Patents
Literature
1132 results about "Safety management systems" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
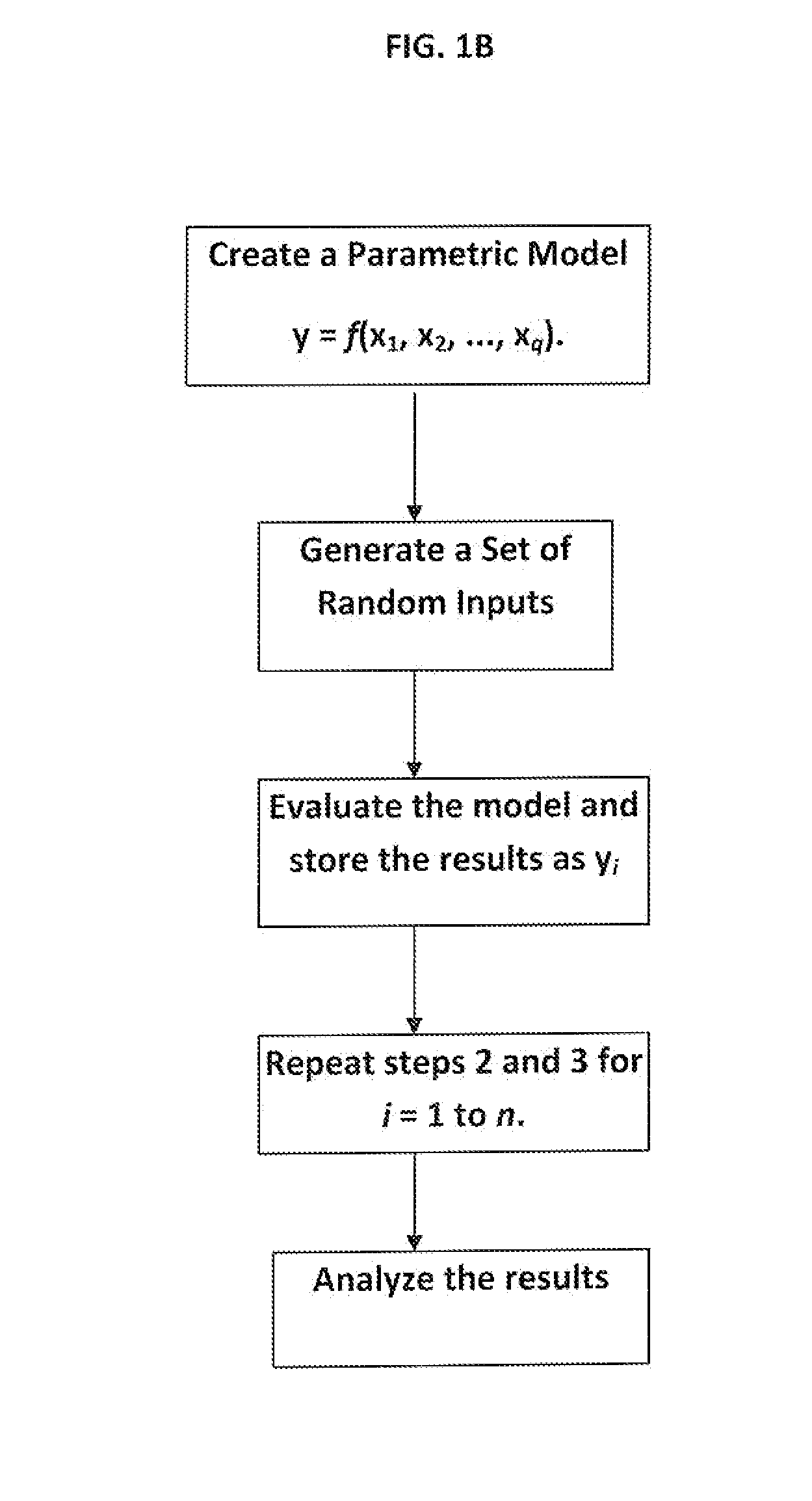
A safety management system (SMS) is a comprehensive management system designed to manage safety elements in the workplace. It includes policy, objectives, plans, procedures, organisation, responsibilities and other measures. The SMS is used in industries that manage significant safety risks, including aviation, petroleum, chemical, electricity generation and others.
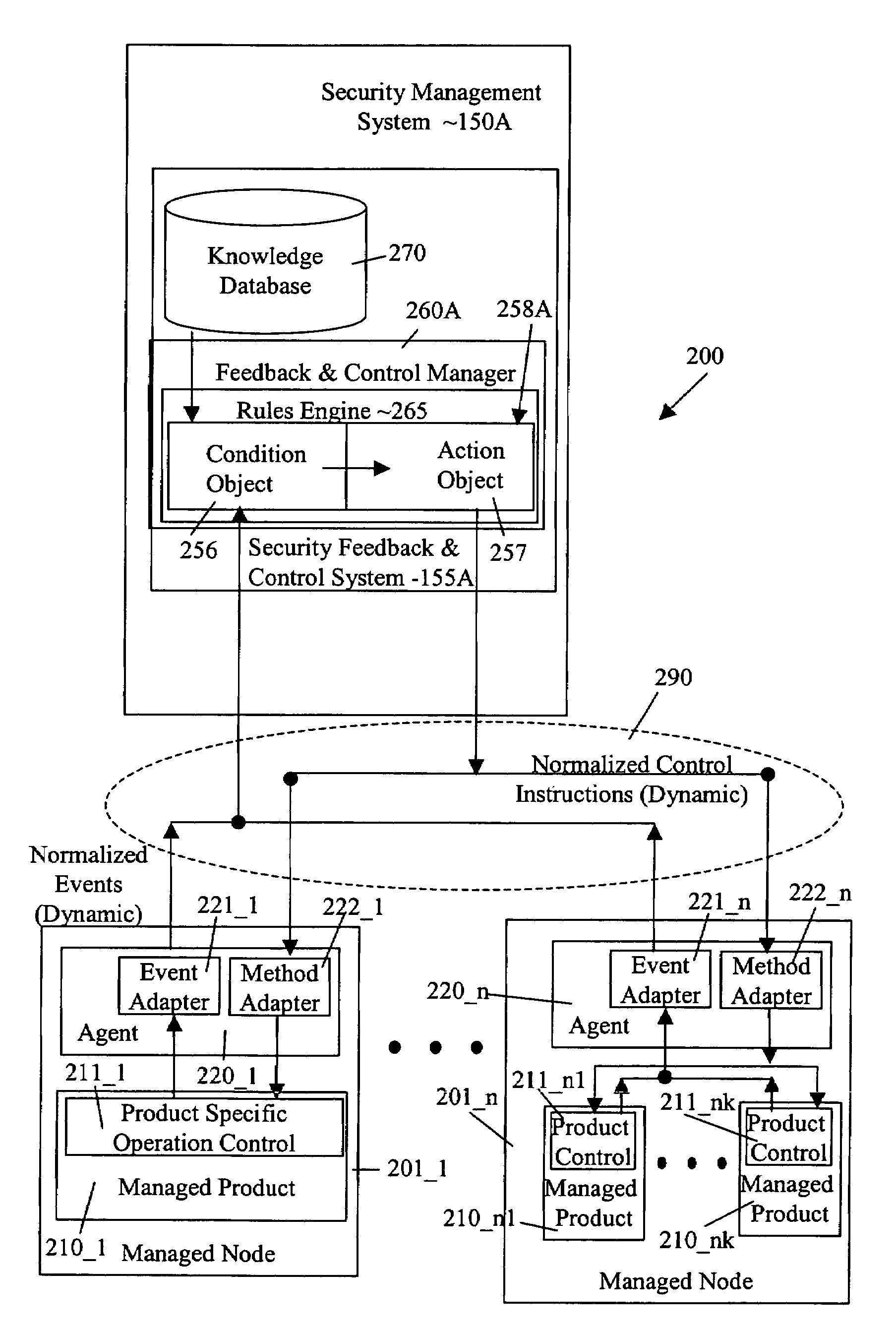
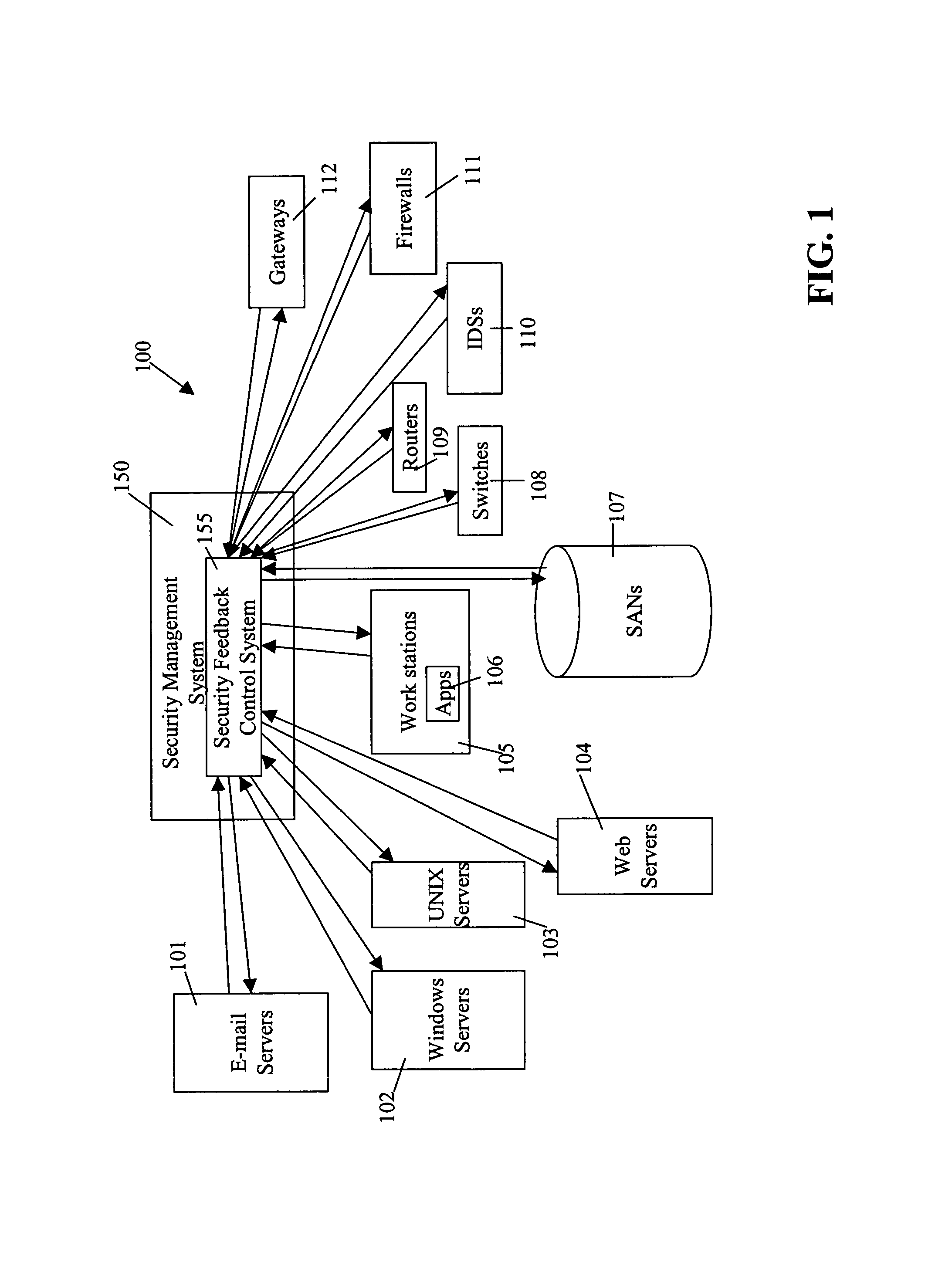
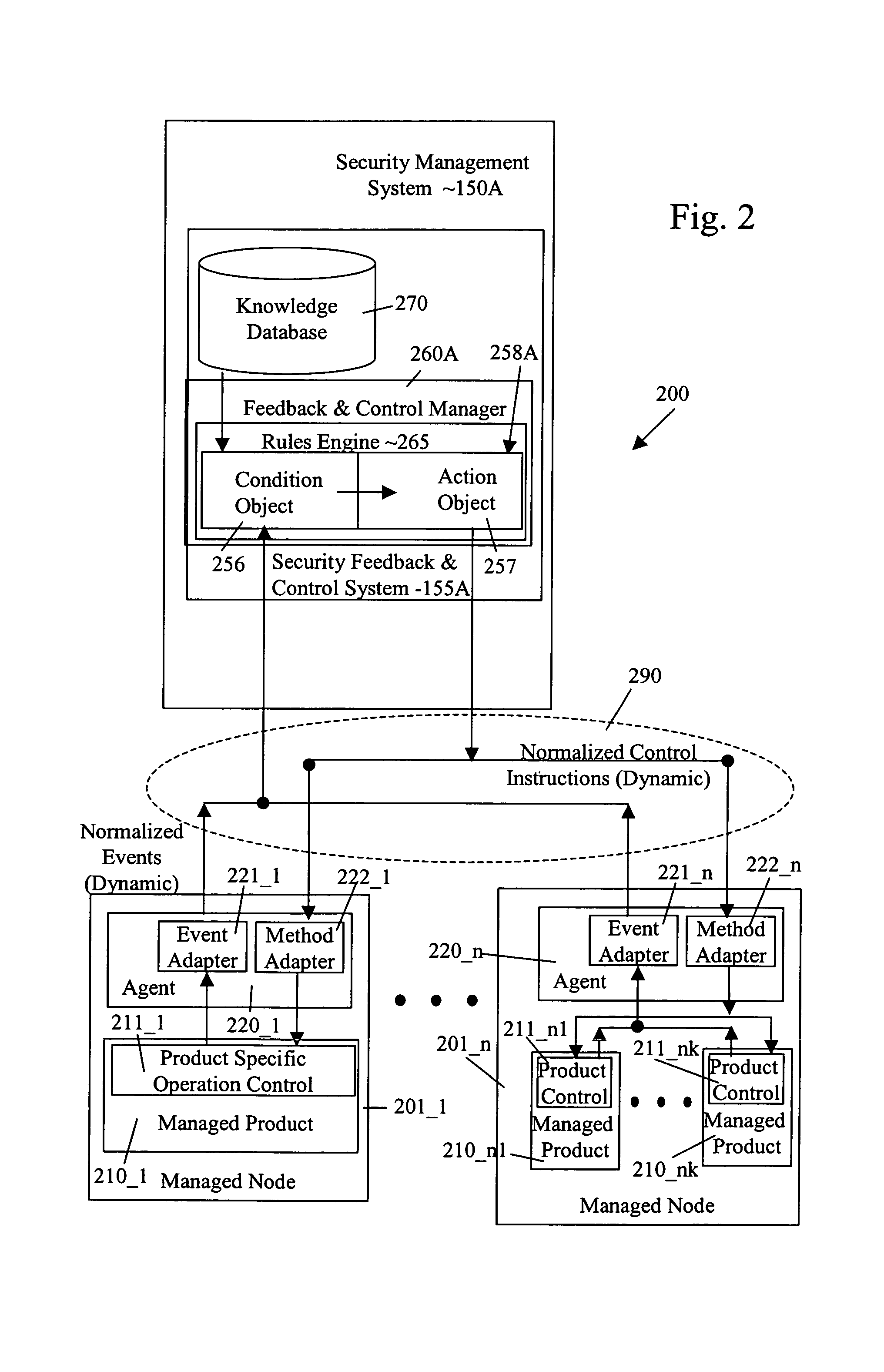
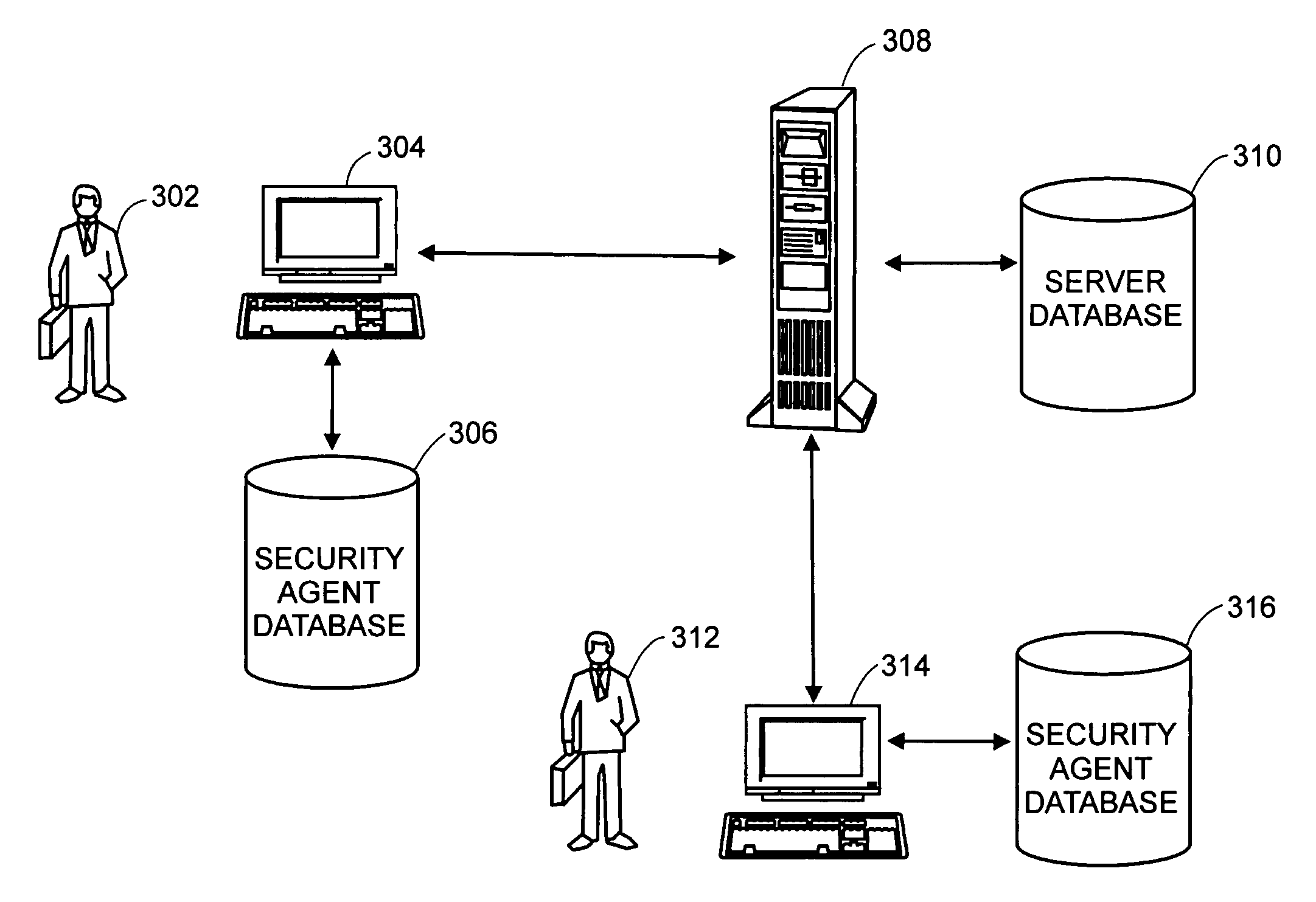
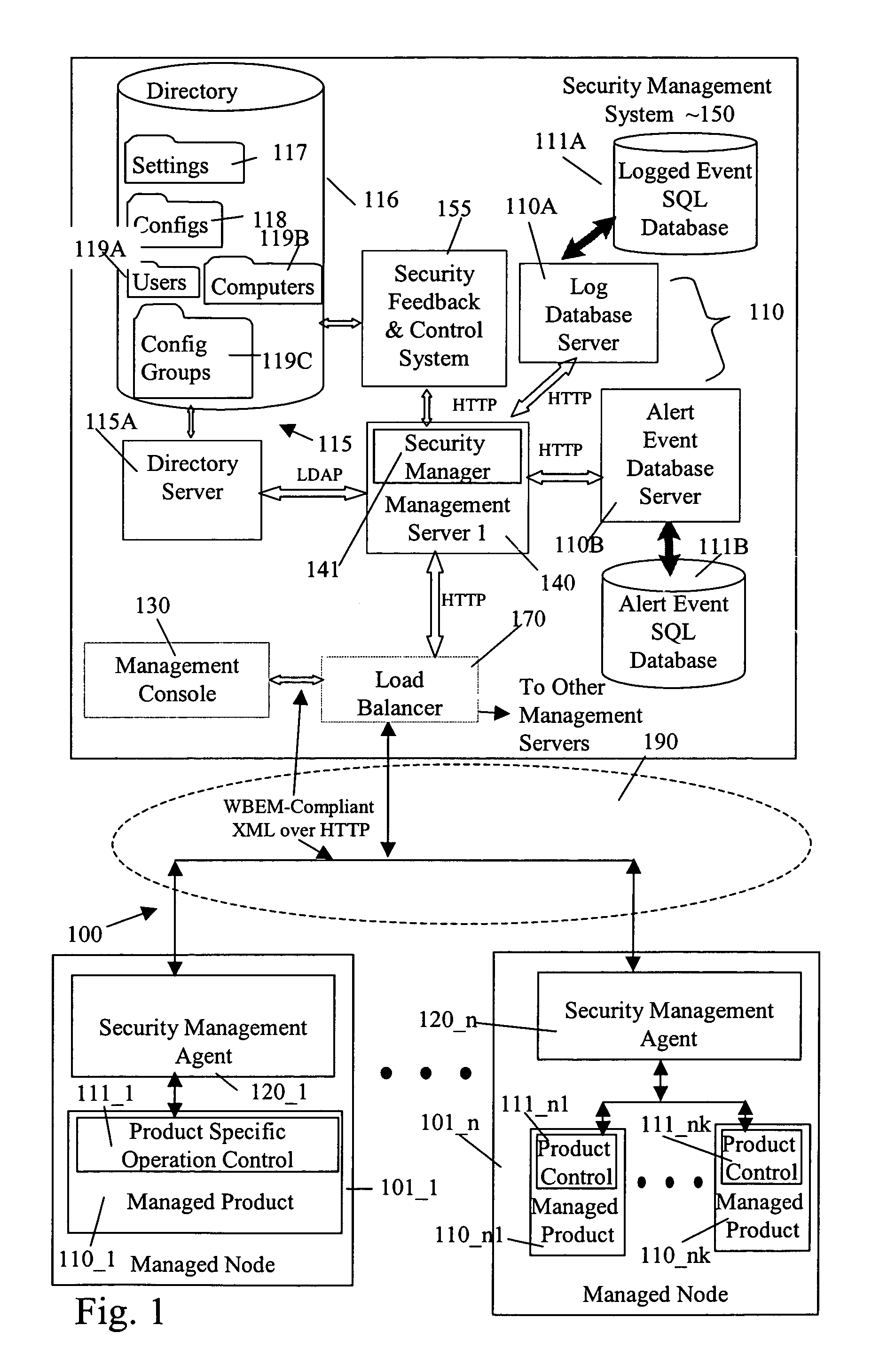
Security management system including feedback and control
InactiveUS7472422B1Memory loss protectionError detection/correctionPolicy decisionSafety management systems
A system uses automatic feedback and control to secure a network infrastructure by iterative convergence of the network's security structure to meet a security policy. Following initialization, a security feedback control system of the security management system makes dynamic adjustments to the system using bi-directional services that are controlled via policy decision components, without user intervention.
