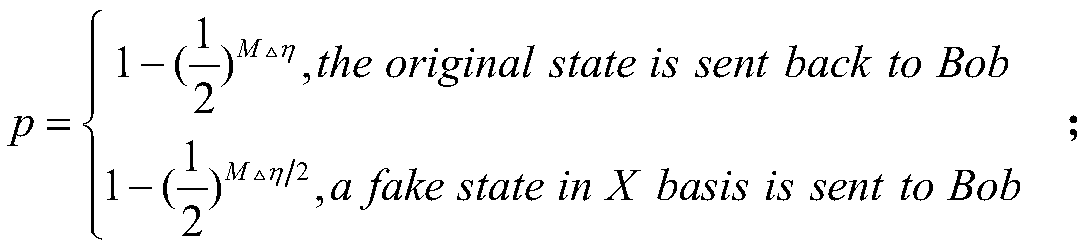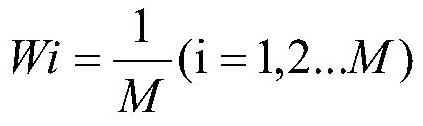Patents
Literature
184 results about "Trojan horse" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, a Trojan horse, or Trojan, is any malware which misleads users of its true intent. The term is derived from the Ancient Greek story of the deceptive Trojan Horse that led to the fall of the city of Troy.
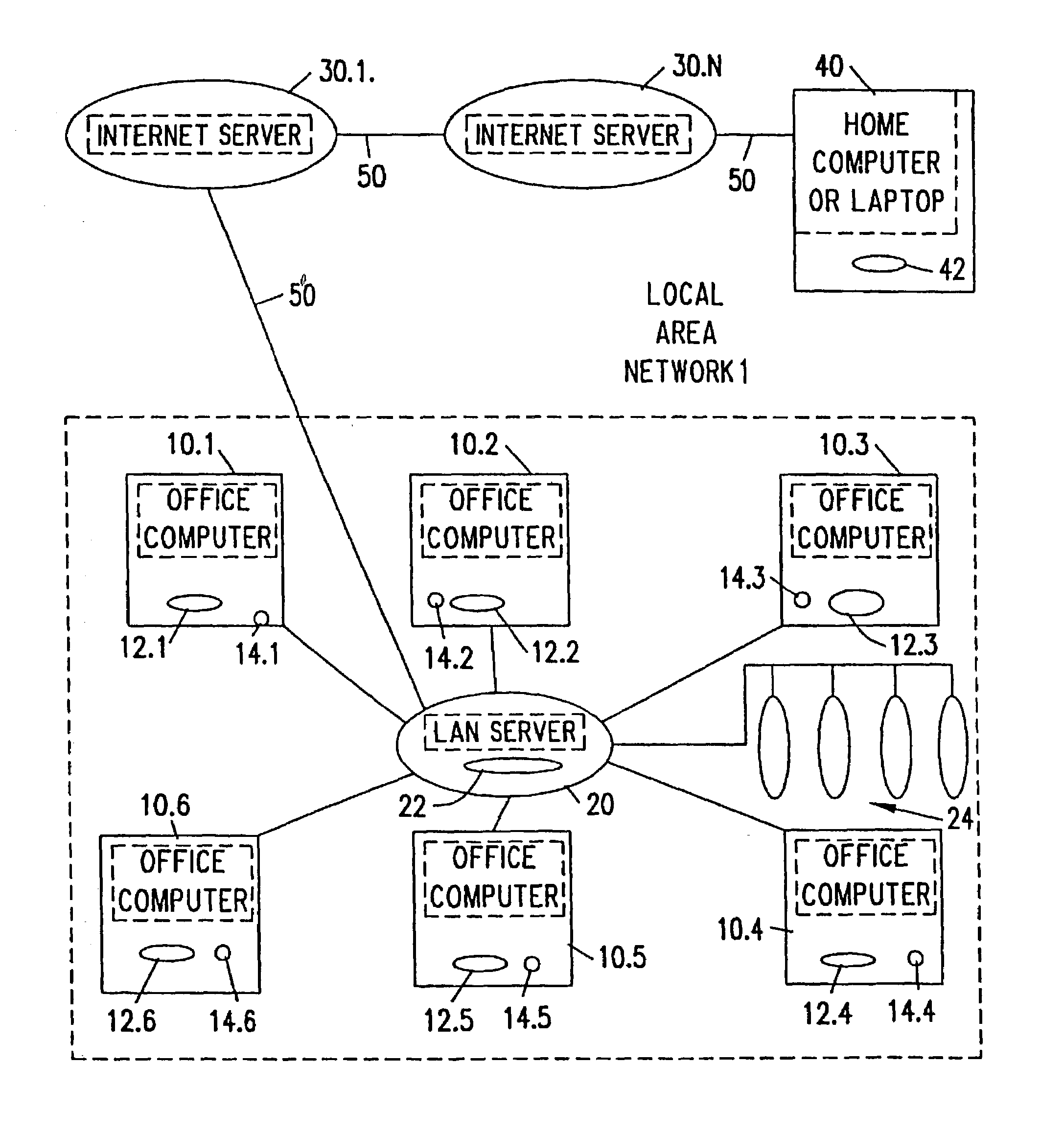
Self-destructing document and e-mail messaging system
InactiveUS7191219B2Robust enforcement of lifetimeDigital data processing detailsUnauthorized memory use protectionMagnetic tapeDocumentation
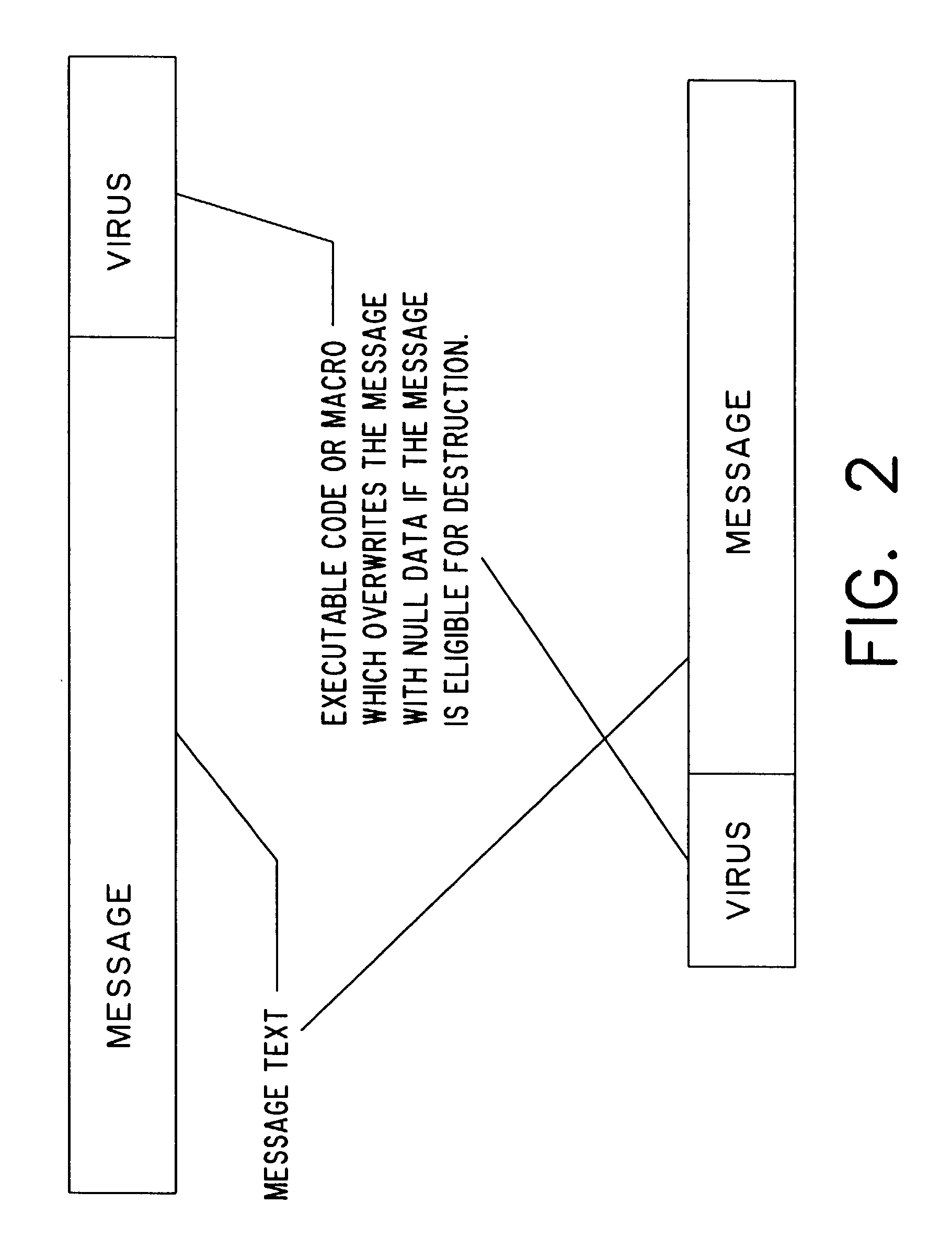
A self-destruction document or e-mail massaging system is provided that automatically destroys documents or e-mail messages at a predetermined time by attaching a “virus” to the document or e-mail message. A virus in the form of a Trojan horse is attached to file (such as an e-mail message or document) when it is created. The virus contains a portion of executable code or an executable program which instructs the computer to overwrite and / or delete the file to which the virus is attached at a desired time. Since the virus is attached to the file, it will travel with the file even when the file is copied, forwarded, or saved to disks or tape drives.
Owner:HANGER SOLUTIONS LLC
Method and system for monitoring Trojan Horse based on network communication behavior characteristic
ActiveCN101605074APerformance is not affectedRealize real-time monitoringData switching networksRe implantationData stream
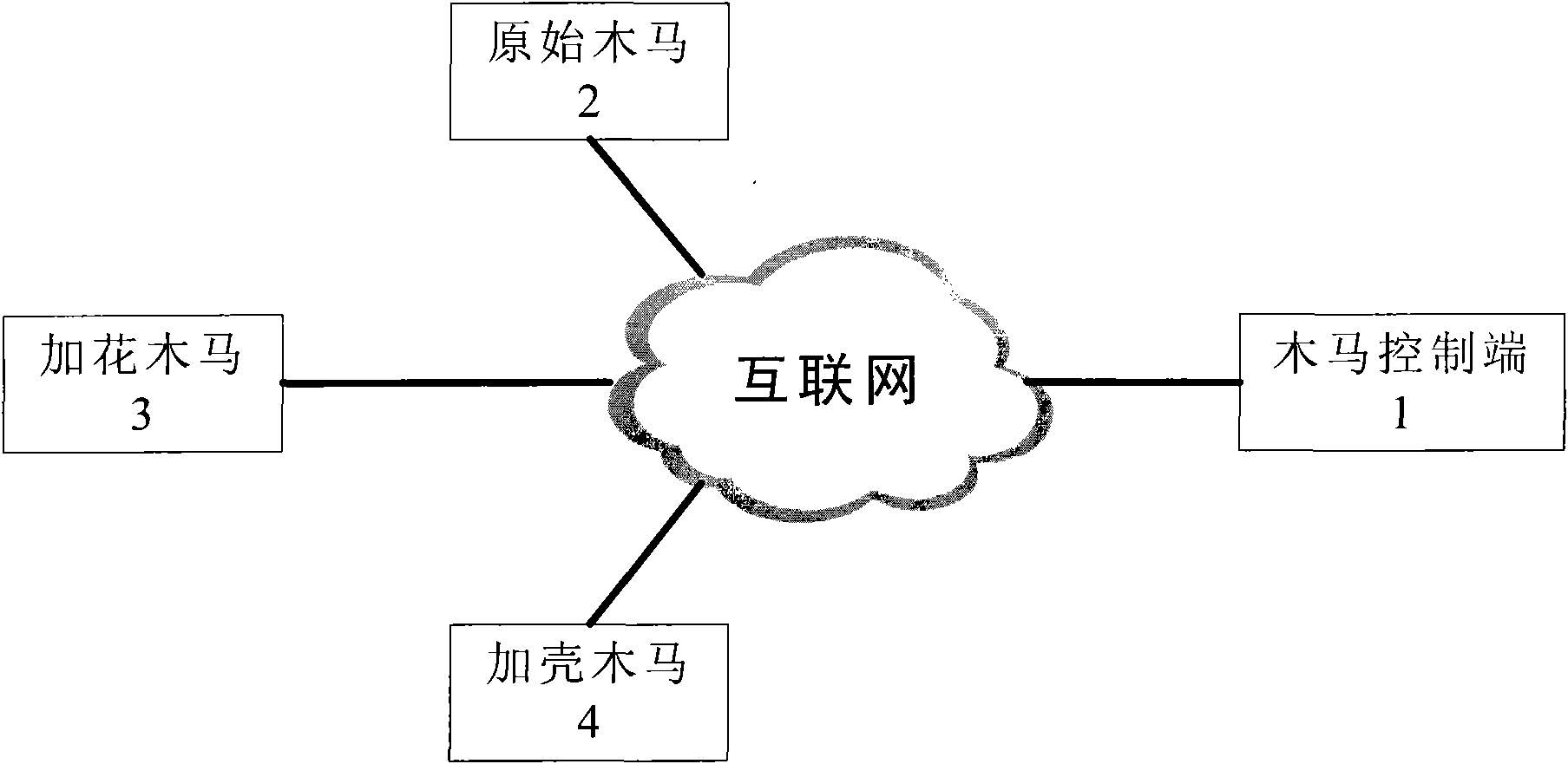
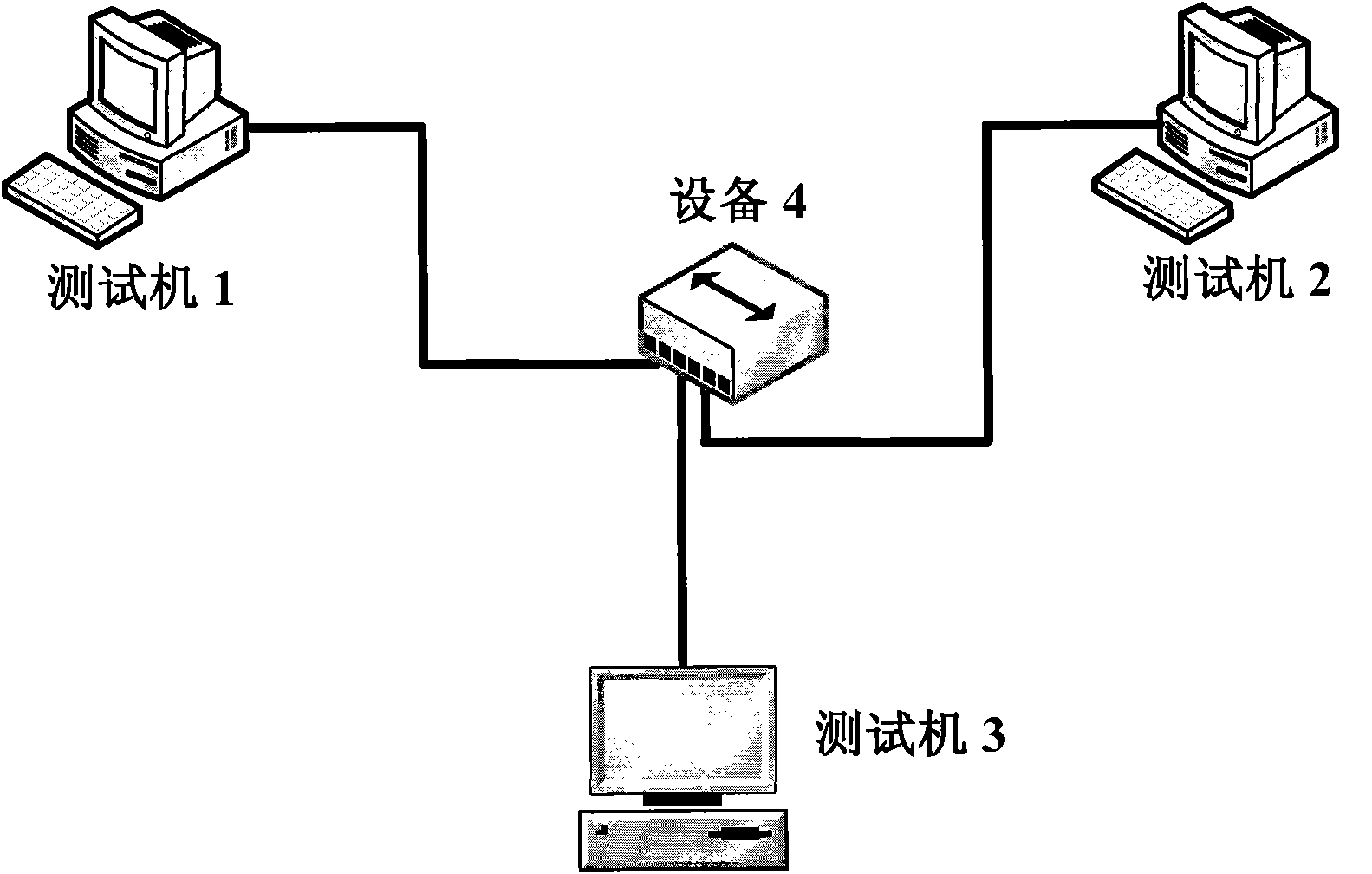
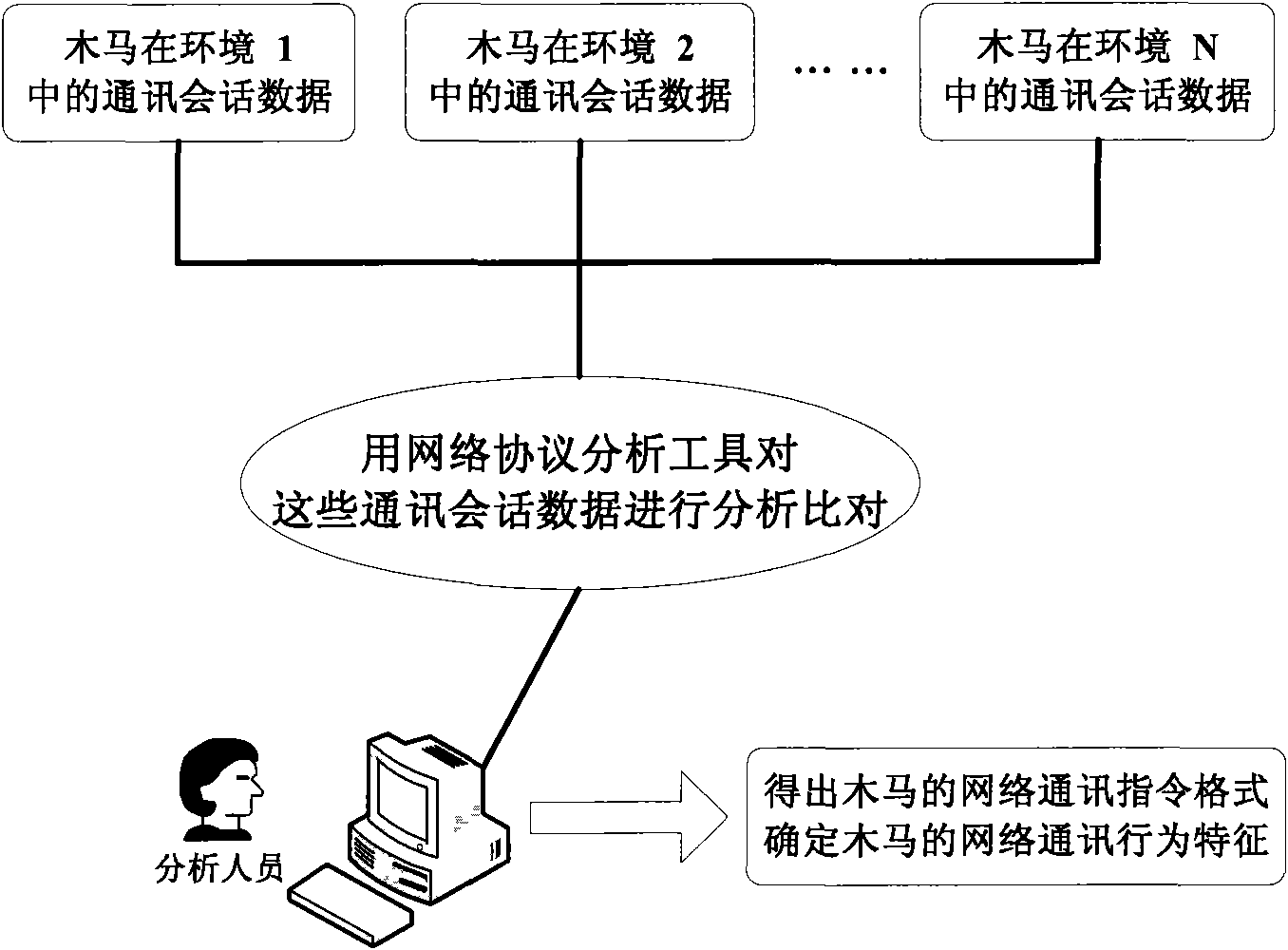
The invention provides a method and system for real-time monitoring Trojan Horse base on network communication behavior characteristic of Trojan Horse in network data flow, which belongs to the field of computer network security. Currently, Trojan Horse is capable of avoiding detection based on file characteristic and host behavior characteristic in prior art by various technical means. But behavior characteristic of Trojan Horse in network communication is relatively stable, that is application communication protocol thereof is unlikely to change. That is because the change to the protocol relates to simultaneous change to programs on both Trojan Horse customer and server, which needs re-implantation of the Trojan Horse, and also relates to the communication problem between different versions of the Trojan Horse program. Accordingly, based on the network communication behavior characteristic during Trojan Horse activation in the network data flow, not only the known Trojan Horses can be monitored, but also unknown flowered, shelled or variant Trojan Horse can be precisely monitored.
