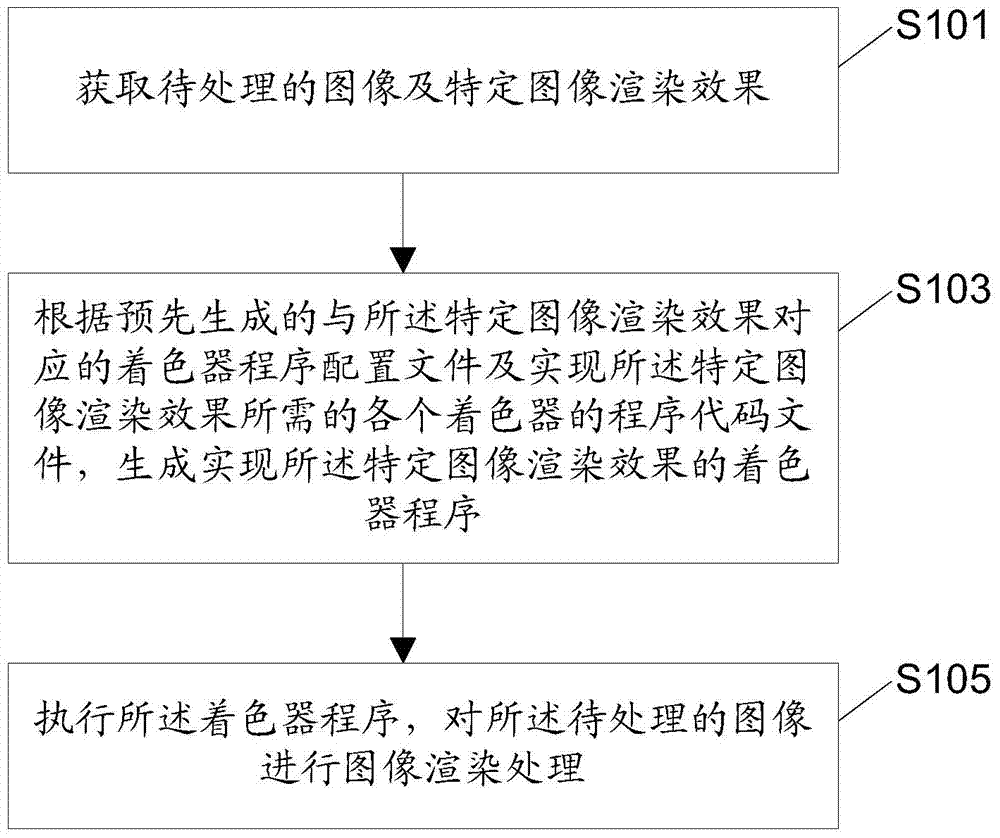
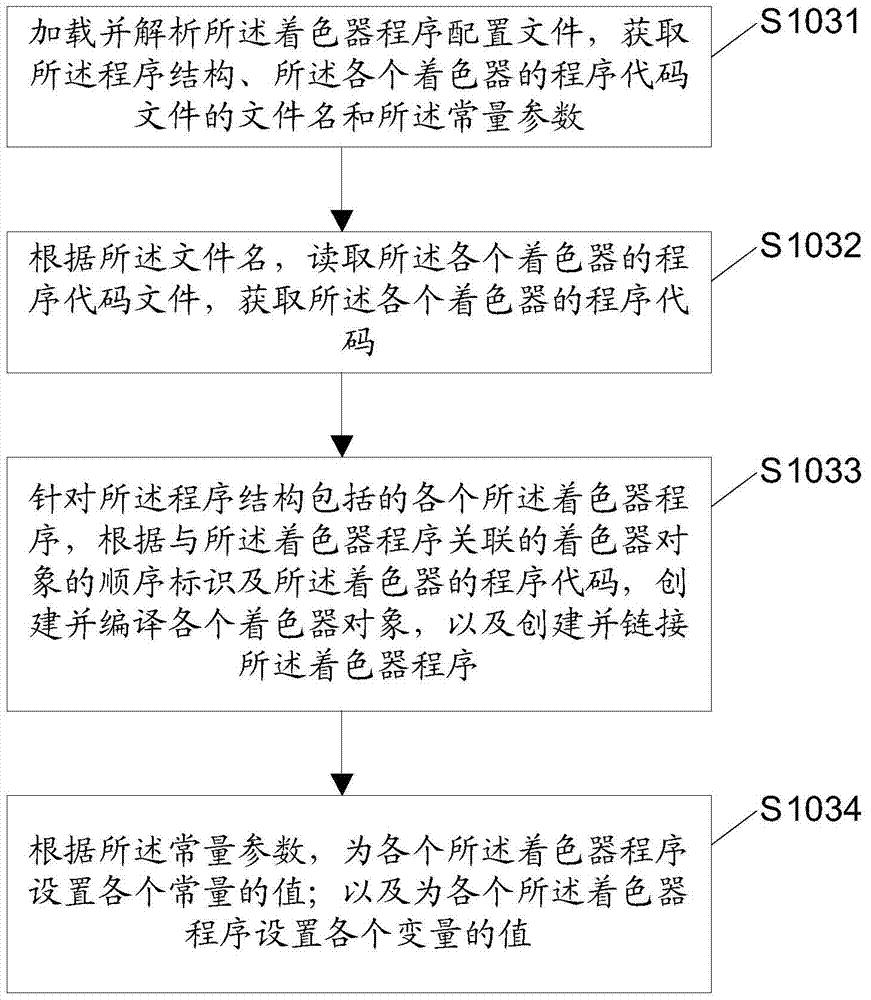
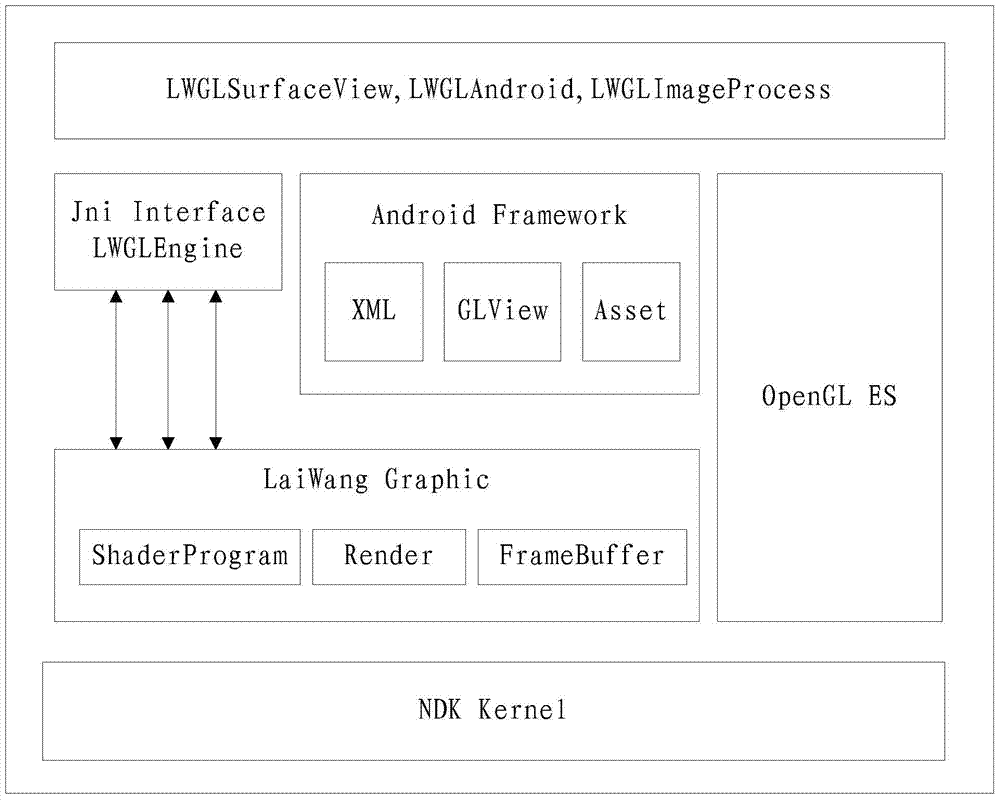
Patents
Literature
261 results about "Program structure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
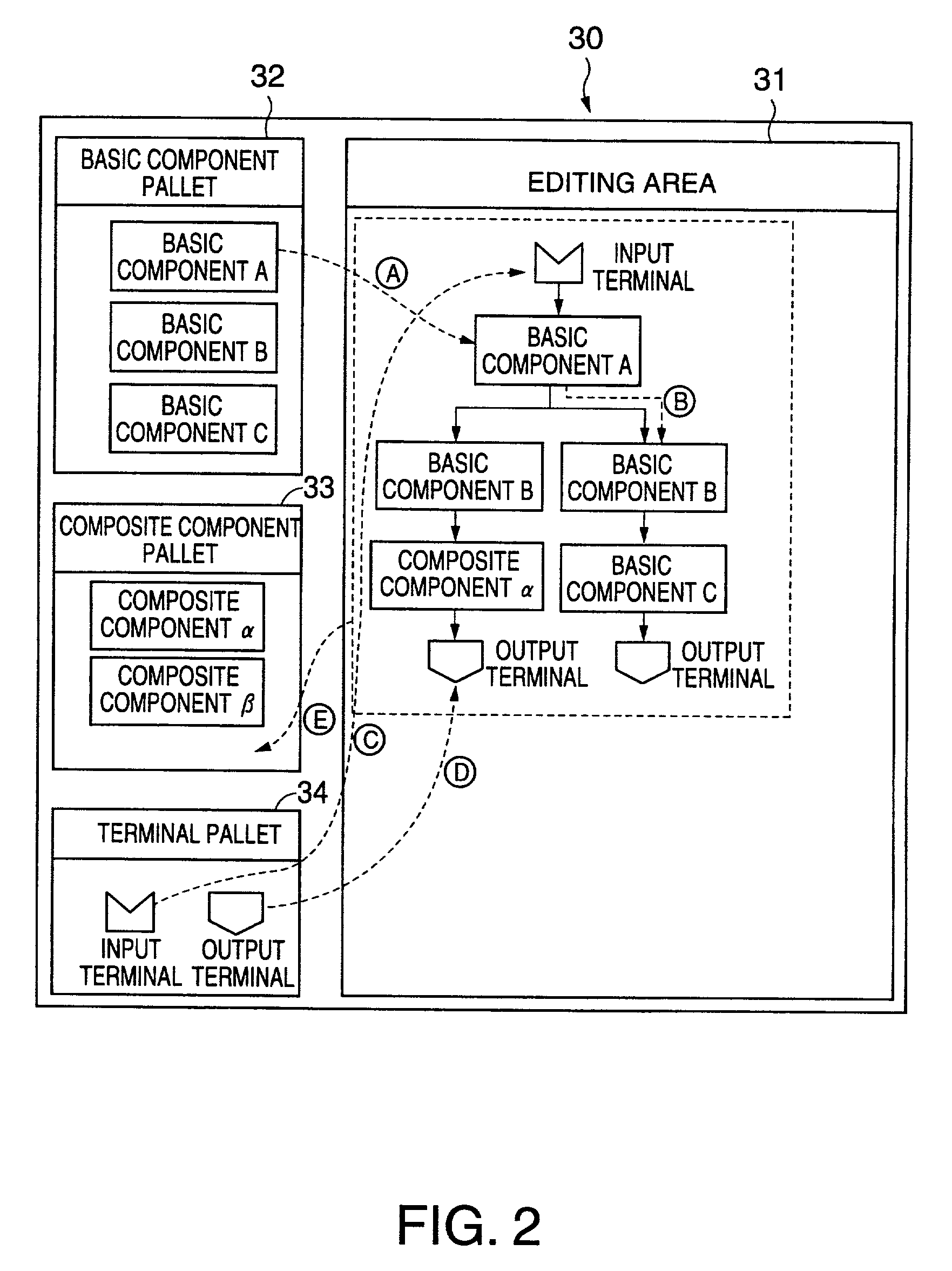
Program structure The overall form of a program, with particular emphasis on the individual components of the program and the interrelationships between these components. Programs are frequently referred to as either well structured or poorly structured.
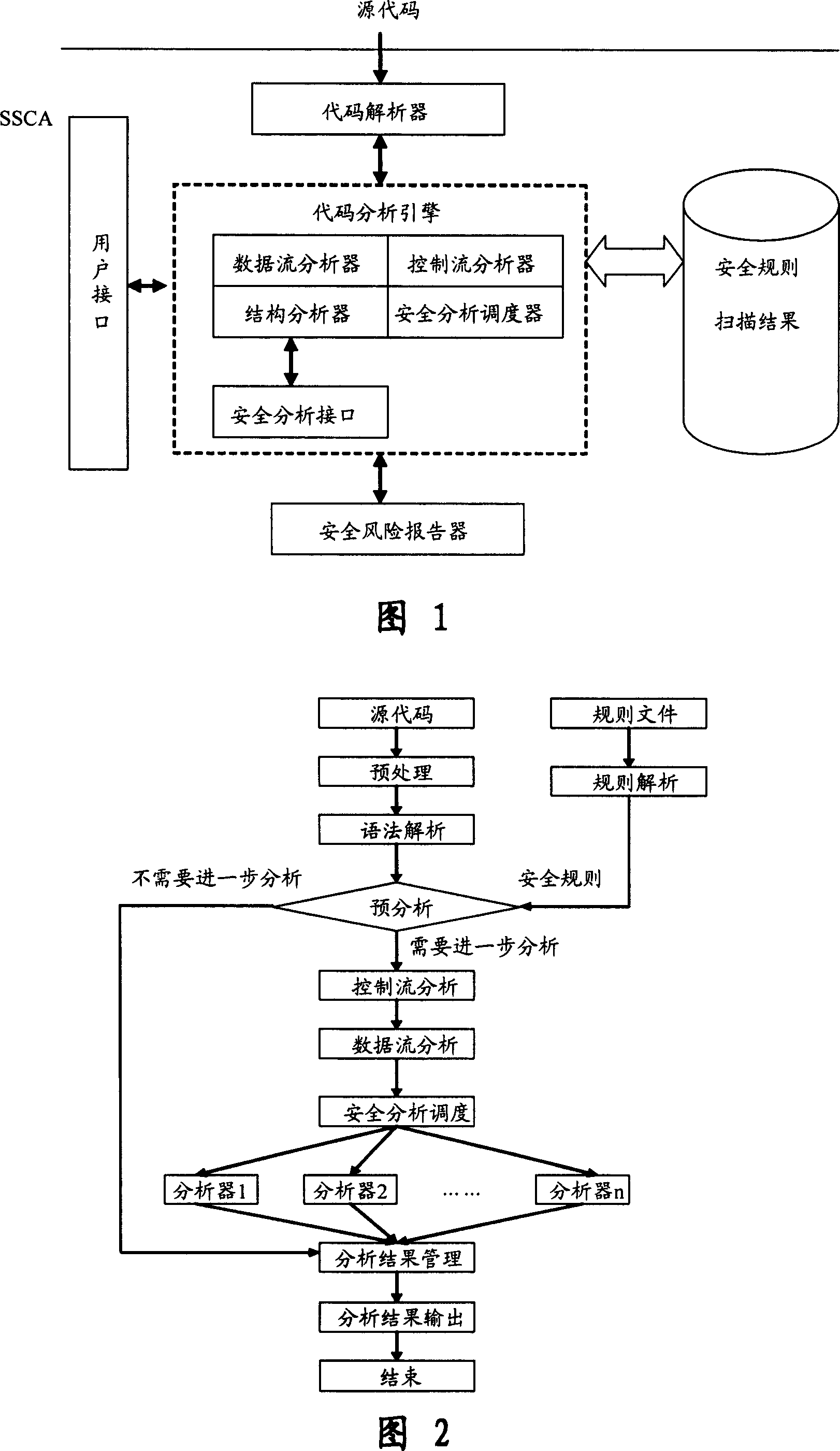
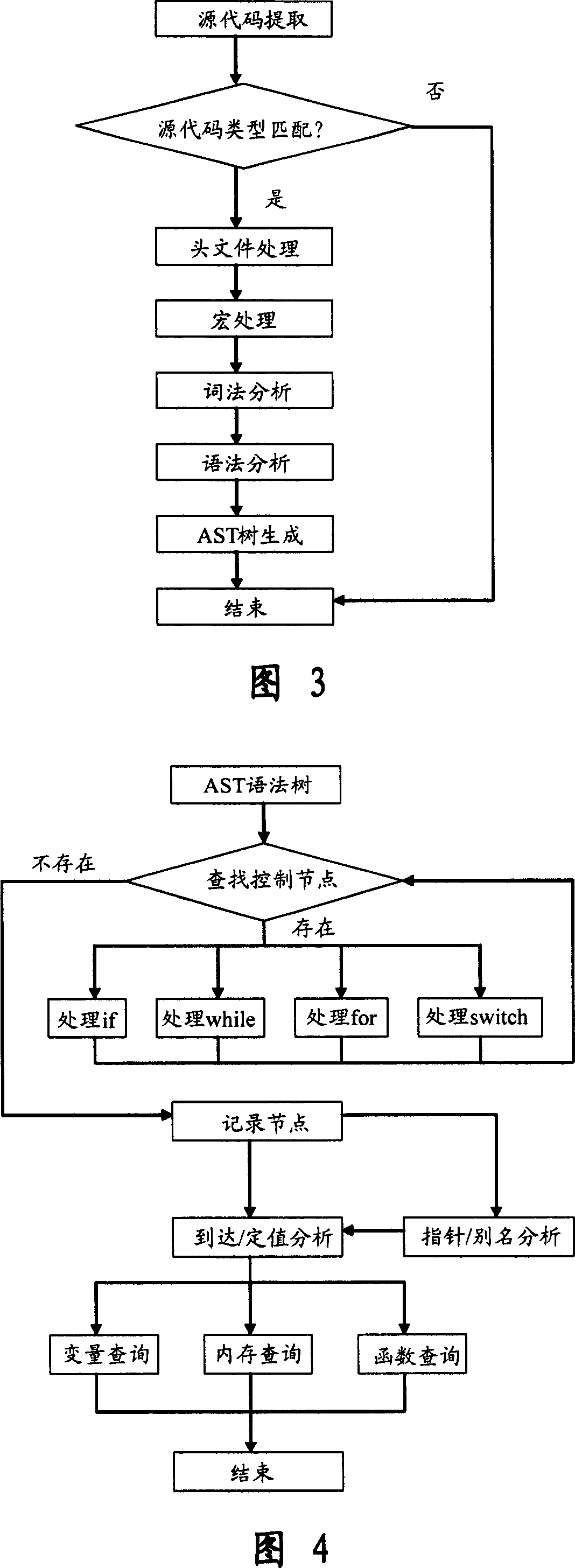
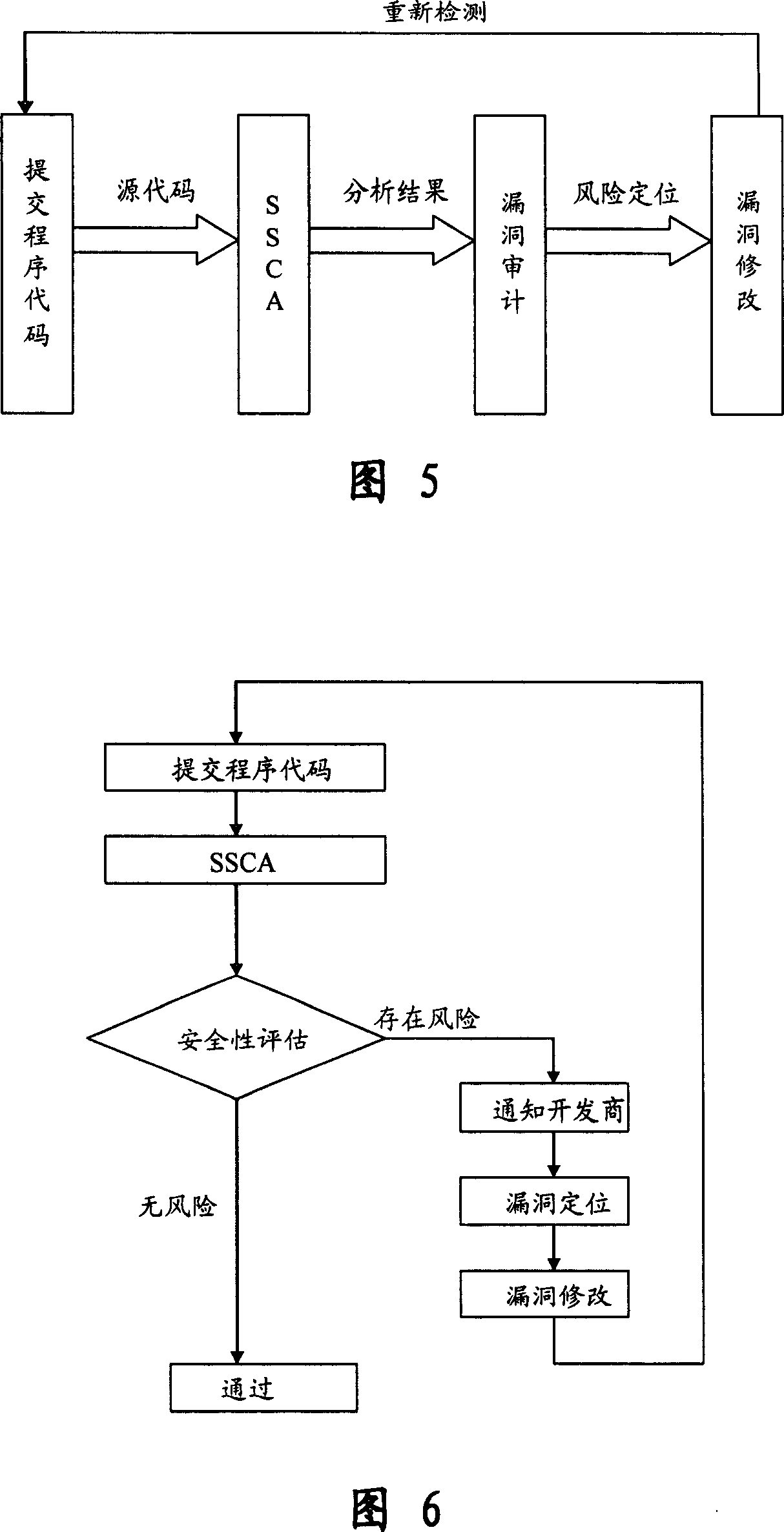
Software safety code analyzer based on static analysis of source code and testing method therefor
InactiveCN101017458AImprove accuracySupport for expansionSoftware testing/debuggingStatic timing analysisStructure analysis
This invention relates to one software analyzer and its test method based on source codes static analysis, wherein the analysis device comprises five function modules of code analysis device, codes analysis engine, safety risk report device, safety rules database and user interface; this invention gets programs safety risk to user according to the source program and grammar and meanings and delivers the safety leak to the user for audit and evaluation.
