Patents
Literature
310results about How to "Protection attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
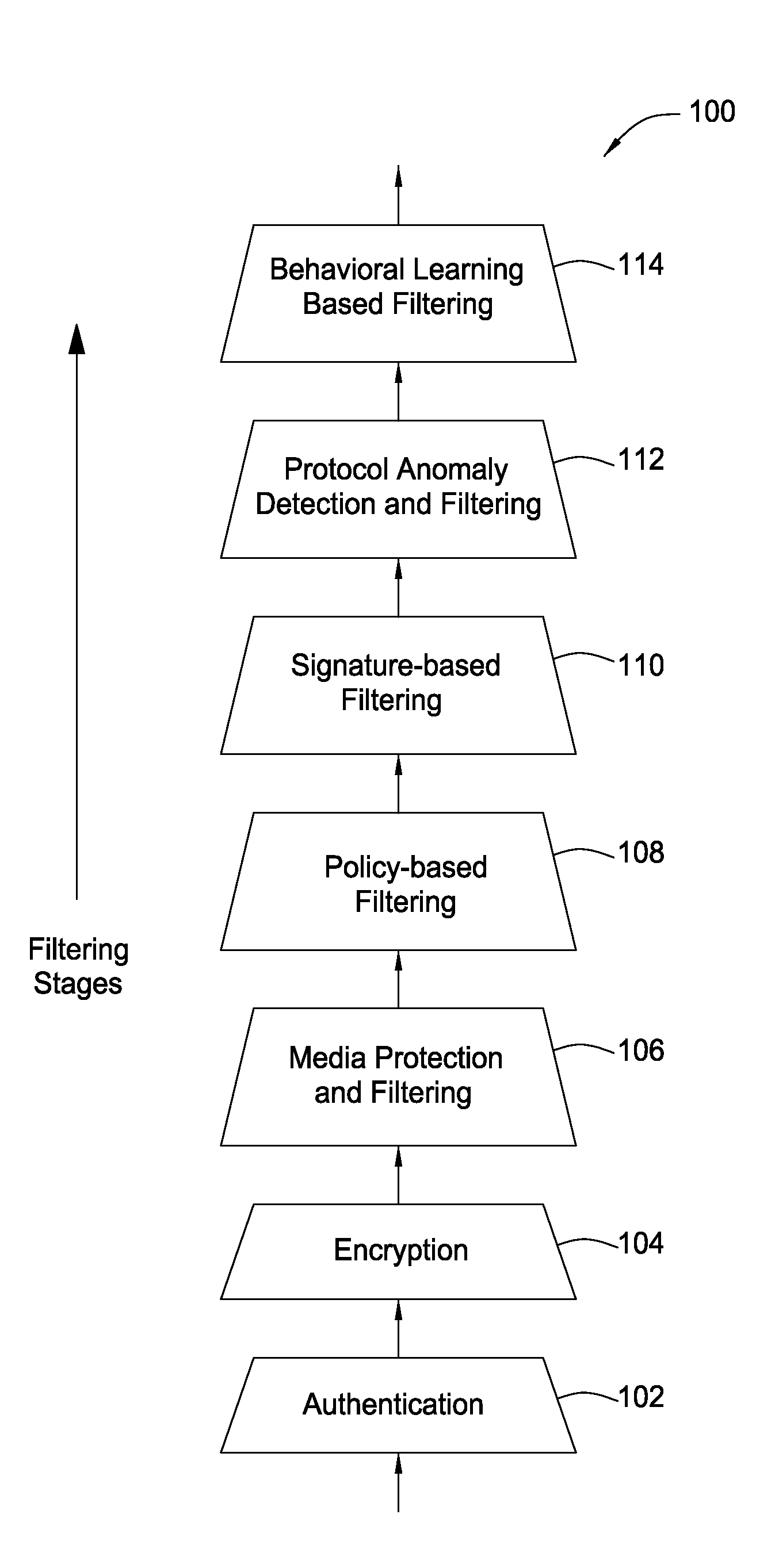
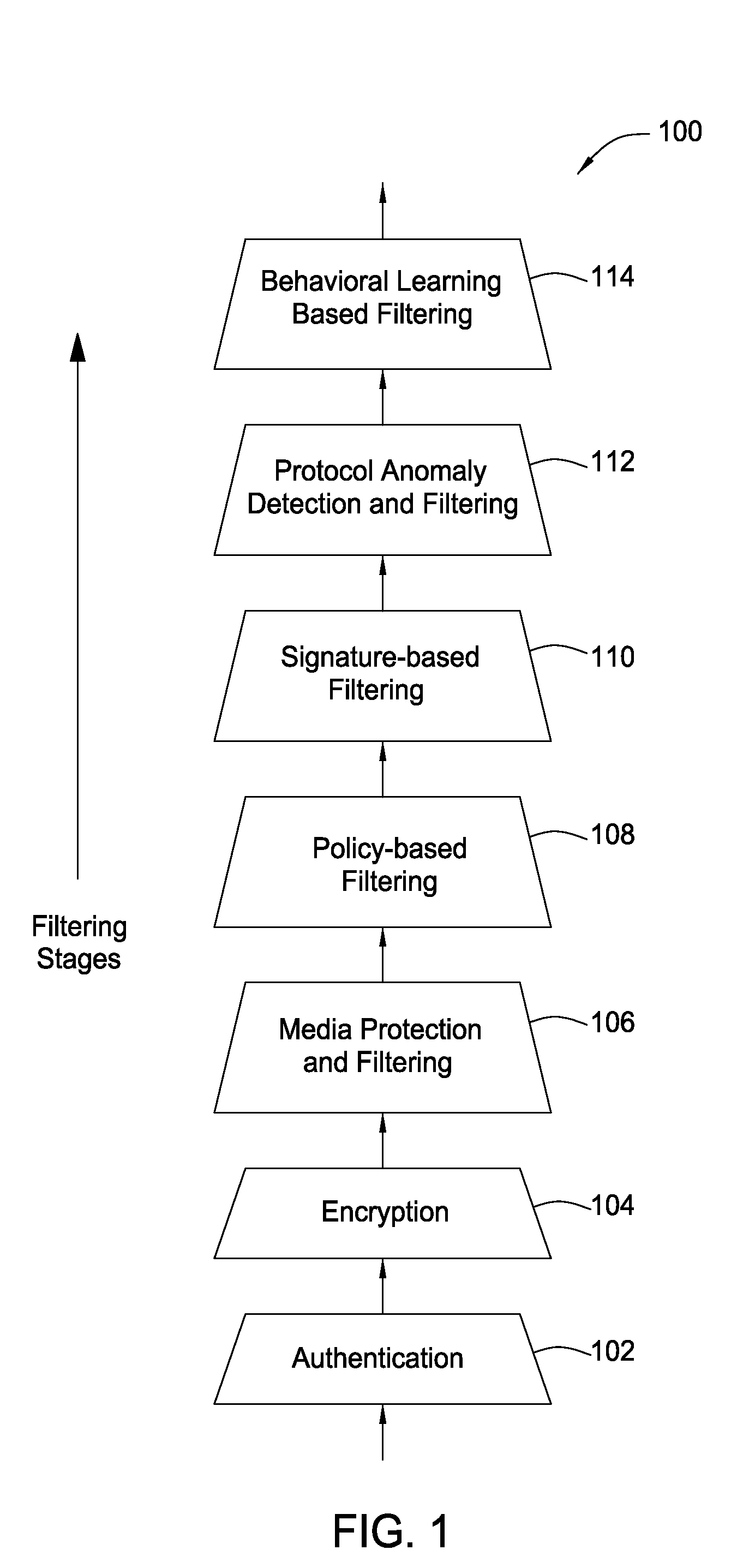
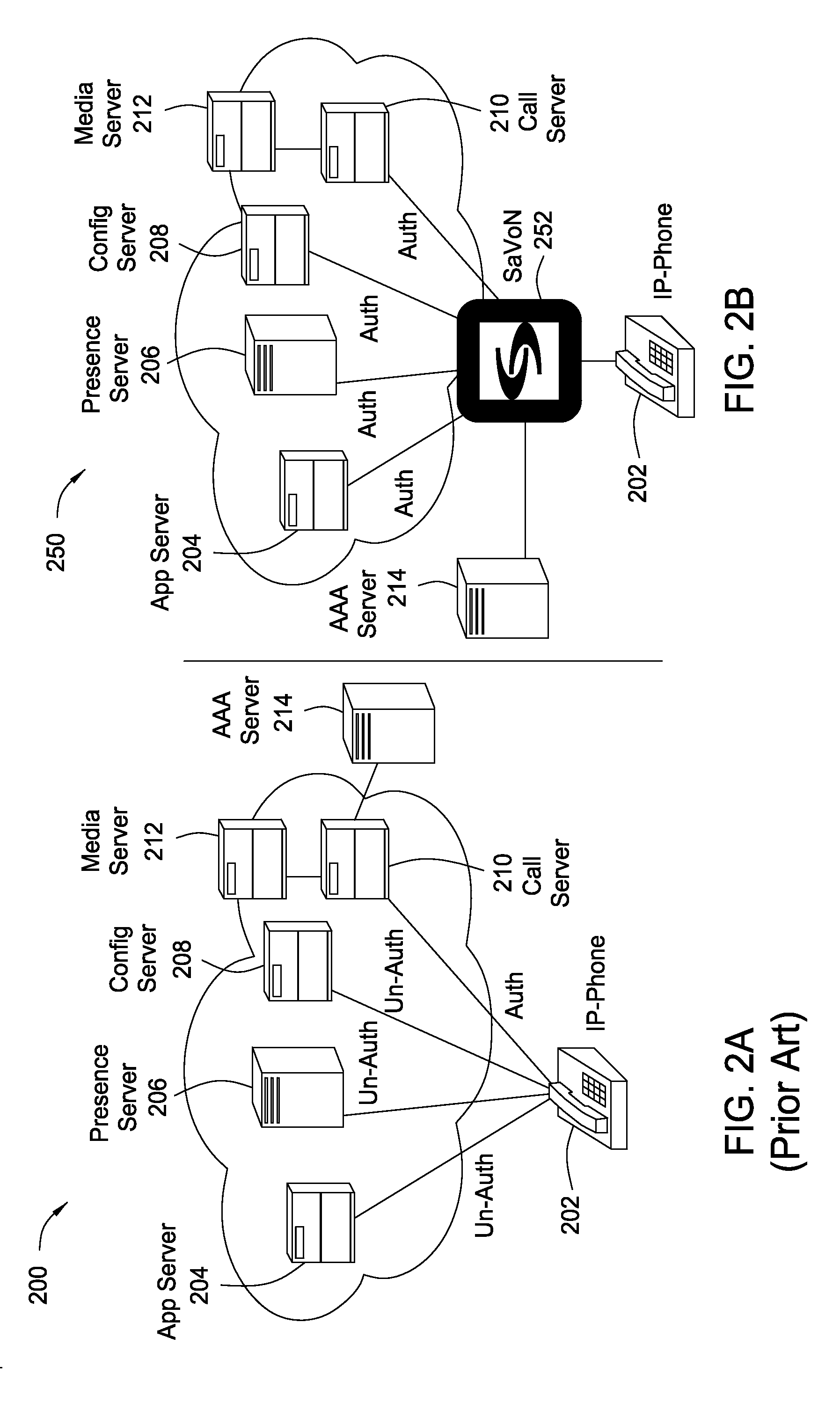
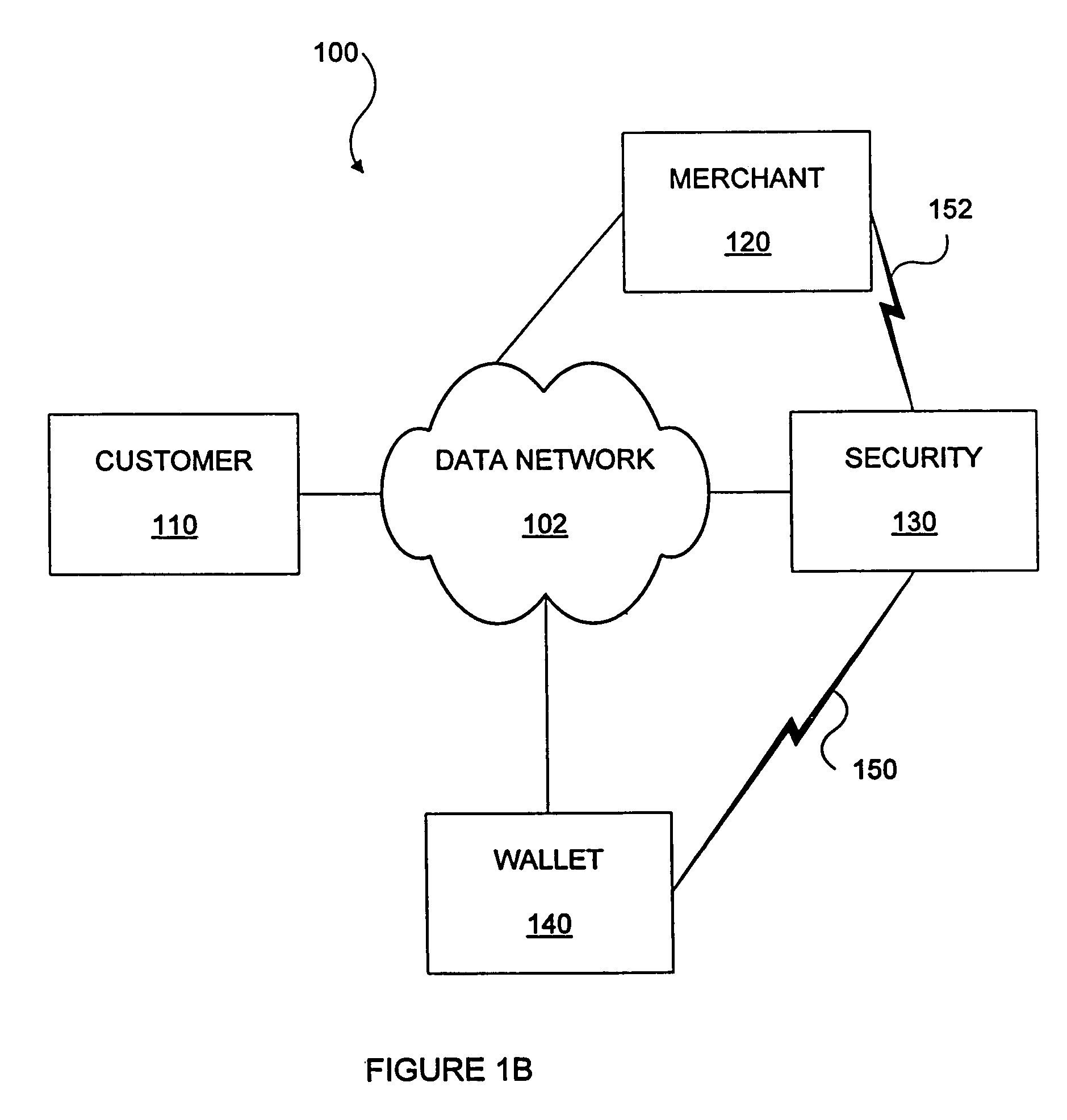
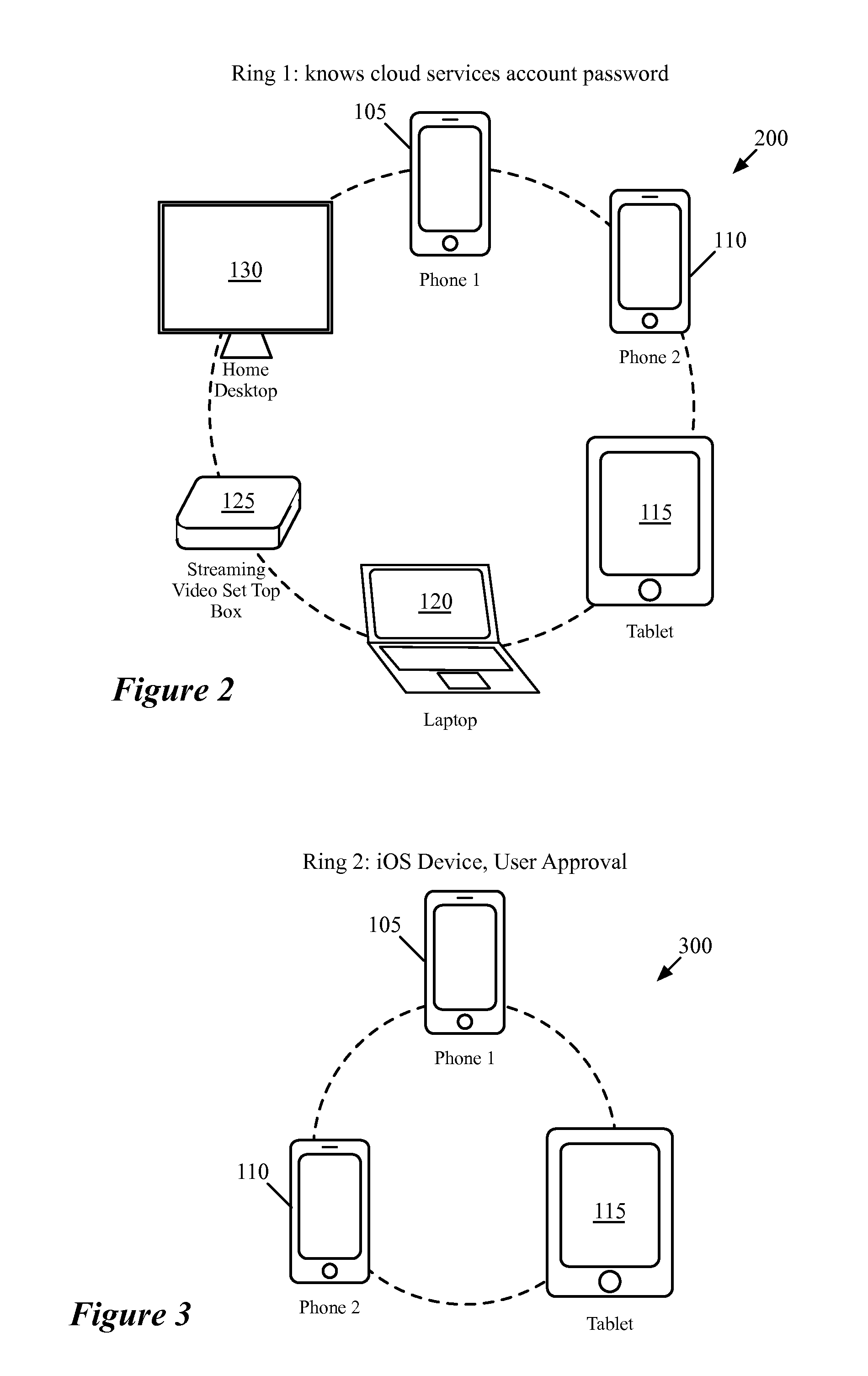
System and method for providing network level and nodal level vulnerability protection in VoIP networks
ActiveUS20070121596A1Unauthorized usePrivacy protectionInterconnection arrangementsAutomatic exchangesComputer networkAnomaly detection
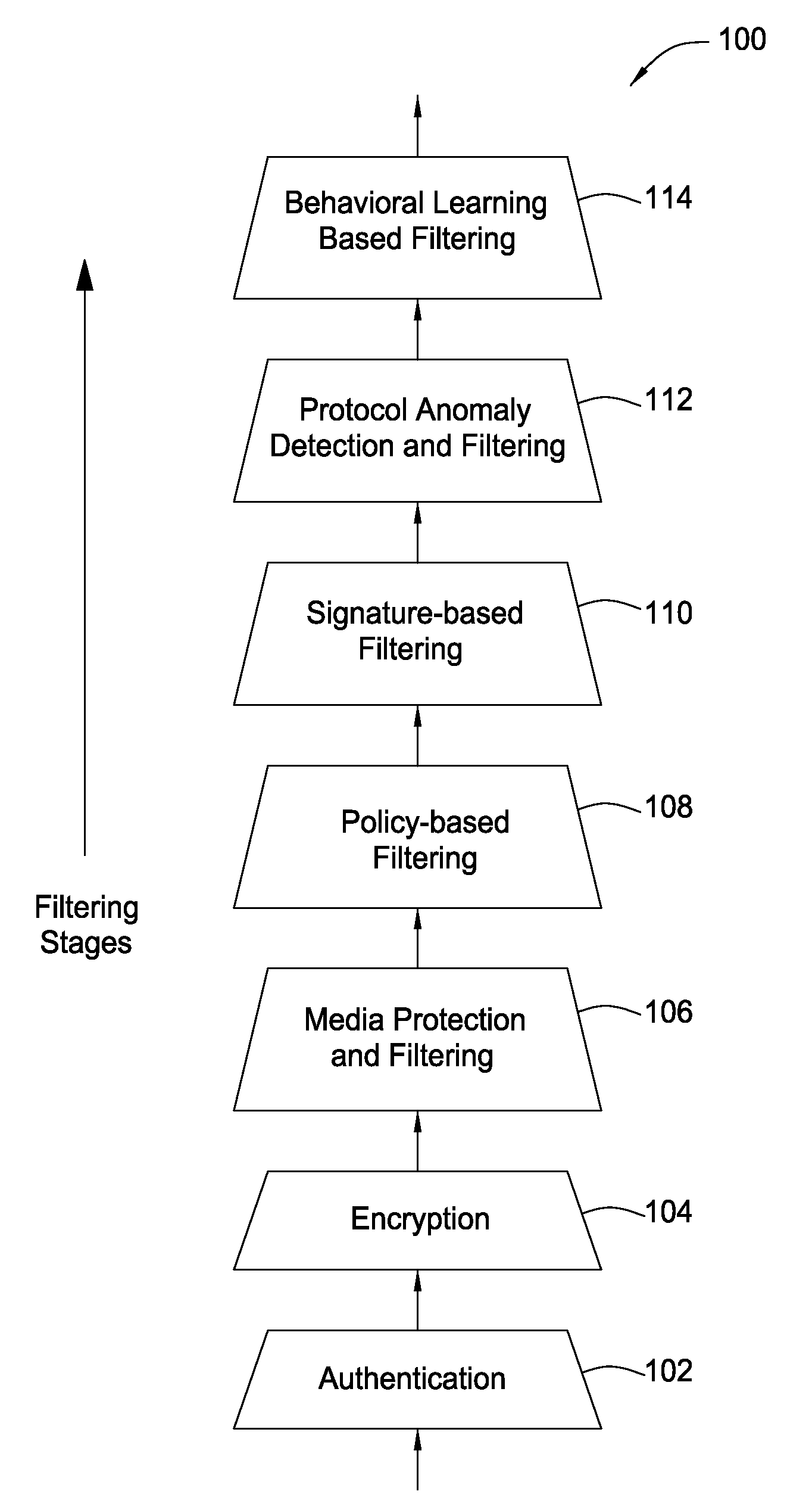
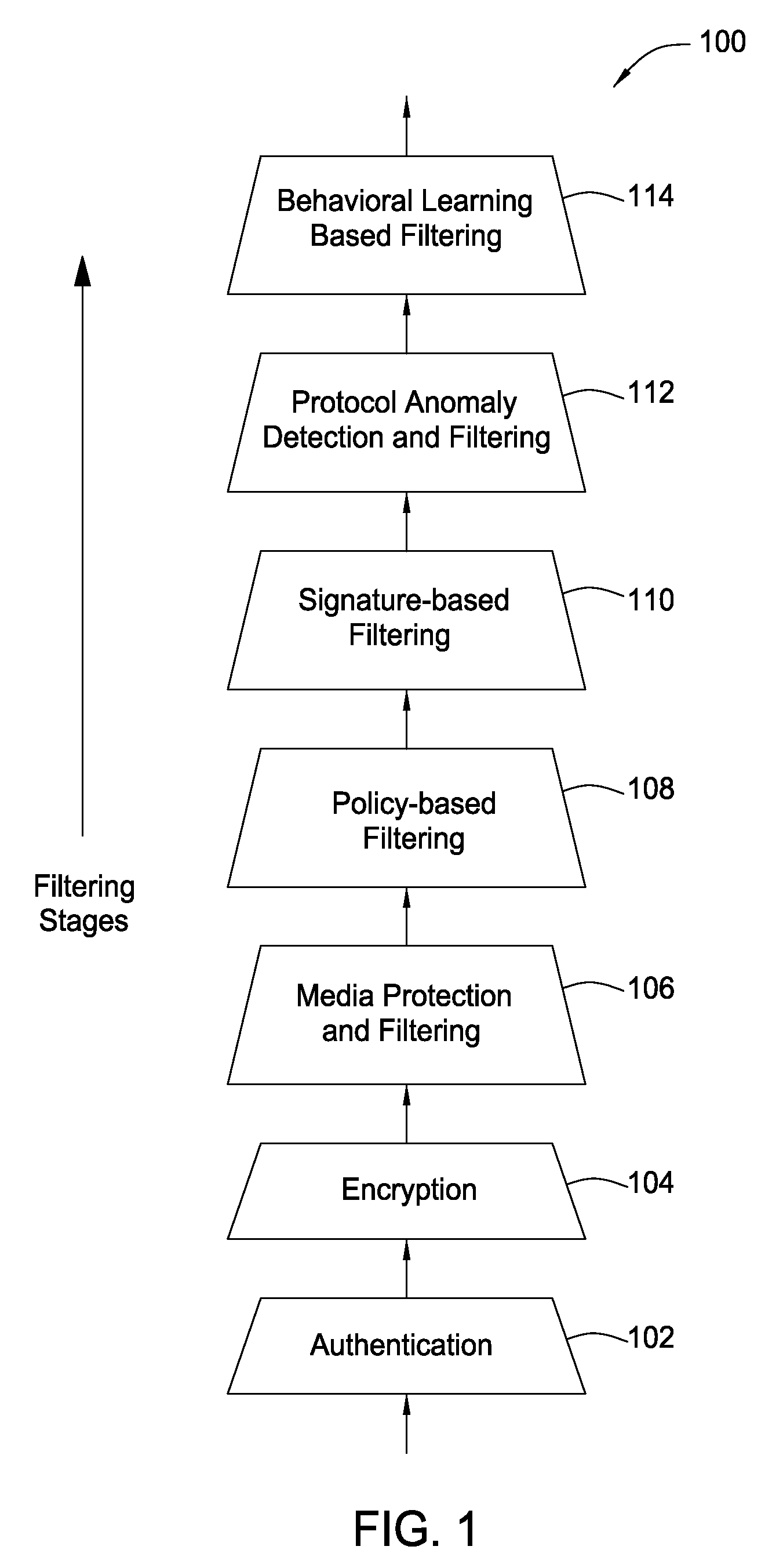
The present invention provides a system, method and apparatus for providing network level and nodal level vulnerability protection in VoIP networks by receiving a communication, filtering the received communication using three or more stages selected from the group comprising a media protection and filtering plane, a policy based filtering plane, a signature based filtering plane, a protocol anomaly detection and filtering plane and a behavioral learning based filtering plane, and either allowing or denying the received communication based the filtering step. The stages are applicable to one or more protocols including SIP, IMS, UMA, H.248, H.323, RTP, CSTA / XML or a combination thereof. In addition, the stages can be implemented within a single device or are distributed across a network (e.g., SIP network, a UMA network, an IMS network or a combination thereof).