Owner:中国人民解放军信息技术安全研究中心 +1
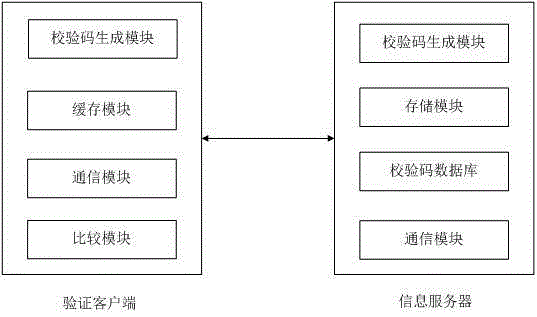
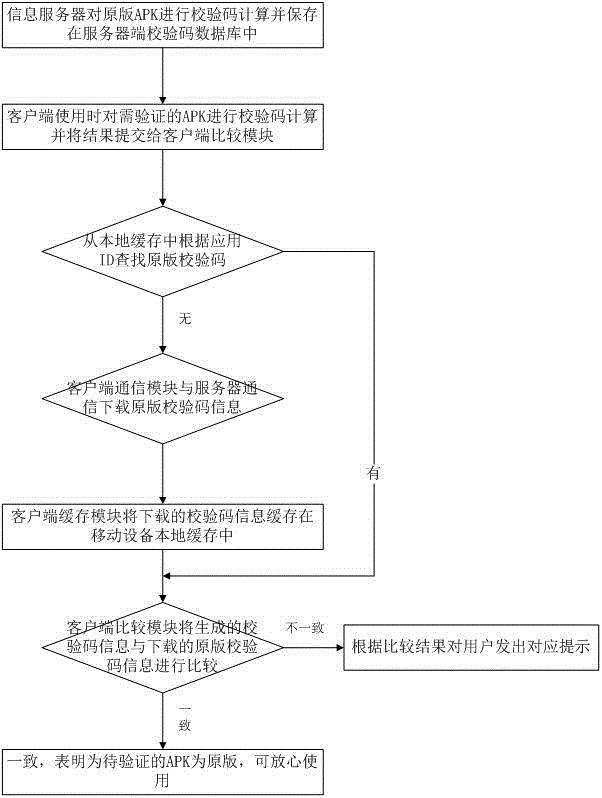
System for conducting original-edition check to mobile application program
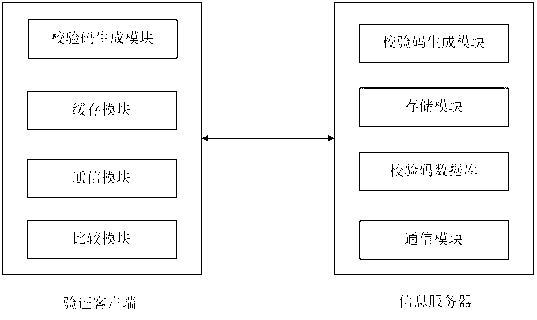
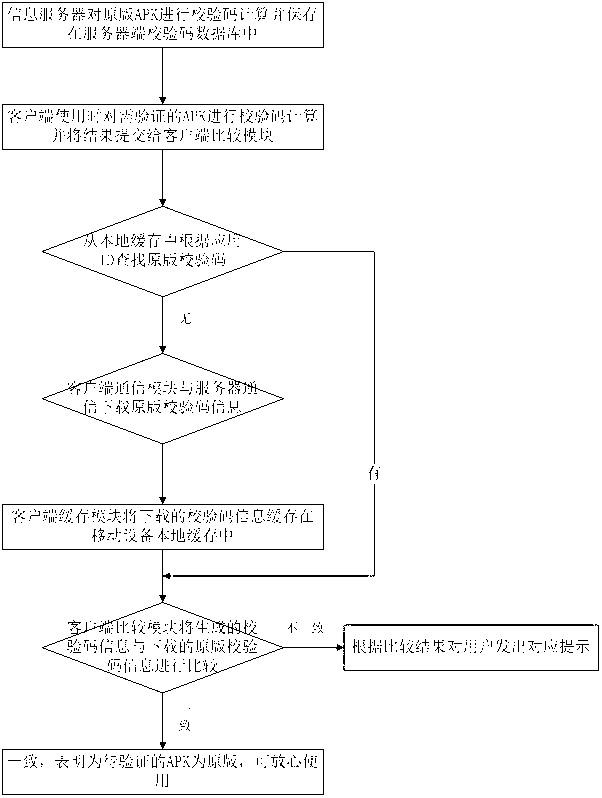
The invention provides a system for conducting original-edition check to a mobile application program. By erecting a specialized original-edition information server, and making a comparison with original-edition information provided by the server in the downloading or installation or using starting process of the mobile application program, whether the mobile application program belongs to an original edition or not is judged. The original-edition check can avoid using trouble and loss caused by the download of the mobile application program contracting virus or Trojan horse or carrying illegal advertising information, and thus the experience and satisfaction of mobile phone users are improved.
Owner:BEIJING SENSESHIELD TECH
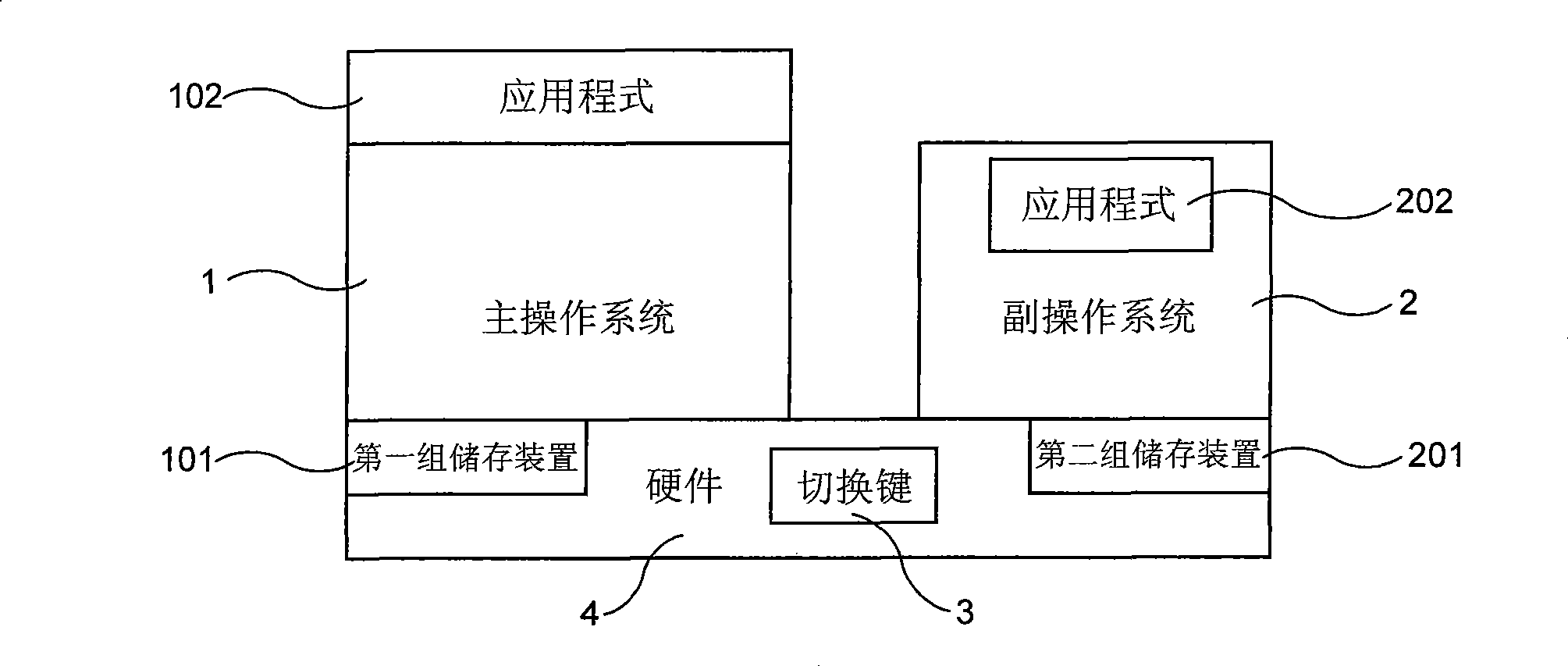
Double operating system computer against worms
InactiveCN101364187AEnsure safetyProgram initiation/switchingUser identity/authority verificationOperational systemThe Internet
The invention relates to a computer with double operating systems, which comprises a primary operating system (1), a secondary operating system (2), a switch key (3) used for selecting a current operational operating system, a first storage device (101) and a second storage device (201), wherein, the first storage device (101) is independently separated from the second storage device (201) in body; and is only used for accessing the main operating system (1); and the second storage device (201) is only used for accessing the auxiliary operating system (2). The main operating system (1) can be used for a majority of application with low safety requirements such as online, playing games and the like; the auxiliary operating system (2) is mainly used for application with high safety requirements such as internet banking service, processing confidential and important files, receiving and sending E-mails and the like, and only can execute a formula prearranged inside, thereby avoiding the intrusion of various viruses and Trojan horse formulae.
Owner:黄金富
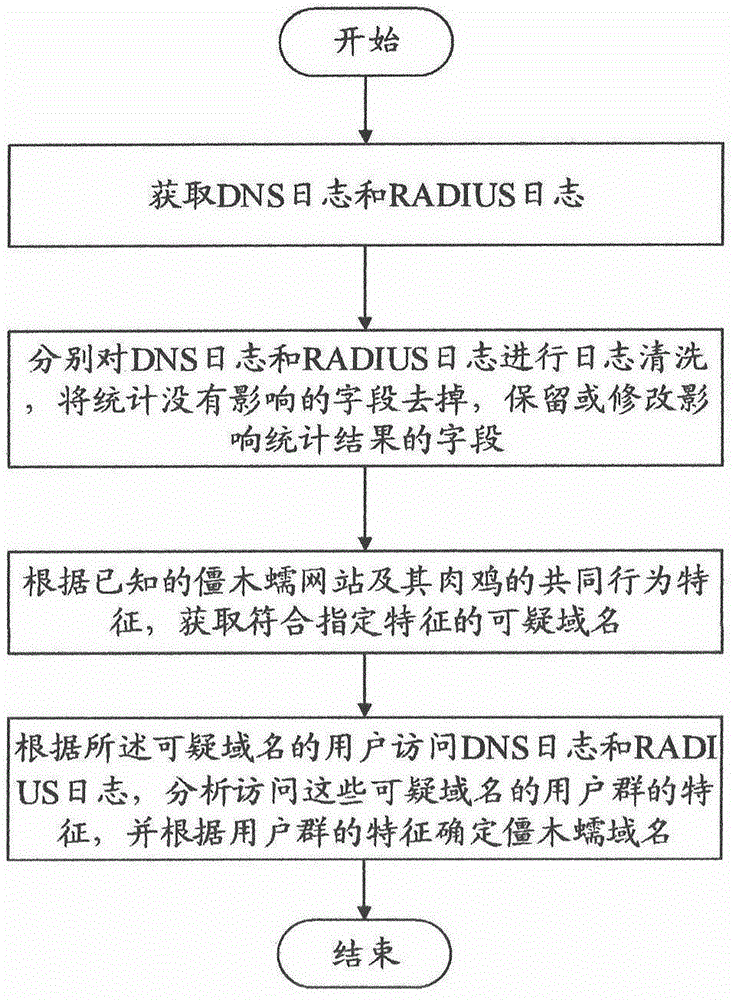
Botnet, Trojan horse and worm network analysis method and system based on logs
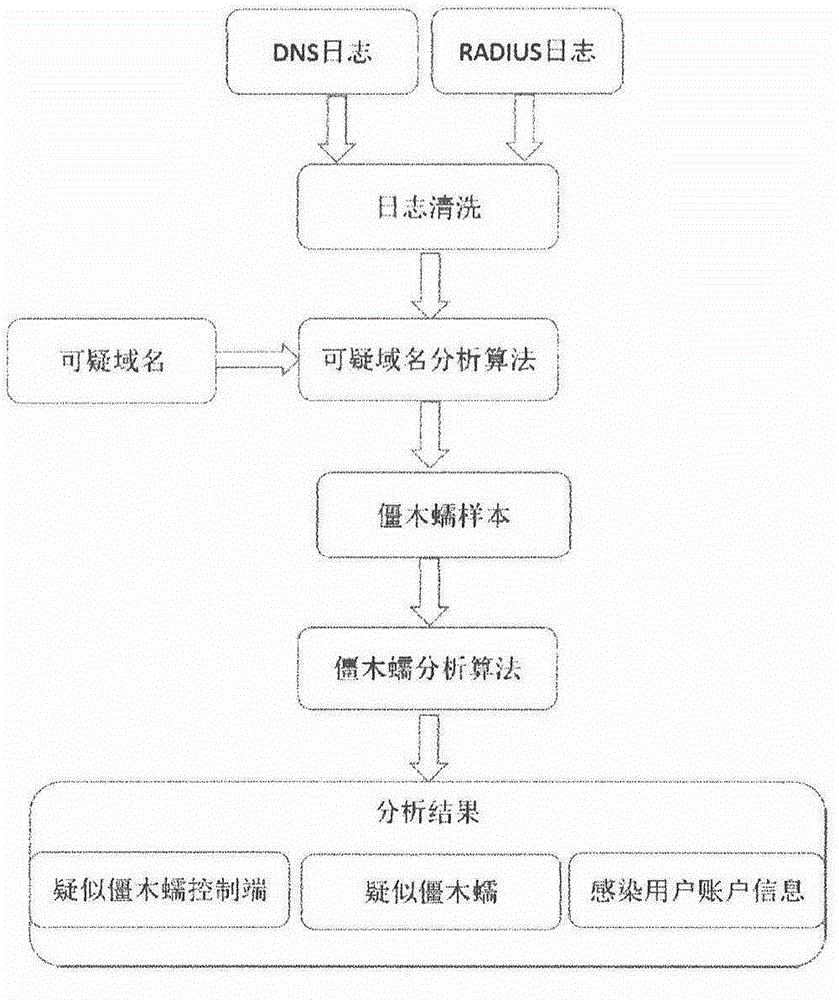
The invention discloses a botnet, Trojan horse and worm network analysis method based on logs. The method comprises the steps that step 1, a DNS log and a RADIUS log are obtained; the DNS log comprises date, time, visit information, IP request information, domain name request information, domain name request characteristics, type analysis, IP information analysis and DNS server characteristic information; step 2, log cleaning is performed on the DNS log and the RADIUS log, fields which have no influence on statistics are deleted, fields which influences a statistical result are retained or modified; step 3, a suspicious domain name which confirms with specific characteristics is obtained according to common behavior characteristics of a known botnet, Trojan horse and worm network and a computer which has virus of botnet, Trojan horse and worm; step 4, according to the user visit DNS log and RADIUS log of the suspicious domain name, the characteristics of user groups which visit the suspicious domain name are analyzed, and a domain name of the botnet, Trojan horse and worm is determined according to the characteristics of the user groups.