Owner:SYMANTEC CORP
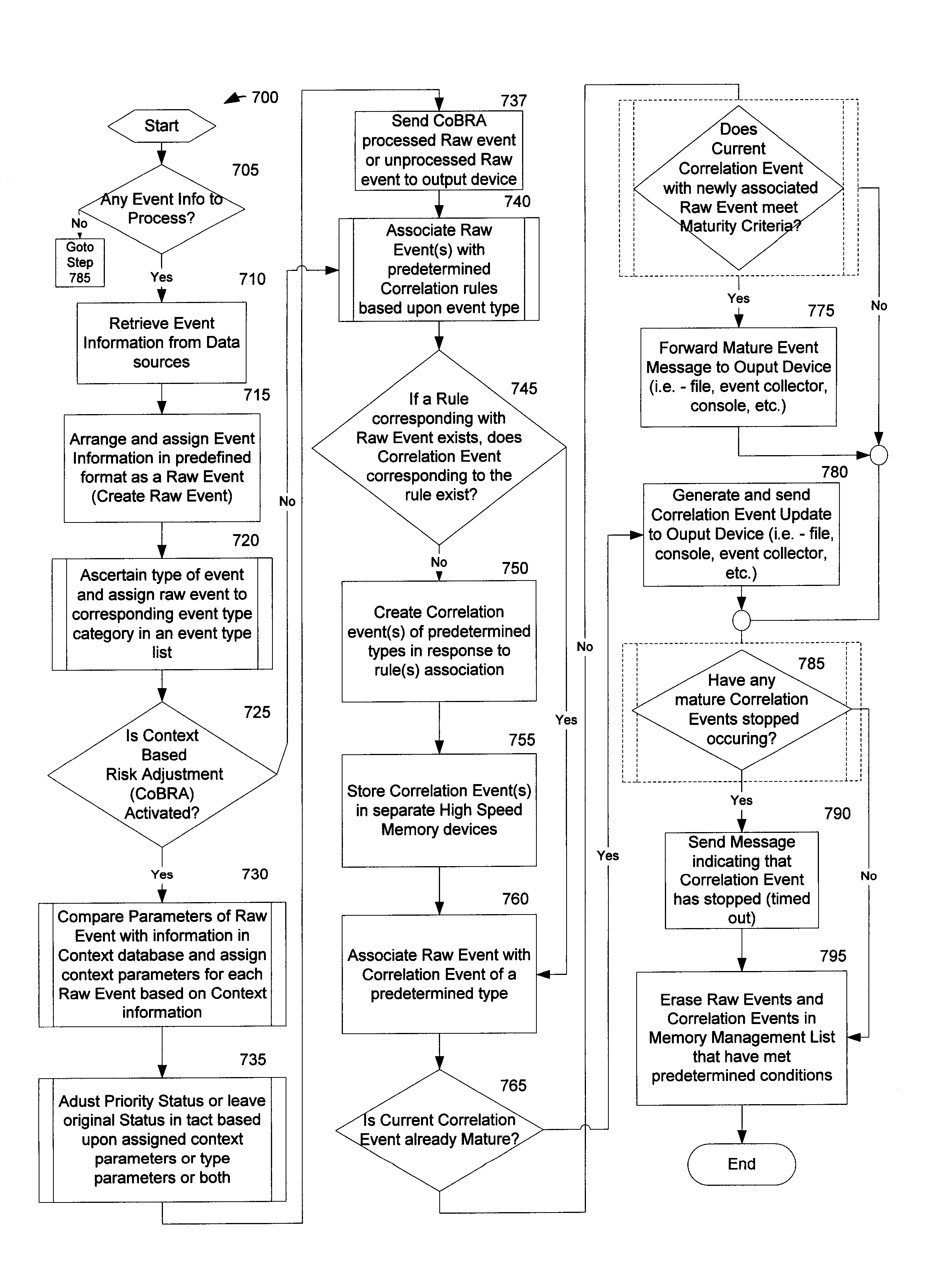
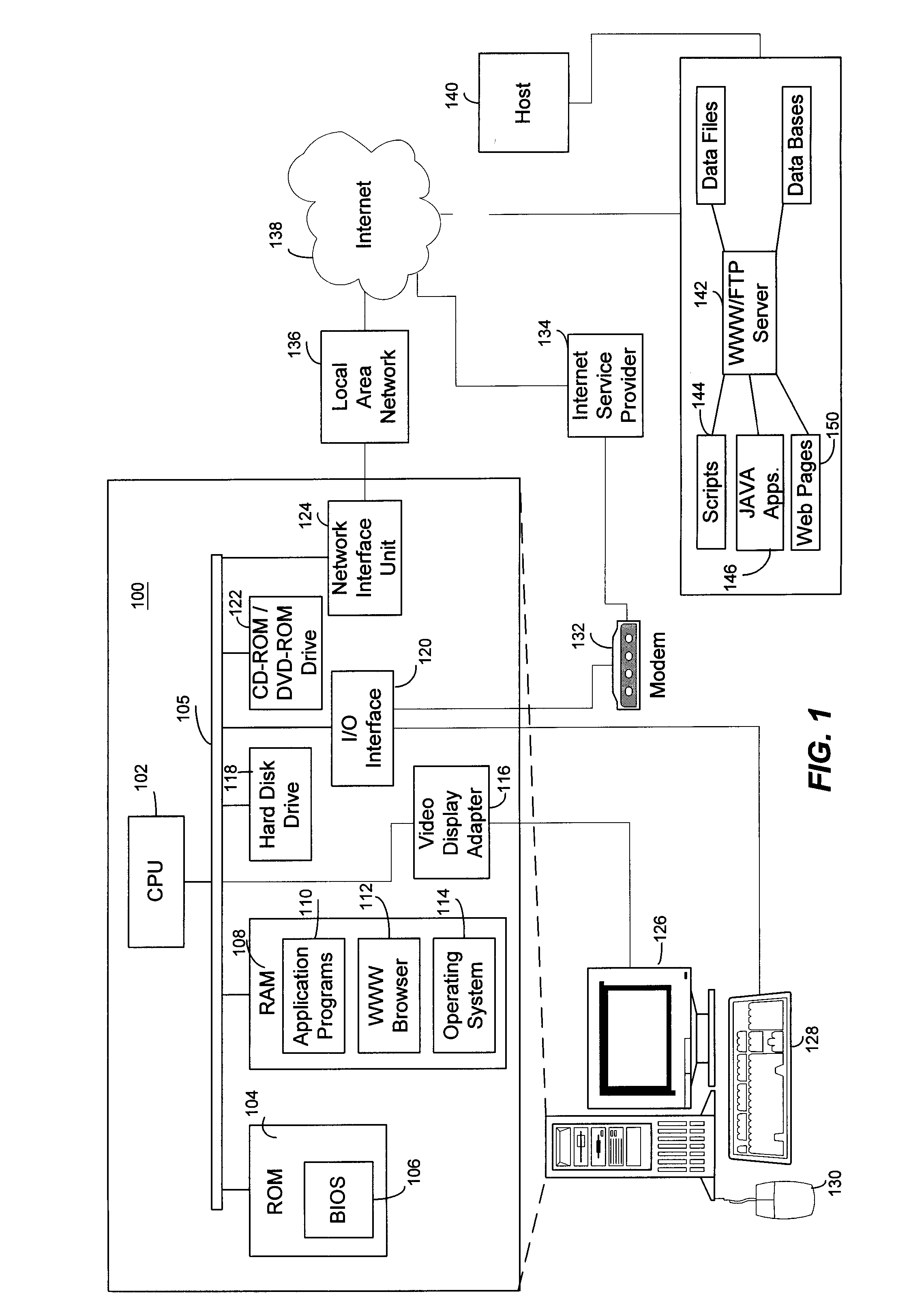
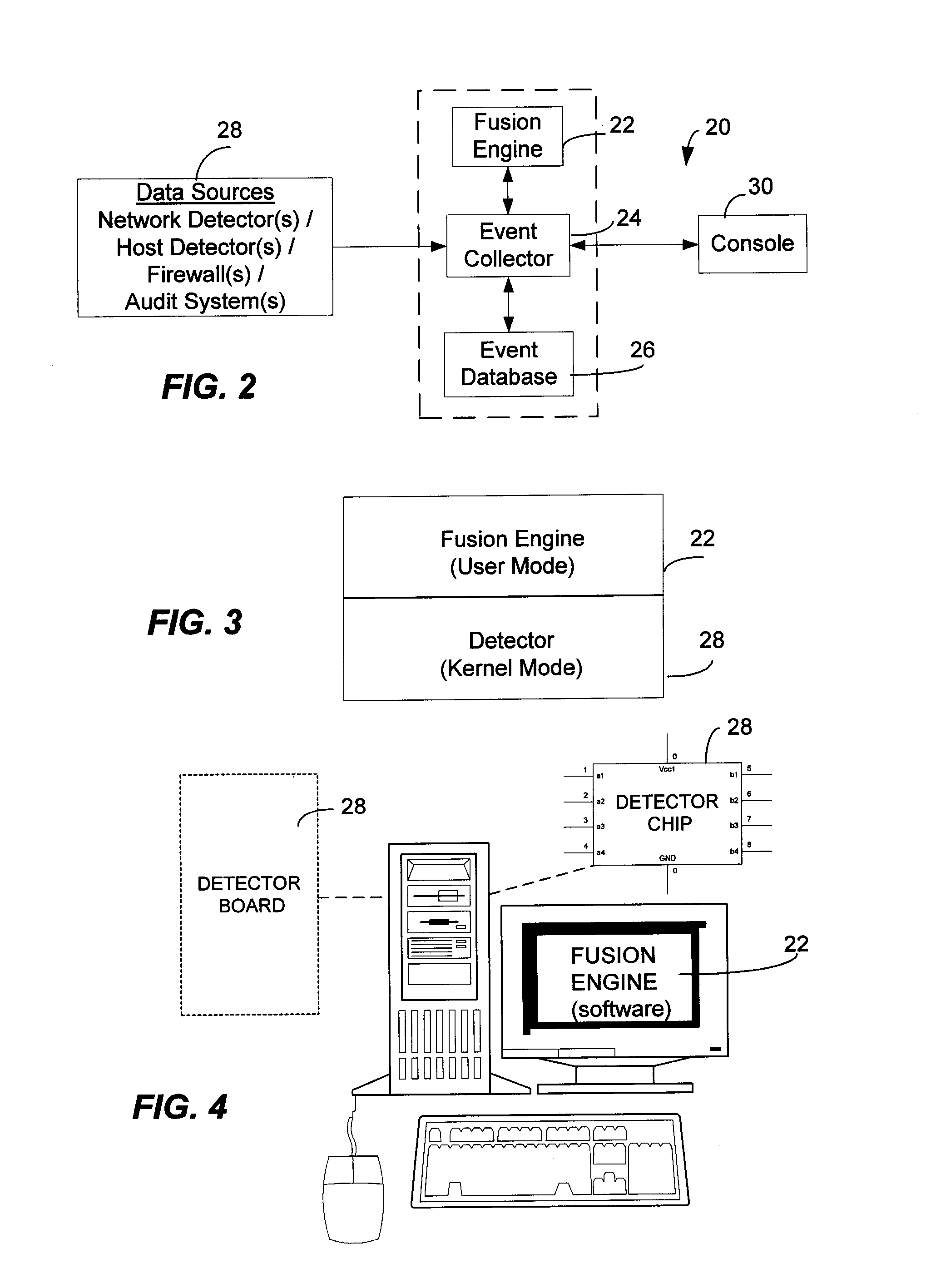
Method and System for Managing Computer Security Information
InactiveUS20020078381A1Efficient managementReduce processing speedMemory loss protectionDigital data processing detailsTraffic capacitySafety management systems
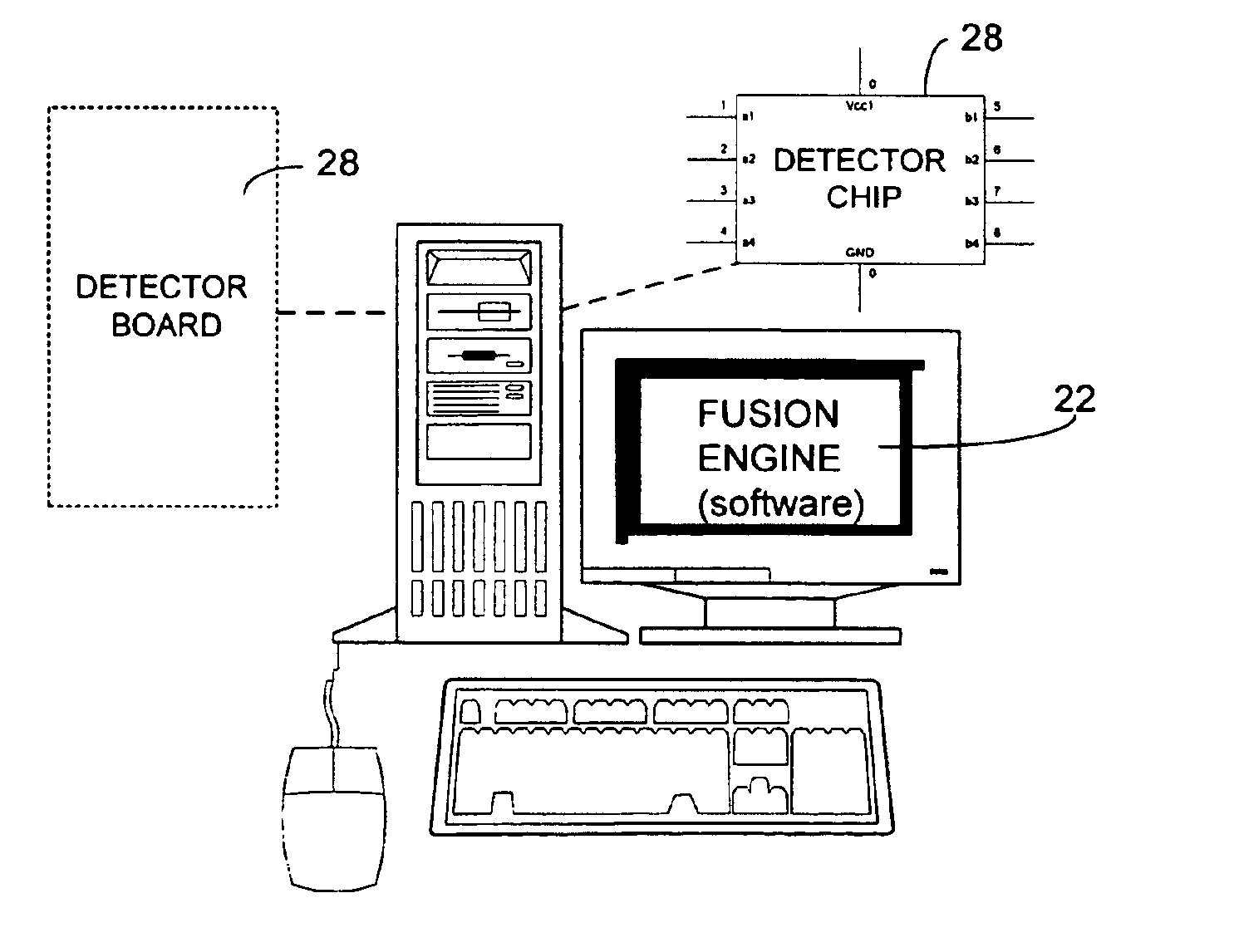
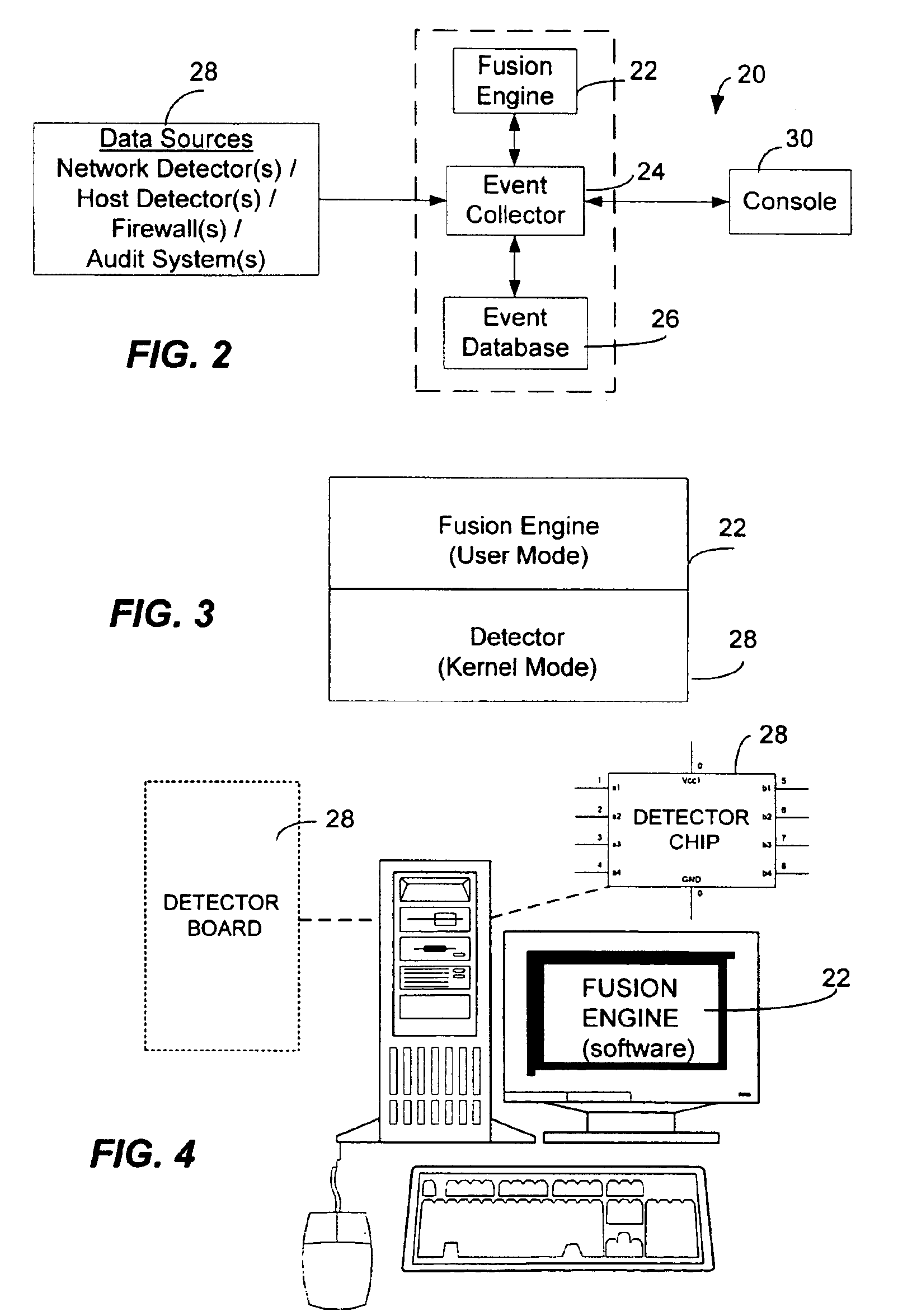
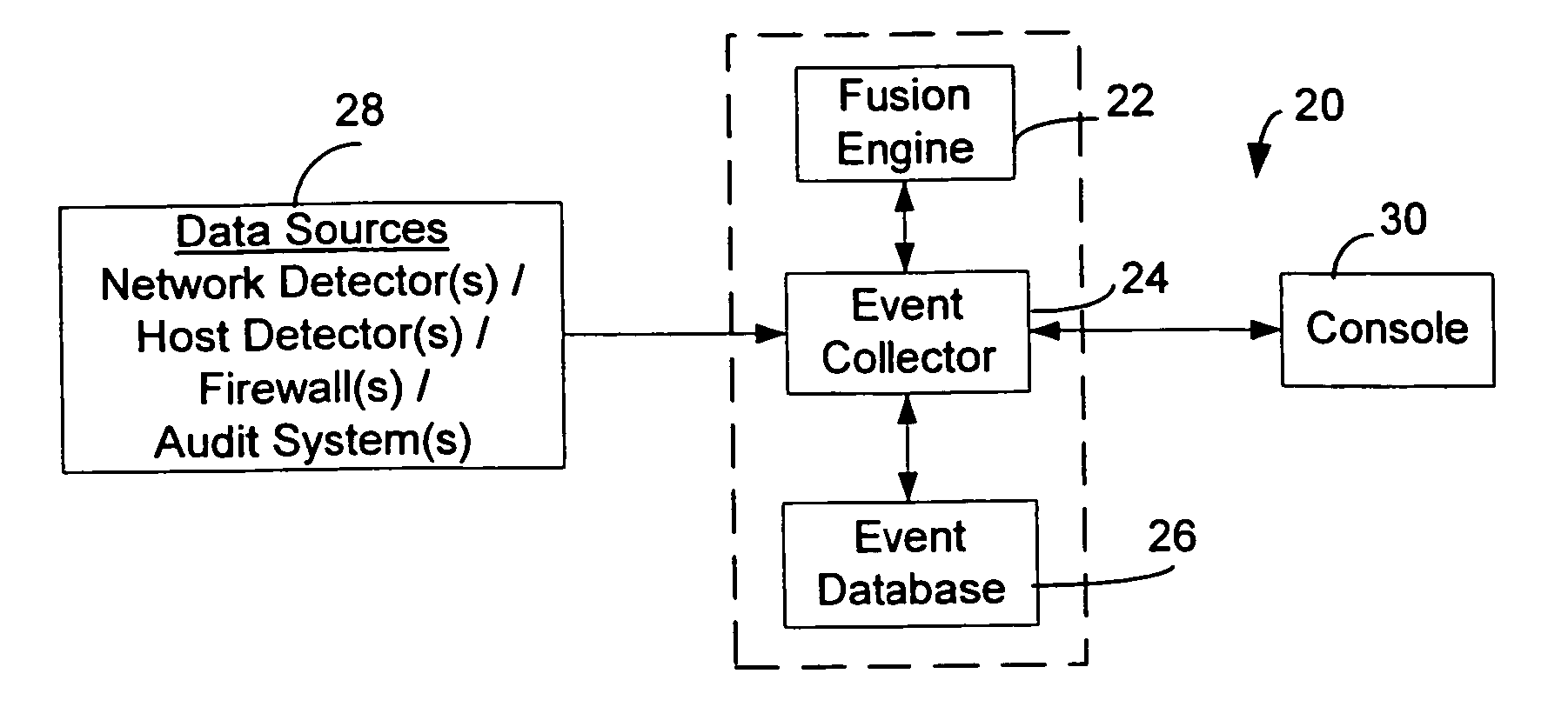
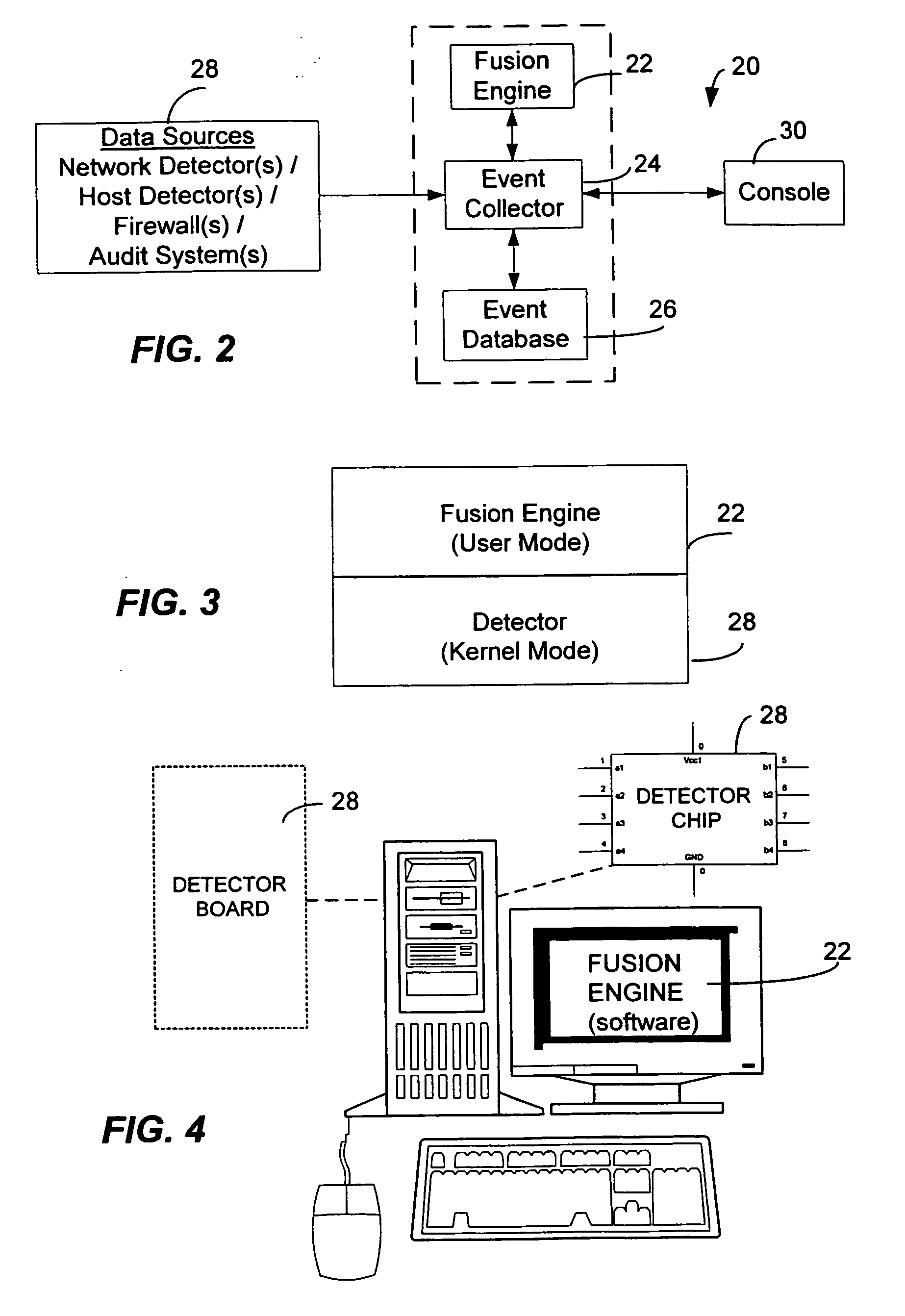
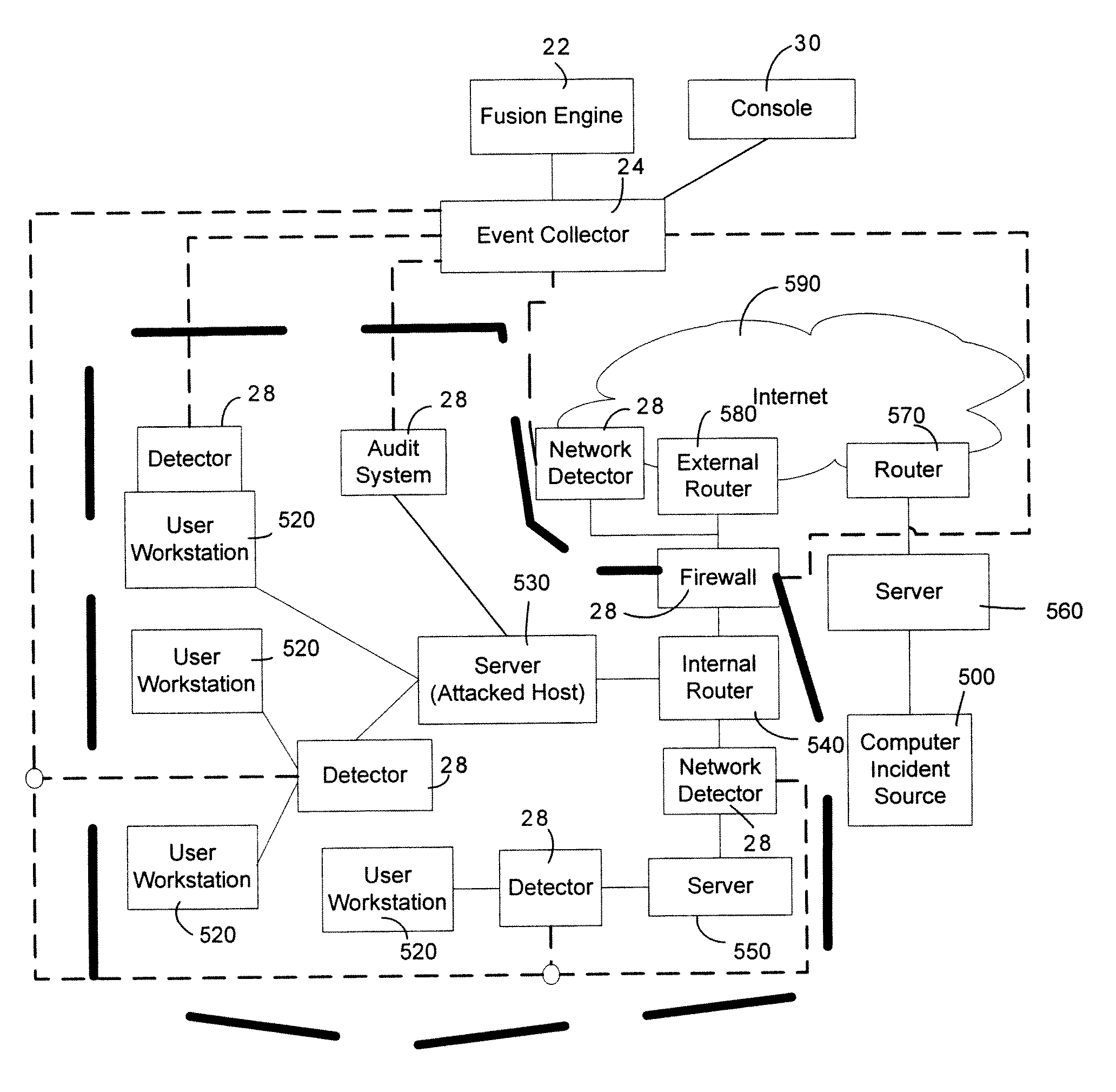
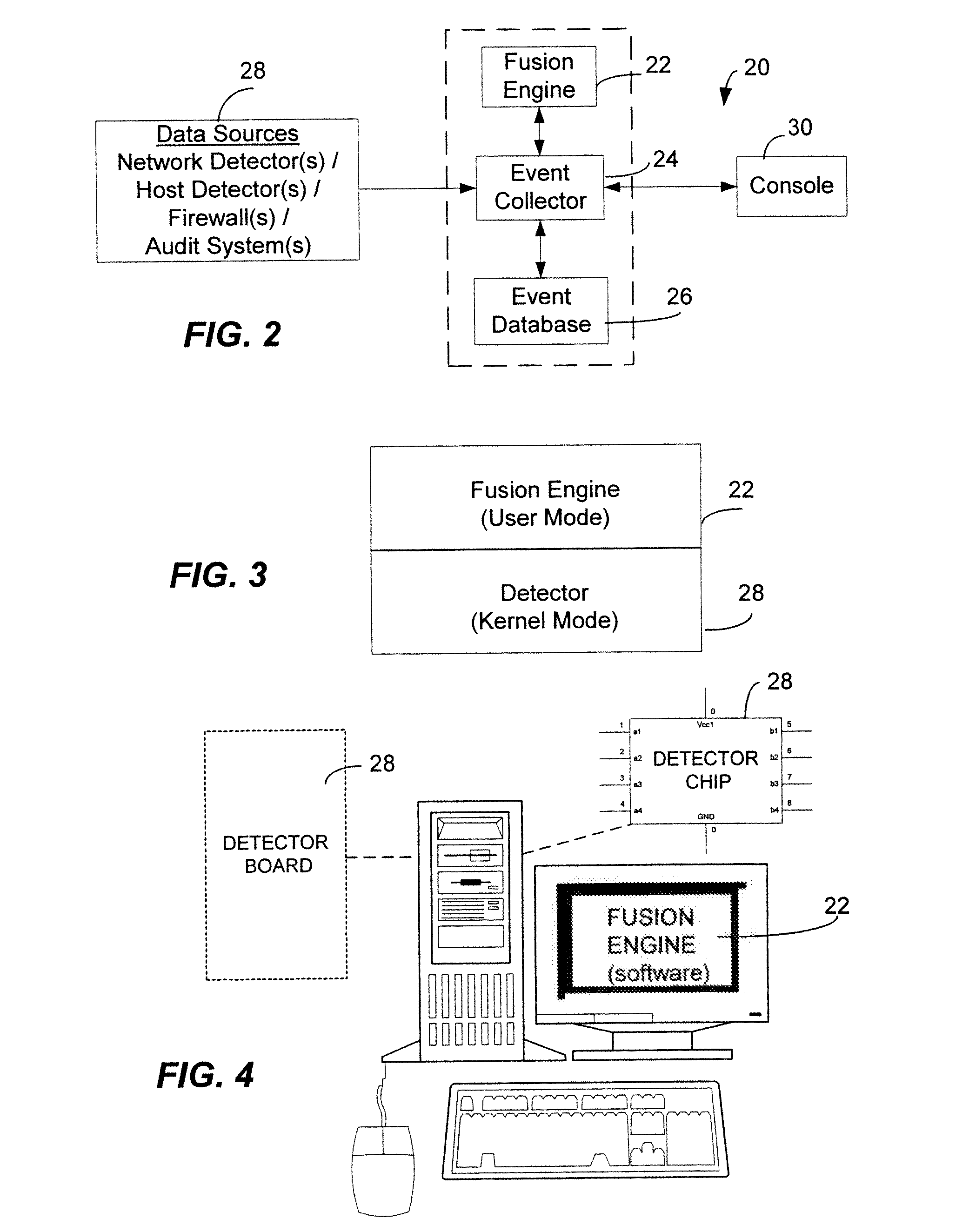
<heading lvl="0">Abstract of Disclosure< / heading> A security management system includes a fusion engine which "fuses" or assembles information from multiple data sources and analyzes this information in order to detect relationships between raw events that may indicate malicious behavior and to provide an organized presentation of information to consoles without slowing down the processing performed by the data sources. The multiple data sources can comprise sensors or detectors that monitor network traffic or individual computers or both. The sensors can comprise devices that may be used in intrusion detection systems (IDS). The data sources can also comprise firewalls, audit systems, and other like security or IDS devices that monitor data traffic in real-time. The present invention can identify relationships between one or more real-time, raw computer events as they are received in real-time. The fusion engine can also assess and rank the risk of real-time raw events as well as mature correlation events.