Owner:AVAYA INC
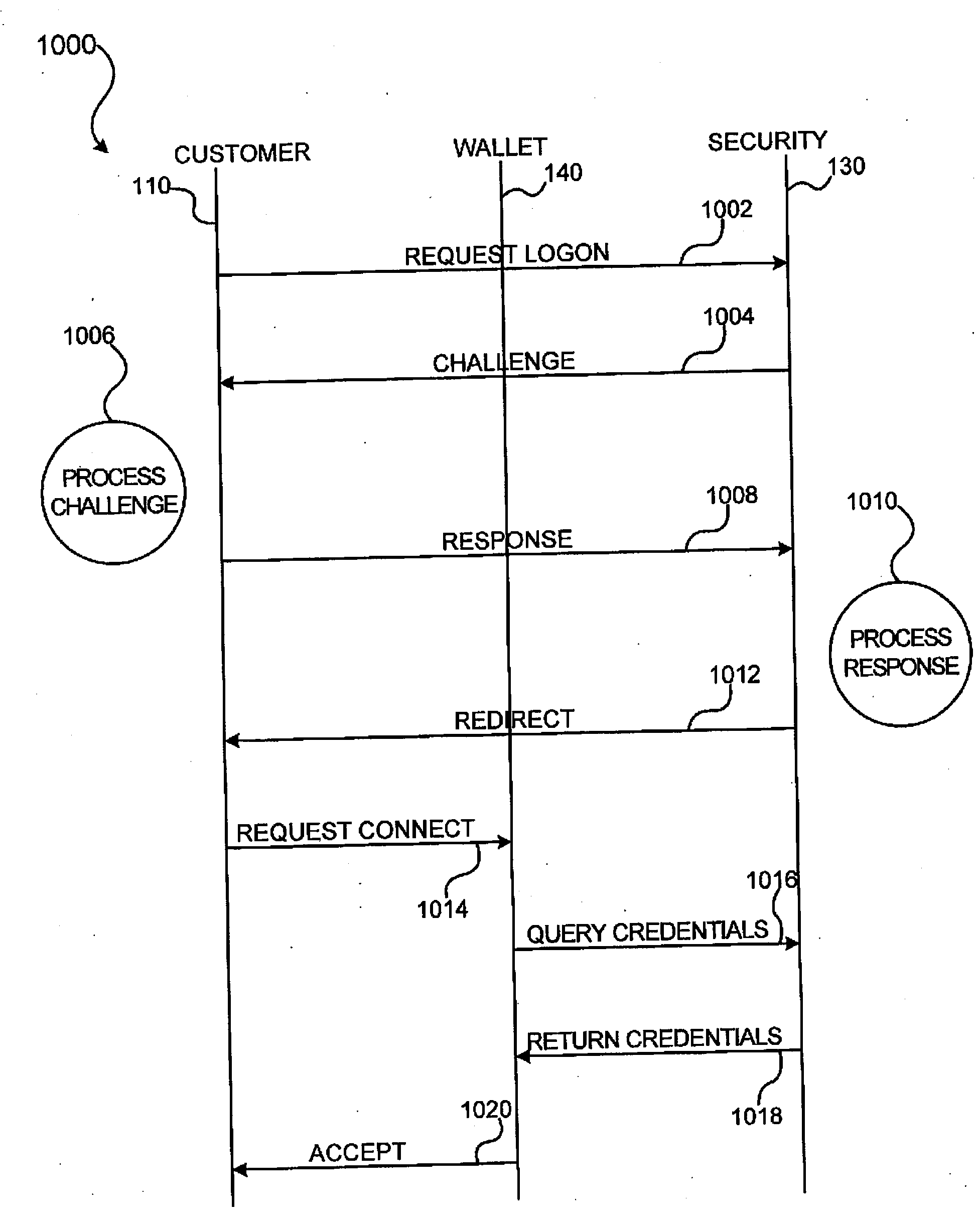
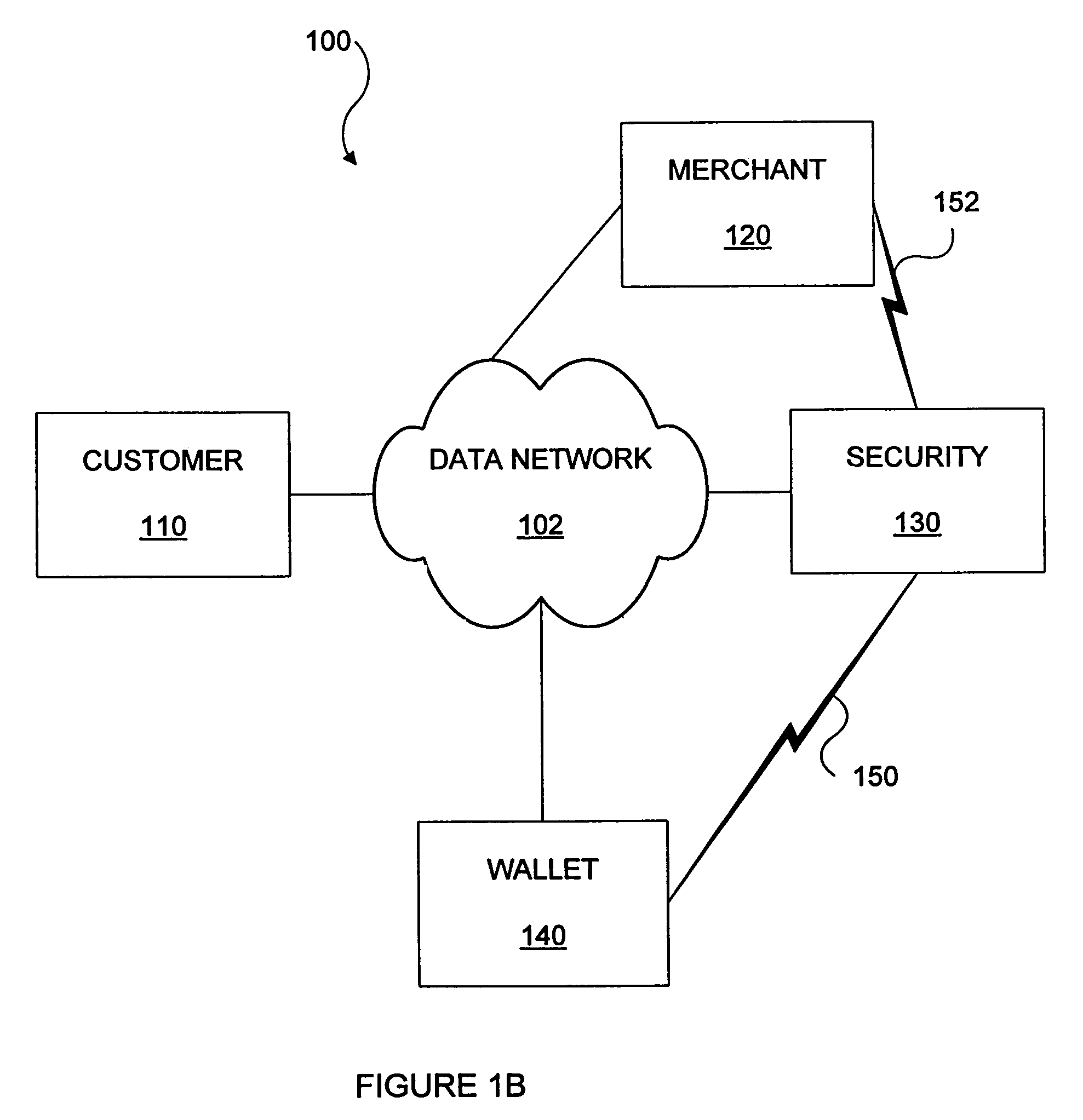
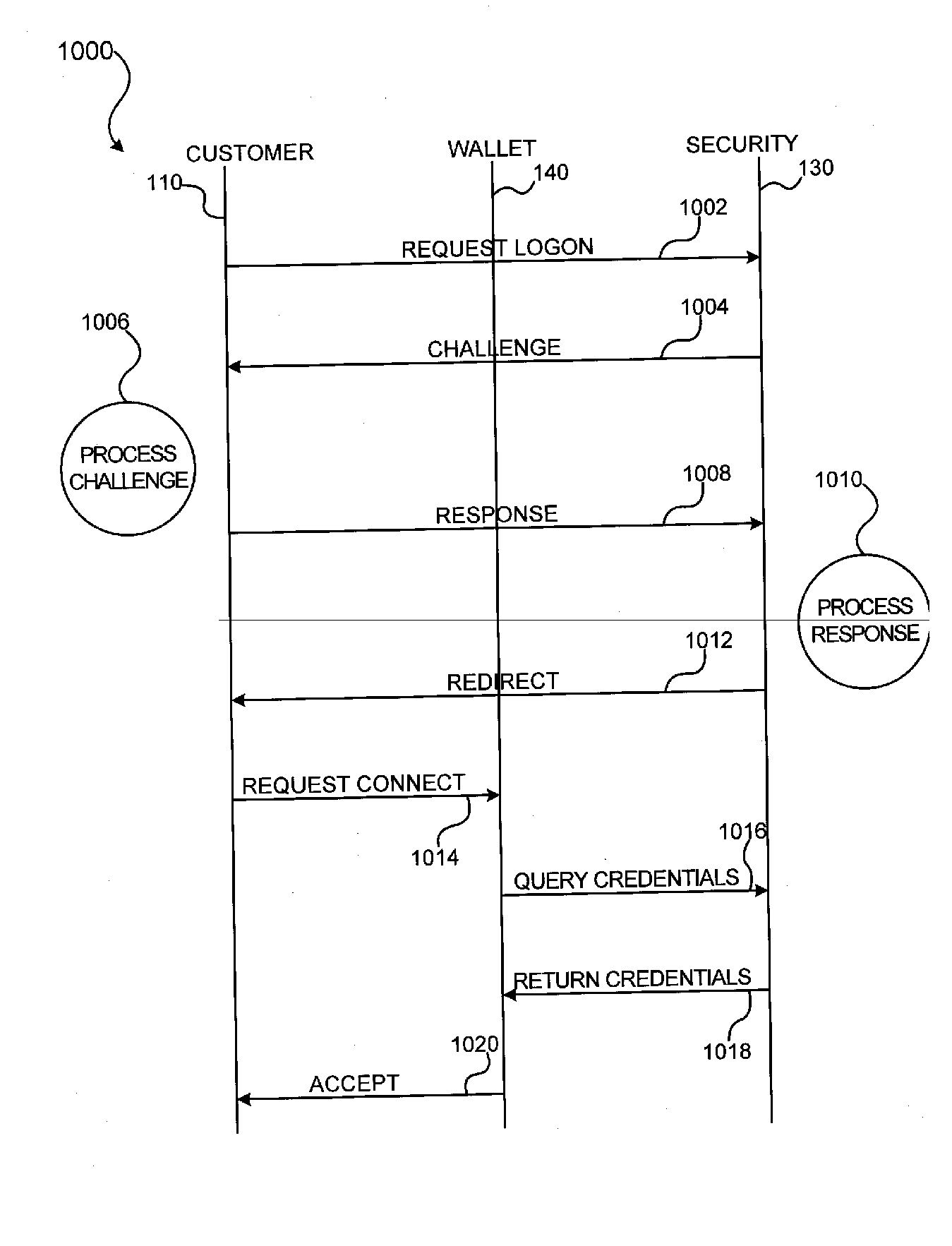
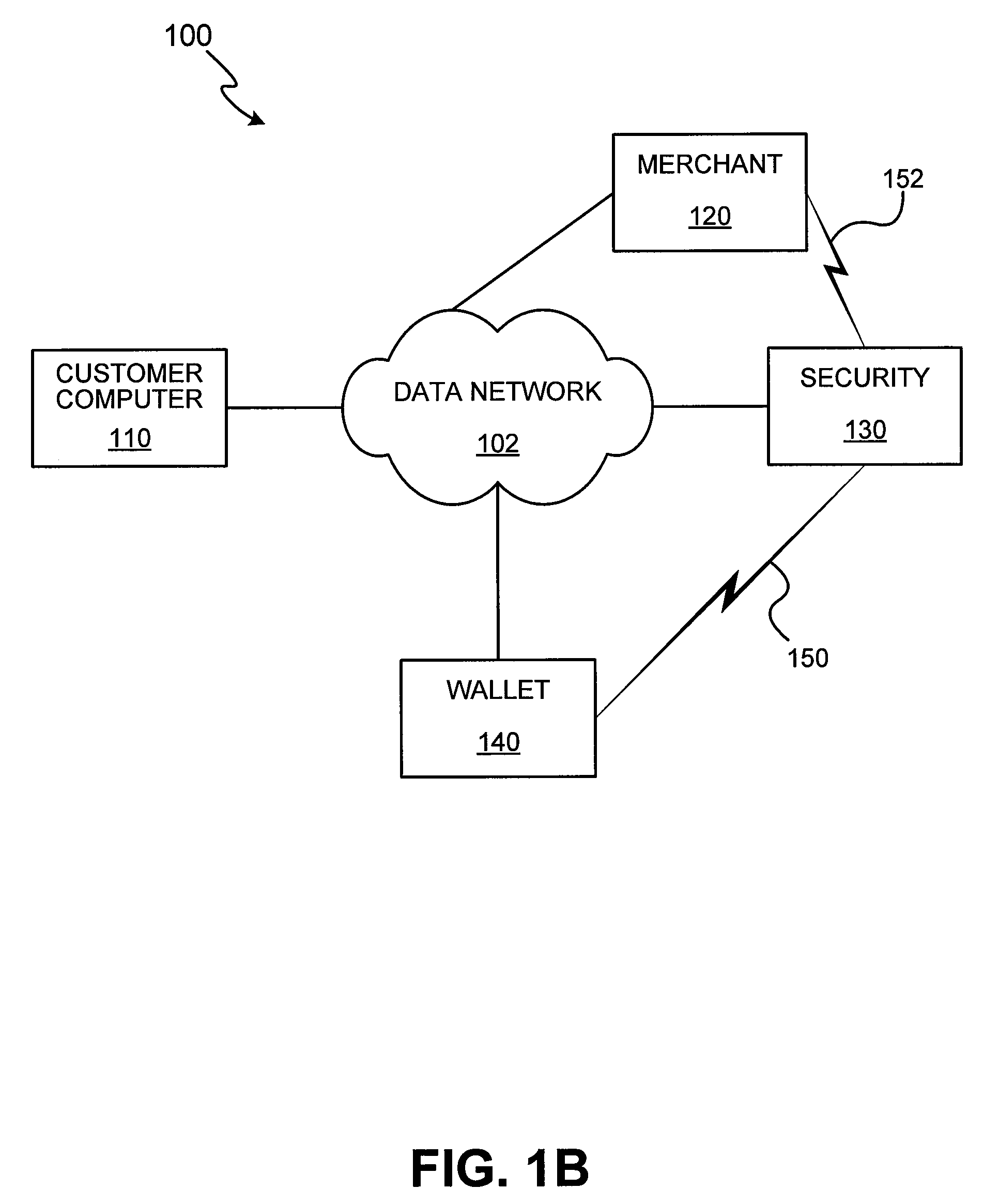
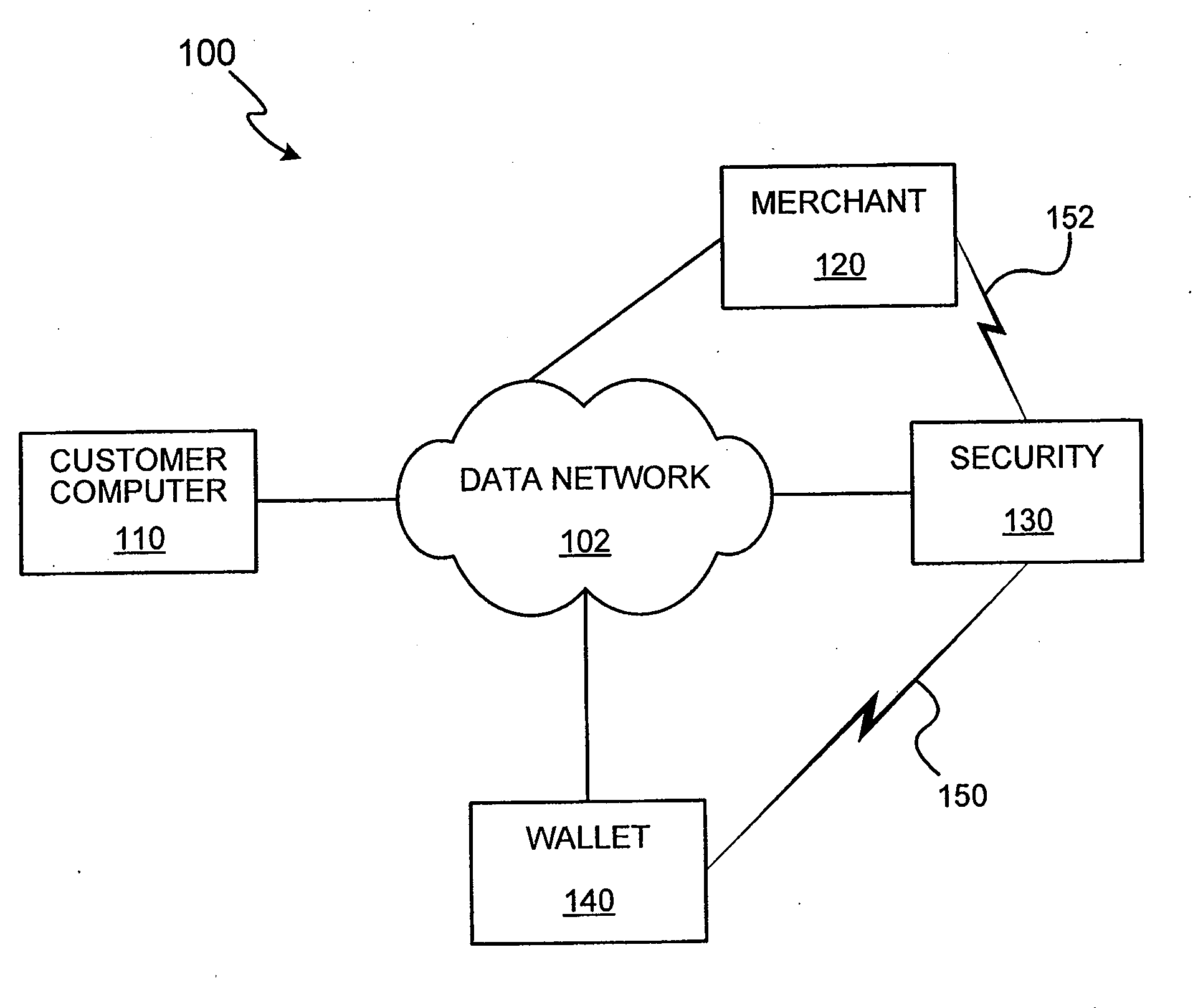
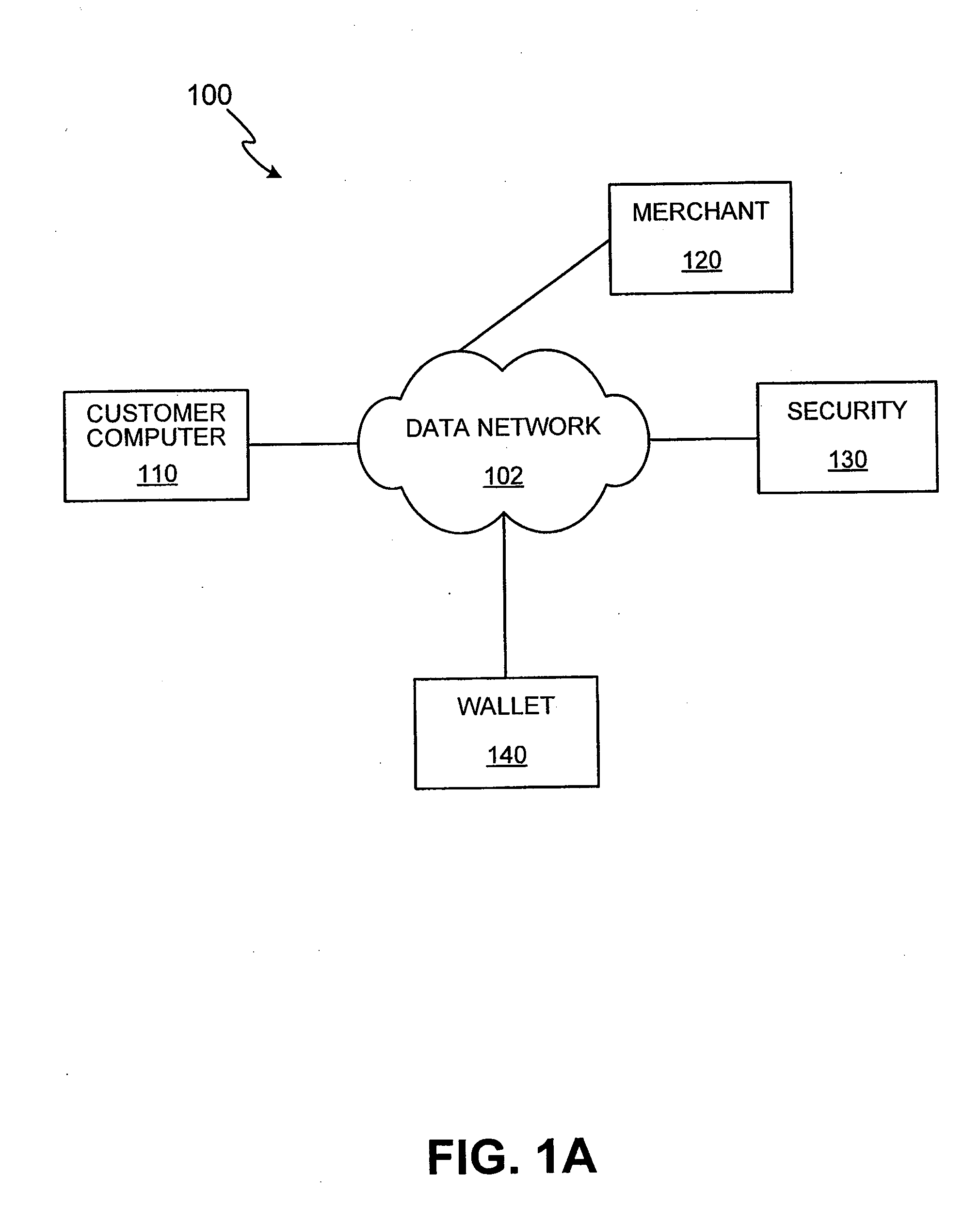
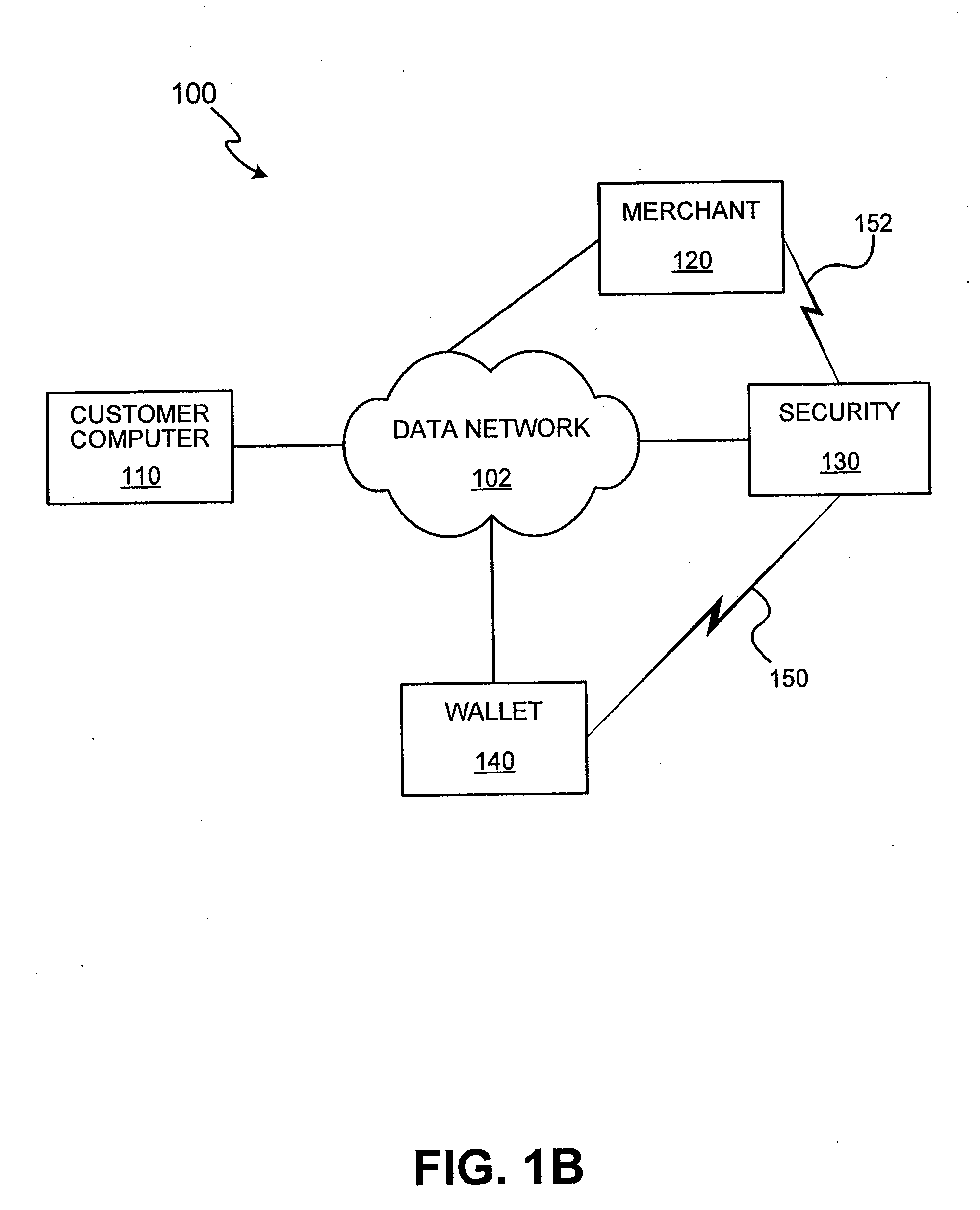
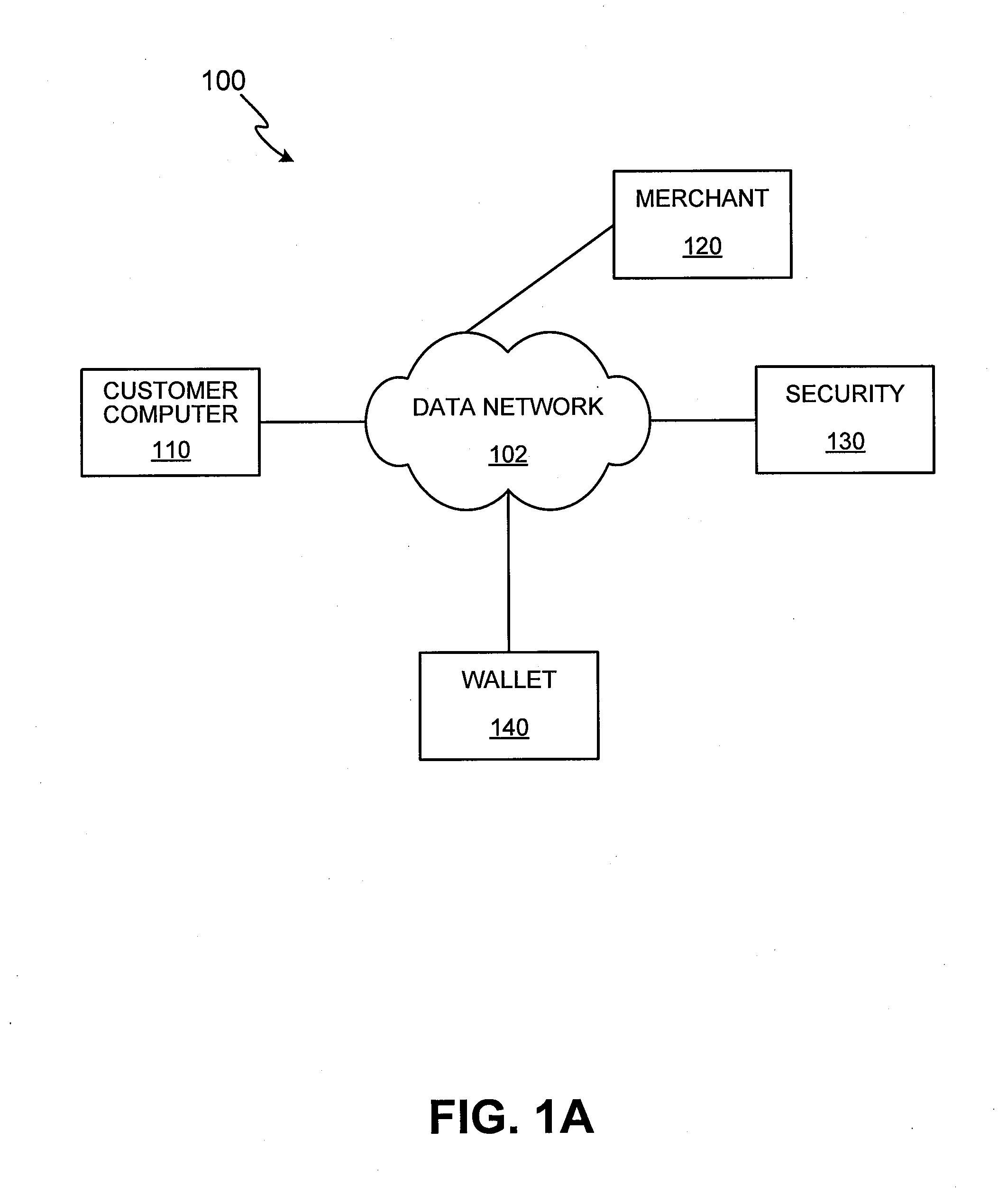
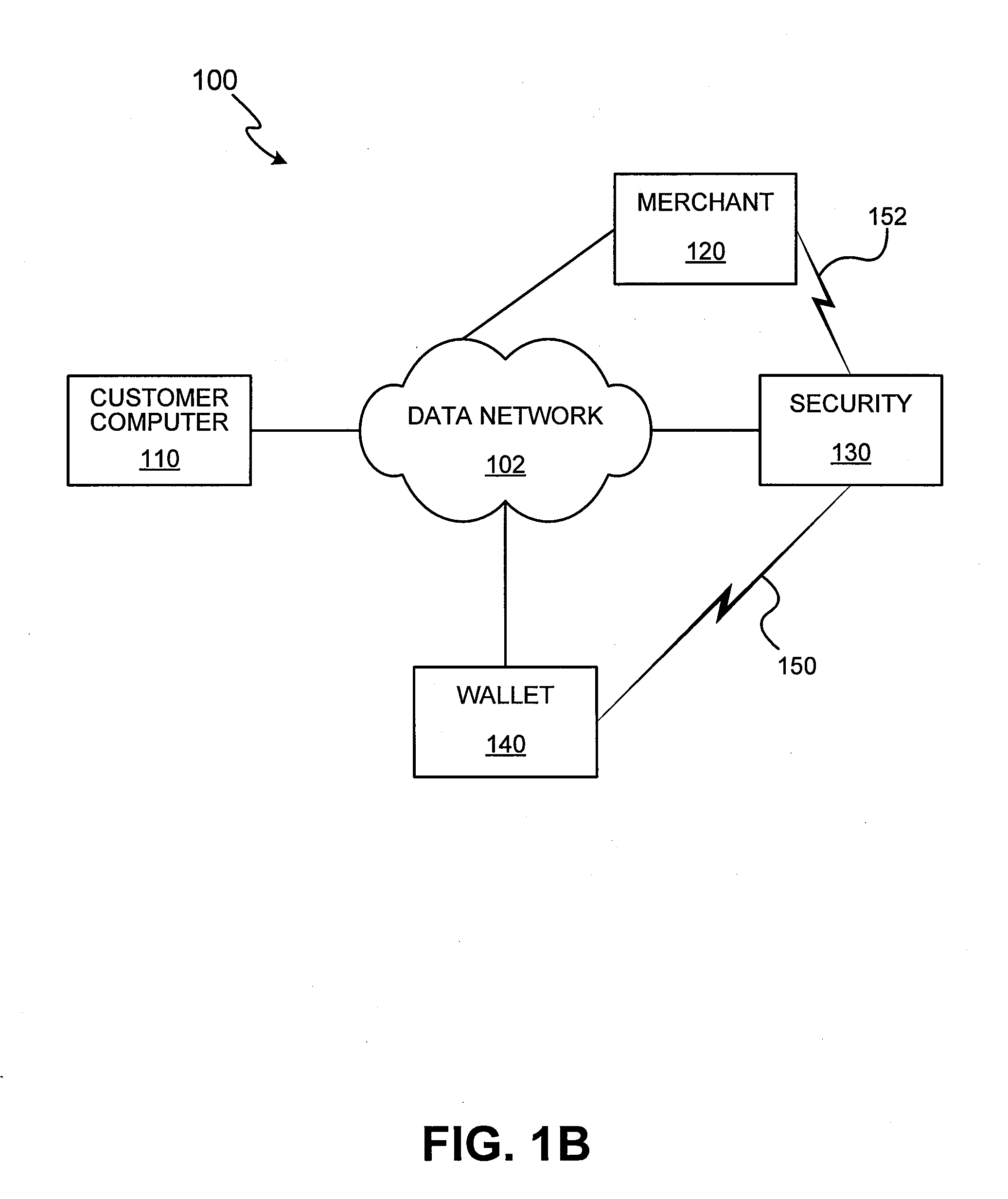
Methods and apparatus for conducting electronic transactions
InactiveUS20090076966A1Enhanced reliability and confidenceReduce security risksComplete banking machinesAcutation objectsAuthorization certificateChallenge response
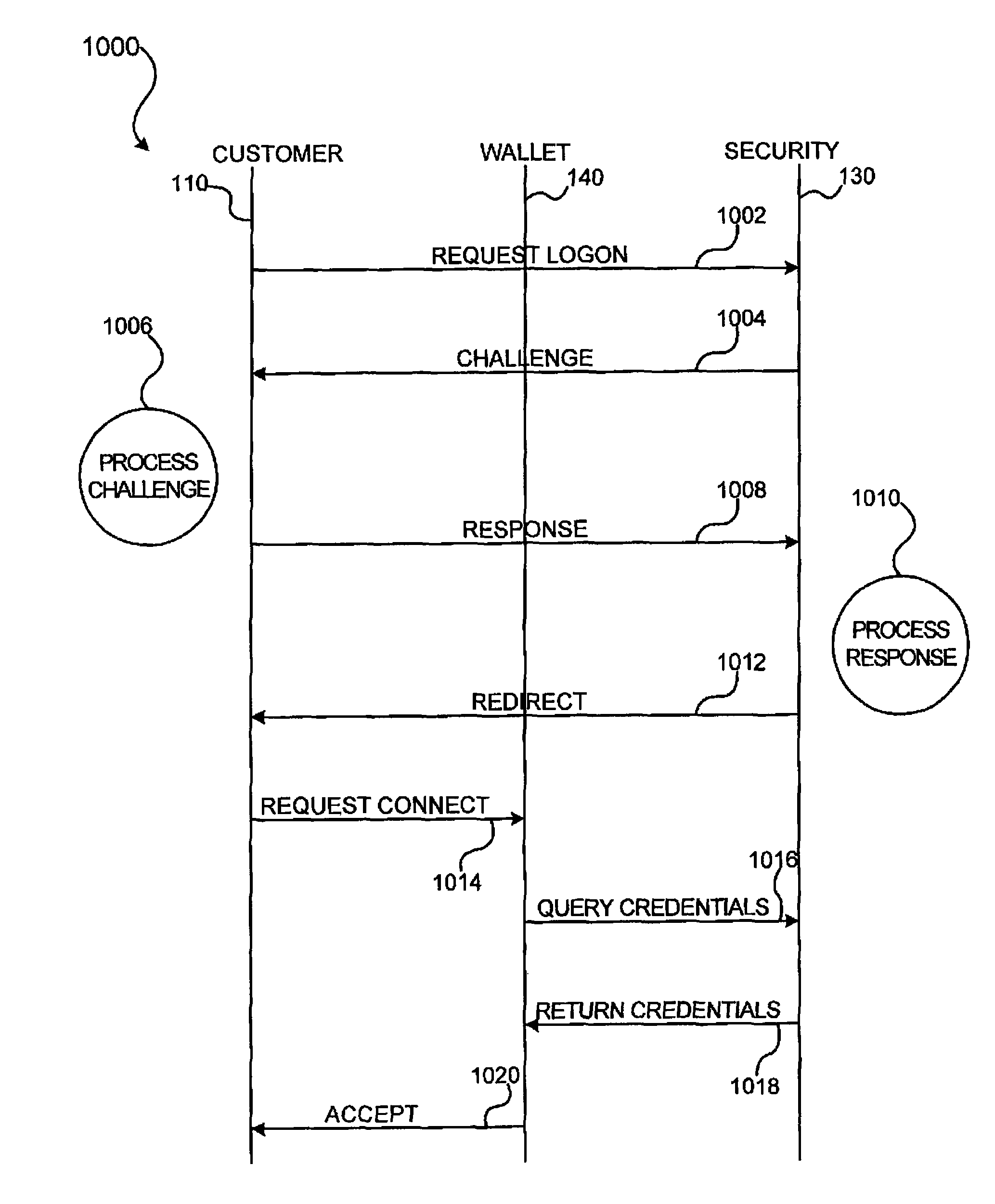
A system and method for facilitating electronic transactions using an intelligent instrument is disclosed. An authorization server enables users to obtain authorization credentials through the use of the intelligent instrument by issuing a challenge to an intelligent token of the intelligent instrument. The intelligent token generates a challenge response and transmits the challenge response to the authorization server, which assembles credentials including a key for the electronic transaction upon validating the response. The authorization server sends the assembled credentials to the intelligent instrument and the intelligent instrument transmits the assembled credentials to the authorization server during a subsequent transaction. The authorization server validates the assembled credentials and provides authorization for the transaction in response to the validating the assembled credentials.
