Patents
Literature
661results about How to "Respond effectively" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
End user risk management
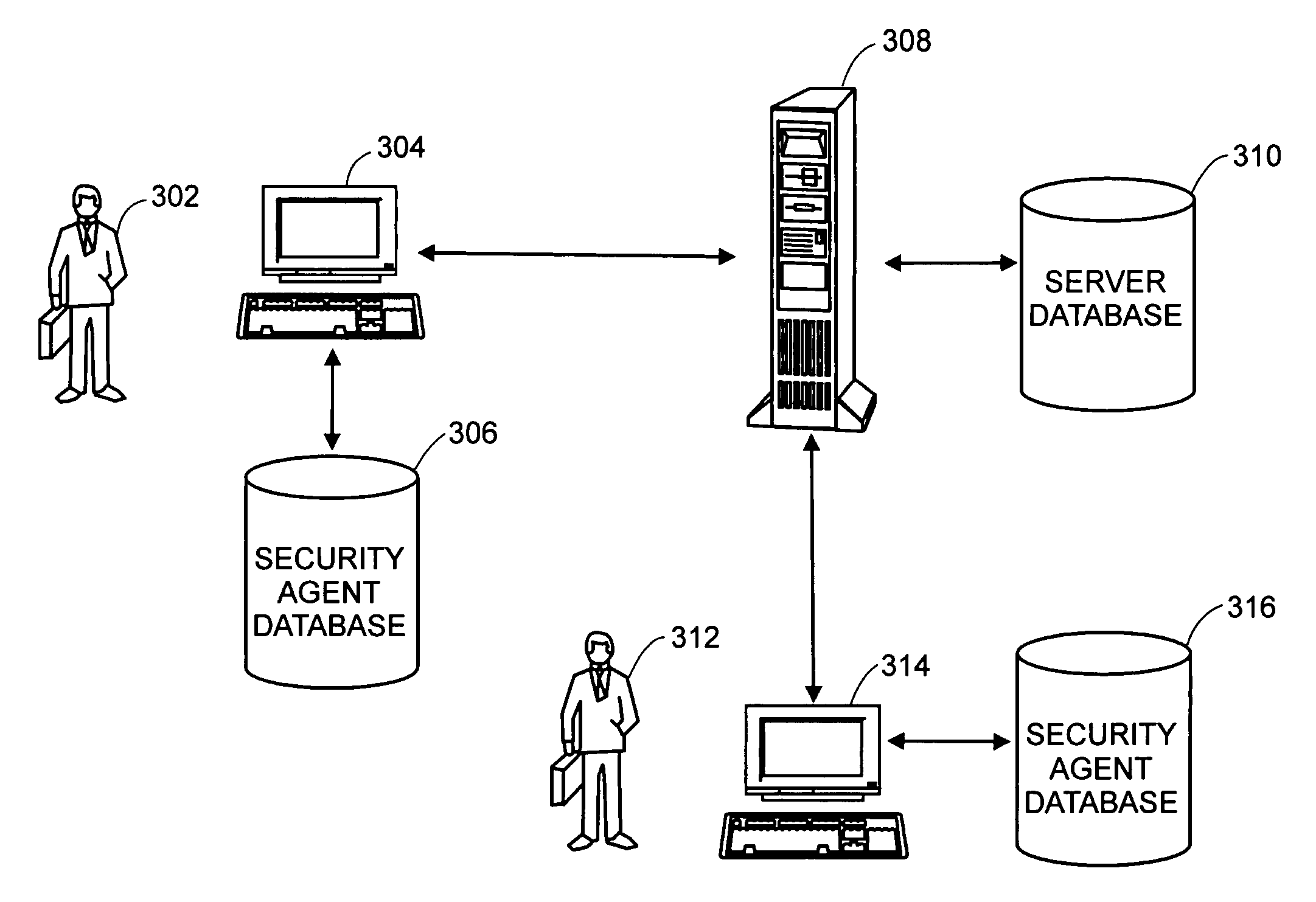
ActiveUS20060020814A1Respond effectivelyMemory loss protectionDigital data processing detailsReal time analysisComputer science
A flexible, efficient and easy-to-use computer security management system effectively evaluates and responds to informational risks on a wide variety of computing platforms and in a rapidly changing network environment. An individual computer system dynamically monitors its end user, without regard to network connectivity, in order to calculate a risk score and to ensure that the end user's behavior does not put corporate information or other assets at risk. Data regarding such risks and responses are analyzed and stored in real-time.
Owner:CITRIX SYST INC
End user risk management
ActiveUS7490356B2Respond effectivelyMemory loss protectionDigital data processing detailsReal time analysisSafety management systems
A flexible, efficient and easy-to-use computer security management system effectively evaluates and responds to informational risks on a wide variety of computing platforms and in a rapidly changing network environment. An individual computer system dynamically monitors its end user, without regard to network connectivity, in order to calculate a risk score and to ensure that the end user's behavior does not put corporate information or other assets at risk. Data regarding such risks and responses are analyzed and stored in real-time.
Owner:CITRIX SYST INC
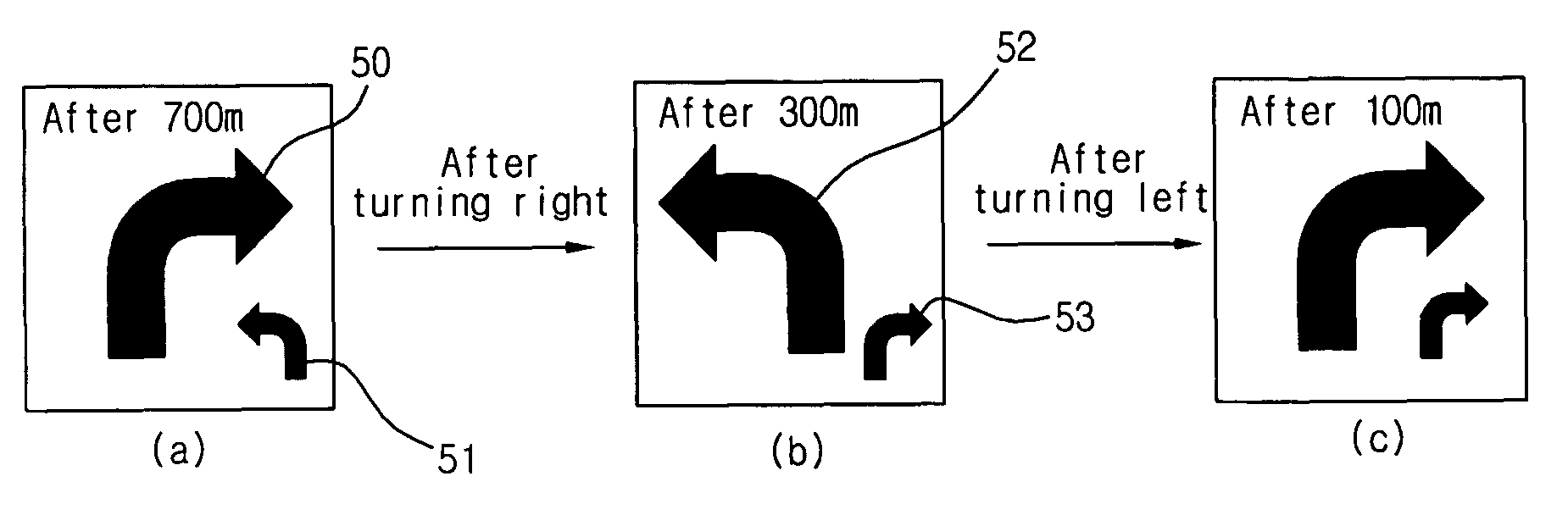
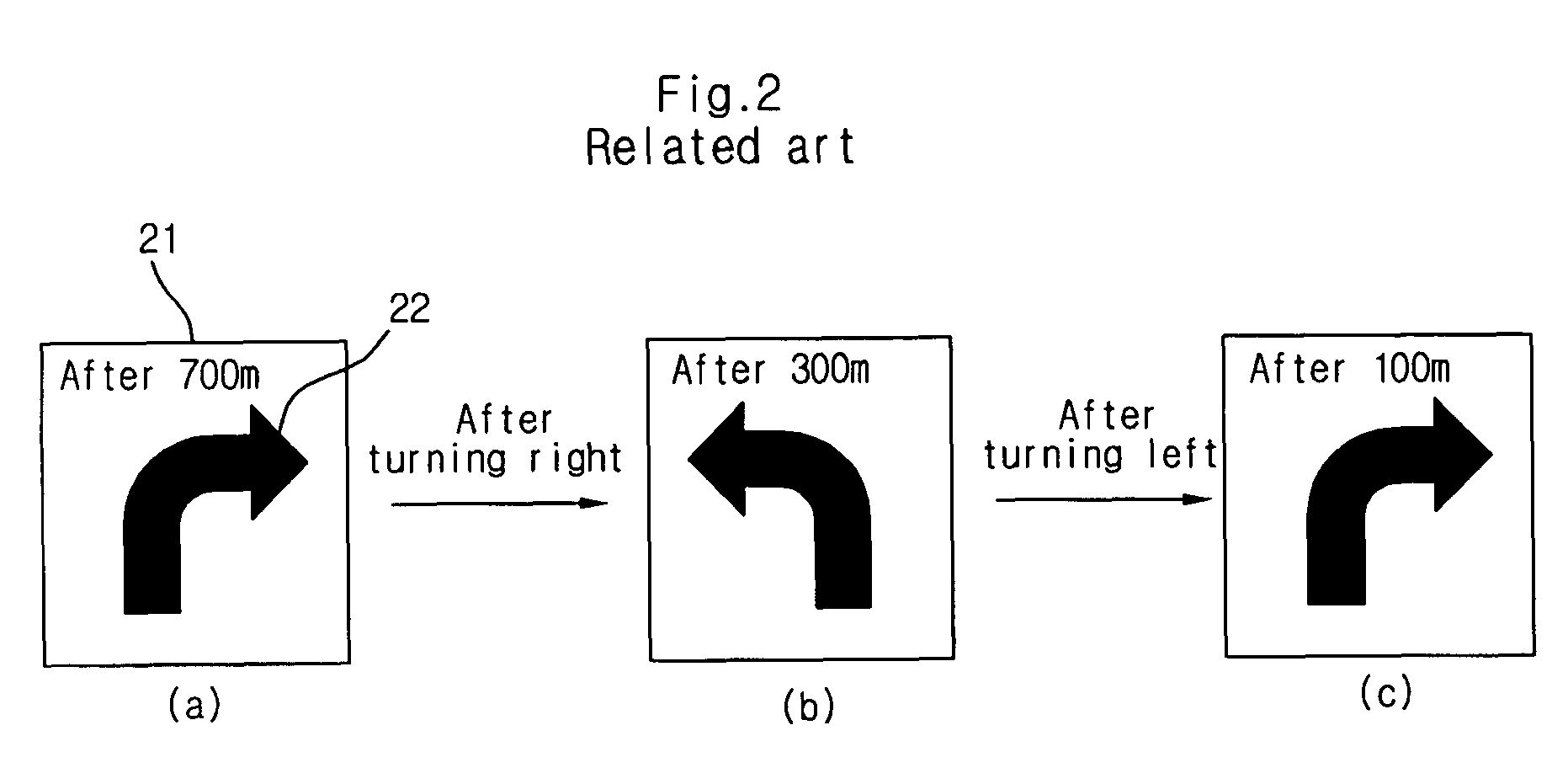
Turn-by-turn navigation system and next direction guidance method using the same
ActiveUS7844394B2Respond effectivelyInstruments for road network navigationRoad vehicles traffic controlGraphicsTurn-by-turn navigation
A turn-by-turn navigation system includes a positioning module receiving position information and updating real time road information on a road where a car is currently located, a map database storing map information required for driving the car, a route planning / route guidance module receiving the real time road information and the map information and generating current guidance information and next guidance information, a turn-by-turn graphic user interface module receiving the current and next guidance information and generating current and next guidance images, and an image display unit displaying the current and next guidance images.
Owner:LG ELECTRONICS INC
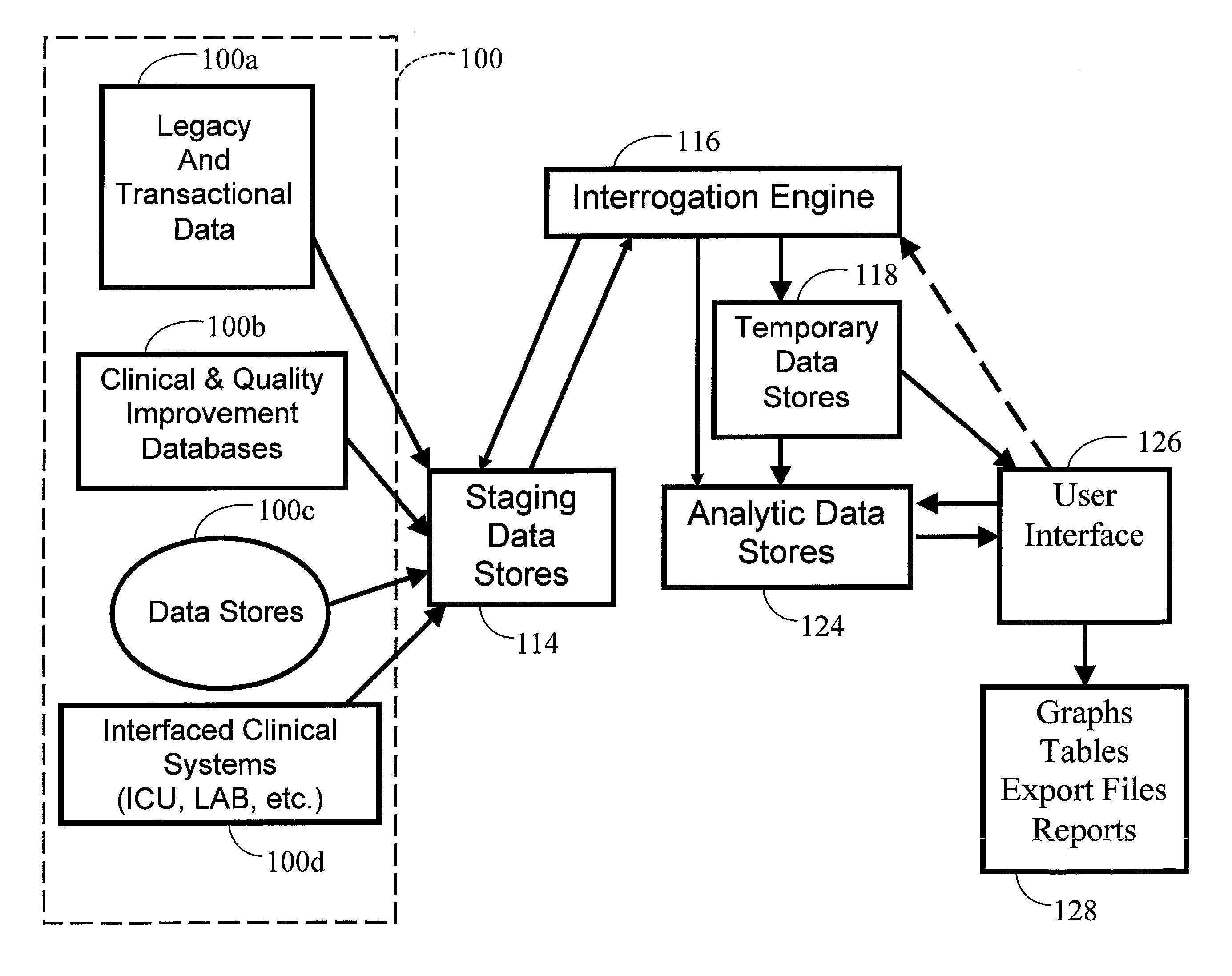
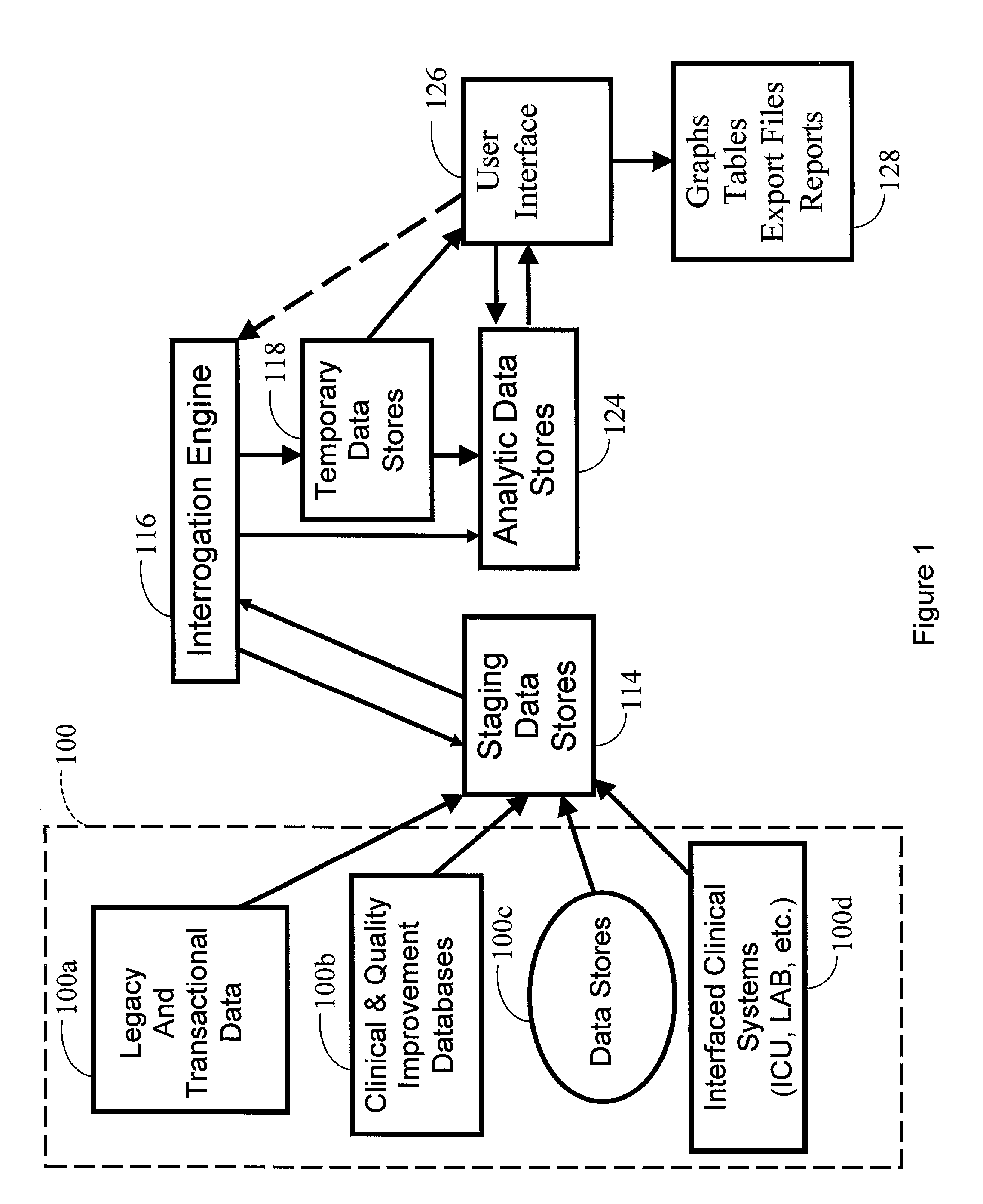
Analytics and data warehousing infrastructure and services
ActiveUS7191183B1Respond effectivelyReduce riskData processing applicationsDigital data processing detailsService systemAnalysis data
An analytics and data warehousing infrastructure and services system that uses an analytic rather than a transactional data model. The system preferably has at least one extracted source data store, at least one staging data store, and at least one analytic data store. The at least one staging data store preferably has at least one staging data table. The at least one analytic data store preferably has at least one analytic data table for storing transformed data. A staging data table loading algorithm may be used for populating the at least one staging data table with source data. A data transformation algorithm may be used for moving and transforming data from a staging data table into an analytic data store. Other algorithms that may be used in the present invention include algorithms for creating derived variables, creating event proxies, and restructuring data. In one preferred embodiment, the system is a data model based on a clinical rather than a financial understanding of healthcare.
Owner:RGI INFORMATICS
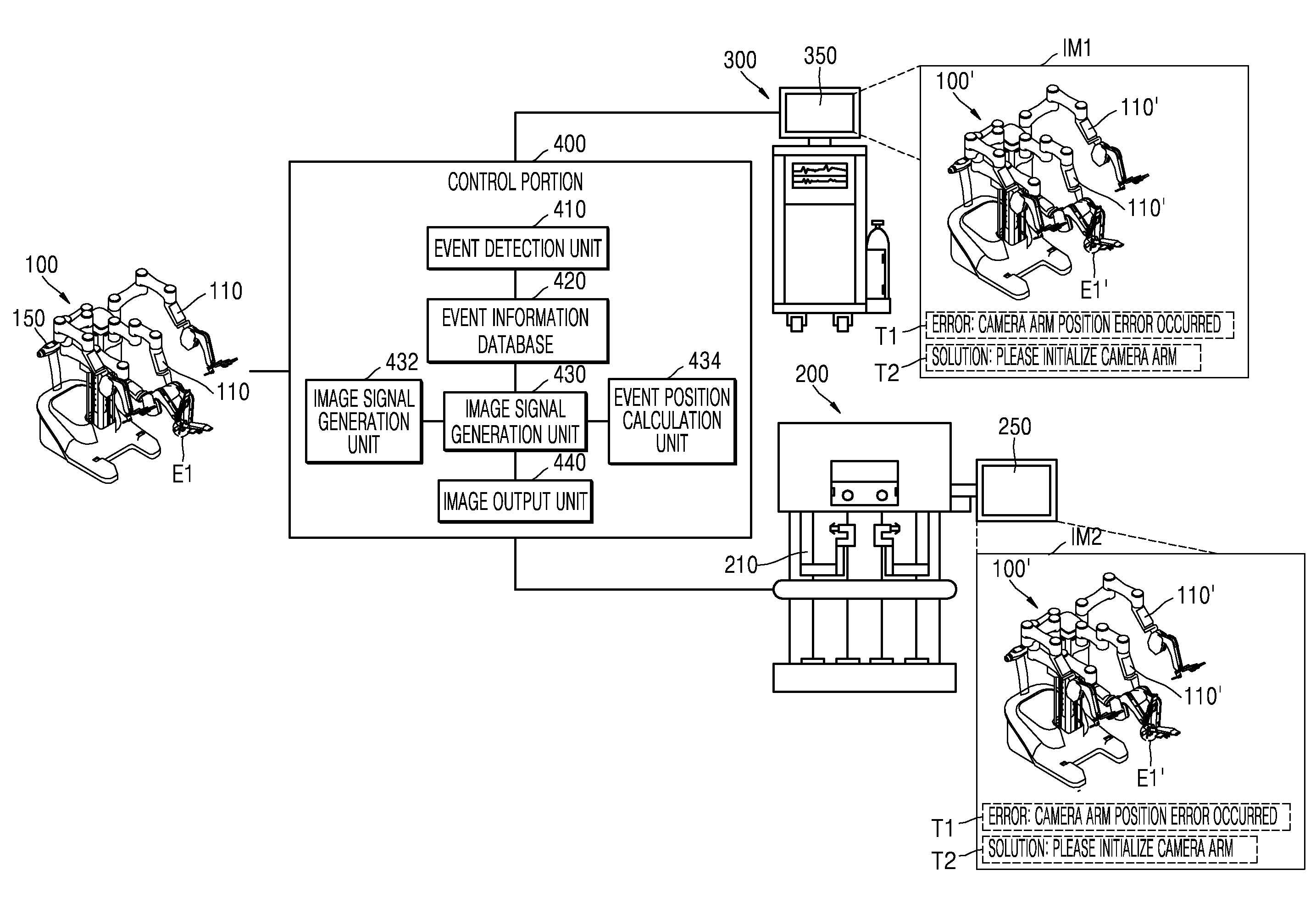
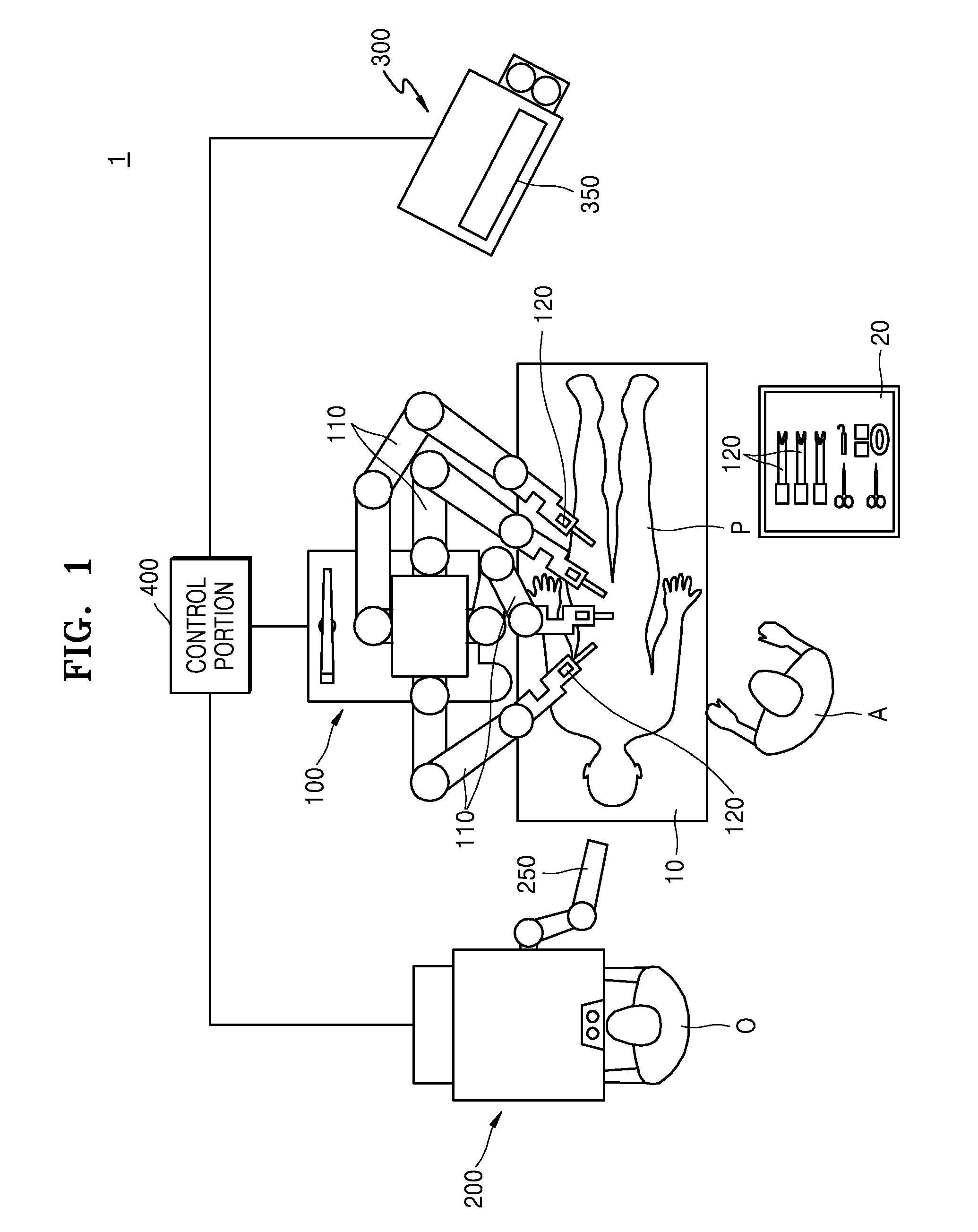
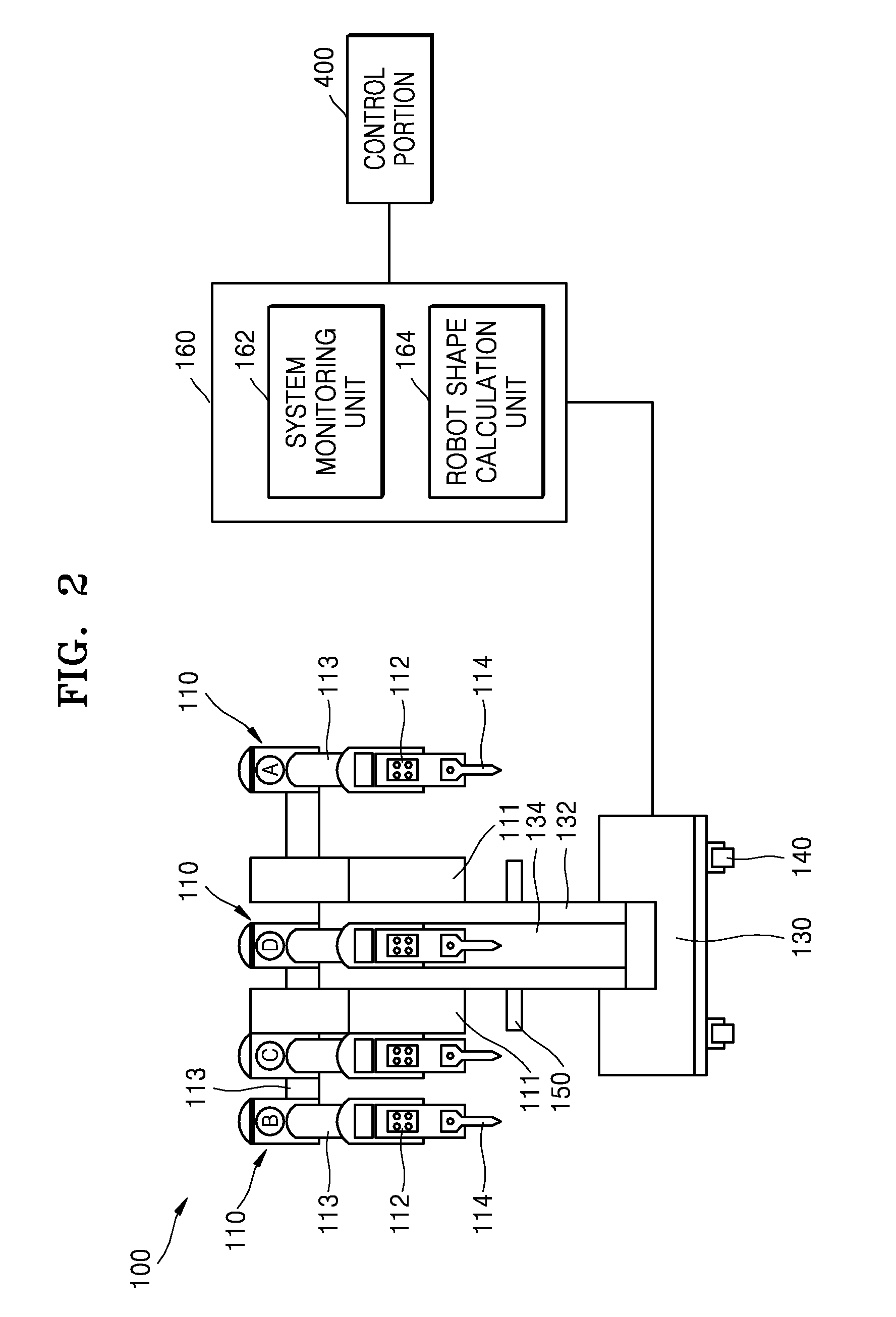
Surgical robot system and method for controlling surgical robot system
ActiveUS9433470B2Respond effectivelyAccurately and quickly transmittingSurgical furnitureSurgical systems user interfaceSurgical robotRemote control
A surgical robot system includes a slave robot, a master console, a first display and a control portion. The slave robot includes a plurality of robot arms at which surgical tools are mounted. The master console performs remote control on the slave robot in response to a manipulation of an operator. The first display is arranged around the slave robot. The control portion outputs image information displaying information about a position of the event on an image corresponding to a shape of the slave robot or the master console to the first display when the event occurs in the slave robot or the master console.
