System for signatureless transmission and reception of data packets between computer networks
a data packet and computer network technology, applied in the field of data packet security, can solve the problem that no one on the public internetwork can determine the contents of packets
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
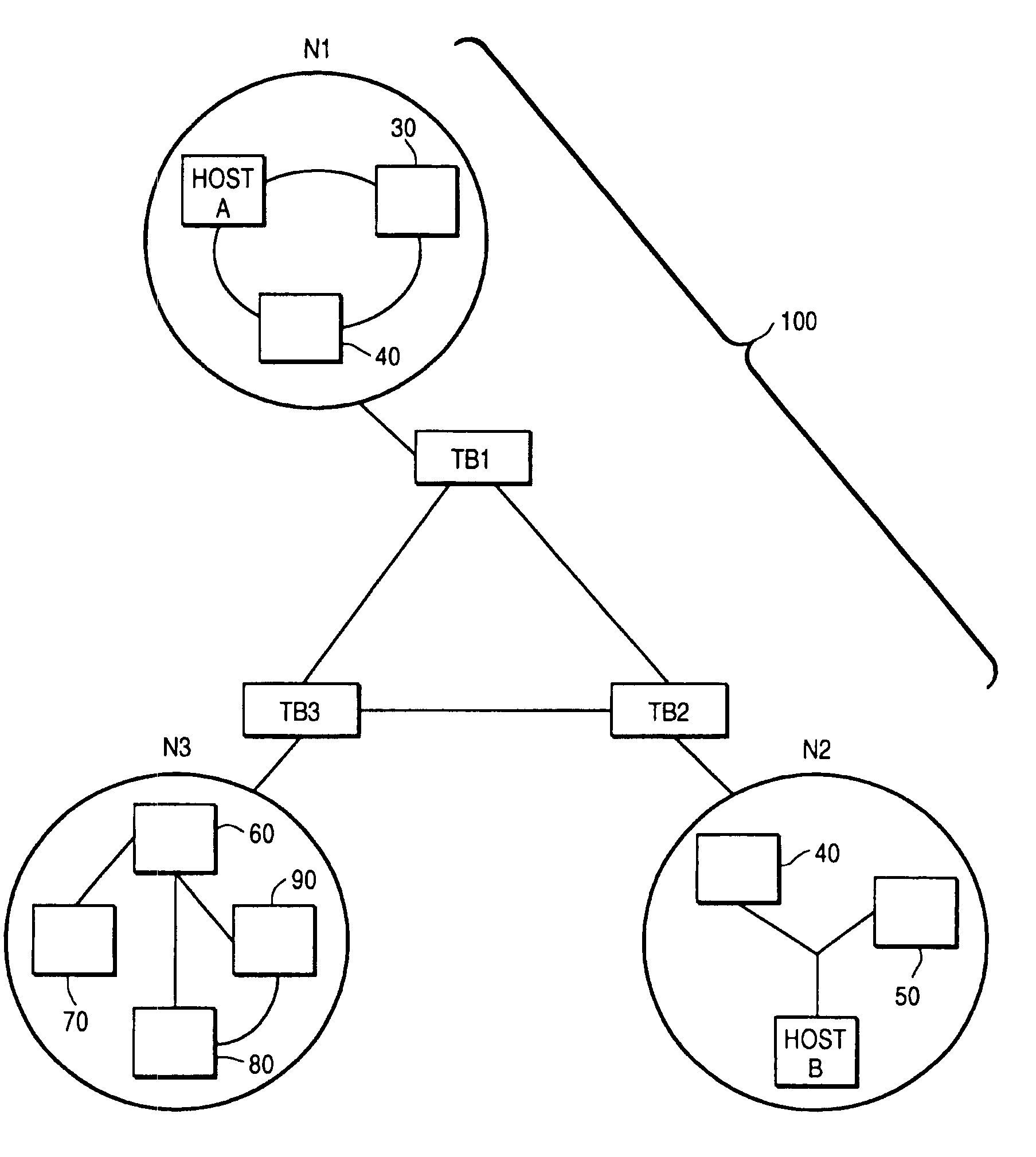
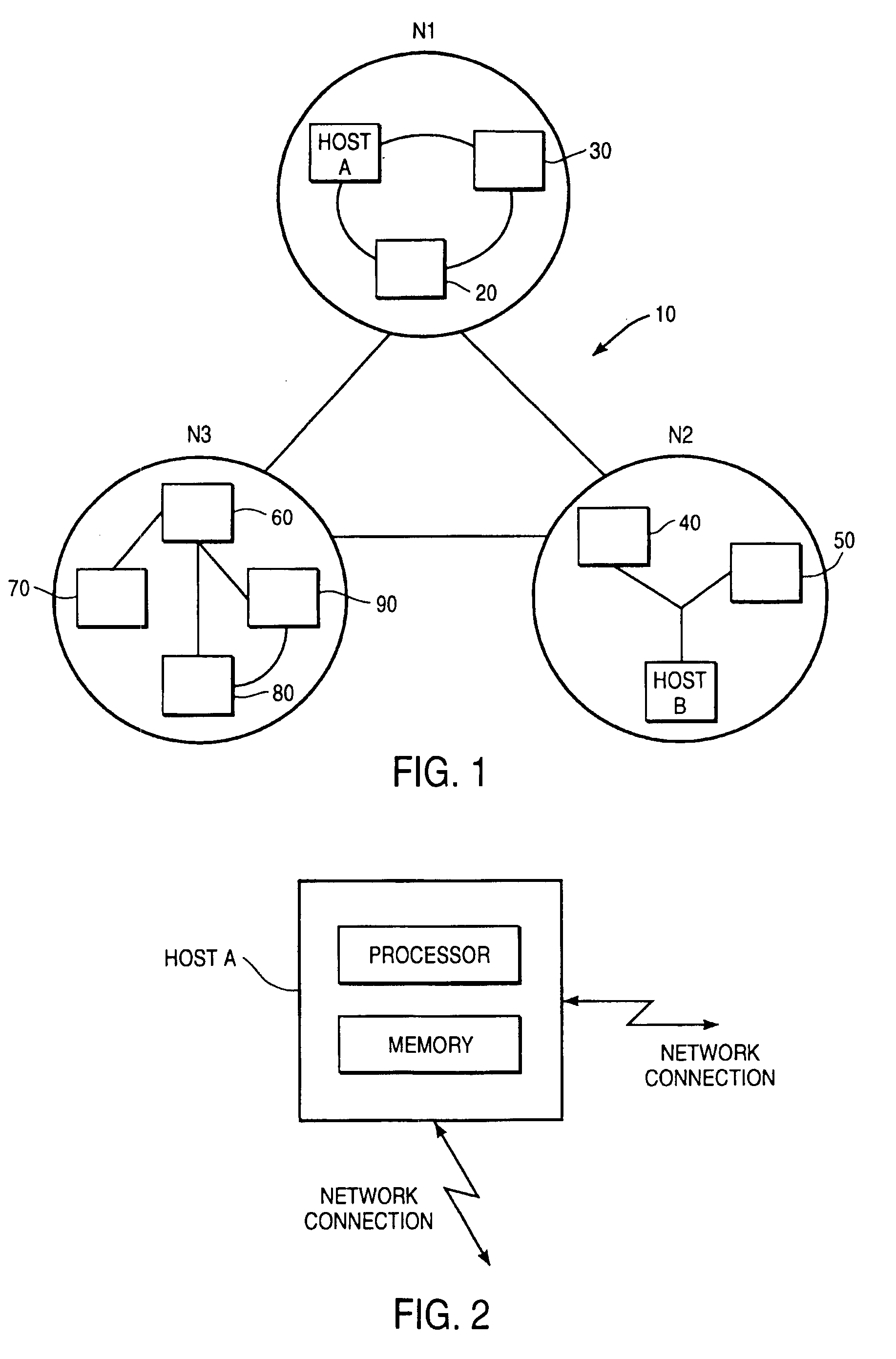
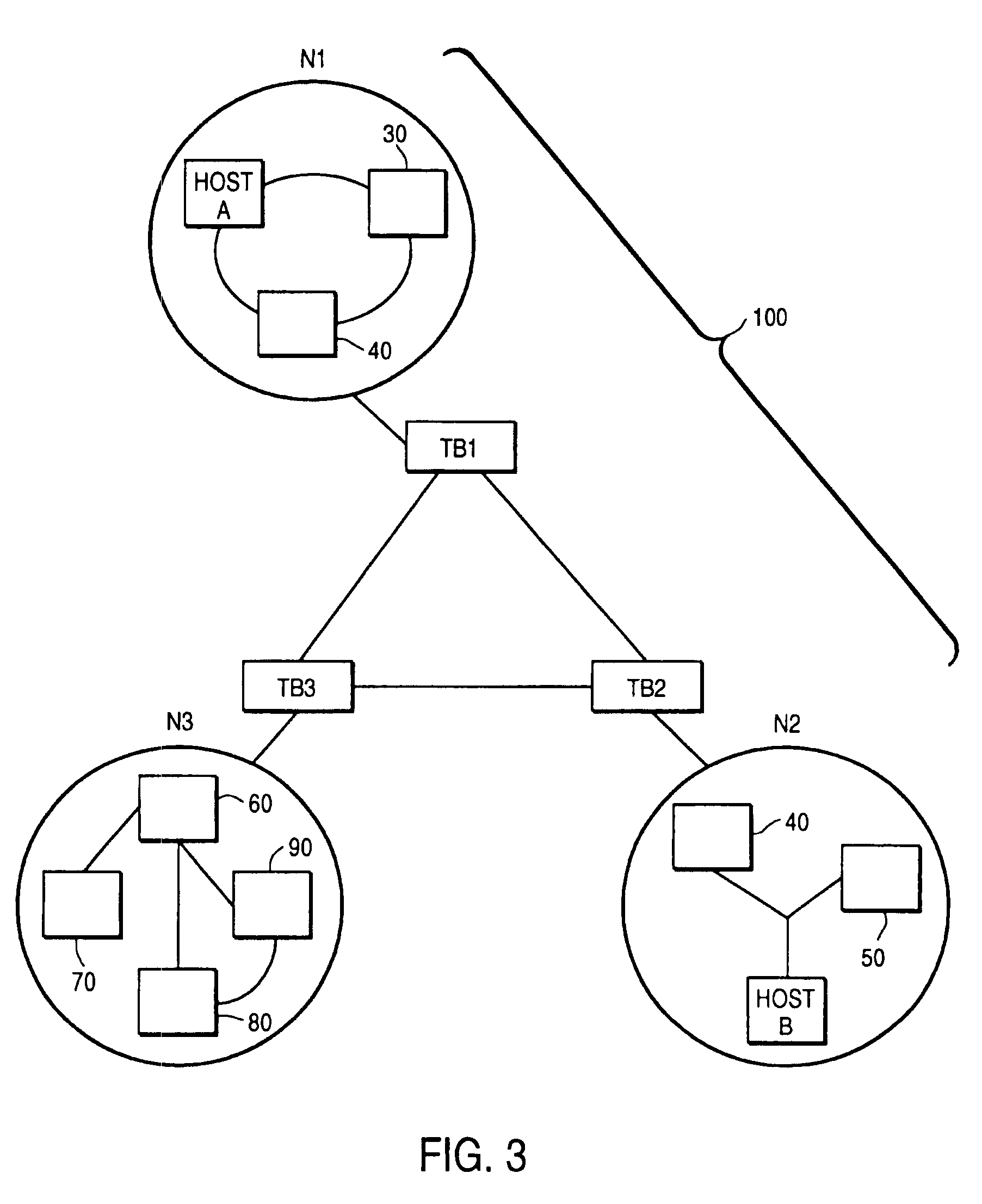
[0023]The system of the present invention is designed to be implemented in existing computer networks, and in the preferred embodiment uses the addition of a tunnelling bridge at junctions between local computer networks and public or larger-scale networks such as the Internet. The mechanisms for carrying out the method of the invention are implemented by computers acting as these tunnelling bridges, incorporating program instructions stored in memories of the tunnelling bridges and appropriate (standard) network connections and communications protocols.
[0024]FIG. 3 shows a network 100 of networks N1, N2 and N3 according to the invention, where each network includes a tunnelling bridge—TB1, TB2 and TB3, respectively—which intercepts all data packets from or to the respective networks. Networks N1-N3 may in other respects be identical to networks N1-N3 in conventional designs. In the following description, any references to networks N1-N3 or hosts A and B should be taken as referring...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com