Owner:IBM CORP
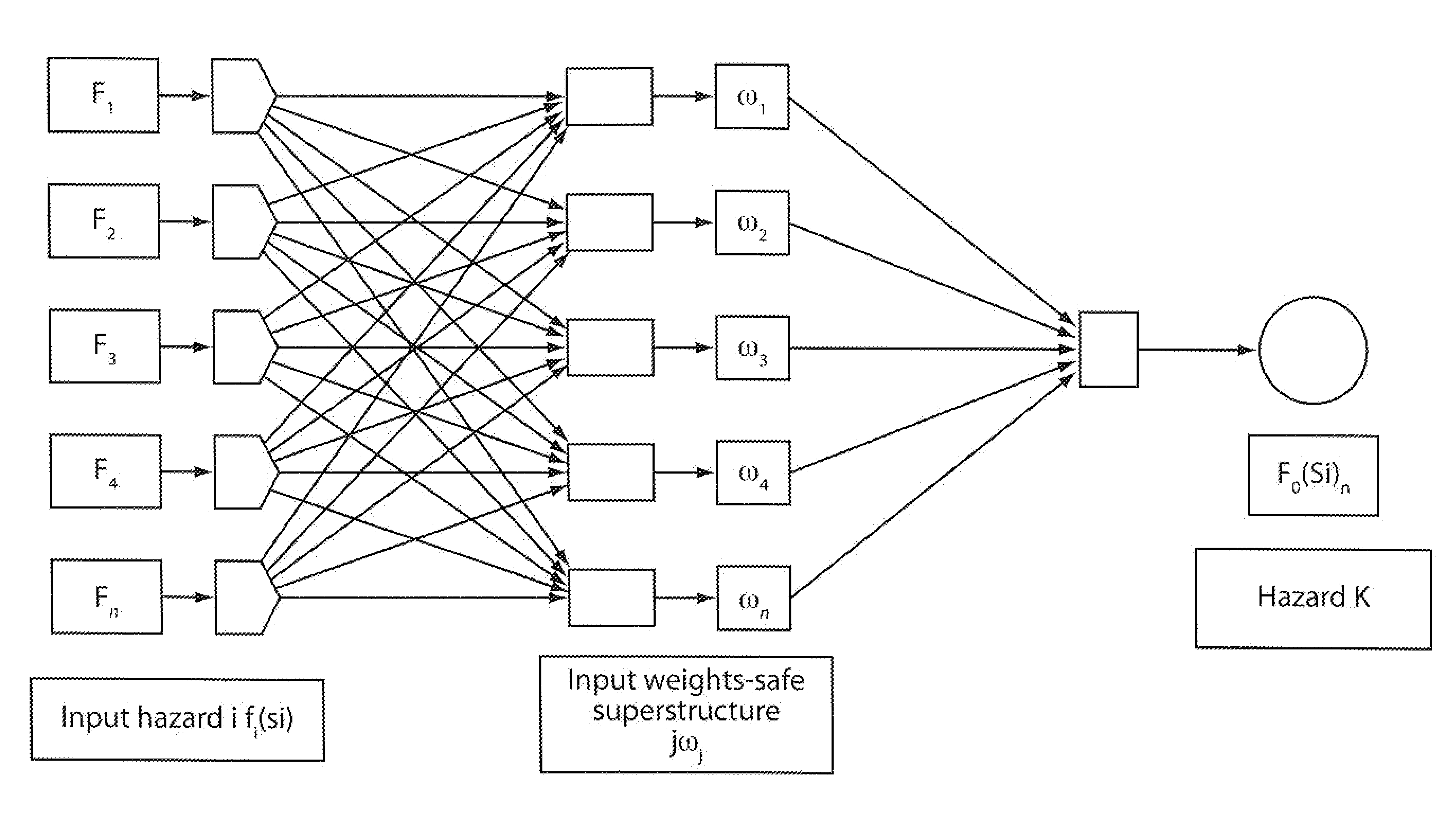
Design of computer based risk and safety management system of complex production and multifunctional process facilities-application to fpso's
InactiveUS20120317058A1Strong robust attributeStrong robust attributesDigital computer detailsFuzzy logic based systemsProcess systemsNerve network
A method for predicting risk and designing safety management systems of complex production and process systems which has been applied to an FPSO System operating in deep waters. The methods for the design were derived from the inclusion of a weight index in a fuzzy class belief variable in the risk model to assign the relative numerical value or importance a safety device or system has contain a risk hazards within the barrier. The weights index distributes the relative importance of risk events in series or parallel in several interactive risk and safety device systems. The fault tree, the FMECA and the Bow Tie now contains weights in fizzy belief class for implementing safety management programs critical to the process systems. The techniques uses the results of neural networks derived from fuzzy belief systems of weight index to implement the safety design systems thereby limiting use of experienced procedures and benchmarks. The weight index incorporate Safety Factors sets SFri {0, 0.1, 0.2 . . . 1}, and Markov Chain Network to allow the possibility of evaluating the impact of different risks or reliability of multifunctional systems in transient state process. The application of this technique and results of simulation to typical FPSO / Riser systems has been discussed in this invention.
Owner:ABHULIMEN KINGSLEY E
End user risk management
ActiveUS20060020814A1Respond effectivelyMemory loss protectionDigital data processing detailsReal time analysisComputer science
A flexible, efficient and easy-to-use computer security management system effectively evaluates and responds to informational risks on a wide variety of computing platforms and in a rapidly changing network environment. An individual computer system dynamically monitors its end user, without regard to network connectivity, in order to calculate a risk score and to ensure that the end user's behavior does not put corporate information or other assets at risk. Data regarding such risks and responses are analyzed and stored in real-time.
Owner:CITRIX SYST INC
End user risk management
ActiveUS7490356B2Respond effectivelyMemory loss protectionDigital data processing detailsReal time analysisSafety management systems
A flexible, efficient and easy-to-use computer security management system effectively evaluates and responds to informational risks on a wide variety of computing platforms and in a rapidly changing network environment. An individual computer system dynamically monitors its end user, without regard to network connectivity, in order to calculate a risk score and to ensure that the end user's behavior does not put corporate information or other assets at risk. Data regarding such risks and responses are analyzed and stored in real-time.
Owner:CITRIX SYST INC
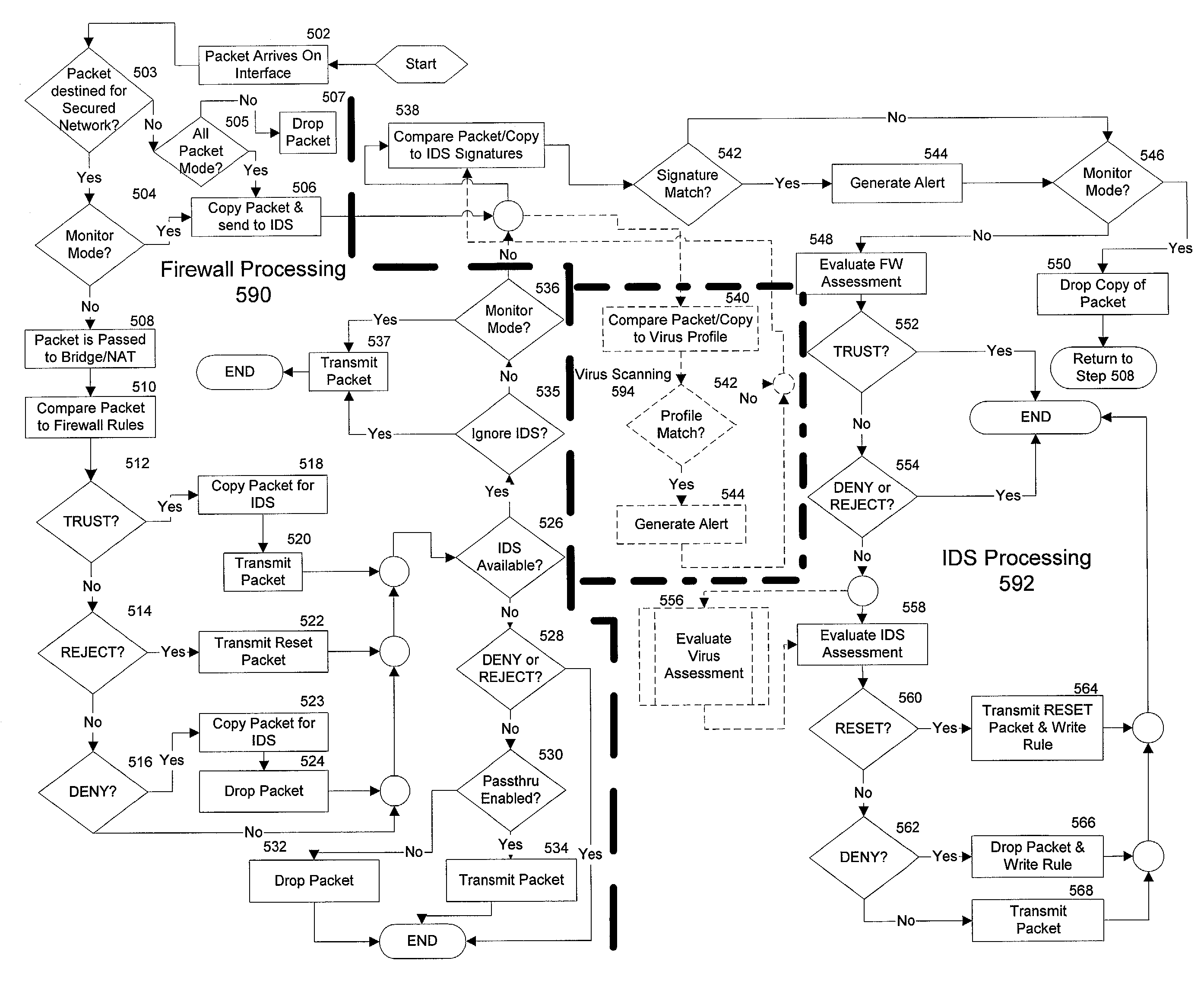
Integrated computer security management system and method
InactiveUS7331061B1Centralized controlIncrease speedMemory loss protectionError detection/correctionSafety management systemsSecurity management
The present invention is generally directed to a computer security management system that integrates a firewall with an intrusion detection system (IDS). In other words, the firewall and IDS of the present invention can be designed to communicate process or status information and packets with one another. The present invention can facilitate centralized control of the firewall and the IDS and can increase the speed at which packets are passed between a secured computer network and an external network. Increased packet processing speed can be achieved in several ways. For example, the firewall and IDS can process packets in series, in parallel, and sometimes singularly when one of the components is not permitted to process a packet. Alternatively, singular processing can also be performed when one component is permitted to pass a packet to the secured computer network without checking with the other component.
Owner:SECUREWORKS
Method and apparatus for an improved security system mechanism in a business applications management system platform
InactiveUS6850893B2Minimizing user input effortMinimize effortSpecific access rightsDigital data processing detailsSafety management systemsImproved method
The present invention provides a solution to the needs described above through an improved method and apparatus for an improved security system mechanism in a business applications management system platform. The security management system partitions a number of business objects into a number of hierarchical domains. A security list is then created and configured to grant a member the right to perform a security operation on the business object located within the hierarchical domain. The security list is created by adding the security operation to the security list, applying the security operation to one of the multiple domains, and adding members to the security list.
Owner:SABA SOFTWARE
Techniques for discovering and managing security of applications
ActiveUS20170251013A1Minimizing security threatMinimizing riskTransmissionSafety management systemsData source
Techniques for discovery and management of applications in a computing environment of an organization are disclosed. A security management system discovers use of applications within a computing environment to manage access to applications for minimizing security threats and risks in a computing environment of the organization. The security management system can obtain network data about network traffic to identify unique applications. The security management system can perform analysis and correlation, including use of one or more data sources, to determine information about an application. The system can compute a measure of security for an application (“an application risk score”) and a user (“a user risk score”). The score may be analyzed to determine a threat of security posed by the application based on use of the application. The security system can perform one or more instructions to configure access permitted by an application, whether access is denied or restricted.
Owner:ORACLE INT CORP
Method and system for managing computer security information
InactiveUS7089428B2Efficient managementMemory loss protectionDigital data processing detailsInternet trafficSafety management systems
A security management system includes a fusion engine which “fuses” or assembles information from multiple data sources and analyzes this information in order to detect relationships between raw events that may indicate malicious behavior and to provide an organized presentation of information to consoles without slowing down the processing performed by the data sources. The multiple data sources can comprise sensors or detectors that monitor network traffic or individual computers or both. The sensors can comprise devices that may be used in intrusion detection systems (IDS). The data sources can also comprise firewalls, audit systems, and other like security or IDS devices that monitor data traffic in real-time. The present invention can identify relationships between one or more real-time, raw computer events as they are received in real-time. The fusion engine can also assess and rank the risk of real-time raw events as well as mature correlation events.
Owner:INT BUSINESS MASCH CORP
Systems and methods for security management based on cursor events
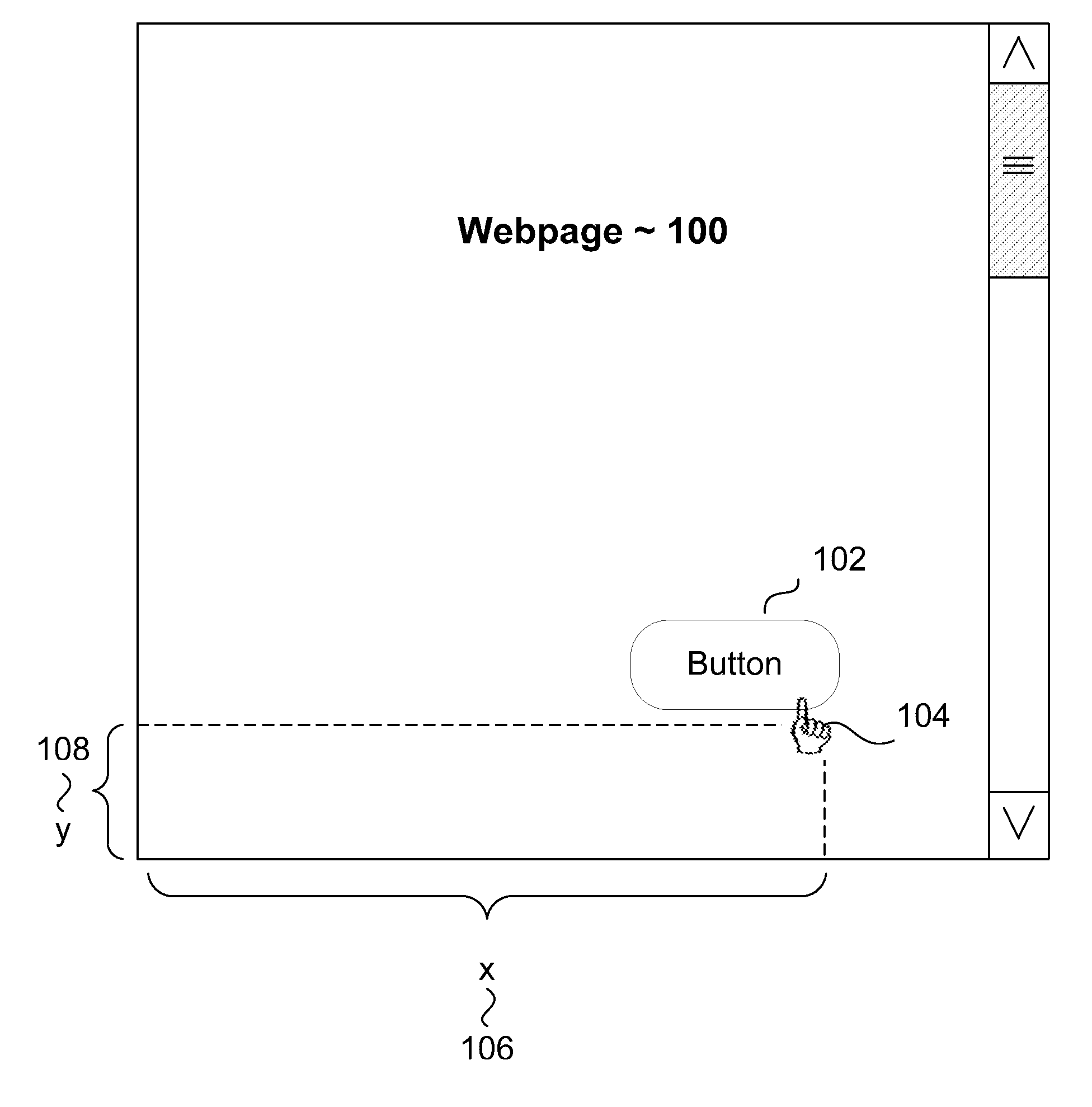
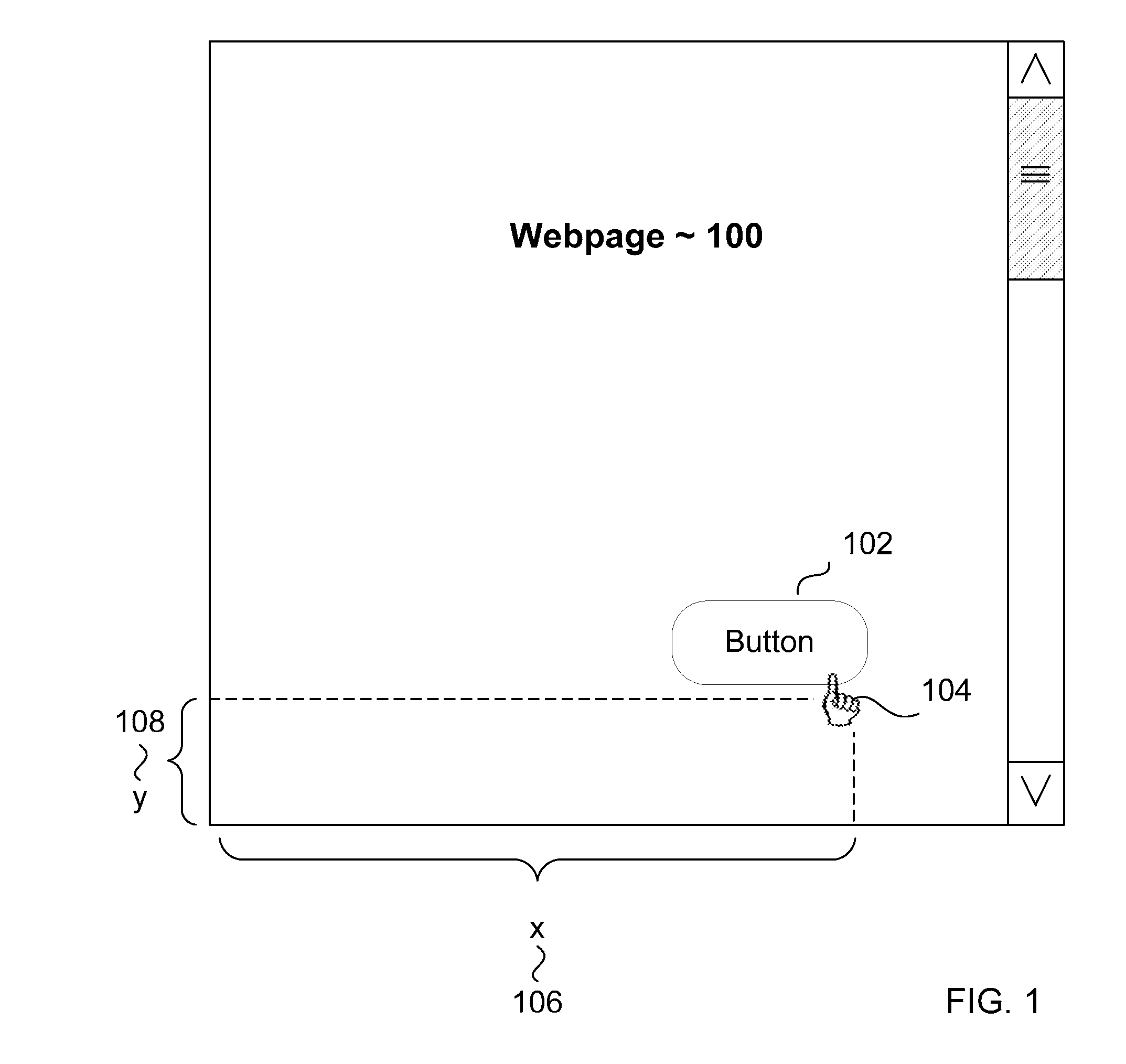
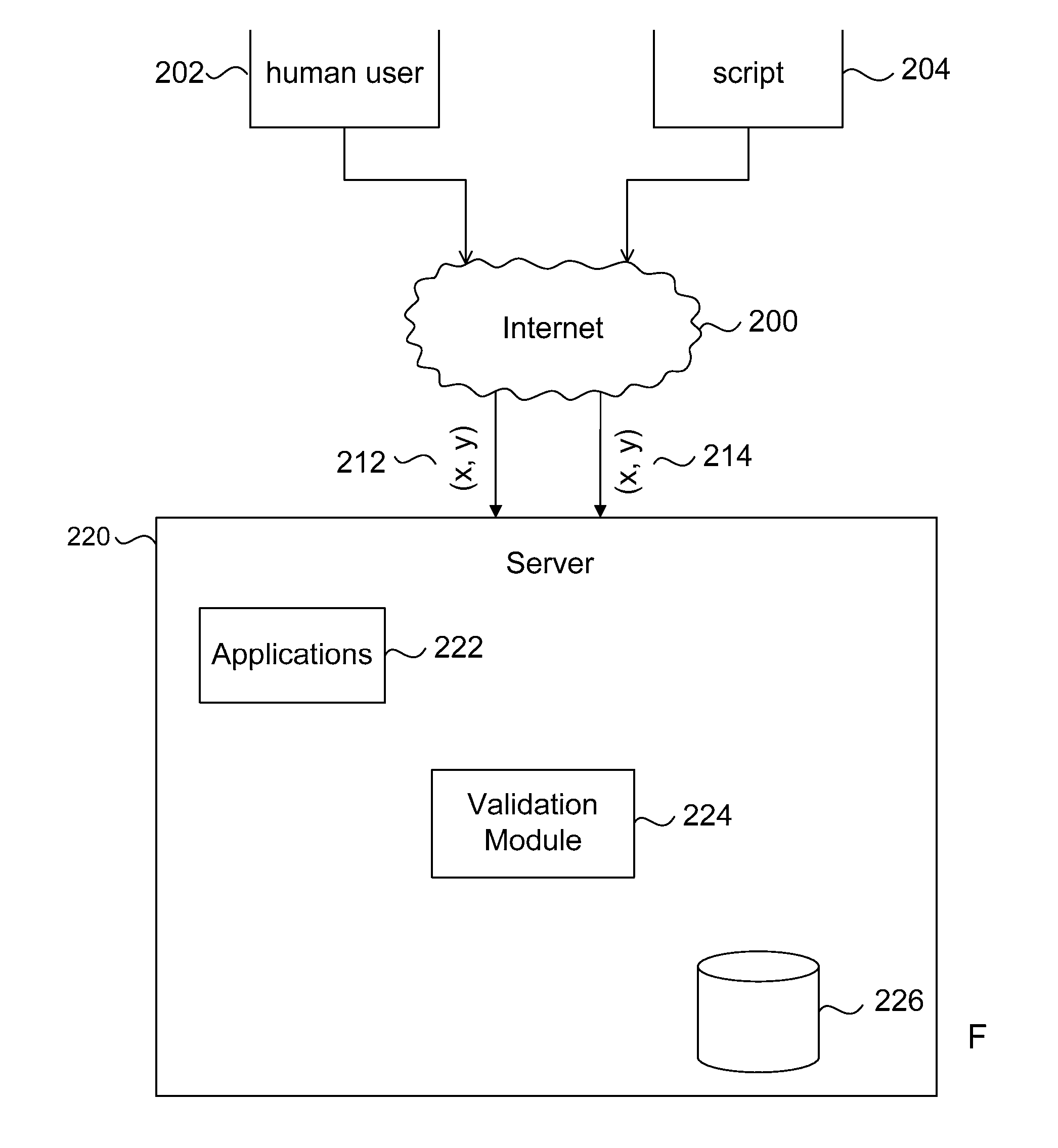
ActiveUS20110113388A1Digital data authenticationInput/output processes for data processingSafety management systemsData mining
Systems and methods for security management based on cursor events. Click coordinates on a webpage of user's activity are logged in order to detect multiple or repeated transactions that bare the same exact coordinates. Such multiple or repeated activity may be helpful in detecting scripted attacks or bot net activity in a variety of environments and transactions. Further, the invention may also capture the coordinates of the location of submit buttons, and similar buttons, on a webpage to analyze whether a click action or other pointer action occurred within the button's parameters.
Owner:THE 41ST PARAMETER
Safety monitoring early warning and safety management system and method for oil gas extracting, gathering and transporting operation
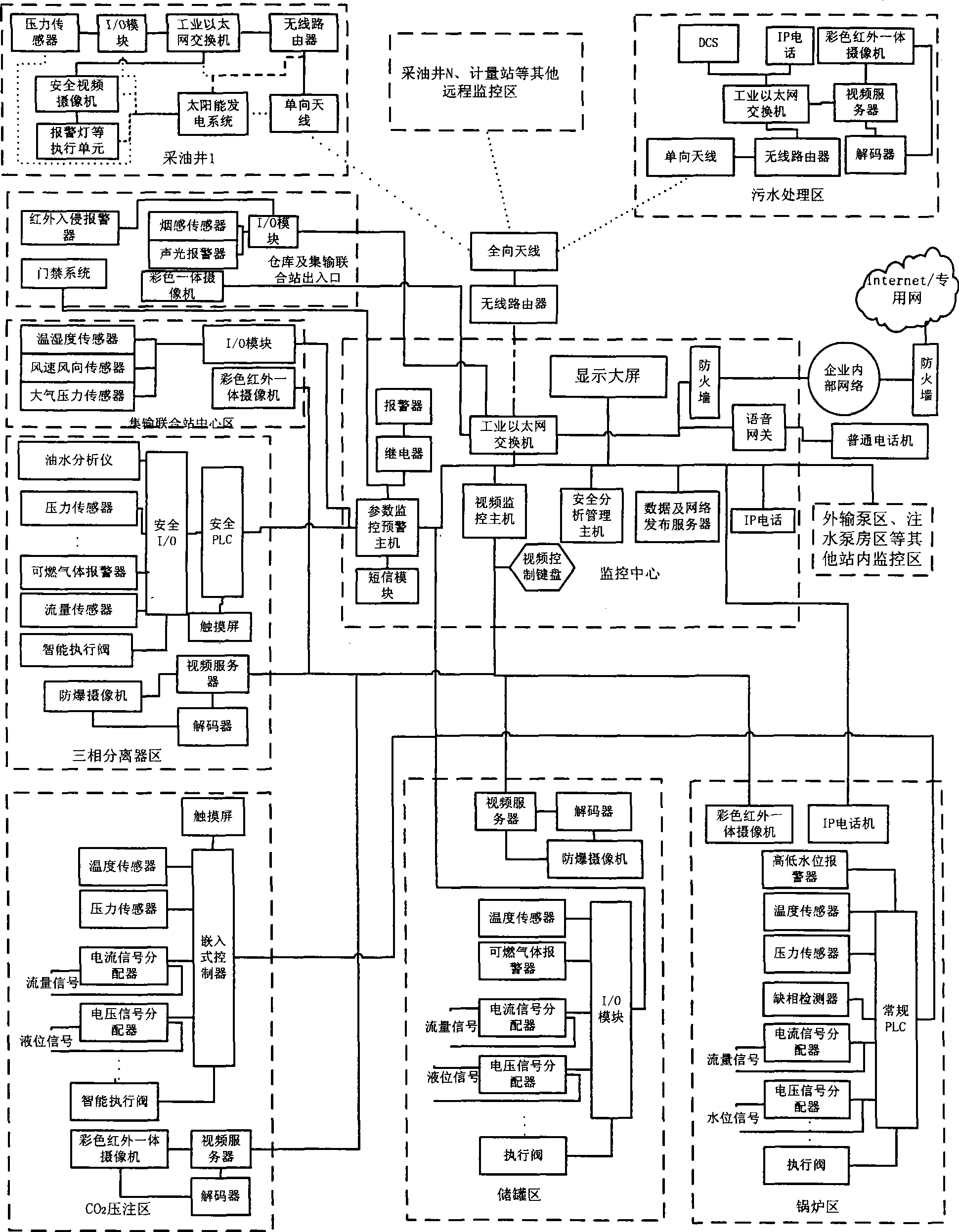
InactiveCN101369152AManagement is easy to strengthenEasy to manageFluid removalProgramme total factory controlVideo monitoringSafety management systems
The invention relates to a safety monitoring early warning and safety management system of oil and gas extraction and gathering operations as well as a method thereof, belonging to the technique field of safety production monitoring and supervision, and the system is composed of a monitoring center arranged at an oil and gas extraction safety monitoring and management department and a plurality of on-site monitoring terminals disposed at all oil and gas extraction operation areas. The method comprises: collecting and transmitting safety-related parameter signals, video signals and audio signals in real time; implementing the analog-digital conversion or signal conversion and compression coding to the signals; then transmitting the signals to all hosts of the monitoring center; processing and analyzing the received three types of signal information by all the hosts and then carrying out the parameter monitoring, video monitoring and audio communication respectively; and outputting the processed three types of information to the spot for being controlled correspondingly. The invention can realize the risk assessment, dynamic intelligent monitoring, safety state analysis, accident early warning and alarming, safety guarantee control and safety management of the whole process of operations ranging from oil and gas extraction, heating, separation processing, storage to transportation for oil and gas production enterprises.
Owner:CHINA ACAD OF SAFETY SCI & TECH
Method to generate a quantitative measurement of computer security vulnerabilities
InactiveUS20060101518A1Memory loss protectionError detection/correctionCollocationSecurity management
The present invention provides a system and method to provide a measurement of the risk that a computer network may have to computer security threats. The system includes a collocation facility that is coupled to a plurality of computer security management systems. Some or all of the vulnerability information is reported to the collocation facility. At the collocation facility, this information is compared to a standard. This comparison yields a number or other measurement of that organization's risk in its computer security. The collocation facility can then report this measurement to any information user that wishes to know what the vulnerability is for that organization.
Owner:SCHUMAKER TROY T +1
Method and system for managing computer security information
InactiveUS20060265746A1Efficient managementReduce processing speedMemory loss protectionError detection/correctionTraffic capacitySafety management systems
A security management system includes a fusion engine which “fuses” or assembles information from multiple data sources and analyzes this information in order to detect relationships between raw events that may indicate malicious behavior and to provide an organized presentation of information to consoles without slowing down the processing performed by the data sources. The multiple data sources can comprise sensors or detectors that monitor network traffic or individual computers or both. The sensors can comprise devices that may be used in intrusion detection systems (IDS). The data sources can also comprise firewalls, audit systems, and other like security or IDS devices that monitor data traffic in real-time. The present invention can identify relationships between one or more real-time, raw computer events as they are received in real- time. The fusion engine can also assess and rank the risk of real-time raw events as well as mature correlation events.
