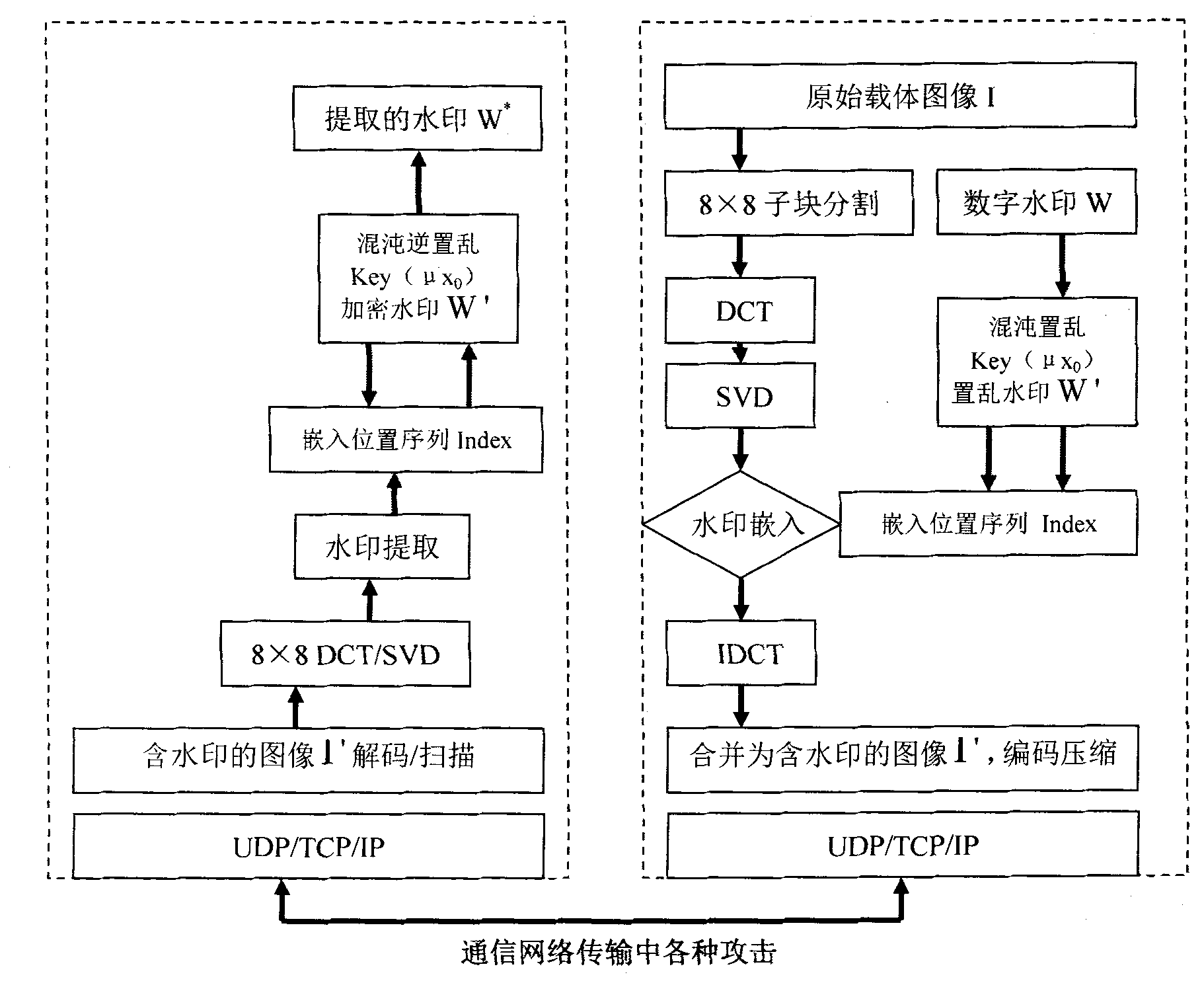
Digital watermark embedding and extraction method based on chaos sequences
InactiveCN101847251AImprove securityGood robustnessImage data processing detailsSingular value decompositionDiscrete cosine transform
The invention discloses a digital watermark embedding and extraction method based on chaos sequences. The digital watermark of the chaos sequences is used for carrying out scrambling, and the pertinence of the original watermark and the scrambled digital watermark is removed through the scrambling, so the digital watermark has the features like flat noise. Thereby, the transparency of the digital watermark is improved. The position of the watermark embedding into a DCT block is determined through the chaos sequences, the safety of the algorithm is improved, and better robustness on the large-area cutting attack can also be realized. In the watermark embedding process, firstly, image sub blocks carry out discrete cosine transform (DCT), and the energy can be converted into low-frequency factor compression blocks; and after the conversation, the obtained low-frequency component matrix A carries out singular value decomposition (SVD), and at the same time, the position of the watermark embedding into the DCT low-frequency compression blocks can be determined and the embedding intensity can be regulated through the chaos sequences. Thereby, the calculation complicity can be reduced, in addition, the embedding quantity is also increased, the robustness of the watermark is improved, and the capability is improved for resisting ordinary attack, so the invention has wider practicability.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
Polymer-fiber composite building material with bulk and aesthetically functional fillers
ActiveUS20060099405A1Reduce resin usageResist attackSynthetic resin layered productsCeramic layered productsFiberMohs scale of mineral hardness
Polymer composite building materials are provided which contain resin, and about 20-75 wt. % fillers and additives, in which the fillers contain at least one bulk filler for reducing the amount of resin needed to make the building material, and at least one aesthetically functional filler for providing the building material with an aesthetic appearance. The bulk filler and the aesthetically functional filler of this embodiment are non-toxic, resistant to microbial attack, and have a Mohs hardness of less than about 5.
