Patents
Literature
5270 results about "System usage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
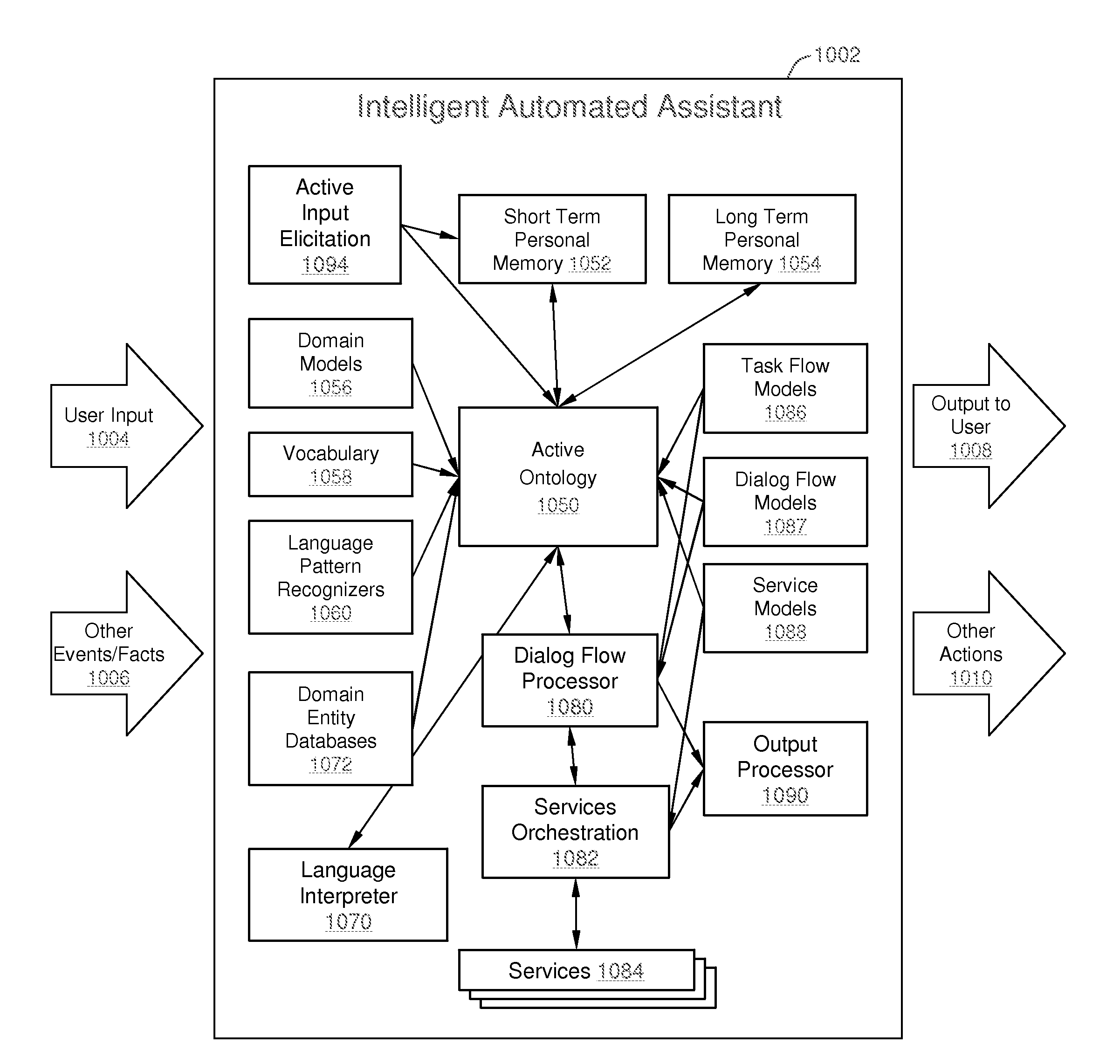
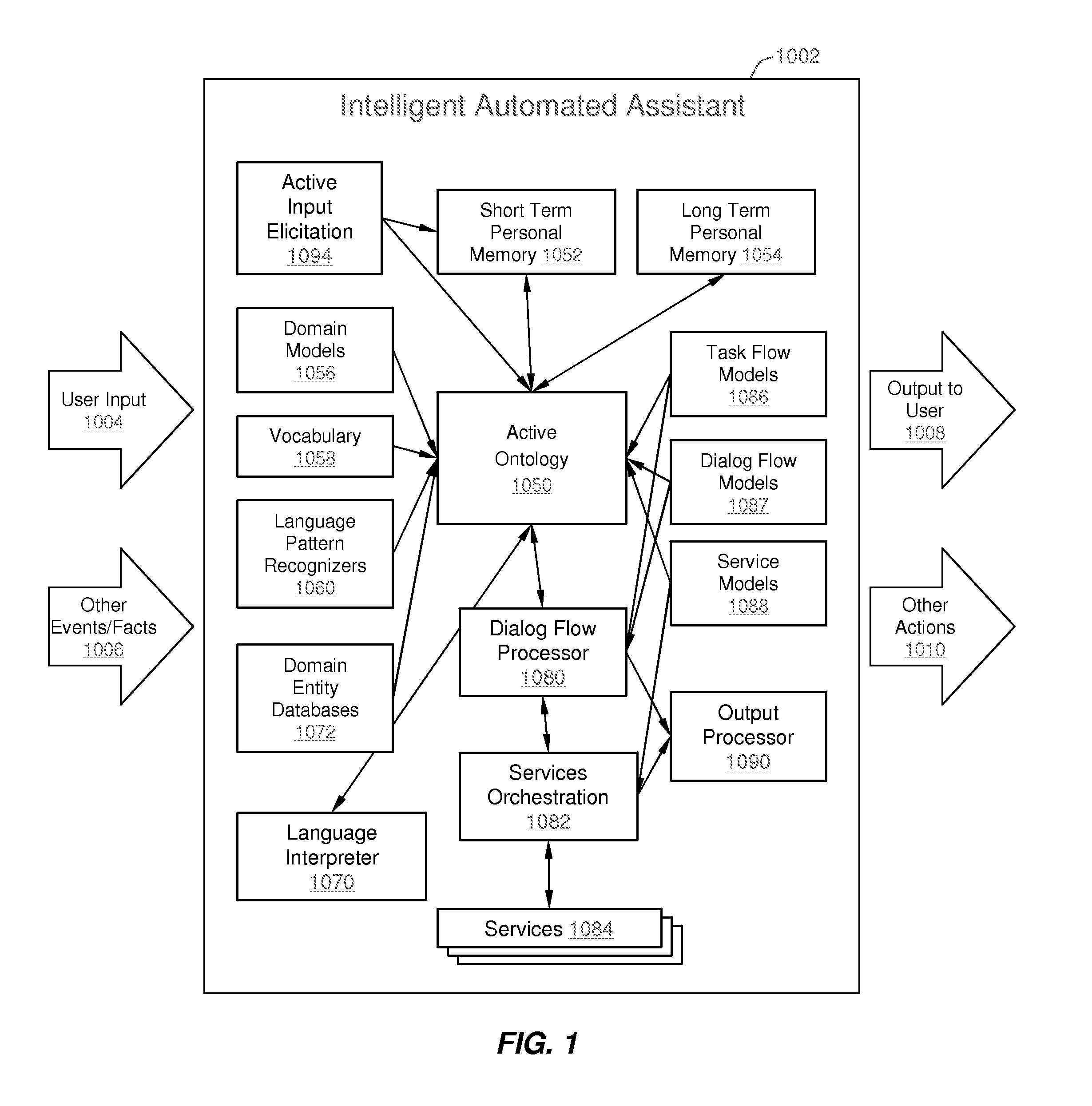
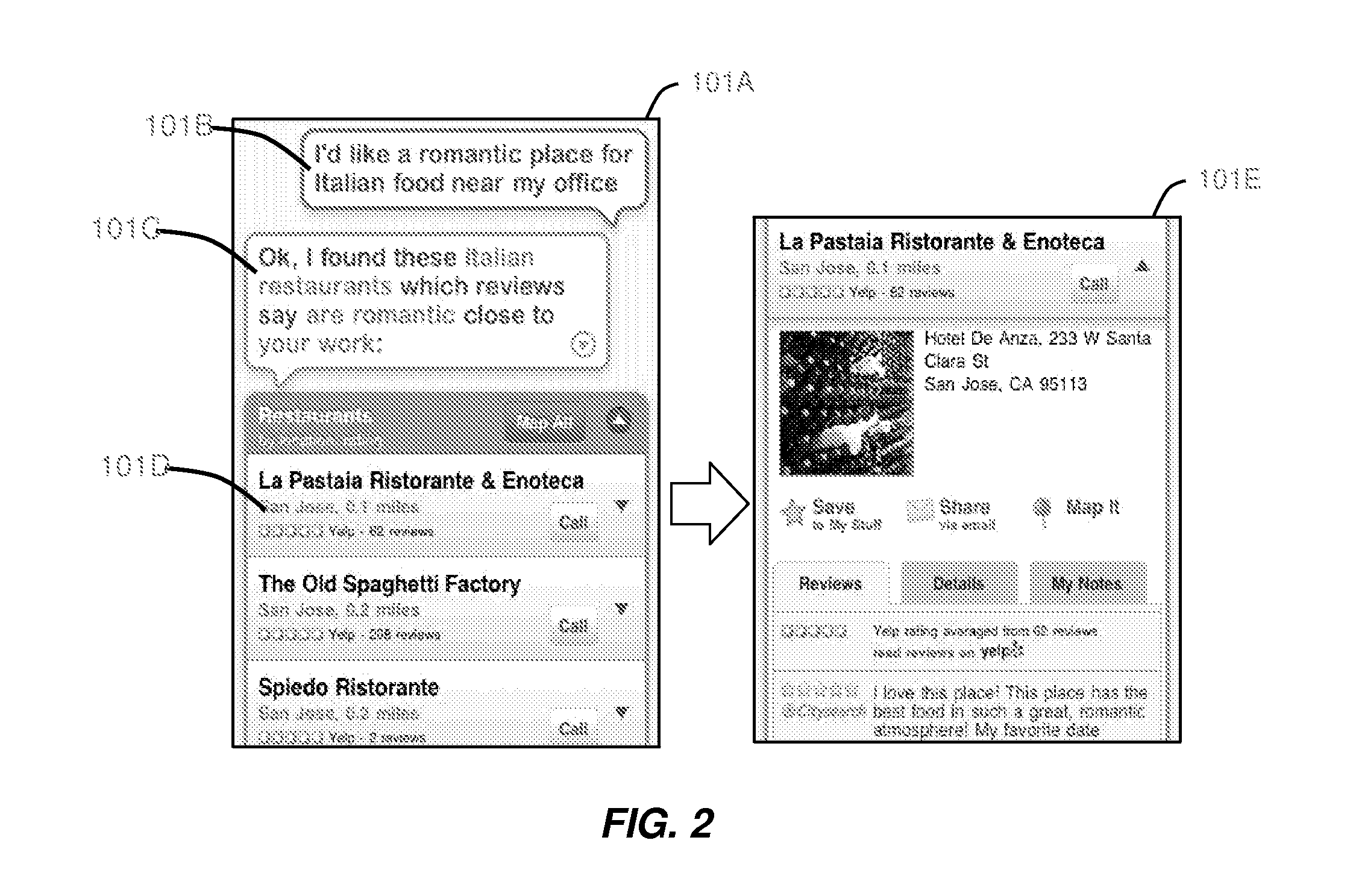
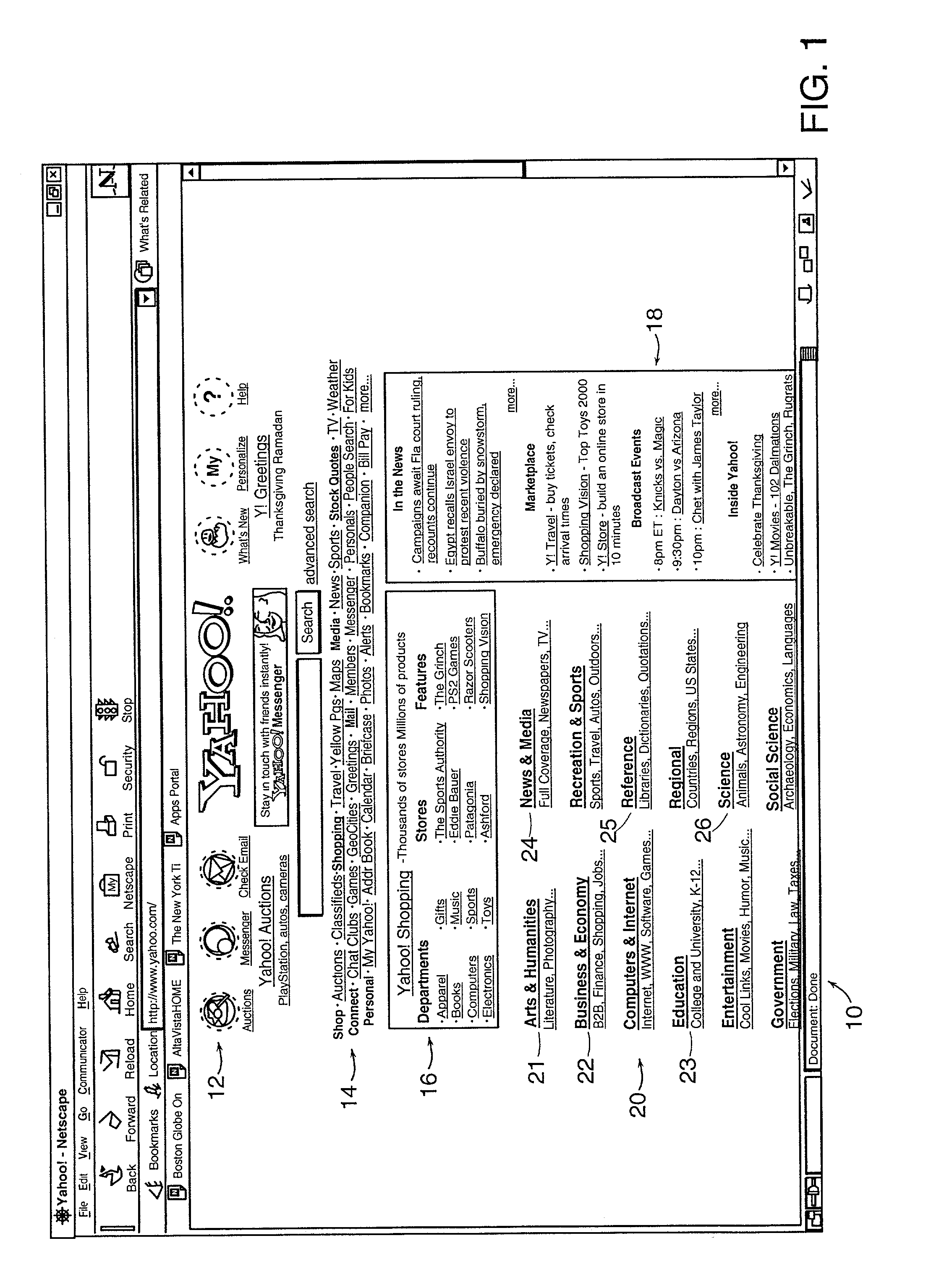
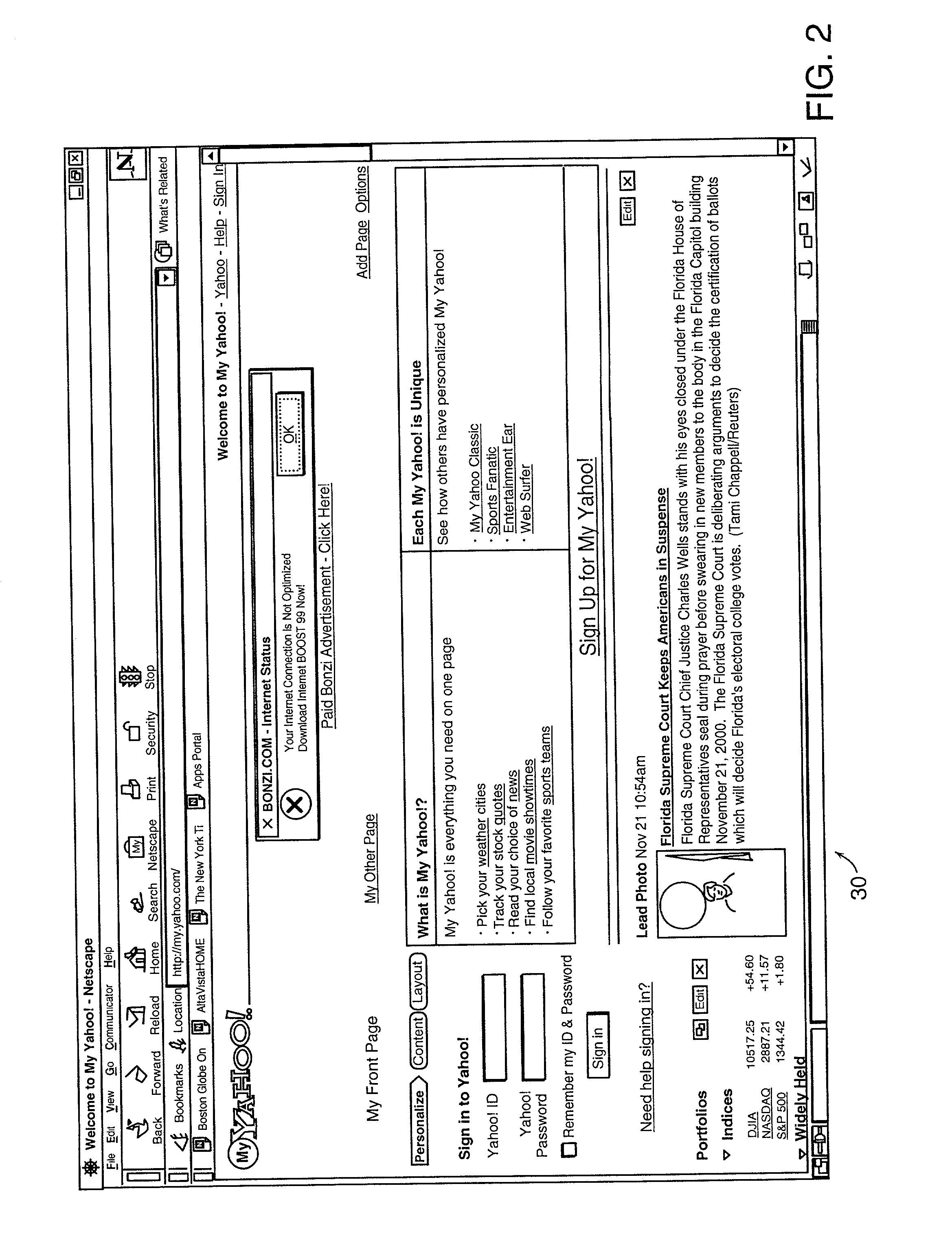
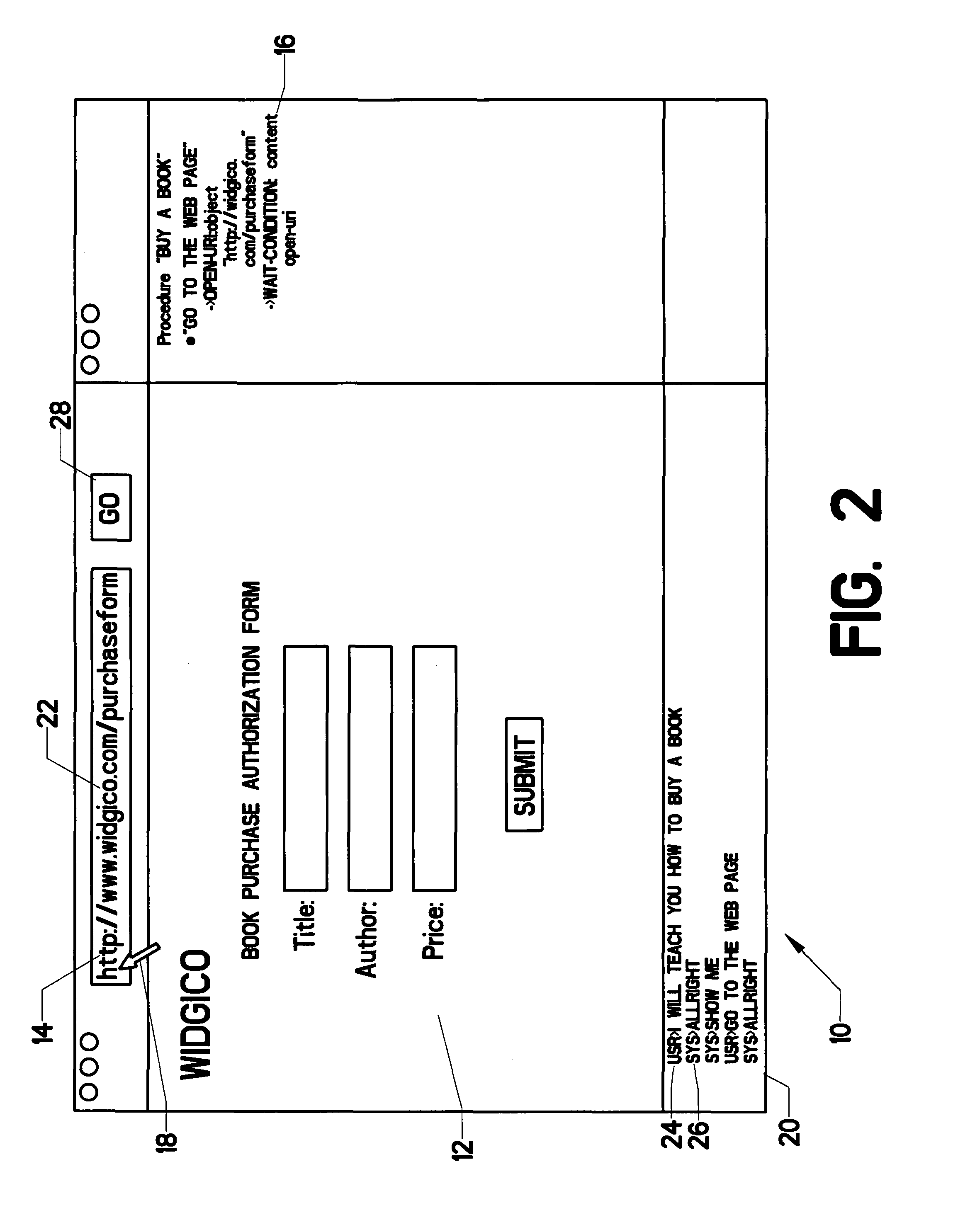
Intelligent Automated Assistant
ActiveUS20120016678A1Improve user interactionPromote effective engagementNatural language translationSemantic analysisService provisionSystem usage
An intelligent automated assistant system engages with the user in an integrated, conversational manner using natural language dialog, and invokes external services when appropriate to obtain information or perform various actions. The system can be implemented using any of a number of different platforms, such as the web, email, smartphone, and the like, or any combination thereof. In one embodiment, the system is based on sets of interrelated domains and tasks, and employs additional functionally powered by external services with which the system can interact.
Owner:APPLE INC
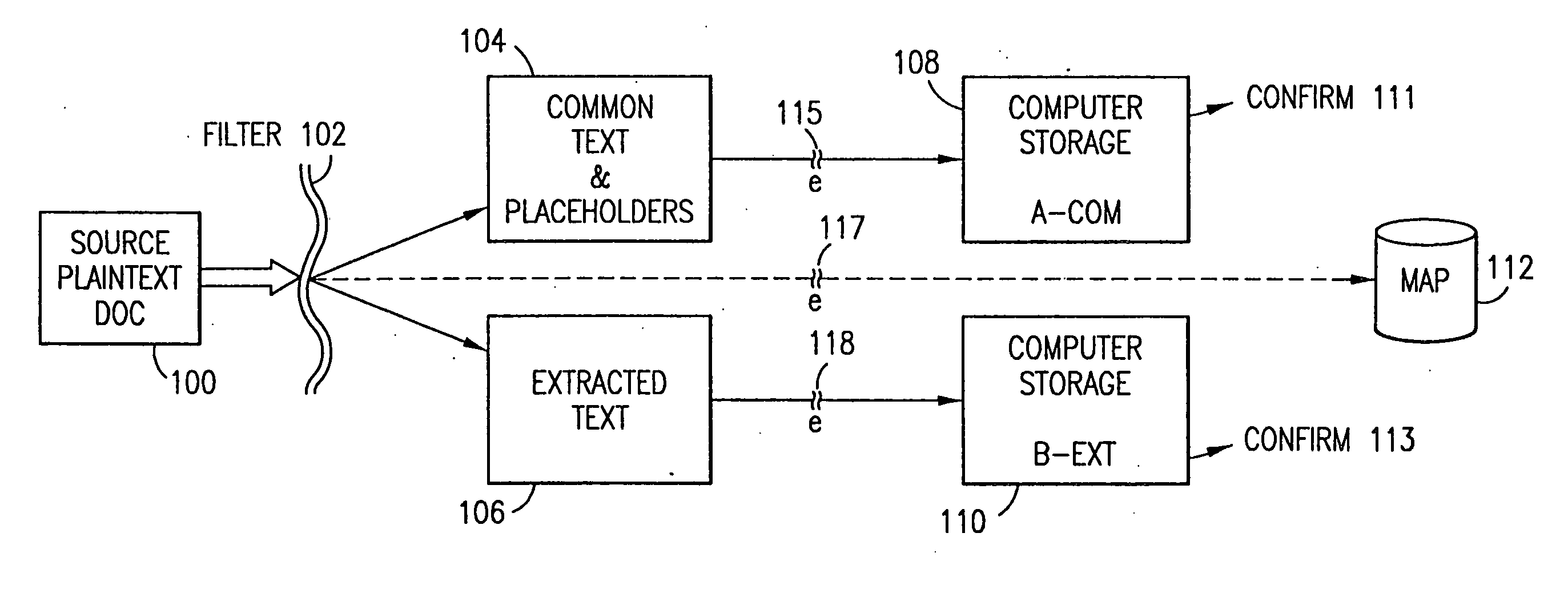
Data security system and method with editor
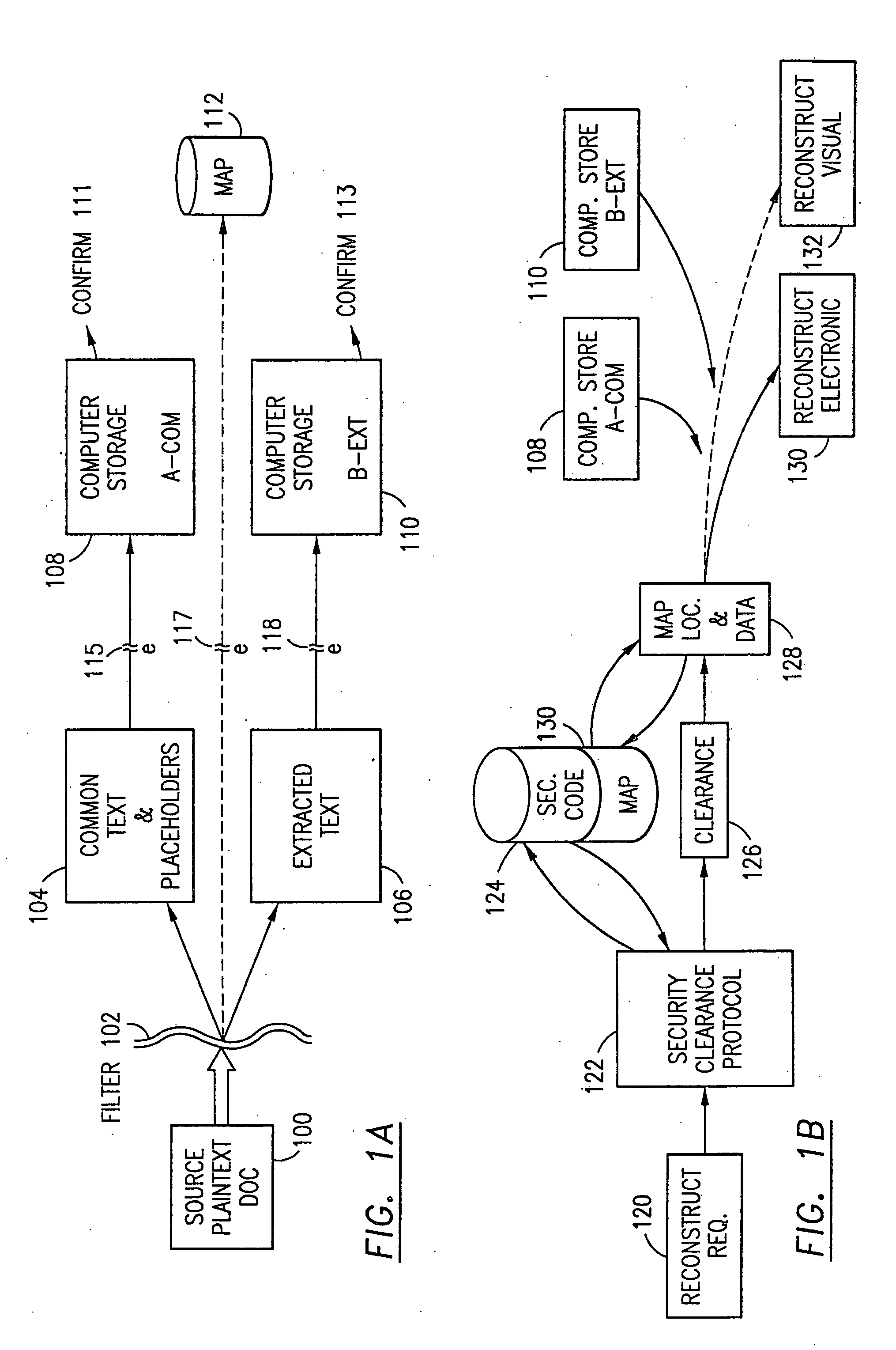
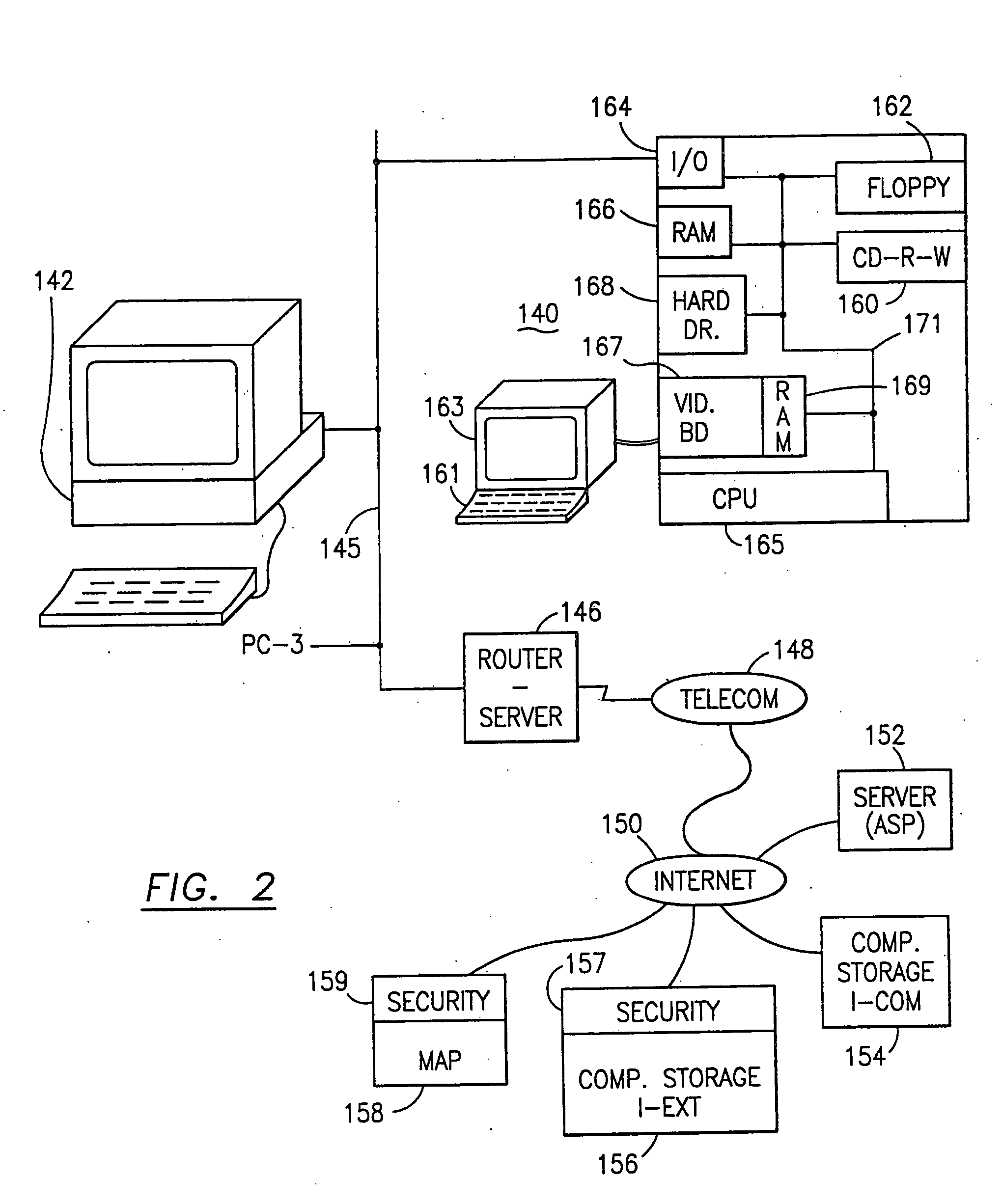
ActiveUS20050132070A1Ease overhead performanceHigh overhead performanceDigital data processing detailsTelephonic communicationFiltrationPaper document
The method, program and system secures sensitive data / objects found in a data source document with an editor. The simple editor identifies and displays, in situ, the sensitive words / objects per each security level. Level tags are inserted and adjunctive words / objects are marked / displayed per the level's protocol. The precursor document is processed to extract sensitive and adjunctive words / objects. The stripped data is either separately stored or partial versions of the secured document are stored per protocol. A comprehensive editor secures content data and meta data contained in a data document object model (DOM). The editor maps the source document root, branch and leaf components as binary files populated with content data and meta data. Security introns, earlier identified based upon the level's informational attributes, are excluded. Security exons are copied from the source content and meta data binary files into a security safe document (template). Filtration, extraction, dispersal and storage follow.
