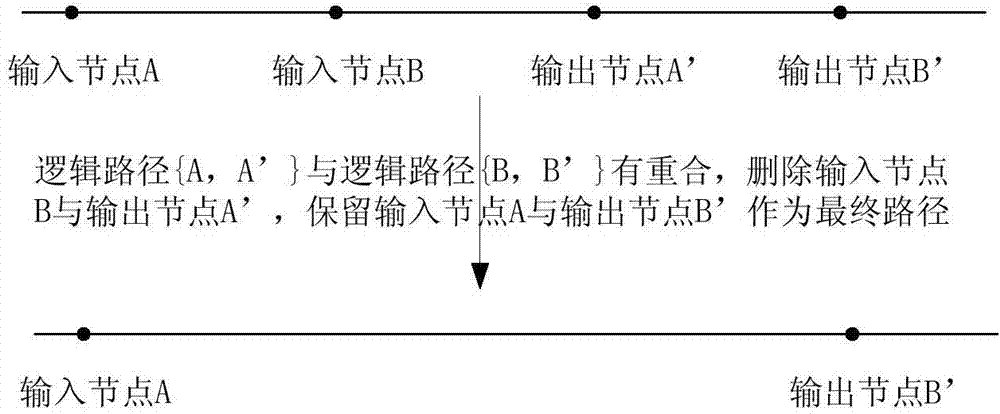
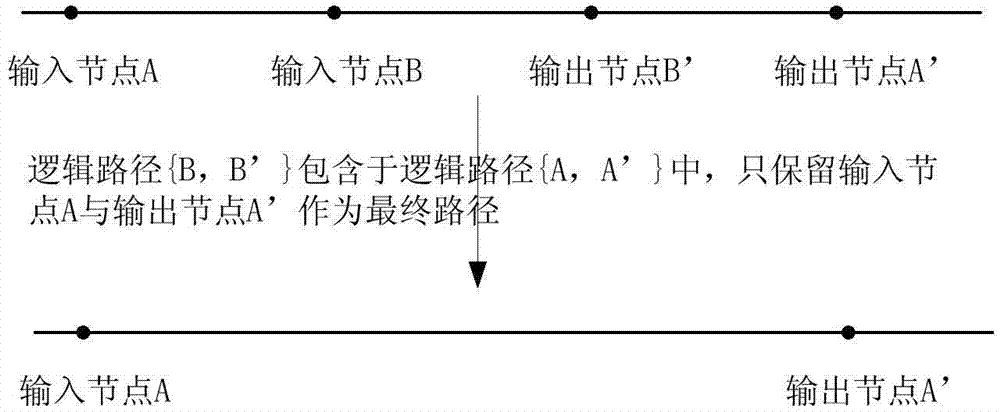
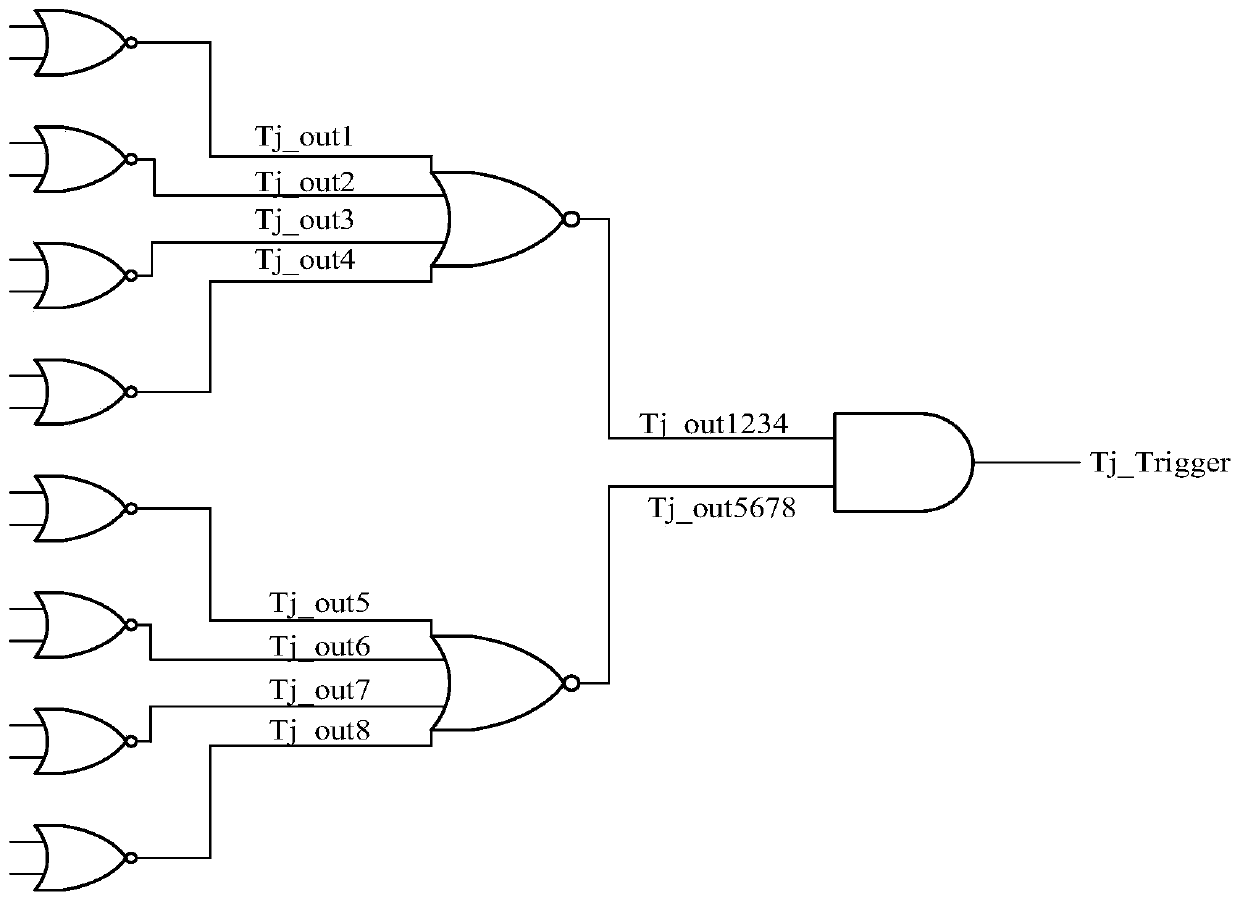
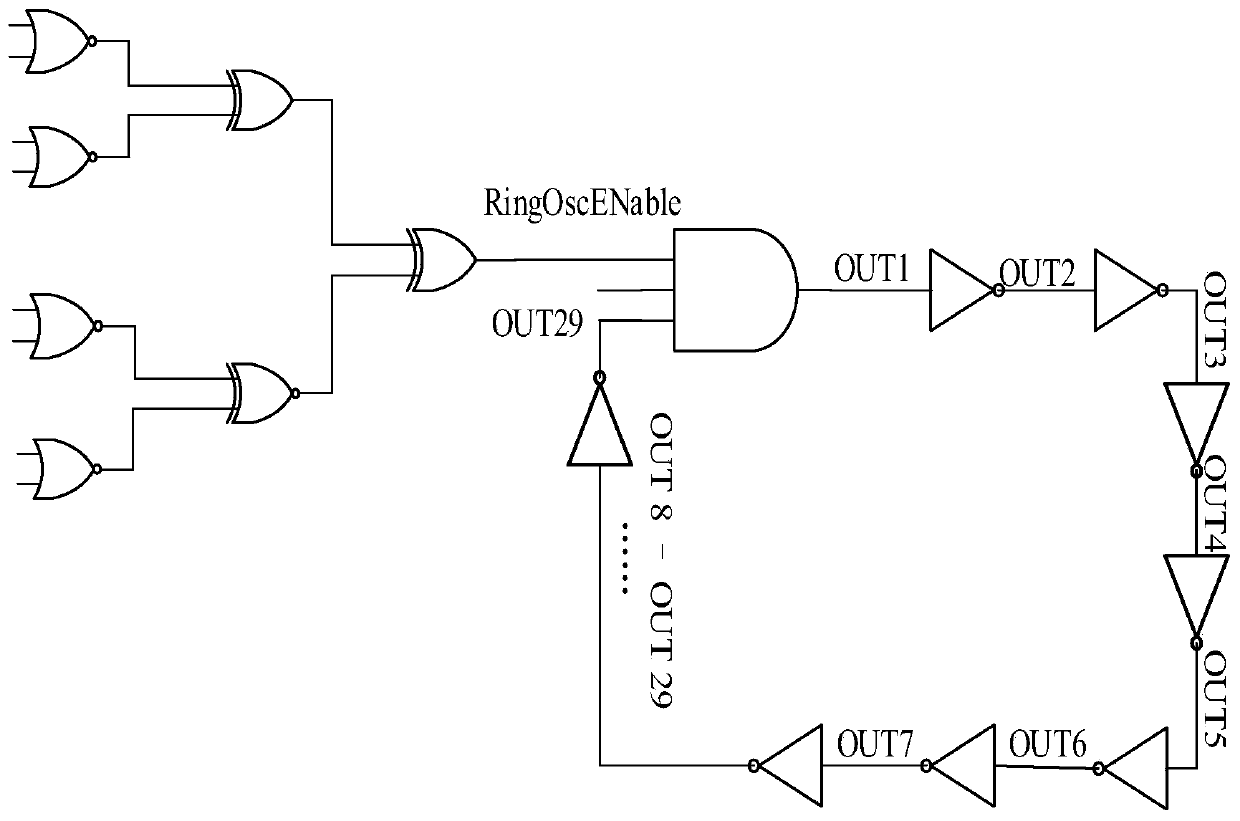
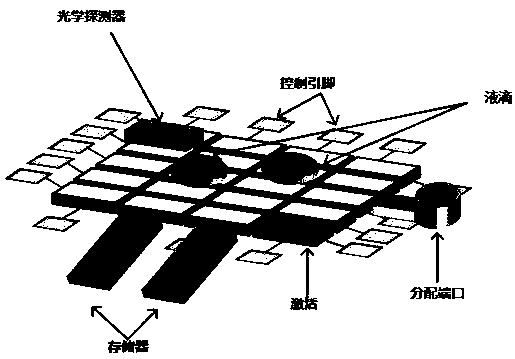
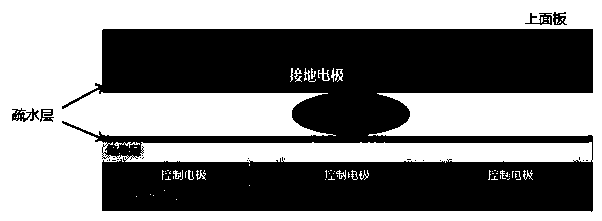
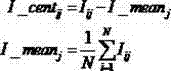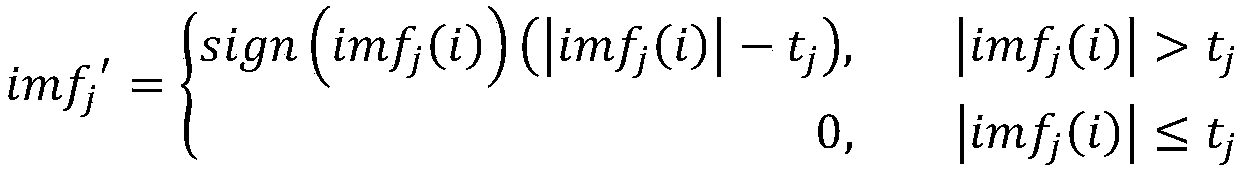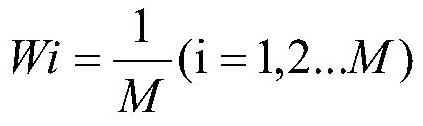Patents
Literature
134 results about "Hardware trojan horse" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
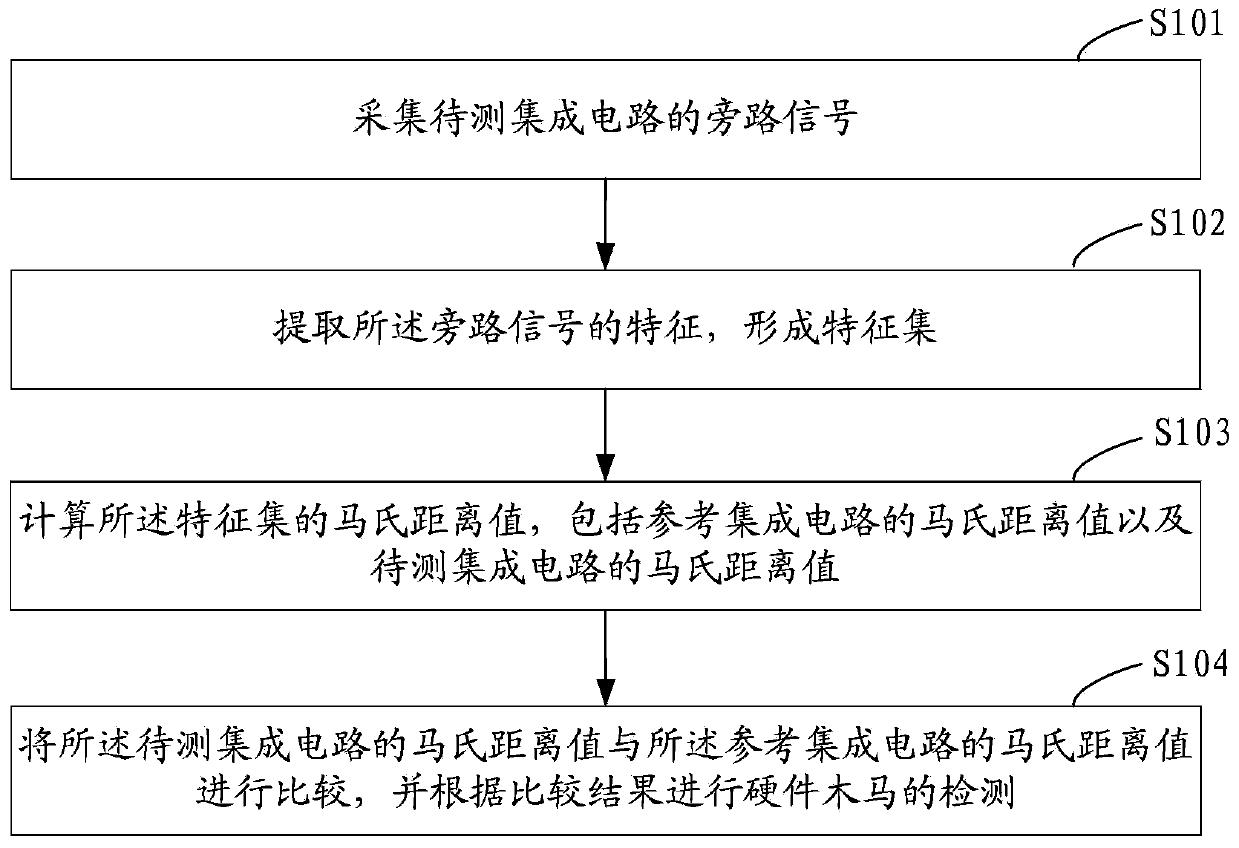
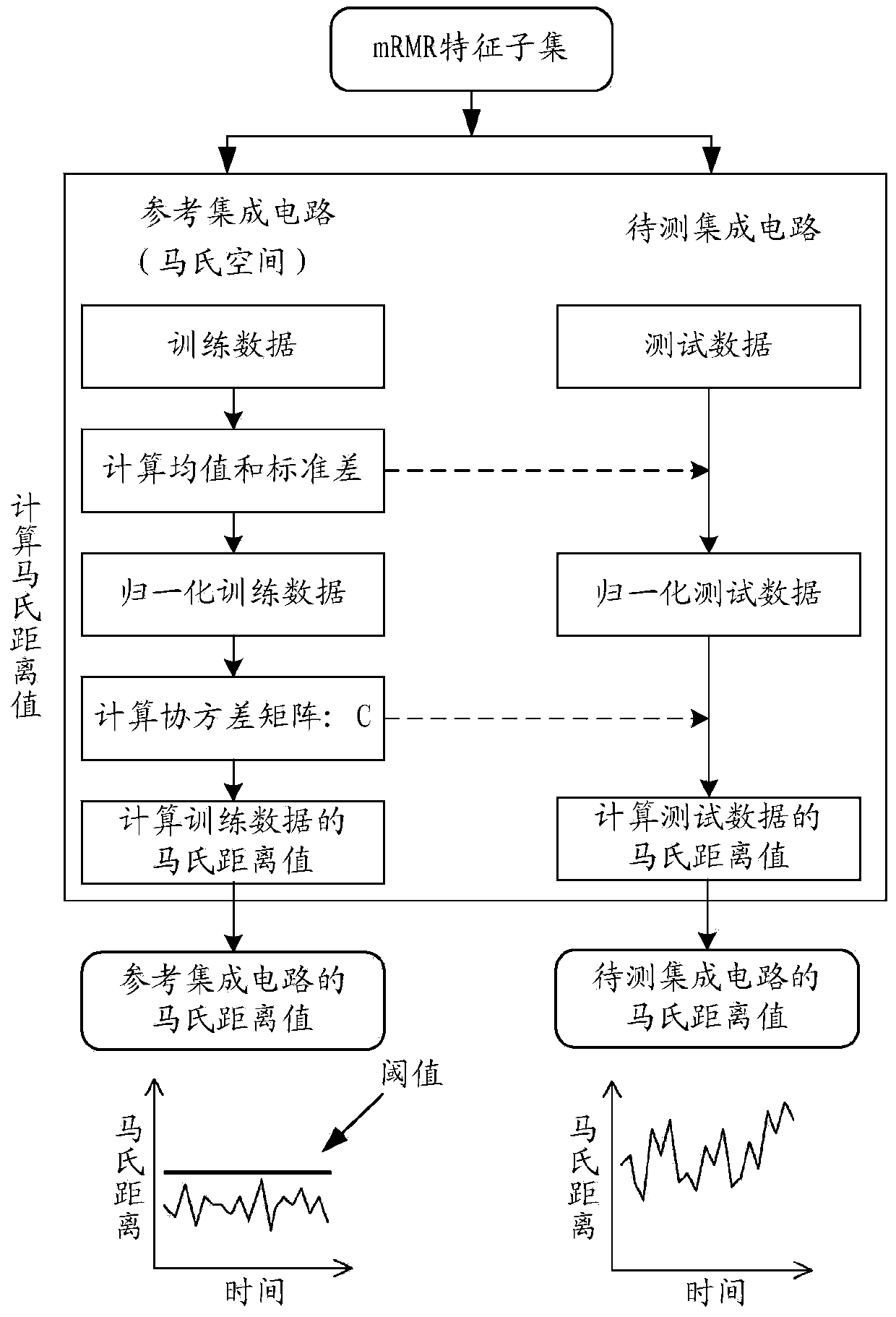
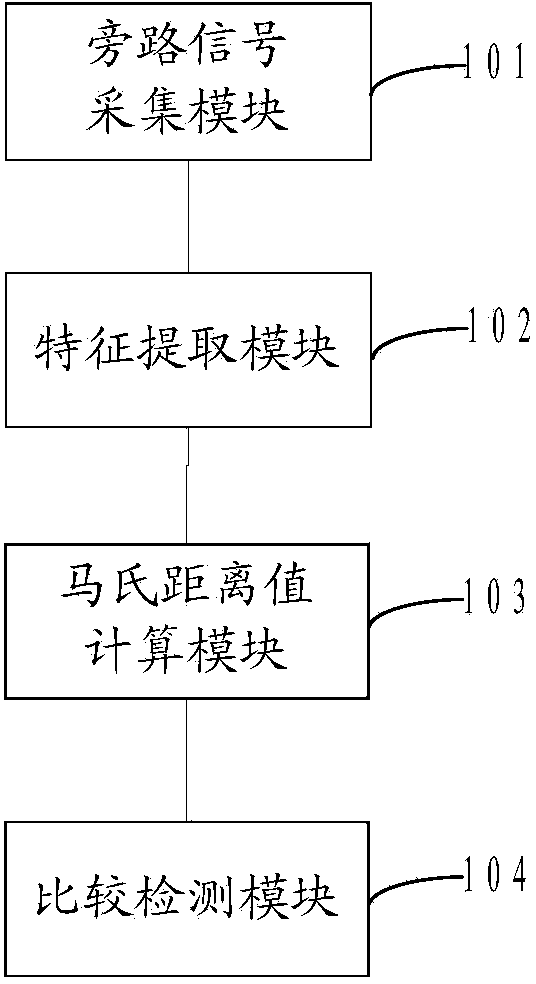
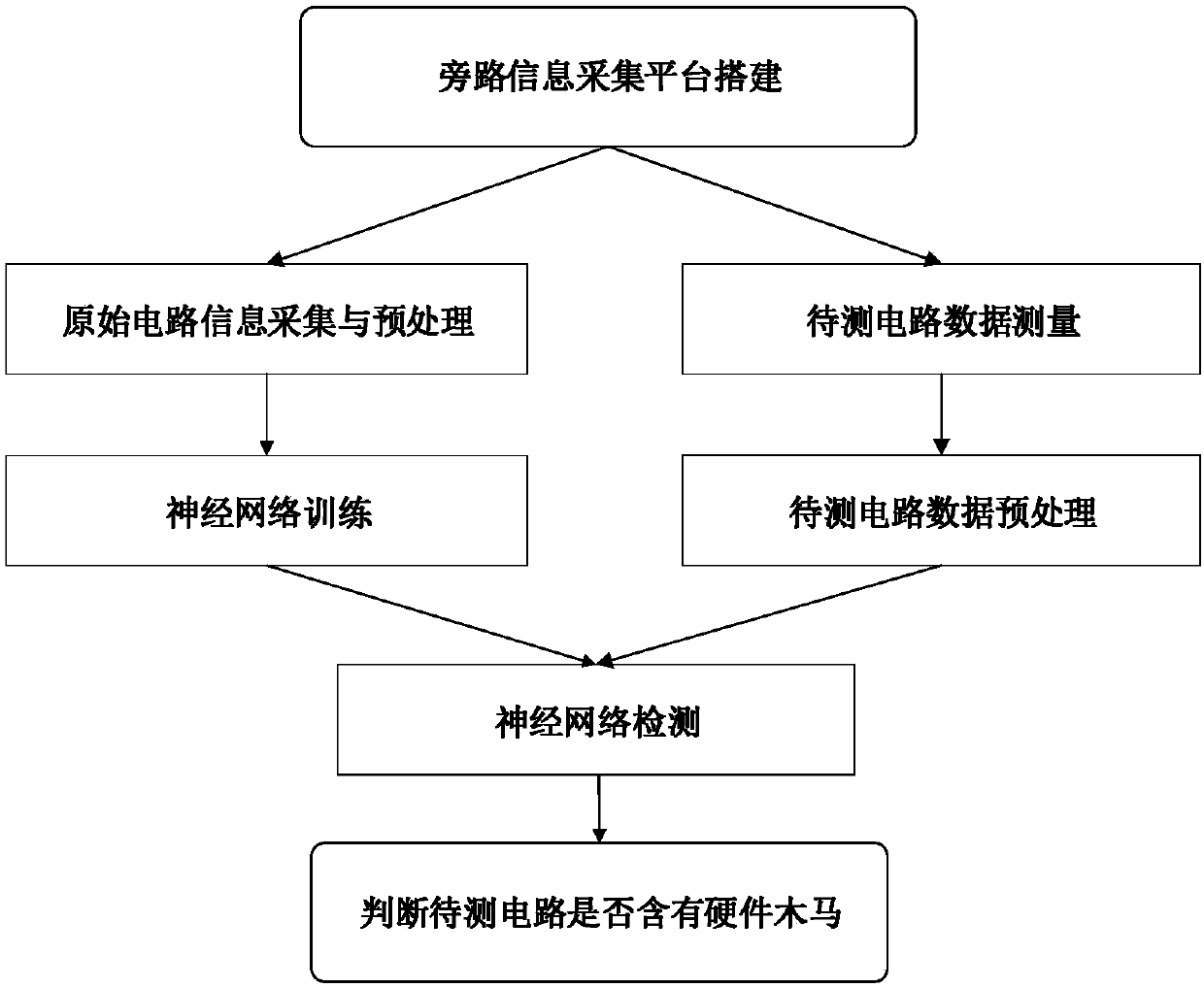
Hardware Trojan horse detection method and hardware Trojan horse detection system
ActiveCN103488941AImprove detection resolutionImprove detection efficiencyPlatform integrity maintainanceComputer hardwareMahalanobis distance
The invention provides a hardware Trojan horse detection method and a hardware Trojan horse detection system. The method includes the following steps: collecting a by-pass signal of a to-be-detected integrated circuit; extracting features of the by-pass signal to form a feature collection; calculating mahalanobis distance values, including a mahalanobis value of a reference integrated circuit and a mahalanobis value of the to-be-detected integrated circuit, of the feature collection; comparing the mahalanobis value of the reference integrated circuit with that of the to-be-detected integrated circuit, and performing hardware Trojan horse detection according to a comparison result. By the hardware Trojan horse detection method and the hardware Trojan horse detection system which have the advantages of simple algorithm and short detection time, distinguishability and efficiency of hardware Trojan horse detection in integrated circuit testing are effectively improved, and any cost for hardware is not generated.
Owner:FIFTH ELECTRONICS RES INST OF MINIST OF IND & INFORMATION TECH
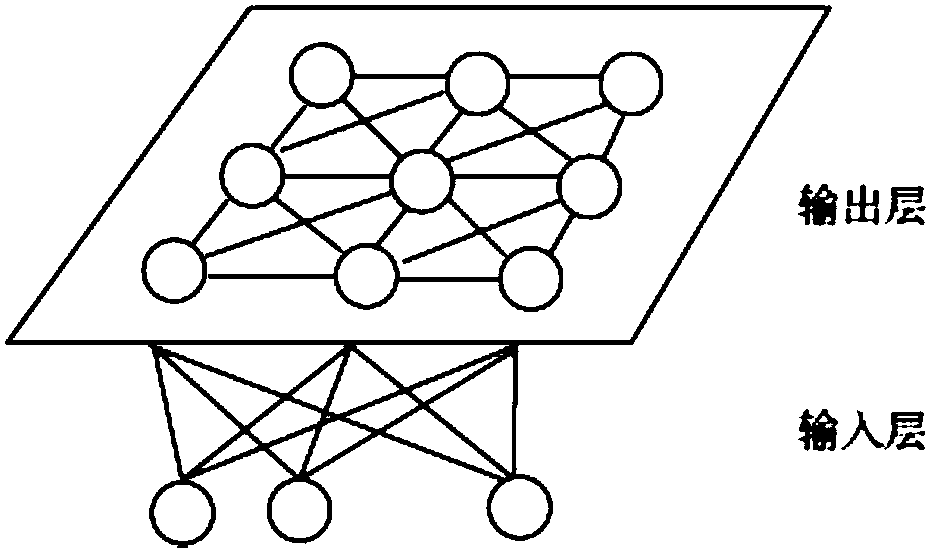
Hardware Trojan horse recognition method based on neural network
InactiveCN103198251AImprove recognition efficiencyImprove recognition accuracyBiological neural network modelsPlatform integrity maintainanceChannel state informationCharacteristic space
The invention provides a hardware Trojan horse recognition method based on a neural network. The problem that an existing recognition method does not need manual observation and is low in efficiency is solved, and recognition intelligentization of a hardware Trojan horse chip is achieved. The method comprises the following steps of first obtaining side channel information of a chip to be detected and performing data pre-processing; selecting a part of the chip to be detected to perform back subdivision analysis and confirming whether a back subdivision chip contains hardware Trojan horse or not; utilizing the back subdivision chip which does not contain the hardware Trojan horse to build a chip characteristic space through pro-processed side channel information; projecting all of chips to be detected into the characteristic space through a pro-processed side channel information matrix to obtain a side channel information characteristic data matrix; utilizing side channel information characteristic data of the back subdivision chip and a corresponding target output value to build and train the neural network; delivering the side channel information characteristic data of a tested chip to the trained neural network to be distinguished and output and achieving hardware Trojan horse recognition.