Owner:LIBERTY PEAK VENTURES LLC
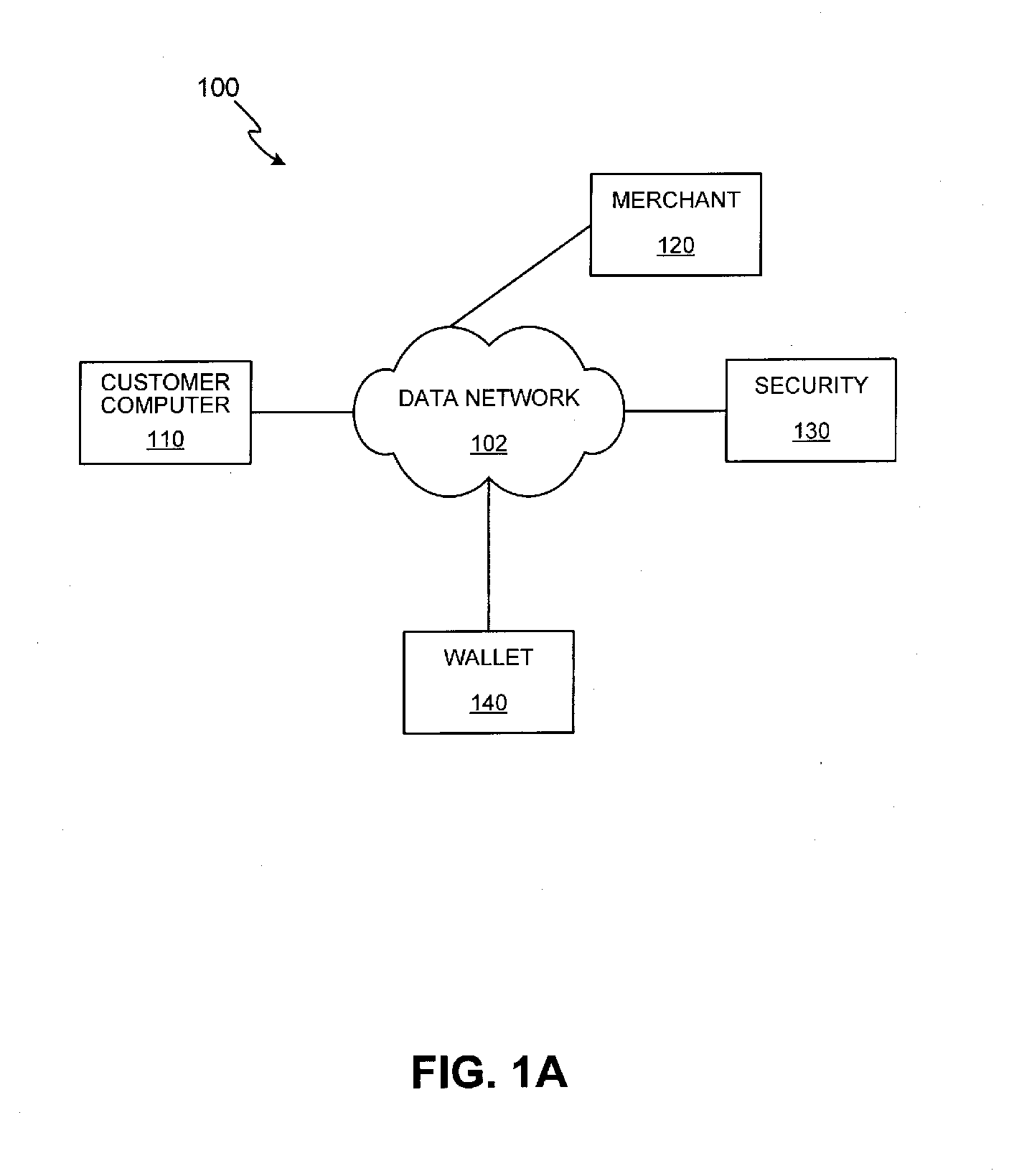
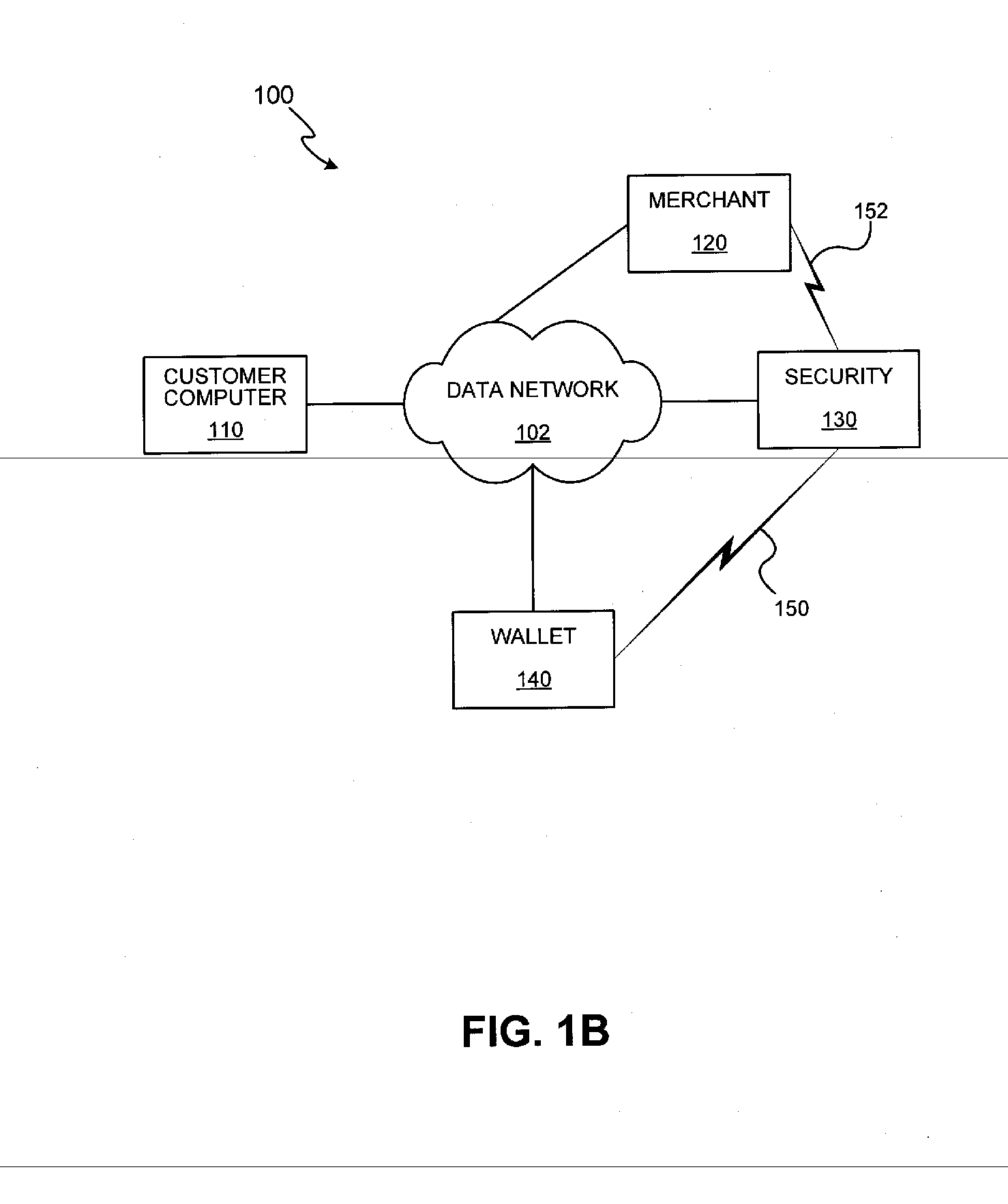
Methods and apparatus for conducting electronic transactions
InactiveUS7343351B1Improve reliabilityConfidenceDigital data processing detailsAnalogue secracy/subscription systemsSmart cardE-commerce
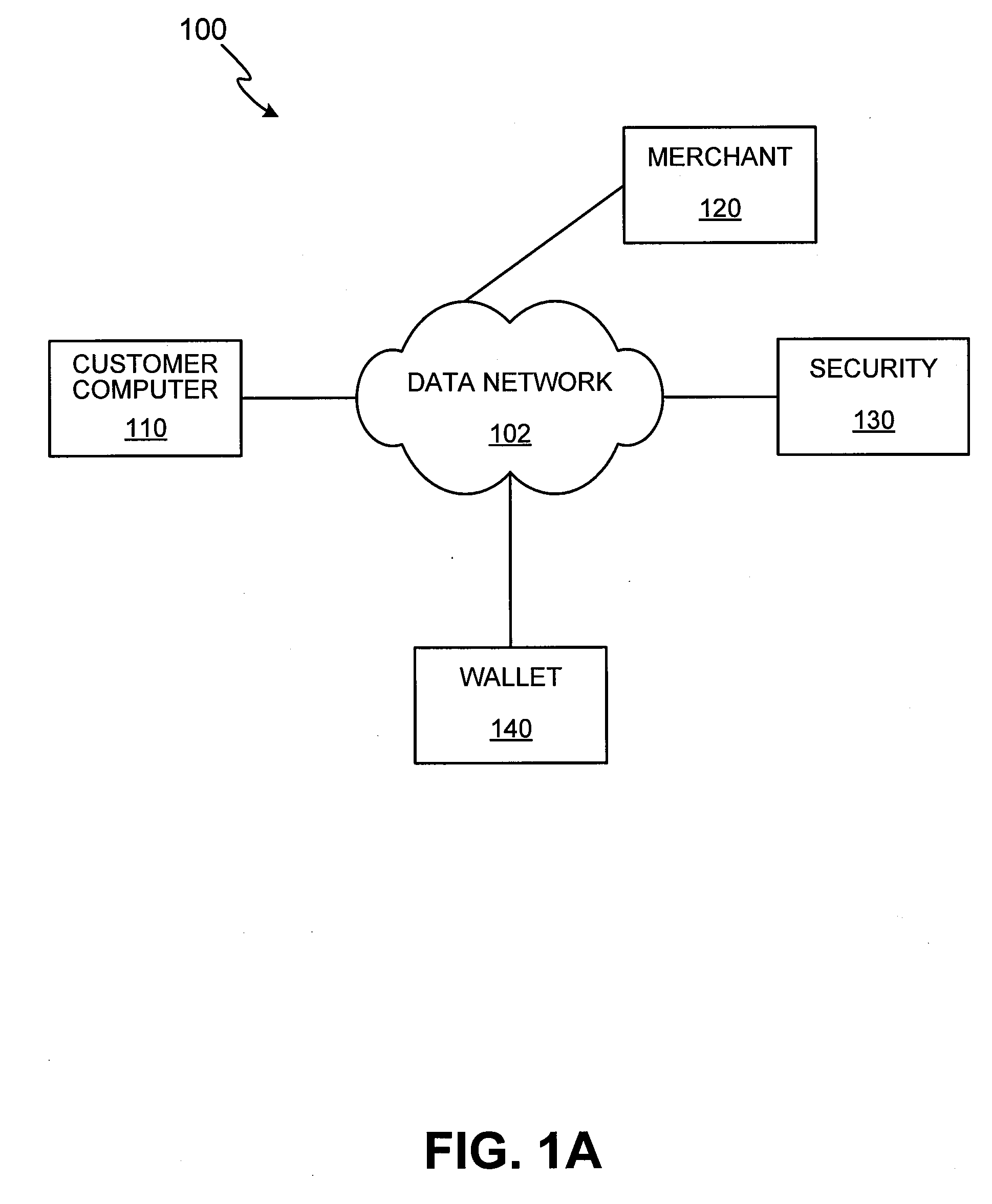
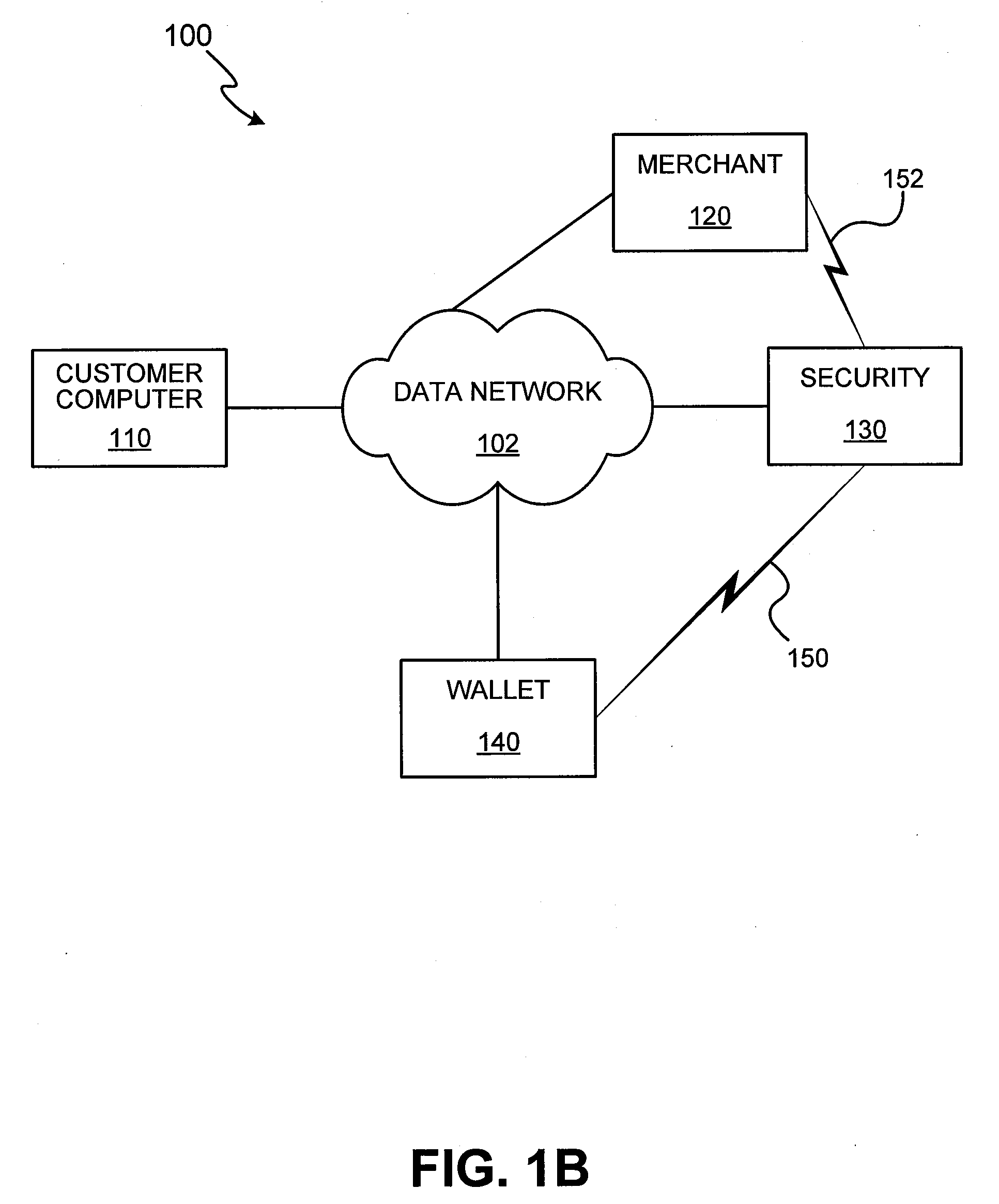
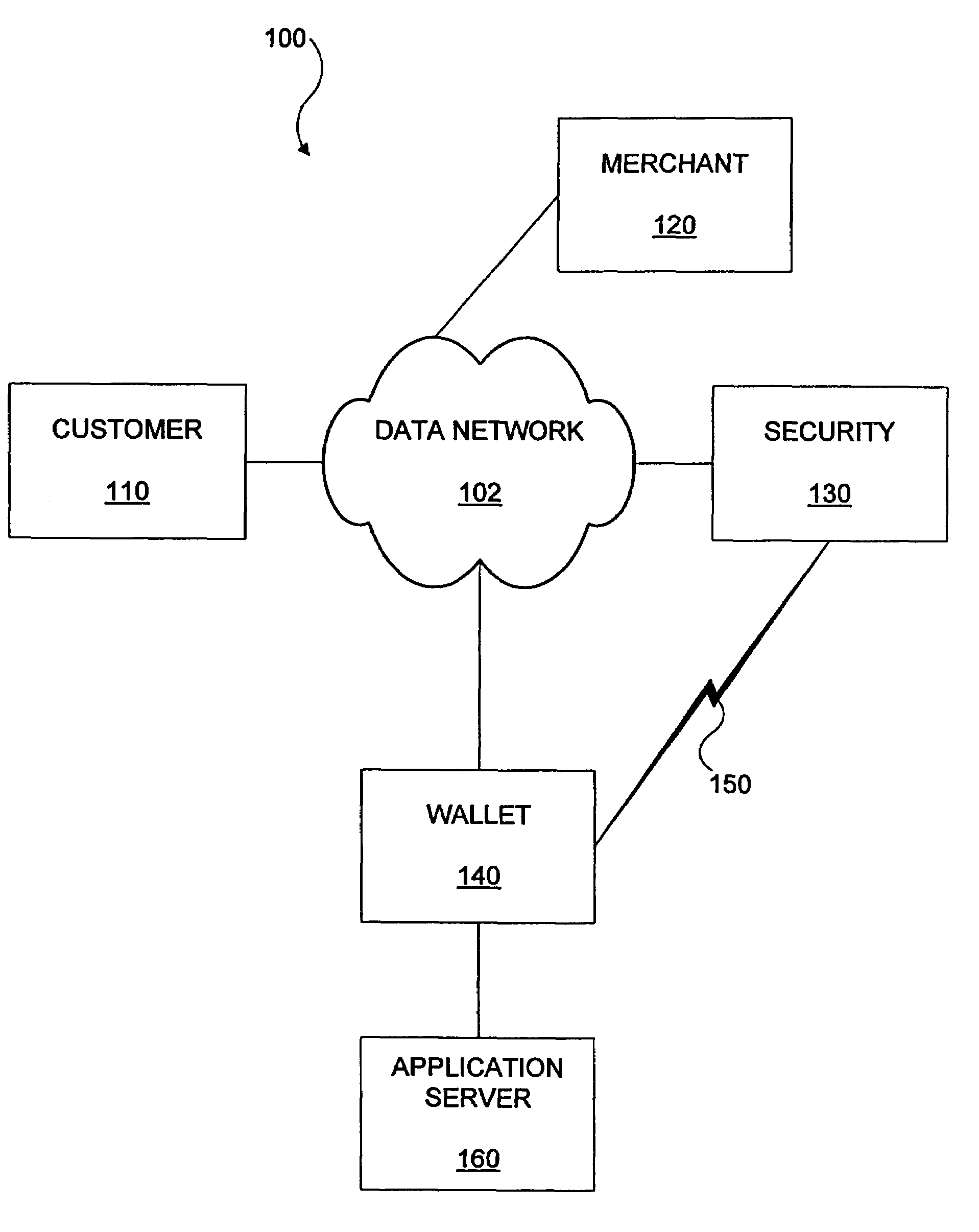
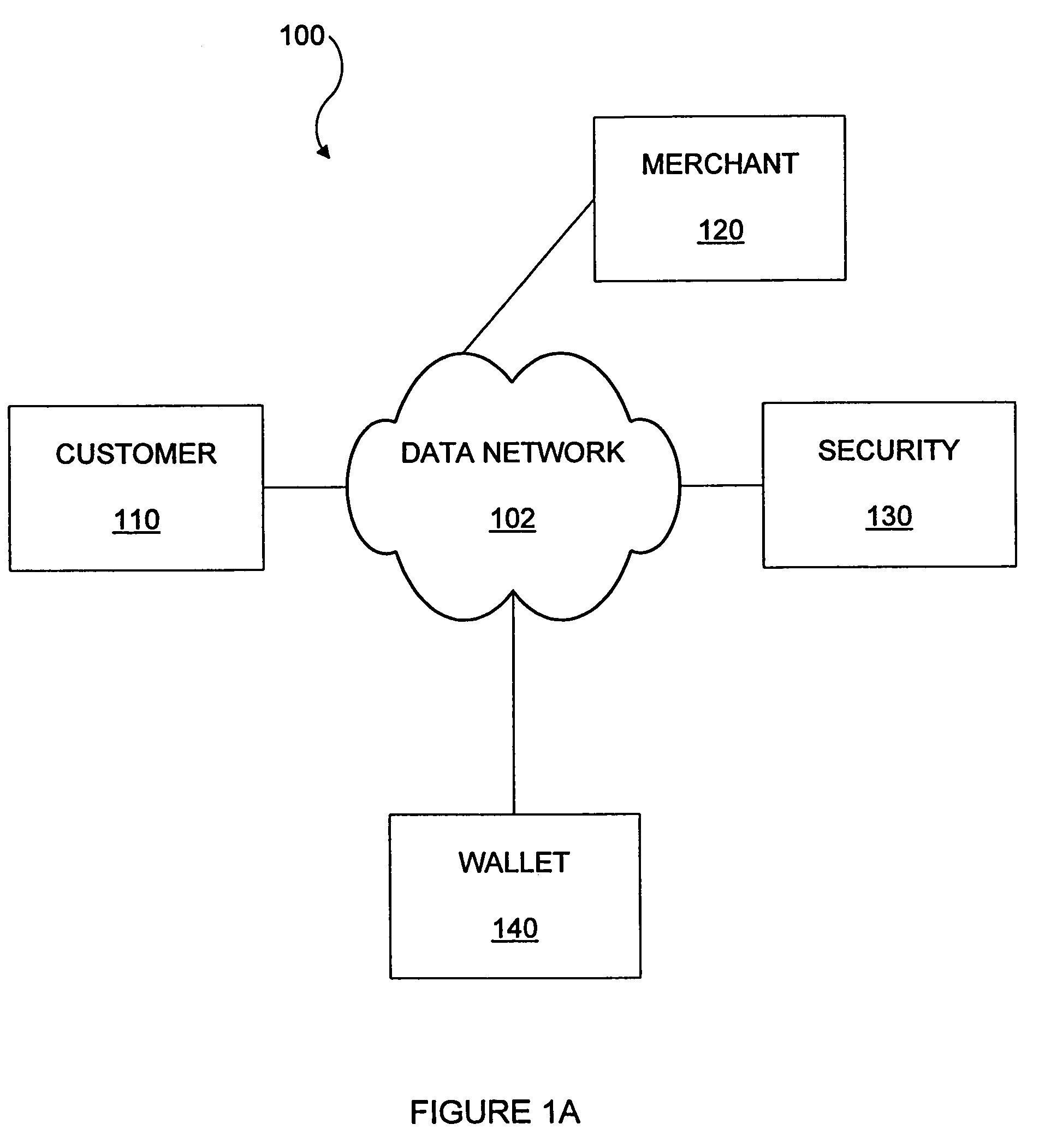
A system and method for conducting electronic commerce are disclosed. In various embodiments, the electronic transaction is a purchase transaction. A user is provided with an intelligent token, such as a smartcard containing a digital certificate. The intelligent token suitably authenticates with a server on a network that conducts all or portions of the transaction on behalf of the user. In various embodiments a wallet server interacts with a security server to provide enhanced reliability and confidence in the transaction. In various embodiments, the wallet server includes a toolbar. In various embodiments, the digital wallet pre-fills forms. Forms may be pre-filled using an auto-remember component.
