Patents
Literature
436 results about "Reboot" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
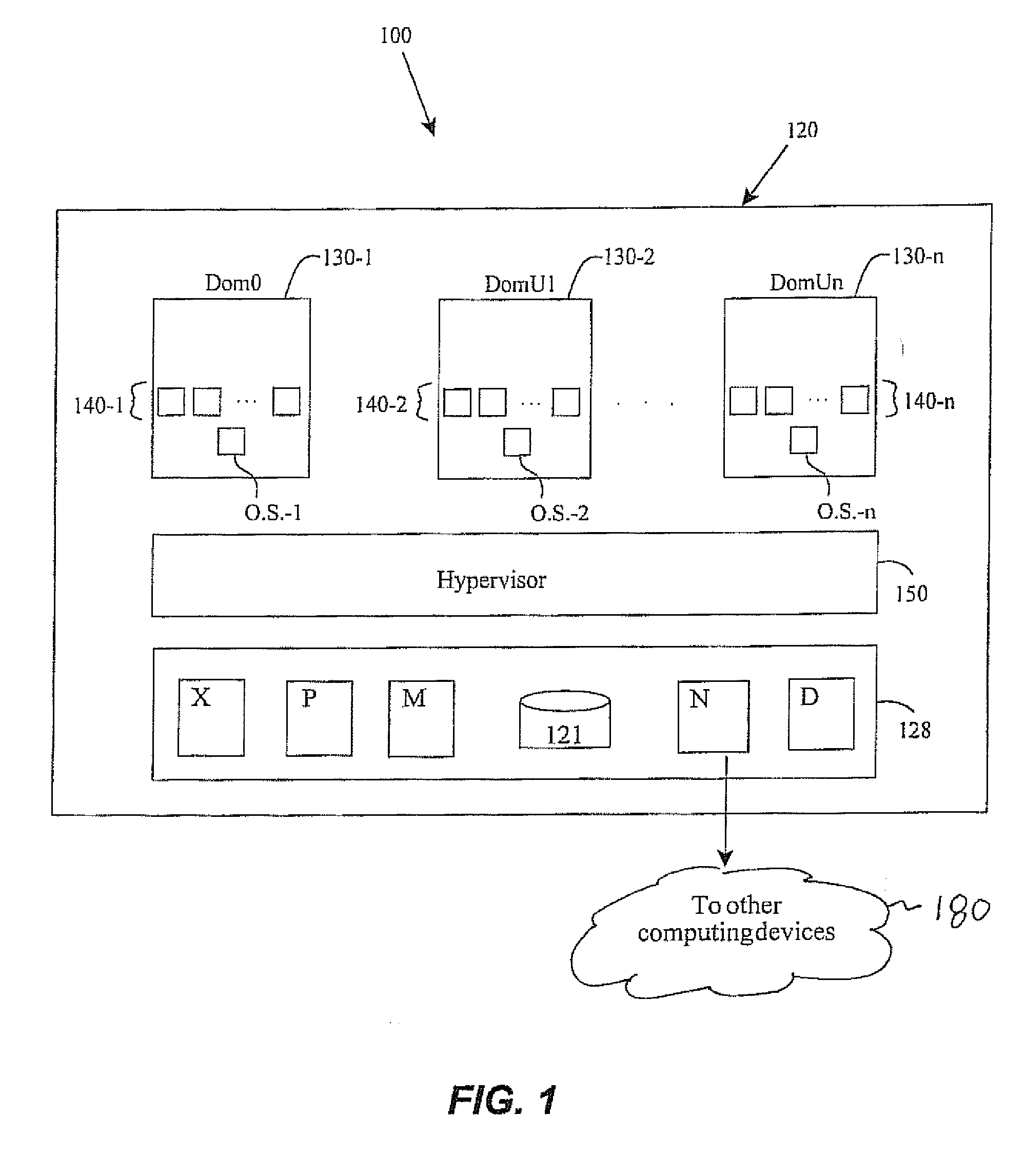
In computing, rebooting is the process by which a running computer system is restarted, either intentionally or unintentionally. Reboots can be either "cold" (alternatively known as "hard") where the power to the system is physically turned off and back on again, causing an initial boot of the machine, or warm (alternatively known as soft) where the system restarts without the need to interrupt the power. The term restart is used to refer to a reboot when the operating system closes all programs and finalizes all pending input and output operations before initiating a soft reboot.
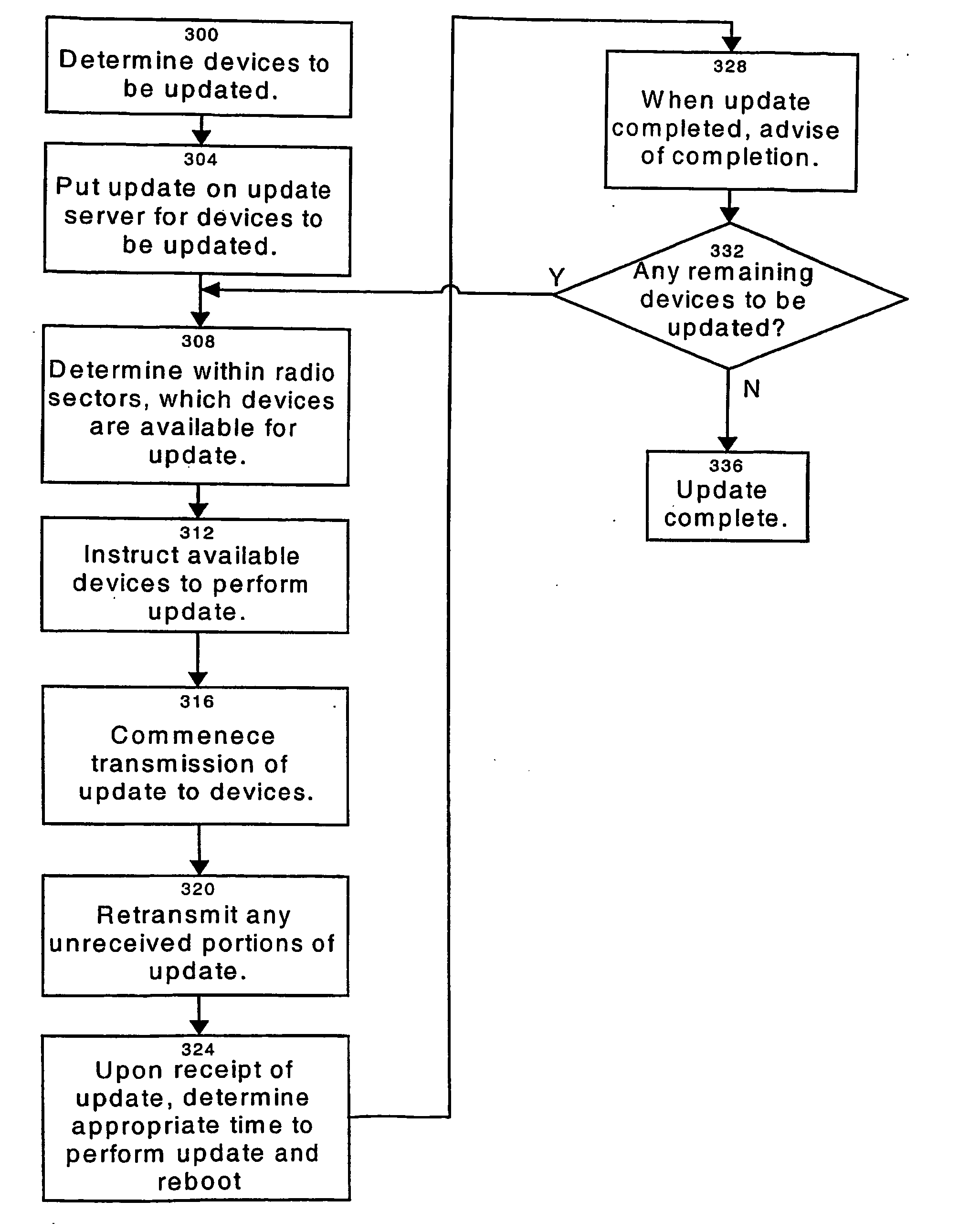
Software update method, apparatus and system
A system for remotely updating software on at least one electronic device connected to a network. The electronic devices have a non-volatile rewritable storage unit divided into at least two partitions, one of which will contain core firmware and the other of which will contain auxiliary software. When an update is received at the device, the updated core firmware is written to overwrite the partition in the rewritable storage unit that contained the auxiliary software. When this is completed and verified, the previous version of the core firmware stored in the storage unit is disabled from execution by the device. Next, the updated auxiliary software is written to overwrite the old version of the core firmware. When this write is complete, the device determines a suitable time for it to be rebooted to execute the updated software. In another embodiment, the present core firmware in the device is copied from the partition it is in to the other partition, overwriting the auxiliary software stored there. The new core firmware received to update the device is overwritten into the first partition, the old copied core firmware being present in case of an upgrade failure, and upon a successful update of the first partition, the auxiliary software is written to the second partition, overwriting the copied old core firmware. In this manner, the position of the core firmware and auxiliary software within the partitions is preserved during normal operation of the device.
Owner:WI LAN INC
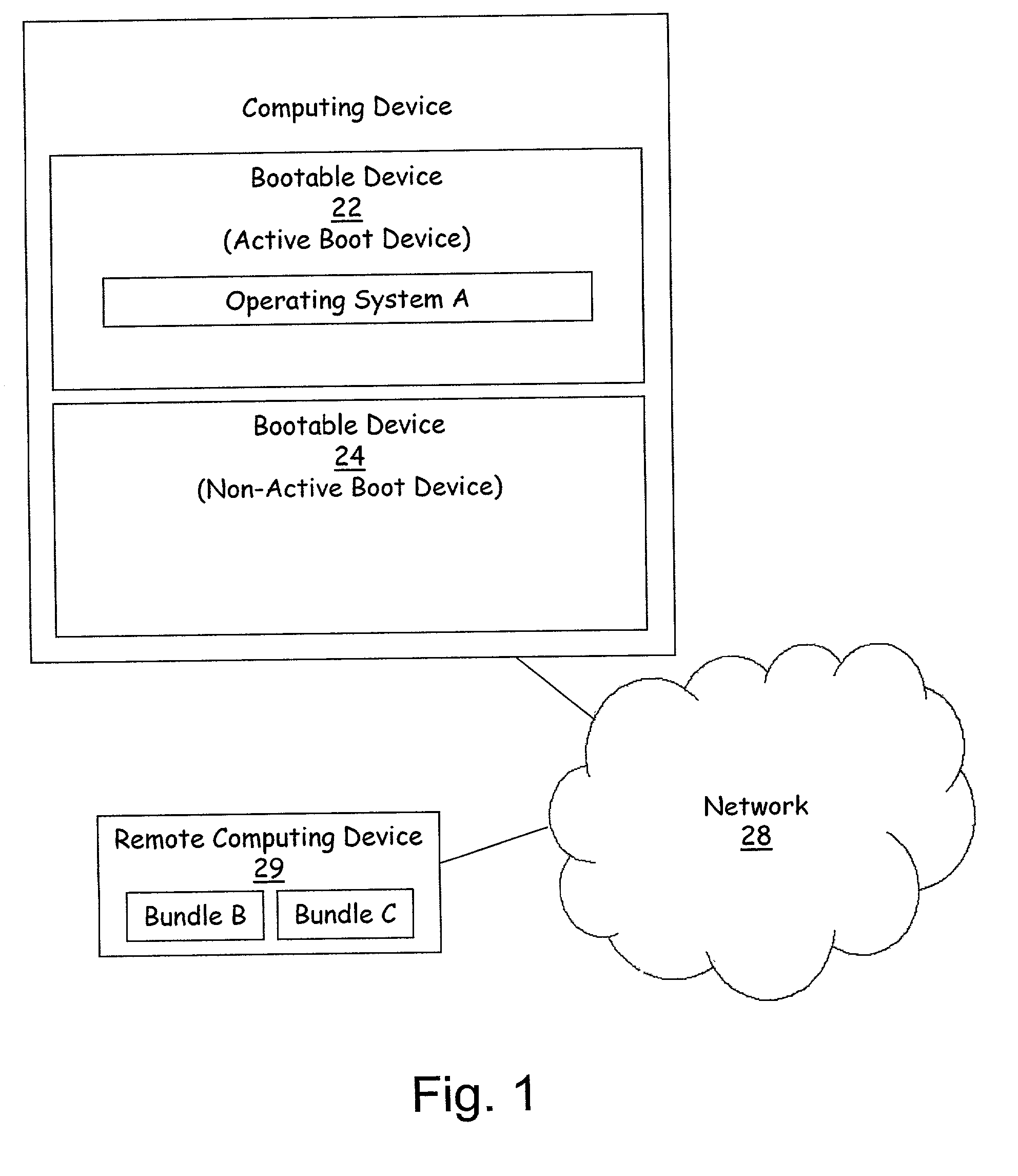
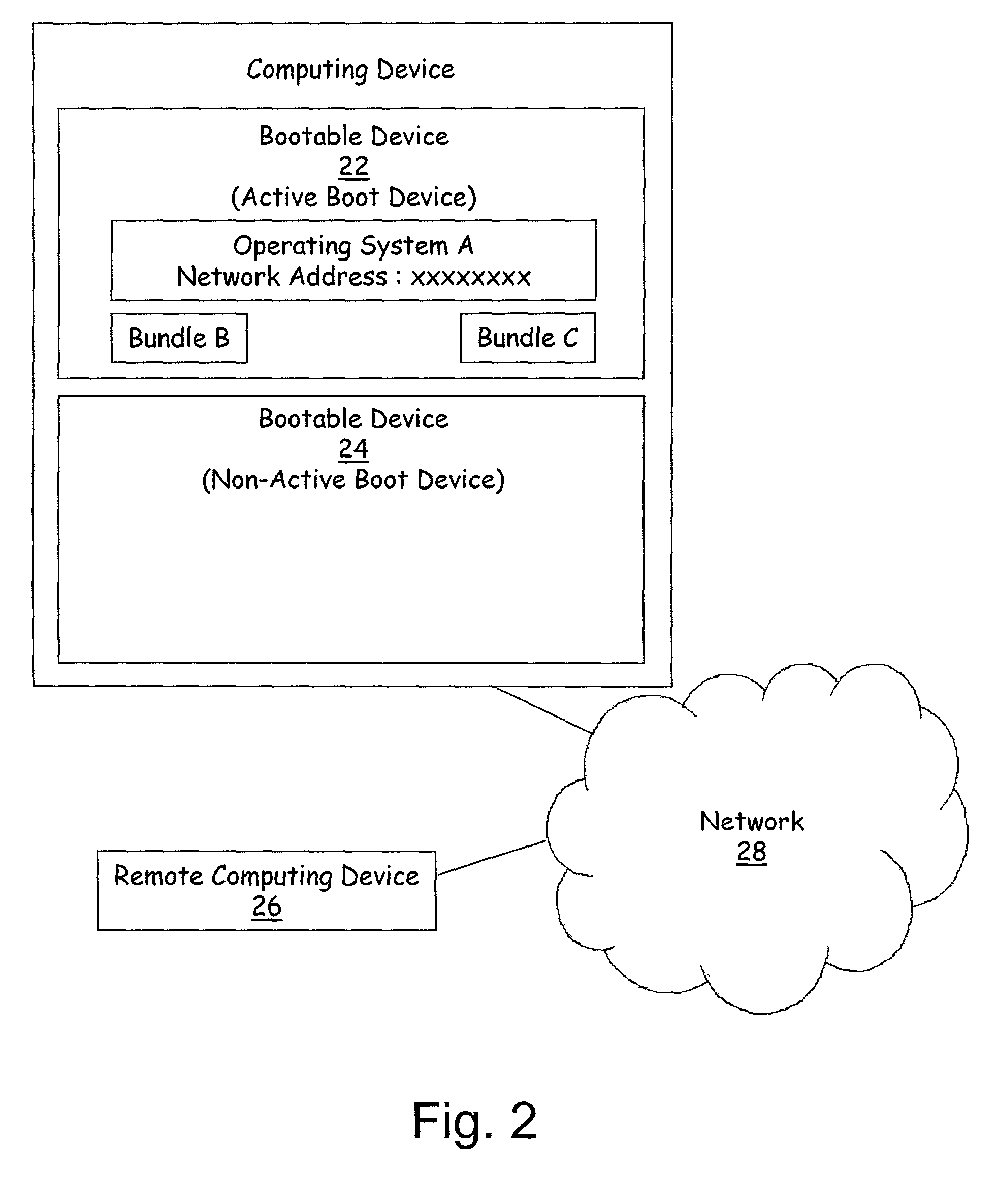
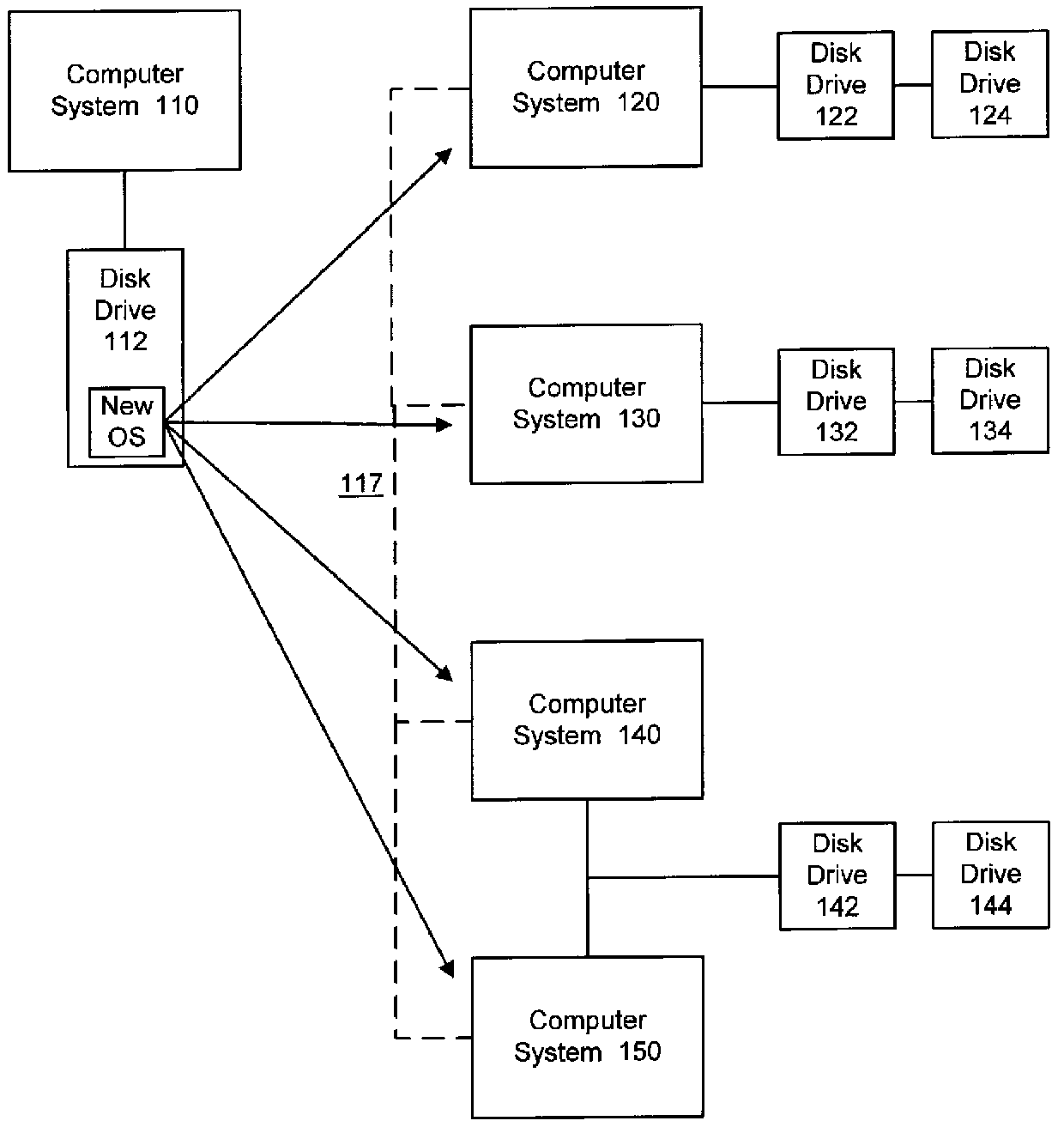
Method and apparatus for remote installation of an operating system over a network connection
InactiveUS6963981B1More securityMemory loss protectionError detection/correctionOperational systemNetwork connection
A method for remote installation of a target operating system is carried out on a machine operating a source operating system. In one embodiment, it is presumed that the source operating system was booted from a first bootable region of a storage associated with the machine. According to the method, a copy of the source operating system together with the target operating system are delivered to the machine and stored in a second bootable region of the storage. The copy of the source operating system may be stored in a first partition of the second bootable region of the storage, and the target operating system may be stored in a second partition of the second bootable region. A boot loader is then configured to boot the copy of the source operating system from the second bootable region of the storage. The machine is then re-booted. At this point, the machine is still running the source operating system, although in this case that operating system was booted from the second bootable region of the storage. The original source operating system (from the first bootable region) is then removed, and the boot loader is re-configured to boot the target operating system from the second bootable region of the storage. The machine is then re-booted again, after which the target operating system is operational. In one embodiment, the first and second bootable regions may be separate hard disks, and the source and target operating systems are Linux and Windows, or vice versa.
