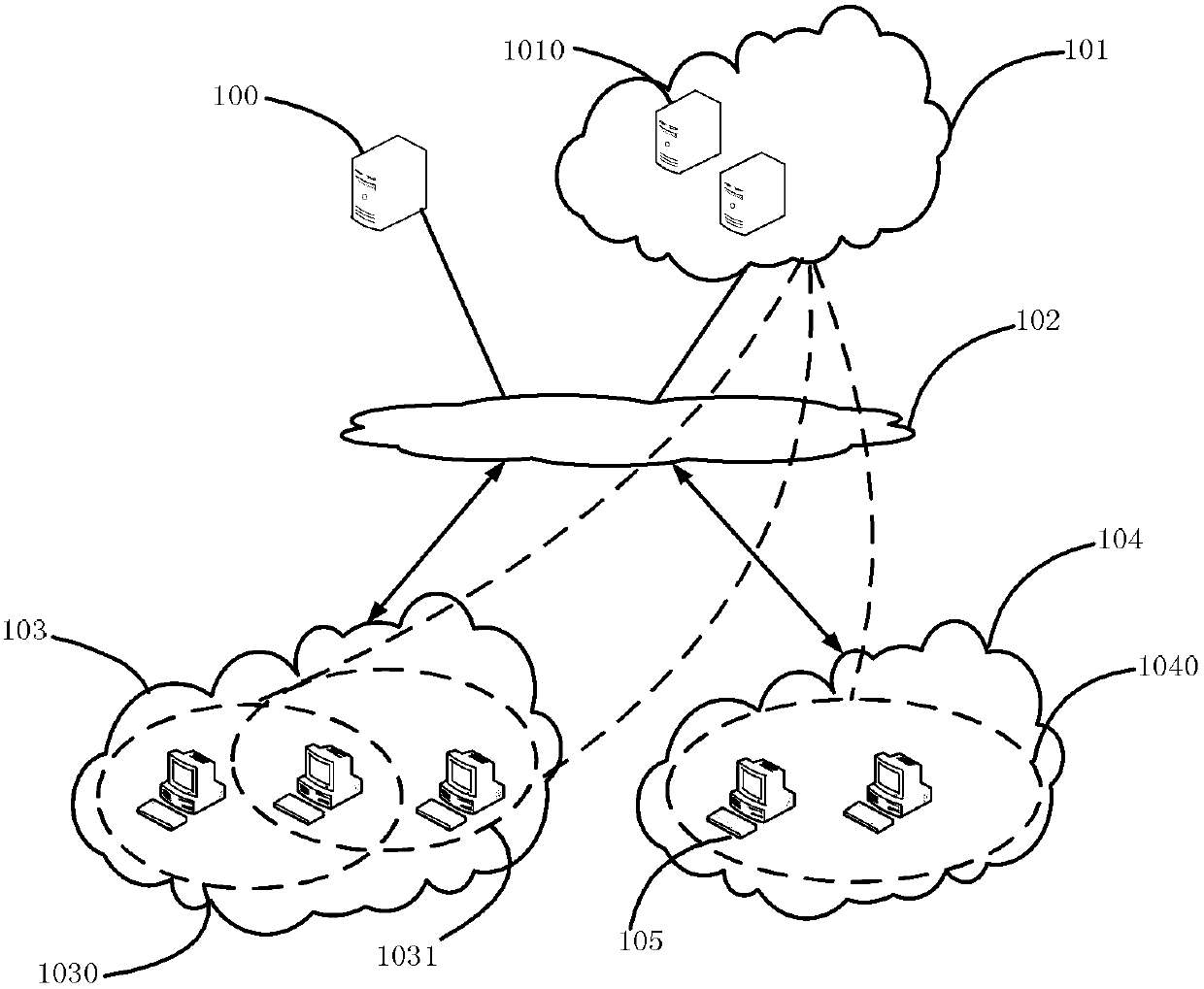
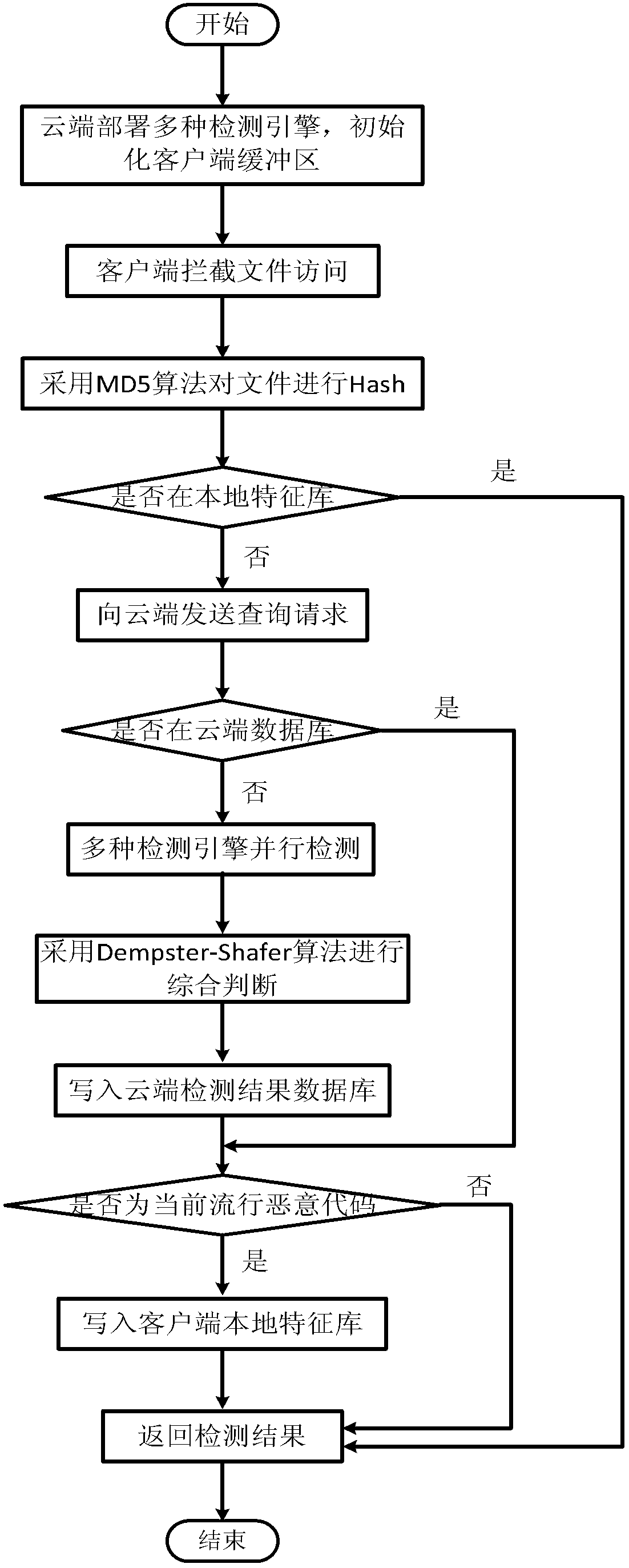
Patents
Literature
1075 results about "Extranet" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
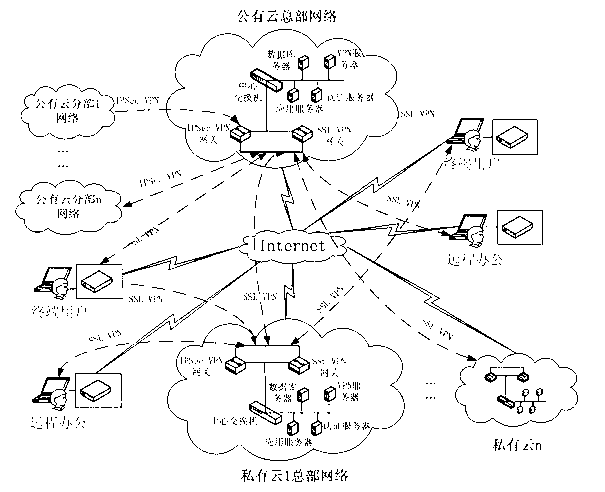
An extranet is a controlled private network that allows access to partners, vendors and suppliers or an authorized set of customers – normally to a subset of the information accessible from an organization's intranet. An extranet is similar to a DMZ in that it provides access to needed services for authorized parties, without granting access to an organization's entire network.
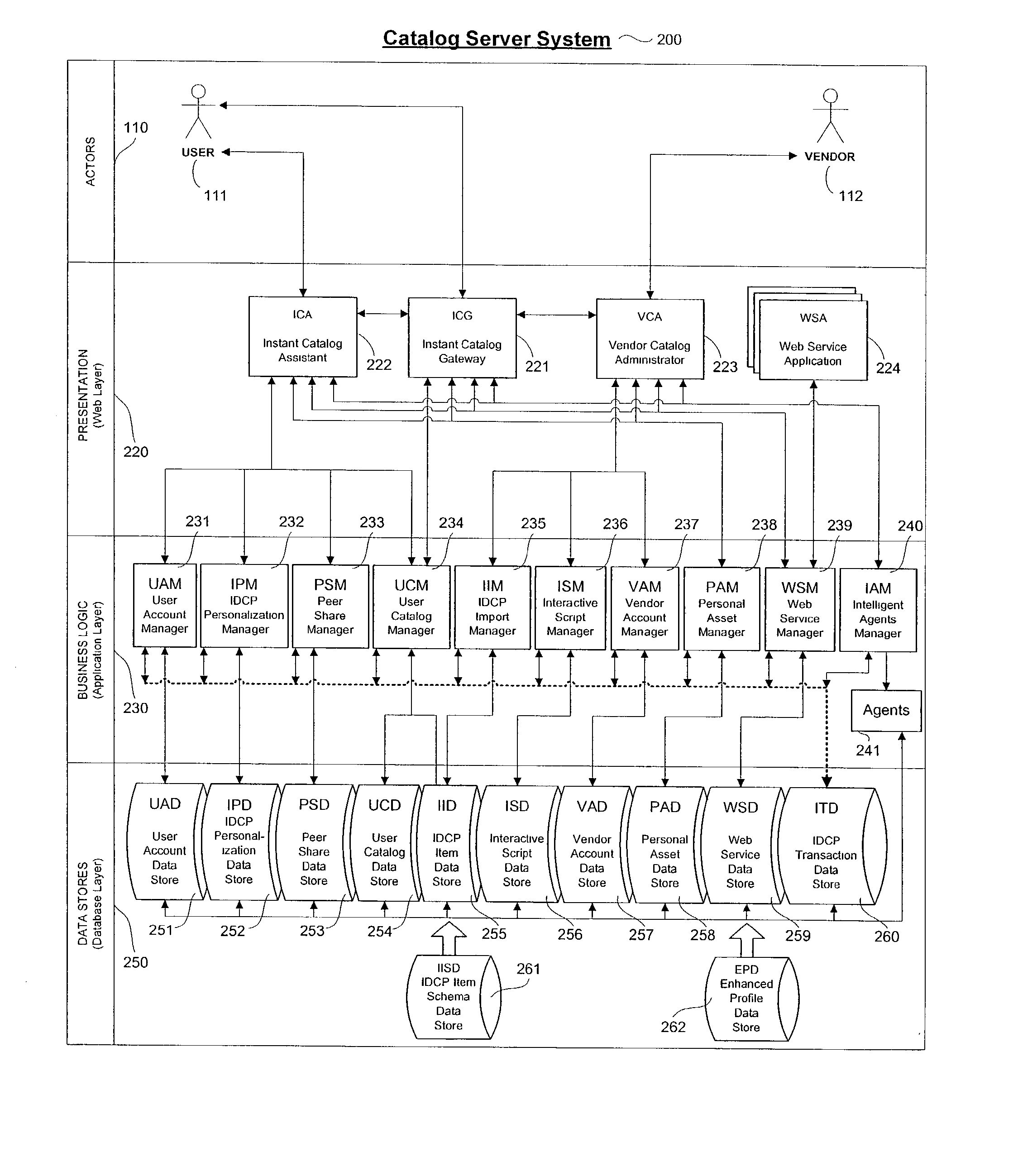
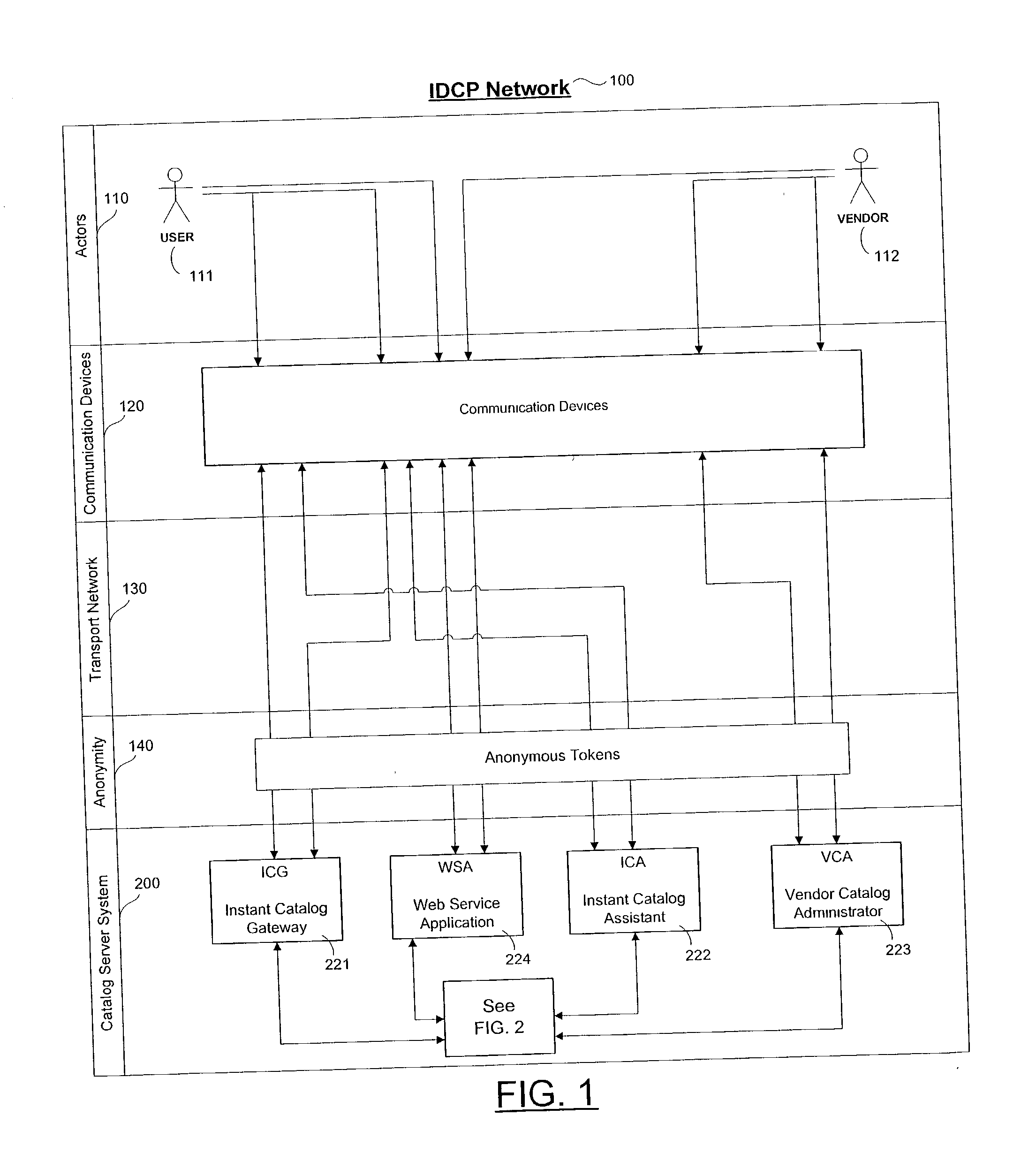
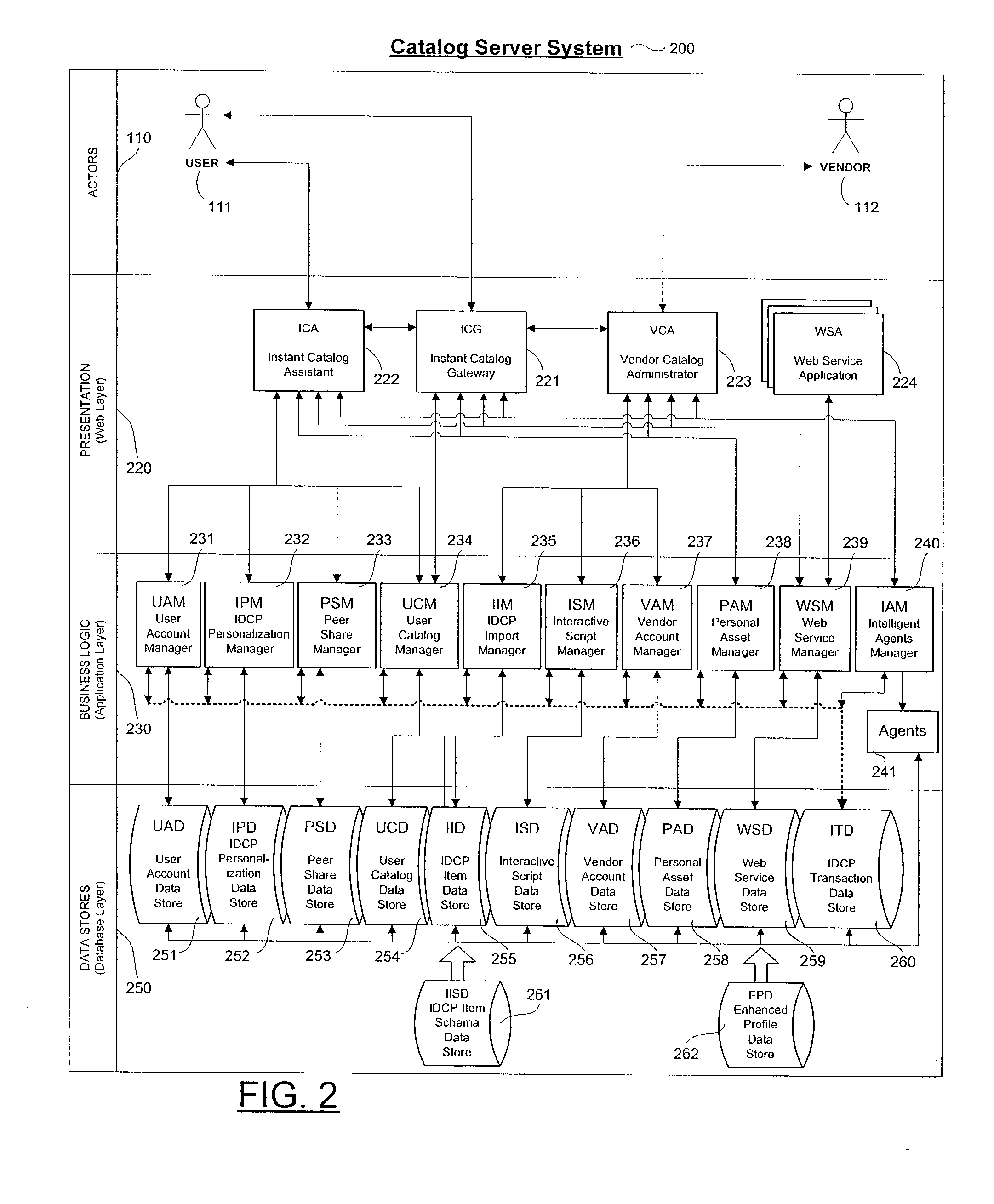
Personalized interactive digital catalog profiling
InactiveUS20030028451A1Facilitate transactionsReduce deliveryDigital data information retrievalComputer security arrangementsPersonalizationWeb browser
An interactive and enhanced digital Instant Catalog of products, services, and information that is personalized or personally profiled, to each unique user of the catalog. The catalog instantly and intelligently captures, stores, manages, and processes self-selected, reusable and "re-distributable" catalog groupings anonymously, for personalizing, enhancing, monitoring, tracking, and peer sharing through multiple mediums and platforms by intelligent agents for a variety of user and vendor specified purposes. The personally profiled cataloged information can be viewed instantaneously and simultaneously by each effected component or member of a supply chain, at the time the product or service has been cataloged, without identifying the cataloger. The user, who preferably employs a Web browser over the Internet, personalizes the interactively produced intelligent catalog content. Products, services, and information groupings are digitally captured and stored by an intelligent catalog agent for enhanced personalized interaction and networking through a peer sharing network, or through an open catalog exchange. The user has the ability to create their own individualized world of products, services, and information that is contextually tailored to each user's unique environment in real-time. Web services hosted within a personal Extranet can anonymously assist and facilitate a context specific task or service insightfully and spontaneously. Through the selective cataloging of multi-vendor products, services, and information, a user is able to fully control, personalize, enhance and share, any lifestyle interest captured from ITV, print, the World Wide Web, businesses, and peers.
Owner:INTENTIONIZE LLC
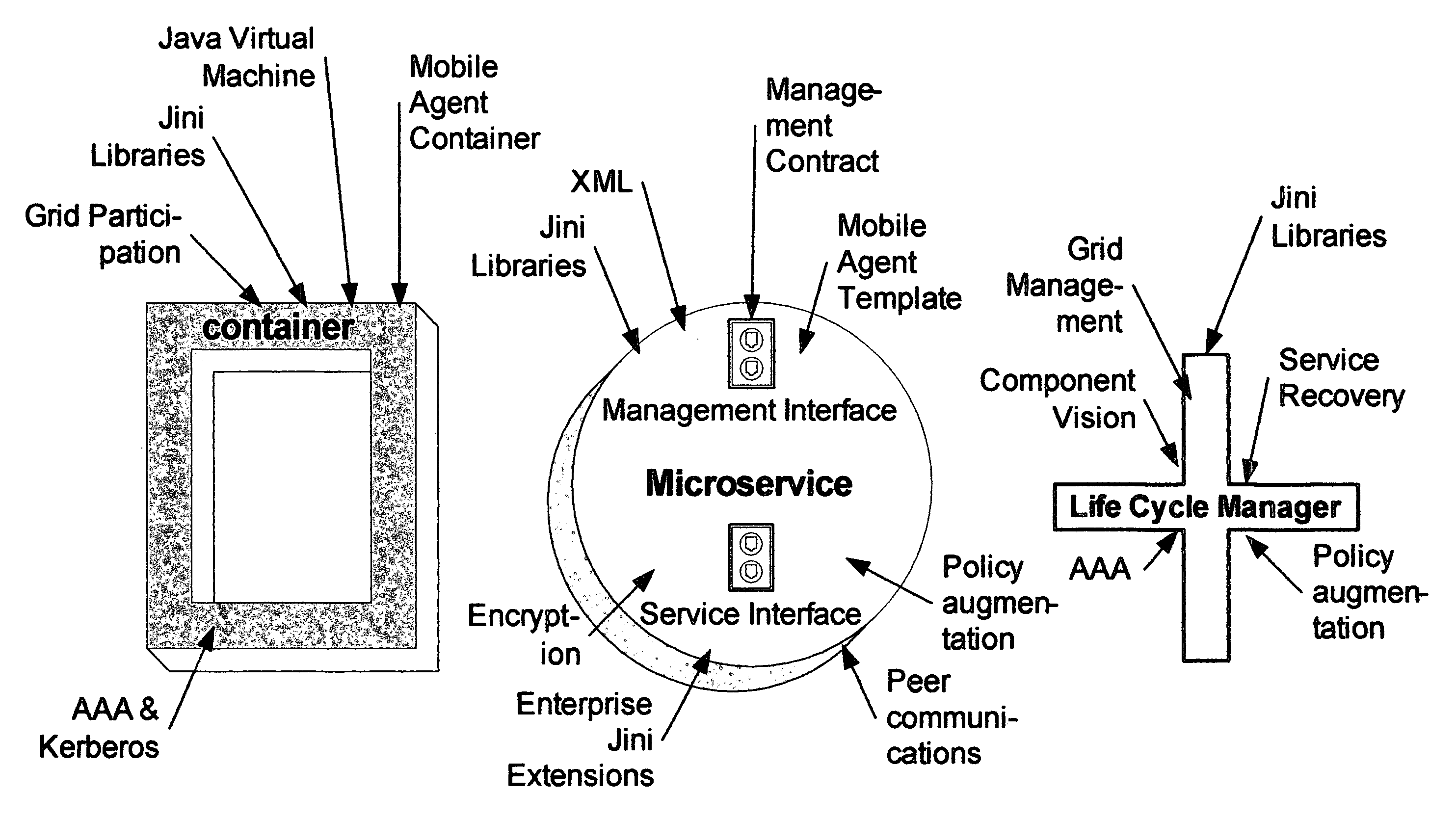
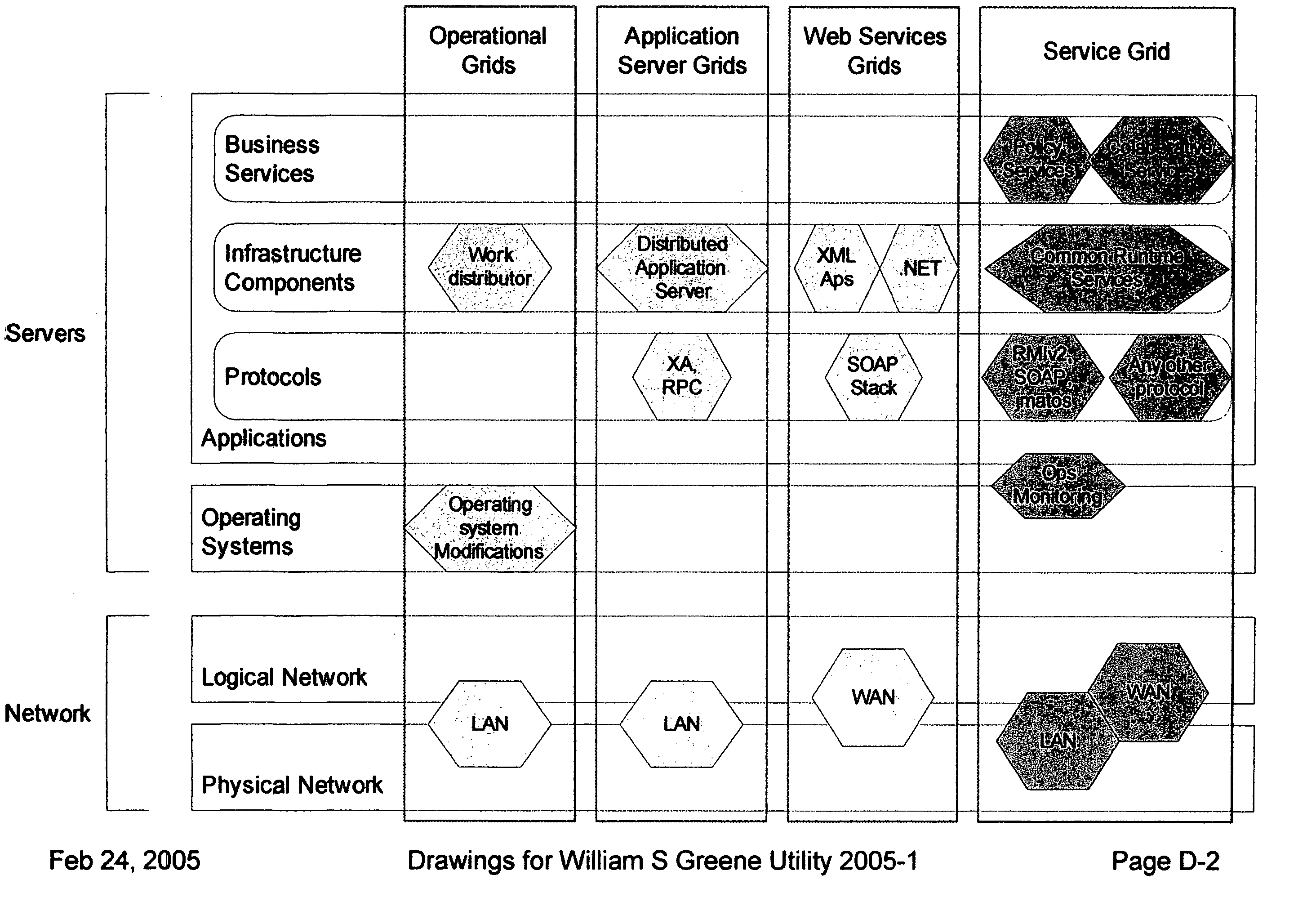
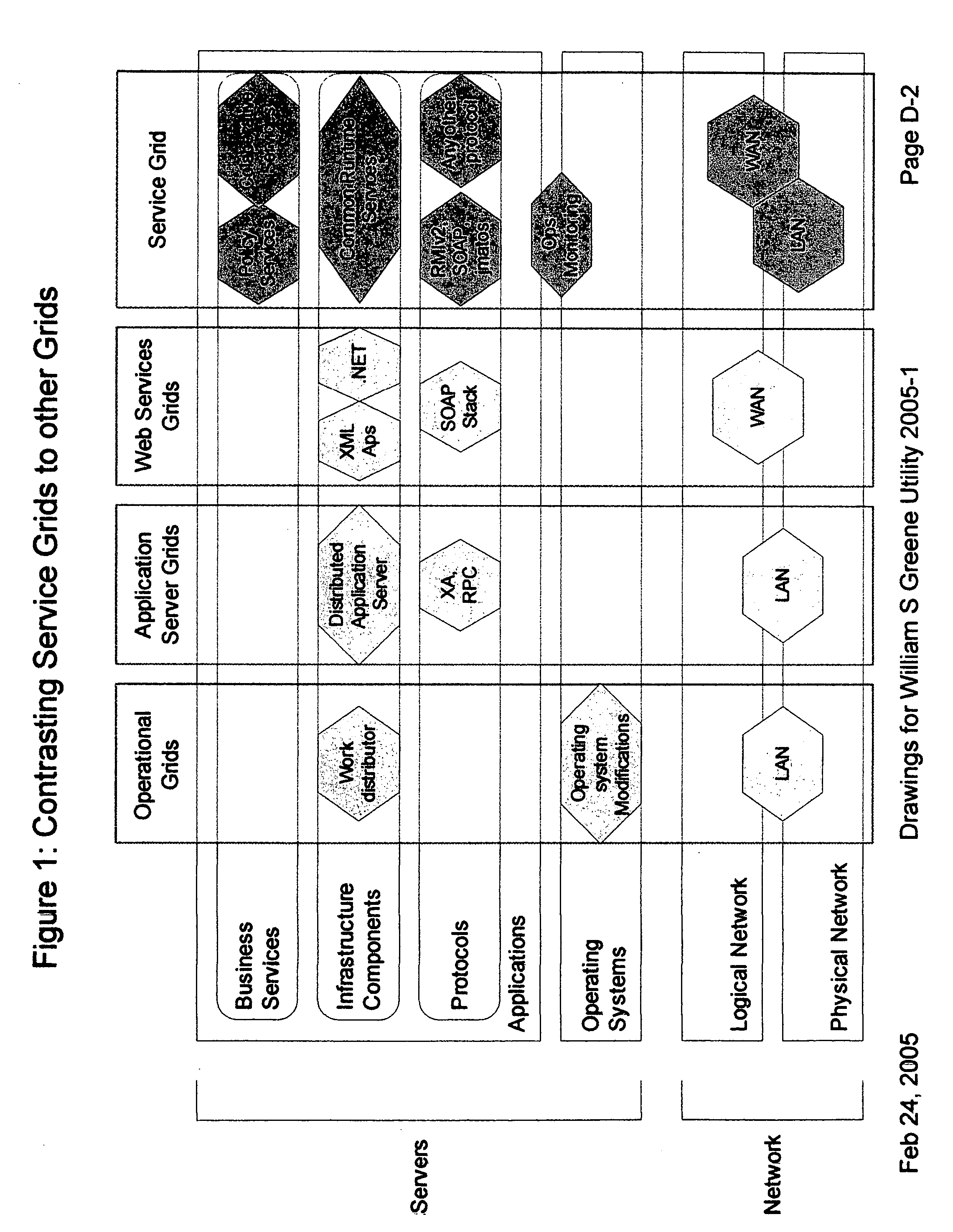
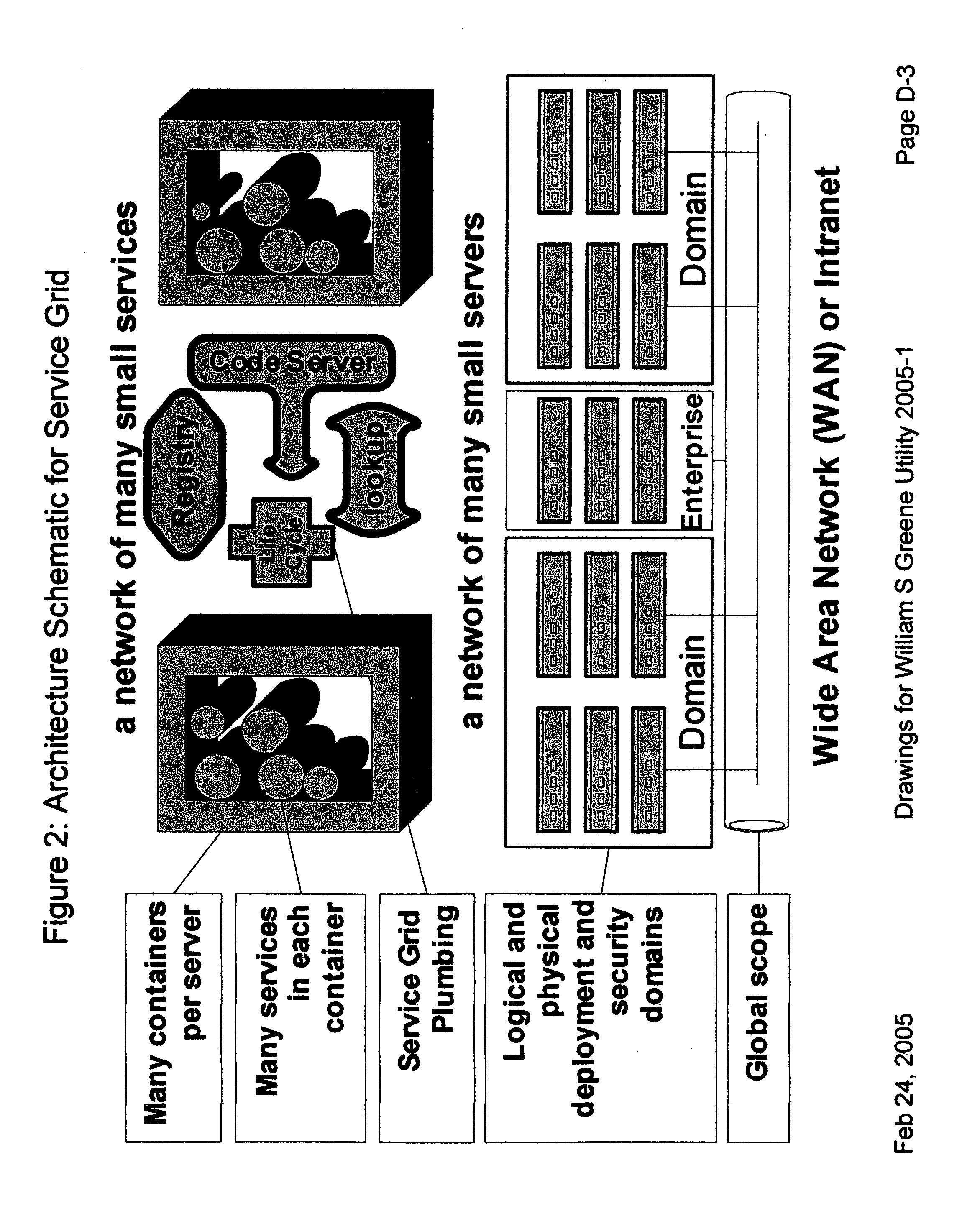
System and method for use of mobile policy agents and local services, within a geographically distributed service grid, to provide greater security via local intelligence and life-cycle management for RFlD tagged items
InactiveUS20070112574A1Low costIntegration costMultiple digital computer combinationsProgram controlDistributed servicesRadio frequency
This invention provides a system, method, and software program for providing software intelligence to Radio Frequency Identity (RFID) tags. Utilizing the unique characteristics of the Service Grid, mobile software agents can relocate in close proximity to RFID tagged items. Once associated with the tag, these RFID agents migrate near where items are identified to provide local control, environmentally responsive policy, and ongoing permanent data capture & history. These RFID agents respond to events as circumstances require. They transport data and policy between supply-chain partners when the partners participate in a secure extranet. Enhanced service grids composed of distributed agents, comprising numerous services, facilitates supply-chain security and integration as virtual software service agents, including virtual RFID tags, are directed from one computer to another computer in response to changing conditions.