Owner:HARBIN INST OF TECH AT WEIHAI
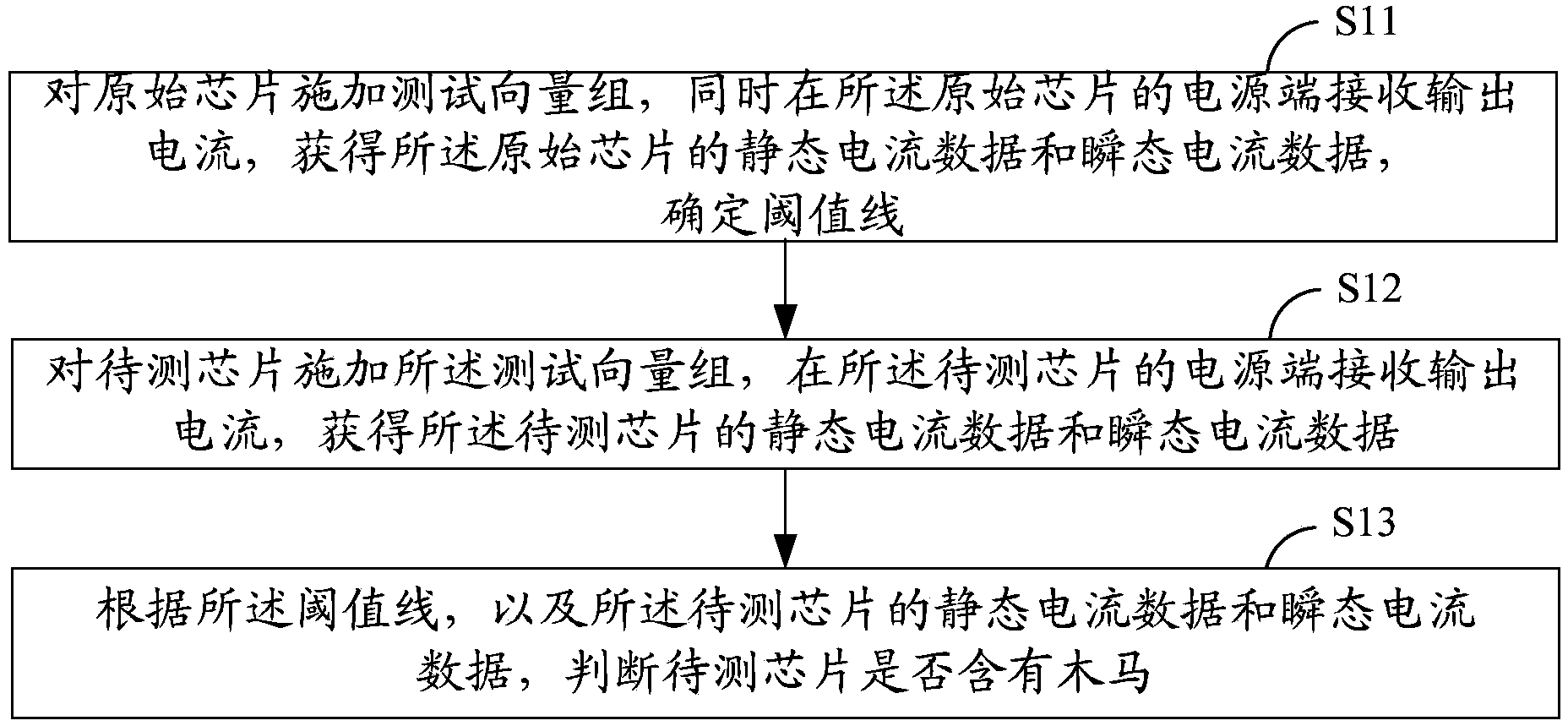
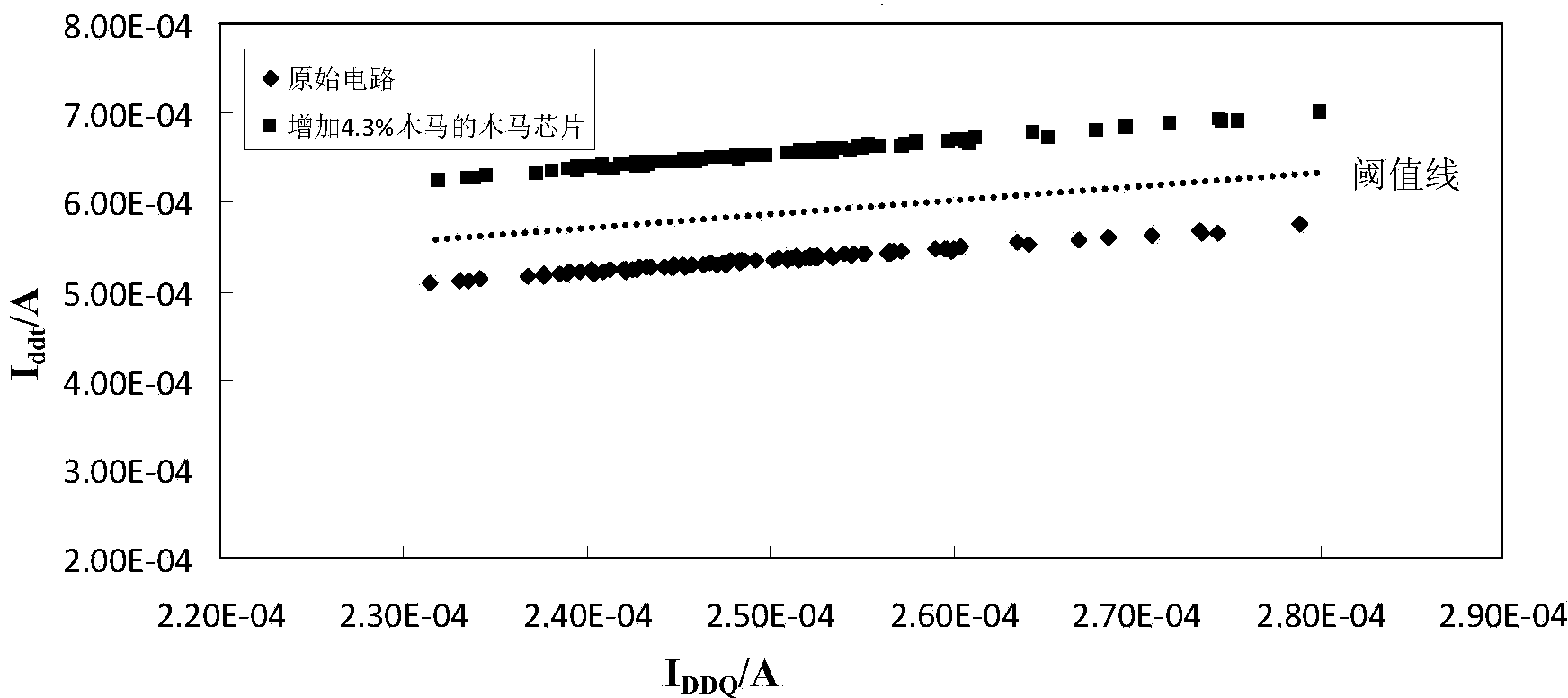
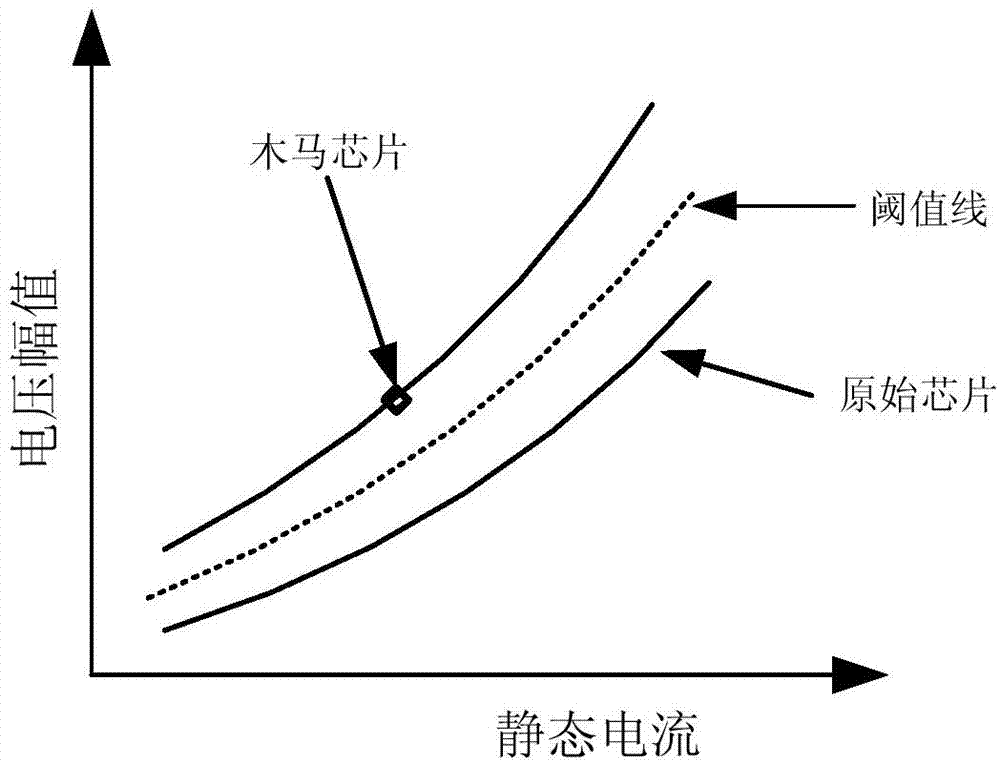
Hardware Trojan horse detection method and system based on supply current
The invention provides a hardware Trojan horse detection method and system based on supply current. The hardware Trojan horse detection method comprises the following steps that a test vector group is applied to a golden IC, the supply current is tested at the power supply end of the golden IC to obtain quiescent current data and transient current data of the golden IC, and a threshold line is determined on the basis of the data, wherein the golden IC is an IC without a hardware Trojan horse; the test vector group is applied to a chip to be detected, and the supply current is tested at the power supply end of the chip to be detected to obtain quiescent current data and transient current data of the chip to be detected; whether the chip to be detected has the Trojan horse or not is judged according to the threshold line, the quiescent current data of the chip to be detected, and the transient current data of the chip to be detected. The invention further provides the corresponding hardware Trojan horse detection system. According to the hardware Trojan horse detection method and system based on the supply current, the test process is simple, the test time is short, and the test result is accurate.
Owner:FIFTH ELECTRONICS RES INST OF MINIST OF IND & INFORMATION TECH
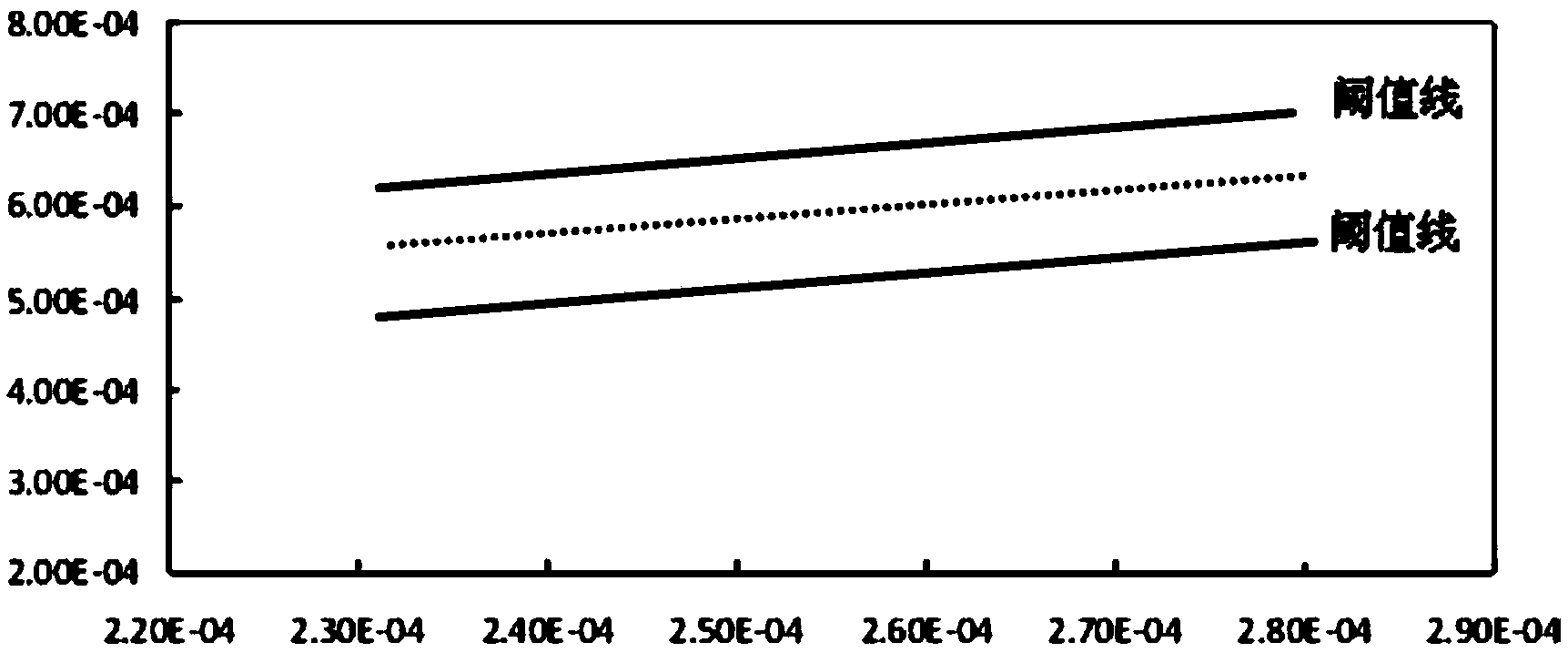
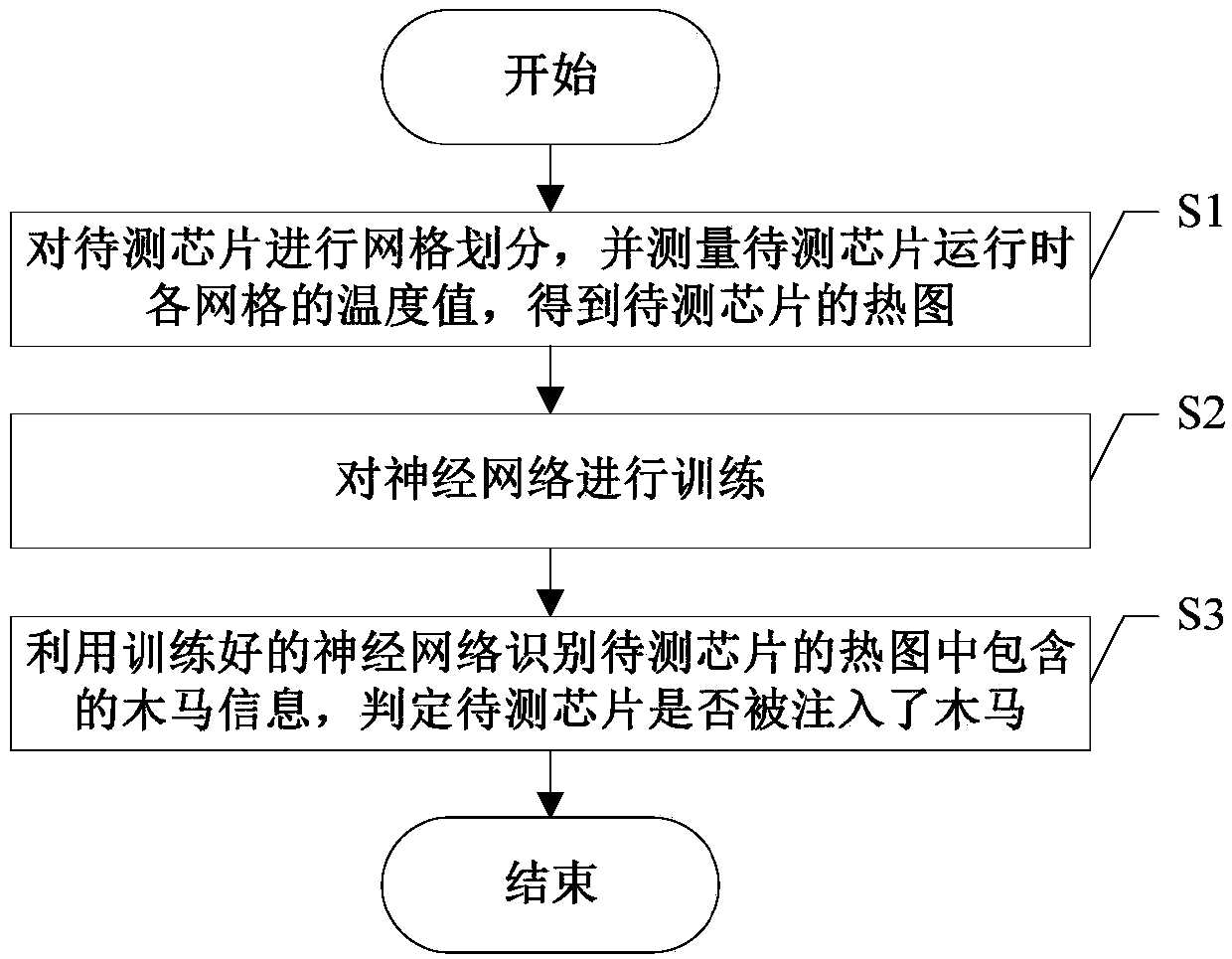
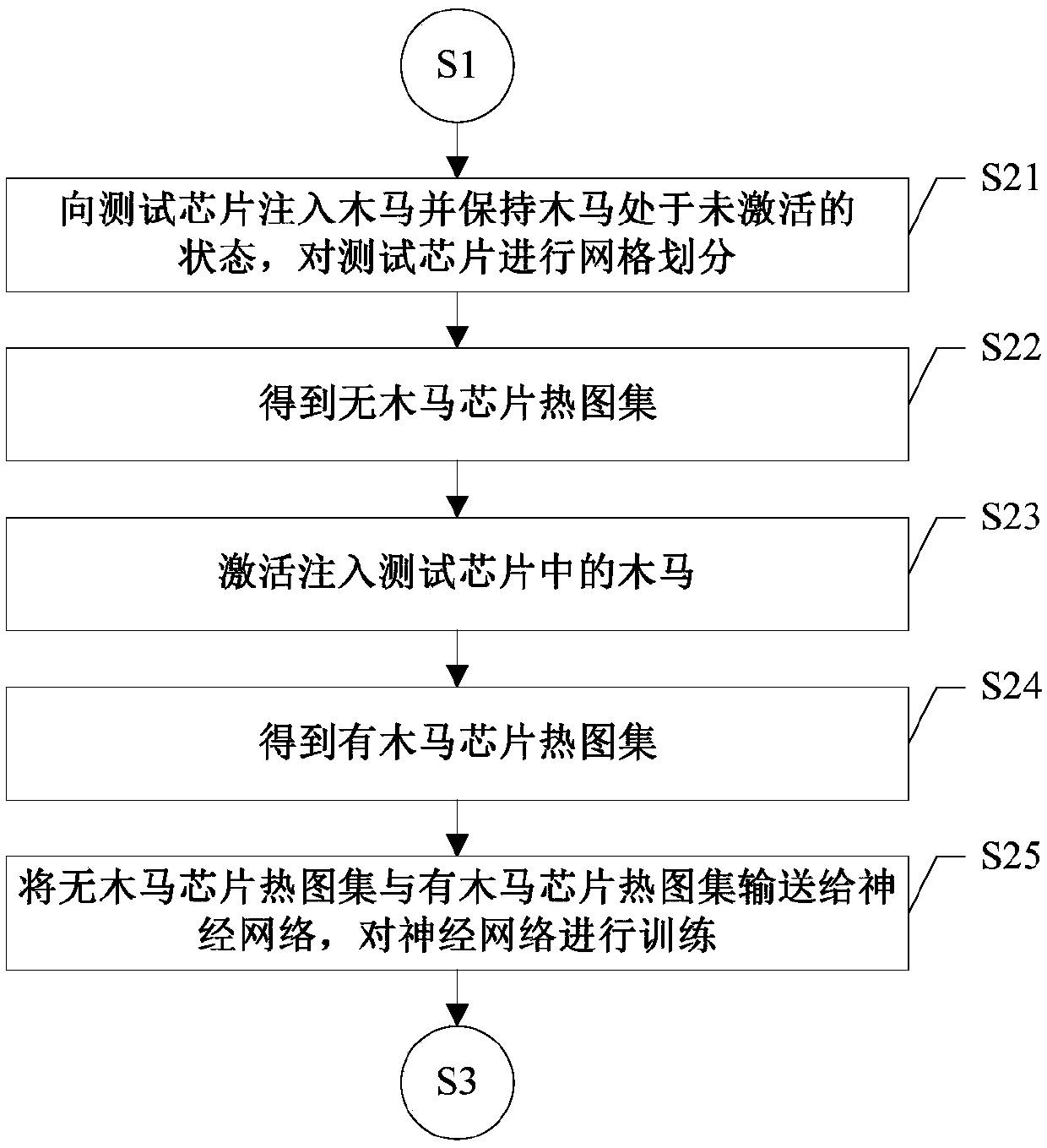
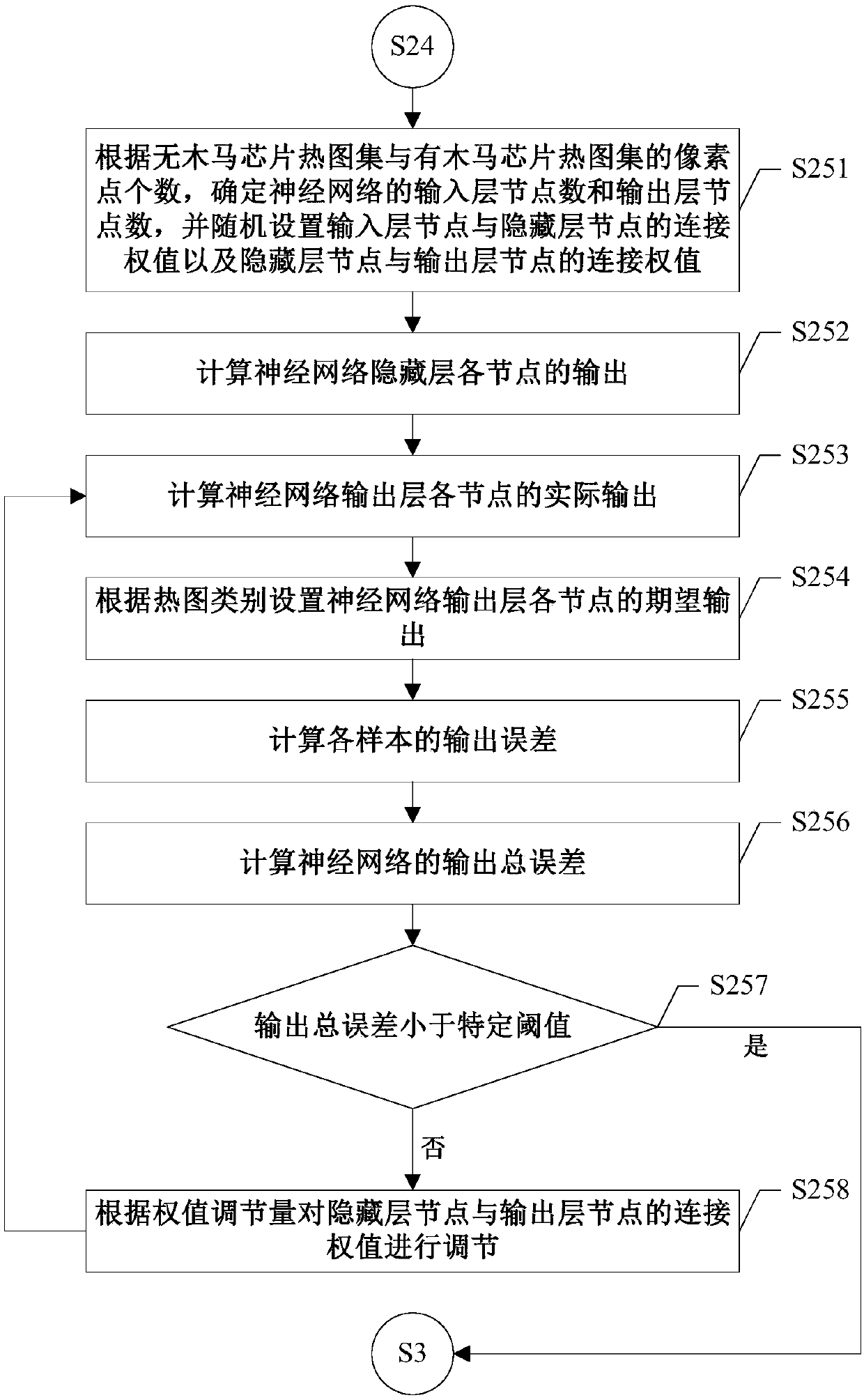
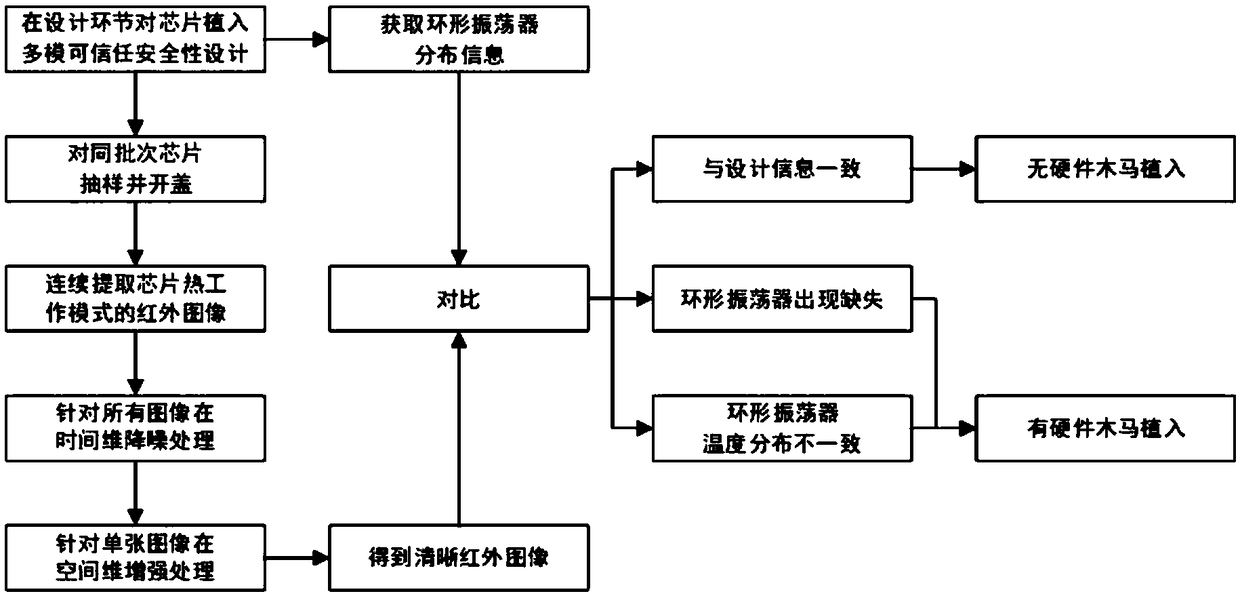
A hardware Trojan horse detection method based on a chip temperature field effect
InactiveCN107703186AImprove detection rateEasy to implementMaterial flaws investigationNeural architecturesEngineeringGrid partition
A hardware Trojan horse detection method based on a chip temperature field effect is disclosed. Based on the chip temperature field effect, a chip to be detected is firstly subjected to grid partition, then a test vector is inputted into the chip to be detected, the temperature in each grid of the chip during operation is measured to obtain a heat map of the chip, and the heat map is used for a neural network to identify Trojan horse information of the heat map. In addition, heat map sets of chips to which a Trojan horse is inputted and chips to which no Trojan horse is inputted are utilized to train the neural network, and then the trained neural network is utilized to detect the chip to be detected so as to determine whether a Trojan horse is inputted to the chip to be detected. The method has characteristics of a high detection rate and easy implementation, and can ensure correct detection of a hardware Trojan horse.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
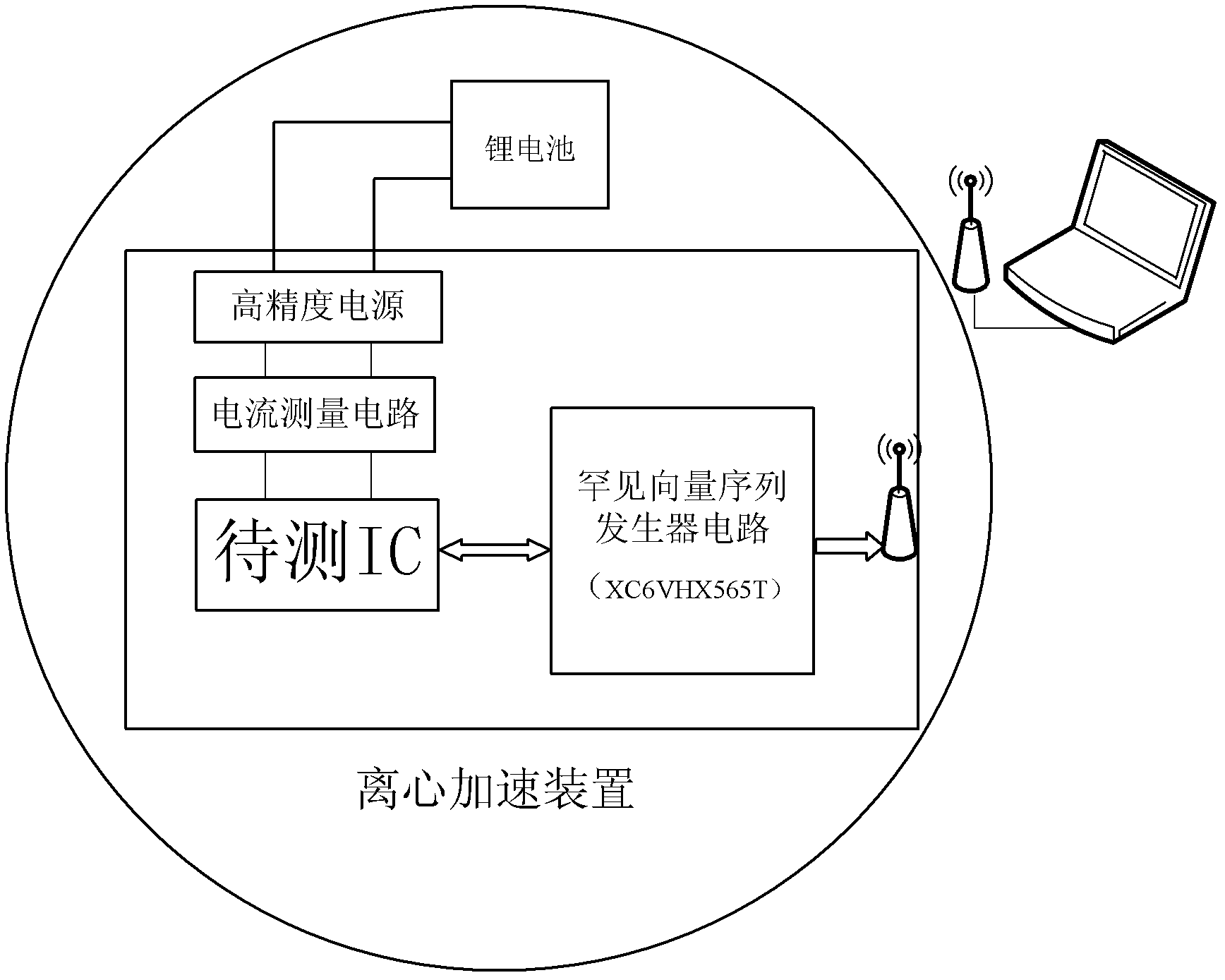
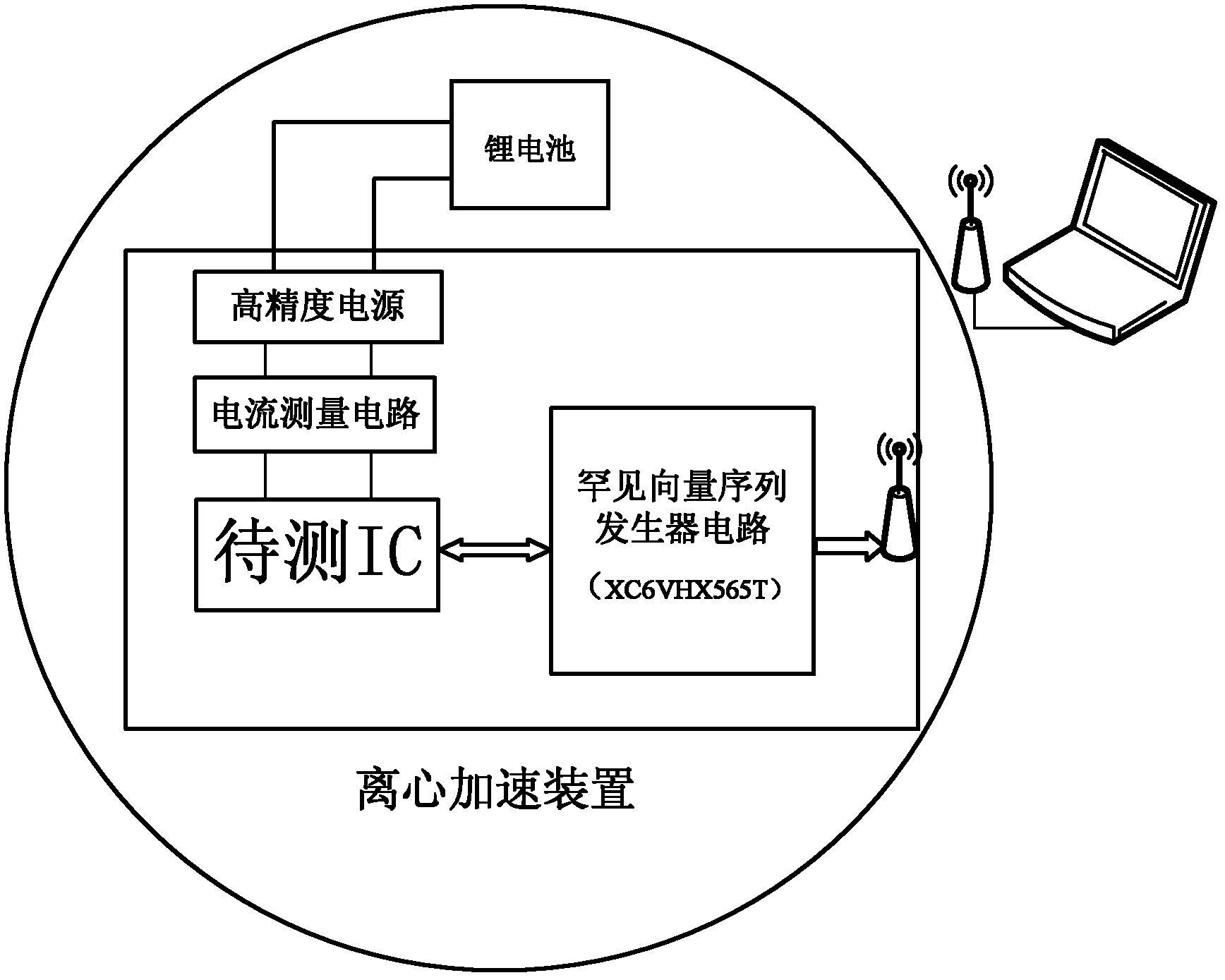
Hardware Trojan horse test system
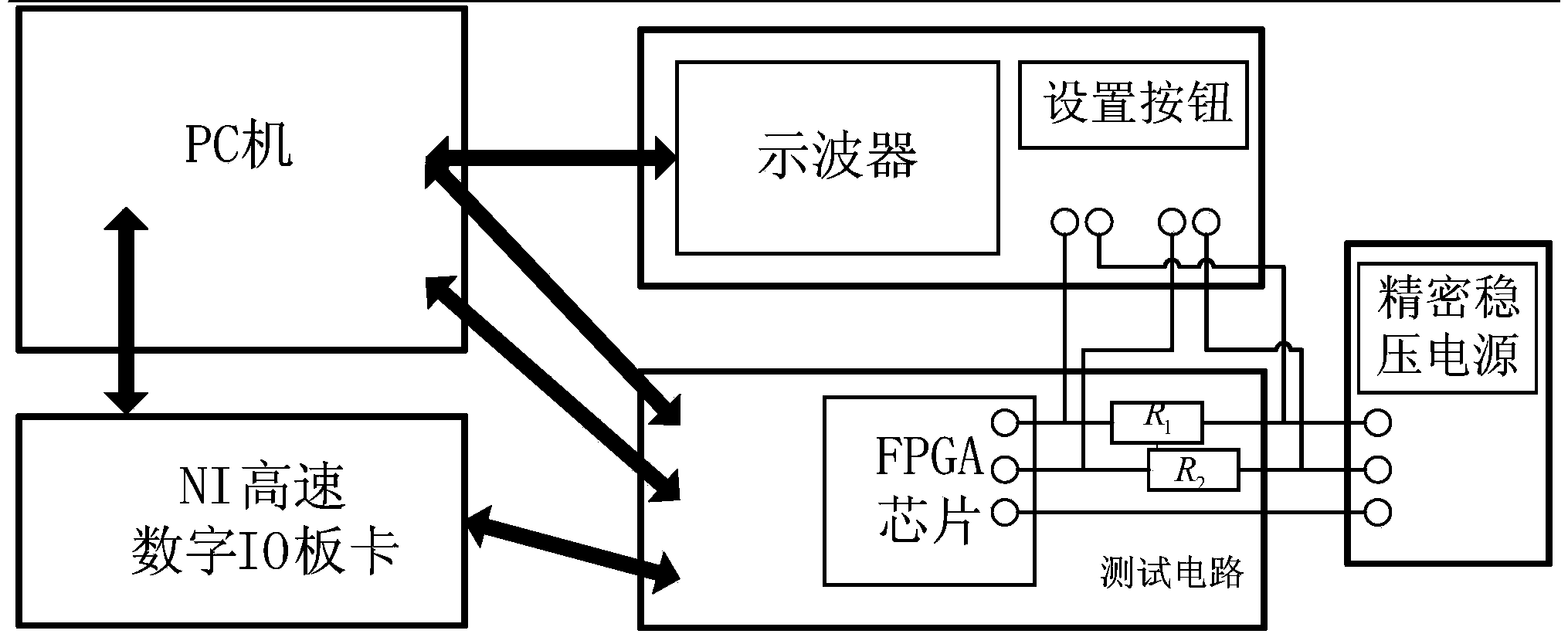
ActiveCN103954904AImprove the level of automated testingEasy to handleDigital circuit testingElectrical resistance and conductanceFpga chip
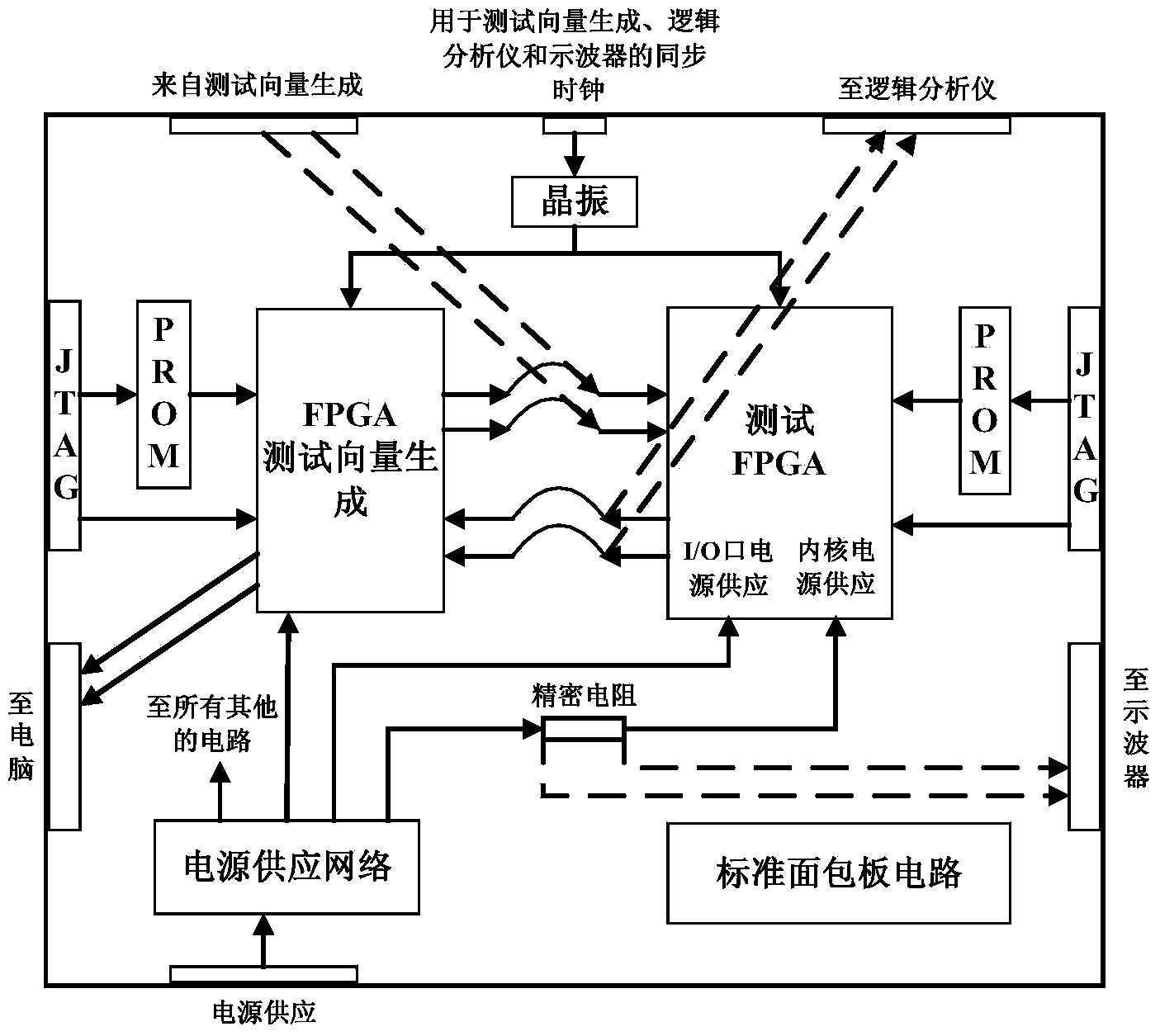
The invention discloses a hardware Trojan horse test system. The hardware Trojan horse test system comprises a PC, an NI high-speed digital I / O board and a test circuit, wherein the PC is used for generating a test vector, conducting programming on an FPGA chip, controlling the NI high-speed digital I / O board, an oscilloscope and the FPGA chip and receiving signals sent by the NI high-speed digital I / O board and the oscilloscope; the NI high-speed digital I / O board is used for outputting the test vector to the FPGA chip, collecting an FPGA response signal and sending back the FPGA response signal to the PC; the testing circuit comprises the FPGA chip and receives the test vector output by the NI high-speed digital I / O board. The hardware Trojan horse test system further comprises a precise resistor R1, a precise resistor R2, the oscilloscope and a precise voltage-stabilized source, wherein the precise resistor R1 and the precise resistor R2 monitor the power consumption change of the kernel voltage and the auxiliary voltage of the FPGA chip, the oscilloscope is used for automatically triggering and collecting signals of power consumption change of the kernel voltage and the auxiliary voltage of the FPGA chip and sending the signals to the PC; the precise voltage-stabilized source is used for supplying power to the test circuit. The hardware Trojan horse test system conducts automatic tests, improves the precision of logic testing and bypass analysis and is high in application value.
