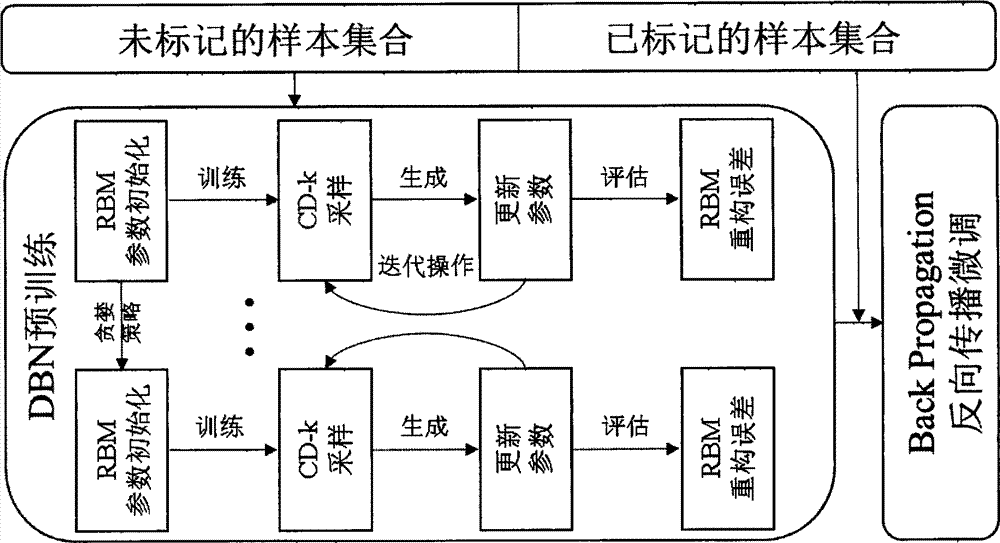
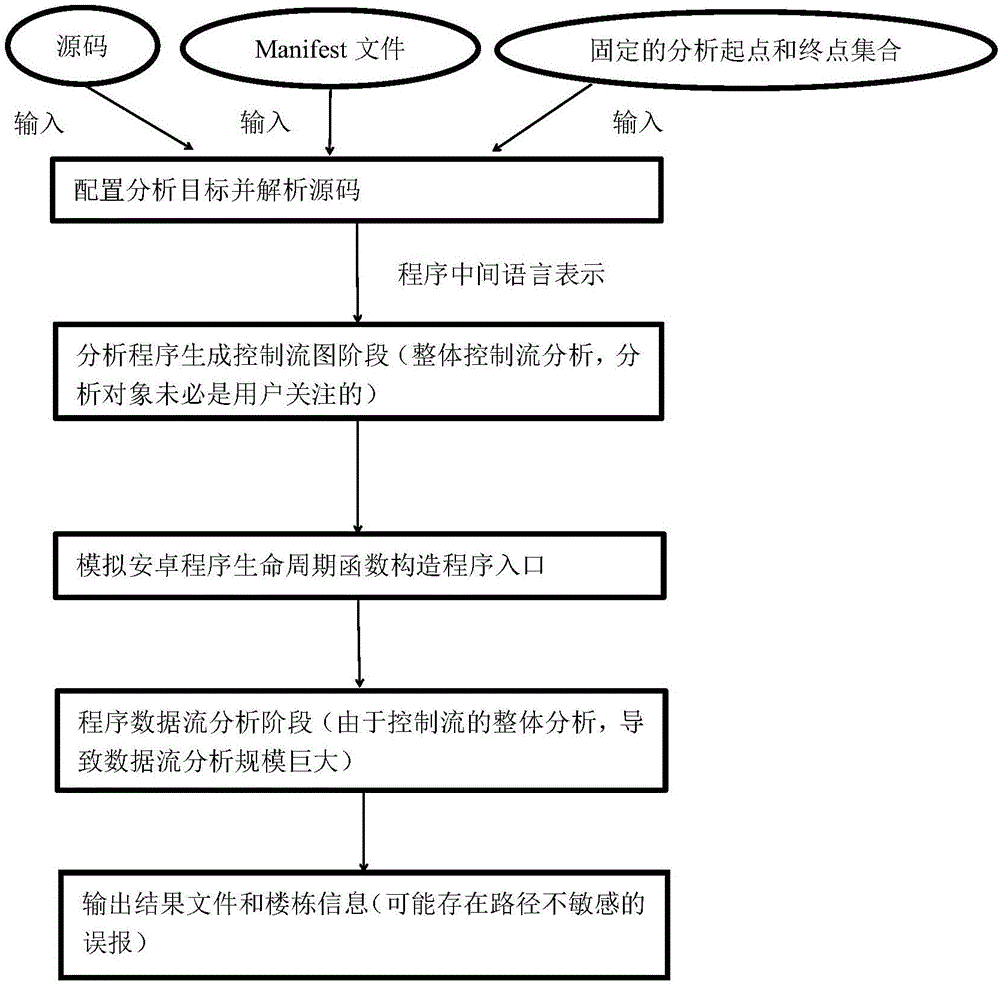
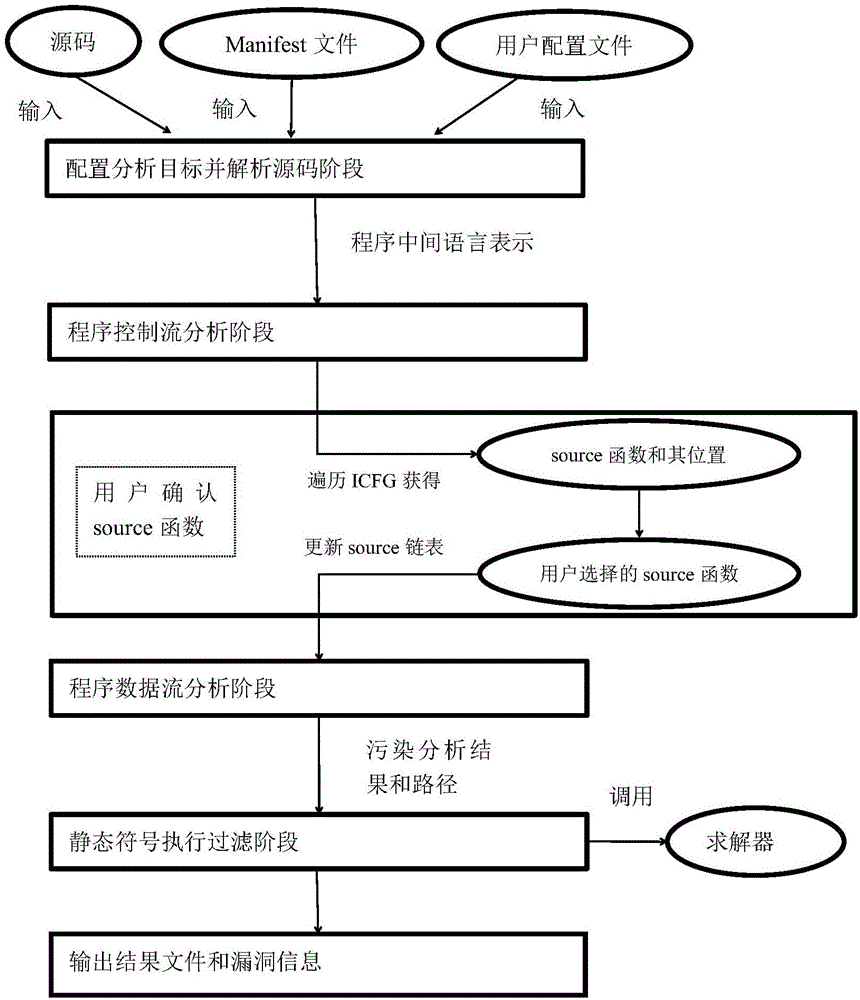
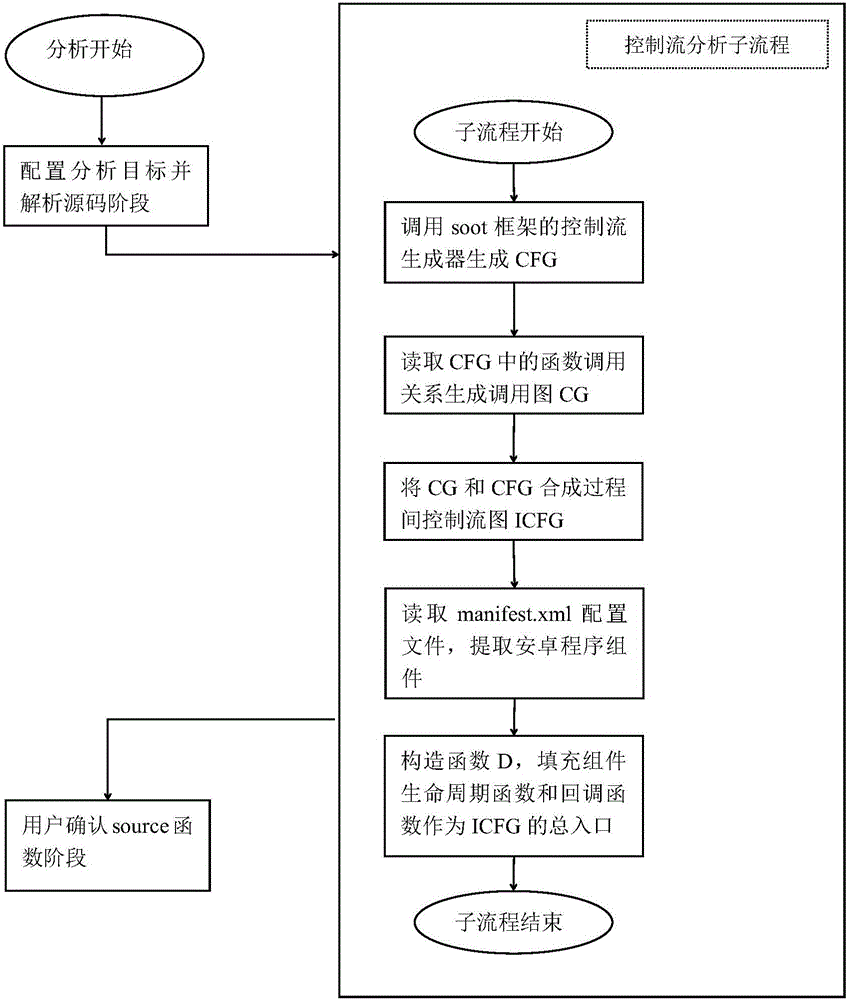
Patents
Literature
1242 results about "Android application" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
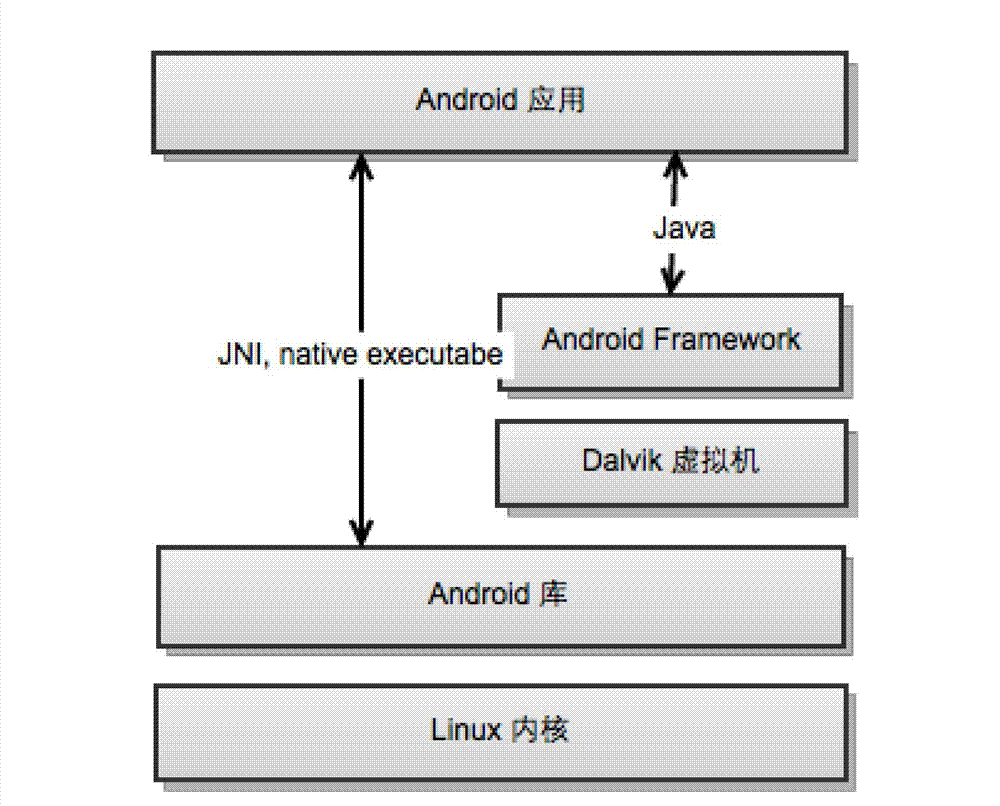
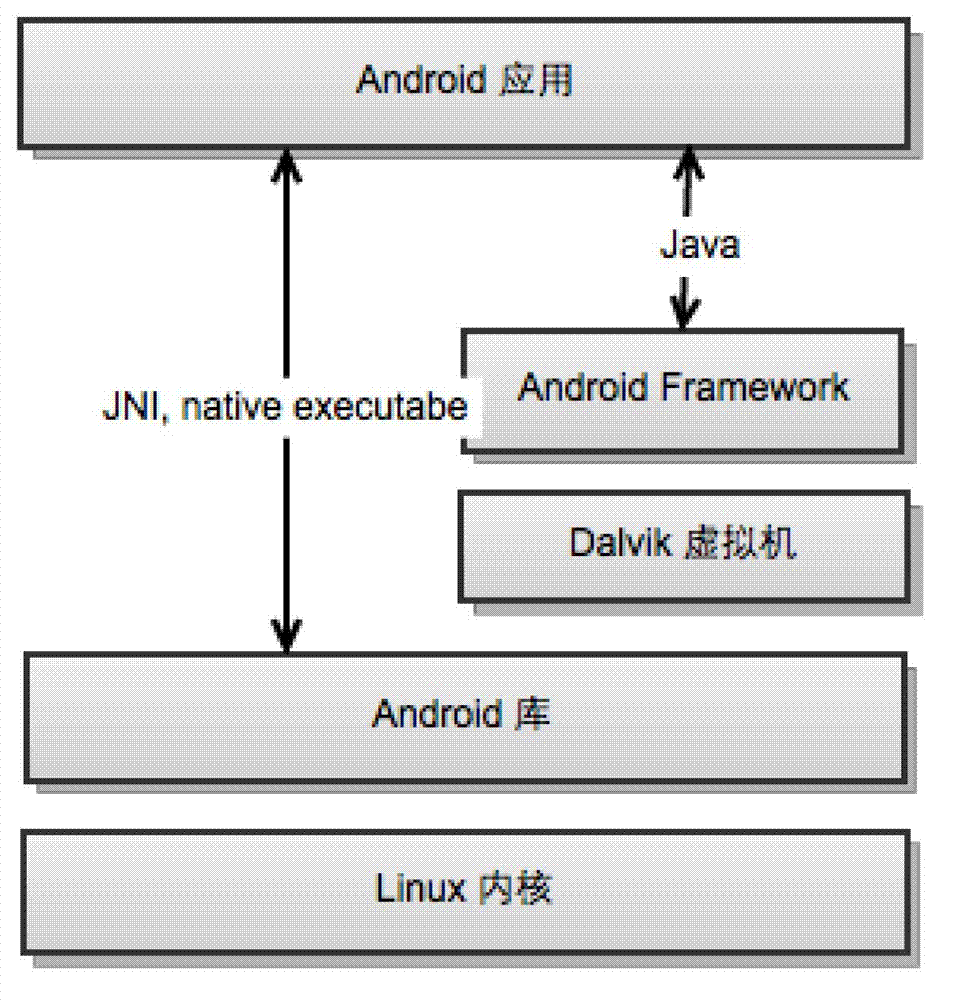
Android App. Definition - What does Android App mean? An Android app is a software application running on the Android platform. Because the Android platform is built for mobile devices, a typical Android app is designed for a smartphone or a tablet PC running on the Android OS.
Security detection method and system of Android application program
ActiveCN102779257ACause harmImprove scanning efficiencyComputer security arrangementsSoftware engineeringApplication software
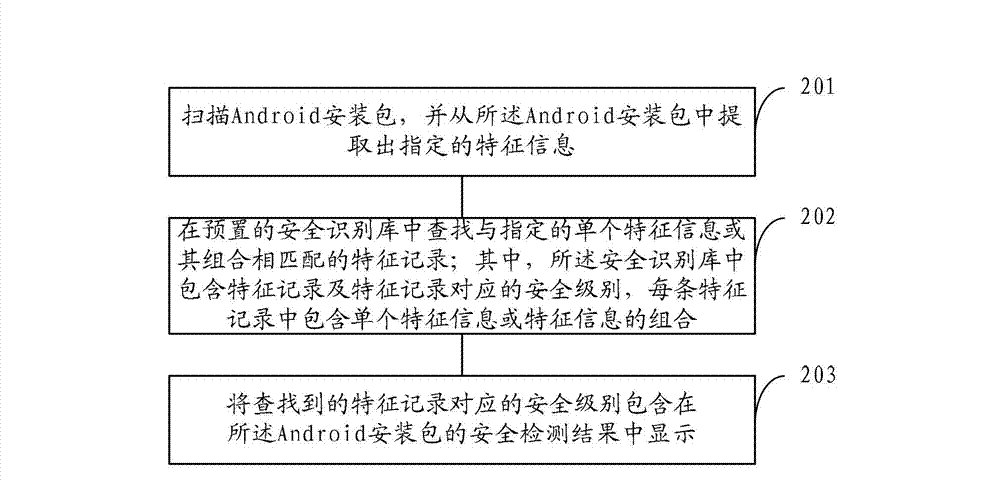
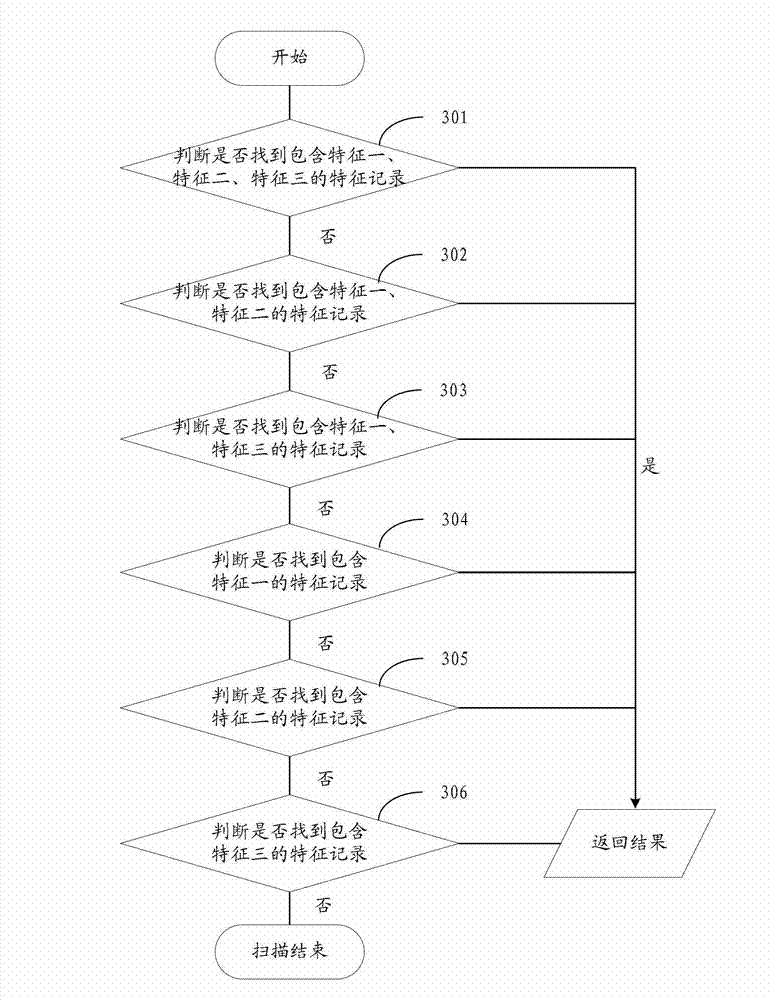
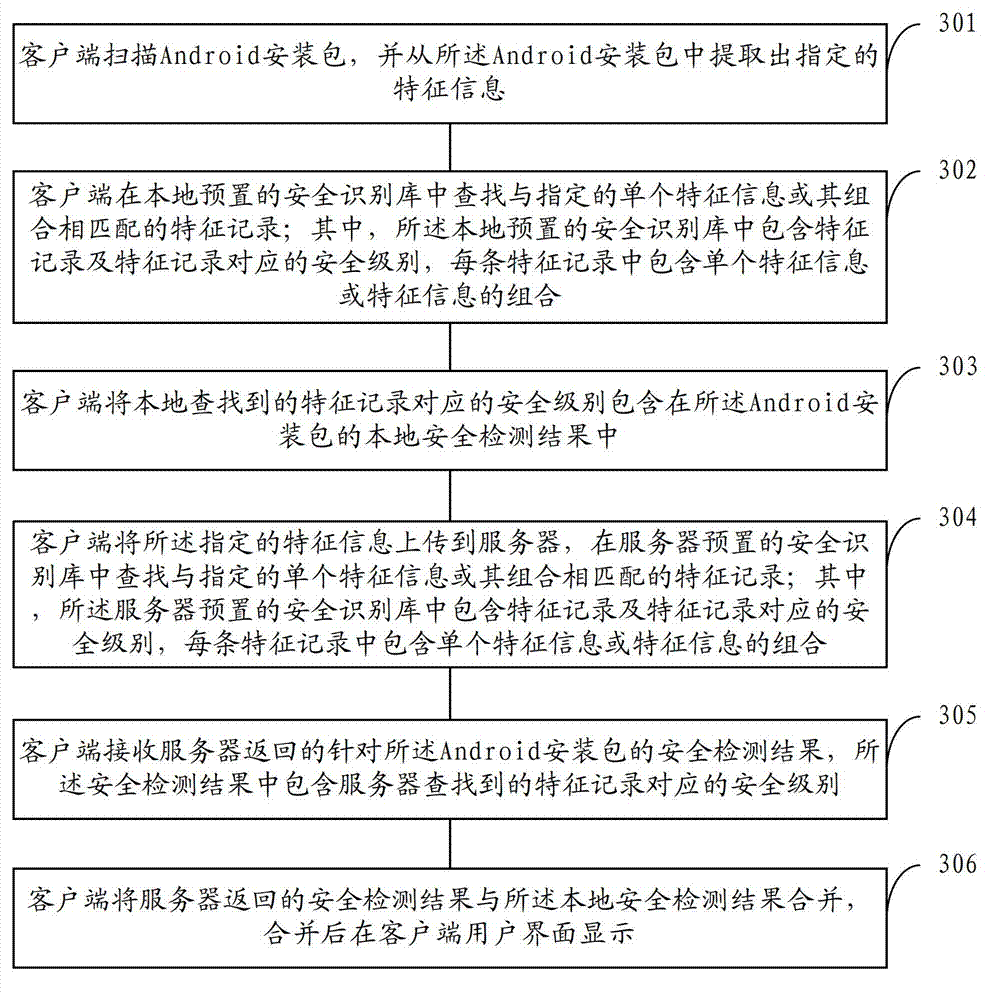
The invention provides a security detection method and system of an Android application program, aiming to solve the problems of an antivirus method of the existing Android platform that the scanning speed is slow and the false positive ratio is high. The method comprises the following steps of: scanning an Android installation package and extracting appointed characteristic information from the Android installation package; finding characteristic records which are matched with the appointed single characteristic information or a combination thereof from a pre-arranged security identification base, wherein the security identification base comprises the characteristic records and security grades corresponding to the characteristic records, and each characteristic record comprises single characteristic information or the combination of the characteristic information; and respectively displaying the security grade corresponding to the found characteristic records in a security detection result of the Android installation package. The security detection method and system of the Android application program disclosed by the invention have the advantages of fast scanning speed and high searching and killing accuracy.