Owner:IBM CORP
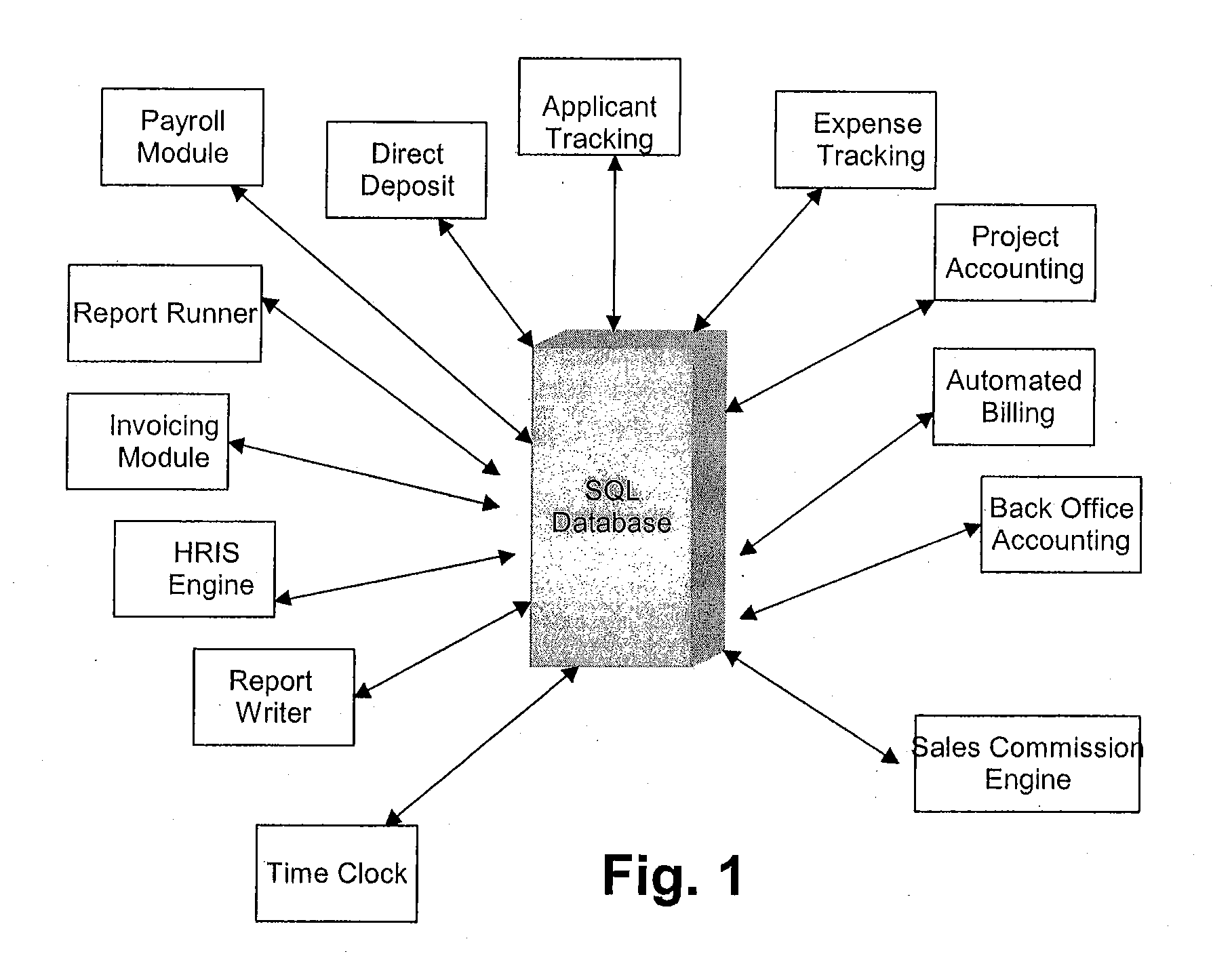
A multi-tasked human resources and payroll accounting system
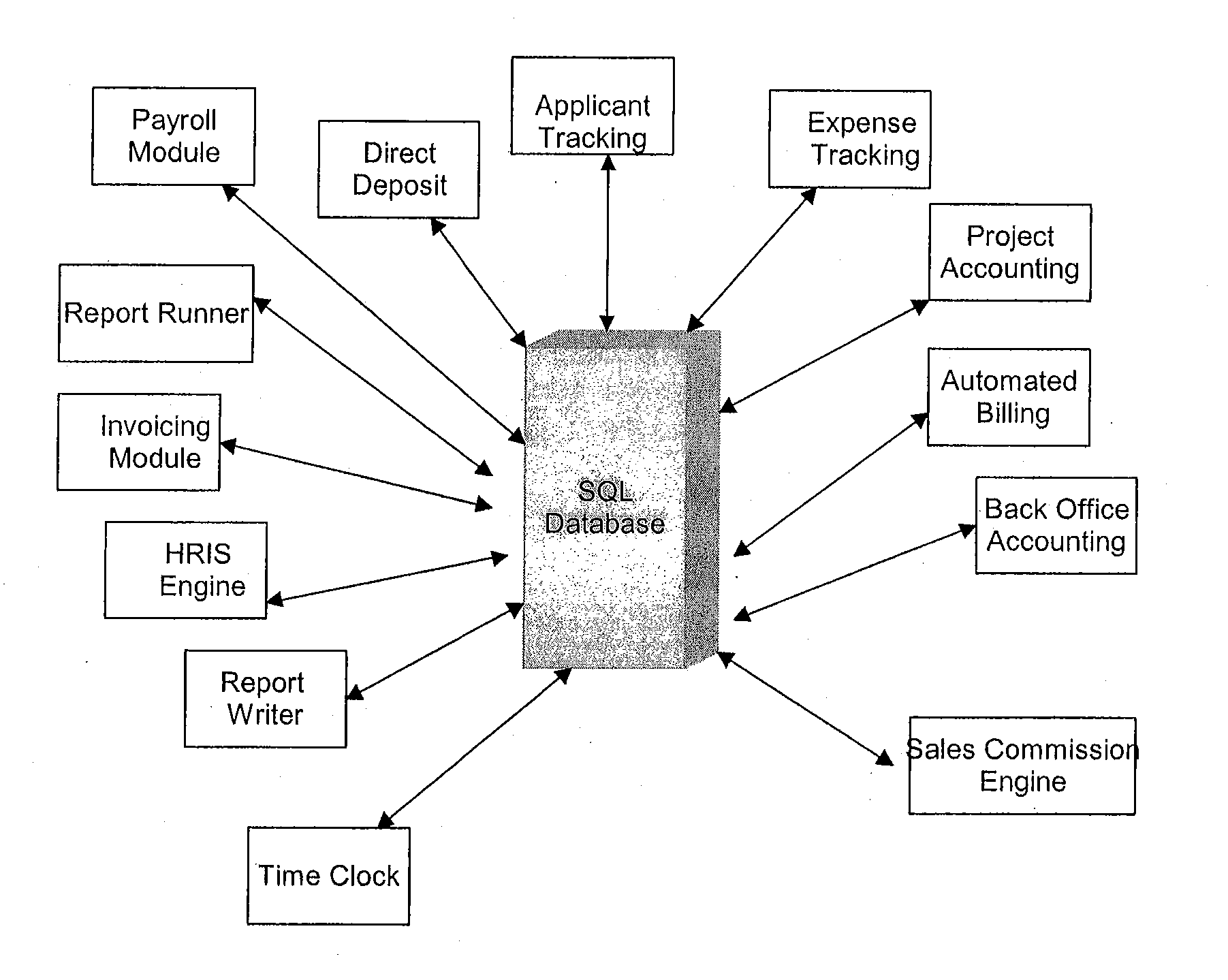
InactiveUS20100100464A1Function optimizationConvenient timeComplete banking machinesFinanceSafety management systemsSql server
A human resources and payroll system having a plurality of separate modules includes a SQL server or alternative server being able to implement a back end database. In one example, each separate module is designed to be integrated seamlessly into the core payroll system. In another example, each separate module is capable of being controlled by a security management system. In one example, each separate module may be activated or deactivated by the security management system based on the needs or contracted arrangements of a client using the system.
Owner:ESTAR
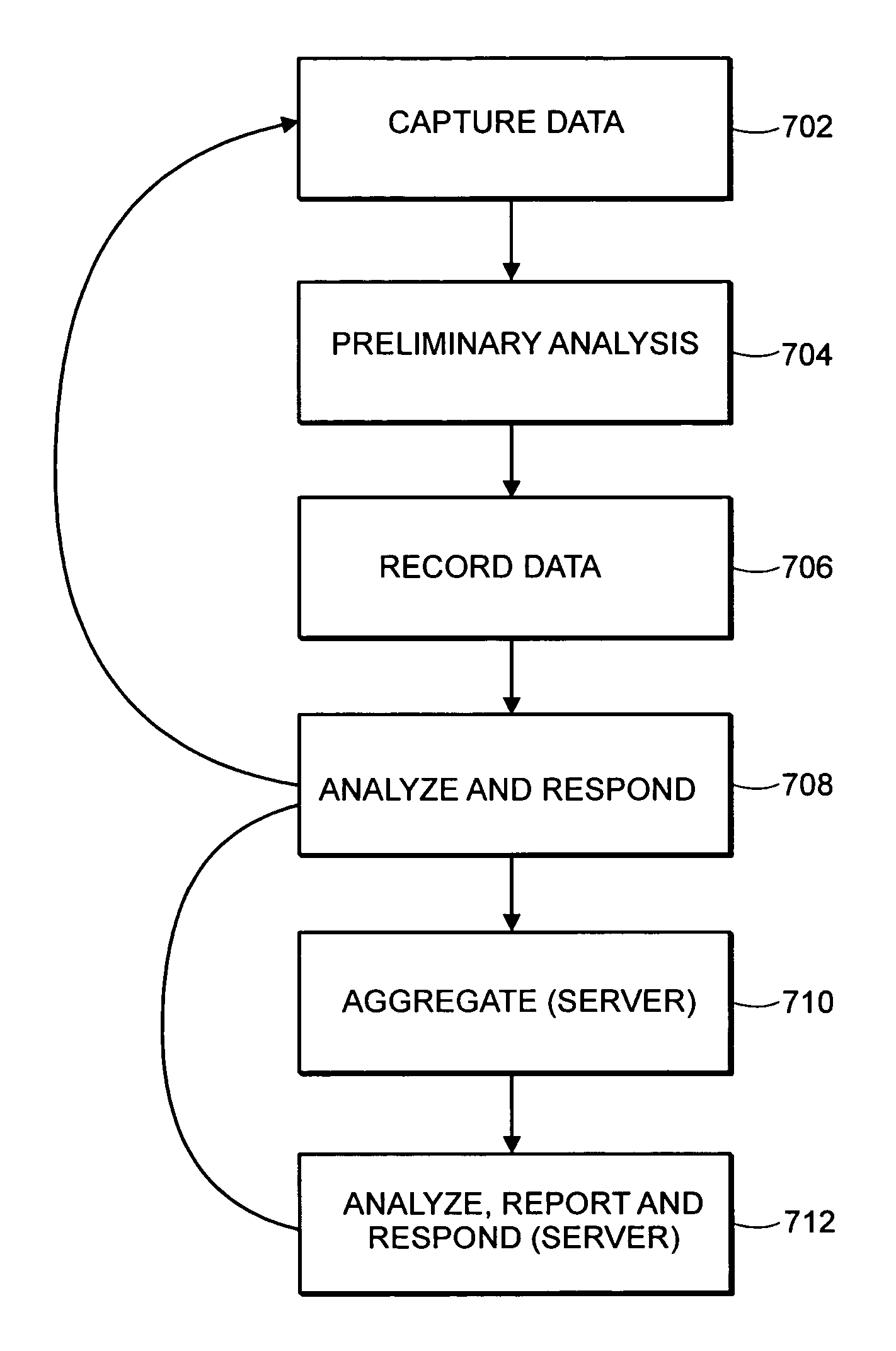
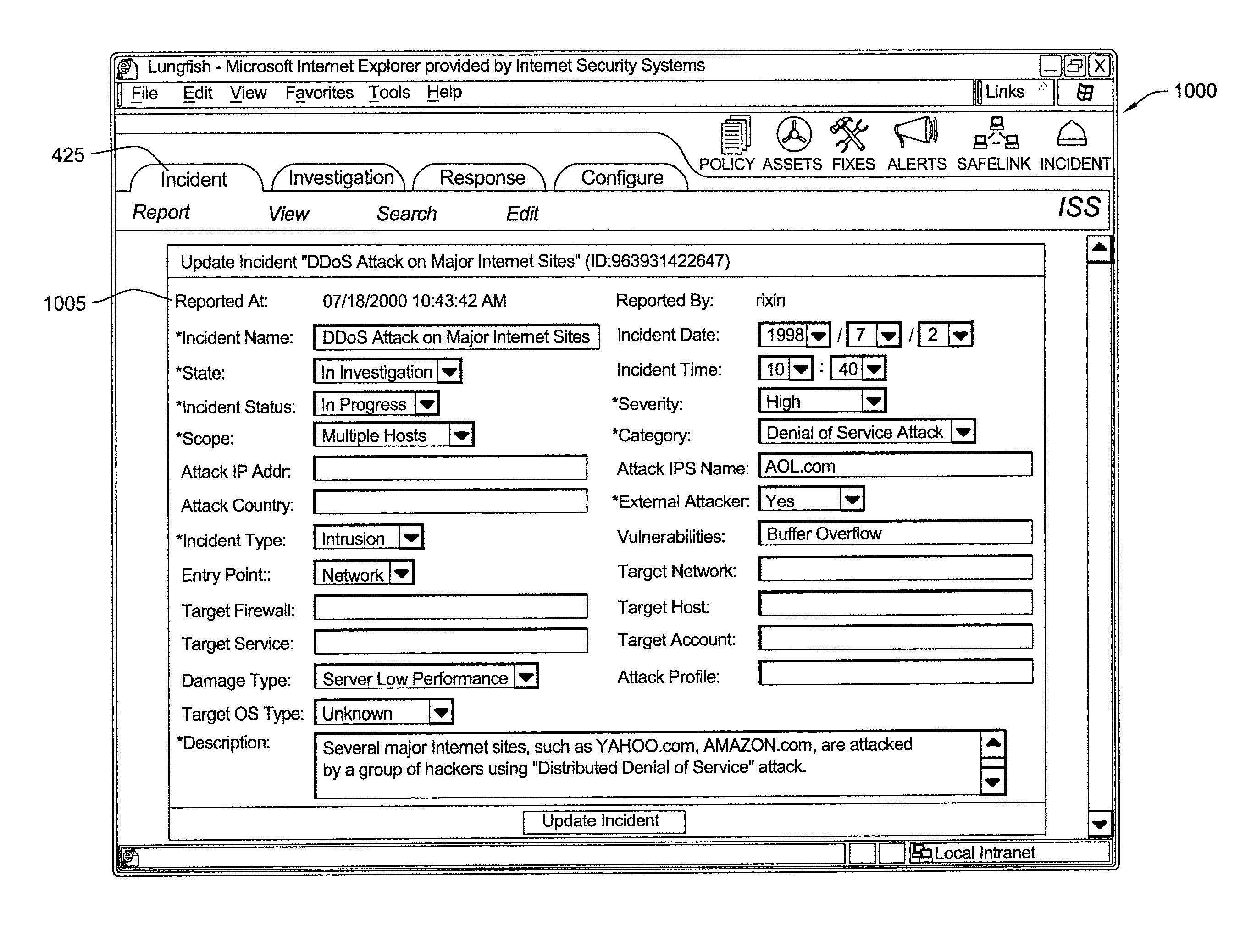
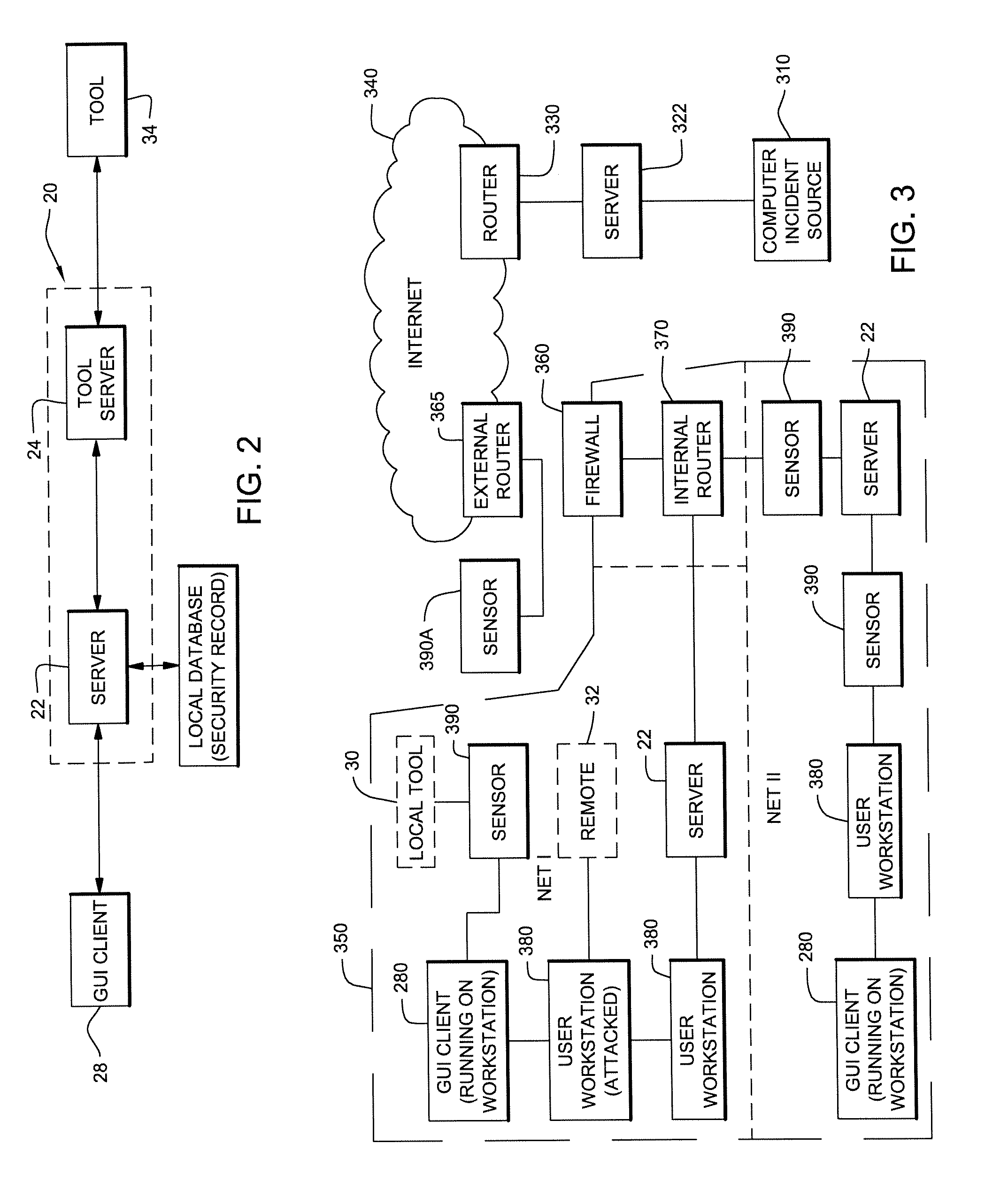
Method and System for Creating a Record for One or More Computer Security Incidents
ActiveUS20080016569A1Avoid unsafe incidentsMemory loss protectionError detection/correctionSafety management systemsDigital Signature Algorithm
A security management system can log, investigate, respond, and track computer security incidents that can occur in a networked computer system. In other words, the security management system can produce a security record of information related to the tracking of suspicious computer activity or actual computer security threats, such as denial of service attacks or other similar compromises to computers or computer networks. The security record can include, but is not limited to, date and times of computer security incidents, a name for a particular security incident, a security management system user, and a potential source of the computer security incident. The security record can be designed as a running log that saves or records all activity of a computer incident source as well as the activity of the security team responding to the computer incident source. To produce the security record, all data that relates to a computer incident and all data that relates to a computer incident response can be sent to a separate protected database, where data is protected by digital signature algorithms (DSAs).
Owner:KYNDRYL INC
Method and System for Managing Computer Security Information
InactiveUS20100083382A1Reduce processing speedEasy to operateMemory loss protectionError detection/correctionTraffic capacitySafety management systems
A security management system includes a fusion engine which “fuses” or assembles information from multiple data sources and analyzes this information in order to detect relationships between raw events that may indicate malicious behavior and to provide an organized presentation of information to consoles without slowing down the processing performed by the data sources. The multiple data sources can comprise sensors or detectors that monitor network traffic or individual computers or both. The sensors can comprise devices that may be used in intrusion detection systems (IDS). The data sources can also comprise firewalls, audit systems, and other like security or IDS devices that monitor data traffic in real-time. The present invention can identify relationships between one or more real-time, raw computer events as they are received in real-time. The fusion engine can also assess and rank the risk of real-time raw events as well as mature correlation events.
Owner:INT BUSINESS MASCH CORP
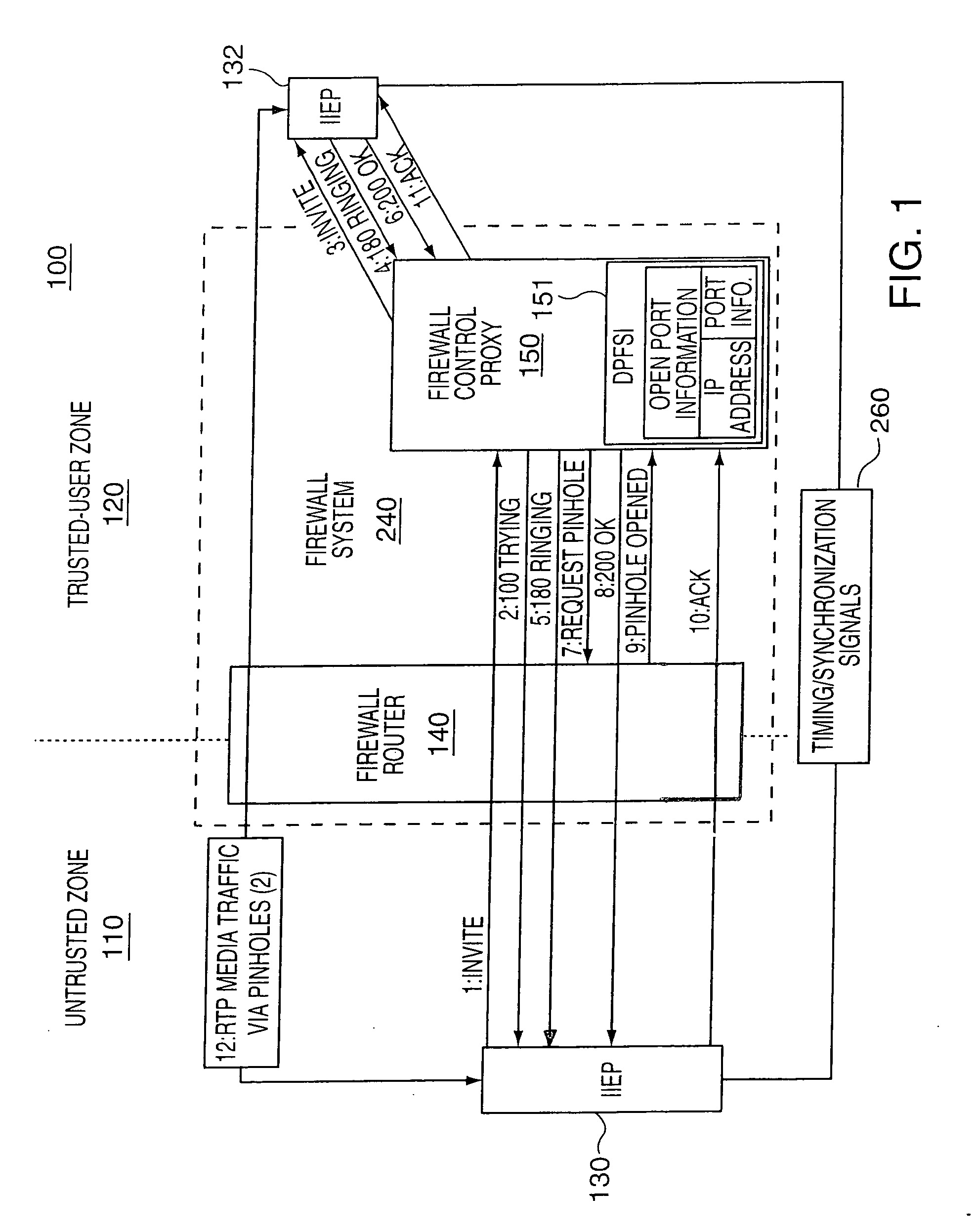
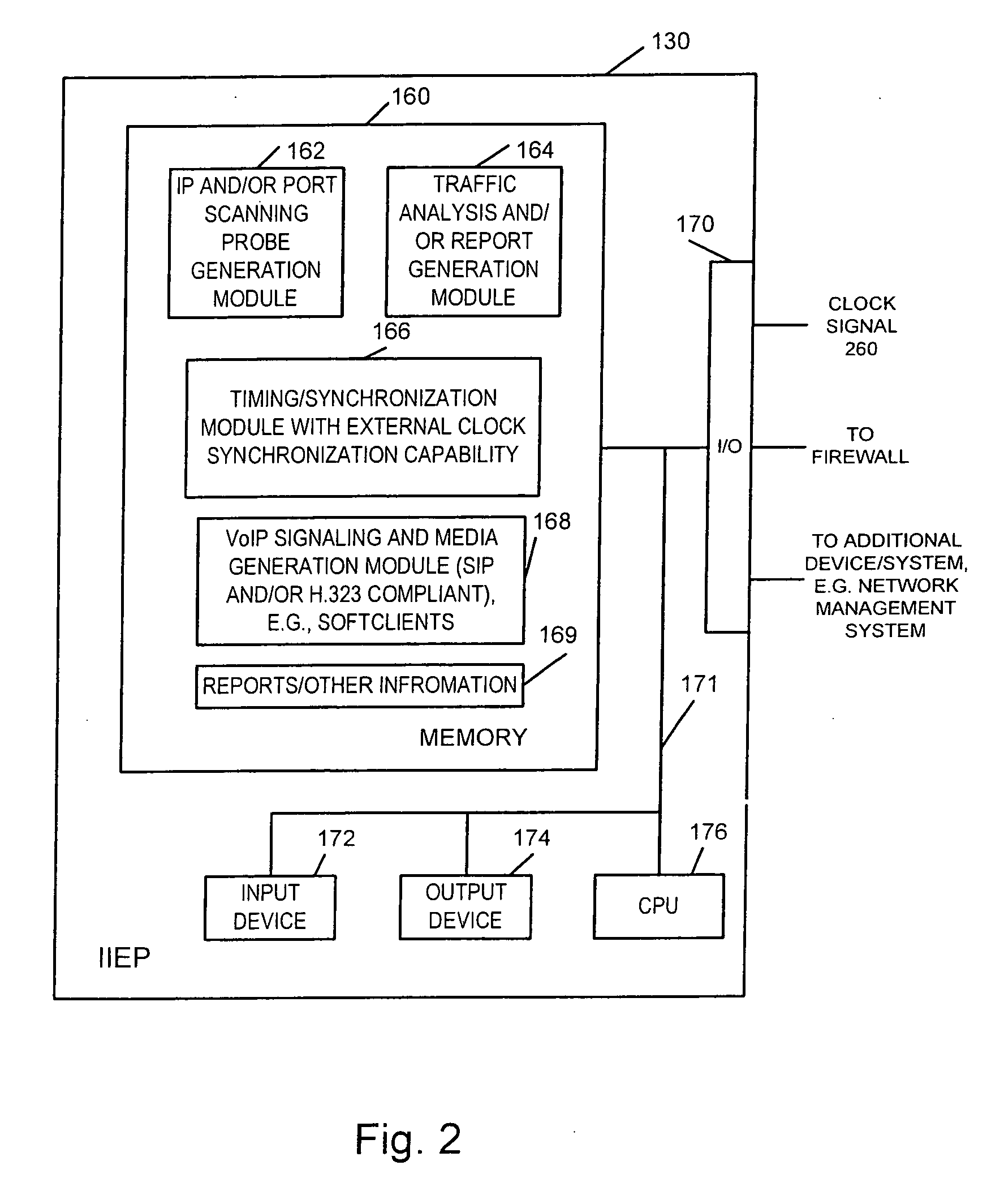
Security management system for monitoring firewall operation
ActiveUS20050076238A1Extra logicReduce loadDigital data processing detailsMultiple digital computer combinationsIp addressSafety management systems
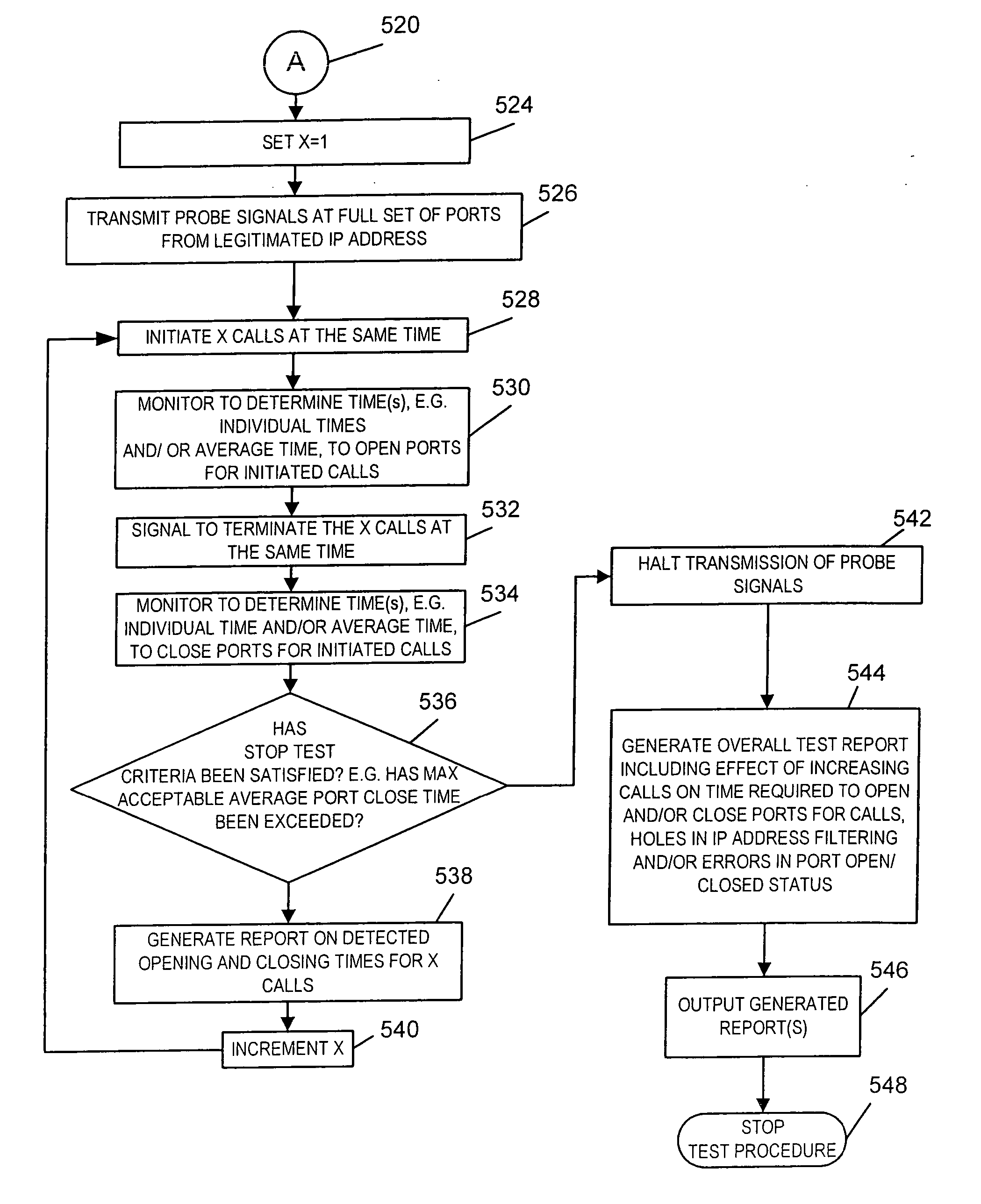
A test method for Internet-Protocol packet networks that verifies the proper functioning of a dynamic pinhole filtering implementation as well as quantifying network vulnerability statistically, as pinholes are opened and closed is described. Specific potential security vulnerabilities that may be addressed through testing include: 1) excessive delay in opening pinholes, resulting in an unintentional denial of service; 2) excessive delay in closing pinholes, creating a closing delay window of vulnerability; 3) measurement of the length of various windows of vulnerability; 4) setting a threshold on a window of vulnerability such that it triggers an alert when a predetermined value is exceeded; 5) determination of incorrectly allocated pinholes, resulting in a denial of service; 6) determining the opening of extraneous pinhole / IP address combinations through a firewall which increase the network vulnerability through unrecognized backdoors; and 7) determining the inability to correlate call state information with dynamically established rules in the firewall.