Owner:BARRETTE OUTDOOR LIVING INC
Secure certification and transaction method with combination of digital certificate and one-time password
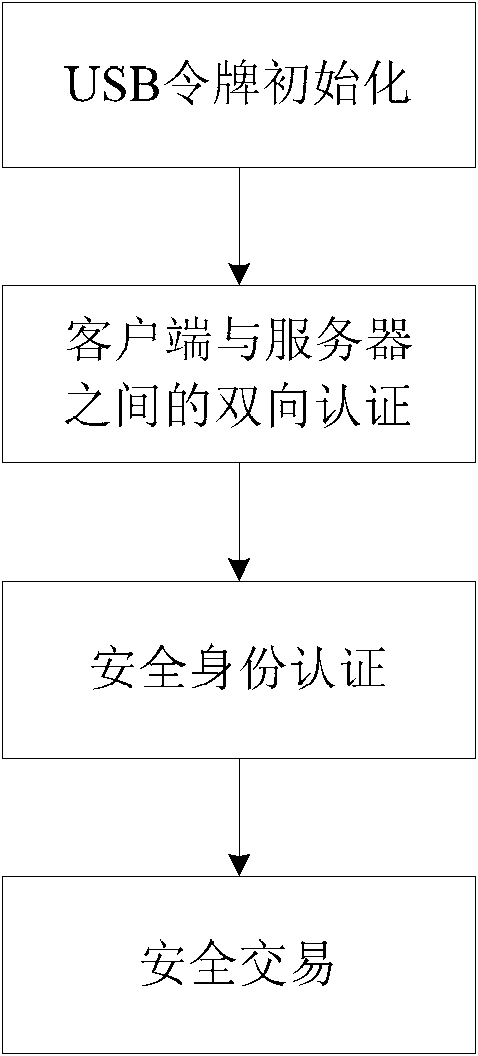
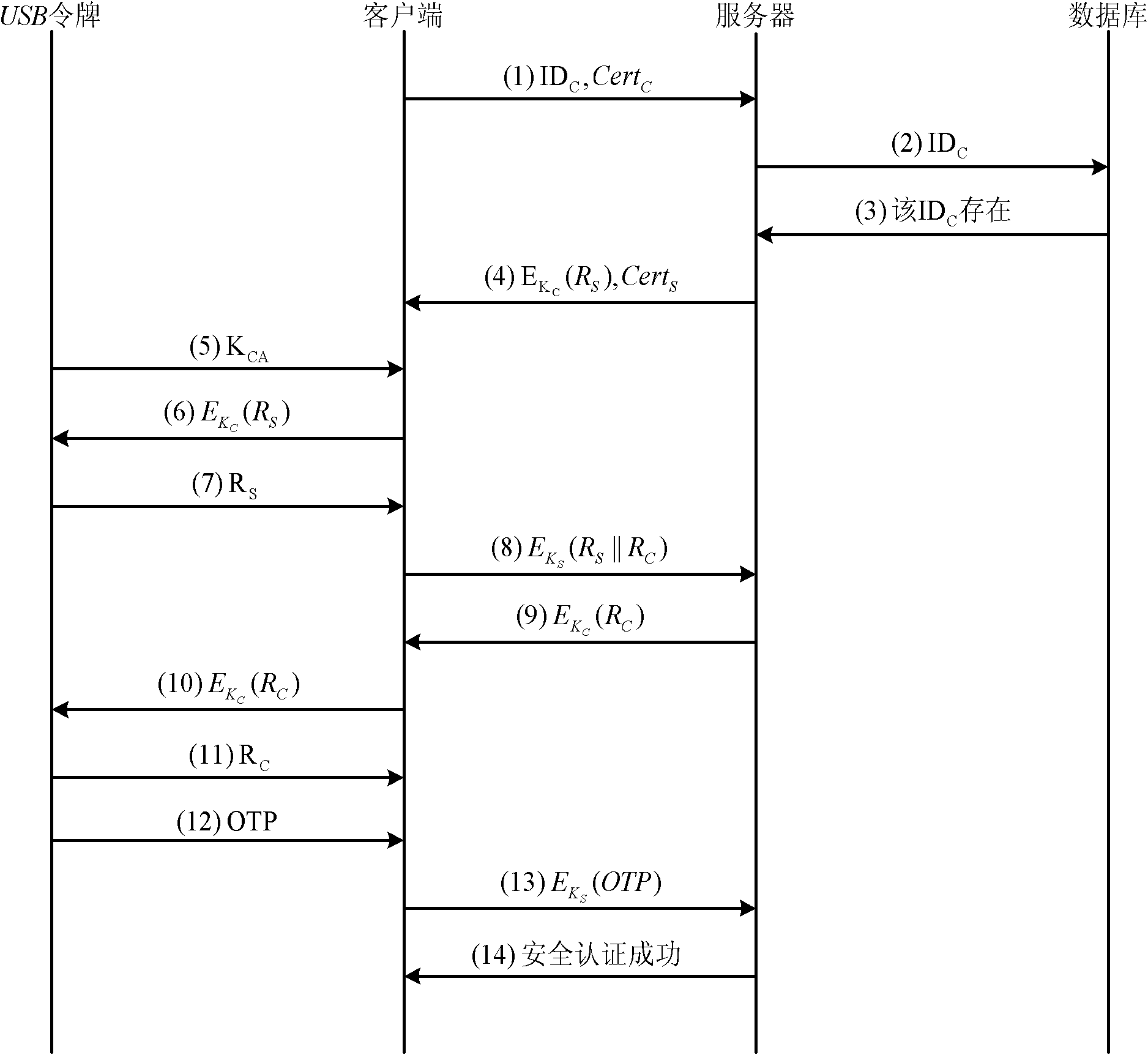
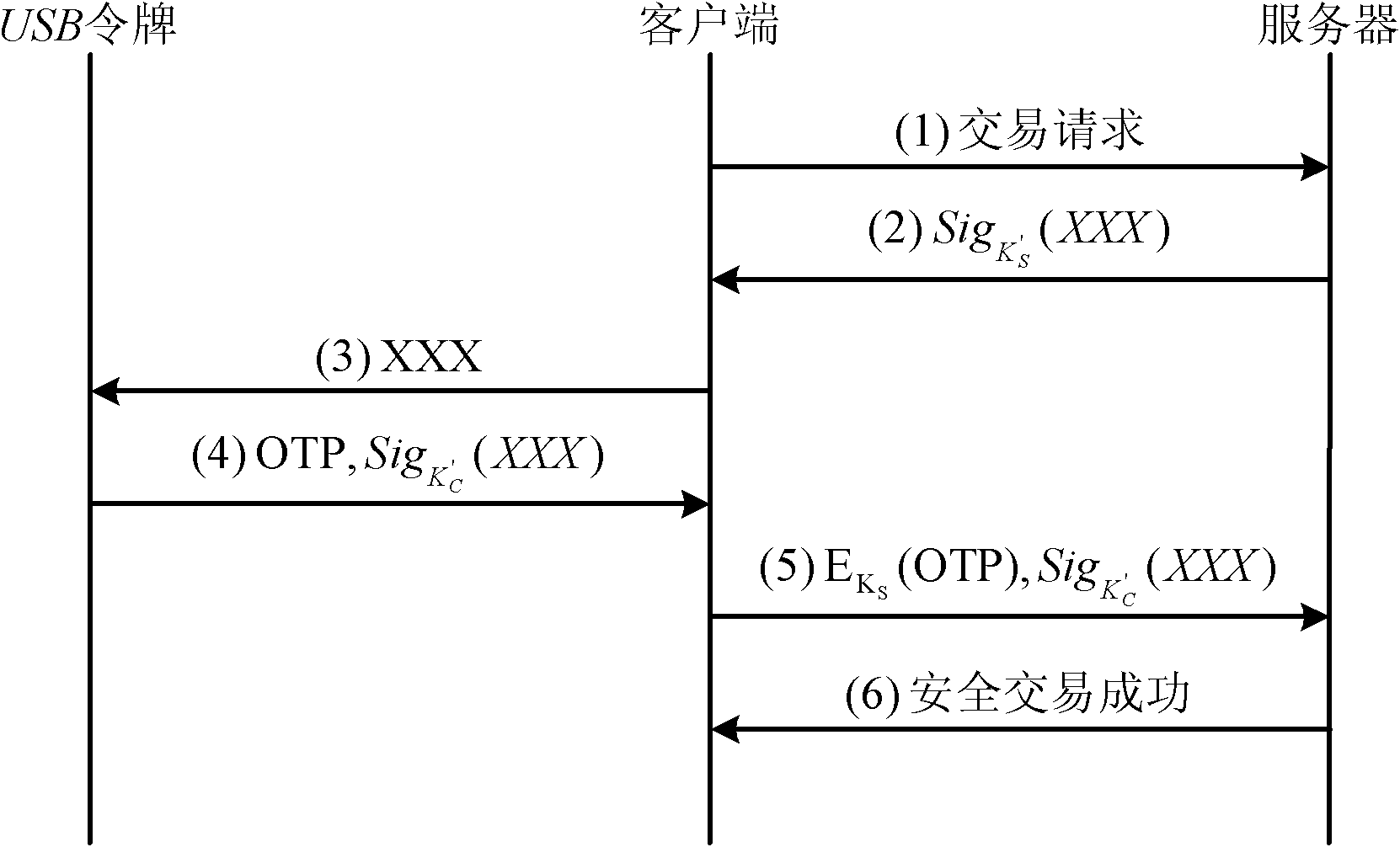
ActiveCN102075522AAvoid safety hazardsMeet the needs of high security applicationsPublic key for secure communicationUser identity/authority verificationOne-time passwordTwo step
The invention discloses a secure certification and transaction method with the combination of a digital certificate and a one-time password. The method comprises two steps of: a secure certification method and a secure transaction method. The secure certification and transaction method specifically comprises the steps of: first, performing bidirectional certification between a client and a server on the basis of the digital certificate; then, realizing secure certification through the combination of the digital certificate and the one-time password on the basis of the bidirectional certification; and finally, realizing secure transaction through the combination of the digital certificate and the one-time password on the basis of the bidirectional certification. By the method, the identities of users are confirmed by combining the digital certificate and the one-time password so as to realize the secure login and secure transaction of various application systems. By the method, the digital certificate and the one-time password are organically combined, so that the safety hidden trouble caused by separately using the digital certificate or the one-time password is avoided, respective security advantages of the digital certificate and the one-time password are fully exerted, various attacks can be resisted, high security is achieved, the demand of various high security application in the network can be met, and the method has higher practical value and broad application prospect in the field of network security technology.