Owner:360 TECH GRP CO LTD
Security detection method and system of Android application program
ActiveCN102831338ACause harmImprove scanning efficiencyComputer security arrangementsSpecial data processing applicationsSecurity levelFalse alarm
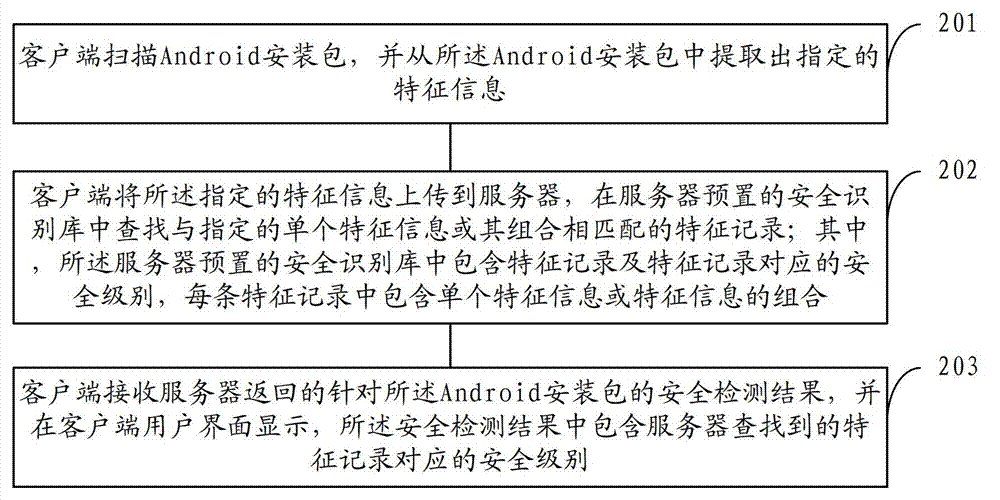
The invention provides a security detection method and system of an Android application program, solving the problems of low scanning speed and high false alarm rate of the traditional virus killing method of an Android platform. The security detection method comprises the steps of: scanning an Android installation package, extracting appointed characteristic information from the Android installation package; uploading the appointed characteristic information to a server, searching a characteristic record matched with appointed single characteristic information or combination from a security identification base preset in the server; and receiving a security detection result returned by the server aiming at the Android installation package, and displaying on a client end user interface, wherein the security detection result includes a security level corresponding to the characteristic record searched by the server. The client end detection is combined with the server detection, thus the security detection method is high in scanning speed and high in killing accuracy rate.
Owner:360 TECH GRP CO LTD
Android malicious application detection method and system based on multi-feature fusion
ActiveCN107180192AImprove detection accuracyReflect malicious appsCharacter and pattern recognitionPlatform integrity maintainanceFeature vectorAnalytical problem
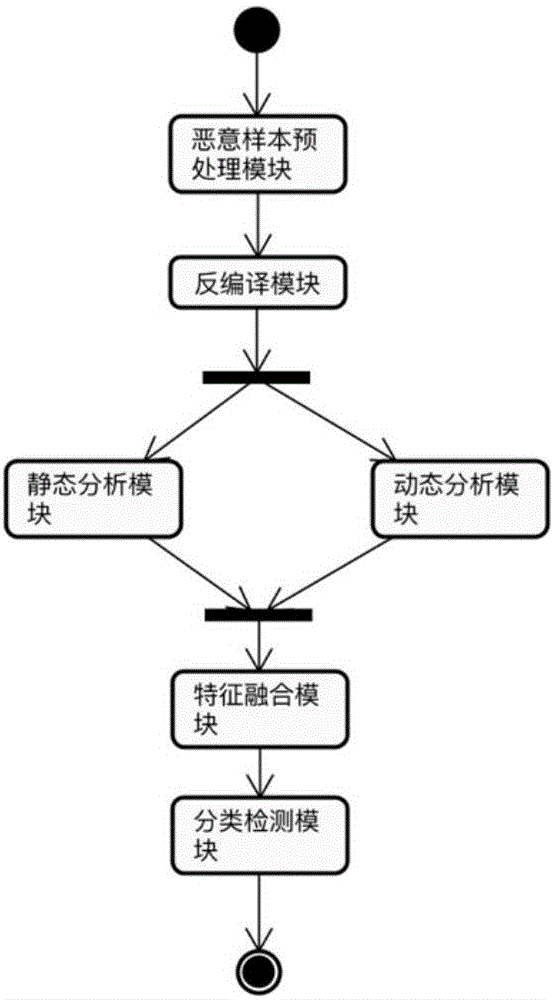
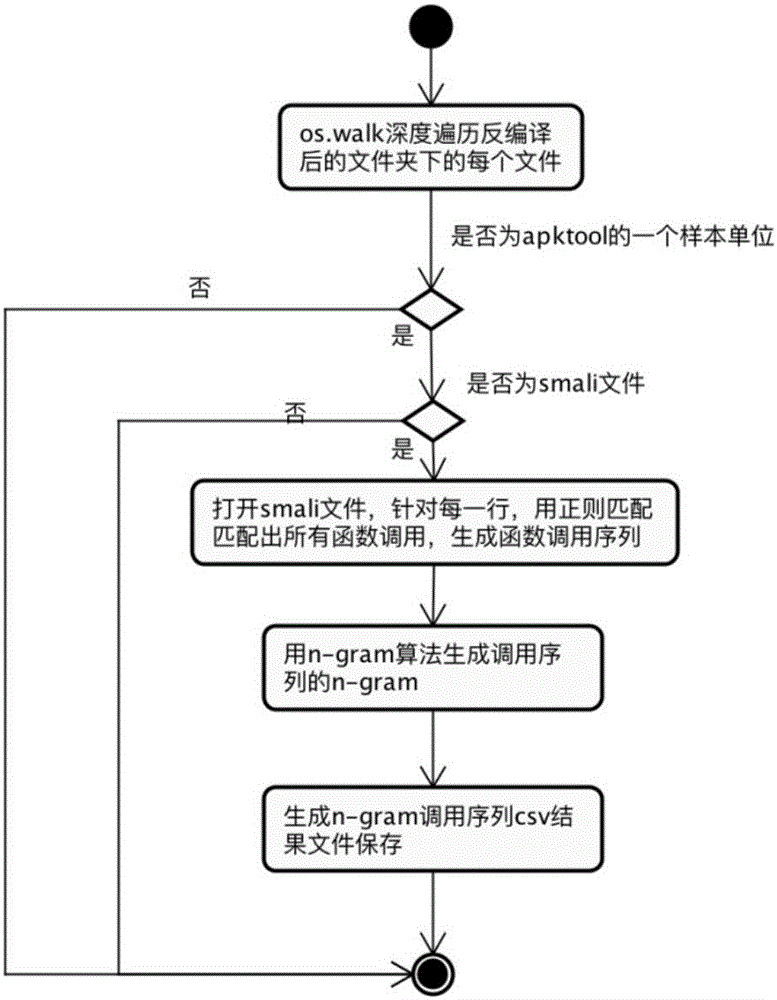
The invention discloses an Android malicious application detection method and system based on multi-feature fusion. The method comprises the following steps that: carrying out decompilation on an Android application sample to obtain a decompilation file; extracting static features from the decompilation file; operating the Android application sample in an Android simulator to extract dynamic features; carrying out feature mapping on the static features and the dynamic features by the text Hash mapping part of a locality sensitive Hash algorithm, mapping to a low-dimensional feature space to obtain a fused feature vector; and on the basis of the fused feature vector, utilizing a machine learning classification algorithm to train to obtain a classifier, and utilizing the classifier to carry out classification detection. By use of the method, the high-dimensional feature analysis problem of a malicious code rare sample family can be solved, and detection accuracy is improved.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Malicious Android application program detection method, system and device
InactiveCN102938040AMalicious behavior detection is accurate and timelyReduce workloadSoftware testing/debuggingPlatform integrity maintainanceWorkloadApplication software
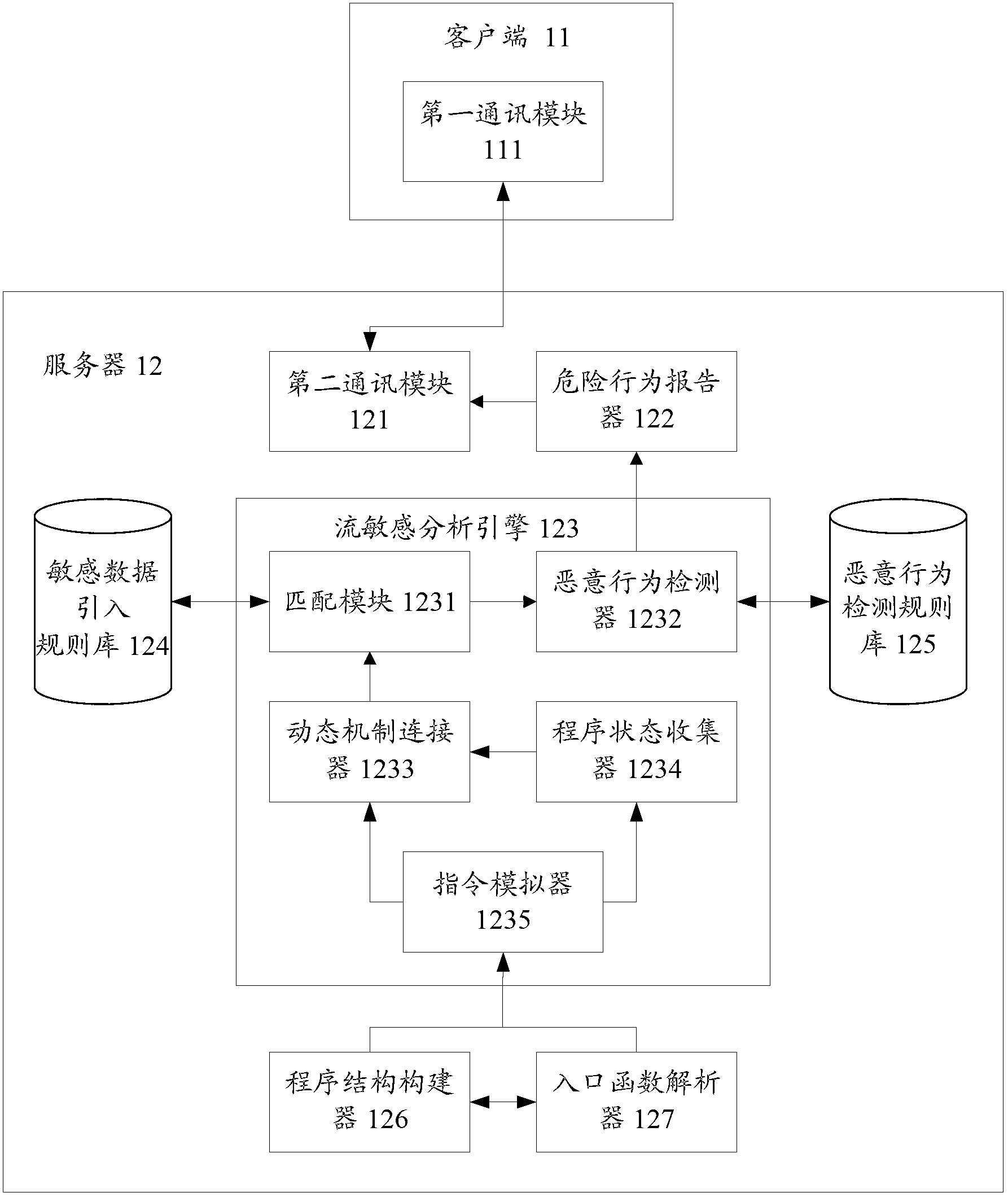
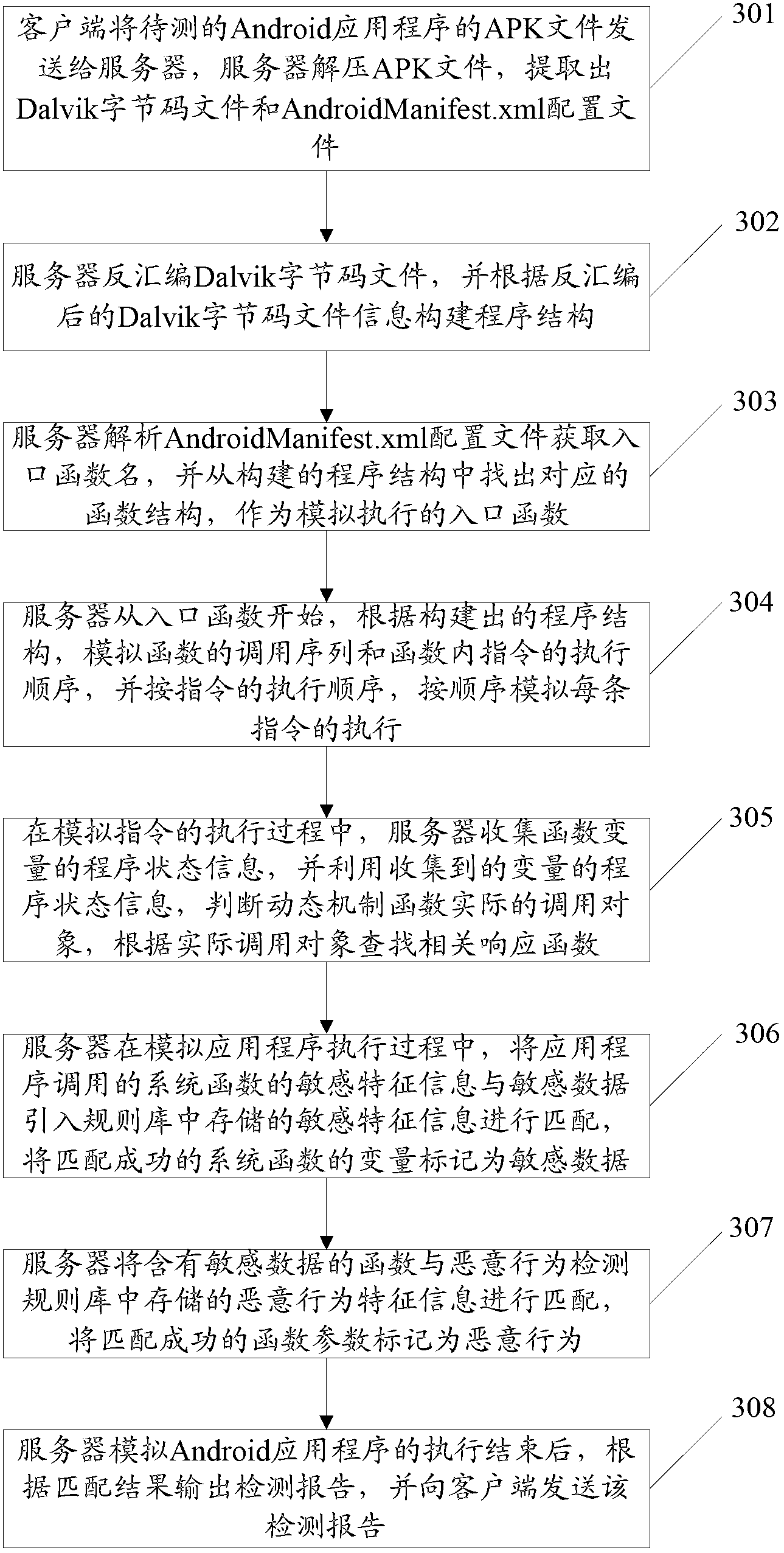
The invention discloses a malicious Android application program detection method, system and device. The method comprises the following steps of: imitating the execution of Android application programs by a server; matching sensitive characteristic information and sensitive date of system functions called by the Android application programs with sensitive characteristic information stored in a rule base, and marking variables of the matched system functions as sensitive data; and matching the functions containing the sensitive data with characteristic information of malicious acts stored in a malicious act detection rule base, and marking parameters of the matched functions as malicious acts. According to the technical scheme, the method, the system and the device can be used for detecting malicious Android application programs on the premise that manual analysis of characteristic codes is not relied on, thus alleviating the workload of technicians.
