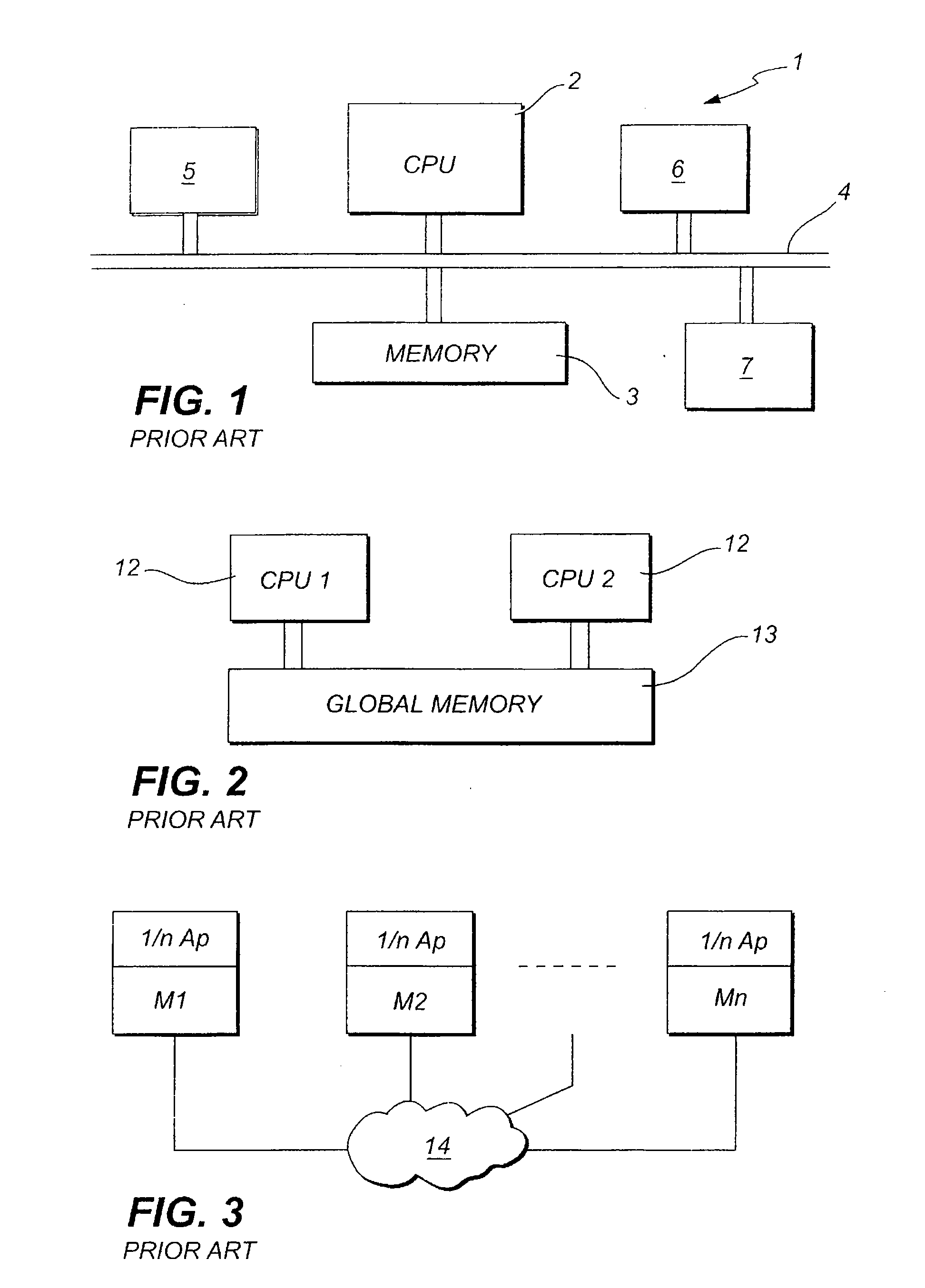
Patents
Literature
281 results about "Code distribution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
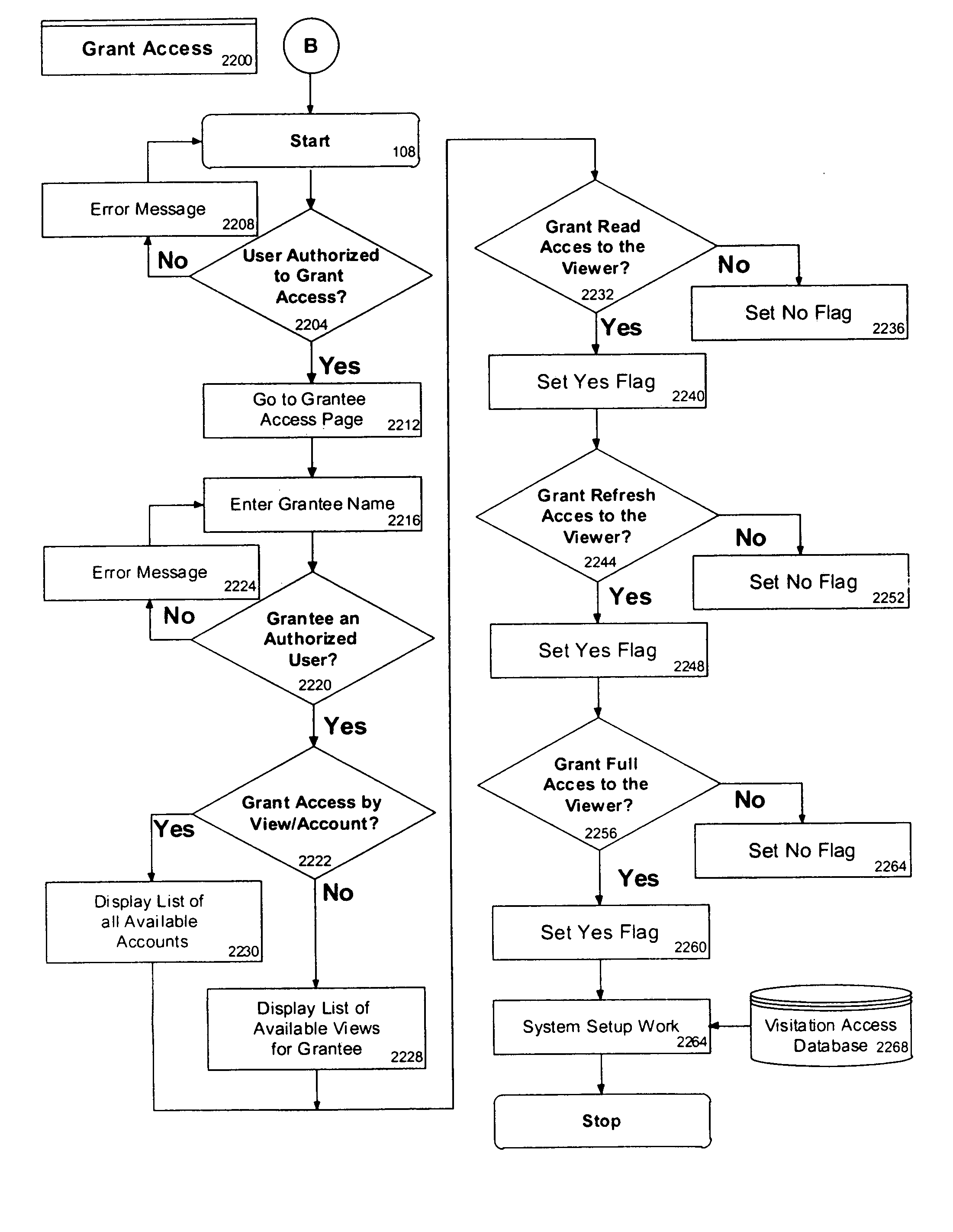
Secure selective sharing of account information on an internet information aggregation system
InactiveUS7120928B2Preserve security and confidentialityCommunication securityDigital data processing detailsUser identity/authority verificationThe InternetCode distribution
Owner:FINASTRA USA CORP
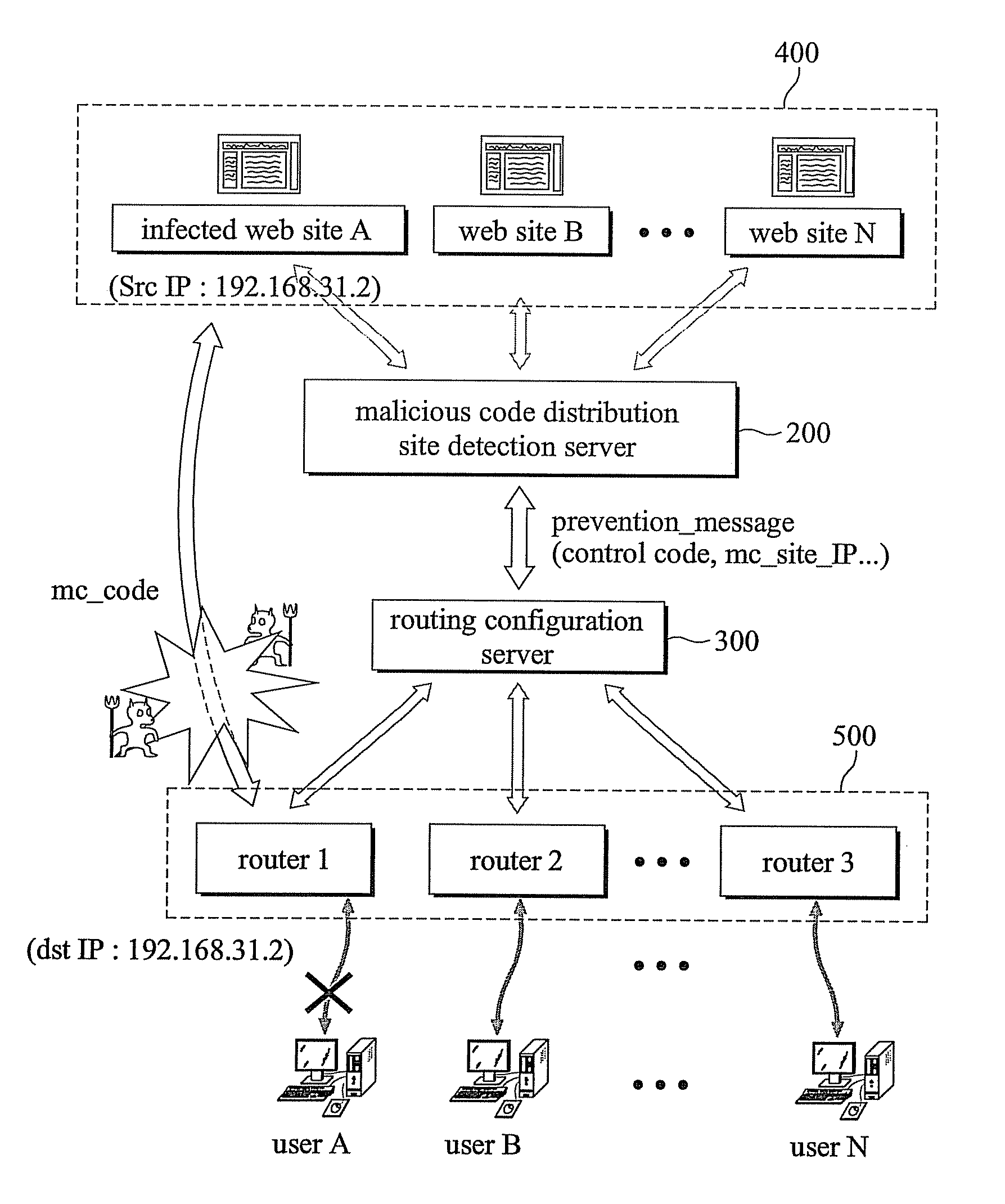
System and method for preventing malicious code spread using web technology
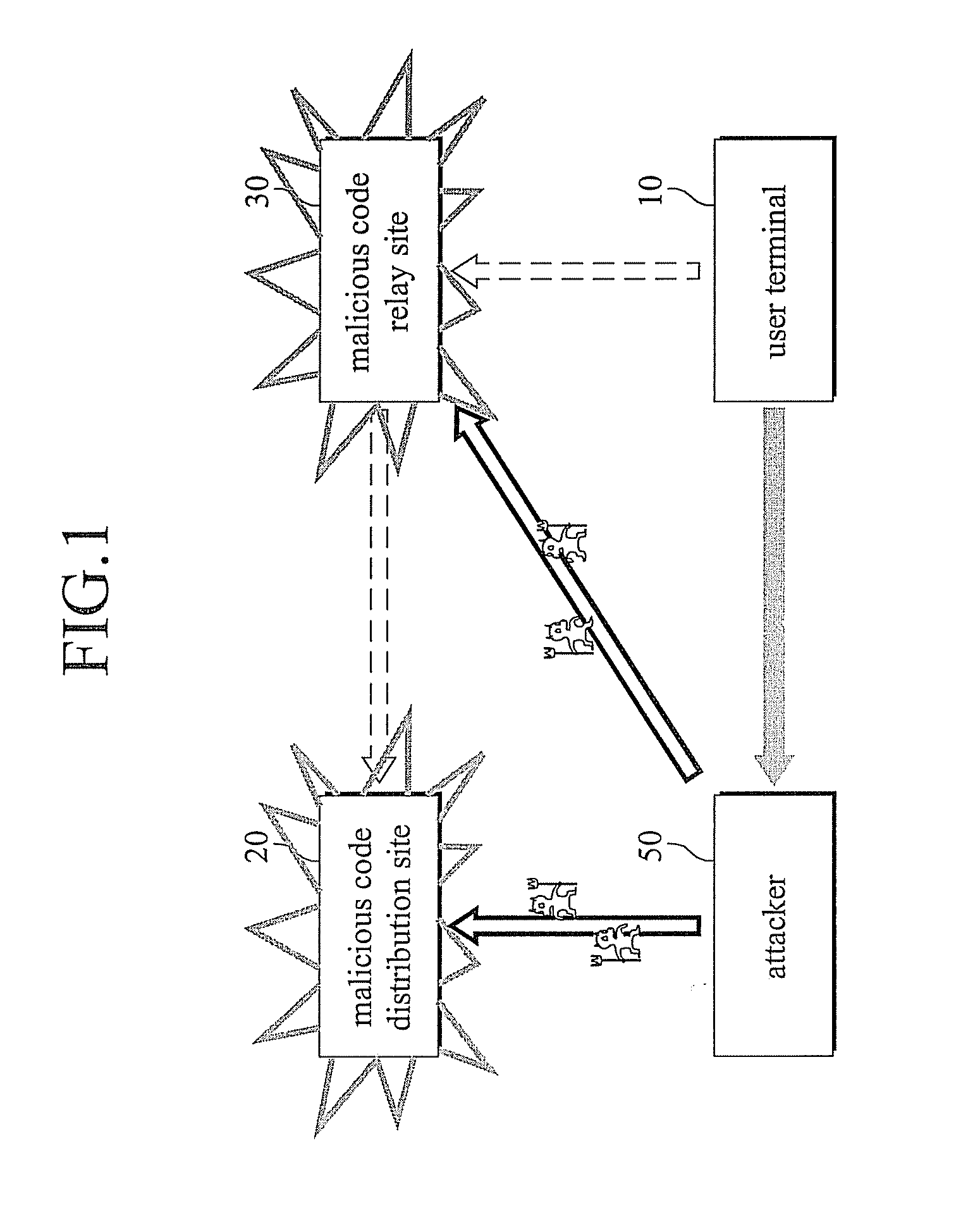
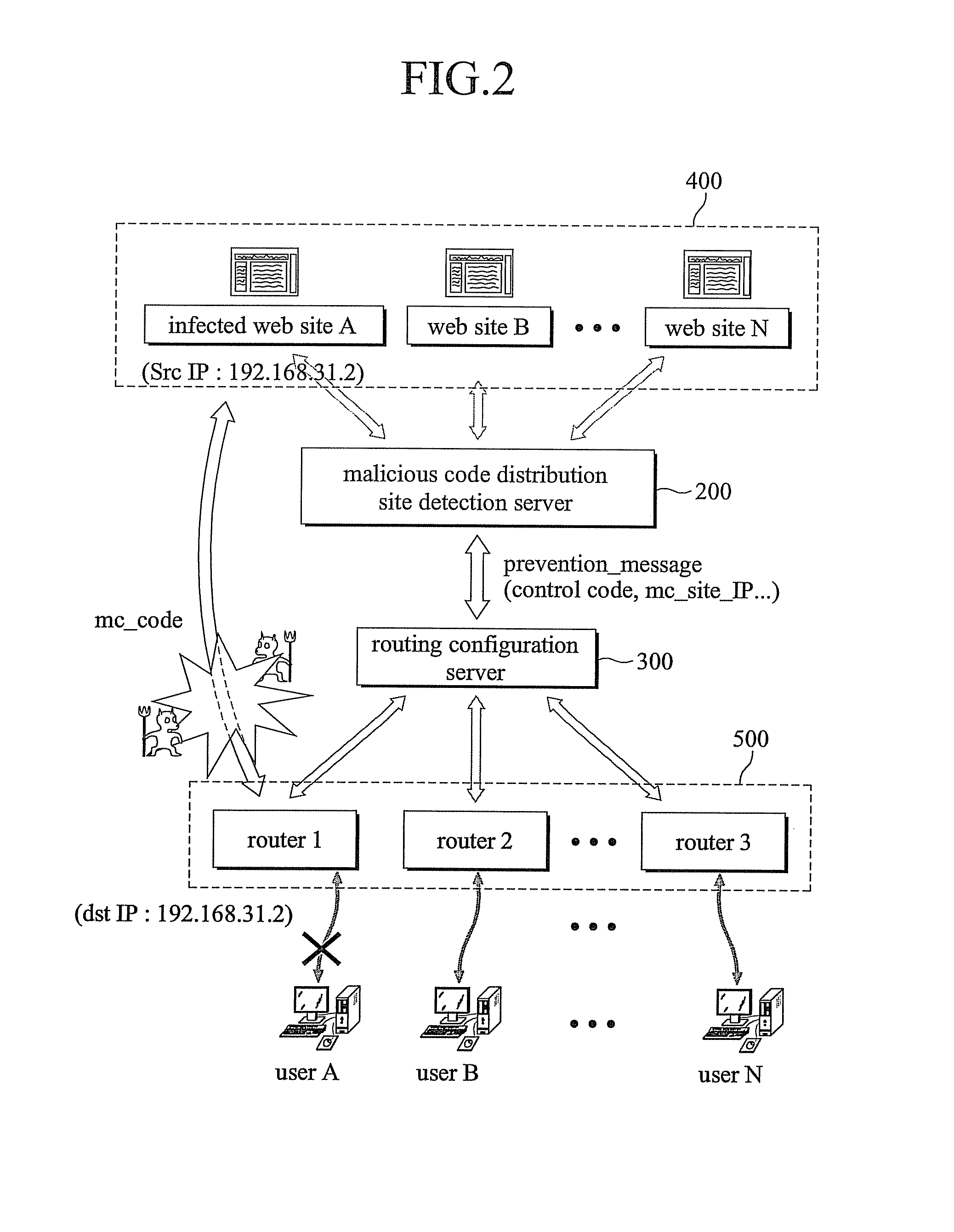
InactiveUS20080127338A1Avoid attackPrevent malicious attacksMemory loss protectionError detection/correctionCode distributionTransmitter
The present invention relates to a system and a method for preventing an attack of a malicious program spread using a web technology comprising a malicious code distribution site detection server comprising a malicious code distribution site detector for detecting a malicious code distribution site, and a prevention message transmitter for transmitting a prevention message to a routing configuration server, wherein the prevention message includes an IP address of the malicious code distribution site detected by the malicious code distribution site detector; a plurality of routers including a virtual IP address; and the routing configuration server for advertising the IP address of the malicious code distribution site such that a routing path of a packet having the IP address of the malicious code distribution site as a target address or an starting address is guided to the virtual IP address according to an reception of the prevention message to block a connection to the malicious code distribution site.
Owner:KOREA INTERNET & SECURITY AGENCY
Method and apparatus for control and routing of wireless sensor networks
ActiveUS20060077918A1Efficient routingReliable data transmissionEnergy efficient ICTElectric signal transmission systemsLine sensorDirectional antenna
A scalable, minimum node complexity, energy efficient, and error-resilient routing method for wireless sensor networks is described. The network is partitioned into regions by power controlled base station scans using a directional antenna. Routing is performed using only local location information and instructions received from the base station at each sensor node with minimum processing and control overhead, thus allowing simple, low-cost sensor designs. Sensors in the network provide to a base station reports of the condition of the sensors themselves, and these reports are analyzed by the base station to determine improved routing instructions, which are then provided to the sensor nodes in control messages. Each data packet is relayed in an interleaved, loop-free mesh of sectors toward the base station, making data delivery robust to sensor failures and transmission errors. The disclosure also contains descriptions for simple edge-based tasking, query, code distribution, and network programming for sensor nodes. The method is suitable for large-scale, dense sensor networks for detection, alarming, and monitoring applications.
Owner:VIRGINIA TECH INTPROP INC
Method and apparatus for control and routing of wireless sensor networks
ActiveUS7304976B2Improve performanceEnergy efficient ICTElectric signal transmission systemsLine sensorWireless mesh network
A scalable, minimum node complexity, energy efficient, and error-resilient routing method for wireless sensor networks is described. The network is partitioned into regions by power controlled base station scans using a directional antenna. Routing is performed using only local location information and instructions received from the base station at each sensor node with minimum processing and control overhead, thus allowing simple, low-cost sensor designs. Sensors in the network provide to a base station reports of the condition of the sensors themselves, and these reports are analyzed by the base station to determine improved routing instructions, which are then provided to the sensor nodes in control messages. Each data packet is relayed in an interleaved, loop-free mesh of sectors toward the base station, making data delivery robust to sensor failures and transmission errors. The disclosure also contains descriptions for simple edge-based tasking, query, code distribution, and network programming for sensor nodes. The method is suitable for large-scale, dense sensor networks for detection, alarming, and monitoring applications.
Owner:VIRGINIA TECH INTPROP INC
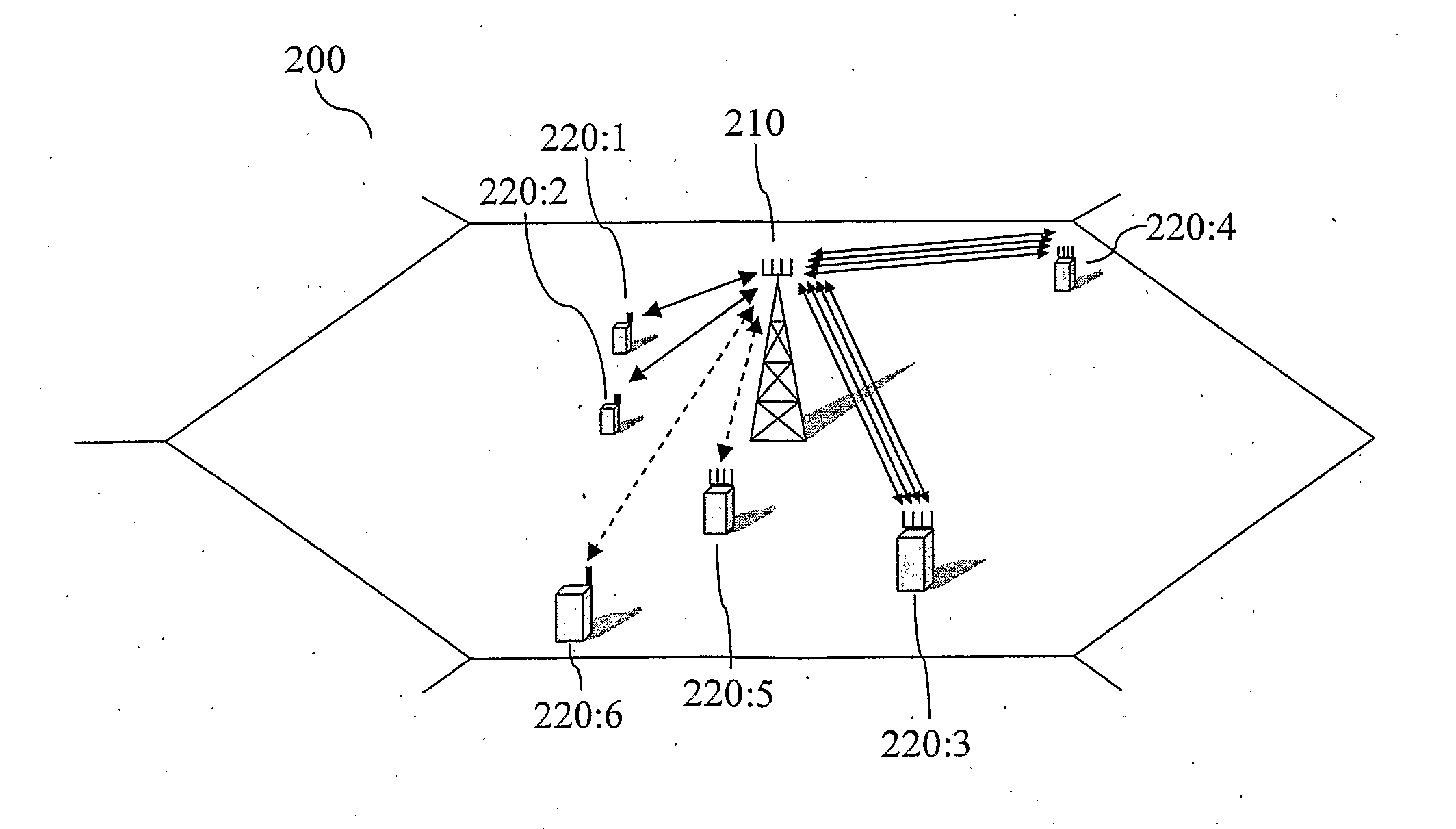
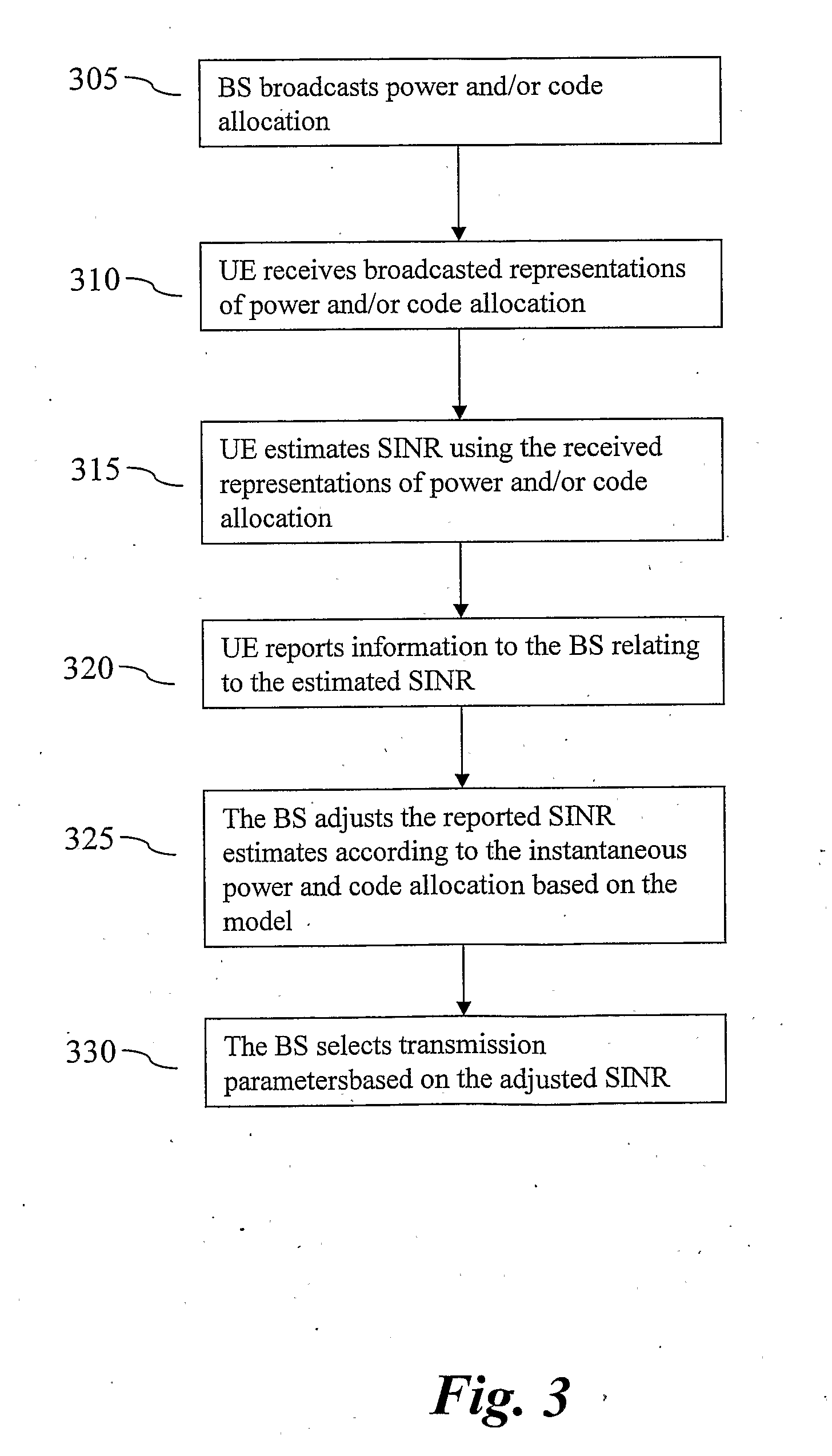
Method and Arrangement for SINR Feedback in MIMO Based Wireless Communication Systems
InactiveUS20100098030A1High throughputHigh qualityPower managementSecret communicationWireless communication systemsMIMO
The present invention relates to a method and arrangement to enhance the communication performance in wireless communication systems. The method of the invention provides better adjustment of reported SINR in MIMO, and PARC-MIMO based communication systems. According to the method information relating to signal-to-interference-plus-noise ratio is determined by the user equipment and reported to the base station. The base station adjust reported SINRs using a model of the SINR dependences of power and code allocation. The dependences is modeled by a function comprising a first parameter relating only to power allocation and a second parameter relating only to code allocation. The first parameter has a power allocation exponent and the second parameter has a code allocation exponent. Both the power allocation exponent and the code allocation exponent are data stream dependent.