Owner:BEIJING RUNSTONE TECH
Network-based detection method of rebound ports Trojan horse
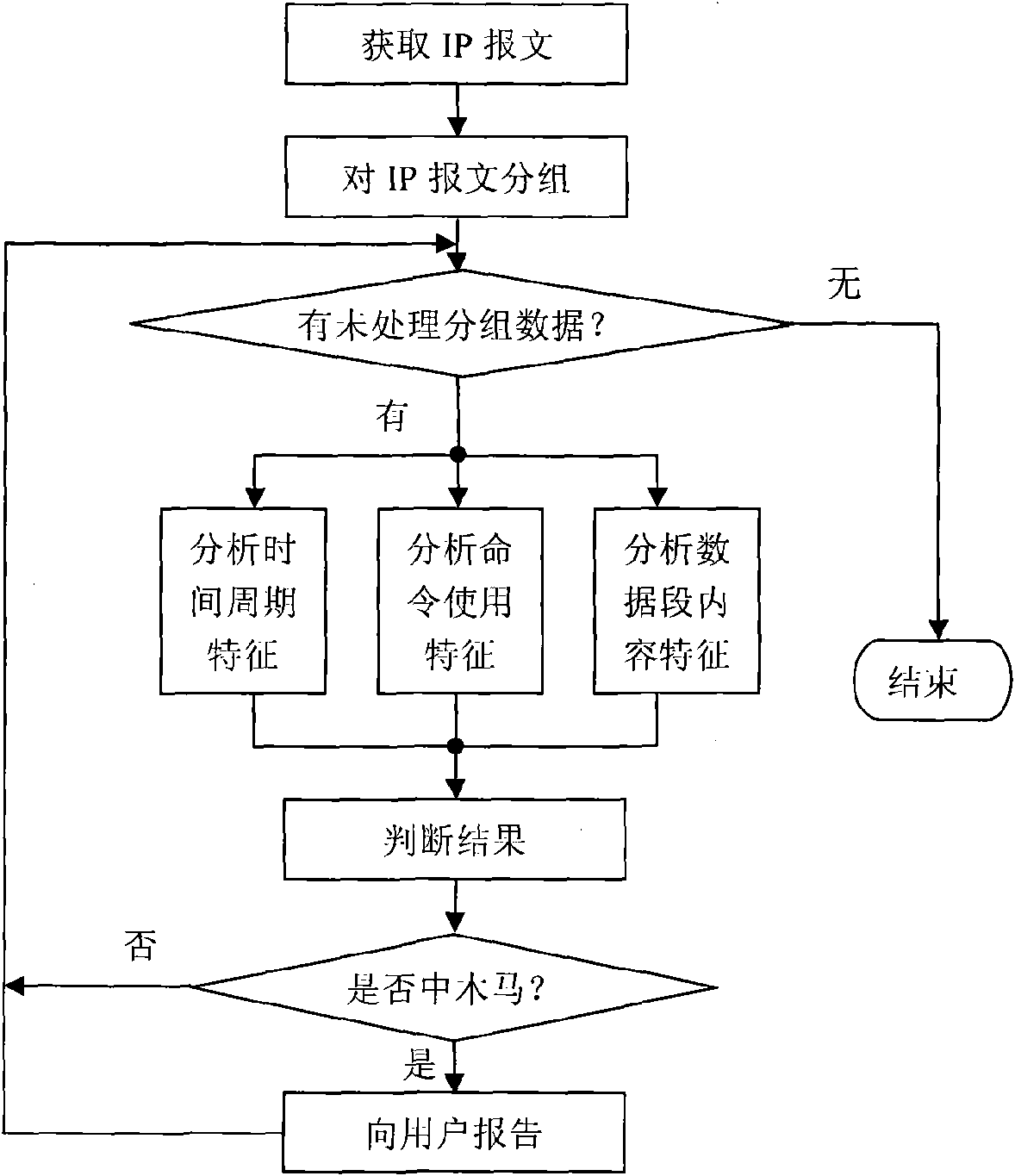
The invention relates to a network-based detection method of rebound ports Trojan horse, belonging to the technical field of network information safety. The method determines whether a corresponding mainframe is attacked by the rebound ports Trojan horse or not by capturing network data packets and utilizing data for carrying out the analysis of time features, application layer protocol and data content. The method can effectively detect the rebound ports Trojan horse which adopts process hiding, file hiding, service hiding and other technologies to a certain extent and does not need to install any proxy software or module, thereby being fully applicable to the situations of having limitations on the installation of a Trojan killing tool on the mainframe.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
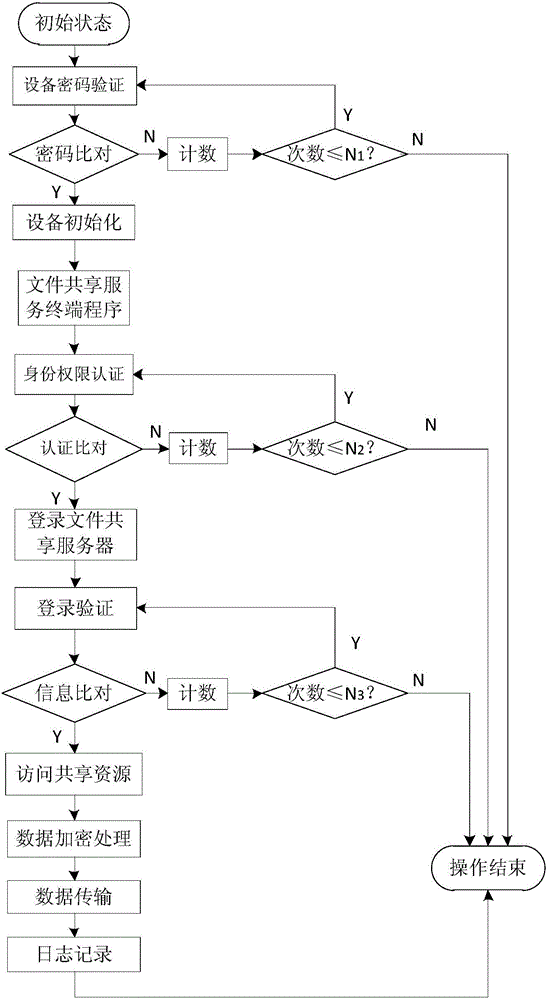
Security and secrecy method for sharing storage files
PendingCN105956496AAvoid churnImprove protectionDigital data protectionInternal/peripheral component protectionStorage securityTrojan horse
The invention relates to a method suitable for information protection security, and discloses a security and secrecy method for sharing storage files. The method is based on independent third-party assurance and encryption equipment, wherein the third-party assurance and encryption equipment comprises a control chip, a memory and a fingerprint reader; a program running on the control chip comprises a control module and a file encryption module; the control chip is used for realizing identity authentication and file encryption through the control module and the file encryption module; the memory consists of an encrypted storage area and a common storage area; the encrypted storage area comprises an equipment command, fingerprint authentication information, a key and an algorithm software carrier; and the common storage file comprises a file sharing service terminal program. According to the security ad secrecy method for sharing storage files, the file sharing service terminal program is adopted to control the data encryption and decryption, and prevent the illegal misappropriation of viruses such as Trojan horses, illegal users and file sharing service providers, so that the data storage security is improved and the security of the user data is ensured.
Owner:新昌县七星街道明盛模具厂
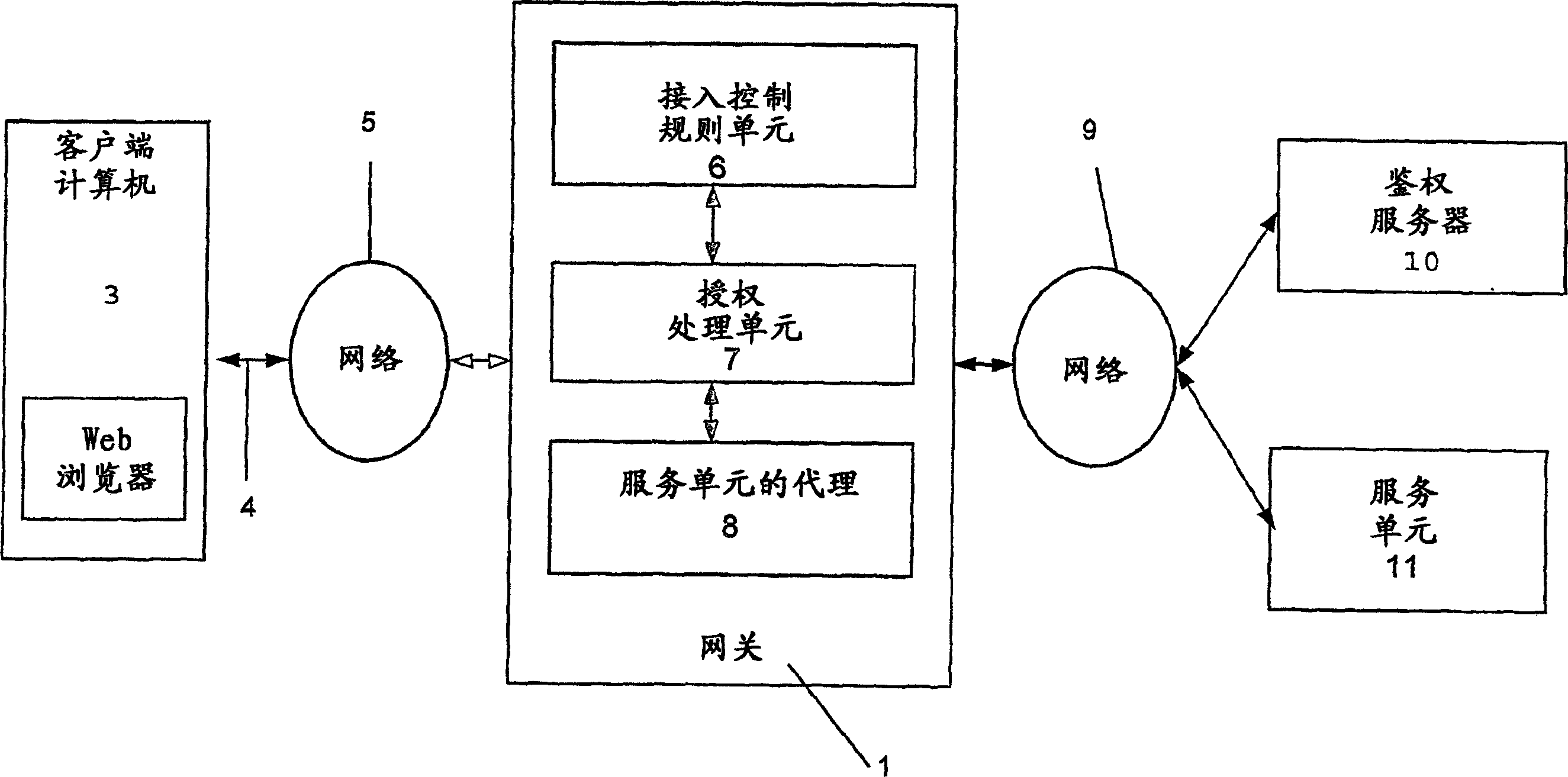
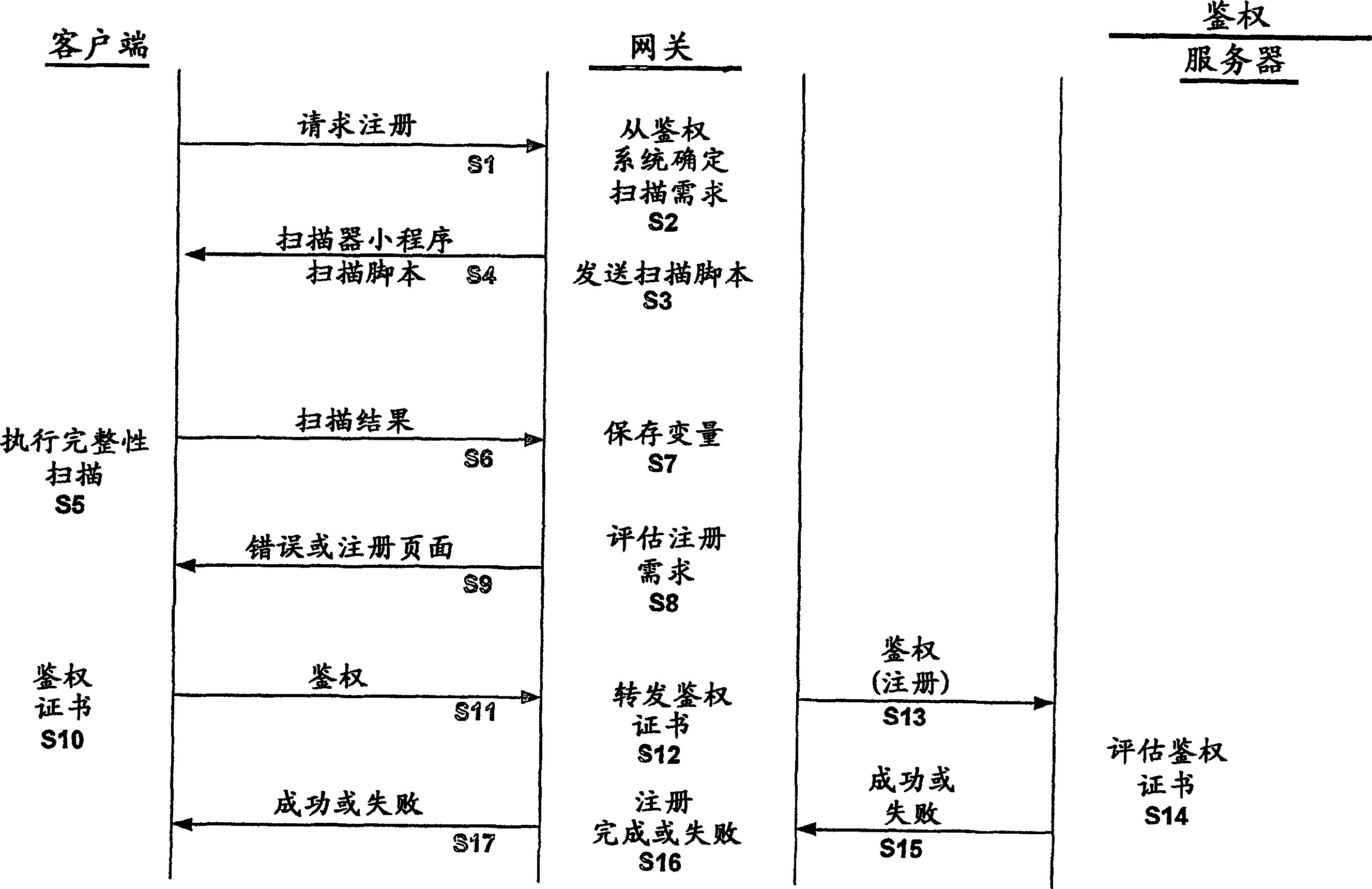
An apparatus, system, method and computer program product for implementing remote client integrity verification
InactiveCN1833228AUser identity/authority verificationUnauthorized memory use protectionAccess networkWeb browser
Owner:NOKIA TECH OY
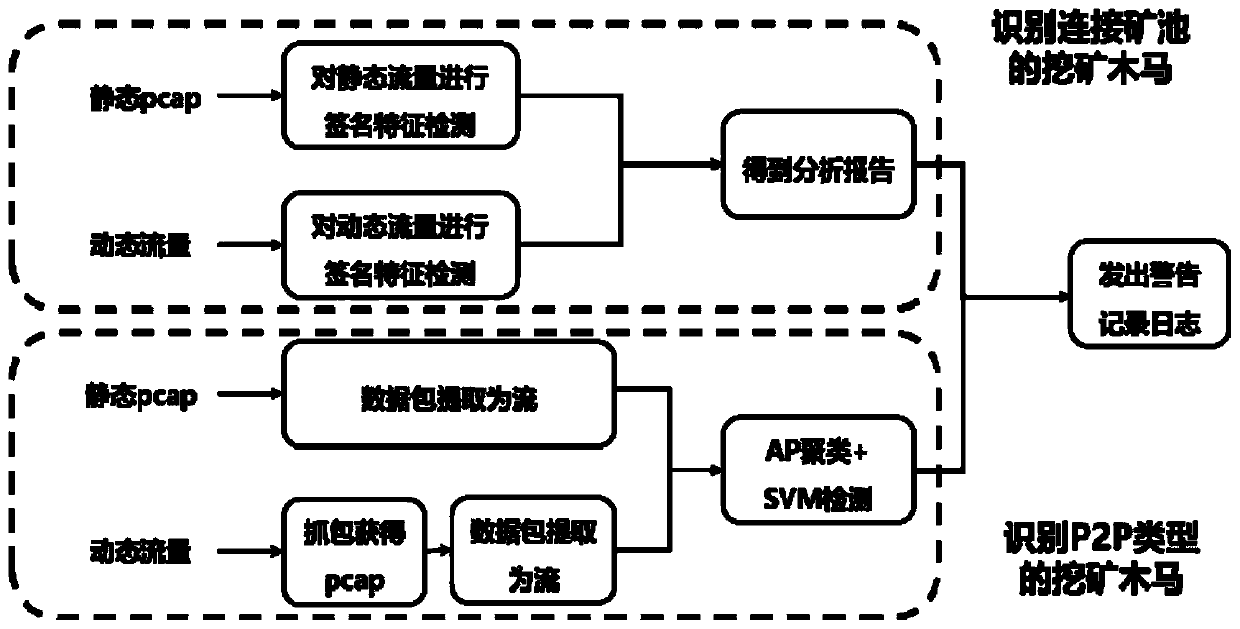
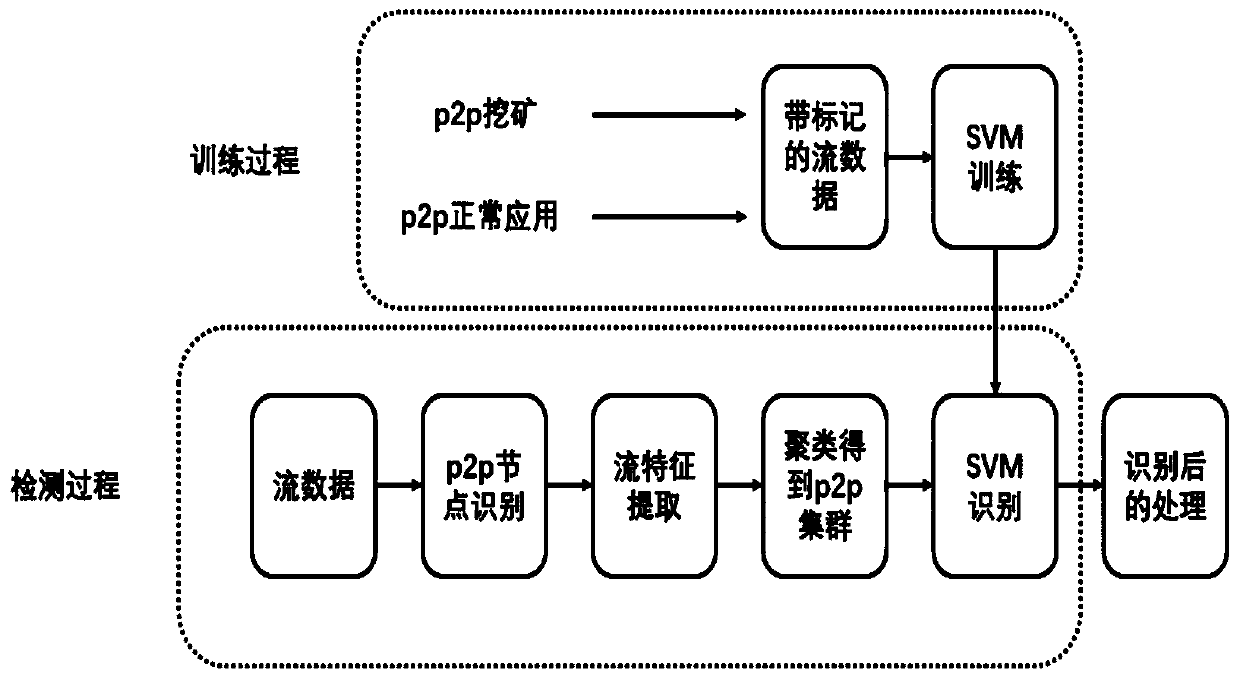
Mining Trojan horse detection system based on flow analysis
ActiveCN110933060APrevent invasionMeet application requirementsData switching networksAlarm messageFeature extraction
The invention discloses a mining Trojan horse detection system based on flow analysis, which relates to the field of computer network security and comprises a connectionmining pool mining Trojan horsebehavior detection subsystem and a p2p mining network mining Trojan horse behavior detection subsystem. According to the invention, the static pcap data packet or the real-time flow is used as the input, two modes of detecting and connecting mine pool mining and p2p mining can be selected, the mining flow is analyzed through the field feature extraction or communication flow feature extraction and identification of the system, and the alarm information is output to the user. Aiming at the conditions of plaintext communication and ciphertext communication, the system has the capability of quickly processing mass data, and can meet the requirements of personal hosts and enterprise-level users at the same time.