Owner:FIFTH ELECTRONICS RES INST OF MINIST OF IND & INFORMATION TECH
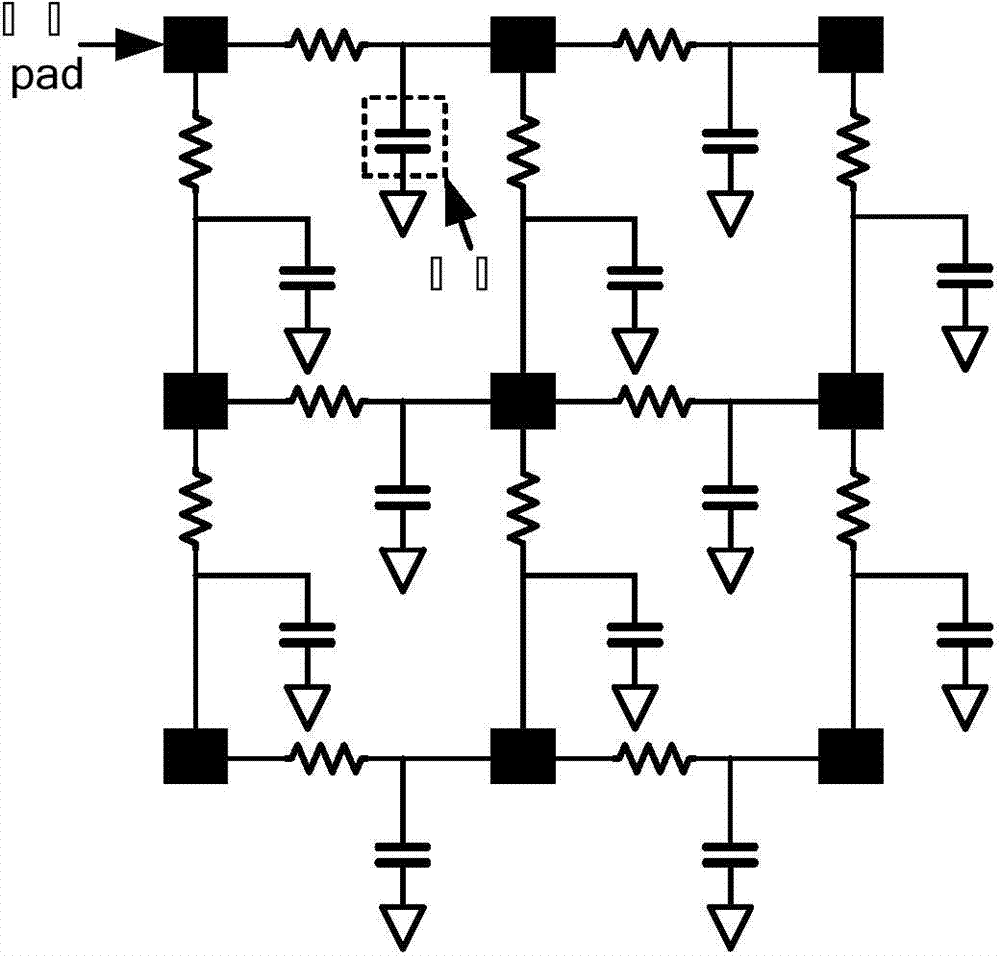
Hardware Trojan horse detecting and positioning method and system based on voltage
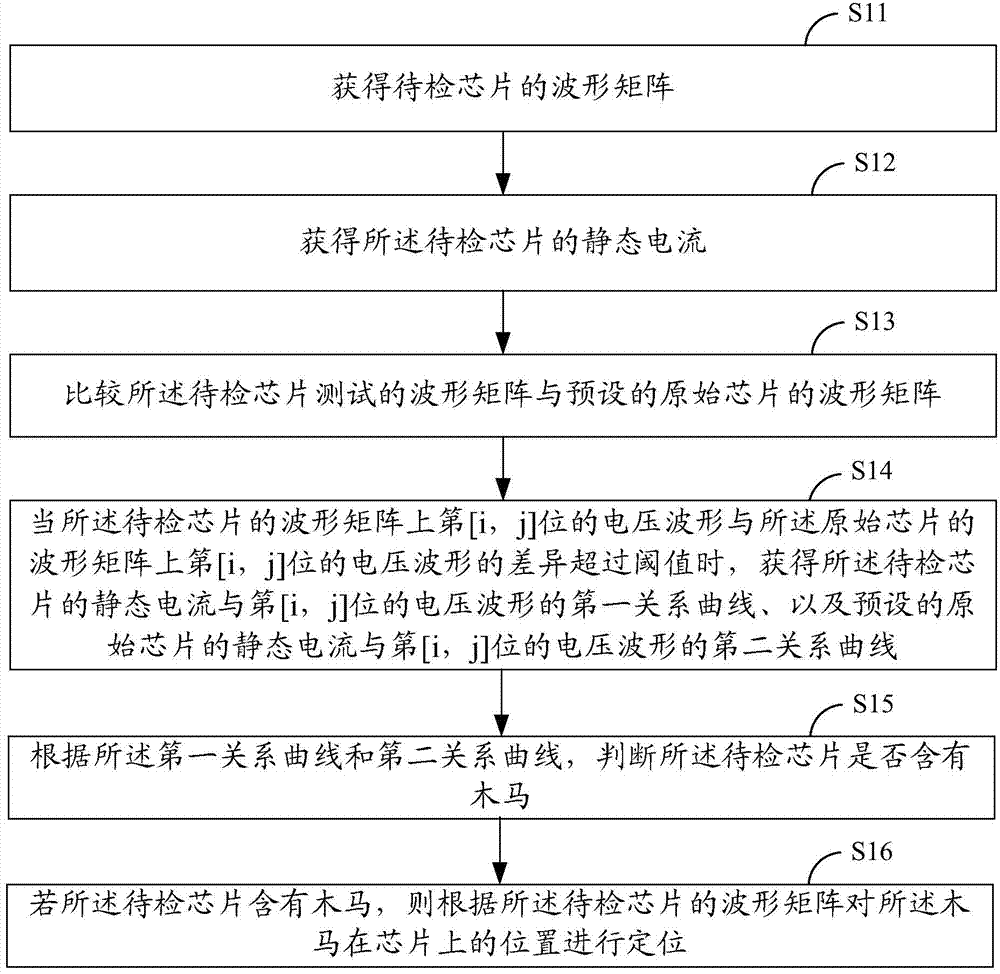
ActiveCN103926522AGuarantee safe and reliableEliminate Process VariationsElectronic circuit testingEngineeringExcitation signal
The invention provides a hardware Trojan horse detecting and positioning method based on voltage. The hardware Trojan horse detecting and positioning method includes the steps that a waveform matrix of a chip to be detected is obtained and includes a voltage waveform, obtained through testing, of a J power source pad of the chip to be detected after a voltage excitation signal is exerted on an i power source pad of the chip to be detected; static currents of the chip to be detected are obtained; the waveform matrix of the chip to be detected is compared with a preset waveform matrix of an original chip; when the difference of voltage waveforms exceeds a threshold value, a first relation curve of the chip to be detected and a second relation curve of the original chip are obtained, and whether the chip to be detected includes Trojan horse or not is judged; according to the waveform matrix of the chip to be detected, the Trojan horse is positioned on the chip. The invention further provides a corresponding system, voltage is used for hardware Trojan horse detecting and positioning, so that technology fluctuation influences can be eliminated, detecting speed is high, and detecting precision is high.
Owner:FIFTH ELECTRONICS RES INST OF MINIST OF IND & INFORMATION TECH
Hardware Trojan horse detection method based on neural network
InactiveCN108052840AImprove visibilityImprove detection accuracyElectronic circuit testingInternal/peripheral component protectionComputer hardwareNerve network
The invention relates to the technical field of integrated circuit credibility detection and aims to improve detection efficiency of a hardware Trojan horse and realize obvious distinction of two types of circuit data so as to realize detection of the hardware Trojan horse. According to a hardware Trojan horse detection method based on a neural network, a training neural network algorithm is utilized to process bypass information, so that recognition of the hardware Trojan horse is realized, wherein the neural network is a self-organized neural network, network parameters are automatically corrected continuously by finding the internal law of input samples, automatic classification of the input samples is realized, and competitive learning is adopted as the network learning rule; and structurally, the self-organized neural network only contains two layers of neurons, wherein the first layer is an input layer, the second layer is a competitive layer, namely an output layer, and the neurons of the two layers are completely interconnected. The method is mainly applied to integrated circuit detection.
Owner:TIANJIN UNIV
Circuit safety design method for defending against threat of hardware Trojan horse based on triple modular redundancy
ActiveCN104715121ADefend against potential threatsGuaranteed to be correctInternal/peripheral component protectionSpecial data processing applicationsNODALSequential logic
The invention provides a circuit safety design method which utilizes triple modular redundancy to guarantee that an original circuit can work stably even if a hardware Trojan horse is maliciously embedded in the original circuit. The circuit safety design method comprises the following steps: firstly, after finishing the design and verification of the original circuit, selecting logical nodes which can not be covered by all conventional testing methods, and taking the logical nodes as output nodes; secondly, backtracking the output nodes as terminal points in a fan-in direction, and determining input nodes according to certain rules; and finally, performing the triple modular redundancy design of paths between the input nodes and the output nodes respectively according to the difference between combinatorial logic and sequential logic. Through the circuit safety design method, final output cannot be affected even after the logic value of a circuit node, which cannot be tested or has high risk, is changed under the influence of a hardware Trojan horse, and the original function of the circuit is kept.
