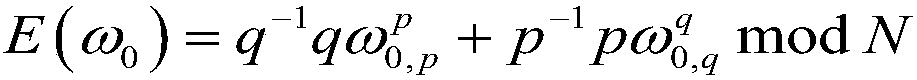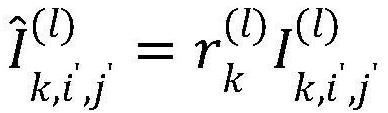Patents
Literature
896results about How to "Avoid getting" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
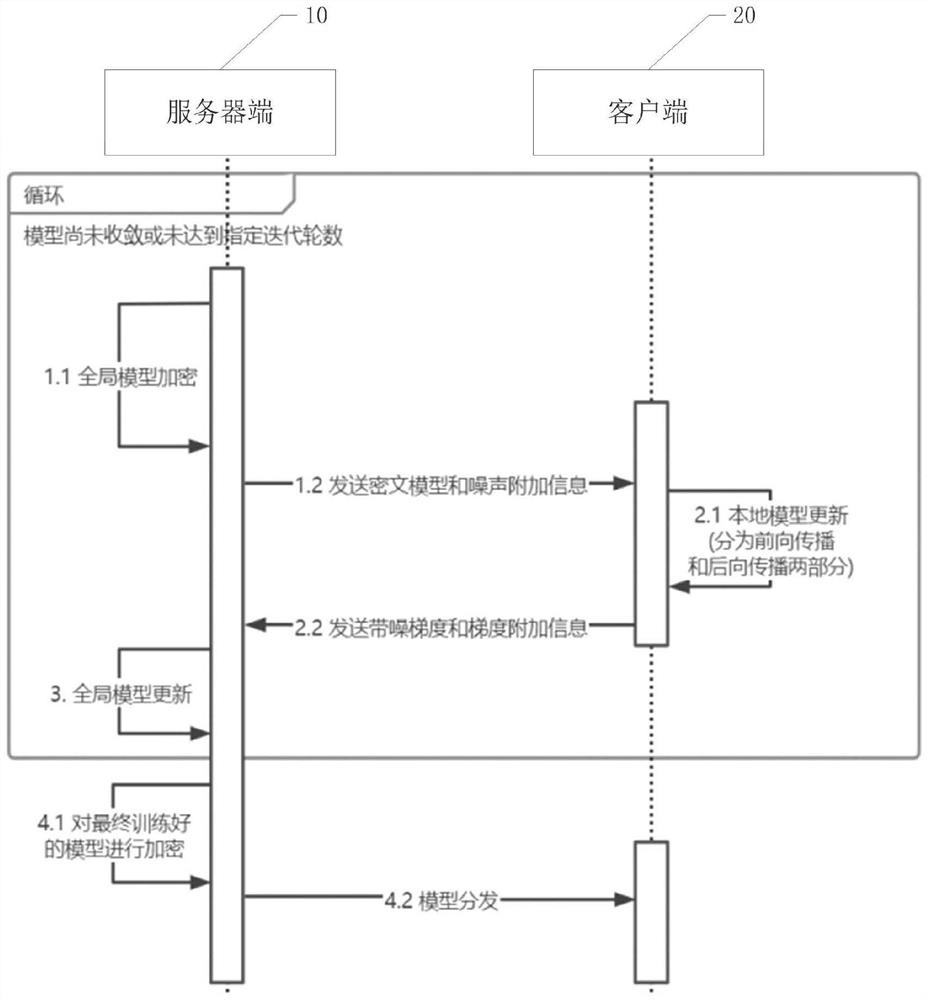
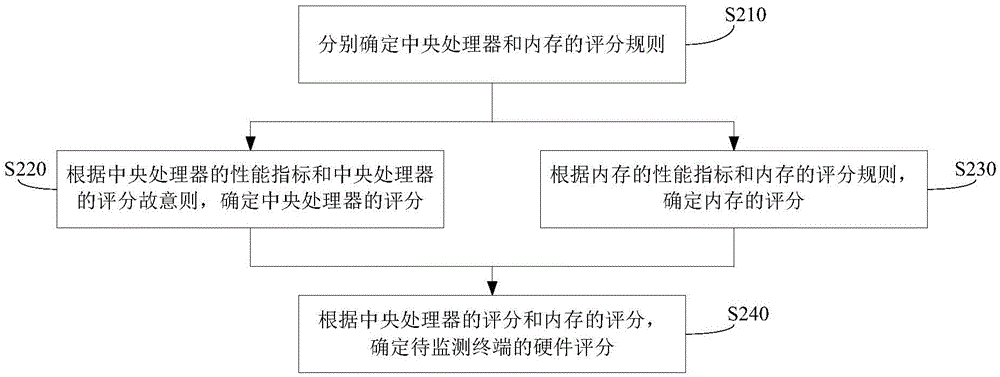
A combined deep learning training method based on a privacy protection technology
ActiveCN109684855AAvoid gettingSafe and efficient deep learning training methodDigital data protectionCommunication with homomorphic encryptionPattern recognitionData set
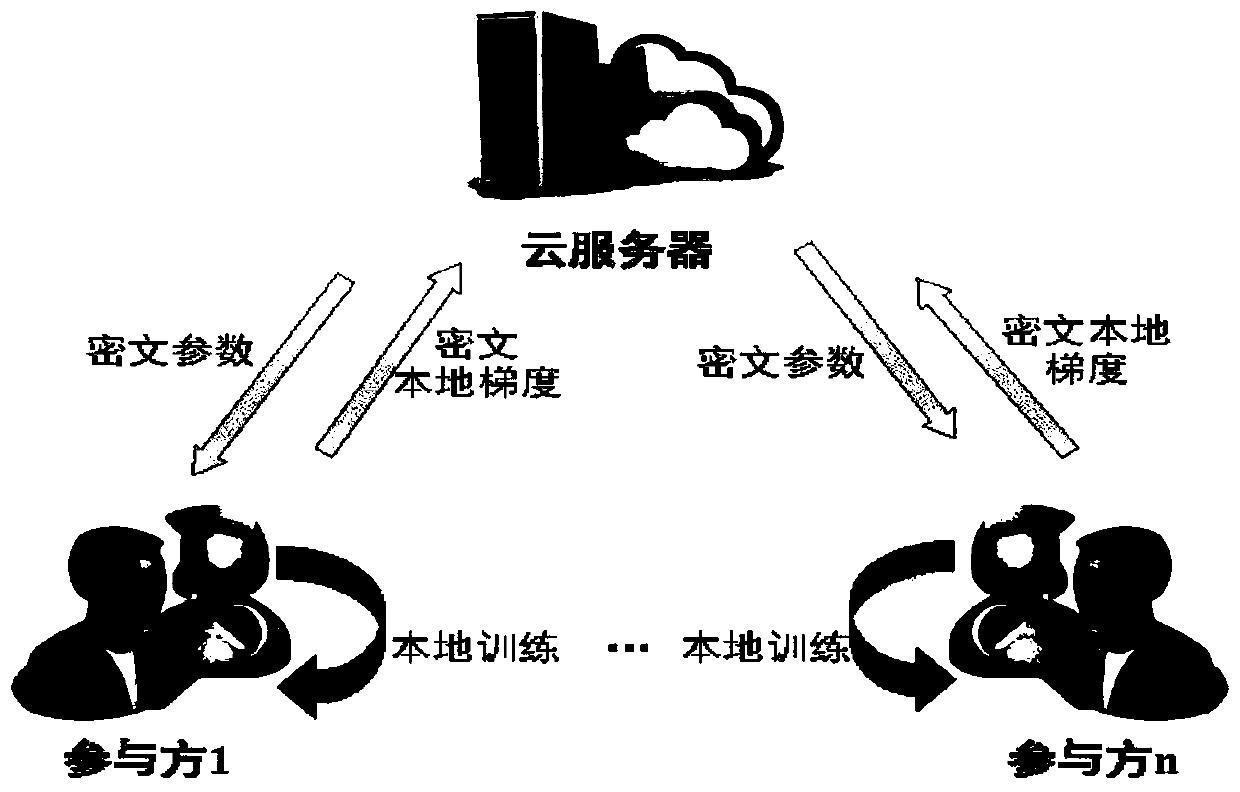
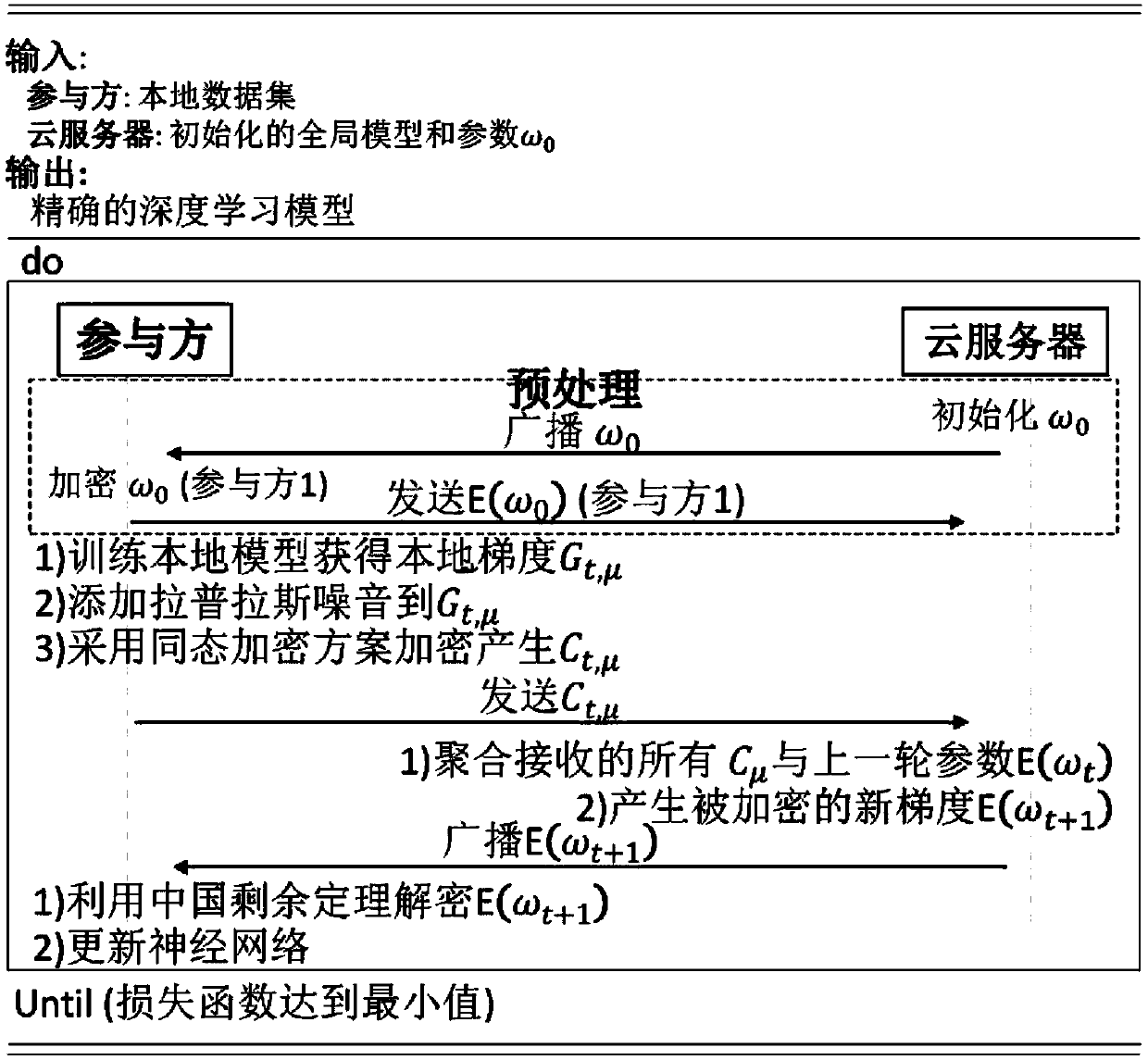
The invention belongs to the technical field of artificial intelligence, and relates to a combined deep learning training method based on a privacy protection technology. The efficient combined deep learning training method based on the privacy protection technology is achieved. In the invention, each participant first trains a local model on a private data set to obtain a local gradient, then performs Laplace noise disturbance on the local gradient, encrypts the local gradient and sends the encrypted local gradient to a cloud server; The cloud server performs aggregation operation on all thereceived local gradients and the ciphertext parameters of the last round, and broadcasts the generated ciphertext parameters; And finally, the participant decrypts the received ciphertext parameters and updates the local model so as to carry out subsequent training. According to the method, a homomorphic encryption scheme and a differential privacy technology are combined, a safe and efficient deep learning training method is provided, the accuracy of a training model is guaranteed, and meanwhile a server is prevented from inferring model parameters, training data privacy and internal attacksto obtain private information.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
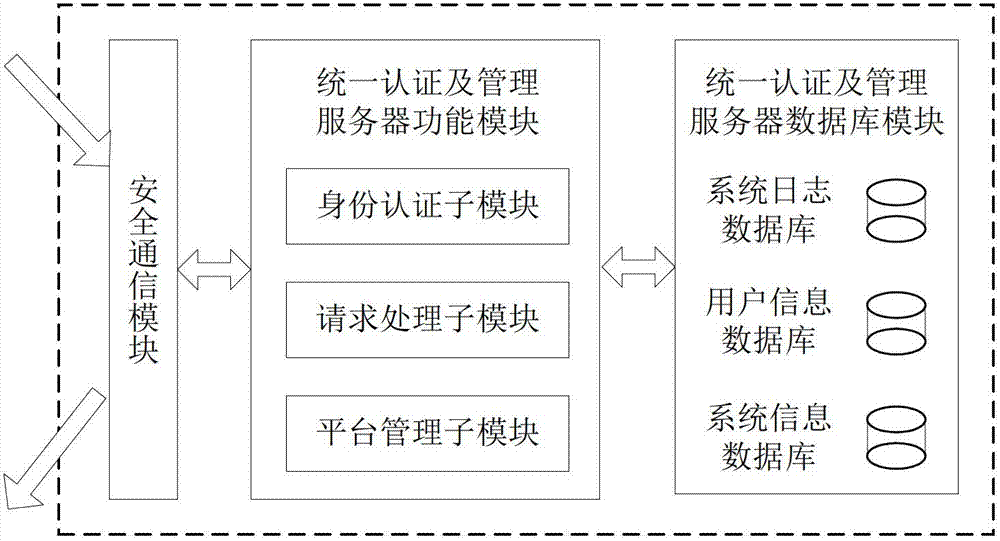
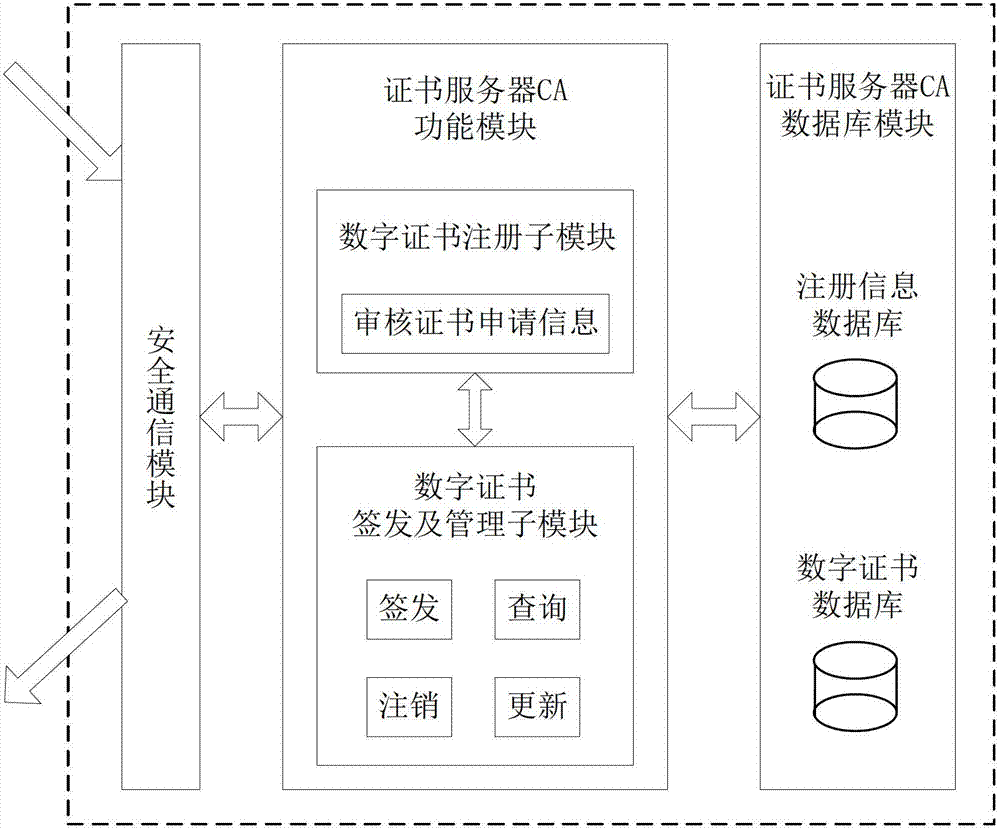
File safe protection system and method thereof
ActiveCN102970299ASimple structureEasy to buildKey distribution for secure communicationUser identity/authority verificationConfidentialityComputer terminal
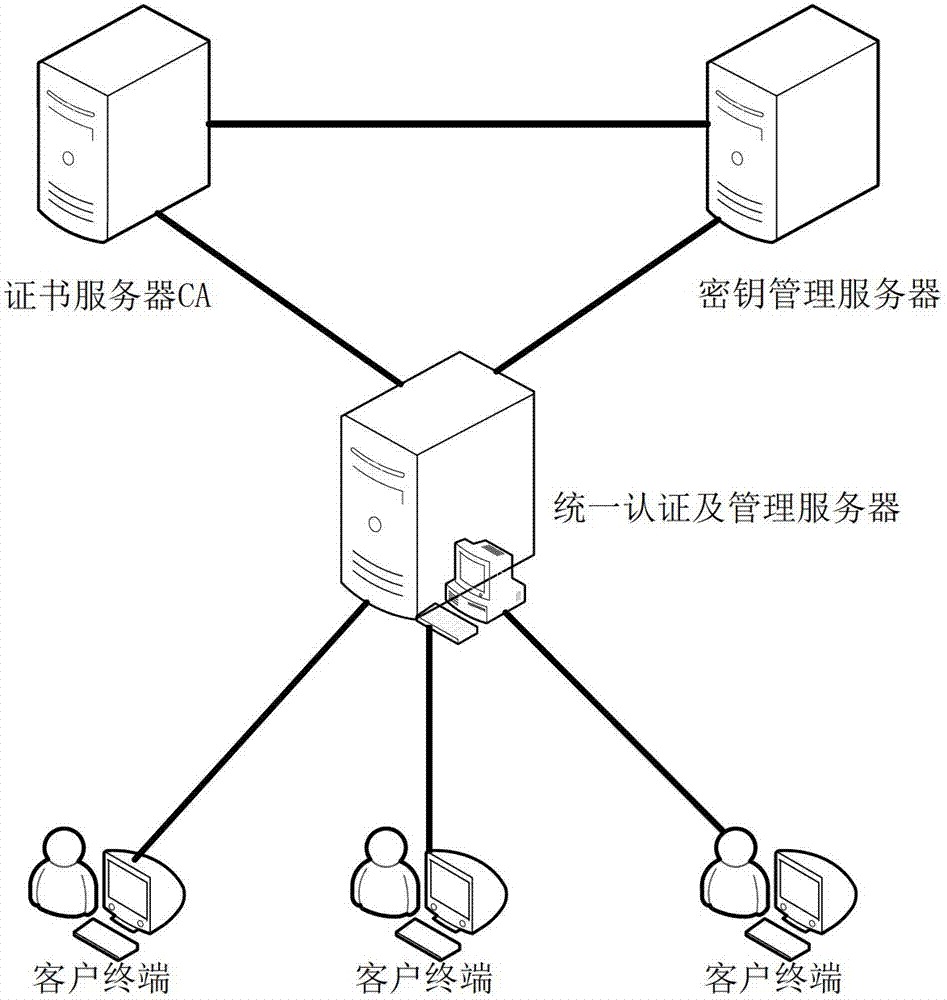
The invention discloses a file safe protection system and a method, which mainly solves the problems of network illegal invasion, information stealing and tamping, impersonation and weak deny resistance in the conventional information system. The file safe protection system consists of a unified authentication and management server, a certificate server CA, a secret key management server and a client terminal; the unified authentication and management server is used as a middle node and is used for processing or transmitting a service request sent by the client terminal; the certificate server CA processes a certificate service request of the client terminal and provides basic support for identification; and the secret key management server processes the secrete key service requests of the client terminal and the certificate server CA, and is used for encrypting and decrypting a file for the client terminal and providing parameter support for a digital certificate signed by the certificate server CA. With the adoption of the file safe protection system and method provided by the invention, identification, confidentiality, integration and non-repudiation services can be provided; and the file can be safely protected in transmission, storage, sharing and access processes.
Owner:XIDIAN UNIV
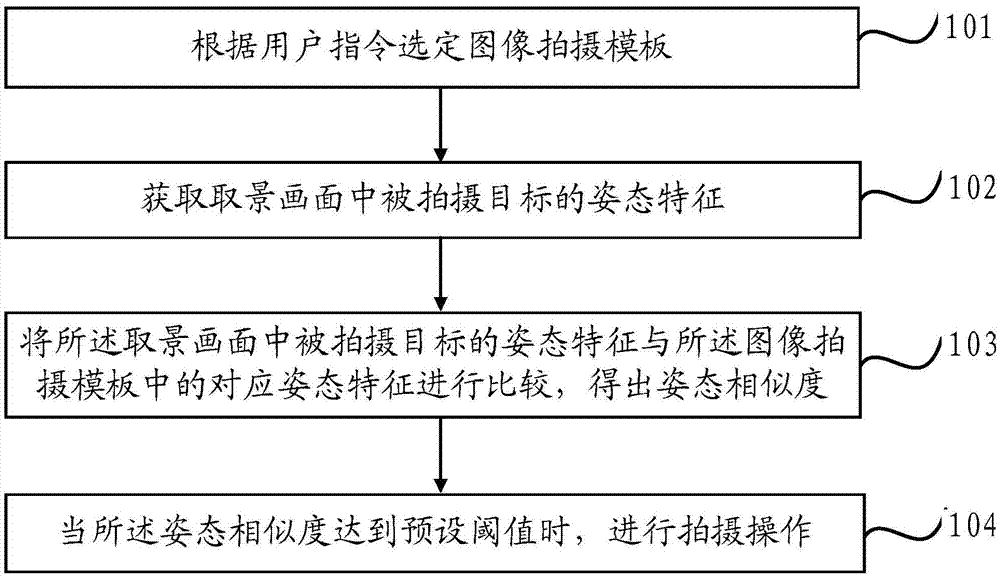
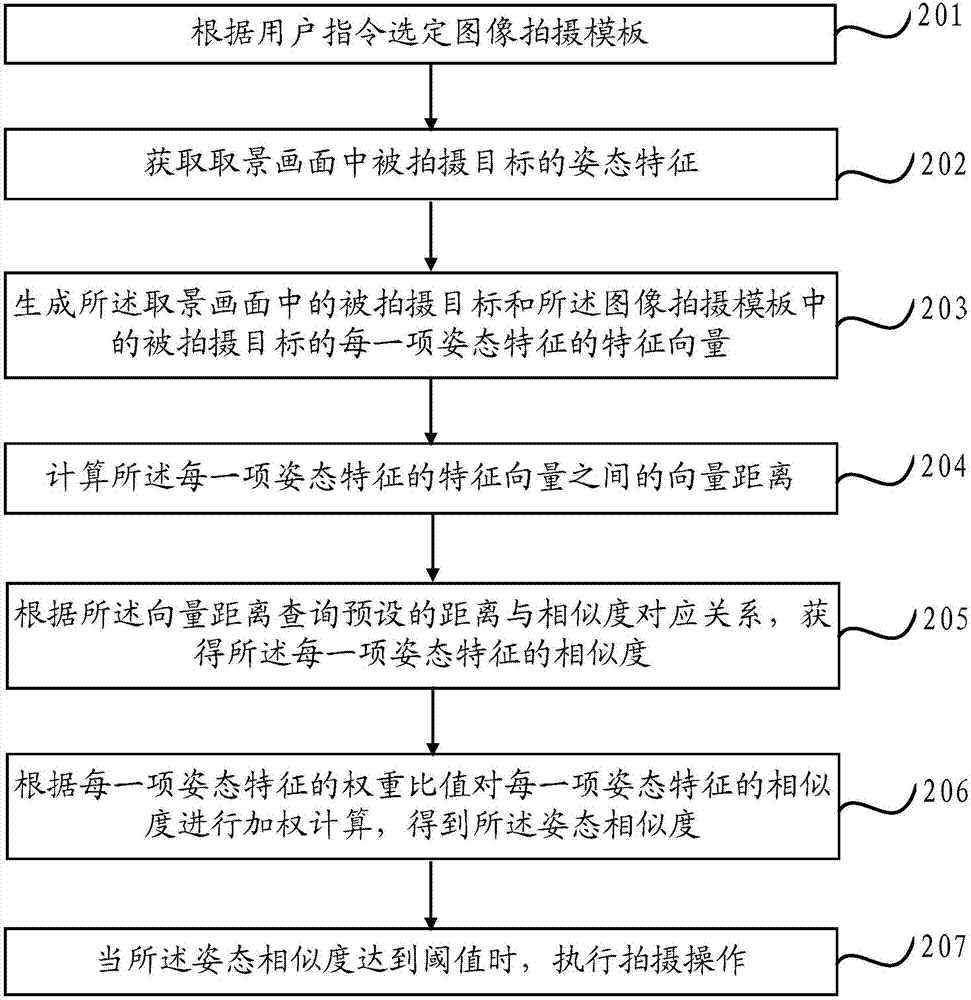
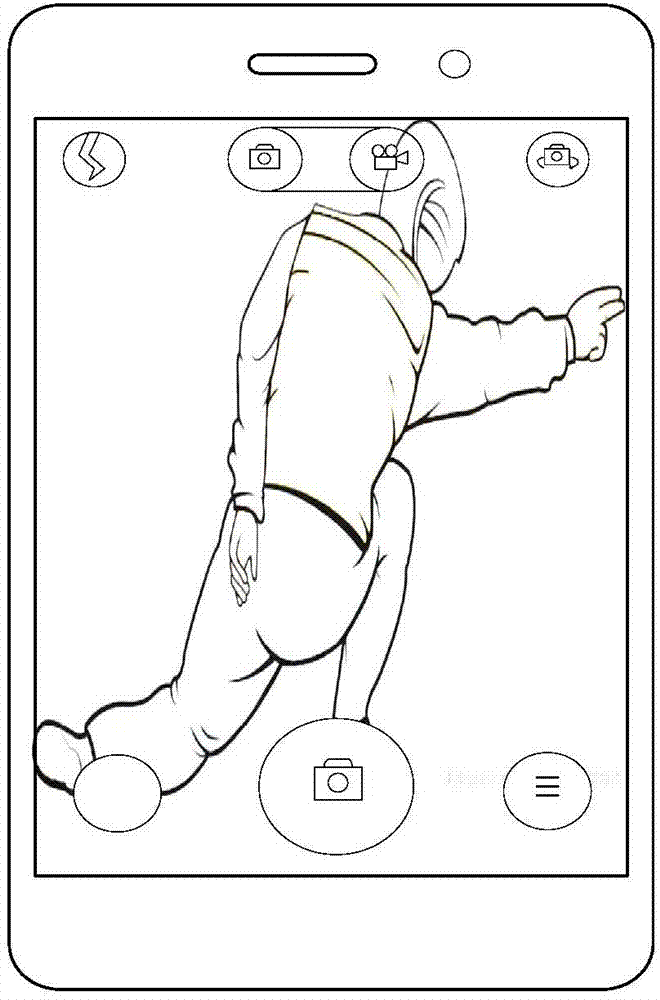
Image shooting method and device
ActiveCN104125396AHigh similarityImprove experienceInput/output for user-computer interactionTelevision system detailsComputer graphics (images)Shooting method
The invention provides an image shooting method and device. The method comprises the following steps: selecting an image shooting template according to a user instruction; acquiring posture features of a shooting object in a capturing picture; comparing the posture features of the shooting object in the capturing picture with the posture features of the shooting object in the image shooting template to obtain posture similarity; shooting as the posture similarity reaches a preset threshold. According to the technical scheme, the image shooting method and device are able to help a user shoot a picture in which the posture is the same as that of the image shooting template and has higher similarity.
