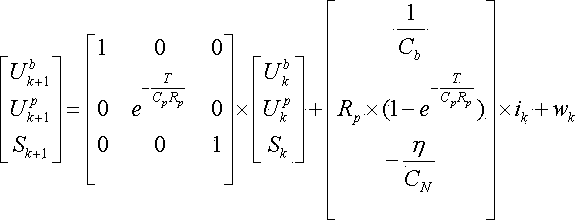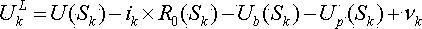Patents
Literature
5315results about How to "Increase the difficulty" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
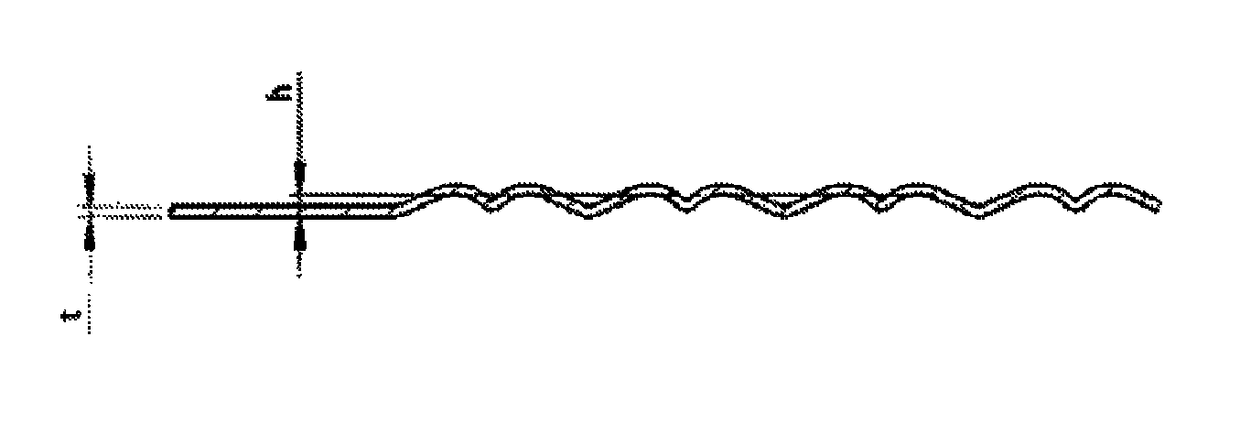
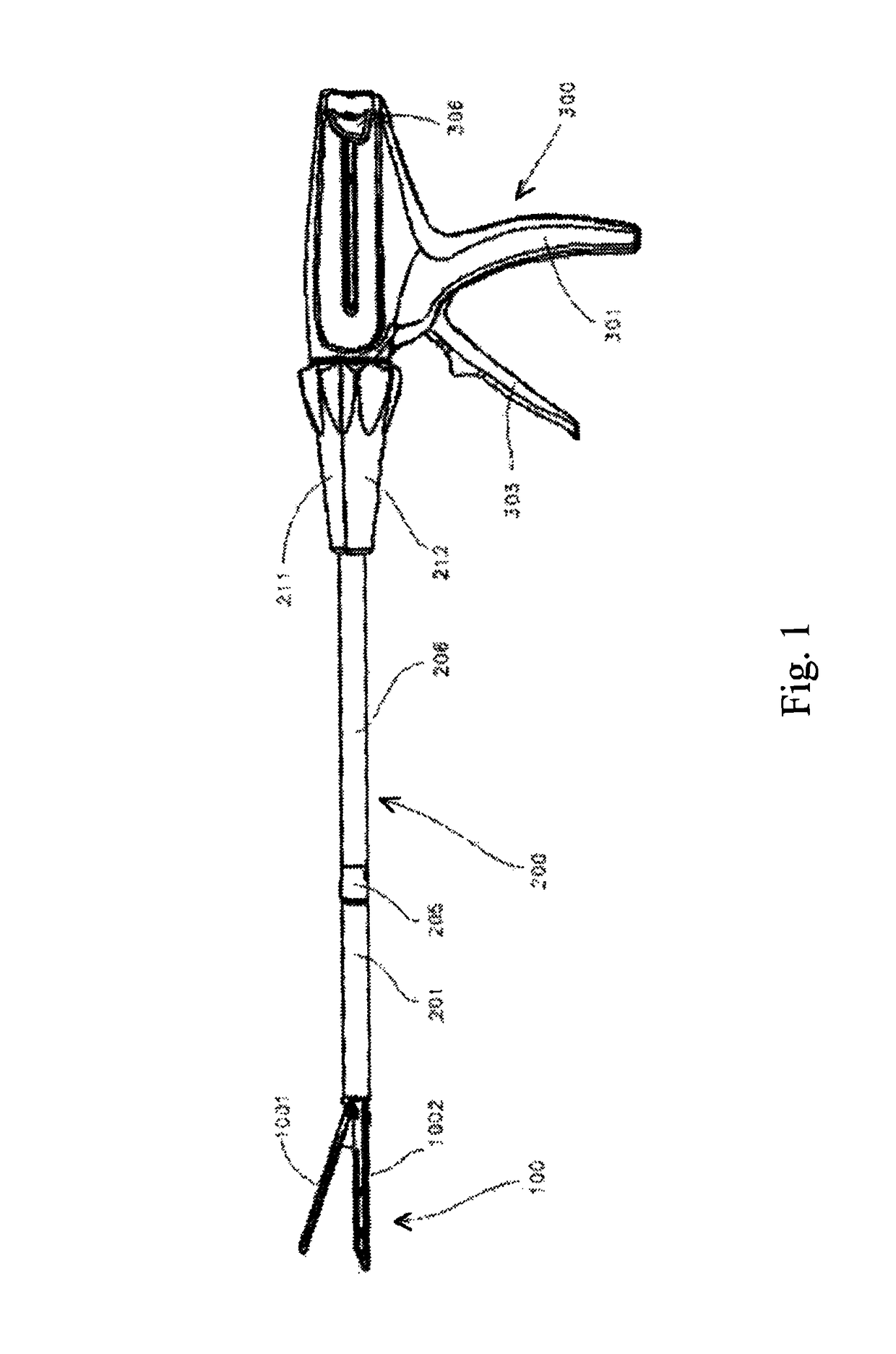
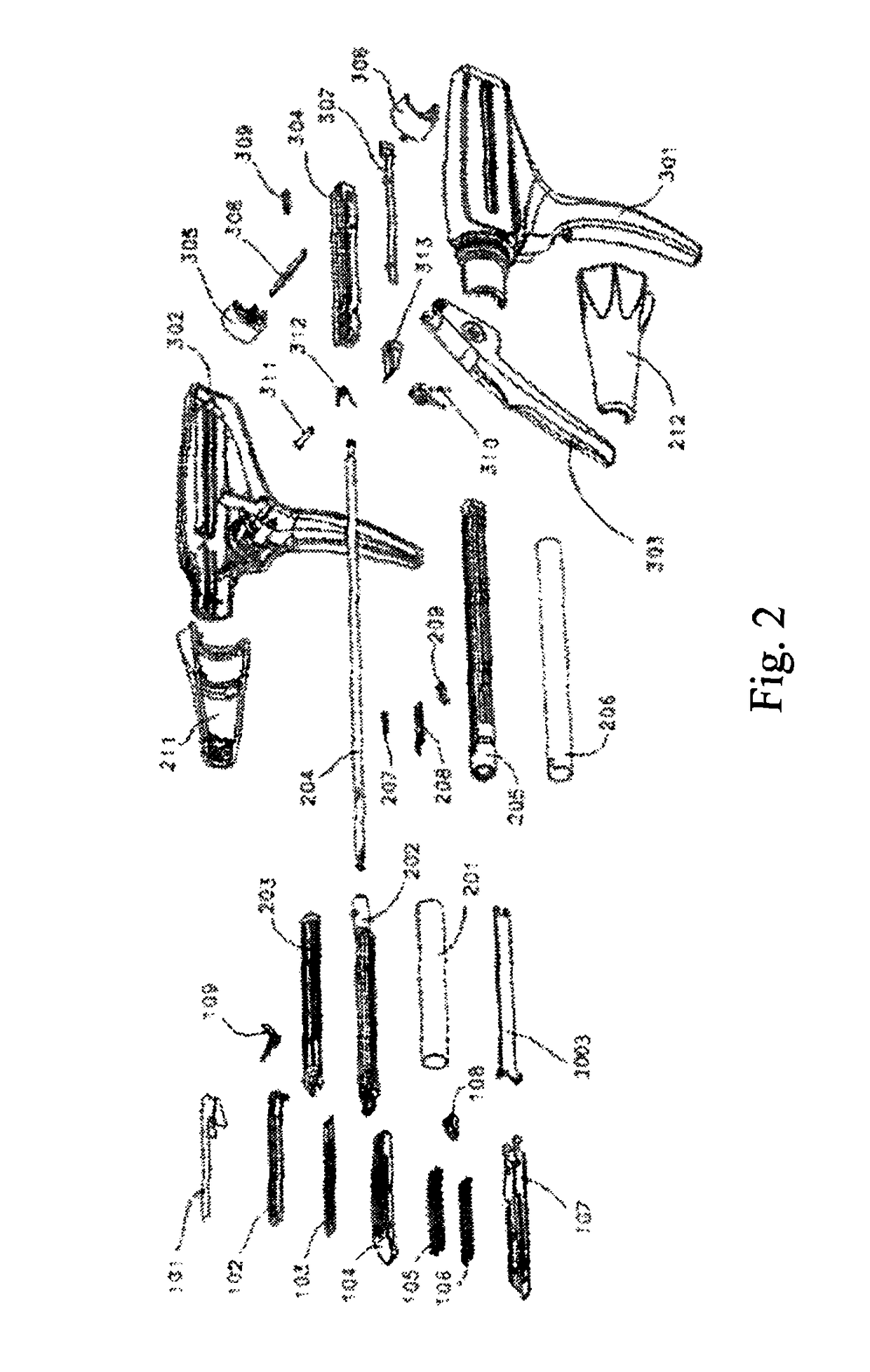
Surgical apparatus actuator
ActiveUS9924945B2Increase the difficultyImprove accuracySurgical staplesEngineeringMechanical engineering
Owner:EZISURG MEDICAL CO LTD
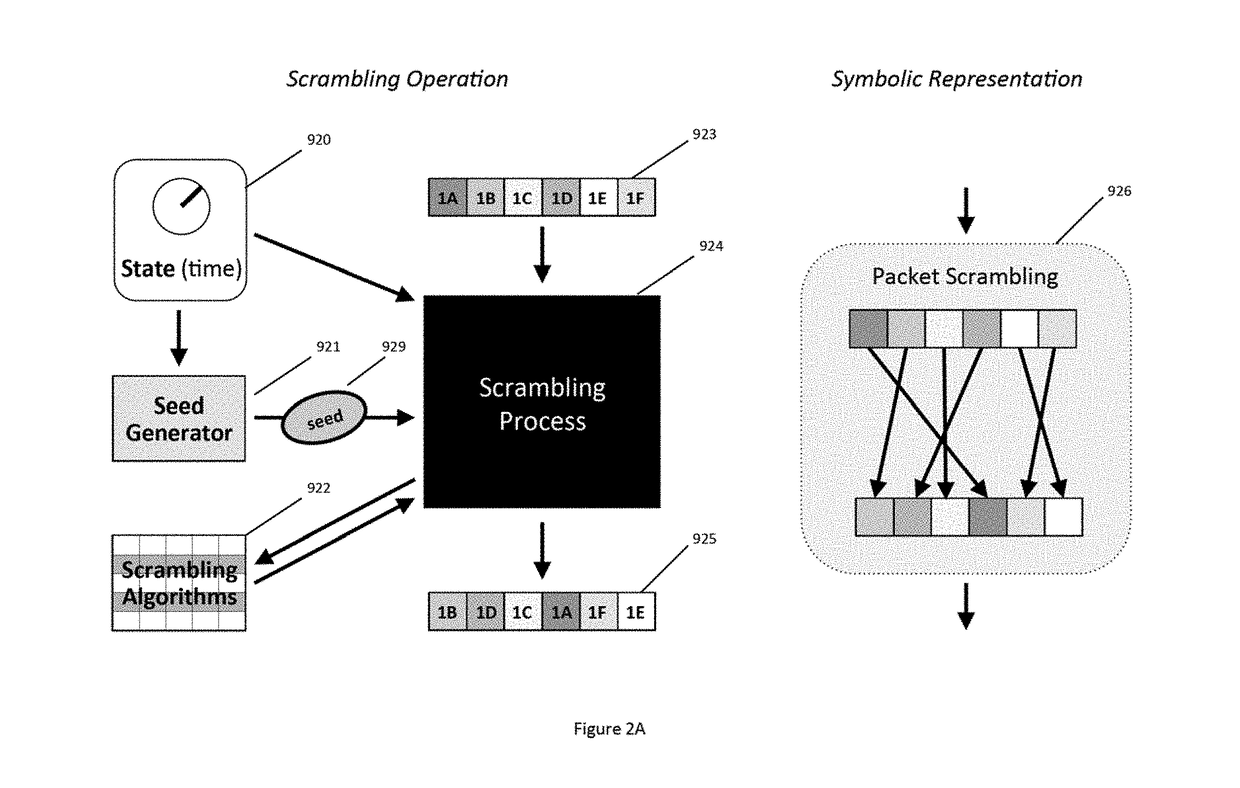
Secure Dynamic Communication Network And Protocol
ActiveUS20160219024A1Increase the difficultyUsefulness of their knowledge would be short-livedMultiple keys/algorithms usageData taking preventionDigital dataData segment
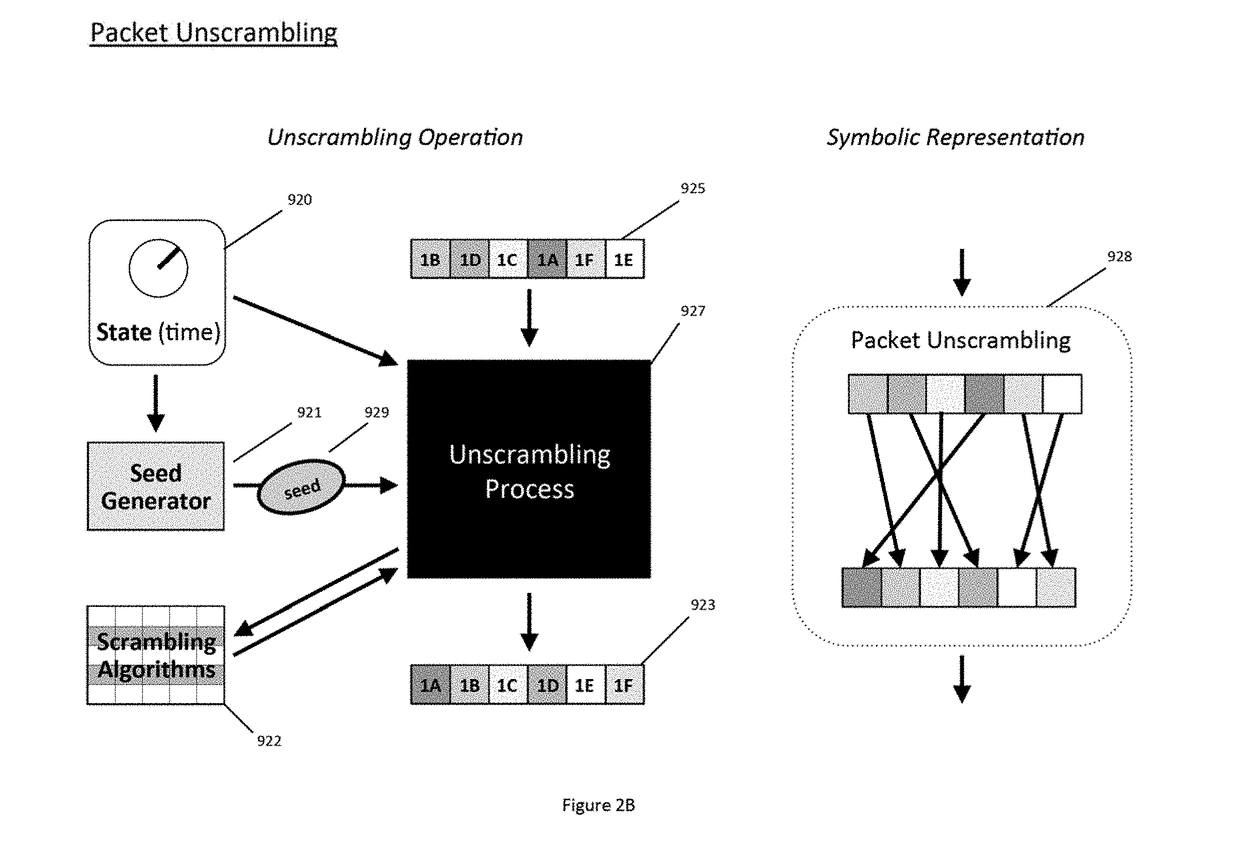
In a secure cloud for transmitting packets of digital data, the packets may be repeatedly scrambled (i.e., their data segments reordered) and then unscrambled, split and then mixed, and / or encrypted and then decrypted as they pass through media nodes in the cloud. The methods used to scramble, split, mix and encrypt the packets may be varied in accordance with a state such as time, thereby making the task of a hacker virtually impossible inasmuch as he or she may be viewing only a fragment of a packet and the methods used to disguise the data are constantly changing.
Owner:LISTAT LTD
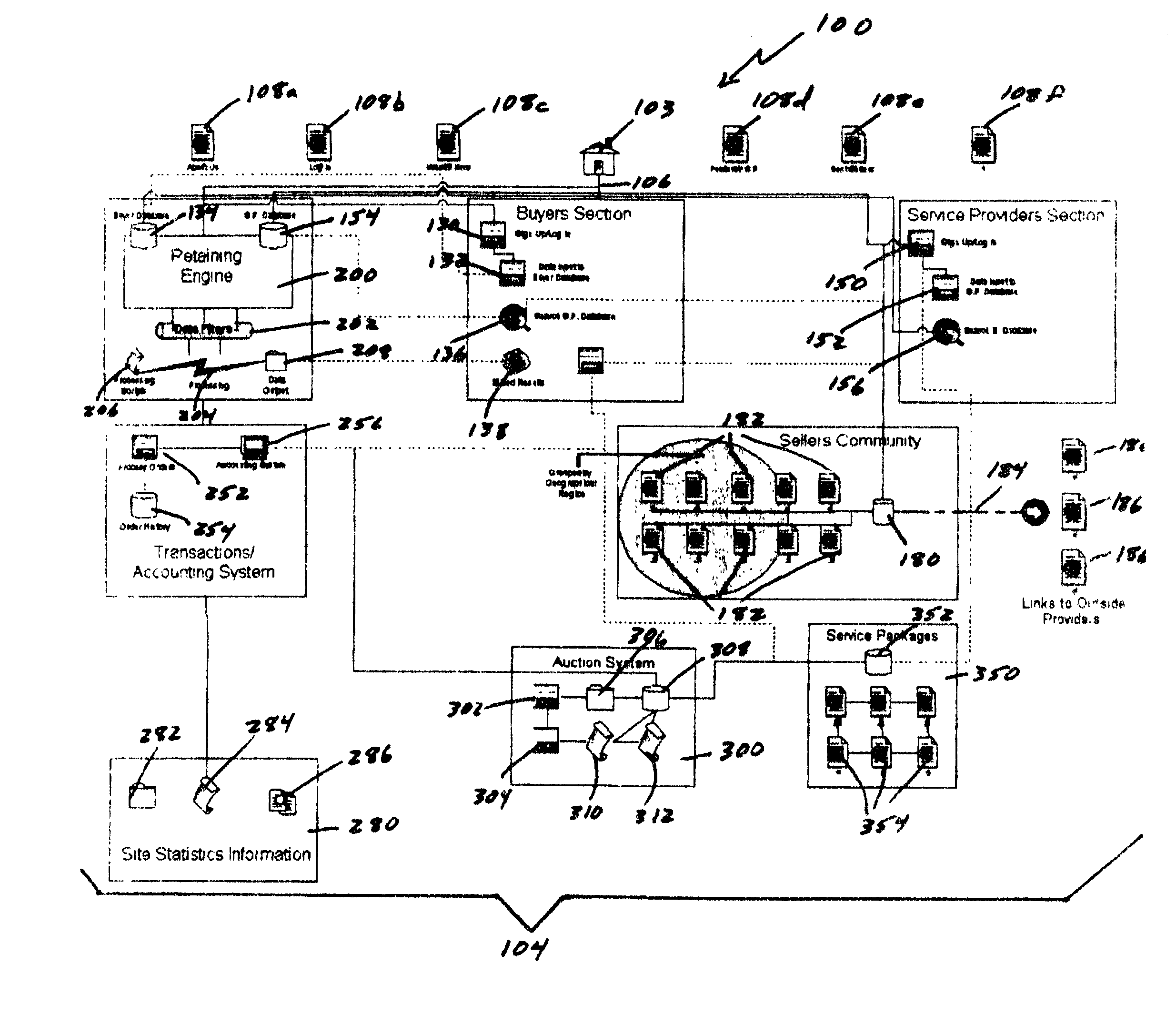
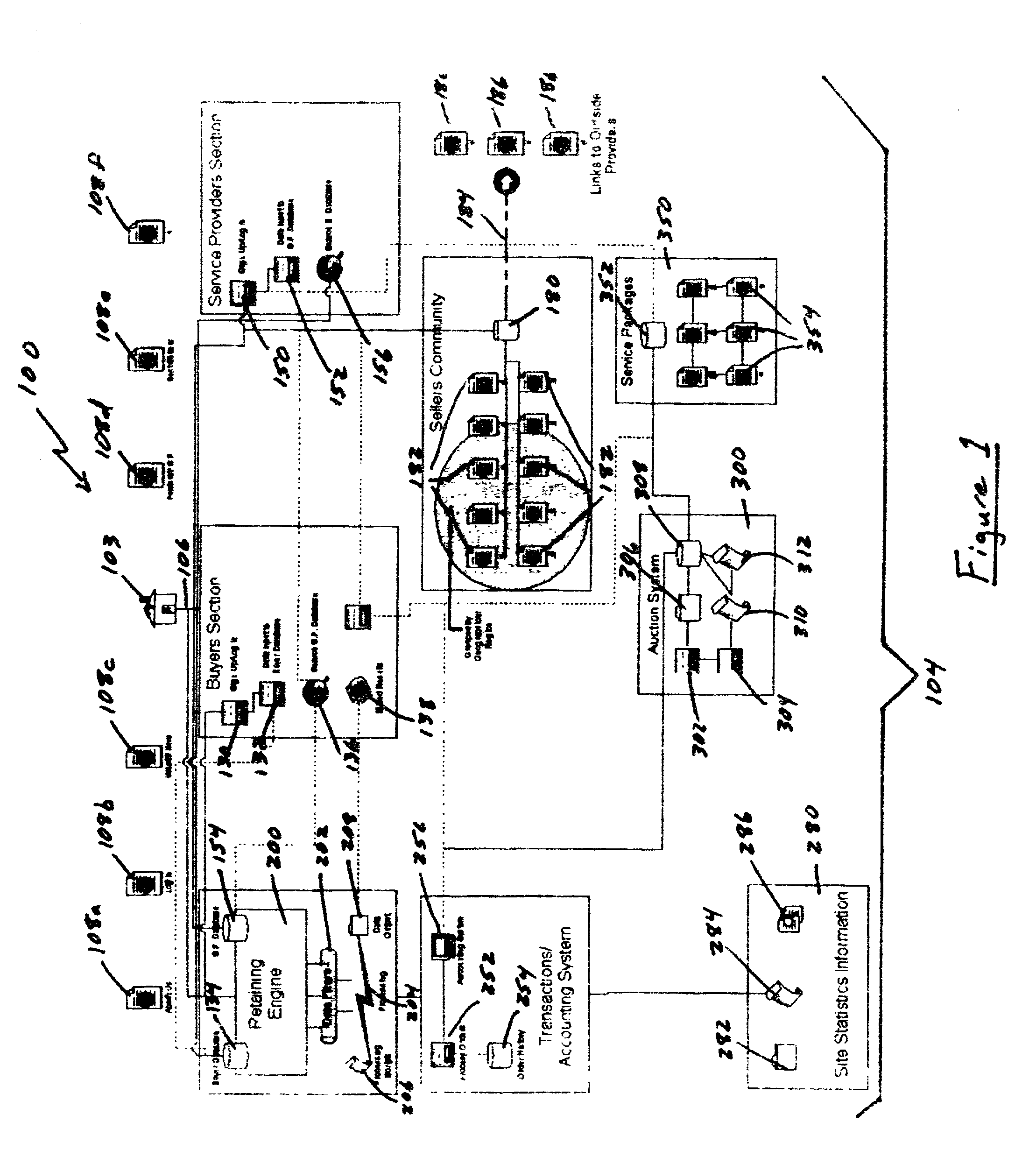
Auction, imagery and retaining engine systems for services and service providers
InactiveUS20020120554A1Facilitates in efficiently accessing latent demandEliminate riskFinancePayment architectureGroup PurchasingService provision
The present disclosure provides a computer-implemented method / system for facilitating communications between service providers and potential customers for services. The computer-implemented method / system provides a marketplace for interactions, both online and off-line, between service providers and potential customers, including purchasing groups, particularly buyer-driven service-related interactions. The marketplace advantageously allows categorization, key word searching, group purchasing, service packaging, data mining, auctions and other commercial features and functionality. The computer-implemented method / system also supports holographic imagery, e.g., in the form of virtual assistants, that facilitates marketplace-related activities. Based on the computer-implemented method / system, service providers are able to efficiently and cost effectively extend the reach of their marketing and promotional activities to a wide range of additional customers, and customers are able to initiate access service providers ideally suited to meet their needs, i.e., buyer-driven commerce, at desirable prices and according to required timeframes.