Owner:GREENE WILLIAM SPROTT
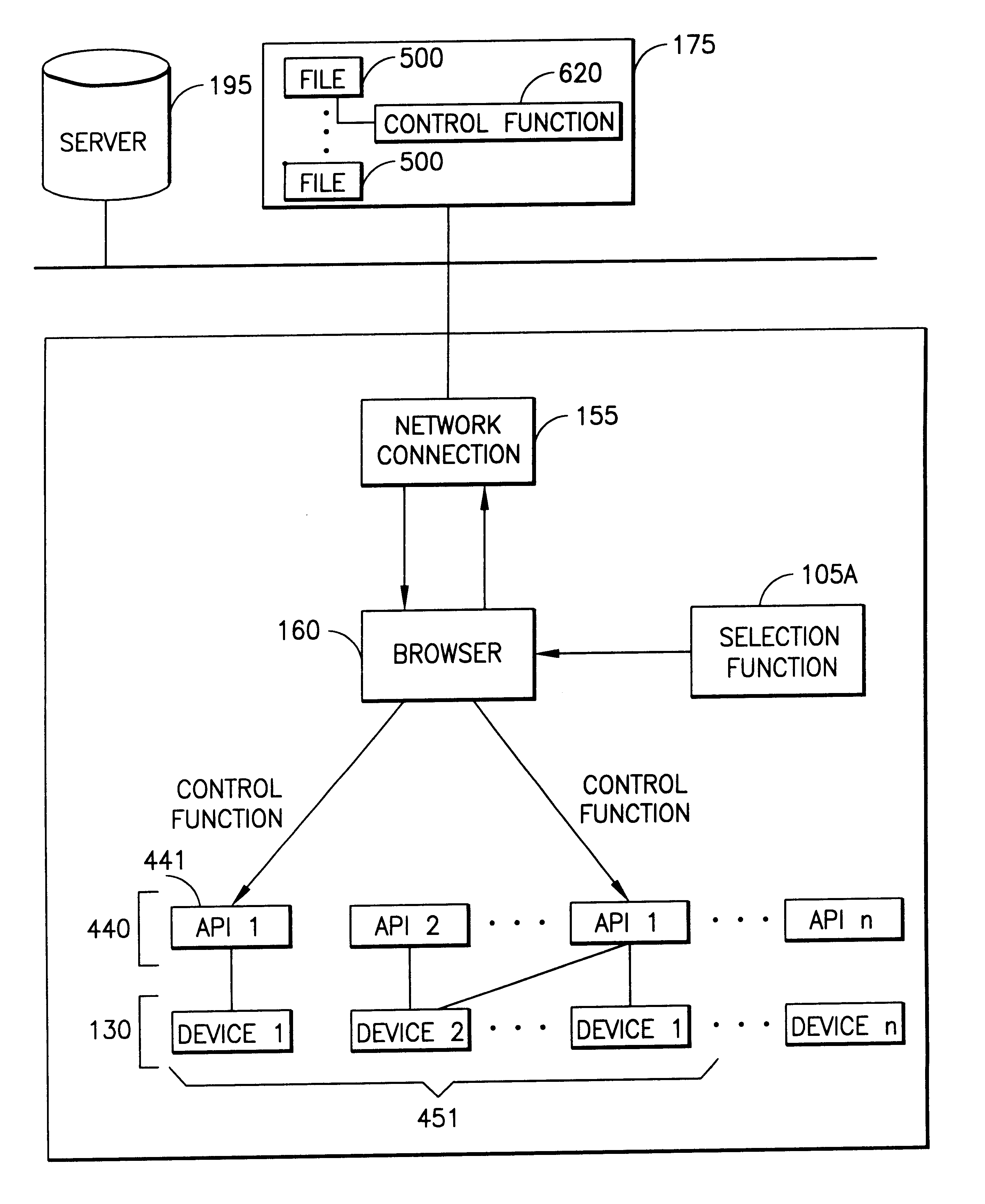
Server for reconfiguring control of a subset of devices on one or more kiosks
InactiveUS6195694B1Faster and reliable accessLow costAcutation objectsData switching by path configurationM-governmentComputer terminal
A server system that is connected to one or more networks, e.g., the Internet, corporate or government intranets, extranets, etc. The server has one or more application files or configuration sets that the server serves to from one or more kiosks on the network. The configuration sets are application specific. (An application is a use for which the kiosks are configured or reconfigured.) One or more of the files in the configuration sets include one or more embedded (control) programs that are used to control the local APIs of one or more of the devices on the kiosk. In this way, the devices are controlled to configure the kiosk to perform the application.
Owner:IBM CORP
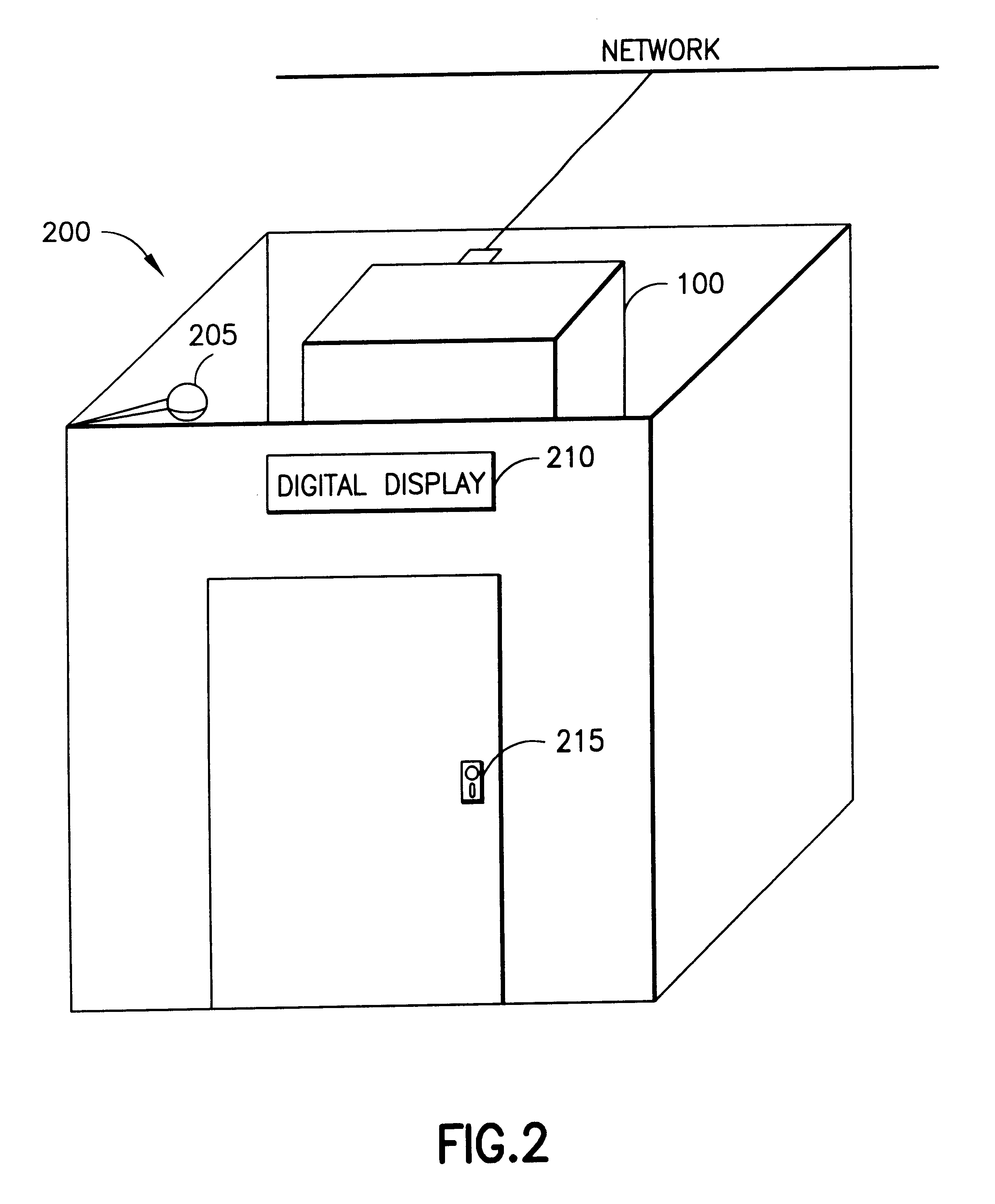
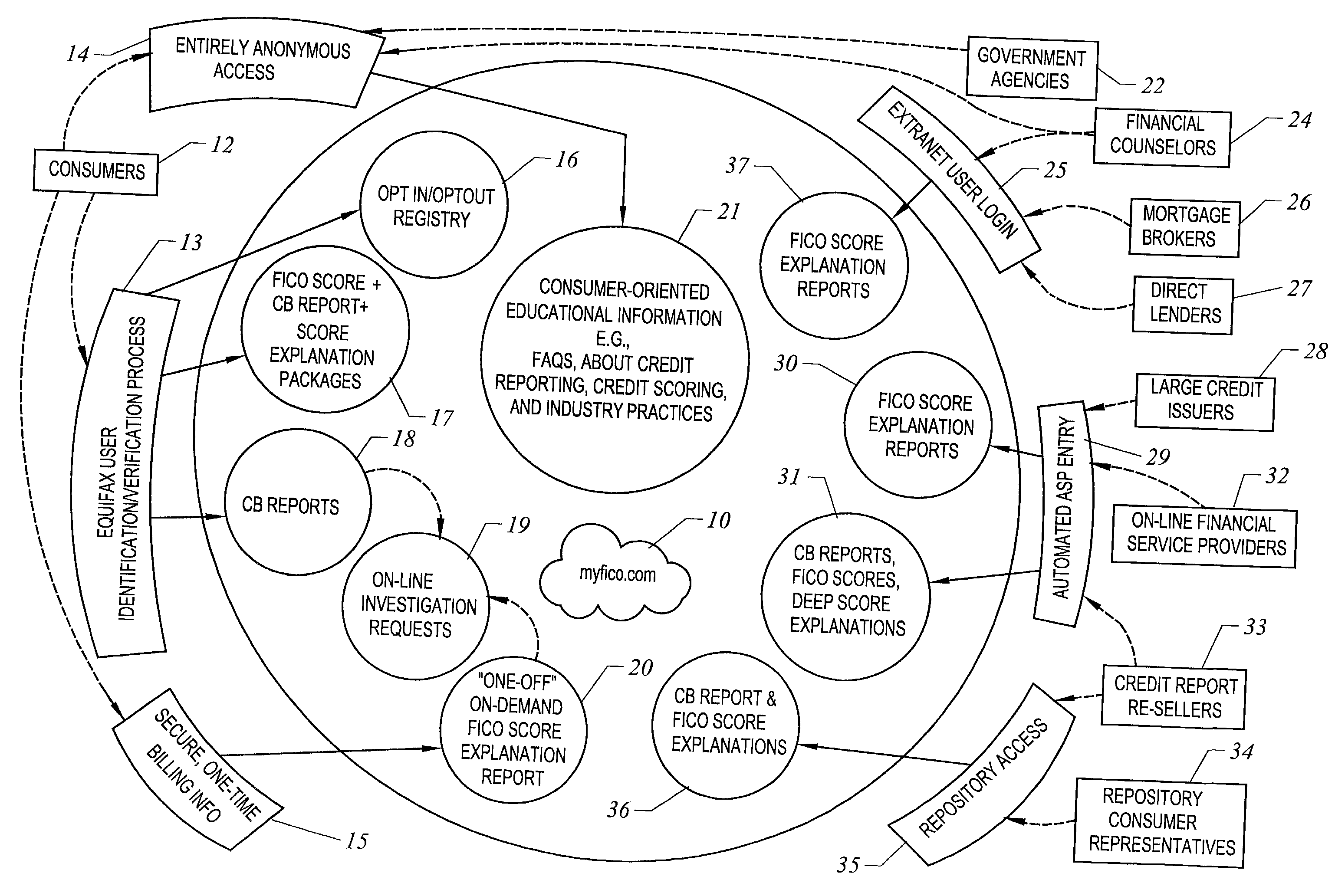
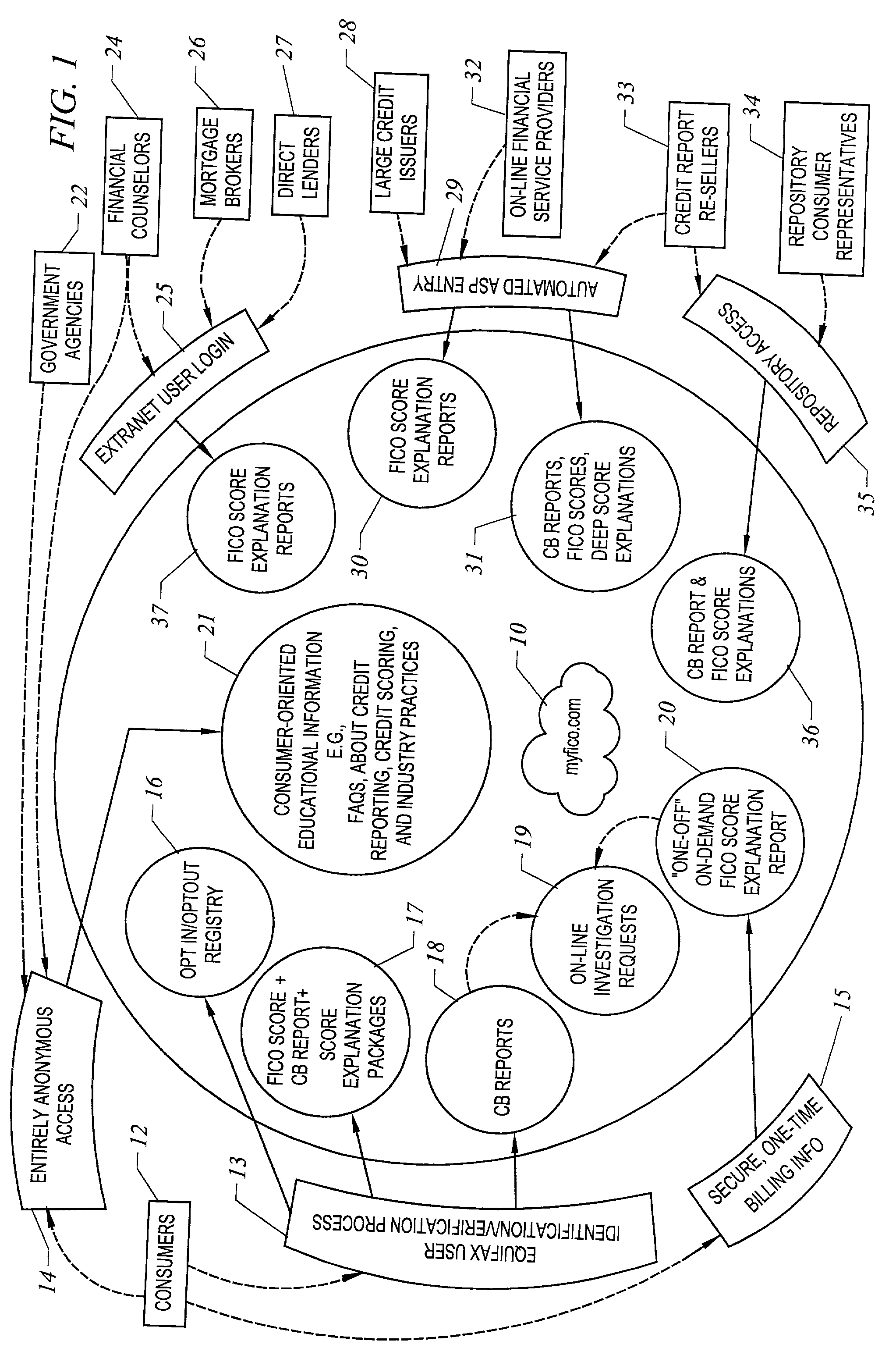
Method and apparatus for explaining credit scores
A Web site is provided that contains an array of informative resources including for-pay services and extranet functions to serve consumers and traditional players in the financial services industry, including financial counselors, mortgage brokers, direct lenders, large national credit issuers, and third-party credit report re-sellers, plus information seekers such as the press, consumer groups, and government agencies. A primary focus is to educate consumers, consumer groups, and the consumer press by offering them access to the exceptionally high-quality information, both general and personal, about the practices of collection, storing, reporting, and evaluating consumer credit data.
Owner:FAIR ISAAC & CO INC
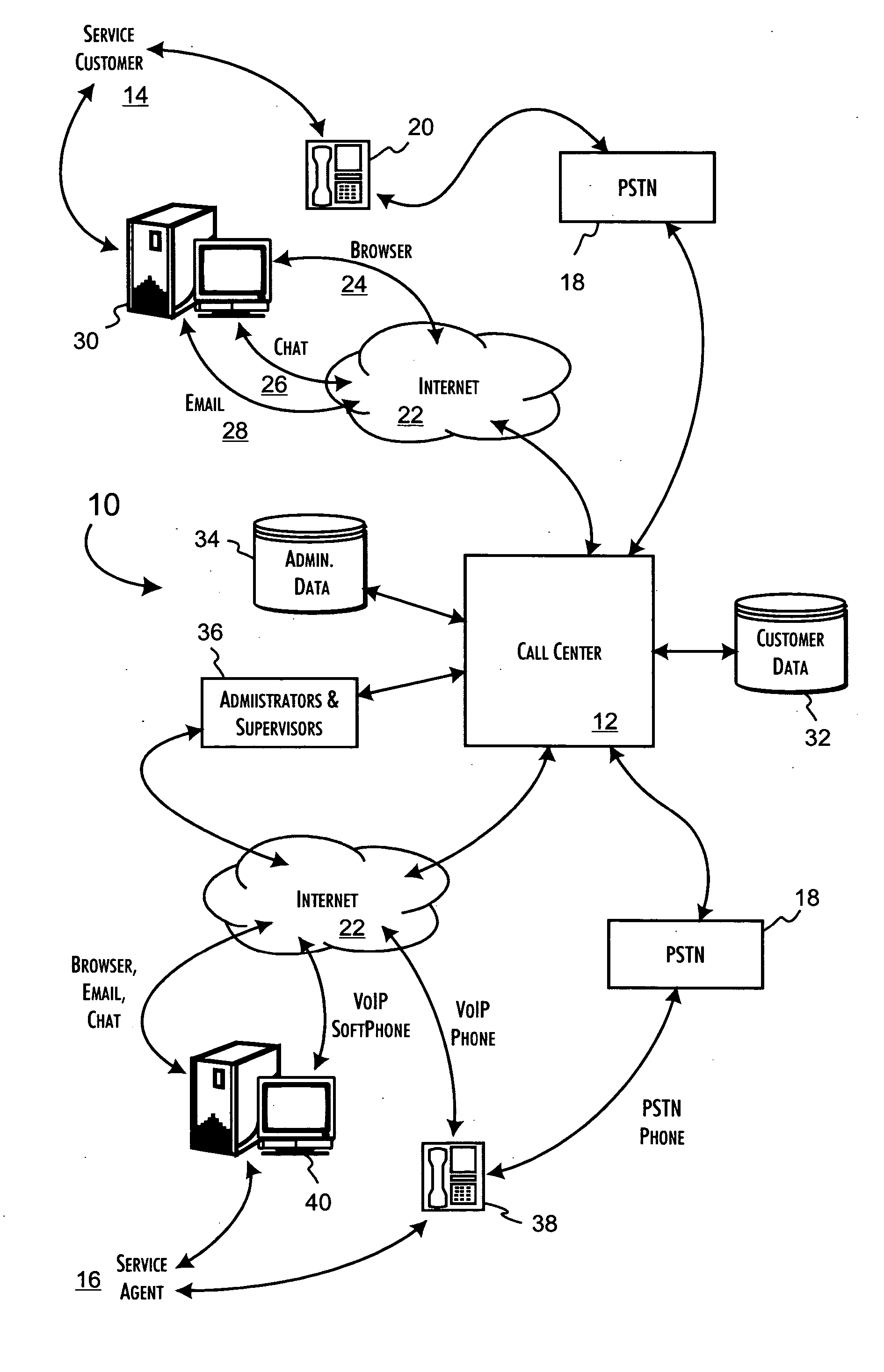
Telecommunication call distribution system
InactiveUS20050047579A1Easy administrative oversightEnsure availabilityInterconnection arrangementsSpecial service for subscribersQuality of serviceDistribution system
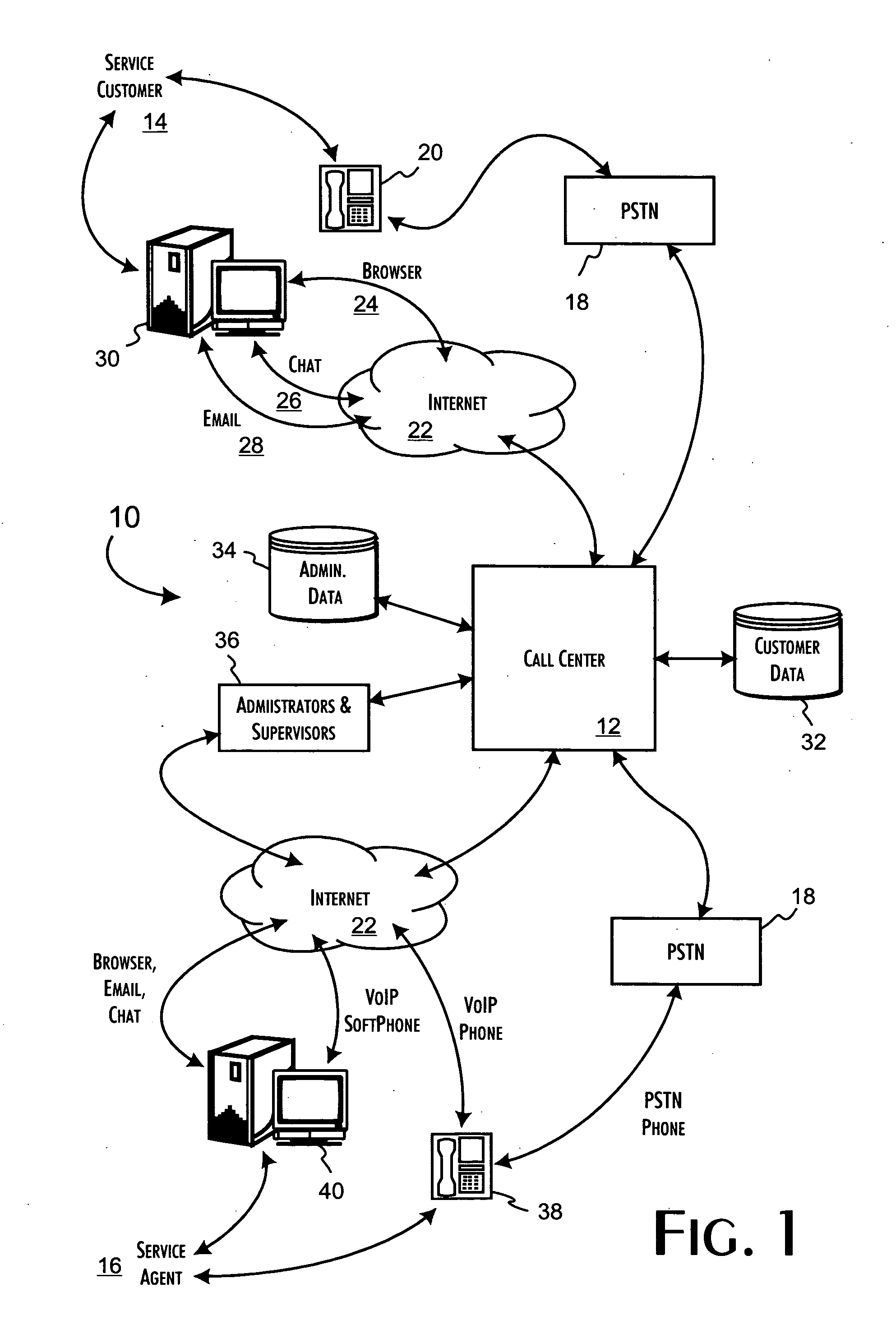
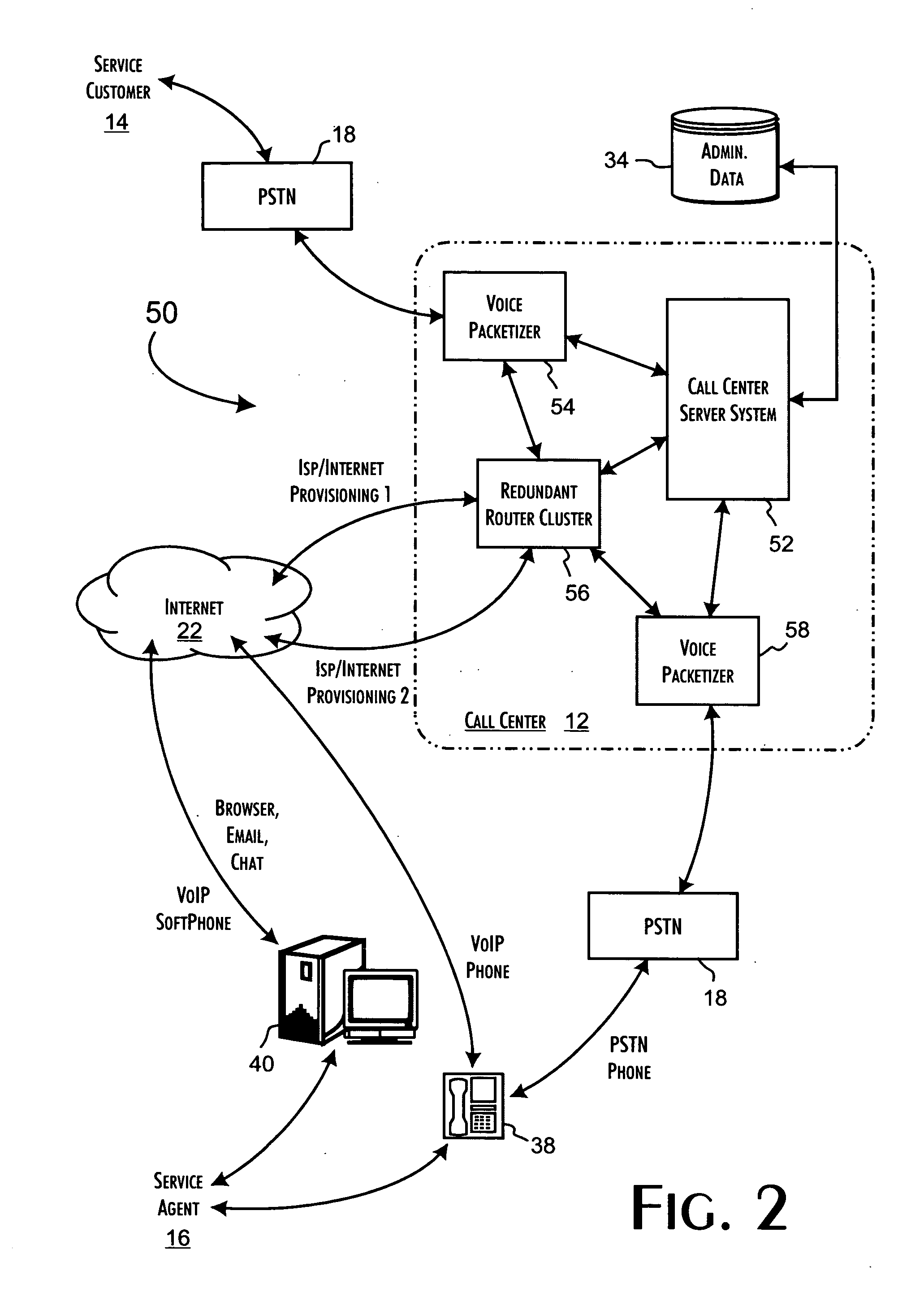
A call center server architecture supporting service transactions between service customers and service agents who can be either local to or in geographic distributed locations relative to the call center. The call center server architecture includes an inbound voice packetizer providing a PSTN line interface to the call center, a call center server system, coupled to said inbound voice packetizer, that provides for the execution of call center server control applications, and a router, coupled among said inbound voice packetizer, the call center server system, and, through a network interface to any combination of intra- and extranets, to service agent terminal equipment. The call center server control applications dynamically determine the routing and distribution of service requests received from service customers to service agents and are dynamically responsive to determinations of inadequate quality of service for individual communications channels. The call center server control applications provide for the controlled interruption of a predetermined service transaction while establishing a new communications channel having an adequate quality of service.