Owner:上海视岳计算机科技有限公司
Payment webpage modification preventing method and device
ActiveCN102999718APrevent malicious tamperingImprove securityPlatform integrity maintainanceTransmissionPaymentE-commerce
The embodiment of the invention discloses a payment webpage modification preventing method and a payment webpage modification preventing device. The method comprises the following steps that whether a request received by a modification webpage interface is an external request or not is judged, and the external request refers to an inter-process request sent by other processes different from the webpage operating process; and when the judgment result shows that the request is the external request, the external request is intercepted. When the method and the device are adopted, the webpage tampering by trojan horse program can be avoided, and the goal of improving the e-commerce safety is reached.
Owner:TENCENT TECH (SHENZHEN) CO LTD
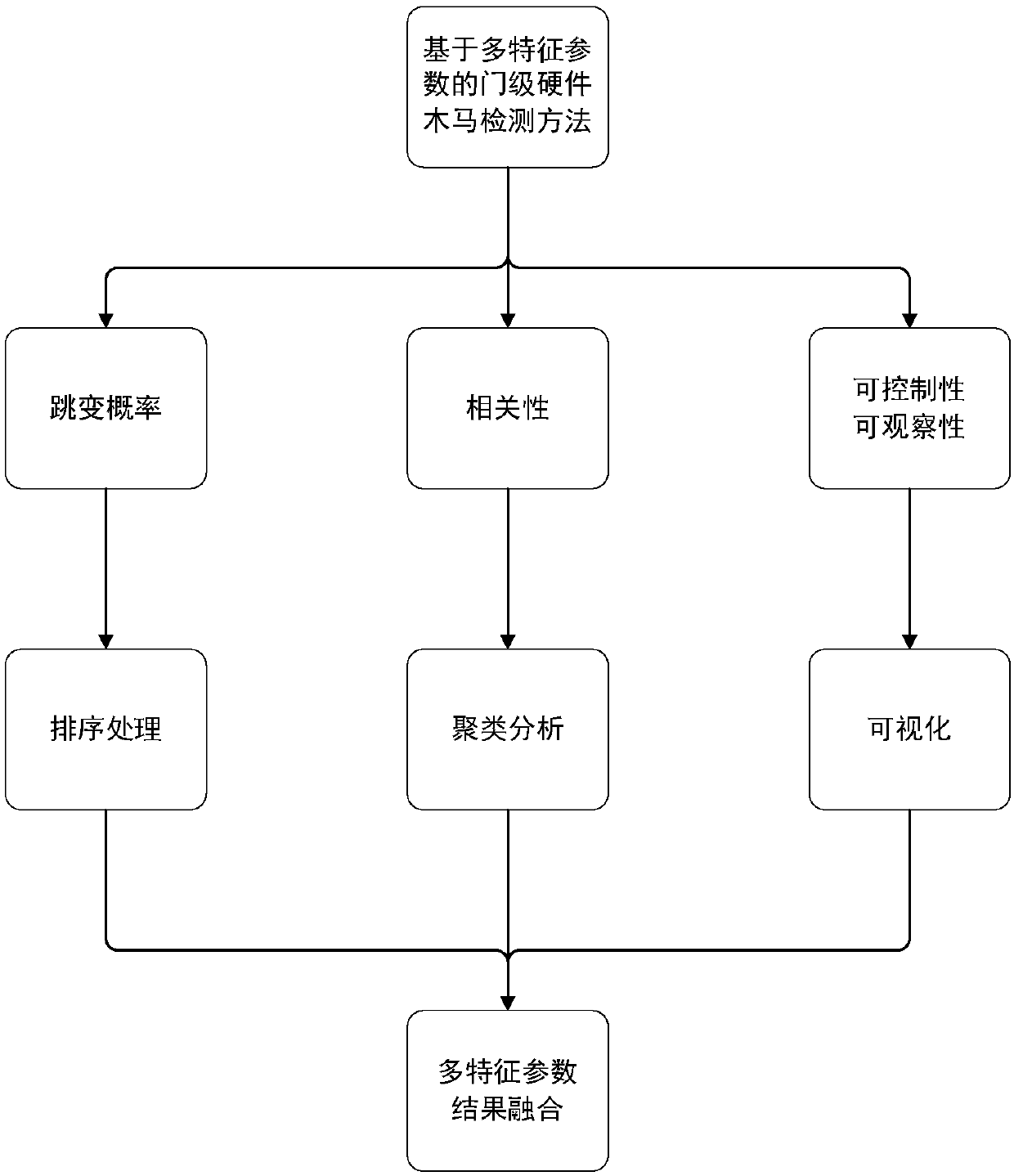
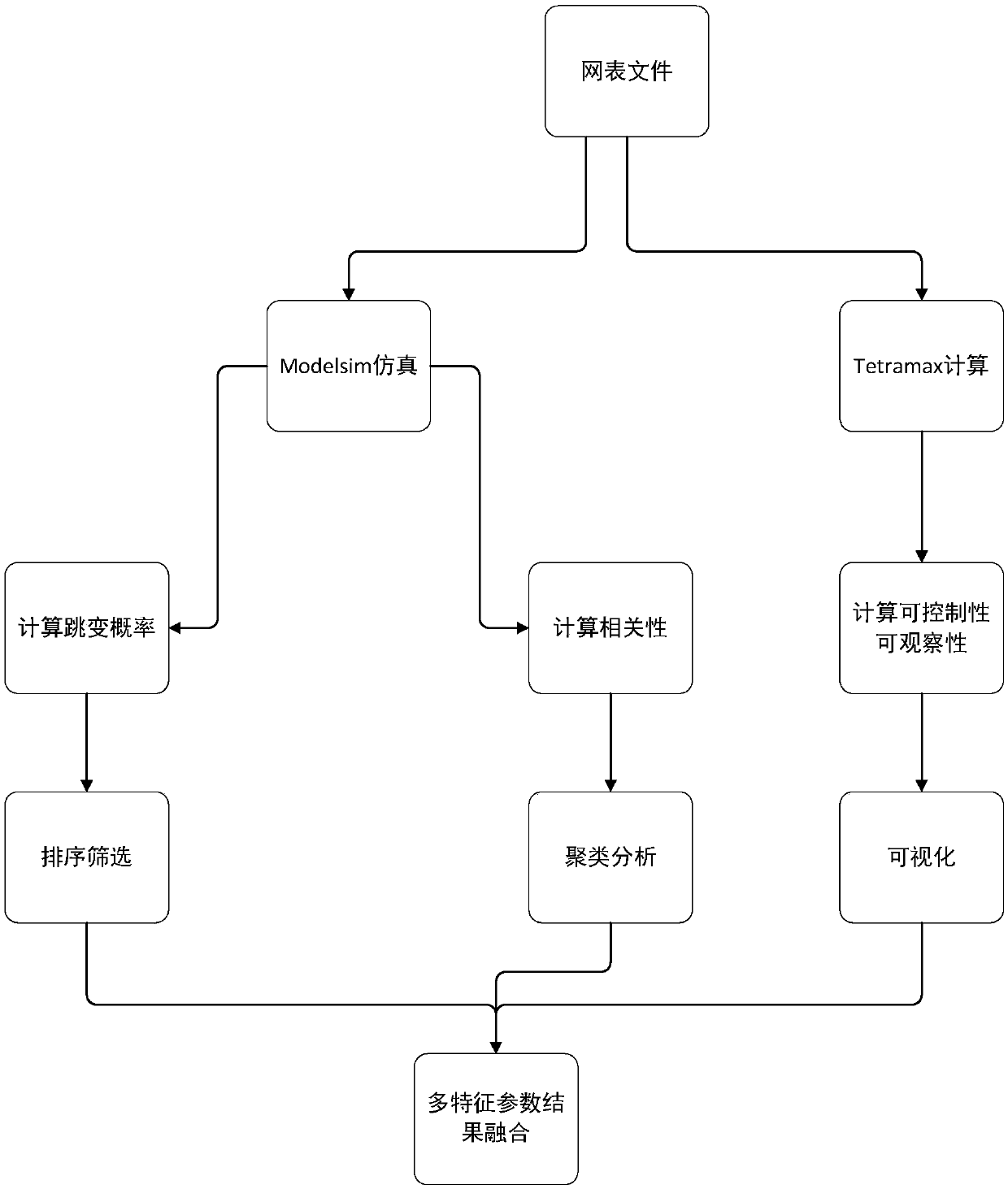
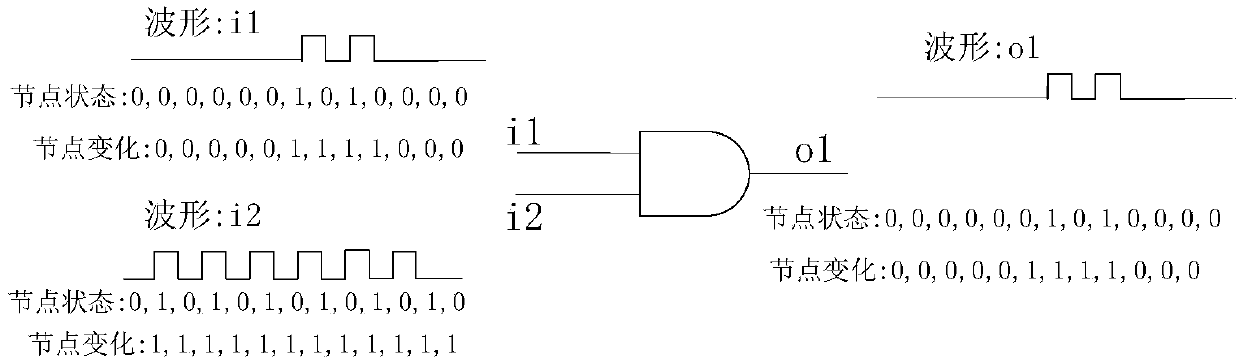
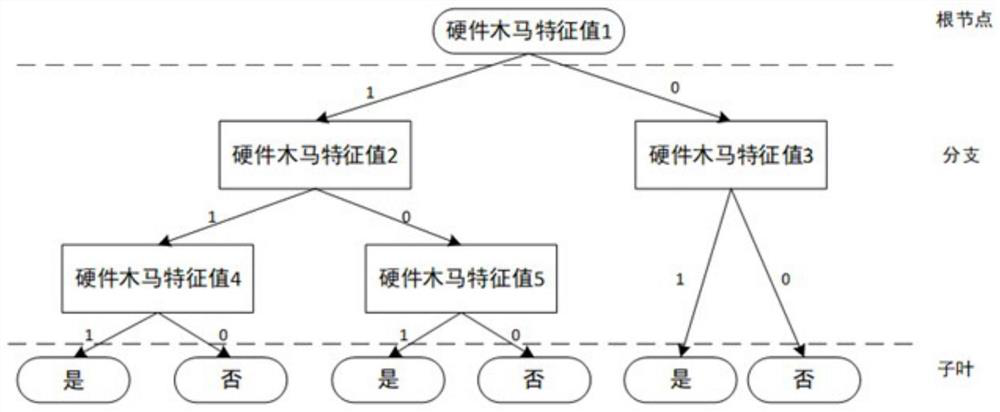
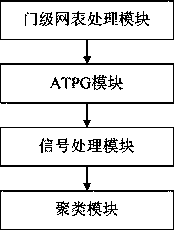
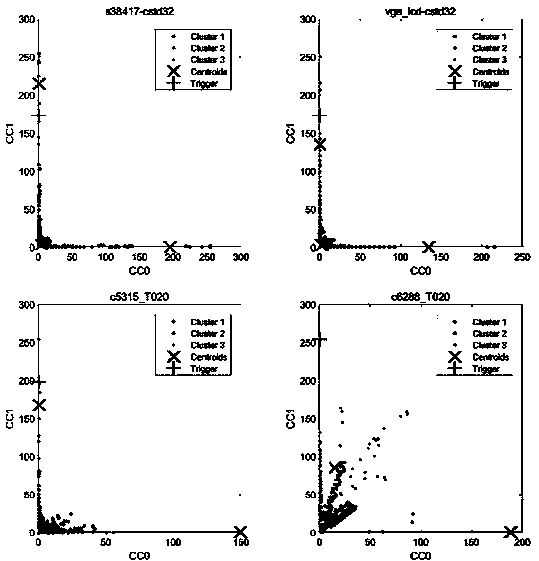
Gate-level hardware Trojan horse detection method based on multiple characteristic parameters
ActiveCN110414277ASolve detection difficultiesImprove detection accuracyInternal/peripheral component protectionThird partyNODAL
The invention relates to a gate-level hardware Trojan horse detection method based on multiple characteristic parameters. The method mainly comprises two parts: characteristic parameter extraction anddata processing. Specifically, characteristic parameters such as hopping probability, correlation, controllability and observability of a gate-level netlist are extracted in the detection process, the hopping probability reflects the activity degree of circuit nodes, the correlation reflects the correlation degree between the nodes, and the controllability and observability indicate the difficulty degree of node control and observation. Then, different algorithms are designed according to different parameter characteristics to distinguish normal nodes and Trojan horse nodes. According to themethod, the gate-level netlist hardware Trojan horse detection effect can be improved; the situation of all nodes in the circuit is reflected through multiple characteristic parameters, the possibility that a design company uses an IP core provided by a third party to introduce a hardware Trojan horse maliciously modifying the circuit in the chip design stage is reduced, and therefore the method can be universally applied to gate-level hardware Trojan horse detection and has high practicability.
Owner:PEKING UNIV
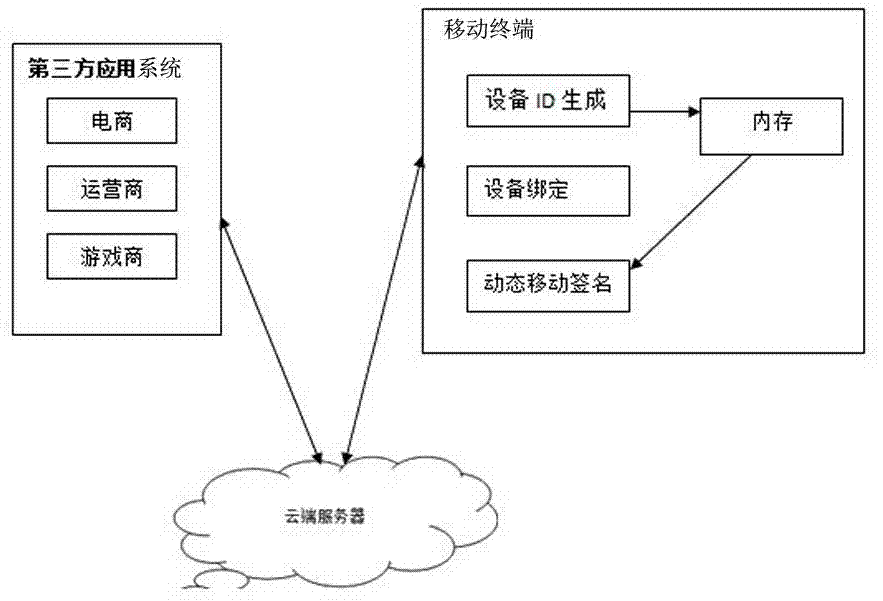
Dynamic mobile signature system and method
InactiveCN103546295AIncrease flexibilityImprove securityUser identity/authority verificationMobile paymentSoftware
The invention discloses a dynamic mobile signature system and method. An improvement is conducted on the software and hardware environment of a mobile terminal, so that the dynamic encryption process and the dynamic decryption process are achieved. The mobile terminal is made to conduct dynamic signature on trade data sent to a commercial tenant through data interaction between a cloud dynamic signature service platform and the mobile terminal and data interaction between the cloud dynamic signature service platform and a commercial tenant platform, then, the trade data are sent to the commercial tenant platform through the cloud dynamic signature service platform to be confirmed after the signature is authenticated, and the operation of mobile payment is permitted according to trade information confirmed by a commercial tenant, wherein the cloud dynamic signature service platform and the mobile terminal are connected through the internet. By means of the dynamic mobile signature scheme, the defects of the hardware signature are overcome, the dynamic signature authentication at the software level is achieved, safety and flexibility of the mobile terminal are greatly improved when the mobile terminal participates in electronic commerce trade information confirming, the signature and authentication process is produced through a dynamic signature algorithm which is unceasingly updated on the basis of a cloud server, and therefore invasion of Trojan horse viruses can be effectively resisted, and safety performance of information confirming can be improved.