Owner:AKAMAI TECH INC
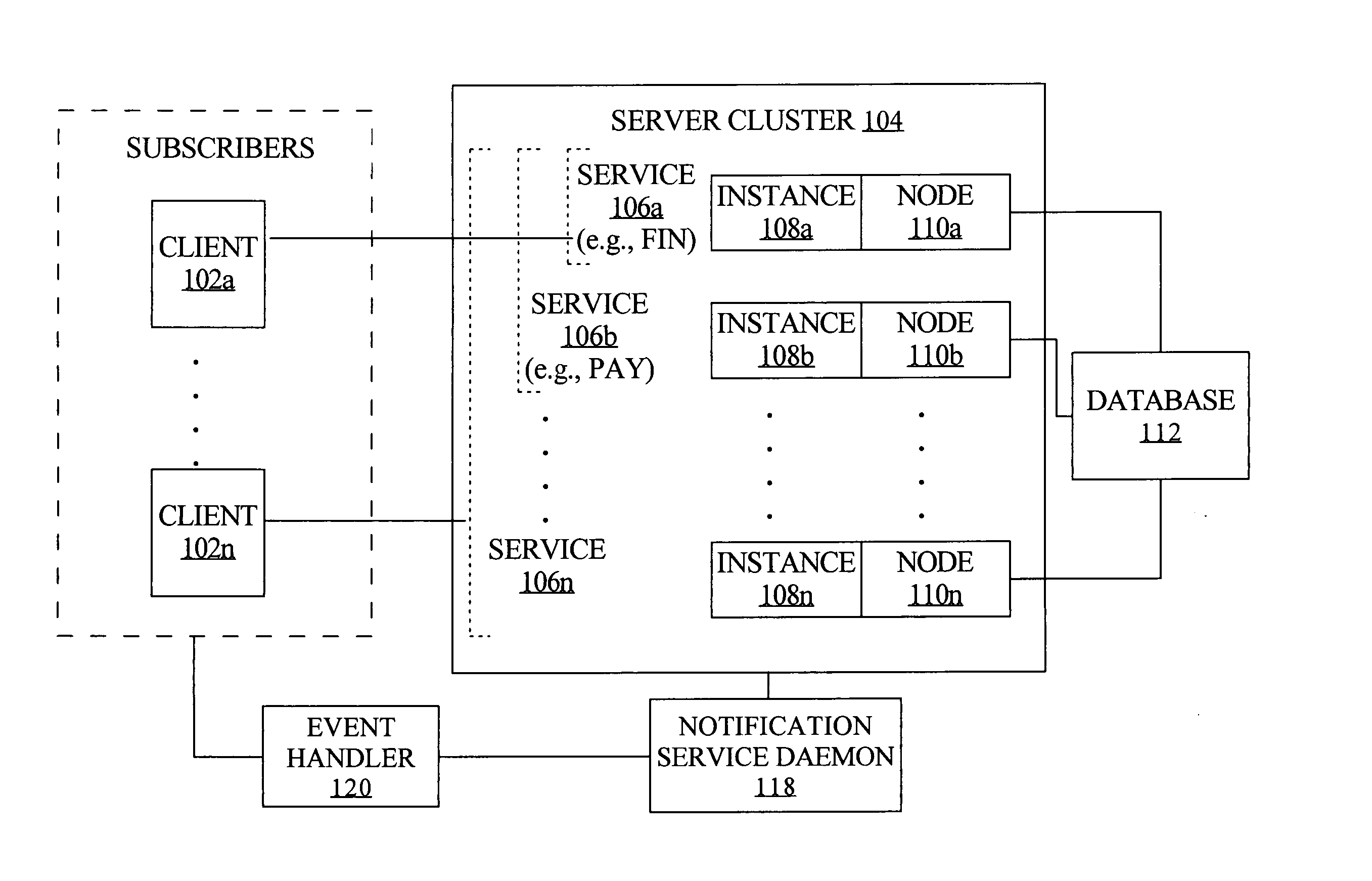
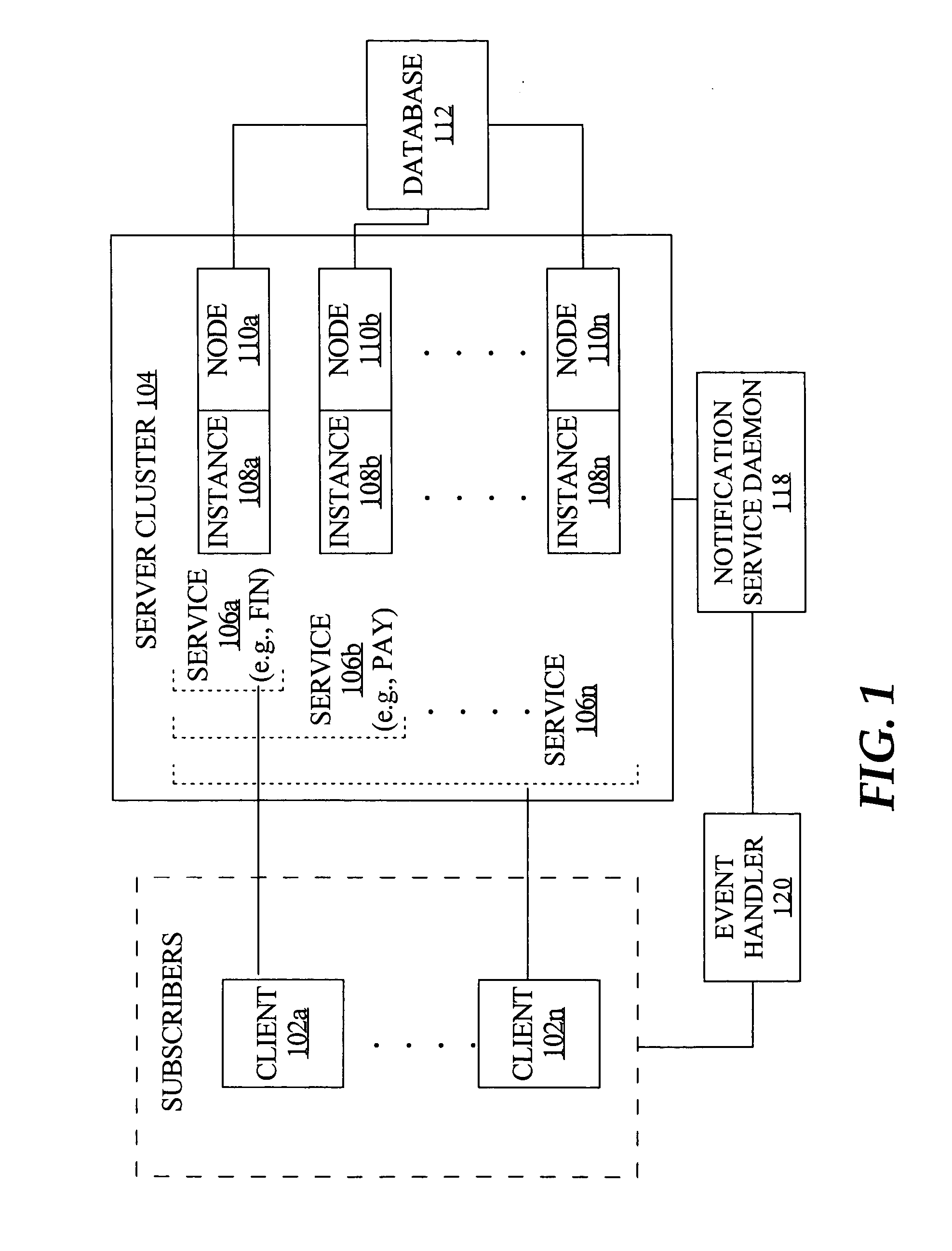
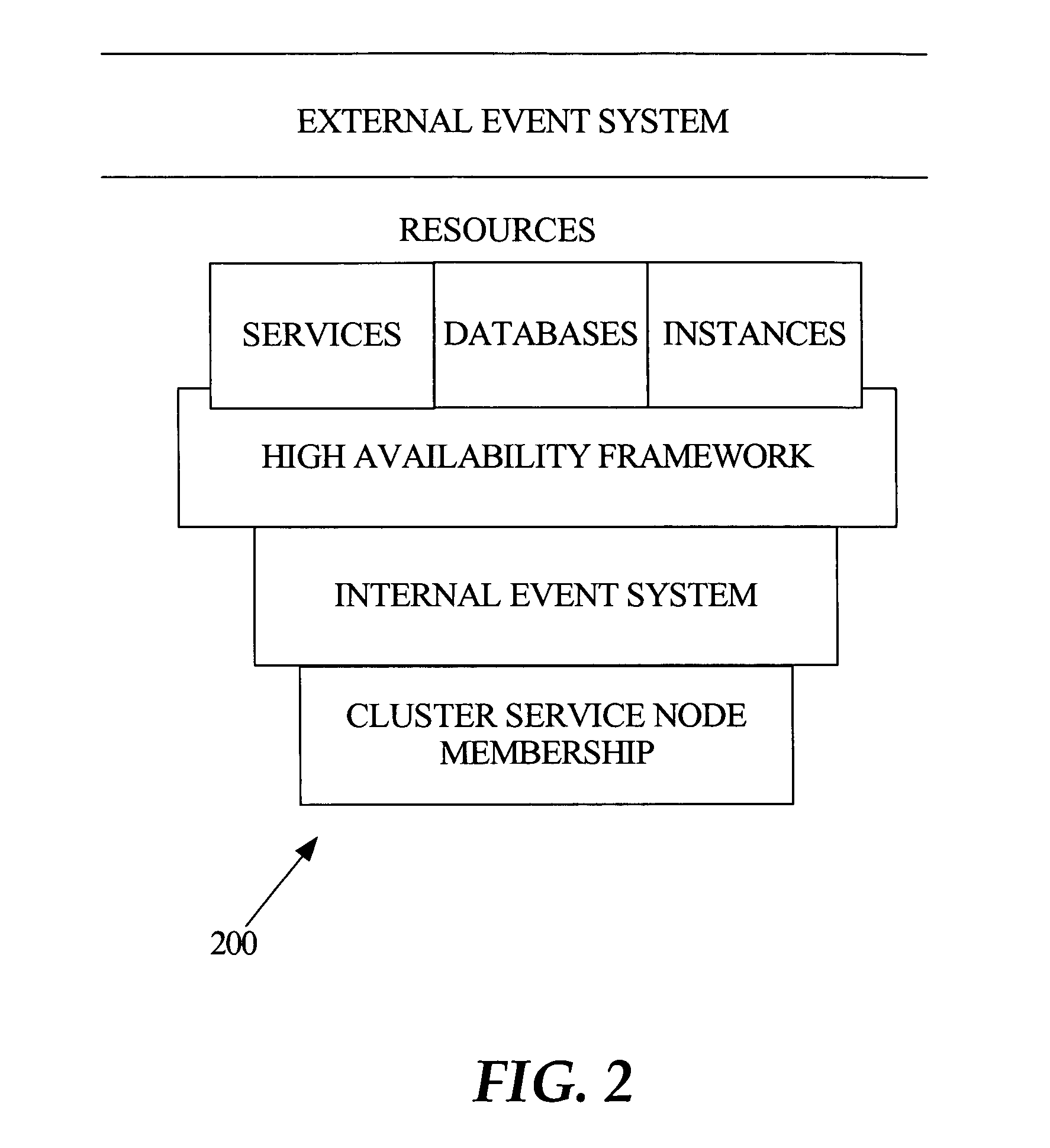
Fast application notification in a clustered computing system
ActiveUS20050038772A1Resource allocationDigital data processing detailsComputer networkService experience
With fast notification of changes to a clustered computing system, through which a number of events are published for system state changes, applications can quickly recover and sessions can quickly be rebalanced. When a resource associated with a service experiences a change in status, such as a termination or a start / restart, a notification event is immediately published. Notification events contain information to enable subscribers to identify, based on matching a session signature, the particular sessions that are affected by the change in status, and to respond accordingly. This allows sessions to be quickly aborted and ongoing processing to be quickly terminated when a resource fails, and allows fast rebalancing of work when a resource is restarted.
Owner:ORACLE INT CORP
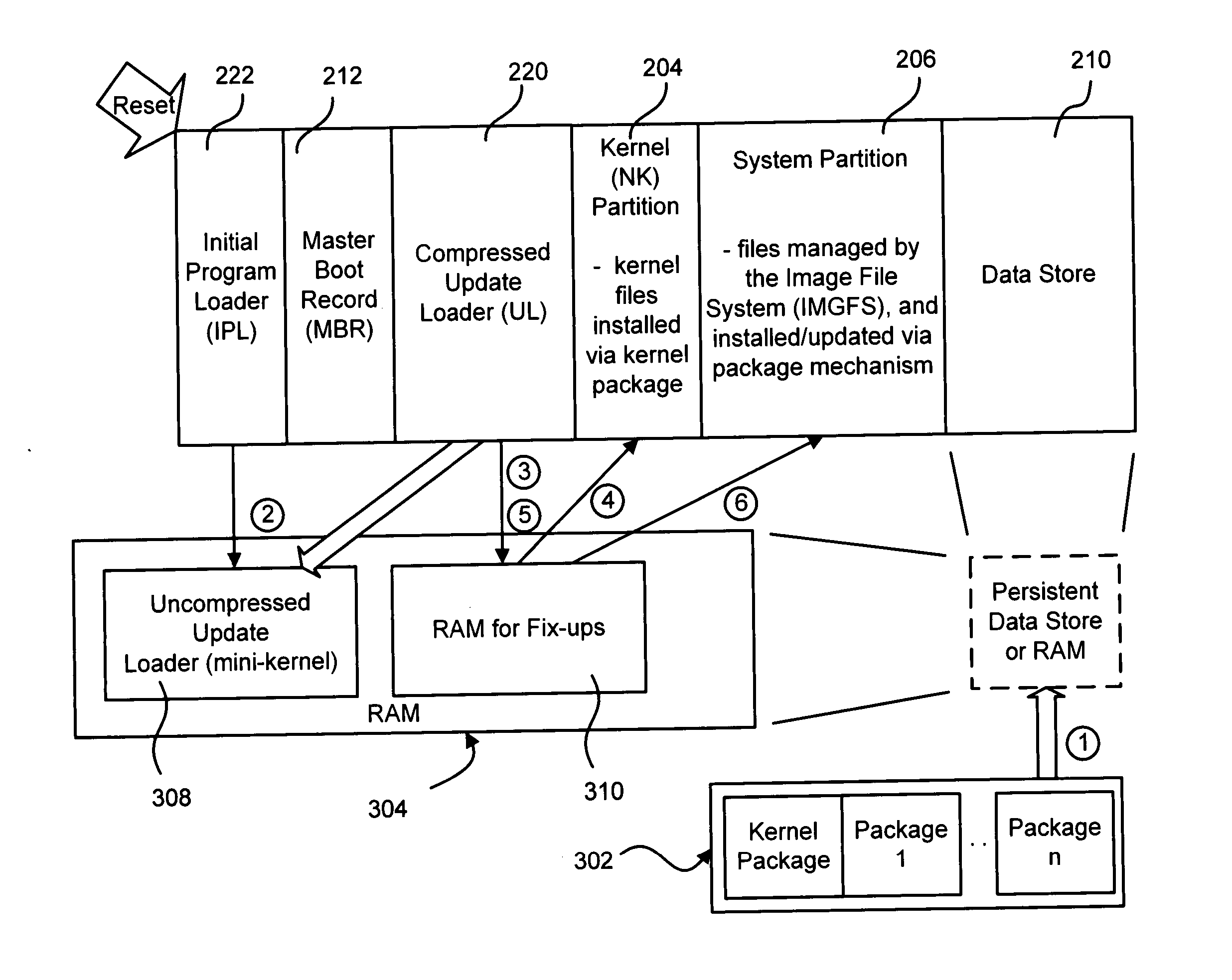
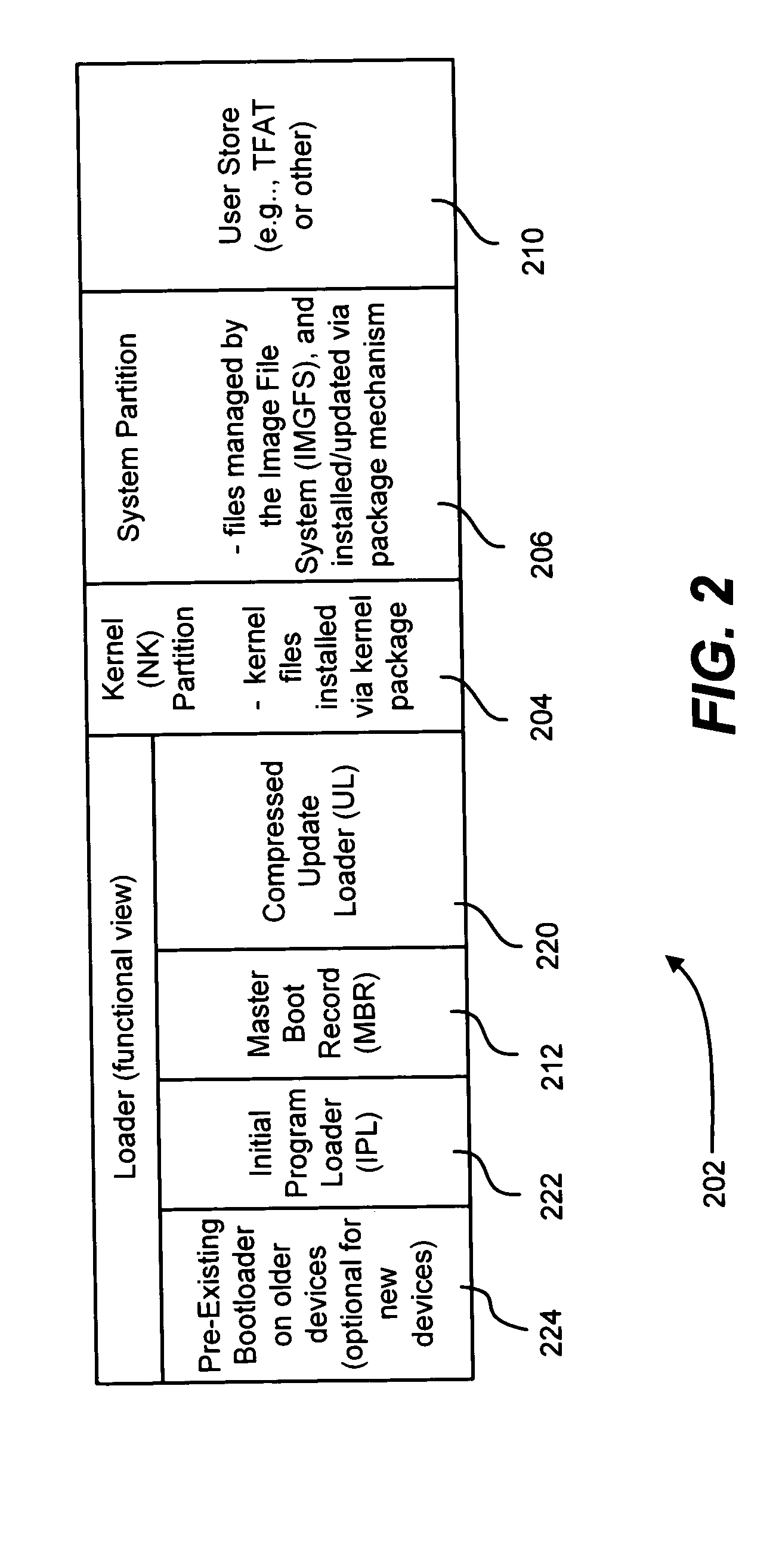
Applying custom software image updates to non-volatile storage in a failsafe manner
Described is a system and method in which software updates in the form of self-contained, secure entities are applied to an embedded device's non-volatile storage in a failsafe manner. Various types of software updates may be applied, and updates may contain executable code and / or data. Following a reboot, an initial program loader determines an update mode, and if updating, boots to a special update loader. The update loader processes update packages to apply the updates. Kernel partition, system partition and reserve section updates may be updated with entire files or binary difference files, with failure handling mechanisms are provided for each type of update. Updates may be simulated before committing them. Updates may be relocated in memory as appropriate for a device.
