Integrated circuit hardware Trojan horse detection method and system
A hardware Trojan detection and integrated circuit technology, applied in electronic circuit testing and other directions, can solve the problems of difficult to guarantee recognition accuracy and low efficiency, and achieve the effect of improving recognition ability and efficiency, improving resolution, and improving feature extraction ability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The specific implementation of the integrated circuit hardware Trojan horse detection method and system of the present invention will be described in detail below in conjunction with the accompanying drawings.
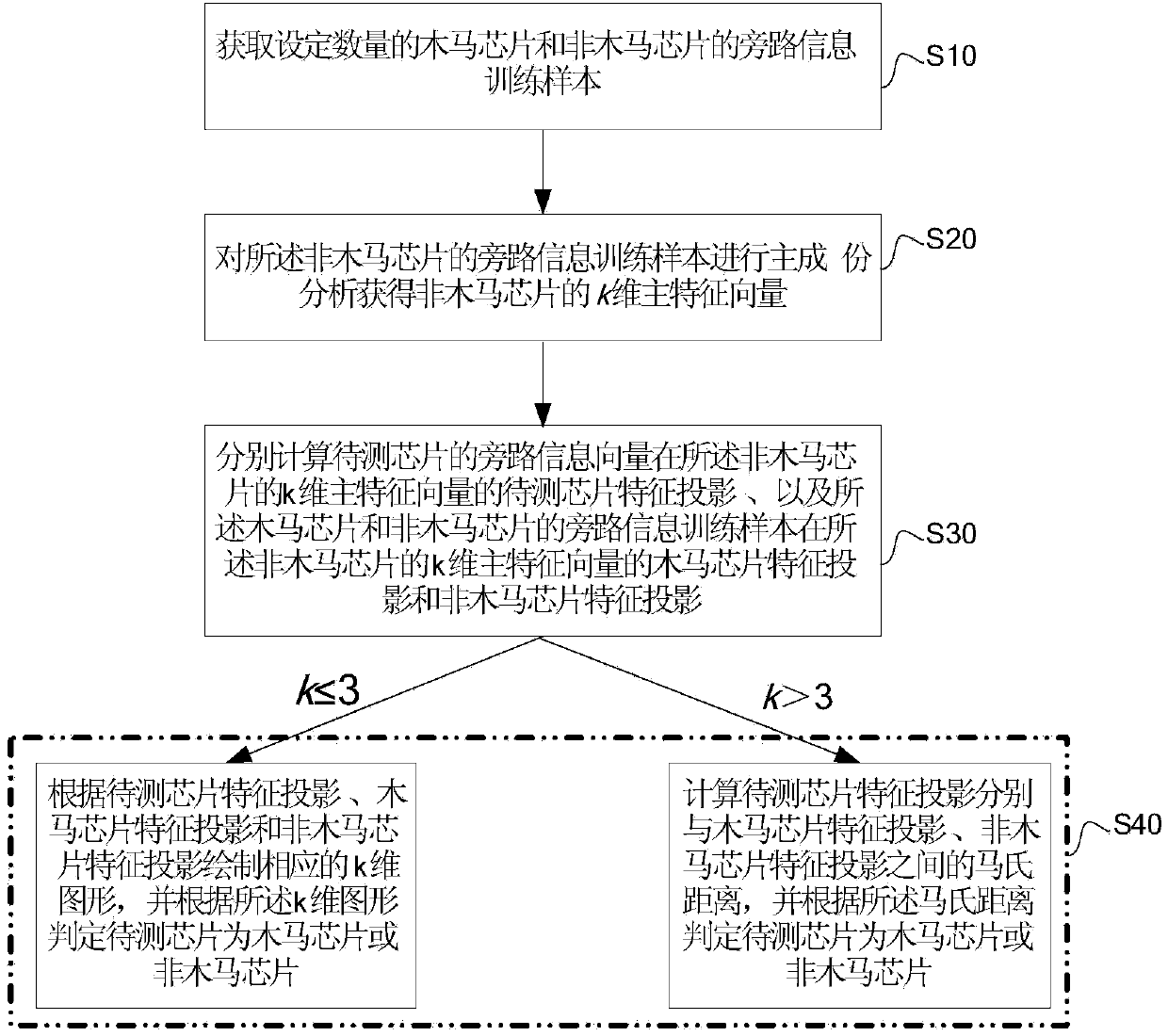
[0029] see figure 1 as shown, figure 1 It is a flowchart of an integrated circuit hardware Trojan horse detection method of an embodiment, including the following steps:
[0030] Step S10, acquiring bypass information training samples of a set number of Trojan horse chips and non-Trojan horse chips.
