Patents
Literature
1079results about "Data taking prevention" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
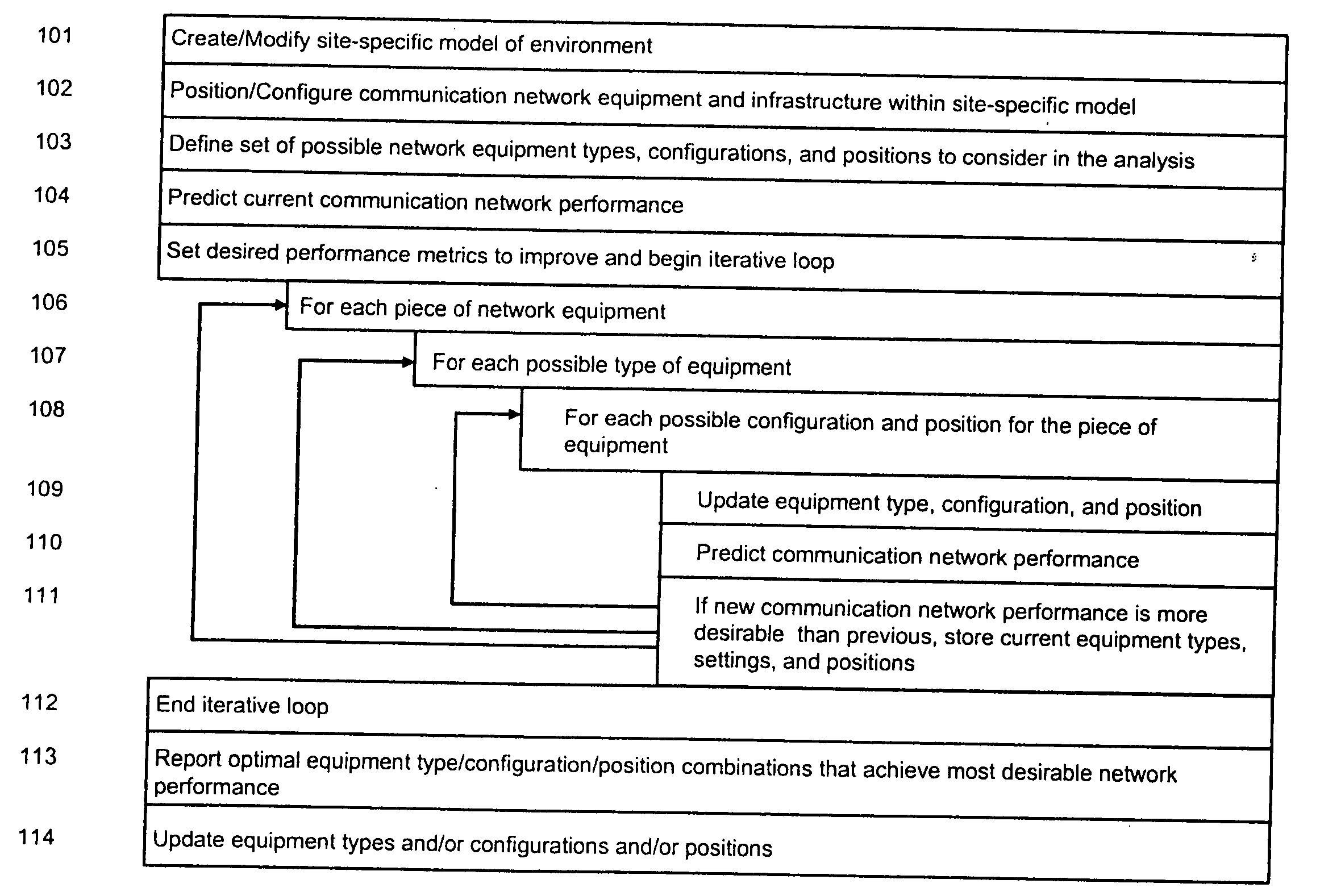
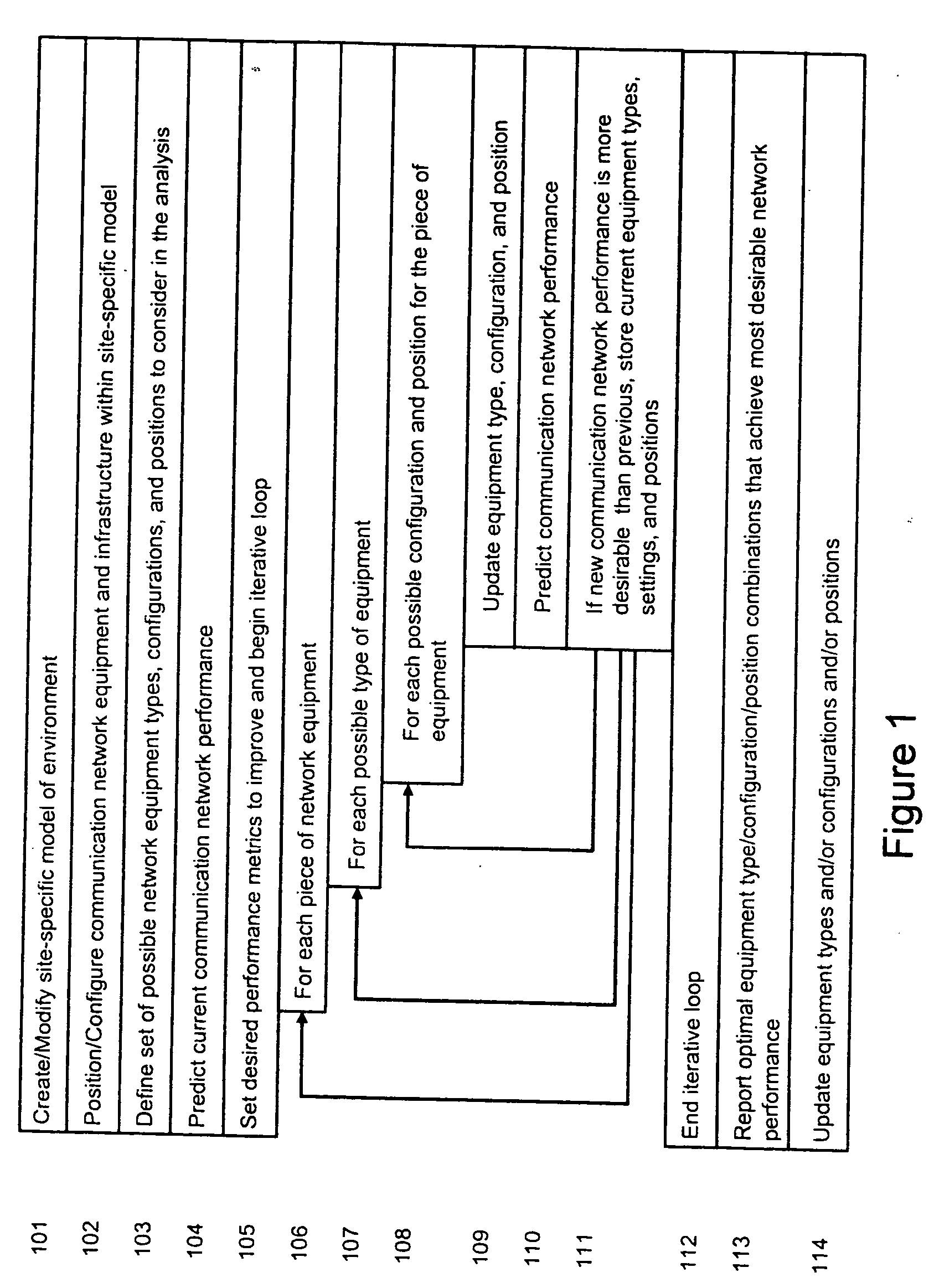
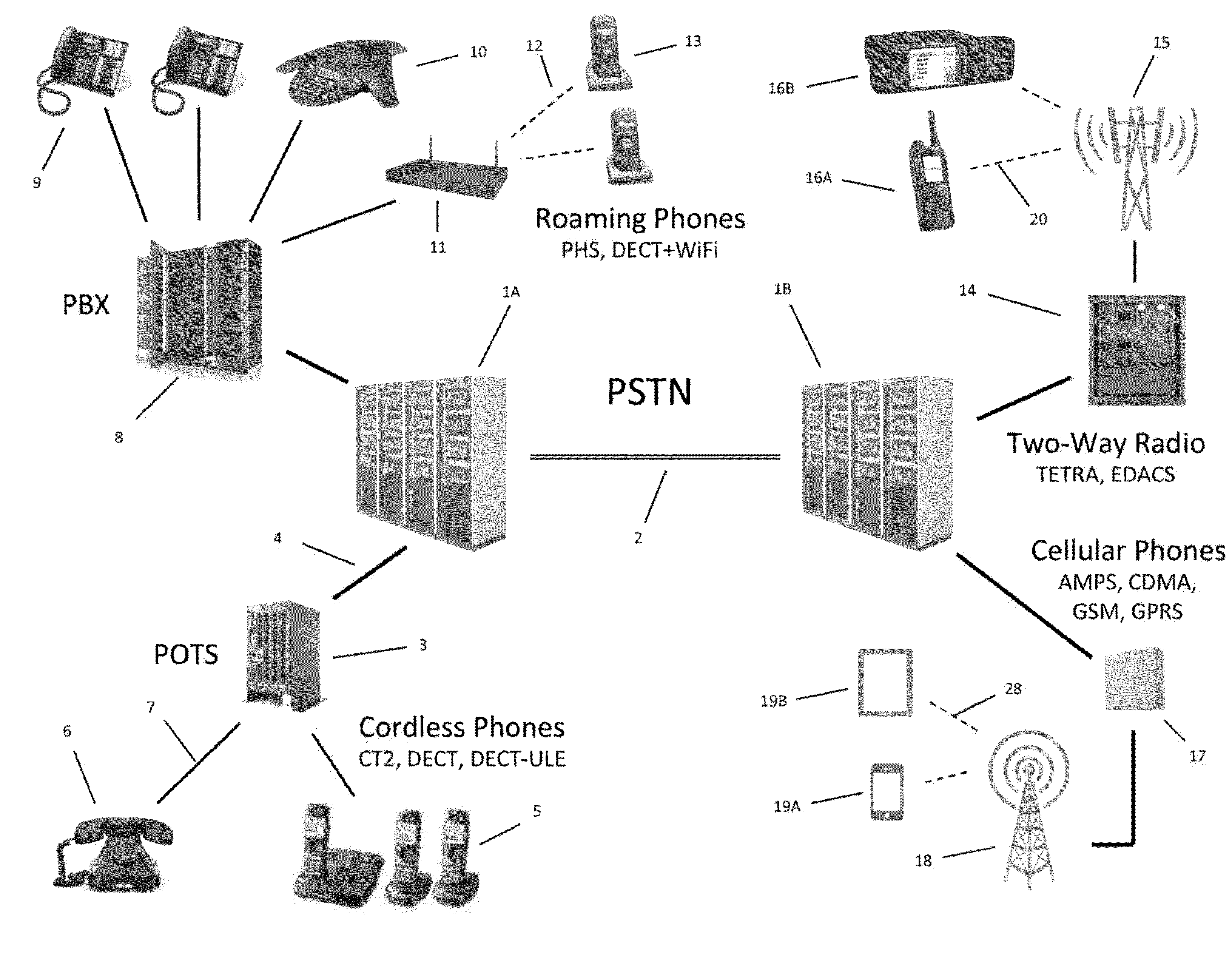
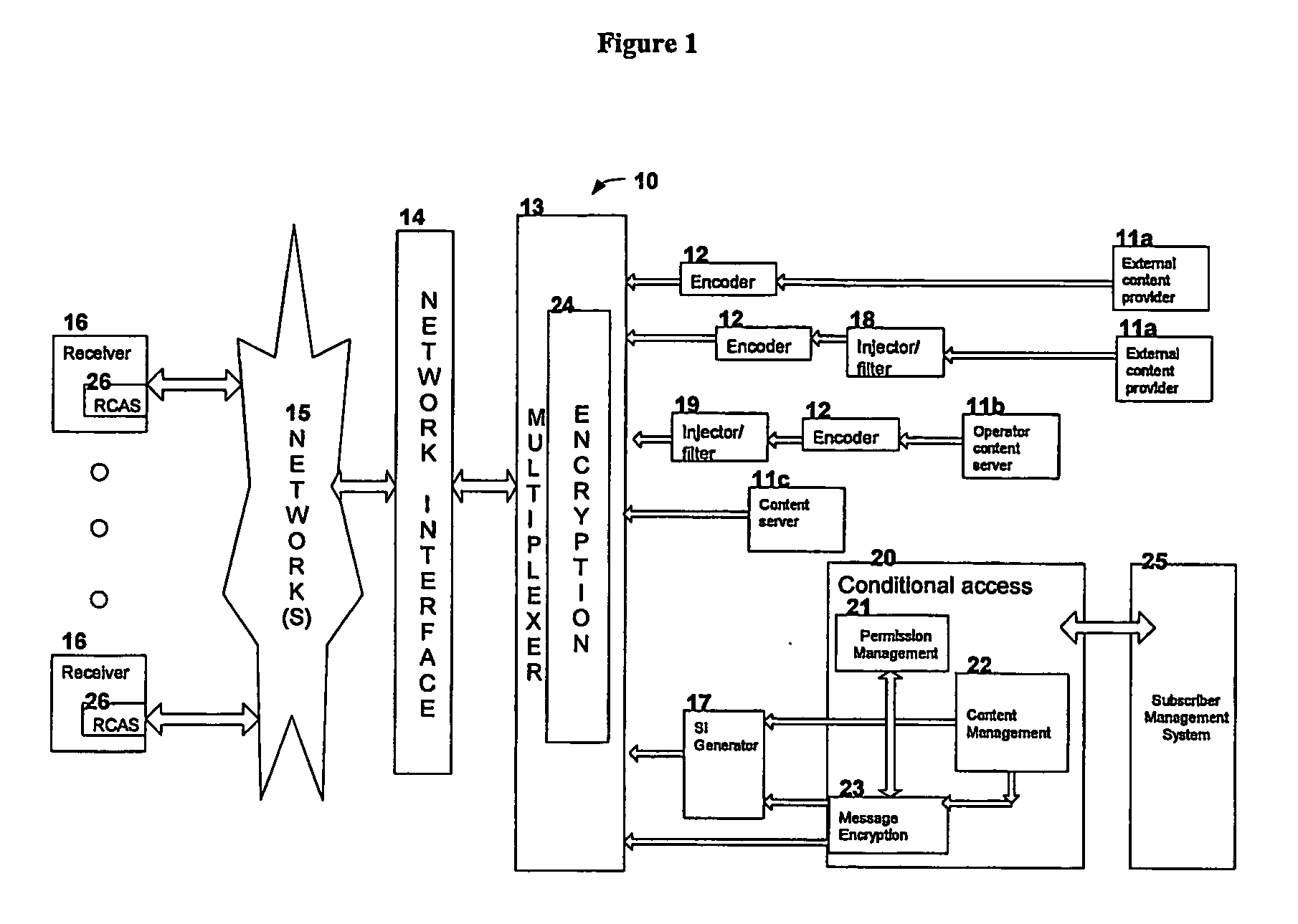
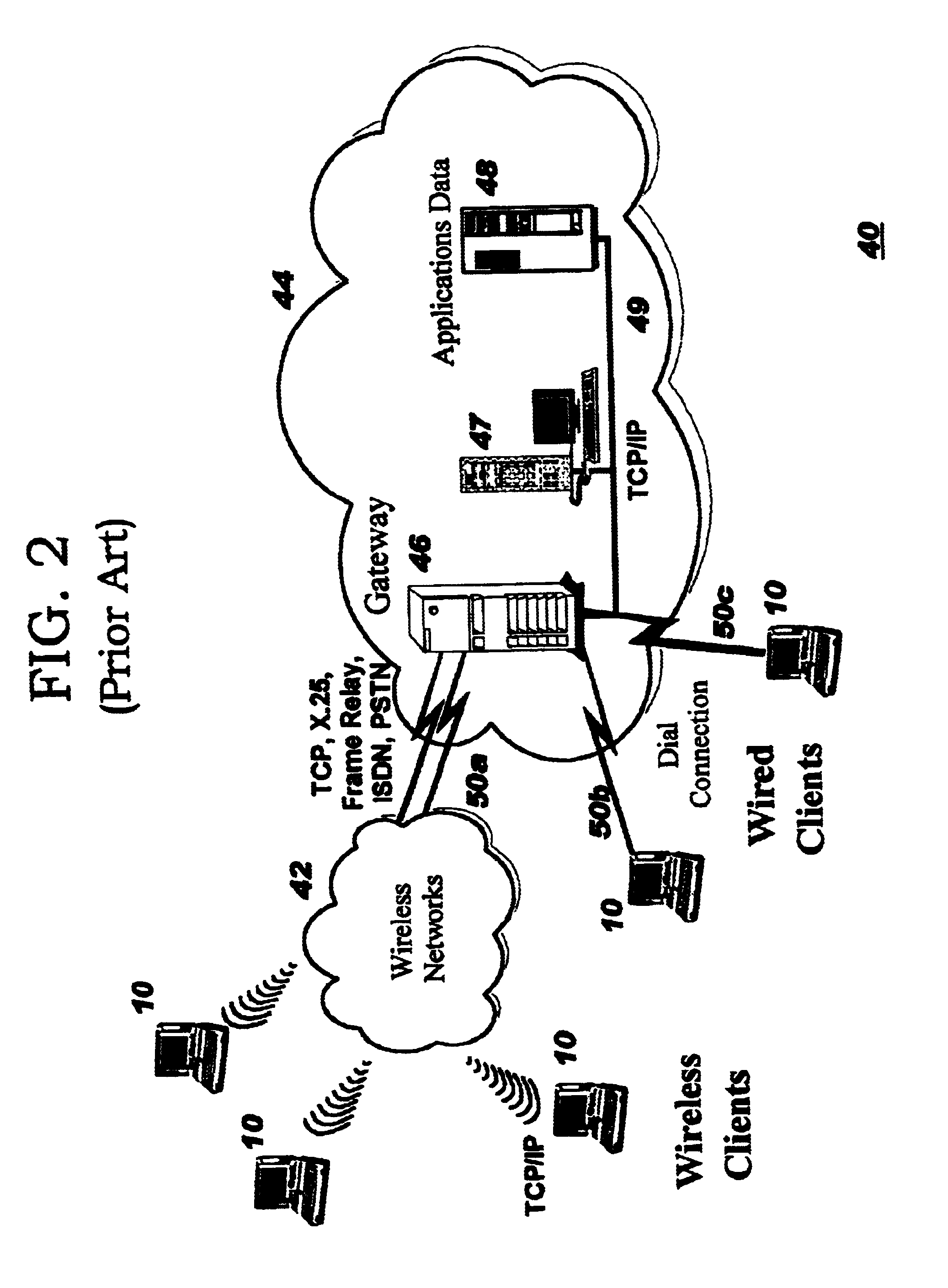
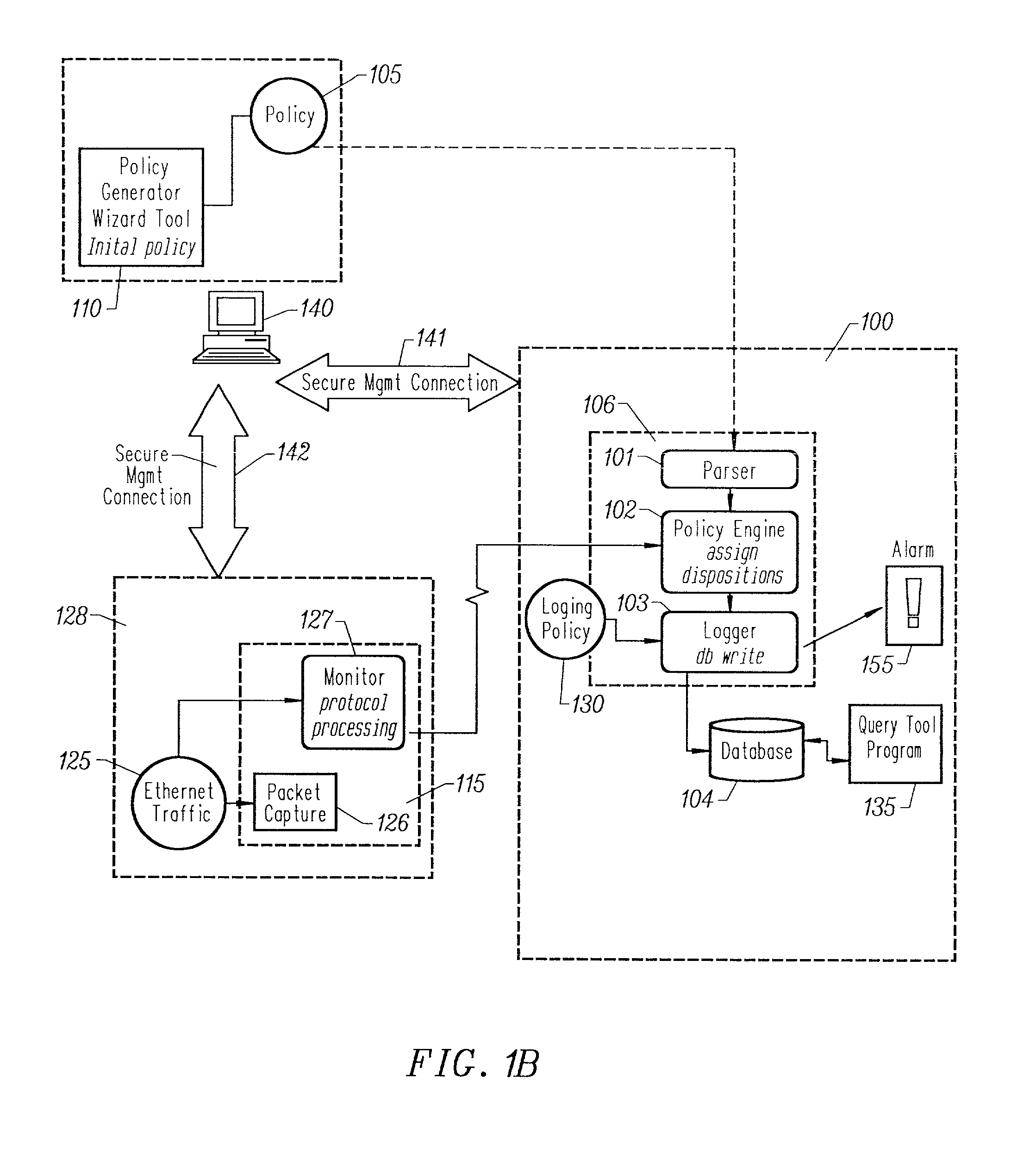
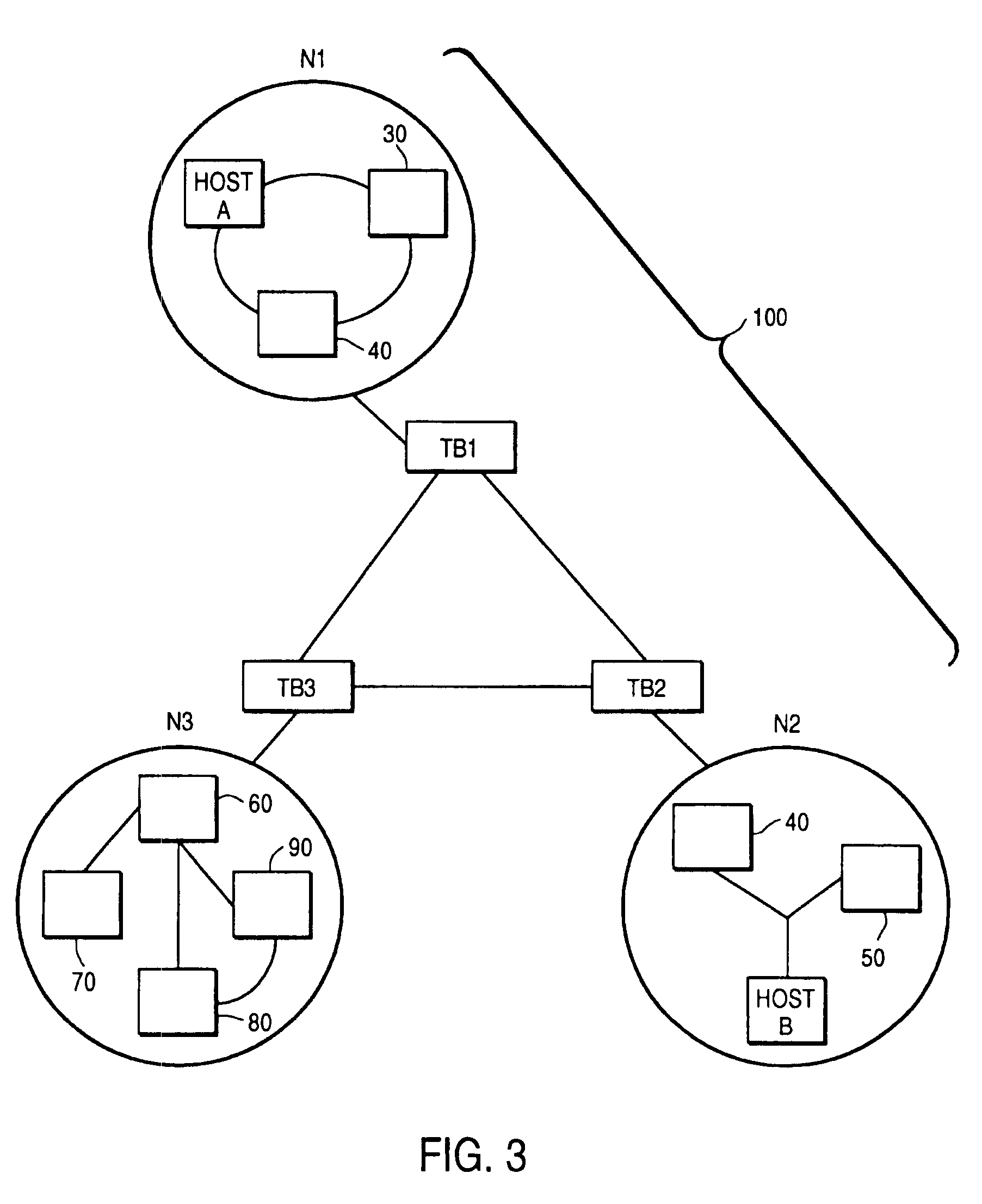
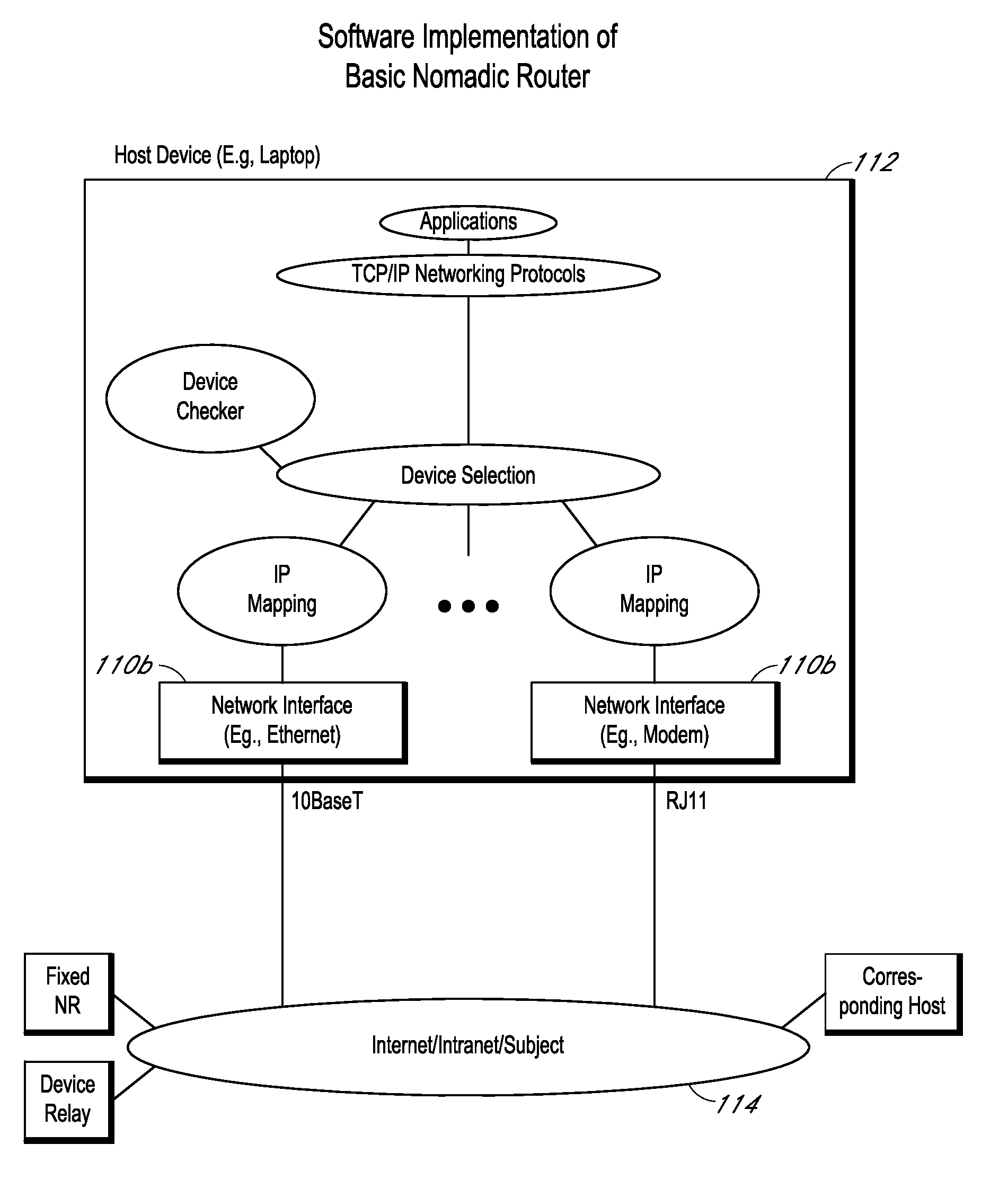
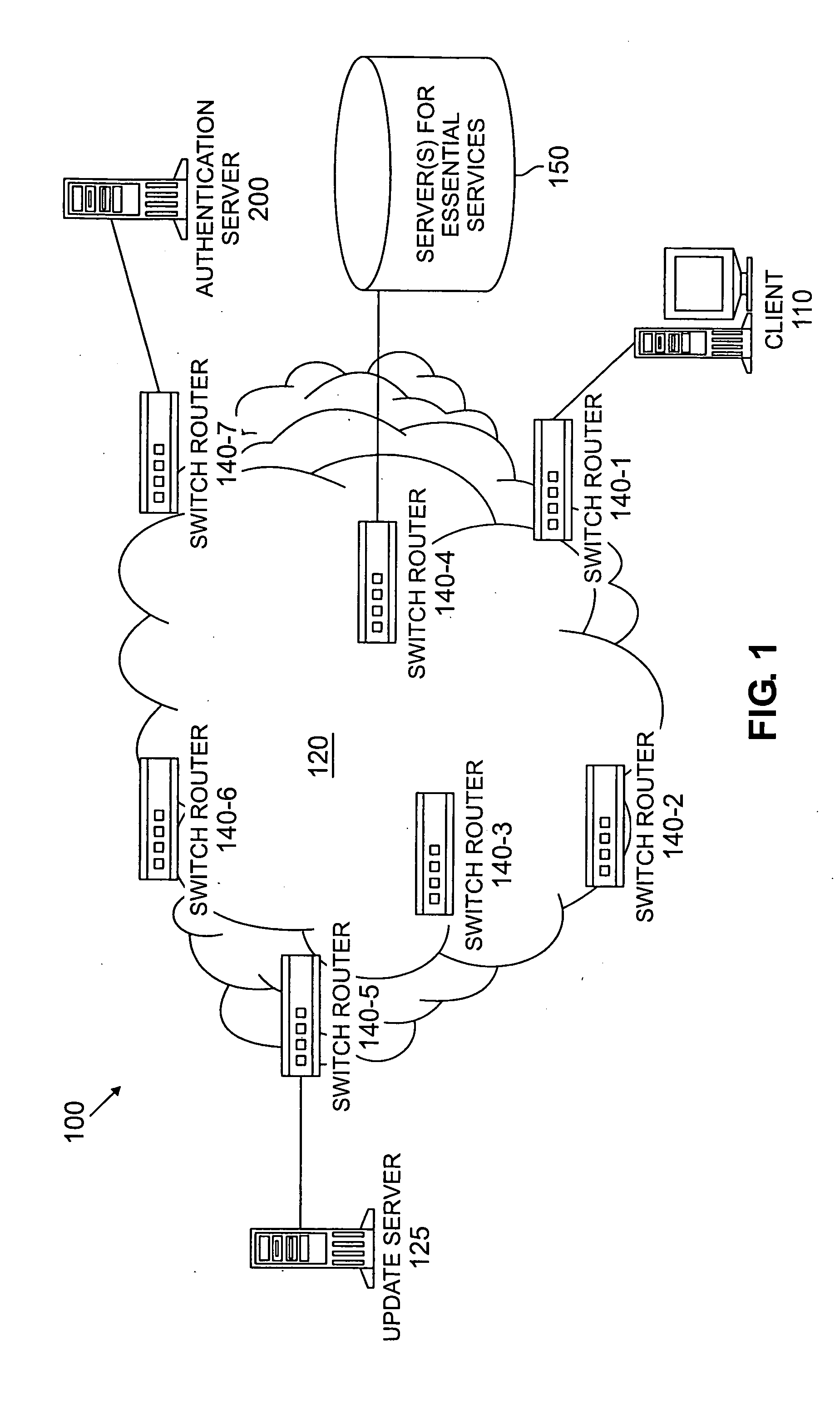
System and method for automated placement or configuration of equipment for obtaining desired network performance objectives and for security, RF tags, and bandwidth provisioning
ActiveUS20040236547A1Significant valueEasy to explainGeometric CADData taking preventionHard disc driveThe Internet
A method is presented for determining optimal or preferred configuration settings for wireless or wired network equipment in order to obtain a desirable level of network performance. A site-specific network model is used with adaptive processing to perform efficient design and on-going management of network performance. The invention iteratively determines overall network performance and cost, and further iterates equipment settings, locations and orientations. Real time control is between a site-specific Computer Aided Design (CAD) software application and the physical components of the network allows the invention to display, store, and iteratively adapt any network to constantly varying traffic and interference conditions. Alarms provide rapid adaptation of network parameters, and alerts and preprogrammed network shutdown actions may be taken autonomously. A wireless post-it note device and network allows massive data such as book contents or hard drive memory to be accessed within a room by a wide bandwidth reader device, and this can further be interconnected to the internet or Ethernet backbone in order to provide worldwide access and remote retrieval to wireless post-it devices.