Owner:MICROSOFT TECH LICENSING LLC
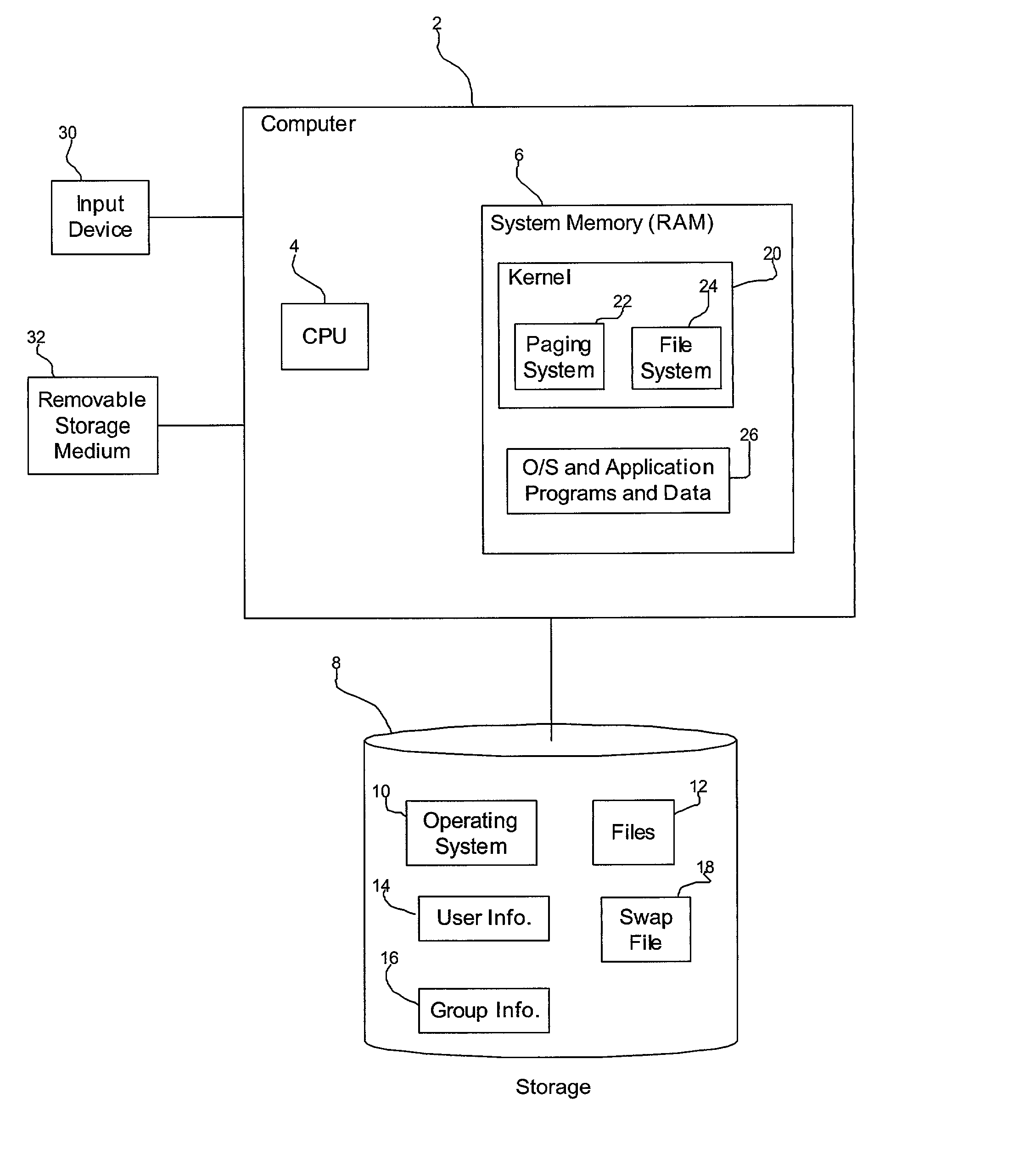
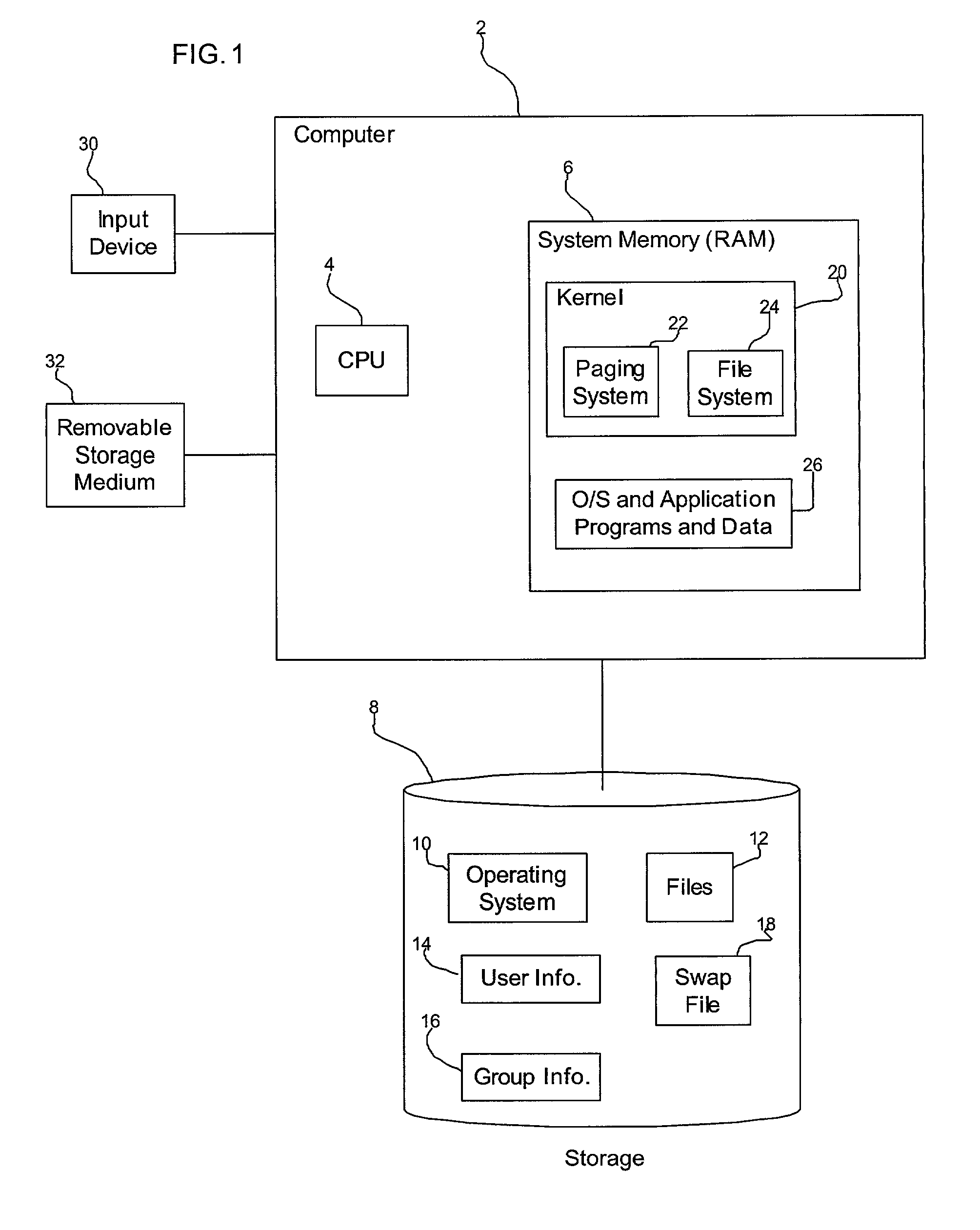
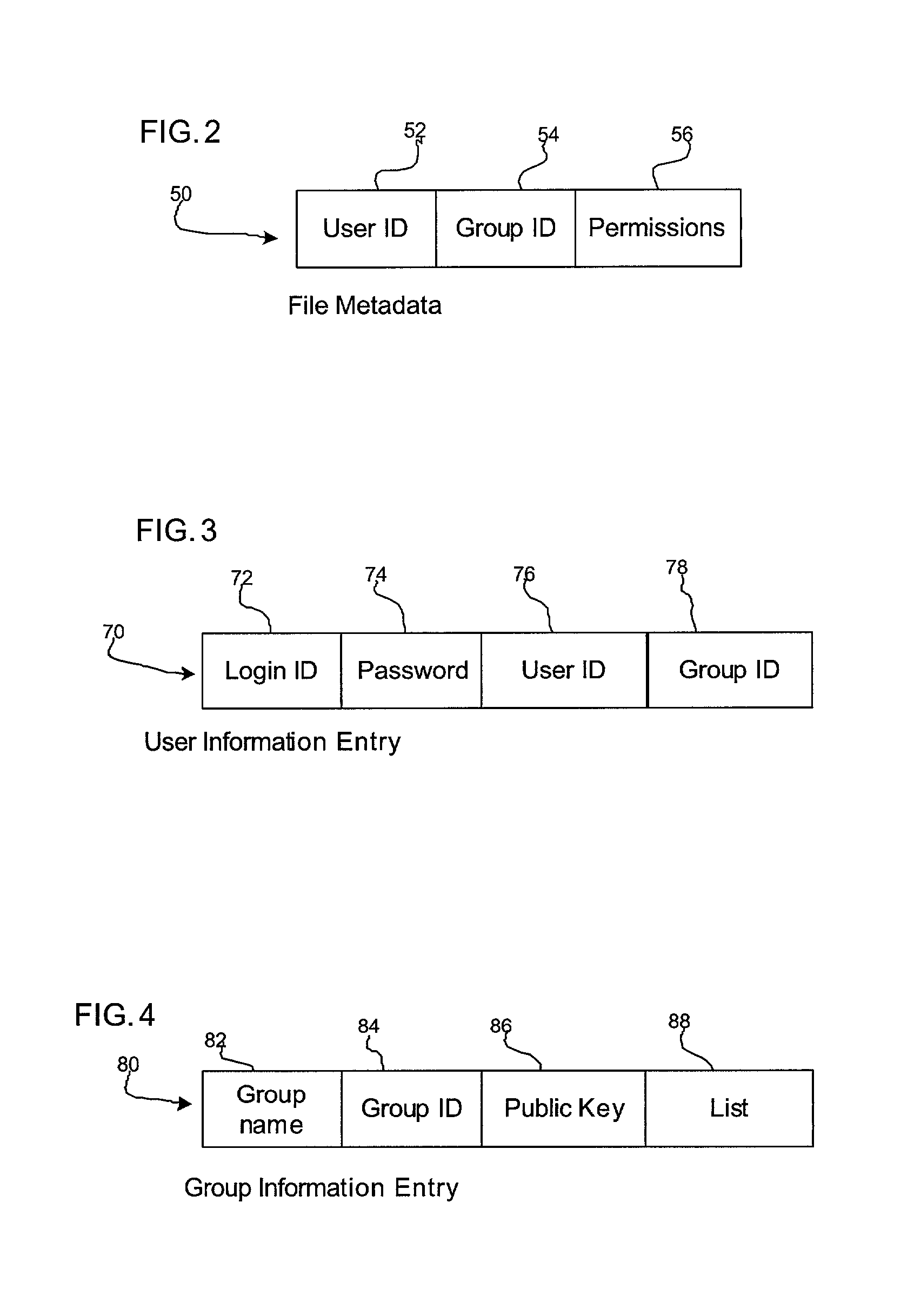
Method, system, and program for encrypting files in a computer system
ActiveUS20020166053A1Prevent accessDigital data processing detailsUser identity/authority verificationEncryptionVolatile memory
Provided is a method, system, and program for encrypting files in a computer in communication with a volatile memory and non-volatile storage device. An encryption code is generated to encrypt a file and a decryption code is generated to decrypt one file encrypted with the encryption code. The decryption code is loaded into the volatile memory, wherein the decryption code is erased from the volatile memory when the computer reboots. Files written to the non-volatile storage device are encrypted using the encryption code and the decryption code in the non-volatile memory is used to decrypt files encrypted with the encryption code to transfer from the non-volatile storage device to the volatile memory.
Owner:ORACLE INT CORP
Performing operating system recovery from external back-up media in a headless computer entity
InactiveUS6845464B2Redundant operation error correctionMemory systemsHard disc driveOperational system
A computer entity, particularly but not exclusively a headless computer entity, has operating systems stored on a non-volatile data storage device e.g. a hard disk drive, and has a back-up data storage device. Operating system backup's are taken from an uncorrupted copy of an operating system stored in a separate partition on the data storage device to the primary operating system which is actually used to run the device, thereby ensuring that if the primary operating system of the computer entity becomes corrupted either gradually or catastrophically, the back-up copy which is stored on a back-up media is not effected. Under failure conditions of the computer entity, a pristine copy of the operating system can be reloaded from the back-up tape data storage media and the computer entity rebooted from the pristine operating system back-up copy.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
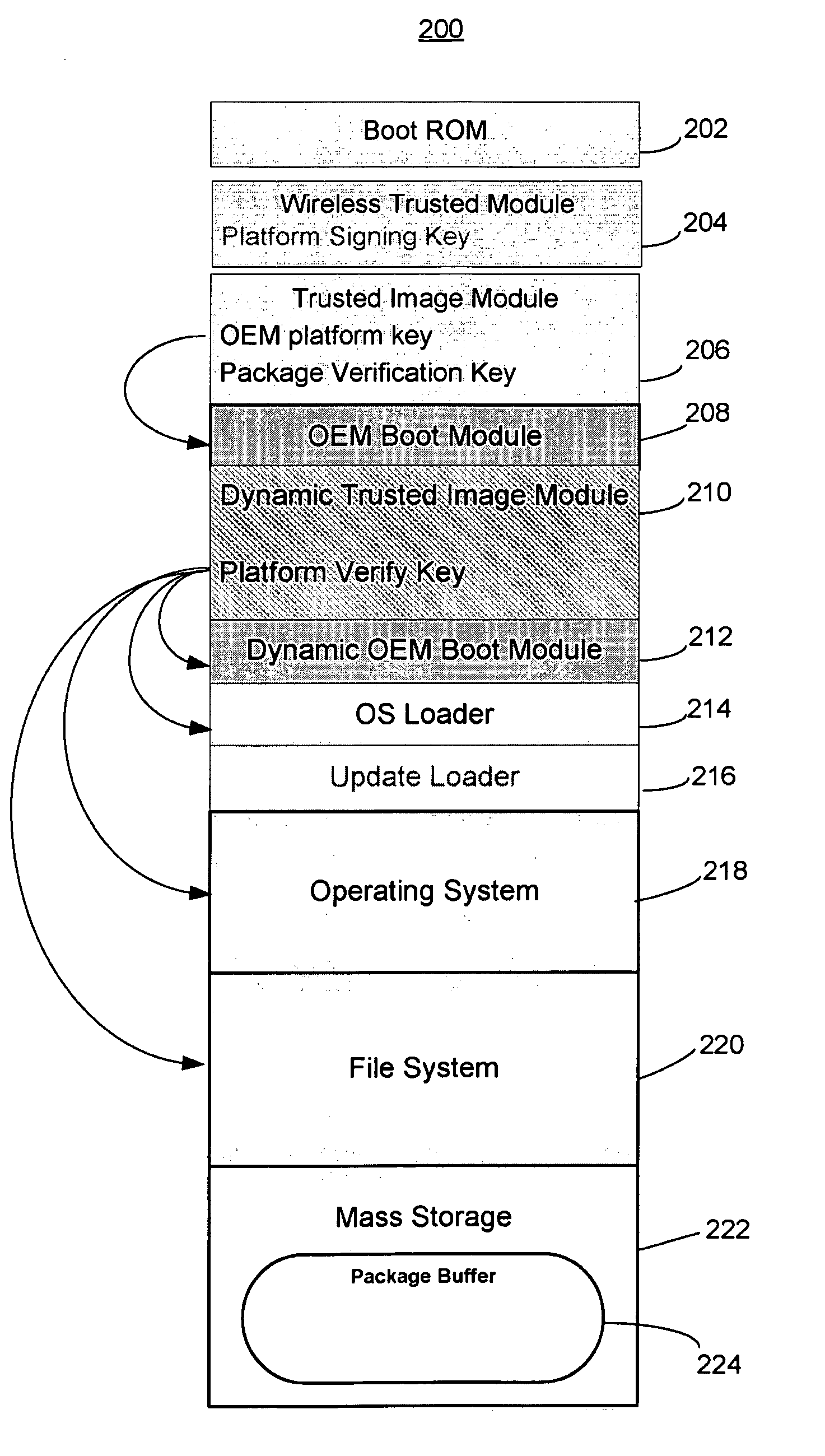
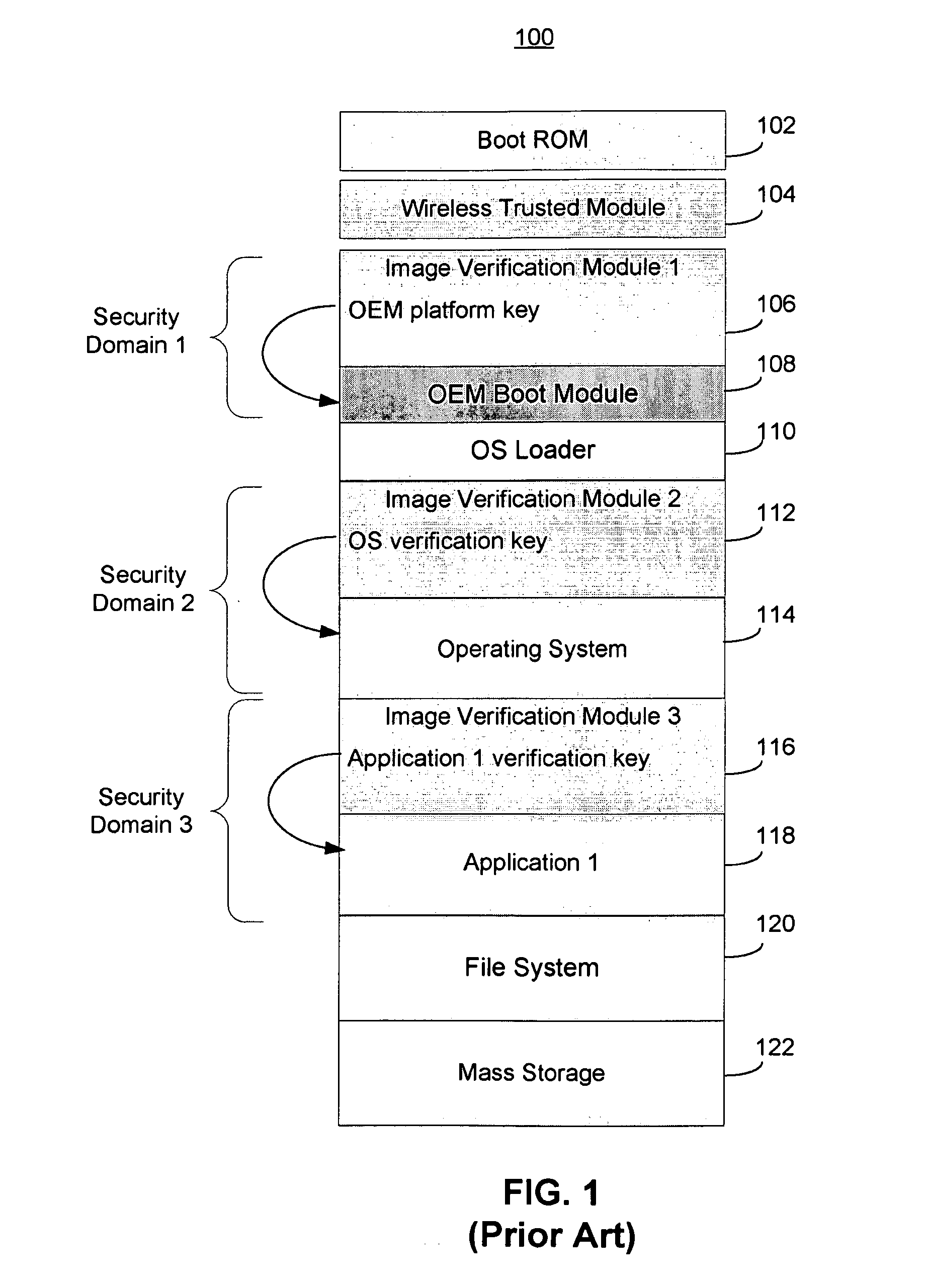
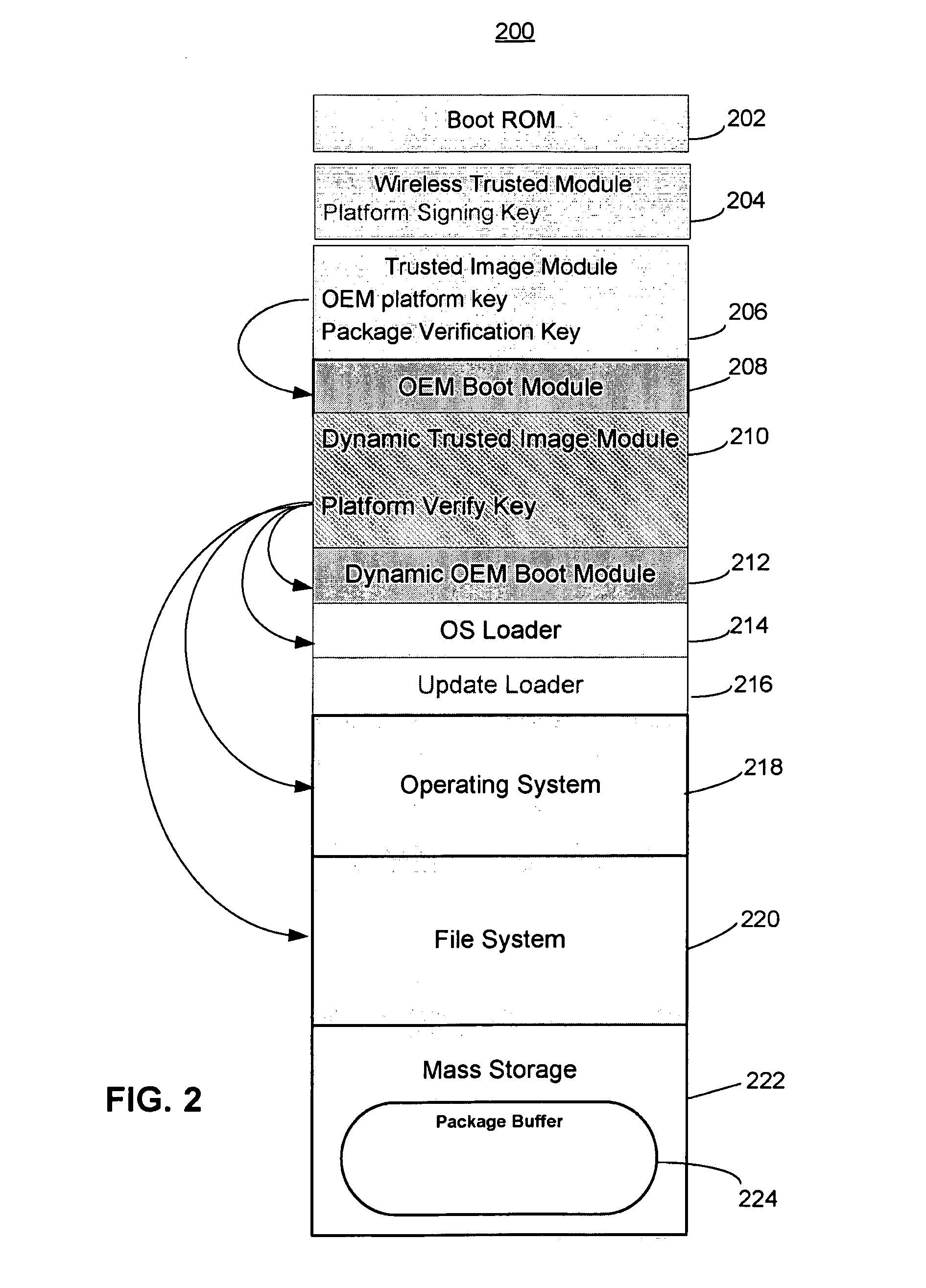
Trusted modular firmware update using digital certificate
An over-the-air firmware update is accomplished in a secure manner using a two-step process. The first step uses an initial boot using a fixed boot program and an authenticated and verified secondary environment to complete starting of only authenticated code. After verifying a pending update, the second step is started with the electronic device being booted into an update mode with an update loader that has exclusive access to a signing key. A dummy update image is loaded into a temporary memory location and a hash is taken. A digital certificate is created corresponding to the update image and signed using the signing key. The update and digital certificate are atomically installed and the signing key is deactivated. Upon reboot, the new image is used for operation and is verified by the hash data and public key in the digital certificate.