Owner:ZTE CORP +1
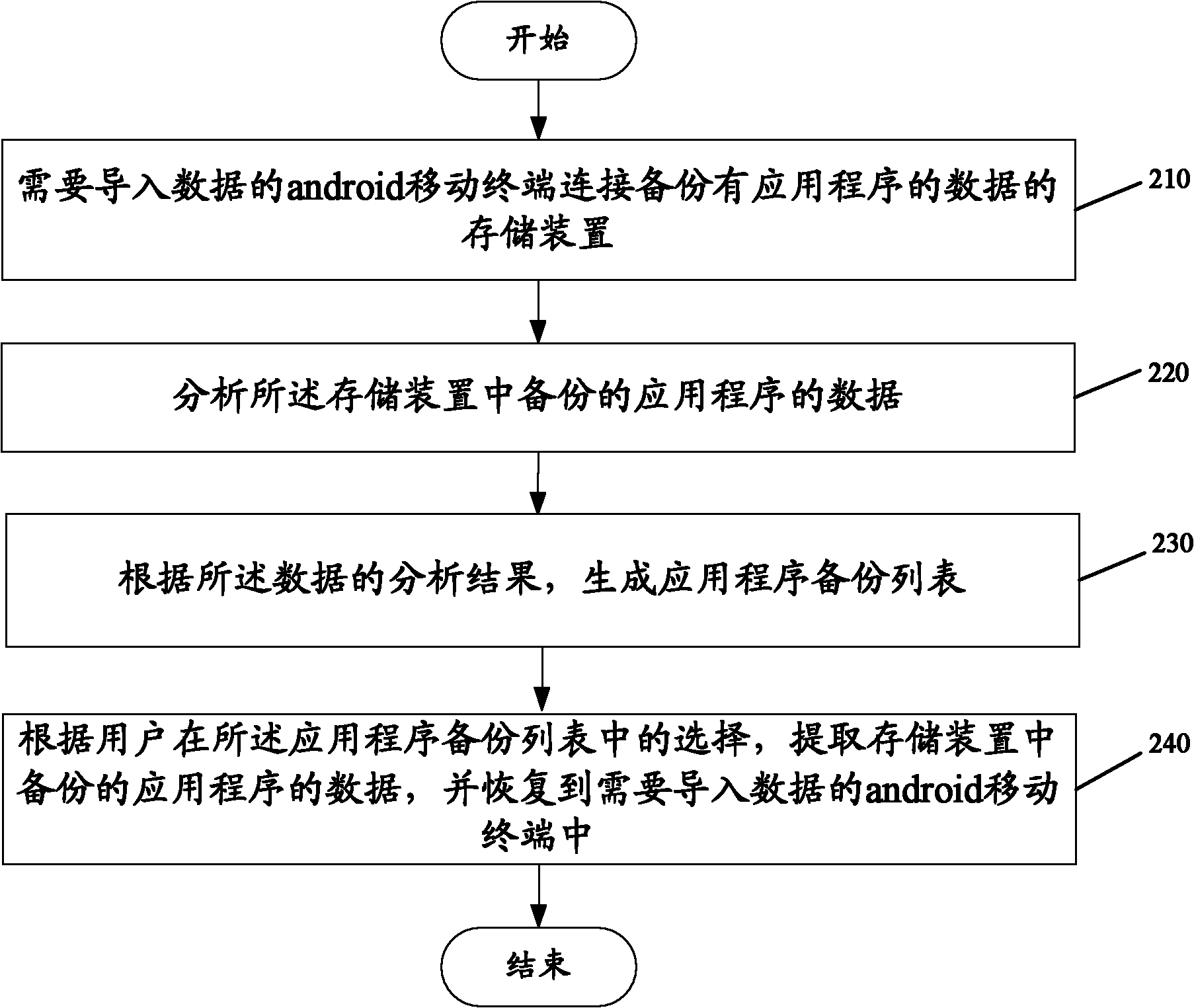
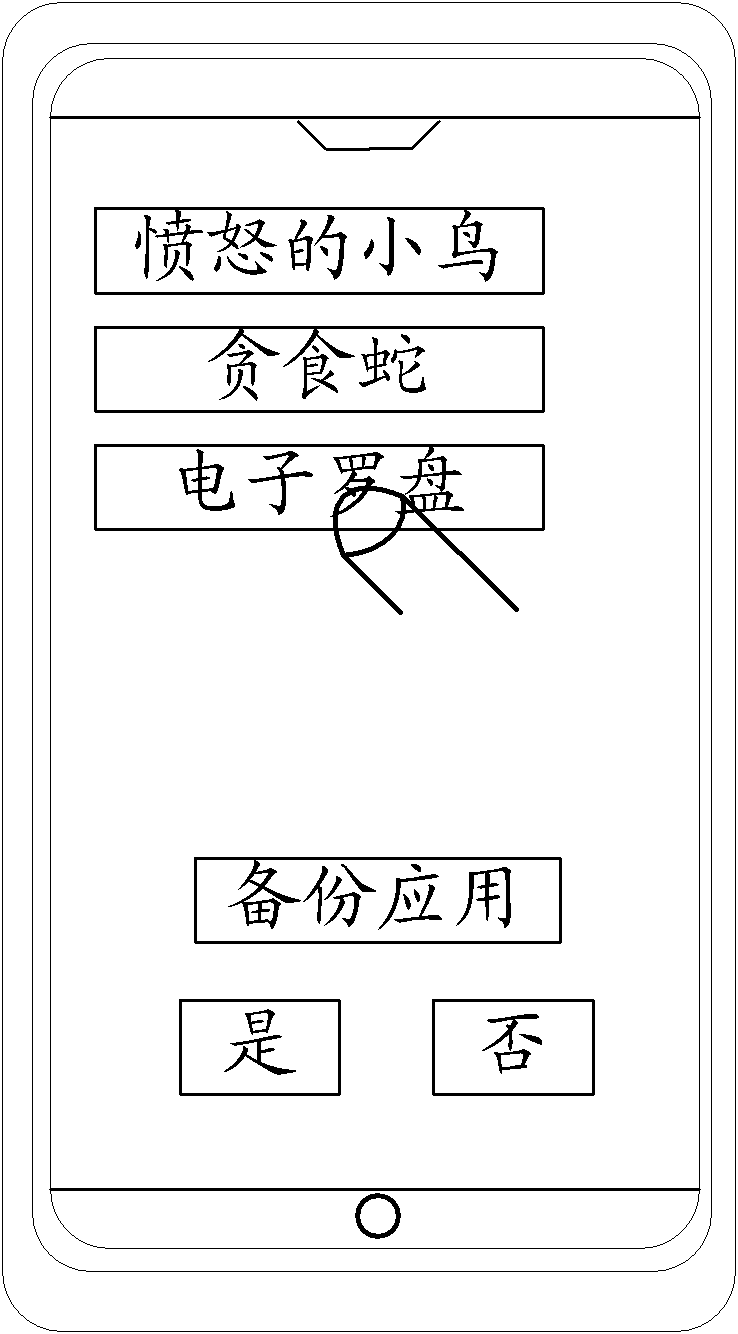
Android system-based application program backup and recovery method
InactiveCN102110031AConsistent configurationContinuation of usage habitsRedundant operation error correctionRecovery methodHabit
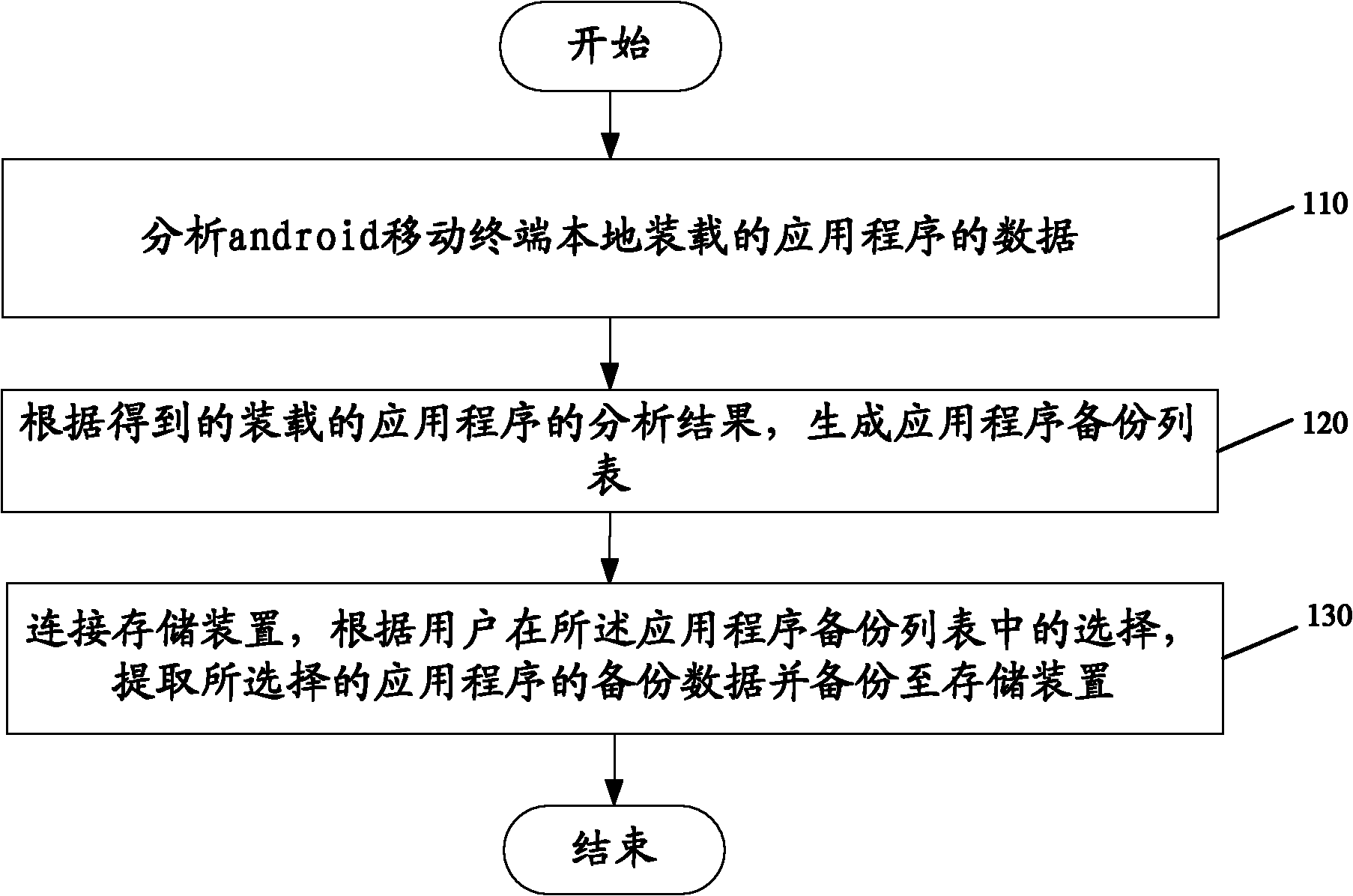
The invention discloses an android system-based application program backup and recovery method, which comprises the following steps of: analyzing data of a local loaded application program of a mobile terminal; generating an application program backup list according to the acquired analysis result of the loaded application program; and extracting the backup data of the selected application program according to the selection of a user in the application program backup list, and backing up the data to a storage device. By using the method, the android application program is subjected to mirror image transfer and used among different android mobile terminals, consistency of application and desktop configuration of two mobile terminals is ensured, the using habit of a user is continued, and the satisfaction of the user is improved.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
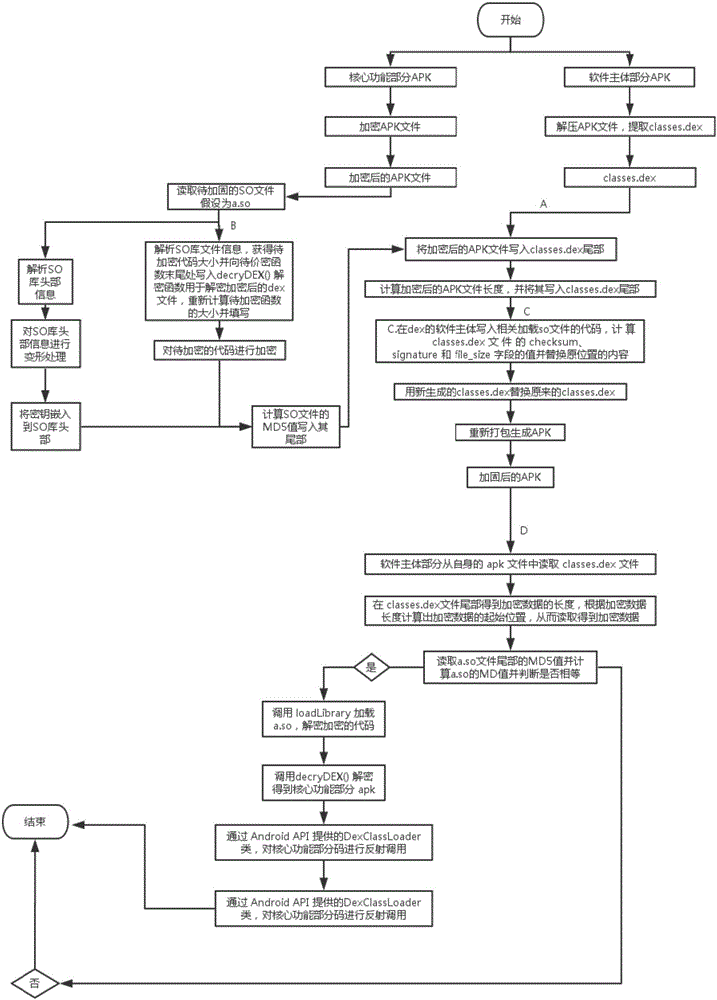
Software protection method and system applicable to Android system
InactiveCN102236757AImprove protectionImprove execution efficiencyProgram/content distribution protectionByteSoftware protection
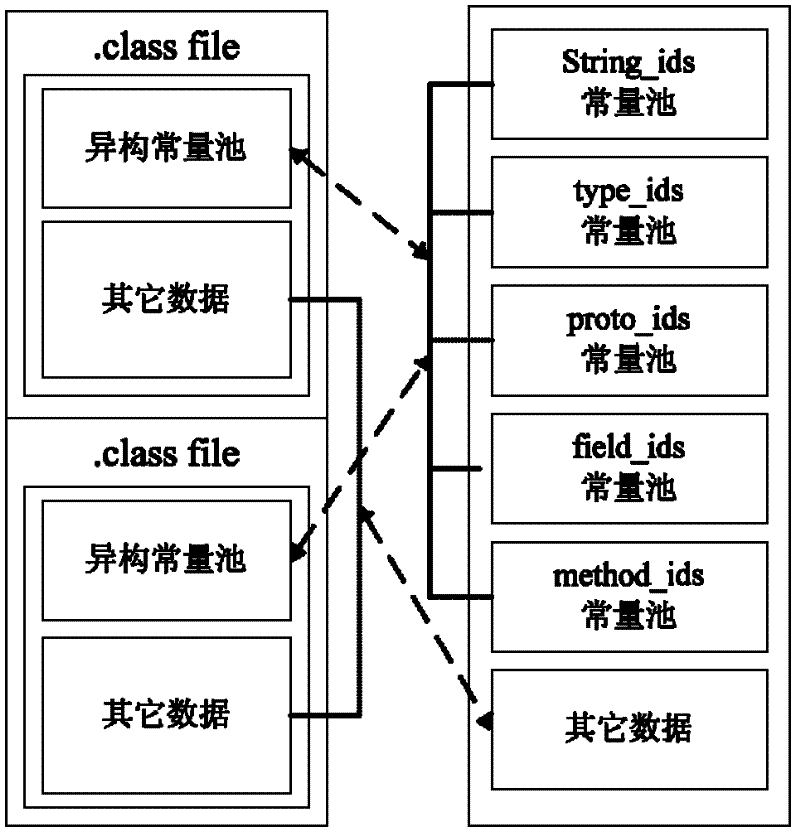
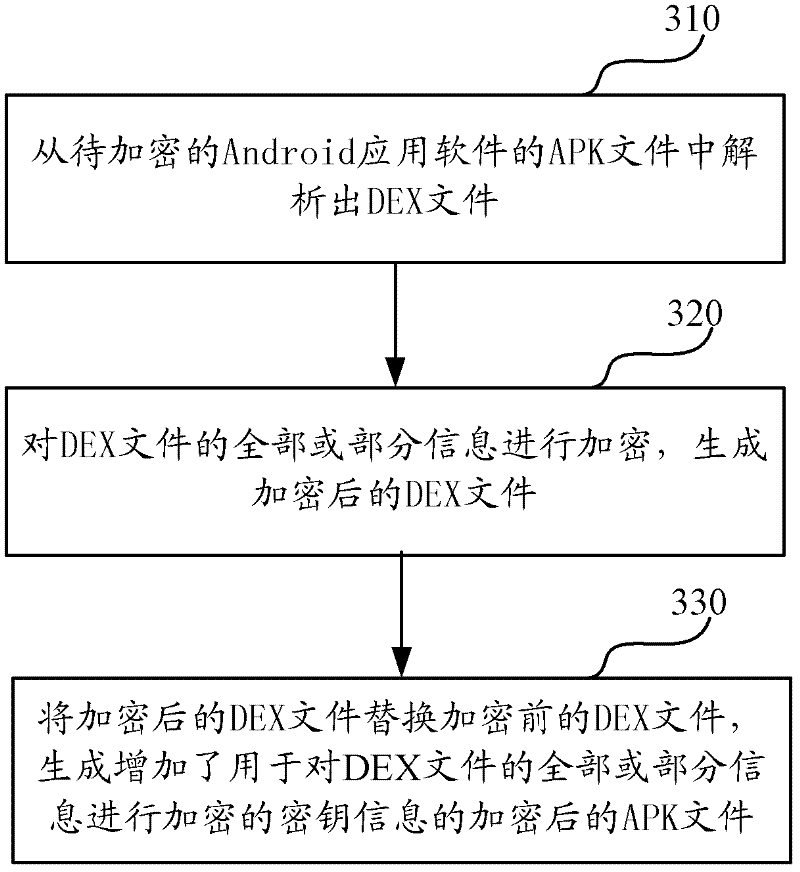
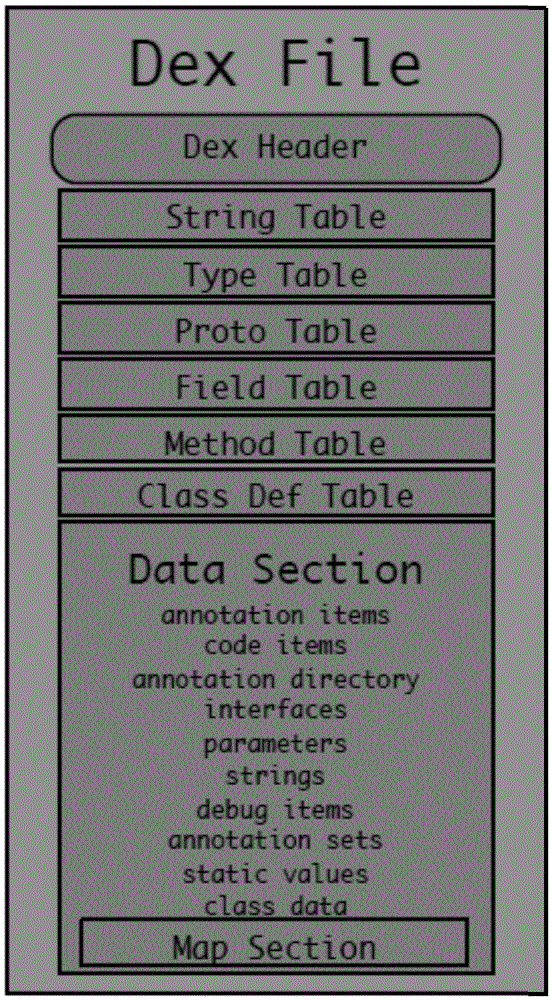
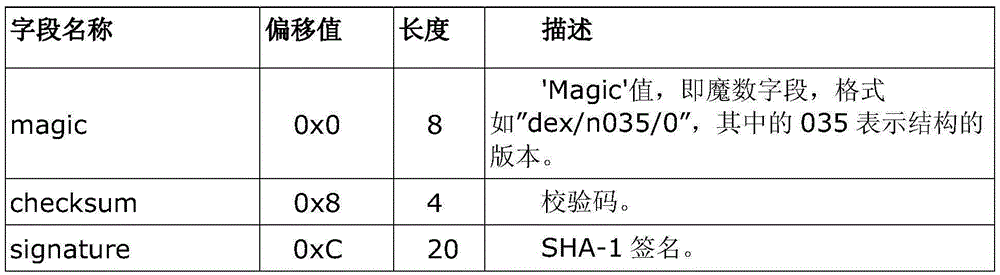
The invention discloses a software protection method and system applicable to an Android system. The method comprises the following steps of: analyzing: analyzing a DEX file from an APK (Android Package) file of Android application software to be encrypted; encrypting: encrypting all or a part of information of the DEX file to generate an encrypted DEX file; and generating, substituting the DEX file before encryption with the encrypted DEX file to generate the APK file formed by encrypting all or a part of the information of the DEX file and a digest file formed by performing MD5 (Message Digest 5) encryption on a key. Since the method only aims at the encryption protection of key information (such as a DEX file header, byte codes in the DEX file and the like) of the DEX file in the APK file, the execution efficiency of encryption and decryption is greatly increased.
Owner:BEIJING UNIV OF POSTS & TELECOMM
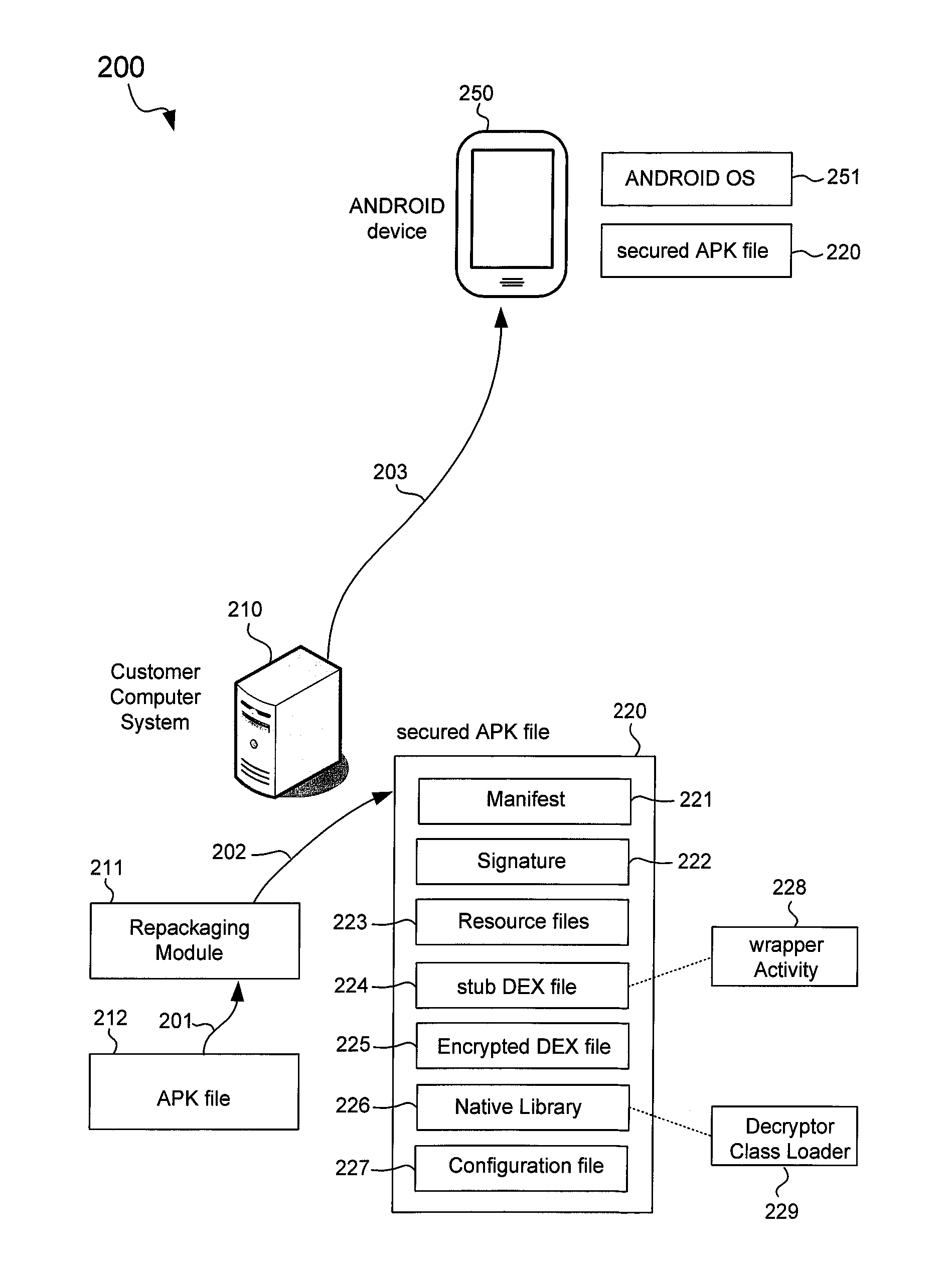
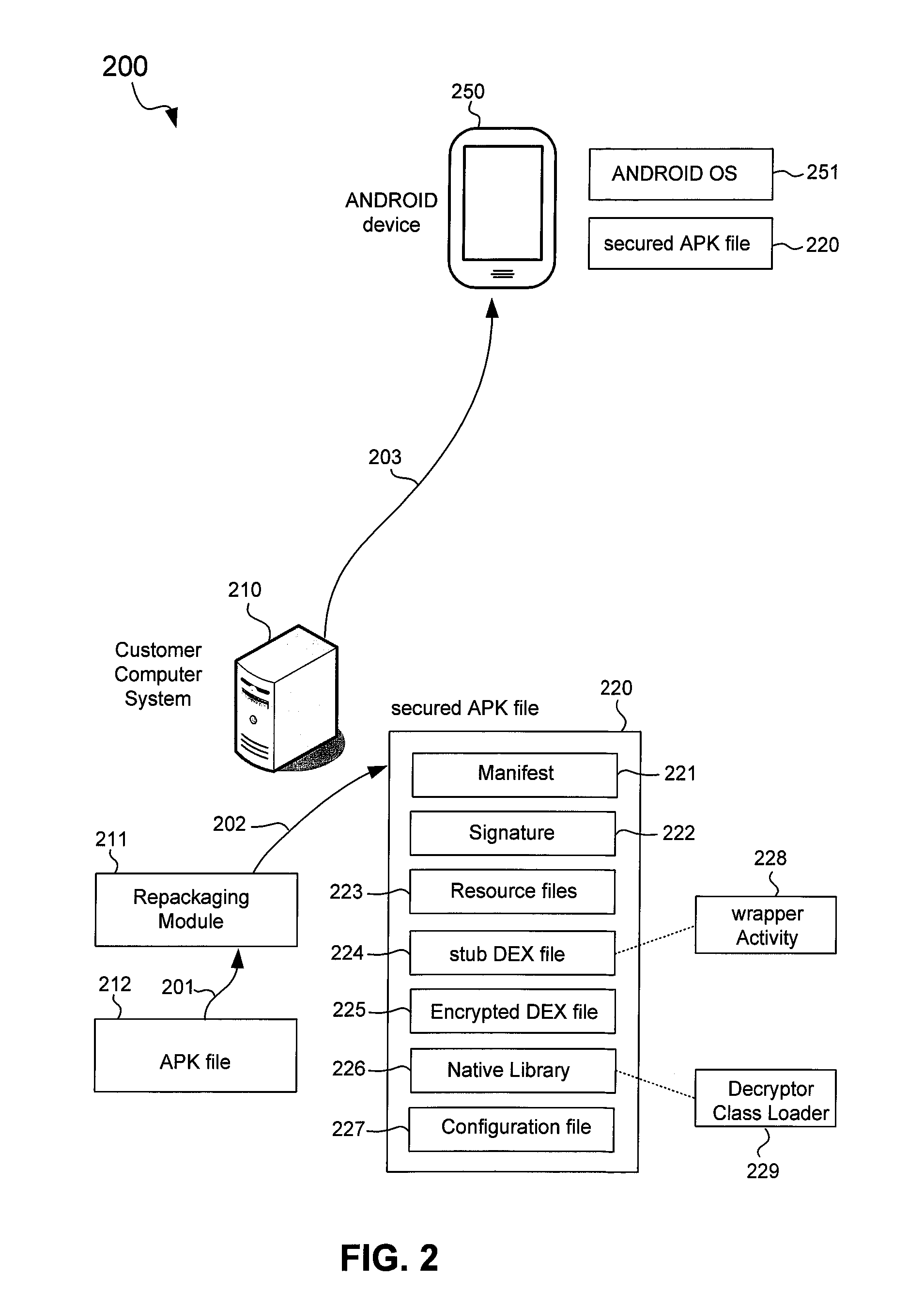
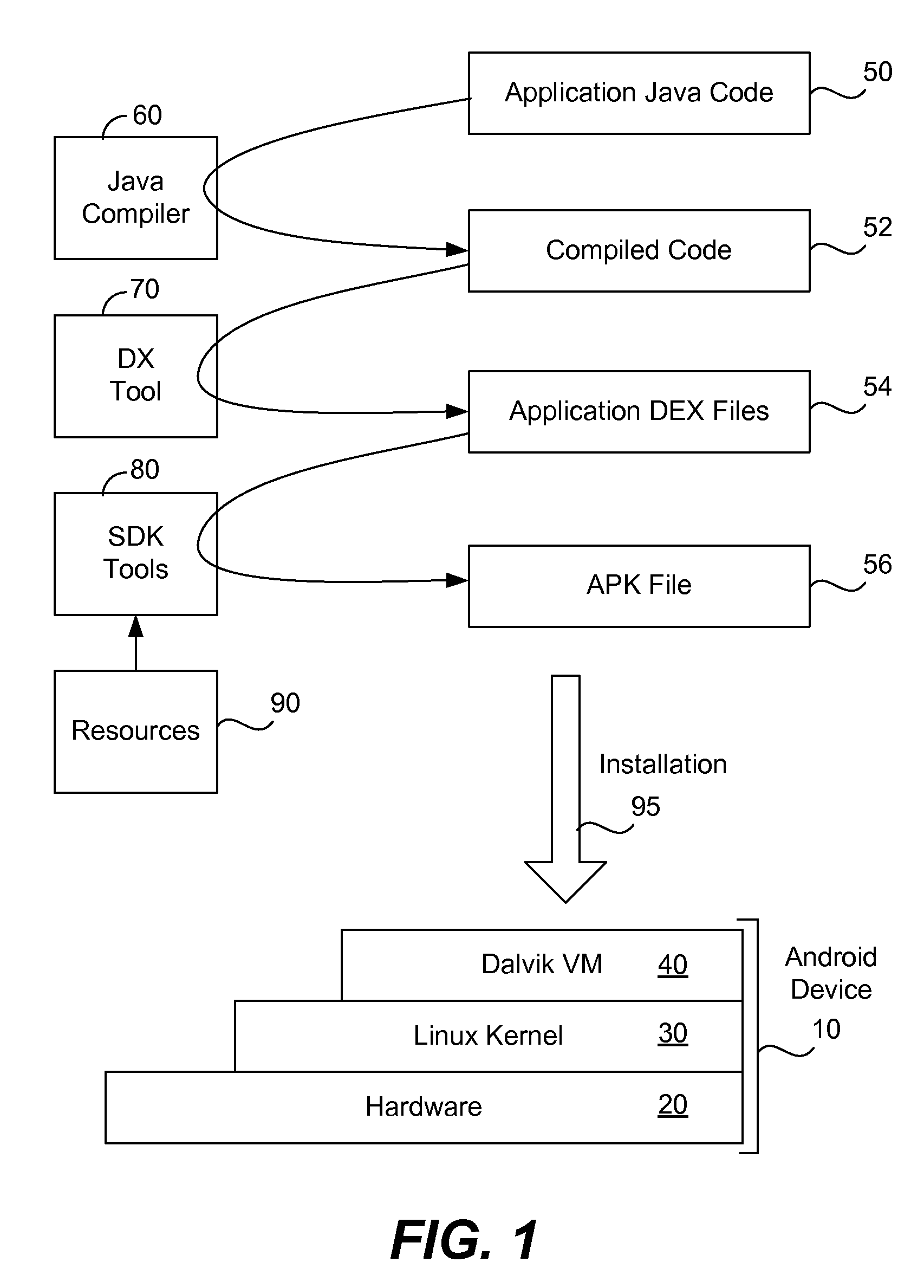
Secured application package files for mobile computing devices
An ANDROID application package (APK) file for an application is repackaged into a secured APK file to protect a Dalvik executable (DEX) file of the application. The DEX file is encrypted to generate an encrypted DEX file that is included in the secured APK file along with a stub DEX file. The secured APK file is received in a mobile computing device where the stub DEX file is started to start a wrapper Activity. The wrapper Activity replaces an APK class loader of a mobile operating system of the mobile computing device with a decryptor class loader. The decryptor class loader decrypts the encrypted DEX file to recover the DEX file, and loads classes of the DEX file into a Dalvik virtual machine. The original Activity of the application is then started to provide the functionality of the application in the mobile computing device.