Owner:DIGITAL DOORS
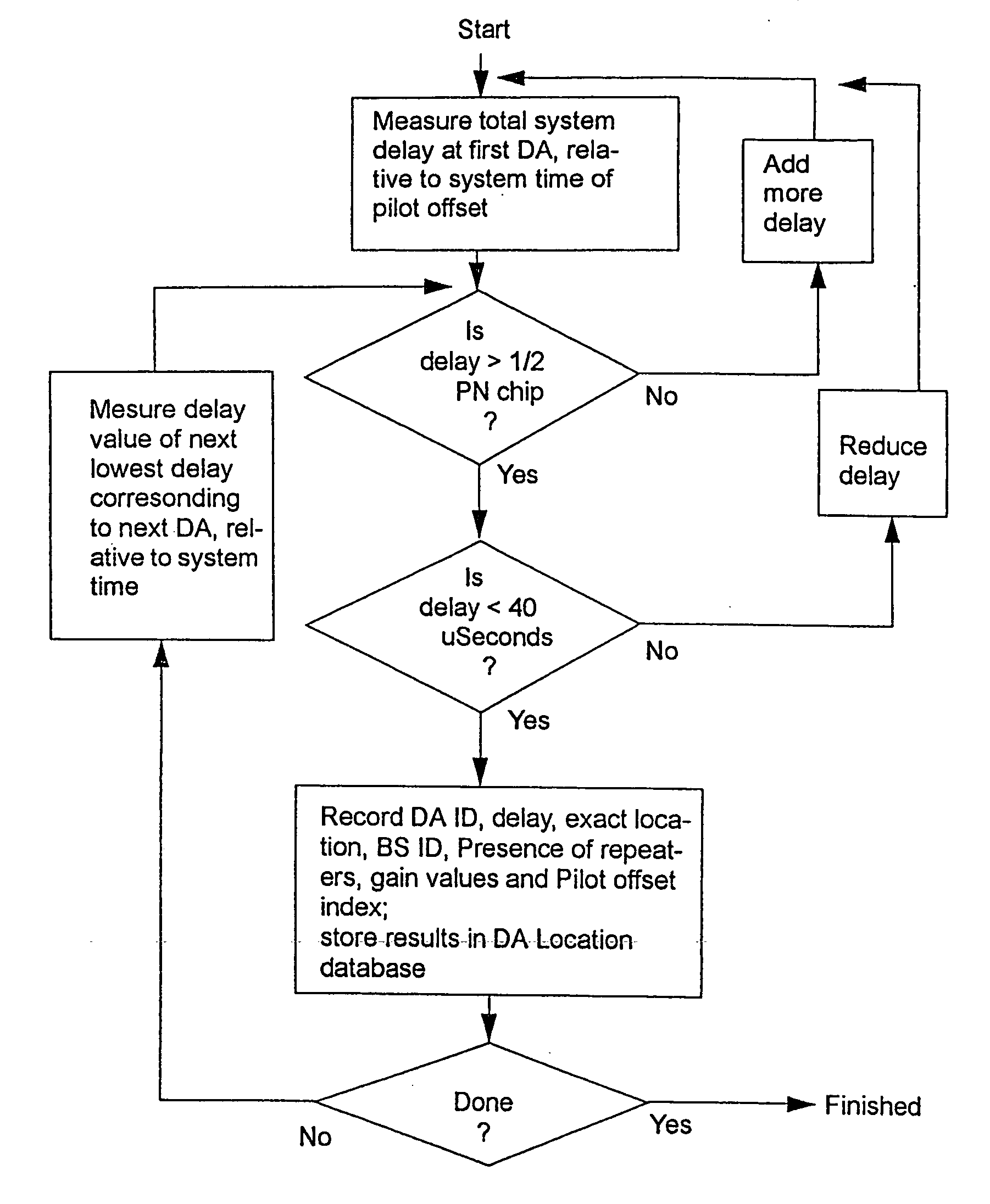
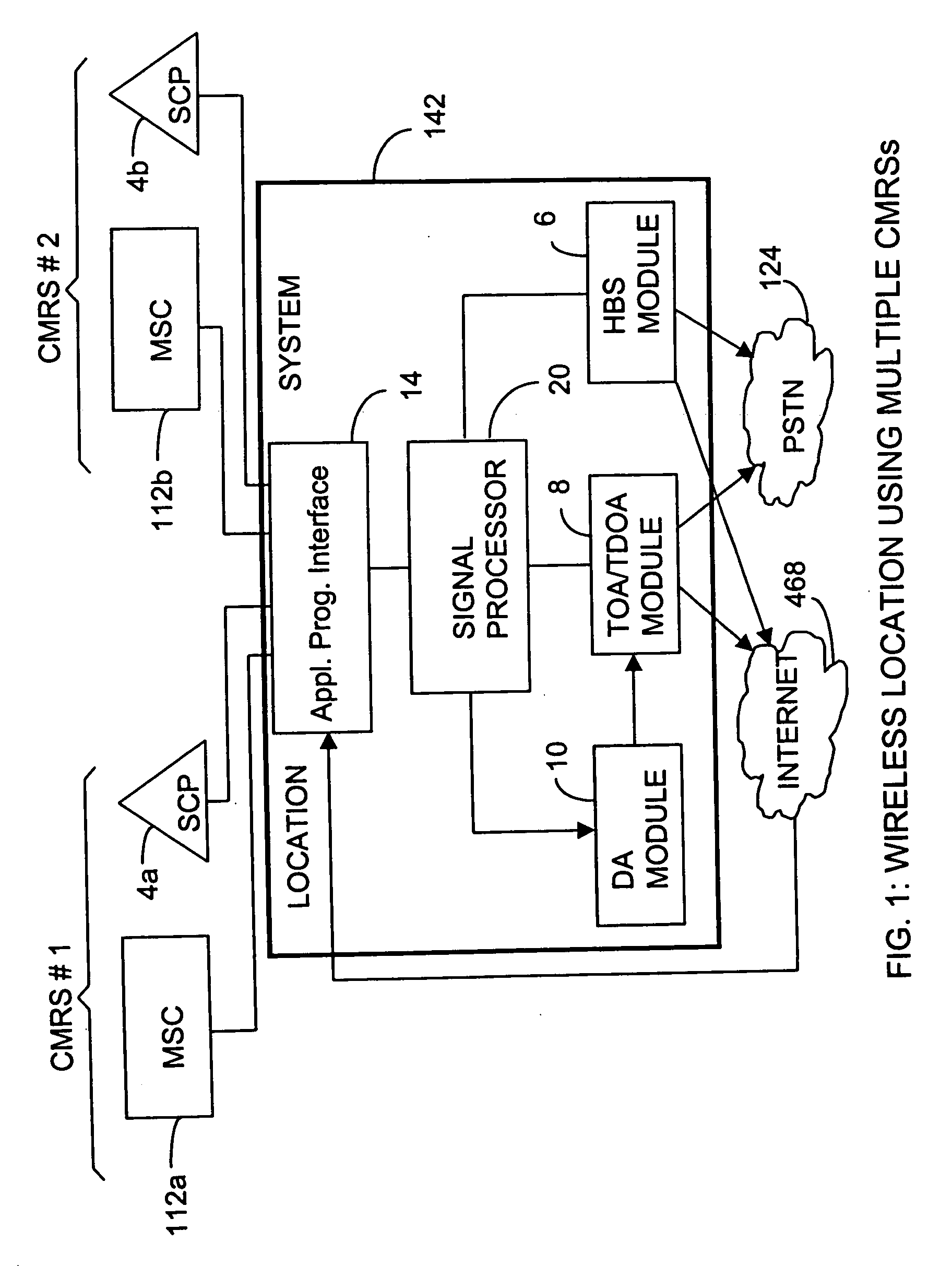
Wireless location using multiple location estimators
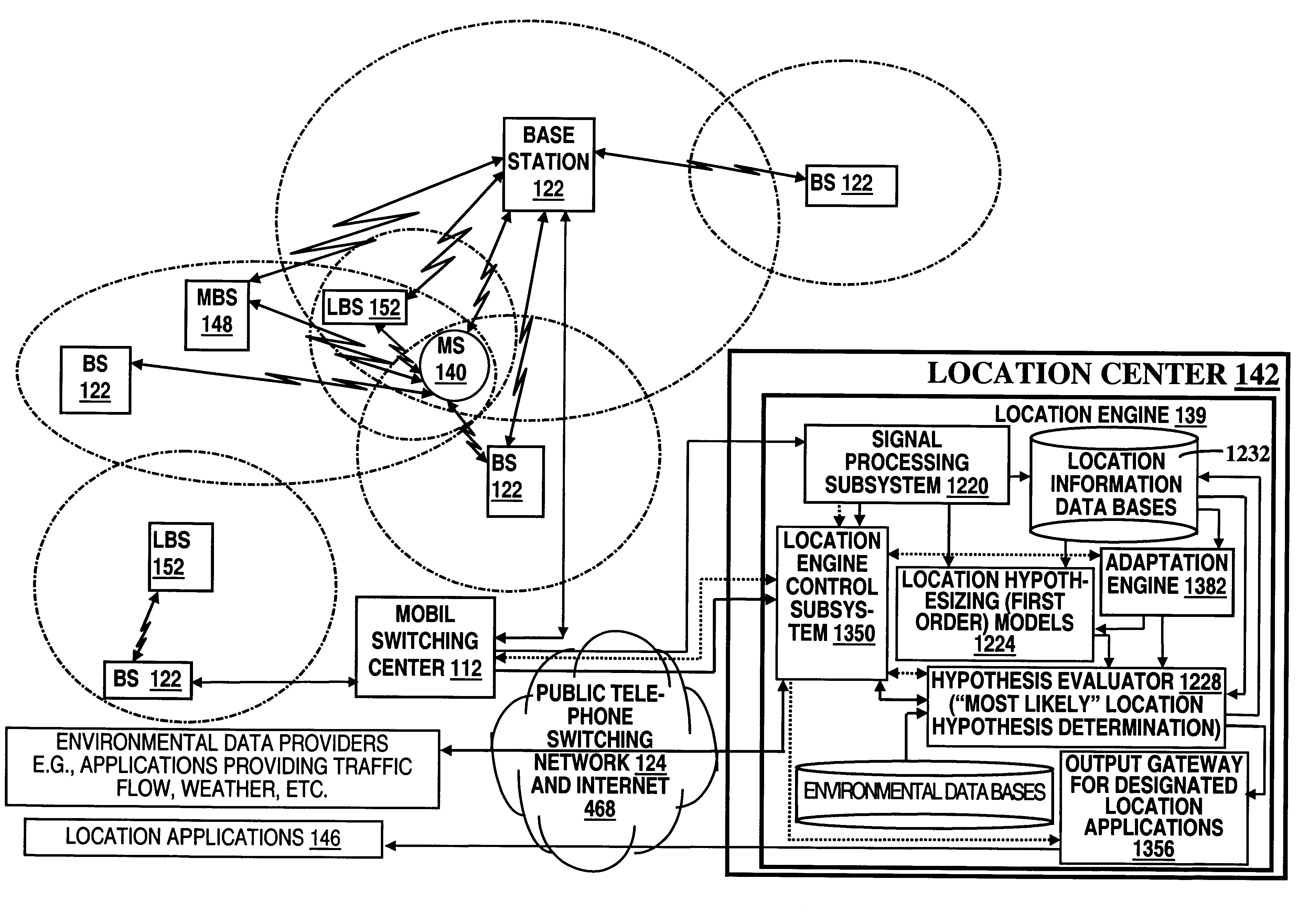
InactiveUS6249252B1Effectively and straightforwardly resolvedAmbiguity and conflictDirection finders using radio wavesBeacon systems using radio wavesTerrainHeuristic
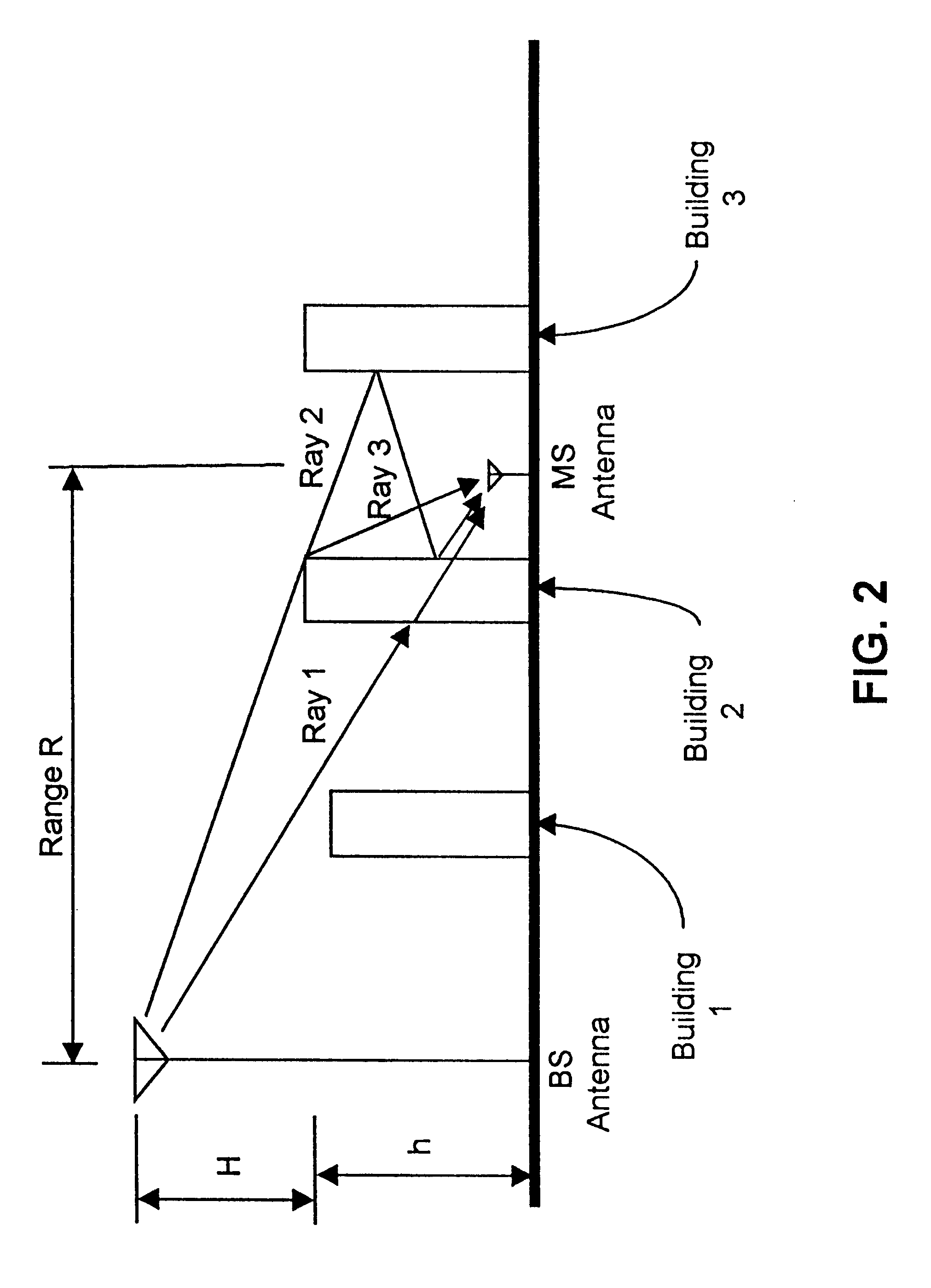
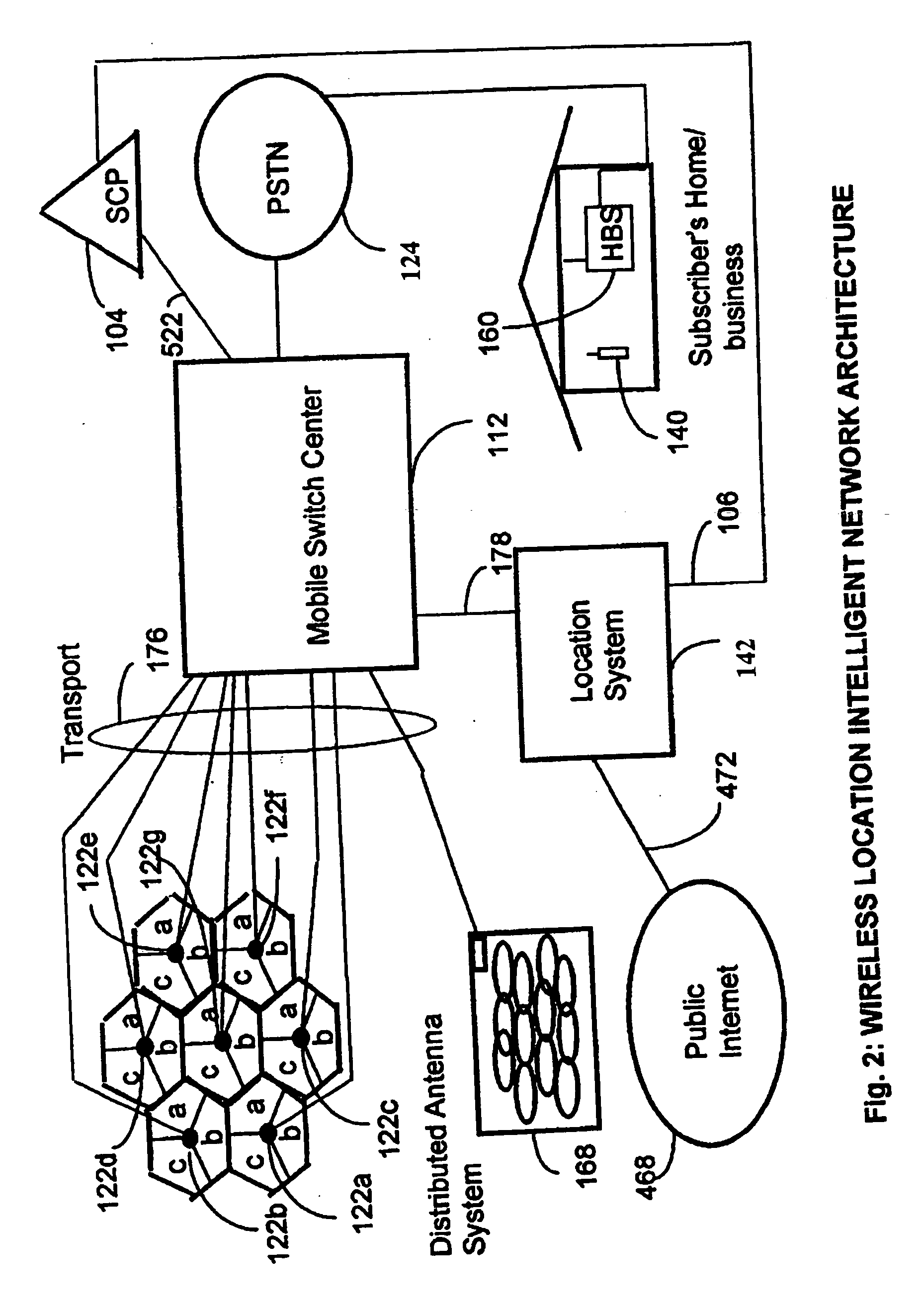
A location system is disclosed for commercial wireless telecommunication infrastructures. The system is an end-to-end solution having one or more location centers for outputting requested locations of commercially available handsets or mobile stations (MS) based on, e.g., CDMA, AMPS, NAMPS or TDMA communication standards, for processing both local MS location requests and more global MS location requests via, e.g., Internet communication between a distributed network of location centers. The system uses a plurality of MS locating technologies including those based on: (1) two-way TOA and TDOA; (2) pattern recognition; (3) distributed antenna provisioning; (5) GPS signals, (6) angle of arrival, (7) super resolution enhancements, and (8) supplemental information from various types of very low cost non-infrastructure base stations for communicating via a typical commercial wireless base station infrastructure or a public telephone switching network. Accordingly, the traditional MS location difficulties, such as multipath, poor location accuracy and poor coverage are alleviated via such technologies in combination with strategies for: (a) automatically adapting and calibrating system performance according to environmental and geographical changes; (b) automatically capturing location signal data for continual enhancement of a self-maintaining historical data base retaining predictive location signal data; (c) evaluating MS locations according to both heuristics and constraints related to, e.g., terrain, MS velocity and MS path extrapolation from tracking and (d) adjusting likely MS locations adaptively and statistically so that the system becomes progressively more comprehensive and accurate. Further, the system can be modularly configured for use in location signing environments ranging from urban, dense urban, suburban, rural, mountain to low traffic or isolated roadways. Accordingly, the system is useful for 911 emergency calls, tracking, routing, people and animal location including applications for confinement to and exclusion from certain areas.
Owner:TRACBEAM
Secure electronic content distribution on CDS and DVDs
InactiveUS6611812B2Key distribution for secure communicationDigital data processing detailsDigital contentComputer terminal
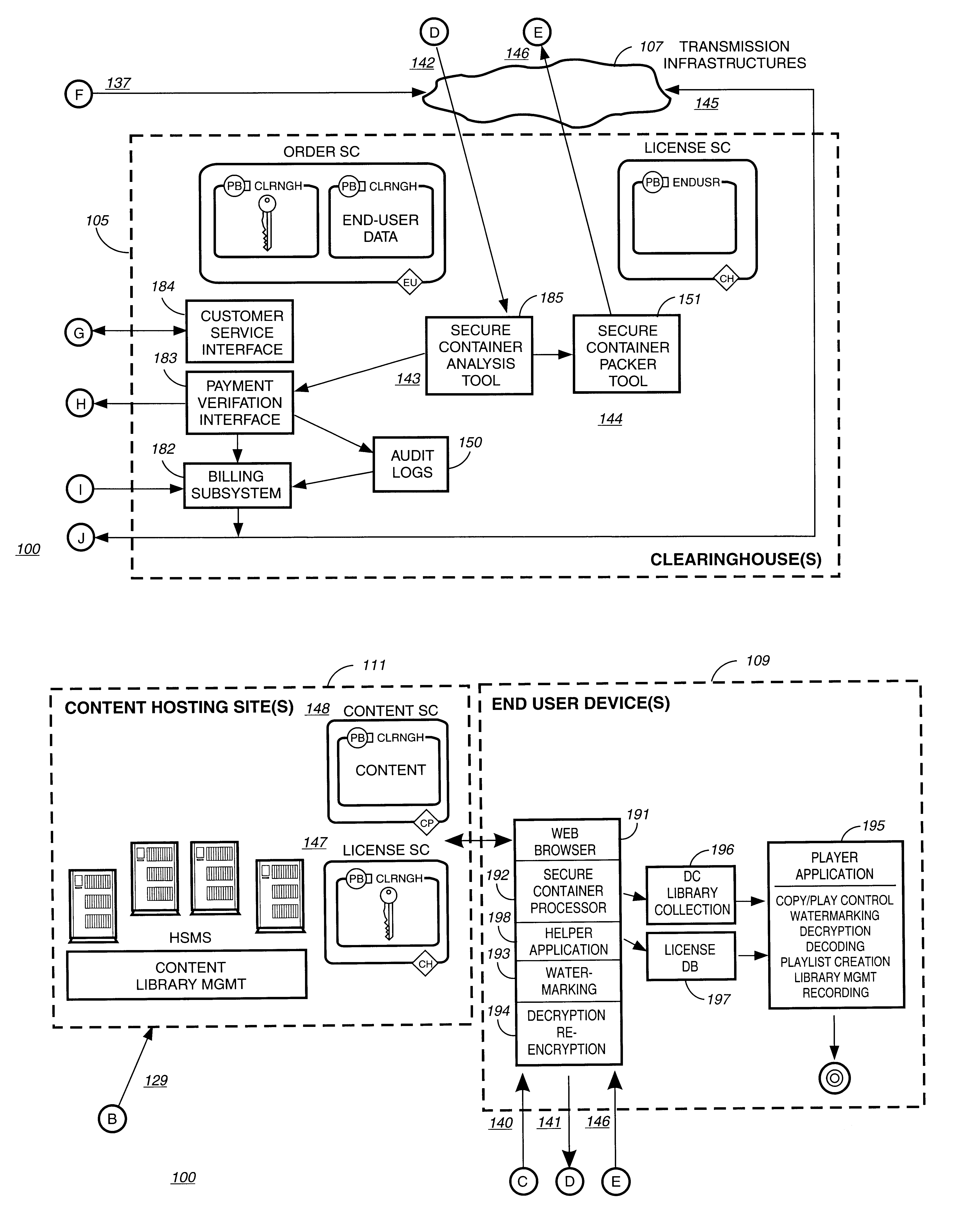
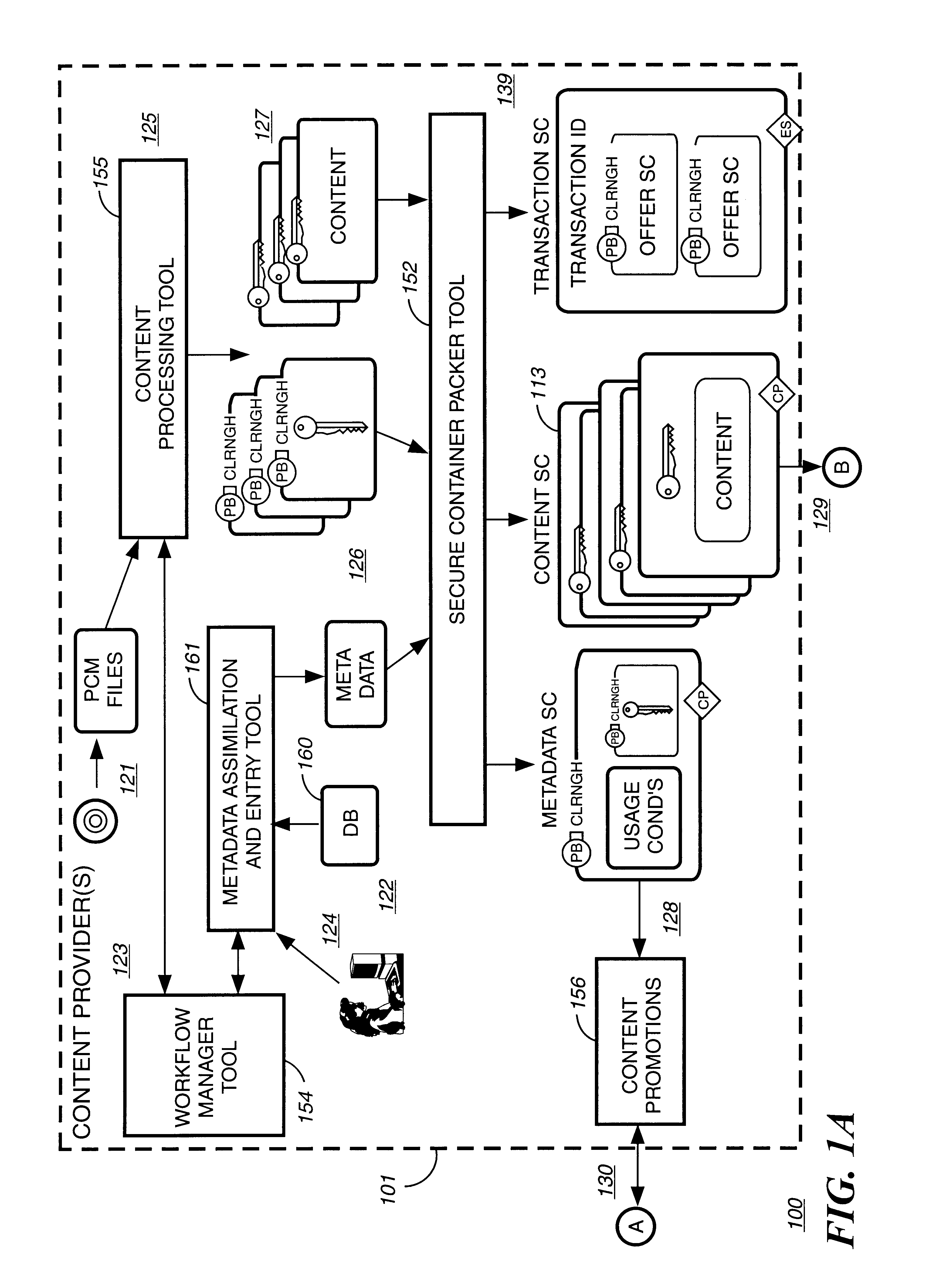
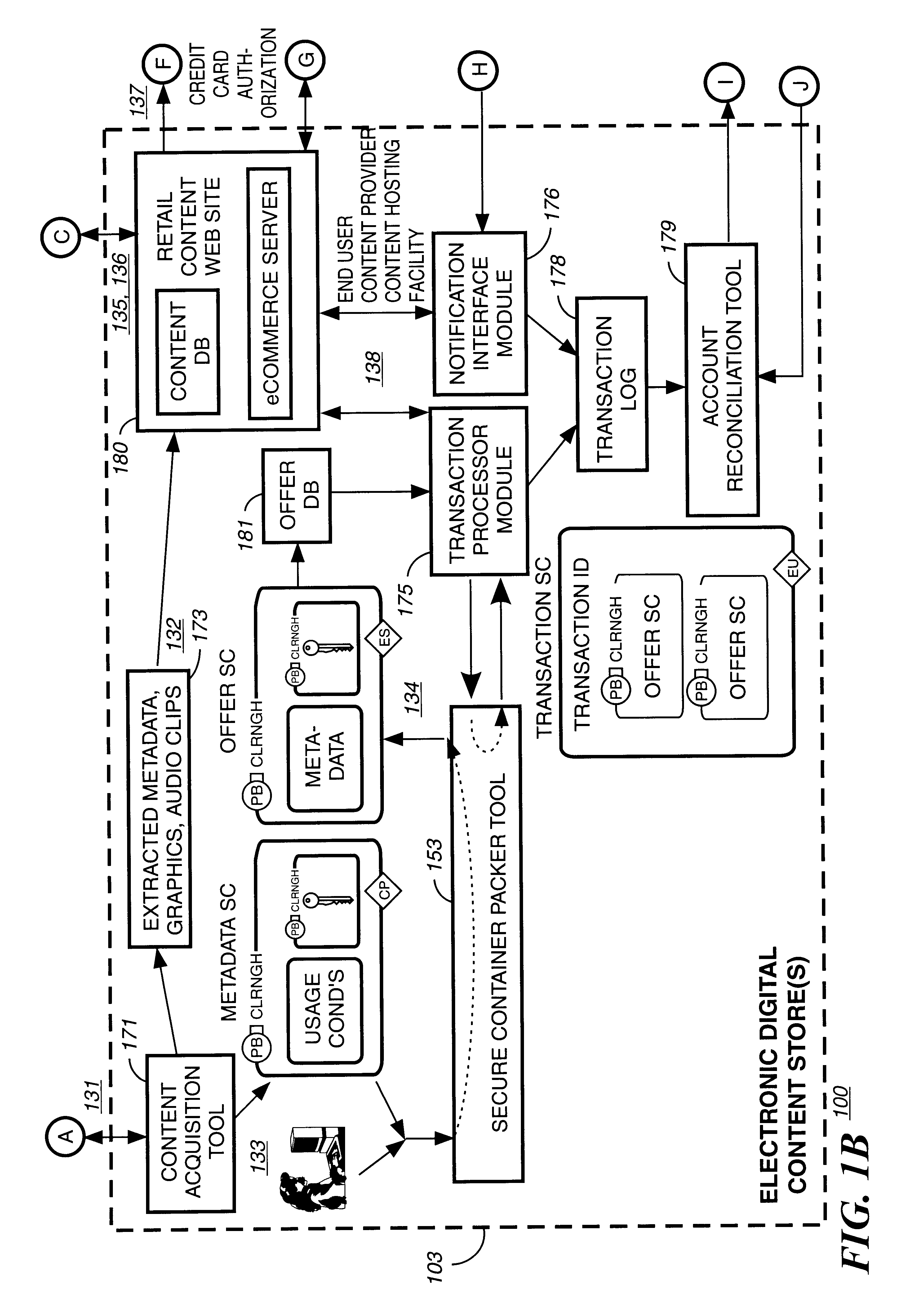
A method to delivery encrypted digital content to a end user system for playing the content comprising the steps of: reading from a computer readable medium metadata which has previously associated with the content. A user selects from the metadata associated content to decrypt and the end user system establishes a secure connection with an authorization authority for decrypting the content. The end user system receives a secure container containing the decrypting key for decrypting at least part of the previously encrypted content as permitted. The system creates a secure container using the encrypting key from a clearing house, wherein the secure container has an encrypting key therein from the end user system; transferring the secure container to the clearing house for authentication of permission to decrypt the content. The system receives from the clearing house, a secure container encrypted using the encrypting key of the end user system containing the decrypting key for decrypting at least part of the previously encrypted content stored on the computer readable medium as permitted; and playing at least part of the previously encrypted content by decrypting the secure container using the encrypting key of the end user system to access the decrypting key for decrypting at least part of the encrypted content.