Owner:58TH RES INST OF CETC
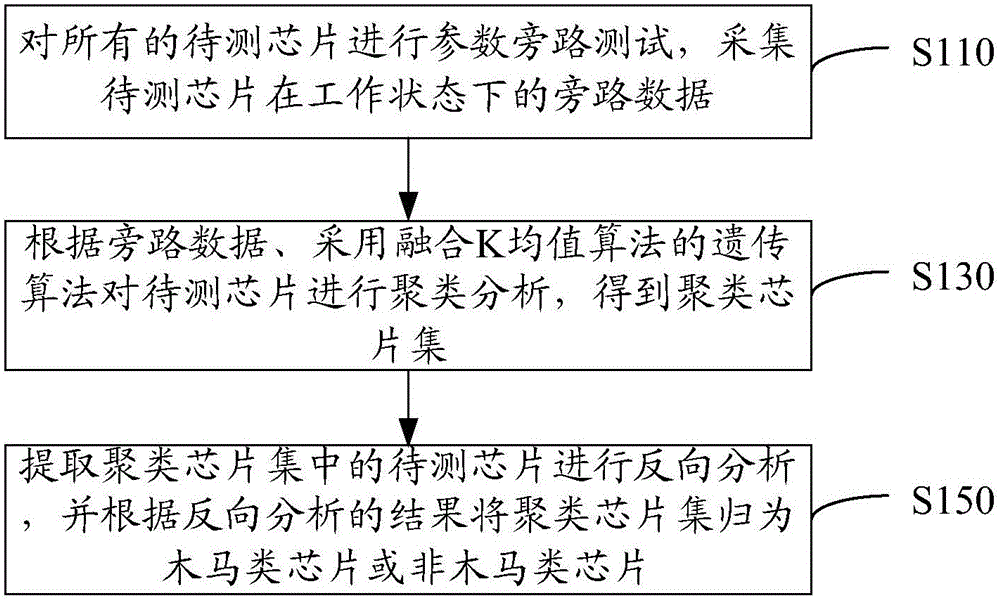
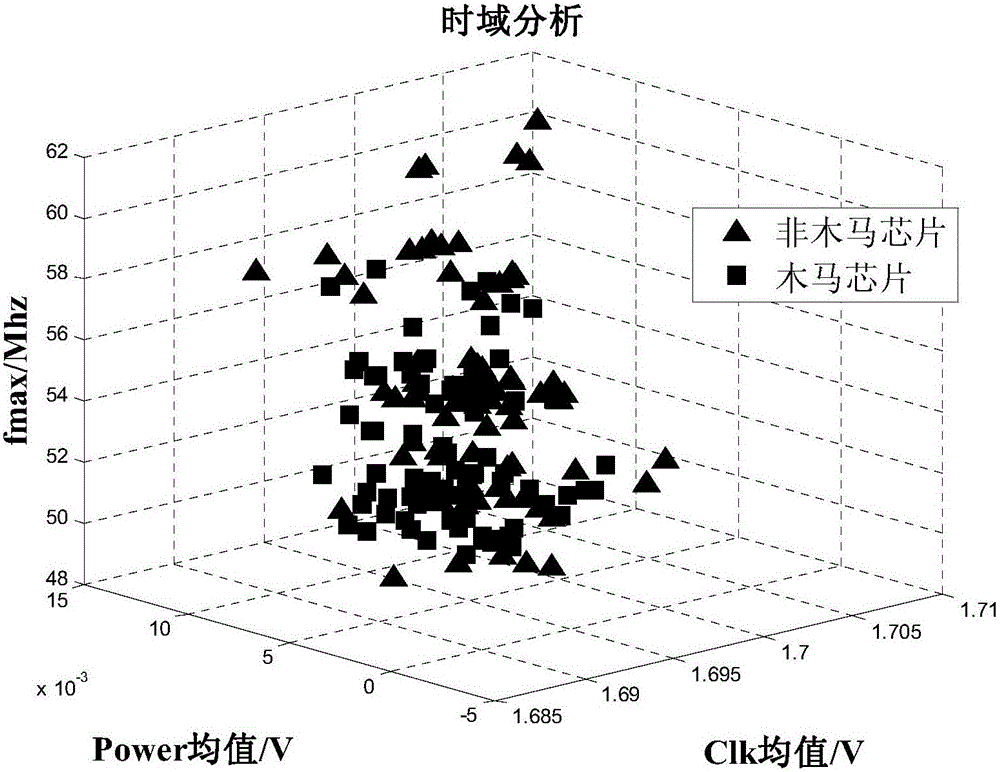
Chip hardware Trojan horse detection method and system
InactiveCN105893876AEfficientStrong local search ability to improve efficiencyInternal/peripheral component protectionGenetic algorithmComputer science
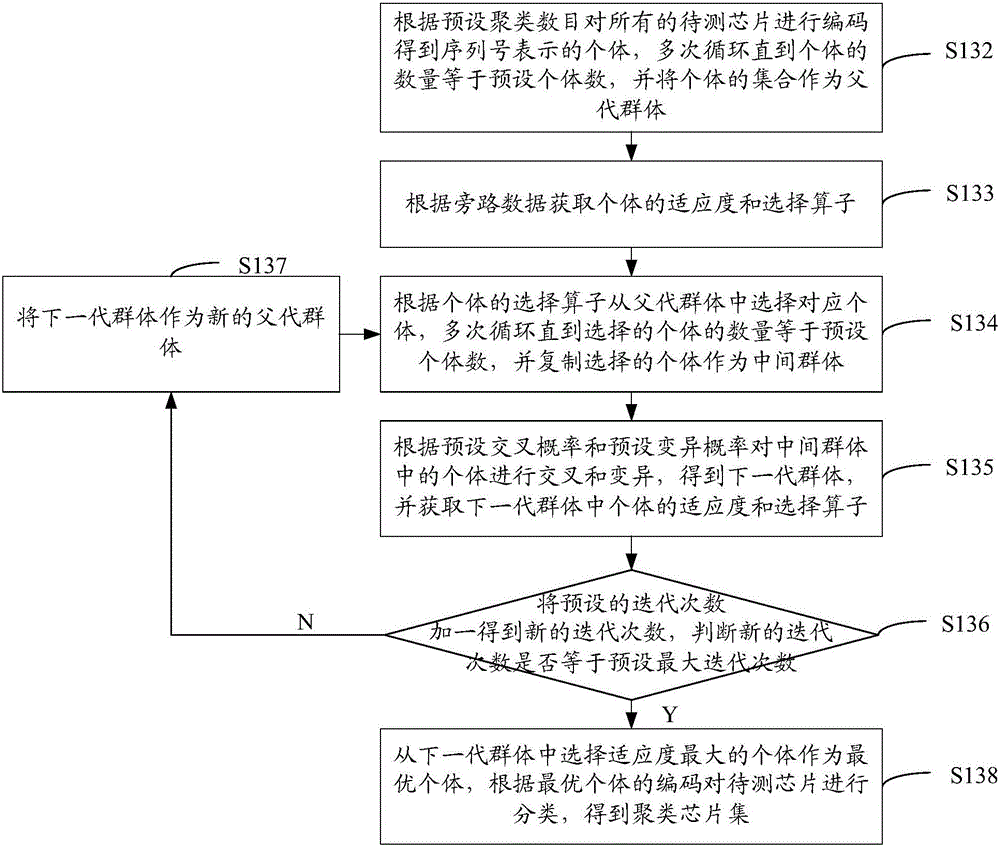
The invention relates to a chip hardware Trojan horse detection method and system. The method comprises the steps that parameter bypass testing is conducted on all chips to be detected, and bypass data of the chips to be detected in a working state is collected; clustering analysis is conducted on the chips to be detected by means of a genetic algorithm fused with an K-means algorithm according to the bypass data, and a clustering chip set is obtained; the chips to be detected in the clustering chip set are extracted for backward analysis, and the clustering chip set is classified as a Trojan horse chip or a non-Trojan horse chip according to a result of backward analysis. The clustering analysis capacity is improved by means of the high local searching capability of the K-means algorithm; by means of the high global searching capability of the genetic algorithm and unceasing iterative optimization, an optimal classification result is automatically screened out, artificial intervention is greatly reduced, the automatic identification capability for characters is improved, the hardware Trojan horse detection capability is high, and the efficiency is high.
Owner:FIFTH ELECTRONICS RES INST OF MINIST OF IND & INFORMATION TECH
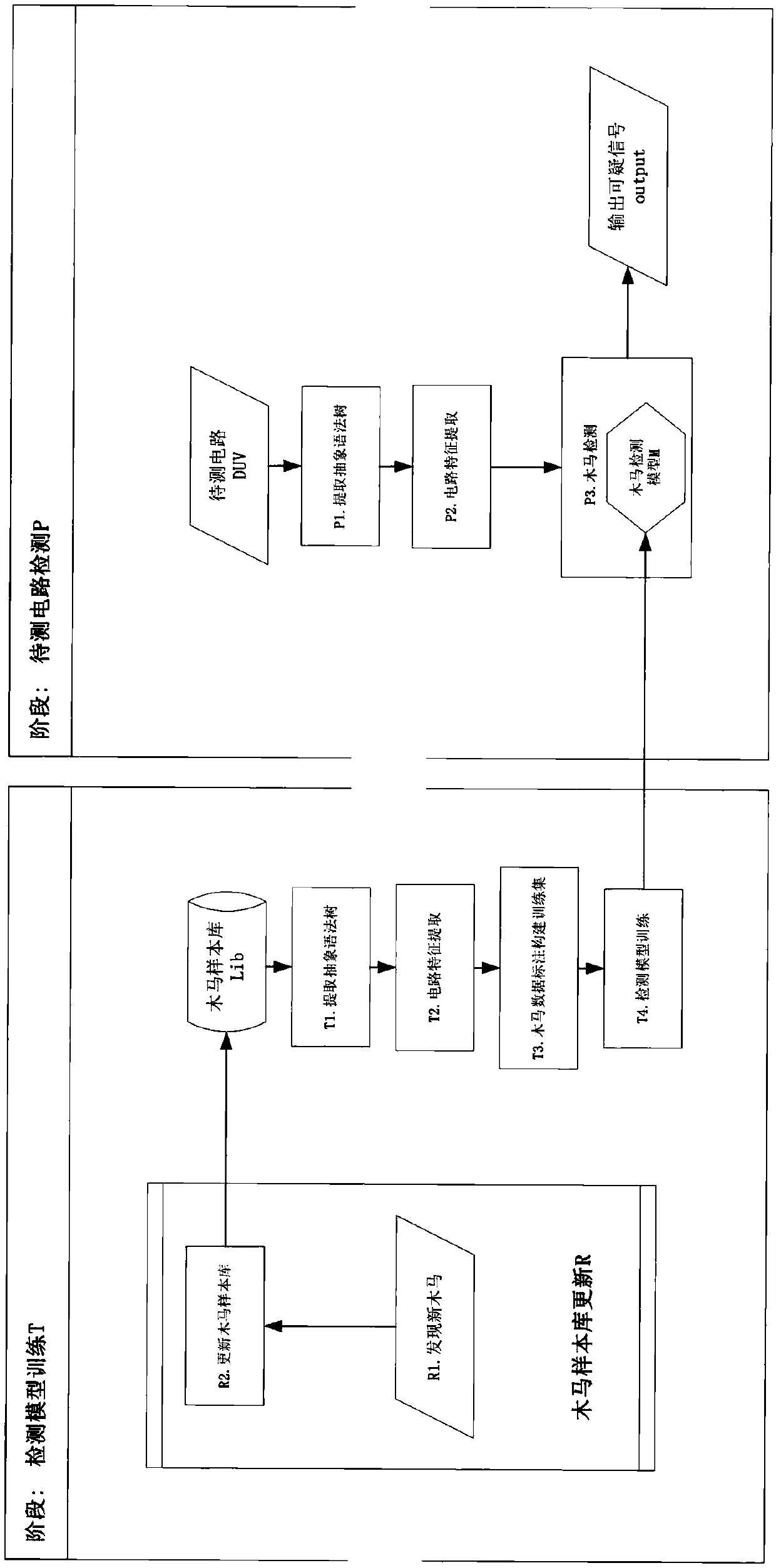
Integrated circuit security assessment and detection method
InactiveCN107656839AAssess securityComprehensive detection contentElectronic circuit testingFaulty hardware testing methodsDependabilityHardware trojan horse
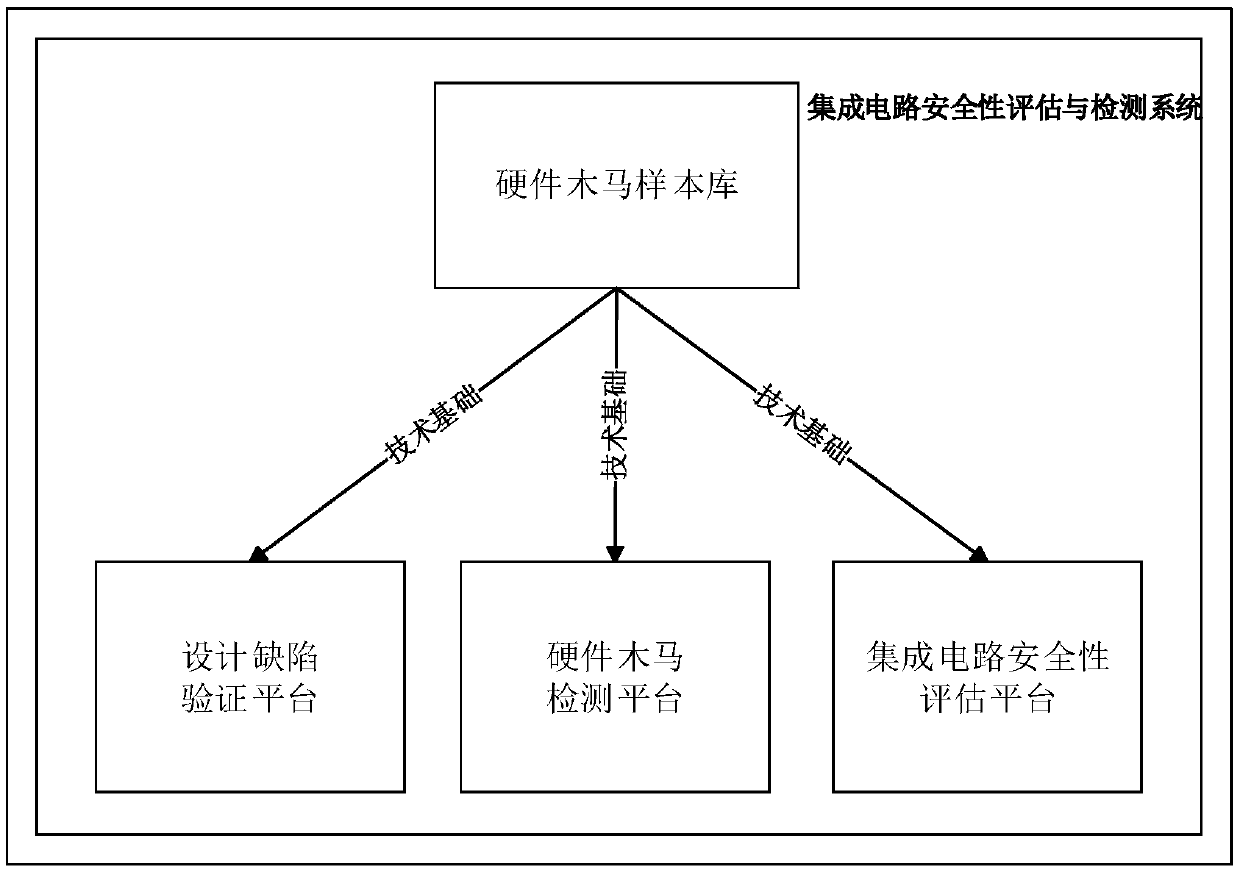
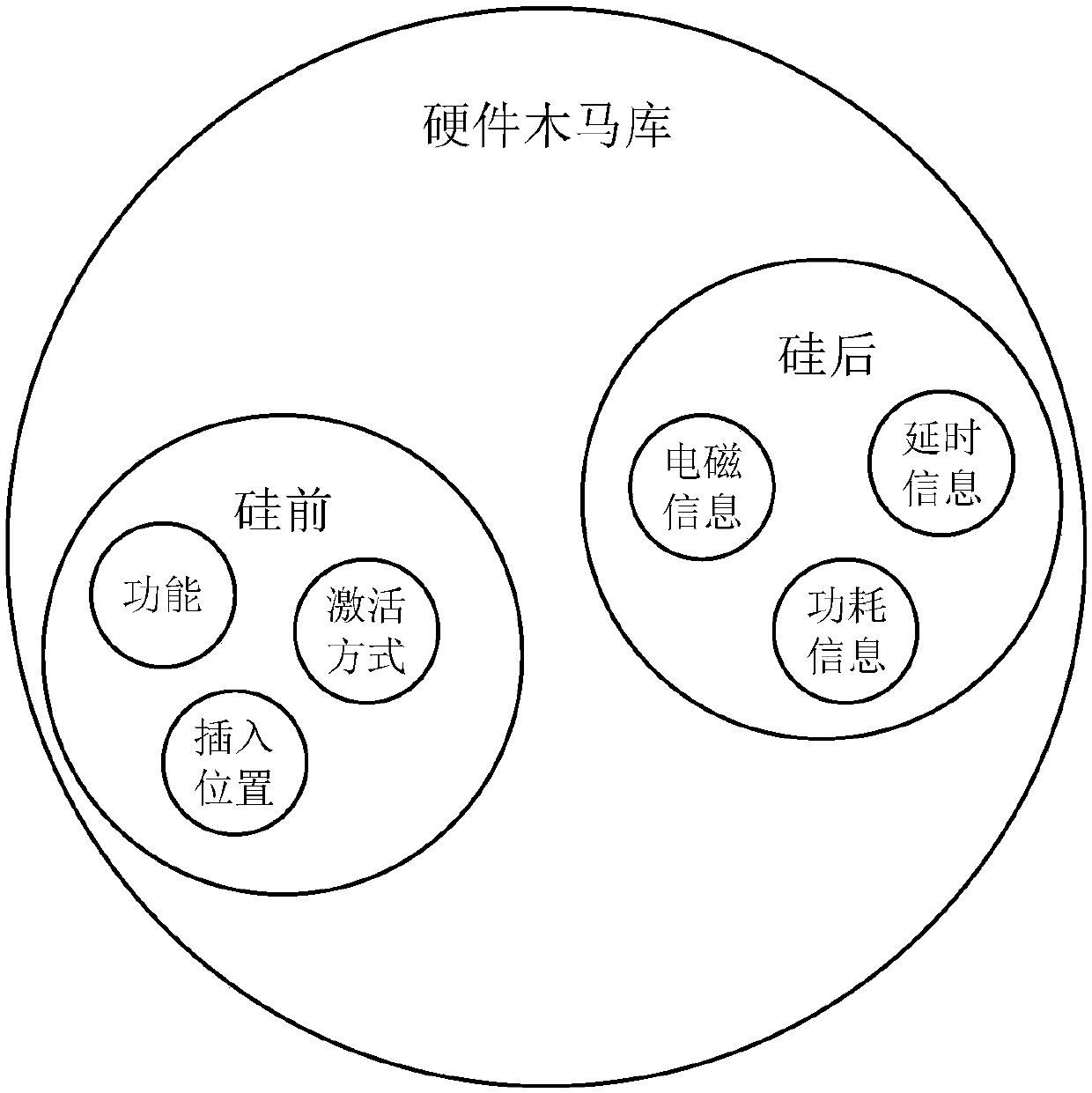
The invention relates to the field of integrated circuit security and provides an integrated circuit security assessment and detection system in order to ensure the reliability of an integrated circuit and enhance the security of a relevant system. Design defect verification and hardware Trojan horse detection are performed on a to-be-detected circuit to realize security assessment on an integrated circuit system. According to the technical scheme, an integrated circuit security assessment and detection method comprises the steps that (1) a hardware Trojan horse base is established, wherein the step is divided into the two aspects of pre-silicon and post-silicon; (2) a design defect is verified, wherein a simulation verification method is adopted to analyze the design defect of the circuit, a simulation result is compared with an expected result through a checking mechanism, and therefore a functional defect of design is discovered; and (3) detection is performed, wherein hardware Trojan horse detection is completed. The integrated circuit security assessment and detection system and method are mainly applied to an integrated circuit security occasion.
Owner:TIANJIN UNIV
Integrated circuit hardware Trojan horse detection method and system
ActiveCN104215894AEasy to identifyImprove efficiencyElectronic circuit testingFeature vectorGraphics
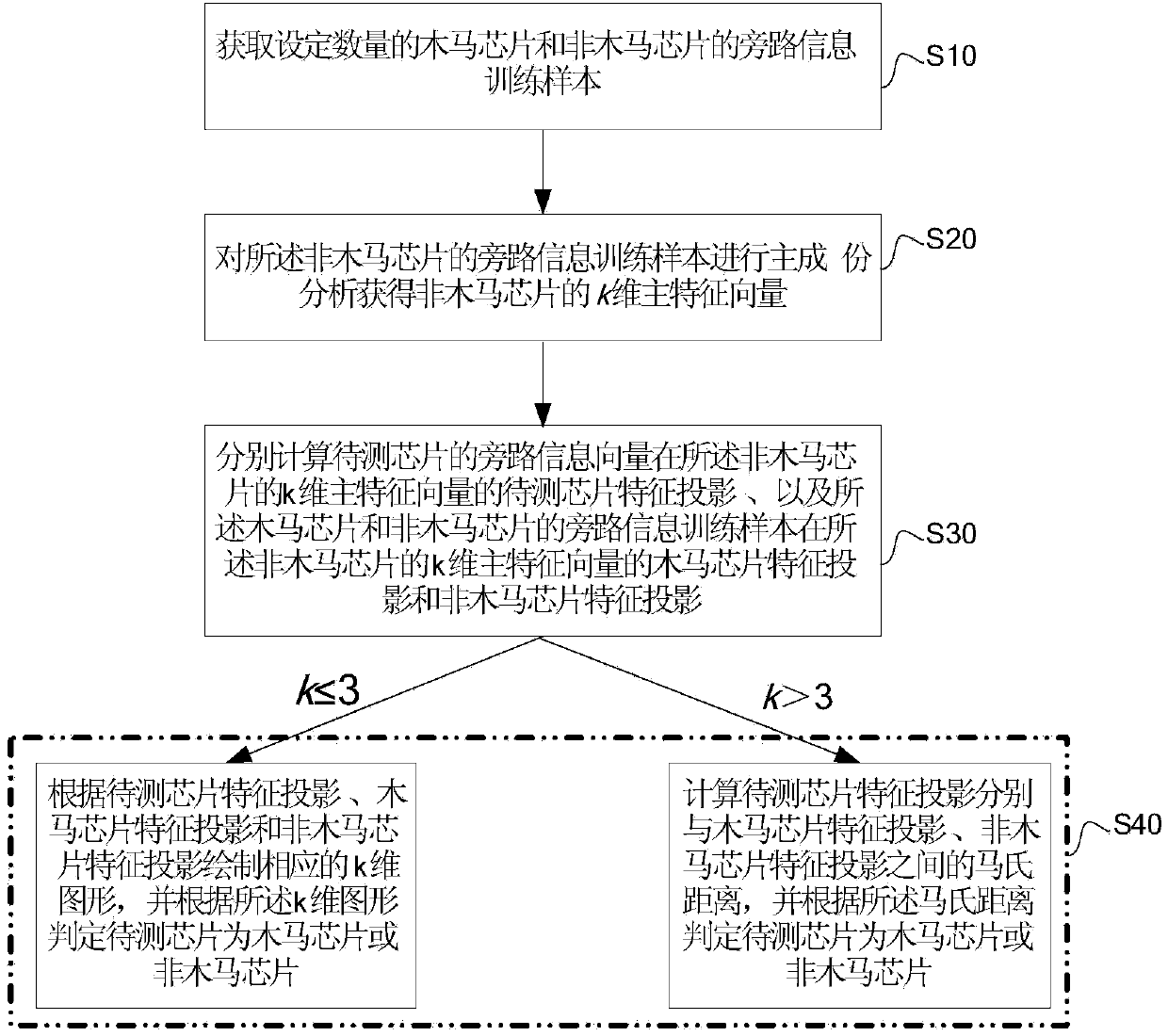
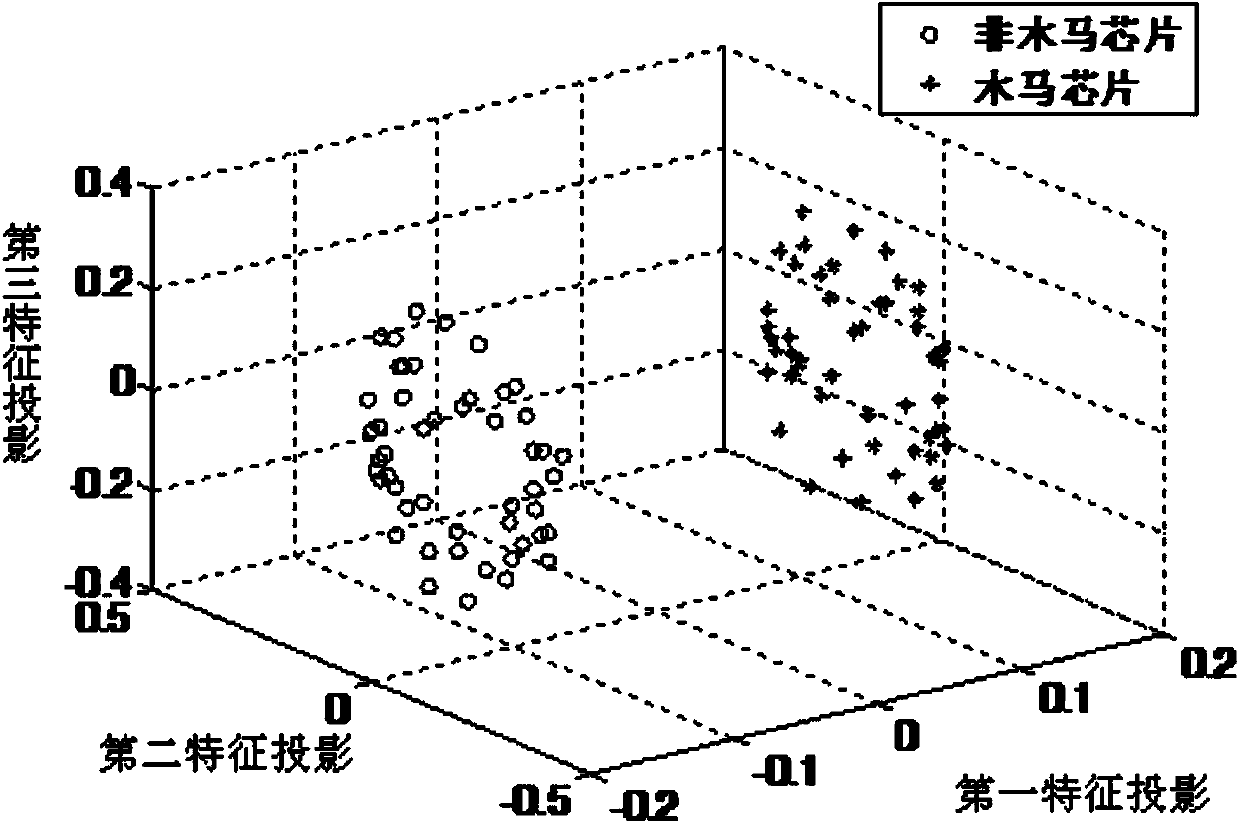
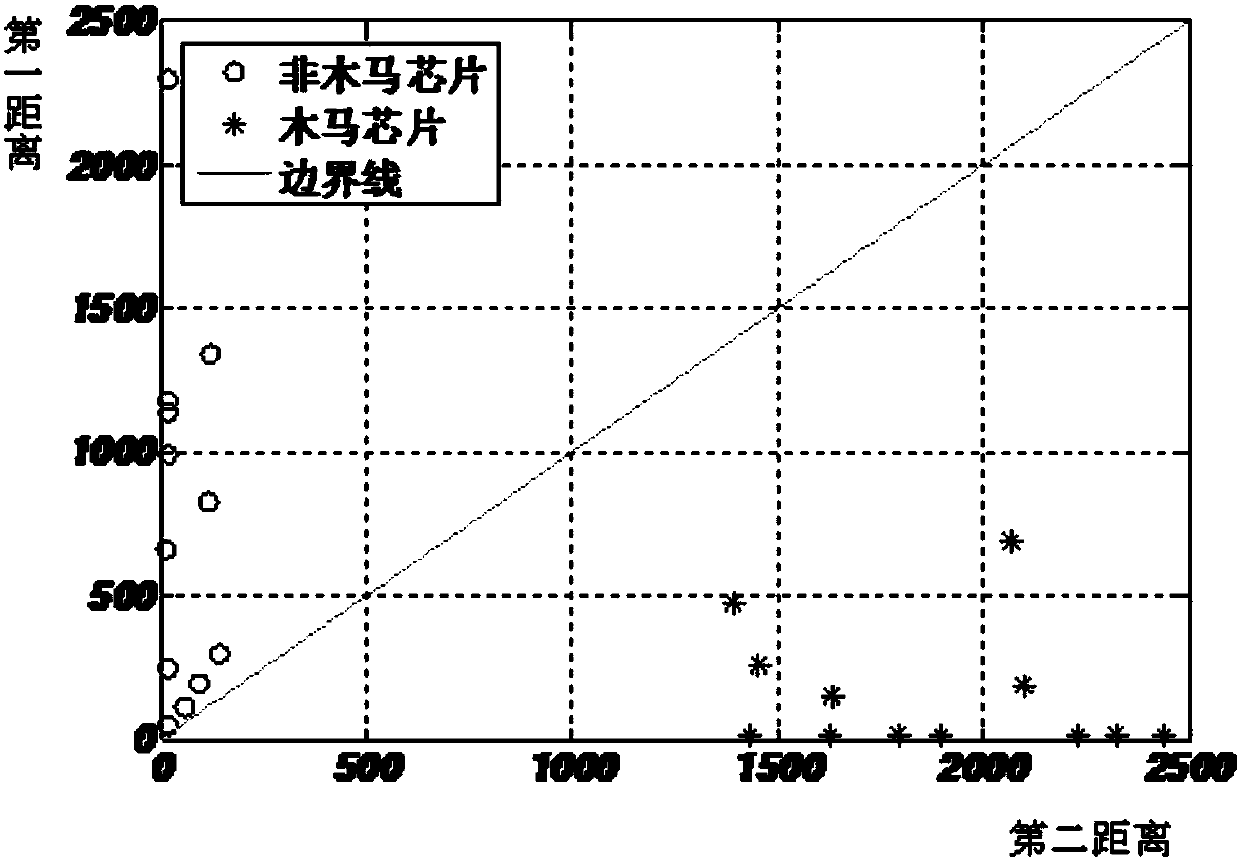
The invention provides an integrated circuit hardware Trojan horse detection method and system. The method includes acquiring bypass information training samples of Trojan horse chips and non Trojan horse chips in the set numbers; performing main component analysis on the bypass information training samples of the non Trojan horse chips to acquire k-dimensional principal eigenvectors; calculating the feature projection of a chip to be detected of bypass information vectors of the chip to be detected on the k-dimensional principal eigenvectors of the non Trojan horse chips and the Trojan horse chip feature projection and non Trojan horse chip feature projection of the bypass information training samples of the Trojan horse chips and non Trojan horse chips on the k-dimensional principal eigenvectors of the non Trojan horse chips respectively; if K< / =3, judging the chip to be detected to be a Trojan horse chip or non Trojan horse chip according to a k-dimensional image; if the k > 3, judging the chip to be detected to be a Trojan horse chip or non Trojan horse chip according to the mahalanobis distance. The method is adaptive to the characteristic of uncertainty of the data dimension, the Trojan horse chip and non Trojan horse chip can be identified accurately, and the integrated circuit pattern identifying capability and efficiency are improved.