Owner:SALAME MANSOUR A
On-line interactive system and method for transacting business
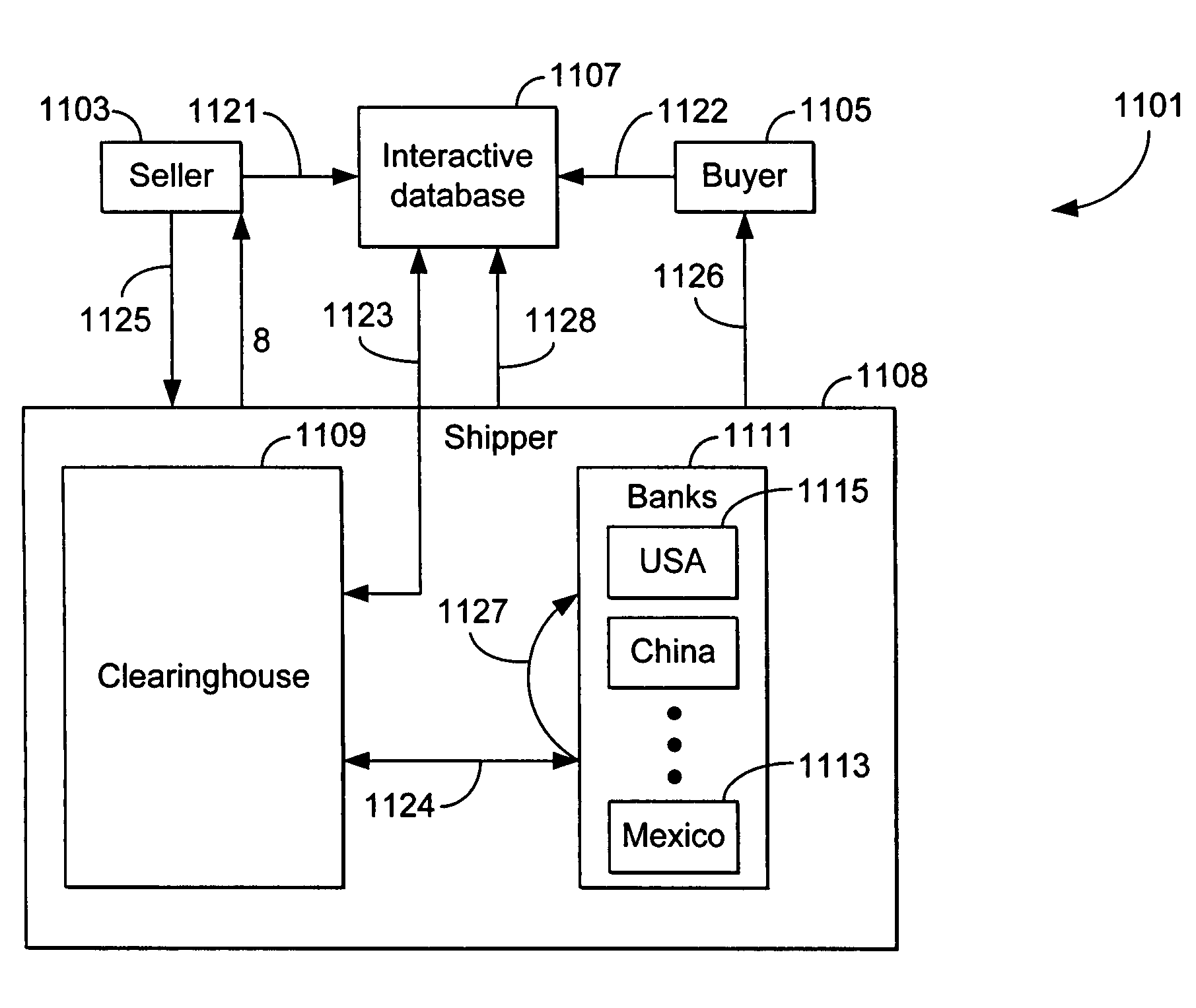
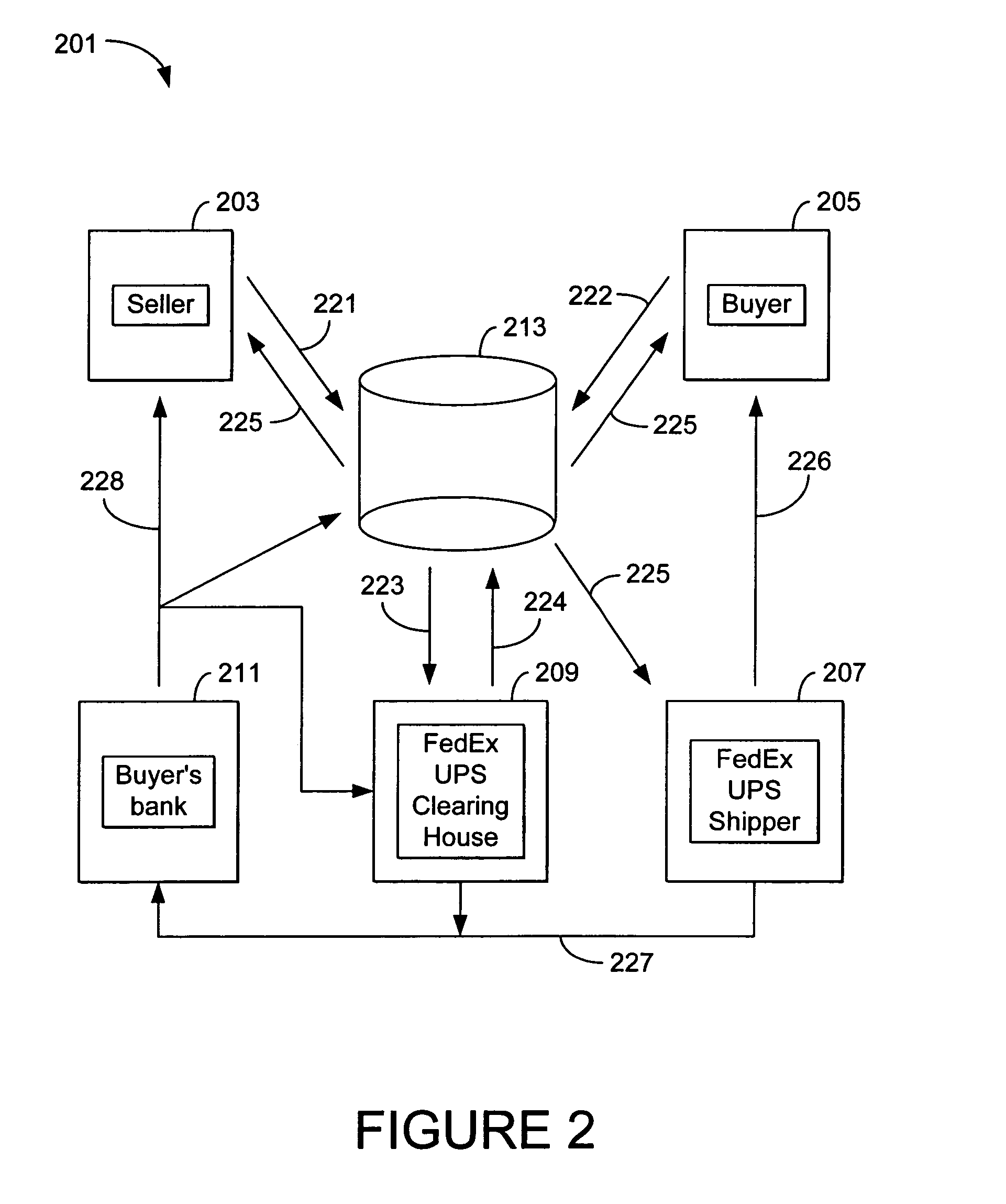
The present invention includes a method for transacting business over a network between multiple buyers and sellers. In an exemplary embodiment, the invention operates within an improved extranet system which is a secure, limited access network which operates within the larger public packet switched network (Internet) and allows only registered buyers and sellers to access the website while the system communicates with, and takes advantage of, existing credit, billing, collection, clearinghouse, insurance, transportation, tracking and banking systems. The interactive database includes real-time information in connection with a transaction, where the buyer submits a request for product and the request for the product locks out the requested product from selection by any other buyers.
Owner:DUNCAN VENTURES INC
Local and remote monitoring using a standard web browser
InactiveUS8914526B1Ensure integrityLow costTelephonic communicationMultiple digital computer combinationsWeb browserPrivate network
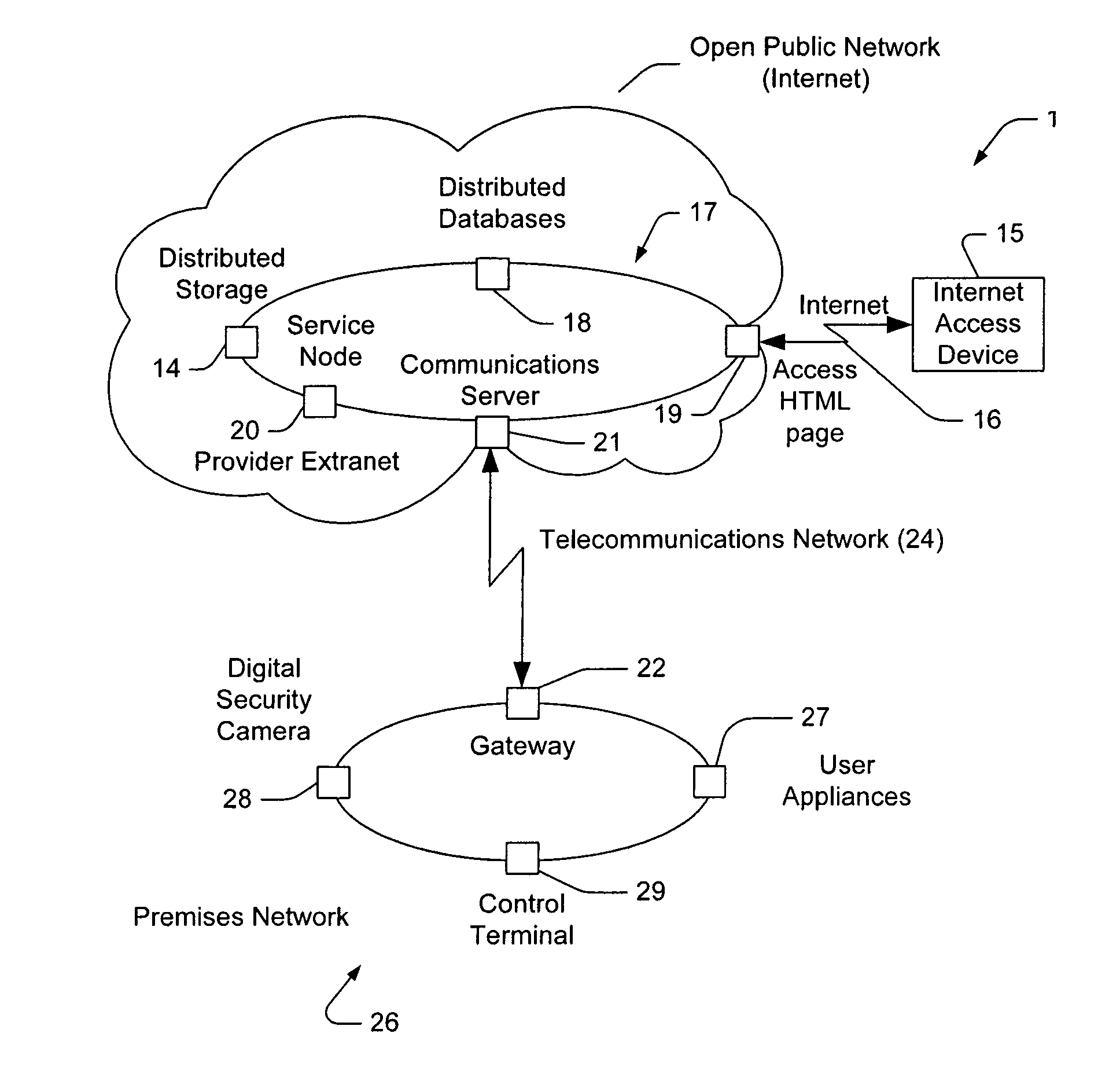
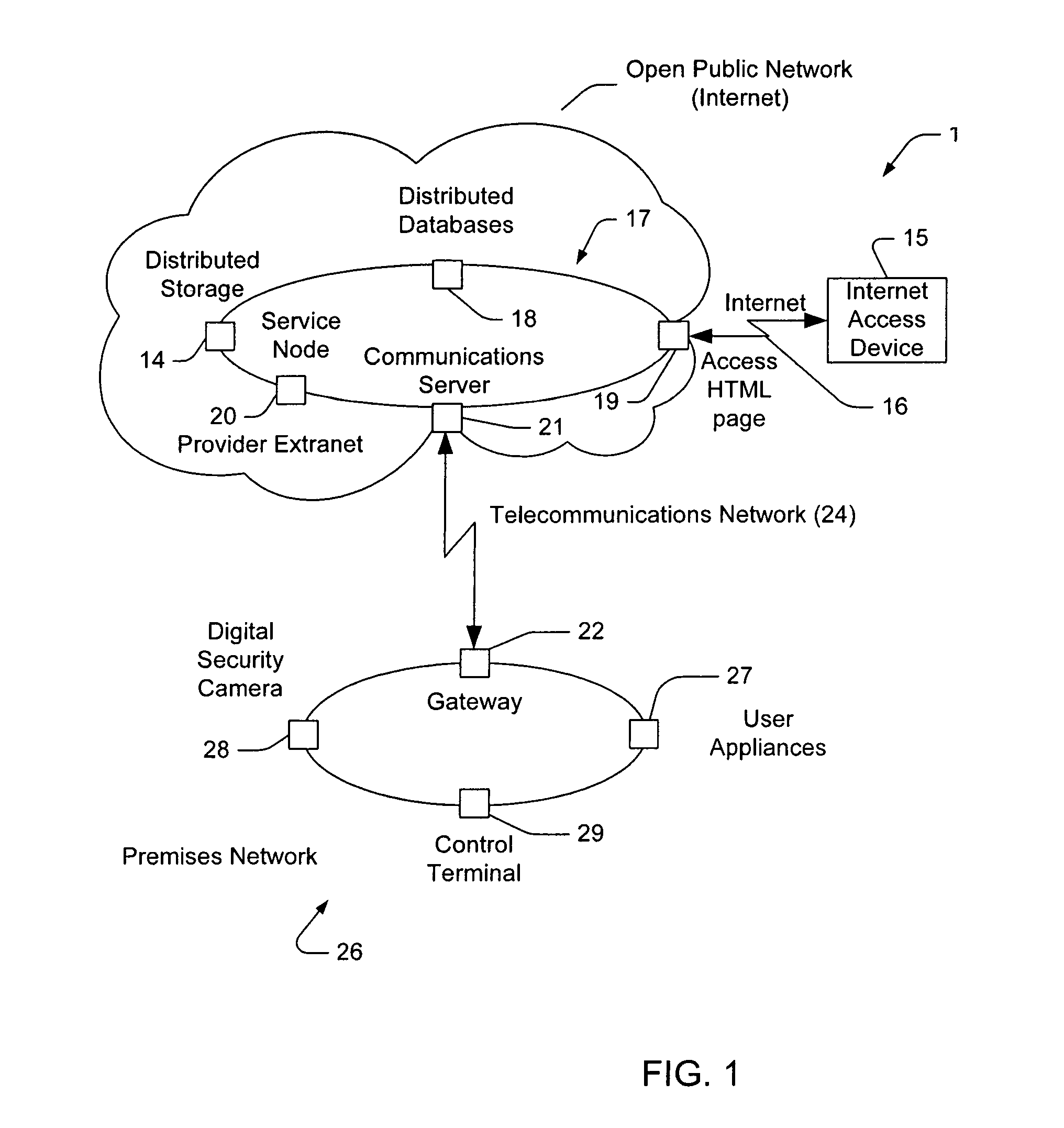
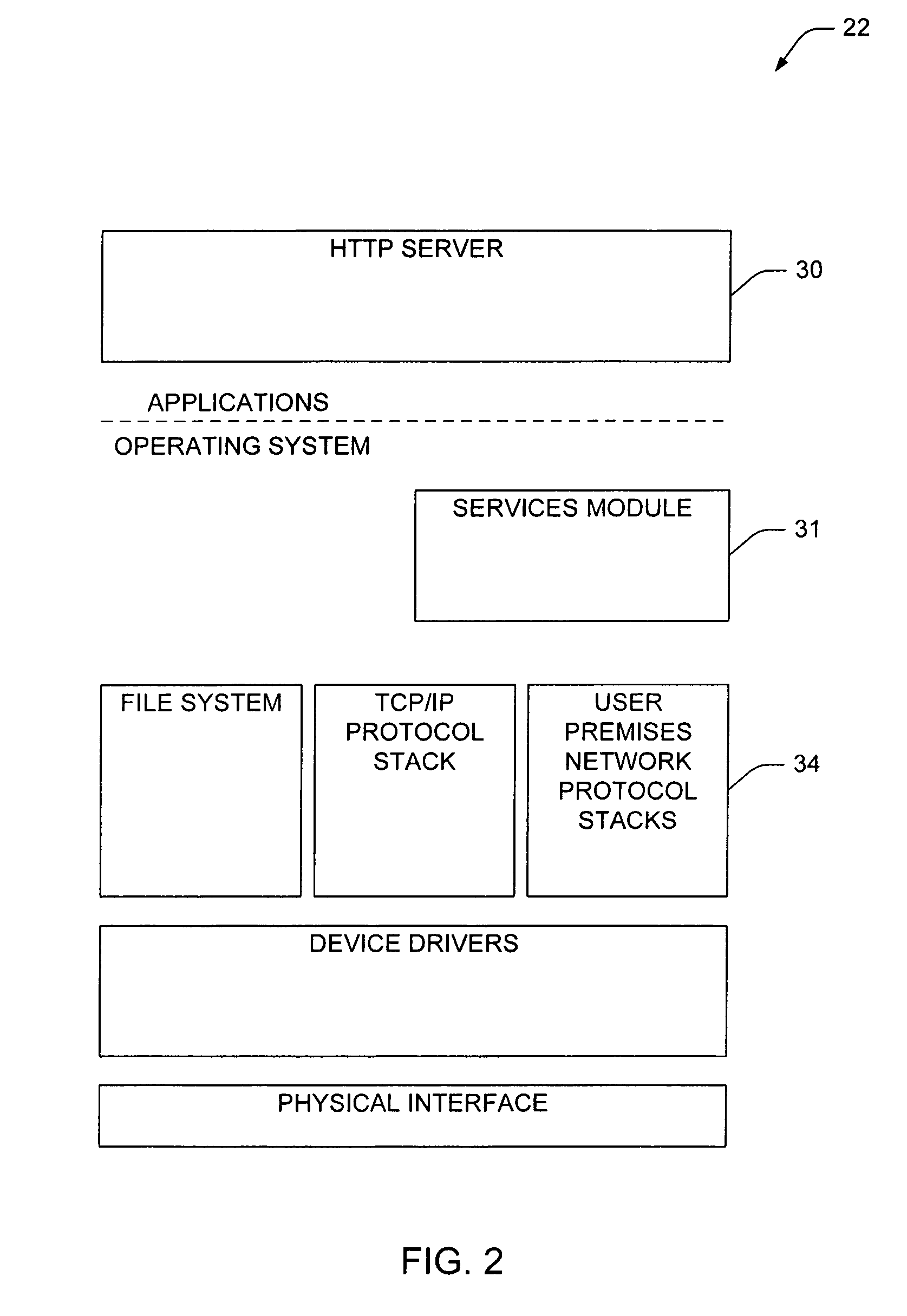
A home security and control system for monitoring and controlling an external environment such as a home environment comprising: an Internet browser connectable to an extranet; an extranet located external to the home environment and accessible via the Internet browser; a communications server located in the extranet and adapted to interconnect on demand with one of a series of connection gateways located in predetermined home environments; and a connection gateway located in the home environment adapted to control and / or monitor the operation of at least one security device in the home environment; wherein upon accessing a predetermined address by the Internet browser on the extranet, the communications server connects to a predetermined one of the connection gateways to control and / or monitor the operation of the security device. The extranet can ideally be implemented as a Virtual Private Network (VPN) across an Internet substrate.
Owner:PORTUS SINGAPORE
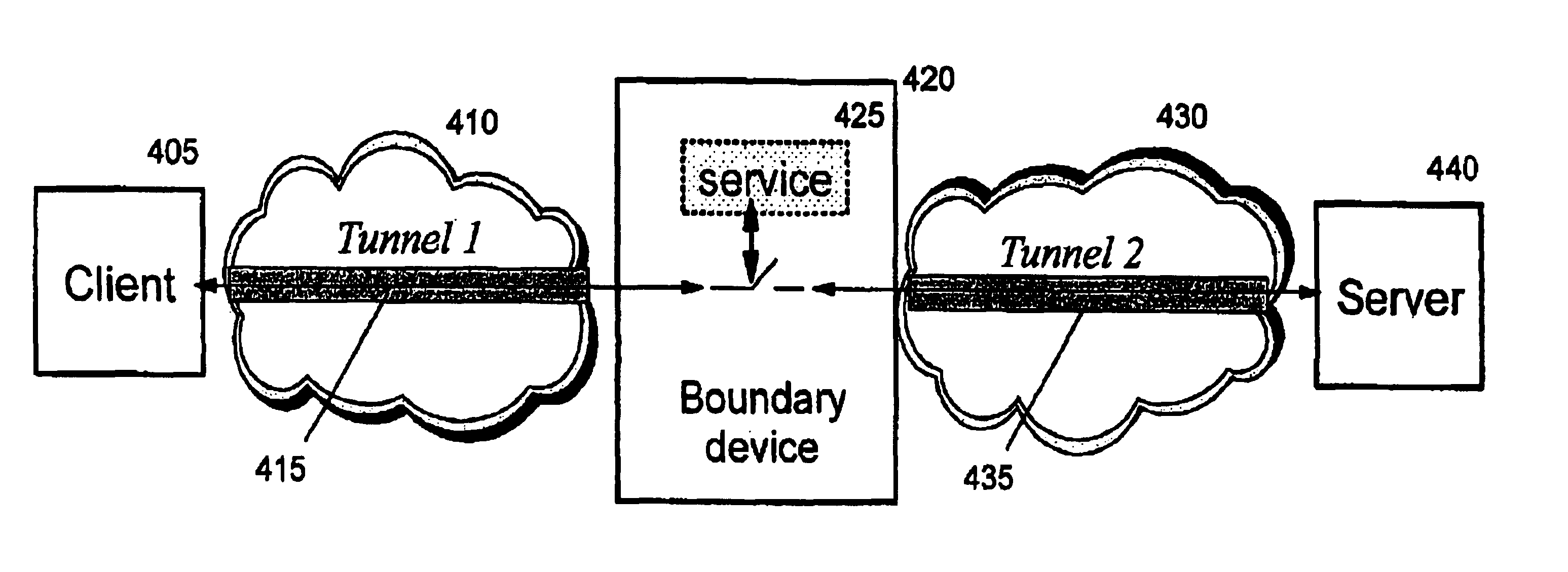
Establishing consistent, end-to-end protection for a user datagram
A method, system, and computer program product for providing consistent, end-to-end protection within a computer network for user datagrams (i.e. packets) traveling through the network. The network may comprise network segments that are conventionally assumed to be secure (such as those found in a corporate intranet) as well as network segments in non-secure networks (such as the public Internet or corporate extranets). Because security breaches may in fact happen in any network segment when datagrams are unprotected, the present invention discloses a technique for protecting datagrams throughout the entire network path by establishing cascaded tunnels. The datagrams may be exposed in cleartext at the endpoints of each tunnel, thereby enabling security gateways to perform services that require content inspection (such as network address translation, access control and authorization, and so forth). The preferred embodiment is used with the “IPSec” (Internet Protocol Security Protocol) and “IKE” (Internet Key Exchange) protocols, thus providing a standards-based solution.
Owner:IBM CORP
Information security management and control method under cloud manufacturing environment
InactiveCN102710605ASolve the problem of update and maintenanceAvoid complex proceduresPublic key for secure communicationUser identity/authority verificationConfidentialityPrivate network
The invention discloses an information security management and control method under a cloud manufacturing environment. On the basis of a network security protocol, a password technology and a public key infrastructure (PKI), comprehensive security guarantee is supplied to information interaction among cloud internal networks, between one cloud and another cloud, and between a user and each cloud by using implementation technologies and methods, such as a virtual private network (VPN) based on multiple layers of protocols, a digital envelope and a password algorithm; Intranet, Extranet and Internet of a cloud manufacturing system are covered; comprehensive management and control technical information files are stored and transmitted to each used loop; a session key (SK) which is randomly produced by using a key production protocol is used for symmetrically encrypting the technical information files; and a receiver public key obtained according to a PKI digital certificate asymmetrically encrypts the SK to form the digital envelope for protecting the technical information files and the SK. The information security management and control method has the characteristics of being high in confidentiality, high inefficiency, flexible in arrangement and the like and can be widely applied to the cloud manufacturing system and other network manufacturing systems.
Owner:CHONGQING UNIV
Providing secure data and policy exchange between domains in a multi-domain grid by use of a service ecosystem facilitating uses such as supply-chain integration with RIFD tagged items and barcodes
InactiveUS20050193222A1Simple methodImprove securityDigital data processing detailsMultiple digital computer combinationsSecurity domainRadio frequency
A system, method, and software implemented system of services provides enhanced security and management to multiple domain grids and allows intercommunications between the different grid domains providing for secure data exchange, policy exchange, and agent exchange between grids or grid domains. Via the exemplary example, utilizing the unique characteristics of the Service Grid and mobile agents, this is extended to provide enhanced security and management to supply chains: providing data exchange, policy exchange, and agent exchange between supply chain nodes and supply chain partners—facilitating enhanced methods of supply chain automation when using barcodes and Radio Frequency Identity (RFID) tags to identify and track goods through supply chains and consumer uses. Agents transport data and policy between supply-chain partners over an extranet, migrating across corporate boundaries and security domains, locating near where items are identified to provide local control, environmentally responsive policy, and ongoing permanent data capture & history.
Owner:GREENE WILLIAM SPROTT
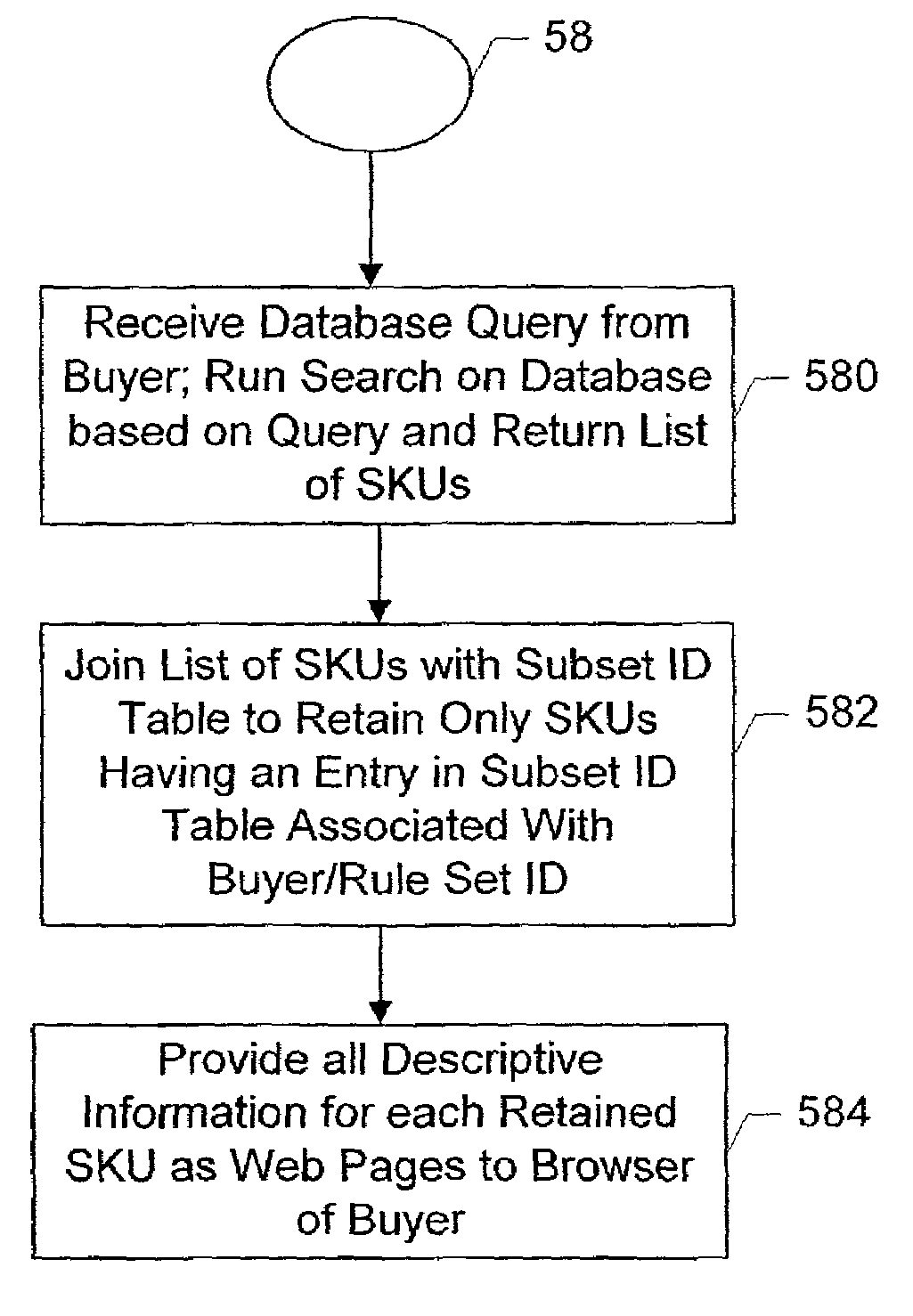
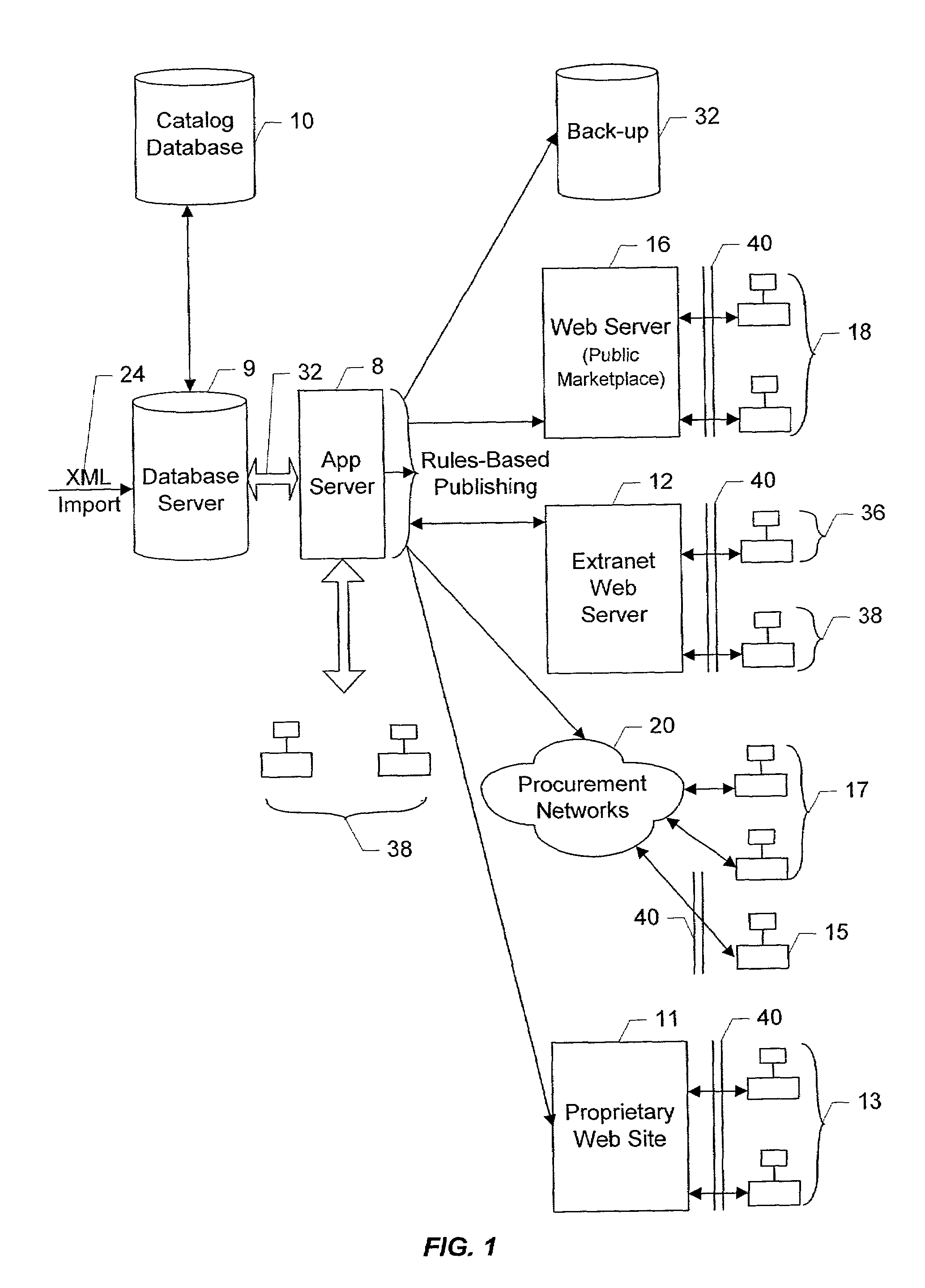
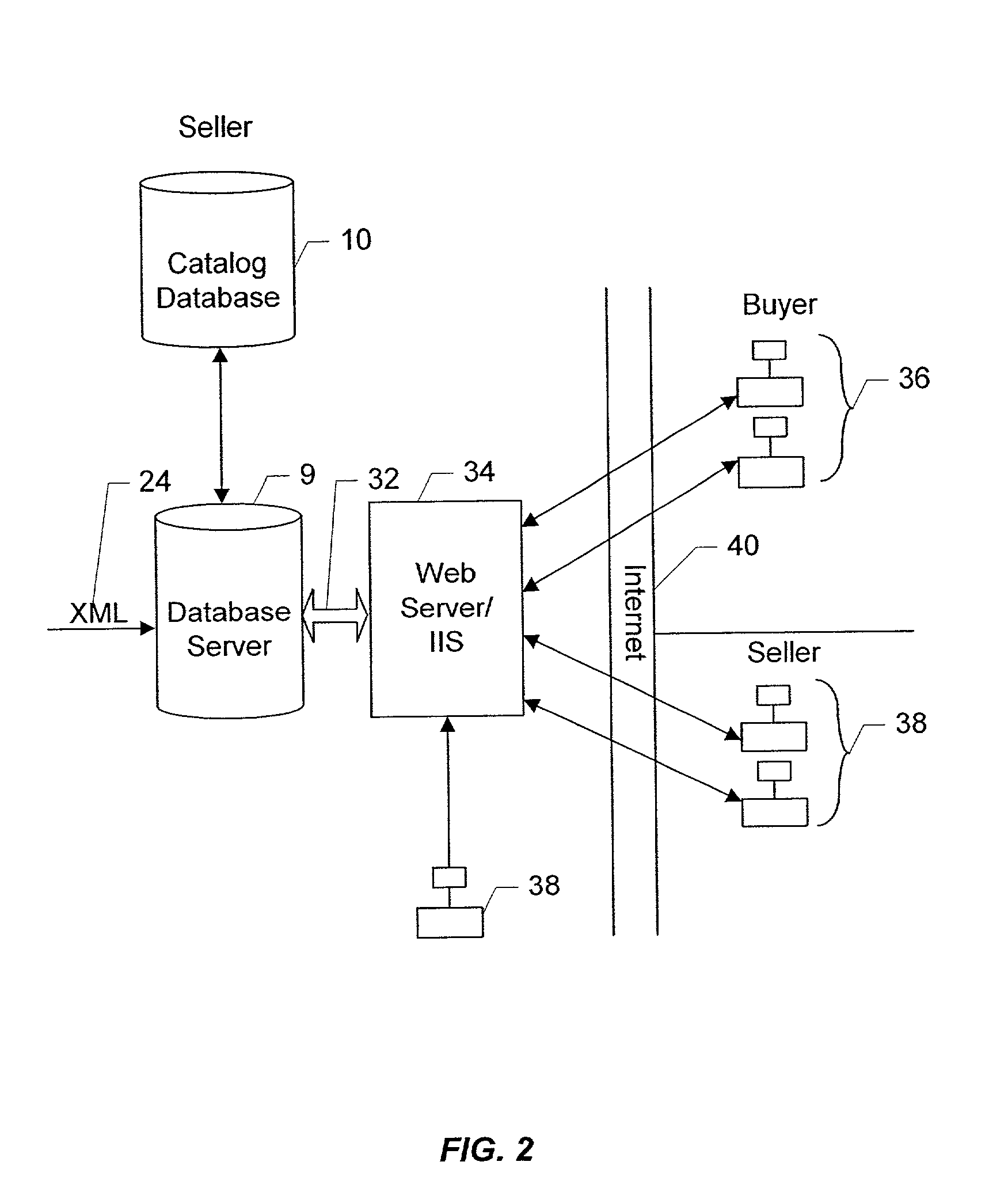
Rules based custom catalogs generated from a central catalog database for multiple entities
An arbitrary number of custom catalogs for an arbitrary number of customers can be published from a centrally maintained database of seller catalog data. The custom catalogs are subsets of the catalog database, and are generated in accordance with a set of rules that defines the scope of the content of the custom catalog. The rule sets define a series of sequential searches by which a subset of the item SKUs contained in the database are returned. For extranet buyers, the subsets for each rule set are maintained in a subset table. Whenever a user authorized by a particular buyer wishes to browse the unique catalog subset assigned to that buyer, any queries regarding the catalog will result first in a search of the full catalog database, and the results from the full search are pared down to only those items the SKUs for which have entries in the subset table associated with the buyer's assigned subset. A buyer-authorized user browses the catalog using a standard PC and browser, and SKUs returned to the user based on the user's query will include descriptive information such as descriptive text, pictures etc., which are displayed by the browser. Buyers who are not coupled to the seller via an extranet connection can have customized subsets of the total catalog database produced in accordance with their own rule sets, and formatted and delivered off-line for incorporation into their web sites and procurement networks.
