Patents
Literature
622 results about "Network isolation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Isolation network. A network inserted in a circuit or transmission line to prevent interaction between circuits on each side of the insertion point.
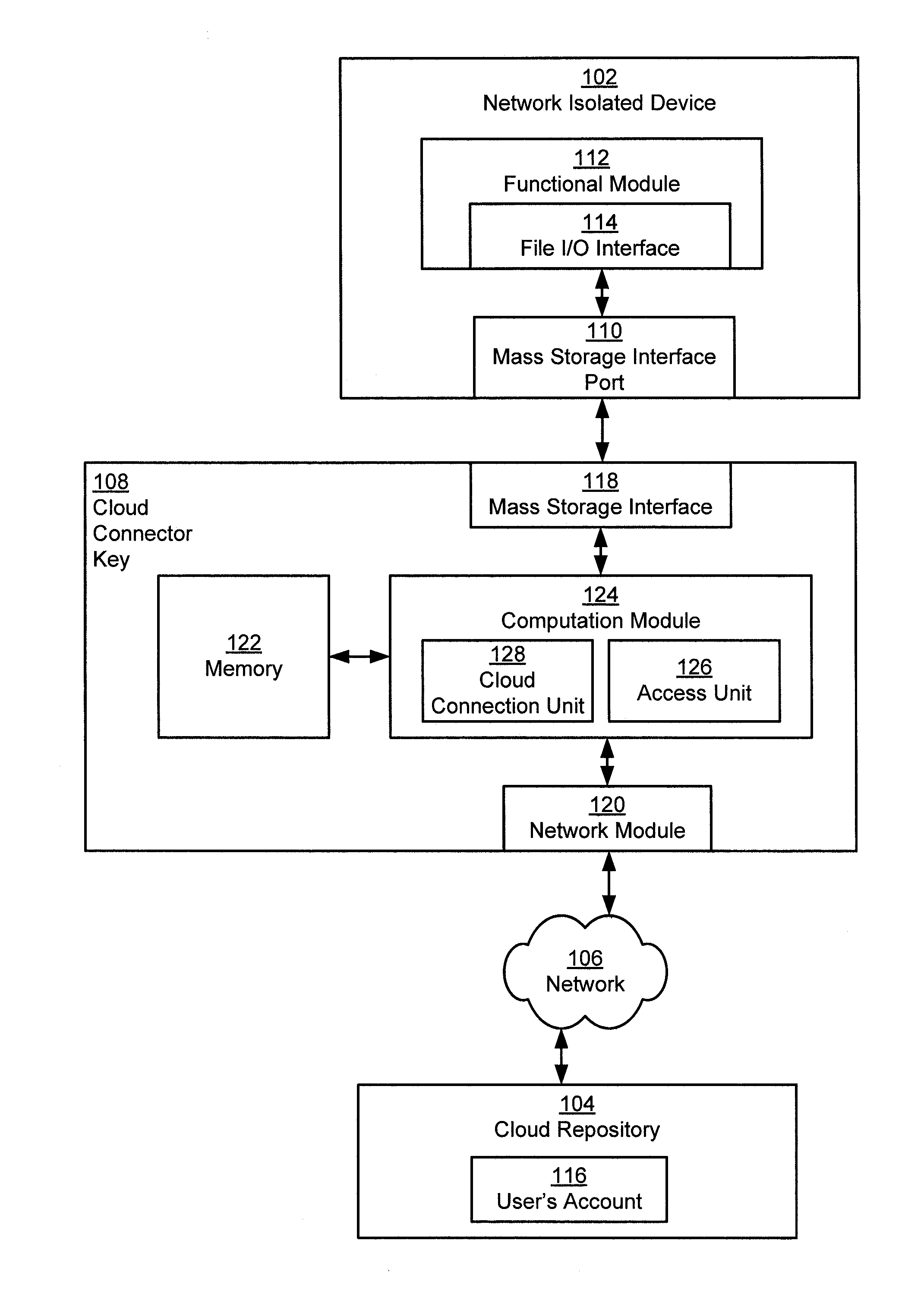
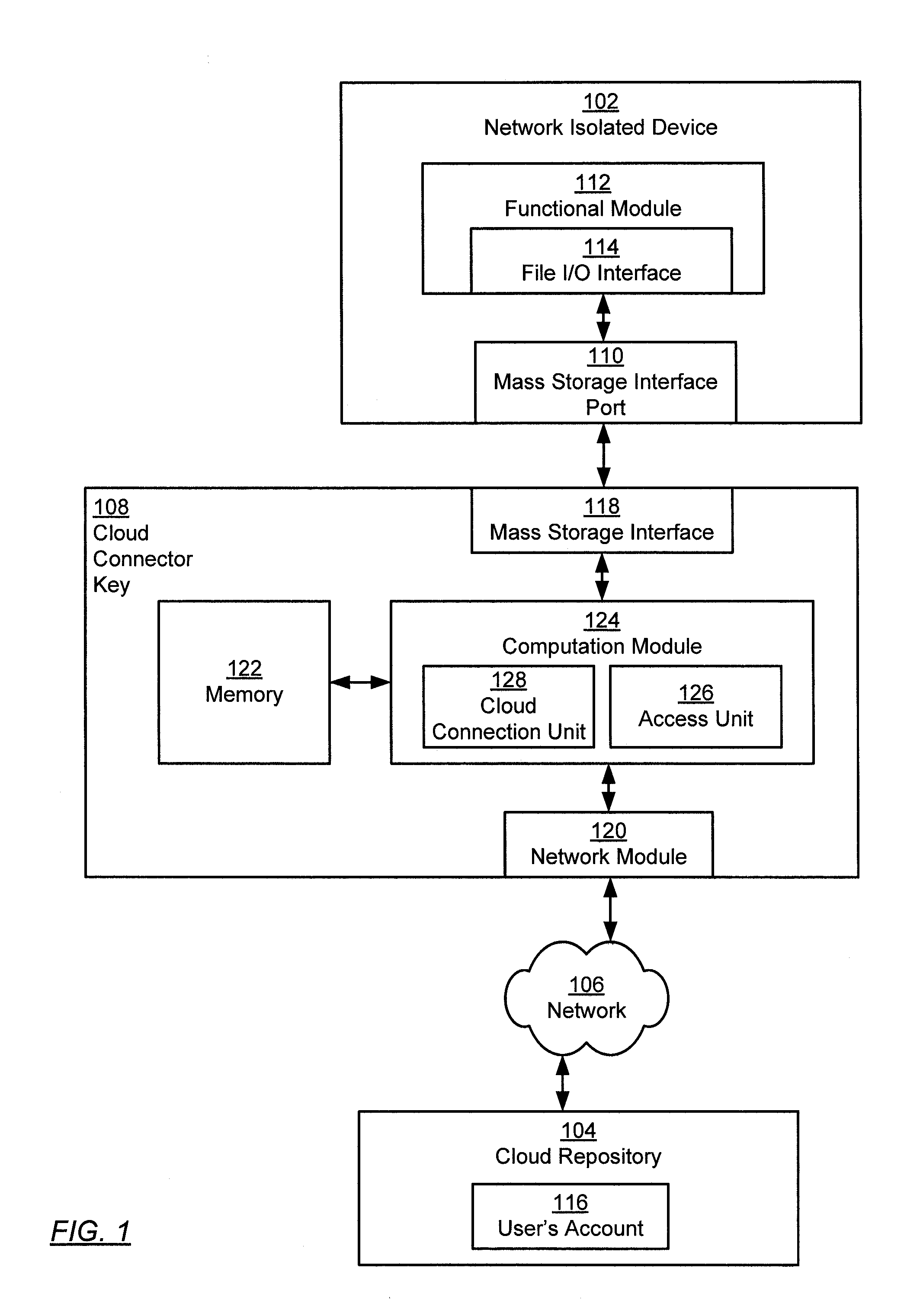
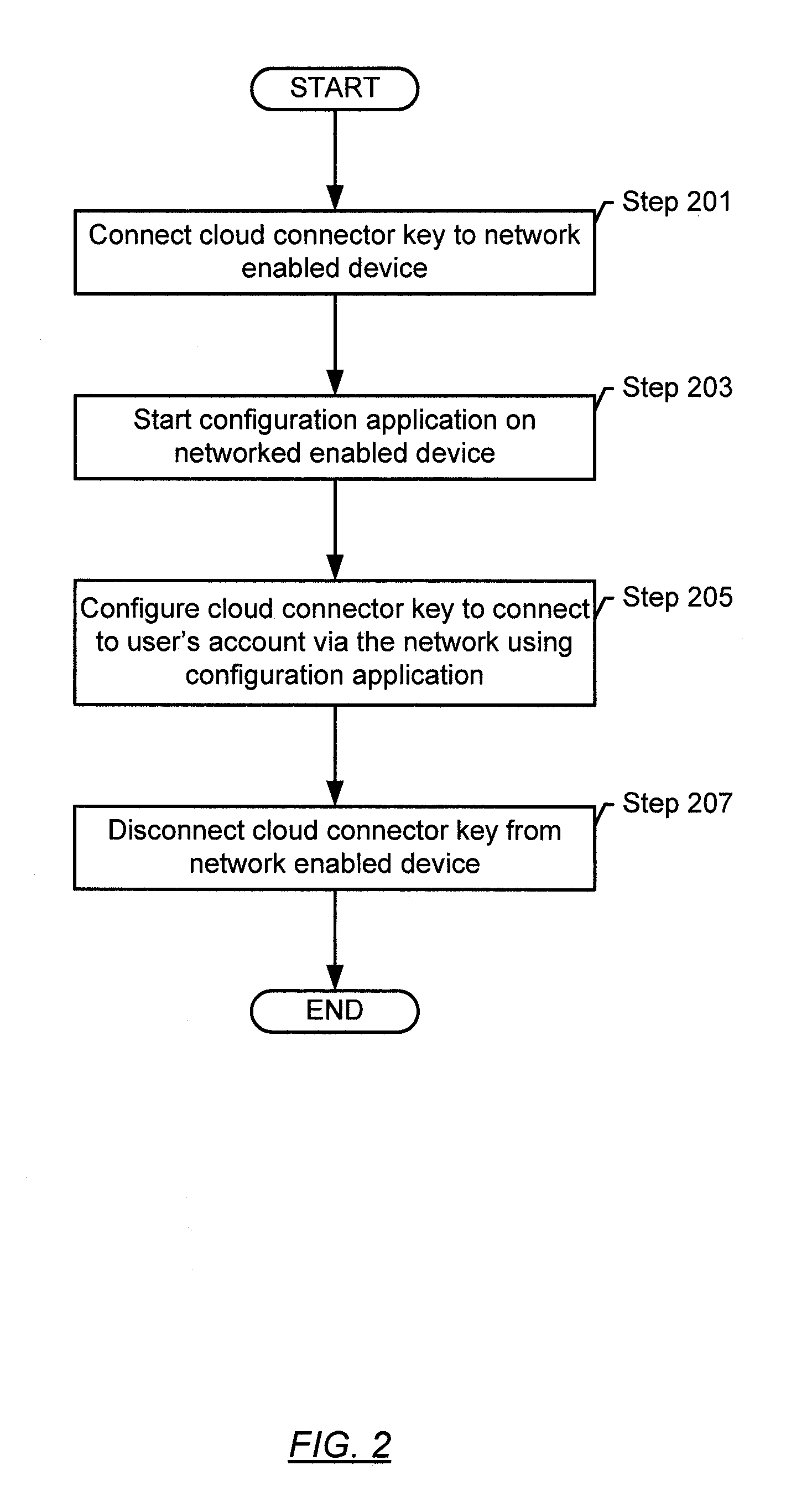
Cloud connector key
ActiveUS20110258333A1Multiple digital computer combinationsWebsite content managementMass storageNetwork addressing
A cloud connector key includes a network interface configured to connect to a network, a mass storage interface configured to connect to a network isolated device, and a computation module operatively connected to the network interface and the mass storage interface. The computational module is configured to connect to a cloud repository using the network interface by obtaining, from storage on the cloud connector key, a network address of the cloud repository, requesting connection to the cloud repository using the network address, and authenticating, using credentials in the storage on the cloud connector key, to an account in the cloud repository. The computational module is further configured to transfer a file between the account in the cloud repository and a network isolated device via the mass storage interface.
Owner:ORACLE INT CORP
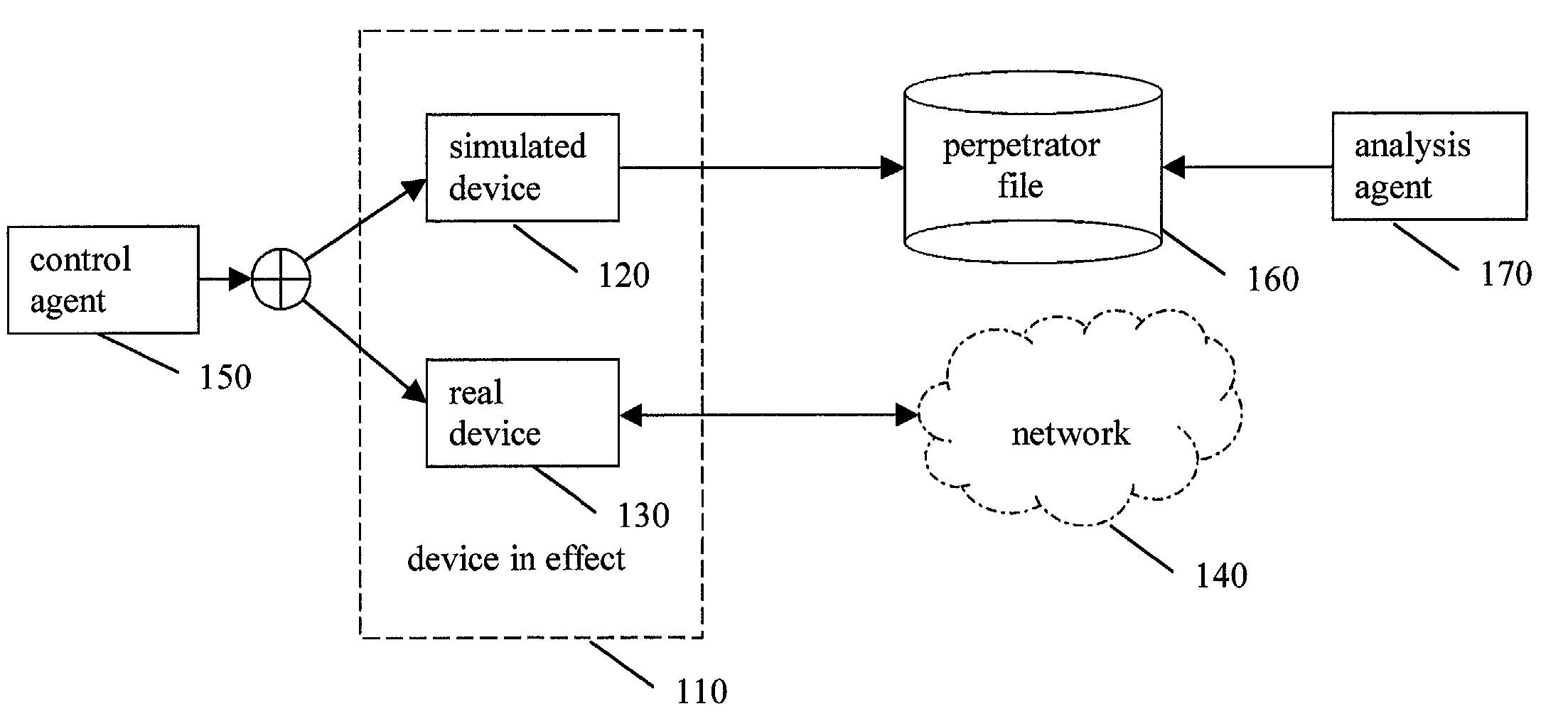
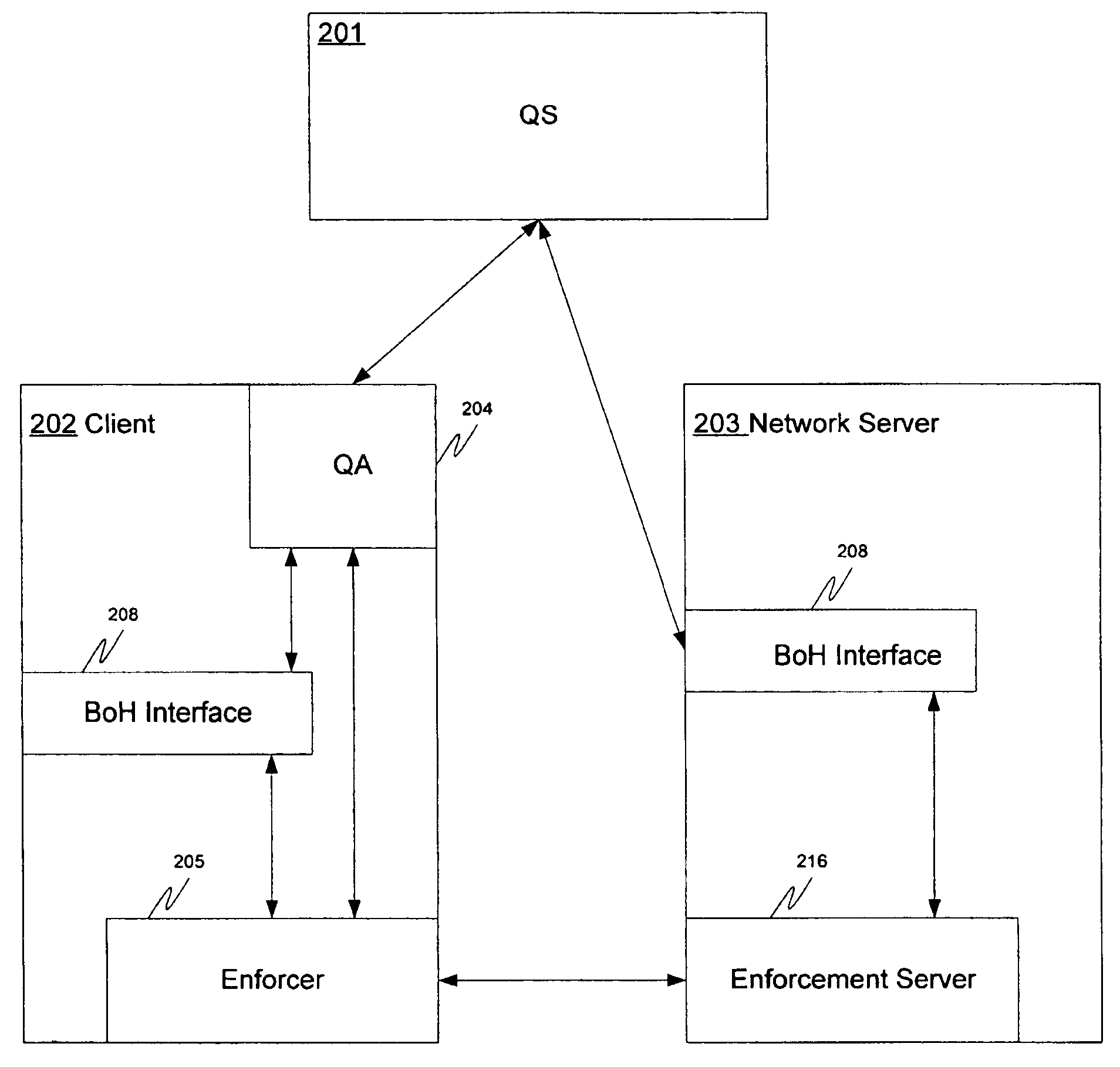
Method and apparatus for security management via vicarious network devices
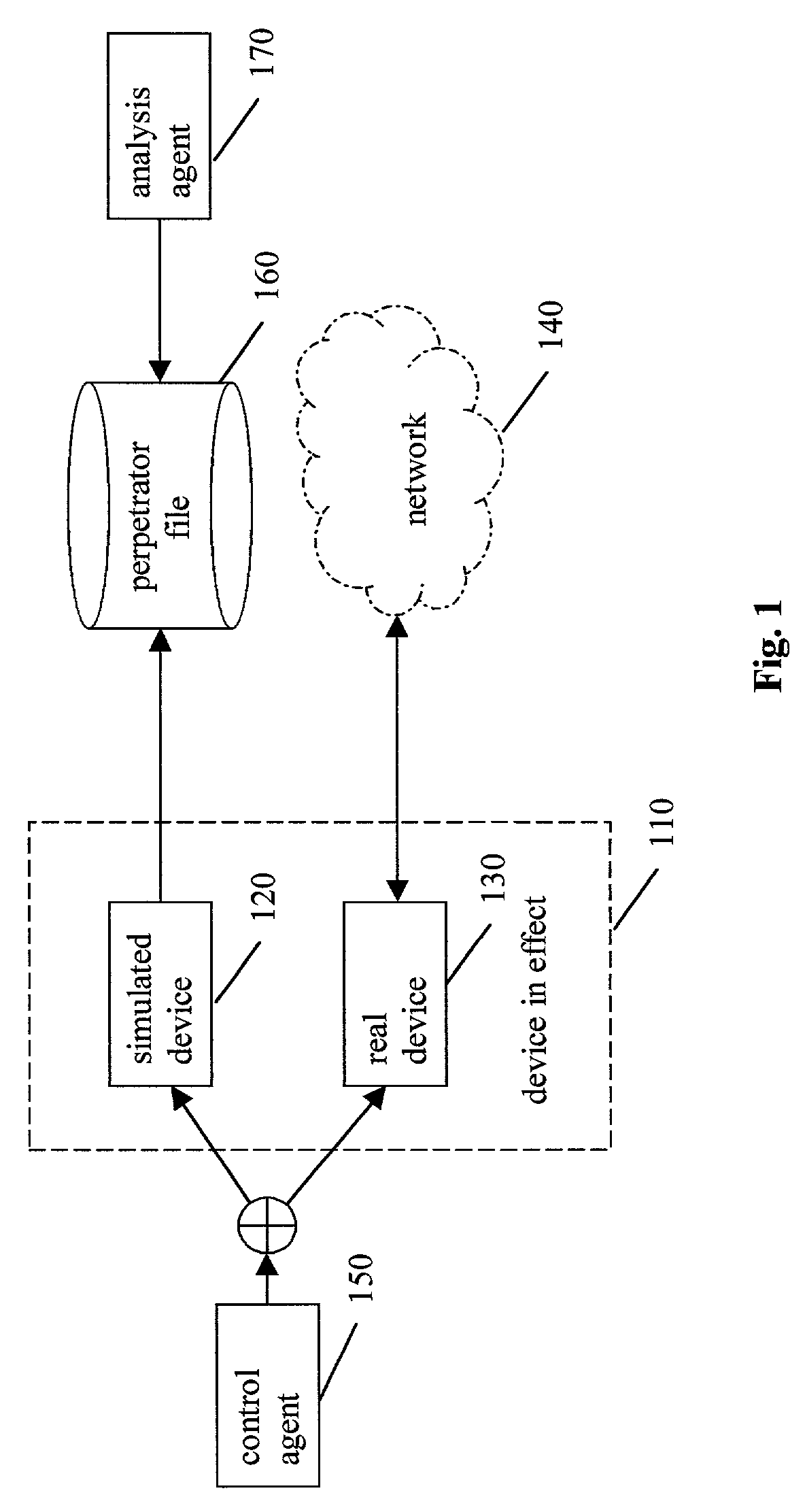
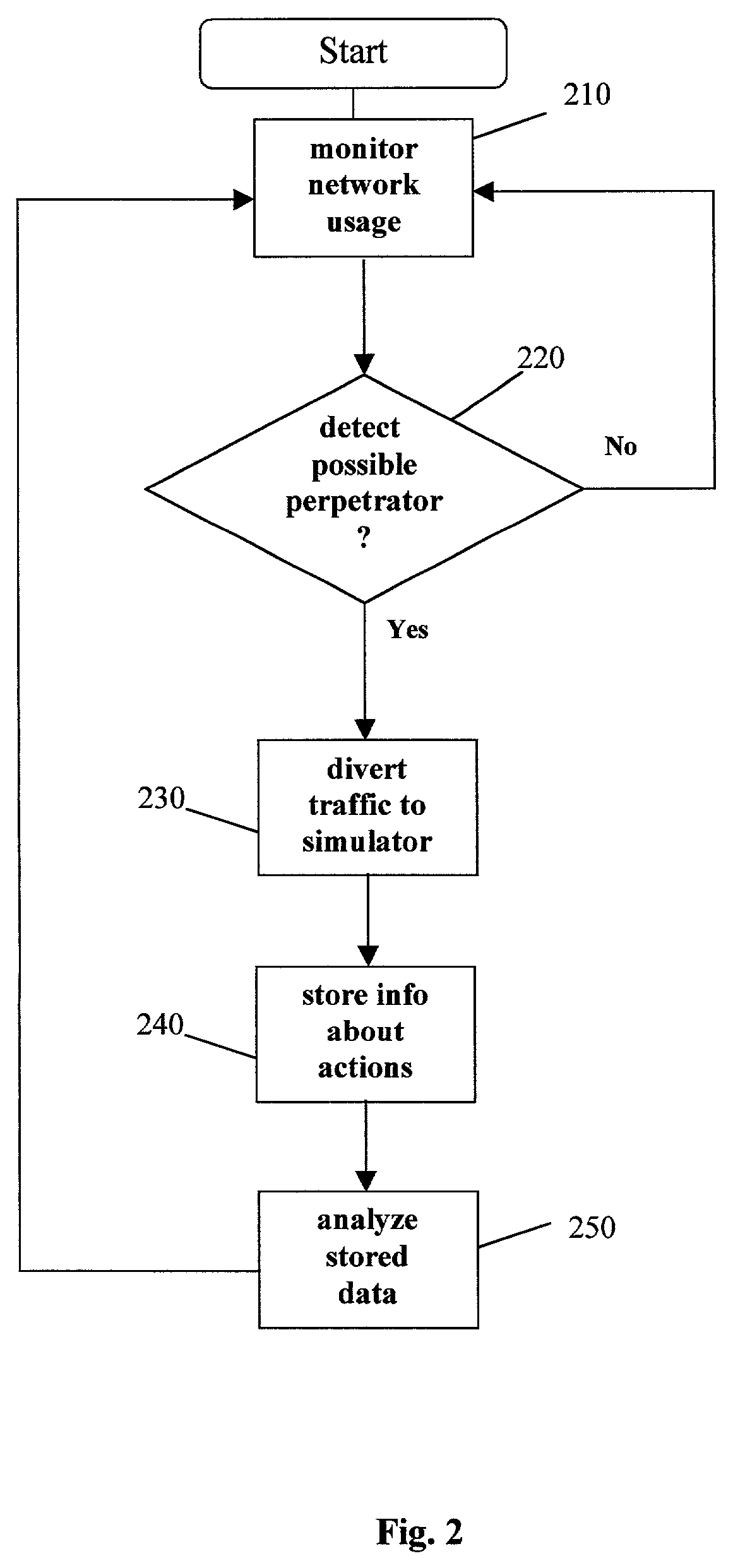
ActiveUS7770223B2Reliable portrayalAvoid data lossMemory loss protectionDigital data processing detailsNetwork isolationSpeech sound
In one embodiment of a method and apparatus for protecting data, voice, and video networks from individuals with malicious intent, a real network or network device has a vicarious simulated counterpart that may take the place of the real device or network upon appropriate triggering. The simulated counterpart behaves like the real device, but records the suspect transactions. The integrity of the real network or device is therefore continuously maintained because the suspect is isolated from the real network and the suspect transactions are not passed on to the actual device or network. The recorded transactions may then be analyzed for purposes of exposing the perpetrator, discovering perpetrator behavior patterns, and identifying device or network security weaknesses.