Owner:MEERE
System and method of automated gunshot emergency response system
InactiveUS20160232774A1Reduce the impactAvoiding obtrusiveCharacter and pattern recognitionBurglar alarmMessage passingCommunication device
A threat sensing system is provided including, in some aspects, a plurality of threat sensing devices distributed throughout a school or facility, with each of the threat sensing devices comprising one or more acoustic sensors, one or more gas sensors, and a communication circuit or communication device configured to output sensor data to a system gateway. The system gateway is configured to receive and process the sensor data output from the threat sensing devices and determine whether the processed sensor data corresponds to one of a predetermined plurality of known threats (e.g., a gunshot) and, if so, to communicate the existence of the threat, the processed sensor information, and / or predetermined messaging information to one or more recipient devices (e.g., first responders, dispatchers).
Owner:ONALERT GUARDIAN SYST INC
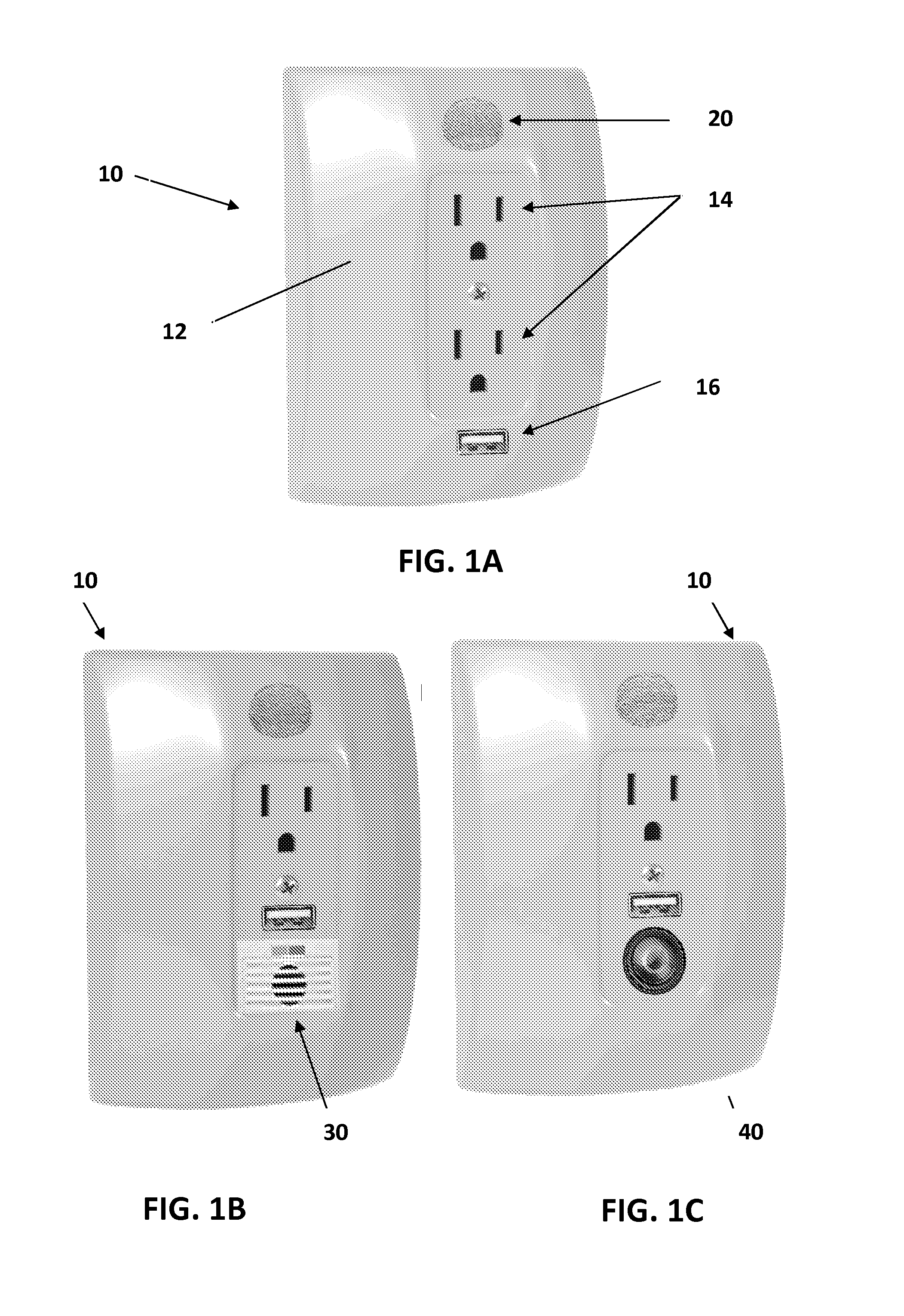
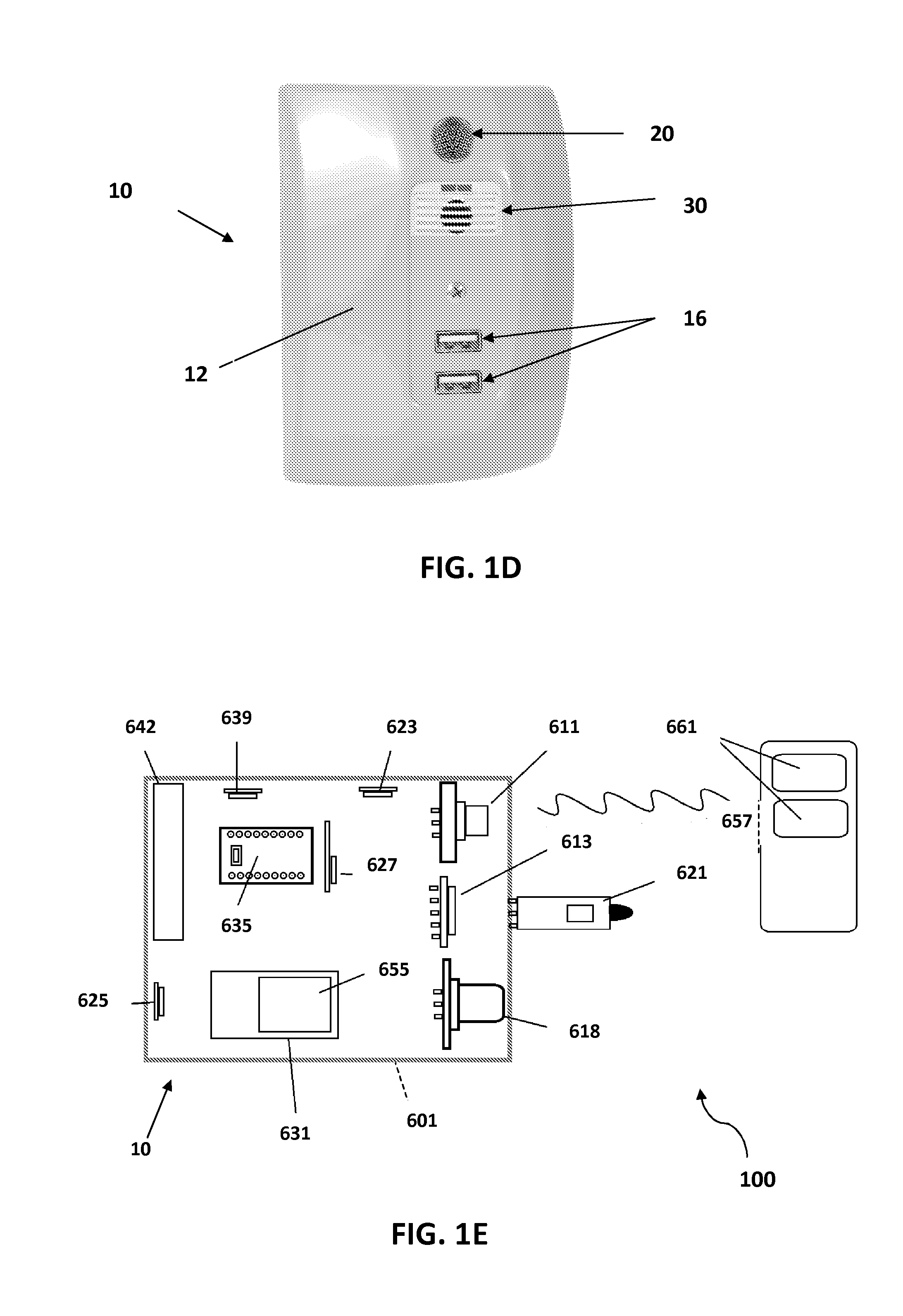
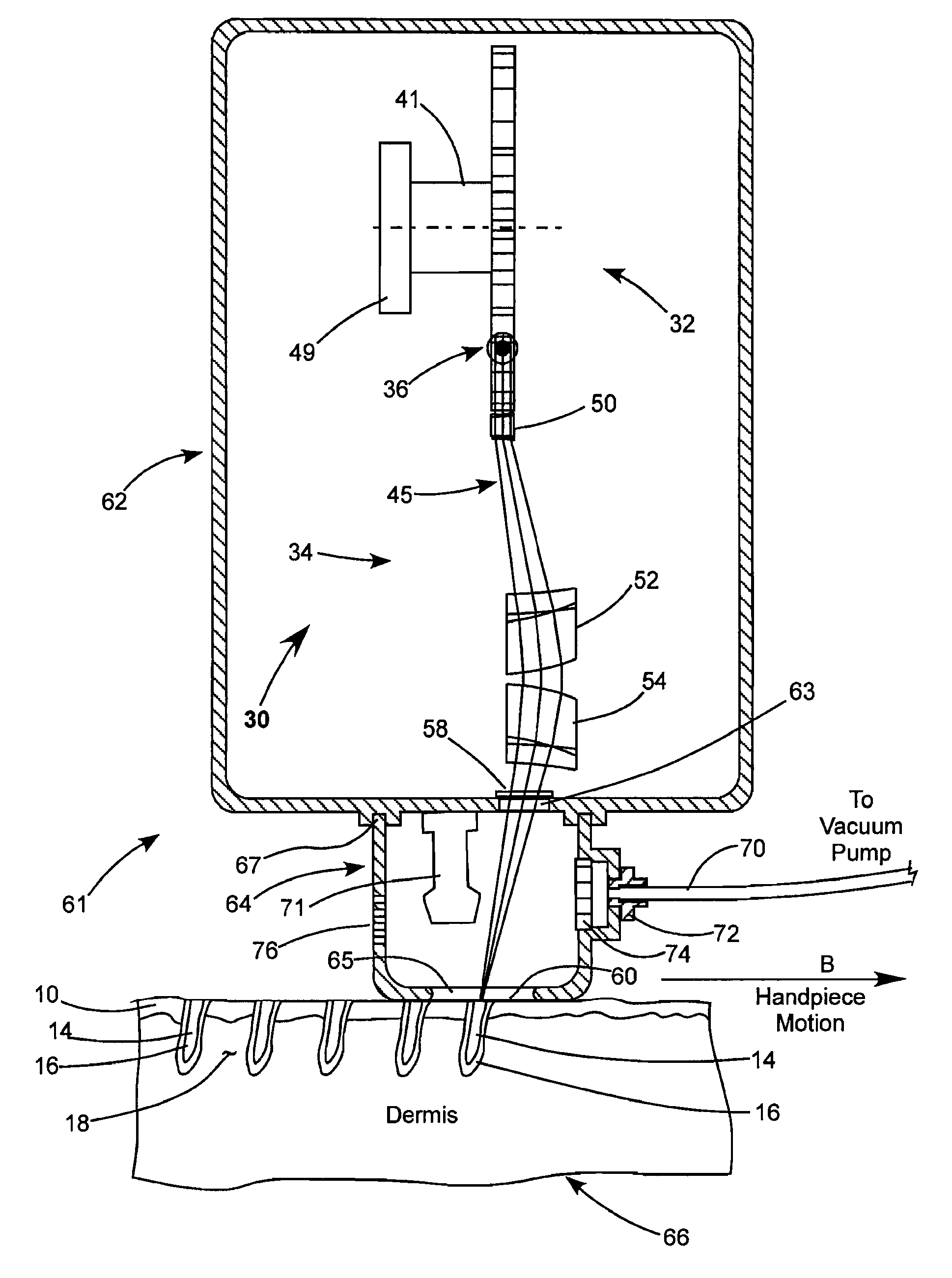
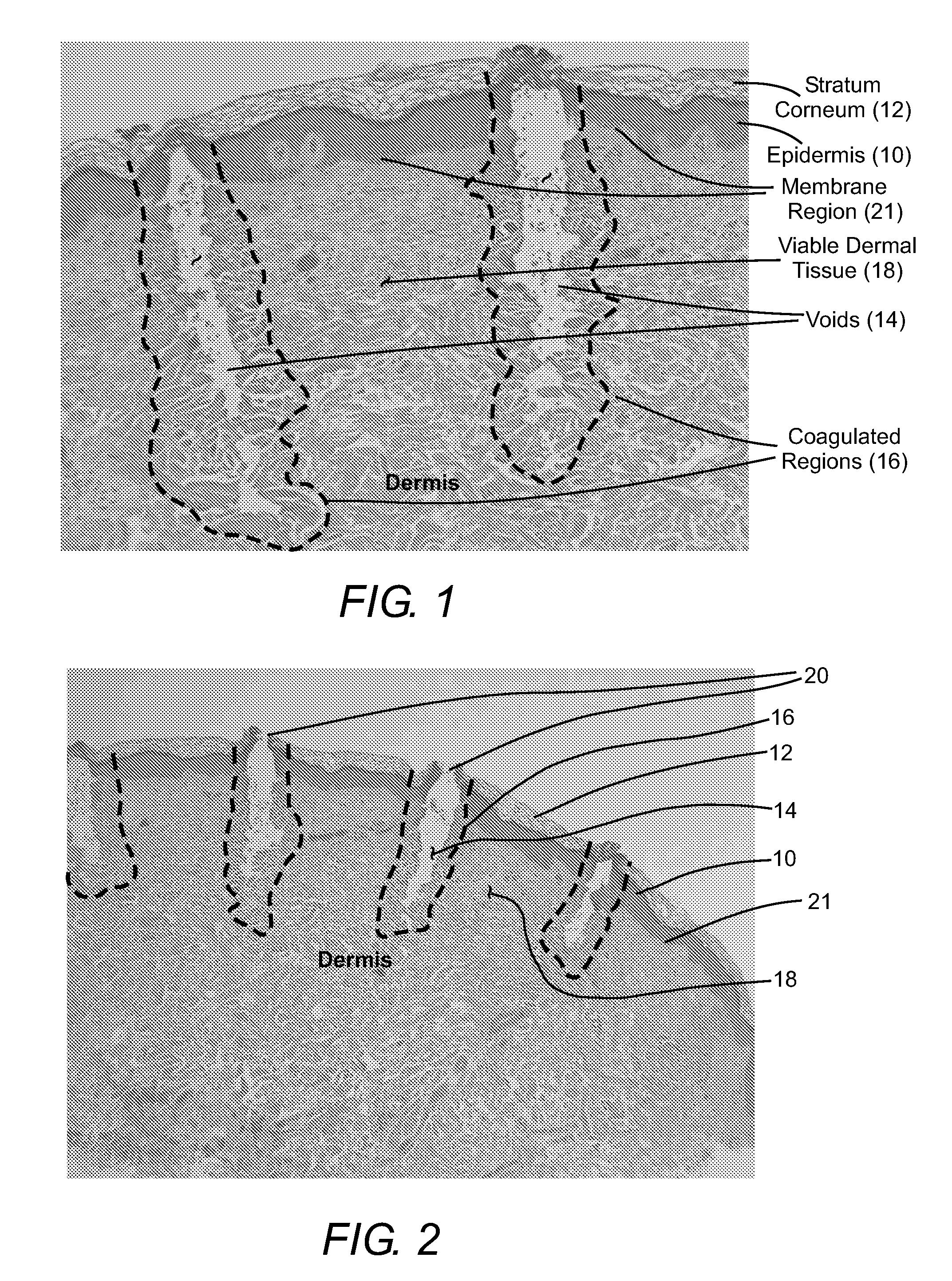
Laser System for Treatment of Skin Laxity
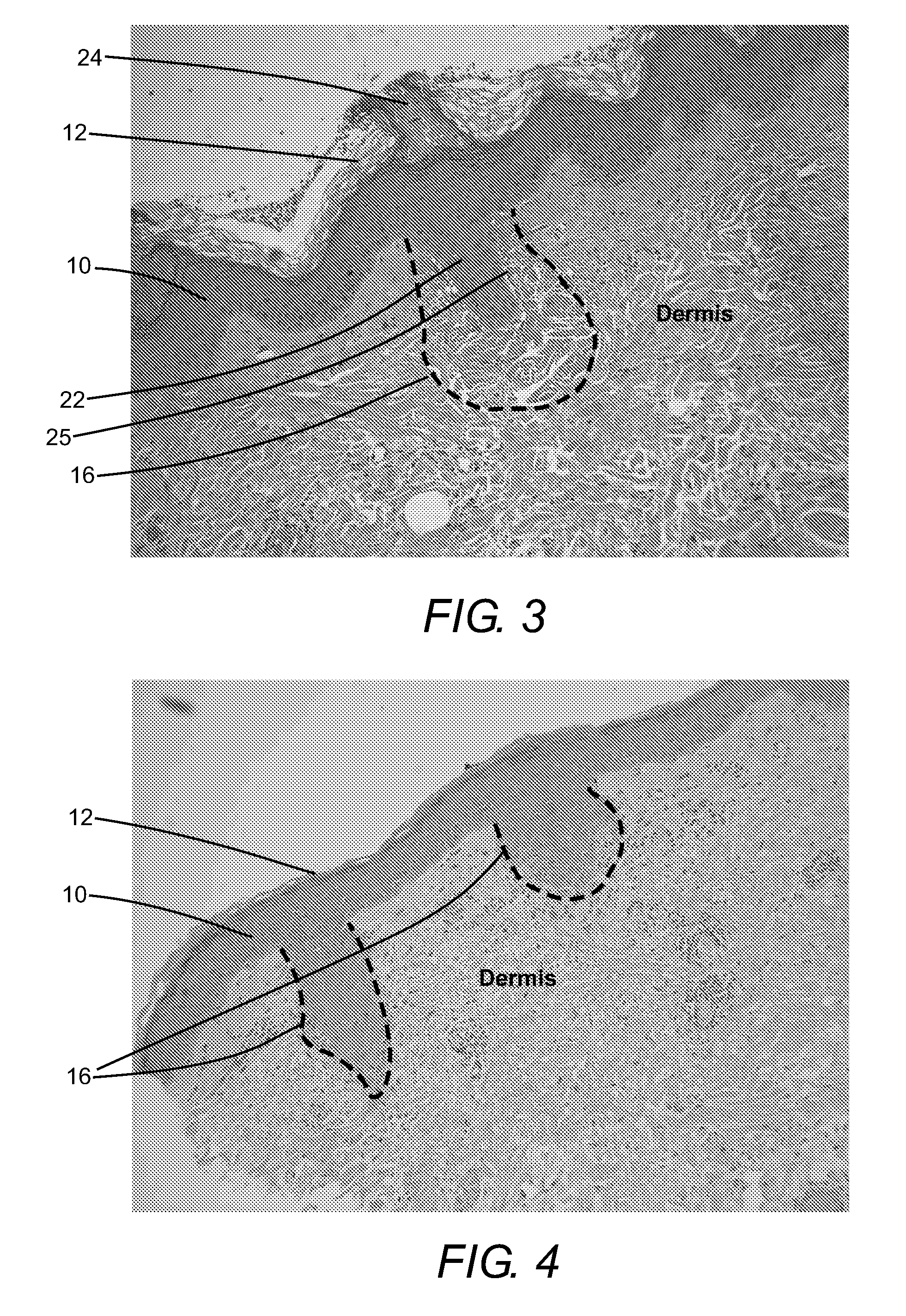
InactiveUS20070179481A1Tighten skinEnhance elasticitySurgical instrument detailsWrinkleBiomedical engineering
A method of reducing wrinkles in skin includes irradiating the skin with laser pulses to ablate an array of spaced apart voids in the skin. A region of coagulated tissue surrounds each of the voids and there viable tissue between the coagulated regions. Tissue in the coagulated regions is in tension due to shrinkage of collagen by the heat generated during the ablation. This tension rapidly closes the voids, tightening the skin and reducing the wrinkles. A healing process replaces the coagulated tissue with new tissue after a period of about one-month. The method is also applicable to lightening abnormally pigmented skin, as the new tissue replacing the coagulated tissue is not abnromally pigmented.