Owner:UNWIRED PLANET
Computer Architecture And Method Of Operation for Multi-Computer Distributed Processing Having Redundant Array Of Independent Systems With Replicated Memory And Code Striping
ActiveUS20080250213A1Avoid accessError detection/correctionMemory adressing/allocation/relocationTelecommunications linkParallel computing
Computers and other computing machines and information appliances having a modified computer architecture and program structure which enables the operation of an application program concurrently or simultaneously on a plurality of computers interconnected via a communications link or network using a special distributed runtime (DRT), and that provides for a redundant array of independent computing systems that include computer code distribution using code-striping onto the plurality of the computers or computing machines. A redundant array of independent computing systems operating in concert and code-striping features.
Owner:WARATEK LTD
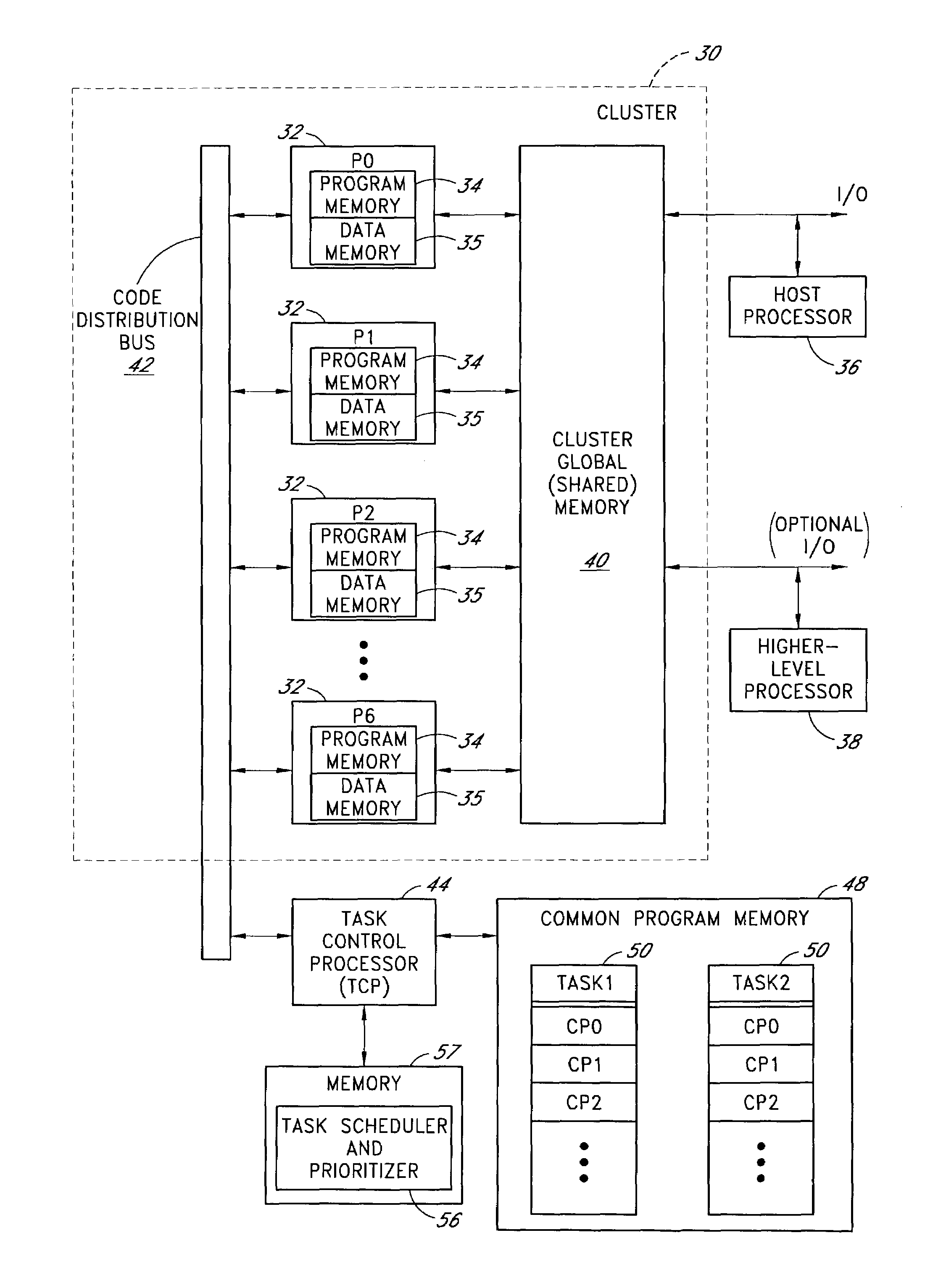
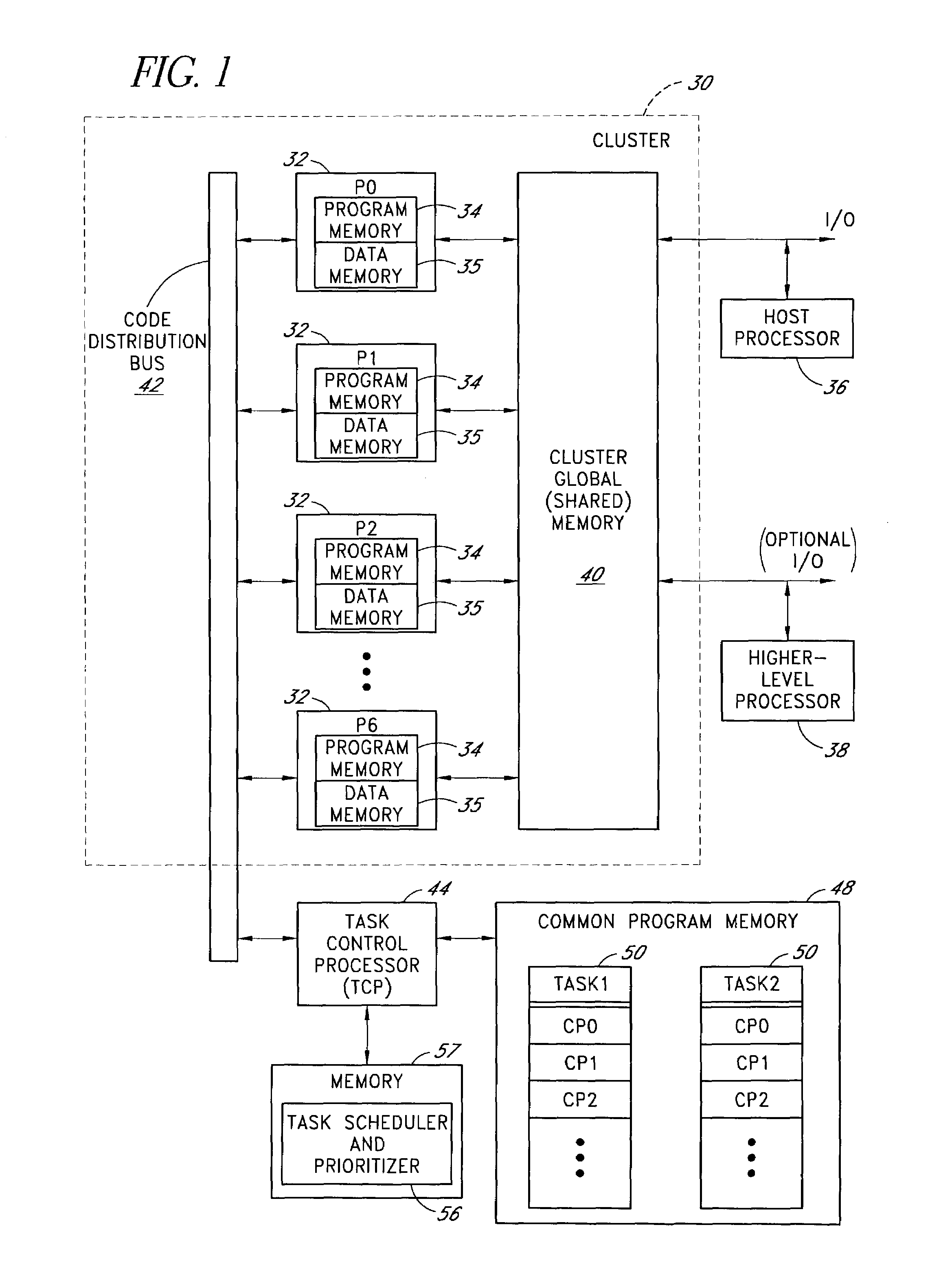
Processor cluster architecture and associated parallel processing methods
ActiveUS6959372B1High level of performanceGeneral purpose stored program computerProgram loading/initiatingCode distributionComputer science
A parallel processing architecture comprising a cluster of embedded processors that share a common code distribution bus. Pages or blocks of code are concurrently loaded into respective program memories of some or all of these processors (typically all processors assigned to a particular task) over the code distribution bus, and are executed in parallel by these processors. A task control processor determines when all of the processors assigned to a particular task have finished executing the current code page, and then loads a new code page (e.g., the next sequential code page within a task) into the program memories of these processors for execution. The processors within the cluster preferably share a common memory (1 per cluster) that is used to receive data inputs from, and to provide data outputs to, a higher level processor. Multiple interconnected clusters may be integrated within a common integrated circuit device.
Owner:NVIDIA CORP
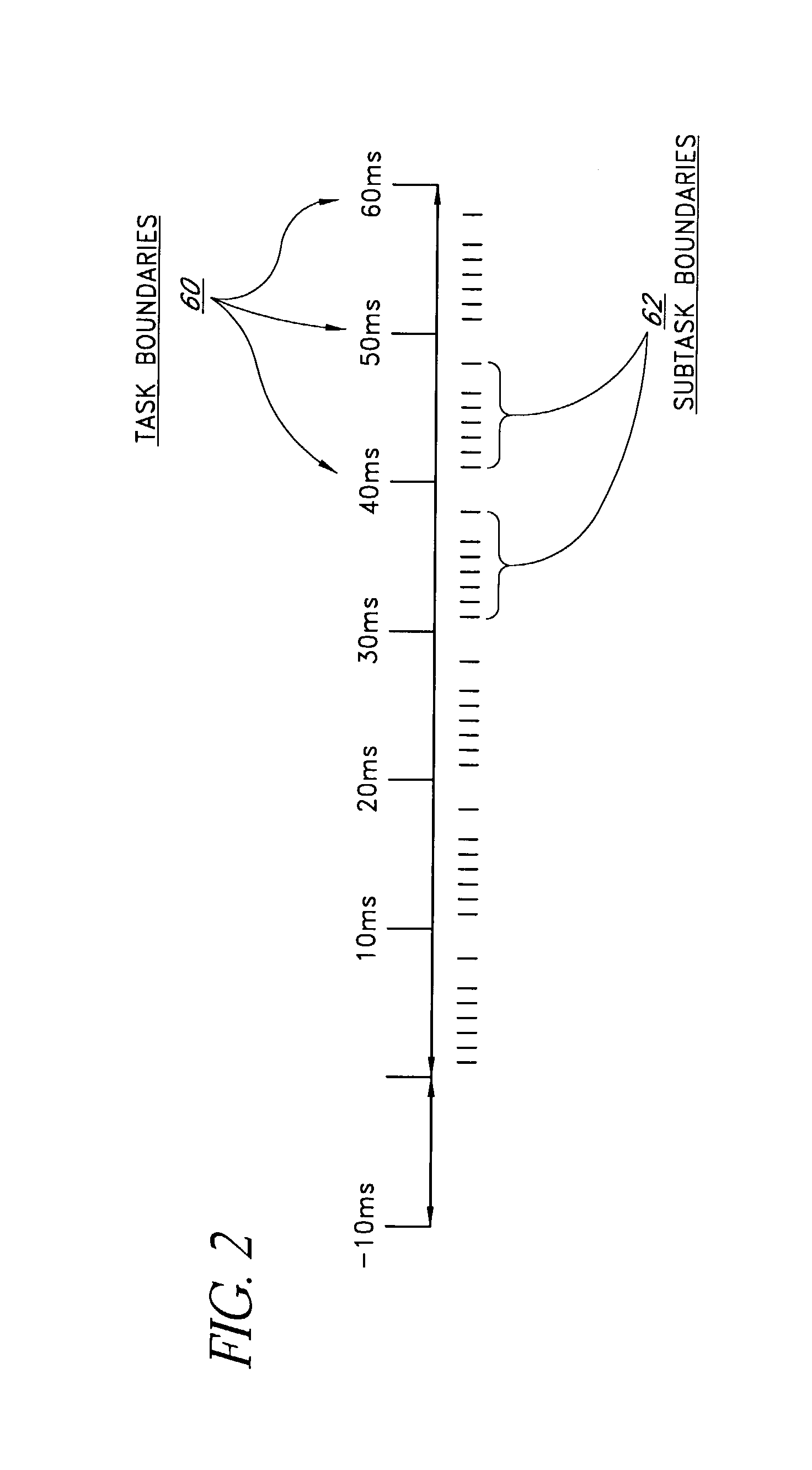
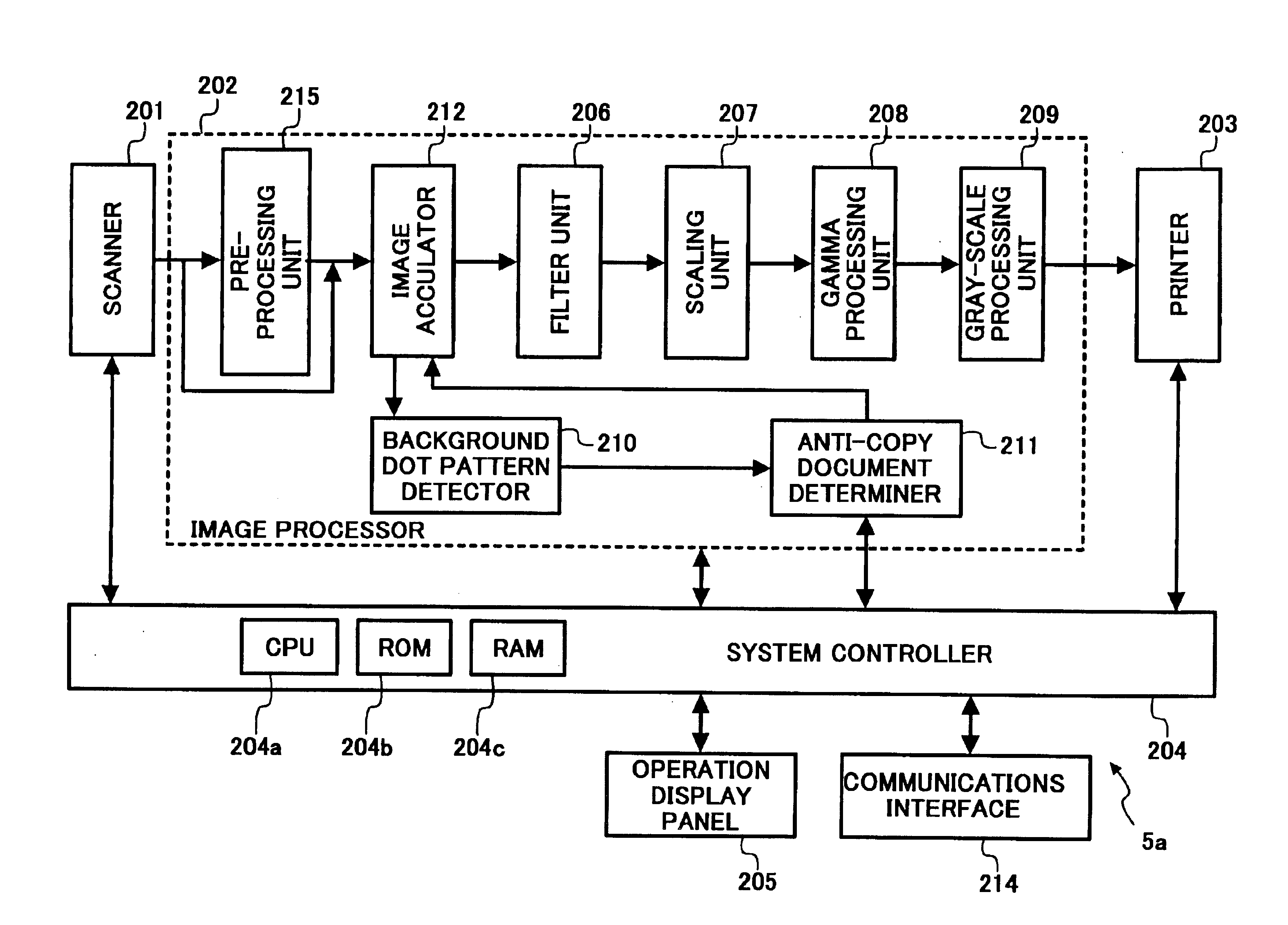
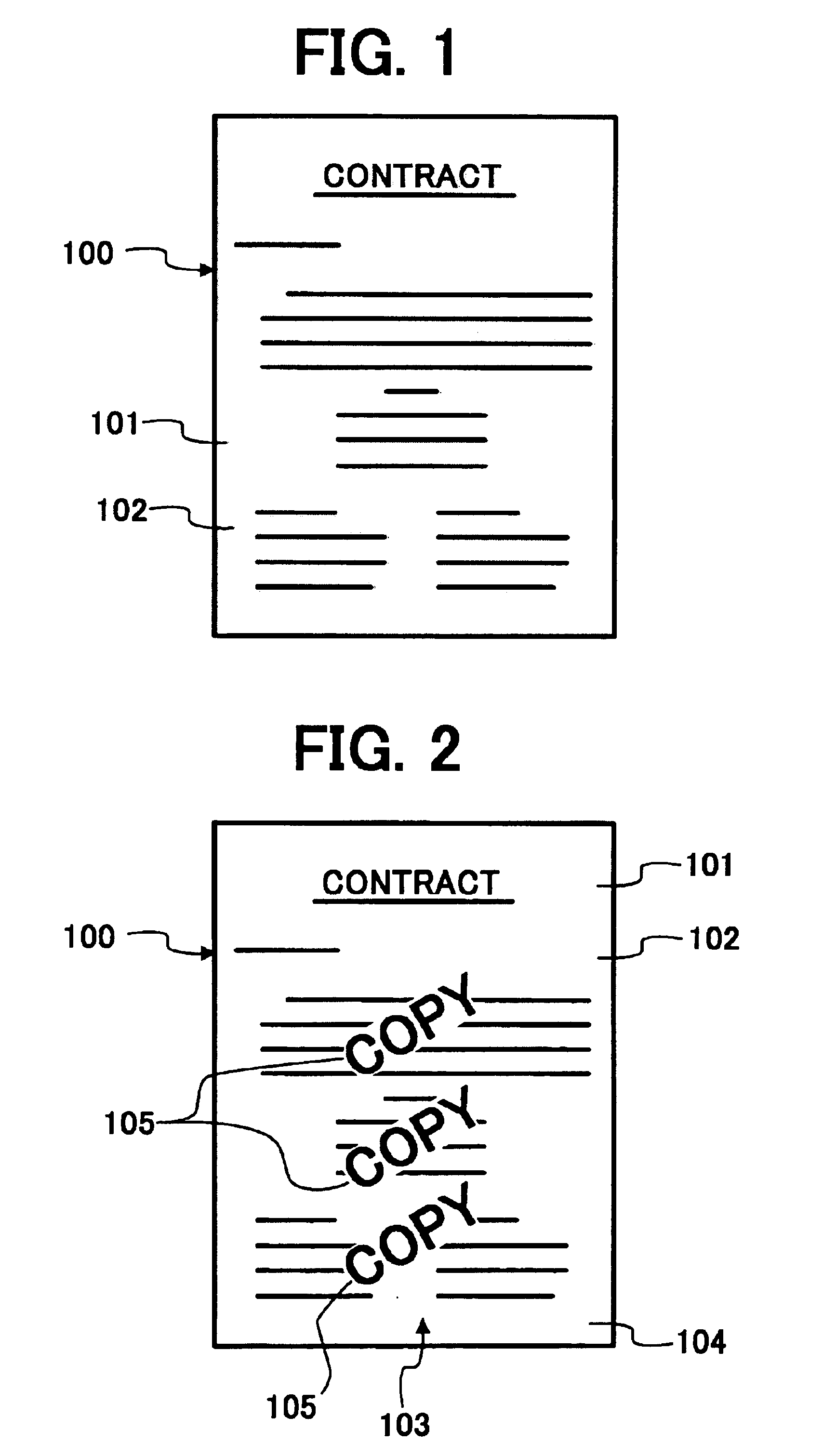
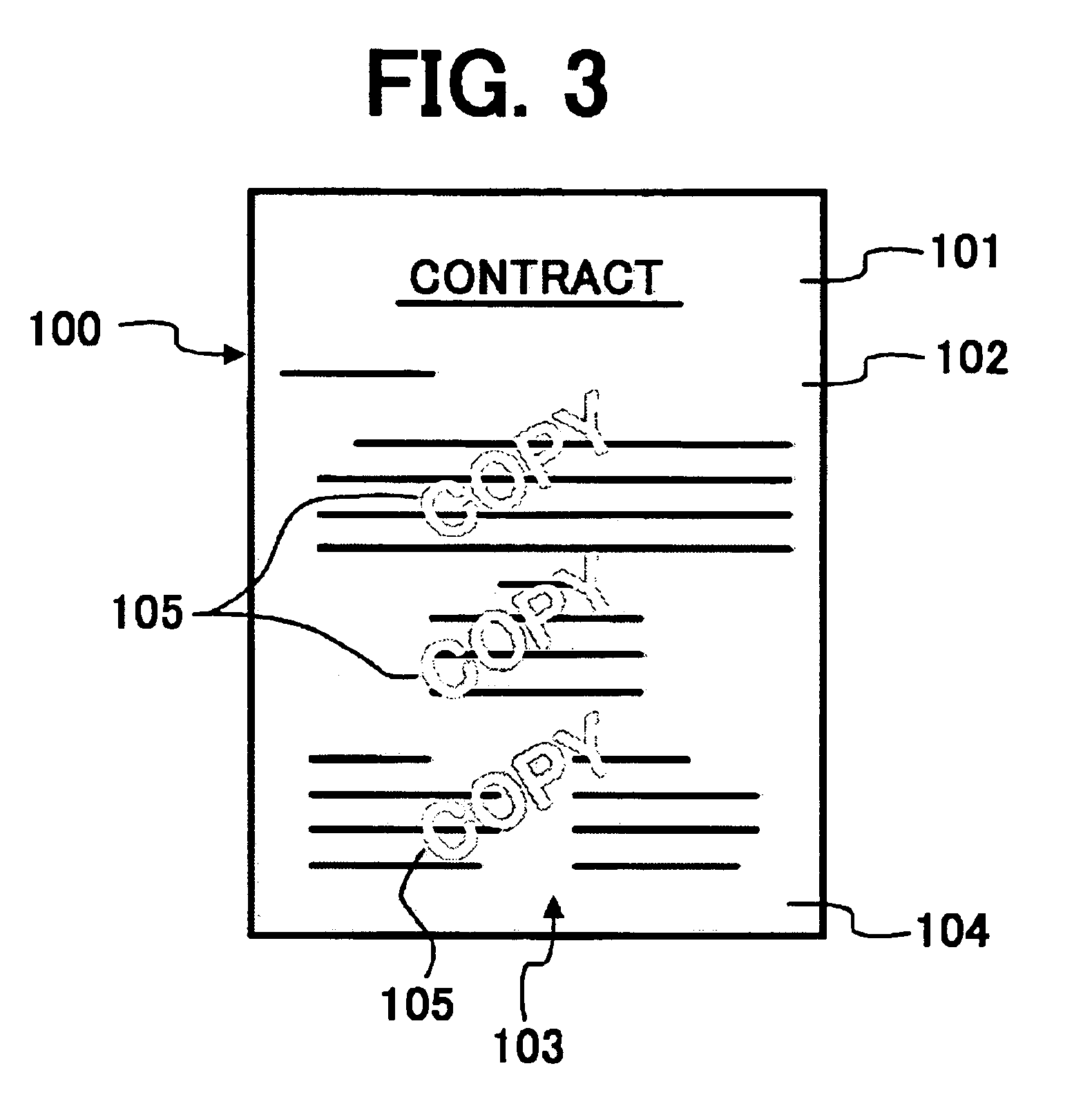
Method, program, and apparatus for preventing a reproduction of an anti-copy document, and a medium storing the program
InactiveUS6901236B2Character and pattern recognitionElectrographic process apparatusPattern recognitionGraphics
An image processing apparatus includes a scanning mechanism, first and second memories, an image accumulating mechanism, a detecting mechanism, a determining mechanism, and a code assigning mechanism. The first memory stores a reference dot pattern indicating an anti-copy background dot pattern. The second memory stores image data. The image accumulating mechanism accumulates image data of an original image into the second memory. The detecting mechanism detects a background dot pattern embedded in a background image included in the image data of the accumulated original image. The determining mechanism compares the detected background dot pattern with the reference dot pattern and determines whether the detected background dot pattern is substantially identical to the reference dot pattern. The code assigning mechanism assigns an identification code to the image data having the detected background dot pattern when the detected background dot pattern is determined as substantially identical to the reference dot pattern.