Owner:COMP ASSOC THINK INC
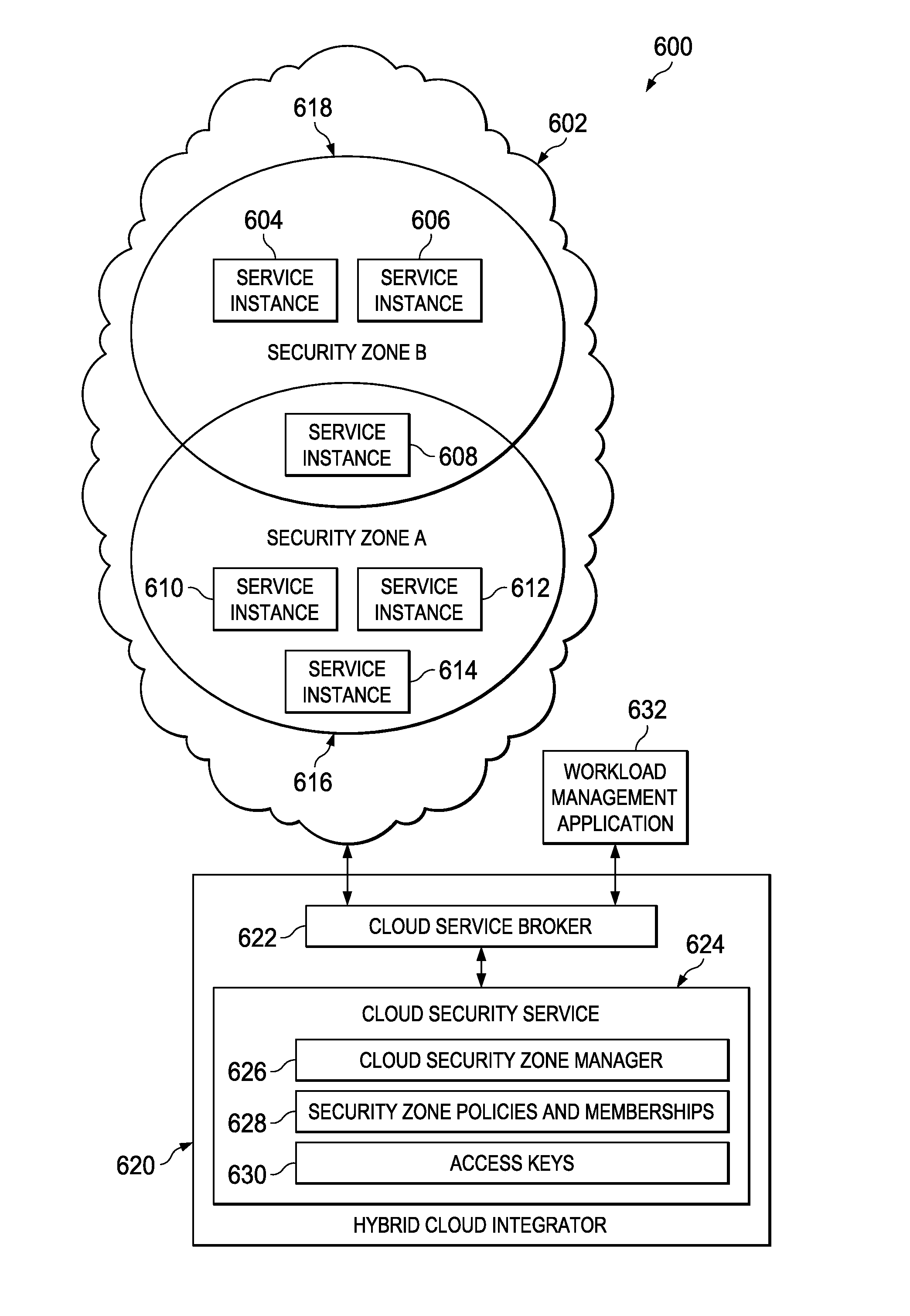
Virtual Securty Zones for Data Processing Environments
InactiveUS20120222084A1Error detection/correctionComputer security arrangementsNetwork isolationSecurity policy
A method, apparatus, and computer program product for providing security and network isolation for service instances comprising data processing resources provided as a service by a provider of data processing resources. Individual service instances may be associated as members of one or more security zones. The security zones comprise security policies that define access of each service instance that is a member of a security zone.
Owner:IBM CORP
Self-healing tree network
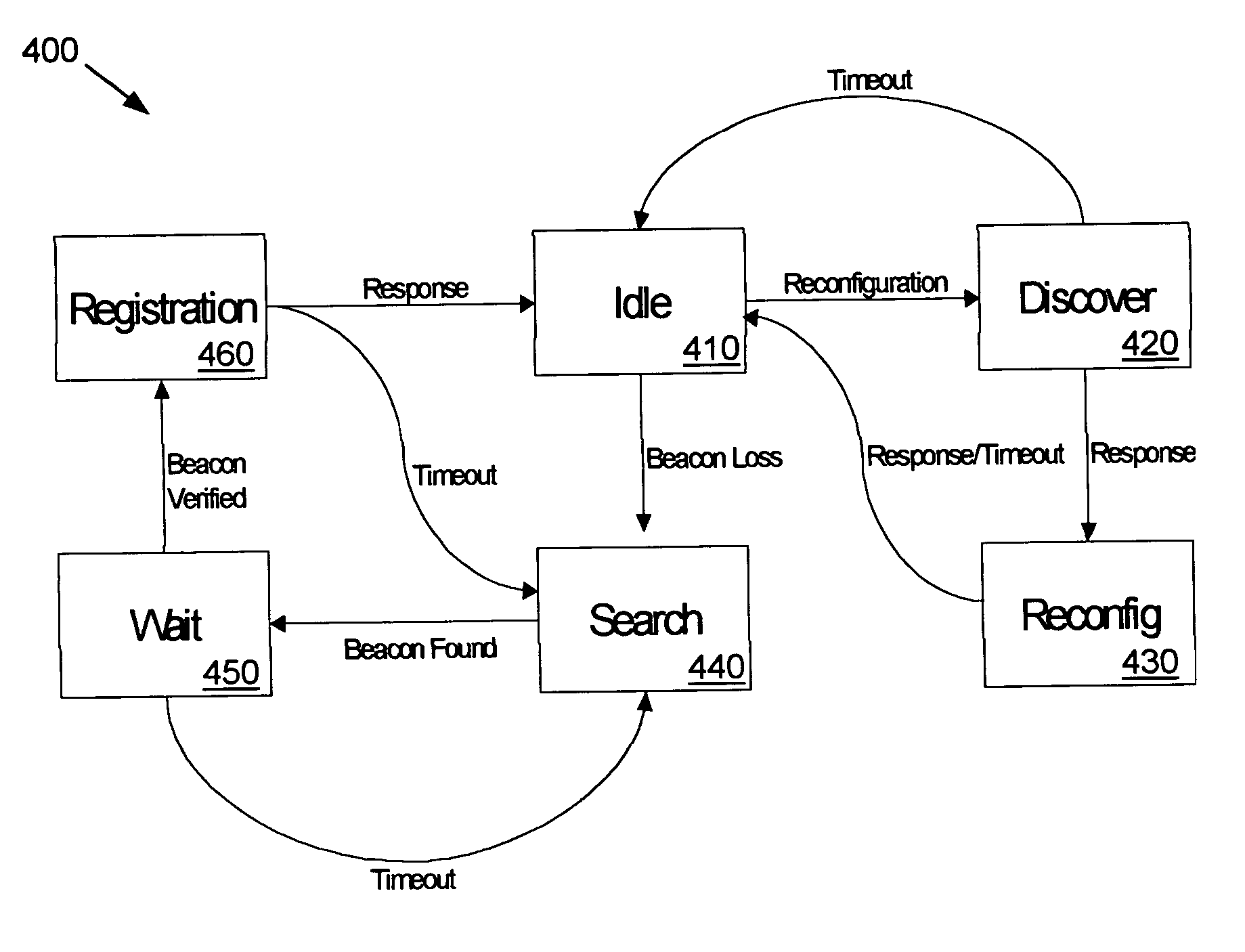
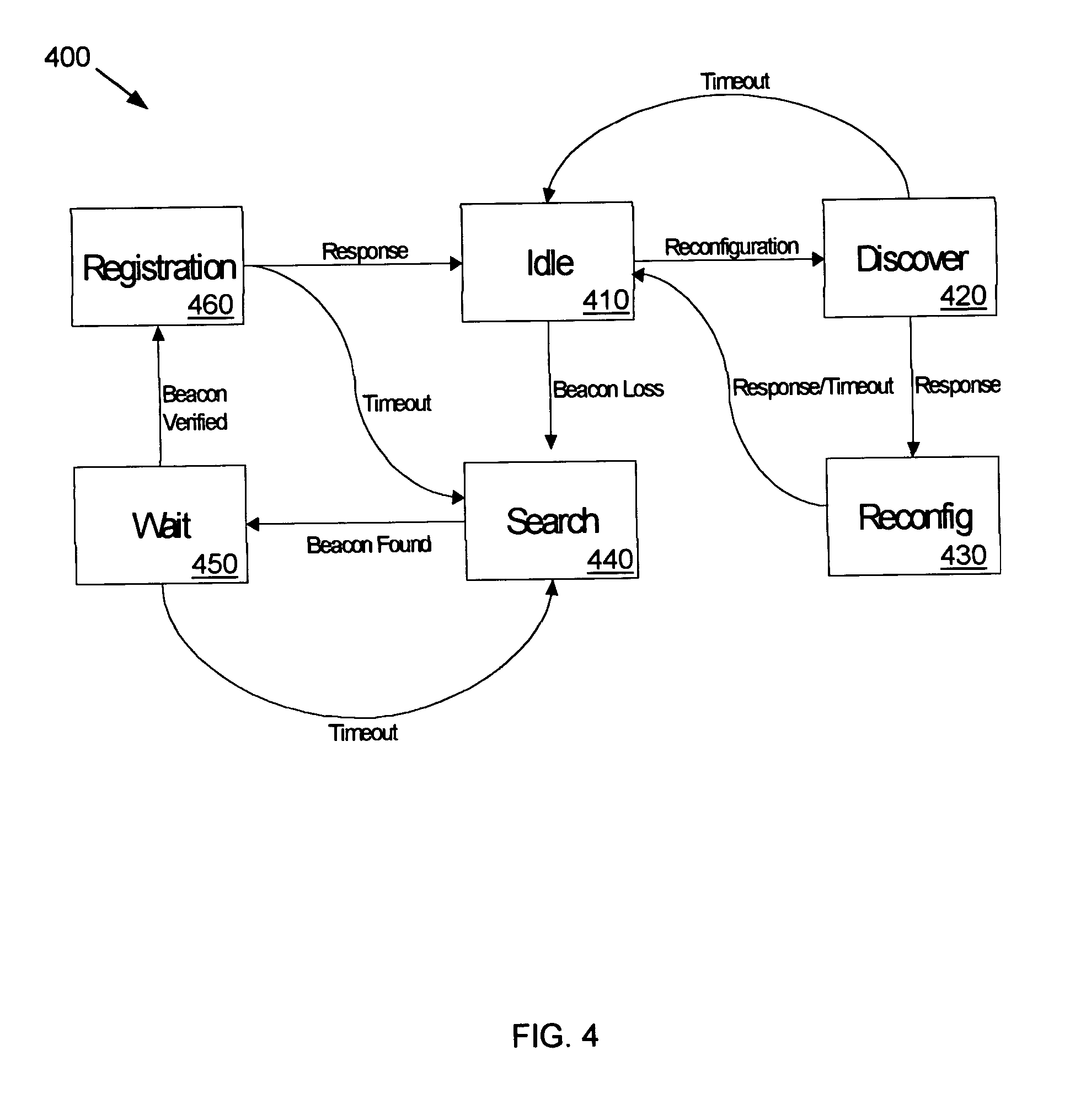
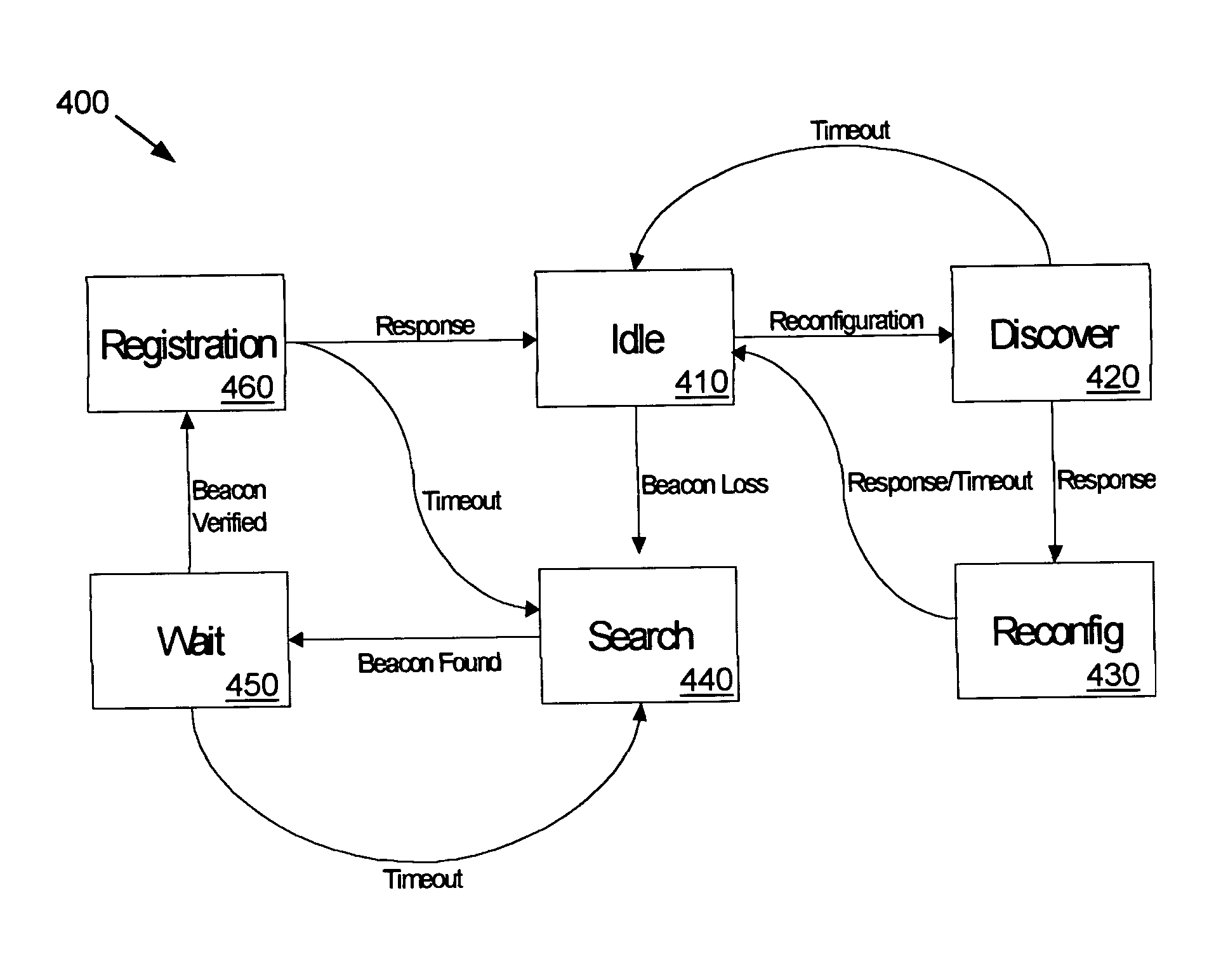
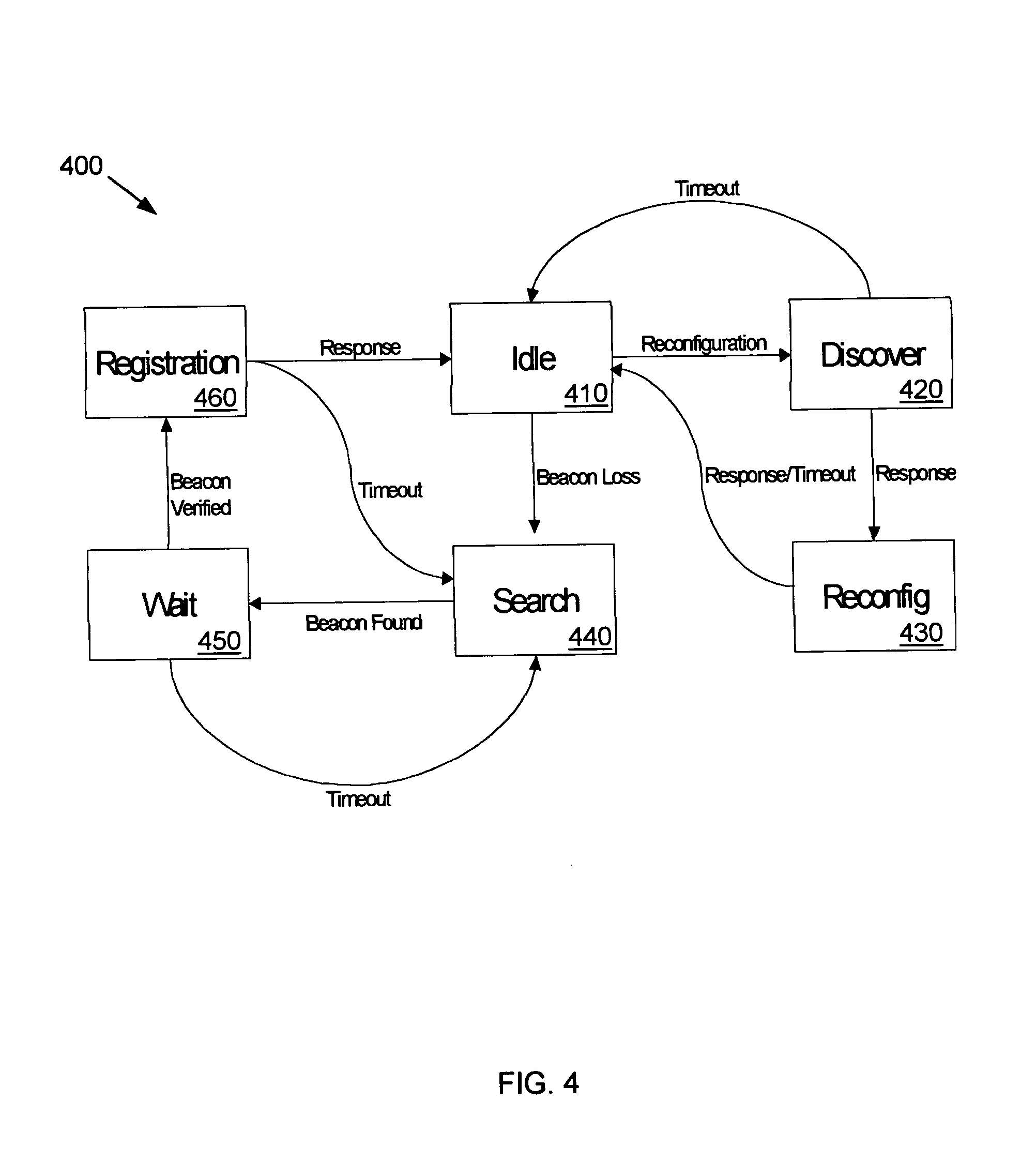
InactiveUS7233991B2Blocking in networkAvoid creatingError detection/correctionData switching by path configurationSelf-healingNetwork isolation
A communications network is provided with a self-healing topological architecture. Each node in the network detects continuously transmitted beacon packets that are propagated through the network at regular intervals by a root node. Upon failure to detect a new beacon packet after a predetermined time from a parent node, a network node determines a network isolation condition and searches for another node that is still actively connected in the network. Algorithms are provided for registering with and identifying active parent node candidates during a network failure so as to prevent the creation of network loops.
Owner:OMNILUX
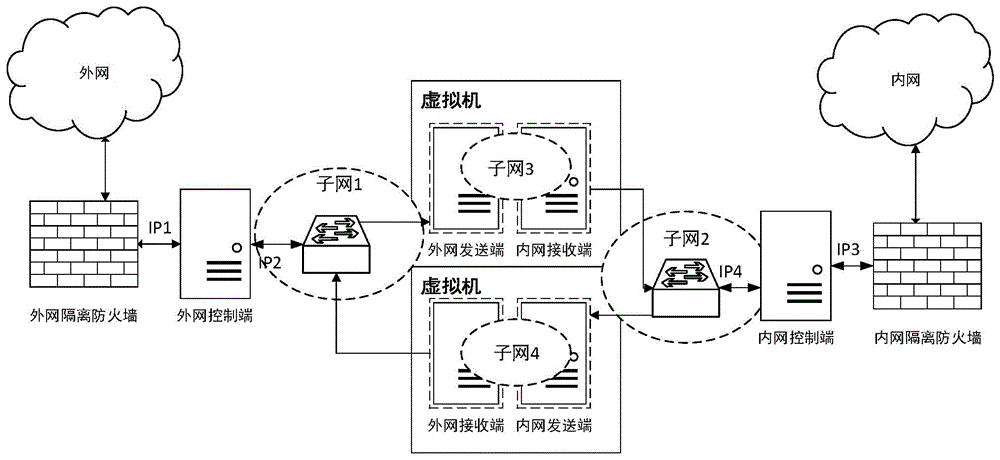
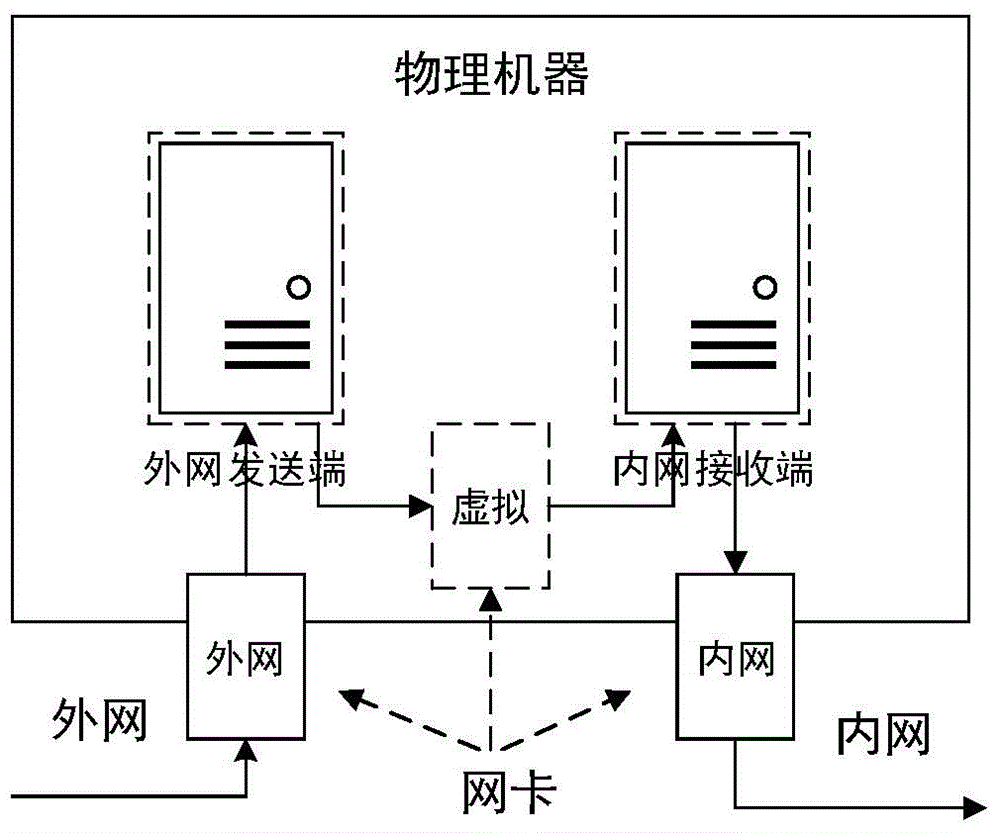
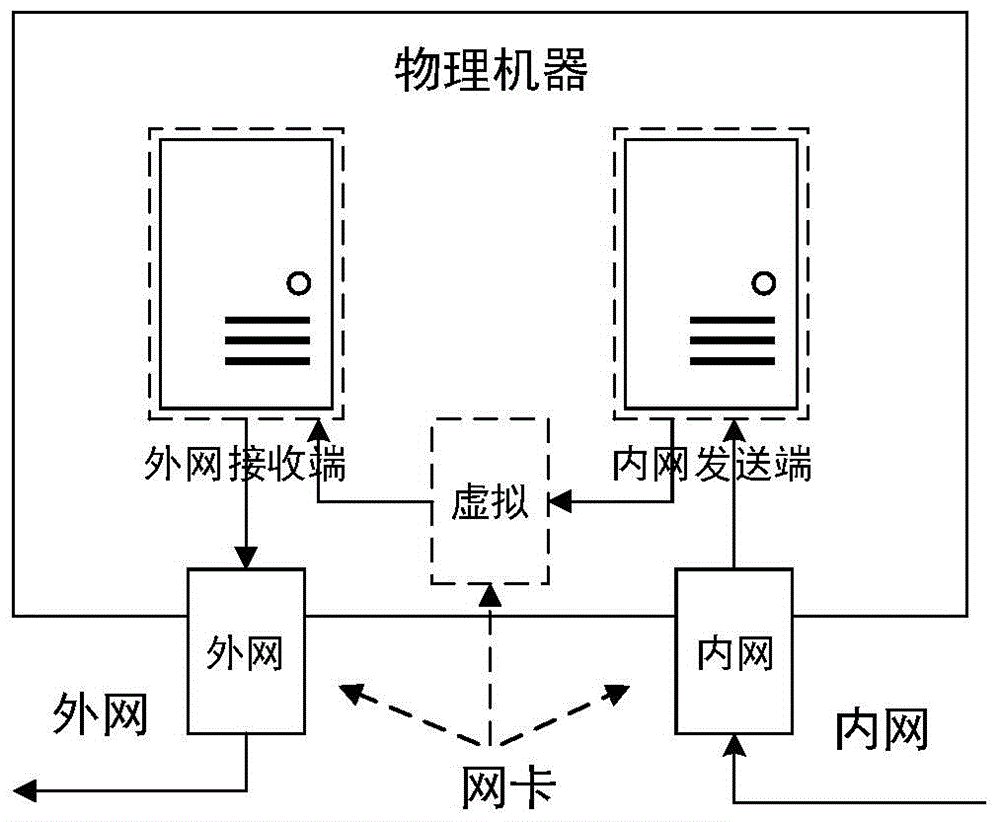
Network safety isolation file transmission control method
InactiveCN104363221AEnsure safetyKeep Content SafeSecuring communicationComputer hardwareConfidentiality
The invention relates to a safety isolation file transmission control method, in particular to a file transmission control method between taxation network safety isolation systems. A transmission control system comprises an external network isolation firewall, an external network control end, an external network transmitting end, an external network receiving end, an internal network transmitting end, an internal network receiving end, an internal network control end and an internal network isolation firewall. A computer system, a virtual machine system and the isolation firewalls are combined to achieved a relatively universal safety data transmission manner, safe and reliable bidirectional data transmission is achieved by the control method with a special safety protocol, confidentiality, completeness and non-repudiation during information transmission are achieved by safety techniques such as data encryption, digital signatures and information authentication codes, data exchanging performance is increased while safety of internal and external network systems is guaranteed, and the whole system can work reliably and stably.