Owner:VERSATA DEV GROUP
System and method for judging cloud safety malicious program
The invention discloses a system for judging a cloud safety malicious program. The system comprises a cloud terminal, a client, a virtual defending group and a station, wherein light malicious code defending software is installed on the client. A local characteristic base maintains the current prevalent malicious code information and keeps relatively stable scale, so that the performance of the client is improved. The client organizes in the form of a virtual defending group, the cloud terminal distributes malicious risk solving schemes with the virtual defending group as a unit, and group members belonging to the same virtual defending group can interact malicious code information, so that the spending of the client terminal is reduced. According to a cloud safety malicious program judging method based on the system, the working mode thereof includes an online mode and an offline mode. The online mode comprises a series of sub steps, and the client updates the local characteristic base through an extranet or an intranet. In the offline mode, the client synchronizes the local characteristic base through the intranet, and the offline safety of the client is guaranteed.
Owner:SHANGHAI MARITIME UNIVERSITY
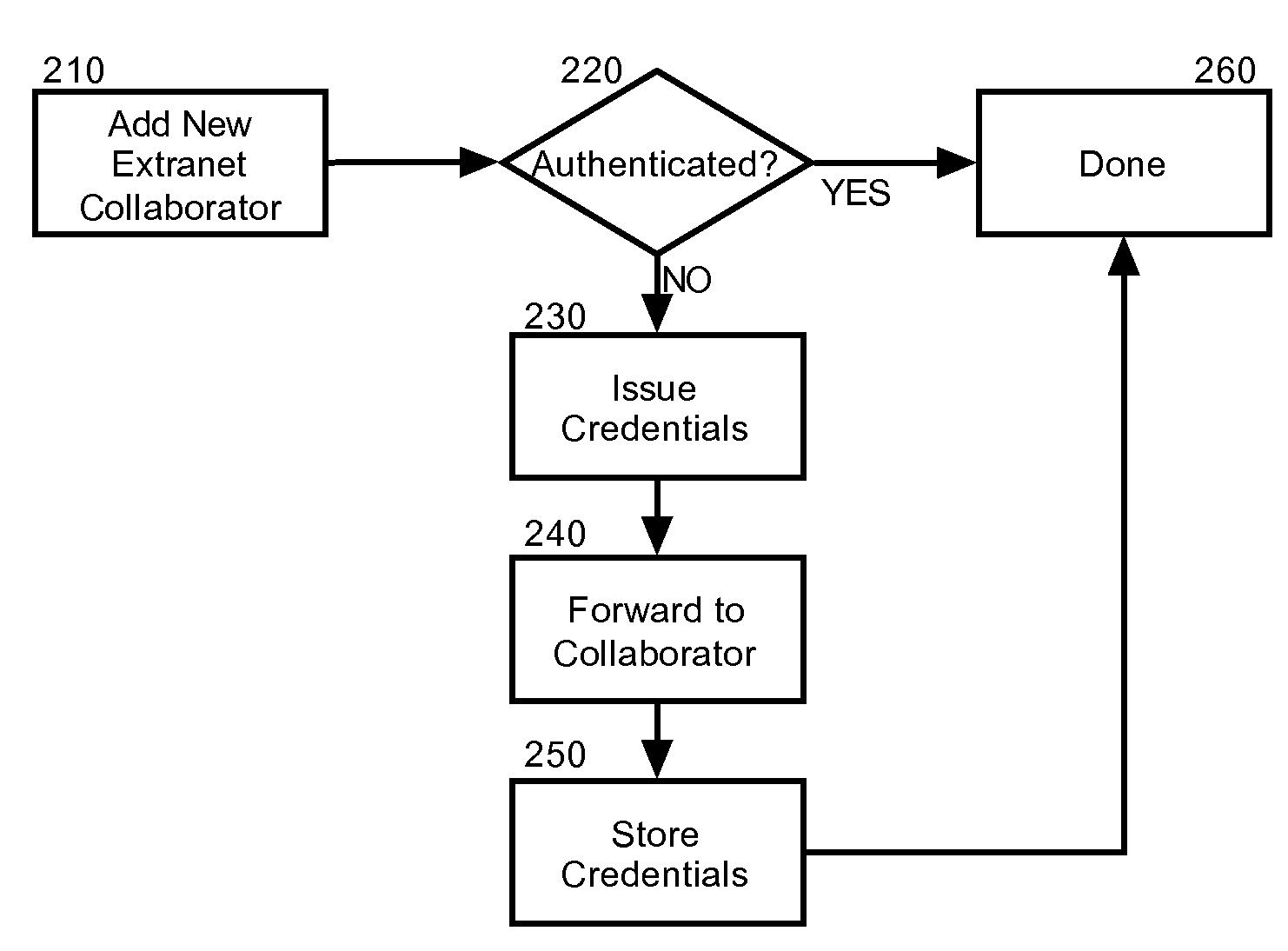
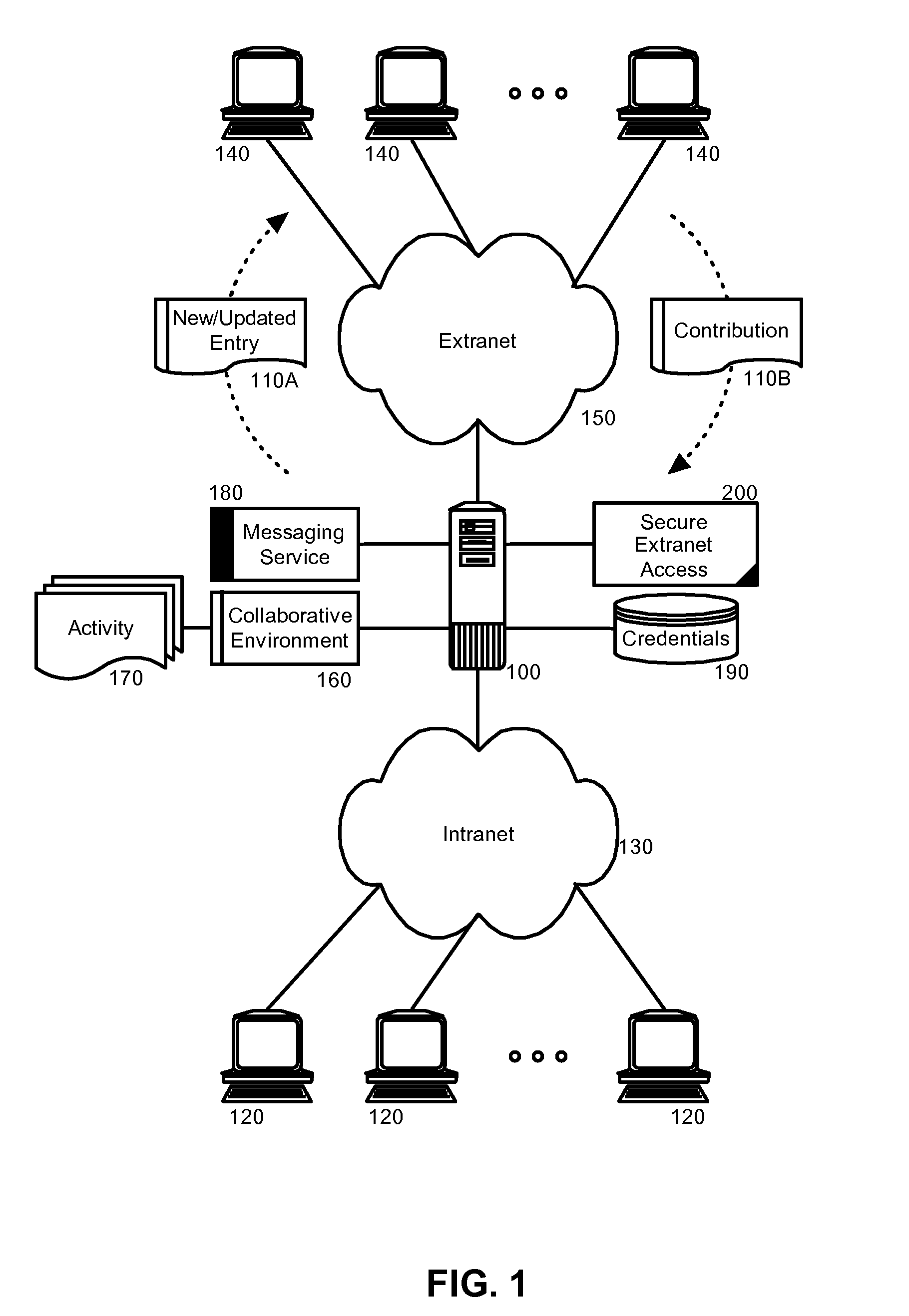
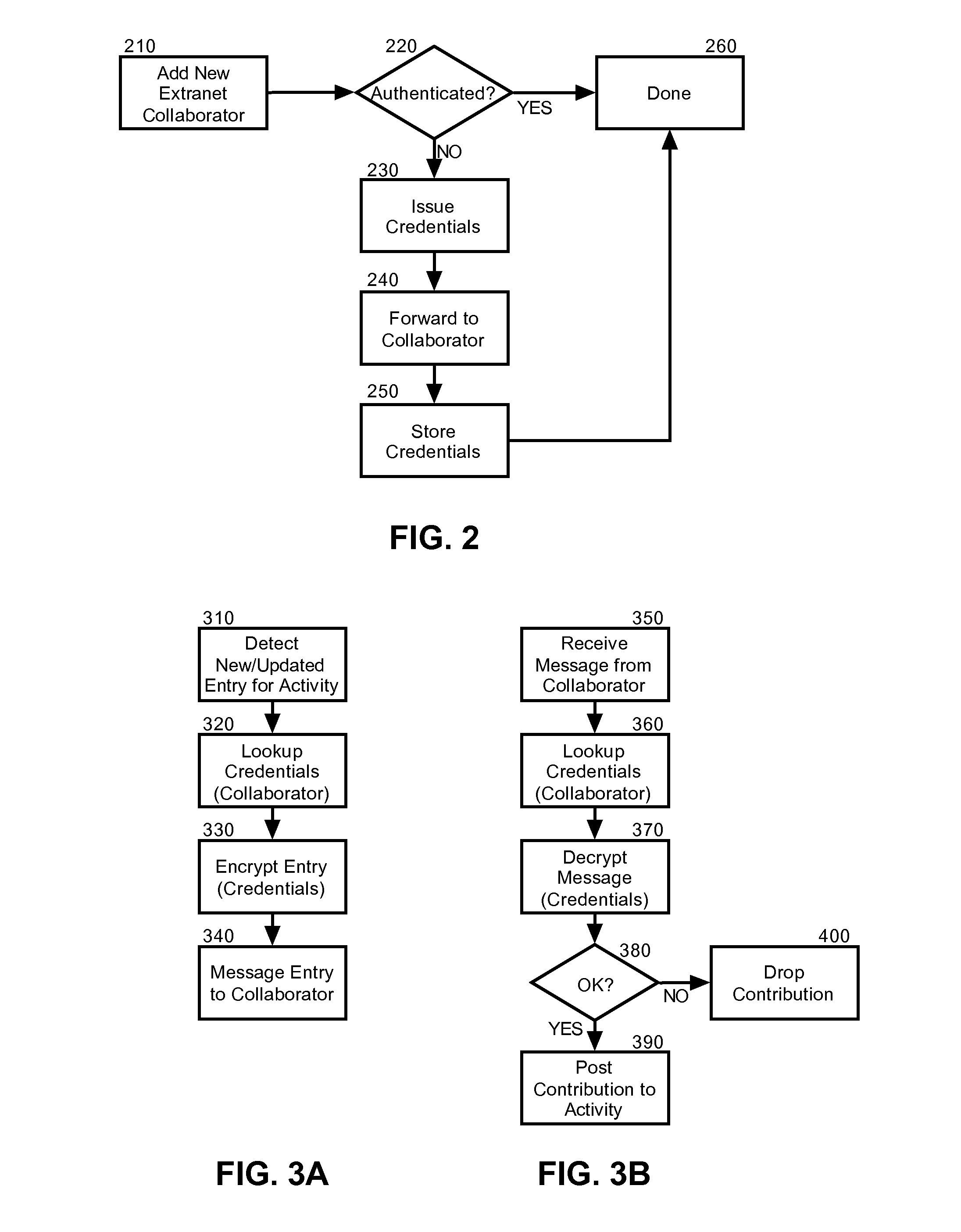
Secure extranet access to collaborative activities in a collaborative computing environment
InactiveUS20080148368A1Easy accessDigital data processing detailsUser identity/authority verificationCollaborative computingKnowledge management
Embodiments of the present invention address deficiencies of the art in respect to securing extranet access to a collaborative environment and provide a method, system and computer program product for secure extranet access to collaborative activities in a collaborative environment. In an embodiment of the invention, a method for secure extranet access to collaborative activities in a collaborative environment can be provided. The method can include adding an extranet collaborator to a collaborative space within a collaborative environment and establishing encryption credentials for the extranet collaborator. Thereafter, in response to detecting a change to the collaborative space, the change can be encrypted with the credentials and the change can be messaged to the extranet collaborator. Notably, a contribution to the activity can be received from the extranet collaborator. Once received, the contribution can be decrypted with the credentials and the contribution can be posted to the activity.
Owner:IBM CORP
Method and apparatus for implementing a workgroup server array
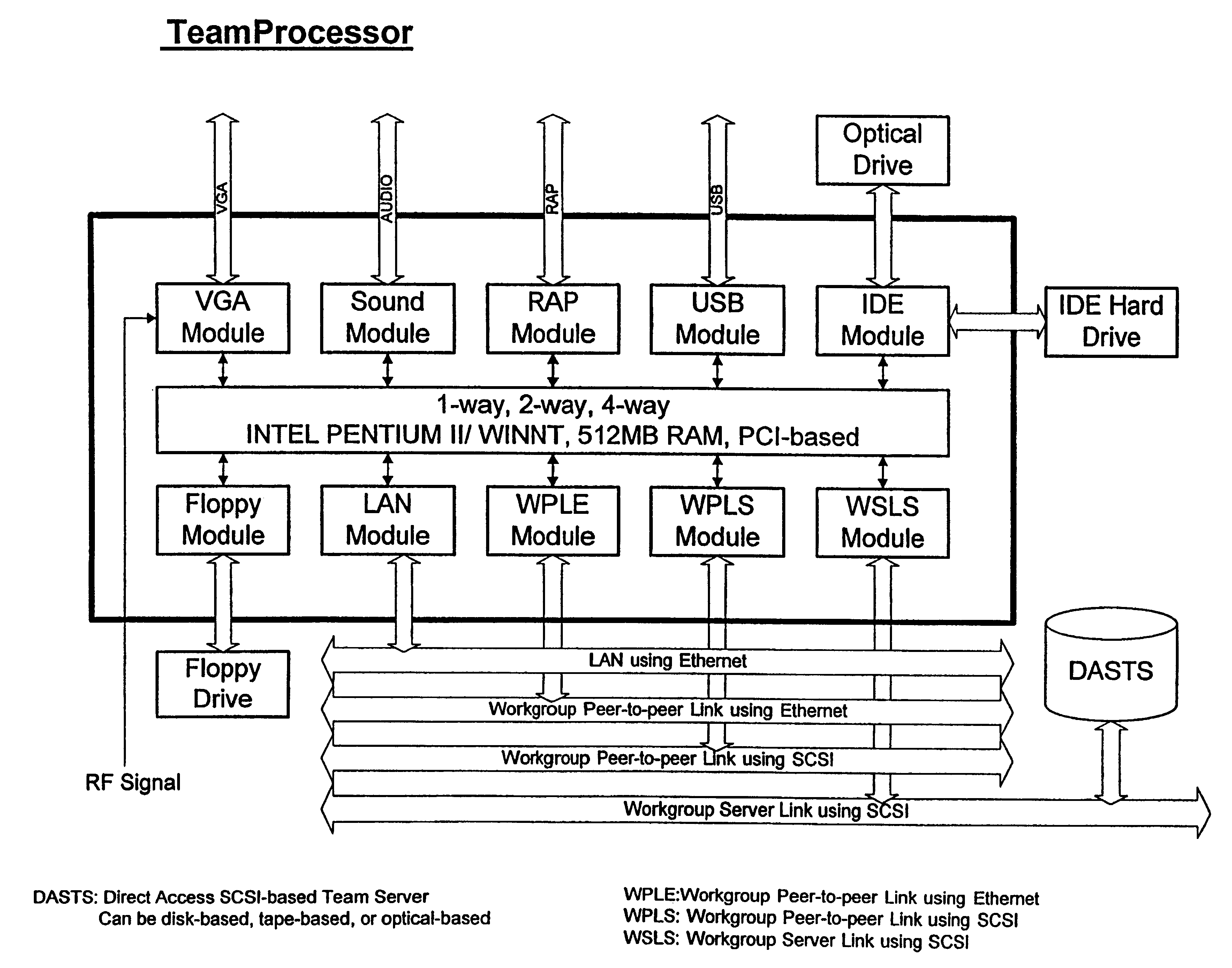
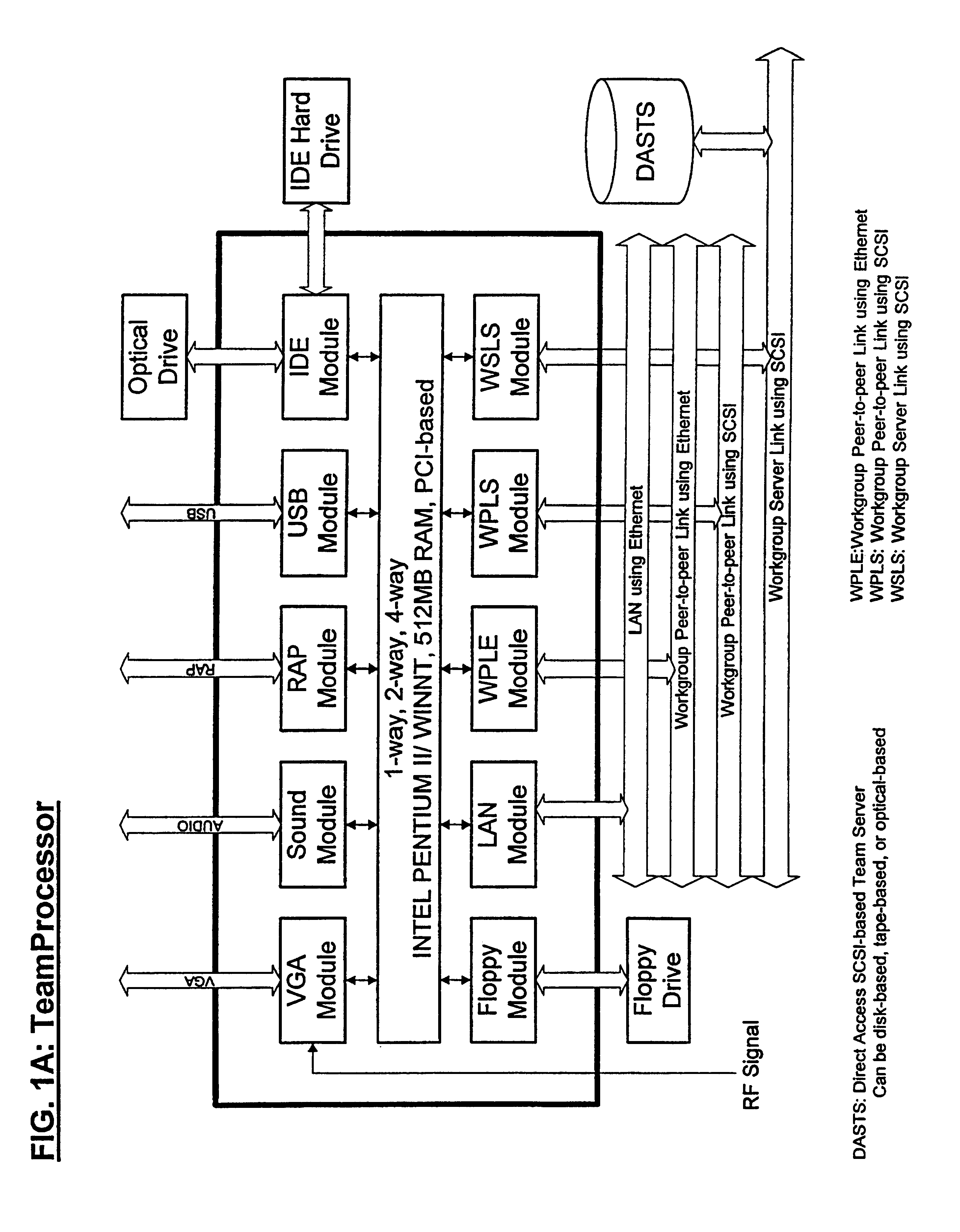
InactiveUS6715100B1Unnecessary network traffic can be reducedReduce in quantityError detection/correctionFailoverHigh availability
A method and apparatus for implementing a workgroup server array ideal for web-based Intranet, Extranet and Internet applications. The inventive server array comprises a plurality of team / workgroup computers (408) equipped with work-group-based direct-access servers and modular controlling devices (1), creating workgroup-based fault-tolerant and fail-over capabilities, providing console-based monitoring and management support, and accommodating highly available and scalable web-based applications with optimal performance. These workgroup server arrays can be used as the basic building blocks to construct large-scale server clusters, so that more users can be served concurrently. Furthermore, workgroup-server-array-based architecture is created for building various highly available, scalable and mission critical server clusters, which enable distributed computing services for enerris-based Intranet, Extranet and Internet mission critical applications.
Owner:HWANG IVAN CHUNG SHUNG
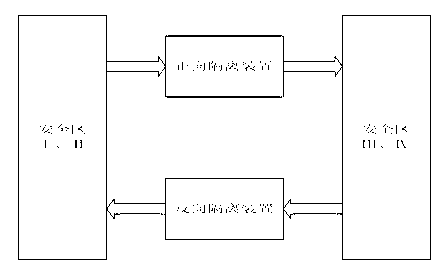
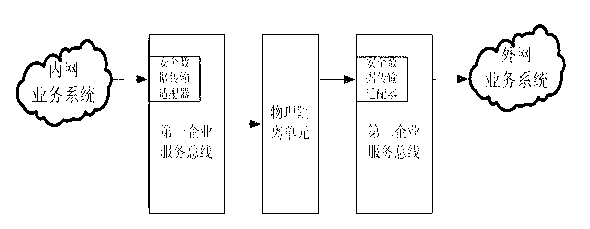
Cross-physical isolation data transparent transmission system and method between intranet and extranet
ActiveCN102843352ARetrofit smallEasy to deployUser identity/authority verificationBus networksEnterprise servicesWorkload
The invention relates to a cross-physical isolation data transparent transmission system between an intranet and an extranet. The system comprises a first enterprise service bus and a second enterprise service bus which are respectively arranged on the two sides of physical isolation, wherein a first safety data transmission adapter and a second safety data transmission adapter are respectively deployed on the first and second enterprise service buses, the physical isolation is arranged between gateways of the intranet and the extranet for performing network safety area isolation, the first and second enterprise service buses are used for respectively providing calling interfaces and simultaneously communicating with the physical isolation, and the first and second safety data transmission adapters are respectively responsible for safety certification and calibration of integrity and effectiveness of data of the intranet and the extranet. The invention further relates to a cross-physical isolation data transparent transmission method of the system. Improvement of data transmission can be performed under a physical isolation environment through the system and the method, the difficulty in transformation and the workload of the service system can be simplified, and the safety in data transmission can be further enhanced through the safety data transmission adapters.
Owner:MAOMING POWER SUPPLY BUREAU GUANGDONG POWER GRID CORP
Multi-way interactive email performing functions of networks and the web
InactiveUS20020107931A1Multiple digital computer combinationsOffice automationInternal managementCustomer relationship management
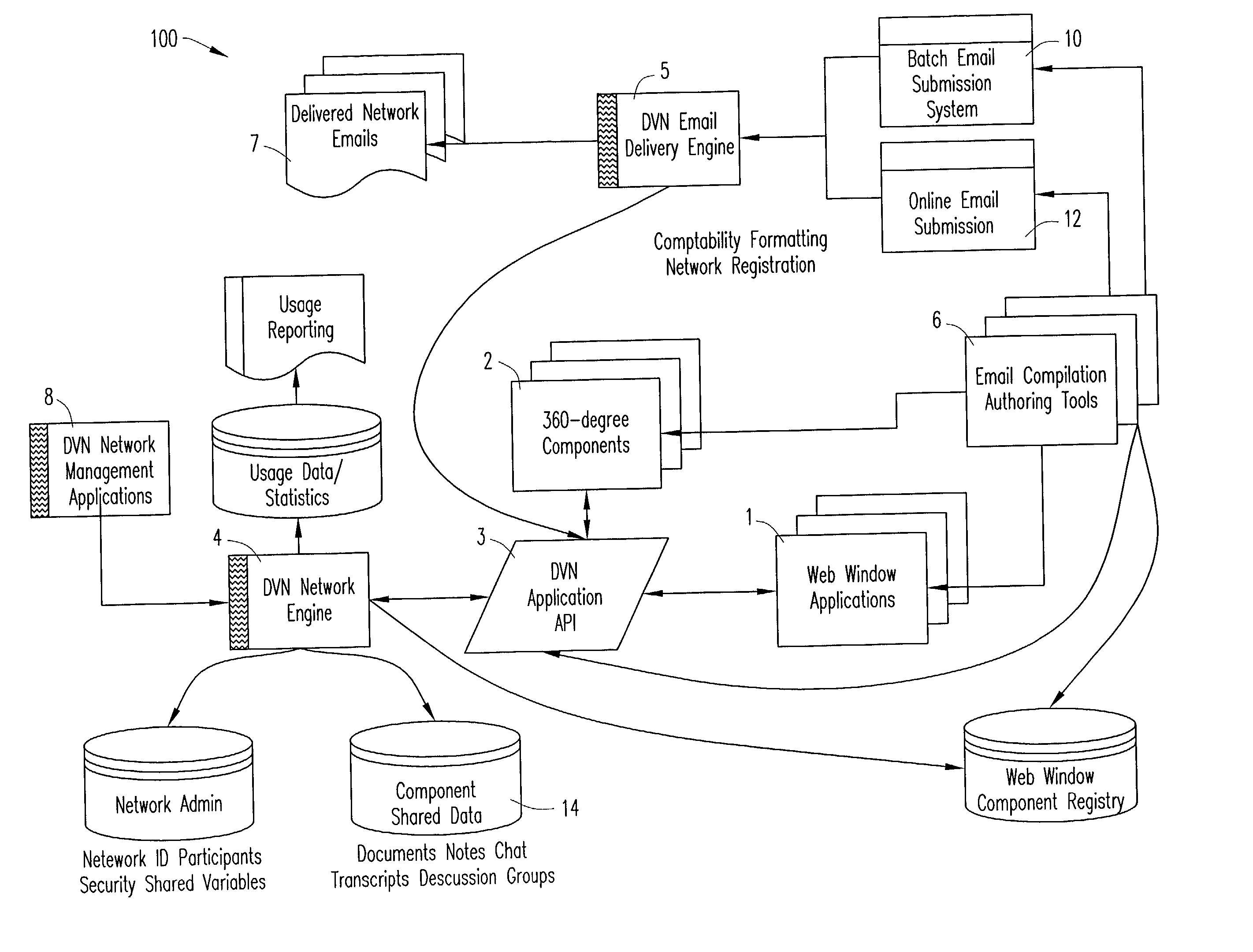
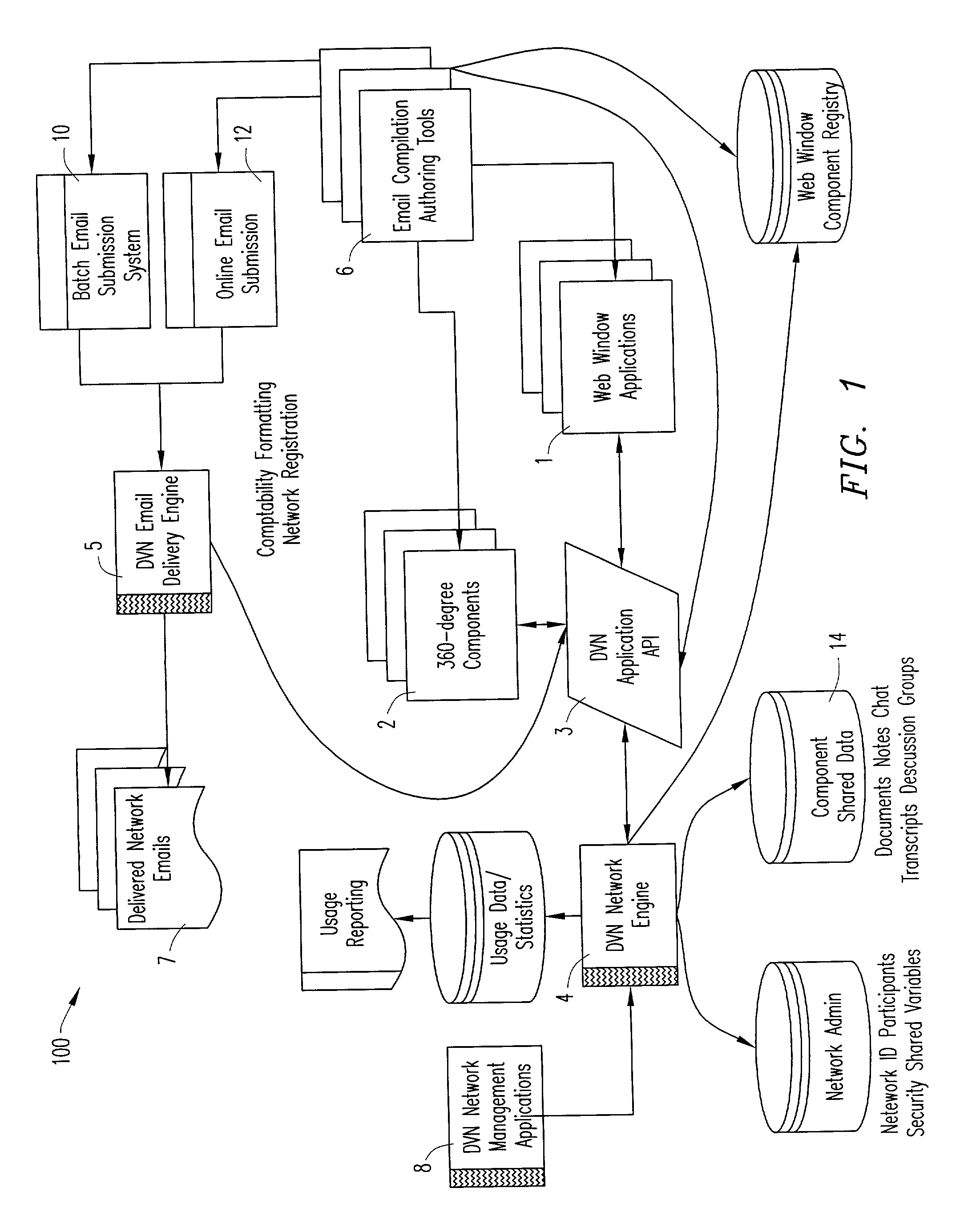
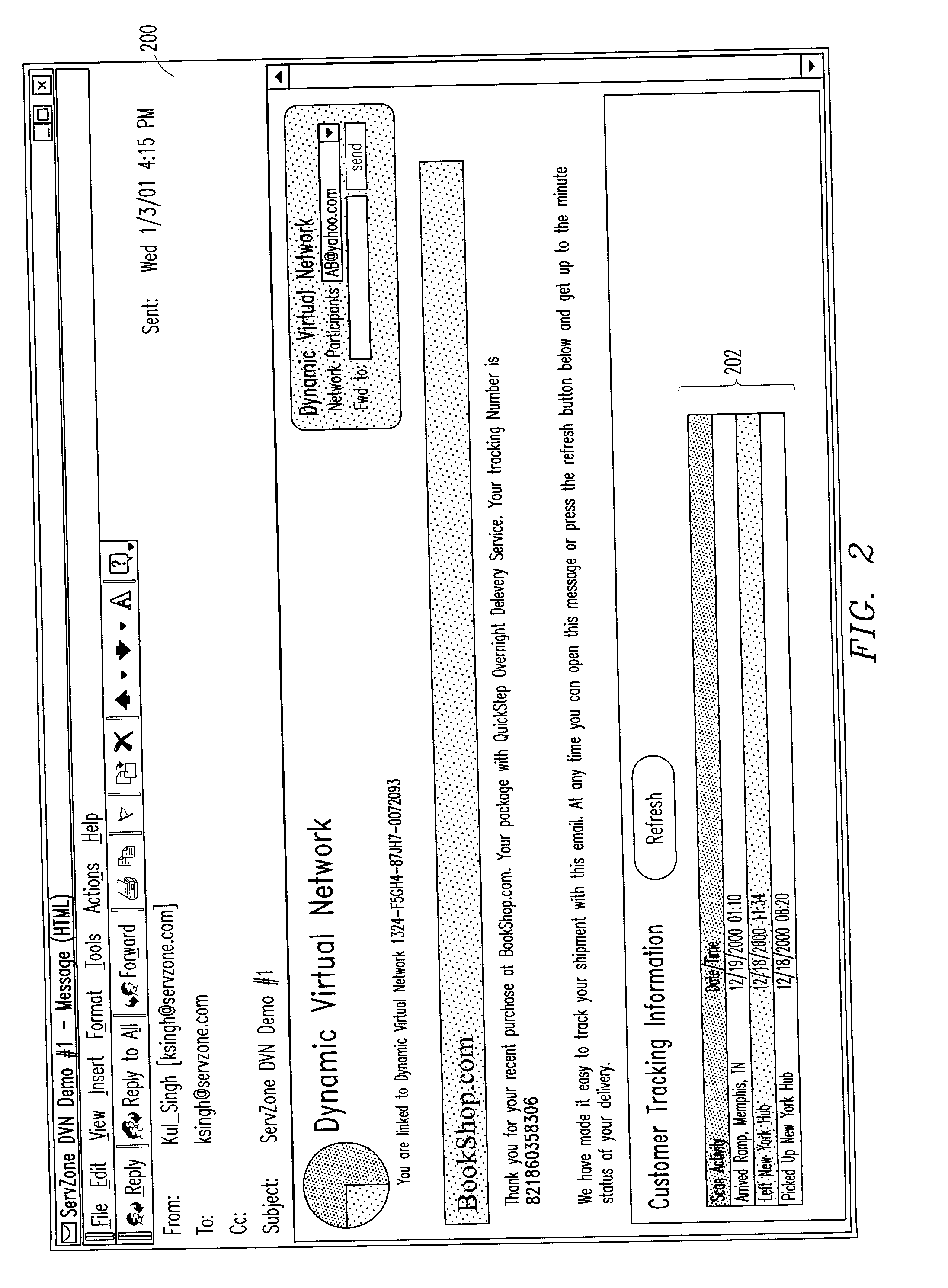
An improved system that enables interactive networks to be configured and delivered to HTML enabled email systems providing common access to applications and data between two or more parties. The system also provides the capability to link interactive components within the email that, upon execution, dynamically affect the content of the email. The system permits the construction and delivery of dynamic network content enabling email to serve as an ad-hoc, impromptu intranet or extranet. The system internally manages the identification of each node of the email network and creates and tracks security authorization and entitlements ensuring that only authenticated recipients see authorized information. The system combines robust networking capability with two-way interactivity, creating efficiencies for the purposes of information sharing, collaboration, customer relationship management, and online marketing. Anytime the recipient either re-opens the email or refreshes it, the body of the email will reflect the latest transmitted data. The system creates a private and secure network when enterprises or individual users email one or more recipients.