Owner:PALO ALTO NETWORKS INC
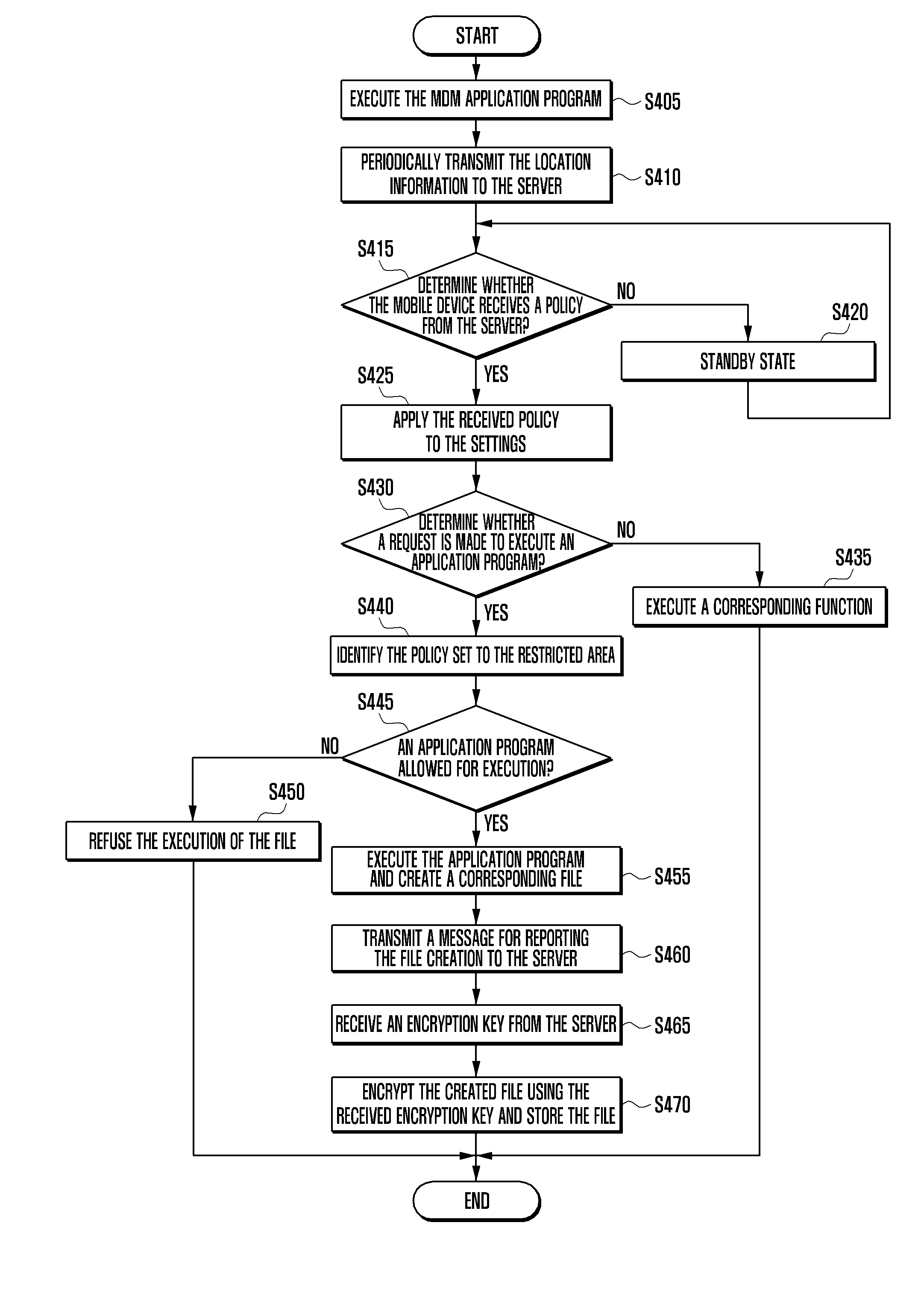
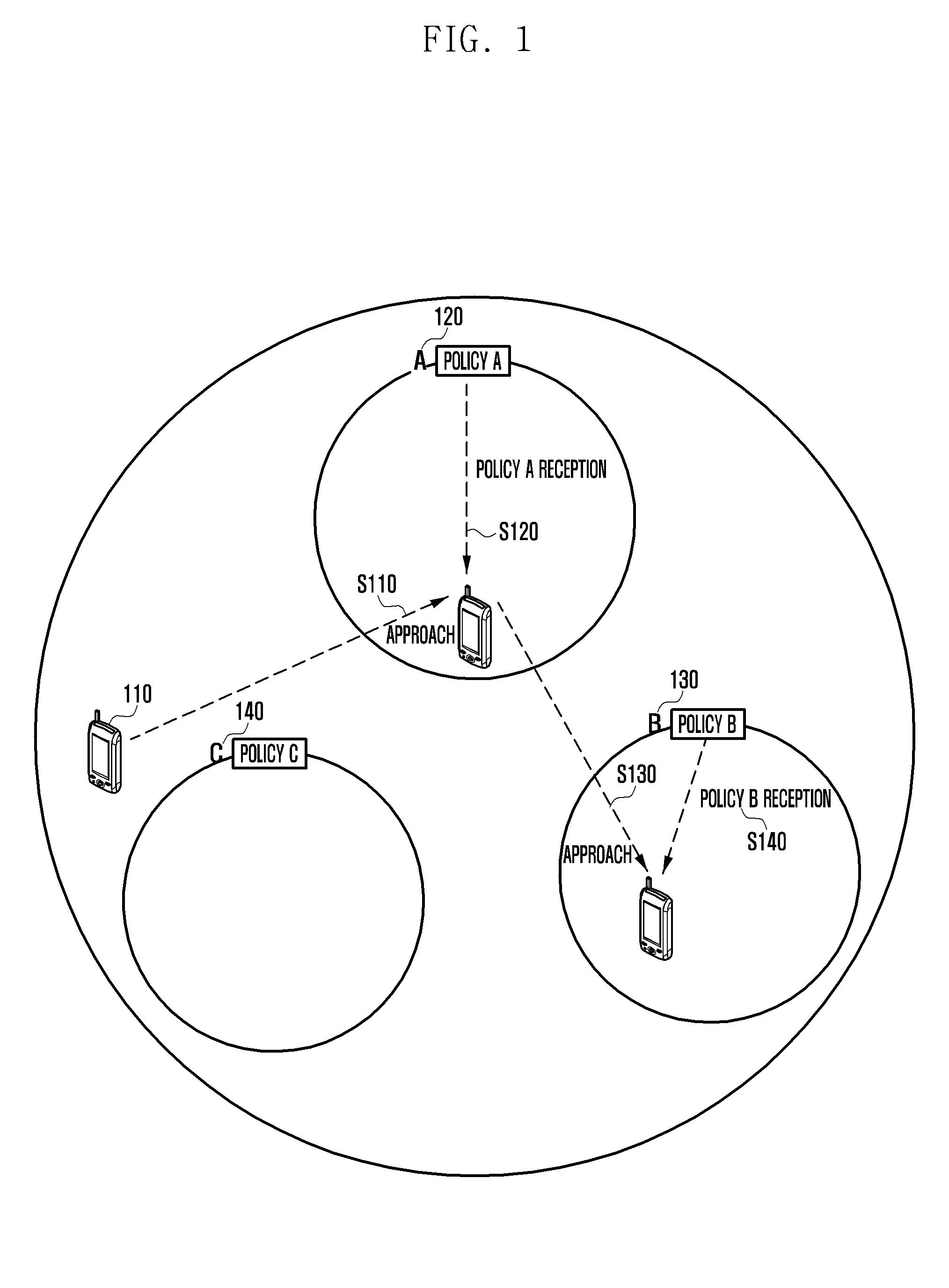
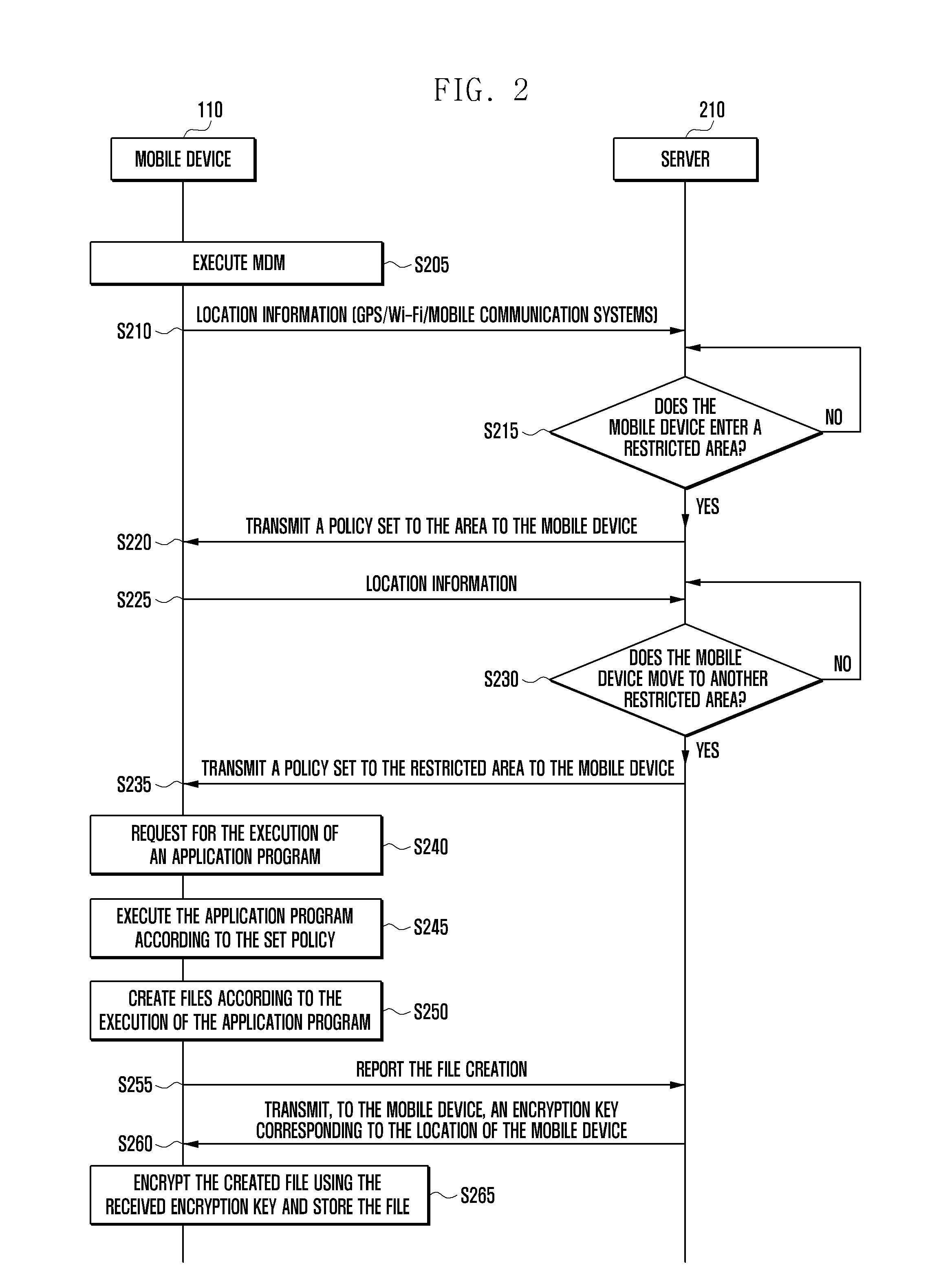
Security management system and method for location-based mobile device
ActiveUS20130013932A1Unauthorized memory use protectionHardware monitoringSafety management systemsMobile device
A method and a system of managing information security for a mobile device in a restricted area based on location information regarding the mobile device are provided. The method includes receiving, by the mobile device, a request for the execution of an application program in a restricted area from a server managing the restricted area, executing, by the mobile device, the application program requested for execution when the program was set to be executable according to a security policy set to the restricted area, encrypting, by the mobile device, a file, created according to the execution of the application program, based on location information regarding the mobile device, and storing the encrypted file.
Owner:SAMSUNG ELECTRONICS CO LTD
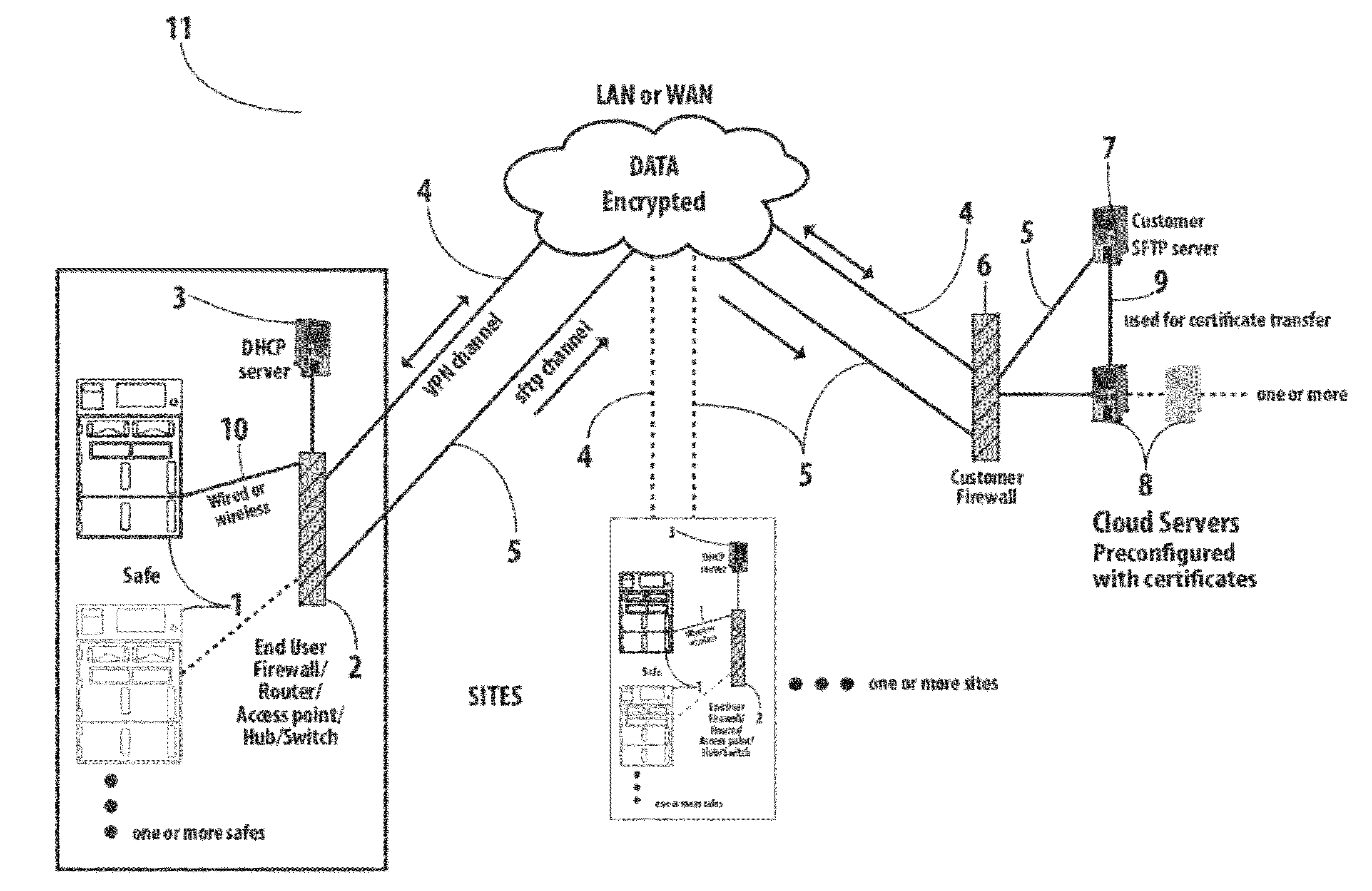
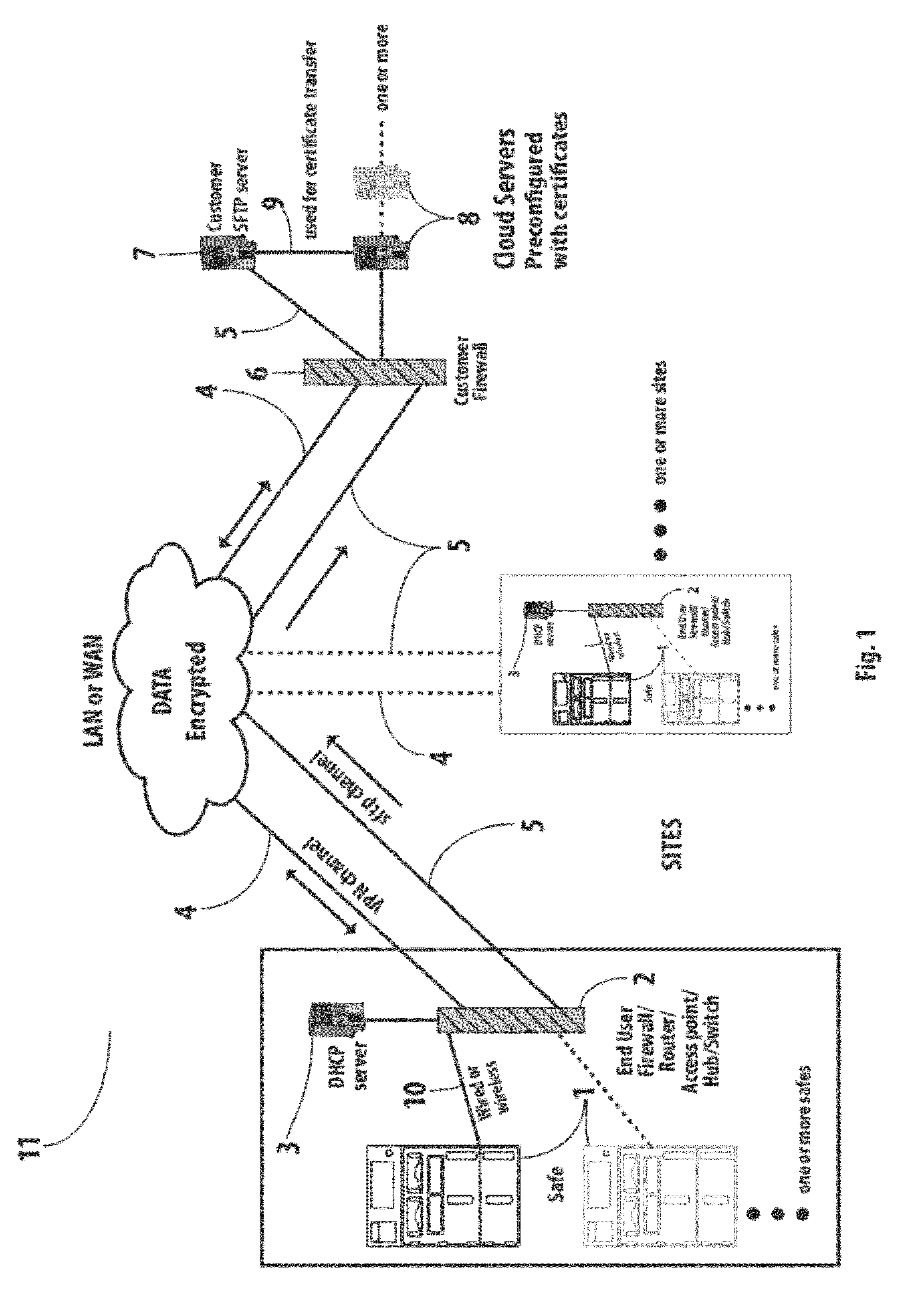
Centrally Controlled Safe Management System
InactiveUS20120073482A1Easy maintenanceImprove securityPayment architectureSafety transaction partitionSafety management systemsService provision
A cash management system utilizes a cloud computing model wherein a cloud of one or more servers may be locally networked or may be geographically dispersed and accessed by the client device over the Internet. The client device is a cash management safe. More than one safe may be employed in a system. Metrics, control functions, and interactions normally handled by an autonomous safe are shunted directly to a cloud server on the network. Usage data, currency validations, coin validations, security entries, etc. are communicated to the cloud server. The cloud server(s), based on database information and software settings, can transmit configuration, updates and information to remote safes. The information transmitted may include user configuration, access rules, currency configuration, alert configuration, and software and firmware updates. The cloud server based cash management system allows the entire cash management of an enterprise to be provided as a service to that enterprise.
