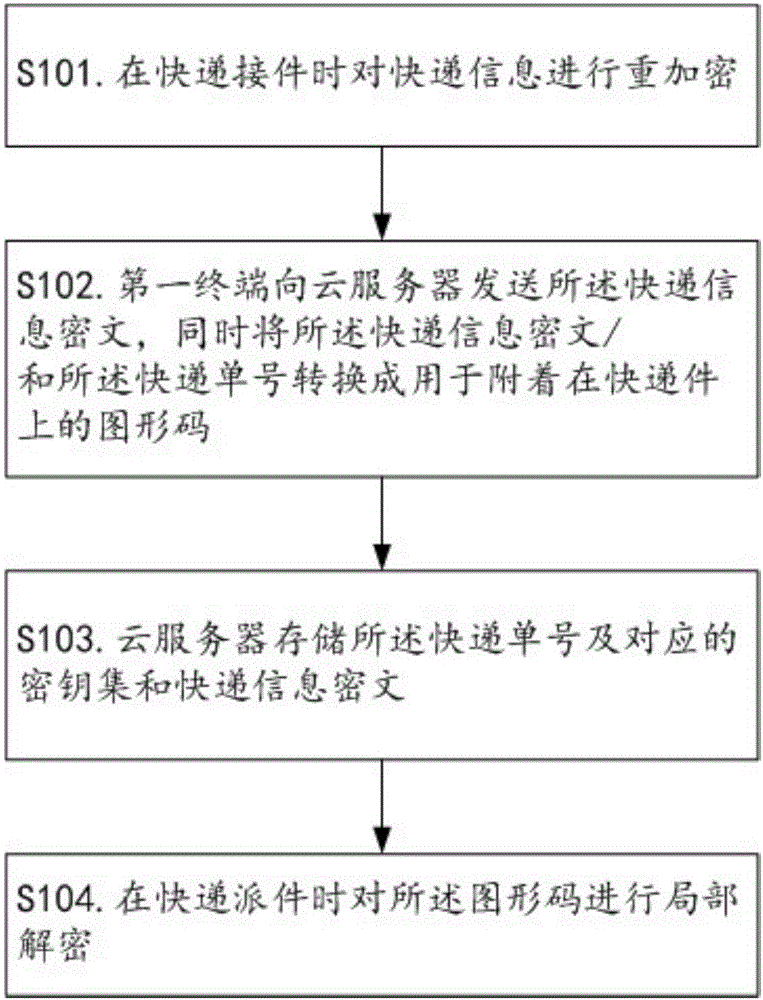
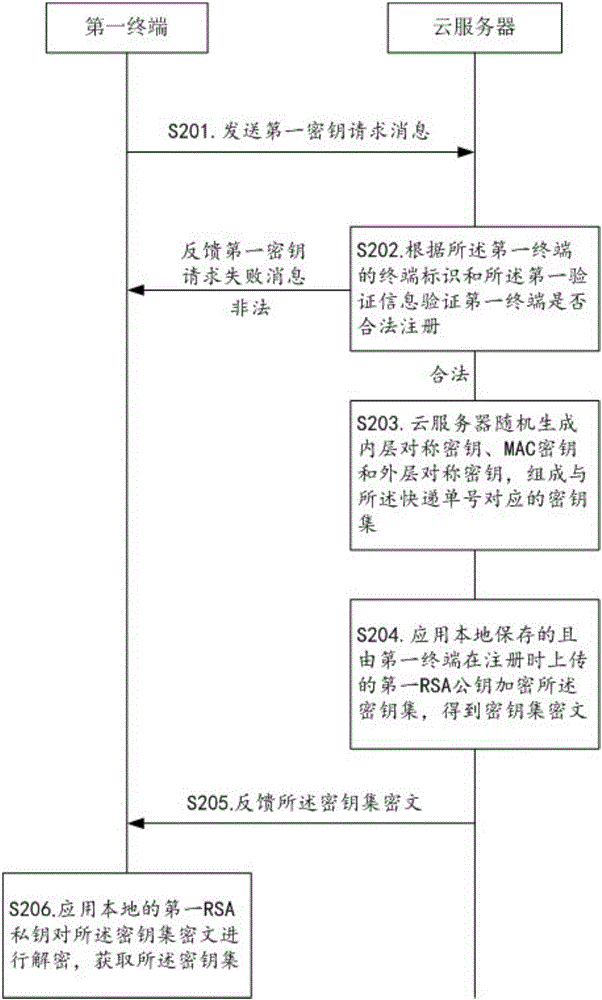
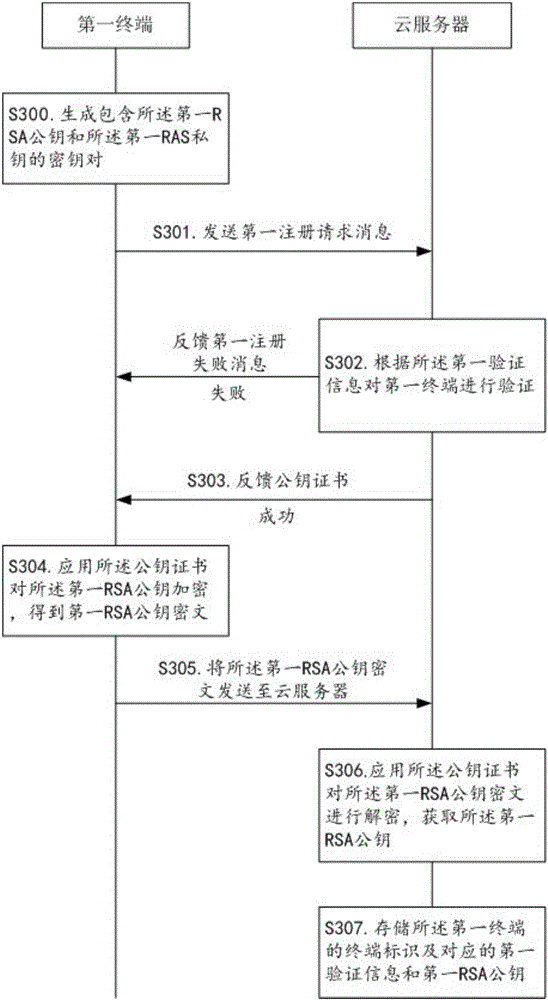
Method for realizing express privacy protection in the logistics process
A privacy protection and logistics technology, applied in the direction of electrical components, transmission systems, etc., can solve problems such as inability to realize express delivery information protection, uneven quality of express delivery employees, and threats to customers' private information security, so as to avoid direct exposure , increase efficiency, prevent the effect of direct acquisition
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0030] figure 1 It shows the flow chart of the method for realizing express privacy protection in the logistics process provided by the present invention, figure 2 It shows the flow chart of information interaction provided by the present invention for the first terminal to request to obtain the key set when picking up the package, image 3 It shows the flow chart of information interaction provided by the present invention in which the first terminal completes the registration before receiving the mail, Figure 4 It shows the flow chart of information interaction provided by the present invention in which the second terminal requests to obtain the outer symmetric key when dispatching the parcel, Figure 5 It shows the flow chart of information interaction provided by the present invention in which the second terminal completes the registration before delivery. The method for realizing express delivery privacy protection in the logistics process provided by this embodiment ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com