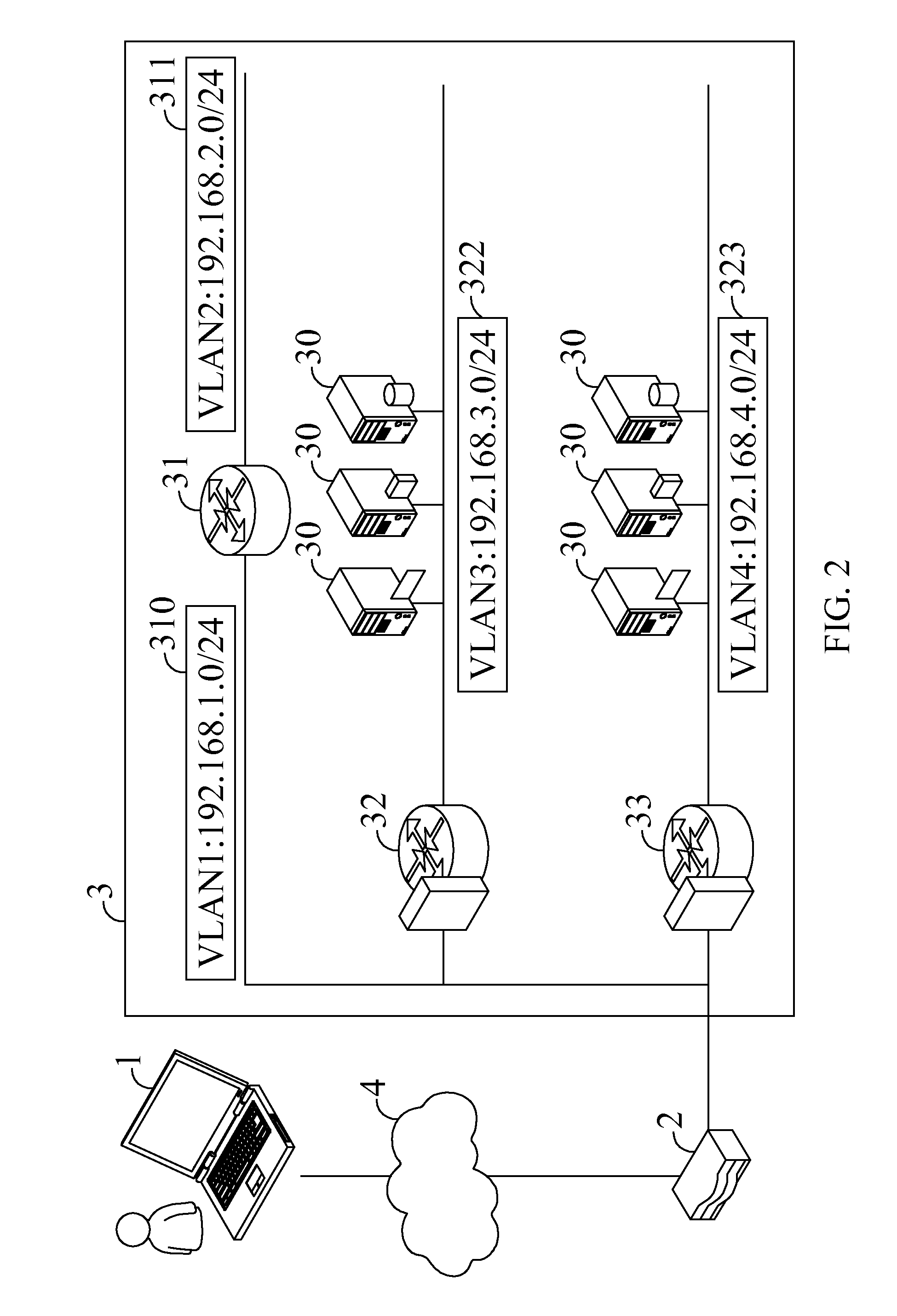
Patents
Literature
484 results about "Virtual IP address" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
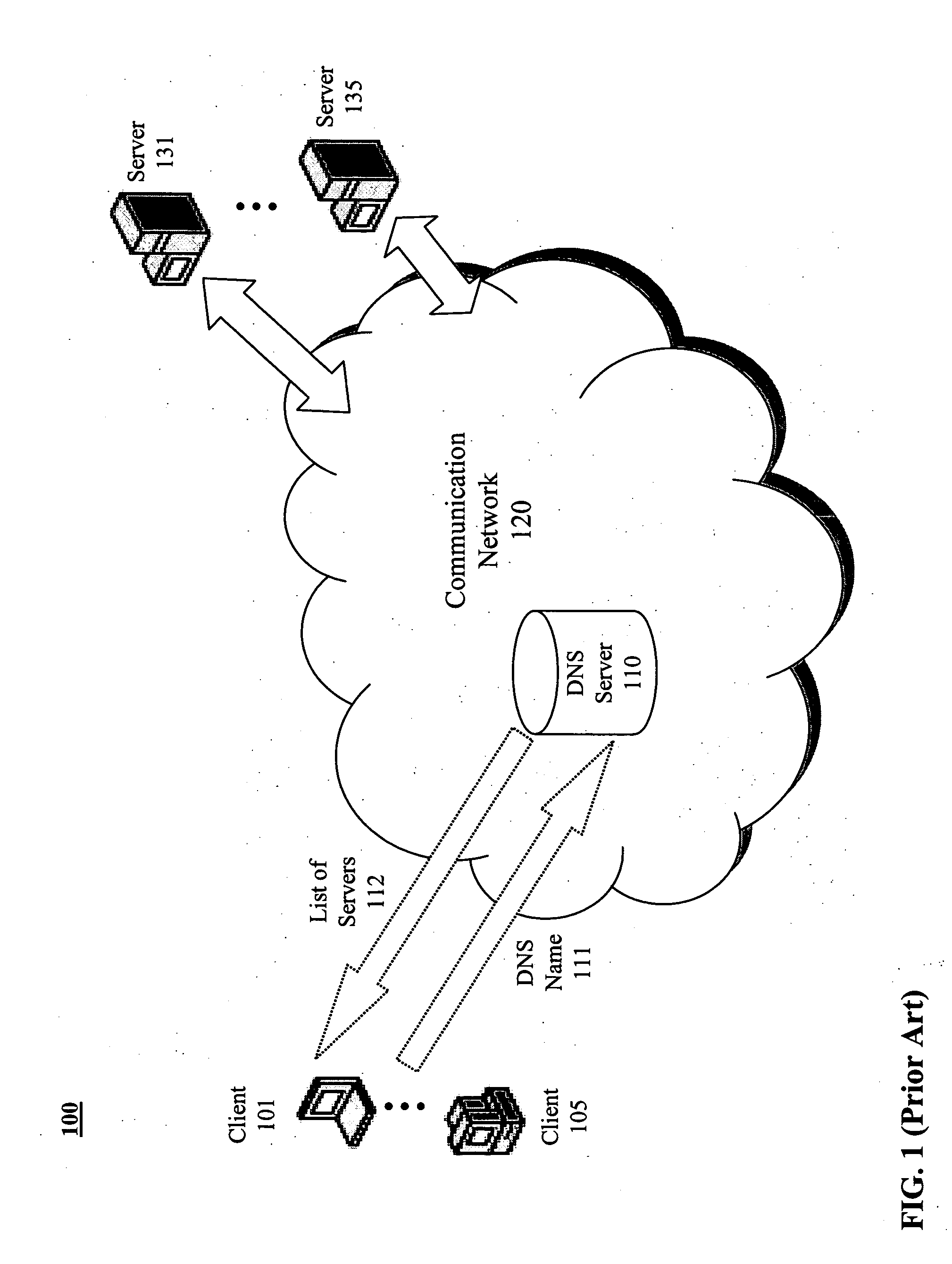
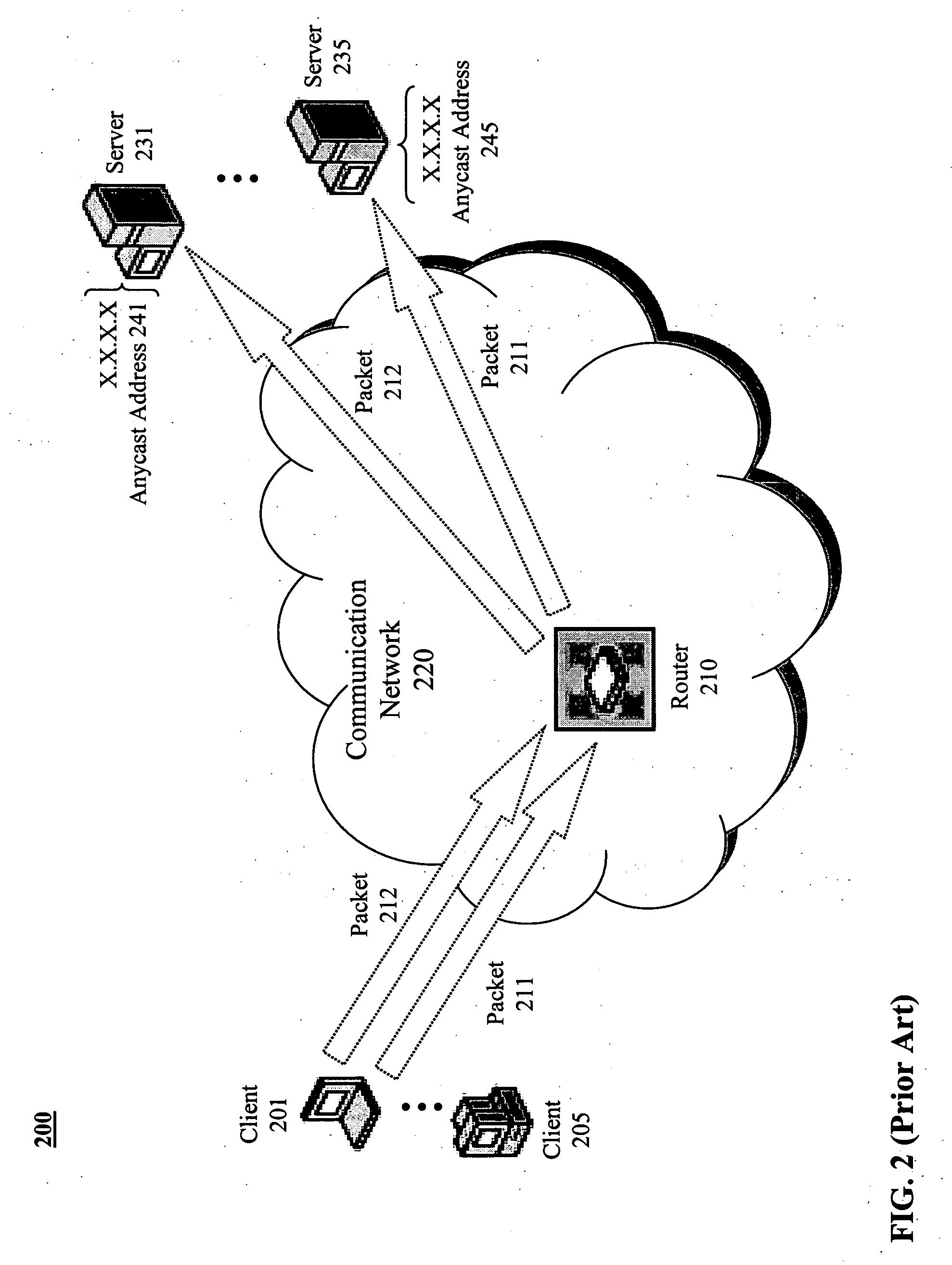
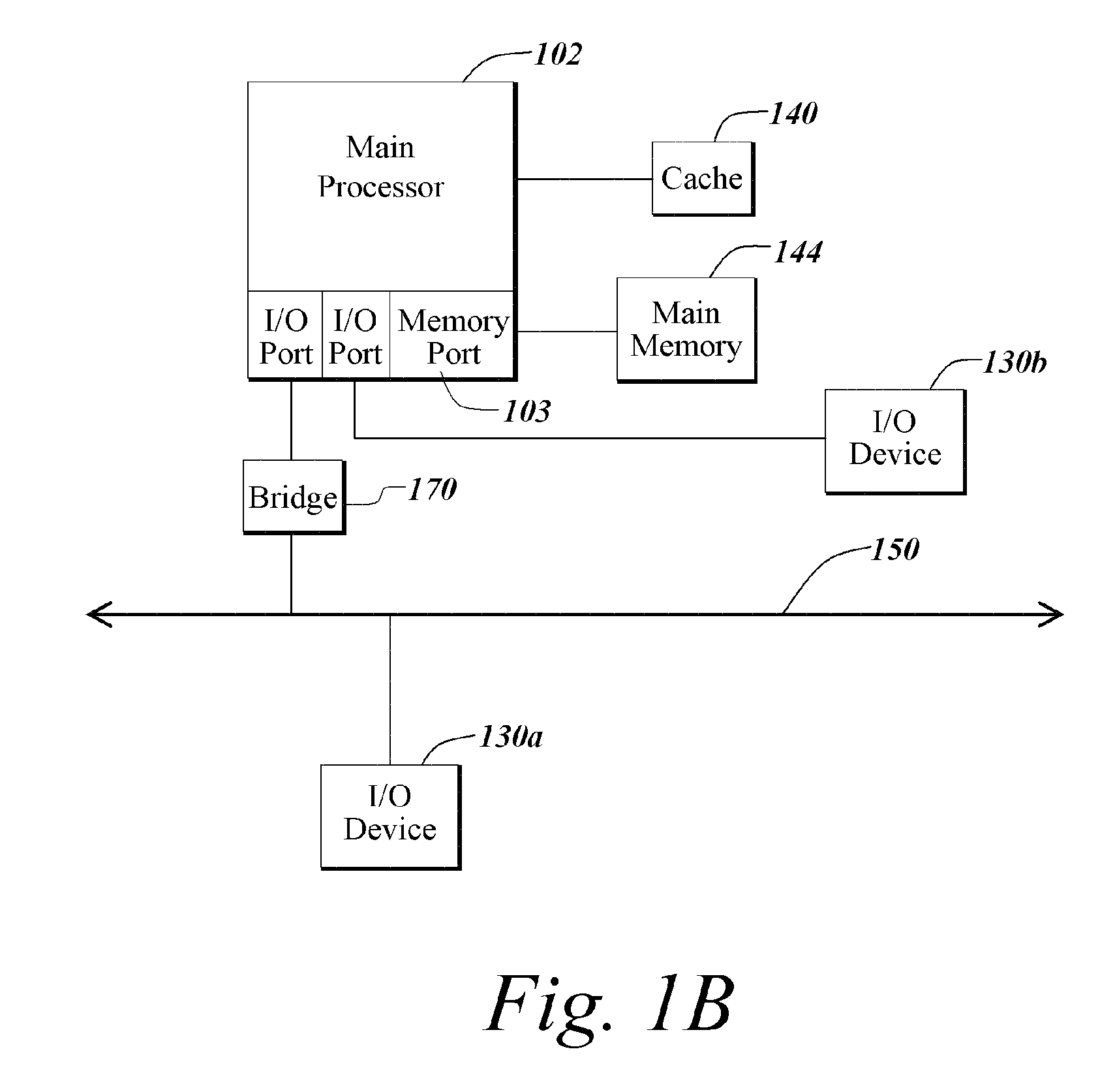
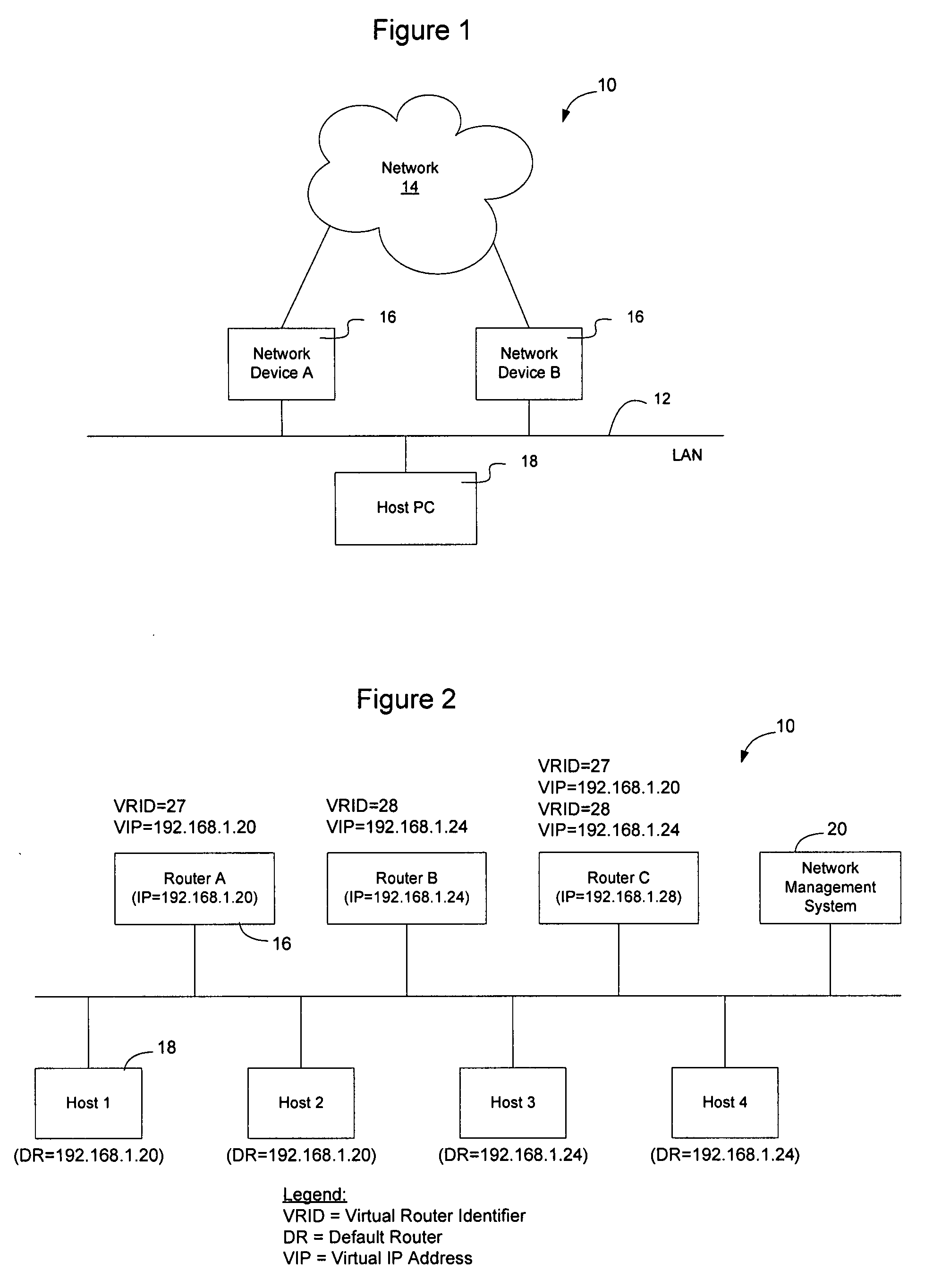
A virtual IP address (VIP or VIPA) is an IP address that doesn't correspond to an actual physical network interface. Uses for VIPs include network address translation (especially, one-to-many NAT), fault-tolerance, and mobility.
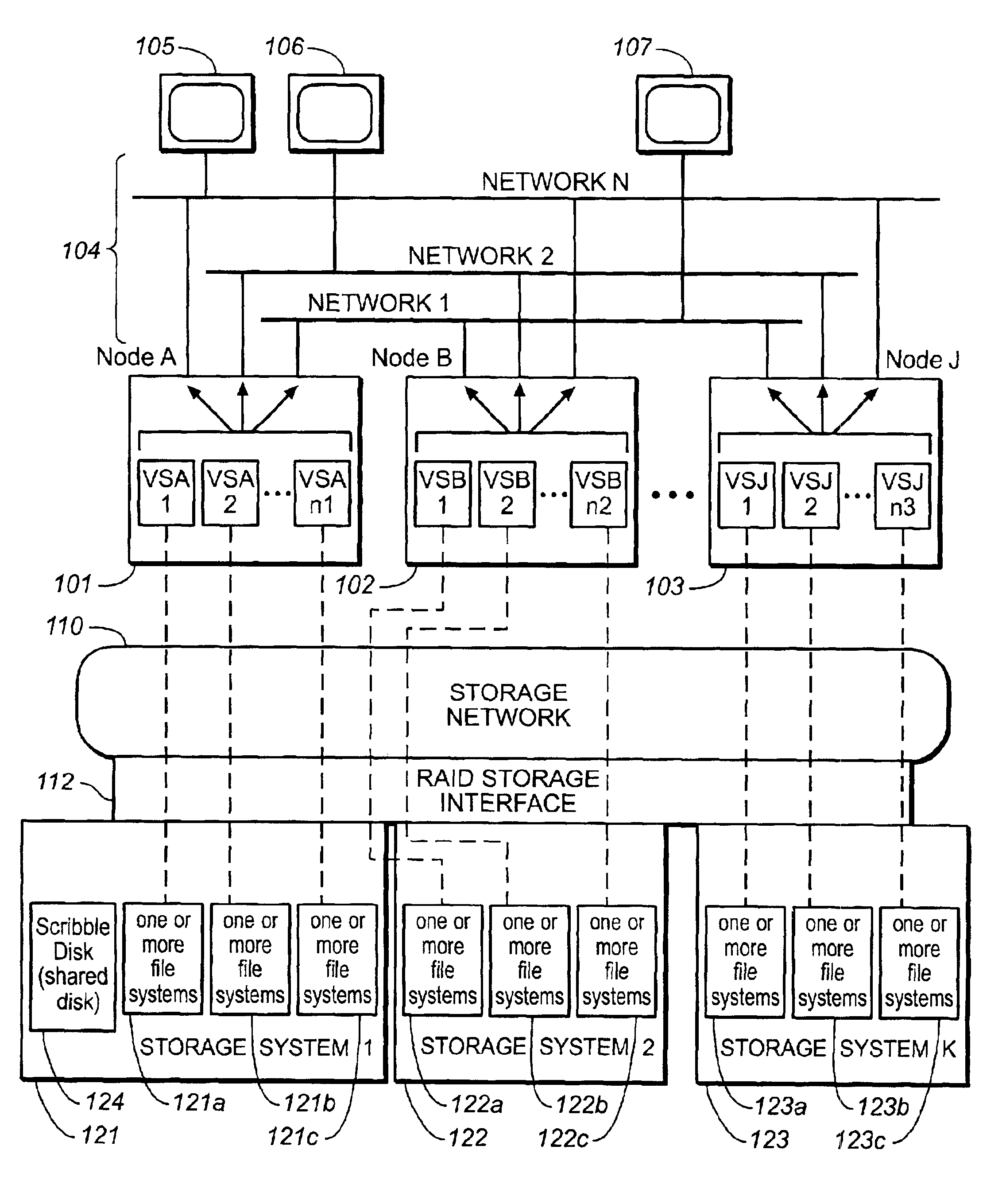
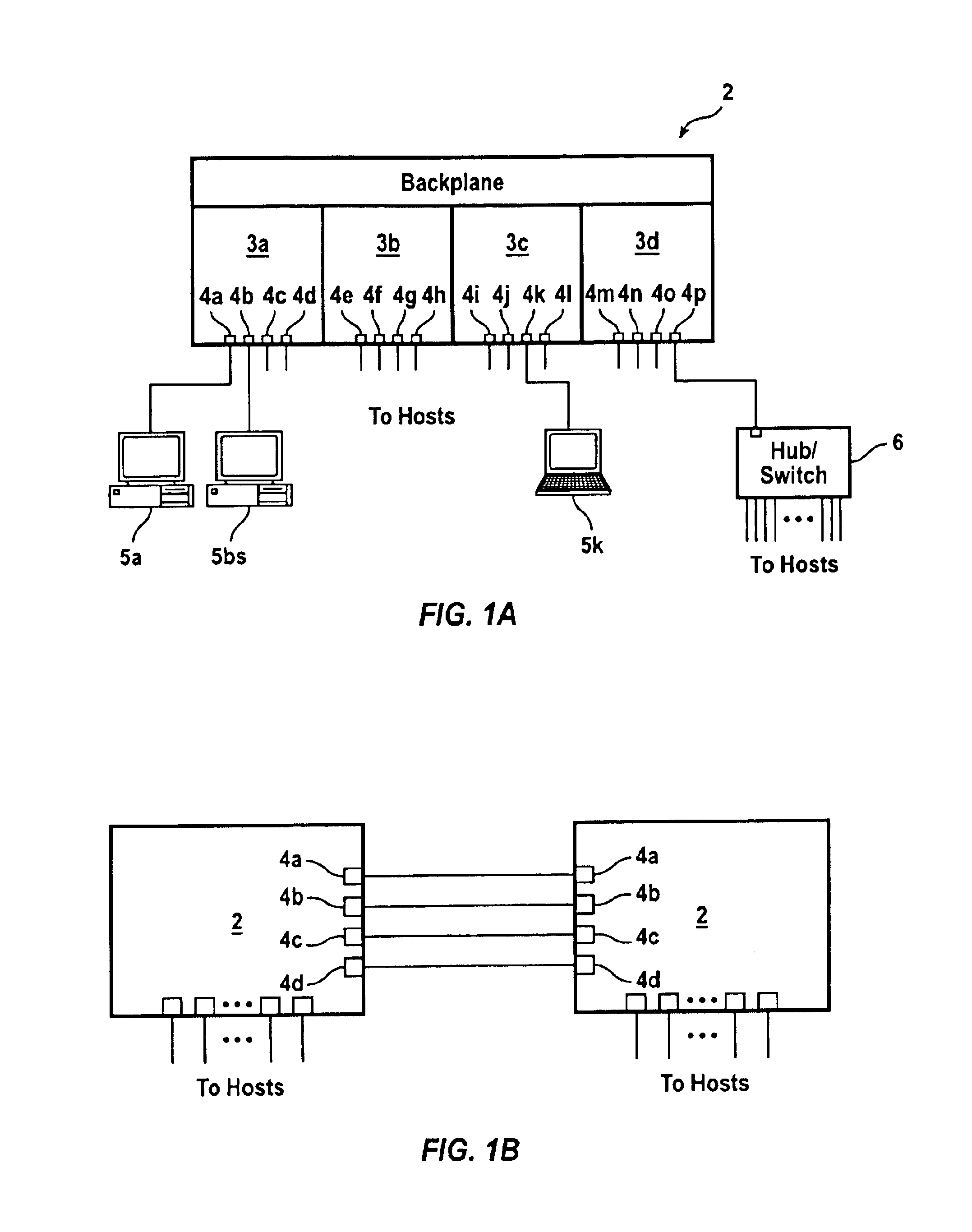
High-availability cluster virtual server system
InactiveUS6944785B2Minimize occurrenceImprove system performanceInput/output to record carriersData switching networksFailoverHigh availability
Systems and methods, including computer program products, providing high-availability in server systems. In one implementation, a server system is cluster of two or more autonomous server nodes, each running one or more virtual servers. When a node fails, its virtual servers are migrated to one or more other nodes. Connectivity between nodes and clients is based on virtual IP addresses, where each virtual server has one or more virtual IP addresses. Virtual servers can be assigned failover priorities, and, in failover, higher priority virtual servers can be migrated before lower priority ones. Load balancing can be provided by distributing virtual servers from a failed node to multiple different nodes. When a port within a node fails, the node can reassign virtual IP addresses from the failed port to other ports on the node until no good ports remain and only then migrate virtual servers to another node or nodes.
Owner:NETWORK APPLIANCE INC
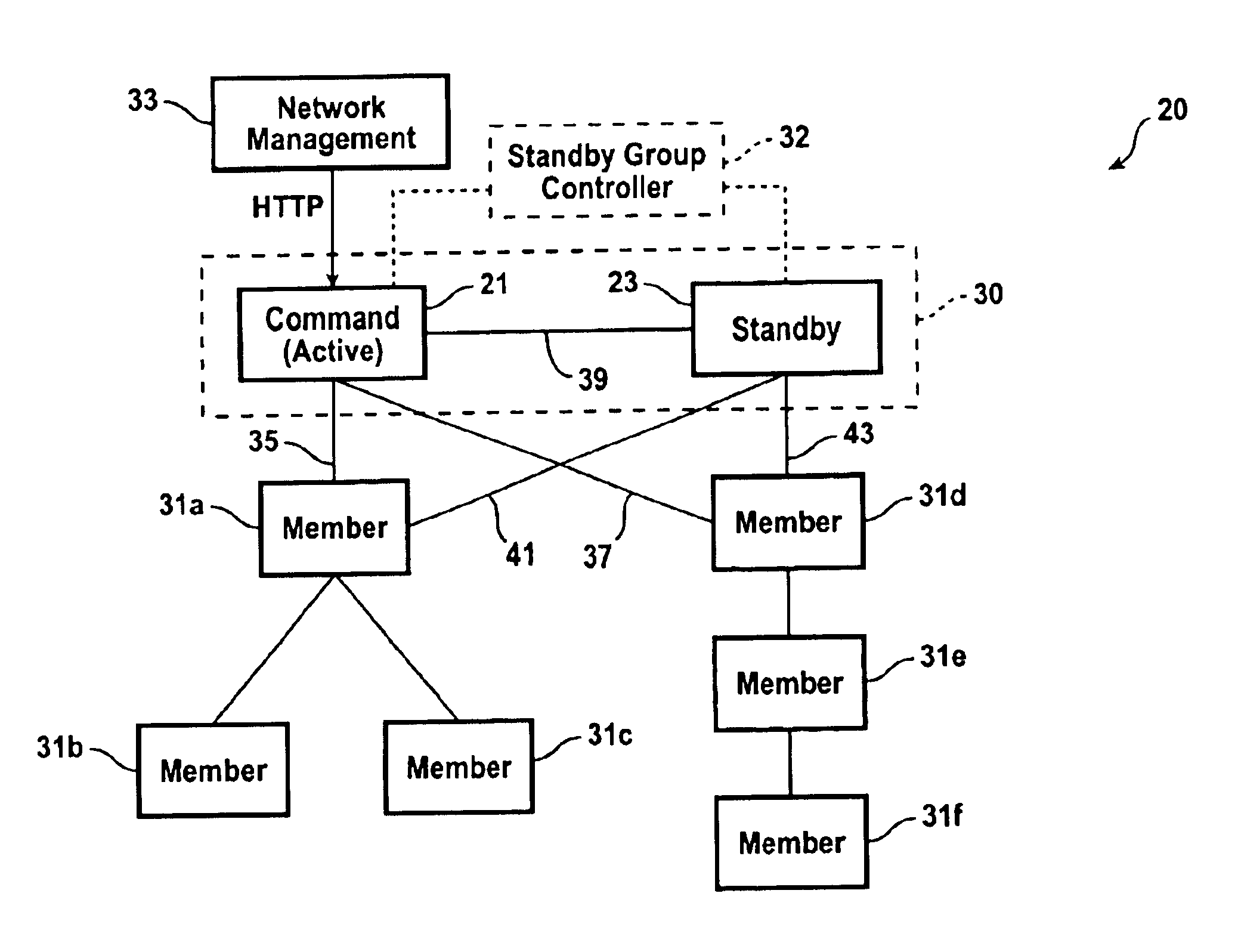
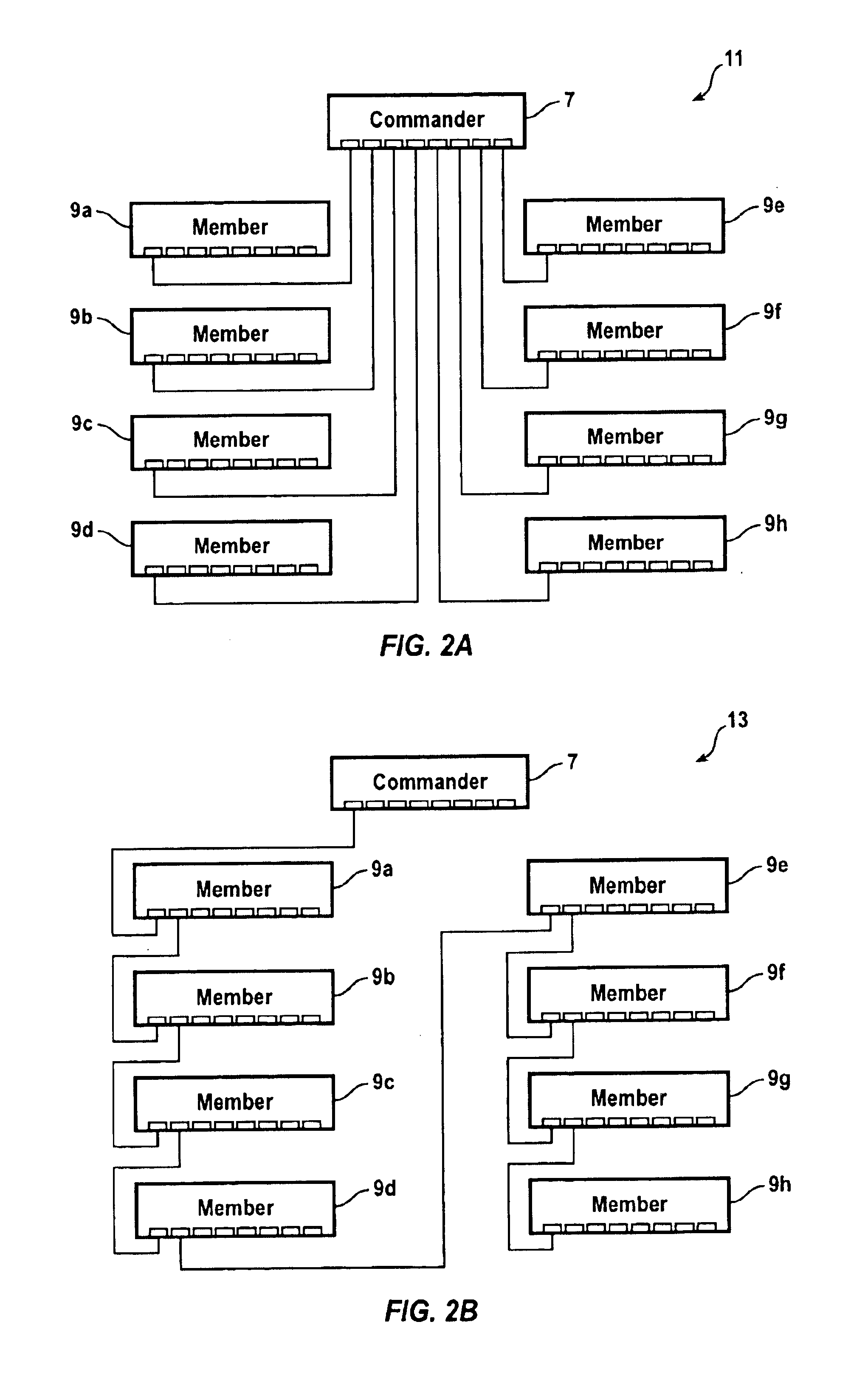
Method and system for high reliability cluster management
InactiveUS6856591B1Improve reliabilityError preventionTransmission systemsDependabilityDistributed computing
A method provides high reliability to management of a cluster of network devices. The cluster including a command network device and at least one member network device. The command network device has a commander IP address and a commander MAC address. The method includes: defining a standby group by assigning a virtual IP address and a virtual MAC address; selecting a first network device; which is the command network device, for the standby group; selecting at least one second network device, which has an IP address, for the standby group; defining a standby priority for each network device in the standby group; and binding the standby group to the cluster, by replacing the commander IP address with the virtual IP address and replacing the commander MAC address with the virtual MAC address. Upon the binding, the network device with a highest priority becomes an active commander, and the network device with a second highest priority becomes a standby commander. The the network device with a third highest priority, if any, becomes a passive commander. The cluster is controlled through the active commander using the virtual IP address. The active commander periodically forwards the cluster configuration information to the passive commander. The control of the cluster is switched from the active commander to the standby commander upon a failure of the active commander, the standby commander becoming a current active commander.