Owner:EXTREME NETWORKS INC
Secure Dynamic Communication Network And Protocol
ActiveUS20160219024A1Increase the difficultyUsefulness of their knowledge would be short-livedMultiple keys/algorithms usageData taking preventionDigital dataData segment
In a secure cloud for transmitting packets of digital data, the packets may be repeatedly scrambled (i.e., their data segments reordered) and then unscrambled, split and then mixed, and / or encrypted and then decrypted as they pass through media nodes in the cloud. The methods used to scramble, split, mix and encrypt the packets may be varied in accordance with a state such as time, thereby making the task of a hacker virtually impossible inasmuch as he or she may be viewing only a fragment of a packet and the methods used to disguise the data are constantly changing.
Owner:LISTAT LTD
Computer security and management system
Owner:CISCO TECH INC
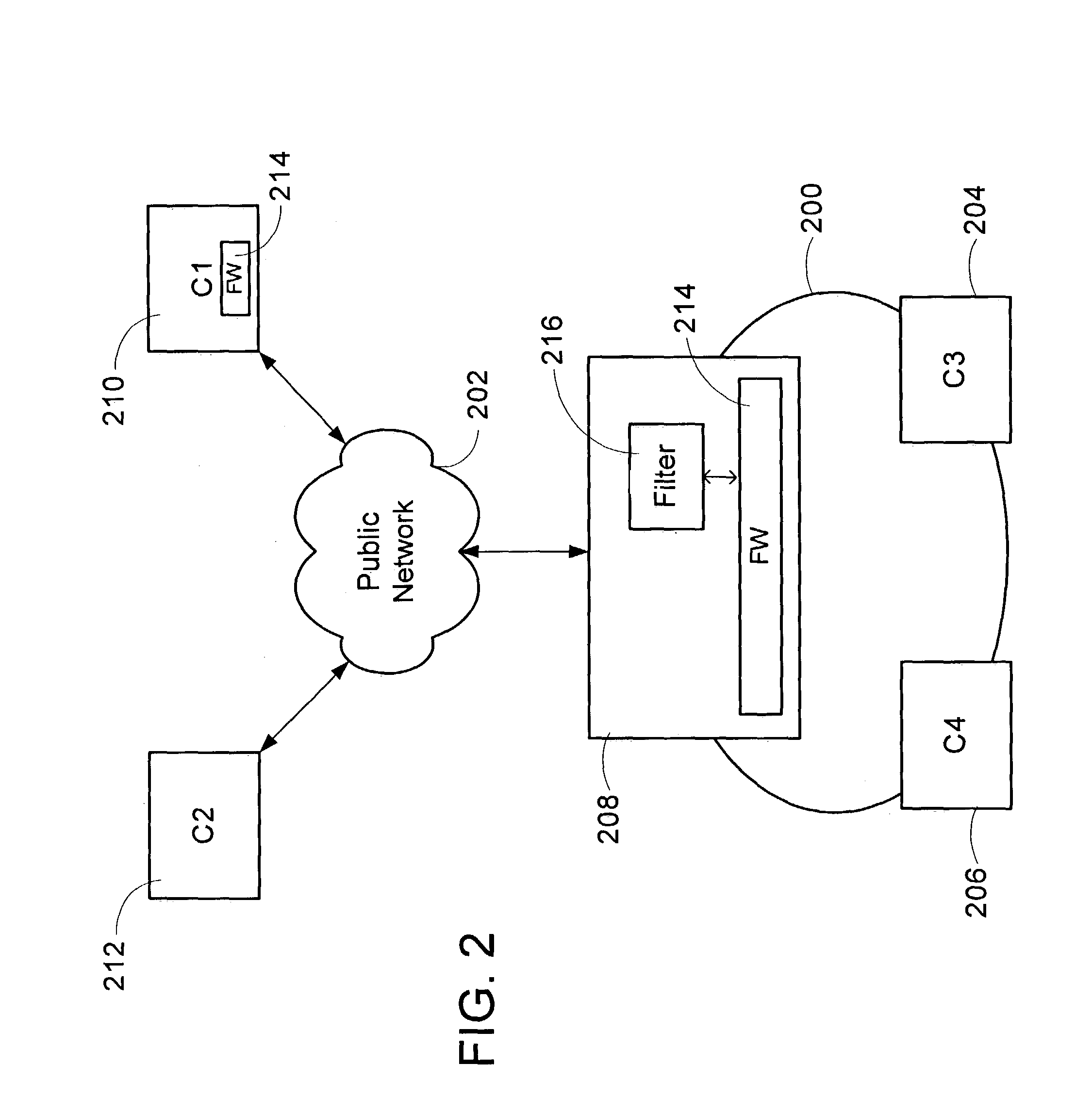
System, device and method for rapid packet filtering and processing
InactiveUS6496935B1Reducing and even eliminating amountImprove efficiencyLaser detailsData taking preventionFiltrationSession control
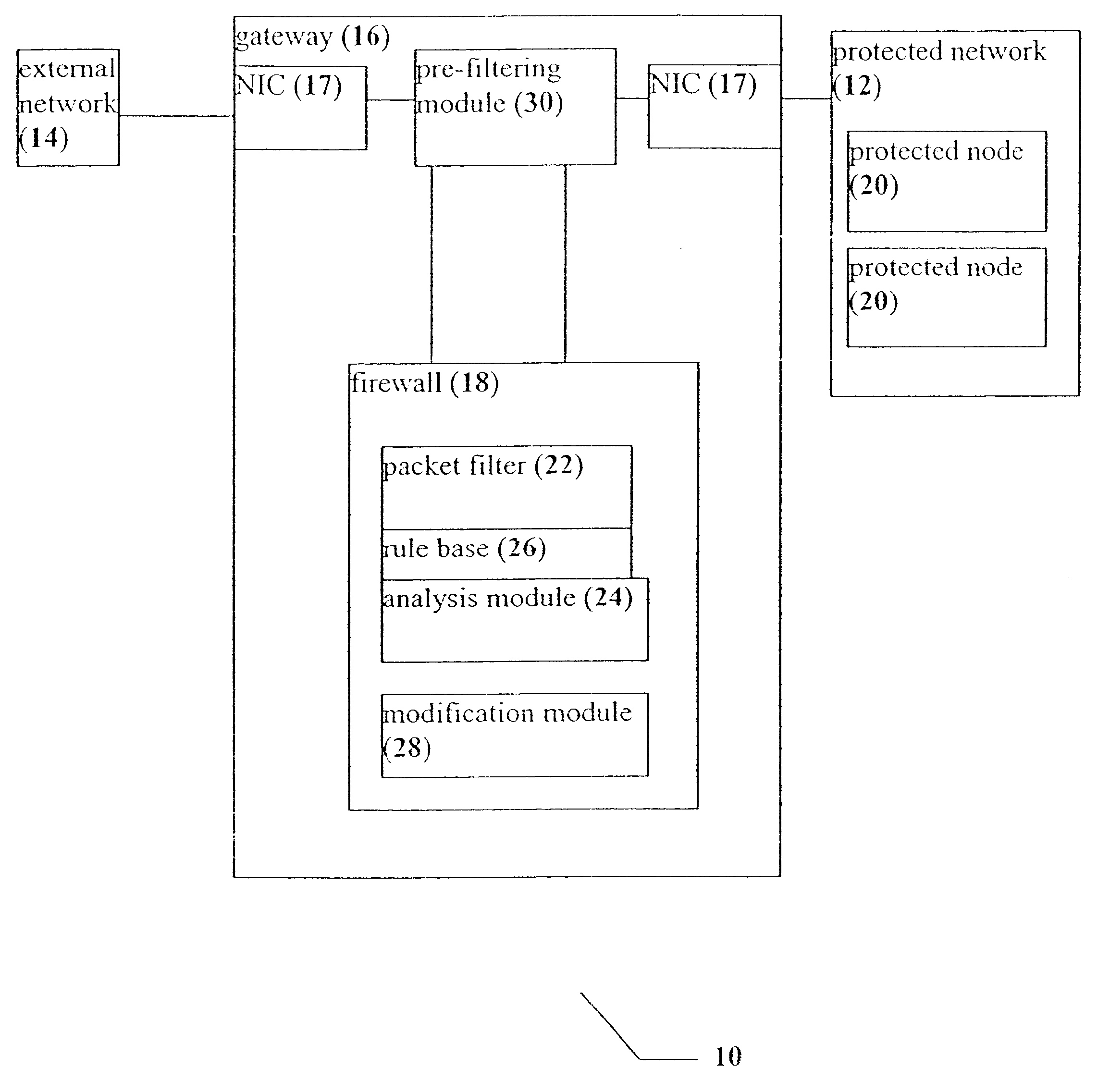
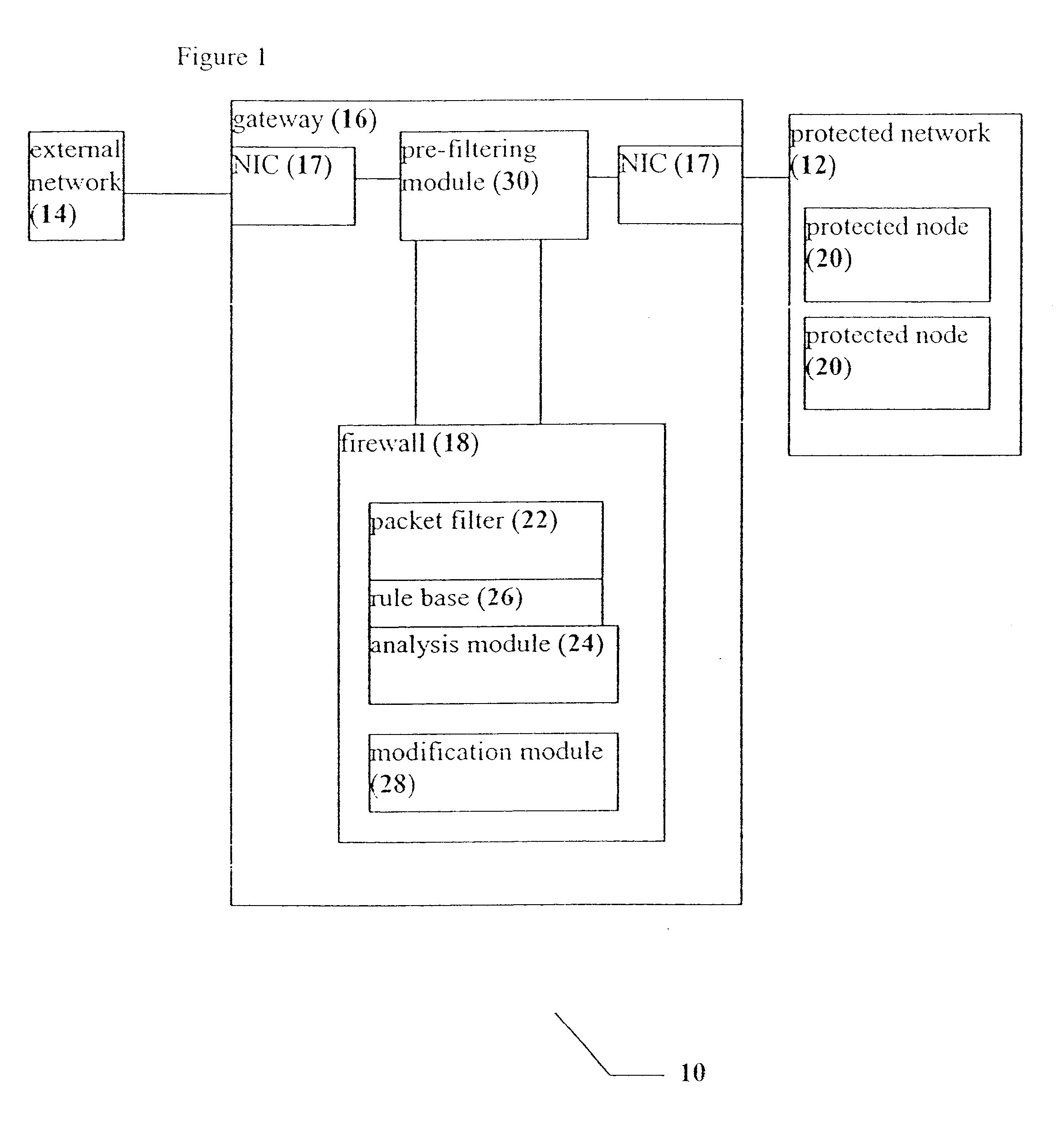
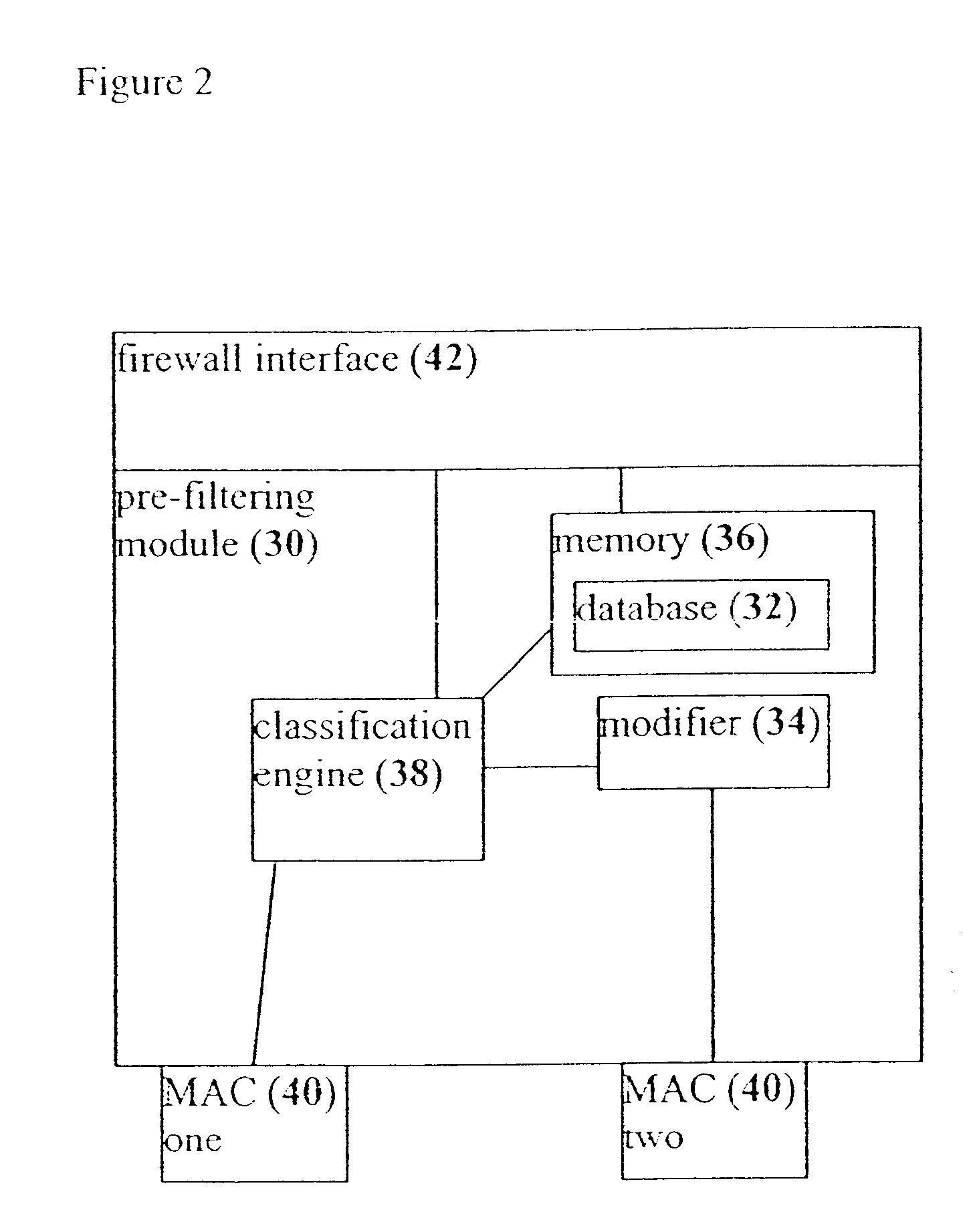
A system, a device and a method for accelerating packet filtration by supplementing a firewall with a pre-filtering module. The pre-filtering module performs a limited set of actions with regard to the packets, according to whether the packets are received from a connection which has been previously permitted by the firewall. If the packets are received from such a permitted connection, then the pre-filtering module forwards the packets to their destination, optionally performing one or more actions on the packets. Otherwise, the packets are forwarded to the firewall for handling. Preferably, once the firewall has transferred responsibility for the connection to the pre-filtering module, or "off-loaded" the connection, the firewall does not receive further packets from this connection until a timeout occurs for the connection, or a packet is received with particular session-control field values, such that the connection is closed. Optionally and preferably, the pre-filtering module is implemented as hardware.
Owner:CHECK POINT SOFTWARE TECH LTD
Apparatus and method for providing secure network communication
InactiveUS20020162026A1Eliminate attackEliminate needData taking preventionDigital data processing detailsFault toleranceIntelligent Network
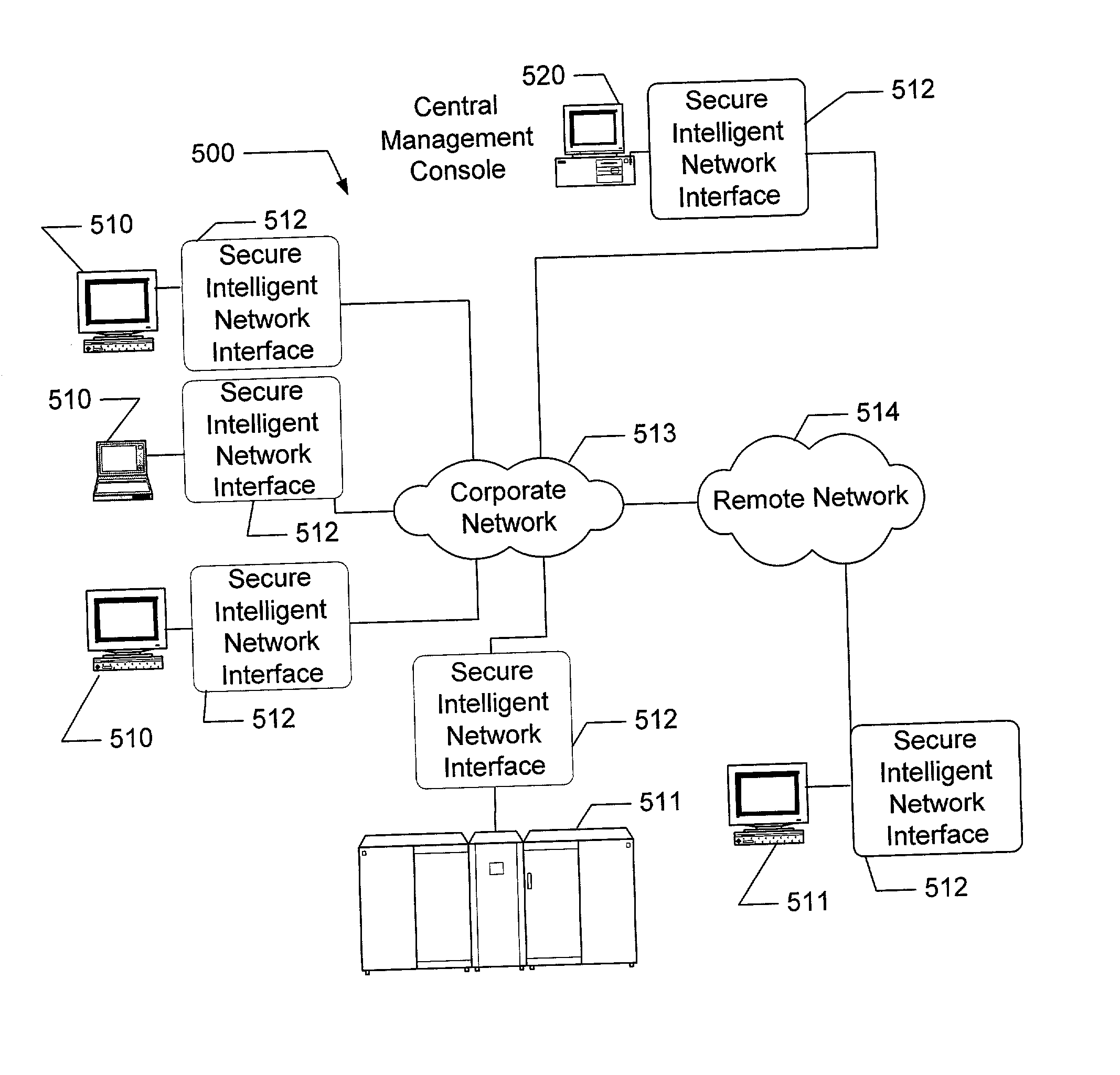
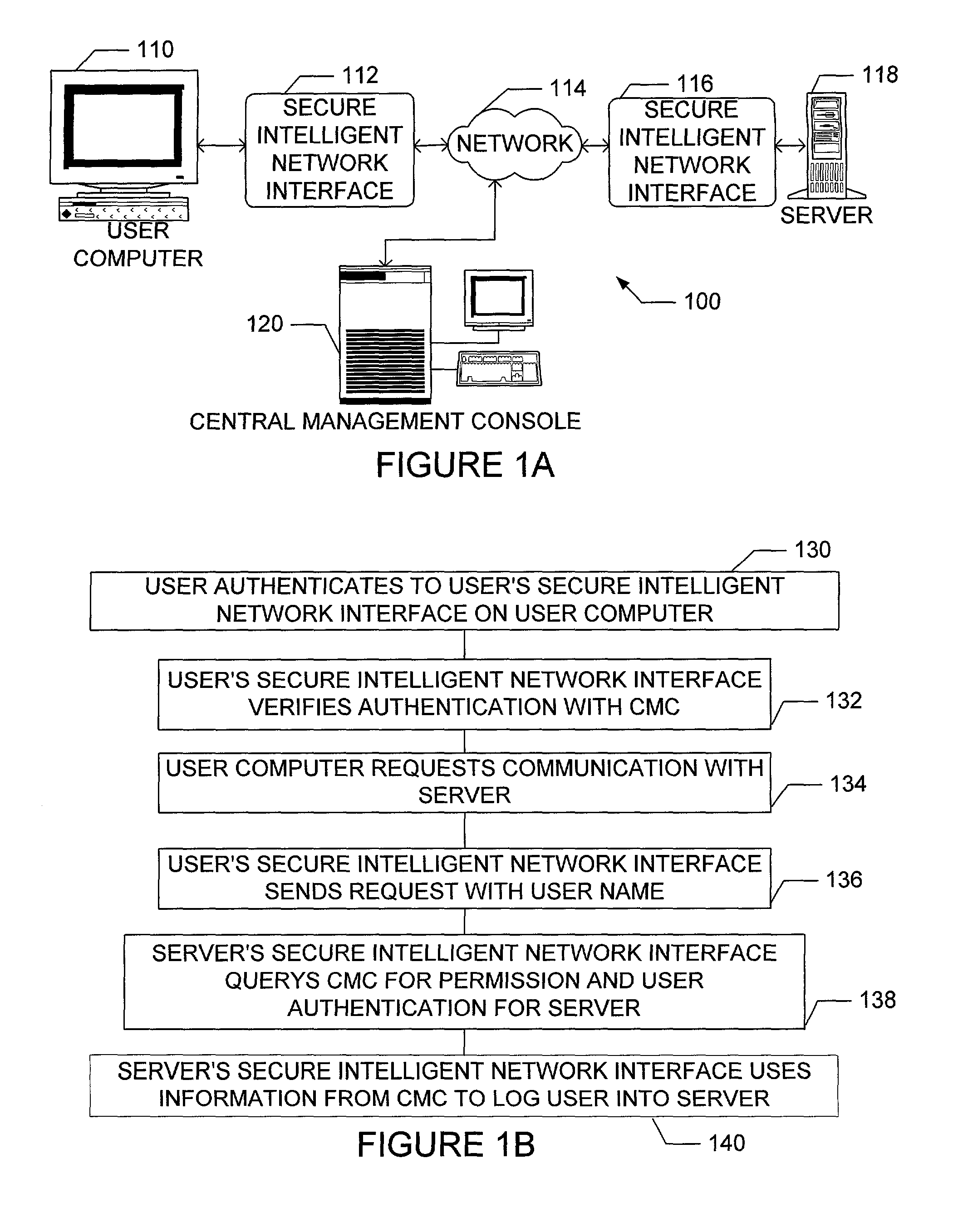
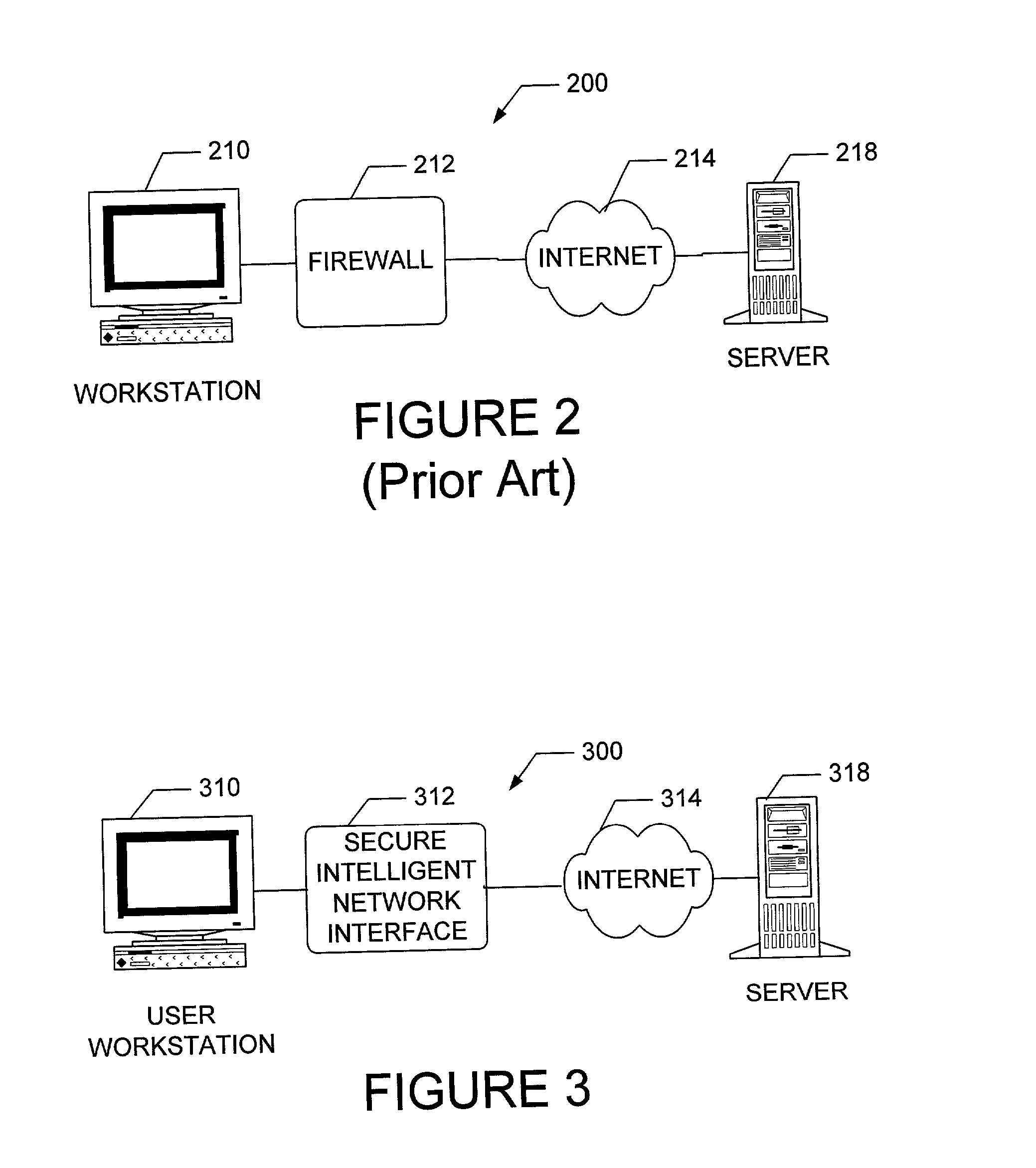
The present invention is drawn to an apparatus and method for providing secure network communication. Each node or computer on the network has a secure, intelligent network interface with a coprocessor that handles all network communication. The intelligent network interface can be built into a network interface card (NIC) or be a separate box between each machine and the network. The intelligent network interface encrypts outgoing packets and decrypts incoming packets from the network based on a key and algorithm managed by a centralized management console (CMC) on the network. The intelligent network interface can also be configured by the CMC with dynamically distributed code to perform authentication functions, protocol translations, single sign-on functions, multi-level firewall functions, distinguished-name based firewall functions, centralized user management functions, machine diagnostics, proxy functions, fault tolerance functions, centralized patching functions, Web-filtering functions, virus-scanning functions, auditing functions, and gateway intrusion detection functions.