Owner:SERVZONE COM
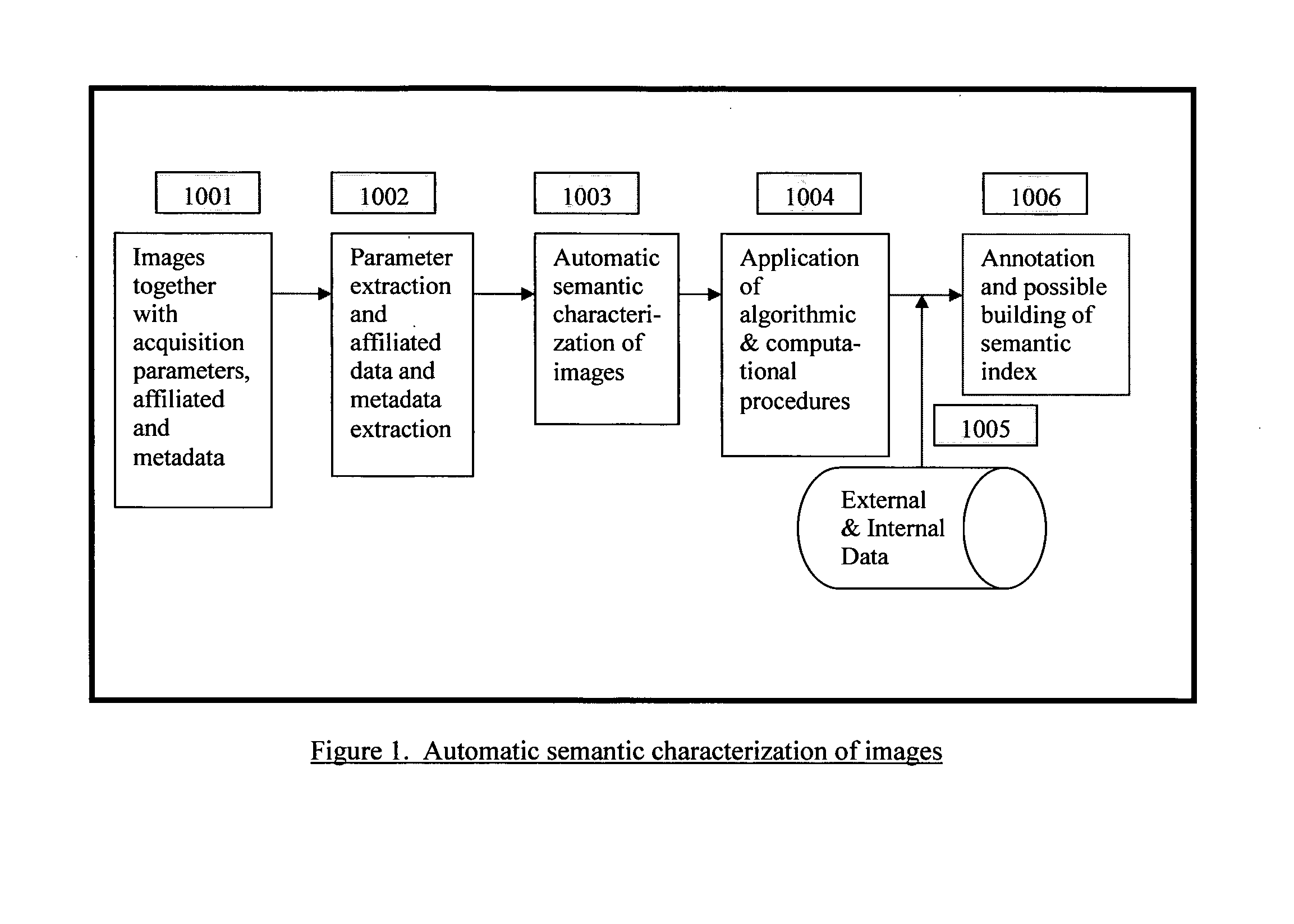
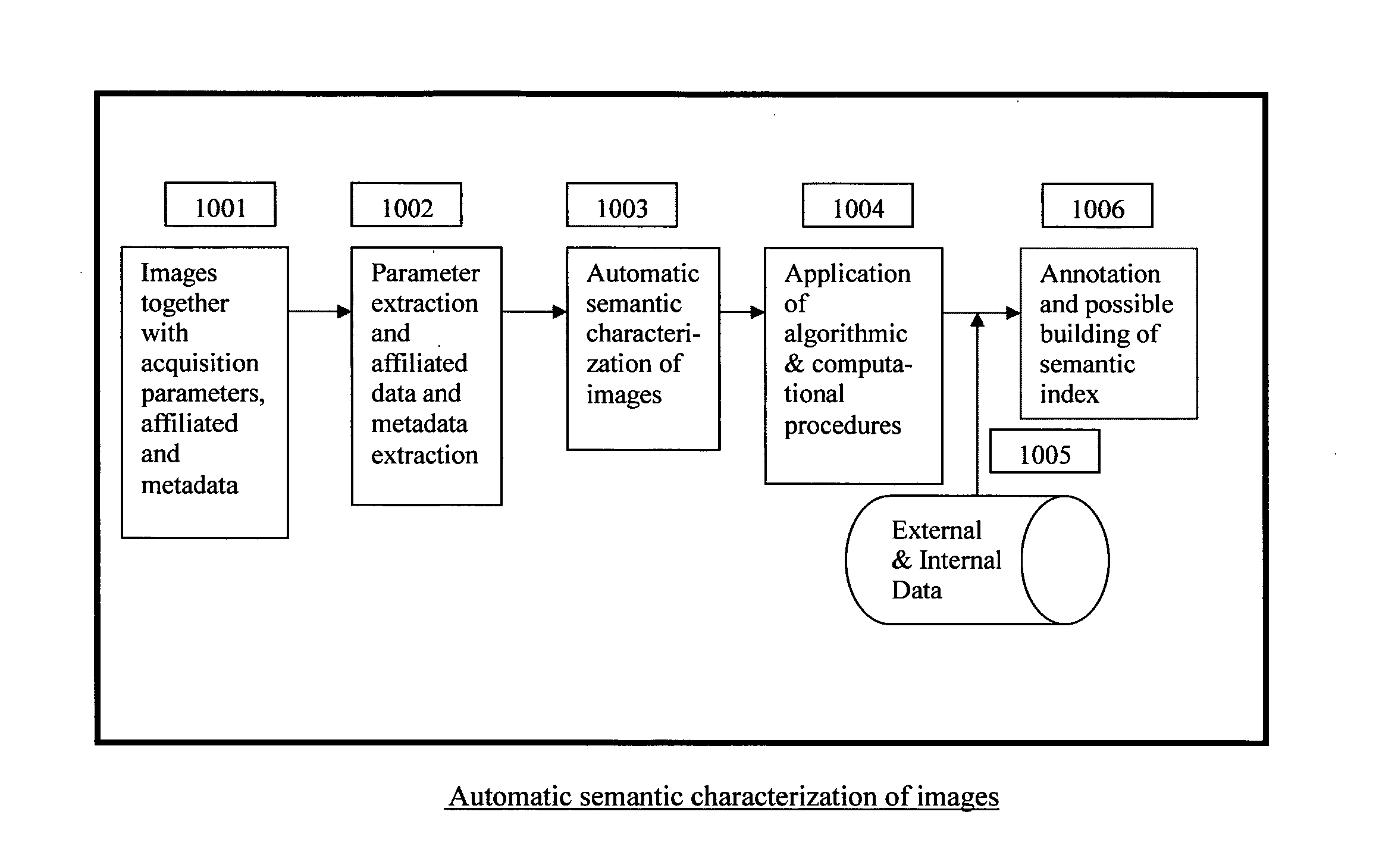
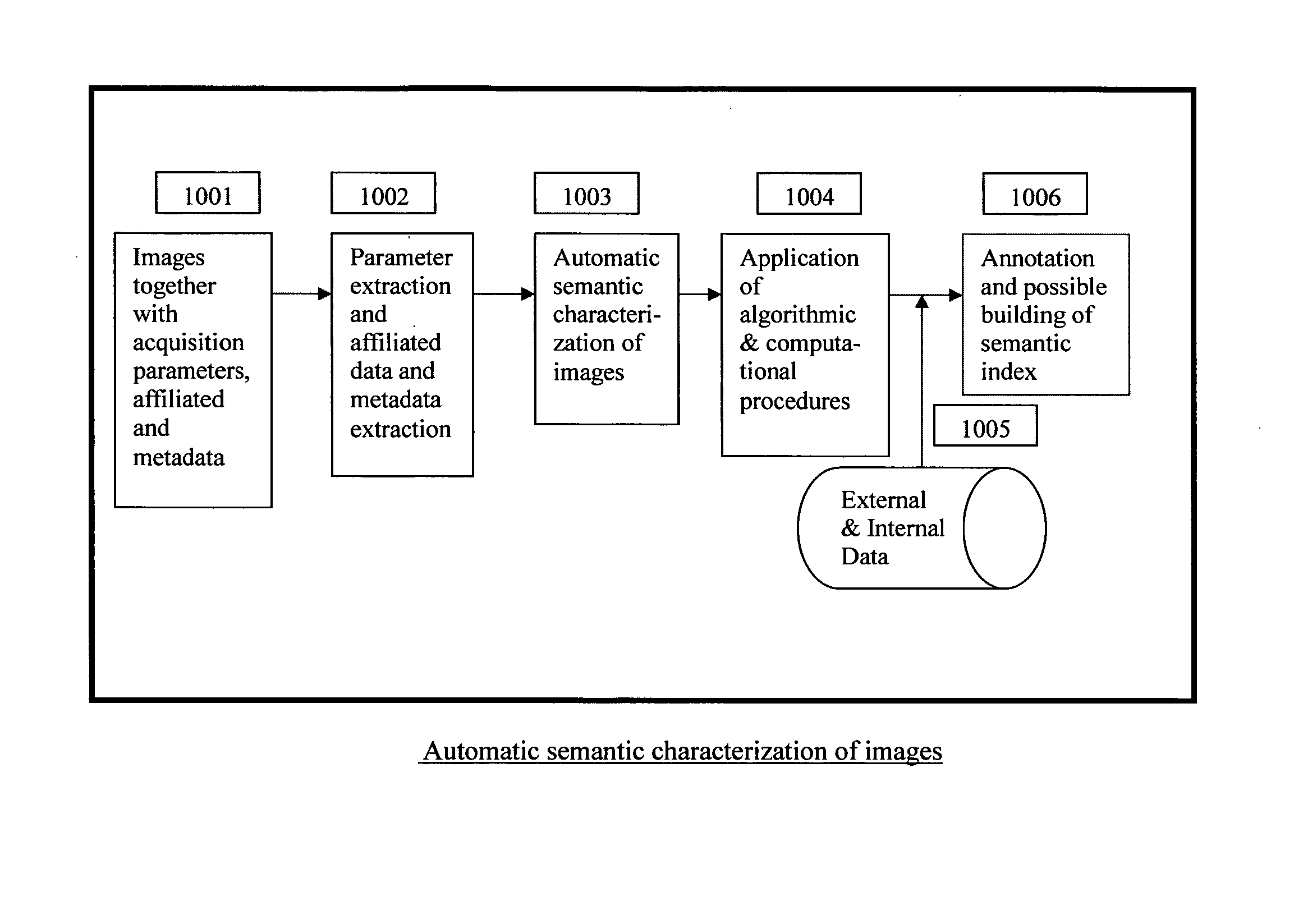
Automatic and Semi-automatic Image Classification, Annotation and Tagging Through the Use of Image Acquisition Parameters and Metadata
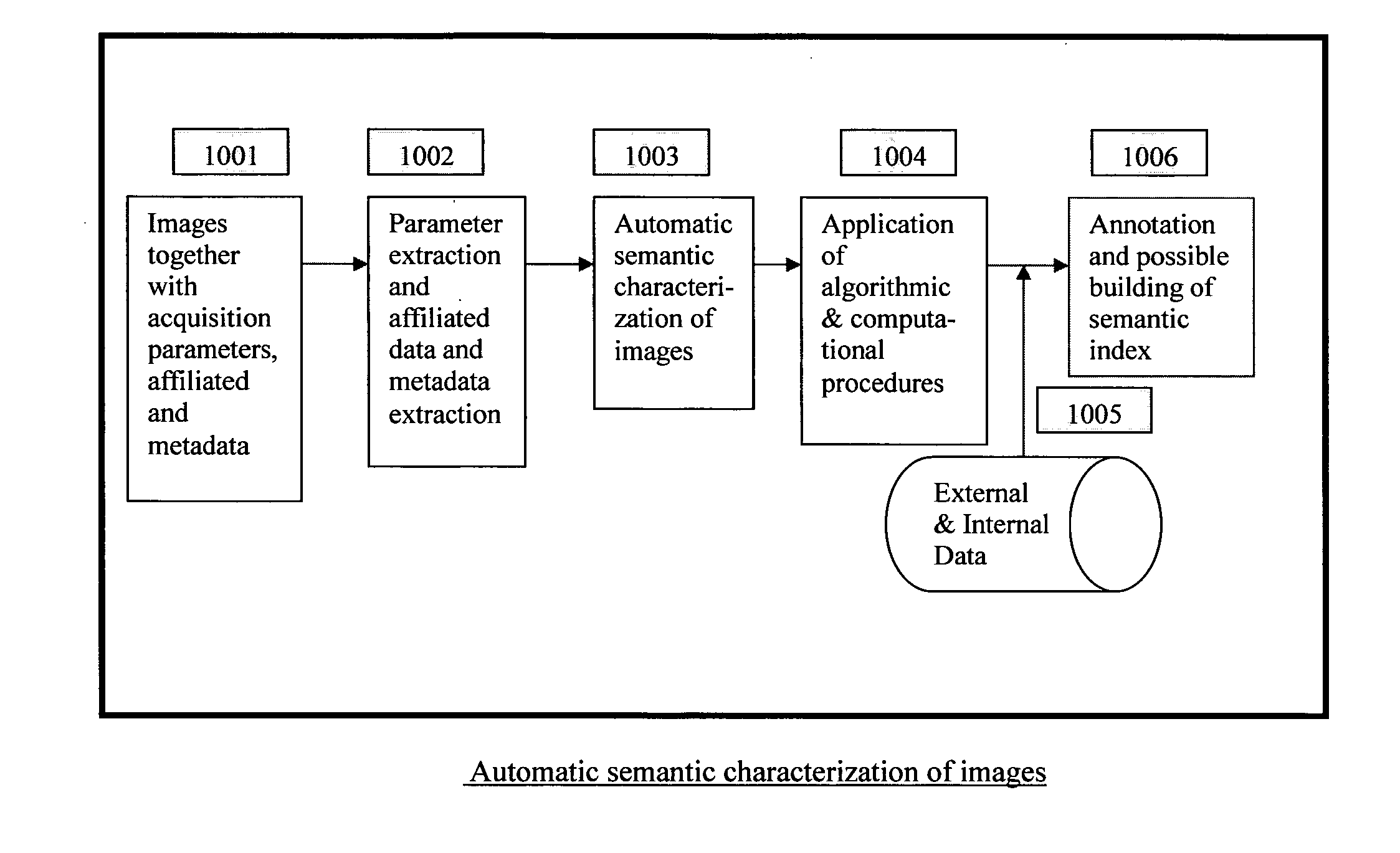
ActiveUS20110317885A1Improve accuracyCharacter and pattern recognitionMetadata still image retrievalTimestampSemi automatic
A method for characterizing image contents automatically or semi-automatically using image acquisition parameters and metadata is presented. The method establishes probabilistic and deterministic relationships between different types of metadata and the semantic attributes and contents of images. It furnishes a mechanism that enables the automatic and semi-automatic classification, annotation, tagging, indexing, searching, identification or retrieval of images based on their contents, semantic properties and metadata characteristics. The method uses, but is not limited to, image capture metadata such as focal length, exposure time, relative aperture, flash information, ISO setting, angle of view, subject distance, timestamp, GPS information as well as other forms of metadata, including but not limited to, captions, keywords, headings, tags, comments, remarks, titles which may be automatically, semi-automatically, or manually generated. The present invention can be applied to image databases, web searching, personal search, community search, broad-based or vertical search engines for internet, intranet, extranet or other usages.
Owner:HONG KONG BAPTIST UNIV
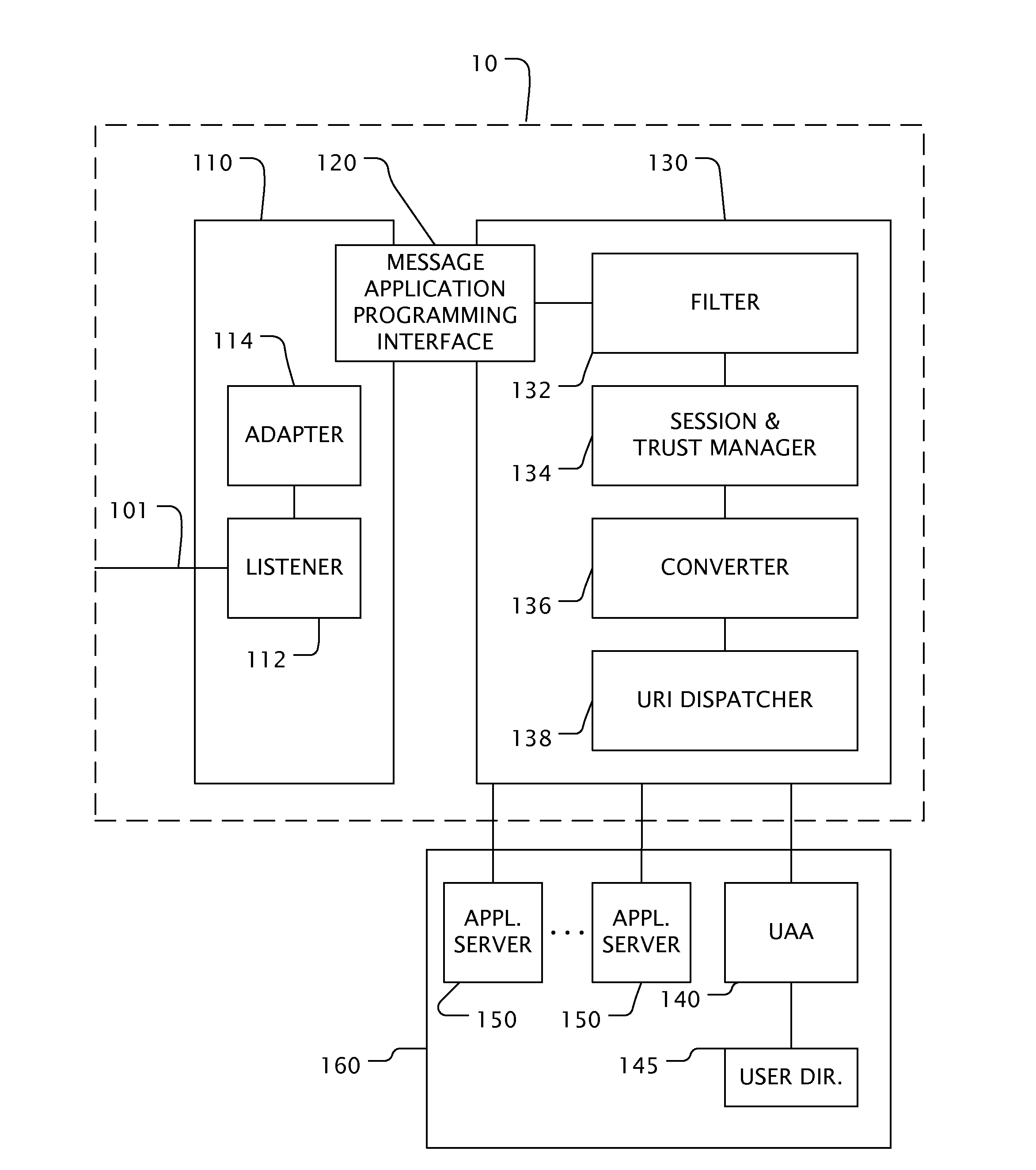
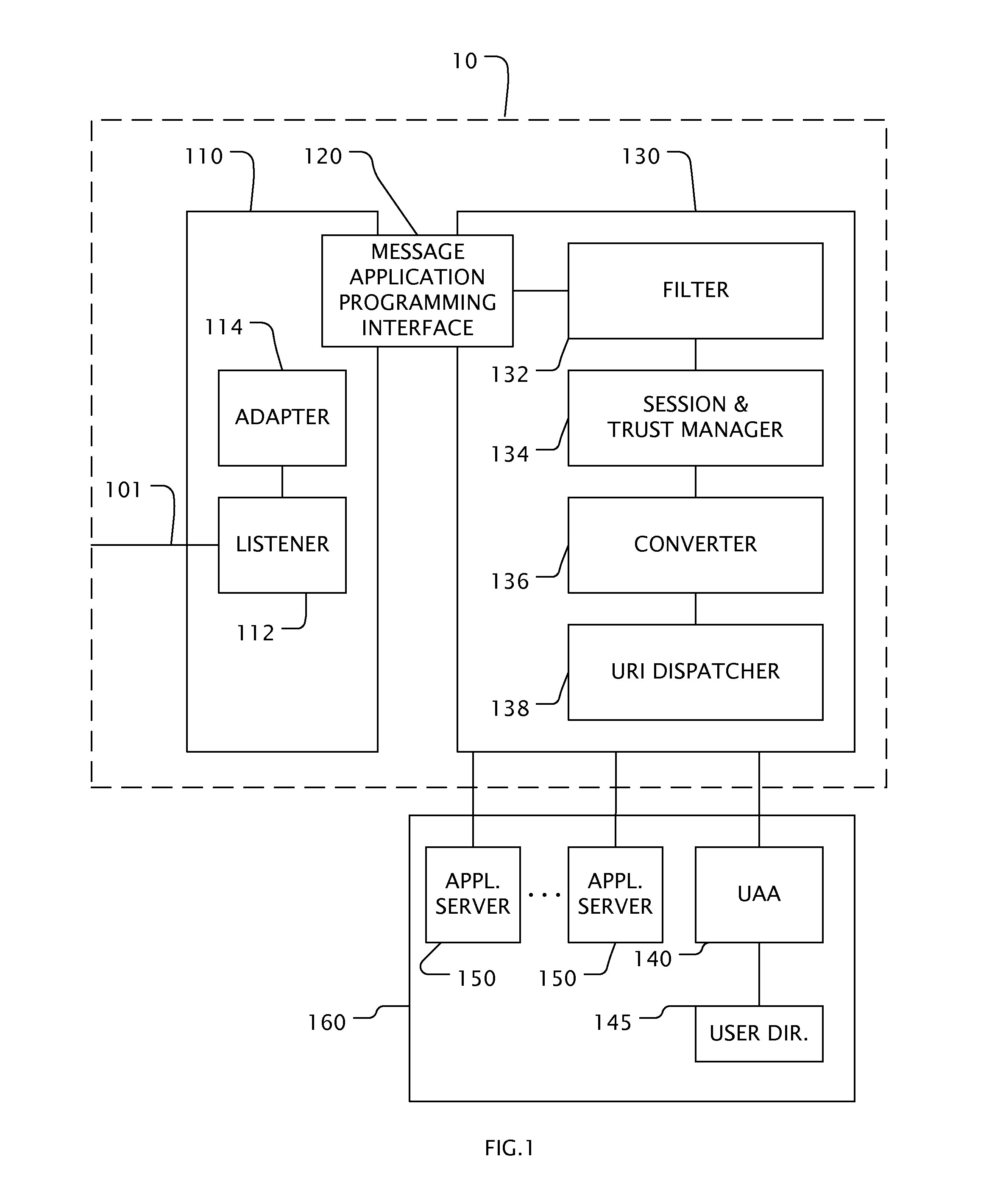
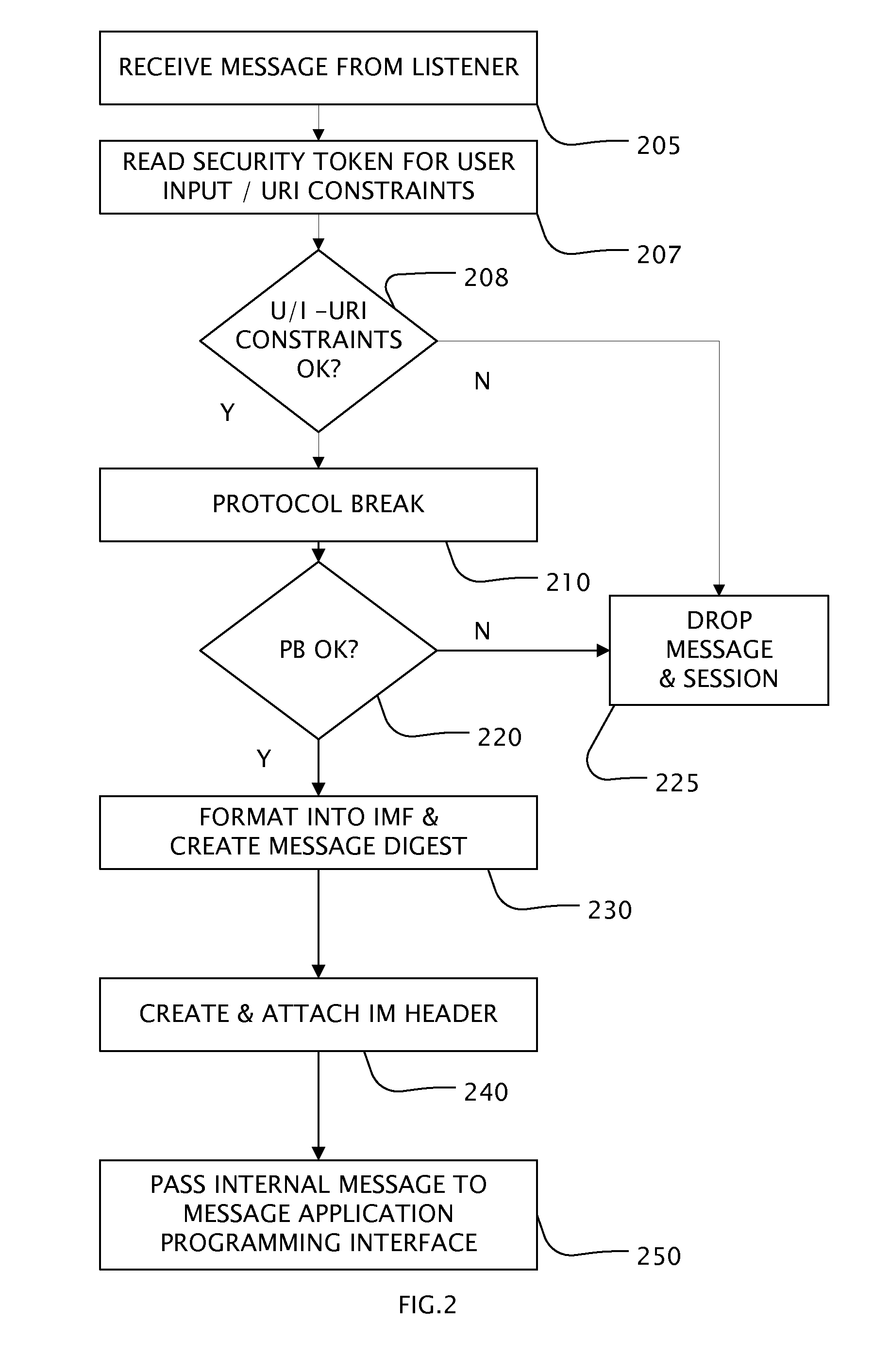
Secure extranet server
A Secure Extranet Server (SES) provides for secure and traceable communication and document exchange between a trusted network and an untrusted network by authenticated users. The SES includes a first partition in communication with the untrusted network and a second partition in communication with the trusted network. The second partition maintains a session table and is in communication with a user authentication and authorization module. Communication between the first and second partition is preferably initiated by a request from the second partition. Security tokens attached to messages provide constraint checking on user inputs, access to documents and servers within the trusted network, checkout and checkin of controlled documents, and a single sign-on capability for on-line applications as well as local applications operating on protected files at remote user computers.
