Gate-level hardware Trojan horse detection method based on multiple characteristic parameters
A feature parameter and multi-feature technology, applied in the direction of internal/peripheral computer component protection, etc., can solve the problems that the accuracy of the detection result is difficult to guarantee, and a single feature parameter cannot fully reflect the node status in the gate-level netlist, so as to improve the detection Accuracy, the effect of improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
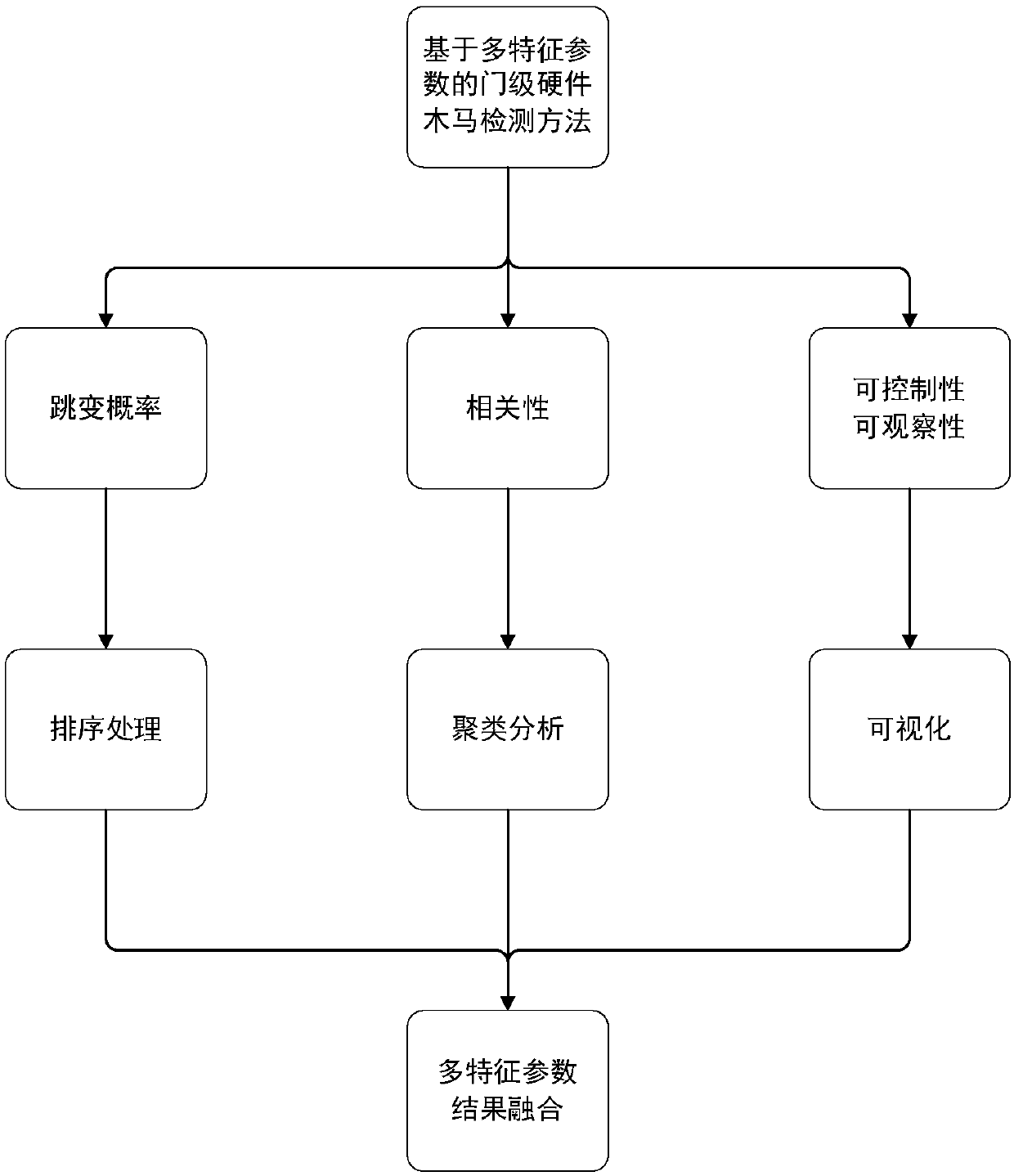
[0019] The multi-feature parameter-based door-level hardware Trojan detection method provided by the present invention will be described in detail below in conjunction with the accompanying drawings, but this does not constitute a limitation to the present invention.