Owner:XIAOMI INC
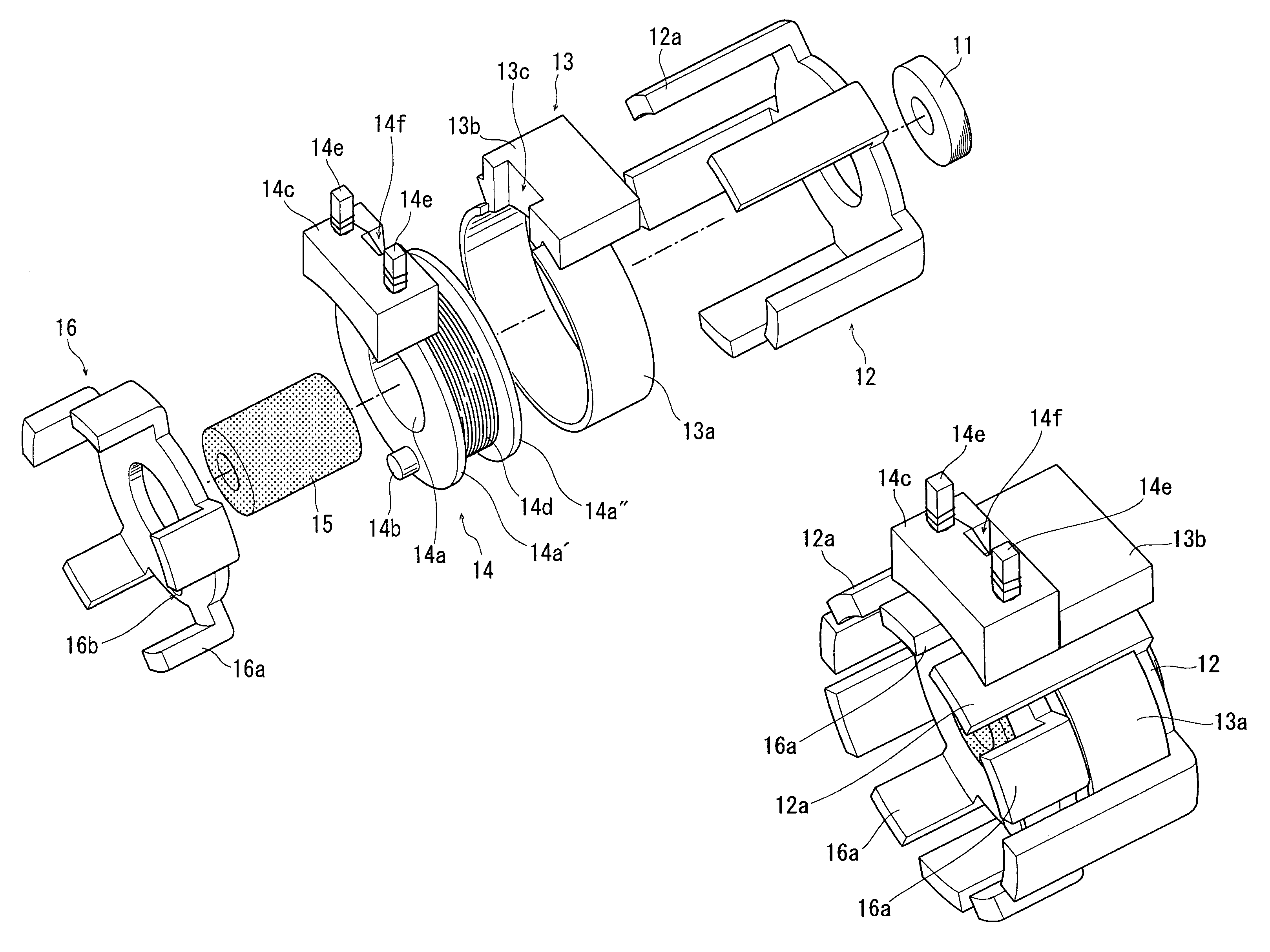
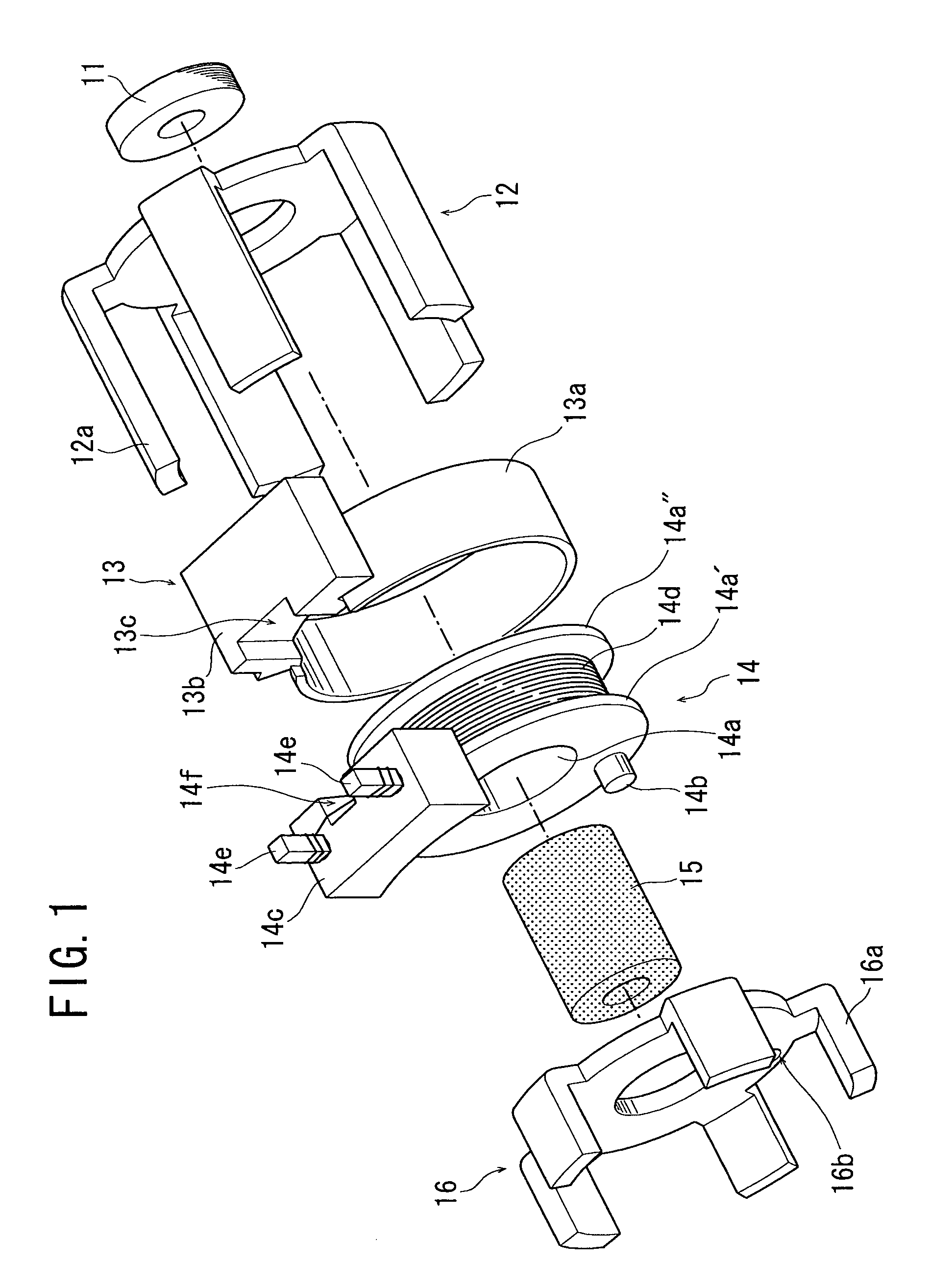
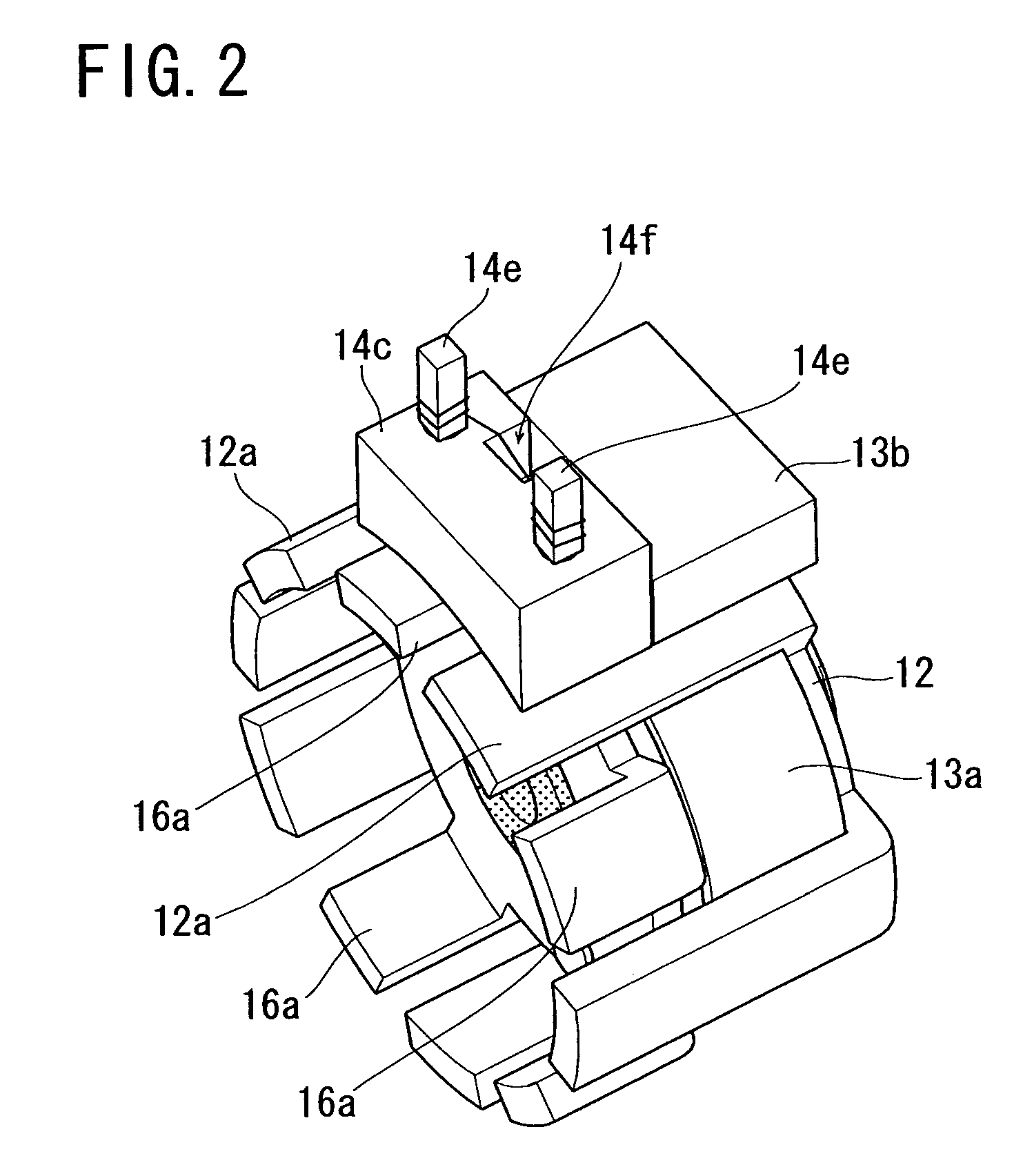
Claw-pole type stepping motor
InactiveUS7071593B2Reduce radial sizeMaintain mechanical strengthSynchronous generatorsWindingsBobbinSolid structure
A claw-pole type stepping motor comprises: a rotor assembly shaped substantially cylindrical, and having a center shaft; and a stator assembly composed of two cup-shaped stator units which are coupled to each other coaxially so as to axially sandwich the rotor assembly, and which each include a bobbin having a magnet wire wound therearound, and two pole tooth arrays magnetically connected to each other and shifted in phase from each other by an electrical angle of 180 degrees. In the motor, each stator unit further includes a cover ring which protects the magnet wire wound around the bobbin against resin injected when the stator unit is resin-molded for an integrated solid structure. The motor structured as described above can be successfully resin-molded so as to enable elimination of a motor case, thus achieving downsizing for the dimension of the eliminated motor case while maintaining a sufficient mechanical strength.
Owner:MINEBEA CO LTD
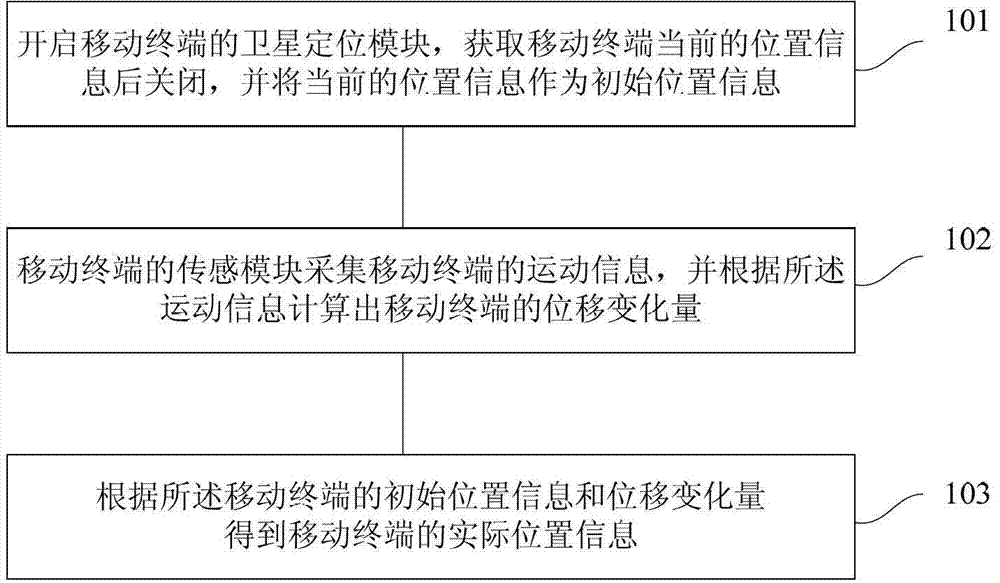
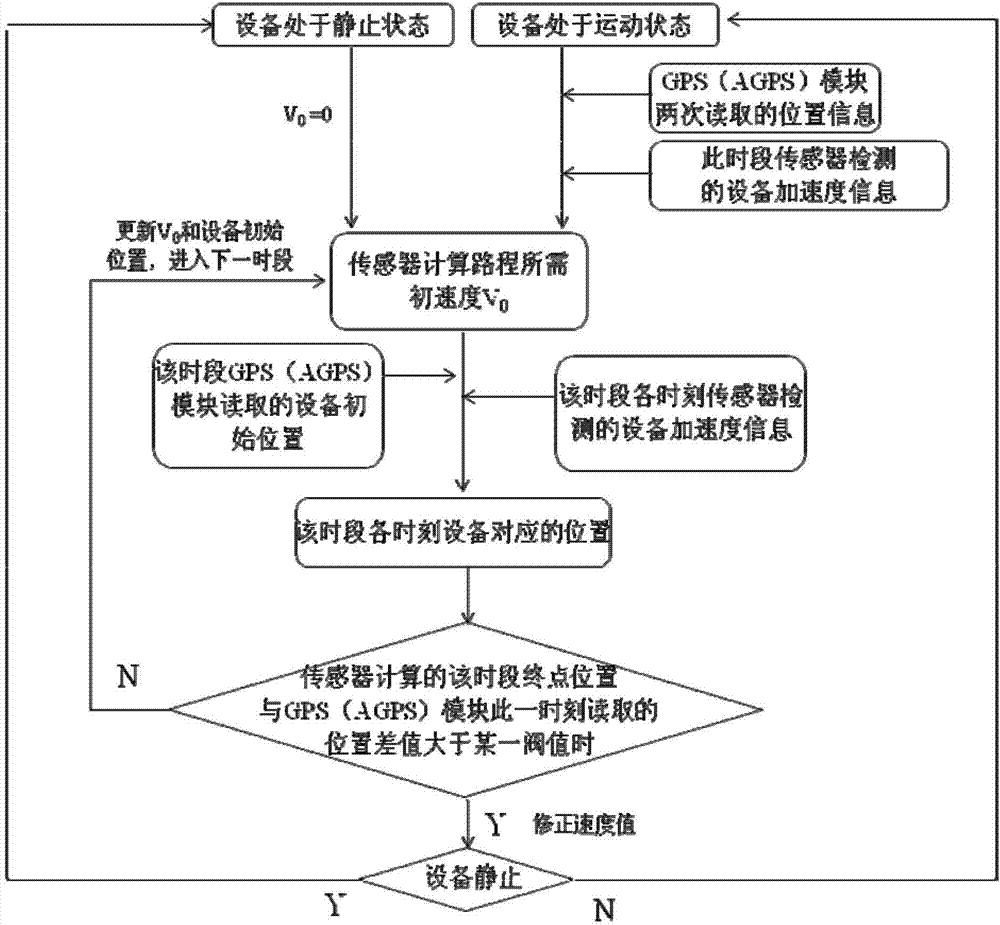
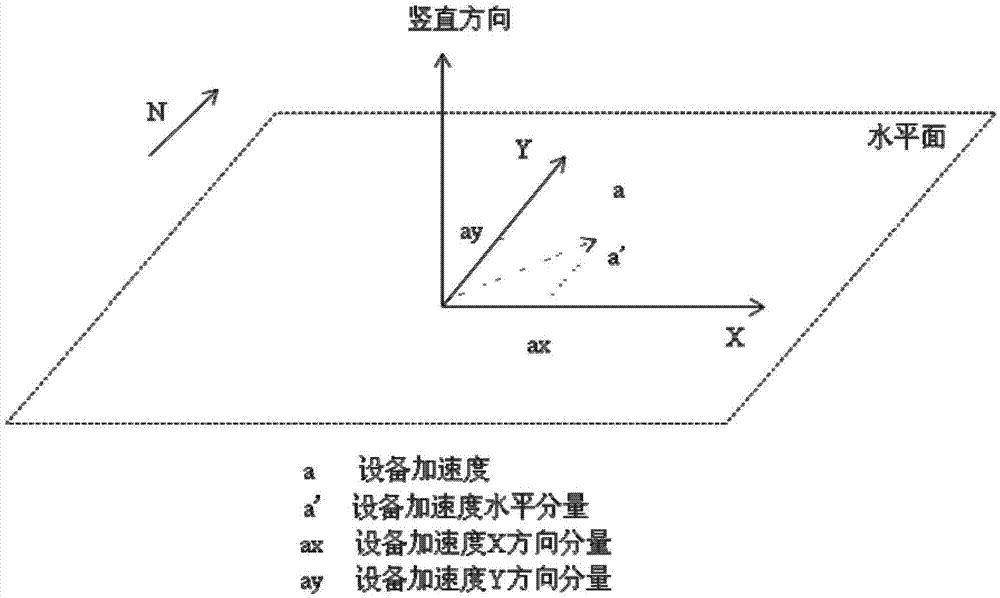
Mobile terminal and method for obtaining position information of mobile terminal
InactiveCN102901975AReduce power consumptionHigh precisionSatellite radio beaconingLocation information based servicePower consumptionSatellite positioning
The invention discloses a mobile terminal and a method for obtaining the position information of the mobile terminal. The method for obtaining the position information of the mobile terminal comprises the following steps that a satellite positioning module of the mobile terminal is turned on and then turned off after the current position information of the mobile terminal is obtained, and the current position information is used as initial position information; the movement information of the mobile terminal is collected by a sensor module of the mobile terminal, and the displacement variation of the mobile terminal is calculated in accordance with the movement information; and the actual position information of the mobile terminal is obtained in accordance with the initial position information and the displacement variation of the mobile terminal. By using the mobile terminal and the method for obtaining the position information of the mobile terminal, the power consumption of the satellite positioning module can be reduced.
Owner:ZTE CORP
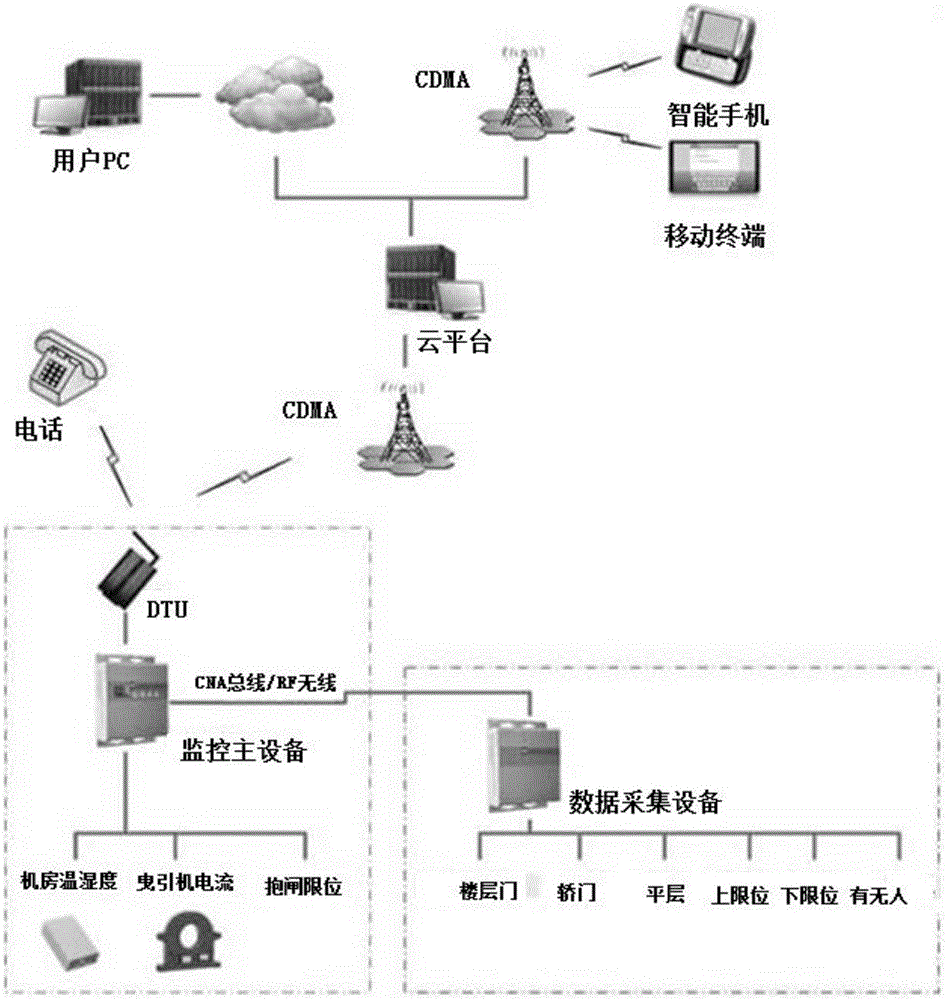
Intelligent monitoring system for elevator safe operation based on IOT (Internet of Things) technology
InactiveCN105035904AImprove your own securityEffectively guide productivityElevatorsInformatizationMonitoring system
The invention discloses an intelligent monitoring system for elevator safe operation based on IOT (Internet of Things) technology. The intelligent monitoring system is mainly designed for government regulation departments, maintenance units, manufacturers, property management companies and the like, and provides the above with a set of intelligent, platform-based total management system which supports wireless access and remote access, so that safe operation, management, maintenance and detection of an elevator can be more effectively realized. While daily needs are met, monitoring on the elevator is more normalized, institutionalized and scientized, so that elevator accidents are further reduced, and speed and quality for solving problems after an accident occurs are improved; by utilizing information for driving, the informatization management level of the intelligent monitoring system is improved through advanced and applicable technology and exploitation and construction pattern innovation by comprehensively utilizing information science and technology as well as decision making and management methods, and an emergency response system of elevator safety is favorably established.