Owner:RELIANT TECH INC
Schedule activated management system for optimizing aircraft arrivals at congested airports
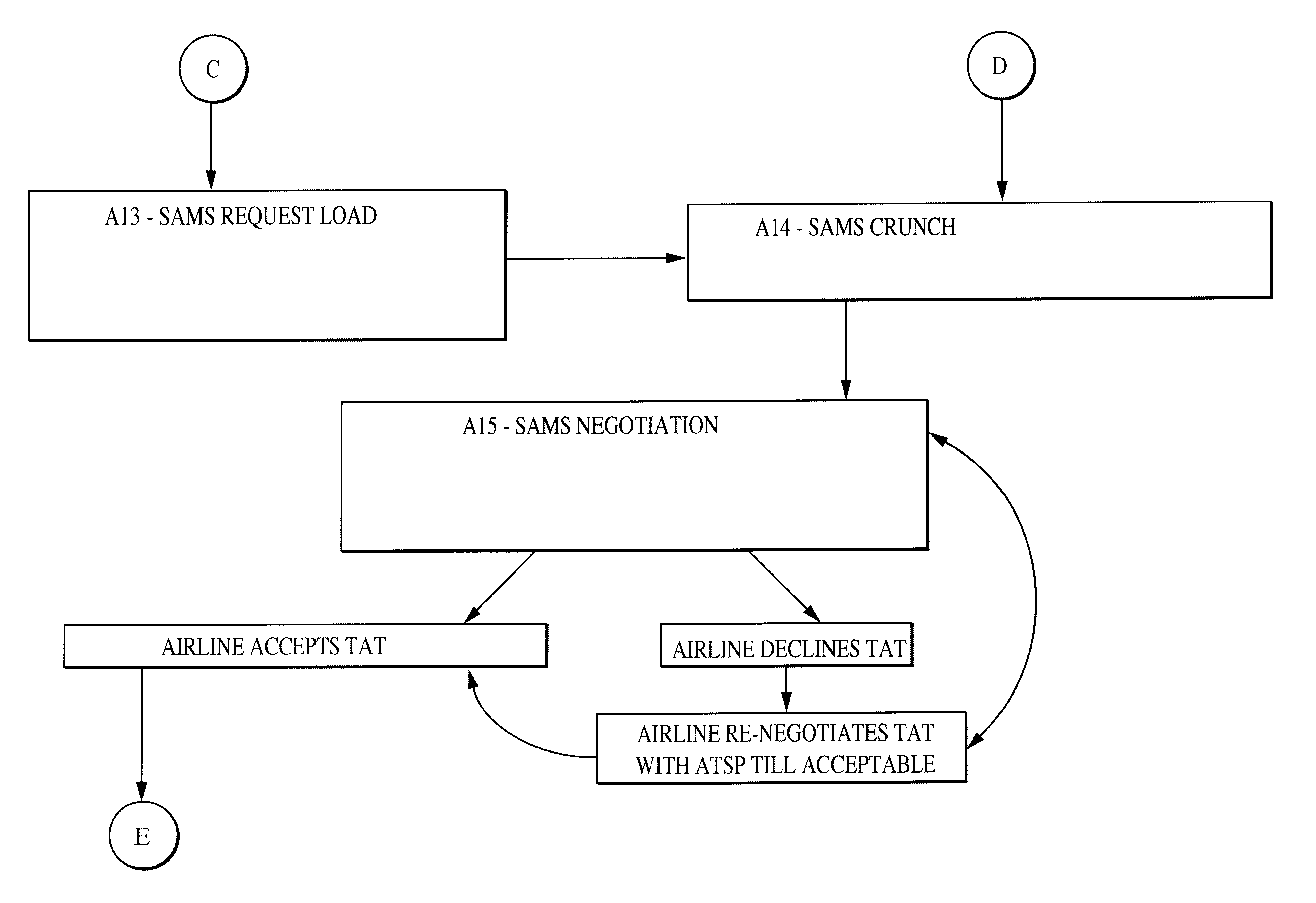
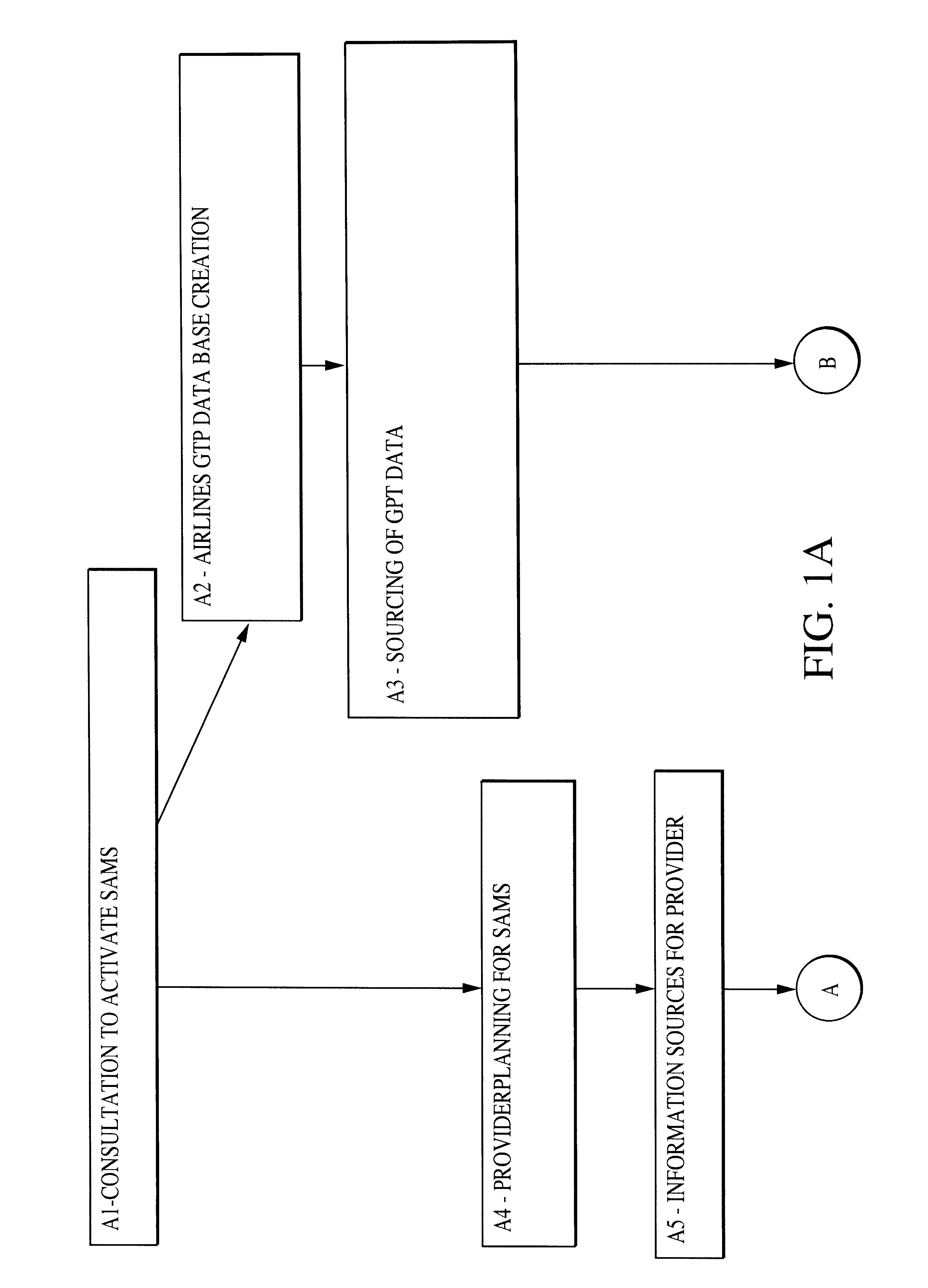
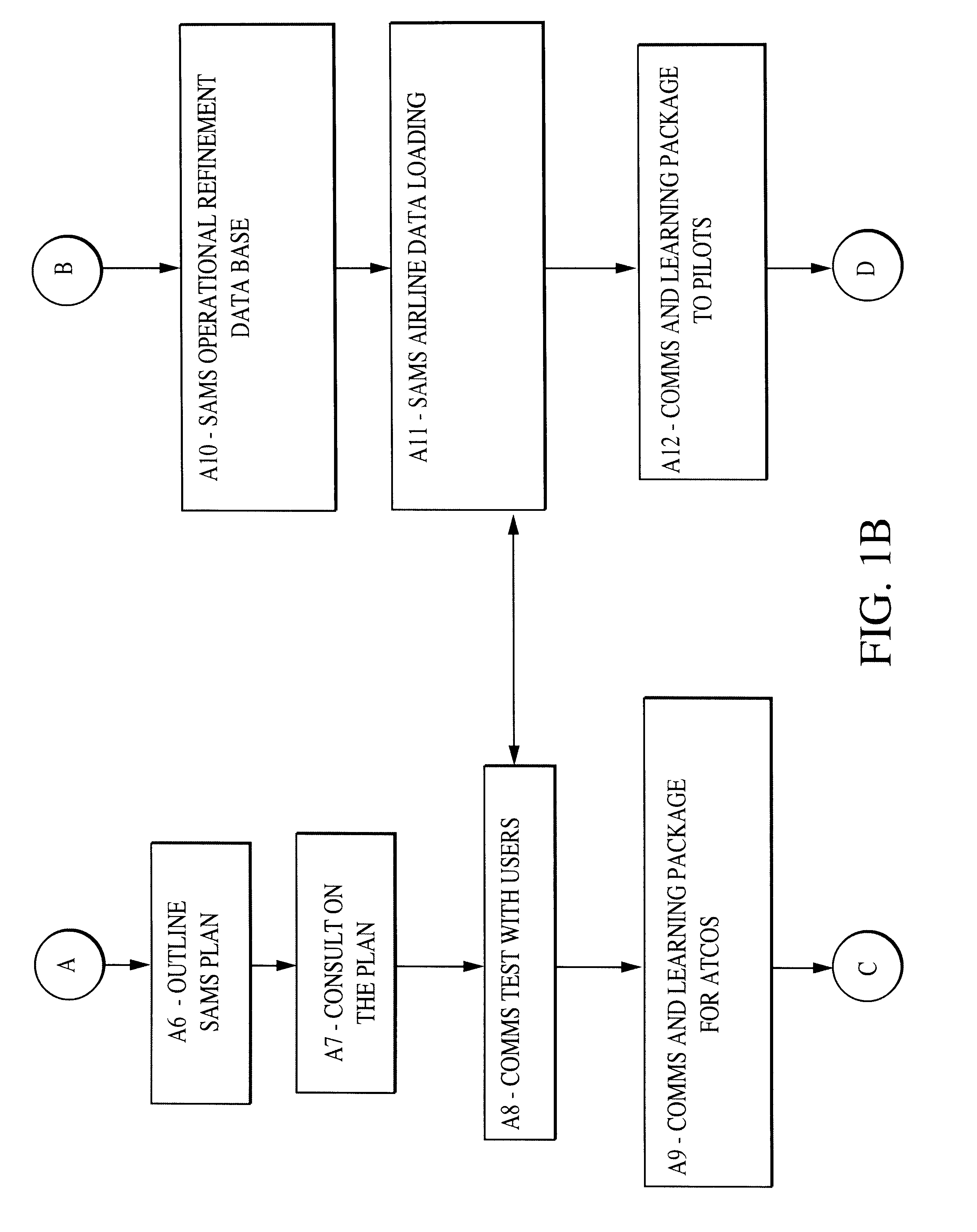
InactiveUS6584400B2Reduced resourceRespond effectivelyAnalogue computers for vehiclesData processing applicationsTraffic capacityAir traffic control
A system is provided for managing the inbound flow of aircraft to an airfield by ensuring that aircraft are sequenced before departure into an arrival stream. Sequencing uses operational data obtained from airlines and then provides a methodology for sharing this data with the air traffic control (ATC) agency. The outcome is a daily arrival schedule providing a predetermined operational arrival time for each aircraft movement. The operational data used by the system relates to airline punctuality, taxi times at departure airfields and actual flight times predicted on a flight-by-flight basis by airline flight planning systems. This information is combined to effect a predictive arrival time at a desired navigational fix.
Owner:BEARDSWORTH LOUIS J C
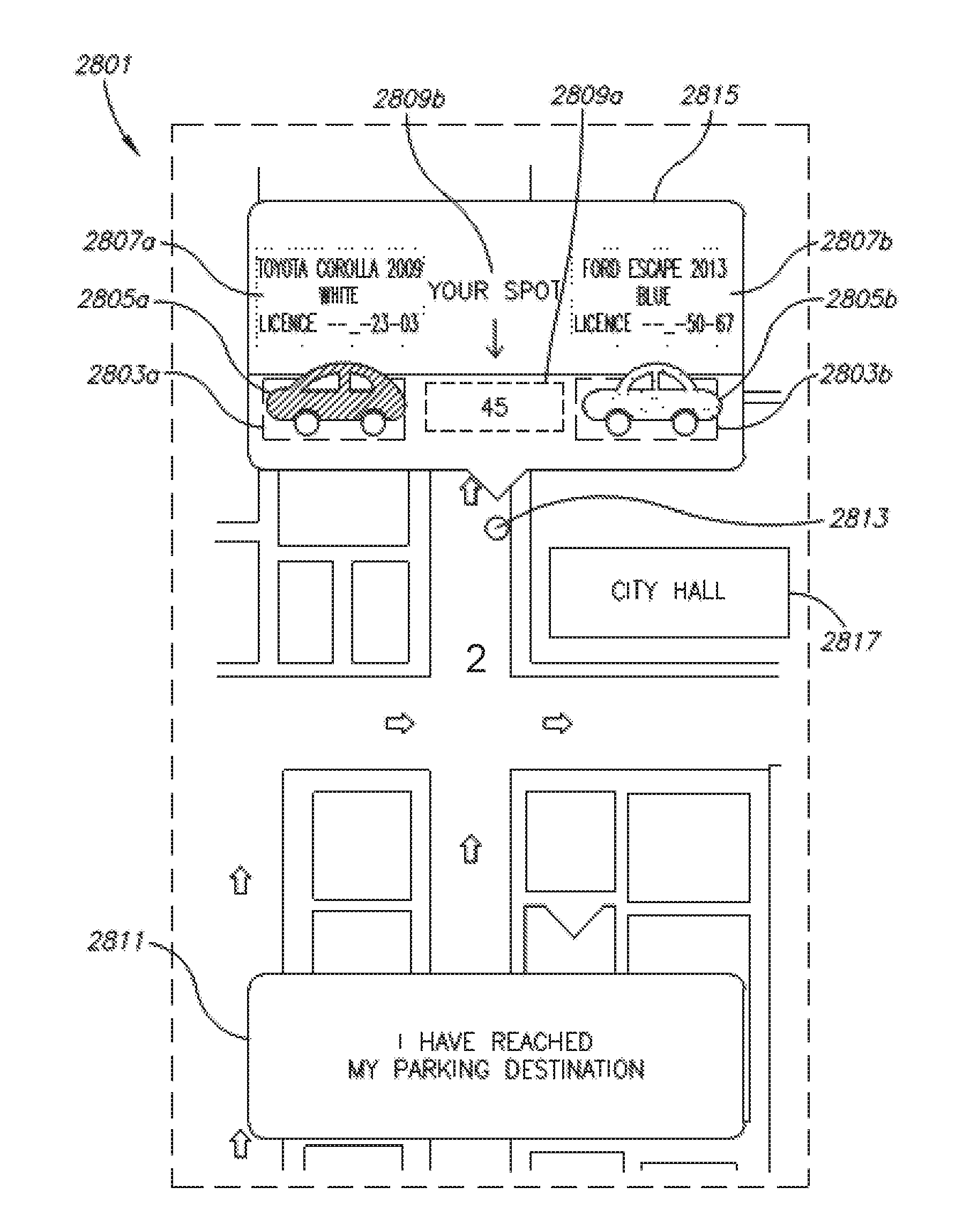
Citywide parking system and method
InactiveUS20160371607A1Improve parking efficiencyDecreasing parking effortInstruments for road network navigationTransportation facility accessComputer moduleParking space
A system including: (a) a database of individual on-street parking spots, and individual off-street parking spots, each of the individual parking spots associated with a unique identifier (UID) and location coordinates; and (b) an off street spot management module in communication one or more external client devices, adapted to receive parking rules from an external client device operated by an owner of each of the individual off-street parking spots.
Owner:SPARKCITY COM
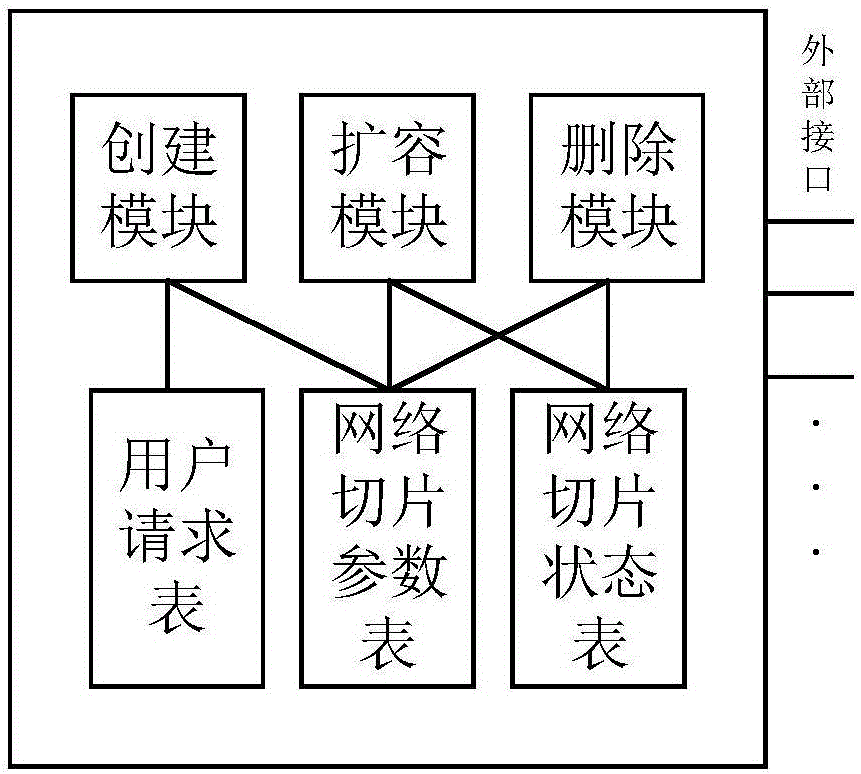
Network slice manager and management method thereof
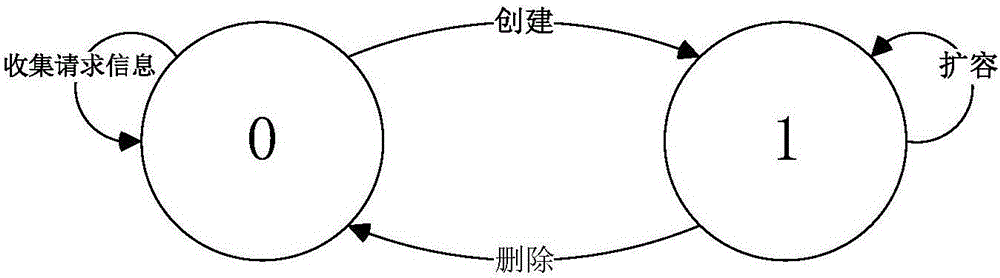
ActiveCN106549806AMaximize UtilizationIncrease profitData switching networksAccess networkResource pool
The invention discloses a network slice manager and a management method thereof, and belongs to the technical field of communication. The manager comprises a creation module, an expansion module, a deletion module, a user request table, a network slice parameter table, a network slice state table and a plurality of external interfaces, wherein the creation module is respectively connected with the user request table and the network slice parameter table; both the expansion module and the deletion module are respectively connected with the network slice parameter table and the network slice state table; the creation module is connected with a core network, an access network, a physical resource pool and a user by the external interfaces; the expansion module is connected with an existing network slice and the physical resource pool by the external interfaces; and the deletion module is connected with the existing network slice by the external interface. The management method of the manager comprises three parts of creation, expansion and deletion of the network slice. According to the network slice manager and the management method thereof, which are disclosed by the invention, the network slice which meets requirements can be created according to user demands, and a utilization rate of the network slice is effectively maximized, so that a utilization rate of network resources is improved.
Owner:TSINGHUA UNIV
Screen mirroring method and apparatus thereof
ActiveUS20130219072A1Efficient processEfficient screen mirroringMultiple digital computer combinationsTransmissionComputer networkComputer science
A screen mirroring method of a source device is provided, including determining whether a reproduction operation of media content is requested while a screen mirroring operation is performed, when the reproduction operation of the media content is requested, streaming the media content to a sink device and stopping the reproduction operation of the media content.
Owner:SAMSUNG ELECTRONICS CO LTD
Impact absorbing device for vehicle
ActiveUS20140062106A1Efficiently distributedReduce distortionSuperstructure subunitsElastic dampersEngineeringMechanical engineering
An impact absorbing device for a vehicle may include a bumper beam disposed to extend in a traverse direction of a vehicle, a side member extending in a longitudinal direction of the vehicle and disposed at a lateral side of the vehicle in the traverse direction thereof, a crash box connecting the bumper beam in the longitudinal direction of the vehicle to the side member, a fender apron member disposed at outer sides of the side member in the traverse direction of the vehicle, a connecting member connecting the fender apron member and the side member, and a side crash box of which a front tip end may be mounted to an outer portion of the bumper beam positioned at an outer direction of the side member in the traverse direction of the vehicle, and of which a rear tip end may be disposed to be spaced apart from the connecting member at a predetermined interval therebetween.
Owner:HYUNDAI MOTOR CO LTD
Three-factor user authentication method for generating otp using iris information and secure mutual authentication system using otp authentication module of wireless communication terminal
InactiveUS20130268444A1Simple and safe processMaximize convenienceDigital data processing detailsMultiple digital computer combinationsSecure Electronic TransactionService provision
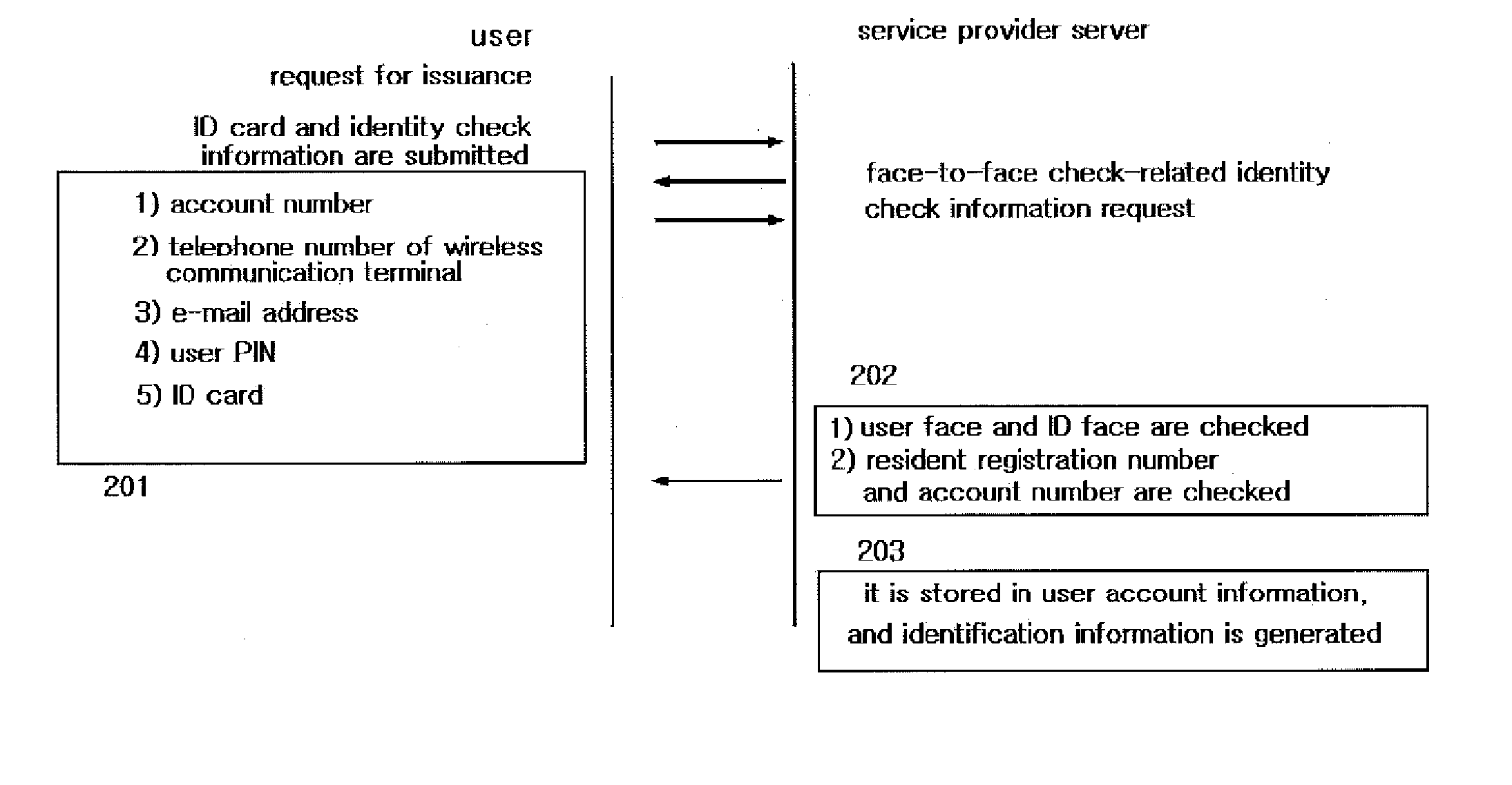
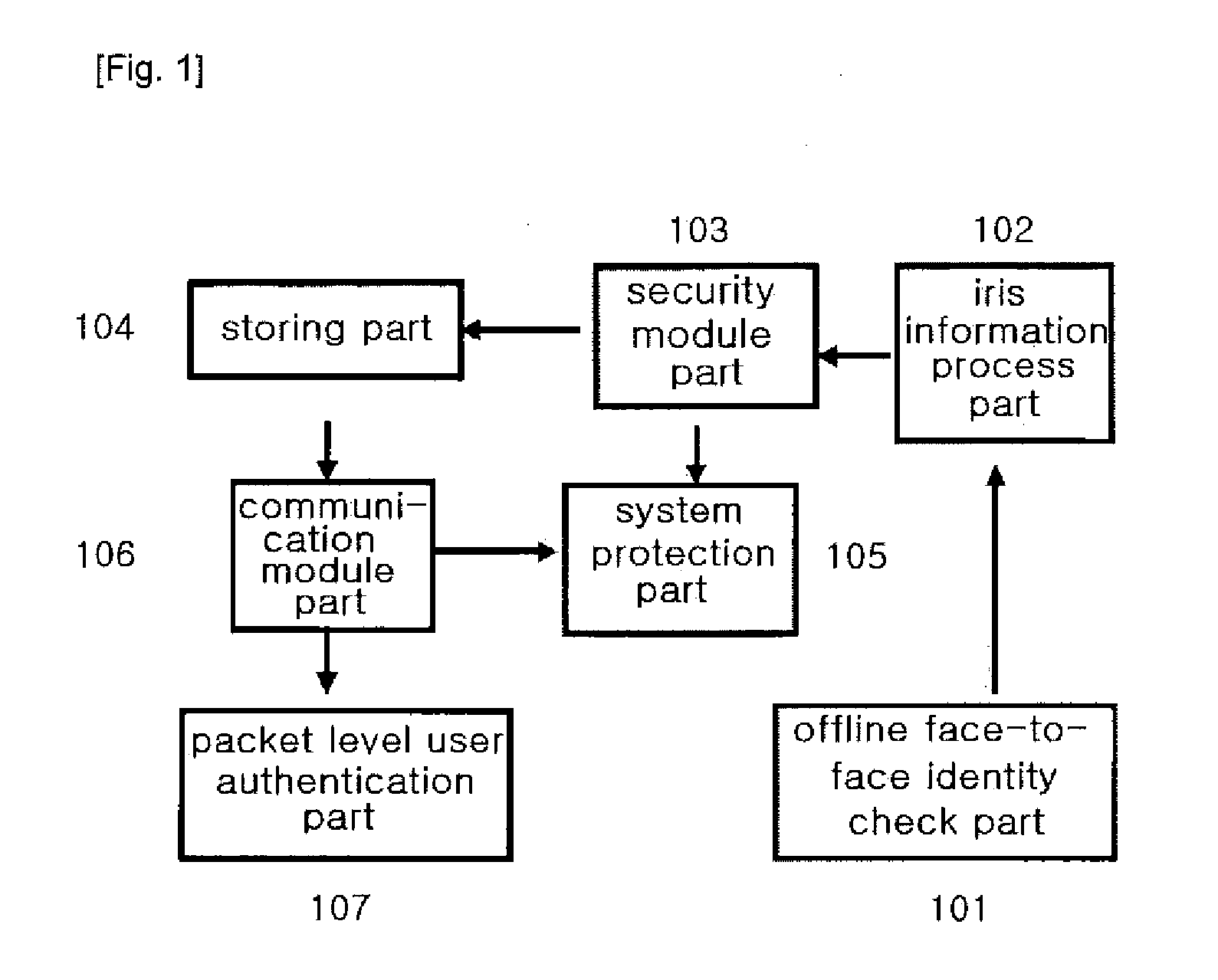
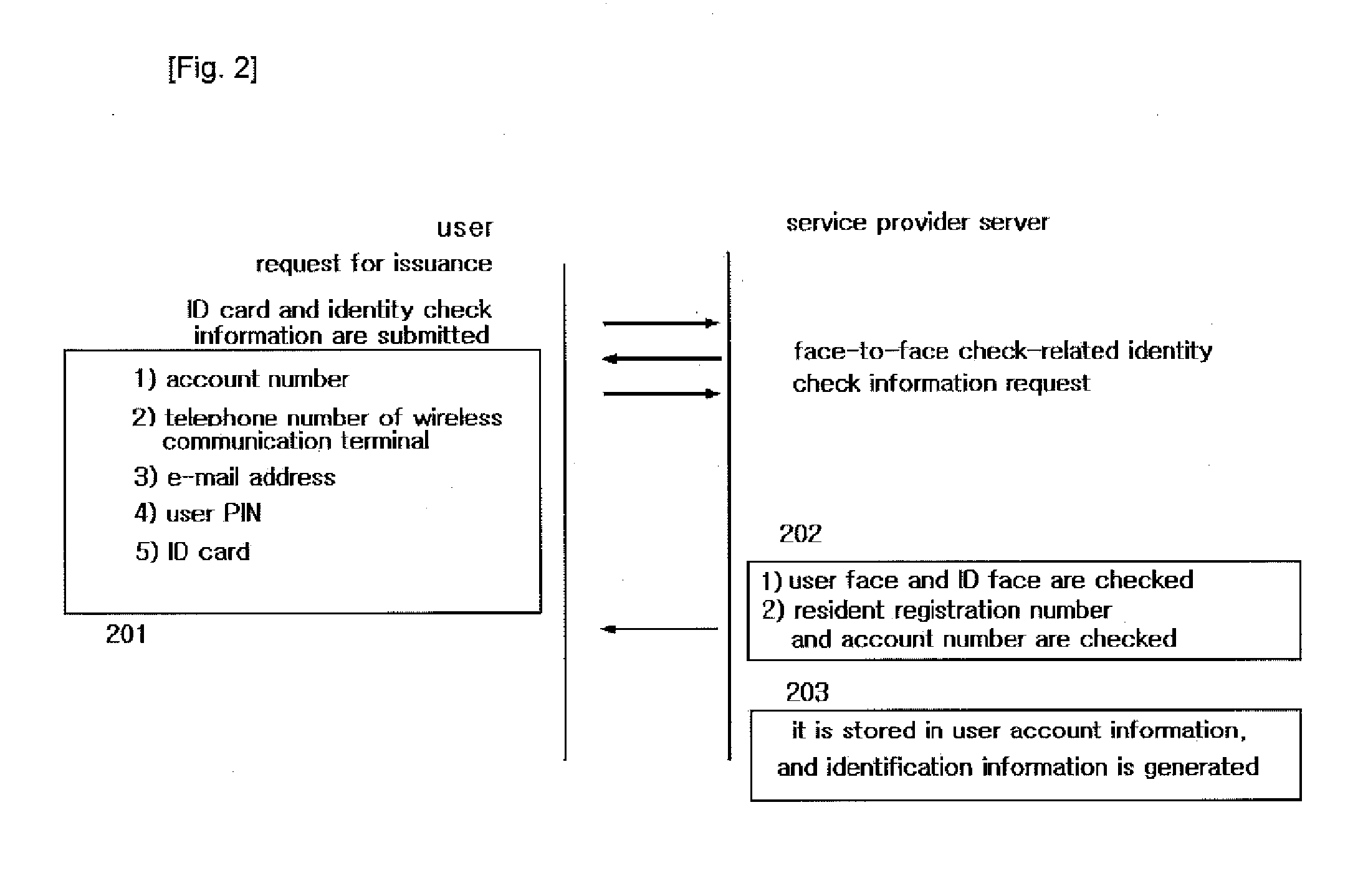
The present invention authenticates a user using iris information in order to generate OTP, generates OTP using a 3-factor authentication method based on HMAC, and performs encryption thereof, and also relates to a security system that secures and controls a wireless communication terminal owned by a user through the following methods: a method for managing the storage of a program memory having a management program and encrypted key values stored therein, by directly inputting the iris information in real-time; a method for authenticating a wireless communication terminal by mutually authenticating two methods having different directions, the methods being an authentication by an OTP integrated authentication server through a service providing server, and an authentication by a public authentication facility through a wireless authentication server; a method for enabling the service usage of packets for communication between a user and a server only through iris authentication in order to prevent a DoS attack during the communication; and a method for protecting the system by protecting the original and patch files of the applications and the drives using iris information and constantly monitoring same, thus enabling secure electronic transaction services.