Owner:FIFTH ELECTRONICS RES INST OF MINIST OF IND & INFORMATION TECH
hardware Trojan horse detection method based on path delay analysis
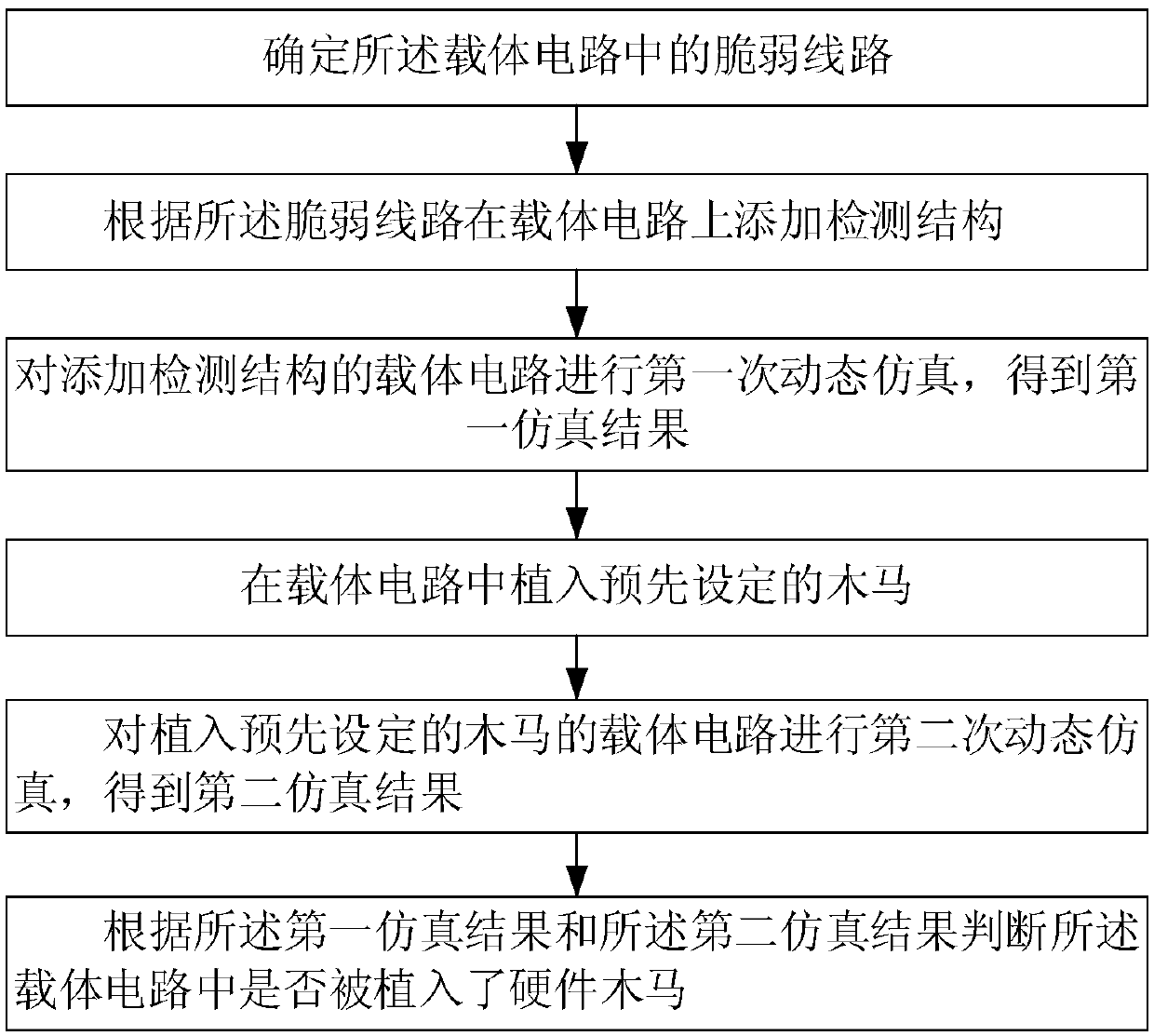
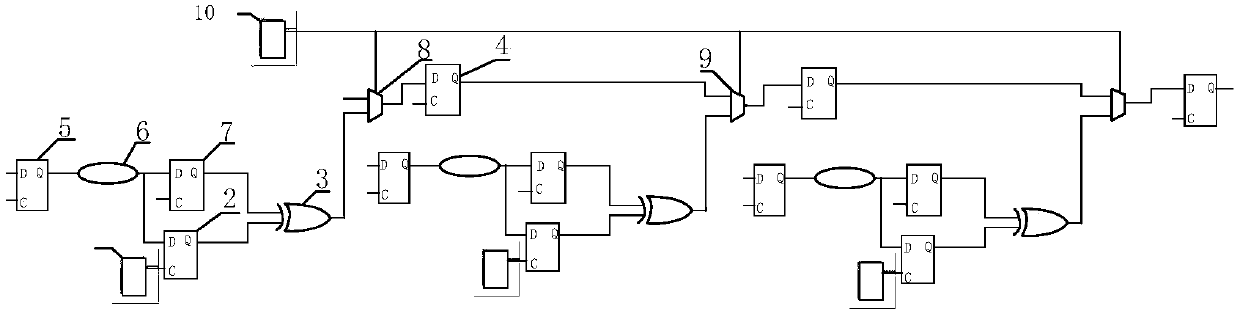
ActiveCN109657464AIncrease credibilityIncrease attack difficultyInternal/peripheral component protectionPlatform integrity maintainanceMultiplexerHardware trojan horse
The invention relates to the technical field of integrated circuit detection, in particular to a hardware Trojan horse detection method based on path delay analysis. The device comprises a detection structure, and the detection structure comprises a detection module, a result output module and a data selector which are connected in sequence; Determining a fragile line in the carrier circuit; Adding a detection structure on the carrier circuit according to the fragile line; Carrying out first dynamic simulation on the carrier circuit added with the detection structure; Embedding a preset Trojanhorse into the carrier circuit; Carrying out second dynamic simulation on the carrier circuit implanted with the preset Trojan horse; And judging whether a hardware Trojan horse is implanted into thecarrier circuit according to the first simulation result and the second simulation result. According to the embodiment of the invention, the credibility of the integrated circuit is improved, and thedifficulty of Trojan attack is increased.
Owner:XIDIAN UNIV
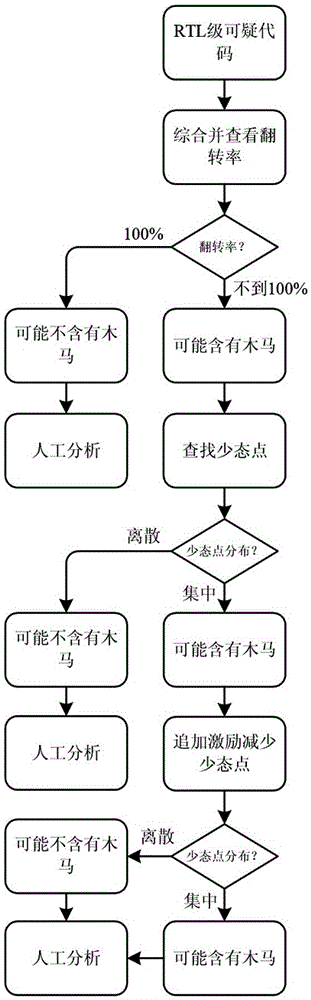
Hardware trojan horse detection method based on few-state point analysis
ActiveCN105046153AImprove recognition efficiencyEasy to implementPlatform integrity maintainanceHardware trojan horseComputer science
A hardware trojan horse detection method based on few-state point analysis comprises the steps of: S1: integrating RTL-level suspicious codes to obtain a gate-level net list of a circuit; S2: applying random excitation to the gate-level net list obtained by integration and checking a turn-over rate; if the turn-over rate is 100%, judging that the circuit does not have trojan horse therein; if the turn-over rate does not reach 100%, primarily judging that the circuit possibly has the trojan horse and going to the step S3; and S3: analyzing data of the turn-over rate in details to find out a few-state point which is rarely turned over, if the distribution of the few-state points is relatively discrete, primarily judging that the circuit does not have the trojan horse therein, and if the distribution of the few-state points is relatively concentrated, primarily judging that the circuit possibly has the trojan horse. The hardware trojan horse detection method based on the few-state point analysis has the advantages of easiness for implementation, high recognition efficiency, low detection cost and the like.
Owner:NAT UNIV OF DEFENSE TECH
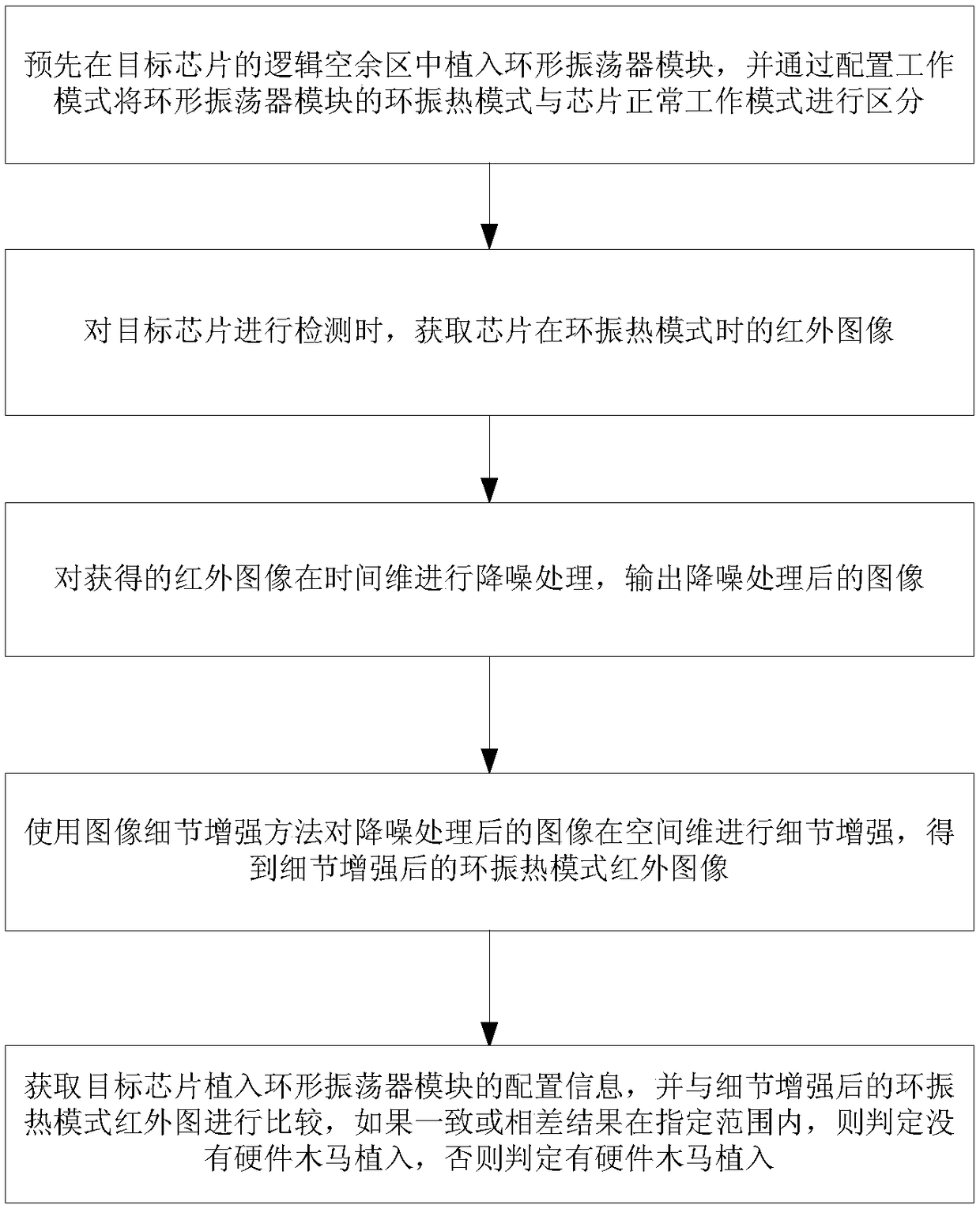
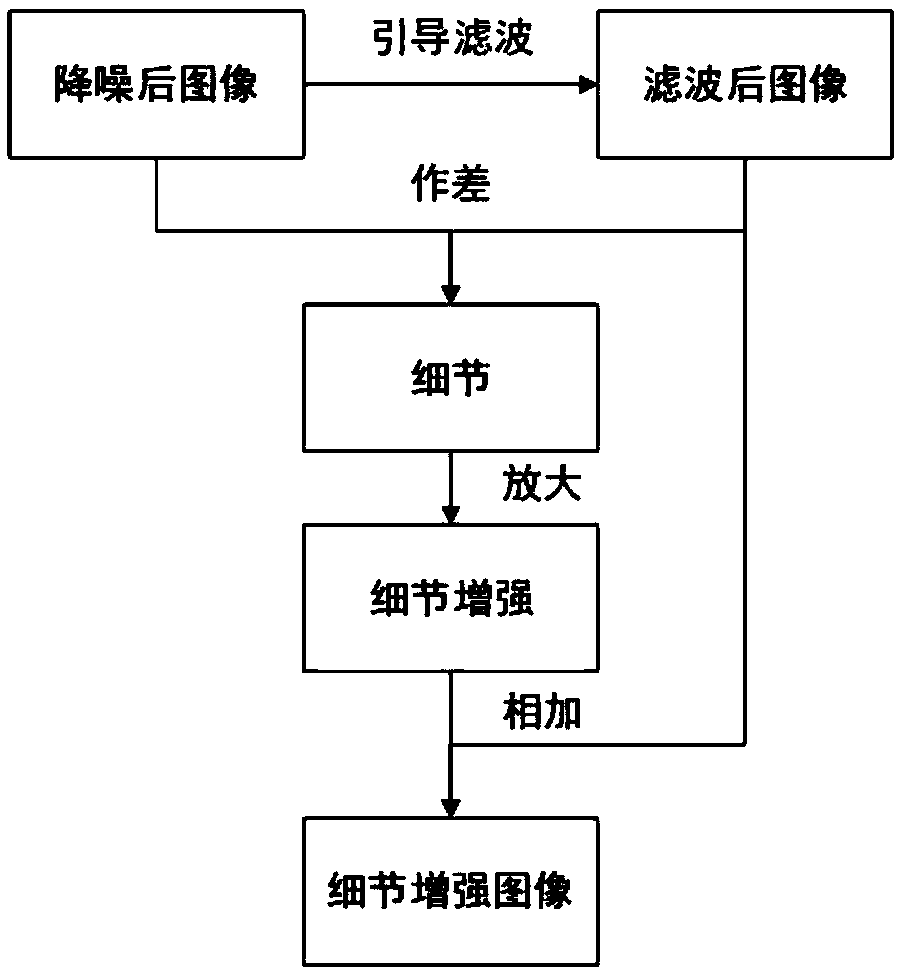
Hardware Trojan horse detection method based on infrared image detail enhancement
InactiveCN108985058AReduce design costReliable hardware Trojan detectionImage enhancementImage analysisPhase differenceComputer module
The invention discloses a hardware Trojan horse detection method based on infrared image detail enhancement. The method comprises the following steps: S1, A ring oscillator module is implanted in a logic spare area of a target chip in advance, and the normal working mode of a ring vibration heat mode chip is distinguished by configuring the working mode; S2, when the target chip is detected, the infrared image of the chip in the ring vibration heat mode is obtained; S3, noise reduction processing is carried out on the obtained infrared image in the time dimension; S4, an image detail enhancement method is utilized to enhance the spatial dimension of the image after noise reduction processing; S5, the configuration information of the chip implanted ring oscillator module is acquired, and iscompared with the ring vibration thermal mode infrared image after detail enhancement, if the consistent or phase difference result is within the specified range, a condition that there is no hardware Trojan horse implantation can be judged. The method has the advantages of simple operation, low cost, high detection accuracy and efficiency.
Owner:NAT UNIV OF DEFENSE TECH
Nondestructive detecting method of mixed activated hardware Trojan horse in integrated circuit
InactiveCN102621480AAvoid threatsEnsure safetyElectronic circuit testingEngineeringHardware trojan horse
The invention relates to a nondestructive detecting method of an acceleration and rare vector sequence mixed activated hardware Trojan horse in an integrated circuit. The nondestructive detecting method comprises the following steps of: providing a corresponding testing environment to the integrated circuit; generating a rare vector sequence set for the integrated circuit; applying maximum acceleration, which is not less than the acceleration born during normal working, to the integrated circuit; exciting the integrated circuit by using the rare vector sequence; testing whether characteristic parameters and function effects of the integrated circuit are abnormal or not; and if so, detecting the integrated circuit implanted with the hardware Trojan horse and recording a destruction method. According to the invention, the integrated circuit implanted with the hardware Trojan horse can be detected before entering an application system so as to prevent the application system from being threatened by the hardware Trojan horse and ensure the safeties of important systems.
Owner:NANKAI UNIV
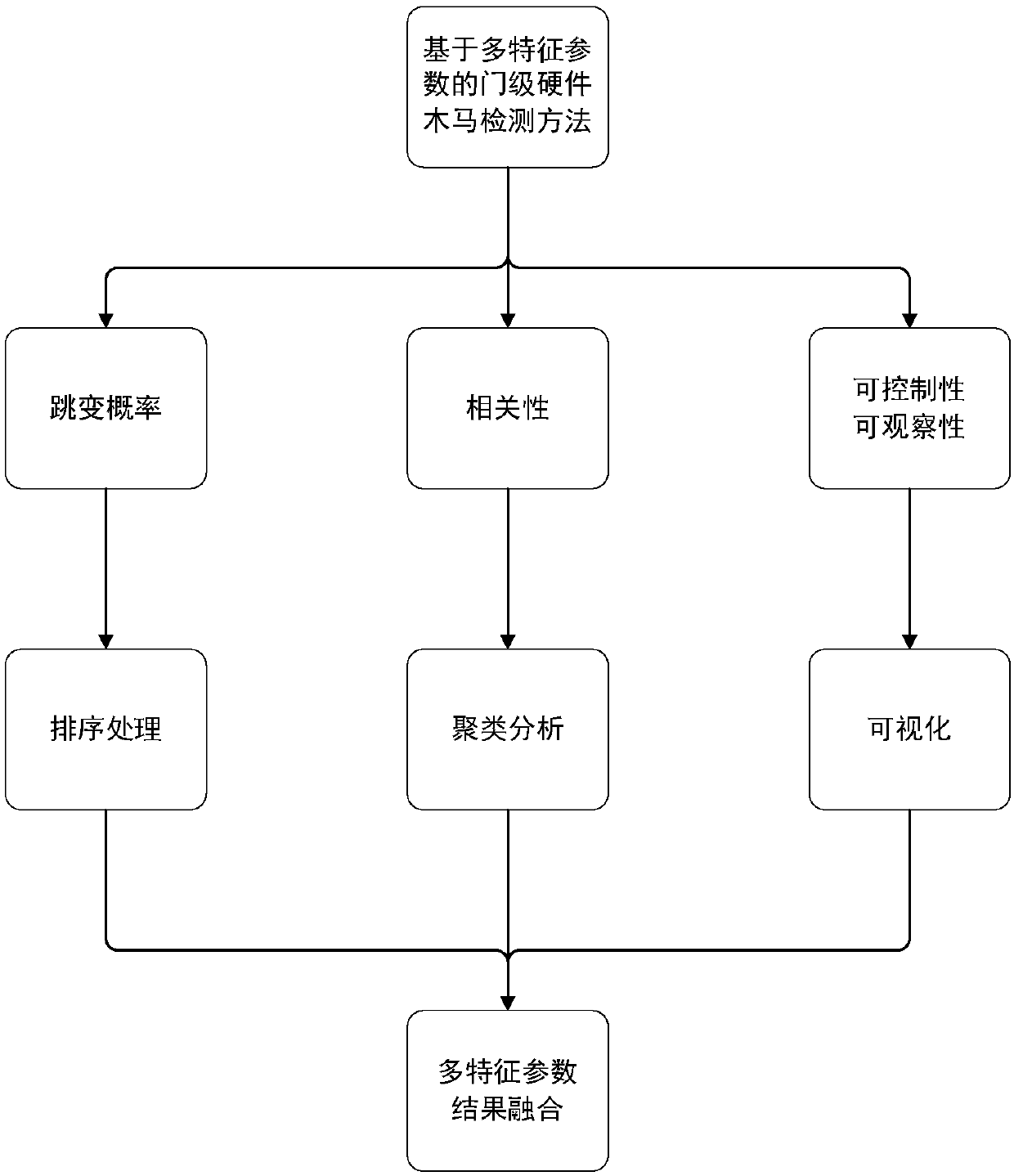
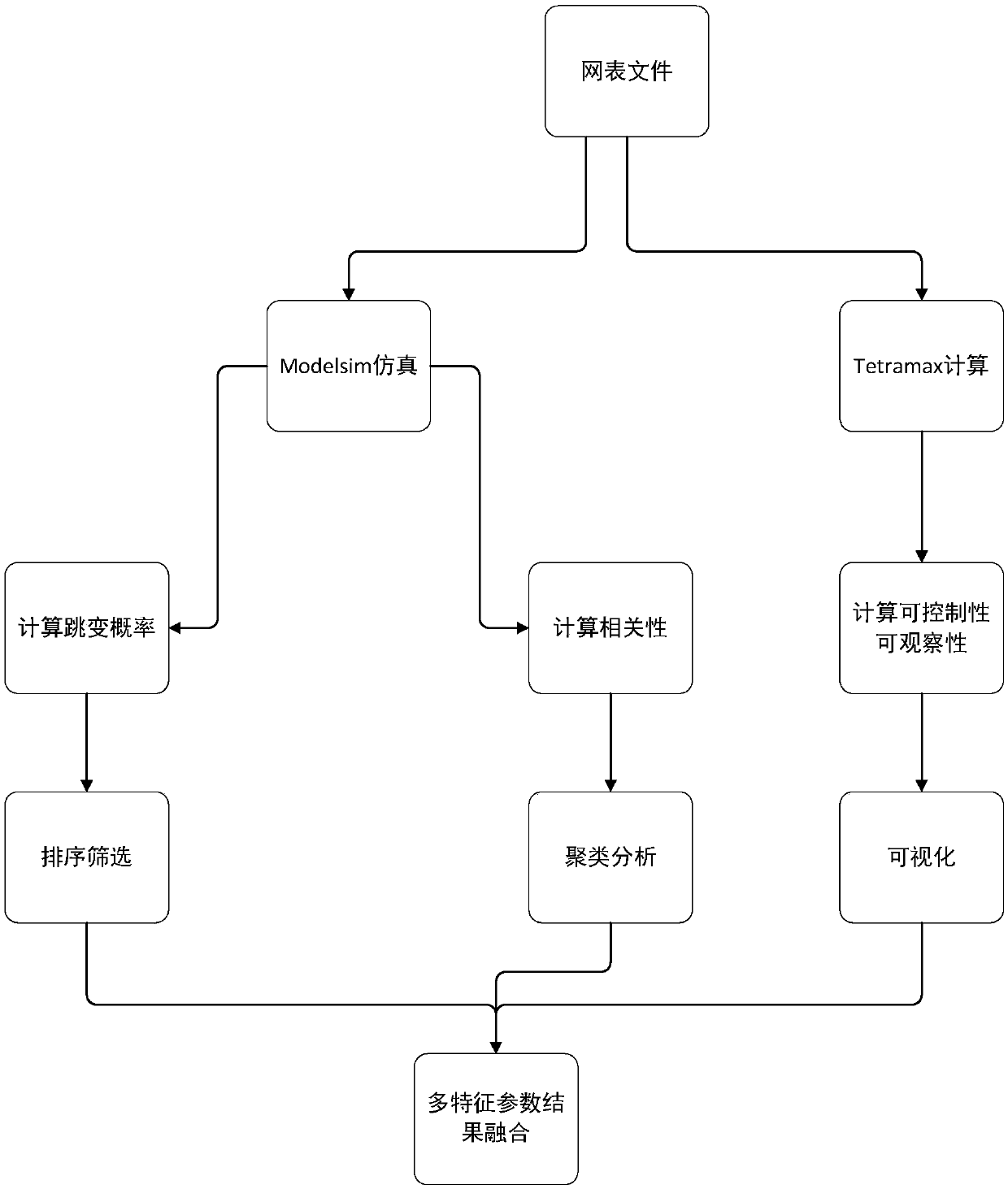
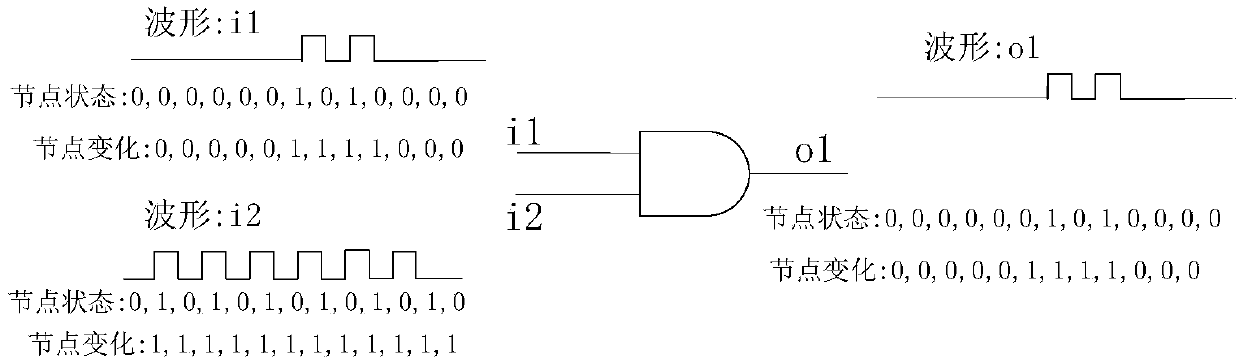
Gate-level hardware Trojan horse detection method based on multiple characteristic parameters
ActiveCN110414277ASolve detection difficultiesImprove detection accuracyInternal/peripheral component protectionThird partyNODAL
The invention relates to a gate-level hardware Trojan horse detection method based on multiple characteristic parameters. The method mainly comprises two parts: characteristic parameter extraction anddata processing. Specifically, characteristic parameters such as hopping probability, correlation, controllability and observability of a gate-level netlist are extracted in the detection process, the hopping probability reflects the activity degree of circuit nodes, the correlation reflects the correlation degree between the nodes, and the controllability and observability indicate the difficulty degree of node control and observation. Then, different algorithms are designed according to different parameter characteristics to distinguish normal nodes and Trojan horse nodes. According to themethod, the gate-level netlist hardware Trojan horse detection effect can be improved; the situation of all nodes in the circuit is reflected through multiple characteristic parameters, the possibility that a design company uses an IP core provided by a third party to introduce a hardware Trojan horse maliciously modifying the circuit in the chip design stage is reduced, and therefore the method can be universally applied to gate-level hardware Trojan horse detection and has high practicability.