Owner:深圳北邮网络科技有限公司
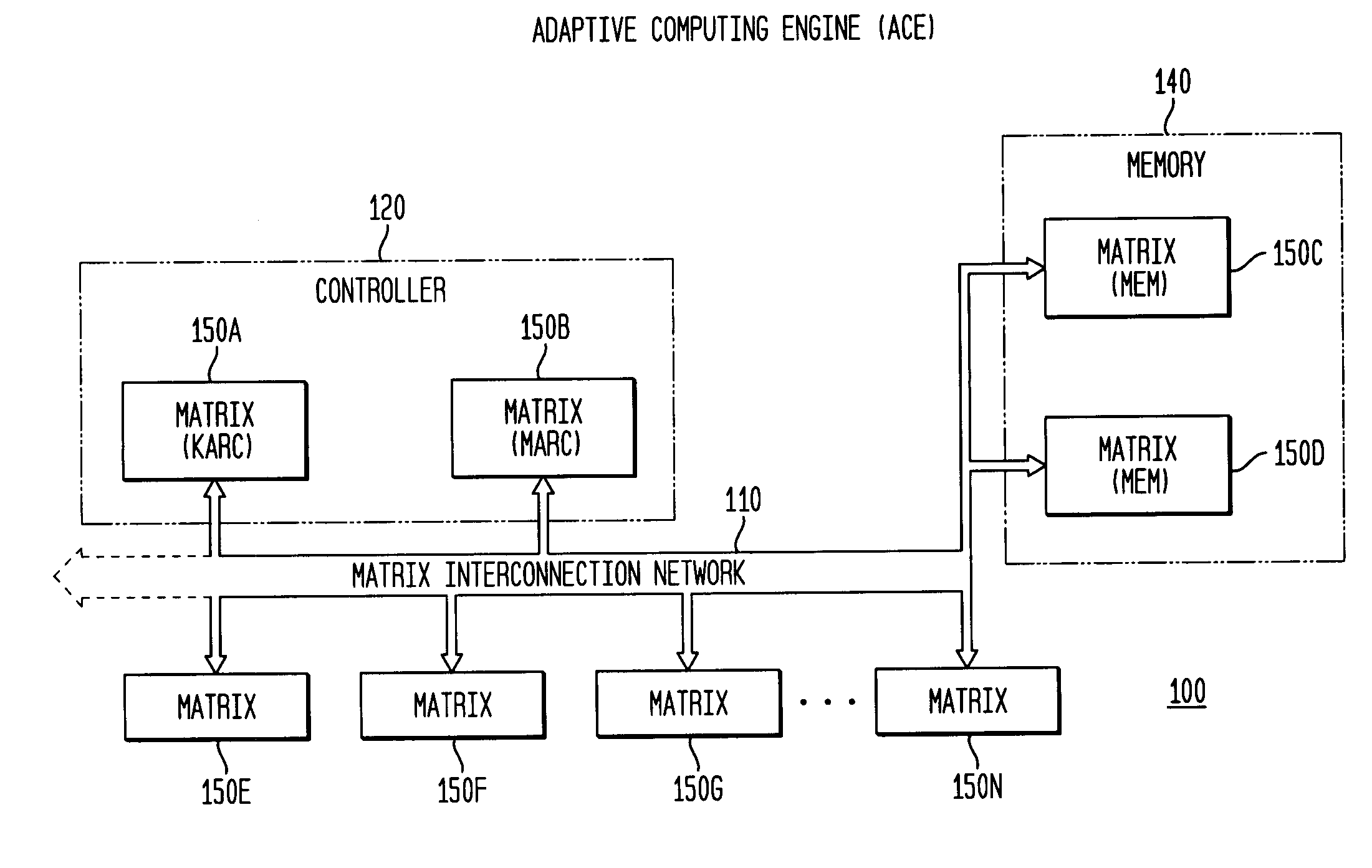
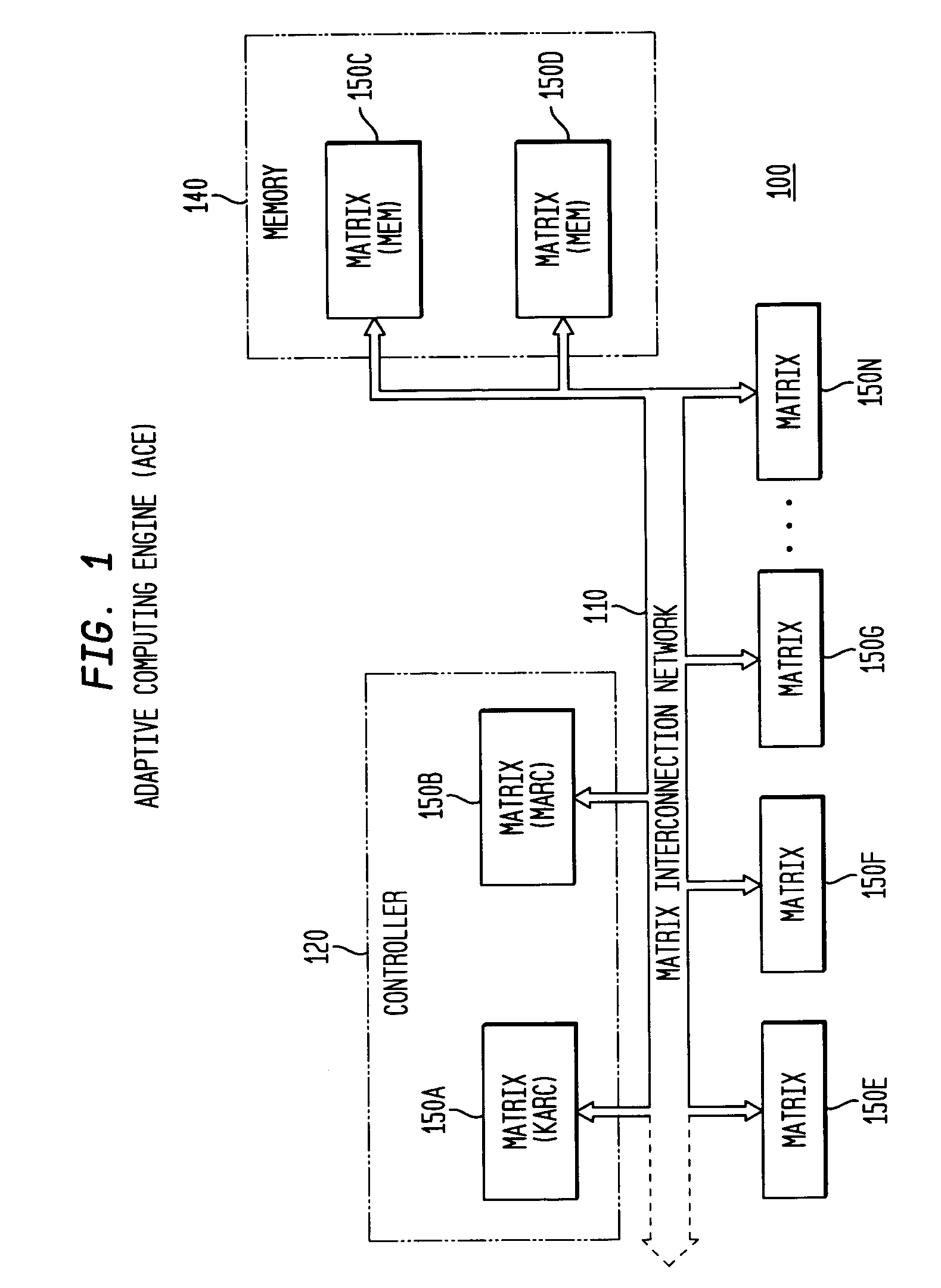
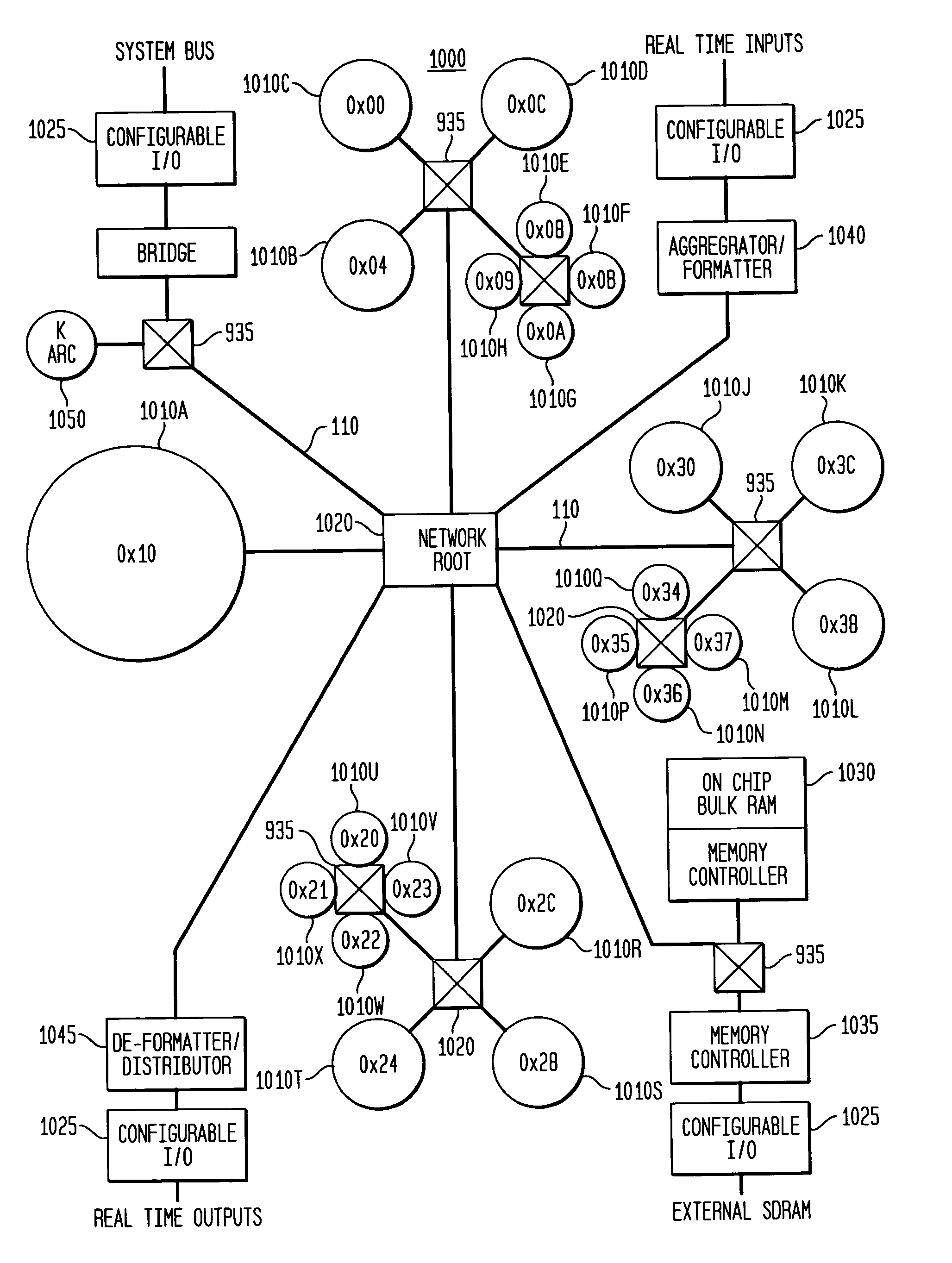
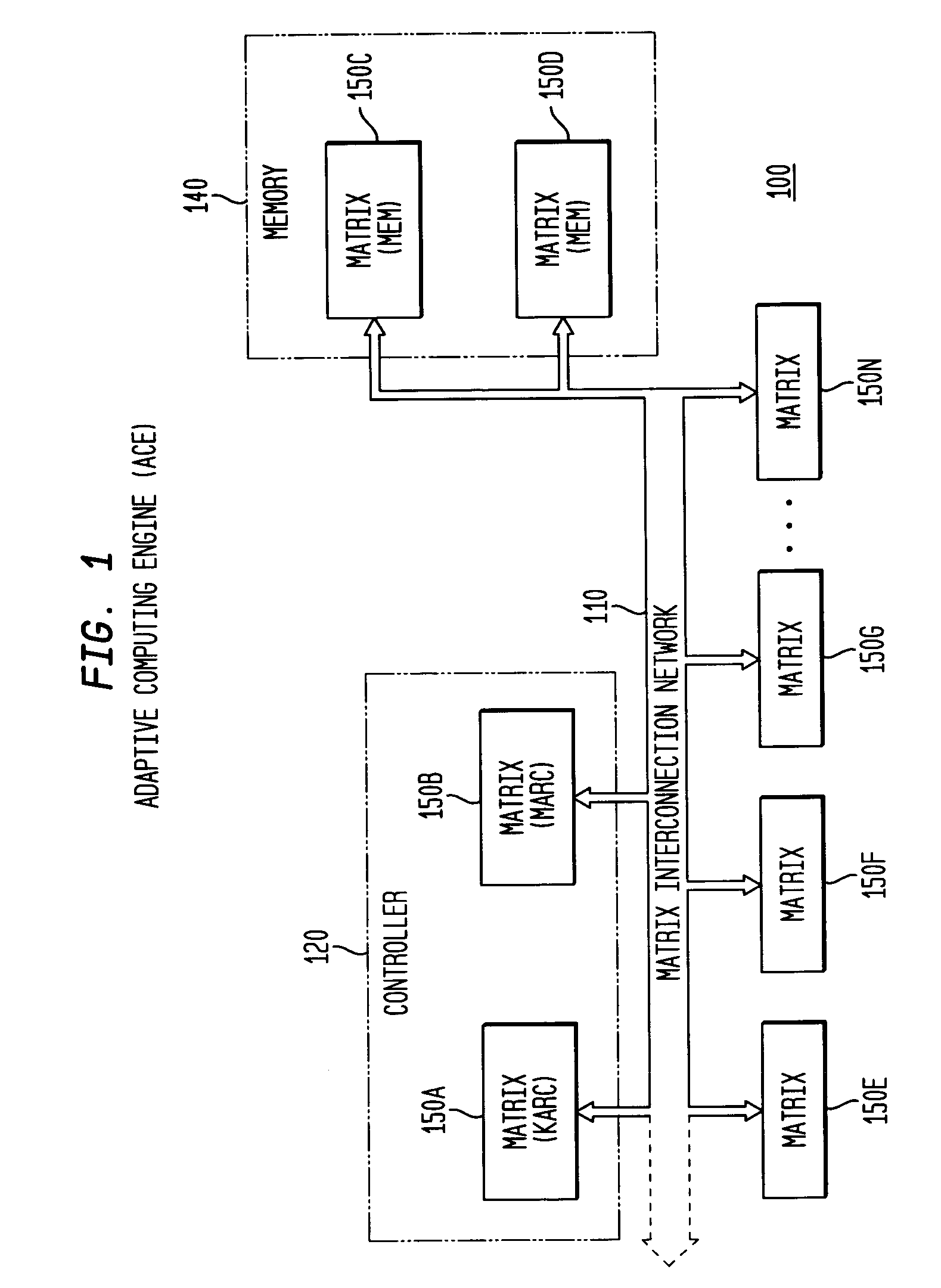
System, method and software for static and dynamic programming and configuration of an adaptive computing architecture
ActiveUS20050044344A1Architecture with single central processing unitSpecial data processing applicationsInterconnectionSystems approaches
The present invention provides a system, method and software for programming and configuring an adaptive computing architecture or device. The invention utilizes program constructs which correspond to and map directly to the adaptive hardware having a plurality of reconfigurable nodes coupled through a reconfigurable matrix interconnection network. A first program construct corresponds to a selected node. A second program construct corresponds to an executable task of the selected node and includes one or more firing conditions capable of determining the commencement of the executable task of the selected node. A third program construct corresponds to at least one input port coupling the selected node to the matrix interconnect network for input data to be consumed by the executable task. A fourth program construct corresponds to at least one output port coupling the selected node to the matrix interconnect network for output data to be produced by the executable task;
Owner:CORNAMI INC
Computer Architecture And Method Of Operation for Multi-Computer Distributed Processing Having Redundant Array Of Independent Systems With Replicated Memory And Code Striping
ActiveUS20080250213A1Avoid accessError detection/correctionMemory adressing/allocation/relocationTelecommunications linkParallel computing
Computers and other computing machines and information appliances having a modified computer architecture and program structure which enables the operation of an application program concurrently or simultaneously on a plurality of computers interconnected via a communications link or network using a special distributed runtime (DRT), and that provides for a redundant array of independent computing systems that include computer code distribution using code-striping onto the plurality of the computers or computing machines. A redundant array of independent computing systems operating in concert and code-striping features.
Owner:WARATEK LTD
Method and apparatus for sociable computing in ad-hoc and configured peer-to-peer networks
ActiveUS20120042000A1Multiple digital computer combinationsOffice automationProgram instructionParallel computing
Executing a program structure for spanning a thread of control and a thread of execution across multiple peers in a peer-to-peer network comprises generating a program structure comprising a plurality of program instructions. A first of a plurality of network peers then executes a portion of the program instructions which initiates the execution of code hosted by said first network peer, where said portion comprising fewer than all program instructions. The first network peer then migrates one or more of the program instructions, including one or more controlling program instructions, together with any requisite data, some of which may include control data, to at least one other of the plurality of network peer. The at least one other network peer then continues execution of the program instructions in accordance with the controlling program instructions and control data until one or more of the objections of the program structure are achieved.
Owner:ZEROTOUCHDIGITAL
Software translation
InactiveUS20080222616A1Faster time to marketIncreased cost-effectivenessProgram controlMemory systemsSource codeHuman language