Owner:WISTRON CORP
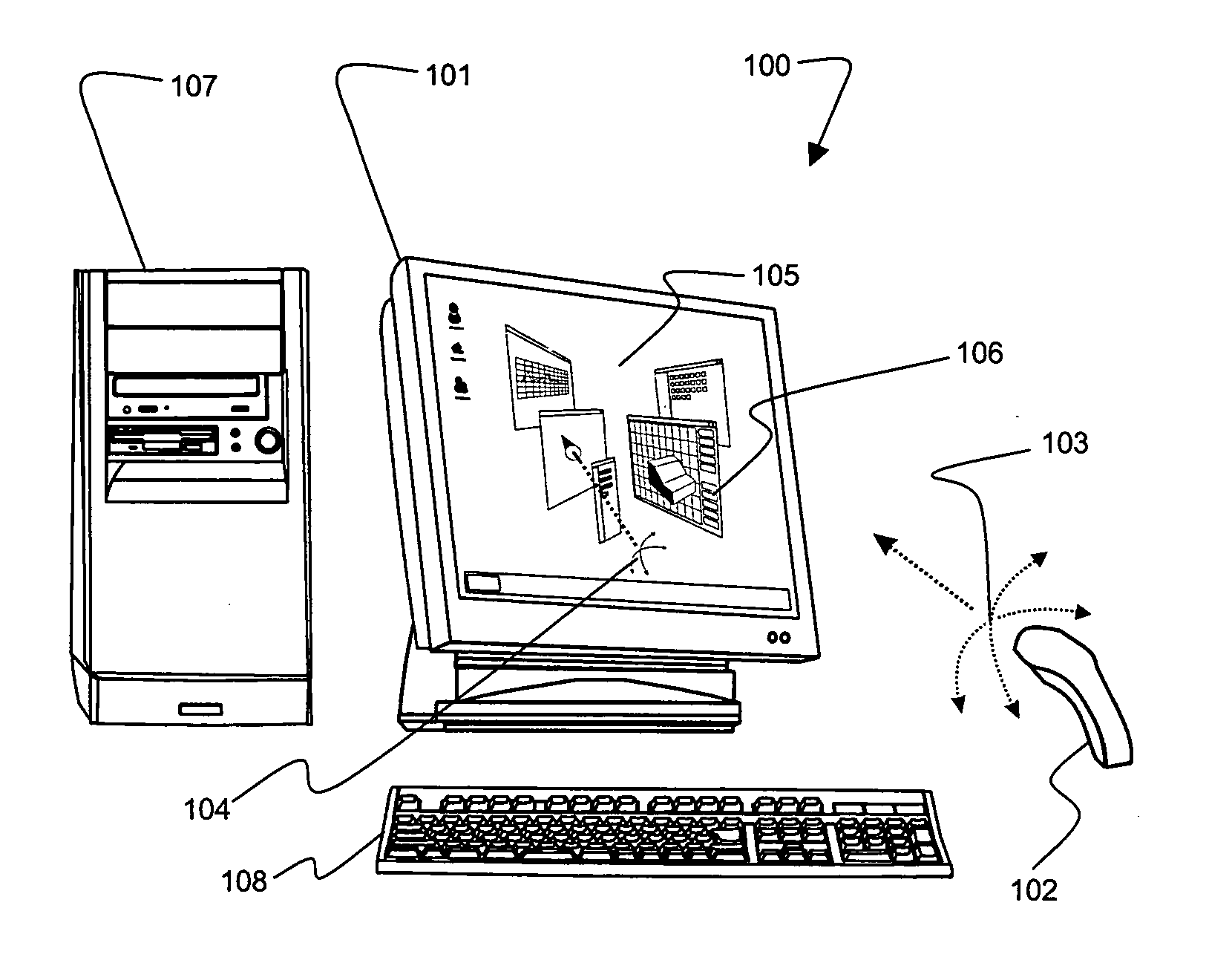
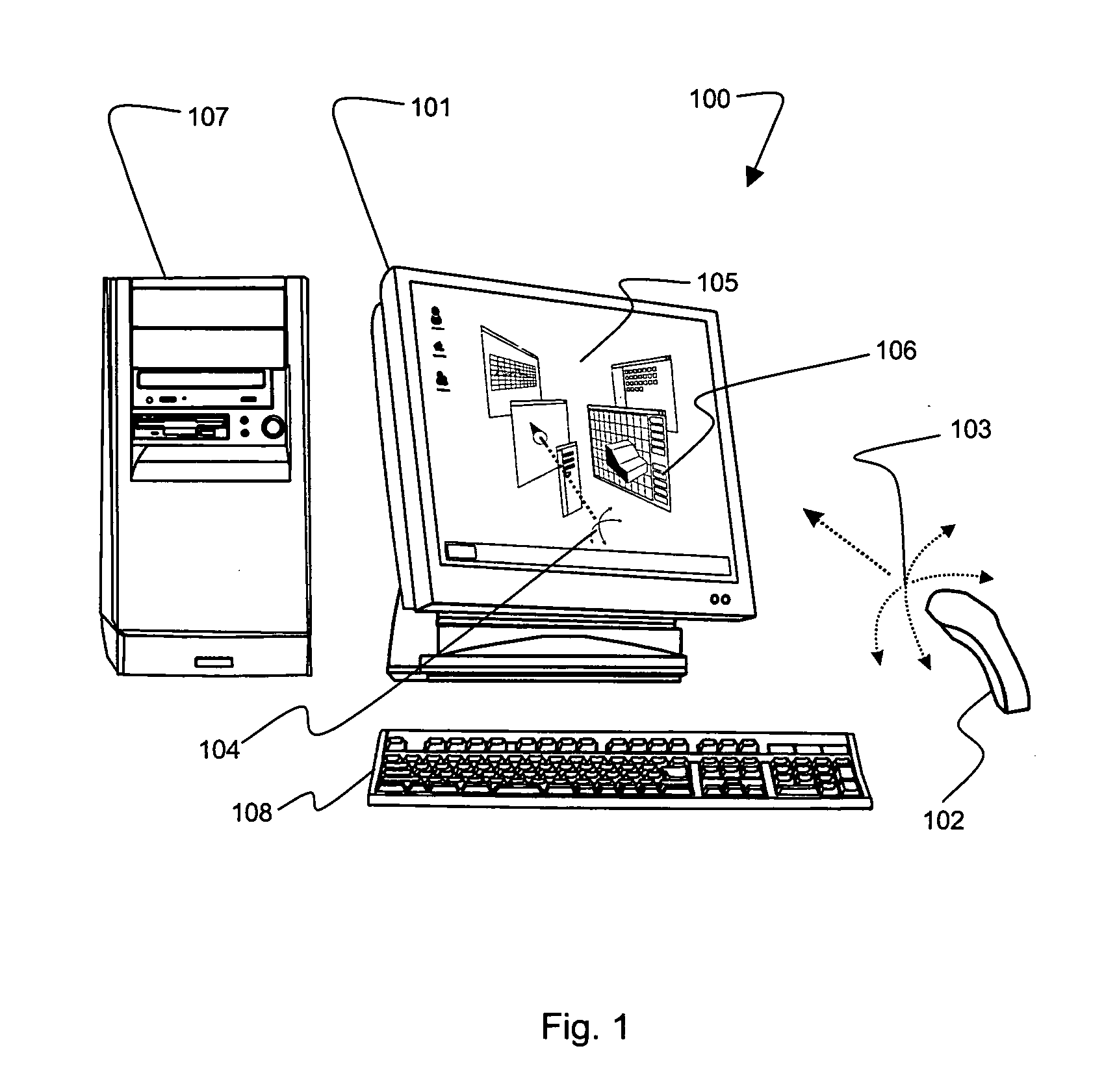
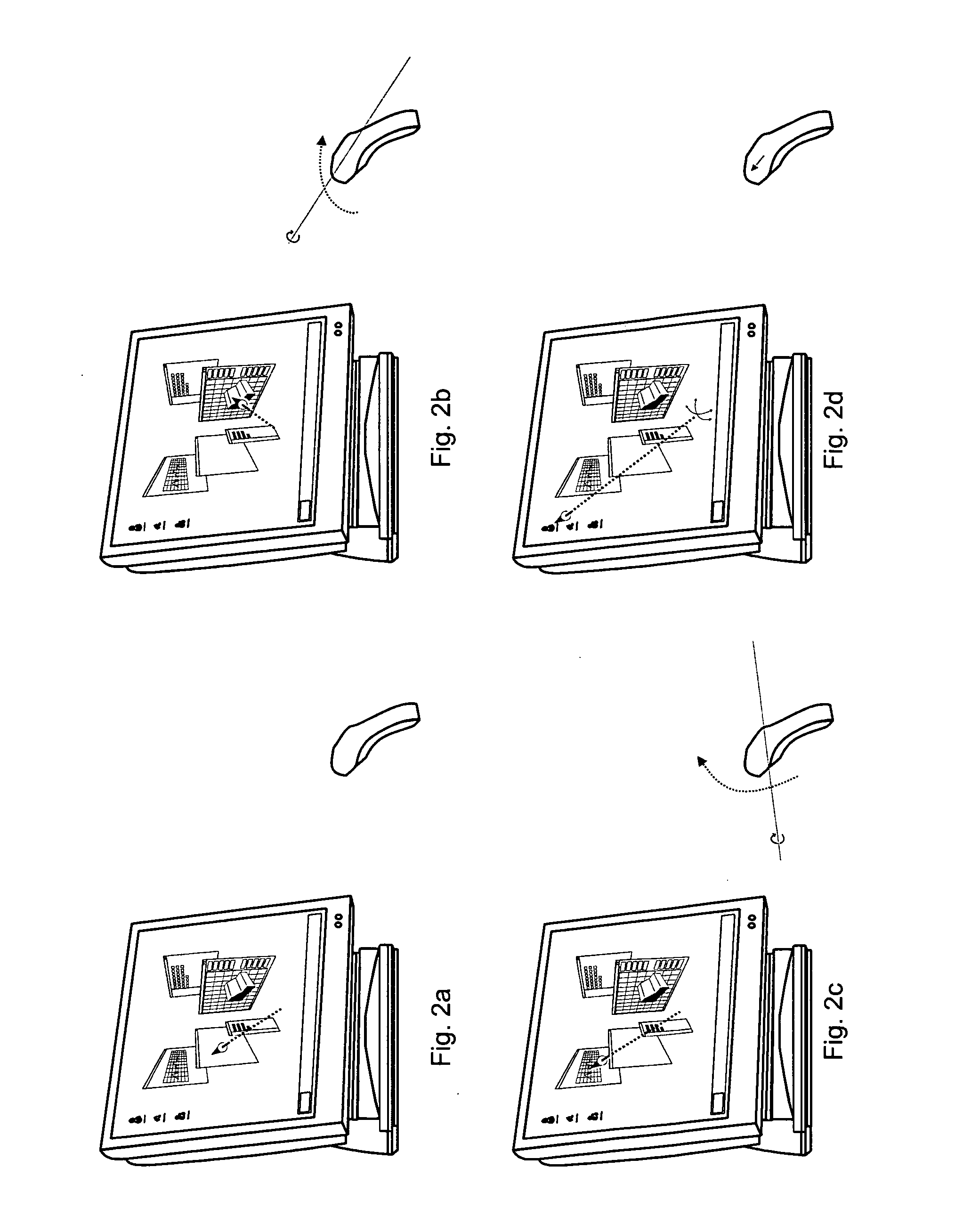
Gesture-based computer interface
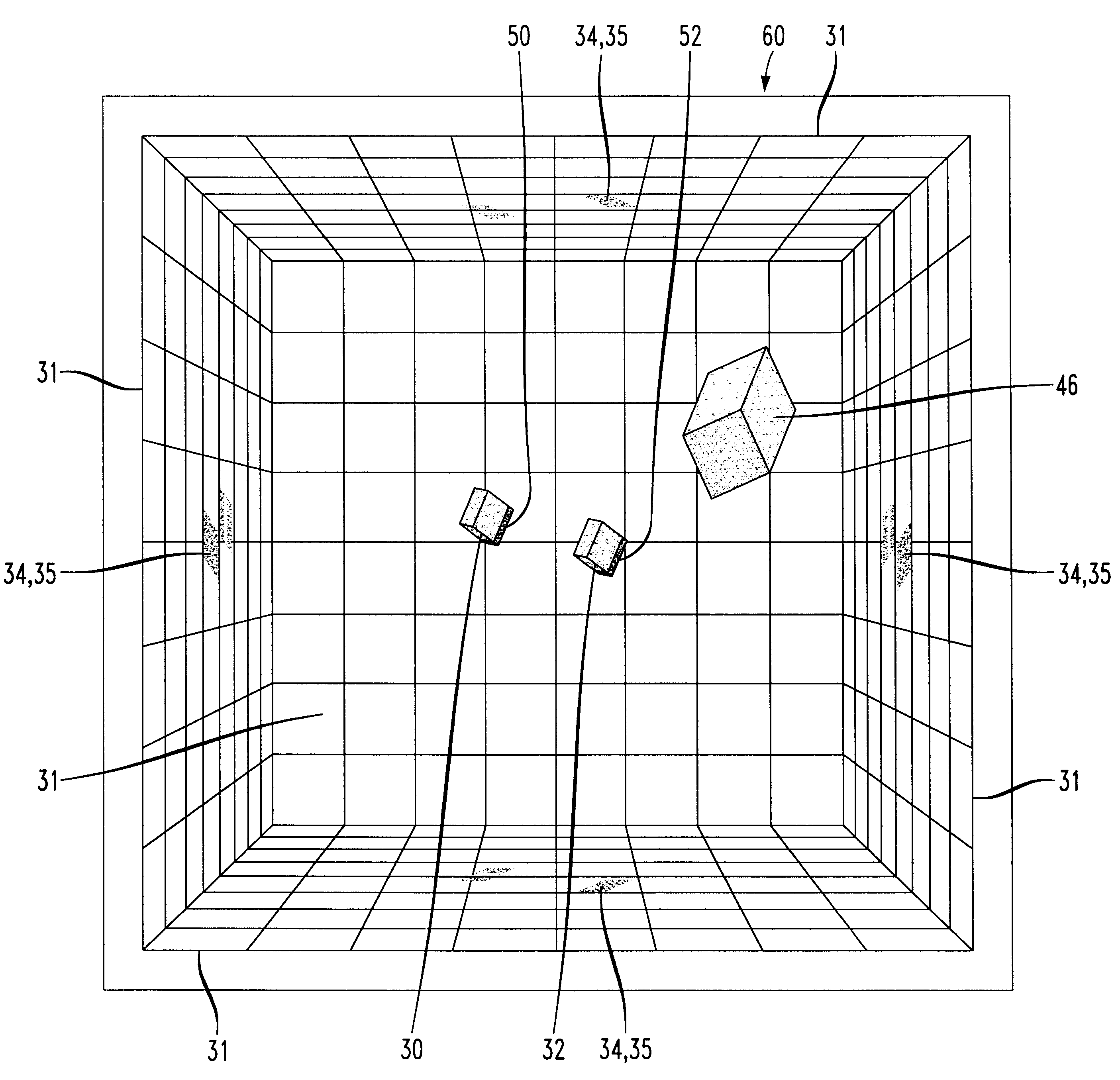
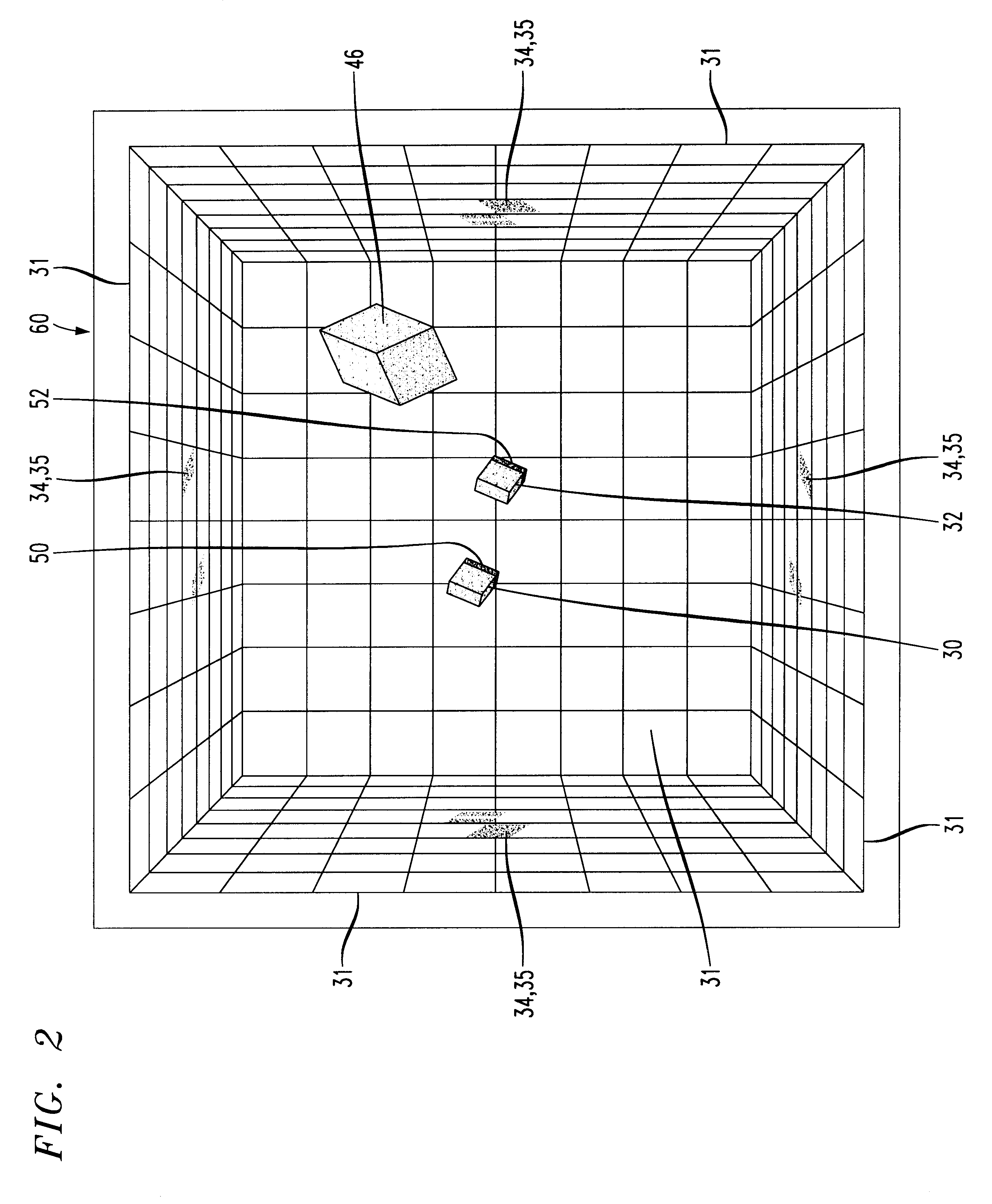
InactiveUS6222465B1Input/output for user-computer interactionCharacter and pattern recognitionFree formHand movements
A system and method for manipulating virtual objects in a virtual environment, for drawing curves and ribbons in the virtual environment, and for selecting and executing commands for creating, deleting, moving, changing, and resizing virtual objects in the virtual environment using intuitive hand gestures and motions. The system is provided with a display for displaying the virtual environment and with a video gesture recognition subsystem for identifying motions and gestures of a user's hand. The system enables the user to manipulate virtual objects, to draw free-form curves and ribbons and to invoke various command sets and commands in the virtual environment by presenting particular predefined hand gestures and / or hand movements to the video gesture recognition subsystem.
Owner:LUCENT TECH INC
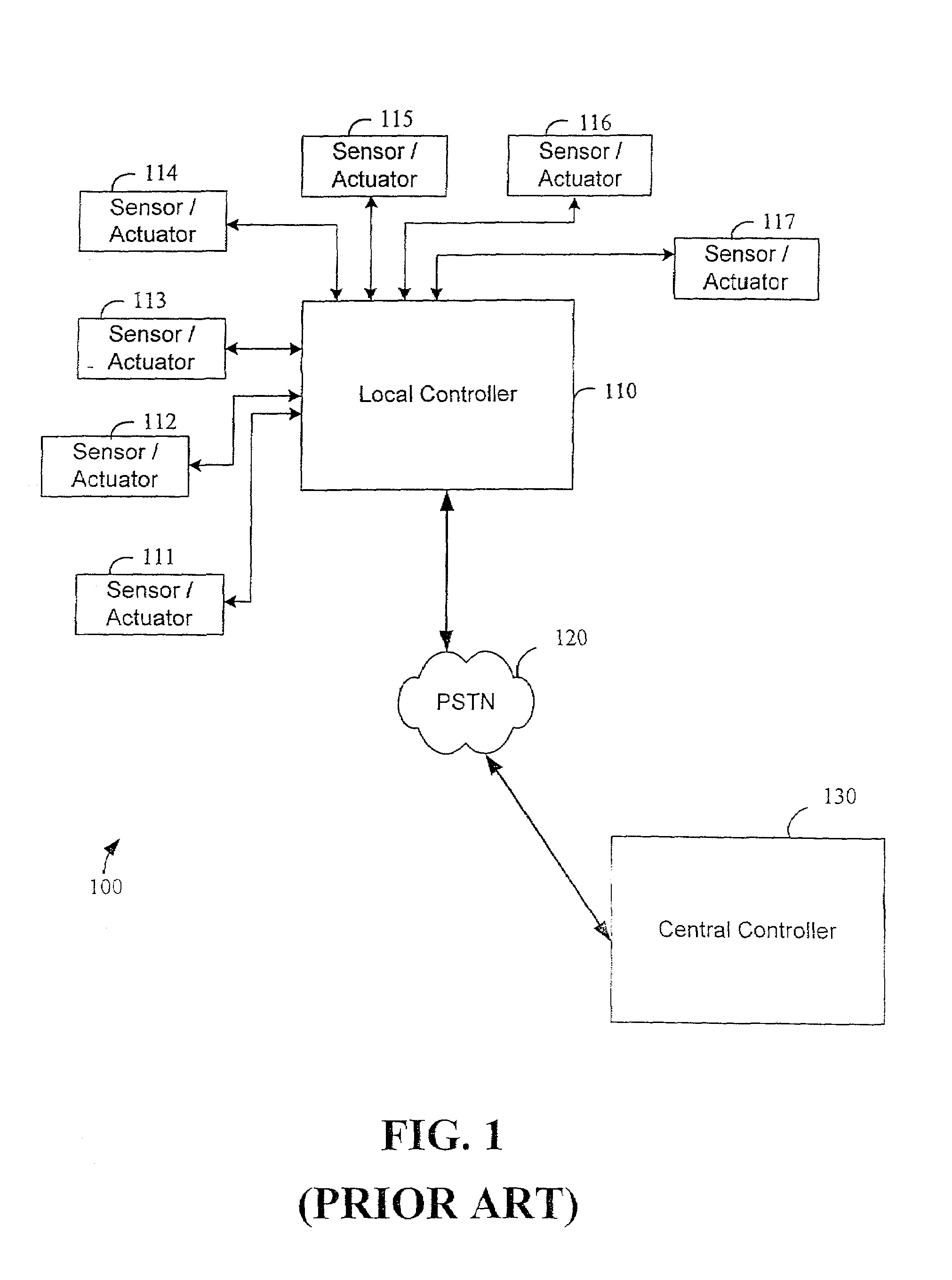
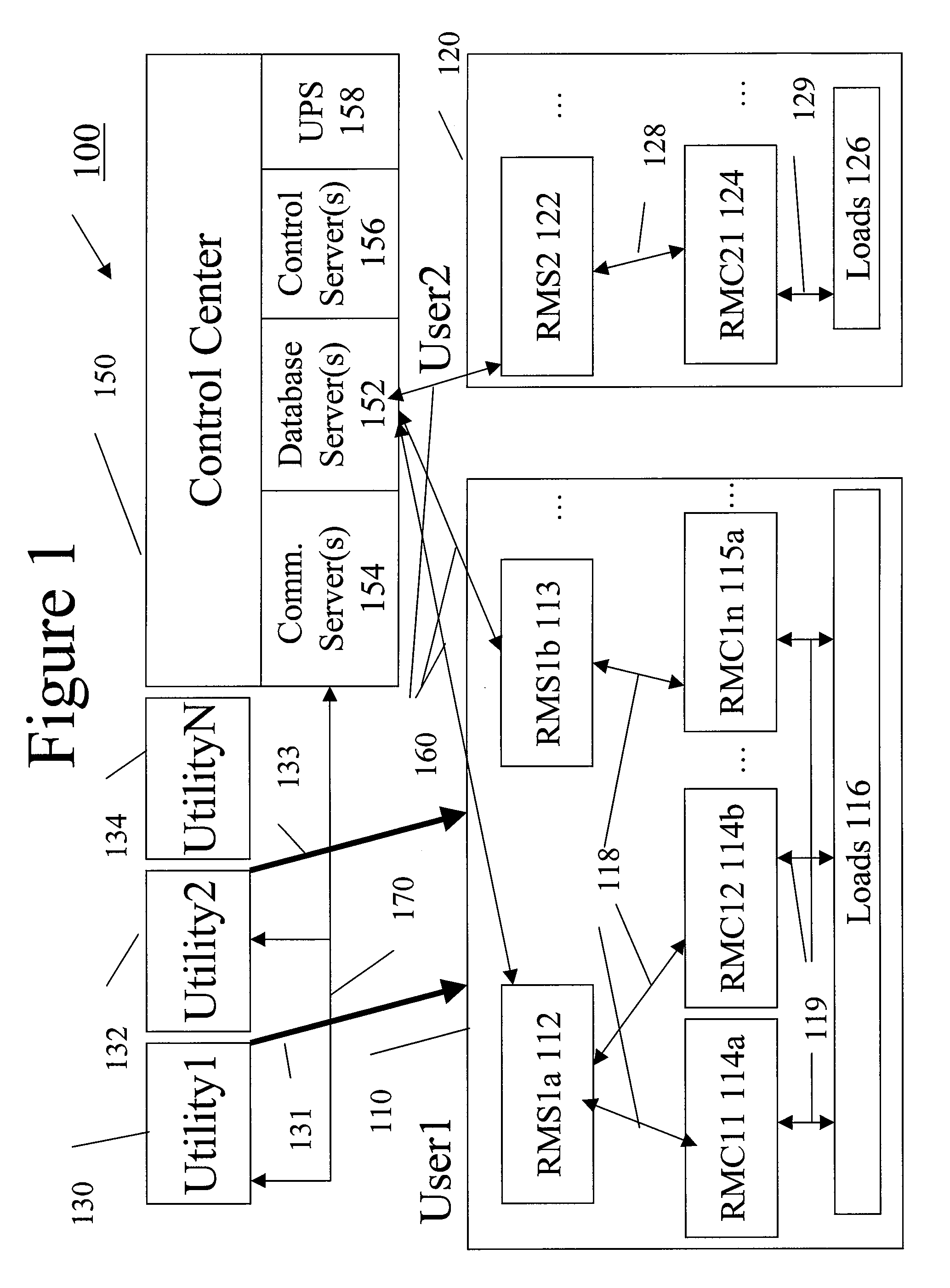
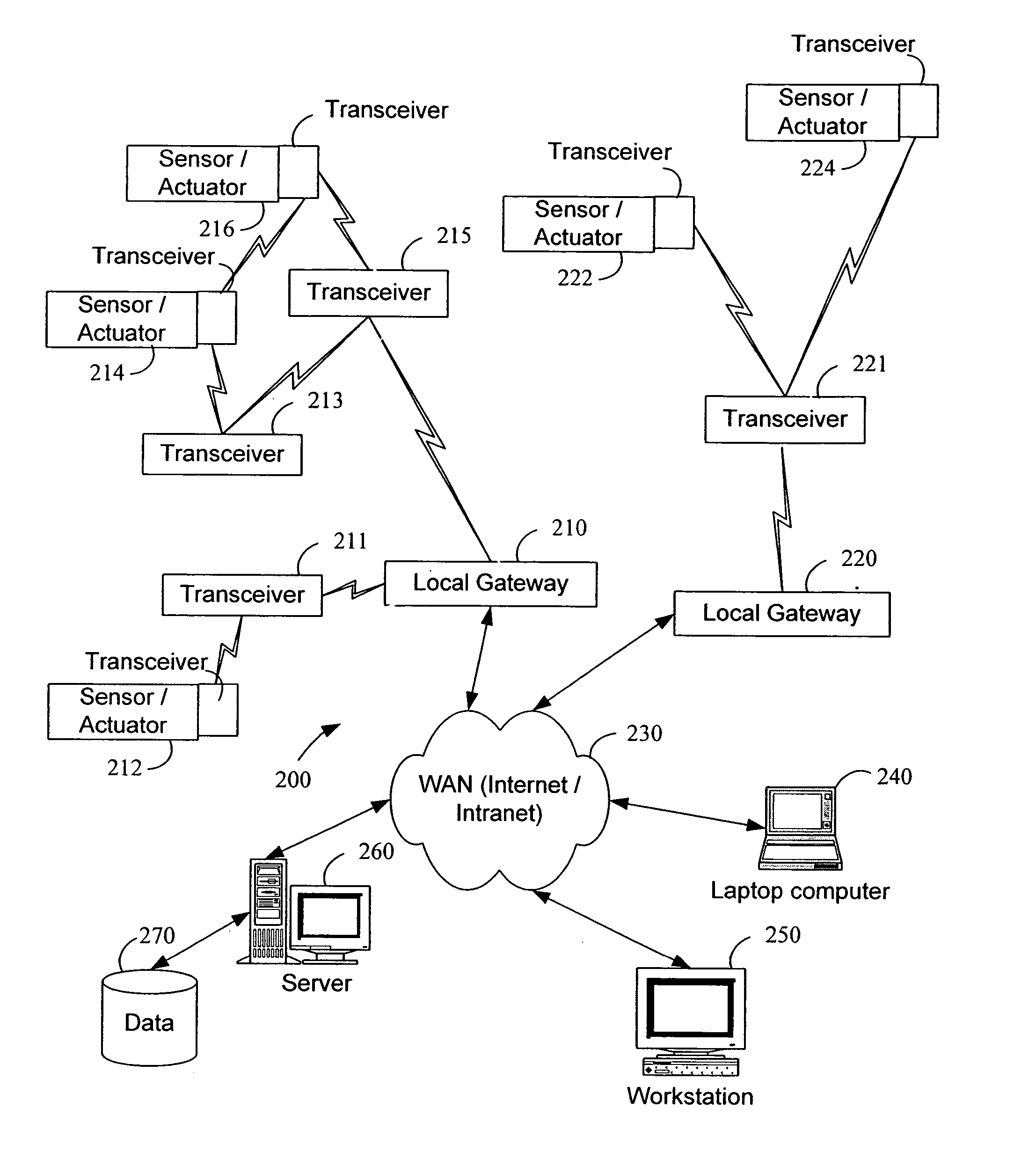
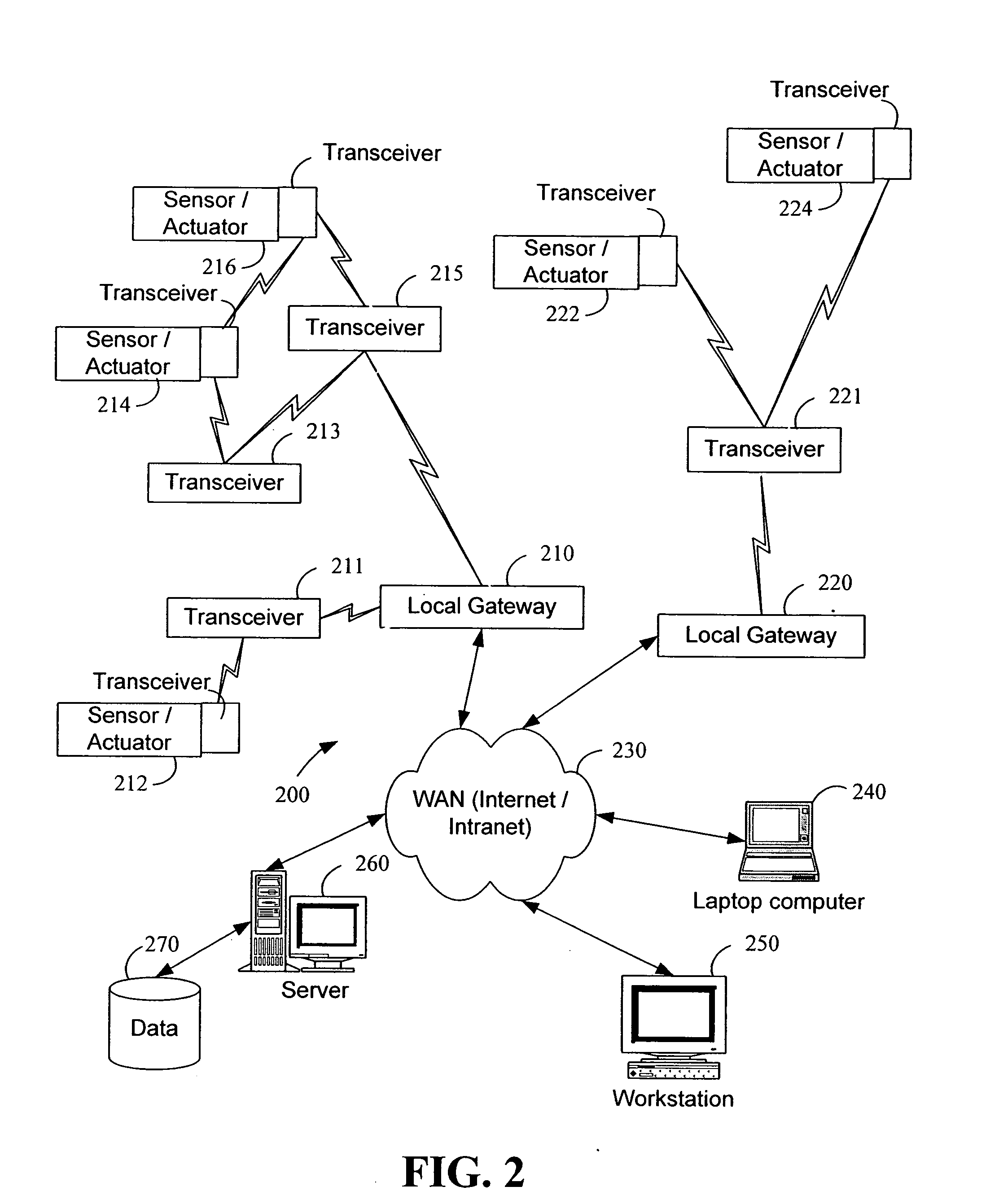
System and method for monitoring and controlling remote devices
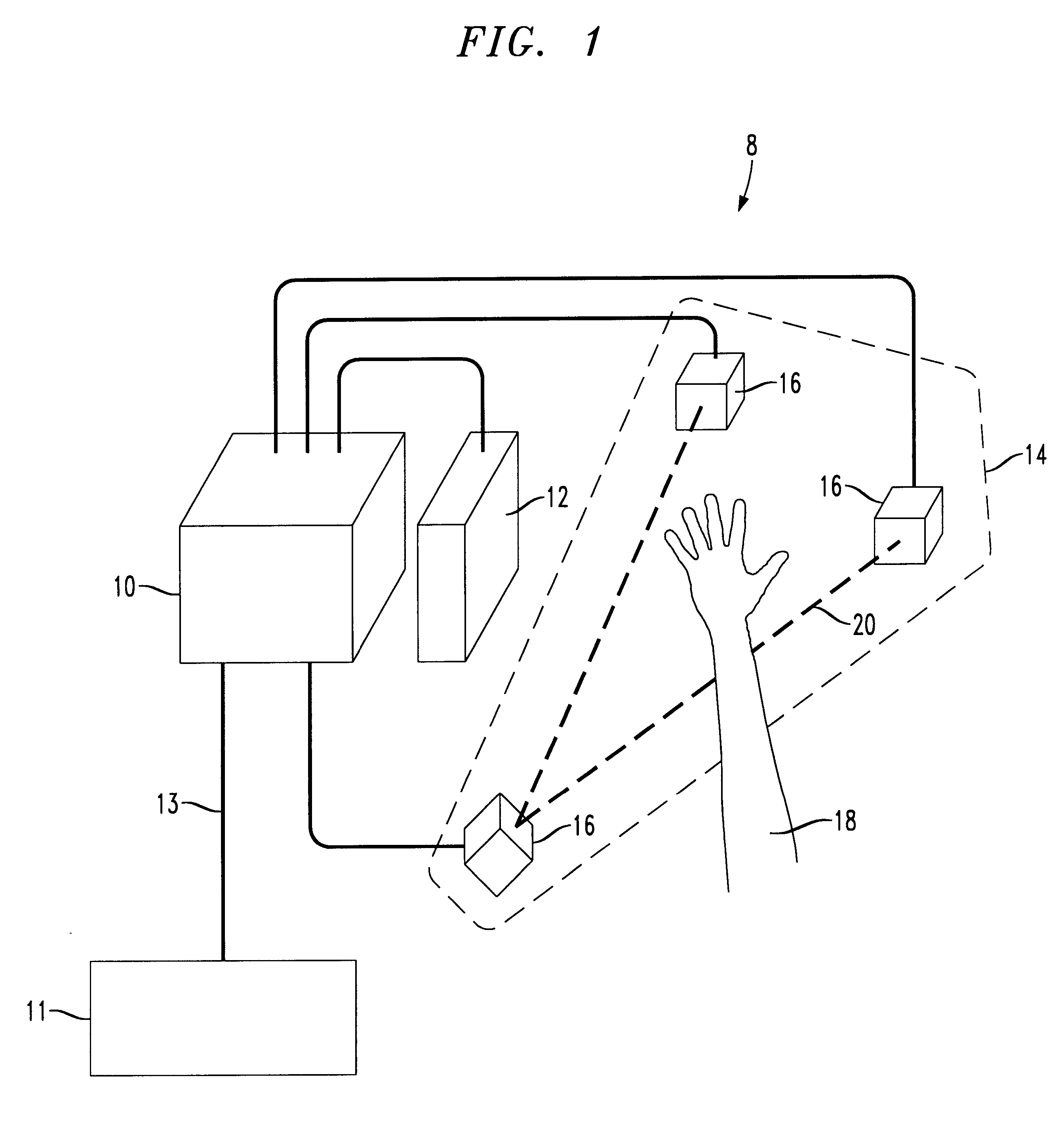
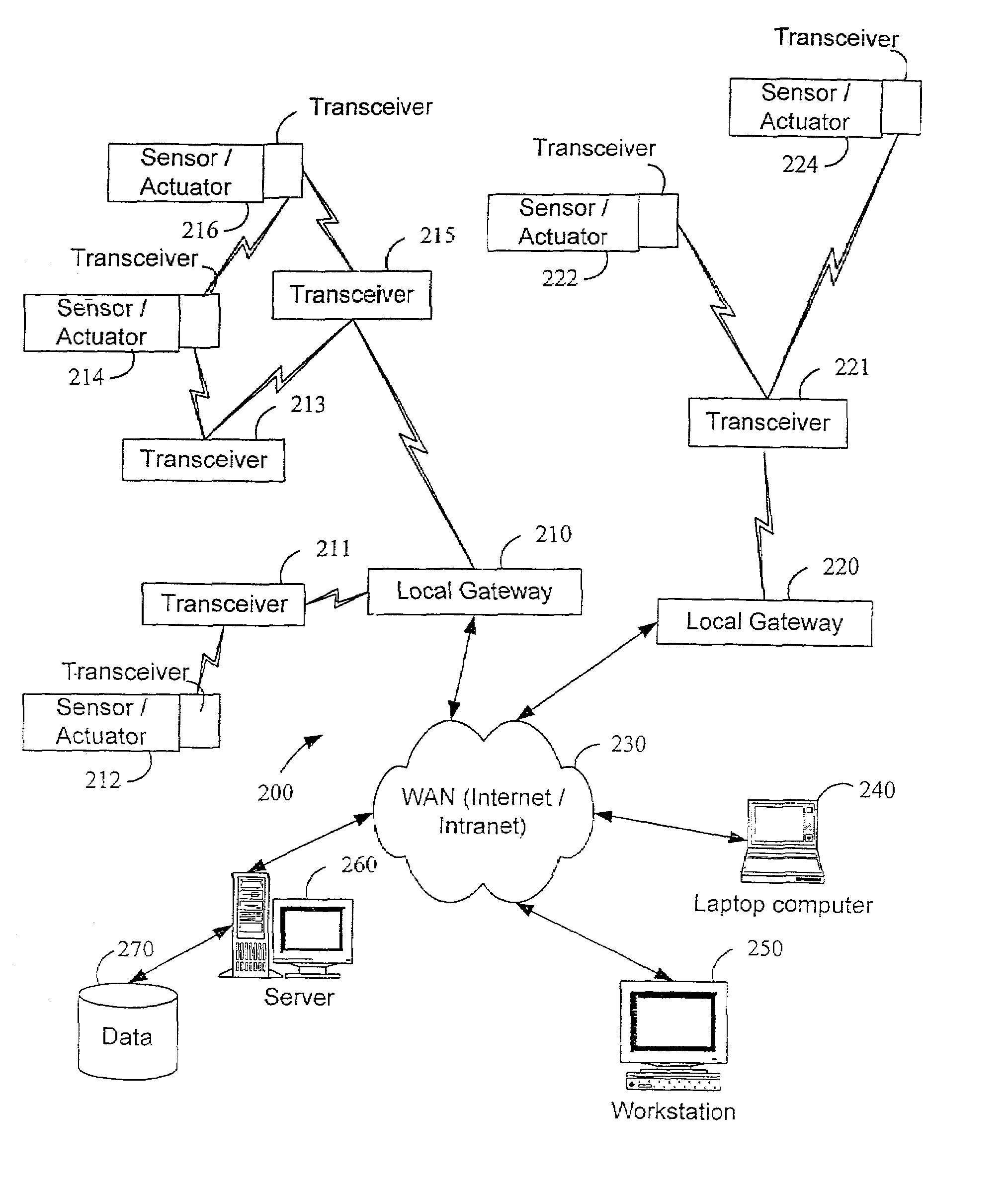
InactiveUS7053767B2Closed feedback loopIntegrated inexpensivelyError preventionFrequency-division multiplex detailsTransceiverControl signal
The present invention is generally directed to a system for monitoring a variety of environmental and / or other conditions within a defined remotely located region. In accordance with one aspect of the invention, a system is configured to monitor utility meters in a defined area. The system is implemented by using a plurality of wireless transmitters, wherein each wireless transmitter is integrated into a sensor adapted to monitor a particular data input. The system also includes a plurality of transceivers that are dispersed throughout the region at defined locations. The system uses a local gateway to translate and transfer information from the transmitters to a dedicated computer on a network. The dedicated computer, collects, compiles, and stores the data for retrieval upon client demand across the network. The computer further includes means for evaluating the received information and identifying an appropriate control signal, the system further including means for applying the control signal at a designated actuator.