Owner:LIBERTY PEAK VENTURES LLC
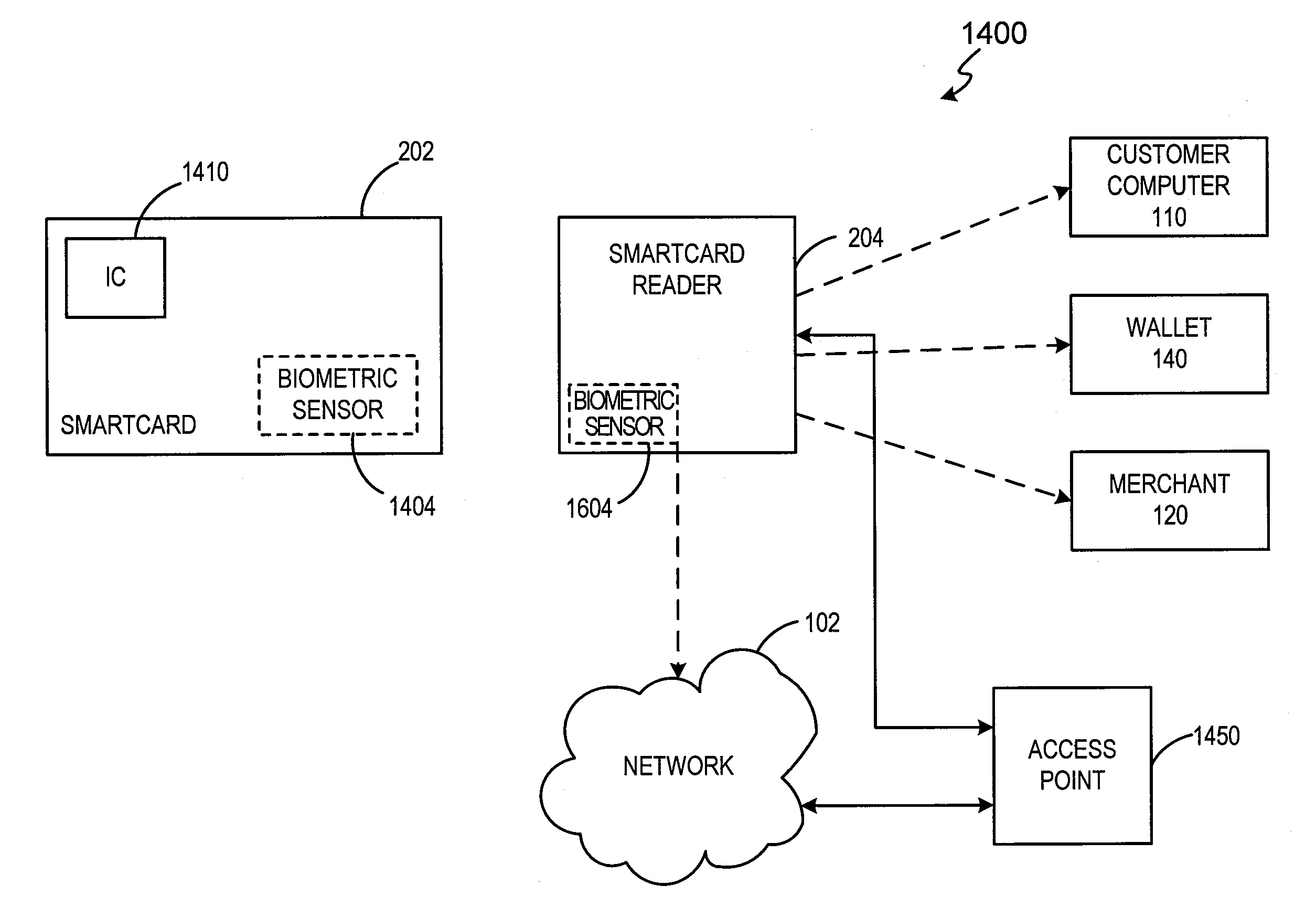
Methods and apparatus for conducting electronic transactions using biometrics
InactiveUS20050187883A1Improve reliabilityConfidenceDigital data processing detailsAnalogue secracy/subscription systemsBiometricsComputer science
A system and method for facilitating electronic transactions using a biometric are disclosed. The system for facilitating electronic transactions using a biometric comprises a smartcard-reader transaction system. The method comprises determining if a transaction violates an established rule, such as a preset spending limit. The method also comprises notifying a user to proffer a biometric sample in order to verify the identity of said user, and detecting a proffered biometric at a sensor to obtain a proffered biometric sample. The method additionally comprises verifying the proffered biometric sample and authorizing a transaction to continue upon verification of the proffered biometric sample.
Owner:LIBERTY PEAK VENTURES LLC
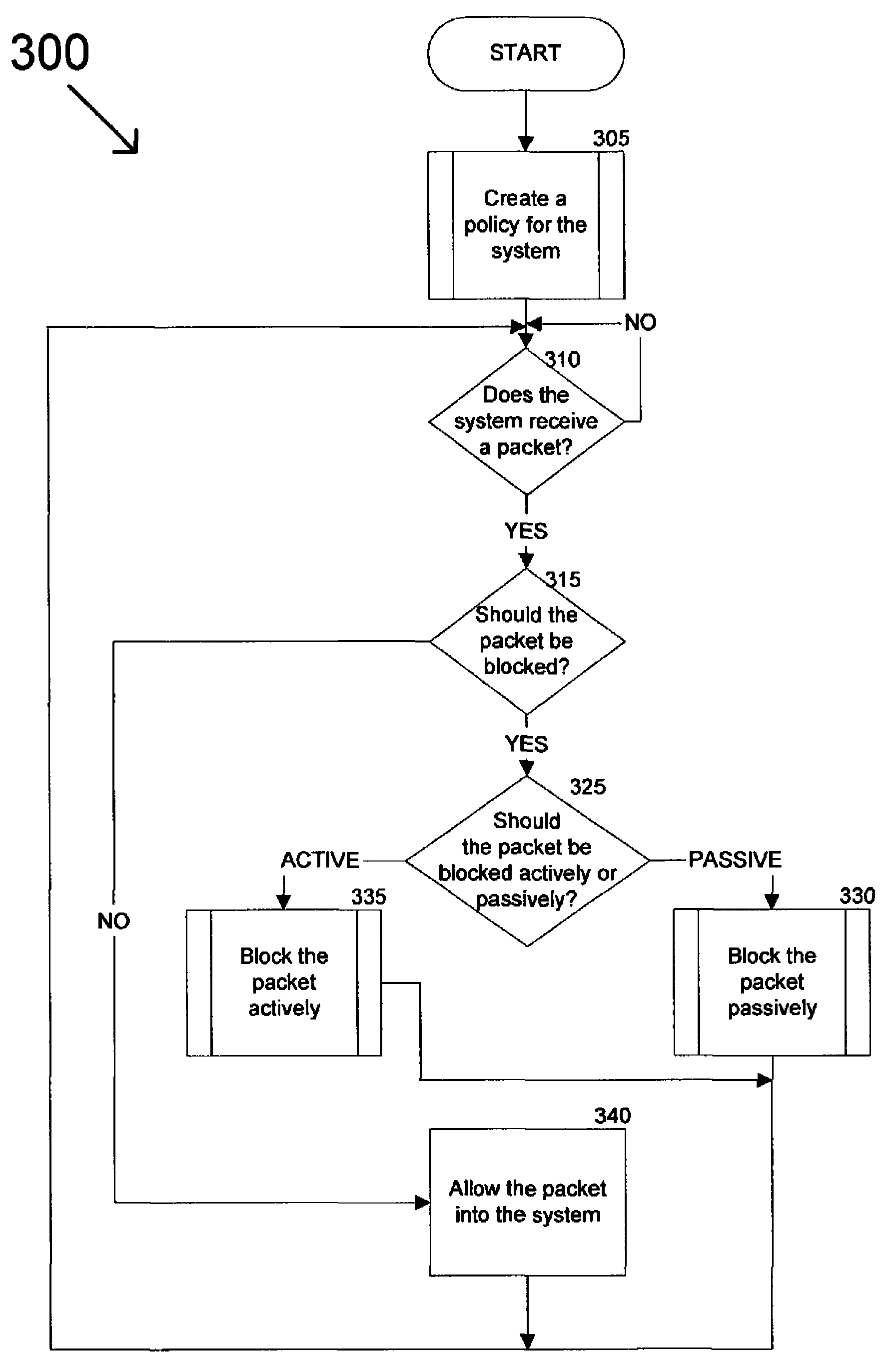
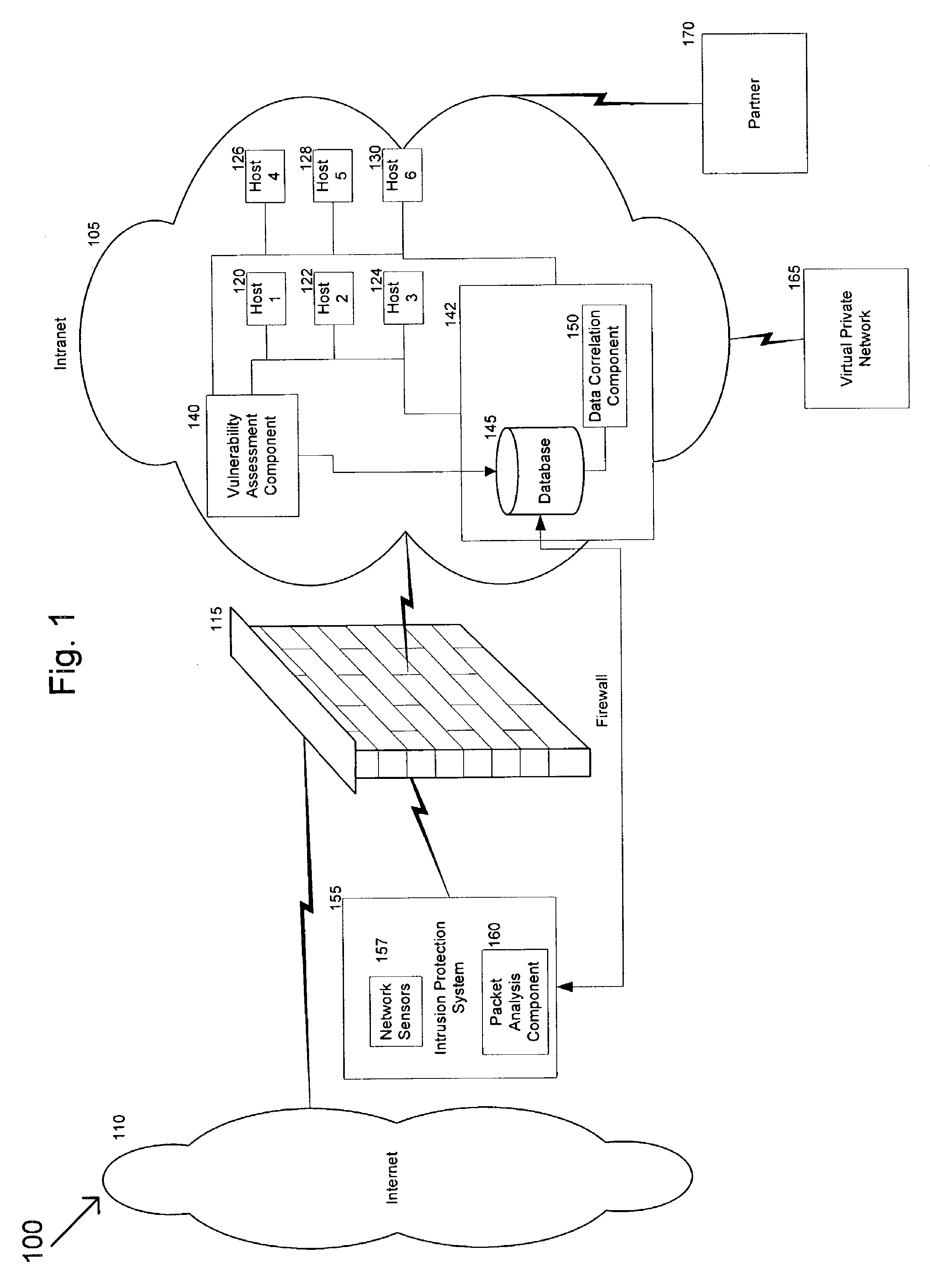
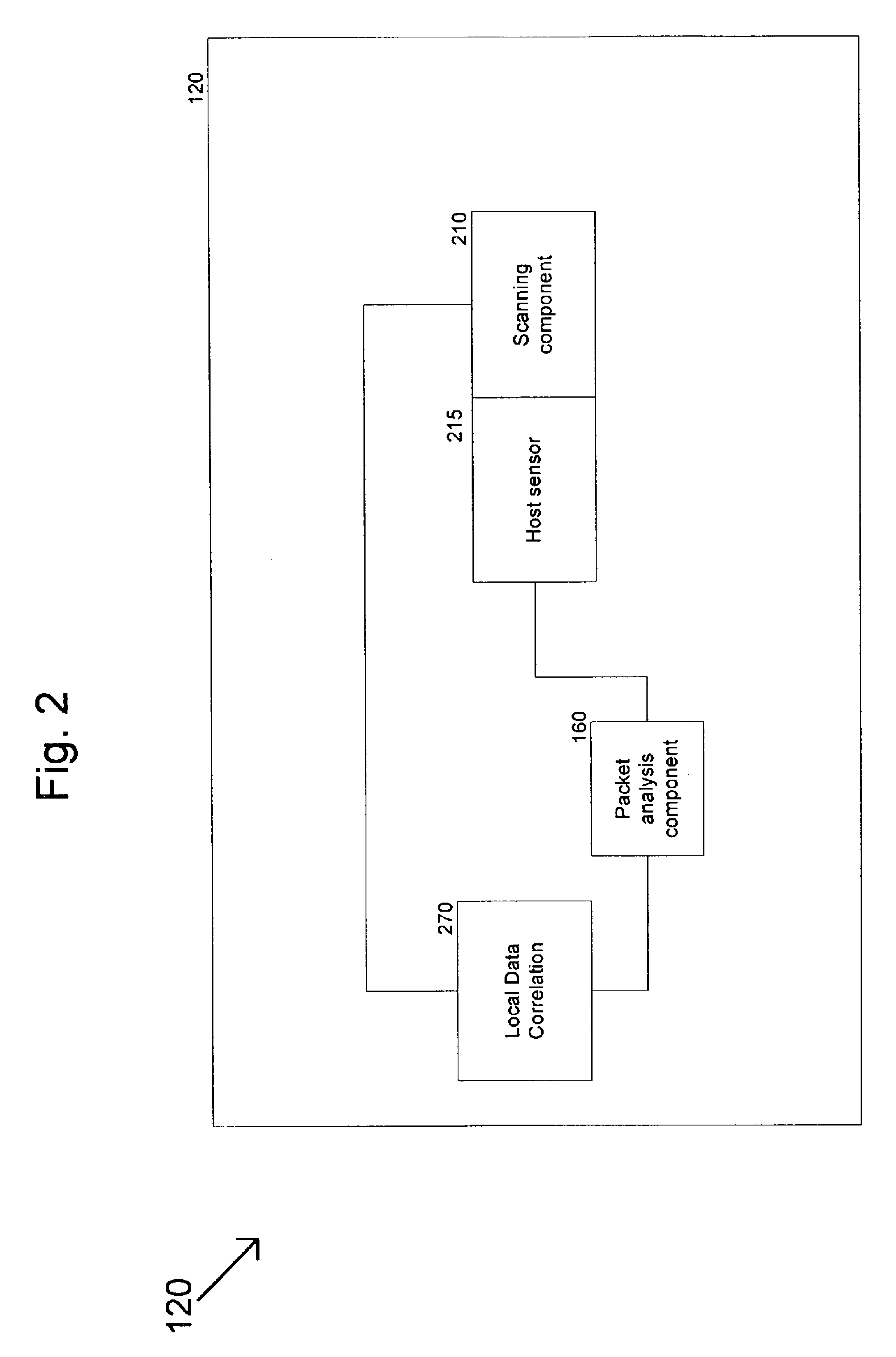
Method and system for dynamically protecting a computer system from attack
ActiveUS7913303B1Protection attackMemory loss protectionUnauthorized memory use protectionProtection systemVulnerability
A dynamic protection system can analyze a computer system to determine its vulnerabilities to attack and generate a policy for protecting the computer system based on the identified vulnerabilities. Data received by the computer system can be analyzed to determine if it poses a threat to the system. This can prevent the data from entering the system or host based on a determination that the data poses a threat. Also, the dynamic protection system can receive policy updates to allow it to protect the system more efficiently and effectively. In other words, the dynamic protection system can protect an evolving computer system operating in an environment that is characterized by constantly changing methods of attack. Furthermore, by minimizing a need for manual intervention, attacks can be rapidly and accurately detected with a minimization of false positives, thereby lowering the cost of operation.
Owner:ALIBABA GRP HLDG LTD
System and methods for run time detection and correction of memory corruption
ActiveUS8510596B1Improve productivitySubstantial time windowNon-redundant fault processingPlatform integrity maintainanceRunning timeBackup
A method or apparatus detects a memory corruption of at least one portion of memory during run-time and corrects the memory corruption of the at least one portion of memory by replacing the at least one portion of memory with a backup of the at least one portion of memory. In this way, memory corruption can be corrected in a timely fashion while minimizing security risks.
Owner:VIRSEC SYST
Methods and apparatus for conducting electronic transactions
InactiveUS7953671B2Enhanced reliability and confidenceReduce security risksComplete banking machinesAcutation objectsChallenge responseAuthorization