A computer implemented method for automatically translating a first source code associated with a first programming language to a second source code associated with a second programming language wherein the first and second source codes are associated with the same functionality, the method comprising the steps of: parsing the first source code to form a program structure representation comprising a plurality of program structure elements associated with the first programming language, analysing the program structure elements, wherein the analysis includes the step of searching for at least one program structure element that has no direct associated representation that produces the same result in the second programming language, and transforming the program structure representation into the second source code based on said analysis.
Owner:INNAWORKS DEV
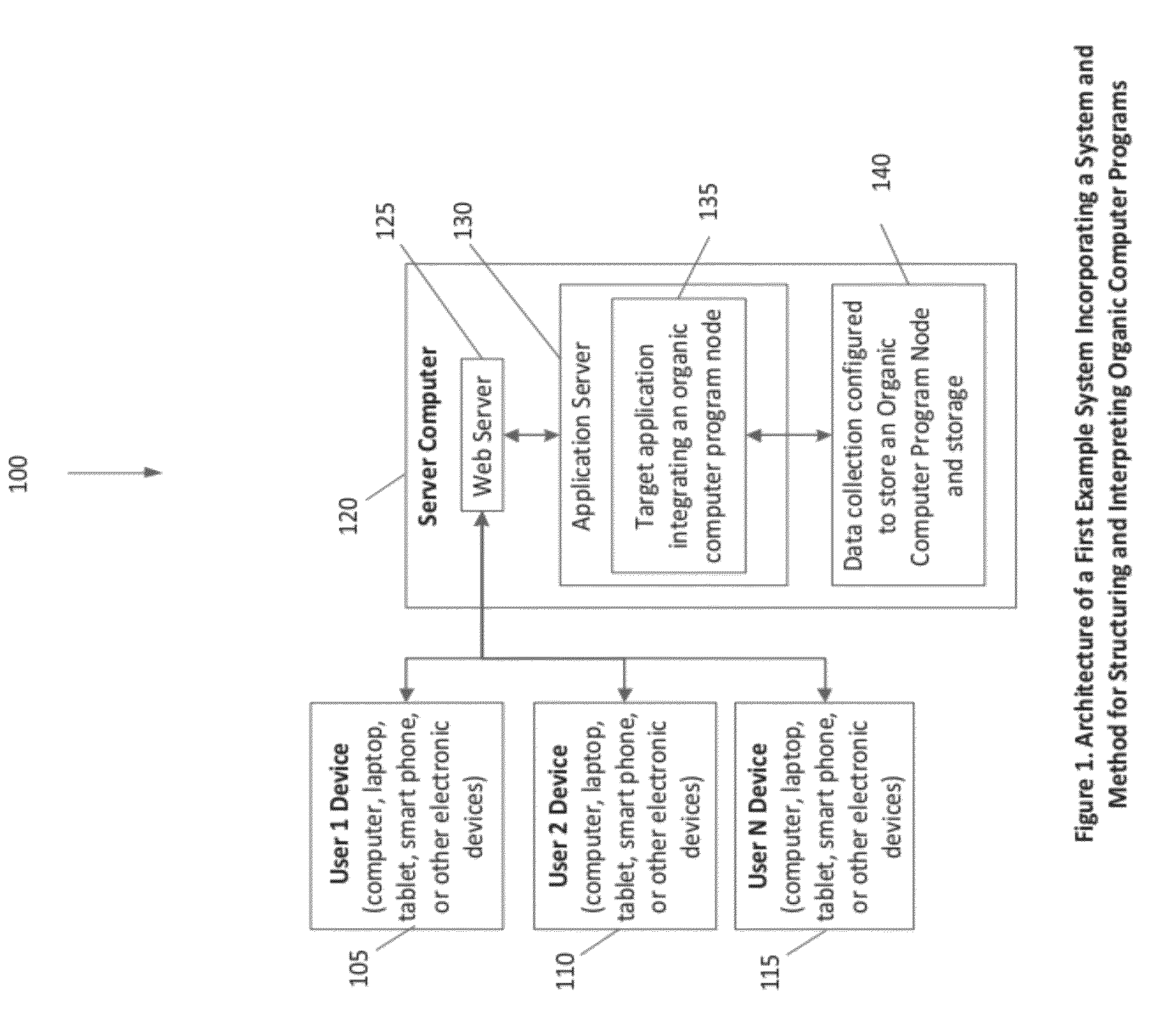
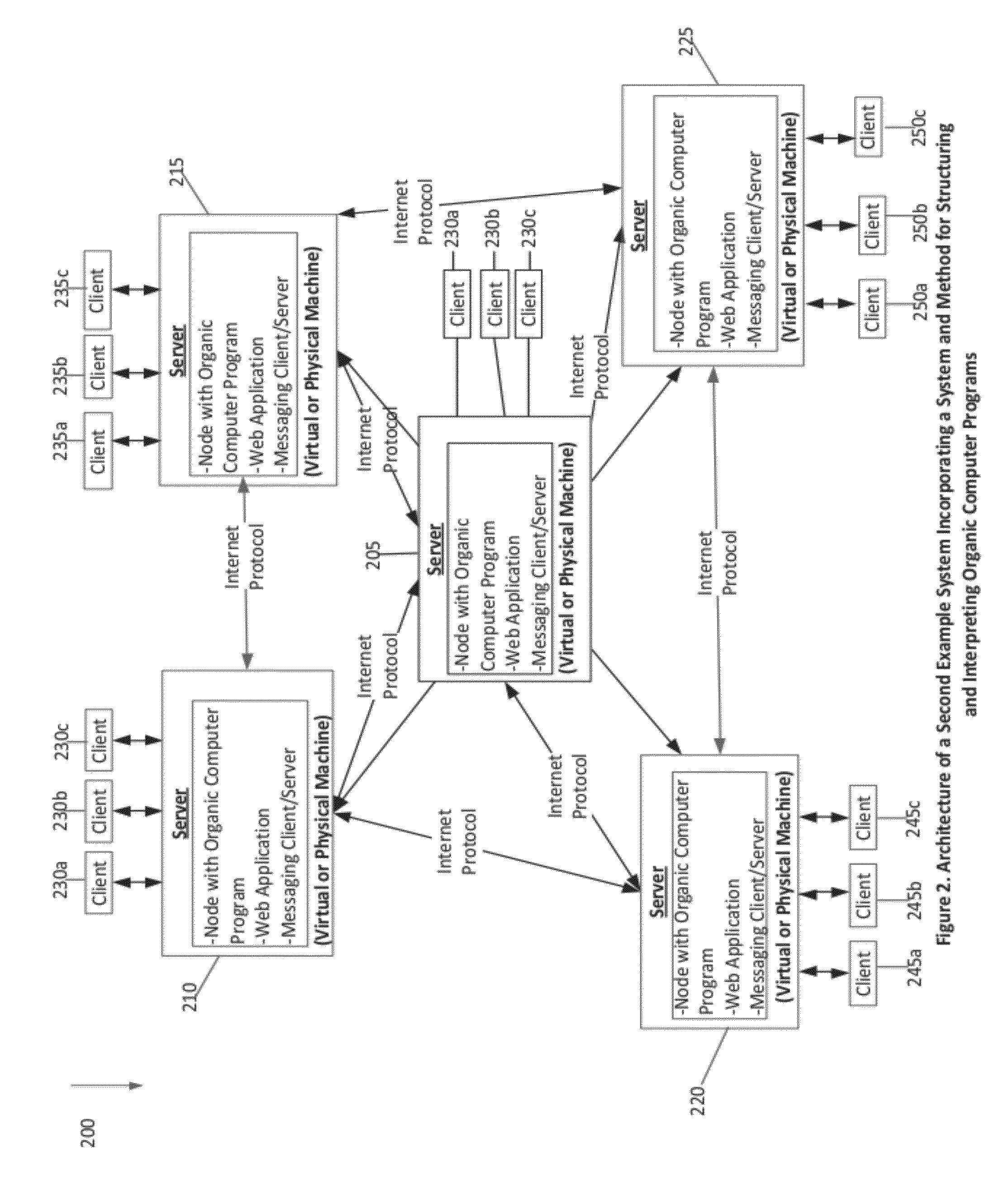
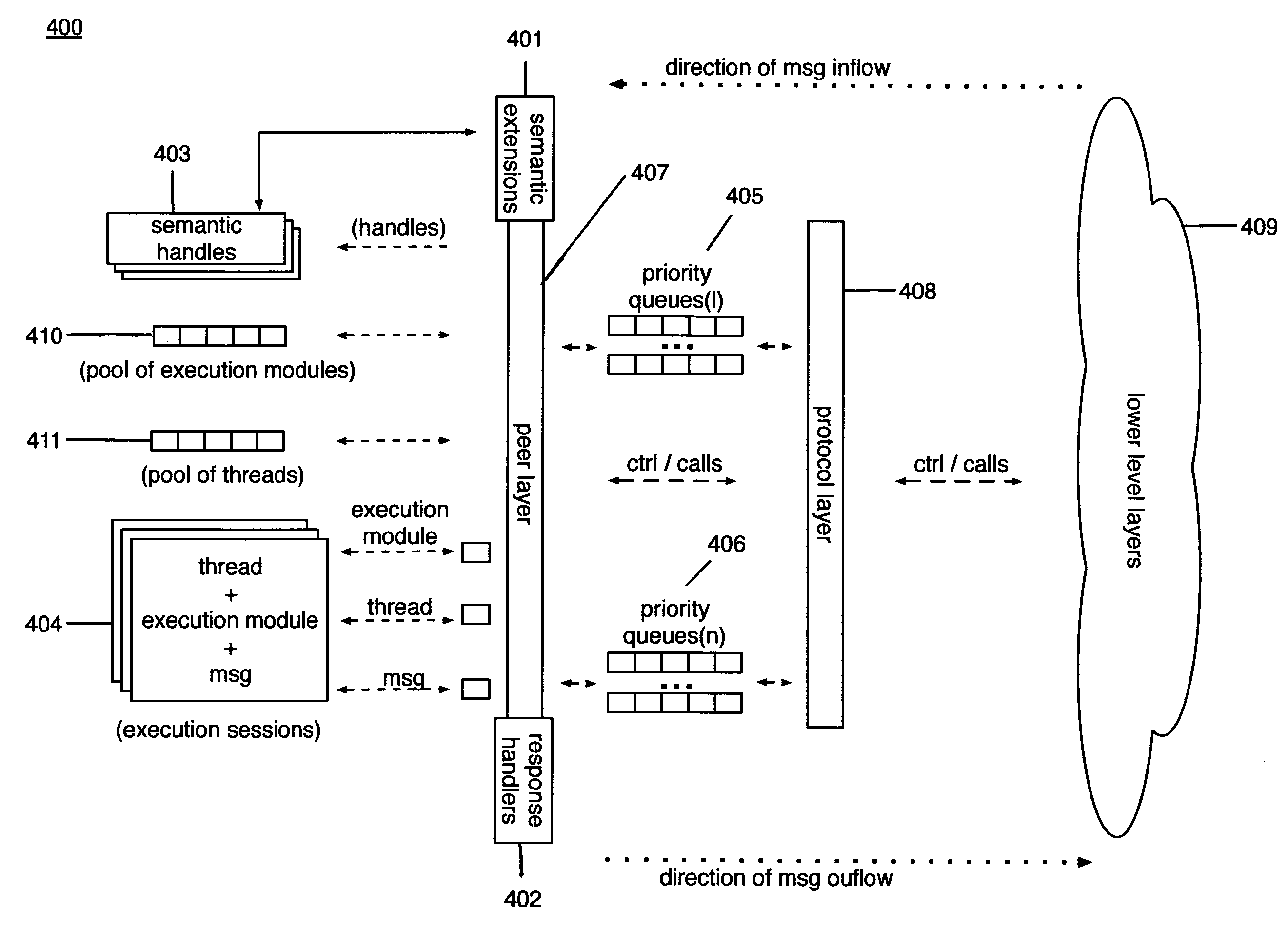
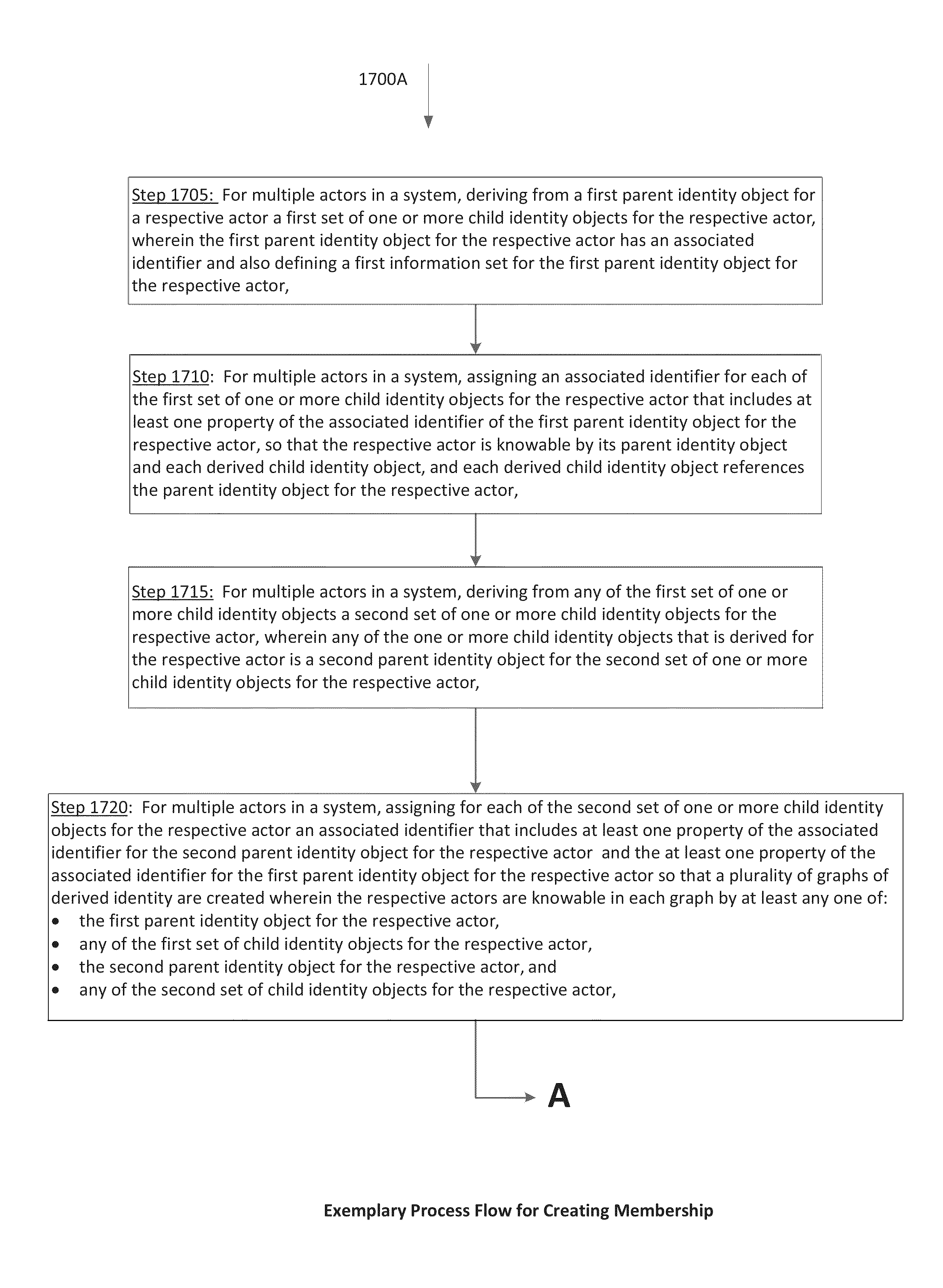
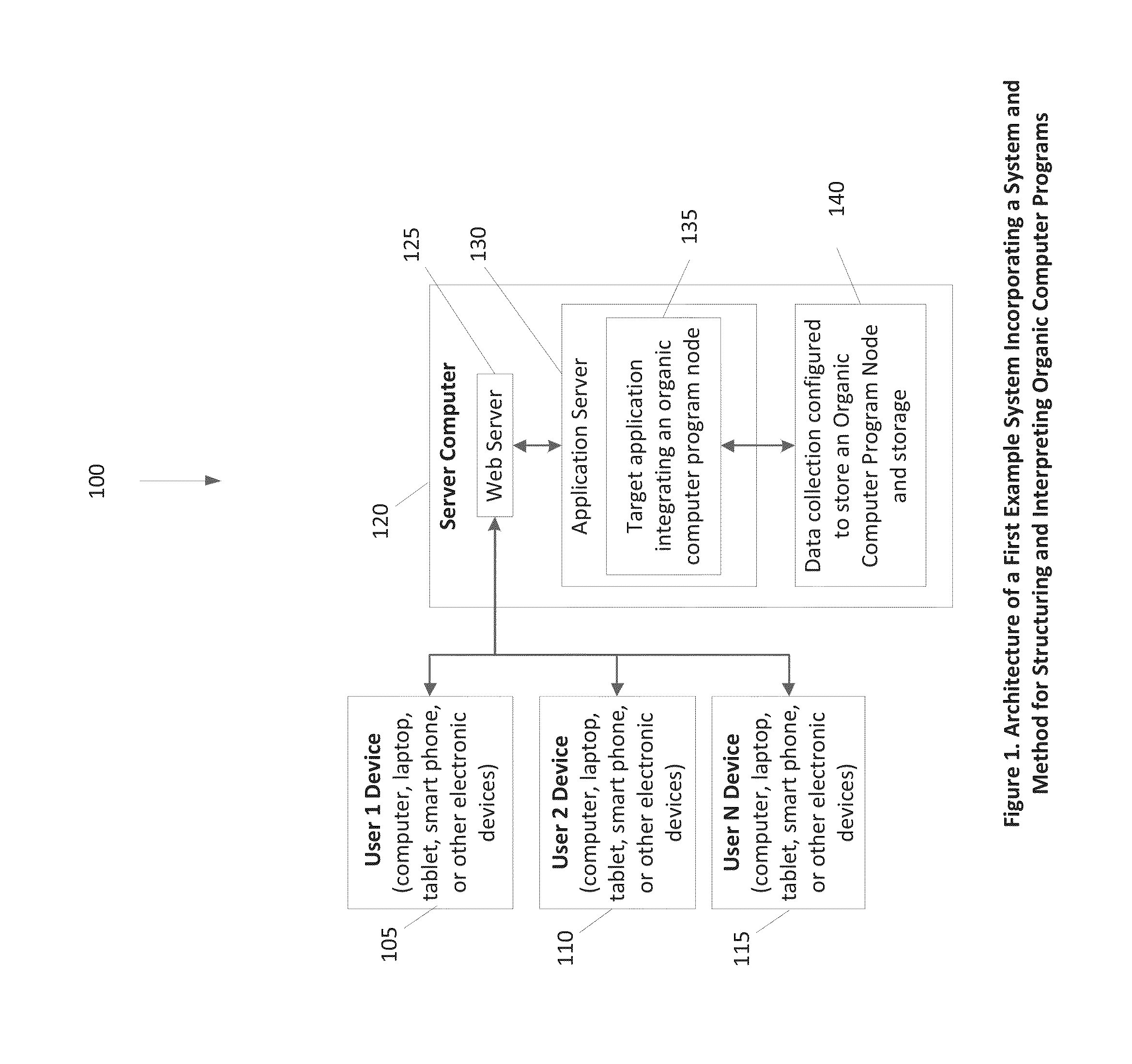
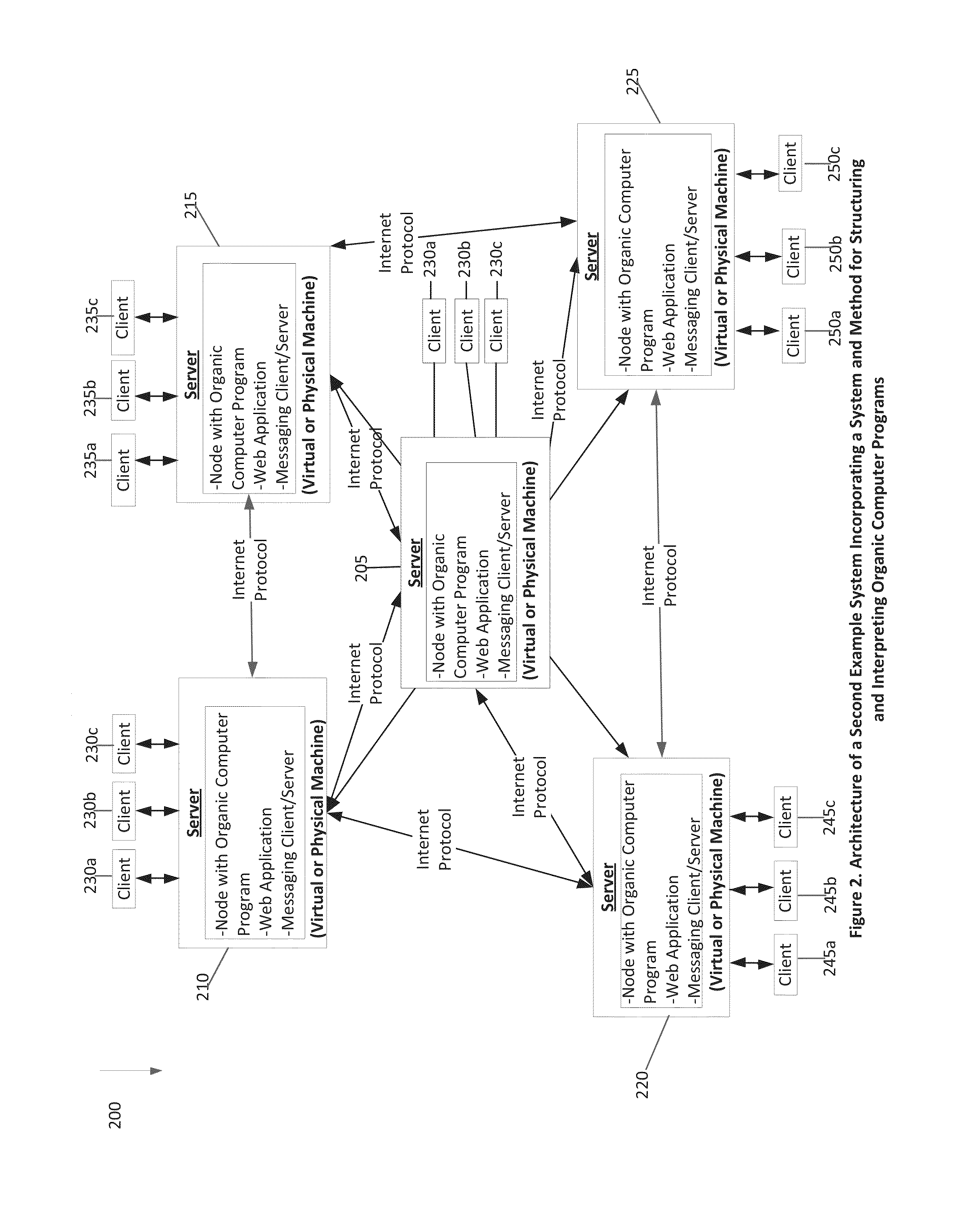
System and method for the structuring and interpretation of organic computer programs
InactiveUS20120254842A1Improve operational capabilitiesImprove computing powerProgram code adaptionSoftware designComputer programmingRunning time
In various aspects, a system and method for structuring and interpreting organic computer programs may provide for programs to expand, grow and evolve analogous to the way plants, animals, and organisms in nature grow and evolve. The organic computing system and method may unify program design time and program run time, may provide for program structure and program state to change at run time, and may provide for programs to continuously change and evolve through the addition of member functions, inputs, and outputs as the program is running. The organic computing system provides continuous means of differentiation, creating asymmetries and the opportunity for competition, and integration, creating symmetries and the opportunity for cooperation. Together, these factors provide a programming system wherein normalization occurs over time through the exchange and integration of differences and evolution and diversification through the creation of new differences, thereby introducing a differential form of computer science.
Owner:SKAI
Method and apparatus for utility computing in ad-hoc and configured peer-to-peer networks
ActiveUS7716286B2Multiple digital computer combinationsOffice automationProgramming languageUtility computing
Owner:ZEROTOUCHDIGITAL
Test program control stream path set creation method based on base path
InactiveCN101216803ASolve the completeness problemSolving automation problemsSoftware testing/debuggingPath generationProgram testing
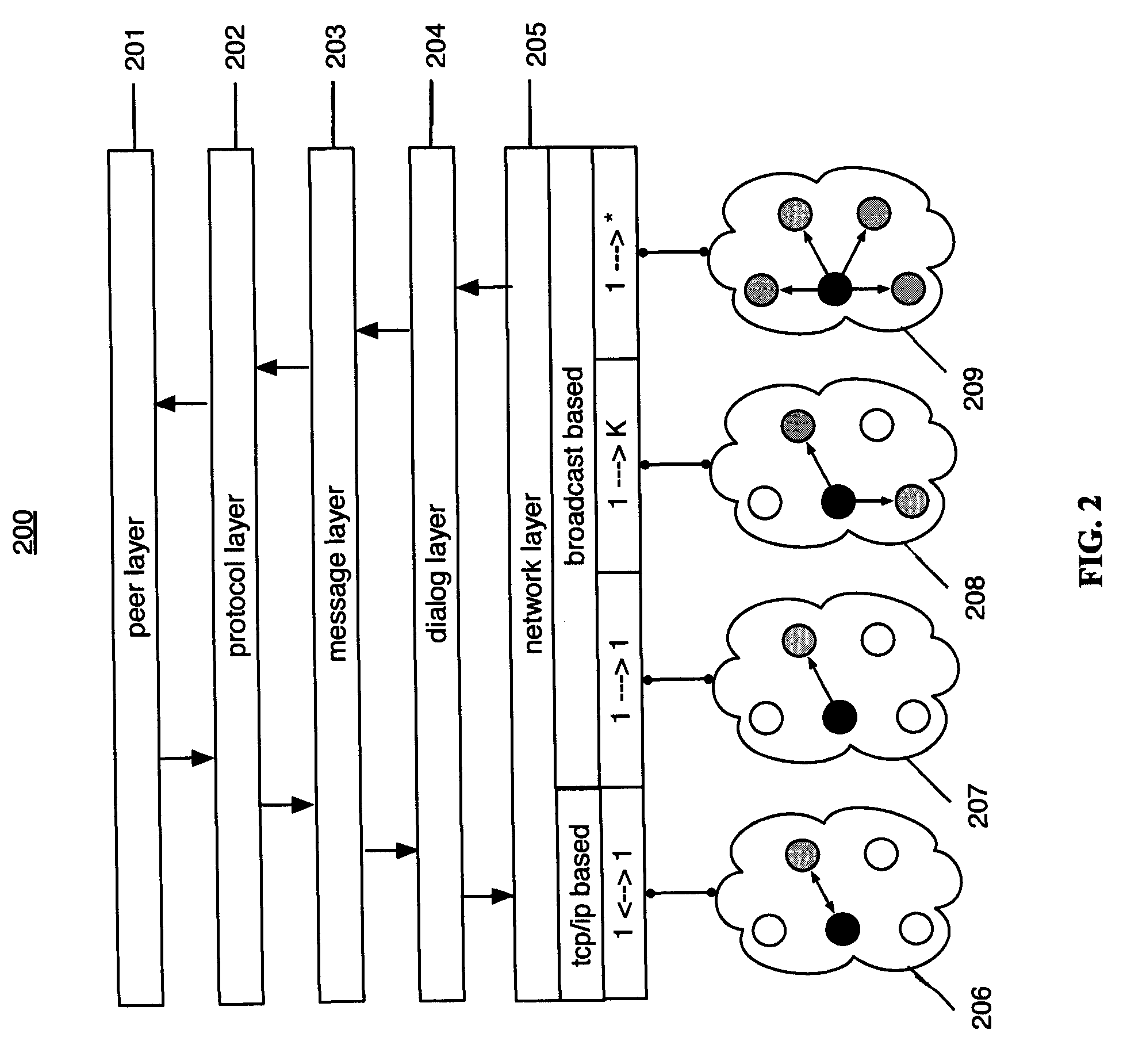
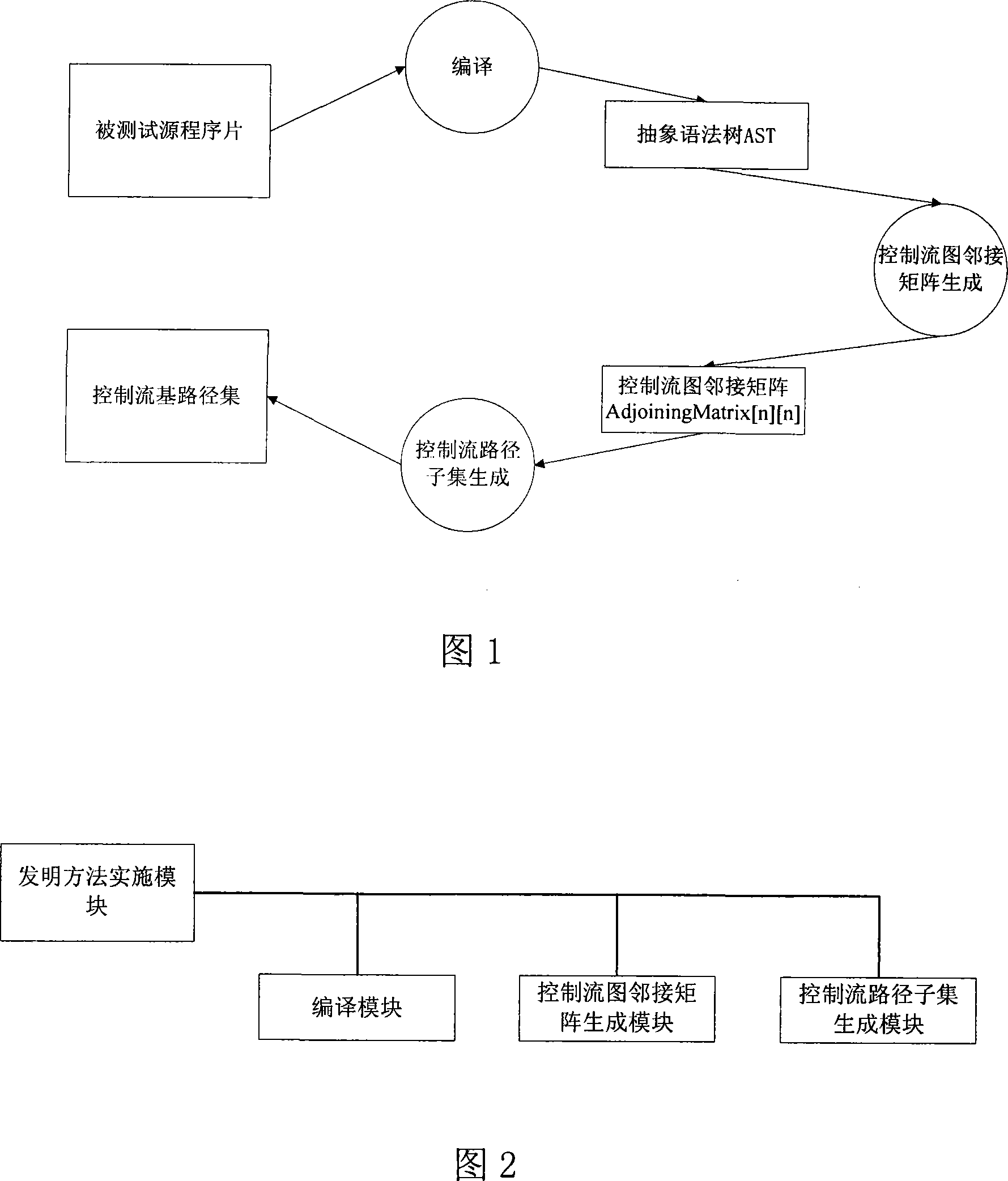
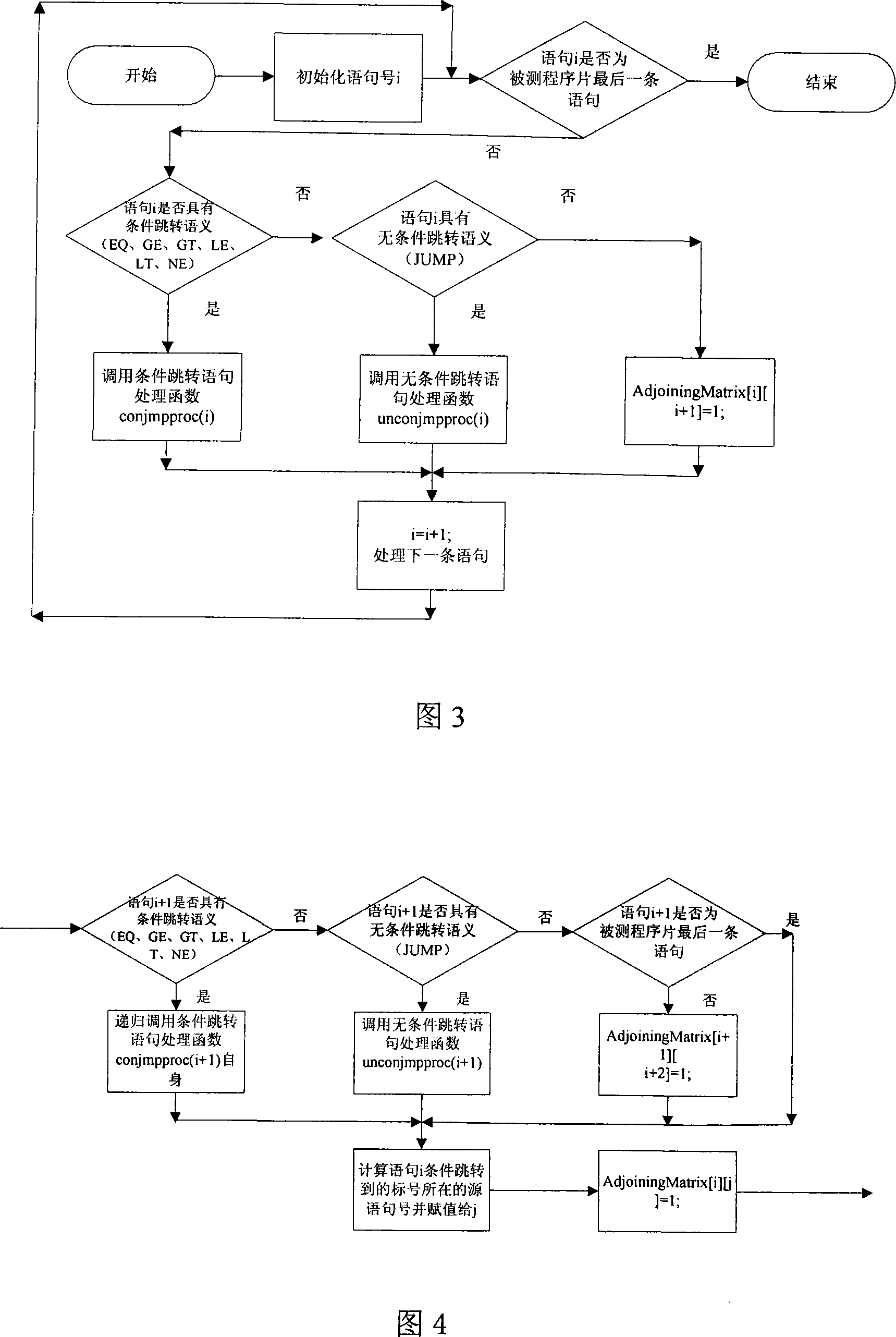
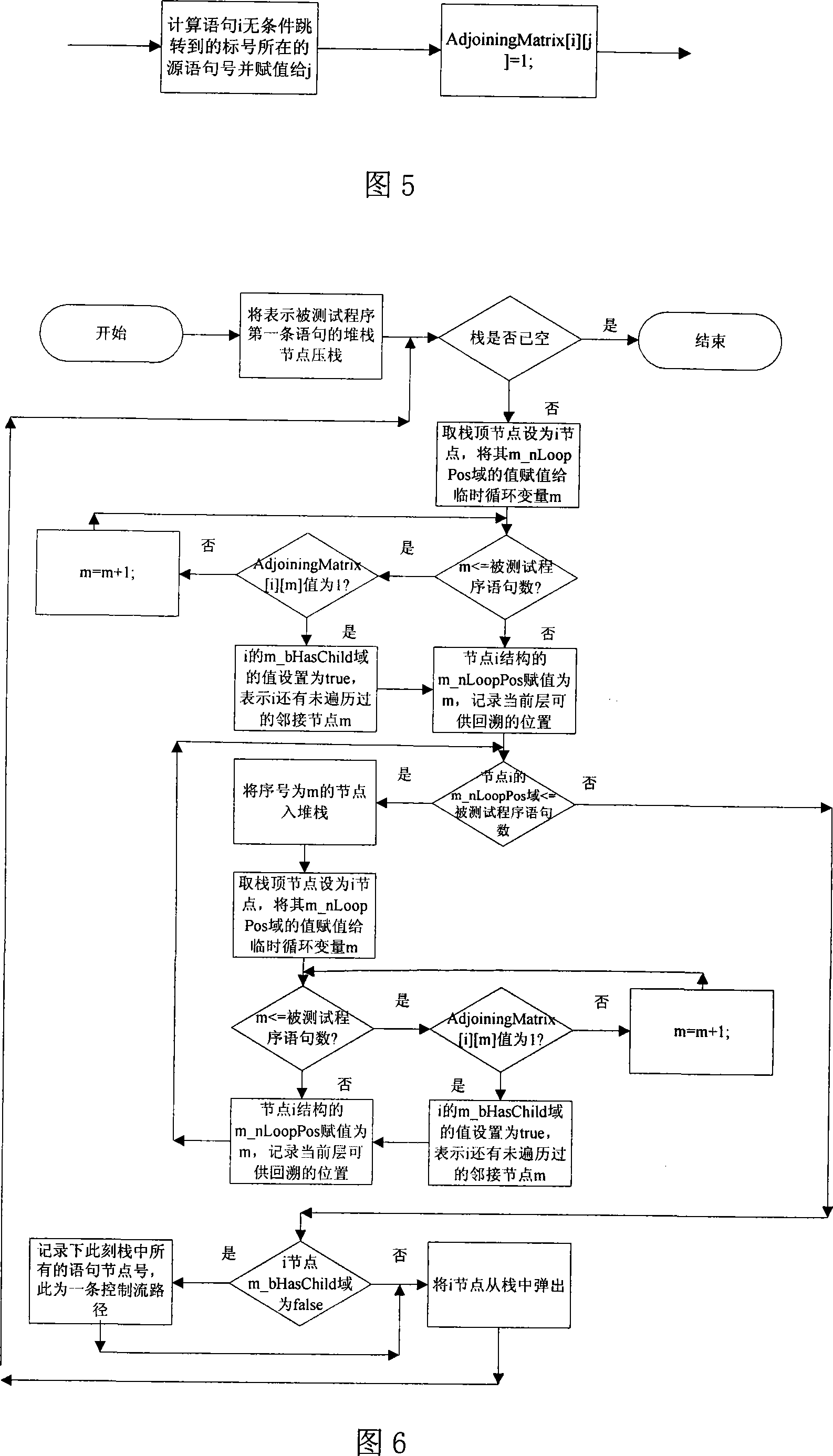
The invention pertains to a path testing in a program testing. The concept of a program control flow base path is defined through bringing in the concept of base in mathematics, a data structure showing a program structure of a source program slice is obtained by using a compiler module first; then through traversing the data structure, a control flow path generating algorithm is utilized to generate a subset compiler module of a program control flow path which is based on a base path to interpret the semanteme on a tested source program, an abstract syntax tree structure showing the structural information of the tested program control flow is output. An adjacency matrix of a control flow graph generates a module ergodicity abstract syntax tree structure, and generates the adjacency matrix representation of a program flow chart. A control flow path subset generating module acquires the control flow information of the tested program through traversing the adjacency matrix, traverses the adjacency matrix by adopting a depth-first multiple backtracking method, and processes sentence nodes, thus a program control flow path subset based on the base path is generated. The method has the outstanding advantages in generating results and flows, and can be widely used in the engineering practice of a path cover testing in a software structure testing.