Owner:JIANGSU PAYEGIS INFORMATION SECURITY TECH CO LTD
Mixed mode multi-level gate-level hardware Trojan horse detection method based on machine learning
ActiveCN111523116AEfficient detectionImprove accuracyPlatform integrity maintainanceMachine learningAlgorithmTrojan horse
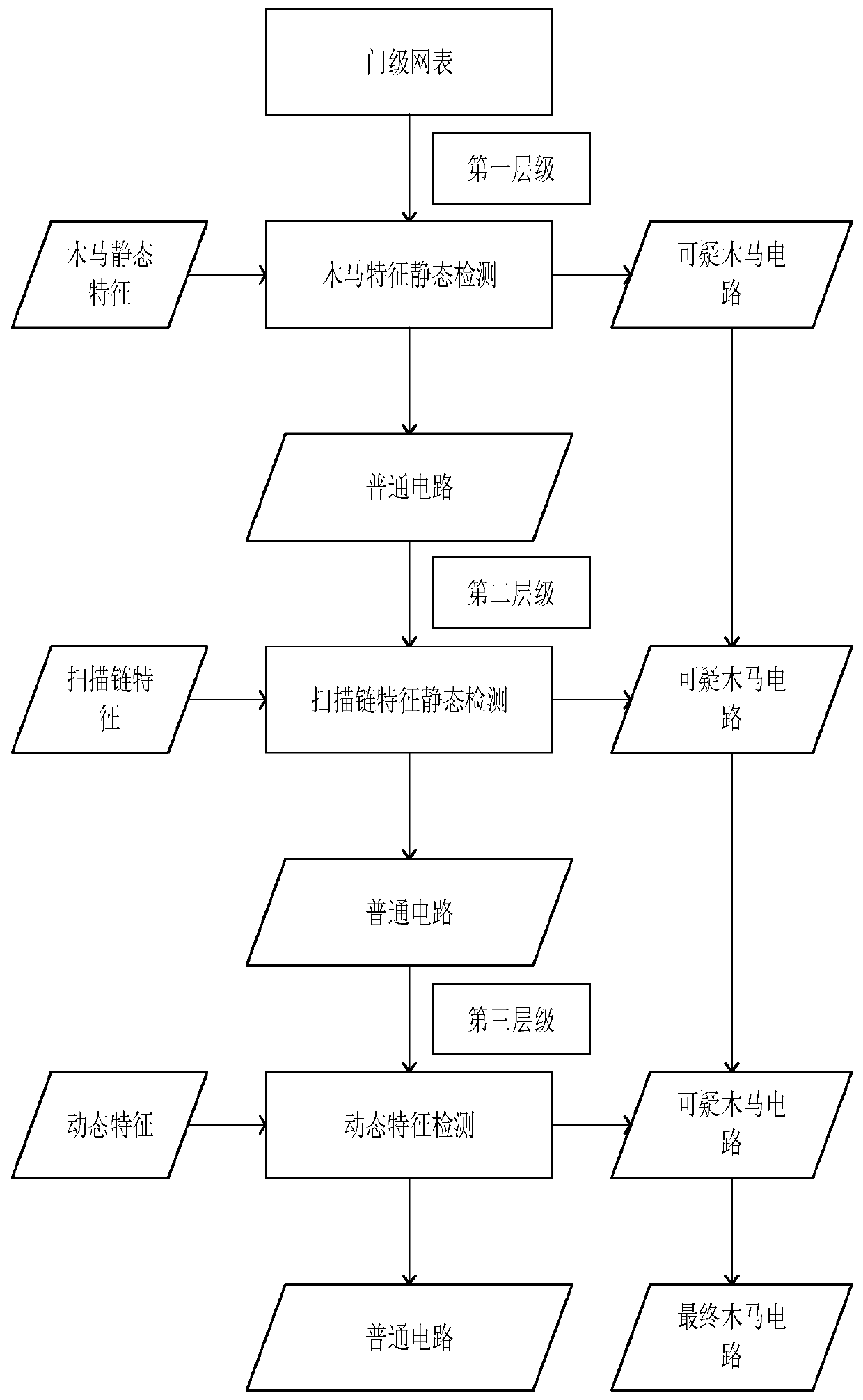
The invention discloses a mixed mode multi-level gate-level hardware Trojan horse detection method based on machine learning, and belongs to the technical field of calculation, reckoning or counting.The mixed mode multi-level gate-level hardware Trojan horse detection method comprises the steps of: firstly, by analyzing a structure and characteristics of a gate-level Trojan horse circuit at a first level, providing two effective Trojan horse circuit characteristics, combining with traditional Trojan horse characteristics, carrying out static detection on a suspicious circuit to be detected through a machine learning algorithm, and separating the Trojan horse circuit and a normal circuit preliminarily; secondly, providing Trojan horse characteristics of two scanning chain structures at a second level, and continuing to perform static detection on the normal circuit separated at the first level by using a scan chain detection method; and finally, dynamically detecting the normal circuitseparated at the second level, and integrating detection results of the three levels to obtain the final Trojan horse circuit. Compared with a traditional gate-level hardware Trojan horse detection method, the mixed mode multi-level gate-level hardware Trojan horse detection method combines a static detection method and a dynamic detection method, and the suspicious circuit to be detected is detected more comprehensively and efficiently by means of the multi-level structure.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
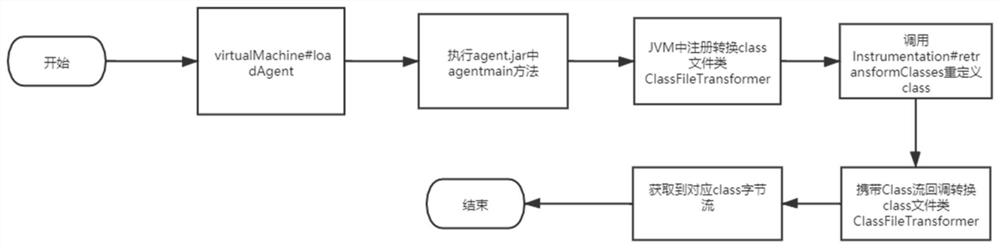
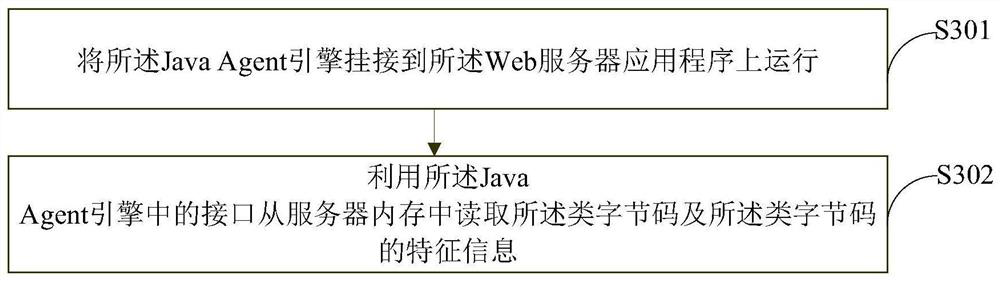
Java Web application memory Trojan horse detection method, terminal equipment and storage medium
ActiveCN113312624AReduce the impactConsume less resourcesPlatform integrity maintainanceEnergy efficient computingWeb applicationTrojan horse
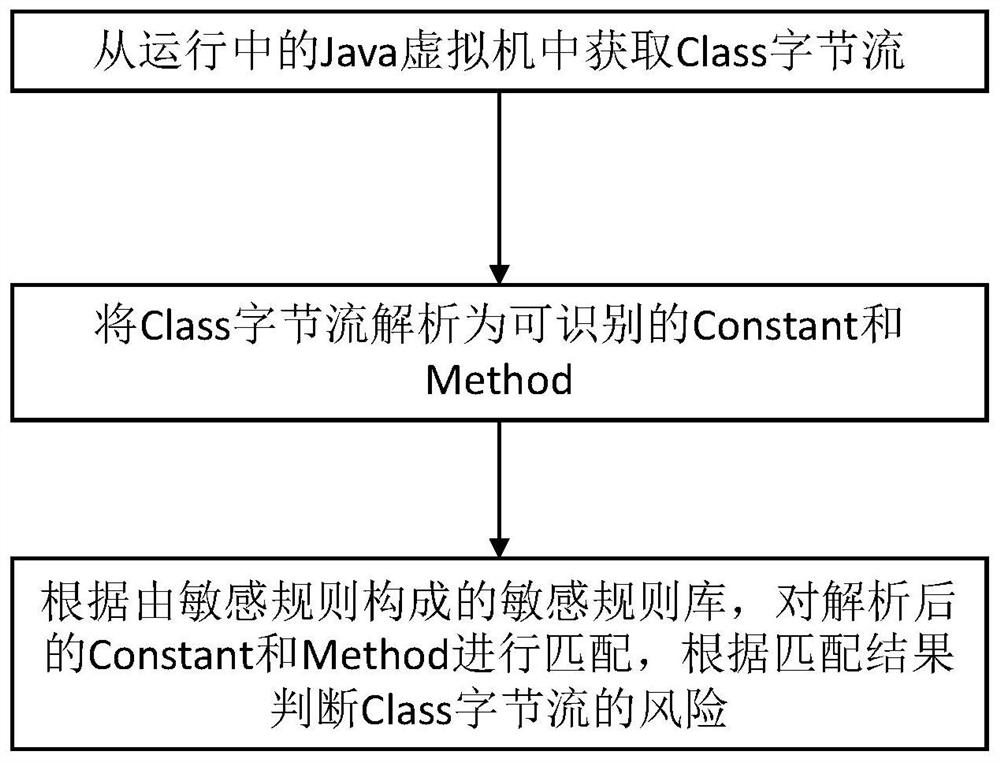
The invention relates to a Java Web application memory Trojan horse detection method, terminal equipment and a storage medium. The method comprises the following steps: S1, acquiring a Class byte stream from a running Java virtual machine; s2, the Class byte stream is analyzed into an identifiable Constance and an identifiable Method, and the Class byte stream is analyzed into the identifiable Constance and the identifiable Method; and S3, according to a sensitive rule base formed by sensitive rules, matching the analyzed Constant with the analyzed Method, According to a matching result, judging the risk of the Class byte stream. Compared with a traditional detection method, the method has the advantages that the resource consumption is lower, the influence on the operation of a service system is smaller, and a large amount of I / O operation is avoided.
Owner:XIAMEN FUYUN INFORMATION TECH CO LTD +1
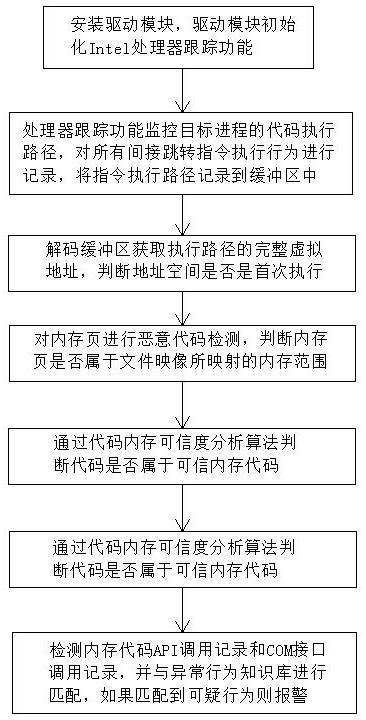
Memory malicious code detection method based on processor tracking
ActiveCN113569244AEasy to detectImprove universalityPlatform integrity maintainanceIntel processorAttack
The invention discloses a memory malicious code detection method based on processor tracking, which belongs to the technical field of information security, and is characterized by comprising the following steps that: a, a driving module initializes an Intel processor tracking function; b, monitoring a code execution path of a target process; c, decoding a buffer area to obtain a complete virtual address of the execution path; d, carrying out malicious code detection on a memory page; e, judging whether the code belongs to a trusted memory code or not; and f, detecting a memory code API calling record and a COM interface calling record, and matching the memory code API calling record and the COM interface calling record with an abnormal behavior knowledge base. Common scenes such as memory codes, shelled malicious codes, encrypted malicious code viruses and Trojan horses used in file-free attacks can be detected, meanwhile, the method also has a detection effect on execution of shellcode codes in the vulnerability utilization process, the detection effect is good, and good universality is achieved.
Owner:COLASOFT
File-free Trojan searching and killing method and device
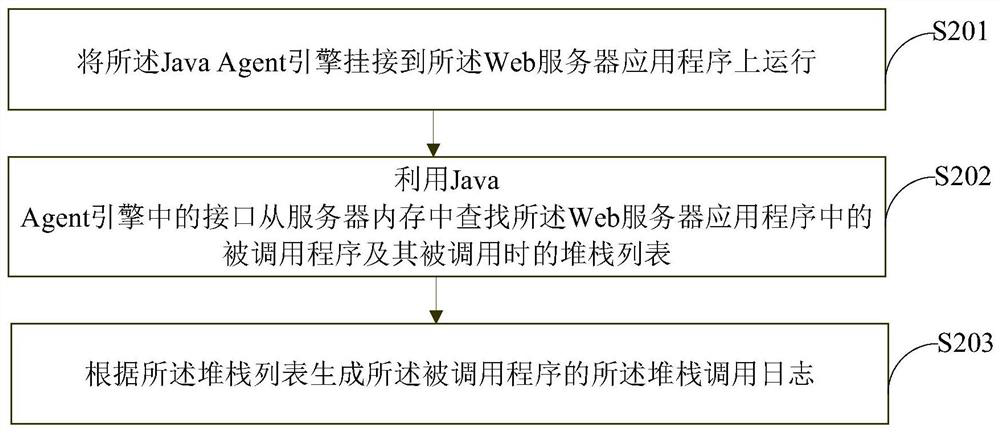
PendingCN114065204AEasy to detectRealize killingPlatform integrity maintainanceSecuring communicationRisk levelWeb application
The invention provides a file-free Trojan searching and killing method and device, and relates to the field of information security. The method can also be used in the financial field, and comprises the following steps: running a Java Agent engine and obtaining a stack calling log and byte-like code information of a called program in a Web server application program; determining the risk level of the called program according to a preset detection rule, the stack calling log and the byte-like code information; and according to a preset searching and killing strategy and the risk level, determining that the called program contains a class file without the file Trojan horse, and searching and killing the class file without the file Trojan horse. According to the method and the device, automatic detection, searching and killing without file Trojan can be realized, and safe operation of the Web application is protected.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Method and circuit for credible design of integrated circuit design process
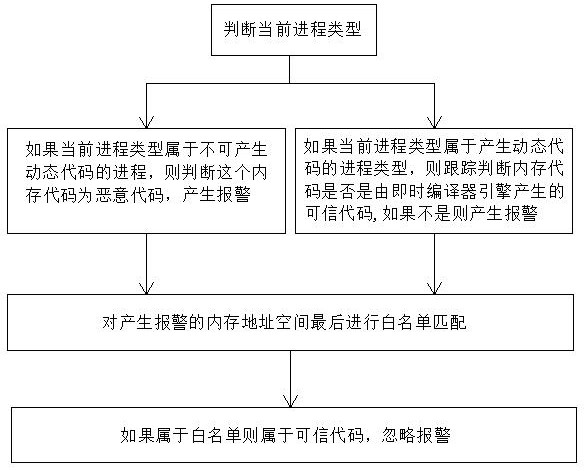
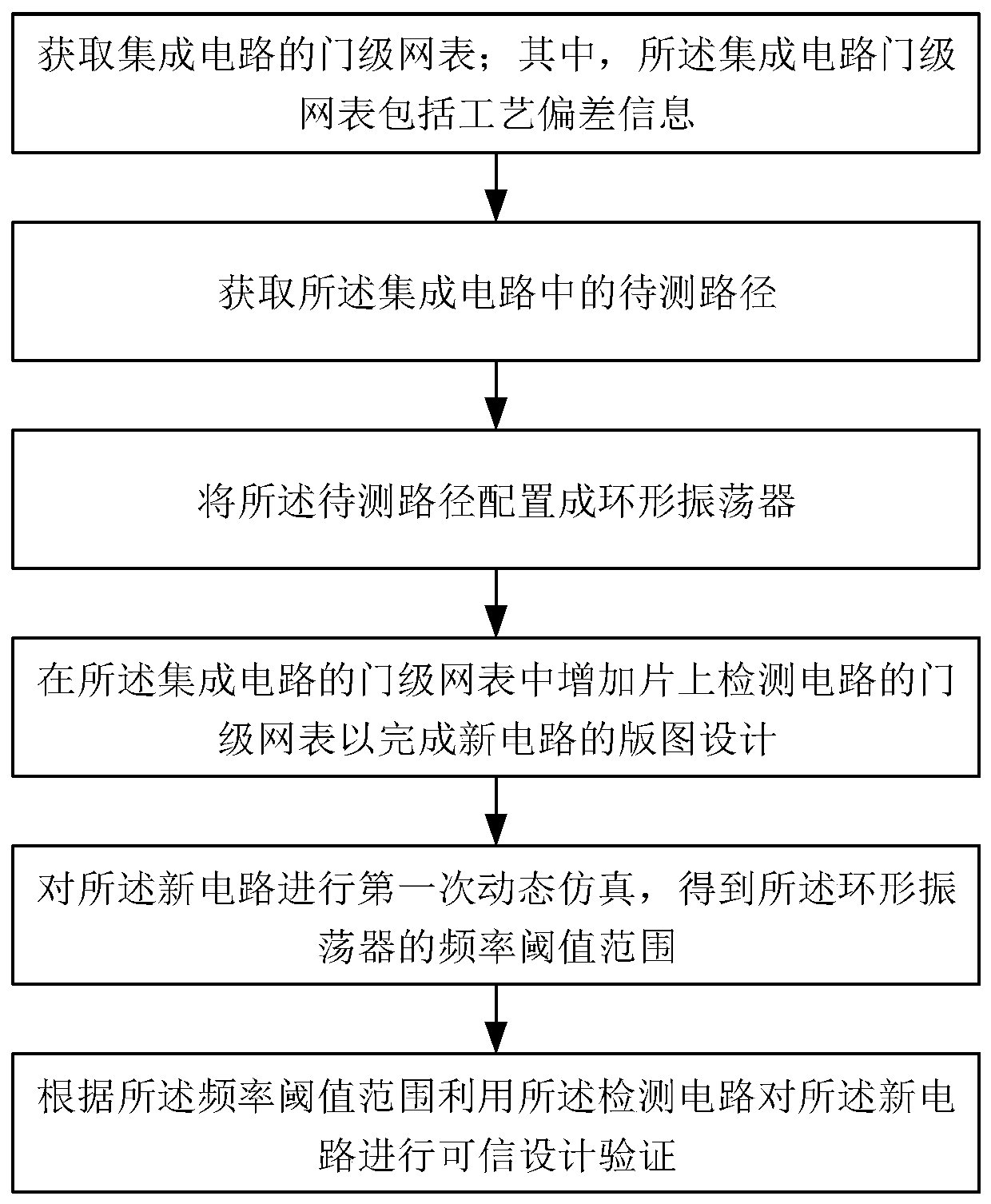
ActiveCN111027270AEliminate the modeling processReduce the impactCAD circuit designSpecial data processing applicationsTrojan horseHemt circuits
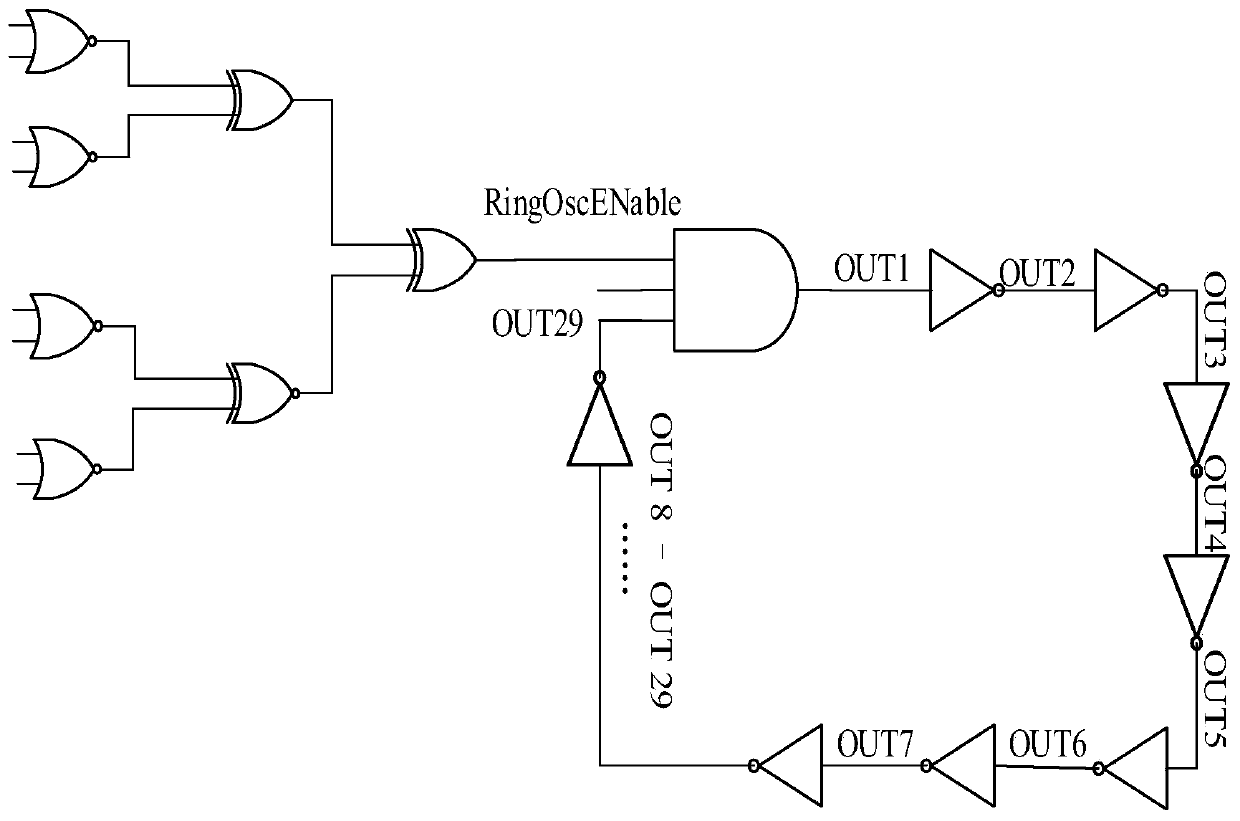
The invention discloses a method and a circuit for credible design of an integrated circuit design process. The method comprises the following steps: acquiring a gate-level netlist of an integrated circuit; wherein the integrated circuit gate-level netlist comprises process deviation information; acquiring a to-be-tested path in the integrated circuit; configuring the to-be-measured path into a ring oscillator; adding a gate-level netlist of an on-chip detection circuit in the gate-level netlist of the integrated circuit to complete the layout design of a new circuit; performing first dynamicsimulation on the new circuit to obtain a frequency threshold range of the ring oscillator; and performing credible design verification on the new circuit by utilizing the detection circuit accordingto the frequency threshold range. According to the credible design method provided by the invention, the influence of the Trojan horse on the side channel information is directly reflected on the pathdelay, so that the process of modeling the Trojan horse is omitted, and the test difficulty is reduced; and meanwhile, the detection circuit is simple in structure and easy to integrate into an integrated circuit design process, so that the measurement accuracy is ensured.