Owner:FIRE KING SECURITY PRODS
Management system and method for user safety authority limit
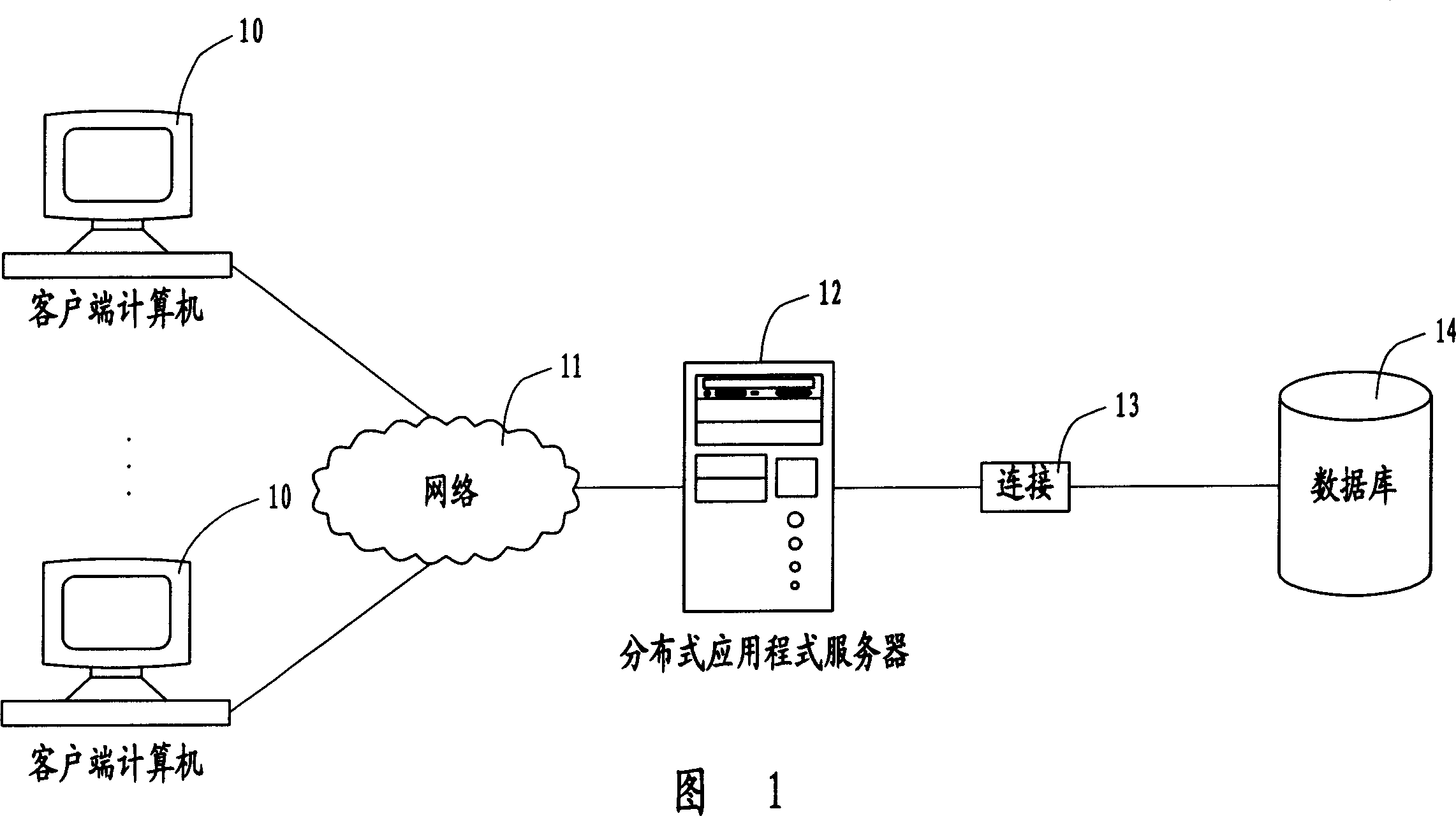
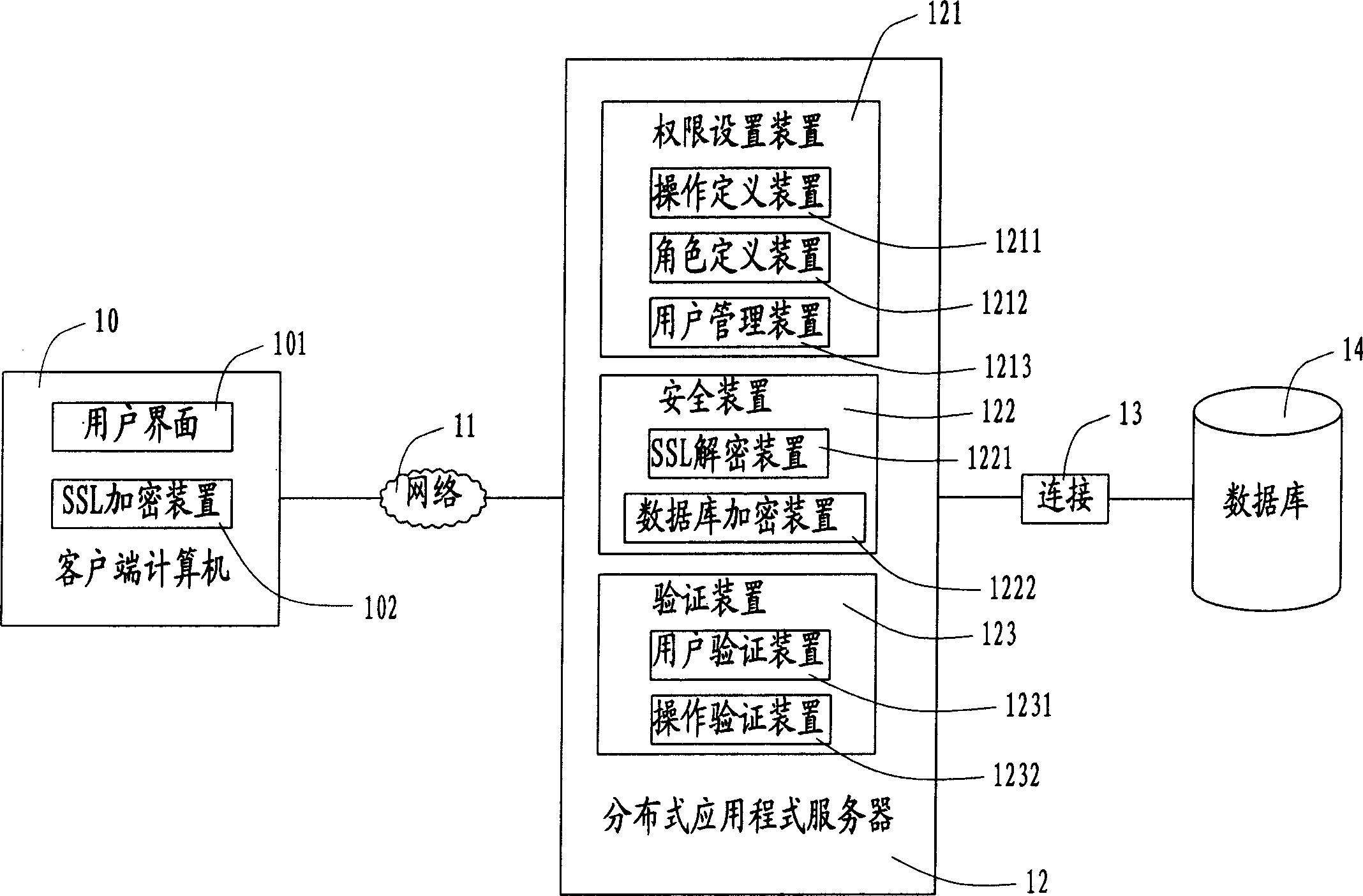
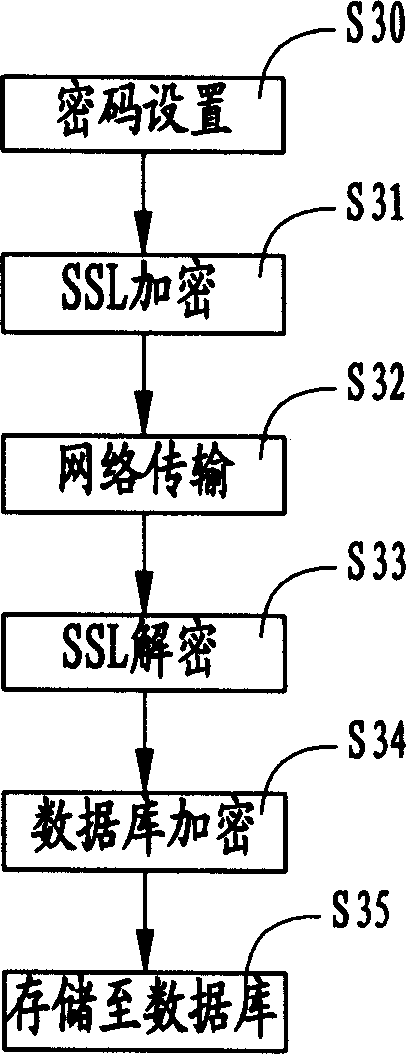
InactiveCN1485746AEnsure safetyGuaranteed scalabilityUnauthorized memory use protectionExtensibilitySafety management systems
The user authority safety management system and method, wherein the system comprises a plurality of client end computers, a distributed application program server and a data base, the user calls the application program device for proceeding operation definition and role definition through the user interface on the client end computer, and store the information into the database. The invention realizes the user authority control based the system operation, thus guaranteeing the expandability of the system.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
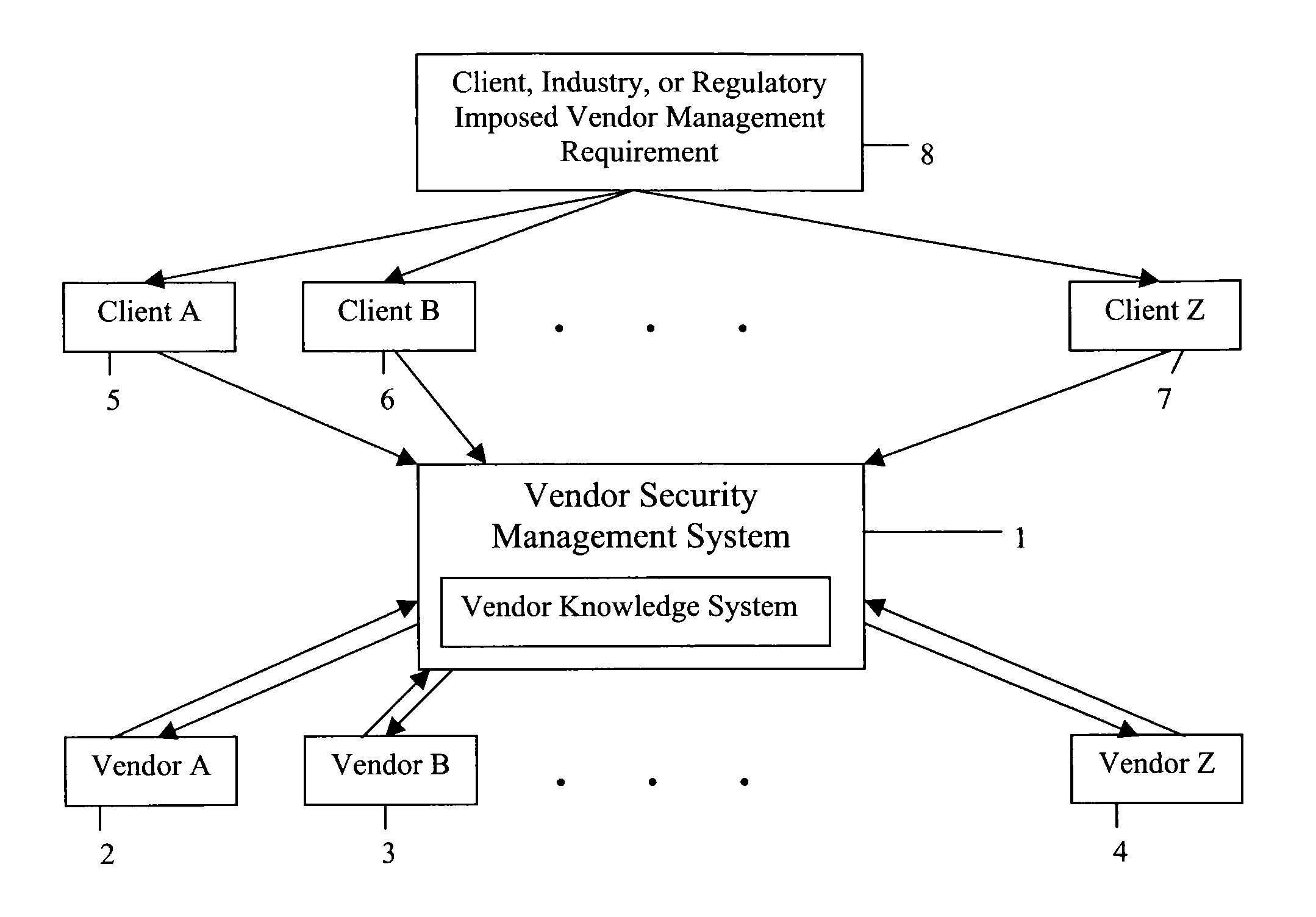
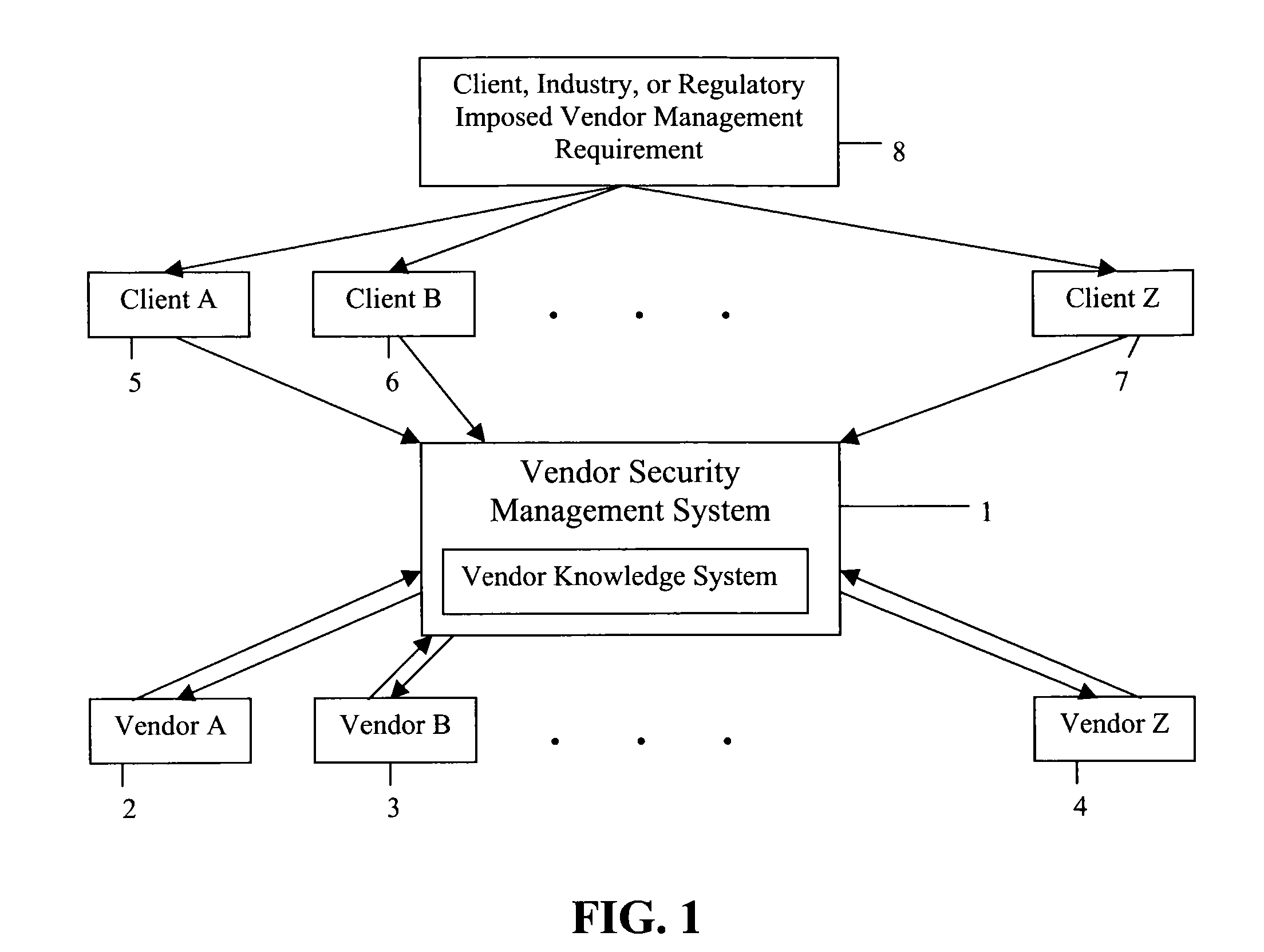
Vendor security management system
InactiveUS7392203B2Fulfil requirementsDigital data processing detailsMultiple digital computer combinationsSafety management systemsSecurity Measure
A management system for determining the security measures of a plurality of vendors. An assessment is performed on a plurality of vendors at a discount. The assessment is placed into a database and is reviewable and accessible by clients who subscribe to the management system. The management system allows clients to review and assess the security information regarding a plurality of vendors without the cost of performing an assessment of each vendor.
Owner:FORTREX LLC
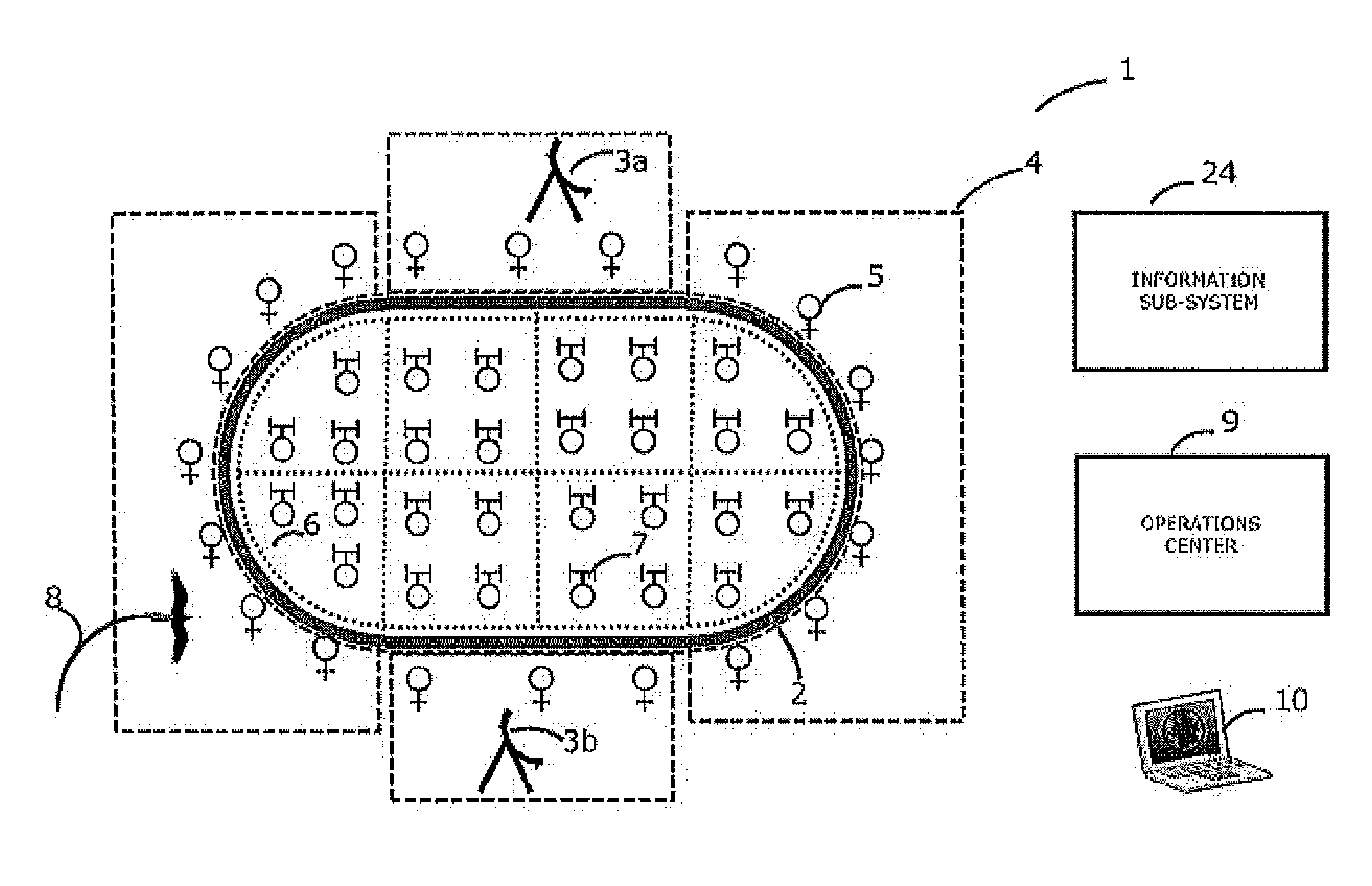
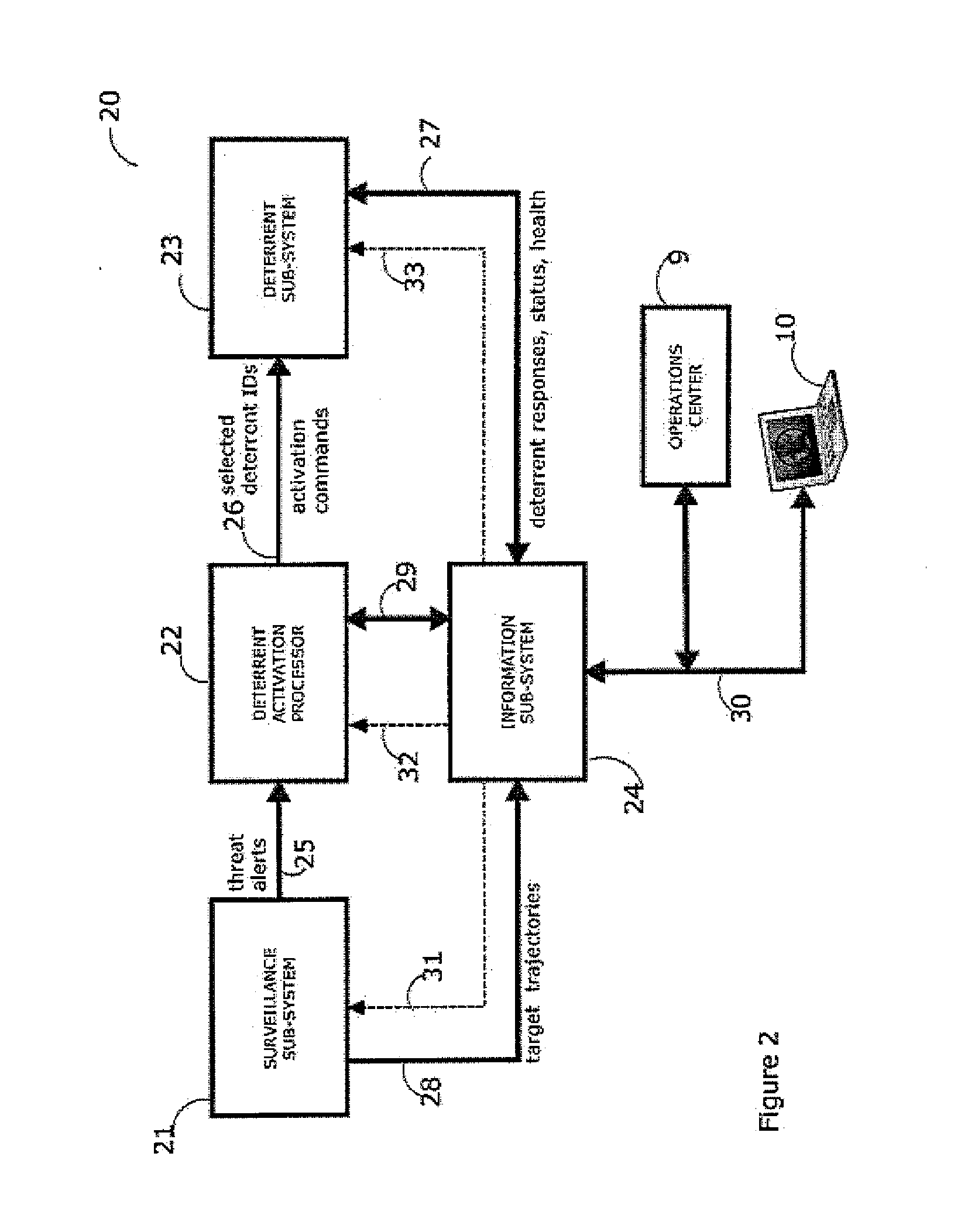
Device & method for smart, non-habituating, automatic bird deterrent system
ActiveUS20130098309A1Improve intelligenceMore automated capabilityAnimal huntingAnimal repellantsWide areaAnalysis data
Operation of a bird deterrent system includes i. measurement of bird habituation to activation of deterrent devices; ii. reduction of habituation through increased selectivity in activating deterrents only for birds posing a threat to or threatened by a protected area, and in particular, those within threat altitudes; iii. provision of analytical data in support of safety management systems, risk management, etc.; iv. integrated, wide-area radar coverage with multiple virtual intrusion zones providing multiple lines of defense around and over very large protected areas.
Owner:ACCIPITER RADAR TECH
Imaging apparatus, imaging system, security management apparatus, and security management system
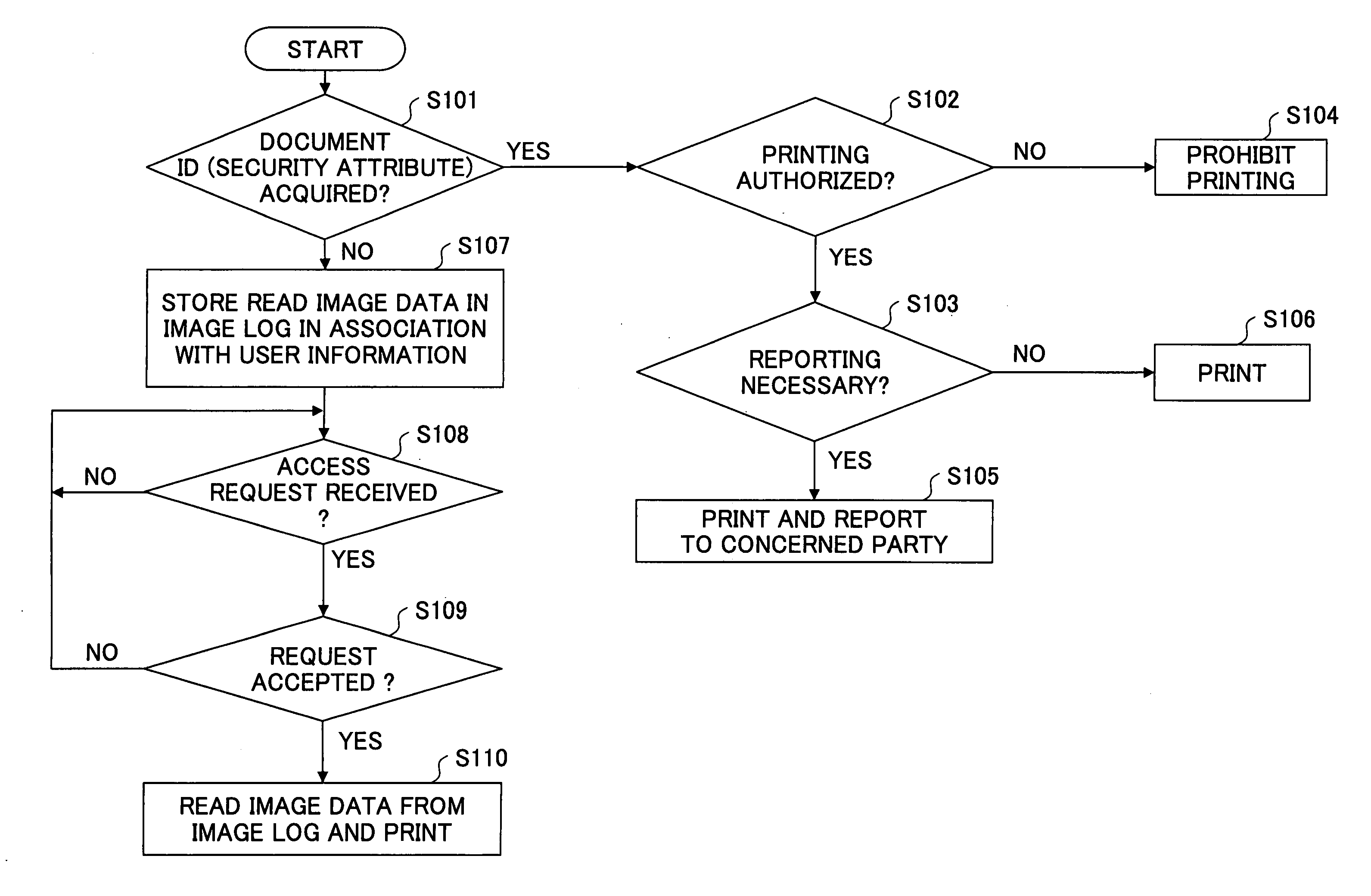
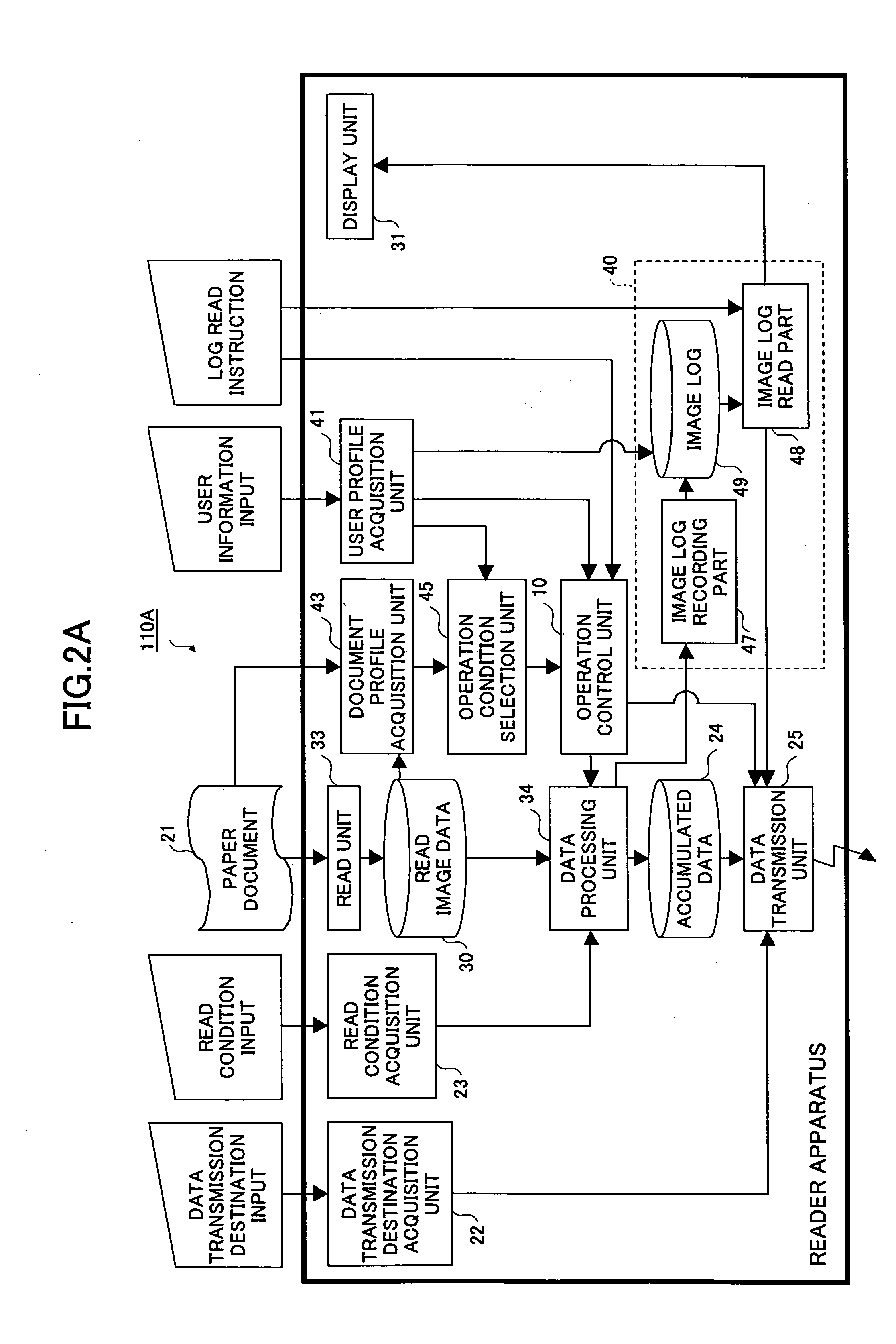
InactiveUS20050144469A1User identity/authority verificationUnauthorized memory use protectionSafety management systemsPaper document
An imaging apparatus is provided that is capable of maintaining document security control even in a case where document ID information cannot be identified from a physical document that is subject to an imaging operation. The imaging apparatus includes a read unit for reading image data from a physical document in response to an imaging request from a user, a user information acquisition unit for acquiring user information including a security attribute of the user, a document information acquisition unit for acquiring document information including a security attribute of the physical document, an operating condition selection unit for determining whether to authorize outputting of the image data read from the physical document based on the user information and the document information by referring to a predetermined rule, and a log management unit for storing the image data in association with the user information without allowing the image data to be output when the document information is not acquired at the document information acquisition unit.