A system and method for facilitating electronic transactions using an intelligent instrument is disclosed. An authorization server enables users to obtain authorization credentials through the use of the intelligent instrument by issuing a challenge to an intelligent token of the intelligent instrument. The intelligent token generates a challenge response and transmits the challenge response to the authorization server, which assembles credentials including a key for the electronic transaction upon validating the response. The authorization server sends the assembled credentials to the intelligent instrument and the intelligent instrument transmits the assembled credentials to the authorization server during a subsequent transaction. The authorization server validates the assembled credentials and provides authorization for the transaction in response to the validating the assembled credentials.
Owner:LIBERTY PEAK VENTURES LLC
Methods of post chemical mechanical polishing and wafer cleaning using amidoxime compositions
InactiveUS20090133716A1Reducing and eliminating corrosion problemSignificant to useOrganic detergent compounding agentsNon-surface-active detergent compositionsDielectric surfaceCompound (substance)
The invention relates to a method for the removal of residues and contaminants from metal or dielectric surfaces and to a method for chemical mechanical polishing of a copper or aluminum surface. The methods of the invention include using an aqueous amidoxime complex agent. Optionally, the pH of the solution can be adjusted with an acid or base. The method includes applying the above composition to the copper or aluminum surface and polishing the surface in the presence of the composition.
Owner:EKC TECH
Wave-power electric device and method
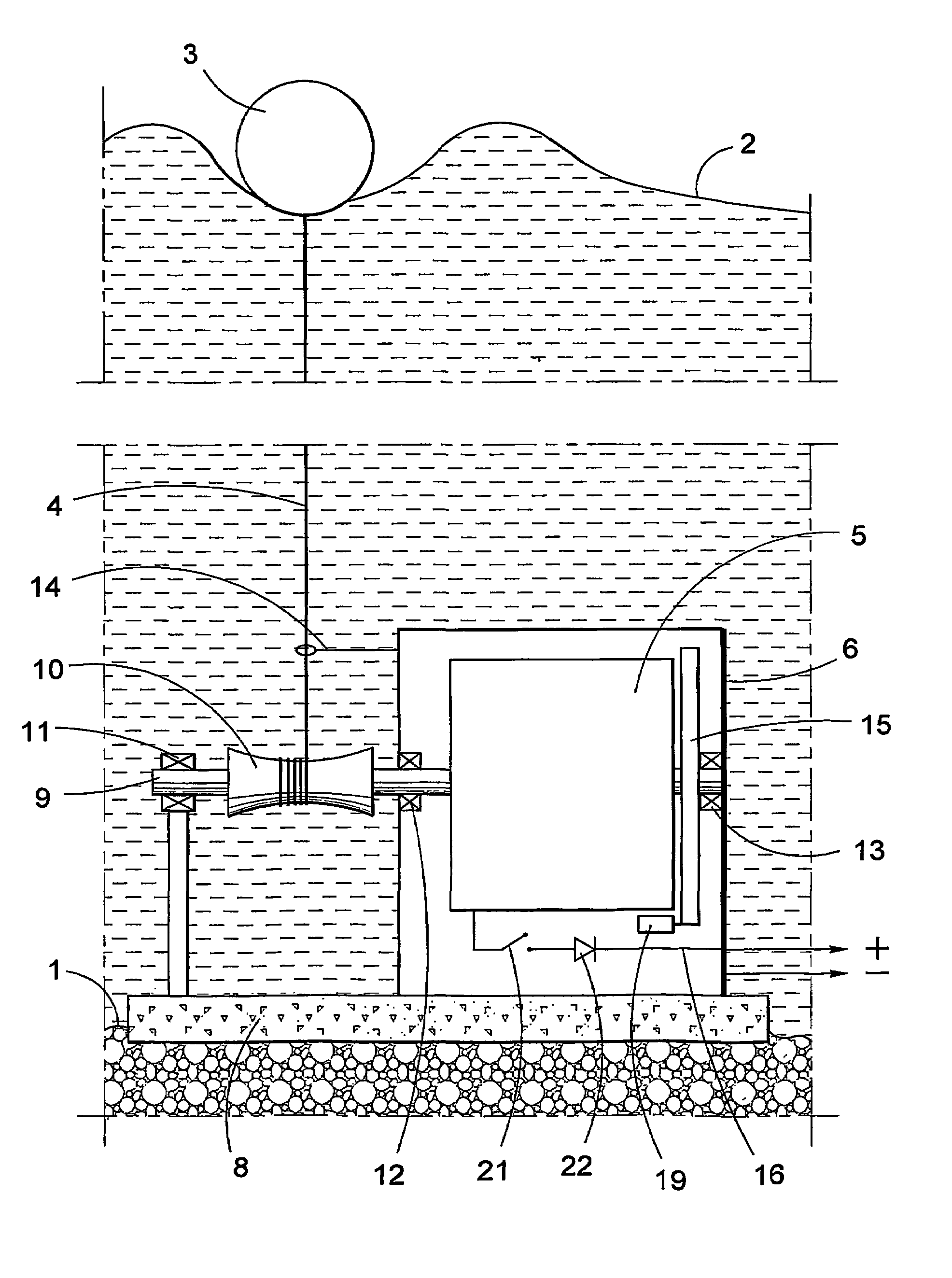
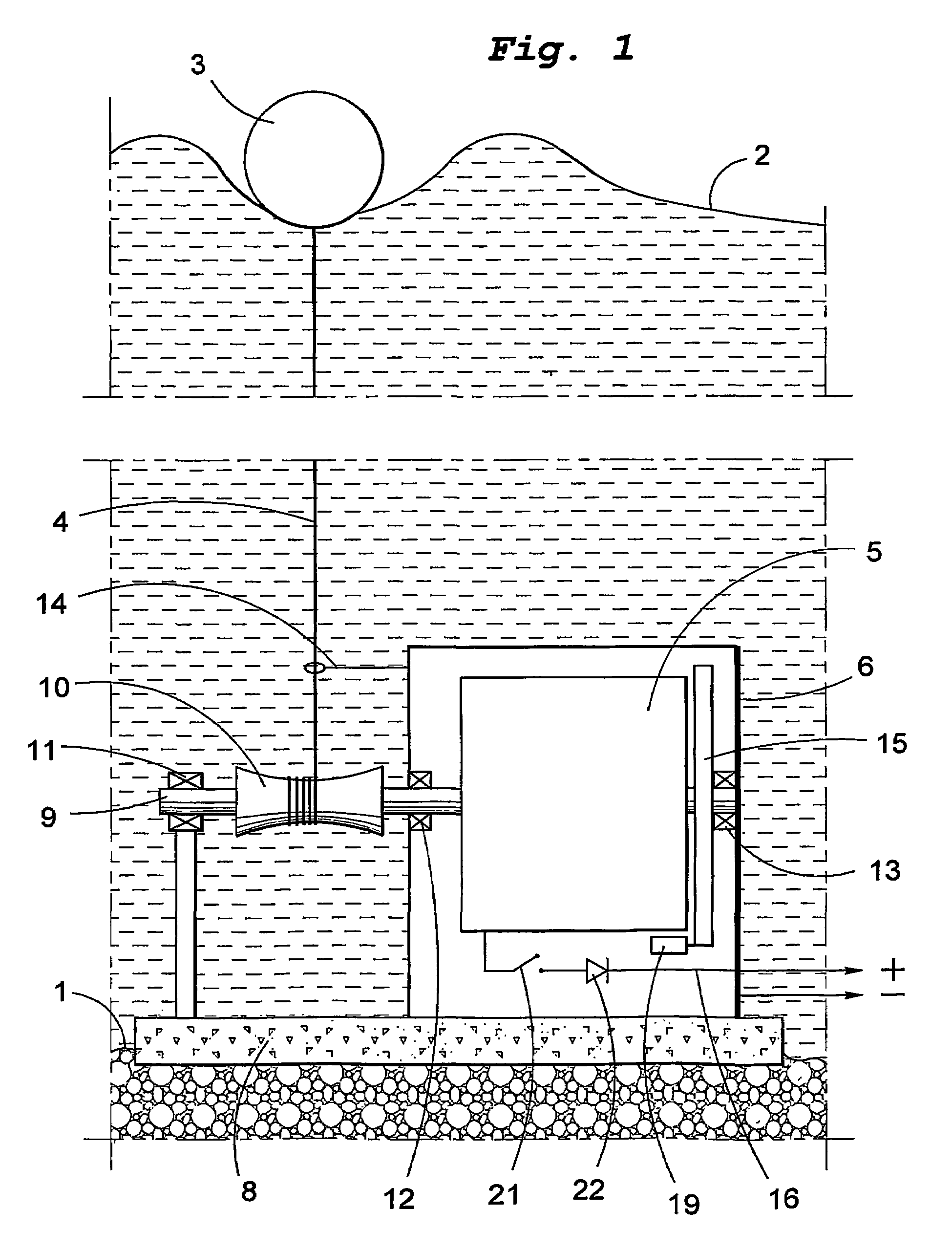
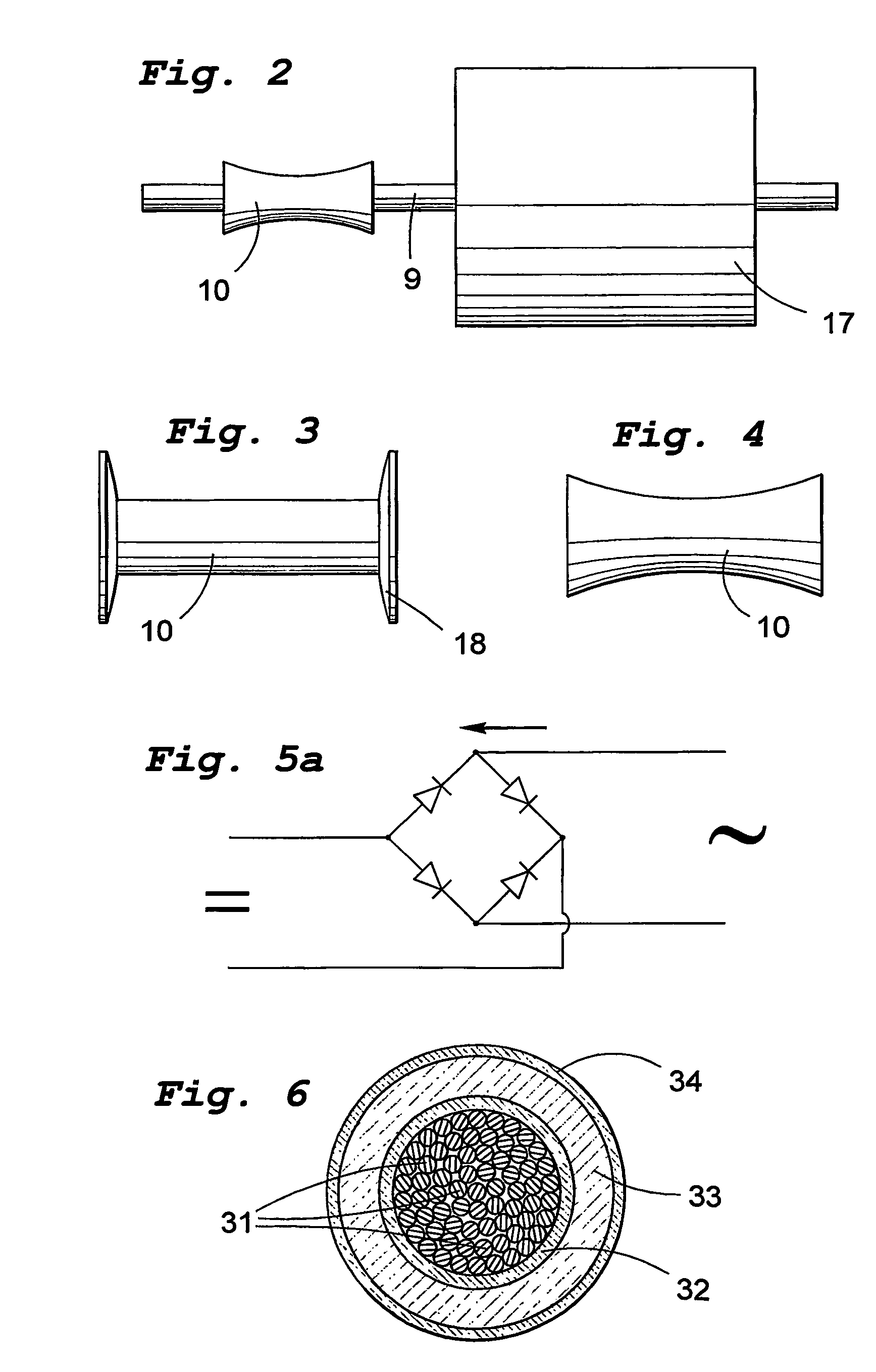
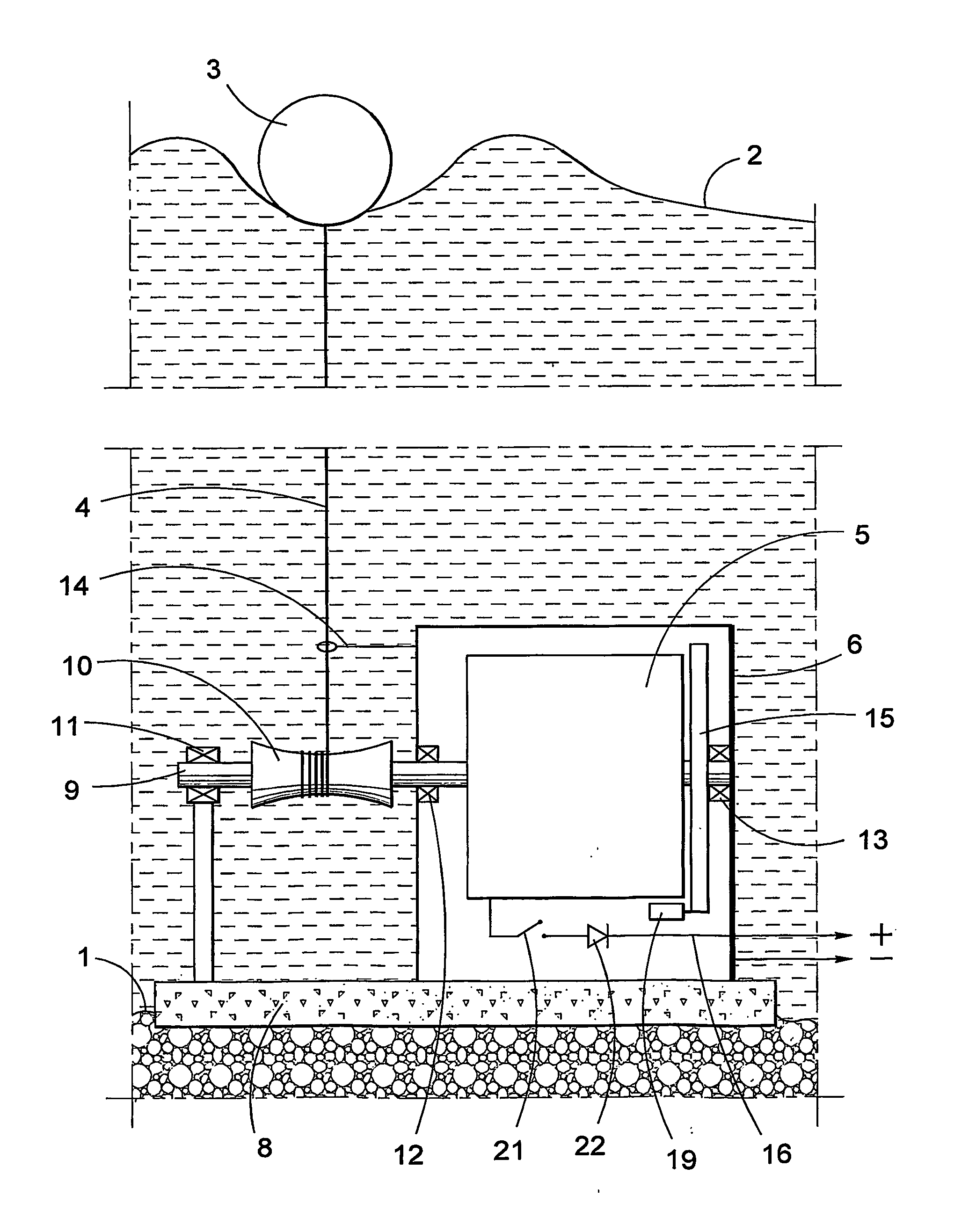
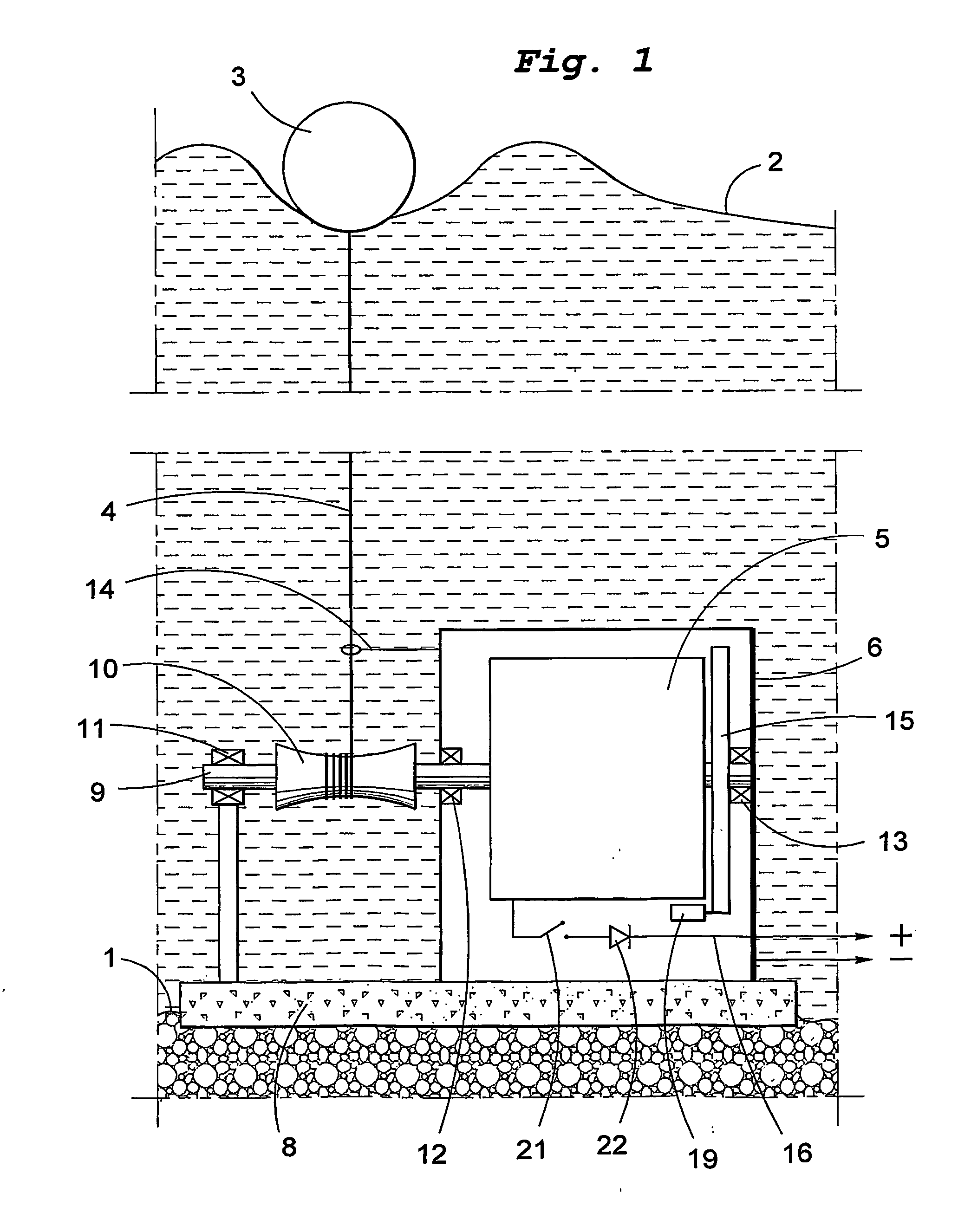
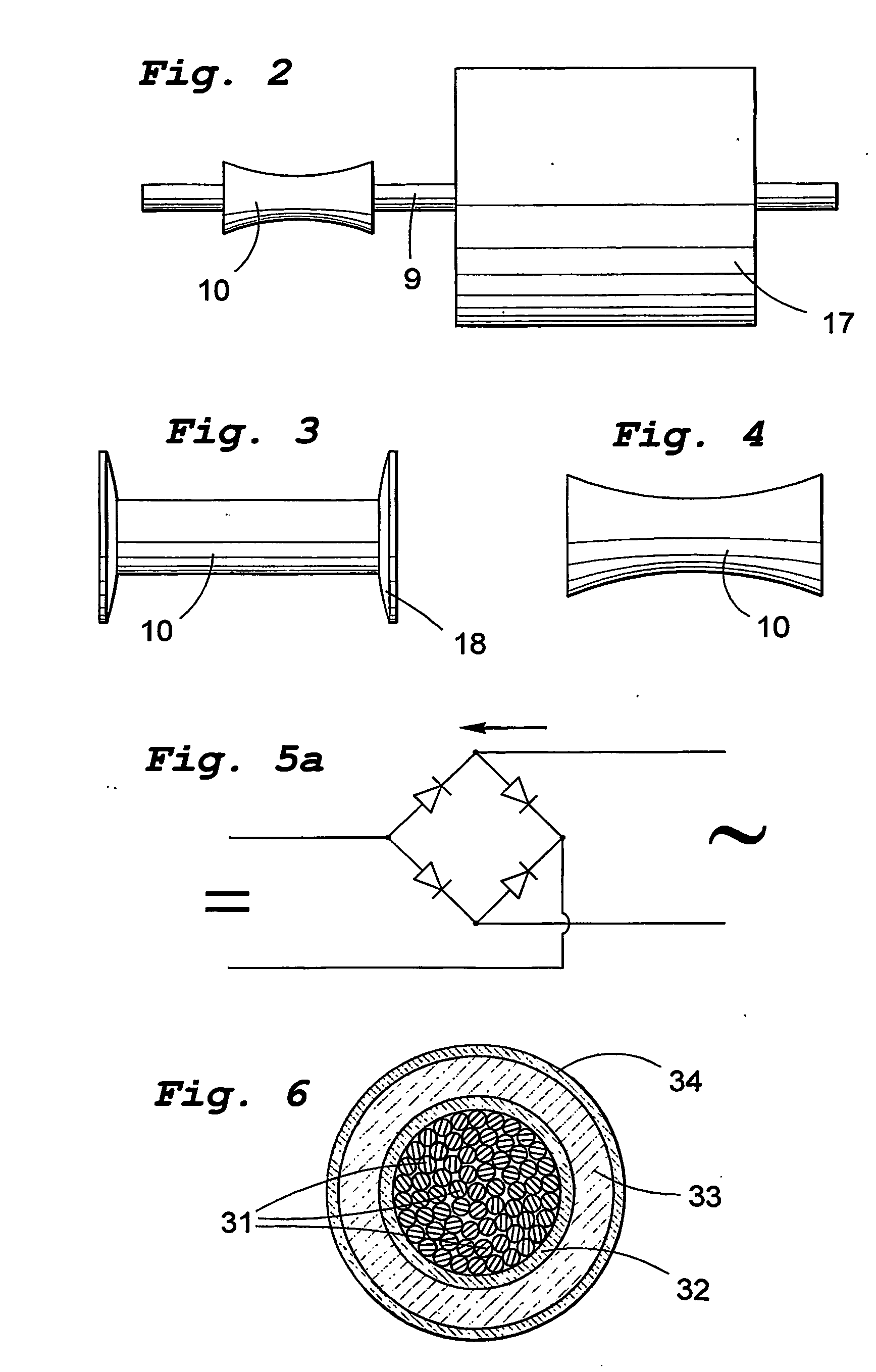
InactiveUS7045912B2Improve overall utilizationProtection attackMachines/enginesEngine componentsEngineeringWave power
The present invention relates to a wave-power unit having a floating body (3) and a rotating electric generator (5) mechanically connected to the floating body (3). In accordance with the invention a mechanically movement transmitting means (4) is arranged for transmission of vertical movements of the floating body (3) to rotary movements of the generator rotor. The invention also relates to a wave-power plant composed of a number of wave-power units in accordance with the invention. The invention also relates to the use of the claimed wave-power unit and method of generating electric energy.
Owner:SEABASED AB
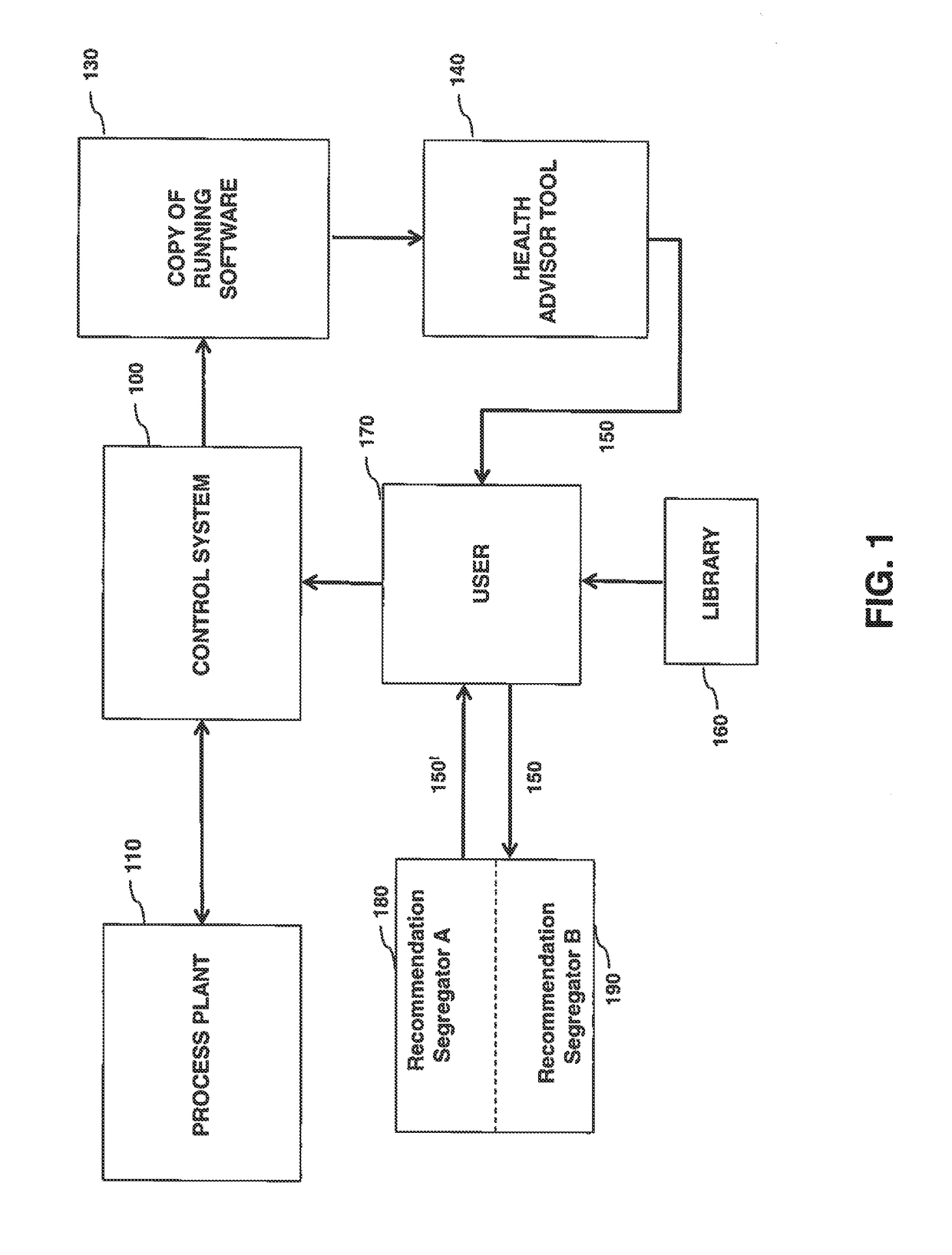
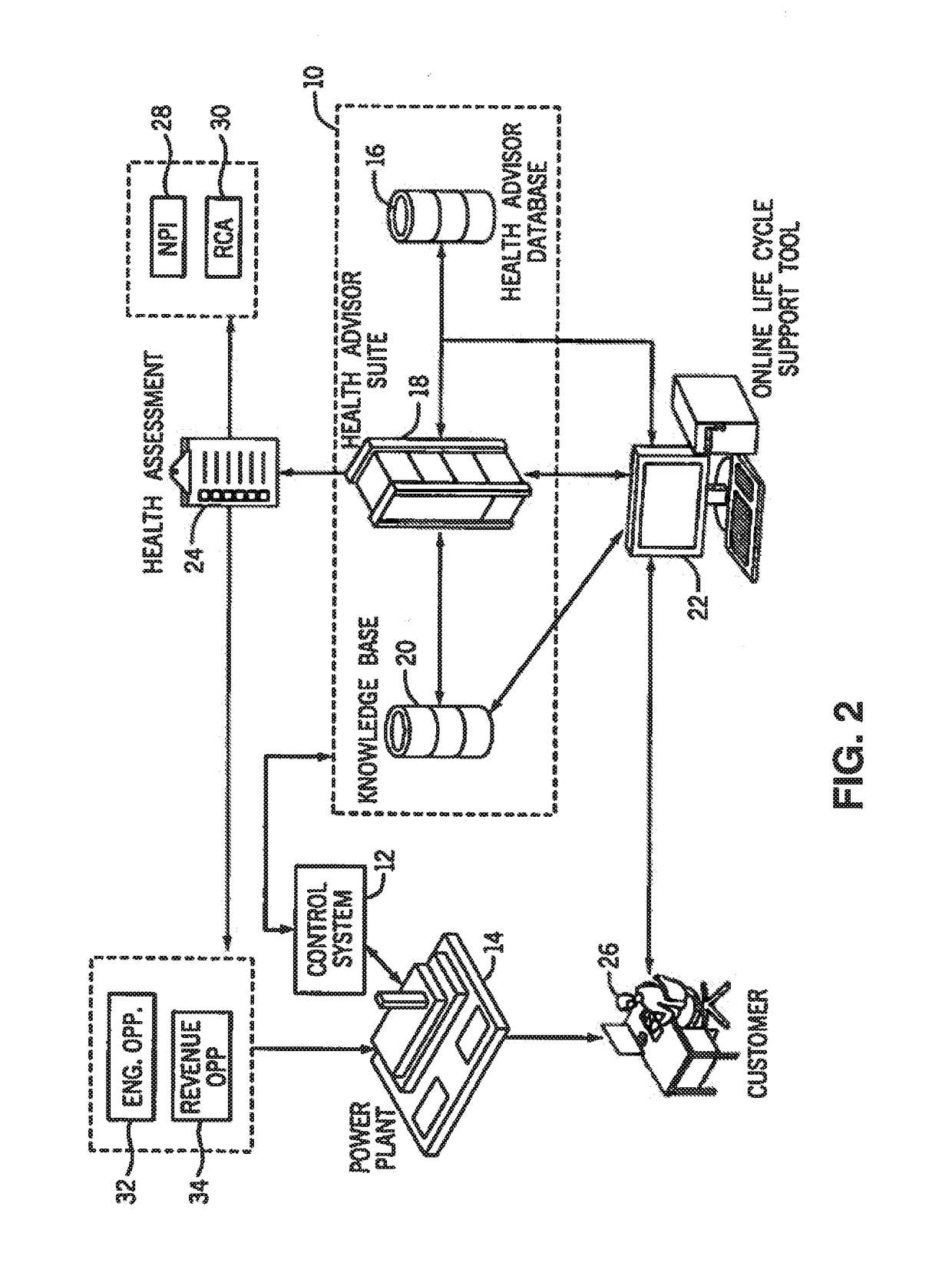
System and method for maintaining the health of a control system
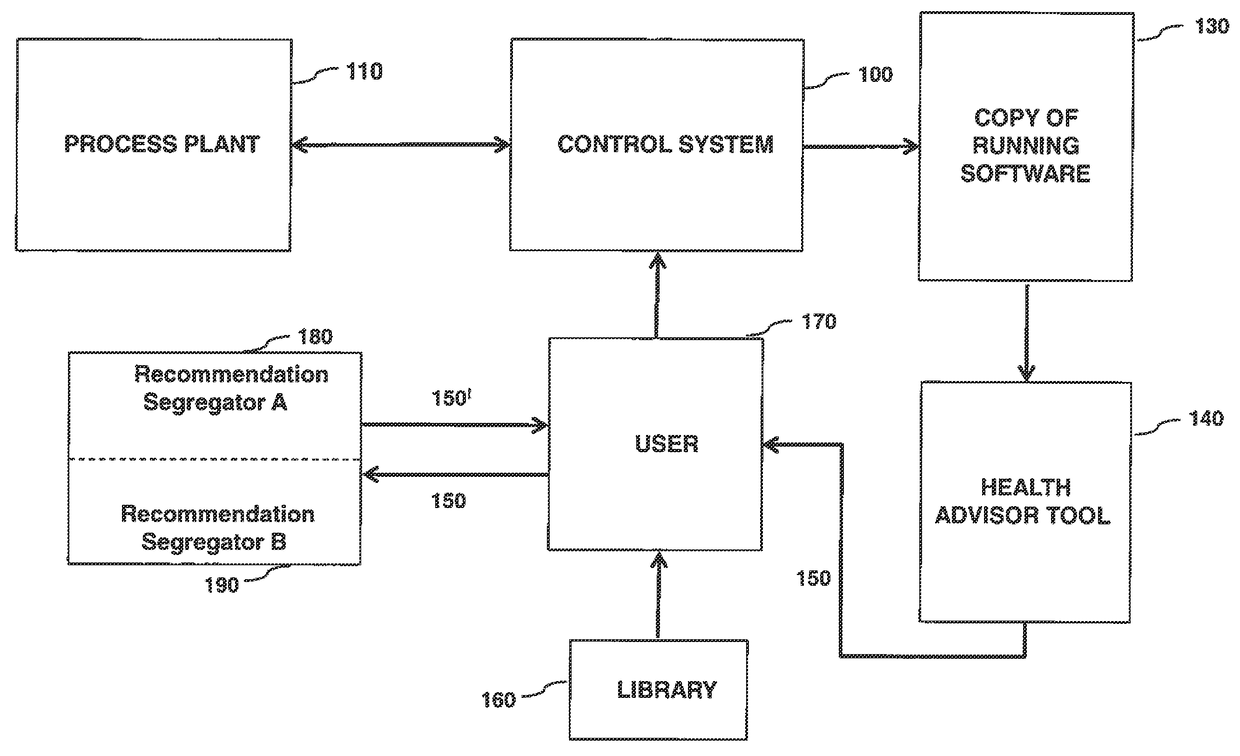
ActiveUS9912733B2Protection attackProgramme controlSafety arrangmentsControl system softwareReliability engineering
Disclosed is a system and method to maintain the health of a control system. A recording of running status of process control system software is performed. Then a health assessment of a process control system is carried out using the recorded running status. Using this information, at least one health maintenance recommendation is generated. The recommendations are then implemented to maintain the health of a process control system.