Owner:CISCO TECH INC
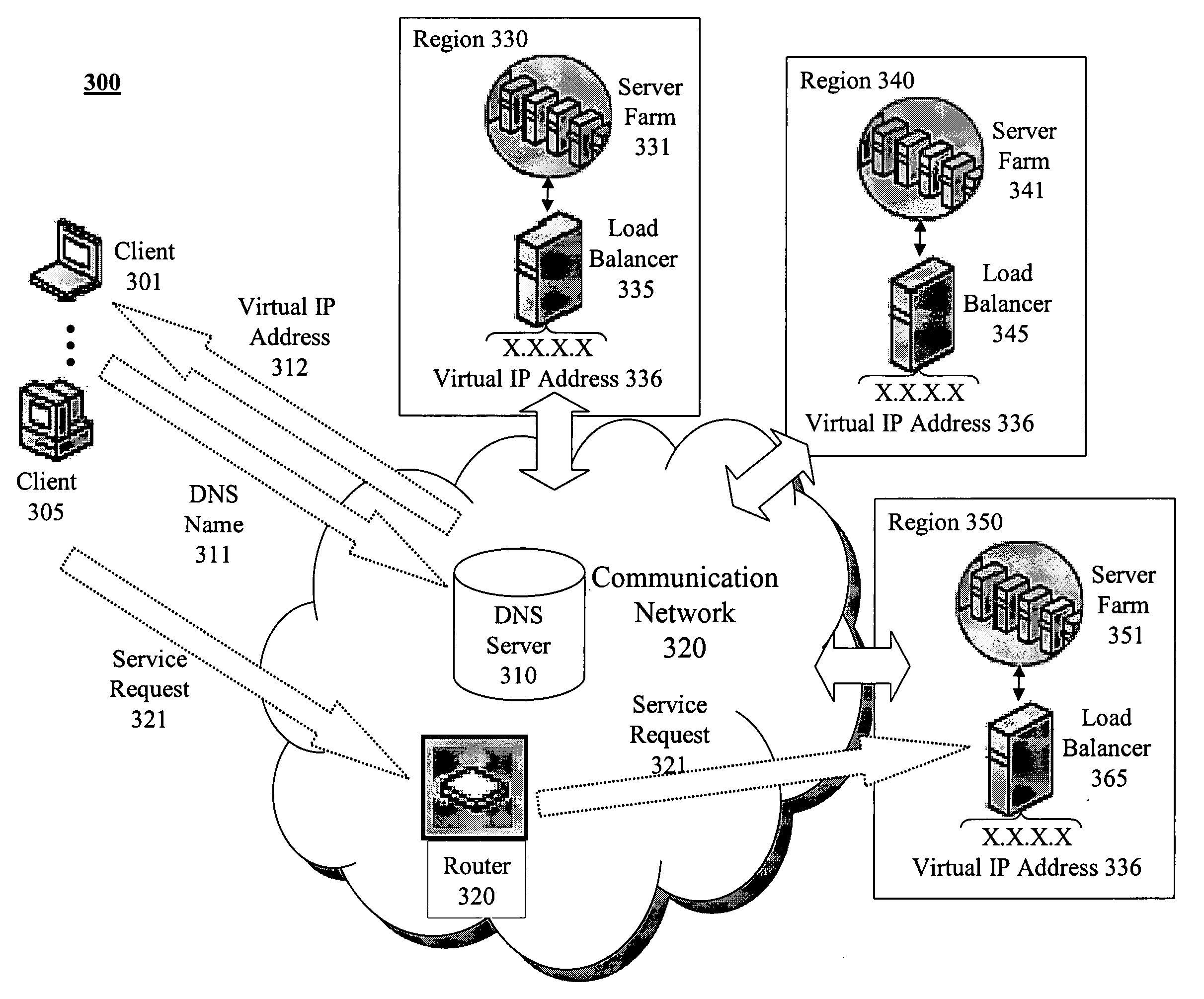
Geo-locating load balancing
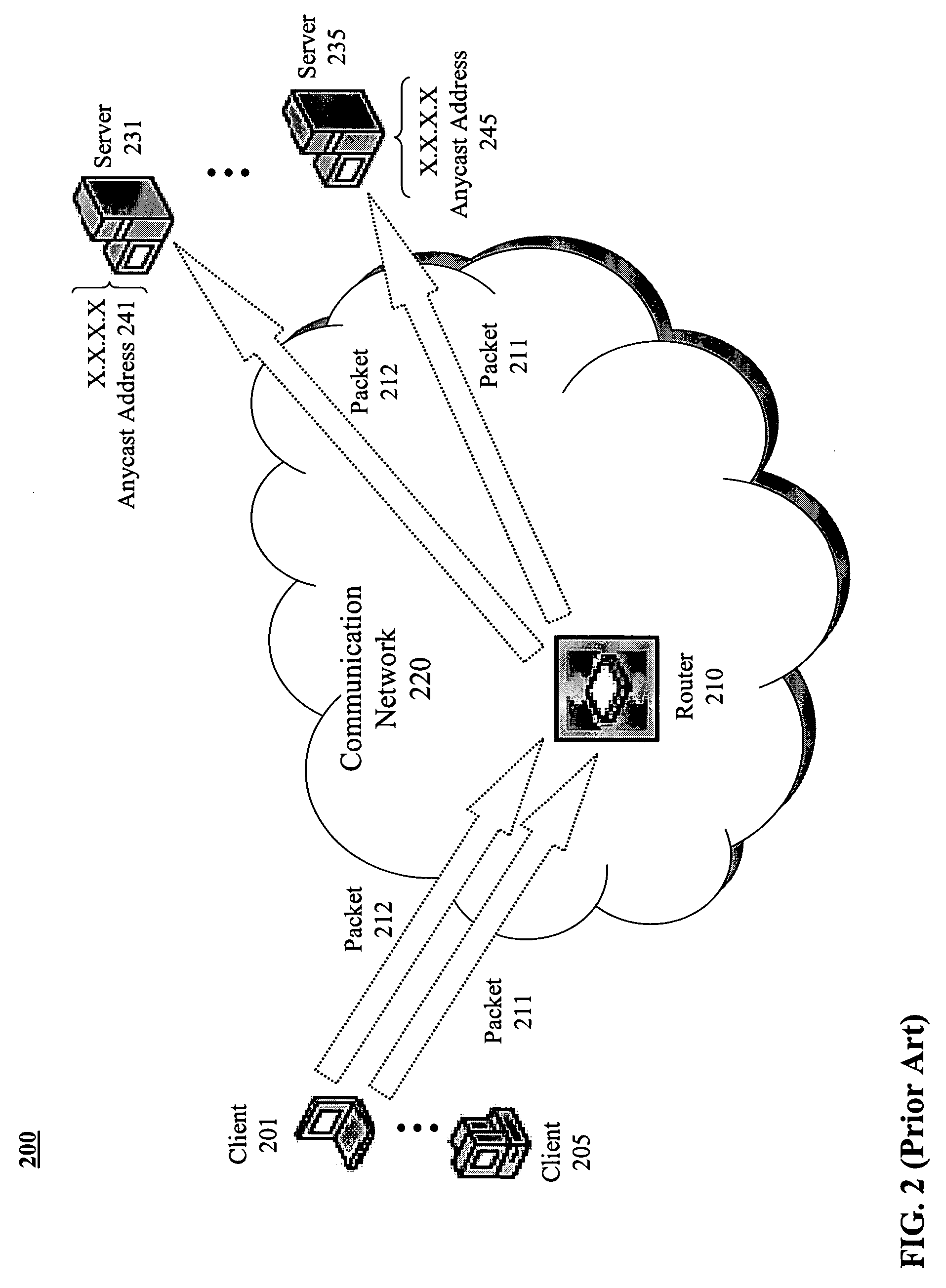
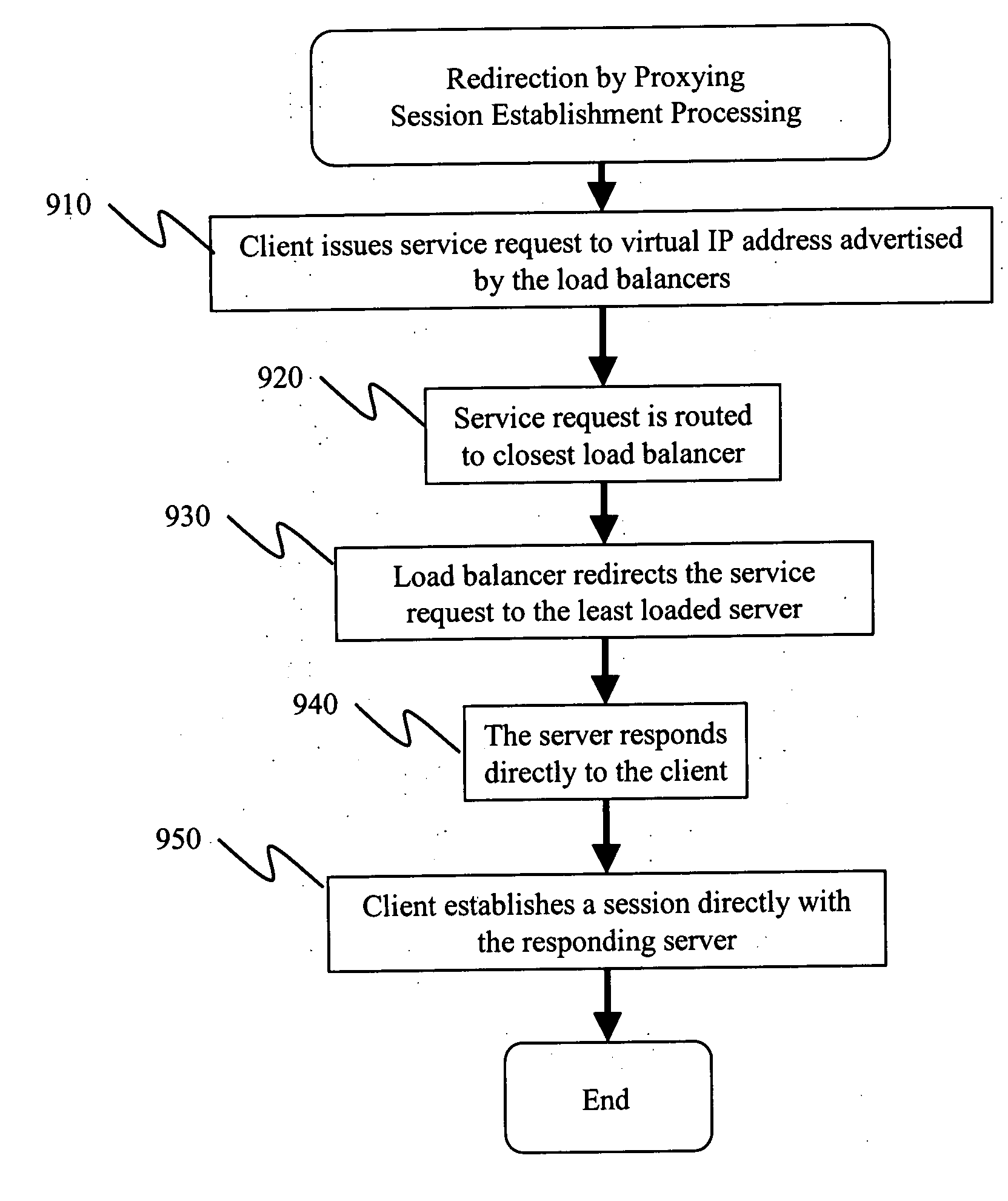
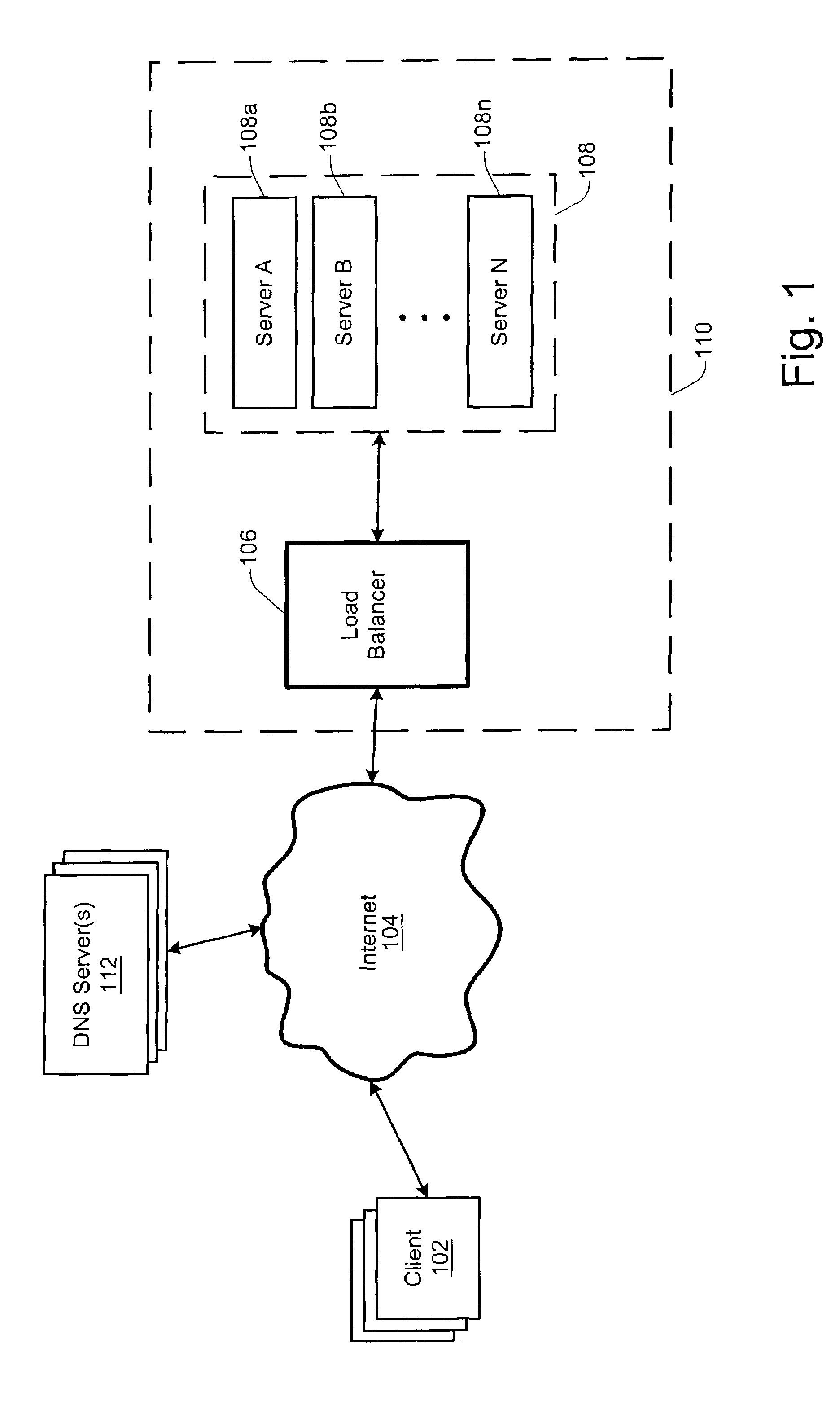
Methods and apparatus are provided for geo-locating load balancing. According to one embodiment, a communication network architecture includes multiple servers, multiple load balancers, and multiple geographically dispersed communication devices. The servers provide services to the communication devices within the communication network. The load balancers each service a shared virtual Internet Protocol (IP) address common to all of the load balancers and perform load balancing of service requests on behalf of two or more of the servers that are located geographically proximate to the load balancer. The communication devices are communicatively coupled with the load balancers and are configured to issue service requests intended for any of the servers to the shared virtual IP address, whereby, upon issuing a service request, a communication device is directed to a particular server selected by a load balancing routine that is associated with a load balancer that is closest to the communication device.
Owner:LEVEL 3 COMM LLC
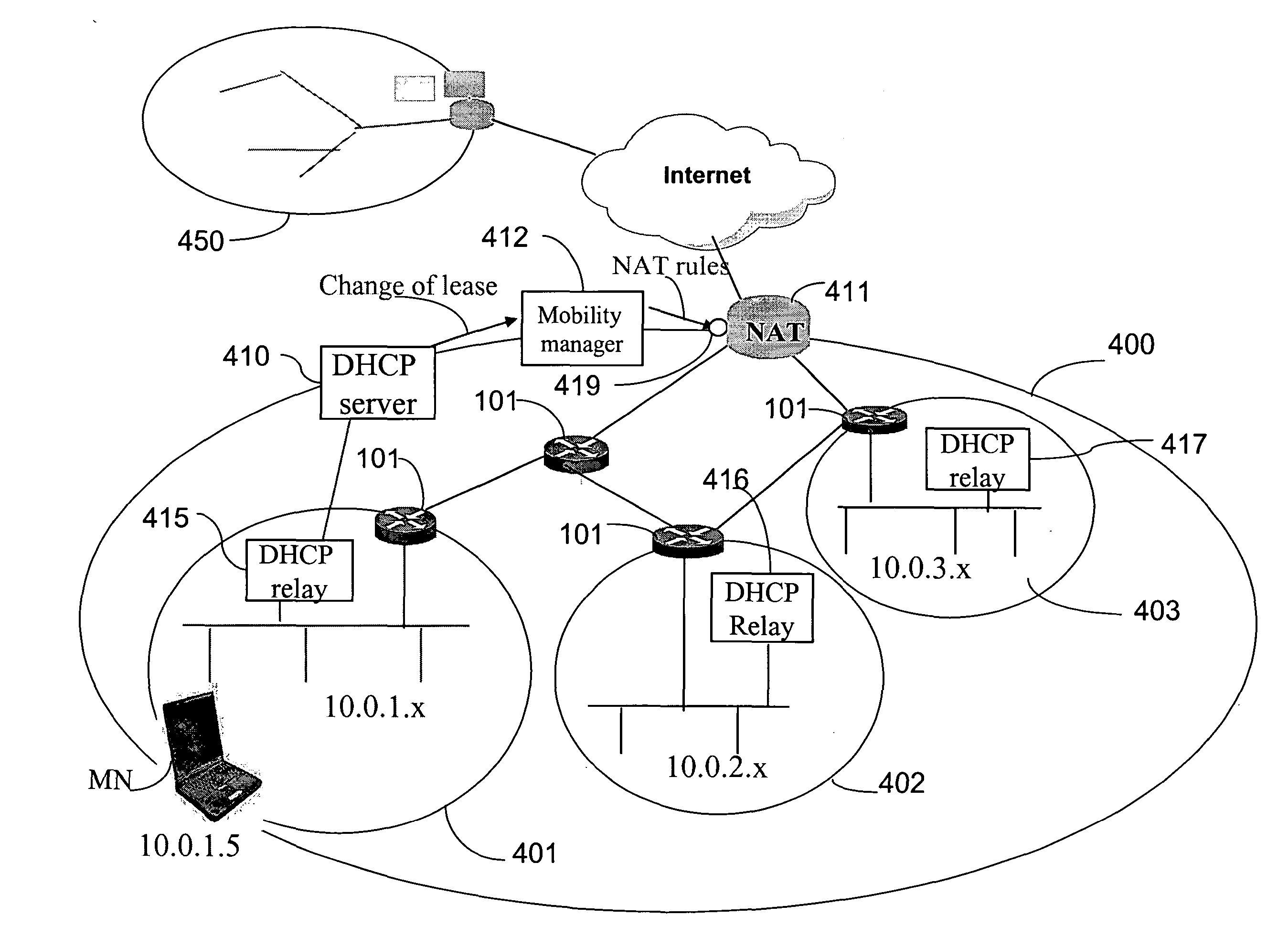
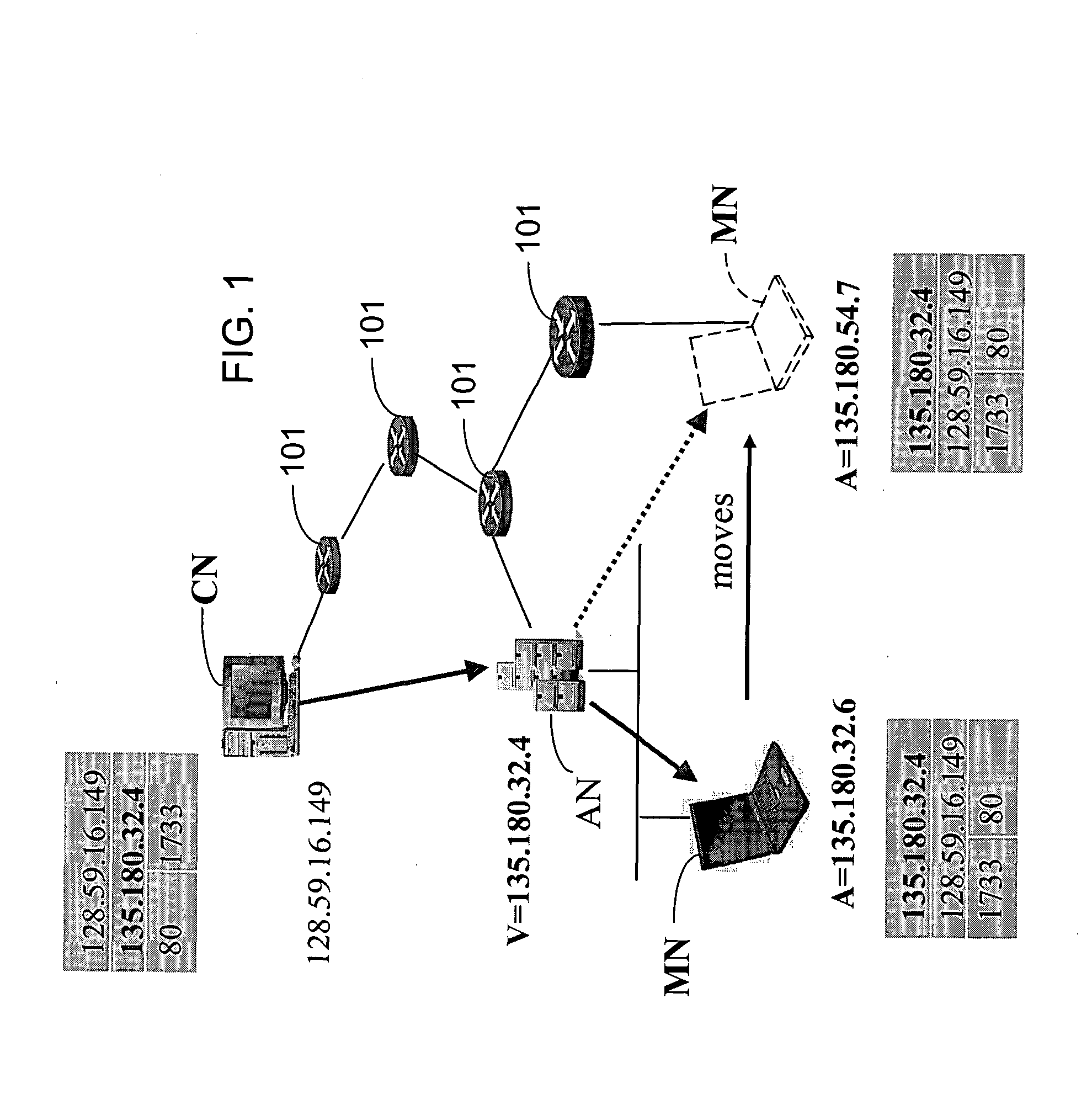
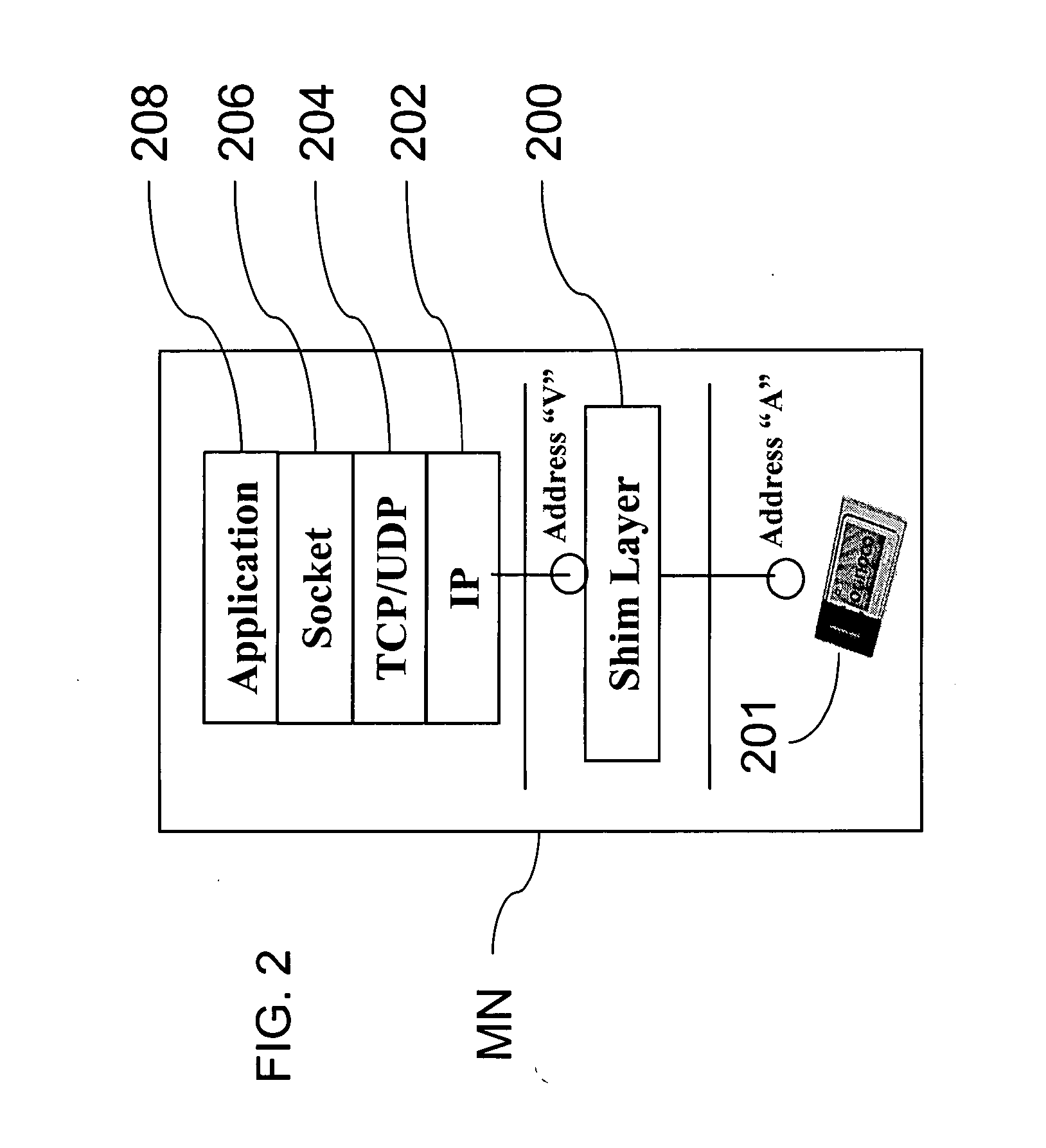
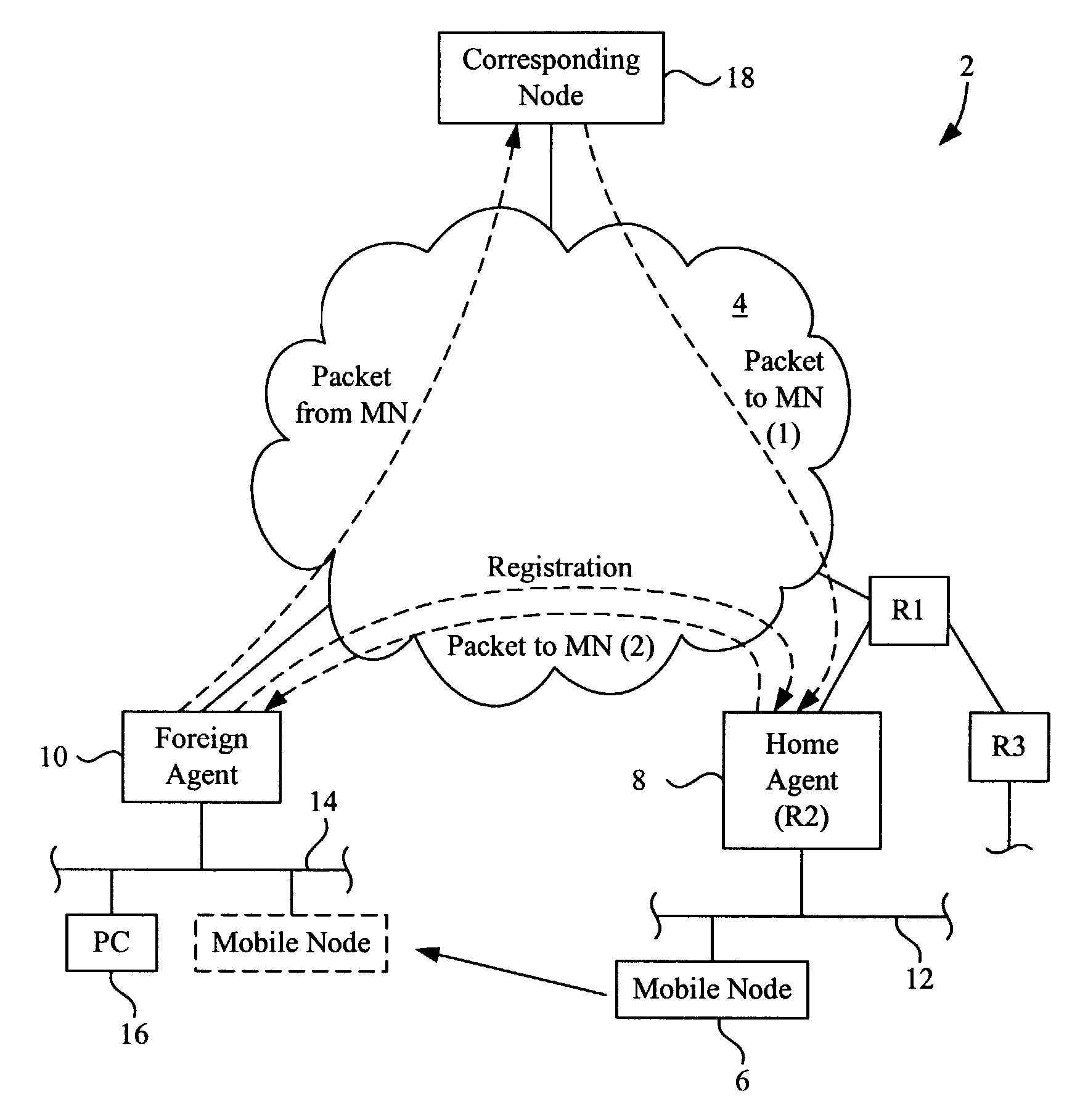
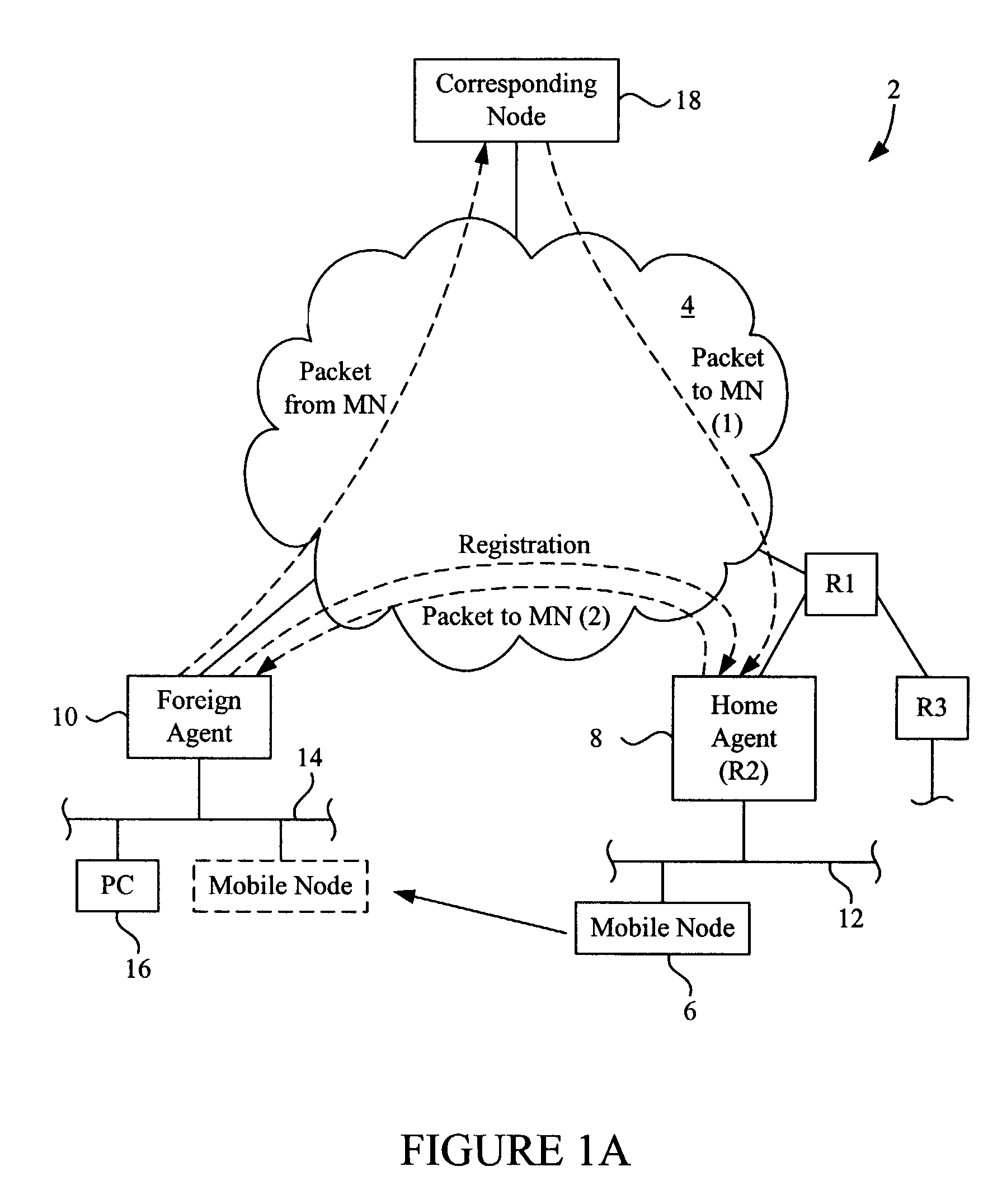
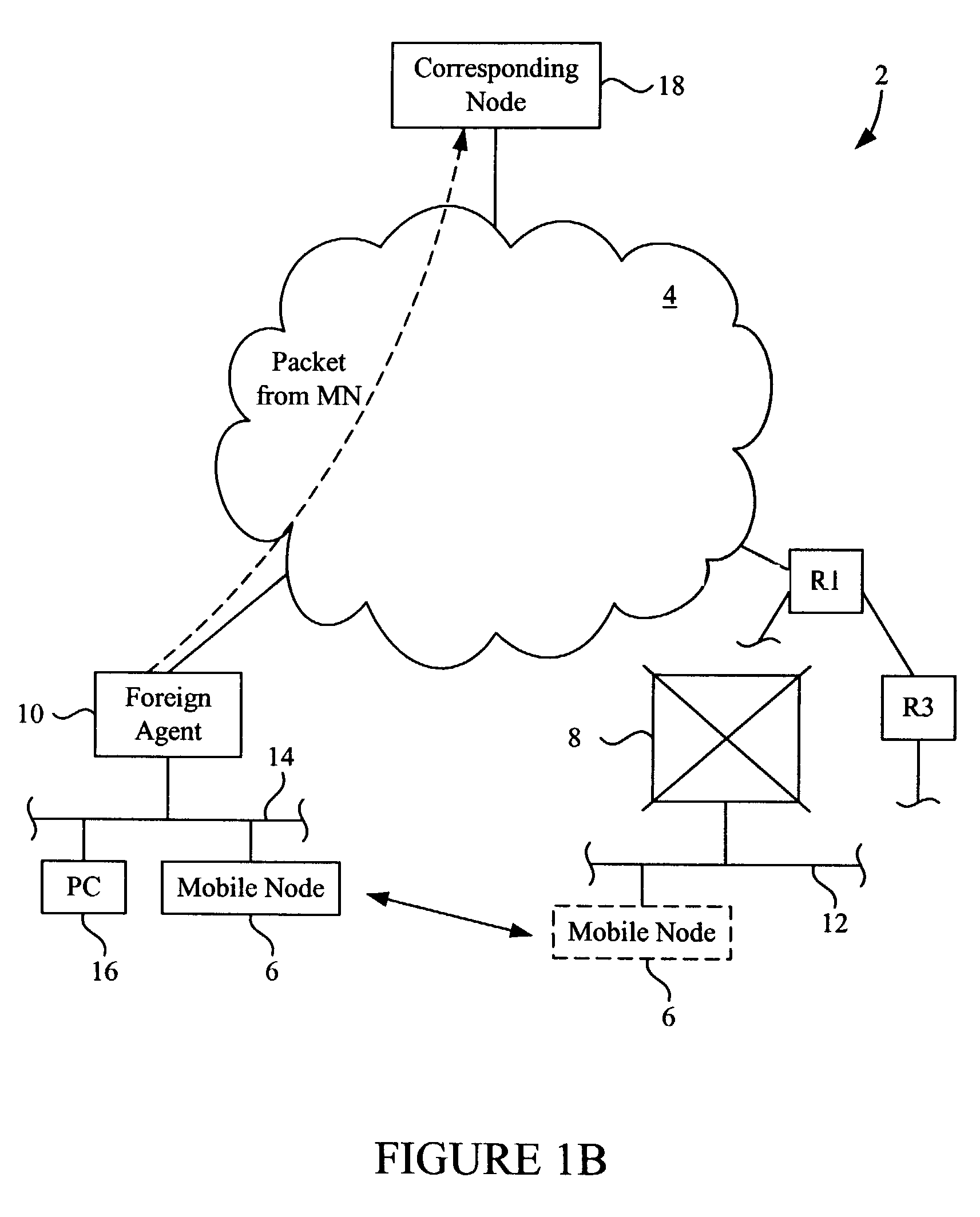
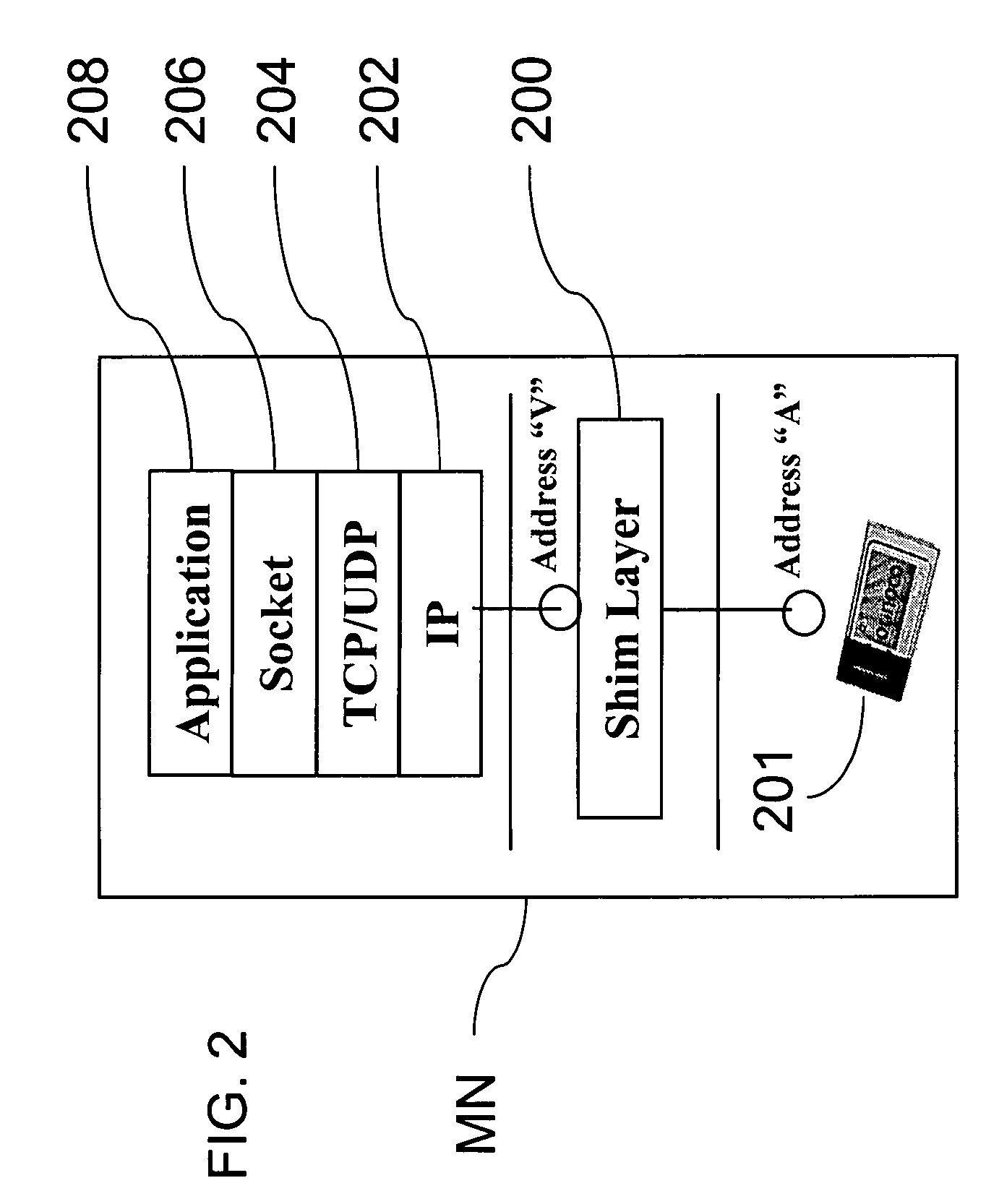
Method and system for mobility across heterogeneous address spaces
ActiveUS20050013280A1Time-division multiplexData switching by path configurationAddress spaceInternet Protocol
A mobile node includes a processor, a network interface, and a storage device having computer program code for execution by the processor. The computer program code includes a network layer for transmitting and receiving packets and an intermediate driver that transmits packets to the network layer and receives packets from the network layer using a virtual internet protocol (IP) address to identify the mobile node. The intermediate driver transmits packets to the network interface and receives packets from the network interface using a routable actual IP address to identify the mobile node. The intermediate driver permits the actual IP address to change when the mobile node moves from a first subnet to a second subnet without a corresponding change in the virtual IP address. A corresponding NAT associates the virtual IP address with a second actual IP address when the NAT is notified that the mobile node is in the second subnet.