Owner:NEUMAN MICHAEL +1
Method and system for detecting and preventing unauthorized signal usage in a content delivery network
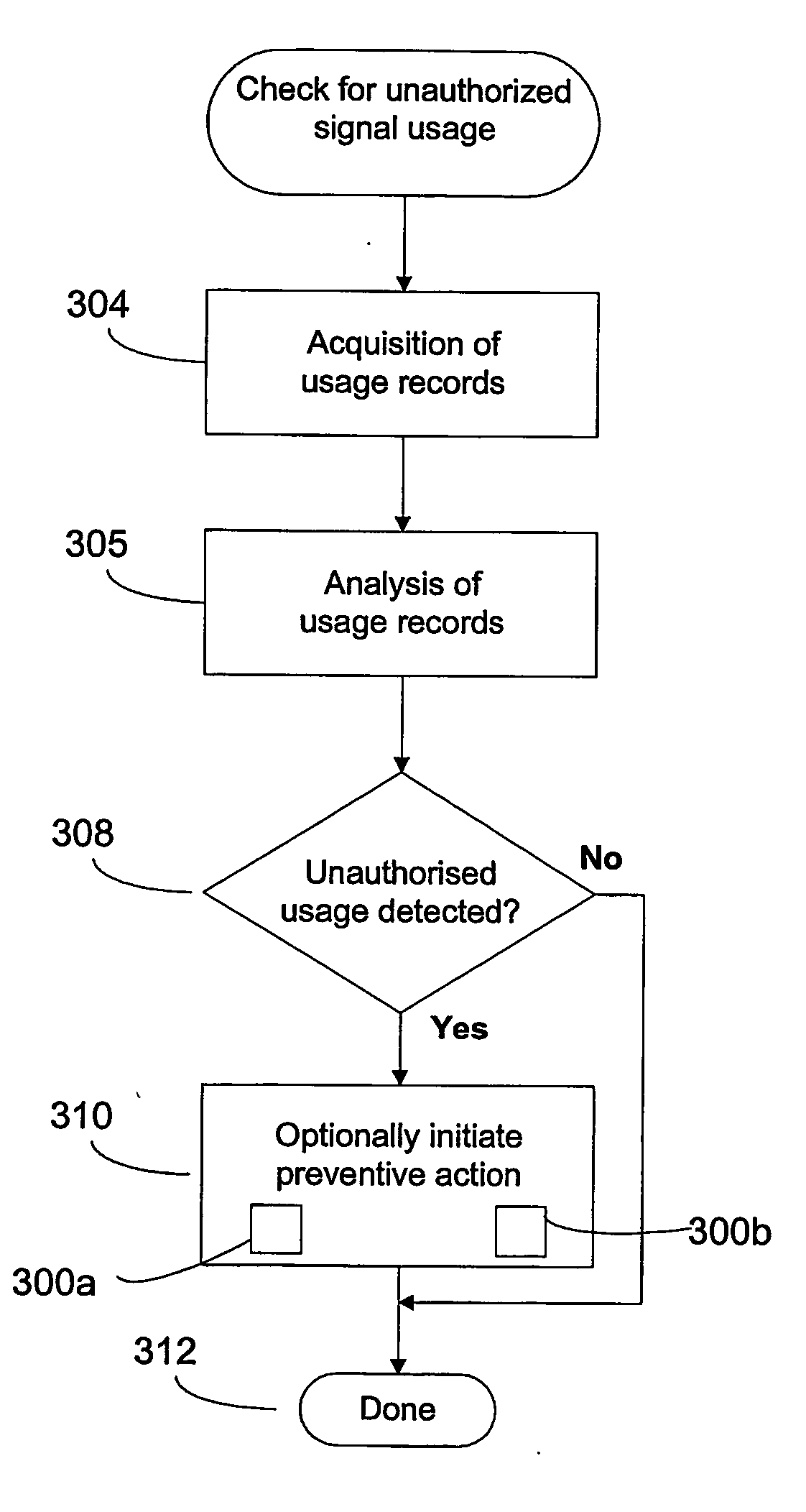
ActiveUS20070076872A1Data taking preventionDigital data processing detailsComputer networkCable television
A method and system for controlling unauthorized signal usage in a content delivery network, such as a television network, is described. The method and system acquires at least two signal usage records for a receiver of the content, evaluates the at least two signal usage records for indicia of usage of a combination of signals not normally authorized on the receiver, and detects unauthorized signal usage upon the at least two signal usage records being consistent with such indicia.
Owner:MAXXIAN TECH
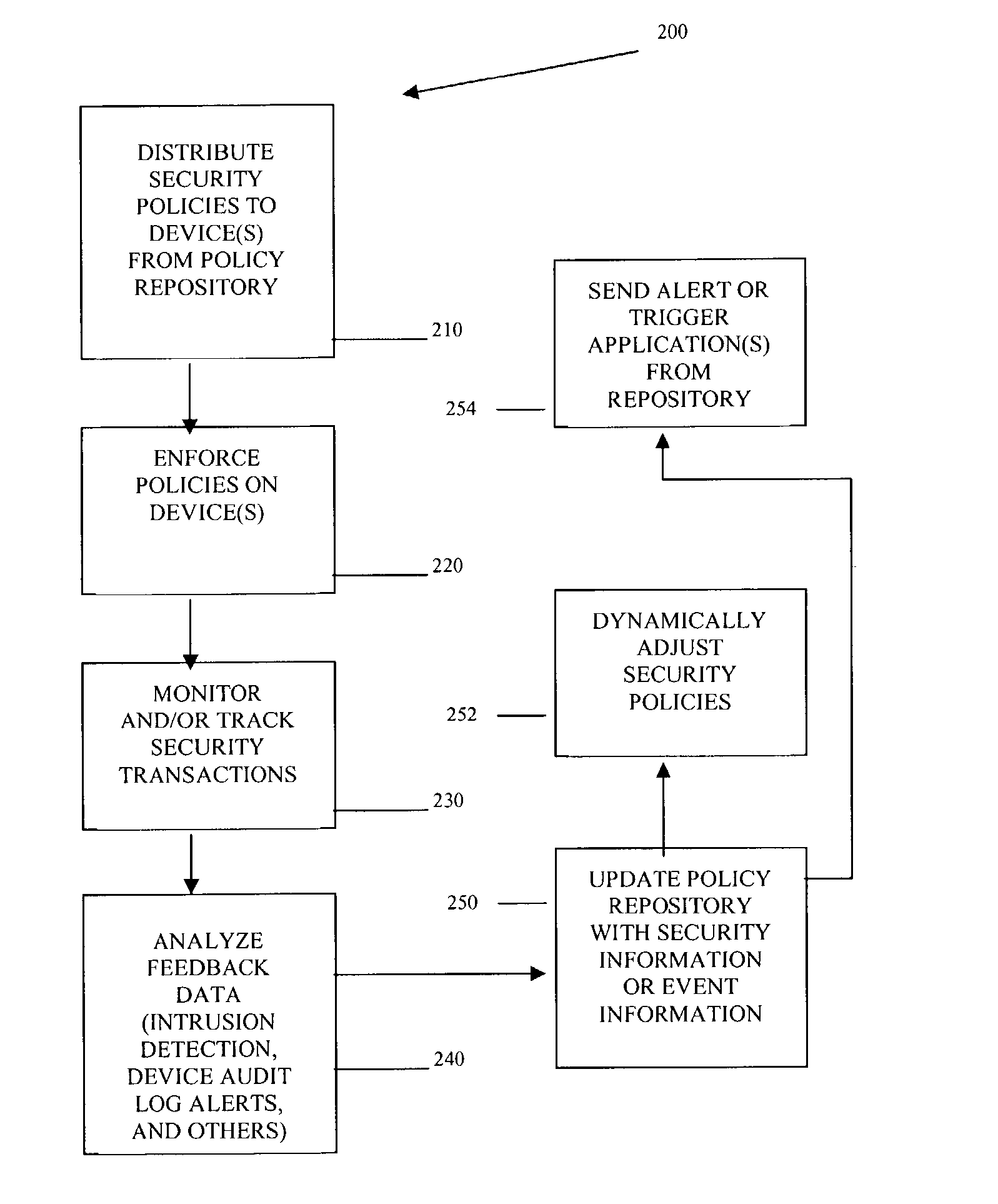
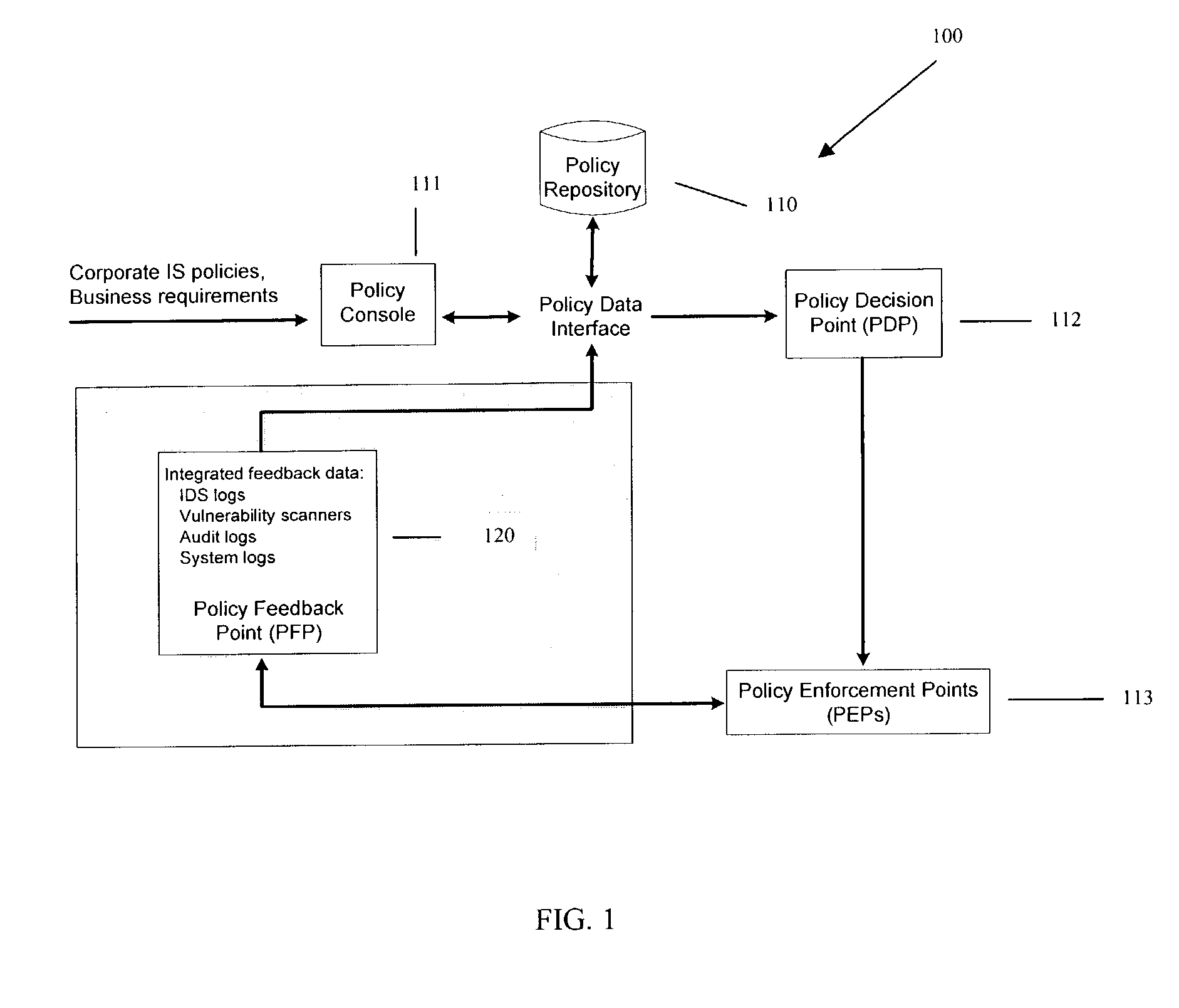
Methods and systems for managing security policies
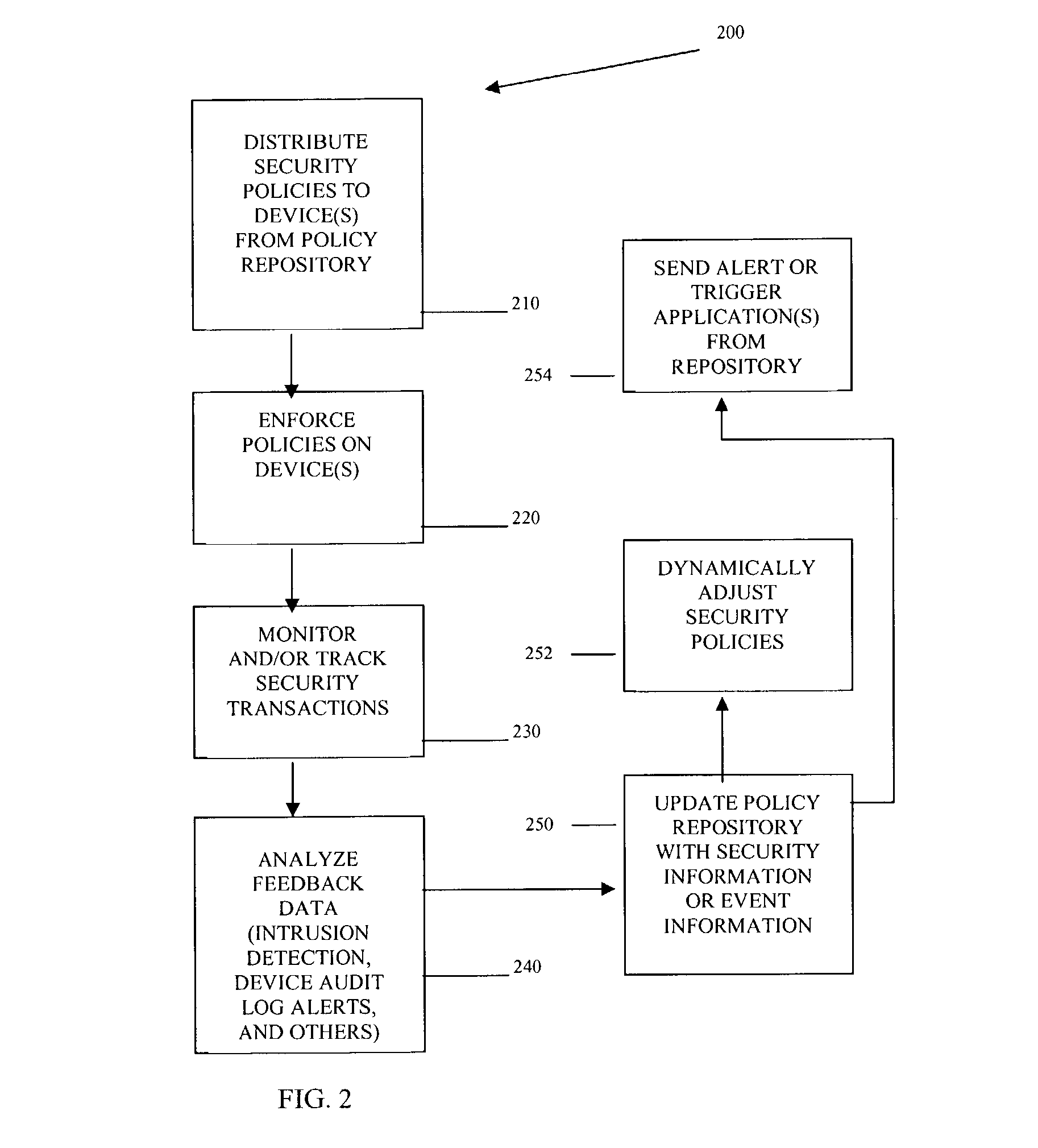
InactiveUS20040193912A1Data taking preventionDigital data processing detailsPolicy decisionSystems management
Methods, machines, and systems manage security policies of heterogeneous infrastructure and computing devices of a network. Security policy repository houses security policies that are pushed over the network by a policy decision point PDP to appropriate security-enabled devices (policy enforcement points (PEPs)) for enforcement. Using a closed feedback loop, a policy feedback point (PFP) collects and processes data from intrusions, alerts, violations, and other abnormal behaviors from a variety of PEPs or logs produced from PEPs. This data is sent as feedback to the policy repository. The PDP detects the data and analyzes it to determine if policy updates (which can be dynamic and automatic) need to be adaptively made and dynamically pushed to PEPs. The PDP can also send console messages or alerts to consoles or administrators.
Owner:INTEL CORP
Device function restricting method and system in specific perimeters
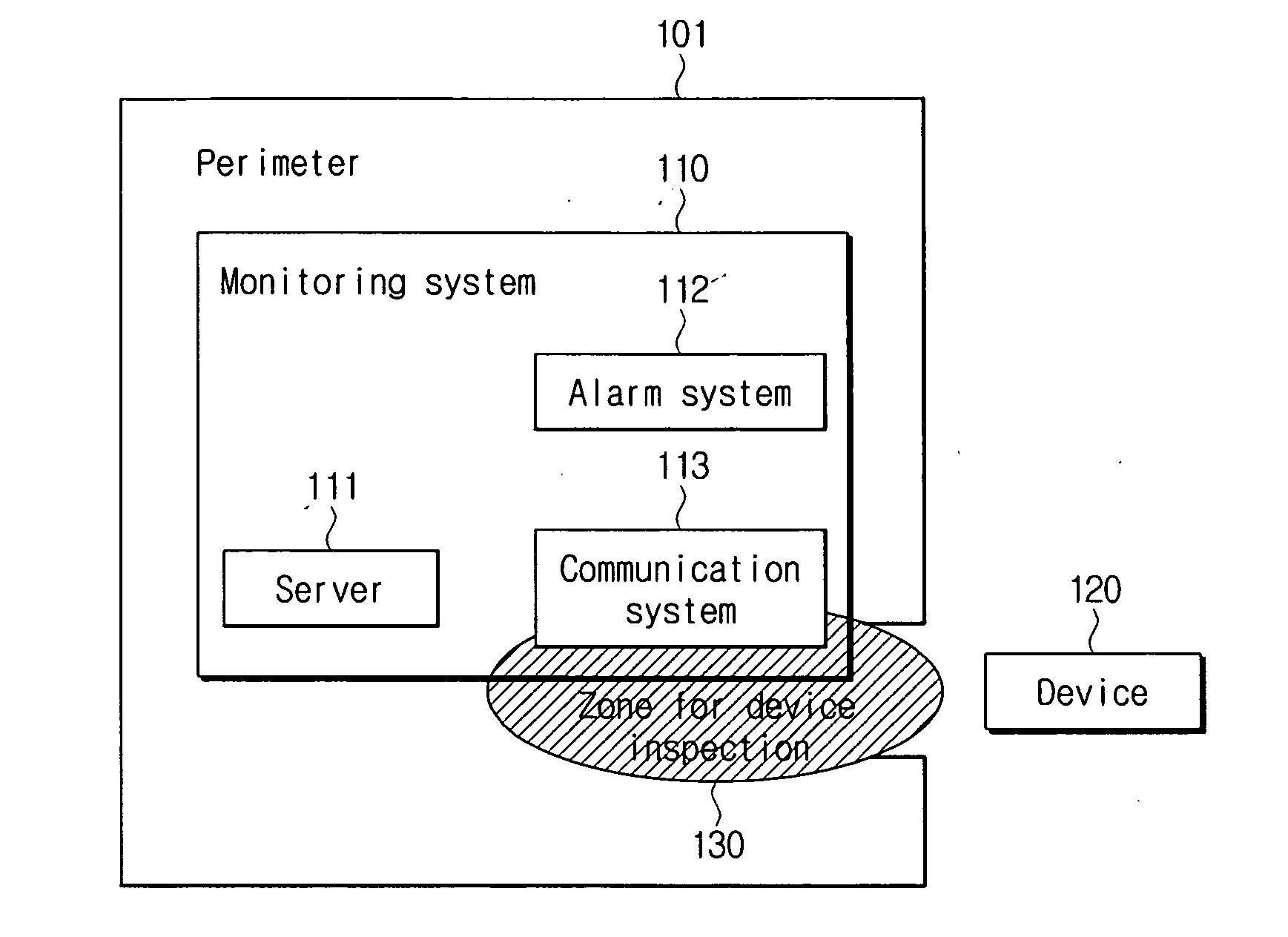
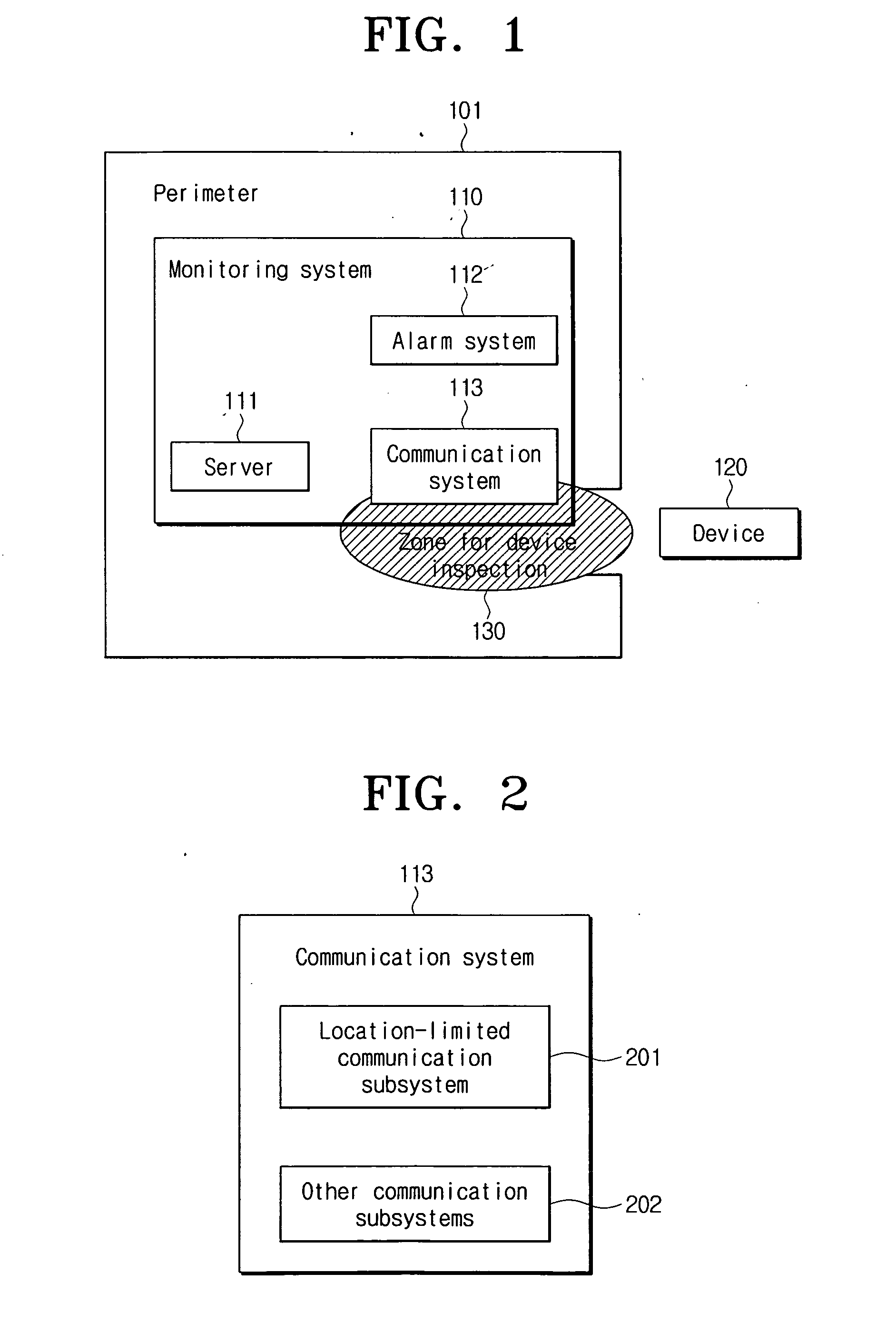
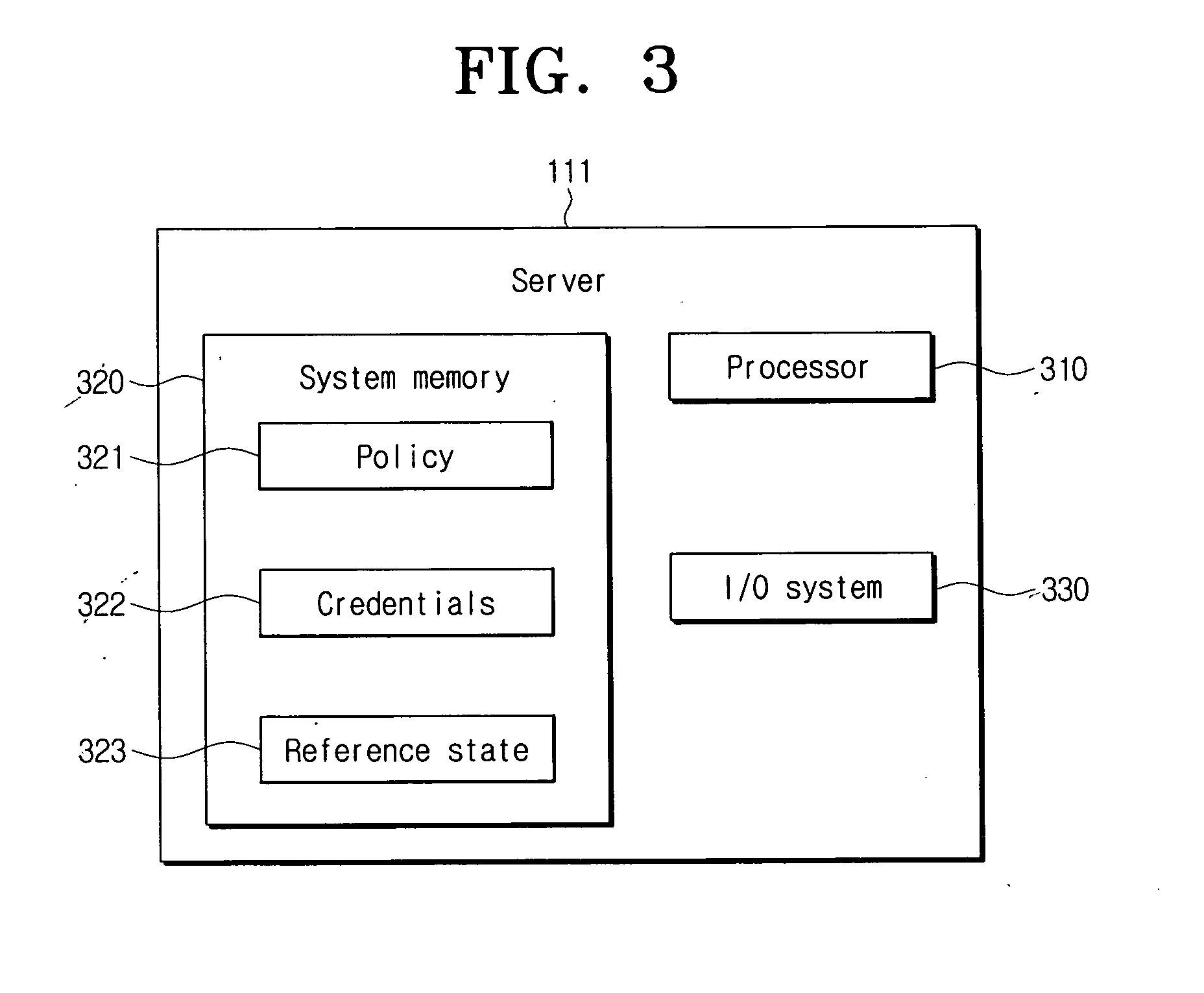
ActiveUS20070101426A1Facilitating information leakageGood informationRandom number generatorsData taking preventionCommunications systemMonitoring system
An apparatus and method for restricting the functions of a device are provided. A restriction monitoring system includes a communication system that provides a location-limited communication channel that detects whether a device entering a perimeter is in an area for device inspection, a server that provides a credential and a security policy to the device and receives a report on whether the device violates the security policy through the location-limited communication channel, and an alarm system which triggers a security alarm when the device violates the security policy.