Owner:RICOH KK
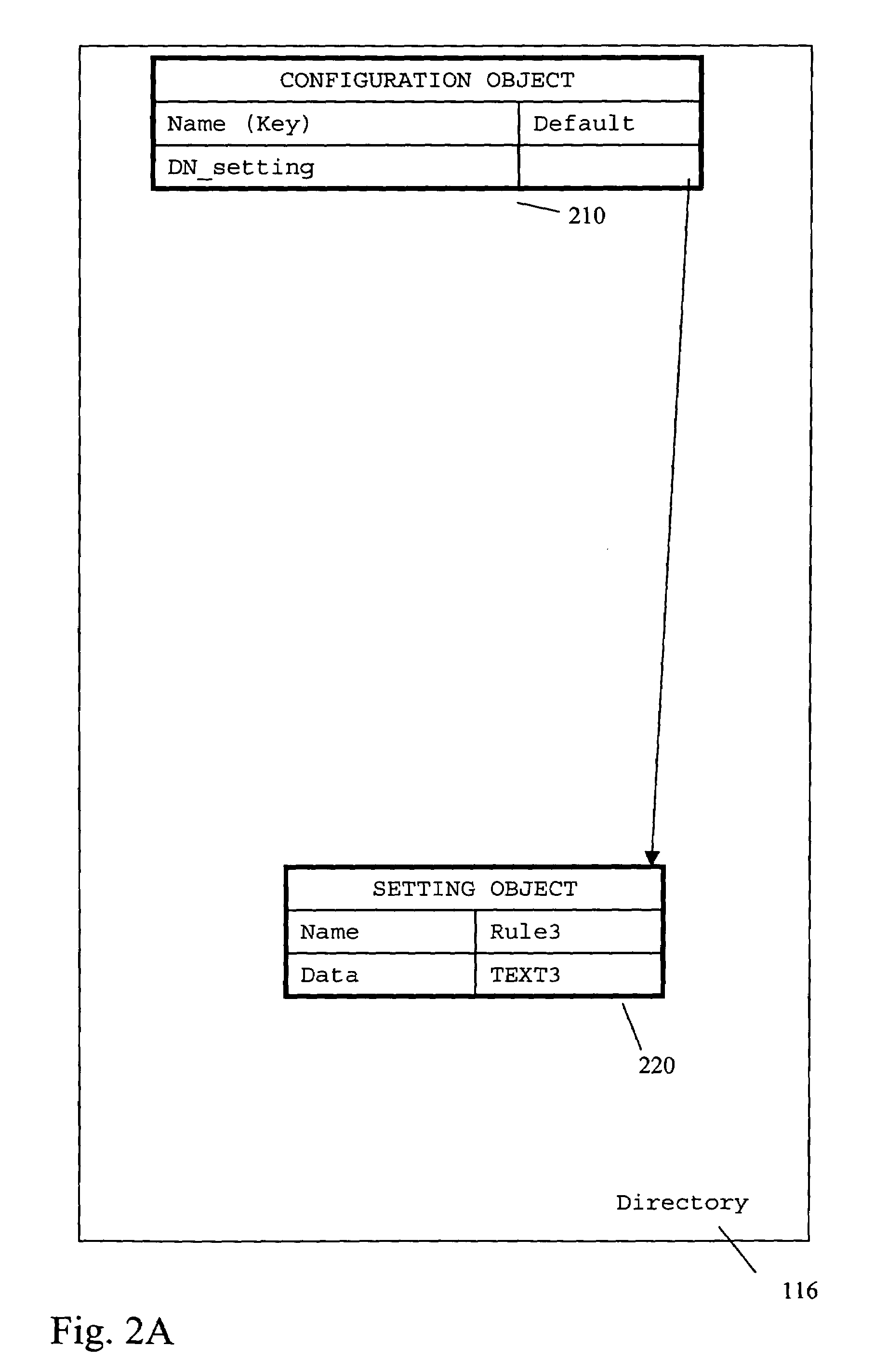
Configuration system and methods including configuration inheritance and revisioning
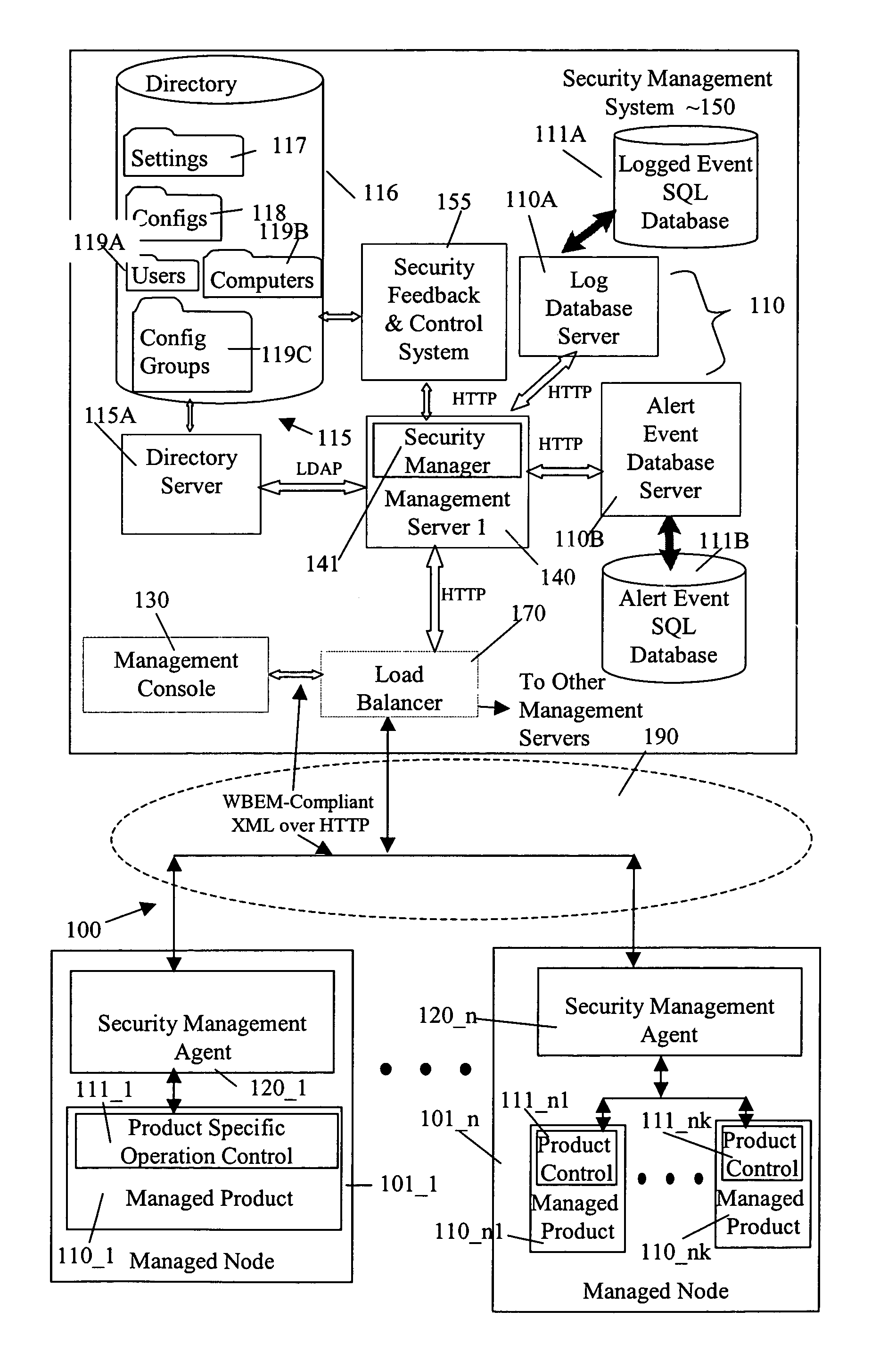
ActiveUS7383534B1Efficient configurationVersion controlSpecific program execution arrangementsSafety management systemsData store
A system includes a security management system for a plurality of managed products. The security management system stores configuration data for managed products and managed nodes in a directory. Configuration data is stored in the directory in the form of configuration objects and setting objects. A revision history of a configuration object and / or a setting object can be maintained. Inheritance between configuration objects is supported so that a configuration inheritance chain is available. To determine an effective configuration at a point in time, a parent-child inheritance merge process is used. To assist the parent-child inheritance process, name attributes and collision resolution mode attributes are used.
Owner:SYMANTEC CORP
Combined secret key dynamic security management system
InactiveCN102170357AIncrease flexibilityImprove securityPublic key for secure communicationUser identity/authority verificationPersonal identification numberSafety management systems
The invention discloses a combined secret key dynamic security management system, which consists of a client device unique identification number SN, a synchronous factor (SF) which is managed by a background main service system, a personal identification number (PIN) which is managed by users themselves, and an additional code (AC) which is managed by a service system. A dynamic protection secretkey KP which is generated by computing the SN, the SF, the PIN and the AC is used for protecting a business private key SK, and by an unique identification number SN of an other person involved, a public key of the other person involved is calculated, a message is safely sent to the other person involved and a signature of the other person involved is verified; and by the private key of the user,encrypted data sent is decrypted and data which is ensured by the user is signed. The user identity and the safety of business application are verified hierarchically by adopting a system of a dynamic factor and the combined secret key system.
Owner:BEIJING HUFU TECH
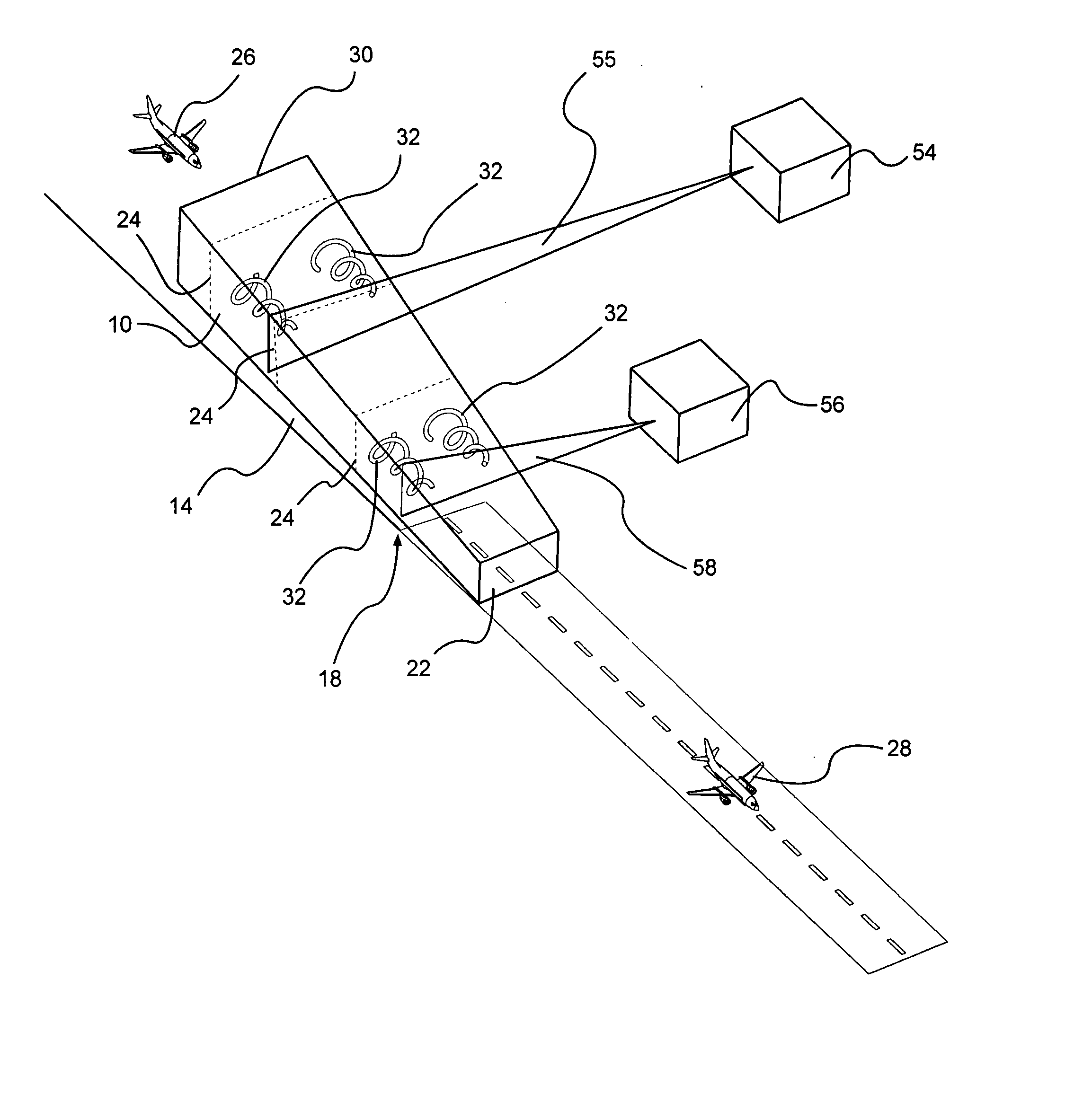
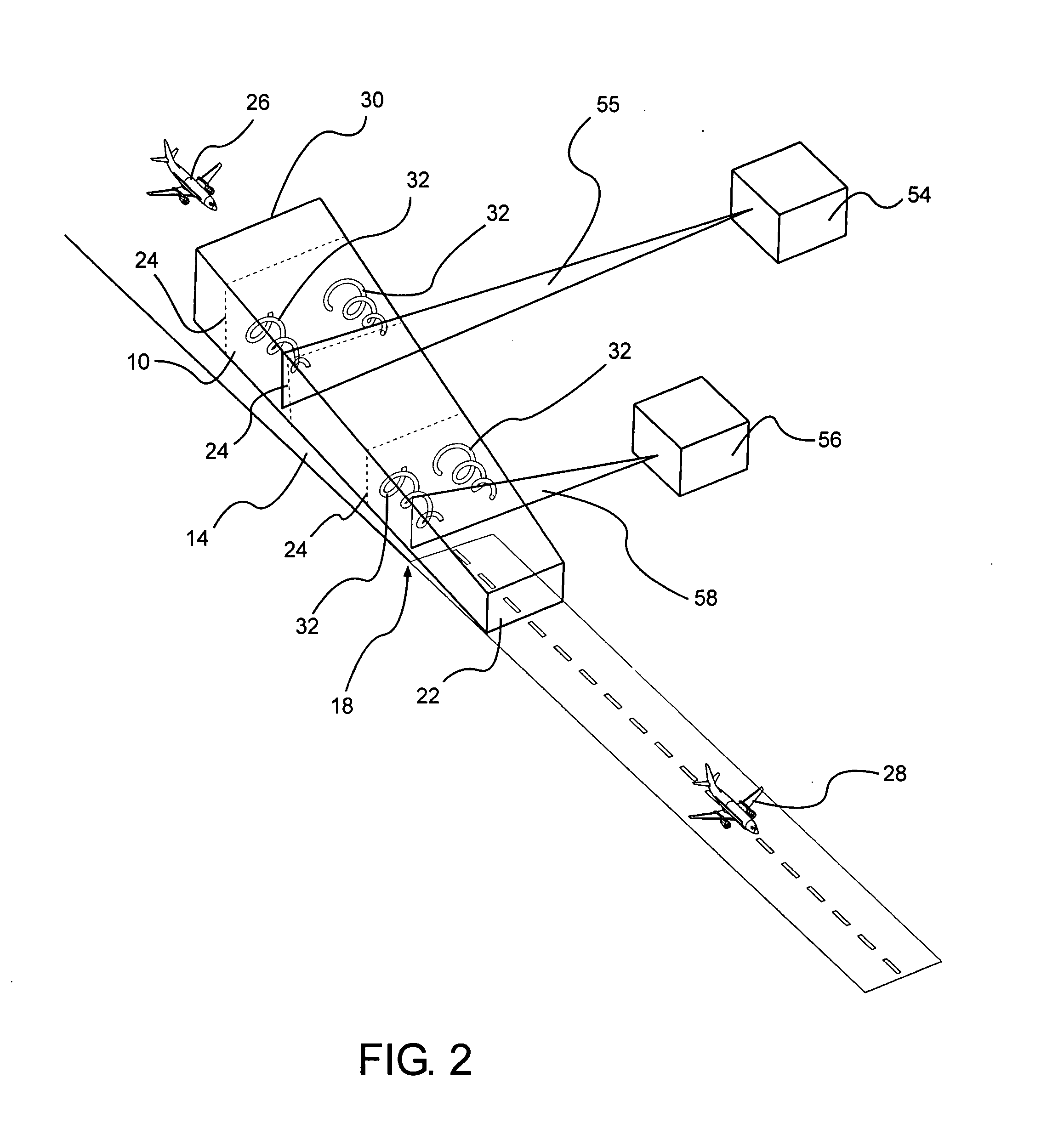
Aircraft wake safety management system
InactiveUS20080030375A1Analogue computers for vehiclesAnalogue computers for trafficRoad traffic controlSafety management systems
The disclosure is directed toward a method for safely managing aircraft separation. The method comprises a data integration host configured for: receiving aircraft information from a first aircraft; receiving weather data from a weather monitoring system; combining the aircraft information of the first aircraft with the weather data; formulating a position prediction of a wake vortex located within a critical safety volume of a runway; receiving from a sensor real time wake vortex data in a path of the first aircraft; comparing the real time wake vortex data to the position prediction to validate the position prediction and to formulate a determination of whether the wake vortex is present in the critical safety volume; and utilizing the determination to transmit spacing data to air traffic control, wherein the spacing data is at least one of standard wake vortex spacing and minimum radar spacing.
Owner:FLIGHT SAFETY TECH
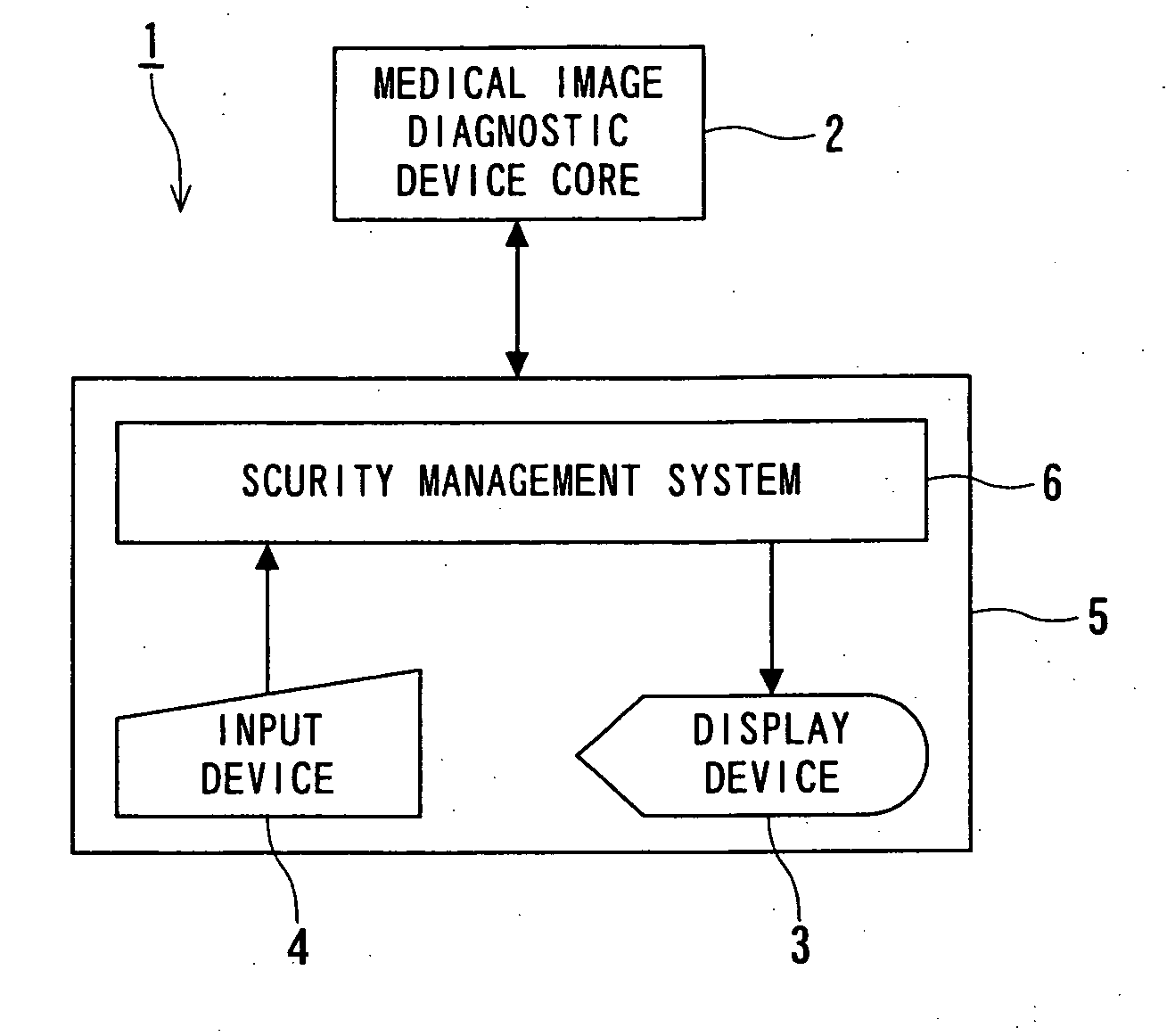
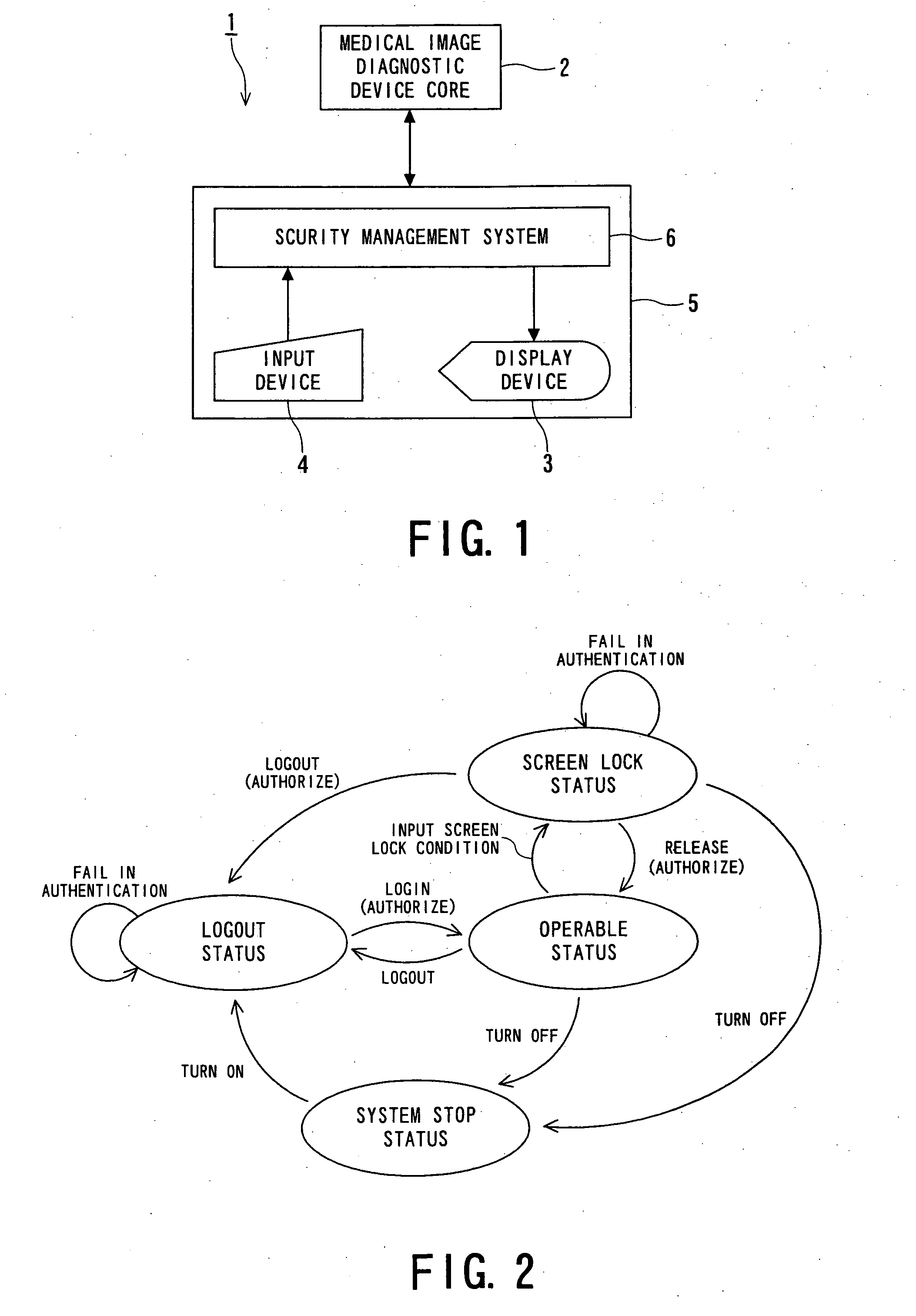
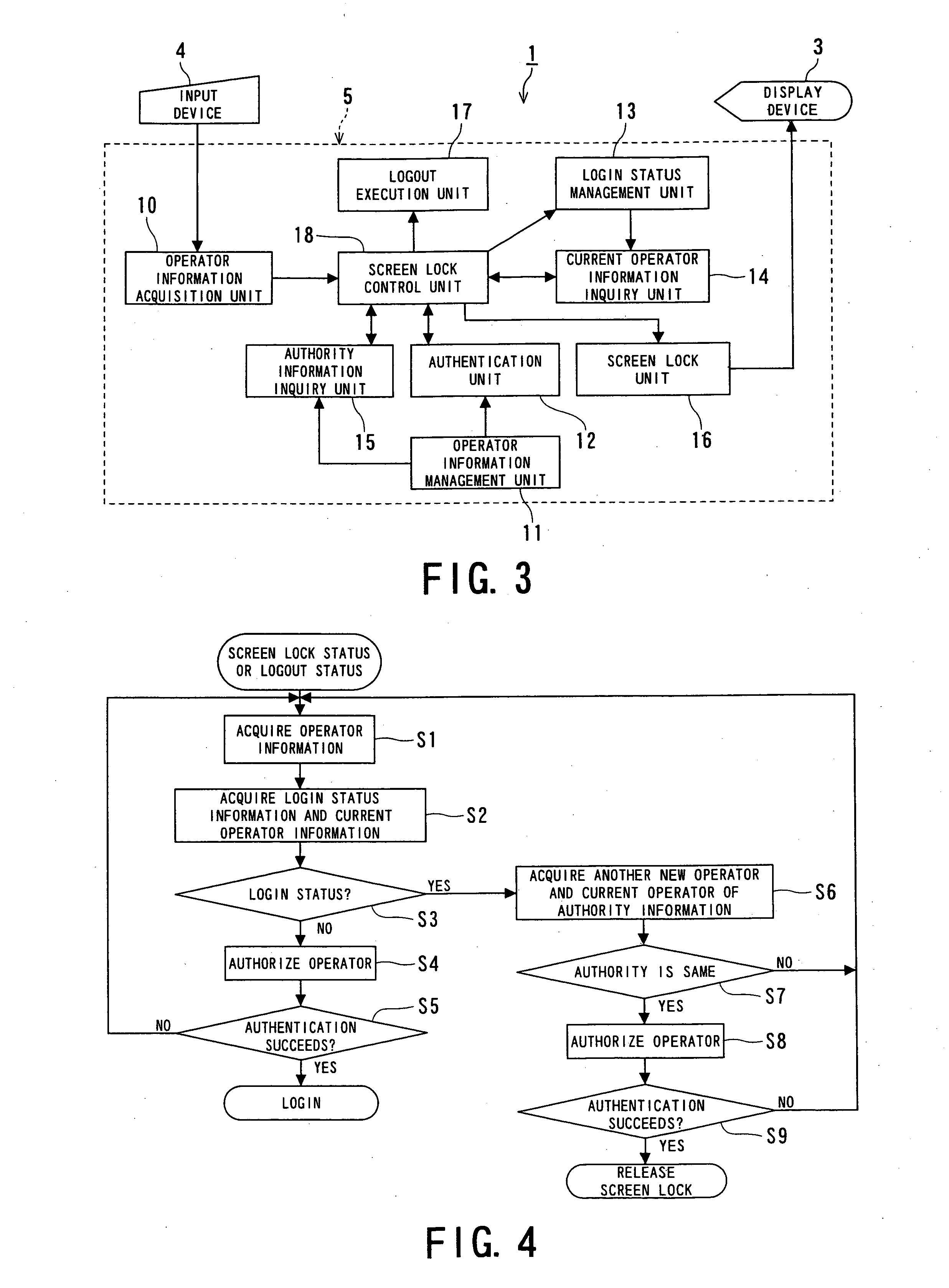
Security management system, medical device and method for managing security
ActiveUS20060136998A1Reduce obstaclesData processing applicationsDigital data processing detailsSafety management systemsMedical device
A security management system, comprising: an authentication unit for authenticating an operator of an operating terminal in order to determine whether the operator is permitted to log in or release a lock; a current operator information inquiry unit for inquiring for login status information and current operator information; an authority information inquiry unit for inquiring for authority information regarding the operator and that regarding the current operator; a lock unit for detecting an event, where a predetermined lock condition is satisfied, in the login status to allow the operating terminal to change to a lock status, and for allowing the operating terminal to change to an operable status in response to a login instruction or an instruction for a release; and a lock control unit for transmitting the instruction for a release to the lock unit when a predetermined condition is satisfied.