Owner:JIESHOU XUNLIDA ELEVATOR CO LTD
User verification method and device and electronic device
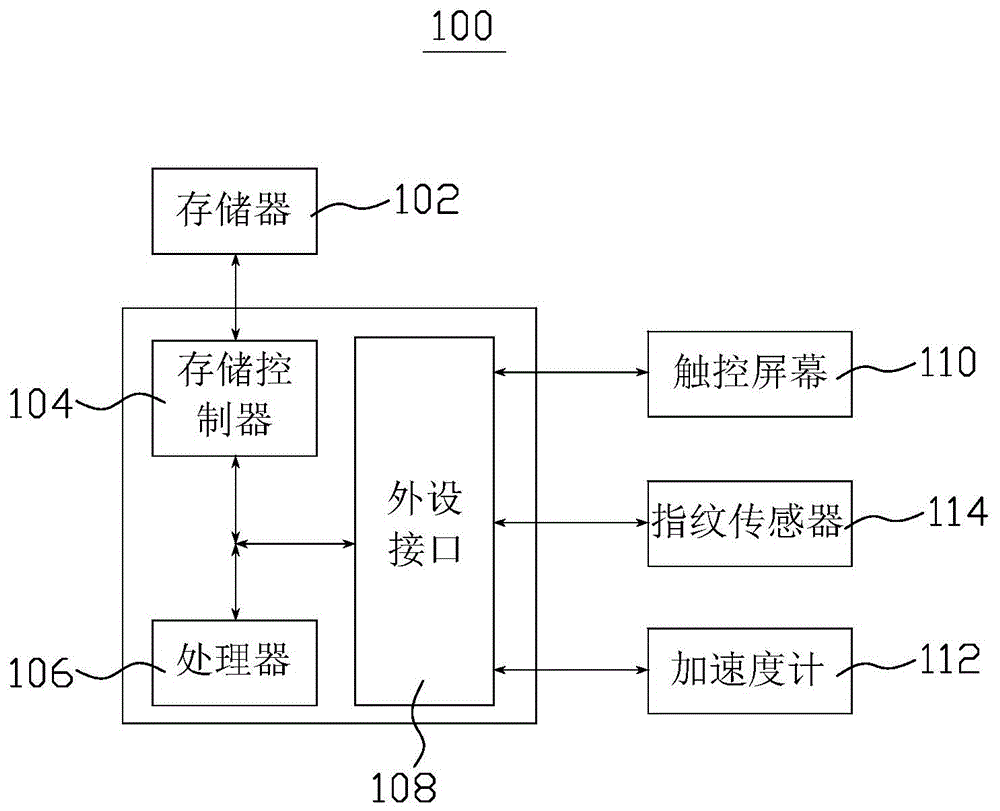
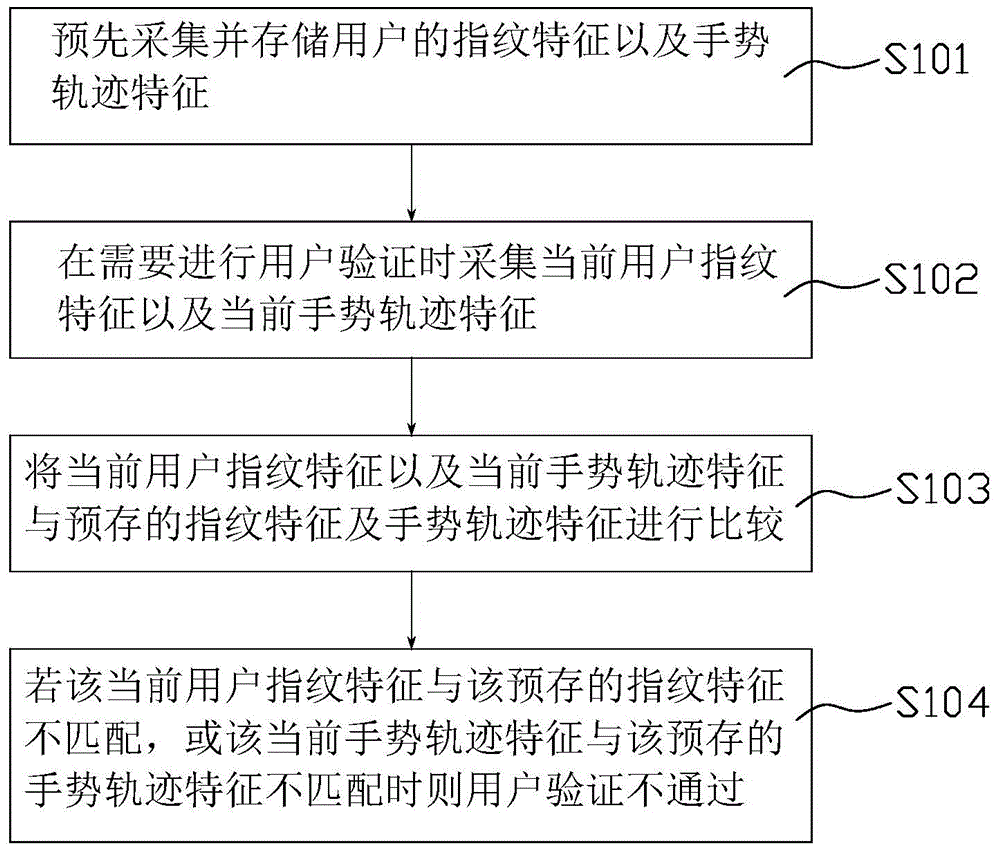
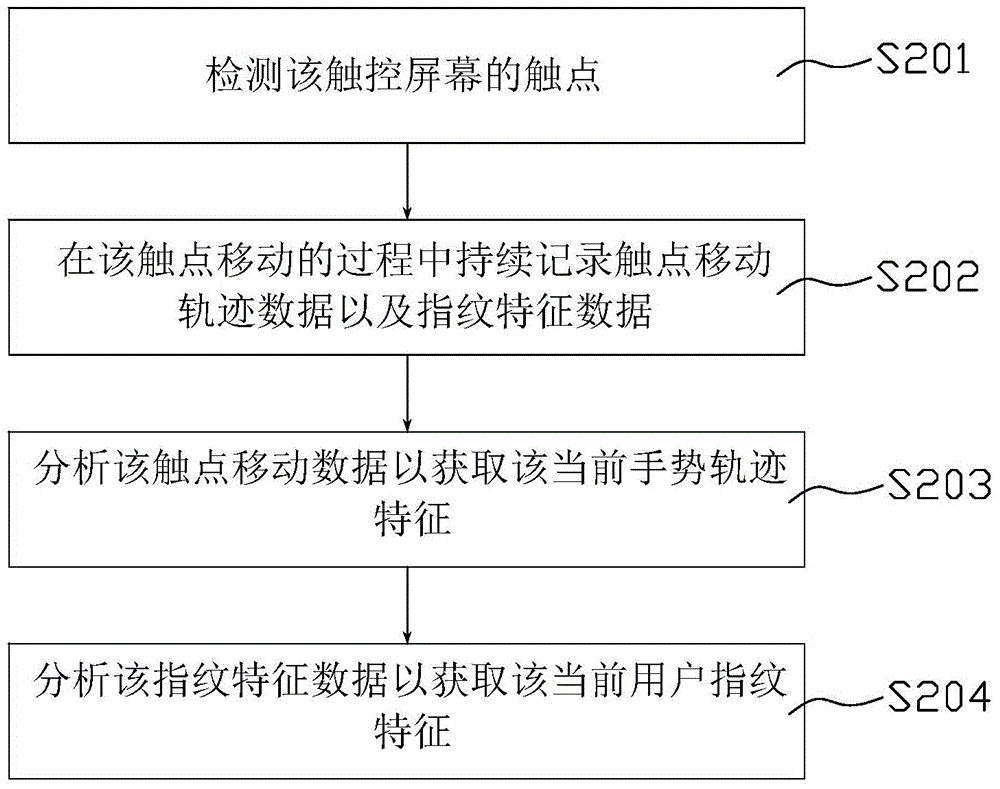
ActiveCN104573451AImprove securityAvoid gettingDigital data authenticationInput/output processes for data processingUser verificationComputer hardware
The invention relates to a user verification method, a user verification device and an electronic device. In one embodiment, the method comprises the following steps that fingerprint features of a user and gesture track features are collected and stored in advance; when the user verification is needed, the current user fingerprint features and the current gesture track features are collected; the current user fingerprint features and the current gesture feature track features are compared with the pre-stored fingerprint features and the gesture track features; if the current user fingerprint features are not matched with the pre-stored fingerprint features, or the current gesture track features are not matched with the pre-stored gesture track features, the user verification is not passed. The device, the device and the electronic device have the advantage that the user verification security can be improved.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
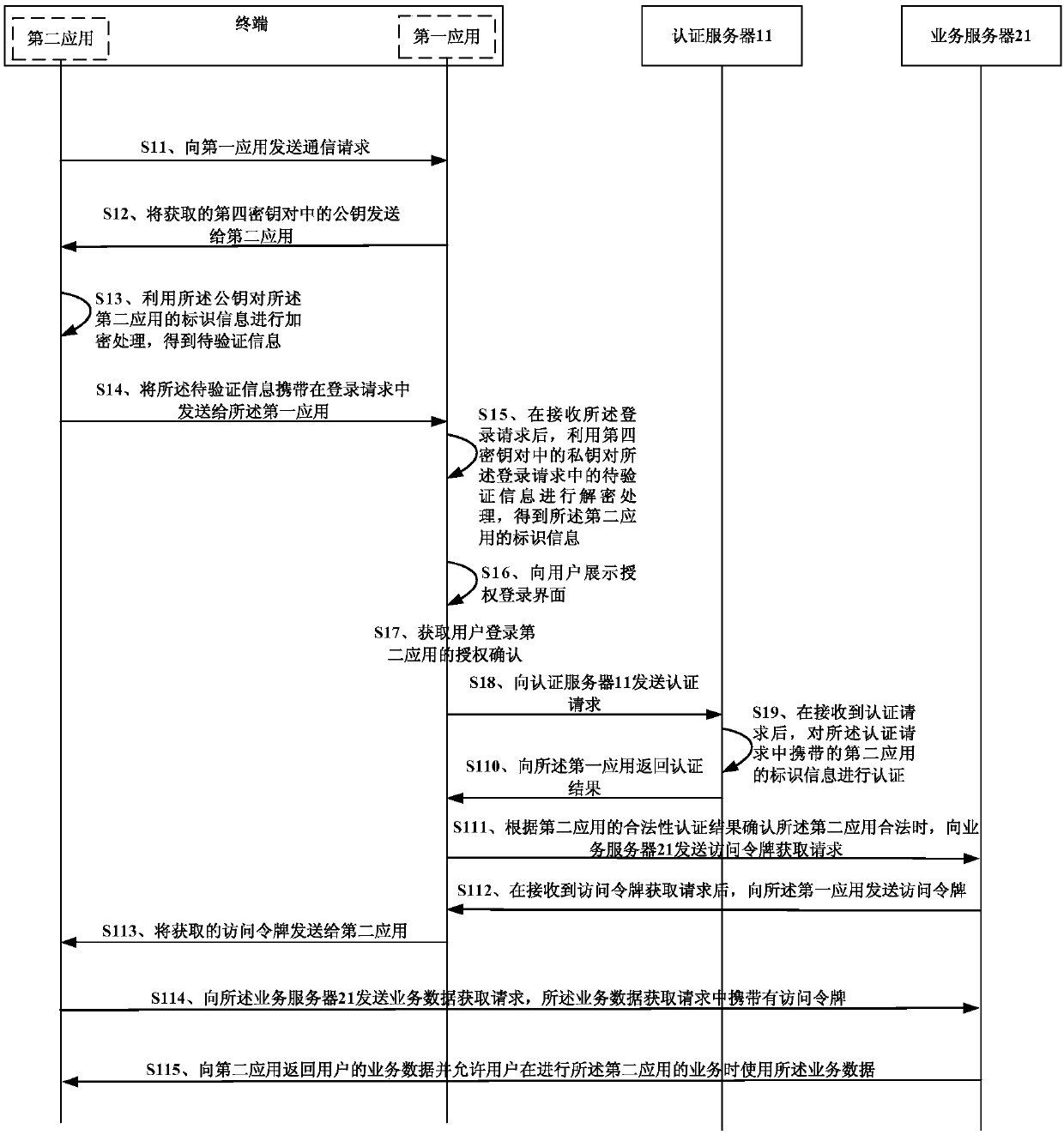
Application login method and system, terminal and electronic equipment
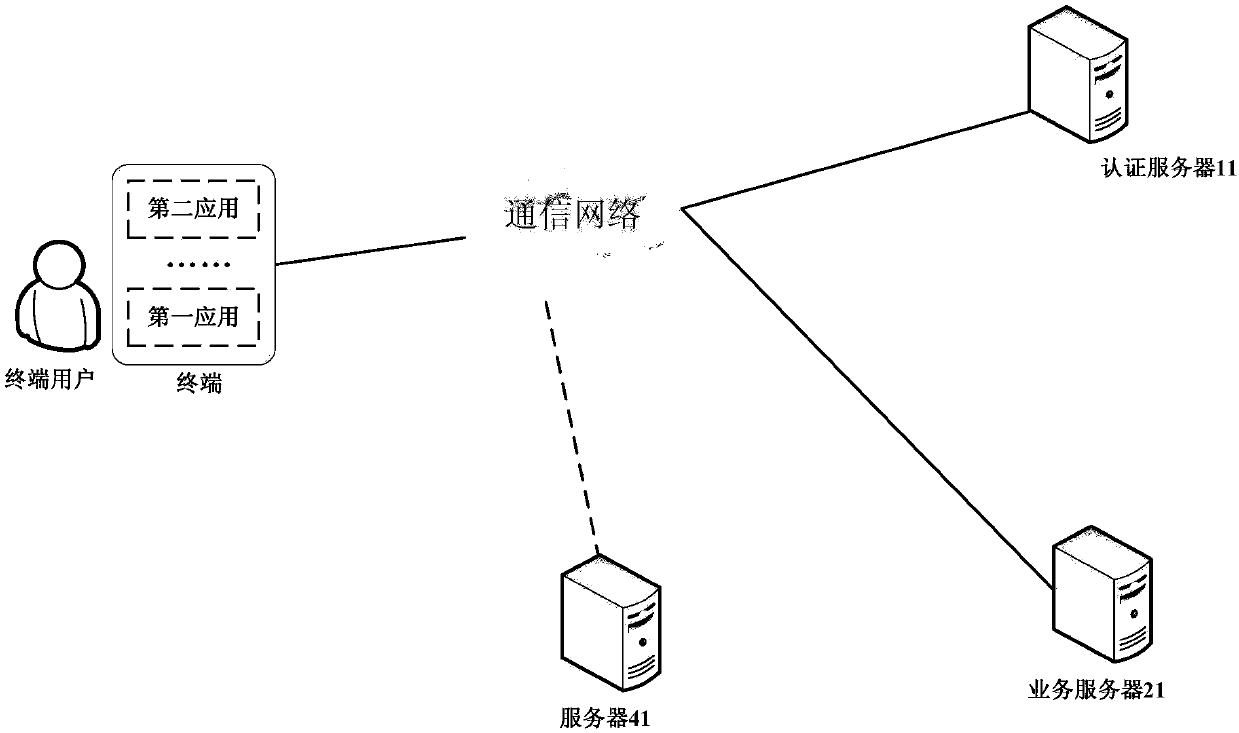
ActiveCN110324276AEnsure safetyPrevent leakageUser identity/authority verificationTransfer procedureBusiness data
The invention discloses an application login method and system, a terminal and electronic equipment, and belongs to the technical field of information security. The method comprises the following steps of: when a first application in a terminal acquires authorization confirmation that a user permits to use user identity information of the first application to log in a second application, sending an authentication request of authentication encryption information carrying the identification information of the second application to an authentication server; when it is determined that the second application is legal according to an authentication result returned by the authentication server, obtaining the access token from the business server of the first application and sending the obtained access token to the second application, so that the second application can obtain the business data of the user from the business server by utilizing the access token, and meanwhile, the user is allowed to use the business data when carrying out the business of the second application. The data is transmitted in an encryption mode, information is prevented from being stolen in the transmission process, and therefore the safety of the data recorded on the service server by a user is guaranteed.
Owner:TENCENT TECH (SHENZHEN) CO LTD
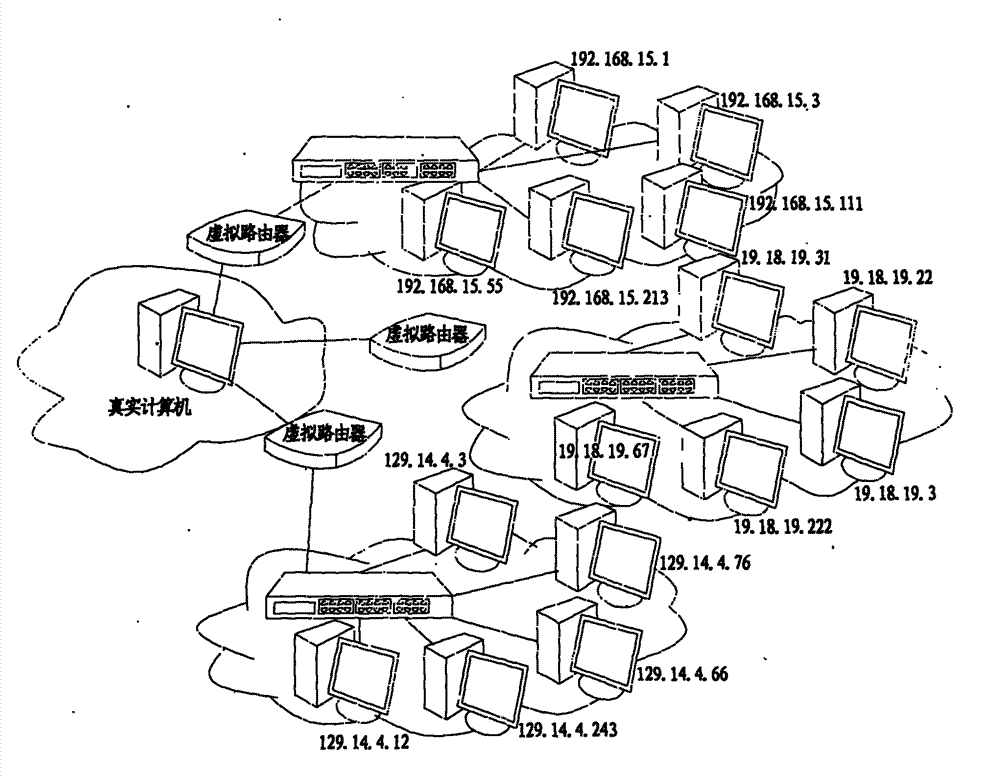
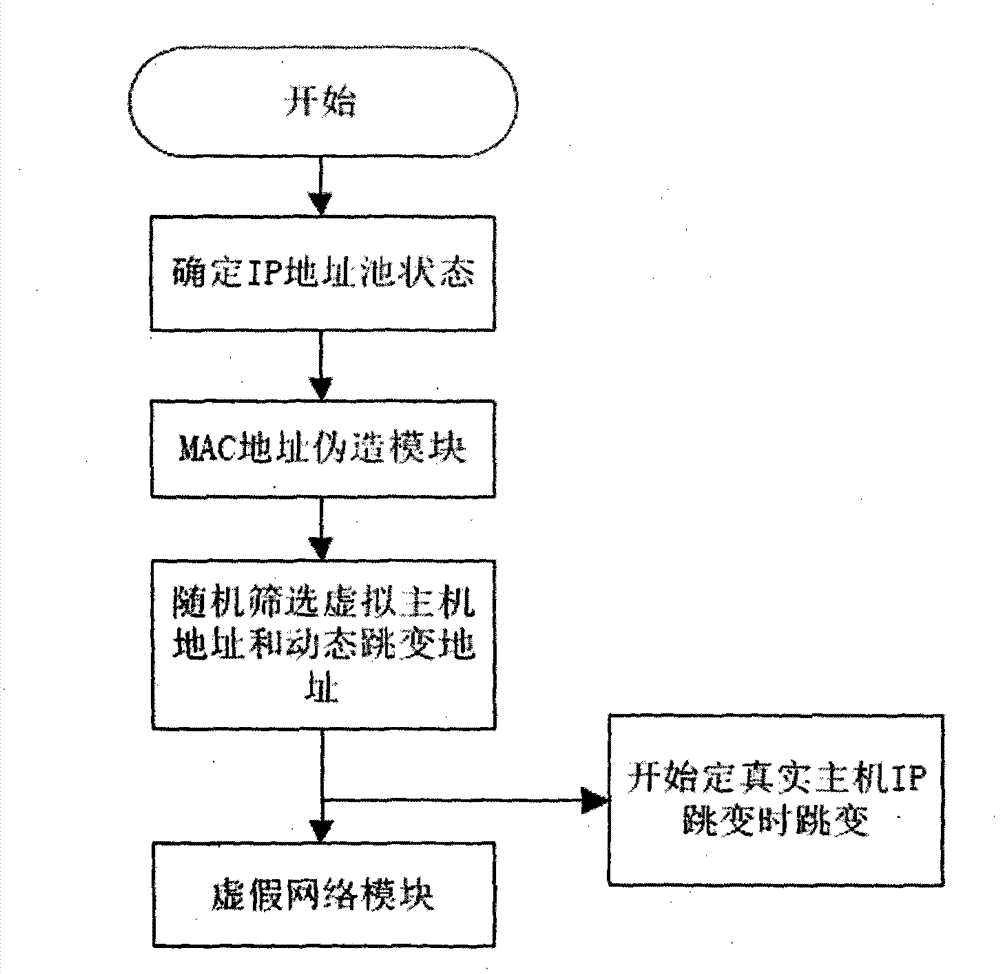
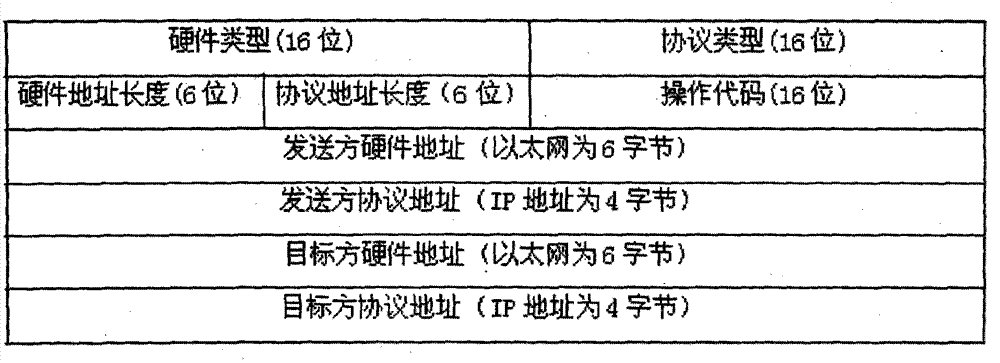
Network hiding method for computer and network hiding system based on method
The invention discloses a network hiding method for a computer and a network hiding system based on the method. In the network hiding method, a passive processing strategy and an active processing strategy are adopted. The active processing strategy comprises the following steps of S1, when a detection behavior is ongoing according to judgment, replying false information to confuse a detector and increase the attacking difficulty; S2, faking false data traffic and a real host network behavior, and disturbing a sniffing behavior; and S3, dynamically and randomly jumping to hide a real host by taking the IP (Internet Protocol) address of the real host as a jumping element. In the network hiding system, four layers of network hiding models, including an access behavior control module, a dynamic multi-address module, a traffic confusing module and a protocol stack fingerprint confusing module are adopted. Due to the adoption of the method and system, unknown security problems can be blocked in advance, the occurrence of malicious network behaviors is blocked at a source, and advance protection is truly realized; due to the hiding characteristic, the aim of nipping in the bud can be fulfilled in the system; and the computer security is well ensured.
Owner:XIDIAN UNIV
Multi-precision-fitting-based automatic detection method for copied sample voice
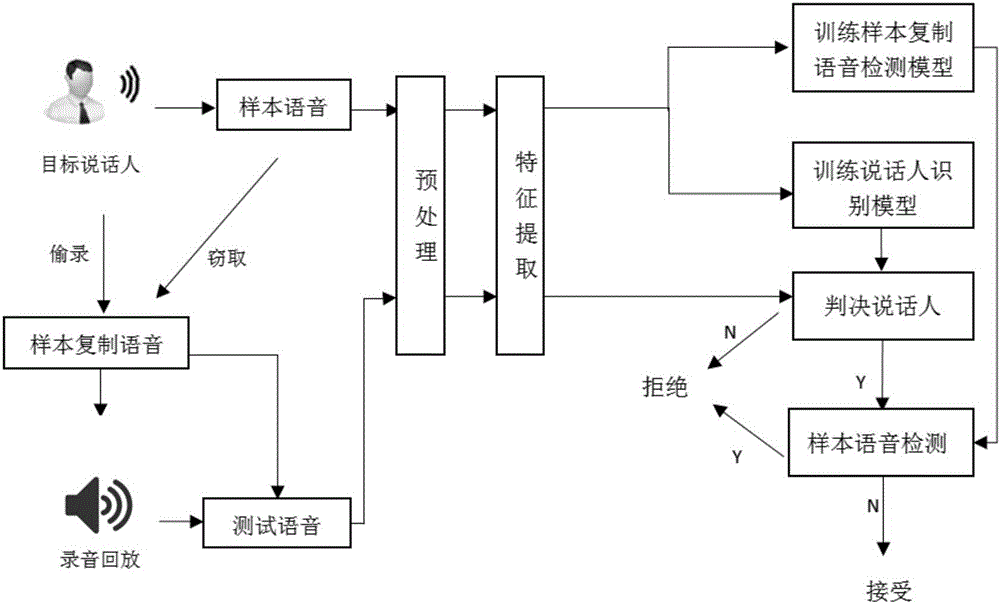
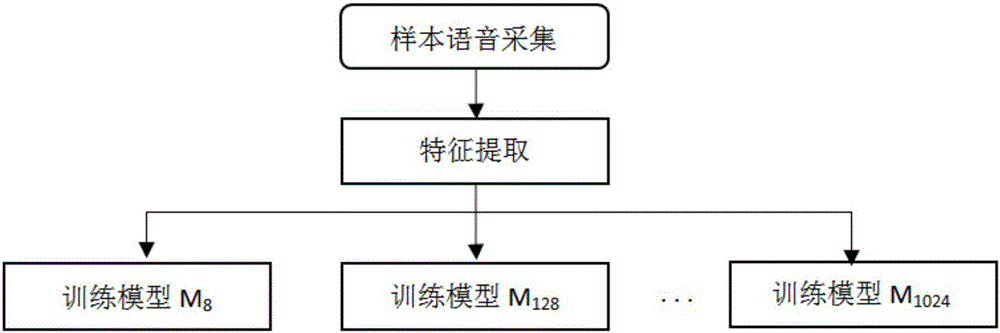
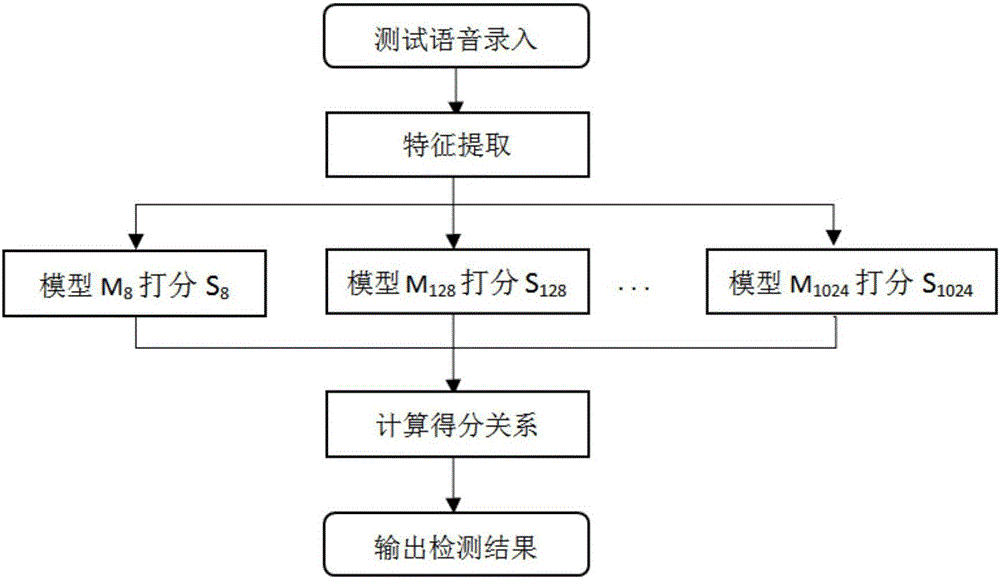
ActiveCN105938716ACases to prevent intrusionImprove securitySpeech analysisSpeech soundSpeaker identification
The invention relates to the voice detection field, especially to a multi-precision-fitting-based automatic detection method for a copied sample voice. The method comprises: S1, a voice feature base is established; S2, a target speaker identification model is trained; S3, a sample copied voice detection model is trained; S4, speaker identification is carried out; and S5, sample copied voice detection. According to the automatic detection method, a phenomenon that a fake user obtains a copied sample voice for a vocal print identification system training model and then tries to invoke a server side interface directly instead of carrying out voice testing collection so as to submit the copied sample voice to the server side of the vocal print identification system directly for intrusion can be avoided; and thus security of the vocal print identification system can be improved.