Owner:SICHUAN UNIV
Image rendering method, image rendering device and electronic device
ActiveCN106997610AAvoid writing directlyImprove development efficiency3D-image renderingComputer graphics (images)Direct writing
Owner:ALIBABA GRP HLDG LTD
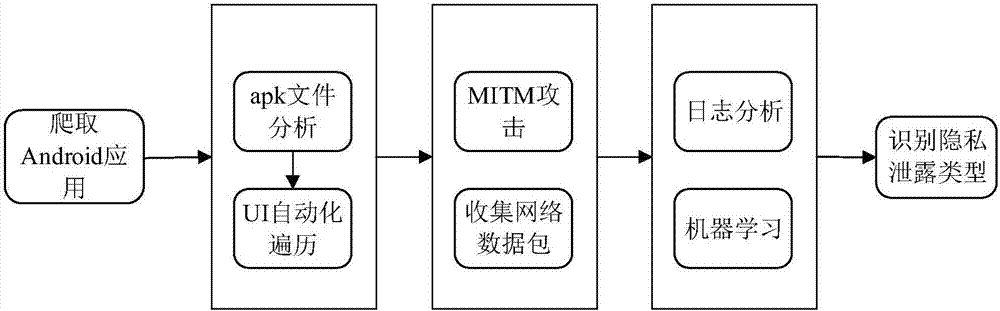
Privacy leaking detecting method and system for android application network communication
ActiveCN107133519AAccurate Privacy Leakage BehaviorAccurate detection of privacy leakage behaviorWeb data indexingPlatform integrity maintainanceMan-in-the-middle attackInternet privacy
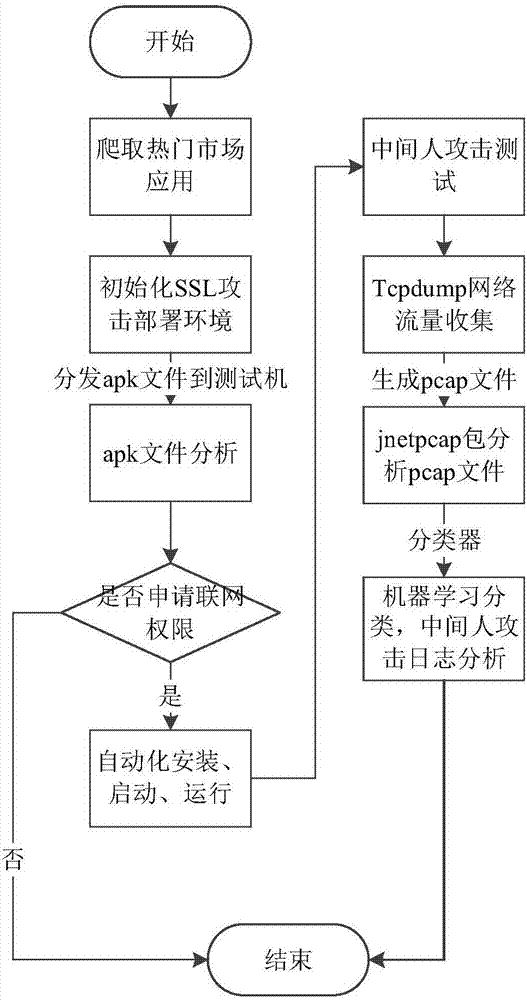
The invention discloses a privacy leaking detecting method and system for android application network communication. The method comprises the following steps: crawling android application to be detected, and building an application set to be detected; building a main-in-the-middle attack server; initializing each tester environment; arranging a multi-tester distributive running scheduling system; analyzing APK files of the application to be detected; installing the application program corresponding to the APK file, and driving the application program to run; analyzing a log file created by the Burp Suite, and acquiring the application set with SSL man-in-the-middle attack; analyzing a network data pack file created in the running process of the collected application program; recognizing the privacy leaking type of the network data pack file according to the application set with the SSL man-in-the-middle attack. The method is flexible to use, and automatic in the whole process; the android system and the android application program structure are not modified; the privacy leaking behavior of the android application in the network communication process can be safely and accurately detected.
Owner:HUAZHONG UNIV OF SCI & TECH
Method and system for automatically generating codes through classification and configuration
InactiveCN102722372AReduce workloadShorten development timeSpecific program execution arrangementsStructure of Management InformationComputer module
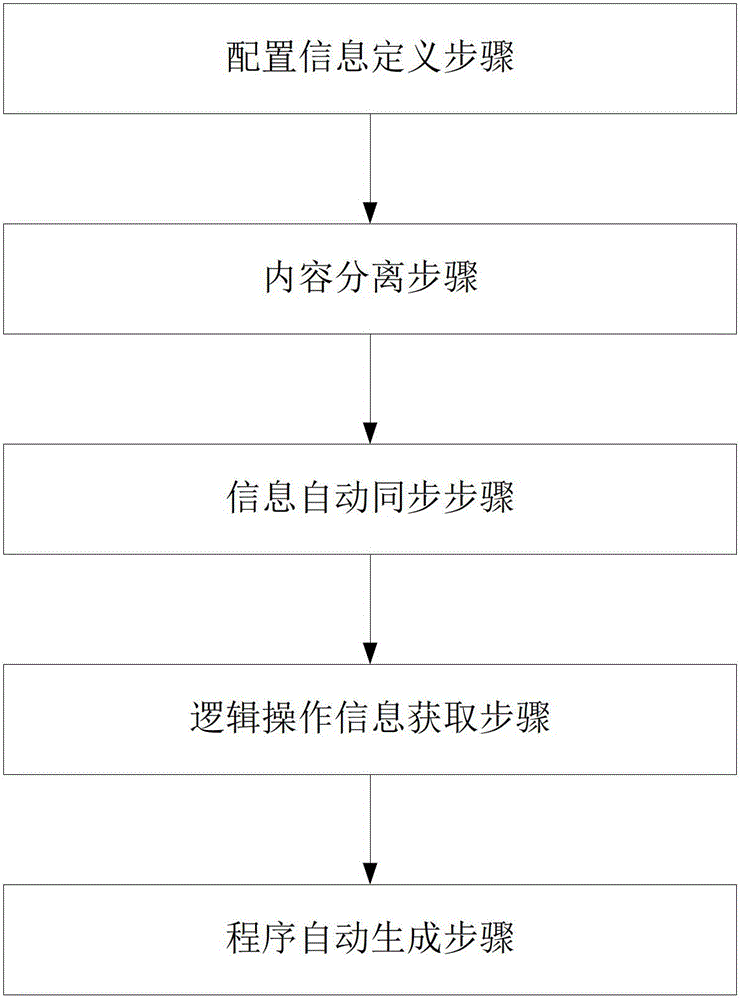
The invention discloses a method and a system for automatically generating codes through classification and configuration. The method for automatically generating codes through classification and configuration comprises the following steps: recording functions of a system menu, a module, functions of each module, and definition and classification of interface content of each module; separating contents of a View layer and a Model layer in the three-layer structure of a model view controller (MVC) of the entire system program structure into files corresponding to every database table; setting a special data binding mechanism to realize the automatic synchronization of presentation content of the View layer and the data of the Model layer according to the configuration information; and enabling a Controller layer to obtain the necessary information of various kinds of logic operation of the present modules according to the configuration information through the synchronization mechanism of the View layer and the Model layer so as to accomplish the realization of the public operation, and expanding Controllers to realize the similar logics. The method and the system disclosed by the invention can automatically generate program codes according to the configuration record, greatly reduce the workload and the development time of the entire software develop period, and greatly enhance the quality of a target system at the same time.
Owner:SHANGHAI XUEZHI TECH
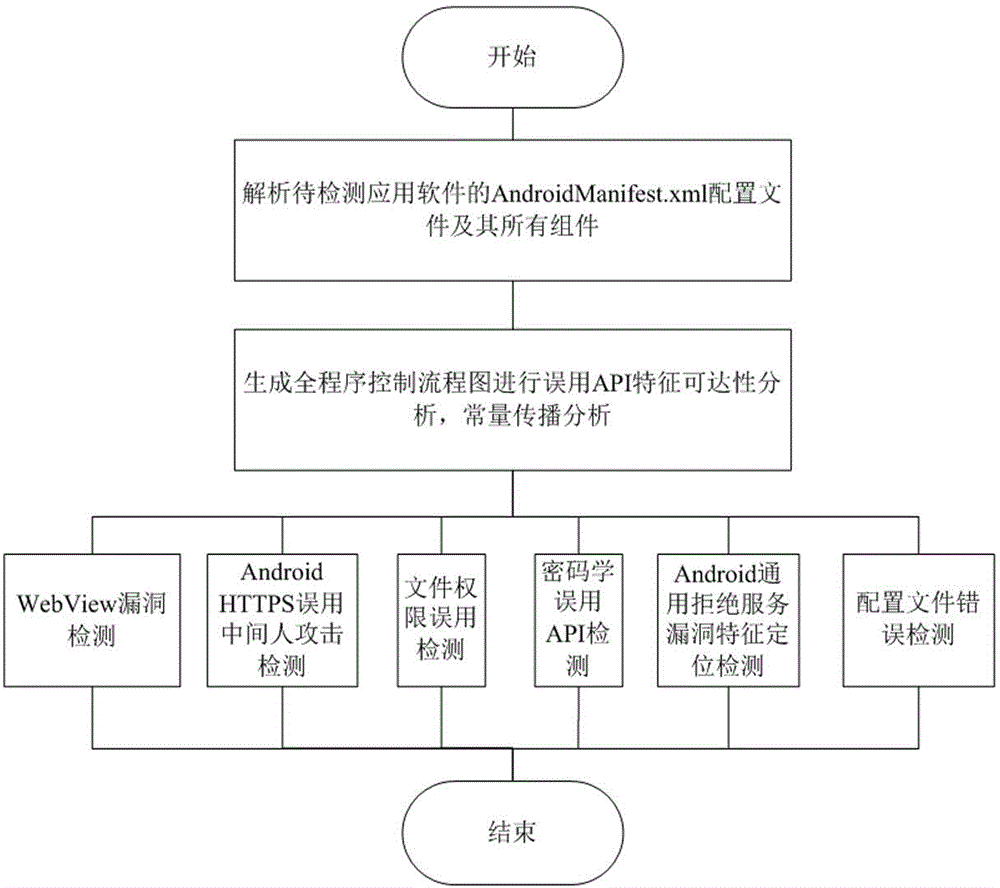
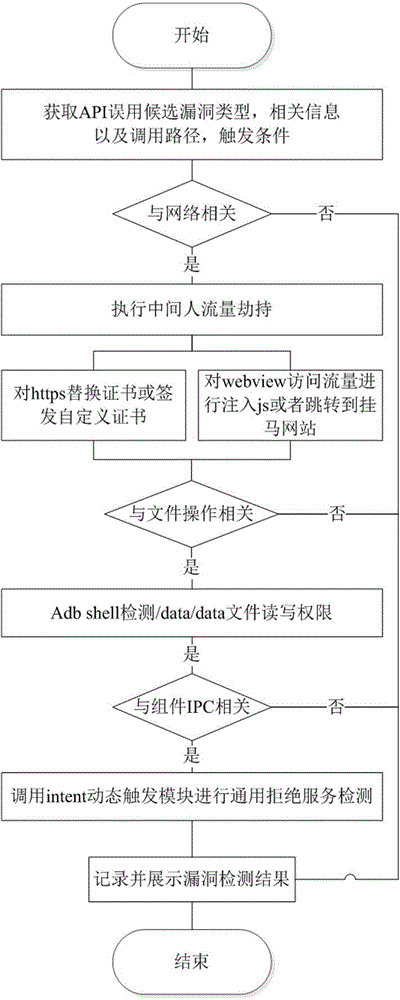
Automatic detection method of API (Application Program Interface) misuse-type bug of Android application software
InactiveCN104933362AImprove detection efficiencyReduce false alarm ratePlatform integrity maintainanceApplication programming interfaceProcedural approach
The invention relates to an automatic detection method of an API (Application Program Interface) misuse-type bug of Android application software. The automatic detection method comprises static analysis and dynamic analysis, wherein the main content of the static analysis comprises the following steps: modeling by combining with the characteristics of the Android application software to construct a full-program control flow chart, and combining with program structure traversal to carry out API misuse accessibility analysis and constant transmission analysis to screen a candidate suspect bug; and the main content of the dynamic analysis comprises the following steps: aiming at different types of bugs to design different modules to carry out bug triggering on the candidate suspect bug obtained by the static analysis, recording the behavior of the candidate suspect bug, and finally giving the bug security evaluation of an application. The automatic detection method adopts a mode of dynamic and dynamic combination to detect the existing API misuse-type bug, reduces a false alarm rate of static detection on the market, and simultaneously improves a coverage rate of dynamic detection.
Owner:FUZHOU UNIV
Software building support system
InactiveUS6966050B2Efficiently building and managing and reusingSoftware designVisual/graphical programmingSupporting systemSoftware engineering
Owner:KK TOSHIBA
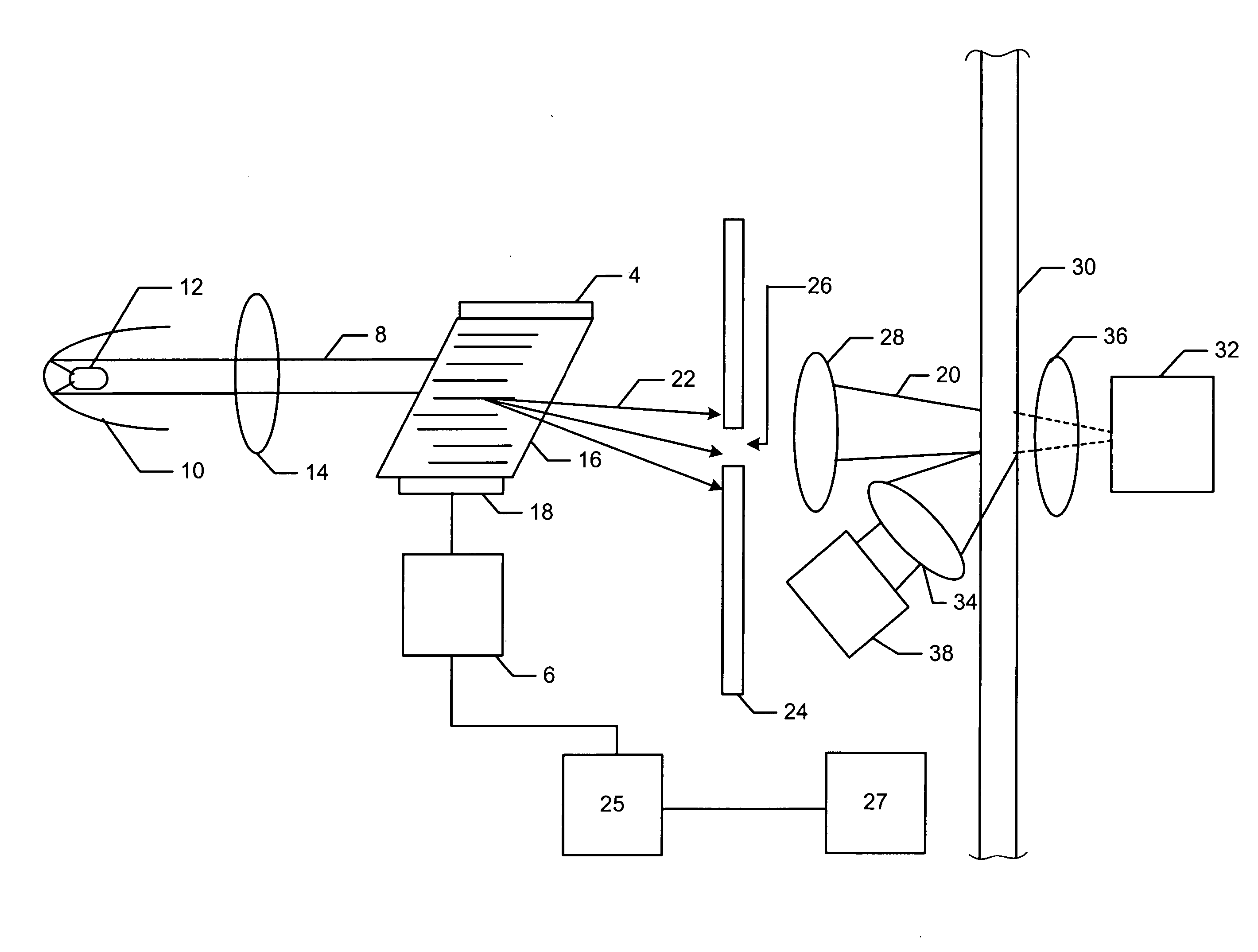
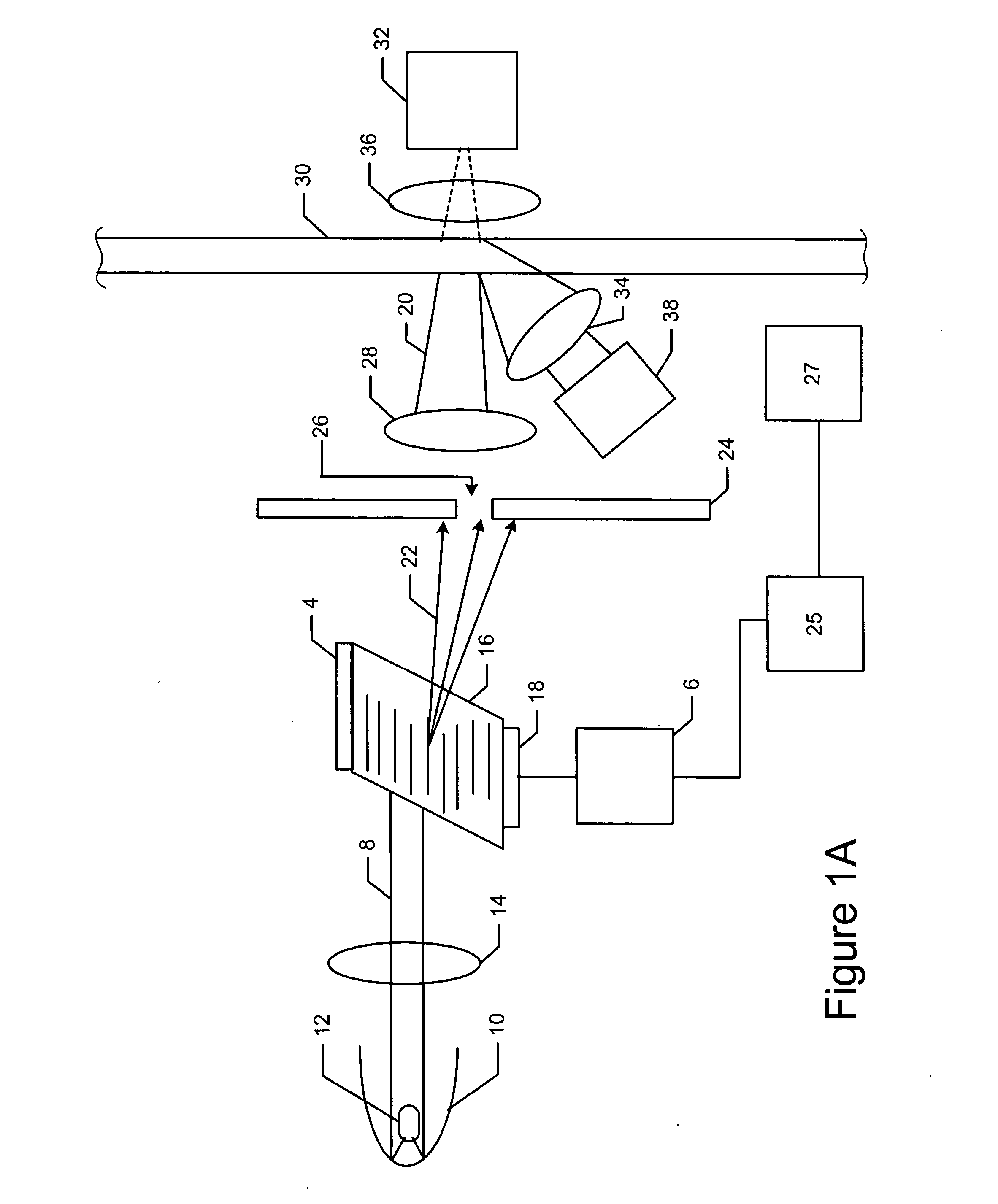
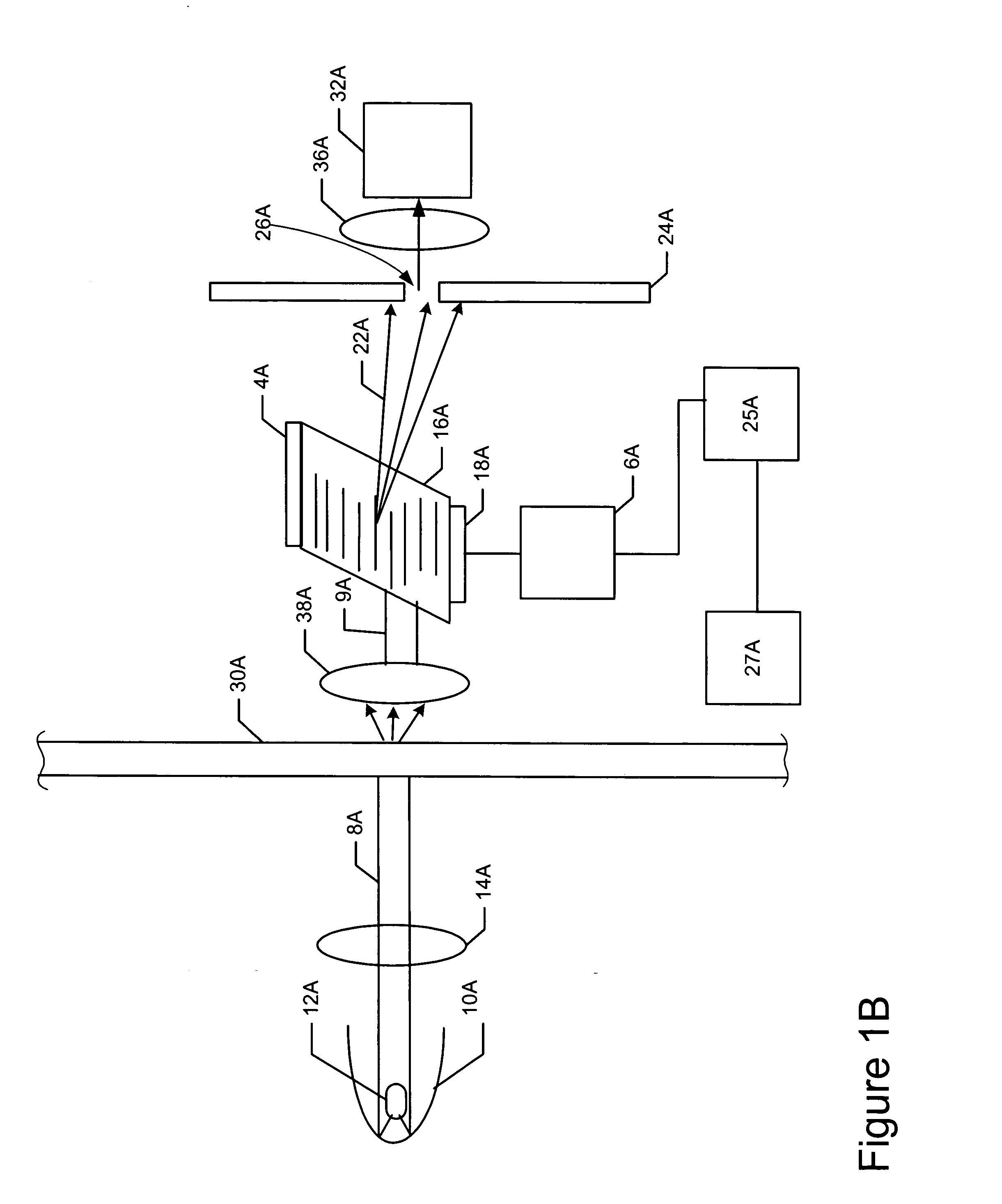
Sensor and methods for measuring select components in sheetmaking systems
ActiveUS20060132796A1Easy to adjustRadiation pyrometrySpectrum investigationLight beamAcousto-optics
An efficient and versatile spectrometric sensor can be configured with an acousto-optic tunable filter. With this diverse spectral filter, the central wavelength and bandwidth of the filter can be quickly tuned to the desired wavelength. A sensor, for measuring at least selected component in a composition, can include: (a) a broadband light source, (b) an acousto-optic tunable filter (AOTF), (c) means for generating a beam of light from the light source and directing the beam of light at the AOTF wherein the AOTF is tuned to pass detection light having a desired wavelength range to detect the presence of the at least one component in the composition, (d) means for directing the detection light of known wavelength to the composition, (e) detection means for receiving light that emerges from the composition, and (f) a program structure that is coupled to the AOTF, the program structure capable of providing the AOTF with at least one desired wavelength range that is characteristic of the least one component in the composition. In addition, the device can be configured so that the AOTF is on the detection side of the sensor. The sensors can be used to measure the thickness of optically transparent films.