Owner:SIPCO
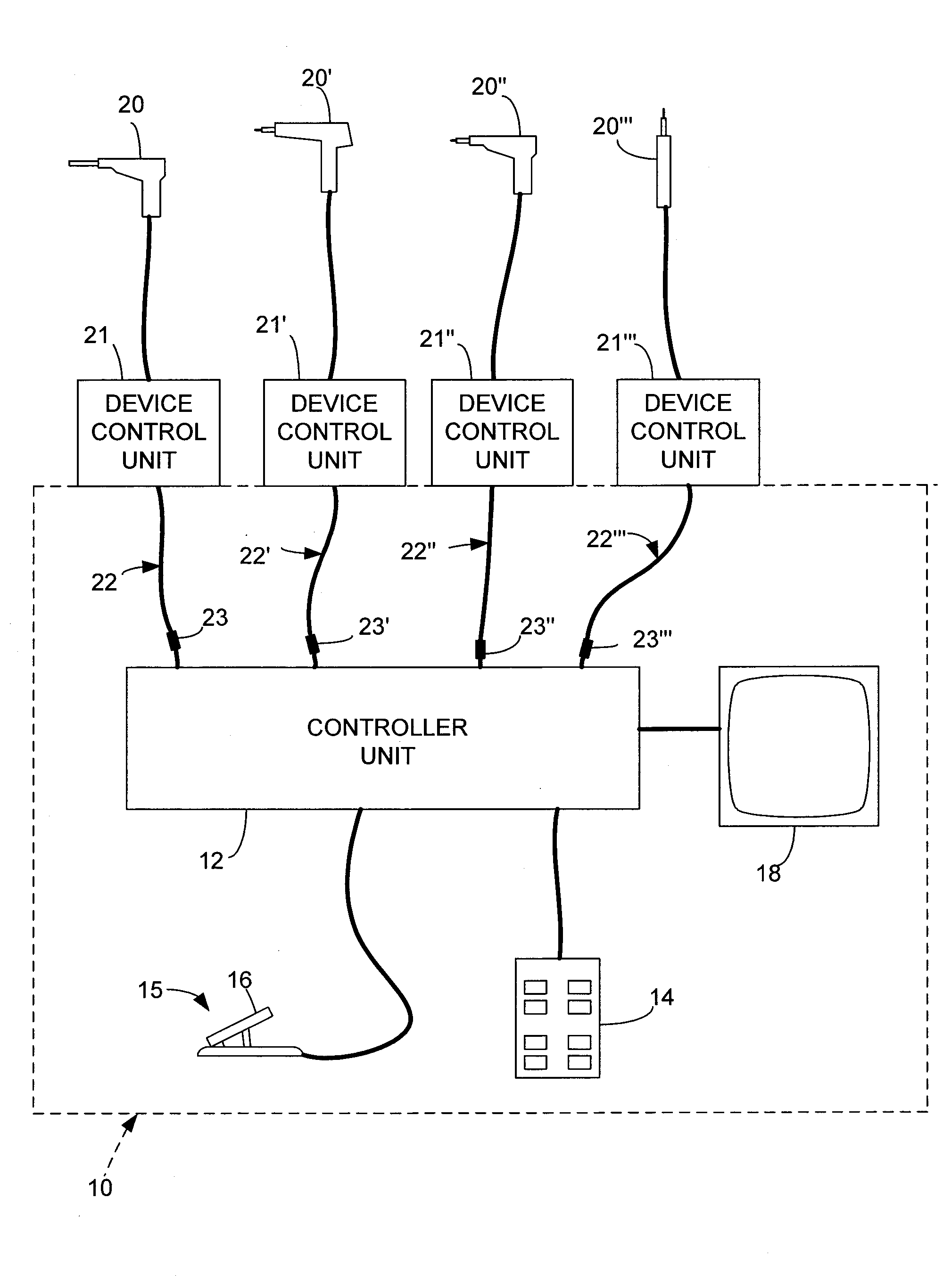
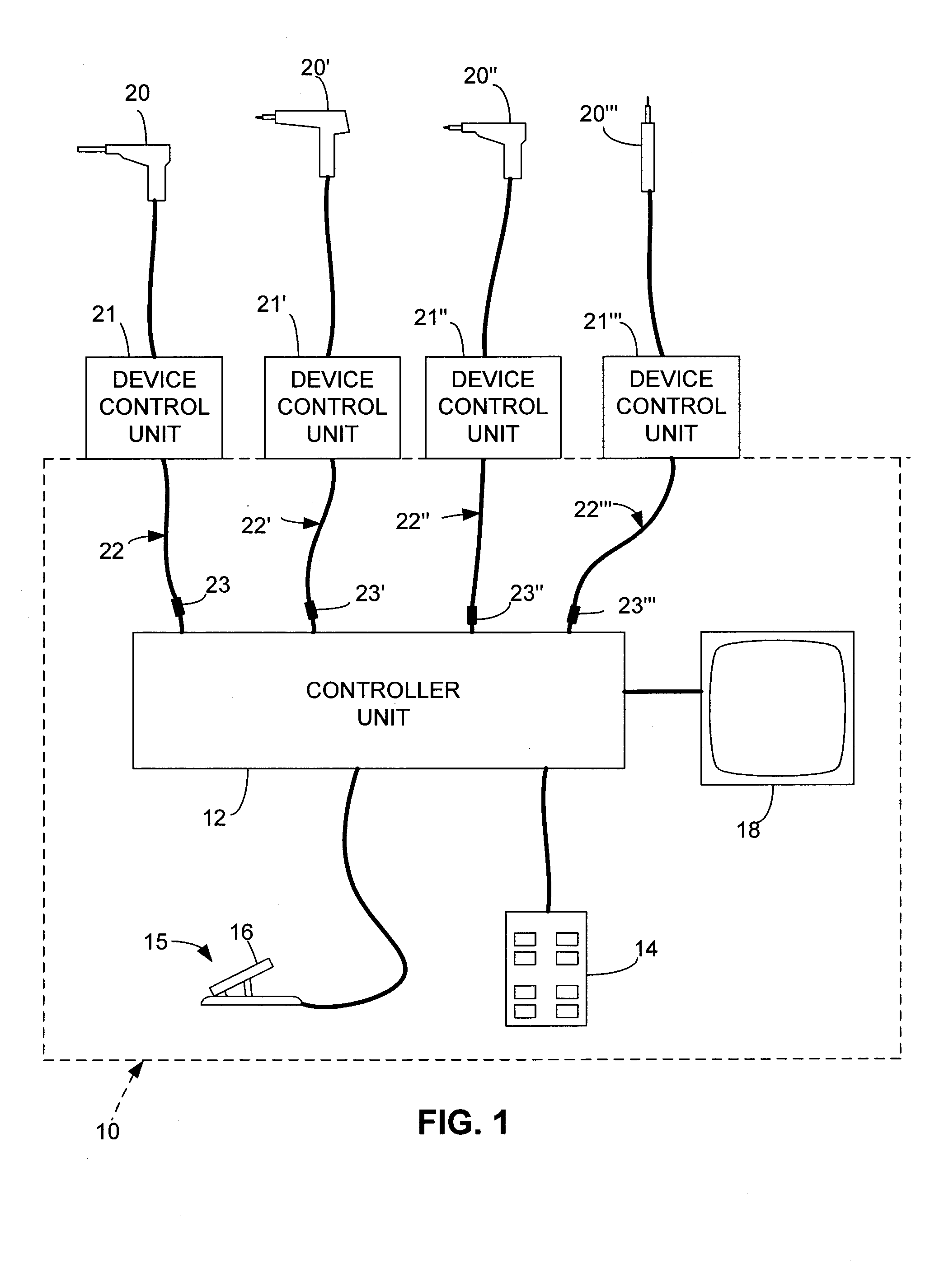
Electrosurgical control system
ActiveUS7217269B2Surgical instruments for heatingSurgical instruments for aspiration of substancesElectricityControl system
An electrosurgical control system includes a selector by which a user can select any of a number of electrosurgical devices or similar devices for use, and a processor system responsive to user actuation of a foot control or other central control by controlling the selected device. Each device has an associated intelligent adapter that communicates information relating to device with which the adapter is associated. The processor system uses the information communicated by the adapter to properly interface the associated device with the control system and its central control.
Owner:STRYKER CORP
Method for allocating files in a file system integrated with a RAID disk sub-system
The present invention is a method for integrating a file system with a RAID array that exports precise information about the arrangement of data blocks in the RAID subsystem. The file system examines this information and uses it to optimize the location of blocks as they are written to the RAID system. Thus, the system uses explicit knowledge of the underlying RAID disk layout to schedule disk allocation. The present invention uses separate current-write location (CWL) pointers for each disk in the disk array where the pointers simply advance through the disks as writes occur. The algorithm used has two primary goals. The first goal is to keep the CWL pointers as close together as possible, thereby improving RAID efficiency by writing to multiple blocks in the stripe simultaneously. The second goal is to allocate adjacent blocks in a file on the same disk, thereby improving read back performance. The present invention satisfies the first goal by always writing on the disk with the lowest CWL pointer. For the second goal, a new disk is chosen only when the algorithm starts allocating space for a new file, or when it has allocated N blocks on the same disk for a single file. A sufficient number of blocks is defined as all the buffers in a chunk of N sequential buffers in a file. The result is that CWL pointers are never more than N blocks apart on different disks, and large files have N consecutive blocks on the same disk.
Owner:NETWORK APPLIANCE INC
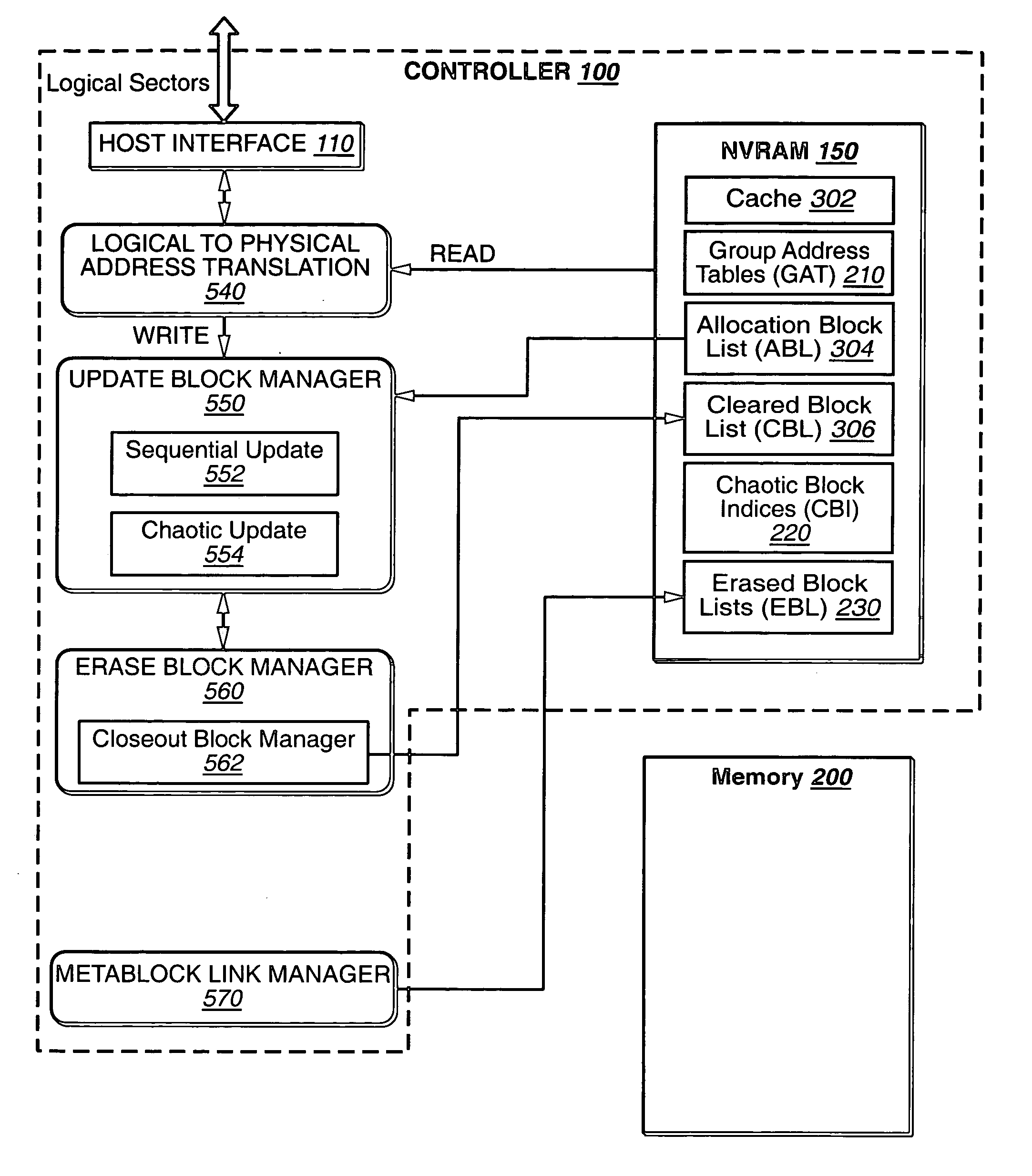
Hybrid non-volatile memory system
InactiveUS20050251617A1Easy accessMemory architecture accessing/allocationInput/output to record carriersData controlControl data
The present invention presents a hybrid non-volatile system that uses non-volatile memories based on two or more different non-volatile memory technologies in order to exploit the relative advantages of each these technology with respect to the others. In an exemplary embodiment, the memory system includes a controller and a flash memory, where the controller has a non-volatile RAM based on an alternate technology such as FeRAM. The flash memory is used for the storage of user data and the non-volatile RAM in the controller is used for system control data used by the control to manage the storage of host data in the flash memory. The use of an alternate non-volatile memory technology in the controller allows for a non-volatile copy of the most recent control data to be accessed more quickly as it can be updated on a bit by bit basis. In another exemplary embodiment, the alternate non-volatile memory is used as a cache where data can safely be staged prior to its being written to the to the memory or read back to the host.
Owner:SANDISK TECH LLC
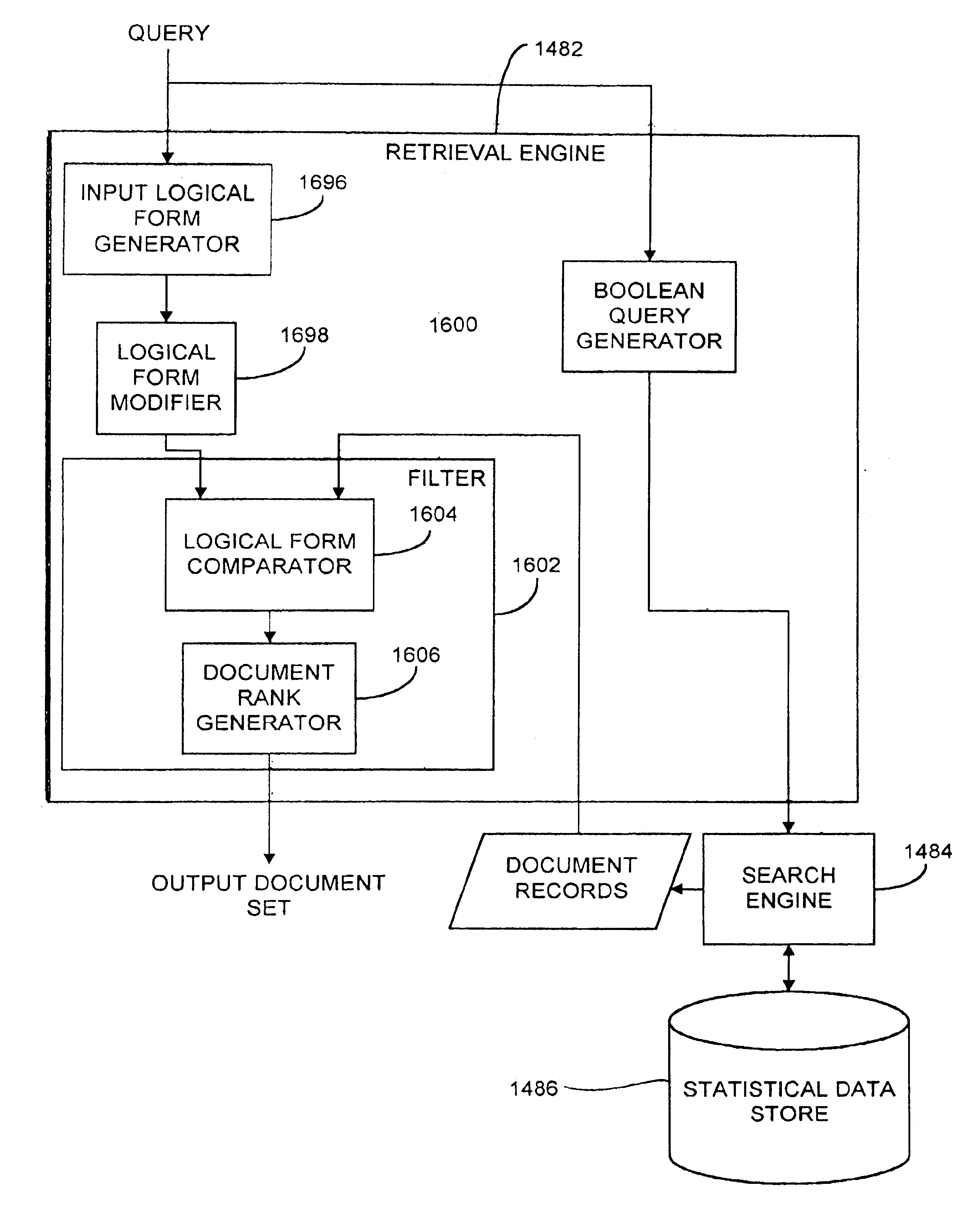
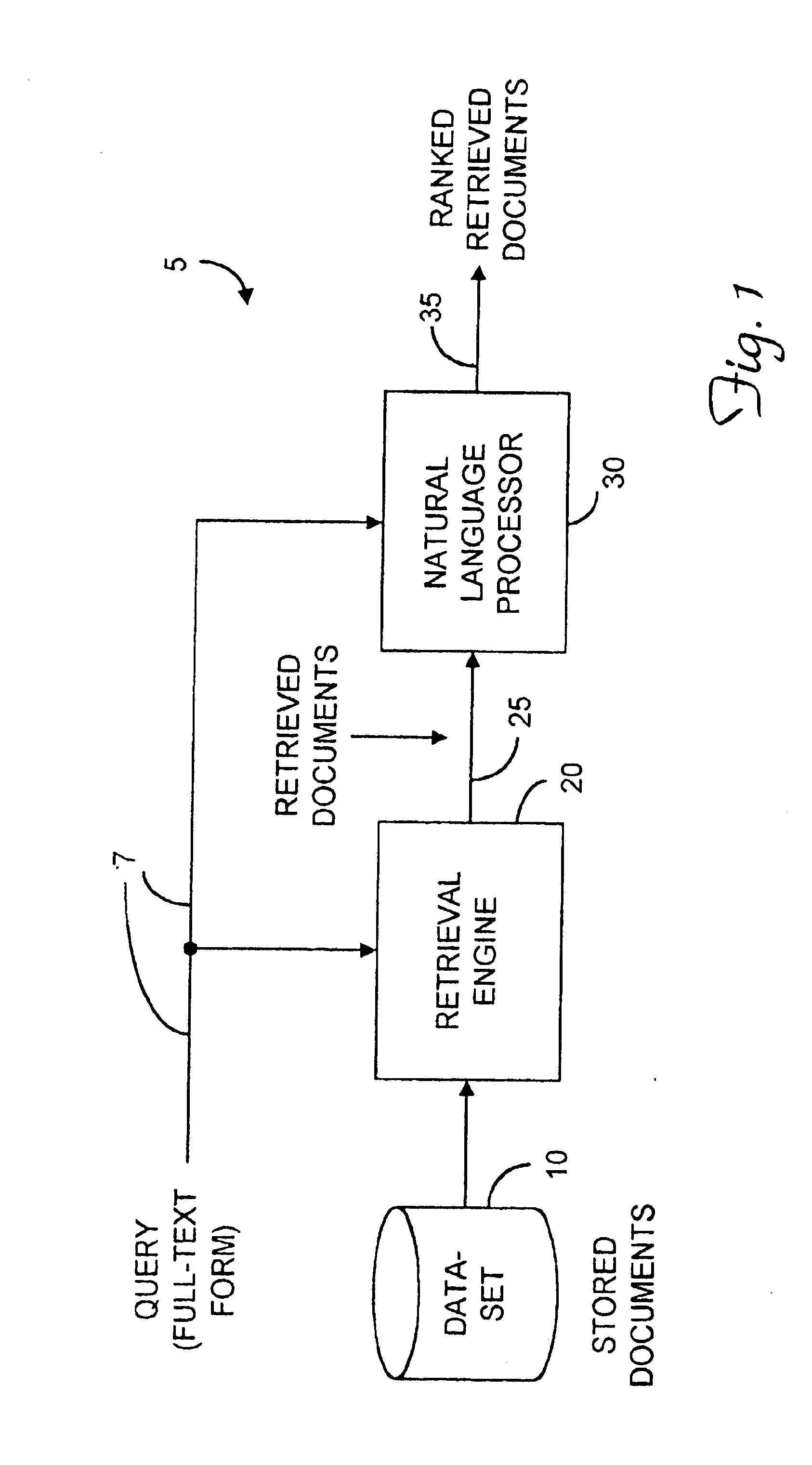
System for processing textual inputs using natural language processing techniques
InactiveUS6901399B1High precisionImprove accuracyData processing applicationsDigital data information retrievalText entryDocument preparation
A system filters documents in a document set retrieved from a document store in response to a query. The system obtains a first set of logical forms based on a selected one of the query and the documents in the document set. The system obtains a second set of logical forms based on another of the query and the documents in the document set. The system then uses natural language processing techniques to modify the first logical forms to obtain a modified set of logical forms. The system filters documents in the document set based on a predetermined relationship between the modified set of logical forms and the second set of logical forms.
Owner:MICROSOFT TECH LICENSING LLC
Locating a mobile station and applications therefor
InactiveUS20060025158A1Accurate locationEmergency connection handlingNetwork traffic/resource managementInternet communicationModularity
A location system is disclosed for wireless telecommunication infrastructures. The system is an end-to-end solution having one or more location systems for outputting requested locations of hand sets or mobile stations (MS) based on, e.g., AMPS, NAMPS, CDMA or TDMA communication standards, for processing both local mobile station location requests and more global mobile station location requests via, e.g., Internet communication between a distributed network of location systems. The system uses a plurality of mobile station locating technologies including those based on: (1) two-way TOA and TDOA; (2) home base stations and (3) distributed antenna provisioning. Further, the system can be modularly configured for use in location signaling environments ranging from urban, dense urban, suburban, rural, mountain to low traffic or isolated roadways. The system is useful for 911 emergency calls, tracking, routing, people and animal location including applications for confinement to and exclusion from certain areas.