Owner:QINGDAO WEIZHIHUI INFORMATION
One-way network transmission interface unit
InactiveUS7260833B1Digital data processing detailsMultiple digital computer combinationsRemote computerWorkstation
A network isolation apparatus is provided that permits data to be sent to a remote computer or network without a return path so that the isolated sensitive network may not be compromised. The isolation device spoofs the network so that the network believes it has a fully functional external connection. The invention has a first media converter for receiving data from a workstation on a sensitive network; this data is then passed to a second media converter and then transmitted to a remote computer. An optical signal generator sends signals to the workstation to imitate a standard transmit and receive connection, and also sends signals to the second media converter to imitate a standard transmit and receive connection. No physical connection exists for the remote computer workstation to compromise the sensitive network.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
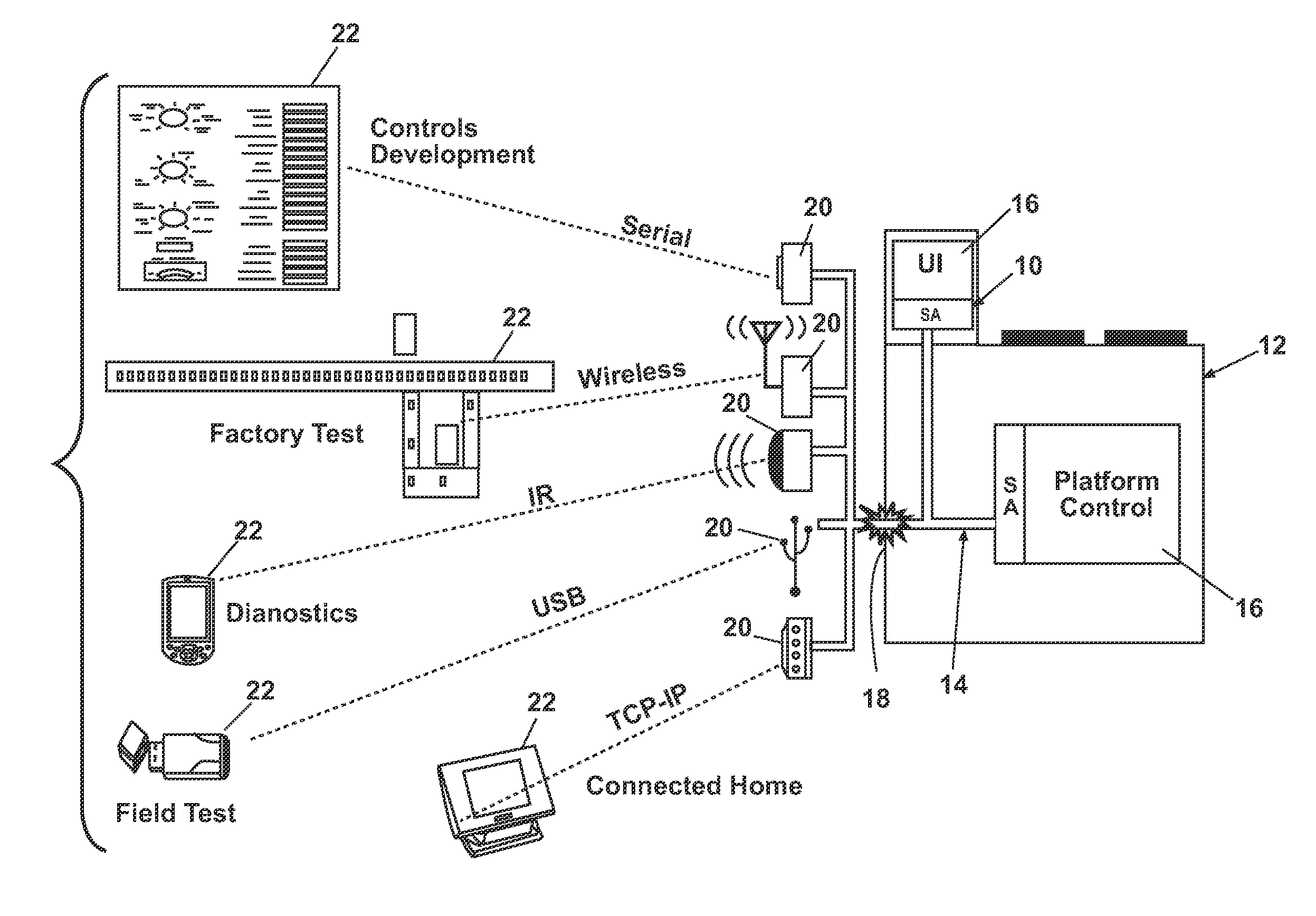
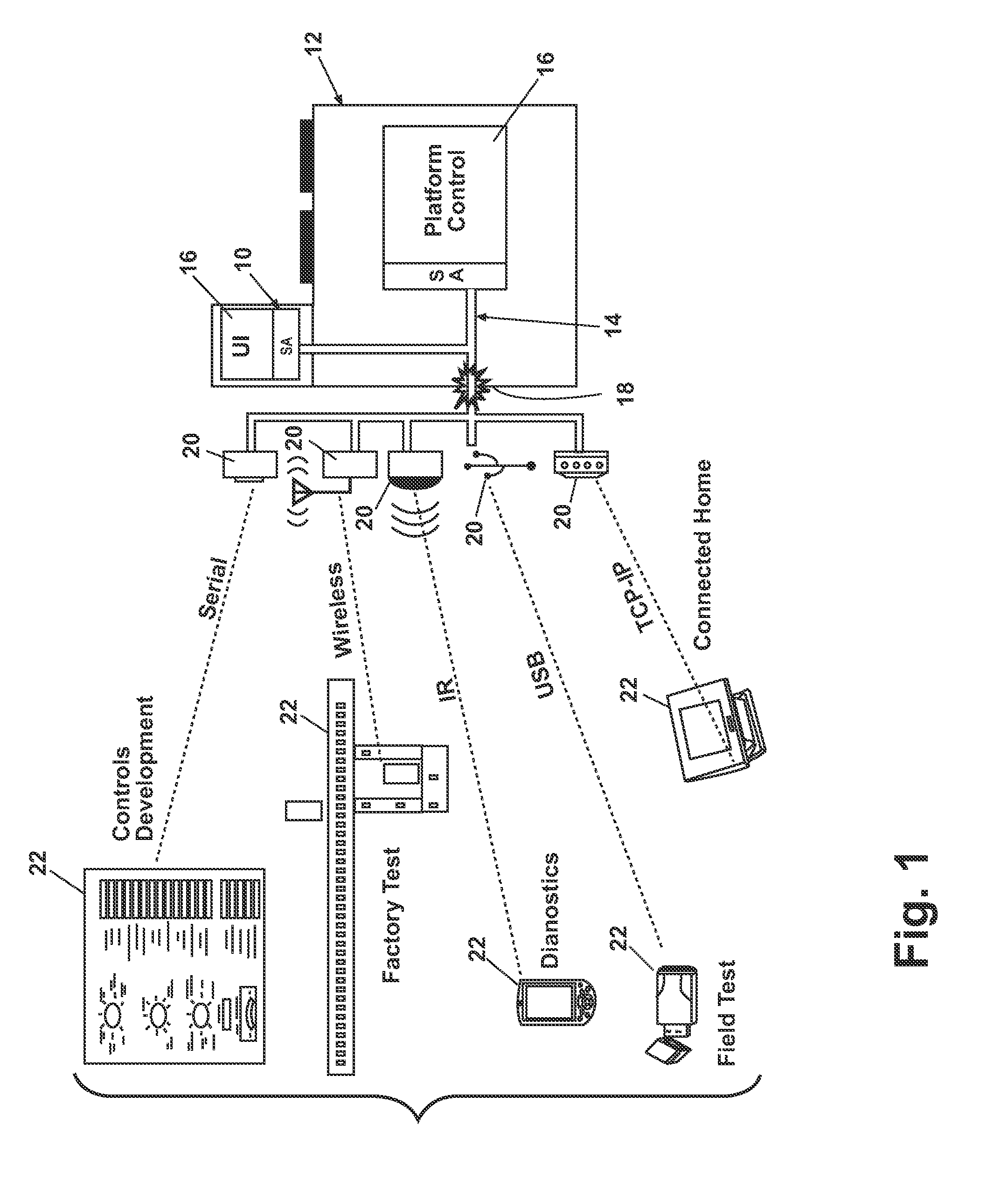
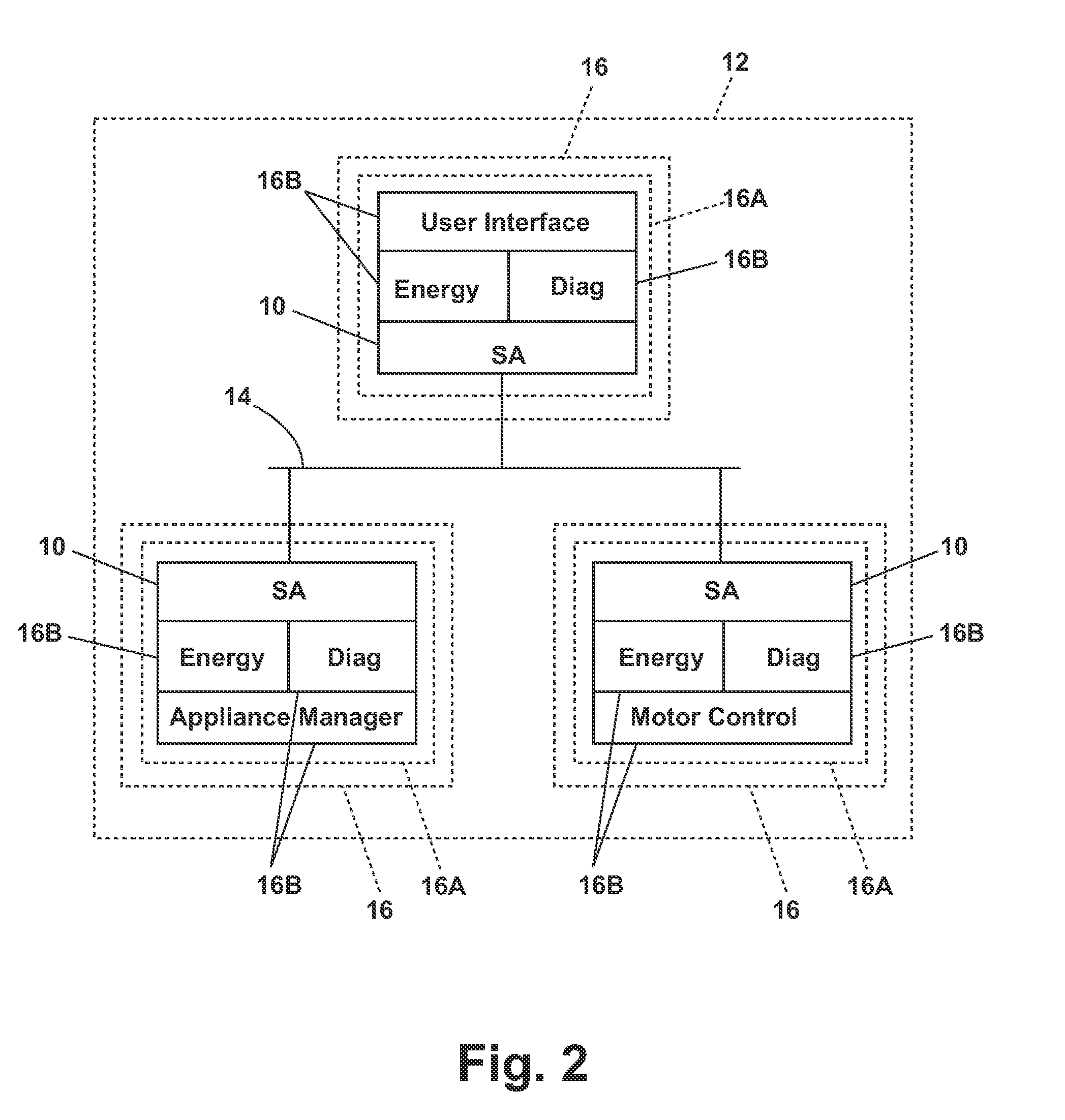
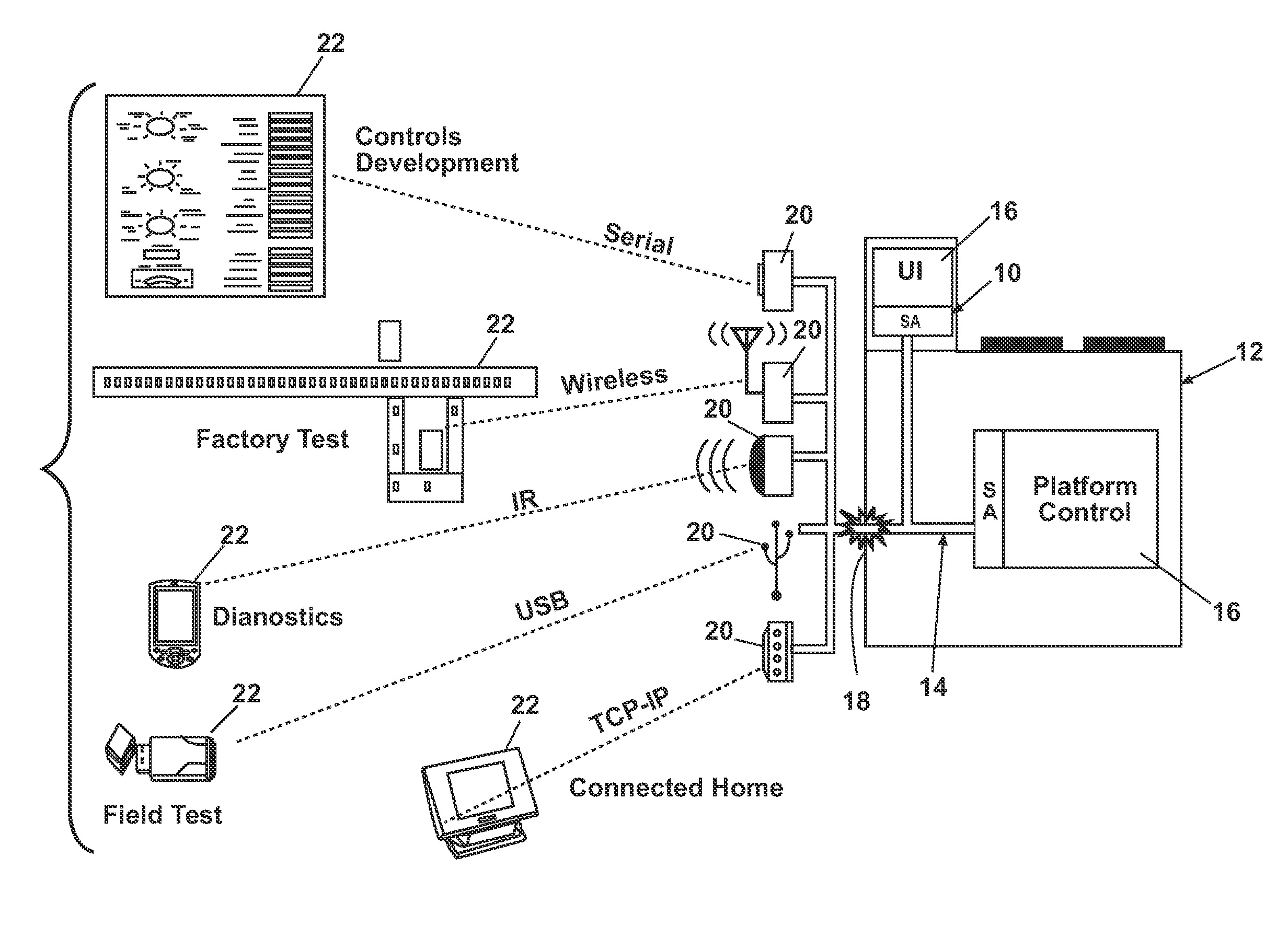
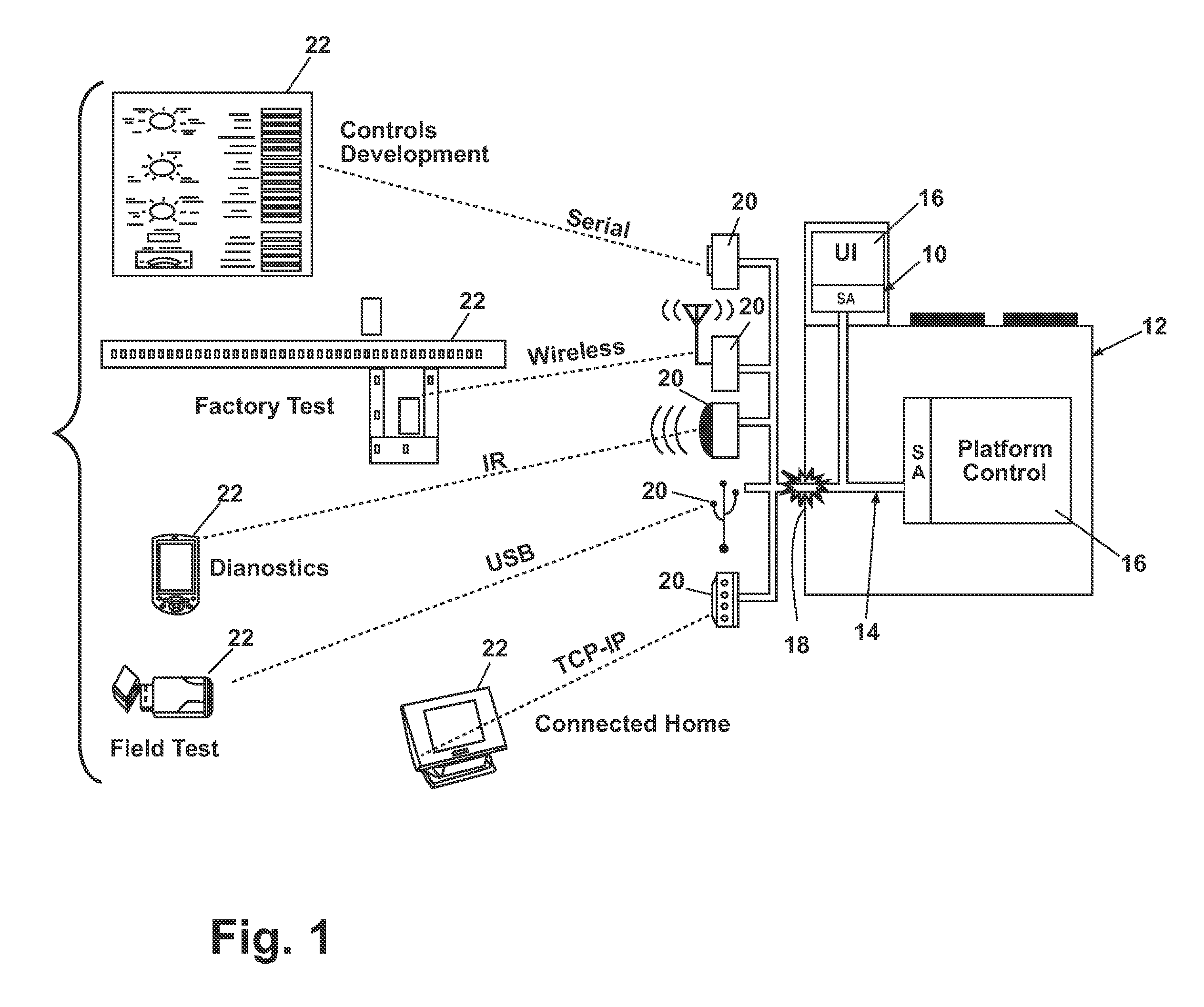
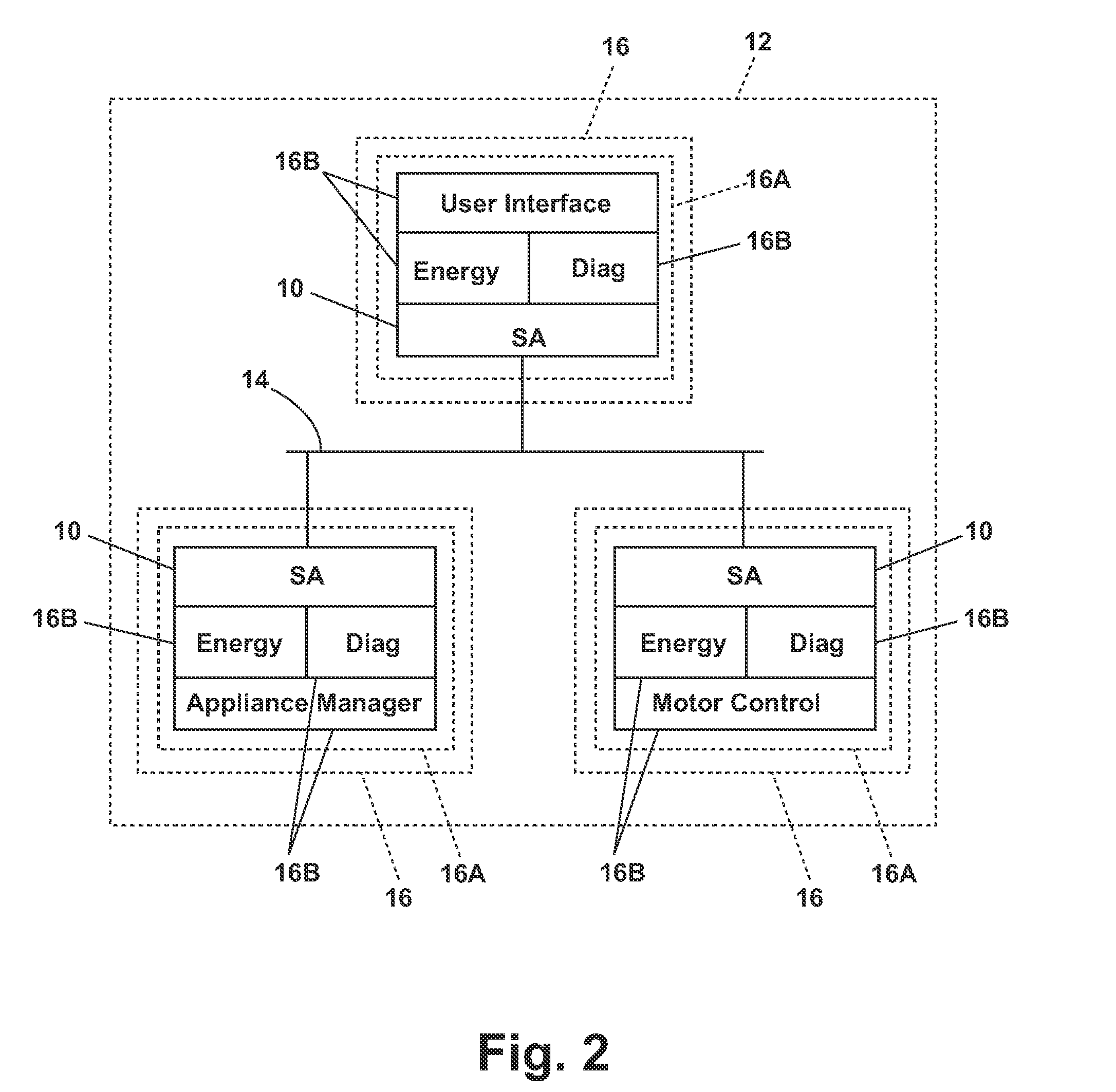
Software architecture system and method for operating an appliance in multiple operating modes
ActiveUS20100087932A1Electric controllersIgnition automatic controlControl systemSoftware architecture
In one embodiment, a system for controlling a plurality of devices having at least two operating modes comprises a first software operating layer configured to control the operation of at least one of the devices in a first operational mode and a second software operating layer configured to control the operation of at least one of the devices in a second operational mode. In another embodiment, a control system for controlling a plurality of devices connected by a communications network comprises a user interface configured to receive the selection of a cycle of operation; a first system element isolated from the network and configured to implement the selected cycle of operation to define a first control state; and a second system element exposed to the network and configured to implement the selected cycle of operation to define a second control state.
Owner:WHIRLPOOL CORP
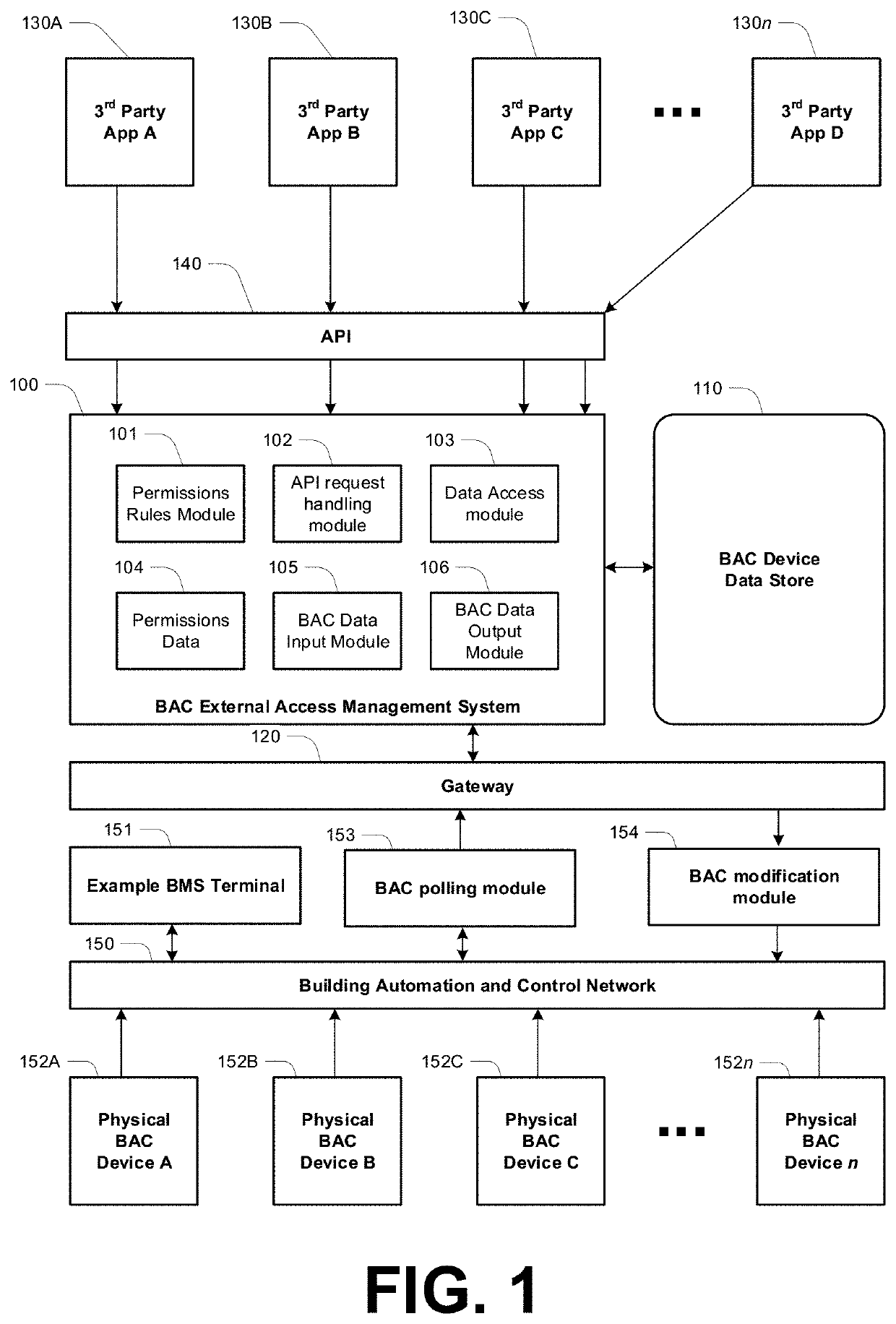
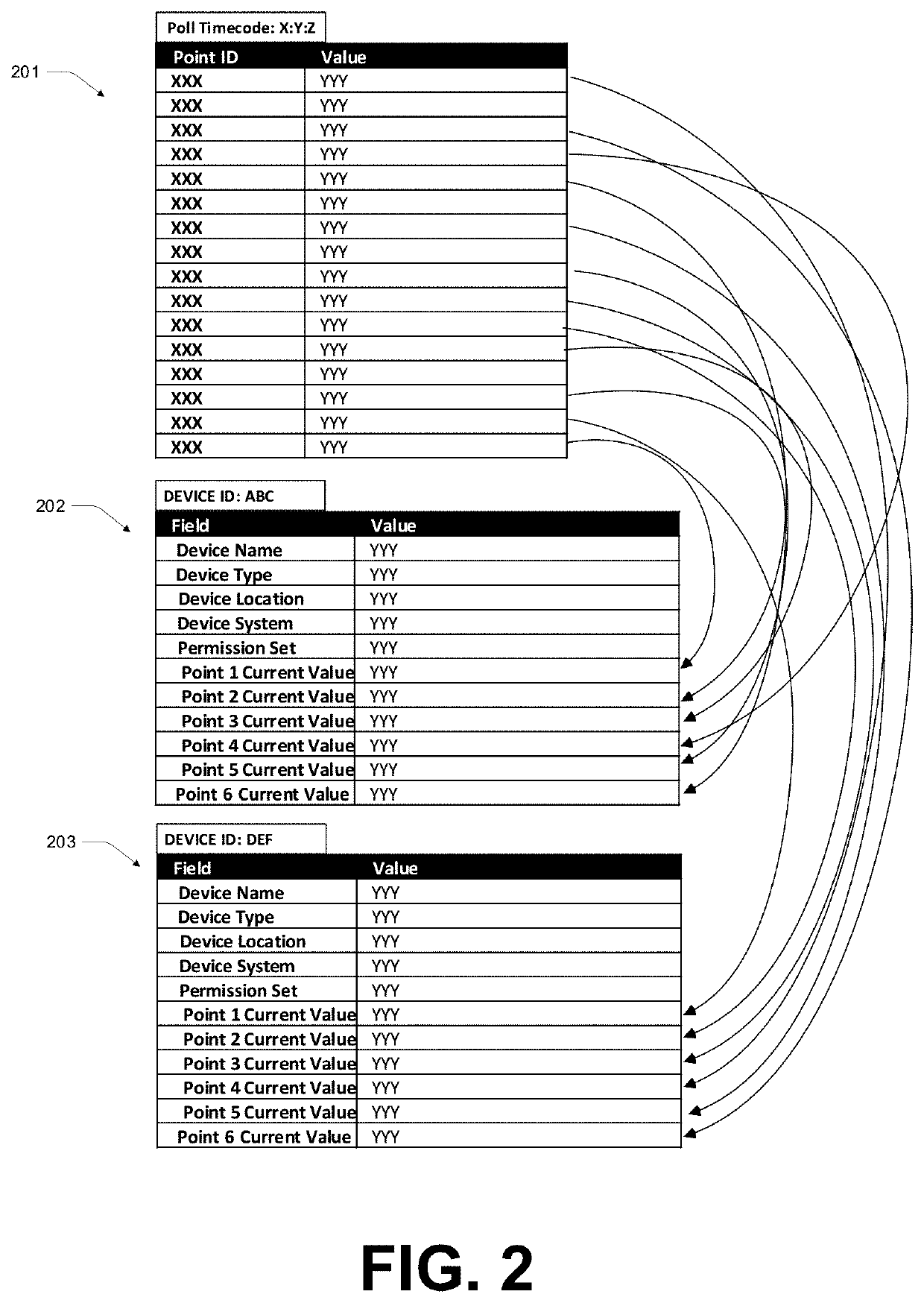
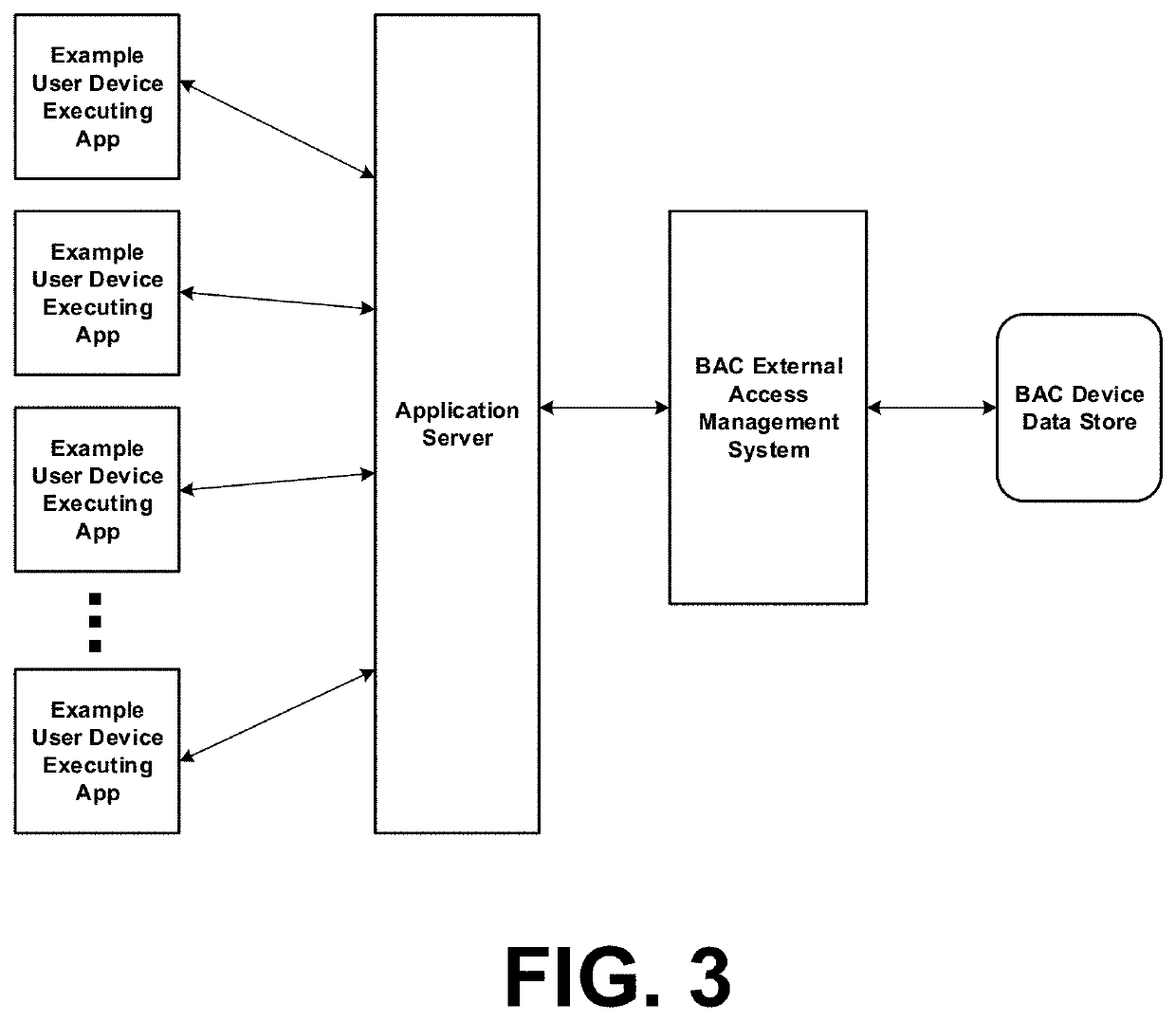
Systems configured to enable isolated client device interaction with building automation and control (BAC) networks, including third-party application access framework
ActiveUS20200396208A1Database management systemsComputer security arrangementsBuilding automationOperating system
Various embodiments employ technology solutions to enable isolated client device interaction with building automation and control (BAC) networks, for example including configuration of a third-party application access framework which enables access to physical devices in a built environment. For example, a data exchange gateway interfaces a system with a BAC (Building Automation and Control) network, wherein the BAC network provides via the gateway, on a periodic basis, data values presented by each of a plurality of physical devices on the BAC network. A data exchange module receives periodic data values and causes recording of those values in a BAC database isolated from the BAC network. A permissions rules module control access to data in the BAC database. An API request handling module handles requests from third-party software platforms via an API.