Owner:RICOH KK
Digital radio communications method using multi-level modulation scheme and transmitter and receiver
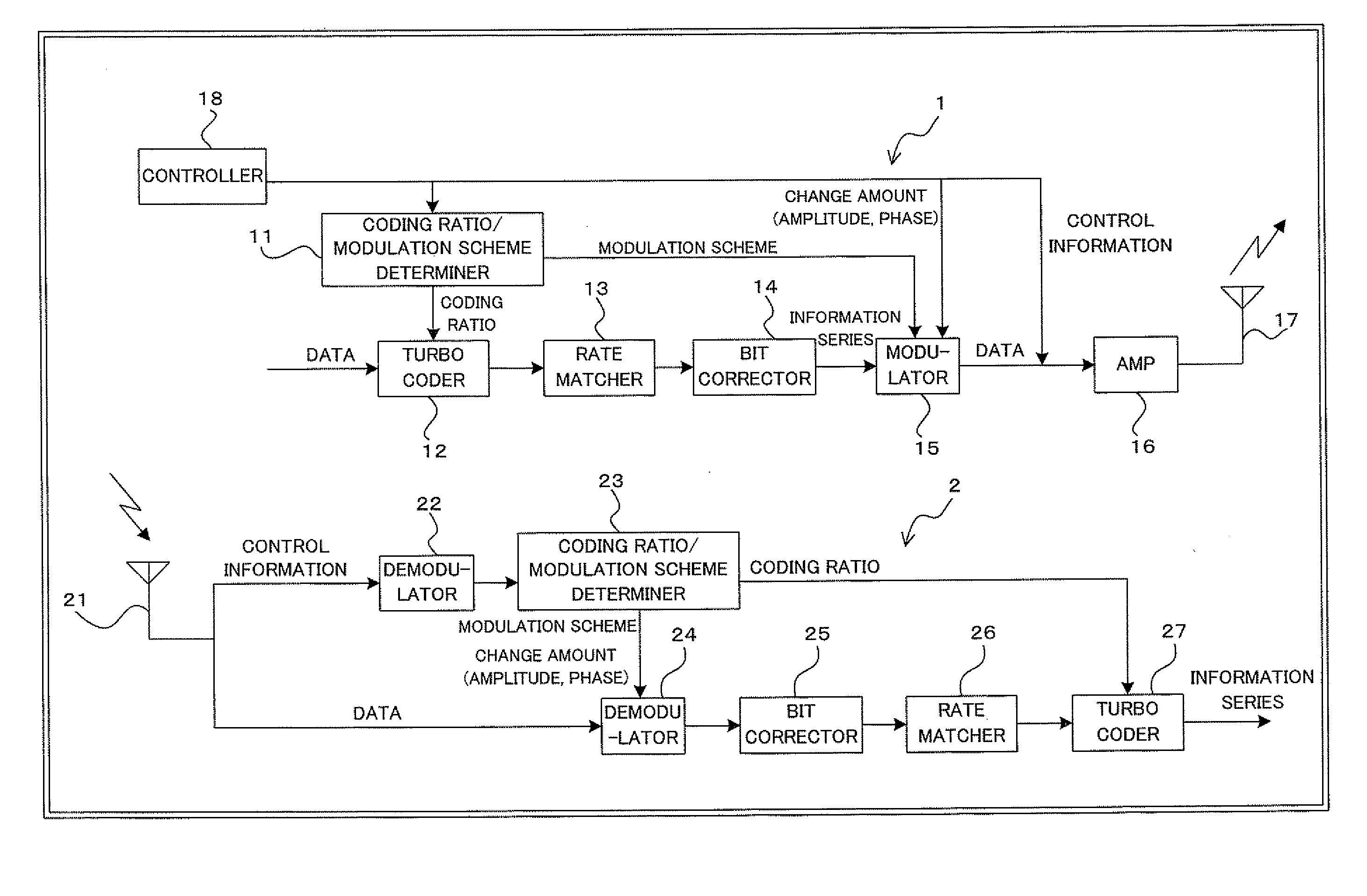
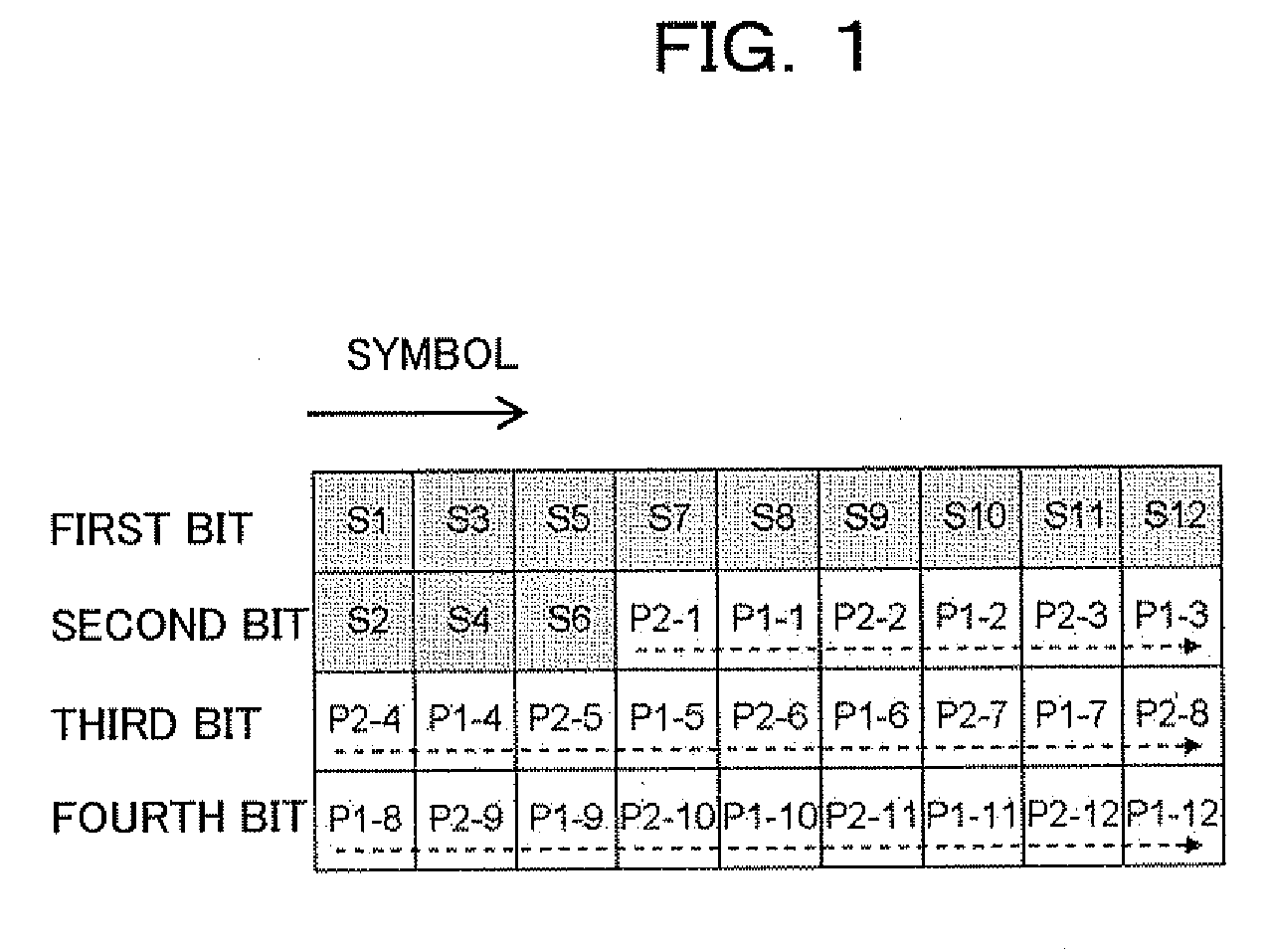
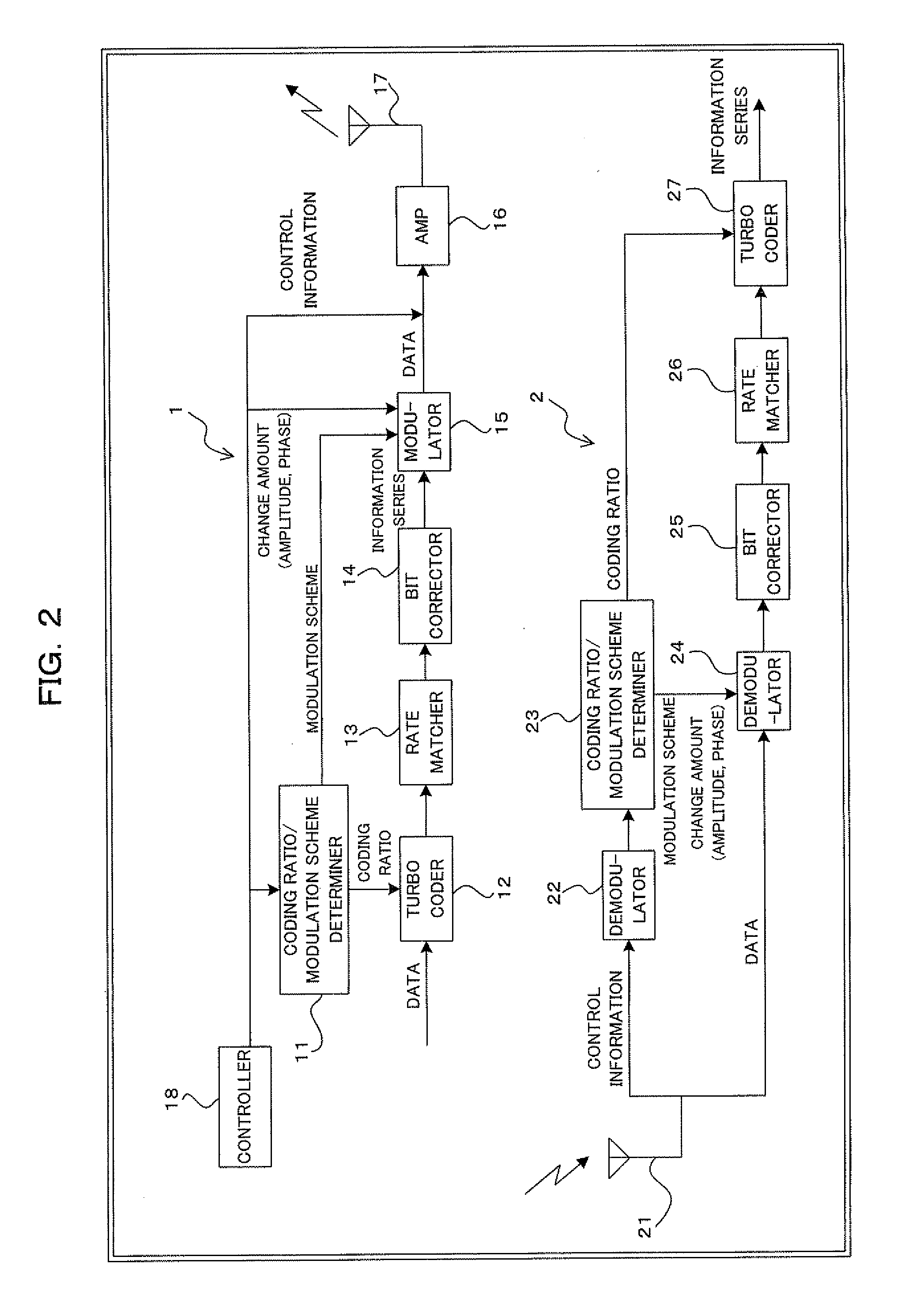
InactiveUS20090161786A1Sufficient effectHigh error rateError correction/detection using trellis codingCode conversionComputer hardwareCommunications system
A transmitter for use in digital radio communications systems includes: a bit corrector controls bit arrangement in such a manner that a code having high significance, out of multiple codes obtained by coding, is allocated with high priority to a bit having a tendency that the likelihood enlarges at the time of symbol decision on a receiver; a multi-level modulator allocates the code to the multiple bits in accordance with a predetermined symbol arrangement; and a symbol arrangement controller controls the symbol arrangement from equal distance arrangement to another arrangement in accordance with a ratio of the codes different in significance. To control symbol arrangement increases the effect of bit correction and improves an error rate on the receiver.
Owner:FUJITSU LTD
Method for selective software rollback
ActiveUS20140075197A1User identity/authority verificationDigital data protectionCode distributionVersion code
A system and method for validating a software file to be installed into a controller. The method includes preparing the software file including assigning a software version code to the software file, assigning a security version code to the software file, and signing the software file with the software file version code and the security version code. The signed software file is presented to the controller for installing on the controller and the controller verifies the software file signature to determine if the software file is valid and the security version code is valid. The controller allows the software file to be installed in the controller if both the signed software file is valid and the security version code is valid.
Owner:GM GLOBAL TECH OPERATIONS LLC
Method and system for code reuse and capacity enhancement using null steering
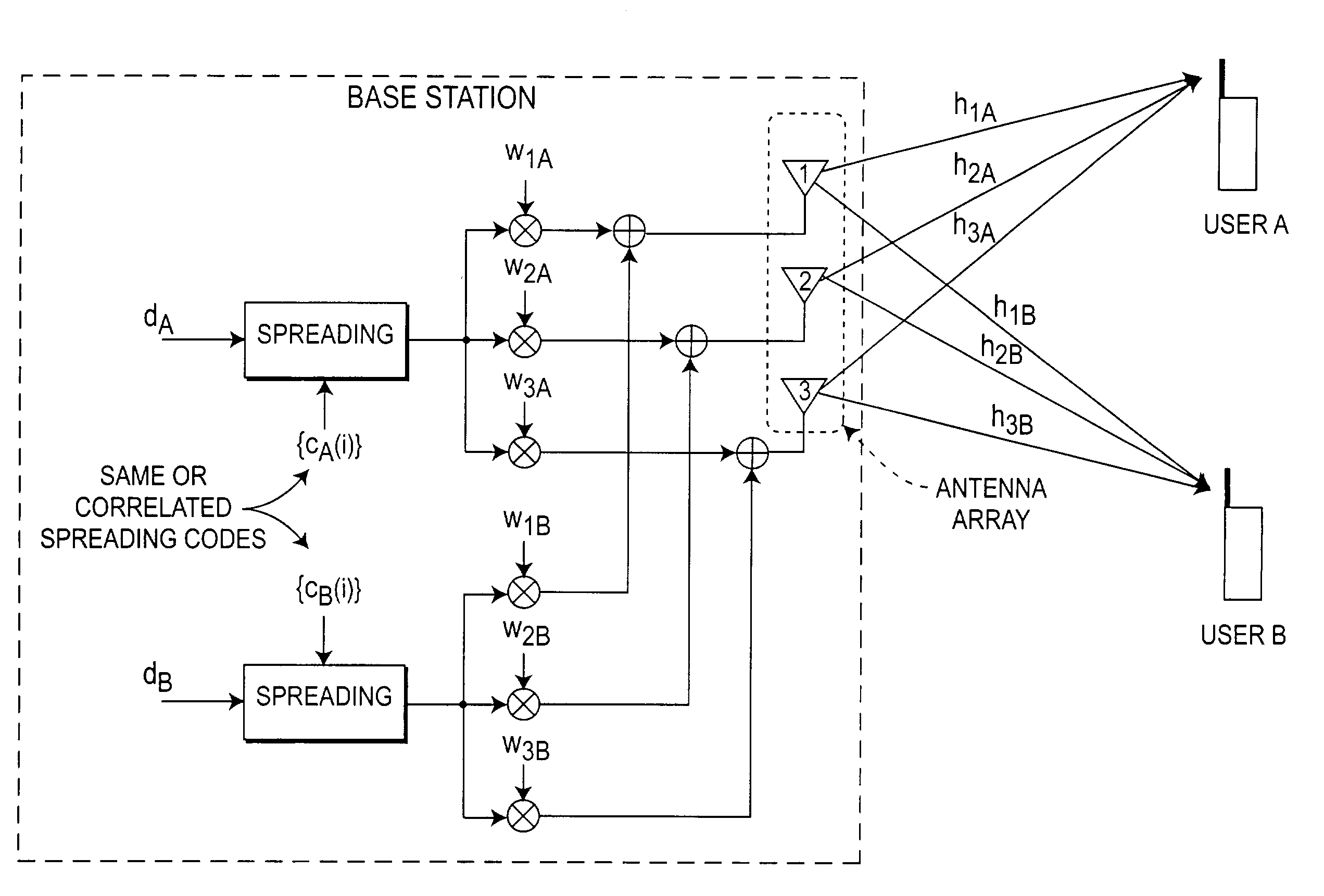
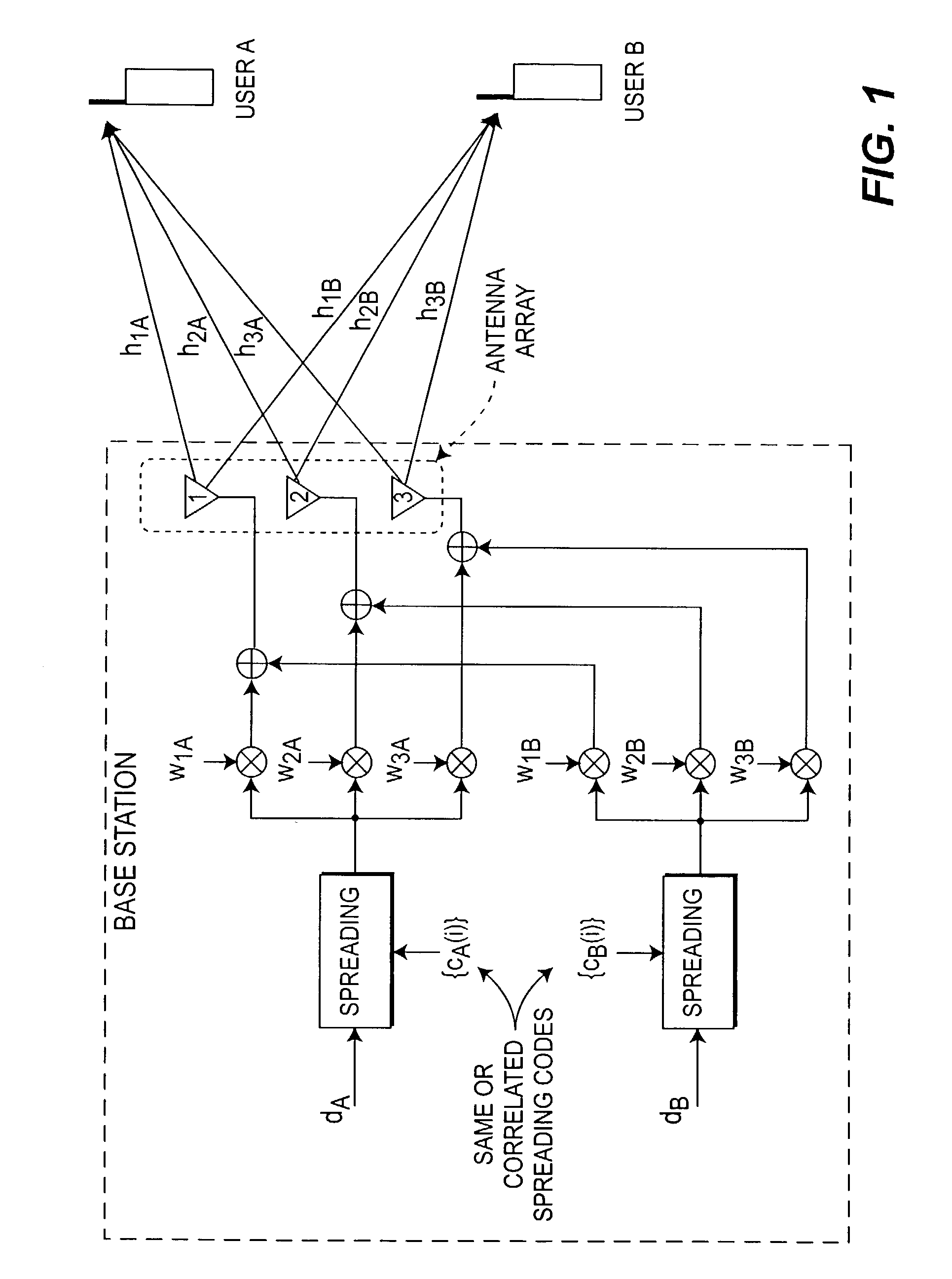
InactiveUS7218684B2Increase capacityMaintain propertiesSpatial transmit diversityAntenna arraysData capacityEngineering
The number of users and data capacity of wireless systems are increased by employing apparatus and method for increasing the number of spreading codes available in the system by providing a mechanism to reuse the already allocated spreading code or use the codes that may correlate to those already being used within the same sector / cell. This, in return, provides capacity improvement proportional to the number of added base station (BS) antennas for each cell. An antenna null steering technique for code allocation maintains the cross correlation properties of the codes only for the desired user and to obtain a gain in capacity improvement.
Owner:INTERDIGITAL TECH CORP
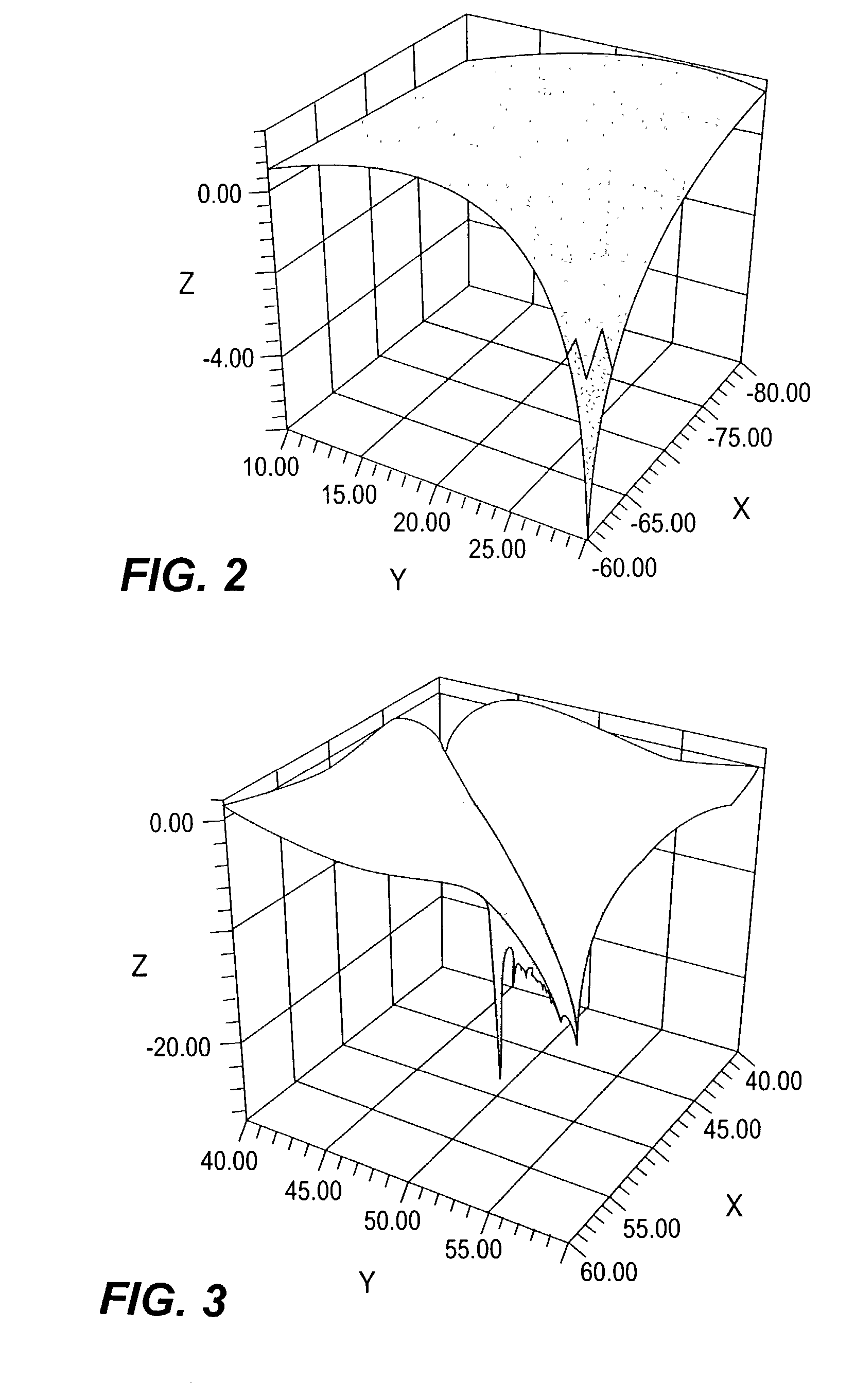
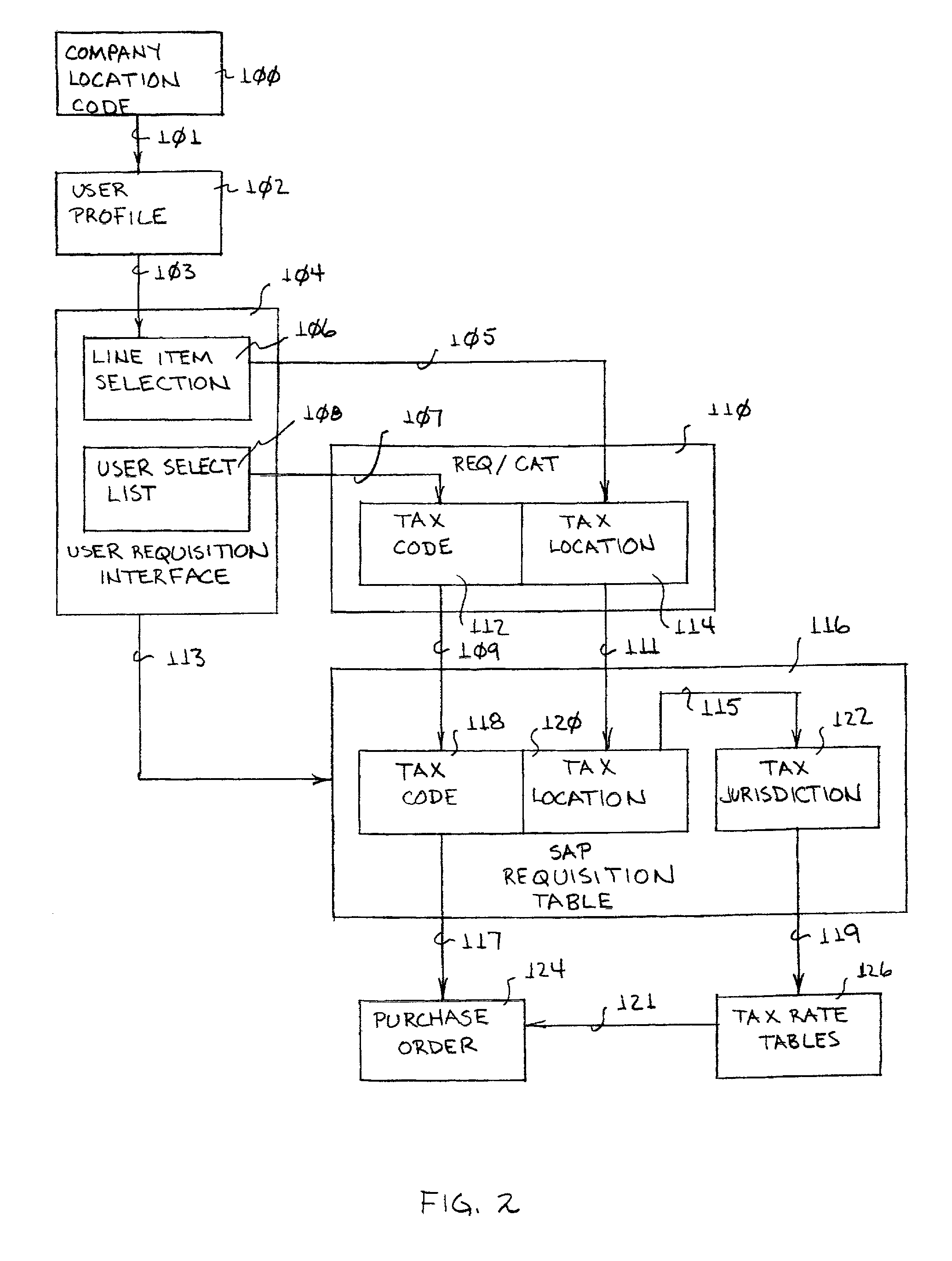
System and method for processing tax codes by company group
A system and method for assigning taxability codes to purchases, and processing tax invoices, by company groups. A user, identified to one of a group of companies, inputs a requisition. Tax code and tax location are identified in a front end process applicable to the object of the requisition and converted into a converted tax code and tax jurisdiction and fed to a back end processor. Responsive to converted tax code and the tax jurisdiction for the corresponding company group, the back end prepares a purchase order which is transmitted to a supplier. Responsive to an invoice from the supplier and company group and tax code indicia from the purchase order, the back end processes and selectively pays, short pays, or rejects the invoice.
Owner:EBAY INC
Method and apparatus for pilot-reuse in reciprocity-based training schemes for downlink multi-user MIMO
A method and apparatus is disclosed herein for employing pilot-reuse for training in the downlink of a wireless communication network. In one embodiment, the method comprises coordinating assignment of pilot codes across base stations in the topology and coordinating assignment of codes across base station-user terminal pairs, including assigning, from a set of pilot codes, a subset of codes to each cell in the topology, and assigning codes in each subset of codes to user terminals in said each cell based on cell dependent criteria; receiving waveforms from user terminals transmitting their assigned pilots; obtaining channel estimate information for channels between base station antennas and user terminals to which the base station is transmitting, the channel estimates based on the received waveforms; and transmitting to user terminals based on the channel estimate information.