Owner:MARVELL ASIA PTE LTD
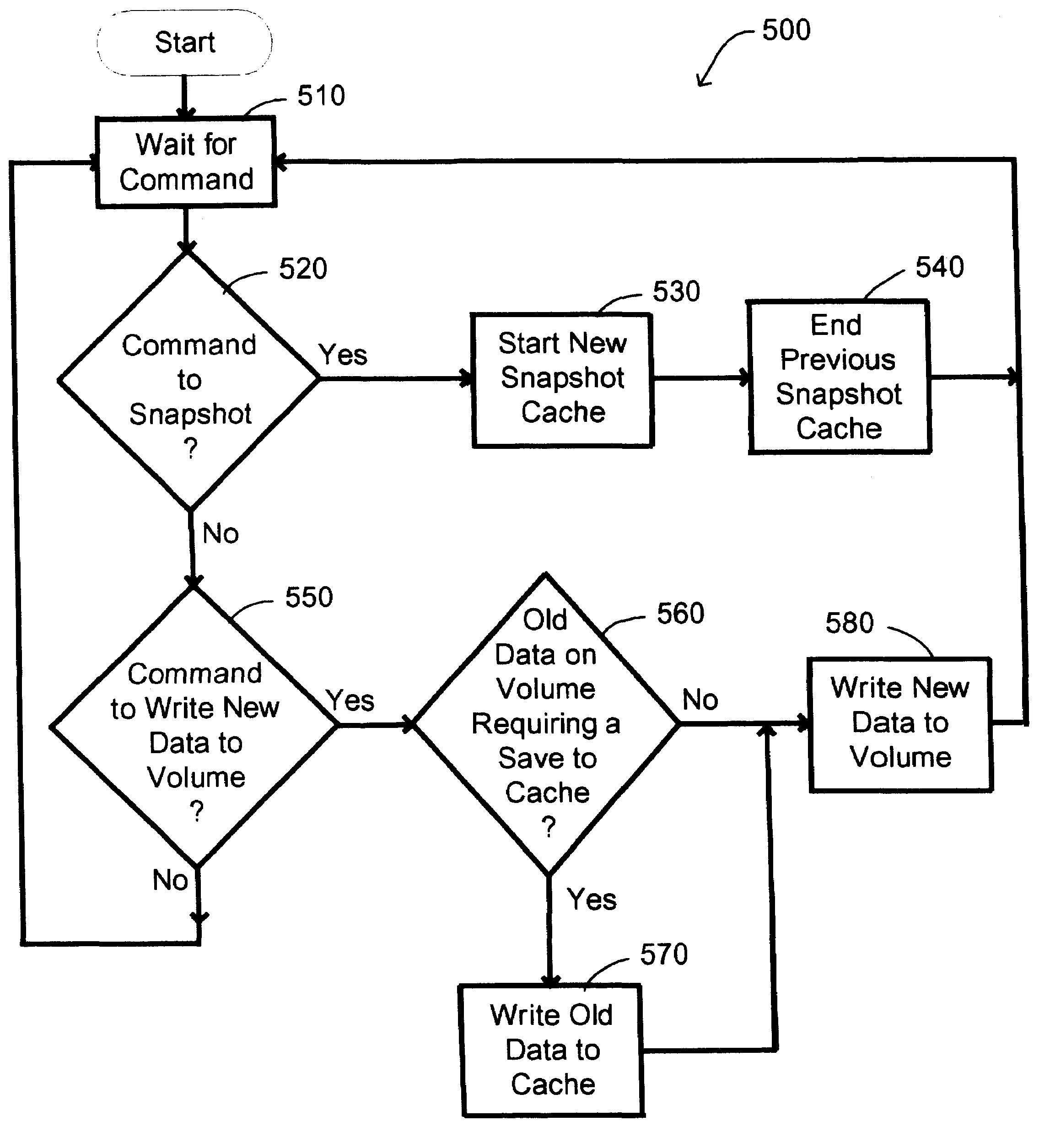
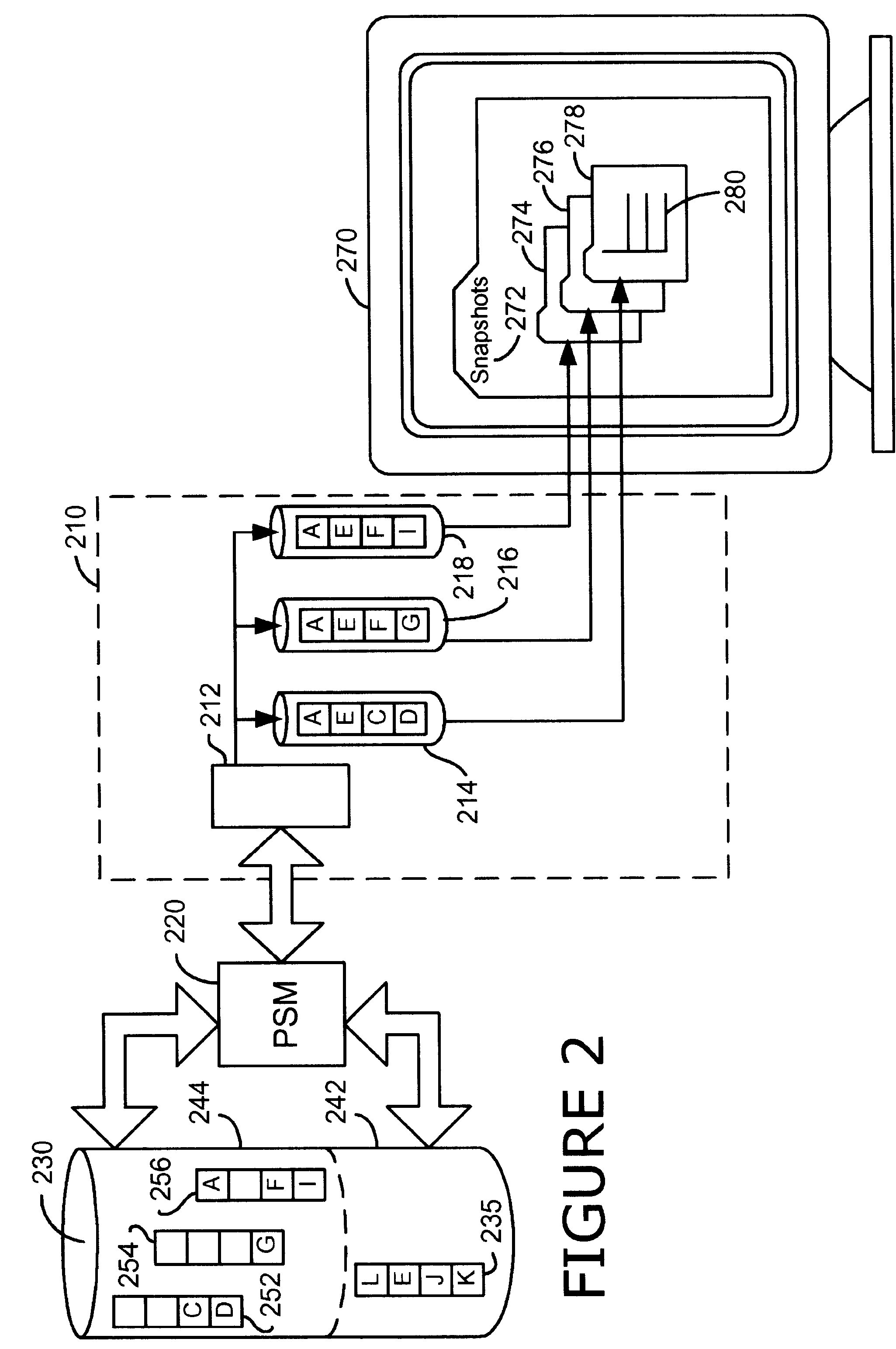
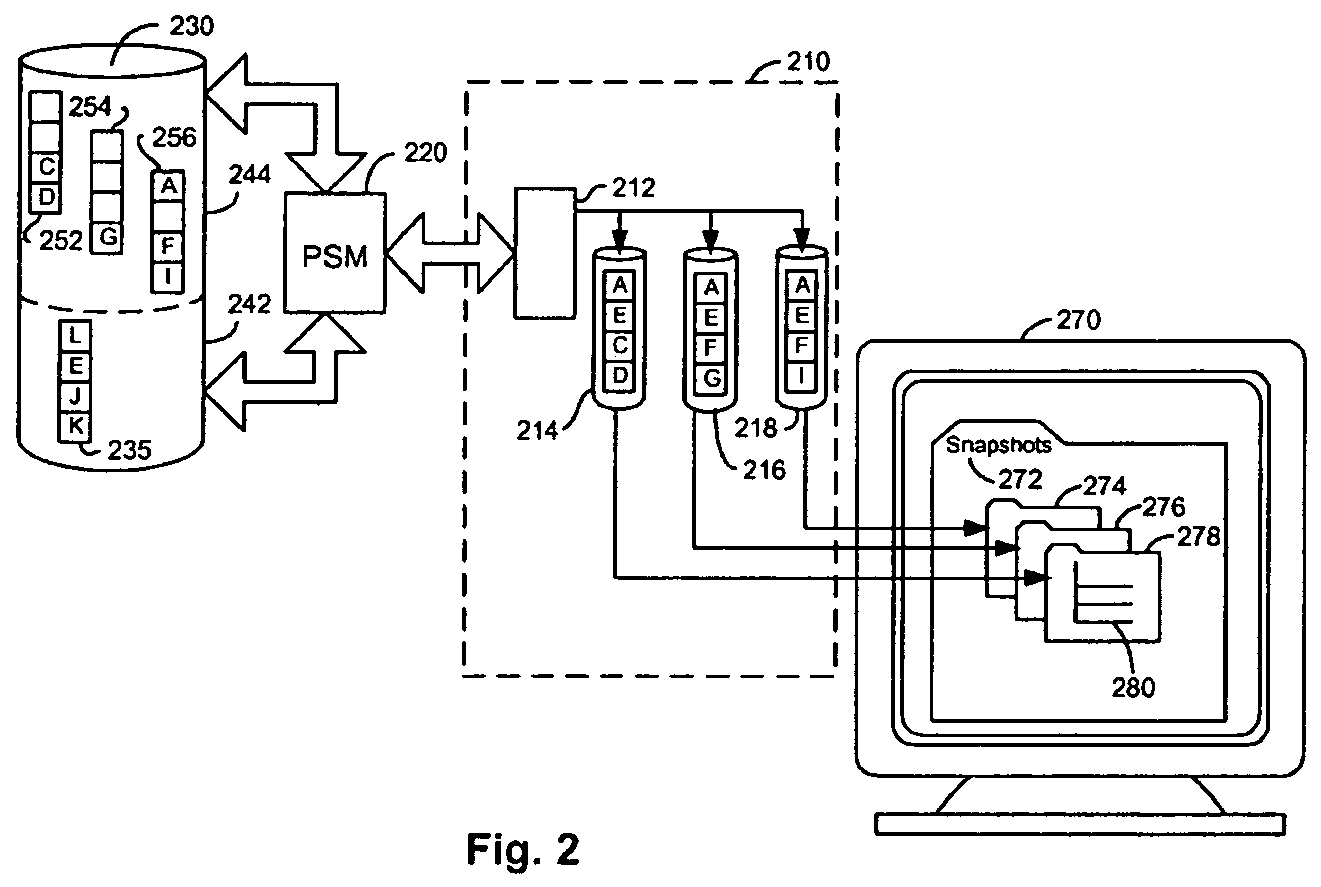
Persistent snapshot methods
A persistent snapshot is taken and maintained in accordance with a novel method and system for extended periods of time using only a portion of a computer readable medium of which the snapshot is taken. Multiple snapshots can be taken in succession at periodic intervals and maintained practically indefinitely. The snapshots are maintained even after powering down and rebooting of the computer system. The state of the object of the snapshot for each snapshot preferably is accessible via a folder on volume of the snapshot. A restore of a file or folder may be accomplished by merely copying that file or folder from the snapshot folder to a current directory of the volume. Alternatively, the entire computer system may be restored to a previous snapshot state thereof. Snapshots that occurred after the state to which the computer is restored are not lost in the restore operation. Different rule sets and scenarios can be applied to each snapshot. Furthermore, each snapshot can be written to within the context of the snapshot and later restored to its pristine condition. Software for implementing the systems and methods of snapshots in accordance with the present invention may comprise firmware of a hard disk drive controller or a disk controller board or within the HDD casing itself. The present invention further comprises novel systems and methods in which the systems and methods of taking and maintaining snapshots are utilized in creating and managing temporal data stores, including temporal database management systems. The implications for data mining and exploration, data analysis, intelligence gathering, and artificial intelligence (just to name a few areas) are profound.
Owner:COLUMBIA DATA PRODUCTS
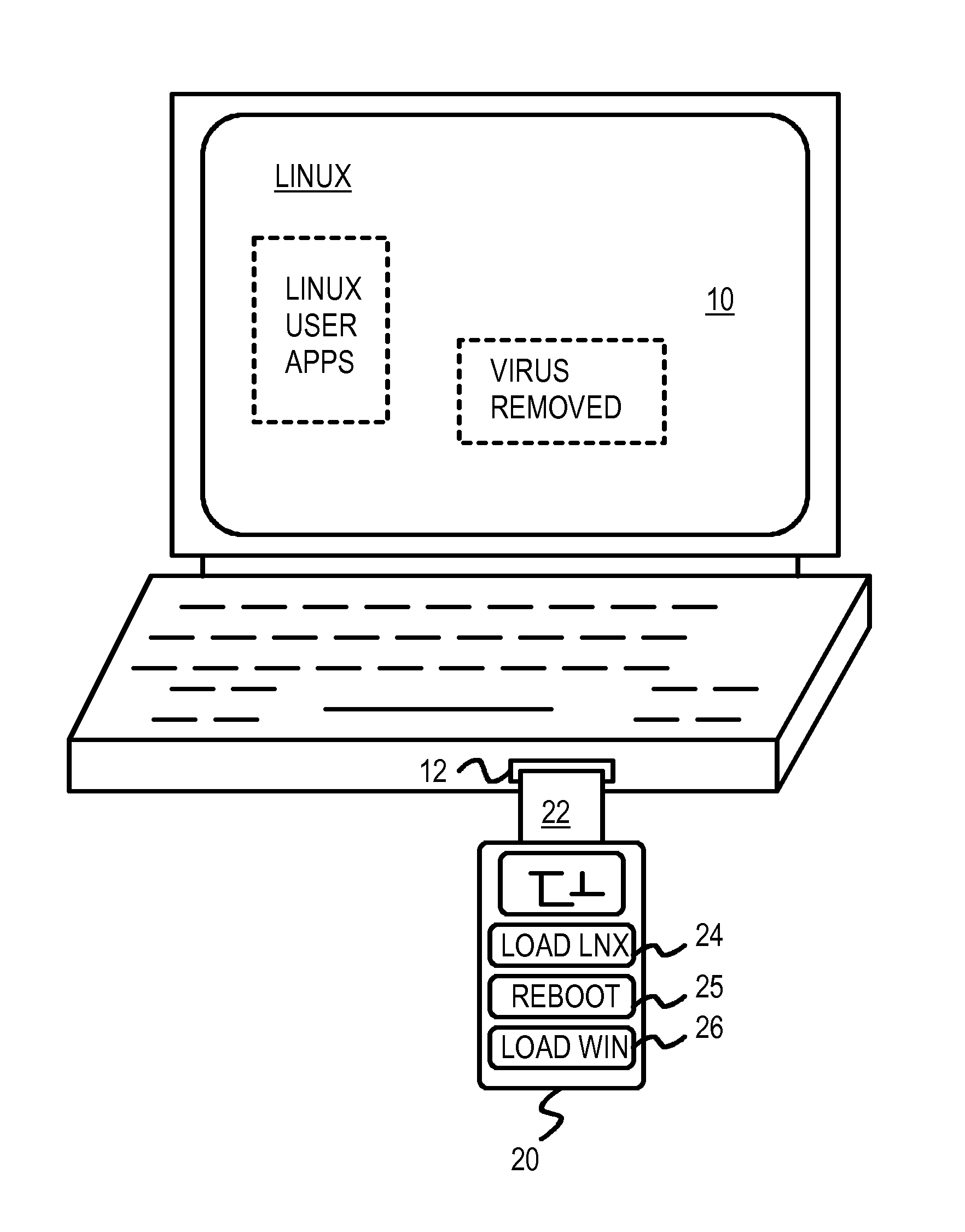
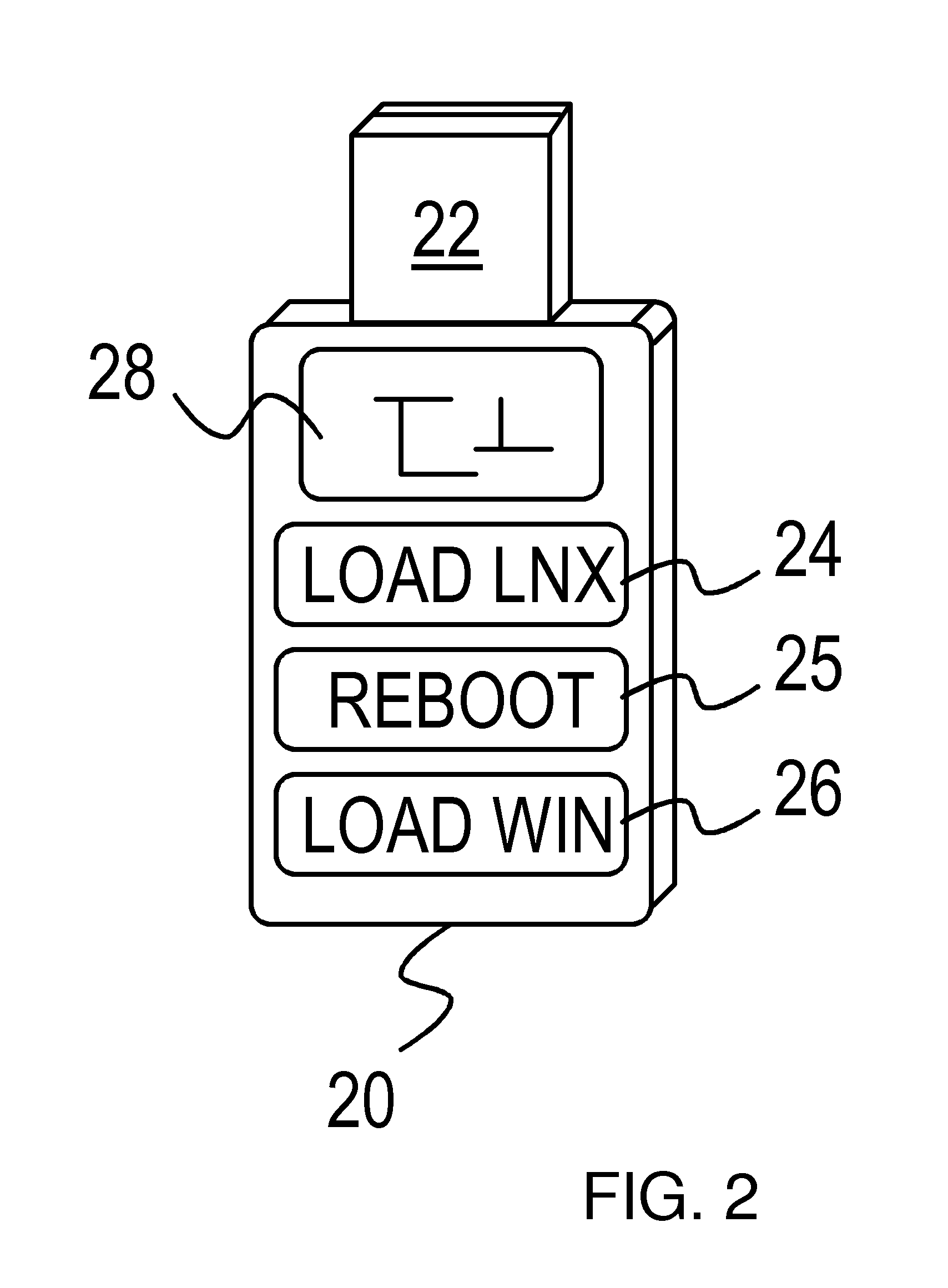
Multi-Partition USB Device that Re-Boots a PC to an Alternate Operating System for Virus Recovery
InactiveUS20080052507A1Program control using stored programsMemory loss protectionInformation controlOperational system
A multi-partition Universal Serial Bus (USB) device has a flash memory with multiple partitions of storage. Some partitions are for different operating systems and store OS images. Another partition has a control program while a user partition stores user data and user configuration information. The control program can test the multi-partition USB device and instruct the host computer BIOS to mount a partition from its flash memory as a drive of the host computer. The host computer can then be rebooted. The OS image from the flash memory is loaded into main memory during rebooting, and the host computer executes a new operating system using the new OS image. The user can press buttons on the multi-partition USB device to select which OS to load, and to begin rebooting. Virus removal programs in the alternate OS can help recover from a virus in the primary OS.