Owner:XIDIAN UNIV
One-time pad bidirectional authentication safe logging technology for internet bank
The invention relates to one-time pad bidirectional authentication safe logging technology for an internet bank. The technology ensures that a user safely logs in a personal e-bank, and the account capital security of the user is protected. A character table disclosed in the technology has electronic and substantial double characteristics and has huge information space. Because all used authentication information is hashed values in the bidirectional authentication process, it is difficult to calculate the character table back through the hashed values, and various network eavesdropping and Trojan horse programs can be sufficiently resisted. An input password must be subjected to bidirectional authentication of the internet bank and the user in a one-time pad mode, and in the process, any failures can prevent the password of the user himself or herself from being divulged. Any ordinary people can easily master the one-time pad bidirectional authentication safe logging technology for the internet bank, and extra auxiliary authentication hardware devices and authentication cost are not needed. The technology can ensure that an ordinary user frequently conducts the operation of logging in a personal e-bank account and an ATM in a long term without reducing the safety of a system.
Owner:YANTAI UNIV
Method and system for indicating an executable as trojan horse
Owner:SAFENET DATA SECURITY ISRAEL
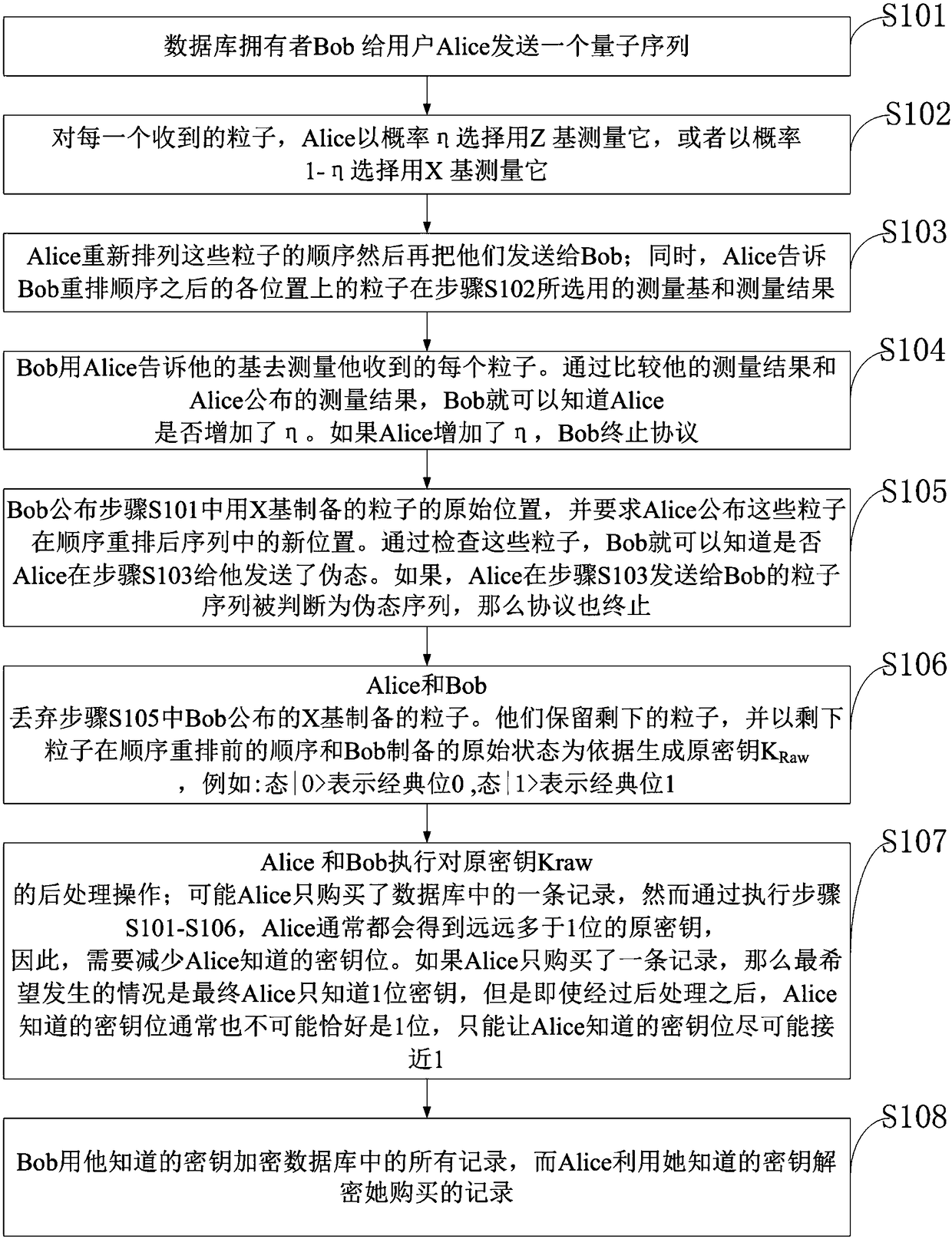
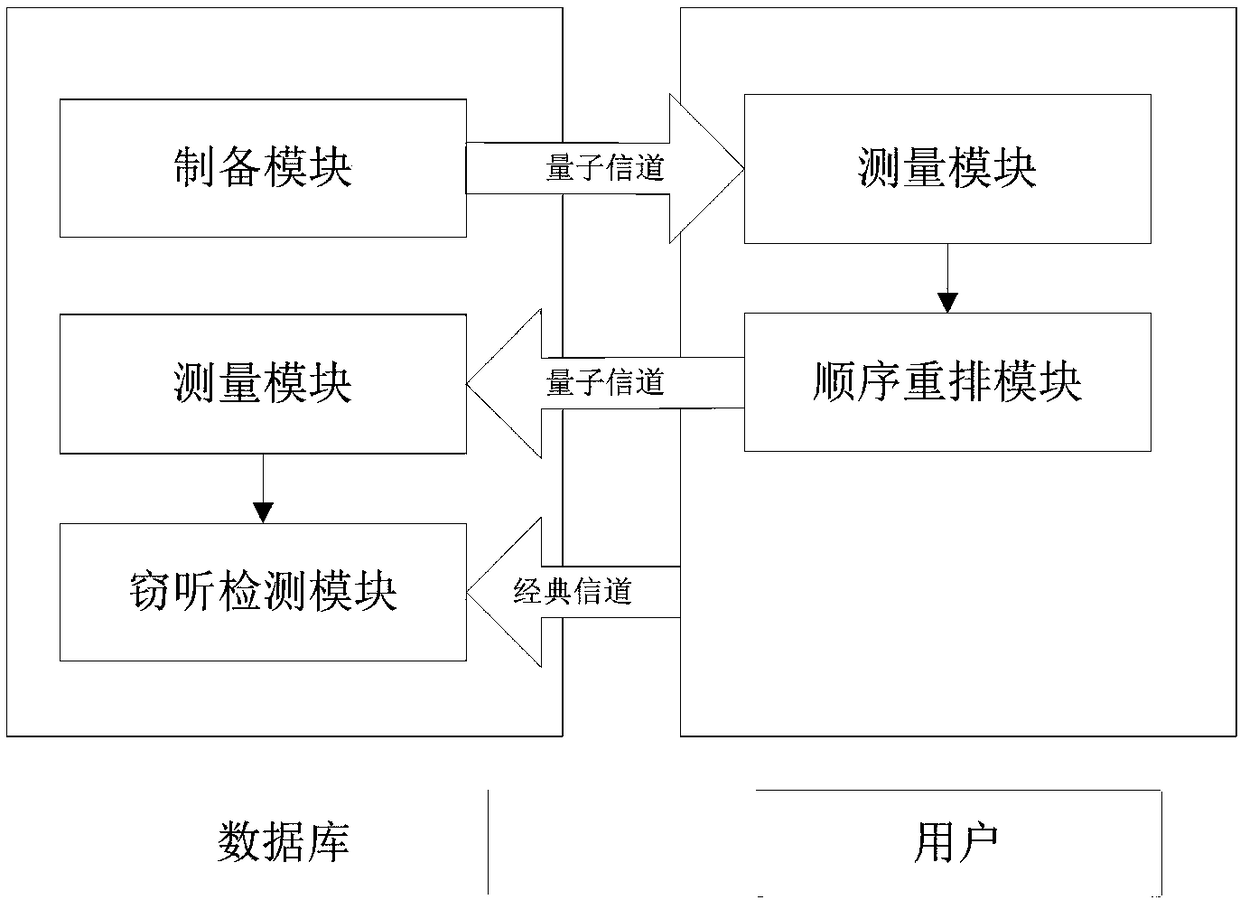
Sequence rearrangement-based quantum database privacy query method with better user privacy performance
ActiveCN108363927AGood user privacy performanceUser privacy protection performance is goodDigital data protectionSpecial data processing applicationsUser privacyDatabase privacy
The invention belongs to the technical field of database privacy query, and discloses a sequence rearrangement-based quantum database privacy query method with better user privacy performance. A database owner Bob sends a quantum sequence to a user Alice; for each received particle, the Alice measures the particle by selecting and using Z base according to a probability eta, or by selecting and using X base according to a probability 1-eta; the Alice rearranges a particle sequence and then sends rearranged particles to the Bob; and meanwhile, the Alice tells the Bob about the measurement baseselected and used for the particle in each position after sequence rearrangement and a measurement result. Through a quantum database privacy query protocol proposed by the method, the user privacy performance better than cheat sensitivity can be obtained; and Trojan horse attack can be resisted in the absence of a wavelength filter and a photon number distributor with an auxiliary monitoring detector.
Owner:哈尔滨同创普润科技有限公司
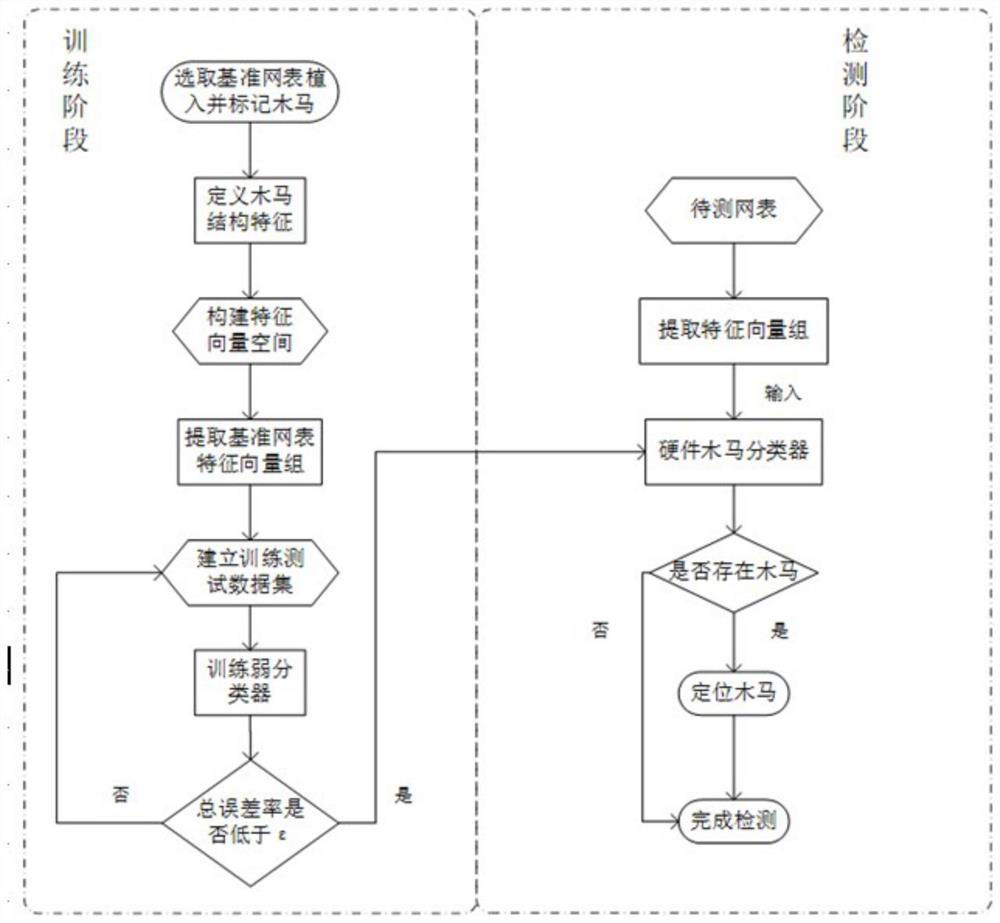
Hardware Trojan horse detection method based on Adaboost algorithm
ActiveCN112231775AShorten the timeReduce resource requirementsInternal/peripheral component protectionPlatform integrity maintainanceFeature vectorData set
The invention discloses a hardware Trojan horse detection method based on Adaboost. The method comprises steps of defining the gate-level structure features of hardware Trojan horses, calibrating thepositions of all hardware Trojan horses in a netlist and the Trojan horse feature vectors of gate-level elements, building a training and testing data set, and building and training an Adaboost hardware Trojan horse detection model according to the data set. When the error rate of the model is lower than a set threshold value, the model can be used for detecting hardware Trojan horses in the circuit netlist to be detected.