Owner:FINETRAK LLC
Method and apparatus for data communication
InactiveUS6094684AInterprogram communicationMultiple digital computer combinationsGraphicsGraphical user interface
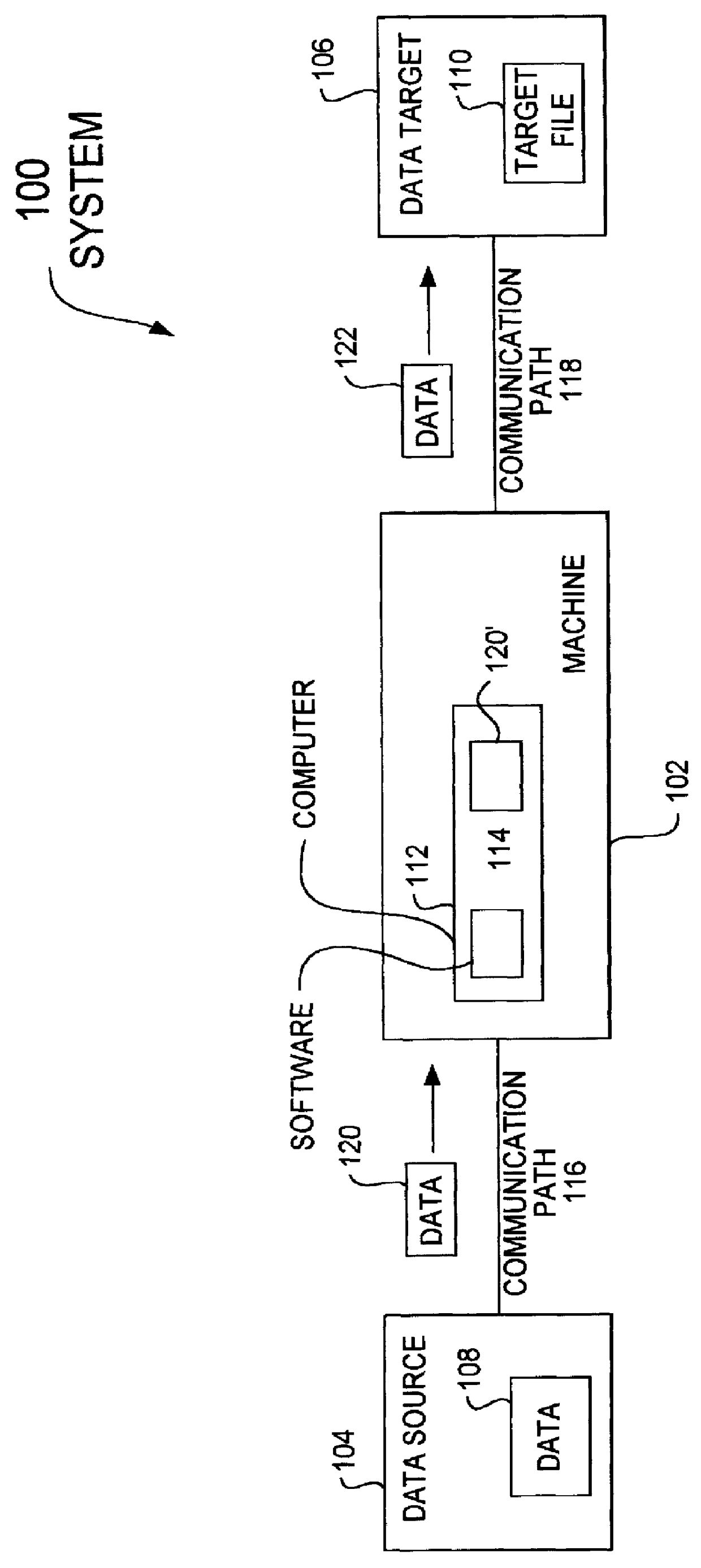
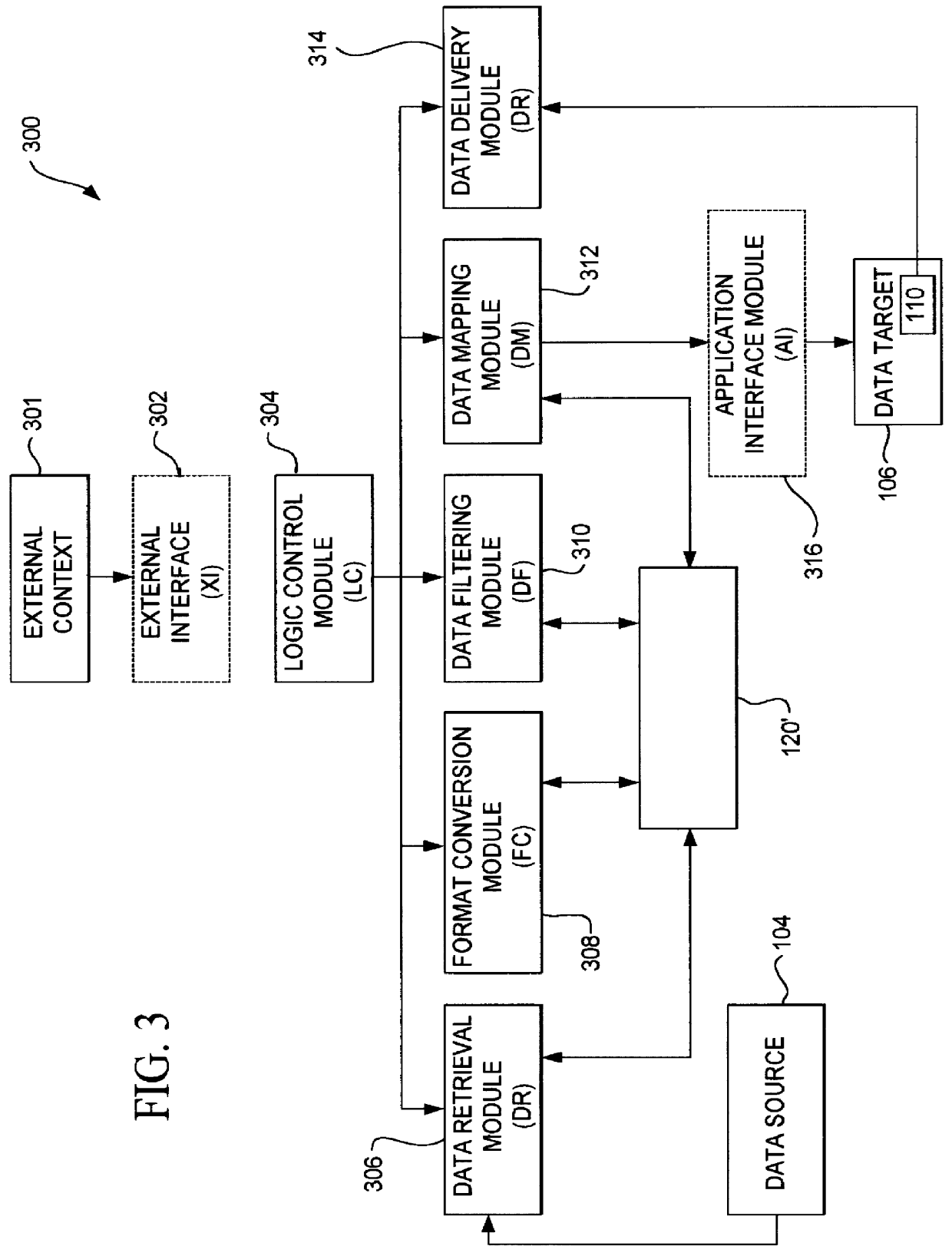
A data acquisition and delivery system for performing data delivery tasks is disclosed. This system uses a computer running software to acquire source data from a selected data source, to process (e.g. filter, format convert) the data, if desired, and to deliver the resulting delivered data to a data target. The system is designed to access remote and / or local data sources and to deliver data to remote and / or local data targets. The data target might be an application program that delivers the data to a file or the data target may simply be a file, for example. To obtain the delivered data, the software performs processing of the source data as appropriate for the particular type of data being retrieved, for the particular data target and as specified by a user, for example. The system can communicate directly with a target application program, telling the target application to place the delivered data in a particular location in a particular file. The system provides an external interface to an external context. If the external context is a human, the external interface may be a graphical user interface, for example. If the external context is another software application, the external interface may be an OLE interface, for example. Using the external interface, the external context is able to vary a variety of parameters to define data delivery tasks as desired. The system uses a unique notation that includes a plurality of predefined parameters to define the data delivery tasks and to communicate them to the software.
Owner:E BOTZ COM INC A DELAWARE +2
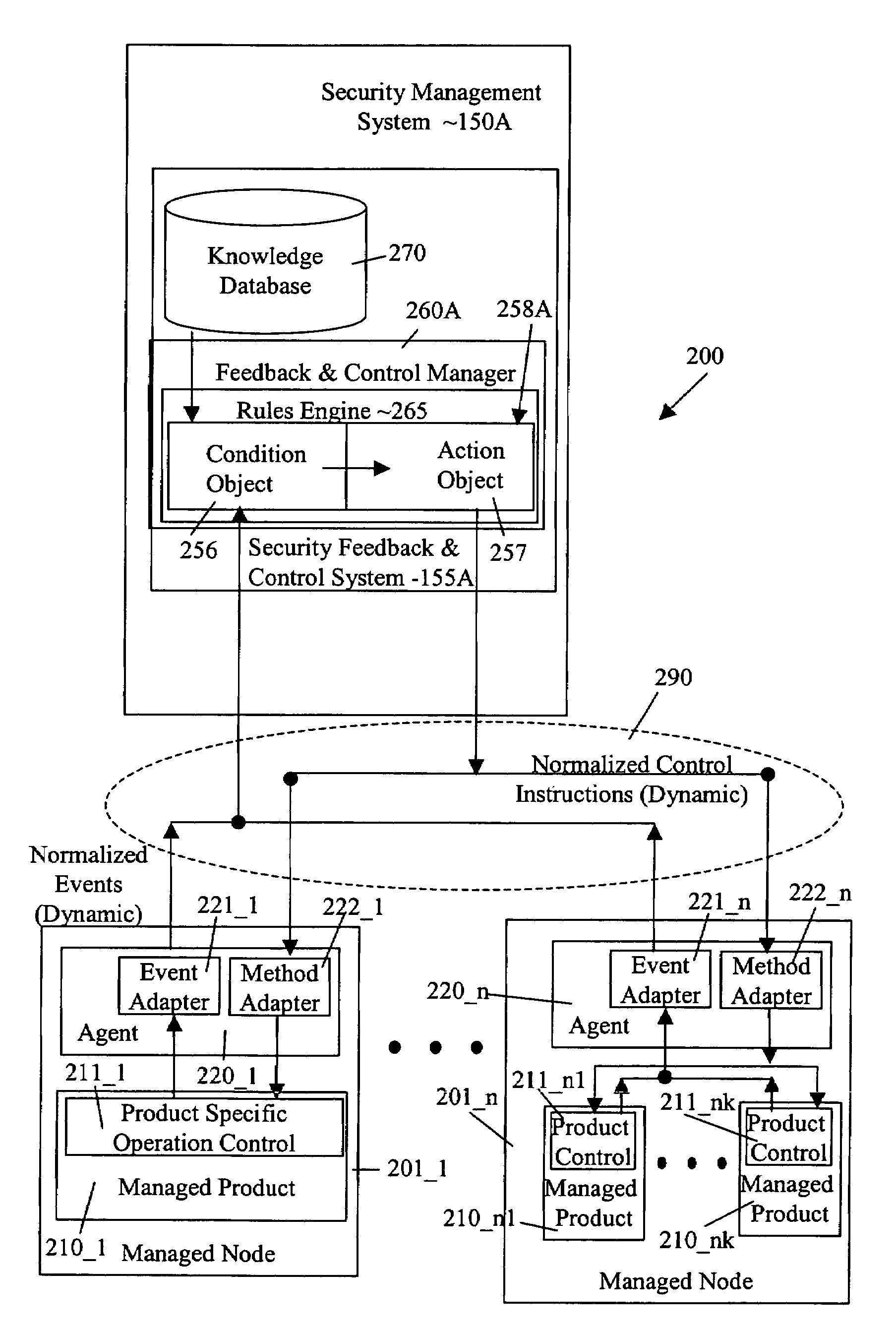
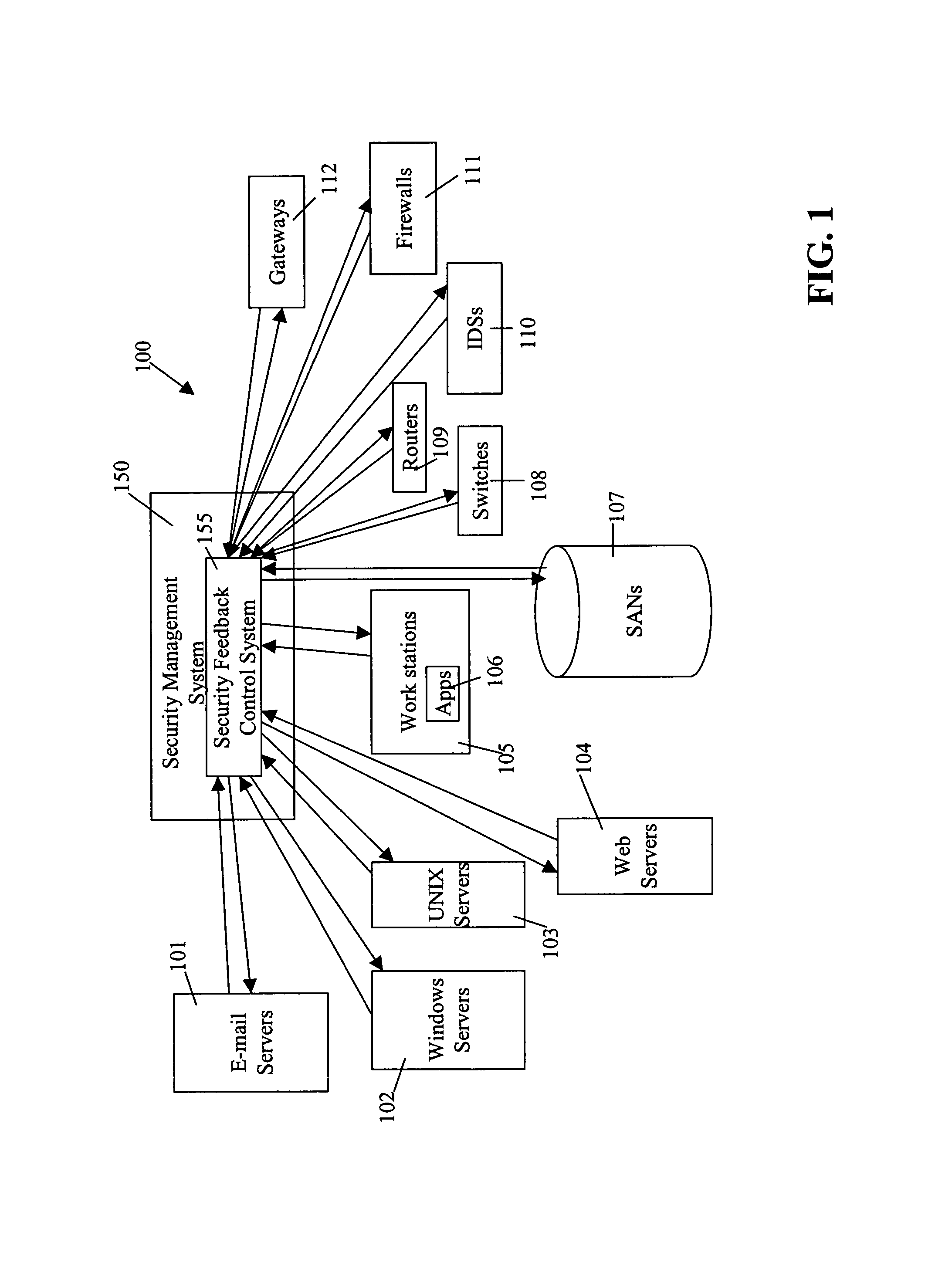
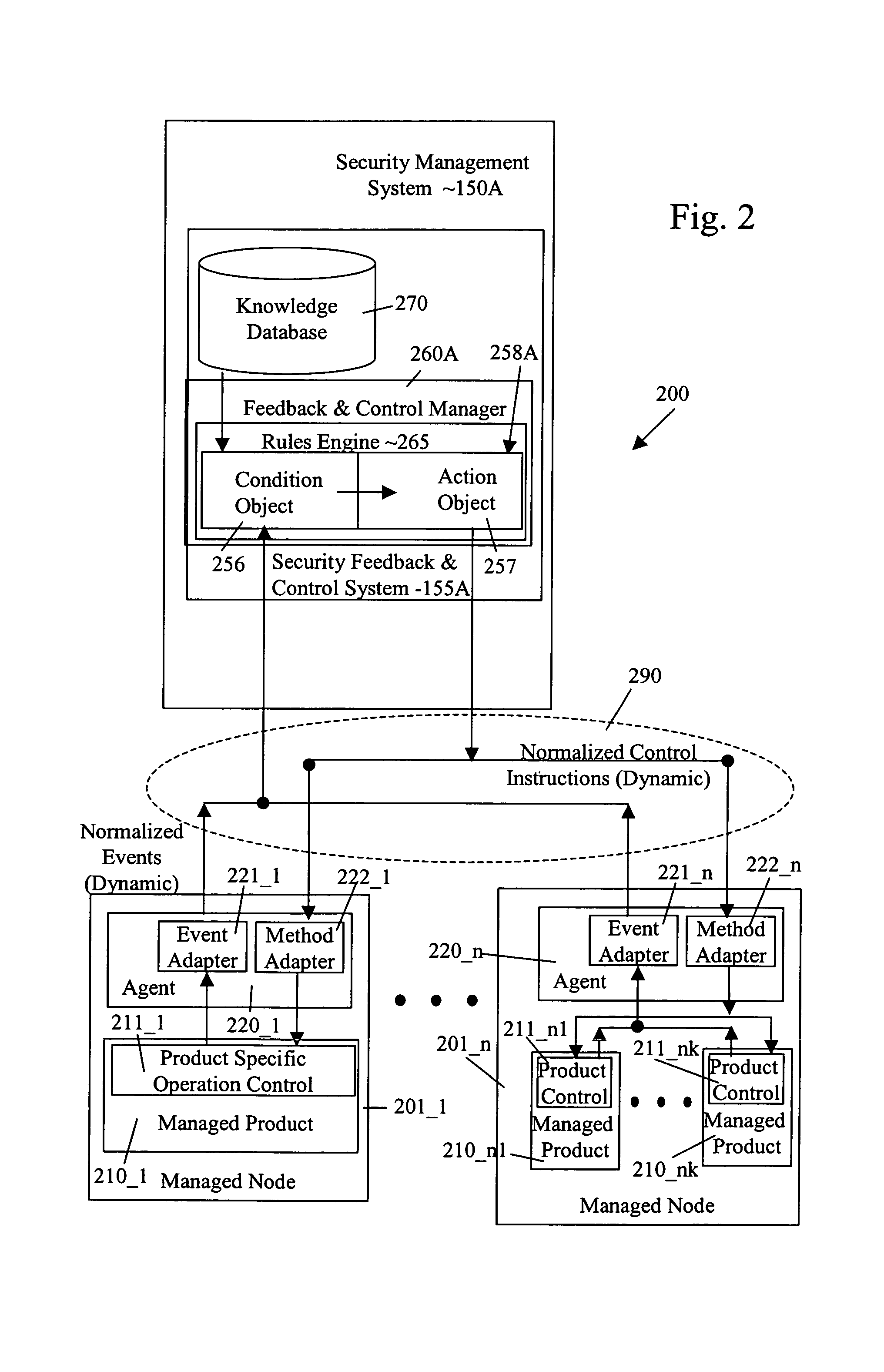
Security management system including feedback and control
InactiveUS7472422B1Memory loss protectionError detection/correctionPolicy decisionSafety management systems
A system uses automatic feedback and control to secure a network infrastructure by iterative convergence of the network's security structure to meet a security policy. Following initialization, a security feedback control system of the security management system makes dynamic adjustments to the system using bi-directional services that are controlled via policy decision components, without user intervention.
Owner:SYMANTEC CORP
Method and system for web page personalization
InactiveUS20020138331A1Digital data information retrievalNatural language data processingPersonalizationWeb service
The invention includes a method and system for personalizing displays of published Web pages provided by Web content providers to meet the interests of Web users accessing the pages, based on profiles of the users. The system preferably provides to the requesting user, through a proxy server, an edited version of the HTML file for the original published Web page that is served by a host Web server. The system uses user profiles that may include demographic and psychographic data to edit the requested Web page. The content of a Web page as published by a host Web server may be coded to correlate components of the Web page with demographic and psychographic data. The user profiles may then be used to filter the content of a coded Web page for delivery to a requesting user. The system may rearrange content on a published Web page so that content determined to be of higher interest to a user is more prominently featured or more easily or quickly accessible. The system may also delete content on a published Web page that is determined to be of low interest to a user. In embodiments of the invention, a single proxy server or proxy server system personalizes Web pages from multiple Web servers, using a single user profile for a user.
Owner:SEDNA PATENT SERVICES
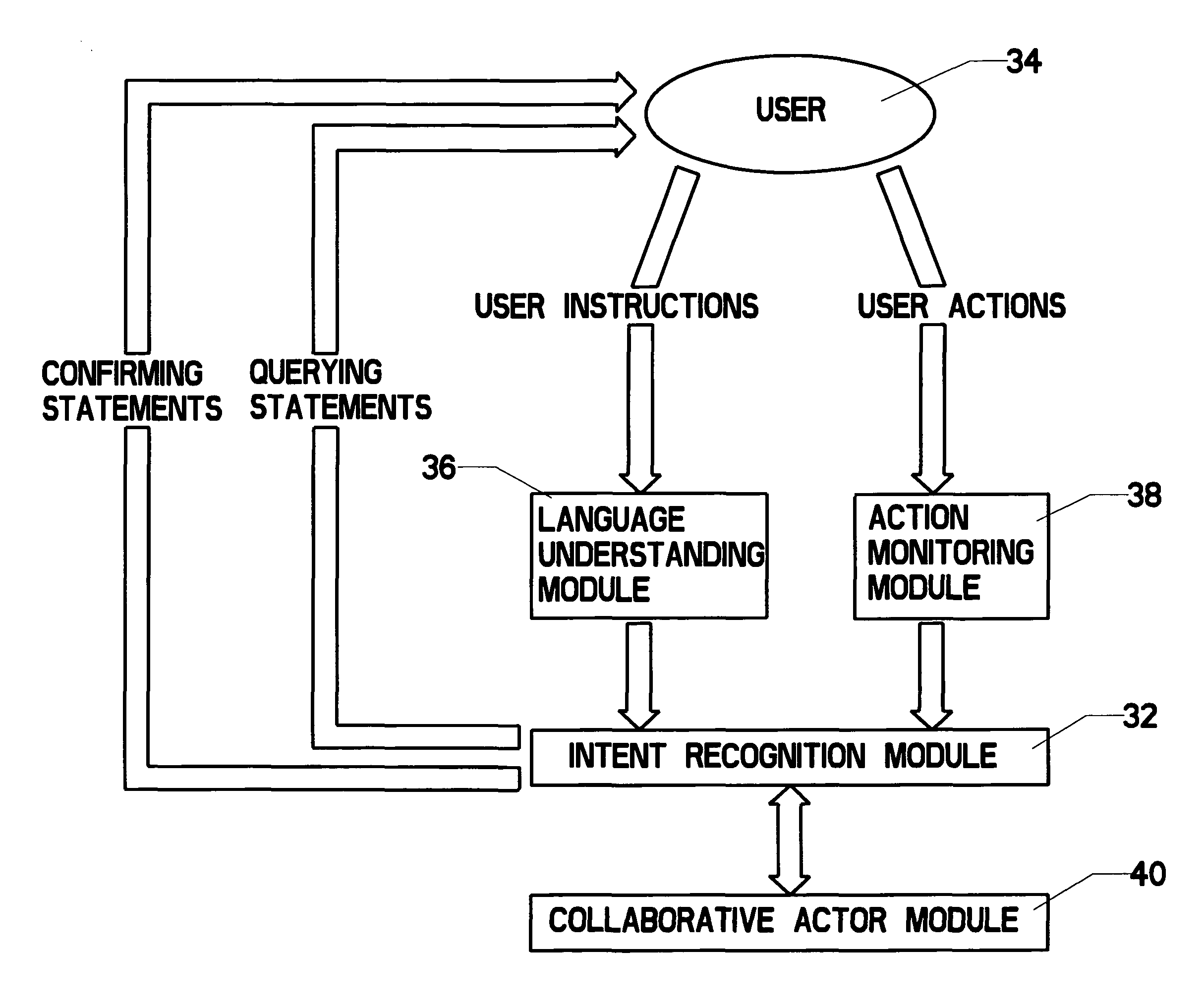
Interactive complex task teaching system that allows for natural language input, recognizes a user's intent, and automatically performs tasks in document object model (DOM) nodes
ActiveUS7983997B2Error detection/correctionDigital computer detailsRepetitive taskComponent Object Model
A system which allows a user to teach a computational device how to perform complex, repetitive tasks that the user usually would perform using the device's graphical user interface (GUI) often but not limited to being a web browser. The system includes software running on a user's computational device. The user “teaches” task steps by inputting natural language and demonstrating actions with the GUI. The system uses a semantic ontology and natural language processing to create an explicit representation of the task that is stored on the computer. After a complete task has been taught, the system is able to automatically execute the task in new situations. Because the task is represented in terms of the ontology and user's intentions, the system is able to adapt to changes in the computer code while still pursuing the objectives taught by the user.
Owner:FLORIDA INST FOR HUMAN & MACHINE COGNITION
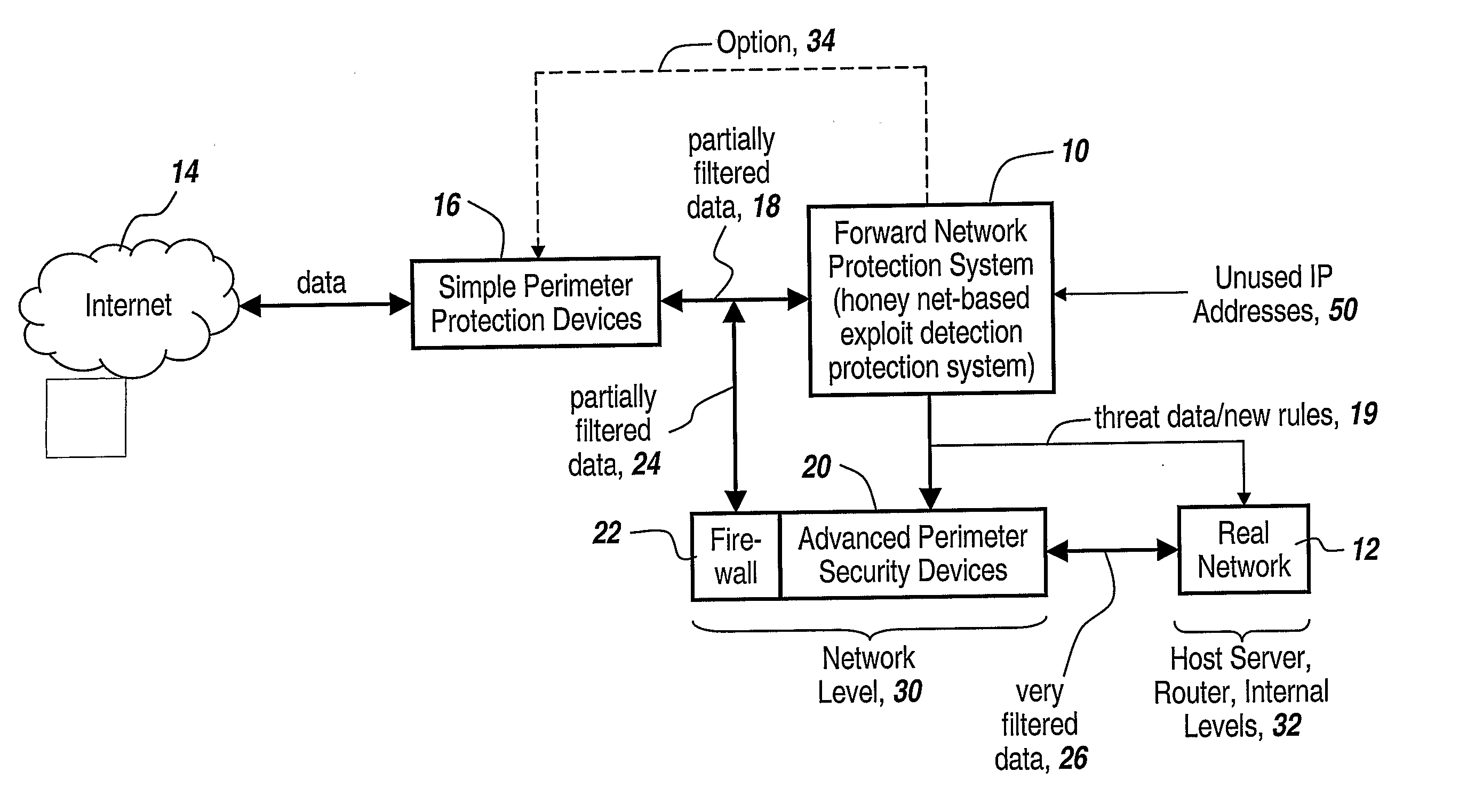
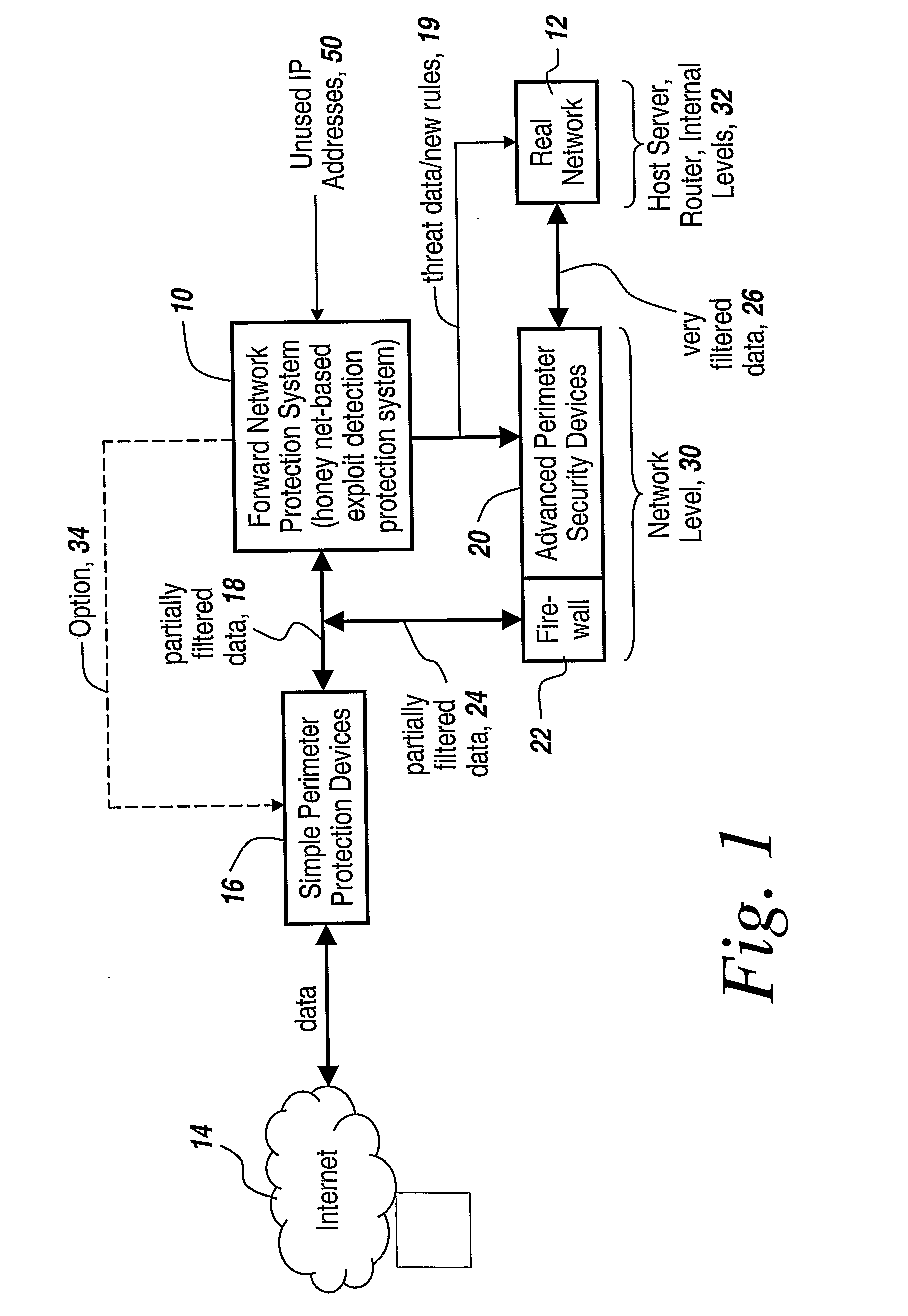
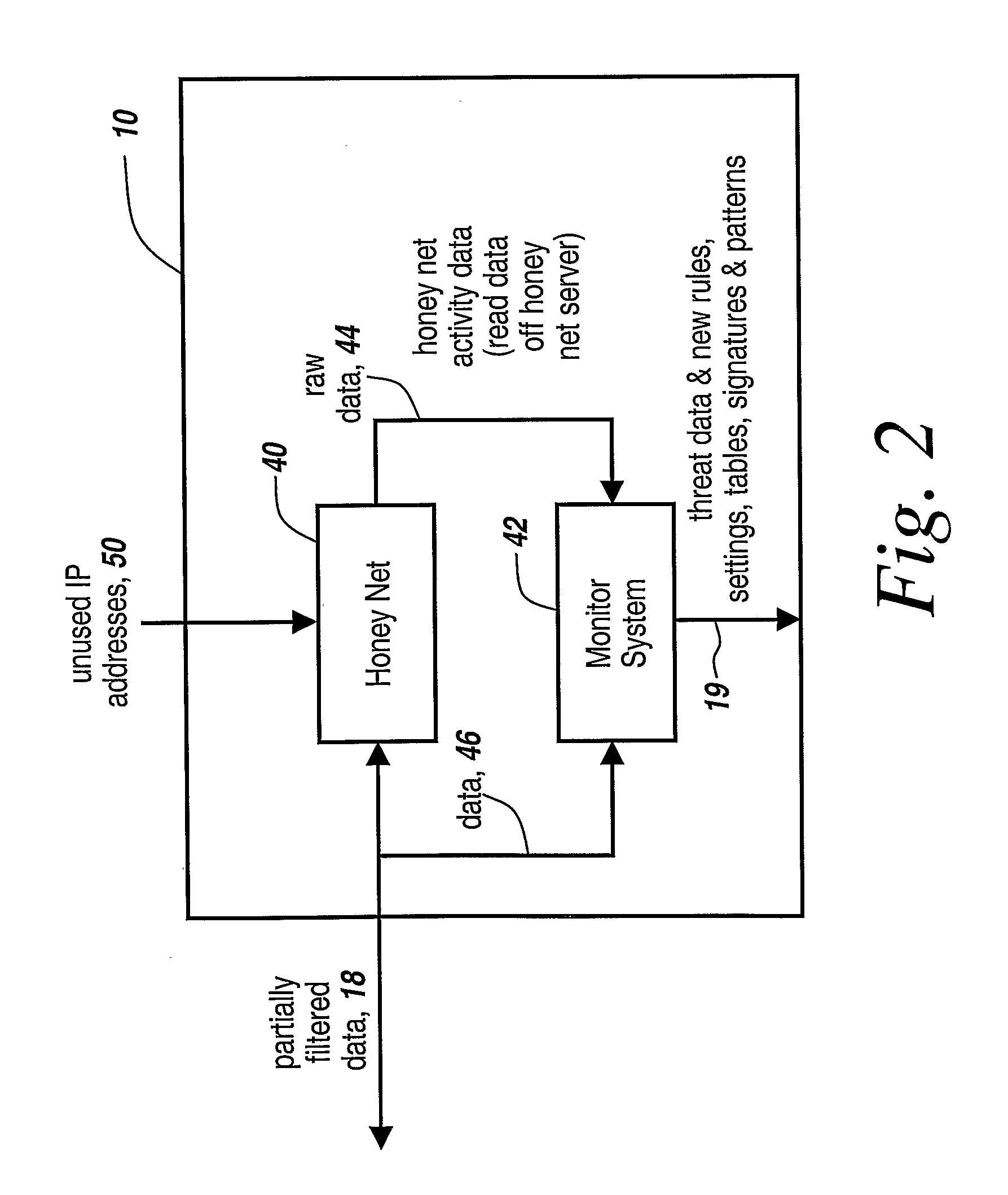
Method and Apparatus for Defending Against Zero-Day Worm-Based Attacks
InactiveUS20080098476A1Curb workloadEliminate usual spam and other simple attackMemory loss protectionError detection/correctionData packOperational system