Owner:SUPER TALENT TECH CORP
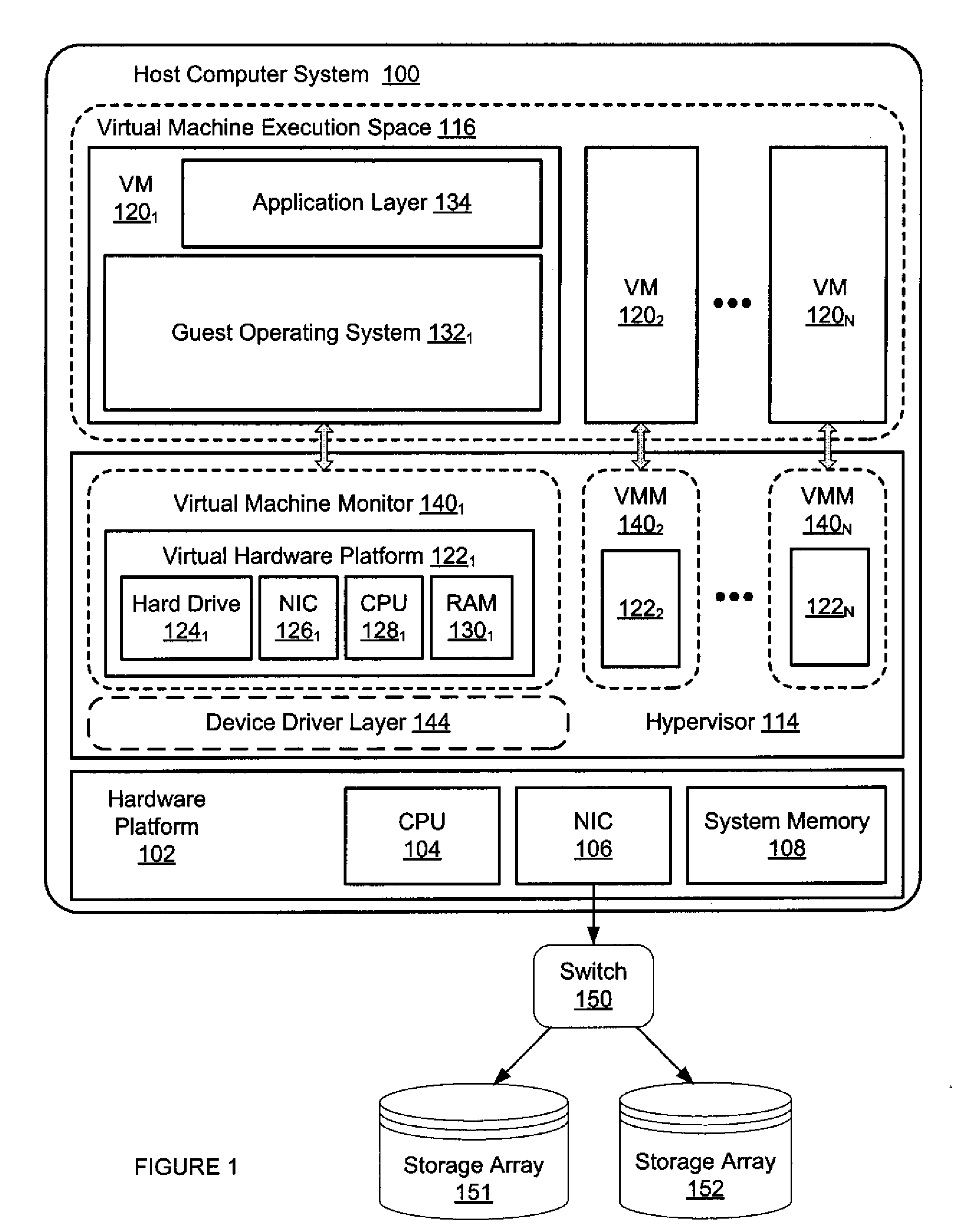
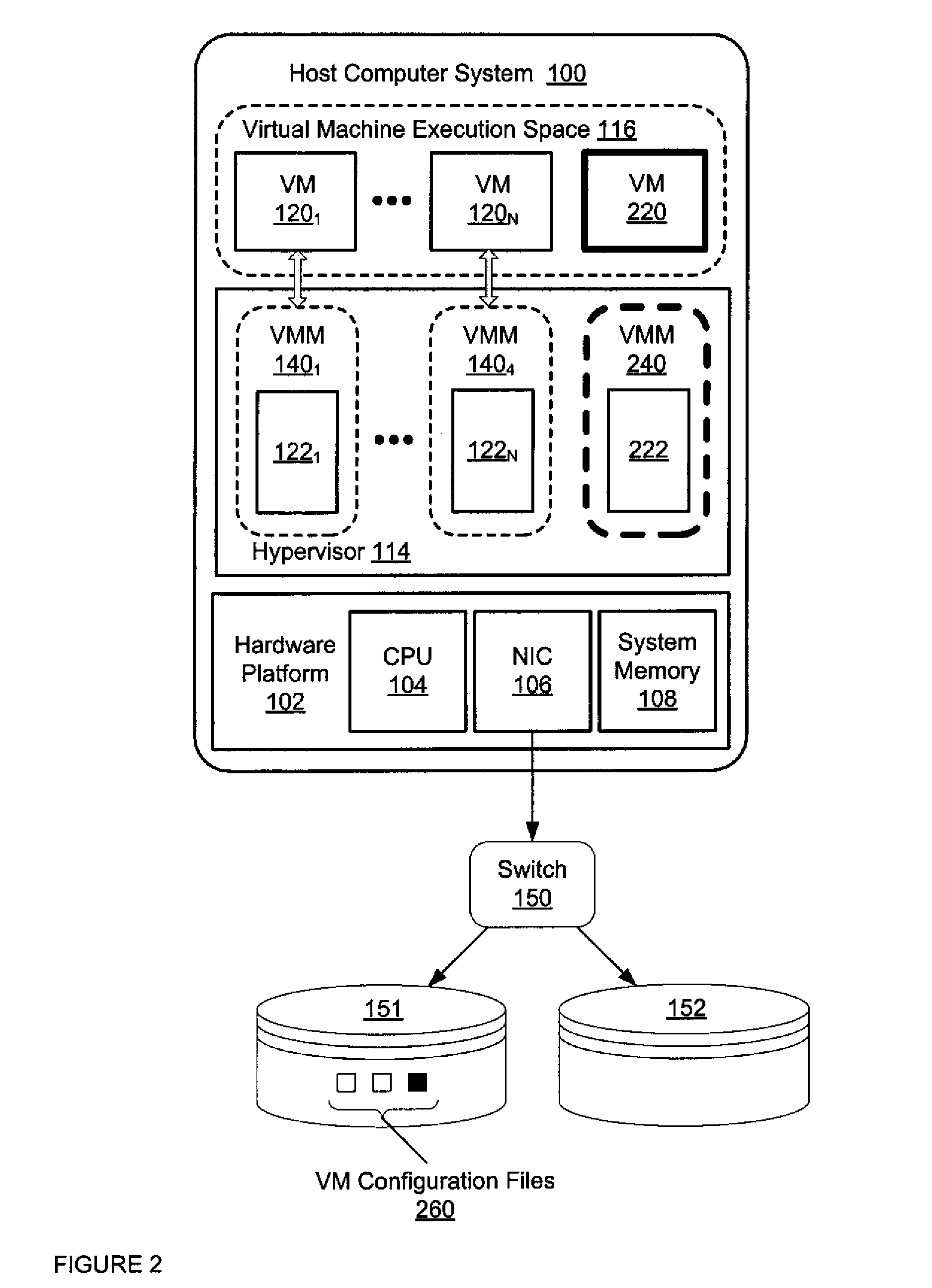
Method of Suspending and Resuming Virtual Machines
ActiveUS20110066786A1Minimize downtimeEfficient use ofMemory adressing/allocation/relocationComputer security arrangementsOperational systemDowntime
A virtual machine is suspended and quickly restarted while maintaining the VM's state. The method is quick enough so that network connections are maintained across the restart and the guest operating system and guest applications running in the VM are not aware of the restart. As a result, users and clients connected to the VM do not notice any downtime or disruption to the VM. After suspension and before the restart, VM configuration changes that would not be possible or be very difficult through code changes alone while the VM was running can be made.
Owner:VMWARE INC
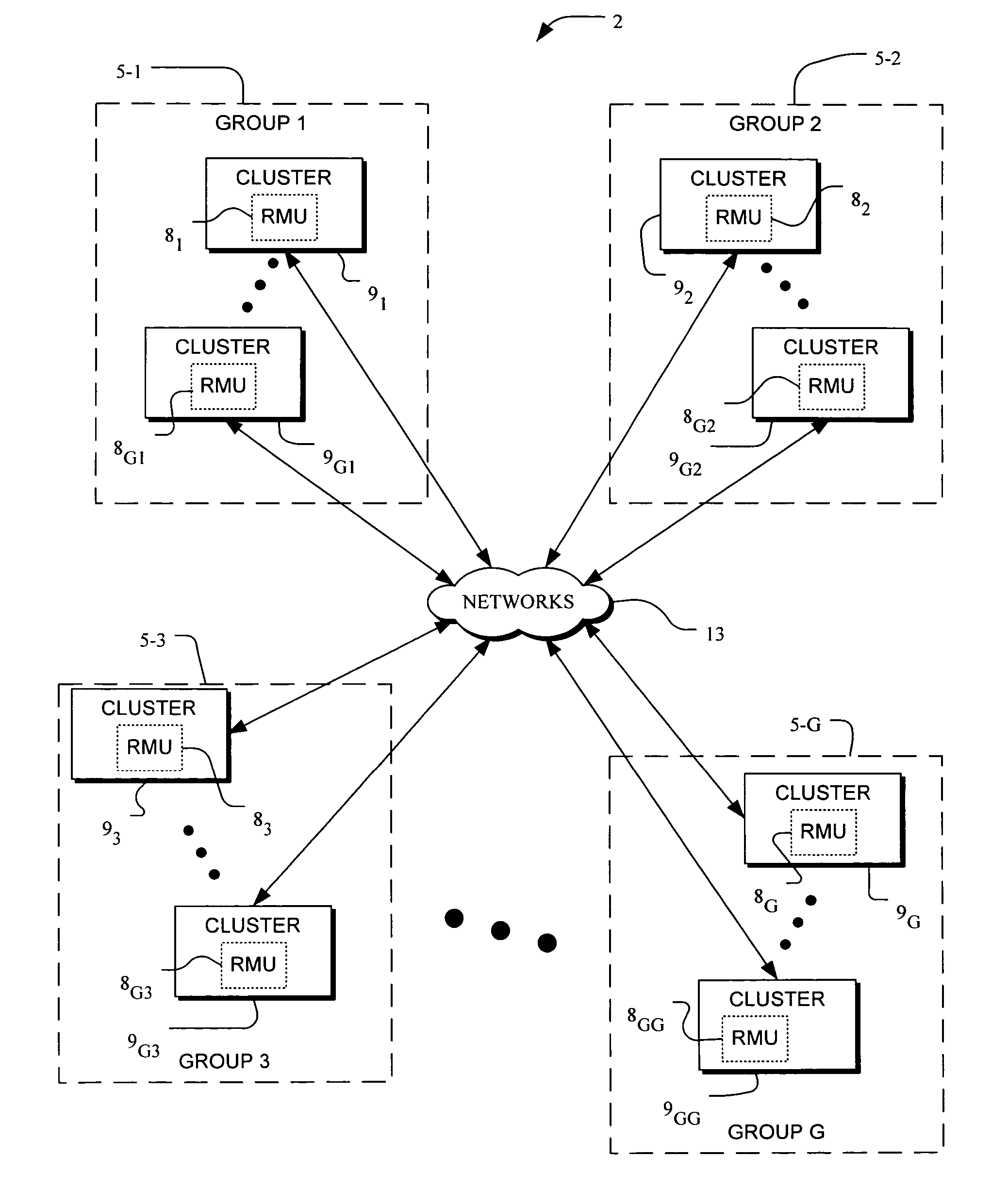
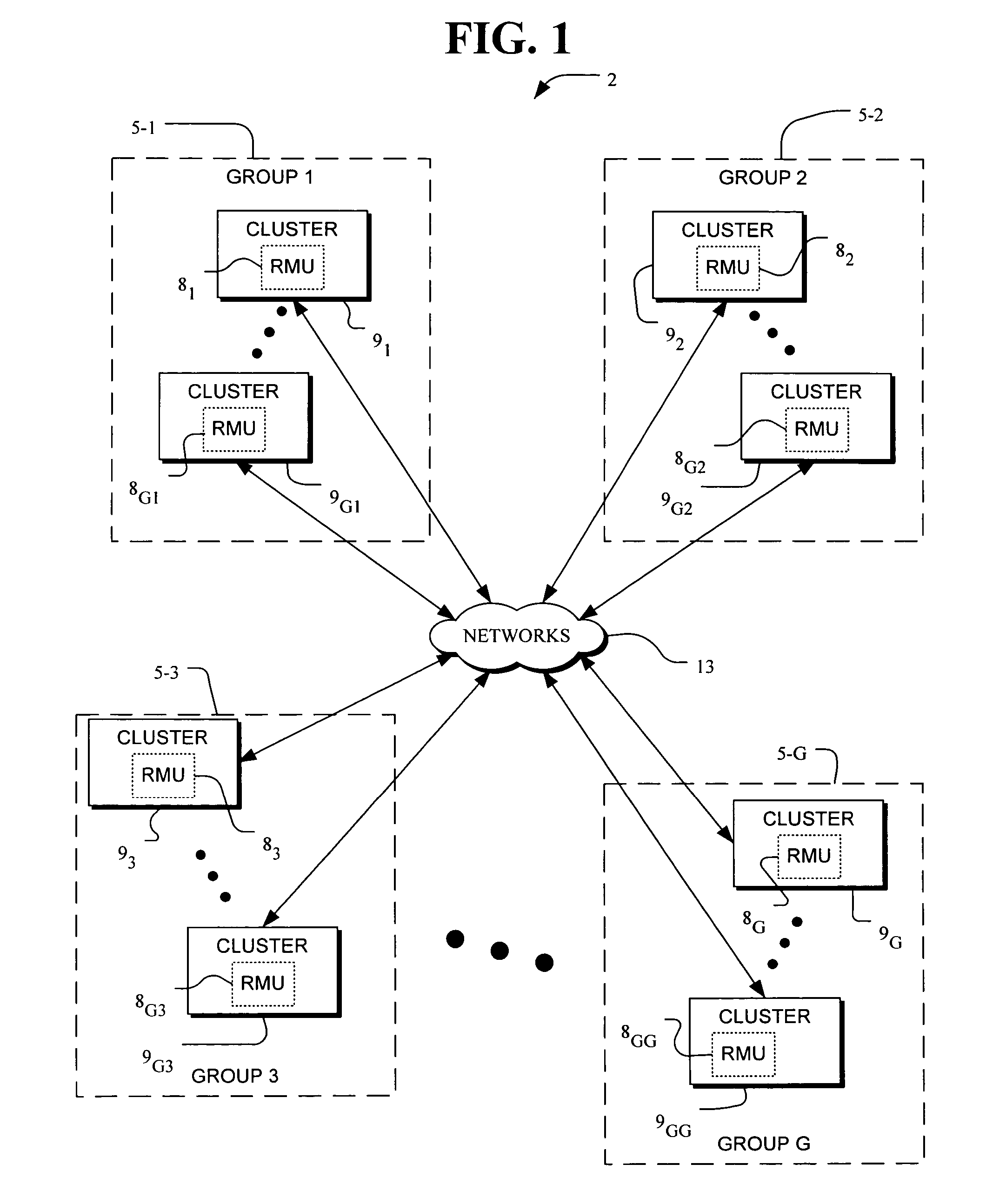
Fault-tolerance framework for an extendable computer architecture
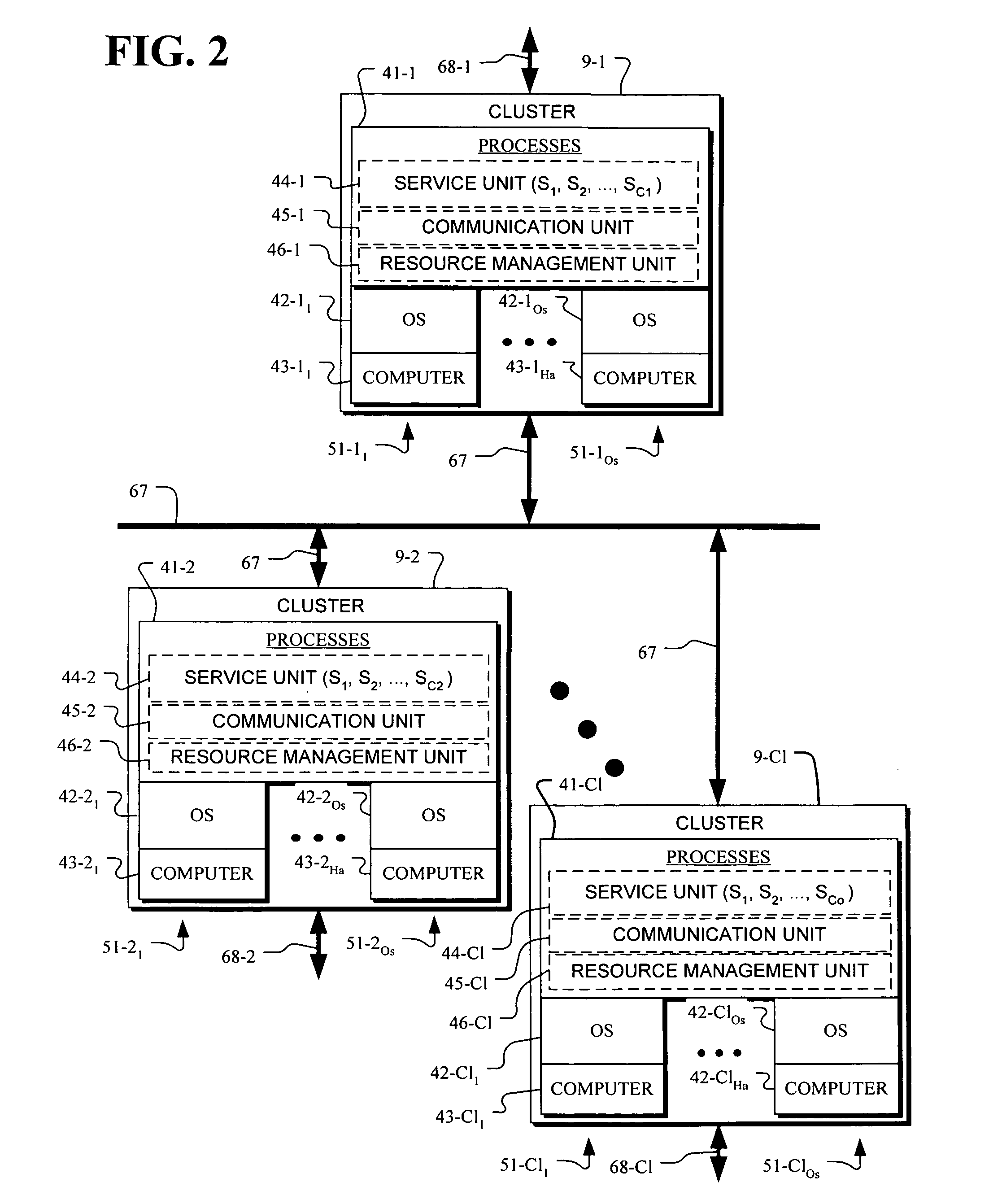
InactiveUS20040205414A1Overcome failureSimple and quickEmergency protective arrangements for automatic disconnectionScalable computingResource management
A computer system having a fault-tolerance framework in an extendable computer architecture. The computer system is formed of clusters of nodes where each node includes computer hardware and operating system software for executing jobs that implement the services provided by the computer system. Jobs are distributed across the nodes under control of a hierarchical resource management unit. The resource management unit includes hierarchical monitors that monitor and control the allocation of resources. In the resource management unit, a first monitor, at a first level, monitors and allocates elements below the first level. A second monitor, at a second level, monitors and allocates elements at the first level. The framework is extendable from the hierarchy of the first and second levels to higher levels where monitors at higher levels each monitor lower level elements in a hierarchical tree. If a failure occurs down the hierarchy, a higher level monitor restarts an element at a lower level. If a failure occurs up the hierarchy, a lower level monitor restarts an element at a higher level. Each of the monitors includes termination code that causes an element to terminate if duplicate elements have been restarted for the same job. The termination code in one embodiment includes suicide code whereby an element will self-destruct when the element detects that it is an unnecessary duplicate element.
Owner:ROSELLI DREW SCHAFFER +2
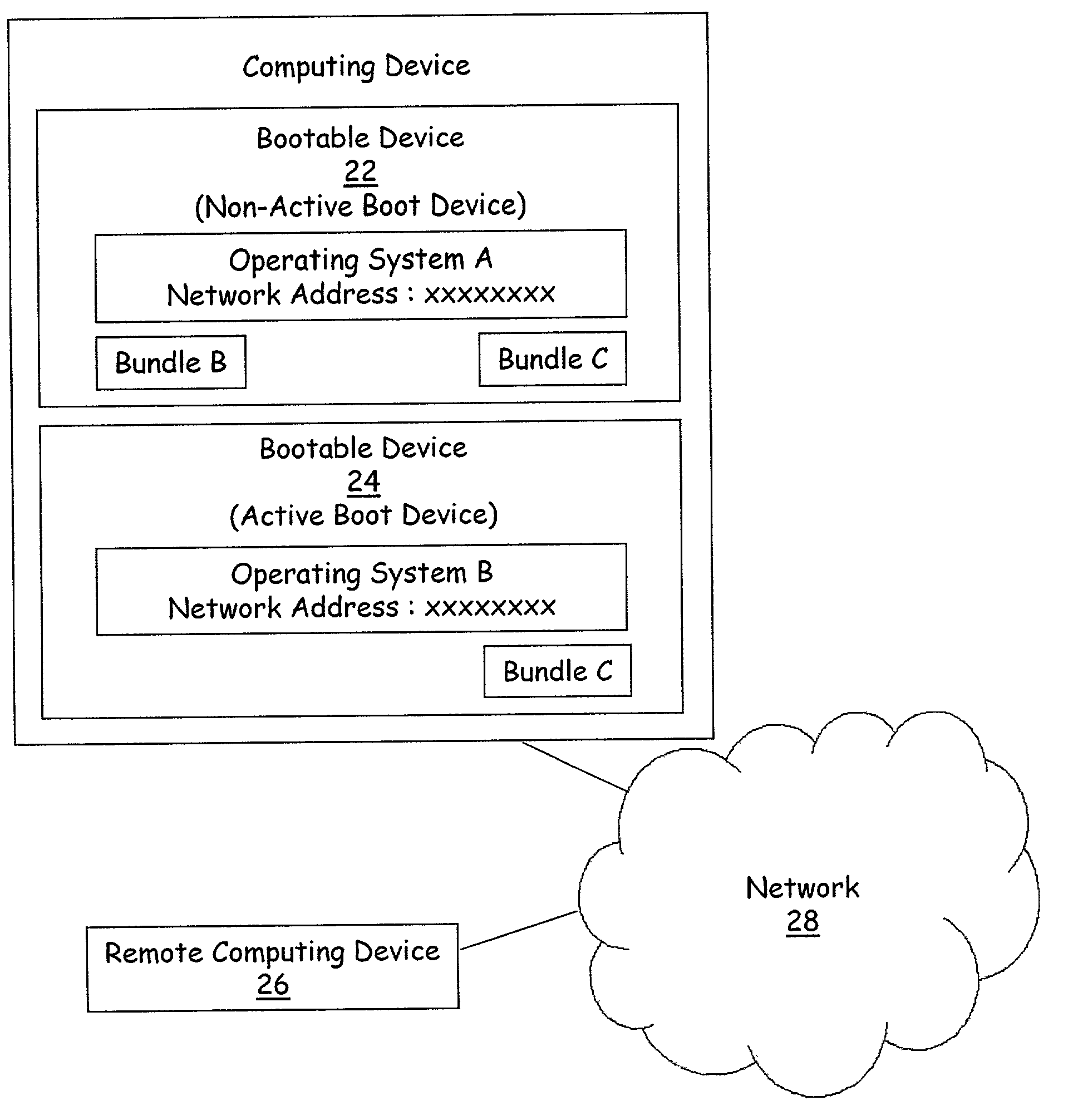
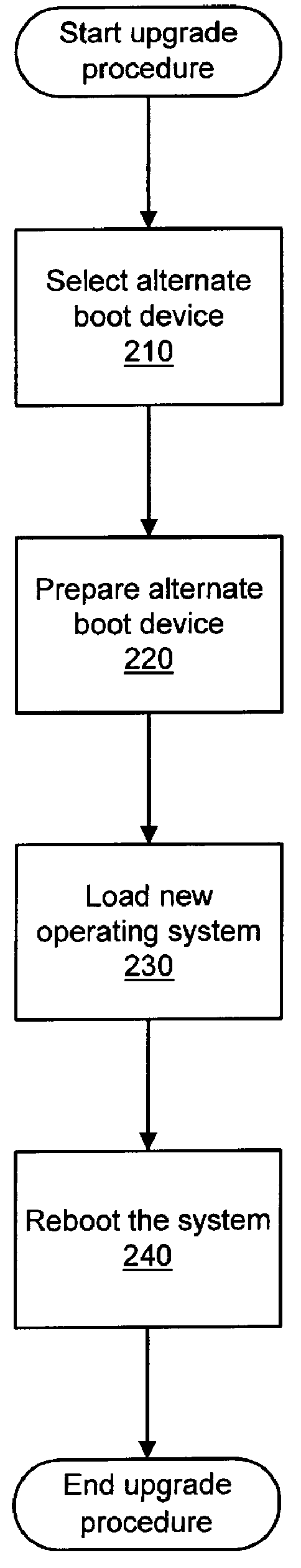
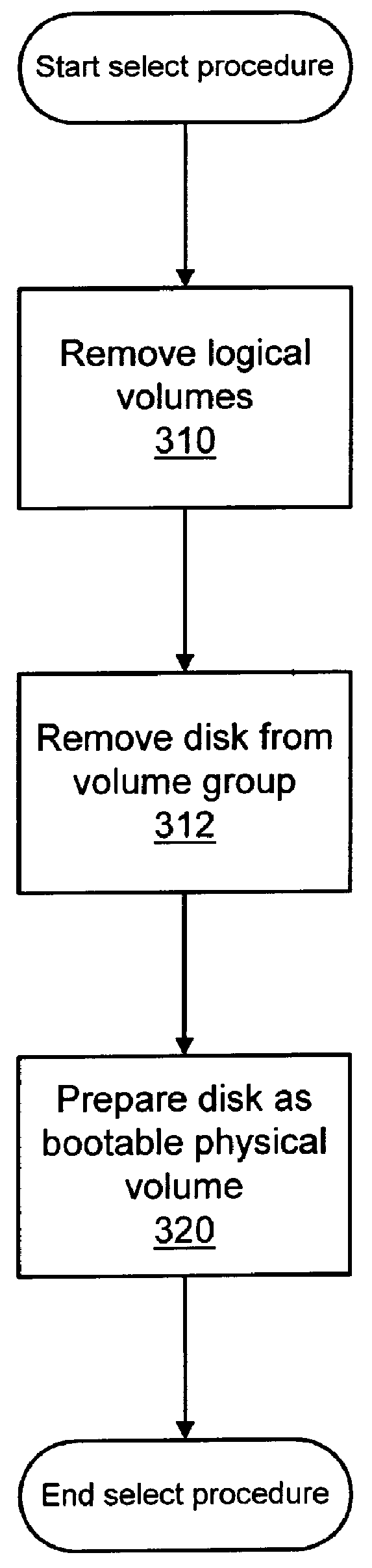
Installing operating systems changes on a computer system
A computer system is upgraded while the computer system is functioning. The computer system has a first boot device with a first operating system and a second device. The method includes: preparing the second device within the computer system as a bootable device while the computer system is functioning under control of the first operating system; preparing the second device within the computer system to receive a second operating system while the computer system is functioning under control of the first operating system; loading the second operating system onto the second device while the computer system is functioning under control of the first operating system; and, rebooting the computer system such that the computer system is under control of the second operating system on the second device.