Owner:NAMGOONG JONG +1
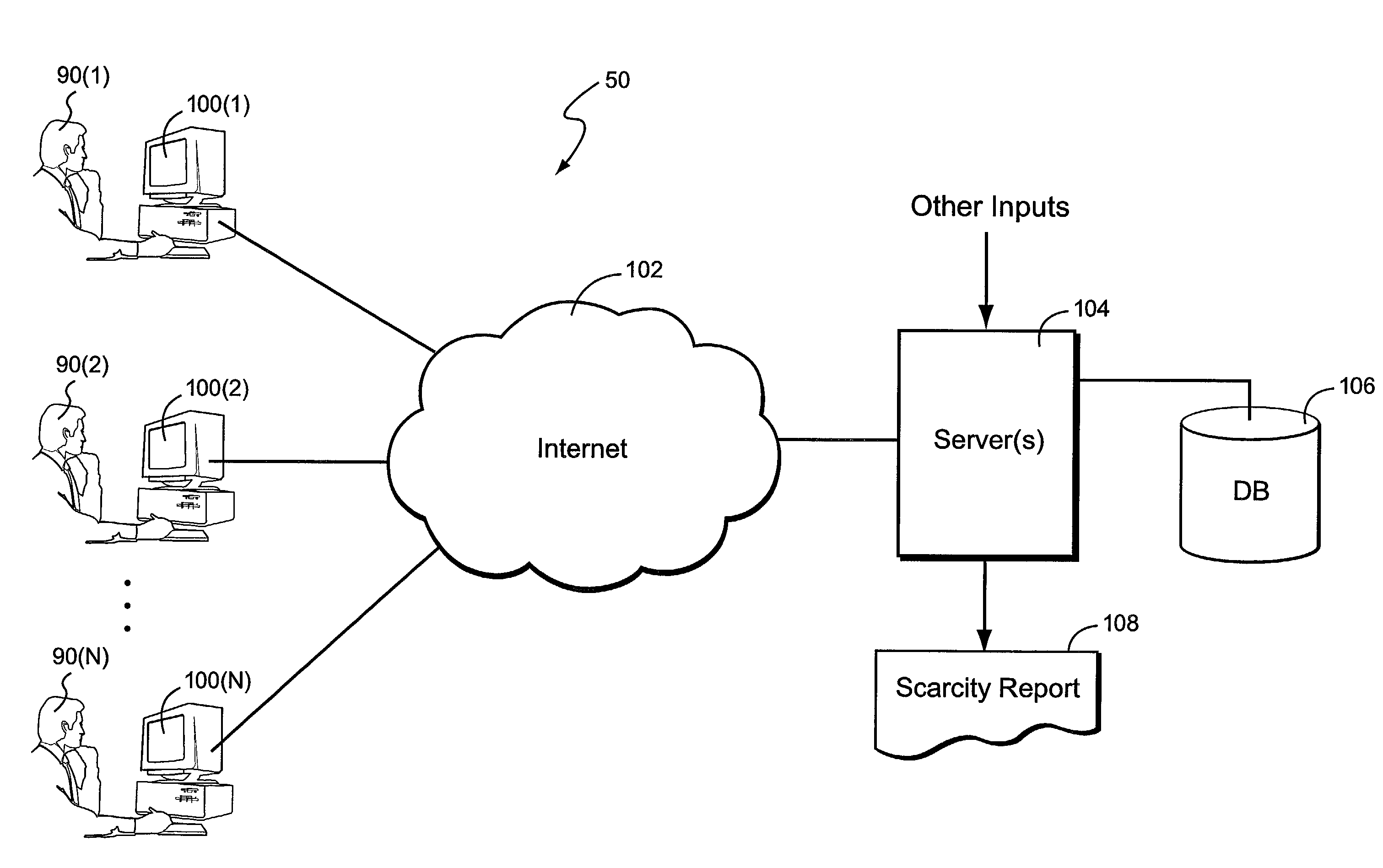
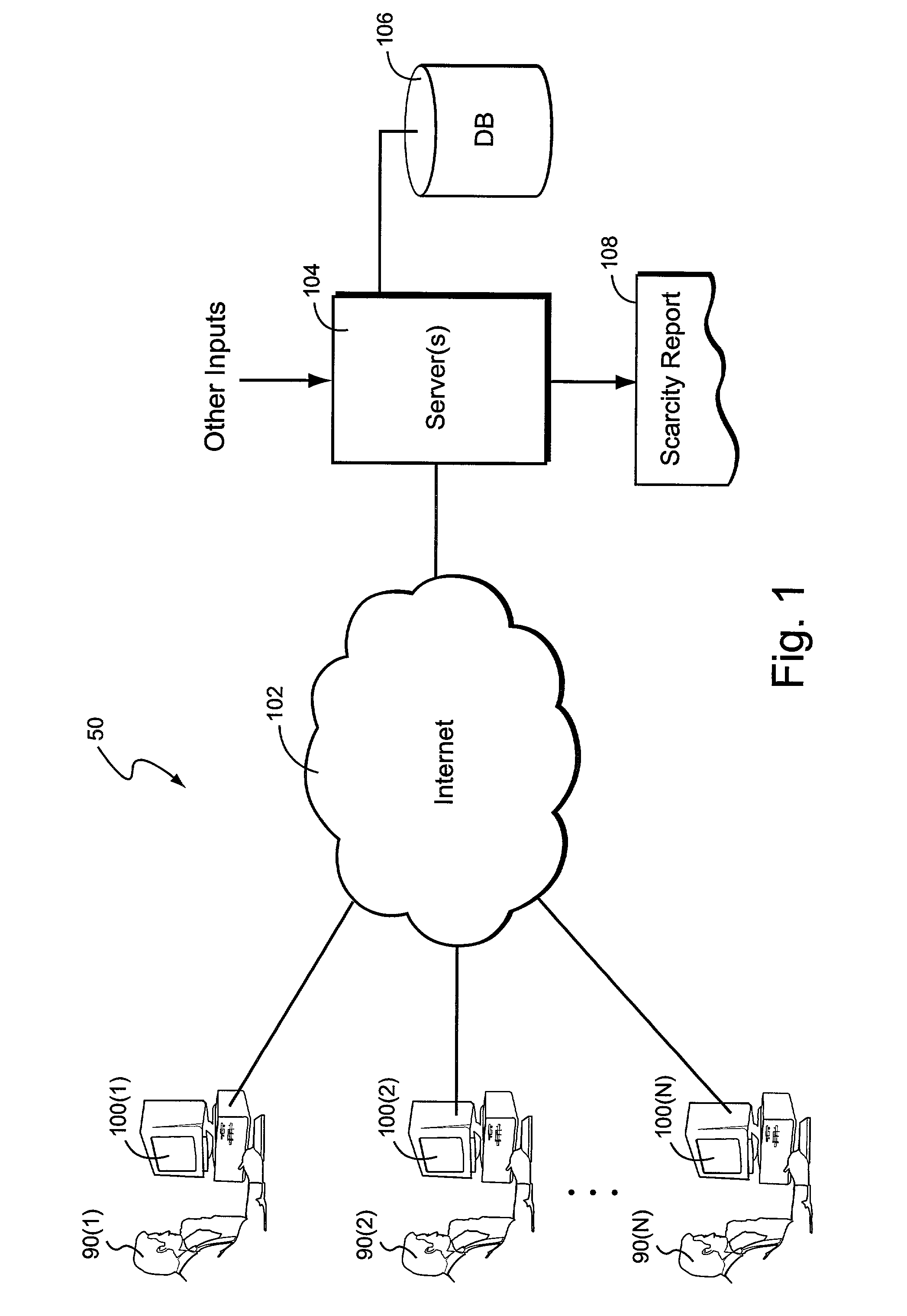
Computer-based system and method for determining a quantitative scarcity index value based on online computer search activities
ActiveUS8521619B2Facilitated and enhanced marketingEfficient searchBuying/selling/leasing transactionsMarketingConsumer demandData mining
An online product or service listing arrangement logs searches performed and uses the logged information to calculate a scarcity index that measures the scarcity of products and services. Scarcity may indicate the number of searches that consumers have conducted compared to available listings. Empirical techniques are used to take into account certain types of searches that may not accurately reflect actual consumer demand. Reports may compare item scarcity within different geographical or other markets to determine relative scarcity. Particularly advantageous but non-limiting applications include new and used motor vehicles, employment opportunities, and real estate.
Owner:AUTOTRADER COM
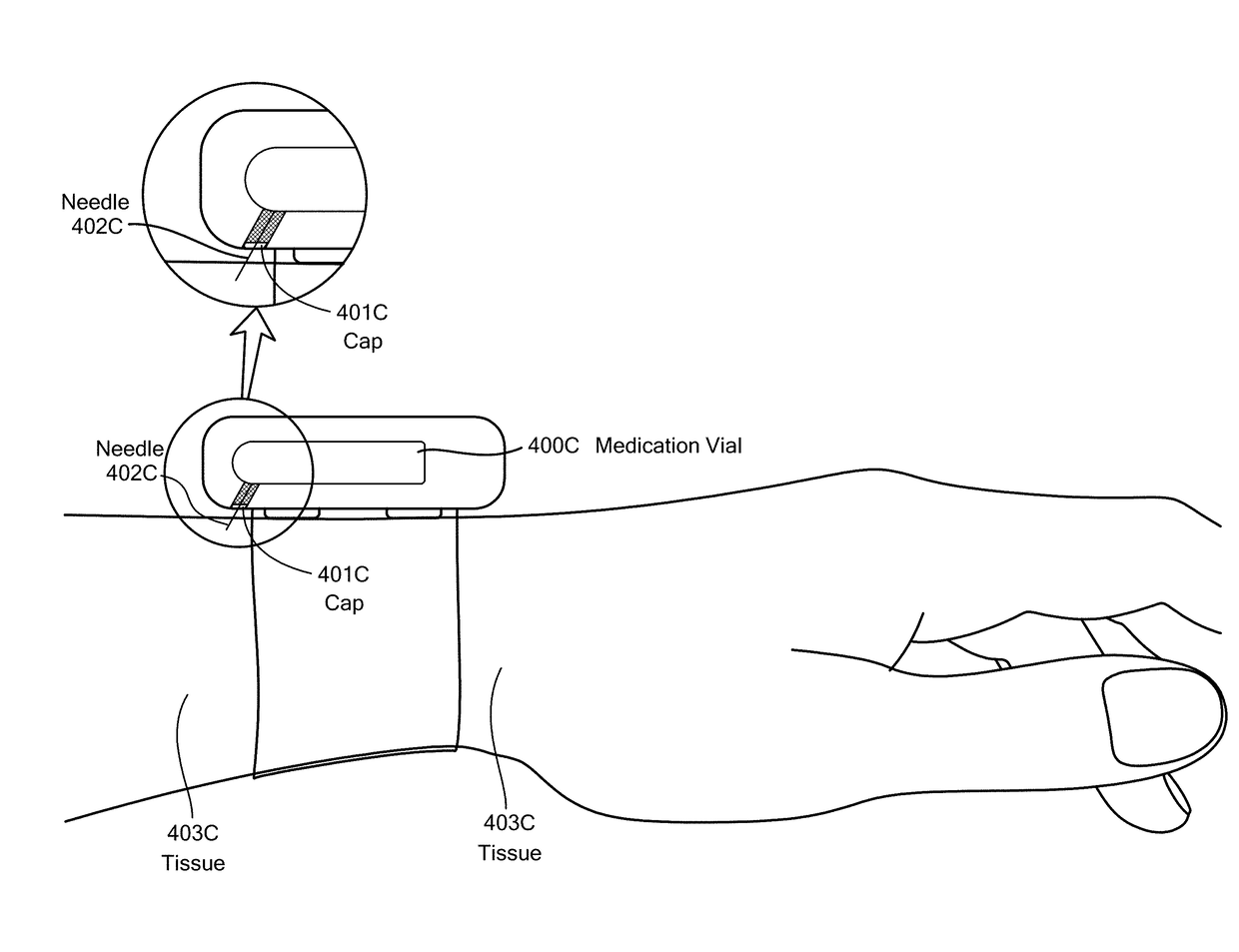
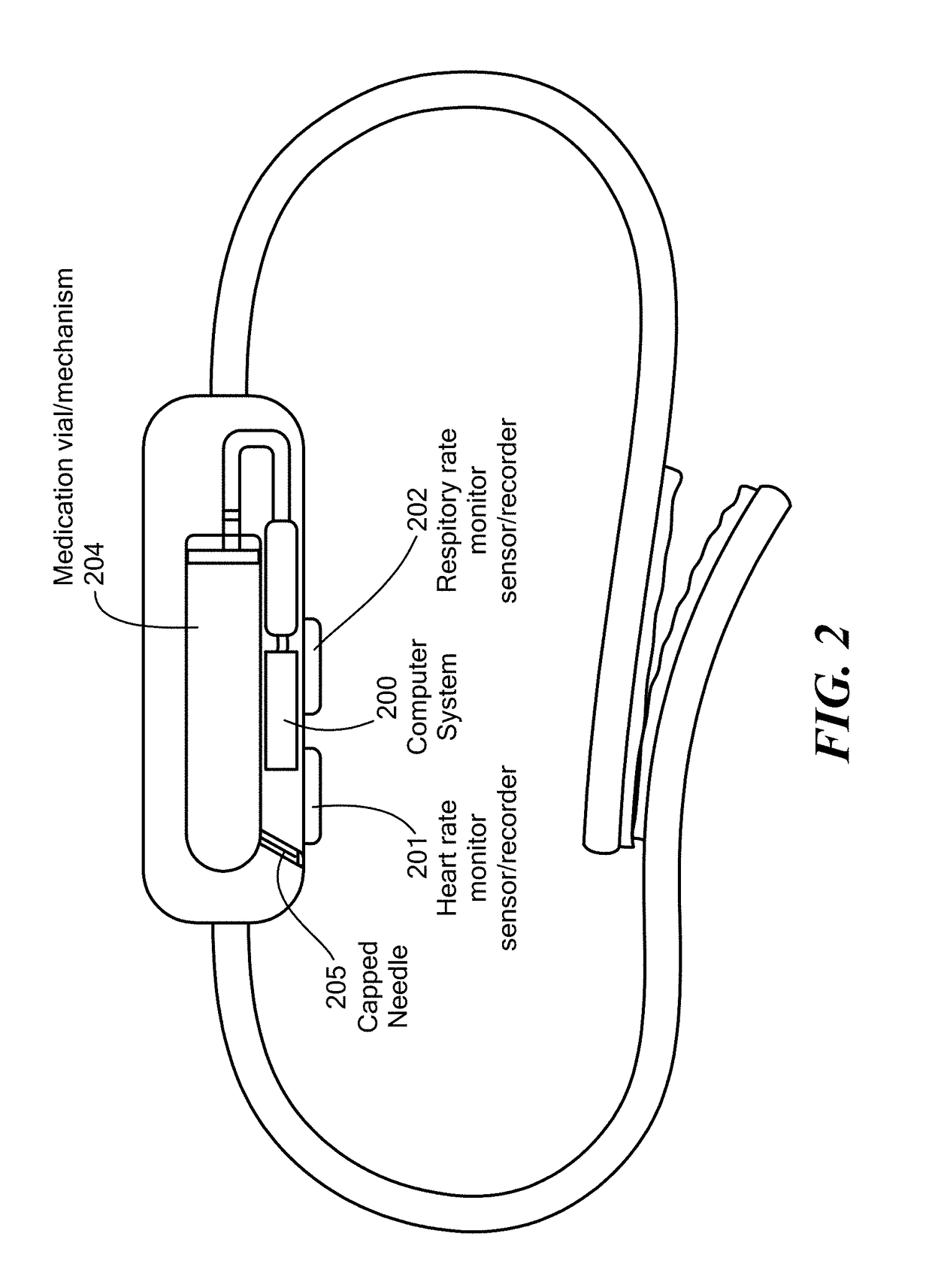
Method and Device for Automatic Identification of an Opioid Overdose and Injection of an Opioid Receptor Antagonist
ActiveUS20170172522A1Constant monitoringRespond effectivelyOrganic active ingredientsAutomatic syringesOpioidergicOpioid overdose
A method for detecting the need for providing assistance to an individual suspected of overdosing on an opiate is provided. The method includes using a wearable device for continuous or intermittent monitoring of one or more physiological parameters of the individual. If the level of one of the one or more physiological parameters exceeds a threshold level specific to that parameter, an alarm is triggered. If the alarm is not aborted, an alert is transmitted to one or more emergency contacts conveying that the individual has overdosed. The method optionally provides for injection of an opioid receptor antagonist into the individual to reverse the effects of the overdose. Also provided is a device for implementing these methods.
Owner:INSLER JOSEPH +1
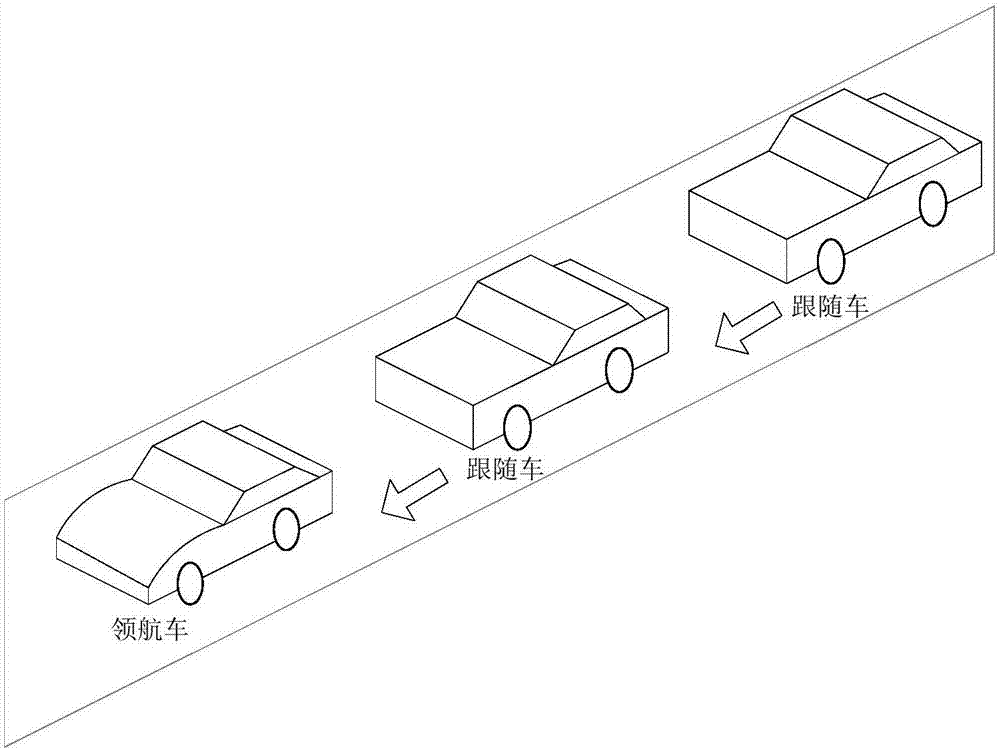
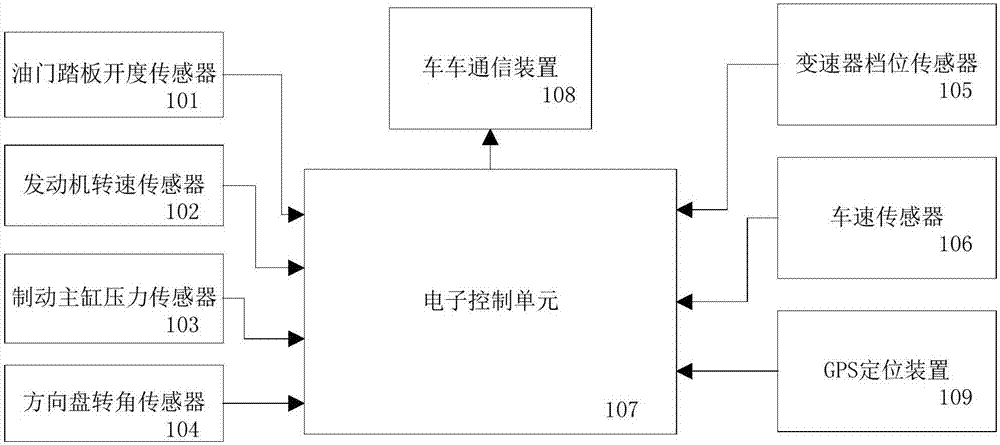
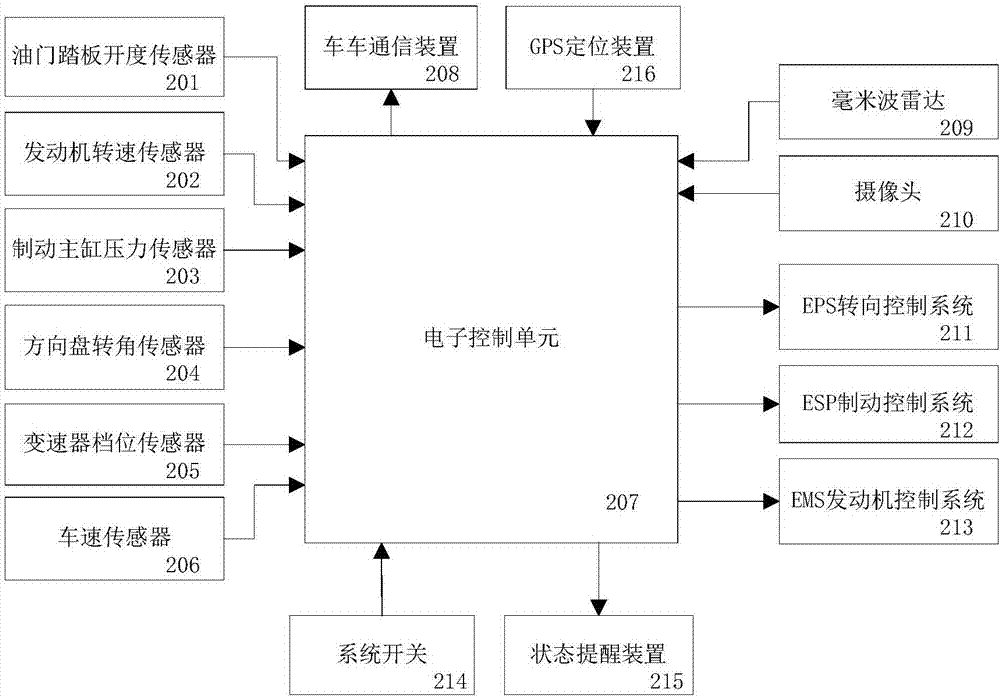
System for controlling automatic car-following operation and method thereof
ActiveCN107089231AImprove reliabilityImprove adaptabilityExternal condition input parametersDriver input parametersControl systemRadar
The invention discloses a system for controlling automatic car-following operation and a method thereof. The system comprises a piloting-car control system and following-car control systems, wherein the piloting-car control system is arranged on a piloting car, and the following-car control systems are arranged on following cars and communicate with the piloting-car control system. The piloting-car control system collects related data about the piloting car through a plurality of sensors and a GPS positioning device which are arranged on the piloting car, and sends the data to the following car through a car-car communicator. Each following-car control system receives the data based on a car-car communicator and collects data through a plurality of sensors, a GPS positioning device, a radar, a camera and the like which are arranged on the following car, and then controls automatic car-following driving of the following car according to the data. Multi-data is integrated to judge the following situation of the following car so that the safety and the reliability of automatic driving can be ensured effectively.
Owner:CHINA FIRST AUTOMOBILE
System and method for digital media server load balancing
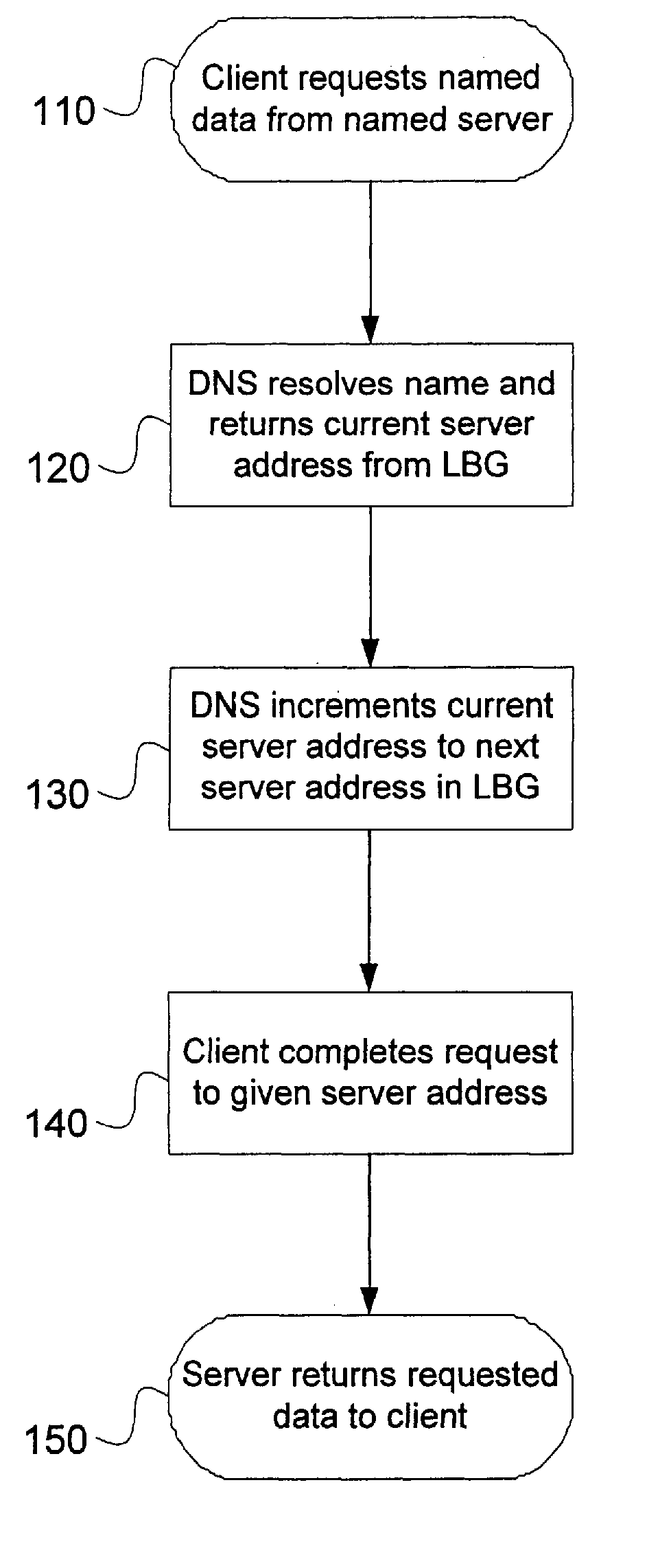
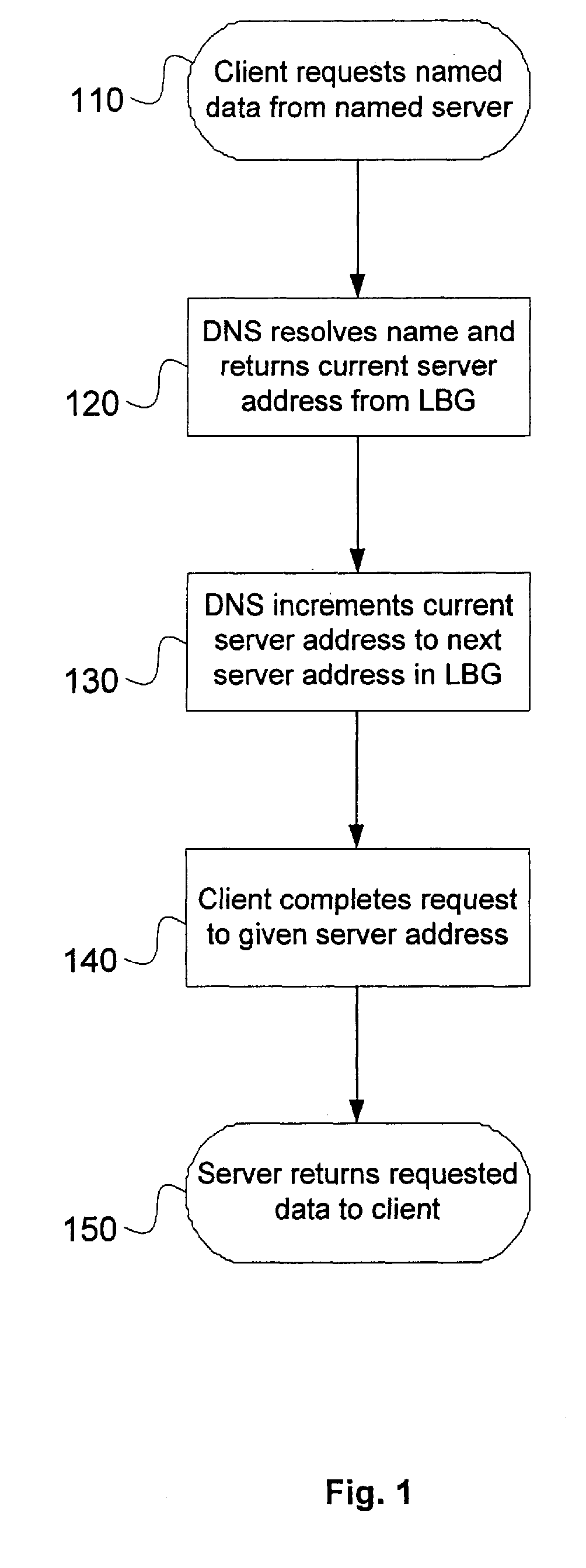
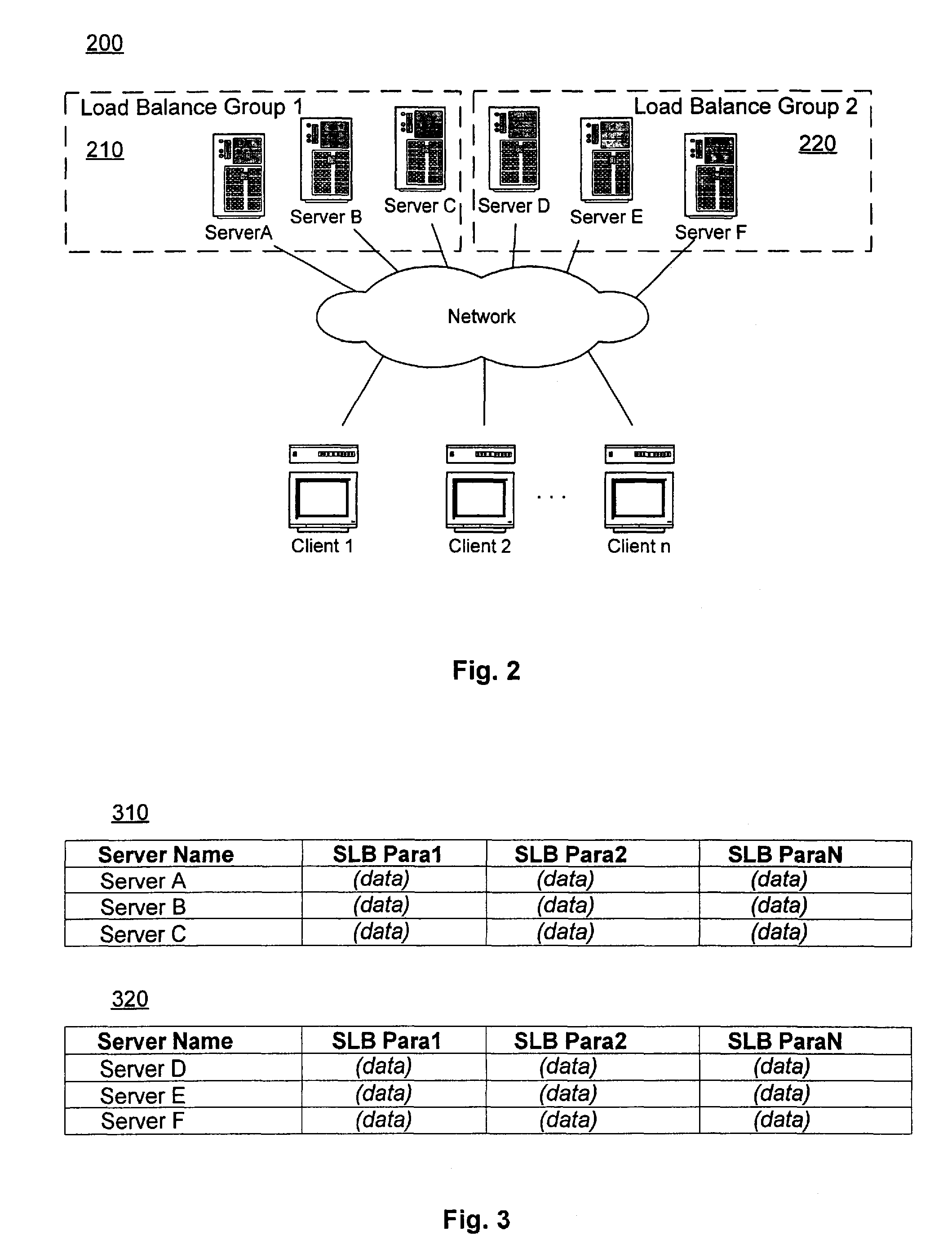
ActiveUS20070124476A1Efficiently respondRespond effectivelyDigital computer detailsTransmissionVideo on demandLoad Shedding
A system and method for load balancing a plurality of servers is disclosed. In a preferred embodiment, a plurality of servers in a video-on-demand or other multi-server system are divided into one or more load-balancing groups. Each server preferably maintains state information concerning other servers in its load-balancing group including information concerning content maintained and served by each server in the group. Changes in a server's content status or other state information are preferably proactively delivered to other servers in the group. When a content request is received by any server in a load-balancing group, it evaluates the request in accordance with a specified algorithm to determine whether it should deliver the requested content itself or redirect the request to another server in its group. In a preferred embodiment, this determination is a function of information in the server's state table.