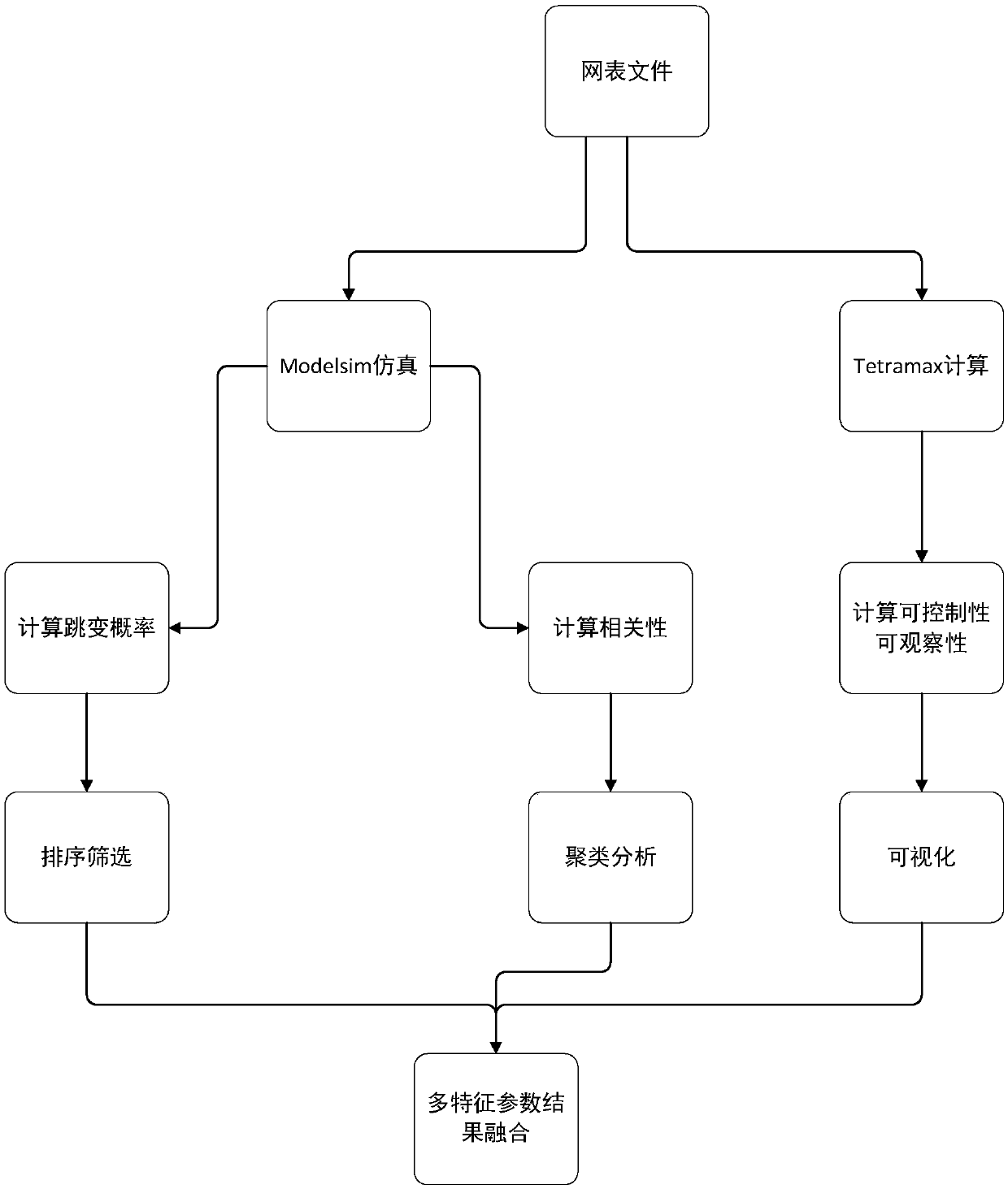
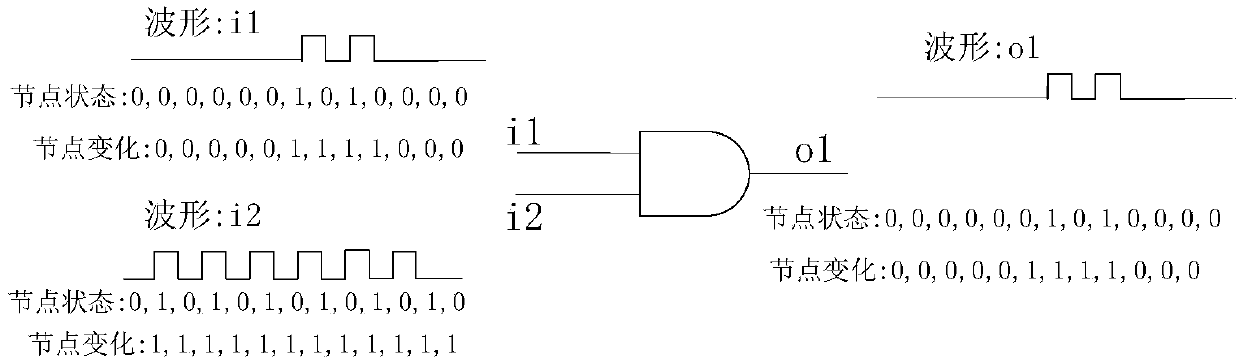
[0020] The method mainly includes two parts, extracting multi-characteristic parameters in gate-level circuits and data processing. Among them, the feature parameters in the gate-level circuit are extracted including the following parts: jump probability, correlation, controllability and observability; the data processing part includes the following parts: sorting processing of jump probability, correlation clustering Analysis algorithms, controllability and observability cluster analysis methods, and multi-feature parameter fusion processing. The implementation steps of extraction of multiple feature parameters and data processing are as follows:
[0021] Part 1: Extract multiple feature parameters
[0022] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com