Owner:WILLOW TECH CORP PTY LTD
Software architecture system and method for operating an appliance in multiple operating modes
In one embodiment, a system for controlling a plurality of devices having at least two operating modes comprises a first software operating layer configured to control the operation of at least one of the devices in a first operational mode and a second software operating layer configured to control the operation of at least one of the devices in a second operational mode. In another embodiment, a control system for controlling a plurality of devices connected by a communications network comprises a user interface configured to receive the selection of a cycle of operation; a first system element isolated from the network and configured to implement the selected cycle of operation to define a first control state; and a second system element exposed to the network and configured to implement the selected cycle of operation to define a second control state.
Owner:WHIRLPOOL CORP
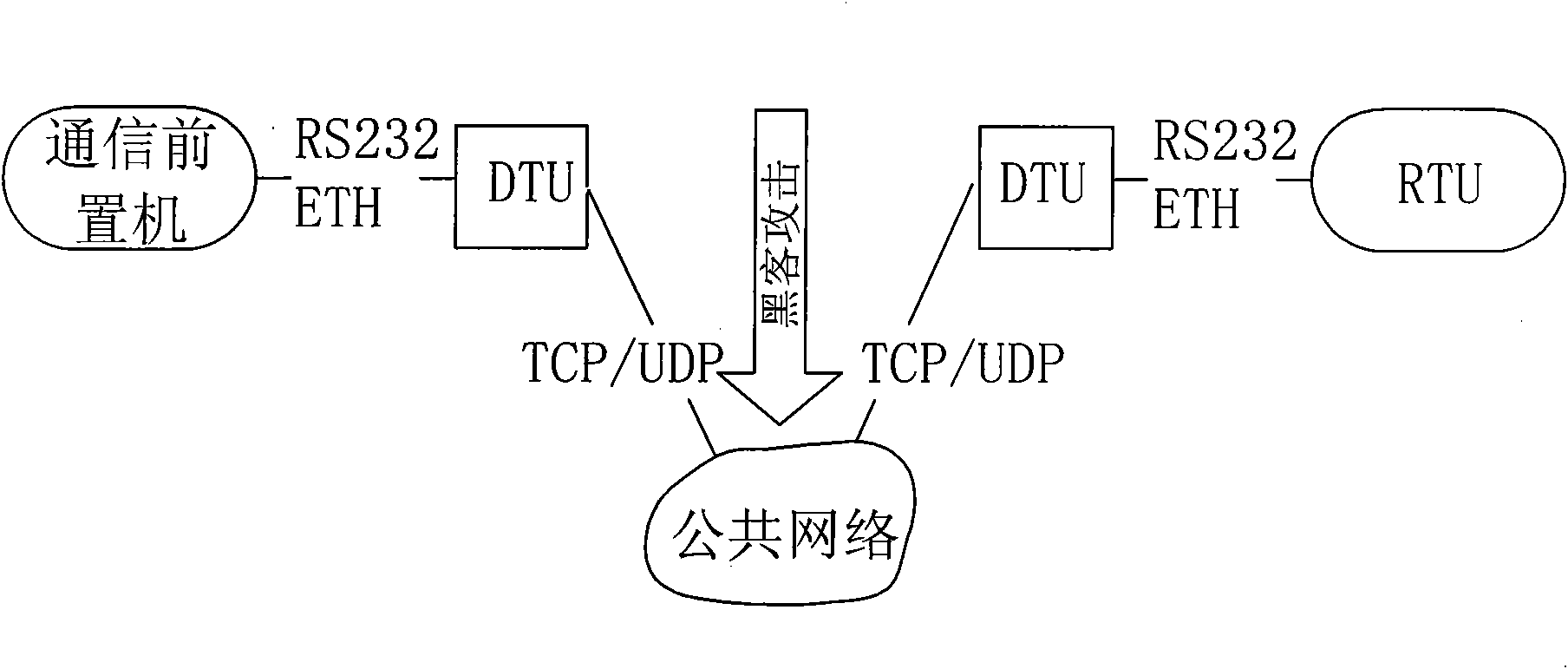
Security protection method of communication data of special electricity public network
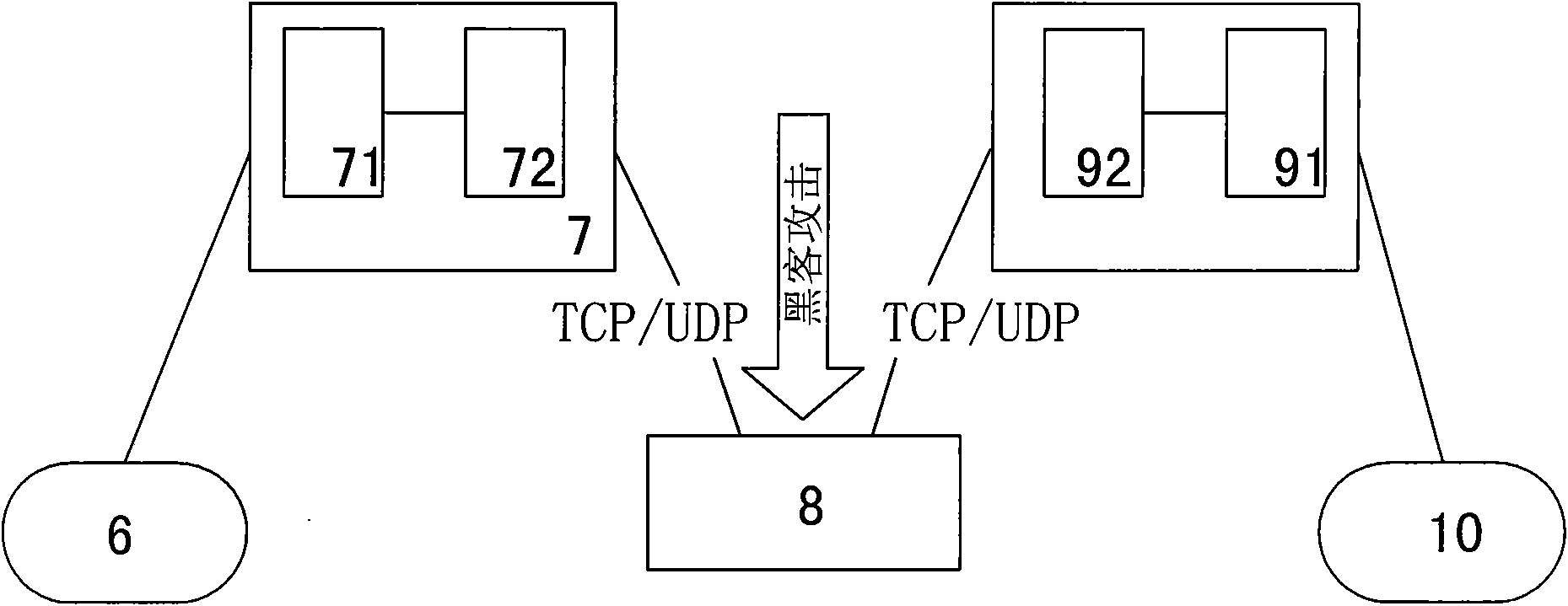
ActiveCN101662359AReal-time uninterruptible productionControl securityNetwork connectionsSecuring communicationCommunications securityElectricity
The invention discloses a security protection method of communication data of a special electricity public network, which provides secure and reliable data communication for the data communication ofthe special electricity public network by adopting the technical means of network isolation, right control, identity authentication and transmission encryption, realizes the purpose of securely usingthe public network for communication at any time and in any places without making any change to the application environment or software. In the process of application, a calling telecontrol communication security gateway (7) and a called telecontrol communication security gateway (9) are connected to a public network (8) by dialing; an encrypted public network communication channel is establishedfor the communication between a communication front-end processor (6) and a remote RTU (10); and the data is connected with the telecontrol communication security gateway (7) from the communication front-end processor (6) through a serial port or network, connected with the public network (8) through the calling telecontrol communication security gateway (7), connected with the called telecontrolcommunication security gateway (9) from the public network (8), and then connected with the remote RTU (10) through the serial port or the network. The invention can be widely applied to the field ofsecurity protection of the communication data of the public network.
Owner:CHINA SOUTHERN POWER GRID COMPANY +1
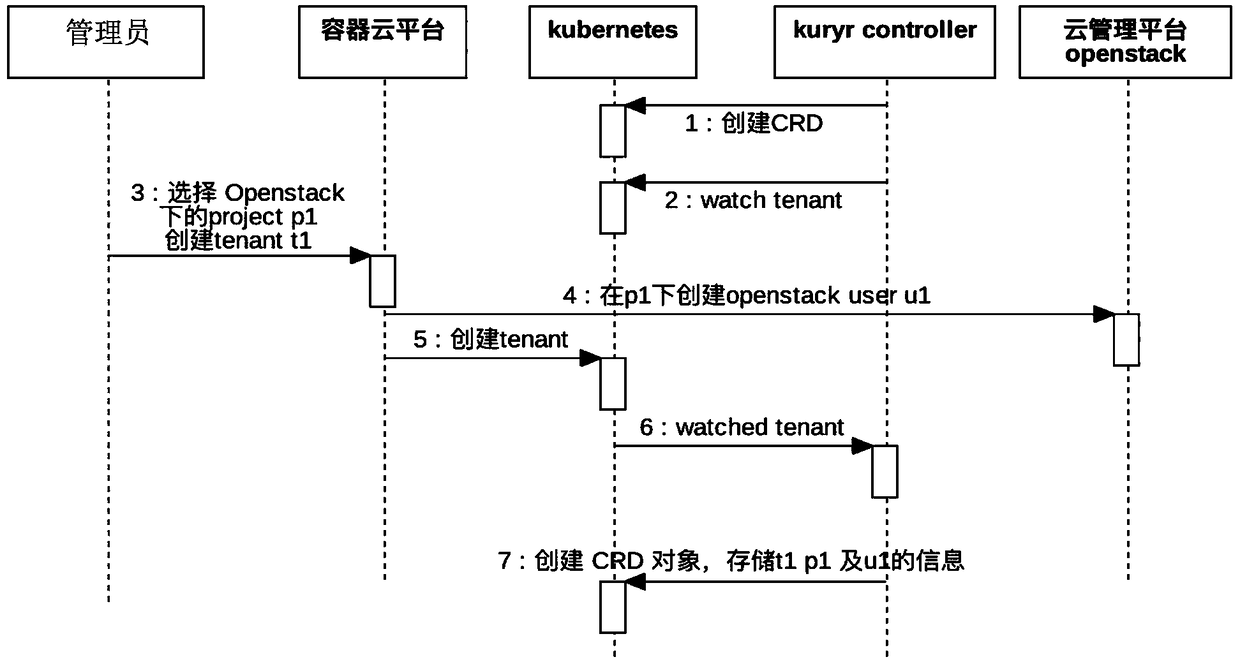
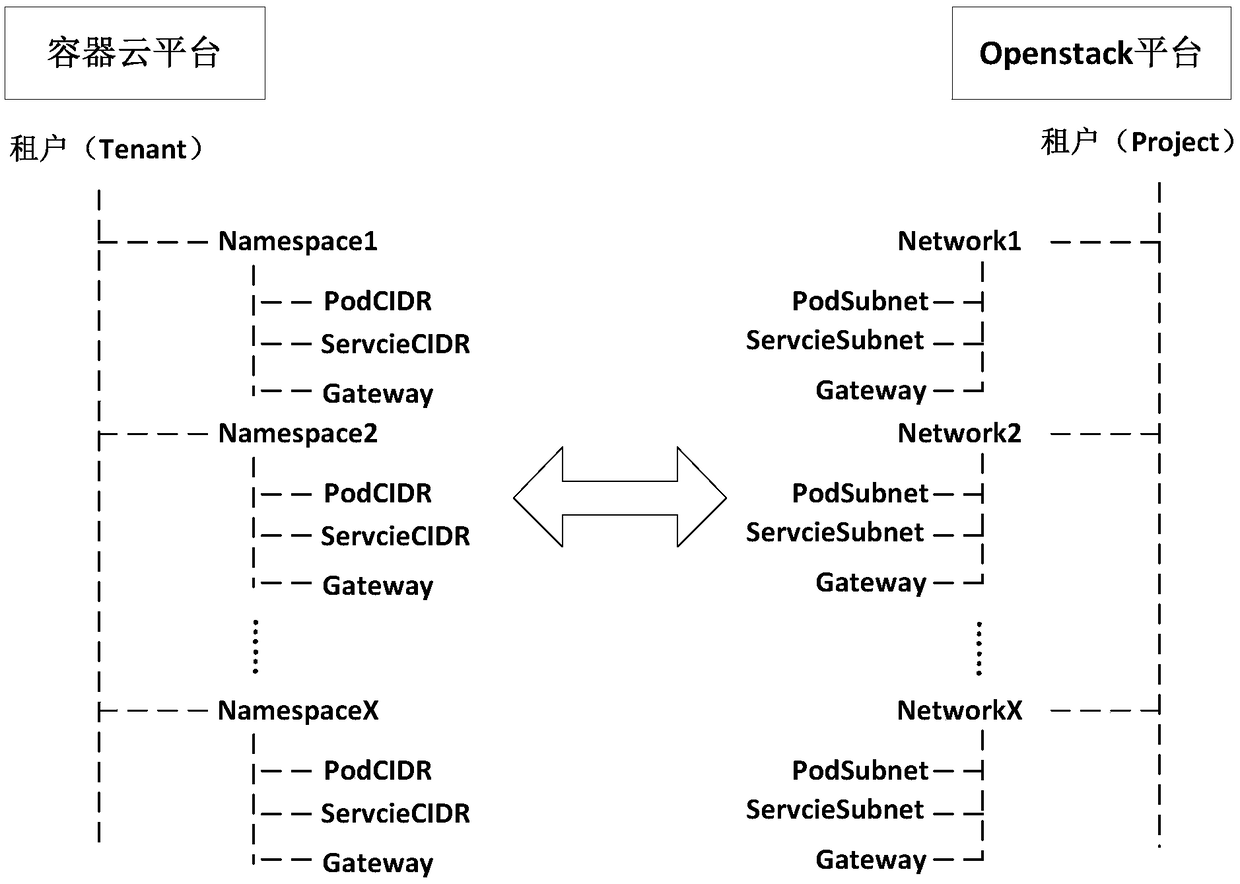
Tenant network isolation method based on kubernetes network, storage medium, and electronic device
ActiveCN108989091AAchieve isolationAchieve mutual accessData switching networksNetwork modelNetwork isolation
The invention provides a tenant network isolation method based on a Kubernetes network, comprising the following steps: selecting an Openstack tenant and creates a corresponding container tenant in aKubernetes cluster by a container cloud platform administrator; monitoring events that create container tenants in the cluster and sends requests to create privileged users; creating CRD object; translating Kubernetes network model into Openstack Neutron network model to generate Neutron information, and sending Neutron information to CNI Driver for pod binding. By interfacing with an Openstack tenant, container tenants in Kubernetes cluster implement complete network isolation among tenants, and each container tenant makes use of Openstack Neutron's powerful SDN network function to plan and configure the network, so as to realize mutual access between tenant's inner container service and virtual machine service.
Owner:杭州才云科技有限公司
System and methods for providing network quarantine
A client quarantine agent requests bill of health from a quarantine server, and receives a manifest of checks that the client computer must perform. The quarantine agent then sends a status report on the checks back to the quarantine server. If the client computer is in a valid security state, the bill of health is issued to the client. If the client computer is in an invalid state, the client is directed to install the appropriate software / patches to achieve a valid state. When a client requests the use of network resources from a network administrator, the network administrator requests the client's bill of health. If the bill of health is valid, the client is admitted to the network. If the bill of health is invalid, the client is placed in quarantine.
Owner:MICROSOFT TECH LICENSING LLC
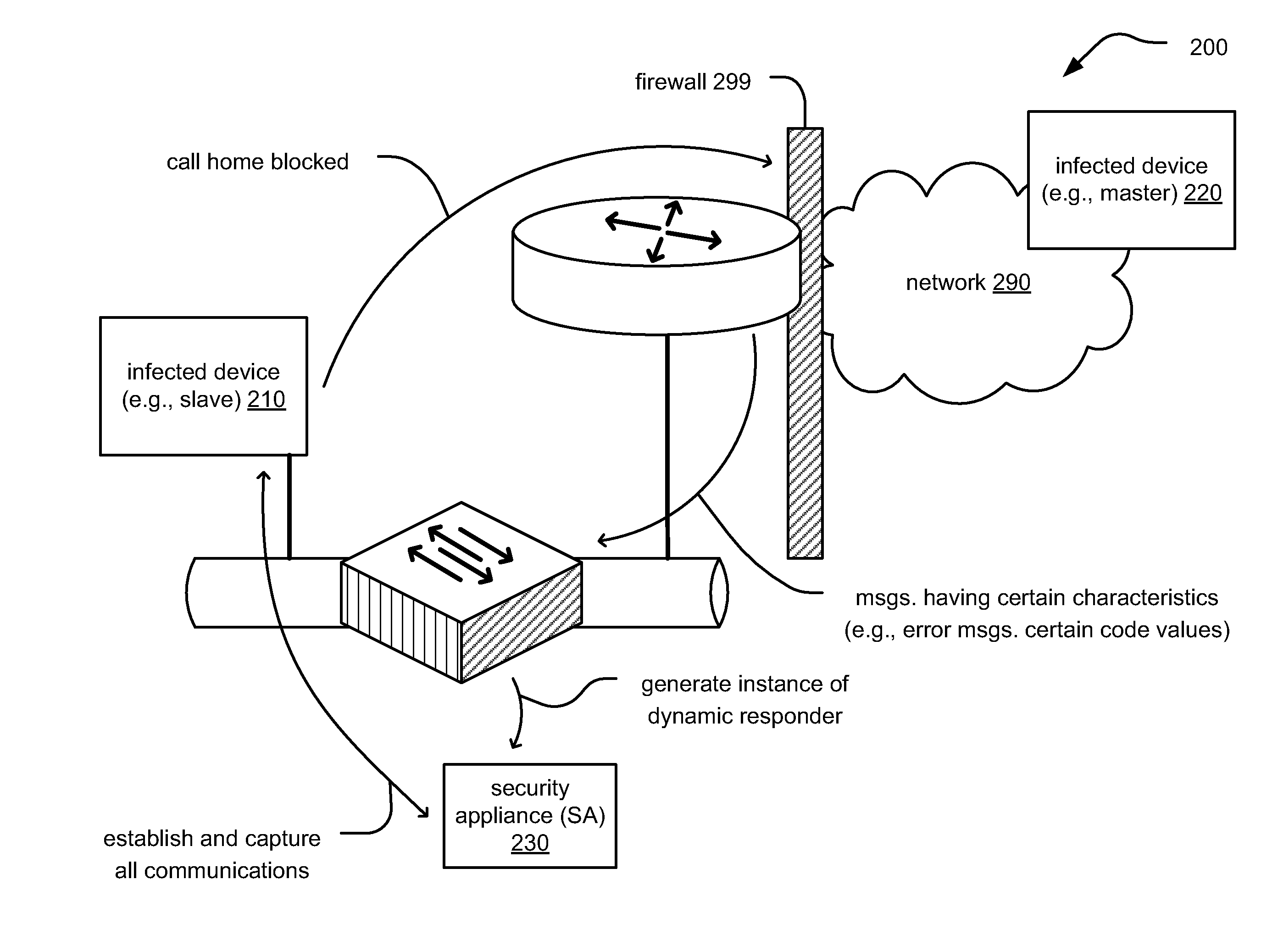
Infiltration of malware communications
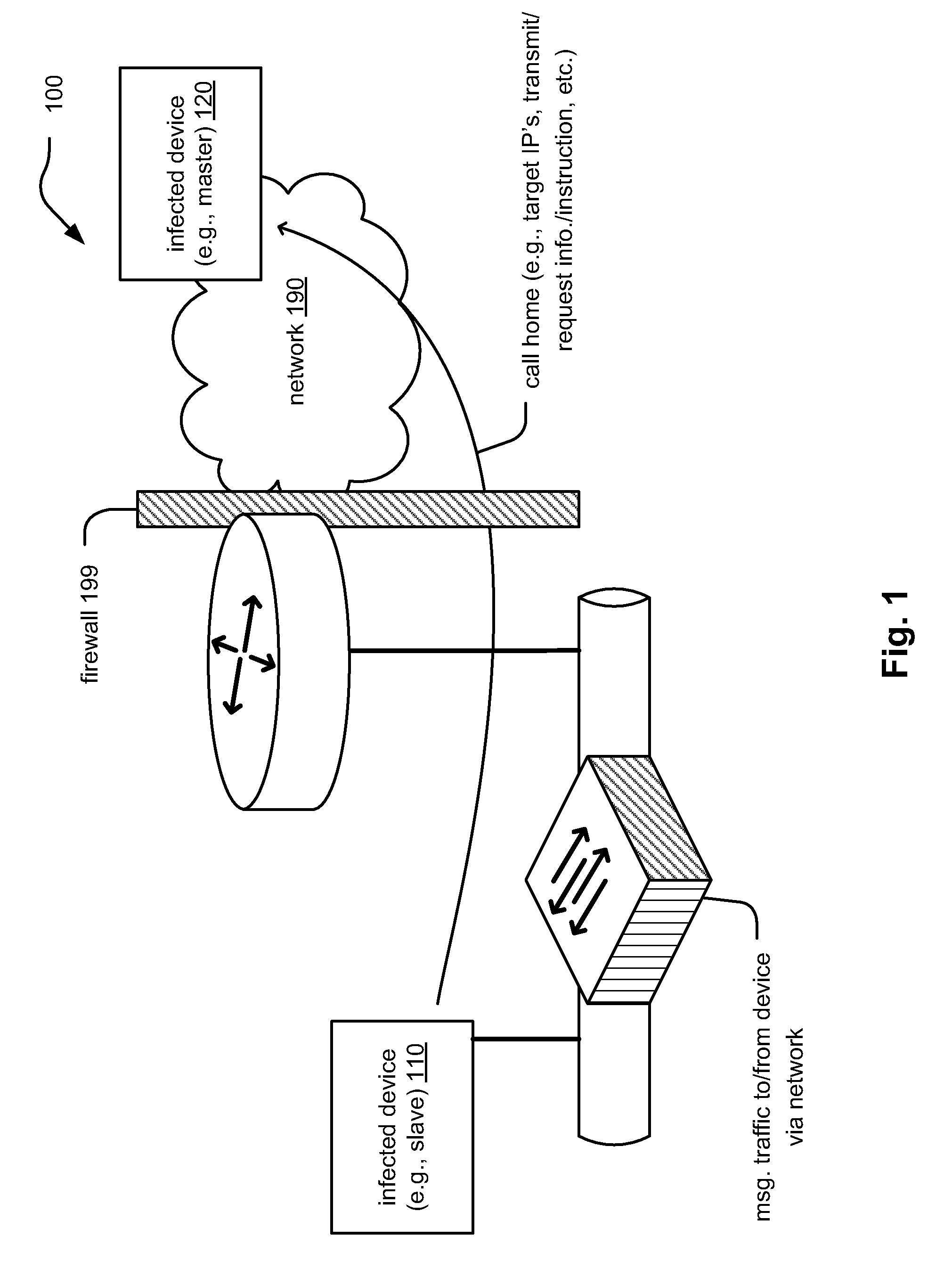
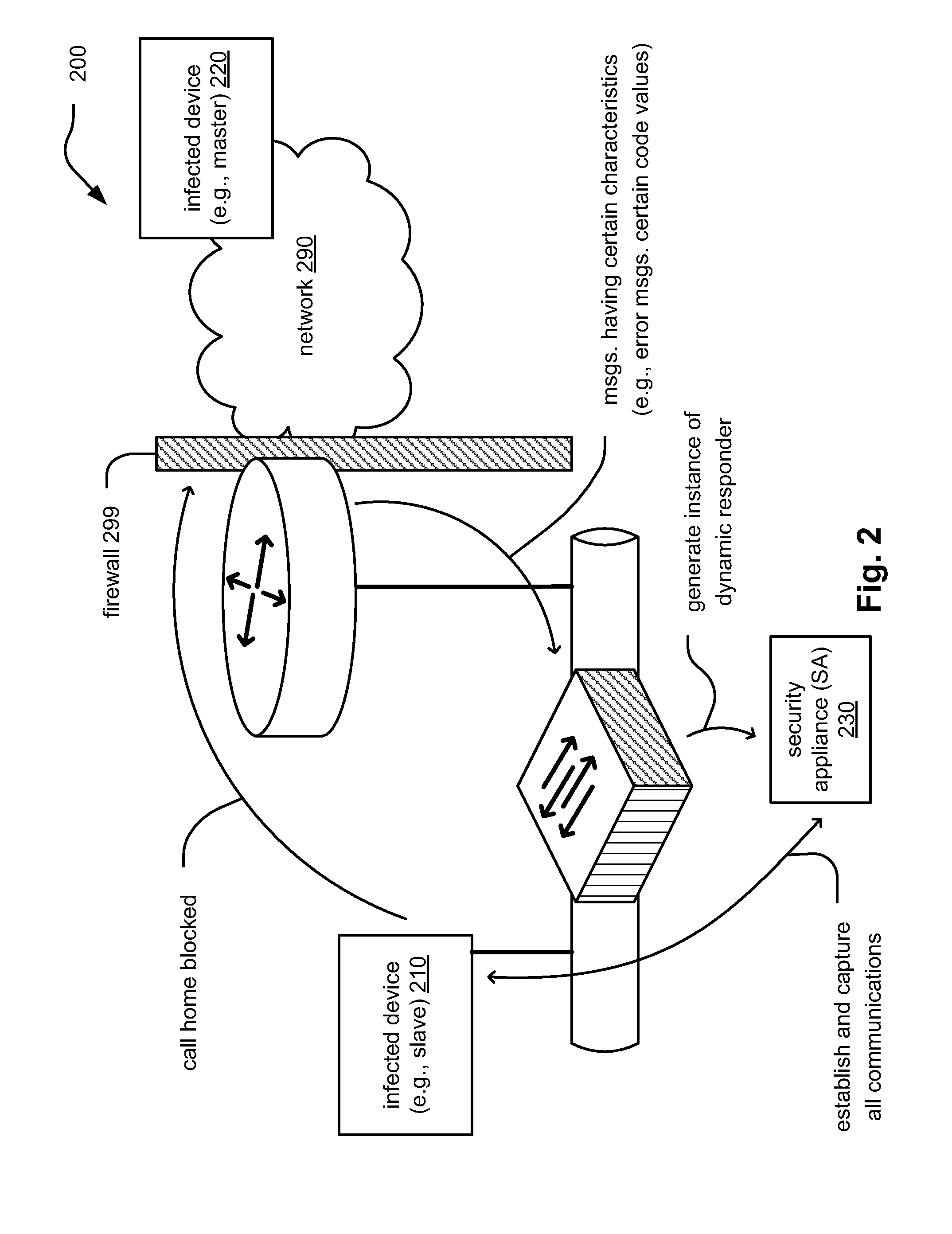
InactiveUS20100071065A1Reduce the possibilityMemory loss protectionError detection/correctionNetwork isolationNetwork service
Infiltration of malware communications. Malicious programs infecting individual devices within a network oftentimes communicate with another infected device (e.g., a master device by which the infection was established on a slave device in the first place). During this call home to a master device (or receiving a call from the master device), vital information about the attack, target, master device, etc. may be transmitted. The call home may include information acquired / retrieved from the infected device, or it may request additional information from the infecting device. By monitoring the network messages associated with such call home attempts (including any errors associated therewith), an infected device may be identified and appropriate action be taken (e.g., continue monitoring, isolate infected device from network, generate call to network help desk, etc.). This approach may be implemented at a network level to help prevent further promulgation of the malicious program to other devices.