Owner:ZHEJIANG UNIV
Privacy protection method and system based on federated learning, and storage medium
PendingCN112199702AAvoid gettingTrue Prediction ResultsDigital data protectionNeural architecturesAlgorithmCiphertext
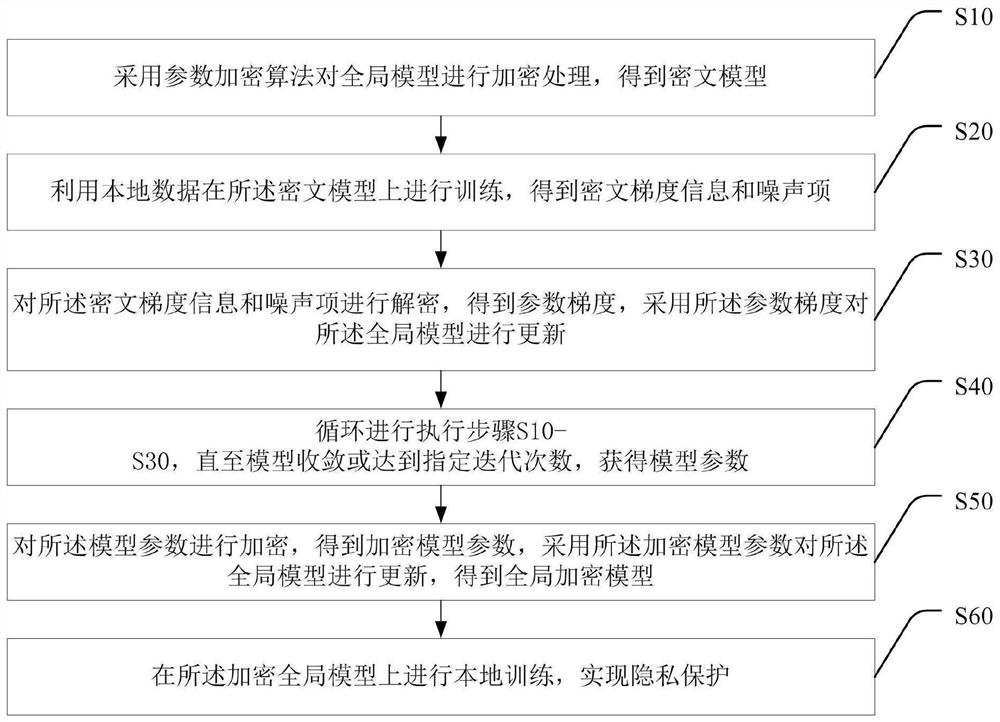
The invention discloses a privacy protection method and system based on federated learning, and a storage medium, and the method comprises the steps: carrying out the encryption of a global model through employing a parameter encryption algorithm, and obtaining a ciphertext model; training on the ciphertext model by using local data, decrypting the obtained ciphertext gradient information and noise item to obtain a parameter gradient, updating the global model by using the parameter gradient, and repeating the steps until the model converges or reaches a specified iteration number to obtain amodel parameter; encrypting the model parameters to obtain encrypted model parameters, and updating the global model by adopting the encrypted model parameters to obtain a global encrypted model; andperforming local training on the encrypted global model to realize privacy protection. According to the method, semi-trusted federated learning participants can be effectively prevented from acquiringreal parameters of the global model and an output result of the intermediate model, and meanwhile, the participants can acquire a real prediction result by utilizing the finally trained encryption model.
Owner:PENG CHENG LAB +1
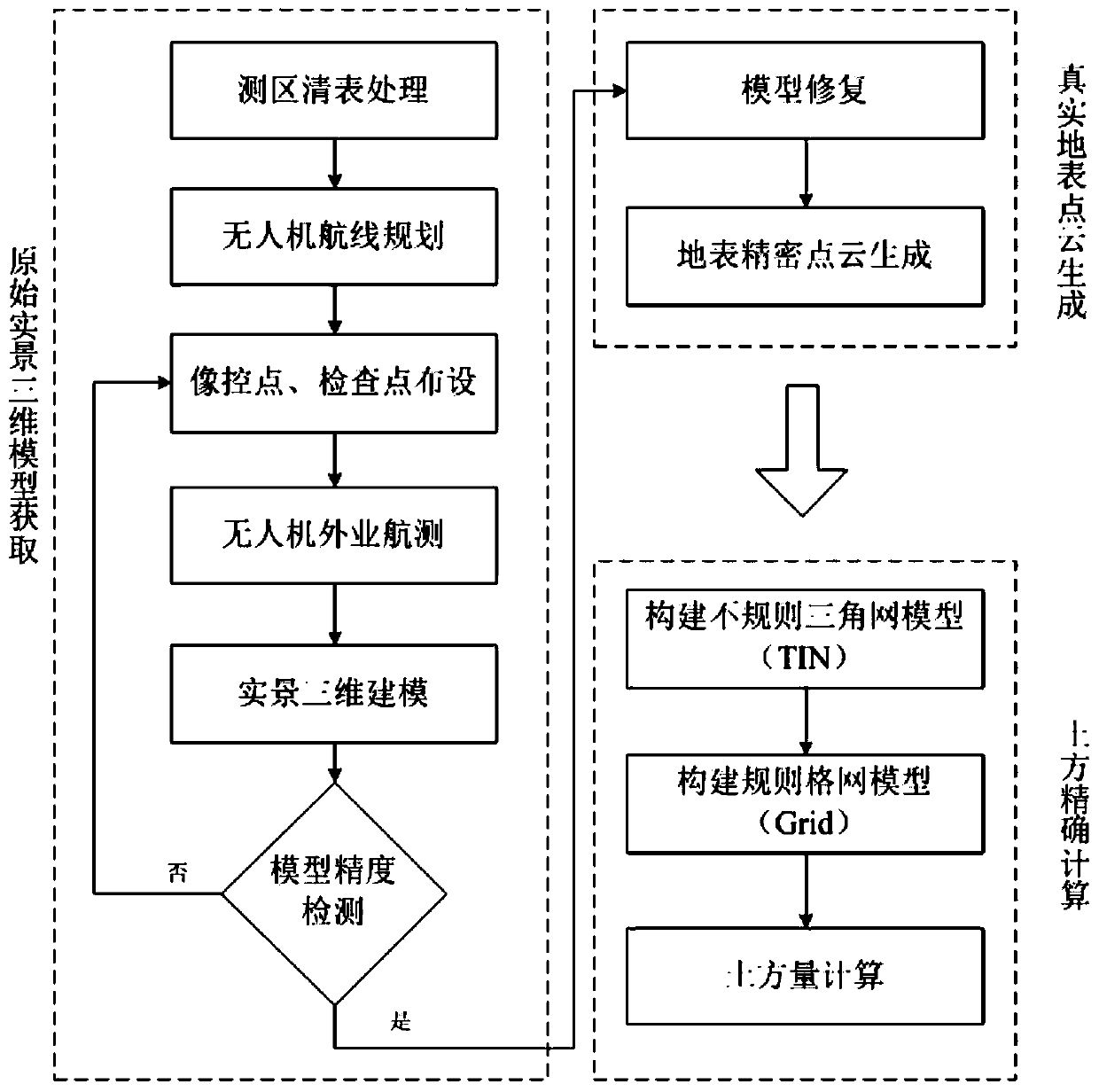
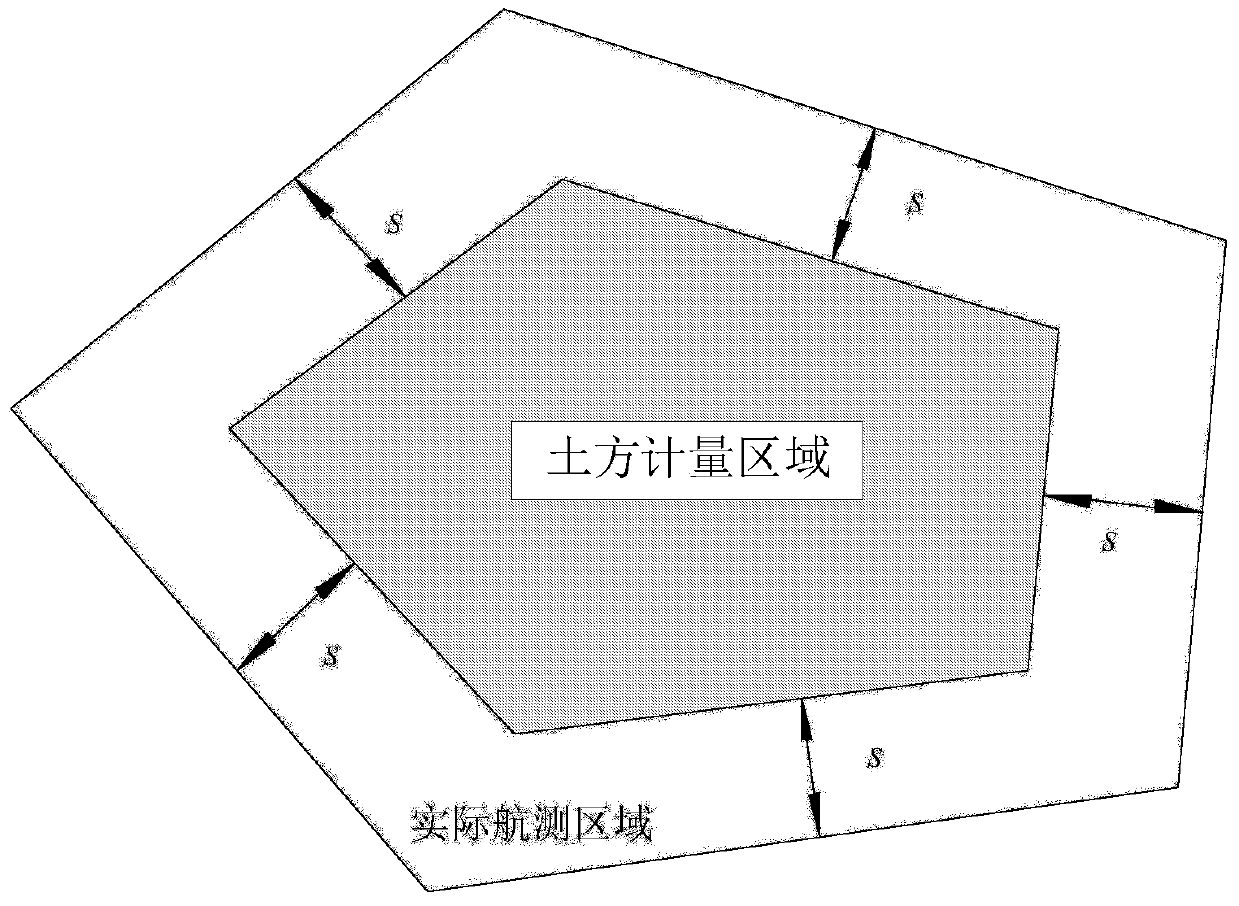
Unmanned aerial vehicle tilt photography fine grid earthwork measurement method
ActiveCN110285792AHigh measurement accuracyReduce intensityPhotogrammetry/videogrammetry3D modellingRegular gridPoint cloud
The invention provides an unmanned aerial vehicle tilt photography fine grid earthwork measurement method. The aerial survey data are obtained by aerial survey of the unmanned aerial vehicle and the data are integrated and processed so as to obtain a three-dimensional model of a real scene; the model restoration technology is applied to eliminate the interference objects such as trees and houses in the real scene three-dimensional model, the elevation around the pores left after the interference objects are deleted is applied to fit the curved surface, and the pores are filled with the curved surface so that the restored real scene three-dimensional model is finally obtained, and the real surface point cloud is generated based on the restored real scene three-dimensional model; and an irregular triangular network model is constructed according to the point cloud and then a regular grid model is further constructed, and the earthwork calculation value is obtained through a fine grid earthwork measurement formula based on the regular grid model. The accurate calculation of earthwork filling and excavation can be realized based on the fine grid, and the method has the advantages of high accuracy, safe operation and saving manpower and time cost.
Owner:SHANDONG TRAFFIC PLANNING DESIGN INST
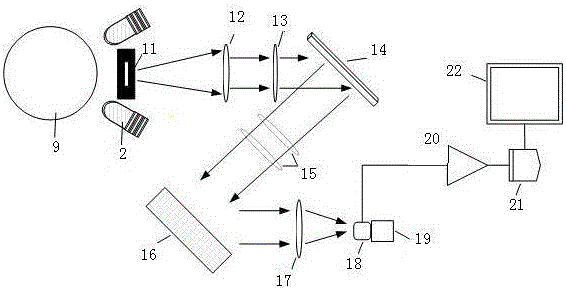
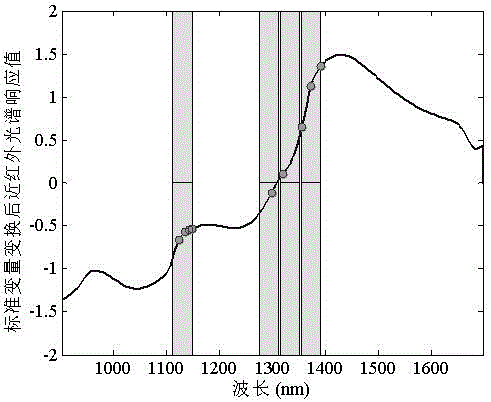
Handheld near infrared spectrum detection system and detection method for quality of fruits and vegetables
The invention discloses a handheld near infrared spectrum detection system and a detection method for the quality of fruits and vegetables, and belongs to the field of quick detection technologies for the quality of foods or agricultural products. The handheld near infrared spectrum detection system and the detection method have the advantages that modulation light paths of a digital micro-mirror device is matched with a single-point detector and other external modules, so that the handheld, low-cost and miniaturized near infrared spectrum detection system for the quality of the fruits and vegetables can be obtained, and high-performance spectrum information can be acquired without expensive linear array detectors; characteristic wave bands are selected at first in the aspect of building fruit and vegetable quality detection models, then wave bands which do not contain information variables and are low in relevancy are removed, then a small quantity of characteristic wavelengths are selected by the id of characteristic wavelength selection processes, internal collinear relations among spectrum data are eliminated, accordingly, model calculation can be reduced, the models can be simplified, and the quality of the models can be improved; the bottleneck problems of high nondestructive detection cost for the quality of fruits and vegetables, carrying inconvenience and poor quality of existing detection models can be solved by the aid of the handheld near infrared spectrum detection system and the detection method.
Owner:JIANGSU UNIV
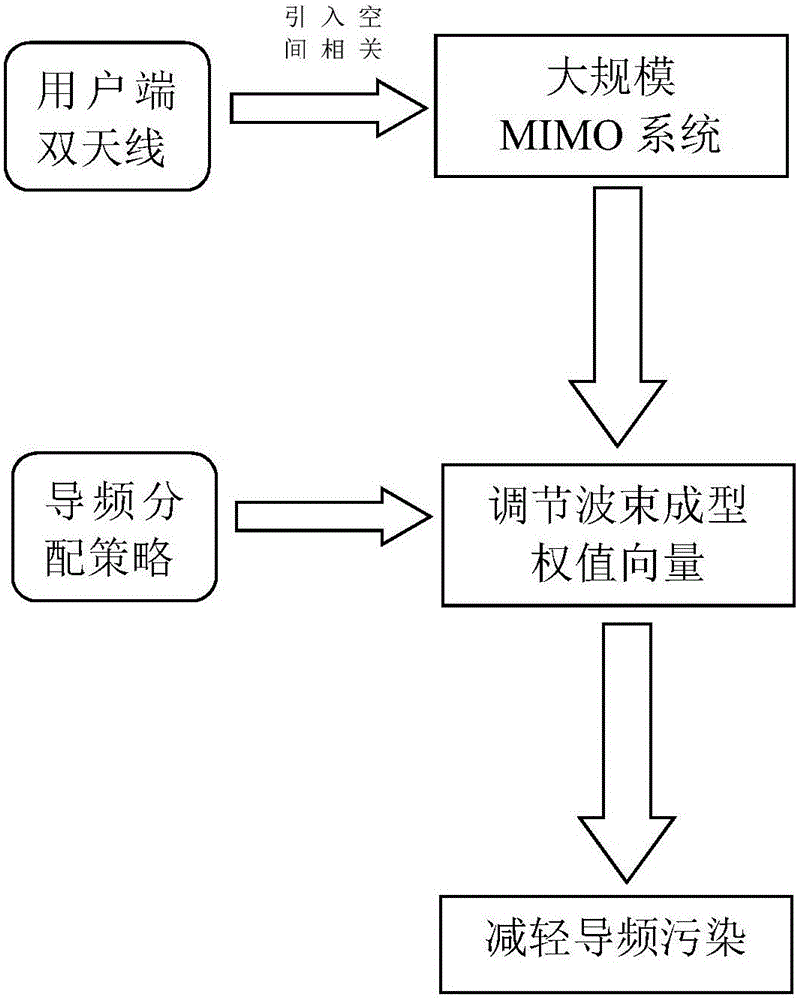
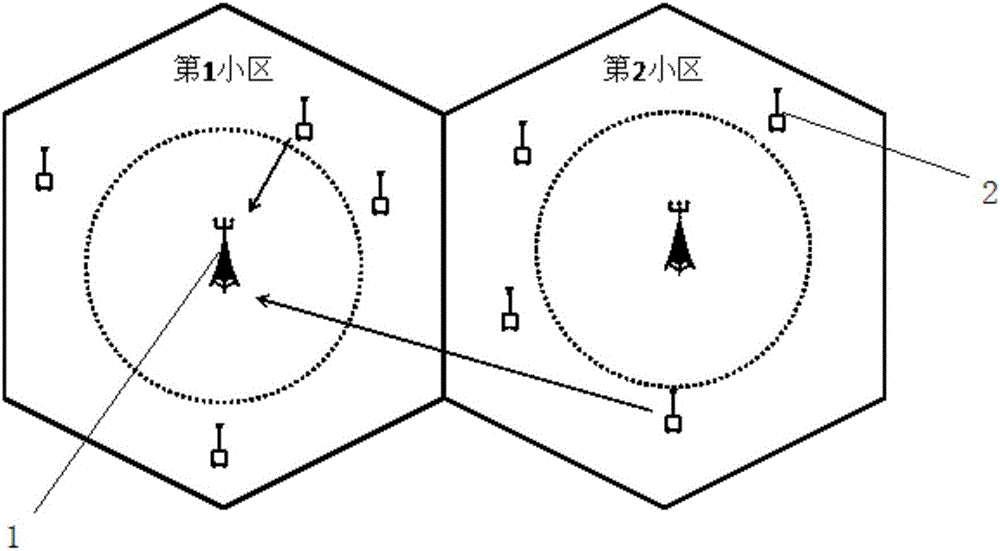
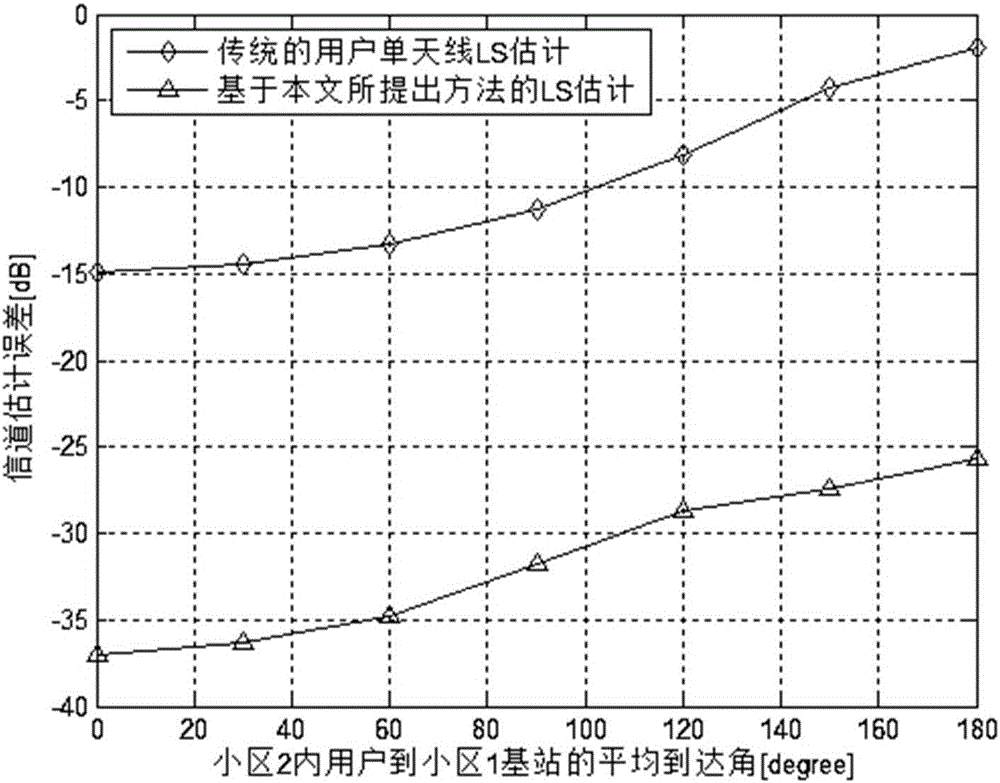
Multi-cell large-scale MIMO system user dual-antenna pilot frequency interference elimination method
InactiveCN105827273AAvoid gettingEliminate and Mitigate Pilot PollutionSpatial transmit diversitySpatial correlationInterference elimination
The invention provides a multi-cell large-scale MIMO system user dual-antenna pilot frequency interference elimination method. Pilot frequency pollution of an uplink and interference in the data transmission process of a downlink are alleviated by considering spatial correlation and controlling the beam forming weight vector of a user side. Meanwhile, pilot frequency distribution is introduced to the method, and a pilot frequency distribution strategy based on a greedy algorithm is put forward so that influence caused by pilot frequency pollution is further alleviated through combination of a user dual-antenna device, and thus the objectives of reducing channel estimation error and enhancing system speed can be achieved.
Owner:SHANGHAI JIAO TONG UNIV
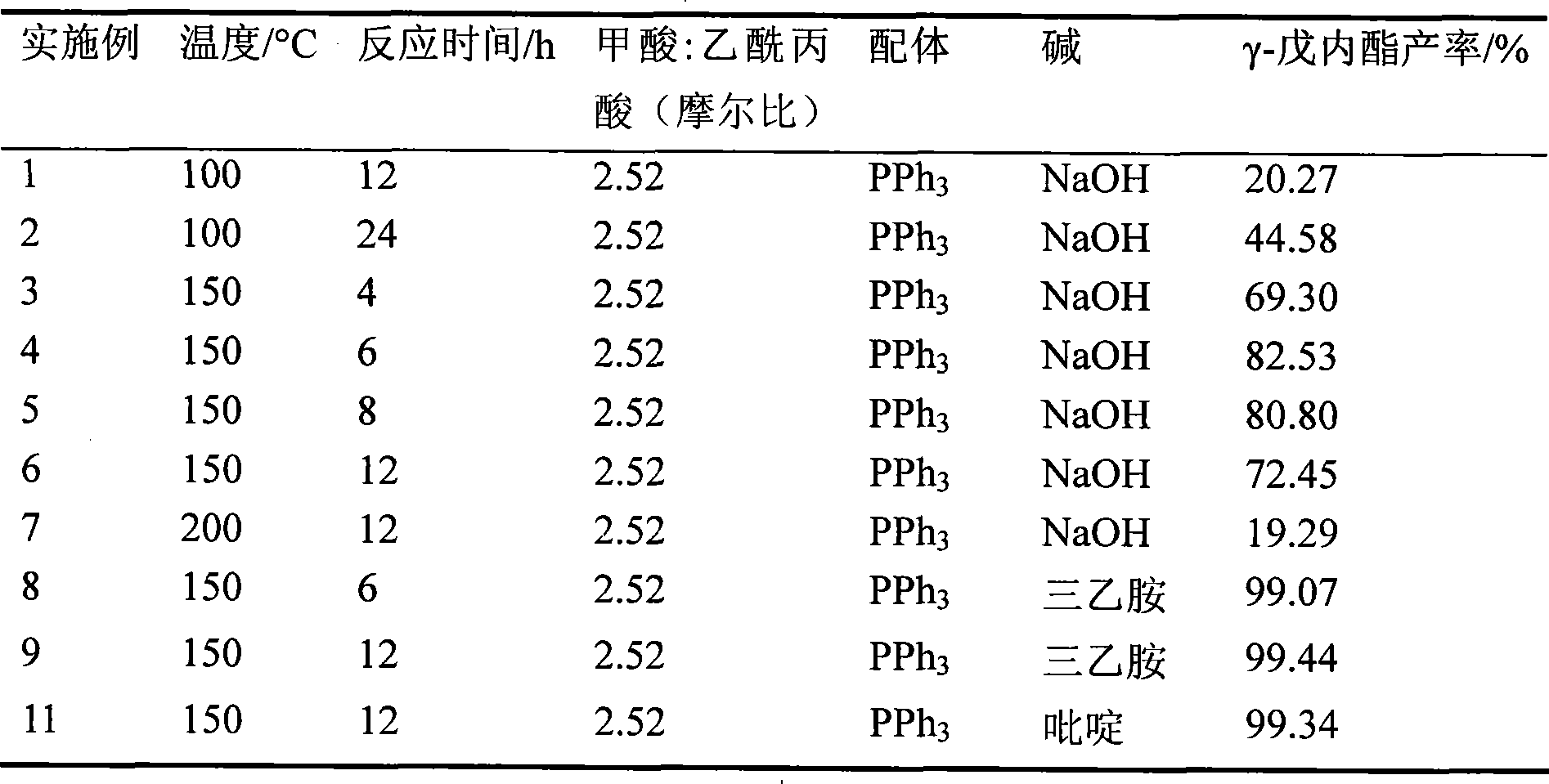
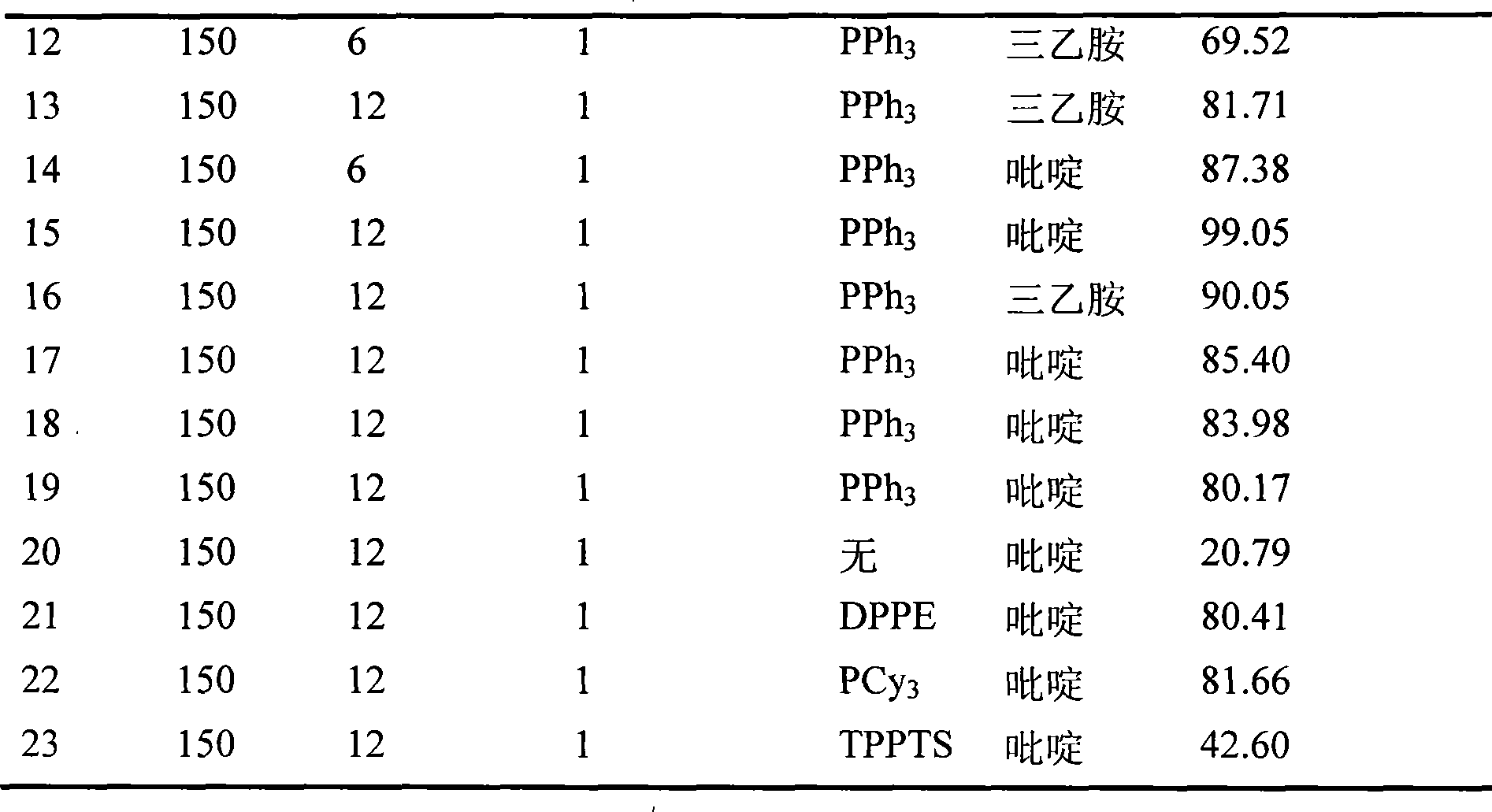
Method for directly preparing gamma-valerolactone from acetylpropionic acid and aminic acid
The invention discloses a method for preparing GAMMA-valerolactone from levulinic acid and formic acid, which is characterized in that the levulinic acid is in situ reduced at 100-200 DEG C in the presence of ruthenium catalyst and formic acid contained in a system as reducer, and distillation is carried out to obtain mixture containing the product GAMMA valerolactone and used catalyst; and mother liquor containing the used catalyst and raw material are mixed to realize circulation of the catalyst, thereby greatly improving environmental friendliness. The method avoids the energy source consumption during valerolactone purification process, avoids hydrogen source acquired from the system exterior, and improves the economy and security of a production system, with the advantages of simple operation process. The formic acid is decomposed to generate large amount of carbon dioxide besides hydrogen, which is convenient for collection and utilization.