Owner:BEIHANG UNIV
Method for carrying out in-vivo detection based on human face recognition
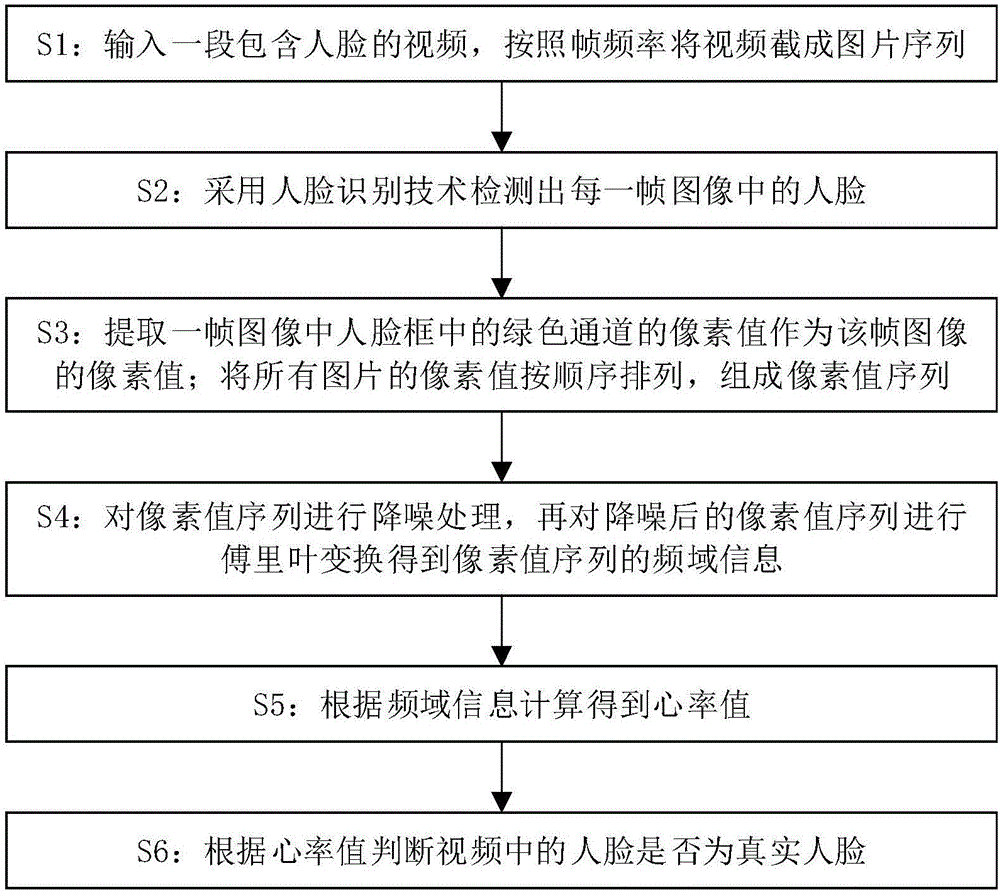
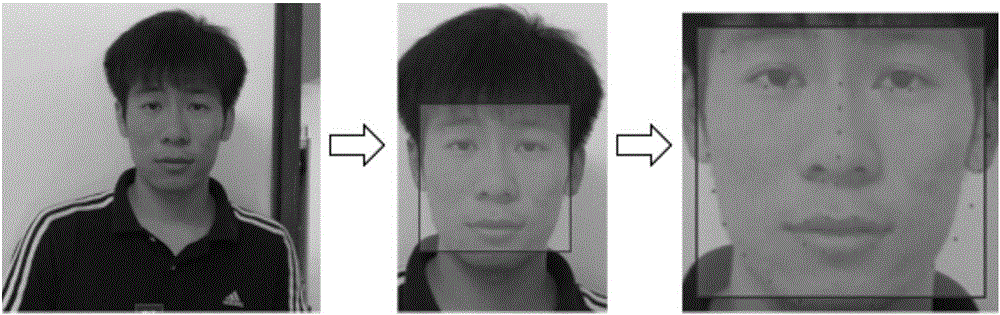
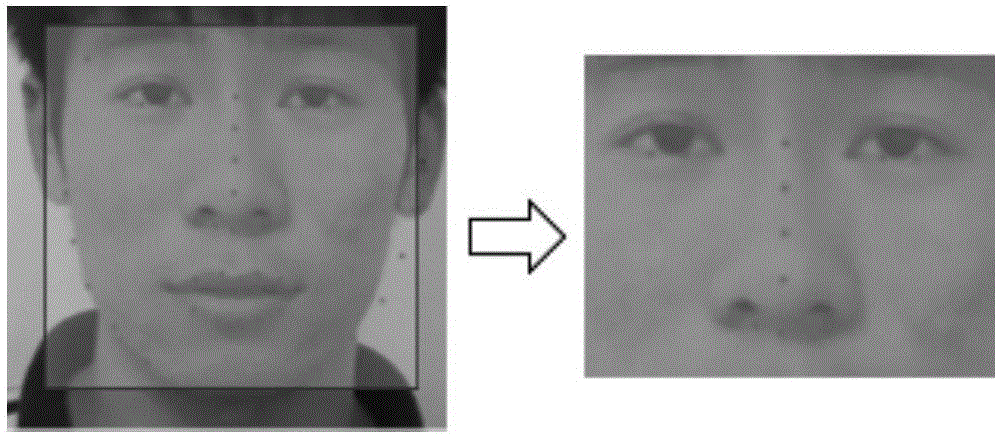
The invention relates to a method for carrying out in-vivo detection based on human face recognition. The method comprises the following steps that a video including human faces is input, and the video is cut into picture sequences according to frame frequency; the human face in each frame of picture is detected out through the human face recognition technology; the pixel value of a green channel in a human face frame in one frame of picture is extracted to serve as the pixel value of the picture, the pixel values of all the pictures are ranked according to the sequence, and a pixel value sequence is formed; the pixel value sequence is subjected to noise reduction, then Fourier transform is carried out, and frequency domain information of the pixel value sequence is obtained; a heart rate value is calculated according to the frequency domain information; whether the human faces in the video are real human faces or not is judged according to the heart rate value. Heartbeat information reflected by the human faces is utilized, human face in-vivo detection is carried out faster in a better interaction mode, a tester does not need to carry out operation according to a voice instruction, and the detection speed is high. Hardware equipment such as infrared cameras or 3D cameras is not needed, the cost is low, and the method can be widely applied.