Owner:GENERAL ELECTRIC CO
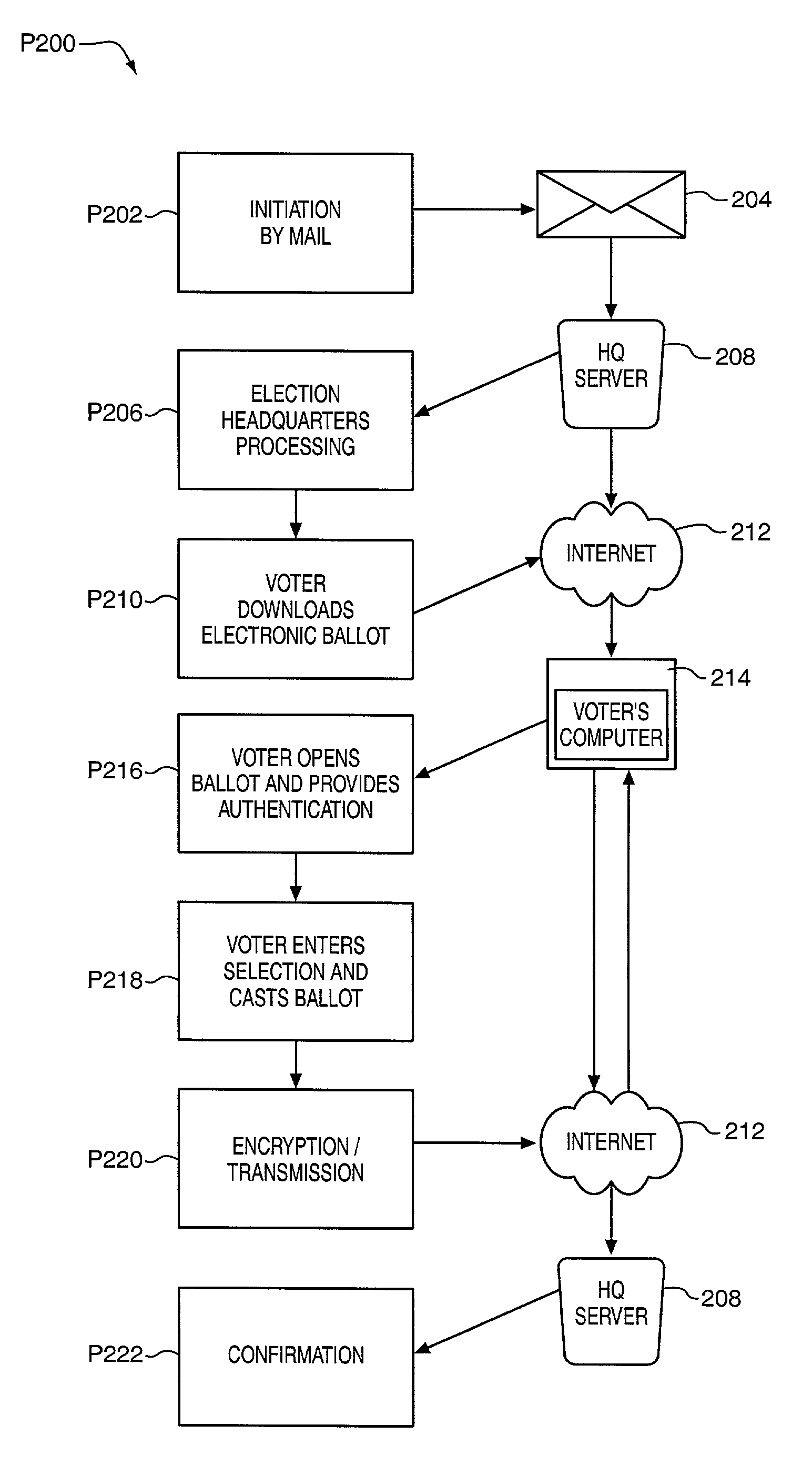
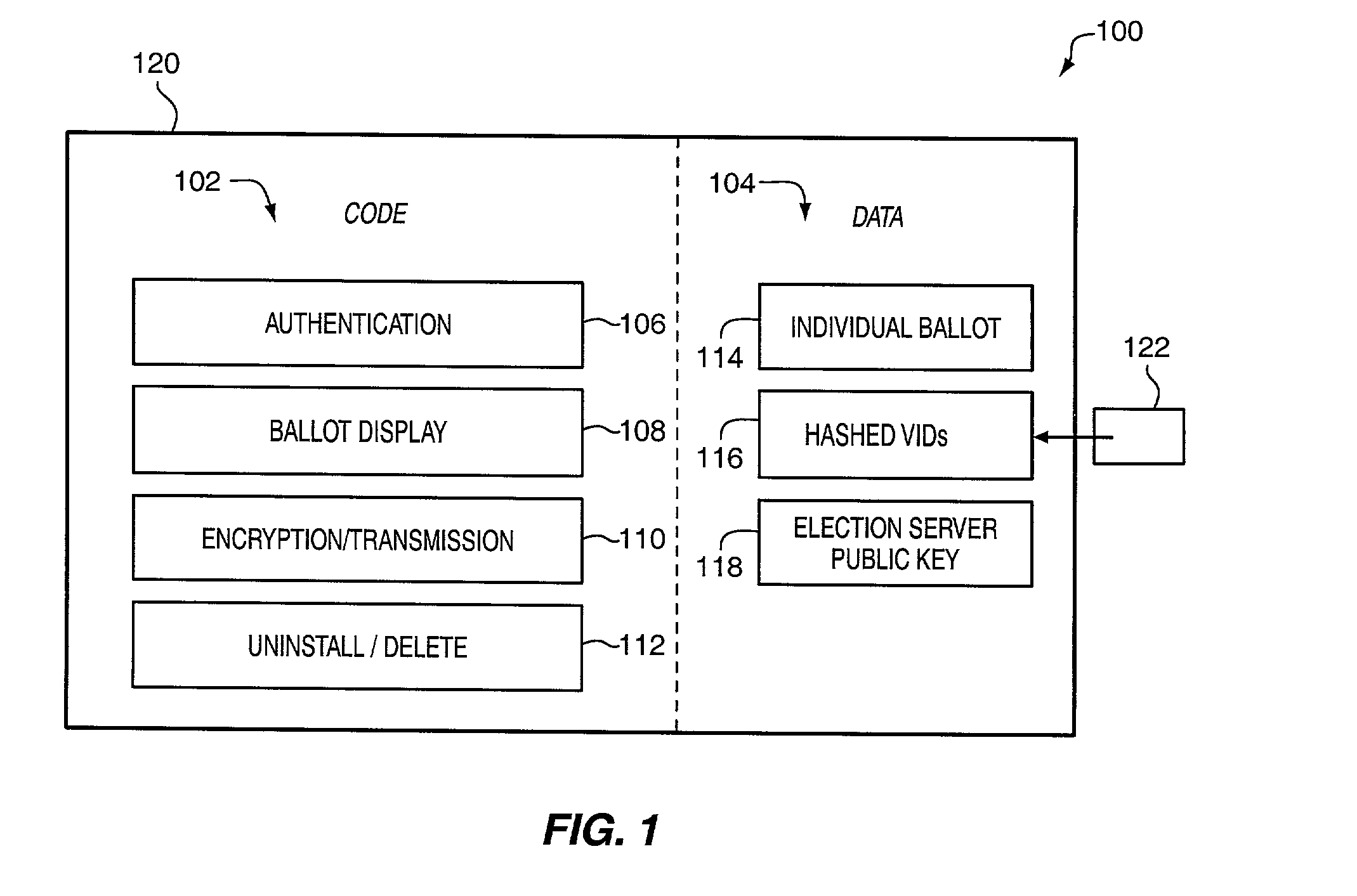
Distributed network voting system
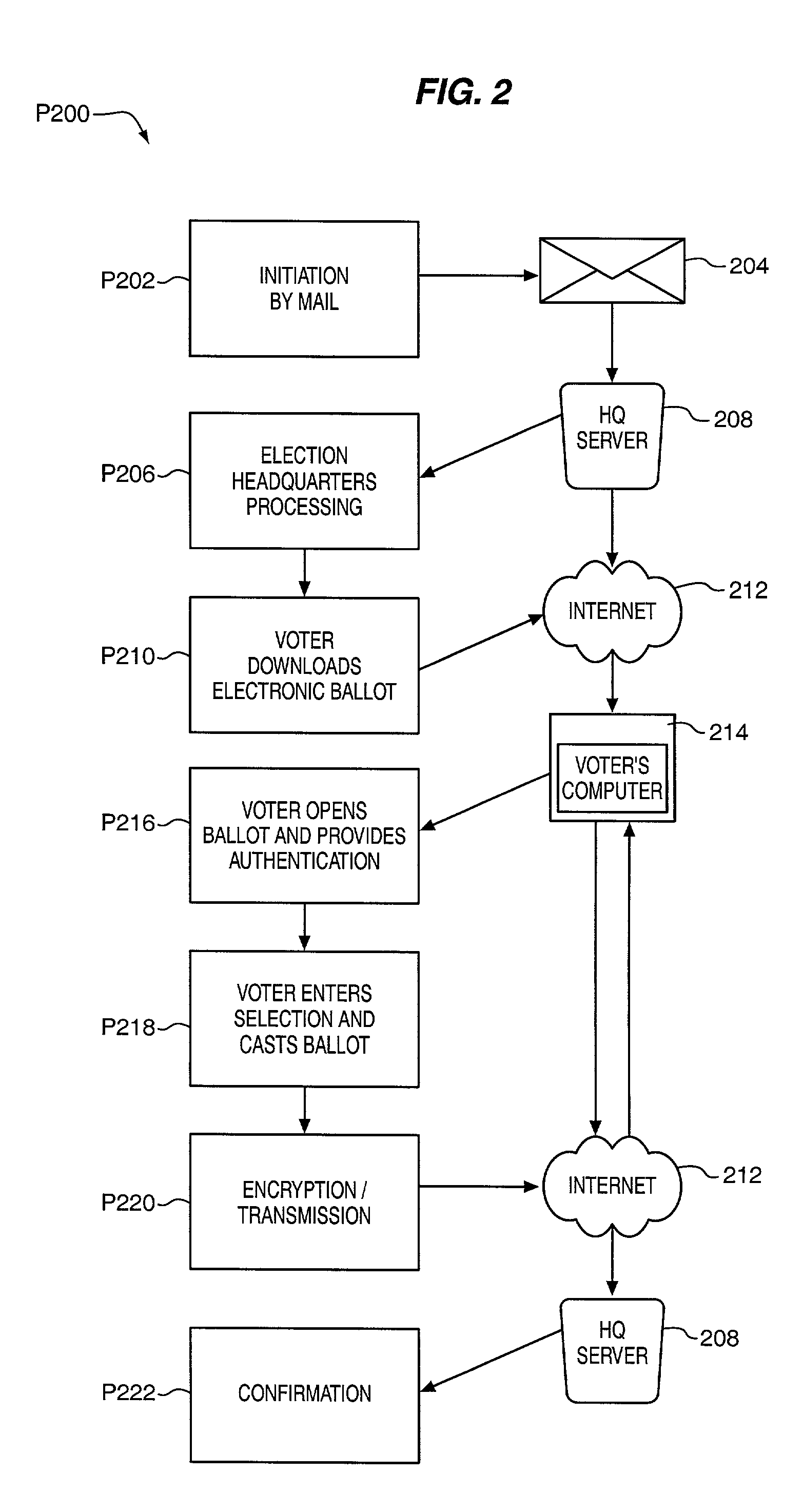
InactiveUS20020019767A1Confirm the accuracyProtection attackVoting apparatusError detection/correctionThe InternetEncryption
A secure election system provides a downloadable ballot viewer object for the casting of ballots. The ballot viewer object authenticates the user, permits user interaction in the casting of ballots, seals the cast ballot image by encryption, and transmits the cast ballot to election headquarters. The ballot viewer object may be used to perform secure voting on the Internet.
Owner:HART INTERCIVIC
Wave-power unit and plant for the production of electric power and a method of generating electric power
InactiveUS20050121915A1Improve overall utilizationProtection attackMachines/enginesEngine componentsPower stationEngineering
A wave-power unit has a floating body and a rotating electric generator mechanically connected to the floating body. A mechanical movement transmitter is arranged for transmission of vertical movements of the floating body to rotary movements of the generator rotor. A wave-power plant employs a plurality of wave-power units. Use of the wave-power unit and a method of generating electric energy as described.
Owner:SEABASED AB
Secure method and system for computer protection
ActiveUS20040268322A1Protection attackMemory loss protectionDigital data processing detailsQuality dataThe Internet
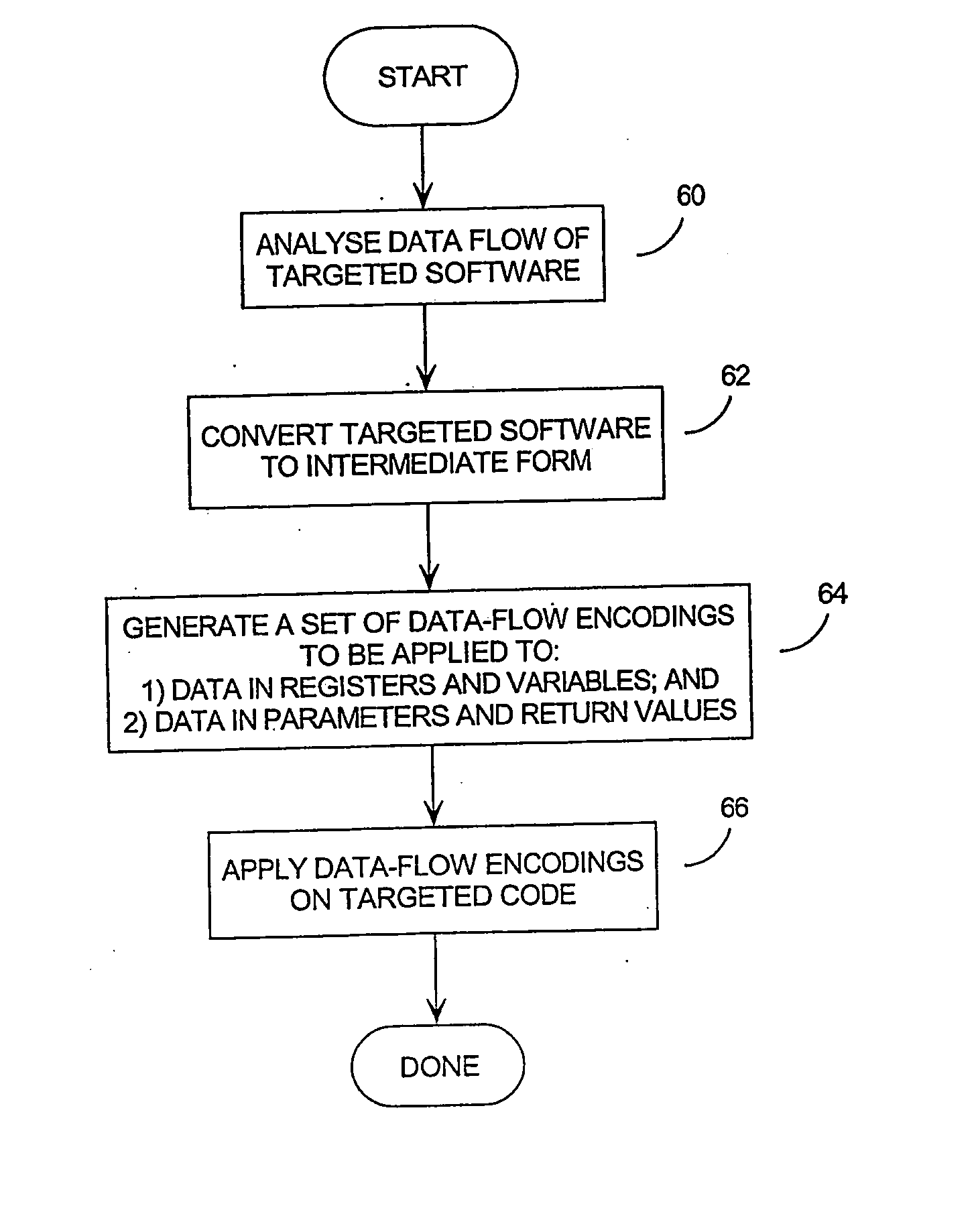
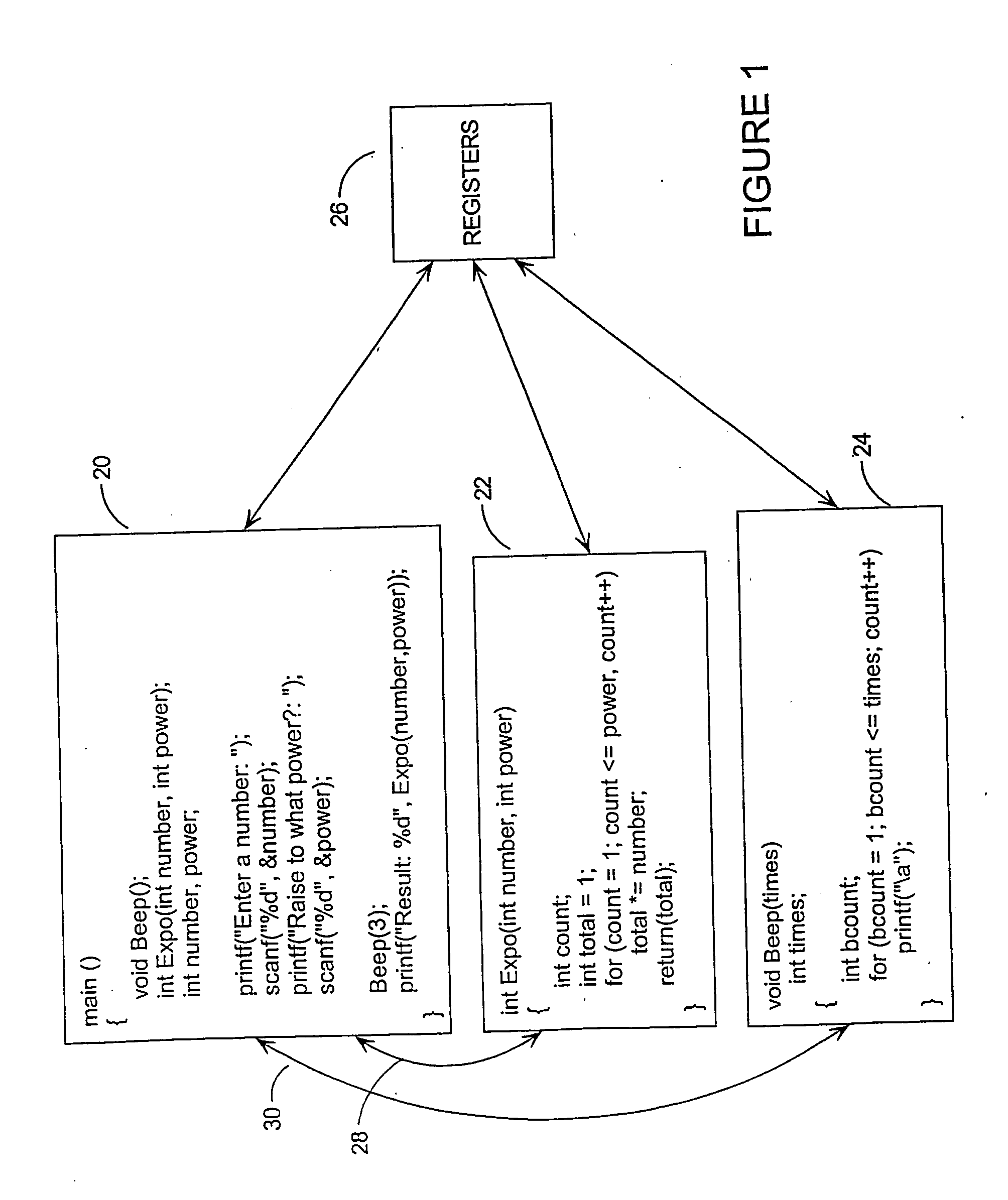
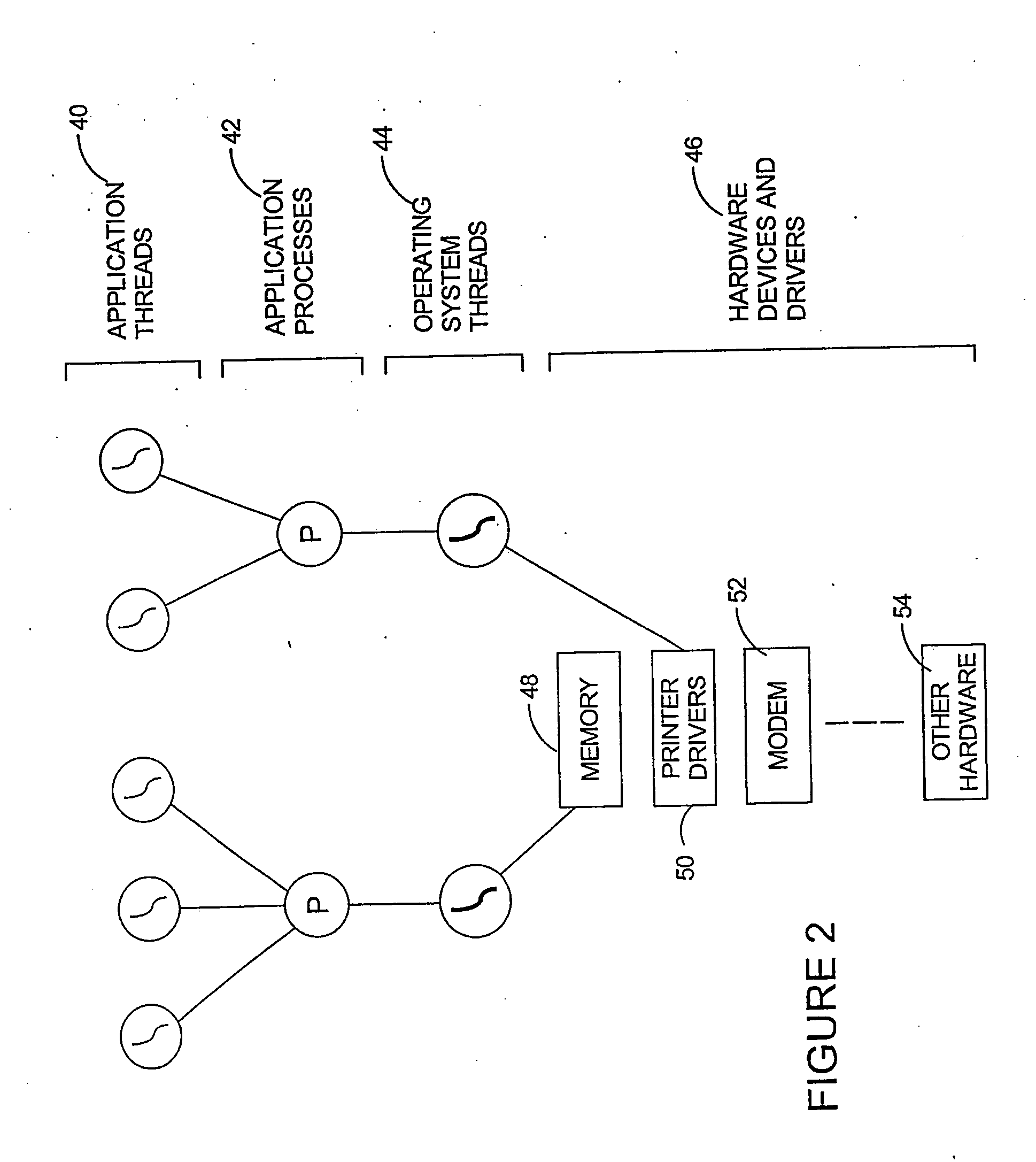
Attacks by computer viruses, worm programs, and other hostile software ('malware'), have become very serious problems for computer systems connected to large communication networks such as the Internet. One potential defence against such attacks is to employ diversity-that is, making each copy of the attacked software different. However, existing diversity techniques do not offer sufficient levels of protection. The invention provides an effective diversity solution by applying tamper resistant software (TRS) encoding techniques, to the communications that take place between software components, with corresponding changes to the code handling those communications. These communications may include, for example, data passed between software routines via parameters or mutually accessible variables, light-weight messages, signals and semaphores passed between threads, and messages passed between software processes. Effective TRS encoding techniques include data-flow encoding and mass-data encoding techniques.
Owner:IRDETO ACCESS
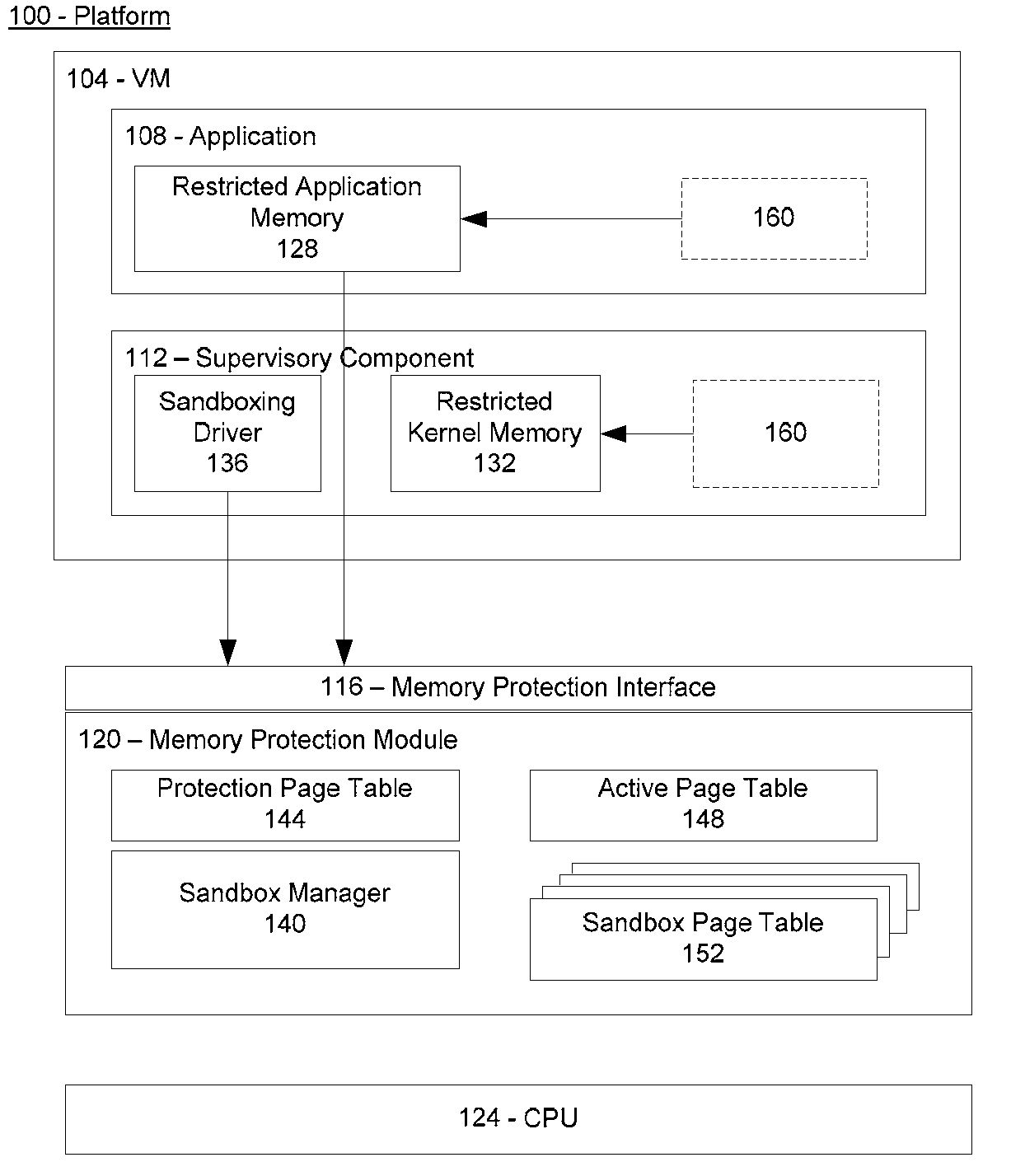
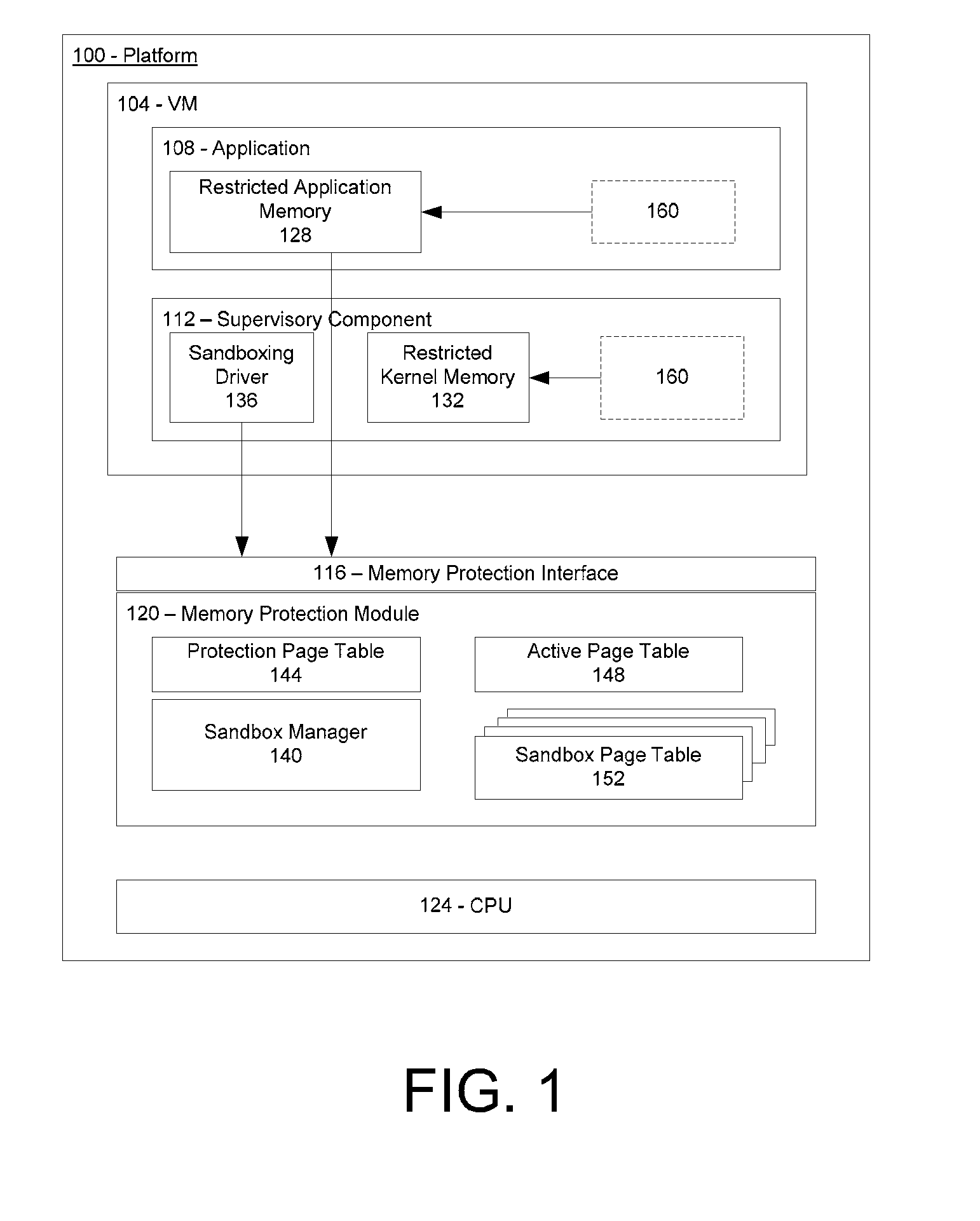
Restricted Component Access to Application Memory
ActiveUS20100082926A1Without riskProtection attackMemory loss protectionError detection/correctionCode moduleApplication software
Owner:INTEL CORP
Methods and apparatus for conducting electronic transactions
InactiveUS7801827B2Enhanced reliability and confidenceReduce security risksDigital data processing detailsUnauthorized memory use protectionSmart cardE-commerce
A system and method for conducting electronic commerce are disclosed. In various embodiments, the electronic transaction is a purchase transaction. A user is provided with an intelligent token, such as a smartcard containing a digital certificate. The intelligent token suitably authenticates with a server on a network that conducts all or portions of the transaction on behalf of the user. In various embodiments a wallet server interacts with a security server to provide enhanced reliability and confidence in the transaction. In various embodiments, the wallet server includes a toolbar. In various embodiments, the digital wallet pre-fills forms. Forms may be pre-filled using an auto-remember component.