Owner:SAMSUNG ELECTRONICS CO LTD
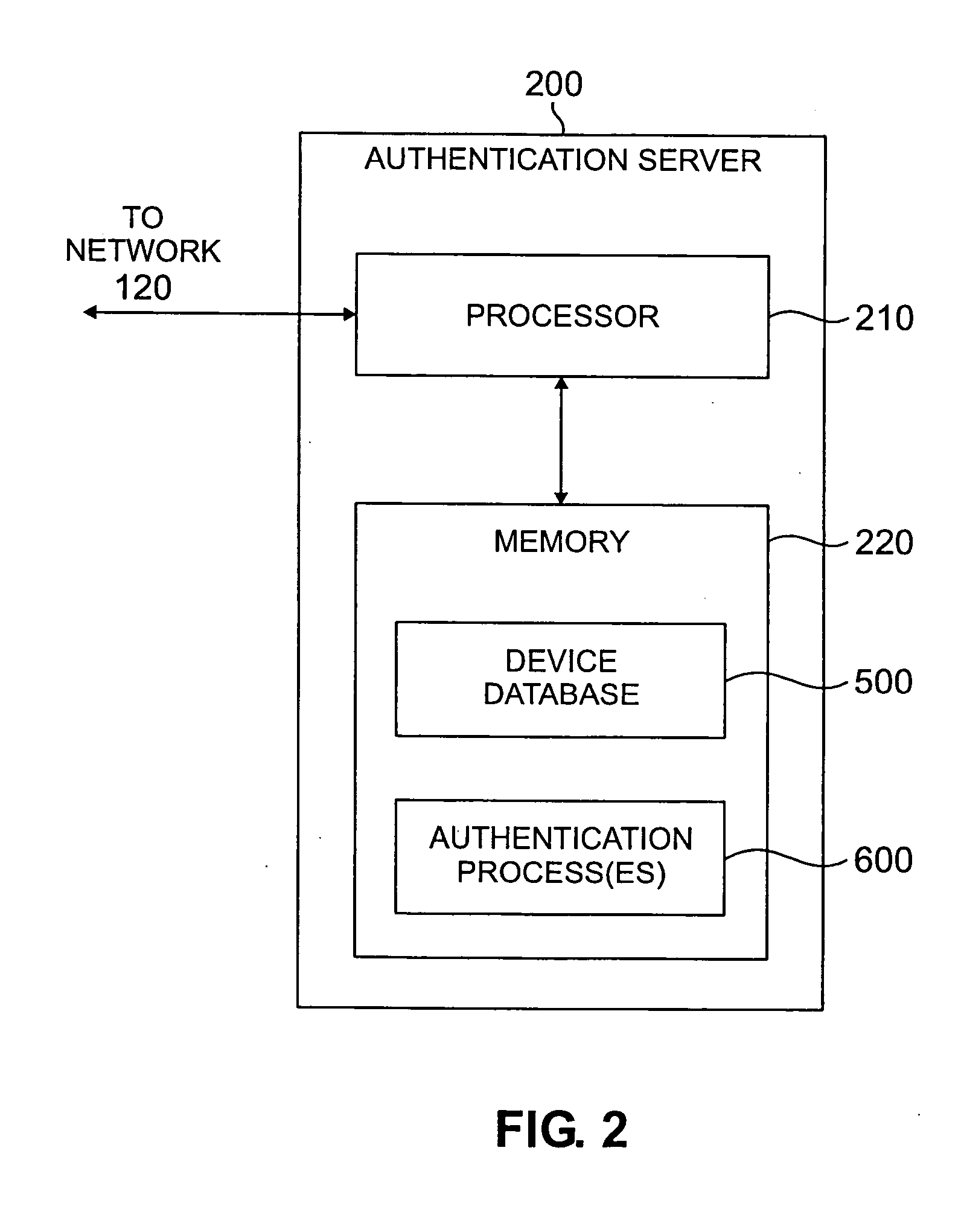
Computer security and management system
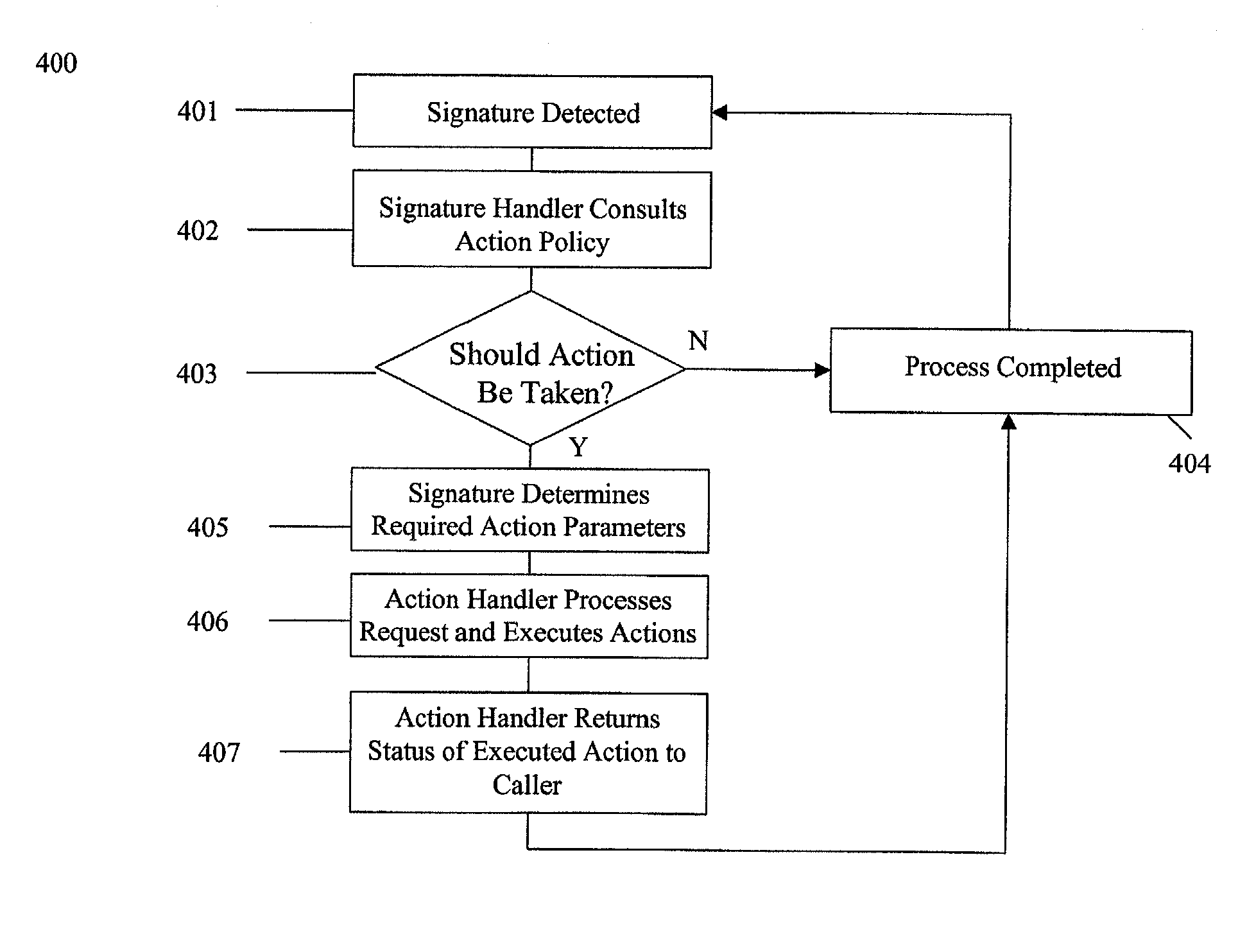
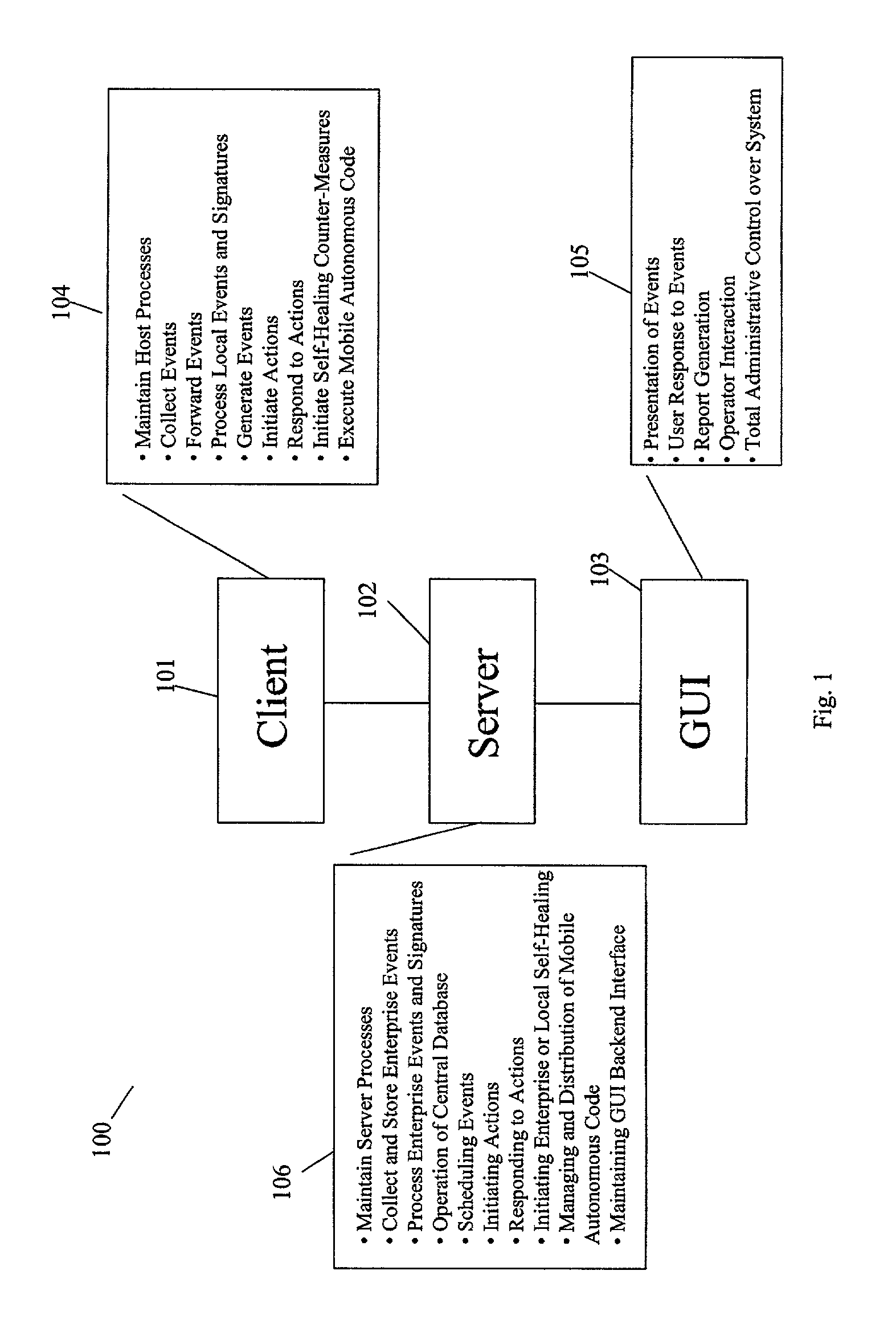
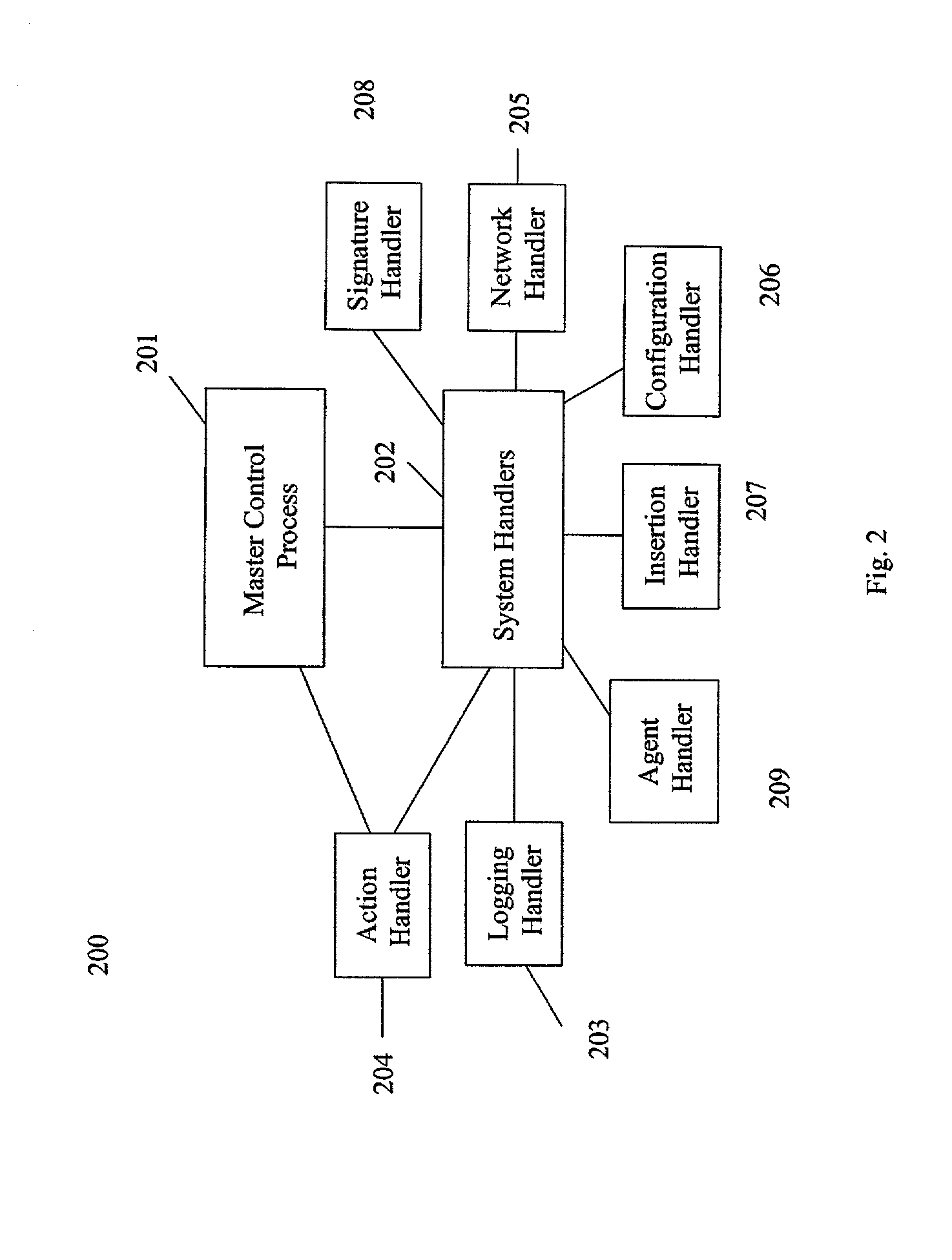
ActiveUS20020129264A1Memory loss protectionData taking preventionComputer security modelDirect execution
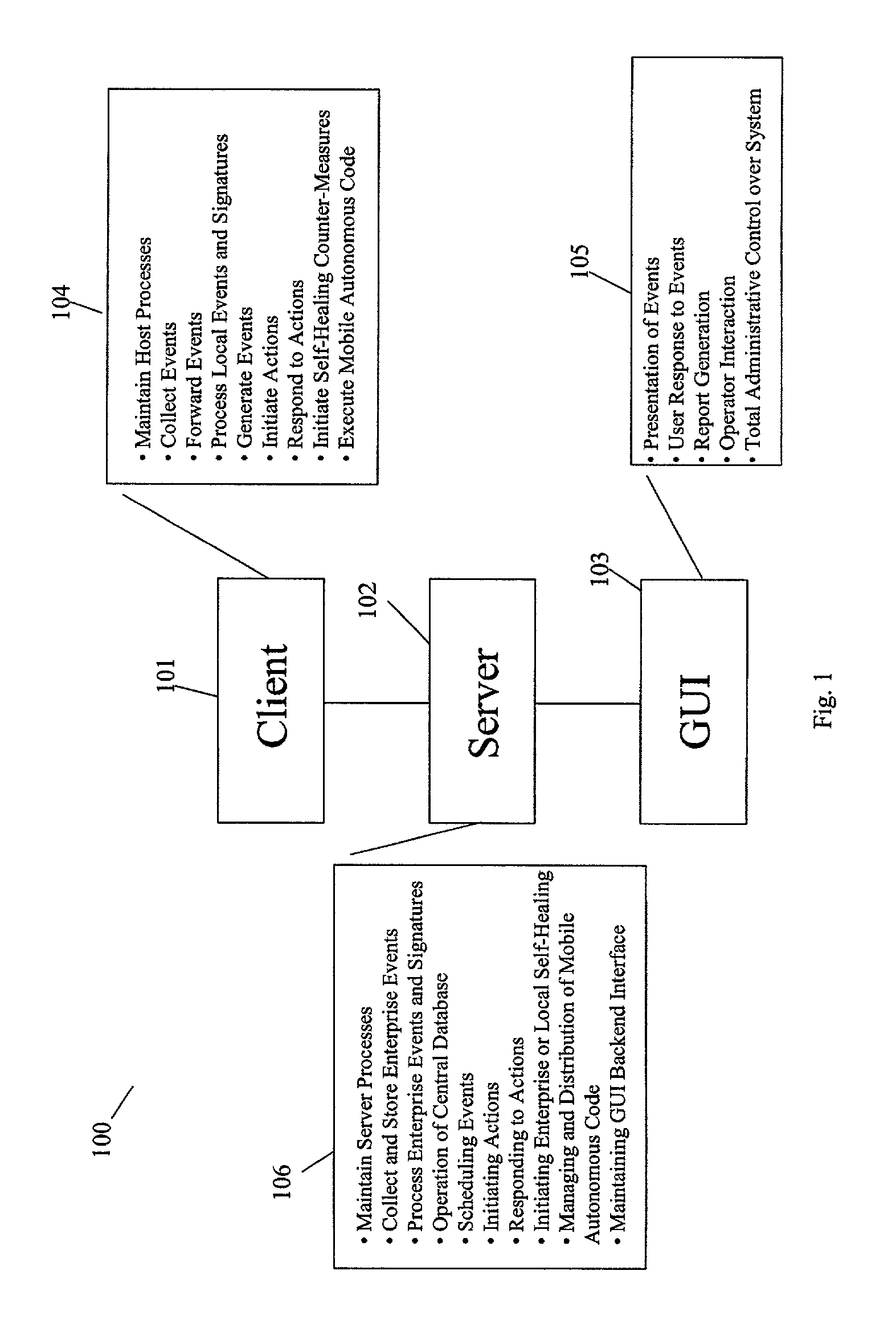
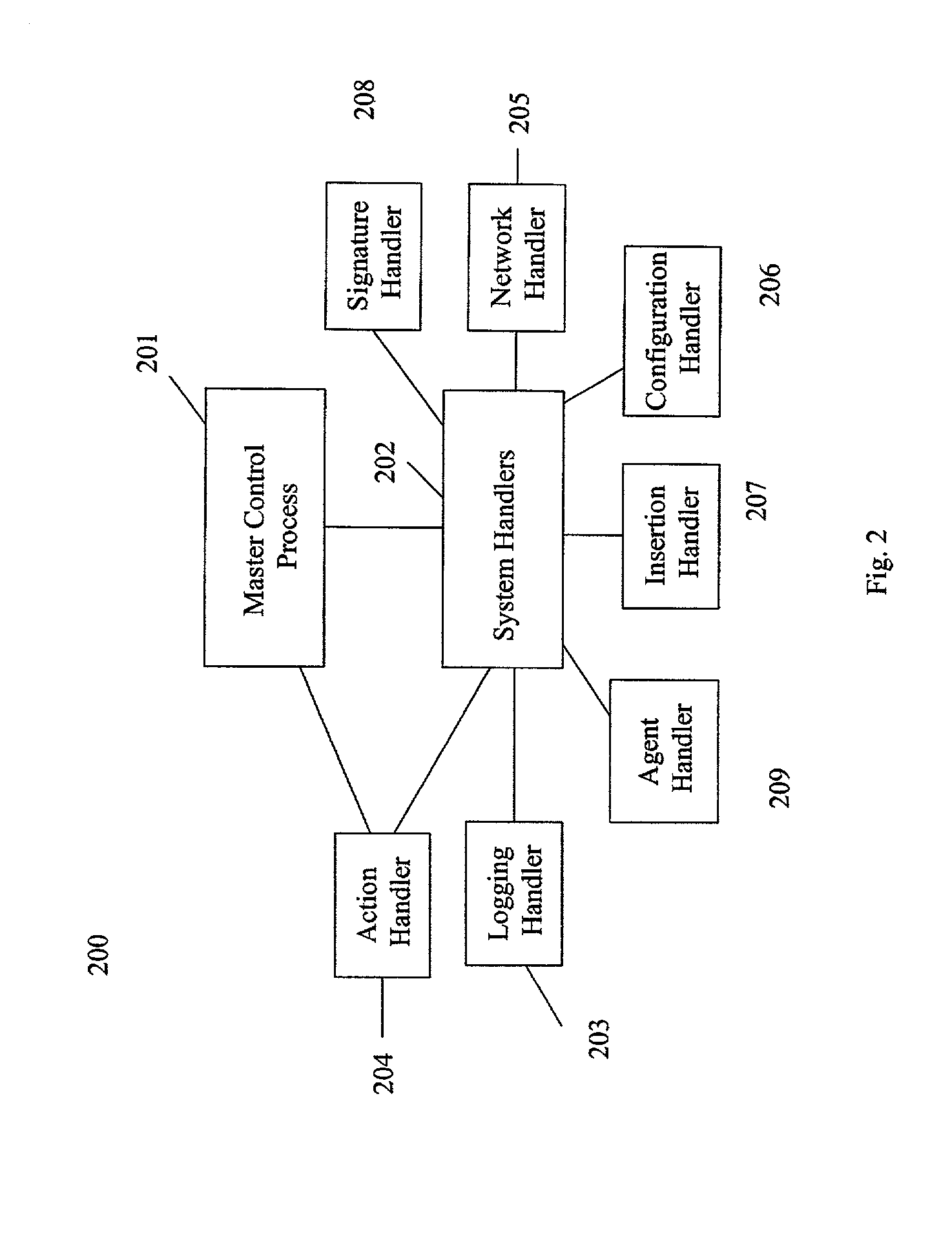
The present invention provides a generic distributed command, control, and communication framework that allows computer systems, devices, and operational personnel to interact with the network as a unified entity. The present invention provides these services by building upon a core communication architecture that permits local or remote execution of mobile program code, static execution of program code, flexible communication formats, self-healing network techniques, and expansion by the addition of new system modules, software handlers, or mobile autonomous agents.