Owner:NTT DOCOMO INC
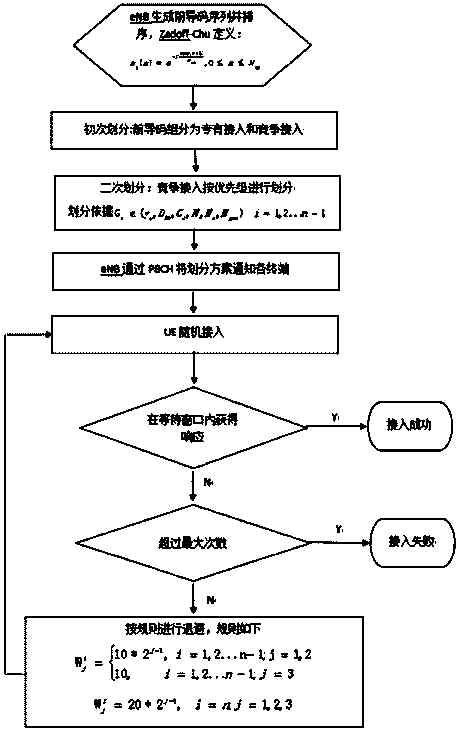
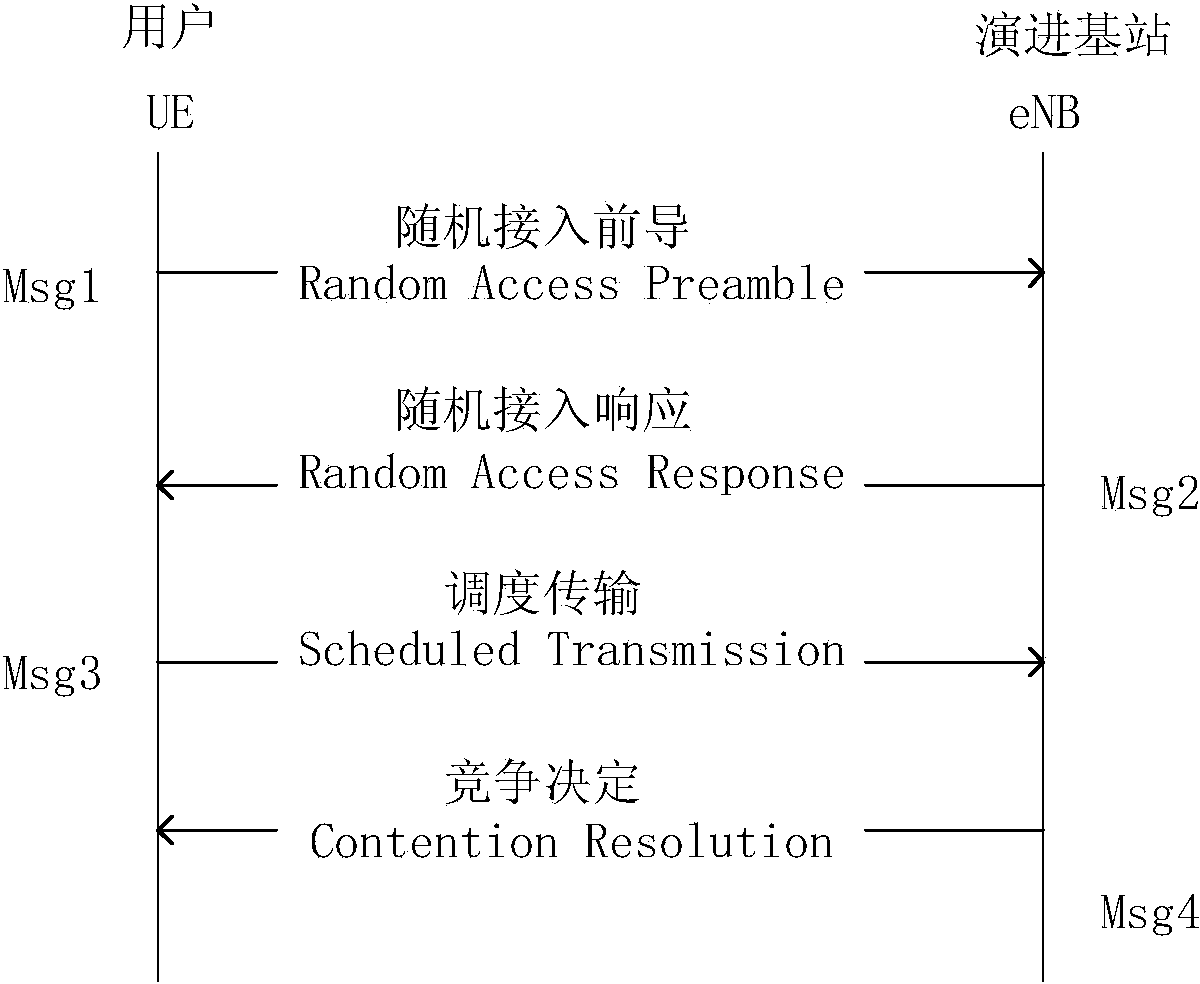
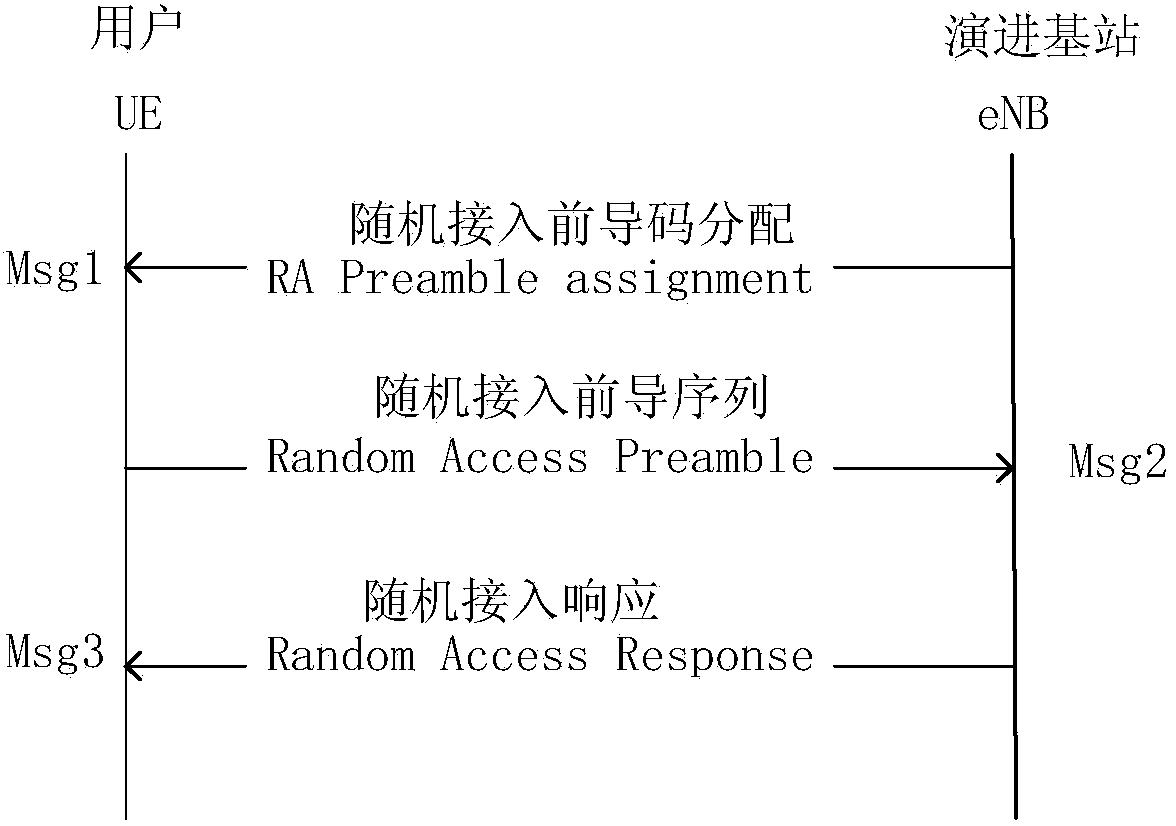
Uplink access method for distribution of lead codes for distinguishing user priority in TD-LTE/TD-LTE-A system
ActiveCN103763784AGuaranteed access throughputReduce latencyWireless communicationAccess methodAccess time
The invention discloses an uplink access method for distribution of lead codes for distinguishing the user priority in a TD-LTE / TD-LTE-A system. The unlink access method is a random access method for achieving different QoS services. The uplink access method includes the steps of (1) a lead code generation sorting stage; (2) a lead code distribution stage, wherein the lead codes are divided into the exclusive lead codes and the competitive lead codes for the first time; during secondary division, the competitive lead codes are divided into n groups according to the user group level number n, G1, G2, ...Gn-1 groups are the priority lead code groups and are used for backoff access of user groups corresponding to the priority lead code groups, and the Gn group is used for public access; an eNB enables the distribution scheme to be notified to all terminals in a broadcasting mode; (3) a random access stage, UE selects the front codes according to broadcast information to have access, a window does not receive any response in the waiting time, collision exists in the access, the terminals back off according to rules and reaccess is performed, and access fails when the maximum access time is exceeded. In random access based on competition, low delay and high throughout of high priority access can be guaranteed, and the requirements for different QoS services of the TD-LTE / TD-LTE-A system are met.
Owner:上海瀚芯实业发展合伙企业(有限合伙)
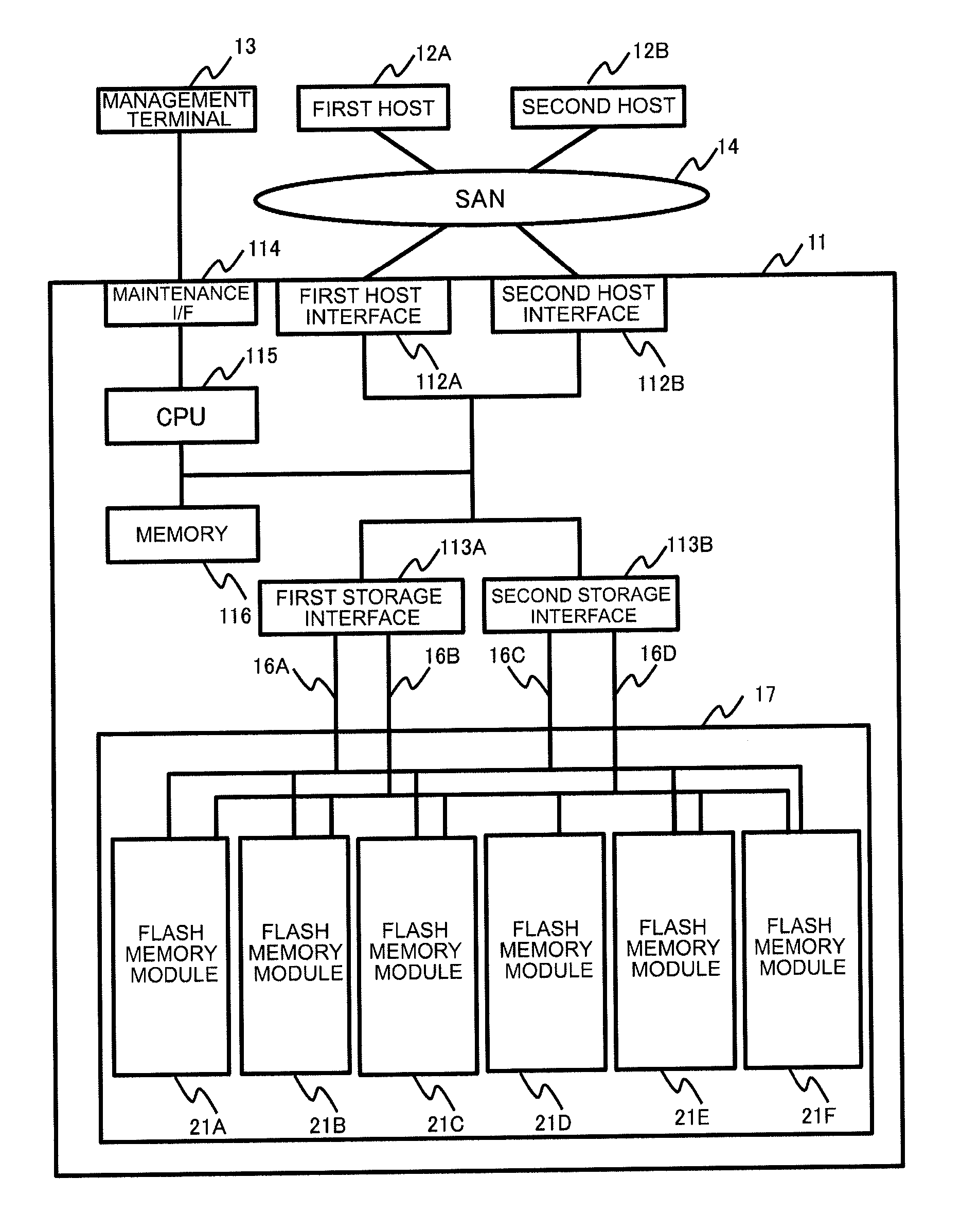
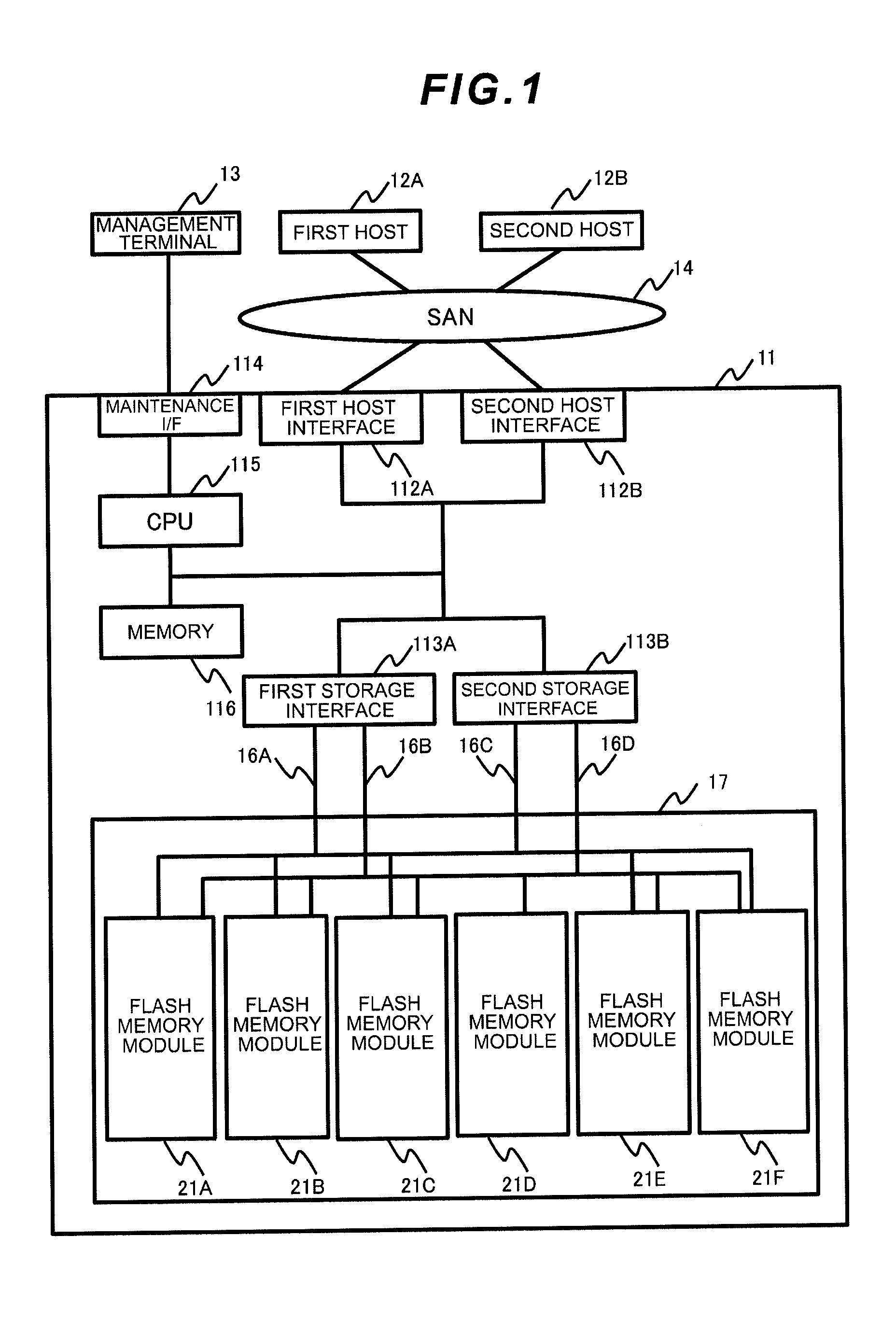
Storage apparatus and data control method
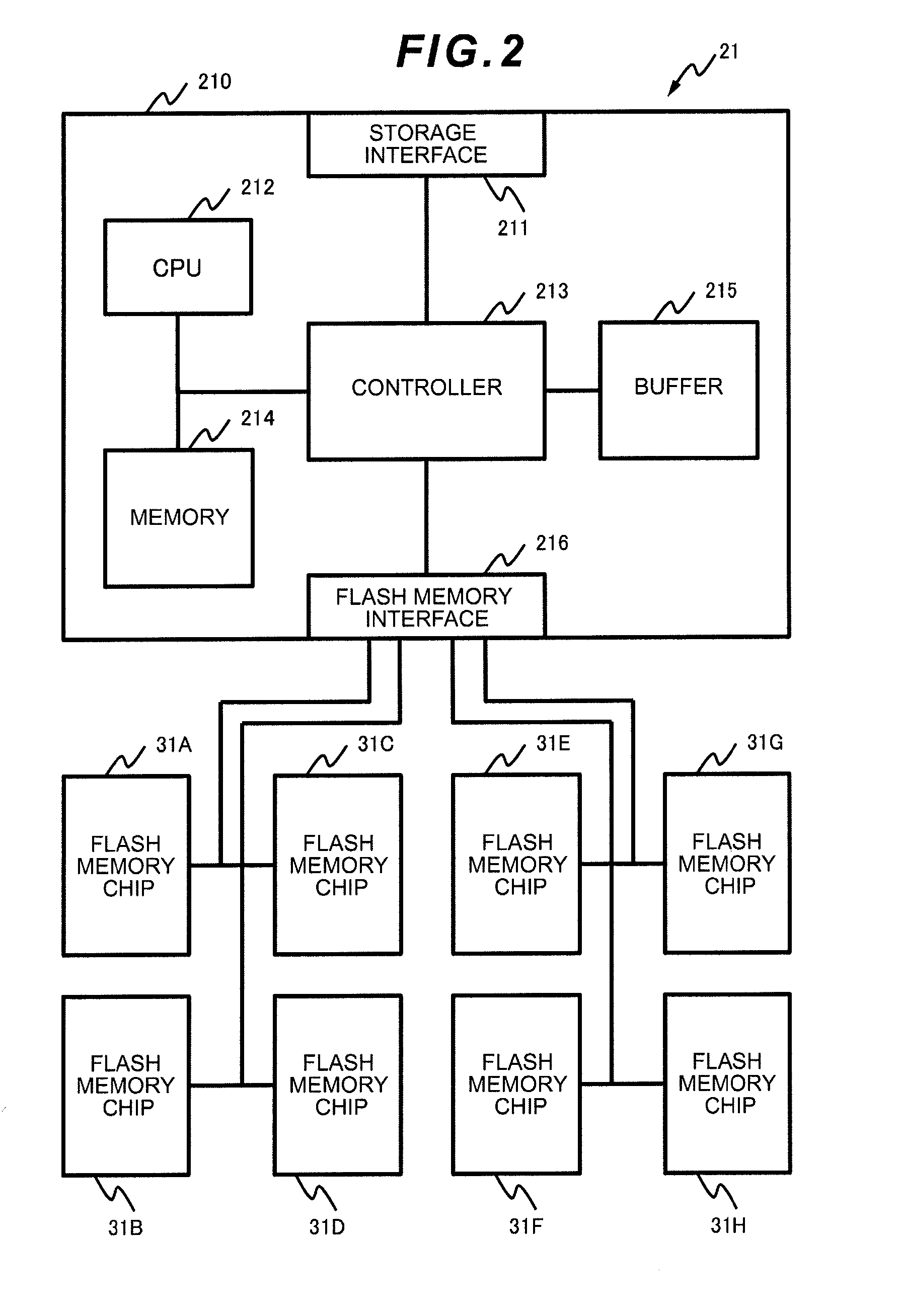
ActiveUS20120102260A1Improve data capacity efficiencyImprove production efficiencyMemory architecture accessing/allocationDigital data processing detailsData controlData capacity
Data capacity efficiency is improved by de-duplicating data assigned with a code that is different for each data.A storage apparatus comprising a flash memory control device equipped with one or more flash memory modules, wherein the flash memory module comprises at least one flash memory chip for providing a storage area, and a controller for controlling writing / reading of data including user data and a guarantee code accompanying the user data to and from the storage area provided by the flash memory chip, wherein the controller respectively divides a plurality of the data having the common user data into the user data and the guarantee code, stores one of the user data in an area of a predetermined unit of the storage area, and links and stores each of the guarantee codes accompanying the plurality of user data in an area of a predetermined unit of the storage area.
Owner:HITACHI LTD
Method, system and computer program product for optimization of data compression
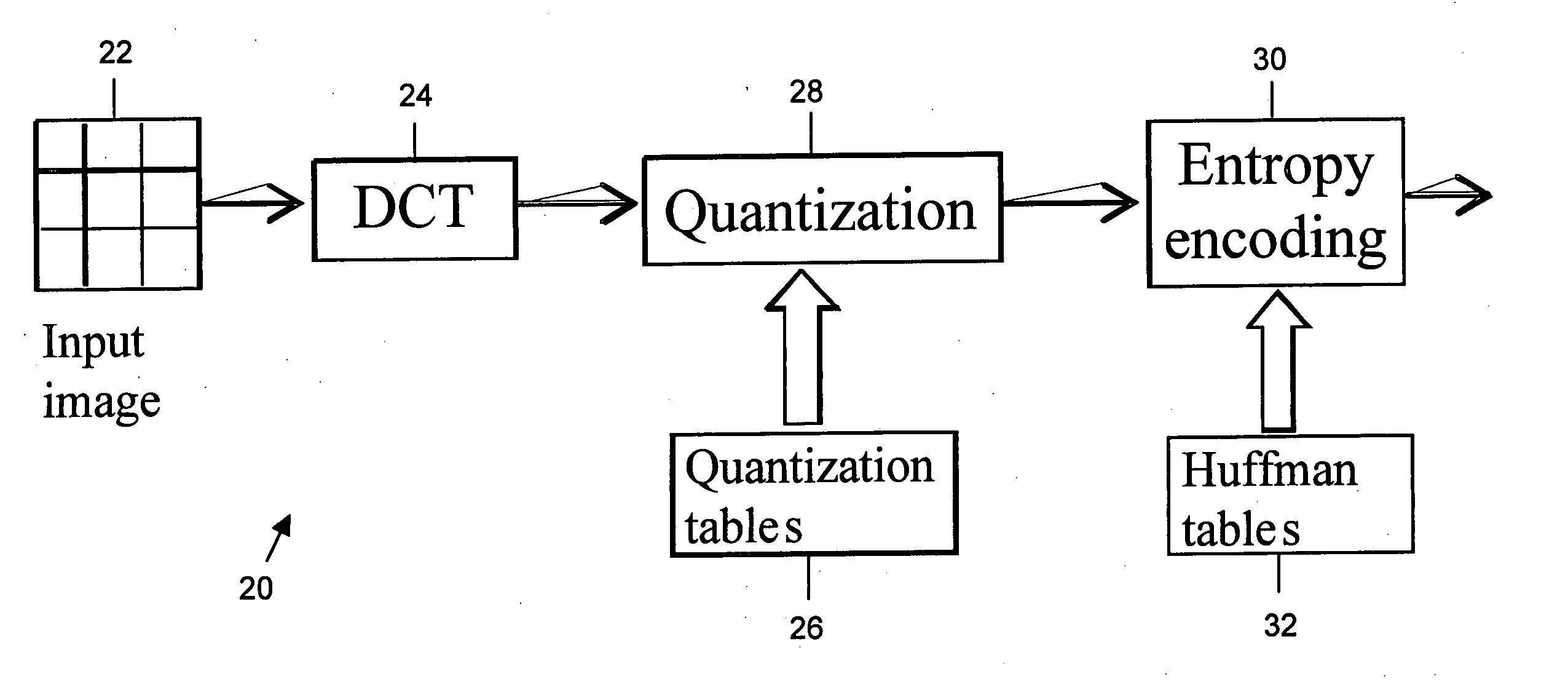
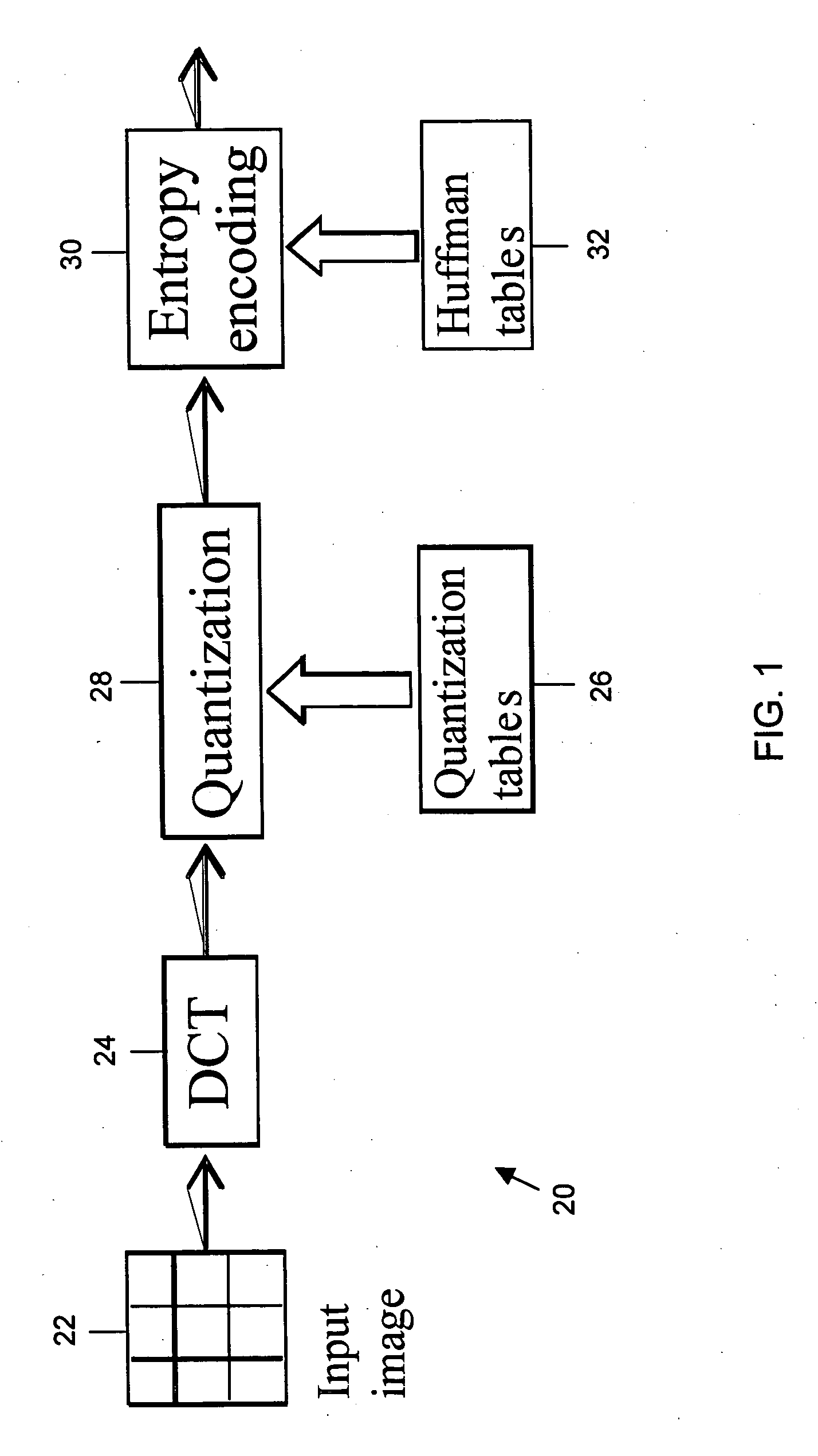
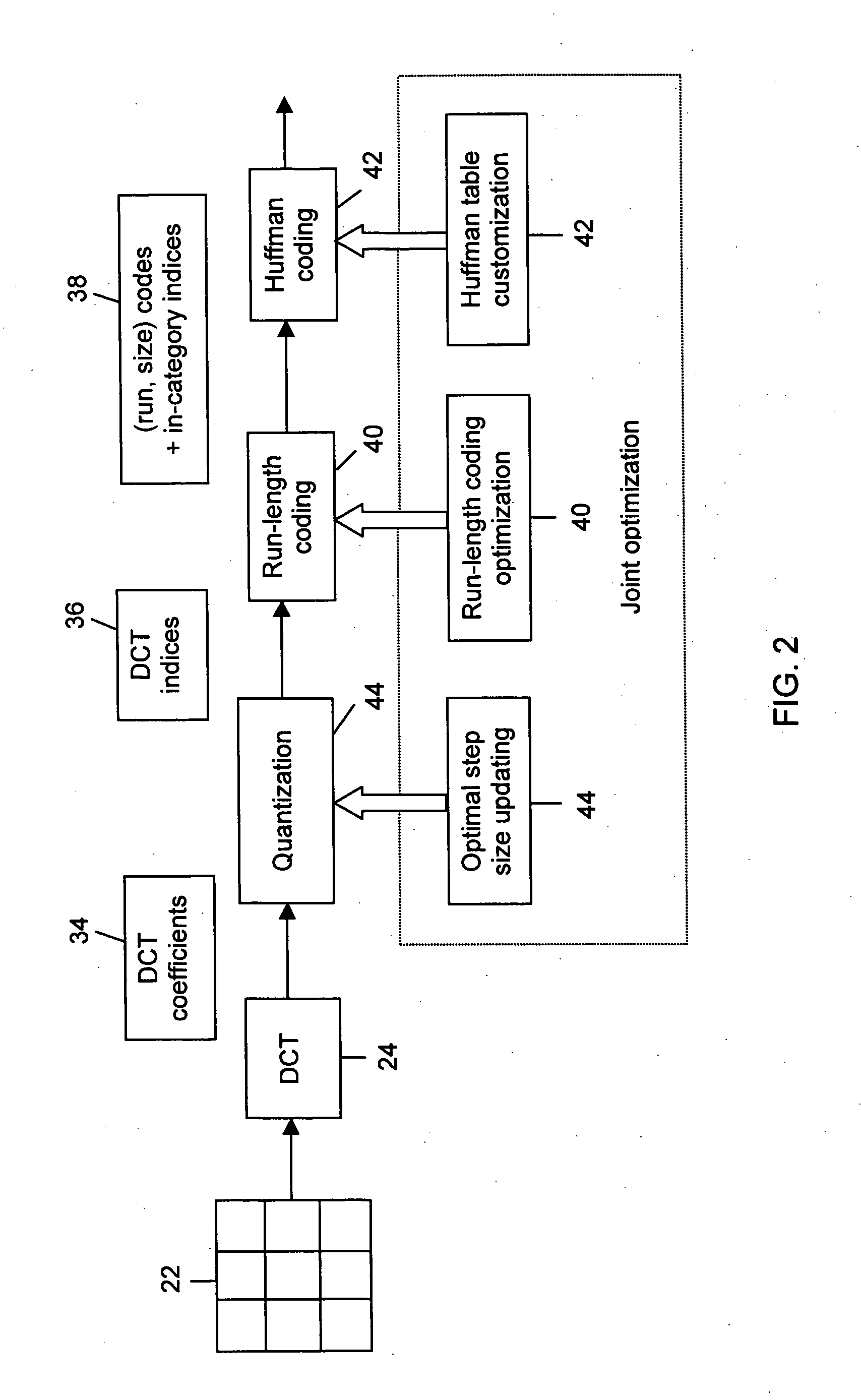
ActiveUS20060013493A1Code conversionCharacter and pattern recognitionDigital numberCode distribution
A sequence of n coefficients is compressed by determining a cost-determined sequence of n coefficient indices represented by a cost-determined sequence of (run, index derivative) pairs under a given quantization table and run-index derivative coding distribution, wherein each sequence of (run, index derivative) pairs defines a corresponding sequence of coefficient indices such that (i) each index in the corresponding sequence of coefficient indices is a digital number, (ii) the corresponding sequence of coefficient indices includes a plurality of values including a special value, and (iii) each (run, index derivative) pair defines a run value representing a number of consecutive indices of the special value, and an index-based value derived from a value of the index following the number of consecutive indices of the special value. This involves (a) using the given quantization table and run-index derivative coding distribution to formulate a cost function for a plurality of possible sequences of (run, index derivative) pairs; (b) applying the cost function to each possible sequence in the plurality of possible sequences of (run, index derivative) pairs to determine an associated cost; and, (c) selecting the cost-determined sequence of (run, index derivative) pairs from the plurality of possible sequences of (run, index derivative) pairs based on the associated cost of each of the plurality of possible sequences of (run, index derivative) pairs; and encoding the corresponding selected cost-determined sequence of (run, index derivative) pairs using entropy coding based on a run-index derivative coding distribution.