Owner:UNIV OF SCI & TECH OF CHINA
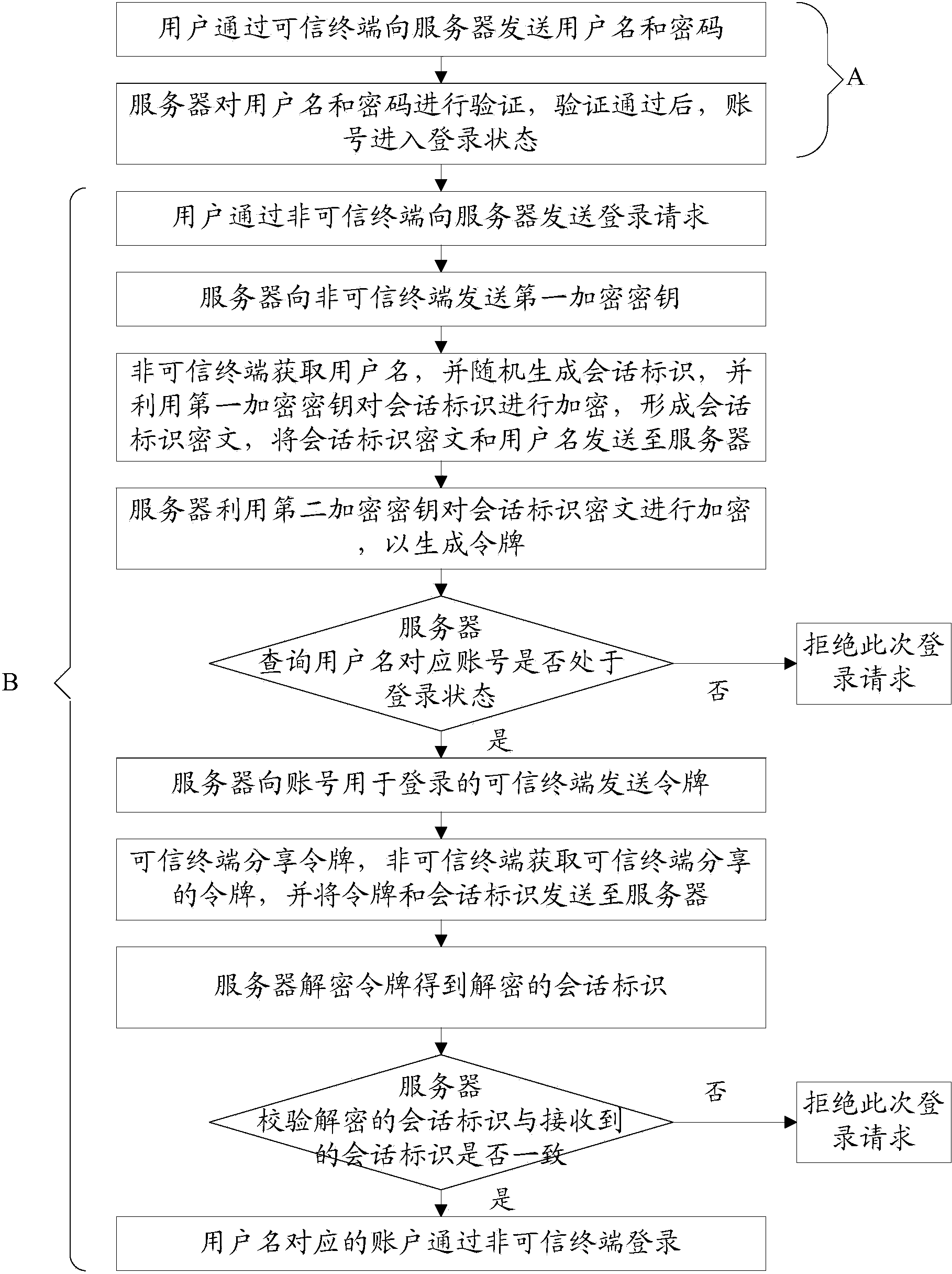
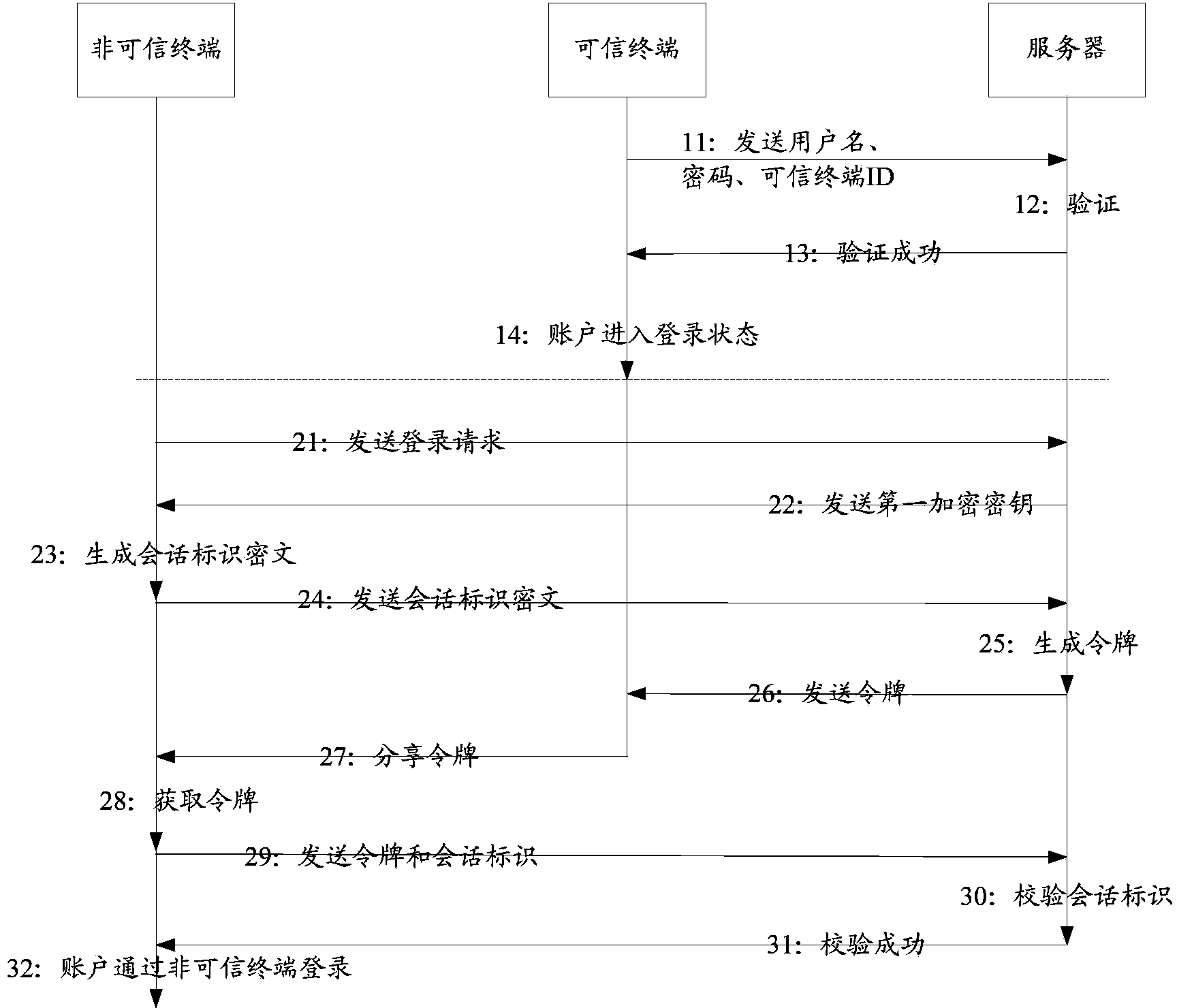
Same-account incredible terminal login method and system based on credible terminal
The invention discloses a same-account incredible terminal login method and system based on a credible terminal. The method includes the steps that firstly, an incredible terminal generates session identification through a first encryption key, a server encrypts the session identification and generates a token, the token is sent to the credible terminal, the incredible terminal acquires the token through the credible terminal and sends the token and the initially-generated session identification back to the server to be checked, and after check is successful, a user can log in through the incredible terminal. Due to the fact that when logging in through the incredible terminal, the user does not need to input both a user name and a password and can successfully log in only through the user name, malicious users are effectively prevented from acquiring integral account information through the incredible terminal, and safety performance of login of accounts on the incredible terminal is improved.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Information provision method and system for social network
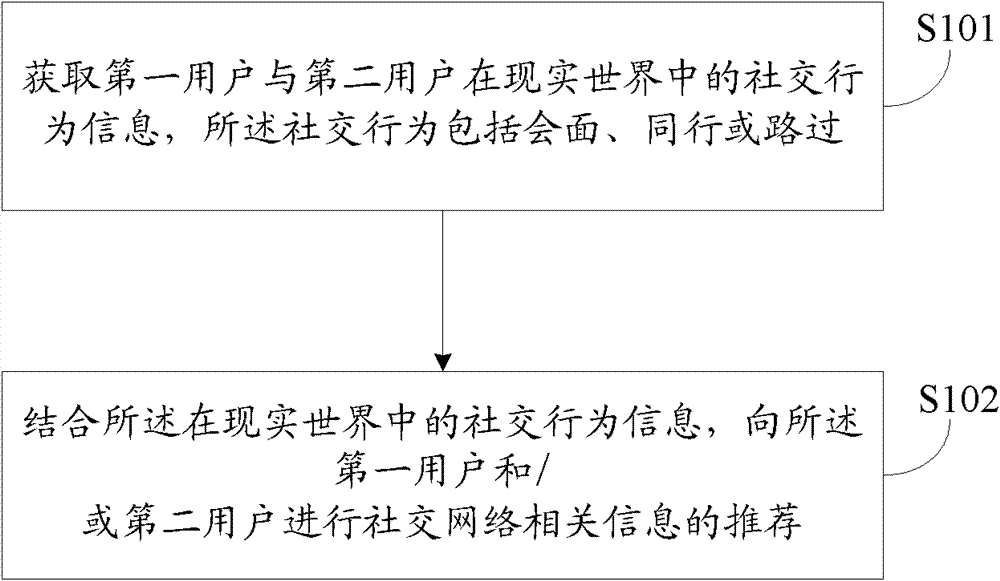
ActiveCN102811179ATo achieve mutual integrationAvoid gettingMessaging/mailboxes/announcementsData switching networksComputer terminalSocial behavior
The invention discloses an information provision method and an information provision system for a social network. The method comprises the following steps of: acquiring the social behavior information of a first user and a second user in a real world, wherein social behaviors comprise meeting, traveling together or passing-by; and suggesting social network related information to the first user and / or the second user by combining the social behavior information in the real world. By the method and the system, virtual social contact and social contact in the real world can be well fused, the user can be prevented from obtaining a great amount of invalid information, and the waste of system resources of a mobile communication terminal also can be avoided.
Owner:北京淘友天下技术有限公司
Method for secure storage of data and electronic equipment
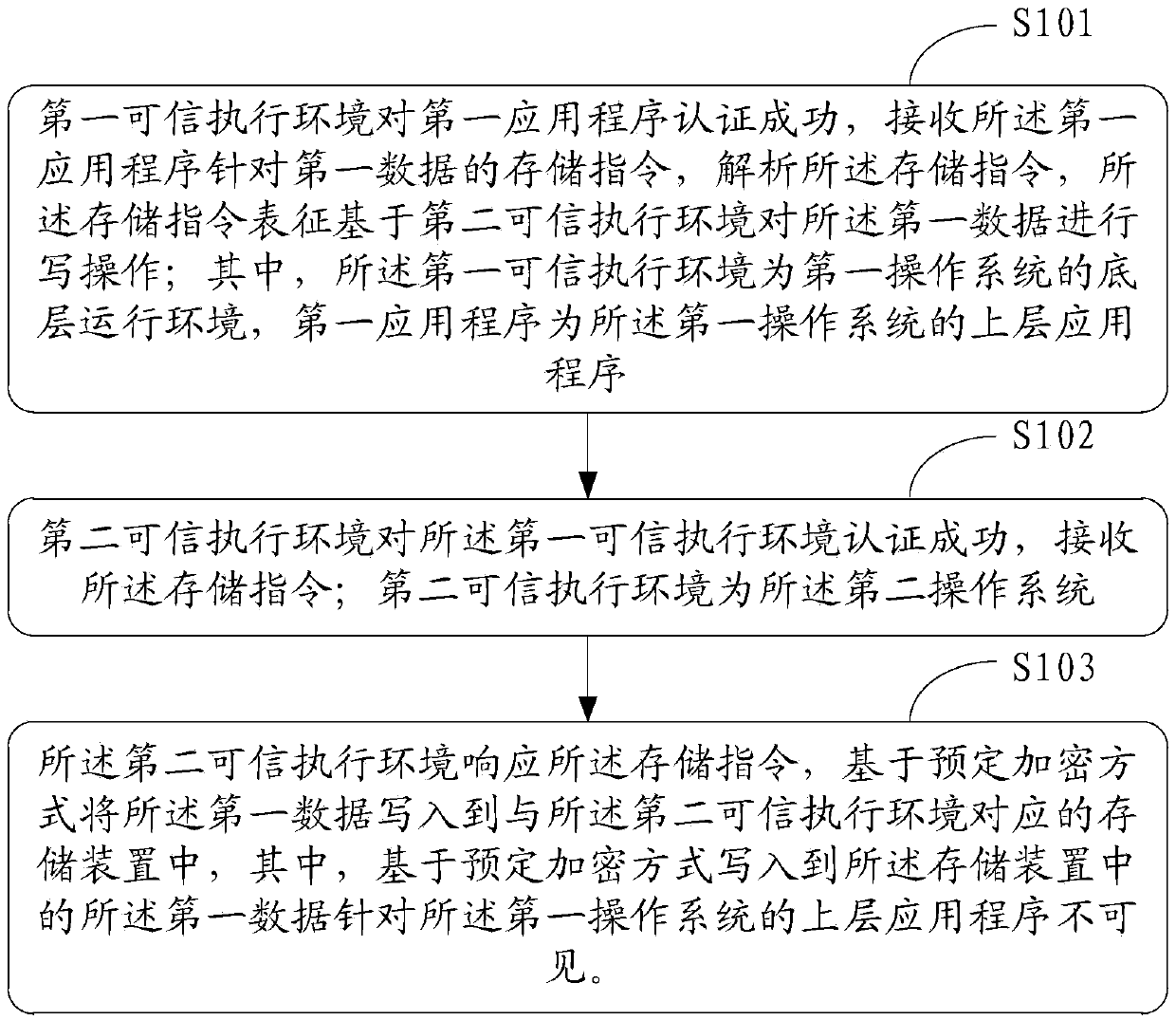
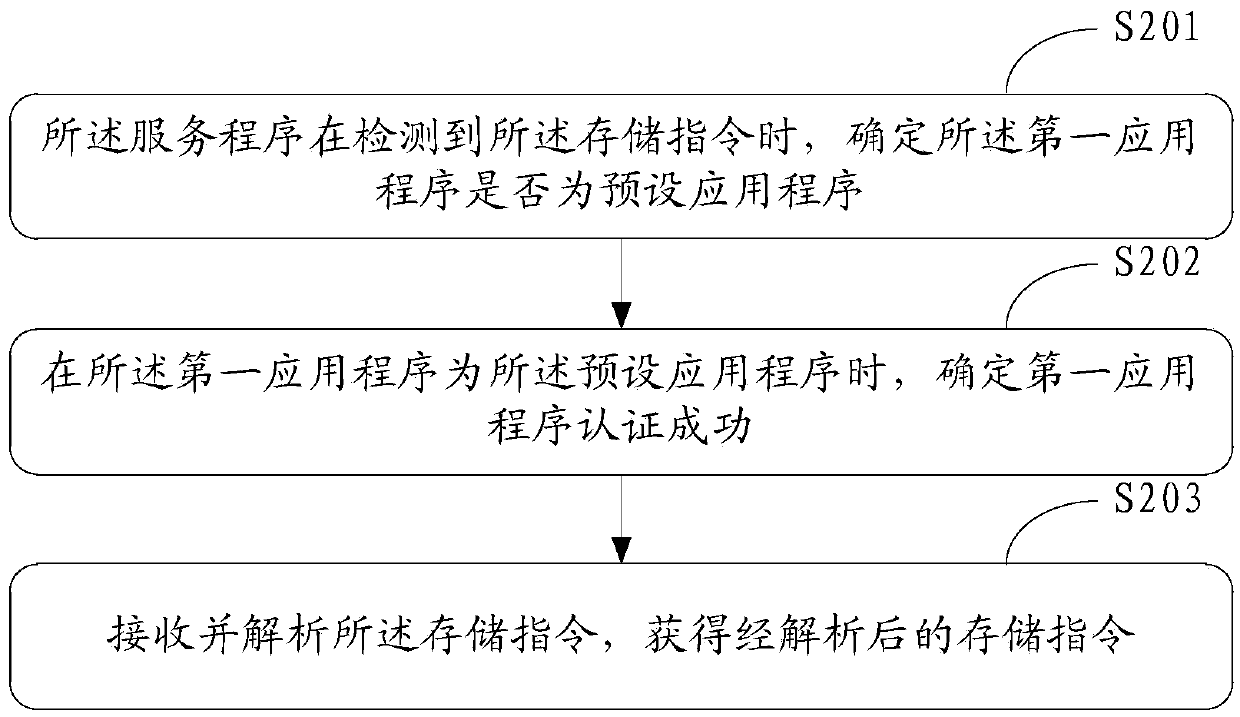
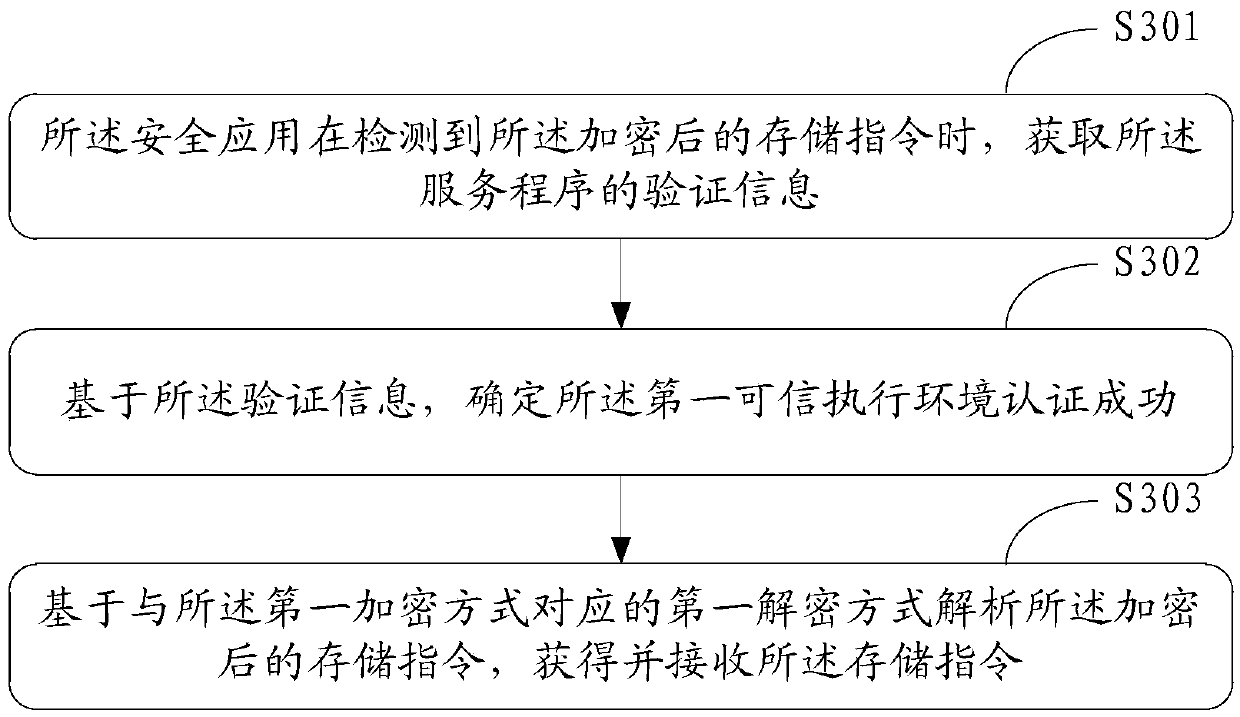
InactiveCN105512576AEnsure communication securityEnsure safetyInternal/peripheral component protectionDigital data authenticationOperational systemApplication software
The invention discloses a method for secure storage of data and electronic equipment. The method comprises steps as follows: a first credible execution environment authenticates a first application successfully, receives a storage instruction of the first application for first data and analyzes the storage instruction, and the storage instruction represents to perform write operation on the first data on the basis of a second credible execution environment; the second credible execution environment authenticates the first credible execution environment successfully and receives the storage instruction; the second credible execution environment is a second operation system; the second credible execution environment responds to the storage instruction and writes the first data in a storage device corresponding to the second credible execution environment in a preset encryption mode, and the first data written in the storage device in the preset encryption mode are invisible to an upper-layer application of a first operation system.