Owner:VEGA LILLY MAE
Method for dynamically adjusting an interactive application such as a videogame based on continuing assessments of user capability
InactiveUS20070066403A1Reduce the differenceIncrease the difficultyVideo gamesSpecial data processing applicationsNegative feedbackEducational game
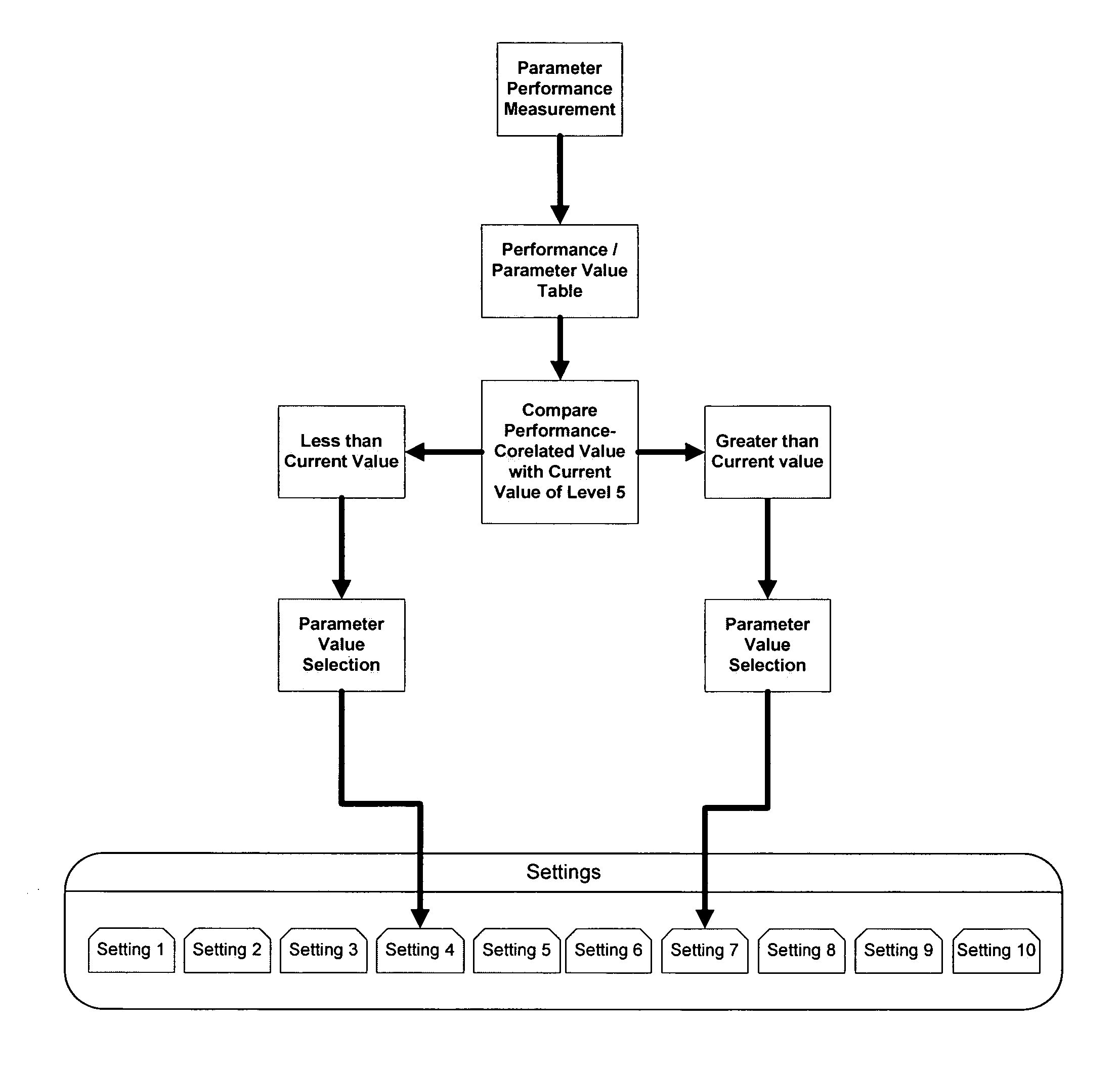
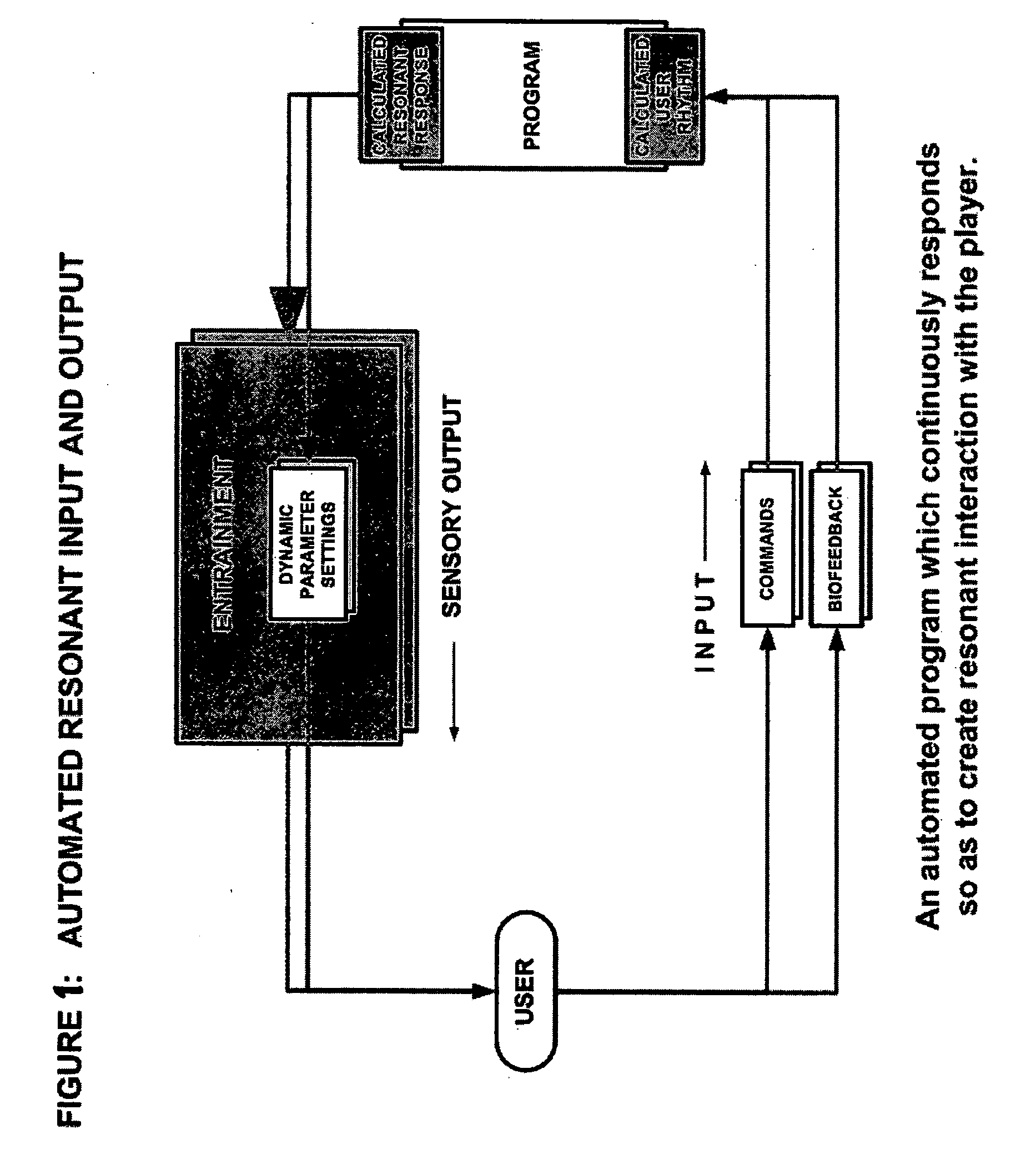
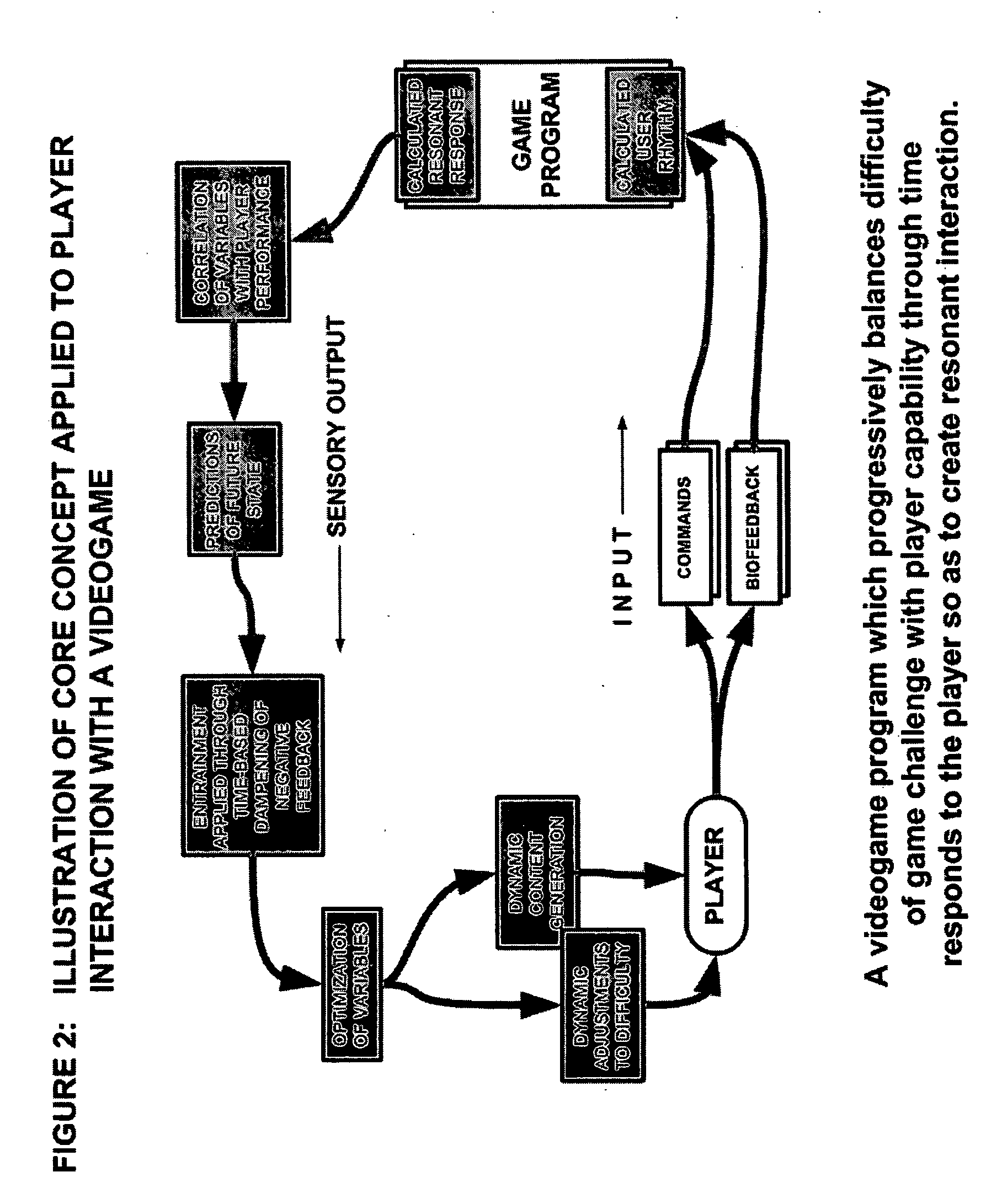
A method of balancing a user's input to an interactive computer program with the program's output is obtained by continually measuring the difference between the user's input and the program's output and adjusting one or more parameters of the program's output so that the difference from the user's performance is progressively reduced. The adjustment may be obtained dynamically through negative feedback dampening of the measured difference (delta) between user input and program output, and / or by selection of predetermined apposite values for program output corresponding to the measurement of user input. The adjustment results in dynamic generation and / or selection of premodeled segments of interactive output in closer balance with user input. The adjustment method can be applied to video games, educational games, productivity programs, training programs, biofeedback programs, entertainment programs, and other interactive programs. In video games, the adjustment method results in balancing user performance with game difficulty for a more engaging game experience. It can also enable embedded advertising to be triggered when the user is in an optimum state of engagement. The adjustment method may be performed by projecting future trends of user performance, selecting predetermined or dynamically determined levels of value, modifying user control of input devices, or even modifying the program's challenges to user capability over time.
Owner:CONKWRIGHT GEORGE COLBY
Method and system for enhancing the security of a transaction
ActiveUS20190012672A1Increasingly difficultHard to removeDigital data protectionDigital data authenticationIntegrated circuitComputer security
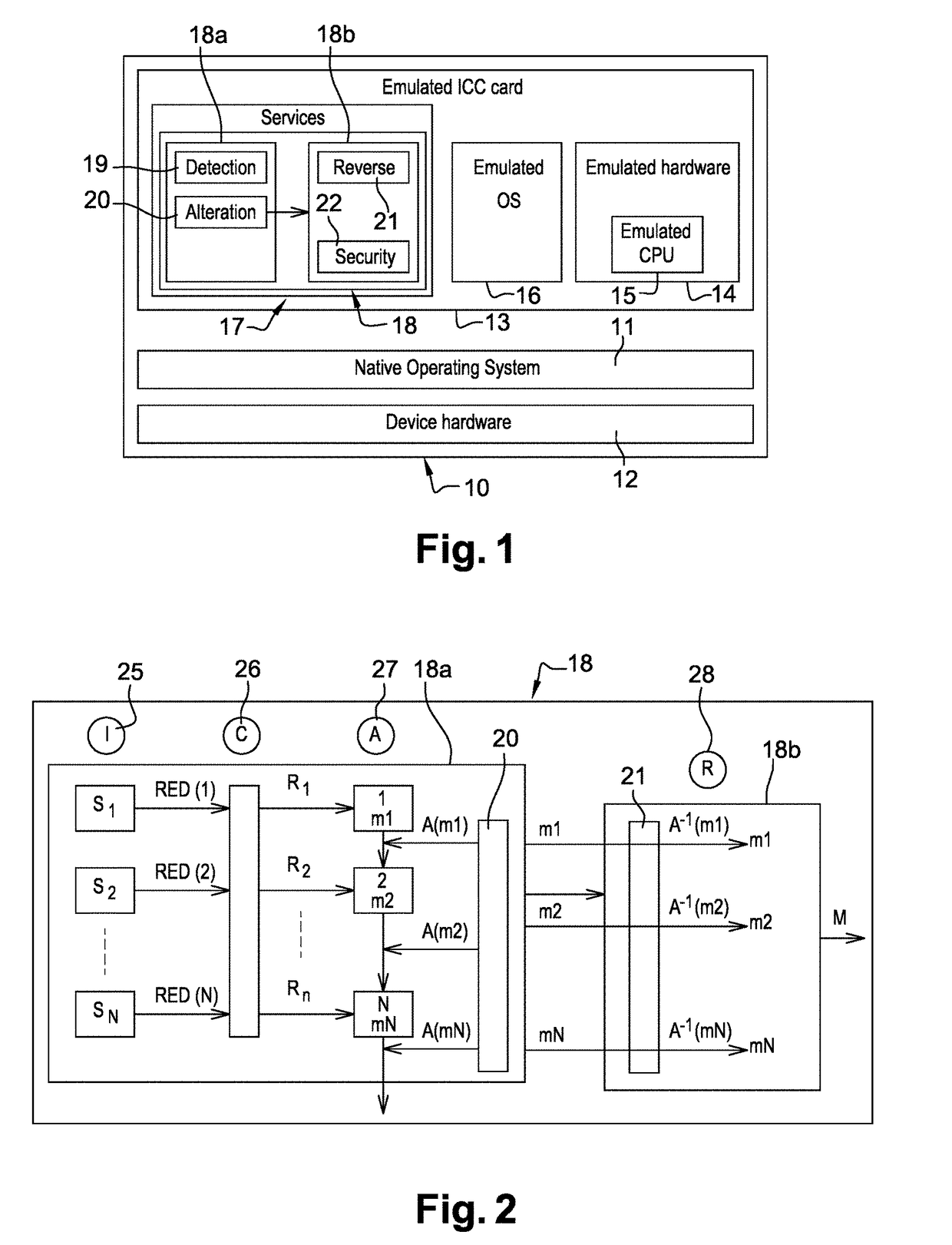
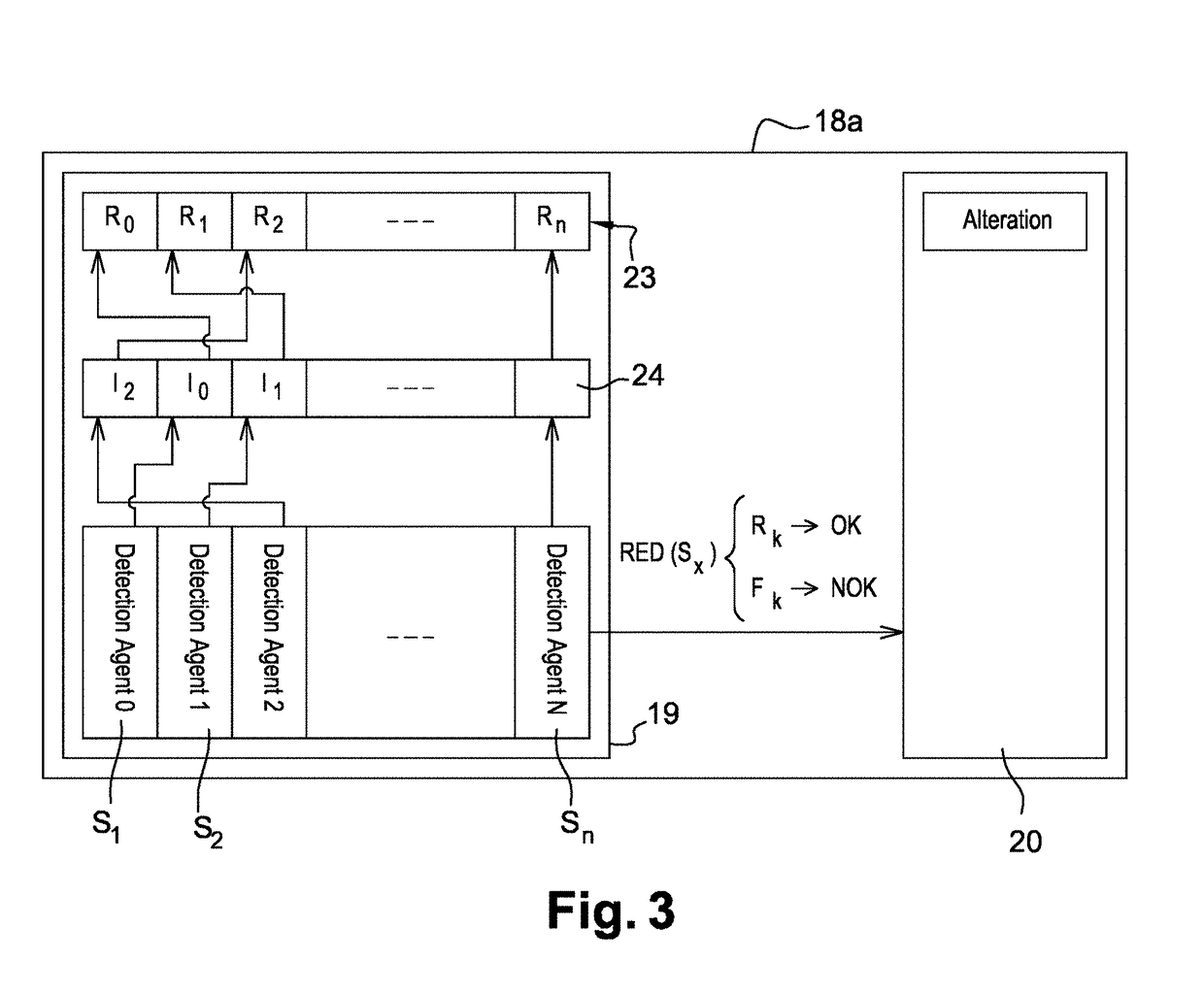
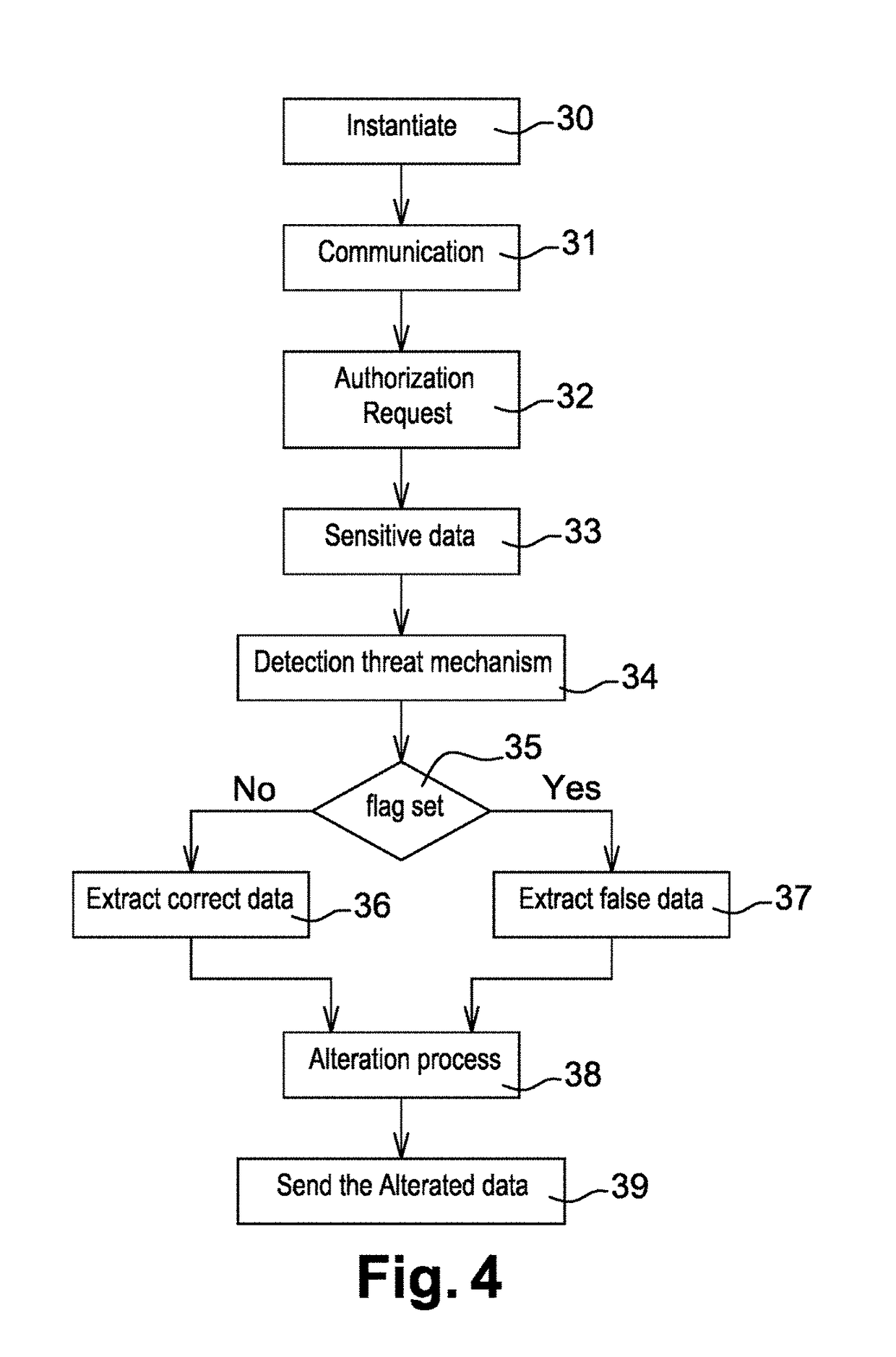
This invention concerns a method and system for improving the security of transaction in an emulated Integrated Circuit. During compilation time of a payment application, at least one detection agent are inserted into the code of the payment application. This detection agent is configured to detect an unauthorized use of the payment application. During a runtime of the payment application, if the detection agent result indicates “no threat detected” the payment application retrieves from a predefined map of “no threat detected”, the right value associated to the detection agent, otherwise a random false value is generated. The payment application alters at least one data manipulated during the transaction with the value retrieved or generated. A reverse mechanism of the payment application retrieve the right value and apply a restoration process to the altered data with the retrieved right value. The payment application computes a cryptogram from the restored manipulated data. From the computed cryptogram, a third party can authorize or reject the transaction.
Owner:THALES DIS FRANCE SA
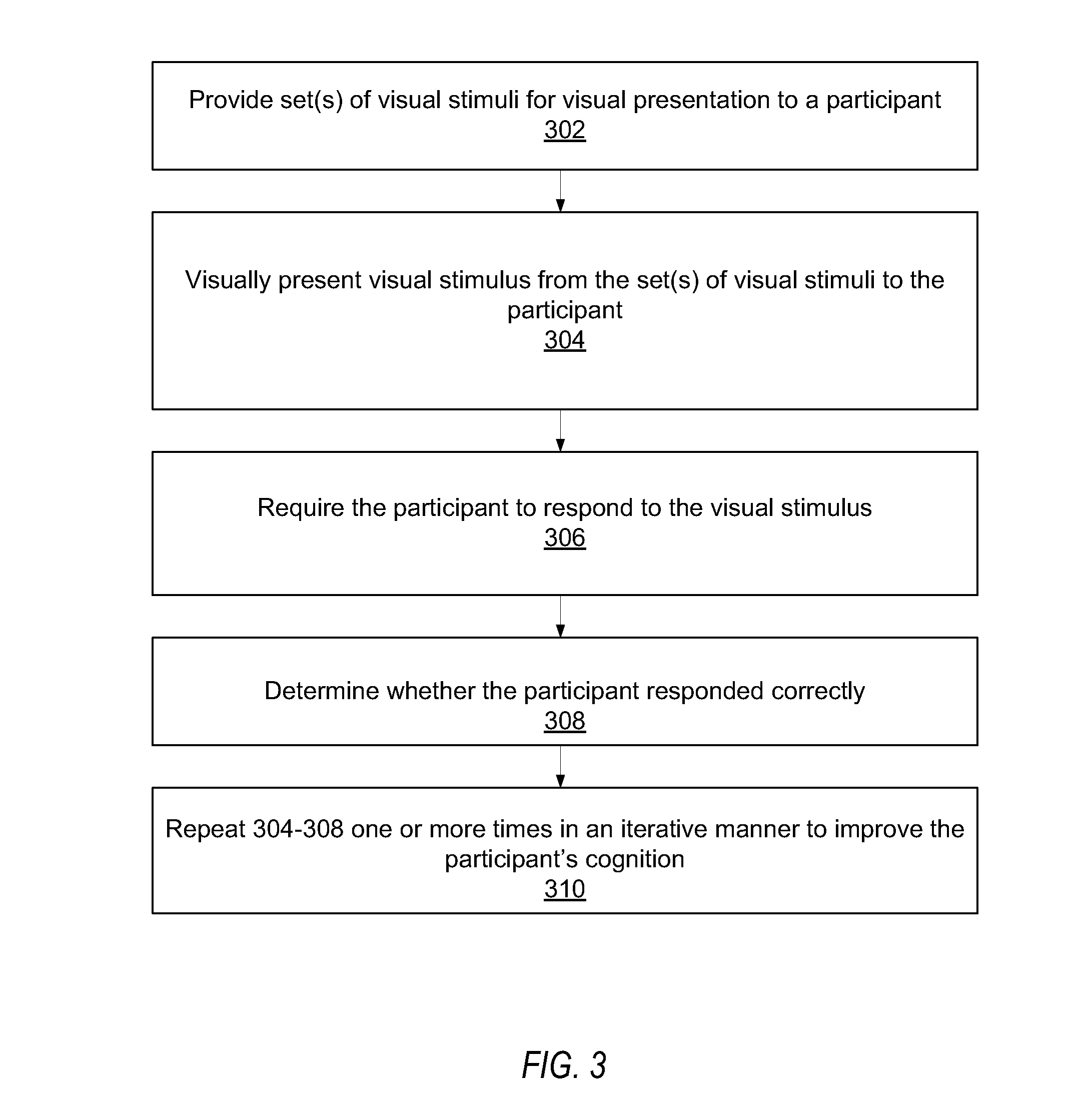
Cognitive training using visual stimuli
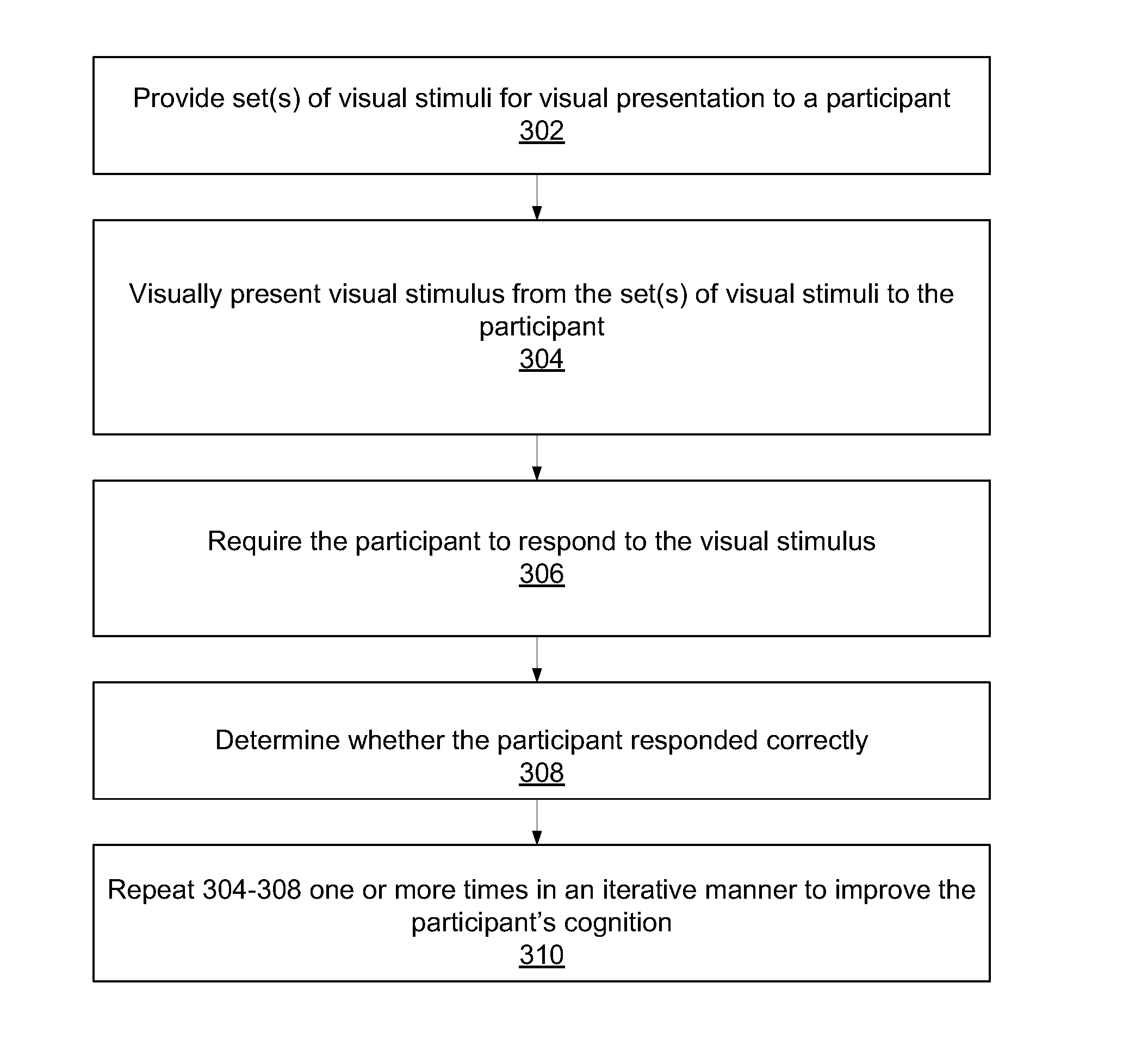
InactiveUS20070166675A1Improve participant 's cognitionEffective capacityElectrical appliancesTeaching apparatusVisual presentationComputer science
A computer-implemented method for enhancing cognition, e.g., for improving cognitive ability of a participant using visual stimuli. A set (or sets) of visual stimuli is provided for visual presentation to the participant. A visual stimulus from the set is visually presented to the participant. The participant is required to respond to the visual stimulus. A determination is made regarding whether the participant responded correctly. The stimulus intensity of the visual stimuli presented may be adjusted based on the correctness / incorrectness of the participant's response according to a single-stair maximum likelihood (e.g., ZEST) or N-up / M-down procedure. The visually presenting, requiring, and determining are repeated one or more times in an iterative manner to improve the participant's cognition, e.g., ability to process visual information, memory, etc. Assessments may be performed during the repeating according to a dual-stair maximum likelihood (e.g., ZEST) or N-up / M-down procedure. The repeating may include performing multiple exercises using visual stimuli.