Owner:MALIKIE INNOVATIONS LTD
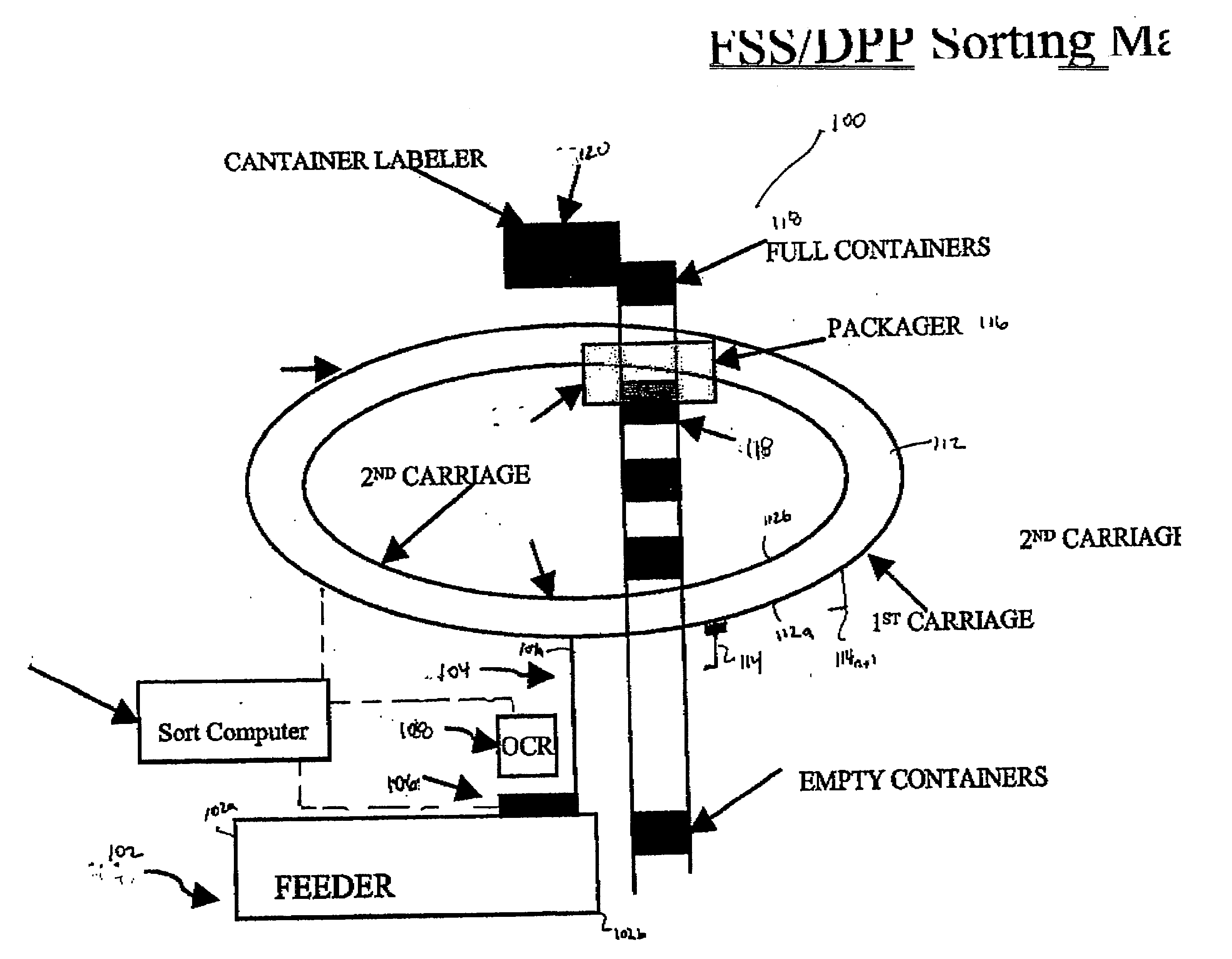
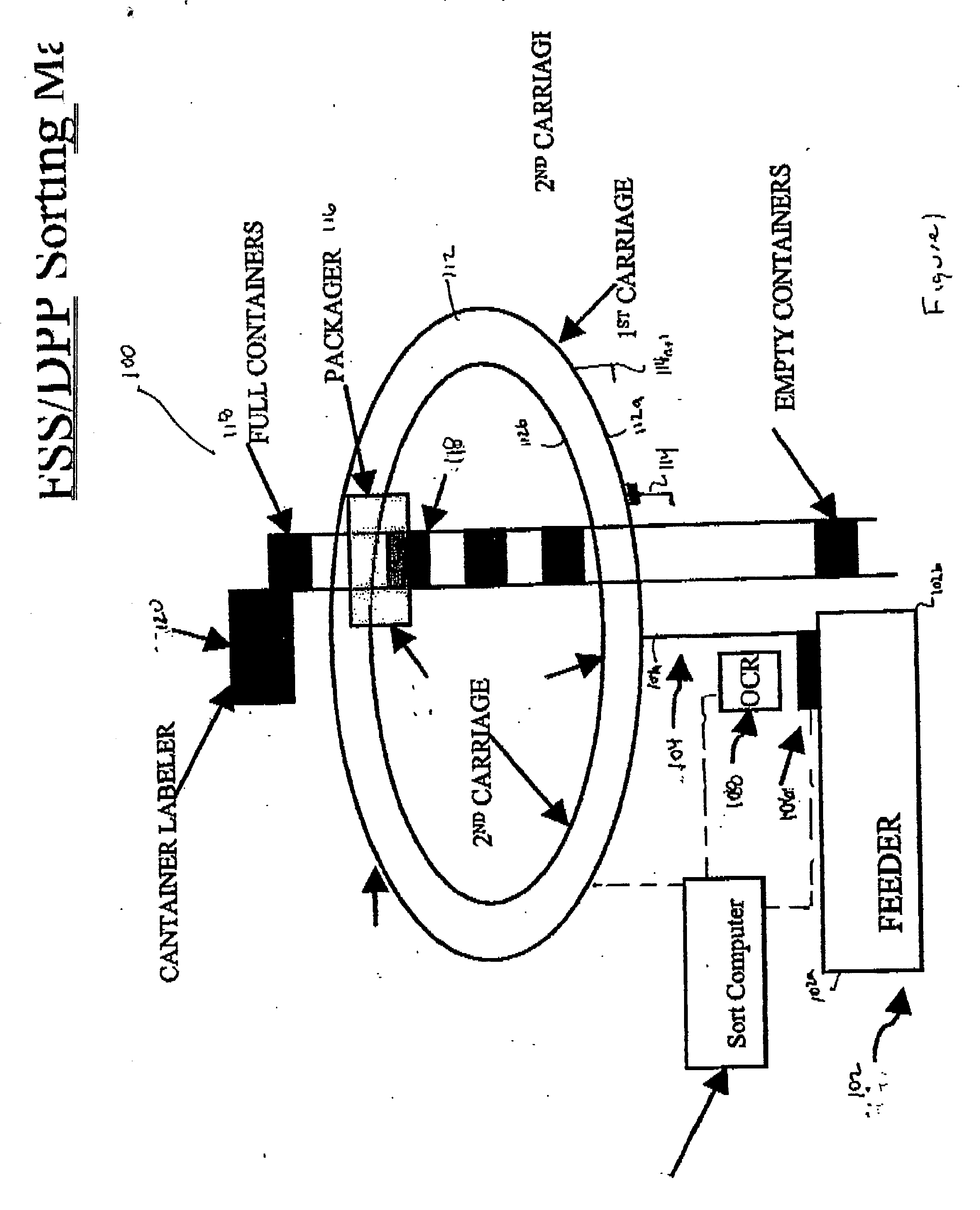
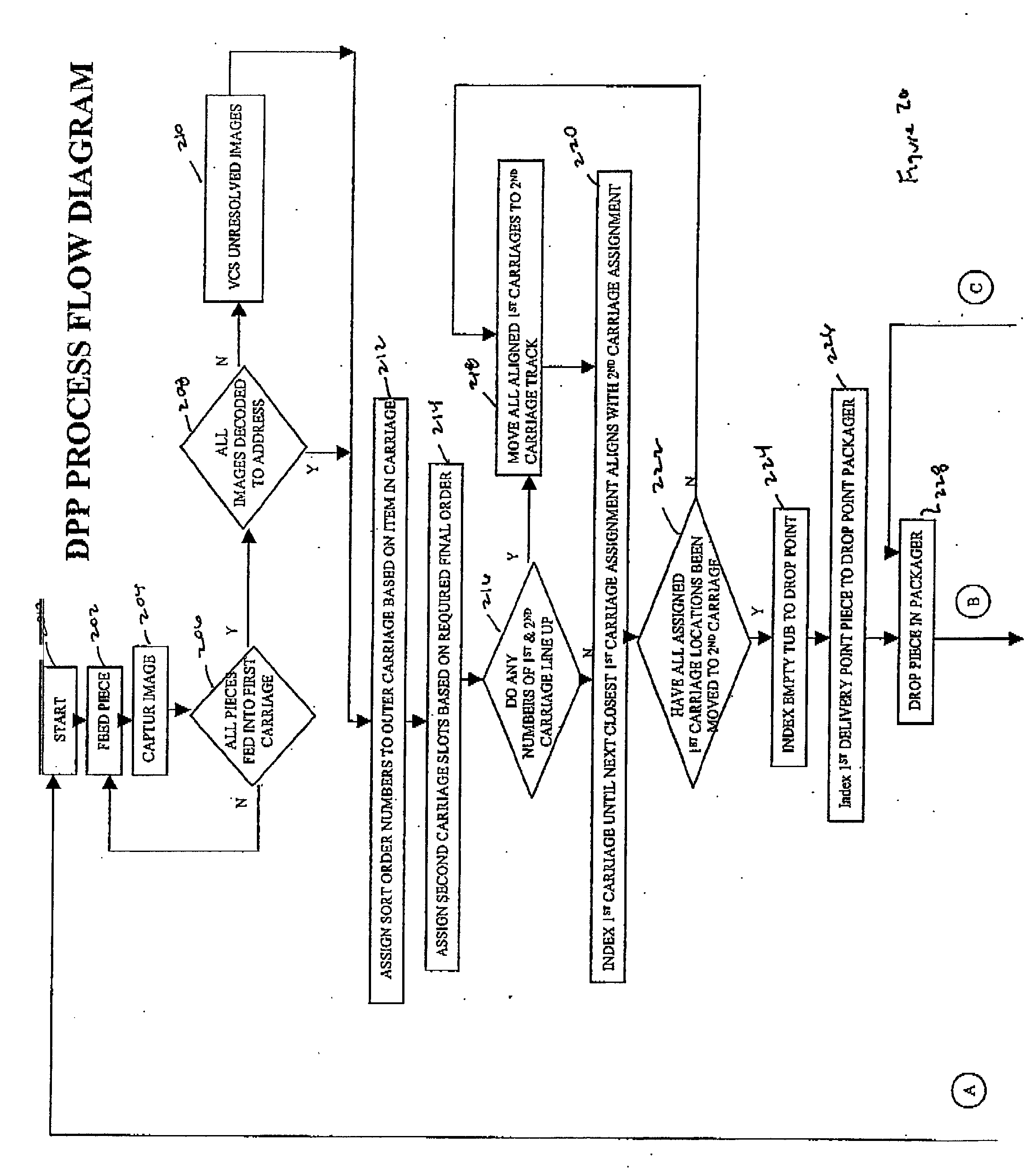
Method for sequentially ordering objects using a single pass delivery point process
InactiveUS20040065597A1Separation devicesCharacter and pattern recognitionTransport systemCode distribution
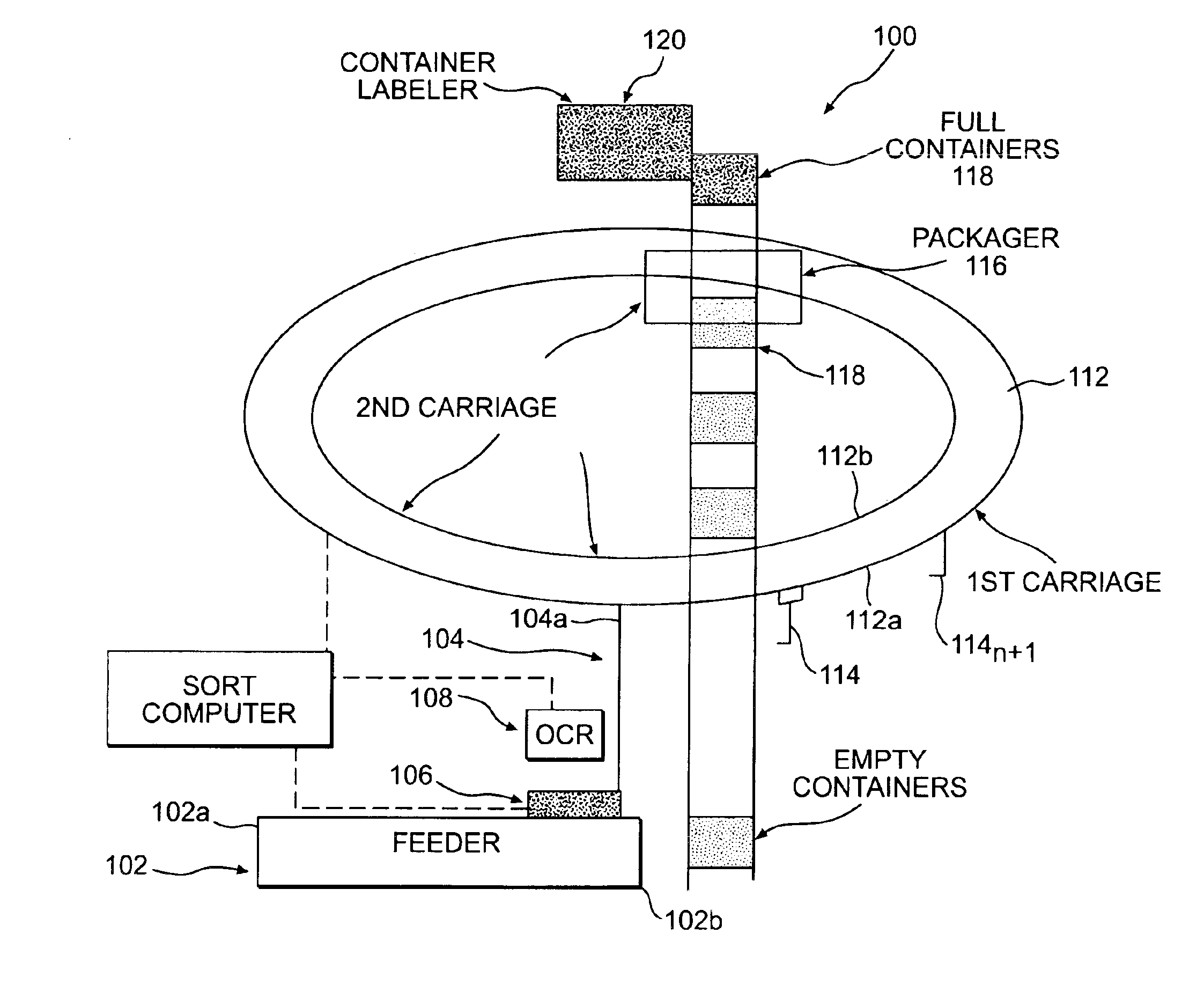
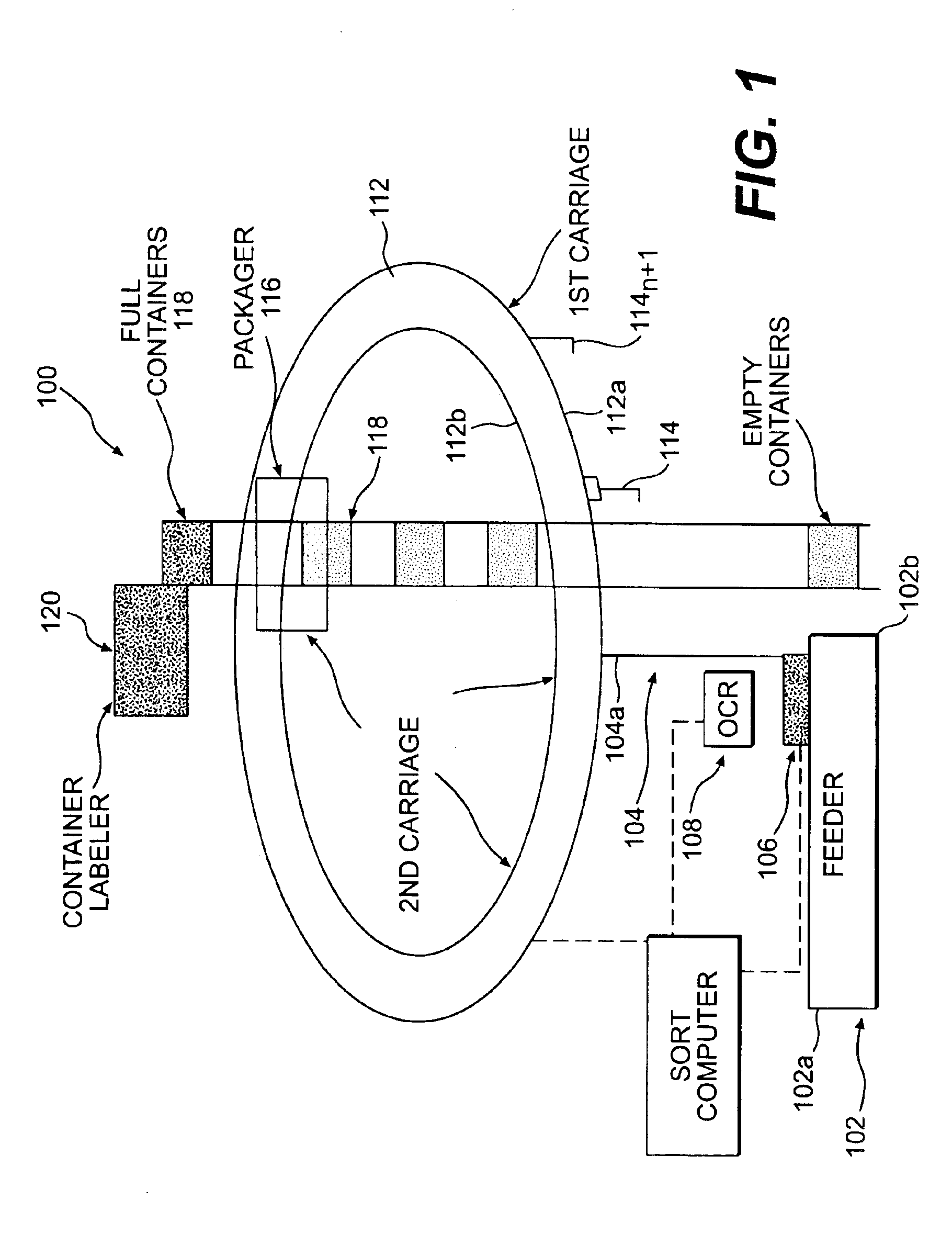
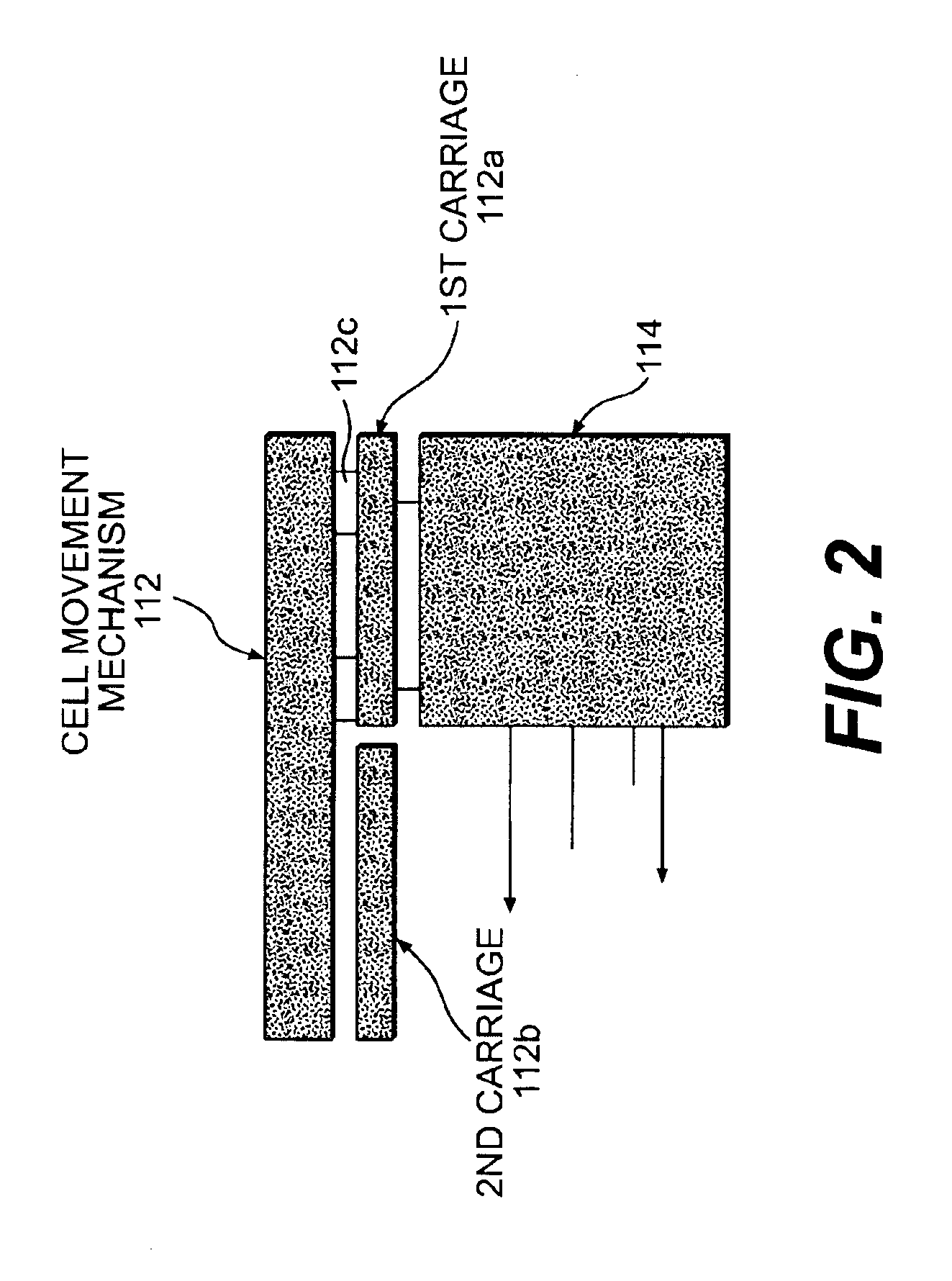
A method using a single pass sequencer having a transport system for transporting the mail pieces to a transport system having a first carriage system and a second carriage system with a plurality of holders slidable between the first carriage system and the second carriage system with packaged output. Each of the plurality of holders holding a mail piece of the mail pieces received from the transport system. The method includes assigning a code to: (i) the mail pieces based on the destination information, (ii) the plurality of holders on the first carriage, and (iii) a position on the second carriage which corresponds to the initial sequence and a destination sequence of the mail pieces. The method instructs movement of the plurality of holders from the first carriage to the second carriage based on the code assigned to the mail pieces, the plurality of holders on the first carriage and the position on the second carriage such that when the mail pieces are moved to the second carriage they are in sequential order of delivery destination, ready to be packaged.
Owner:LOCKHEED MARTIN CORP
Signal processing apparatus and method, signal processing system, and printer
InactiveUS7137136B1Easily and reliably performingEasy to implementTelevision system detailsAnalogue secracy/subscription systemsCode distributionInformation searching
A signal processing apparatus has a search unit for searching input program information in accordance with a predetermined search condition, an assignment unit for assigning a code to a program corresponding to the program information searched by the search unit, and a processing unit for executing a process for the program in accordance with the code assigned by the assignment unit.
Owner:CANON KK
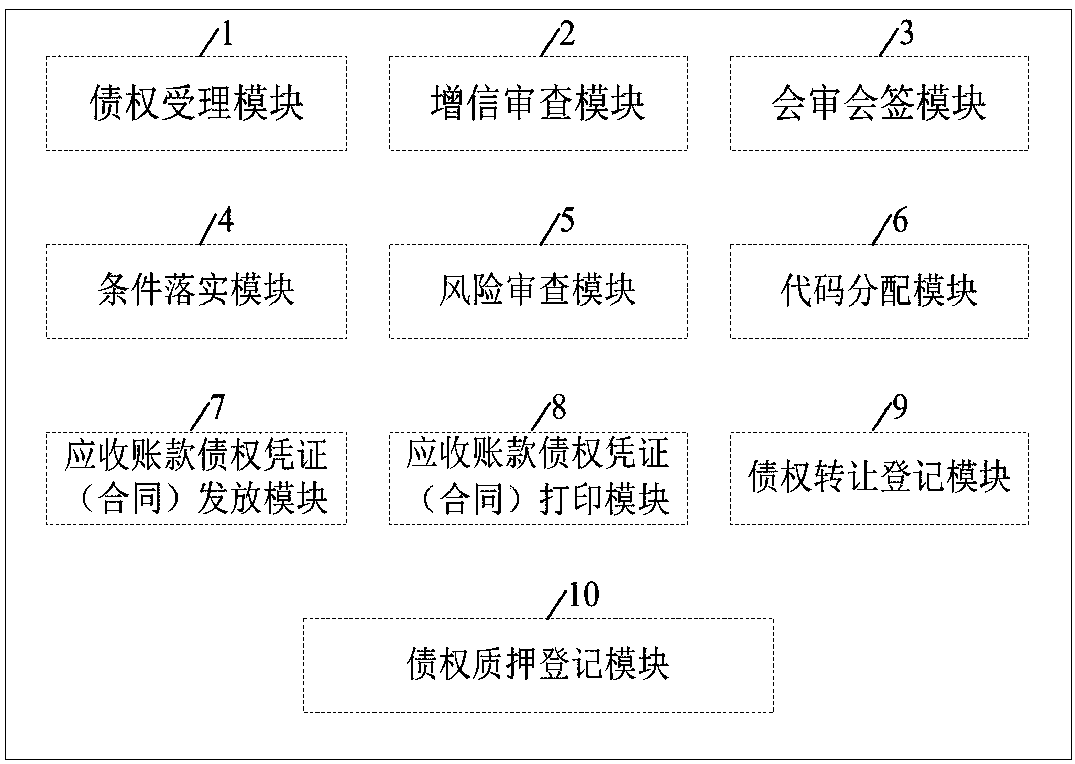
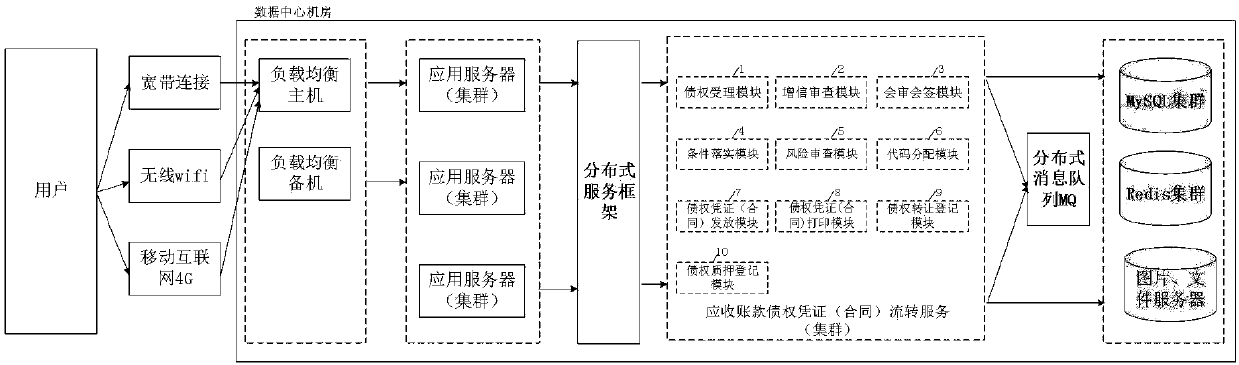
Account receivable creditor's rights certificate (contract) transfer system
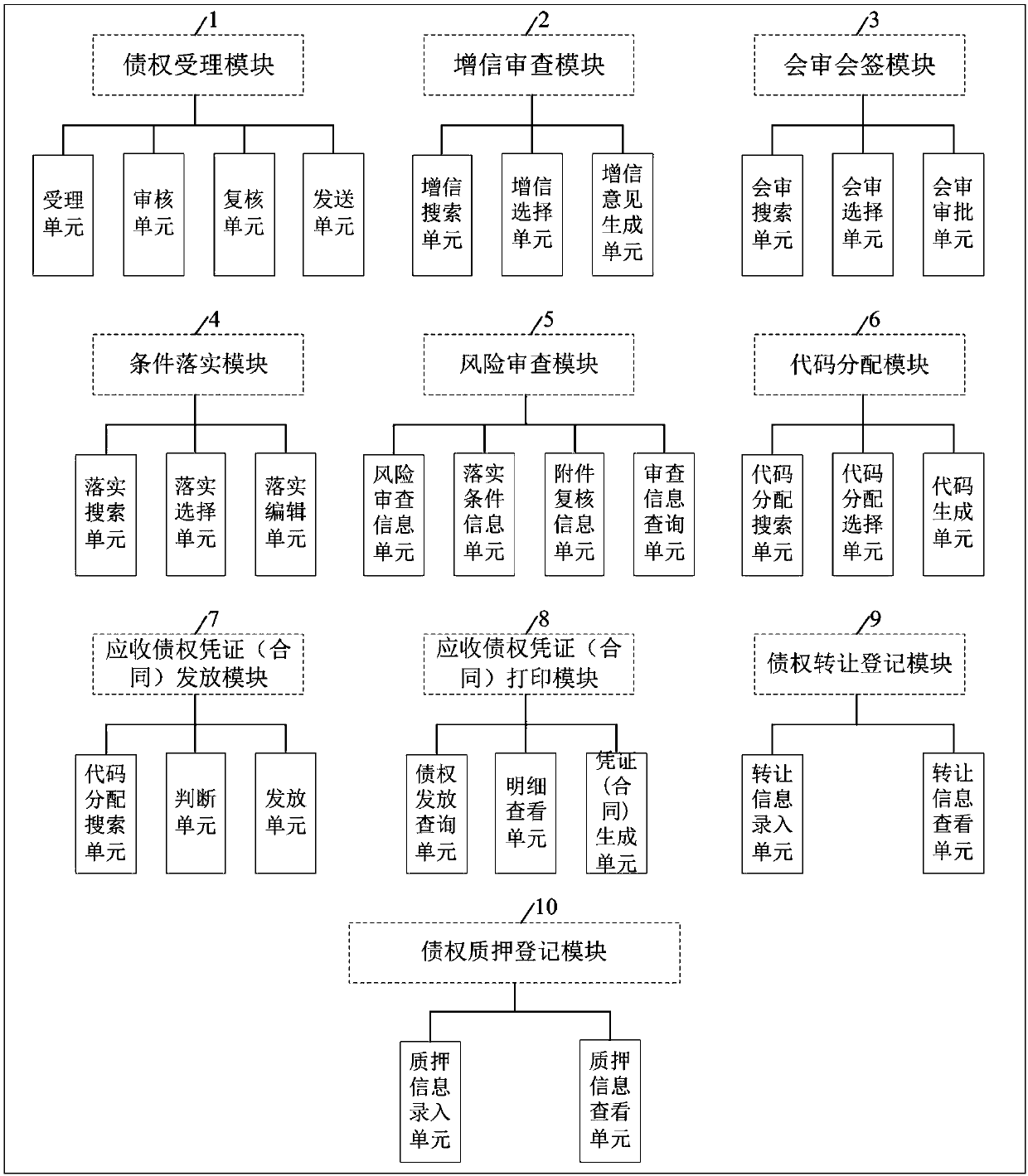
ActiveCN108038781AEffectively resolve debtDiversified solutions to social conflicts and disputesFinanceCredit systemMedium enterprises
The invention discloses an account receivable creditor's right certificate (contract) transfer system and method. The system comprises a creditor's right acceptance module, a risk review module, a code distribution module, an account receivable creditor's right certificate (contract) issuing module, an account receivable creditor's right certificate (contract) printing module, a creditor's right assignment module and a pledge registration module. Through sciences and technologies and a credit enhancement manner, account receivables, in static state, among various economic subjects are converted into paper or electronic account receivable certificates (contracts) which integrates the functions of financing, commodity financing, transfer, transaction and refunding (countervailing); in practice, solely state-owned account receivable creditor's right management companies are established by local governments or group applications are organized via mediation such as people mediation, industrial mediation and commerce chamber mediation; and through the system, account receivable creditor's right certificate (contract)s are issued for account receivables which accords with conditions so asto carry out transfer, so that a positive role is played in solving difficult financing of small and medium enterprises, resolving chain debts, resolving the debts of local governments and pushing the construction of credit systems.