Owner:ALCATEL LUCENT SAS
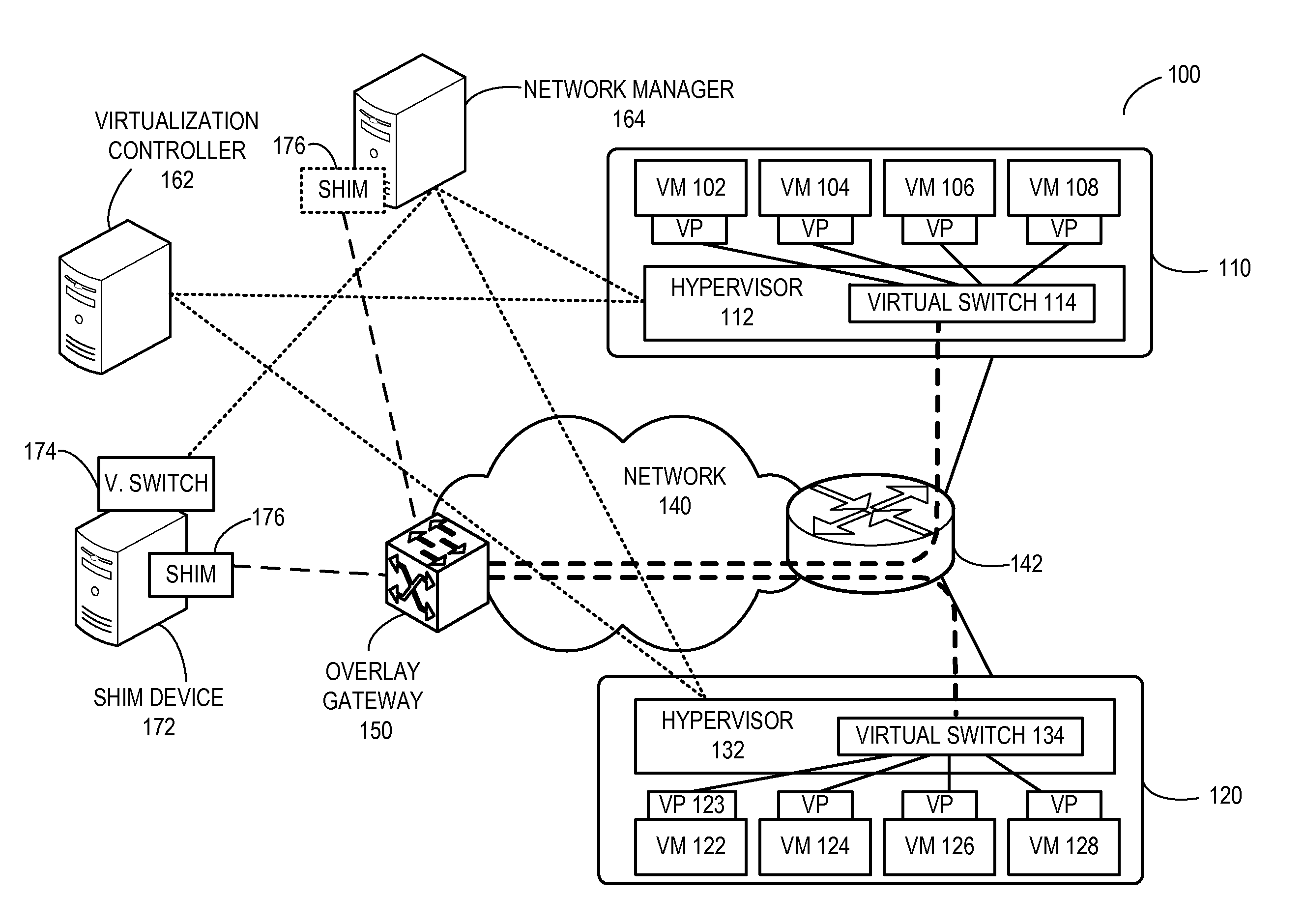
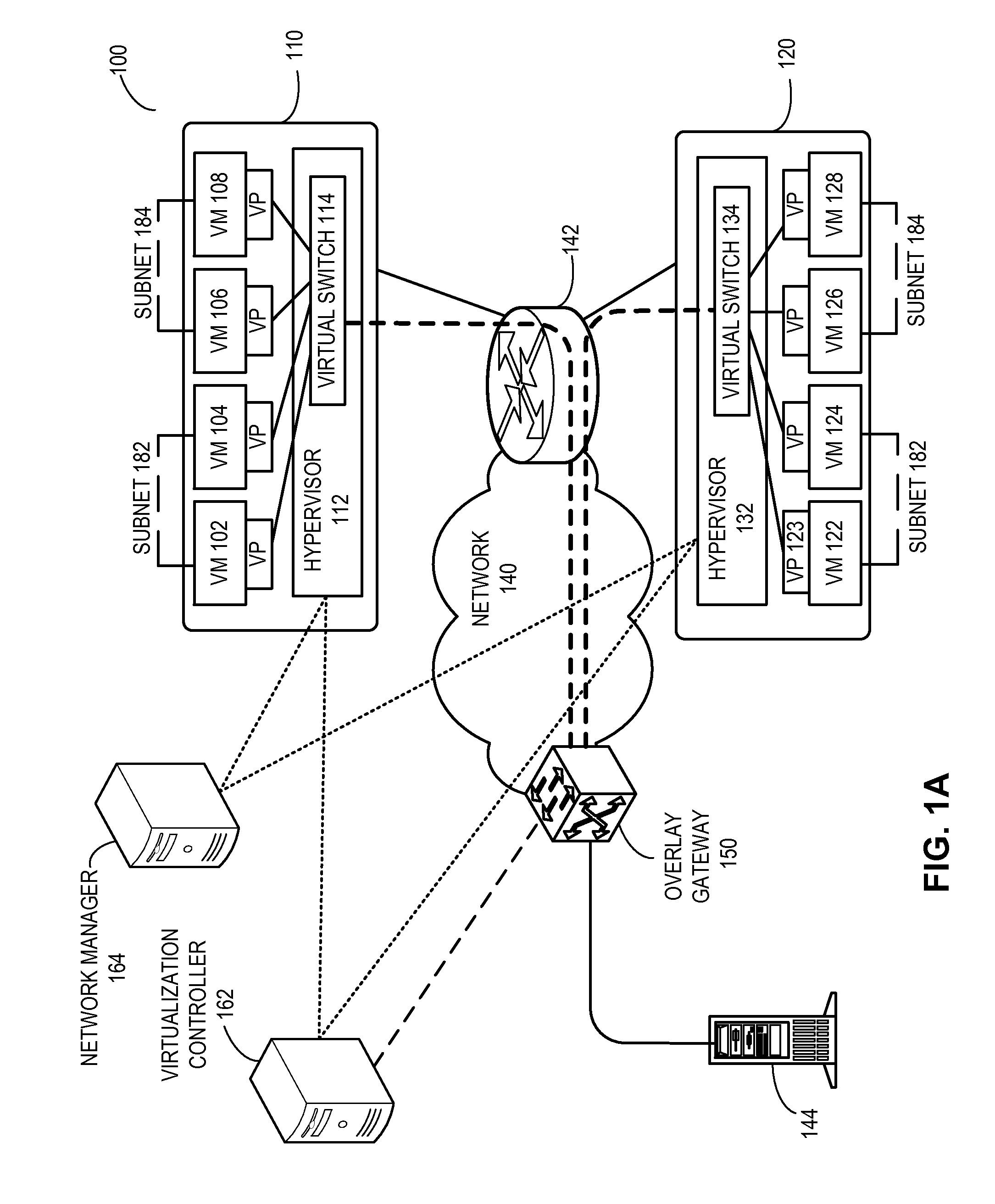
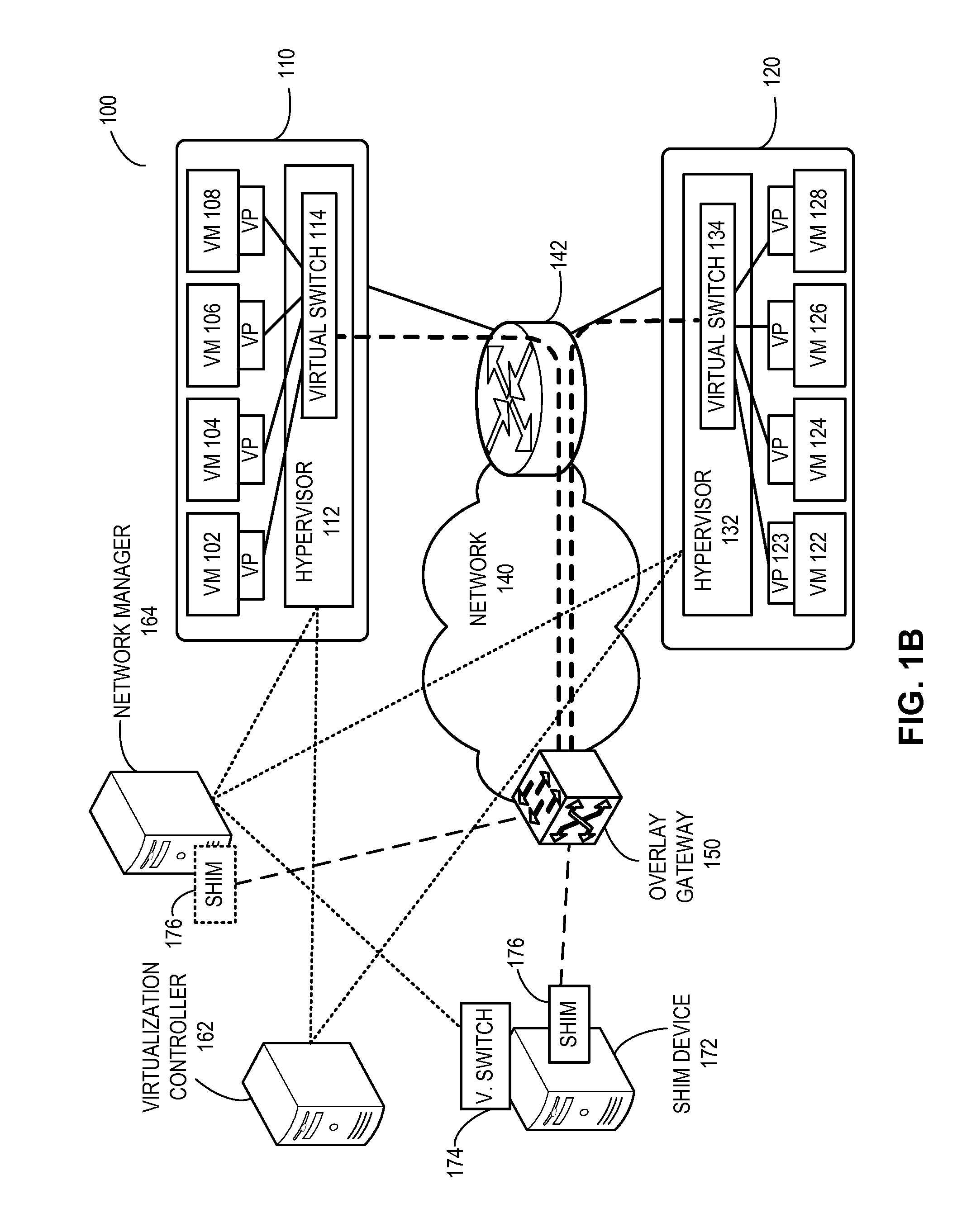
Layer-3 overlay gateways
ActiveUS20130318219A1Digital computer detailsData switching networksInternet ProtocolStore instruction
One embodiment of the present invention provides a computing system. The computing system includes a processor and a computer-readable storage medium for storing instructions. Based on the instructions, the processor operates the computing system as an overlay gateway. The computing system initiates and terminates an overlay tunnel associated with a virtual machine. During operation, the computing system maps a virtual Internet Protocol (IP) address of the virtual machine to a second IP address used to terminate the overlay tunnel based on information received from a configuration system. The computing system then determines an output port for a data packet based on the second IP address. The data packet comprises an inner packet and the destination address of this inner packet corresponds to the virtual IP address.
Owner:AVAGO TECH INT SALES PTE LTD
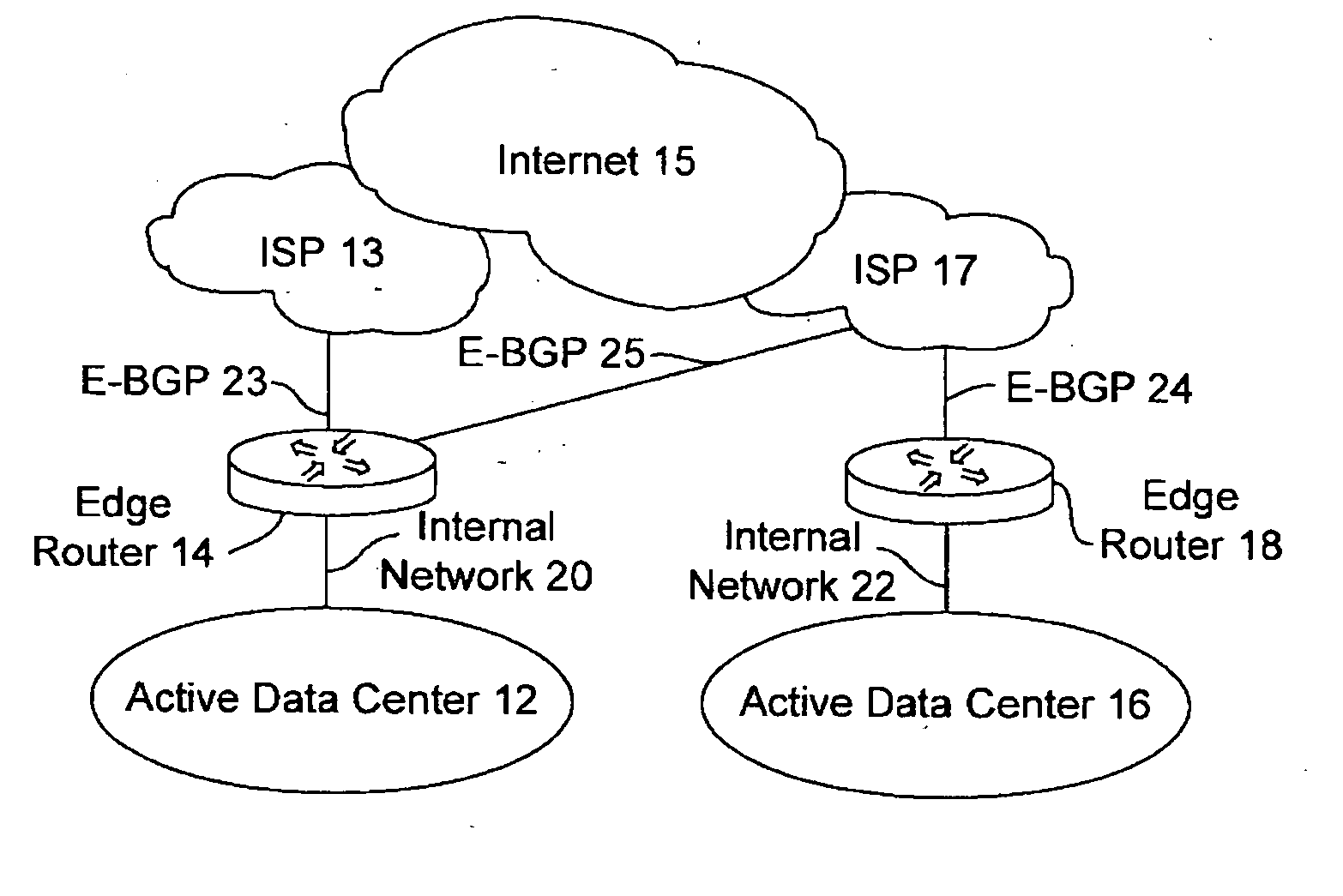
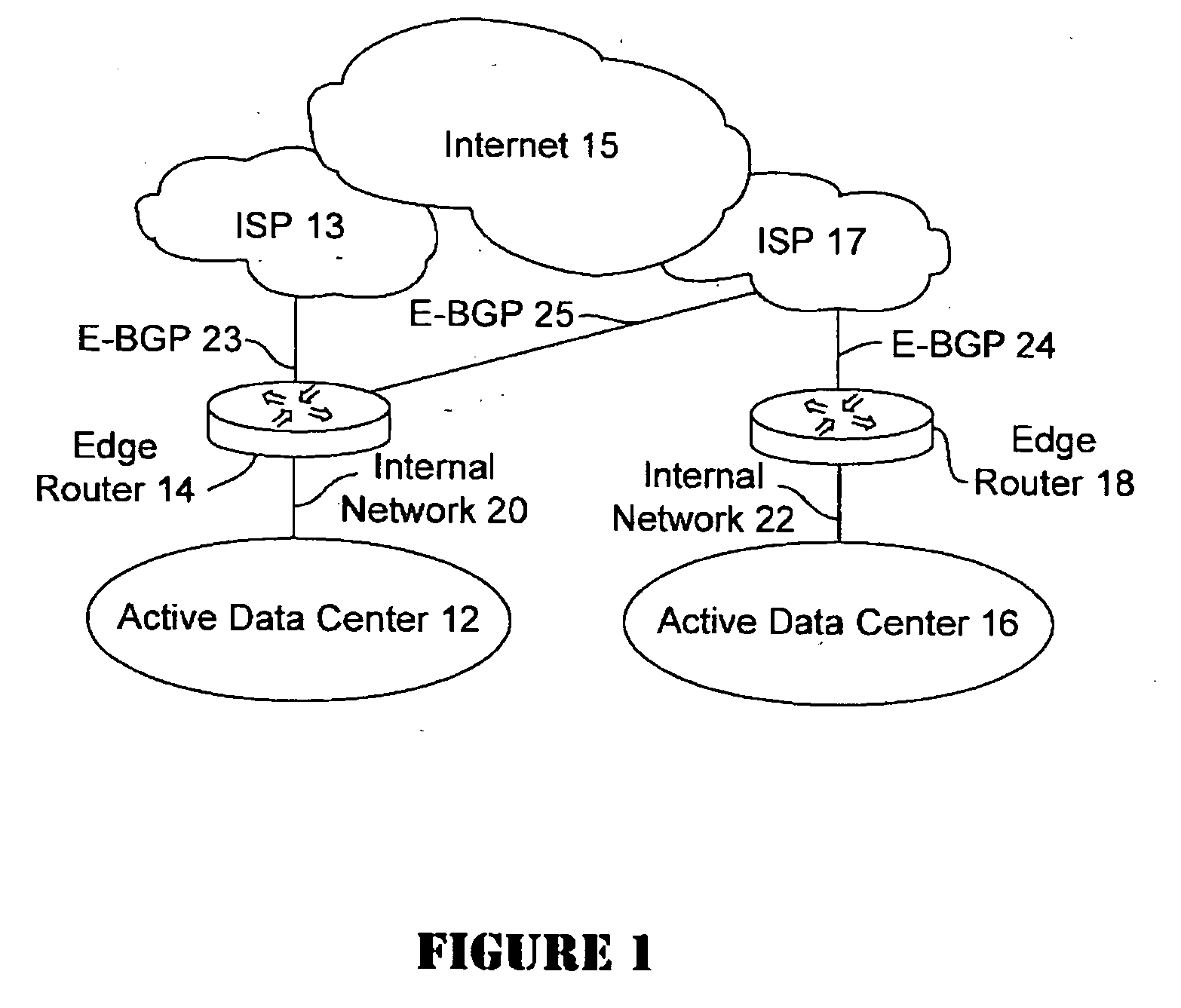
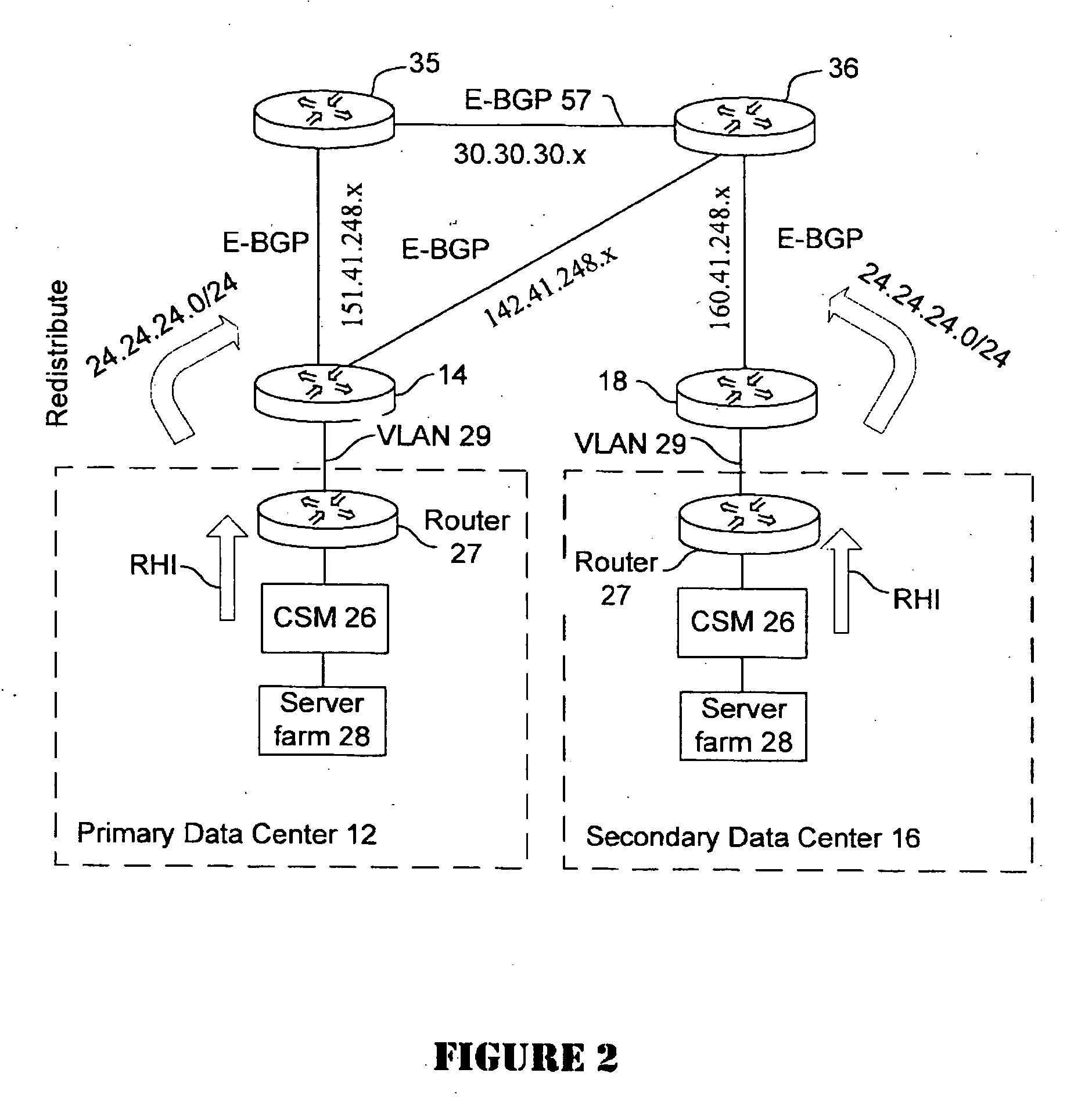
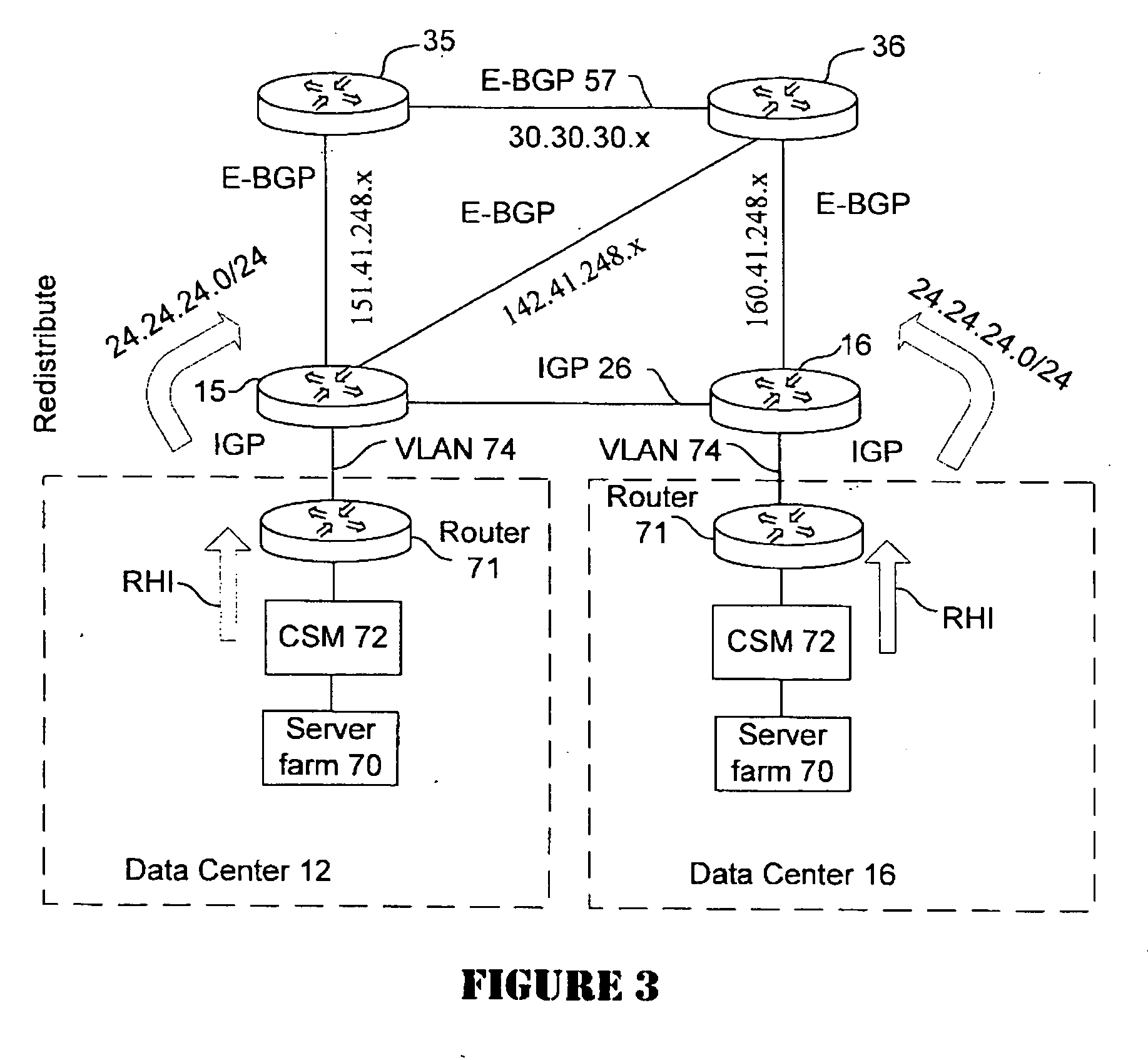
Active-active data center using RHI, BGP, and IGP anycast for disaster recovery and load distribution
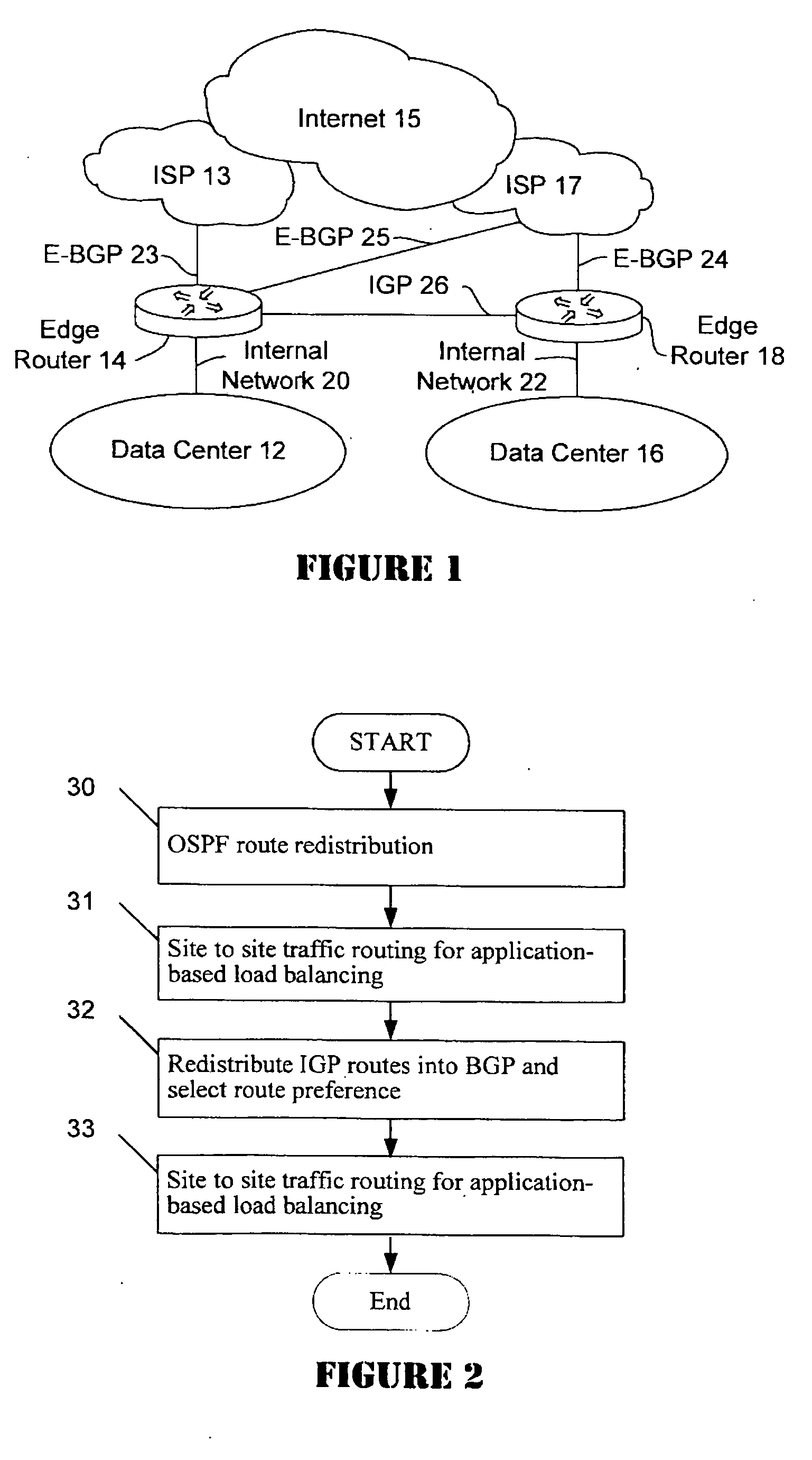
A distributed data center topology having at least a pair of active data centers that can recover from a disaster at one of the data centers and achieves load balancing using IGP (Interior Gateway Protocol) between data centers. The distributed data centers use virtual IP addresses, route health injection and Border Gateway Protocol (BGP) for business continuance, disaster recovery and load balancing. The active / active topology supports load balancing where each site concurrently hosts active applications or applications can be hosted in a logical active / standby mode. IGP and RHI (Route Health Injection) are used to propagate routes to an edge router and BGP (Border Gateway Protocol) and IP Anycast are used for site-to-site recovery and load balancing between data center sites.