Owner:XYLON LLC
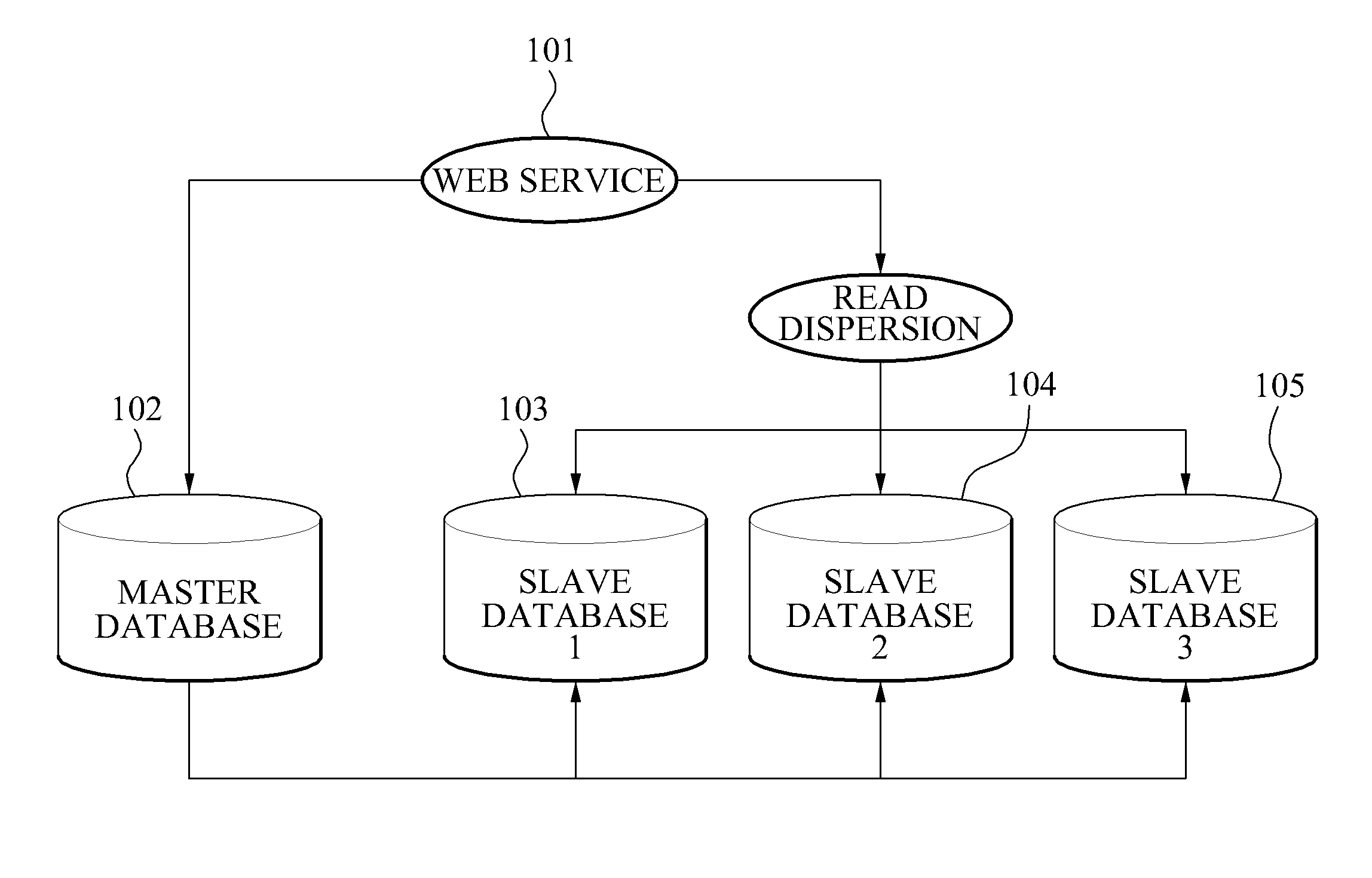
Data replication method and system for database management system
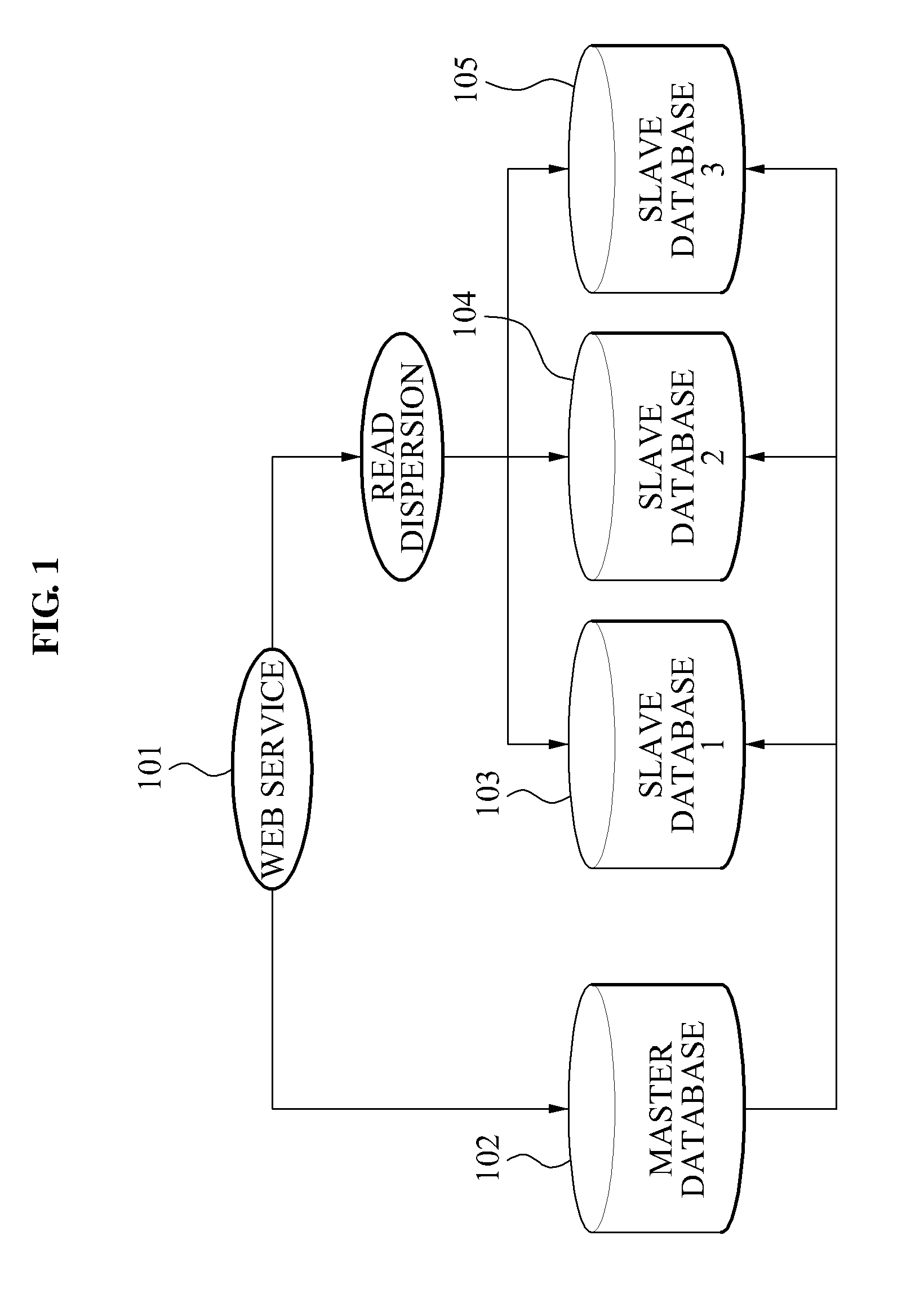
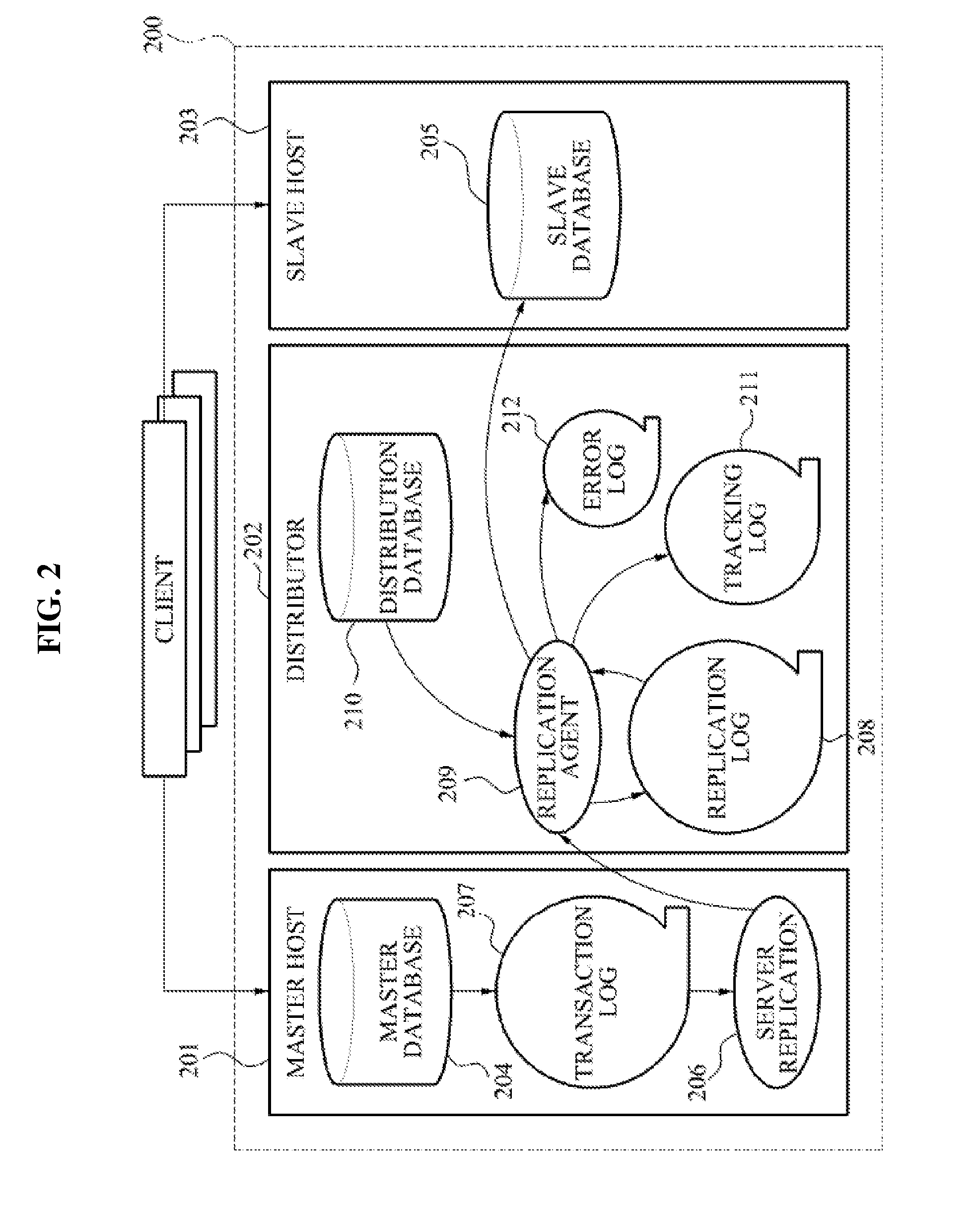
ActiveUS8874512B2Respond effectivelyQuick collectionDigital data processing detailsDatabase distribution/replicationReplication methodTransaction log
Disclosed is a data replication method in a Database Management System (DBMS). The data replication method includes generating a replication log through a transaction log of a master database to thereby transmit the generated replication log to a distributor, determining a slave host distributing the replication log to thereby distribute the replication log to the corresponding slave host, and reflecting the replication log in a slave database.
Owner:NAVER CORP
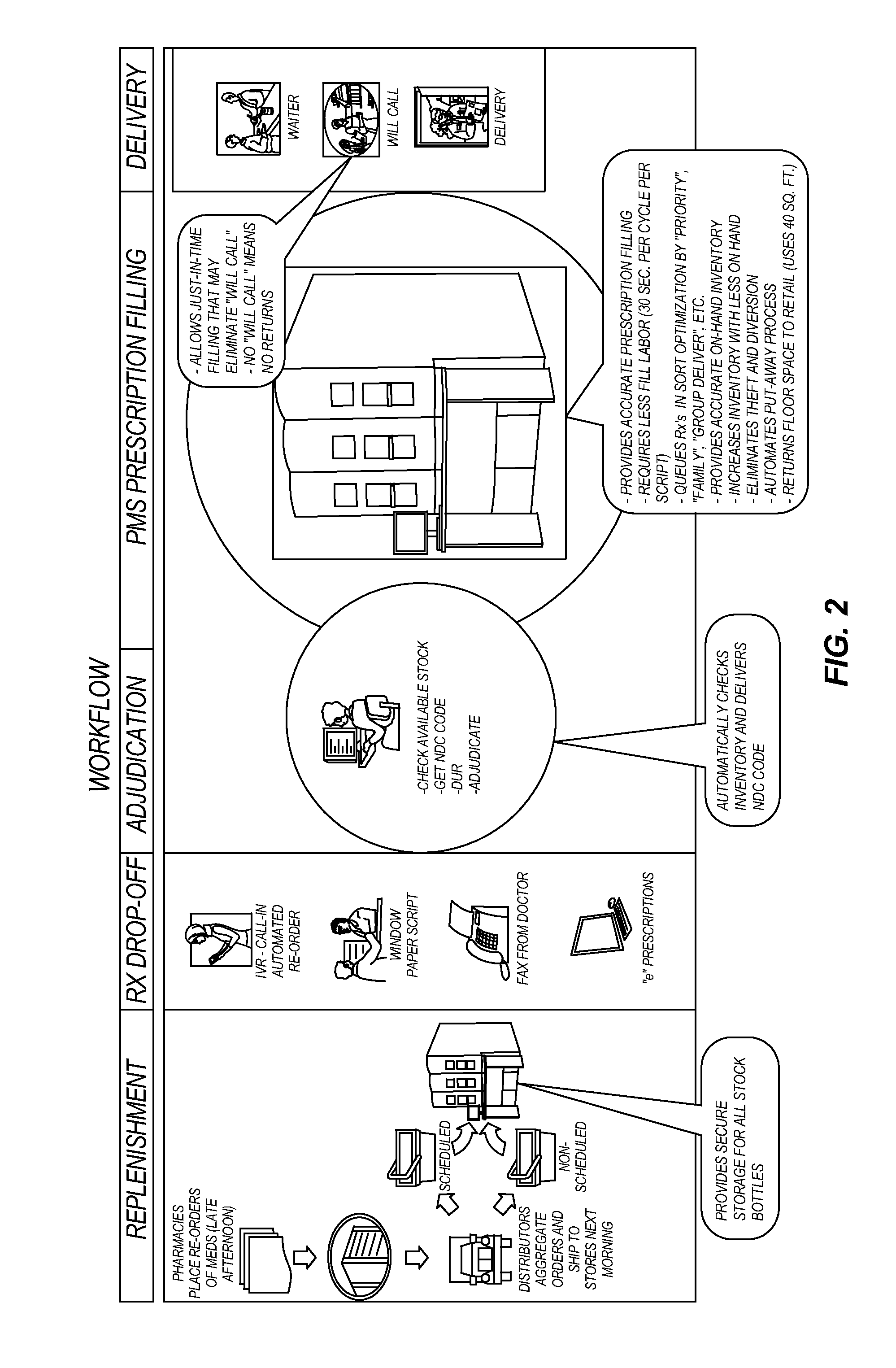
Pharmaceutical storage and retrieval system and methods of storing and retrieving pharmaceuticals
ActiveUS20110054668A1Reduce transaction costsEasy to controlSmall article dispensingDigital data processing detailsDrug productAuthorization
A pharmaceutical storage and retrieval system and a method of storing and retrieving pharmaceutical containers from the system. The system includes a pharmaceutical storage and retrieval and a controller operatively coupled to the device to control storage and retrieval functions of the device. The device includes a gantry assembly, a shelving assembly, a user access assembly, and a user authorization system that function in a coordinated manner to carry out the storage and retrieval functions of the device.
Owner:RXSAFE
Plasma display apparatus
InactiveUS20050243106A1Easy to takeImprove cooling effectCathode-ray tube indicatorsSolid cathode detailsEngineeringWall mount
A plasma display apparatus is capable of enhancing the heat dissipating ability of a plasma display panel, and of reducing the total weight of the plasma display apparatus. The plasma display apparatus comprises a plasma display panel, a frame to which the plasma display panel is attached and by which the plasma display panel is supported, and a boss plate fixed to a rear surface of the frame and fitted with driving circuit boards. The frame is formed in the shape of a rectangular frame which contacts edges of the plasma display panel. A vertical member is vertically disposed in the rectangular frame. The vertical member has wall-mounted bosses which support the total weight of the plasma display apparatus. Other features include a thermally conductive member formed on the rear surface of the frame, and formation of an air passage between the thermally conductive member and the driving circuit boards.
Owner:SAMSUNG SDI CO LTD
Method and apparatus for scheduling in a wireless communication system
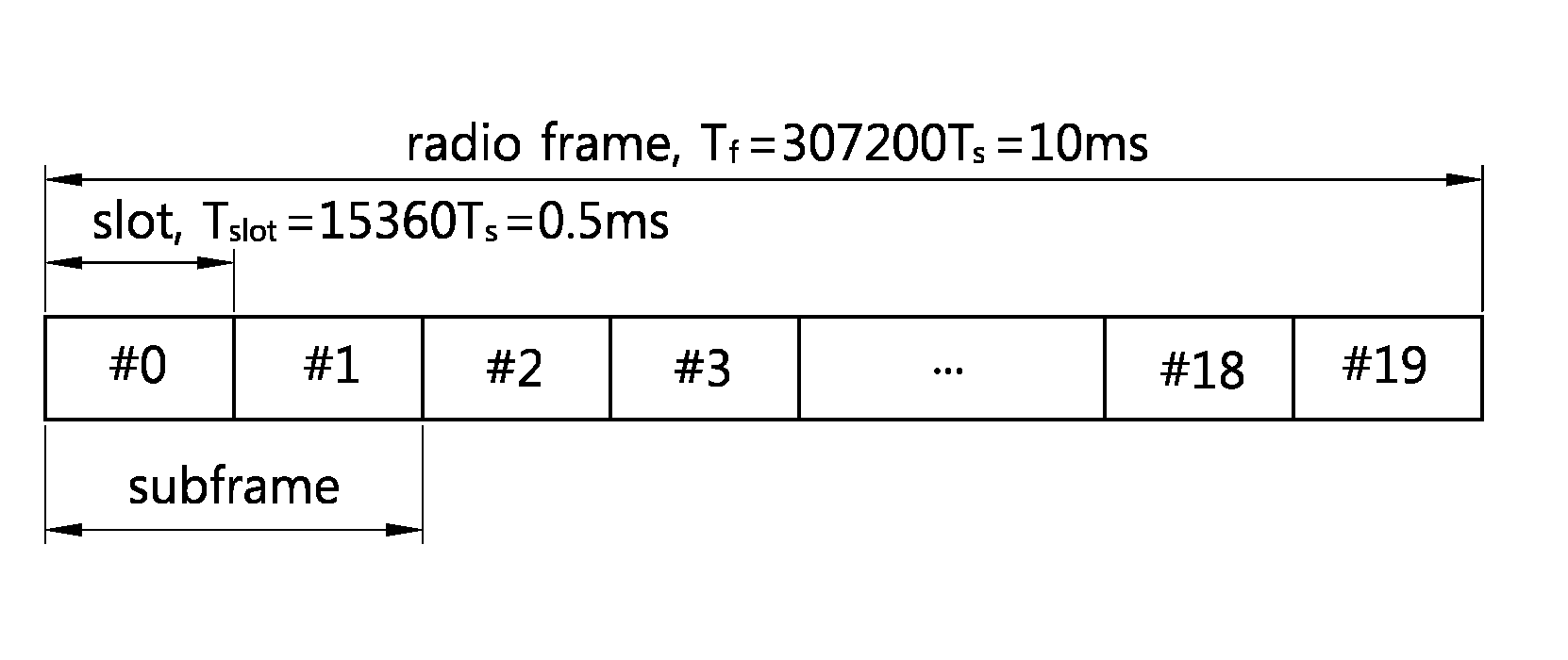
ActiveUS20140185539A1Effective distributionImprove resource utilizationRadio transmissionWireless commuication servicesCommunications systemReal-time computing
Provided is a method and apparatus for scheduling in a wireless communication system. In the method, if frame configuration information is transmitted, the frame configuration information sets each sub-frame within a frame to either a default sub-frame or a variable sub-frame and transmits scheduling information which schedules the configured variable sub-frame; and if a signal based on the scheduling information from the configured variable sub-frame is transceived, the default sub-frame becomes a sub-frame for which the transmission direction is fixed, and the configured sub-frame is used as an uplink sub-frame or a downlink sub-frame according to the scheduling information.