Owner:北京飞搜科技有限公司
Polyurethane in intimate contact with fibrous material
InactiveUS7267288B2Excellent abrasion resistanceImprove adhesionRecord information storageLight beam reproducingFiberPolymer science
A sprayable polymeric material and a process for preparing the material which contains a fibrous material, dispersed throughout the polymeric material. A restriction free spray nozzle is provided for mixing and spraying the polymeric material having a fibrous material, the nozzle having a restriction free check valve. A reinforced structure, and a method of making the structure are provided, the structure having layers of the polymeric material (both film and foam) containing the fibrous material. A flexible liner is provided of a porous geotextile fabric and a polyurethane composition comprising the fibrous material sprayed over the geotextile fabric.
Owner:NEVADA SUPPLY CORP
Method for Scalar Multiplication in Elliptic Curve Groups Over Prime Fields for Side-Channel Attack Resistant Cryptosystems
InactiveUS20090214025A1Secure performancePrevent internal leakageDigital data processing detailsSecret communicationEllipseElliptic curve cryptosystem
A method and device for transforming data with a secret parameter in an elliptic curve cryptosystem based on an elliptic curve defined over an underlying prime field, includes multiplying a point of the elliptic curve; representing the data to be transformed, by a scalar representing the secret parameter, wherein the multiplying includes performing at least one point addition operation and at least one point doubling operation on points of the elliptic curve; providing a representation in affine coordinates of the elliptic curve point to be multiplied and a representation in projective coordinates of intermediate elliptic curve points obtained during the multiplying; performing both the point addition operation and the point doubling operation by means of a sequence of elementary prime field operation types, the elementary prime field operation types including: a first type of prime field operations including field multiplication and field squaring of coordinates of the elliptic curve points and a second type of prime field operations including field addition, field doubling, and field subtraction of coordinates of the elliptic curve points.
Owner:TELECOM ITALIA SPA
Pseudonym-based anonymous authentication and key negotiation optimization method and optimized authentication analysis method for Internet of Things
ActiveCN106657124AAchieve non-traceabilityAvoid attackTransmissionKey-agreement protocolThe Internet
The invention provides a pseudonym-based anonymous authentication and key negotiation optimization method and optimized authentication analysis method for the Internet of Things. The method comprises the following steps: S1, a user and a sensor node separately register a gateway node, and for the difference of the user and the sensor node, a user registration protocol and a sensor node registration protocol different from each other are adopted; and S2, after the registration, the user logs in the system through a user login protocol and an authentication and key negotiation protocol, and under the assistance of the gateway node, the sensor node requiring access realizes mutual authentication and a negotiation shared session key. By adoption of the method provided by the invention, better anonymity, non-traceability and security are realized.
Owner:YICHUN UNIVERSITY
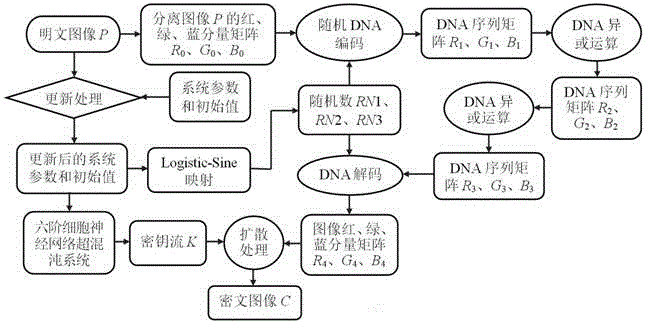
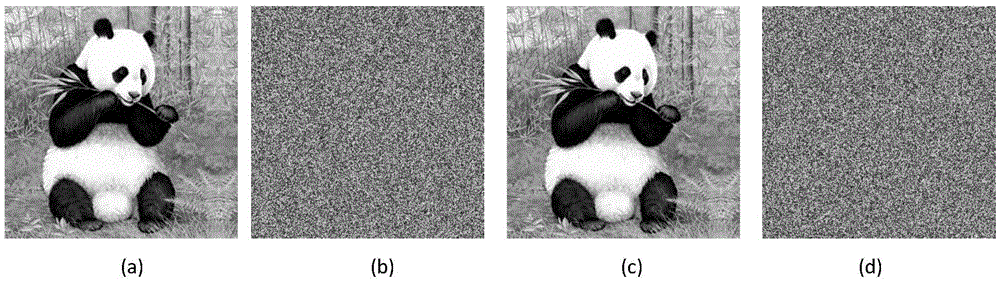
Color image encryption method based on cellular neural network hyperchaos and DNA sequence
The invention belongs to the technical field of information security, and particularly relates to a color image encryption method based on cellular neural network hyperchaos and a DNA sequence. The method provided by the invention comprises the steps of separating red, green and blue three primary color components of a color plaintext image; updating and generating parameters and initial values of a six-order cellular neural network hyperchaotic system and a Logistic-Sine mapping system through the plaintext image, respectively carrying out iterative operation on the two chaotic systems, and obtaining red, green and blue components of an encrypted image according to a DNA encoding rule and a DNA decoding rule; and finally, changing the pixel values of the encrypted image through key stream and a bitwise XOR operation to obtain a final ciphertext image. The decryption is a reverse operation of the encryption process. Compared with the existing image encryption method, the color image encryption method provided by the invention has the advantages of high security, good encryption effect, strong robustness, no information loss and the like, and thus being capable of being widely used in military, remote sensing, remote medical treatment, commerce and other fields.