Honey pots are used to attract computer attacks to a virtual operating system that is a virtual instantiation of a typical deployed operational system. Honey nets are a collection of these virtual systems assembled to create a virtual network. The subject system uses a forward deployed honey net combined with a parallel monitoring system collecting data into and from the honey net, leveraging the controlled environment to identify malicious behavior and new attacks. This honey net / monitoring pair is placed ahead of the real deployed operational network and the data it uncovers is used to reconfigure network protective devices in real time to prevent zero-day based attacks from entering the real network. The forward network protection system analyzes the data gathered by the honey pots and generates signatures and new rules for protection that are coupled to both advanced perimeter network security devices and to the real network itself so that these devices can be reconfigured with threat data and new rules to prevent infected packets from entering the real network and from propagating to other machines. Note the subject system applies to both zero-day exploit-based worms and also manual attacks conducted by an individual who is leveraging novel attack methods.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC
Method and system for conducting sentiment analysis for securities research
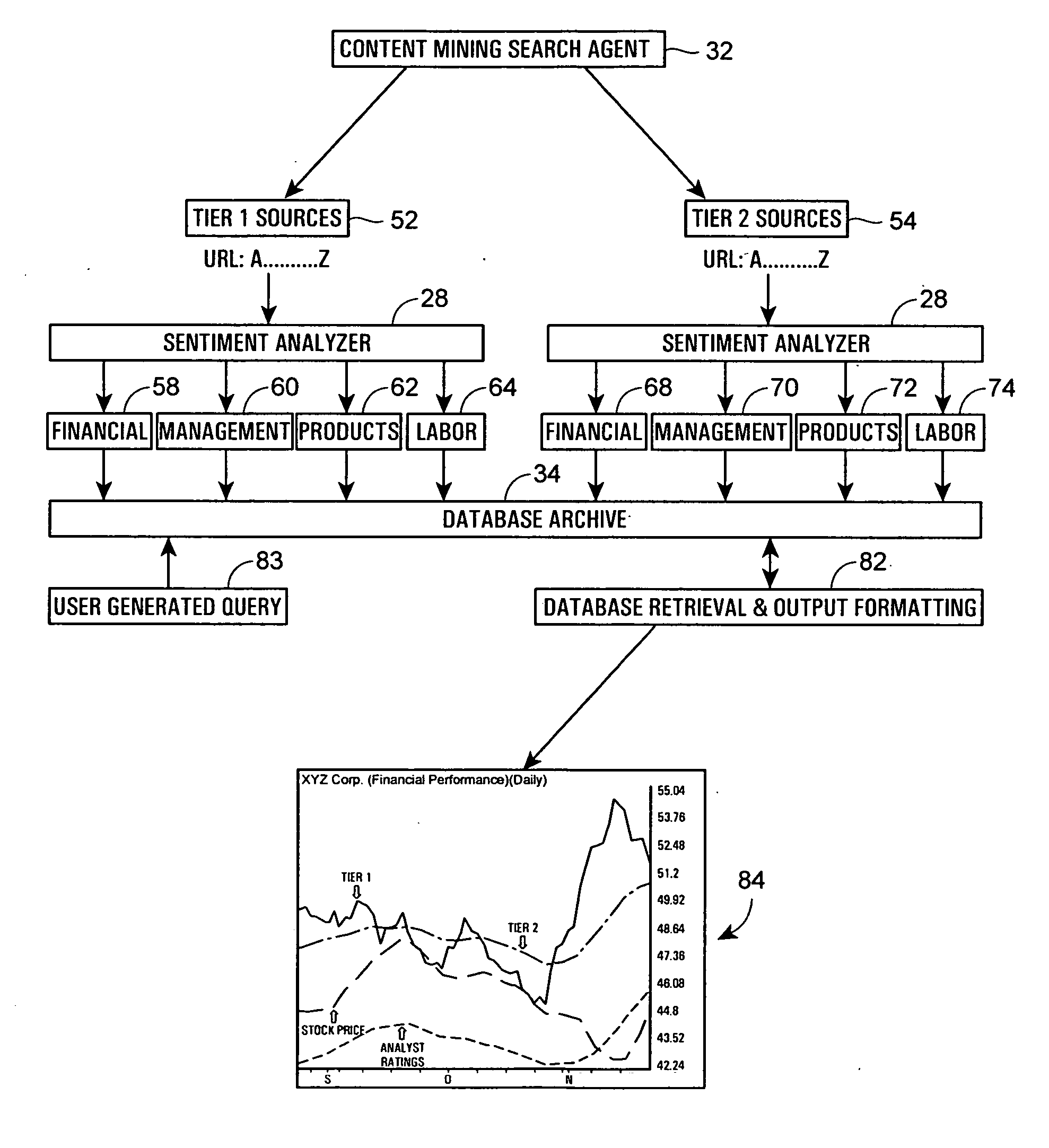
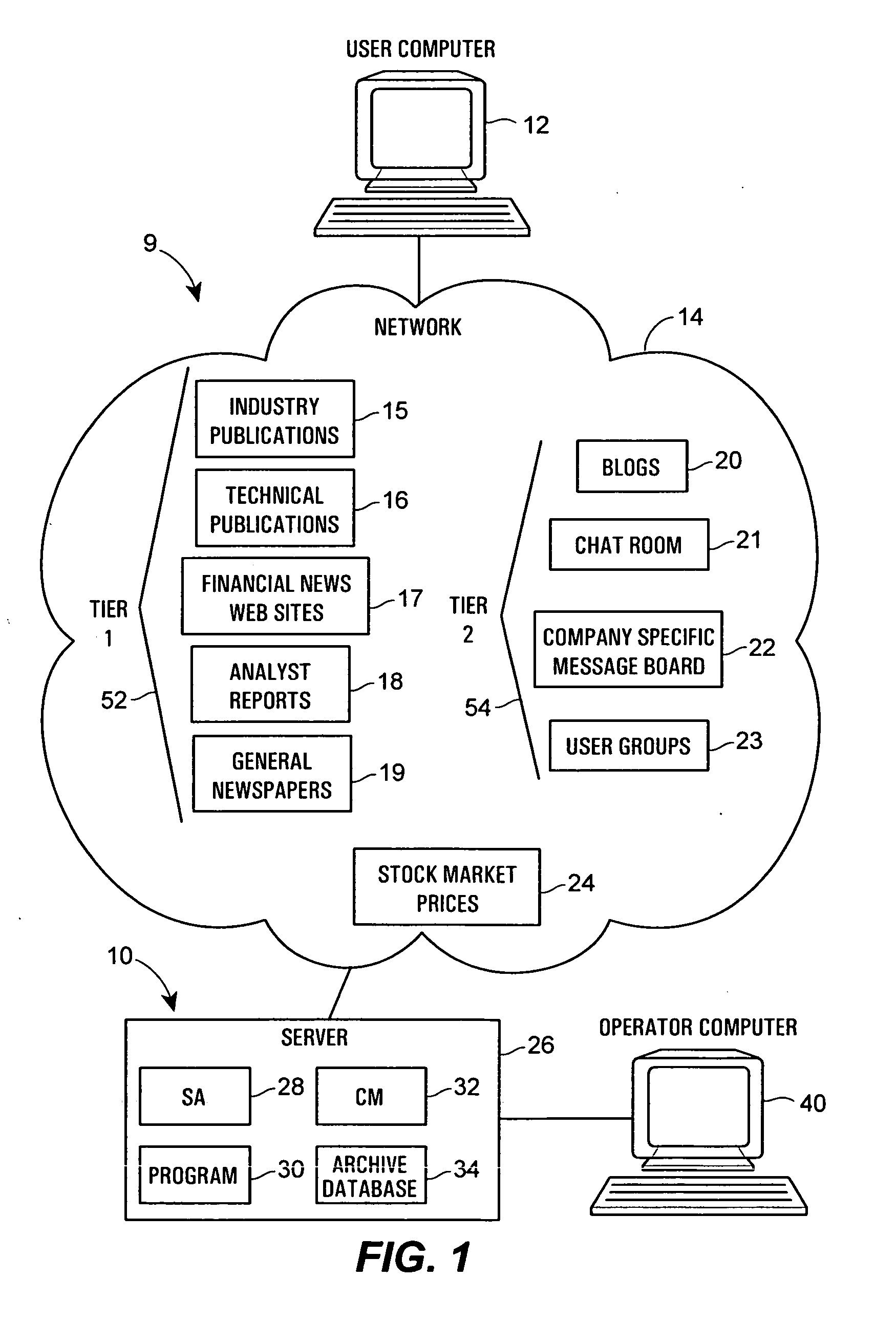
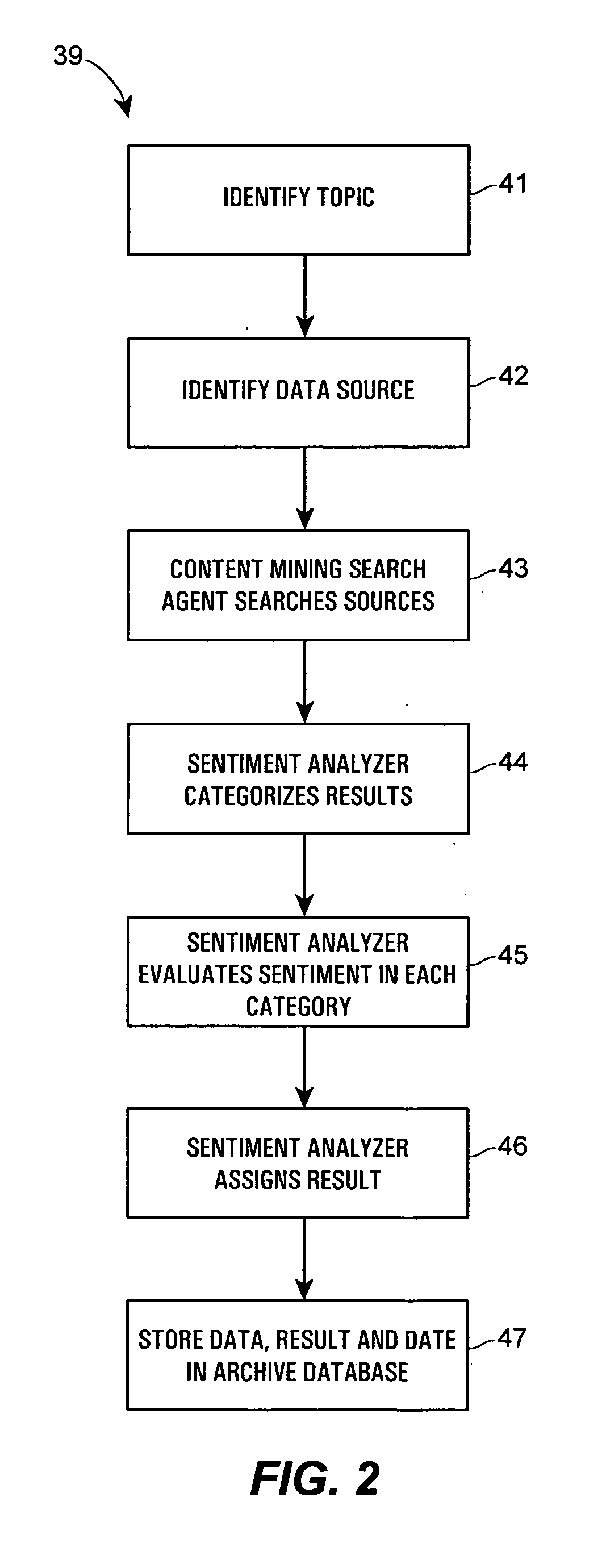
A computer system performs financial analysis on one or more financial entities, which may be corporations, securities, etc., based on the sentiment expressed about the one or more financial entities within raw textual data stored in one or more electronic data sources containing information or text related to one or more financial entities. The computer system includes a content mining search agent that identifies one or more words or phrases within raw textual data in the data sources using natural language processing to identify relevant raw textual data related to the one or more financial entities, a sentiment analyzer that analyzes the relevant raw textual data to determine the nature or the strength of the sentiment expressed about the one or more financial entities within the relevant raw textual data and that assigns a value to the nature or strength of the sentiment expressed about the one or more financial entities within the relevant raw textual data, and a user interface program that controls the content mining search agent and the sentiment analyzer and that displays, to a user, the values of the nature or strength of the sentiment expressed about the one or more financial entities within the data sources. This computer system enables a user to make better decisions regarding whether or not to purchase or invest in the one or more financial entities.
Owner:AIM HLDG LLC
Method and system for consolidating and distributing information
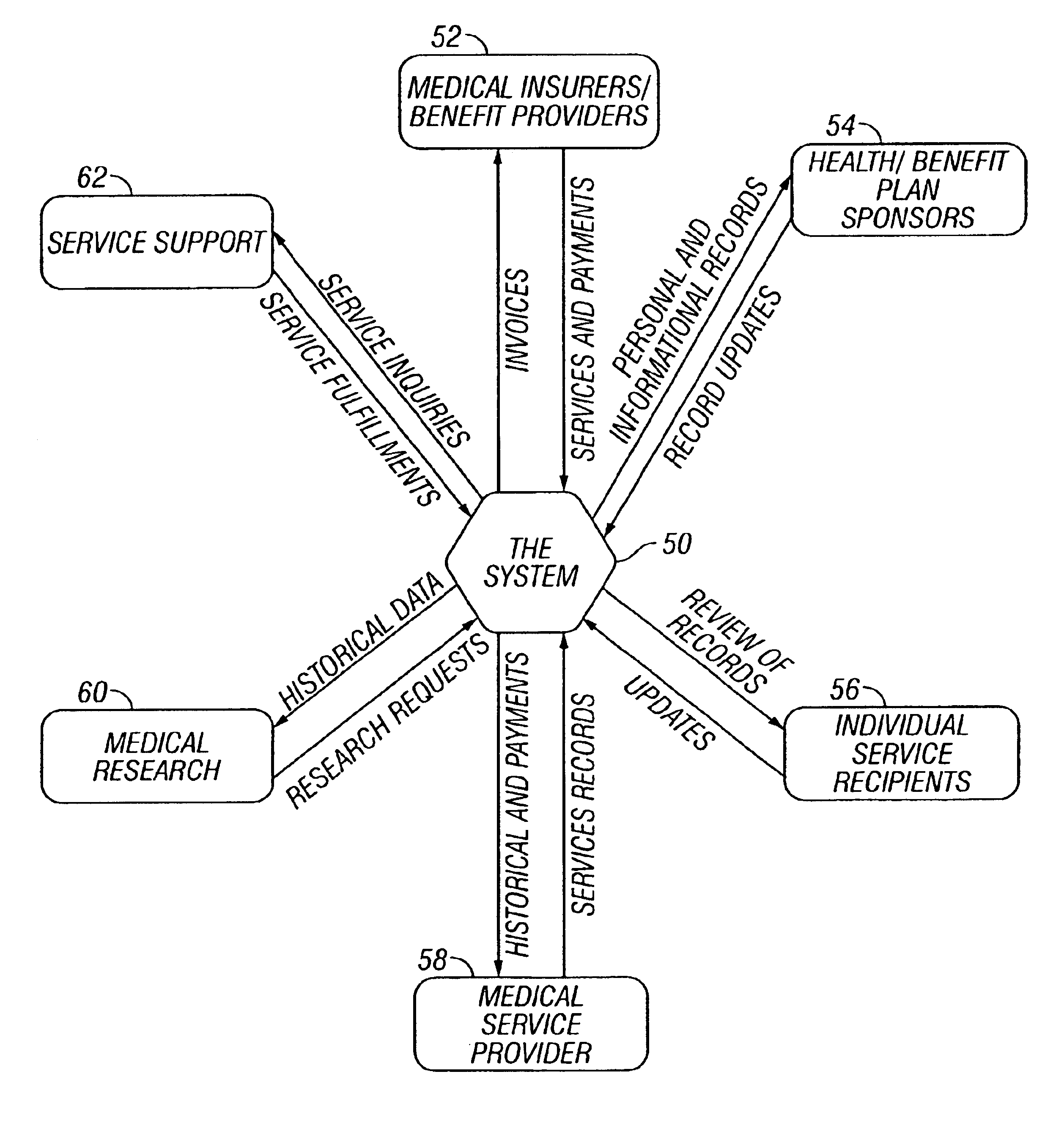
InactiveUS6915265B1Easy accessEasy transferDrug and medicationsOffice automationNetwork linkInformation device
A method and system are provided for consolidating and distributing information. Implementation of system functionalities for both restricted local and unrestricted system-wide uses are permitted. Open standards for hardware, software and firmware components and standardized medical codes, definitions and formats are supported. The preferred embodiment of the invention provides an integrated health care system. The invention can also be used to allow secure access to Social Security, annuity, retirement account, and benefit information, allowing individuals a unified view of their benefit and payment status. A centralized host maintains, consolidates, and redistributes information generated at all networked locations. Information is electronically transferred among the system components to link an individual's local records to those stored remotely. The individual information device, centralized host computer, and any other computers or networks linked to the system can therefore be automatically updated. An individual information device stores a service recipient's insurance information, a emergency records and critical health care histories. This information is accessed by the system for use in managing any aspect of the service recipient's health care. Portable terminals can be used to access the system. A portable terminal can also be used independently from the system to perform health care functions. Unrestricted system-wide, or restricted local uses are supported. Insurance coverage for services and treatments can be determined and the information transmitted directly from the carrier(s) to the service recipient and service provider(s). Supported features include service authorization, messaging, diagnostic services,coverage determination, billing, and electronic payment.
Owner:JOHNSON JANICE
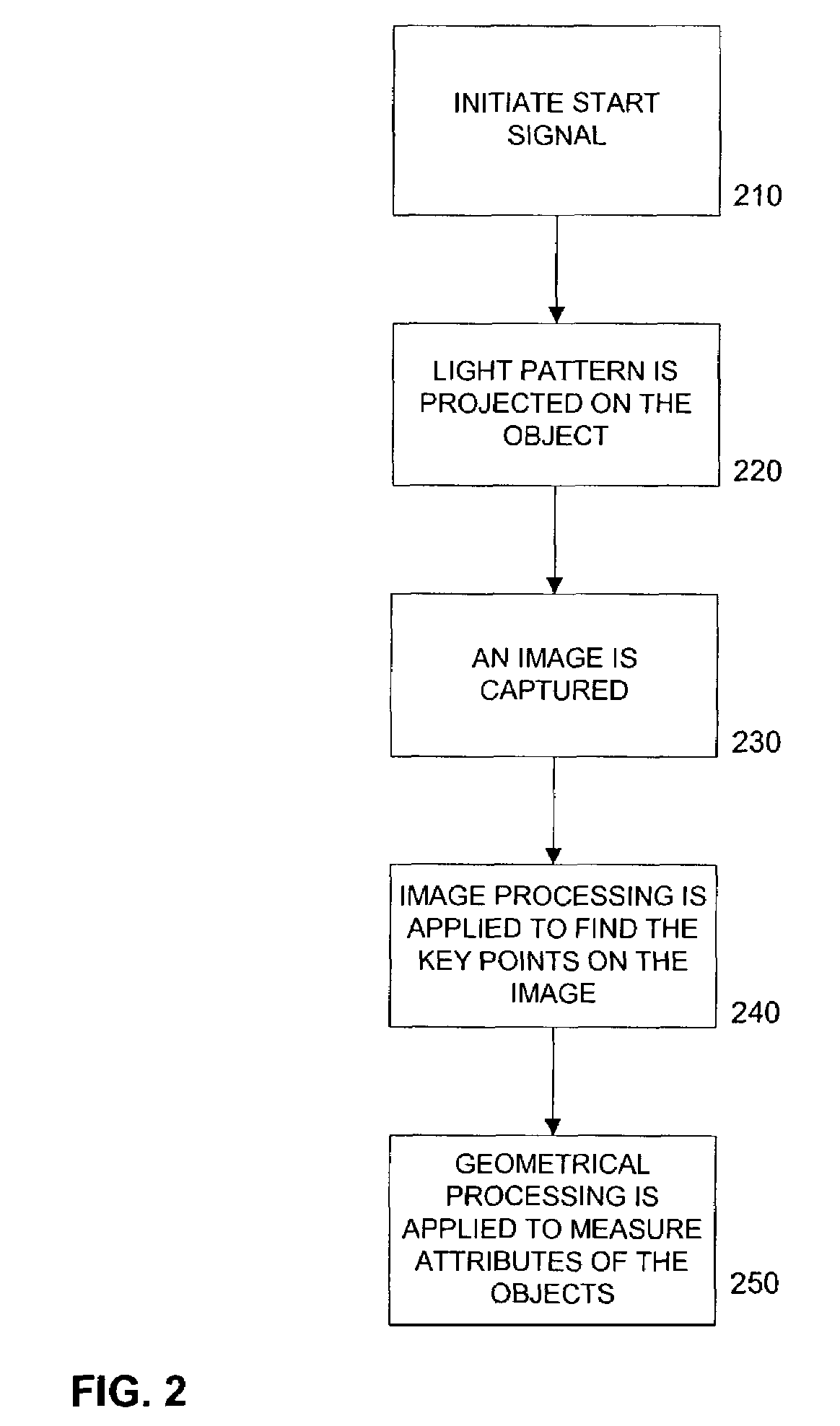
Optical methods for remotely measuring objects
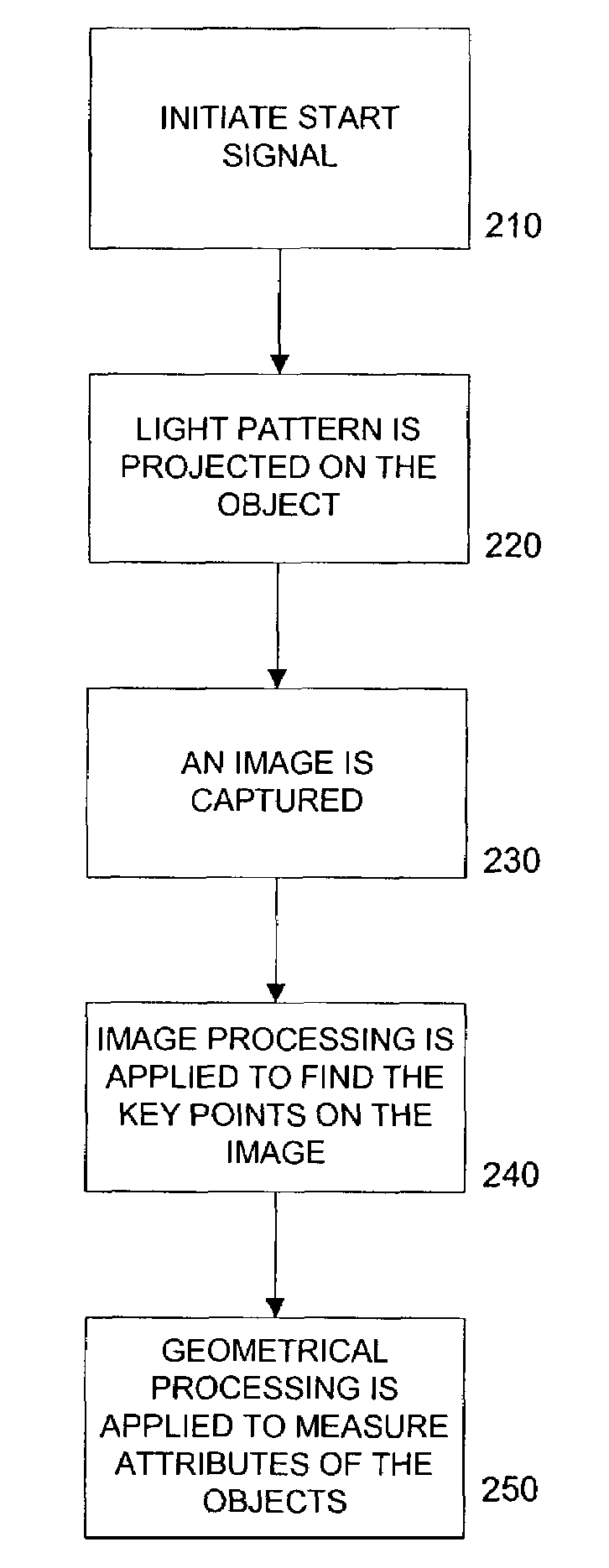
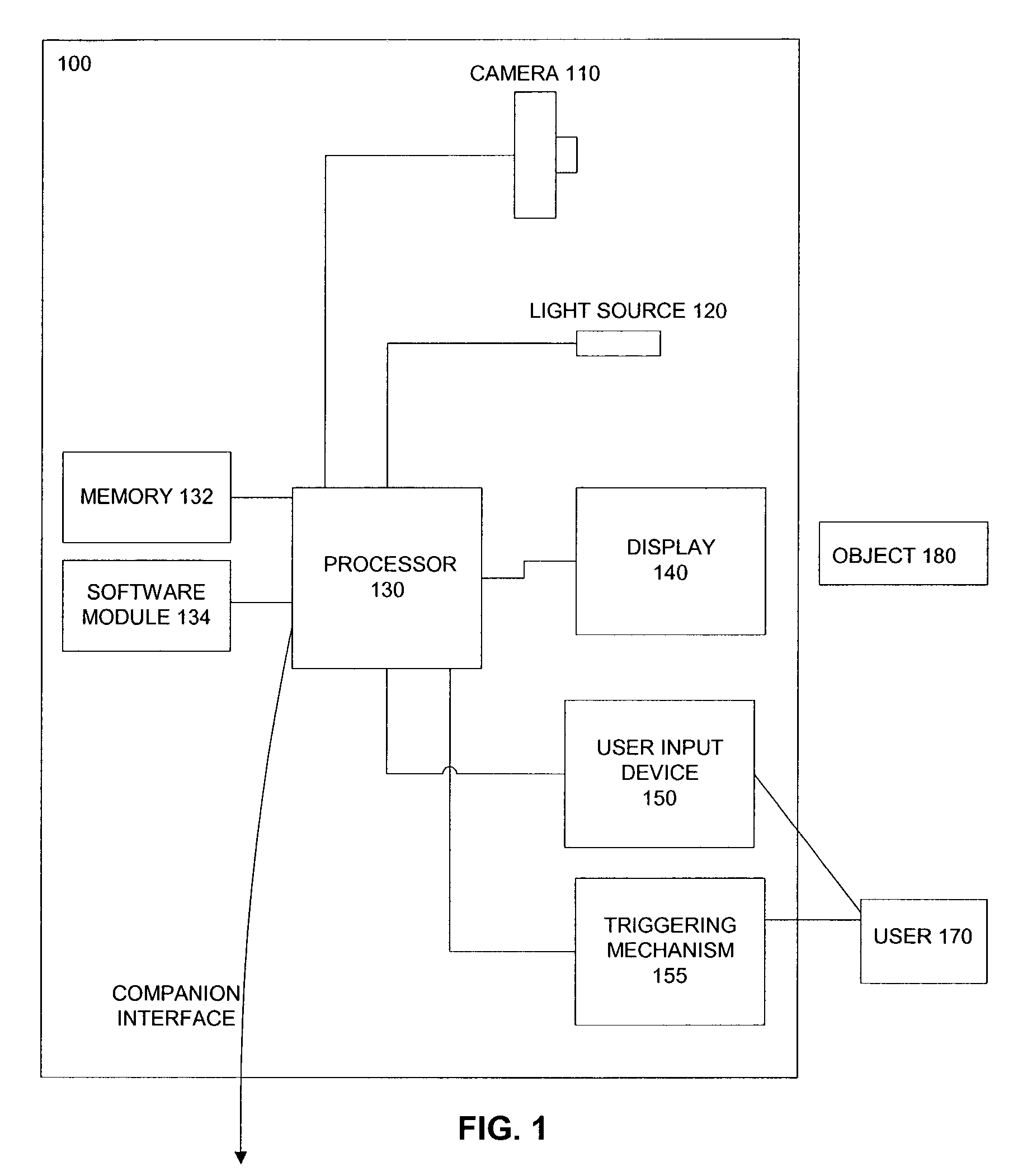
A class of measurement devices can be made available using a family of projection patterns and image processing and computer vision algorithms. The proposed system involves a camera system, one or more structured light source, or a special pattern that is already drawn on the object under measurement. The camera system uses computer vision and image processing techniques to measure the real length of the projected pattern. The method can be extended to measure the volumes of boxes, or angles on planar surfaces.
Owner:MICROSOFT TECH LICENSING LLC
System and method for resource management
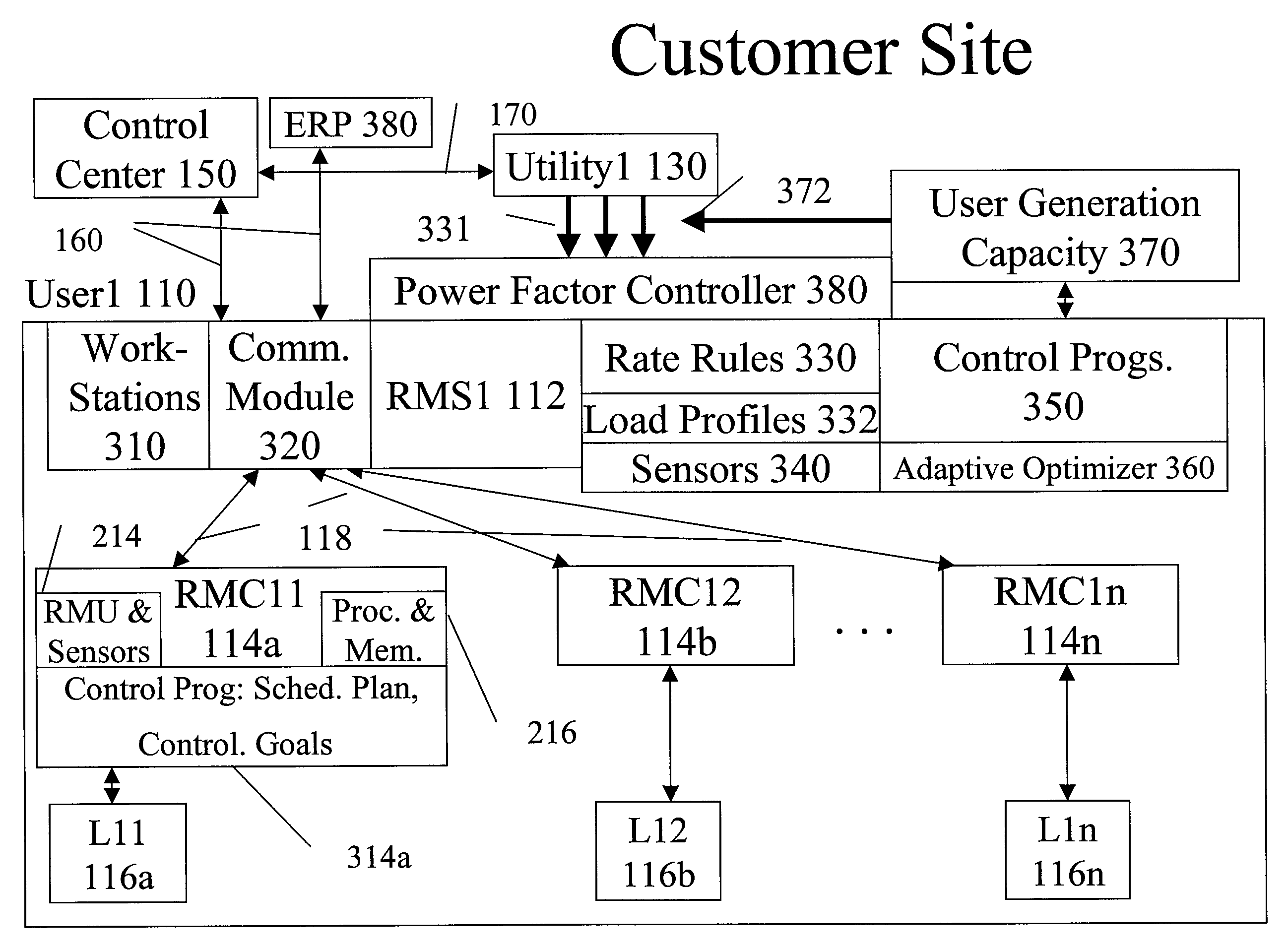
InactiveUS20080172312A1Low costImprove efficiencyElectric signal transmission systemsLevel controlResource managementSystem usage
A system uses an intelligent load controller for managing use of a consumable resource at an associated load. The controller has a resource measuring component for measuring the rate of use of the resource by the associated load, including measuring at least one of an instantaneous usage rate and a usage rate over an integration period and a load status component for receiving load status data for the associated load. The controller also has a communication component for receiving control messages from and sending load status messages to other associated controllers; a memory for storing a load control goal set; and a load control computer program responsive to the resource measuring component, the load status component, the control messages from other associated controllers and the load control goal set, to determine a load operating level for, and provide control commands to, the associated load.