Owner:LG ELECTRONICS INC
Data storage device provided with function for user's access right
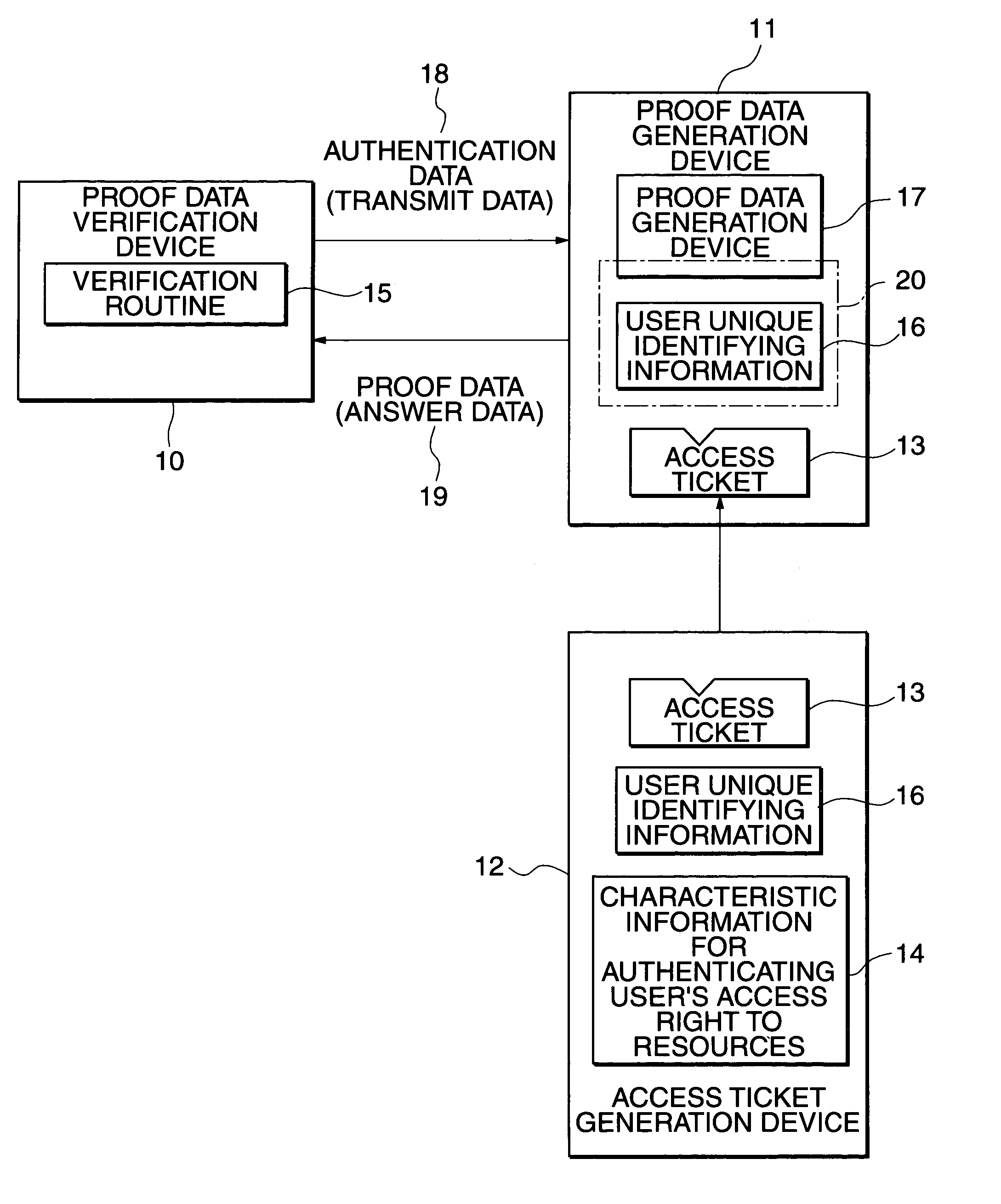
InactiveUS7155745B1Protection technologyImprove abilitiesProgram control using stored programsDigital data processing detailsHard disc driveSource Data Verification
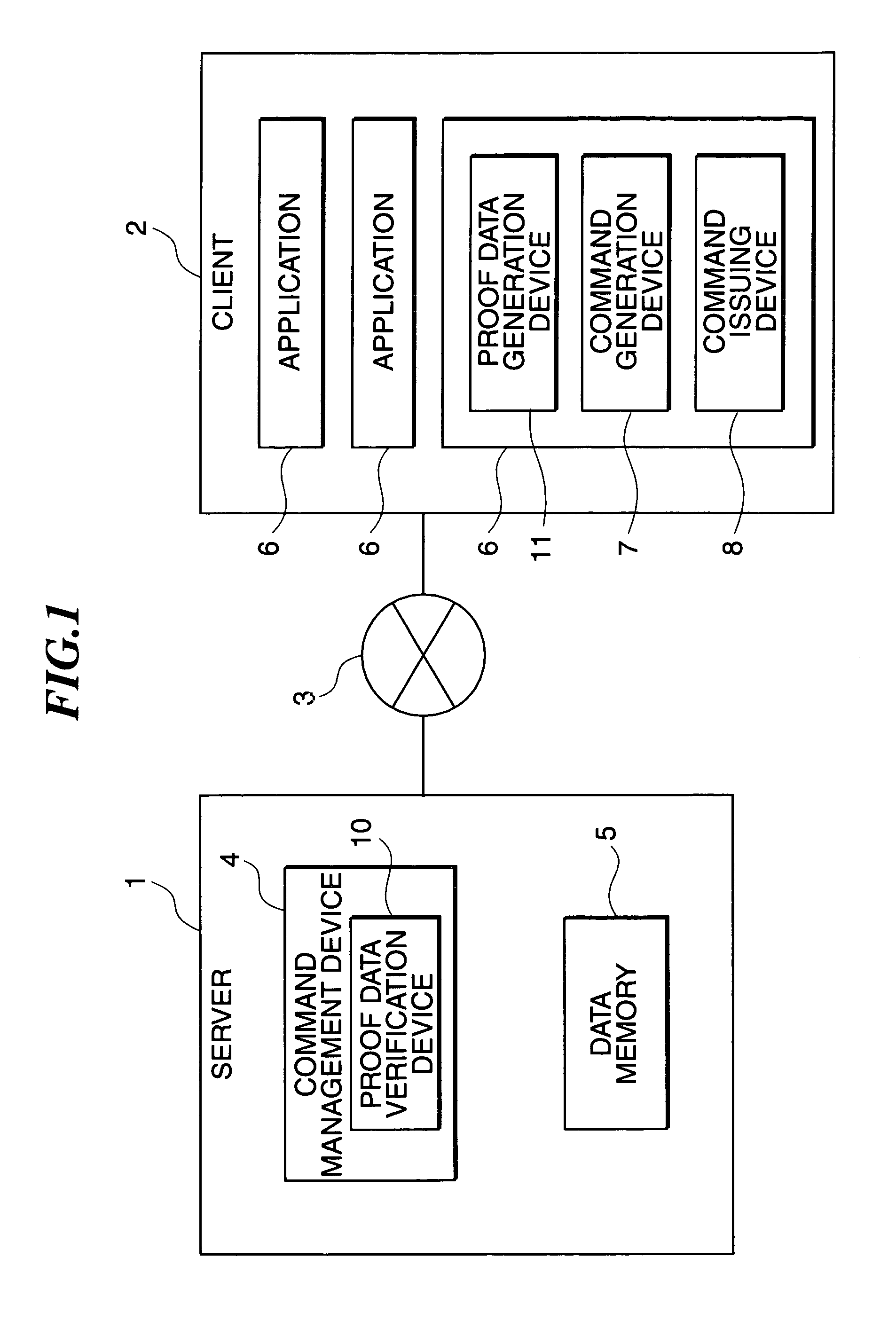
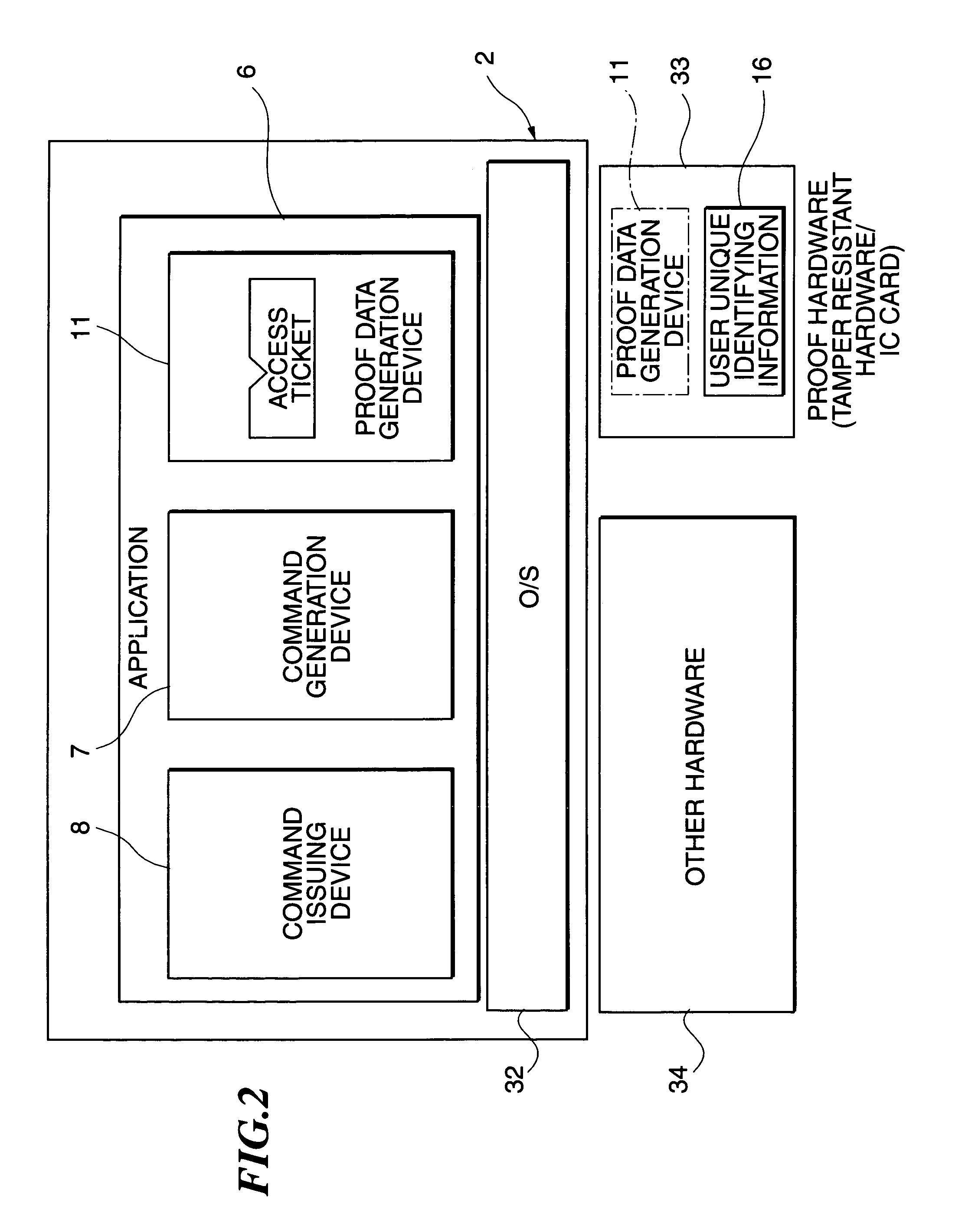
An application of a client includes a proof data generation device, a command generation device, and a command issuing device. A command and proof data are sent to a server from the application of the client, and a command management device of the server receives them. A proof data verification device verifies the access right of a user to the application on the basis of the proof data, and enables a data storage device to be accessed in accordance with the command, if the verification is successful. The data storage device, used instead of a commonly used hard disk drive, includes a phase change type optical memory or a phase separation type optical memory to execute write once recording. Thus, the access to the data storage device is flexibly controlled.
Owner:FUJIFILM BUSINESS INNOVATION CORP
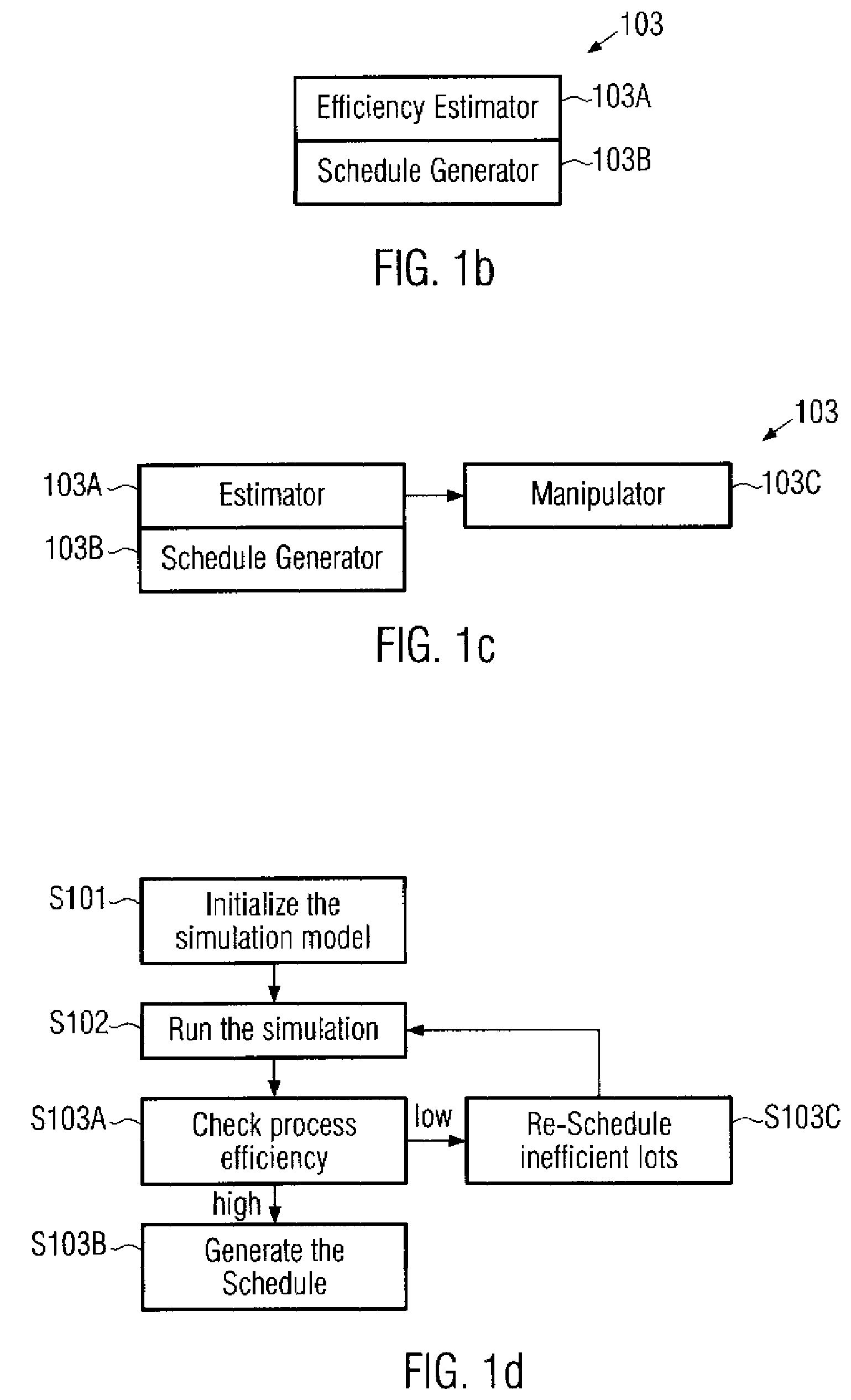
Method and system for scheduling a stream of products in a manufacturing environment by using a simulation process
InactiveUS20070179652A1Efficiently determinedIncrease flexibilityProgramme controlAnalogue computers for electric apparatusProcess efficiencyComputer science
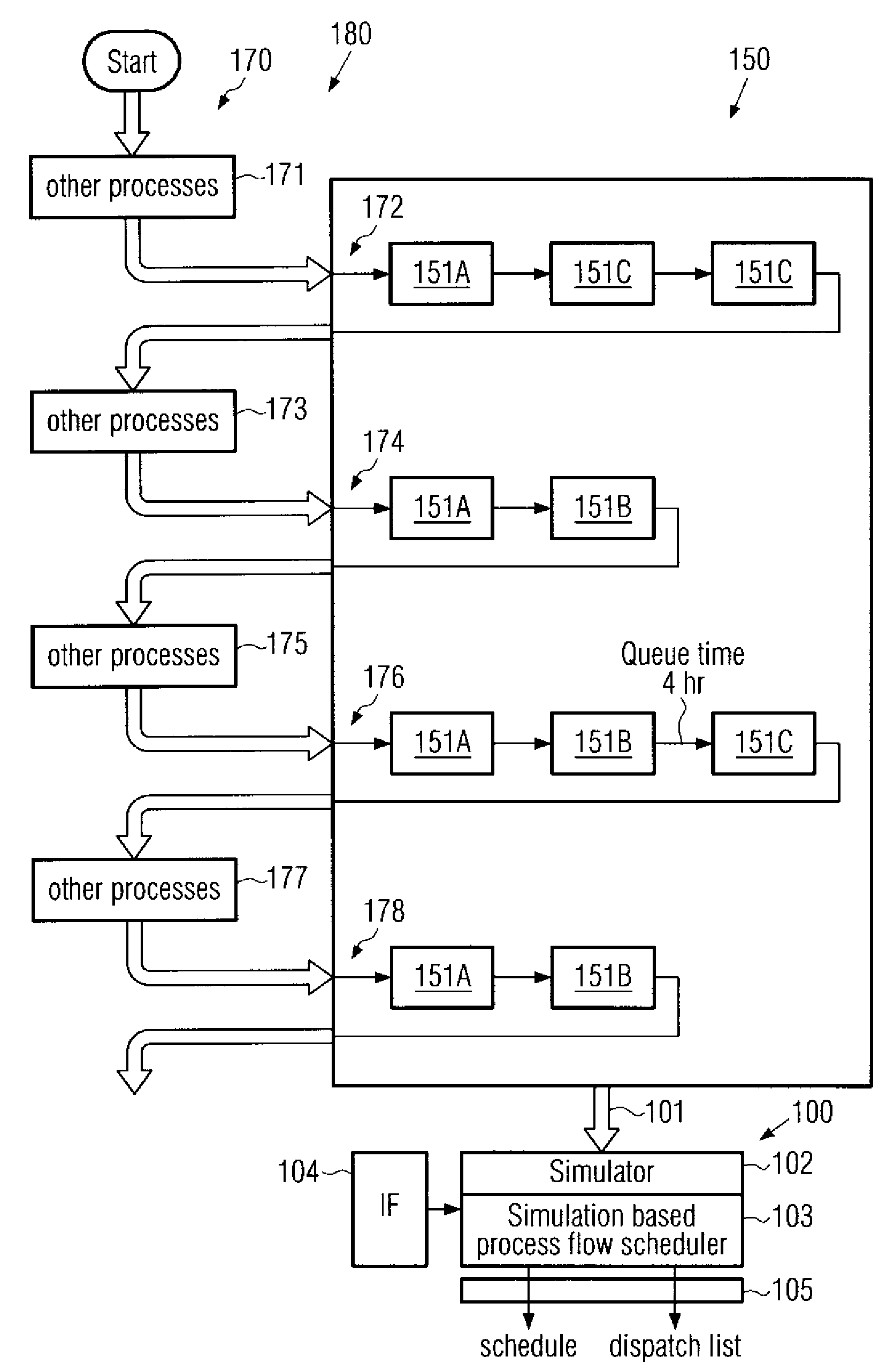
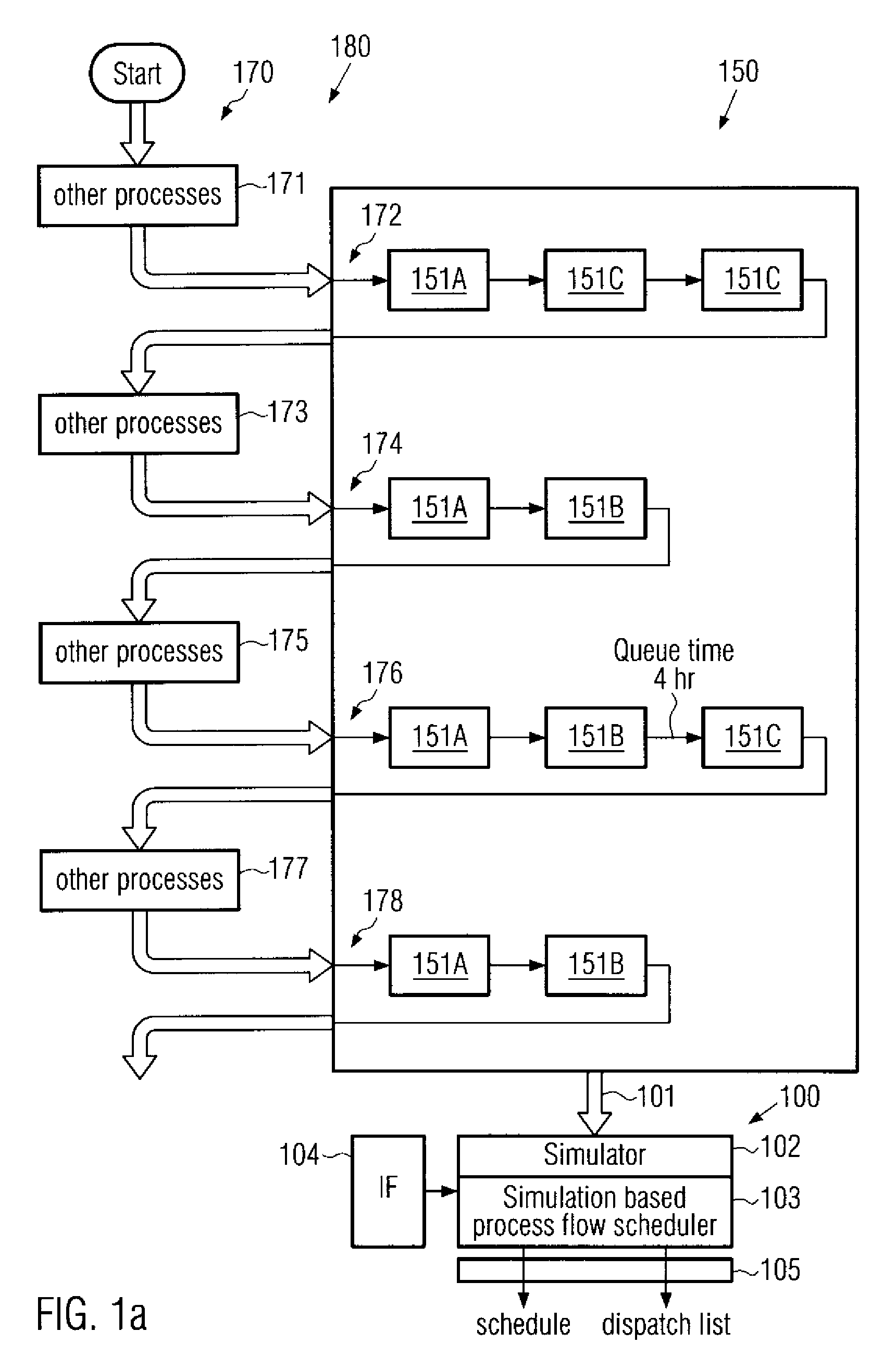
By simulating a manufacturing environment on the basis of appropriate simulation models, a schedule may be established in which process restrictions, tool availability and product entity status are automatically taken into consideration. Moreover, by estimating the process flow efficiency provided by a simulated time progression of the process flow in the environment, an optimized schedule may be established, which may be accomplished by identifying less efficient product entities and re-scheduling one or more product entities in order to obtain an enhanced process flow efficiency. The technique of the present invention may be advantageously applied to the processing of advanced mass products requiring sophisticated process tools and process sequences, such as the processing of semiconductor devices.