Owner:FUDAN UNIV
Method of generating program, information processing device and microcomputer
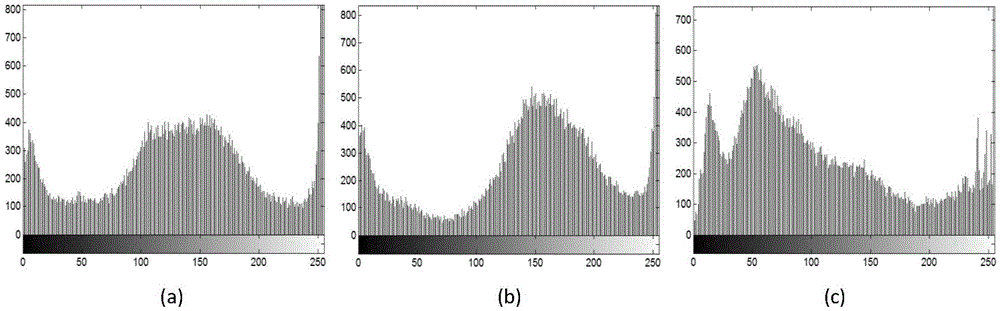
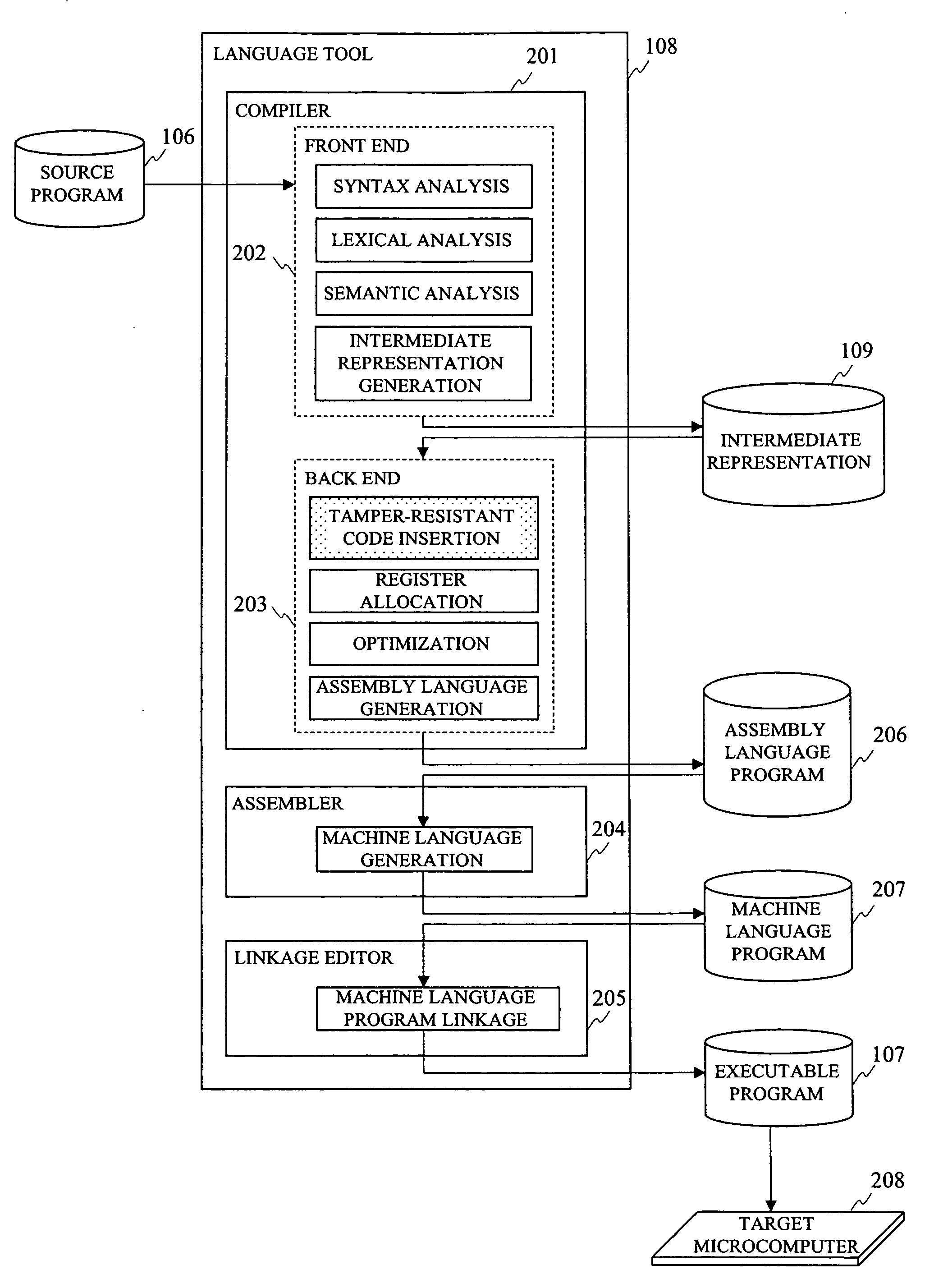
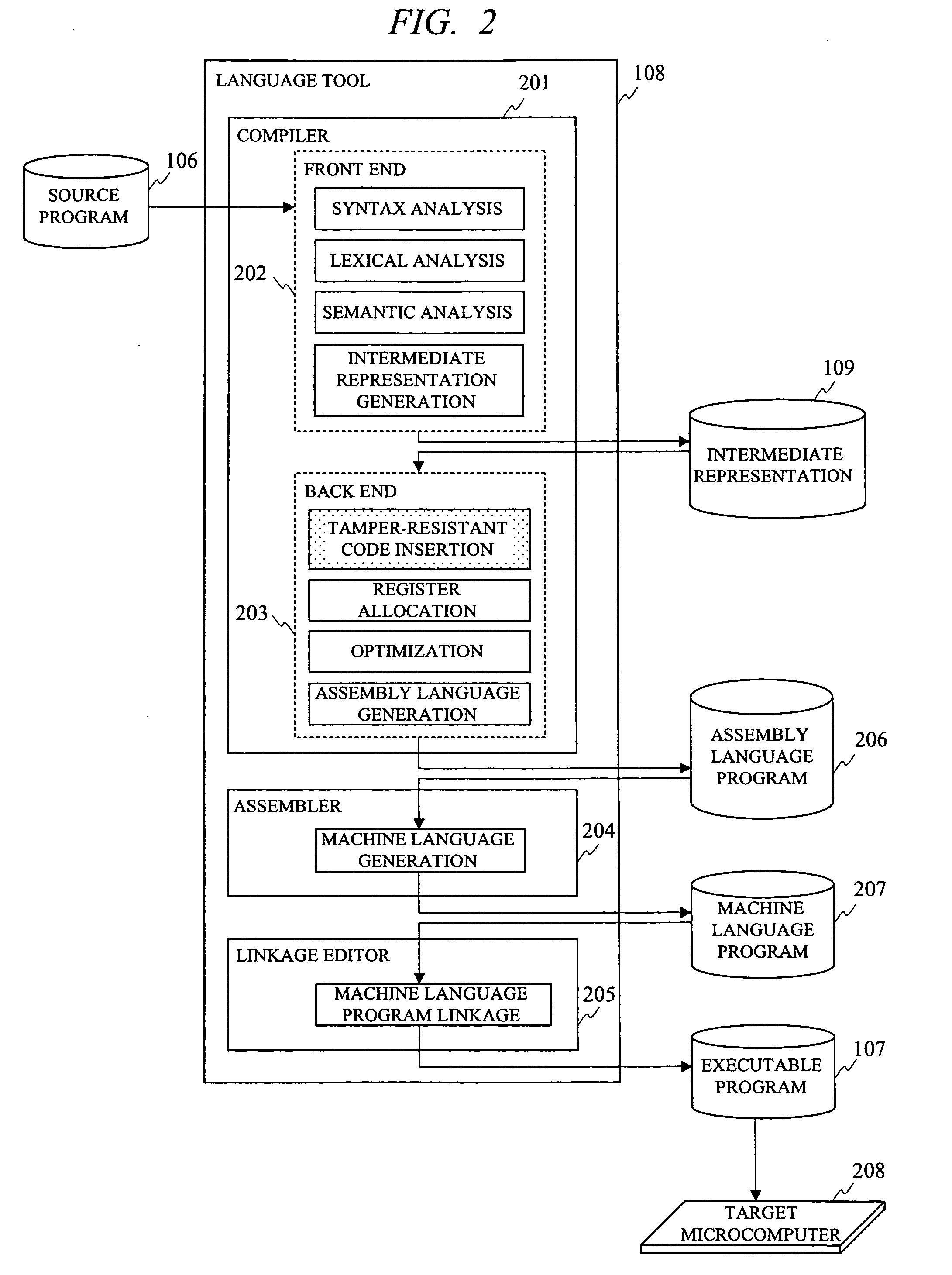
InactiveUS20080271001A1Improve developmentAvoid attackInternal/peripheral component protectionProgram controlSyntaxTamper resistance
In programming in high-level language, a method of generating a program supporting external specifications for generating secure codes having high tamper-resistance and automatically generating an executable program having tamper-resistance with regard to a portion designated by a user is provided. A syntax analysis step, an intermediate representation generation step, a register allocation step, an optimization processing step, an assembly language generation step, a machine language generation step and a machine language program linkage step are executed. And between finish of reading of the source program and generating the executable program, a tamper-resistant code insertion step of automatically generating a code having tamper-resistance coping with unjust analysis of an operation content of the executable program is executed to the source program, the intermediate representation, the assembly language program or the machine language program based on an instruction of a user.
Owner:RENESAS ELECTRONICS CORP
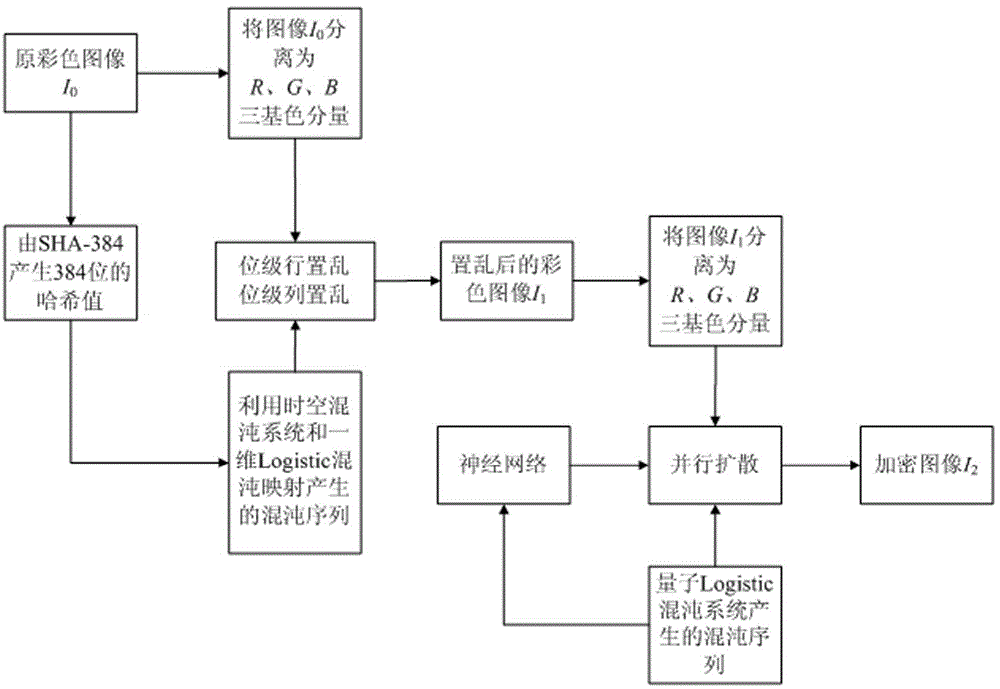
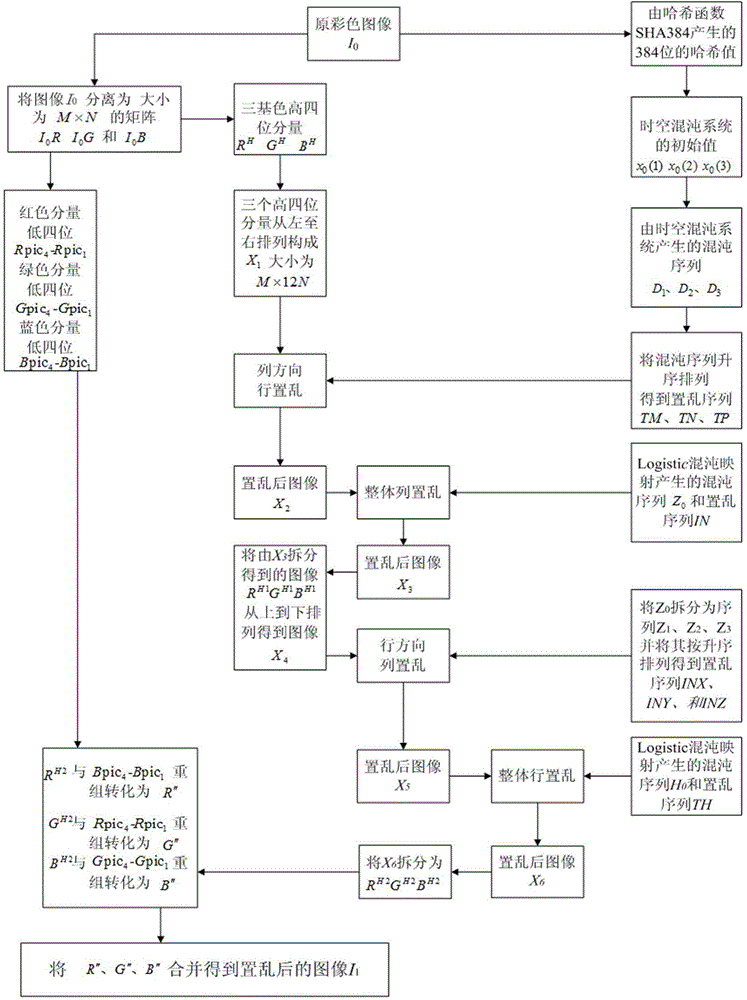
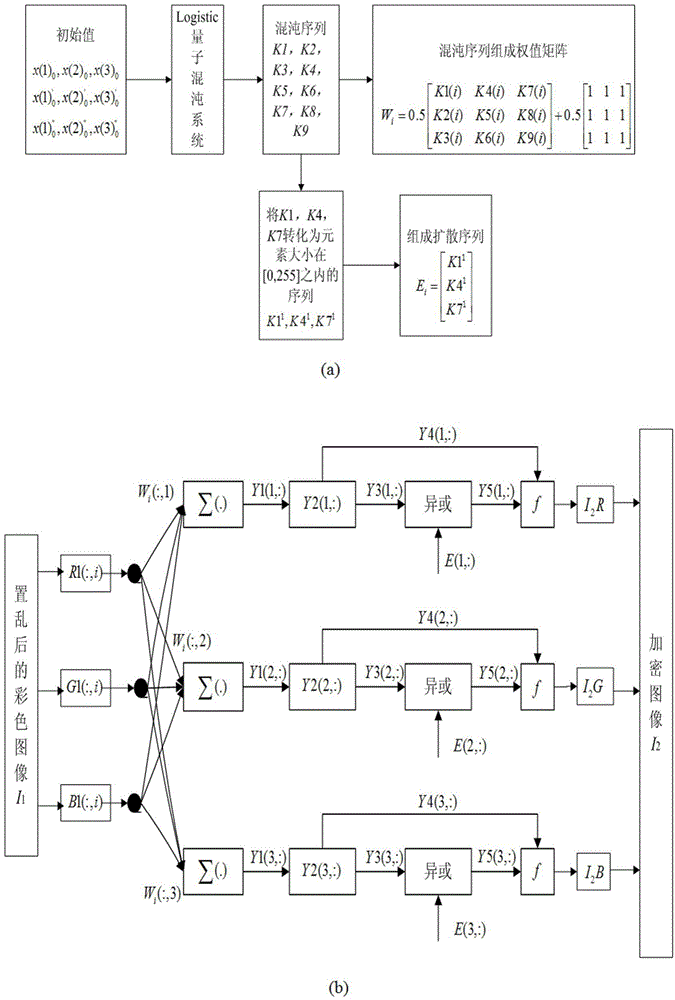
Color image encryption method based on SHA-384 function, spatiotemporal chaotic system, quantum chaotic system and neural network