Owner:安徽海汇金融投资集团有限公司 +1
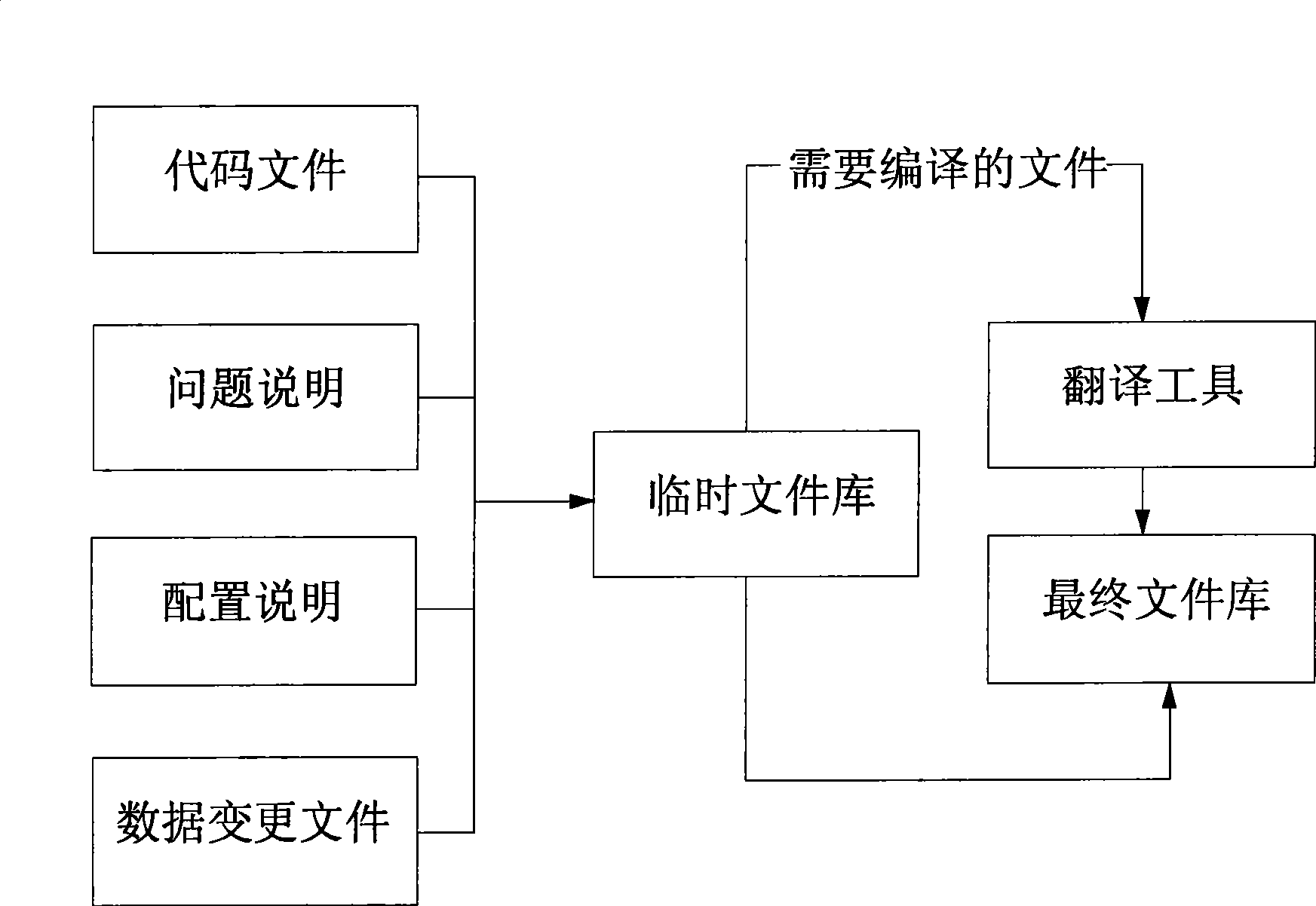
Project code releasing method
The invention provides a method for distributing item codes. The method comprises the following steps: automatically checking out needed codes from a configuration library, putting in a specified compiling directory; automatically calling the compilation method of a compiler to convert codes into execution codes, and packing the execution codes to a complete product package or an independent upgrade package. A configuring administrator just needs to check relevant logs and judges whether the codes are compiled correctly or not, if yes, the packed software is released to a target environment. The invention has the advantages that the problems, such as the code selection by the configuring administrator, and the compilation, are solved; the releasing time is greatly compressed; the releasing promptness is improved; and the operation on tools compiled according to the method after the completion of the intraday work by the configuring administrator can enable the upgrade package to be finished, so that the item codes distribution can be finished by just sending the upgrade package to the target environment and just costs 0.5-1 hour.
Owner:INSPUR SOFTWARE CO LTD
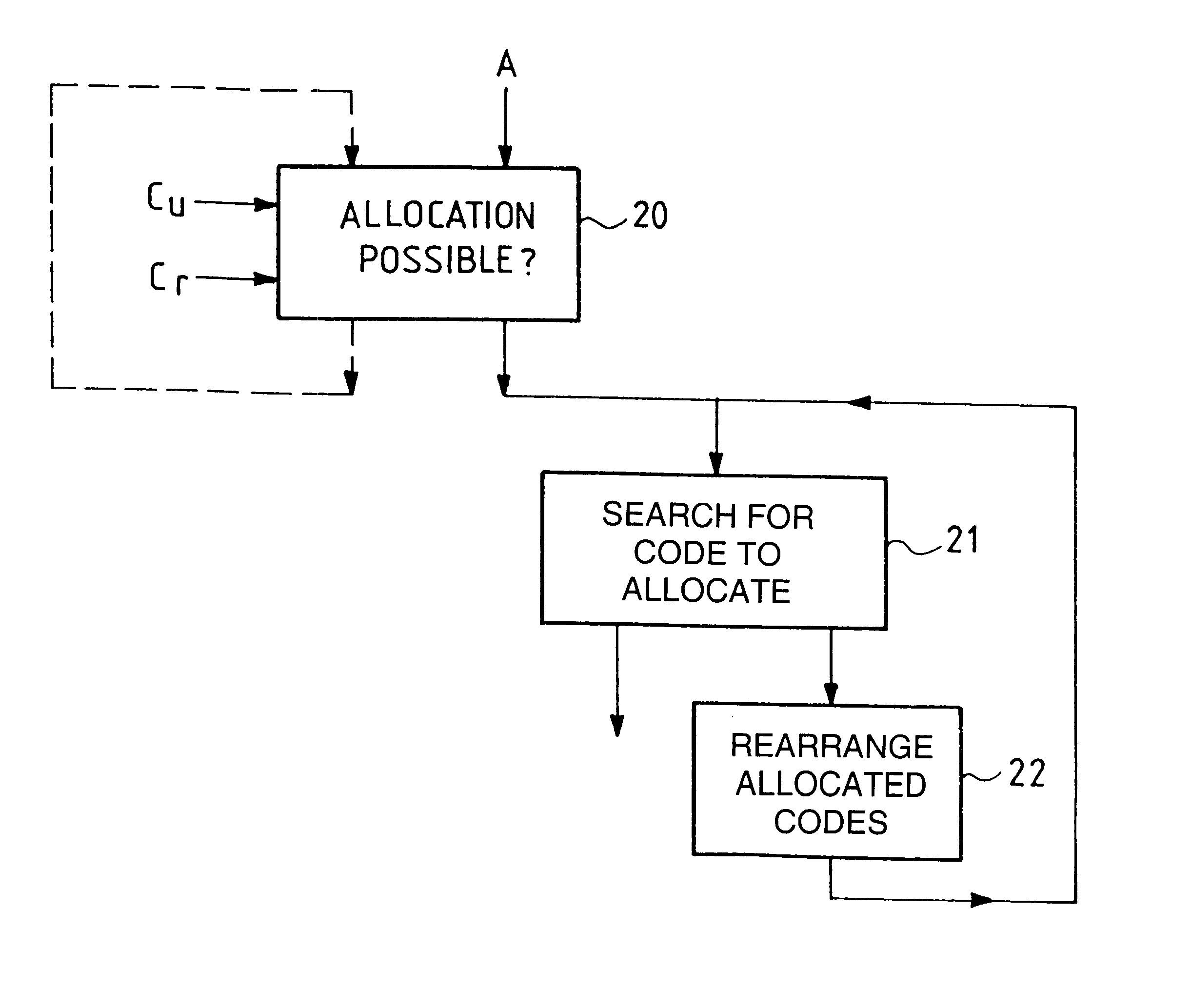
Method of allocating orthogonal codes in a code division multiple access mobile radio system using codes of variable length
InactiveUS6560194B1The method is simple and fastReduce stepsCode conversionRadio transmissionCode division multiple accessCode distribution
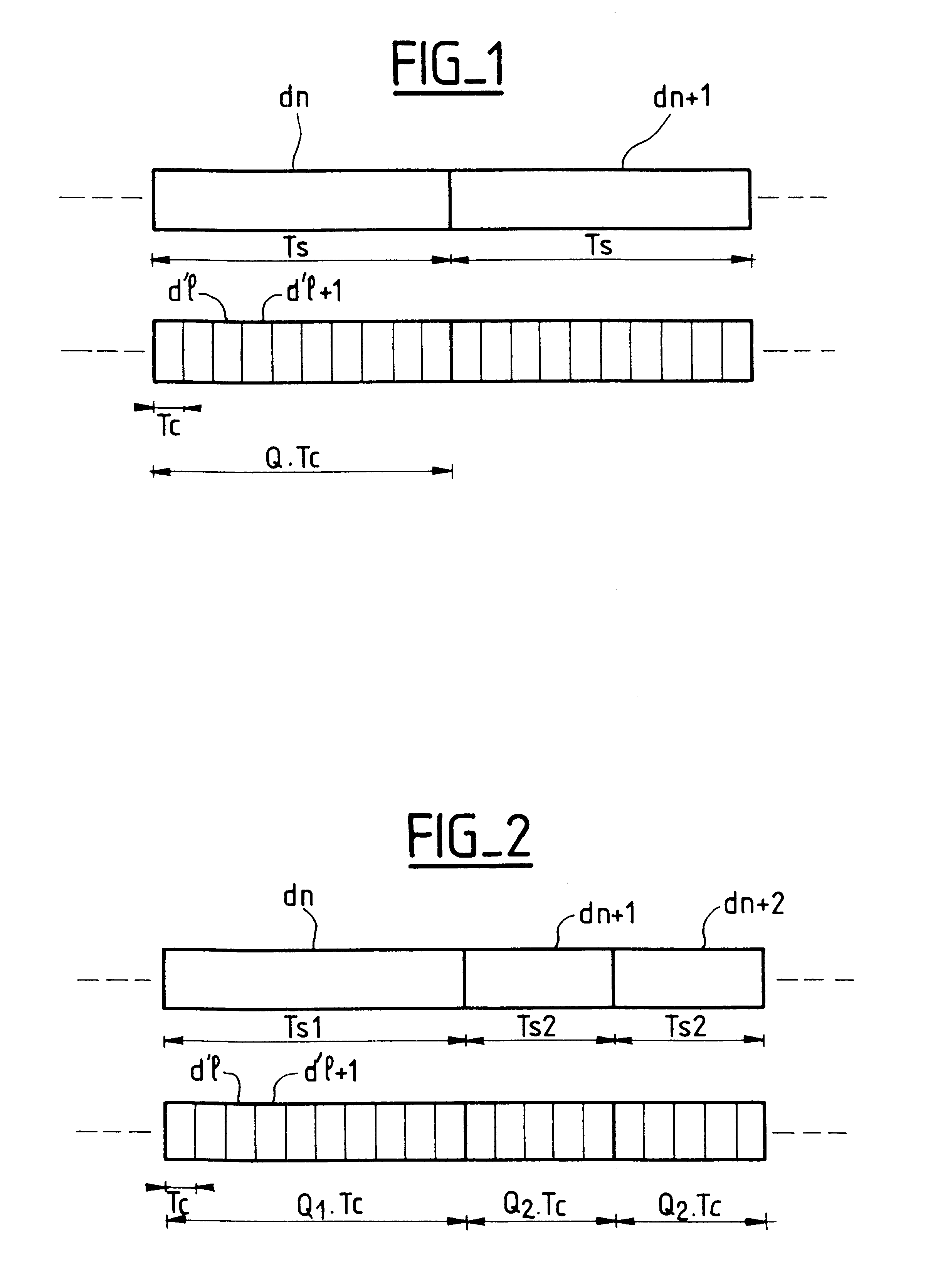
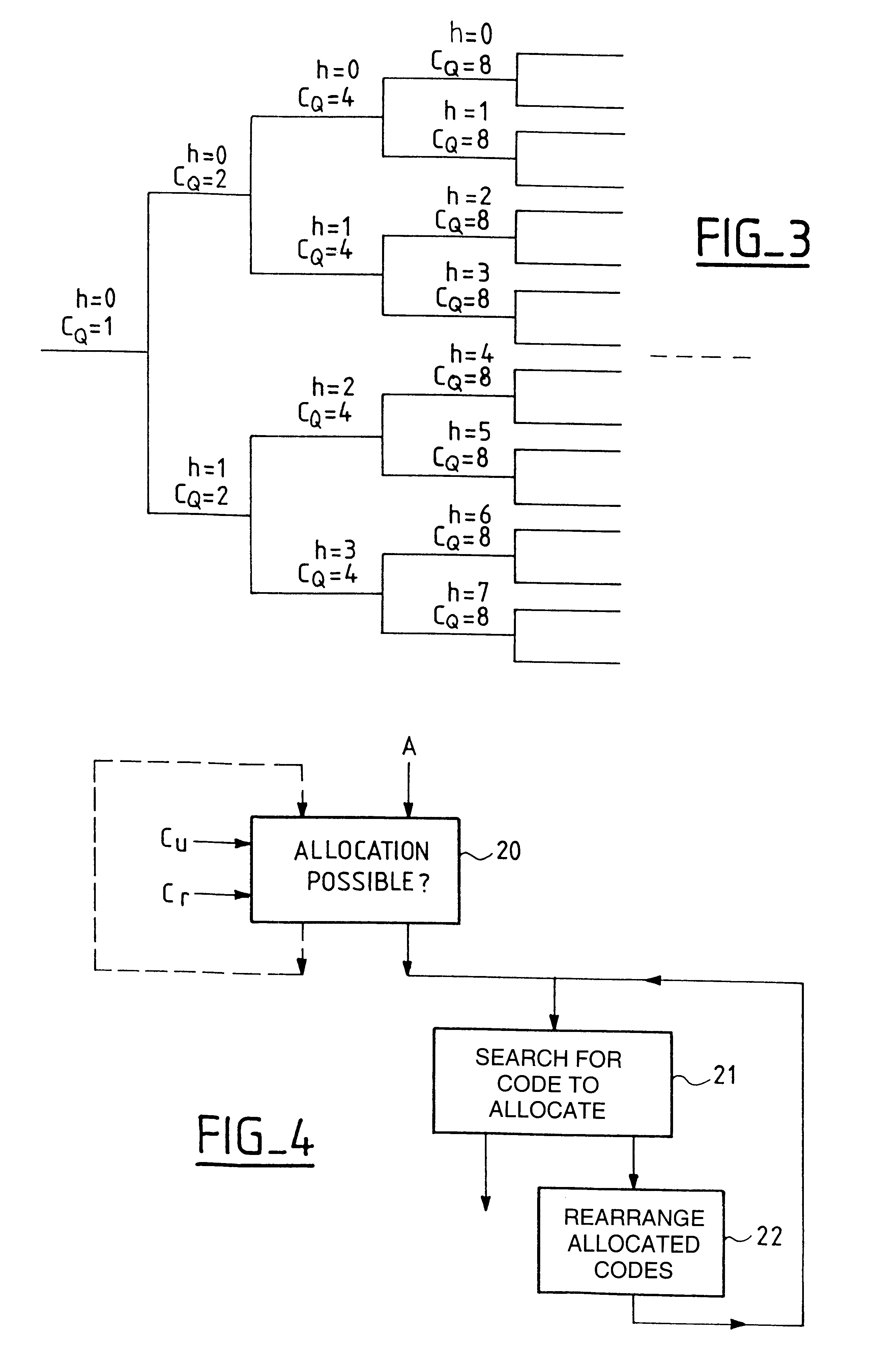
Method of allocating orthogonal codes in a code division multiple access mobile radio system using codes of variable length which are generated in such a way that they can be represented in the form of a tree, said method including, in response to a code allocation request, a first step of determining, in accordance with the tree capacity used, corresponding to codes already allocated, and the tree capacity required, corresponding to the code allocation requested, if such allocation is possible.
Owner:RPX CORP
History based rights computation for managed code
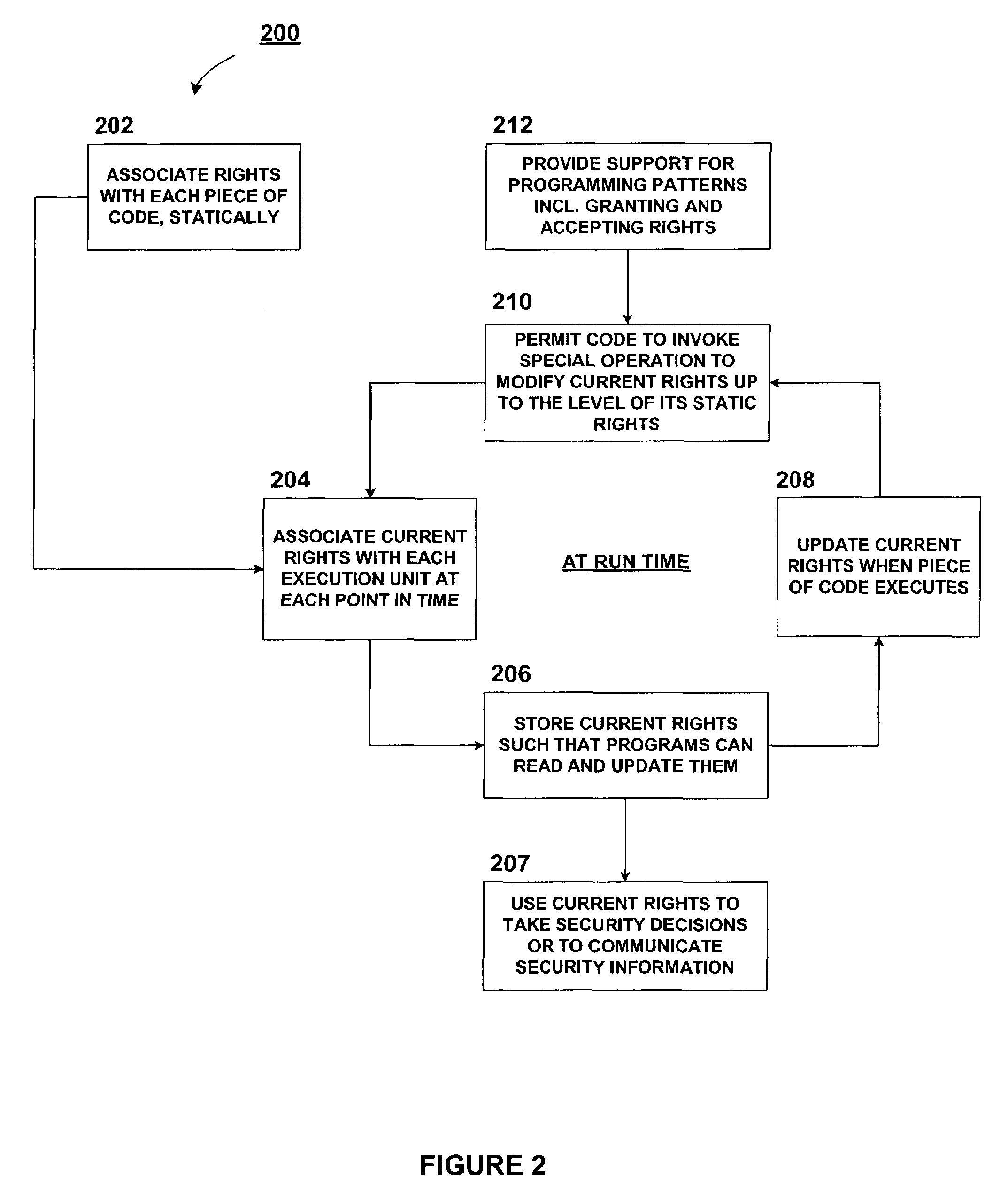
InactiveUS7203833B1Memory loss protectionError detection/correctionAccess control matrixManaged code
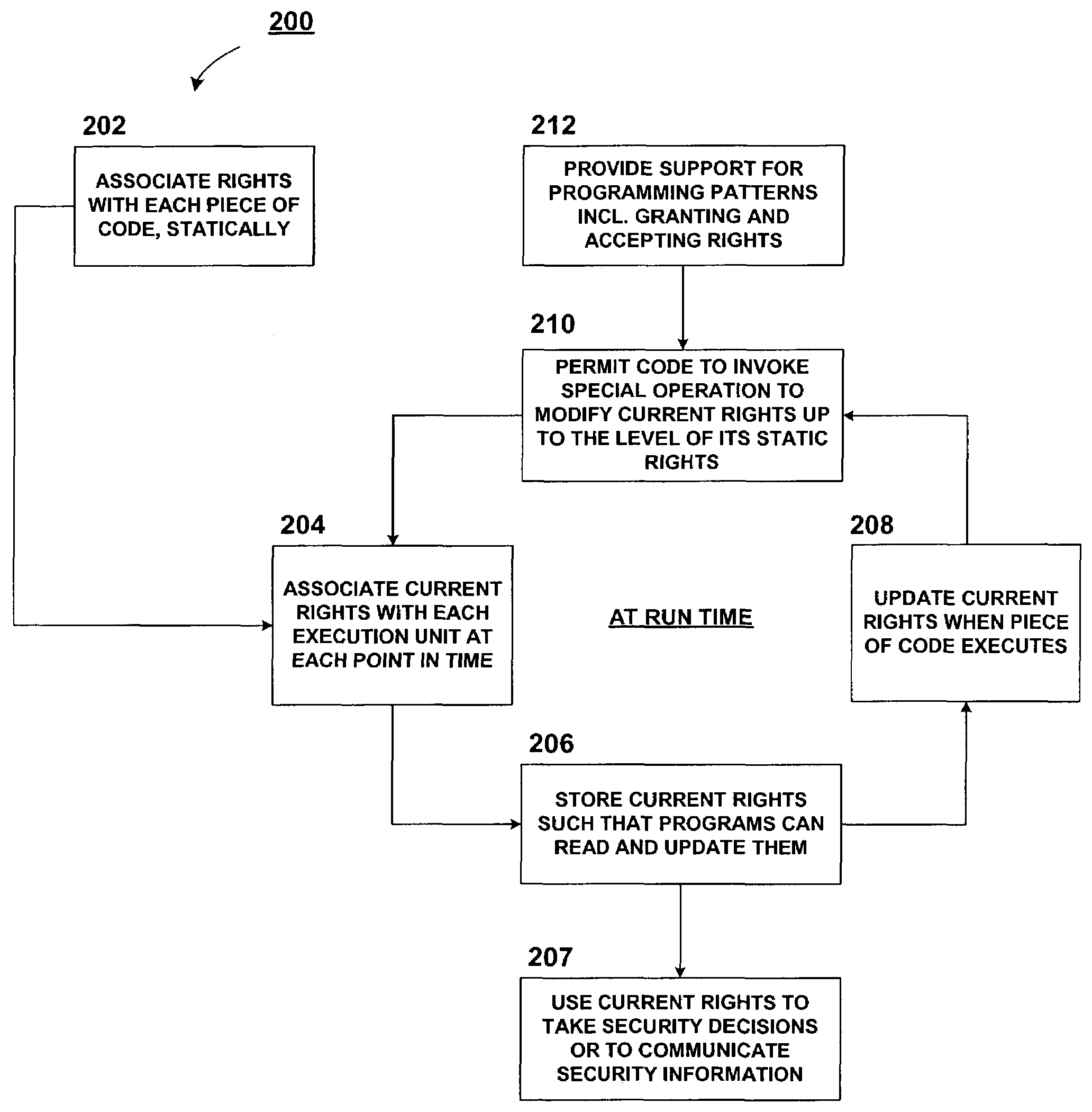
In the access control model of security, an access control matrix associates rights for operations on objects with subjects. An approach for assigning rights to code at run-time involves determining the run-time rights of a piece of code by examining the attributes of the pieces of code that have run (including their origins) and any explicit requests to augment rights. Thus, this approach relies on the execution history for security. This history based approach reduces the difficulties and the error-proneness of securing extensible software systems.