Owner:POSIT SCI CORP
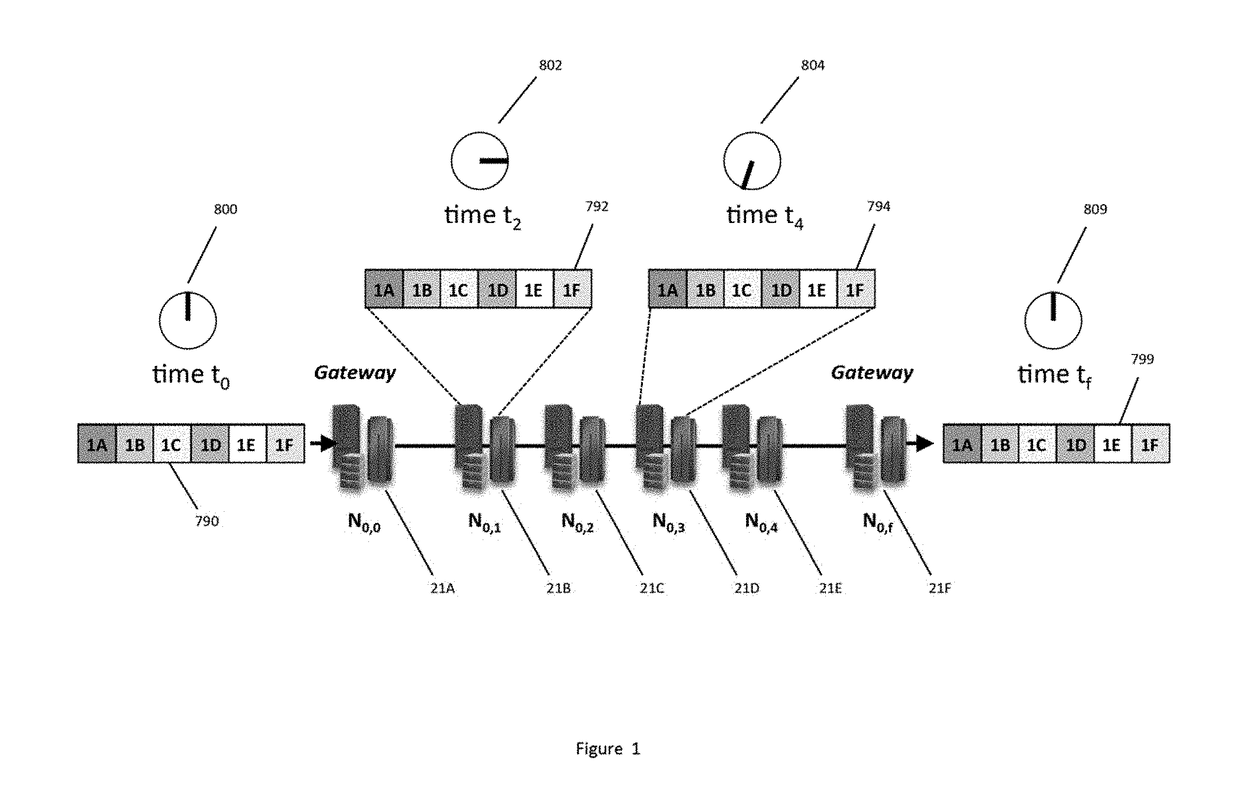
Methods And Apparatus For HyperSecure Last Mile Communication
ActiveUS20180359811A1Simplified challengeSacrificing network latencyNetwork traffic/resource managementNetwork topologiesData fileClient-side
A variety of techniques for concealing the content of a communication between a client device, such as a cell phone or laptop, and a network or cloud of media nodes are disclosed. Among the techniques are routing data packets in the communication to different gateway nodes in the cloud, sending the packets over different physical media, such as an Ethernet cable or WiFi channel, and disguising the packets by giving them different source addressees. Also disclosed are a technique for muting certain participants in a conference call and a highly secure method of storing data files.
Owner:LISTAT LTD
Specie limitation-free eucaryote gene targeting method having no bio-safety influence and helical-structure DNA sequence
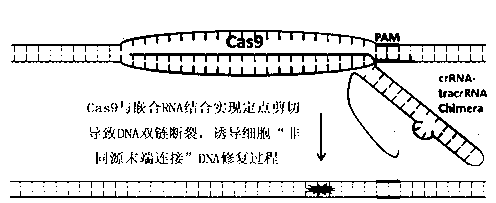
ActiveCN103233028AUnable to cutImprove accuracyFermentationVector-based foreign material introductionDNA repairEucoenogenes
The invention discloses a specie limitation-free eucaryote gene targeting method having no bio-safety influence and a helical-structure DNA sequence, and belongs to the field of gene engineering. The specie limitation-free eucaryote gene targeting method comprises the following steps of 1, designing and constructing CRISPR / Cas9 and chimeric RNA, and 2, carrying out Cas9mRNA internal translation so that Cas9 nuclease and the chimeric RNA are bonded, carrying out fixed point clipping so that DNA double-chain cleavage is realized after the clipping, and introducing an exogenous DNA by induction of a natural DNA restoration process which is a non-homologous end bonding process of cells so that cell endogenous gene modification is realized. The specie limitation-free eucaryote gene targeting method has simple processes, realizes flexible site recognition and has low energy consumption.
Owner:NANJING SYNC BIOTECH
System and methods of determining computational puzzle difficulty for challenge-response authentication
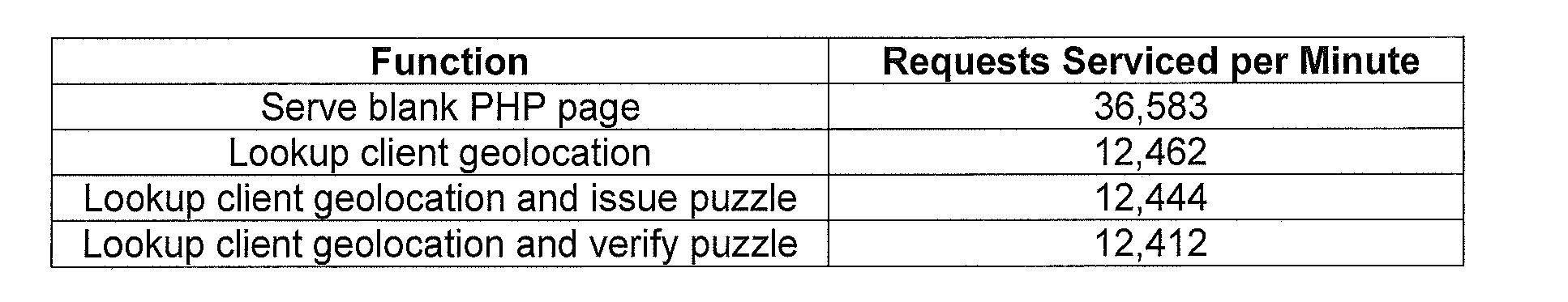
InactiveUS20110231913A1Low costEnsure correct executionDigital data processing detailsMultiple digital computer combinationsGeographic siteComputational intelligence
Computational puzzles are parameterized by a difficulty variable which may be assigned based on at least one component from the group of components: time component, location component, reputation component, usage component, content component, and social networking component. For example, in one embodiment, the proof-of-work puzzle comprises a location component directed by the geographic location of the client that can be applied to any web transaction or application. One such application involves online ticket sales including those that employ purchasing robots. Another application involves accessing and using webmail.
Owner:THE OREGON STATE BOARD OF HIGHER EDUCATION ACTING BY & THROUGH PORTLAND STATE UNIV
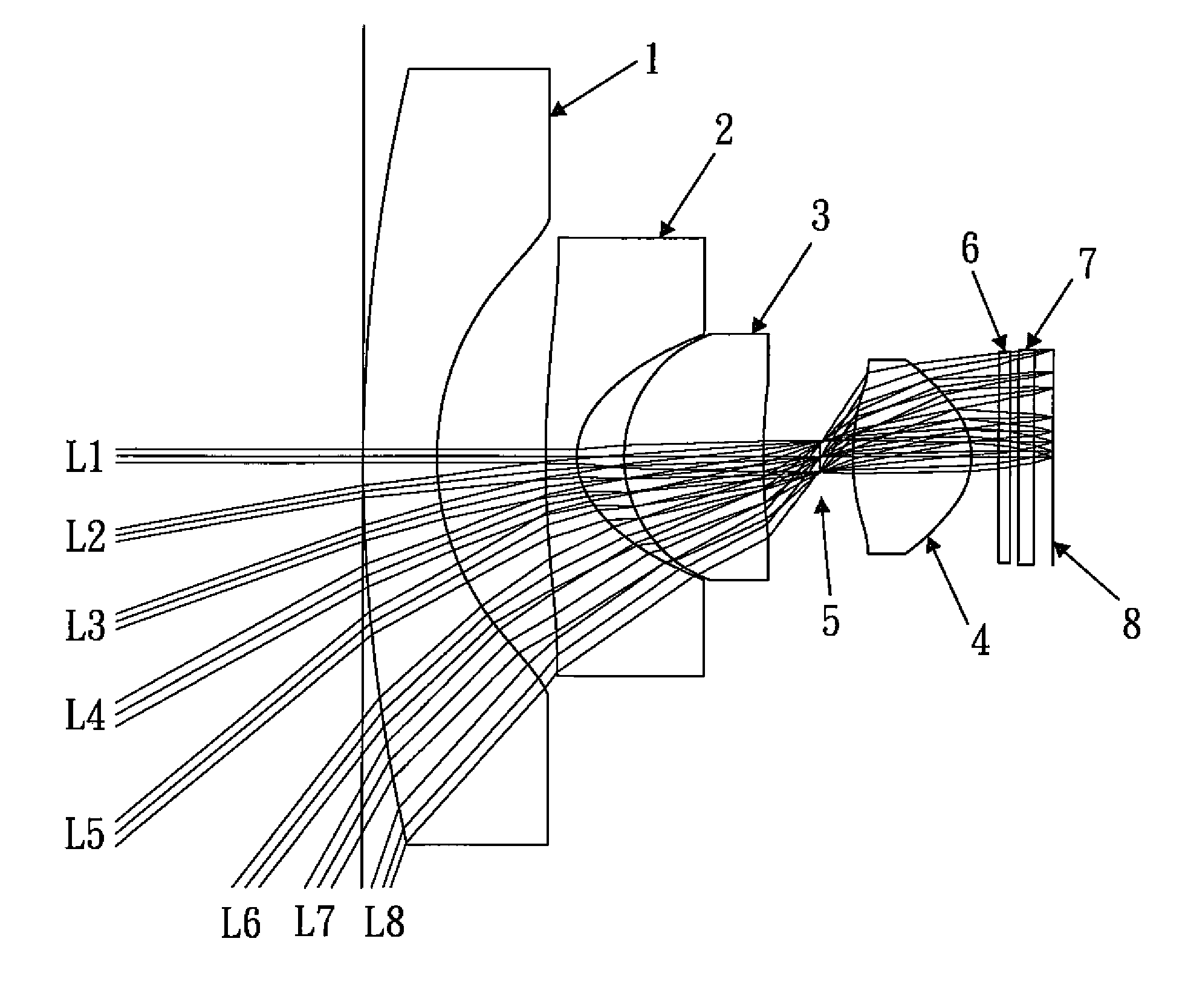
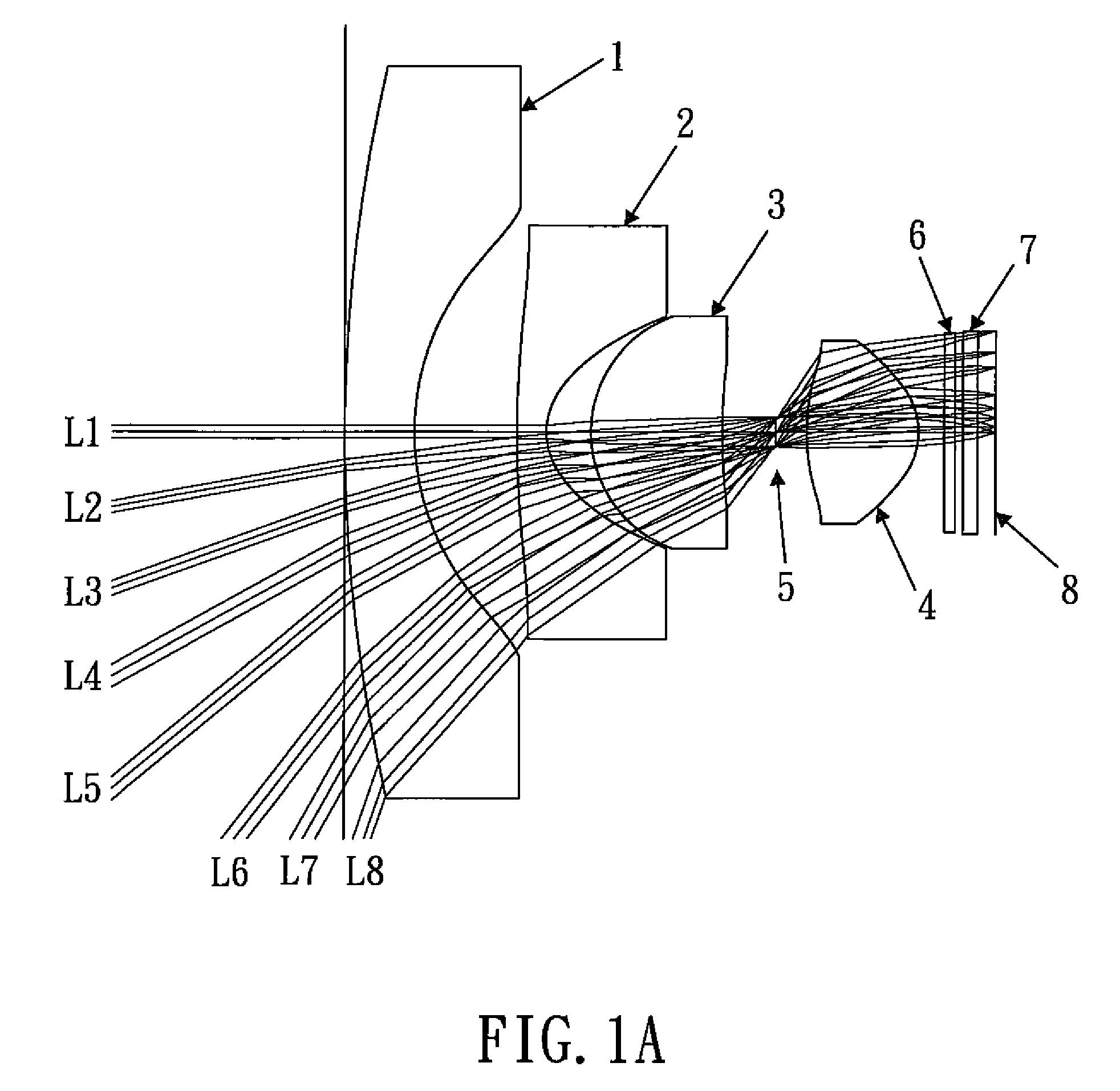
Wide-angle lens system
A wide-angle lens system comprises, sequentially from the object side to the image side: a first lens element, a second lens element, a third lens element, an aperture and a fourth lens element. If the field of view of the wide-angle lens system is as high as 140 degrees, the extreme distortion of the image edge can be prevented with only four lens elements, and the image has a high sharpness. Therefore, it is very suitable for use in the monitor and vehicle-related lens system.
Owner:LARGAN PRECISION
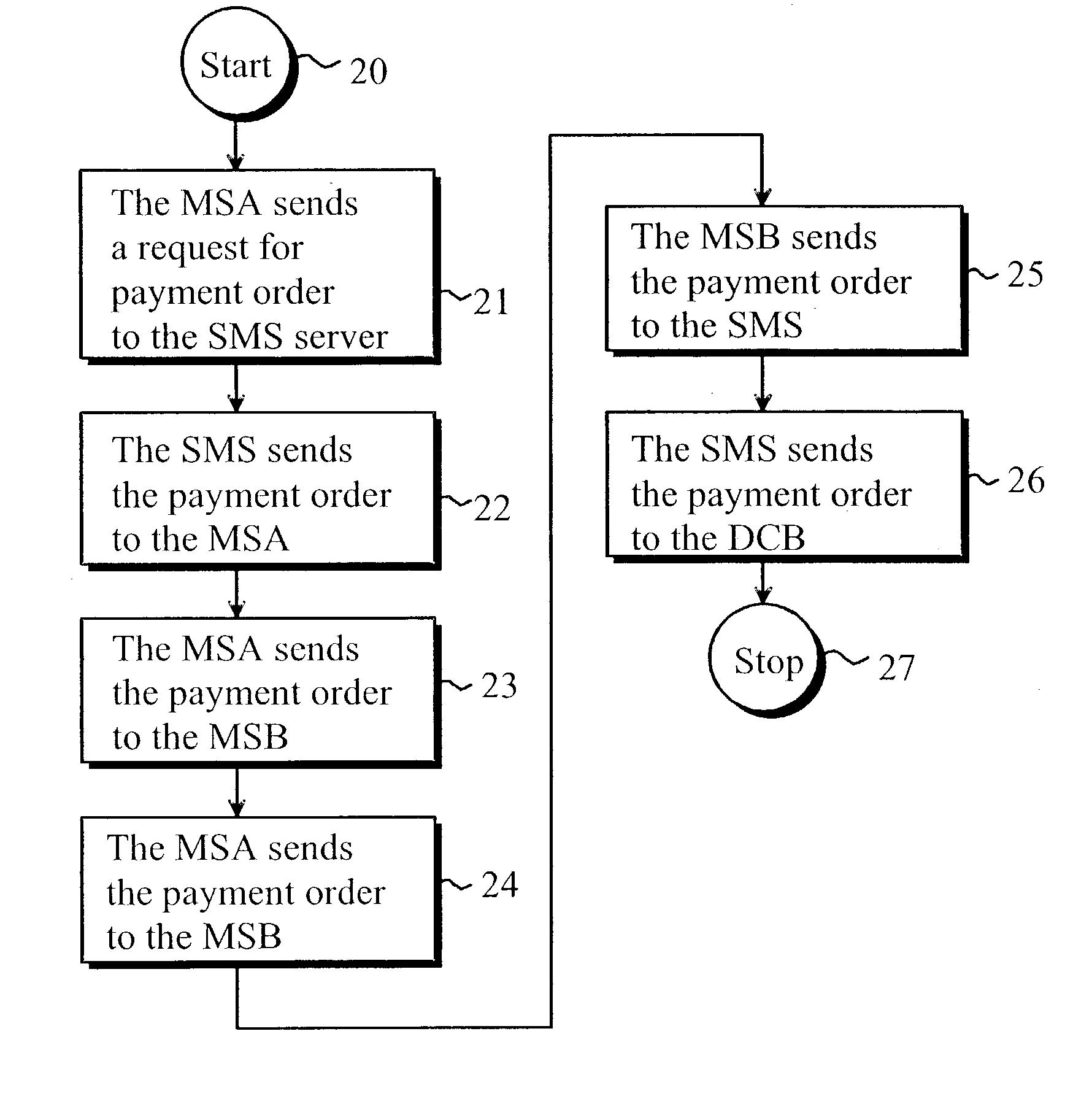
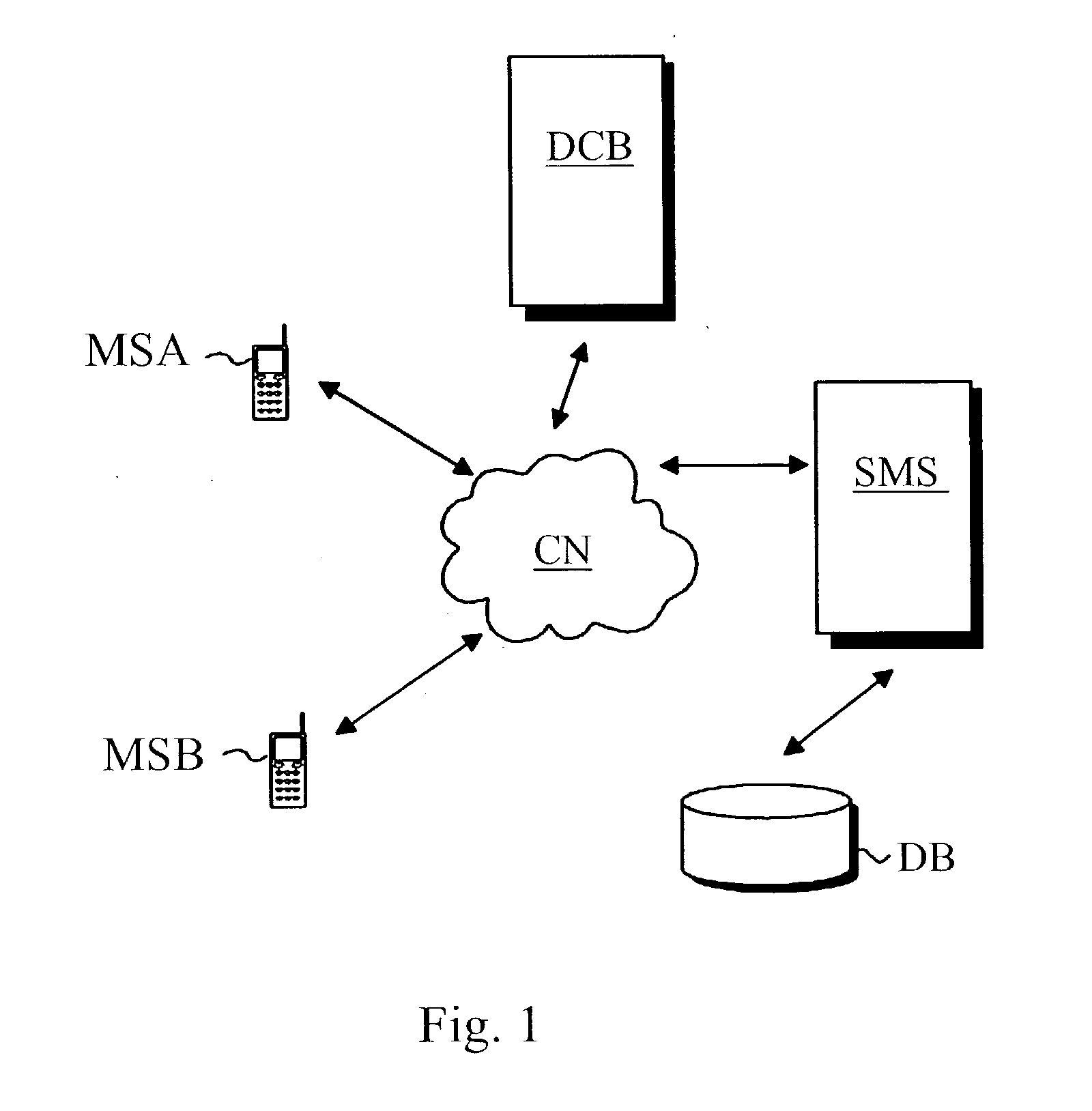
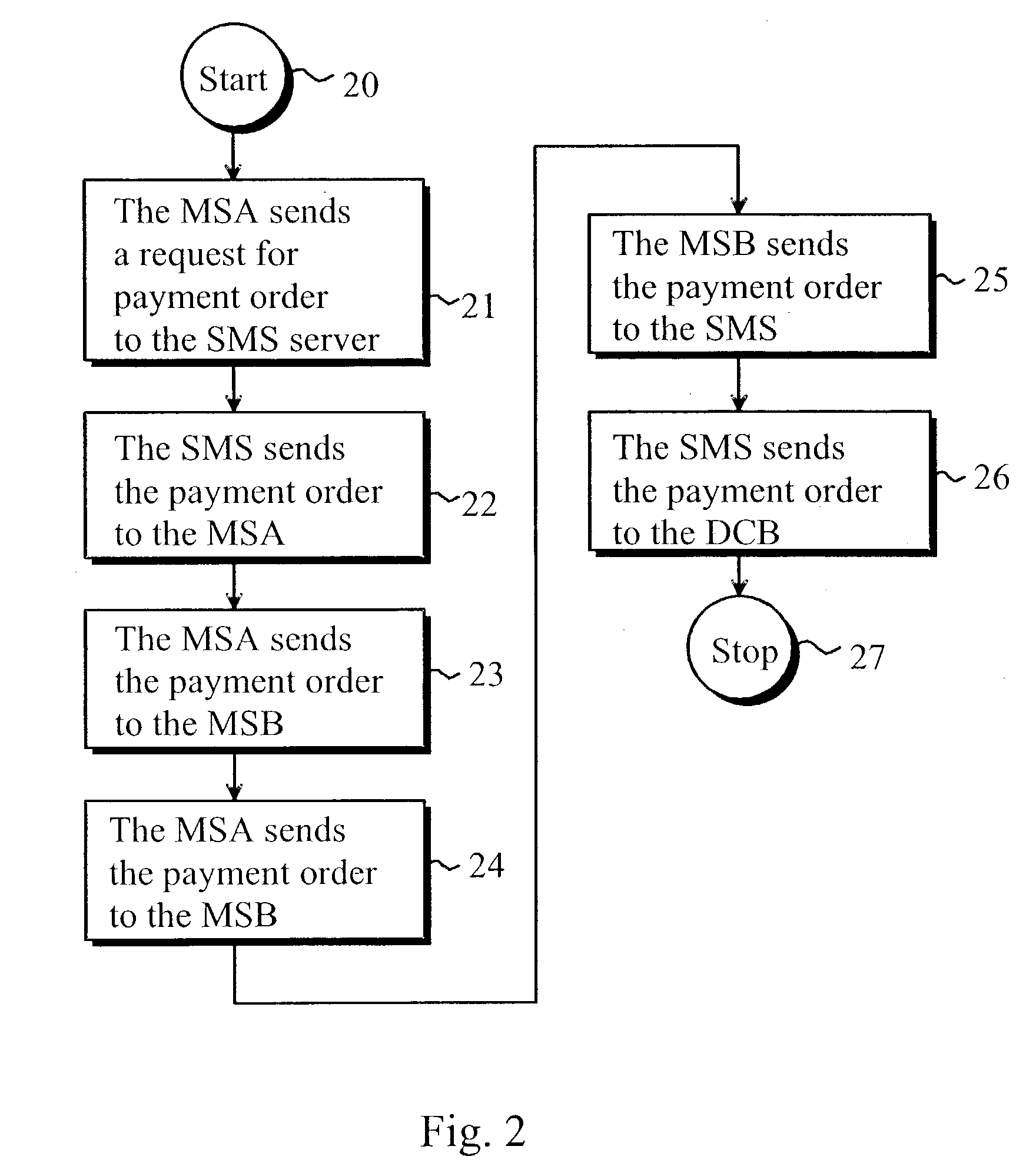
Method of implementing digital payments
ActiveUS20030126078A1Eliminate, orAlleviate, the drawbacks and deficienciesFinanceComputer security arrangementsPaymentTerminal equipment
A method for transferring a digital payment order from a first terminal device to a second terminal device, and for saving the payment order on a payment order server. A payment order request is sent from the first terminal device to the payment order server and, in response, the requested payment order is sent from the payment order server to the first terminal device. The payment order is thereafter transmitted from the first terminal device to the second terminal device, and the payment order is then transferred from the second terminal device to the payment order server to be honored. A message confirming the honoring of the payment order is sent to the second terminal device.