Owner:LIBERTY PEAK VENTURES LLC
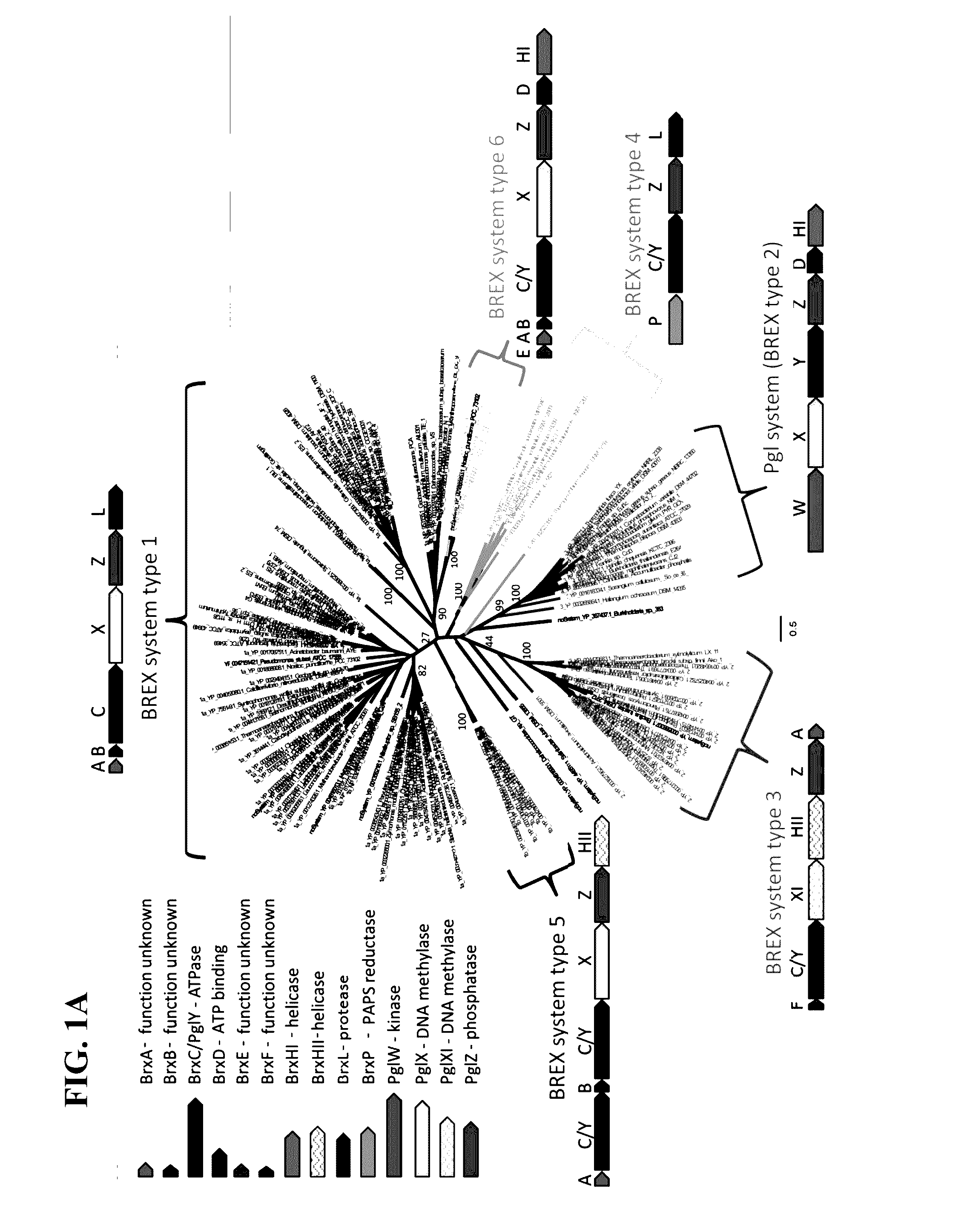
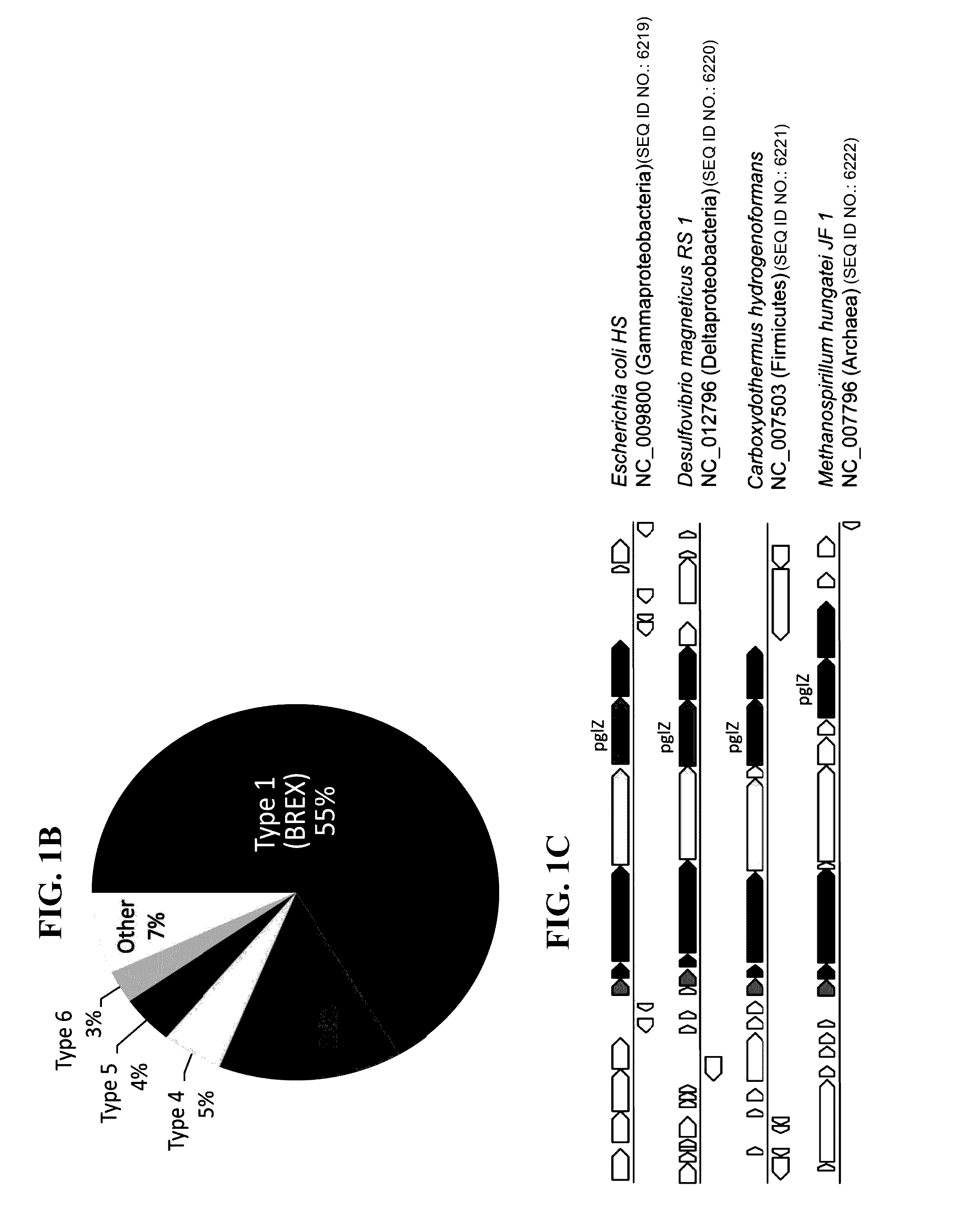
Polynucleotides encoding brex system polypeptides and methods of using same
Isolated polynucleotides encoding a BREX system are provided. Accordingly there is provided an isolated polynucleotide encoding a BREX system comprising a nucleic acid sequence encoding the BREX system comprising brxC / pglY, pglZ and at least one of pglX, pglXI, brxP, brxHI, brxHII, brxL, brxD, brxA, brxB, brxF, and brxE, with the proviso that said BREX system does not comprise pglW, and wherein said BREX system confers phage resistance to a bacteria recombinantly expressing same; Also provided is an isolated polynucleotide encoding a BREX system comprising a nucleic acid sequence encoding the BREX system comprising brxC / pglY, pglZ, pglX, pglW and at least one of brxD and brxHI, and wherein said BREX system confers phage resistance to a bacteria recombinantly expressing same. Also provided are compositions and methods for conferring phage resistance to bacteria or for conferring bacterial susceptibility to phages.
Owner:YEDA RES & DEV CO LTD
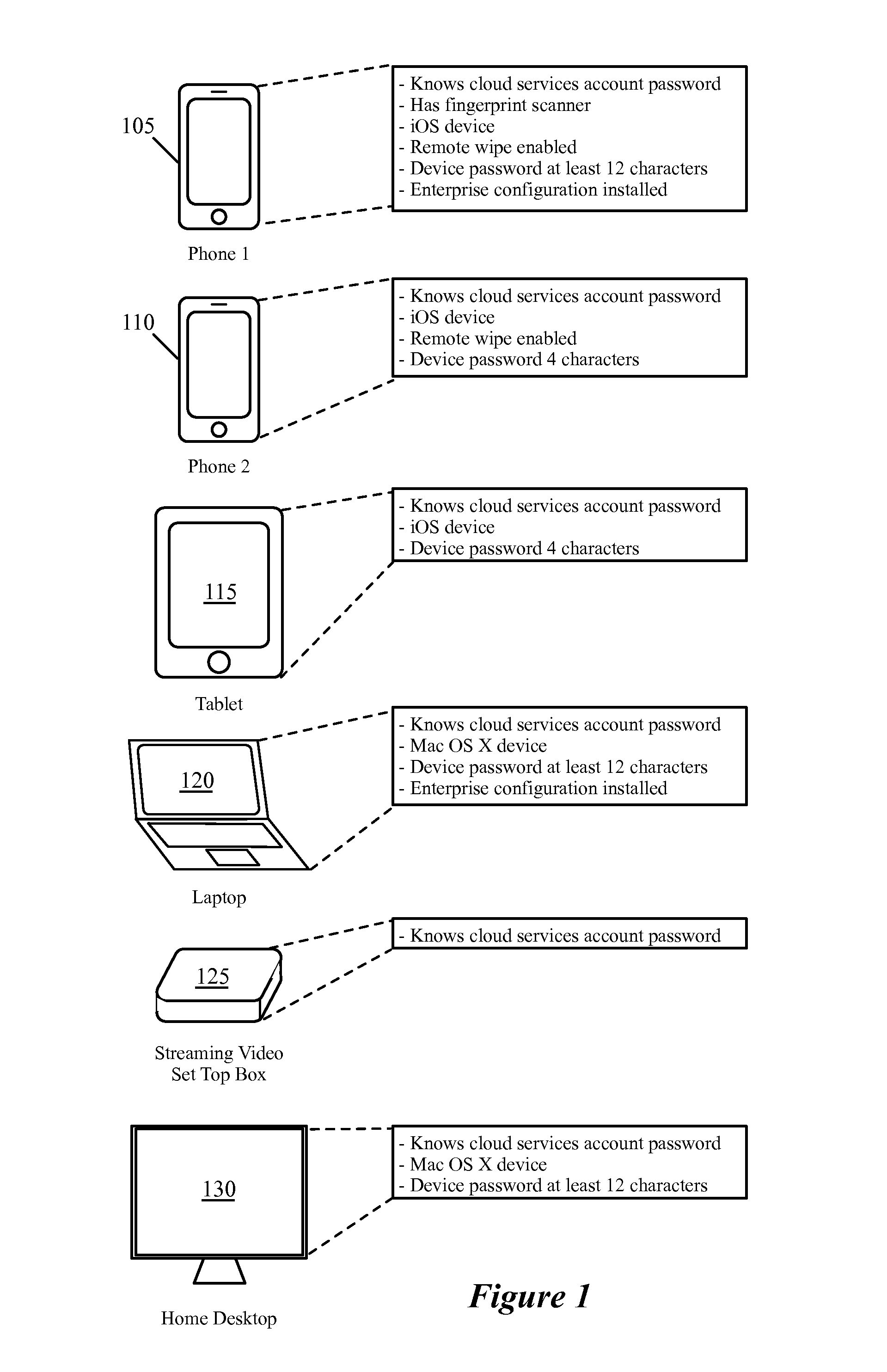
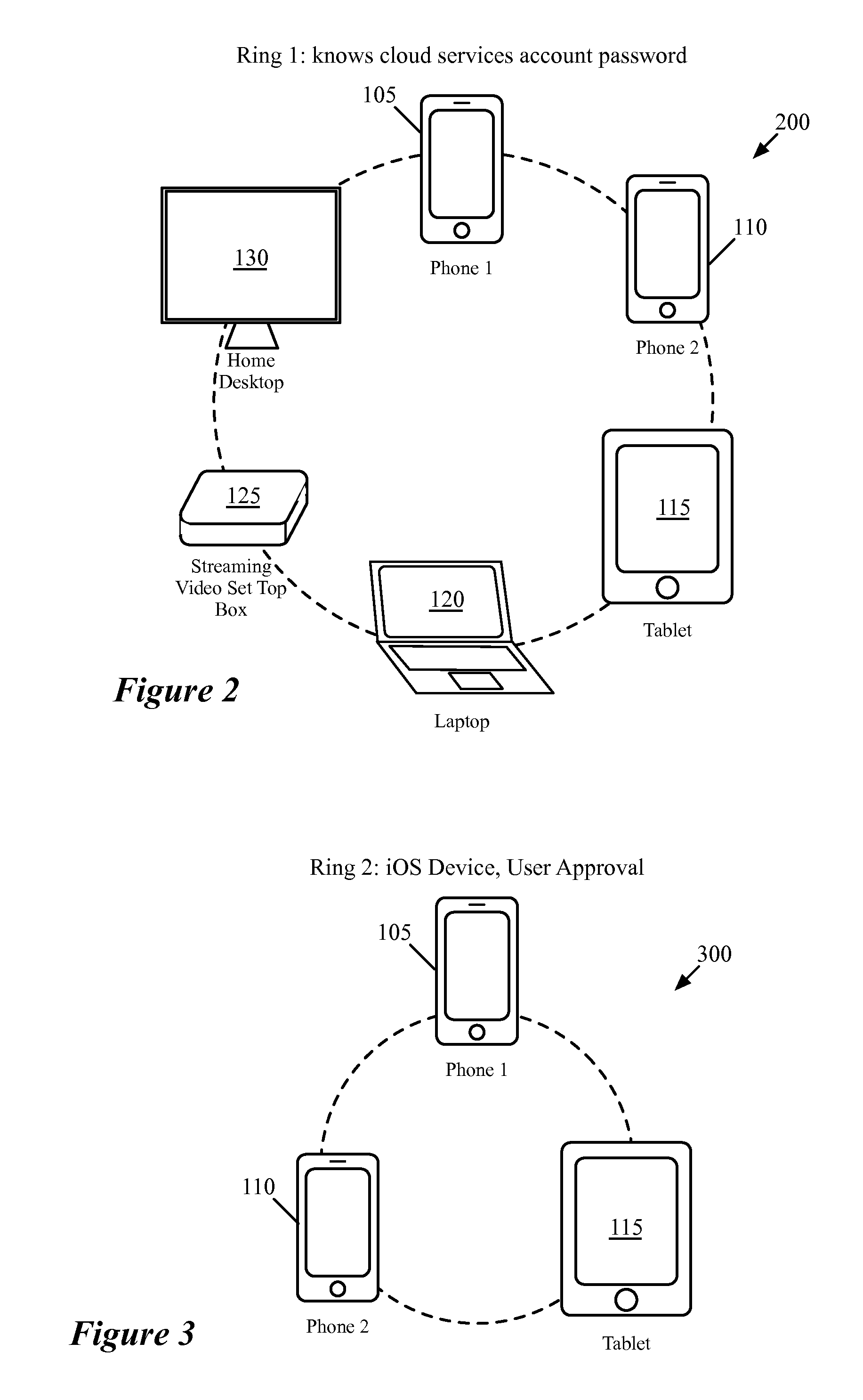
Synchronization And Verification Groups Among Related Devices
ActiveUS20160349999A1Protection attackInput/output to record carriersBroadcast service distributionDistributed computingSecure channel
Some embodiments provide a method for a first device to synchronize a set of data items with a second device. The method receives a request to synchronize the set of data items stored on the first device with the second device. The method determines a subset of the synchronization data items stored on the first device that belong to at least one synchronization sub-group in which the second device participates. Participation in at least one of the synchronization sub-groups is defined based on membership in at least one verification sub-group. The first and second devices are part of a set of related devices with several different verification sub-groups. The method sends only the subset of the synchronization data items that belong to at least one synchronization sub-group in which the second device participates to the second device using a secure channel.
Owner:APPLE INC
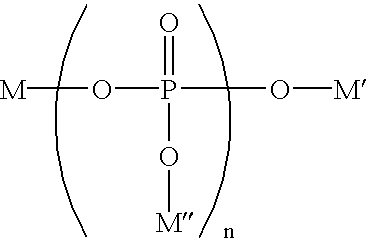
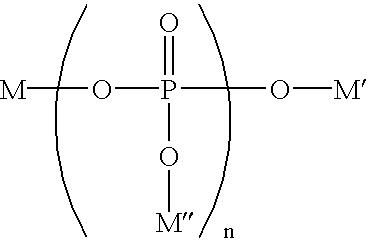
Methods of inhibiting dental erosion/discoloration using a beverage composition comprising a long chain polyphosphate
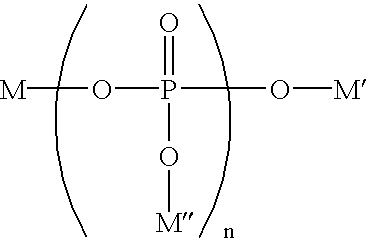
InactiveUS6984376B2Low efficacyProtection attackCosmetic preparationsInorganic phosphorous active ingredientsTooth discolorationErosion
The present invention is directed to a method of treating dental erosion, preventing dental discoloration or both comprising orally administering to a mammal (preferably, a human) a beverage composition having a pH of greater than about 5.5; wherein the beverage composition comprises a compound having the structure: wherein n is an integer averaging from about 7 to about 100 and M, M′, and M″ are each, independently, selected from the group consisting of sodium and potassium. The present invention is further directed to kits comprising the foregoing beverage composition and information that use of the beverage composition provides treatment against dental erosion, dental discoloration or both.
Owner:THE PROCTER & GAMBLE COMPANY
Tamper detection system for securing data
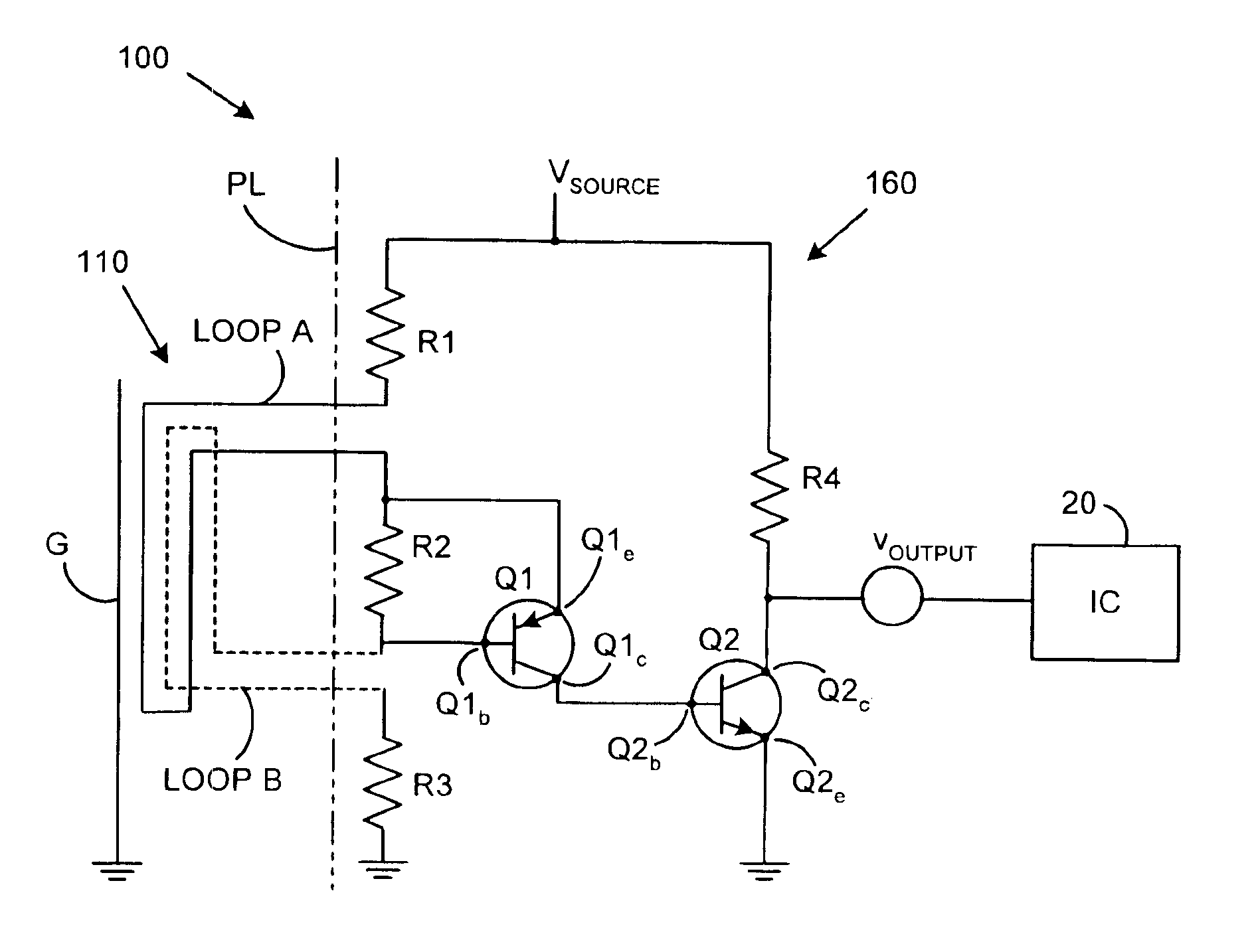
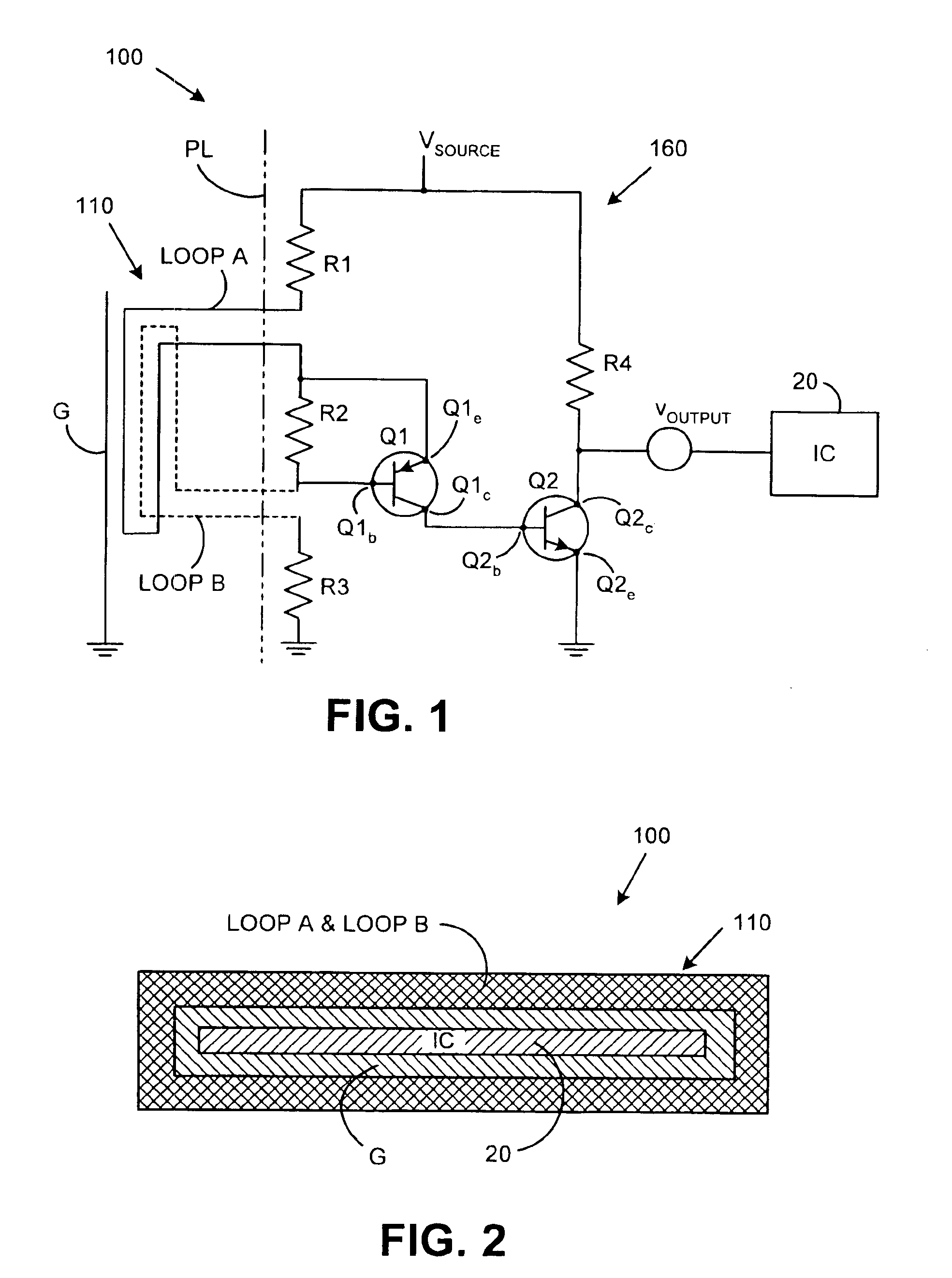
InactiveUS6895509B1Easy to operateProtection attackEqual length code transmitterMemory loss protectionEngineeringIntegrated circuit
A tamper detection system includes a trigger mechanism system and a detection circuit that operate in combination to protect an integrated circuit from attack. The detection circuit connects to the trigger mechanism system that is basically a protective mesh that consists of two separate loops of wire held in close proximity to each other and an optional ground layer. The mesh is such that an attempted penetration is highly likely to cause an open of either loop or a short of one loop to the other. The detection system recognizes shorts and opens in the mesh. The detection circuit is intended to be very simple in its operation it that it does not require a sophisticated stimulus and response set to operate. It is designed to be polled on a regular basis for indications of a change in its operation.
Owner:PITNEY BOWES INC
Translucent or opaque colored glass-ceramic article providing a cooking surface and its use
InactiveUS20050252503A1Minimizing contentEasy resistanceCooking-vessel materialsStoves/ranges foundationsChemical reactionAdditive ingredient
The translucent or opaque colored glass-ceramic article provides a cooking surface and has an adjustable light transmission in a visible range under 15%, as measured for a 4 mm sample thickness; a flaw-free upper surface with an impact resistance of greater than 18 cm breaking height, as tested with a 200 g steel ball in a falling ball test; a temperature difference resistance of greater than 500° C.; a high crystallinity with keatite mixed crystals as principal crystal phase in an interior of the glass-ceramic article and with a residual glass phase fraction of less than 8% by weight; a glassy upper surface layer of from 0.5 to 2.5 μm thick, which is substantially free of high quartz mixed crystals and which inhibits chemical reactions, and a content of enriched ingredients in the residual glass phase in the interior of the glass-ceramic and in the glassy surface layer of ΣNa2O+K2O+CaO+SrO+BaO+F+refining agents of from 0.2 to 1.6% by weight.
Owner:SCHOTT AG
Oral formulation for gastrointestinal drug delivery
InactiveUS7097851B1Prevent penetrationImprove bioavailabilityOrganic active ingredientsPeptide/protein ingredientsControl layerAdhesive
An oral formulation for gastrointestinal drug delivery which comprises an adhesion site-controlling layer for attaching the formulation to the selected site in the digestive tract, a drug-carrying layer for containing a drug and an adhesive and a protecting layer for protecting the drug in the drug-carrying layer, wherein the drug-carrying layer exists between the protecting layer and the adhesion site-controlling layer, and the adhesion site-controlling layer may attach to the protecting layer. The formulation can improve bioavailability of drugs which have low bioavailability.
Owner:TAKADA
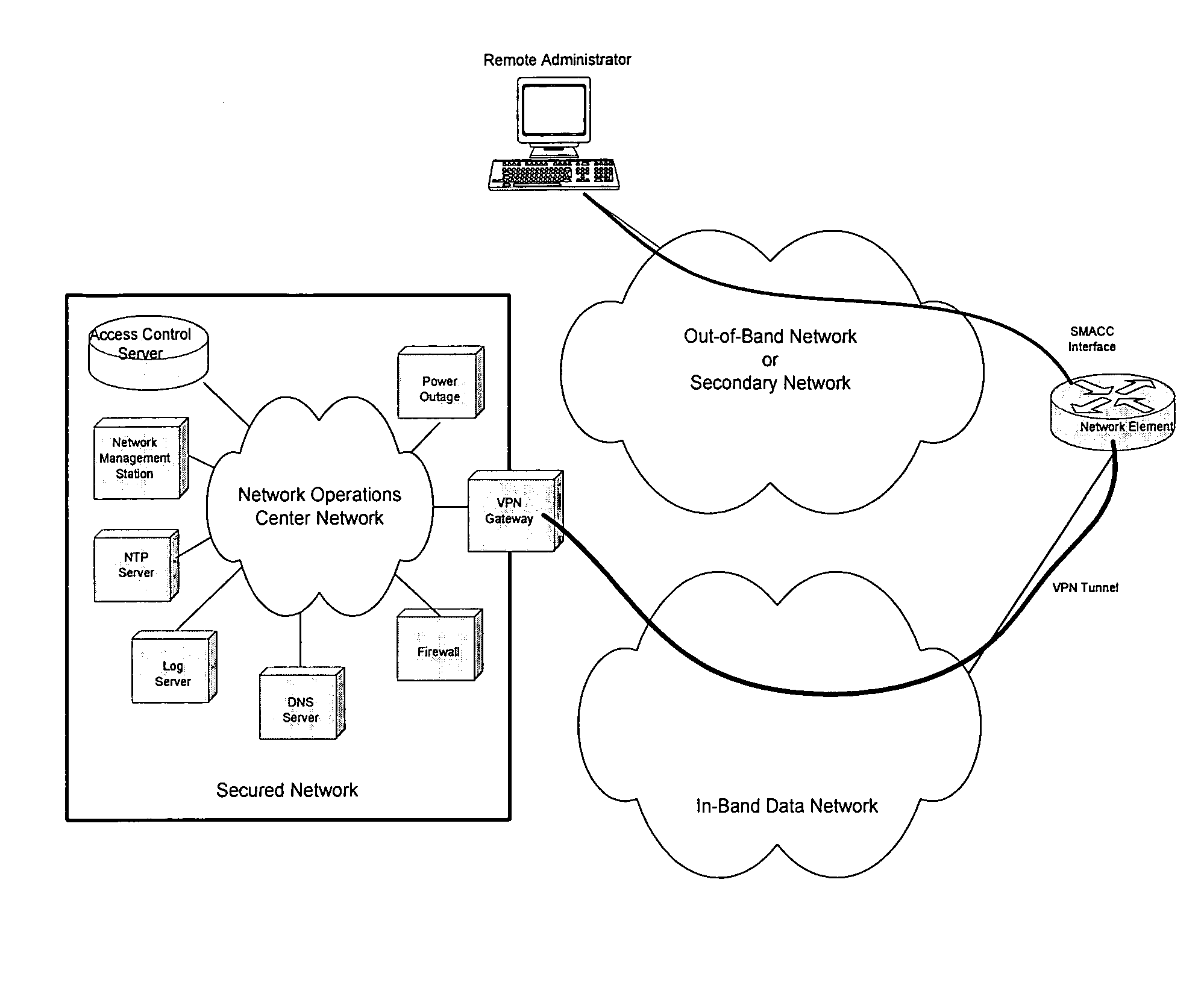
Secure management access control for computers, embedded and card embodiment
ActiveUS20050086494A1Great opportunityConvenient remote managementDigital data processing detailsMultiple digital computer combinationsDirect communicationAuthorization
A computer network management system for remotely managing a network device. The system includes a secure management access controller which is in direct communication with the network device. The secure management access controller provides access for remotely and securely managing a network. The secure management access controller further separates management communications from user communications to ensure the security of the management communications. The system further includes network and power monitoring and notification systems. The system further provides authentication and authorization capabilities for security purposes.
