Application proxy-based network management system isolation control device
A technology for applying agents and control devices, applied in the network field, to achieve the effect of enhanced control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
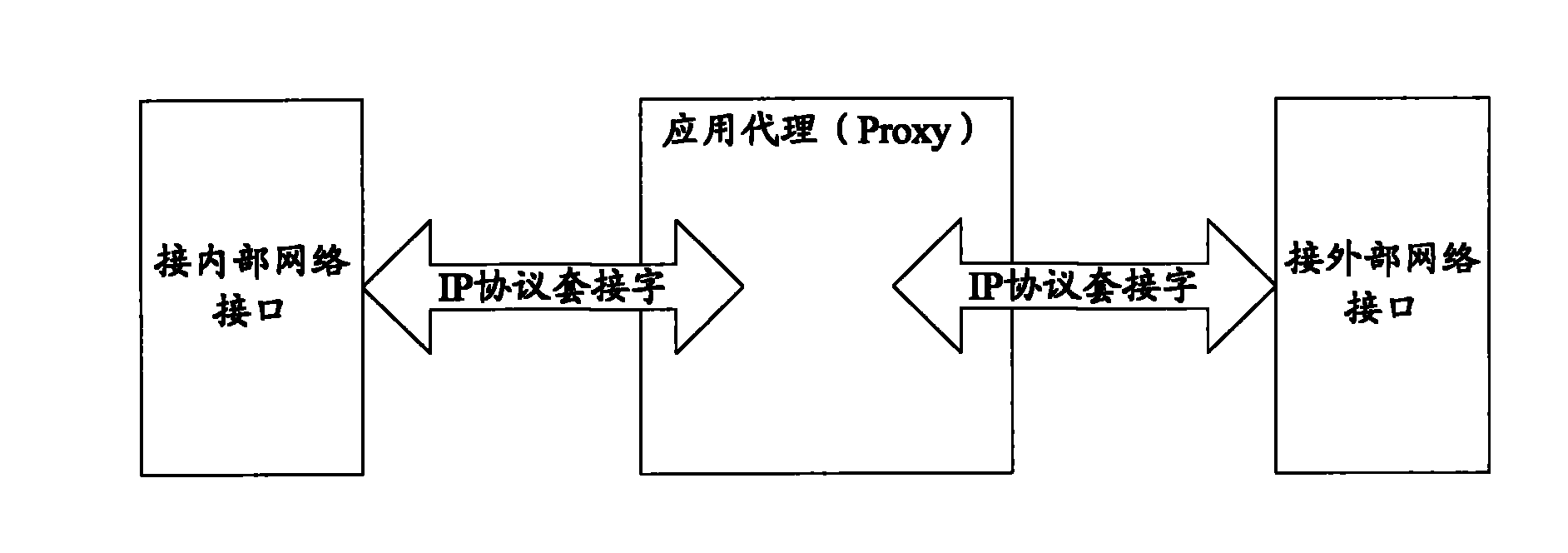
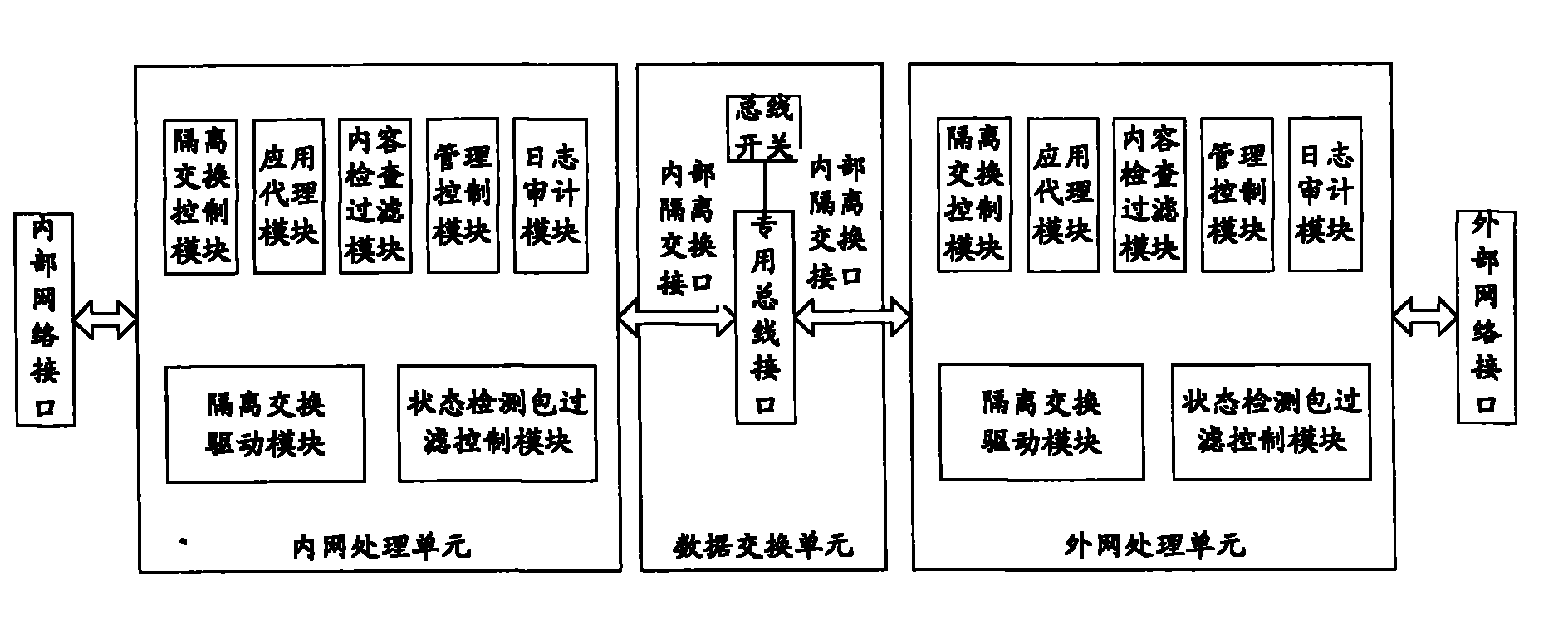
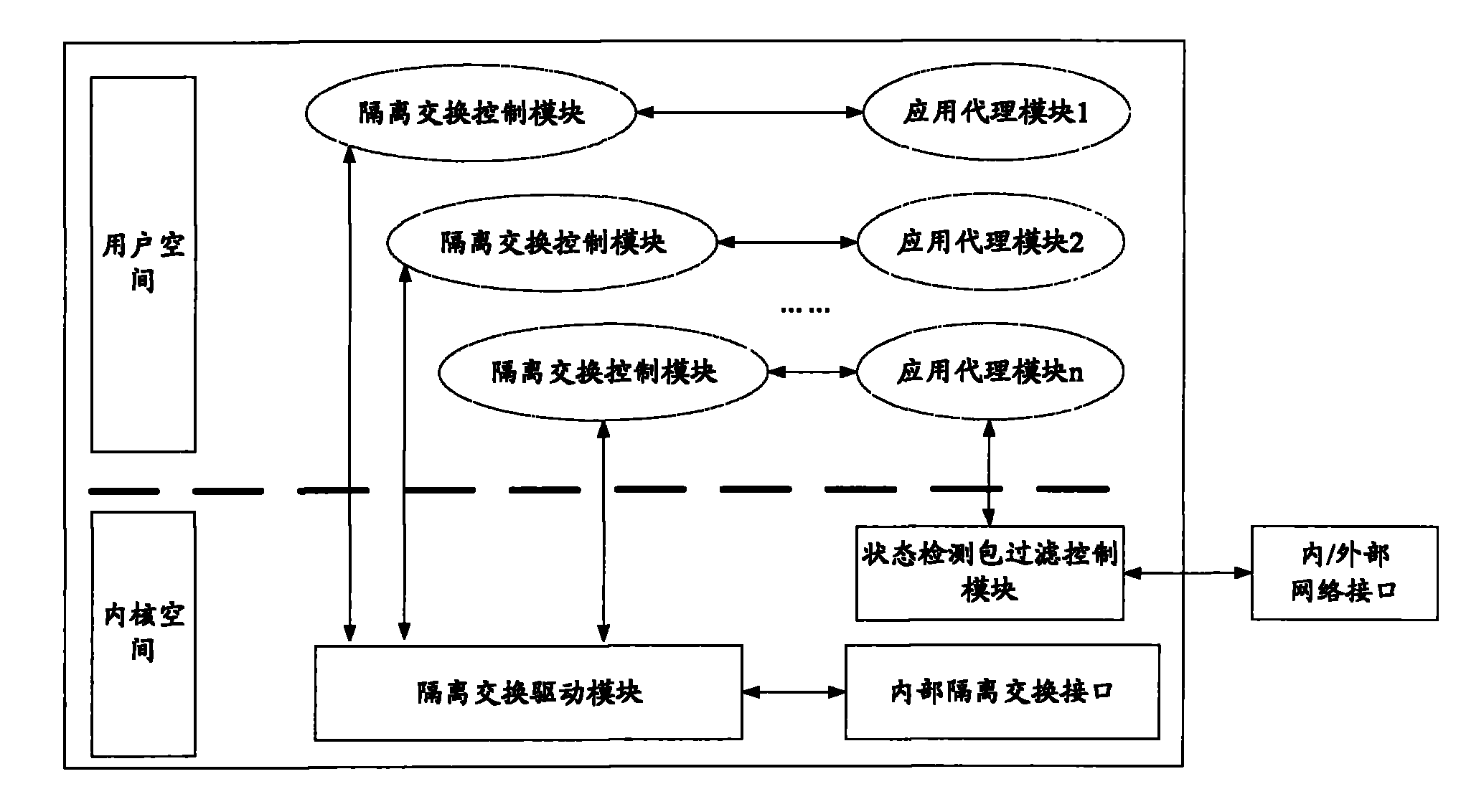
[0026] Below, refer to the attached Figure 1~5 The application agent-based network management system isolation control device of the present invention is described in detail.
[0027] like figure 2 As shown, the application agent-based network management system isolation control device of the present invention includes an internal network processing unit, an external network processing unit and a data exchange unit.
[0028] Among them, the intranet processing unit includes an isolated switching control module and an application agent module, wherein the isolated switching control module of the intranet processing unit is used to realize the encapsulation and restoration of the special format of data transmitted between the internal and external network processing units, that is, from the bottom layer The driver obtains the data transmitted by the external network processing unit, encapsulates and restores it from the data link layer to the application layer in turn, and di...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com