Owner:ALCATEL LUCENT SAS
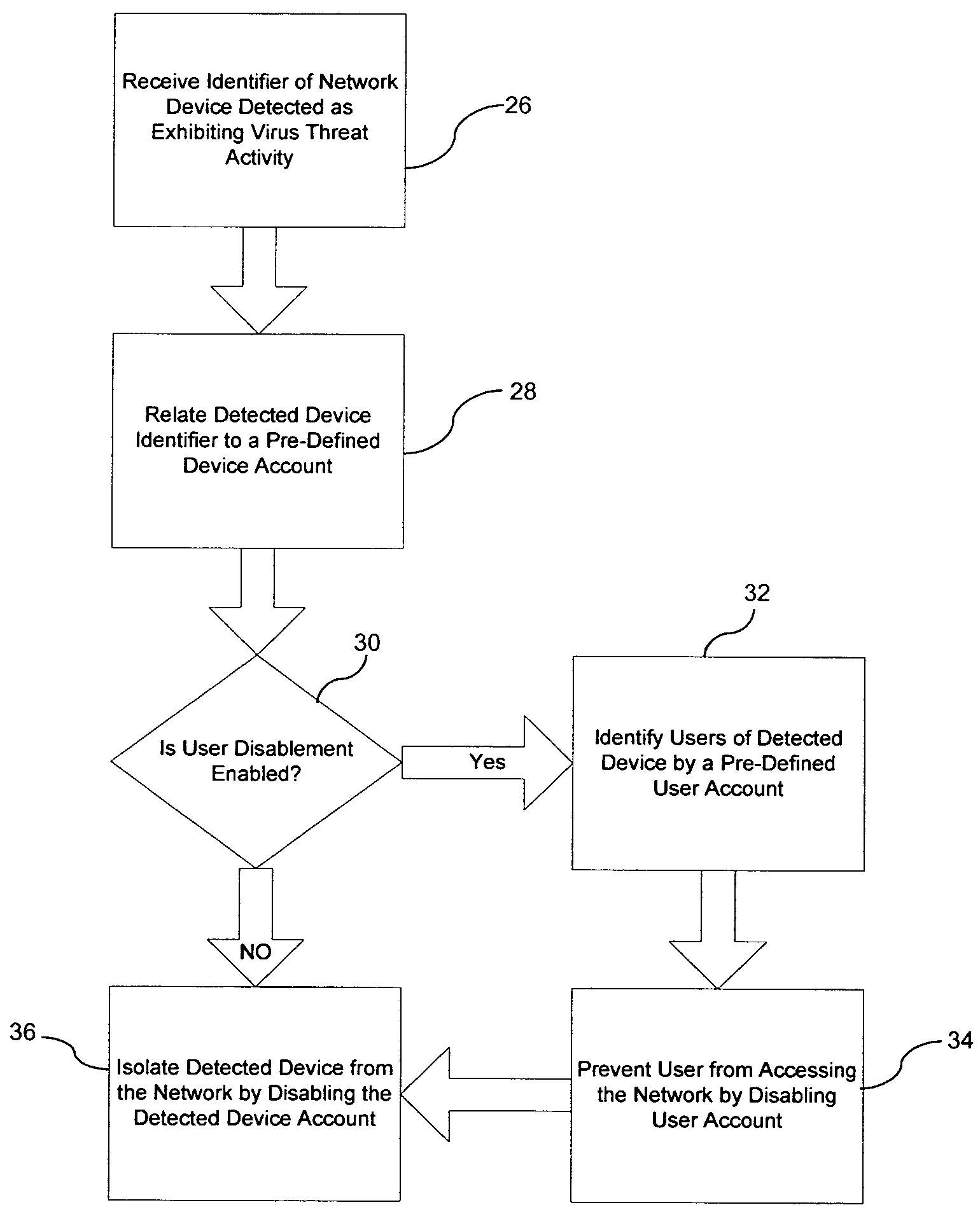
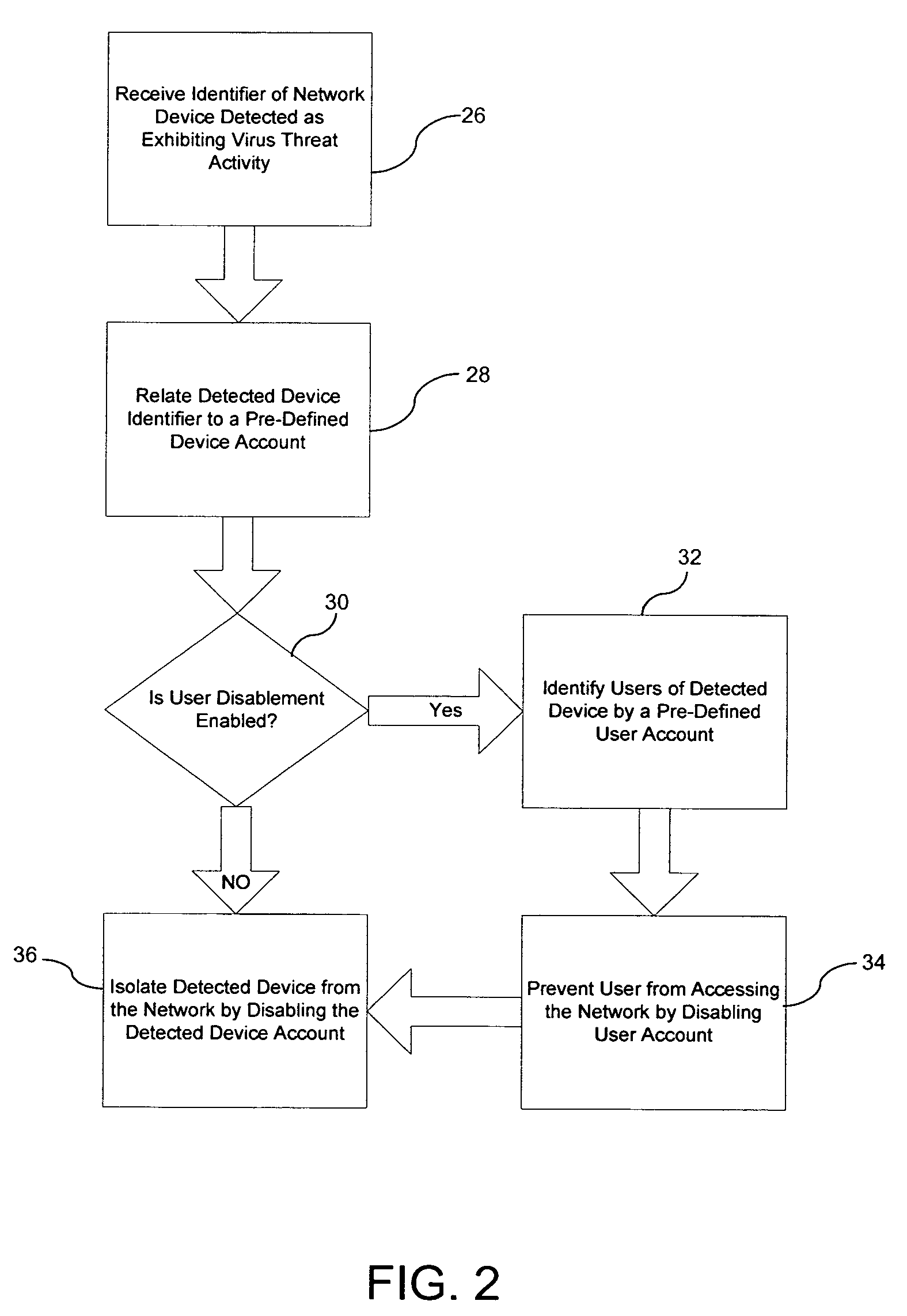
System and method for reducing the vulnerability of a computer network to virus threats
ActiveUS7571483B1Avoid infectionReduce vulnerabilityMemory loss protectionError detection/correctionNetwork isolationVirus
A method for reducing vulnerability of a computer network to a detected virus threat includes receiving an identifier of a network device detected as a source of virus activity. The method also includes relating the identifier to a predetermined account of the detected device and then automatically disabling the device account. Accordingly, the detected device is isolated from the network to prevent infection of the network by the detected device.
Owner:LOCKHEED MARTIN CORP
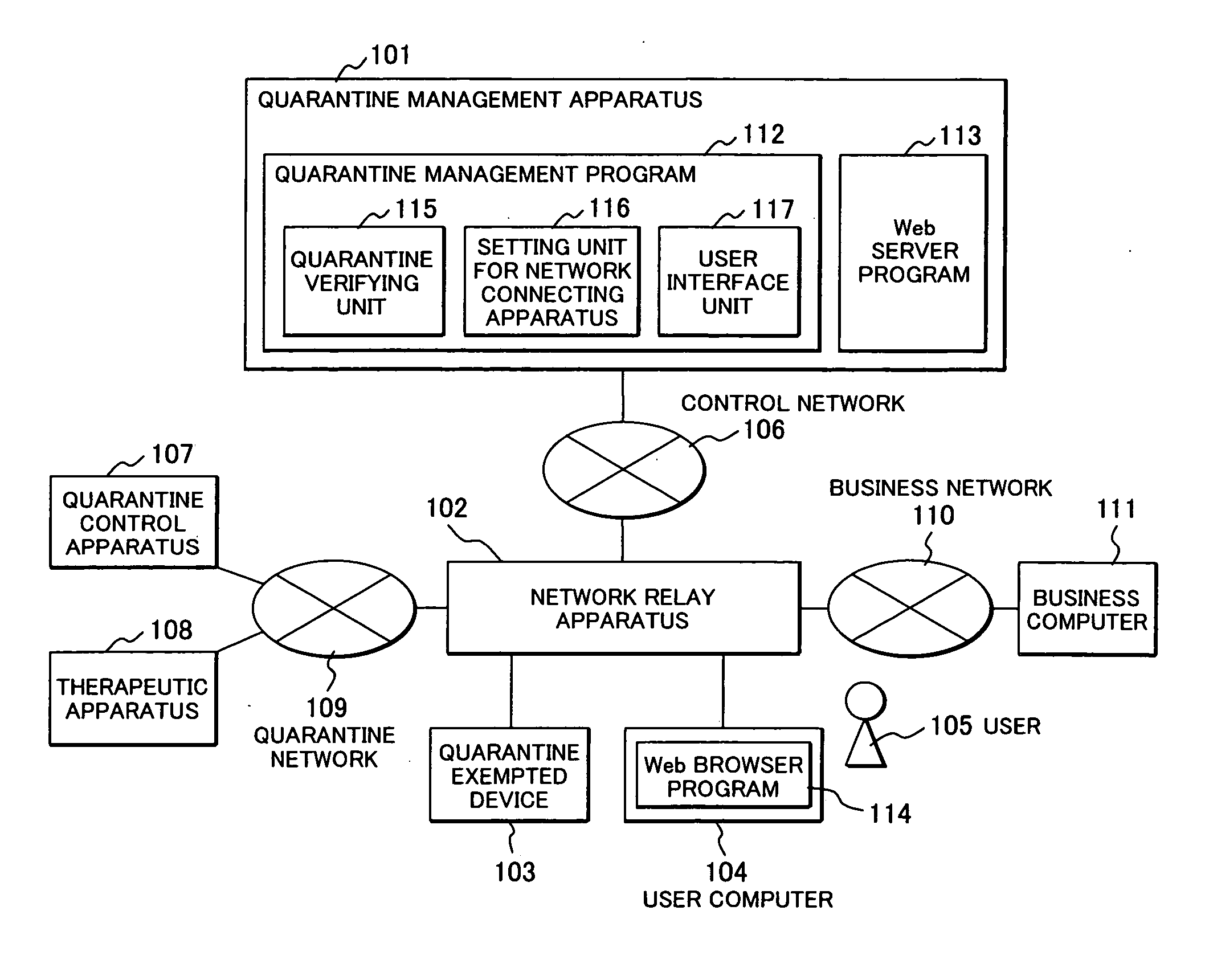
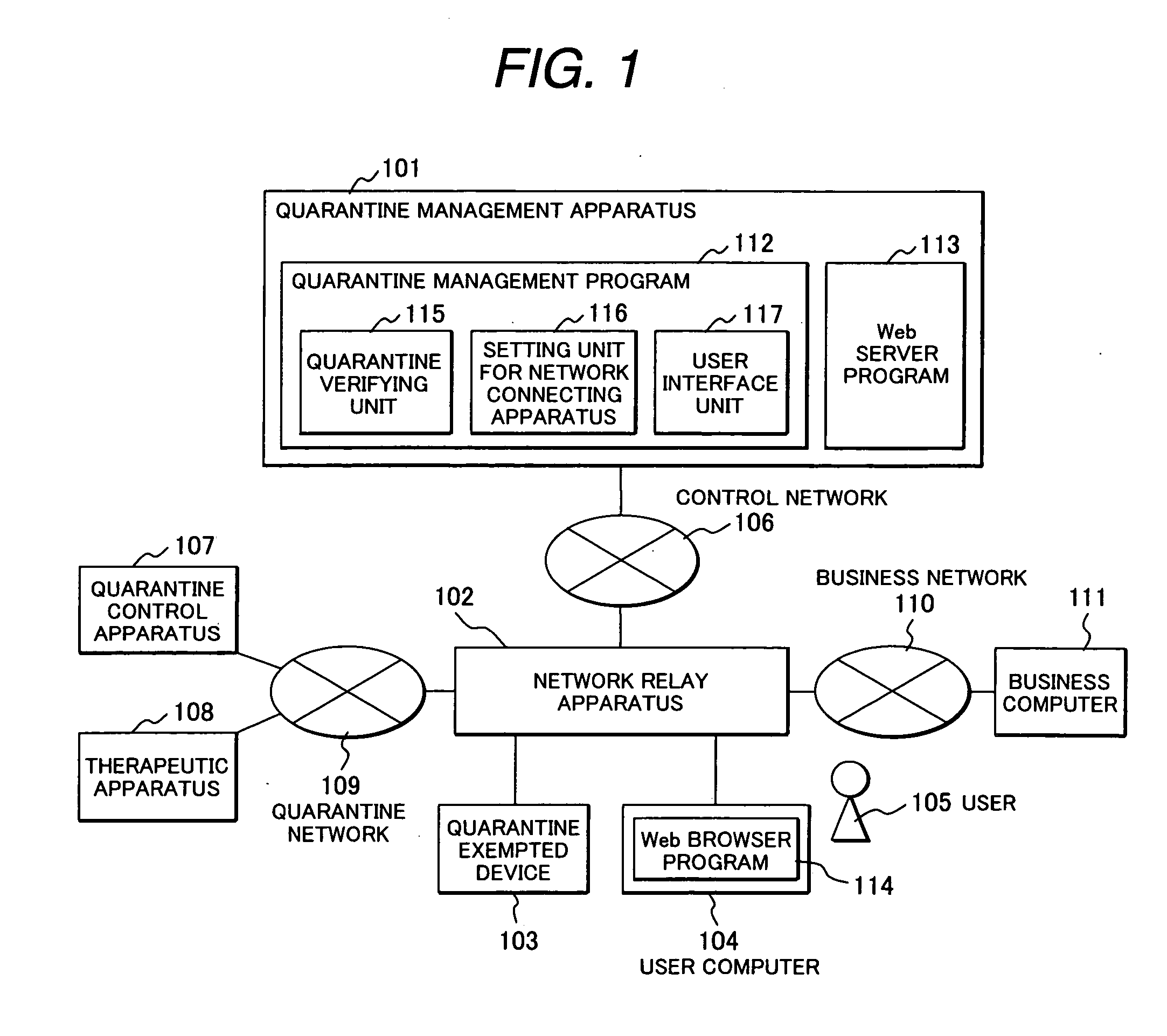
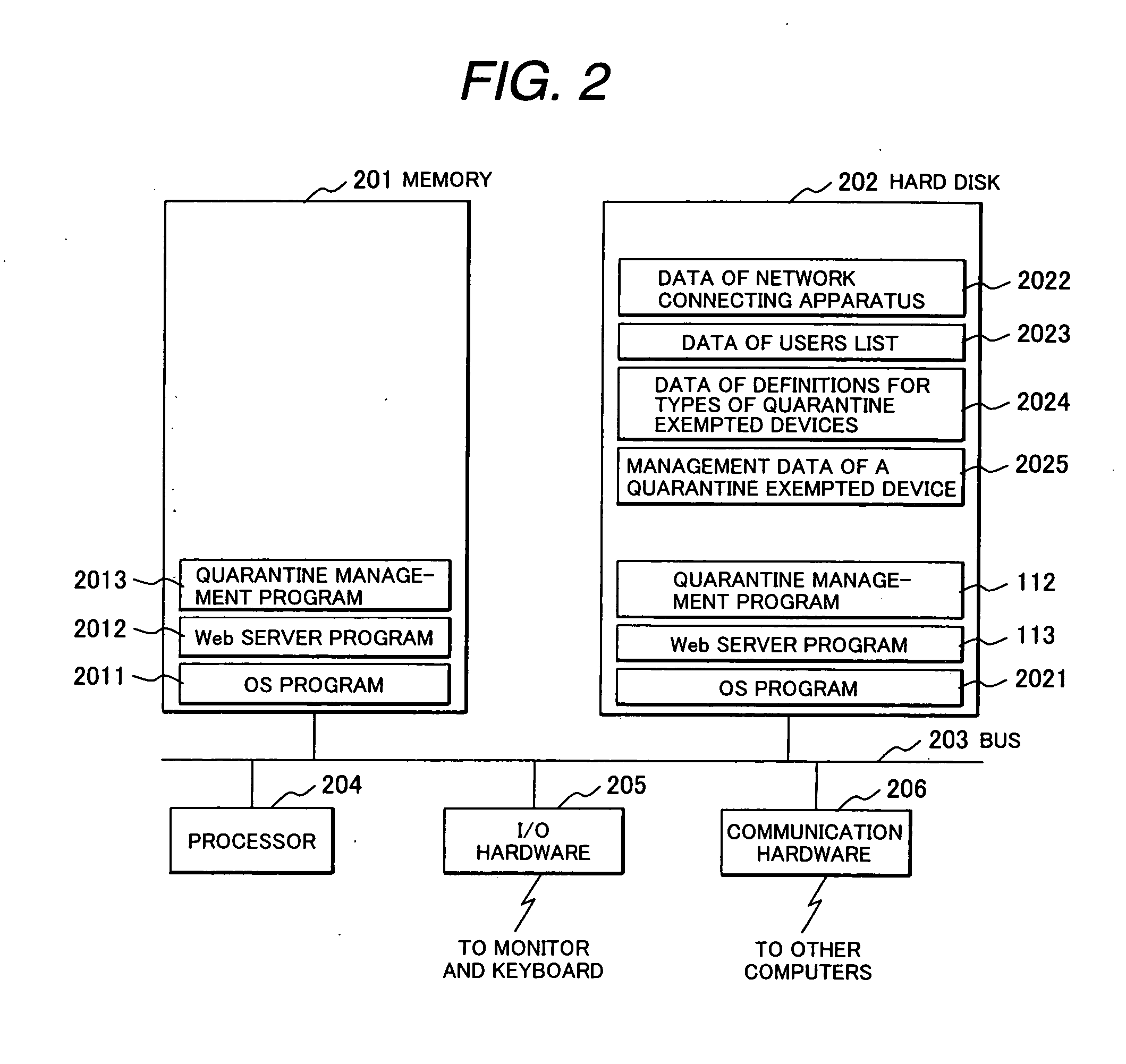
Method for device quarantine and quarantine network system
InactiveUS20070118567A1Avoid connectionMemory loss protectionError detection/correctionDevice typeNetwork connection
A network quarantine management system eliminates registration or updating work of a quarantine-exempted device and prevents a fraudulent device from abusing authorized network information registered as a quarantine-exempted device and from impersonation. when a quarantine management system detects network connection of a new device, the system judges the type (printer, NAS, etc.) of the device by port scanning. The system enables the device to communicate with another device coupled to a business network without an inspection for connecting the device to the business network, if the newly coupled device is judged to be of an authorized type. The device type judgment is conducted whenever a connection is made and is repeatedly conducted after establishment of the connection to check that the type is of an authorized type and, if the type is found to be an unauthorized type, the device is isolated for inspection.