Owner:PHION
Message transmission method, device and network system
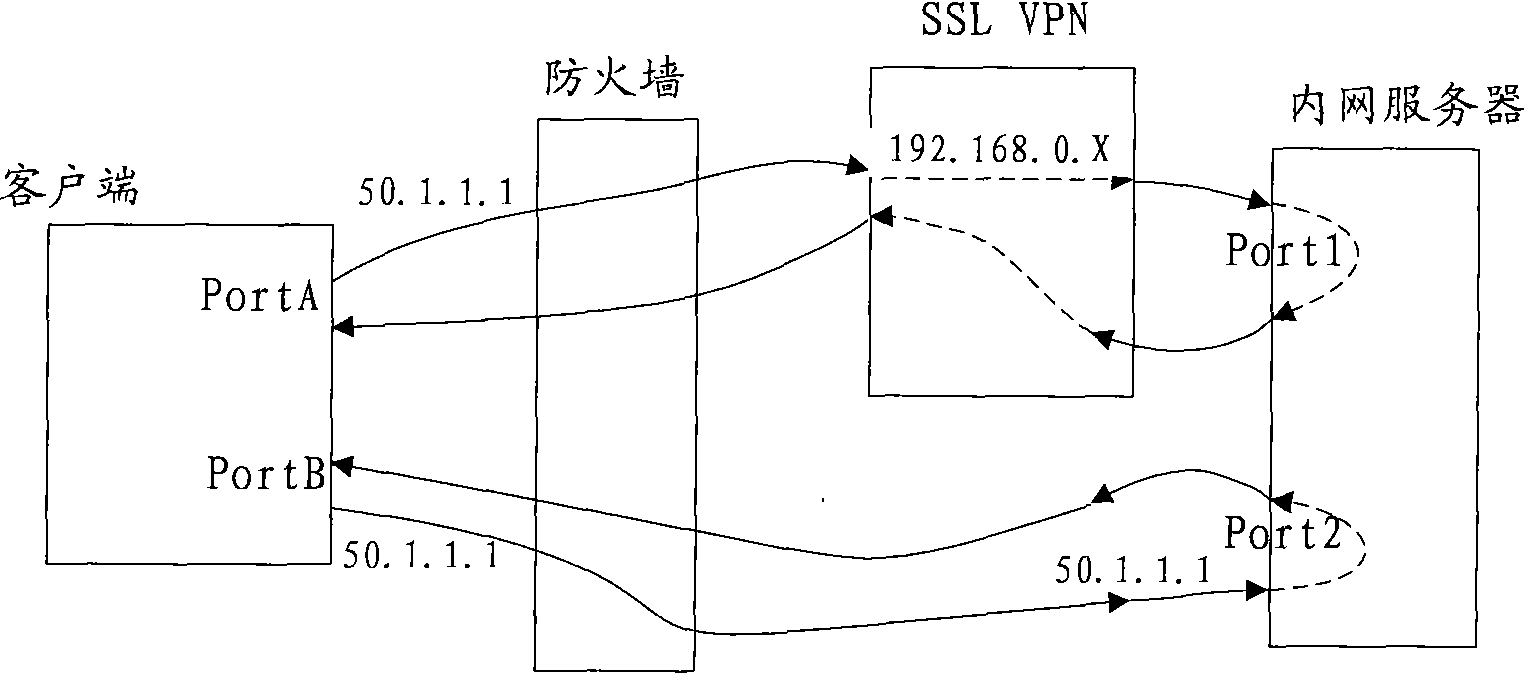
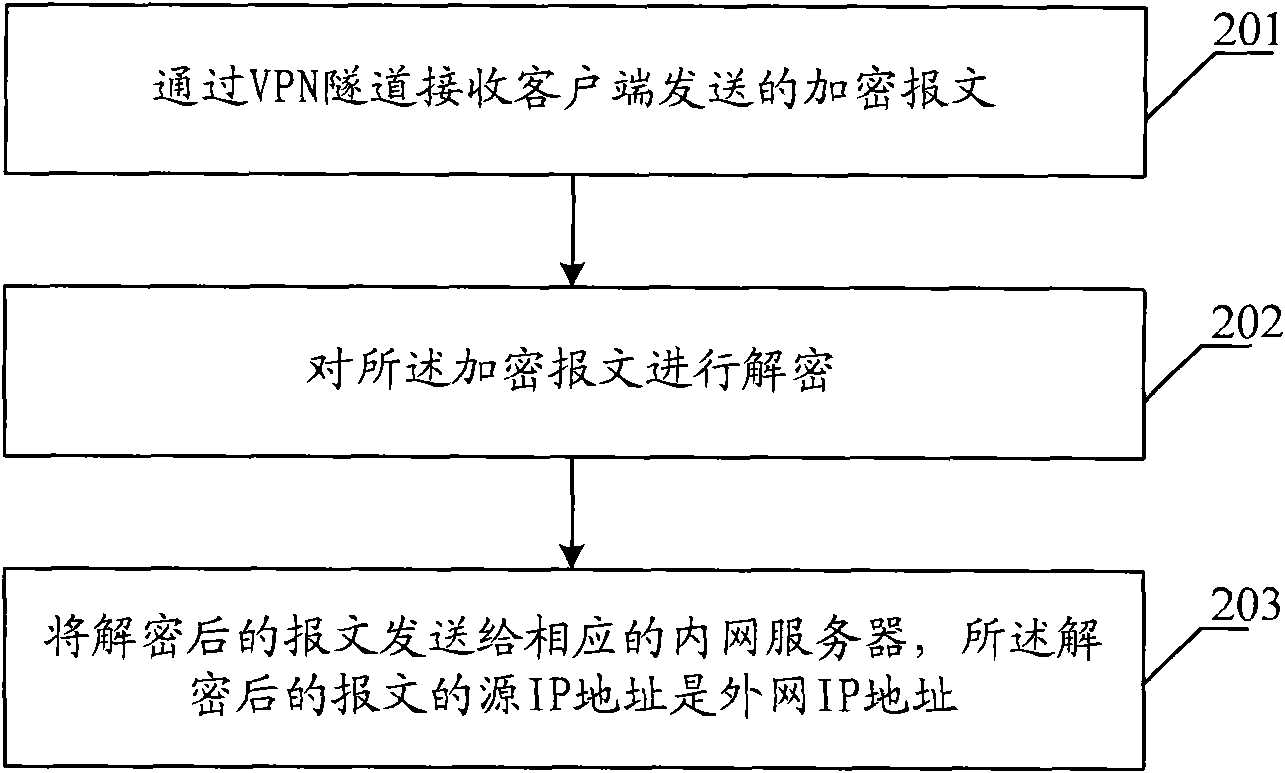
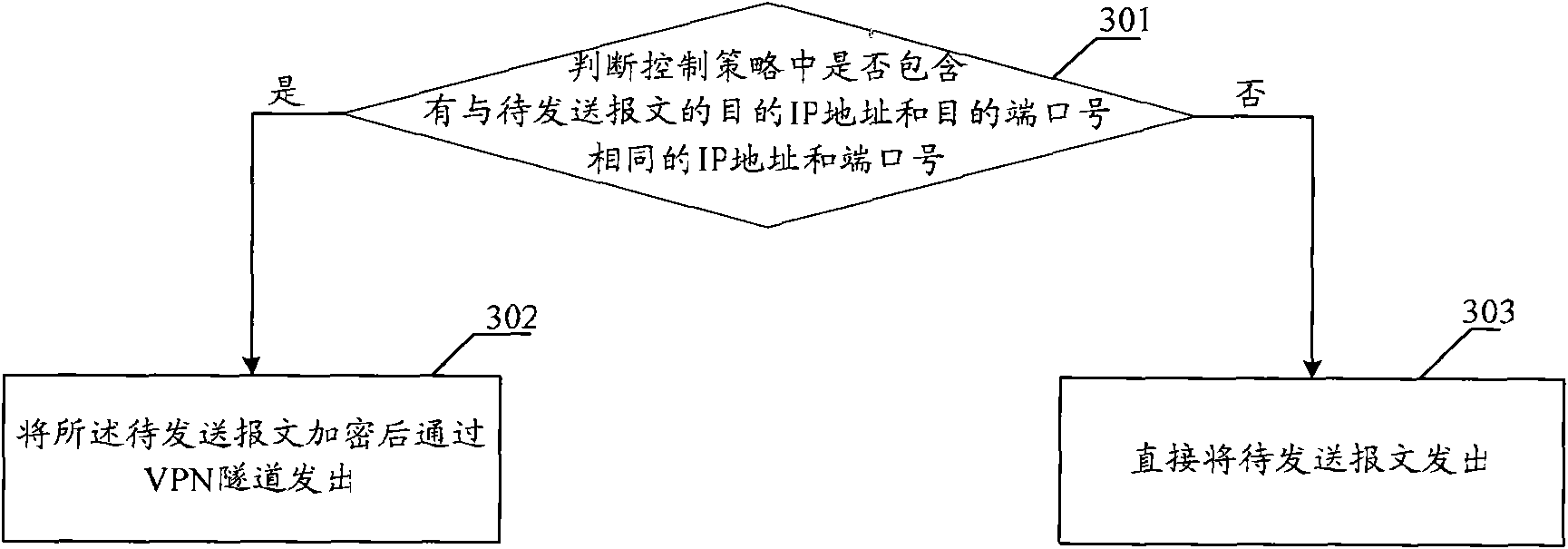
The embodiment of the invention provides a message transmission method, a device and a network system, wherein the message transmission method comprises the following steps of: receiving an encrypted message transmitted by a client through a VPN (Virtual Private Network) tunnel, decrypting the encrypted message and transmitting the decrypted message to a corresponding intranet server, wherein the encrypted message is transmitted by encrypting the message to be transmitted when the client determines that a control strategy comprises an IP address and a port number which are the same with the IP address and the port number of a destination of the message to be transmitted according to the pre-set control strategy; the control strategy comprises the information of the IP address and the port number of the intranet server which can carry out message interaction with a secure socket layer virtual private network (SSLVPN) server; and the source IP address of the decrypted message is an extranet IP address. The message between an intranet and an extranet can be transferred through a secure socket layer virtual private network (SSLVPN) under the condition of unchanging the topology structure of the intranet by utilizing the technical scheme provided by the embodiment of the invention.
Owner:CHENGDU HUAWEI TECH
Method and device for viewing, archiving and transmitting a garment model over a computer network
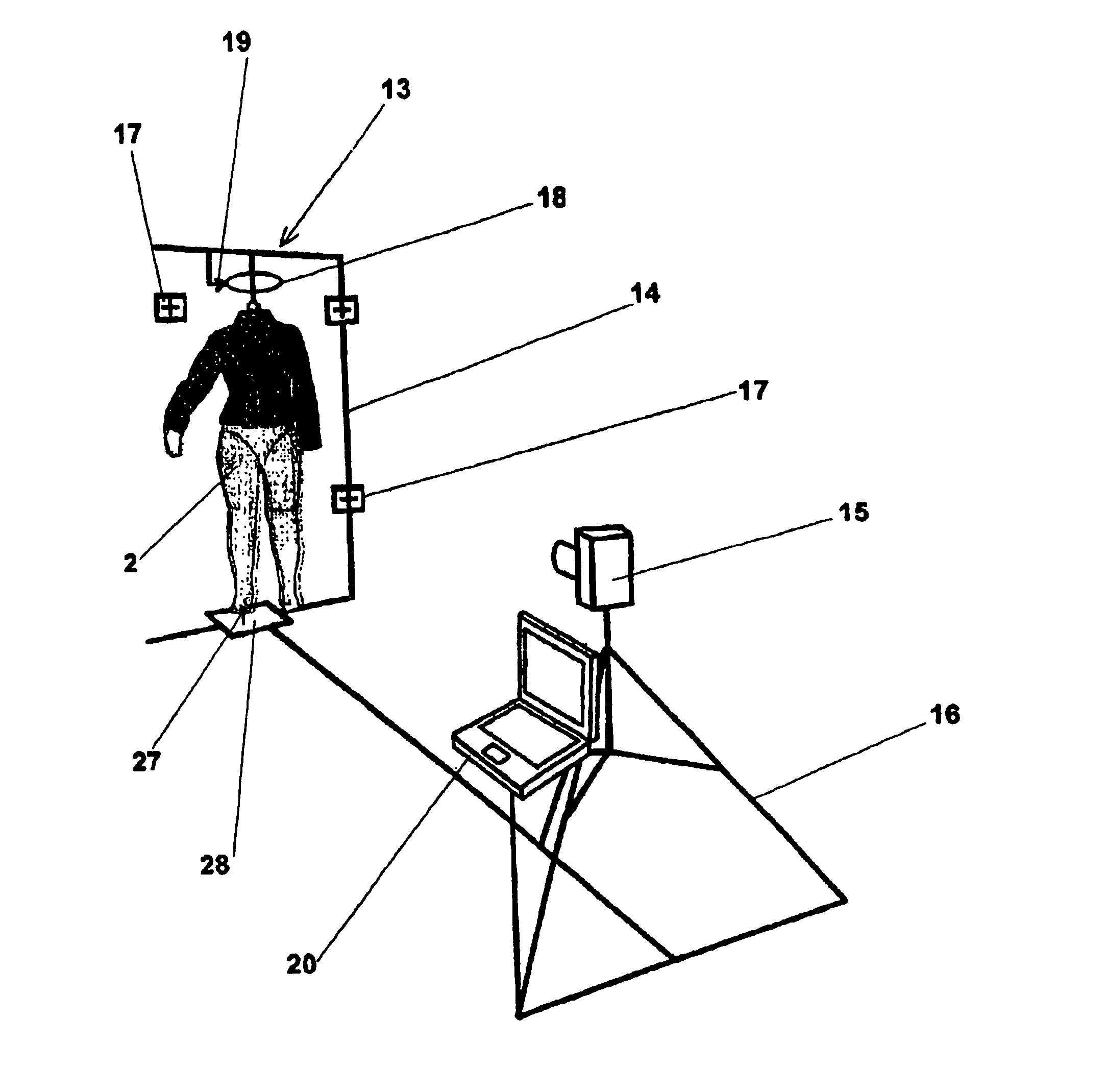
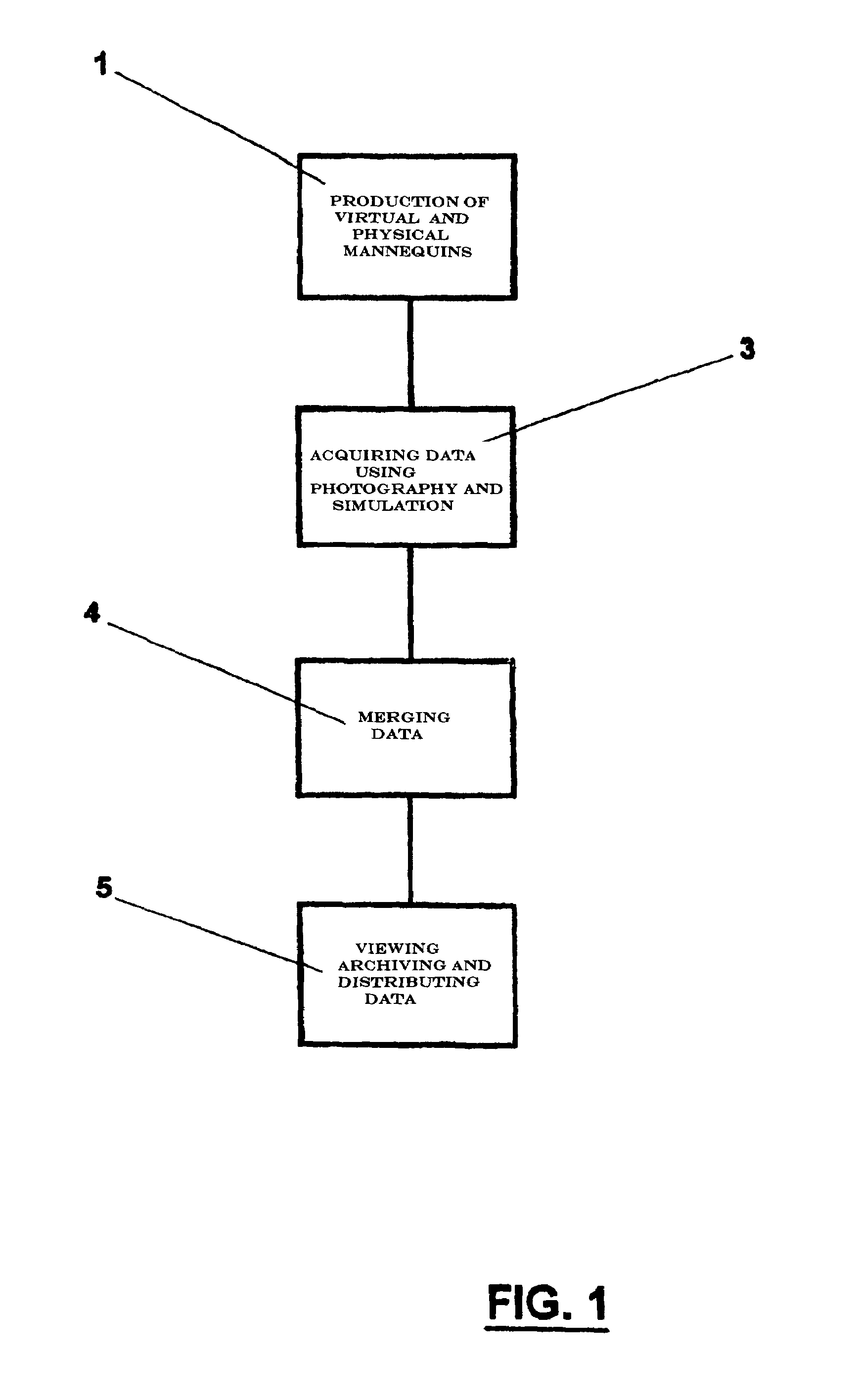
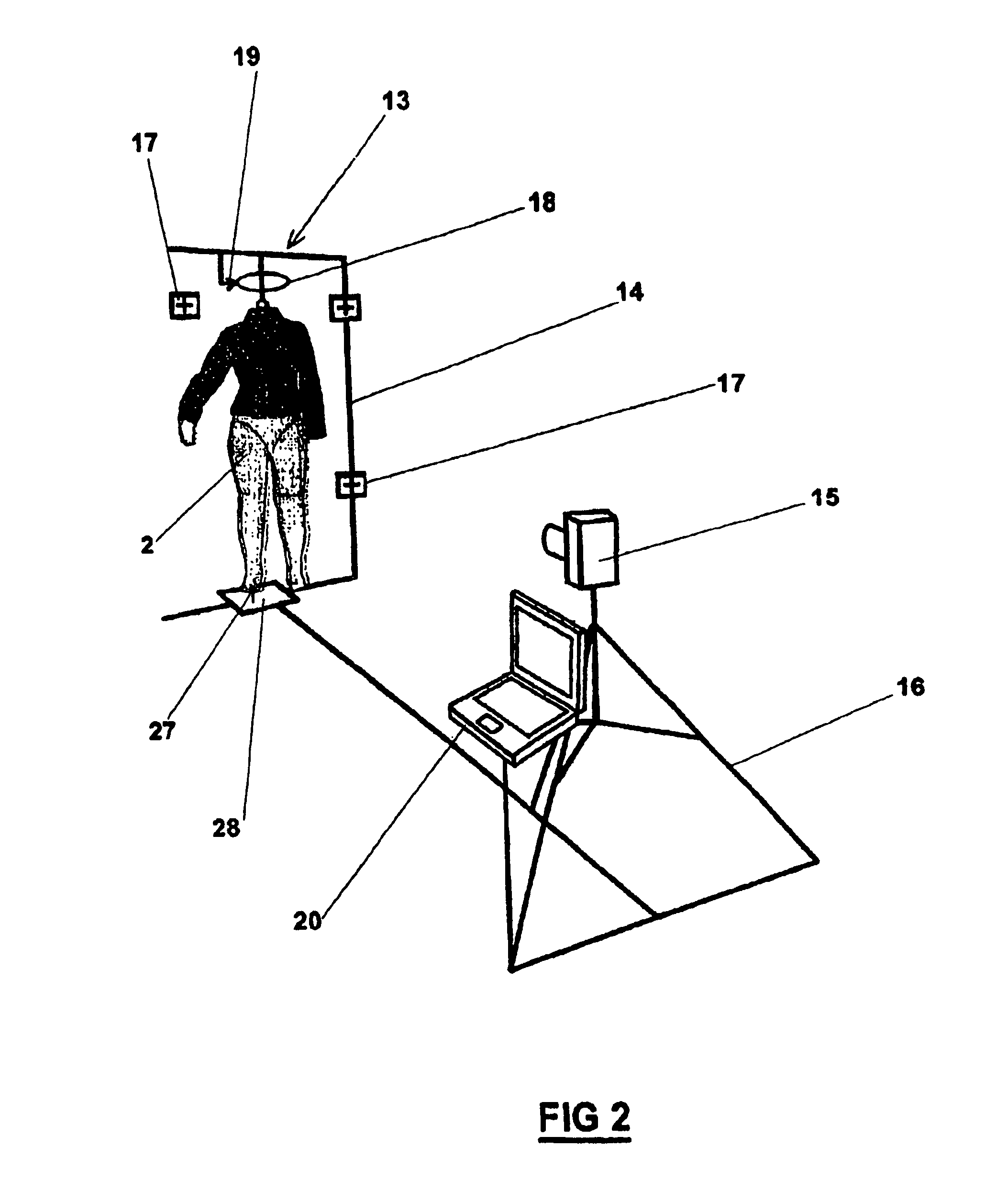
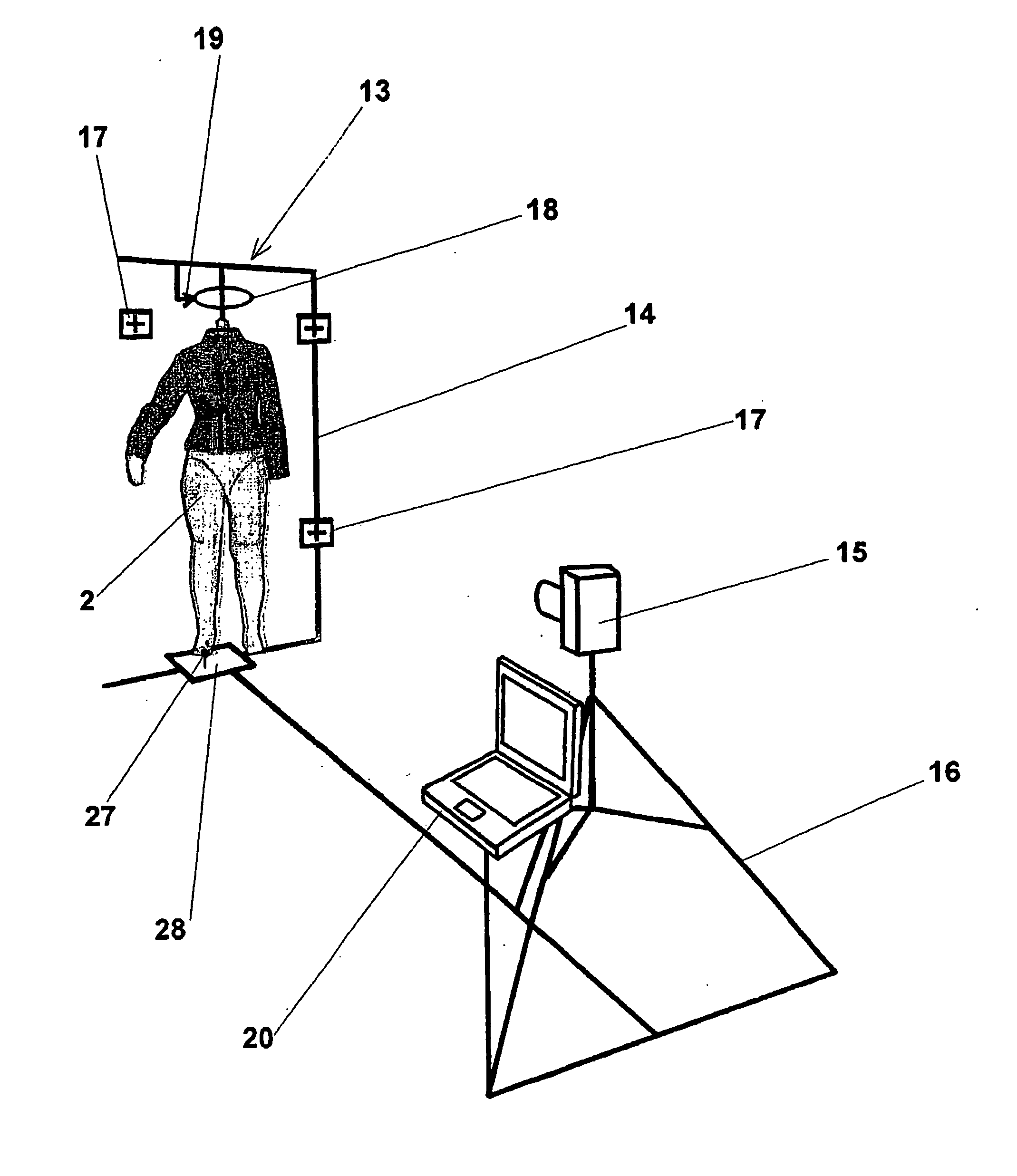
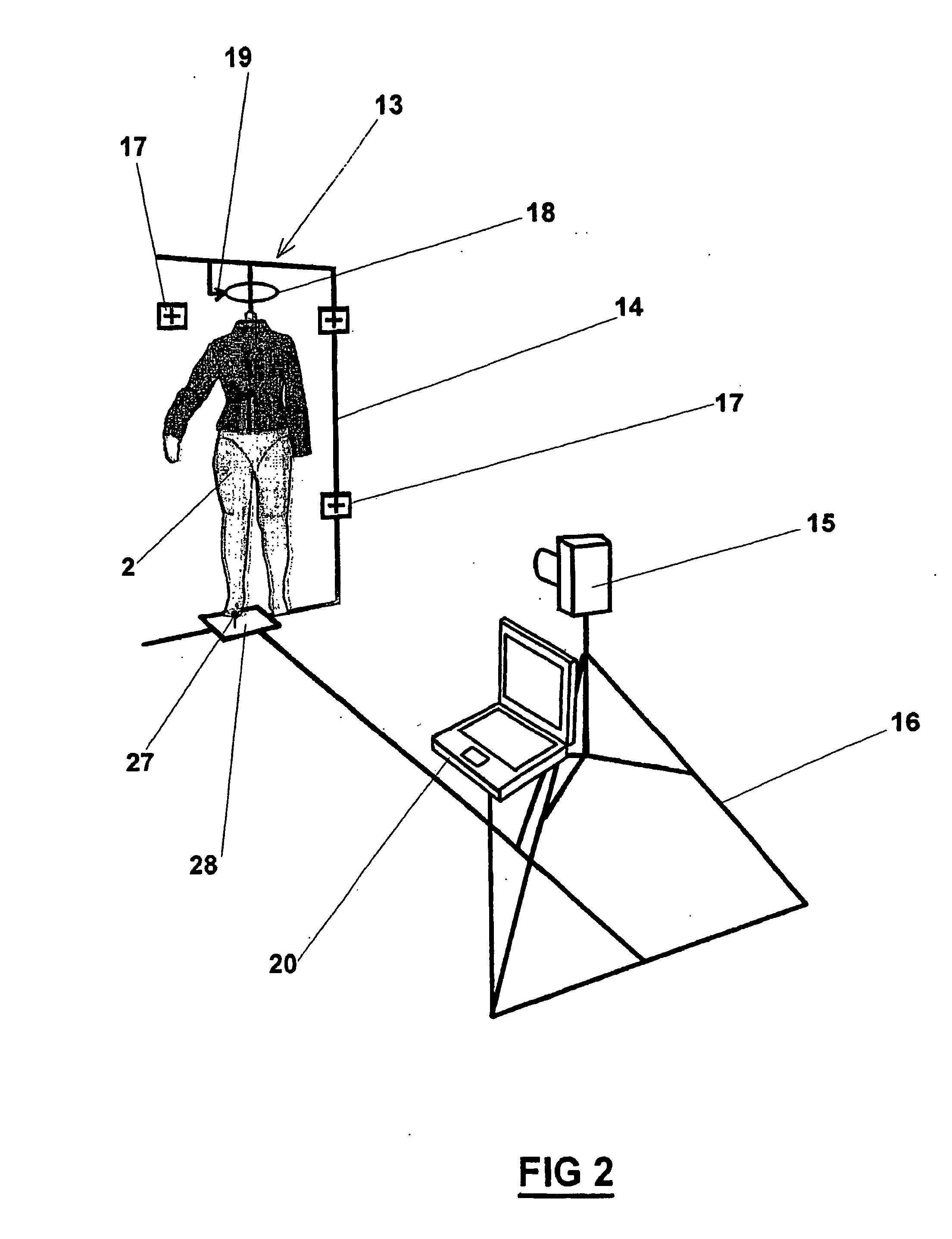
InactiveUS7039486B2Efficient communicationPrecise positioningMeasurement devicesSurgeryDigital imageReference line
A method and device for viewing, archiving and transmitting a garment model over a computer network. The method comprises photographing a physical mannequin from several different directions, the mannequin being a copy of a virtual human model which is representative of the target consumer. The virtual mannequin viewing layers and the garment model are generated from digital images of the naked or clothed mannequin which is suspended from the photography stand. A laser beam is used to determine the exact position of the mannequin. Subsequently, crop marks and recorded reference lines can be used to merge the viewing layers and the model precisely. The data are archived in a base and transmitted over an intranet, an extranet or the Internet for the purpose of remote viewing. The method and device are particularly suitable for the design, manufacture and inspection of clothing samples in the clothing industry.
Owner:WANG KENNETH KUK KEI
Method and device for viewing, archiving and transmitting a garment model over a computer network
InactiveUS20050154487A1Efficient communicationPrecise positioningMeasurement devicesSurgeryComputer graphics (images)Engineering
A method and device for viewing, archiving and transmitting a garment model over a computer network. The method comprises photographing a physical mannequin from several different directions, the mannequin being a copy of a virtual human model which is representative of the target consumer. The virtual mannequin viewing layers and the garment model are generated from digital images of the naked or clothed mannequin which is suspended from the photography stand. A laser beam is used to determine the exact position of the mannequin. Subsequently, crop marks and recorded reference lines can be used to merge the viewing layers and the model precisely. The data are archived in a base and transmitted over an intranet, an extranet or the Internet for the purpose of remote viewing. The method and device are particularly suitable for the design, manufacture and inspection of clothing samples in the clothing industry.