Owner:CISCO TECH INC
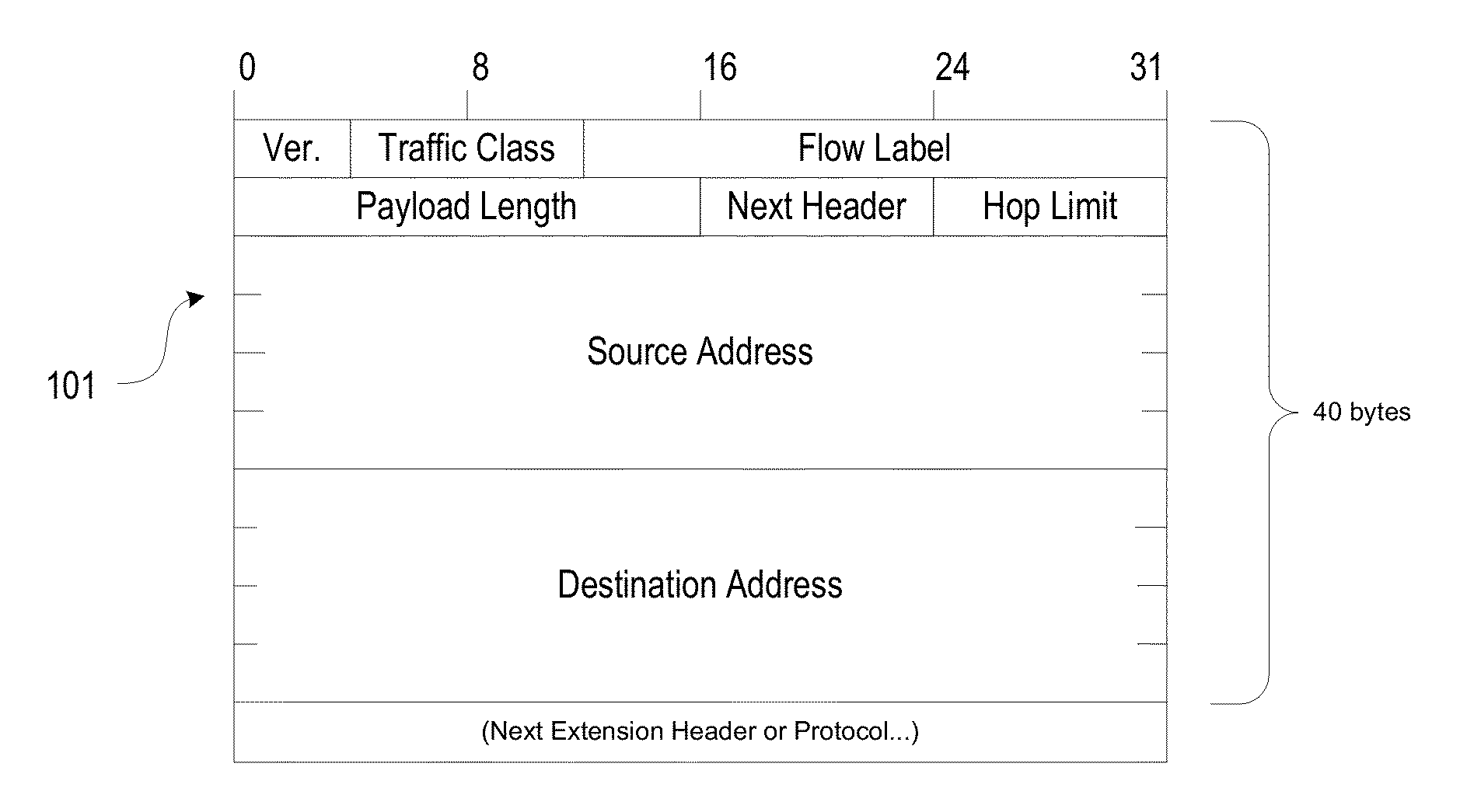
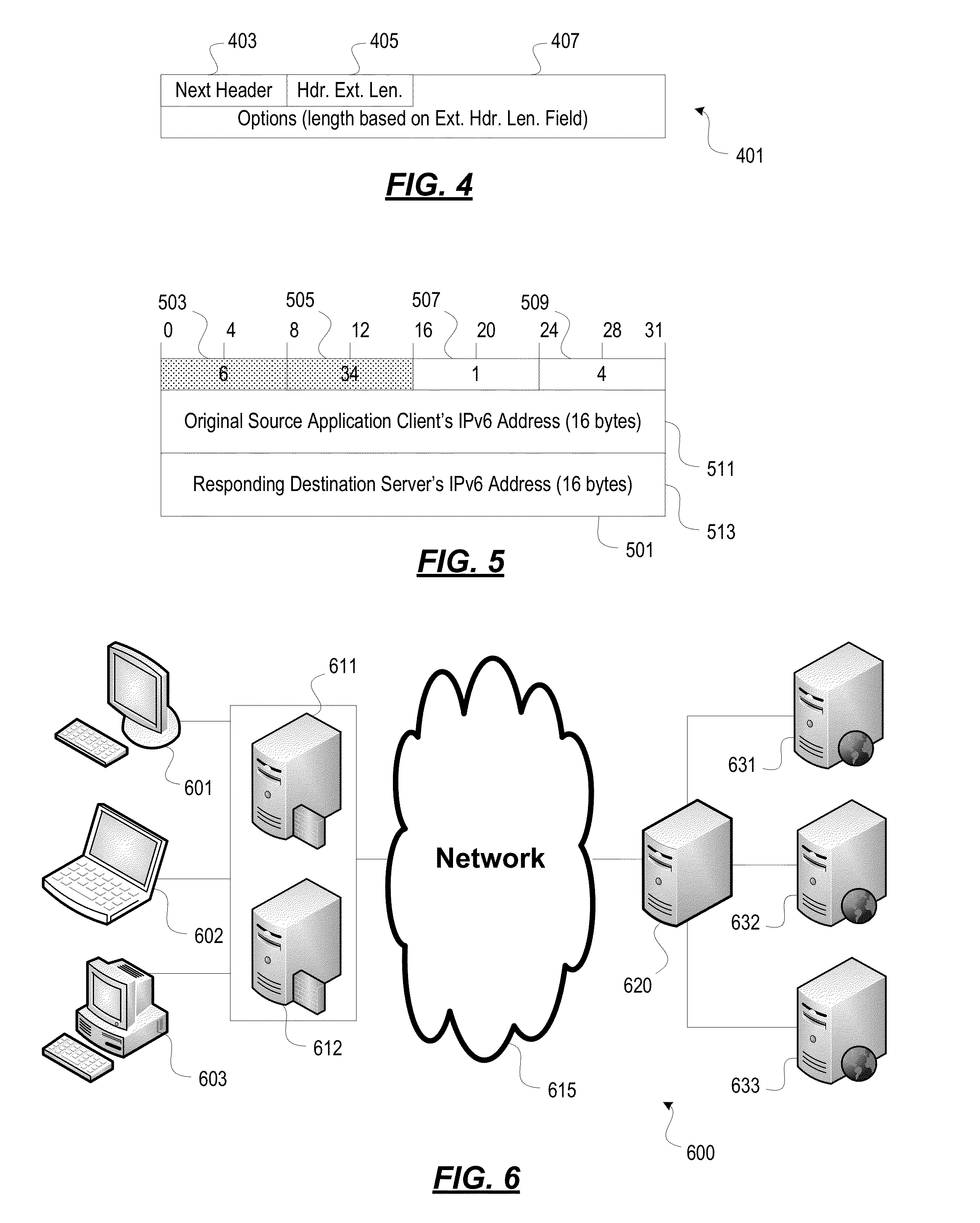
Load Balancing and Session Persistence in Packet Networks
Methods and systems for performing load balancing and session persistence in IP (e.g., IPv6) networks are described herein. Some aspects relate to a destination options extension header that may be defined as a load balancing session persistence option (LBSPO) for storing a client identifier and a server identifier for each of a client and a server during a session. Packets sent between the client and the server may include the LBSPO with the client and server identifiers. A load balancer with a virtual IP address of a target application can perform session persistence and assign a destination server to a client based on a preexisting session between the server and the client, as determined by the LBSPO information. While a target VIP node may process data packets based on the LBSPO information, once established, the LBSPO information may remain unchanged for the duration of the session.
Owner:COMCAST CABLE COMM LLC
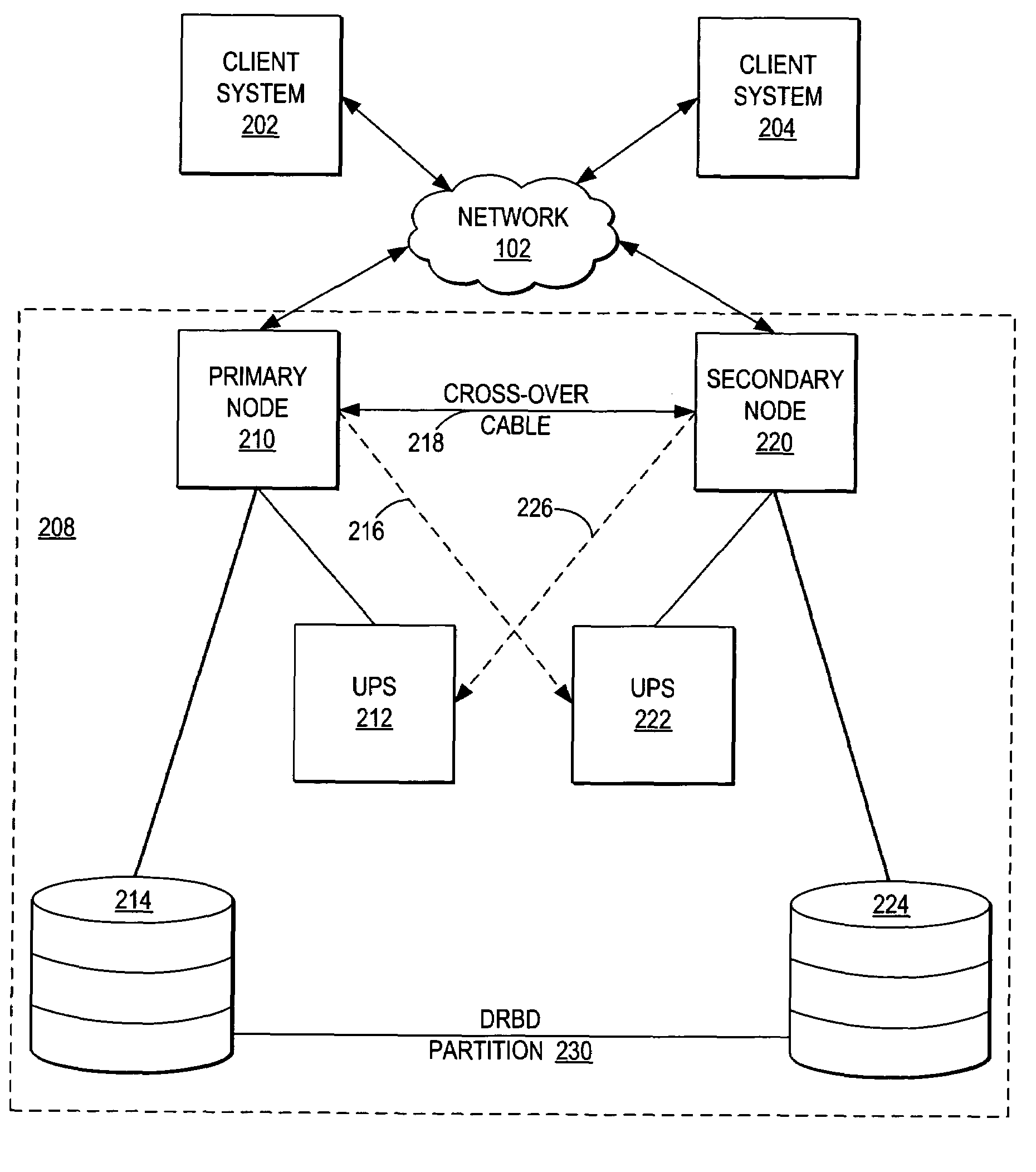
Managing failover of J2EE compliant middleware in a high availability system
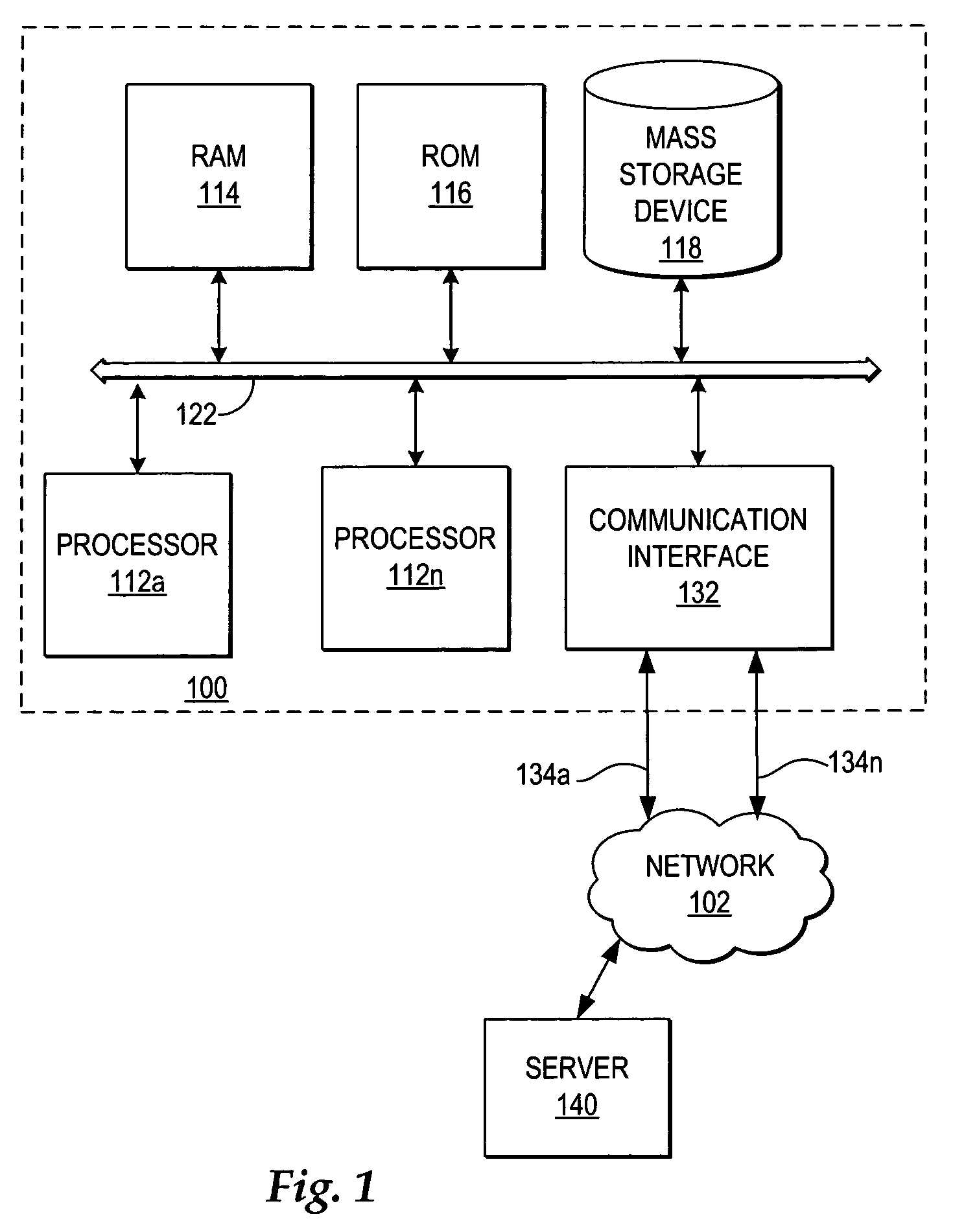
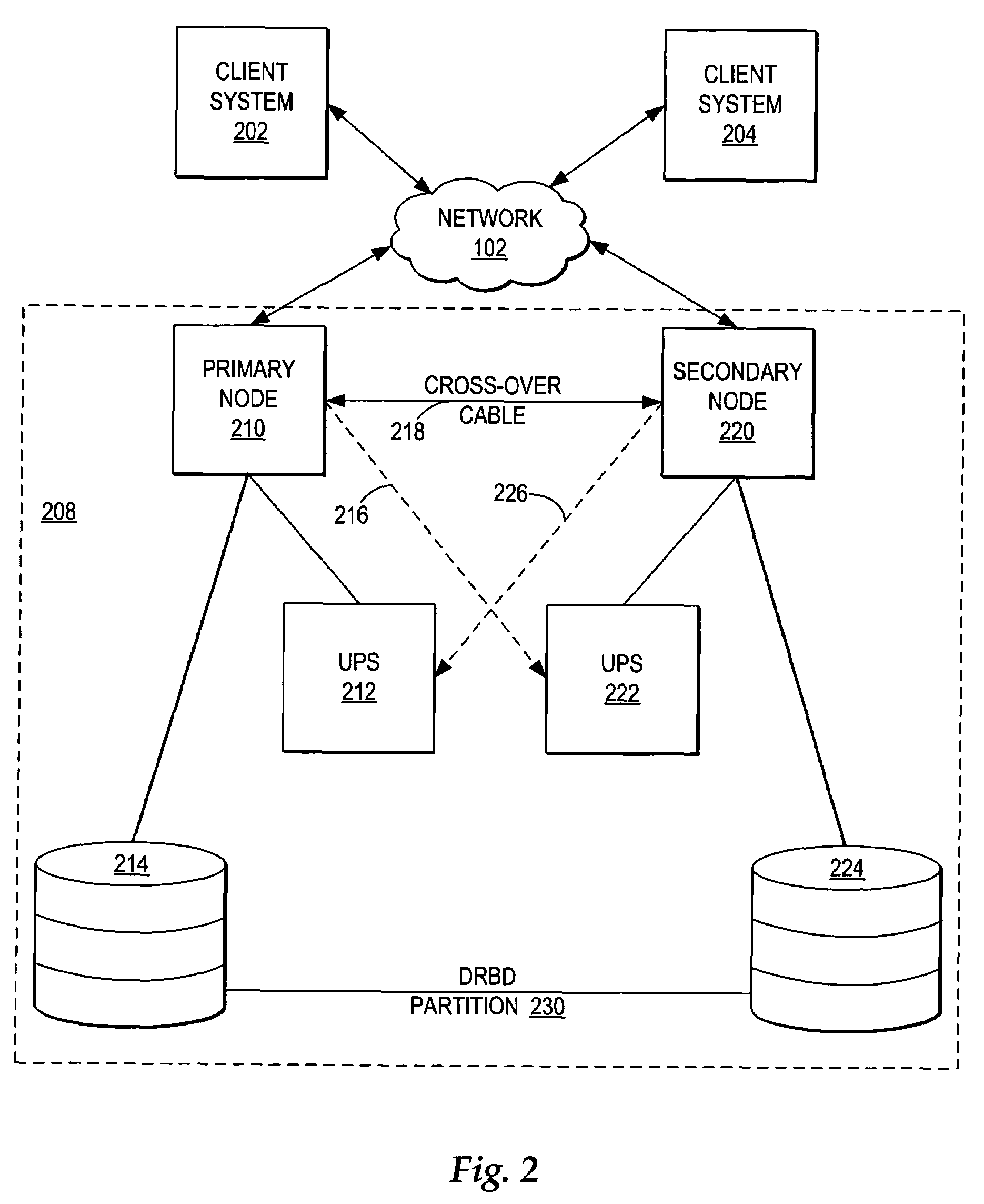
InactiveUS20050172161A1Short recovery timeMinimal data lossRedundant hardware error correctionFailoverWeb application
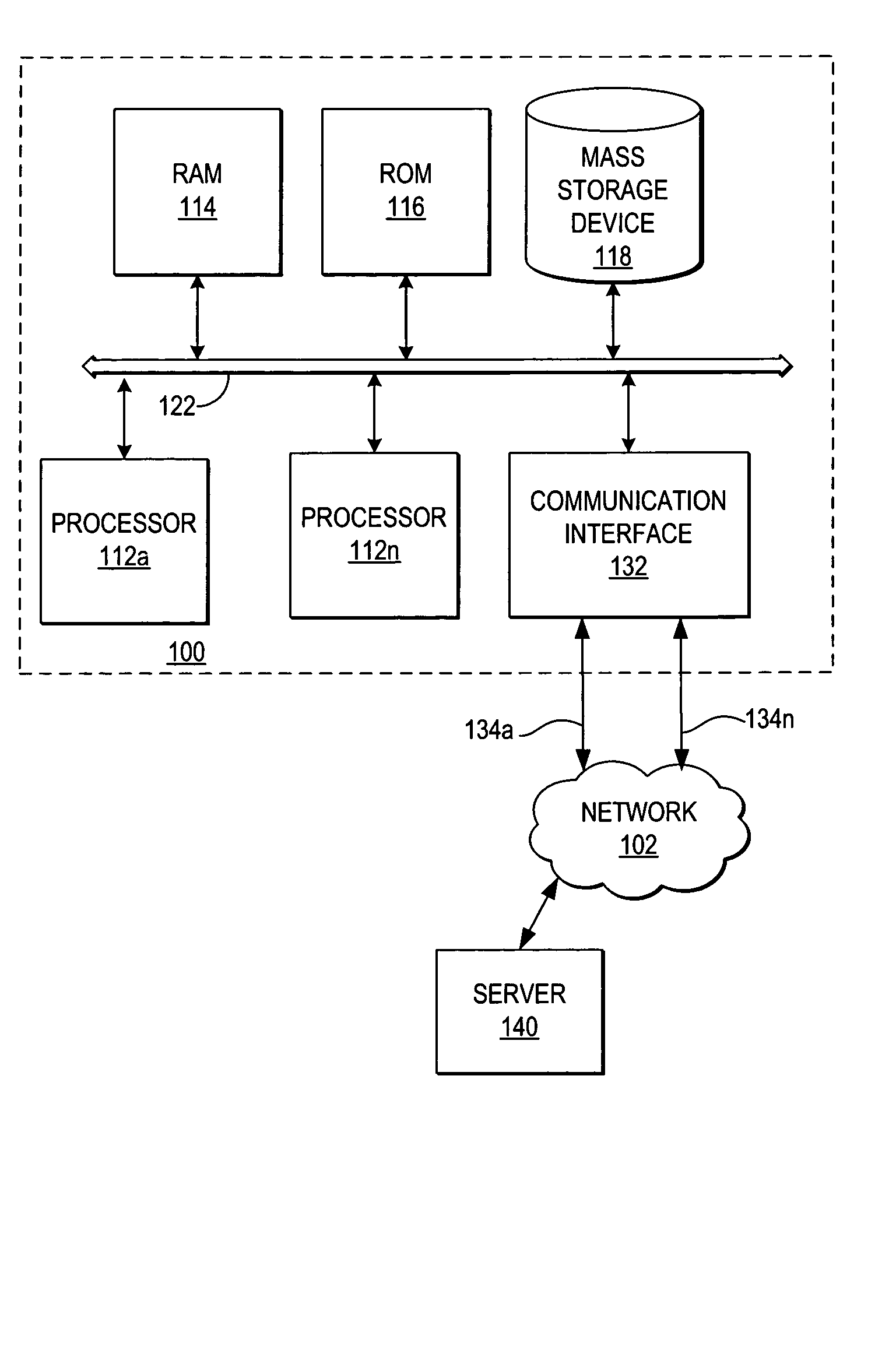
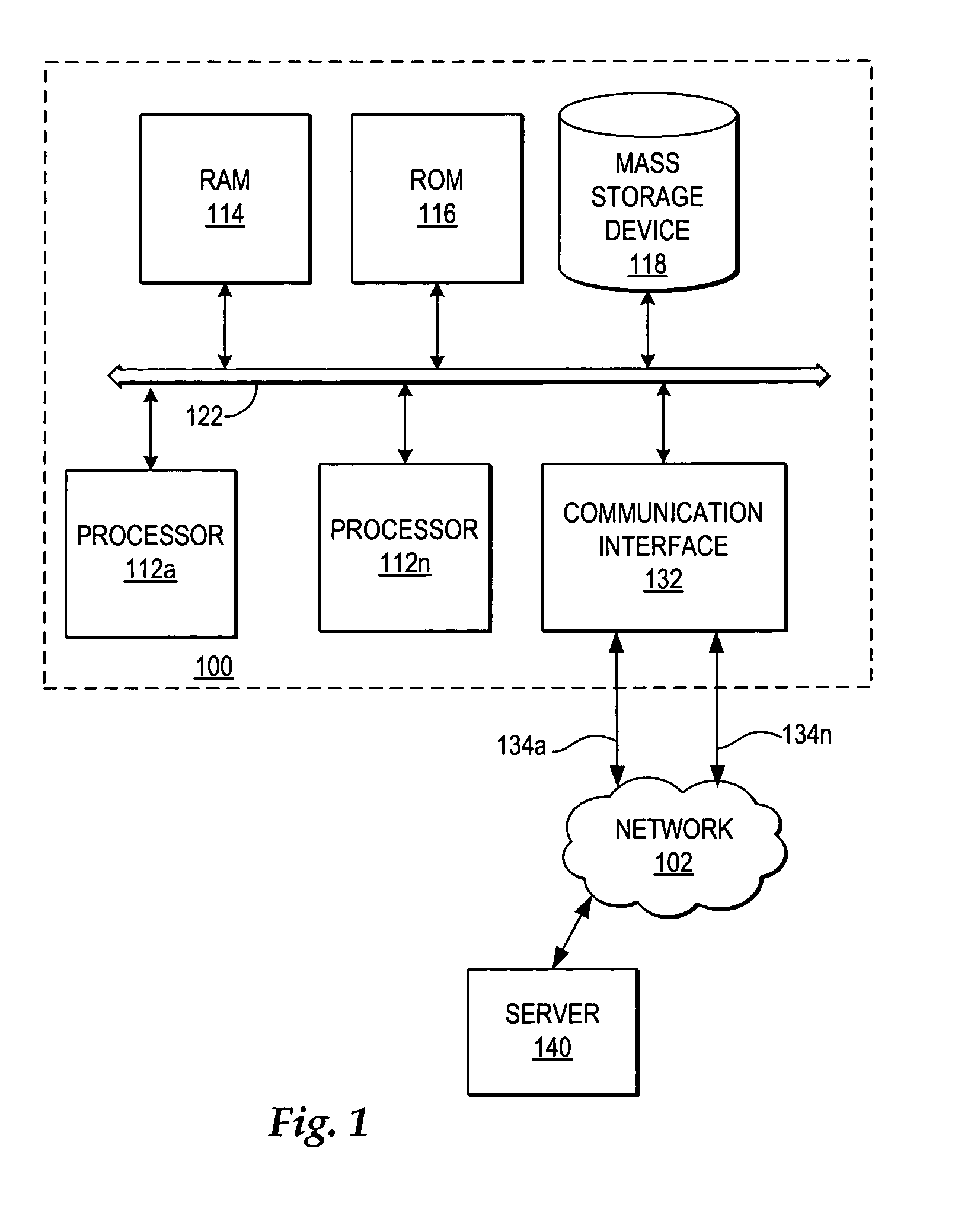
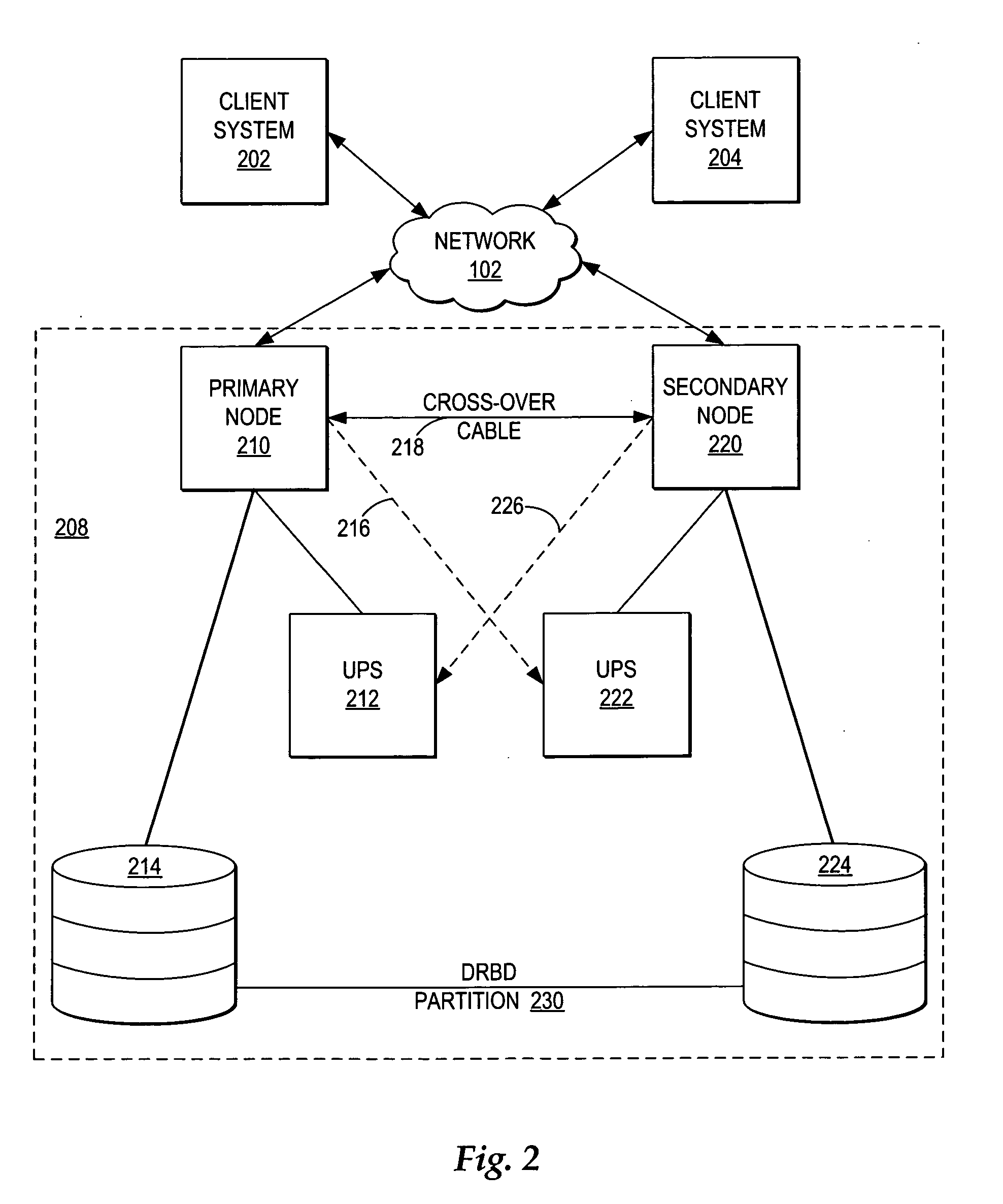
A method, system, and program for managing failover of J2EE compliant middleware in a high availability system are provided. A primary node and a secondary node each run the same J2EE compliant middleware stack comprising layers including a load balancer, a web server, a web application server, a message control server, a monitoring server, and a database control server. In the primary node, all layers are active. In the secondary node, part of the layers are active and part of the layers are in standby. A data replication partition shared between the primary node and the secondary node includes persistent resource data accessible to a selection of the layers of the primary node. A heartbeat controller monitors each node, including the middleware stack, and upon detection of a failure, controls transfer of the services provided by the primary node to the secondary node by transferring virtual IP addresses from the primary node to the secondary node, remounting the data replication partition for access by the secondary node, and activating the standby layers which require access to the data in the data replication partition.
Owner:IBM CORP
Geo-locating load balancing
Methods and apparatus are provided for geo-locating load balancing. According to one embodiment, a communication network architecture includes multiple servers, multiple load balancers, and multiple geographically dispersed communication devices. The servers provide services to the communication devices within the communication network. The load balancers each service a shared virtual Internet Protocol (IP) address common to all of the load balancers and perform load balancing of service requests on behalf of two or more of the servers that are located geographically proximate to the load balancer. The communication devices are communicatively coupled with the load balancers and are configured to issue service requests intended for any of the servers to the shared virtual IP address, whereby, upon issuing a service request, a communication device is directed to a particular server selected by a load balancing routine that is associated with a load balancer that is closest to the communication device.
Owner:LEVEL 3 COMM LLC
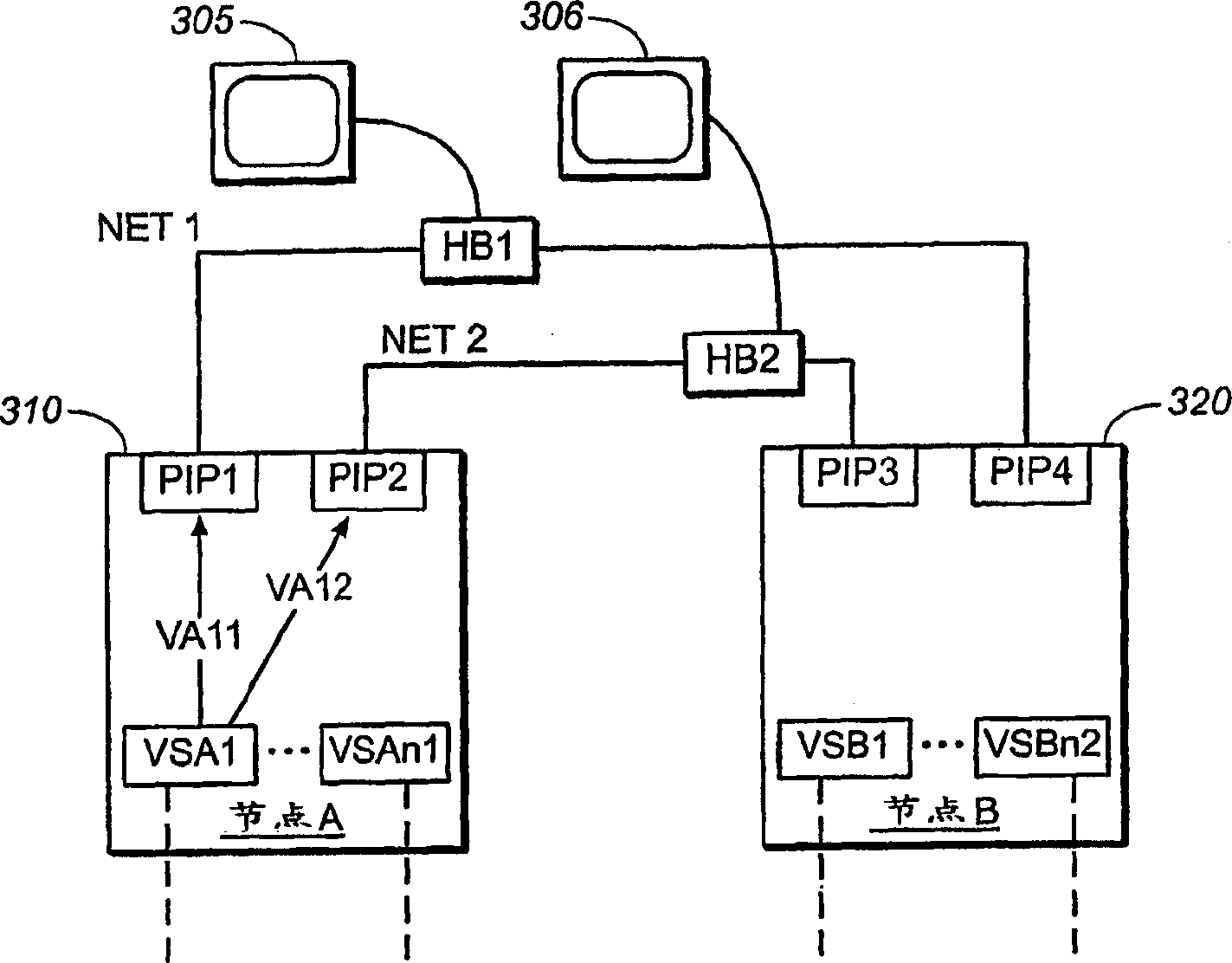
System and method for managing virtual IP addresses
ActiveUS20060075123A1Multiple digital computer combinationsTransmissionNetwork communicationVirtual IP address
The invention relates to systems and methods for assigning a unique network identifier to one or more programs invoked on a computer. The computer obtains a plurality of network identifiers and associates a first network identifier to a first program invoked on the computer and associates a second network identifier, different from the first network identifier, to a second program invoked on the computer. The program may be a user session hosted by the computer, an application or an application isolation environment. The computer through a network communication interface transmits the first network identifier with the network communication of the first program and transmits the second network identifier with network communication of the second program.