Owner:LENOVO (BEIJING) CO LTD
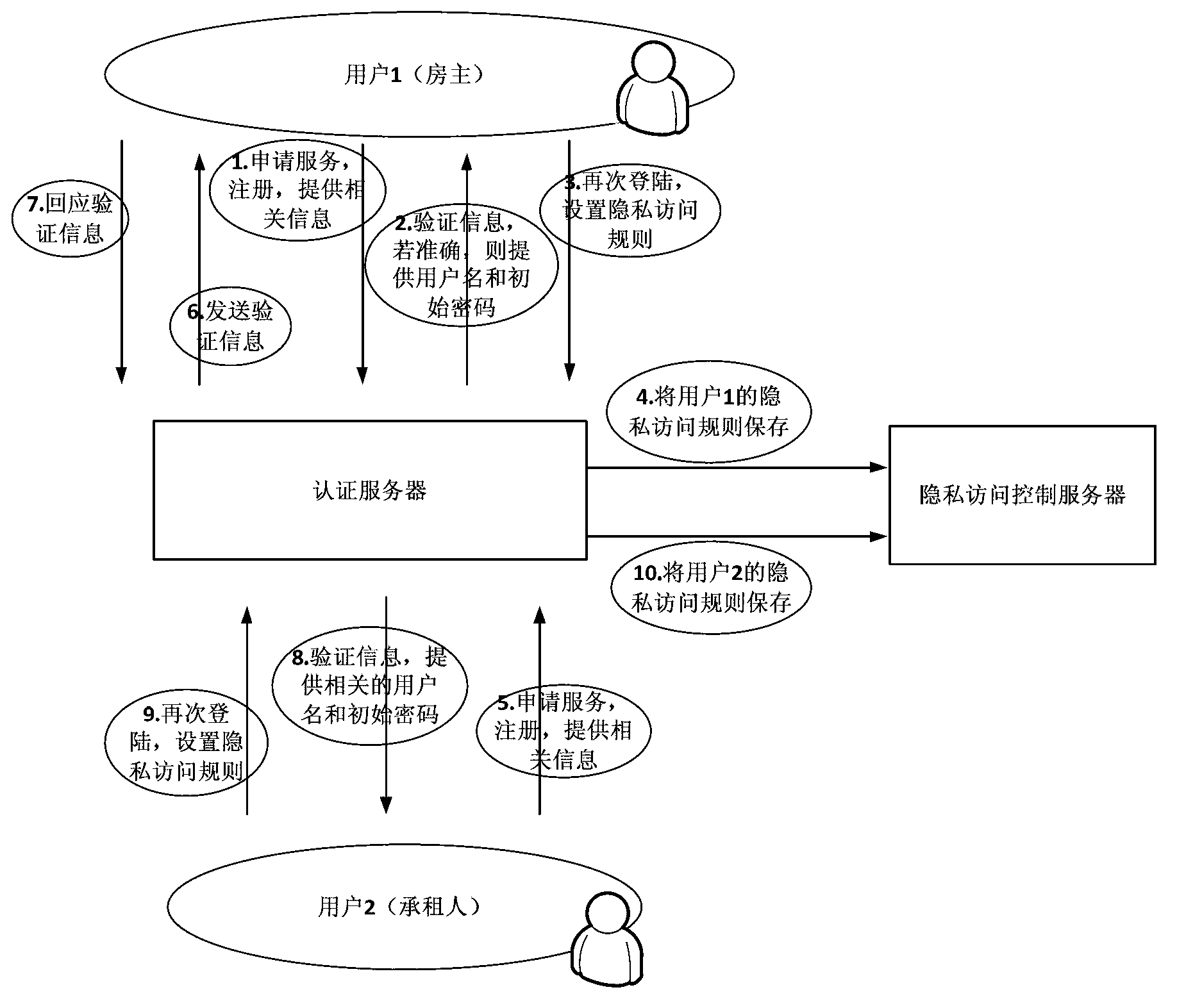
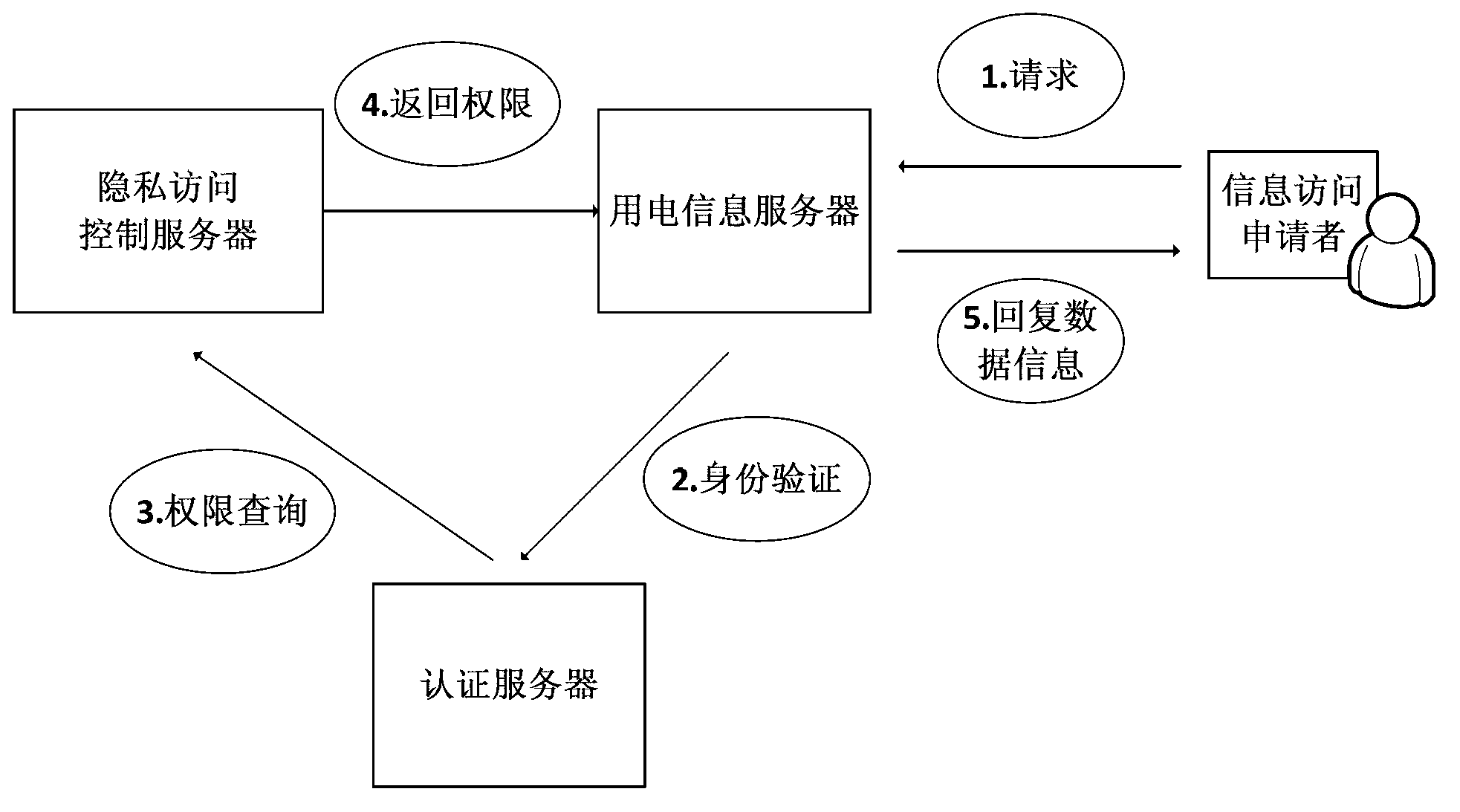
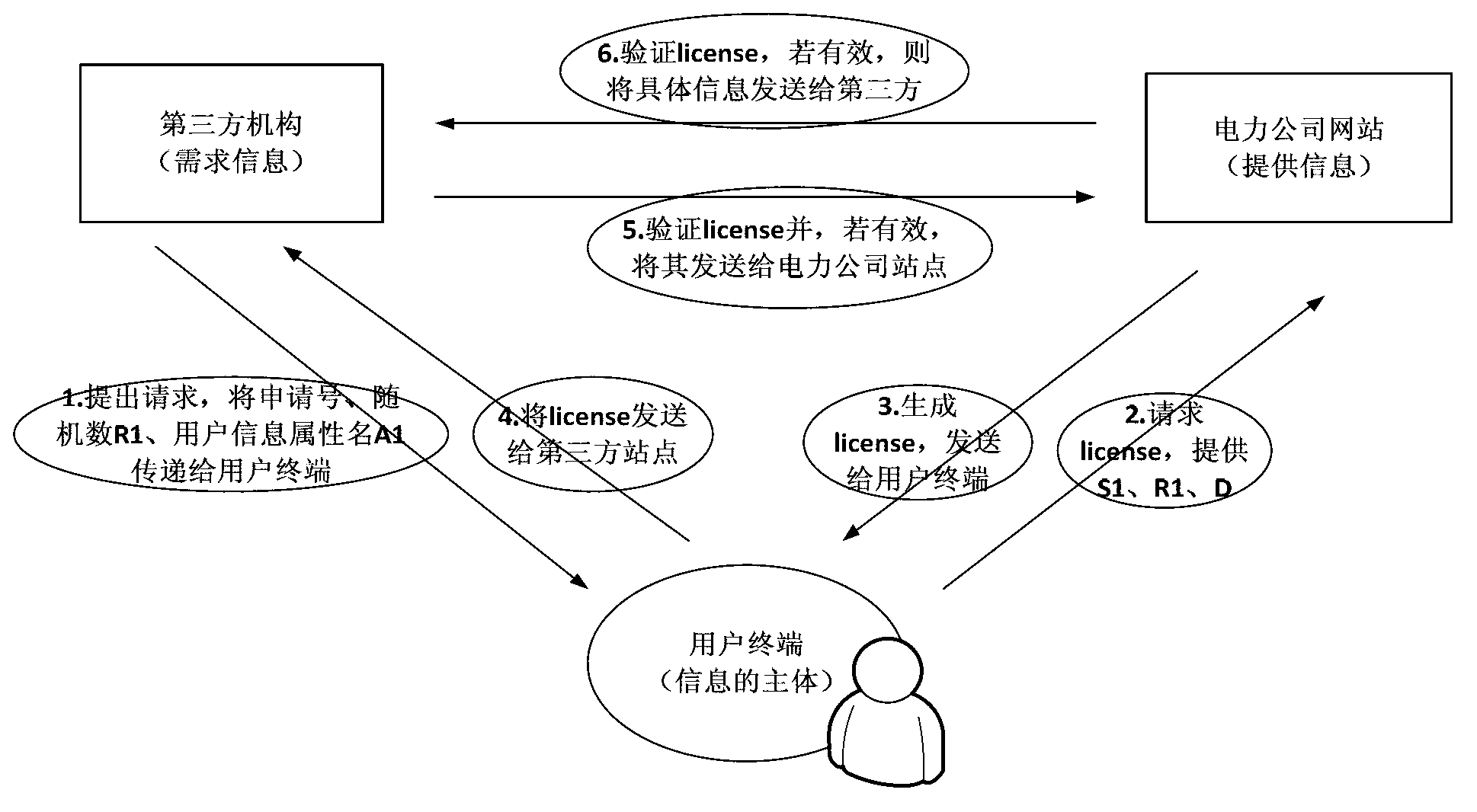
Intelligent grid electricity information privacy protection method based on multi-party interaction
The invention provides an intelligent grid electricity information privacy protection method based on multi-party interaction. The method comprises the following steps that the user sets a privacy access rule; the user requests to access the electricity information; the third party requests to obtain the electricity information. With the adoption of the method, the user can make an access control aiming at his / her own electricity information and prevent others from getting the detailed electricity information without the consent, and meanwhile, the third party gets permit through users when requiring to get the electricity information, and the corresponding safety mechanism is provided, thereby effectively protecting the privacy of the user.
Owner:CHINA ELECTRIC POWER RES INST +2
Method and system for network access
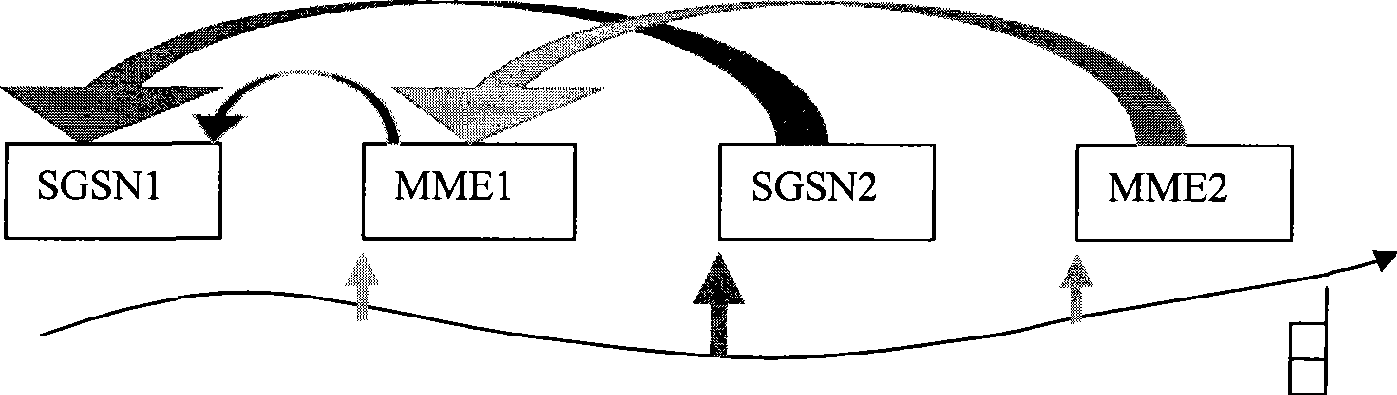
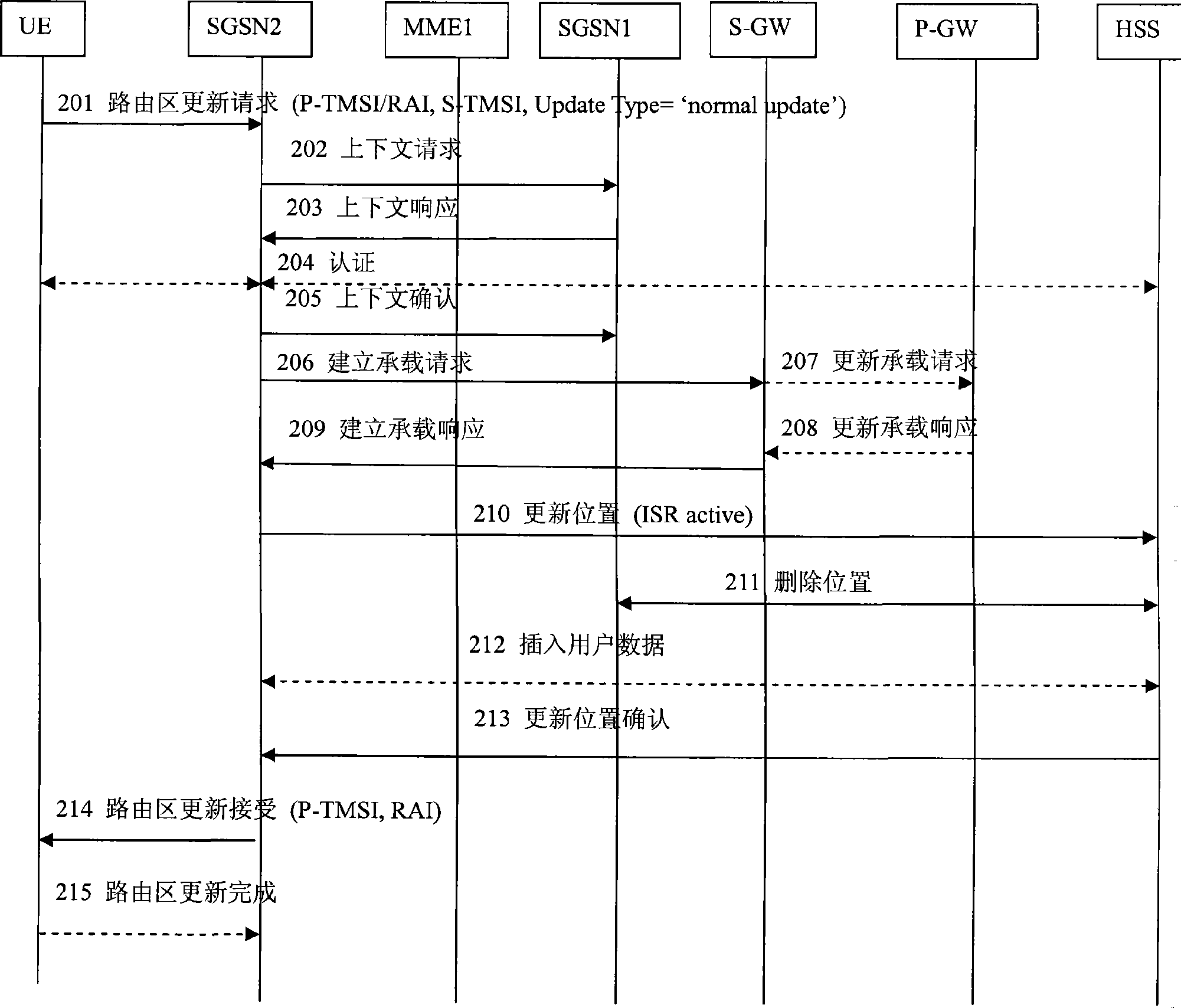
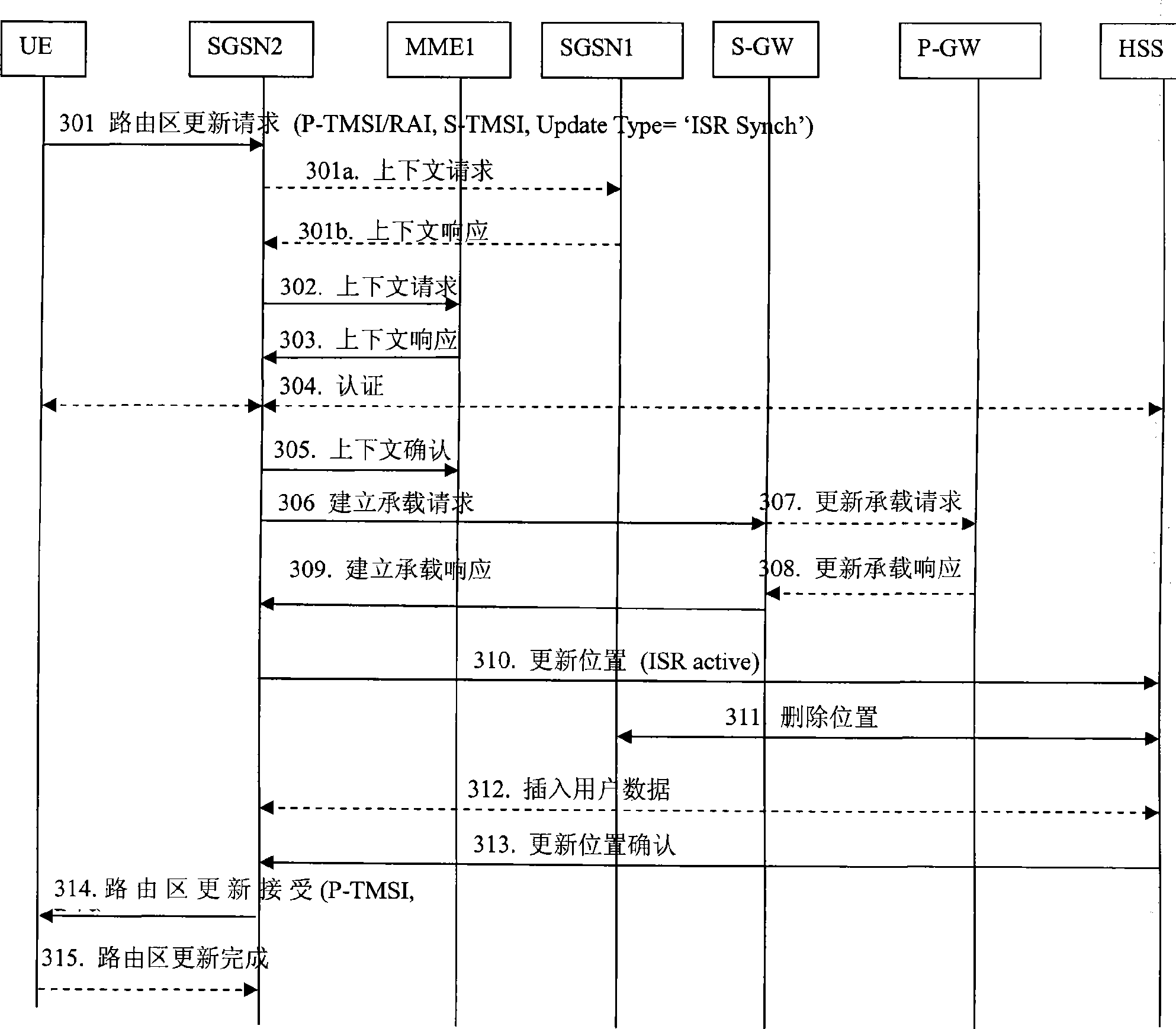
ActiveCN101483850AAvoid gettingReduce idle state signalingRadio transmission for post communicationNetwork data managementTelecommunicationsNetwork Access Device
The invention provides a method and a system for accessing to network; wherein the method for accessing to network comprises: if a terminal UE activates ISR, when the bearer is changed in a fist RAT, 'ISR Synch' demand is set; when a second RAT node is accessed to, the position update with 'ISR Synch' update type is initiated, wherein the first RAT and the second RAT are different. If the UE fails to activate ISR or the UE does not have 'ISR Synch' demand, when the UE initiates position update and is accessed to the RAT node, the update type is 'Normal Update'. If the UE activates ISR, when the bearer is changed in the fist RAT, the signaling in the idle state is set and synchronous 'ISR Synch' demand is reduced; when the UE initiates position update and is accessed to the same RAT node with the first RAT, the update type is 'Normal Update'.
Owner:HUAWEI TECH CO LTD
Auxiliary driving vehicle gateway for multi-CPU hard isolation of intelligent interconnection
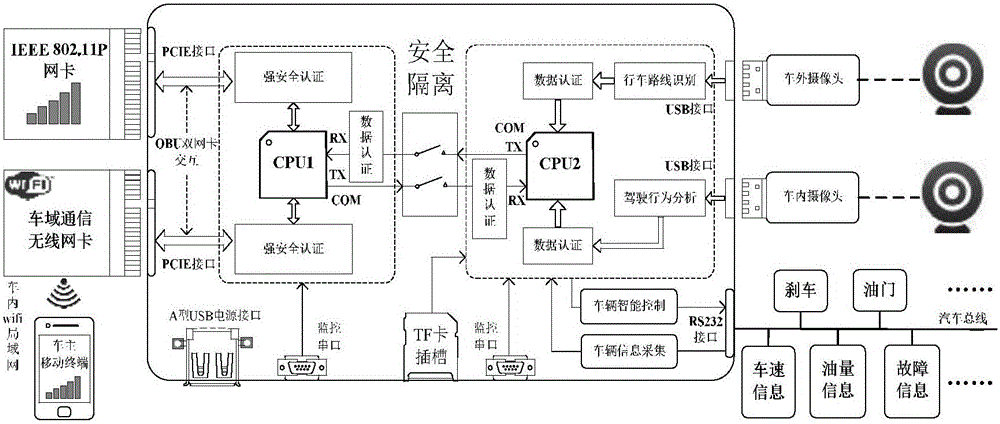
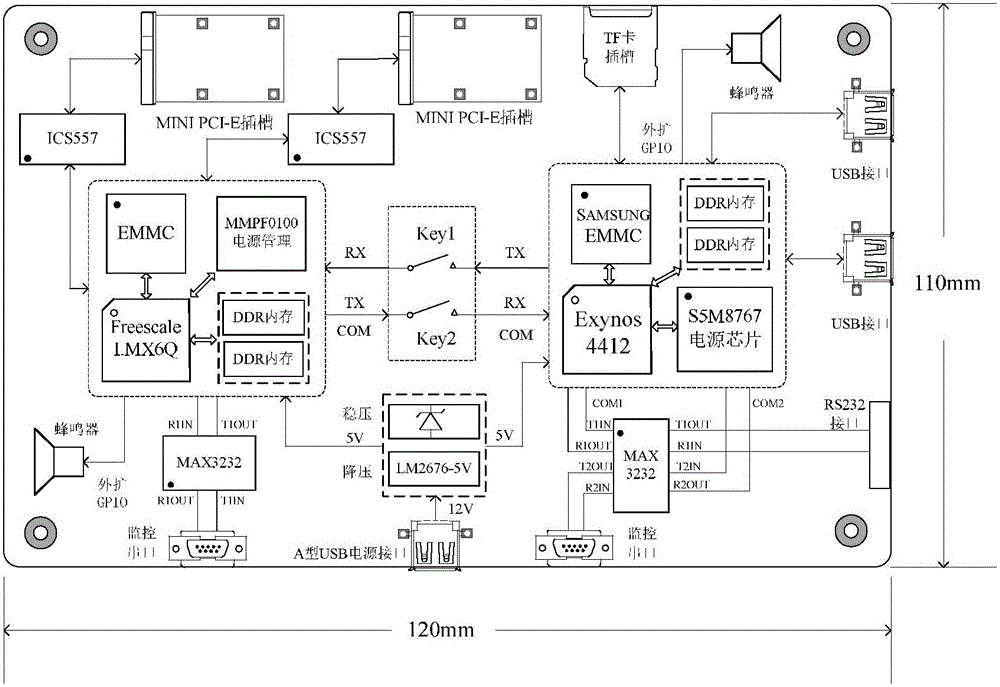
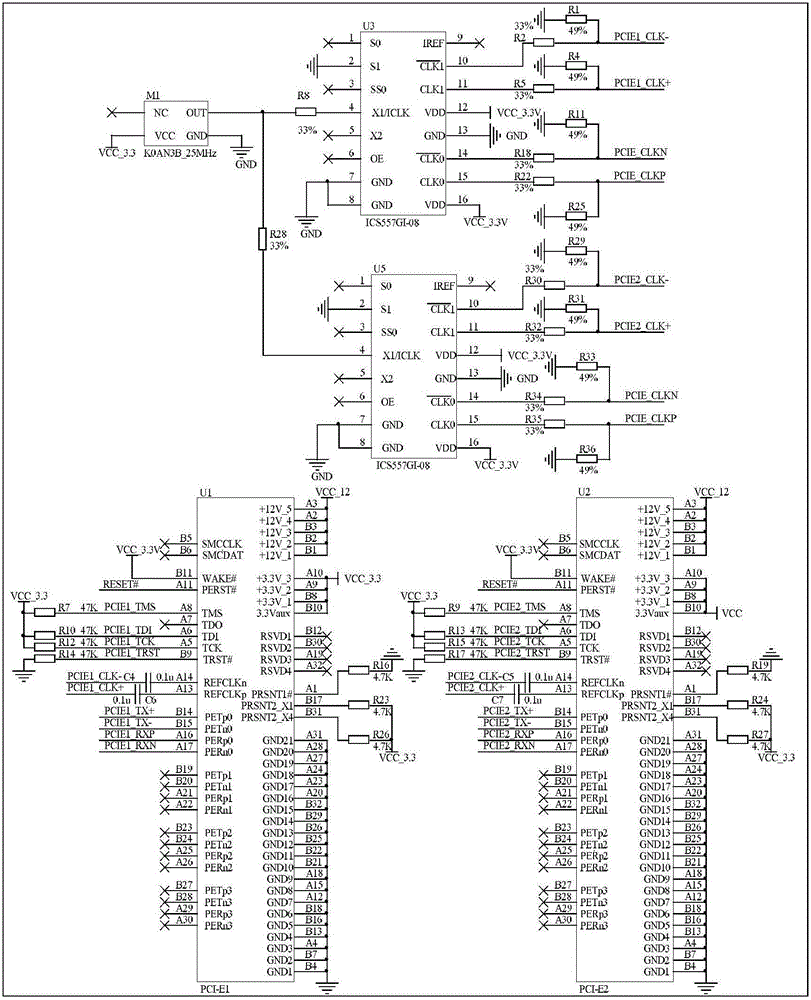
ActiveCN105743902APrevent intrusionAvoid gettingTransmissionSecurity arrangementCommunications securityInformation analysis
The invention discloses an auxiliary driving vehicle gateway for multi-CPU hard isolation of intelligent interconnection. The auxiliary driving vehicle gateway comprises a vehicle security communication system and a vehicle information analysis and control system, wherein the vehicle security communication system comprises a vehicle gateway double-wireless network card structure composed of an inter-vehicle wireless communication module and a vehicle domain wireless communication module, and a vehicle owner mobile terminal, and the vehicle security communication system carries out CPU control by an I.MX6Q processor; and the vehicle information analysis and control system carries out CPU control by an Exynos4412 processor, and comprises a driving route identification module, a driving behavior analysis module, a vehicle information collection module and an intelligent vehicle controller. The auxiliary driving vehicle gateway disclosed by the invention can realize the communication security of the vehicle gateway, realize driving security by driver fatigue state analysis based on Opencv face recognition and driving route recognition and analysis, as well as effectively resisting against Sybil attack and other various types of attacks from a hardware level to prevent hackers from invading the vehicle gateway to obtain vehicle information and controlling the vehicle.