Owner:TIANJIN UNIV
Machine learning Trojan horse detection method based on structural feature screening and load expansion
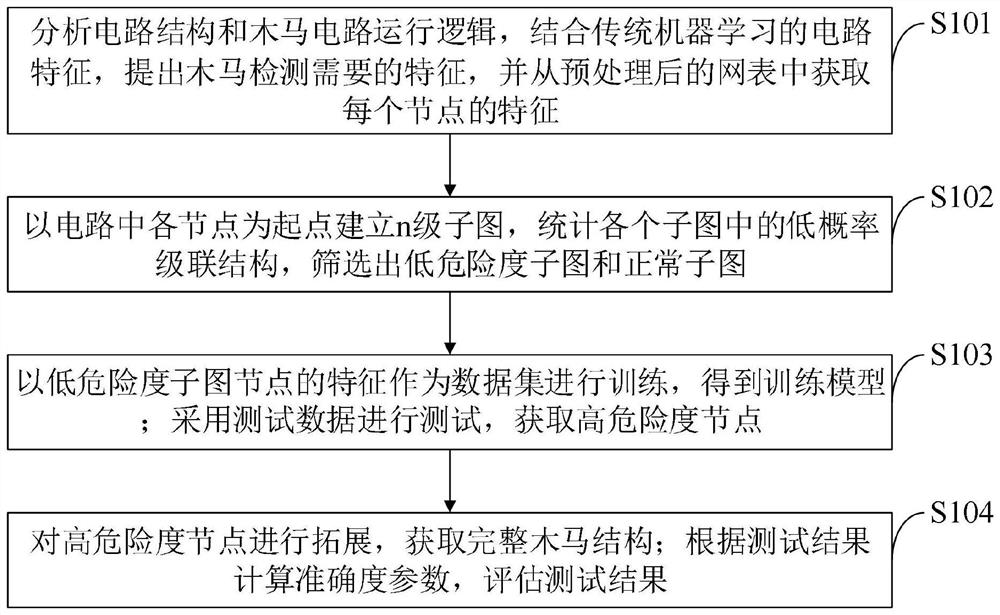
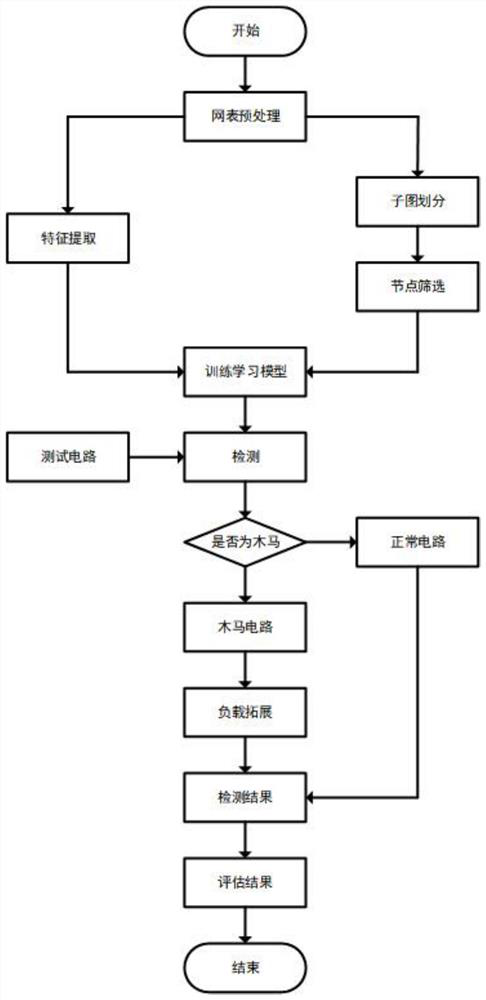
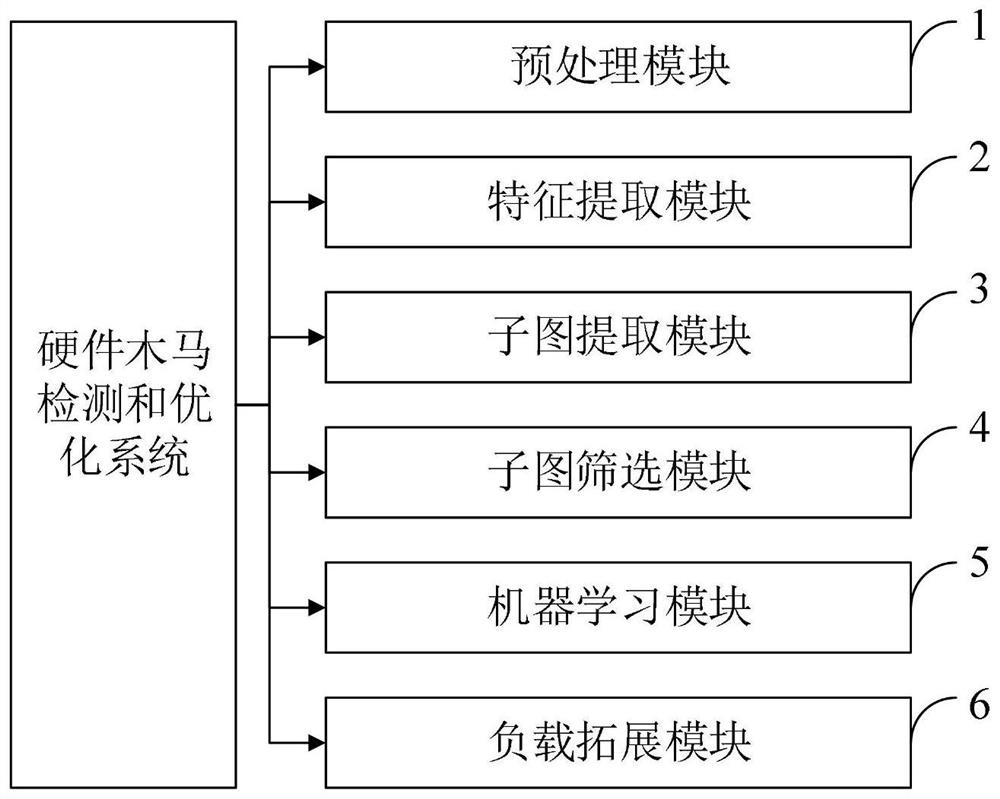
PendingCN113626812AReduce training timeImprove accuracyPlatform integrity maintainanceMachine learningData setFeature extraction
The invention belongs to the technical field of hardware security, and discloses a machine learning Trojan horse detection method based on structural feature screening and load expansion, which comprises the following steps: firstly, converting a netlist of a circuit into a quantifiable mathematical model, and performing feature extraction through a mathematical method based on the model; then, in combination with hardware Trojan trigger structure characteristics, screening nodes to obtain a more balanced data set, and carrying out Trojan detection in combination with a machine learning classification method; and finally, according to the structural characteristics of the hardware Trojan load, carrying out backward expansion on Trojan nodes so as to obtain a complete hardware Trojan circuit. According to the method, the structural features of the Trojan horse with low trigger probability and the circuit static features used by machine learning are creatively combined, the data set of machine learning is preliminarily screened, the data set for training is balanced, the efficiency and accuracy of machine learning are effectively improved, a new thought is provided for subsequent related research, and the detection effects of most hardware Trojan horse detection methods are improved.
Owner:XIDIAN UNIV
A system for authenticating mobile applications
The invention proposes a system for verifying the original version of a mobile application program. By setting up a dedicated original information server, in the process of downloading, installing or enabling the mobile application, by comparing with the original information provided by the server, it is judged whether the mobile application belongs to the original version. The original version verification can prevent mobile phone users from using troubles and losses caused by downloading mobile applications infected with viruses, Trojan horses or other illegal advertising information, thereby improving mobile phone users' experience and satisfaction.
Owner:BEIJING SENSESHIELD TECH
Mining Trojan horse detection method and device, electronic device and storage medium
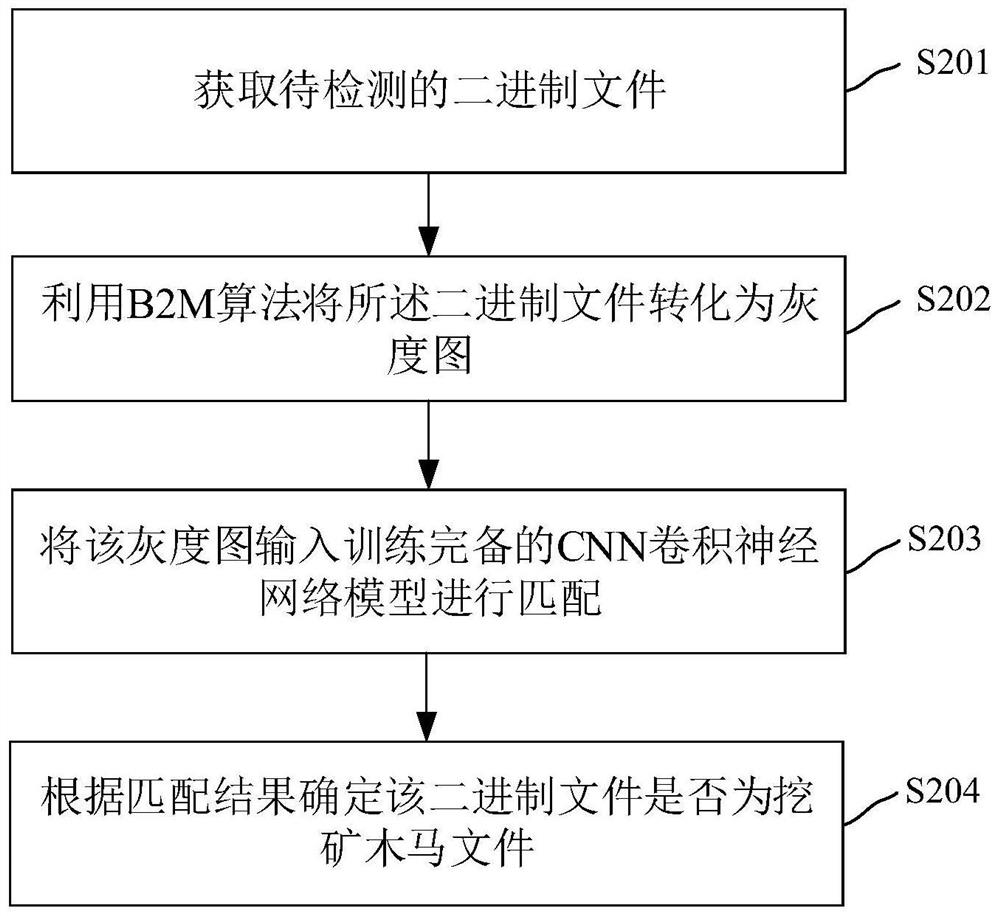
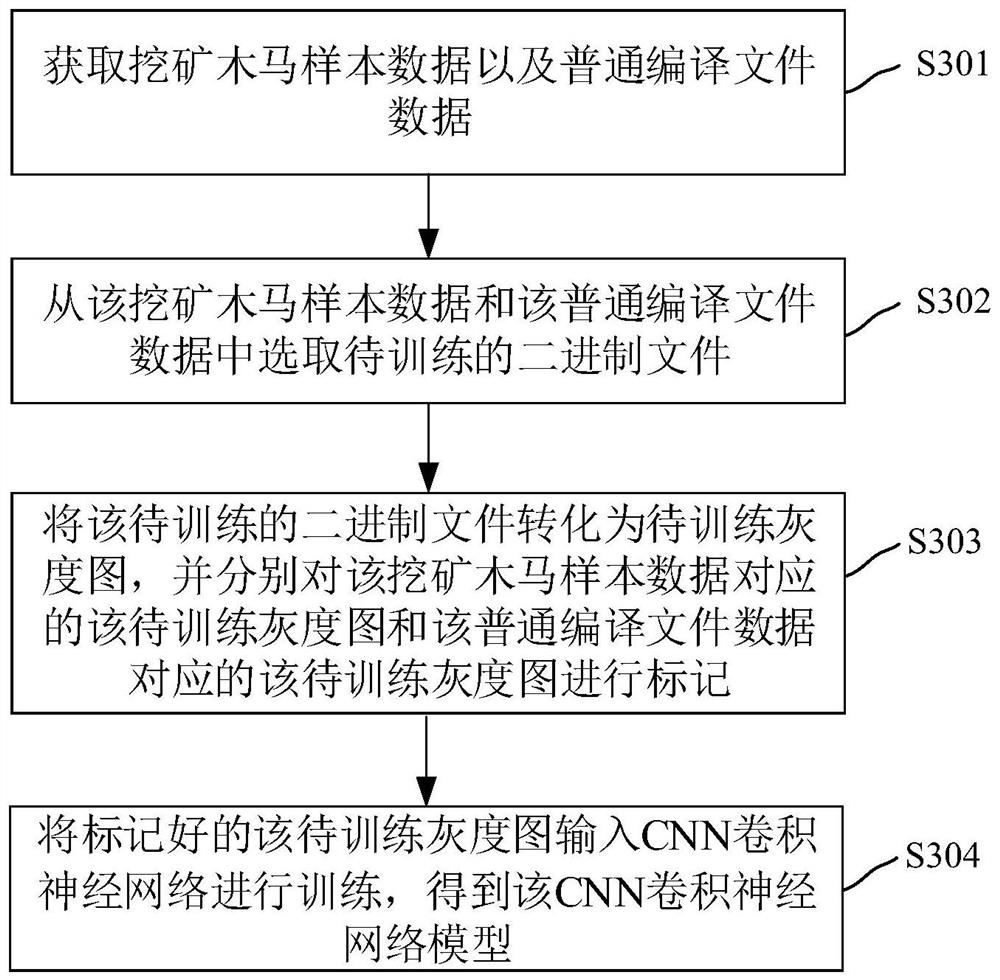
PendingCN112214766AEfficient detectionSolve the problem of large memory usagePlatform integrity maintainanceNeural architecturesAlgorithmTrojan horse
The invention relates to a mining Trojan horse detection method and device, an electronic device and a storage medium, and the method comprises the steps: obtaining a to-be-detected binary file; converting the binary file into a grey-scale map by using a B2M algorithm; inputting the grey-scale map into a completely trained CNN convolutional neural network model for matching; and determining whether the binary file is a mining Trojan file or not according to a matching result. The mining Trojan horse detection method and device solve the problem of how to solve the problem of large memory occupation on the terminal device for detecting the mining Trojan horse by the neural network application, and can quickly and effectively detect the mining Trojan horse on the premise of occupying littlestorage space.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Webshell detection method and device, medium and equipment
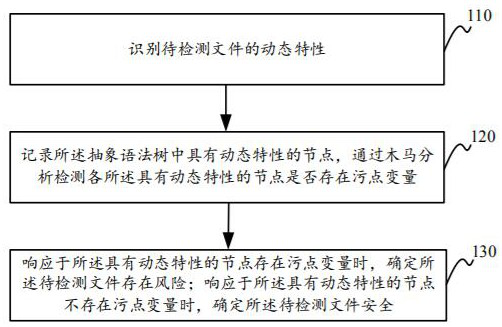
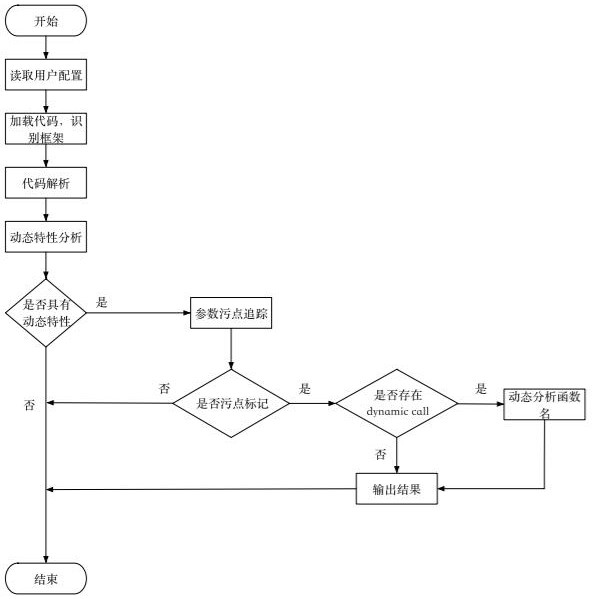
InactiveCN112688966AEasy to detectPrecise positioningPlatform integrity maintainanceTransmissionAlgorithmLexical analysis
The embodiment of the invention provides a webshell detection method and device, a medium and equipment, and the method comprises the steps: recognizing the dynamic characteristics of a to-be-detected file, and generating an abstract syntax tree of the to-be-detected file after the grammatical analysis and lexical analysis of the to-be-detected file; recording nodes with dynamic characteristics in the abstract syntax tree, and detecting whether the nodes with the dynamic characteristics have stain variables or not through Trojan horse analysis; determining that the to-be-detected file has a risk in response to the fact that the node with the dynamic characteristic has the stain variable; and determining that the to-be-detected file is safe in response to the fact that the node with the dynamic characteristic does not have the stain variable. According to the method, the dynamic characteristics of the to-be-detected file are taken as core characteristics, and the dynamic and static analysis technology is matched, so that the detection accuracy and the response efficiency of the webshell are improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM +1
Computer credible authentication system, method and equipment and readable storage medium
PendingCN113190853AEnsure safetyObvious superiorityDigital data protectionBootstrappingOperational systemAttack
The invention discloses a computer credible authentication system, method and equipment and a readable storage medium, and a trusted computing technology is incorporated into the overall security of the system. The credible PC based on the platform can guarantee the integrity of software and hardware in the use process of the PC, an attacker cannot reach an attack directory by means of refreshing an ROM, replacing accessories, replacing an operating system, implanting Trojan horses and the like, and the credible PC always runs in a safe and credible environment. According to the invention, the software and hardware environment of the trusted PC equipment can be ensured to be always in a safe and trusted state from starting of bottom hardware to starting of an operating system to running of actual software and the like, unauthorized software, illegal programs, Trojan viruses and the like cannot be installed in the system and cannot be executed, and the safety of an office environment can be effectively ensured. The credible computing has outstanding superiority and strong defense capability for network attack weapons and attack modes.
Owner:CHINA ELECTRIC POWER RES INST
System chip hardware Trojan horse detection method and system based on differential amplification controllability
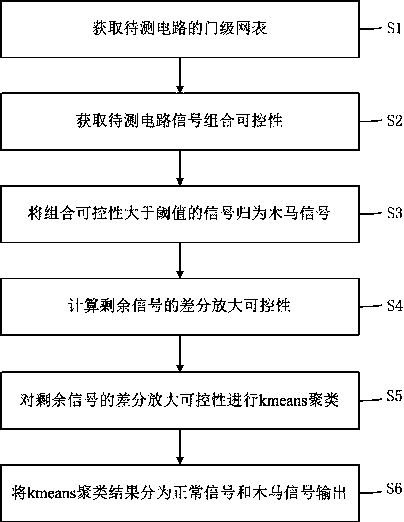
ActiveCN111488629AEmbodies hidden featuresDemonstrate testabilityCharacter and pattern recognitionInternal/peripheral component protectionTrojan horseHemt circuits
The invention discloses a system chip hardware Trojan horse detection method and system based on differential amplification controllability. The detection method comprises the following steps of S1, obtaining a gate-level netlist of a to-be-detected circuit; s2, acquiring the controllability of the signal combination of the circuit to be tested; s3, classifying the signals of which the combined controllability is greater than a threshold value into Trojan signals; s4, calculating the differential amplification controllability of the residual signals; s5, carrying out kmeans clustering on the differential amplification controllability of the residual signals; and S6, dividing the kmeans clustering result into a normal signal and a Trojan signal to be output. According to the method, the gate-level netlist is analyzed, and all Trojans inserted before chip manufacturing can be detected theoretically; the combined controllability of the signals in the circuit is analyzed, the controllability of differential amplification is calculated and utilized, the testability of the signals can be reflected, the static overturning probability of the signals can also be reflected, the concealment characteristic of Trojan horses can be better reflected, and a good detection effect is achieved.