Owner:GLOBALFOUNDRIES INC
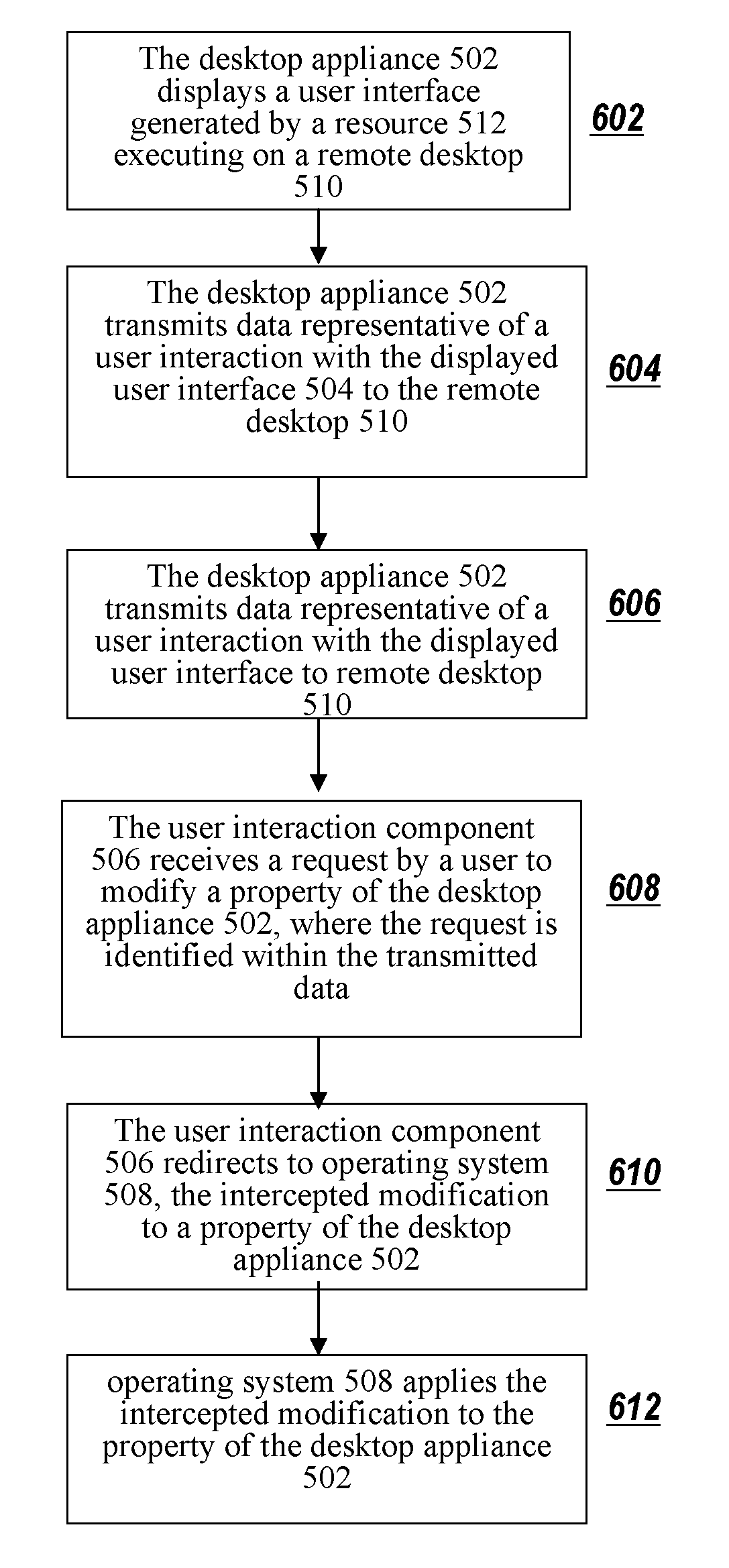
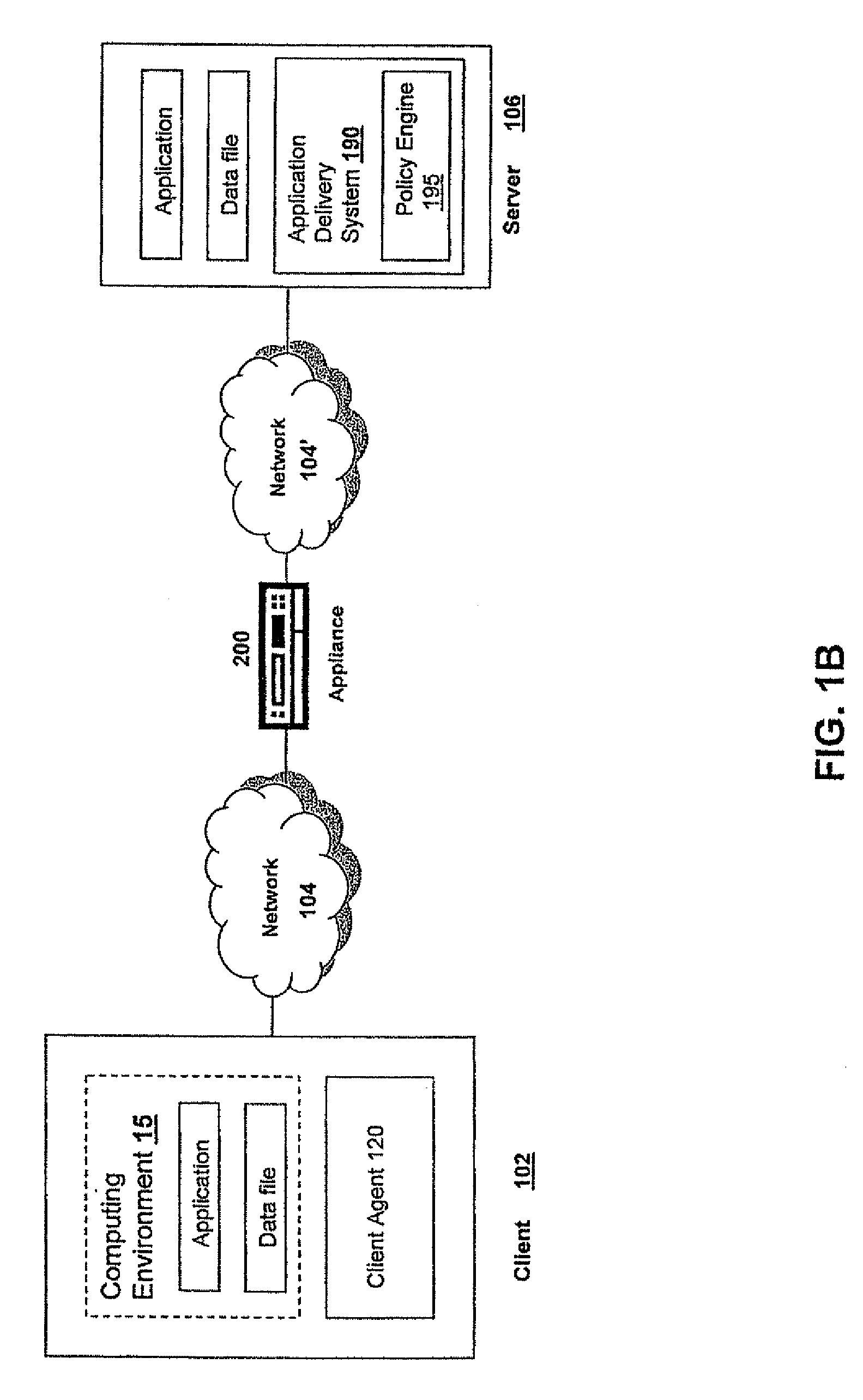
Methods and systems for providing a modifiable machine base image with a personalized desktop environment in a combined computing environment
A method and system for modifying, in a combined computing environment, a machine base image having a personalized desktop environment includes executing an operating system associated with a base disk; intercepting, by a filter driver, an instruction from at least one of a plurality of resources to modify a setting stored in at least one of a file system and a registry, the plurality of resources executing inside an isolation environment; storing, in a delta disk, a copy of the modified setting; restarting the operating system; replacing the setting stored in the at least one of the file system and the registry with the copy of the modified setting stored on the delta disk; and restarting at least one operating system process incorporating the modified setting.
Owner:CITRIX SYST INC
Method and apparatus for performing timing synchronization
A method, apparatus and computer program product are provided in order to cause a timing alignment timer or a plurality of timing alignment timers to be reset based on a timing alignment timer message. In this regard, a method is provided that provides receiving a message. The method further includes determining whether the message includes a restart indication. The method additionally includes causing a plurality of timing alignment timers to be restarted in an instance in which the message includes a restart indication.
Owner:NOKIA CORP
Performing operating system recovery from external back-up media in a headless computer entity
InactiveUS20020042892A1Redundant data error correctionRedundant operation error correctionHard disc driveOperational system
A computer entity, particularly but not exclusively a headless computer entity, has operating systems stored on a non-volatile data storage device e.g. a hard disk drive, and has a back-up data storage device. Operating system backup's are taken from an uncorrupted copy of an operating system stored in a separate partition on the data storage device to the primary operating system which is actually used to run the device, thereby ensuring that if the primary operating system of the computer entity becomes corrupted either gradually or catastrophically, the back-up copy which is stored on a back-up media is not effected. Under failure conditions of the computer entity, a pristine copy of the operating system can be reloaded from the back-up tape data storage media and the computer entity rebooted from the pristine operating system back-up copy.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
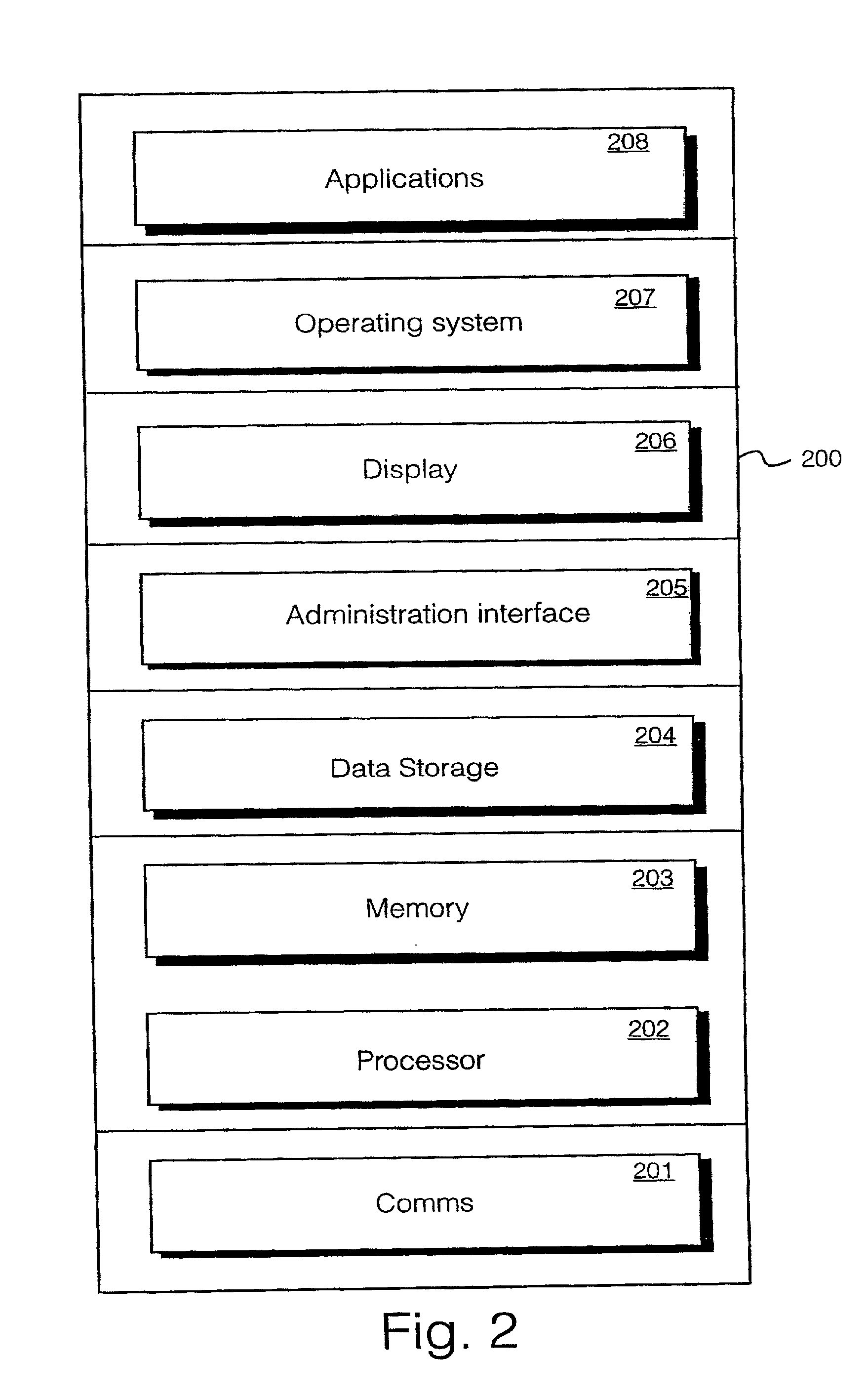
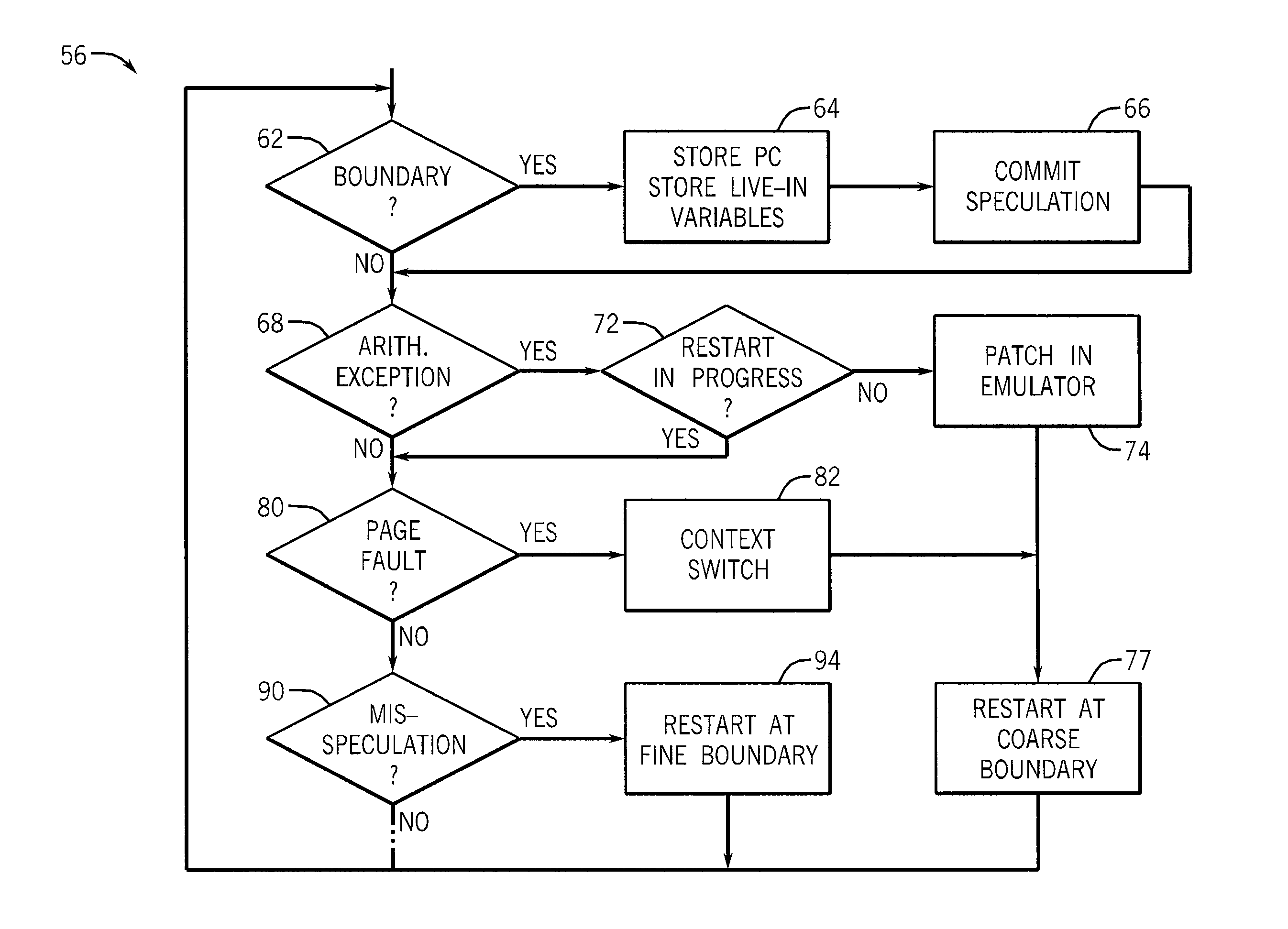
Computer Processor Providing Exception Handling with Reduced State Storage
ActiveUS20140019735A1Reduce hardware overheadSimple methodInstruction analysisDigital computer detailsArchitecture of Integrated Information SystemsException handling
A computer architecture allows for simplified exception handling by restarting the program after exceptions at the beginning of idempotent regions, the idempotent regions allowing re-execution without the need for restoring complex state information from checkpoints. Recovery from mis-speculation may be provided by a similar mechanism but using smaller idempotent regions reflecting a more frequent occurrence of mis-speculation. A compiler generating different idempotent regions for speculation and exception handling is also disclosed.
Owner:WISCONSIN ALUMNI RES FOUND
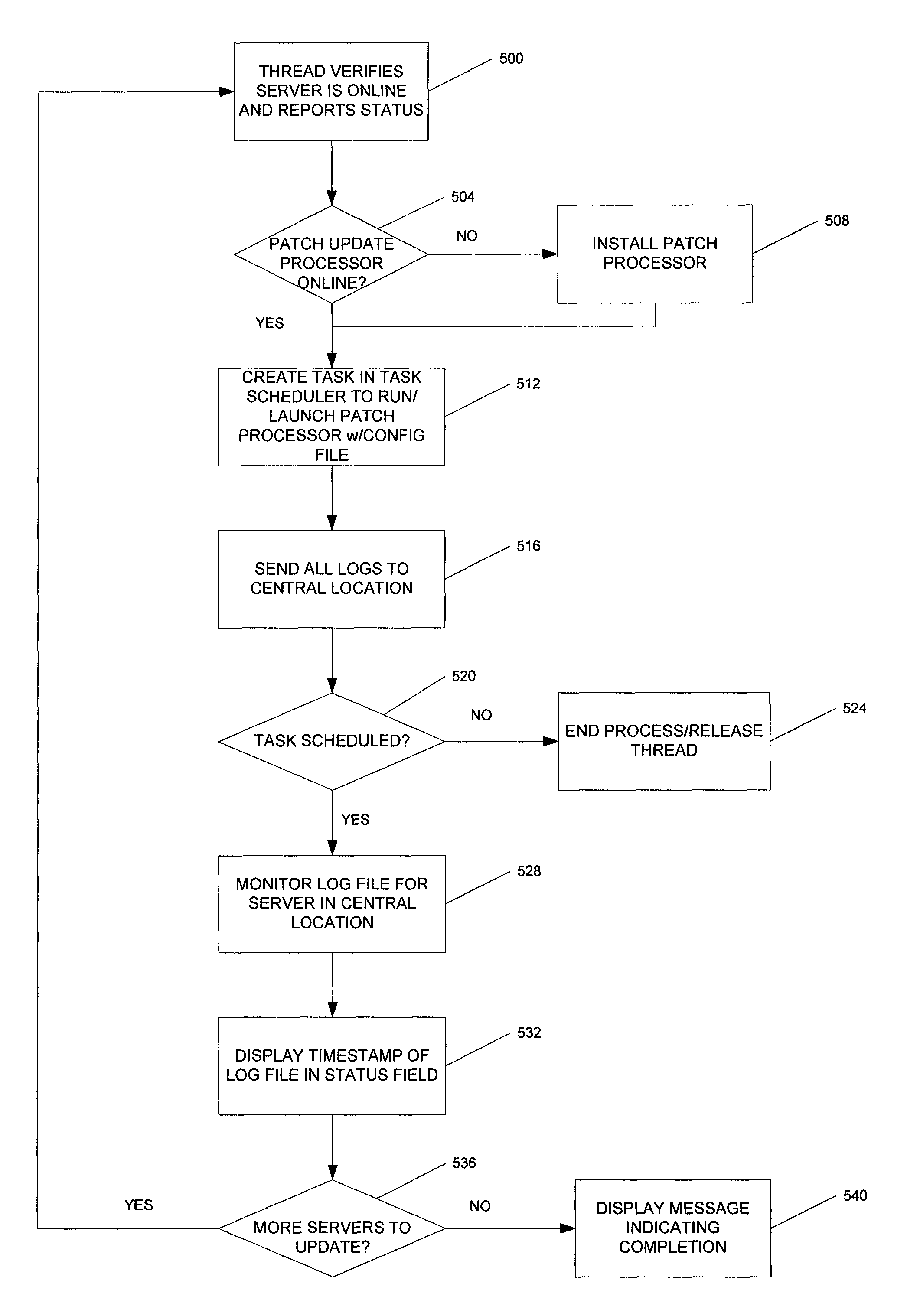
Patch cycle master records management and server maintenance system
ActiveUS8296756B1Reduce gapSoftware engineeringSpecific program execution arrangementsBusiness enterpriseEnterprise computing
A method, system, and computer readable storage medium for managing the deployment of software patch updates on a plurality of computers in an enterprise computer network during a patch cycle wherein each computer receives and installs periodic software patch updates automatically. An inventory is maintained of the computers in a central database that stores a status of each computer for each patch during the patch cycle. The computers are filtered into at least one filter group and a list of computers in the filter group is displayed along with the status for each patch. The status of each patch is verified and displayed for each computer in the filter group. A controlled software patch update is performed for each non-compliant computer in the filter group. A controlled reboot of each computer in the filter group is performed following the completion of the software patch updates for the patch cycle.