Owner:PEKING UNIV
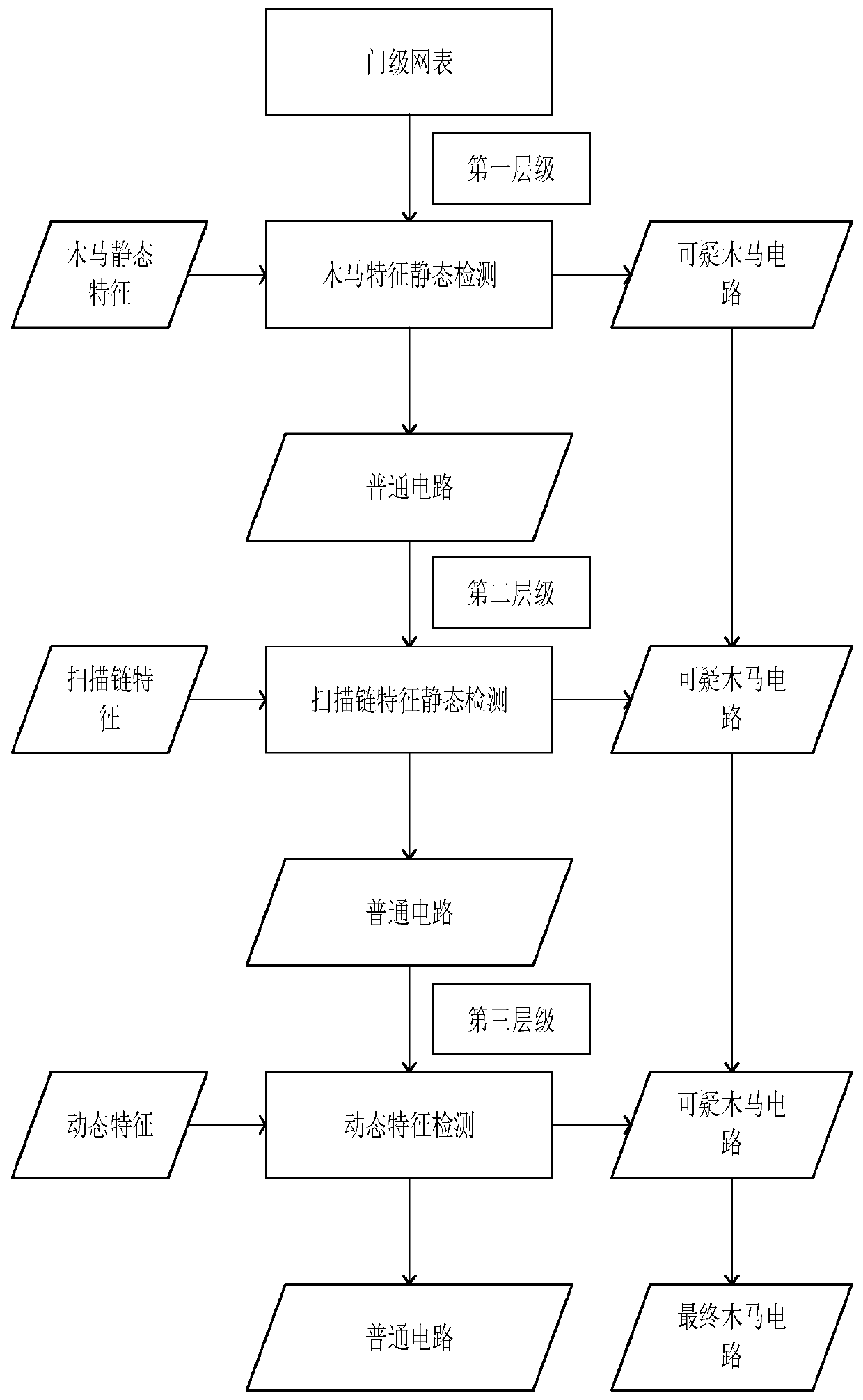
Mixed mode multi-level gate-level hardware Trojan horse detection method based on machine learning
ActiveCN111523116AEfficient detectionImprove accuracyPlatform integrity maintainanceMachine learningAlgorithmTrojan horse
The invention discloses a mixed mode multi-level gate-level hardware Trojan horse detection method based on machine learning, and belongs to the technical field of calculation, reckoning or counting.The mixed mode multi-level gate-level hardware Trojan horse detection method comprises the steps of: firstly, by analyzing a structure and characteristics of a gate-level Trojan horse circuit at a first level, providing two effective Trojan horse circuit characteristics, combining with traditional Trojan horse characteristics, carrying out static detection on a suspicious circuit to be detected through a machine learning algorithm, and separating the Trojan horse circuit and a normal circuit preliminarily; secondly, providing Trojan horse characteristics of two scanning chain structures at a second level, and continuing to perform static detection on the normal circuit separated at the first level by using a scan chain detection method; and finally, dynamically detecting the normal circuitseparated at the second level, and integrating detection results of the three levels to obtain the final Trojan horse circuit. Compared with a traditional gate-level hardware Trojan horse detection method, the mixed mode multi-level gate-level hardware Trojan horse detection method combines a static detection method and a dynamic detection method, and the suspicious circuit to be detected is detected more comprehensively and efficiently by means of the multi-level structure.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Hamming distance-based digital microfluidic biochip field-level hardware Trojan horse detection method
ActiveCN111414618ACutting costsImprove efficiencyPlatform integrity maintainanceThird partyAnimal science
The invention relates to a Hamming distance-based digital microfluidic biochip field-level hardware Trojan horse detection method. The method comprises: acquiring a biochemical protocol stored in a digital microfluidic biochip platform; assuming that a malicious third party is tampered, giving two character strings, one being a gold drive sequence sold by a manufacturer and a series of field-levelimplemented drive sequences, and then from the beginning to the end of the reaction, entering the cyclic utilization difference of each time step to calculate the Hamming distance of the third party;and in each step of circulation, judging whether the calculated Hamming distance is greater than 0 or not by utilizing the calculated Hamming distance to obtain a key value, namely whether the key value is tampered or not. Once the on-site hardware Trojan horse is detected, operation is stopped immediately, and errors are prevented from becoming larger and larger. The program is continuously andcircularly executed through feedback processing. The method is low in cost, does not need special detection equipment, and is not affected by noise.
Owner:FUZHOU UNIV
Hardware Trojan horse detection device and method based on weak same paths
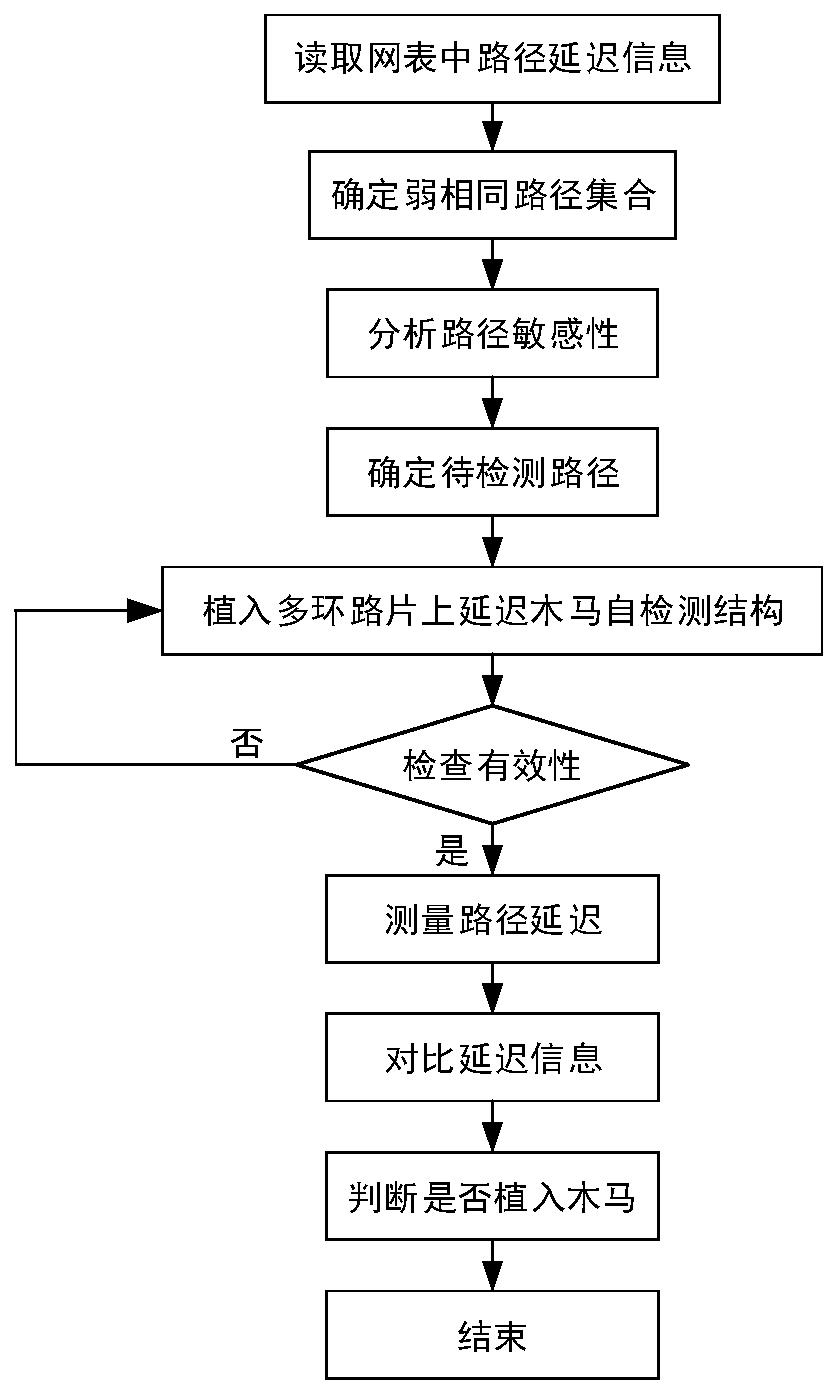
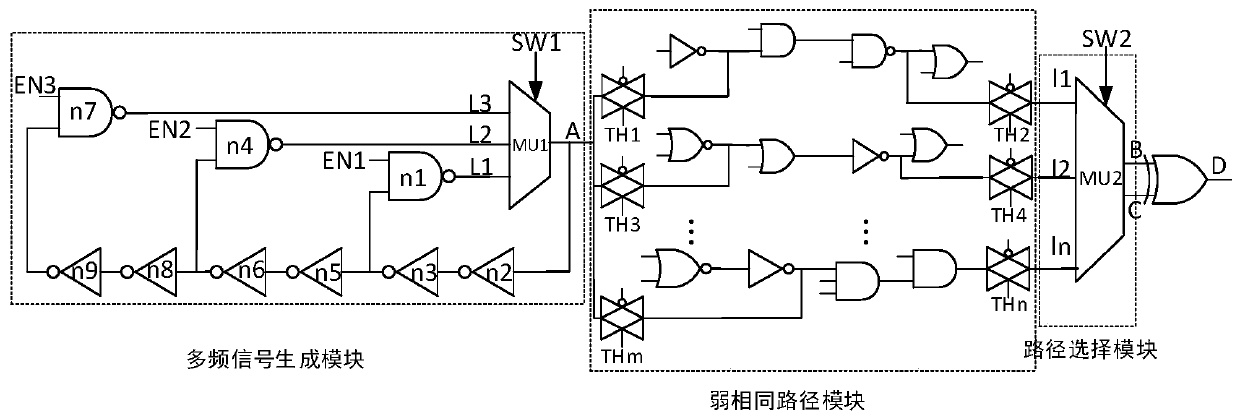
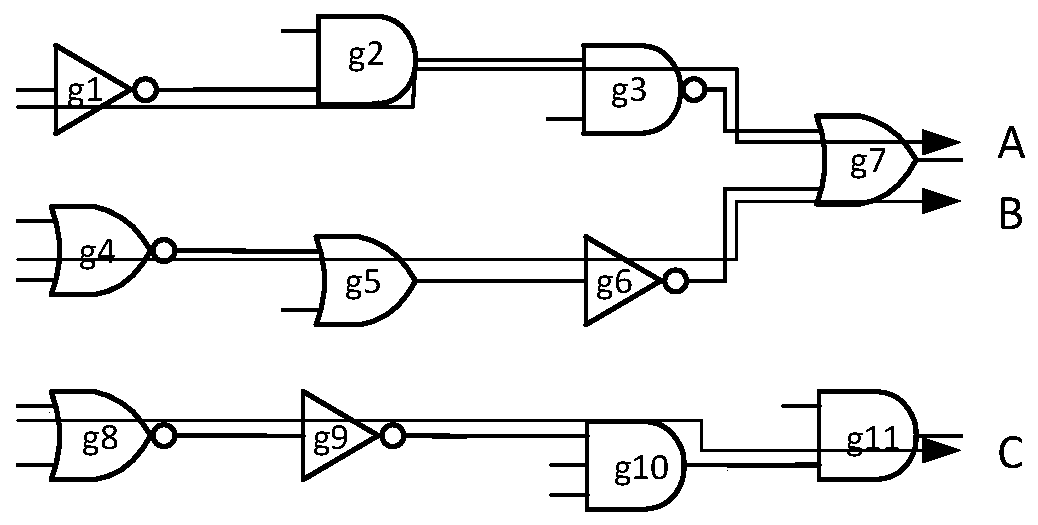
ActiveCN110598399AReduce complexityImprove accuracyInternal/peripheral component protectionPlatform integrity maintainanceStatic timing analysisProcess deviations
The invention belongs to the field of integrated circuit hardware Trojan horse detection methods. Time delay information on a weak same path can be rapidly and effectively detected so that complexityand the cost of chip detection are reduced and the influence of process deviation is eliminated. The invention discloses a hardware Trojan horse detection device and method based on weak same paths. The method comprises the following steps: 1) performing static timing analysis on an integrated circuit layout; 2) setting a weak same path delay threshold, and analyzing and determining a weak same path set R; 3) analyzing the sensitivity of the weak same path, and screening the weak same path set; 4) implanting a multi-loop on-chip delay Trojan horse self-detection structure, and analyzing the effectiveness; 5) testing the delay information of the path after chip manufacturing; and 6) comparing the difference values of the delay information, and judging the path suspected to be implanted intothe Trojan. The method is mainly applied to integrated circuit design and manufacturing occasions.
Owner:TIANJIN UNIV
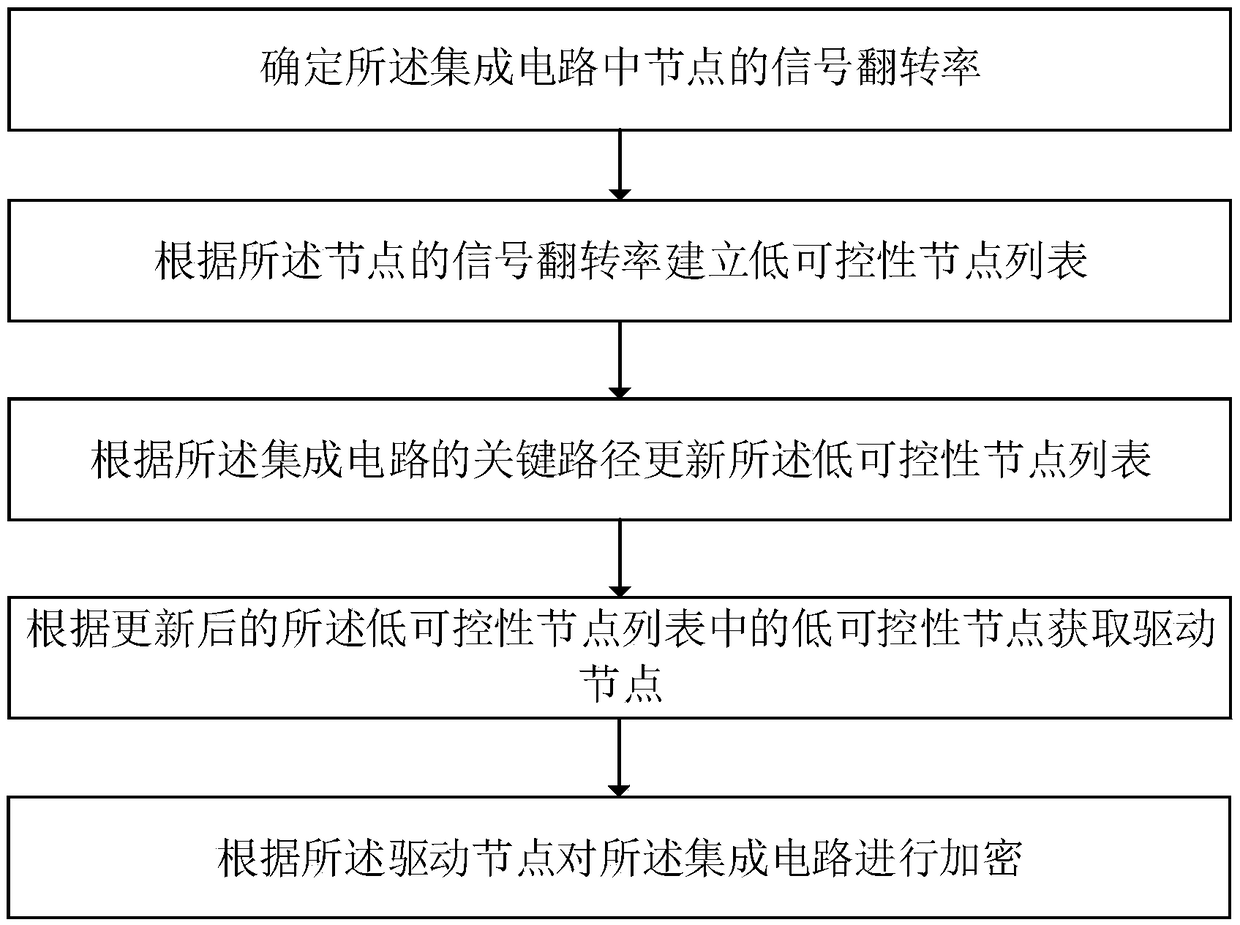
An integrated circuit based on logical encryption and an encryption method thereof
ActiveCN109284637ALittle impact on performanceOvercome performance-impacting issuesInternal/peripheral component protectionComputer hardwareIntegrated circuit layout
The invention relates to an integrated circuit based on logic encryption and an encryption method thereof. The invention includes that the signal flip rate of a node in the integrated circuit is determined; a low controllability node list is established according to the signal flip rate of the node, wherein the first low controllability node list comprises a plurality of low controllability nodes;updating a low controllability node list according to a critical path of the integrated circuit; acquiring a driving node according to the low controllability node in the updated low controllabilitynode list; the integrated circuit is encrypted according to the driver node to obtain an encrypted integrated circuit. The encryption method of the integrated circuit of the invention is a method fordefending hardware Trojan horse based on logic encryption. The invention avoids the low controllability node on the critical path and does not perform any treatment on the low controllability node, avoids inserting additional and useless circuits on the critical path, reduces the influence on the integrated circuit performance, and thus overcomes the problem that the prior art method of defendingthe hardware Trojan horse has great influence on the integrated circuit performance.
Owner:XIDIAN UNIV
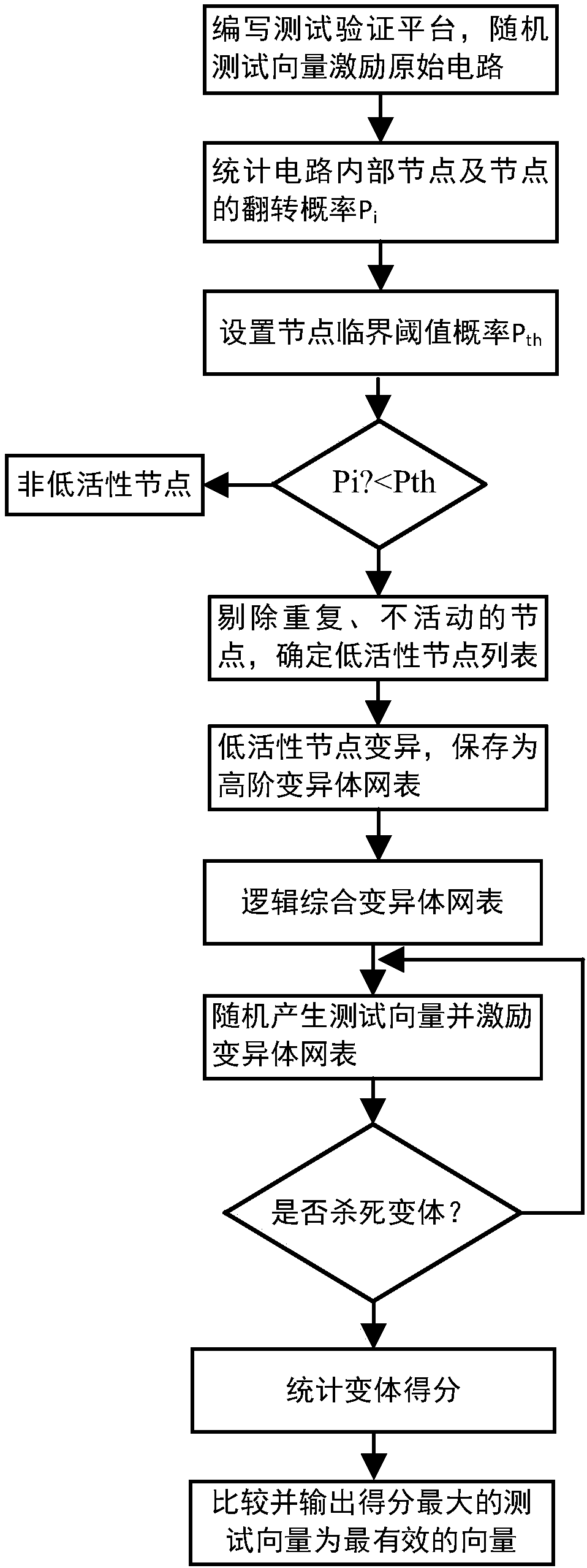
Testing vector generating method based on variation analysis for effectively activating hardware trojan horses
PendingCN107783877AVulnerability testing methods are maturePurposefulError detection/correctionTest efficiencyLow activity
The invention relates to the technical field of credibility of integrated circuits, and discloses a testing vector generating method for effectively activating hardware trojan horses. The method is high in purposiveness, low in testing cost, high in testing efficiency and capable of more effectively activating the hardware trojan horses and has certain actual meaning and reference value for manifesting the hardware trojan horses and analyzing bypass signals, and generated testing sequences are more simplified. In order to achieve the advantages above, according to the adopted technical scheme,the testing vector generating method based on the variation analysis for effectively activating the hardware trojan horses comprises the steps of analyzing the structural characters of a mother circuit, screening out nodes with low activity, utilizing a variation method to execute a variation operation on the circuit structure of the nodes with the low activity to generate high-level variants, and utilizing a functional testing method to screen out testing vectors capable of killing the variants. The method is mainly applied to the safety detection occasion of an integrated circuit.
Owner:TIANJIN UNIV
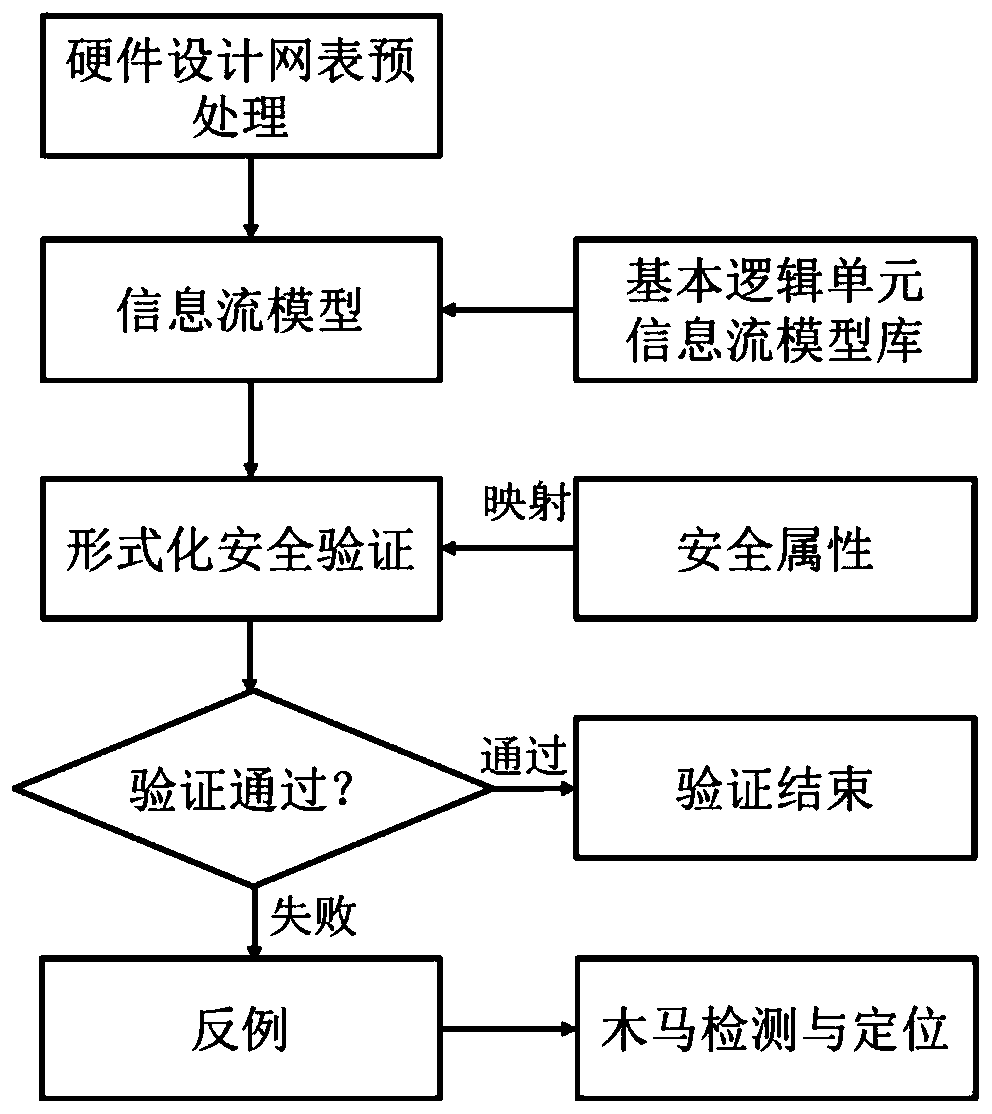
Hardware Trojan horse detection method based on information flow security verification
ActiveCN110096907AAchieve precise positioningAvoid additional design overheadInternal/peripheral component protectionPlatform integrity maintainanceComputer architectureSecurity validation
The invention provides a hardware Trojan horse detection method based on information flow security verification. The method includes constructing an information flow model for integrated circuit hardware design; defining information flow security attributes required to be met by hardware design; adopting an EDA formal verification tool for information flow safety verification, detecting potentialTrojans in hardware design by capturing the situation that information flow safety attributes violate, and achieving accurate positioning of Trojan design and triggering mechanism revealing of the Trojan design by means of the reverse tracking capacity provided by the information flow model. The method can effectively avoid additional design expenditure caused by semantic difference between the hardware design language and the verification language, and improves the efficiency of security verification and Trojan horse detection.