Owner:FOSHAN POWER SUPPLY BUREAU GUANGDONG POWER GRID
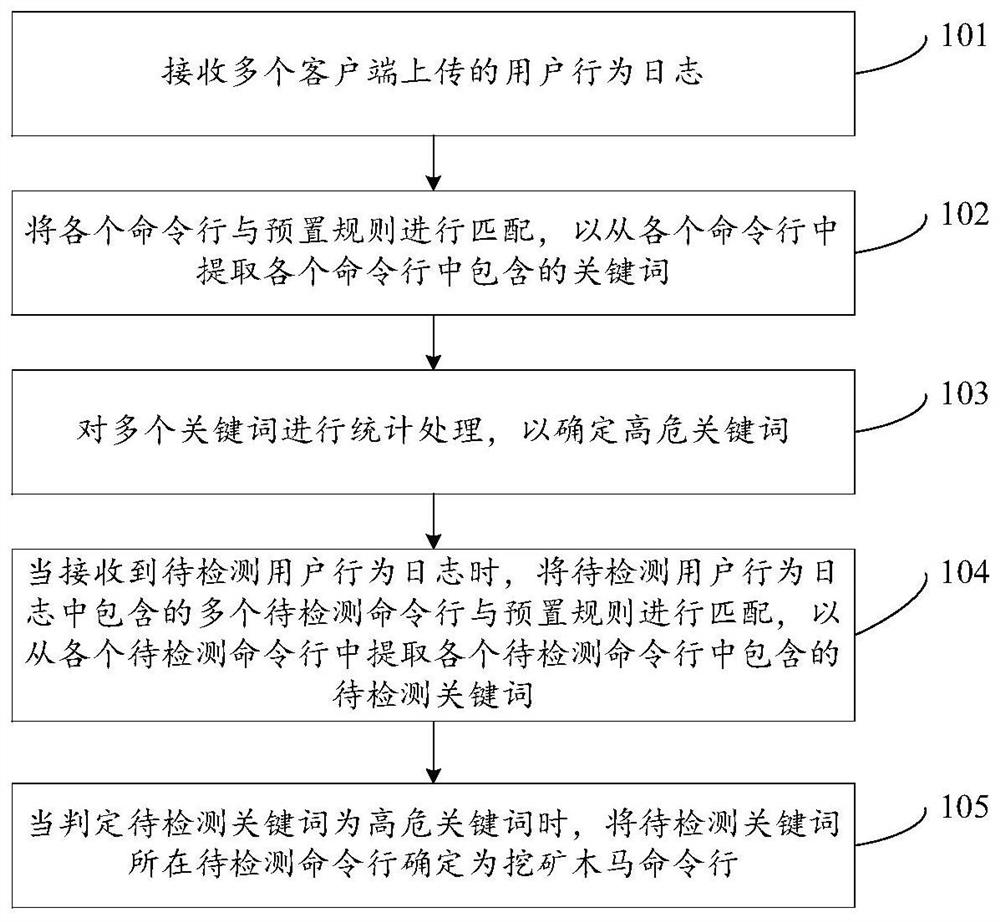
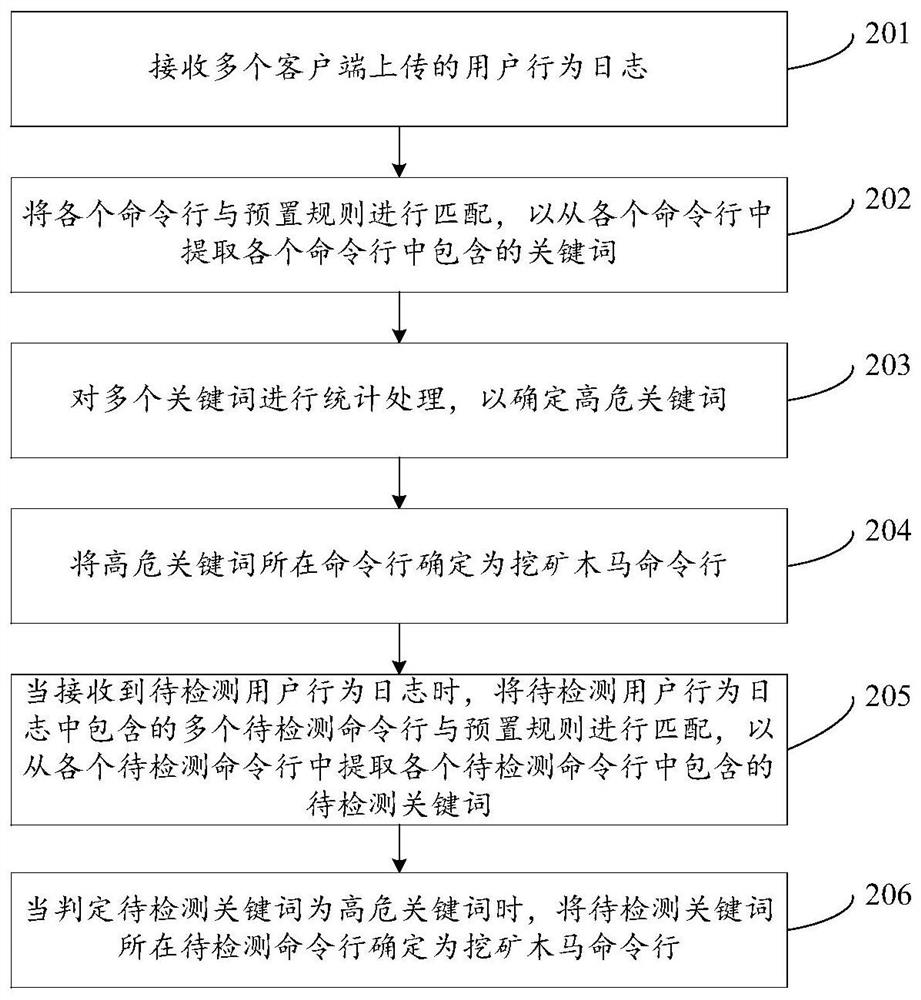
Mining Trojan horse detection method and device
PendingCN112087414AEfficient detectionPlatform integrity maintainanceTransmissionTrojan horseTerminal equipment
The invention discloses a mining Trojan horse detection method and device, relates to the technical field of network security, and aims to effectively detect whether a mining Trojan horse program is implanted into terminal equipment. The method comprises the following steps: receiving user behavior logs uploaded by a plurality of clients; matching each command line with a preset rule so as to extract keywords contained in each command line from each command line; performing statistical processing on the plurality of keywords to determine high-risk keywords; when a to-be-detected user behaviorlog is received, matching a plurality of to-be-detected command lines contained in the to-be-detected user behavior log with a preset rule so as to extract to-be-detected keywords contained in each to-be-detected command line from each to-be-detected command line; when it is judged that the to-be-detected keyword is the high-risk keyword, determining the to-be-detected command line where the to-be-detected keyword is located as a mining Trojan horse command line. The method and the device are suitable for the process of detecting whether the mining Trojan horse program is implanted into the terminal equipment.
Owner:BEIJING QIHOO TECH CO LTD
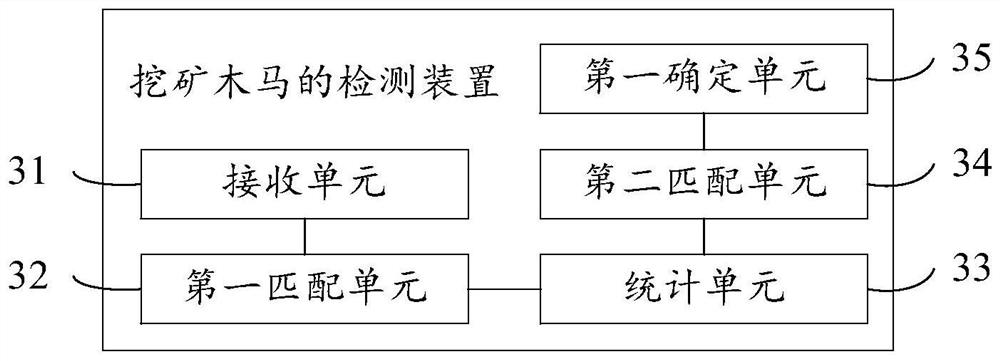
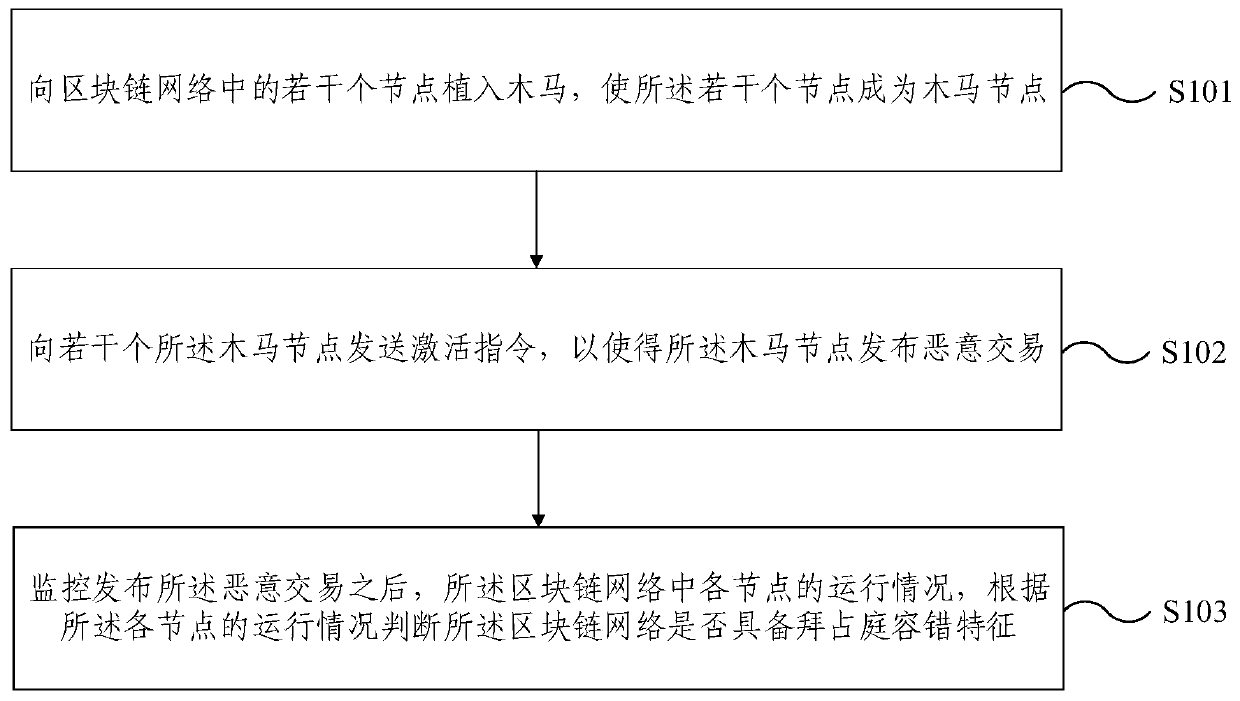
Safety monitoring method and device for block chain network
The embodiment of the invention provides a safety monitoring method and device for a block chain network. The method comprises the following steps: implanting Trojans into a plurality of nodes in a blockchain network, so that the plurality of nodes become Trojan nodes; sending an activation instruction to a plurality of Trojan horse nodes to enable the Trojan horse nodes to publish malicious transactions; and after the malicious transaction is issued, monitoring the operation condition of each node in the blockchain network, and judging whether the blockchain network has the Byzantine fault tolerance feature or not according to the operation condition of each node. According to the security monitoring method and device for the blockchain network provided by the embodiment of the invention,the Byzantine node is constructed for attacking, and other Byzantine nodes are discovered, so that whether the block chain network has the Byzantine fault tolerance characteristic or not can be judged, and security monitoring is carried out on the block chain network.
Owner:北京笔新互联网科技有限公司
Trojan horse virus detection method based on DNS
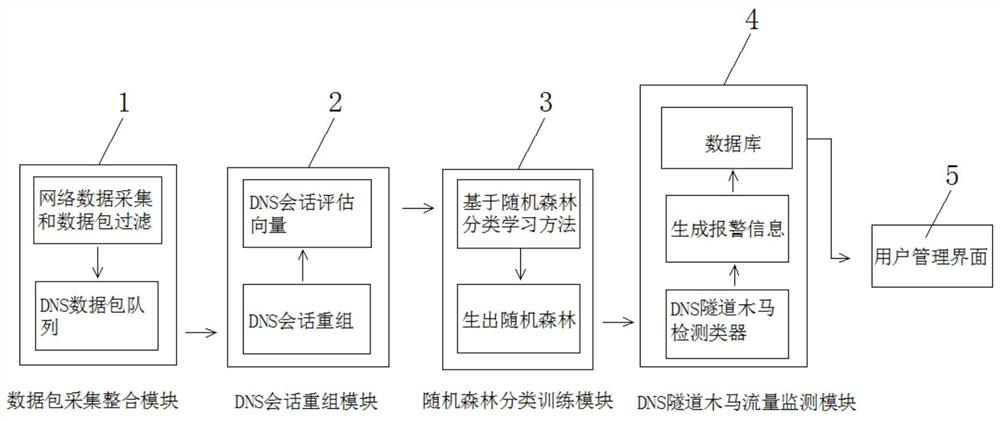
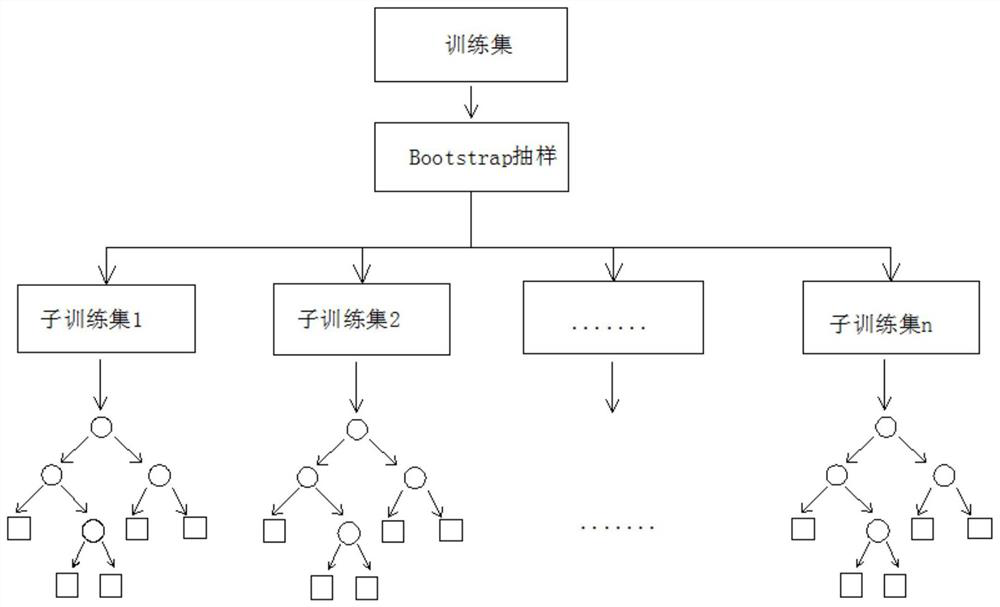
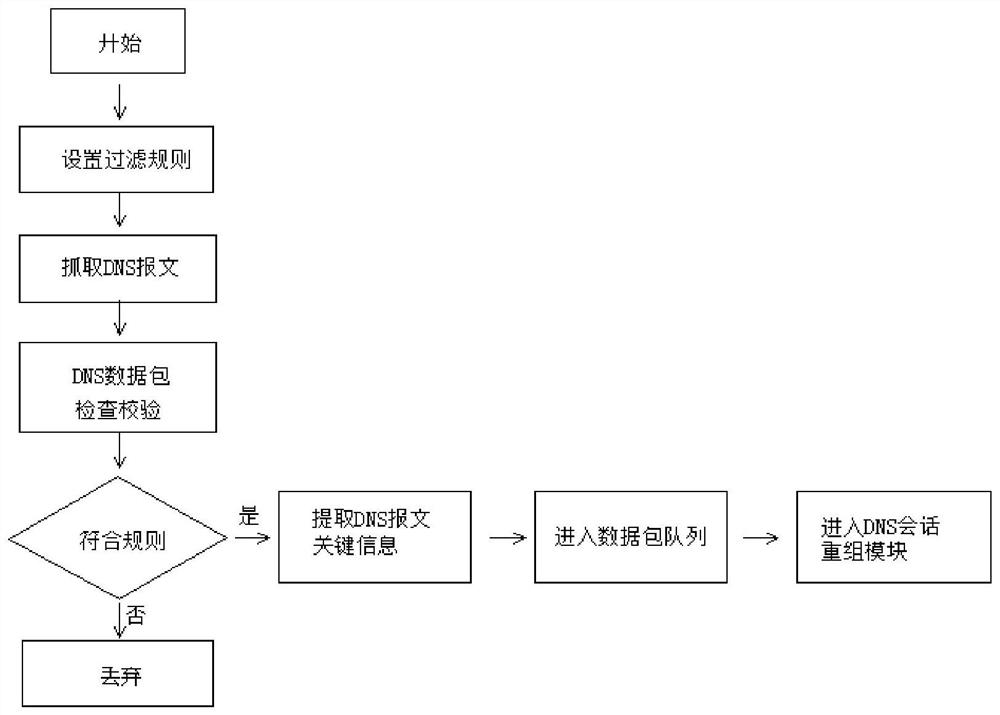
PendingCN112272175AReduce false positivesImprove accuracyCharacter and pattern recognitionPlatform integrity maintainanceData packTrojan horse
The invention relates to the technical field of network security and discloses a DNS-based Trojan horse virus detection method. The method comprises a data packet acquisition and integration module, aDNS session recombination module, a random forest classification training module, a DNS tunnel Trojan horse traffic monitoring module and a user management interface. The Trojan horse virus detectionmethod based on the DNS comprises steps that the first sample information is acquired, and the first sample information comprises the domain name information of the DNS and flow behaviors of the DNS;a characteristic value of the first sample information is extracted; weighted summation is conducted on feature values to obtain a score value; the DNS suspicious model is established according to the score value, so that weighted summation is performed on the feature value, the DNS suspicious model is established according to the score value after the score value is obtained, and the DNS suspicious model can be used for subsequent suspicious judgment on DNS information, namely, multi-dimensional recognition is performed on the feature value, so many problems such as misinformation generatedby a conventional algorithm are reduced; and DNS information detection and identification accuracy is improved.
Owner:江苏今浪信息技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com