Owner:CISCO TECH INC
Wireless sensor network and adaptive method for monitoring the security thereof
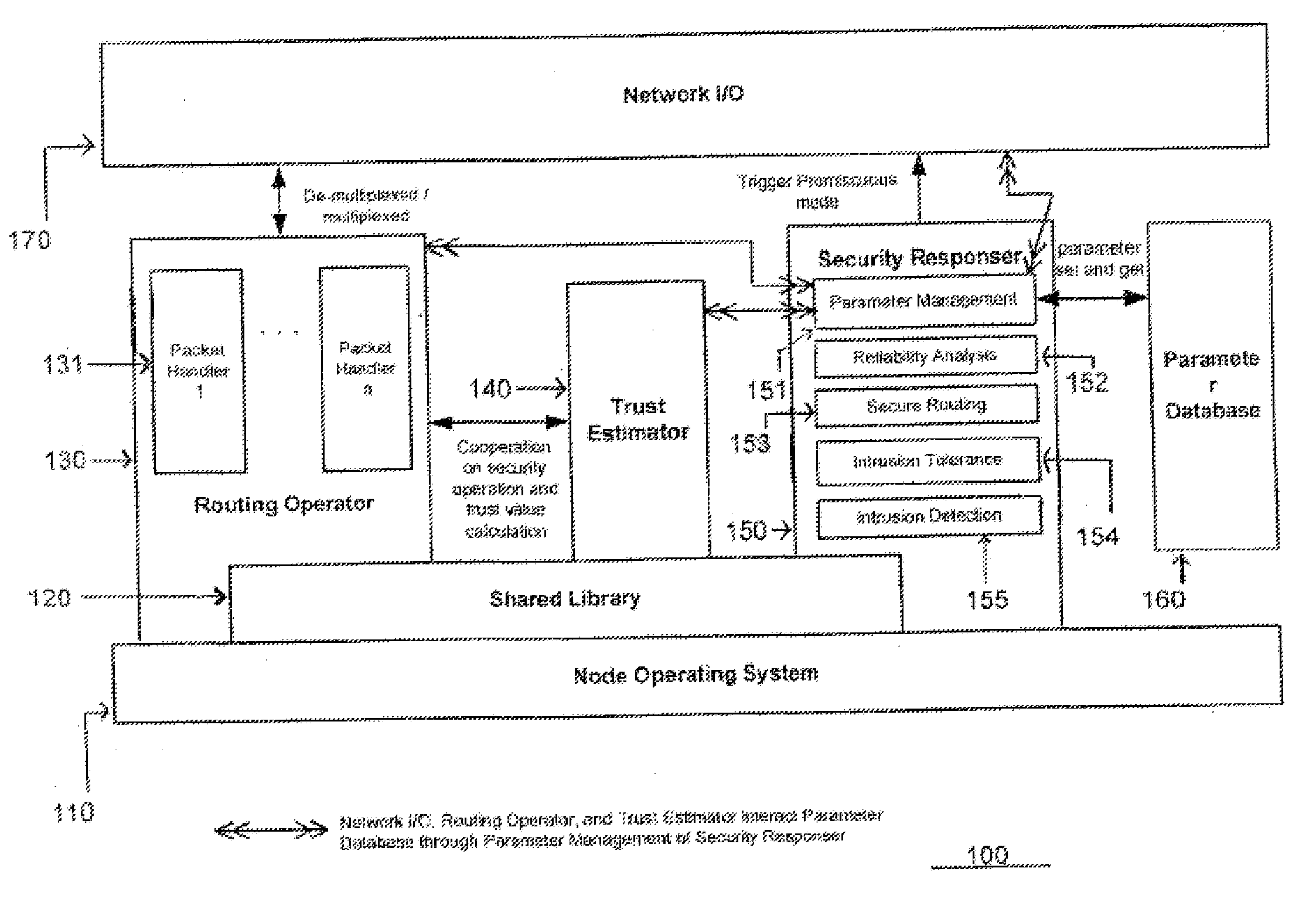
InactiveUS20080084294A1Data taking preventionNetwork topologiesWireless mesh networkWireless sensor networking
The present invention relates to a sensor network having node architecture for performing trust management of neighboring sensor nodes, and to an adaptive method for performing trust management of neighboring sensor nodes for monitoring security in the sensor network. The sensor network includes a base station and a plurality of sensor nodes for reporting sensed information packets to the base station through radiofrequency signals relayed by other sensor nodes. A judge sensor node may have a trust estimator in its node architecture to evaluate trustworthiness of a neighboring suspect sensor node by determining a personal reference and receiving personal references from jury sensor nodes. Based on the trustworthiness of the suspect, the judge may modify a route for transmitting packets to the base station.
Owner:ELECTRONICS & TELECOMM RES INST
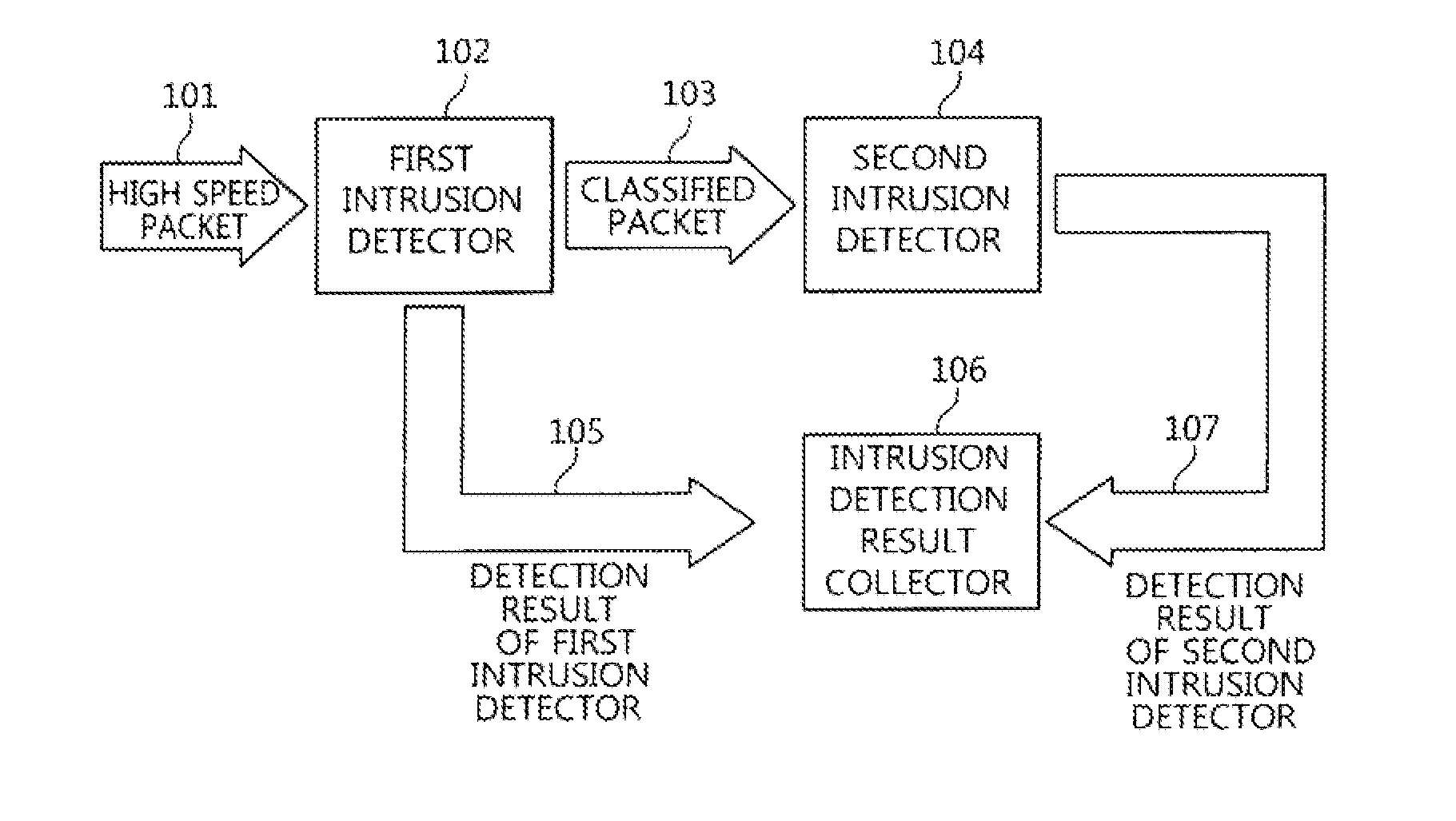
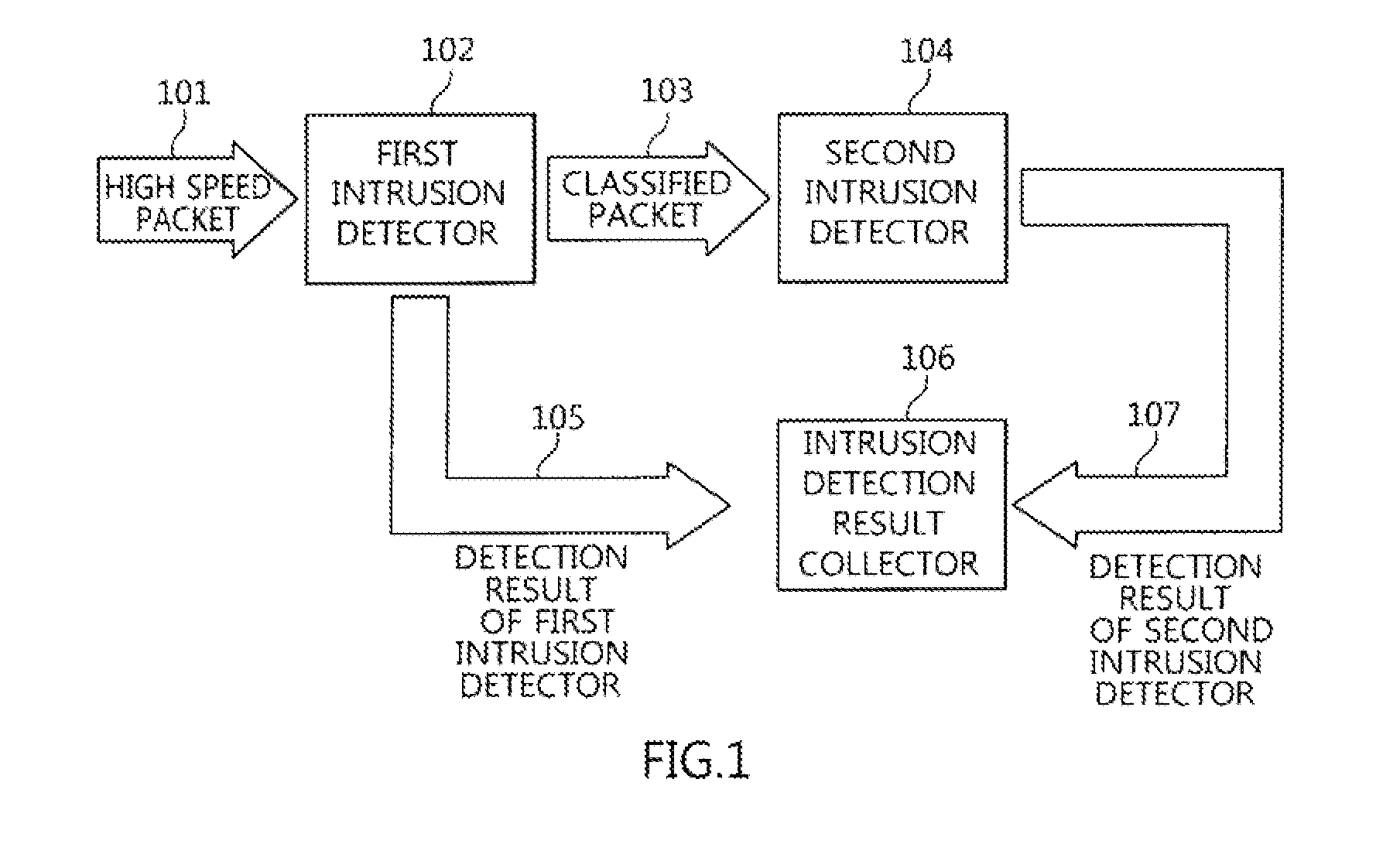
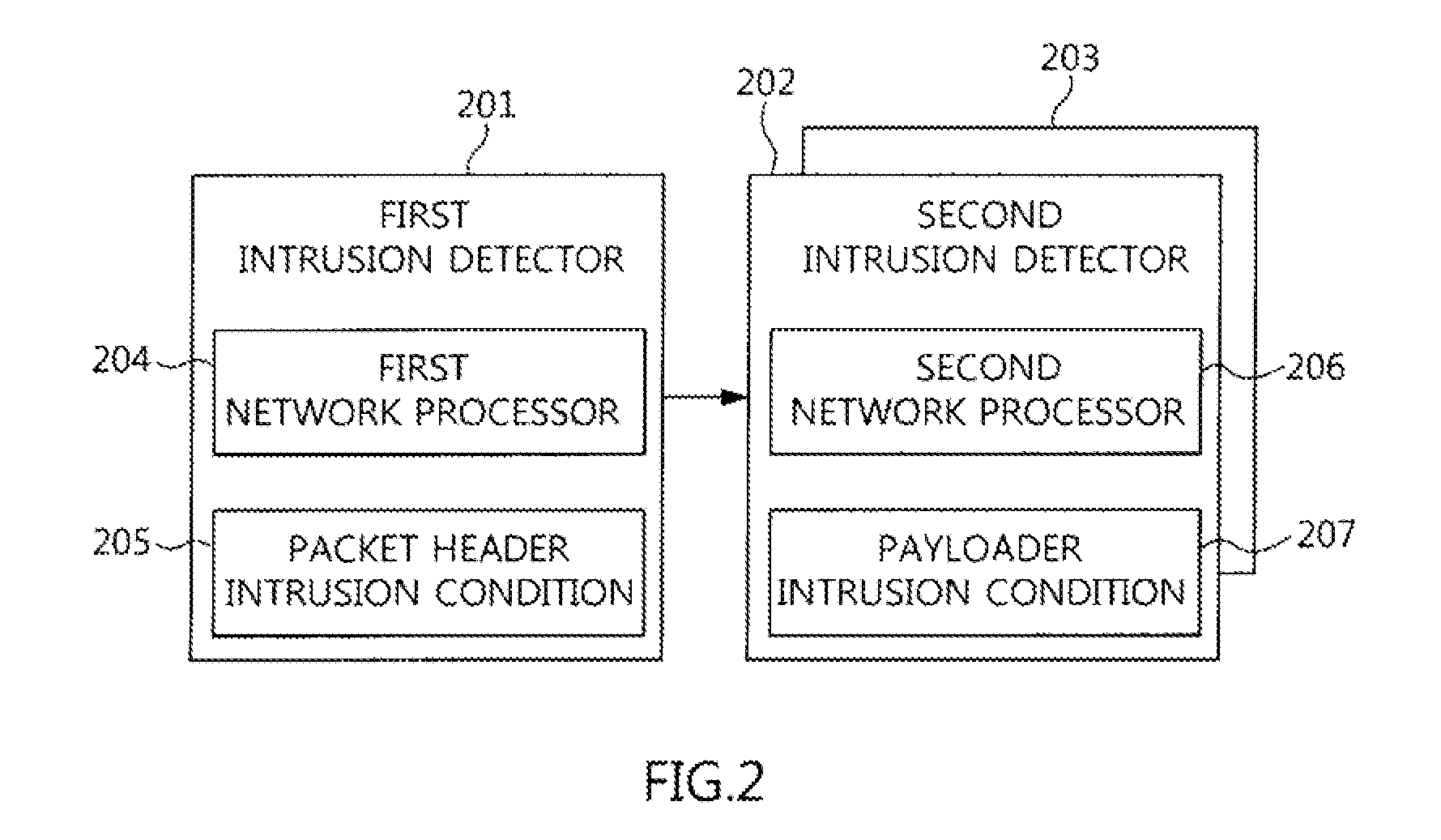
Two-stage intrusion detection system for high-speed packet processing using network processor and method thereof
ActiveUS20130160122A1Memory loss protectionData taking preventionNetwork processorDistributed computing
A system and method for detecting network intrusion by using a network processor are provided. The intrusion detection system includes: a first intrusion detector, configured to use a first network processor to perform intrusion detection on layer 3 and layer 4 of a protocol field among information included in a packet header of a packet transmitted to the intrusion detection system, and when no intrusion is detected, classify the packets according to stream and transmit the classified packets to a second intrusion detector; and a second intrusion detector, configured to use a second network processor to perform intrusion detection through deep packet inspection (DPI) for the packet payload of the packets transmitted from the first intrusion detector. Thereby, intrusion detection for high-speed packets can be performed in a network environment.
Owner:ELECTRONICS & TELECOMM RES INST
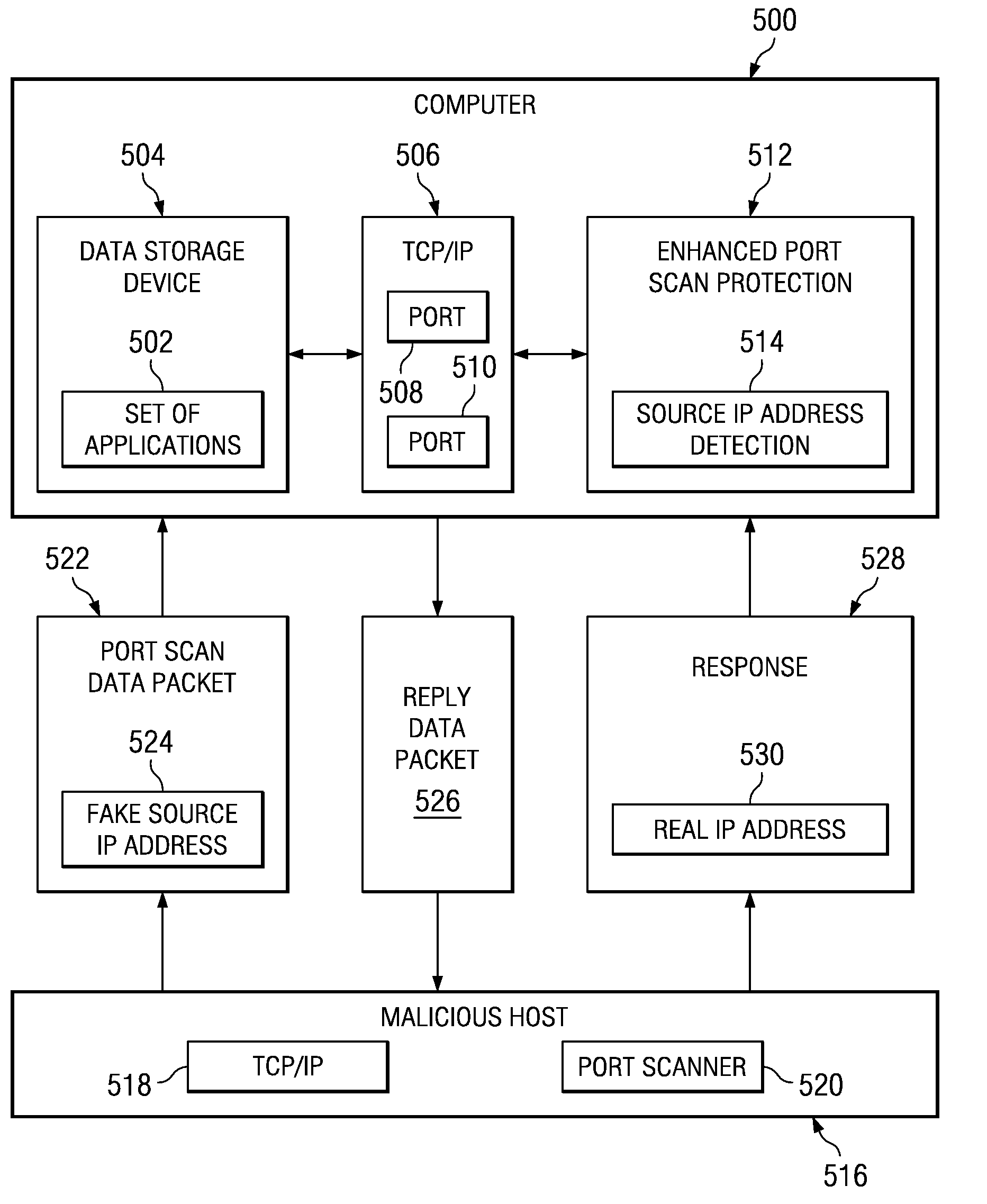
Method and apparatus for detecting port scans with fake source address
Owner:INT BUSINESS MASCH CORP
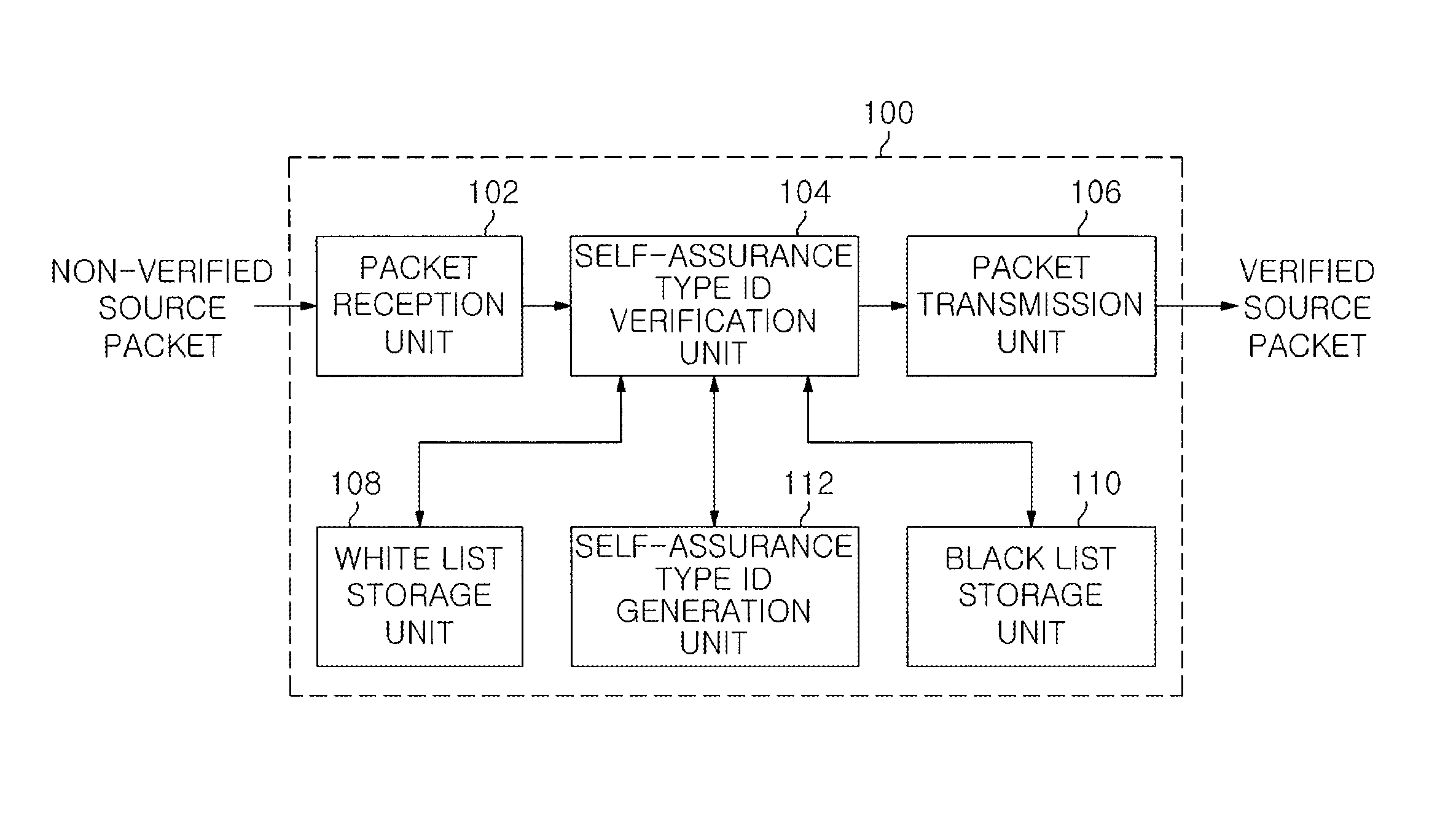
Authentication method and apparatus for detecting and preventing source address spoofing packets
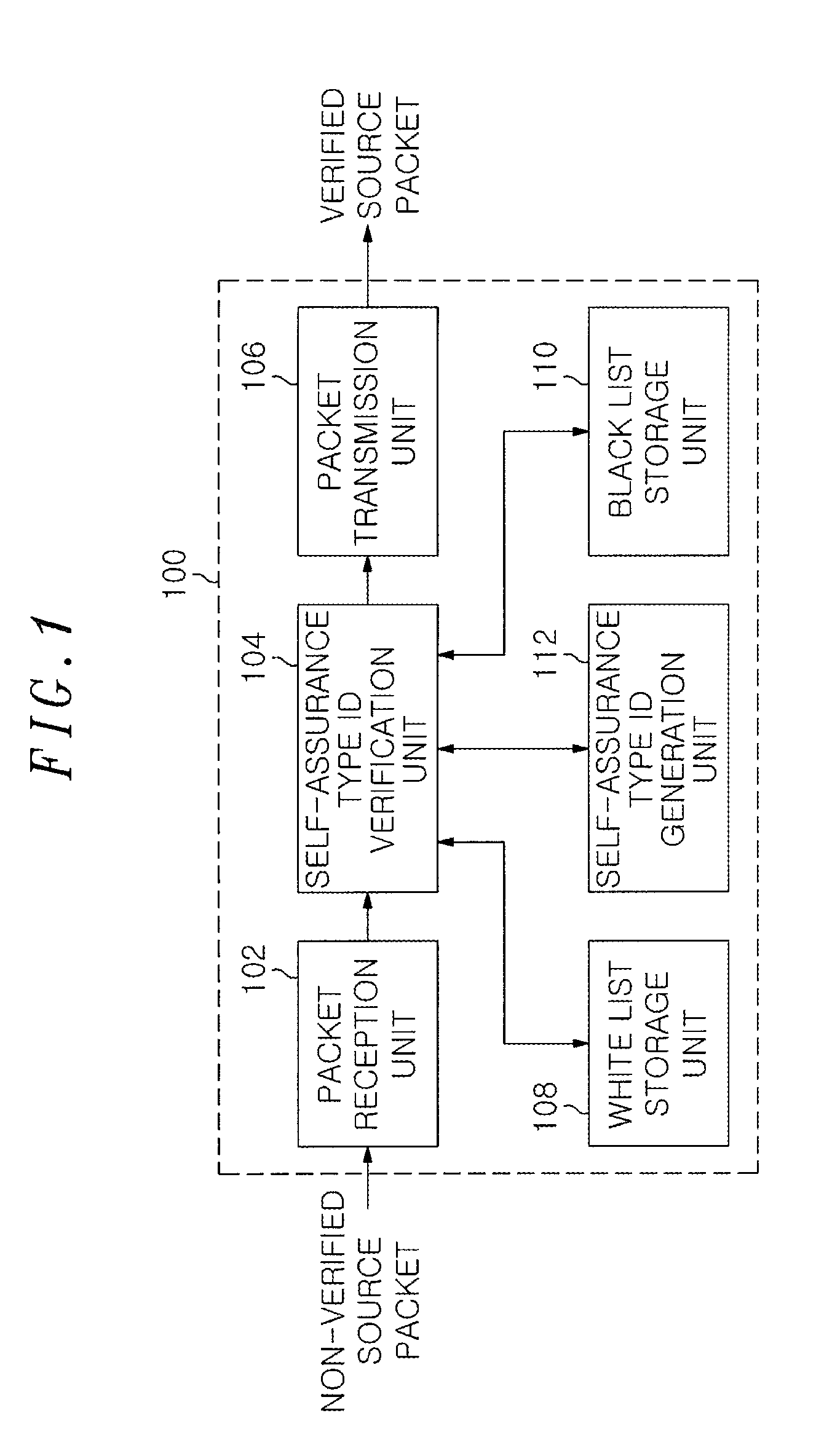
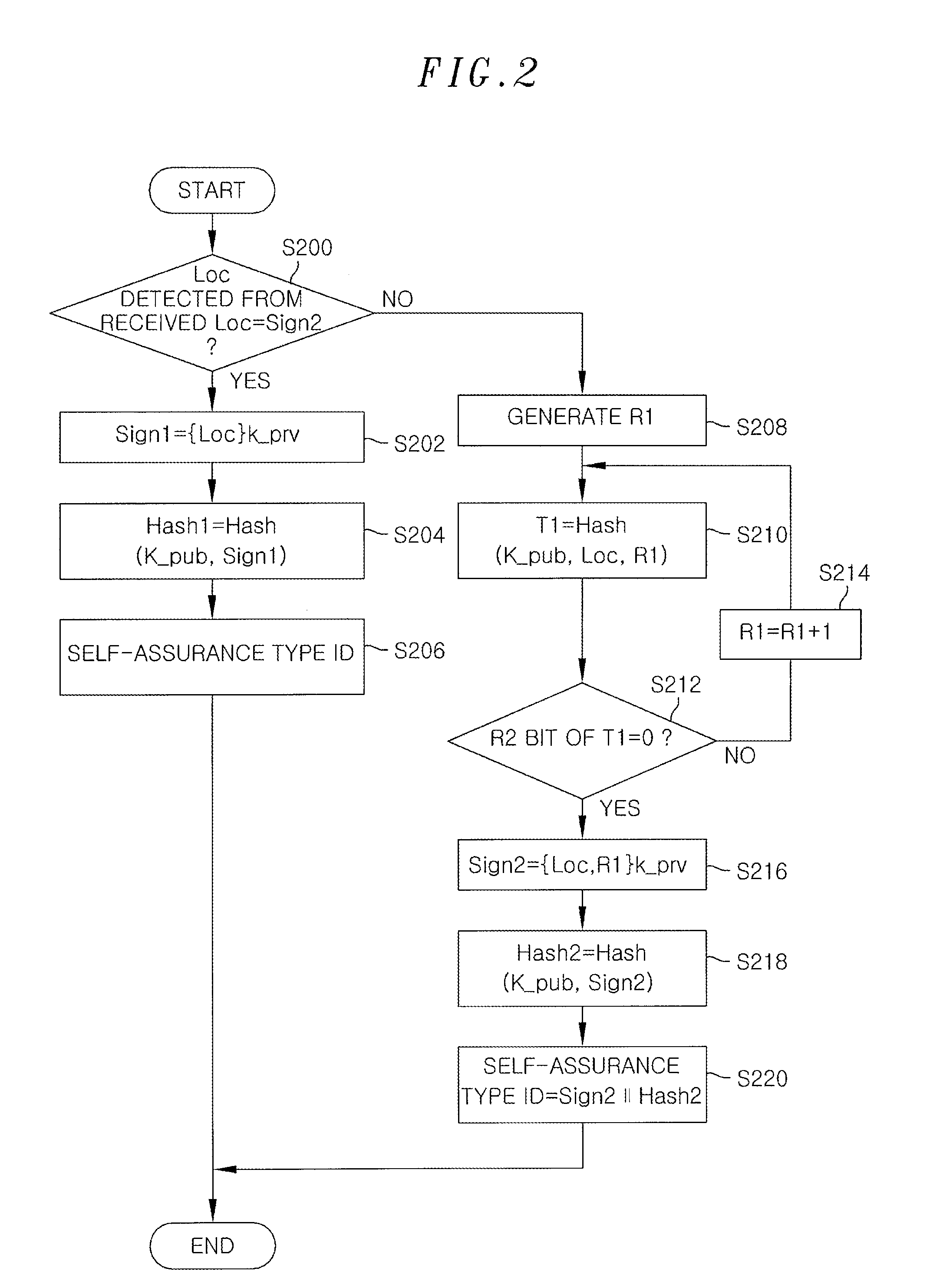
An authentication apparatus for detecting and preventing a source address spoofing packet, includes a packet reception unit configured to receive a packet from a previous node or a user host; a self-assurance type ID generation unit configured to generate a self-assurance type ID of a source node of the received packet; and a self-assurance type ID verification unit configured to determine whether the source address of the received packet has been spoofed. Further, the authentication apparatus includes a white list storage unit configured to store a reliable source node; a black list storage unit configured to store an unreliable source node; and a packet transmission unit configured to transmit the packet whose source has been verified through the self-assurance type ID verification unit to a next network node.