Owner:SYNESIOU ANDREAS JOANNI +1
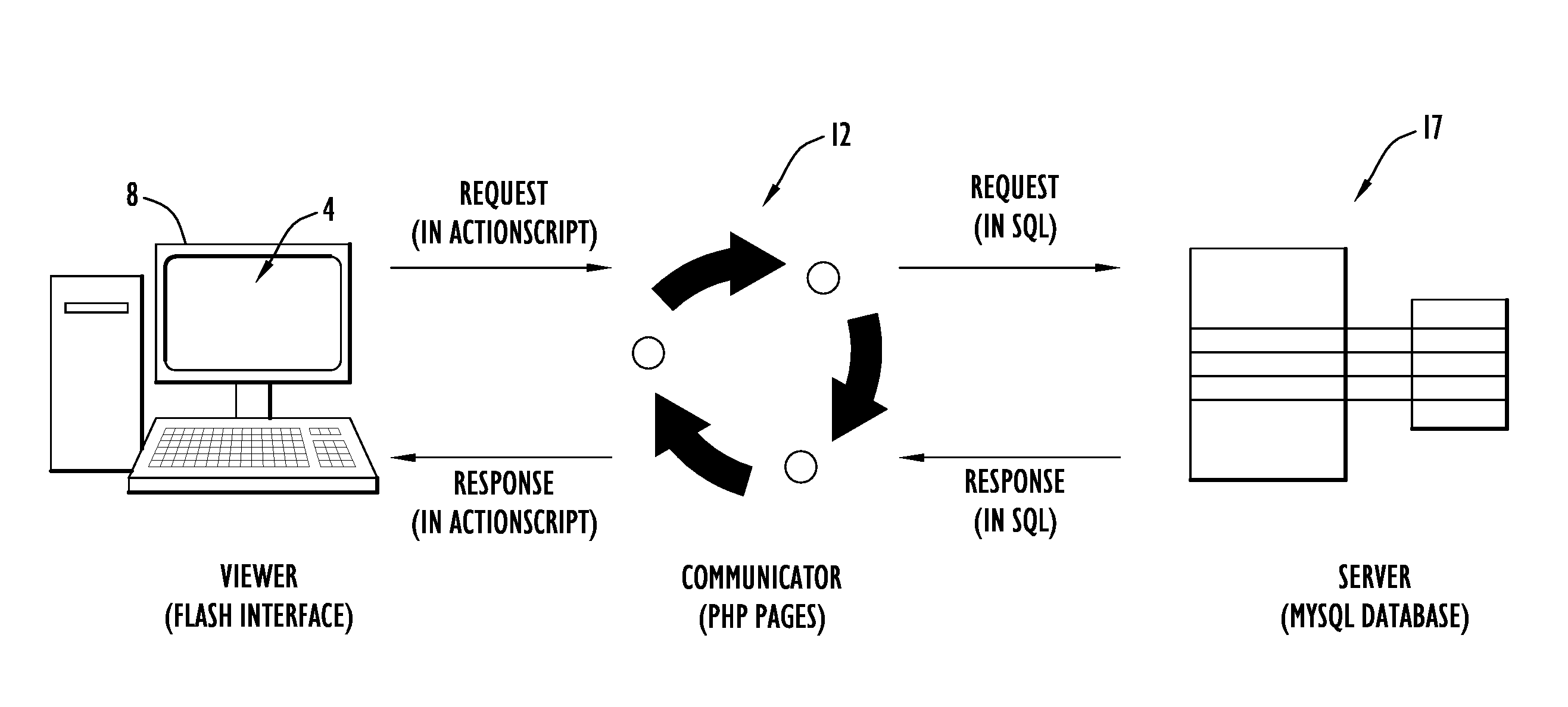
System and Method of Overlaying and Integrating Data with Geographic Mapping Applications
InactiveUS20080059889A1Comprehensive geographic breadthComprehensive detailDigital data processing detailsRadio transmissionRelational databaseTopic analysis
Owner:PARKER CHERYL +1
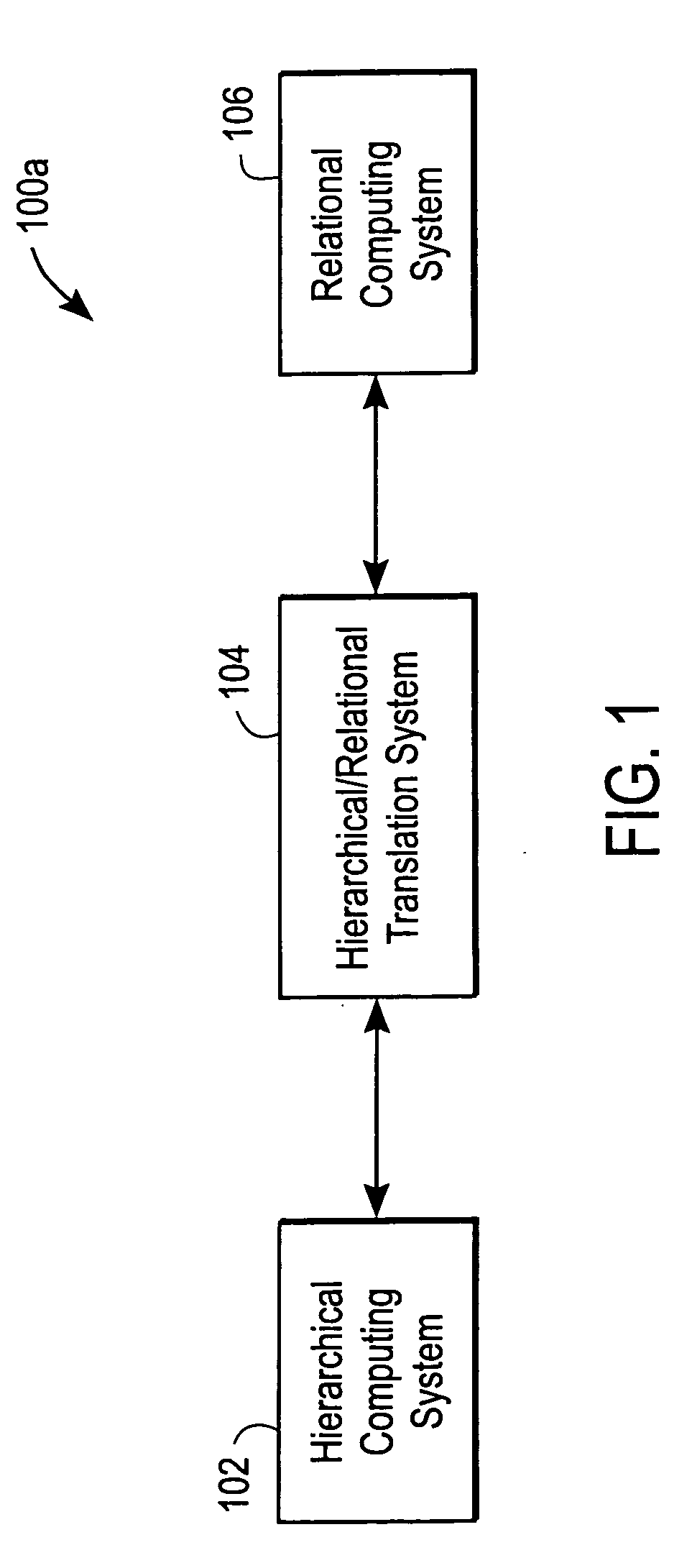
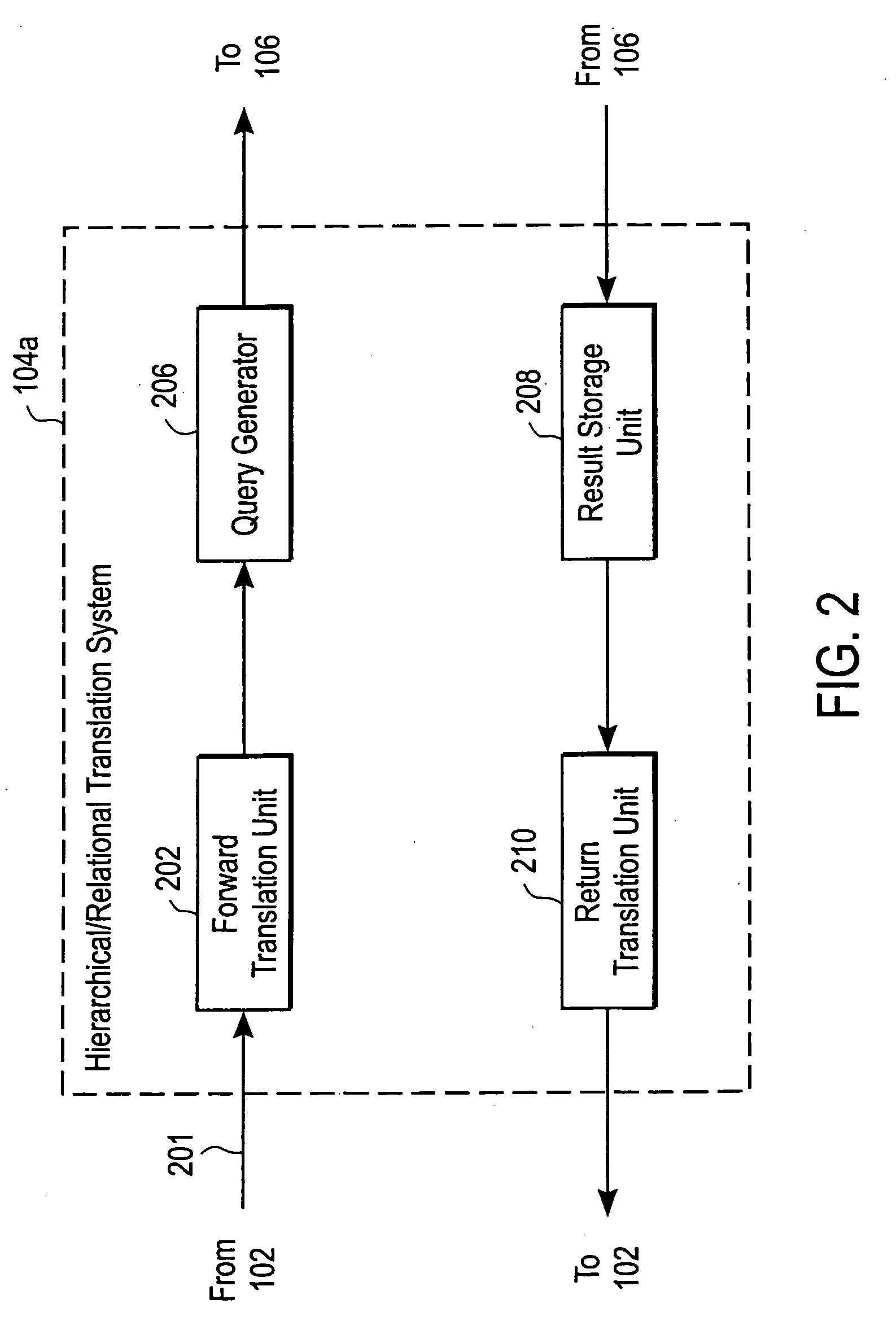
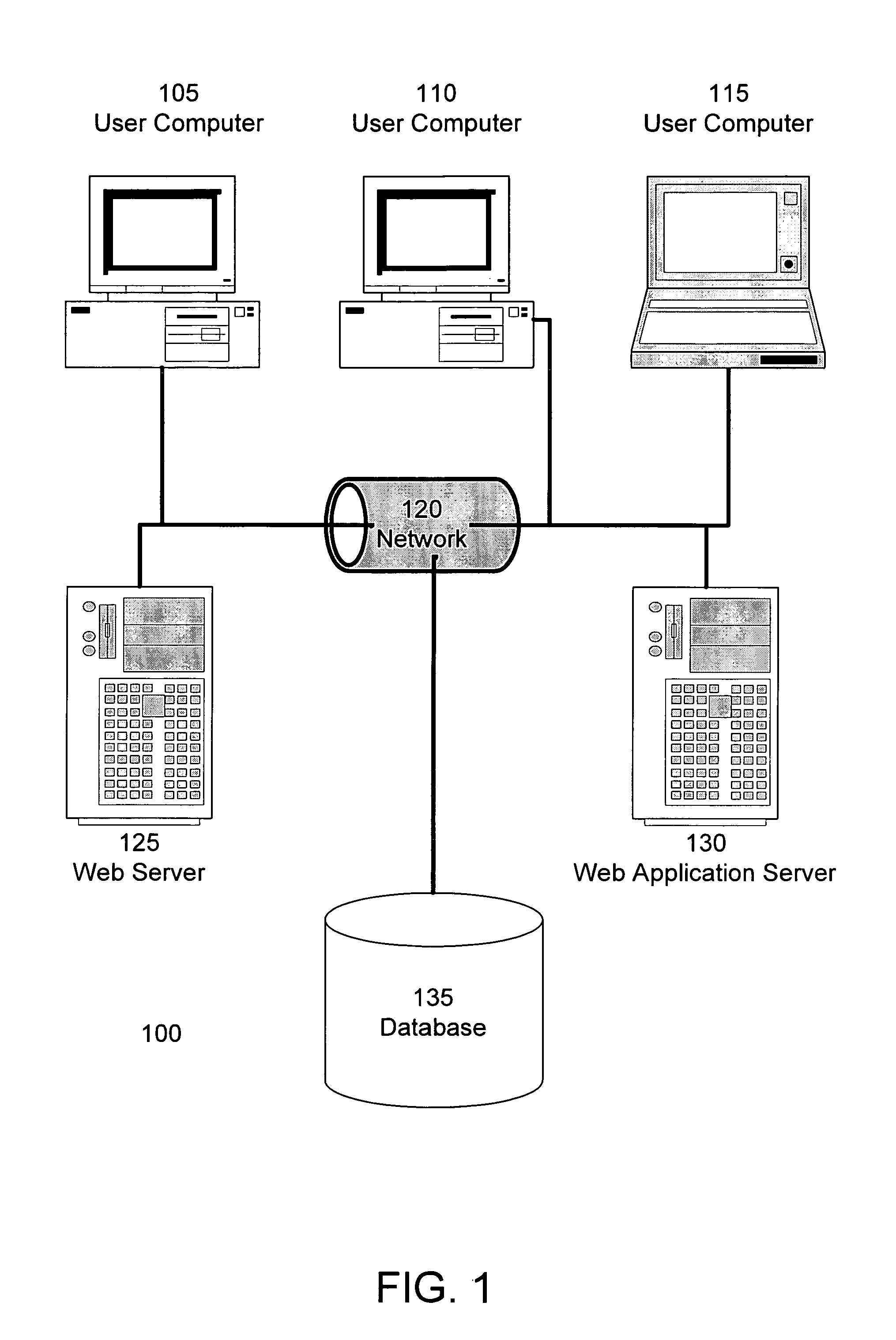
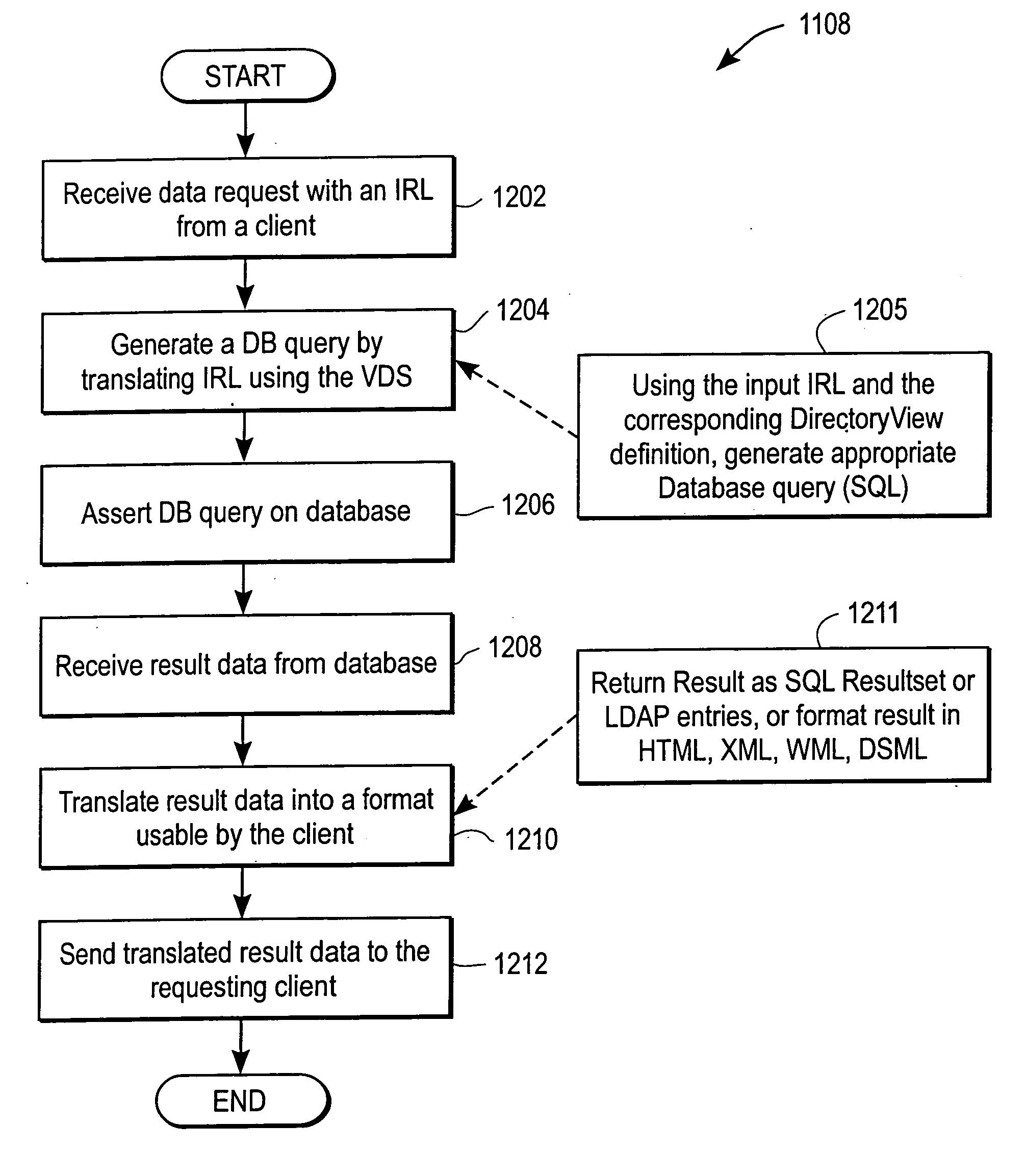
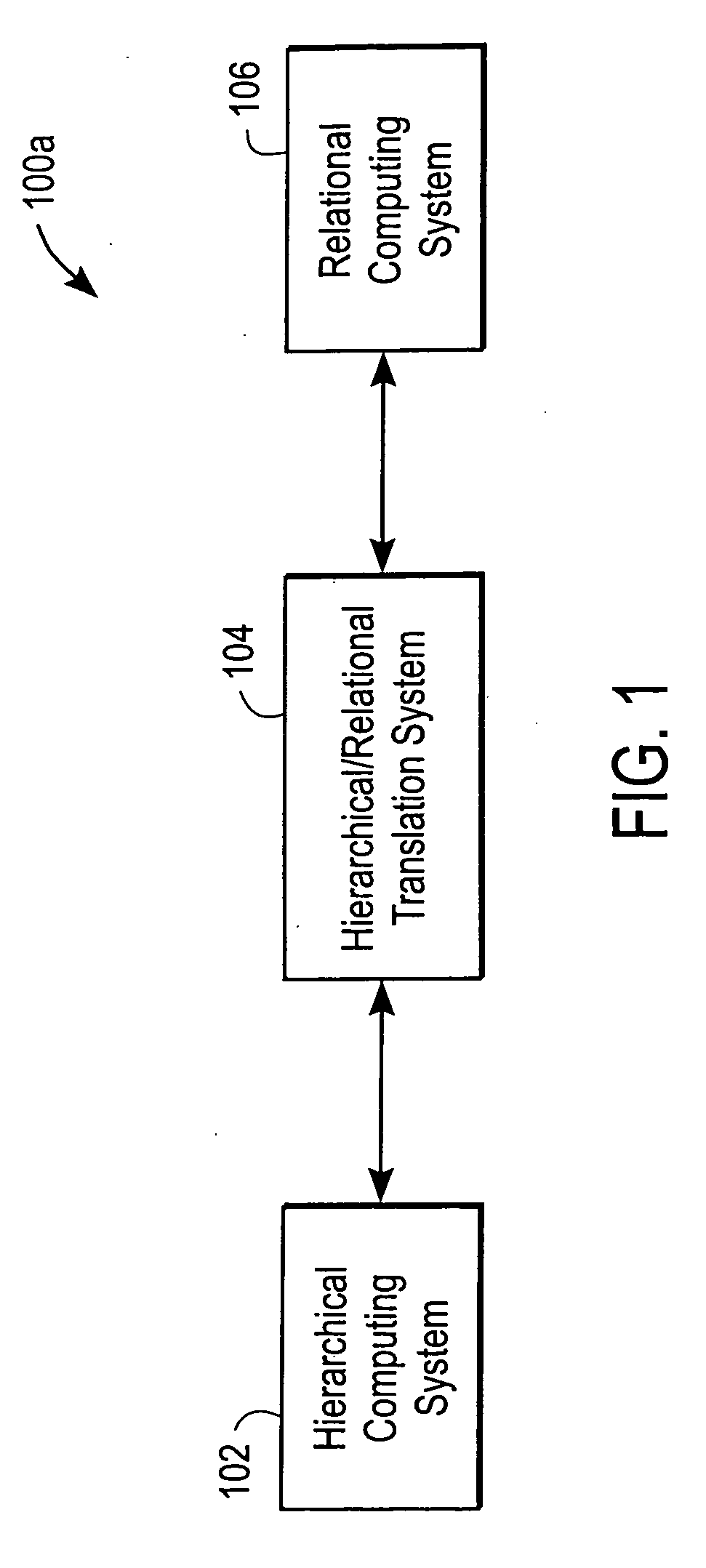
System and method for providing access to databases via directories and other hierarchical structures and interfaces
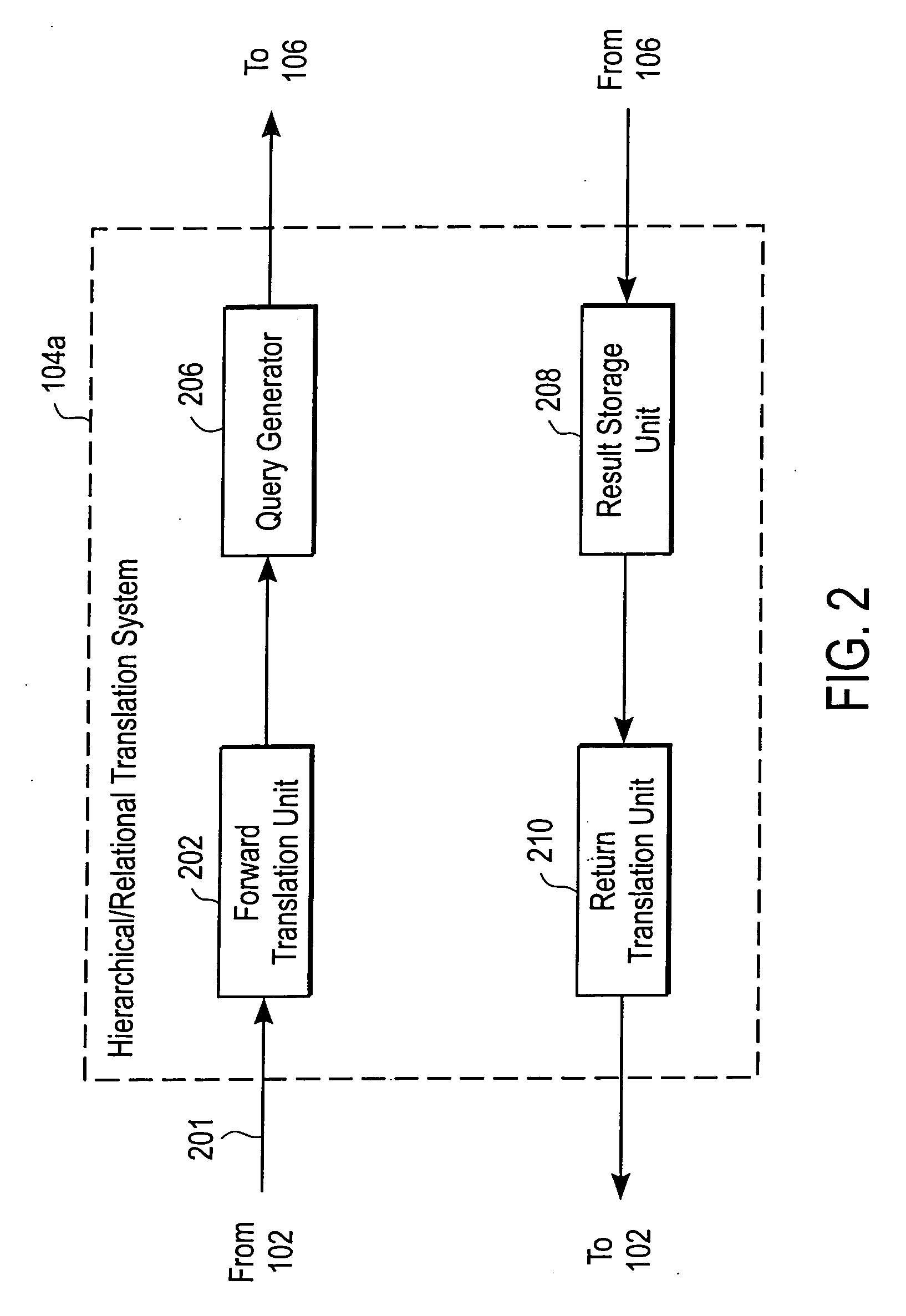
InactiveUS20060020586A1High cost of deploymentData processing applicationsWebsite content managementSystem usageRelational database schema
A hierarchical / relational translation system is provided for enabling information from unrelated heterogeneous relational computing systems to be accessed, navigated, searched, browsed, and shared over a hierarchical computing system. In one embodiment, the hierarchical / relational translation system includes a virtual directory server for capturing information in the nature of relational database schema and metadata. The captured schema and metadata are then translated into virtual directories that are universally compatible with standard communication protocols used with hierarchical computing systems. A virtual directory of information organizes an index of data records and a standard addressing schema is provided to enable customizable access to relevant views of relational computing systems. Several embodiments for presenting the virtual directory information tree are included. In one embodiment, the virtual directory is displayed using browser format. In another embodiment, the virtual directory is presented in electronic mail format. Still, in another embodiment the virtual directory is presented over a wireless medium and through portable devices.
Owner:PROMPT MICHEL +1
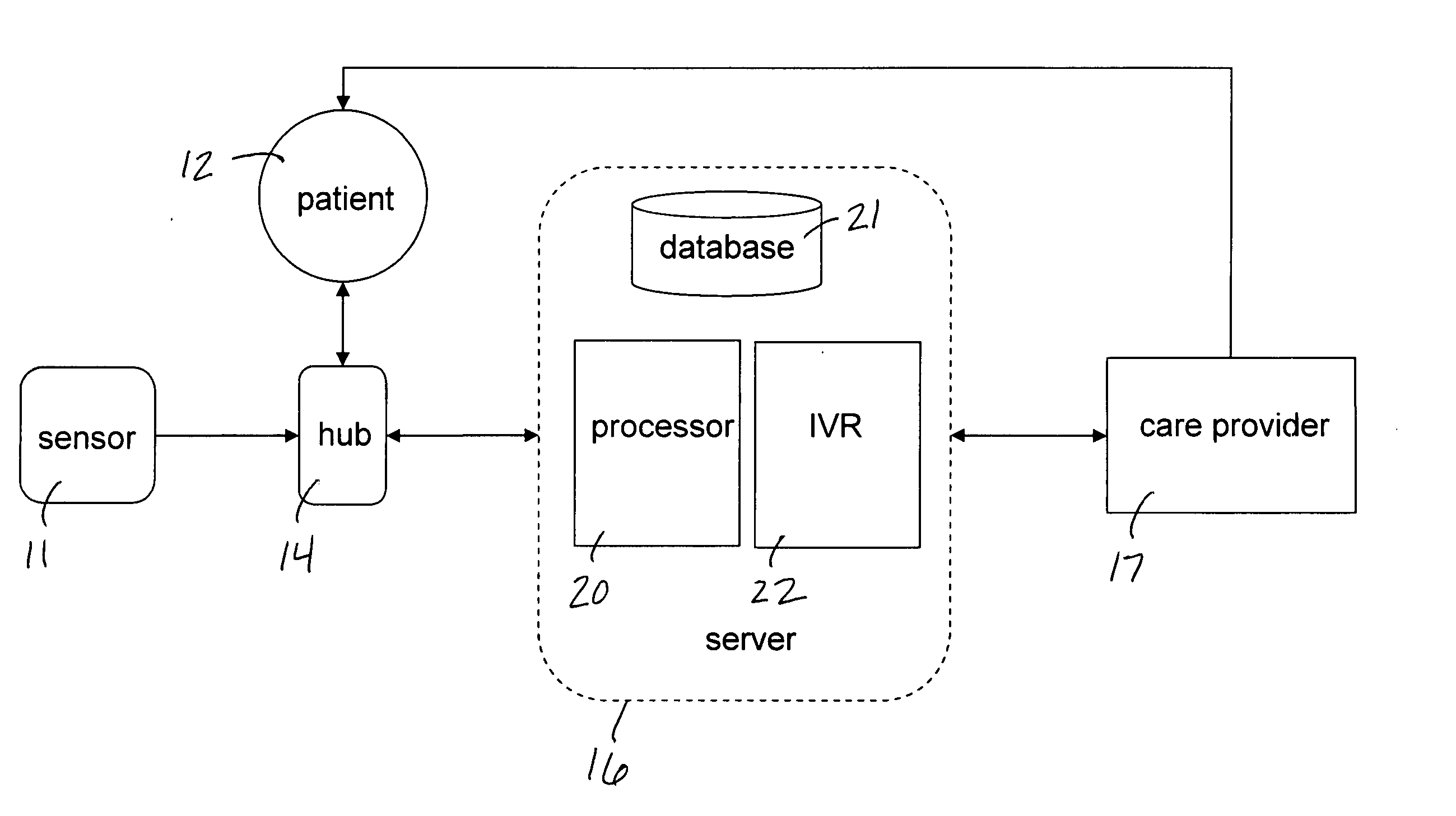
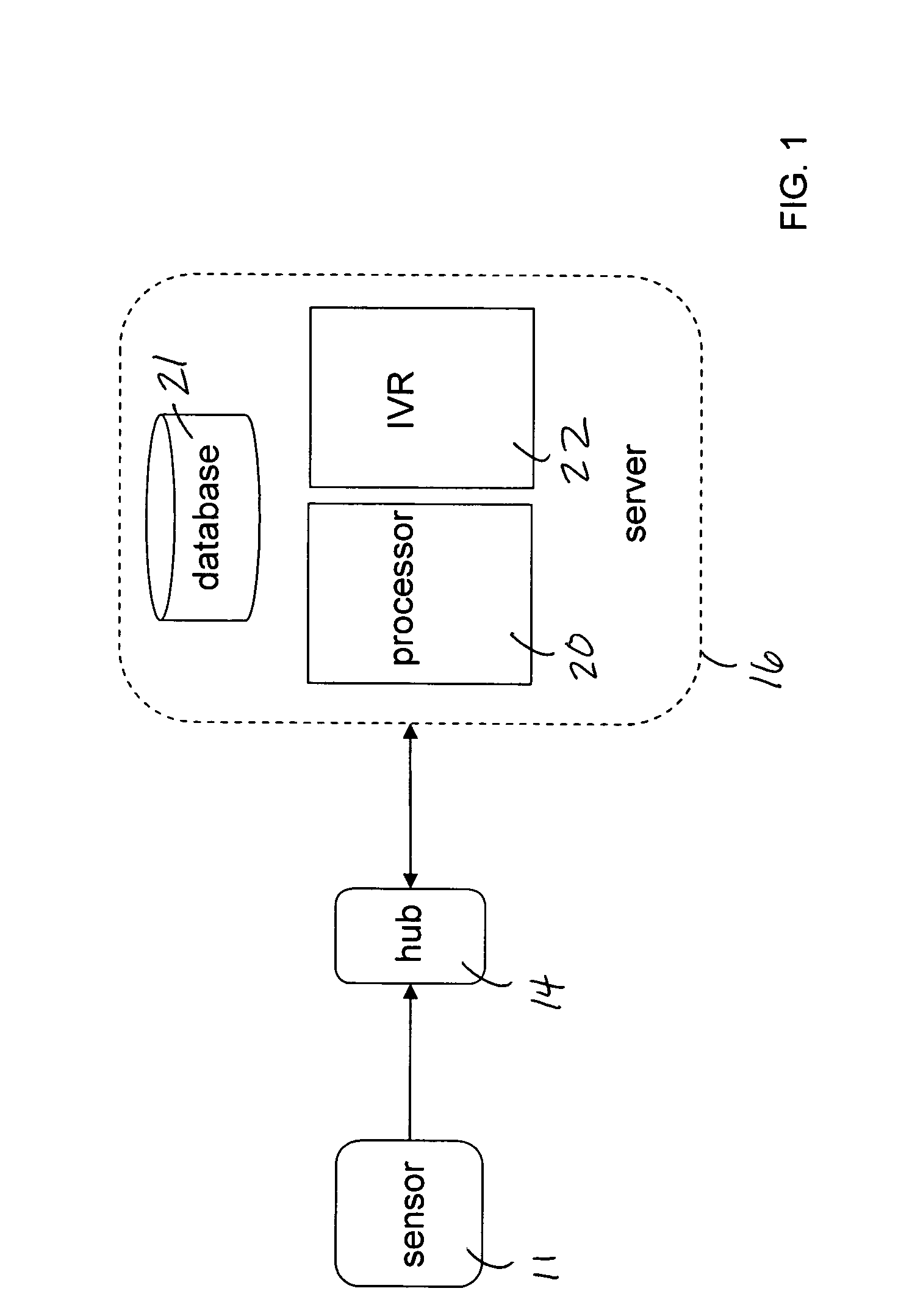
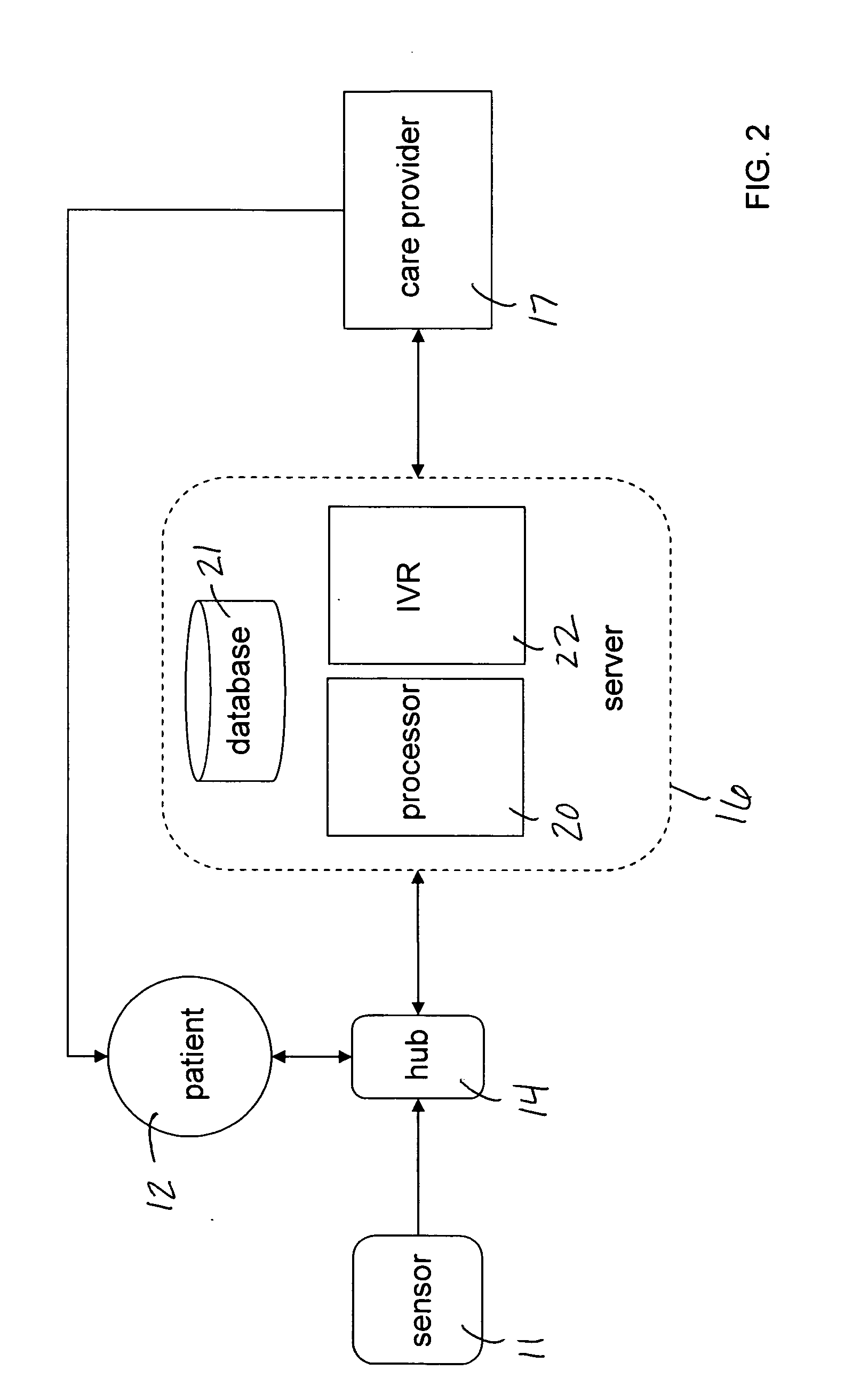
Mobile patient monitoring system with automatic data alerts
InactiveUS20060089542A1Improve complianceLower cost of careMedical communicationSurgeryPatient complianceEmergency medicine
A system to increase compliance with patient monitoring protocols for patients with chronic disease. The system uses a wireless telecommunication device as the hub of the system. The hub is configured to increase patient compliance with a monitoring protocol by being integrated with a mobile device, such as a cellular phone or PDA, that the patient normally carries or wears. The hub is further configured to increase compliance by displaying games that incorporate monitored conditions and providing rewards to the patient when he complies with the monitoring protocol. The hub receives physiological data about the patient from a medical sensor then collates the sensed data with certain data input by the patient. The reading is transmitted to a server that uses a software application to automatically examine and interpret the data. Alerts are sent to the health care provider only when the reading is outside specified parameters. The health care provider may contact the patient about the outlying event via the network.