Owner:GLOBALFOUNDRIES INC
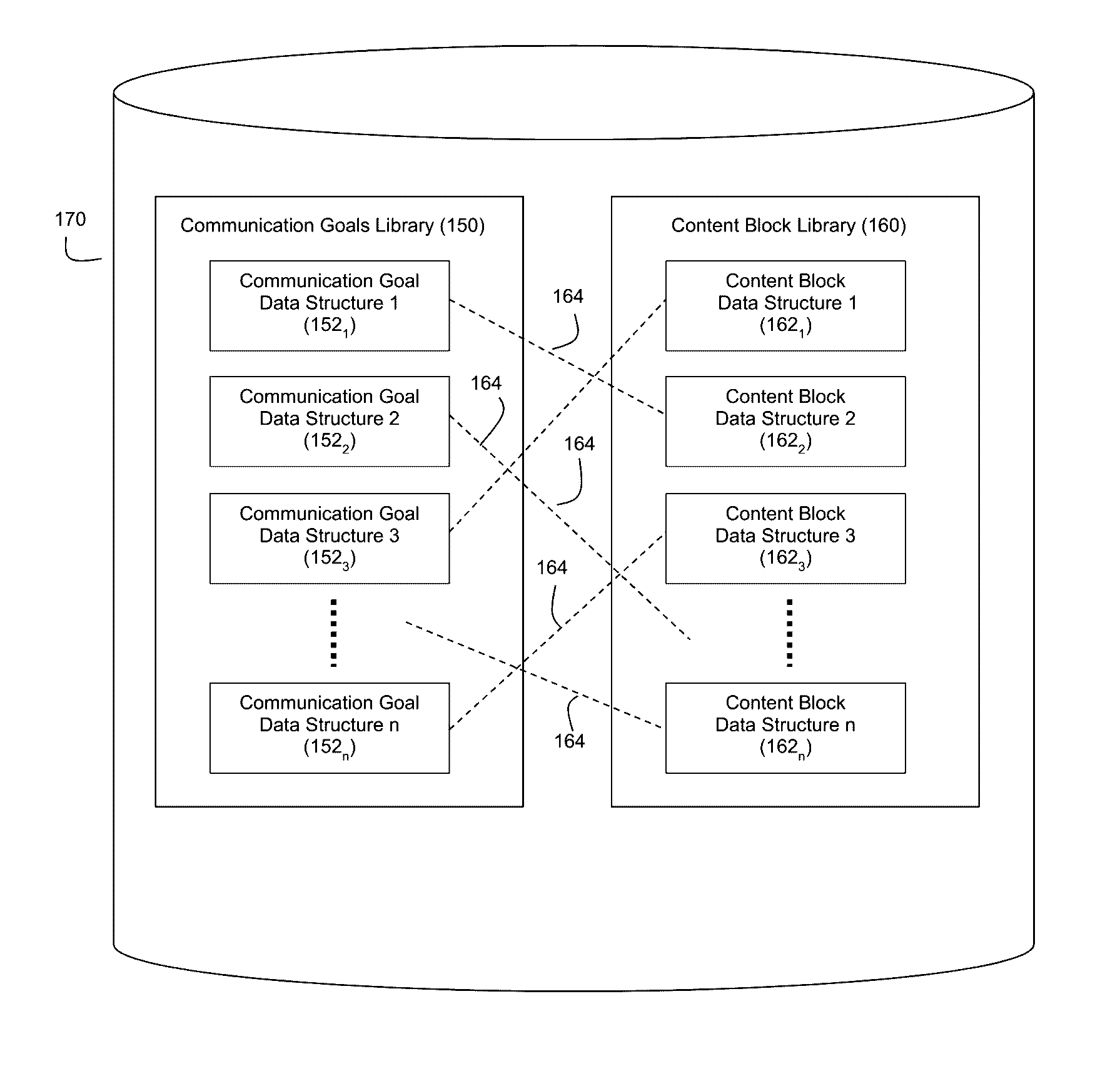
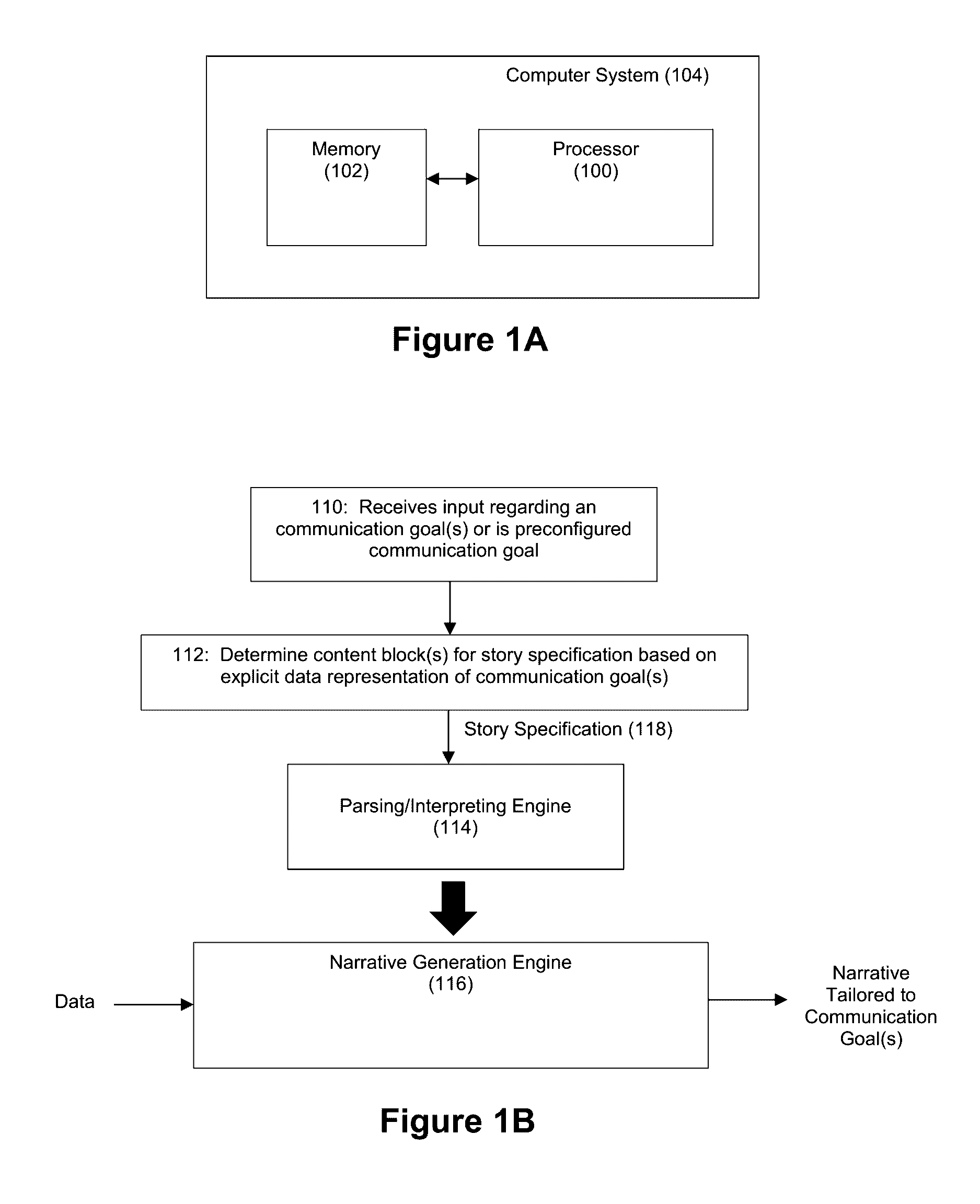
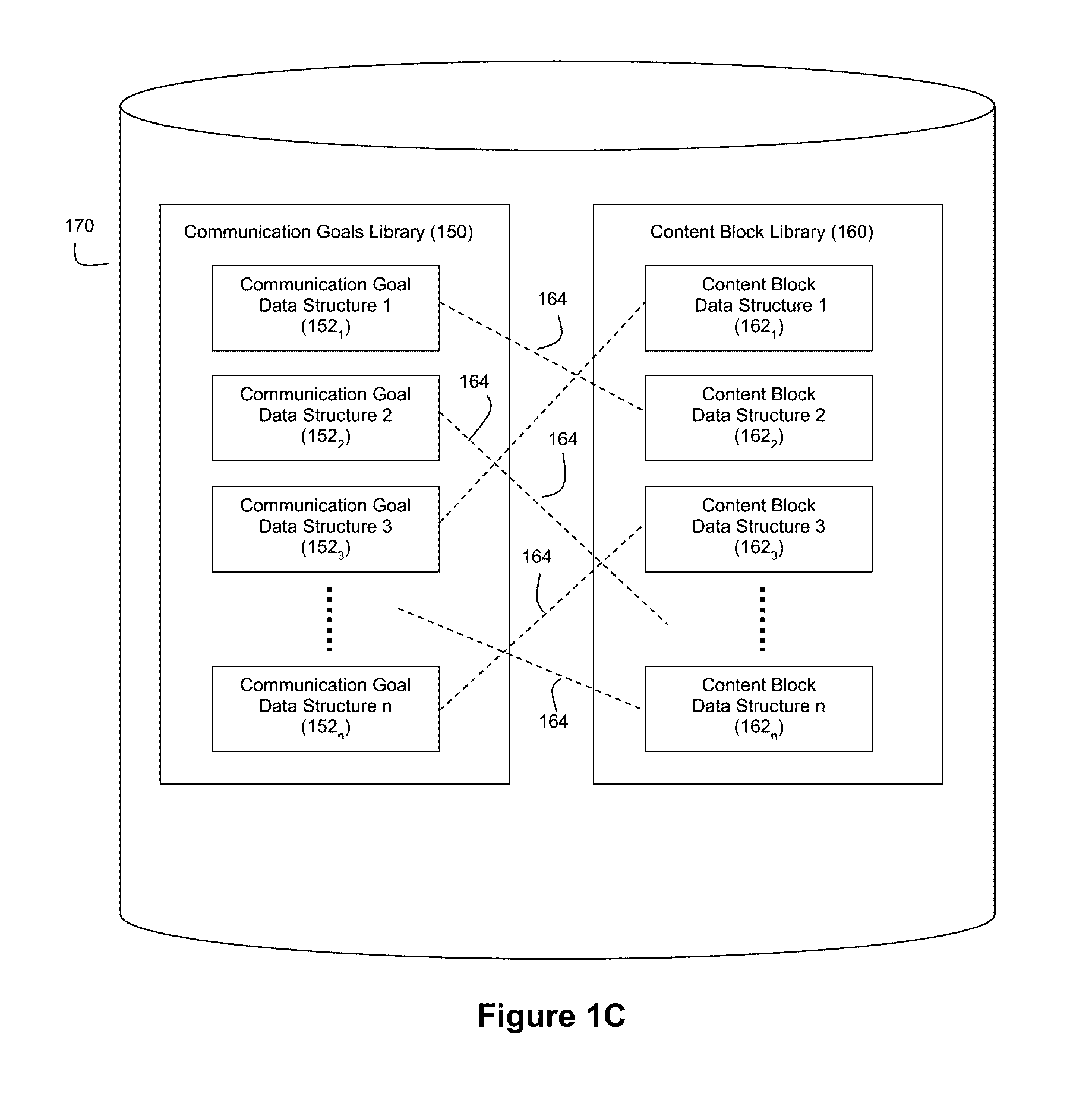
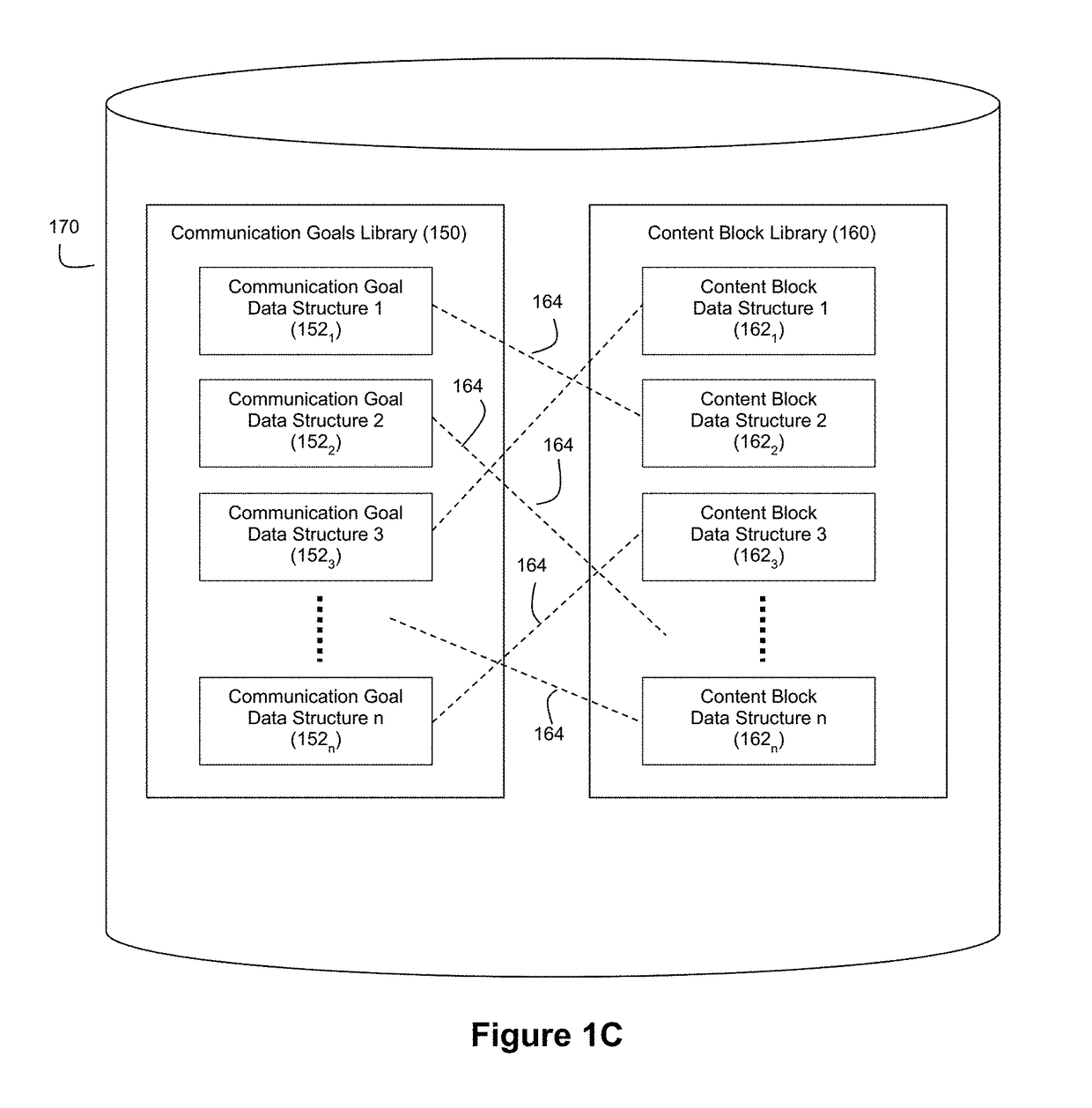
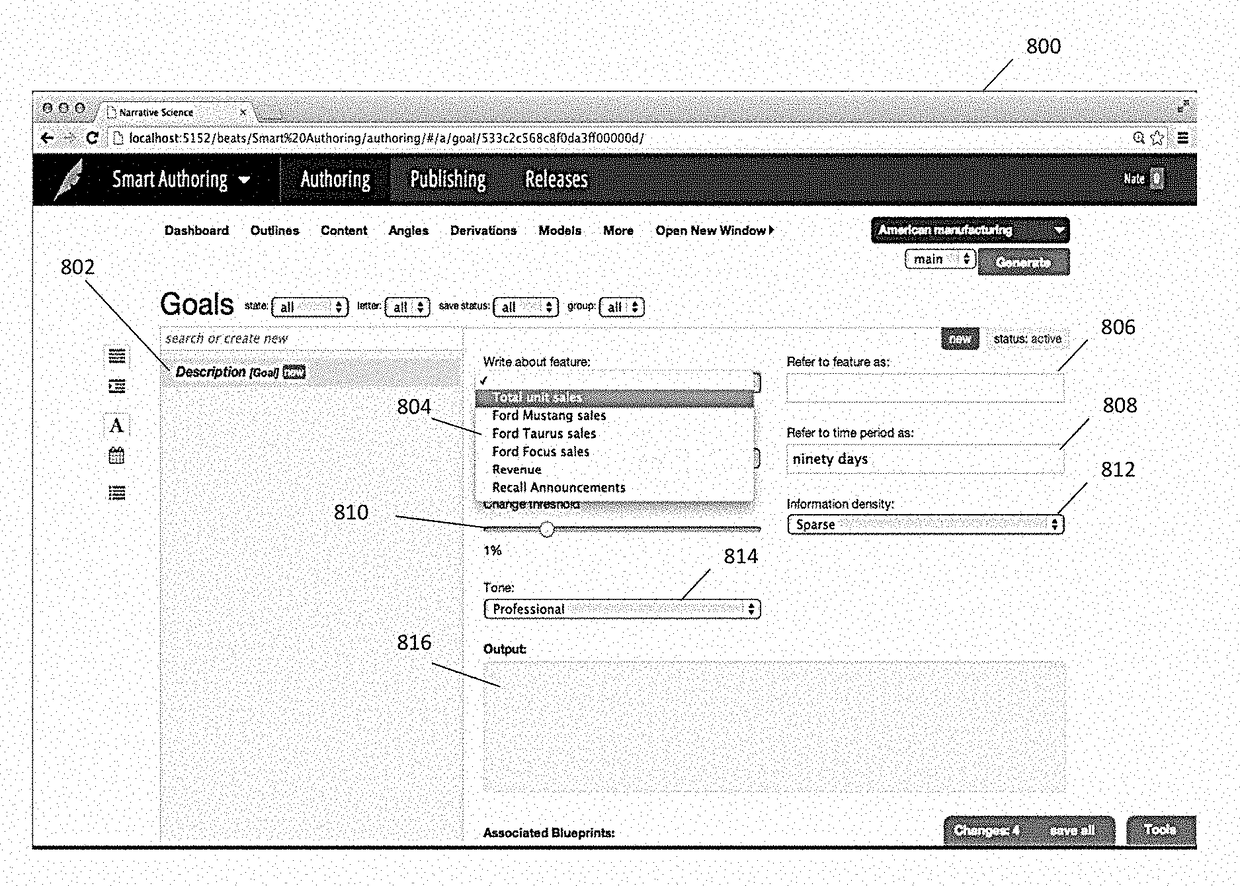
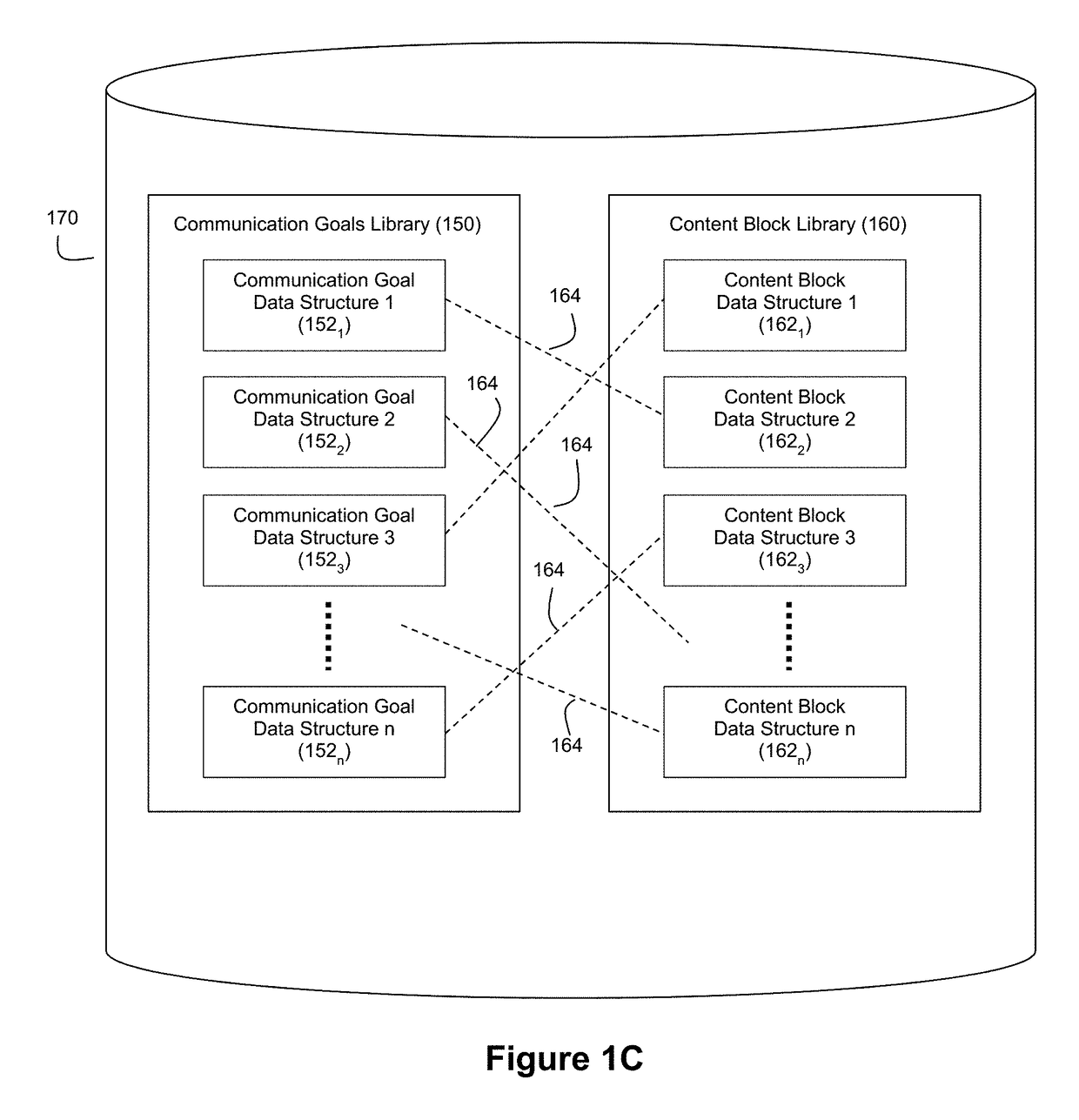
Automatic generation of narratives from data using communication goals and narrative analytics
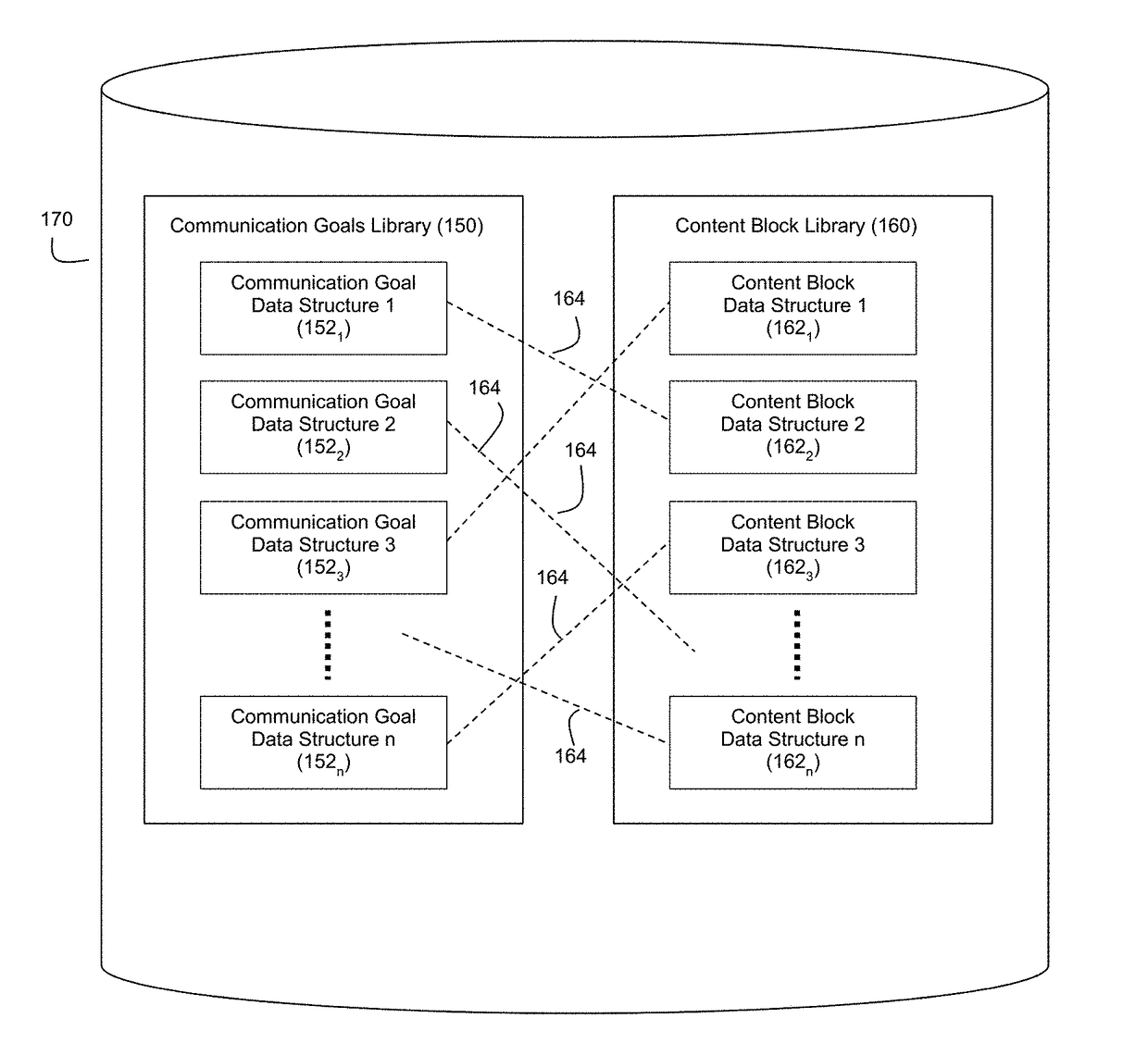
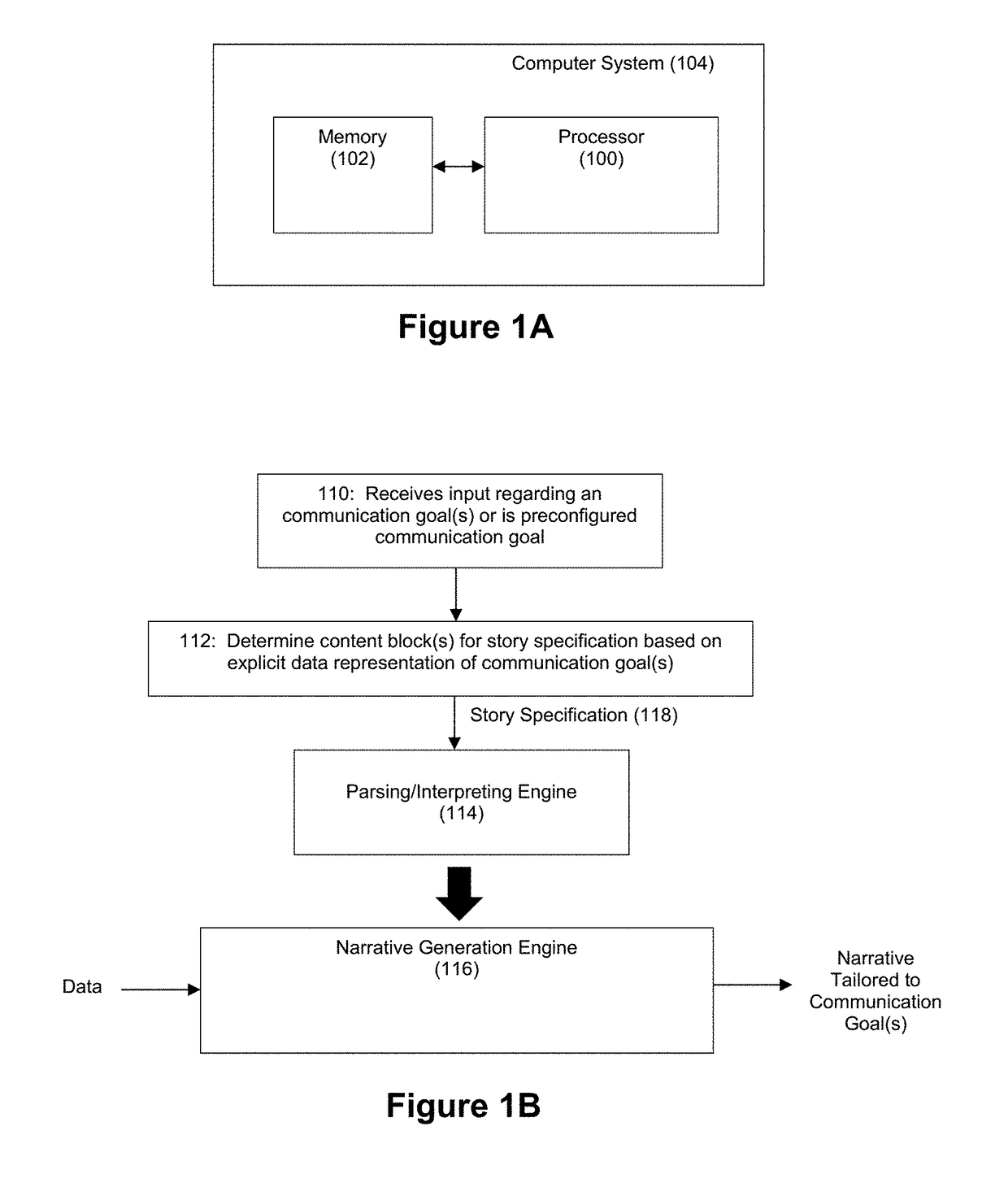
ActiveUS9576009B1Satisfactory communicationEasy to understandDigital data information retrievalOffice automationOperation modeData structure
The exemplary embodiments described herein are related to techniques for automatically generating narratives about data based on communication goal data structures that are associated with configurable content blocks. The use of such communication goal data structures facilitates modes of operation whereby narratives can be generated in real-time and / or interactive manners.
Owner:NARRATIVE SCI
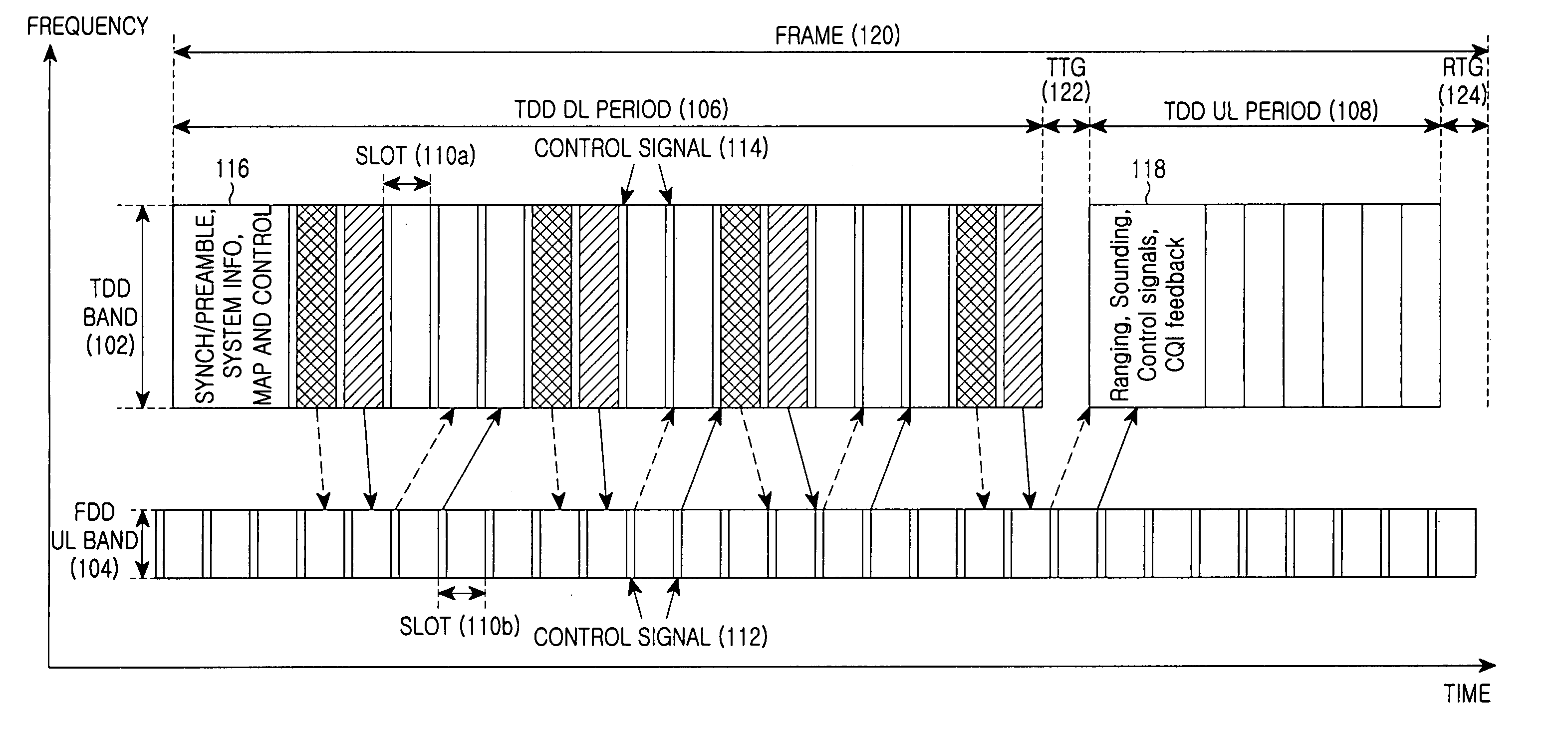
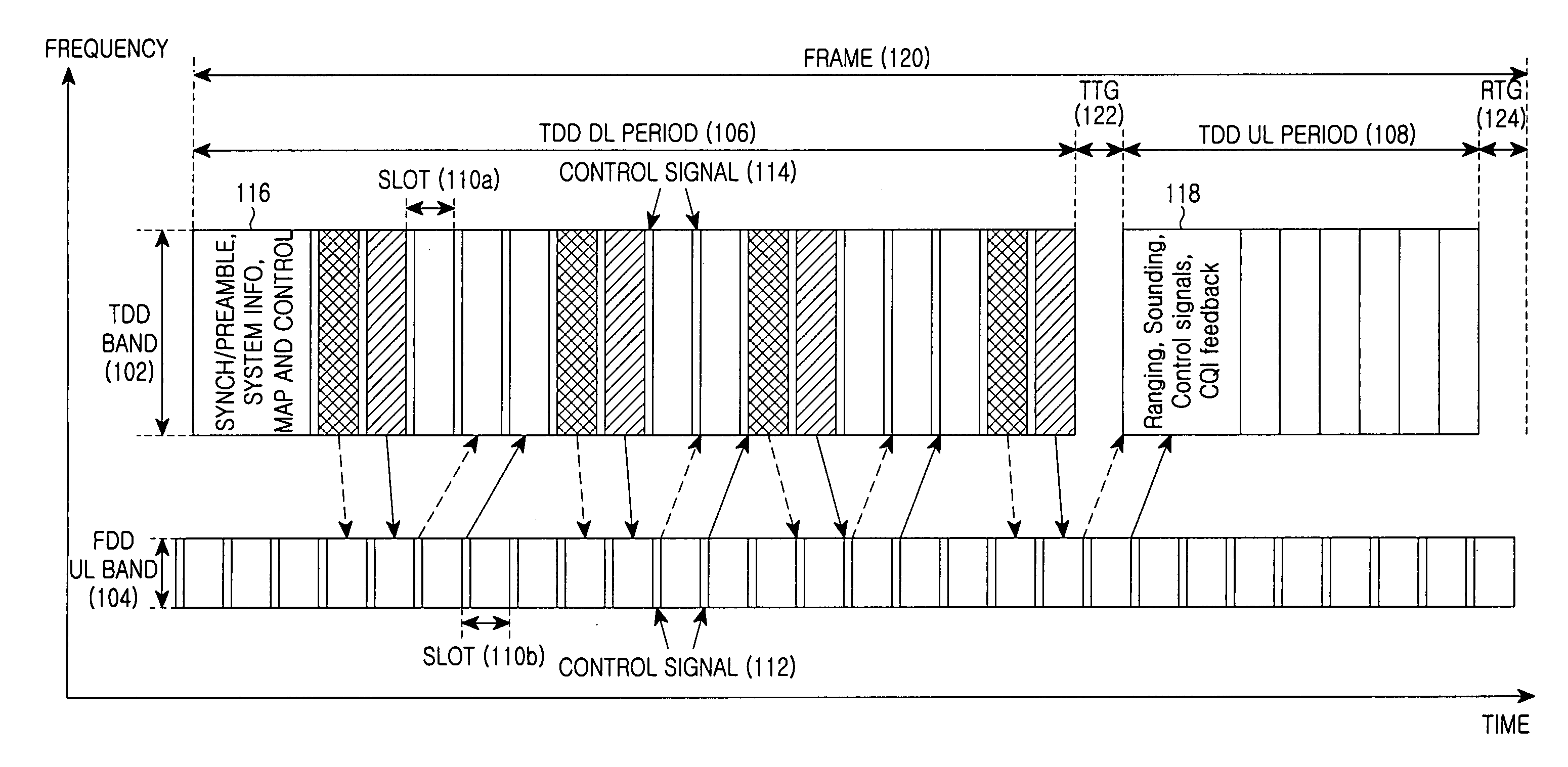
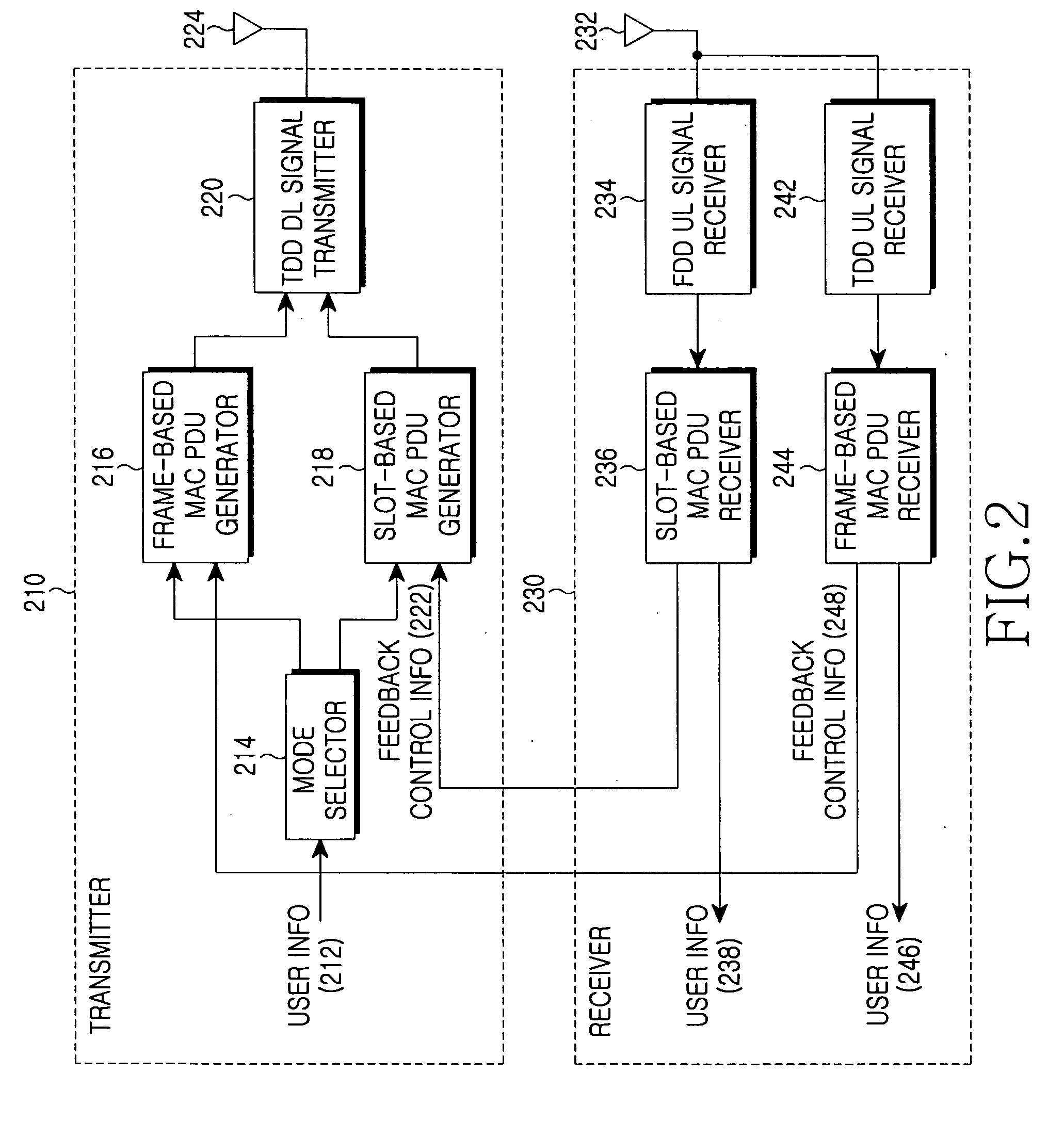
Communication method and system using time division duplex scheme and frequency division duplex scheme
InactiveUS20070097887A1Reduce transmission delayRespond effectivelyMultiplex communicationRadio/inductive link selection arrangementsCommunications systemFrequency division duplex
A communication method in a communication system includes a base station that transmits downlink information to a terminal through a frequency band of a first communication scheme for a downlink period. The terminal transmits uplink information to the base station through the frequency band of the first communication scheme or a frequency band of a second communication scheme that is different from the frequency band of the first communication scheme, for an uplink period.