Owner:MICROSOFT TECH LICENSING LLC
Dynamic sortation of items in a containerization system
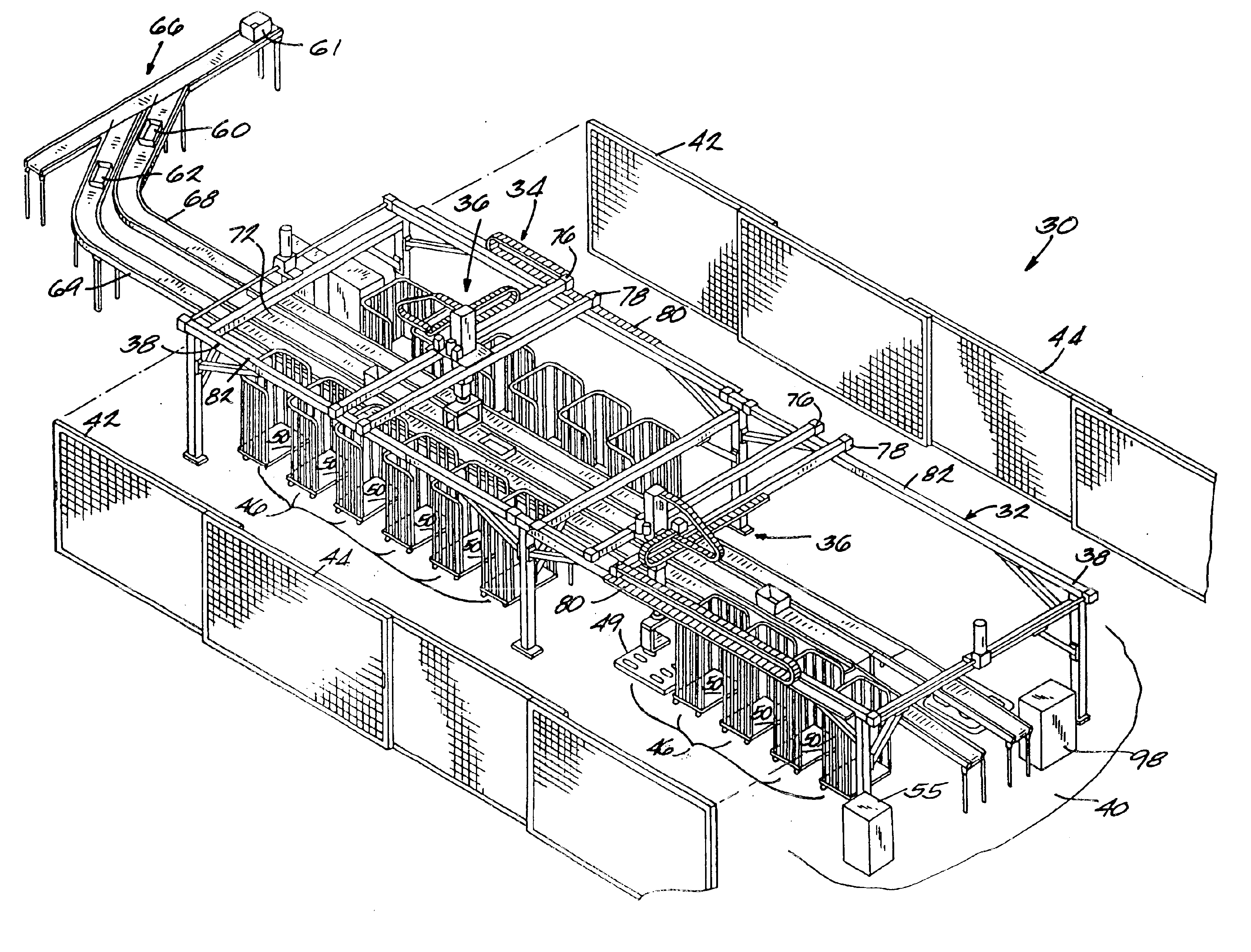
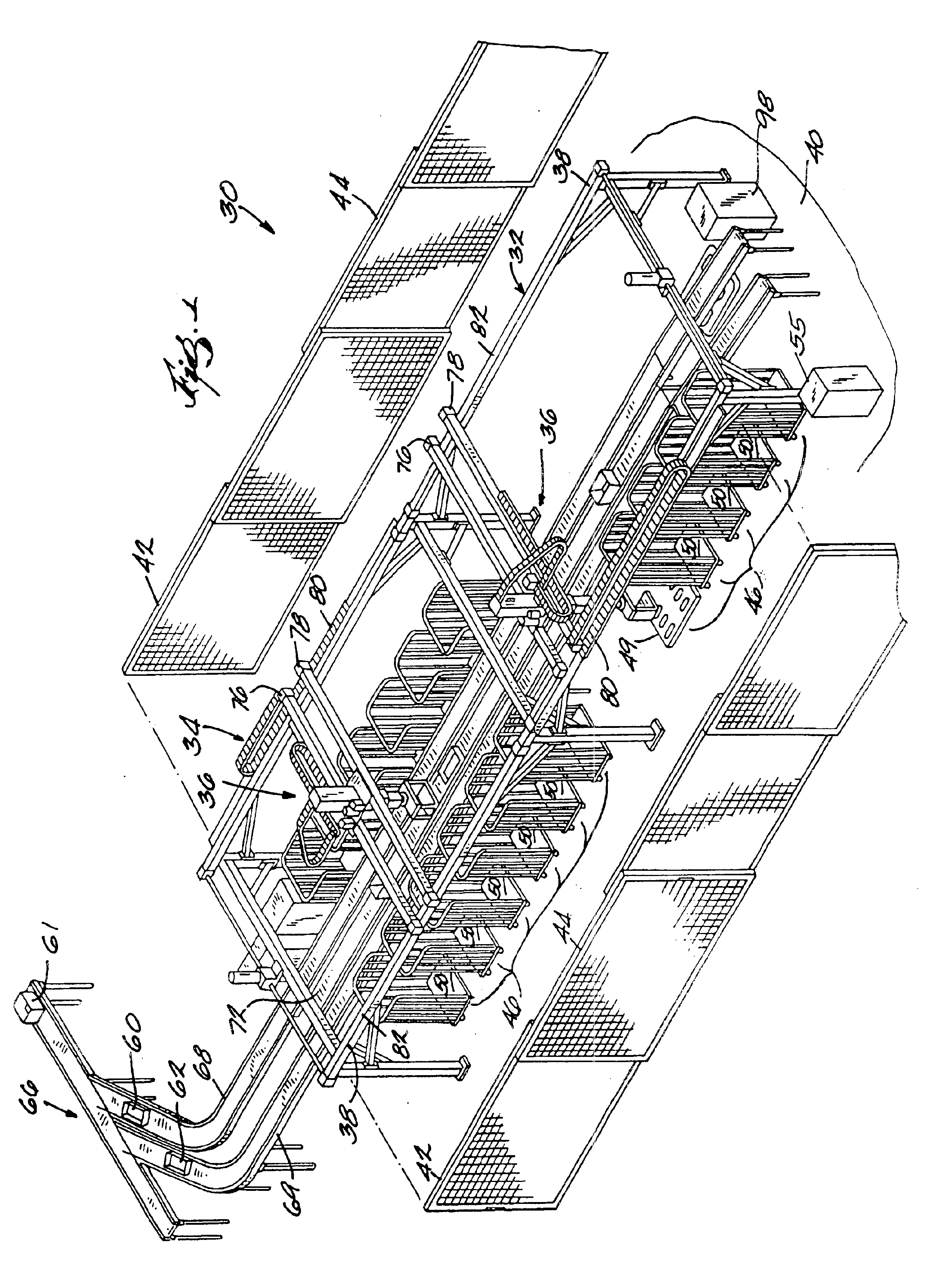
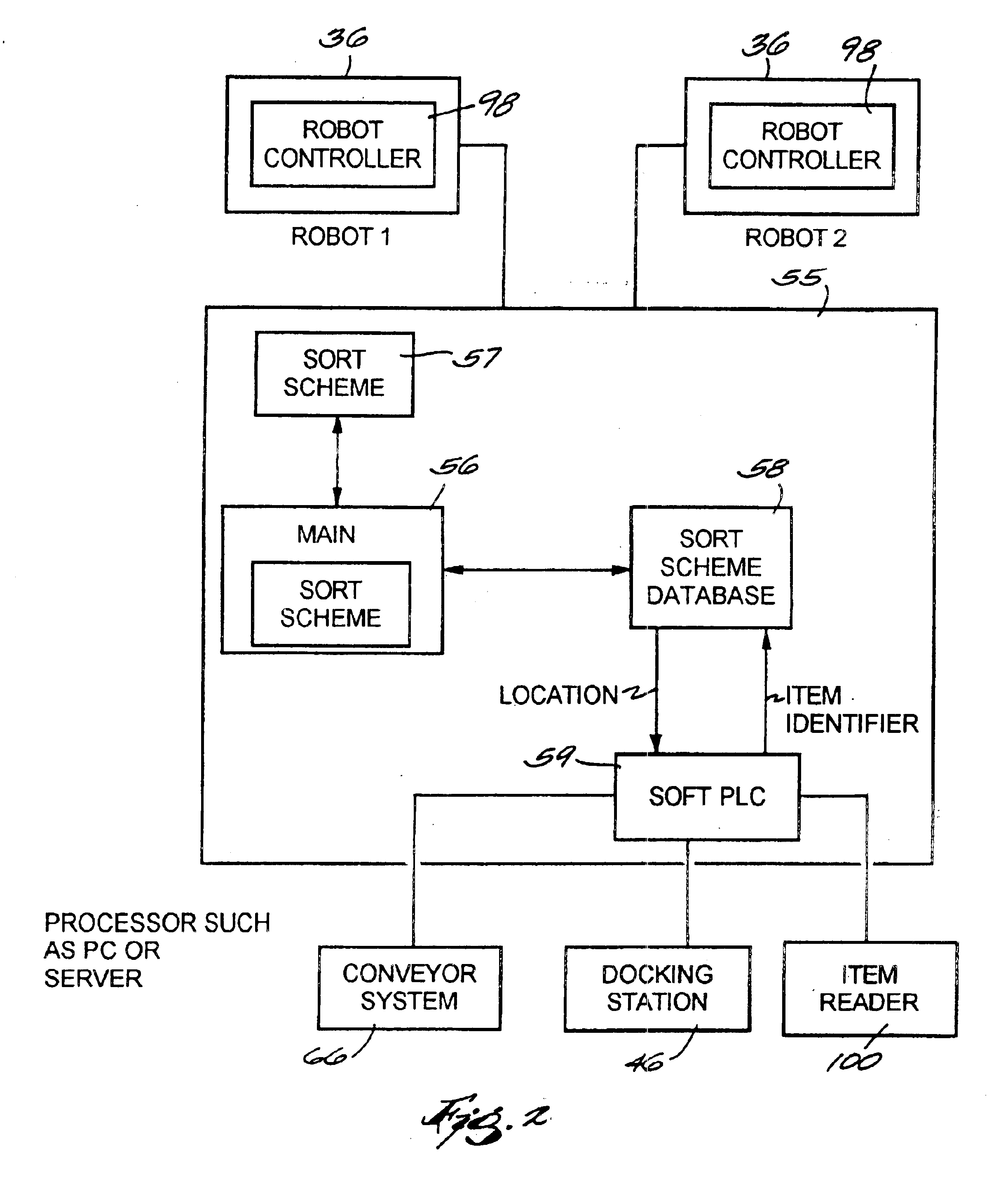
InactiveUS6892890B2Digital data processing detailsCharacter and pattern recognitionContainerizationObject code
A dynamic sortation system and method. The invention is preferably utilized in a robotic containerization system having a number of locations for containers such as carts or pallets. Each location may be assigned a speed of loading rating that represents the time needed for a robot to load an item to a location. The system may be preprogrammed with a simplified, base scheme of destinations. After these initial steps, the system reads destination codes from each of the plurality of items in a load of items sent to the system for sortation. The system may store the destination code of each read item in a historical database. The system then determines whether the read destination code is assigned a location. If the destination code is assigned a location, the item is loaded in a container at the assigned location. If the destination code is not assigned a location, the system determines whether to assign the destination code a location based on whether the destination code is in the scheme of destinations, the projected or historical number of items having the same destination code, and the speed of loading rating for each location.
Owner:ABB AUTOMATION INC
Single pass sequencer
A single pass sequencer having a transport system for transporting the mail pieces and a character recognition system proximate to the transport system for reading destination information associated with the mail pieces. The system includes a first carriage system and a second carriage system with a a plurality of holders slidable between the first carriage system and the second carriage system. Each of the plurality of holders holding a mail piece of the mail pieces received from the transport system. A sorting device stores information from the mail pieces and assigns a code to: (i) the mail pieces based on the destination information, (ii) the plurality of holders on the first carriage based on an initial sequence of each of the plurality of holders on the first carriage, and (iii) a position on the second carriage which corresponds to the initial sequence and a destination sequence of the mail pieces. The sorting device instructs movement of the plurality of holders from the first carriage to the second carriage based on the code assigned to the mail pieces, the plurality of holders on the first carriage and the position on the second carriage such that when the mail pieces are moved to the second carriage they are in sequential order of delivery destination.
Owner:LOCKHEED MARTIN CORP
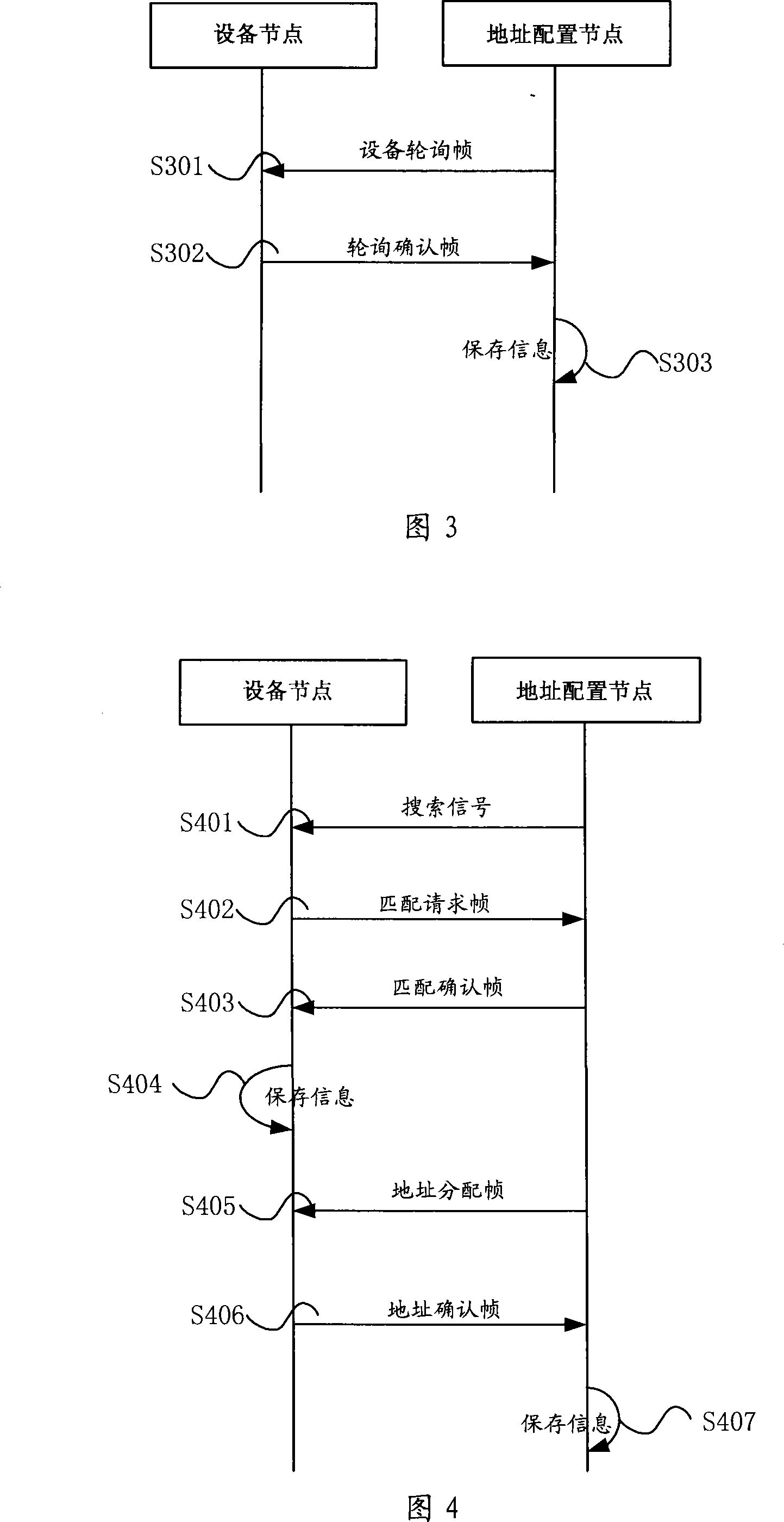
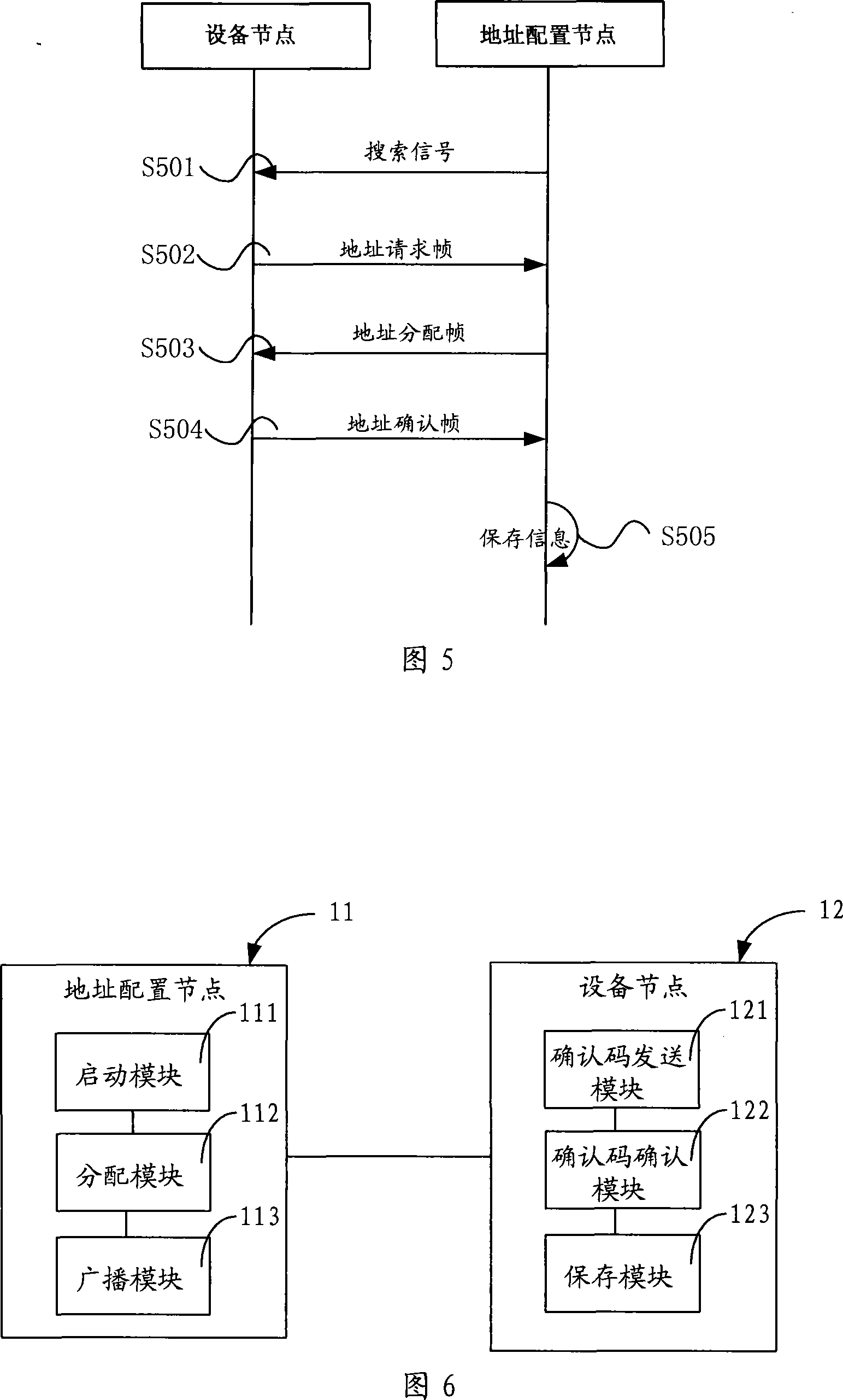
Equipment node address code distribution method and distributing system, and address configuration node
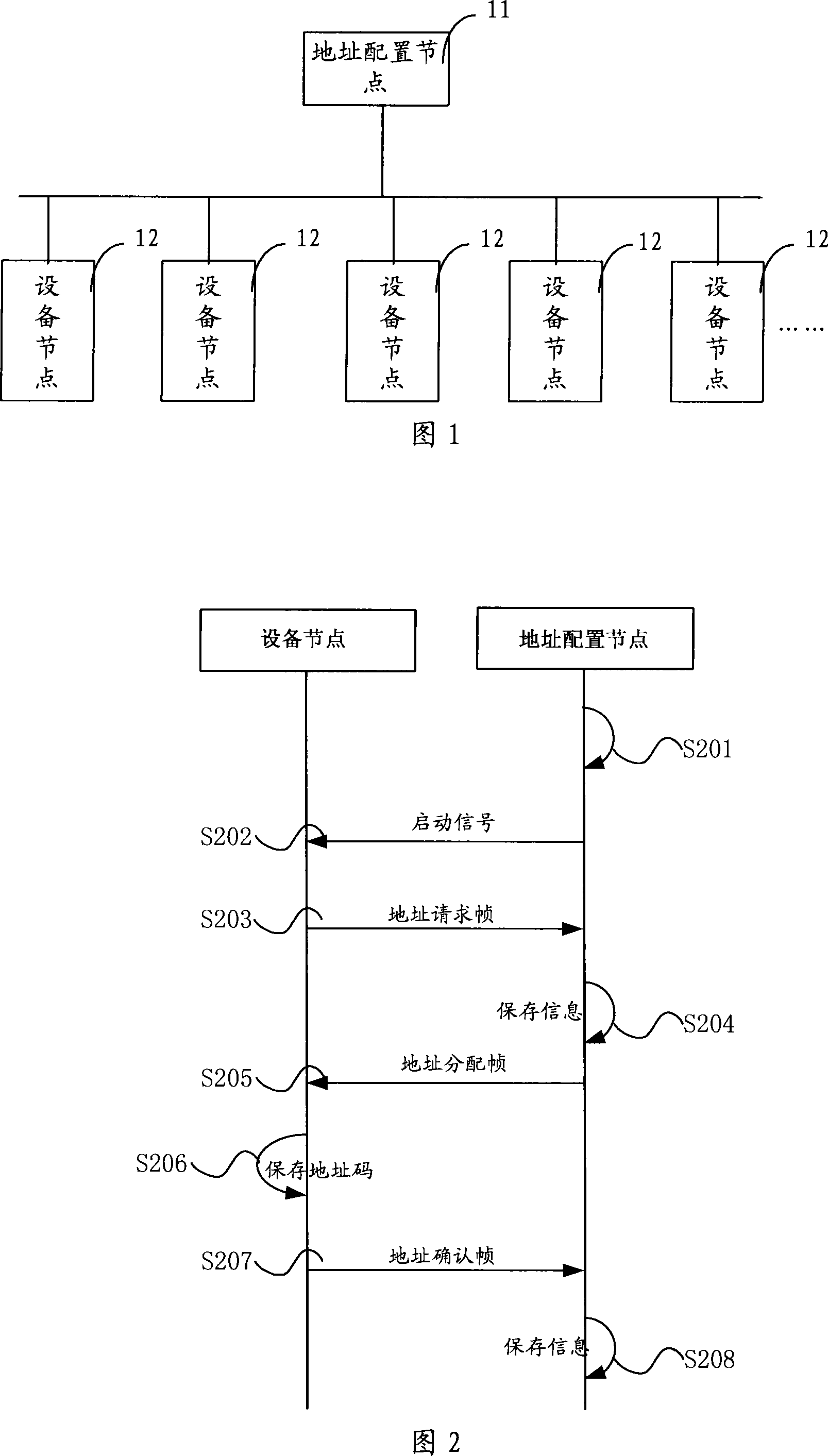
InactiveCN101197855AAvoid the problem of high setting error rateEasy to implementData switching networksDistribution methodDistribution system
The present invention relates to a distribution method for equipment node address codes, comprising the following steps that: an address configuration node in a system configures starting signals are allocated for each equipment node broadcast address; the equipment nodes receives the starting signals and respectively returns a unique confirmation code to the address configuration node; the address configuration node distributes unique equipment node address codes, and broadcasts the equipment node address codes as well as the confirmation codes; the equipment nodes determine that the confirmation codes accord with the own confirmation codes, and saves the equipment node address codes. Meanwhile, the present invention also discloses a distribution system for equipment node address code, as well as an address configuration node. The present invention solves the problem that the prior art is high in error rate when setting address codes, and has the advantages of easy realization, low cost, low error probability, etc.