Owner:MIND FUSION LLC
Protecting software from unauthorized use by applying machine-dependent modifications to code modules
ActiveUS7188241B2Prevents illegal copyingEliminating opportunityDigital data processing detailsUser identity/authority verificationCode moduleApplication program software
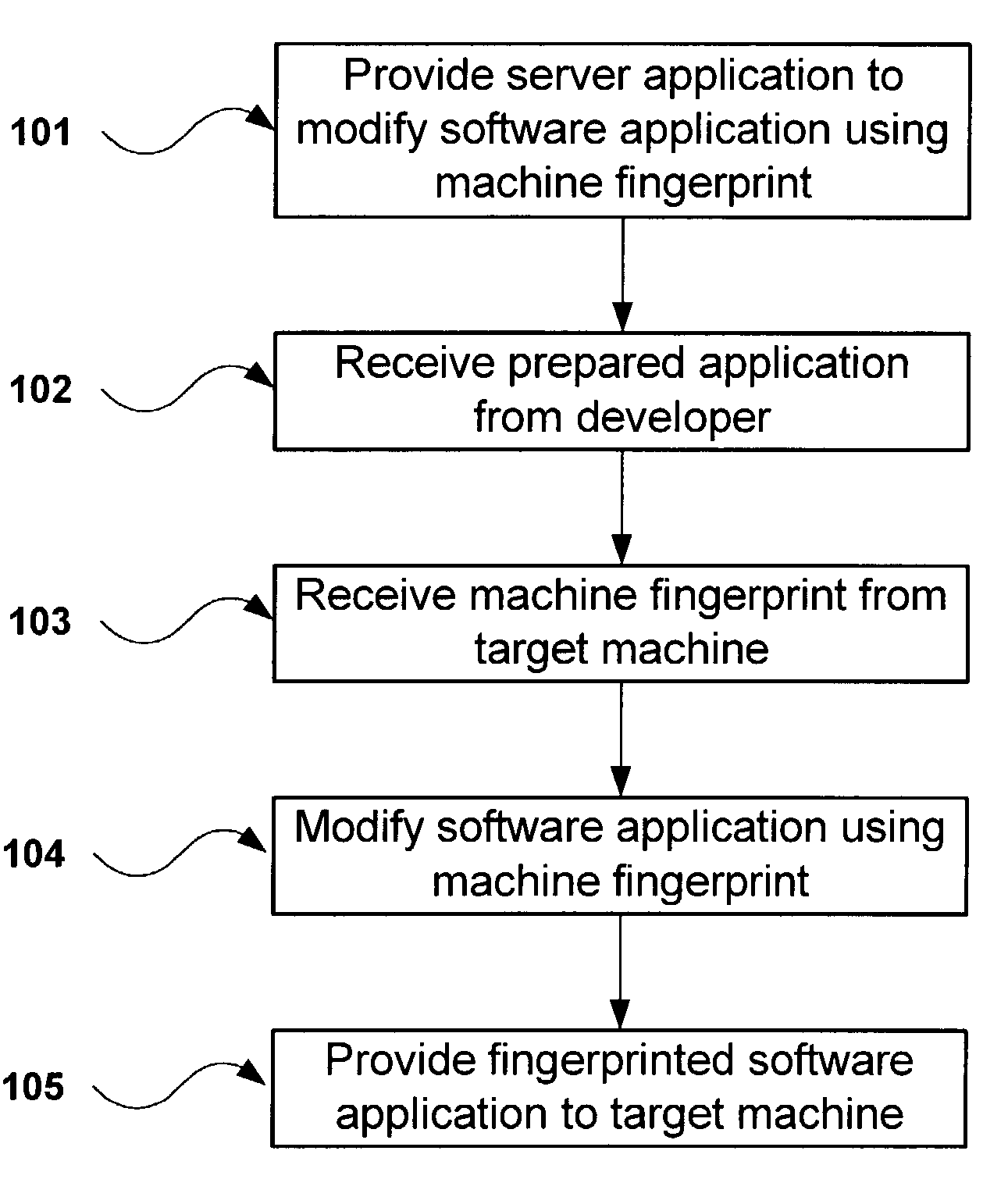
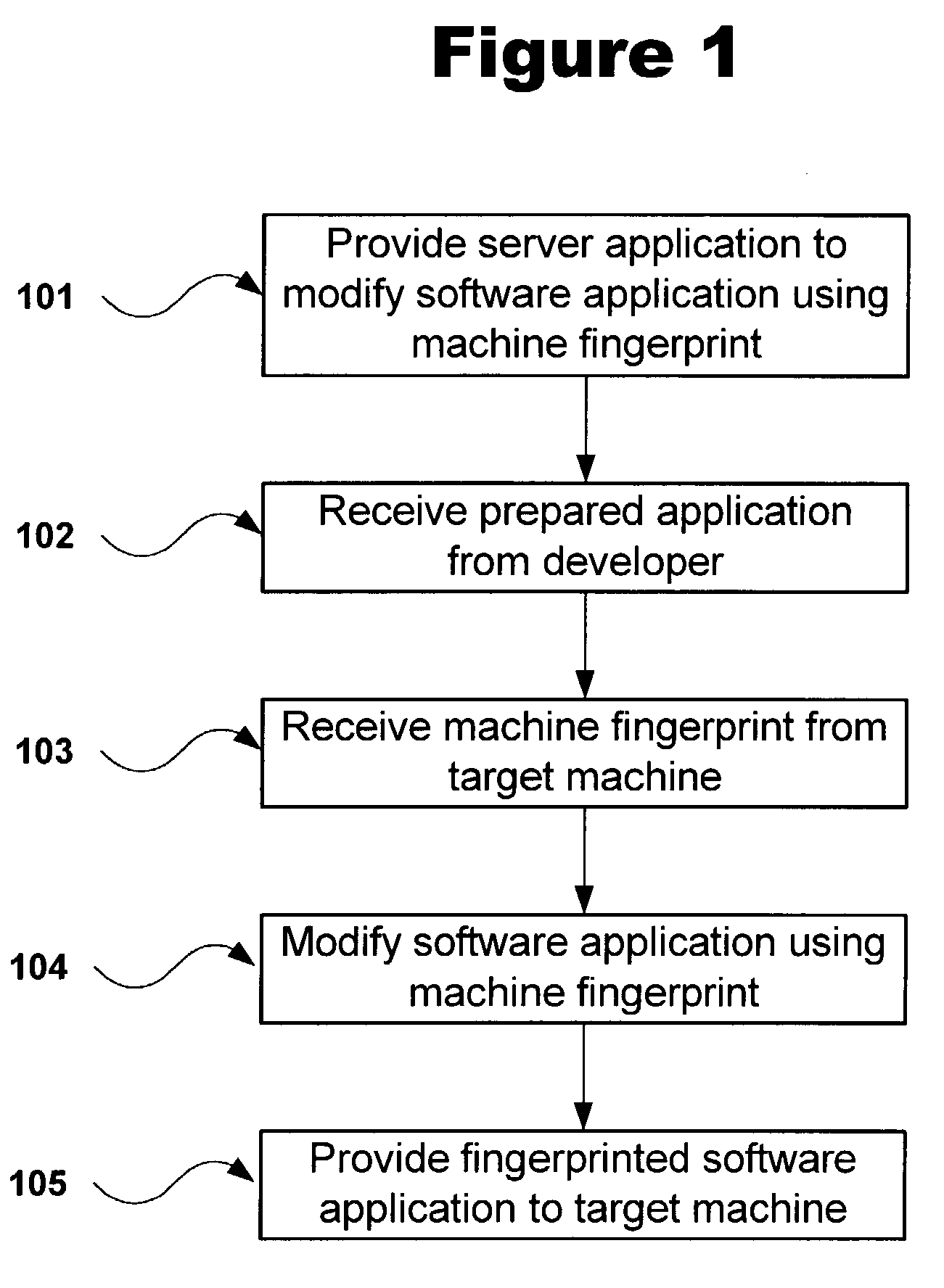
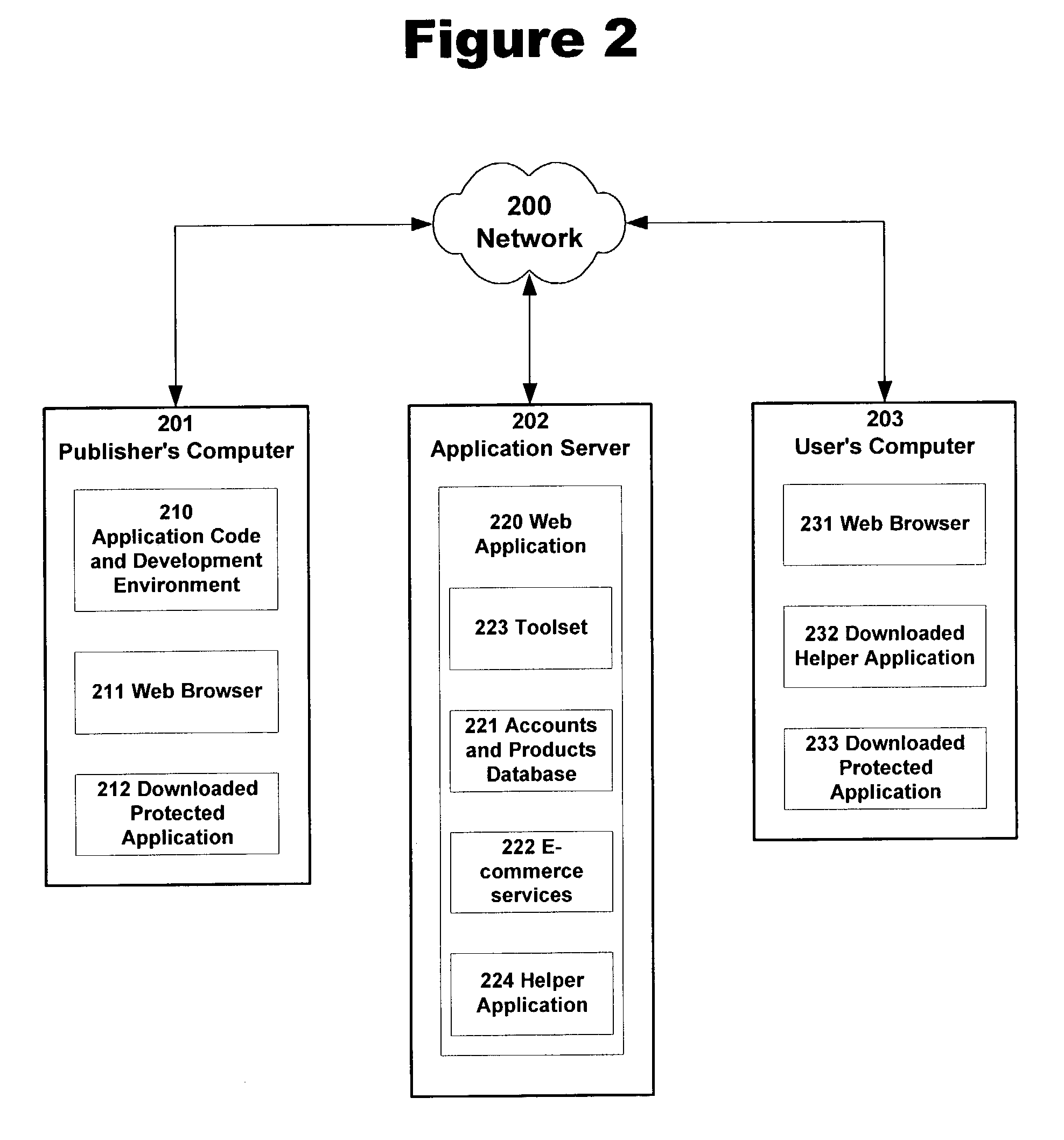
A method and system for providing anti-piracy protection to a software application on a server connected to a target machine over a network is described. The method includes providing a server with a server application for modifying the application software based on a machine fingerprint of the target machine, and for receiving and storing the application software. The server application receives the target machine fingerprint in conjunction with a license transaction between the server and the target machine. The server then modifies the application software using the received machine fingerprint, and provides the resulting modified software to the target machine, wherein the supplied software will only operate correctly on the target machine.
Owner:PACE ANTI PIRACY
Flexible display device and production method thereof
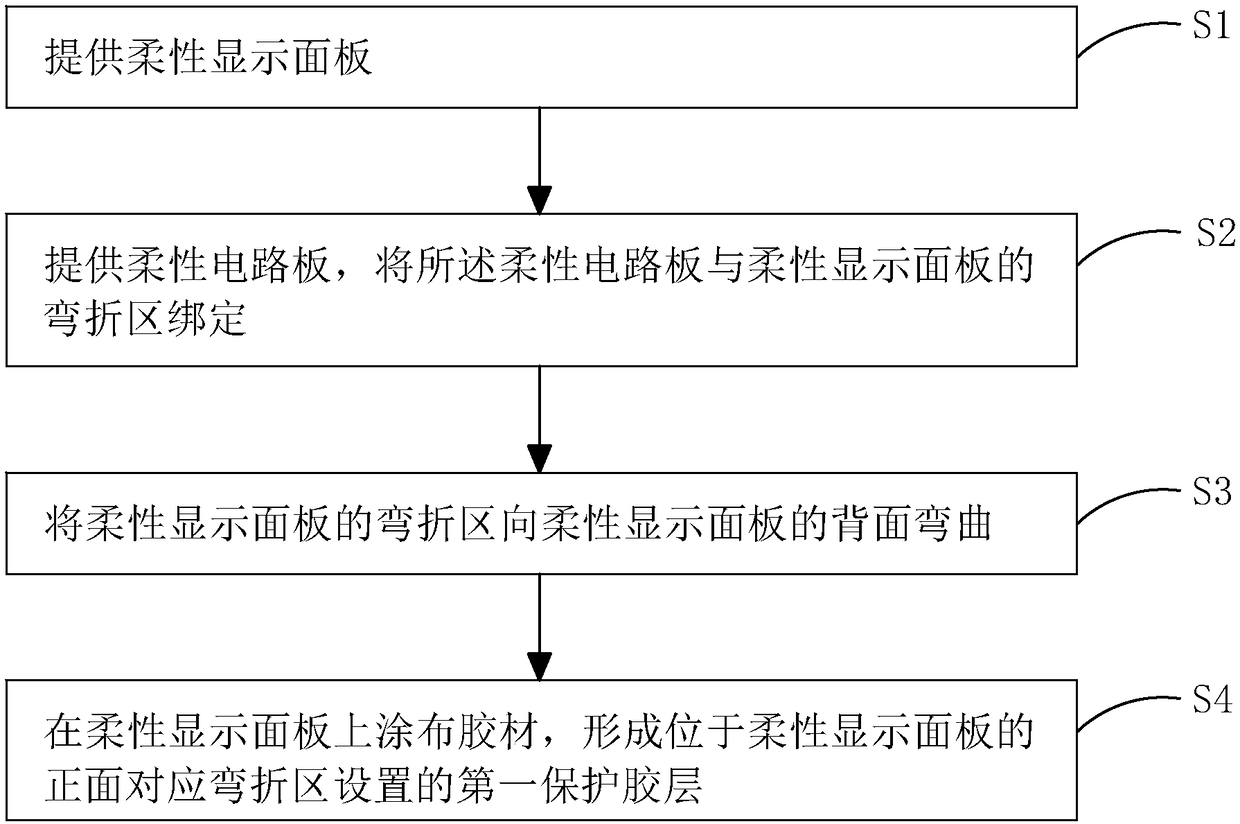
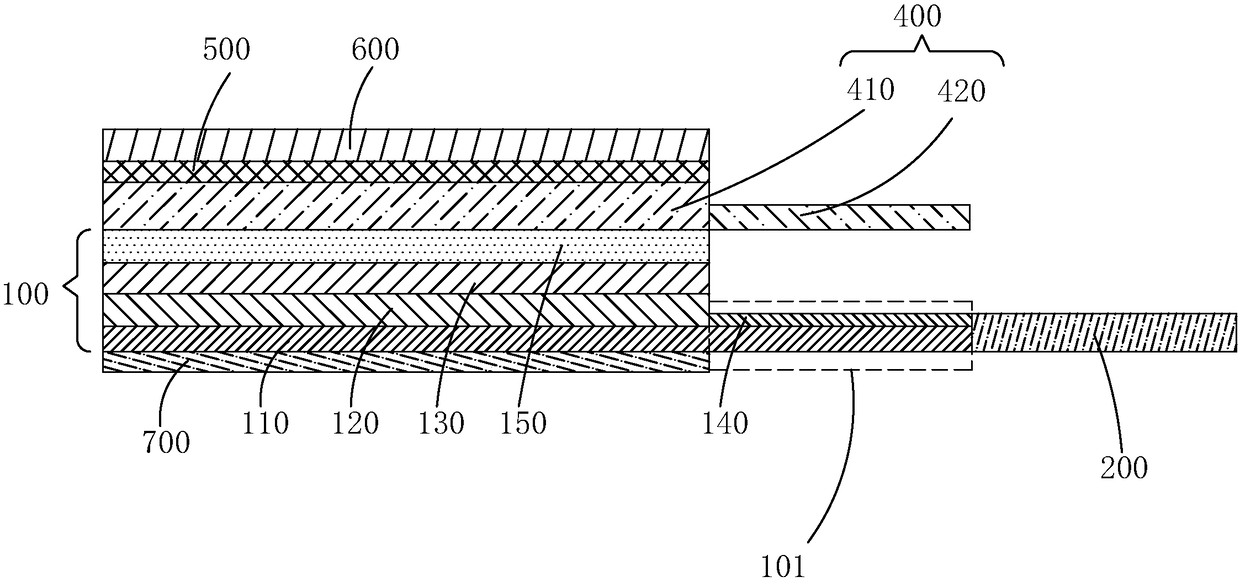
ActiveCN108281387AReduce difficultyIncrease the difficultyFinal product manufactureSemiconductor/solid-state device detailsFlexible circuitsEngineering
The invention provides a flexible display device and a production method thereof. The production method of the flexible display device includes: firstly, binding the bending area of a flexible displaypanel to a flexible circuit board; secondly, bending the bending area of the flexible display panel to the reverse of the flexible display panel; then making a first protective rubber layer on the front of the flexible display panel corresponding to the setting of the bending area. Compared with the prior art, the flexible display device and the production method thereof have the advantages thatrouting in the bending area is protected by the aid of the first protective rubber layer, difficulty in bending the bending area of the flexible display panel is lowered after the first protective rubber layer is bent on the bending area, the stress on the bending area of the flexible display panel is reduced in bending, and product quality is improved.