Owner:TOSHIBA MEDICAL SYST CORP
Electronic document safety management system and method
ActiveCN103530570AGuaranteed security controlImprove offline securityDigital data protectionElectronic documentOperational system
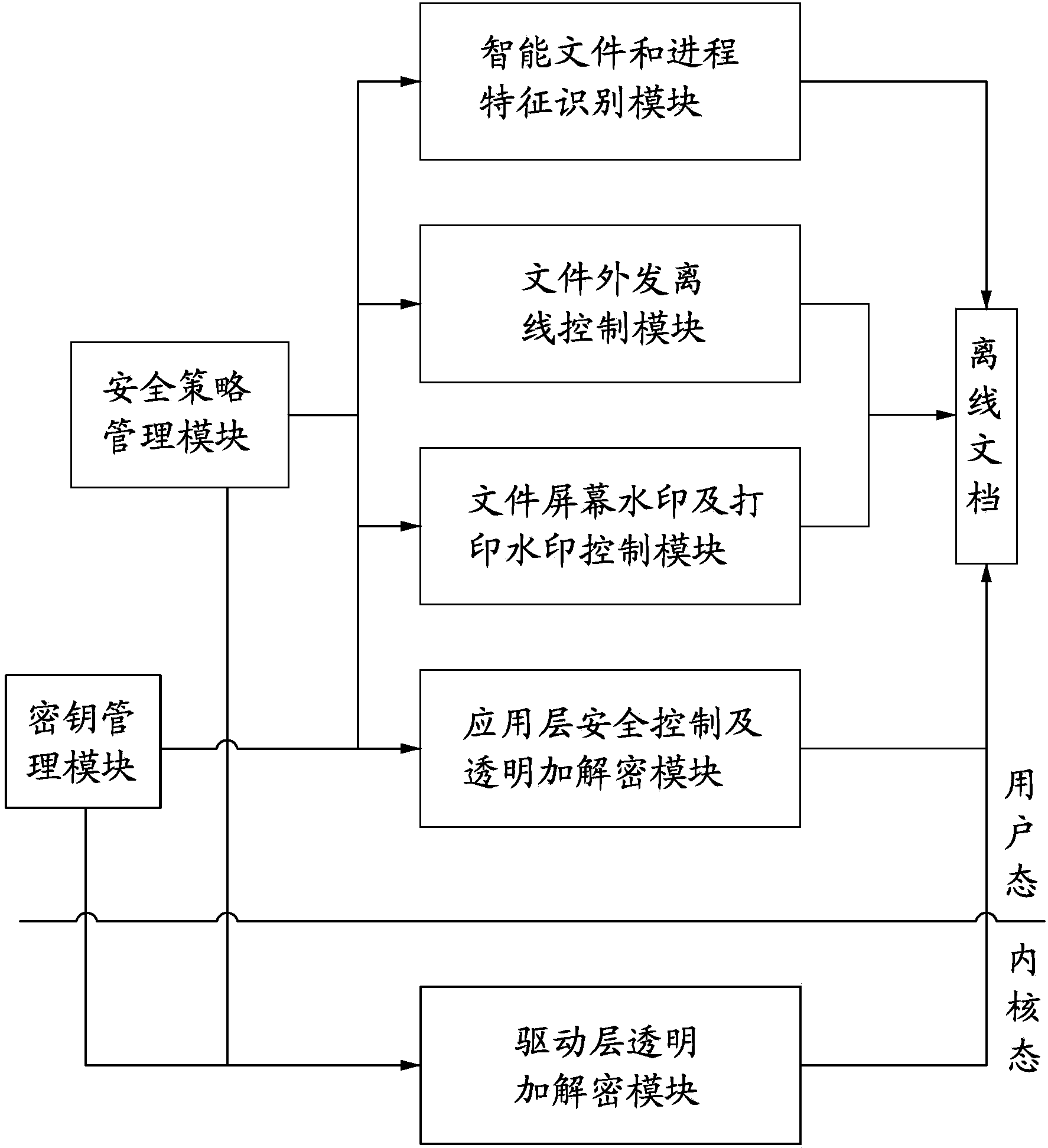
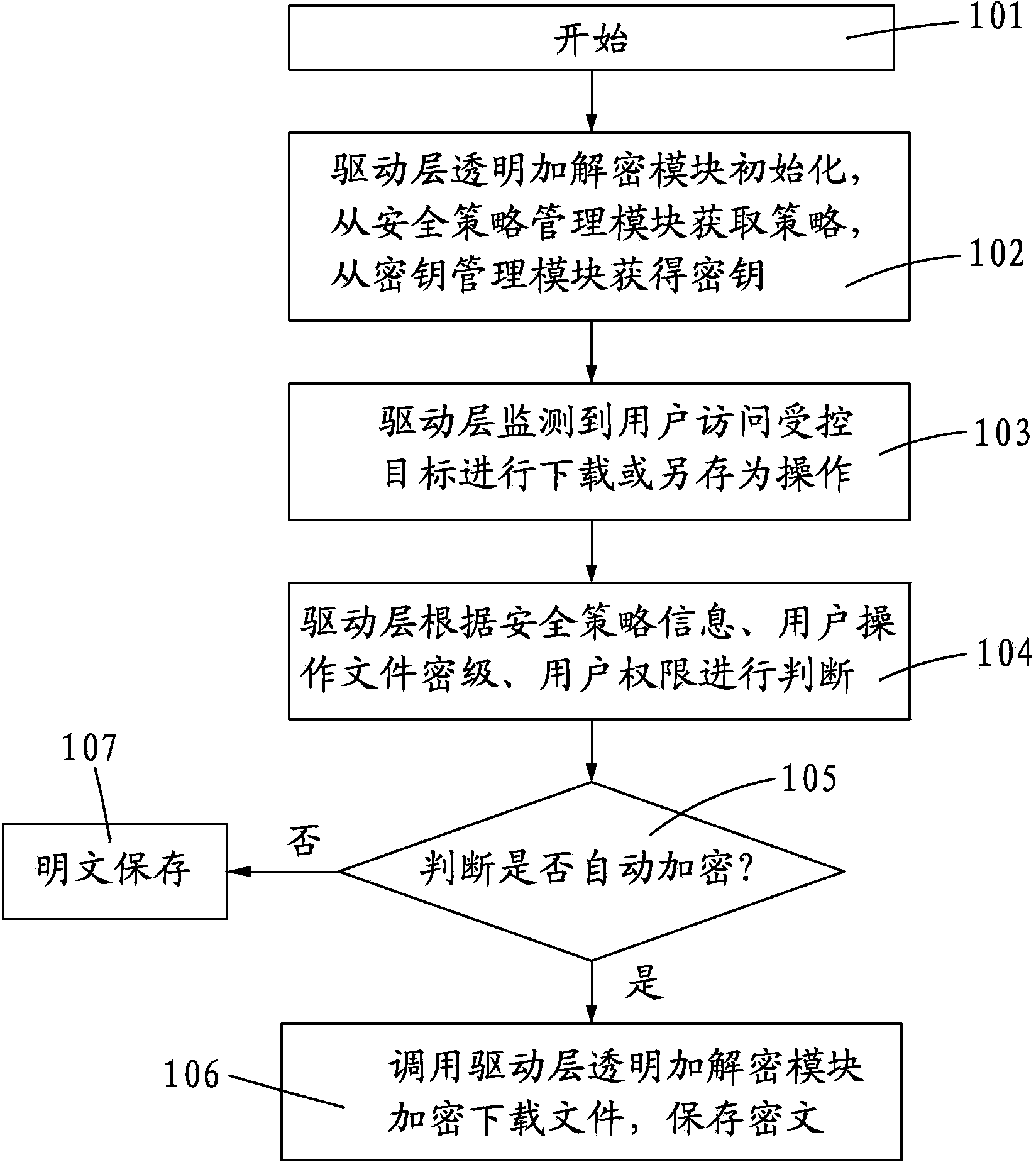
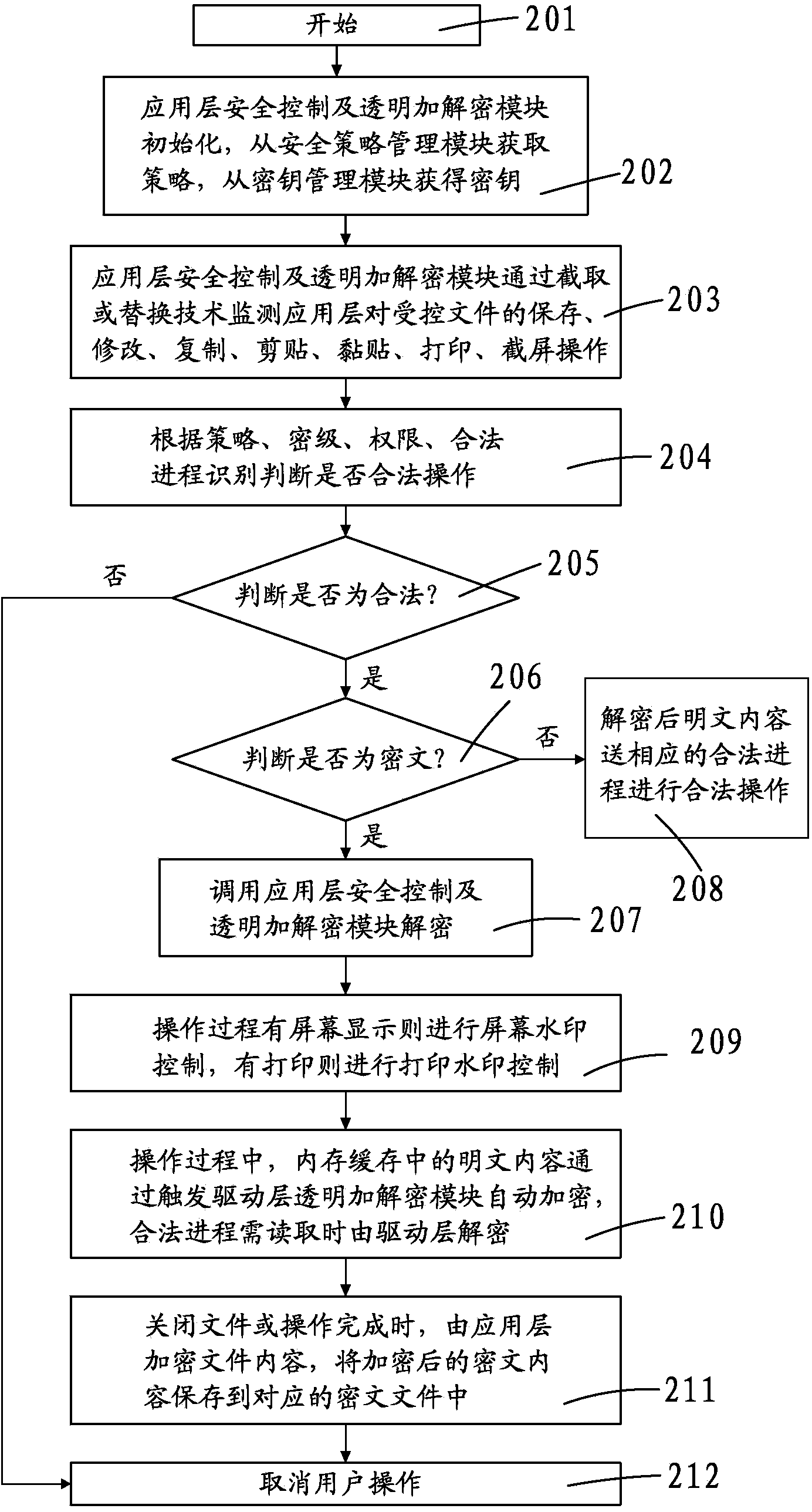
The invention discloses an electronic document safety management system and method. The electronic document safety management system comprises a driving layer transparent encryption and decryption module, an application layer safety control and transparent encryption and decryption module, an intelligent file and process characteristic identification module, a file outside issuing off-line control module, a file screen watermark and printing watermark control module, a safety strategy management module and a secret key management module. The core technology of the system is managed in the driver of a client terminal, is operated in the core of the Windows operating system, and is called by an I / O manager to meet the demand of a file system. A data encryption platform of the system will take over the file system of the whole Windows operating system, and is responsible for providing the transparent encryption and decryption data services for the file system in real time. According to the electronic document safety management system and method, due to the fact that the electronic file safety protection measures are improved and the transparent encryption and decryption methods are imported, the off-line high safety and user friendliness of the electronic files are achieved.
Owner:STATE GRID CORP OF CHINA +1
Security policy based network security management system and method
InactiveCN1604541ASecurity Unified PlanningDeployment securityData switching networksSecurity policySafety management systems
Owner:沈明峰 +3
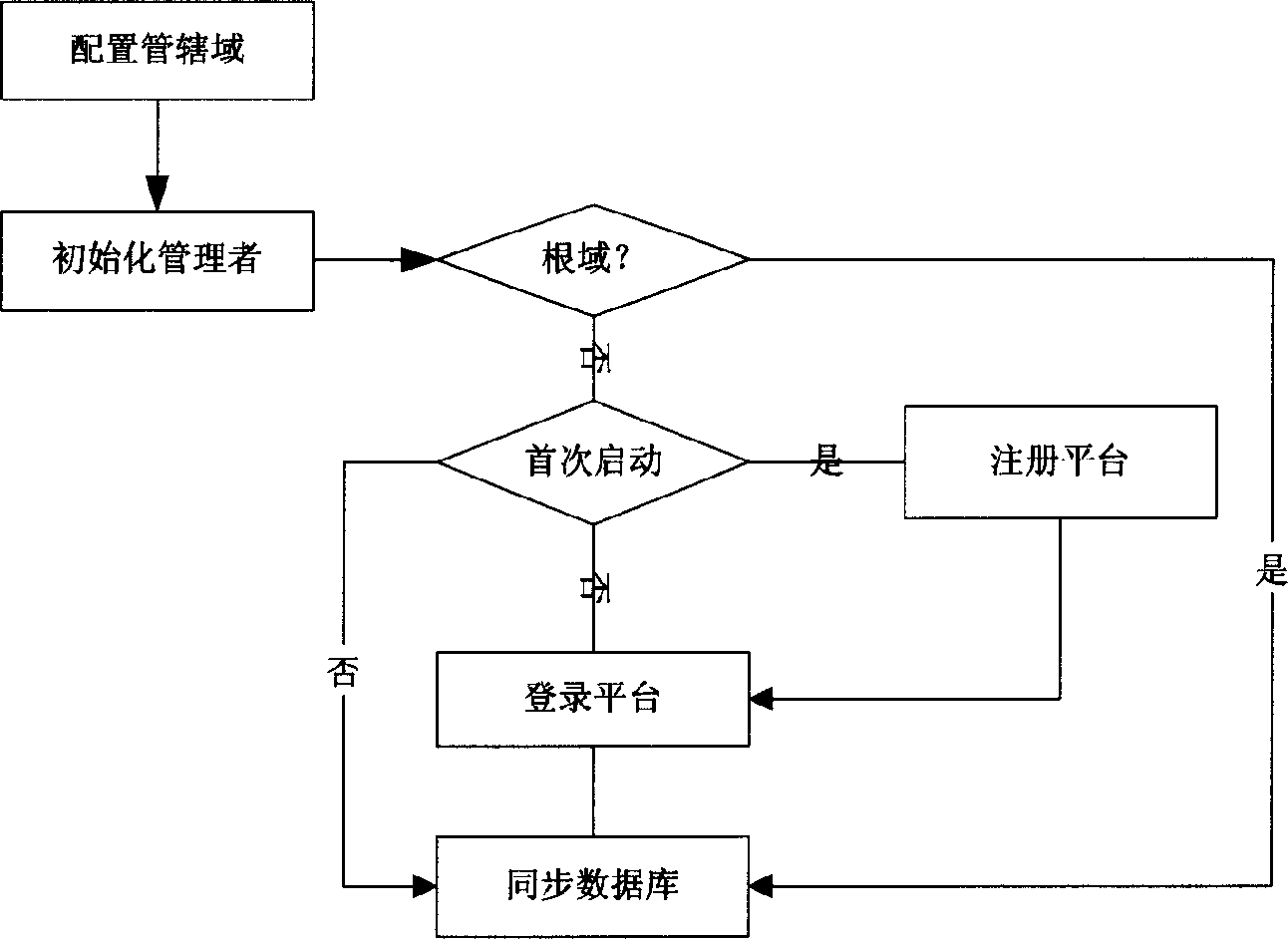
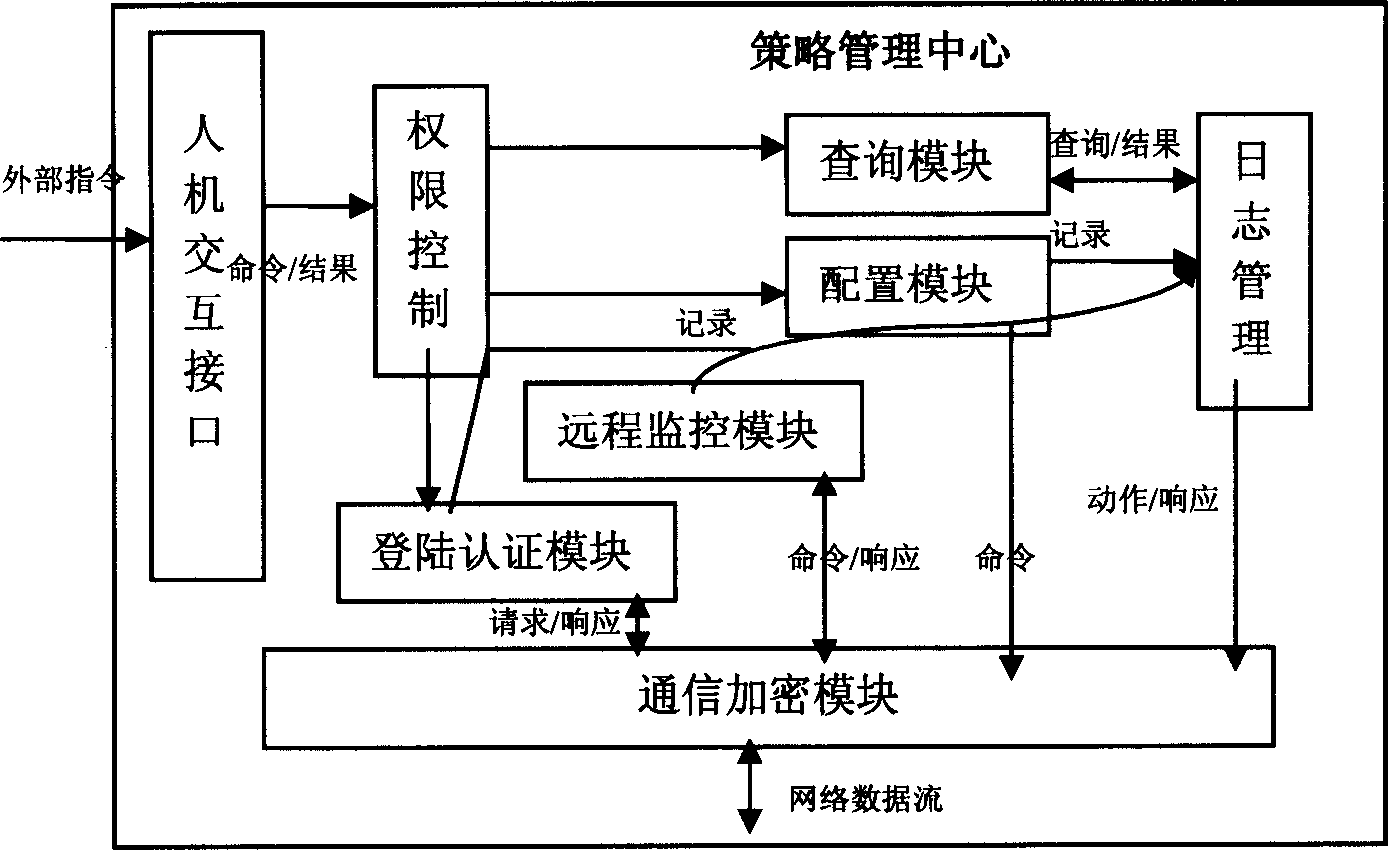
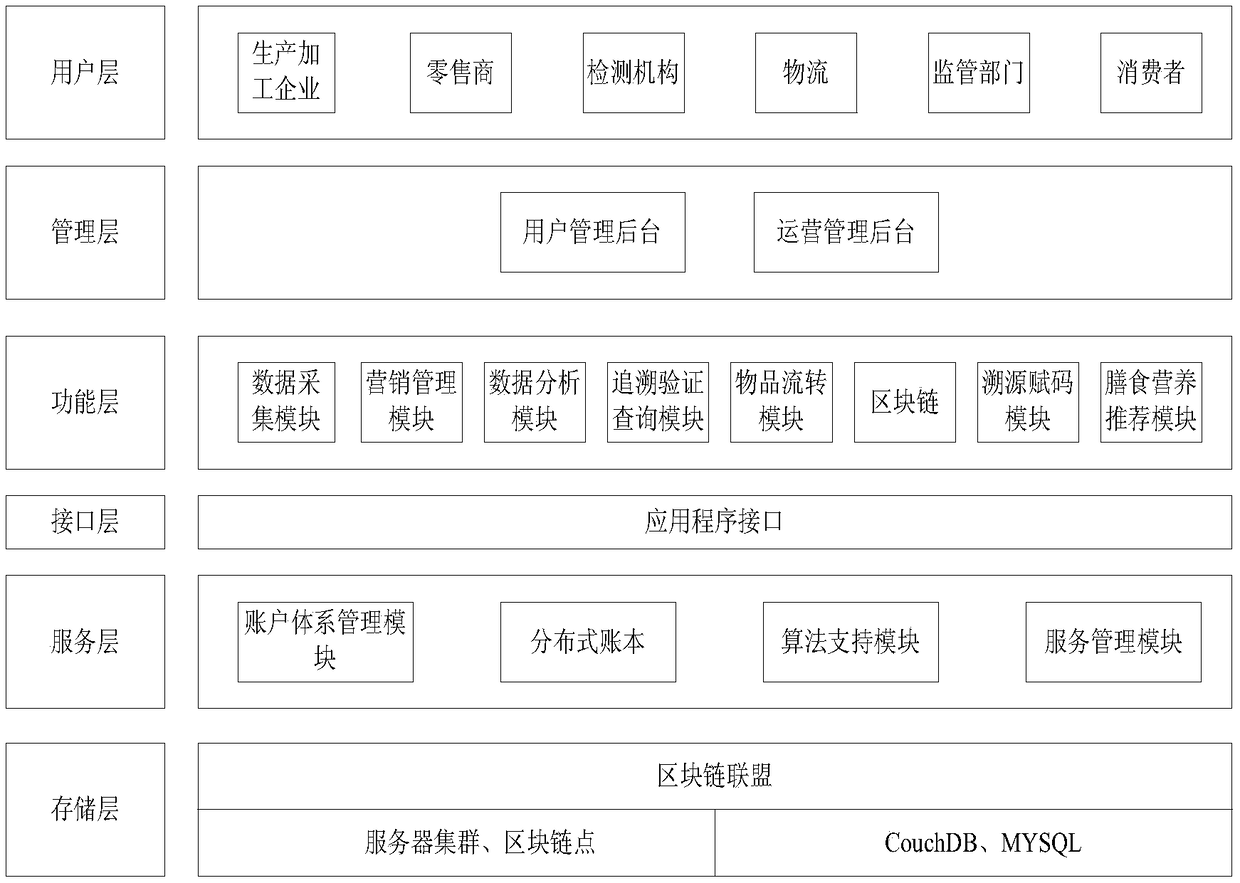
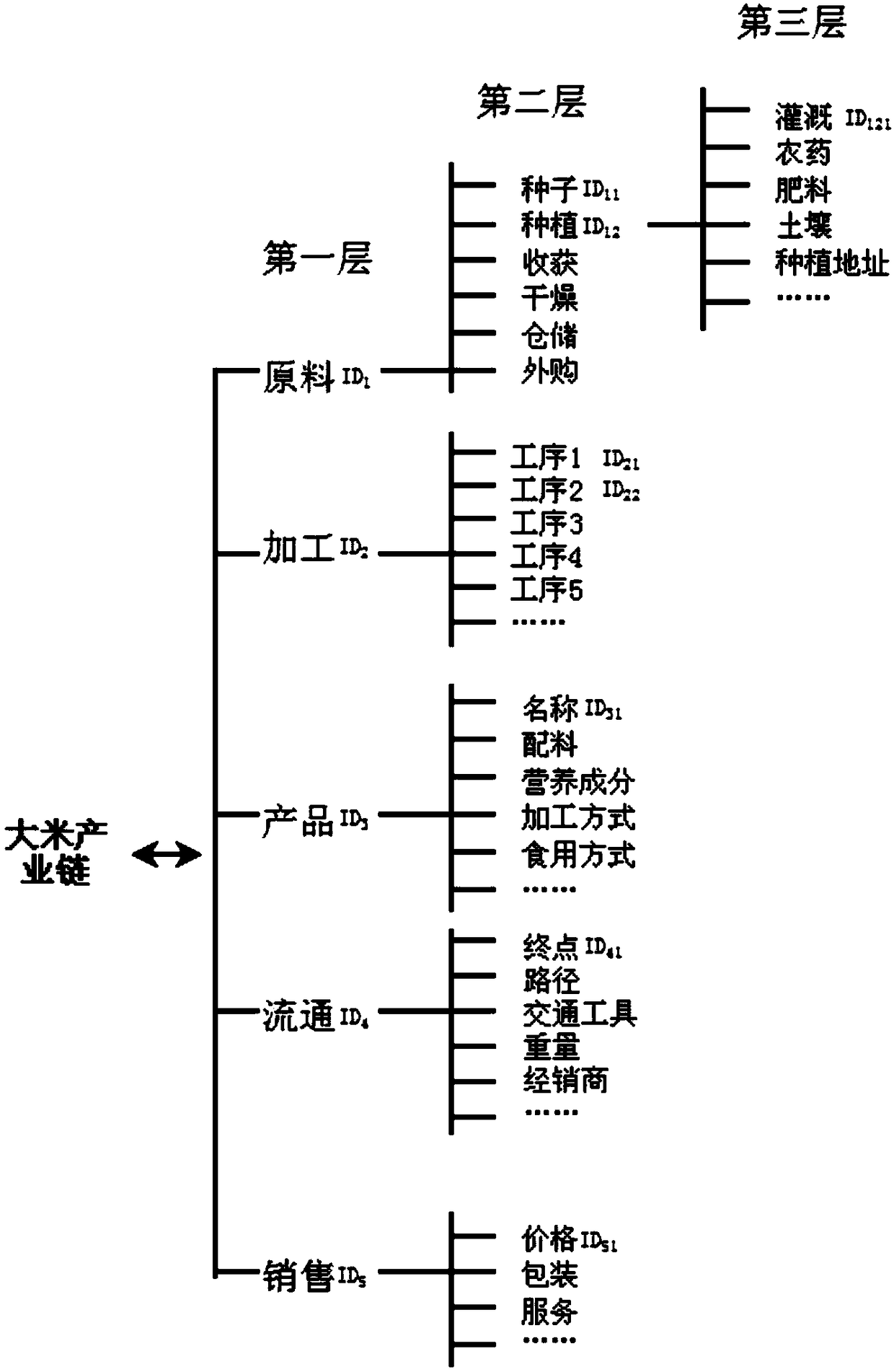
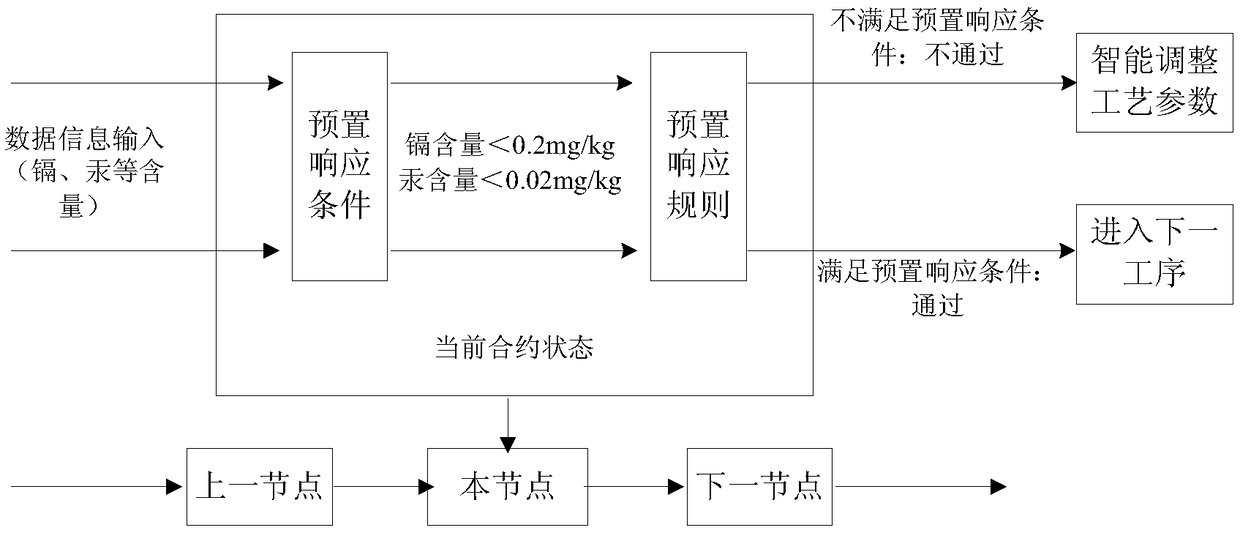
Block chain technology-based food quality safety management system and food quality safety management method
The invention discloses a block chain technology-based food quality safety management system and a food quality safety management method. The system comprises a storage layer, a service layer, an interface layer, a function layer, a management layer and a user layer. The method comprises the steps of food quality intelligent management and food quality safety control. According to the invention, the block chain technology has the advantages of de-centralization, information transparency, non manipulation and the like. In combination with the internet of things sensor technology, the automaticdata acquisition is realized. Through the big data technology, the data information can be mined and analyzed. Therefore, a distributed, efficient and reliable food safety source tracing system is established. In addition, an intelligent contract is established, so that the automatic processing of the information is realized. A trust relationship between nodes is established according to a mathematical method. As a result, the third-party guarantee is not needed, and the transaction can be directly carried out between enterprises. The enterprise efficiency is greatly improved, and the cost isreduced.
Owner:WUHAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com