Owner:SANY HEAVY IND CO LTD (CN)
Two-dimension code image generating method and device
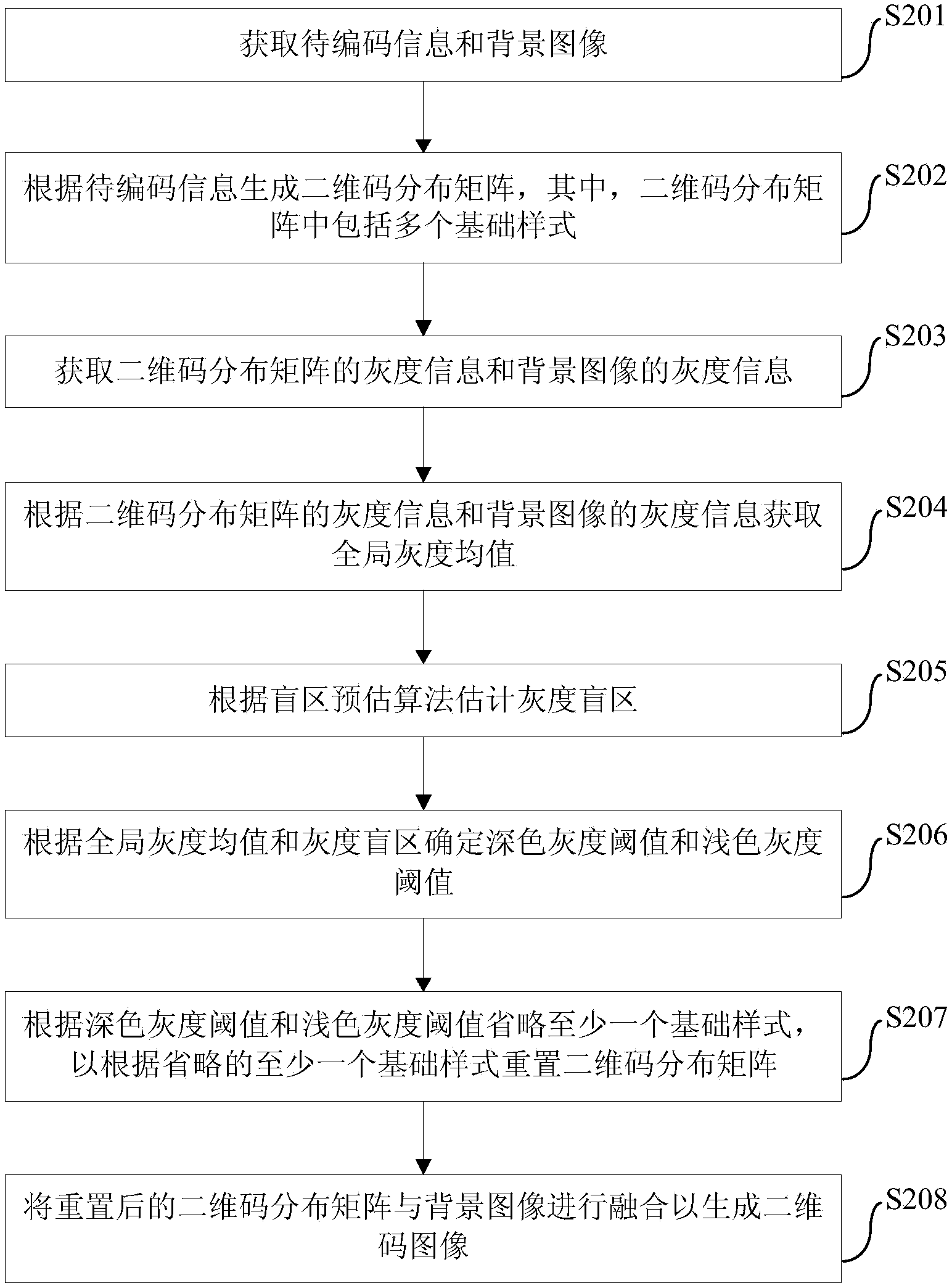
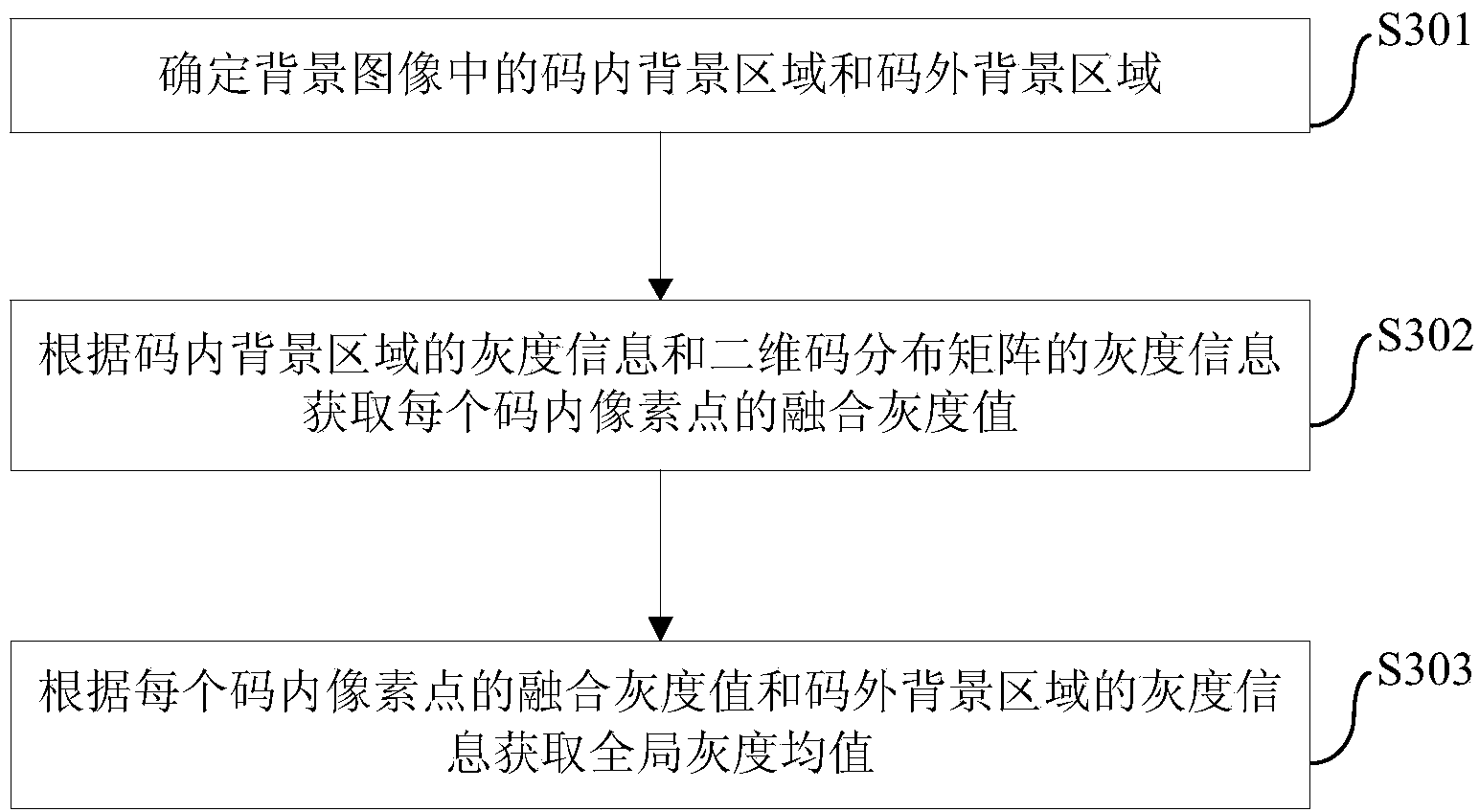
ActiveCN103886628AImprove immersionGuarantee screen2D-image generationRecord carriers used with machinesCode distributionBackground image
The invention provides a two-dimension code image generating method and device. The method comprises the steps of obtaining messages to be coded and a background image, and generating a two-dimension code distribution matrix according to the messages to be coded, wherein the two-dimension code distribution matrix comprises a plurality of basic patterns; obtaining the grey information of the two-dimension code distribution matrix and the grey information of the background image; eliminating at least one basic pattern according to the grey information of the two-dimension code distribution matrix and the grey information of the background image so as to reset the two-dimension code distribution matrix according to the at least one eliminated basis pattern; mixing the rest two-dimension code distribution matrix and the background image together so as to generate a two-dimension code image. The two-dimension code image generating method reduces coverage on the background image so as to further improve the immersion degree of the two-dimension code in the background image, make the background image prominent, and ensure the completeness of the environment color of the background image and the picture harmony sense of the two-dimension code image to a large degree, and increase the display effect of the two-dimension code image.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
E-mail security audit system for company security
InactiveUS20030188196A1Avoid spreadingMemory loss protectionError detection/correctionInternet privacyEngineering
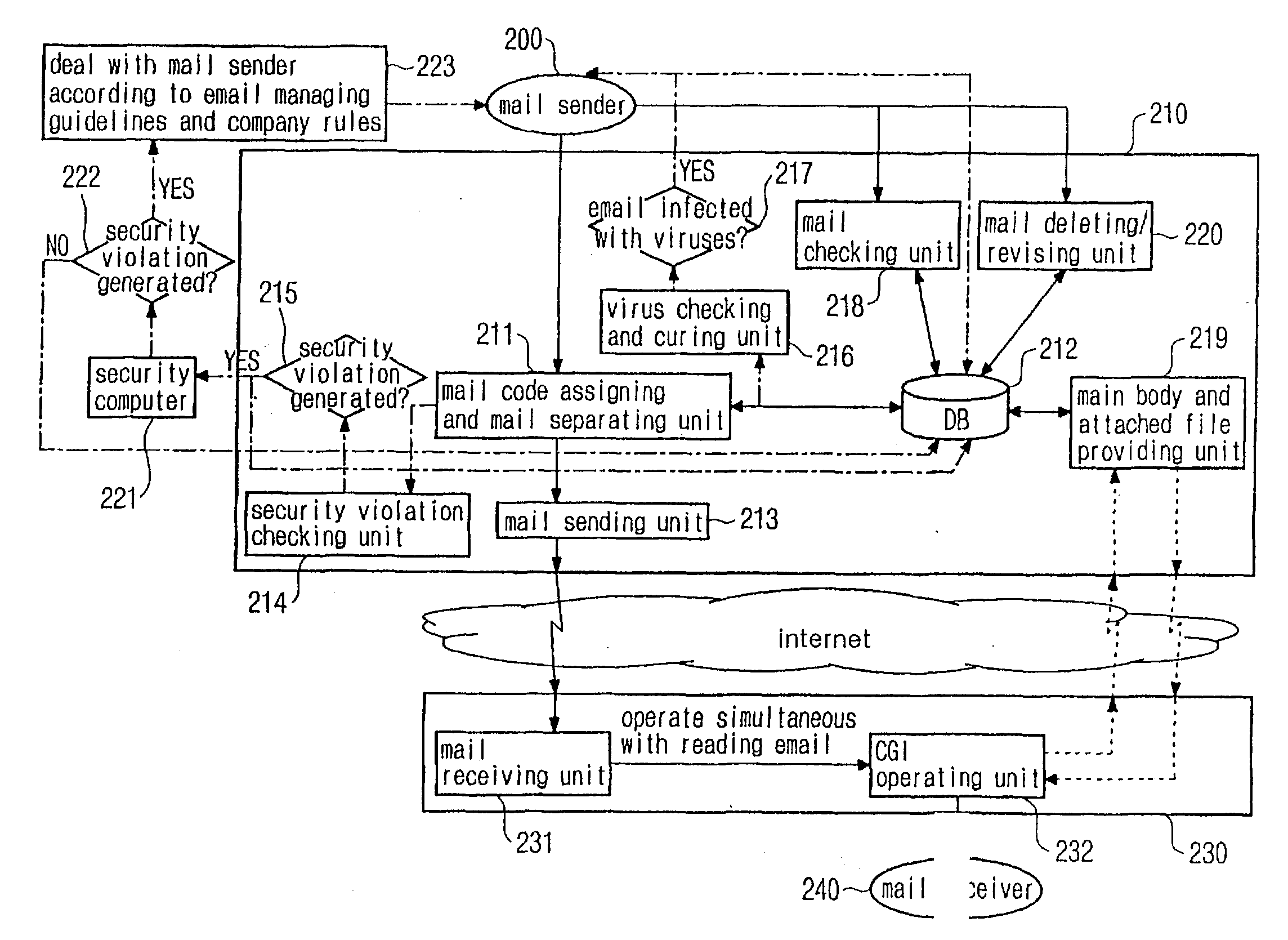
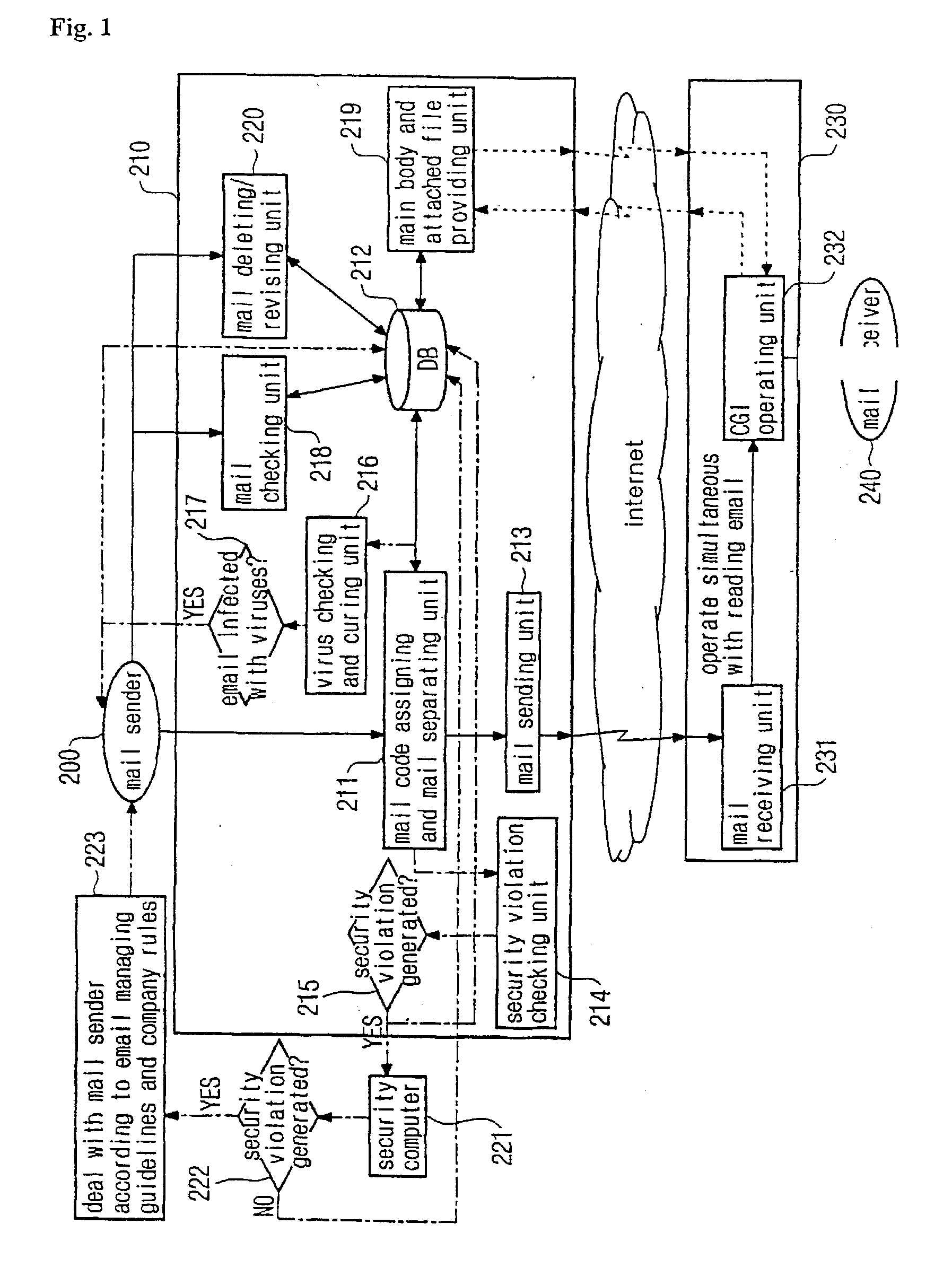
An email security system for company security is disclosed. The email security system has a transmission server and a reception server. The transmission server has a mail code assigning and mail separating unit, a database, a security violation checking unit, a virus checking and curing unit, and a mail sending unit; and the reception server has a CGI operating unit. The security violation checking unit checks whether or not the email written and sent by a mail sender violates security, and sets a flag to prevent a mail receiver from reading the email if the email violates the security. The virus checking and curing unit checks whether the main body and the attached file are infected with computer viruses, and sets the flag to prevent the mail receiver from reading the email if the main body and the attached file are infected with the computer viruses.
Owner:CHOI JEONG HWAN
One-bit digital coding antenna unit and digital phase array antenna system
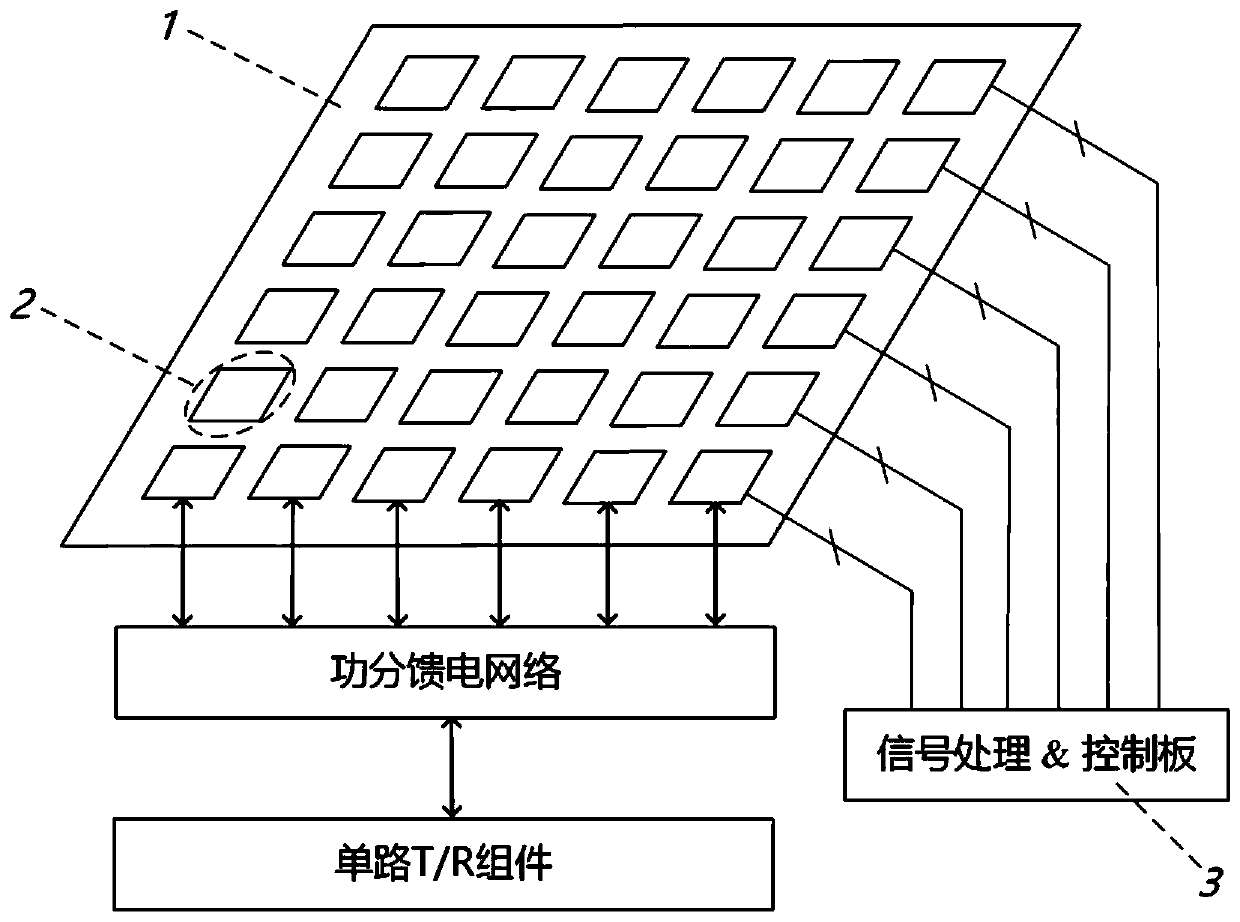
ActiveCN110767999ALow costReduce Design ComplexityParticular array feeding systemsRadiating elements structural formsTelecommunicationsScanning beam
The invention provides a one-bit digital coding antenna unit and a digital phase array antenna system. A PIN diode is integrated on a radiating patch of a direct radiation type digital coding antennaunit provided by the invention; by applying different biases to the PIN diode, radiation beams of the antenna unit take on two phase positions, that is, 0 degree and 180 degrees, which correspond to numerical codes "0" and "1", respectively. By arranging each unit periodically to form an array and feeding through a power division network, a novel phase array antenna is formed; and as code distribution of units on the array is controlled through the optimization algorithm, scanning beams in different orientations or shaped-beams in different shapes can be generated. Compared with the traditional phase array antenna, the digital phase array antenna system reduces system cost and complexity; and compared with digital coding super-surface based phase array antenna, the digital phase array antenna system reduces the profile and volume of the system, avoids energy leakage caused by spacial irradiation feed and improves overall efficiency of the antenna.
Owner:SHANGHAI AEROSPACE ELECTRONICS CO LTD +1
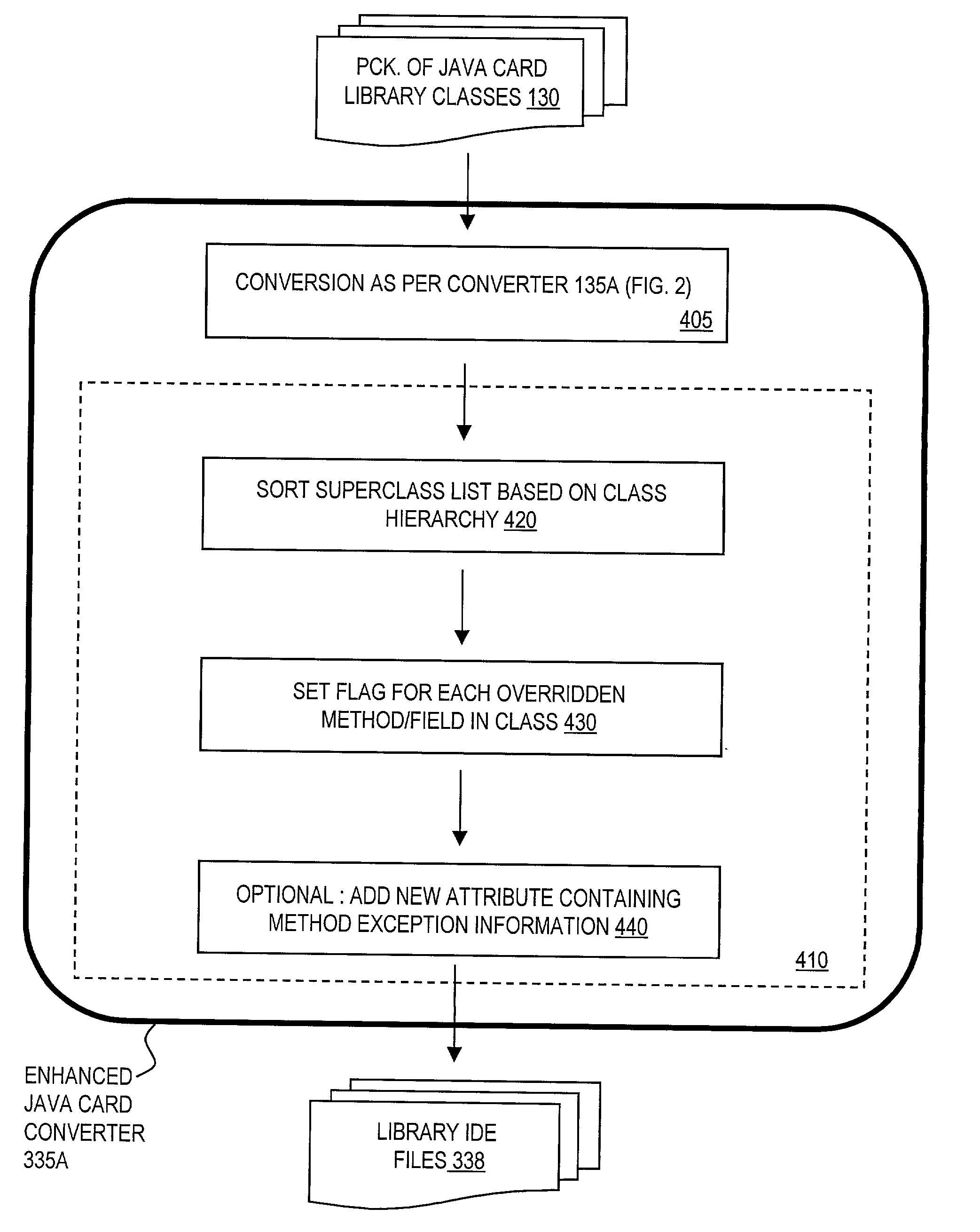
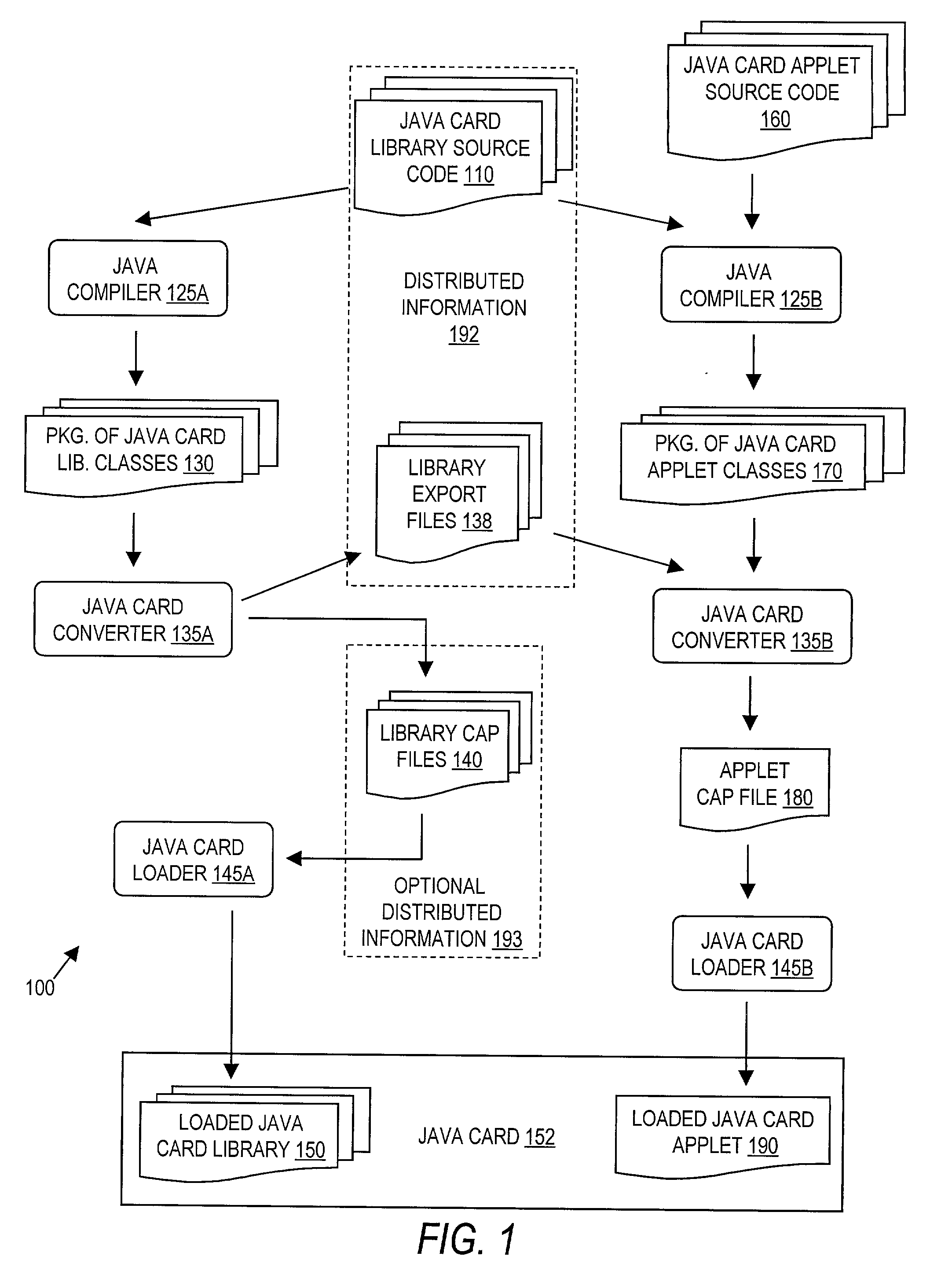
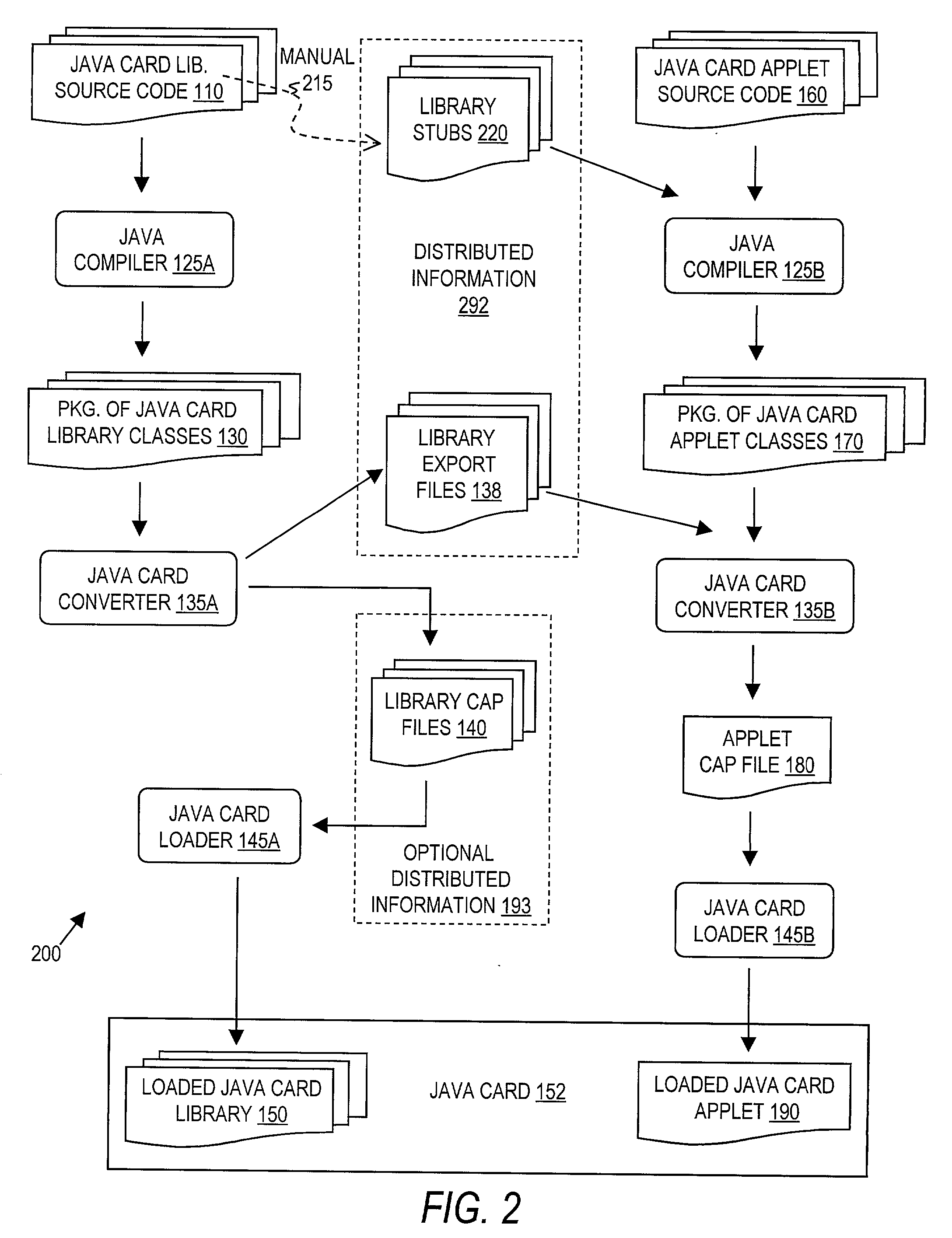
Code distribution and synthesis
InactiveUS20030051233A1Specific program execution arrangementsMemory systemsCode distributionSource code
A first software program is capable of being referenced by a second software program. For compiling the second program, information, including an interface definition, is generated by a converter for the first program. Also, a generator is provided for generating first source code from the interface definition, so that second source code may be developed and the second program may be compiled from the first and second source code.
Owner:AXALTO INC
Registration mail system with a sent e-mail check function on internet and method for the same
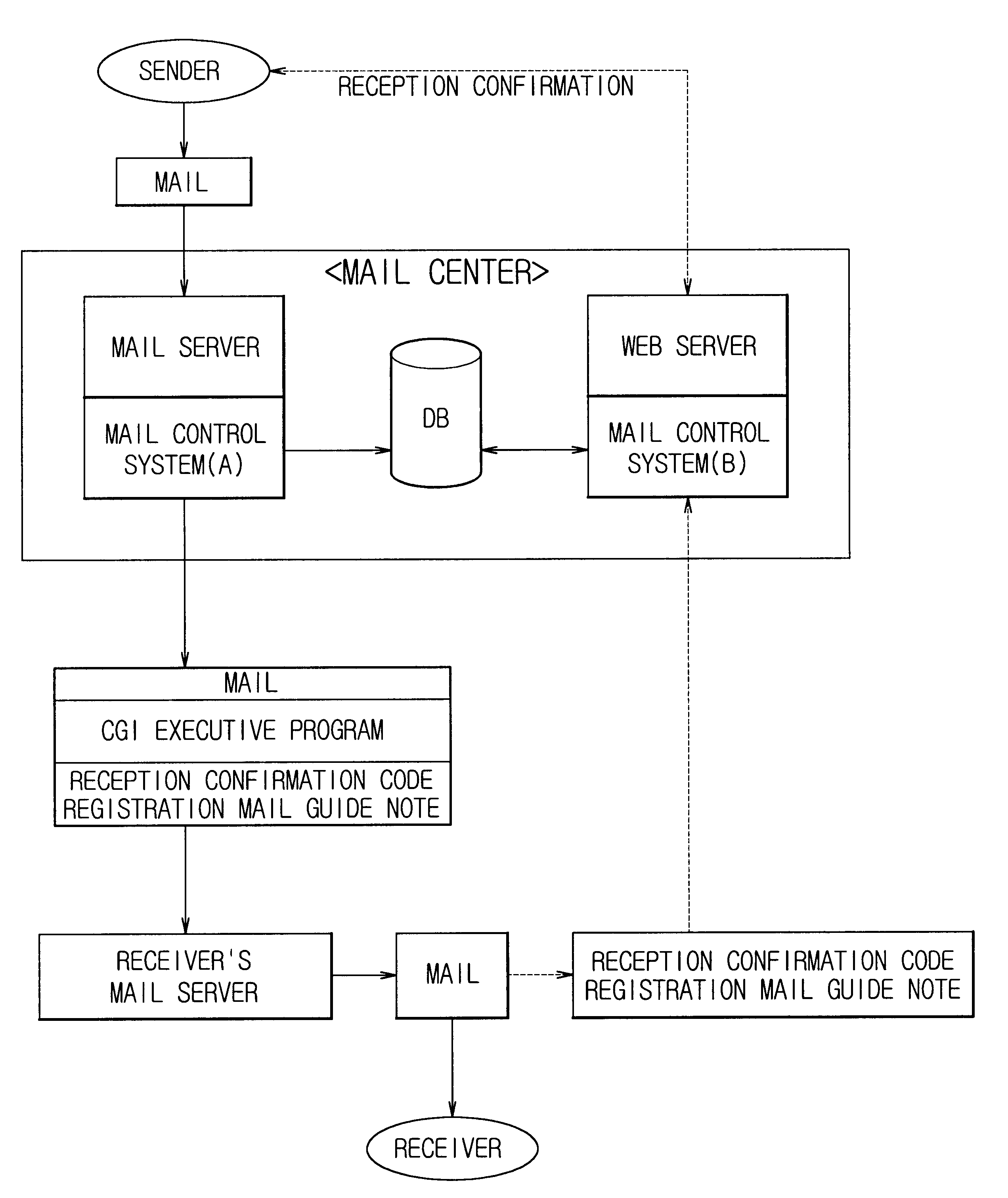
An electronic mailing method on the Internet with a function of reception confirmation is described. The method is comprising the steps of (a) assigning a unique code to the e-mail of a sender and recording the unique code in a database; (b) attaching to the e-mail a CGI executive program that automatically sends the unique code to the web server of the sender when the receiver receives the e-mail; (c) sending the unique code to the web server of the sender by the automatic execution of the CGI executive program when the e-mail is received by the receiver; and (d) comparing the unique code sent in the step (c) and the unique code recorded in the step (a) and, if they are identical, sending reception confirmation information to the sender.
Owner:NEXEN
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com