Owner:HONEYWELL INT INC
System, method and software for static and dynamic programming and configuration of an adaptive computing architecture
ActiveUS7200837B2Architecture with single central processing unitSpecial data processing applicationsInterconnectionSelf adaptive
The present invention provides a system, method and software for programming and configuring an adaptive computing architecture or device. The invention utilizes program constructs which correspond to and map directly to the adaptive hardware having a plurality of reconfigurable nodes coupled through a reconfigurable matrix interconnection network. A first program construct corresponds to a selected node. A second program construct corresponds to an executable task of the selected node and includes one or more firing conditions capable of determining the commencement of the executable task of the selected node. A third program construct corresponds to at least one input port coupling the selected node to the matrix interconnect network for input data to be consumed by the executable task. A fourth program construct corresponds to at least one output port coupling the selected node to the matrix interconnect network for output data to be produced by the executable task.
Owner:CORNAMI INC
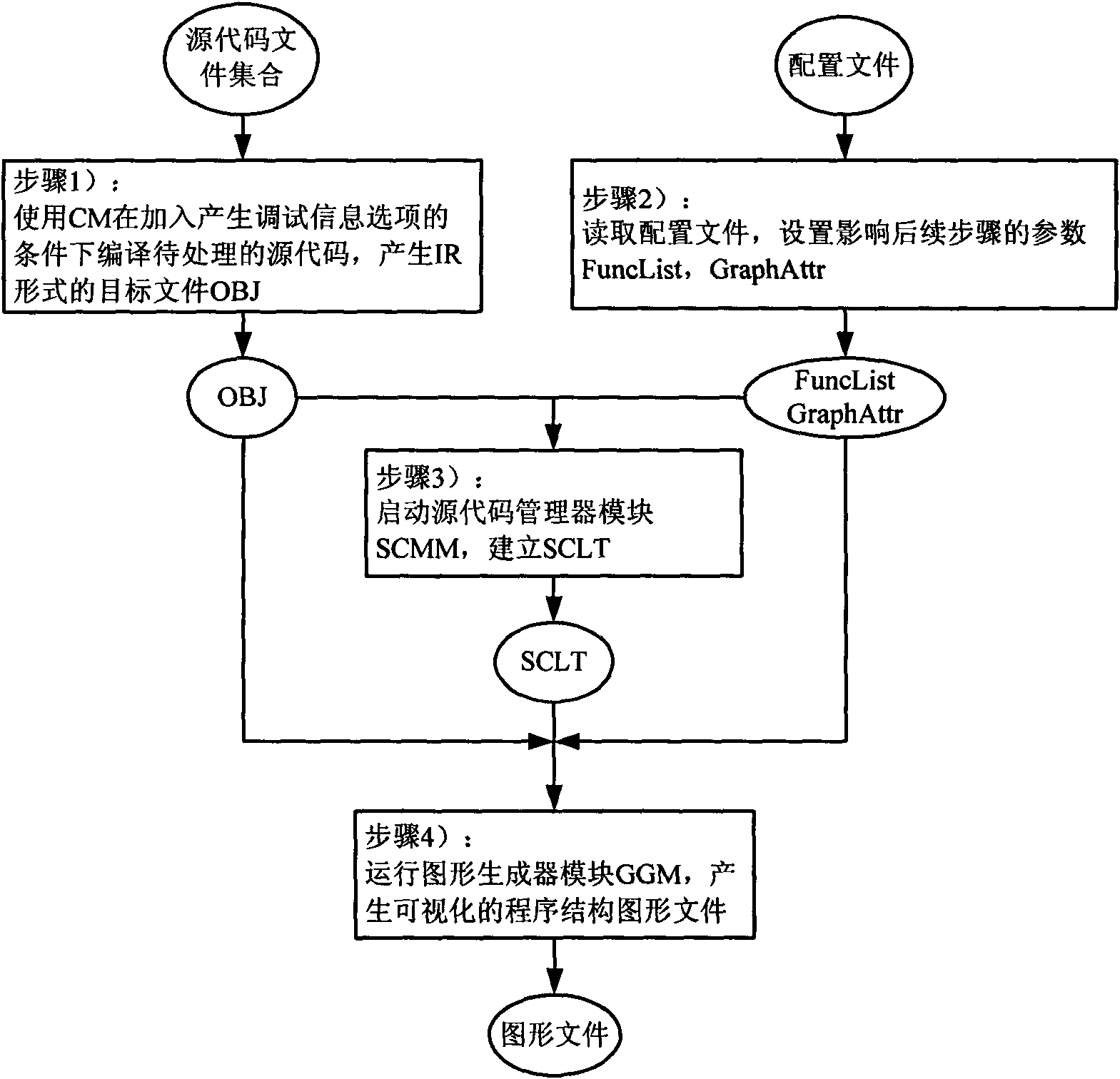
Visualizing method of source code level program structure
InactiveCN101650651AIntuitively understand the structureStrong structural analysis abilitySpecific program execution arrangementsMemory systemsControl flowExtensibility
The invention discloses a visualizing method of a source code level program structure. The method can analyze morphology, syntax and semanteme of a source code programmed by different programming languages, can analyze the program structure in deep level, and can display the information of various analysis structures, such as a function call graph, a control flow chart, a data flow graph, a strongly communicated region and a dominator tree, at the source code level in a graphical form. Compared with the prior visualizing method aiming at specific programming languages and only displaying the control flow, the method has better universality and extensibility and has stronger program structure analysis capability.
Owner:ZHEJIANG UNIV
Method and apparatus for utility computing in ad-hoc and configured peer-to-peer networks
ActiveUS20090259720A1Multiple digital computer combinationsOffice automationProgramming languageUtility computing
Executing a program structure by leveraging a peer-to-peer network comprises generating a program structure comprising a plurality of program instructions. A first of a plurality of network peers then executes a portion of the program instructions which initiates the execution of code hosted by said first network peer, where said portion comprising fewer than all program instructions. The first network peer then migrates one or more of the program instructions, together with any requisite data, to at least one other of the plurality of network peer. The at least one other network peer then continues execution of the program structure until one or more of the objections of the program structure are achieved.
Owner:ZEROTOUCHDIGITAL
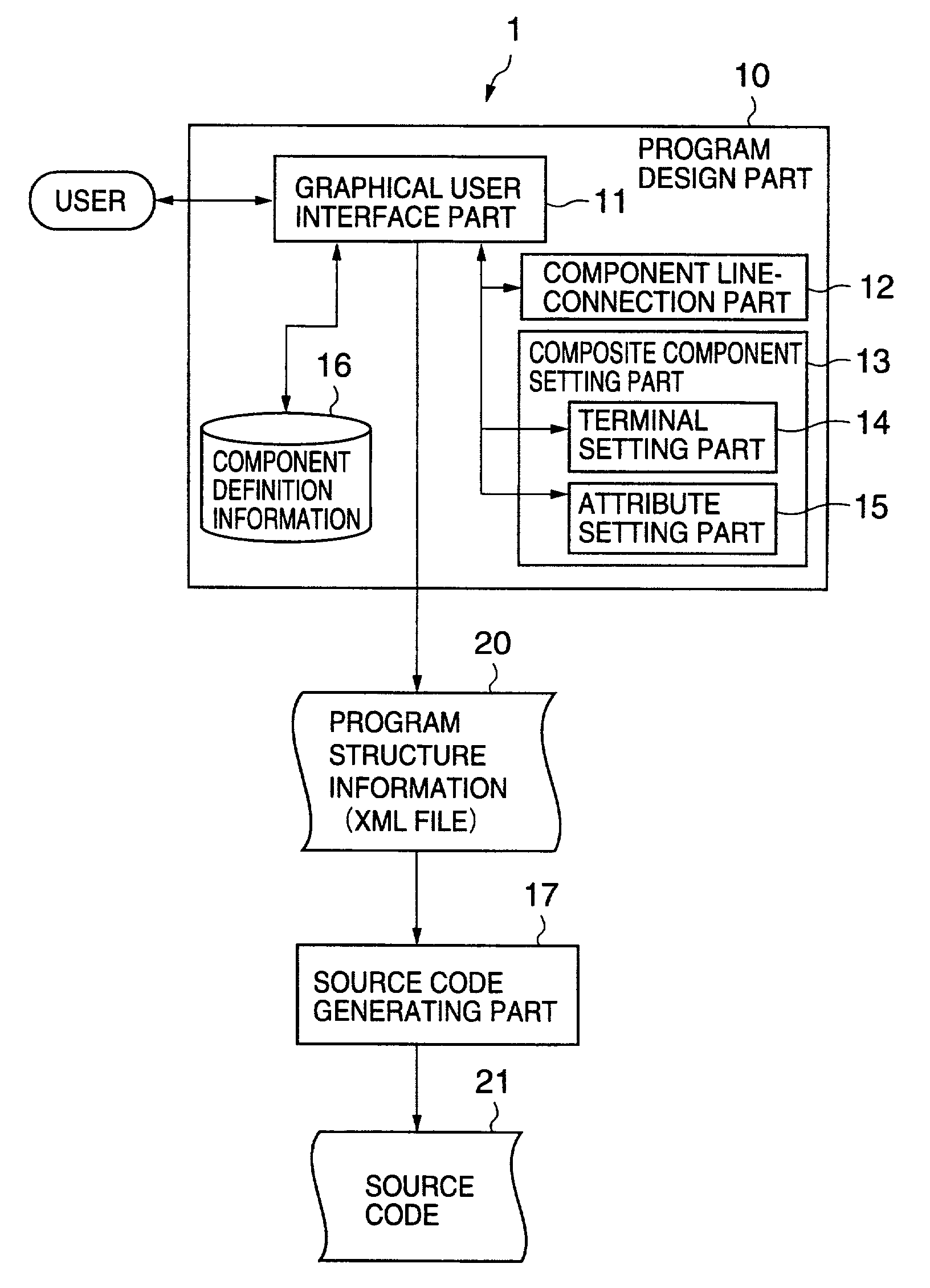
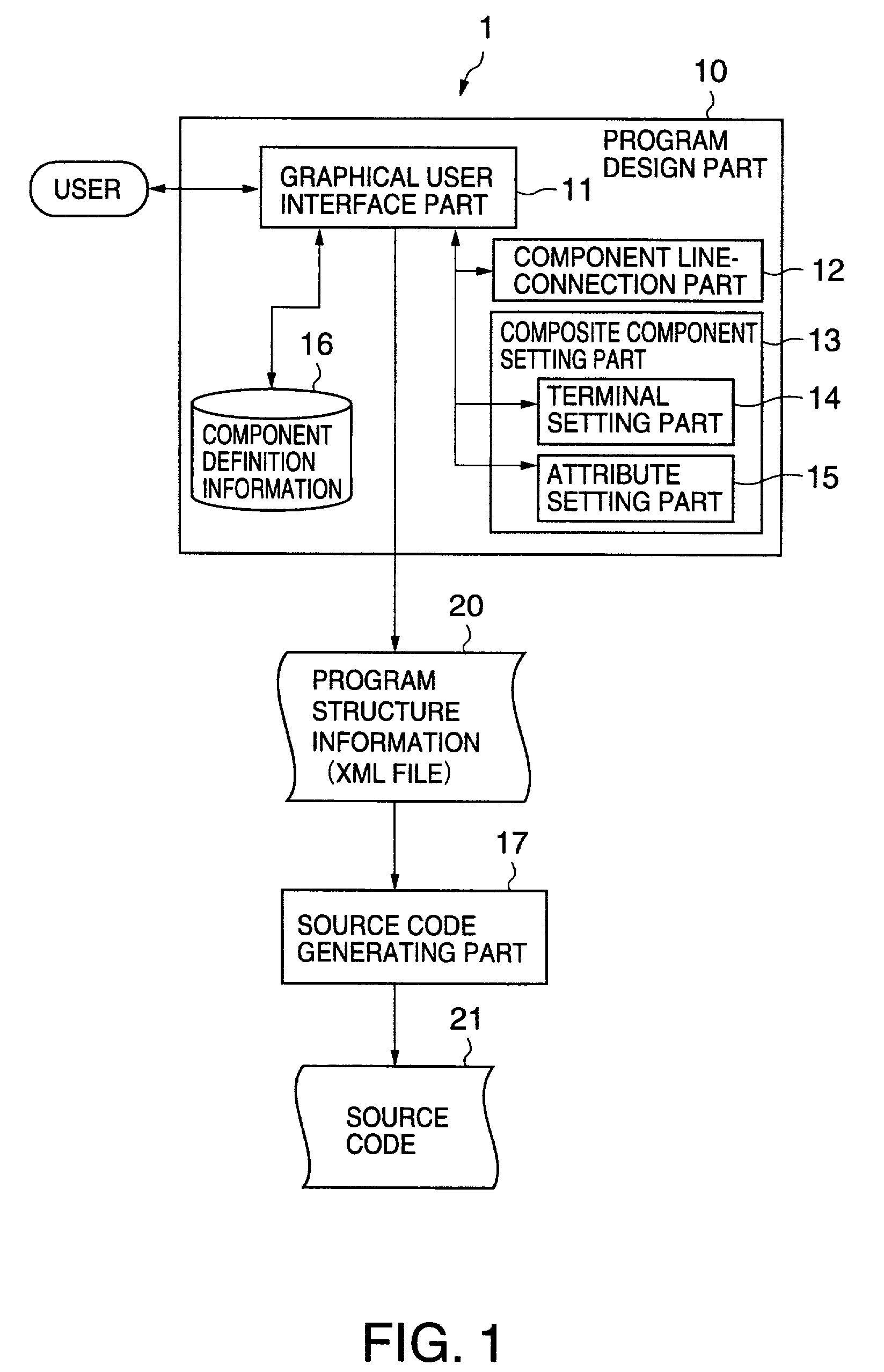
Orchestration designer
InactiveUS20050015746A1Visual/graphical programmingSpecific program execution arrangementsProgramming languageSemantics
The present invention supports the design of a process using a drawing surface that specifies the process with underlying programmatic constructs. In response to a user's command, a construct corresponding to a shape is selected from a palette and inserted onto a design region that shows the specified process. The command is verified to be consistent with semantics of an associated process type. If so, a visual image of the specified process is updated. If not, an indicator is generated in a proximity of a relevant portion of the visual image in order to help the user resolve the inconsistency. The user is able to correct errors before generating computer-executable instructions from a high-level code emission. Computer-executable instructions are also generated from high-level code emission. A process engine is cognizant of the associated high-level lines of code and an infrastructure knowledge base while executing the computer-executable instructions.
Owner:MICROSOFT TECH LICENSING LLC
Method of using a distinct flow of computational control as a reusable abstract data object
InactiveUS7140018B1Less interactionInterprogram communicationConcurrent instruction executionControl flowParallel processing
A method of parallel processing in which there is first provided a first thread which represents an independent flow of control managed by a program structure, the first thread having two states, a first state processing work for the program structure and a second state undispatched awaiting work to process; and a second thread which represents an independent flow of control managed by a program structure separate from the first thread. The method includes using the second thread to prepare work for the first thread to process and placing the work prepared by the second thread in a queue for processing by the first thread. If the first thread is awaiting work to process when the work prepared by the second thread is placed in the queue, the method includes dispatching the first thread and using it to process the work in the queue. If the first thread is processing other work when the work prepared by the second thread is placed in the queue, the method includes using the first thread to complete processing of the other work, access the work in the queue, and then process the work in the queue.
Owner:IBM CORP
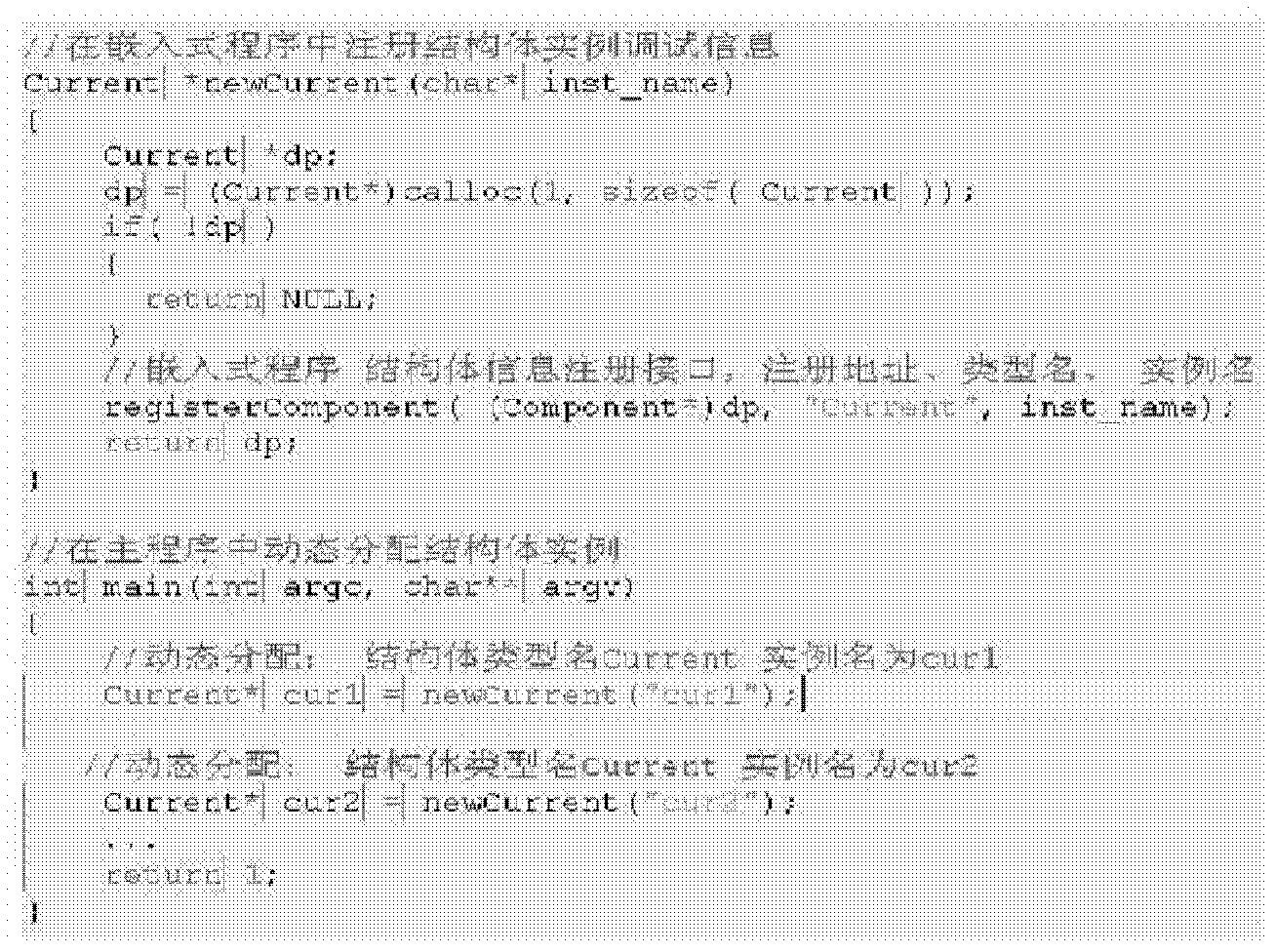
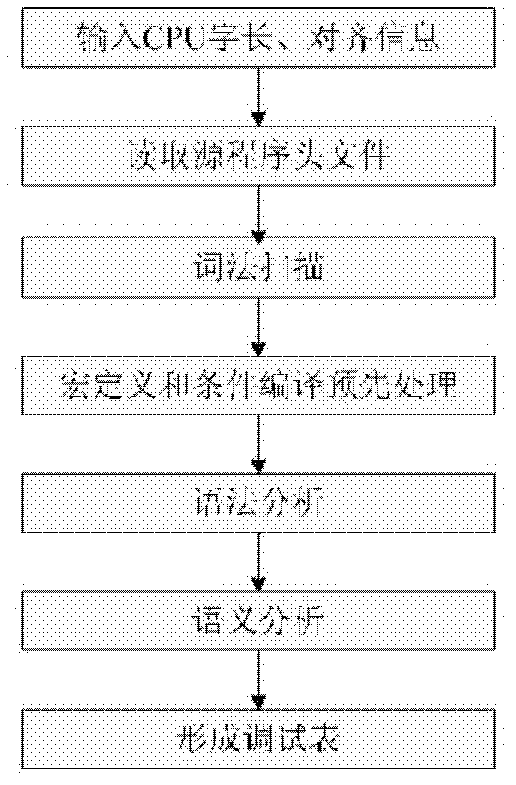
Variable debugging method of embedded program dynamic storage allocation
InactiveCN103136107AImprove diagnostic efficiencyExpand the scope of debuggingMemory adressing/allocation/relocationAnalysis dataMember variable
A variable debugging method of embedded program dynamic storage allocation is characterized in that the logining of an interface of the structural body of an embedded program is achieved, an upper computer is provided with a program sum of debugging the structural body of the embedded program, the communication protocol of the debugging of variables is achieved, the communication protocol is debugged through an upper computer program and the embedded program, the variable name of a level to be debugged is input on an upper computer software by a user, the upper computer software reads program header files, analyzes a data structural body, and calculates the relative offset address and the data type information of each member variable, and a variable debugging table is formed, and is downloaded in a device. The software records a structural body example word address of dynamic application in a constructor, and inquires an relative address according to a debugged level variable name, the structural body word address is added, the absolute address of each member variable is obtained, and the data of the absolute address are accessed and are sent to the upper computer to display. The variable debugging method of the embedded program dynamic storage allocation overcomes the defect that in the past only the global variable of the static allocation of a compiler can be debugged, and improves the diagnosis efficiency of the program.