Owner:CITRIX SYST INC
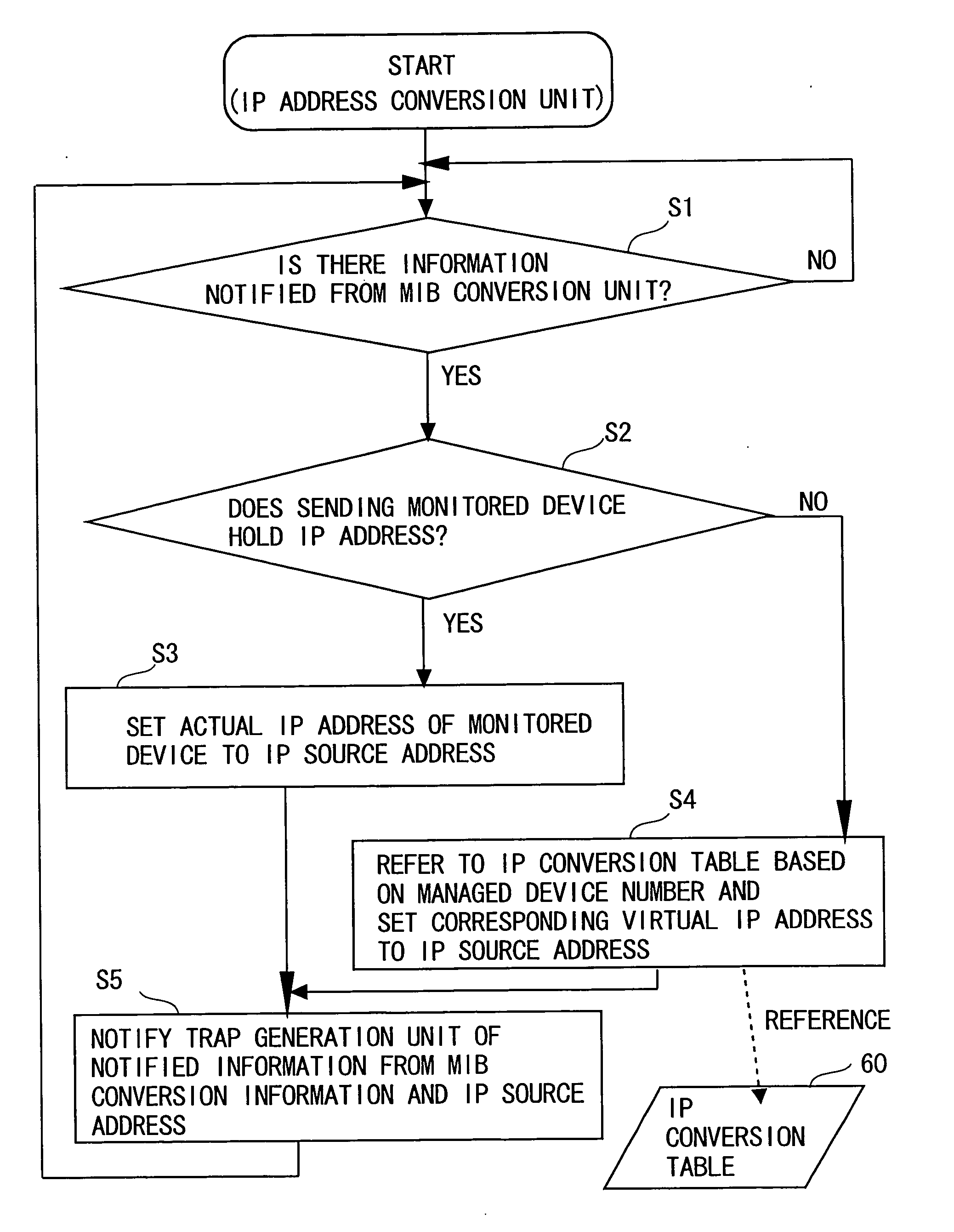
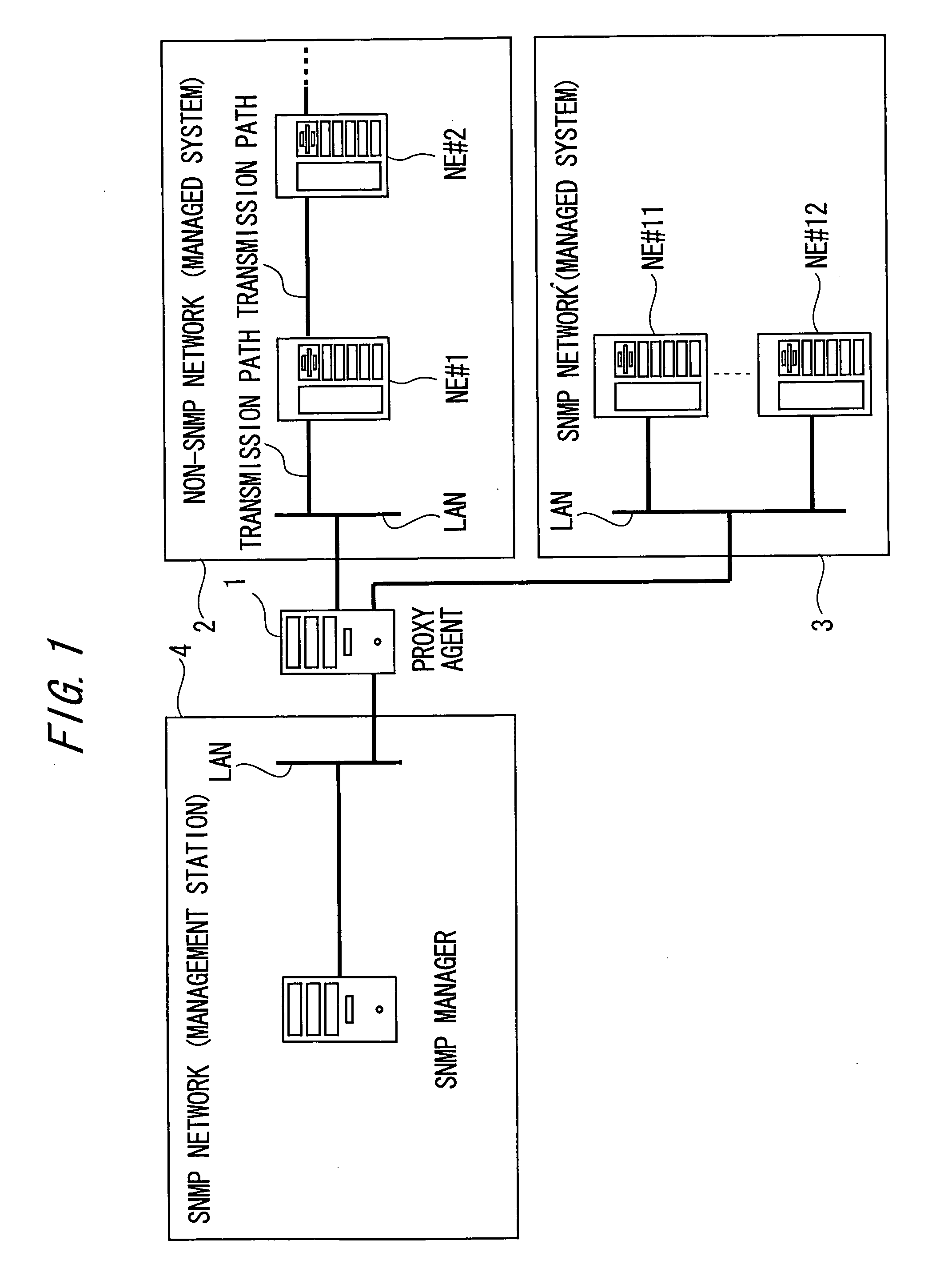
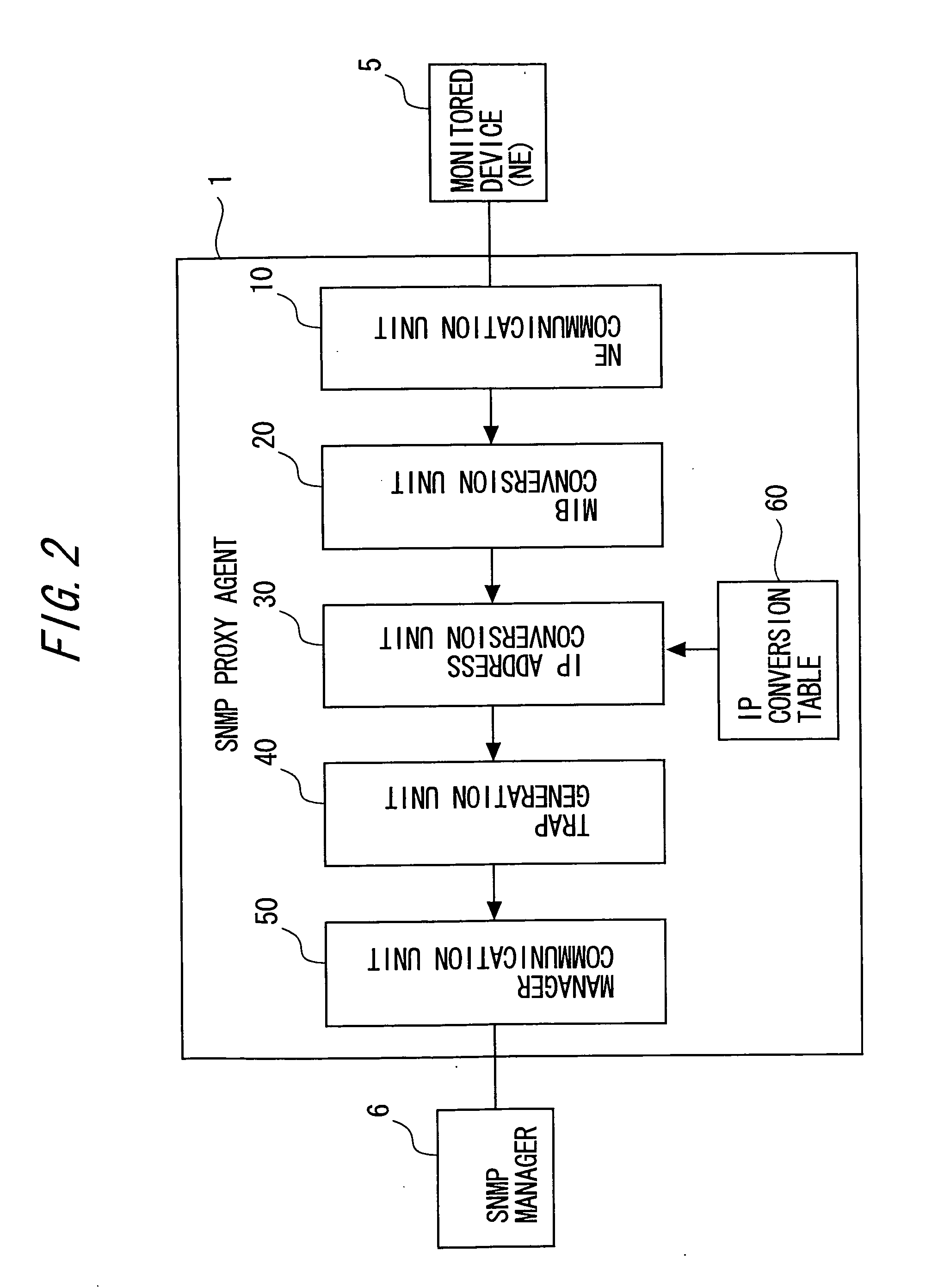
SNMP proxy agent
InactiveUS20060026301A1Simplified managementEasy to operateMultiple digital computer combinationsData switching networksWorld Wide WebVirtual IP address
An SNMP proxy agent includes a format conversion unit for converting management information received from a monitored device not using the SNMP as a management protocol, into a format corresponding to the SNMP, an IP address conversion unit for converting the particular information on the monitored device included in the management information into a virtual IP address indicating the monitored device, a trap generation unit for generating an SNMP trap having the virtual IP address set as a transmission origin and containing the management information after the conversion, and a transmission unit for transmitting the generated SNMP trap to an SNMP manager.
Owner:FUJITSU LTD
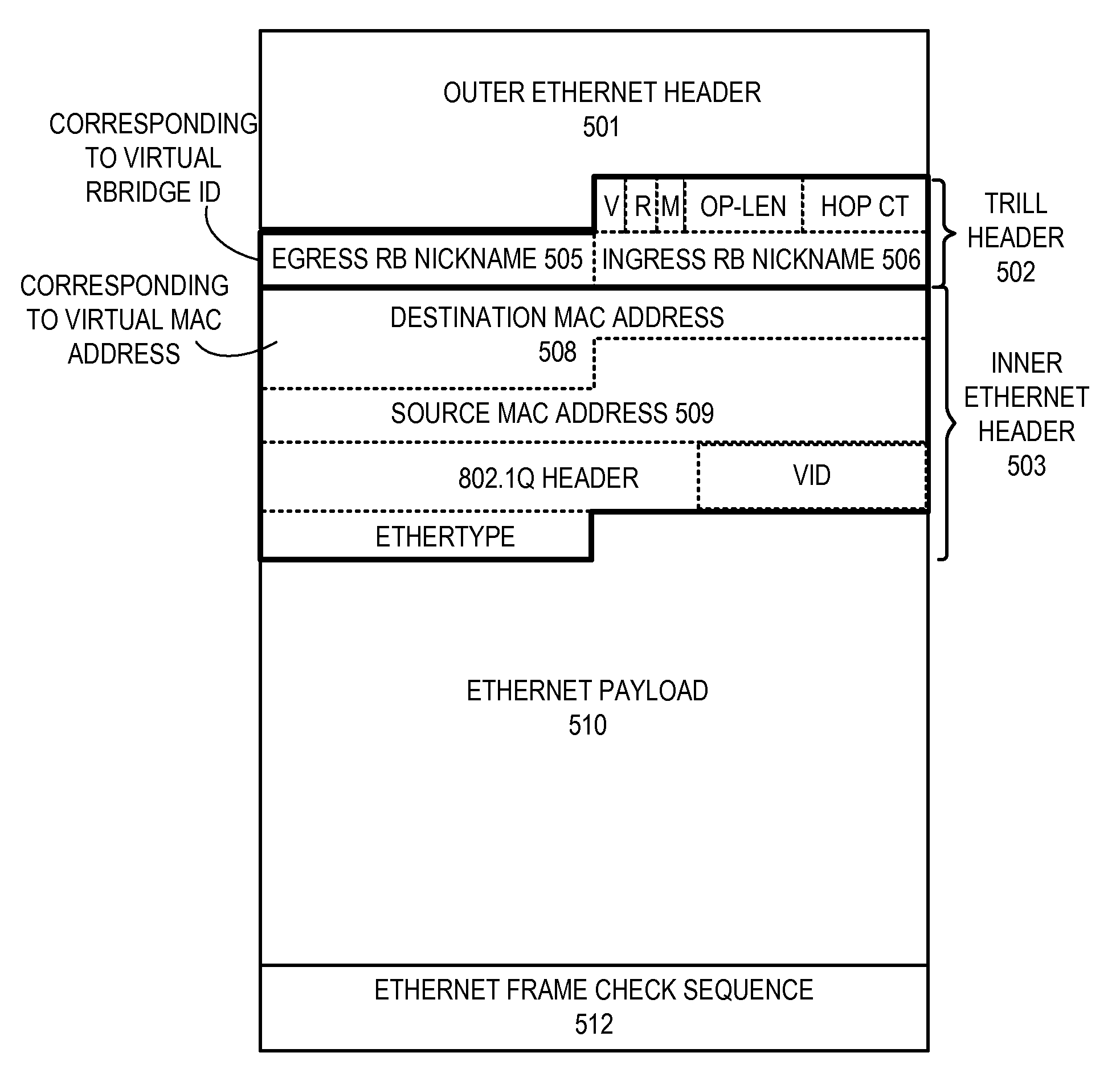
Trill based router redundancy
One embodiment of the present invention provides a switching system. The switching system includes a Transparent Interconnection of Lots of Links (TRILL) header processor and an Internet Protocol (IP) header processor. The TRILL header processor is configured to identify a virtual routing bridge (RBridge) identifier in a packet, and the IP header processor is configured to identify a virtual IP address in the packet. The virtual IP address is assigned to a virtual IP router associated with the virtual RBridge identifier.
Owner:AVAGO TECH INT SALES PTE LTD
Managing failover of J2EE compliant middleware in a high availability system
InactiveUS7246256B2Improved high availability cluster managementShort recovery timeRedundant hardware error correctionFailoverWeb application
A method, system, and program for managing failover of J2EE compliant middleware in a high availability system are provided. A primary node and a secondary node each run the same J2EE compliant middleware stack comprising layers including a load balancer, a web server, a web application server, a message control server, a monitoring server, and a database control server. In the primary node, all layers are active. In the secondary node, part of the layers are active and part of the layers are in standby. A data replication partition shared between the primary node and the secondary node includes persistent resource data accessible to a selection of the layers of the primary node. A heartbeat controller monitors each node, including the middleware stack, and upon detection of a failure, controls transfer of the services provided by the primary node to the secondary node by transferring virtual IP addresses from the primary node to the secondary node, remounting the data replication partition for access by the secondary node, and activating the standby layers which require access to the data in the data replication partition.
Owner:IBM CORP
Application based active-active data center network using route health injection and IGP
A distributed data center topology having at least a pair of active data centers that can recover from a disaster at one of the data centers and achieves load balancing using IGP (Interior Gateway Protocol) between data centers. The distributed data centers use virtual IP addresses, route health injection and Border Gateway Protocol (BGP) for business continuance, disaster recovery and load balancing. Active applications are deployed at each data center to provide a logical active / standby configuration for certain applications. Alternatively, active applications are deployed at both sites and BGP routes traffic to the closest data center edge router. Load balancing occurs over an internal IGP link between sites.
Owner:CISCO TECH INC
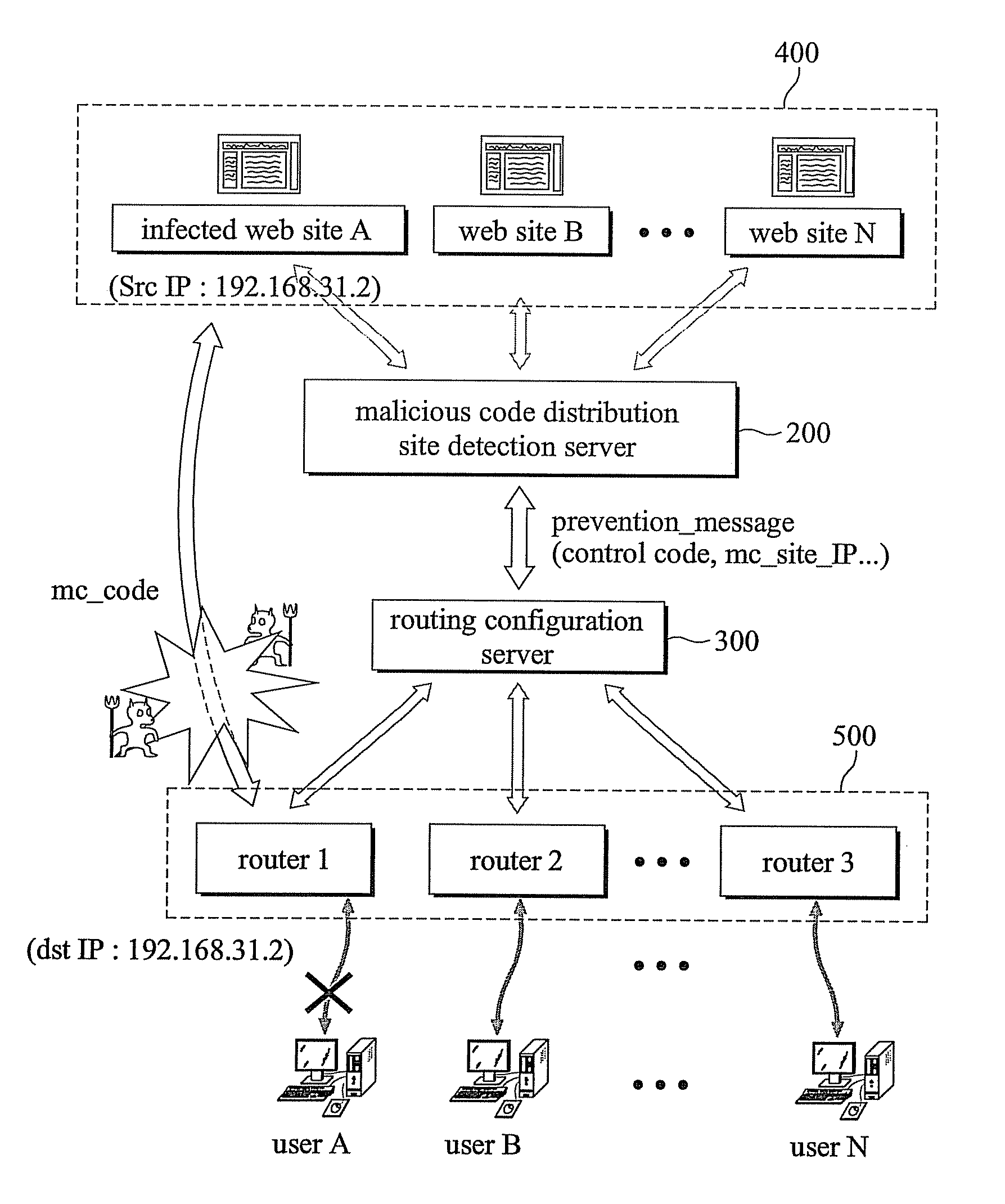
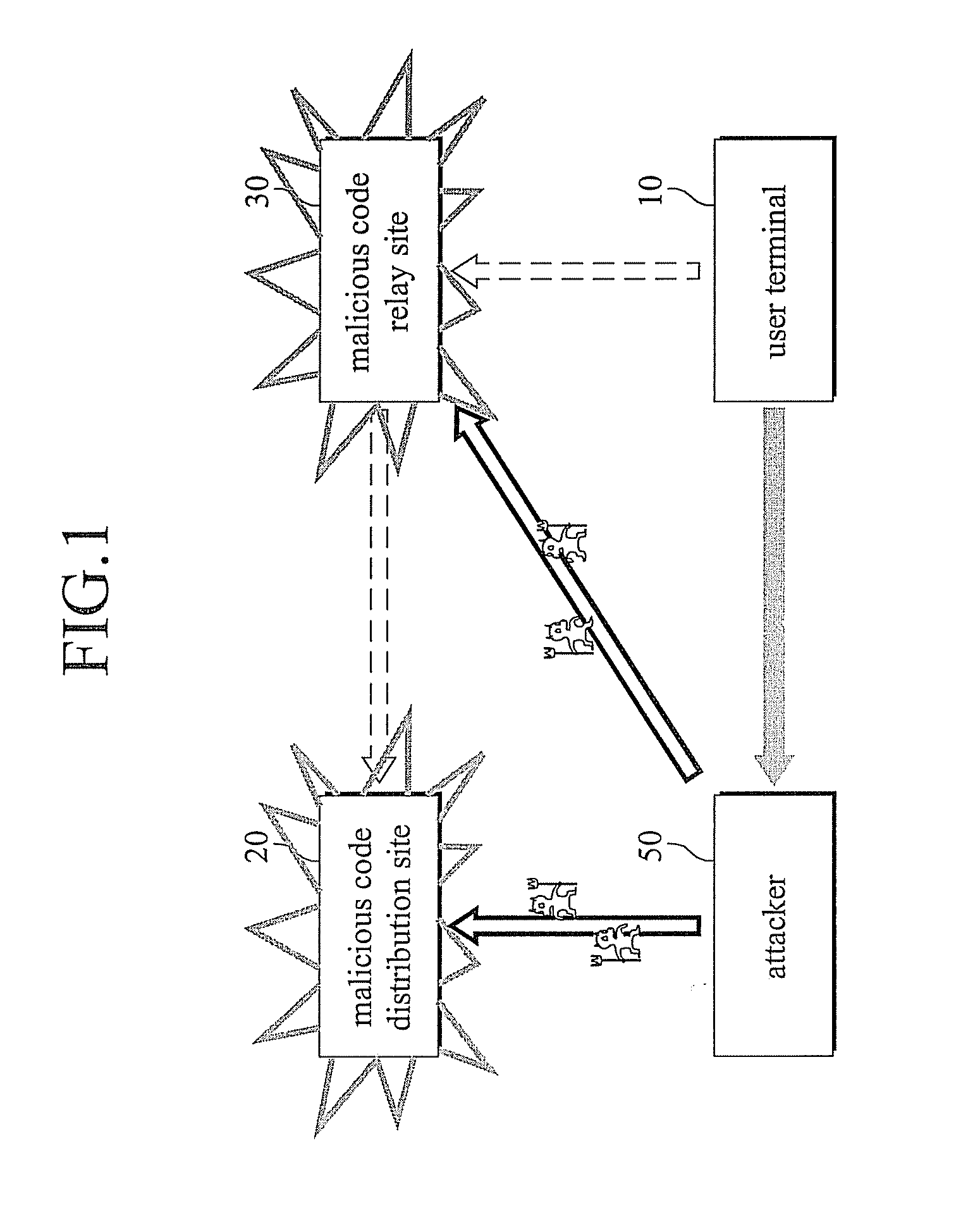
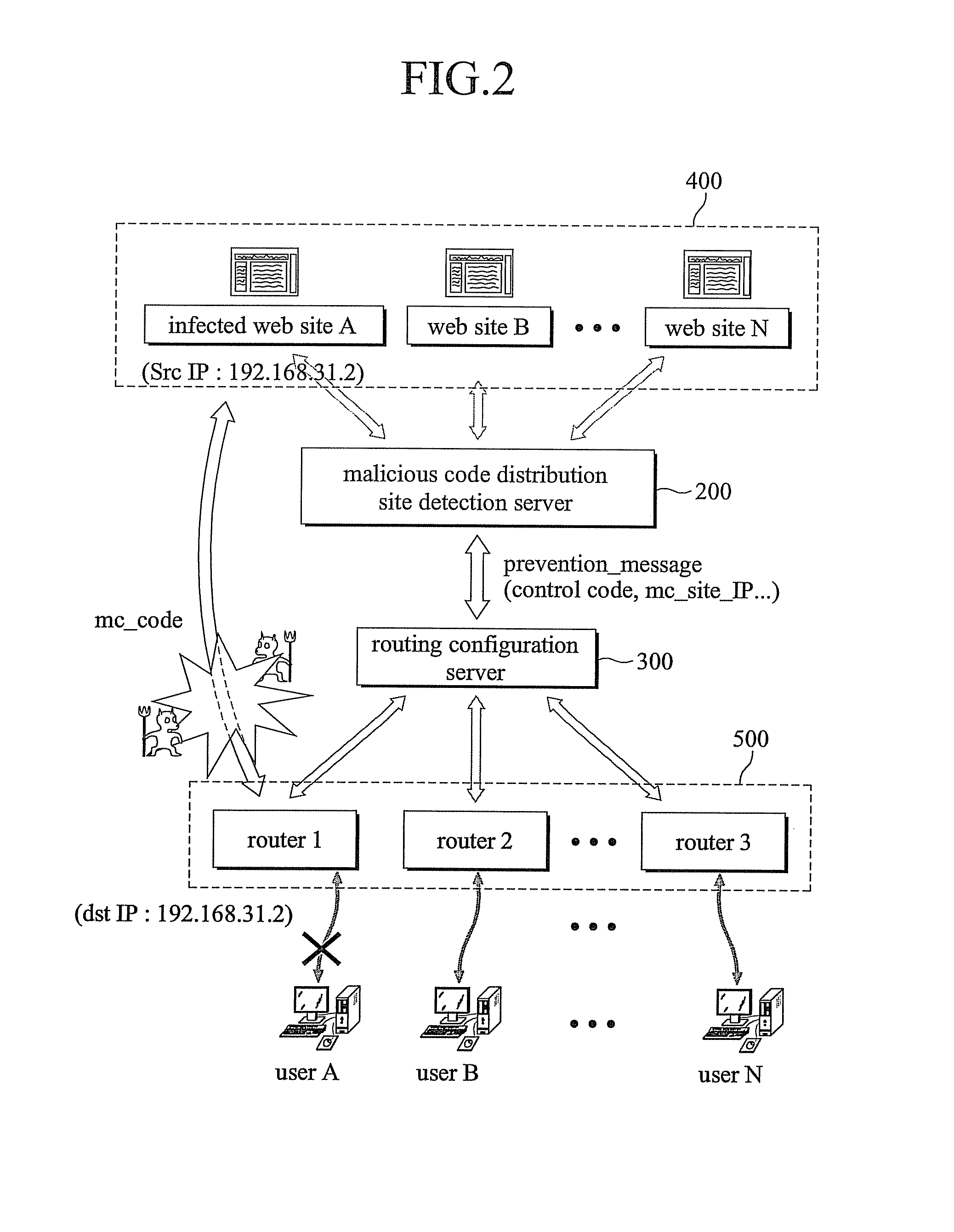
System and method for preventing malicious code spread using web technology
InactiveUS20080127338A1Avoid attackPrevent malicious attacksMemory loss protectionError detection/correctionCode distributionTransmitter
The present invention relates to a system and a method for preventing an attack of a malicious program spread using a web technology comprising a malicious code distribution site detection server comprising a malicious code distribution site detector for detecting a malicious code distribution site, and a prevention message transmitter for transmitting a prevention message to a routing configuration server, wherein the prevention message includes an IP address of the malicious code distribution site detected by the malicious code distribution site detector; a plurality of routers including a virtual IP address; and the routing configuration server for advertising the IP address of the malicious code distribution site such that a routing path of a packet having the IP address of the malicious code distribution site as a target address or an starting address is guided to the virtual IP address according to an reception of the prevention message to block a connection to the malicious code distribution site.
Owner:KOREA INTERNET & SECURITY AGENCY
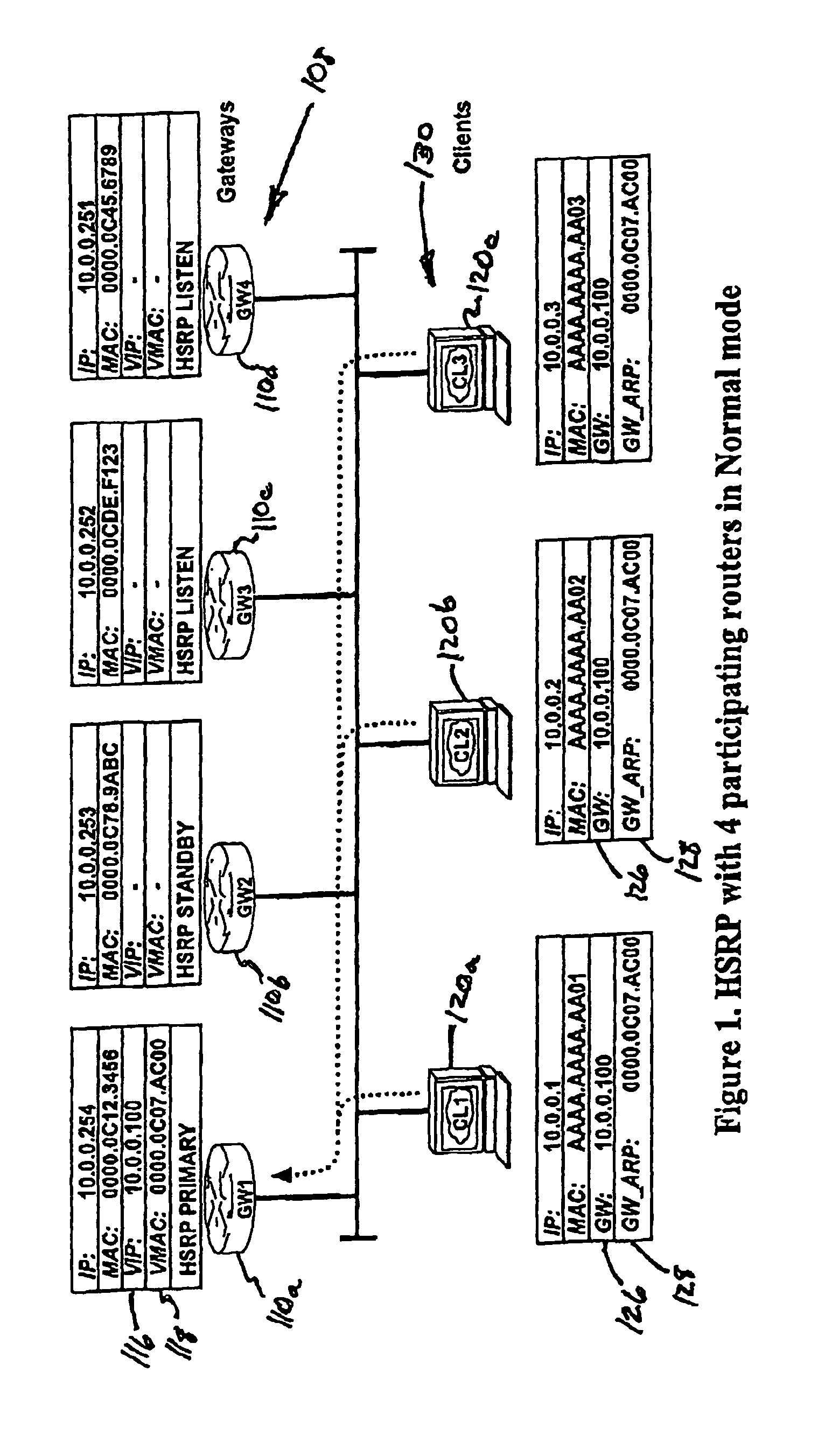
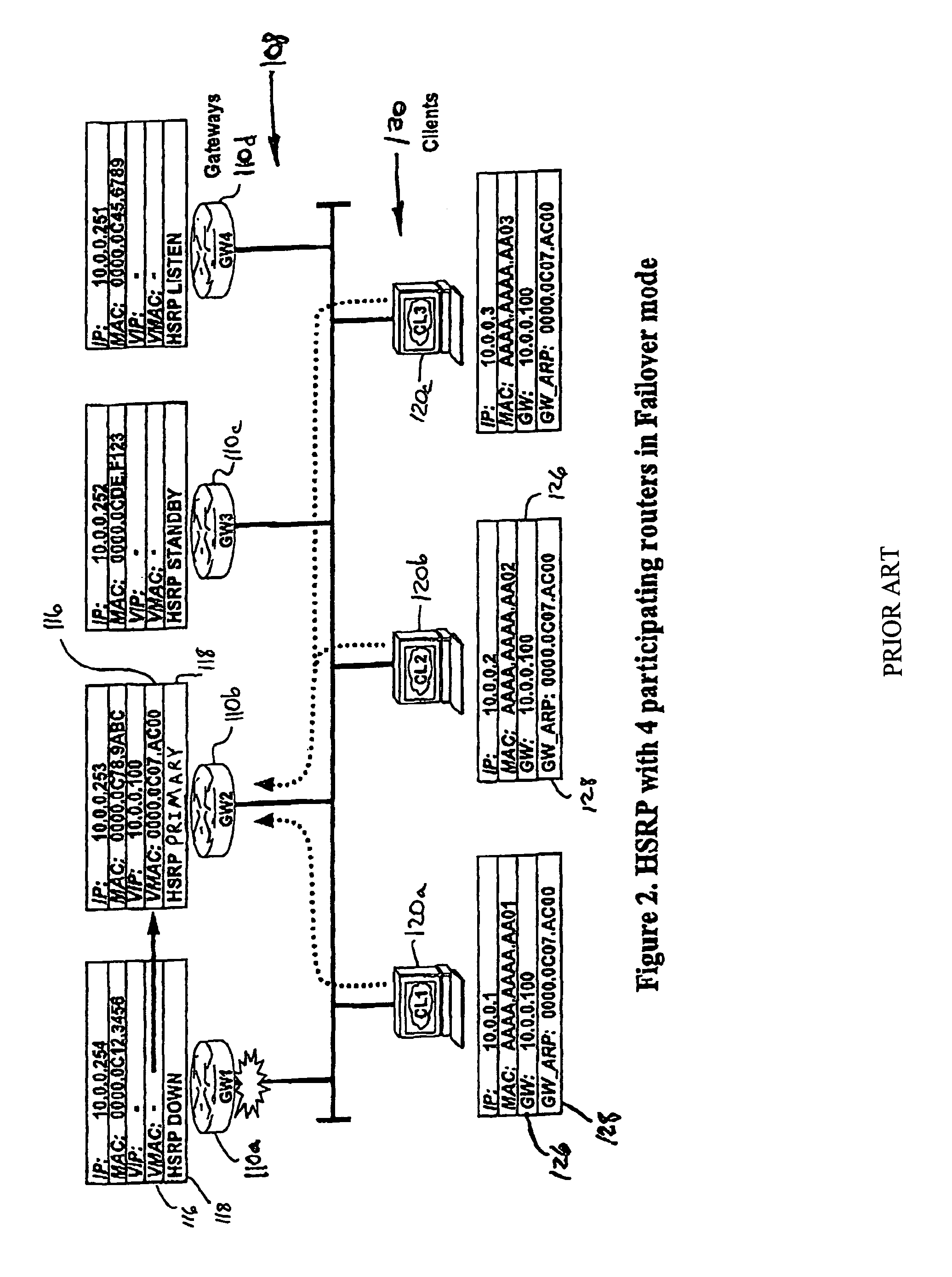
Gateway load balancing protocol
ActiveUS7881208B1Ensure continuityError preventionFrequency-division multiplex detailsFailoverPrimary station
Gateway load balancing and failover methods, apparatus and systems use more than one gateway device in a gateway device group for communications directed outside of a LAN. In the load balancing arrangement, hosts that send ARP messages to a shared virtual IP address receive replies from one of the gateway devices in the gateway device group, directing the host to address outgoing communications to a virtual MAC address assigned to one of the gateway devices. Hosts are assigned virtual MAC addresses for the gateway devices according to a prescribed algorithm or methodology. In the event that one member of the gateway device group fails, the outgoing communications that would have been handled by the failed gateway device are re-assigned to another member of the gateway device group. A master gateway device controls address assignment and failover features. In the event that the master fails, additional steps are taken to appoint or elect a new master and ensure continuity in the load balancing function.