Owner:ELECTRONICS & TELECOMM RES INST
Authentication method to enable servers using public key authentication to obtain user-delegated tickets
InactiveUS6643774B1Key distribution for secure communicationData taking preventionPublic key authenticationDelegation model
A method, system, and computer-readable code for delegating authority in a public key authentication environment from a client to a server machine or process, in order that the server machine or process can then securely access resources and securely perform tasks on behalf of the client. The authority is delegated by obtaining tickets (or other equivalent representation of user credentials) from a private key system, such as the Kerberos system, where the tickets identify a user's access rights or privileges. The present invention provides several alternative techniques with which this delegation model can be implemented. In these techniques, the client does not directly access the private key system.
Owner:IBM CORP
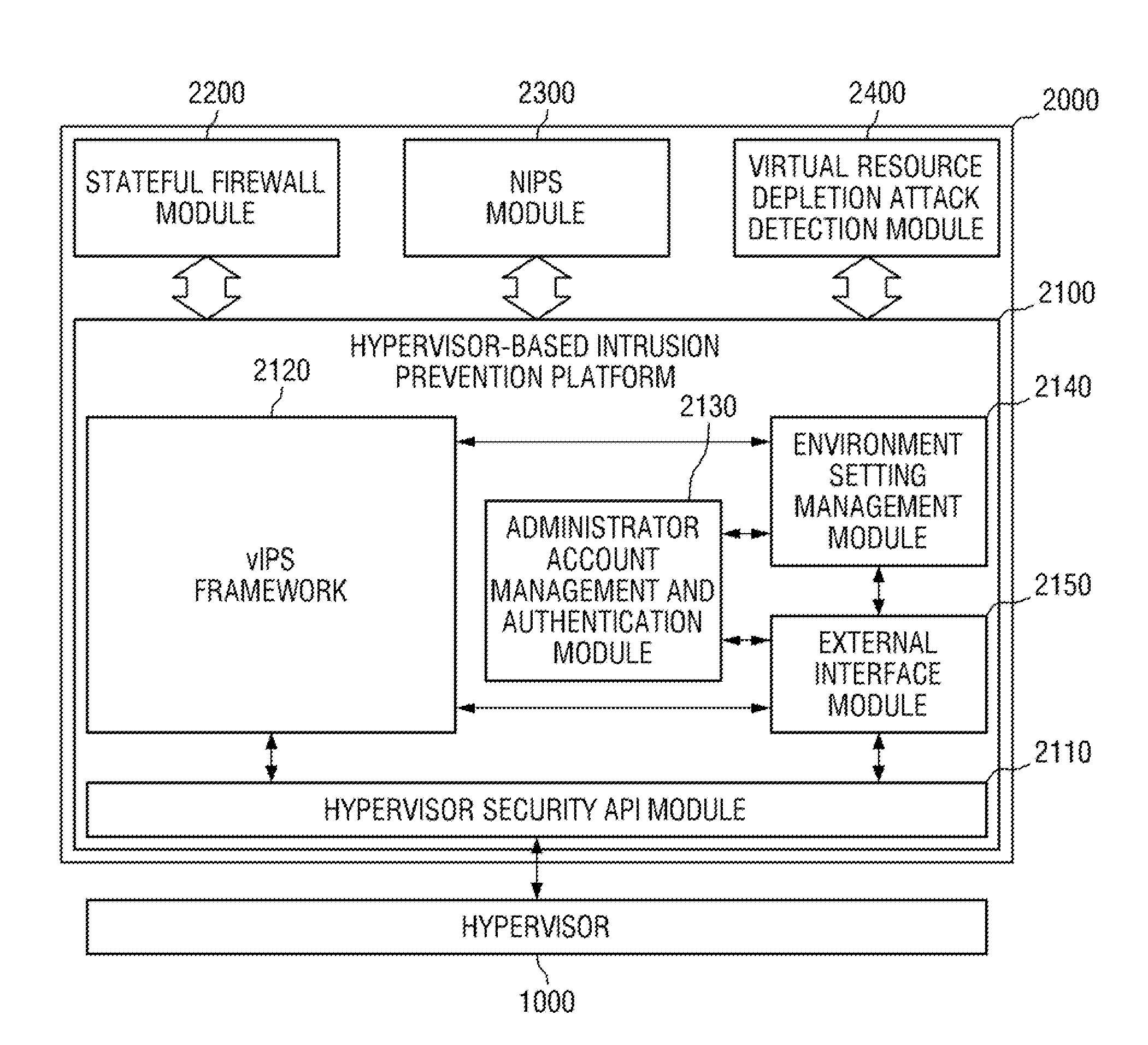
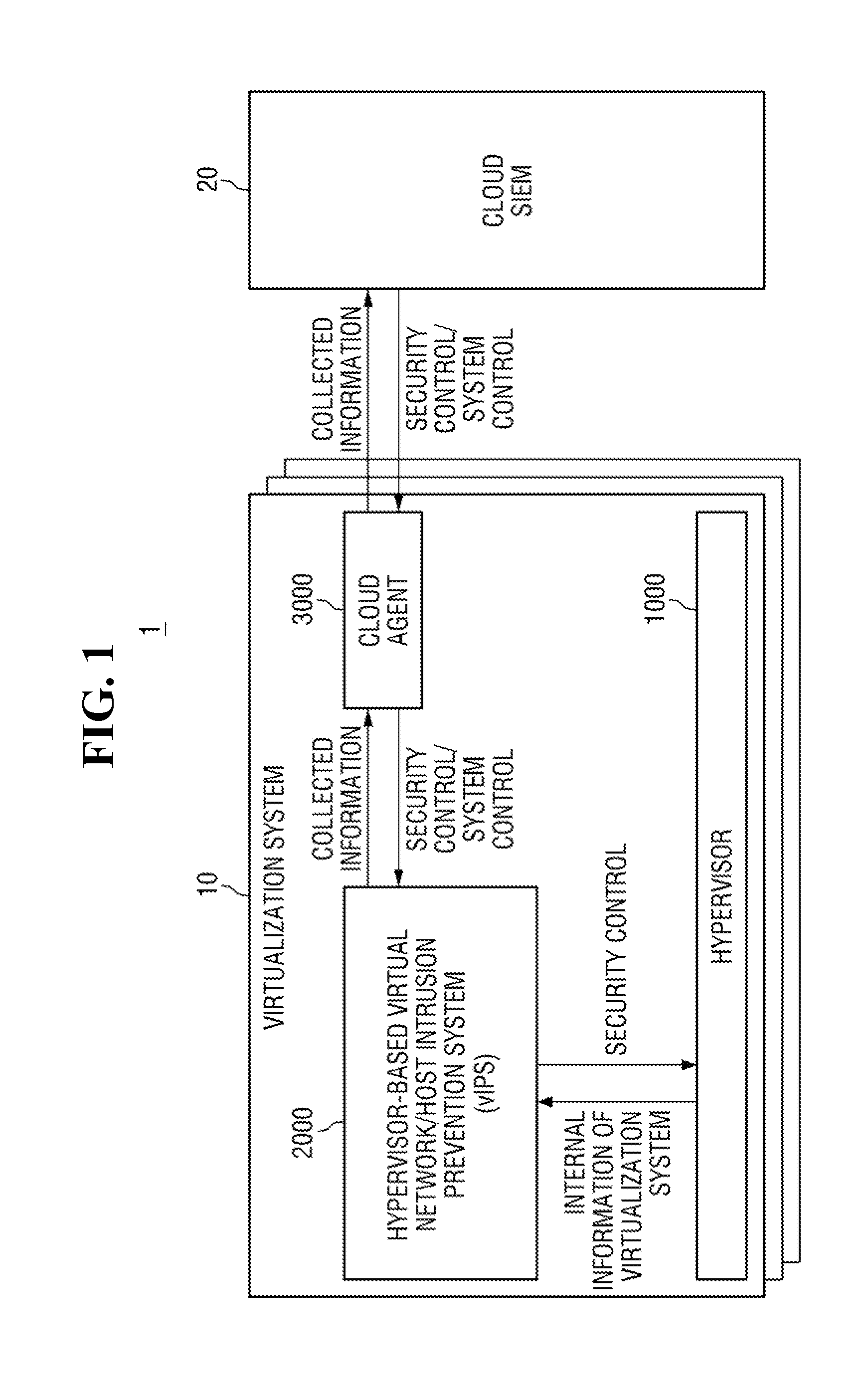
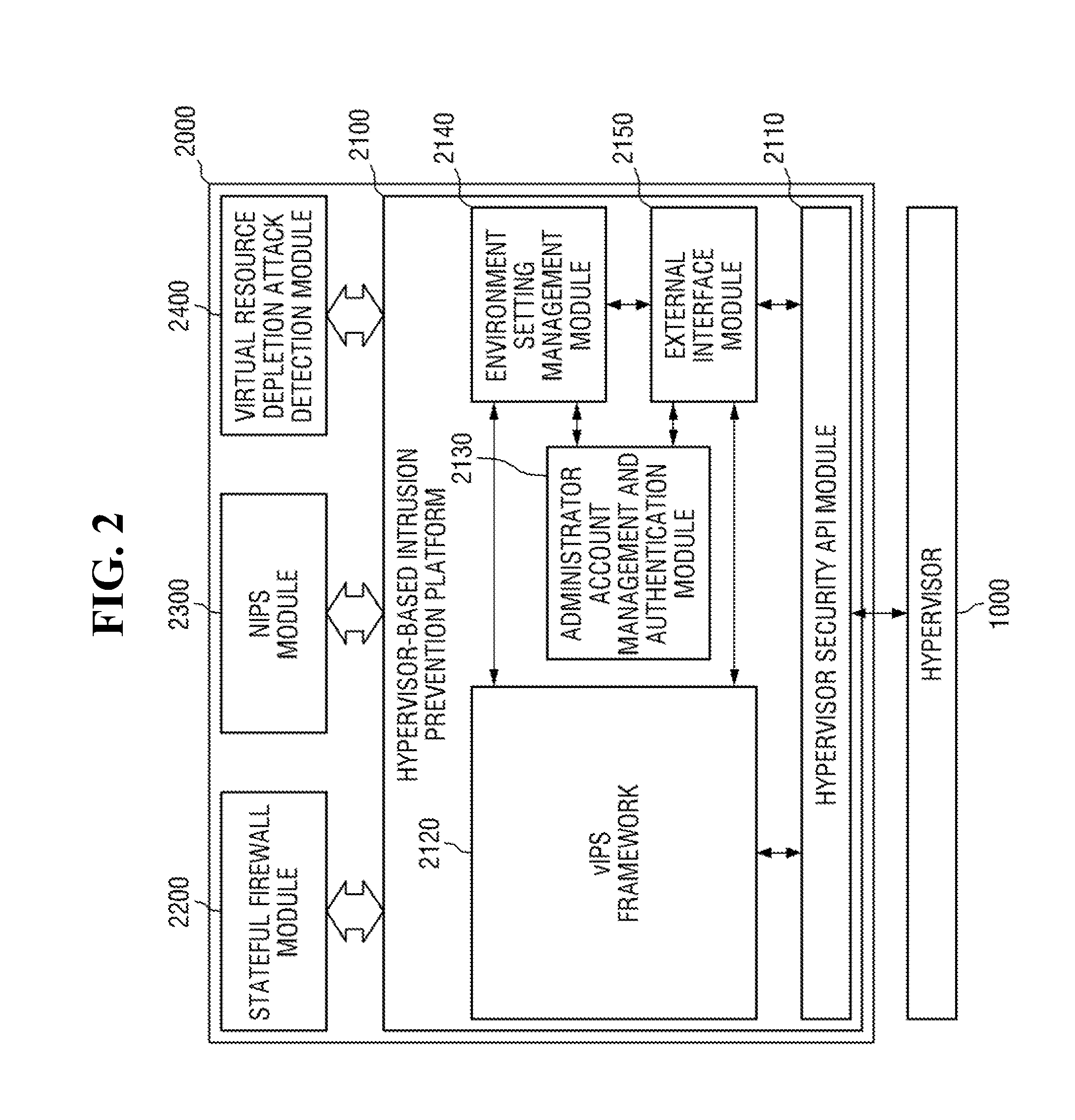
Hypervisor-based intrusion prevention platform and virtual network intrusion prevention system
InactiveUS20140317737A1Memory loss protectionData taking preventionApplication programming interfaceIntrusion prevention system
Hypervisor-based intrusion prevention platform is provided. The hypervisor-based intrusion prevention platform comprises a virtual network intrusion prevention system (vIPS) framework which obtains internal information of a virtualization system from a hypervisor and performs security control on the hypervisor in response to the result of intrusion detection carried out by using the internal information of the virtualization system, a hypervisor security application programming interface (API) module which provides an API used by the vIPS framework to access the hypervisor, an administrator account management and authentication module which manages an administrator account of a vIPS and authenticates the administrator account, an environment setting management module which manages environment setting values of modules within the vIPS, and an external interface module which provides an interface for system control and security control.
Owner:KOREA INTERNET & SECURITY AGENCY
Apparatus and method for the server-sided linking of information
InactiveUS20050033747A1Special service provision for substationData taking preventionHyperlinkClient-side
The invention pertains to an apparatus for the client-sided receiving, transmitting, delivering, representing, outputting and displaying of server-sided stored data by means of unambiguous or unique content signatures, which together with additional data, are stored on the server-side. Server-sided additional data are called via this content signature on the server-side by a client-sided program. Additional data are displayed on the client-side and can be used as hyperlinks for further searches or linking. Further additional data can be inserted on the client-side by creators related to content signatures, which are transmitted to the server and stored on the server-side. Via the assignment of predetermined category names, server-sided additional assignments can be defined for category terms and upon client requests, after which it is sent to the client.
Owner:WITTKOTTER ERLAND
Systems and methods for providing content and services on a network system
InactiveUS20100332615A1Metering/charging/biilling arrangementsData taking preventionNetwork File SystemClient-side
Owner:NOMADIX INC
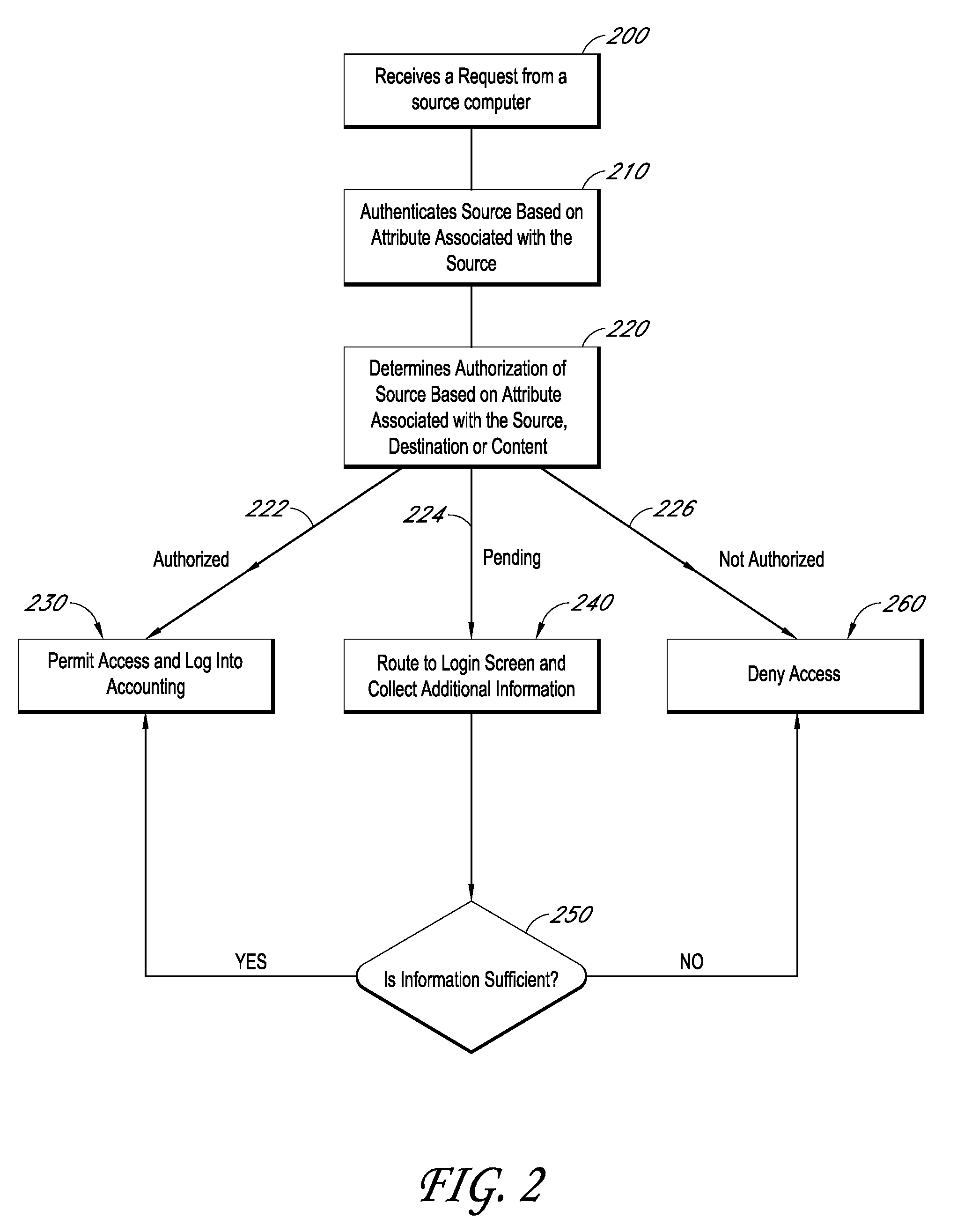
Credential/condition assertion verification optimization
InactiveUS20020053033A1Data taking preventionDigital data processing detailsNetwork security policySecurity policy
A method and apparatus ascertain which credential and which condition both from a network security policy best describe, respectively, information about initiator and target principals involved in an interaction, and tests performed on a state of an associated protocol event.
Owner:MCAFEE LLC
Method for sharing functionality and/or data between two or more linked entities
InactiveUS20080091763A1Secure and flexible and simpleKey distribution for secure communicationData taking preventionNetwork connectionOperating system
A method for sharing functionality and / or data between two or more linked entities using a network. The method comprising the steps of creating on at least one entity at least one real object, each real object providing access to the functionality and / or data of the entity. The method further comprising the step of creating on each entity at least one virtual object, each virtual object providing access to the functionality and / or data of a real object on the entity, each virtual object containing at least one object action. The method further comprising the step of creating on at least one entity at least one remote object for connection to a virtual object on a remote entity via the network; the remote object allowing an entity to access functionality and / or data of a remote entity.
Owner:QUIPA HLDG
Method and apparatus for protecting legitimate traffic from dos and ddos attacks
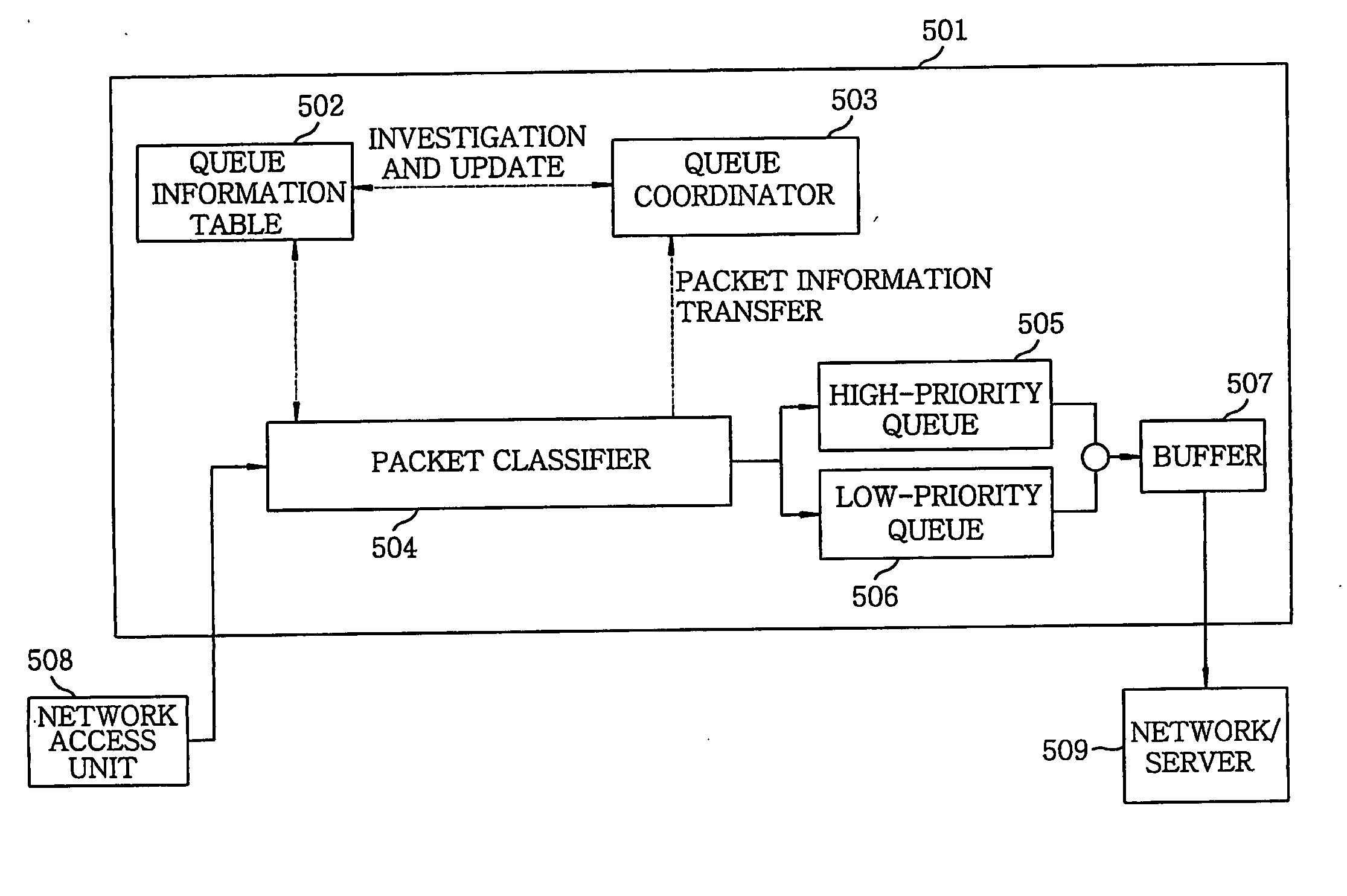
InactiveUS20060041667A1Protection attackError preventionFrequency-division multiplex detailsDistributed computingLower priority
An apparatus for protecting legitimate traffic from DoS and DDoS attacks has a high-priority (505) and a low-priority (506) queue. Besides, a queue information table (402) has STT (Source-based Traffic Trunk) service queue information of a specific packet. A queue coordinator (502) updates the queue information table (502) based on a load of a provided STT and a load of the high-priority queue (505). A packet classifier (504) receives a packet from the network access unit (508), investigates an STT service queue of the packet from the queue information table (502), selectively transfers the packet to the high-priority (505) or the low-priority (506) queue and provides information on the packet to the queue coordinator (503). A buffer (507) buffers outputs of the high-priority (505) and the low-priority (506) queue and provides outputs to the network (509) to be protected.
Owner:ELECTRONICS & TELECOMM RES INST
Method and framework for integrating a plurality of network policies
ActiveUS20050010765A1Data taking preventionDigital data protectionNetwork strategyDistributed computing
A method and system is disclosed for managing and implementing a plurality of network policies in a network device. Each of the plurality of policies are defined by one or more filters. The filters are installed in a policy engine. A layer identifies the network policy to be applied to a packet by sending a request to the policy engine. The policy engine then returns the policy to the requesting layer. The method and system may be used to implement a programmable, host-based, distributed, authenticating firewall that enables security and other policies to be applied at several protocol layers.