Owner:JIANGSU UNIV
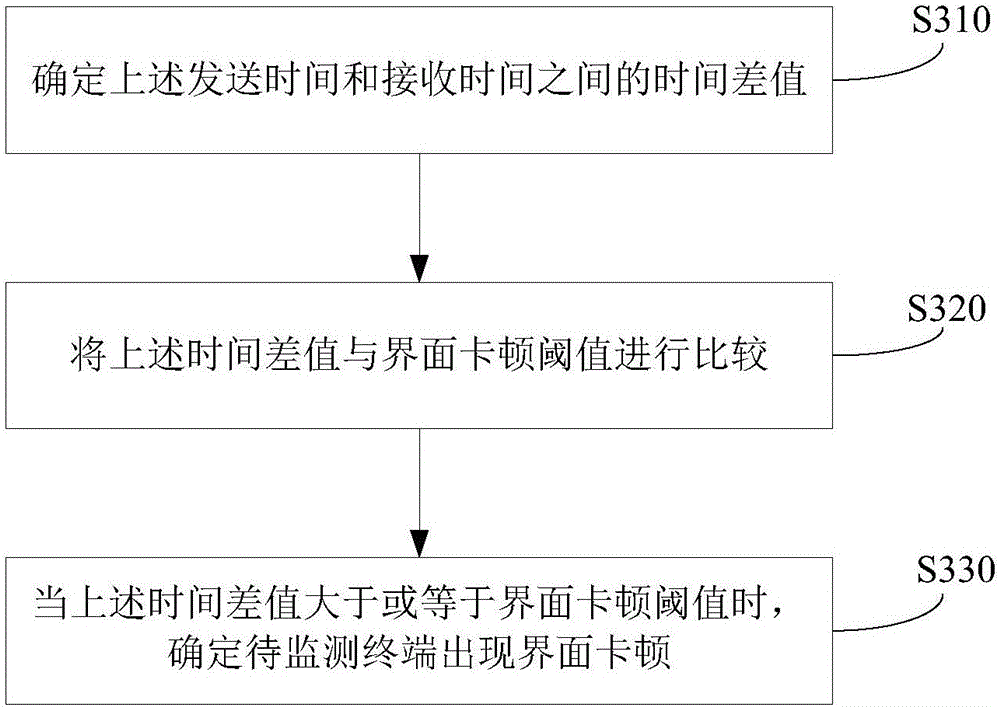
Method and device for monitoring interface jamming
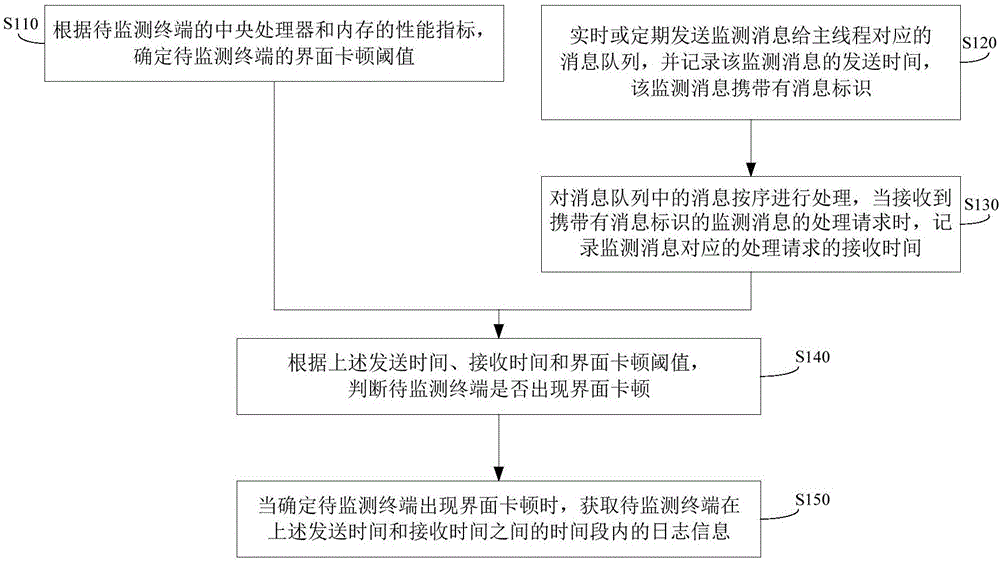
ActiveCN106776253ARealize automatic monitoringAvoid gettingHardware monitoringMessage queuePerformance index
The invention provides a method and device for monitoring interface jamming. The method comprises the steps of determining an interface jamming threshold of a to-be-monitored terminal according to a central processing unit of the to-be-monitored terminal and performance indexes of a memory; sending a monitoring message to a message queue corresponding to an interface thread in real time or at regular intervals, and recording sending time, wherein the monitoring message carries a message identifier; sequentially processing messages in the message queue, and when a processing request on the monitoring message is received, recording receiving time; determining whether interface jamming occurs according to the sending time, the receiving time and the interface jamming threshold; when it is determined that the interface jamming occurs, obtaining log information of the to-be-monitored terminal in a jamming time period. In the method and device for monitoring interface jamming, the interface jamming is automatically monitored; when it is monitored that the interface jamming occurs, the log information during the jamming period is obtained so that developers can conveniently analyze reasons for the jamming conveniently, the obtaining of the log information during the jamming period through problem reoccurring is avoided, and plenty of manpower and time are saved.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
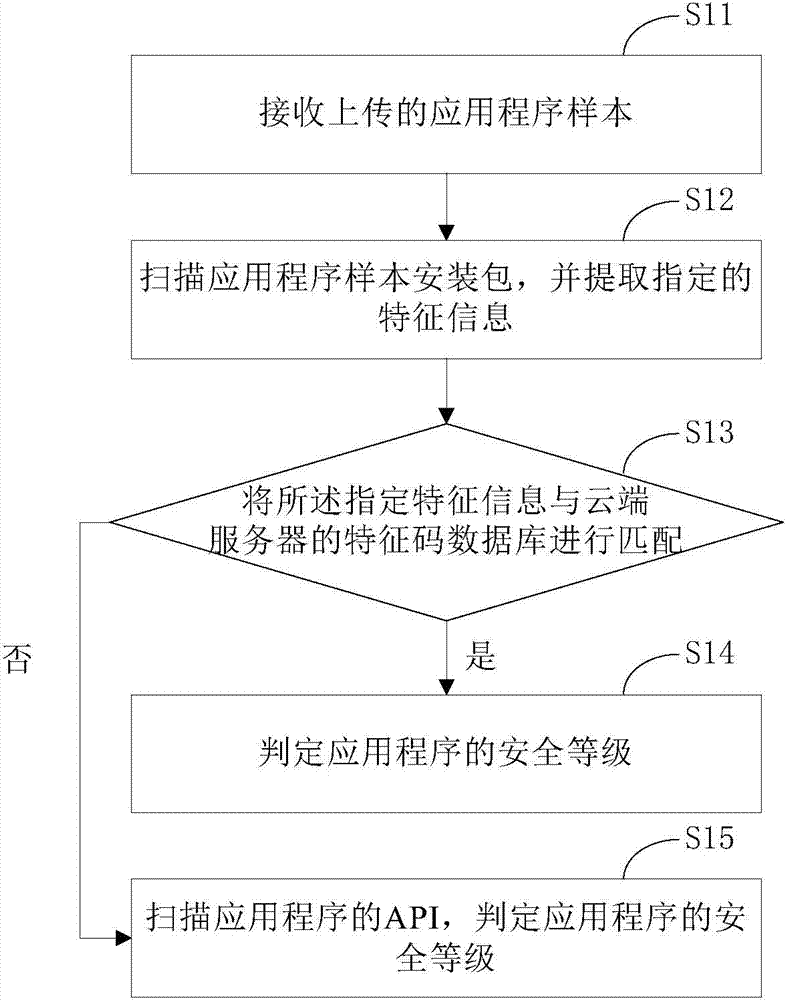
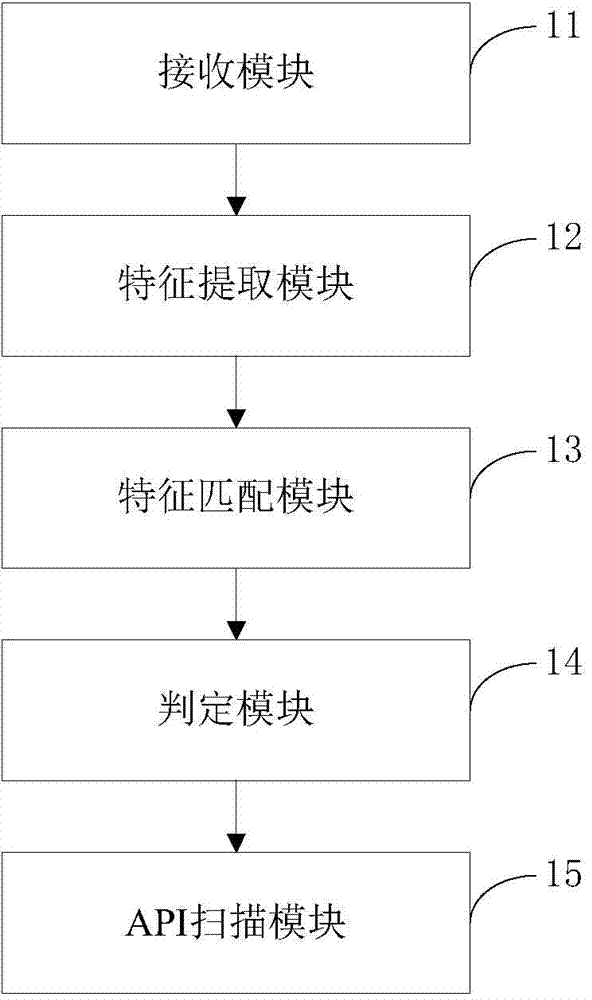
Static analysis method and system of smart phone application program
ActiveCN104715196AFast scanningImprove detection accuracyPlatform integrity maintainanceAnalysis methodAutomatic testing
The invention provides a static analysis method of a smart phone application program. The static analysis method comprises the steps of receiving an uploaded application program sample; scanning an installation package of the application program sample and extracting specified feature information; matching the specified feature information with a feature code database of a cloud server; judging the safety level of the application program if matching is successful; scanning an API of the application program and judging the safety level of the application program if matching is unsuccessful. In addition, the invention further provides a static analysis system of the smart phone application program. According to the static analysis method and system, automatic detecting of the safety level of the application programs of an Android system and an IOS system can be achieved, the detection efficiency is high, and the accurate rate is high.
Owner:BEIJING QIHOO TECH CO LTD
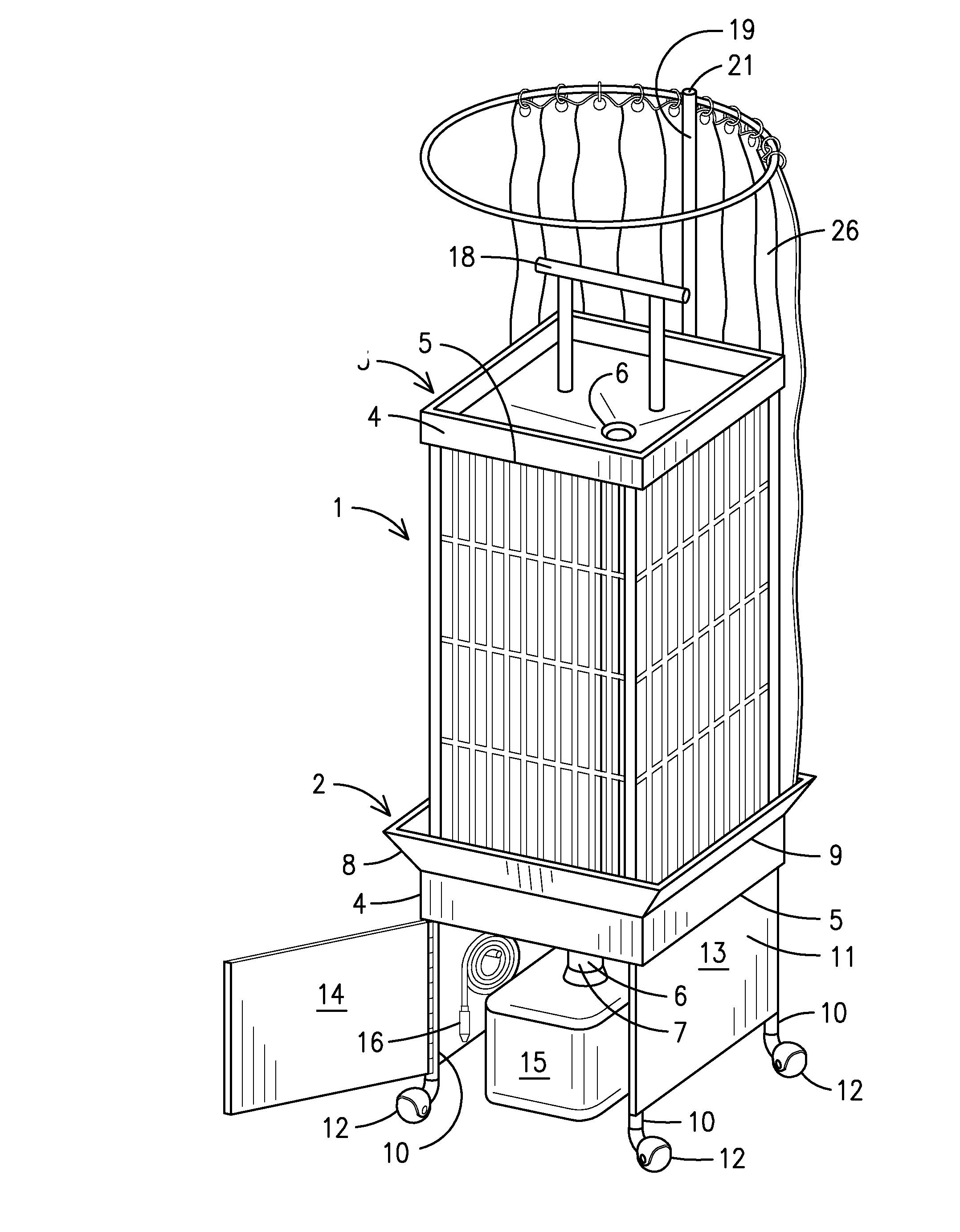
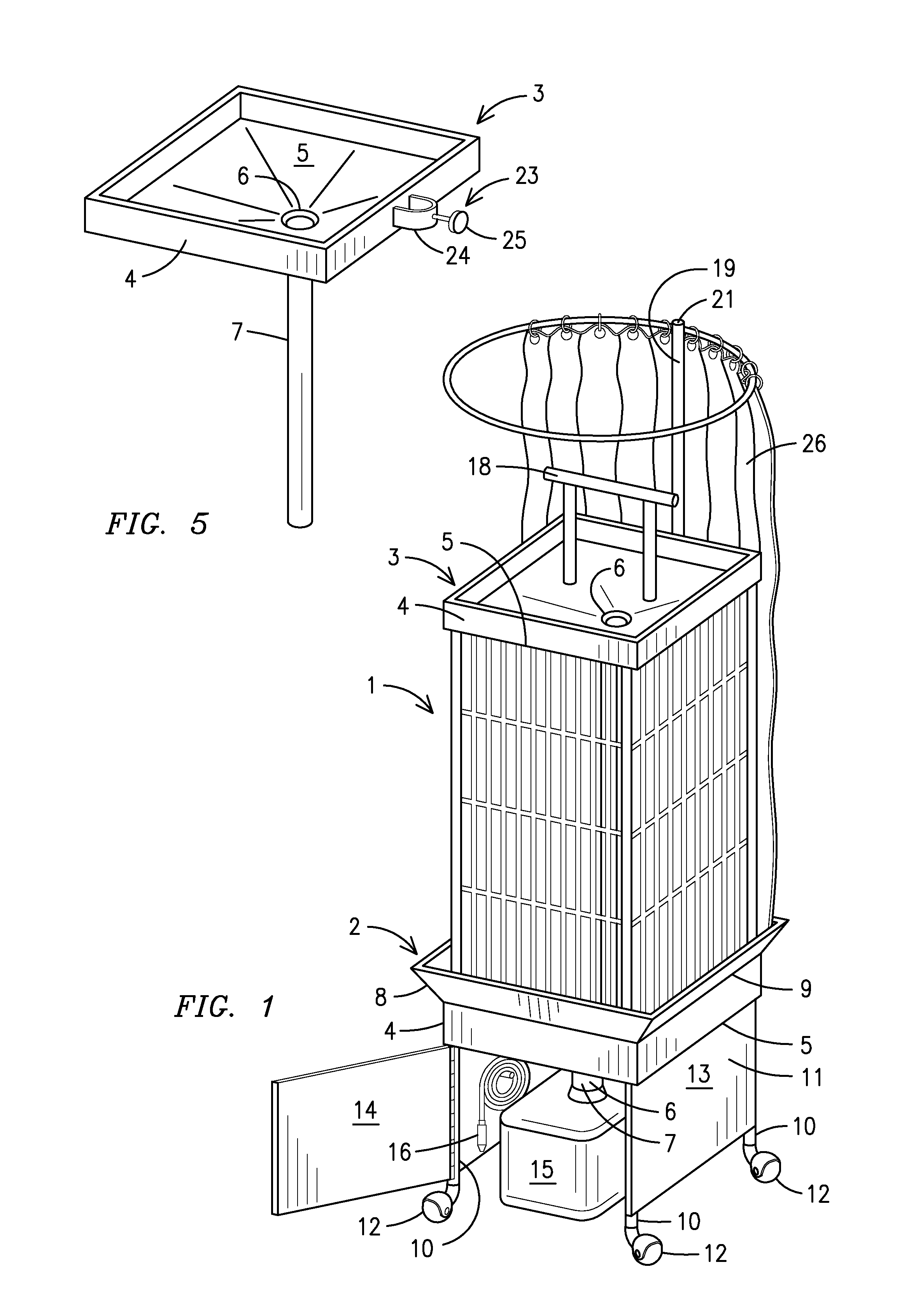
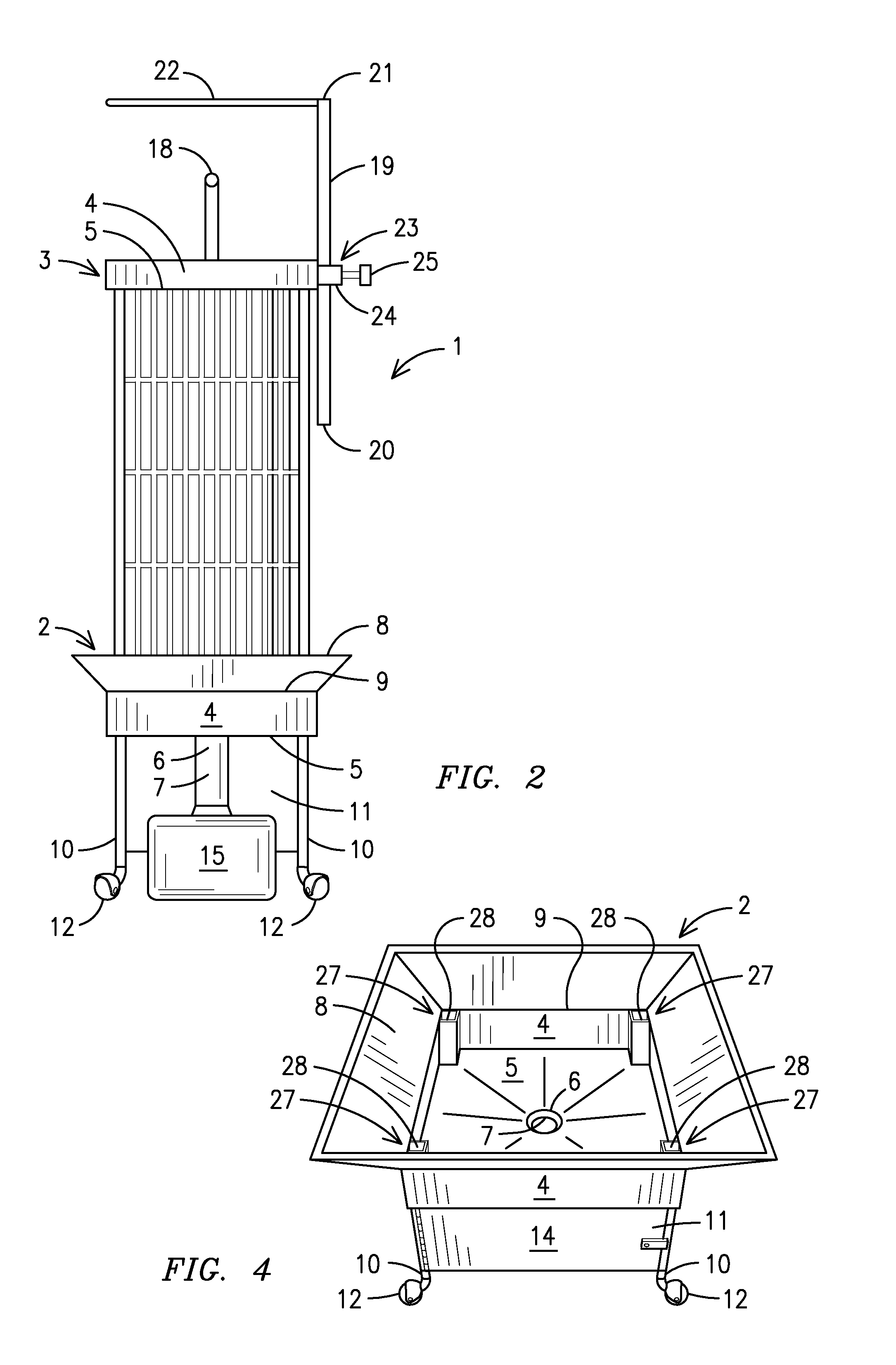
Bird cage assembly with cleaning sinks
A bird cage assembly with cleaning sinks that allows a user to clean a bird cage (1) without having to move the bird cage or dirtying the area around the bird cage. The bird cage rests in a lower cleaning sink (2) having a perimeter wall (4) extending upward from a floor (5) that angles downward towards a drain (6) having a drain pipe (7) extending from the drain. A flange (8) extends outward at an upward angle from an upper edge (9) of the perimeter wall and acts as a gutter to catch debris and water used to clean the bird cage. An upper cleaning sink (17) may be attached to the top of the bird cage to collect debris and water from a perch (18) located above the upper cleaning sink. The upper cleaning sink comprises a perimeter wall extending upward from a floor that angles downward towards a drain having a drain pipe extending downward from the drain. The drain pipe empties into the lower cleaning sink. A removable curtain (26) may be closed around the bird cage, thereby enclosing the entire birdcage to prevent any water from getting on surrounding areas while cleaning the bird cage.
Owner:EUSE PETER F
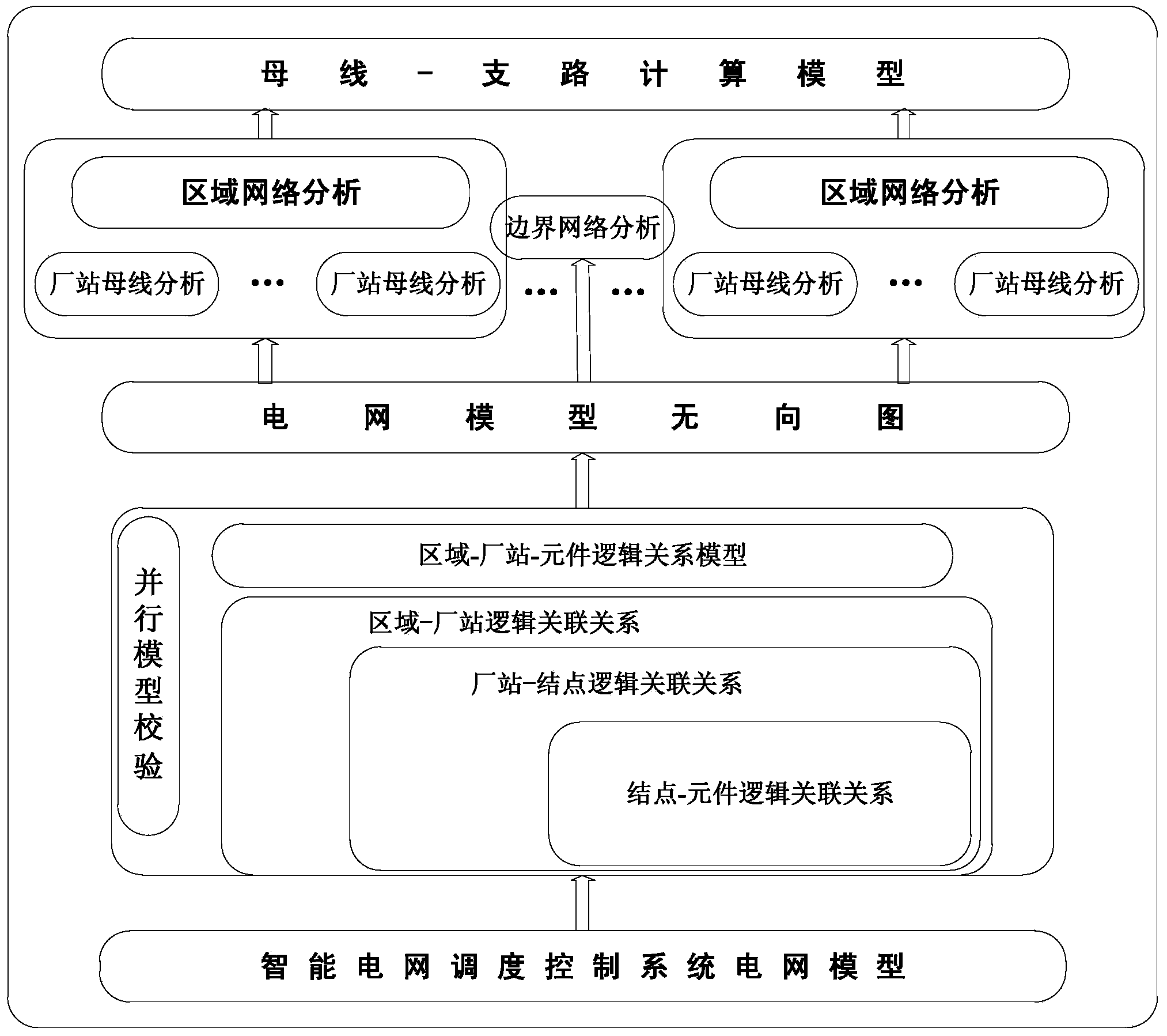
Large power grid parallel network topology analyzing method
ActiveCN104167736AAvoid gettingImprove execution efficiencyAc network circuit arrangementsControl systemSmart grid
The invention provides a large power grid parallel network topology analyzing method. The method comprises the following steps that a smart power grid dispatcher control system power grid model is read, parallel verifying is carried out on the smart power grid dispatcher control system power grid model, and the large power grid parallel network topology is analyzed. According to the large power grid parallel network topology analyzing method, data of the power grid model are divided according to areas and stations, the topology searching function is packaged, parallel processing is carried out on the model data according to the different areas and the different stations, and accordingly parallel computation on the power grid topology analyzing is achieved. The result of the measurement on the actual power grid shows that the method has good stability and real-time performance, and the requirements for the topology analysis of the online system simulation, analysis and control application are met.