Owner:RES & DEV INST OF NORTHWESTERN POLYTECHNICAL UNIV IN SHENZHEN +1
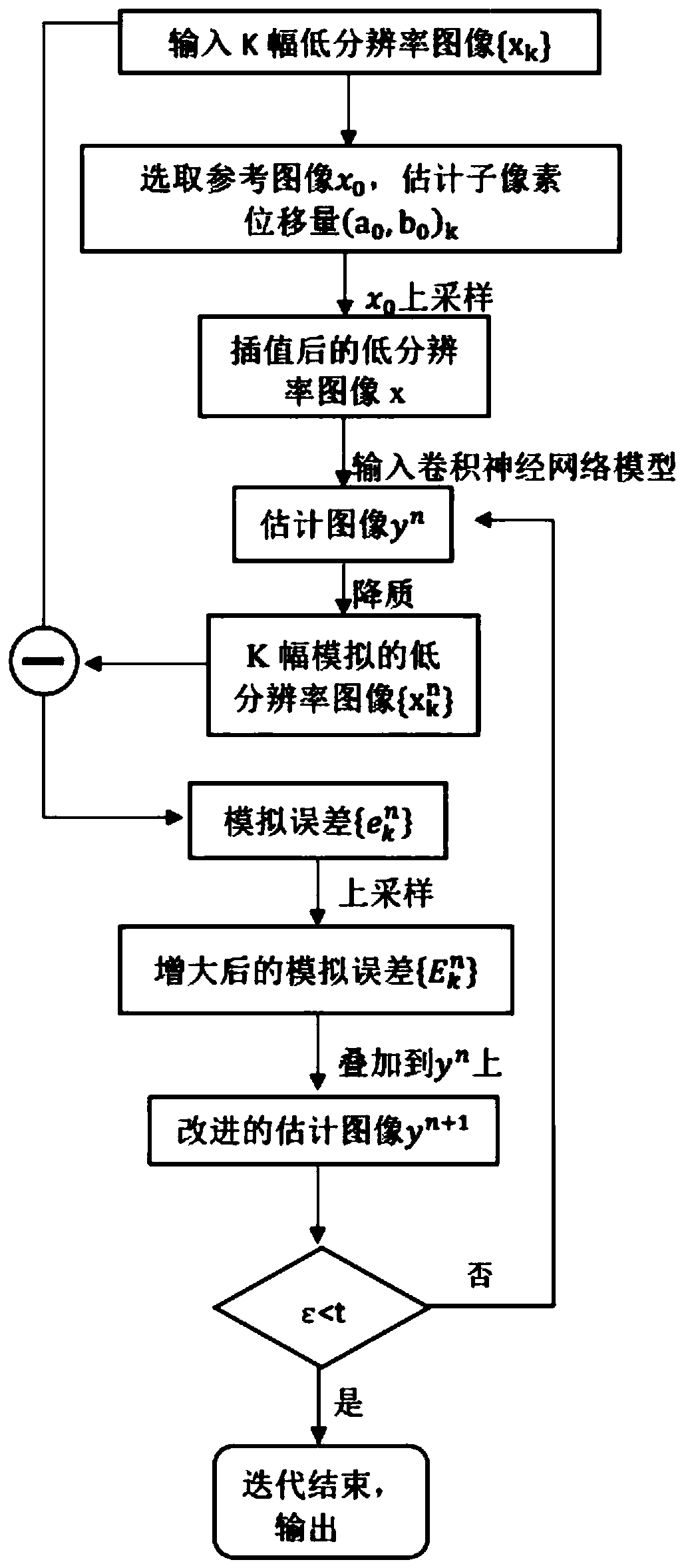
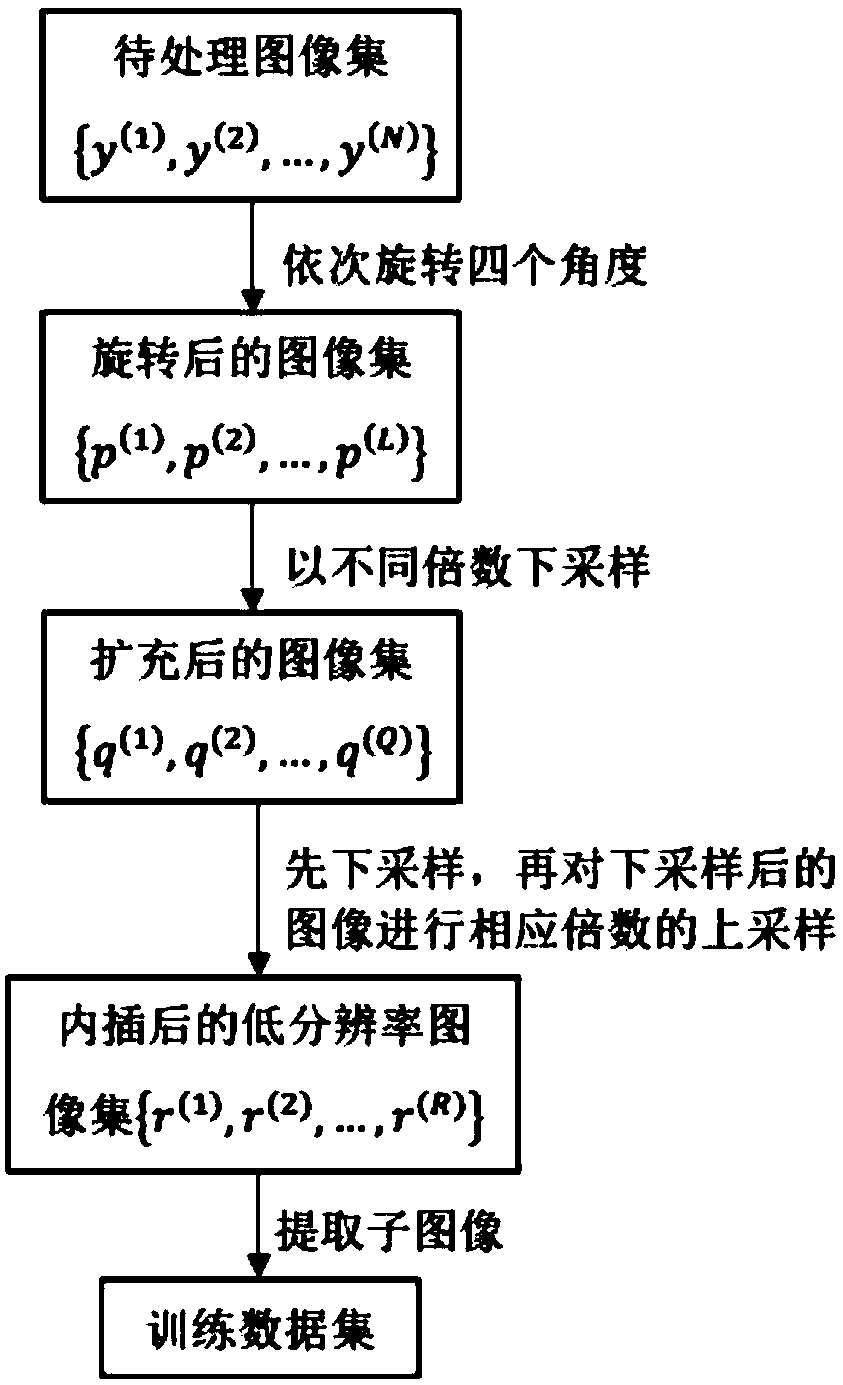
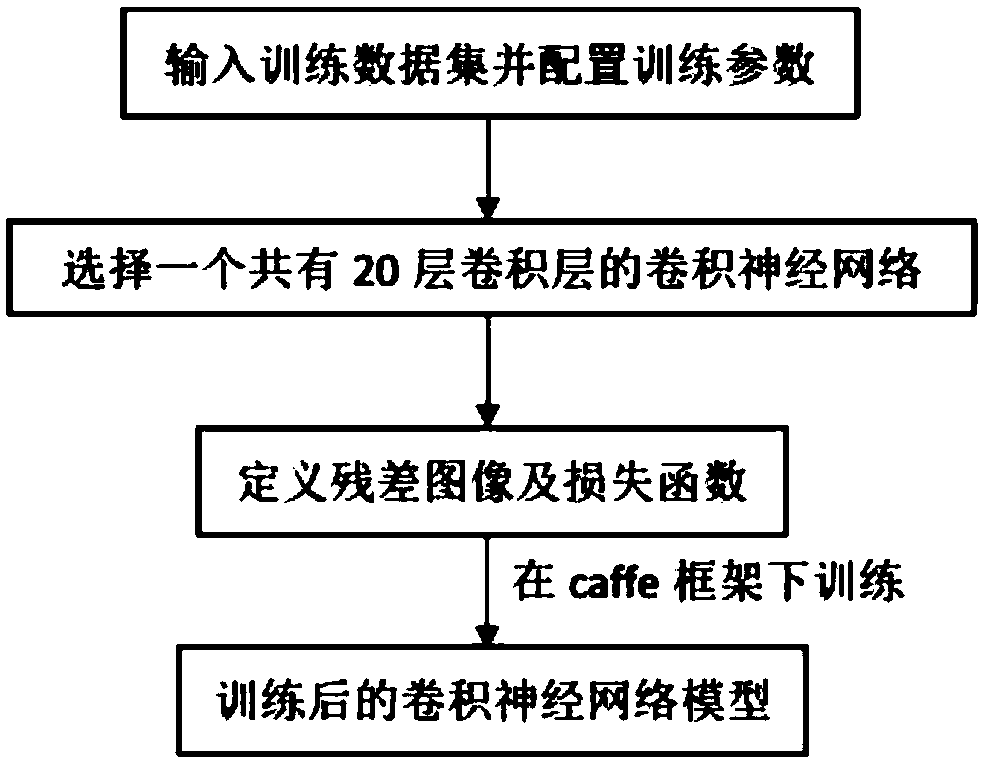
Chip image super-resolution reconstruction method based on depth learning
ActiveCN109146792AImproving super-resolution reconstruction performanceGeometric image transformationNeural architecturesPattern recognitionData set
The invention discloses a chip image super-resolution reconstruction method based on depth learning, which mainly solves the problem of low resolution at the dense part of the circuit of the chip image reconstruction in the prior method. The technical scheme is as follows: 1. dividing the image set and constructing the training data set; 2. training the training data set; 3. estimating the sub-pixel displacement of K low-resolution images and reference images; 4. carrying out up-sampling on that reference image, inputting the reference image into the train model, and outputting the estimated image; 5. degrading the estimated image, and calculating the simulation error between the degrade image and the K low-resolution images; 6. superimposing the simulation error on the estimated image toobtain an improved estimate image; 7. Iteration being performed on steps 5 to 6 until that error function is less than the error threshold, and the resulting improved estimated image being output. Theinvention improves the super-resolution reconstruction effect of the circuit dense part in the chip image, and can be used for detecting the hardware Trojan horse at the circuit dense part of the chip.
Owner:XIDIAN UNIV
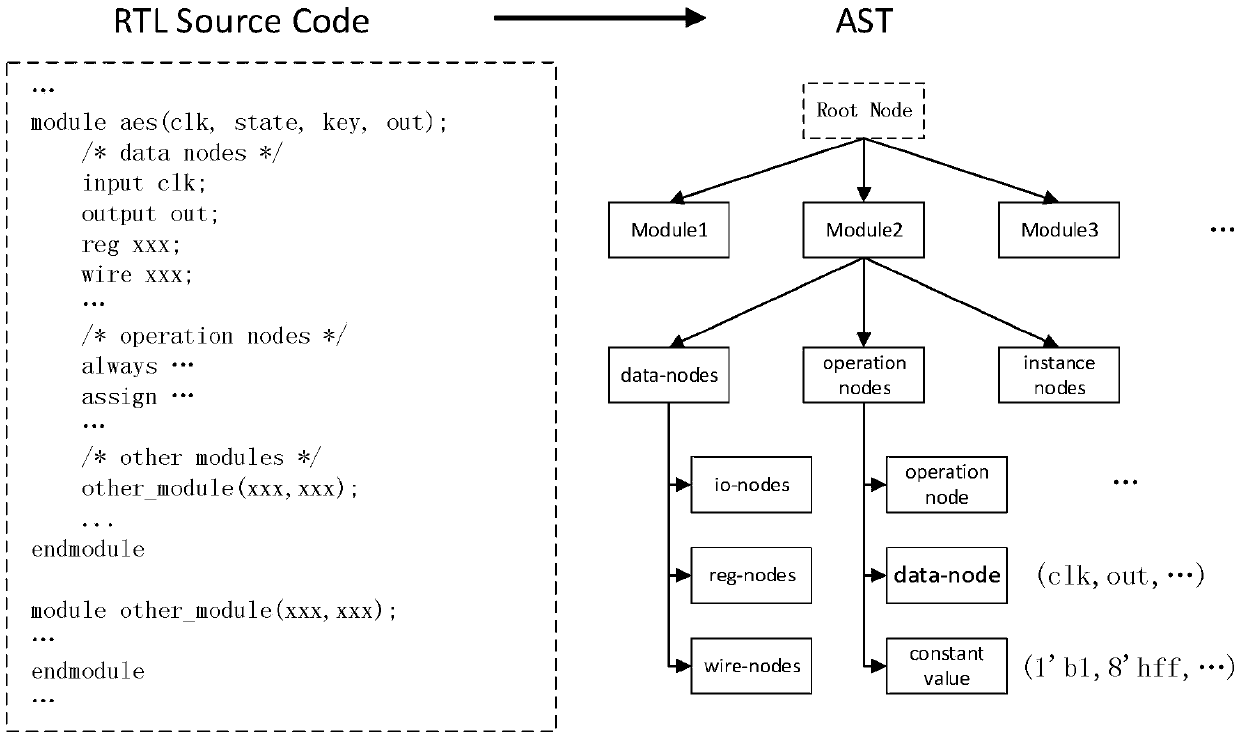
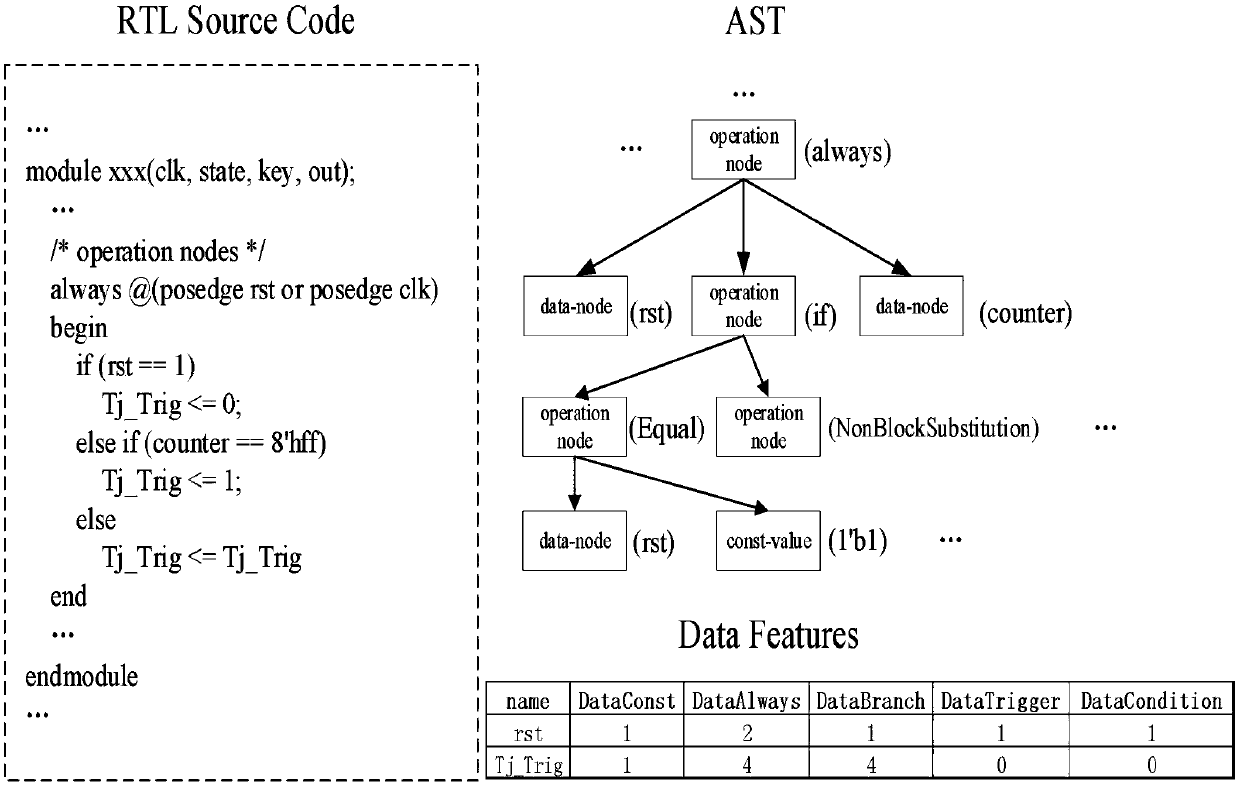
RTL hardware Trojan horse detection method based on a gradient lifting algorithm
ActiveCN109657461AImprove detection accuracyReduce false alarm ratePlatform integrity maintainanceNODALDescent direction
The invention provides an RTL hardware Trojan horse detection method based on a gradient lifting algorithm, and the method comprises the steps: firstly, carrying out the extraction of an abstract syntax tree of a to-be-detected circuit, carrying out the construction and extraction of circuit features of the to-be-detected circuit according to the extracted abstract syntax tree, and obtaining the vectorization feature of each signal node in the to-be-detected circuit; And inputting the vectorized features into a Trojan detection model, detecting the vectorized features by the Trojan detection model, and outputting a label corresponding to each signal node so as to obtain a Trojan detection result corresponding to the signal node. Wherein the Trojan horse detection model is obtained based onXgboost framework training realized by a gradient lifting algorithm; a decision tree model is adopted as a base classifier I for gradient lifting, a new decision tree model is added in the gradient descent direction of a loss function to serve as a base classifier II for improving the classification effect, and an appropriate loss function and an appropriate parameter range are selected through hyper-parameter configuration; The method has the advantages of high detection accuracy, low false alarm rate and high detection efficiency.
Owner:ZHEJIANG UNIV
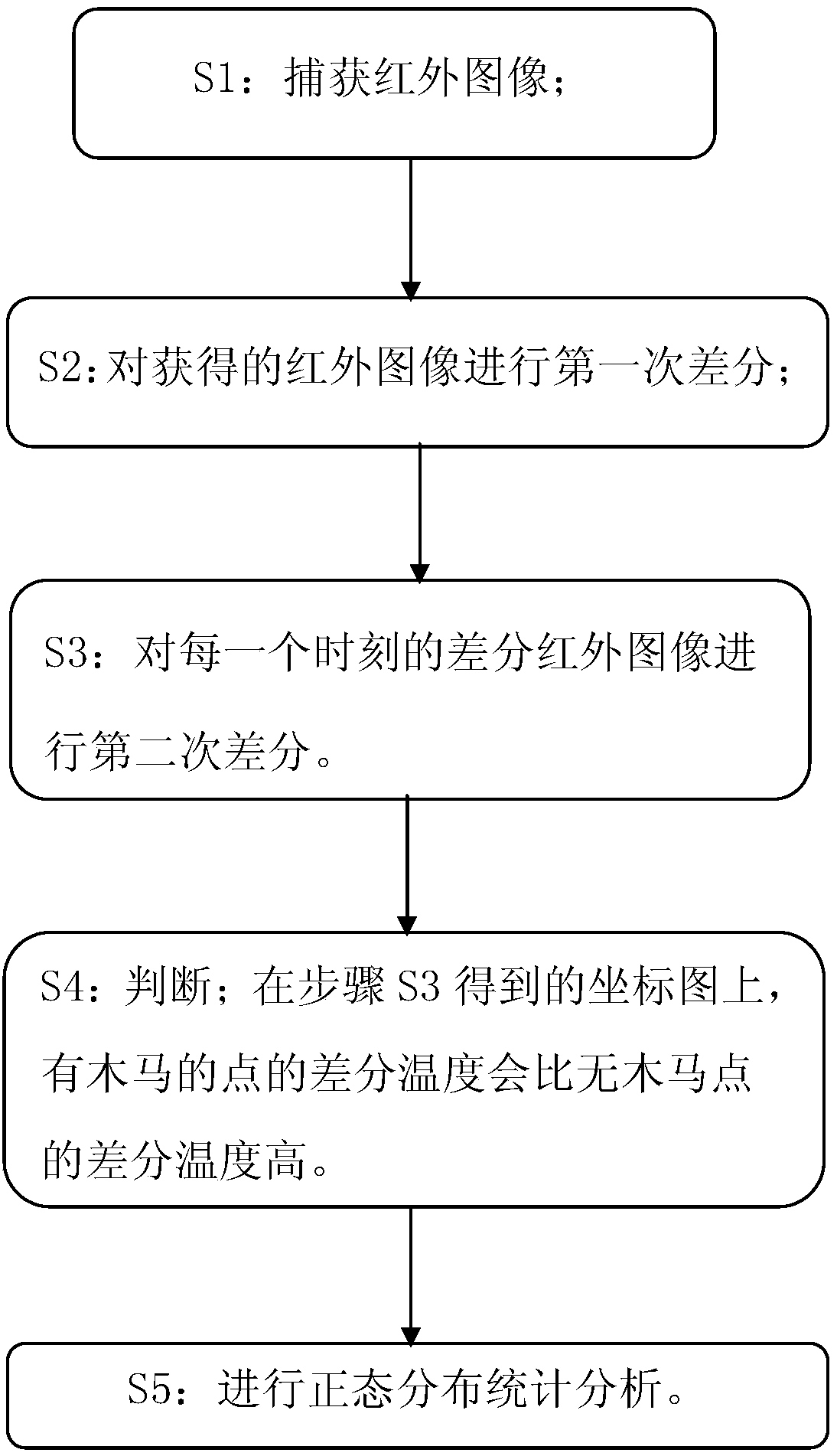
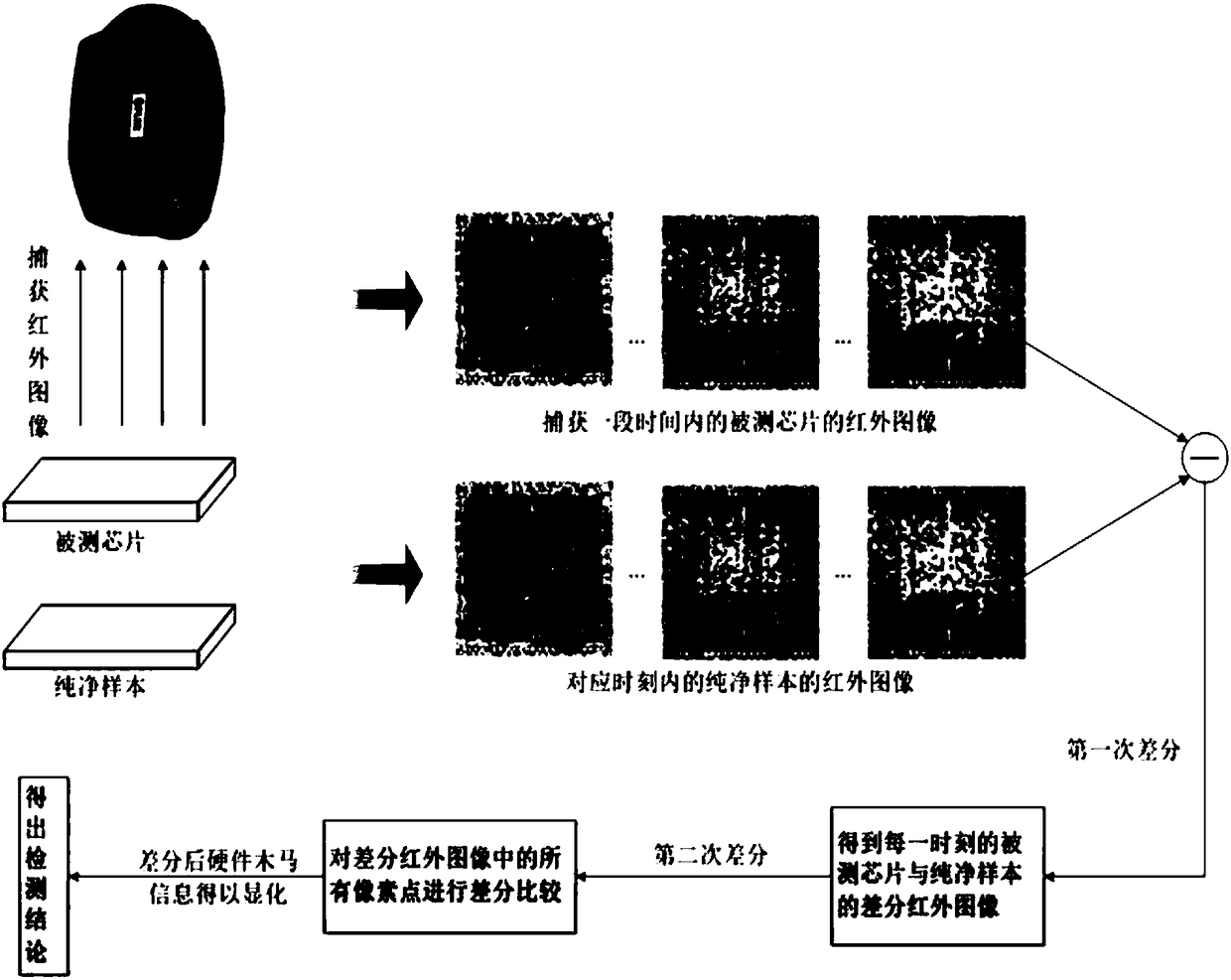
Detecting method of combining infrared imagery and normal distribution analysis for hardware trojan horse
ActiveCN108256357ALow costCause damageTelevision system detailsRadiation pyrometryInfrared imageryComputer science
Provided is a detecting method of combining infrared imagery and normal distribution analysis for a hardware trojan horse. The detecting method comprises the steps that S1: the infrared imagery is captured; a pure chip sample without the hardware trojan horse and a detected chip with a same model simultaneously starts to work, and the infrared imagery of the two chips over a period of time is captured by imagery collecting equipment; S2: a first difference is carried out on the acquired infrared imagery; in the period of sampling time, a pair of infrared imagery is generated at each sampling moment, the difference is carried out on the pair of infrared imagery, infrared imagery after the difference is obtained; S3: a second difference is carried out on the differential infrared imagery ateach moment. Each pixel point in the obtained differential infrared imagery in the first difference is extracted, and differential temperature is drew on a coordinate graph with taking time as an abscissa; S4: judgement is carried out, and the differential temperature of the pixel point with the trojan horse is higher; S5: the normal distribution analysis is carried out. The detecting method has the advantages of high detecting precision, low detecting cost, high detecting efficiency and the like.