Owner:MICROSOFT TECH LICENSING LLC
Node device and method to prevent overflow of pending interest table in name based network system
ActiveUS8826381B2Prevent overflowMemory loss protectionData taking preventionTraffic capacityReal-time computing
Owner:SAMSUNG ELECTRONICS CO LTD
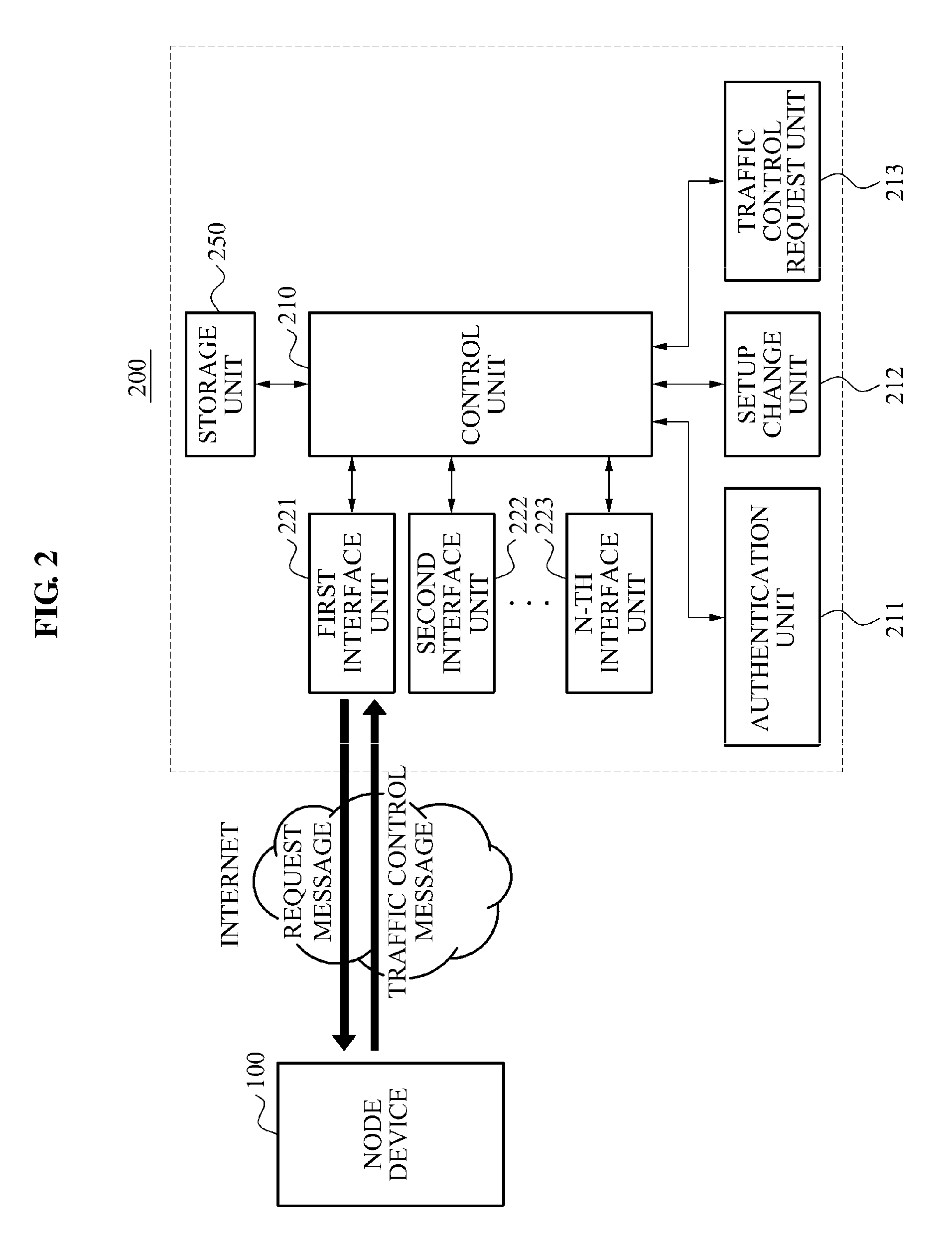
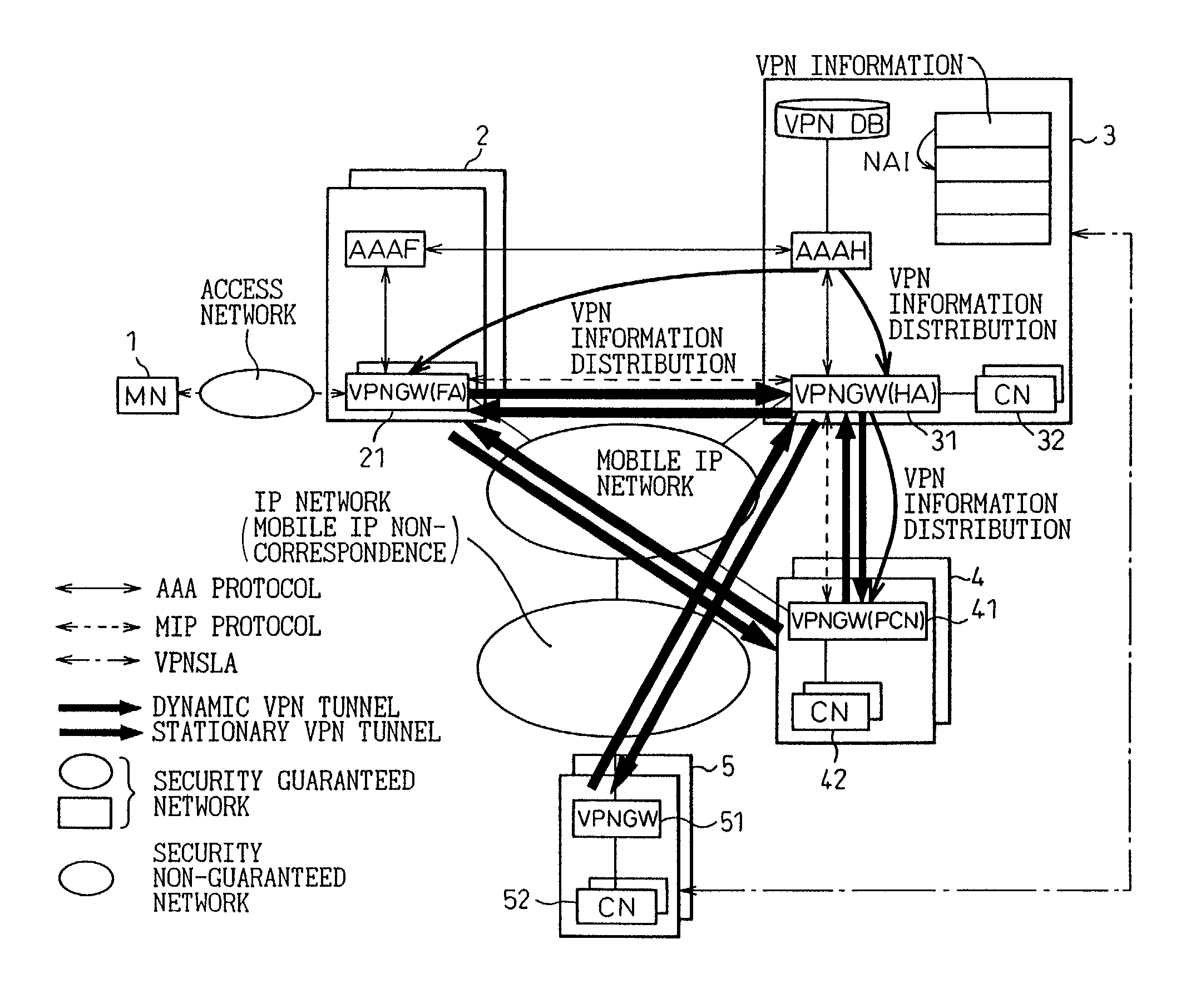
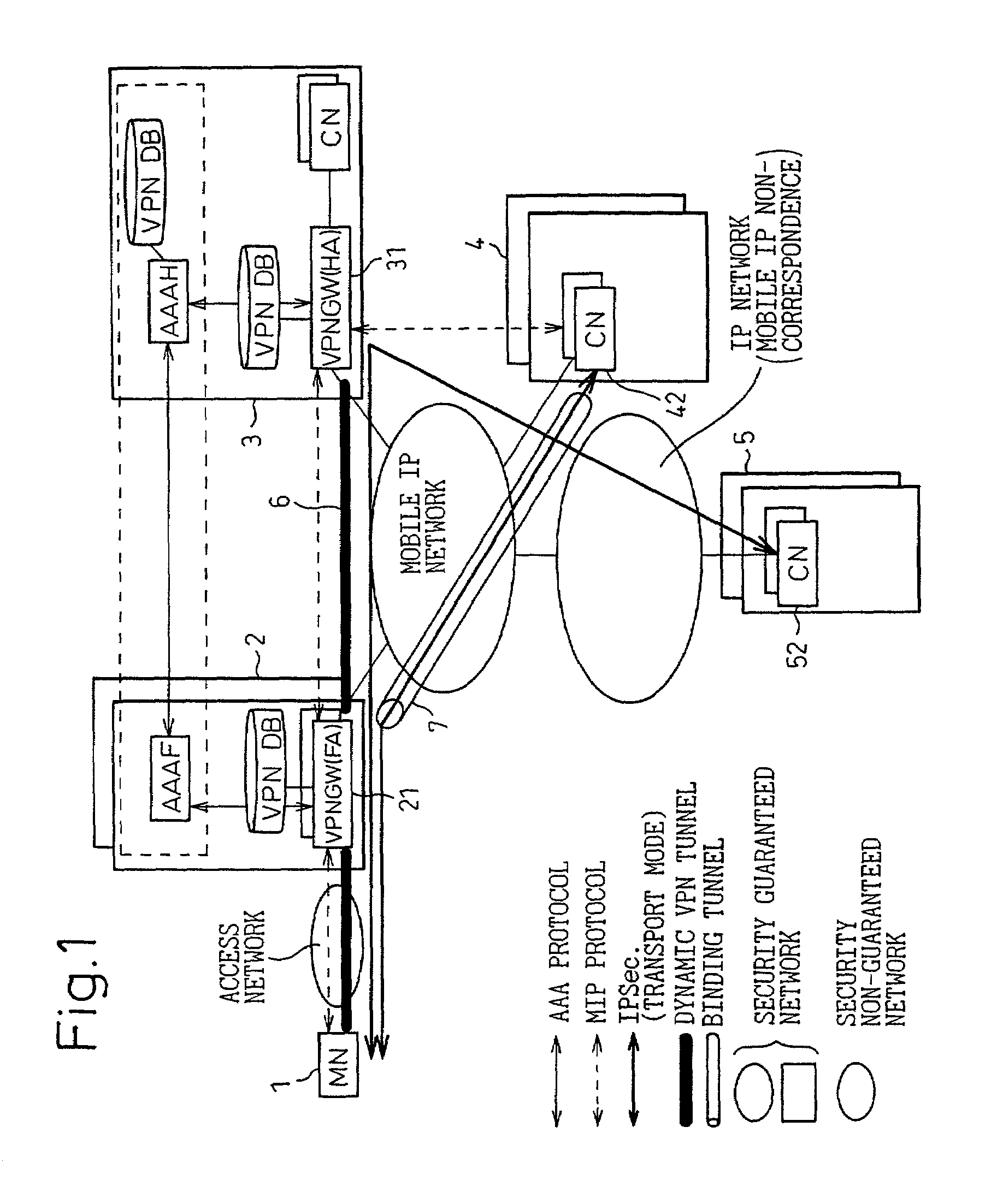
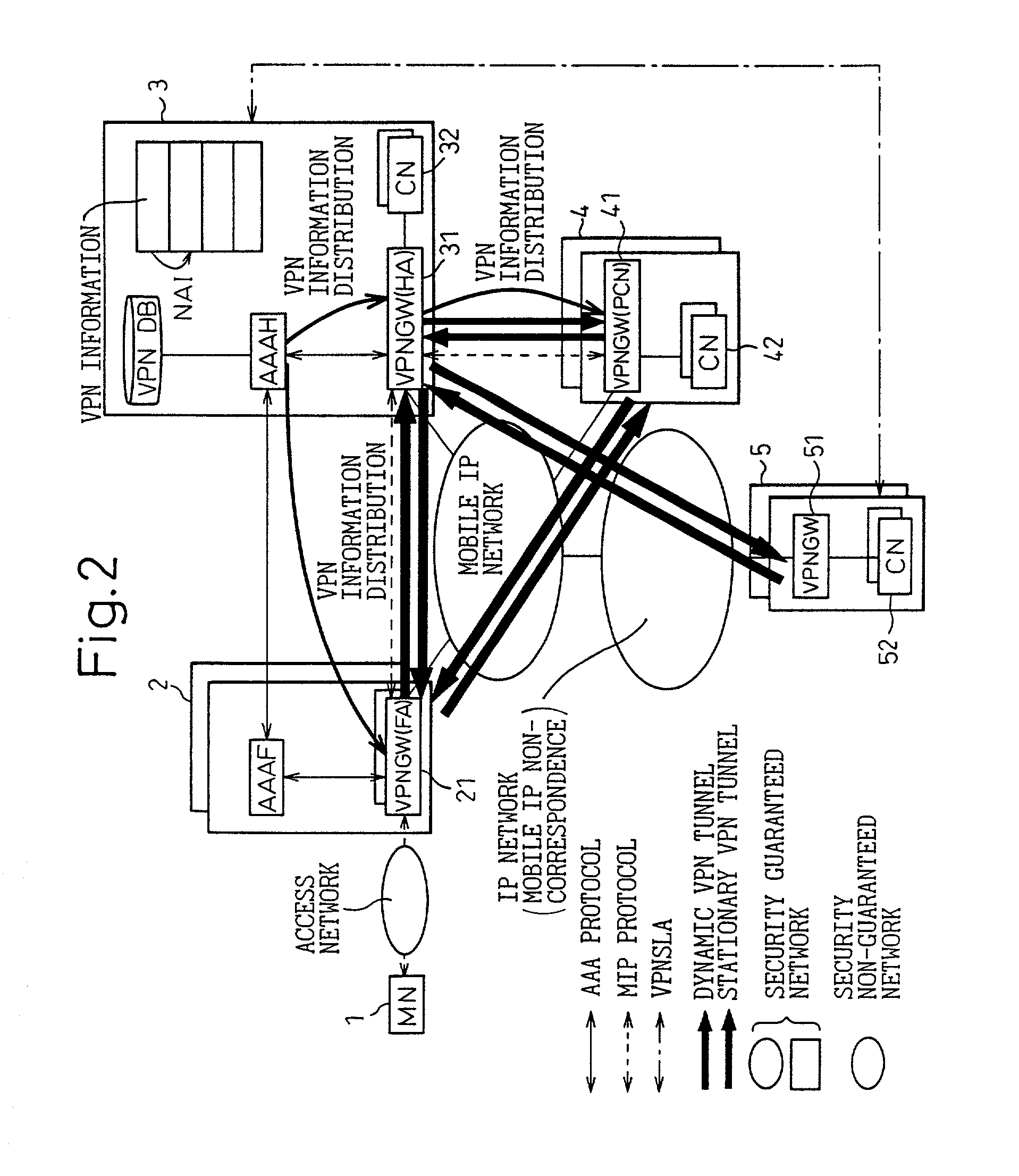
VPN system in mobile IP network, and method of setting VPN
InactiveUS7068640B2Improve user convenienceData taking preventionTime-division multiplexAuthentication serverMobile IP
Linked with a position registration procedure in a mobile IP, the invention provides a VPN setting service using an IP Sec. tunnel between optional terminals without requiring these terminals to have a specific VPN function. This service is provided by a mobile terminal, authentication servers, a VPN database, and network apparatuses. A home authentication server extracts from the VPN database the VPN information of a user who has requested the authentication at the time of making a position registration request from the mobile terminal. The home authentication server then posts the VPN information to each network apparatus using a predetermined position registration message and an authentication response message. Based on the posted VPN information, the network apparatuses set a VPN path by the IP Sec. to between a home network apparatus and an external network apparatus, between the home network apparatus and a predetermined network apparatus, and / or the external network apparatus and the predetermined network apparatus, respectively.
Owner:FUJITSU LTD
Distributed hierarchical identity management system authentication mechanisms
ActiveUS20050283614A1Data taking preventionUser identity/authority verificationThird partyInternet privacy
A set of methods, and systems, for use in an identity management system are disclosed herein. A modular user identity information datastore using hardware accelerated encryption for user data security operates in a network for receiving requests for, and issuing responses containing user information including third party accredited assertions.
Owner:CALLAHAN CELLULAR L L C
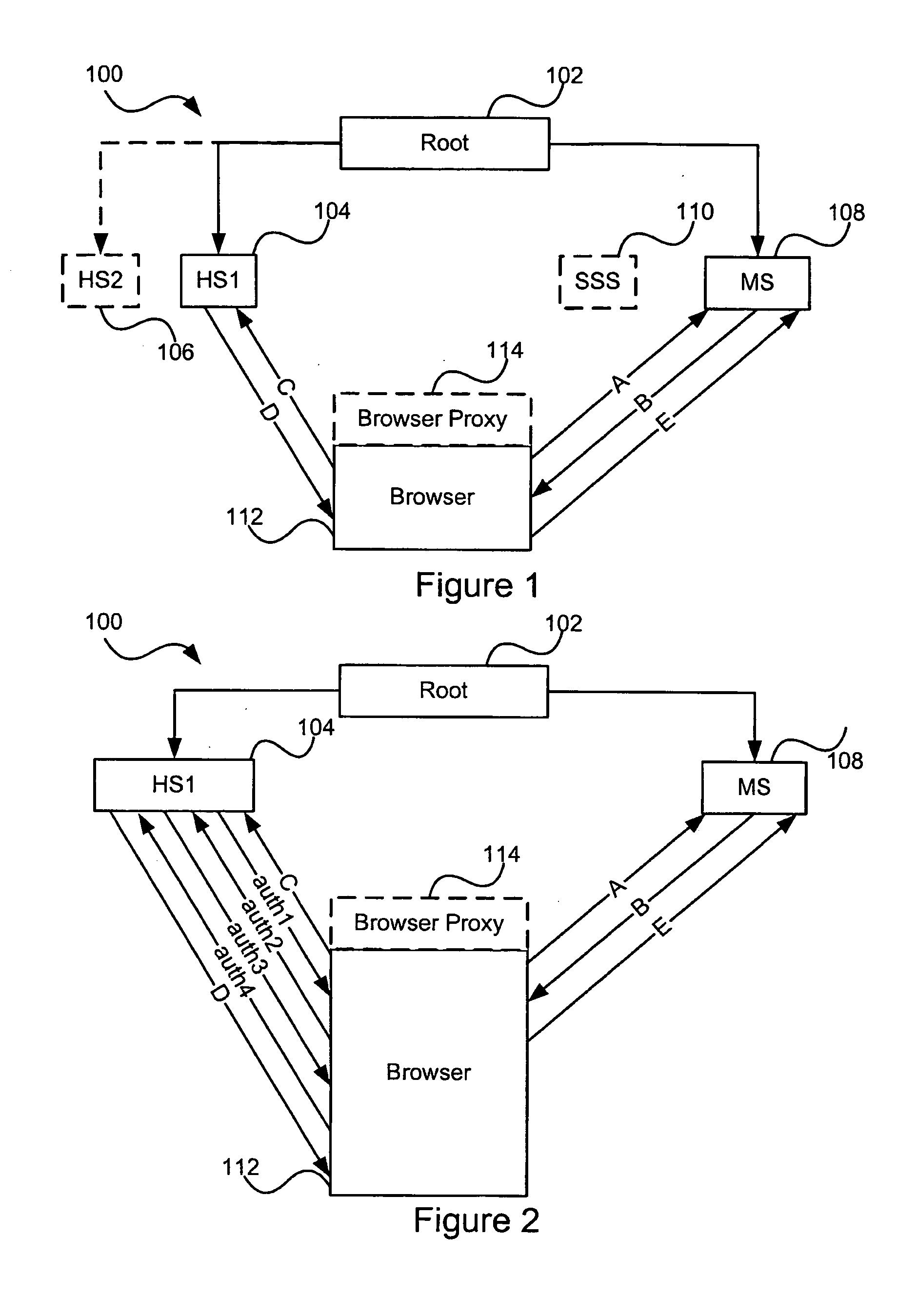
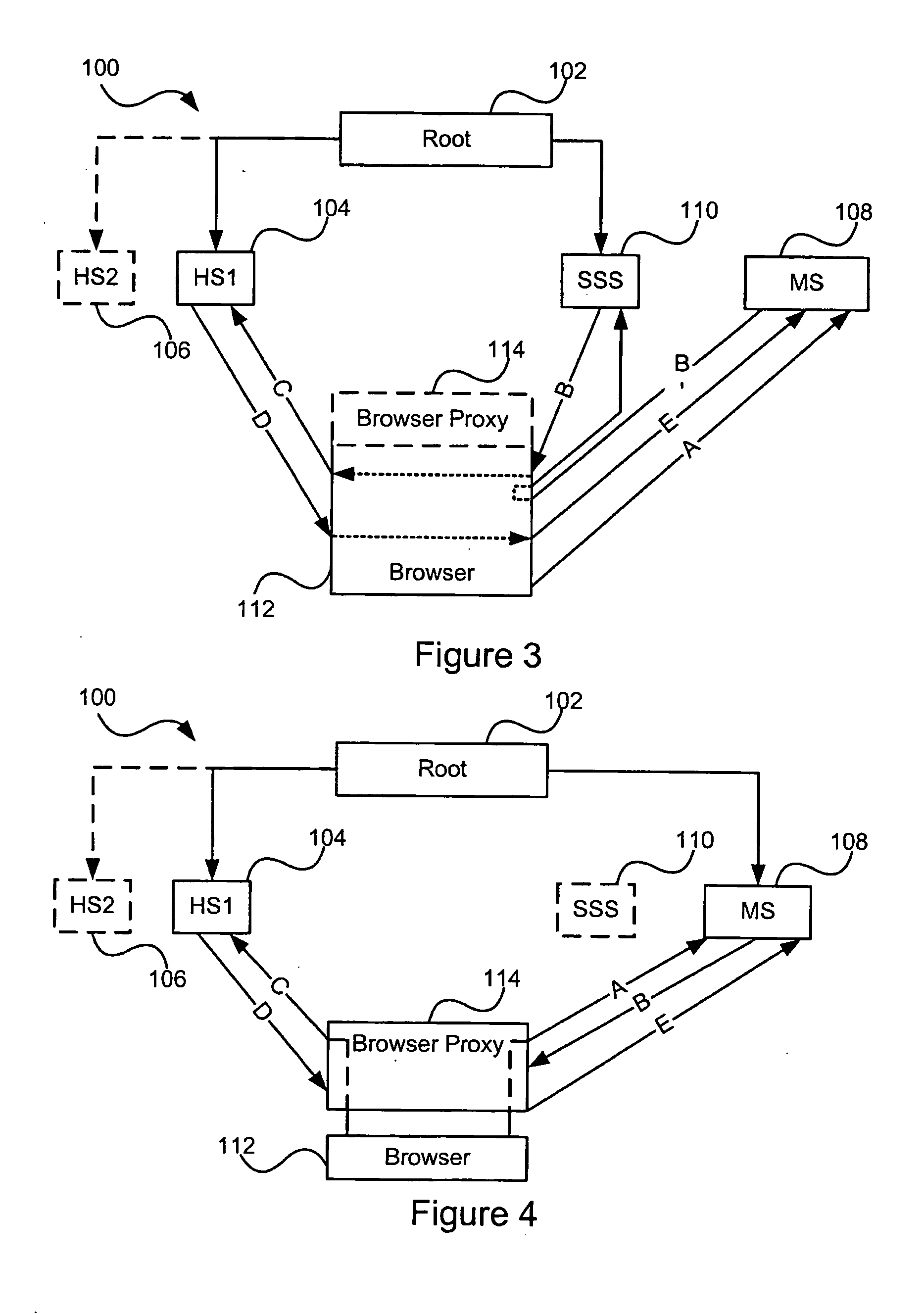
Accessing protected data on network storage from multiple devices
ActiveUS20050193199A1Easy to manageKey distribution for secure communicationData taking preventionPlaintextAuthorized domain
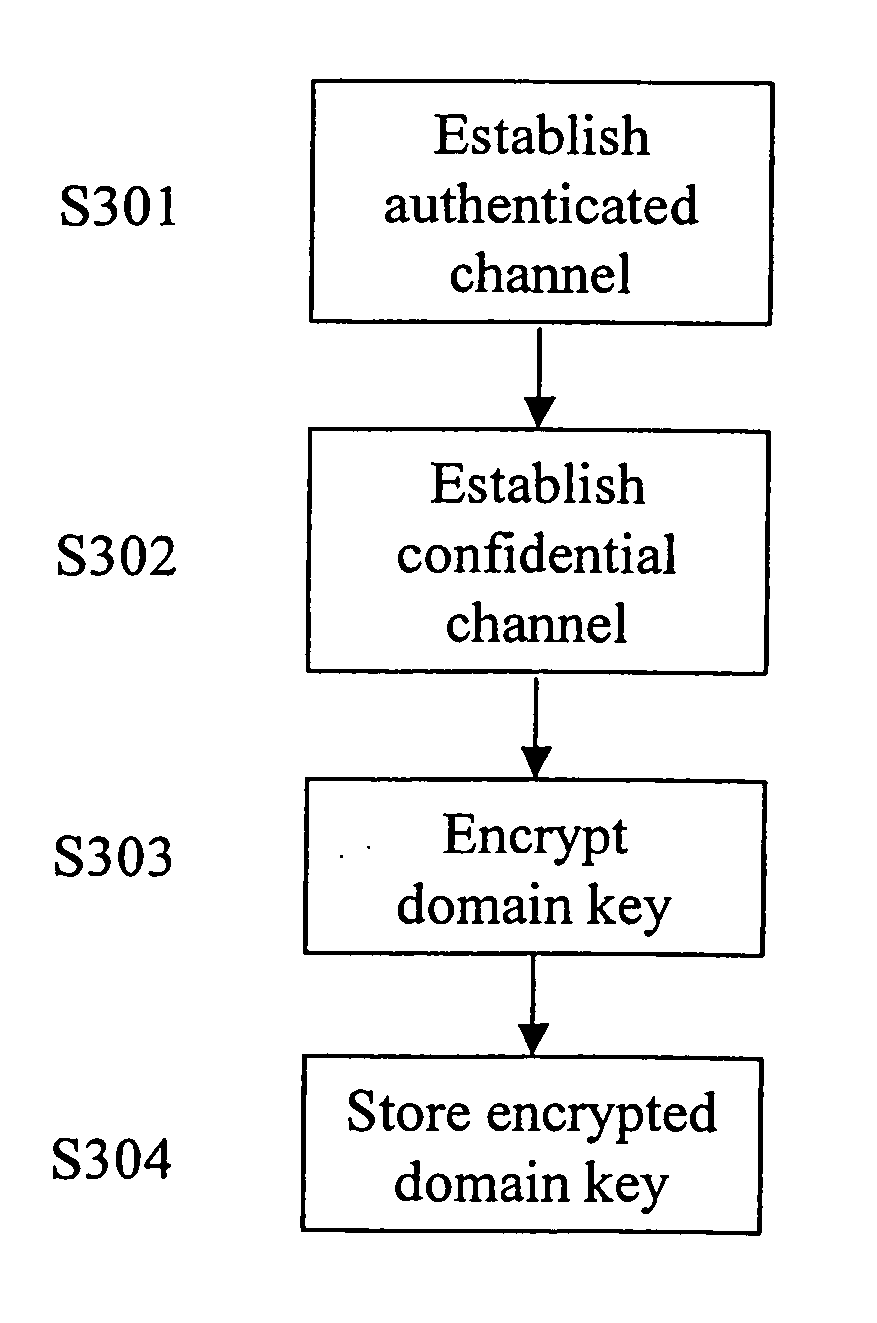
The present invention relates to a method and a system of securely storing data on a network (100) for access by an authorized domain (101, 102, 103), which authorized domain includes at least two devices that share a confidential domain key (K), and an authorized domain management system for securely storing data on a network for access by an authorized domain. The present invention enables any member device to store protected data on the network such that any other member device can access the data in plaintext without having to communicate with the device that actually stored the data.
Owner:NOKIA TECHNOLOGLES OY
System for signatureless transmission and reception of data packets between computer networks
InactiveUSRE39360E1Key distribution for secure communicationData taking preventionObjective informationEncryption
A system for automatically encrypting and decrypting data packet sent from a source host to a destination host across a public internetwork. A tunnelling bridge is positioned at each network, and intercepts all packets transmitted to or from its associated network. The tunnelling bridge includes tables indicated pairs of hosts or pairs of networks between which packets should be encrypted. When a packet is transmitted from a first host, the tunnelling bridge of that host's network intercepts the packet, and determines from its header information whether packets from that host that are directed to the specified destination host should be encrypted; or, alternatively, whether packets from the source host's network that are directed to the destination host's network should be encrypted. If so, the packet is encrypted, and transmitted to the destination network along with an encapsulation header indicating source and destination information: either source and destination host addresses, or the broadcast addresses of the source and destination networks (in the latter case, concealing by encryption the hosts' respective addresses). An identifier of the source network's tunnelling bridge may also be included in the encapsulation header. At the destination network, the associated tunnelling bridge intercepts the packet, inspects the encapsulation header, from an internal table determines whether the packet was encrypted, and from either the source (host or network) address or the tunnelling bridge identifier determines whether and how the packet was encrypted. If the packet was encrypted, it is now decrypted using a key stored in the destination tunnelling bridge's memory, and is sent on to the destination host. The tunnelling bridge identifier is used particularly in an embodiment where a given network has more than one tunnelling bridge, and hence multiple possible encryption / decryption schemes and keys. In an alternative embodiment, the automatic encryption and decryption may be carried out by the source and destination hosts themselves, without the use of additional tunnelling bridges, in which case the encapsulation header includes the source and destination host addresses.