Owner:SAFE N SOUND SOLUTIONS
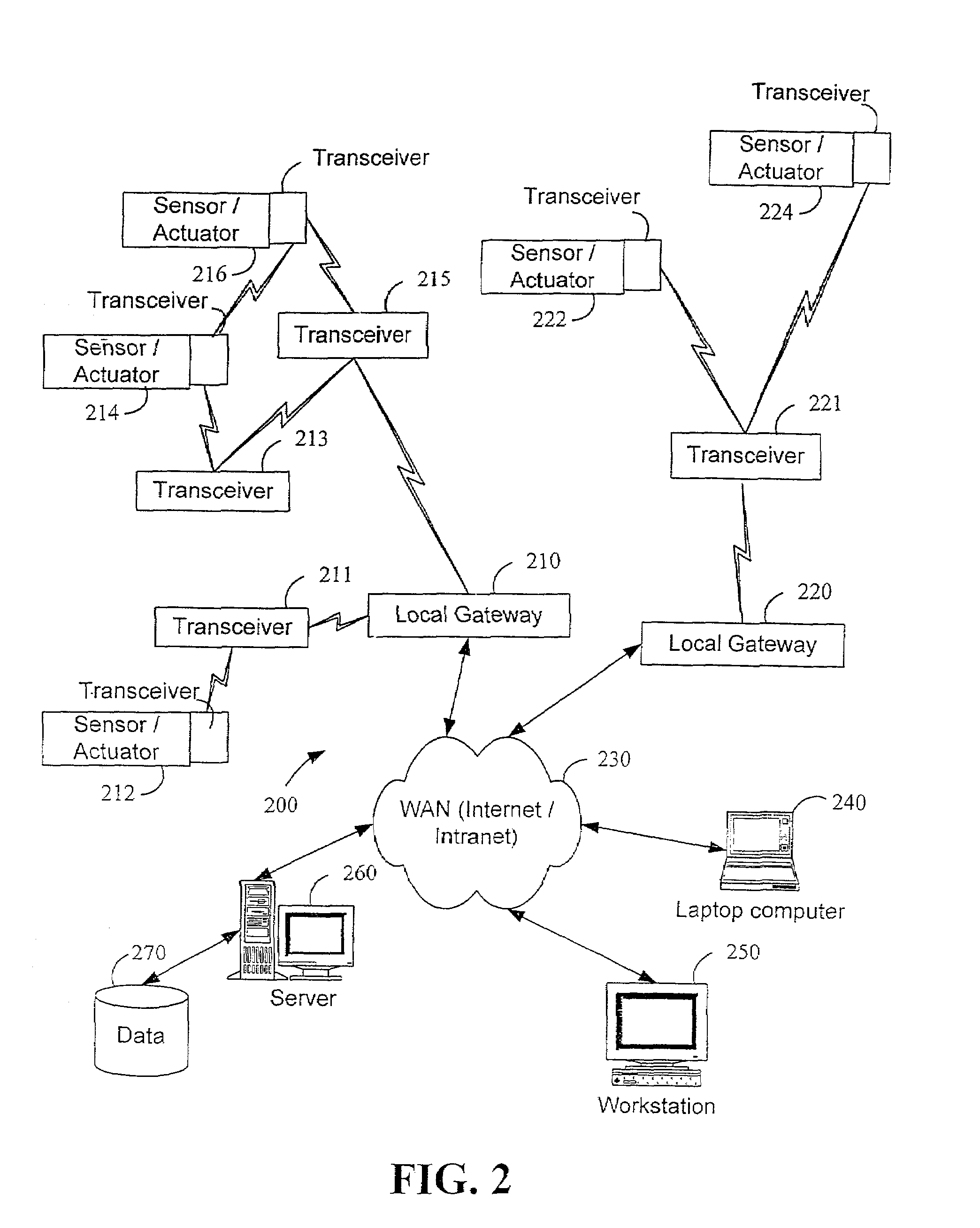
System and method for monitoring and controlling remote devices
InactiveUS20060181406A1Closed feedback loopIntegrated inexpensivelyFrequency-division multiplex detailsRegistering/indicating working of vehiclesTransceiverControl signal
The present invention is generally directed to a system for monitoring a variety of environmental and / or other conditions within a defined remotely located region. In accordance with one aspect of the invention, a system is configured to monitor utility meters in a defined area. The system is implemented by using a plurality of wireless transmitters, wherein each wireless transmitter is integrated into a sensor adapted to monitor a particular data input. The system also includes a plurality of transceivers that are dispersed throughout the region at defined locations. The system uses a local gateway to translate and transfer information from the transmitters to a dedicated computer on a network. The dedicated computer, collects, compiles, and stores the data for retrieval upon client demand across the network. The computer further includes means for evaluating the received information and identifying an appropriate control signal, the system further including means for applying the control signal at a designated actuator.
Owner:SIPCO
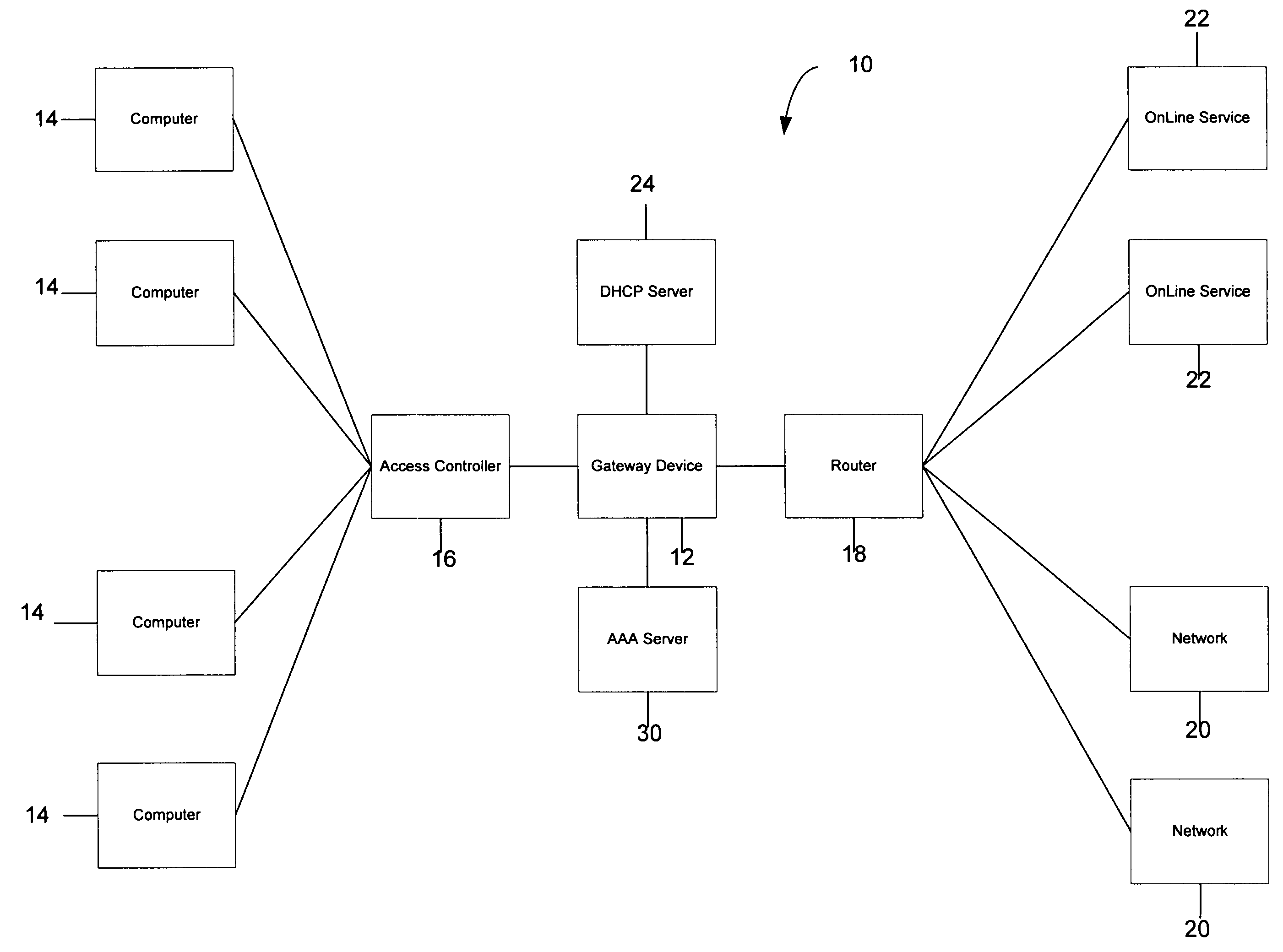
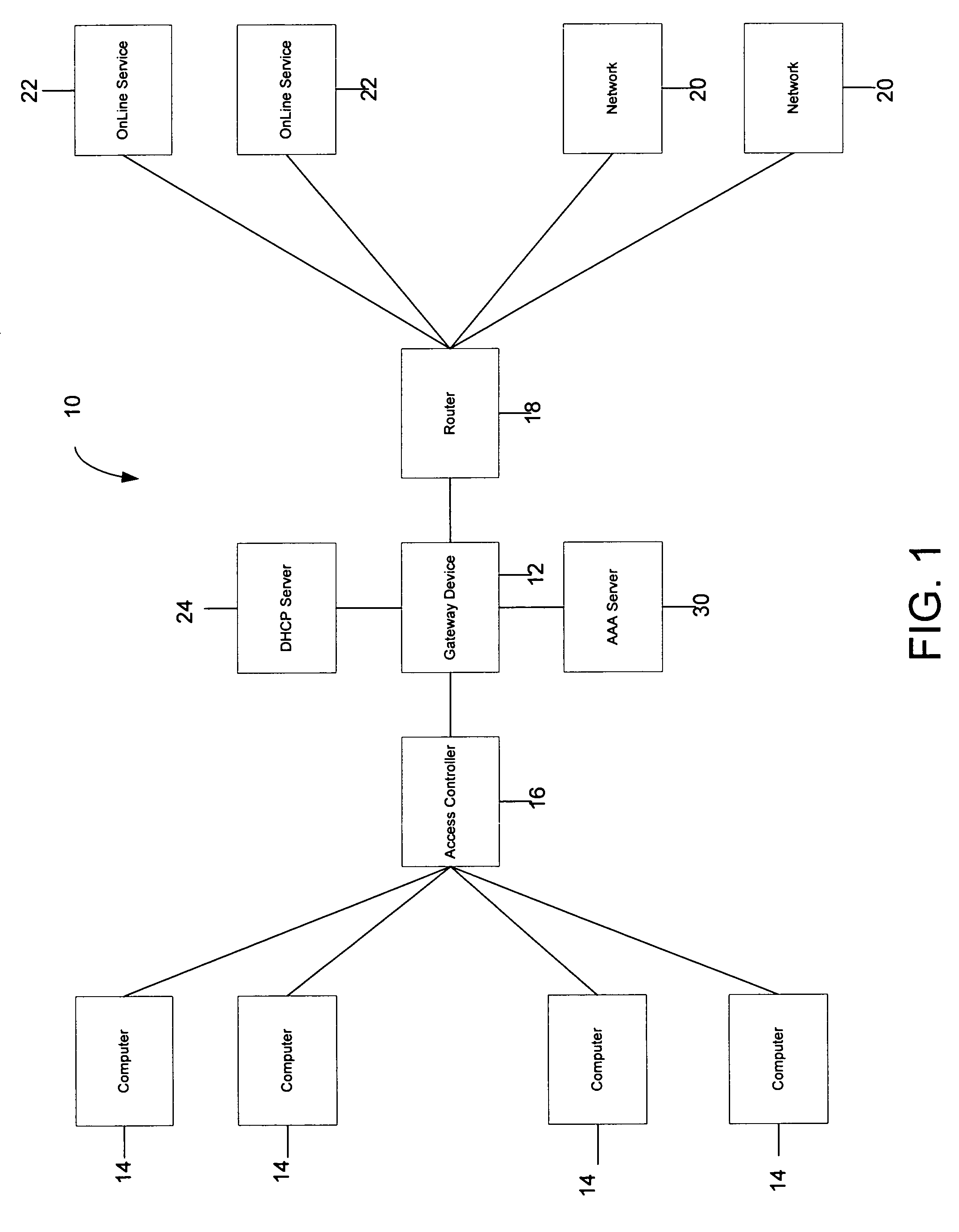
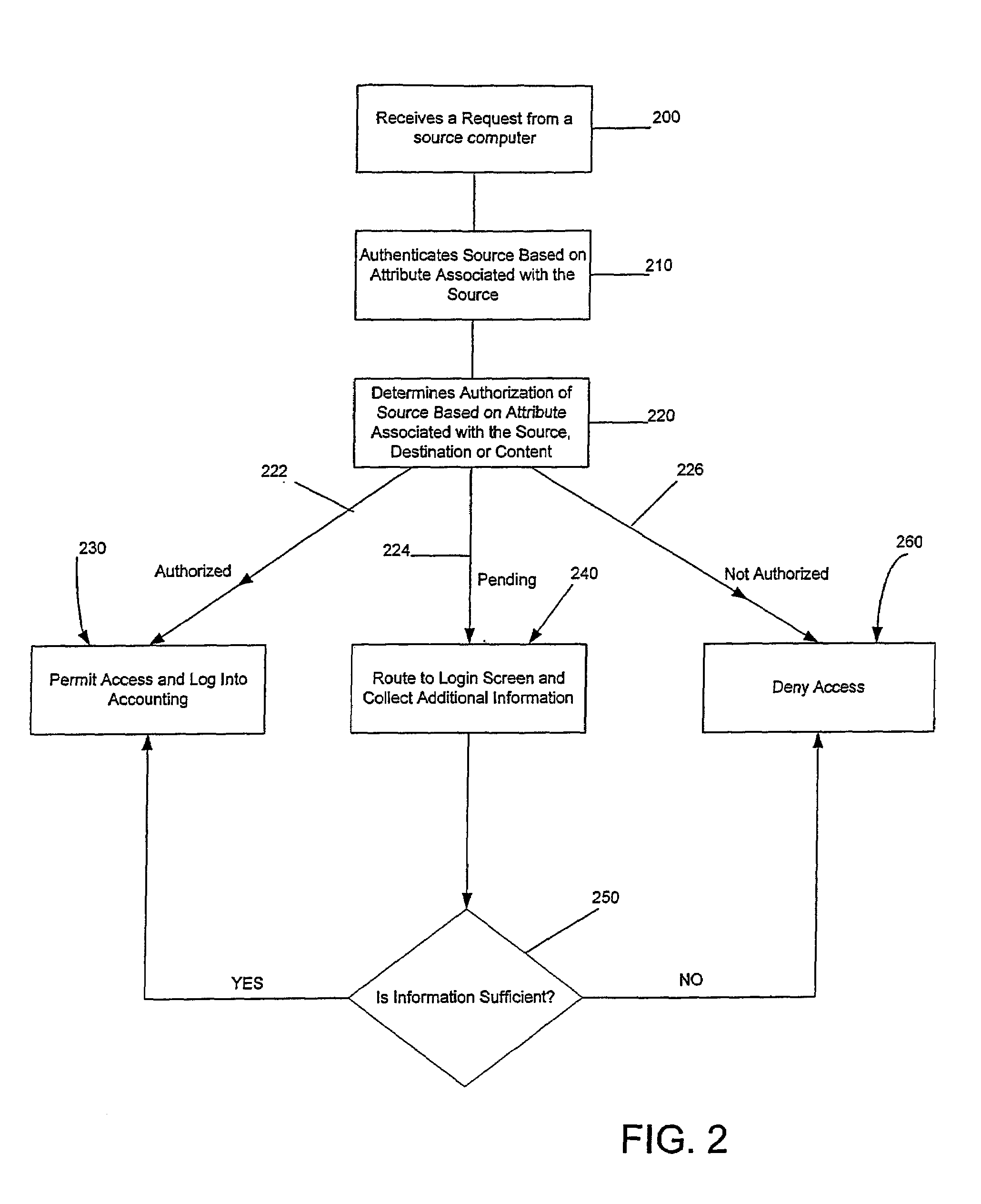
Systems and methods for providing dynamic network authorization authentication and accounting
InactiveUS7194554B1Connection managementMultiple digital computer combinationsInternet privacyDirectory Access Protocol
Systems and methods for selectably controlling and customizing source access to a network, where the source is associated with a source computer, and wherein the source computer has transparent access to the network via a gateway device and no configuration software need be installed on the source computer to access the network. A user may be prevented access from a particular destination or site based upon the user's authorization while being permitted to access to other sites that the method and system deems accessible. The method and system can identify a source without that source's knowledge, and can access customizable access rights corresponding to that source in a source profile database. The source profile database can be a remote authentication dial-in user service (RADIUS) or a lightweight directory access protocol (LDAP) database. The method and system use source profiles within the source profile database to dynamically authorize source access to networks and destinations via networks.
Owner:NOMADIX INC
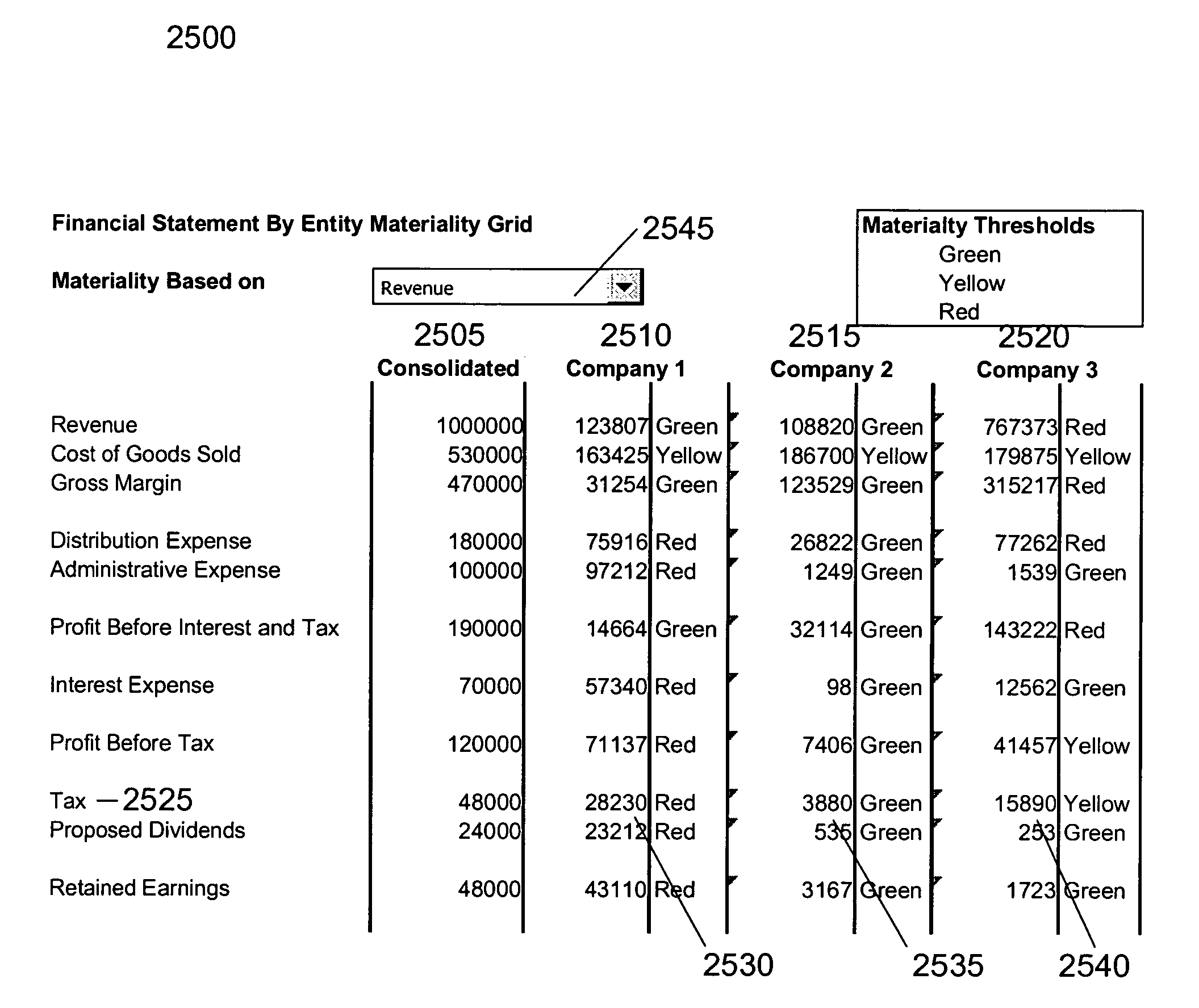
Audit planning
An audit planning system enables users to plan effective audits by identifying audit units having potentially large impacts and risks on an enterprise and enabling users to select audit units to include in audits based on a variety of different criteria. The audit planning system displays the audit units of the enterprise and a visual indicator of the impact and risk associated with each audit unit. The audit planning system enables users to select the displayed audit units to plan an audit. The audit planning system may display audit units in an impacted financial statement, a tree map, a graph, and / or a table. The audit planning system may sort and / or display audit units with visual indicators specifying associated risks, impacts, materiality values, exposures, coverages, and / or audit costs. The audit planning system can further display visual indications of the changes in audit units' associated attributes over time.
Owner:ORACLE INT CORP
System and method for providing access to databases via directories and other hierarchical structures and interfaces
InactiveUS20060173873A1High cost of deploymentDigital data processing detailsRelational databasesSystem usageRelational database schema
A hierarchical / relational translation system is provided for enabling information from unrelated heterogeneous relational computing systems to be accessed, navigated, searched, browsed, and shared over a hierarchical computing system. In one embodiment, the hierarchical / relational translation system includes a virtual directory server for capturing information in the nature of relational database schema and metadata. The captured schema and metadata are then translated into virtual directories that are universally compatible with standard communication protocols used with hierarchical computing systems. A virtual directory of information organizes an index of data records and a standard addressing schema is provided to enable customizable access to relevant views of relational computing systems. Several embodiments for presenting the virtual directory information tree are included. In one embodiment, the virtual directory is displayed using browser format. In another embodiment, the virtual directory is presented in electronic mail format. Still, in another embodiment the virtual directory is presented over a wireless medium and through portable devices.
Owner:RADIANT LOGIC
Methods and systems for automatic evaluation of electronic discovery review and productions
ActiveUS20120296891A1Well formedDigital data information retrievalDigital data processing detailsInformation retrievalSystem usage
Techniques are provided for automatic sampling evaluation. An automatic sampling evaluation system enables users to evaluate convergence of one or more search processes. For example, given a set of searches that were validated by human review, a system can implement a retrieval process that samples one or more non-retrieved collections. Each individual document's similarity in the one or more non-retrieved collections is automatically evaluated to other documents in any retrieved sets. Given a goal of achieving a high recall, documents with high similarity can then be analyzed for additional noun phrases that may be used for a next iteration of a search. Convergence can be expected if the information gain in the new feedback loop is less than previous iterations, and if the additional documents identified are below a certain threshold document count.
Owner:VERITAS TECH
3D mouse and game controller based on spherical coordinates system and system for use
InactiveUS20060092133A1Cathode-ray tube indicatorsInput/output processes for data processingAccelerometerDisplay device
A computer input device constructed from at least one tilt accelerometer and at least one linear input element is disclosed. This input device can be used in a computer system to specify a position on a display using radial coordinates, cylindrical coordinates, or spherical coordinates.
Owner:TOUMA PIERRE A
Informing a user of gestures made by others out of the user's line of sight
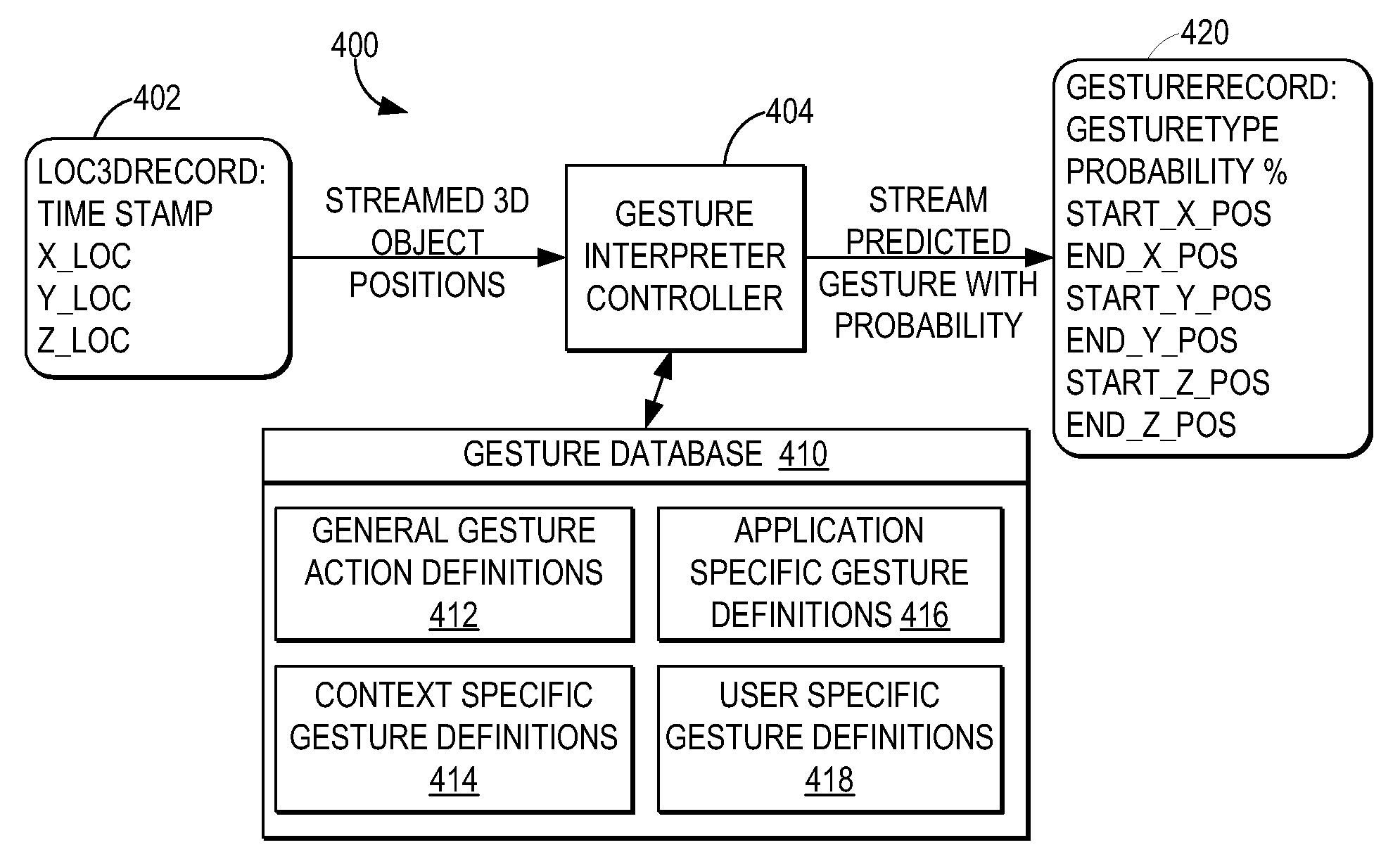
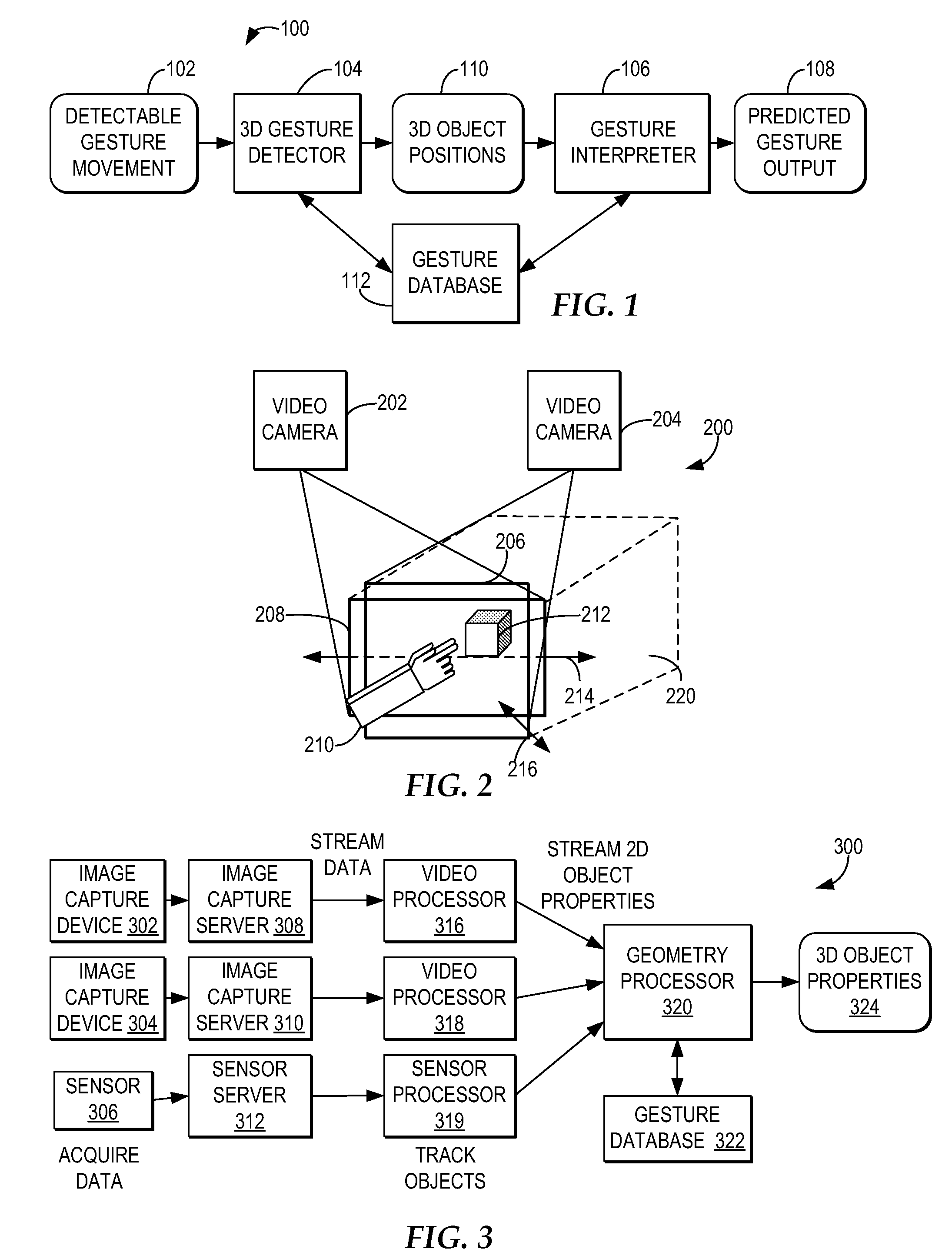
InactiveUS7725547B2Easy to identifyProjectorsCharacter and pattern recognitionElectronic communicationSystem usage
A gesture-enabled electronic communication system informs users of gestures made by other users participating in a communication session. The system captures a three-dimensional movement of a first user from among the multiple users participating in an electronic communication session, wherein the three-dimensional movement is determined using at least one image capture device aimed at the first user. The system identifies a three-dimensional object properties stream using the captured movement and then identifies a particular electronic communication gesture representing the three-dimensional object properties stream by comparing the identified three-dimensional object properties stream with multiple electronic communication gesture definitions. In response to identifying the particular electronic communication gesture from among the multiple electronic communication gesture definitions, the system transmits, to the users participating in the electronic communication session, an electronic object corresponding to the identified electronic communication gesture.
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com