Owner:NR ELECTRIC CO LTD +1
System and method for the structuring and interpretation of organic computer programs
InactiveUS8631387B2Improve computing powerRobust and flexible environmentProgram code adaptionSoftware designSoftware engineeringComputer programming
Owner:SKAI INC
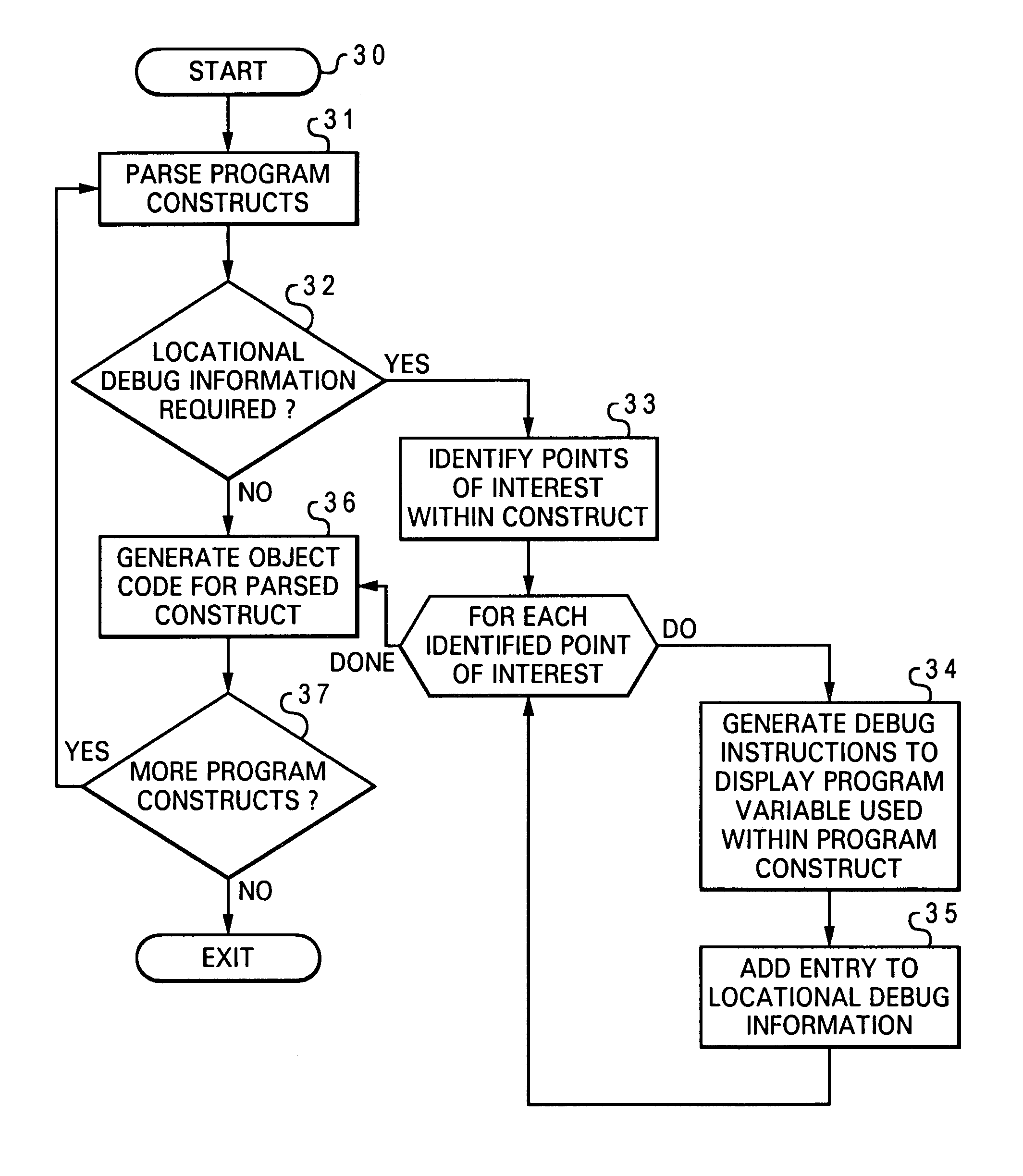
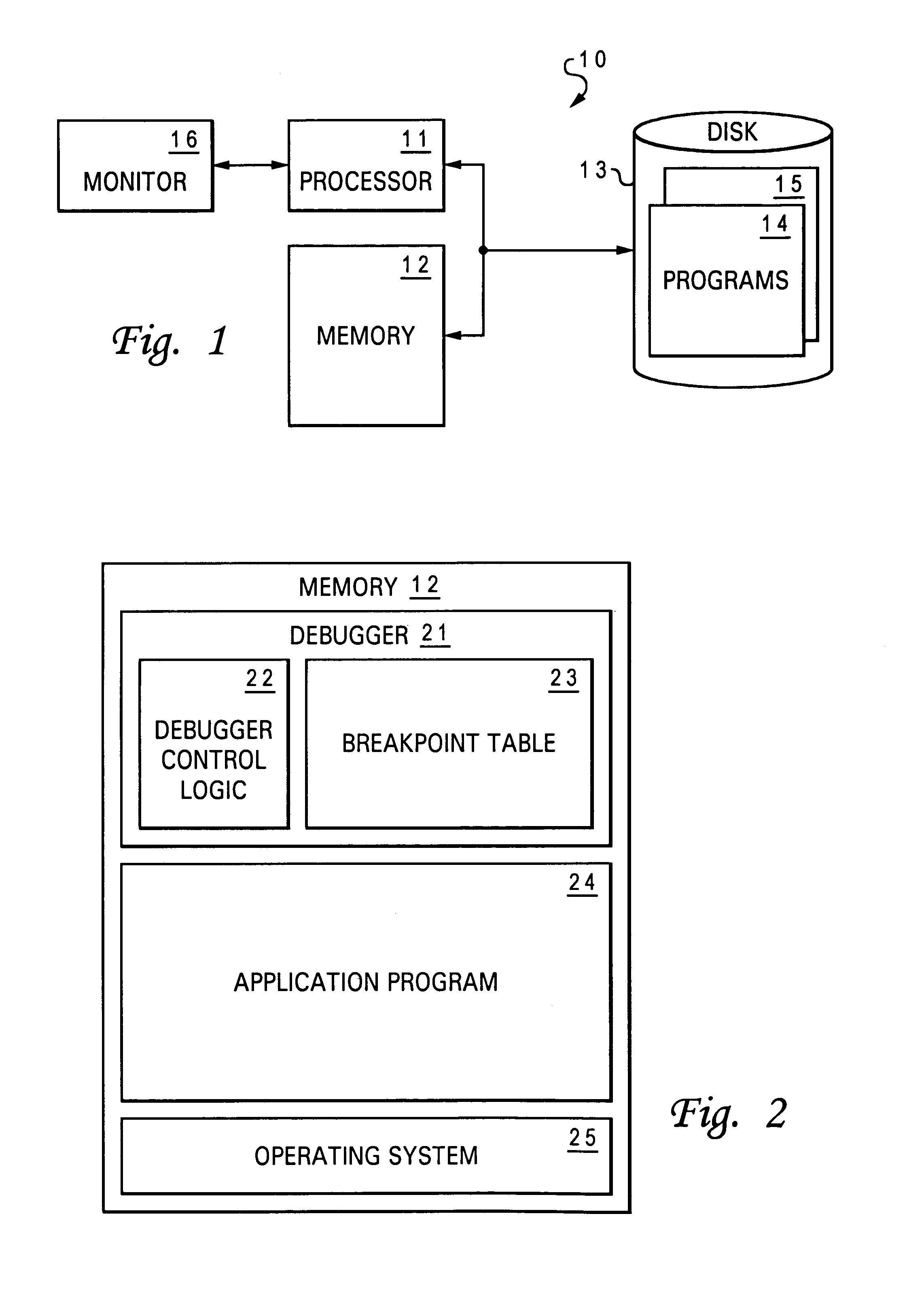
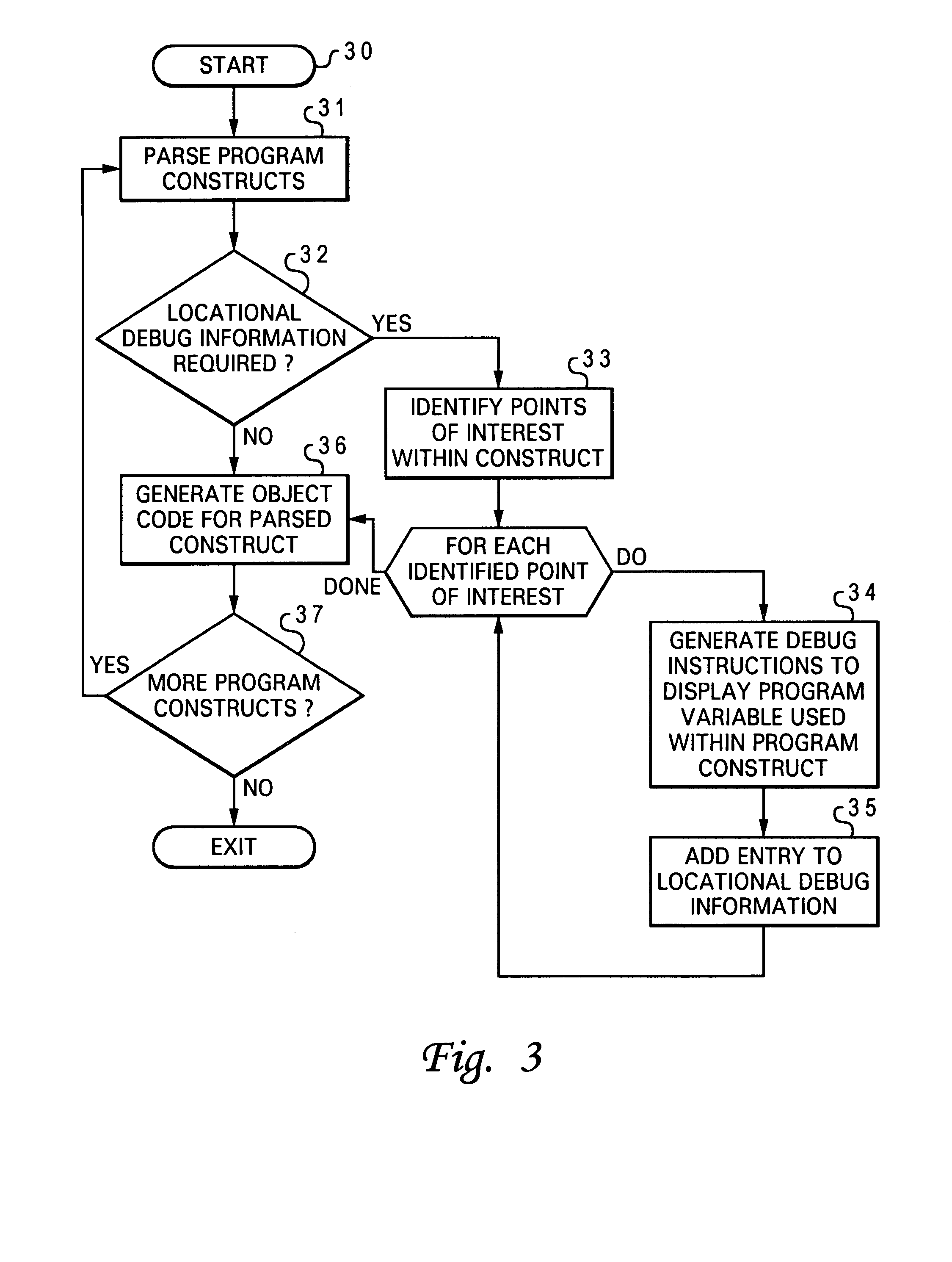
Software debugger having a monitor for monitoring conditional statements within a software program
InactiveUS7086033B2Software testing/debuggingSpecific program execution arrangementsSoftware debuggingDebugger
A software debugger having a monitor for monitoring conditional statements within a software program is disclosed. A program construct is initially identified within a software program. After identifying a point of interest within the program construct, a group of debug instructions is associated with the point of interest within the program construct. In response to a debug stop occurred at the point of interest, the information related to the associated program construct according to the group of debug instructions as a result of executing the instructions within the program construct is displayed.
Owner:INT BUSINESS MASCH CORP
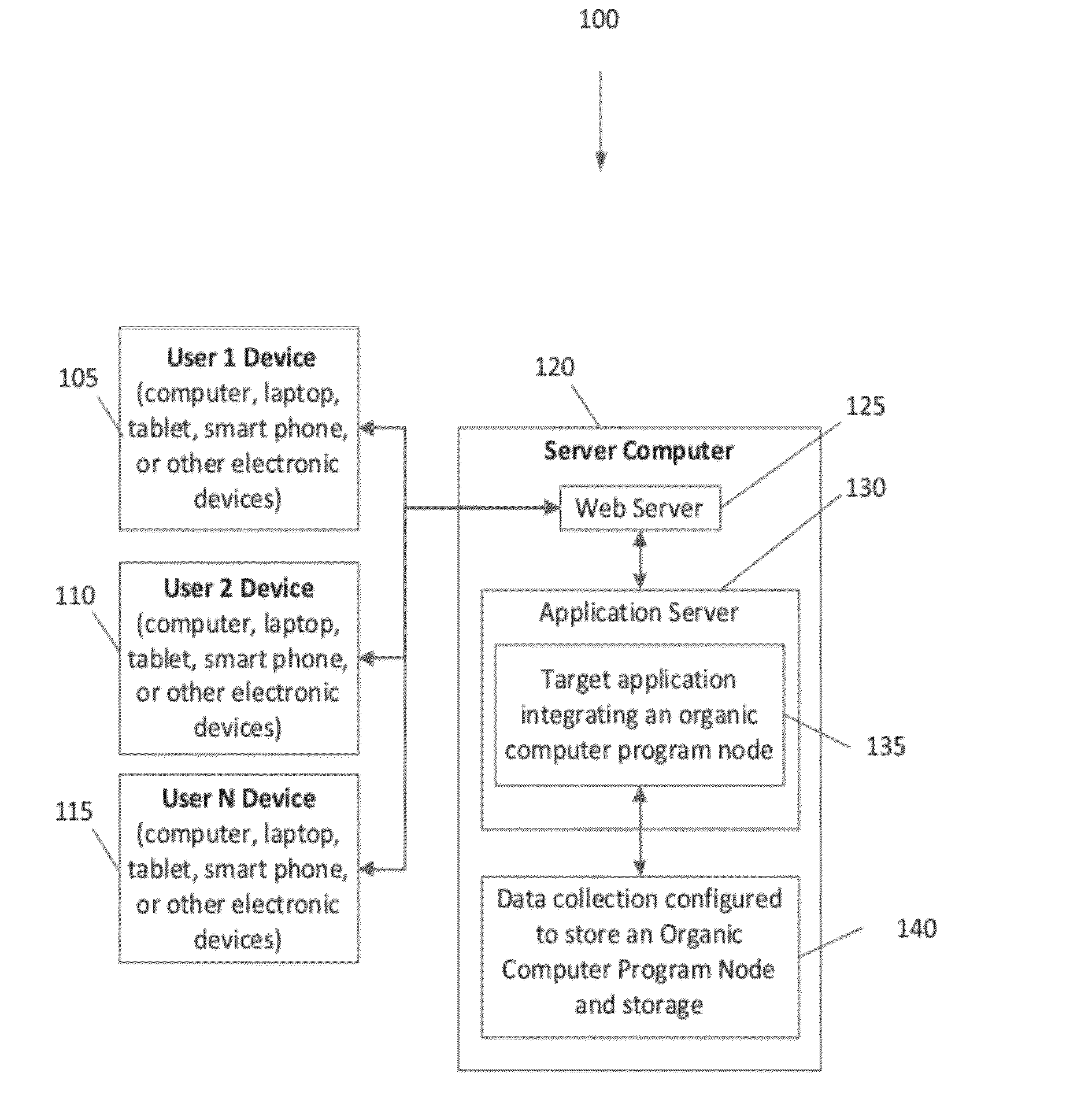
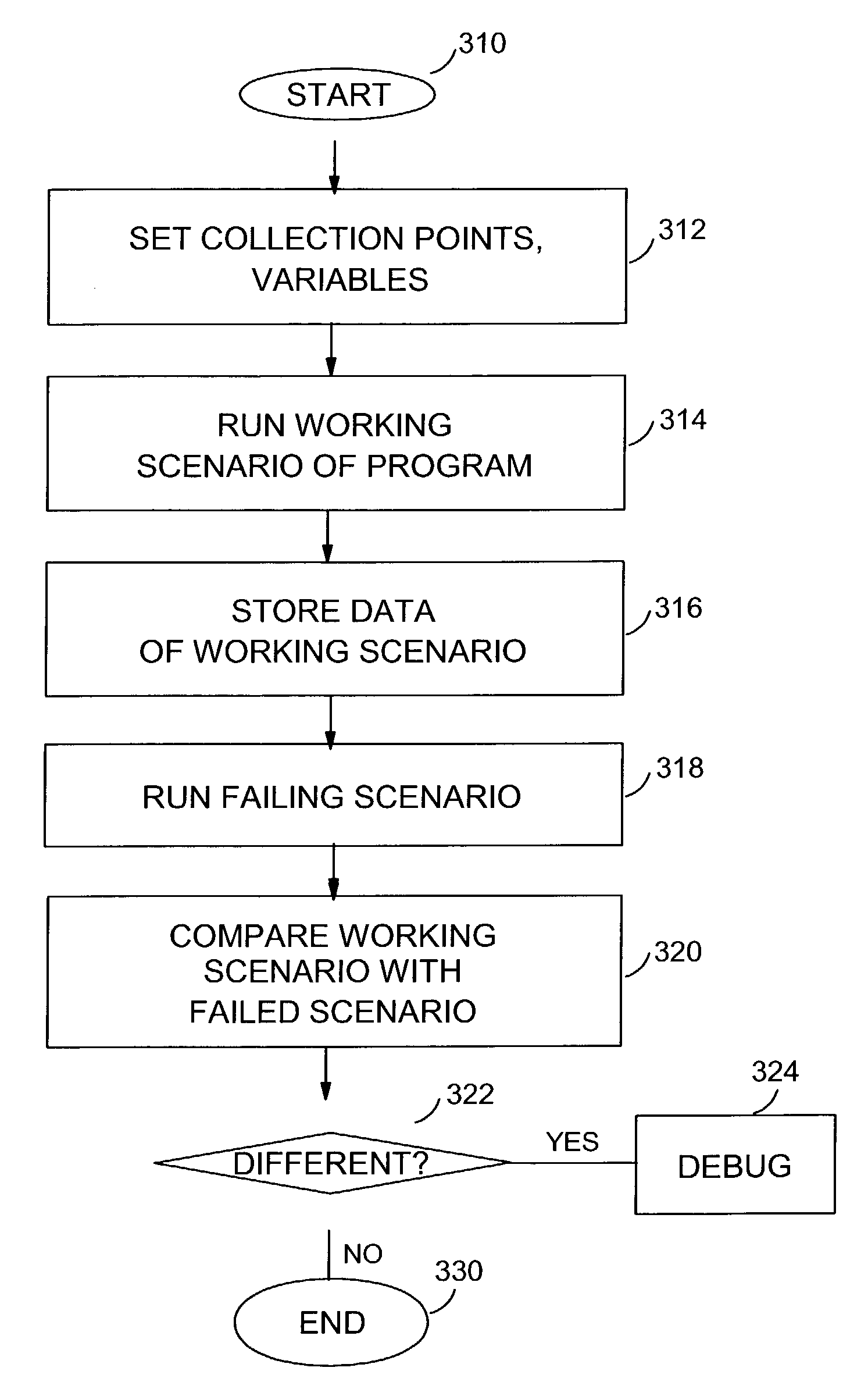
Collection and detection of differences of values of expressions/variables when debugging a computer process
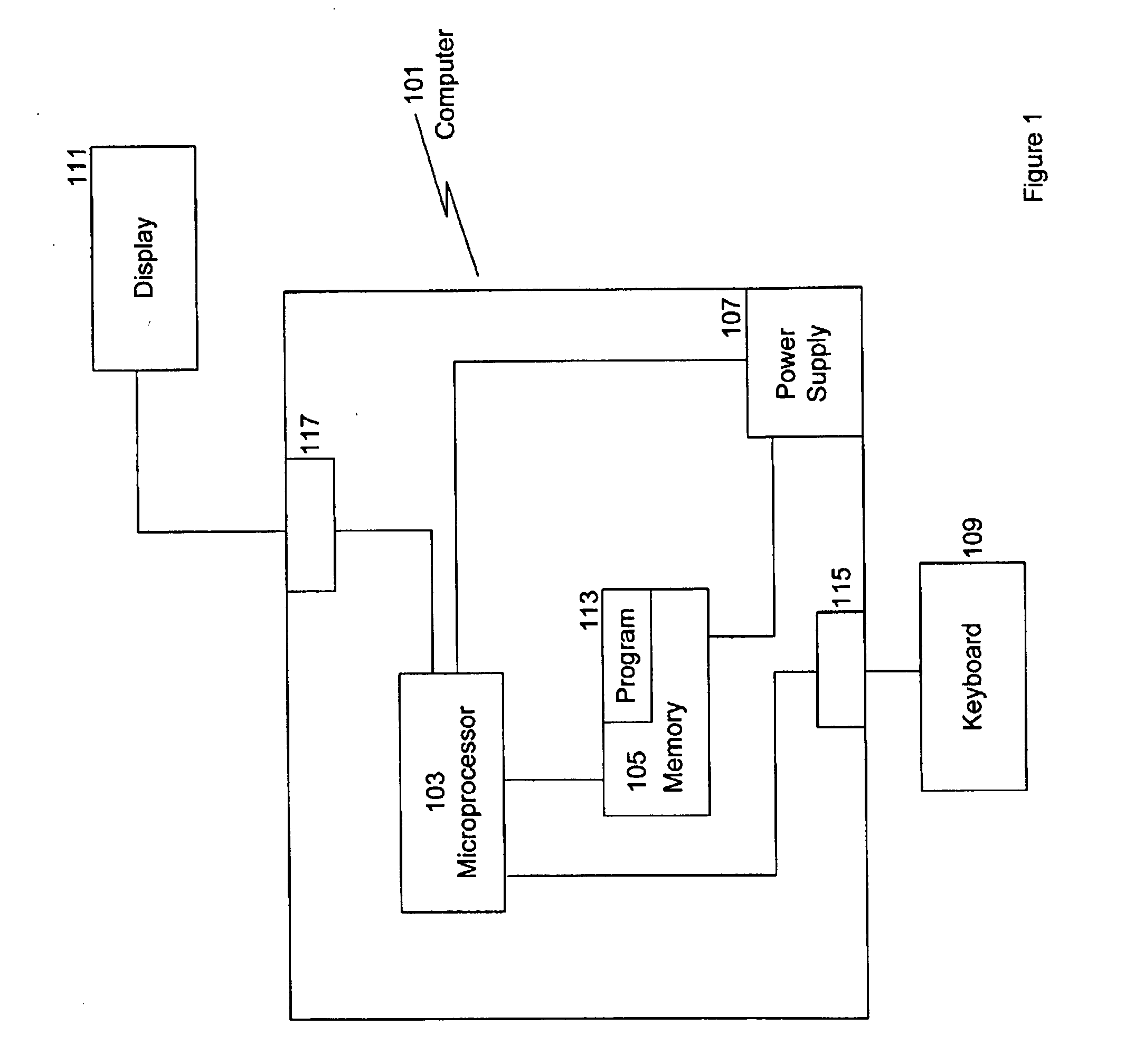
ActiveUS7739664B2Software testing/debuggingSpecific program execution arrangementsProcedure callsExit point
An automated way to detect differences in the values of program variables / expressions and the order of execution between one run and another. A collection mode saves the values of expressions / variables at collection points in the program. On a subsequent execution during the detection mode, these saved values of the same expressions / variables are recalled and compared with the current values. Advantageously, the user selects the collection points within the program at which variable information can be gathered and compared; and these collection points may include: breakpoints set by a debugging program or by the user; collection points set by the user, and entry and / or exit points and / or points within program structures, such as procedure calls, control blocks, etc. Setup of the collection mode includes the capability to modify the expressions / variables, the tolerance or the acceptable alternatives, and the position and number of collection points.