Owner:TREND MICRO INC
Android application program permanent Root permission acquiring method
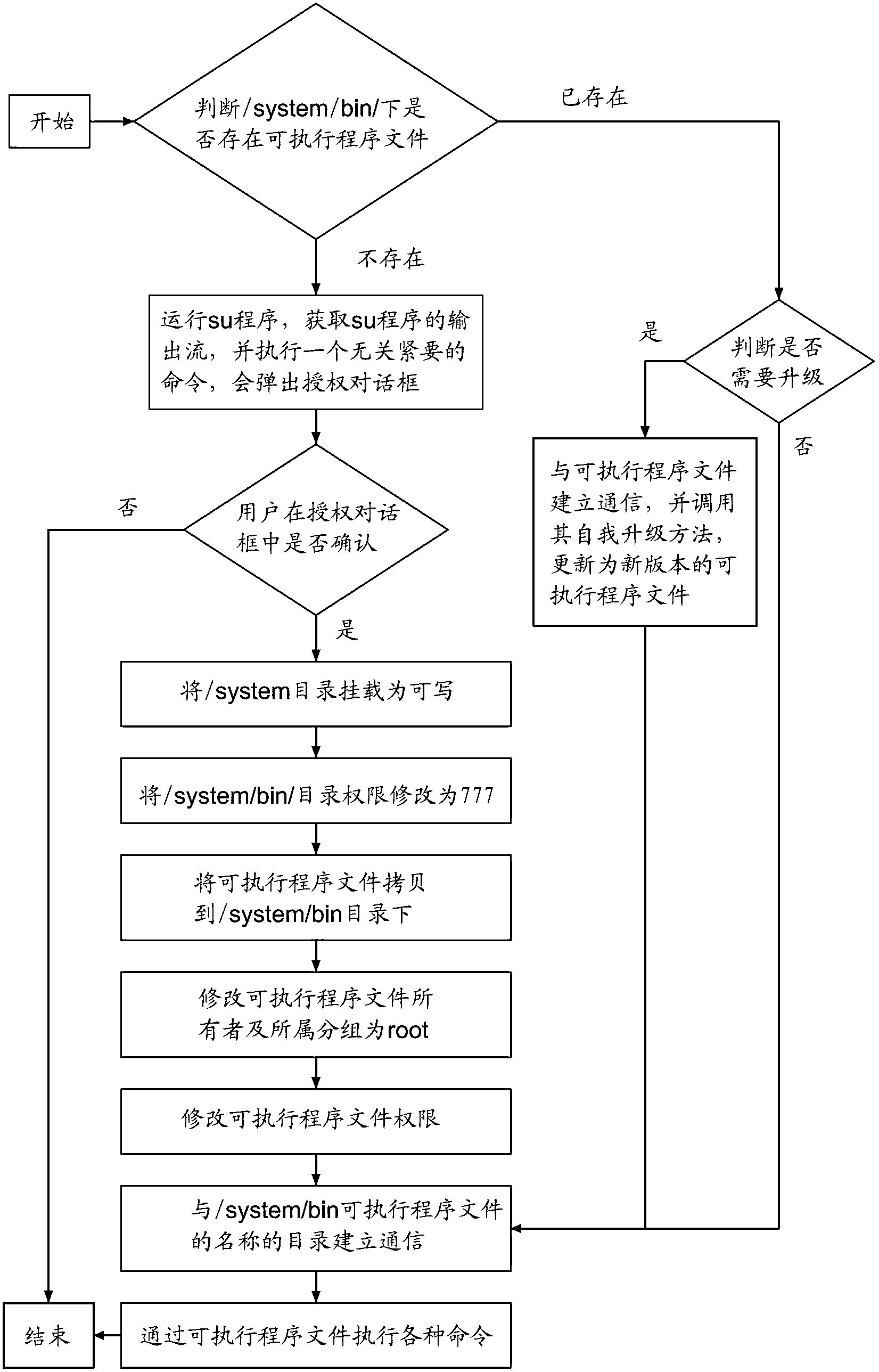
ActiveCN102981835AEasy to useAvoid popping againProgram loading/initiatingProgramming languageApplication software
The invention provides an android application program permanent Root permission acquiring method. The method includes the steps of editing operations where Root permission is needed, compiling the operations into an executable program document, containing the executable program document into an application program which is authorized through a one-time subscriber unit (su) program, copying the executable program document to a / system / bin directory, modifying an owner and a group of the executable program document to be a root, and setting the subscriber unit identification (suid) position. As a result, the executable program document can have the Root permission every time the executable program document is executed so as to prevent an authorized window from popping out again. Due to changes of requirements, the executable program document is likely to need upgrading. Therefore, the executable program document needs achieving a self-upgrading function so as to prevent the authorized window from popping out again when upgrading. The android application program permanent Root permission acquiring method executes various operations with the identification of the Root. Even if the application program is reinstalled and upgraded, the su program authorization operation does not need repeating again. Therefore, the android application program permanent Root permission acquiring method brings great convenience to users.
Owner:BAIDU COM TIMES TECH (BEIJING) CO LTD
Android application program risk assessment method based on dynamic monitoring
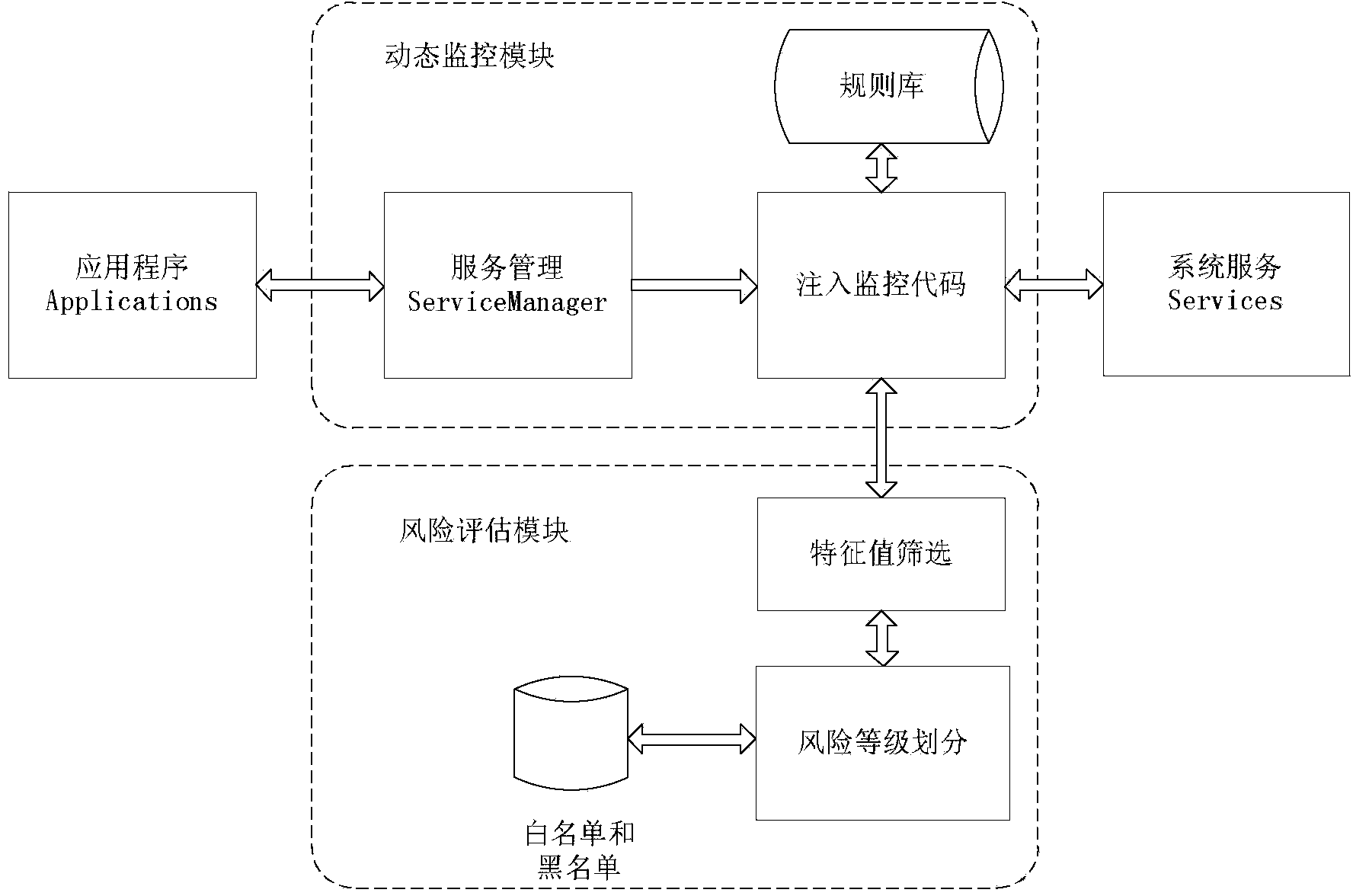
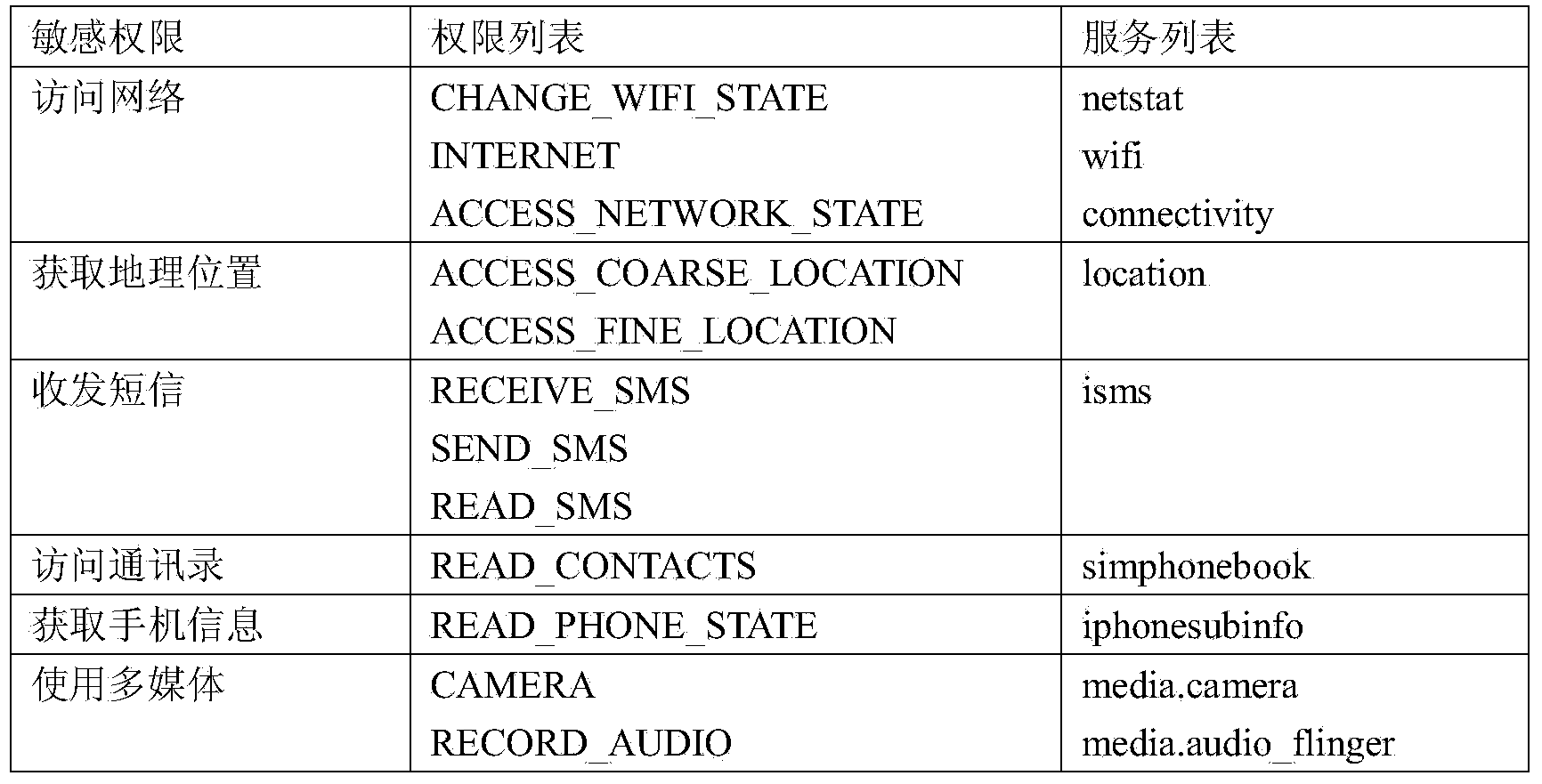
InactiveCN103927485ADetect security risksPredict maliciousnessPlatform integrity maintainanceDynamic monitoringInformation security
The invention discloses an Android application program risk assessment method based on dynamic monitoring, and belongs to the technical field of information safety. The method comprises the steps that firstly, monitoring codes are dynamically injected to a ServiceManager system process, and the aim of monitoring behaviors is achieved by monitoring an application service of an application program; then the risk grade of the application program is determined according to the behavior features of the application program, wherein the behavior features comprise whether a sensitivity operation is executed or not, whether operating is carried out in a background or not, whether operation frequency exceeds a certain threshold value or not and the like. The risk is divided into five grades, and meanwhile a white list and black list mechanism is set up to improve efficiency and accuracy. According to the method, maliciousness of unknown (malicious) software can be predicated, and potential safety hazards of an Android platform can be detected.
Owner:SOUTHEAST UNIV
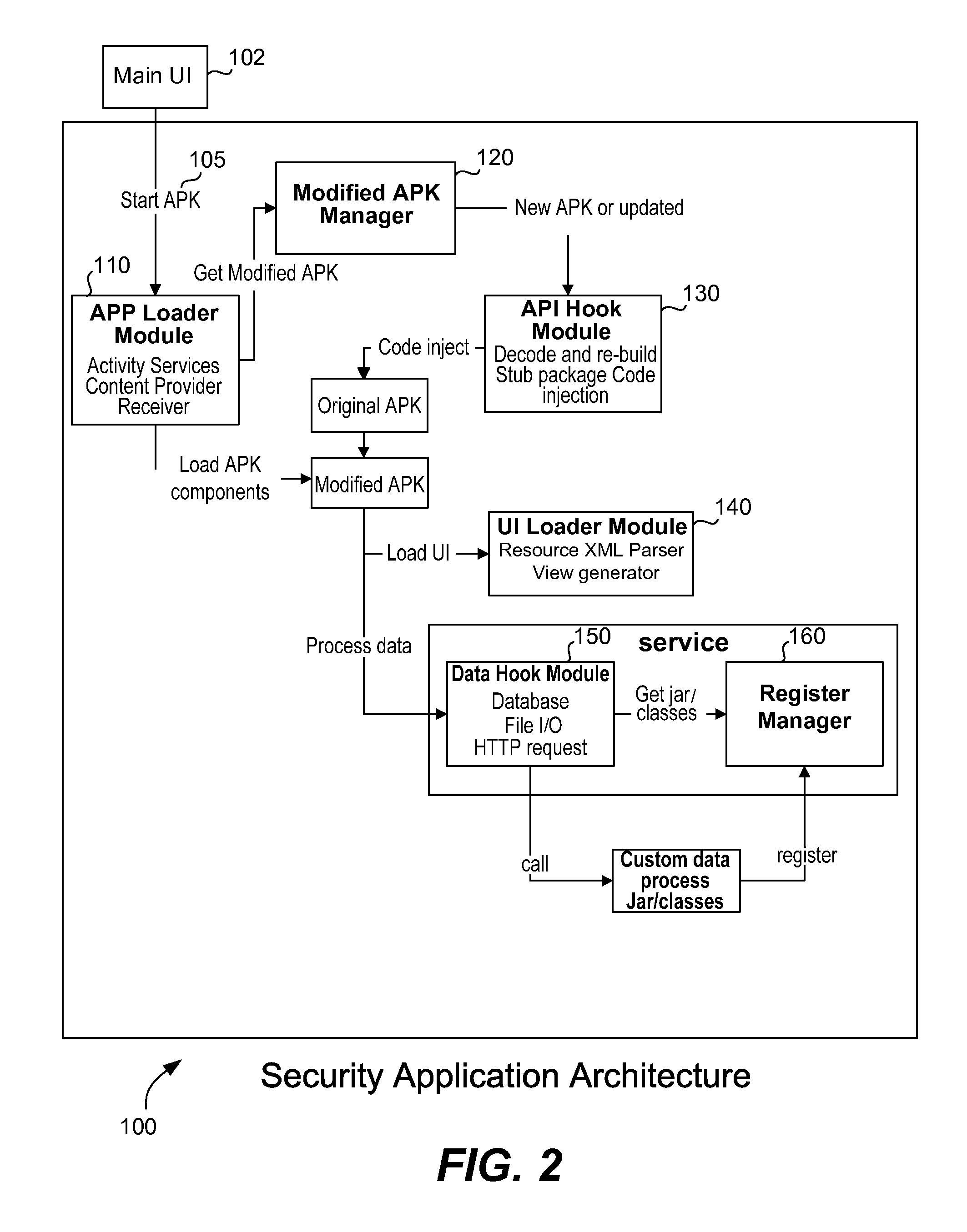
Android application virtual environment
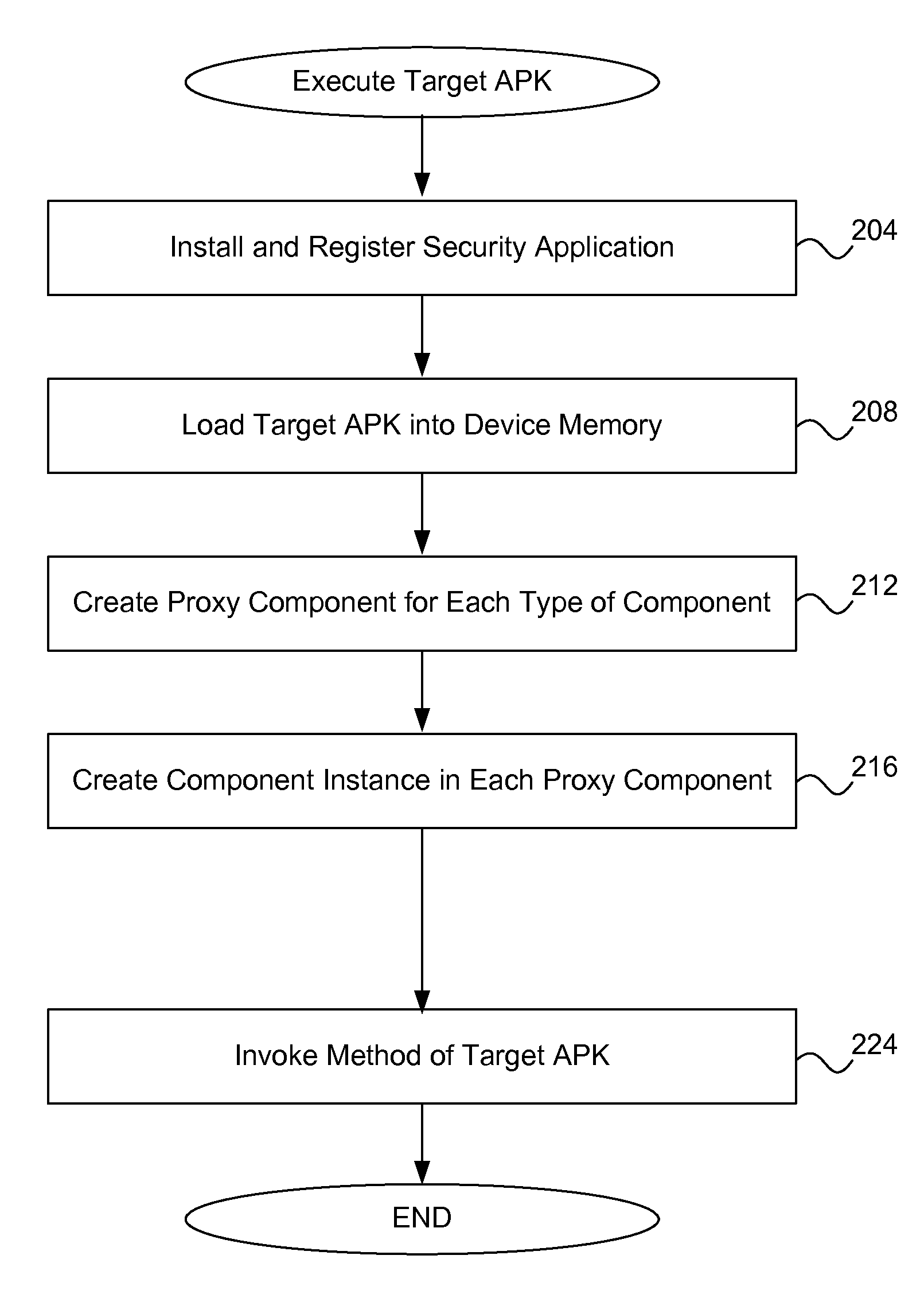
ActiveUS8887152B1Automatically change behaviorConsume lot of powerProgram loading/initiatingMemory systemsApplication softwareAndroid device
The behavior of an installed application within the Android device is modified. The program code is modified to allow a security application to load and run the application within its own context. The modified program code is repacked into a modified APK file, executed within the context of the security application. A component within a target application includes APIs for starting other components. These APIs are modified to use a new intent object which points to a proxy component. A modified target application is executed. The security application loads the target application into memory without installing it. The security application includes a component of each type and creates a proxy component instance for each component in the target application. A proxy component under control of the security application is created for each component within the target application. The target application is executed under the control of the security application.