Owner:CISCO TECH INC
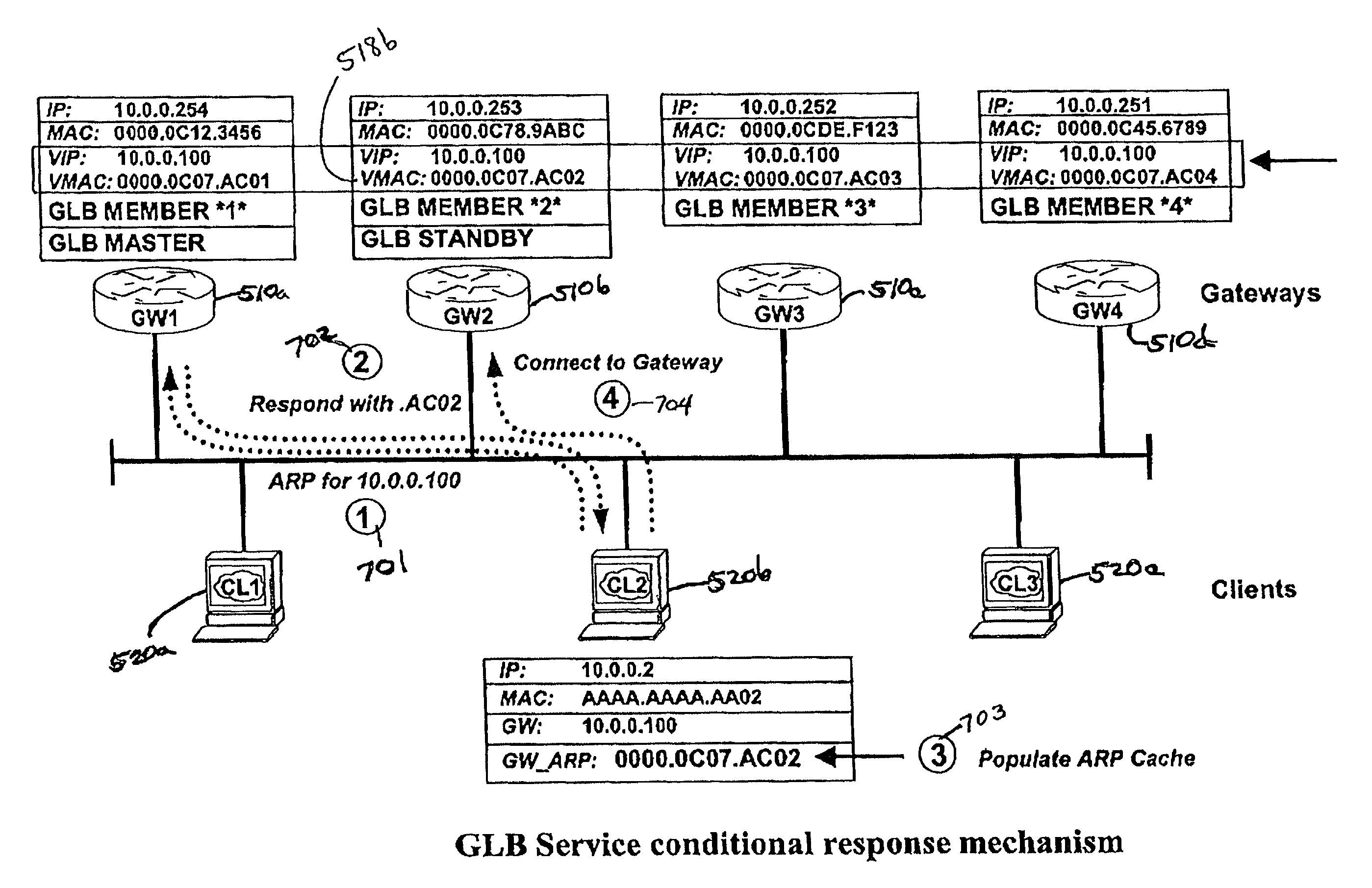
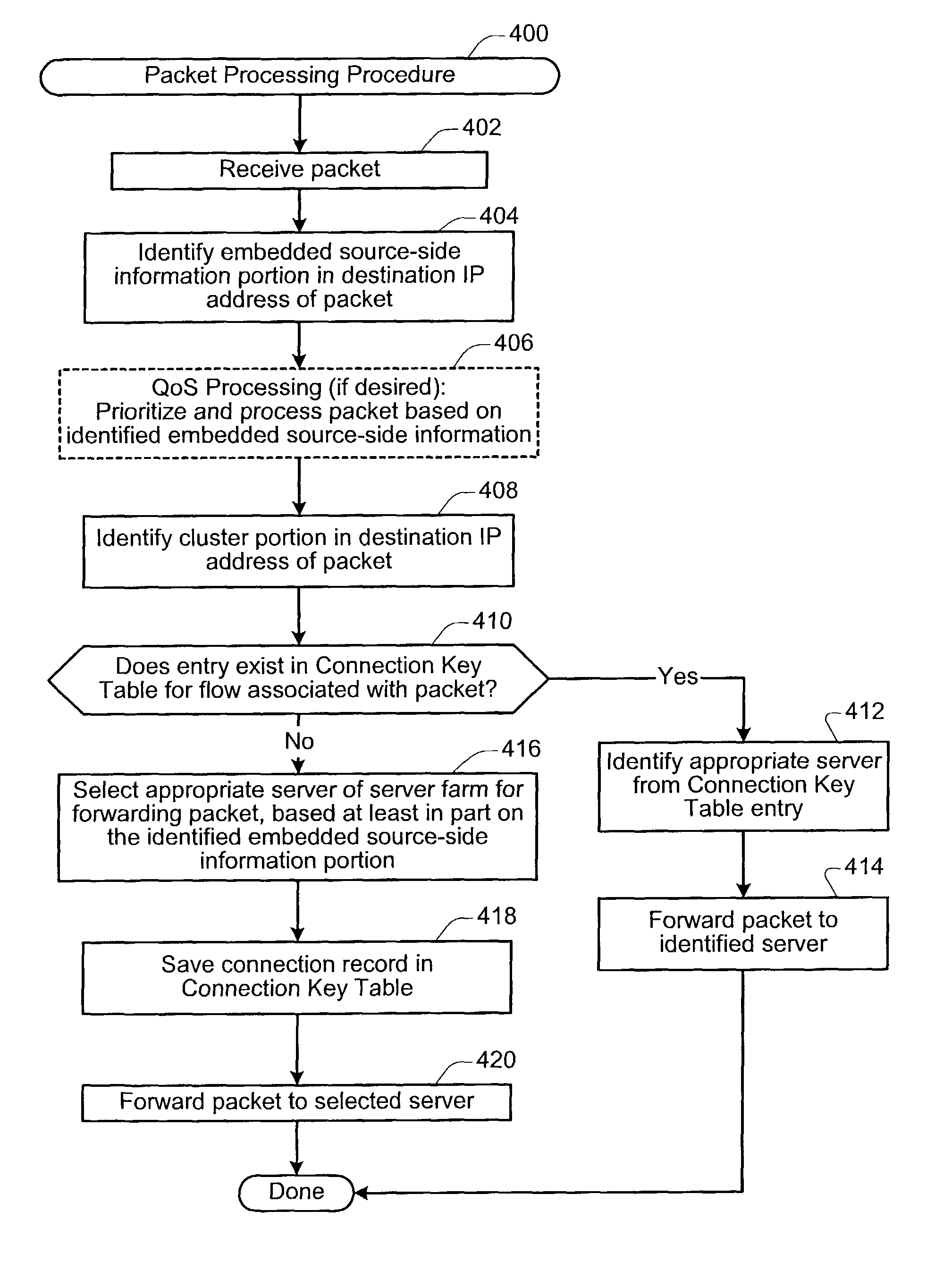
Technique for improving load balancing of traffic in a data network using source-side related information
ActiveUS7328237B1Data switching by path configurationMultiple digital computer combinationsTraffic capacityRelevant information
According to various aspects of the present invention, a technique is described for improving load balancing of traffic in a data network using source-side related information embedded into the destination IP address field of packets received at a load balancing device. One aspect of the present invention relates to assigning more than one virtual IP address to a server cluster in order to enable different clients to select a virtual cluster address which corresponds to each clients' respective rights and / or profiles, and to use the selected virtual cluster address to access a desired site or service. Another aspect of the present invention relates to a mechanism which allows for load balancing operations to be implemented using source-side information which is embedded into the destination IP address of a packet header. In this way, load balancing decisions may be quickly performed at initial or early stages of a connection flow.
Owner:CISCO TECH INC
Methods and apparatus for implementing home agent redundancy
InactiveUS7227863B1Time-division multiplexData switching by path configurationComputer networkMobile IP
Methods and apparatus for maintaining Mobile IP operation in a Home Agent are disclosed. In a Home Agent, a Mobile Node is registered and a registration entry is created in a mobility binding table for the Mobile Node. A multicast message is then sent to a virtual router group to which the Home Agent belongs and with which the Home Agent shares a virtual IP address. The multicast message notifies the virtual router group of the registration. A similar process may be performed when a Mobile Node is de-registered. When an active or non-active Home Agent is initialized, it sends a multicast mobility binding table request to the redundancy group indicating that bindings are requested. The Home Agent may then receive bindings in response to the request and update its mobility binding table with the received bindings.
Owner:CISCO TECH INC
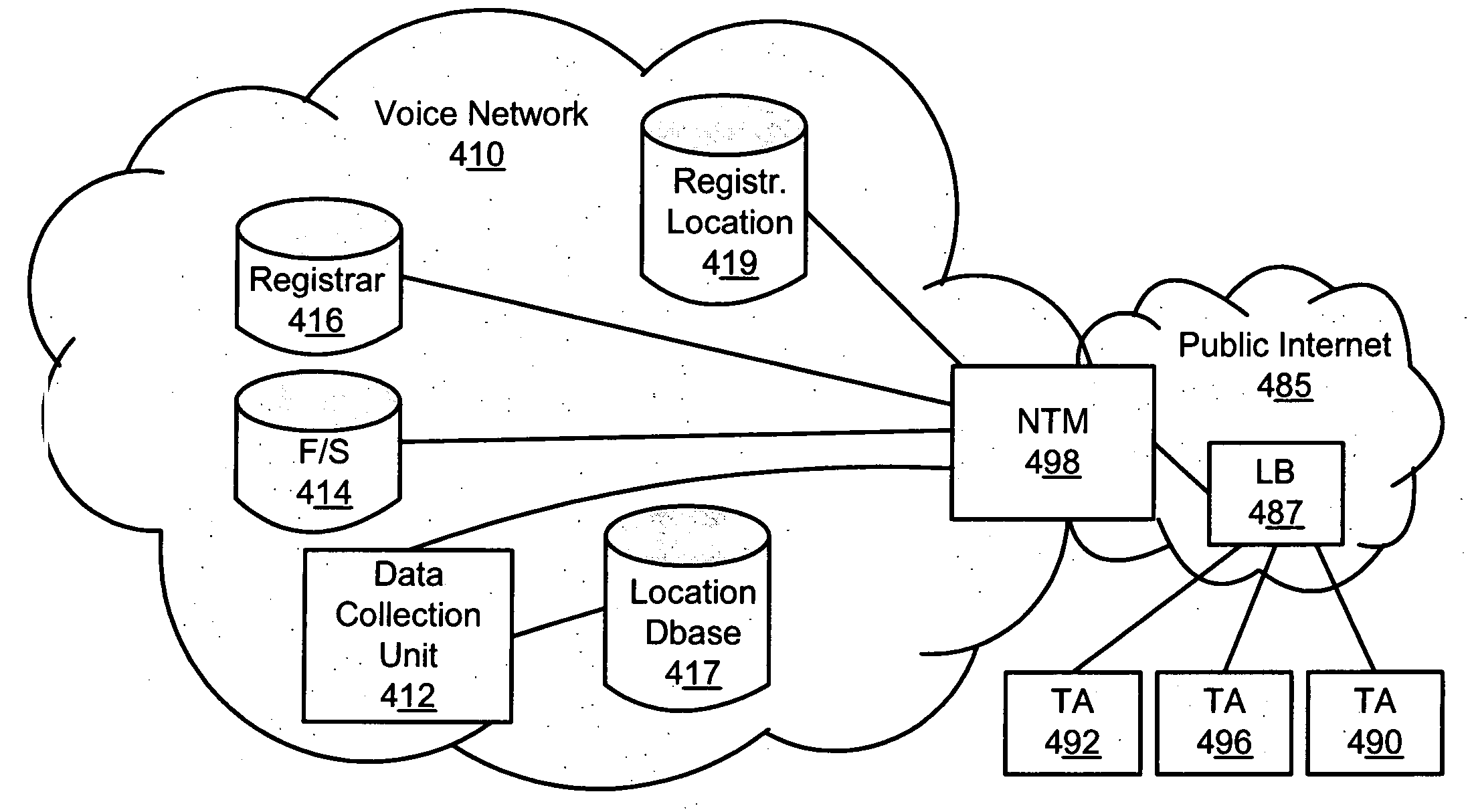
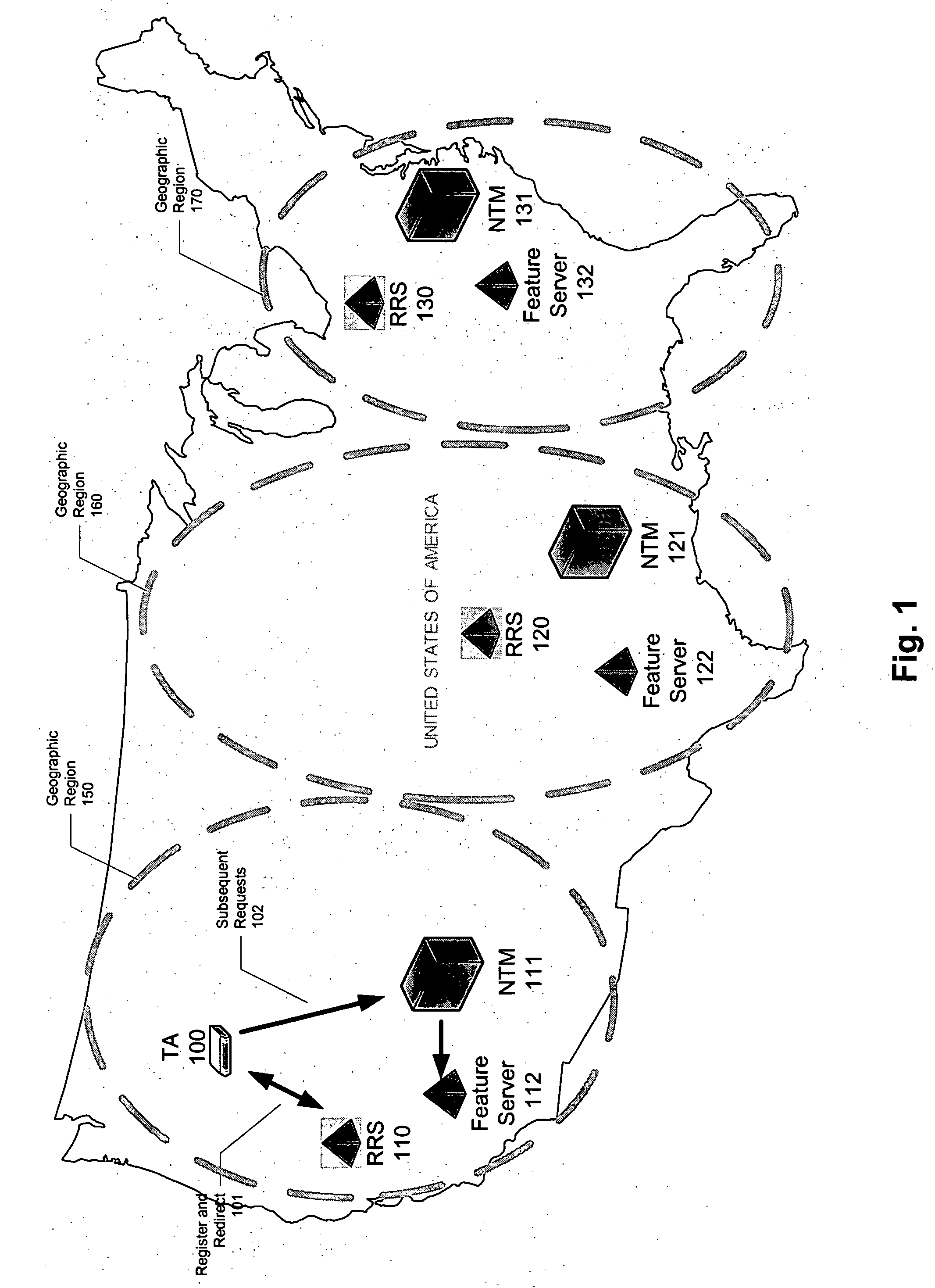
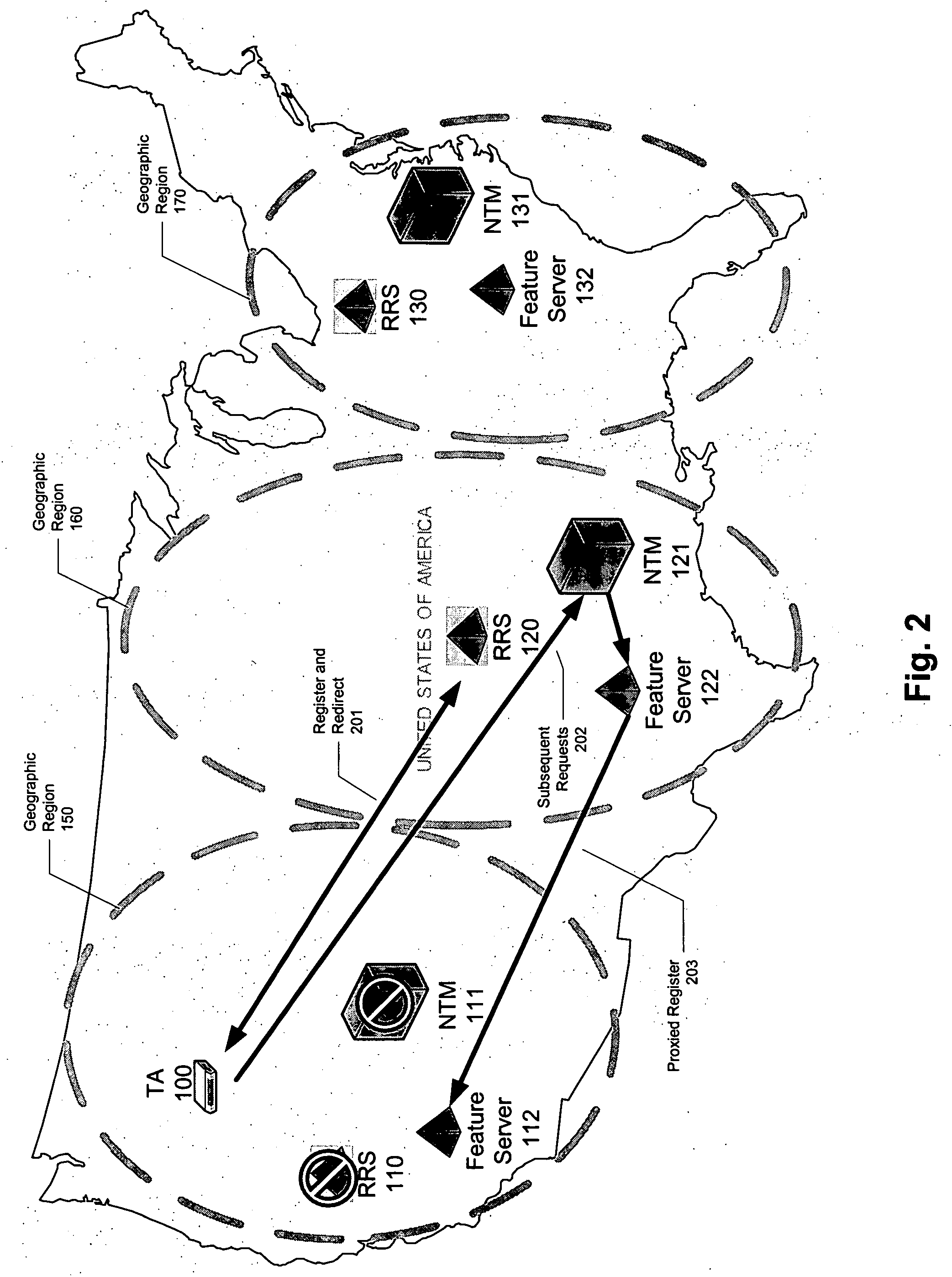
Registration redirect server
ActiveUS20060013147A1Error preventionFrequency-division multiplex detailsNetwork architectureCommunication device
Systems and methods for dynamically registering a communication device are disclosed. As one example, a communication network architecture is disclosed that includes multiple feature servers, multiple registration redirect servers (RRSs), and multiple communication devices. The feature servers provide services to the communication devices. The RRSs each service a shared virtual Internet Protocol (IP) address and perform load balancing of registration requests on behalf of multiple feature servers located geographically proximate to the RRS. The communication devices are configured to issue initial registration requests intended for any of the feature servers to the shared virtual IP address, whereby upon issuing an initial registration request, a communication device is directed to a particular feature server that is associated with a RRS that is closest to the communication device, and where the particular feature server is selected by a load balancing routine executing on the RRS.
Owner:LEVEL 3 COMM LLC
Secure and private mobile web browser
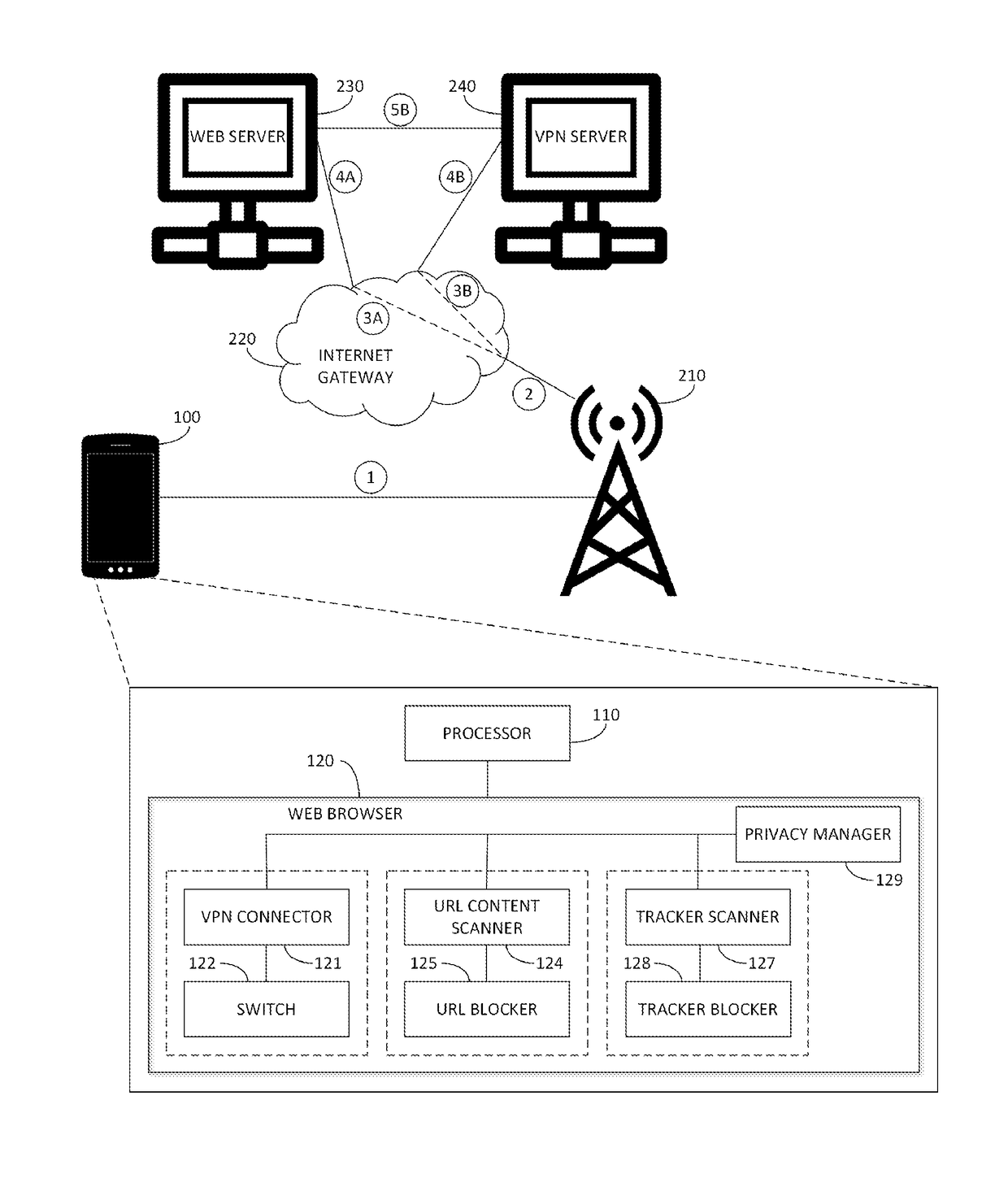
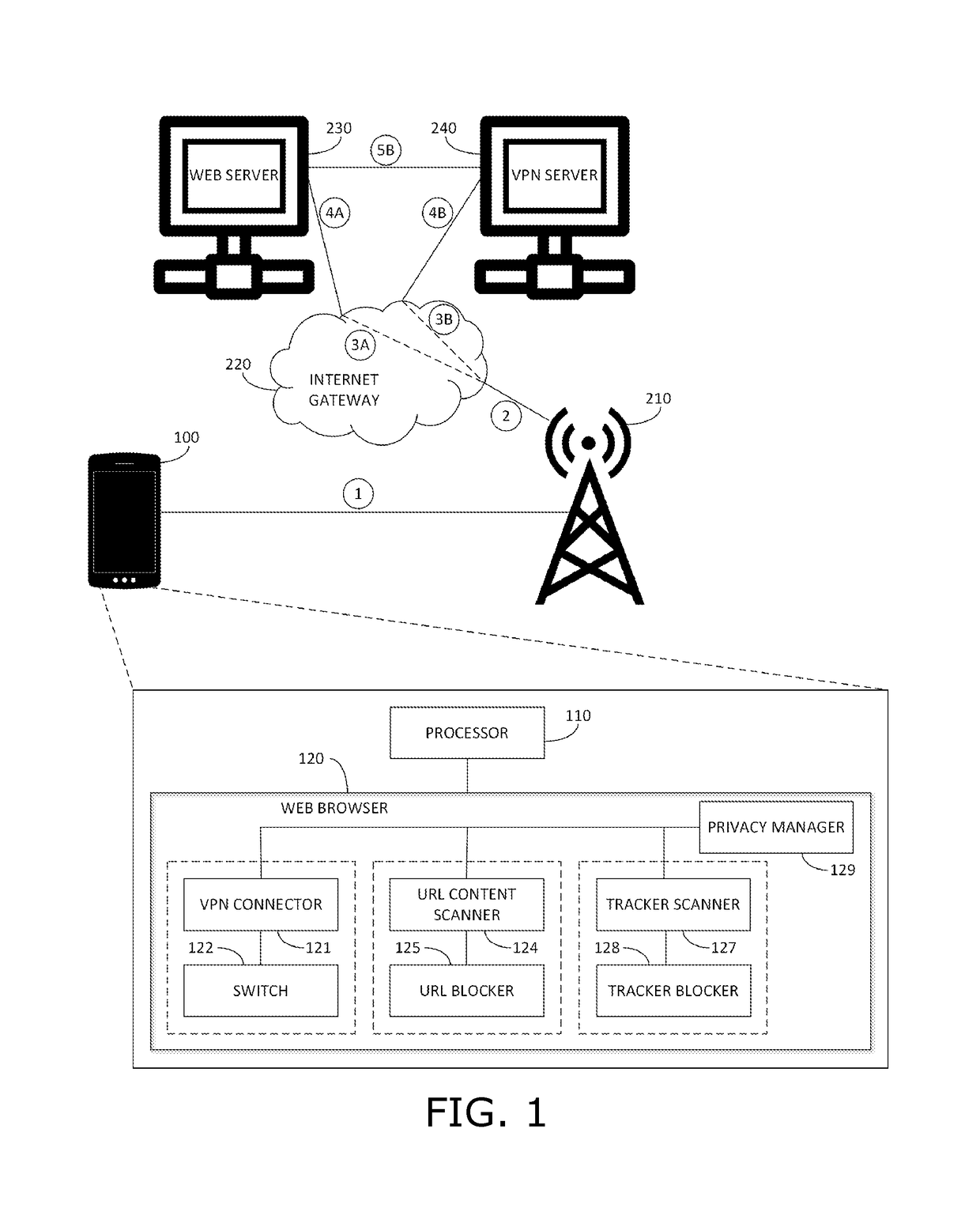
ActiveUS10069858B2Protected from riskEnsuring user privacyWireless network protocolsPlatform integrity maintainanceEngineeringMalware
A mobile web browser embedded in a smartphone operative to open a secure and private session with a web server on the Internet via one or more cell towers, using a mobile IP address of the smartphone, the mobile web browser including a VPN connector operative to connect the smartphone to a secure VPN server and to establish a virtual IP address for the smartphone, the virtual IP address corresponding to the location of the VPN server, a switch operable to change a current IP address of the smartphone used by the mobile web browser from a non-VPN mobile IP address to the virtual IP address of the VPN server, in a seamless manner without interrupting a current session with a web server, a URL content scanner causing a URL of a web page to be scanned for potential malware, a URL blocker, a tracker scanner and a tracker blocker.
Owner:FINJAN MOBILE LLC
High-availability cluster virtual server system
InactiveCN1554055ARestrict accessibilityImprove system performanceInput/output to record carriersMultiple digital computer combinationsFailoverHigh availability
Systems and methods, including computer program products, providing high-availability in server systems. In one implementation, a server system is cluster of two or more autonomous server nodes, each running one or more virtual servers. When a node fails, its virtual servers are migrated to one or more other nodes. Connectivity between nodes and clients is based on virtual IP addresses, where each virtual server has one or more virtual IP addresses. Virtual servers can be assigned failover priorities, and, in failover, higher priority virtual servers can be migrated before lower priority ones. Load balancing can be provided by distributing virtual servers from a failed node to multiple different nodes. When a port within a node fails, the node can reassign virtual IP addresses from the failed port to other ports on the node until no good ports remain and only then migrate virtual servers to another node or nodes.