Owner:WUHAN CHINA STAR OPTOELECTRONICS SEMICON DISPLAY TECH CO LTD
Large-scale distributed network safety data acquisition method and system
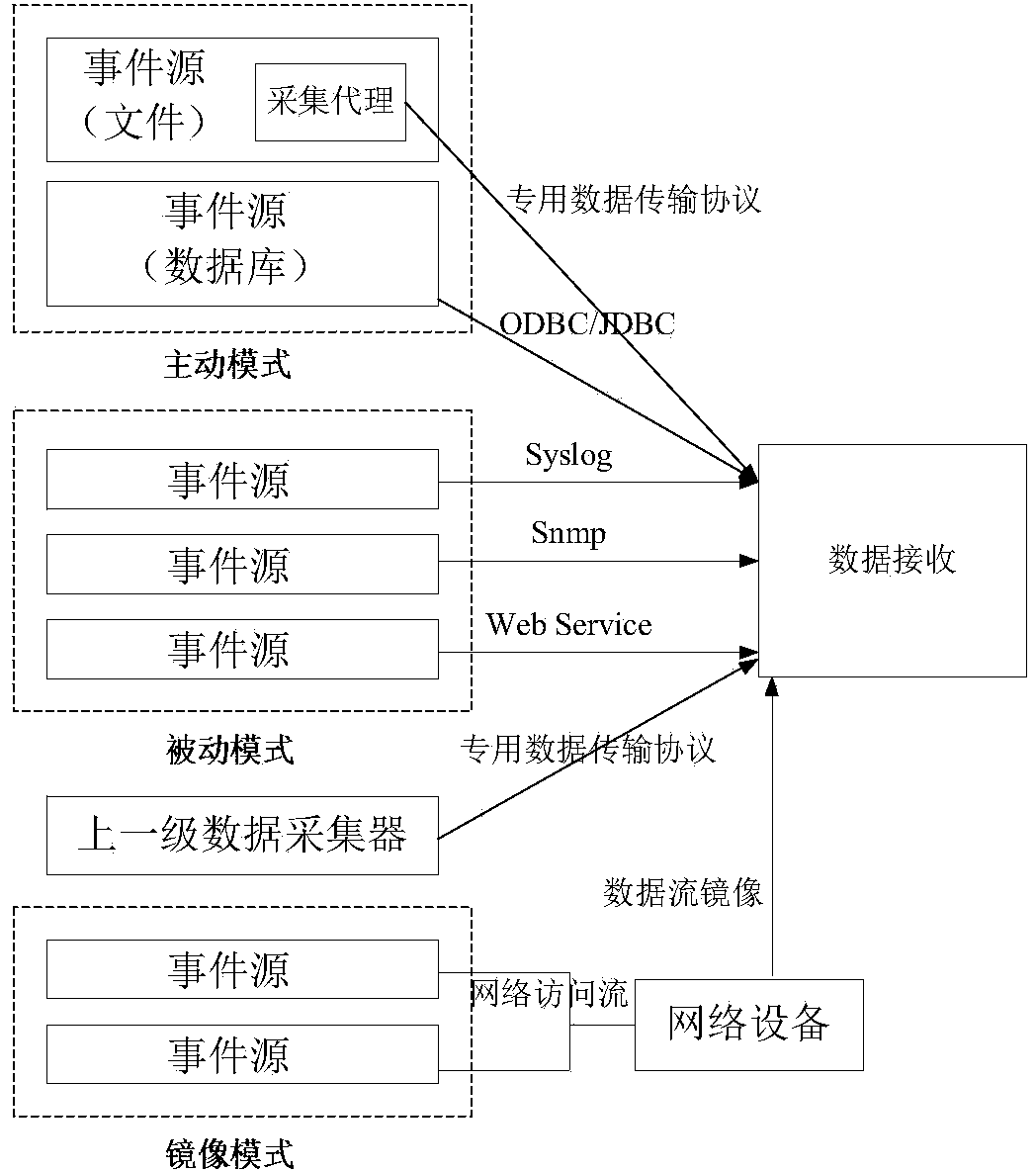
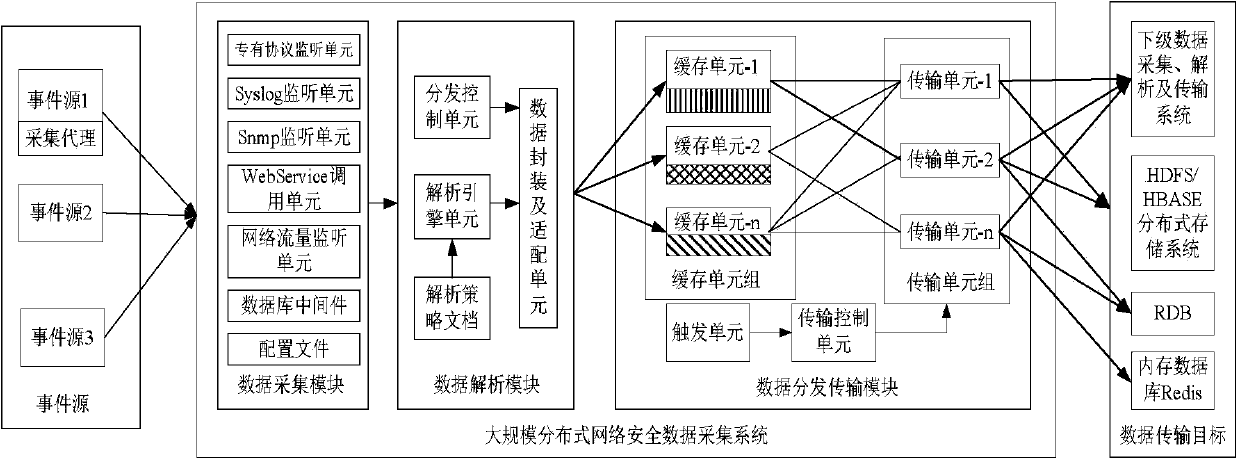
InactiveCN103731298AAvoid lossMeet the needs of comprehensive collectionData switching networksData streamOriginal data
The invention relates to a large-scale distributed network safety data acquisition method and system. The method comprises the steps of multimode data acquisition, data analysis and standardization and data distribution and transmission. The system comprises an acquisition agent module, a data acquisition module, a data analysis module and a data distribution and transmission module. With respect to data acquisition, multiple modes such as an active mode, a passive mode and a data stream mirror image mode are adopted, and comprehensive acquisition of various types of data is realized; with respect to data analysis, a data analysis and standardization mechanism based on strategies is adopted, original data are extracted, mapped, replaced, supplemented and the like by means of writing analysis strategies, and therefore quick analysis of a newly added data format and data standardization oriented to multiple application systems are realized; with respect to transmission, the multi-stage connection technology and the multi-path distribution technology are adopted, elastic combination, cascading deployment and multi-path distribution between acquisition systems are realized, and the requirements for vertical and horizontal expansion of a network environment and acquisition of mass data information are met.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND +1
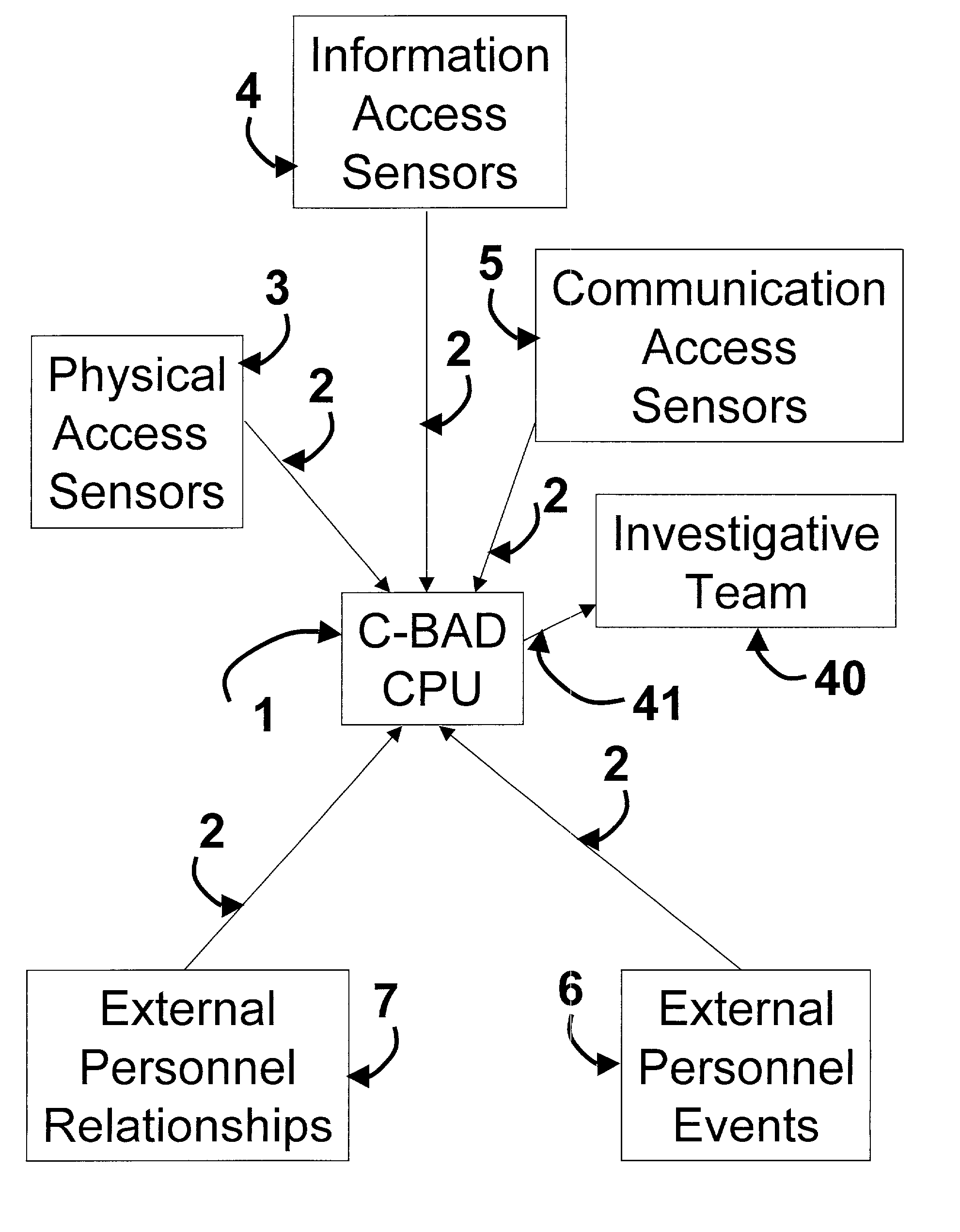
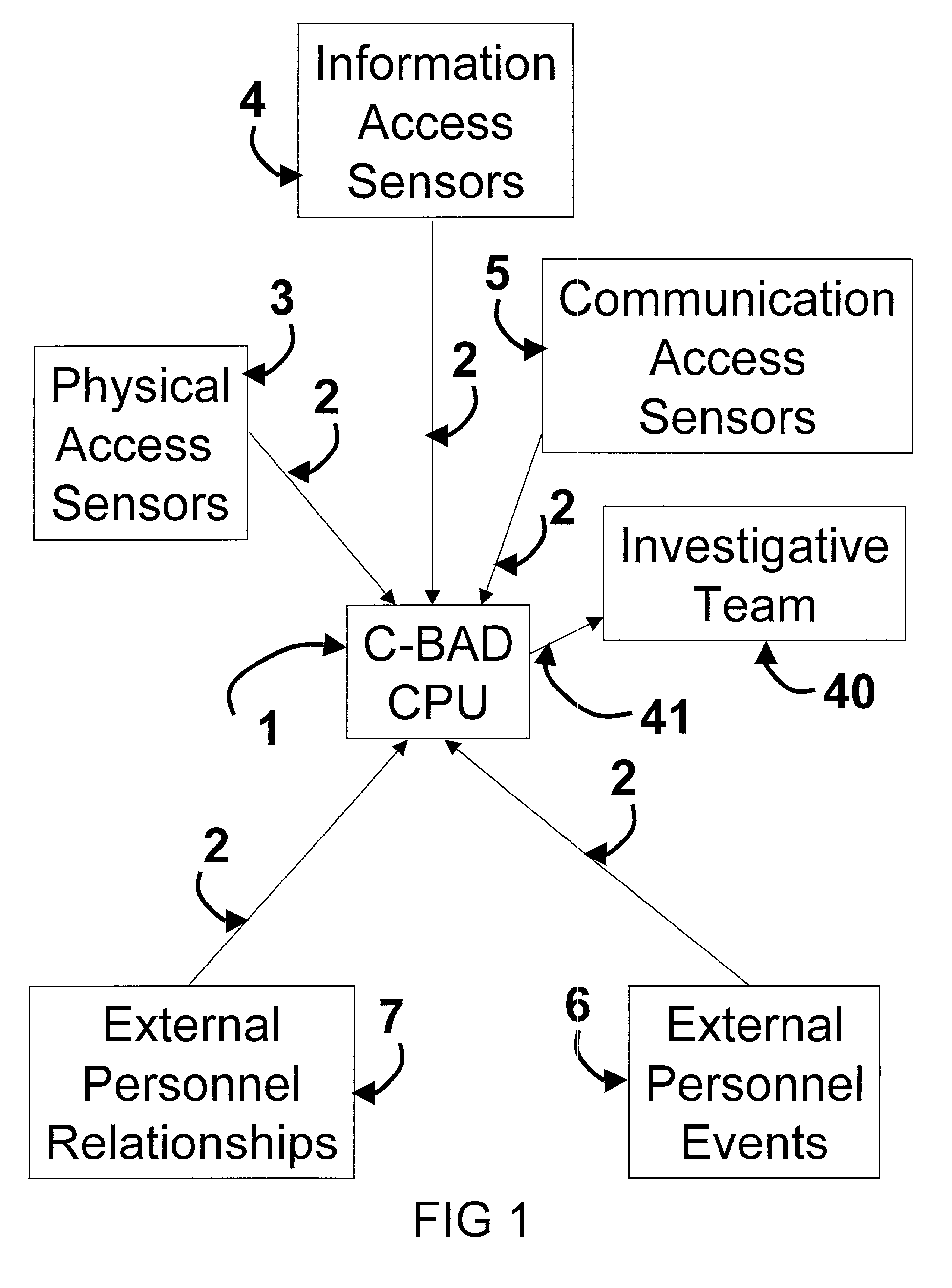
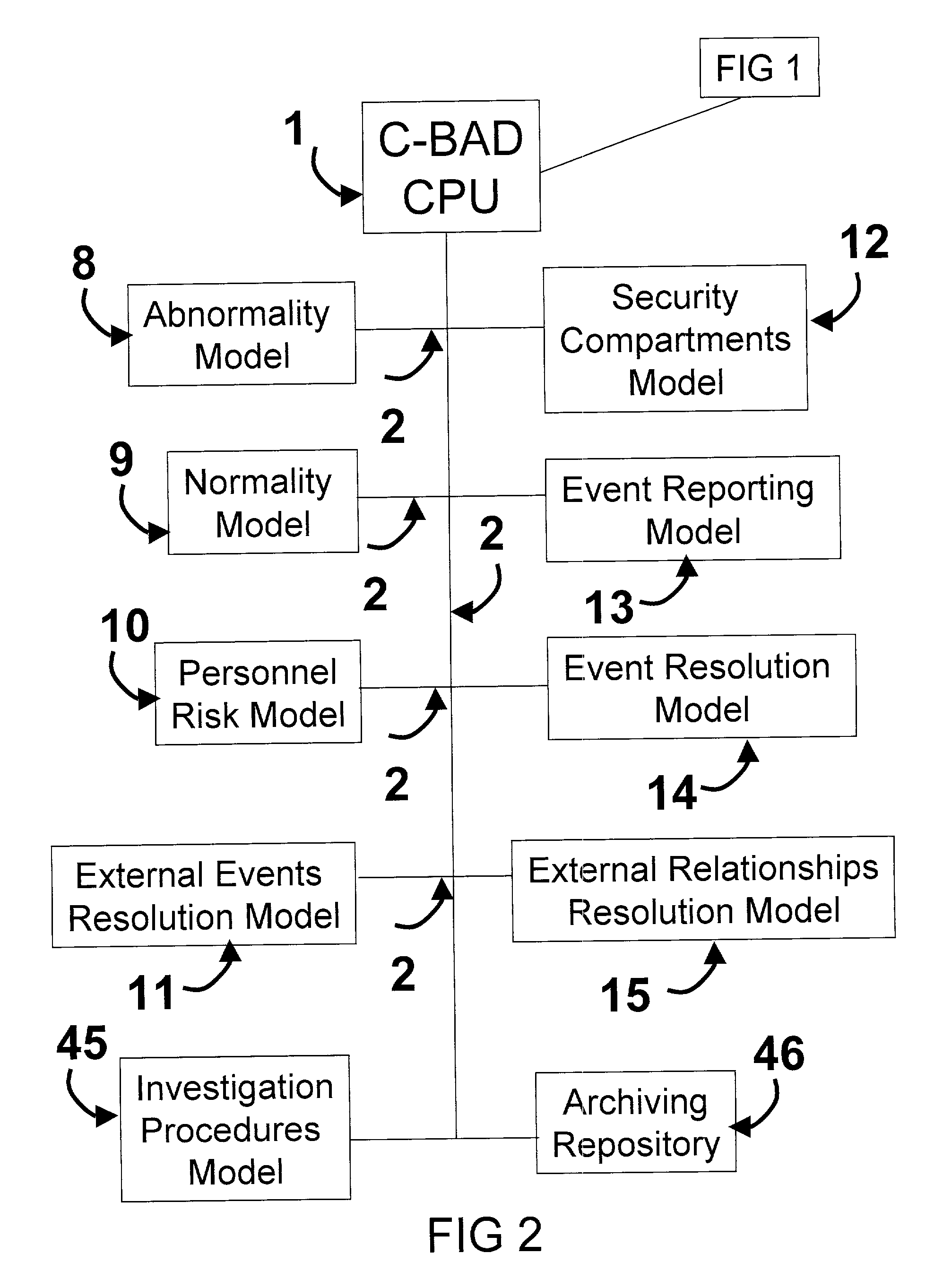
Cooperative biometrics abnormality detection system (C-BAD)
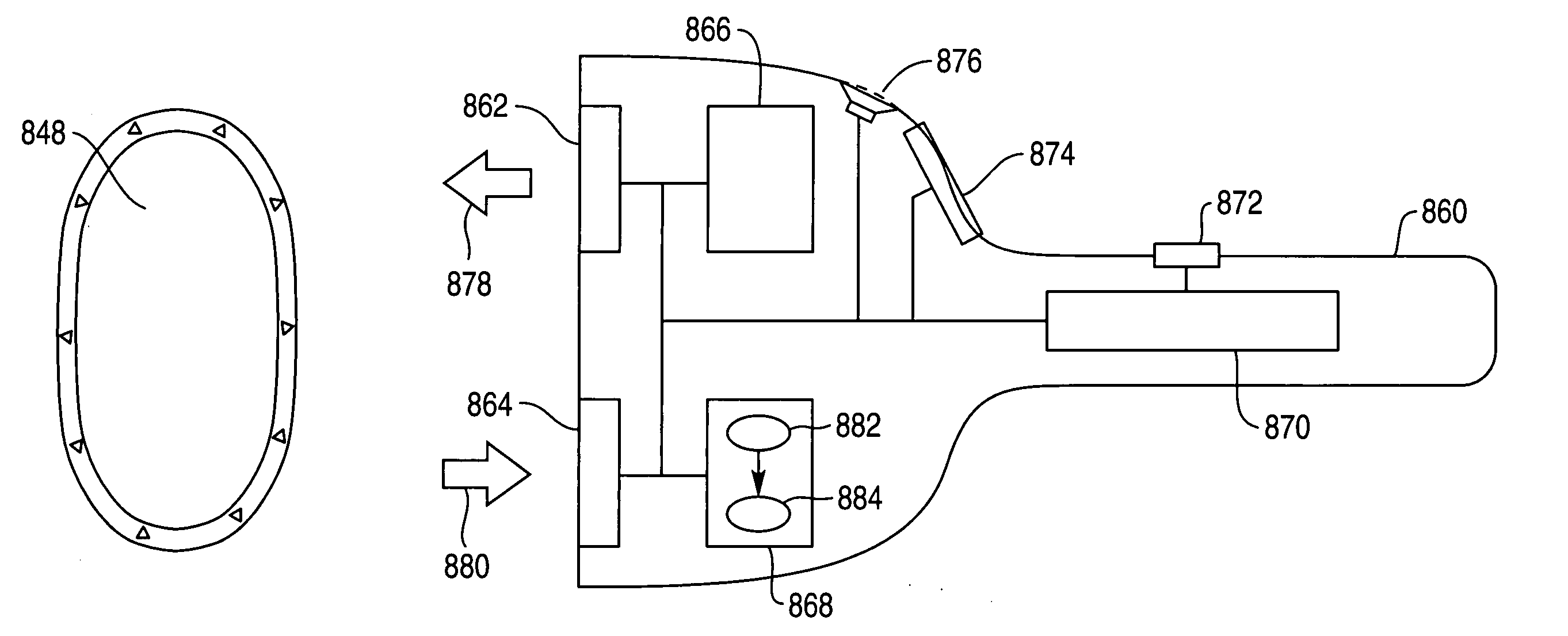
ActiveUS20030217024A1Increase the difficultyElectric signal transmission systemsMultiple keys/algorithms usagePaper documentSmart card
The Cooperative Biometrics Abnormality Detection (C-BAD) system is a network of sensors that track personnel throughout physical locations, communications, and computer systems. These systems are then linked to a central computer that contains detailed information on the individual, and rule-based risk, relationship, and abnormality models that will deter, detect, and document possible insiders. It is only at this point that C-BAD will then objectively report suspicious activities to a supervisory team for further investigation. (C-BAD) This System replaces previous current labor-intensive, subjective analysis, which has proven to be a weak deterrent and fraught with human error. C-BAD uses a full spectrum of sensors that identify personnel through the use of contact, contactless, biometrics, smart cards, or a combination of any one of these. The C-BAD central monitoring computer contains an inference engine based on artificial intelligence or a rule-based system, which reviews databases and furnished information.
Owner:THE RIGHT PROBLEM
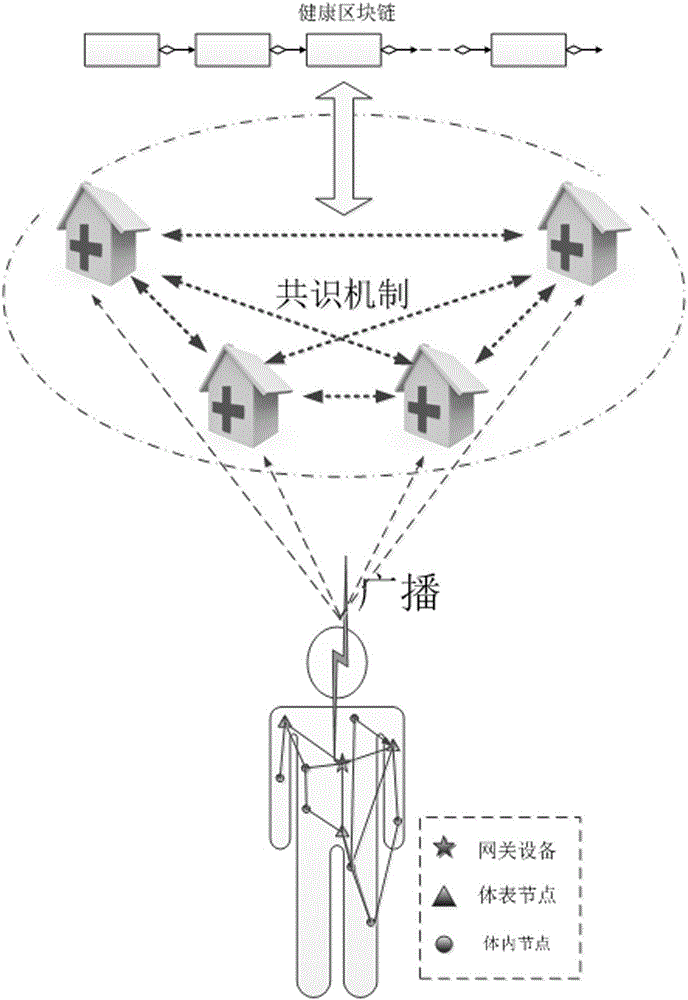
Lightweight back-up and efficient restoration method of health block chain data encryption keys
InactiveCN105812126AReduce management complexityAvoid heavy burdenKey distribution for secure communicationBody area networkRestoration method
The invention provides a lightweight back-up and efficient restoration method of health block chain data encryption keys.Body area networks achieve physiological parameters acquisition of healthy body health, health block chains are produced by a group of credible IT devices appointed by multiple health institutions and used for receiving and storing health data of the body area networks, the health block chain data encryption keys are produced by utilizing a fuzzy technology fuzzy vault and physiological signals acquired by the body area networks, human physiological data acquired in different time periods is encrypted by utilizing different data encryption keys and then is saved in the block chains of the IT devices without storage of historical data encryption keys; historical secret keys are restored by utilizing the health data acquired by the body area networks in real time.The lightweight back-up and efficient restoration method integrates the body area networks with the health block chains, avoids huge burden brought by secret key splitting related in a traditional secret key restoration method and safe storage and retrieval of shadow secret keys and greatly reduces management complexity of the health block chain data encryption keys.
Owner:QILU UNIV OF TECH
Authentication techniques in a monitoring system
InactiveUS6844816B1Improve abilitiesReduce the possibilityElectric signal transmission systemsMultiple keys/algorithms usageMonitoring systemTransmitter
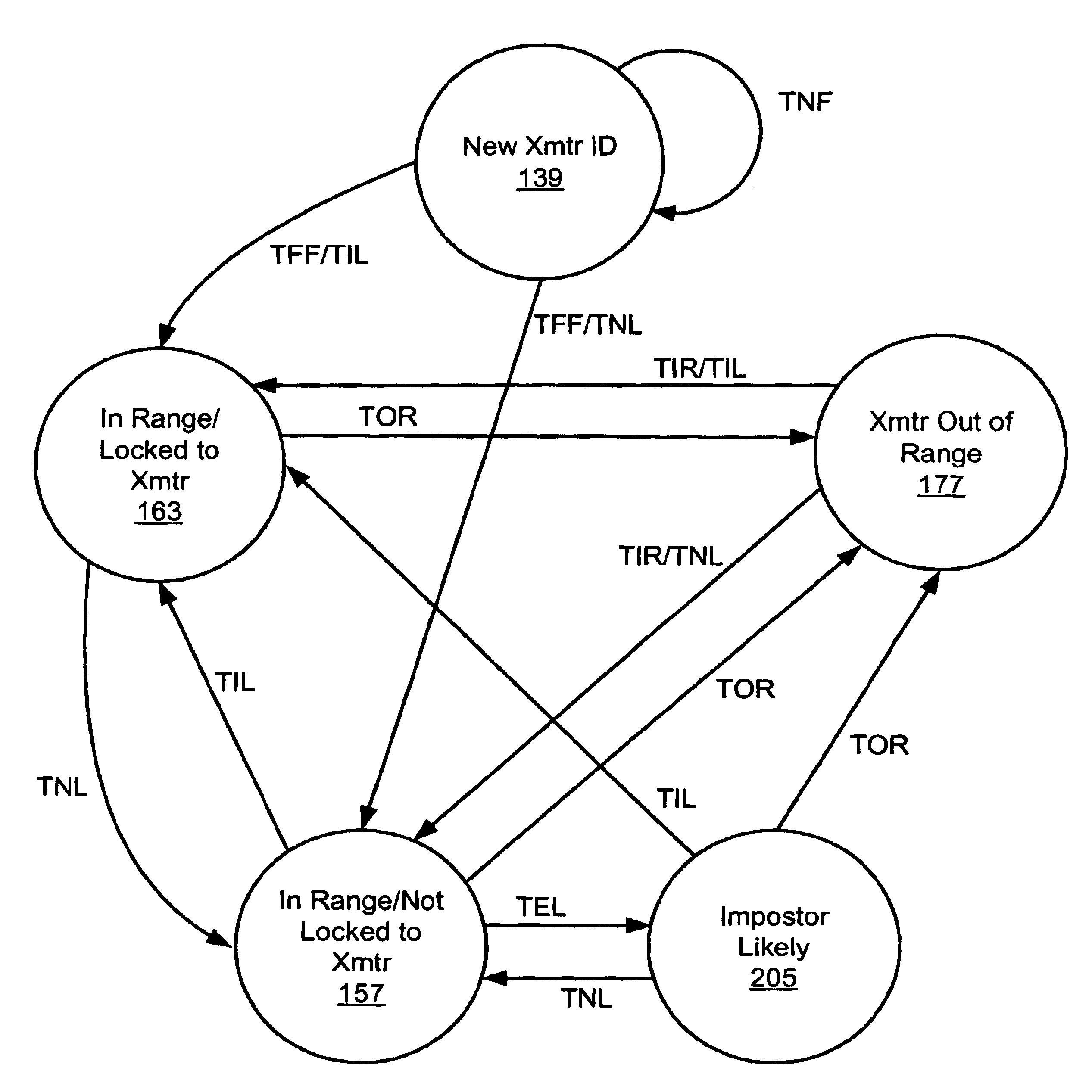
An Electronic House Arrest Monitoring (EHAM) system of the present invention includes a transmitter attached to a monitored offender and a receiver positioned in the vicinity of the desired monitoring location. The transmitter and the receiver each have a pattern stored or generated therein for determining the interval of time between signal transmissions and receptions. The pattern is pseudo-random to offer improved protection against imposter transmitters, in other words the time intervals are selected to be unequal and randomly varying but the pattern is repeated or cycled to allow continuing signal transmission by the transmitter. The transmitter transmits signals at varying time intervals according to this pattern, and the receiver authenticates signals it receives as coming from the monitored transmitter based on the expected time intervals from the pattern. The pattern may include any number of time intervals and, in one embodiment, includes more than one subpattern to extend the length of the repeat cycle to increase the difficulty of defeating the monitoring system. As further protection against imposter devices, the receiver may verify the signals based on information unique to the transmitter included in each signal. The receiver may further use the received signals and unique time interval patterns to determine a number of operating states, including New Transmitter ID Received, Transmitter In Range and Locked to Transmitter, Transmitter In Range and Not Locked, Transmitter Out of Range, and Imposter Likely. The monitoring system may also include a remote host computer linked to the receiver or receivers to enable these operating states to be monitored remotely by enforcement personnel.