Owner:TREND MICRO INC
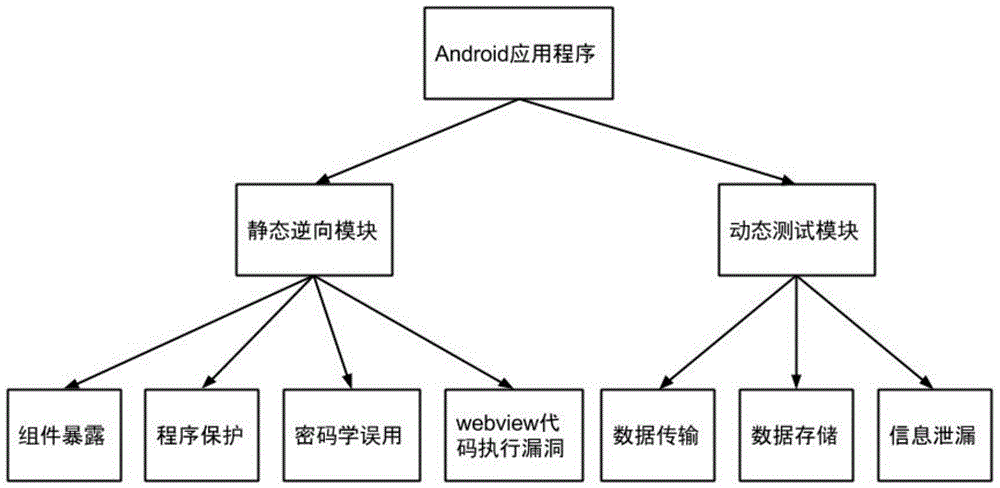
Universal method and universal system for performing safety testing on Android application programs
InactiveCN104484607AReduce false alarm ratePlatform integrity maintainanceApplication softwareSafety testing
The invention discloses a universal method and a universal system for performing safety testing on Android application programs. The universal method comprises the following steps of unpacking and decompiling a to-be-tested program to obtain an XML (extensive markup language) source code; then, through static analysis on configuration files and the code of the to-be-tested program, performing vulnerability detection and safety testing on the aspects of component exposed vulnerability, cryptology misuse, webview code execution vulnerability and code protection; then, performing actual running on the to-be-tested program, and configuring a network detection environment; finally, performing dynamic analysis, and performing dynamic vulnerability detection and the safety testing on three aspects of information leakage, data transmission safety and data storage safety, thus obtaining a vulnerability detection and safety testing report. According to the universal method and the universal system disclosed by the invention, by performing a static analysis and dynamic analysis combination mode on an optional Android application program and through a series of steps of detection and estimation, safety flaws and potential safety hazards existing in the aspects of design and implementation of the application program can be finally given out.
Owner:SHANGHAI JIAO TONG UNIV +1
Increment upgrading method based on Android application software
InactiveCN102707977ALess waitingReduce consumptionProgram loading/initiatingSoftware simulation/interpretation/emulationApplication softwareWaiting time
The invention relates to an increment upgrading method based on Android application software. The increment upgrading method comprises the following steps of: comparing a current version with a latest server version; downloading corresponding increment upgrading plug-in packs according to the differences of the versions; installing and running the increment upgrading plug-in packs; and modifying application program packs in increment upgrading manners set in the packs, wherein the application program pack is modified by modifying functional files and resource files in the packs. According to the increment upgrading method provided by the invention, the contents of increment upgrading comprise two different file targets, namely the functional files and the resource files, so that the increment upgrading plug-in packs only comprise modified upgrading files to the greatest extent. Therefore, the Android application software can carry out increment update on the aspects of functions and resources. Furthermore, the waiting time of a user and the flow consumption can be reduced, and the upgrading is more efficient, convenient and rapid.
Owner:JIANGSU LEMOTE TECH CORP
Android platform software protecting system, method and equipment
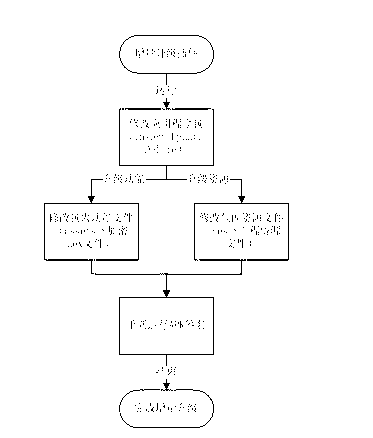
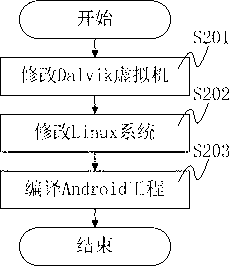
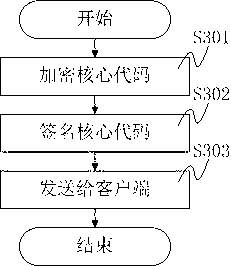
The invention mainly discloses a system and method for protecting application software in an Android system from reverse analysis and decryption. The method mainly comprises the following steps: increasing interfaces for a LiDalvik virtual machine and a Linux system library in the Android system, so that the Android has a capability of directly loading a DEX format file and an SO format file from a memory; storing a core code of the application software in an online server, encrypting and signing the core code, sending the core code to the application software installed at a client end; after receiving the core code, verifying the signature and decrypting the core code by the application software; storing a plaintext into the memory, and directly loading the plaintext into the system; invoking the code; and releasing the memory. The method greatly improves the difficulty in performing reverse analysis and decryption by an attacker, so that the safety of the Android application software can be effectively protected.
Owner:BEIJING ANTIY NETWORK SAFETY TECH CO LTD
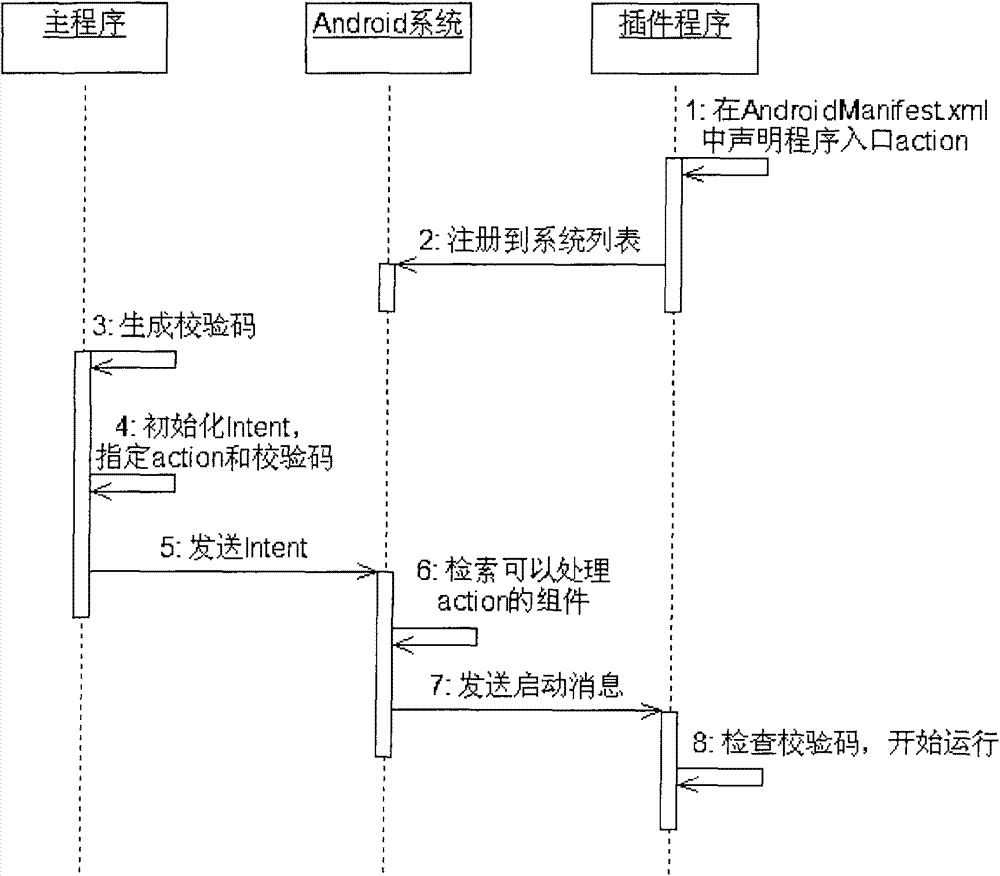
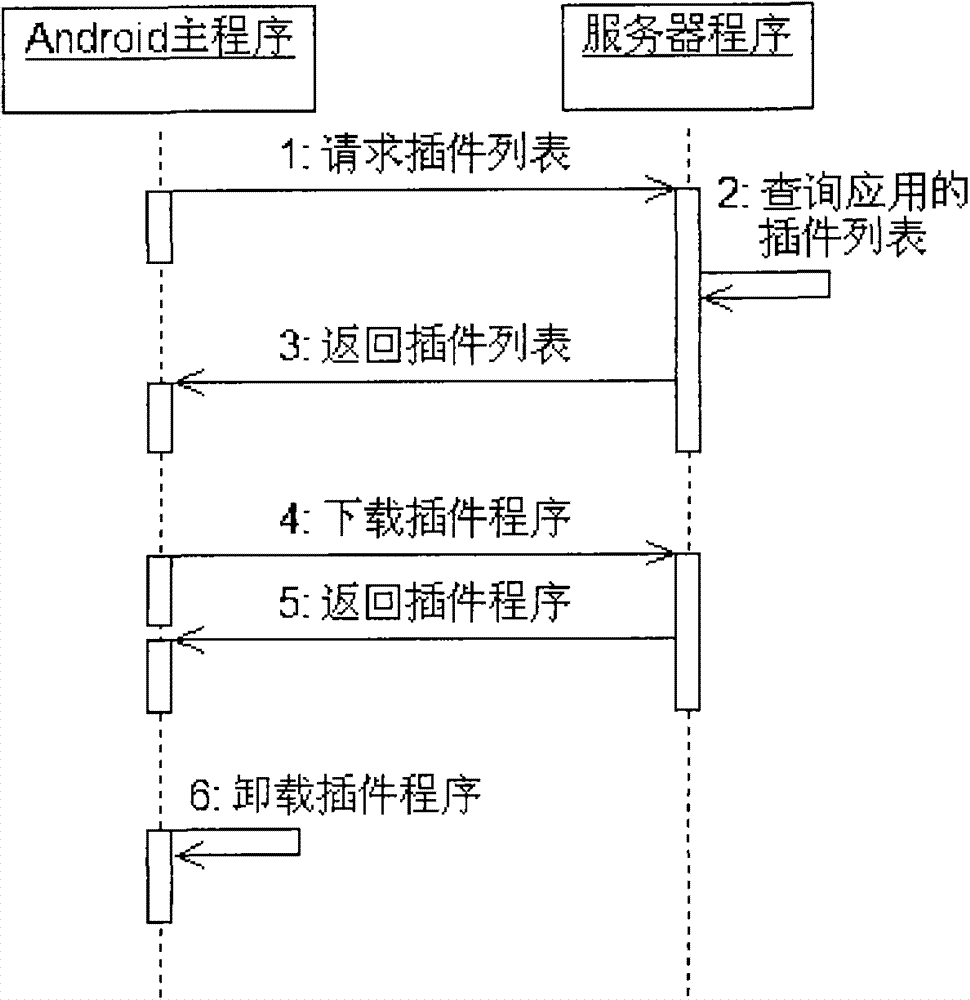
Implementation scheme of Android-based plug-in applications
The invention discloses an implementation scheme of Android-based plug-in applications. The scheme is mainly applied to the development of plug-in Android applications so as to solve the problems of large size, functional complexity and failure of partial update in applications. The implementation scheme is characterized in that as to a plug-in Android application, a non-core core function and a main application are separated, and accordingly the main application is smaller and resource consumption is less; plug-ins of the Android application can be configured dynamically and include configuration plug-ins and plug-in versions; the plug-ins are used for expanding the function of the Android application, and the plug-ins are dynamically updated through a plug-in list provided by a server; the plug-in versions are used for comparing the current version and a latest version for each plug-in; when the current version of each plug-in is older than the latest version, the Android application is allowed to update the plug-ins.
Owner:PCI TECH GRP CO LTD
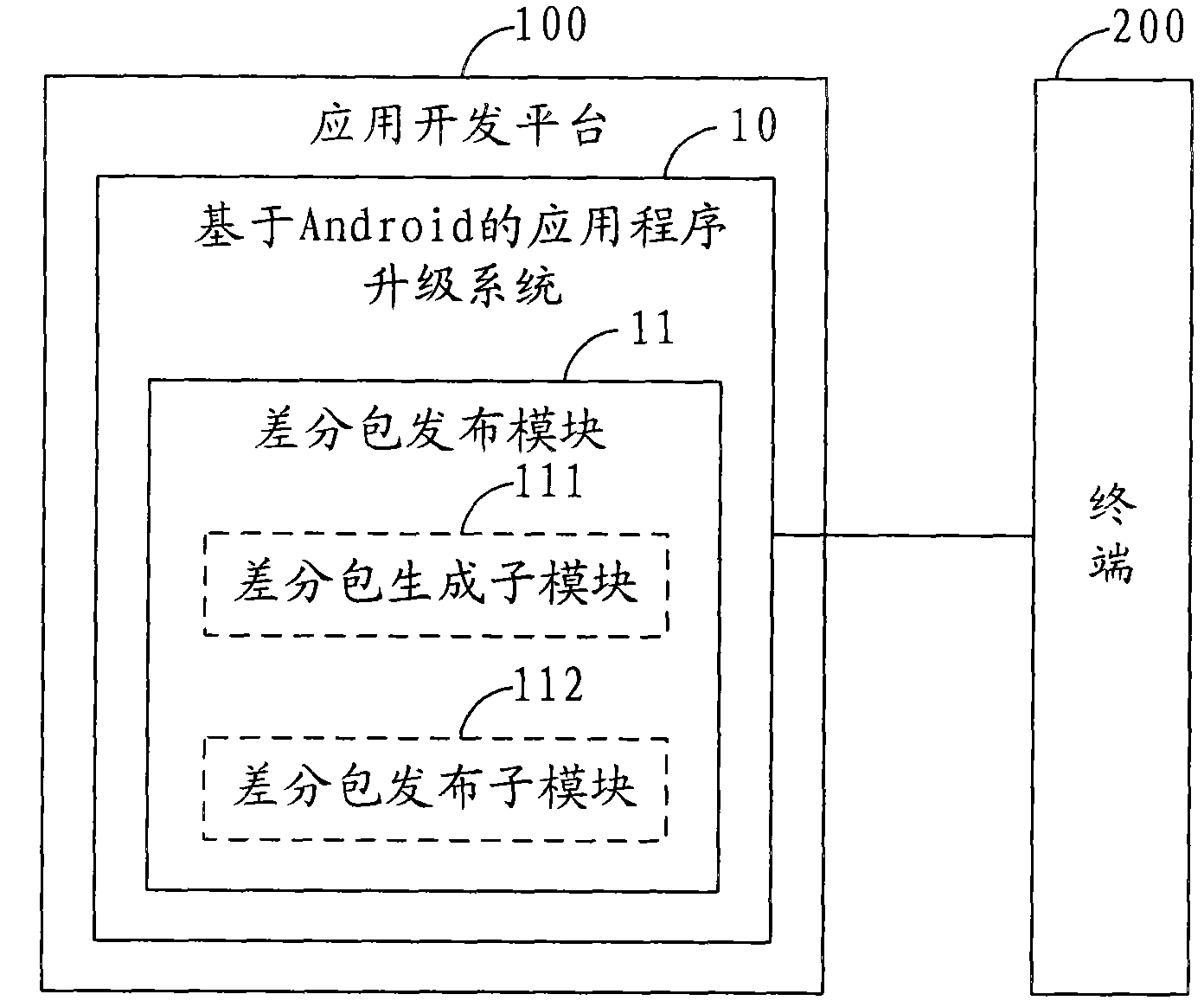
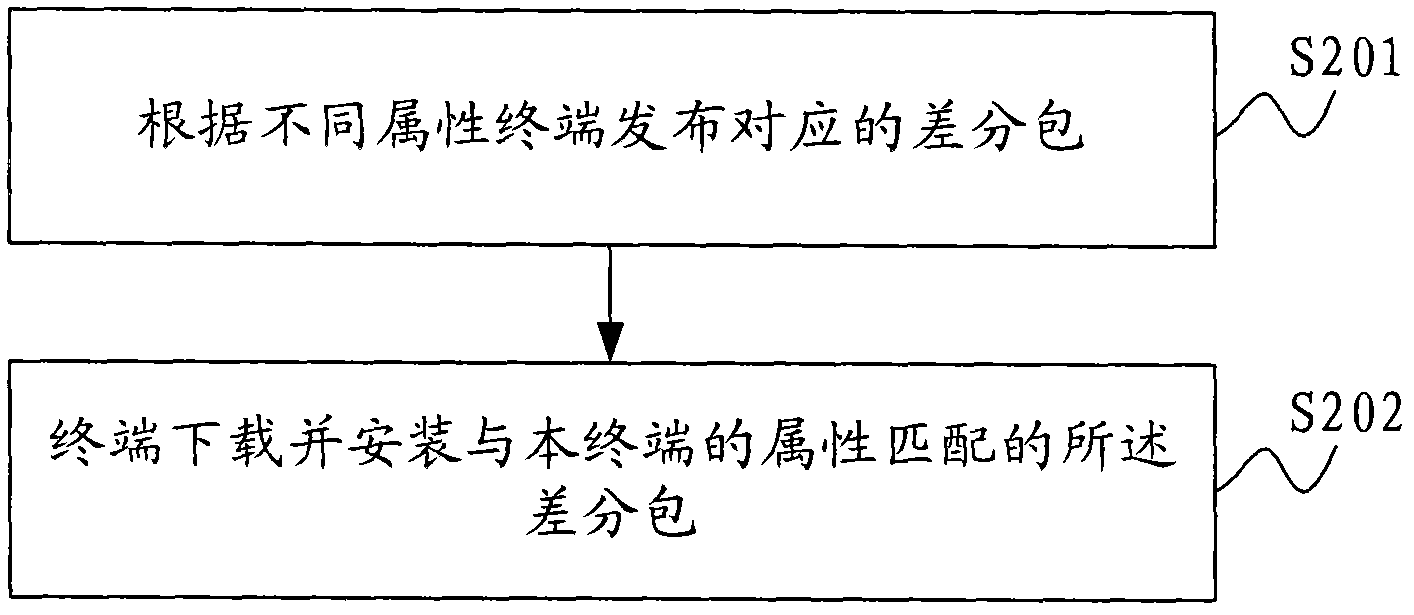
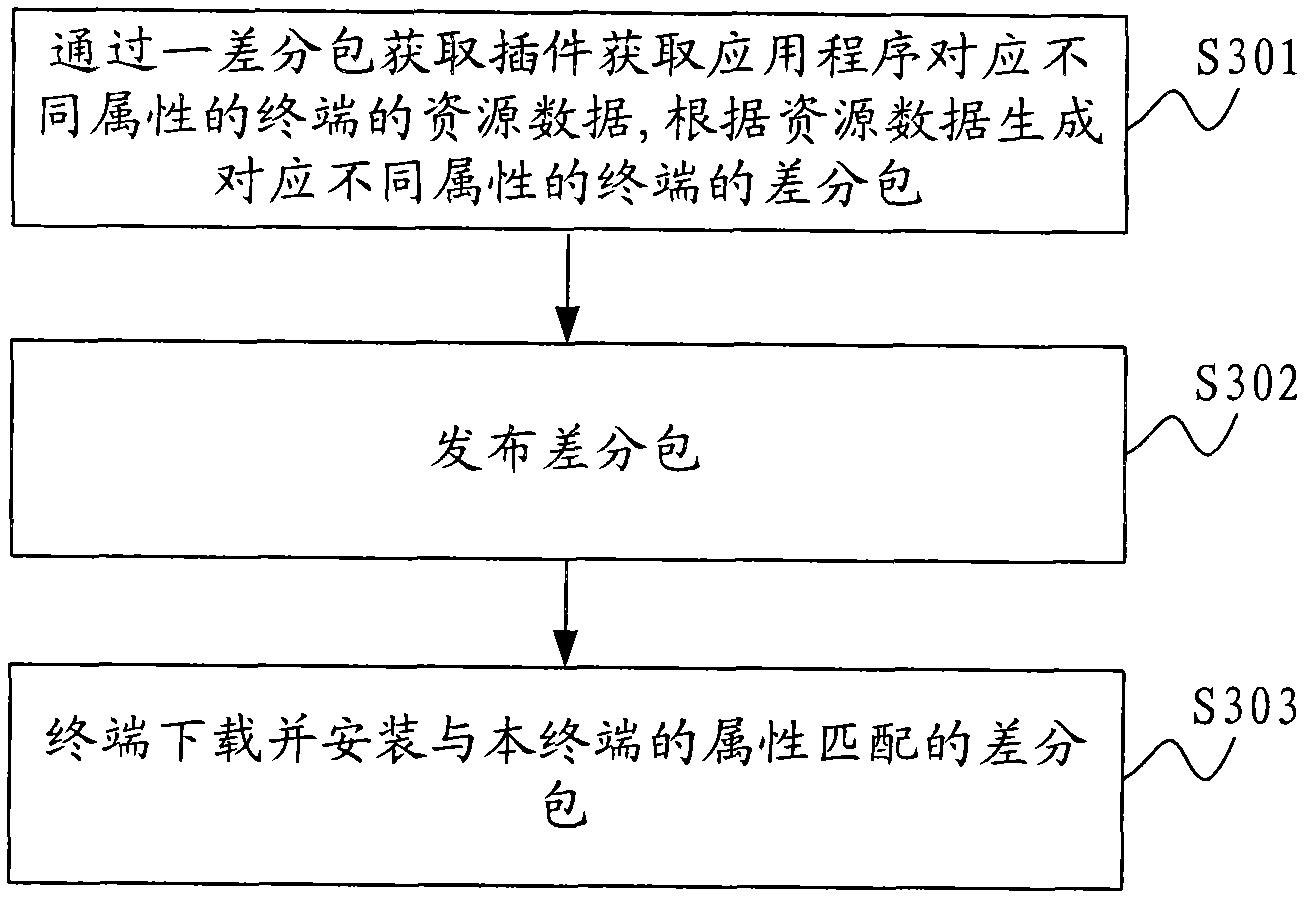
Android-based application program upgrading method and system and application development platform
ActiveCN102081535AAchieve upgradeEfficient upgradeProgram loading/initiatingComputer terminalApplication software
The invention is applicable to the technical field of communication and provides an Android-based application program upgrading method, an Android-based application program upgrading system and an application development platform. The method comprises the following steps of: releasing a corresponding difference packet from a terminal according to different attributes; and downloading and installing a difference packet matched with the attribute of the terminal through the terminal. In the process of upgrading an application program, difference packets of the application program corresponding to the terminal with different attributes can be rapidly released, namely that the same application program adapts to the terminal with different attributes can be met, while whole application development and release of different versions are not needed to be performed. Moreover, the terminal can upgrade the installed application program only by downloading and installing the difference packet without downloading and installing the whole application program of related versions. Therefore, the Android application program can be efficiently and conveniently upgraded at low cost.