Owner:WANG KENNETH KUK KEI
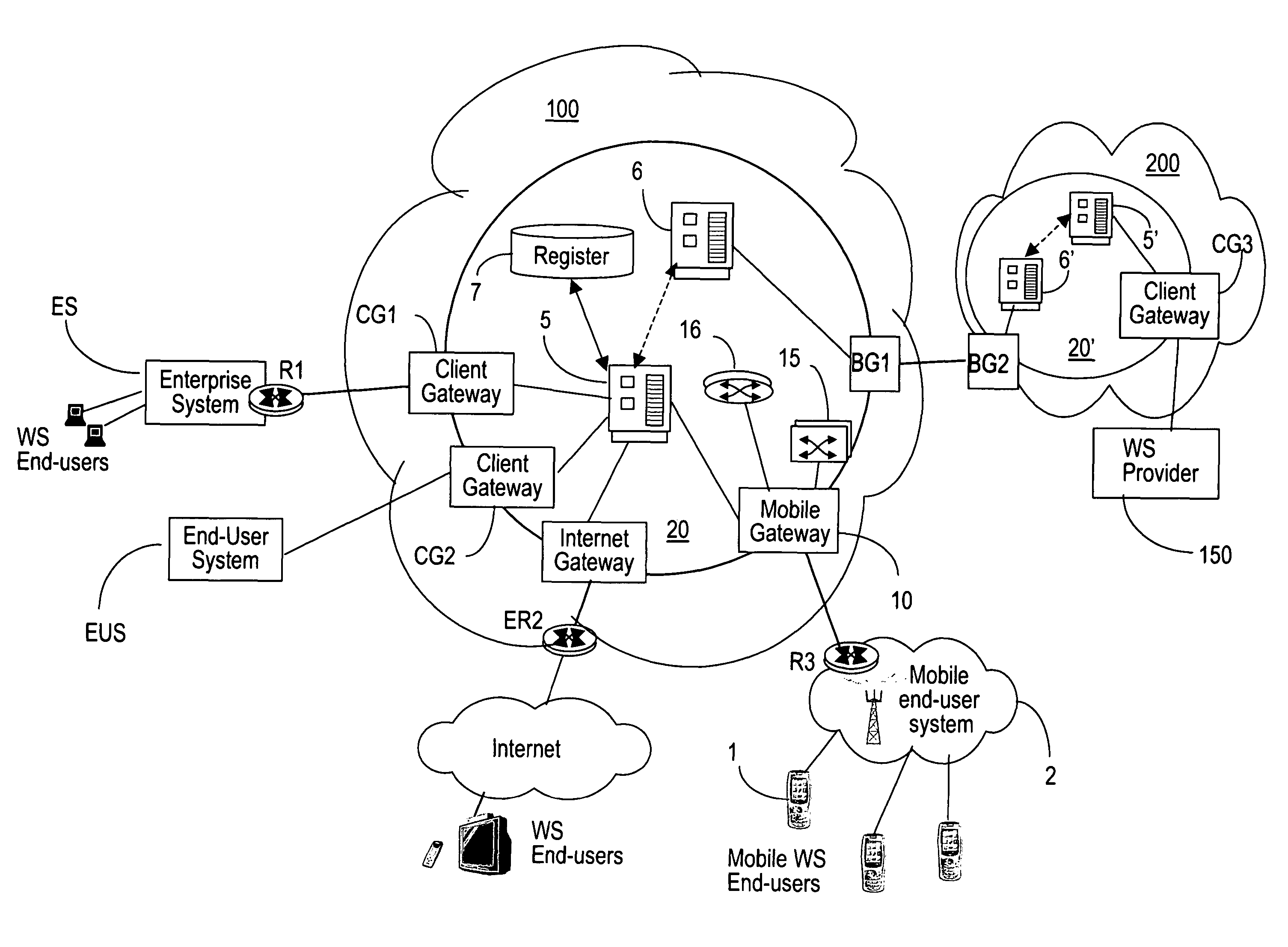
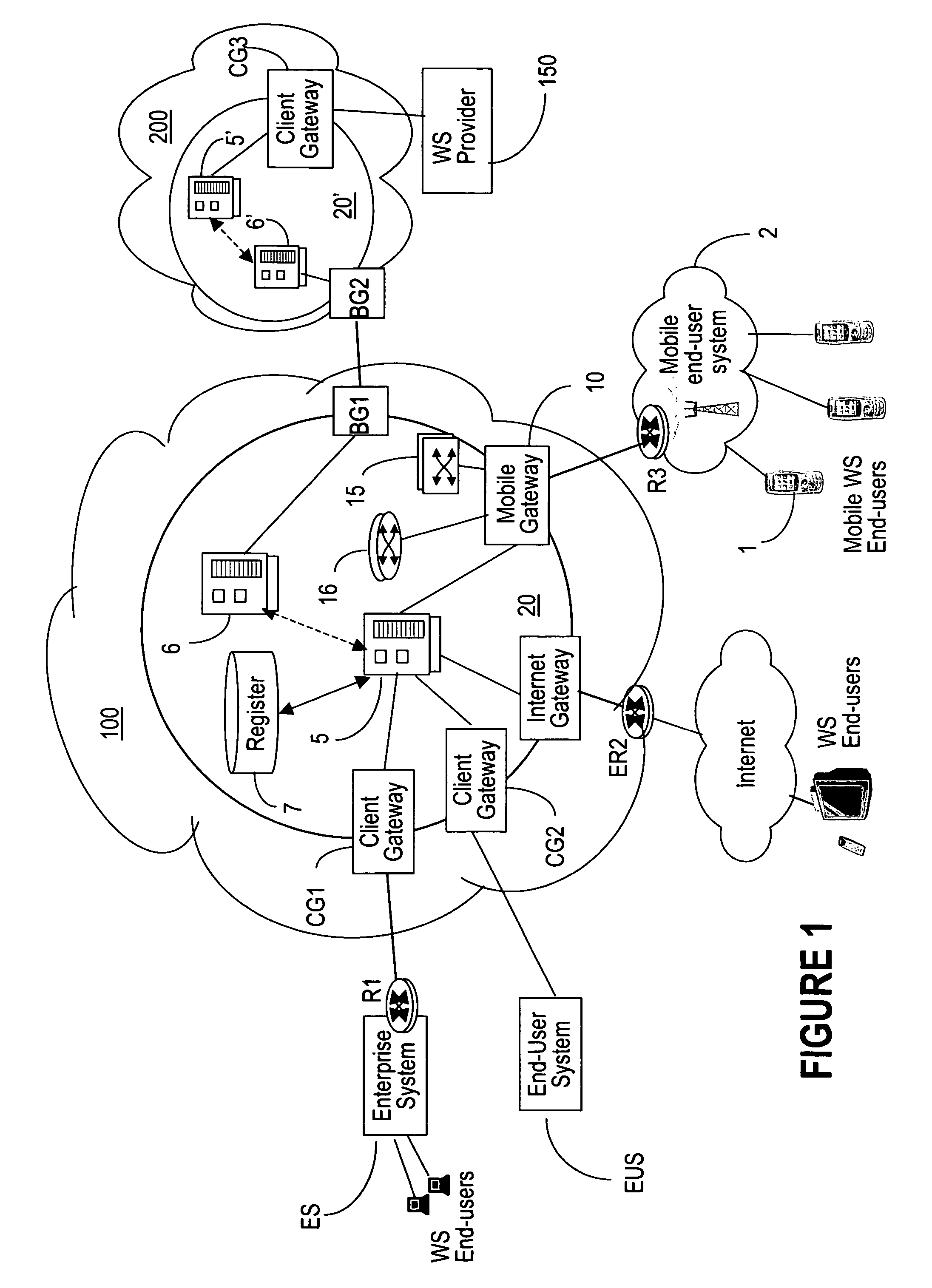
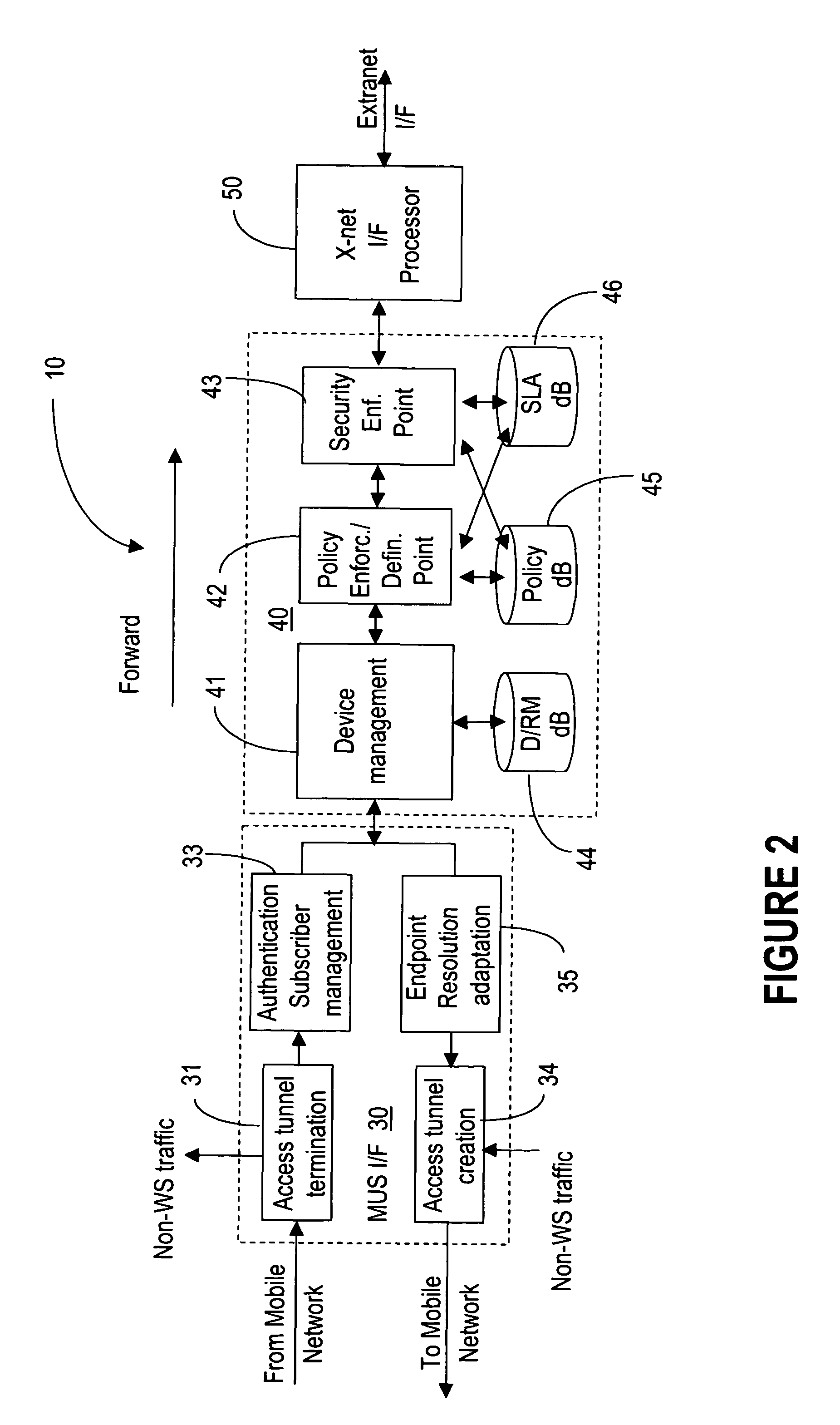
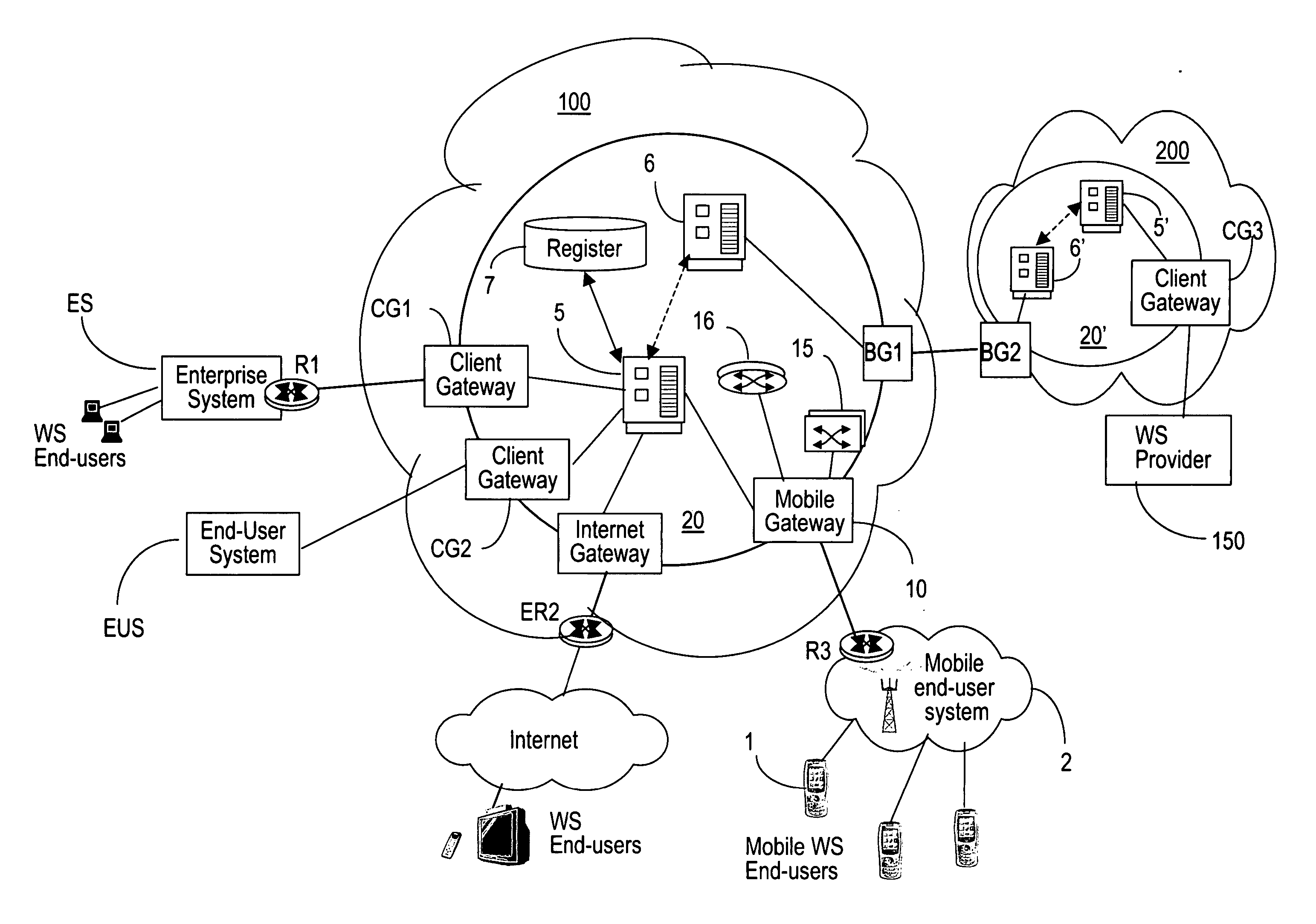
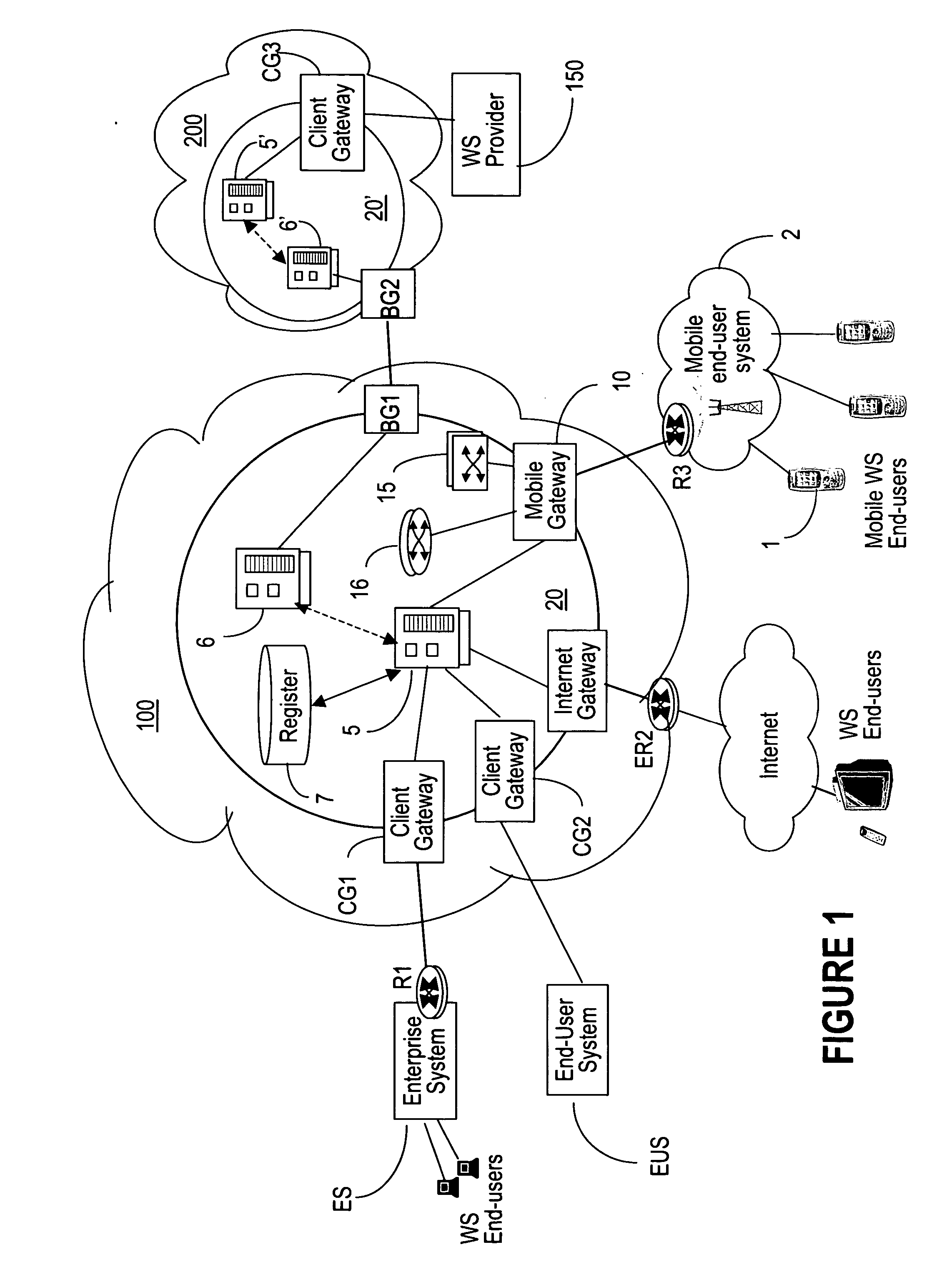
Mobile gateway device
InactiveUS7769877B2Easy accessConnection managementMultiple digital computer combinationsWeb serviceMobile end
Owner:ALCATEL LUCENT SAS
Automated text generation process
InactiveUS20050120002A1Natural language translationDigital data processing detailsGenerative processExternal application
The process of text generation / creation is automated. The text to be processed is used as seed for the text generation process. The text to be processed can be in any language and can be passed to text generation process through any internal / external application or process, through speech technology or through manual entry. At the first step, word(s) are extracted from the text. Each word is considered as seed and this seed is grown up into different word(s) / sentence(s) lists according to the selected criteria. The generated lists are then processed and combined / jointed through a simple mechanism to generate text. This generated text then can be saved, analyzed, filtered or searched on the internet, intranet, extranet, in database(s) or in user defined data repositories again according to the criteria selected by the user or by some external application or process.
Owner:BEHBEHANI HASSAN
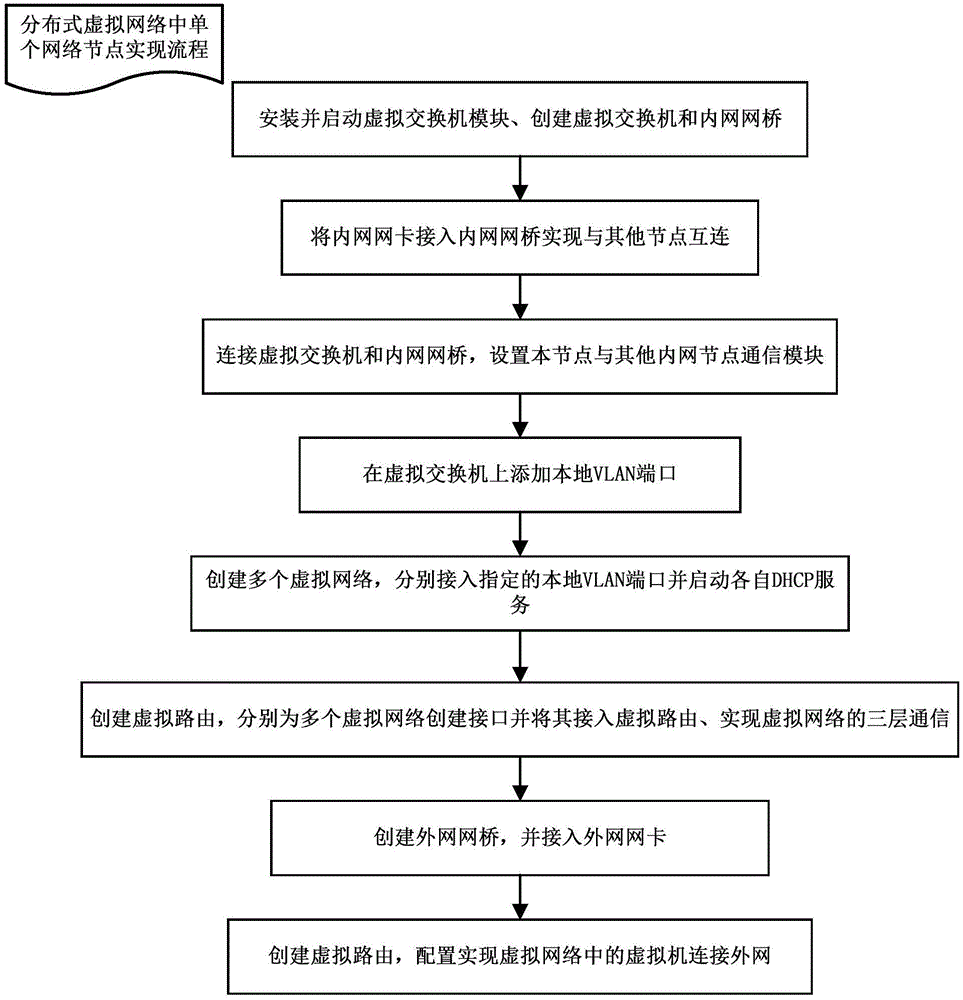
Method for realizing distributed virtual networks applicable to cloud platform
InactiveCN104468746AAvoid single point of failure problemsDoes not affect the normal provision of network servicesNetworks interconnectionComputer moduleVirtual switch
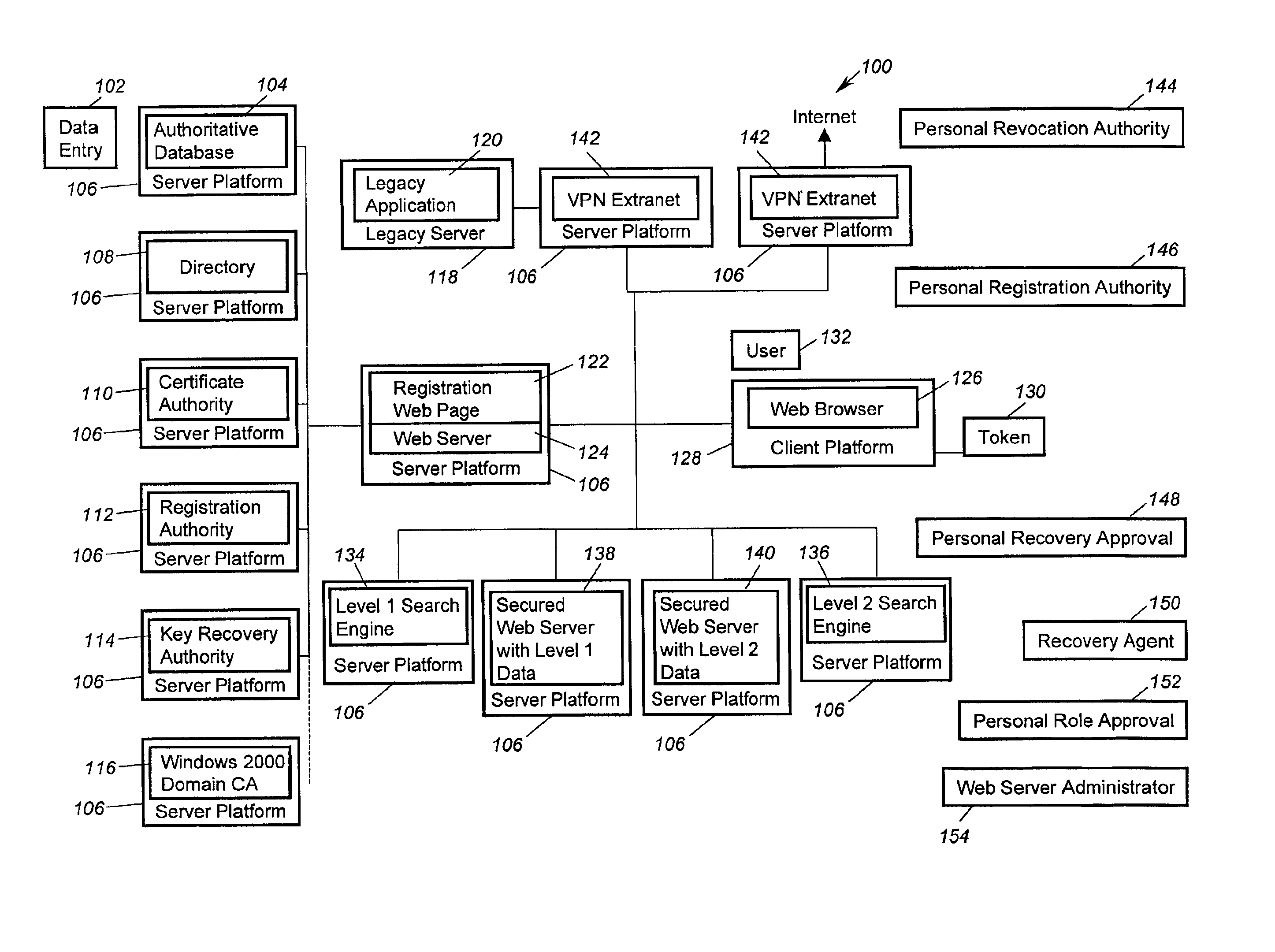
The invention relates to the technical field of cloud computing management, in particular to a method for distributed virtual networks applicable to a cloud platform. According to the method, any number of physical nodes are selected as network nodes of the cloud platform, and the network nodes establish and provide virtual network service; establishment of the network nodes includes the steps that (1), a virtual switch module is installed and started, and a virtual switch and an intranet network bridge are established; (2), an intranet network card is connected into the intranet network bridge; (3), the virtual switch and the intranet network bridge are connected, and a communication module for the node and other intranet nodes is set; (4), local VLAN ports are added; (5), the multiple virtual networks are established; (6), a virtual route is established; (7), an extranet network bridge is established, and an extranet network card is connected in; (8), a virtual route is established. Single-point failures of centralized network service of the cloud platform can be avoided, load balance of the network service nodes is achieved, the virtual networks can be managed flexibly and conveniently, and the method can be used for realizing the distributed virtual networks.
Owner:G CLOUD TECH
Mobile gateway device
InactiveUS20070255852A1Easy accessConnection managementMultiple digital computer combinationsWeb serviceMobile end
The WS-Mobile Gateway is the interworking gateway between users of a mobile network and a WS extranet. The mobile gateway comprises a mobile end-user interface on the side of the mobile network, for user authentication and for separating the web services (WS) traffic from the non-WS traffic. A logic unit performs protocol conversion, address resolution, policy enforcement / definition and publishing operations on the WS traffic. An extranet interface processor routes the WS packets carrying control messages between the gateway and a WS controller which maintains the services registry, while the WS packets carrying data are routed between the mobile gateway and the WS provider.
Owner:ALCATEL LUCENT SAS
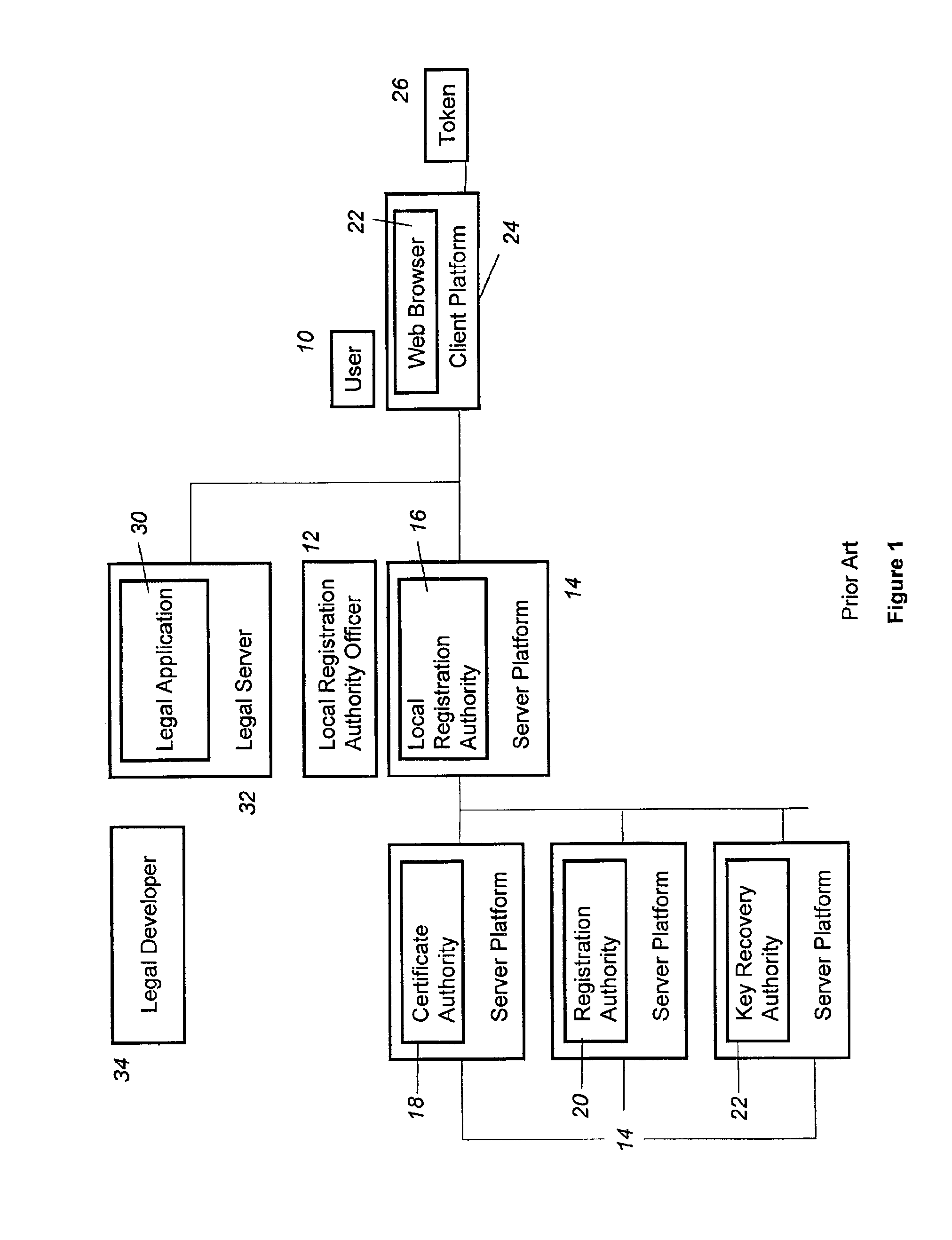
System and method for secure legacy enclaves in a public key infrastructure
InactiveUS6898710B1User identity/authority verificationUnauthorized memory use protectionPrivate networkApplication software
System and method for secure legacy enclaves in a Public Key Infrastructure that includes one or more legacy servers, client platforms, directories, and a Virtual Private Network extranet gateway. The servers contain one or more legacy applications and are connected to a first network. The client plafforms are connected to a second network and contain legacy software employable by users to access the legacy applications. The directories are connected to the second network and contain information on user authorization to access the servers. The gateway is connected between the servers and the second network. The gateway requests a signature certificate of each user attempting access to a legacy application; queries the directory to confirm the user is allowed access to the server after authenticating the user; and establishes a connection between the legacy software and the legacy application if the user is allowed access to the server.