Owner:NETWORK APPLIANCE INC
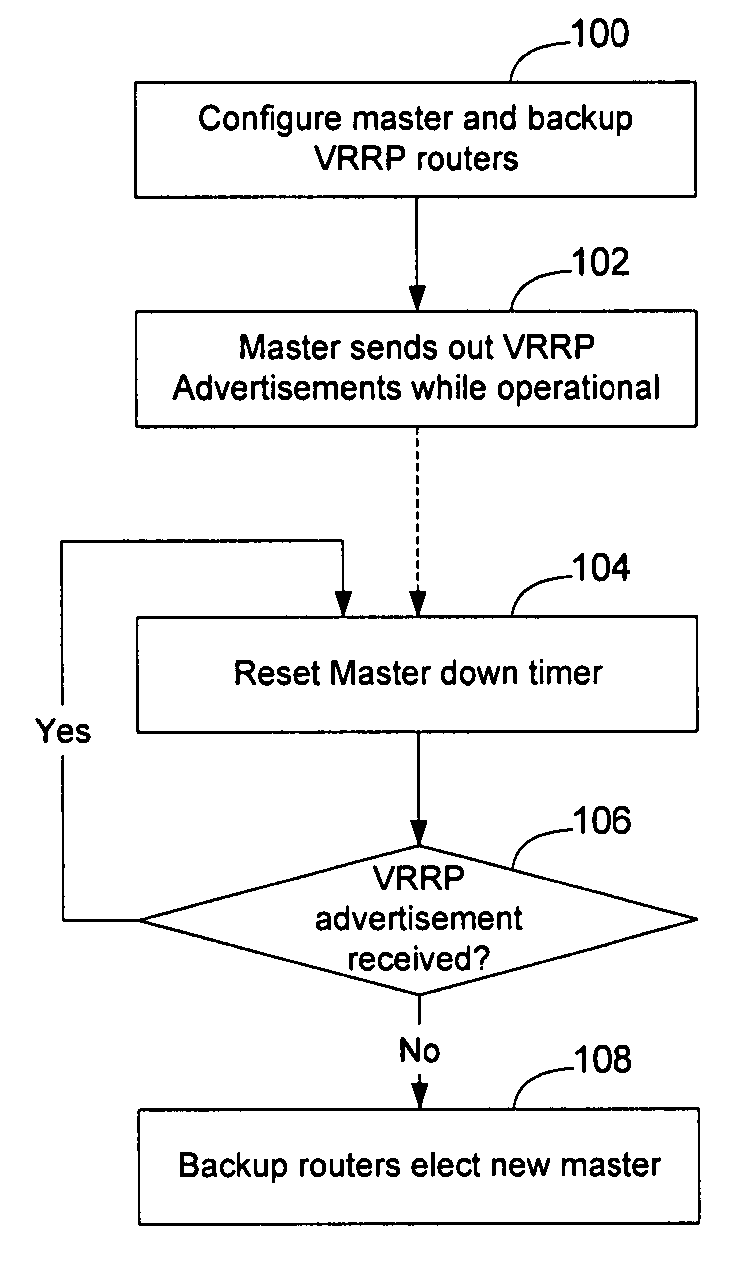
Method and apparatus for learning VRRP backup routers
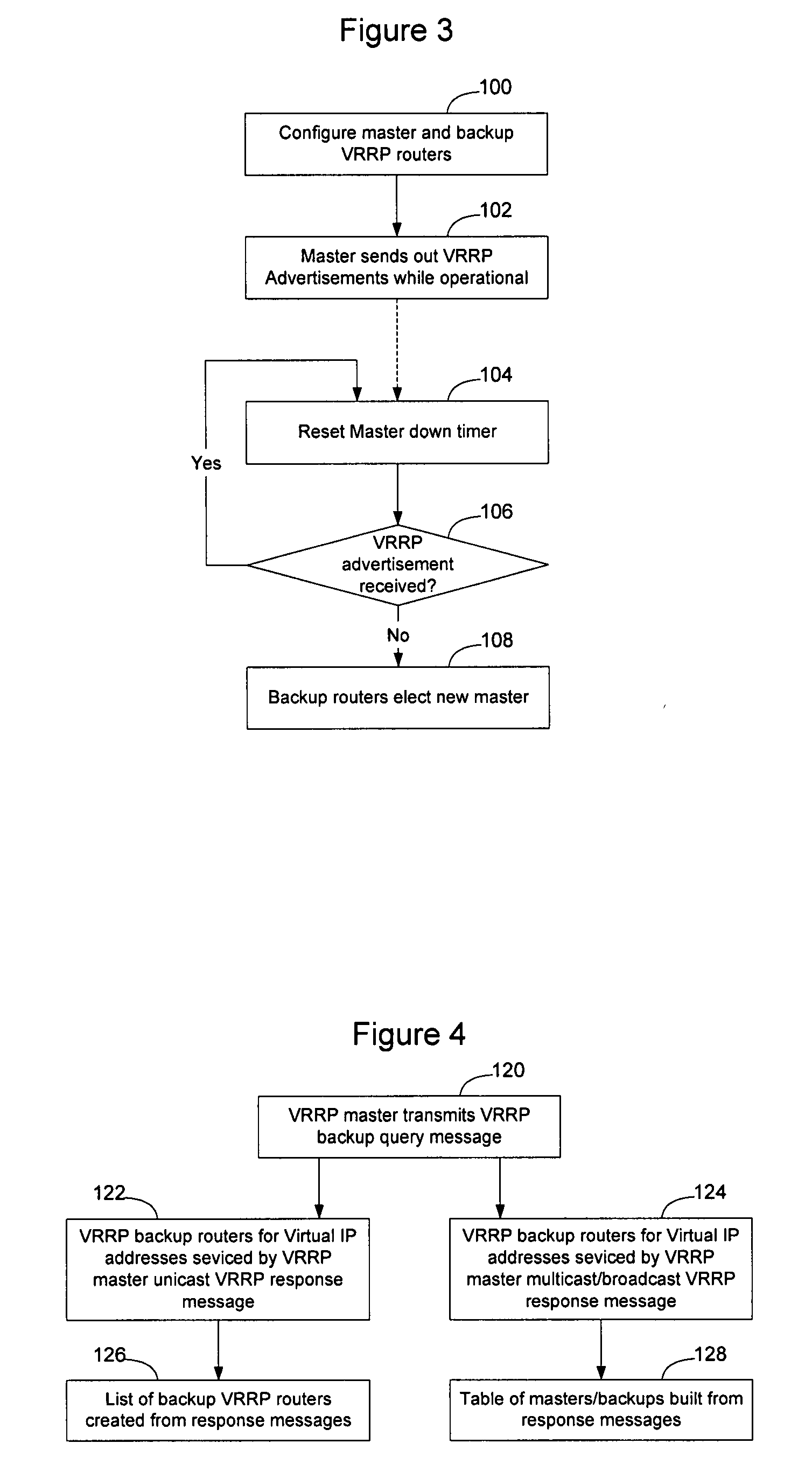
ActiveUS20070230472A1Overcomes drawbackQuick fixSpeech analysisData switching by path configurationMessage typeNetwork management
A method and apparatus for learning the identity of VRRP backup router(s) for a VRRP master router enables the identity of VRRP backup routers to be determined quickly on demand, or enables a table of VRRP master and backup routers to be established over time. A VRRP query message type is defined as a type of VRRP message that will enable the routers on the network to be queried to determine which router(s) are VRRP backup routers for a virtual IP address associated with a VRRP master. The VRRP query message may be initiated by the VRRP master, a network management system, or another entity. The VRRP backup routers may respond with a VRRP response message, which is also defined as a type of VRRP message. The VRRP response message may be unicast to the VRRP master or network management system, or broadcast to enable a table of VRRP master / backup routers to be created.
Owner:AVAYA INC
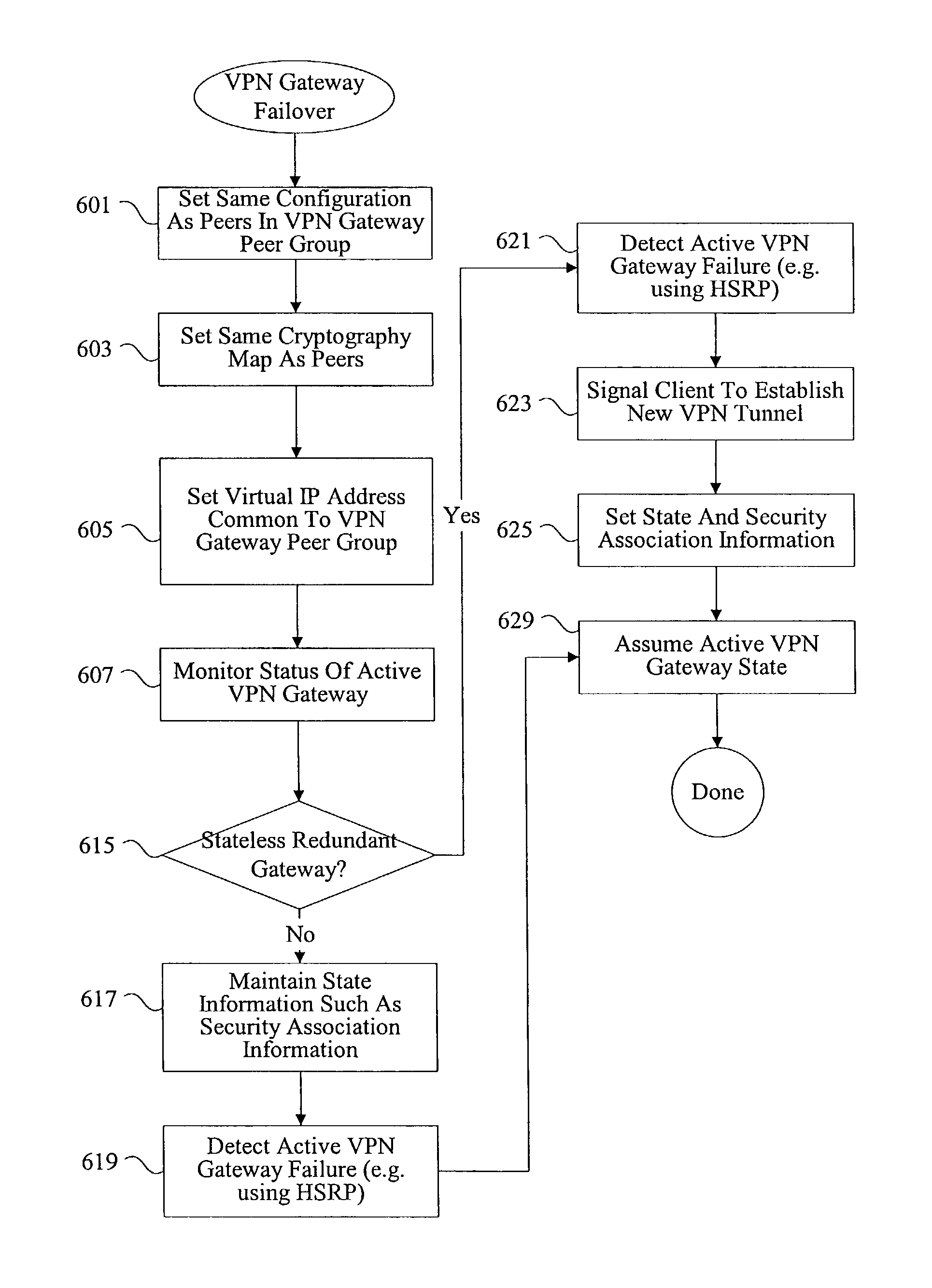
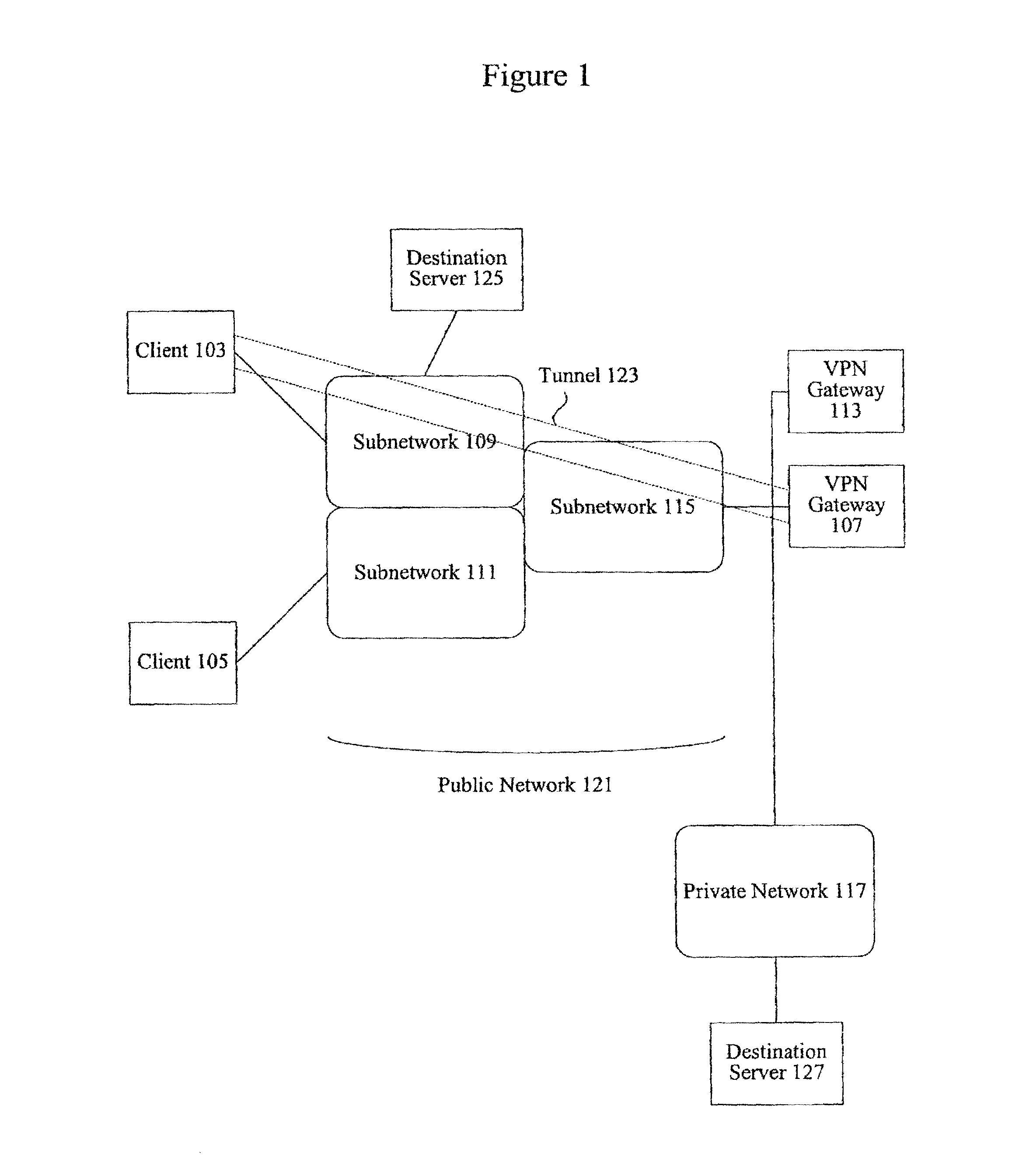
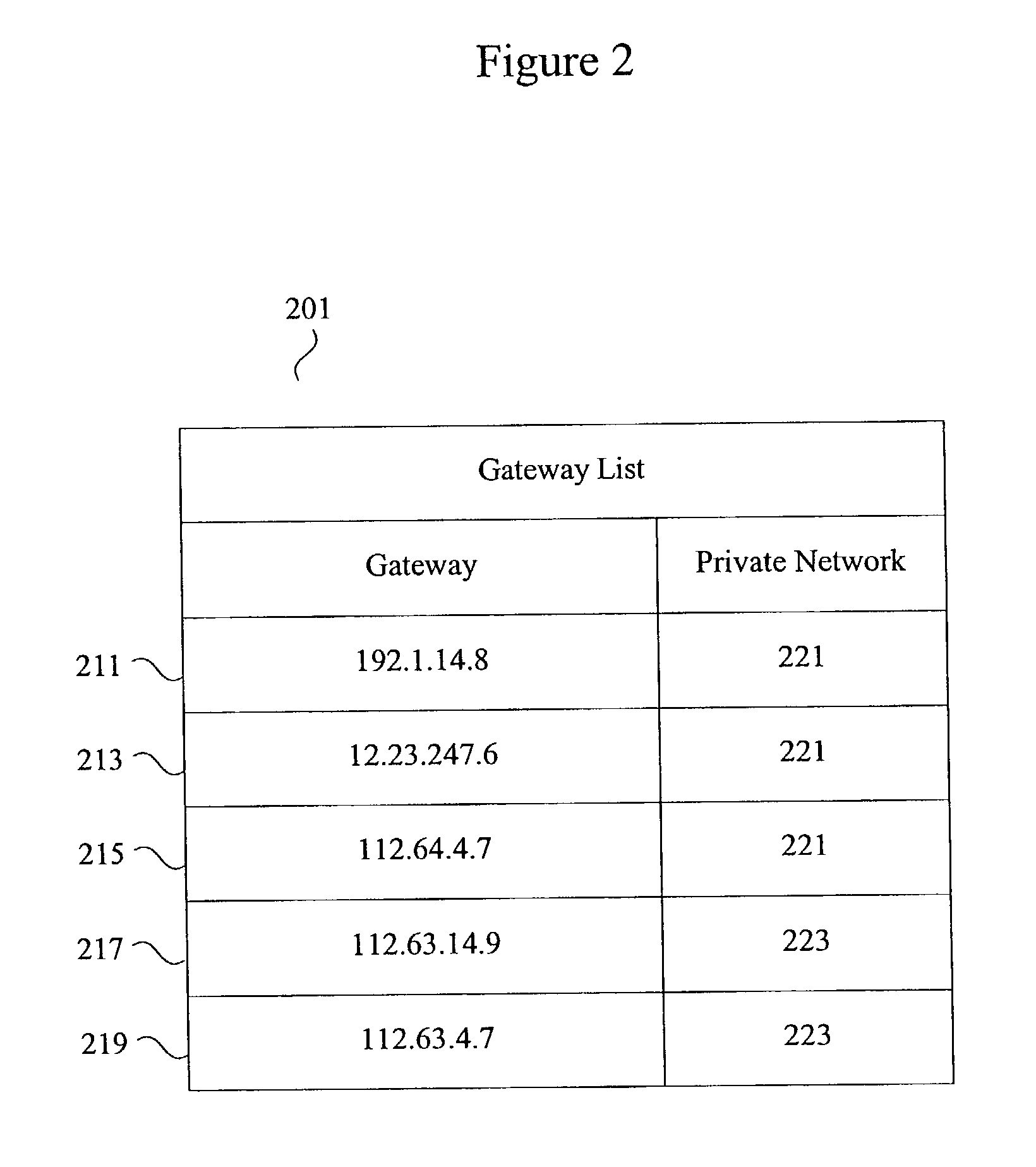
Methods and apparatus for virtual private network fault tolerance
InactiveUS7689722B1Improve fault toleranceImprove securityUser identity/authority verificationMultiprogramming arrangementsFailoverFault tolerance
Methods and apparatus are provided for enhancing security and fault tolerance for VPN gateways connecting clients in a public network with entities in a private network. According to various embodiments, primary and standby VPN gateways serving the same private network are configured with the same virtual IP address to allow public network clients the ability to efficiently switchover to a standby VPN gateway upon failure of the primary VPN gateway. Cryptography operations are executed using the virtual IP address. Routes can also be injected into the private network to enhance failover efficiency.
Owner:CISCO TECH INC
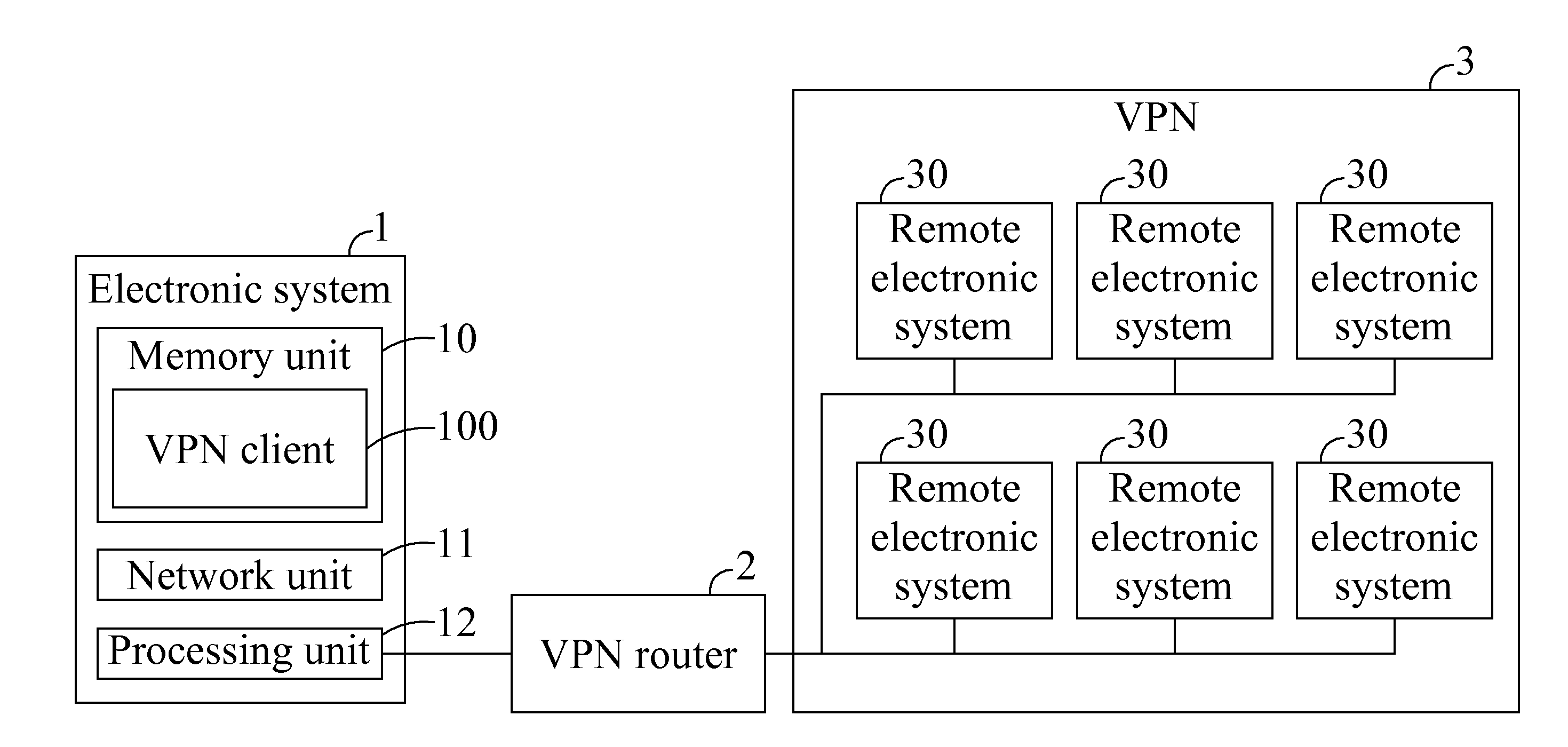
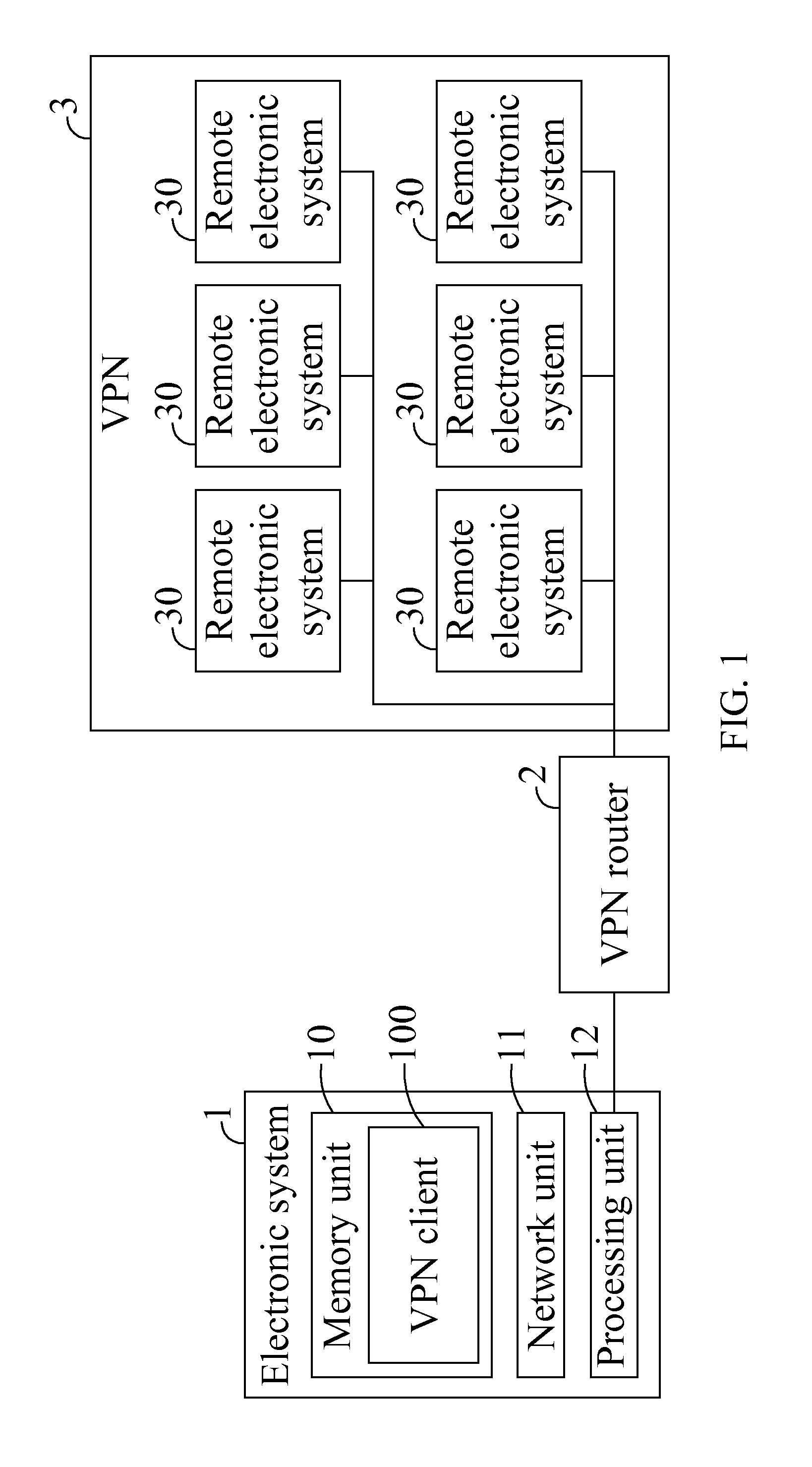
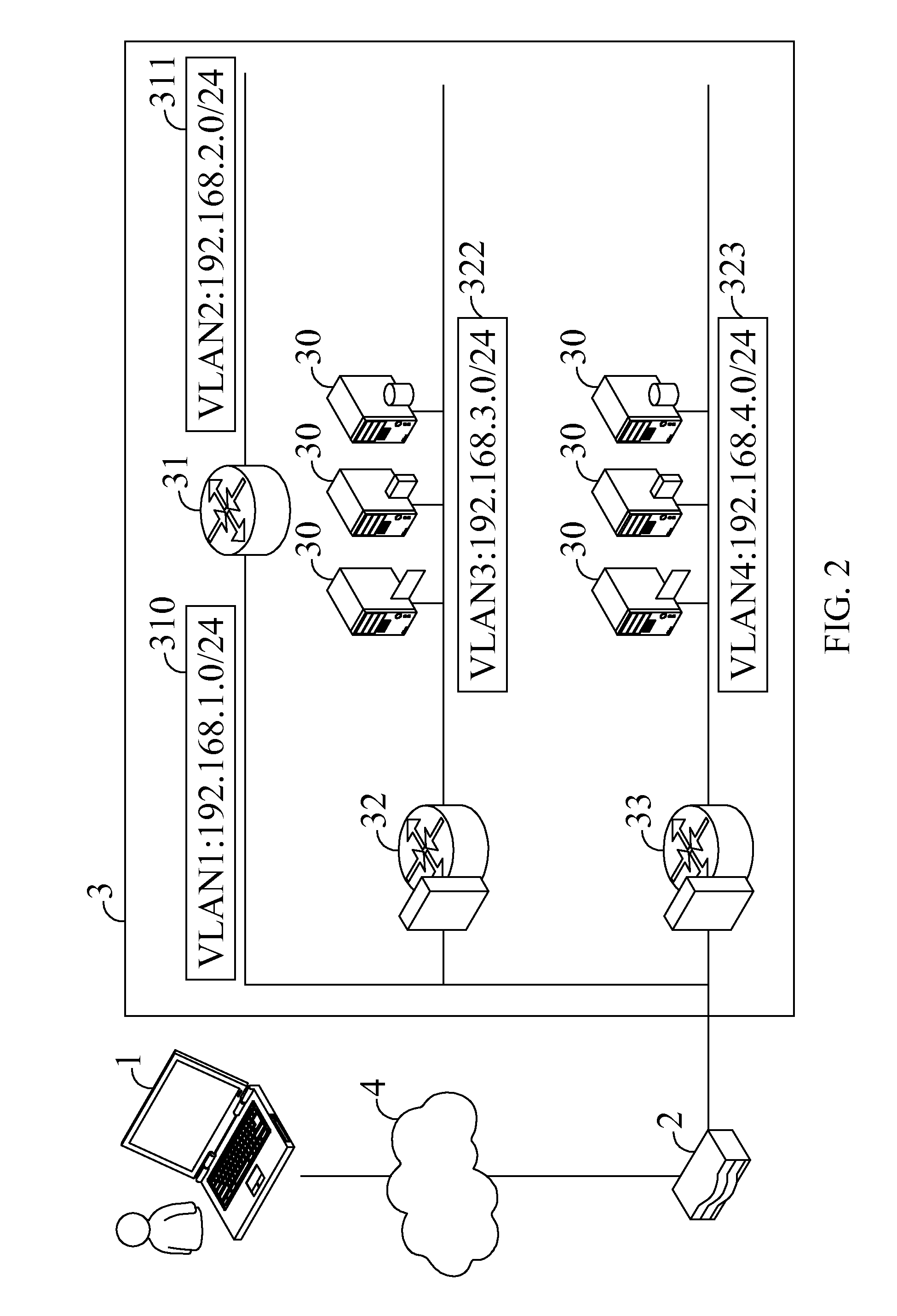
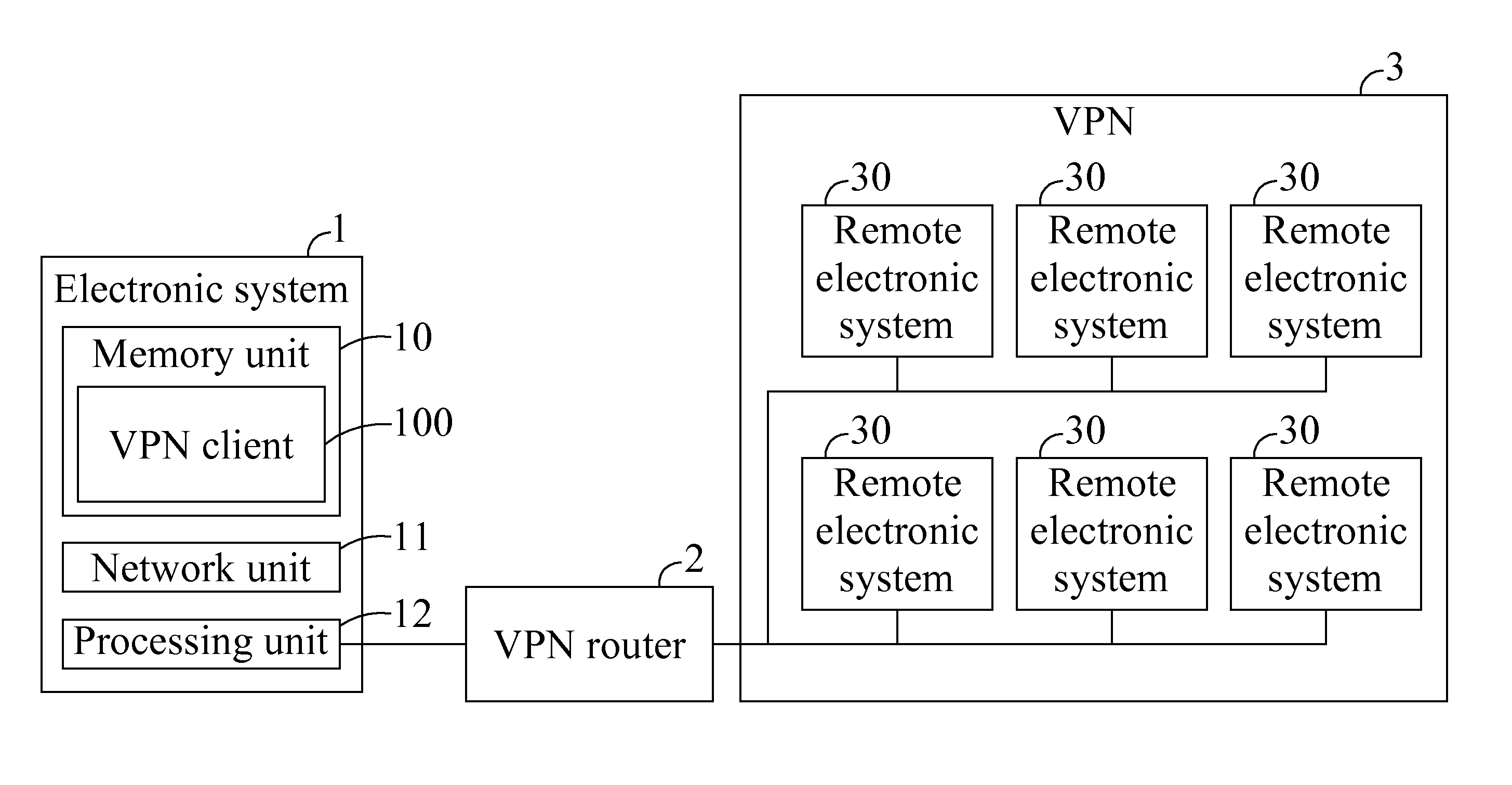
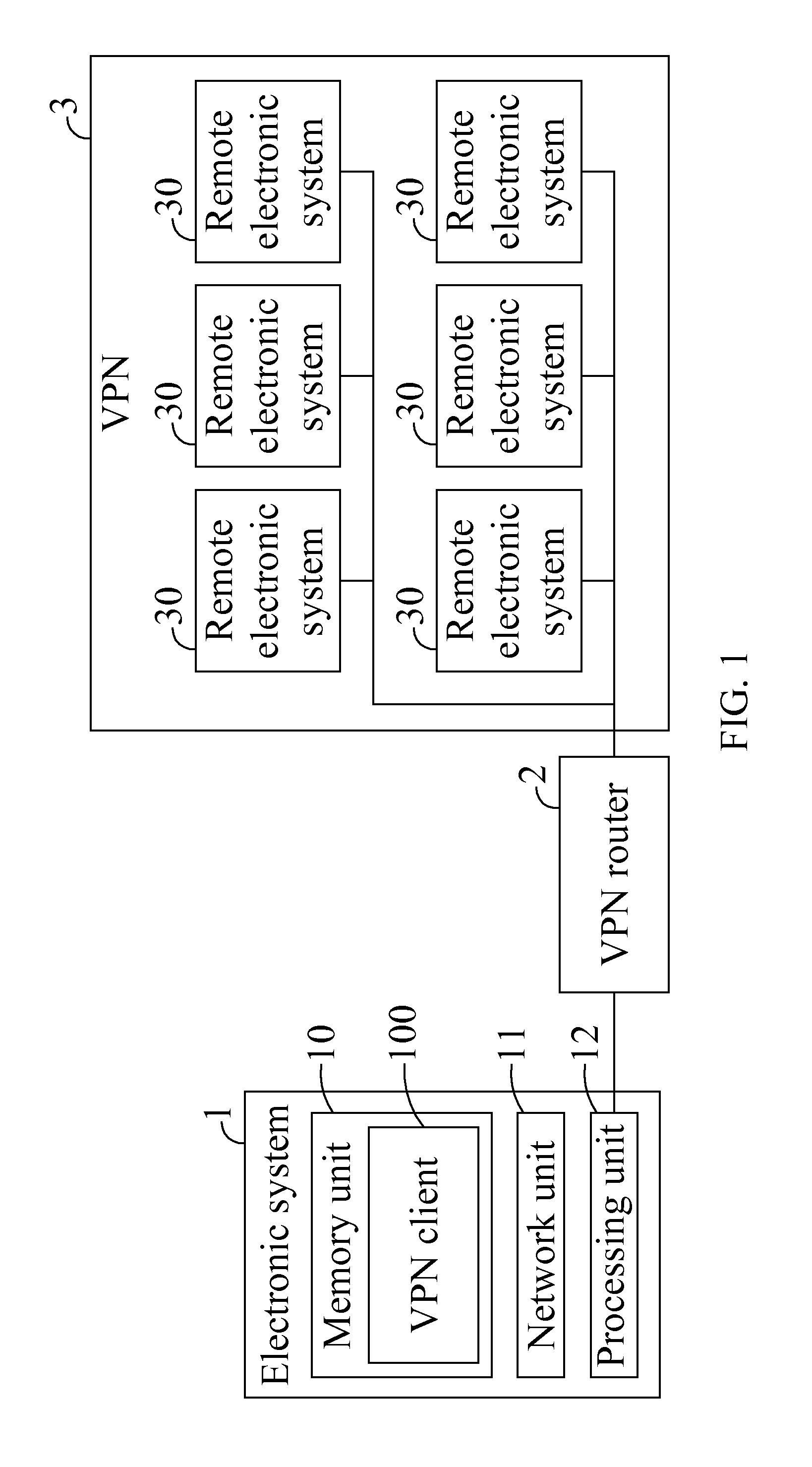
Data transfer system enabling access to multiple subnets and method thereof
ActiveUS20110206052A1Improve accessibilityIncrease flexibilityData switching by path configurationComputer hardwareElectronic systems
A data transfer system enabling access to multiple subnets and method thereof is disclosed. The data transfer method includes the following steps: executing a virtual private network (VPN) client installed on an electronic system; connecting the VPN client to a VPN router; the VPN client assigning a virtual IP address to a virtual interface; and the VPN client accessing a subnet corresponding to the virtual IP address through the virtual IP address.