Owner:DONGGUAN YULONG COMM TECH +1
Processing method and device of data file of android system
The invention discloses a processing method and a device of a data file of an android system. The processing method of the data file of the android system comprises the following steps. A relevance directory is configured in android equipment, and the relevance directory is stored with an android application program and location information of a corresponding data file of the android application program. When the operation of unloading the android application program executed by a user or scanning the garbage file of the data file executed by the user is detected, the android application program and the corresponding data file of the android application program are eliminated according to the relevance directory. According to the processing method and the device of the data file of the android system, the data file can be unloaded through two methods of deleting the data file or scanning the remaining data file in the process of unloading.
Owner:ZHUHAI JUNTIAN ELECTRONICS TECH +3
Android application strengthening method based on dynamic execution of dex and so files
PendingCN106203006AAvoid exposureAvoid gettingDigital data protectionProgram/content distribution protectionComputer hardwarePlaintext
The invention discloses an Android application strengthening method based on dynamic execution of dex and so files. Through an encryption method, key codes of an Android application are strengthened such that codes of the Android application are protected. The strengthening method comprises an encryption process and a decryption process and comprises following steps: strengthening key codes of the Android application during the encryption process; and decrypting when dynamic execution of the Android application. The Android application strengthening method based on dynamic execution of dex and so files has following beneficial effects: the C++ language is utilized for writing core dex decryption functions so that difficulty in decompilation is increased and the dex decryption functions are present in the form of a dynamic link library and encrypted; compared with the method of core dex dual encryption, key codes of the dynamic link library are encrypted and a JNI calling mechanism is removed during encryption; therefore, plaintext so files encrypted during encryption do not exist in a hard disk and stored in a memory; and the Android application strengthening method is higher in safety.
Owner:北京鼎源科技有限公司
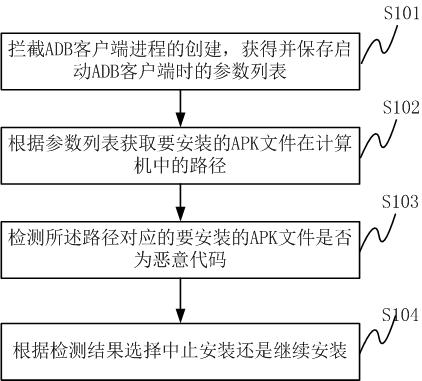
Method and system for detecting and intercepting malicious code of mobile terminal
InactiveCN102254113AStrong computing powerDoes not occupy and consume system resourcesPlatform integrity maintainanceTransmissionThird partyComputer terminal
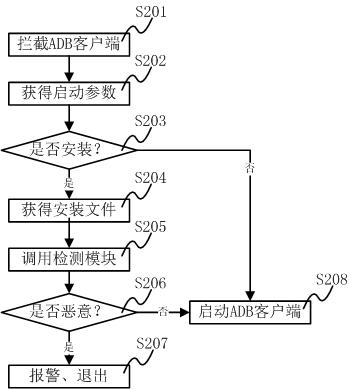
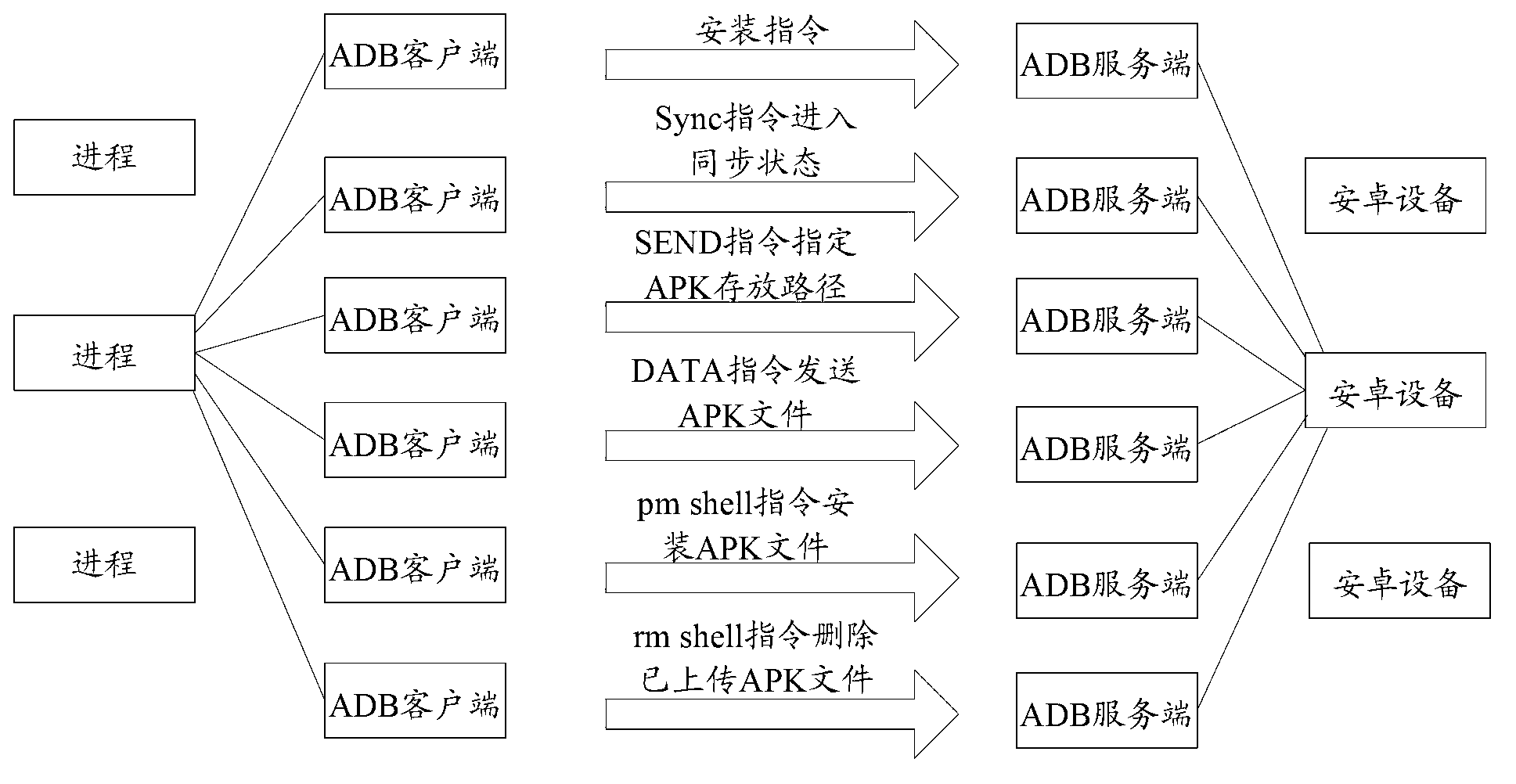
The invention discloses a method for detecting and intercepting a malicious code of a mobile terminal. The method comprises the following steps of: intercepting creating process of an Android debug bridge (ADB) client in a computer, and acquiring and saving a parameter list when the ADB client is started; judging whether an APK file (Android application program) is required to be installed according to the parameter list, if so, acquiring the route of the APK file to be installed in the computer; detecting whether the APK file to be installed corresponding to the route is the malicious code; and selecting stopping installing or continuously installing according to the detection result. The invention further discloses a system for detecting and intercepting a malicious code of a mobile terminal. The method and the system do not consume system resources of the mobile phone; the method and the system are suitable for the existing various installation methods and the third party mobile phone aided software; and the method and the system can effectively prevent the malicious code from spreading to the intelligent mobile phone through the computer.
Owner:SHENZHEN ANZHITIAN INFORMATION TECH
Android platform malicious application detection method and device based on deep learning
ActiveCN104123500AImprove securitySolving the detection problem of Android malicious applicationPlatform integrity maintainanceFeature extractionComputer science
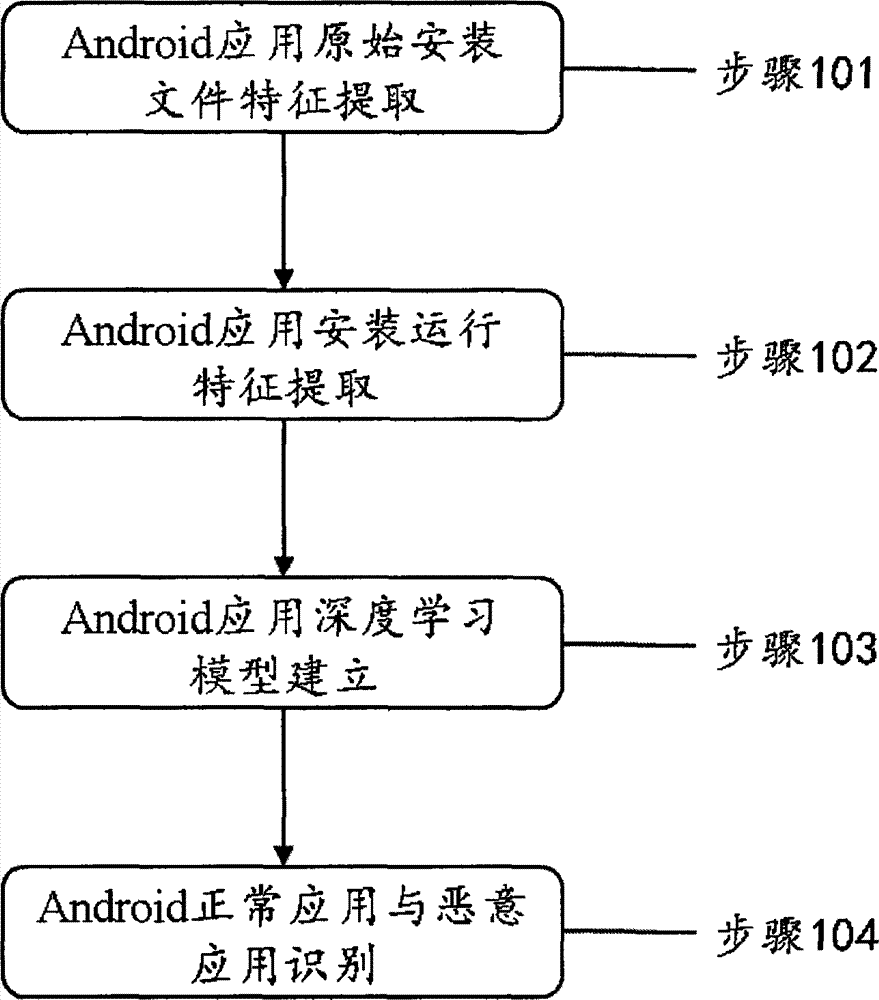
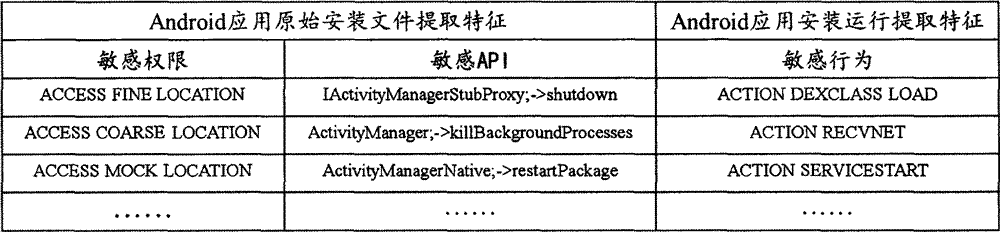
The invention discloses an Android platform malicious application detection method and device based on deep learning. The method comprises the first step of extracting Android application original installation files, the second step of extracting Android application installation operating features, the third step of setting up an Android application deep learning model and the fourth step of recognizing Android normal applications and Android malicious applications.
Owner:北京赋乐科技有限公司
Static taint analysis and symbolic execution-based Android application vulnerability discovery method
ActiveCN106709356ATargetedImprove efficiencyPlatform integrity maintainanceStatic timing analysisData stream
The invention discloses a static taint analysis and symbolic execution-based Android application vulnerability discovery method, and mainly aims at solving the problems that the analysis range is fixed, the memory consumption is huge and the analysis result is mistakenly reported in the process of discovering vulnerabilities by using the existing static taint analysis method. The method is realized through the following steps of: 1) configuring an analysis target and decompiling a program source code; 2) carrying out control flow analysis on the decompilation result; 3) selecting a source function by a user according to the control flow analysis result, so as to narrow an analysis target; 4) carrying out data flow analysis according to the control flow analysis result, so as to generate a vulnerability path; and 5) filtering the data flow analysis result by adoption of a static symbolic execution technology, taking the residual parts after the filtration as discovered vulnerabilities, warning the user and printing the vulnerability path. On the basis of the existing static taint analysis technology, the method disclosed by the invention has the advantages of extending the vulnerability discovery range, decreasing the memory consumption of vulnerability discovery and improving the accuracy of vulnerability discovery results, and can be applied to the discovery and research of Android application program vulnerabilities.
Owner:XIDIAN UNIV
Android application vulnerability detection method and Android application vulnerability detection system
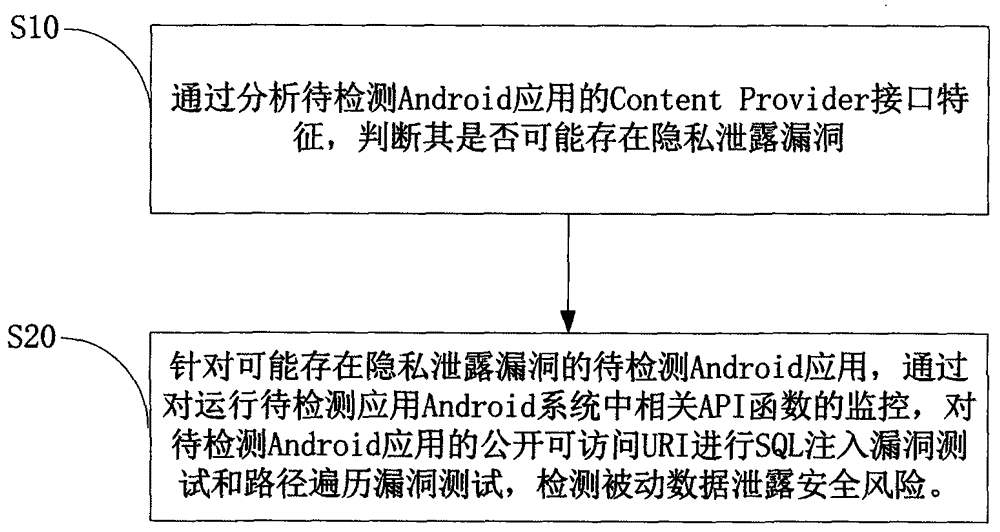
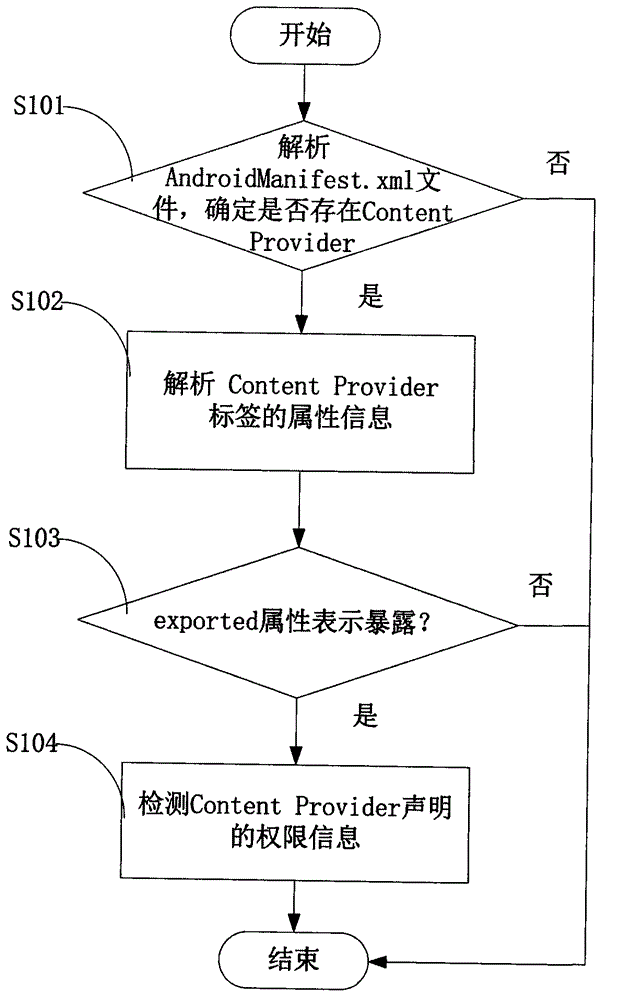
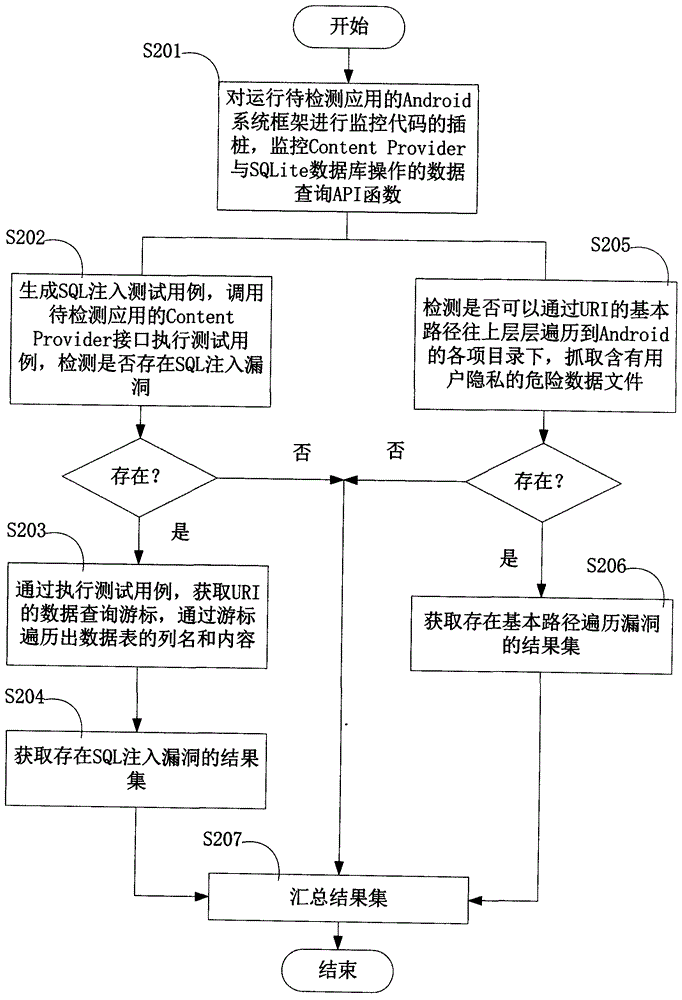
InactiveCN103984900AAvoid false positivesEfficient discoveryPlatform integrity maintainanceSQL injectionUniform resource identifier
The invention provides an Android application vulnerability detection method which comprises the following steps: 1, judging whether a privacy leakage vulnerability possibly exists or not by virtue of analyzing Content Provider interface characteristics of a to-be-detected Android application; 2, if the privacy leakage vulnerability possibly exists, performing an SQL (Structured Query Lanaguge) injection vulnerability test and a path traversal vulnerability test on a public accessible URI (Uniform Resource Identifier) of the to-be-detected Android application which possibly has the privacy leakage vulnerability by virtue of monitoring a related API (Application Program Interface) function in an Android system, and then detecting passive data leakage safety risks. The invention also provides an Android application vulnerability detection system. The method and the system can be used for rapidly discovering privacy leakage and data pollution vulnerabilities possibly existing in the Android application, avoiding misdeclaration, and providing a powerful support for discovering the privacy leakage and data pollution vulnerabilities in the Android application on a large scale.