[0031] In one embodiment, a set number of bypass information training samples of Trojan horse chips and non-Trojan horse chips can be obtained through reverse engineering.
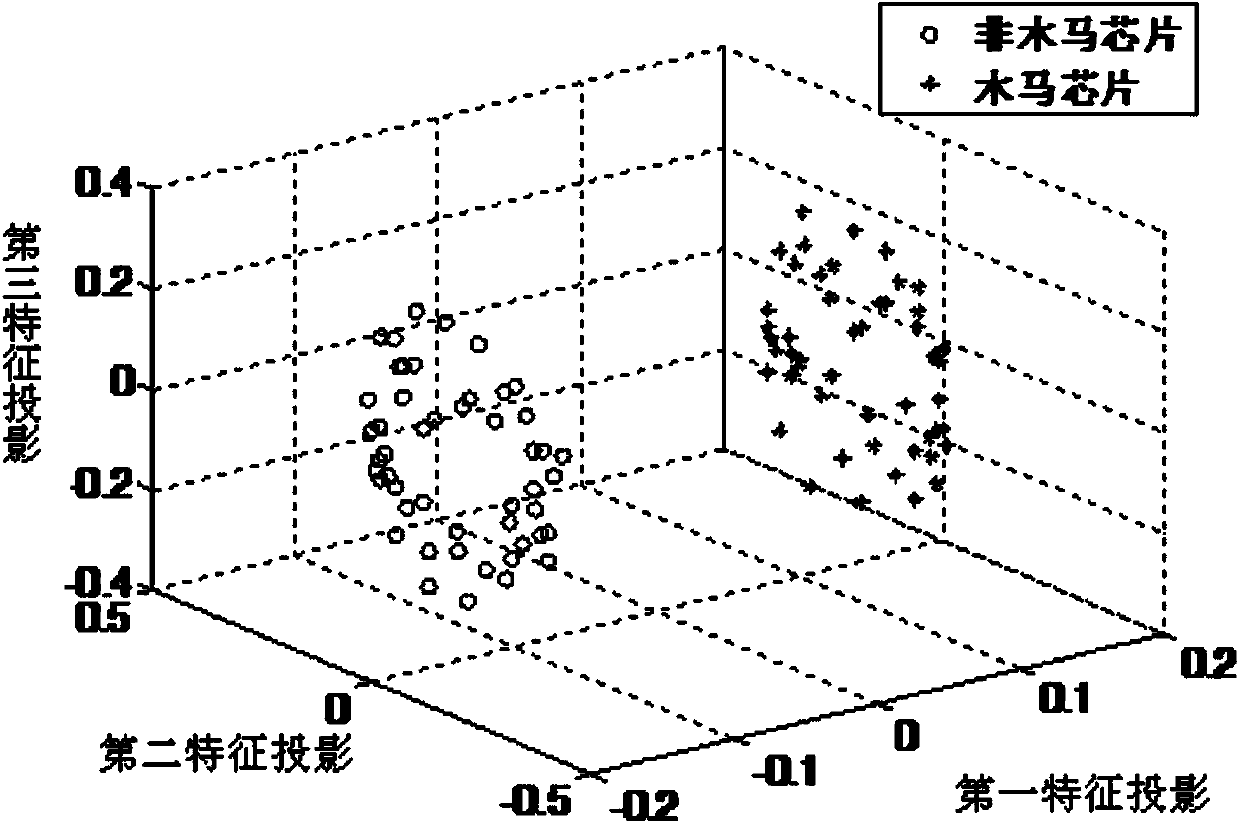
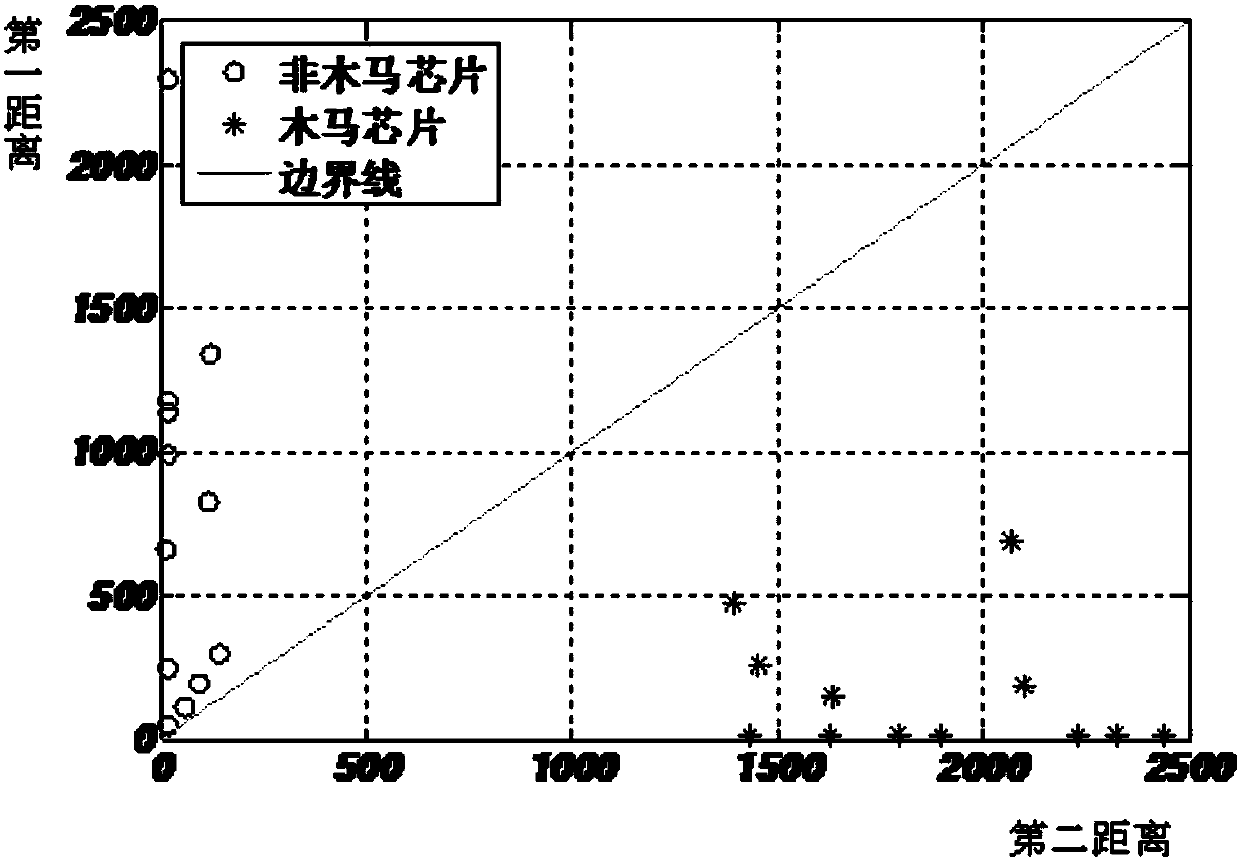
[0032] Step S20, performing principal component analysis on the bypass information training samples of the non-Trojan chip to obtain a k-dimensional principal feature vector of the non-Trojan chip.
[0033] In one embodiment, the k-dimensional principal eigenvector of the non-Trojan chip byp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com