Owner:GEMTEK TECH CO LTD
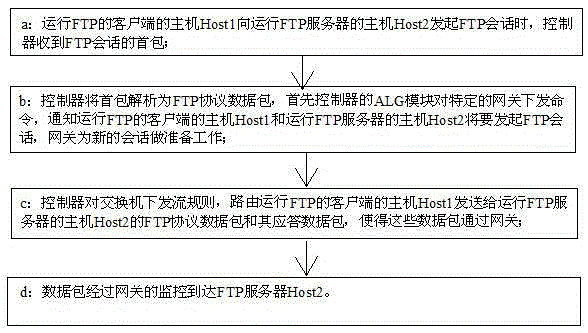
IP address jump safety communication method based on SDN framework
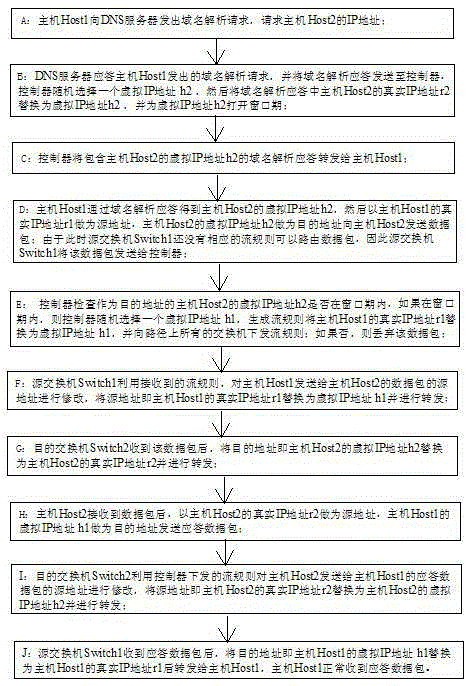
InactiveCN105429957AIncrease attack difficultyRealize IP hoppingData switching networksDomain nameSafety Communications
The invention discloses an IP address jump safety communication method based on an SDN framework. The method comprises steps that A, an IP address of a Host2 is requested by a Host1; B, a real IP address r2 of the Host2 is replaced by a virtual IP address h2 through a controller; C, a domain analysis response is forwarded by the controller to the Host1; D, an r1 is taken as a source address and the h2 is taken as a target address by the Host1 to send a data packet to the Host2; E, a flow rule is generated by the controller to replace the r1 by a virtual IP address h1, and the flow rule is issued; F, the r1 is replaced by the h1 through the source switch, and forwarding is carried out; G, the h2 is replaced by the r2 through the target switch, and forwarding is carried out; H, the r2 is taken as a source address and the h1 is taken as a target address by the Host2 to send a response data packet; I, the r2 is replaced by the h2 through the target switch, and forwarding is carried out; J, the h1 is replaced by the r1 through the source switch, and forwarding to the Host1 is carried out. Through the method, jump IPs can be dynamically distributed to a host computer in the IPH network, one-time one-change access to the host computer IP is transparently realized, attack based on scanning and DDoS attach can be effectively fought against.
Owner:芦斌
Data transfer system enabling access to multiple subnets and method thereof
ActiveUS8218558B2Improve accessibilityIncrease flexibilityData switching by path configurationComputer hardwareElectronic systems
A data transfer system enabling access to multiple subnets and method thereof is disclosed. The data transfer method includes the following steps: executing a virtual private network (VPN) client installed on an electronic system; connecting the VPN client to a VPN router; the VPN client assigning a virtual IP address to a virtual interface; and the VPN client accessing a subnet corresponding to the virtual IP address through the virtual IP address.
Owner:GEMTEK TECH CO LTD
Network communication method for carrying out load division
InactiveCN1531262AFully utilize processing powerData switching by path configurationNetwork connectionsNetwork communicationMessage passing
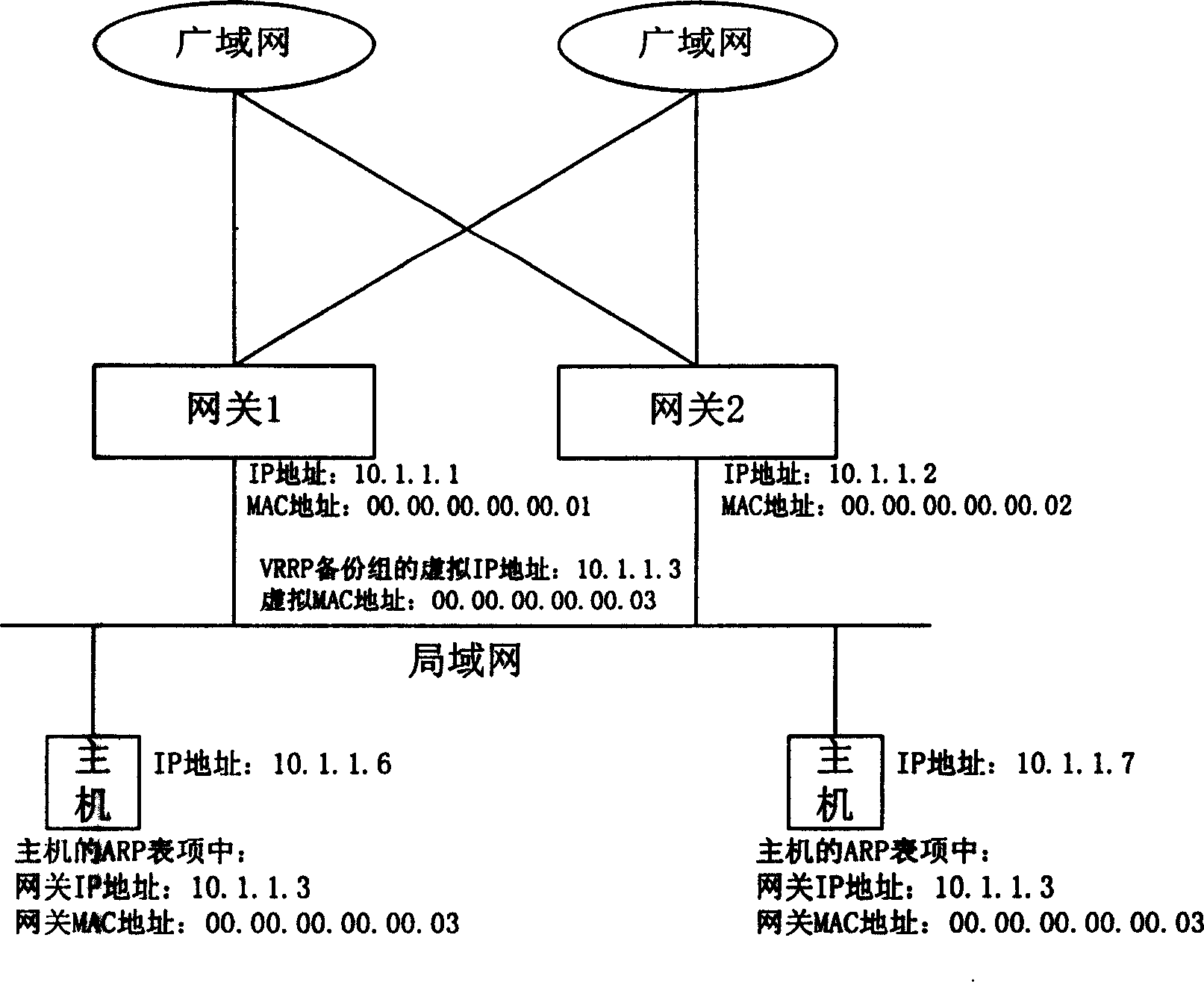
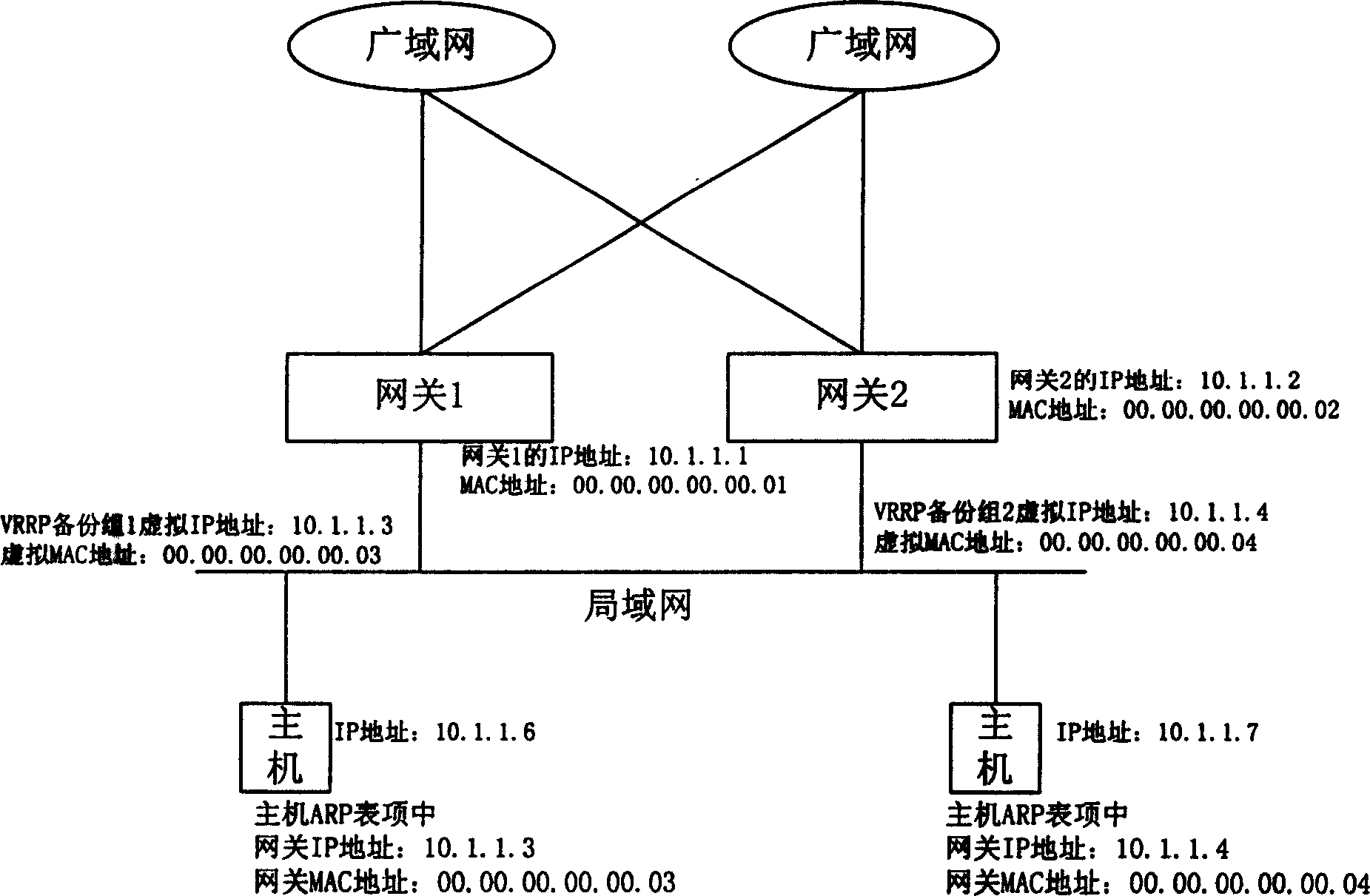
A network communication method implementing the function of network load sharing and the function of redundancy backup, including WAN, LAN host and multi gateway used for connecting WAN with LAN host. The gateway includes main gateway and standby gateway. Within LAN the gateway address configured by each host is the virtual IP address of the gateway. This method includes following steps: when the messages are passed between the host and WAN, the host will send ARP request according to configured gateway address to get MAC address of gateway IP address; the main gateway confirms the gateway providing service for message passing according to the states of each gateway, and uses the virtual MAC address of the pointed gateway to answer the ARP request; then this pointed gateway will provide message passing service for this host. This invention can make the host in LAN enjoys the benefit of load sharing and redundancy backup as no need of any special configuration.
Owner:HUAWEI TECH CO LTD
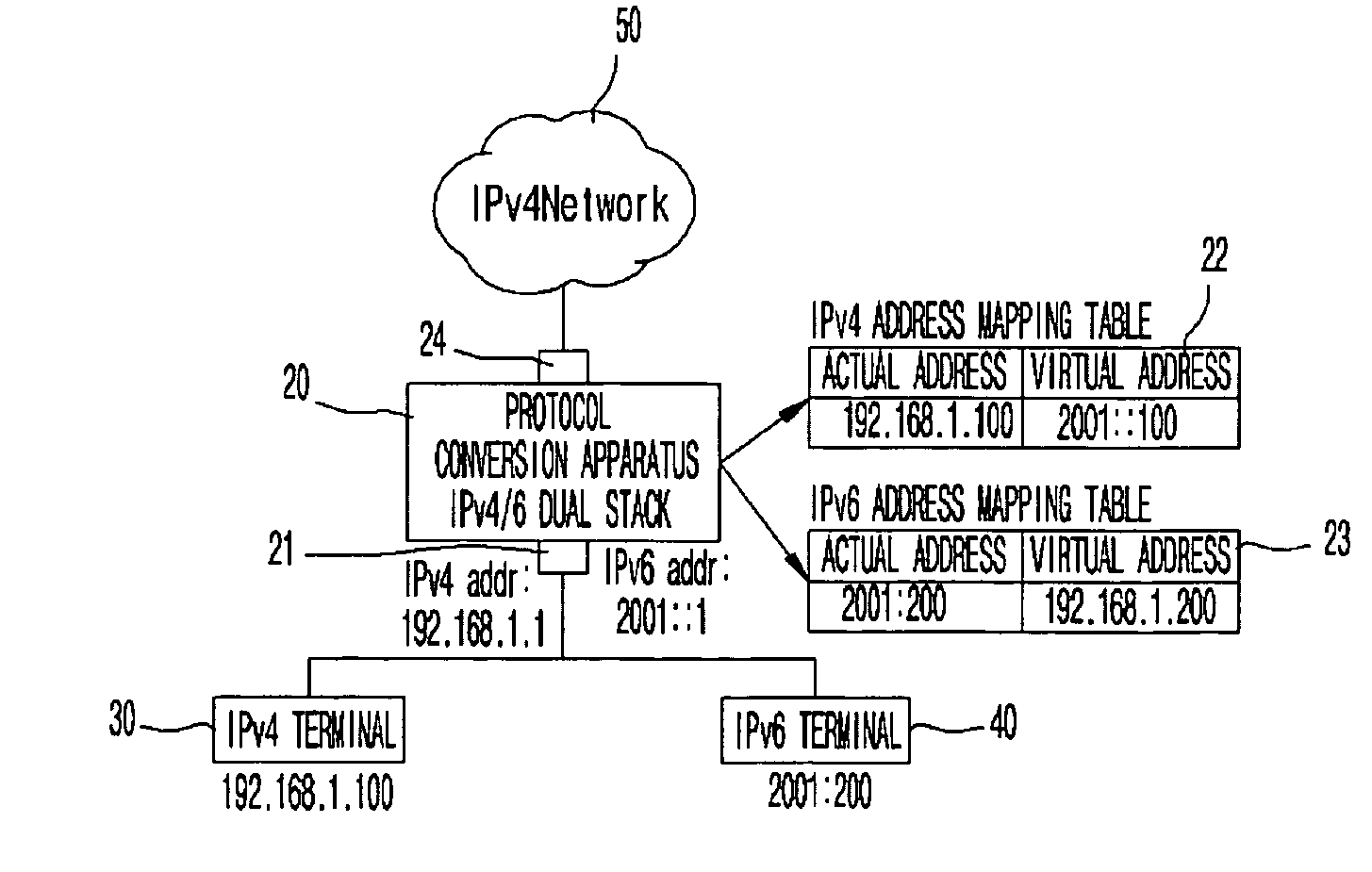
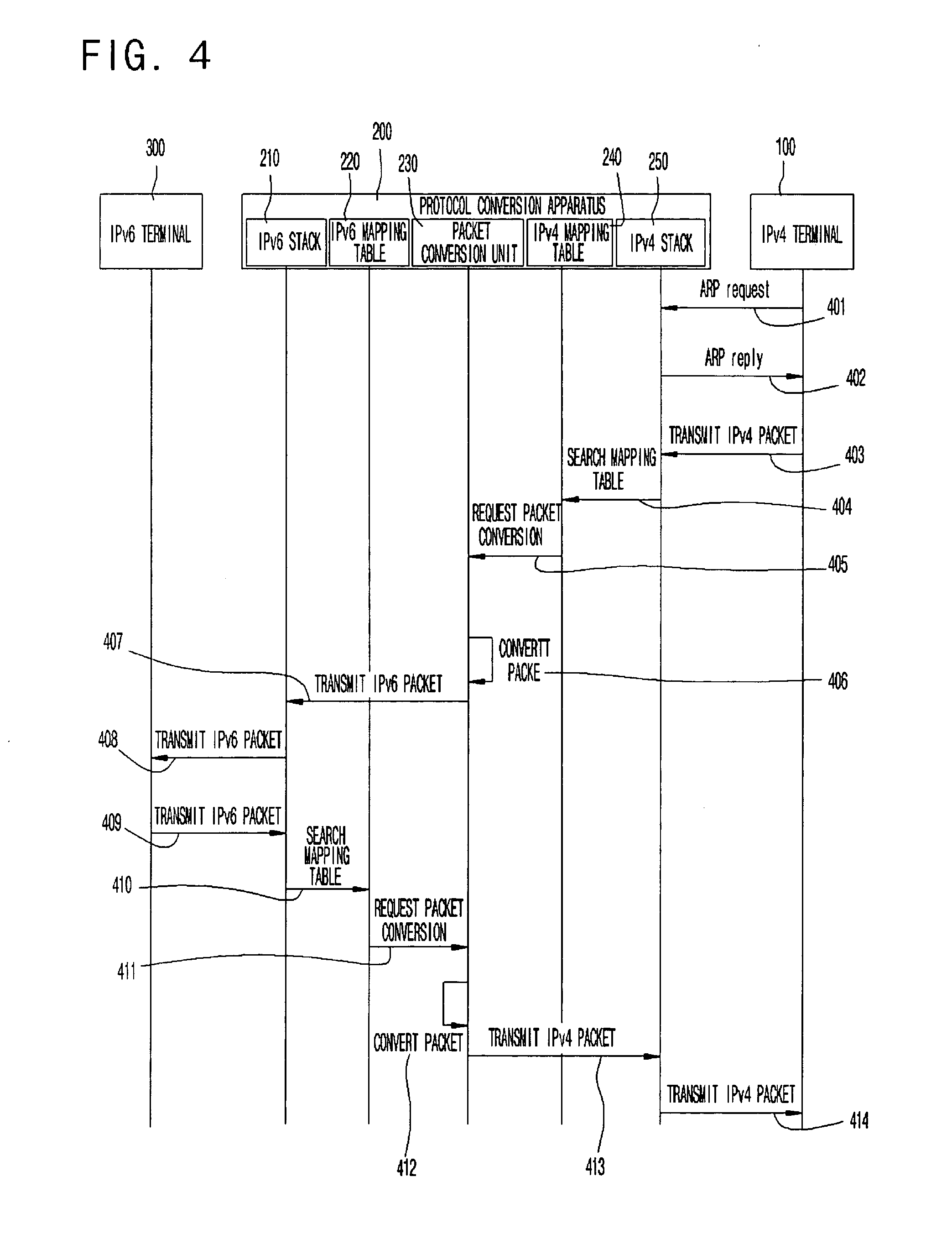
Protocol conversion apparatus and method between IPv4 terminal and IPv6 terminal or between application programs using mapping table, and method of generating mapping table of protocol conversion apparatus
InactiveUS20080080519A1Time-division multiplexData switching by path configurationPhysical networkVirtual IP address
Provided is a protocol conversion apparatus and method supporting communication between terminals through a protocol conversion when IPv4 / IPv6 terminals coexist or a terminal supports an IPv4 / IPv6 dual stack in one physical network but an application service supports a specific protocol. A conventional SIIT protocol conversion technique can be used by receiving a communication request through an IPv4 and IPv6 dual stack for a communication request of an IPv4 terminal or an IPv6 terminal, and supporting a protocol conversion between the IPv4 / IPv6 terminal through a mapping table mapping respective actual IP address and virtual IP address of the IPv4 and IPv6, and performing communication between the IPv4 / IPv6 terminals. Therefore, it is possible to transparently communicate to each other in an IP protocol version. Moreover, a terminal communicates with another terminal in an external network through a conventional protocol or a protocol conversion technique without modification.
Owner:ELECTRONICS & TELECOMM RES INST
Method and system for mobility across heterogeneous address spaces
ActiveUS7453852B2Data switching by path configurationWireless network protocolsAddress spaceNetwork interface
A mobile node includes a processor, a network interface, and a storage device having computer program code for execution by the processor. The computer program code includes a network layer for transmitting and receiving packets and an intermediate driver that transmits packets to the network layer and receives packets from the network layer using a virtual internet protocol (IP) address to identify the mobile node. The intermediate driver transmits packets to the network interface and receives packets from the network interface using a routable actual IP address to identify the mobile node. The intermediate driver permits the actual IP address to change when the mobile node moves from a first subnet to a second subnet without a corresponding change in the virtual IP address. A corresponding NAT associates the virtual IP address with a second actual IP address when the NAT is notified that the mobile node is in the second subnet.
Owner:ALCATEL LUCENT SAS
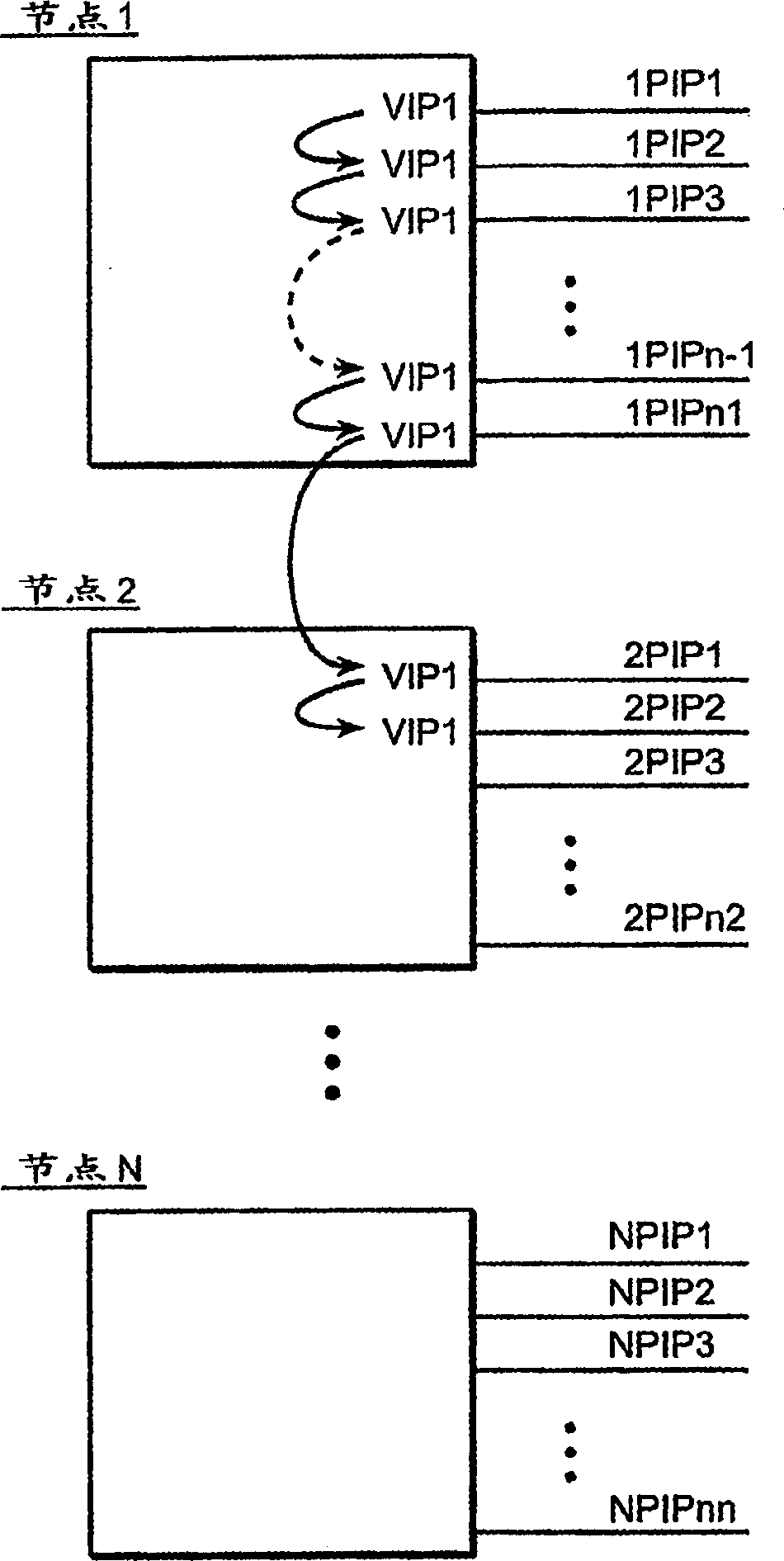
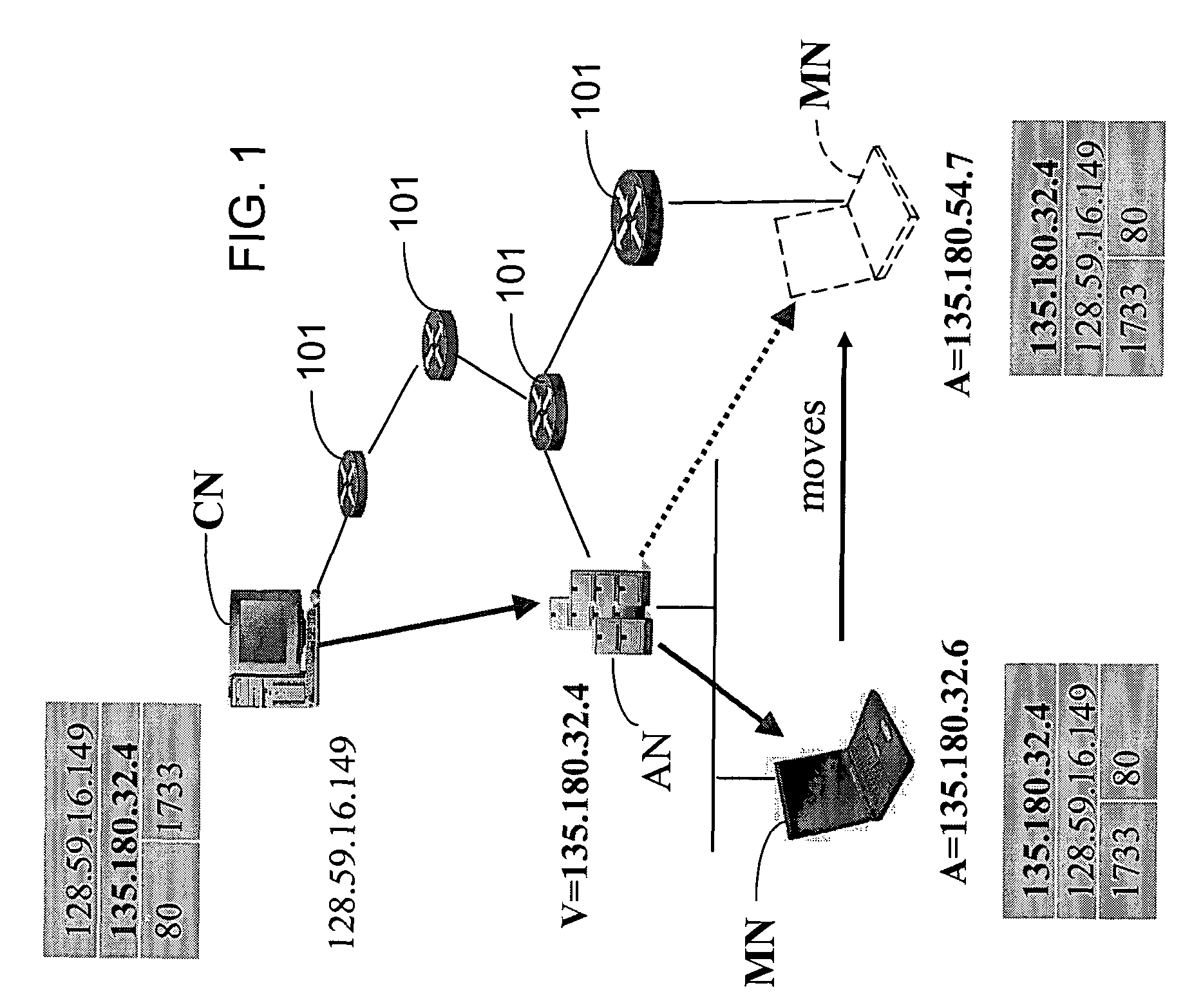
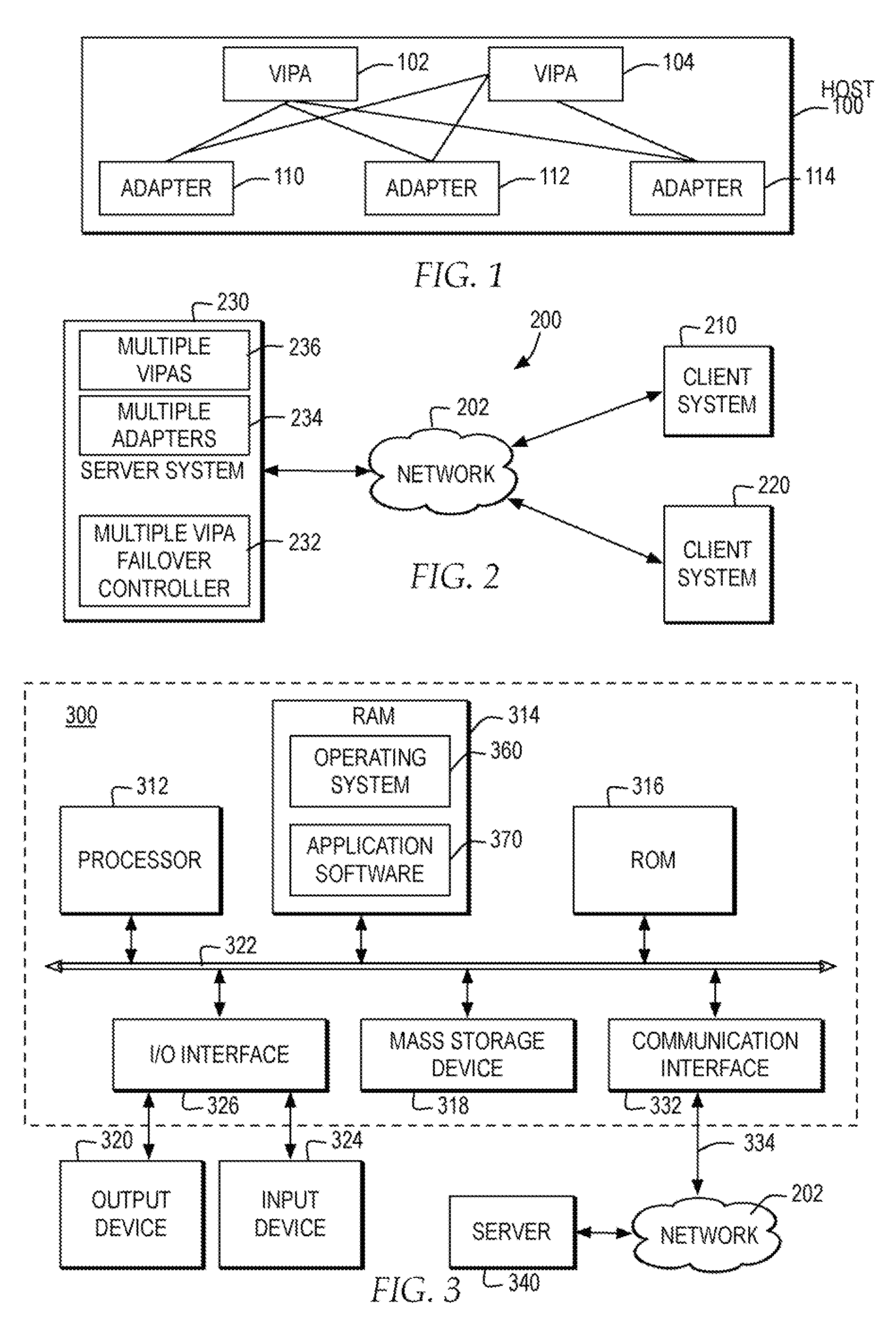
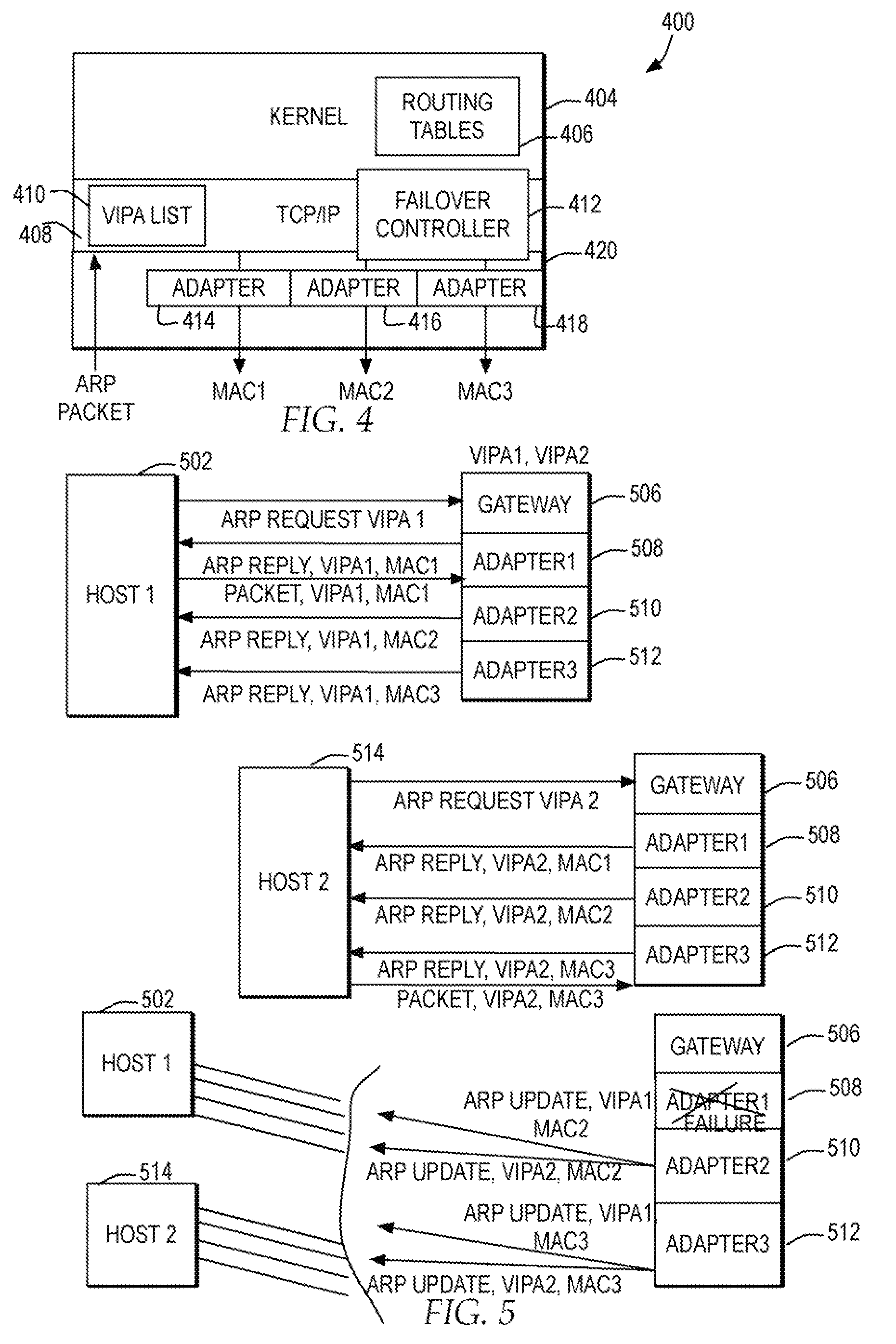
Failover in a host concurrently supporting multiple virtual IP addresses across multiple adapters
ActiveUS20090158082A1Efficient failoverTransmissionRedundant hardware error correctionFailoverHost machine
A host enables any adapter of multiple adapters of the host to concurrently support any VIPA of the multiple VIPAs assigned to the host. Responsive to a failure of at least one particular adapter from among the multiple adapters, the host triggers the remaining, functioning adapters to broadcast a separate hardware address update for each VIPA over the network, such that for a failover in the host supporting the multiple VIPAs the host directs at least one other host accessible via the network to address any new packets for the multiple VIPAs to one of the separate hardware addresses of one of the remaining adapters.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com