Owner:南京赛宁信息技术有限公司 +1
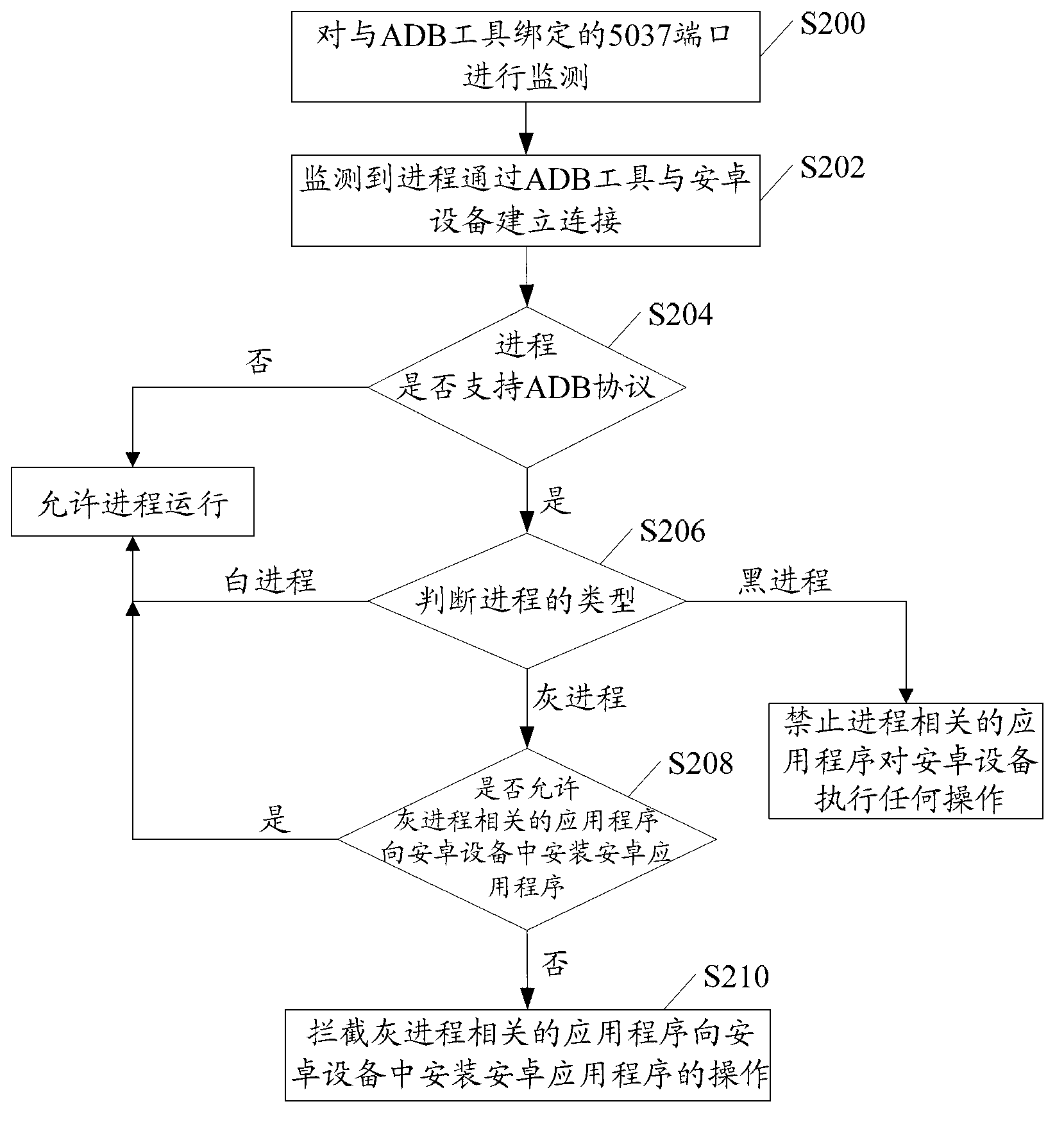
Method and device for intercepting installation of Android application program in mobile terminal
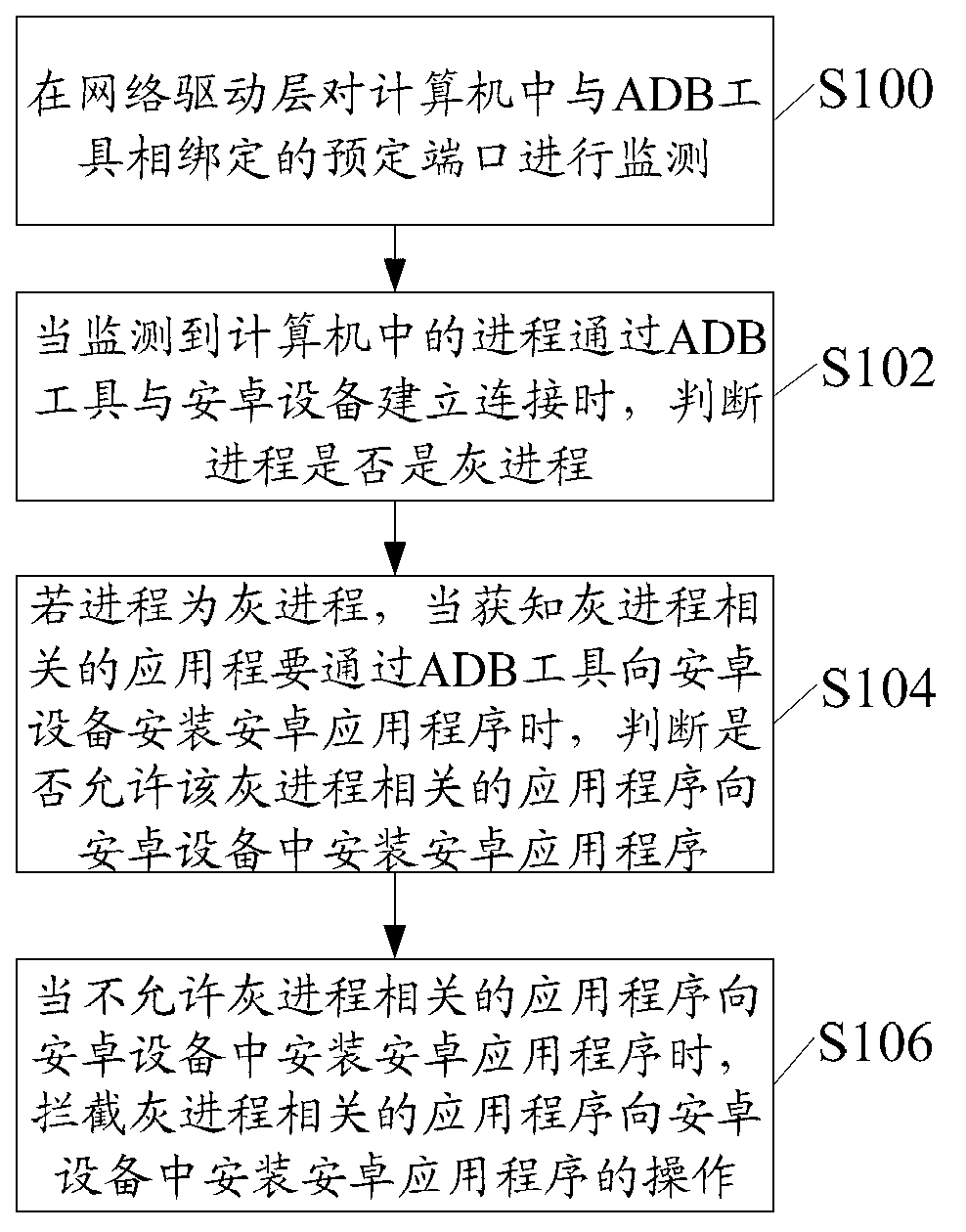
ActiveCN103279706AEnsure safetyEasy to usePlatform integrity maintainanceComputer terminalAndroid application
The invention discloses a method and a device for intercepting installation of an Android application program in a mobile terminal. The method comprises the steps of monitoring a preset port bound with an Android debug bridge (ADB) tool in a computer in a network driver layer; when the fact that a process in the computer is connected with the mobile terminal through the ADB tool is detected, judging whether the process is a grey process; if the process is the grey process, judging whether to allow application programs related to the grey process to install the Android application program in the mobile terminal or not when the application programs related to the grey process are to install the Android application program in the mobile terminal through the ADB tool; and intercepting the operation that the application programs related to the grey process install the Android application program in the mobile terminal when the application programs related to the grey process are not allowed to install the Android application program in the mobile terminal.
Owner:北京鸿享技术服务有限公司
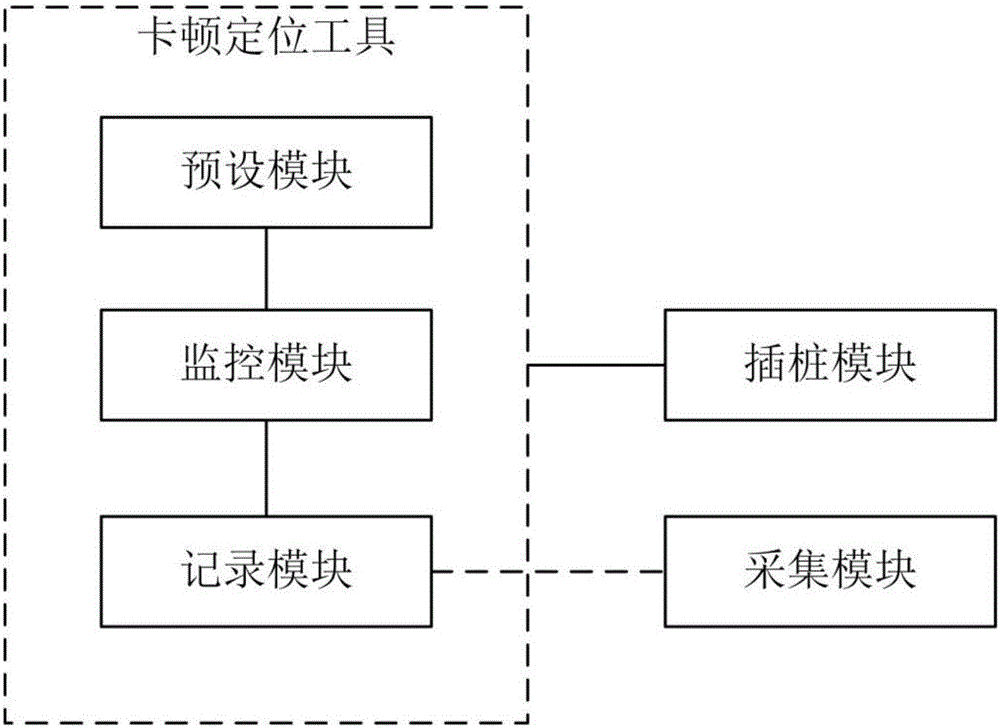
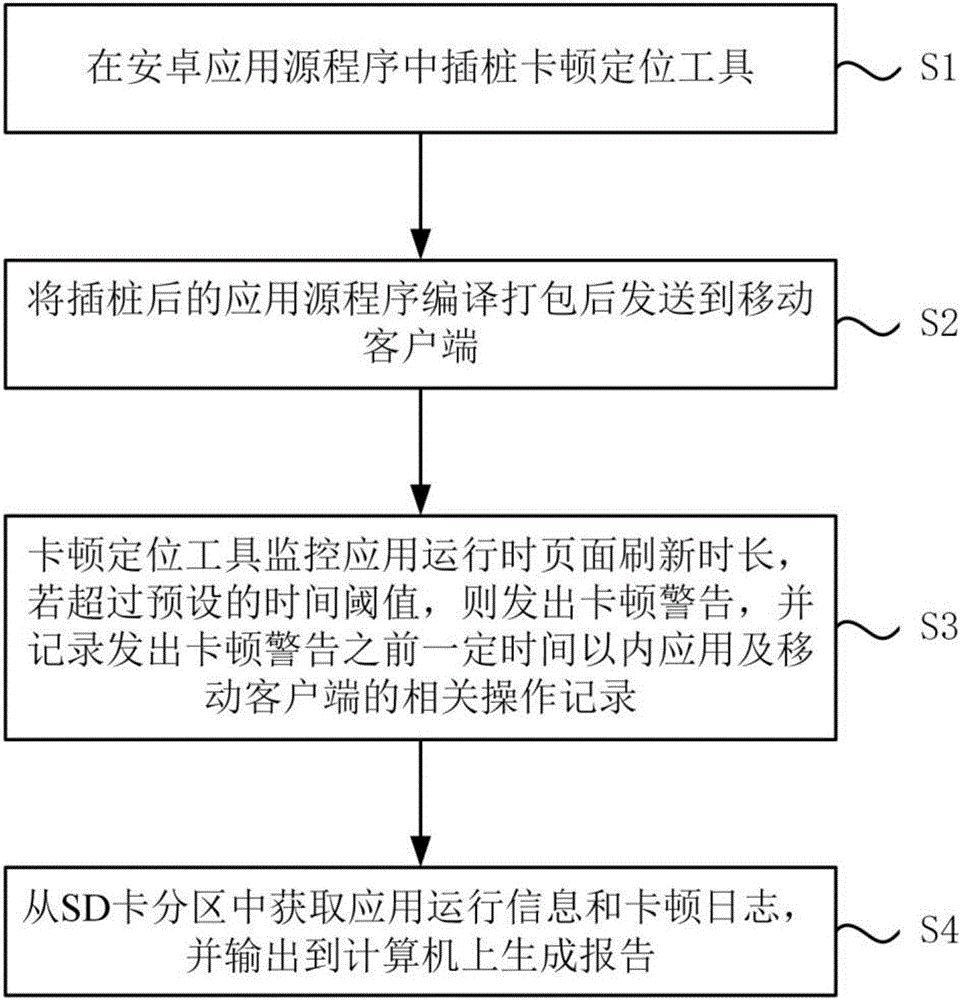
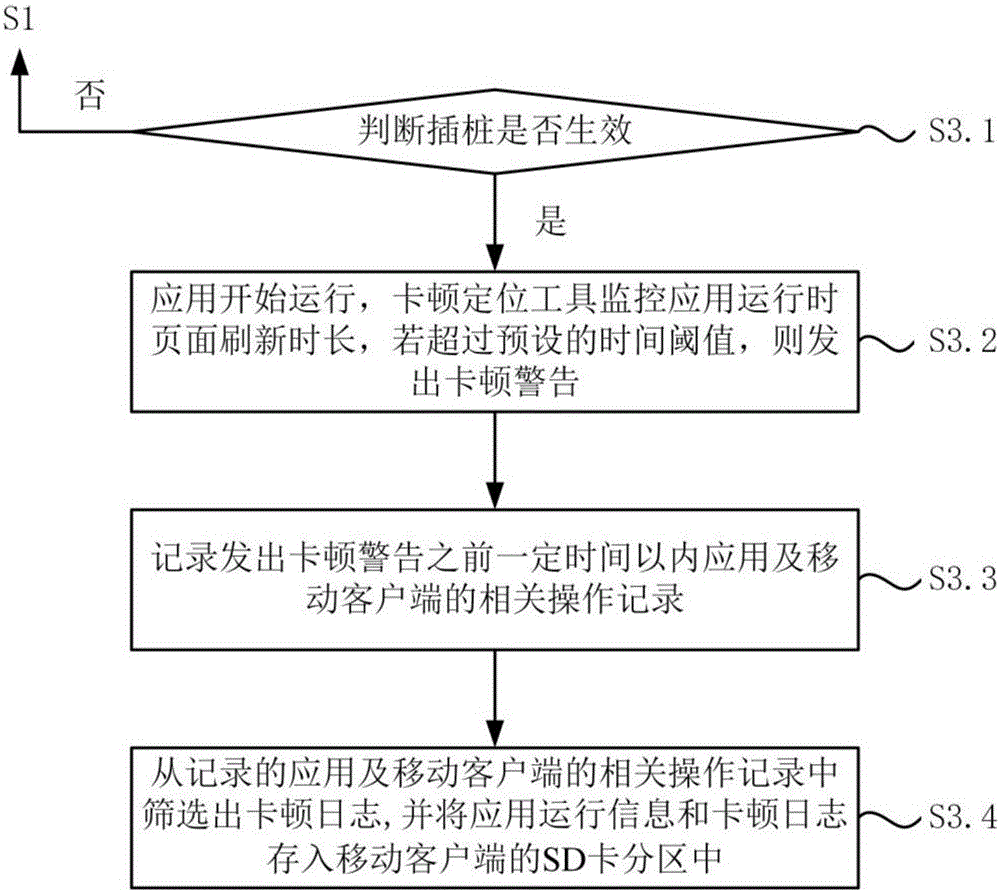
Application not responding positioning system and method
InactiveCN106681913ARapid positioningPrecise positioningSoftware testing/debuggingPositioning systemMobile client
The invention discloses an application not responding positioning system and method, and relates to the technical field of networks. The application not responding positioning system includes a plugging module which is used for plugging an application not responding positioning tool in an Android application source program, compiling and packing the plugged application source program, and then sending the packed application source program to a mobile client. The application not responding positioning tool includes: a preset module for predetermining the time threshold of application not responding before an application runs; a monitoring module which is used for monitoring the page refreshing time length while the application runs, and sending an application not responding alarm while the page refreshing time length exceeds the time threshold; and a recording module which is used for acquiring and recording the application not responding alarm, and recording relative operation records of the application and the mobile client within certain time before the application not responding alarm is sent. The application not responding positioning system and method can rapidly and accurately position the root of application not responding, can help a developer to perform further analysis and improvement on defects of the application, can improve the development efficiency of the application, and can reduce the development cost.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
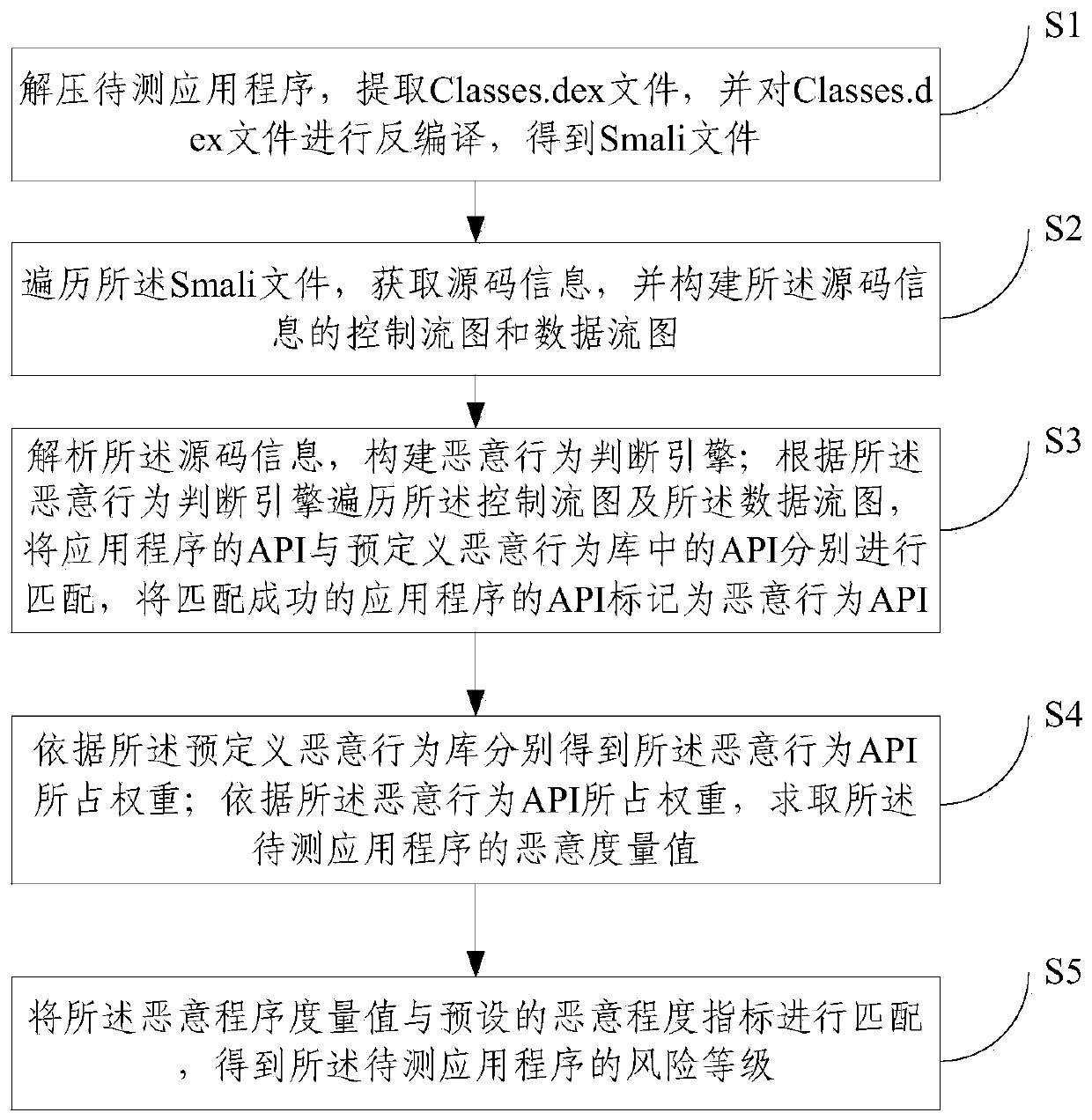
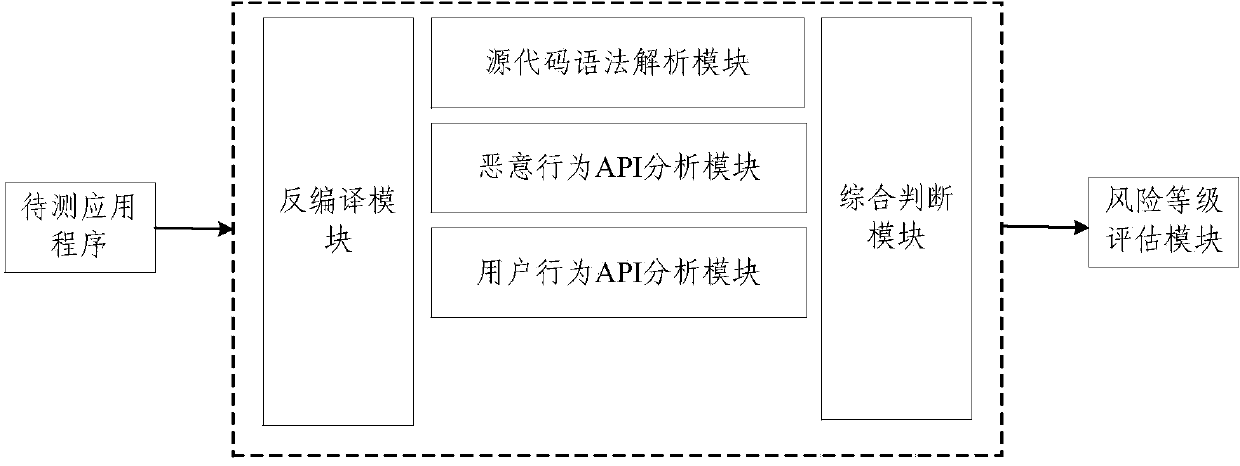
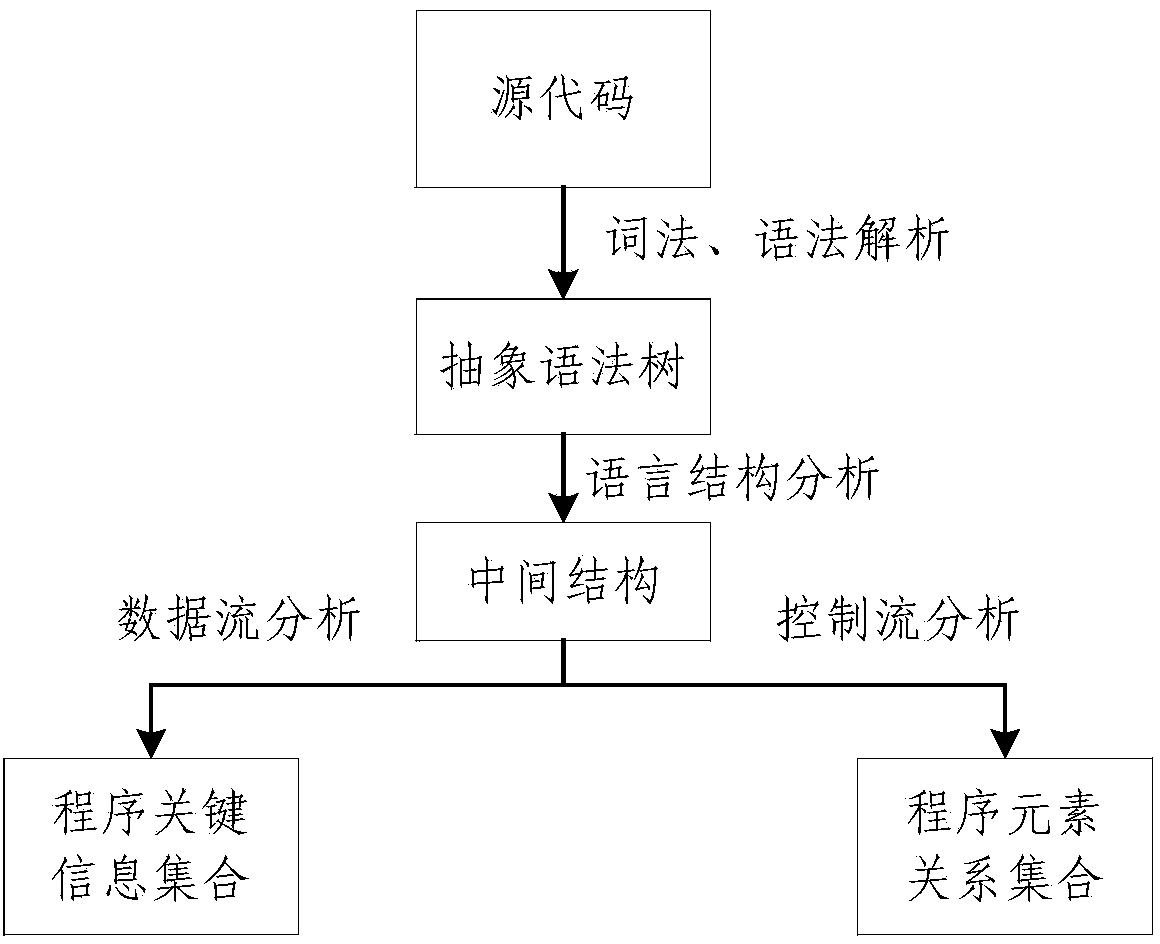
Static analysis method and static analysis device for Android application program
InactiveCN103793650AReduce the risk of miscalculationReduce misjudgmentPlatform integrity maintainanceRisk levelData stream
The invention provides a static analysis method and a static analysis device for an Android application program and relates to the technical field of security detection. The static analysis method includes: S1, unzipping an application program to be detected to obtain a Smali file; S2, traversing the Smali file to acquire a source code information and structuring a control flow diagram and a data flow diagram of the source code information; S3, traversing the control flow diagram and the data flow diagram according to a malicious behavior judging engine to respectively match an API (application program interface) of the application program with another API in a predefined malicious behavior library and marking the successfully matched API of the application program as the malicious behavior API; S4, calculating the malicious measuring value of the application program to be detected; S5, matching the malicious measuring value with a predefined malicious degree index to acquire risk level of the application program to be detected. Through behavior analysis and comprehensive judgment of combined rules, misjudgment rate of virus detection upon the Android application program can be reduced.