Owner:BI
Security markers for determining composition of a medium
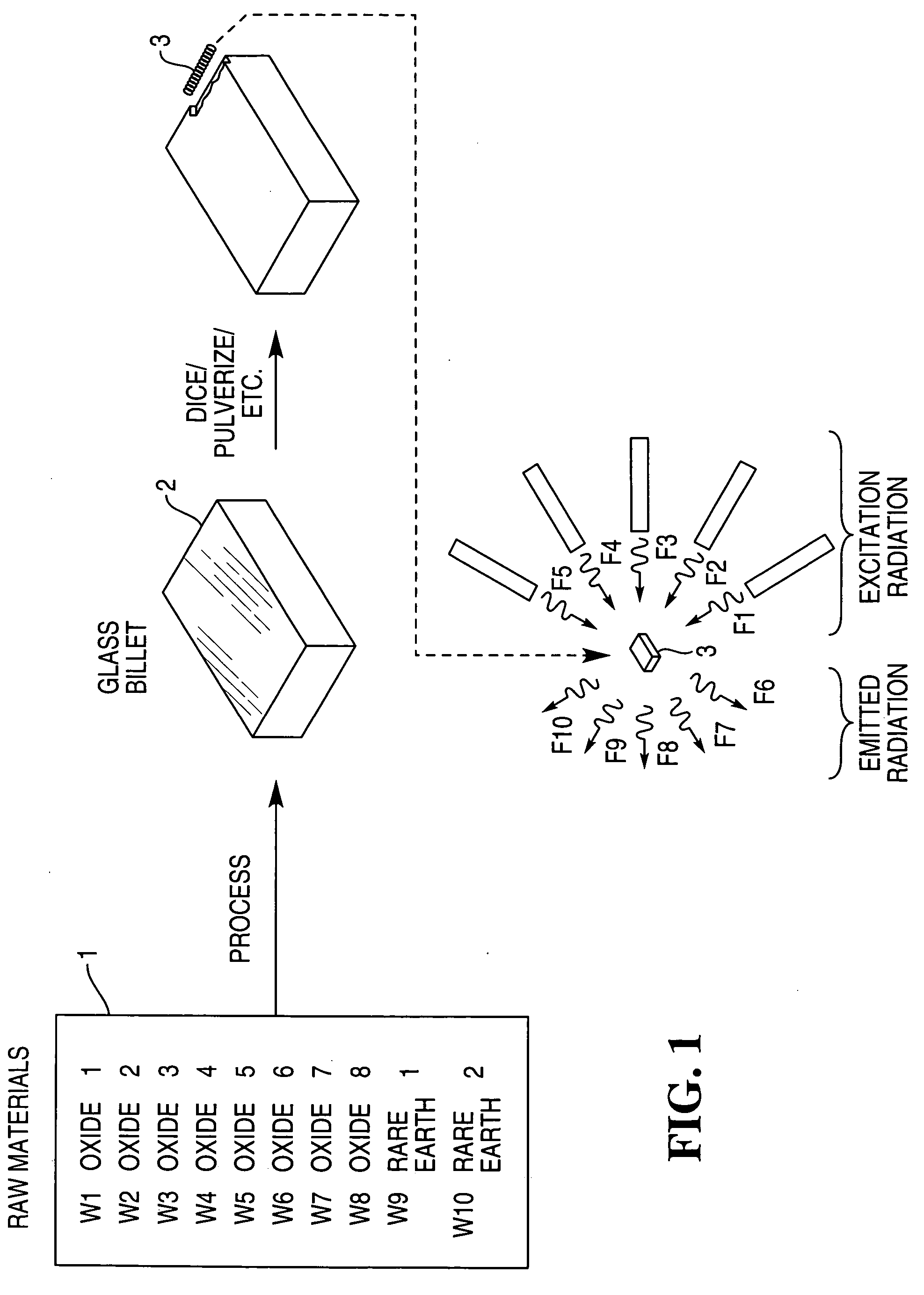
ActiveUS20060131518A1Increase the difficultyMaterial analysis by optical meansInksPhotoluminescencePhysics
Owner:NCR CORP +1
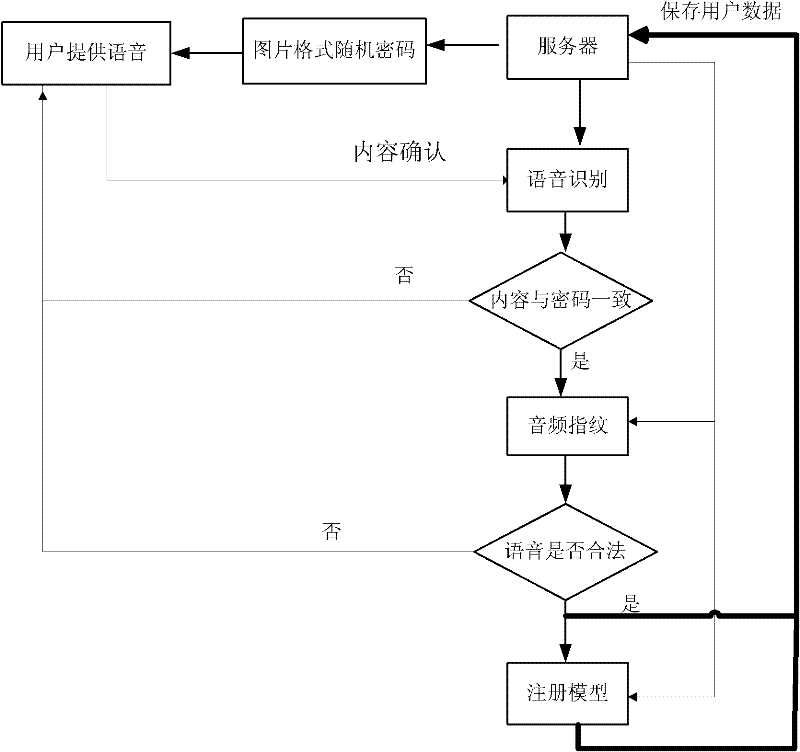
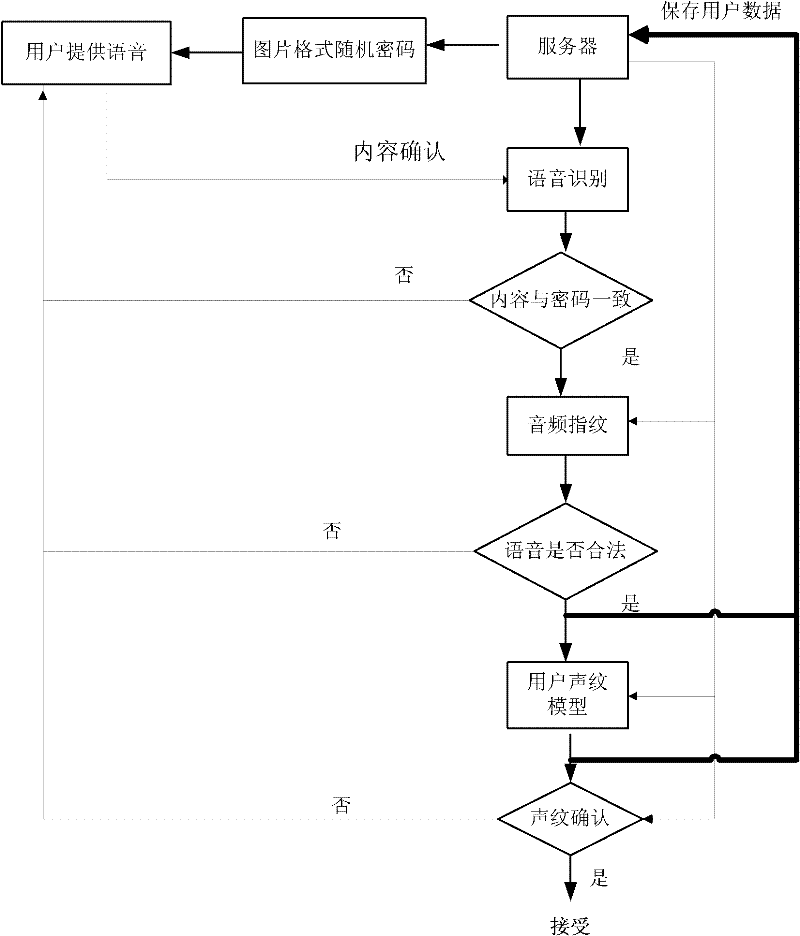
Online voiceprint recognition system and implementation method thereof
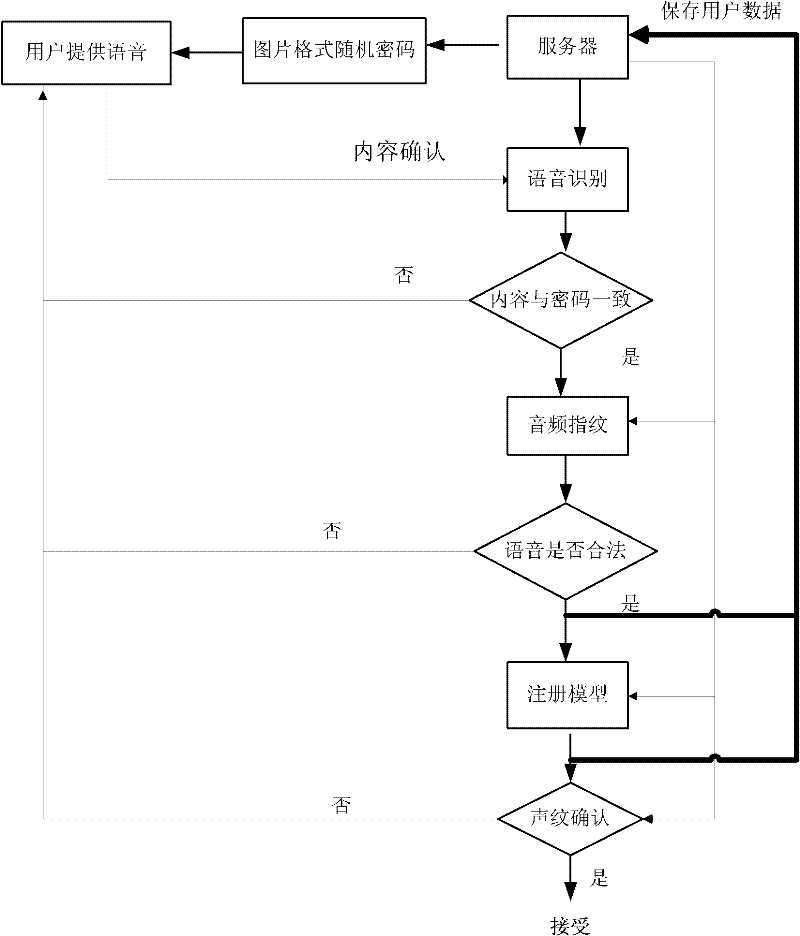
InactiveCN102543084APrevent recording attack problemImprove accuracySpeech analysisTransmissionPasswordAuthentication server
The invention discloses an online voiceprint recognition system and an implementation method thereof. The online voiceprint recognition system comprises a user recording module and an online voiceprint recognition server, and the implementation method comprises the following steps of: (1) providing generated password content for a user through the online voiceprint recognition server; (2) recording the voice of the user by utilizing the user recording module and providing the voice for a voice recognition module; (3) performing mode matching analysis on voice content provided by the user and the password content through the voice recognition module; (4) judging whether an audio fingerprint of the voice provided by the user is of the legal voice or not through an audio fingerprint recognition module; and (5) inspecting the matching degree between the voice provided by the user and a voiceprint module established by the registered user through a voiceprint recognition module, and regarding login is the real user login and receiving the login of the user if the degree achieves a set value. According to the online voiceprint recognition system and the implementation method thereof, disclosed by the invention, simple, easy-to-use and high-efficient online identity authentication can be realized.
Owner:SHENGLE INFORMATION TECH SHANGHAI
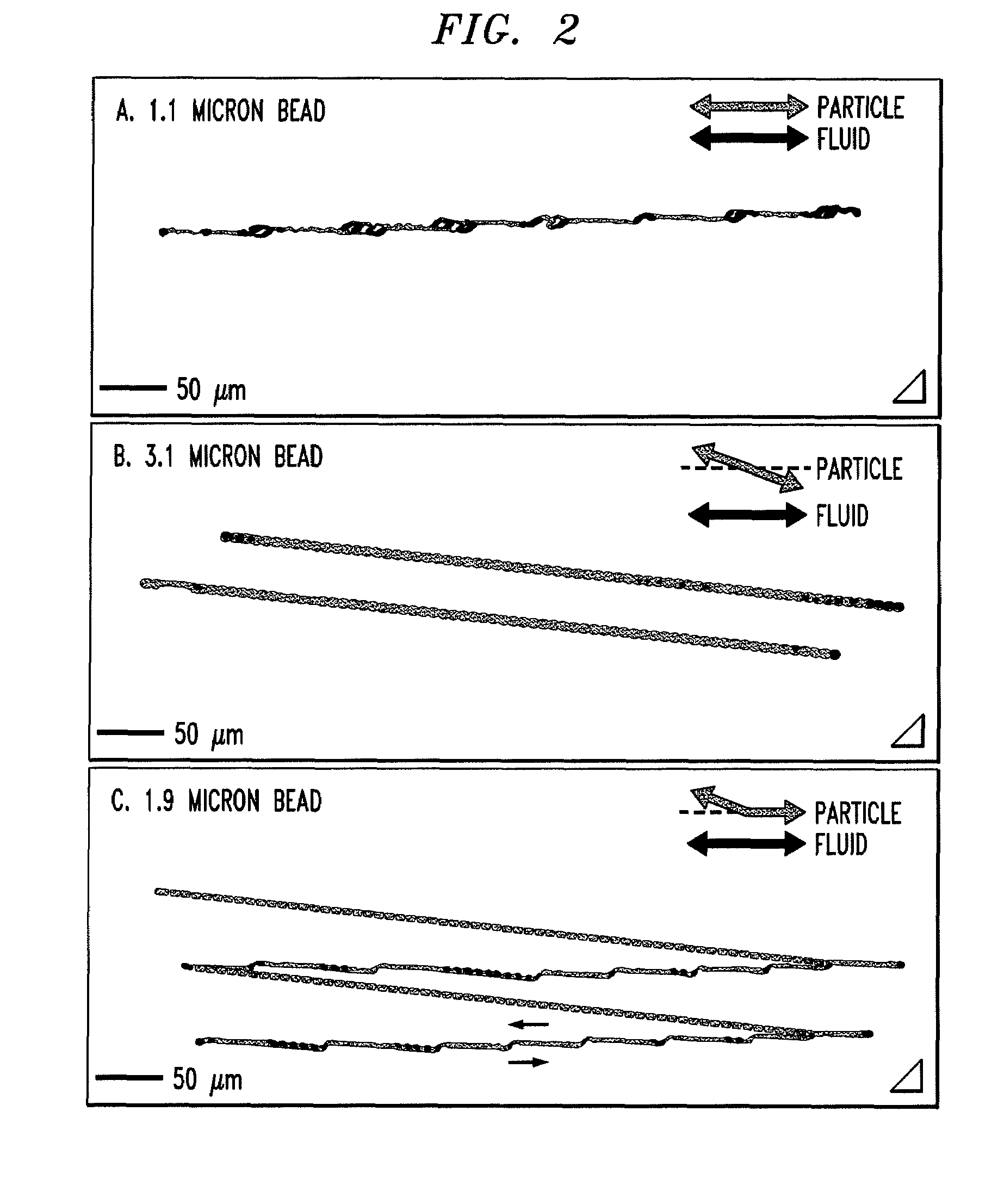
Bump array device having asymmetric gaps for segregation of particles
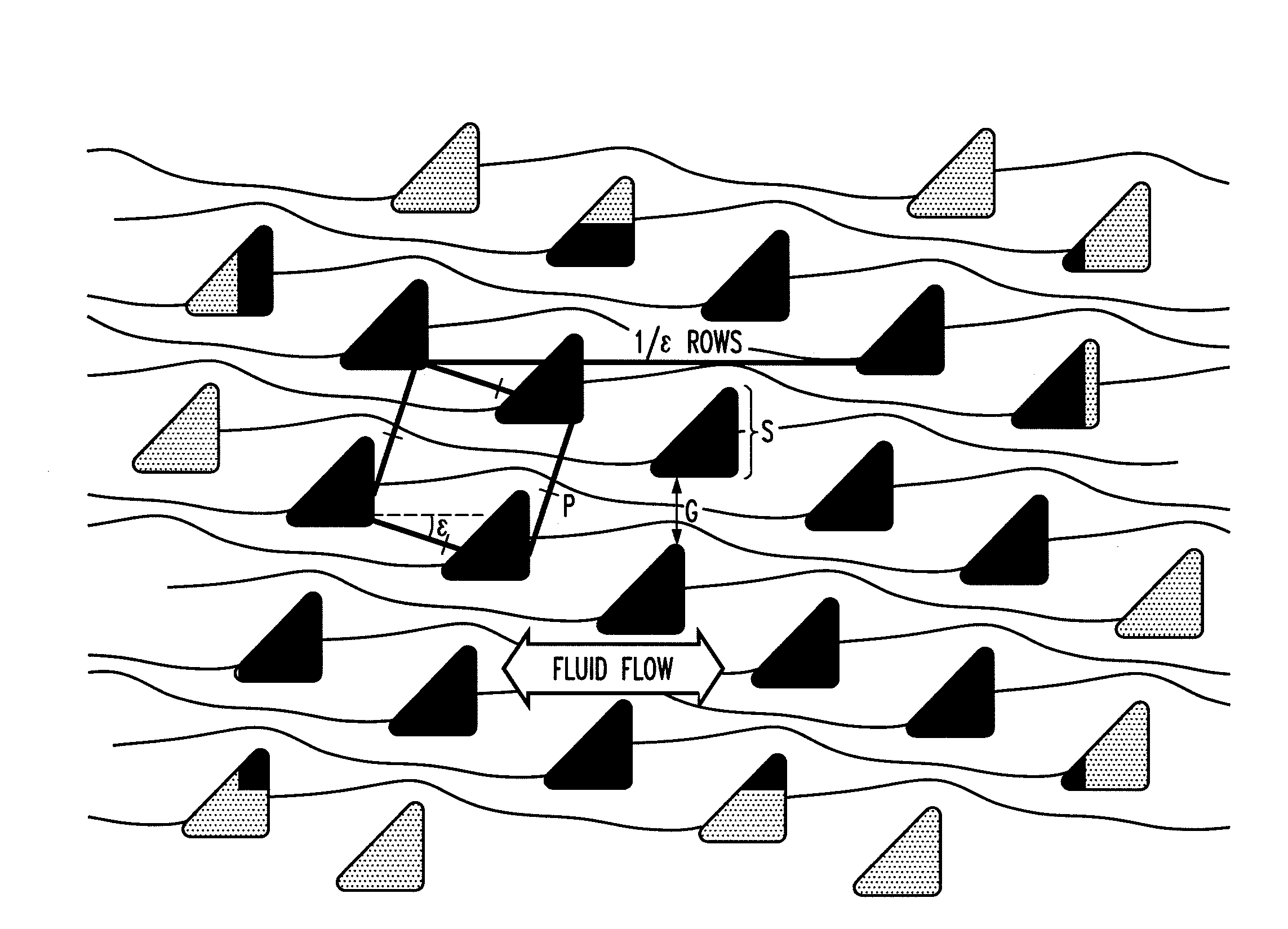
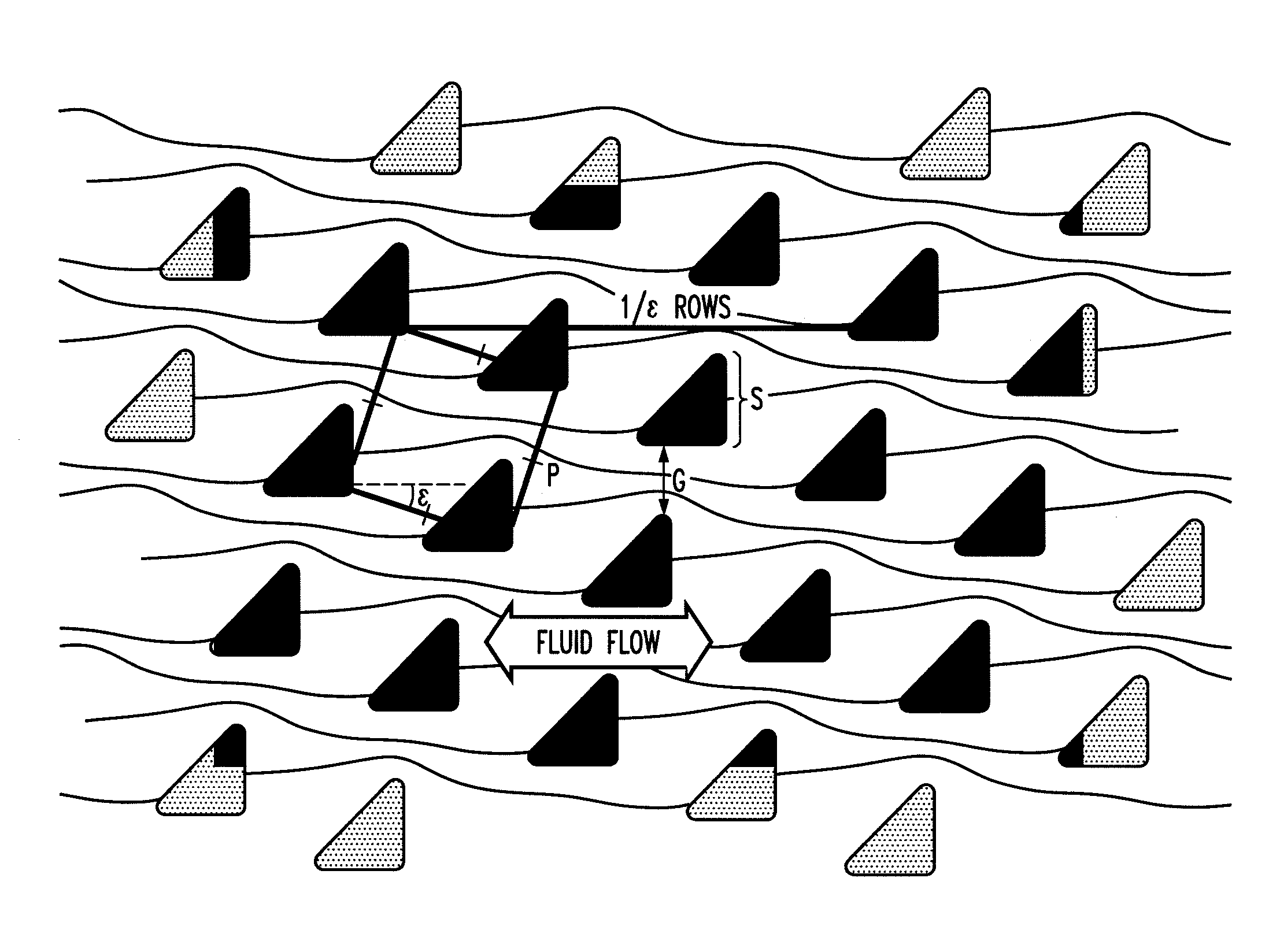
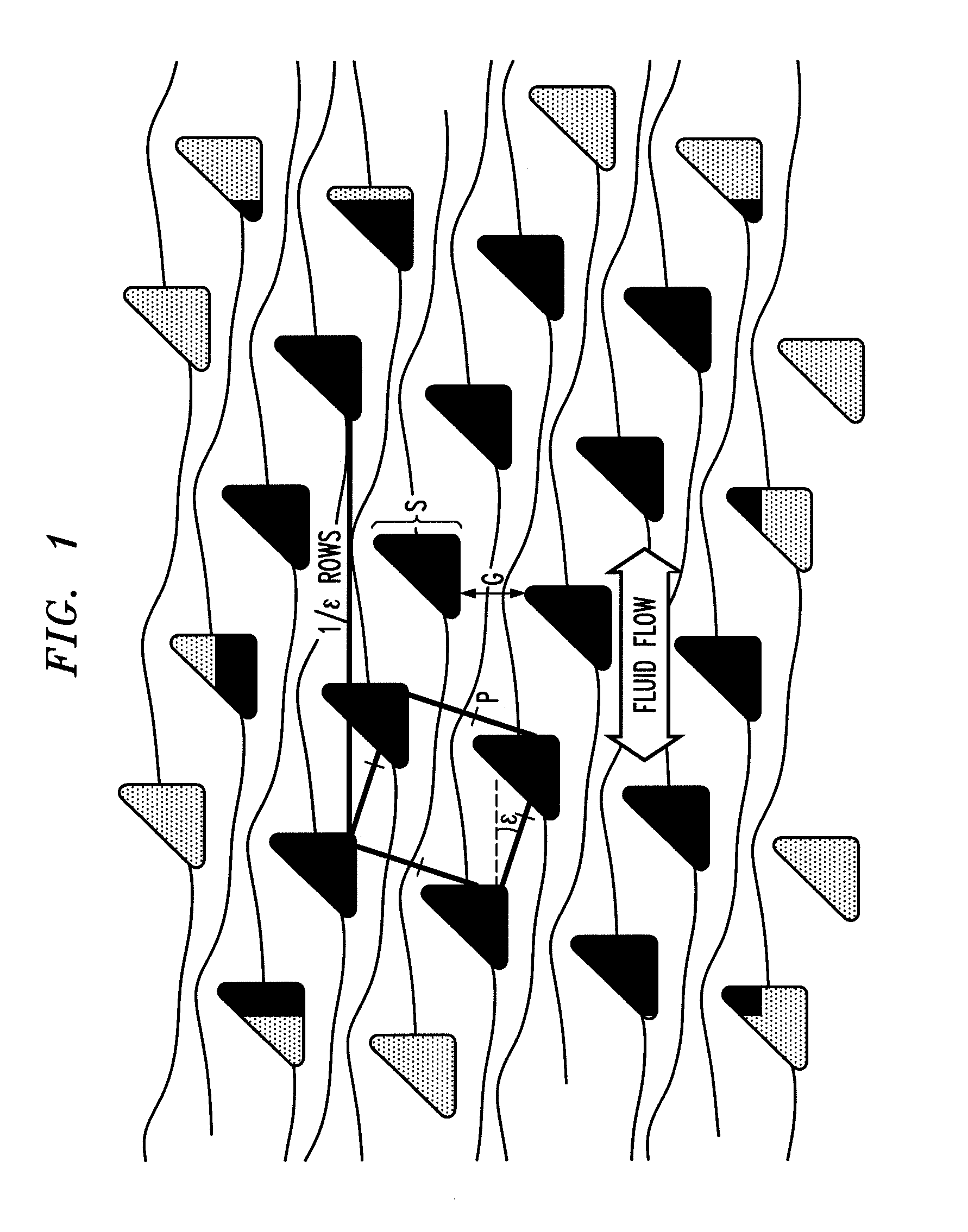
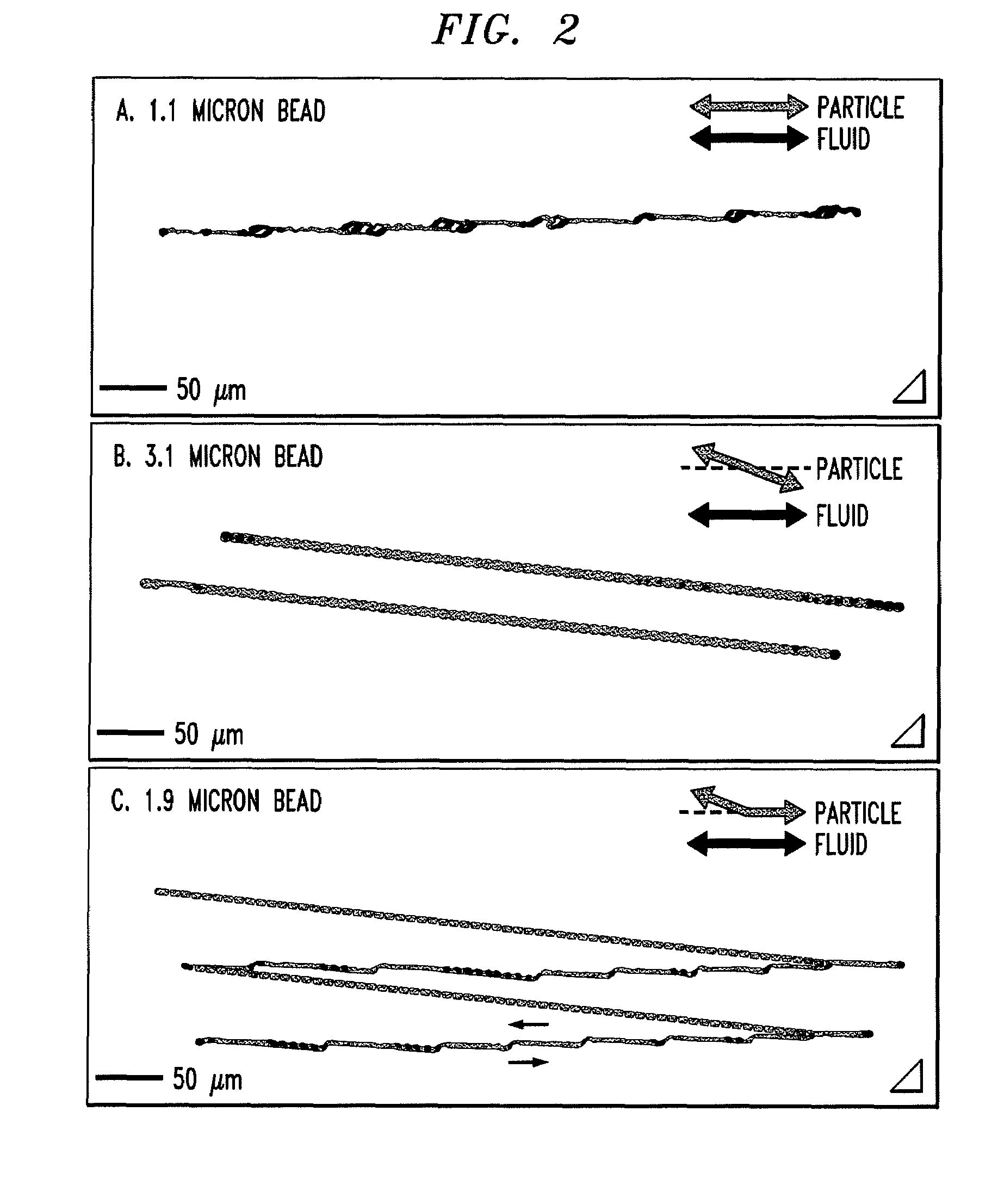
ActiveUS20100059414A1Easy to operateReduce gapGas current separationComponent separationEngineeringMechanical engineering
The disclosure relates to obstacle array devices (also known as bump array devices) for separating populations of particles by size. Improvements over previous obstacle array devices are realized by causing the fluid velocity profile across gaps between obstacles to be asymmetrical with respect to the plane that bisects the gap and is parallel to the direction of bulk fluid flow. Such asymmetry can be achieved by selecting the shape(s) of the obstacles bounding the gap such that the portions of the obstacles upstream from, downstream from, or bridging the narrowest portion of the gap are asymmetrical with respect to that plane. Improvements are also realized by using obstacles that have sharp edges bounding the gaps. Other improvements are realized by selecting obstacle shapes such that the critical particle dimensions defined by the gaps in two different fluid flow directions differ.