Owner:SOUTHERN COMPANY SERVICES
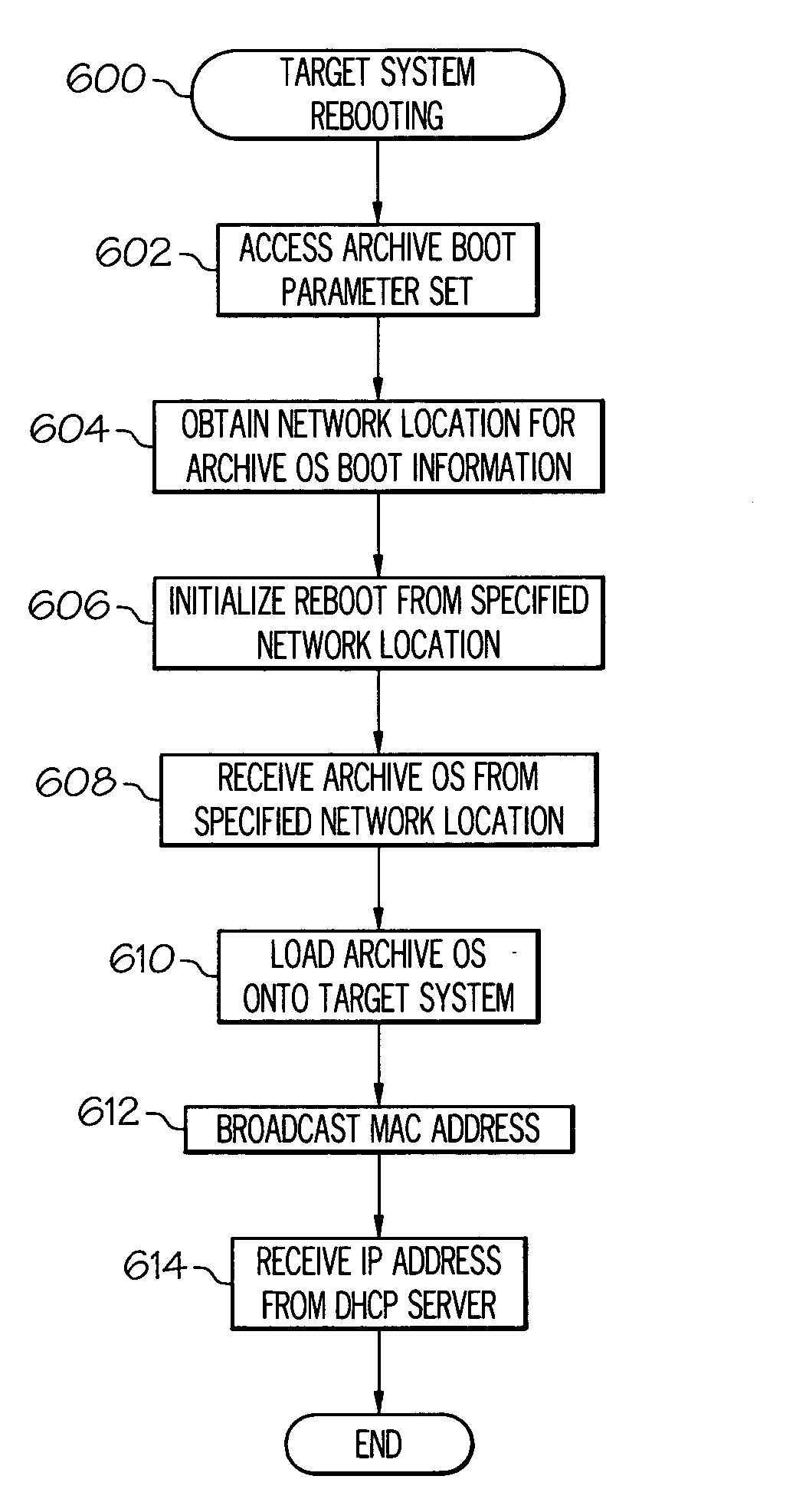
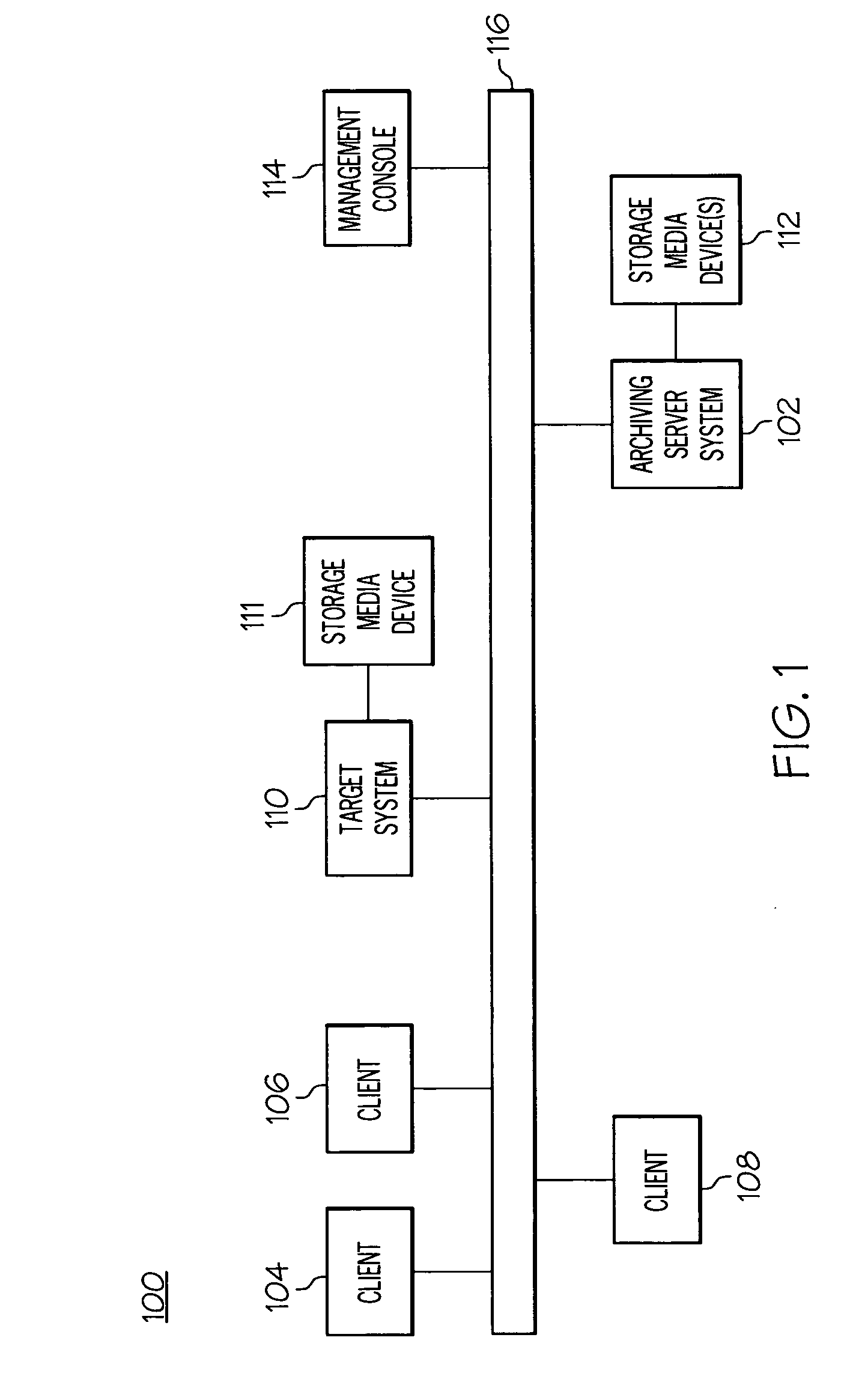
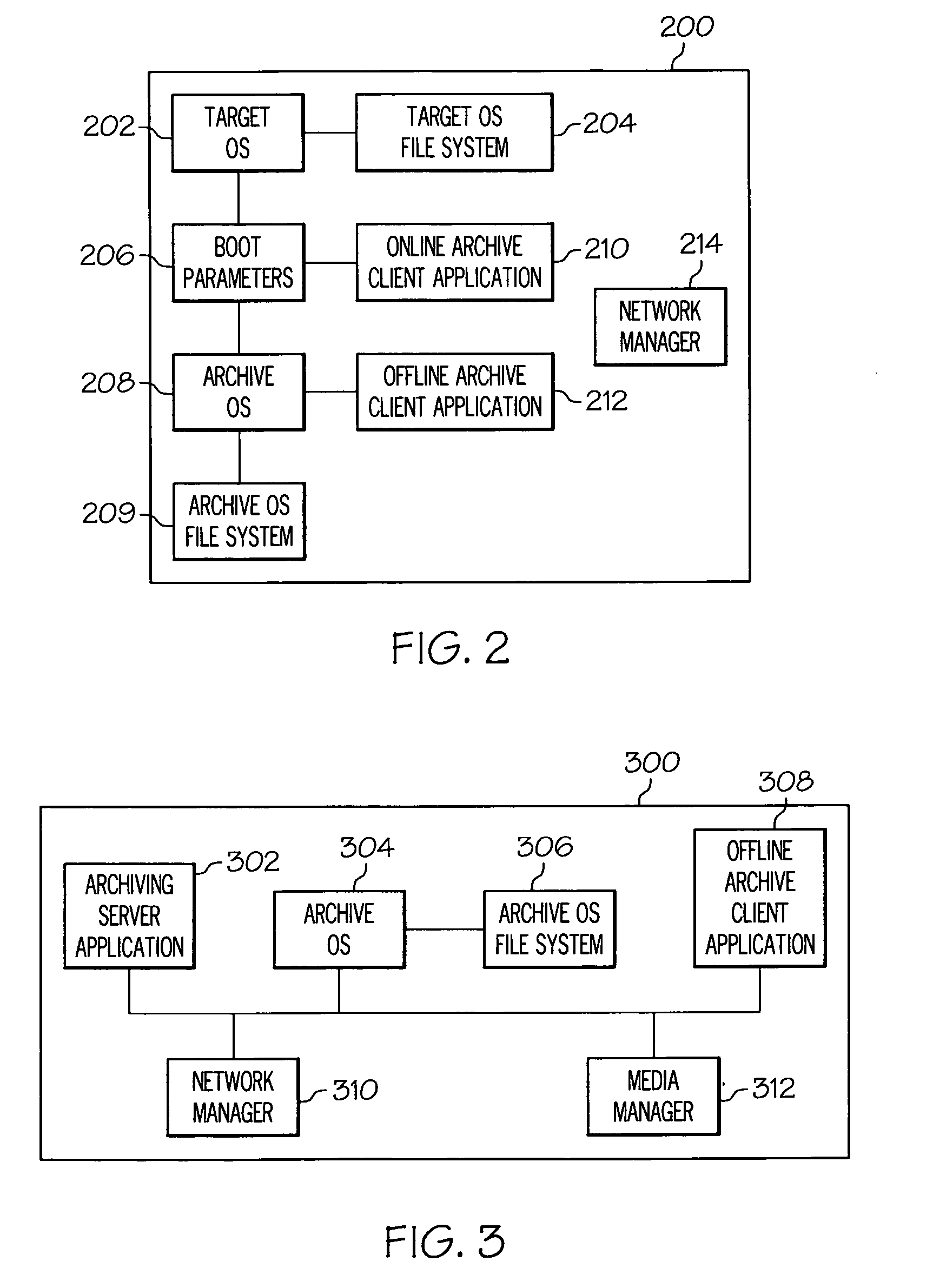
System and method for offline archiving of data
InactiveUS20060080521A1Reduce the amount requiredQuantity minimizationDigital computer detailsProgram controlOperational systemFile system
A data archiving system according to the invention performs offline backup of data stored at a target system connected to a network. To minimize downtime of the target system, the data is archived at a low level of abstraction, e.g., at the block level, rather than at the file system level. The offline backup is accomplished by closing open files and application, and rebooting the target system with an archiving operating system that manages the data backup process. After the target data has been archived, the target system is rebooted with the normal operating system.
Owner:BAKBONE SOFTWARE INC
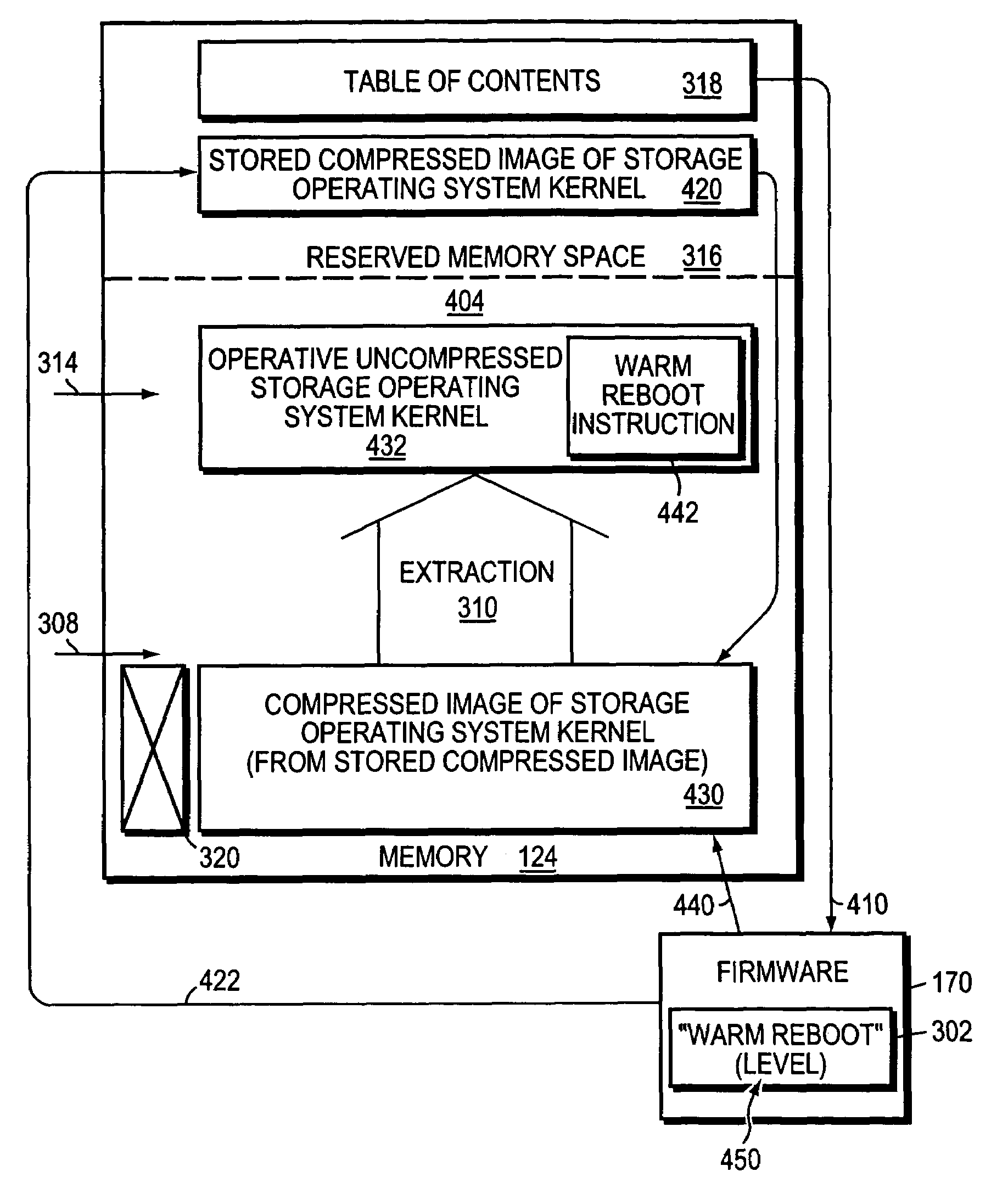
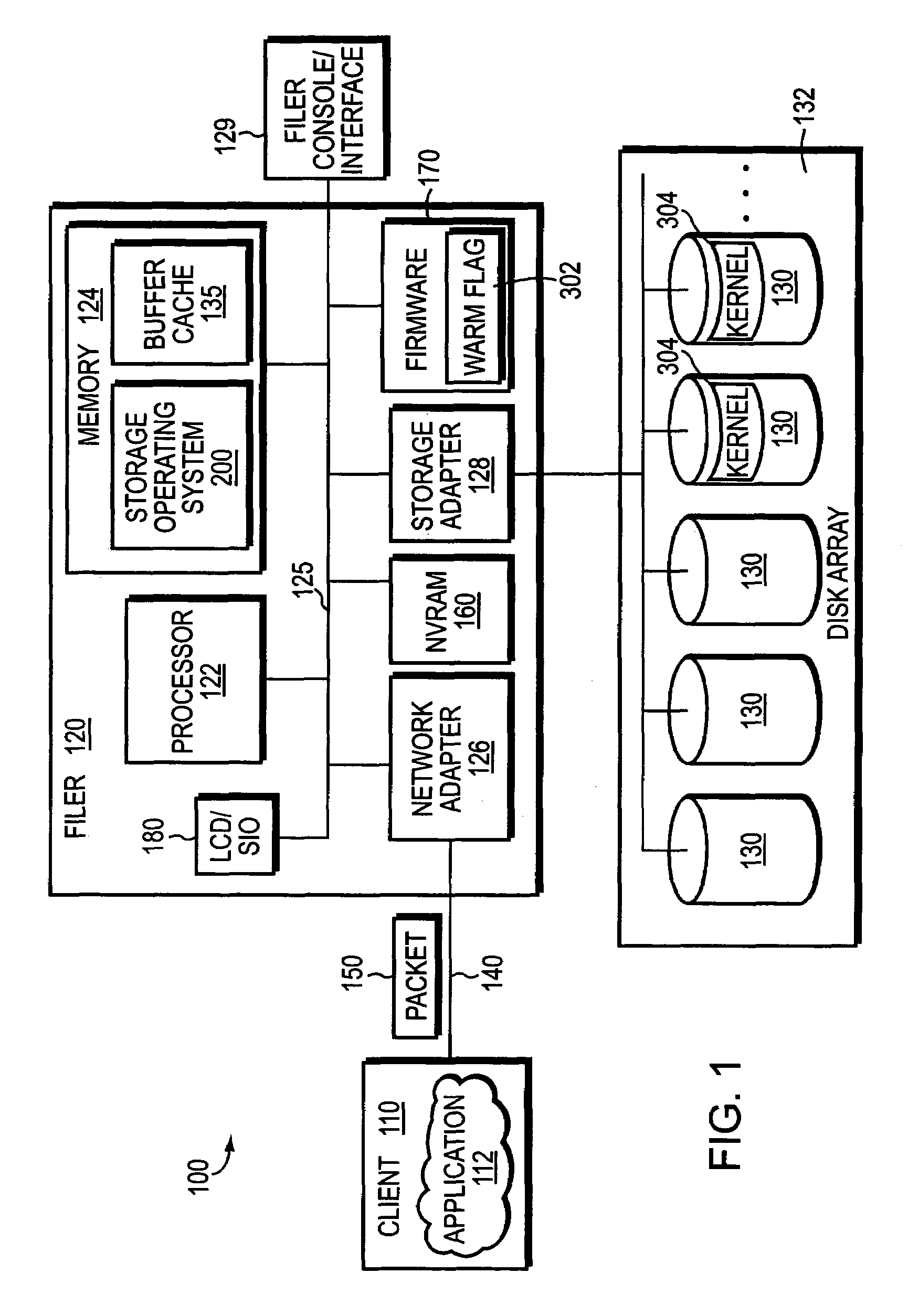
System and method for fast reboot of a file server
InactiveUS6965989B1Fast (“warm”) rebootReduce server downtimeDigital computer detailsData resettingOperational systemDowntime
A system and method for fast (“warm”) reboot of a file server is provided, which skips certain conventional boot processes when circumstances warrant, in order to reduce server downtime. In particular, time is saved by avoiding a full shutdown of the processor and memory, and by causing the firmware to refrain from a full clearance of the file server memory. Instead, the firmware accesses a retained copy of the storage operating system kernel from a reserved location in the file server memory so that an operative version of the kernel is reestablished at the appropriate address space in memory without requiring a time-consuming read of the kernel image from disk. In addition, other “normal” (cold) reboot operations such as full memory tests, hardware checks and memory zeroing are avoided as appropriate—saving further time in the overall reboot process, while still attaining the desired reinitialization of key applications and functions.