Owner:SAMSUNG ELECTRONICS CO LTD
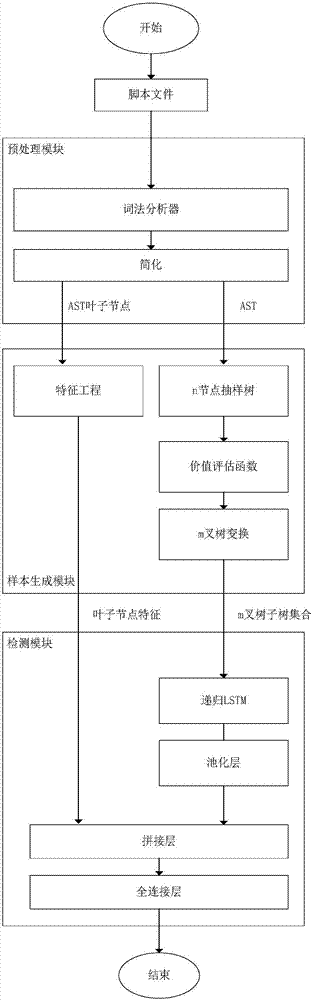
Webshell detection method based on deep neural network, and system thereof
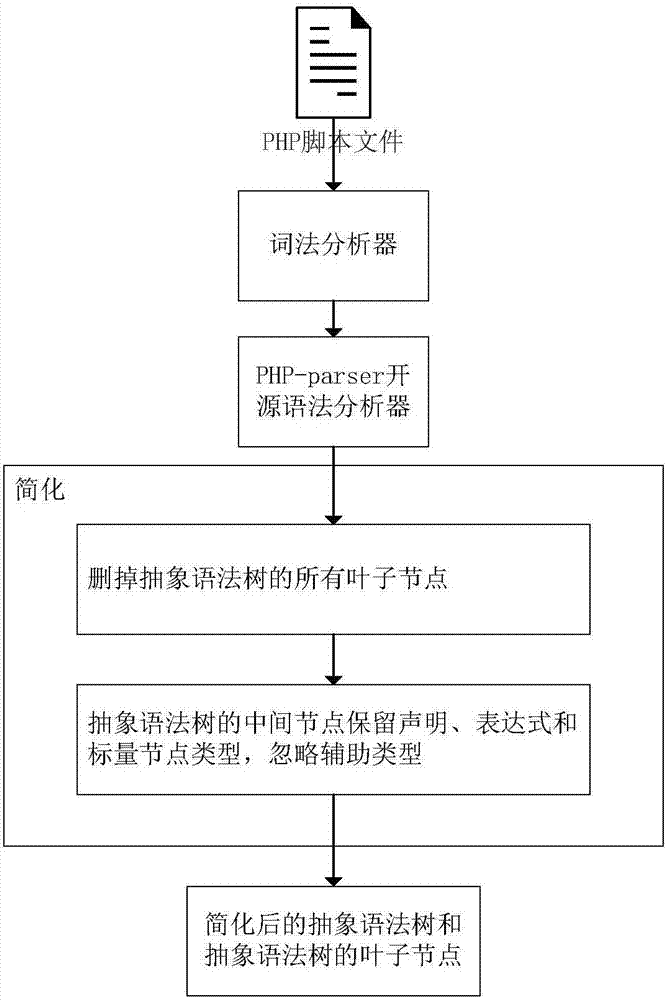
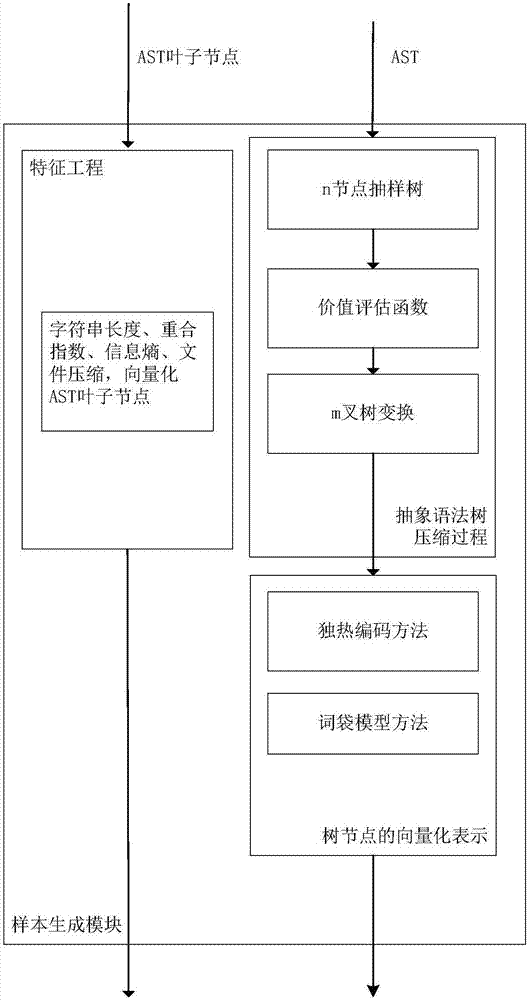
ActiveCN107516041AImprove portabilityRespond effectivelySoftware testing/debuggingPlatform integrity maintainanceScripting languageTheoretical computer science
The invention discloses a Webshell detection method based on a deep neural network, and a system thereof. A recursion loop neural network based on an abstract syntax tree automatically obtains the morphology and grammar information of a script by aiming at a script language, the hierarchical structure characteristics of the abstract syntax tree is used for finishing feature abstraction and WebShell detection, including preprocessing, sample generation and WebShell detection; firstly, the morphology and grammar information of the script is automatically obtained, and then, the recursion loop neural network based on the abstract syntax tree is used for finishing the feature abstraction and the WebShell detection. The method disclosed by the invention has the advantages of being low in deployment cost, good in portability and high in detection accuracy.
Owner:BEIJING ANPRO INFORMATION TECH
Automatic generation of narratives from data using communication goals and narrative analytics
ActiveUS9720899B1Satisfactory communicationEasy to understandNatural language analysisWeb data retrievalOperation modeData structure
The exemplary embodiments described herein are related to techniques for automatically generating narratives about data based on communication goal data structures that are associated with configurable content blocks. The use of such communication goal data structures facilitates modes of operation whereby narratives can be generated in real-time and / or interactive manners.
Owner:NARRATIVE SCI
Automatic generation of narratives from data using communication goals and narrative analytics
ActiveUS9697492B1Satisfactory communicationEasy to understandNatural language analysisWeb data retrievalAutomatic Generation ControlOperation mode
The exemplary embodiments described herein are related to techniques for automatically generating narratives about data based on communication goal data structures that are associated with configurable content blocks. The use of such communication goal data structures facilitates modes of operation whereby narratives can be generated in real-time and / or interactive manners.
Owner:NARRATIVE SCI
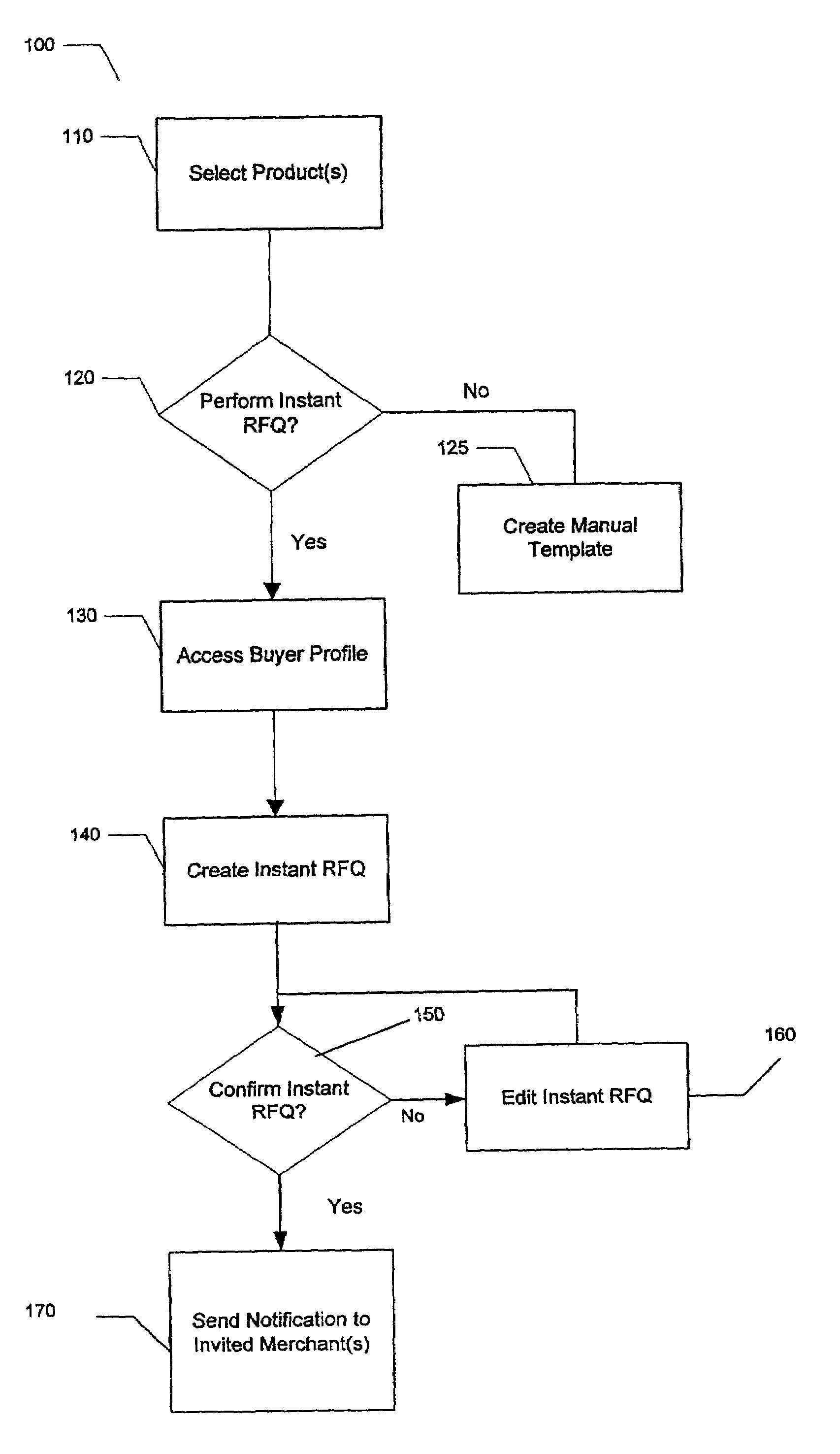
Method and apparatus for efficiently generating electronic requests for quote
InactiveUS7908200B2Effectively respondEfficient deliveryFinanceAnimal feeding devicesRequest for quotationWorld Wide Web
A system and method for efficiently responding to electronic requests for quote (“RFQ”). Through use, a user, such as a merchant, can automatically create and deliver an electronic RFQ response, without need for any interaction by the merchant. The merchant may establish certain criteria in order to allow the system and method to automatically respond to electronic RFQ's received by the merchant.
Owner:VERSATA SOFTWARE INC
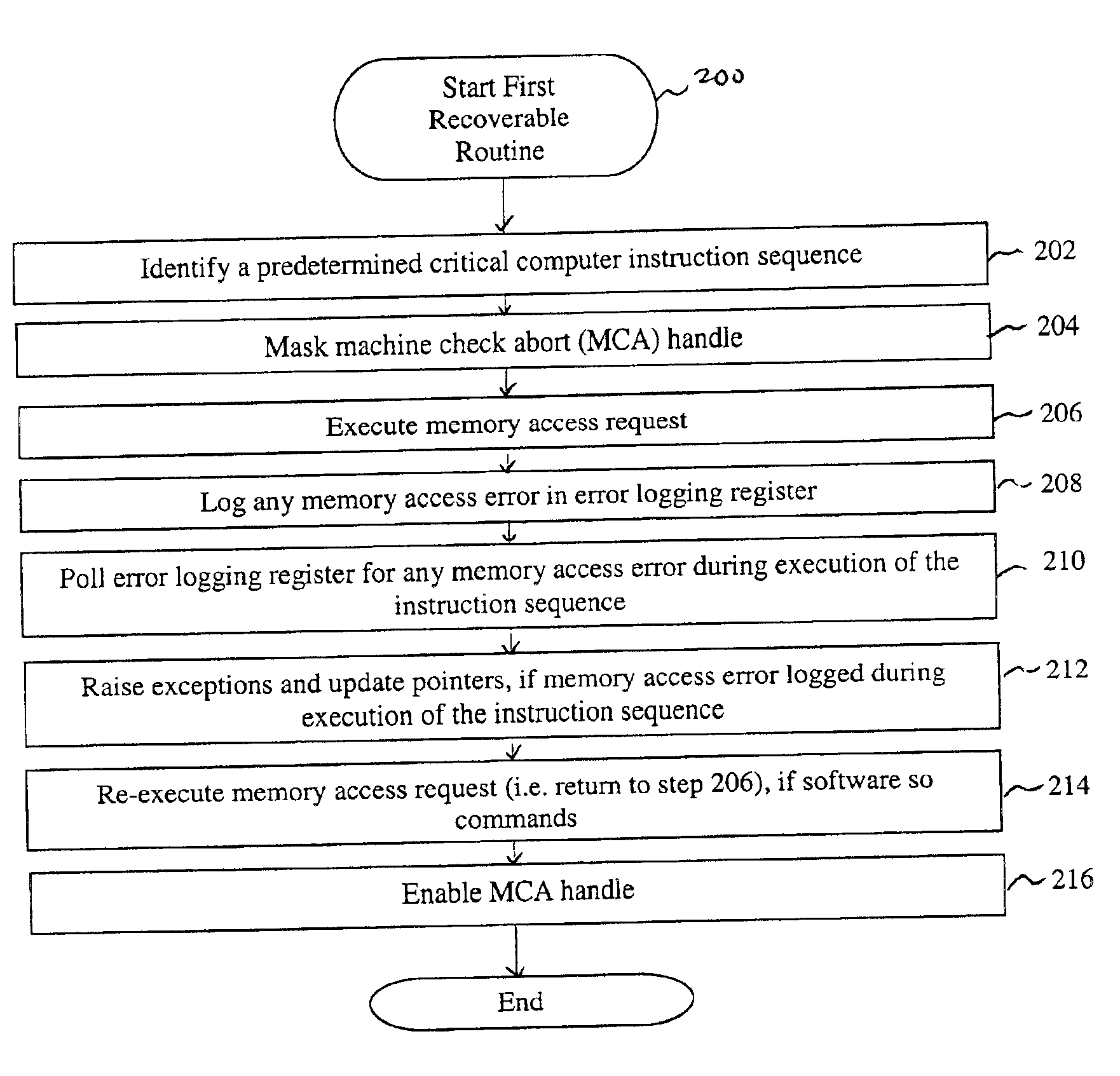
System and method for recovering from memory failures in computer systems
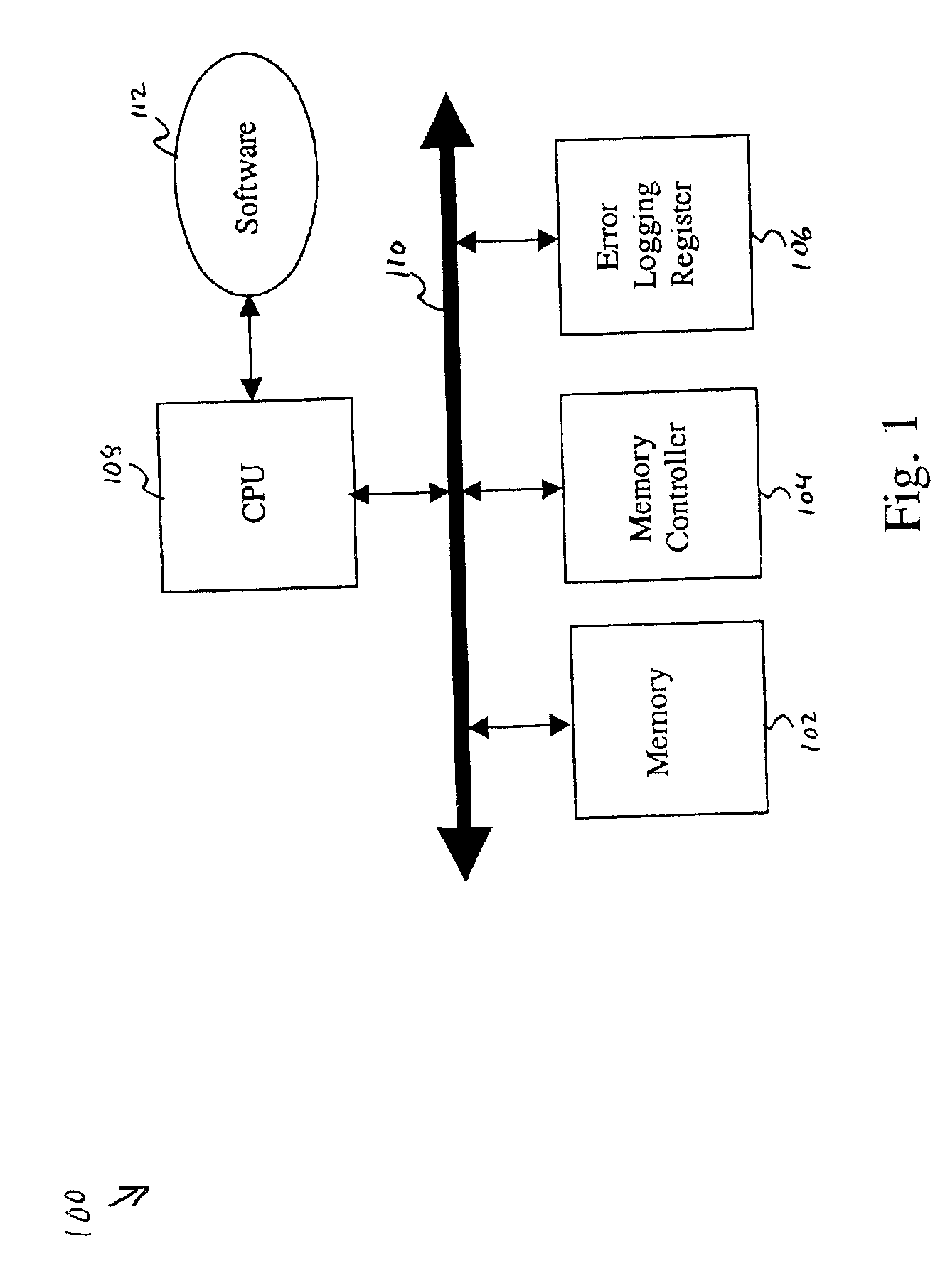
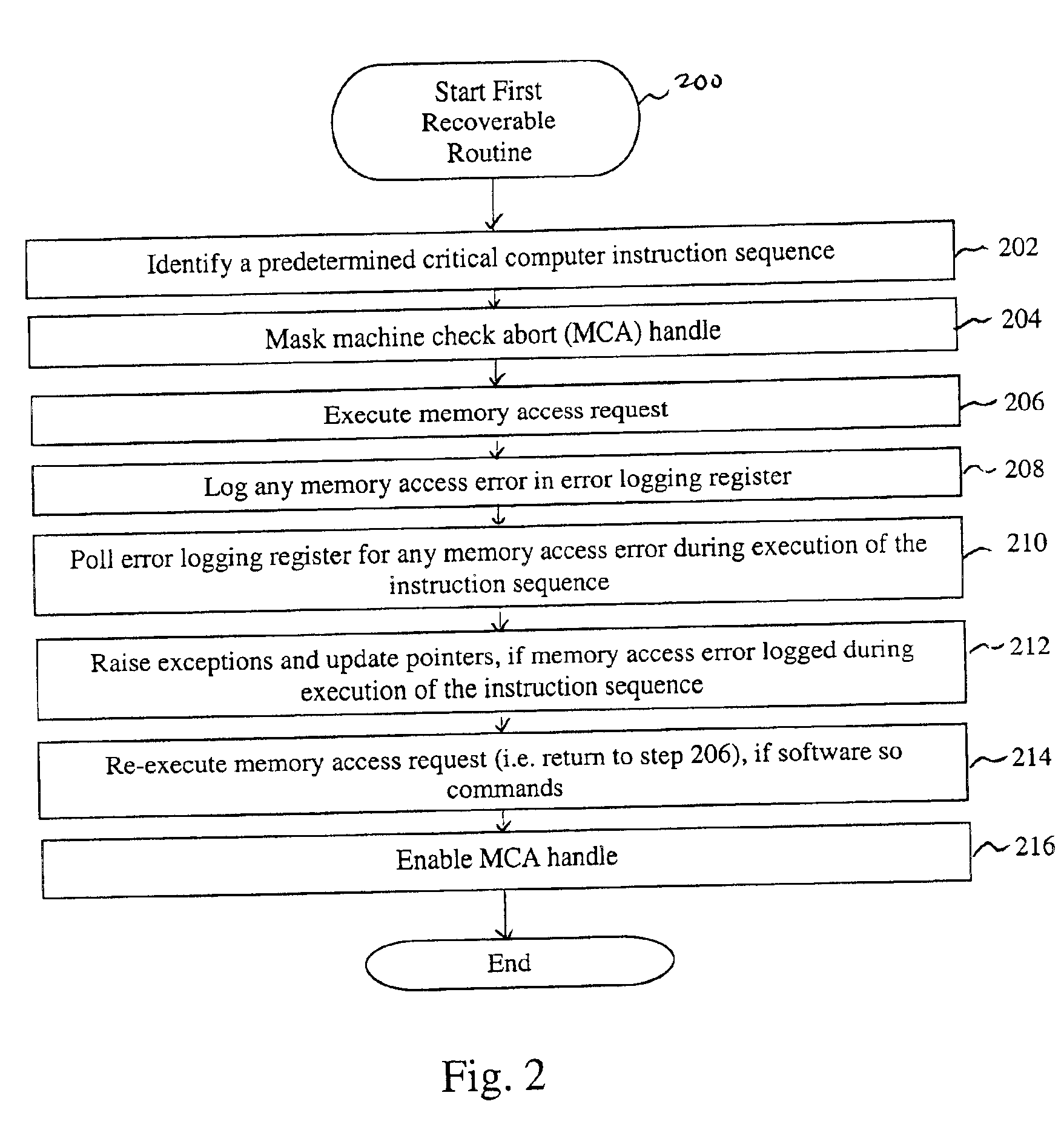
InactiveUS6851074B2Responding to errorRespond effectivelyNon-redundant fault processingRedundant operation error correctionProcessor registerComputerized system
The present invention is a system and method for recovering from memory failures in computer systems. The method of the present invention includes the steps of: identifying a predetermined instruction sequence; monitoring for memory access errors in response to the request; logging a memory access error in an error logging register; polling the register for any logged memory access error during execution of the instruction sequence; and raising exceptions, if the memory access error is logged. Within the system of the present invention, memory access errors are stored in an error logging register, machine check abort handles are masked, and memory controllers are under full control of the software so that memory access errors can be intercepted and responded to without necessitating a system reboot or application restart. The present invention is particularly applicable to O / S code which can not otherwise recover from memory errors except by rebooting.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com