Owner:TWITTER INC
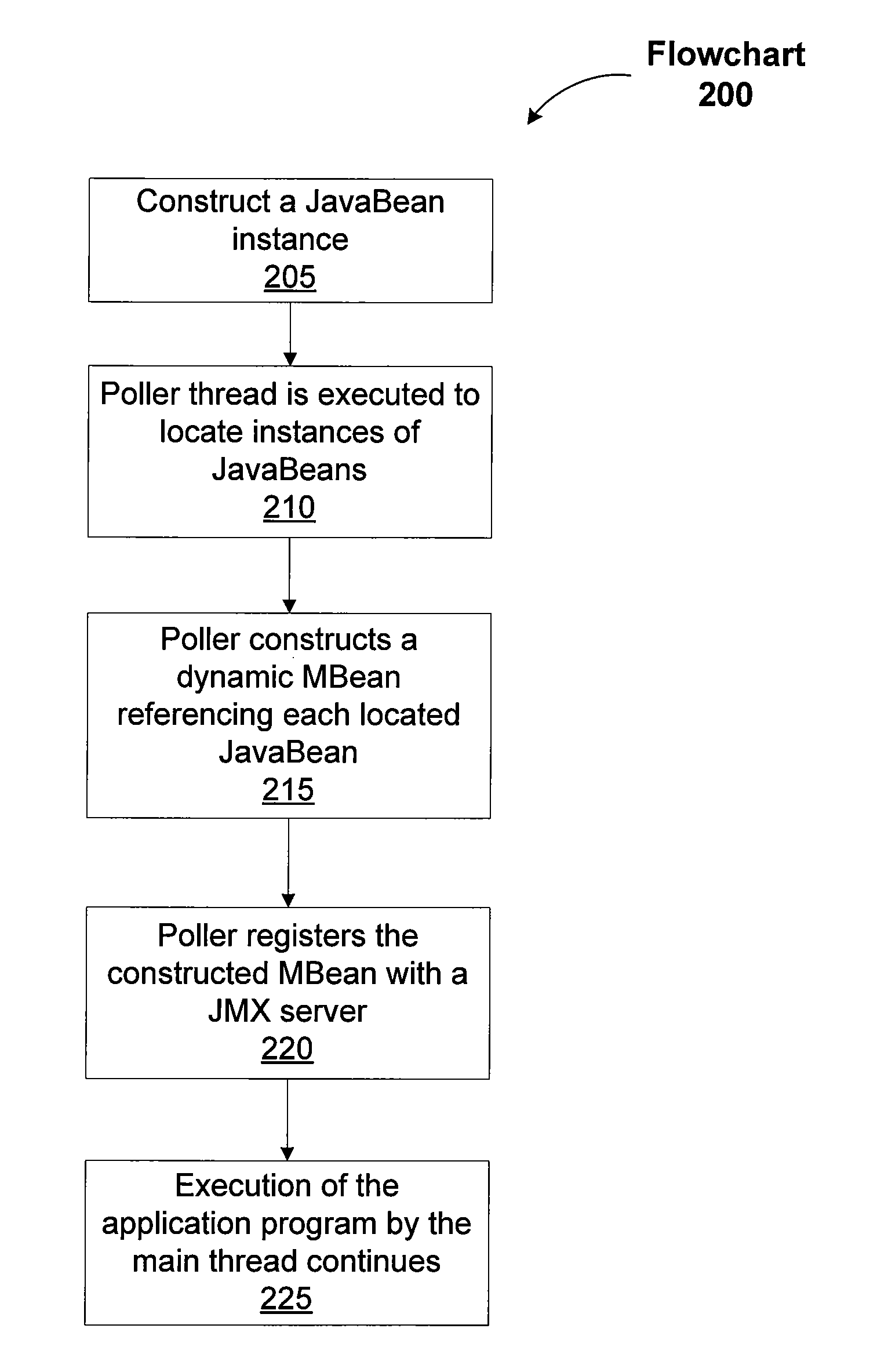
System and method of instrumenting code for in-production monitoring
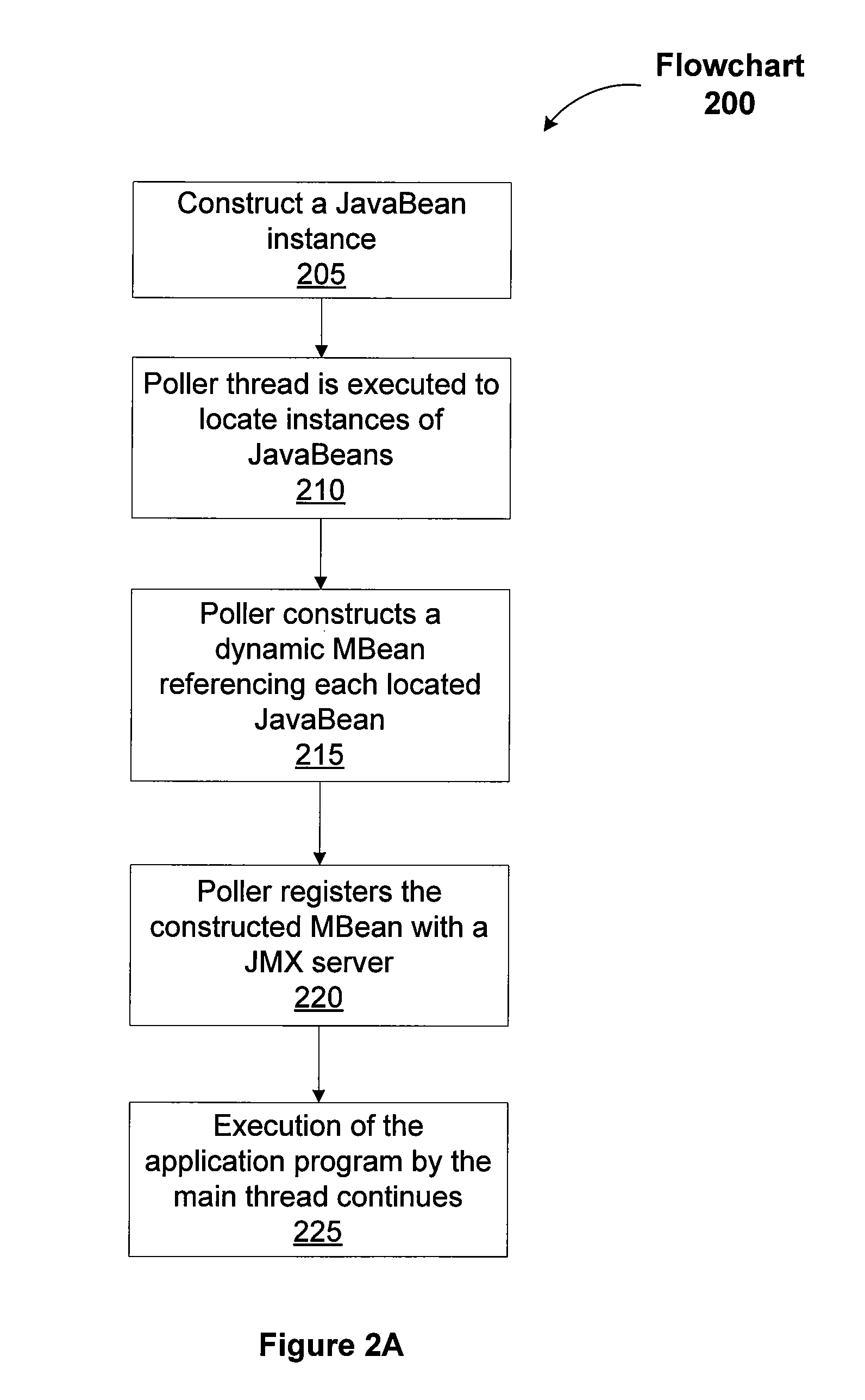
ActiveUS8667472B1Not reduce performanceSimple processHardware monitoringSpecific program execution arrangementsProgram structureManagement object
A system and method configured to instrument code for in-production monitoring provides a polling thread. A main thread executes the code of an instrumented application program and the polling thread executes in the background. Therefore the polling thread does not reduce the performance of the application program execution while monitoring activities are performed. Additionally, the polling thread is configured to simplify the process of instrumenting code for Java management extensions (JMX) by navigating the application program structure to locate administrative objects to bind to JMX and registering the administrative objects with JMX to enable monitoring of the instrumented code.
Owner:DISNEY ENTERPRISES INC
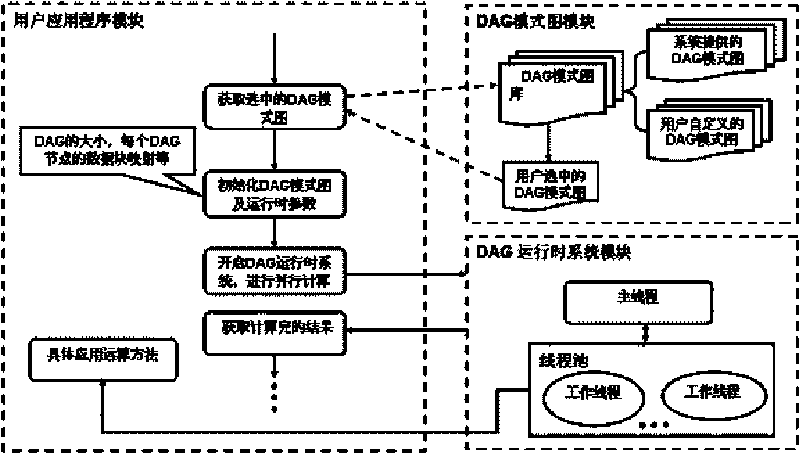
Parallel programming model system of DAG oriented data driving type application and realization method
InactiveCN101710286AReasonable structureImprove performanceConcurrent instruction executionSpecific program execution arrangementsFault toleranceParallel programming model
The invention discloses a parallel programming model system of DAG oriented data driving type application and a realization method. The parallel programming model system of DAG oriented data driving type application comprises a DAG mode chart module, a user application program module and a DAG runtime system module, wherein the DAG mode chart module comprises a DAG mode chart bank; the user application program module is used for user initialization setup and confirmation of specific parallelization algorithm; and the DAG runtime system module comprises a main thread and a thread pool. The main thread is used for analyzing and updating the DAG mode chart, issuing and dispatching data block, and controlling fault-tolerance; the thread pool comprises a thread pool queue buffer zone and a work thread, wherein the thread pool queue buffer zone is a data interface for the main thread and the work thread, the work thread is used for constantly acquiring computing tasks from the queue buffer zone and carrying out computing. Compared with the prior art, the invention decreases difficulty in designing and developing a parallel computing application program for non-computer professionals, shortens development period of parallel software, and enables the completed parallel computing application program to have more reasonable structure and more optimized performance.
Owner:TIANJIN UNIV
Large-scale application regression testing information processing method based on Java bytecode
InactiveCN103425584AImprove test qualityLow costSoftware testing/debuggingInformation processingRegression testing
The invention relates to a large-scale application regression testing information processing method based on Java bytecode. The large-scale application regression testing information processing method based on Java bytecode comprises a plug-in step of injecting an object code; a step of acquiring an operating path of the object code at high efficiency, a mapping and storing step of an established relationship between the object code and a testing case; a step of comparing an object code in a new version and an object code in a cold version; an involved analysis step of automatically selected cases which need to be subjected to regression testing; a step of continuously improving the regression testing based on a version stream; a step of automatically generating all code structures and calling relationship of an object application; a step of carrying out data comparison based on a program structure and code semantic; a step of plugging exploration logic in the object application bytecode so as to dynamically acquire a complete code-operating path and coverage data; a step of controlling regression testing trigger of testing cases; and a step of representing a mapping relationship and an involvement relationship between the testing case and the code on a friendly interface. According to the large-scale application regression testing information processing method, the testing case is subjected to deep analysis, an original progress black-box state is converted into a semitransparent state, so that testing personnel can implement testing better.
Owner:SHANGHAI FAIRYLAND INFORMATION TECH CO LTD
Formal Verification of Graphical Programs
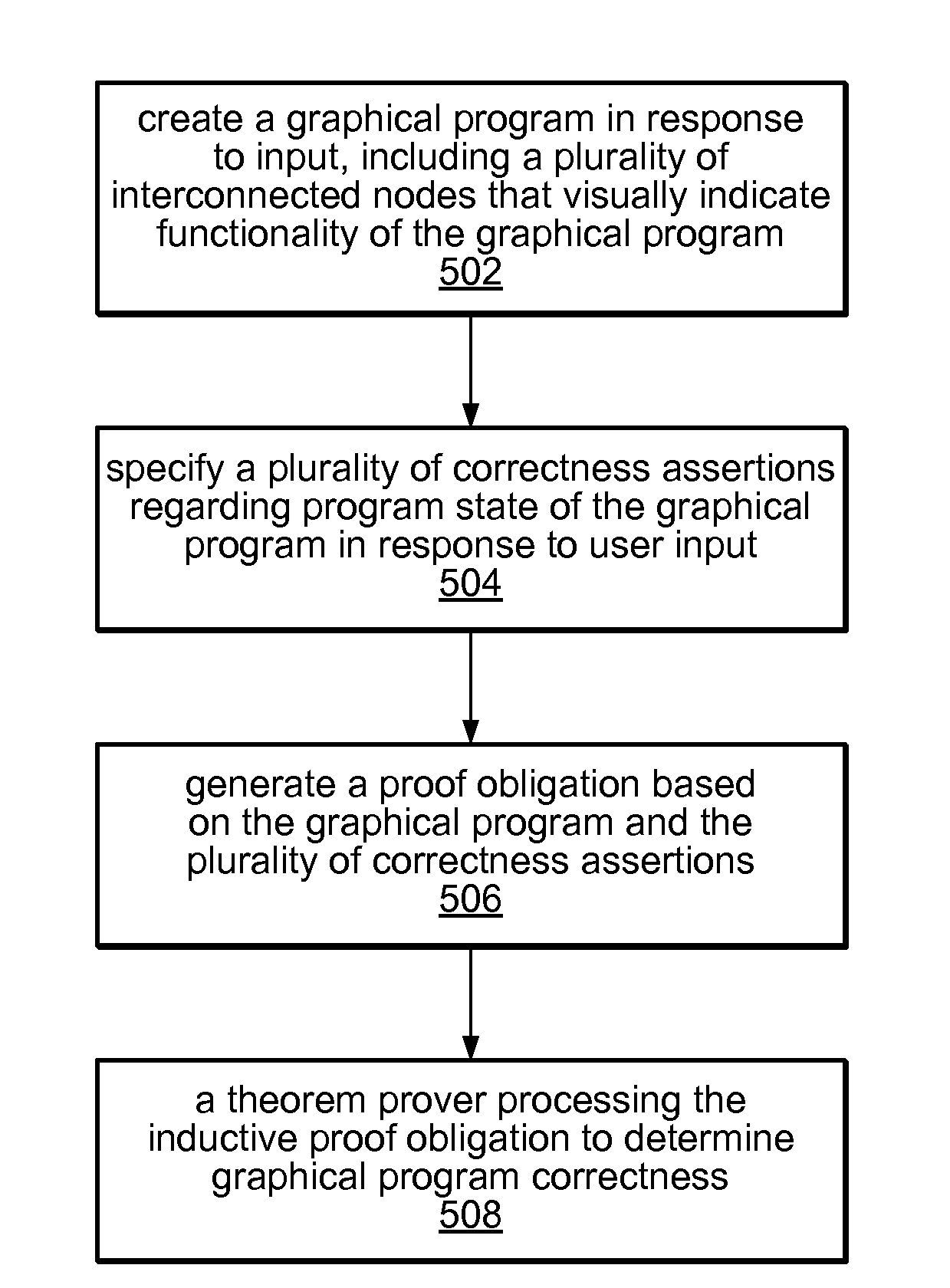
InactiveUS20090064111A1Error detection/correctionVisual/graphical programmingObject levelHuman language
System and method for formal verification of a graphical program. A graphical program comprising a plurality of interconnected nodes is created in response to input. One or more correctness assertions regarding program state of the graphical program are specified in response to user input, and a proof obligation generated based on the graphical program and the correctness assertions, which is usable by a theorem prover to determine correctness of the graphical program. The proof obligation may be generated by compiling the graphical program to generate an object-level diagram, parsing the correctness assertions to generate an intermediate logical form of the one or more correctness assertions, and analyzing the object-level diagram, the intermediate logical form, and / or semantics of the graphical programming language in which the graphical program is written to generate the proof obligation. A theorem prover may then process the proof obligation to determine whether the graphical program is correct.
Owner:NATIONAL INSTRUMENTS
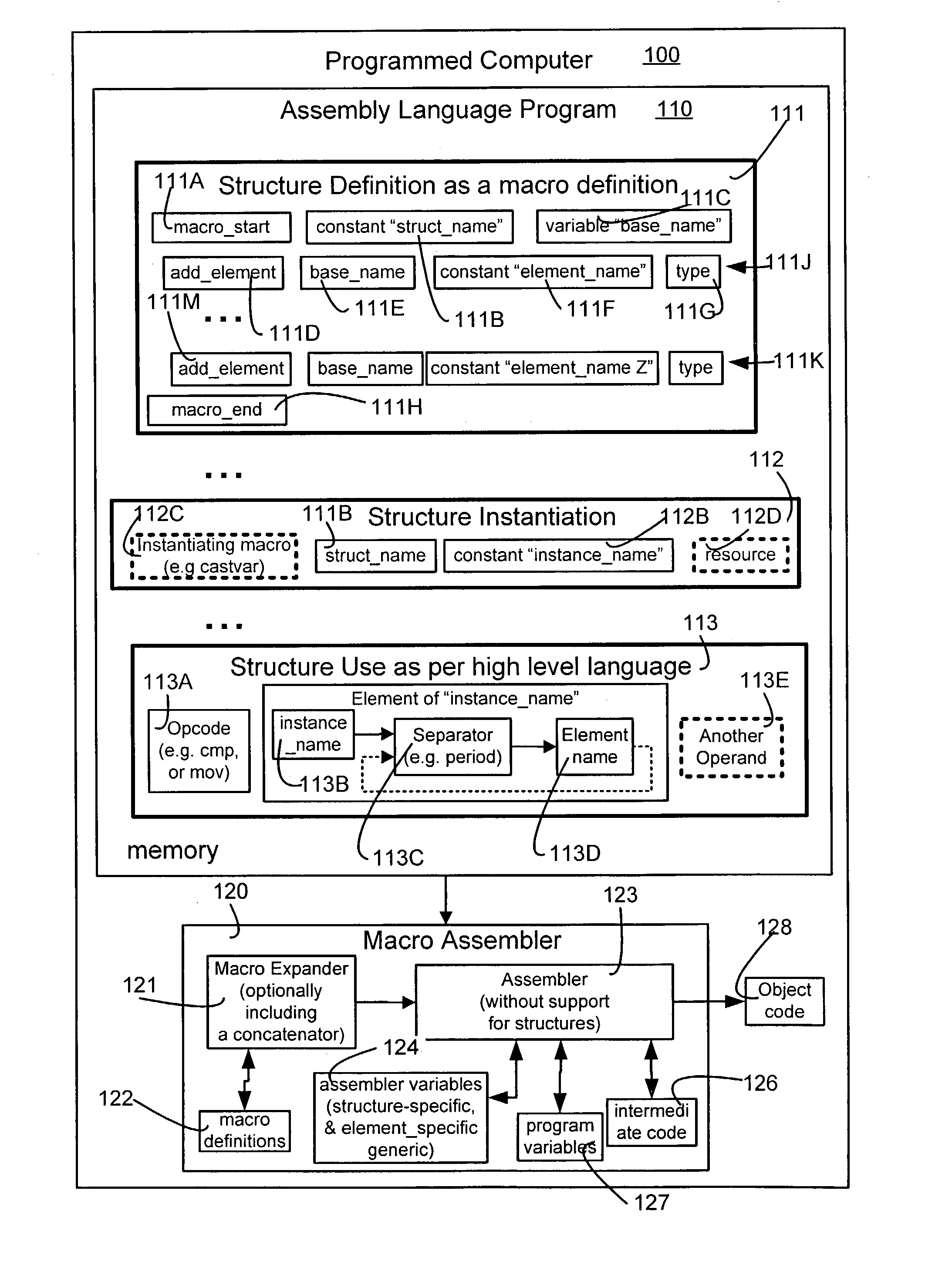
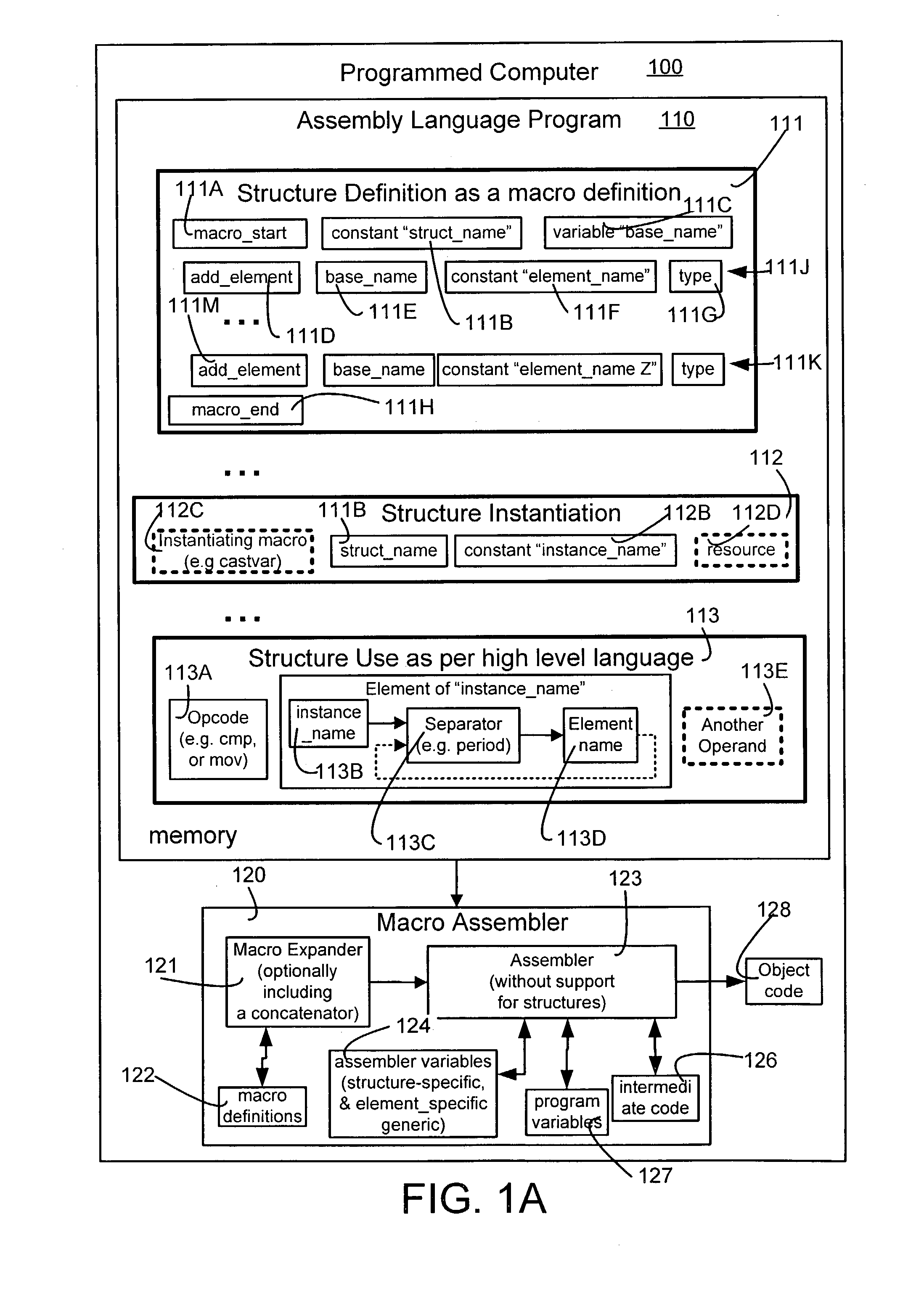
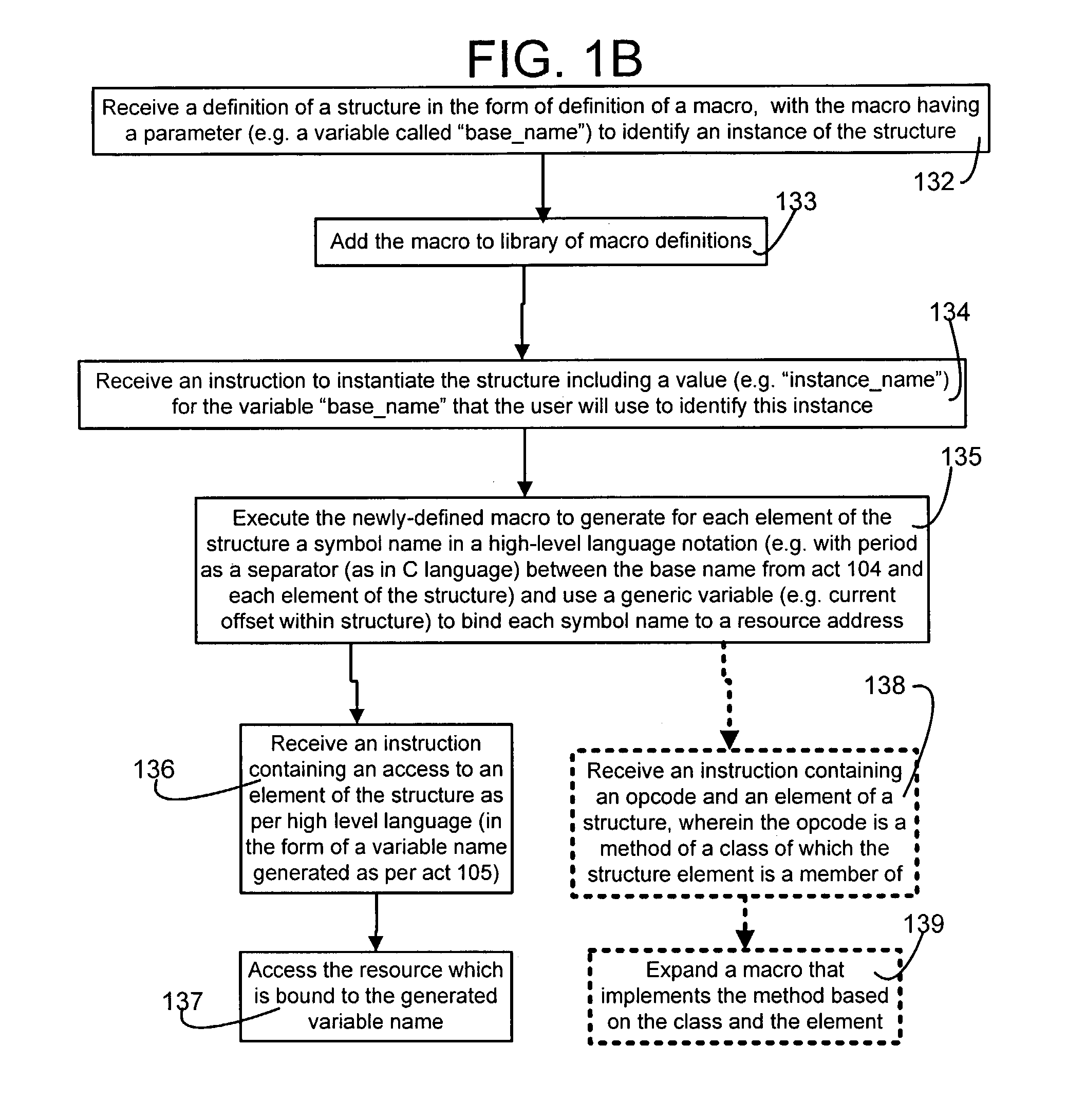
Macros to support structures for an assembler that does not support structures
An assembler incapable of supporting structures of the type supported in the “C” language receives and processes an assembly language program that contains one or more definitions of structures, structure instantiations and structure uses. Specifically, structure definitions are presented in the form of macro definitions. Moreover, a name to be used to identify the structure is passed as a parameter to the macro being defined (also called “structure-definition macro”). Furthermore, one or more members of a structure are presented in the form of arguments to a respective number of one or more macros that are invoked between the beginning and end of the structure-definition macro. During instantiation, variable names are created for each member of the structure, and these names are bound to appropriate addresses of resources. Thereafter, these variable names are used in the assembly language program to access data mapped to the member name.