ActiveCN104008520AImprove securityLarge key spaceImage data processing detailsComputer hardwareDiffusion
The invention relates to a color image encryption method based on an SHA-384 function, a spatiotemporal chaotic system, a quantum chaotic system and a neural network. The method includes the steps that an original color image I0 is calculated through the SHA-384 function, a Hash value is obtained as a secret key, the Hash value, a CML and one-dimension Logistic chaotic mapping are utilized for generating a chaos sequence, bit-level line-column scrambling is carried out on high four-digit images of components of three primary colors of the I0 through the chaos sequence, and a scrambled image I1 is obtained; the Logistic quantum chaotic system is utilized for generating a chaos sequence for encrypting the scrambled image, and is combined with the neural network to carry out parallel diffusion processing on all pixel values of components of three primary colors of the I1, and a final encrypted image I2 is obtained. By the method, the space of the secret key is greatly enlarged, the safety, encryption effect and secret key sensibility are higher, the attack resistance capacity is higher, the scrambling process and the encryption time are shorter, and hardware implementation is easier.
Owner:HENAN UNIVERSITY
Systems and methods for controlling interior climates
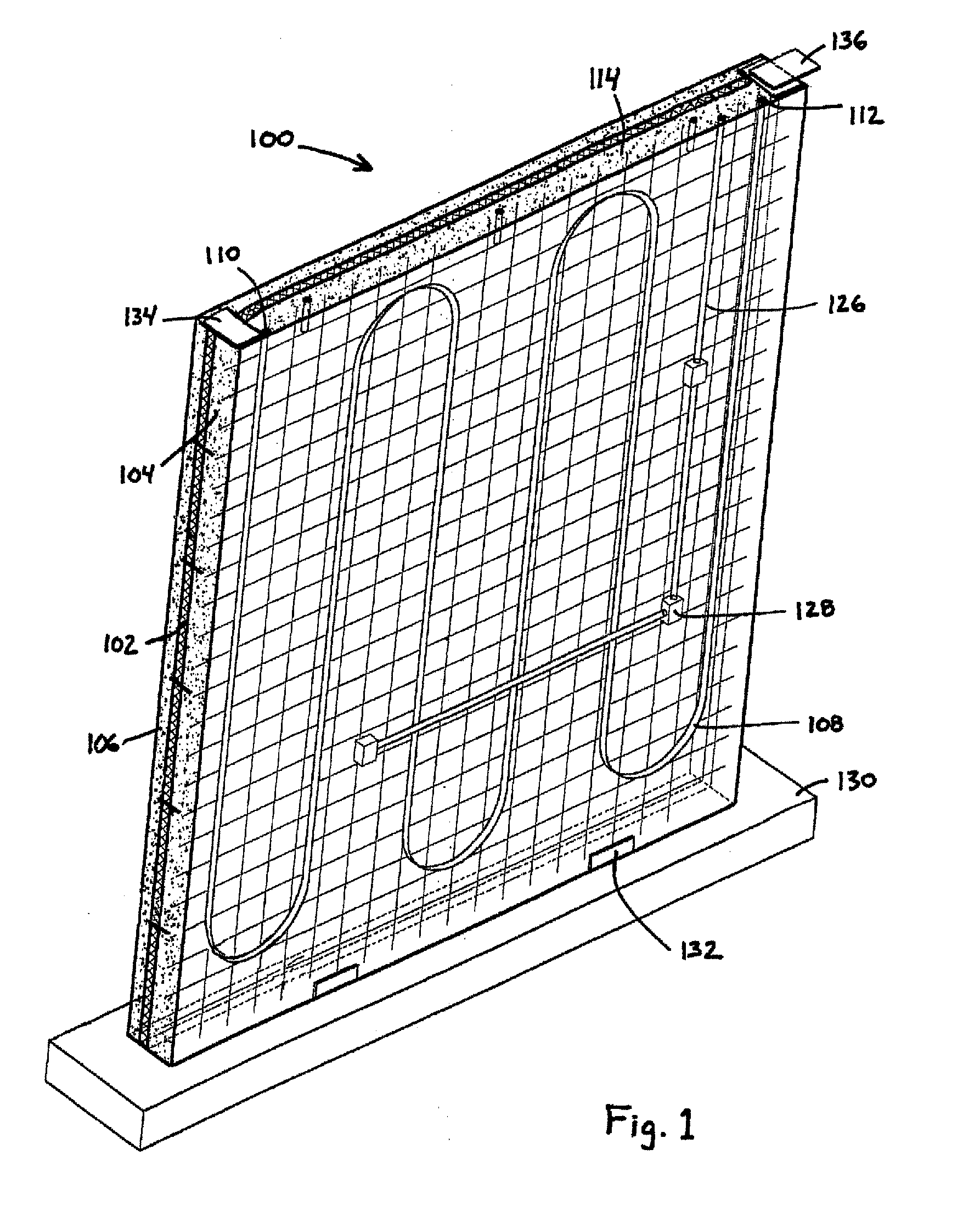
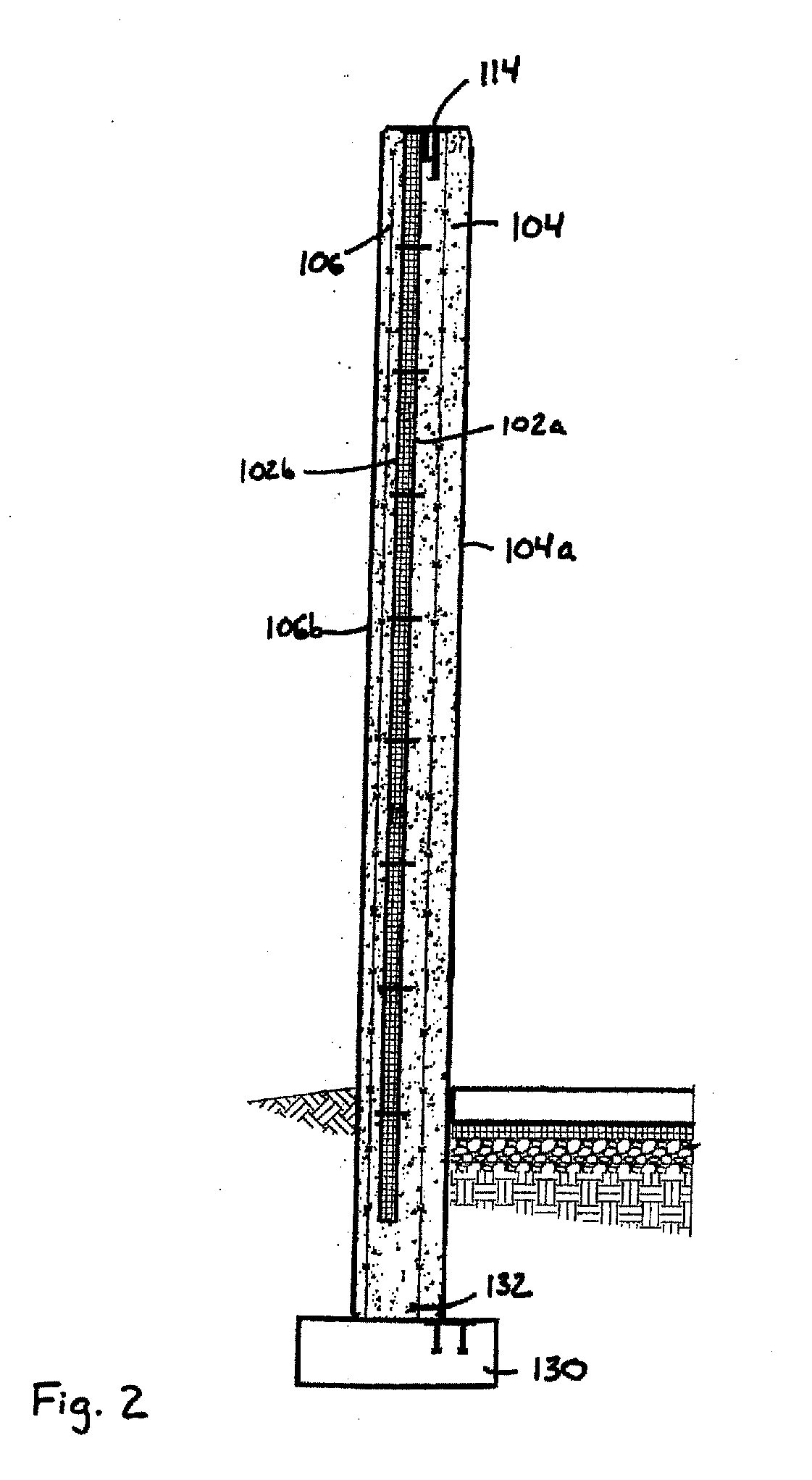
InactiveUS20100198414A1Minimize potentialImprove efficiencySampled-variable control systemsComputer controlThermal insulationEngineering