Owner:HITACHI LTD
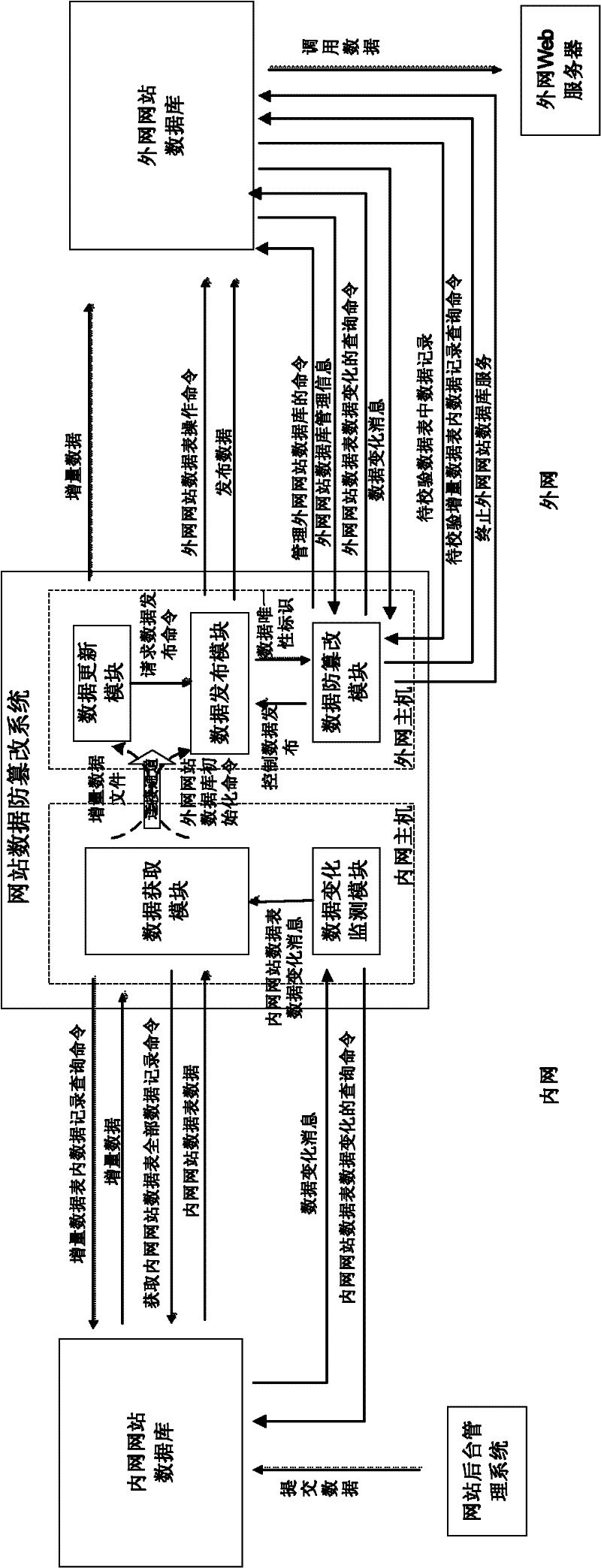
Website data tampering preventing method based on network isolation structure
ActiveCN102609645AEnsure safetyPlatform integrity maintainanceSpecial data processing applicationsWeb siteSQL injection
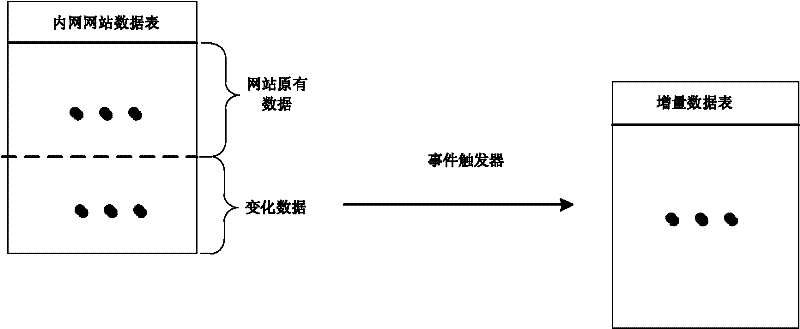
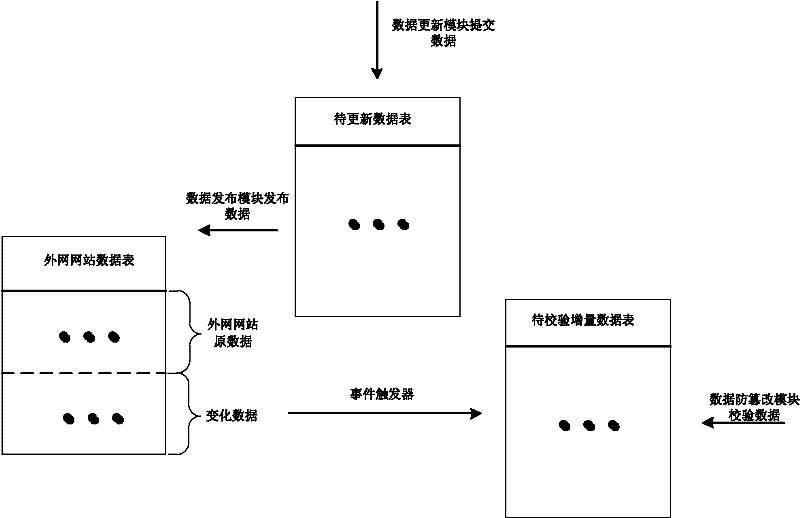
A website data tampering preventing method based on a network isolation structure belongs to the technical field of network safety. The website data tampering preventing method includes: disposing a database server storing website data to the high-safety-level network, publishing the content in a database to a database server of the low-safety-level network connected with the internet unidirectionally and protecting the website data in the low-safety-level network. Therefore, a website data tampering preventing system consisting of an intranet mainframe and an outer net mainframe which are connected to each other is built, in the outer net mainframe, a data updating module submits incremental data to a data sheet to be updated, and a data publishing module publishes the incremental data to an outer net website data sheet. A data tampering preventing module inquires system configuration and data variation in an incremental data sheet to be checked at regular time, starts corresponding operation when detecting data variation and ensures operations of the outer net website data sheet to be authorized. By the aid of the website data tampering preventing method based on the network isolation structure, attacks to the database, such as SQL (structured query language) injection and the like, can be effectively avoided and data safety of the website database is guaranteed.
Owner:北京中关村银行股份有限公司
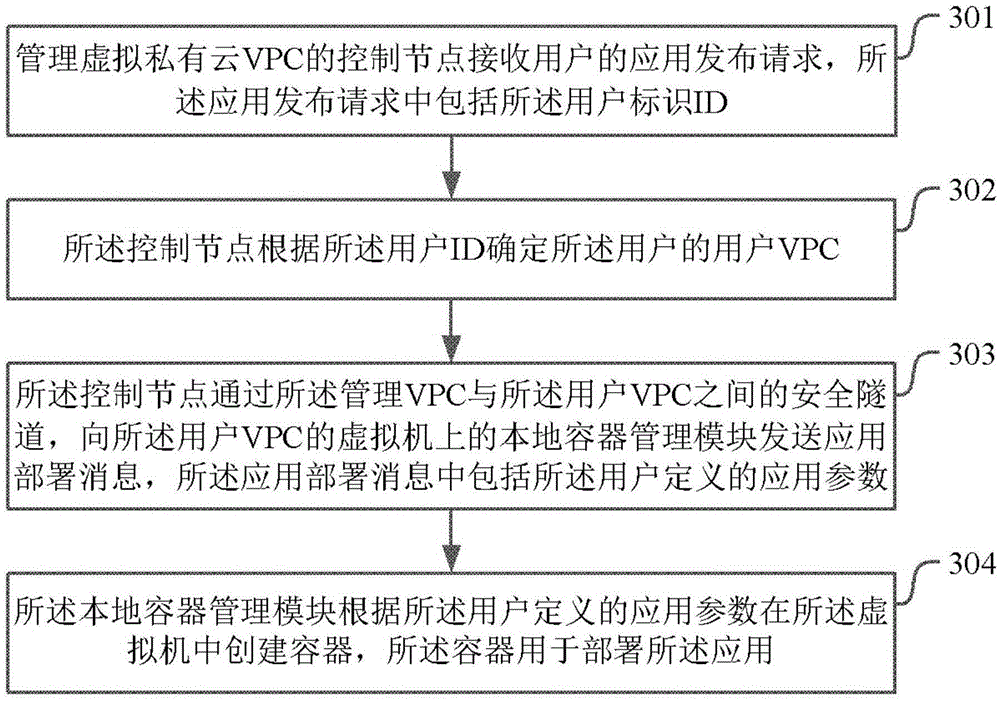
Application deployment method and apparatus
ActiveCN105354076AImprove securityMake sure you can't communicateSoftware simulation/interpretation/emulationNetwork isolationUser identifier
The present application provides an application deployment method and apparatus. The method comprises: a control node of a management VPC (Virtual Path Connection) receiving an application publishing request of a user, wherein the application publishing request comprises a user identifier ID; the control node determining a user VPC of the user according to the user ID; by means of a secure channel between the management VPC and the user VPC, the control node sending an application deployment message to a local vessel management module on a virtual machine of the user VPC, wherein the application deployment message comprises a user-defined application parameter; and the local vessel management module creating a vessel in the virtual machine according to the user-defined application parameter, wherein the vessel is used for deploying an application. According to the application deployment method and apparatus provided by the present invention, resources of the user VPC is unifiedly managed by the management VPC, and the secure channel exists between the management VPC and the user VPC, so that network isolation between different user VPCs is ensured, thus the application of each user will not be attacked by other users, and security of the user application is improved.
Owner:CLOUDMINDS SHANGHAI ROBOTICS CO LTD
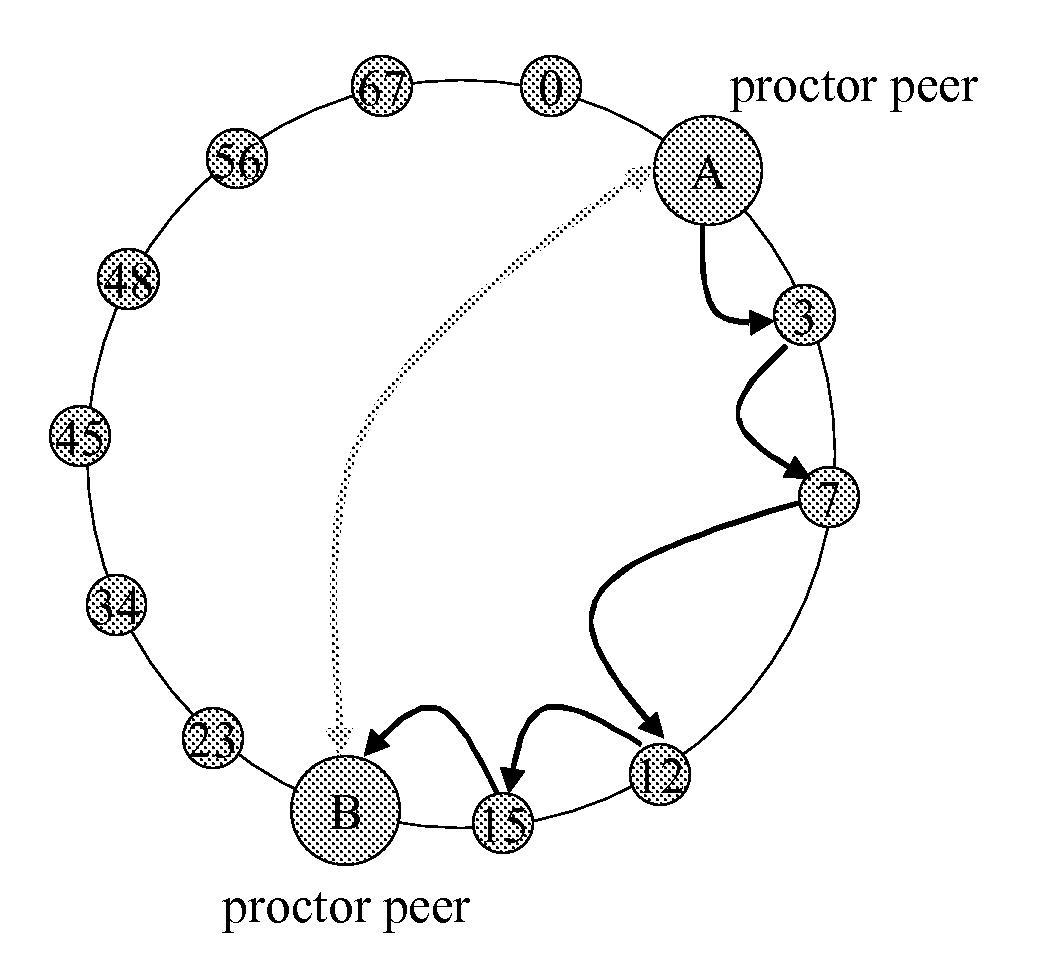
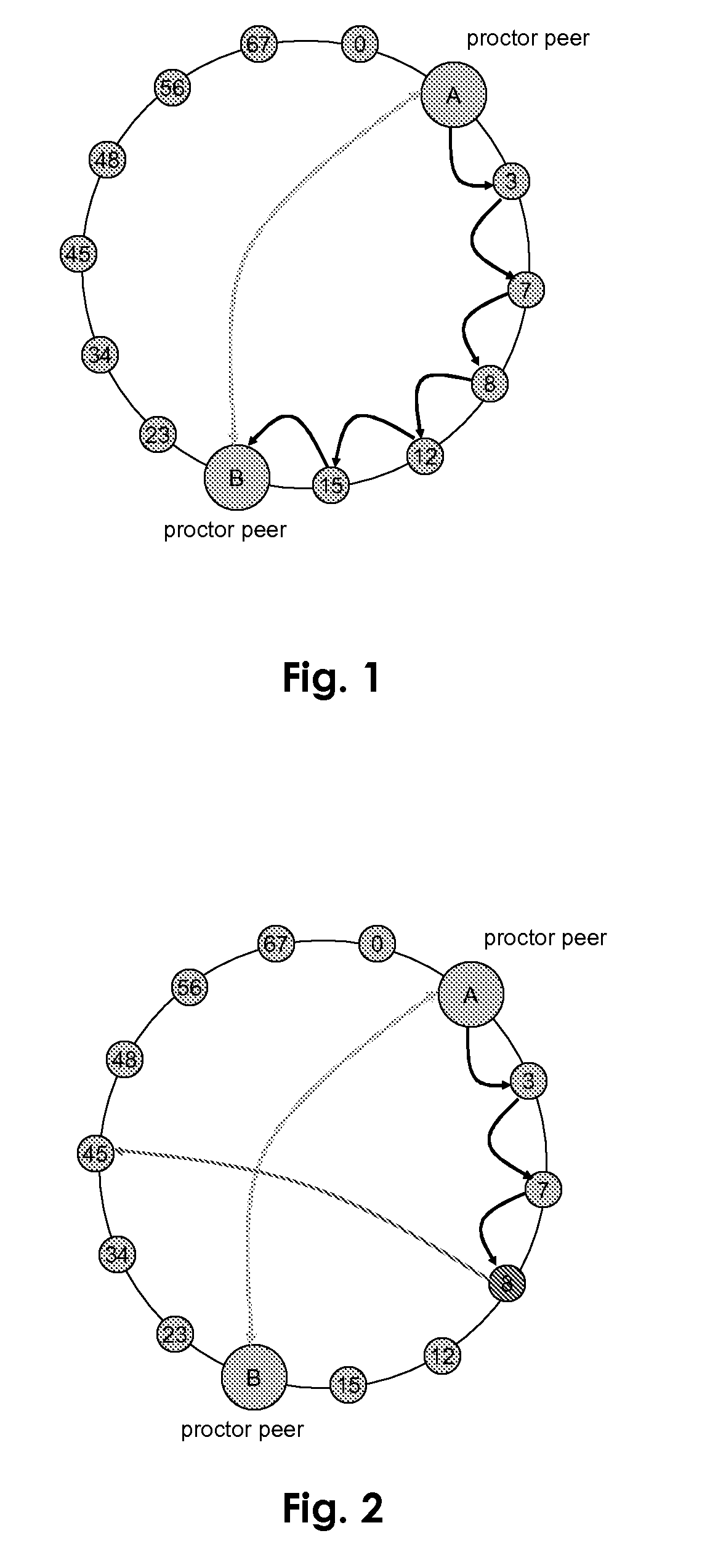
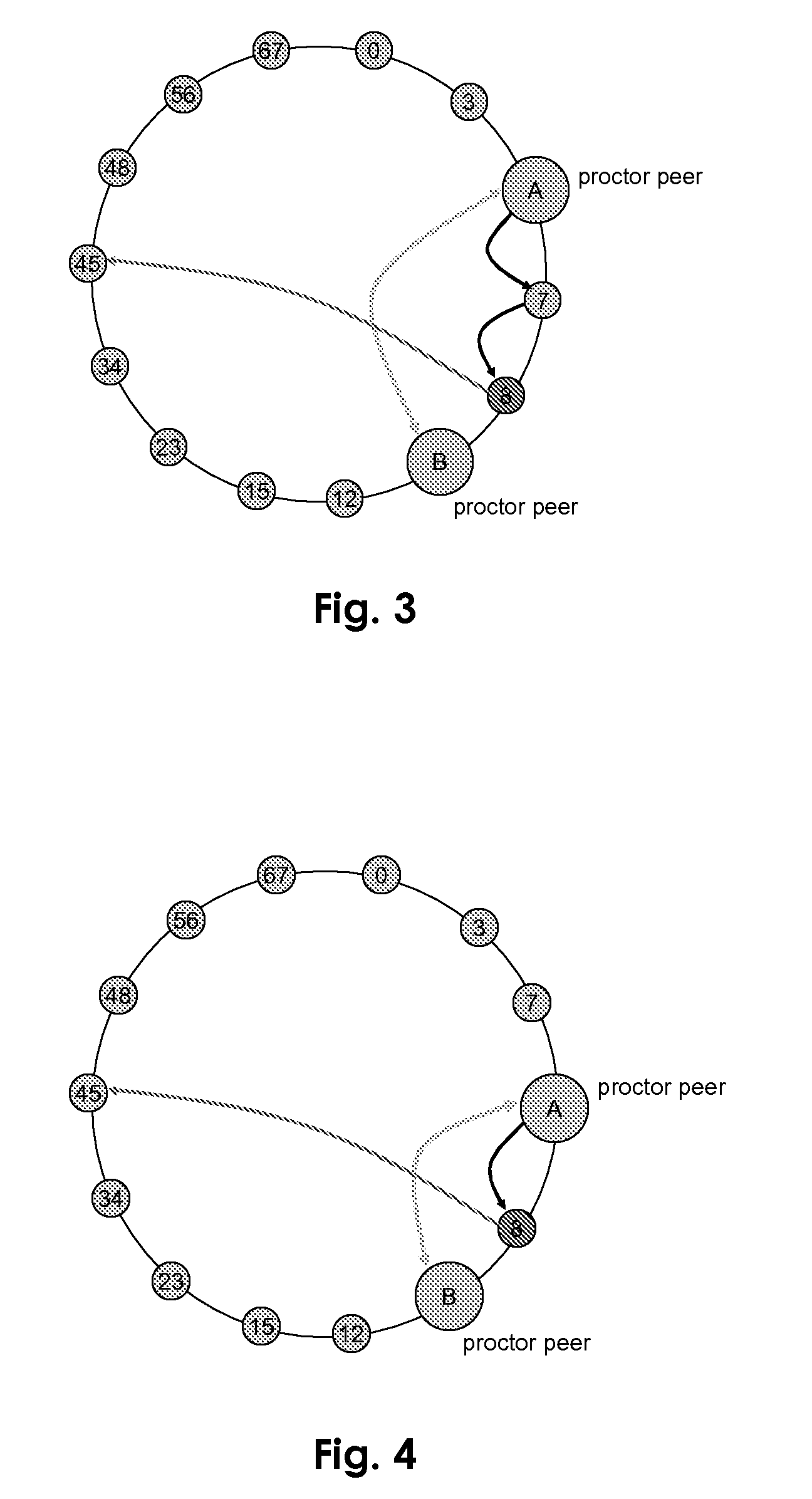
Proctor peer for malicious peer detection in structured peer-to-peer networks
ActiveUS20080313500A1Hardware monitoringData switching networksTest requirementsDistributed computing
Owner:AREIX ANALYTICS LTD
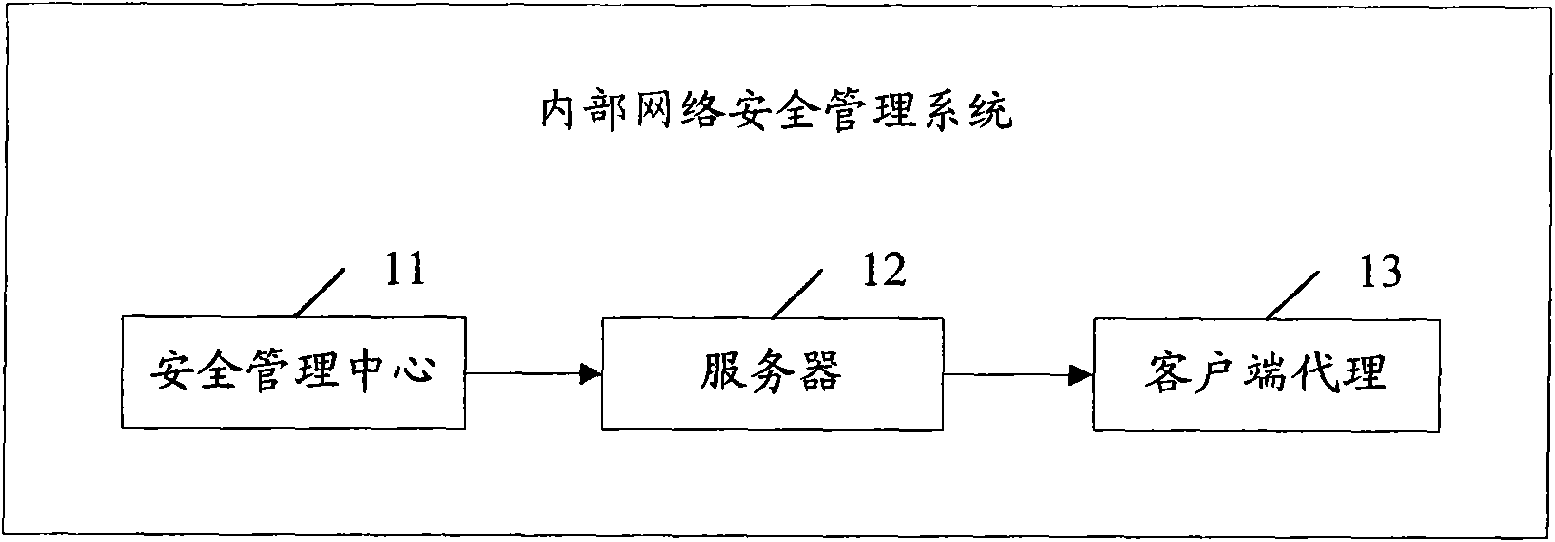
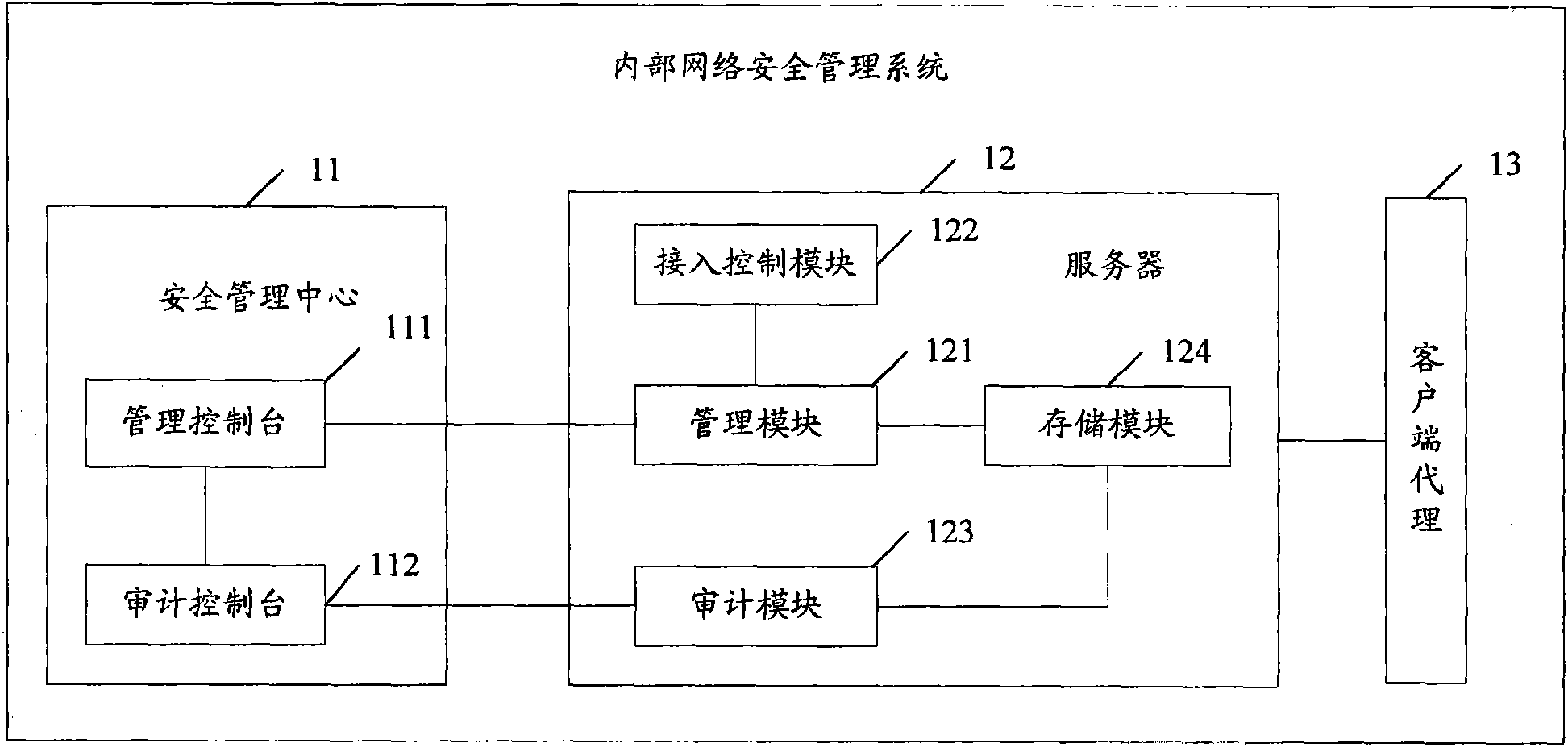
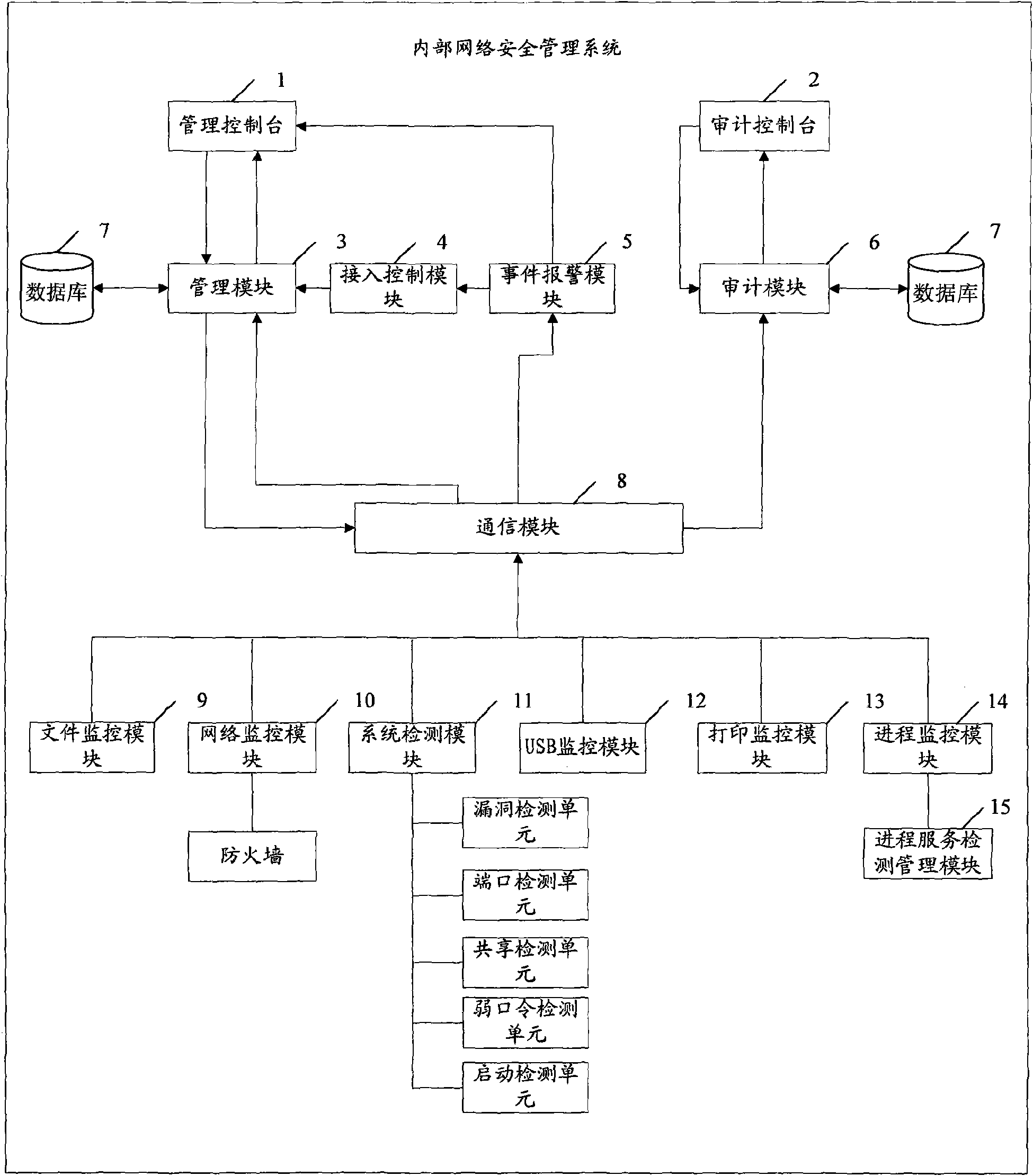
Associated equipment and method for internal network security management
InactiveCN101588360AIntegrity guaranteedAvoid abuseData switching by path configurationTerminal equipmentNetwork isolation
The invention provides associated equipment and method for internal network security management, wherein, through generating and maintaining a security management strategy and an audit strategy; the invention ensures that all the terminals accessible to internal network submit to the strategies; with respect to an piece of equipment unqualified to the strategies, the system processes the equipment as follows: providing a network isolation and locking device, and sending an warning, with the purpose of ensuring that the equipment does not bring the whole network with bad influence on the security and management. The invention not only implements an active defense mechanism of the system, but also effectively prevents some malicious acts of validated user, such as misapplication of network resource, information theft, and active attack by means of internal computers.