Owner:THE TRUSTEES FOR PRINCETON UNIV
Visceral anastomotic device and method of using same
InactiveUS6926724B1Compromising strengthEasy to reconnectBlood vesselsSurgical staplesInsertion stentPERITONEOSCOPE
A temporary biocompatible stent and method for visceral anastomosis. The stent is provided with integral means for maintaining the structural stability of the stent while providing substantial flexibility. The method comprises fitting the luminal stumps of the viscus over either end of a stent of the invention, and joining the ends of each stump together. A short time after completion of the anastomosis, the stent dissolves and is absorbed safely into the body. The stent and method can be beneficially used in laparoscopic or more invasive traditional surgical procedures. The stent and method are particularly well suited for anastomosis of the bowel.
Owner:CITY OF HOPE
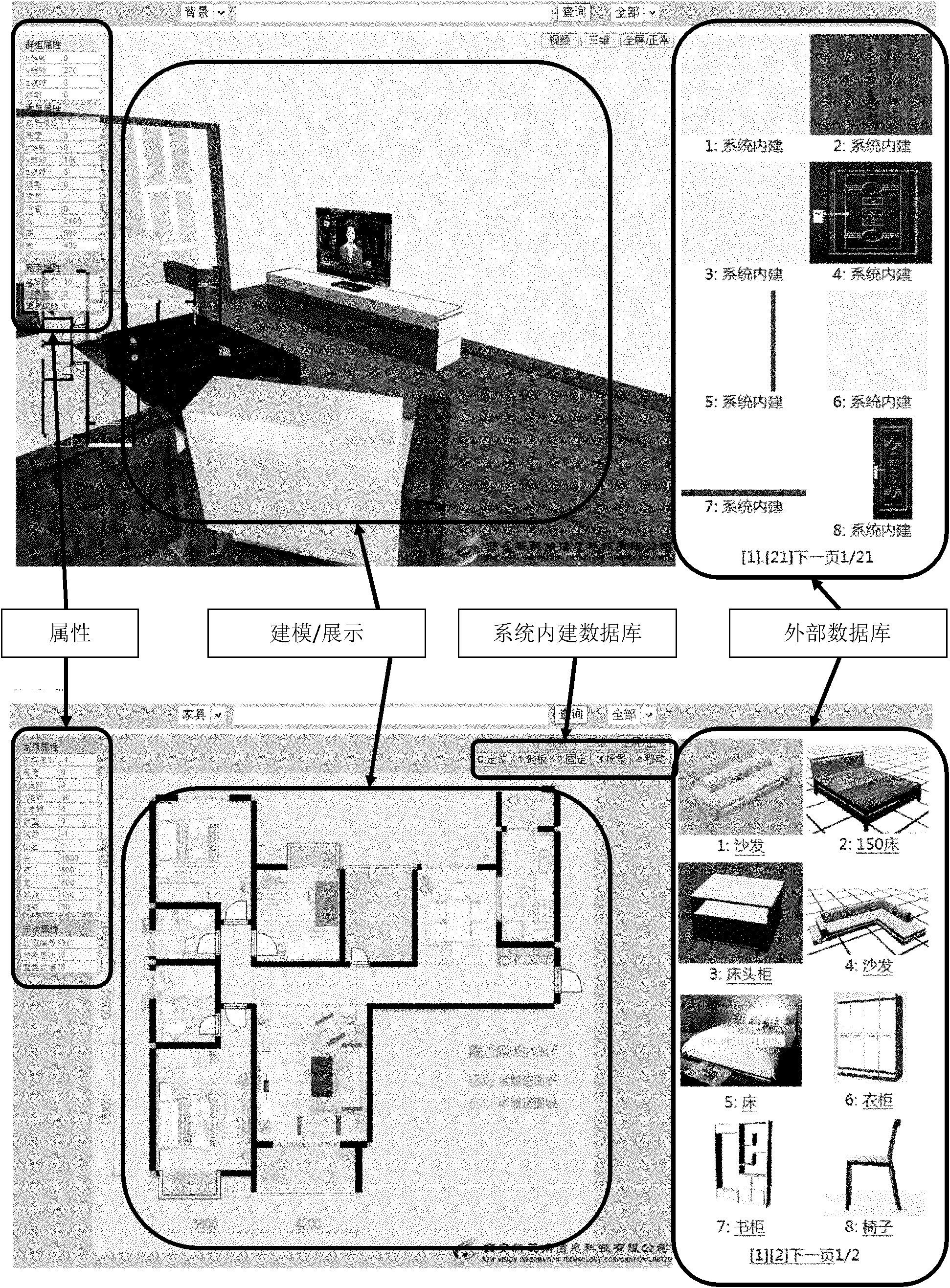
Three-dimensional dwelling size modeling method based on two-dimensional dwelling size diagram
InactiveCN101930627AIncrease the difficultyImprove modeling efficiencySpecial data processing applications3D modellingComputer scienceModelling methods
The invention relates to a three-dimensional dwelling size modeling method based a two-dimensional dwelling size diagram, which comprises the following steps: (1) constructing a database consisting of two-dimensional dwelling size diagram modeling elements and three-dimensional dwelling size diagram modeling elements; (2) selecting the two-dimensional dwelling size diagram in the form of an imageformat and performing vectorization on the two-dimensional dwelling size diagram on the basis of the database consisting of the two-dimensional dwelling size diagram modeling elements and the three-dimensional dwelling size diagram modeling elements; and (3) automatically constructing the three-dimensional diagram on the basis of the vectorized two-dimensional dwelling size diagram. The inventionprovides a three-dimensional dwelling size modeling method based on a two-dimensional dwelling size diagram, which has the advantages of low modeling difficulty and high efficiency.
Owner:XIAN NEW VISION INFORMATION TECH CORP
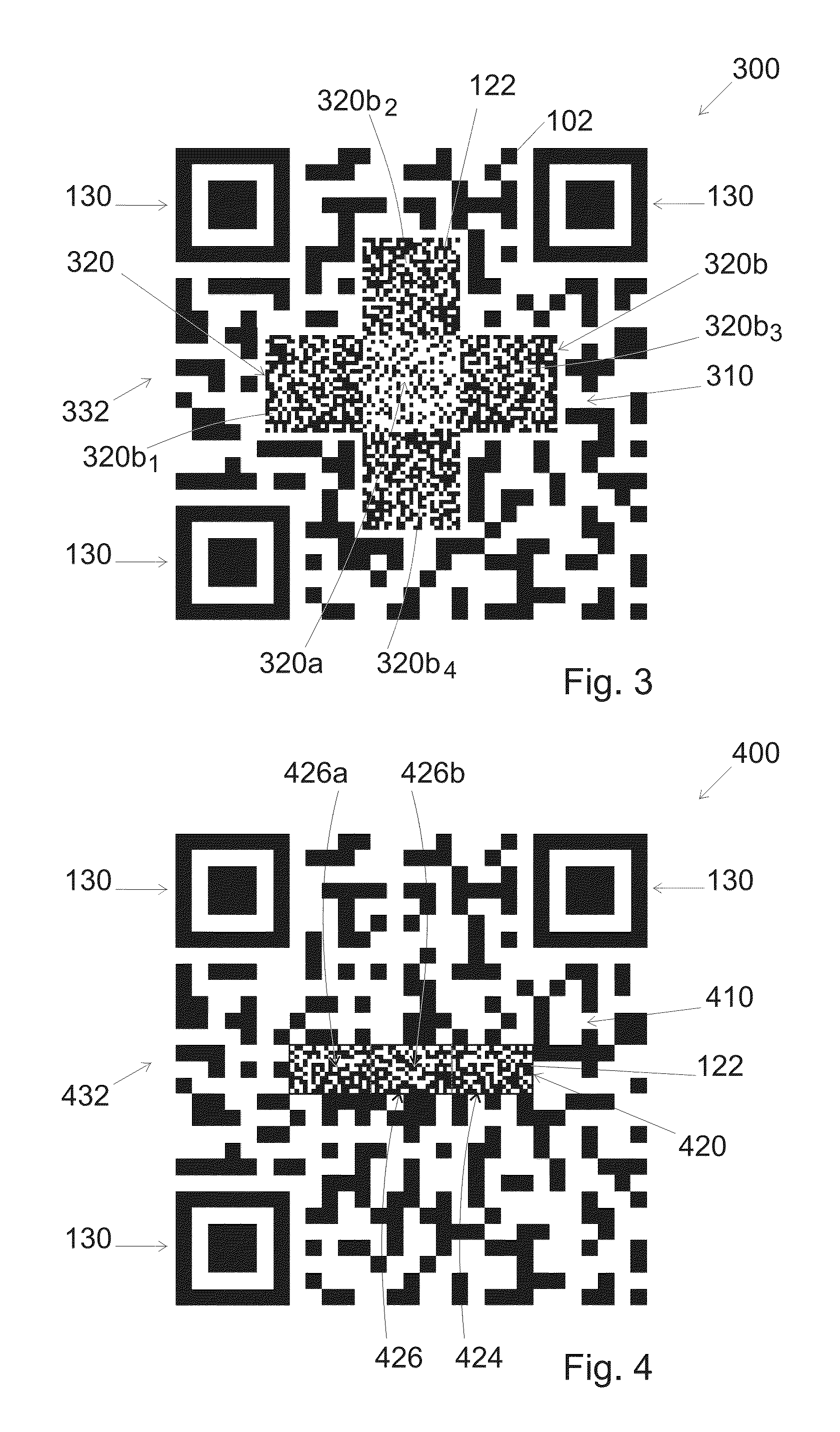
Two dimensional barcode and method of authentication of such barcode
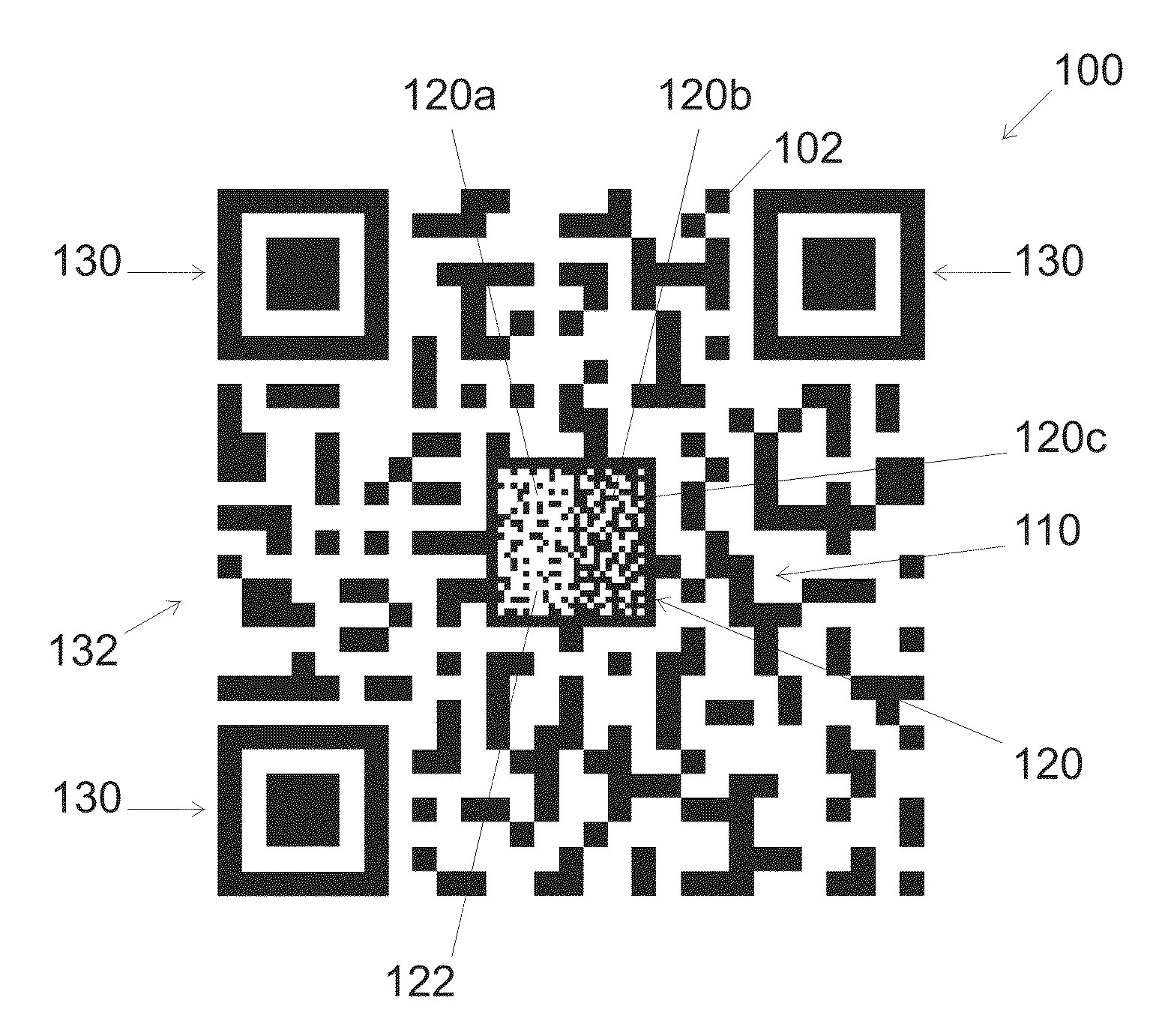
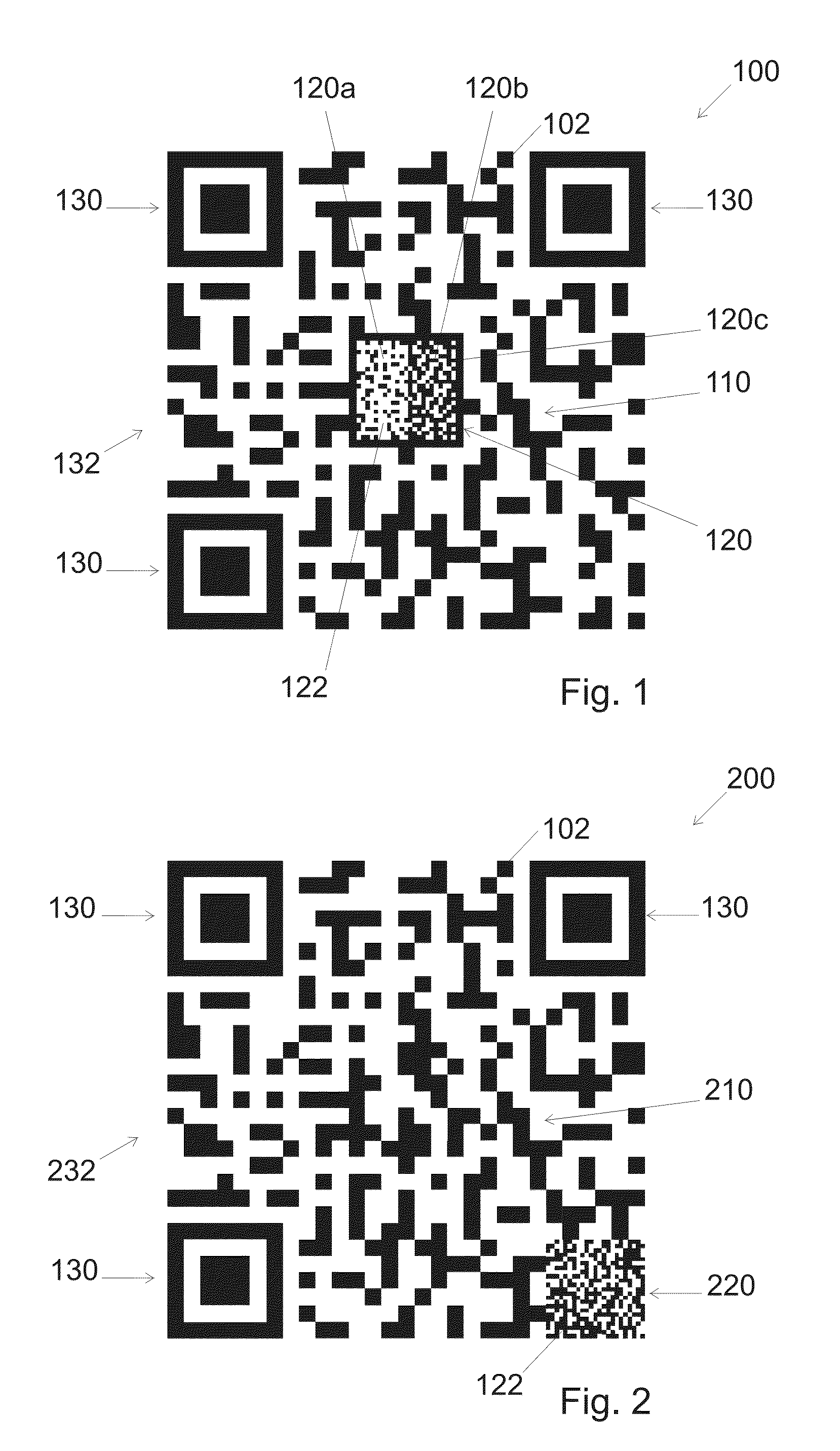
ActiveUS20160267369A1Easy to detectConvenient verificationPaper-money testing devicesRecord carriers used with machinesGraphicsBarcode reader
A method is disclosed for creating a 2D barcode. In an embodiment, the method includes: embedding primary information that can be read by a 2D-barcode-reader in a primary information pattern, and embedding secondary information that is made difficult to reproduce without alteration in a visible pattern. In an embodiment, the visible pattern is embedded within the barcode in at least one area that does not contain any primary information
Owner:SCANTRUST
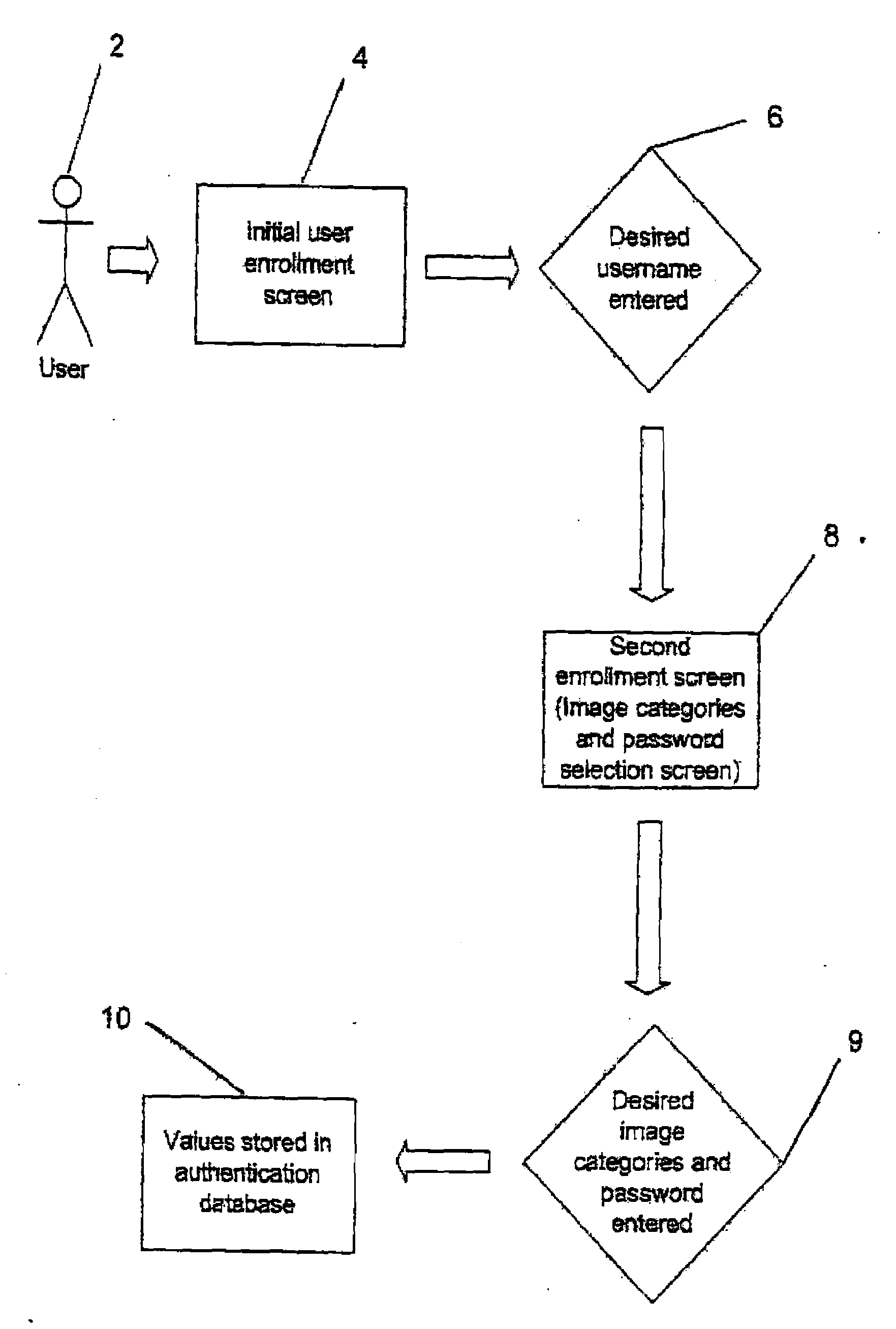
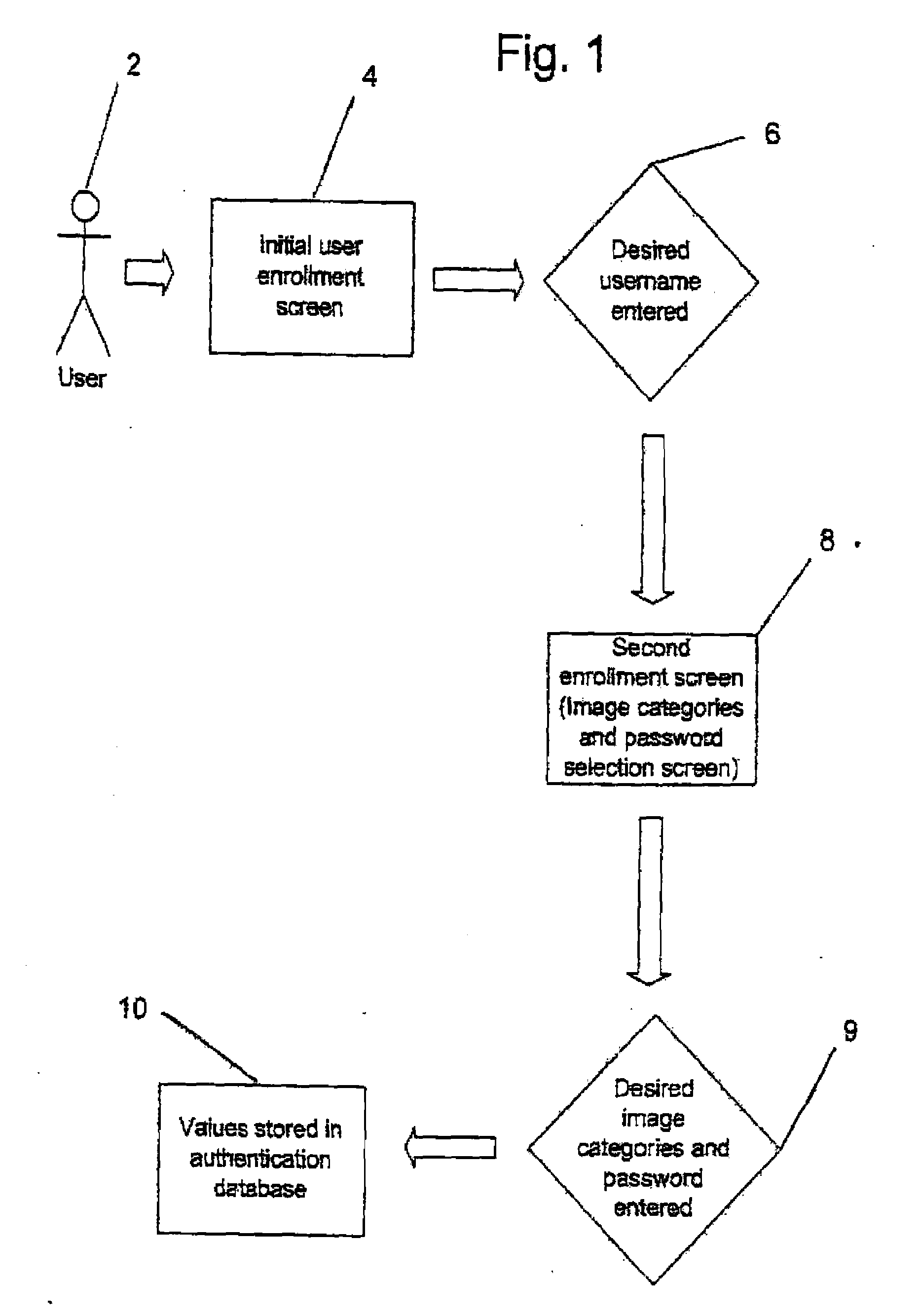
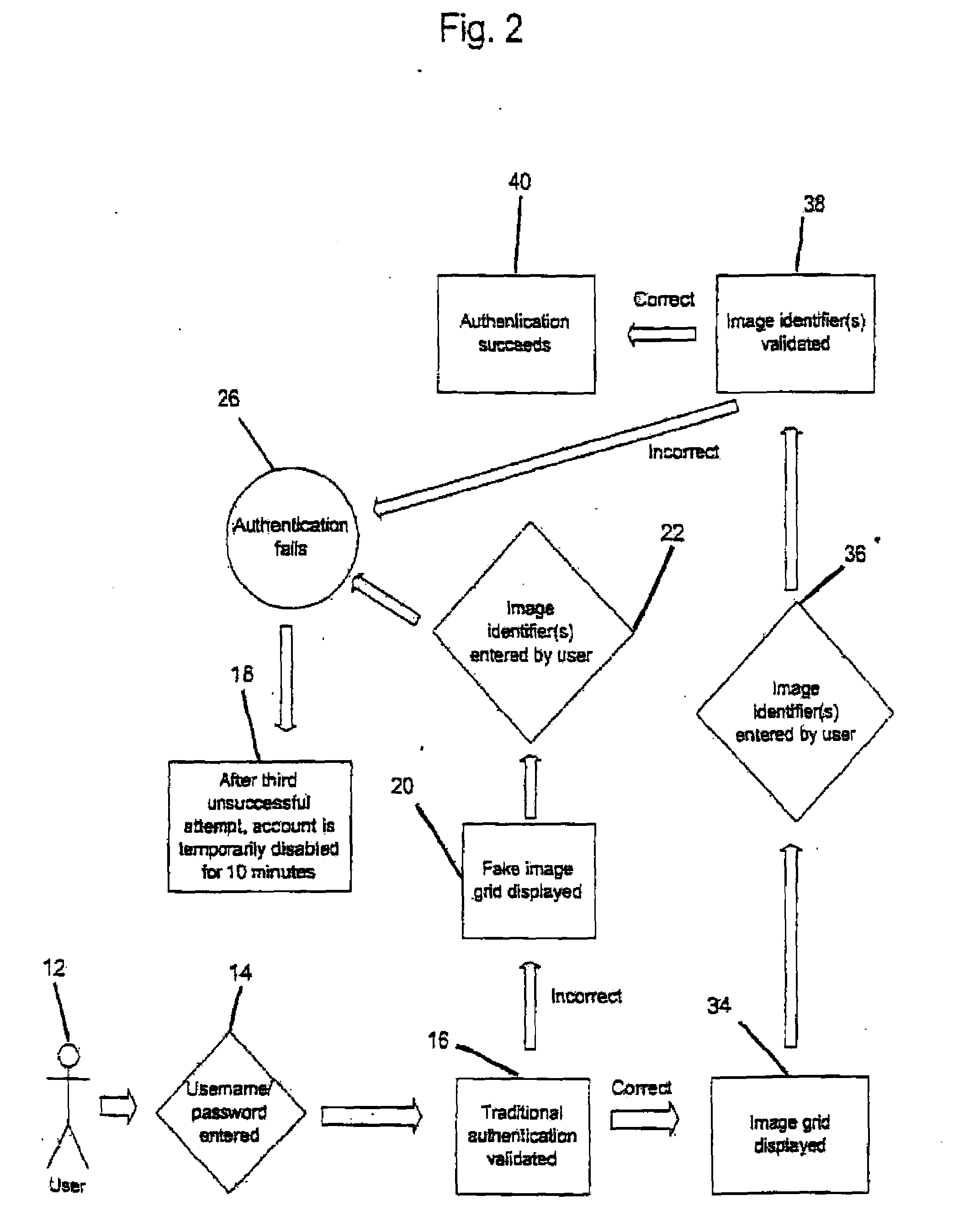
Graphical Image Authentication And Security System
ActiveUS20090077653A1Increase the lengthLock time be increasedDigital data processing detailsUnauthorized memory use protectionSafe systemInternet privacy
A method and system for protection of and secure access to a computer system or computer network from a portable device. The method includes the steps of receiving a first login account identifier, such as a user name from a user in communication with the computer system or network. A determination is made if the user is recognized and enrolled from the first login account identifier. If the user is recognized, a series of randomly generated visual images is displayed including one visual image from an image category which has been pre-selected by the user upon enrollment. An image category identifier is randomly assigned to each visual image in the series. An image category identifier is entered and received. If the login account identifier and the image category are validated, access is permitted to the computer system or network from the portable device.