Owner:SUN MICROSYSTEMS INC
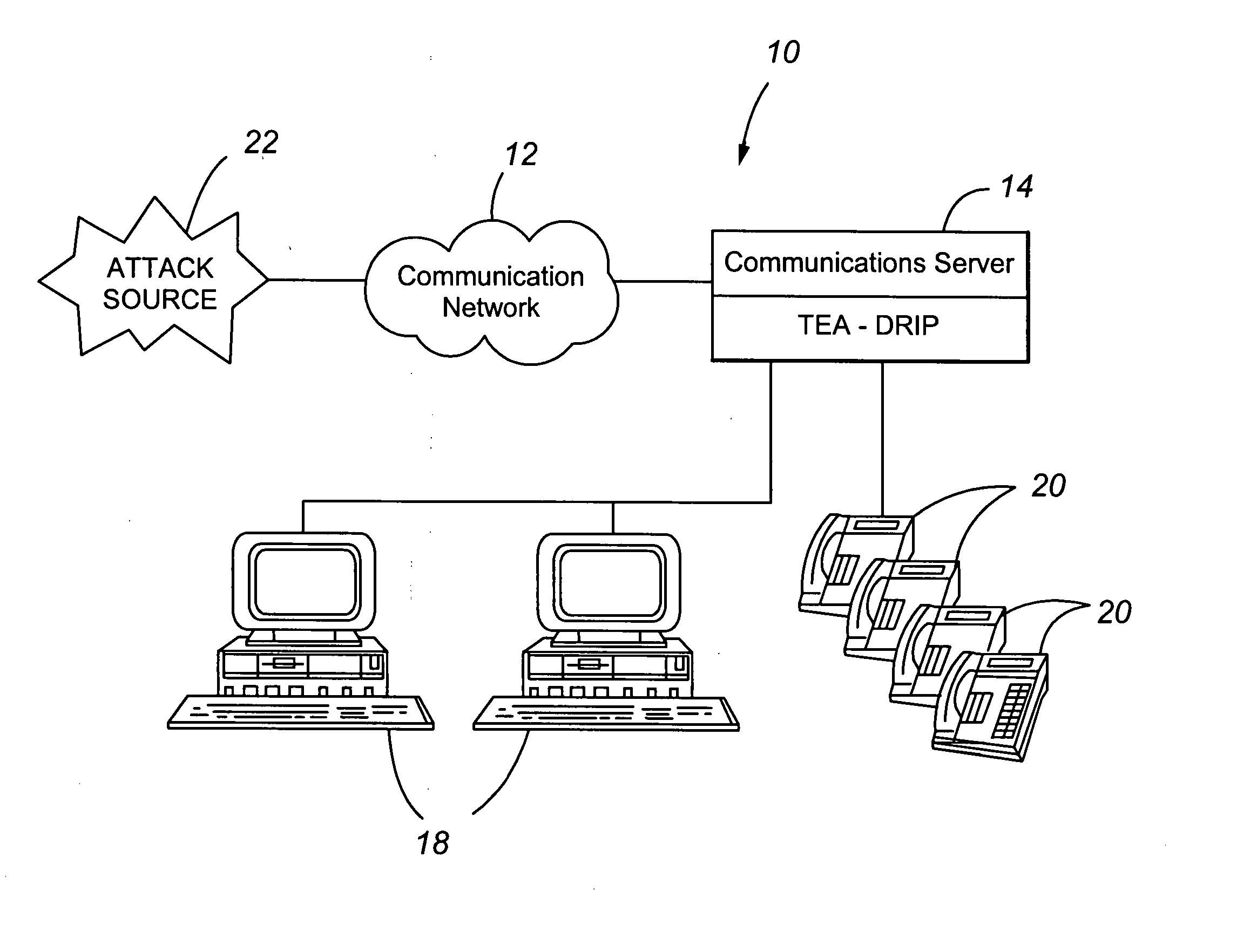
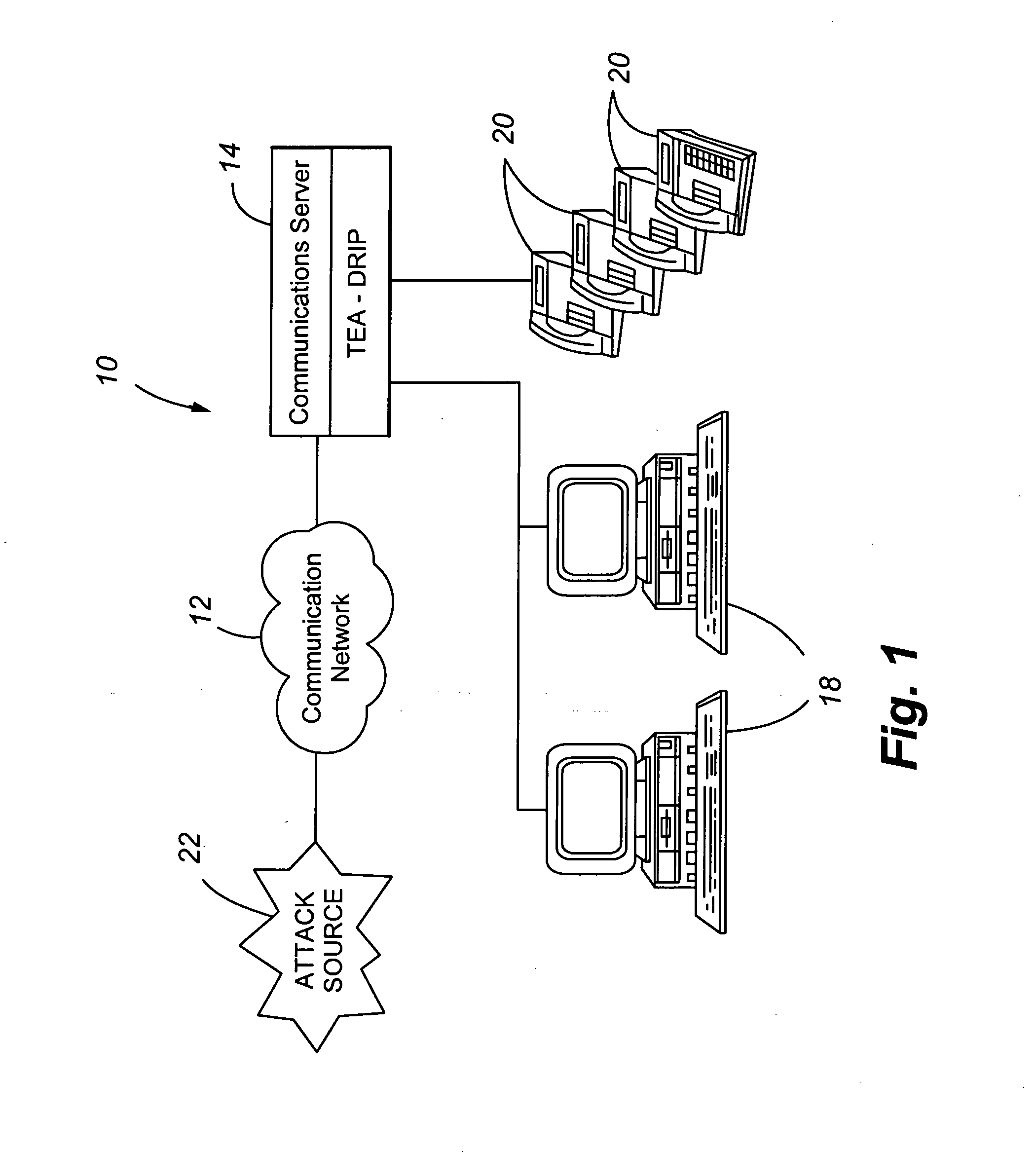
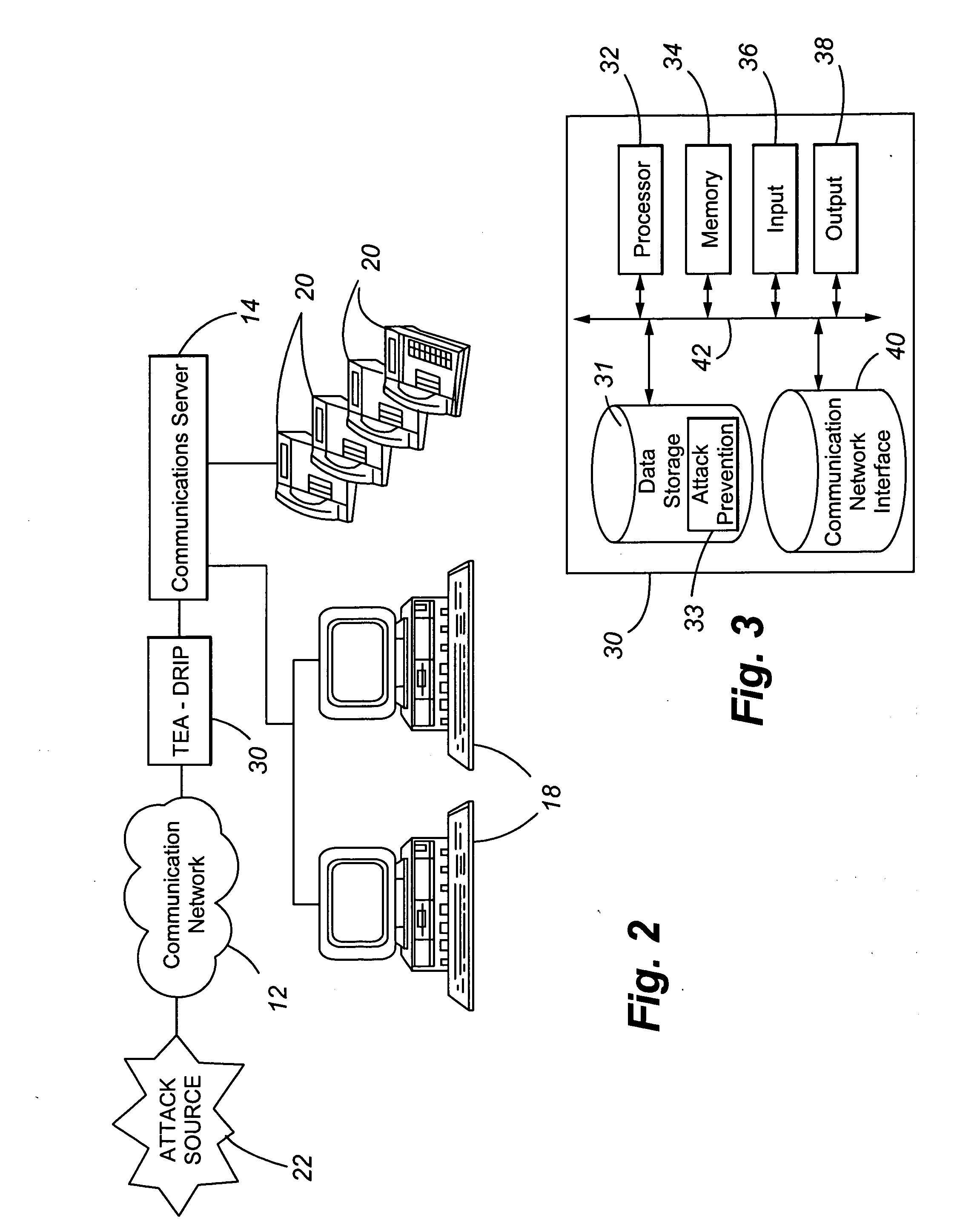
Telephony extension attack detection, recording, and intelligent prevention
ActiveUS20070036314A1Effectively prevent future attackAvoid attackData taking preventionAutomatic exchangesCommunication endpointRemedial action
A system and method are provided for detecting extension attacks made to a communication enterprise, and taking appropriate remedial action to prevent ongoing attacks and future attacks. One or more attributes of a suspect call are analyzed, and a risk is associated with each analyzed attribute. An overall risk or assessment is then made of the analyzed attributes, attack attributes are logged, and one or more remedial actions may be triggered as a result of the analyzed call attributes. The remedial actions may include recording the call, notifying an administrator of a suspect call, or isolating the communication enterprise from the attack by terminating the call or shutting down selected communication endpoints to prevent calls being made to those extensions. Rules may be applied to the analyzed attributes in order to trigger the appropriate remedial action. The call attributes analyzed may include call destination, call direction, call type, time of day of the call, call duration, whether a call source is spoofed, call volume from a particular call source, and hash values created for a suspect media stream.
Owner:AVAYA INC
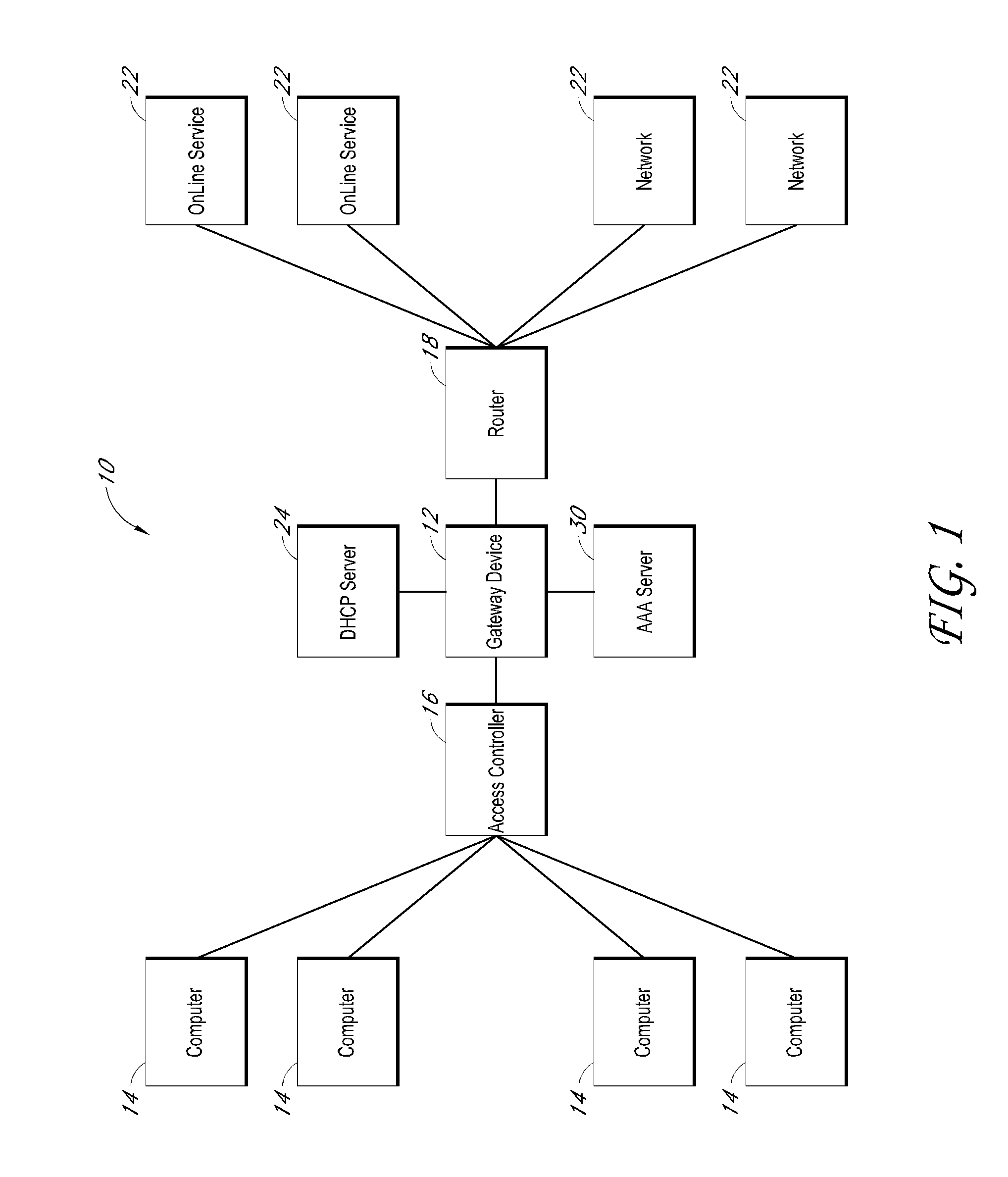
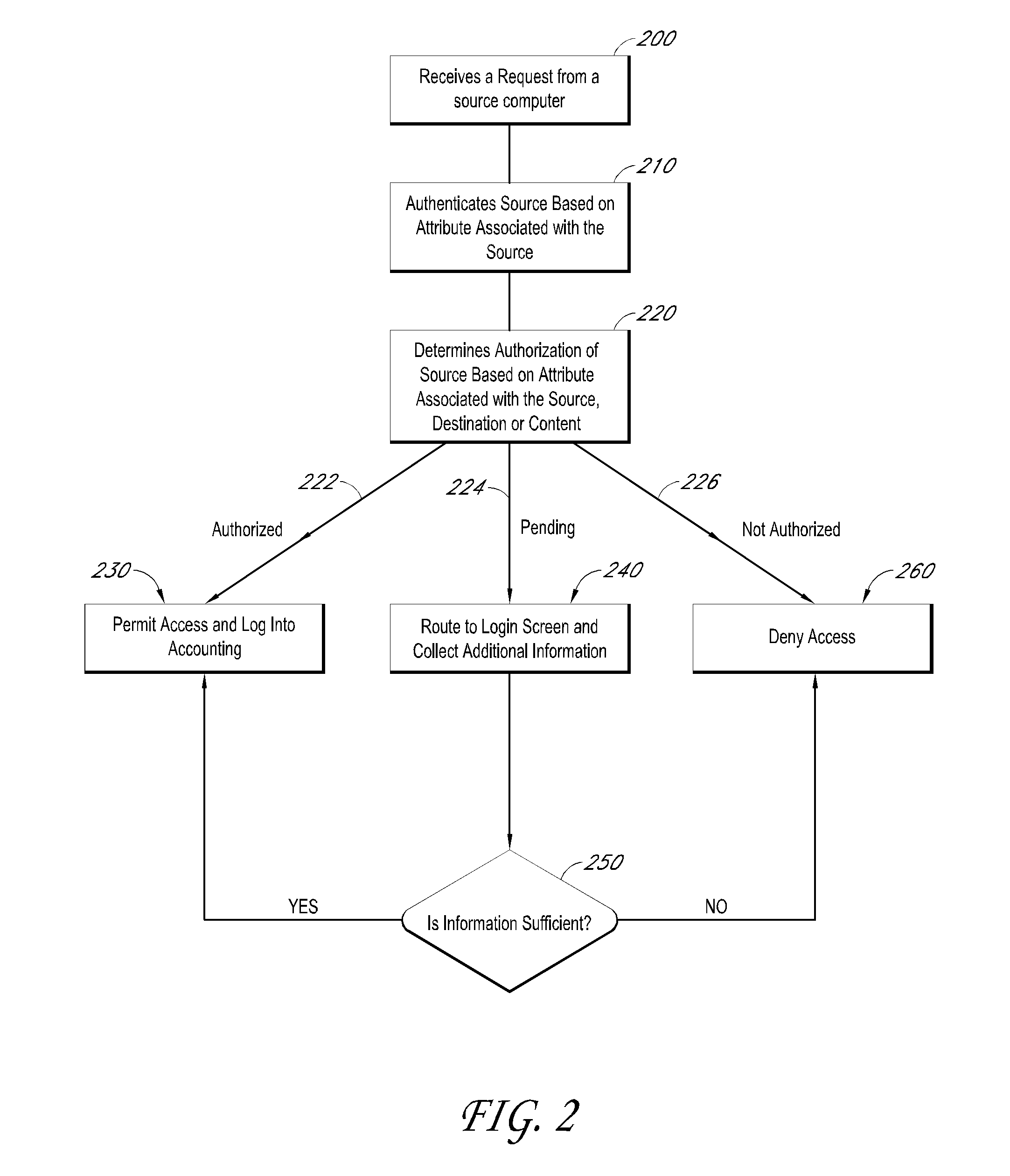
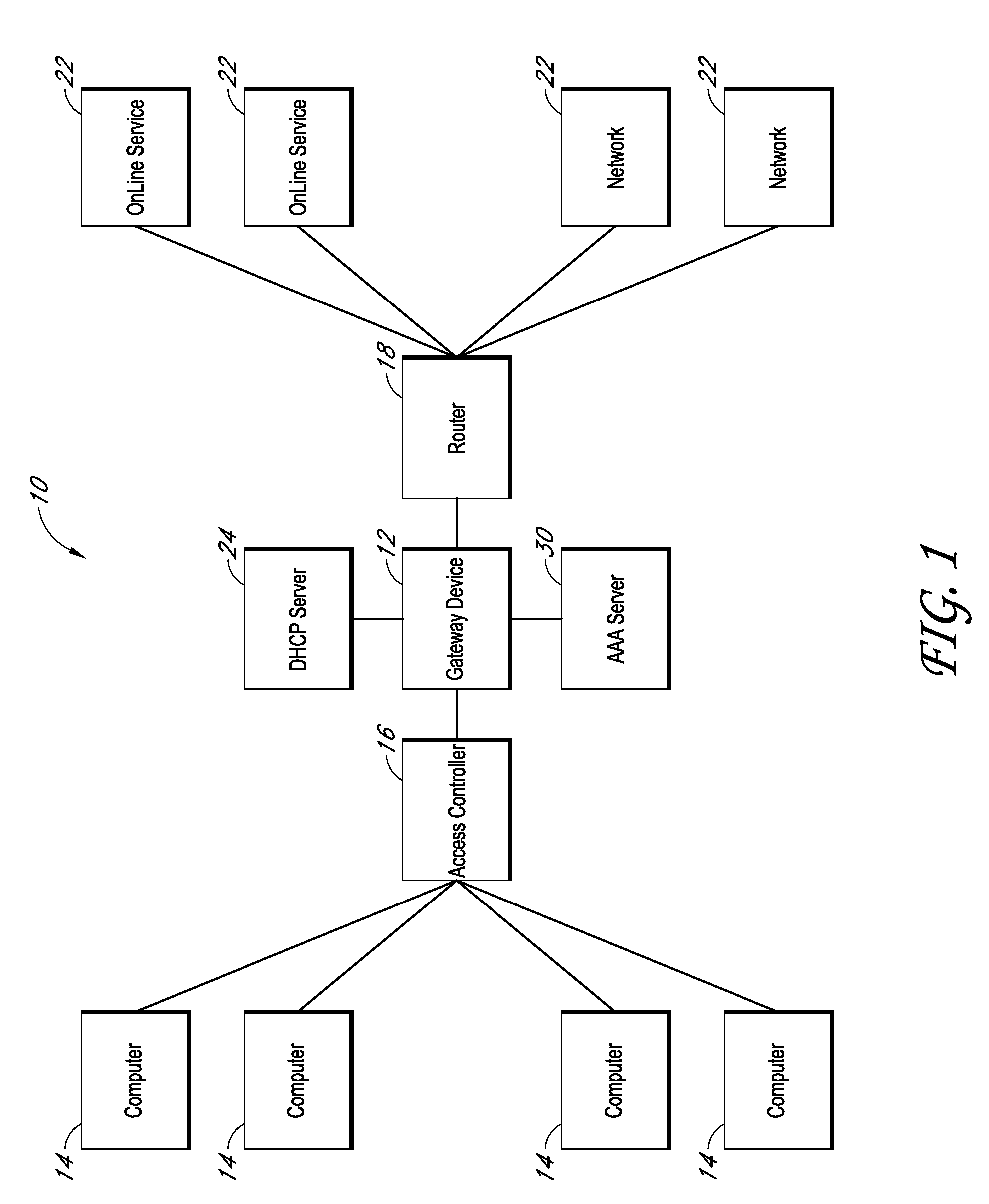
Systems and methods for providing dynamic network authorization, authentication and accounting
InactiveUS20100115113A1Soft handoffImprove throughputMetering/charging/biilling arrangementsData taking preventionInternet privacyDirectory Access Protocol
Systems and methods for selectably controlling and customizing source access to a network, where the source is associated with a source computer, and wherein the source computer has transparent access to the network via a gateway device and no configuration software need be installed on the source computer to access the network. A user may be prevented access from a particular destination or site based upon the user's authorization while being permitted to access to other sites that the method and system deems accessible. The method and system can identify a source without that source's knowledge, and can access customizable access rights corresponding to that source in a source profile database. The source profile database can be a remote authentication dial-in user service (RADIUS) or a lightweight directory access protocol (LDAP) database. The method and system use source profiles within the source profile database to dynamically authorize source access to networks and destinations via networks.
Owner:NOMADIX INC
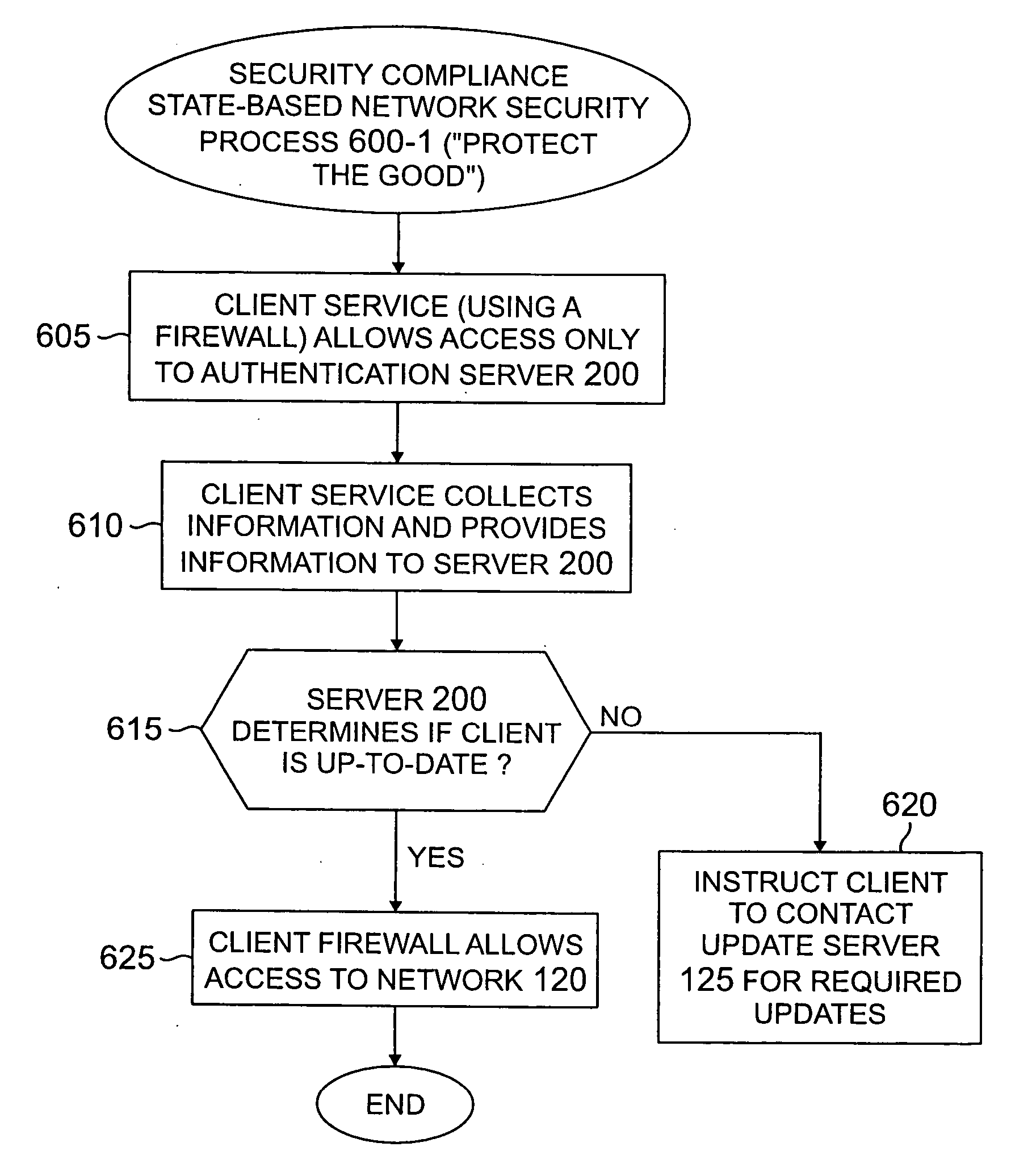
Method and apparatus for network security based on device security status
A method and apparatus are provided for network security based on a security status of a device. A security update status of a device is evaluated; and one or more of a plurality of security policies are selected to apply to the device based on the security update status. The available security philosophies may include, for example, a “protect the good” philosophy, an “encourage the busy” philosophy and a “shut off the non-compliant” philosophy. The security update status can evaluate, for example, a version level of one or more security features installed on the device or can be based on a flag indicating whether the device satisfies predefined criteria for maintaining one or more computer security protection features up-to-date.
Owner:AVAYA INC
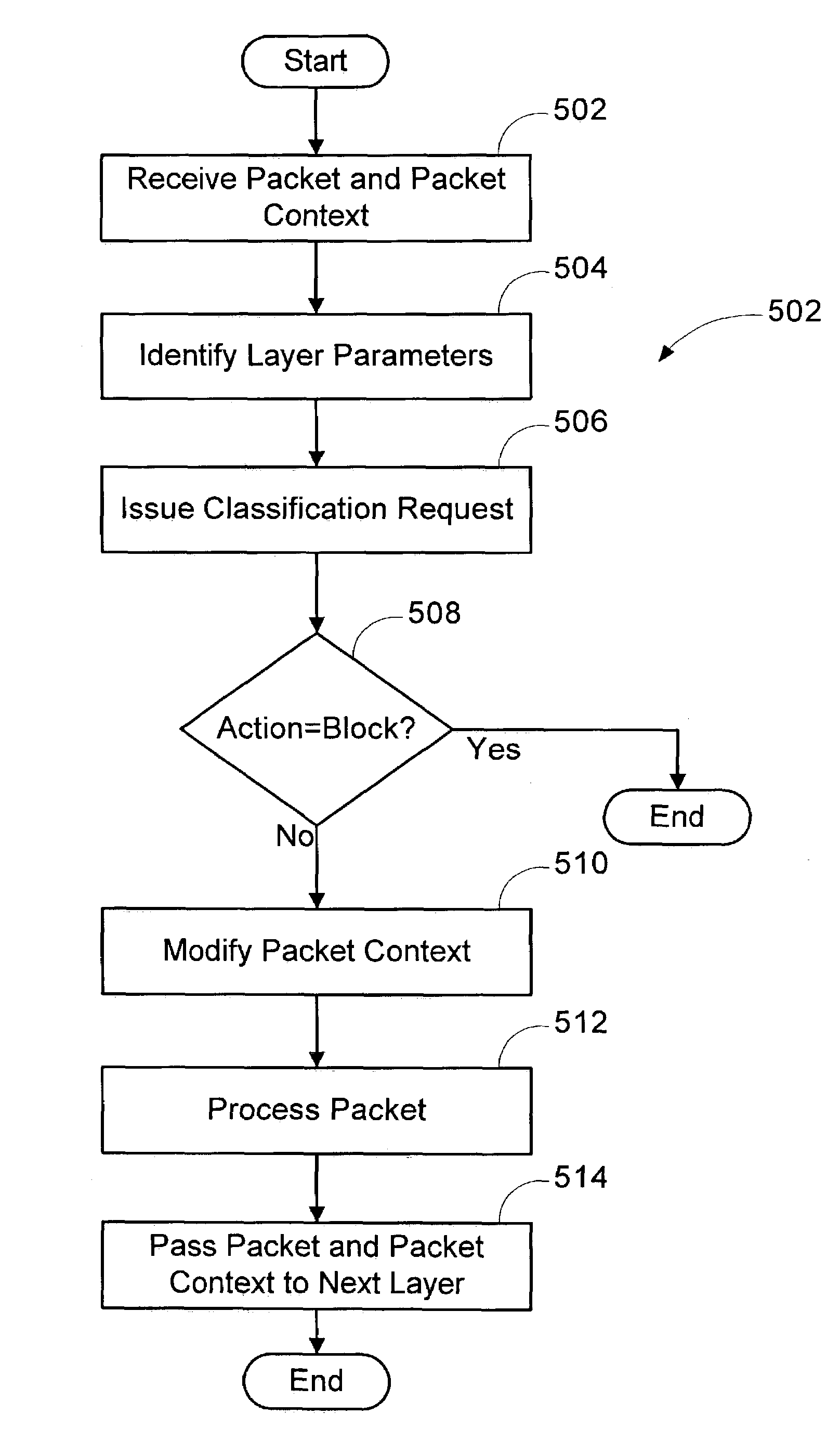
Multi-layer based method for implementing network firewalls
A method is provided for implementing a firewall in a firewall architecture. The firewall architecture includes a plurality of network layers and a first firewall engine. The layers send packets and packet information to the first firewall engine, maintain and pass packet context to subsequent layers, and process the packets. The first firewall engine compares the packet information to one or more installed filters and returns an action to the layers indicating how to treat the packet.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com