Owner:SHENZHEN CITY ANLUODACHENG TECH
Self-healing tree network
InactiveUS20050044211A1Blocking in networkAvoid creatingError detection/correctionData switching by path configurationNetwork isolationTree network
A communications network is provided with a self-healing topological architecture. Each node in the network detects continuously transmitted beacon packets that are propagated through the network at regular intervals by a root node. Upon failure to detect a new beacon packet after a predetermined time from a parent node, a network node determines a network isolation condition and searches for another node that is still actively connected in the network. Algorithms are provided for registering with and identifying active parent node candidates during a network failure so as to prevent the creation of network loops.
Owner:OMNILUX
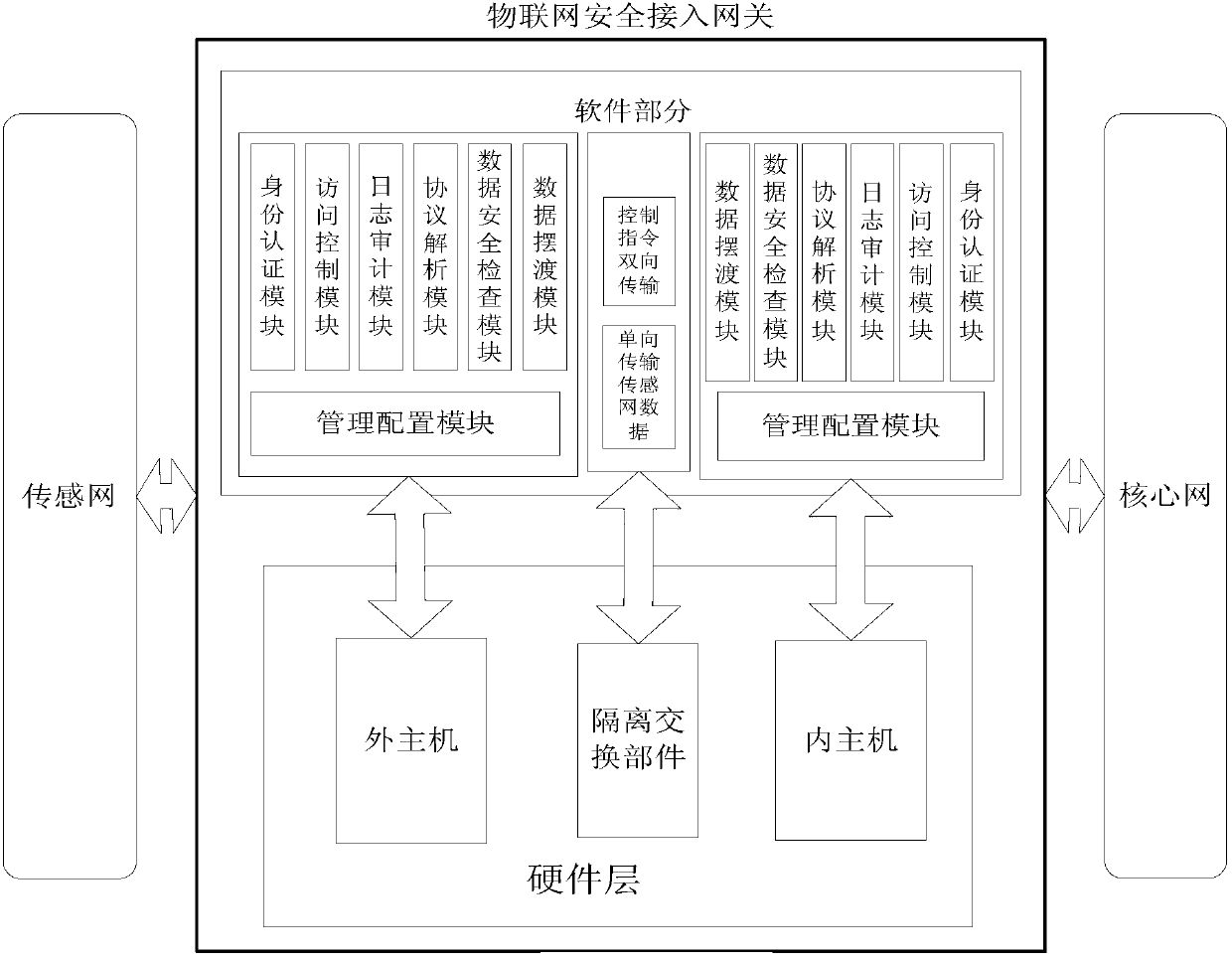
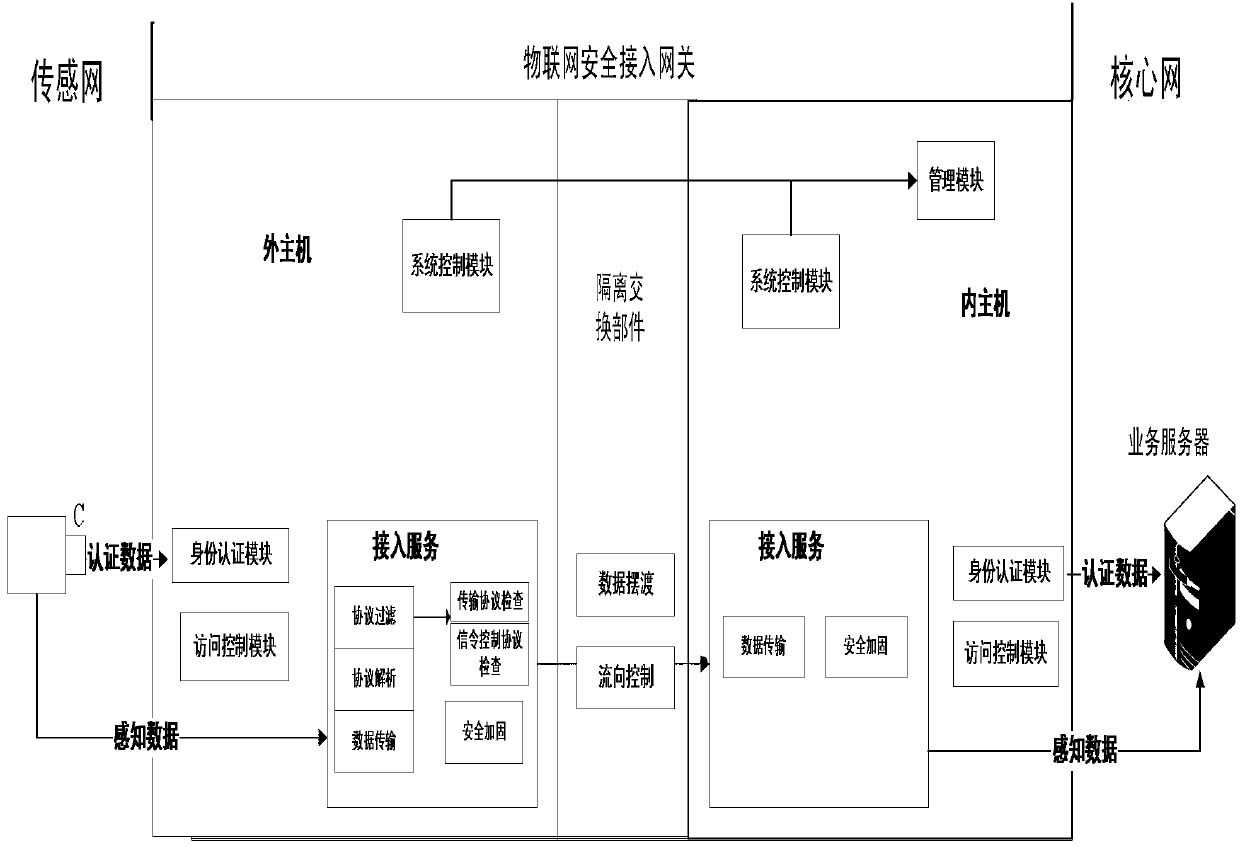
Internet of things security access gateway
InactiveCN103139058ARealize security border controlMeeting Multi-Protocol Complexity RequirementsNetwork connectionsGate arrayThe Internet
The invention discloses an internet of things security access gateway. A three component framework of 2+1 is adopted in a hardware layer of the gateway. The three component framework comprises an outer host machine, an isolation exchange component and an inner host machine. A filed programmable gate array (FPGA) card based on hardware serves as the isolation exchange component so that isolation of a network and safe and rapid exchange of data are achieved. Device certification, access control, protocol analysis, data security check, data ferry service and audit service are achieved through software layers on the inner host machine and the outer host machine and action of the services can be traced. The internet of things security access gateway has the advantages that relative requirements that data collected by an internet of things perception terminal is introduced to a core network safely are satisfied, network attack, Trojan horse virus transmission and denial of service attack are prevented from being launched through a sensing layer network with weak safety protection to the core network, safe exchange of data is achieved under the condition that the sensing network and the core network are in network isolation, and practical application of the internet of things is achieved under the condition that safety is guaranteed.
Owner:THE FIRST RES INST OF MIN OF PUBLIC SECURITY +1
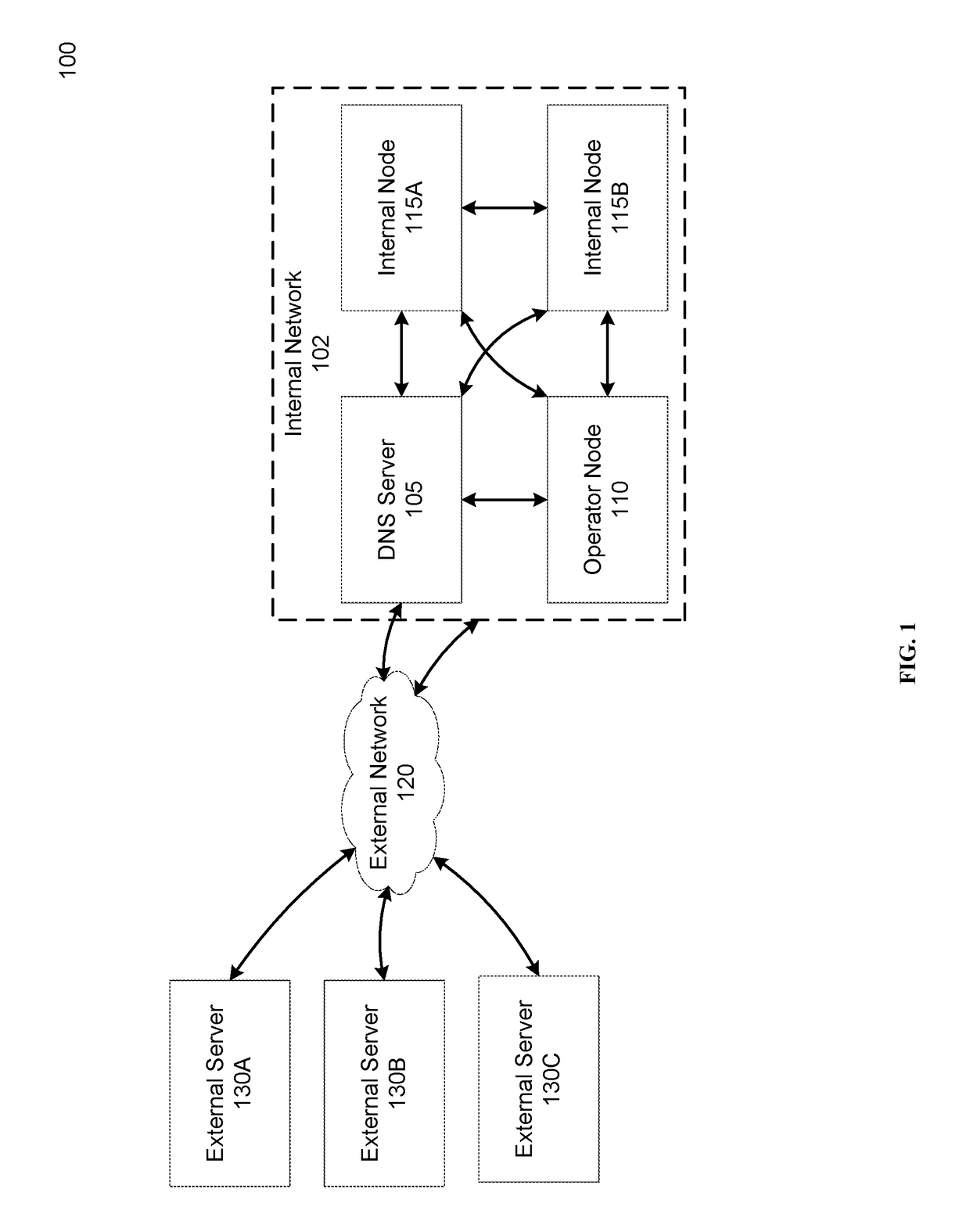
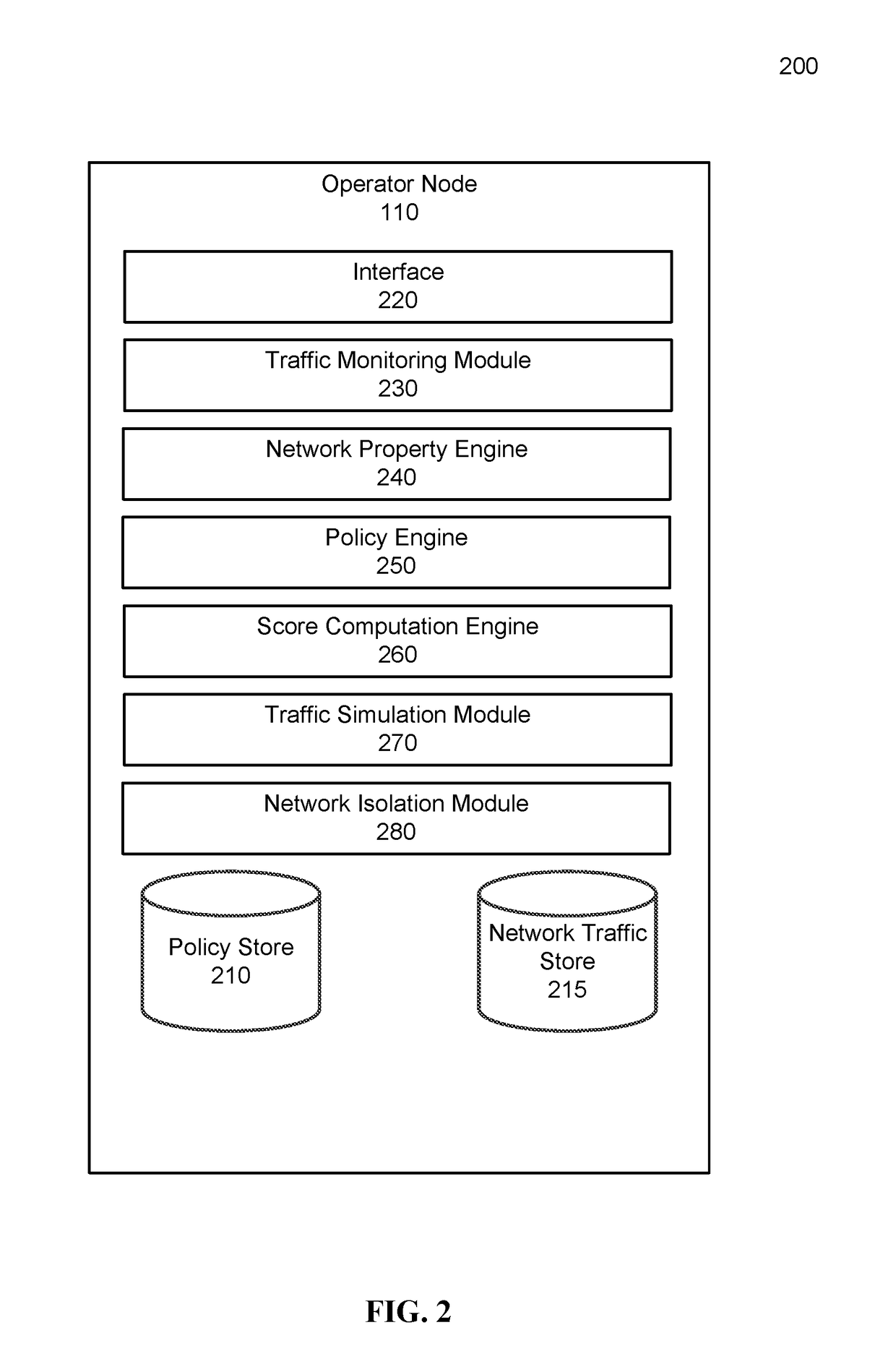
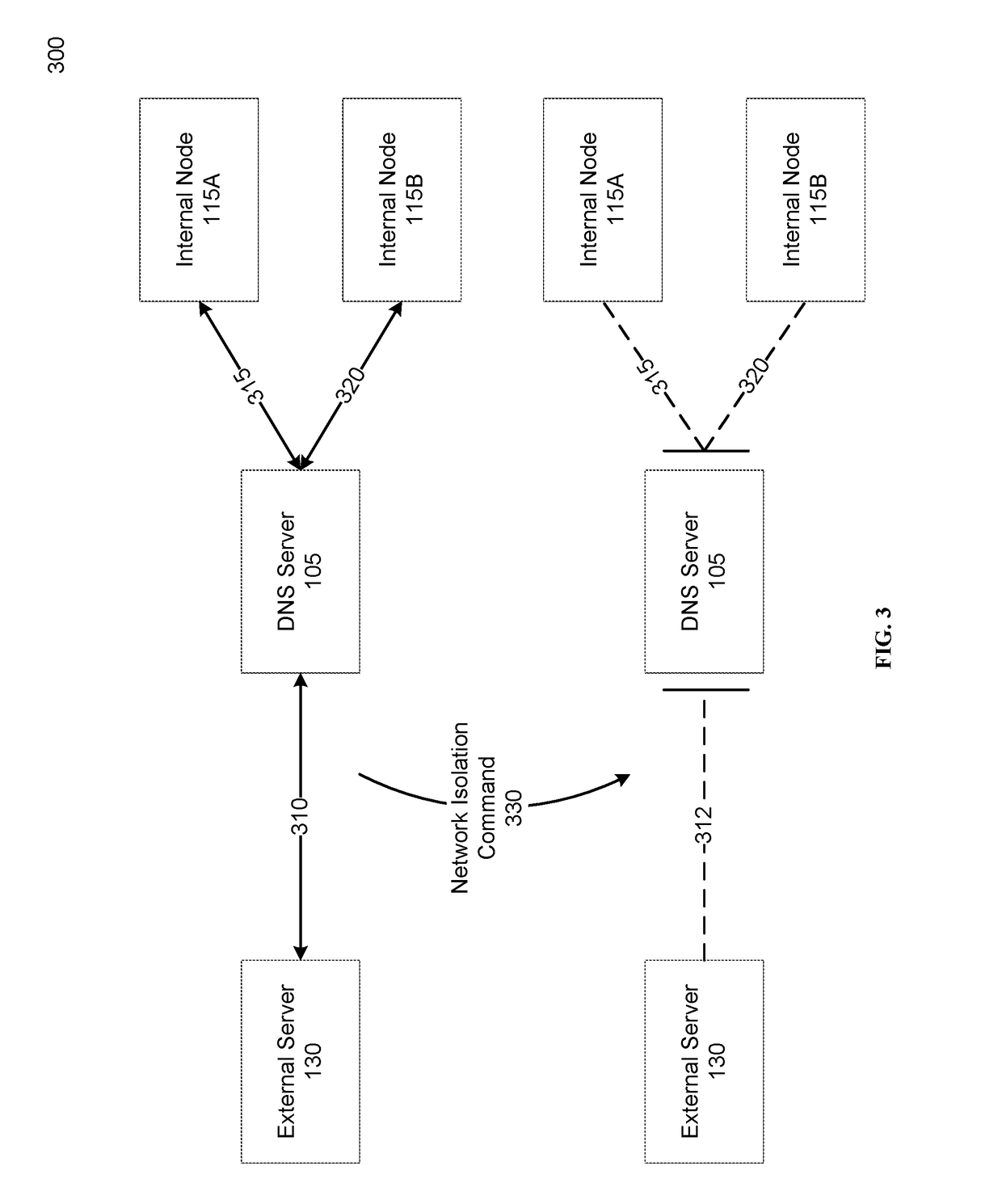
Network isolation by policy compliance evaluation
An internal network can include a plurality of linked internal nodes, each internal node being configured to communicate with other internal nodes or with one or more external servers over an external network. The internal network can analyze the configuration of the internal nodes and the network traffic between internal nodes of the internal network and external servers. Based on the analysis, a network vulnerability score measuring the vulnerability of the internal network to attack can be determined. If the vulnerability score is below a threshold, the internal network can be isolated from the external network, for example by preventing internal nodes from communicating with or over the external network.
Owner:UPGUARD INC
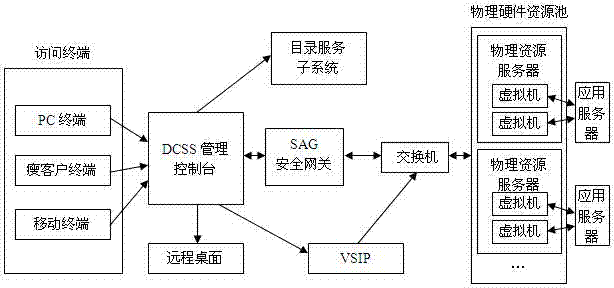
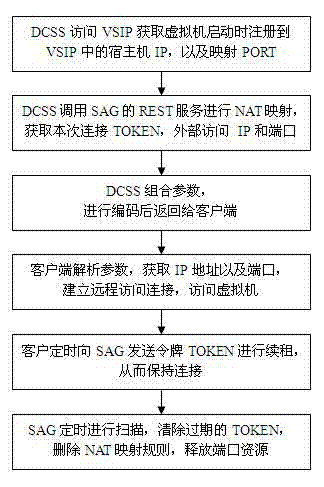
Cloud desktop management system based on security gateway and security access control method thereof
ActiveCN104753930AEnsure manageabilityEnsure safetyTransmissionCloud data managementNetwork address translation
The invention discloses a cloud desktop management system based on a security gateway and a security access control method thereof. The method comprises the steps of providing a uniform security entrance by an SAG (Security Access Gateway) security gateway, and shielding an internal network; supporting a cluster, and dispatching and distributing requests by a management node; adopting a token mechanism; providing a management interface. The method provided by the invention comprising the steps of building the mapping between an external connecting port and the internal network by adopting a linux firewall NAT (Network Address Translation) technology, and providing the uniform security entrance to shield the internal network; supporting the cluster, supporting a frame of a plurality of management nodes and a plurality of Agent nodes by adopting a flexible frame and a flexible deployment way, and distributing requests by the management nodes; adopting the token mechanism to map the port and keeping the connection, and ensuring the manageability of client access and connection. The network isolation between the client and an application server can be realized, i.e. the client and the applying server are arranged at different network segments, therefore the client cannot directly visit the applying server, but can visit the resource of the applying server through a virtual machine, and the security of the virtual resources can be ensured.
Owner:HAIYU SCI & TECH DEV GUIZHOU PROV +1
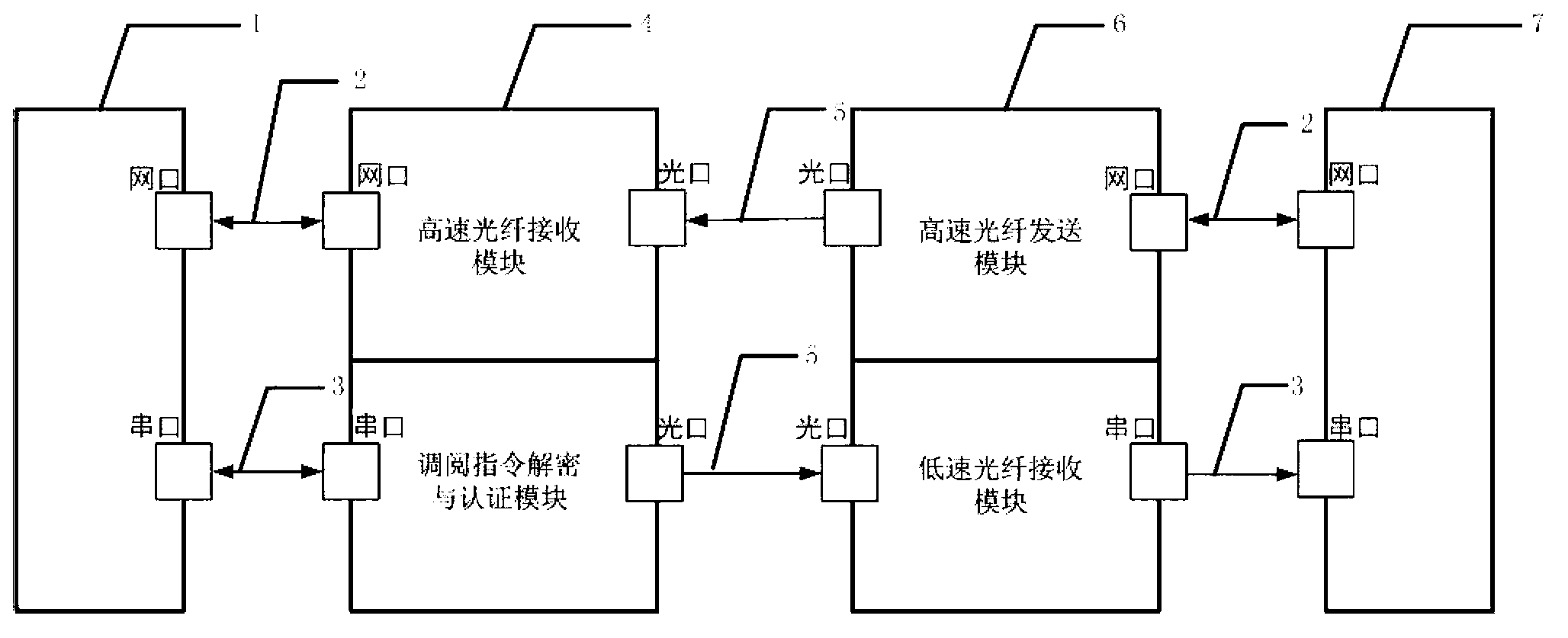
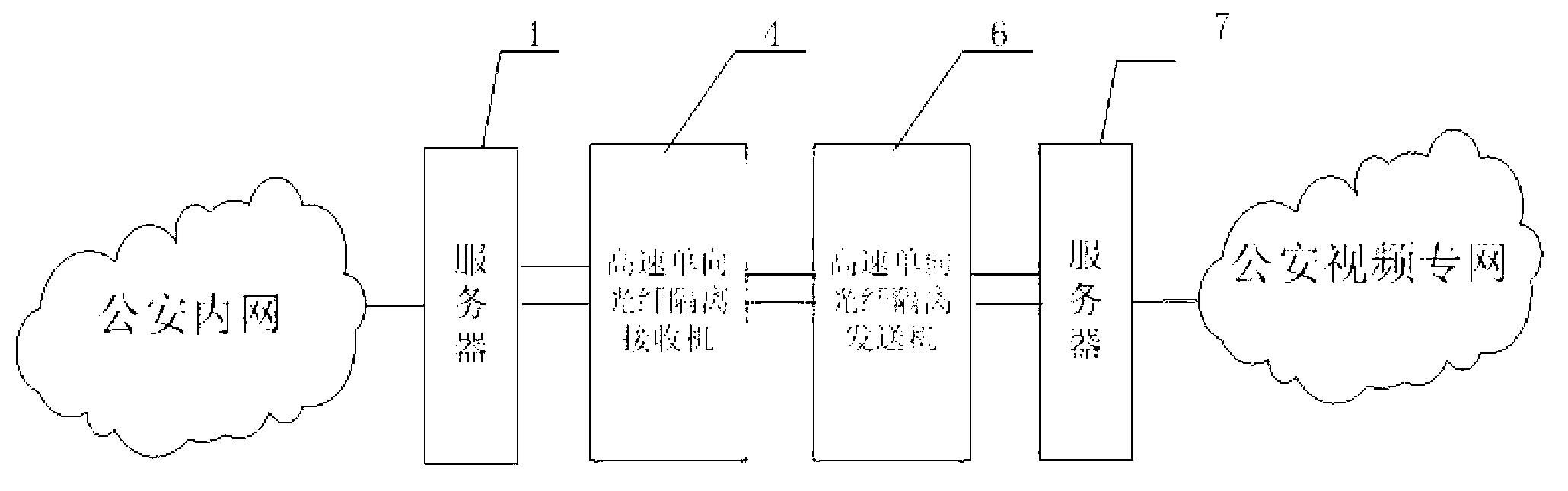
Public-security inner network and special video network isolation system and method
ActiveCN103200201AIntranet protectionClosed circuit television systemsTransmissionNetwork packetNetwork isolation
The invention discloses a public-security inner network and special video network isolation system and method. A limited unidirectional serial channel and a high-speed unidirectional network channel are creatively selected for connection; according to the method, a user-defined encryption protocol and a packet format are used for carrying out unidirectional video access instruction transmission; and an attacker cannot obtain decryption methods, so that even in the most extreme case that an internal network video server is manipulated by the attacker and data are sent out through a serial port, the data can be intercepted by a high-speed unidirectional optical-fiber isolating receiver and cannot be transmitted to special video networks, and then, an inner network is effectively protected.