Owner:OL SECURITY LIABILITY CO
Tablet computer utility structure
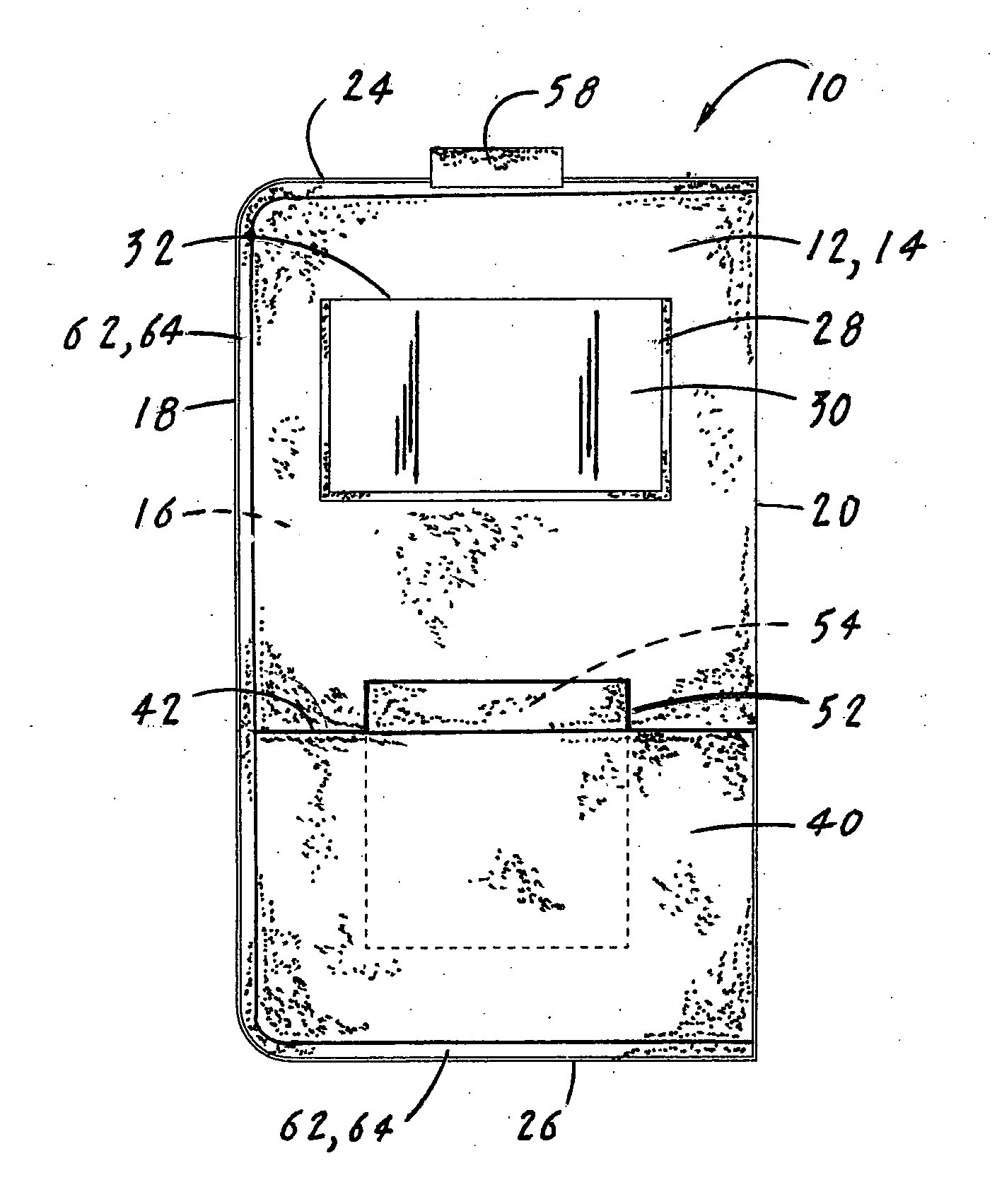
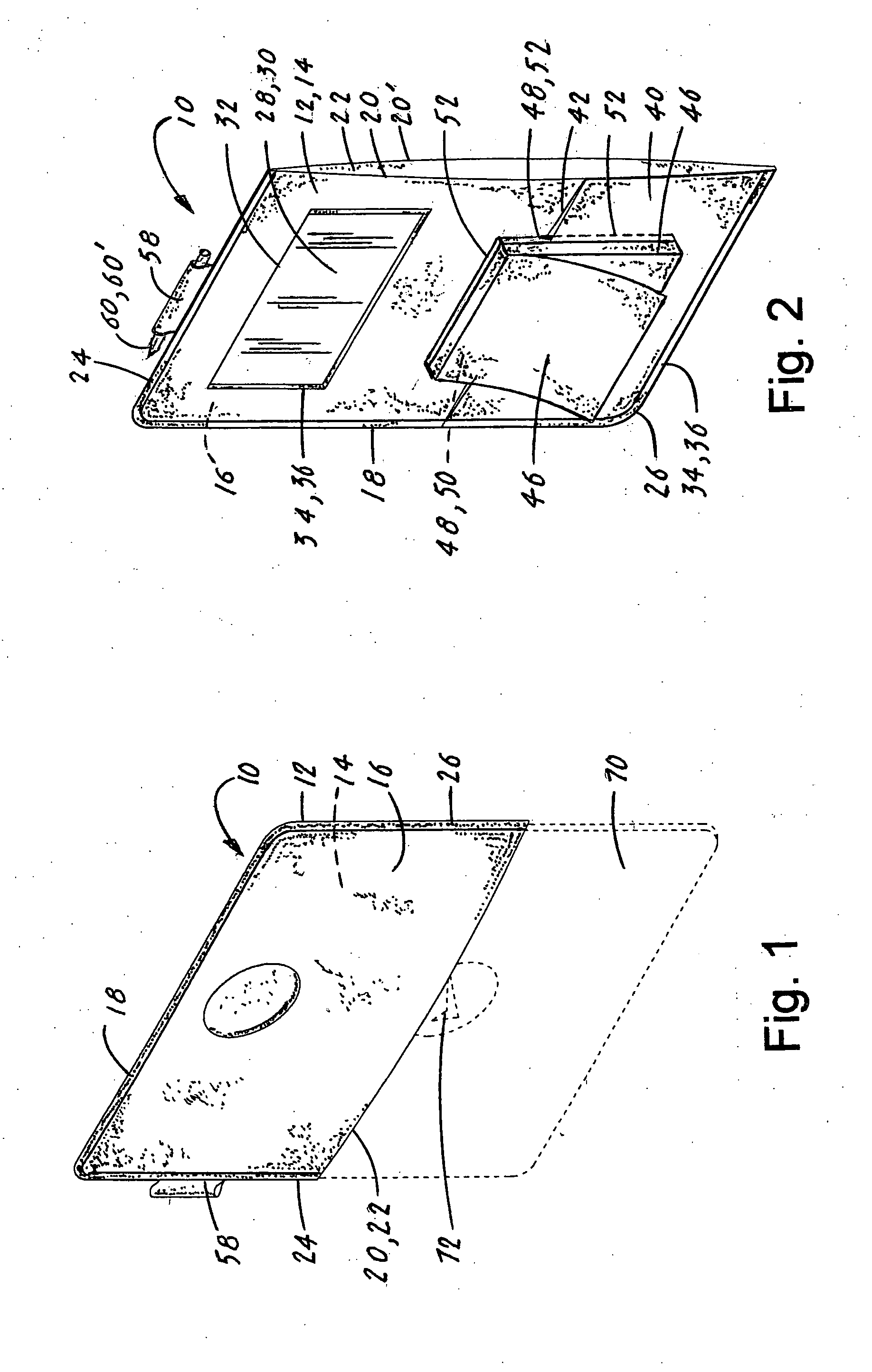
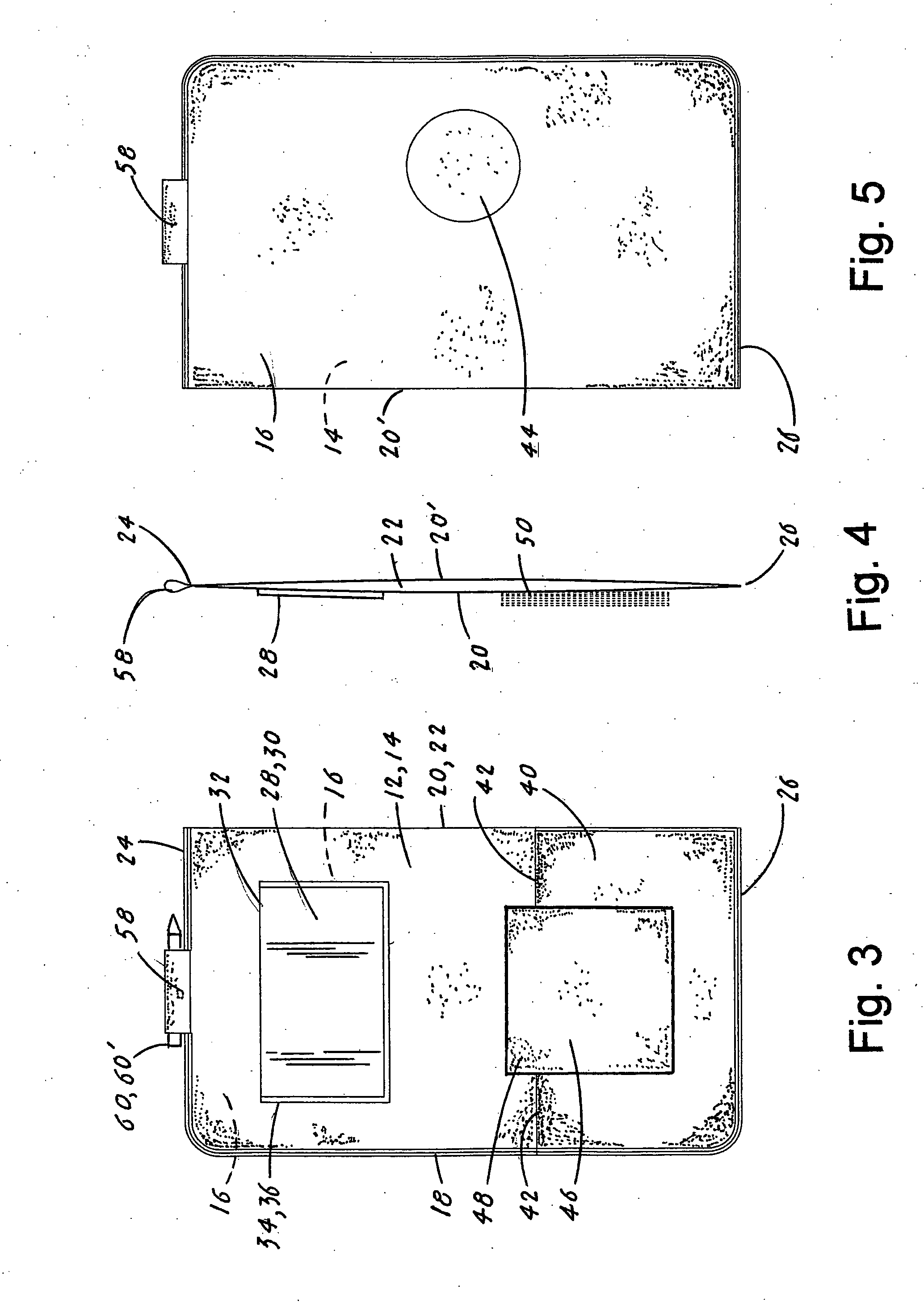
InactiveUS20120247989A1Easy to insertEasy to removePursesDigital data processing detailsTablet computerBusiness card
A tablet computer utility structure (TCUS 10) that is designed to protect and enhance the utility of the tablet computer (70). The enhancement is accomplished by having the TCUS (10) include a cover (12) that includes on its the front surface (16), a business card holder (28), a pocket (40) that has inserted a paper pad (46) and a pen (59), pencil (60) or stylus (61) retaining loop 58. The TCUS (10) can be dimensioned to be utilized with a variety of tablet computers (70) and can further include on the cover (12) a stylistic logo opening (44) that is in alignment with a tablet logo (72) located on the front surface of the tablet computer (70).
Owner:COOPER CHRISTOPHER A
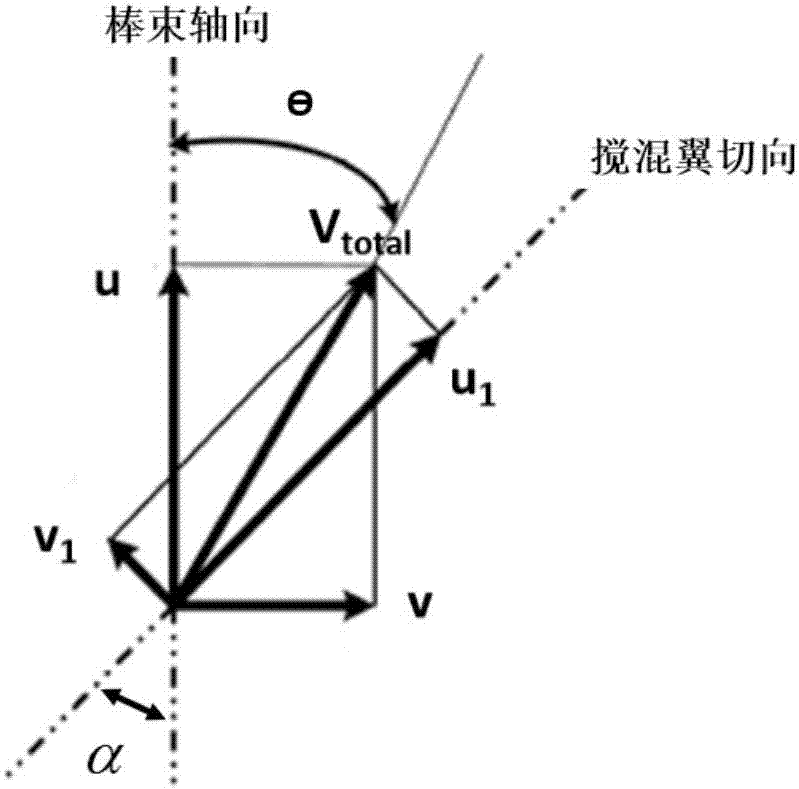
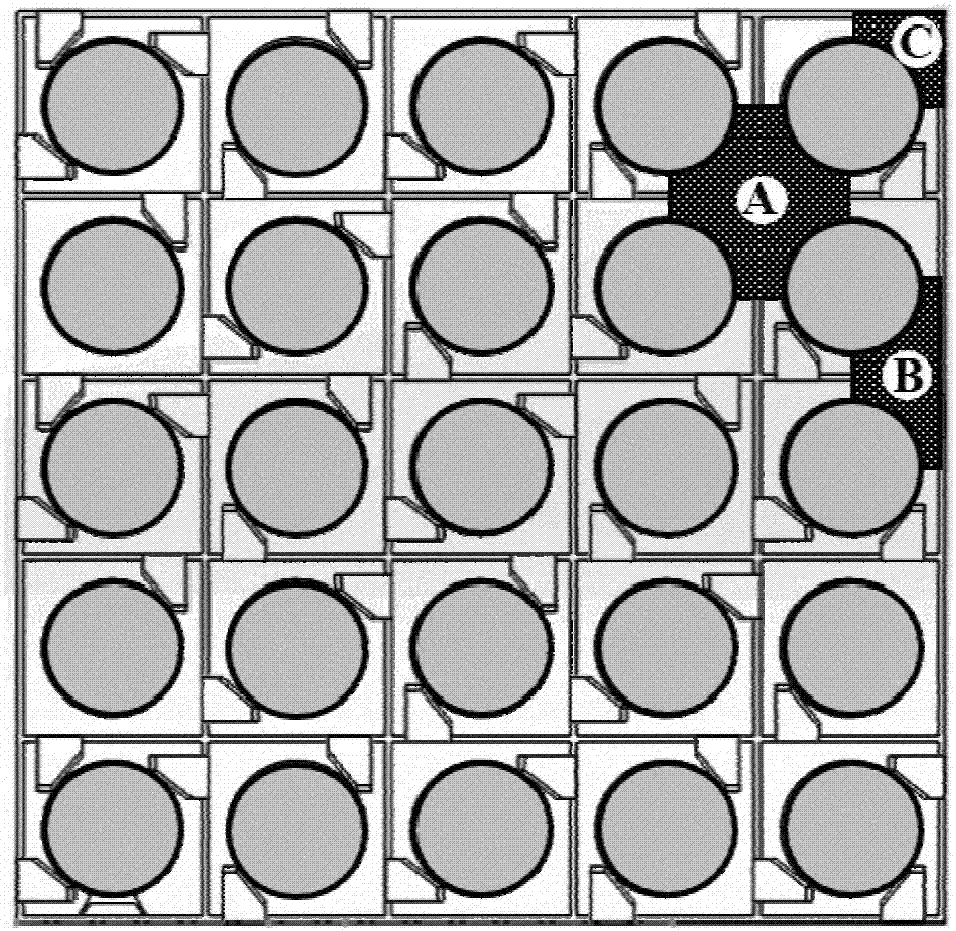
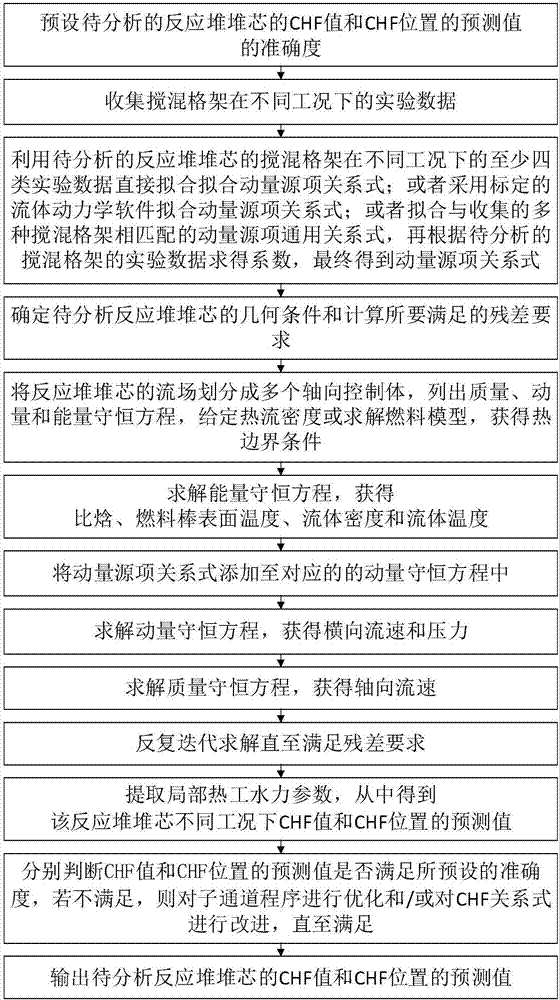
Resistance distribution-based method for analyzing sub-channel with grid mixing effect
ActiveCN106897478AAccurately reflectImprove accuracyDesign optimisation/simulationSpecial data processing applicationsAnalysis methodMixing effect
The invention discloses a resistance distribution-based method for analyzing a sub-channel with a grid mixing effect. The method comprises the steps of collecting experimental data of multiple mixing grids including a mixing grid of a to-be-analyzed reactor core in different working conditions, fitting a momentum source term relational expression capable of reflecting mixing performance of key parts of the mixing grids, and adding the momentum source term relational expression to a corresponding momentum conservation equation; and by solving a mass conservation equation, the momentum conservation equation and an energy conservation equation, obtaining more accurate local thermo-hydraulic parameters in the reactor core, thereby enabling prediction of a critical heat flux (CHF) value and a CHF position to be more accurate. The method is not limited by a structure and a solving method of a sub-channel program, and can be widely applied to the calculation of various types of sub-channel programs including a sub-channel program of a uniform flow model, a drift flow model or a two-fluid model.
Owner:青岛德能创新科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com