Owner:NAT UNIV OF DEFENSE TECH
Hardware trojan horse detection method based on waveform superposition
ActiveCN105046171AImprove recognition efficiencyThe principle is simpleInternal/peripheral component protectionComputer hardwareHardware trojan horse
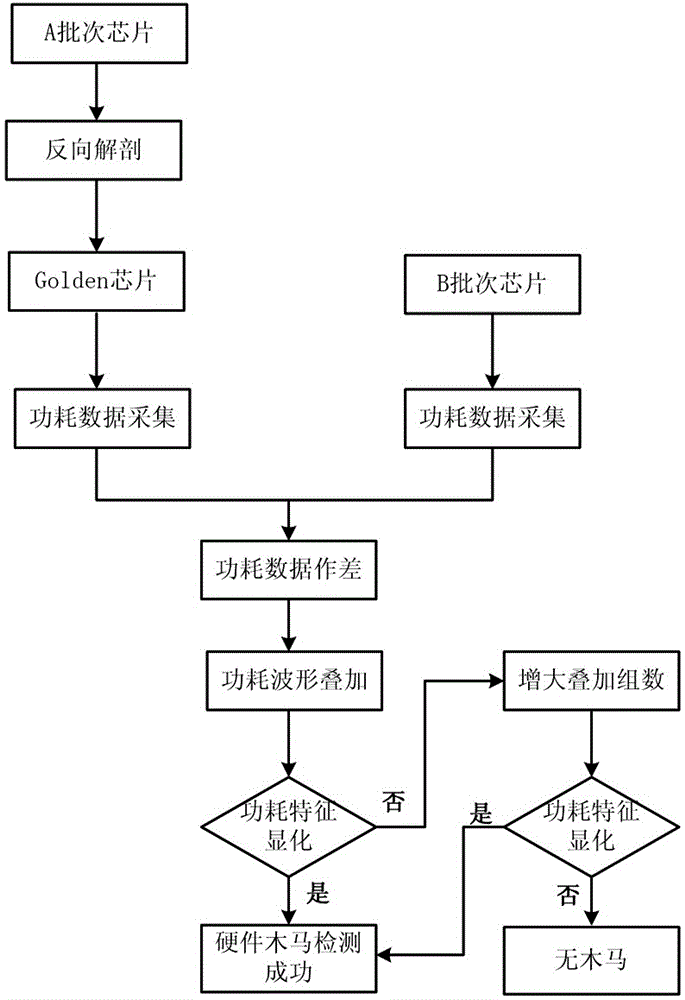
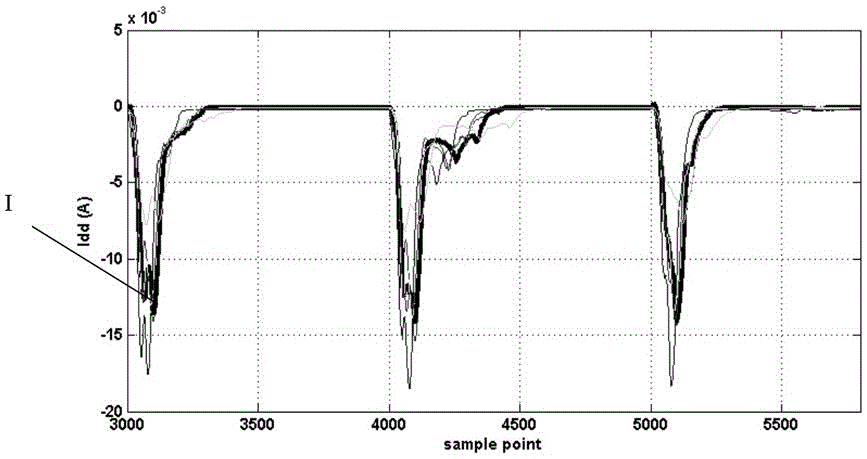
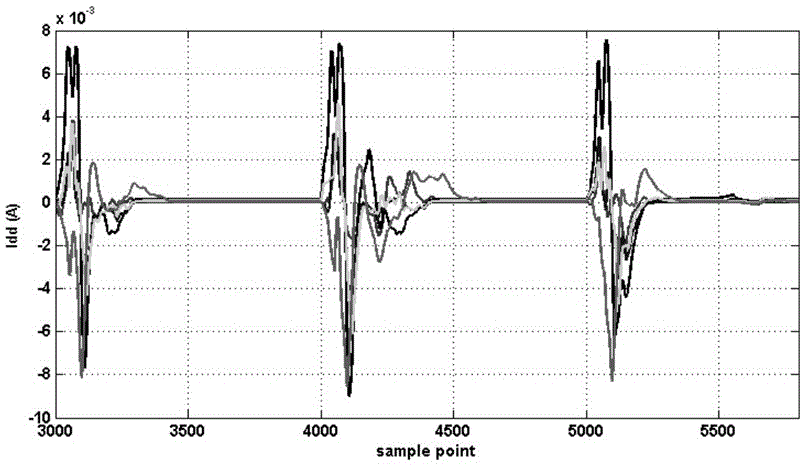
A hardware trojan horse detection method based on waveform superposition comprises the steps of: S1: acquiring a clean chip as reference; S2: extracting a plurality of chips from the other batch as to-be-detected chips; S3: acquiring power consumption data of the clean chip and the to-be-detected chips; S4: subtracting the power consumption data of the clean chip by the power consumption data of the to-be-detected chips respectively; S5: carrying out superposition processing on waveforms of the power consumption data obtained by the subtraction in the step S4; and S6: making a judgment according to a processing result obtained in the step S5, if a power consumption feature in a period is effectively clear after the superposition and the power consumption exceeds a preset threshold value, determining that a hardware trojan horse circuit possibly exists in the to-be-detected chips, and conversely, determining that the to-be-detected chips are normal. The hardware trojan horse detection method based on the waveform superposition has the advantages of simple principle, simplicity and convenience for operation, high detection efficiency, low detection cost and the like.
Owner:NAT UNIV OF DEFENSE TECH
Hardware Trojan horse detection method and device
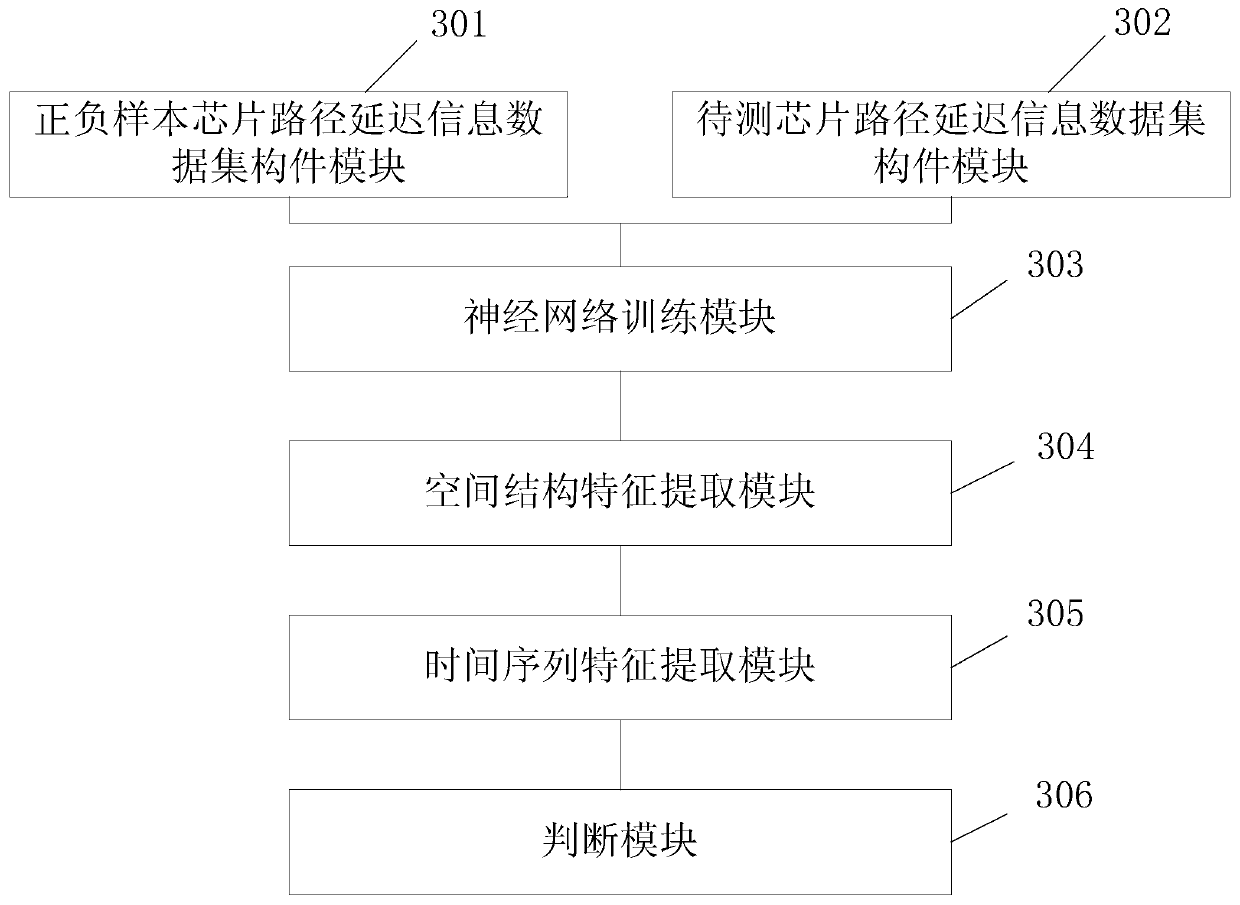
ActiveCN110059504AImprove detection efficiencyImprove detection accuracyInternal/peripheral component protectionNerve networkData set
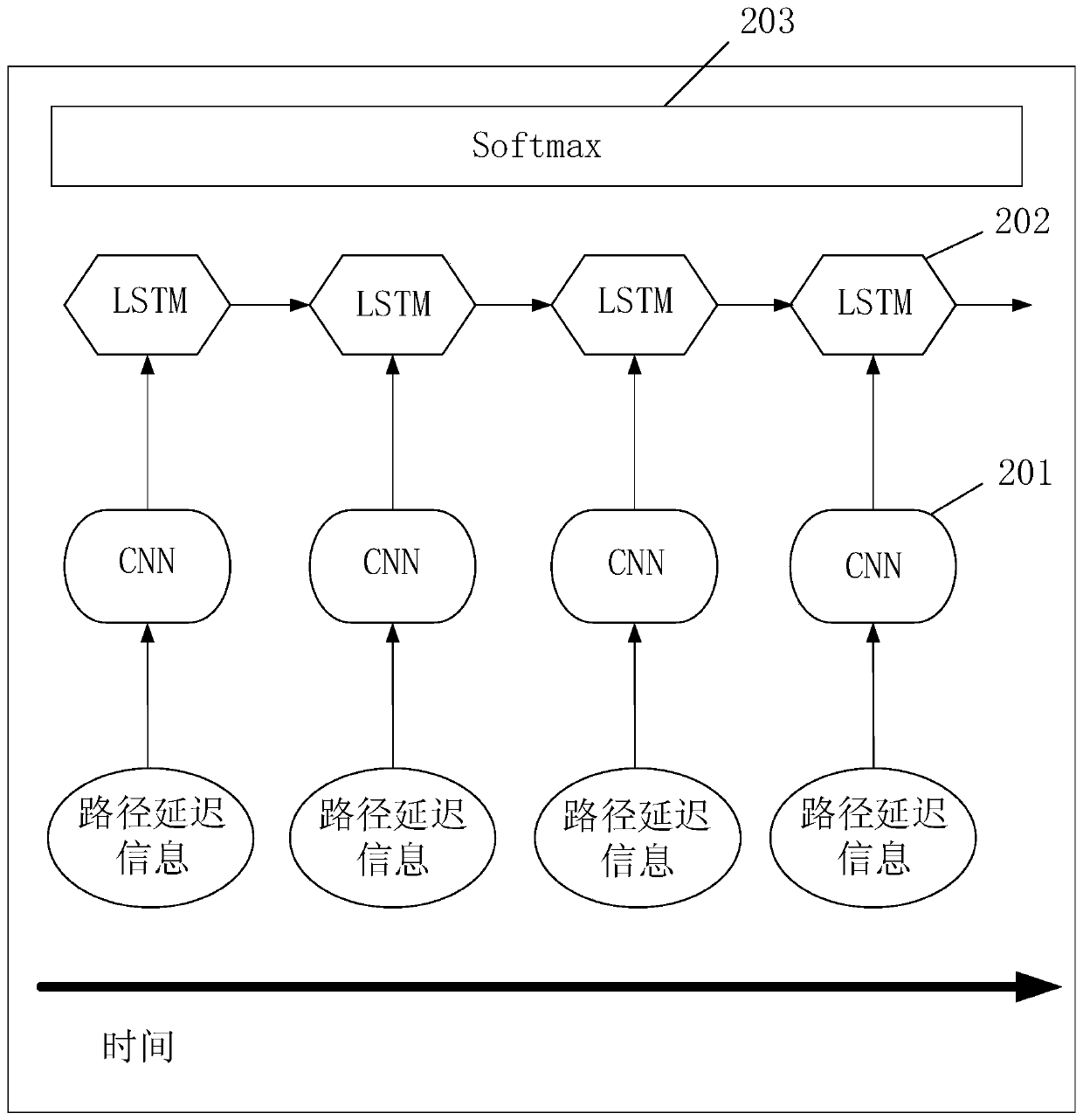
The invention provides a hardware Trojan horse detection method and device. The method comprises the following steps: sampling path delay information of positive and negative sample chips, and constructing a path delay information data set of the positive and negative sample chips; performing path delay information sampling on the chip to be tested, and constructing a path delay information data set of the chip to be tested; sending the positive and negative sample chip path delay information data set into a to-be-trained neural network for training to obtain a neural network hardware Trojan horse detector; sending the path delay information data set of the chip to be tested into the neural network hardware Trojan detector, and extracting spatial structure characteristics of the path delaydata of the chip to be tested; taking the spatial structure characteristics of the path delay data of the chip to be tested as a time sequence, sending the time sequence into a neural network, and extracting the time sequence characteristics of the path delay data of the chip to be tested; and sending the time sequence characteristics of the path delay data of the chip to be tested to a classifier network, and judging whether the chip to be tested is infected with the hardware Trojan horse or not and which hardware Trojan horse is infected.
Owner:XIDIAN UNIV
A hardware Trojan horse detection optimization method based on EMD noise reduction data preprocessing
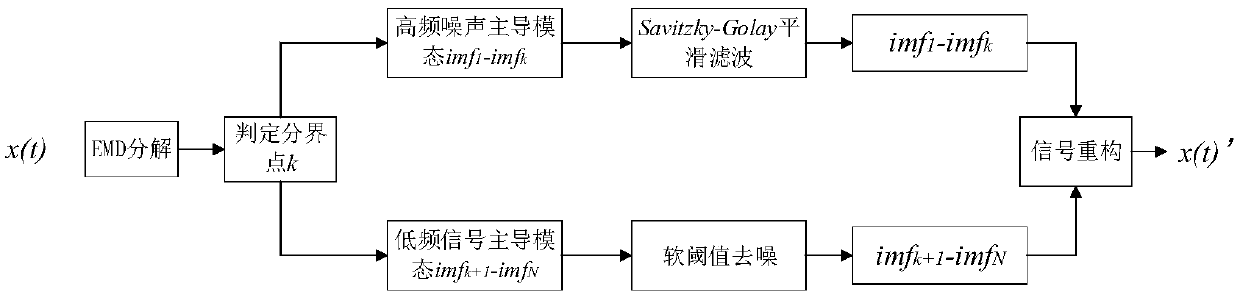
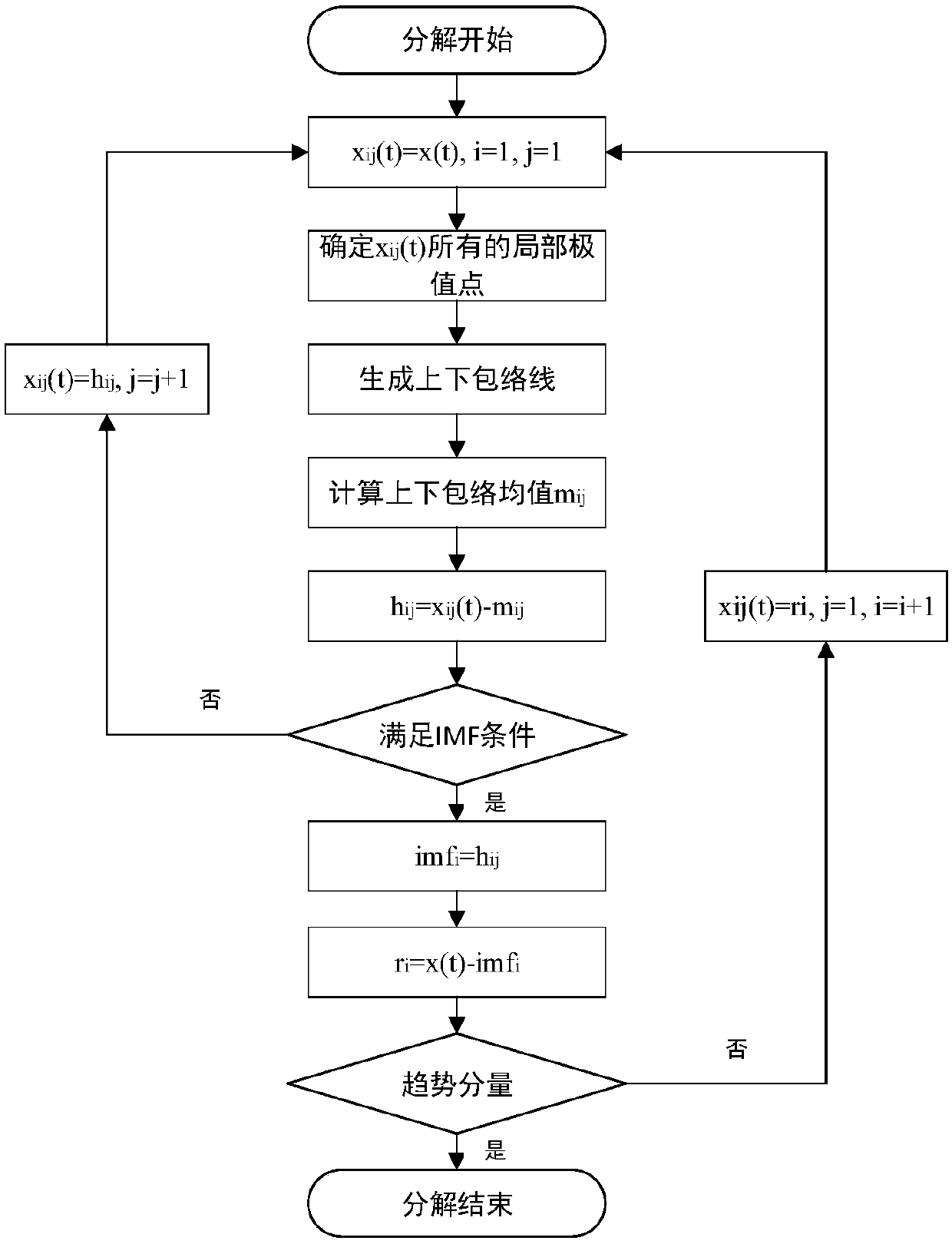
PendingCN109598152AAdaptableKeep useful informationInternal/peripheral component protectionDemarcation pointChannel data
The invention relates to the technical field of integrated circuit credibility, and provides a hardware Trojan horse detection optimization method, which not only can better keep the smoothness characteristic of a low-frequency part of data, but also can keep the useful information of a high-frequency part of side channel data to a greater extent, thereby effectively keeping the characteristics ofa hardware Trojan horse and further improving the hardware Trojan horse detection precision. Therefore, the technical scheme adopted by the invention is as follows: the hardware Trojan horse detection optimization method based on EMD noise reduction data preprocessing Includes: determining a demarcation point of the noise dominant mode and the signal dominant mode by combining the characteristics of the autocorrelation function of each intrinsic mode function IMF, performing noise reduction on the high-frequency mode function by adopting a threshold selection denoising method, and performingSavitzky-on the low-frequency mode function by adopting a Savitzky-method; and filtering by using a Golay filter, reconstructing by using an IMF component to obtain noise-reduced data, and judging the hardware Trojan horse by using a Mahalanobis distance. The method is mainly applied to the trustworthiness detection occasion of the integrated circuit.
Owner:TIANJIN UNIV
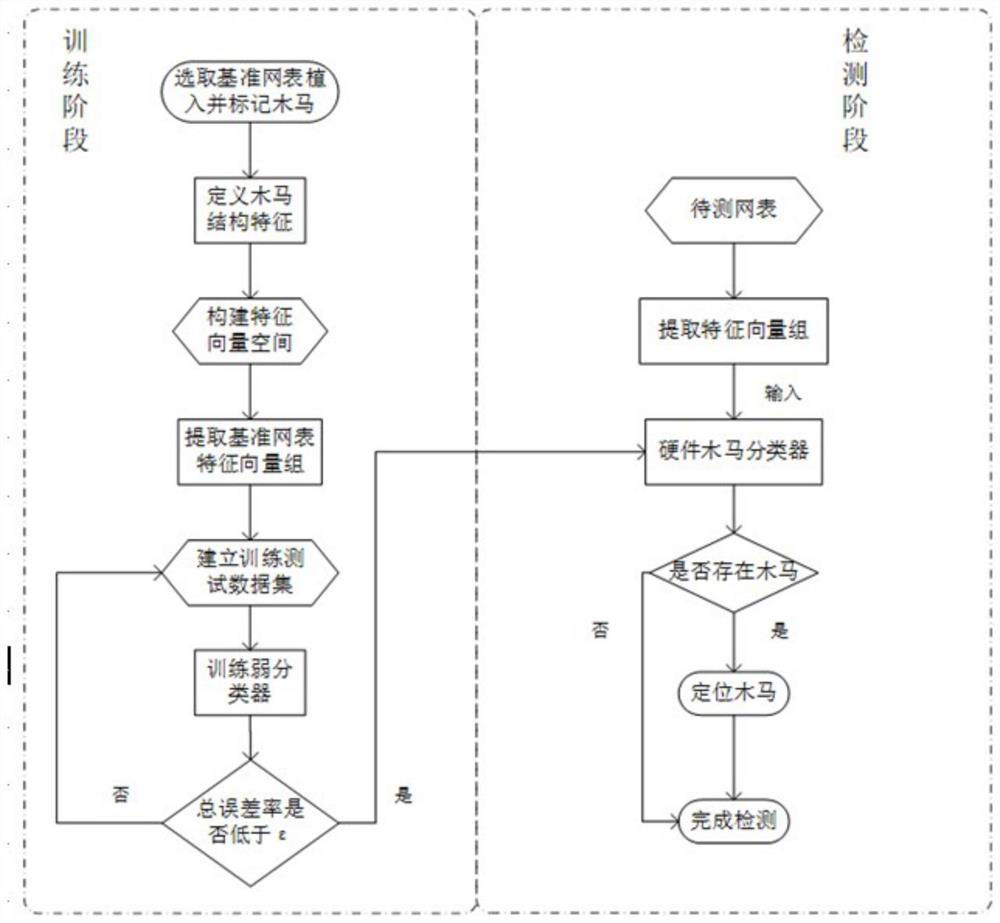
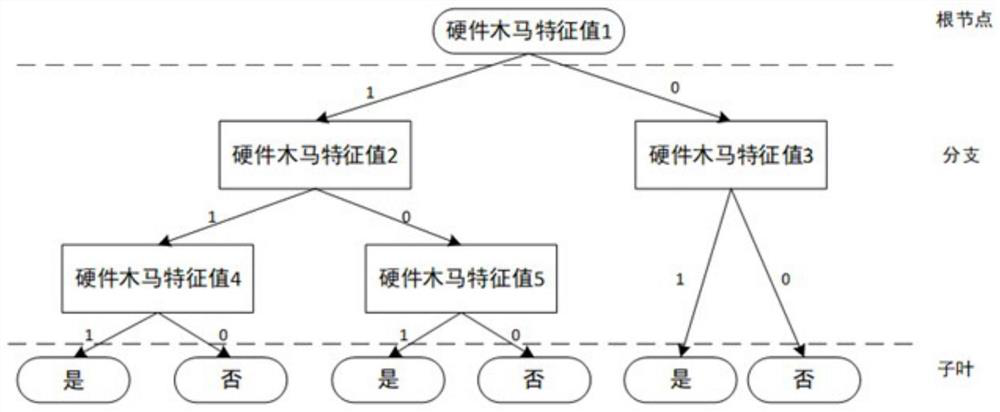
Hardware Trojan horse detection method based on Adaboost algorithm
ActiveCN112231775AShorten the timeReduce resource requirementsInternal/peripheral component protectionPlatform integrity maintainanceFeature vectorData set
The invention discloses a hardware Trojan horse detection method based on Adaboost. The method comprises steps of defining the gate-level structure features of hardware Trojan horses, calibrating thepositions of all hardware Trojan horses in a netlist and the Trojan horse feature vectors of gate-level elements, building a training and testing data set, and building and training an Adaboost hardware Trojan horse detection model according to the data set. When the error rate of the model is lower than a set threshold value, the model can be used for detecting hardware Trojan horses in the circuit netlist to be detected.
Owner:TIANJIN UNIV
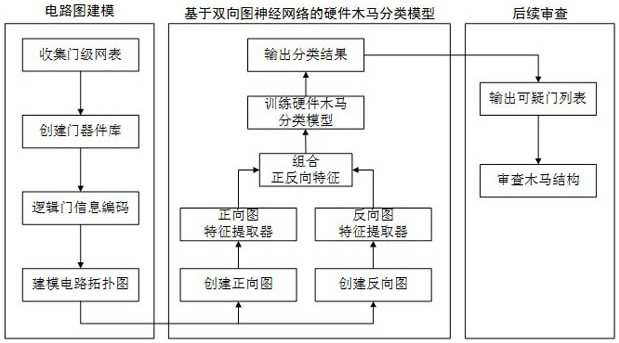
Hardware Trojan horse detection method and system based on bidirectional graph convolutional neural network
PendingCN114065307ARetain structural informationGet rid of the burdenCharacter and pattern recognitionInternal/peripheral component protectionAlgorithmEngineering
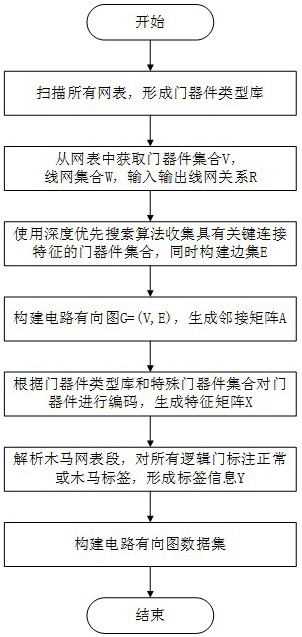
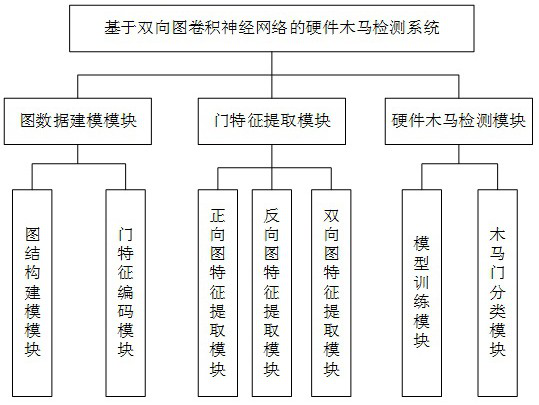
The invention relates to a hardware Trojan horse detection method and system based on a bidirectional graph convolutional neural network. The method comprises the following steps of firstly, preprocessing a netlist file, creating a corresponding directed graph representation, encoding gate device information as a feature representation X, and constructing circuit directed graph data, respectively creating a forward circuit diagram for describing a circuit signal propagation structure and a reverse circuit diagram for describing a circuit signal dispersion structure, respectively constructing corresponding graph neural network feature extractors to extract structural features, and combining the structural features into final gate device features, constructing a multi-layer perceptron classification model, forming a hardware Trojan horse gate classification model by the multi-layer perceptron classification model and a graph neural network feature extractor, and learning model parameters by using a weighted cross entropy loss function to obtain a trained hardware Trojan horse gate classification model, and converting a to-be-detected netlist into a directed graph, inputting the directed graph into the trained hardware Trojan horse gate classification model for detection, and outputting a suspicious door device list. According to the method, the exit-level hardware Trojan horse can be effectively detected.
Owner:FUZHOU UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com