Owner:OB TELECOM ELECTRONICS
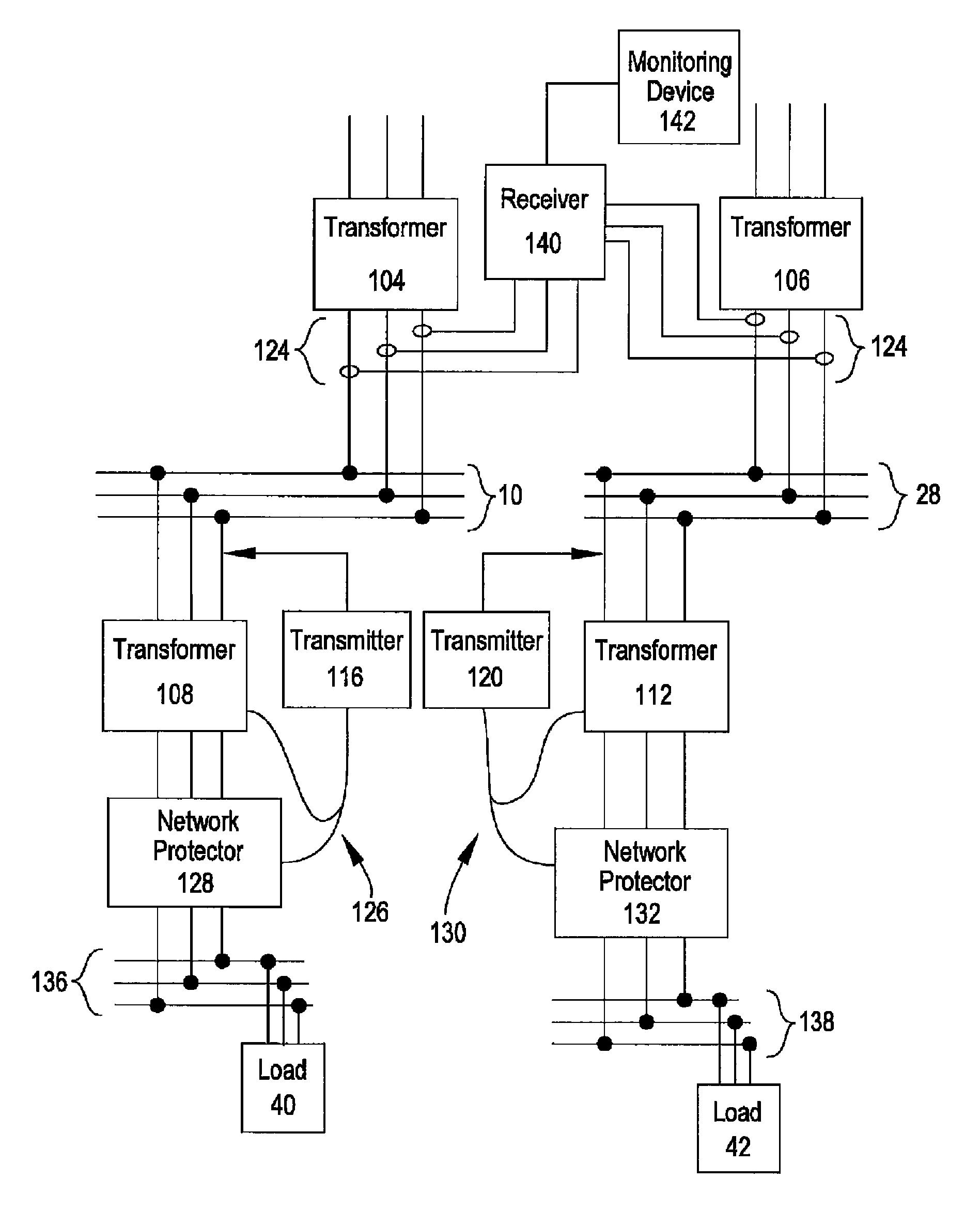
Remote monitoring of control decisions for network protectors
ActiveUS7808128B1Resonant long antennasBoards/switchyards circuit arrangementsNetwork protectorCarrier signal
Network protectors isolate the secondary side of a transformer from a load distribution network. It is useful to have information about the electrical parameters for the transformer and the load side of an open network protector and it is useful to have access to electrical parameters for a closed network protector. Information about a network protector can be provided to a transmitter used to convey information about the transformer associated with that network protector so that information about the network protector can be sent over power liner carrier to a centralized receiver.
Owner:DGI CREATIONS
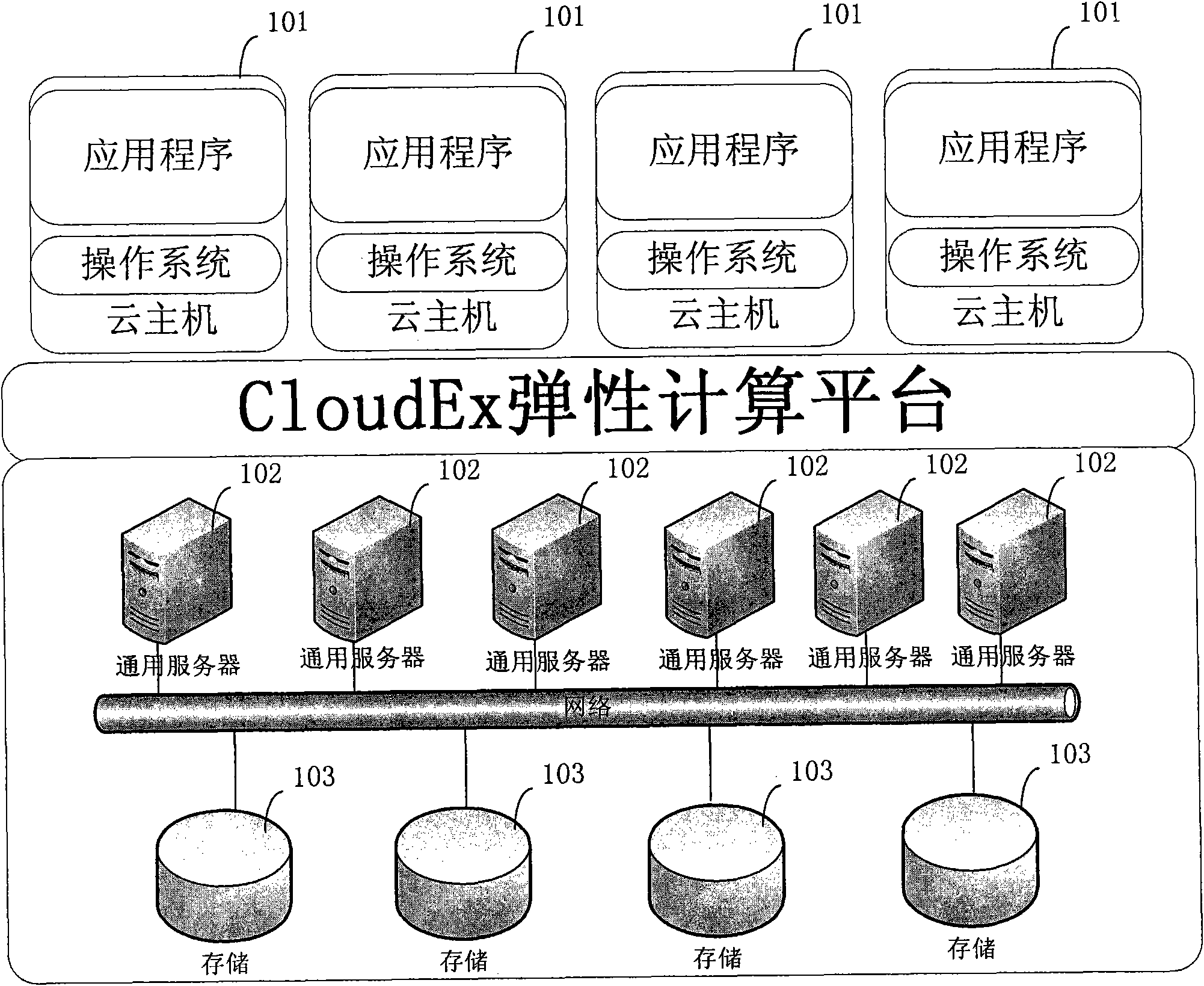
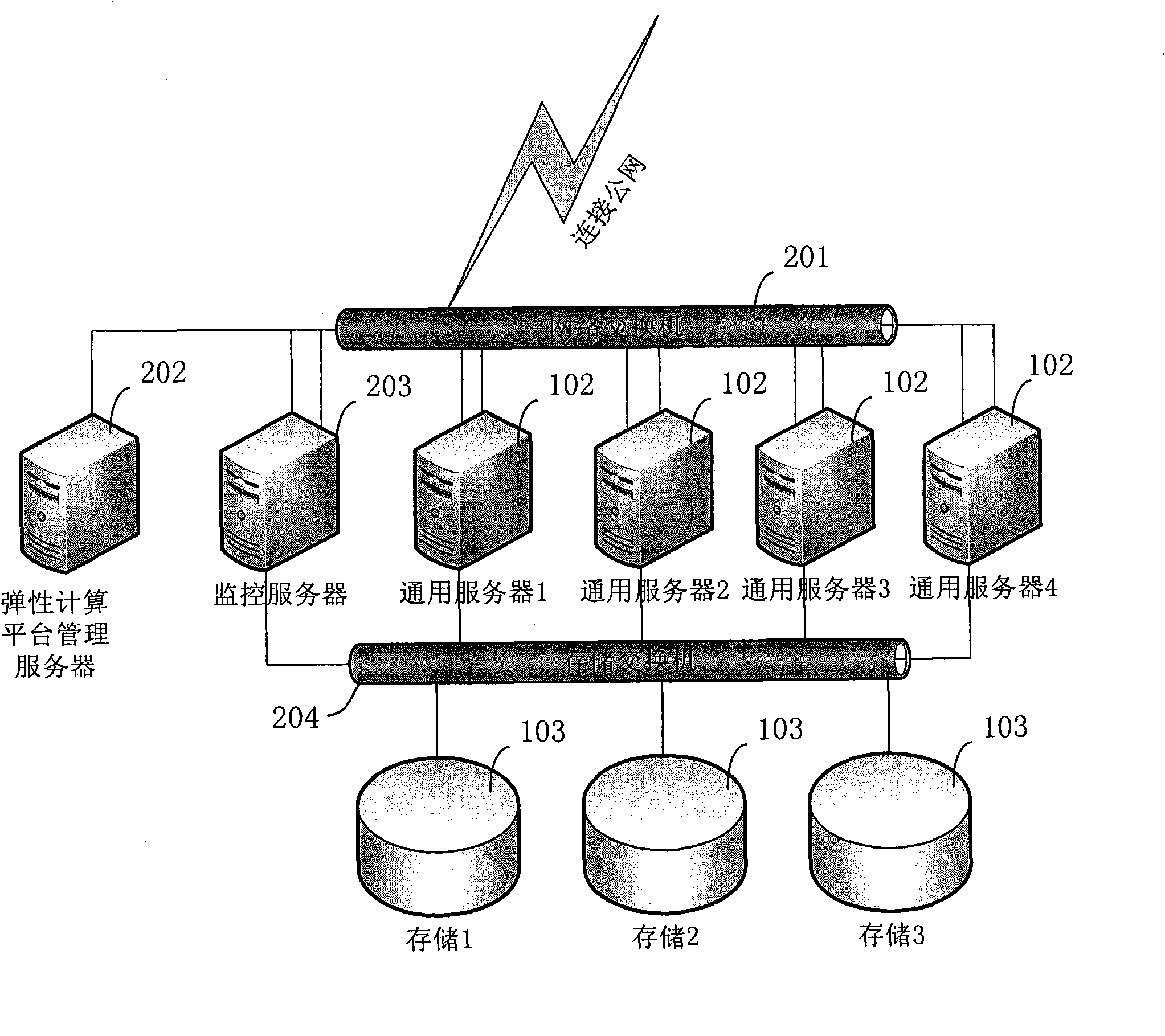
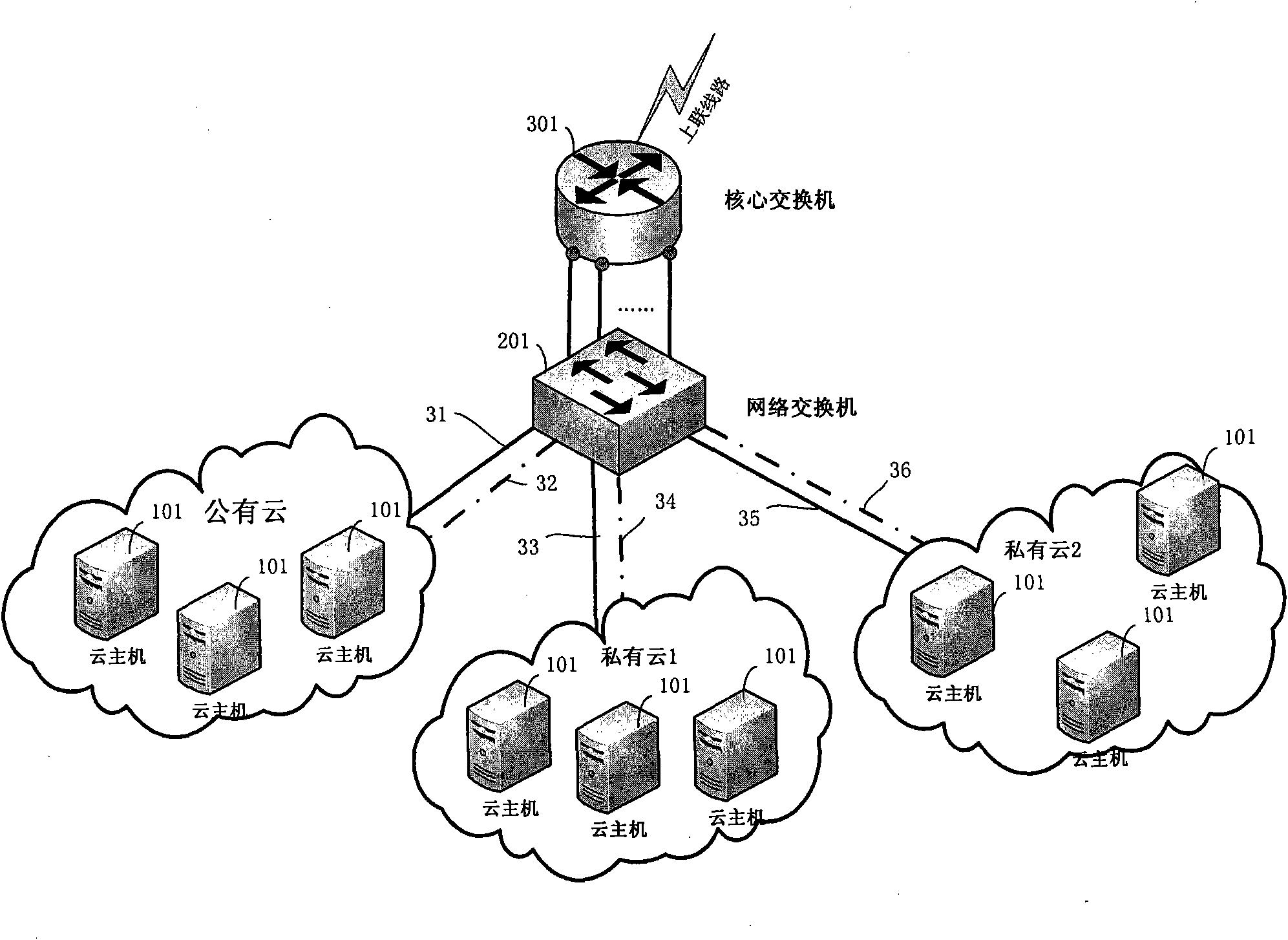
Virtual local area network-based speed limiting method and system for cloud hosts
ActiveCN101841451ATroubleshoot bandwidth sharing issuesSolve the speed limit problemNetworks interconnectionVirtual LANPrivate network
The invention discloses a virtual local area network-based speed limiting method and a virtual local area network-based speed limiting system. A core switch is arranged in an elastic compute node network and is connected with a network switch. A gateway is configured for public cloud and private cloud respectively on the core switch; and a public cloud public network and each private cloud publicnetwork WLAN between the core switch and the network switch are connected through independent links. Each common server in a CloudEx network is respectively connected to the network switch through two lines, wherein one line is used for public network communication; the other line is used for private network communication. Each common server is respectively connected to the network switch throughat least two lines, wherein one line is used for public network communication and used for bearing the public cloud public network VLAN and all private cloud public networks VLAN, and the other line is used for private network communication; and the public cloud public network VLAN and each private cloud public network VLAN between the core switch and the network switch are communicated through mutually independent links respectively. The method and the system make a plurality of cloud hosts share the network bandwidth and realize network isolation between users.
Owner:BEIJING 21VIANET DATA CENT
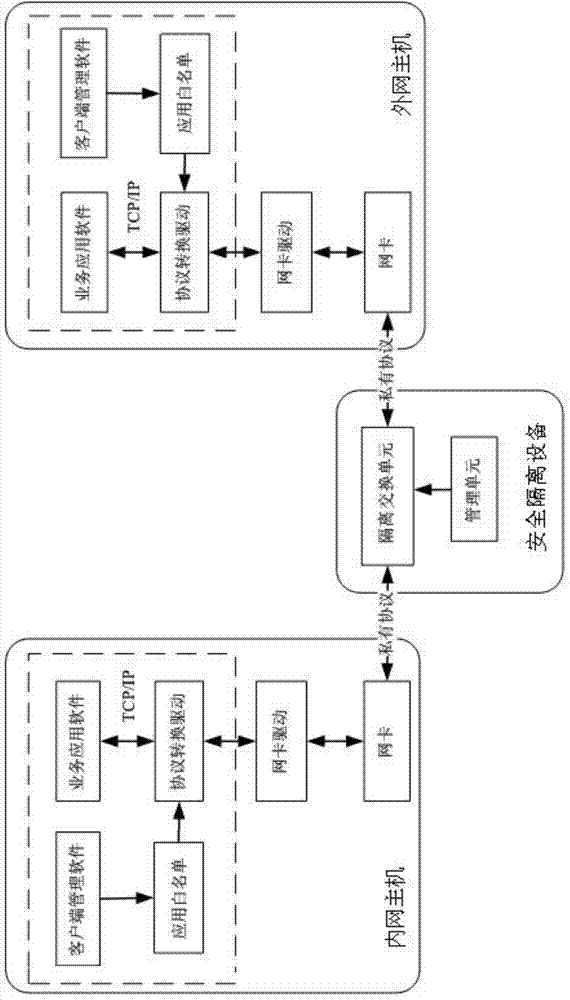
Distributed network isolating system and method
InactiveCN104767752AImprove real-time communicationIncrease flexibilityTransmissionElectricityNetwork packet
The invention discloses a distributed network isolating system and method. The system comprises an inner-network host, an outer-network host and a security isolation device. The security isolation device is arranged at the boundary of an inner network and an outer network, and comprises a plurality of communication ports for transceiving inner-network and outer-network data packets and being in communication with manager computers. The security isolation device is connected with the inner-network host and the outer-network host through a light opening or an electricity opening by means of a cable or an optical fiber. Client side software is arranged on the inner-network host and the outer-network host. A security channel based on a private protocol is established between cores of operation systems of the inner-network host and the outer-network host. Data exchange can be conducted between an inner-network designated application and an outer-network designated application through the security channel. Meanwhile, the data packets between the networks are filtered at the boundary between the inner network and the outer network, the security of the inner network and the outer network is ensured, various existing applications are supported, and the distributed network isolating system has the advantages of being high in communication efficiency, simple in strategy configuration and high in universality.
Owner:XIAN HUIJING ZHUOYUAN INFORMATION TECH CO LTD
VLAN (Virtual Local Area Network) isolation method
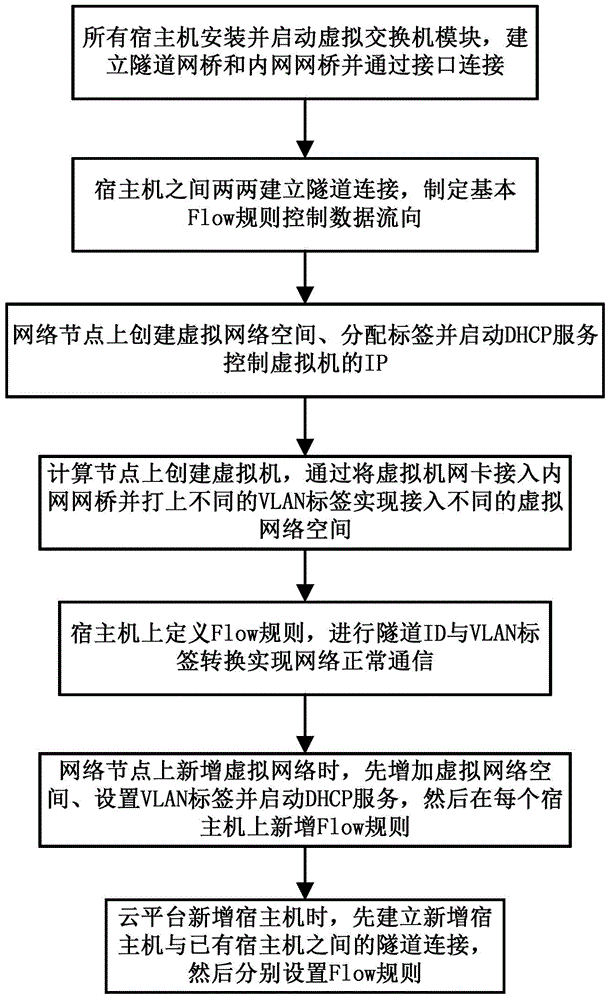
ActiveCN104486192AImprove controllabilityEasy to checkNetworks interconnectionNetwork connectionControl data
The invention relates to the technical field of cloud computing, in particular to a VLAN (Virtual Local Area Network) isolation method. The VLAN isolation method comprises the steps of firstly, installing and starting virtual switch modules on all host computers of a cloud platform, establishing a tunnel network bridge and an intranet network bridge, and connecting the tunnel network bridge with the intranet network bridge through an interface; then, establishing tunnel connection between every two host computers, and assigning a basic Flow rule to control the data flow direction; then, selecting network nodes to create virtual network space and to provide network service, and selecting compute nodes to create virtual computers and to access each virtual network; further, respectively defining a Flow rule on the network nodes and the compute nodes, carrying out conversion between tunnel ID (Identification) and VLAN tags, and realizing VLAN normal communication; finally, flexibly extending VLAN on the network nodes and newly adding a host computer to the cloud platform according to needs. According to the VLAN isolation method disclosed by the invention, the problems that VLAN isolation in the cloud platform is not strong in universality, the network connection is uncontrollable, and the like are solved; the VLAN isolation method can be used for the VLAN isolation.
Owner:G CLOUD TECH
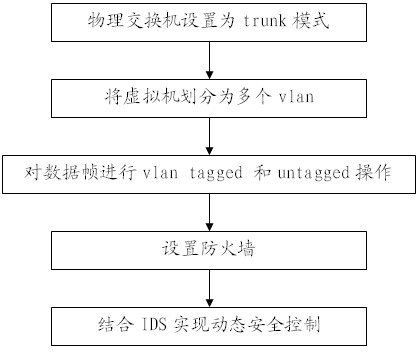
Safety isolation method for virtual network and physical network of cloud computing
InactiveCN102255903AImplement security controlsControl accessTransmissionSafety controlNetwork isolation
The invention provides a safety isolation method for a virtual network and a physical network of cloud computing, wherein the isolation between the both layers of networks is realized by carrying out VLAN (Virtual Local Area Network) tagged and untagged operations on data frames, the access control of three layers is realized by a fire wall, the dynamic safety control is realized with the addition of IDS (Intrusion Detection System) software, so that not only can the communication between different VLANs be controlled, but also the access of other machines in the inner network to the cloud inner network can be controlled. Simultaneously, the network isolation can be performed between virtual machines or between virtual machines and physical machines by employing the VLAN, so that the physical machines and the virtual machines are divided in the different VLANs, namely, the isolation between the physical network and the virtual network can be realized.
Owner:GCI SCI & TECH
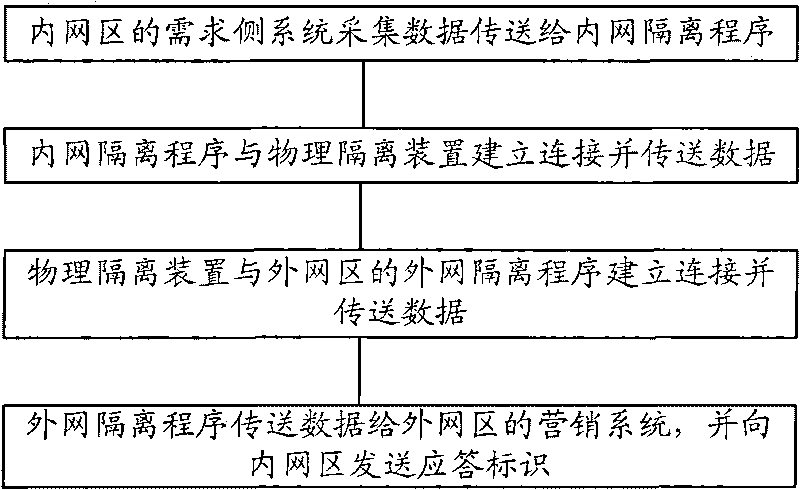
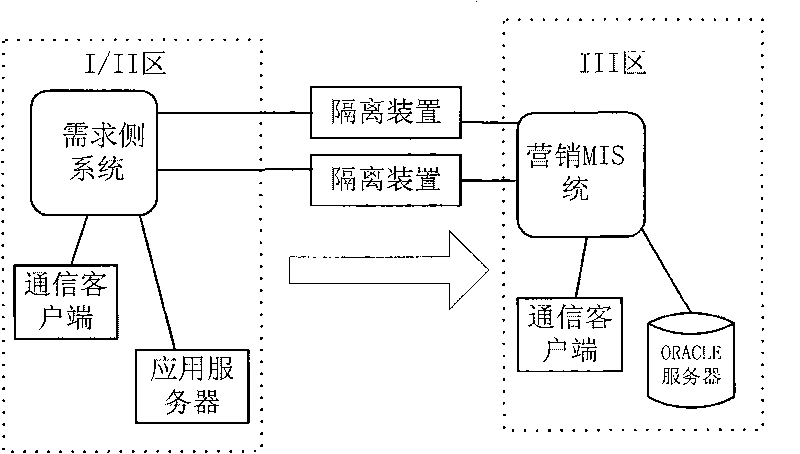
Method for transmitting mass data in real time by penetrating positive physical isolation device
InactiveCN101697536ASolve the blockageComplete in real timeSecuring communicationService flowElectricity
The invention relates to the technical field of electricity and communication, and discloses a method for transmitting mass data in real time by penetrating a positive physical isolation device, which comprises the following steps of S1, acquiring data by a requirement side system of an internal network zone and transmitting the data to an internal network isolation program; S2, establishing a connection between the internal network isolation program and the physical isolation device and transmitting the data; S3, establishing a connection between the physical isolation device and an external network isolation program of an external network zone and transmitting the data; and S4, transmitting the data to a marketing system of the external network zone by the external network isolation program and transmitting a response identification to the internal network zone. The invention ensures that the requirement side system acquires the mass data and effectively transmits the data to the marketing system in real time through the positive physical isolation device, solves the problem of block of the mass data transmitted through the positive physical isolation device among the traditional systems, and enables the marketing system to immediately and completely acquire the data of charge and the like so as to accurately complete the service flow in real time.
Owner:深圳市联创知识产权服务中心
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com