Owner:STATE GRID CORP OF CHINA +2
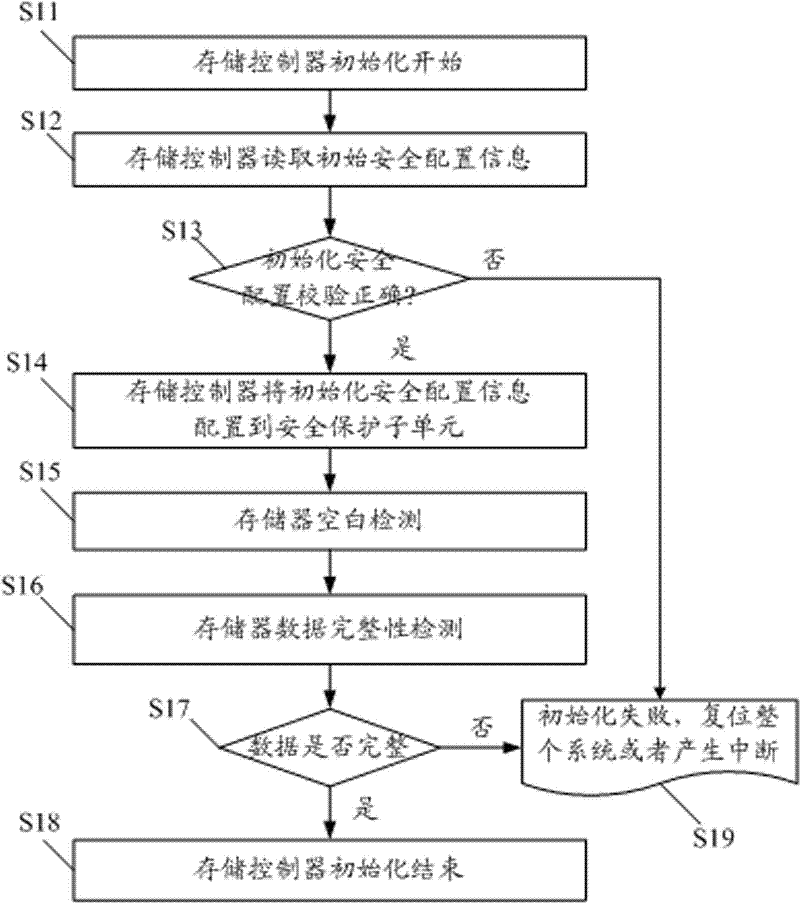
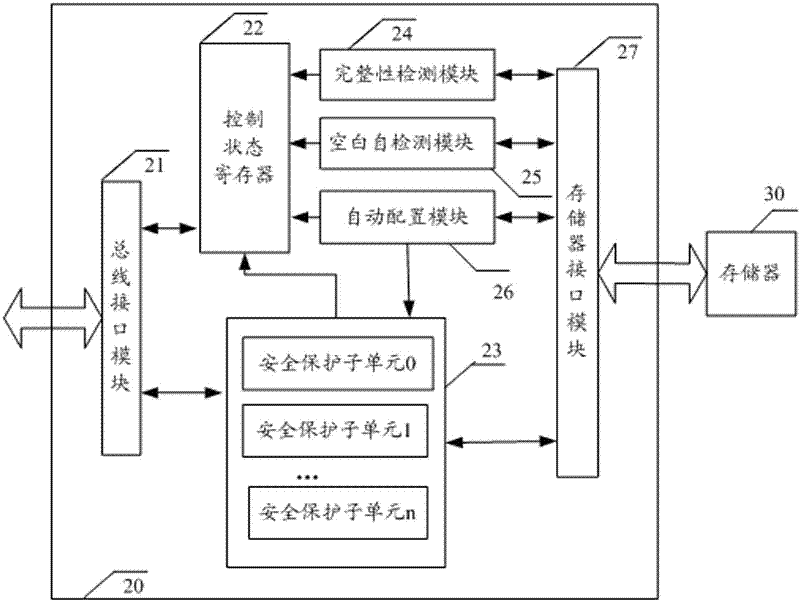
Memory controller for system on chip (SOC) chip system and method for implementing memory controller
ActiveCN102567245AReduce dependenceSimplify storage protection structureUnauthorized memory use protectionMemory interfaceControl store
The invention discloses a memory controller for a system on chip (SOC) chip system and a method for implementing the memory controller. The memory controller comprises a bus interface module, a memory interface module connected with a nonvolatile memory, and a safety protection subunit module connected between the bus interface module and the memory interface module, wherein the safety protection subunit module comprises a plurality of safety protection subunits of which the safety attributes can be independently configured; each safety protection subunit is used for performing access protection on one safety memory space in the nonvolatile memory; and by setting different safety attributes of the safety protection subunits, each piece of main equipment on a bus has different access authority on each safety memory space. The memory controller can effectively protect the safety information of the nonvolatile memory and is particularly suitable for an SOC chip which is needed to divide a memory space into different blocks with different sizes and ensure that the access attributes of the blocks are different.
Owner:SHENZHEN STATE MICRO TECH CO LTD
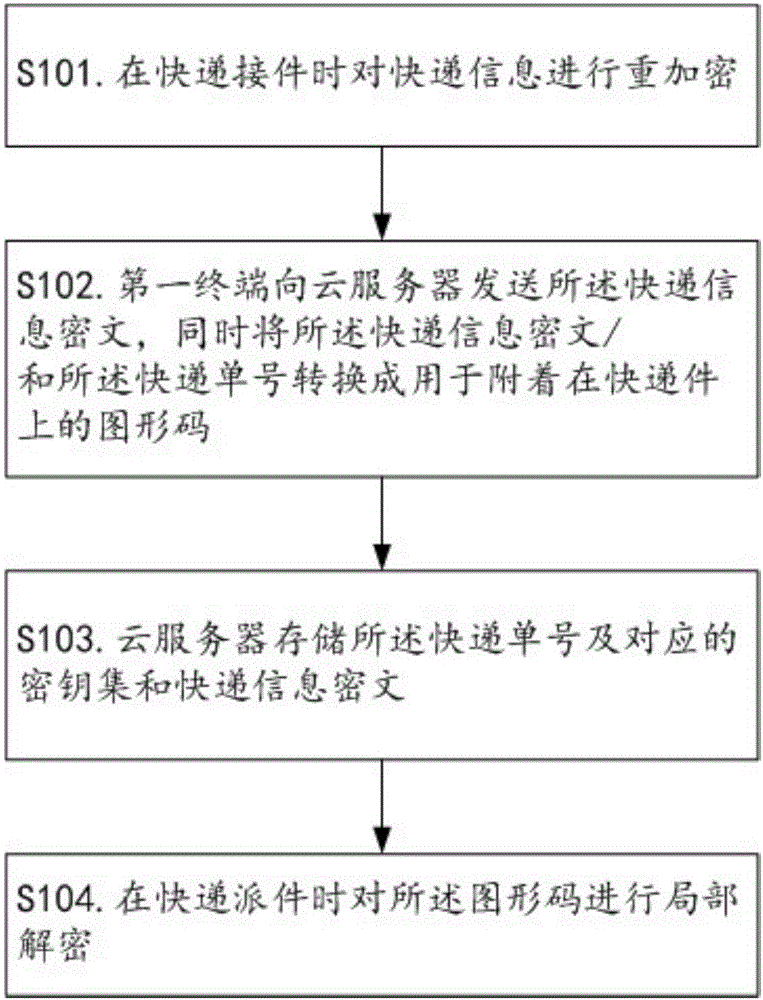
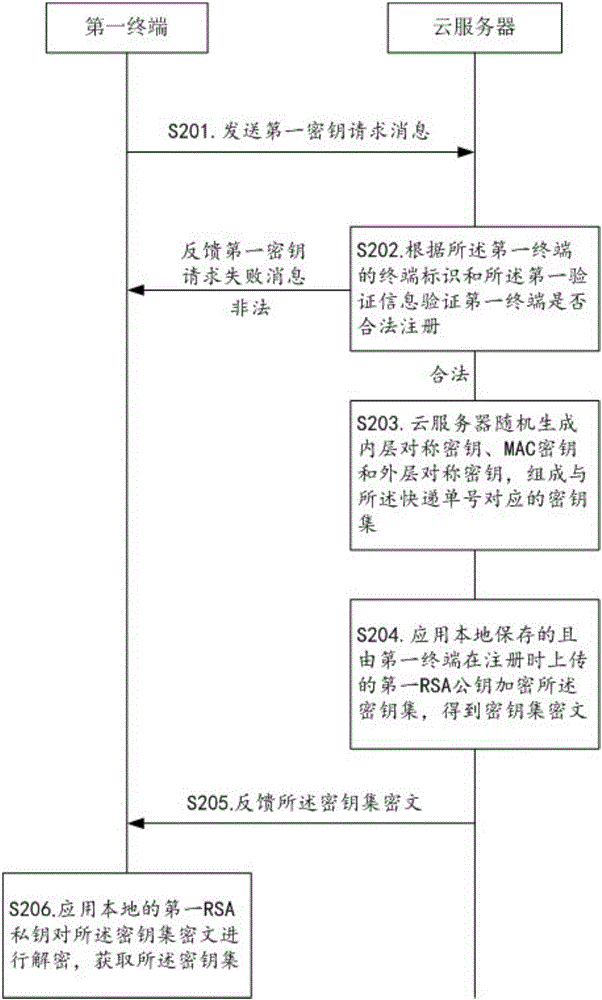
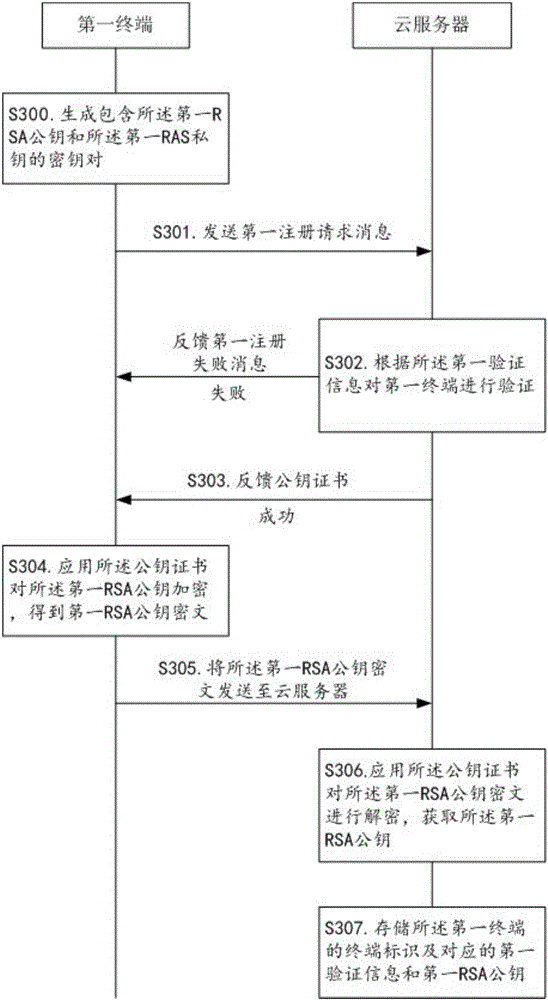
Method for realizing express privacy protection in the logistics process
ActiveCN106453268AAvoid direct nudityPrevent direct accessTransmissionInternet privacyLogistic process
The invention relates to the technical field of the logistics security, and discloses a method for realizing express privacy protection in the logistics process. The method comprises the following steps: performing re-encryptions at different levels on delivery information and privacy information of a user by use of a secret key set from a cloud server when sending and receiving an express, and then managing the secret key set through the cloud server, granting different decryption permissions aiming at different decryption requesters, thereby limiting the decryption permission of a courier in delivering the express, wherein the courier can only use partial secret key from the cloud server to decrypt to acquire the delivery information. Therefore, an illegal person cannot directly acquire the express information since the direct exposure of the express information is avoided, and the condition that the courier uses the position to acquire the privacy information of a customer can be prevented, thereby realizing the safety protection of the express privacy, inhibiting the illegality of dealing the express list, and facilitating the popularization of the real-name system of the express.
Owner:SICHUAN UNIV
Sleeve activated compressed fluid dispensing device with internal seal
ActiveUS20130320045A1Avoid gettingAvoid getting foam on their handsSpray nozzlesSingle-unit apparatusCompressed fluidEngineering
A dispensing device for dispensing compressed fluid from a can through a valve stem of the can has a hollow tube with a channel extending through it from an entrance end to an opposing dispensing end, a connector defining a conduit therethrough that is in fluid communication with the channel of the hollow tube and that attaches to a valve stem of a can, a plug located within the channel of the hollow tube that forms a sealing configuration within the channel when pressed towards the dispensing end of the channel, and a sleeve that wraps at least partially around the hollow tube and that has a protrusion that upon activating the sleeve extends through the dispensing end of the hollow tube and prevents the plug from establishing a sealing configuration with the hollow tube.
Owner:DOW GLOBAL TECH LLC
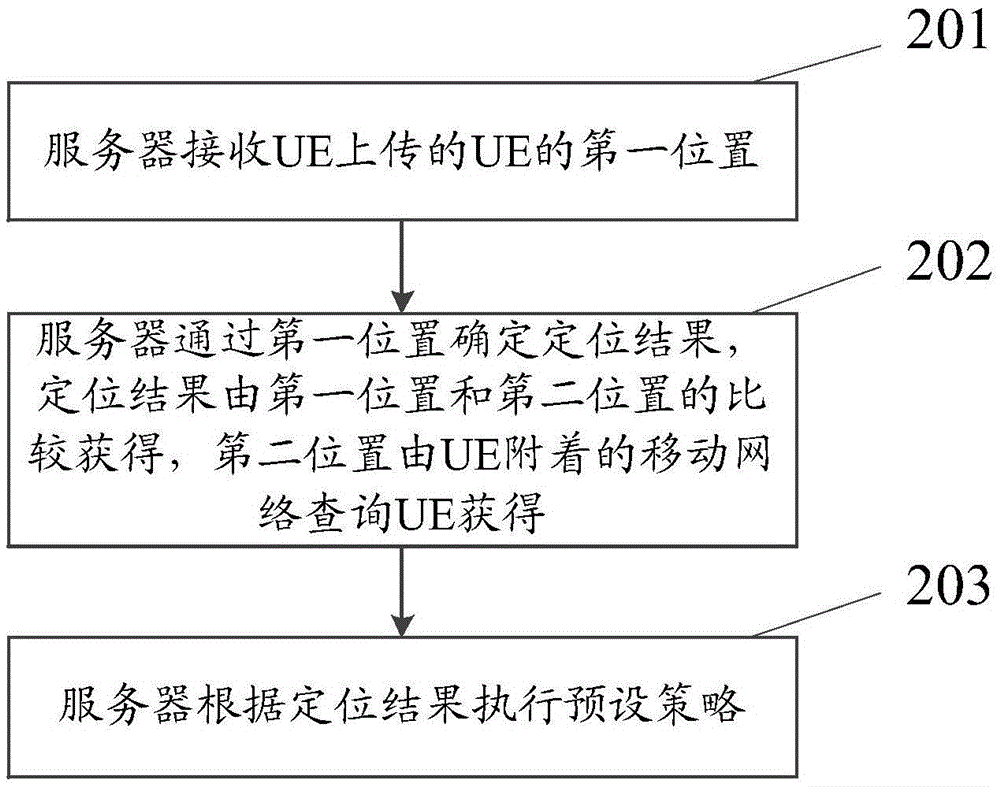
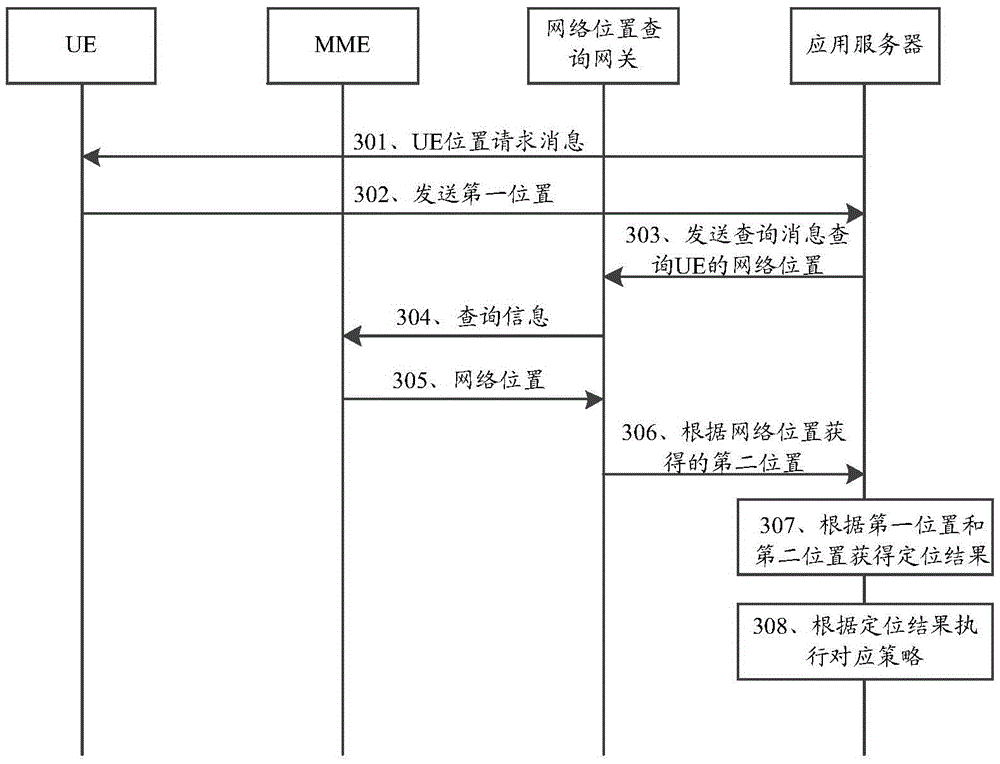
Terminal positioning method and server
The invention relates to the communication field, specifically a terminal positioning method and a server. The method comprises that: the server receives the first position of the UE (user equipment) uploaded by a user equipment UE; the server determines a positioning result according to the first position, the positioning result is obtained by comparing the first position to a second position, the second position is obtained through searching the mobile network attached on the UE by the server; the server executes a preset strategy according to the positioning result. The invention can assist to judge whether the position uploaded by the UE is its actual position, the reliability of the position of the UE is learned in advance before providing service to the UE, and the UE is prevented from using fake position to obtain the service of the server.
Owner:SHANGHAI HUAWEI TECH CO LTD
Input equipment and input method
InactiveCN101667060AEasy to operatePrevent security breachesInput/output for user-computer interactionComputer security arrangementsCommunication interfaceUser input
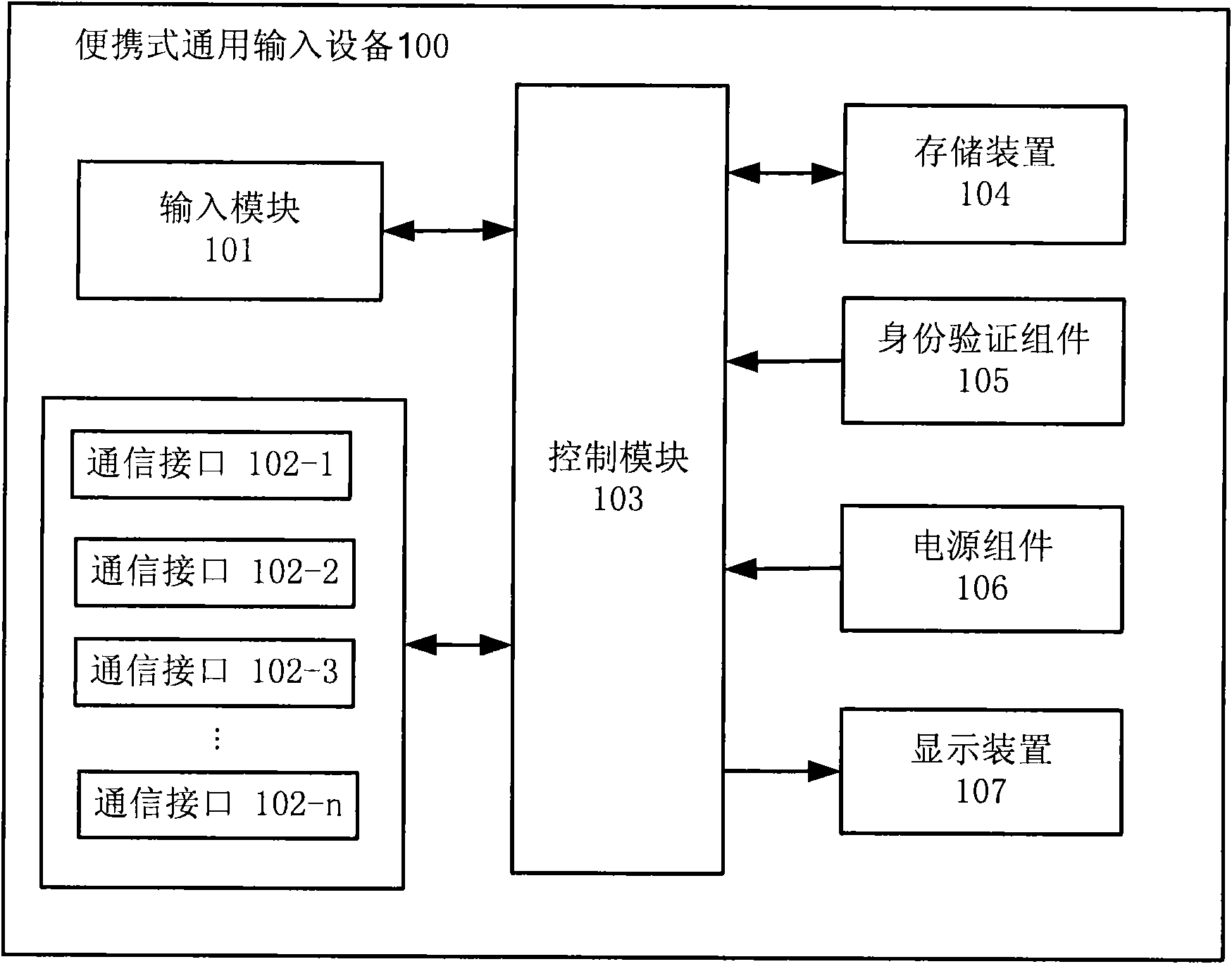
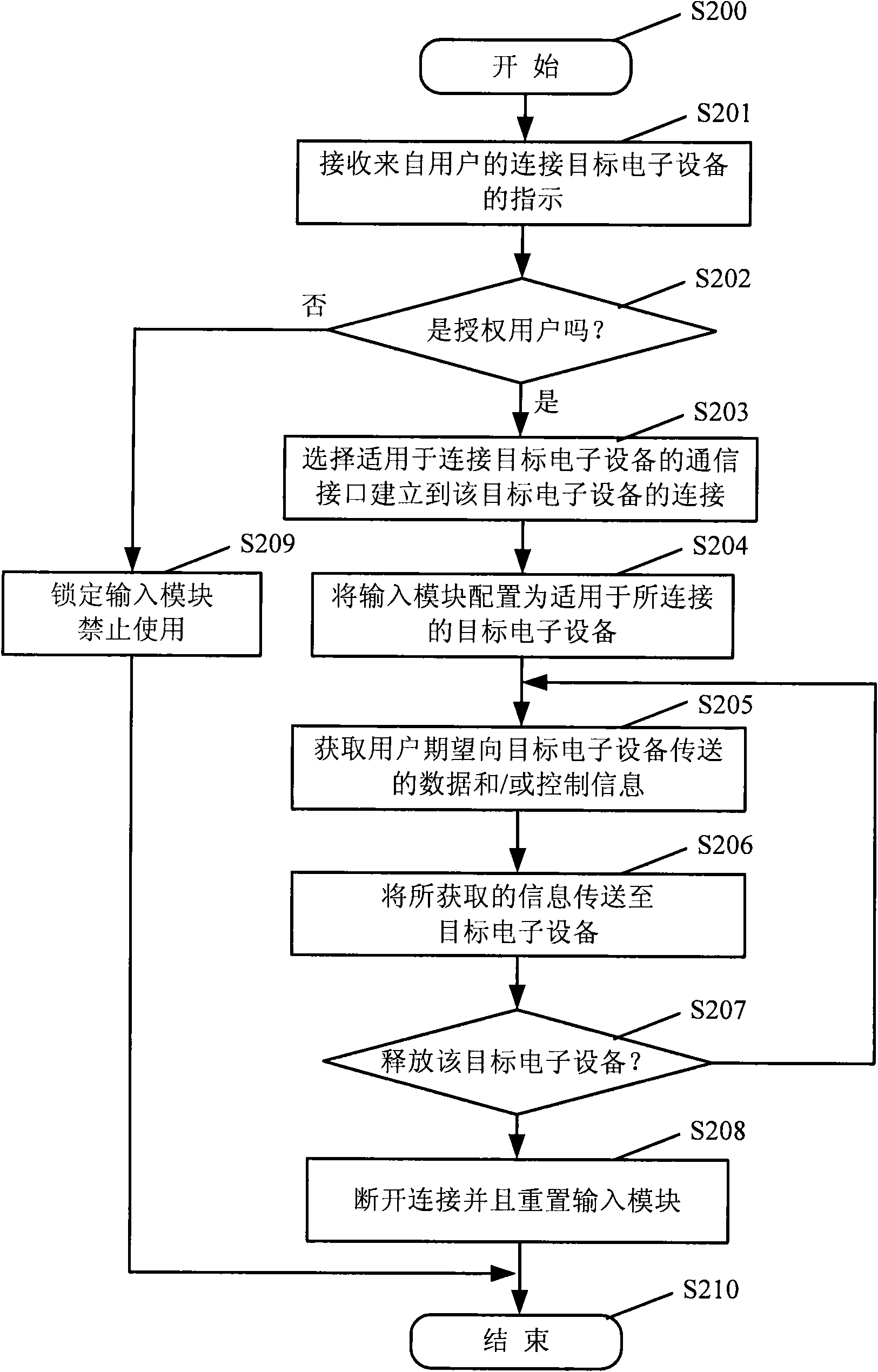
The invention provides portable universal input equipment, which comprises an input module configured to input information by a user, one or more communication interfaces configured to be communicatively connected with various pieces of target electronic equipment, and a control module configured to select the proper communication interface for establishing a connection with the target equipment,wherein the input module is configured to be suitable for performing inputting for the target electronic equipment; and the information input by the input module is transmitted to the target electronic equipment through the established connection so as to input data information or send a control instruction to the target electronic equipment. The invention also provides a corresponding input method. According to the technical scheme of the invention, the input control for the electronic equipment can be implemented in a centralized way in one piece of portable universal input equipment so as to provide extra safety protection to human-computer interactions needing safety protection.
Owner:黄轶 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com