Owner:NORTHROP GRUMMAN SYST CORP
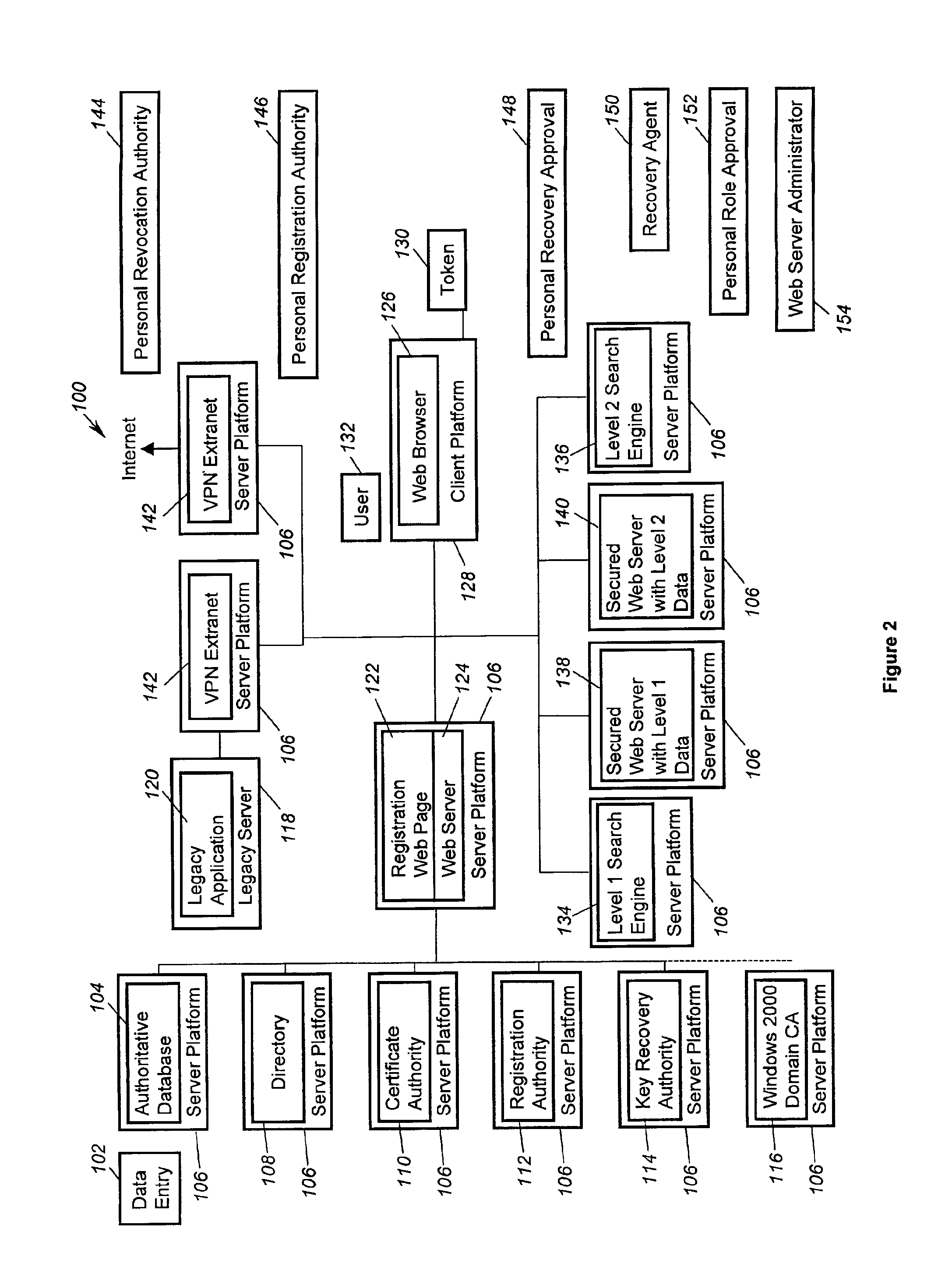
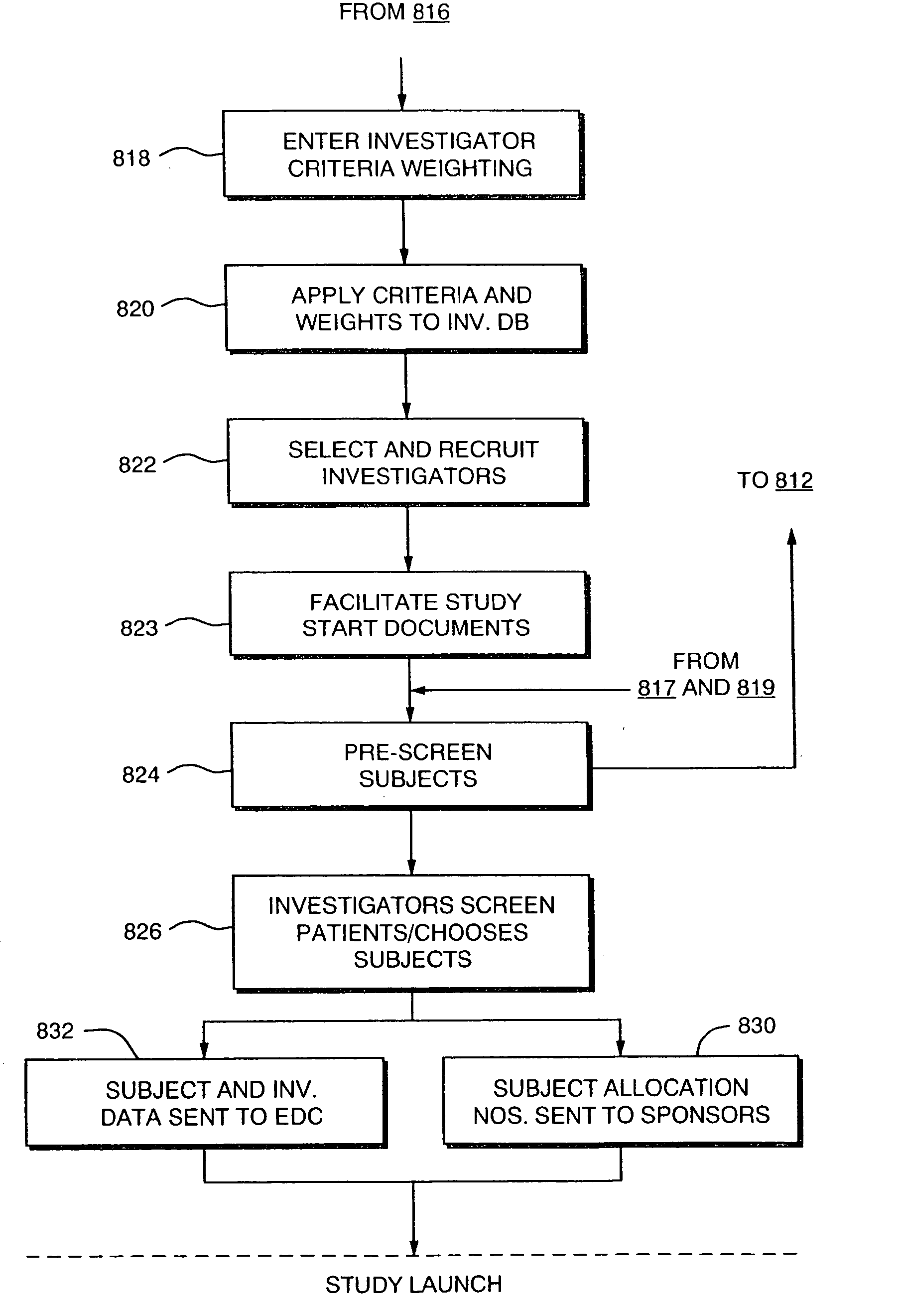
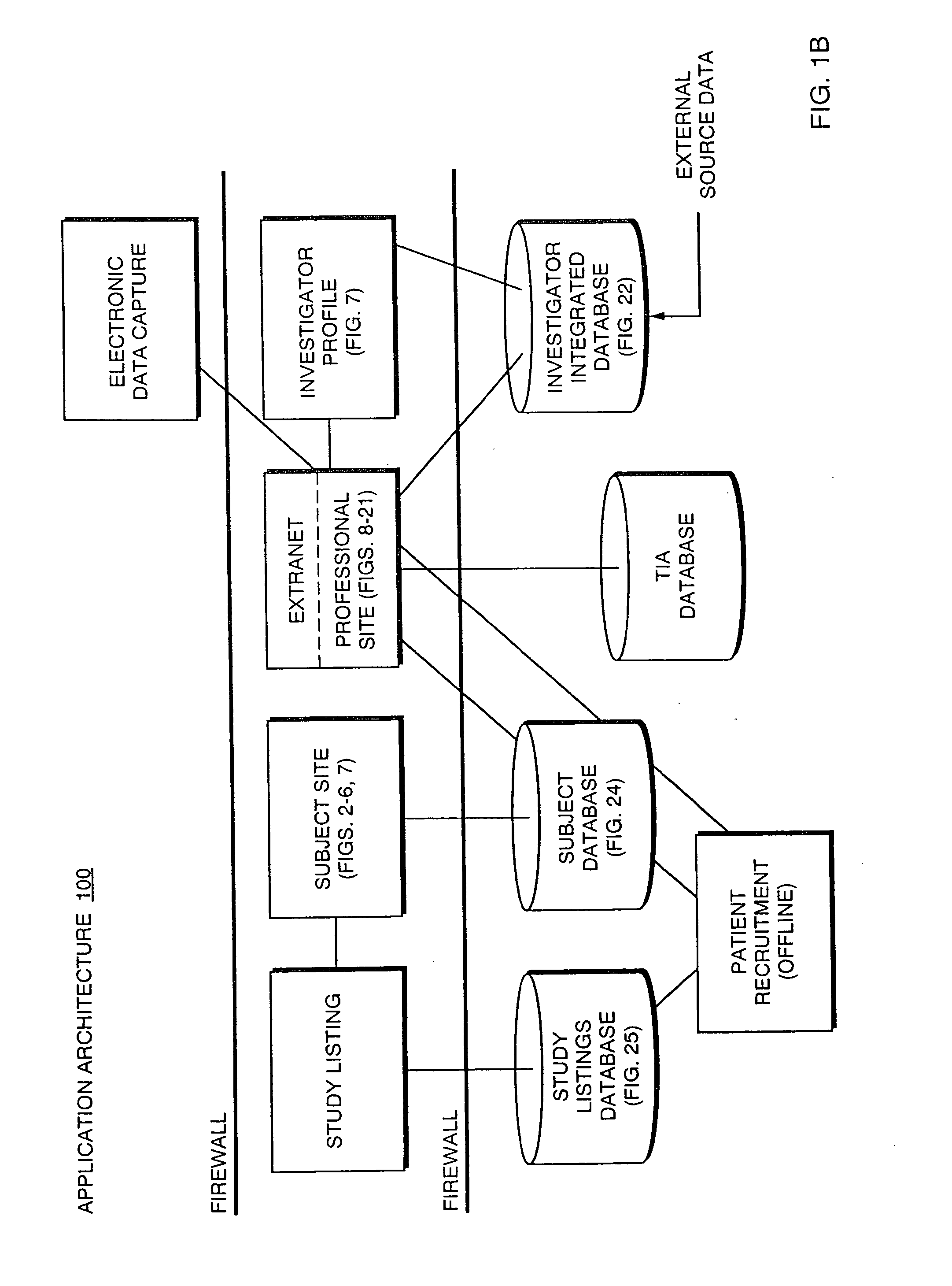
Systems and Methods for Selecting and Recruiting Investigators and Subjects for Clinical Studies
InactiveUS20080133270A1Computer-assisted medical data acquisitionOffice automationMedicineSubject matter
The present invention is directed to an integrated on-line interactive forum that promotes exchange of information among clinical study sponsors, clinical study investigators, and potential clinical study subjects. The forum includes an investigator database that contains information suitable for identification of qualified investigators for clinical studies and a subject database that contains information suitable for identification of eligible subjects for clinical studies. An extranet is coupled to the investigator database and the subject database. The extranet allows sponsors and investigators to exchange securely documents required to start a clinical study. The forum also optionally includes one or more web pages that provide information describing clinical studies to potential clinical study subjects and permit potential clinical study subjects to register for inclusion in the subject database. A therapeutic incidence area database is also optionally integrated into the forum
Owner:MICHELSON LESLIE DENNIS +2
Automatic and semi-automatic image classification, annotation and tagging through the use of image acquisition parameters and metadata
ActiveUS8520909B2Improve accuracyCharacter and pattern recognitionMetadata still image retrievalTimestampSemi automatic
A method for characterizing image contents automatically or semi-automatically using image acquisition parameters and metadata is presented. The method establishes probabilistic and deterministic relationships between different types of metadata and the semantic attributes and contents of images. It furnishes a mechanism that enables the automatic and semi-automatic classification, annotation, tagging, indexing, searching, identification or retrieval of images based on their contents, semantic properties and metadata characteristics. The method uses, but is not limited to, image capture metadata such as focal length, exposure time, relative aperture, flash information, ISO setting, angle of view, subject distance, timestamp, GPS information as well as other forms of metadata, including but not limited to, captions, keywords, headings, tags, comments, remarks, titles which may be automatically, semi-automatically, or manually generated. The present invention can be applied to image databases, web searching, personal search, community search, broad-based or vertical search engines for internet, intranet, extranet or other usages.
Owner:HONG KONG BAPTIST UNIV
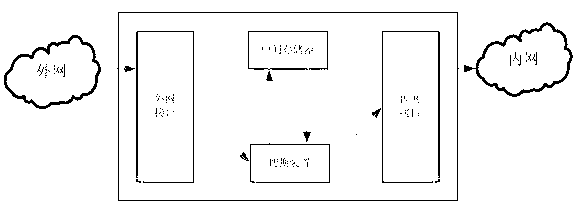
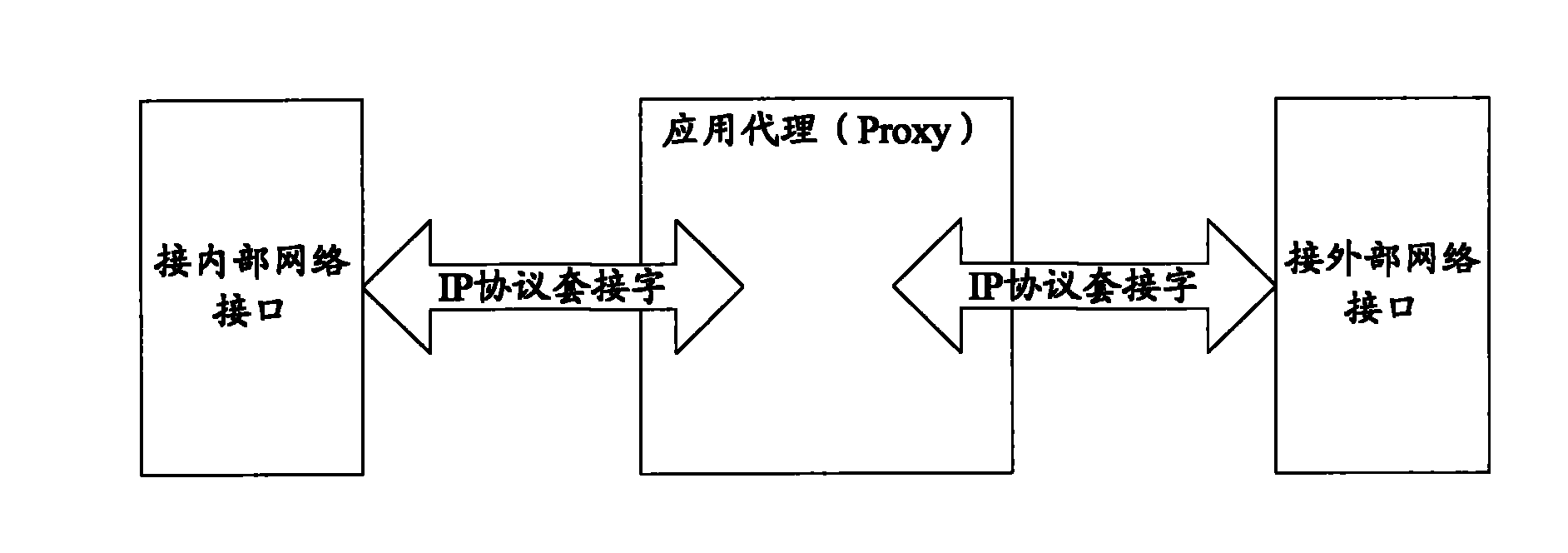
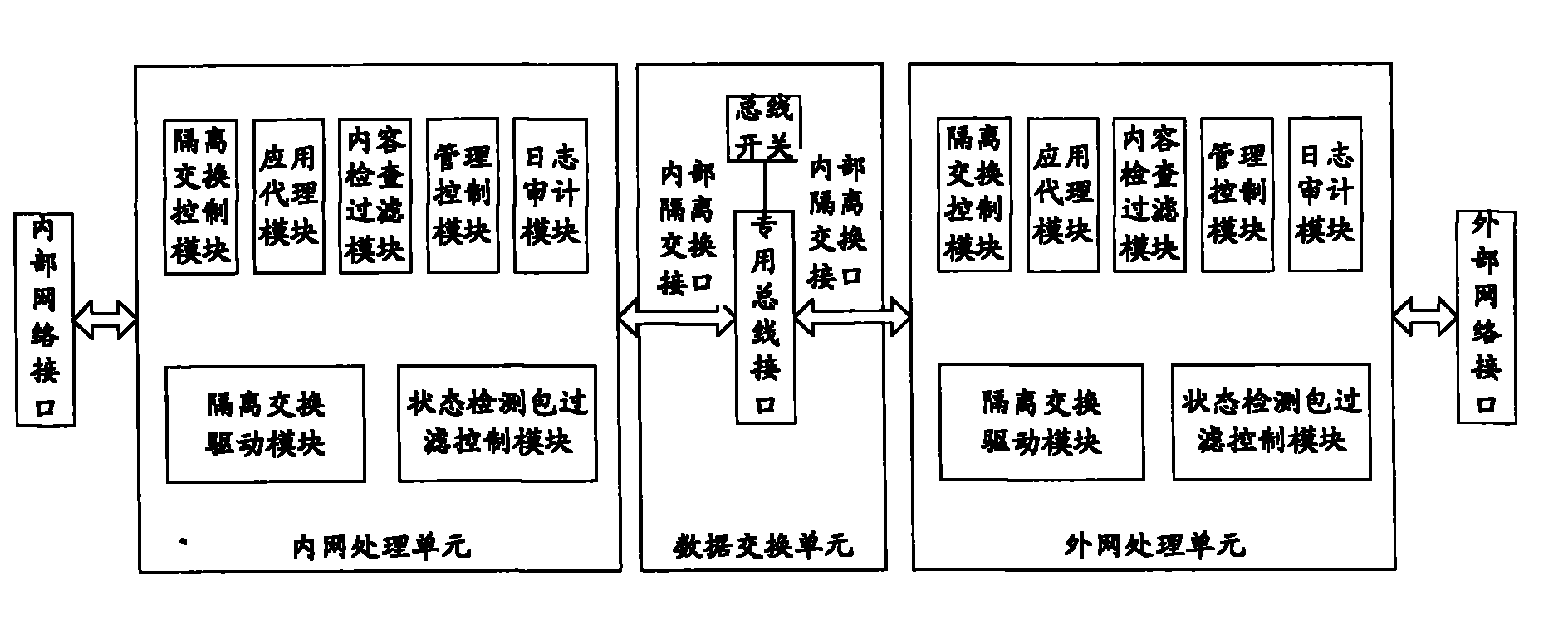
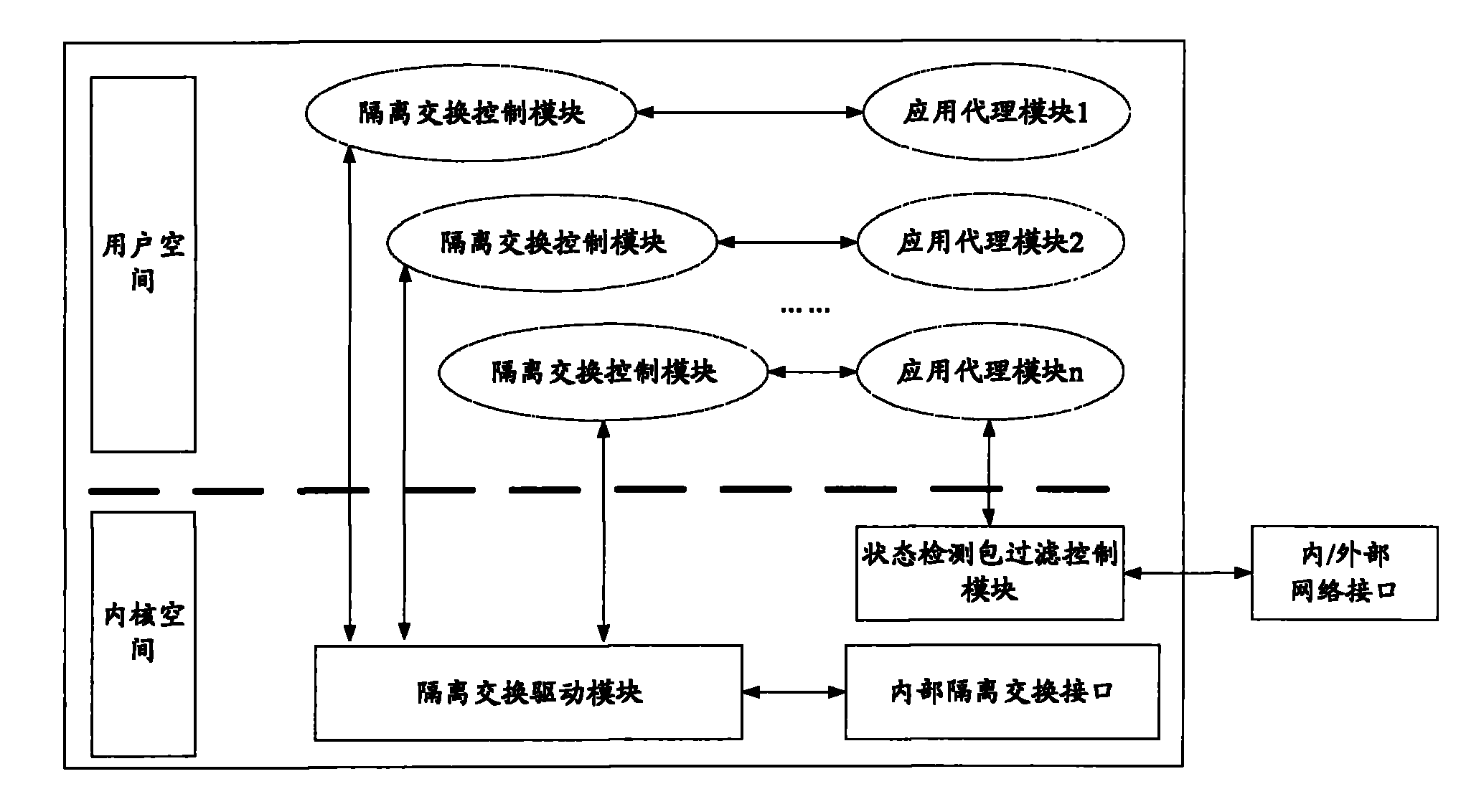
Application proxy-based network management system isolation control device
InactiveCN102006307ASolve data exchange problemsIncrease controlData switching networksComputer moduleBus interface
The invention provides an application proxy-based network management system isolation control device, which comprises an intranet processing unit, an extranet processing unit and a data exchange unit, wherein the intranet processing unit comprises an isolation exchange control module and an application proxy module; the extranet processing unit comprises an isolation exchange control module and an application proxy module; and the data exchange unit consists of a special bus interface and a bus switch and is based on an non-(internet protocol) IP protocol, the special data bus exchanges the data between the intranet processing unit and the extranet processing unit, and prevents attack from the leaks of the transmission control protocol (TCP) / IP. In the invention, the network attack behavior aiming at a TCP stack can be prevented by adopting a specific non-IP protocol and an internal isolation exchange interface.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Method and system for sending information on an extranet
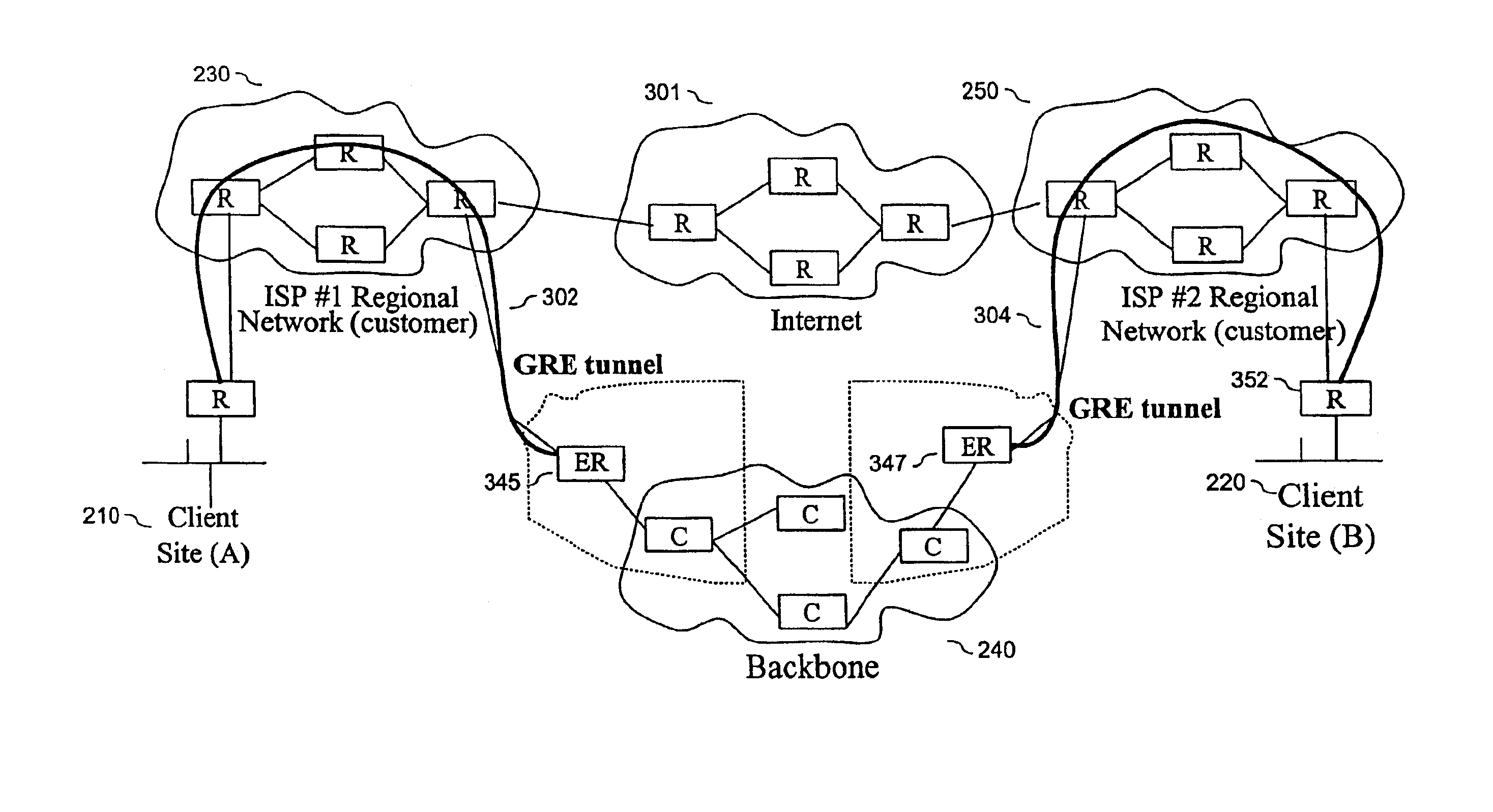
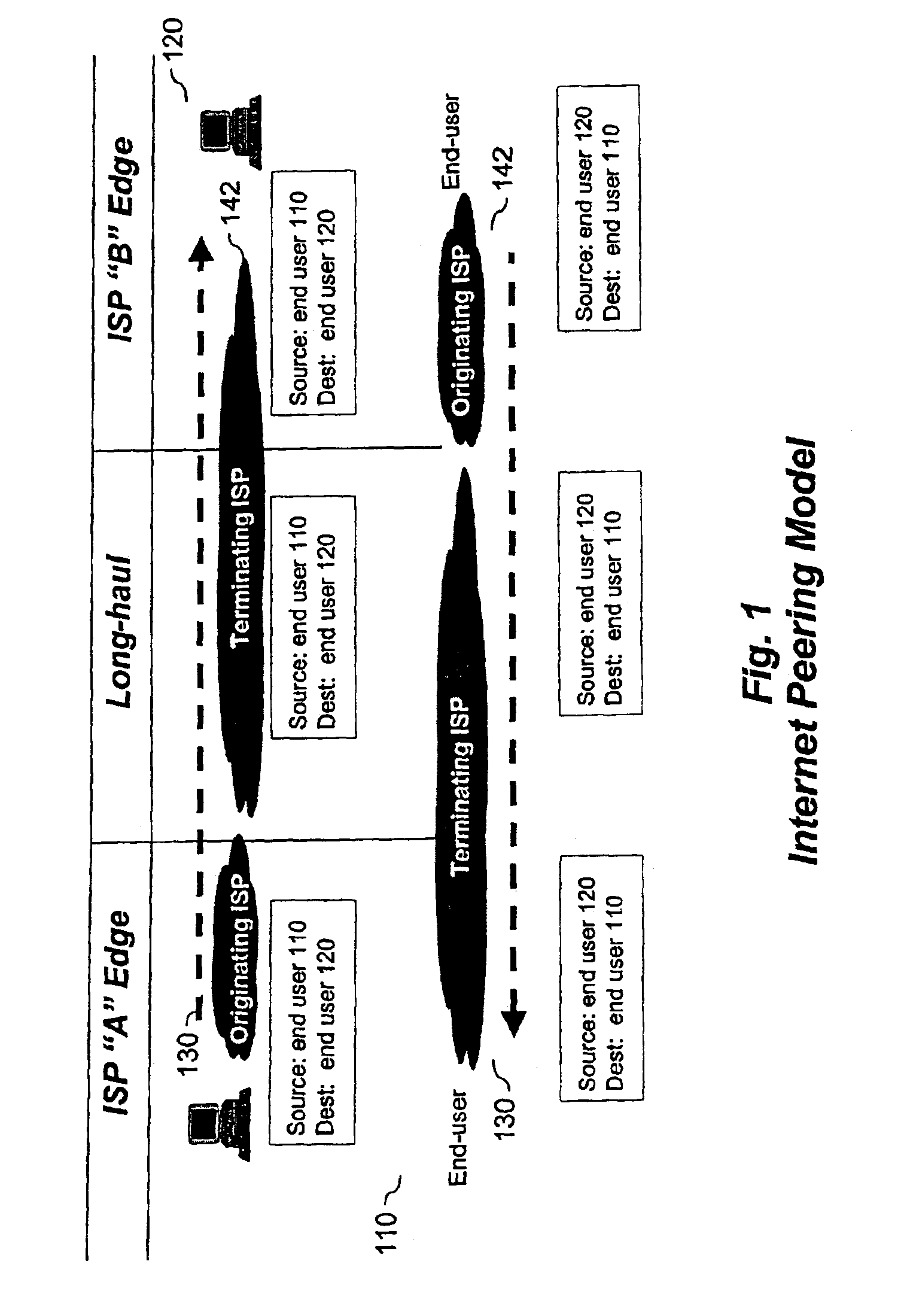
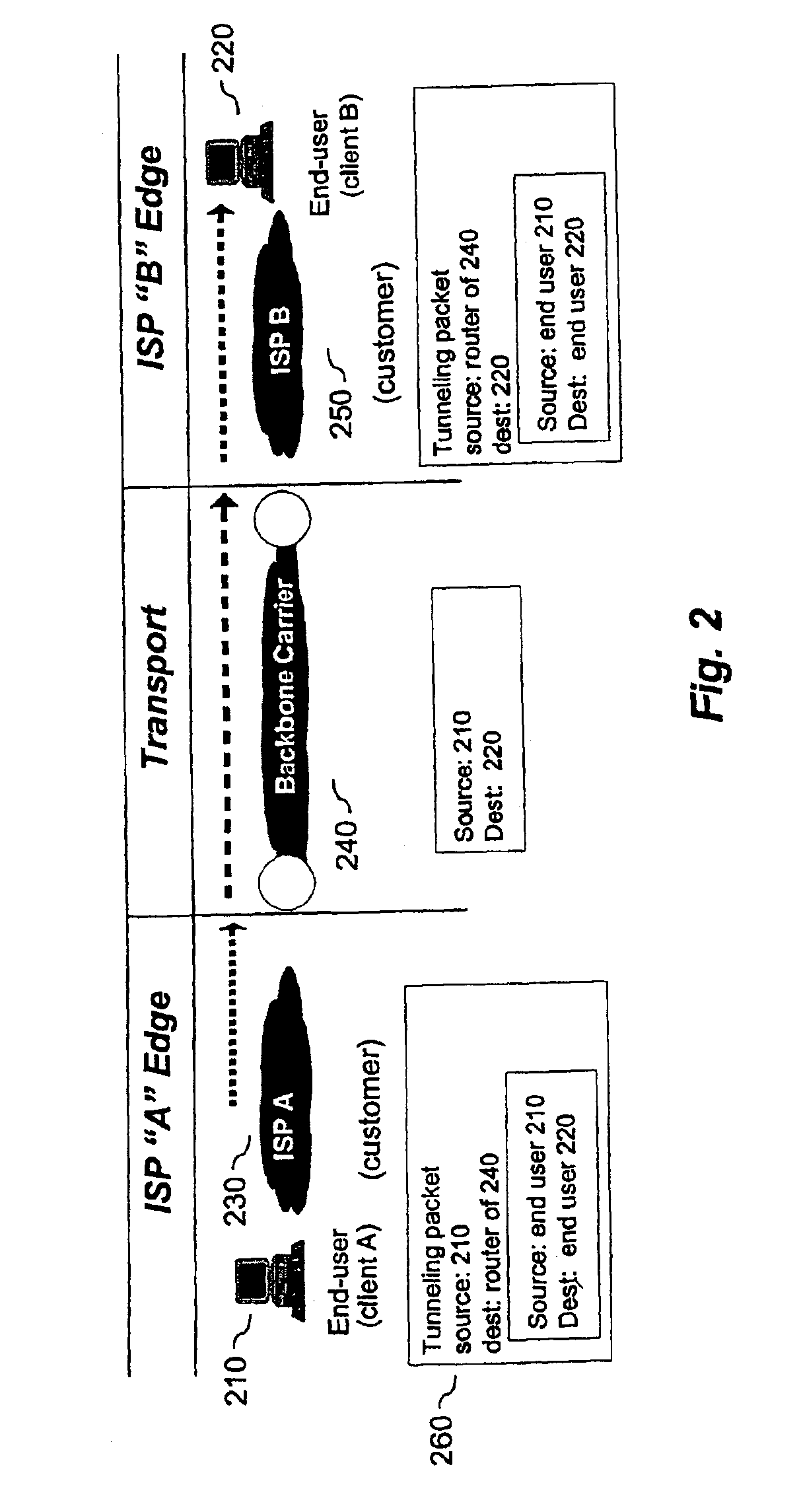
InactiveUS6965937B2Few hopImprove transmission qualityMetering/charging/biilling arrangementsTelephonic communicationDistributed computingExtranet
A method and system providing a single, symmetric path for forward and return traffic between two points on a network.
Owner:COREEXPRESS +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com