Owner:DEFENDERS OF THE AMERICAN DREAM LLC
Storage battery state of charge estimation method based on self-adaptive unscented Kalman filtering
InactiveCN103744026AReal-time accurate measurementLow real-timeElectrical testingBattery state of chargeEstimation methods
The invention discloses a storage battery state of charge estimation method based on self-adaptive unscented Kalman filtering. The method comprises that: performance of a storage battery is tested via an HPPC test so that HPPC test data of the storage battery are acquired; parameter identification is performed on the basis of the acquired HPPC test data of the storage battery so that storage battery model parameters are acquired; and an SOC of the storage battery is estimated on the basis of the acquired storage battery model parameters via an AUKF algorithm. According to the storage battery state of charge estimation method based on the self-adaptive unscented Kalman filtering, defects in the prior art that manual amount of labor is large, real-time performance is poor, operation difficulty is high, test and calculation accuracy is low, etc. can be overcome so that advantages of being small in manual amount of labor, great in real-time performance, low in operation difficulty and high in test and calculation accuracy can be realized.
Owner:GUANGXI UNIVERSITY OF TECHNOLOGY
Bump array device having asymmetric gaps for segregation of particles
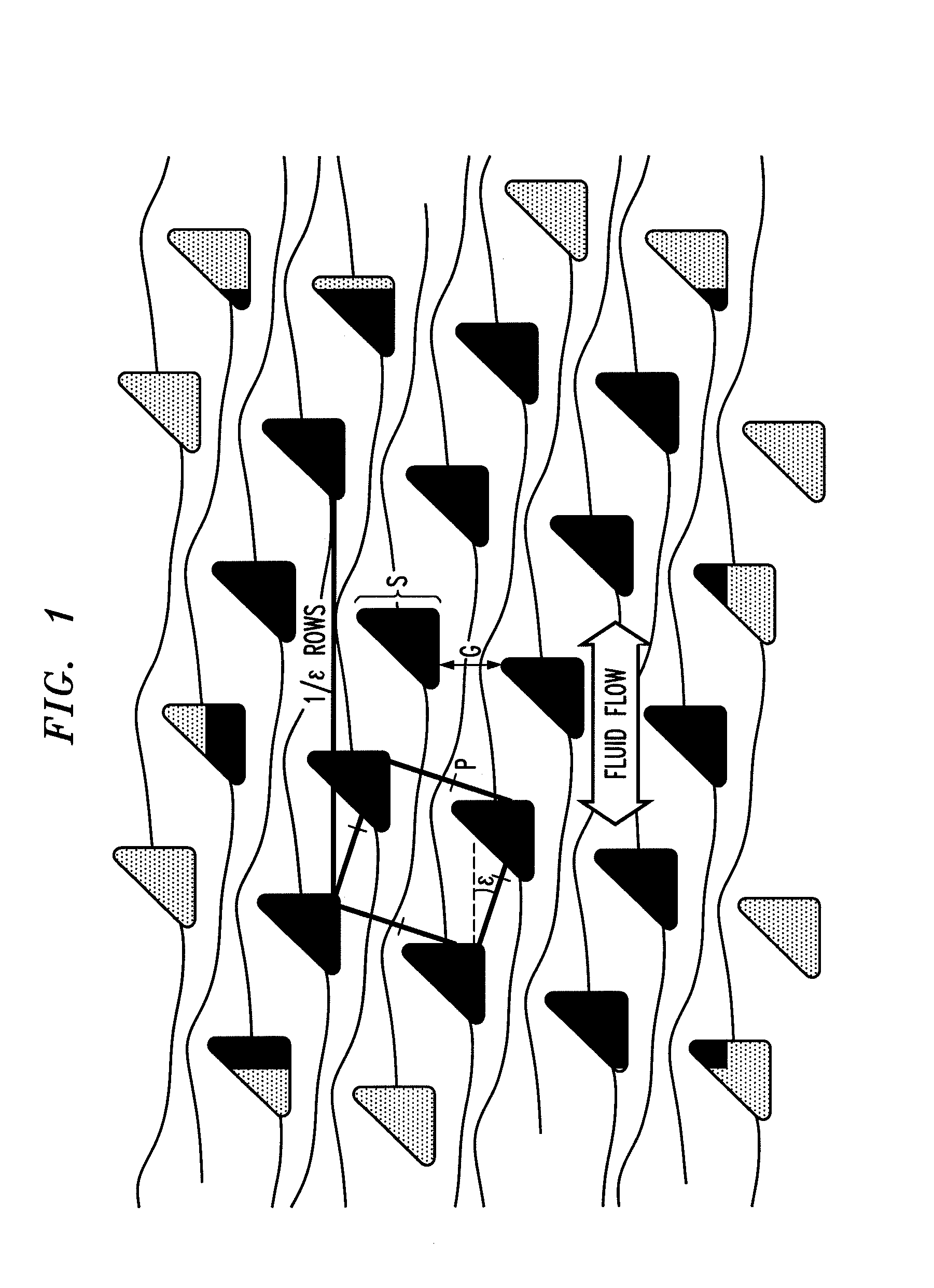
ActiveUS8579117B2Easy to operateReduce gapGas current separationComponent separationEngineeringAsymmetry
The disclosure relates to obstacle array devices (also known as bump array devices) for separating populations of particles by size. Improvements over previous obstacle array devices are realized by causing the fluid velocity profile across gaps between obstacles to be asymmetrical with respect to the plane that bisects the gap and is parallel to the direction of bulk fluid flow. Such asymmetry can be achieved by selecting the shape(s) of the obstacles bounding the gap such that the portions of the obstacles upstream from, downstream from, or bridging the narrowest portion of the gap are asymmetrical with respect to that plane. Improvements are also realized by using obstacles that have sharp edges bounding the gaps. Other improvements are realized by selecting obstacle shapes such that the critical particle dimensions defined by the gaps in two different fluid flow directions differ.
Owner:THE TRUSTEES OF PRINCETON UNIV
Pet exercise toy
InactiveUS20080083378A1Increase dispensing rateSmall sizeAnimal feeding devicesOther apparatusEngineeringCompanion animal
The invention relates to a pet toy that may be filled with food or scented material to attract and maintain the animal's interest while the pet tries to extract the material contained inside. The toy is preferably made with two nested housings with each housing containing one or more holes in the sidewall. Some of the holes in the housings may be adjustably aligned to create a opening in the side wall of the toy that permits materials inside the toy to fall out. The space between the housings is configured to trap crumbs or other particulate material that might create an undesirable mess if allowed to fall out of the toy.
Owner:PEARCE ROGER
Three-dimensional object detection method based on view cone point cloud
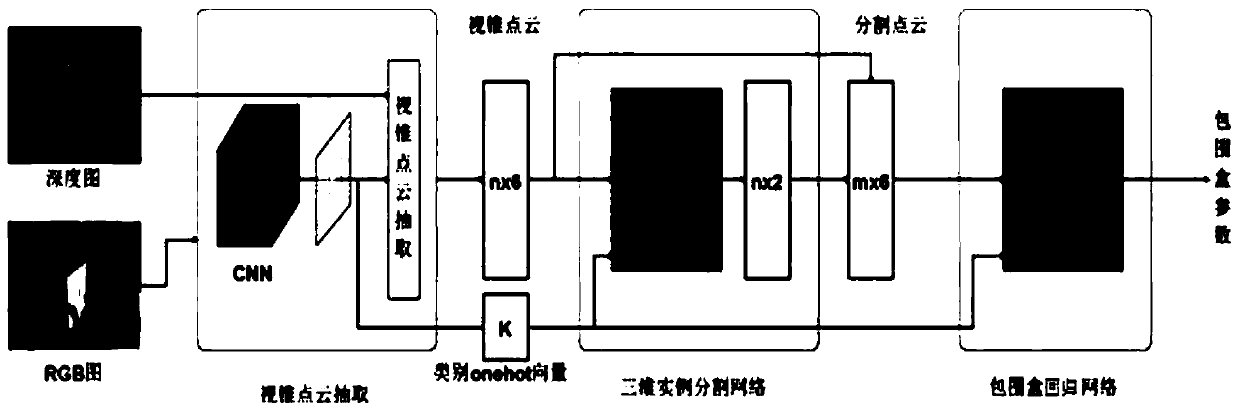
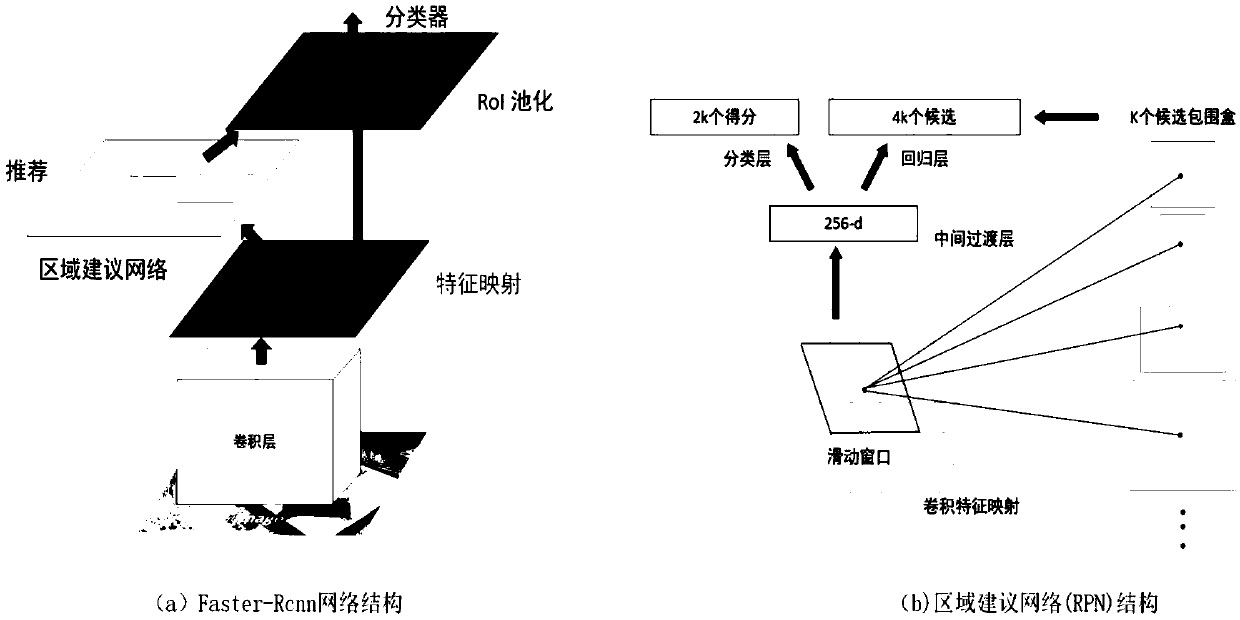
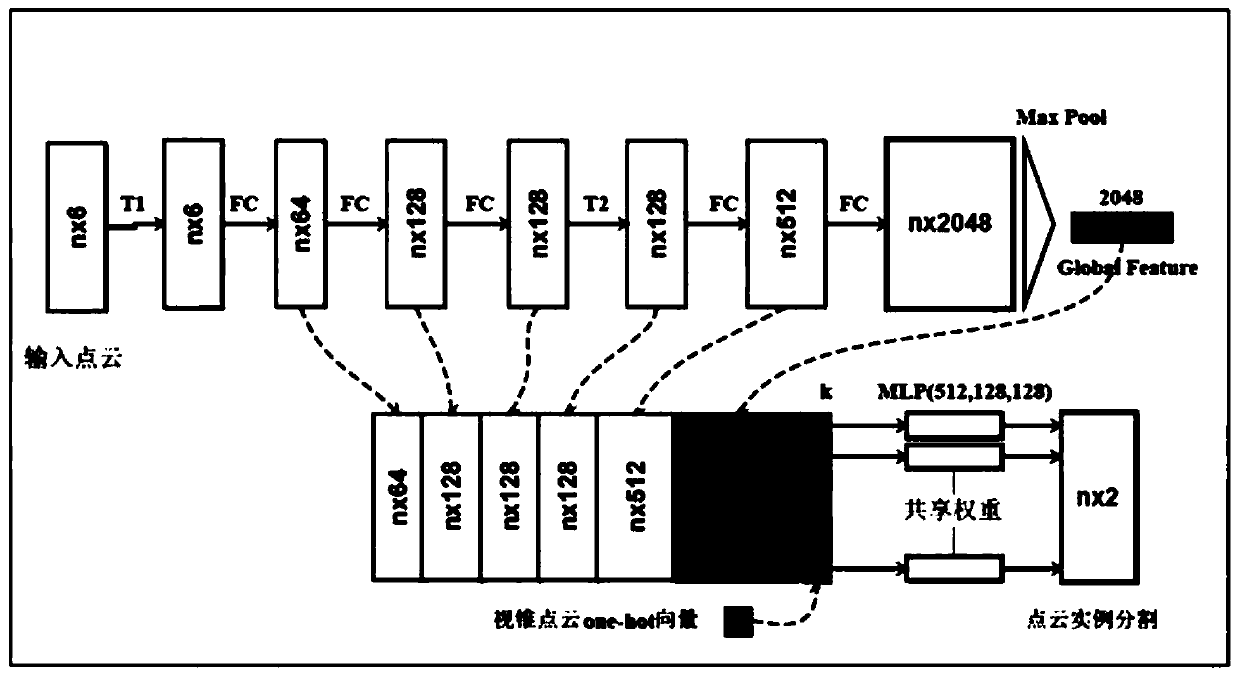
The invention discloses a three-dimensional object detection method based on a view cone point cloud. The RGB image and the point cloud image are collected and annotated, the annotated RGB image dataset and the point cloud image data set are obtained, and the data set is used as a training sample and a test sample. It mainly consists of three networks: cone point cloud extraction network based ontwo-dimensional object detection, three-dimensional object segmentation network based on Point net and three-dimensional bounding box regression network based on offset residuals. The three networksare trained in turn, and the training output of the previous network is used as the input of the next network. The super parameters of each neural network model are set, and the three-dimensional object detection network model is trained by Tensorflow. When the cost loss function is reduced to the ideal degree and the training reaches the required maximum iteration number, the training model is generated. The point cloud image data set is inputted into the trained model, and the 3D object detection result is output. The method of the invention is more perfect and more difficult than the existing three-dimensional object detection method.
Owner:QINGDAO ACADEMY OF INTELLIGENT IND
Flexible Intramedullary Nail
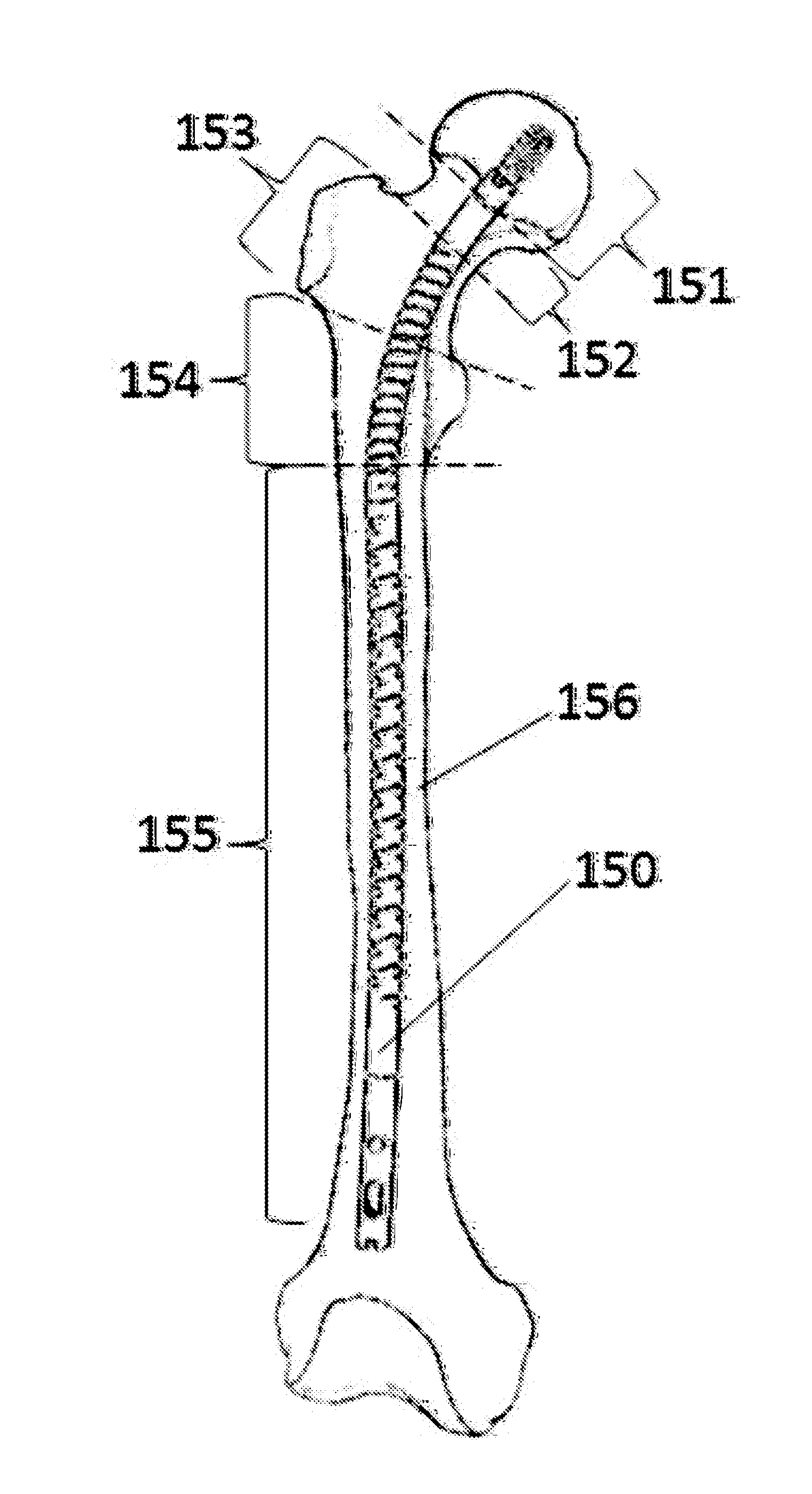
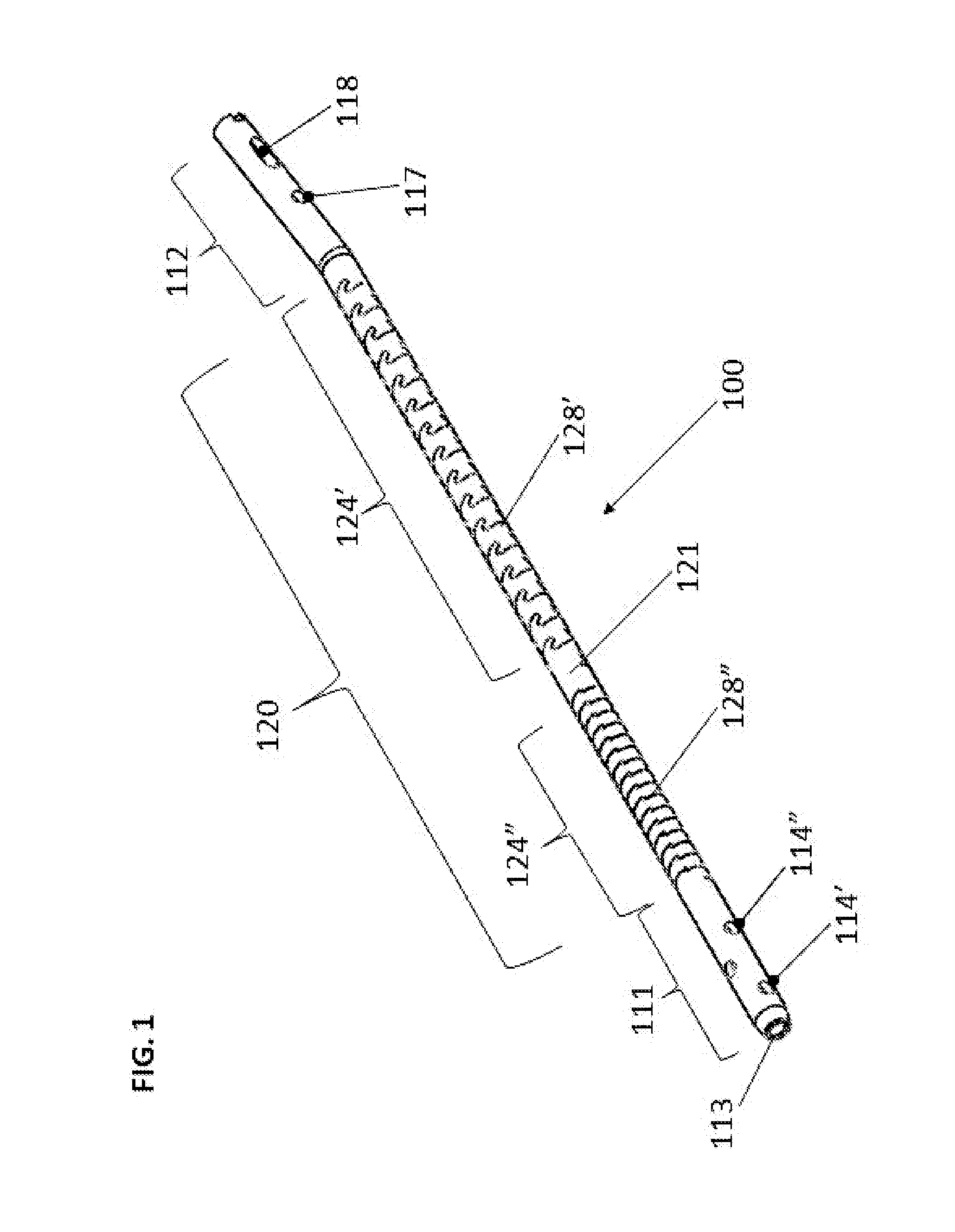
ActiveUS20140114312A1Prevent penetrationErosion is goodInternal osteosythesisJoint implantsFlexible intramedullary nailEngineering
A flexible intramedullary nail is disclosed that is manufactured from a biocompatible rigid material and having a substantially cylindrical hollow body, a leading segment with an entry hole at a distal end and at least one securing means and a trailing segment having a trailing edge and an attachment mechanism. The body has at least one flexible center section, each having at least one slot to provide flexibility. In one embodiment the at least one slot follows a sinuous, serpentine path to form a plurality of interlocking teeth that can follow a helical or a concentric path. Each of the slots has a proximal end and a distal end, with the proximal end being spaced from the trailing segment and the distal end being spaced from the leading segment. When multiple slots are incorporated, the proximal end of a slot is spaced from a distal end of a subsequent slot. The first of the at least one flexible center section and a second of the at least one flexible center section can be separated by a non-slotted section. The nail can be used with a flexible insertion shaft or a locking shaft.
Owner:FLEX TECH
High-purity fishy smell and foreign odor-free fish collagen protein peptide and preparation method thereof
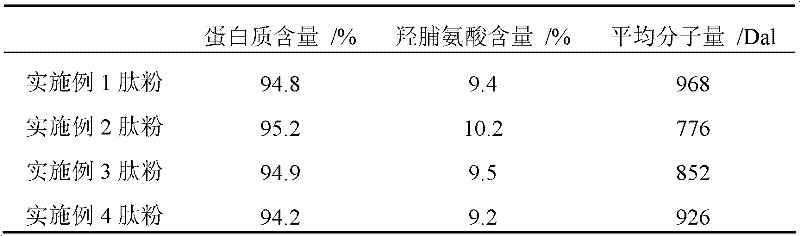
The invention discloses a high-purity fishy smell and foreign odor-free fish collagen protein peptide and a preparation method thereof. The preparation method comprises the following steps: cleaning fish skins, and then cutting into blocks and mincing; performing stirring treatment with NaCl solution; centrifugally degreasing to remove paraprotein; adding water to regulate the pH value of initial slurry to be 8.0-8.5; performing combined gradient enzymolysis on alkali protease and neutral protease; deactivating enzyme after the enzymolysis is ended; performing adsorption bleaching by activated carbon; and then performing rough filtration, fine filtration, evaporation concentration and spray drying to prepare the high-purity fishy smell and foreign odor-free fish collagen protein peptide. The high-purity fishy smell and foreign odor-free fish collagen protein peptide disclosed by the invention has a simple process and is easy to industrial production; fishy smell, foreign odor and non-collagen proteins are fully removed in production; the low-temperature biological enzymolysis technology is adopted, and other substances are not added, thereby, the product quality is improved; an obtained fish collagen protein peptide powder has the characteristics the content of amino acid hydroxyproline is not less than 9 percent, and the average molecular weight is lower than 1000Dal; no fishy smell or foreign odor cannot generated, and obvious fishy smell or foreign odor also cannot be generated through heating treatment under the acid conditions. The high-purity fishy smell and foreign odor-free fish collagen protein peptide can be widely applied to processing of various foods and cosmetics as a green functional ingredient.
Owner:广州合诚实业有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com