Structural wall panels and methods and systems for controlling the interior temperature of a building are provided. The structural wall panels advantageously include a fluid conduit disposed within an interior concrete layer of the structural wall panel where the conduit is adapted to convey a thermal transfer fluid through the interior concrete layer. A thermal insulation layer may be provided between the first concrete layer and an exterior surface of the wall. The thermal transfer fluid can be heated and / or cooled to regulate the temperature of the interior concrete layer and thereby control the temperature of the interior of the building. The interior concrete layer may have a high thermal mass to increase the thermal efficiency of the system.
Owner:CORVID
Shared secret key establishment method under quantum computing environment
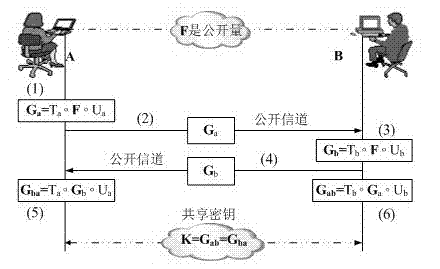
ActiveCN103200000AImprove efficiencyImprove securityPublic key for secure communicationQuantum computerShared secret
The invention relates to the technical field of information security, in particular to a shared secret key establishment method under quantum computing environment. The shared secret key establishment method comprises two steps of establishing a system and establishing a shared secret key between A and B which are communicated. The shared secret key establishment method is provided by adopting of a multinomial homomorphism problem and has the advantages that realizing efficiency is high, a cryptographic algorithm coprocessor is not needed, safety is high, and the attack from a quantum computer is resisted. In the safety fields such as intelligent cards and wireless sensor networks, the shared secret key establishment method has the advantages over traditional secret key exchange protocols such as a Diffie-Hellman secret key exchange protocol. The shared secret key establishment method can be widely applied to information security system fields such as network security and electronic commerce.
Owner:WUHAN UNIV
Authenticated encryption method of public key and digital signature method
ActiveCN101834724AResist attackImprove securityPublic key for secure communicationUser identity/authority verificationHash functionCoprocessor
The invention relates to the technical field of information safety and particularly discloses an authenticated encryption method of a public key and a digital signature method. The invention adopts a multivariable public key password system as a main body part, is combined with a Hash function authentication technology and provides double safety protection by efficiently compounding the multivariable public key password system and the Hash function authentication technology. When applying the scheme to carry out encryption or digital signature, the invention has the advantages of high realization efficiency, no need for a password algorithm coprocessor high safety, impact resistance of a quantum computer and the like and has more superiority in the safety field of intelligent cards, wireless sensing networks and the like compared with the traditional public key encryption algorithm such as RSA (Rivest-Shamir-Adleman), ECC (Elliptic Curve Crypto) and the like. The methods can be widely applied to the field of information safety systems of network safety, electronic commerce, bill, identity authentication and the like.
Owner:常熟紫金知识产权服务有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com