Owner:BEIJING UNIV OF POSTS & TELECOMM +1
Privacy leaking detecting method and system for android application network communication
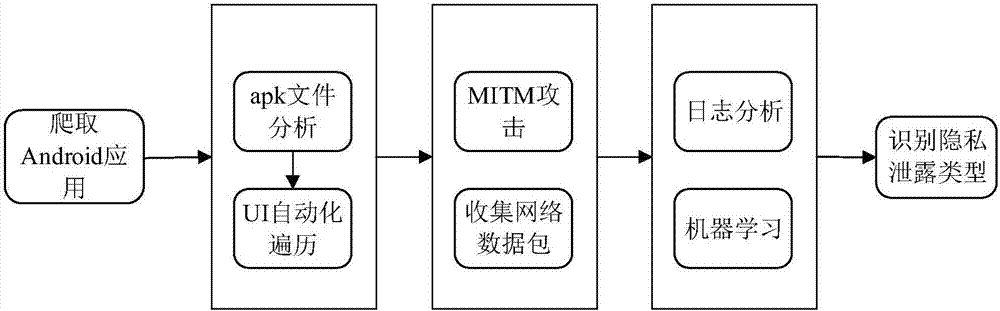
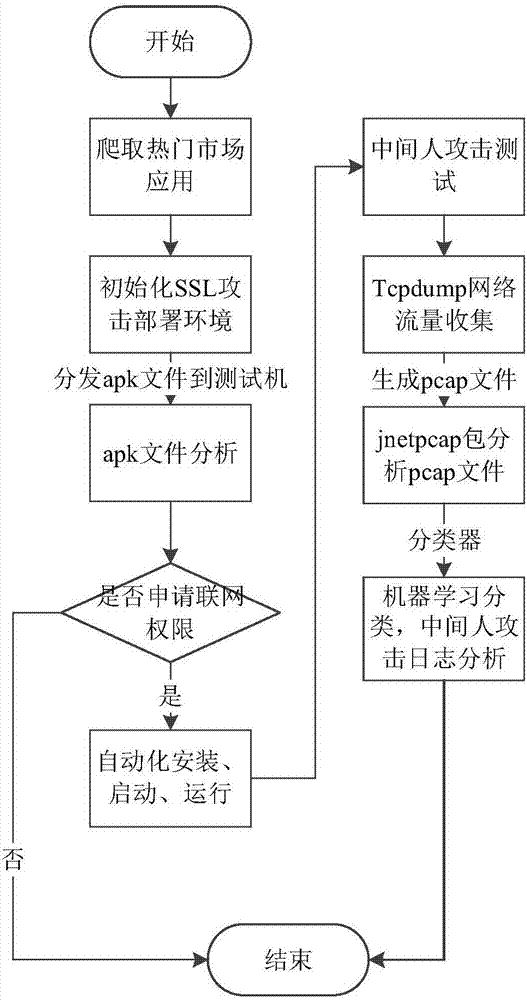
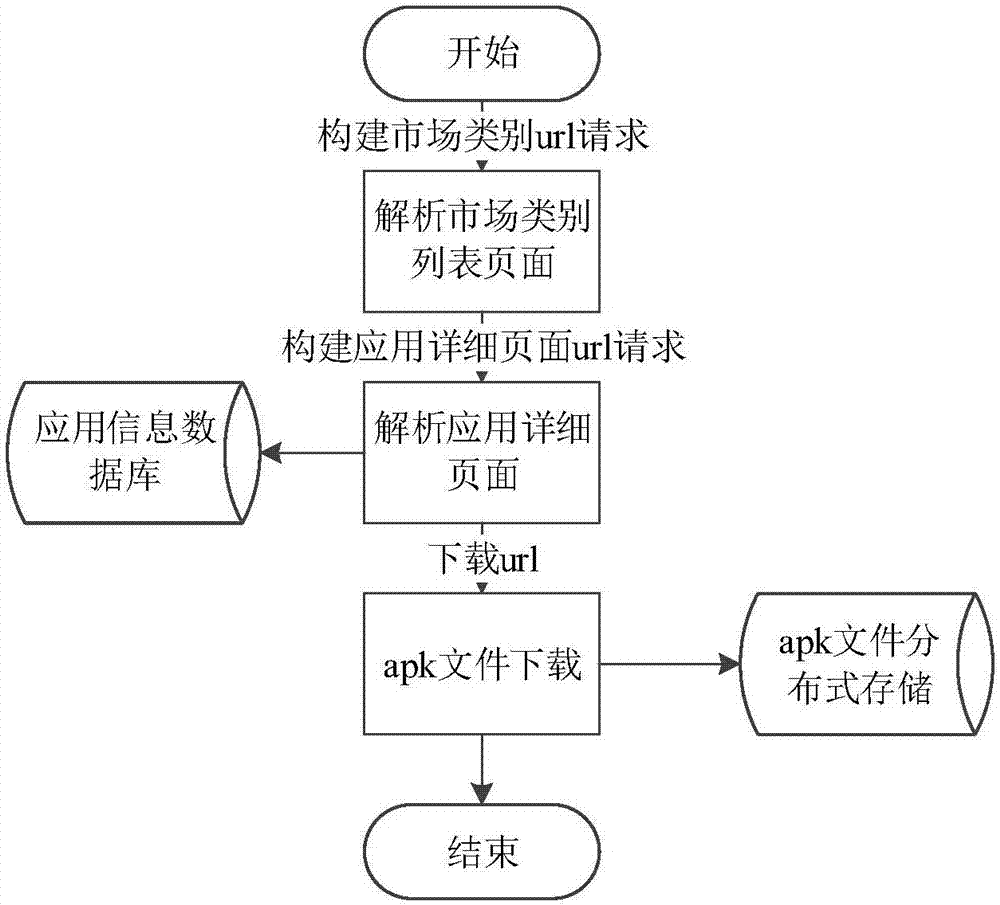
ActiveCN107133519AAccurate Privacy Leakage BehaviorAccurate detection of privacy leakage behaviorWeb data indexingPlatform integrity maintainanceMan-in-the-middle attackInternet privacy
The invention discloses a privacy leaking detecting method and system for android application network communication. The method comprises the following steps: crawling android application to be detected, and building an application set to be detected; building a main-in-the-middle attack server; initializing each tester environment; arranging a multi-tester distributive running scheduling system; analyzing APK files of the application to be detected; installing the application program corresponding to the APK file, and driving the application program to run; analyzing a log file created by the Burp Suite, and acquiring the application set with SSL man-in-the-middle attack; analyzing a network data pack file created in the running process of the collected application program; recognizing the privacy leaking type of the network data pack file according to the application set with the SSL man-in-the-middle attack. The method is flexible to use, and automatic in the whole process; the android system and the android application program structure are not modified; the privacy leaking behavior of the android application in the network communication process can be safely and accurately detected.
Owner:HUAZHONG UNIV OF SCI & TECH
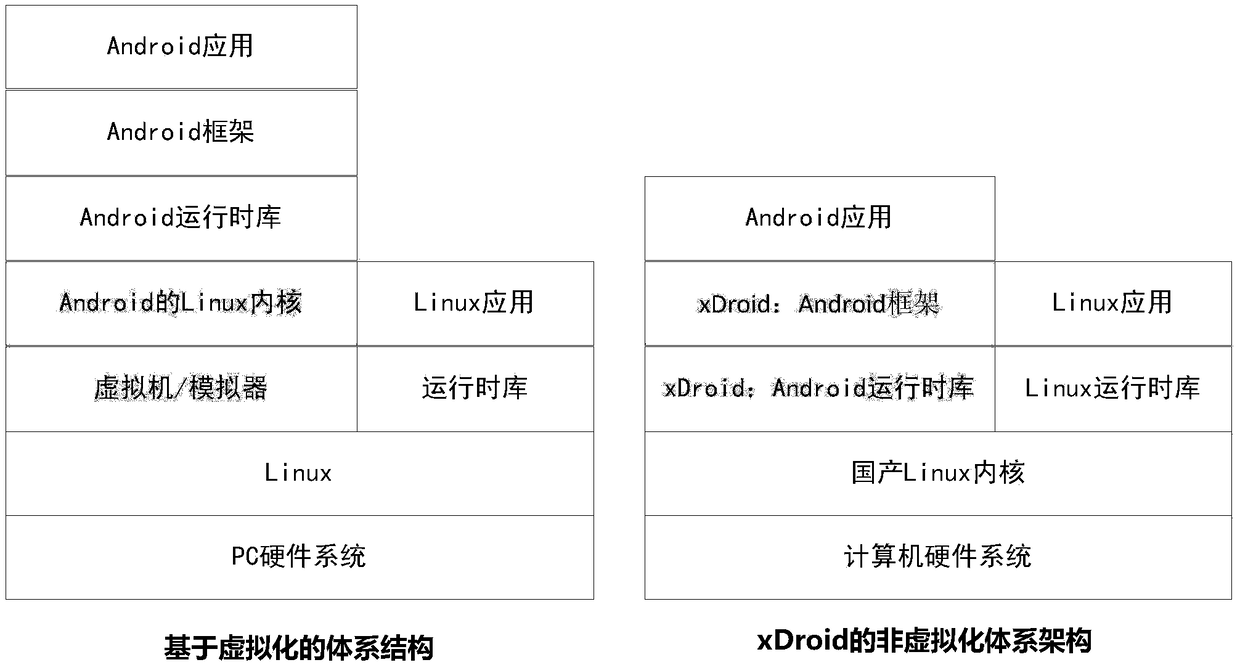
Android running environment realization method based on non-virtualized system architecture
The invention belongs to the field of computer basic software and relates to an Android running environment realization method based on a non-virtualized system architecture. According to the method,an Android running environment is constructed on an existing Linux kernel and recorded as xDroid, and an Android application framework and an Android running time library are migrated to a standard Linux kernel. The xDroid does not need the virtualization technology but stands from a basic library and a basic running mechanism provided by a desktop operating system kernel, an Android bottom running supporting library needed for Android application running is realized layer by layer from bottom to top, then efficient migration of the Android running time library is realized, and the Android running environment is realized on a desktop operating system platform. Compared with a virtualization-based technology, ecological complete fusion of desktop applications and Android applications is realized in a true sense through the xDroid, and the applications are high in starting speed and high in performance; and meanwhile realization is based on different platforms, so that cross-platform running is easy to realize.
Owner:北京麟卓信息科技有限公司
Implementation method of version management tool for Android application development
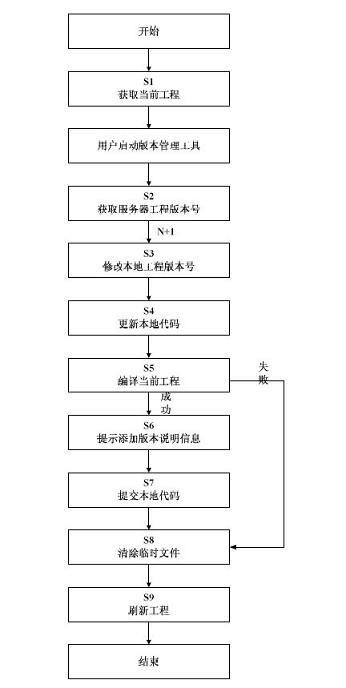
ActiveCN102053836AEasy to operateSimple interfaceSpecific program execution arrangementsSoftware engineeringVersion management
The invention discloses an implementation method of a version management tool for Android application development. The whole version management process of modifying an encapsulation version number, updating a local code, compiling the current project, submitting the local code and adding version description information can be completed by adopting one key operation, thus an interactive interface is realized. Compared with the traditional operation method, the method provided by the invention has the advantages that the whole process can be completed by means of one key operation, operating steps of SVN (subversion) are simplified, and the version number of an Android project and the version number of the SVN can be ensured to be consistent; and meanwhile an Eclipse plug-in form is adoptedfor release, the complete integration with an Android application development environment can be realized, the good interactive interface is realized, the working efficiency of a developer is improved, and the cost is reduced.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Reinforcing method of application program of Android system
InactiveCN105426708AGuaranteed operating efficiencyIncrease reading difficultyProgram/content distribution protectionComputer hardwareChecksum
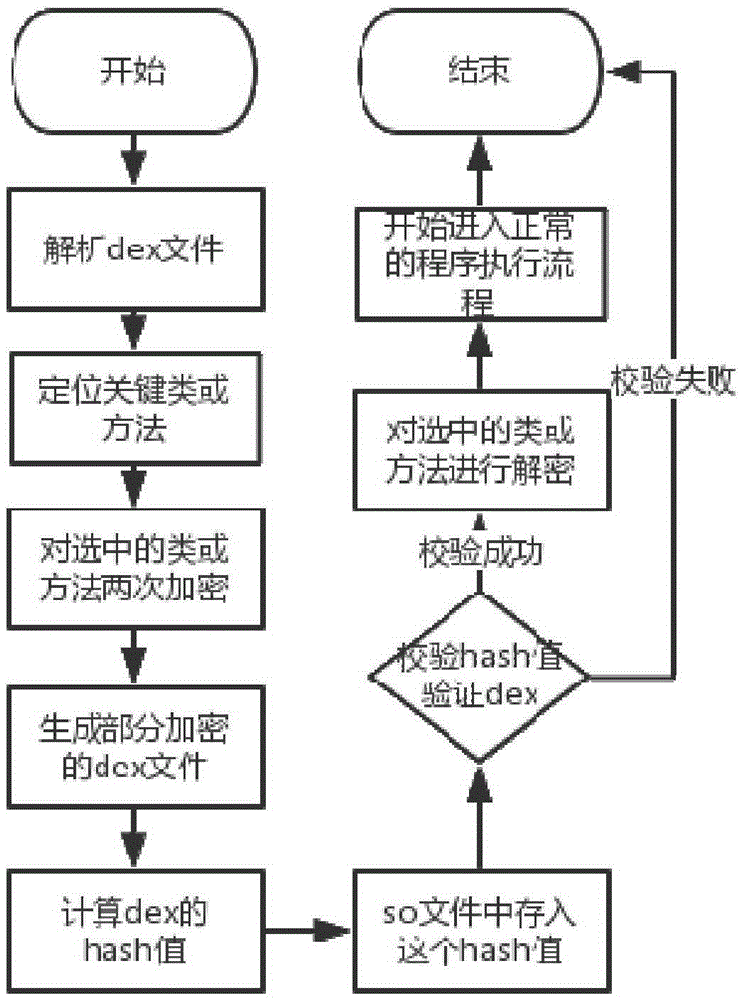
The invention discloses a reinforcing method of an application program of an Android system. The method comprises: reinforcing a key code in the Android application program by binary system flow encryption and protecting a code of the application program; comprising: analyzing a classes.dex file; positioning to a key method; performing primary encryption to obtain intermediate data; performing secondary encryption on the intermediate data; calculating a new Hash value of the dex file, and storing into a so file after the encryption; calculating to obtain new checksum and signature values of the dex file, and updating the dex file; regenerating an apk, thus finishing the encryption process. During decryption, the Hash value of the dex file is calculated, and the Hash value obtained by encryption is compared with the value in the so file; secondary decryption is performed to obtain the key code. Due to the reinforcing method, an Android source code cannot be checked by a decompilation tool, only the key code is protected by encryption, completeness of the code is protected, a static analysis is effectively resisted, the code of the Android program is prevented from being tampered, and operation efficiency of the program is ensured.
Owner:北京鼎源科技有限公司
Method for improving protection strength of application program in Android system
ActiveCN102831342AImprove securityPlatform integrity maintainanceProgram/content distribution protectionApplication softwareComputer engineering
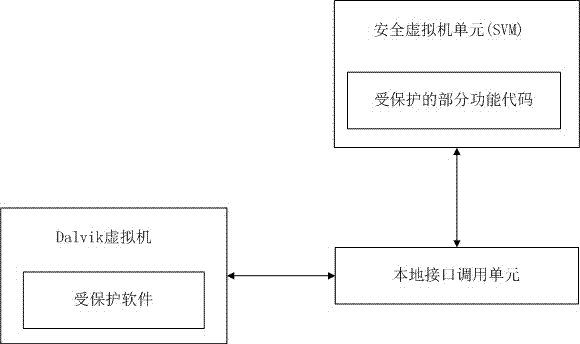
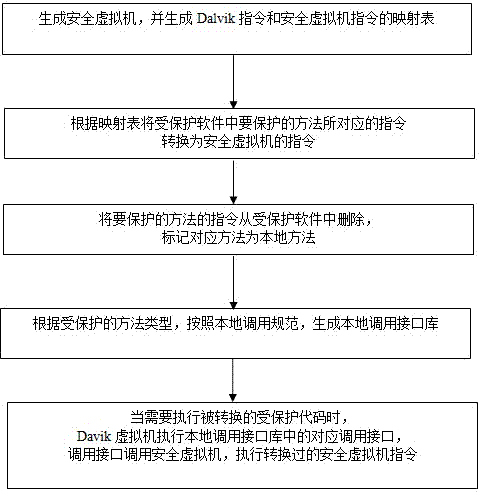
The invention discloses a method for protecting an application program of an Android system. By using a local transfer interface and a secure virtual machine, a key code of the application program of the Android system is seamlessly transplanted to a security environment to operate, so that the difficulty in decompiling and tracking can be greatly improved, and the method has a great practical value.
Owner:BEIJING SENSESHIELD TECH
Testing method and testing device of Android application programs
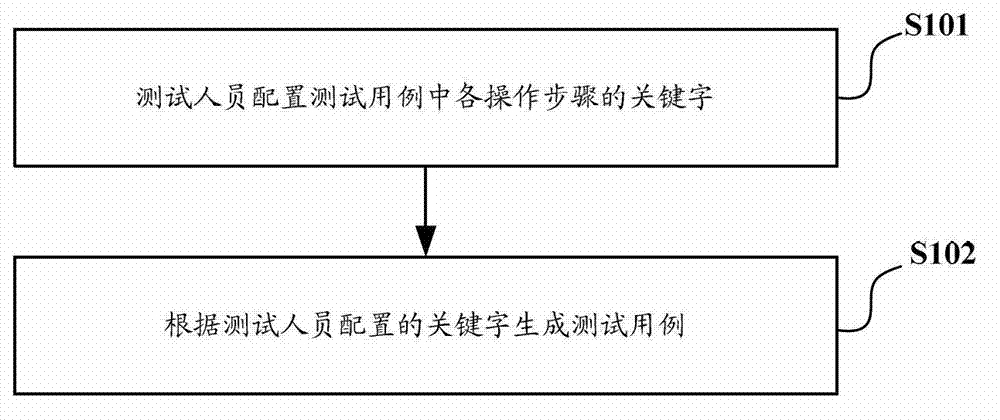
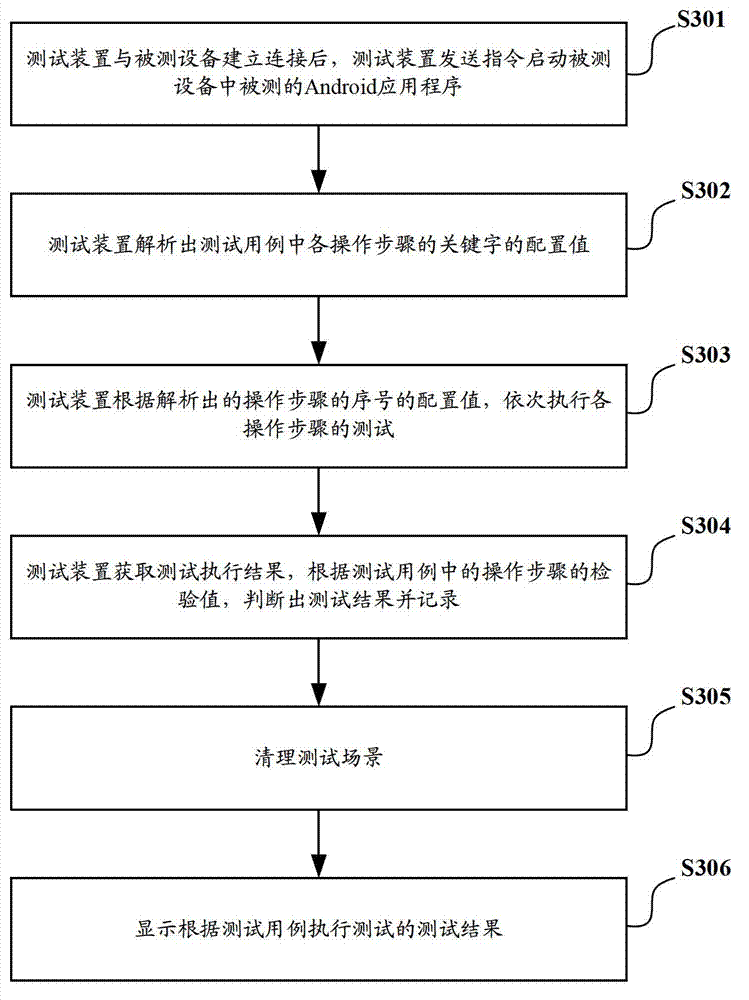
The invention discloses a testing method and a testing device of Android application programs. The method comprises steps of analyzing configuration values of key words of various operation processes from a testing example; sequentially executing tests of operation processes in accordance with analyzed configuration values of the serial number of operation processes; and executing the test for an operation process as follows: calling an element operation tool, wherein element operation tool conducts corresponding operation for corresponding user interface (UI) elements of tested Android application programs in accordance with operation types and configuration values of operation objects of the operation process. Therefore, a tester can configure testing examples based on key words conveniently, conducts the analyzing through key words of testing examples and calls relative tools to operate UI elements of tested application programs, and the testing process is completed automatically, and the testing is convenient.
Owner:QINGDAO HISENSE MEDIA NETWORKS CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com