Owner:INTELLECTUAL VENTURES II
Dynamic Group Membership For Devices
ActiveUS20160352526A1Protection attackUser identity/authority verificationBroadcast service distributionDistributed computing
Owner:APPLE INC
System and method for providing network level and nodal level vulnerability protection in VoIP networks
ActiveUS8582567B2Unauthorized usePrivacy protectionInterconnection arrangementsAutomatic exchangesComputer networkAnomaly detection
Owner:AVAYA INC
Methods and Apparatus for Conducting Electronic Transactions
InactiveUS20110191250A1Enhanced reliability and confidenceReduce security risksAcutation objectsDigital data processing details
A system and method for facilitating electronic transactions using an intelligent instrument is disclosed. An authorization server enables users to obtain authorization credentials through the use of the intelligent instrument by issuing a challenge to an intelligent token of the intelligent instrument. The intelligent token generates a challenge response and transmits the challenge response to the authorization server, which assembles credentials including a key for the electronic transaction upon validating the response. The authorization server sends the assembled credentials to the intelligent instrument and the intelligent instrument transmits the assembled credentials to the authorization server during a subsequent transaction. The authorization server validates the assembled credentials and provides authorization for the transaction in response to the validating the assembled credentials.
Owner:LIBERTY PEAK VENTURES LLC
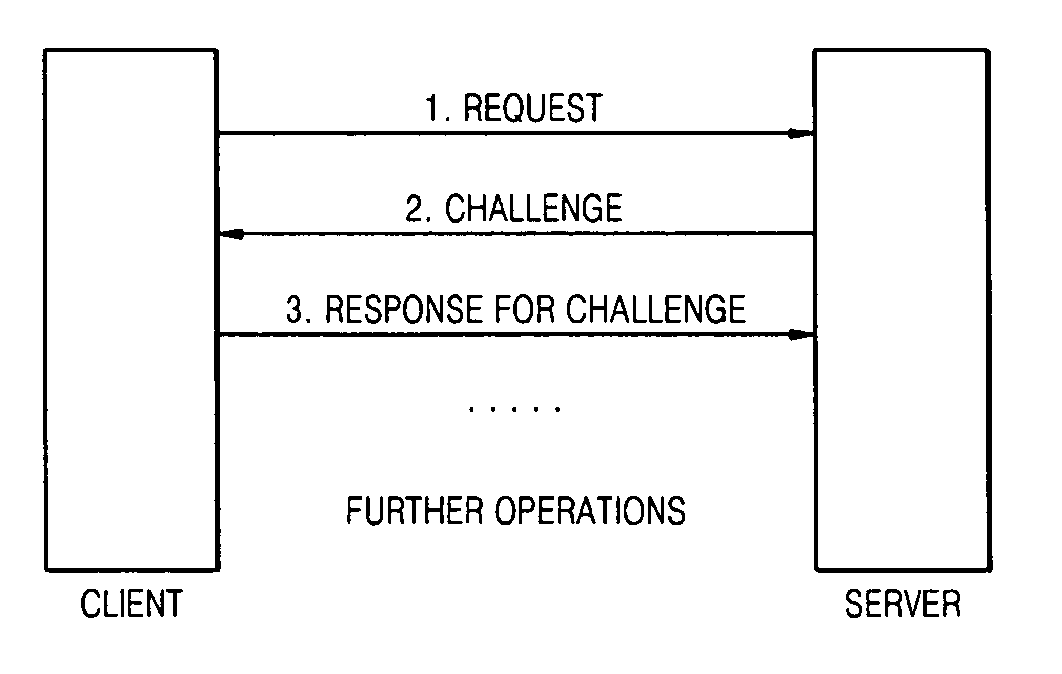
Method and apparatus to protect server from DOS attack
InactiveUS20070157300A1Protection attackData taking preventionDigital data processing detailsClient-sideComputer security
A challenge-response method and apparatus to defend a system against Denial of service (DOS) / Distributed Denial of Service (DDOS) attacks, especially resource consumption attack, the method including: before committing resources to a client, throwing a challenge to the client, verifying a result generated by the client, and committing resources only if the verification is successful. When the client mounts an attack against a server by throwing multiple requests, the server will throw multiple challenges to the client and the client will get overloaded in resolving challenges thrown by the server as the server is able to control a cost of the challenge and verify responses generated for the challenge by investing minimal resources. Thus, the server's resources are free for legitimate users.
Owner:SAMSUNG ELECTRONICS CO LTD
Fast-acting oral peptide pharmaceutical products
ActiveUS8093207B2Increase delivery speedImprove bioavailabilityTetrapeptide ingredientsSkeletal disorderActive agentDrug product
Owner:ENTERIS BIOPHARMA
Authentication password storage method and generation method, user authentication method, and computer
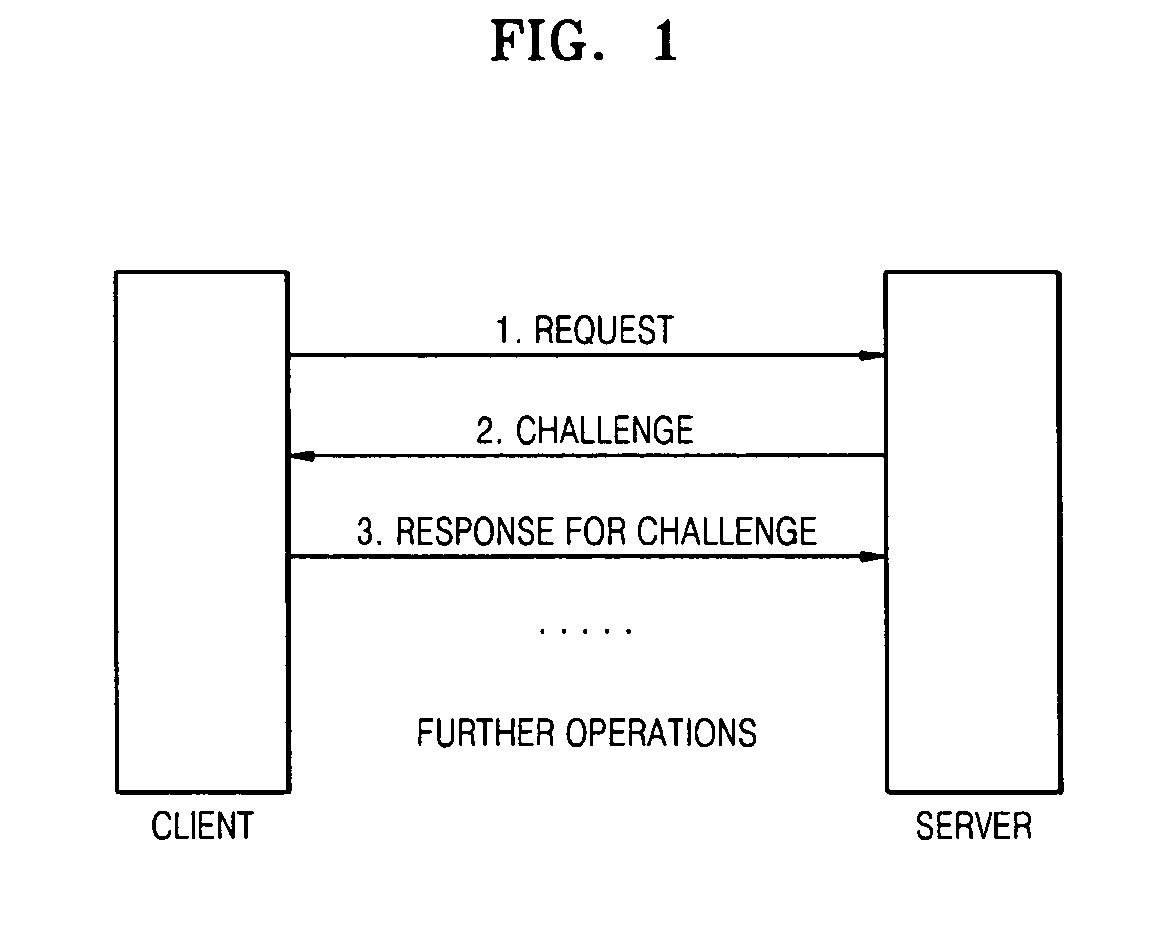
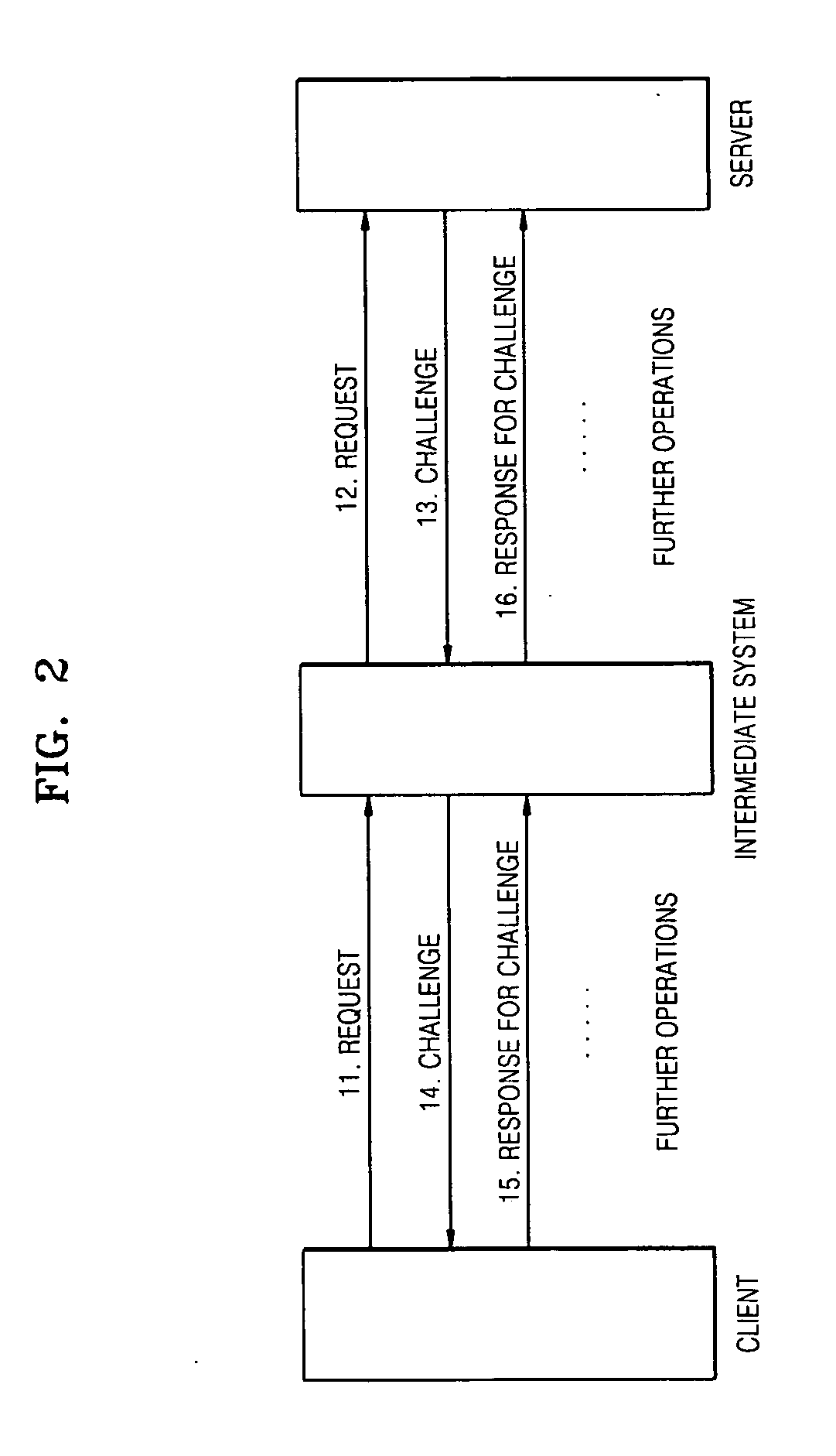
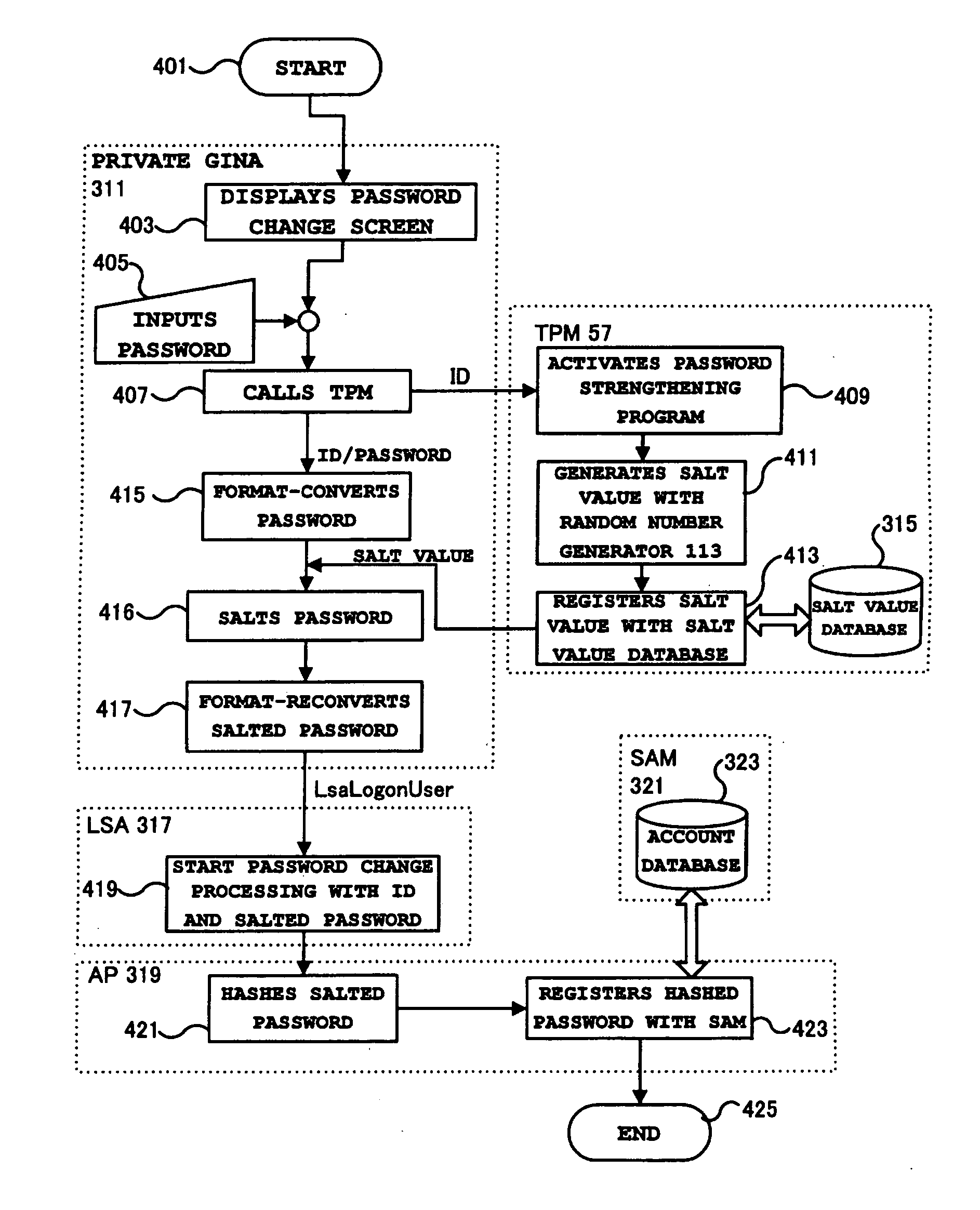
ActiveUS20080092216A1Protection attackImprove protectionDigital data processing detailsUser identity/authority verificationOperational systemPassword
Protection of an authentication password stored in a database held by a SAM of Windows® is strengthened. A GINA, a part of the OS, receives an authentication password in ASCII codes. The authentication password is converted to first UNICODES, and the first UNICODES are salted with a random number and converted to second UNICODES. The random number used for salting is associated with a user account and a password and stored in a read / write protected non-volatile memory or a non-volatile memory which can be accessed only by a BIOS. An LSA of the OS can process UNICODES without being changed.
Owner:LENOVO PC INT
Method for protecting client and server
ActiveUS20090193074A1Access be blockEasily and promptly useComputer security arrangementsMultiple digital computer combinationsClient-sideSystem service
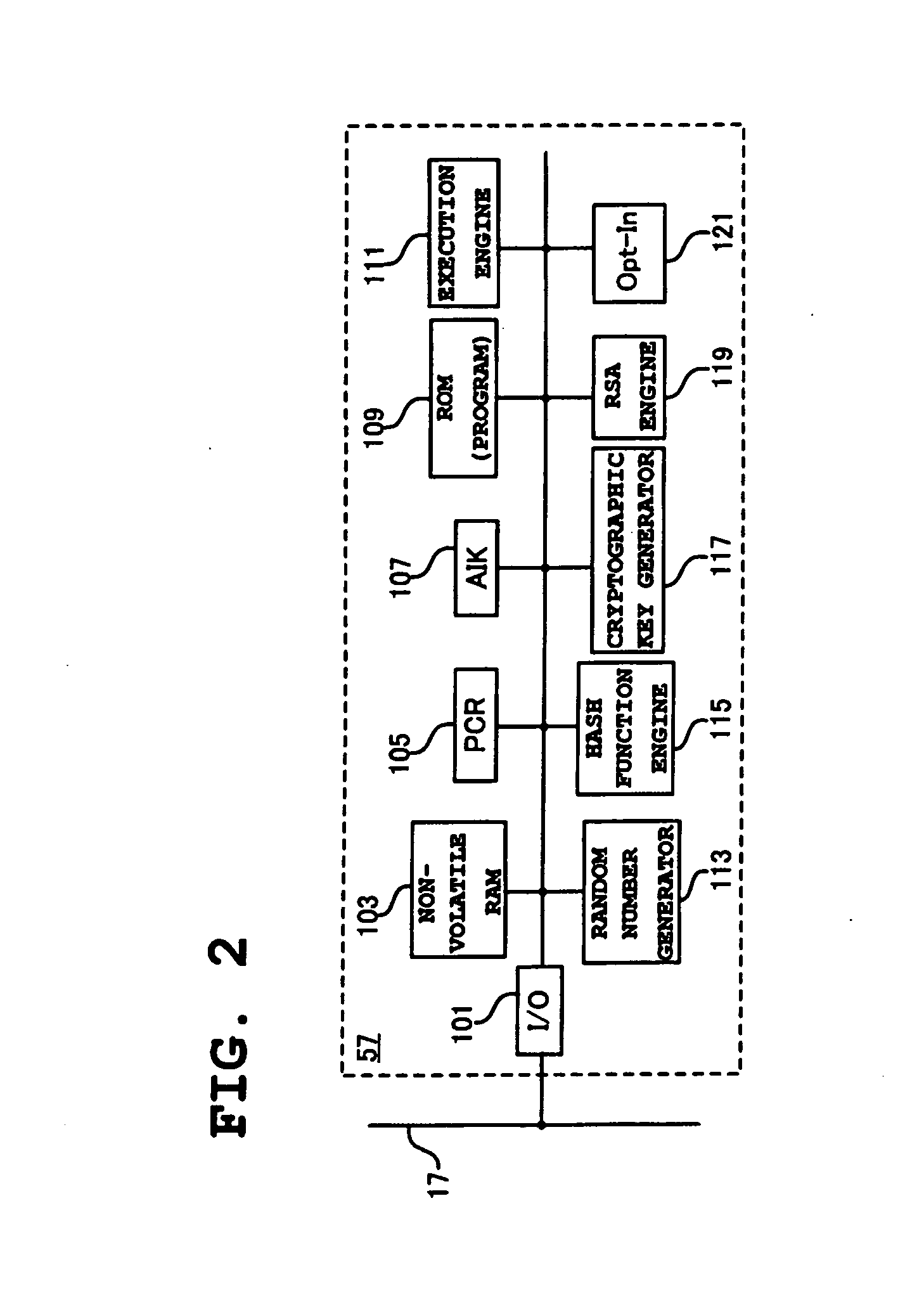
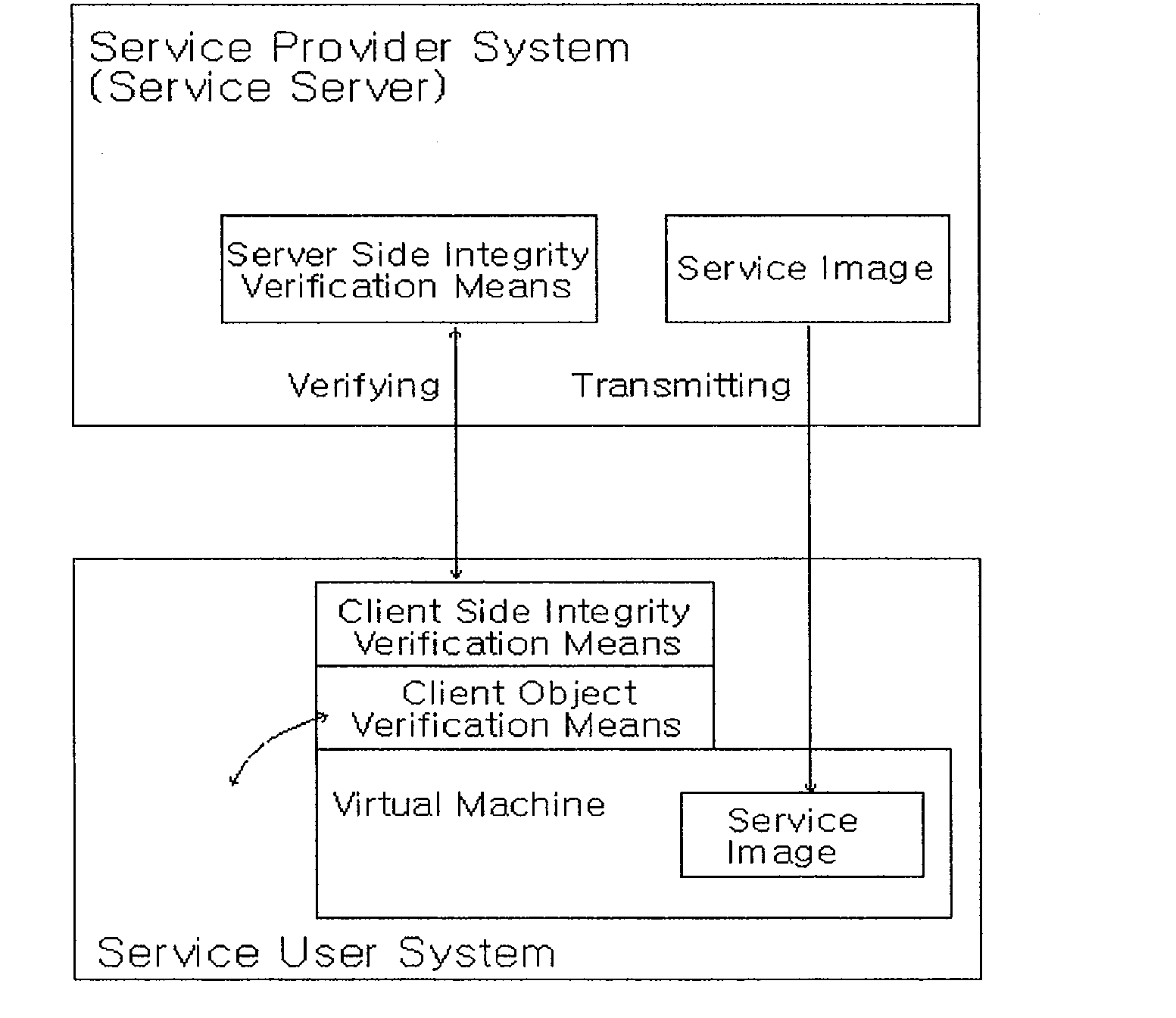
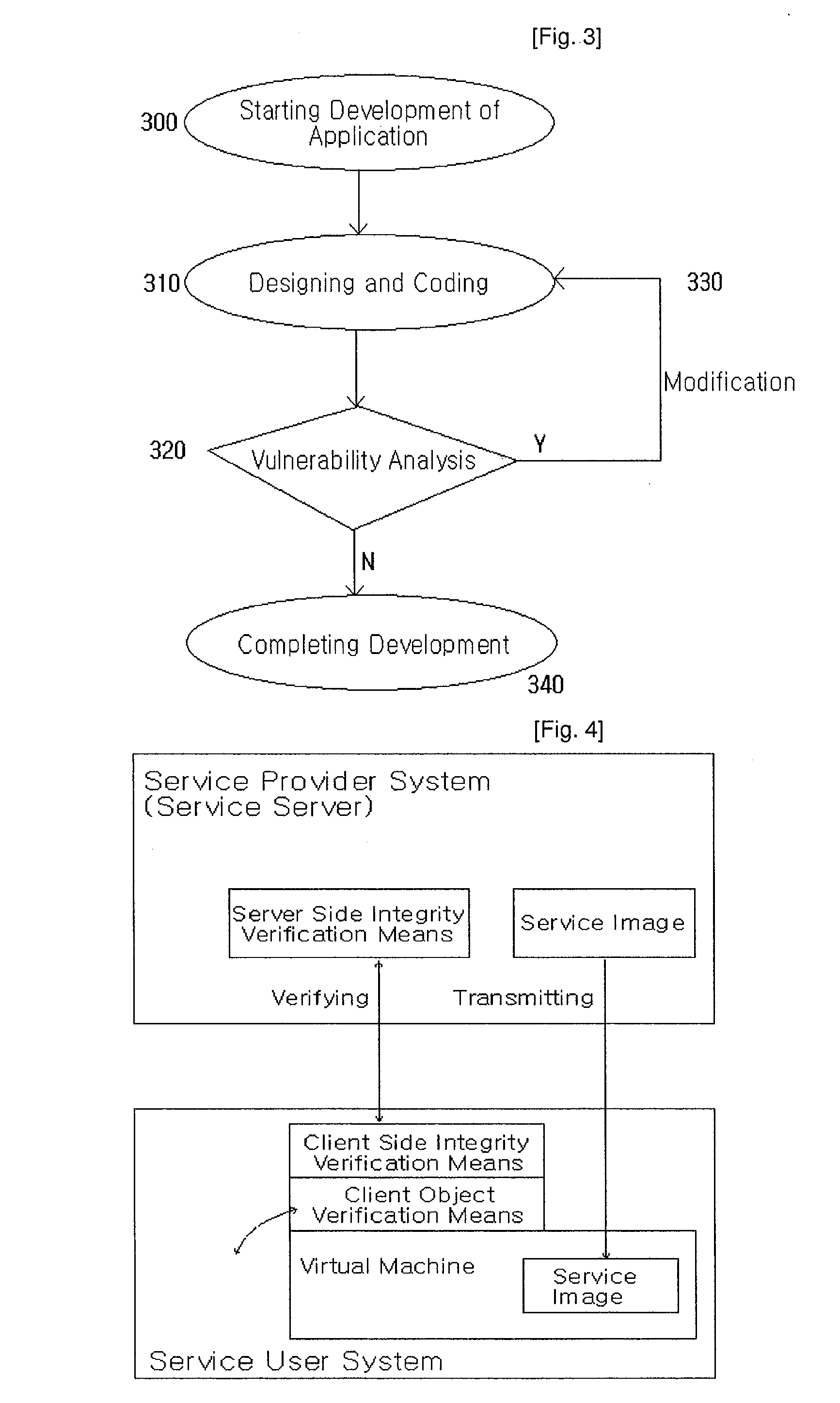
A service provider provides a service to a service user using a client server based system executed in network, such as Internet, Intranet and Extranet. If the service user request a service to the service provider, the service provider installs a protection space within system of the service user and executes programs requested by the service user within the protection space, thereby both the system of the service user and the system of the service provider are securely protected. A software distritution based on distribution of virtual machine makes a user who is not familiar with a computer use the PC in a easy and speedy way.
Owner:LEE SANGGYU
Methods and apparatus for conducting electronic transactions using biometrics
InactiveUS7505941B2Enhanced reliability and confidenceReduce security risksDigital data processing detailsAnalogue secracy/subscription systemsFinancial transactionBiometrics
A system and method for facilitating electronic transactions using a biometric are disclosed. The system for facilitating electronic transactions using a biometric comprises a smartcard-reader transaction system. The method comprises determining if a transaction violates an established rule, such as a preset spending limit. The method also comprises notifying a user to proffer a biometric sample in order to verify the identity of said user, and detecting a proffered biometric at a sensor to obtain a proffered biometric sample. The method additionally comprises verifying the proffered biometric sample and authorizing a transaction to continue upon verification of the proffered biometric sample.
Owner:LIBERTY PEAK VENTURES LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com