Owner:NETWORK APPLIANCE INC
Interdependent virtual machine management
ActiveUS20150154046A1Program initiation/switchingSoftware simulation/interpretation/emulationNetwork connectionSoftware engineering
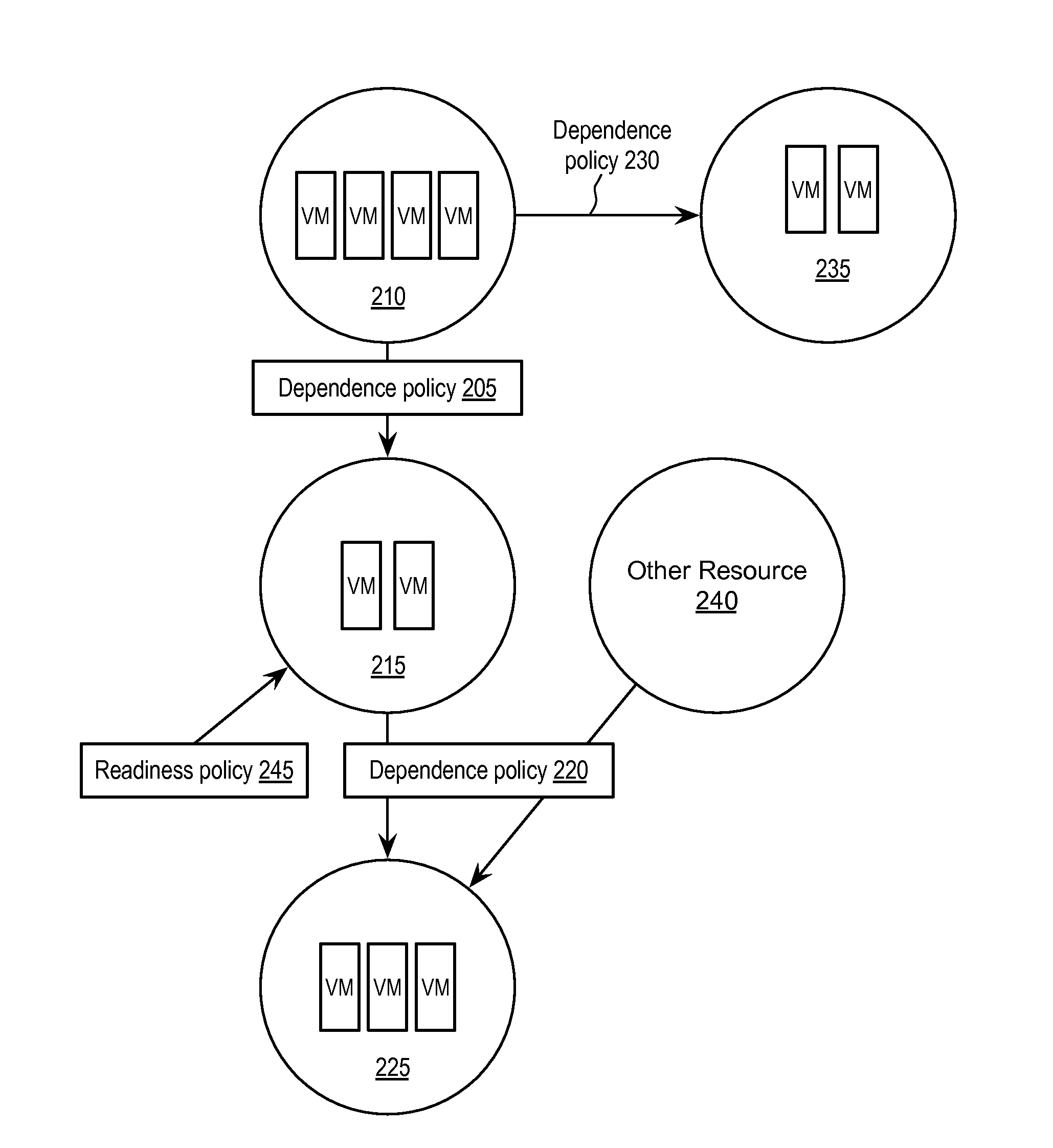
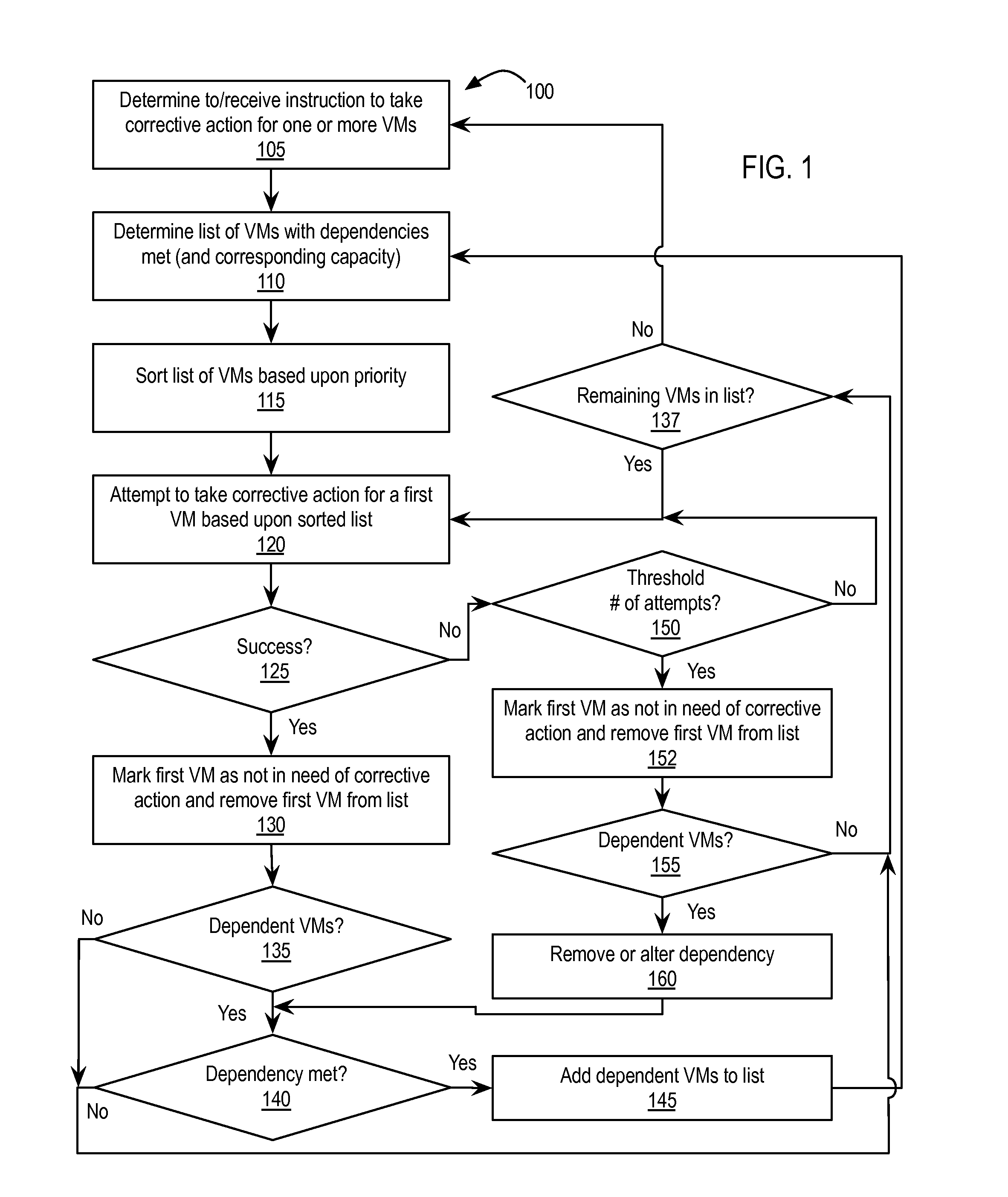
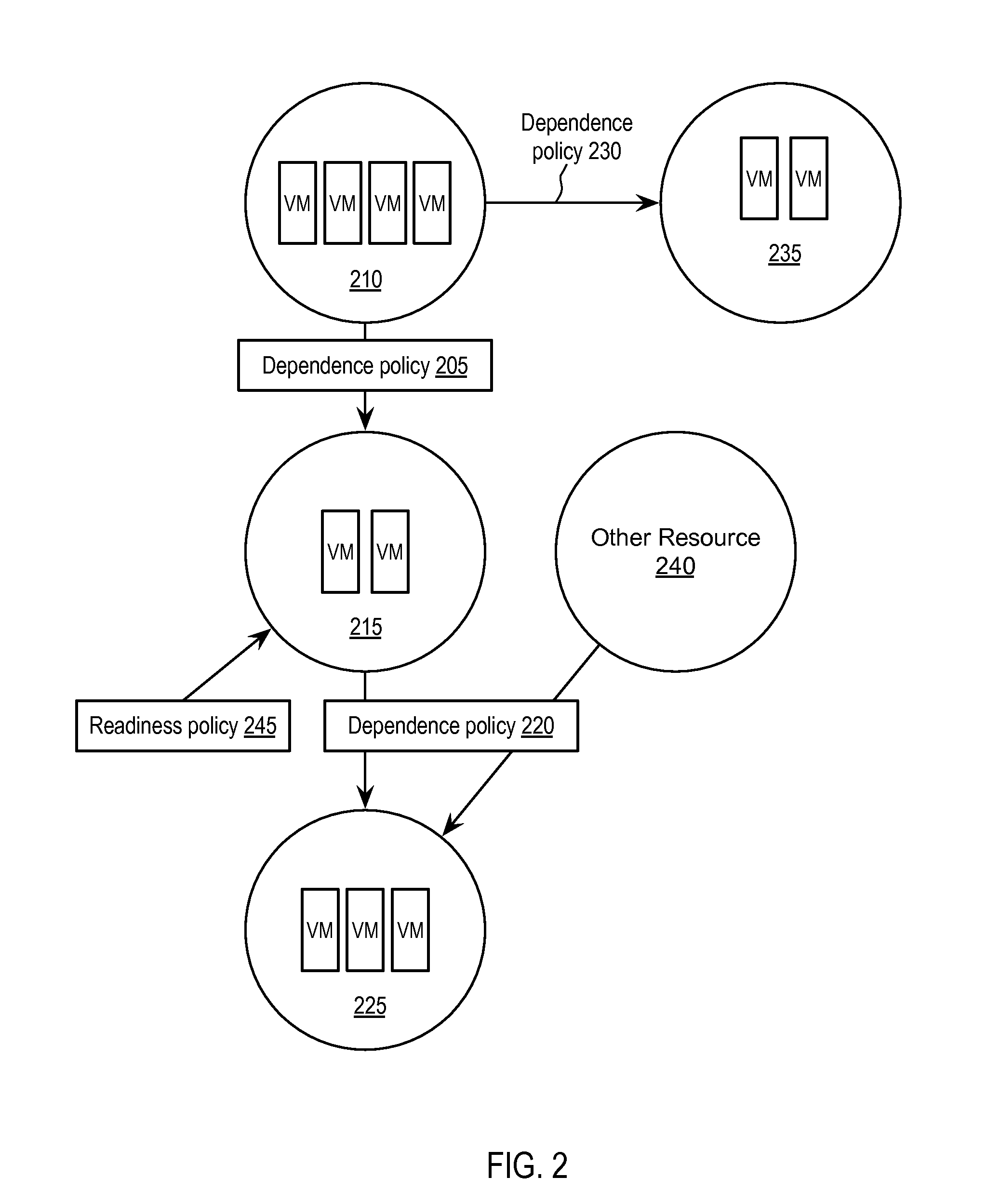
Exemplary methods, apparatuses, and systems determine a list of virtual machines to be subject to a corrective action. When one or more of the listed virtual machines have dependencies upon other virtual machines, network connections, or storage devices, the determination of the list includes determining that the dependencies of the one or more virtual machines have been met. An attempt to restart or take another corrective action for the first virtual machine within the list is made. A second virtual machine that is currently deployed and running or powered off or paused in response to the corrective action for the first virtual machine is determined to be dependent upon the first virtual machine. In response to the second virtual machine's dependencies having been met by the attempt to restart or take corrective action for the first virtual machine, the second virtual machine is added to the list of virtual machines.
Owner:VMWARE INC
Systems and Methods of Installing An Application Without Rebooting
ActiveUS20080046371A1Efficiently administeringEfficient deploymentComputer security arrangementsSecuring communicationClient agentClient-side
A method for automatically changing a version of a client agent for a non-administrative user account without rebooting the user's machine uses a service having installation privileges. The service executes on the client and installs a client agent. The client agent communicates with a network appliance. The client agent detects a difference between its version and a version of the client agent identified by the network appliance. The agent signals the service that it has detected the difference and, in response, the service executes an installation program that installs, without rebooting the client, the version of the client agent identified by the appliance. A corresponding system is also described.
Owner:CITRIX SYST INC
Method and apparatus for software loading and initialization in a distributed network
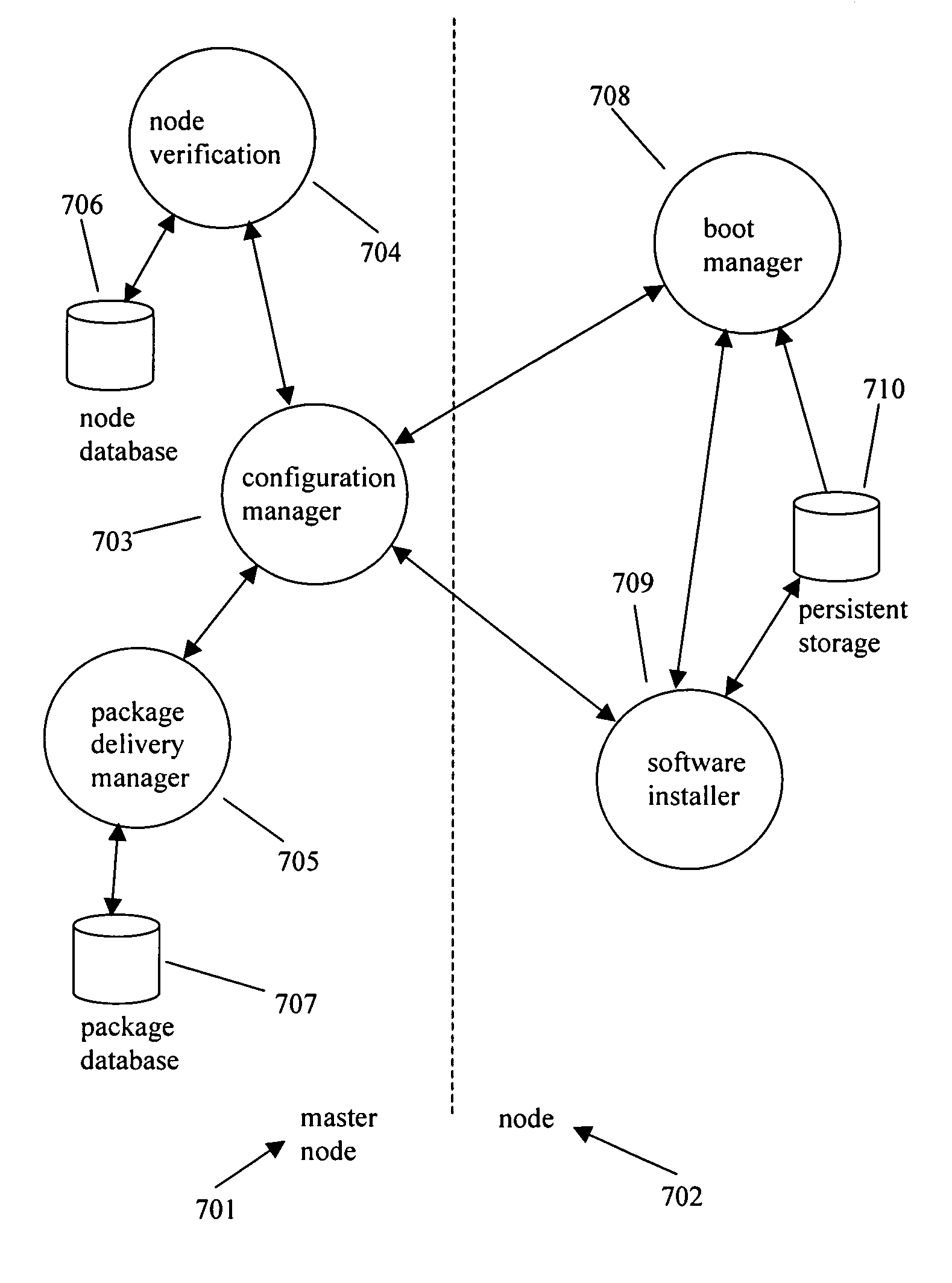
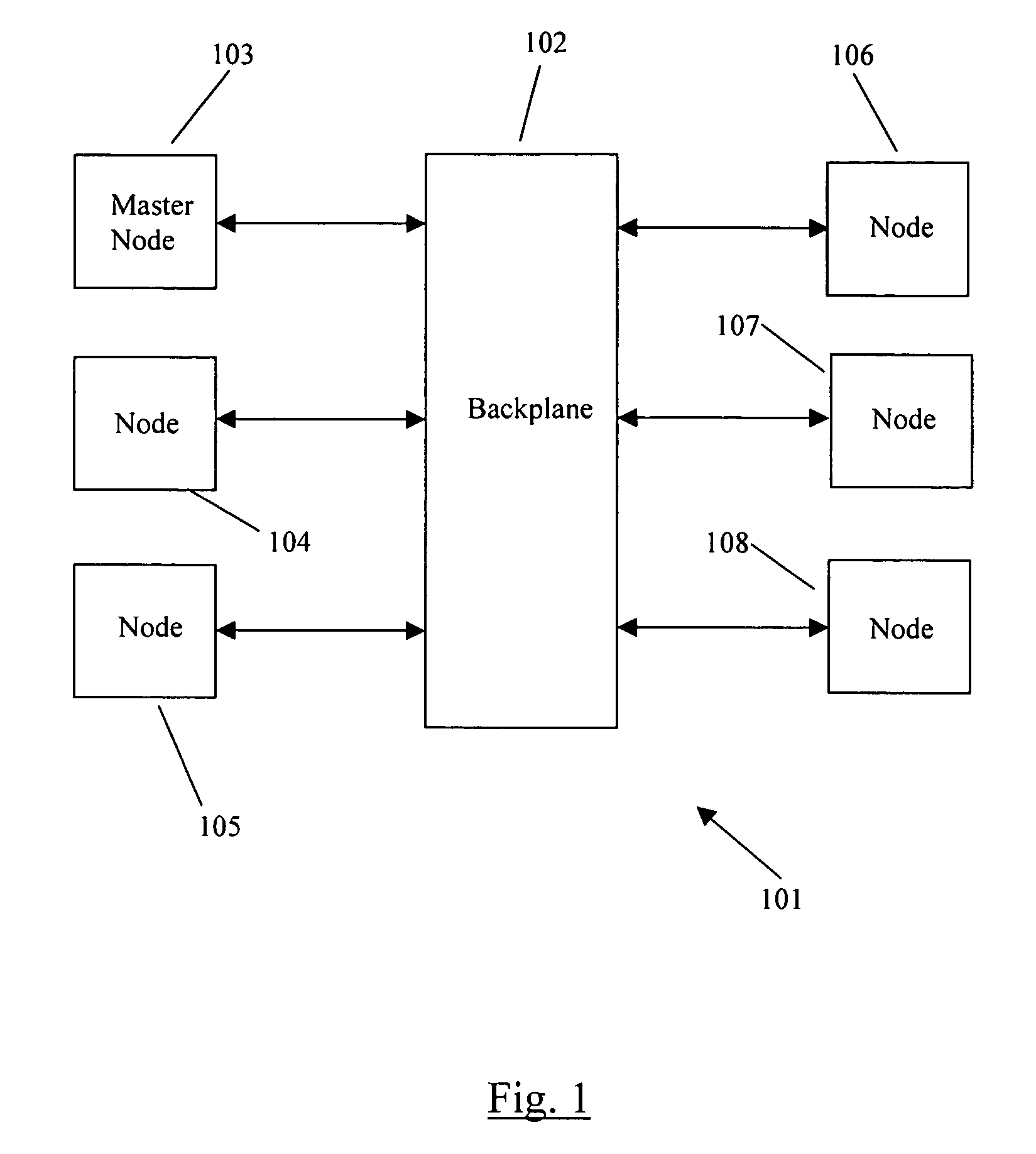
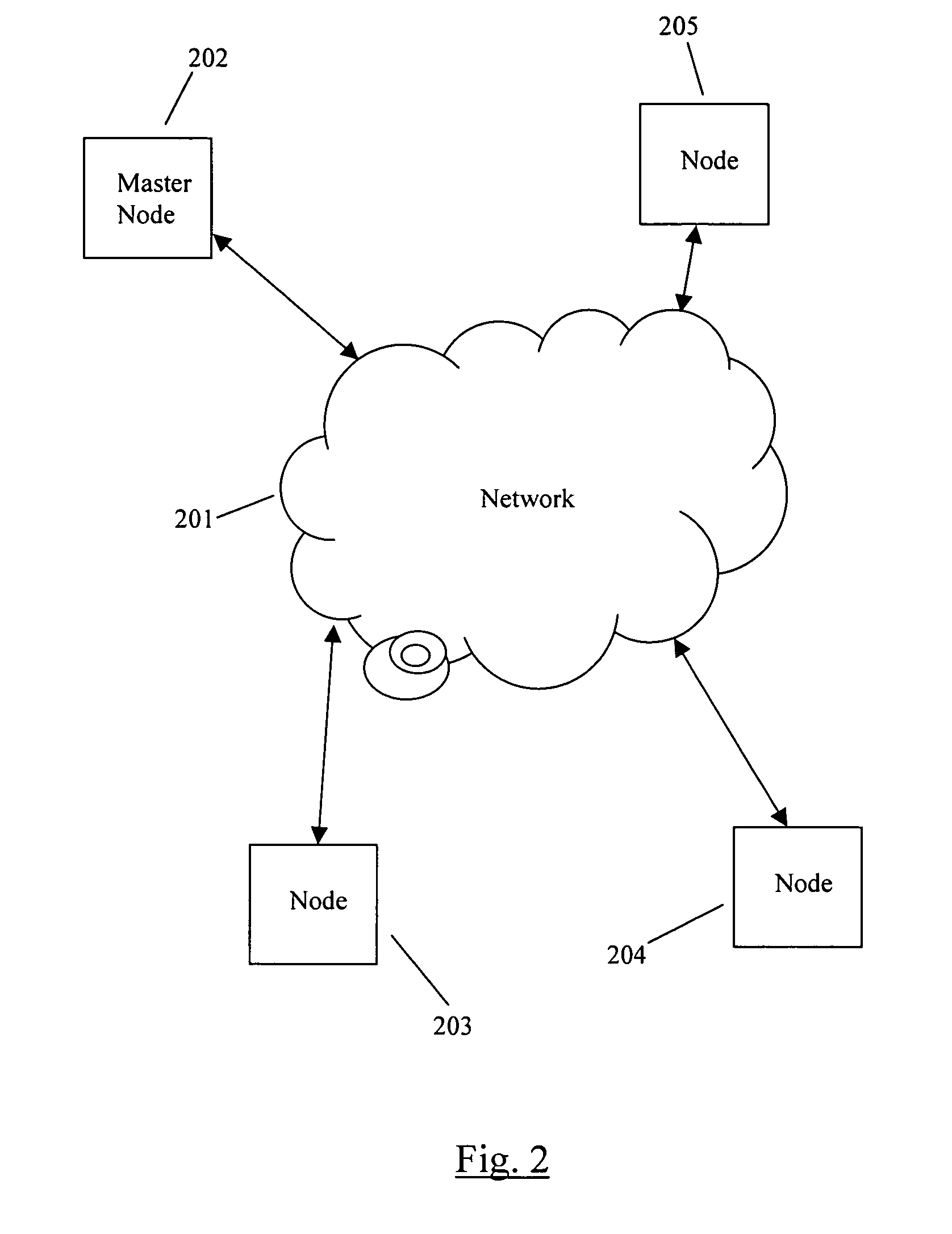
InactiveUS7506335B1Specific program execution arrangementsMemory systemsComputer hardwareSoftware package
A method for software loading and initialization in a distributed network of nodes. A master node provides a node information database and a software package database. A node performing an initial boot requests a boot image and software package download from the master node. The master node finds the node's software configuration information in the node information database and sends the boot image and software packages to the node from the software package database. The node reboots into the boot image and verifies the software versions with the master node. If the node has the correct software, then it completes the boot sequence, otherwise, the master node sends the correct software packages to the node which then continues with the boot sequence.
Owner:CISCO TECH INC
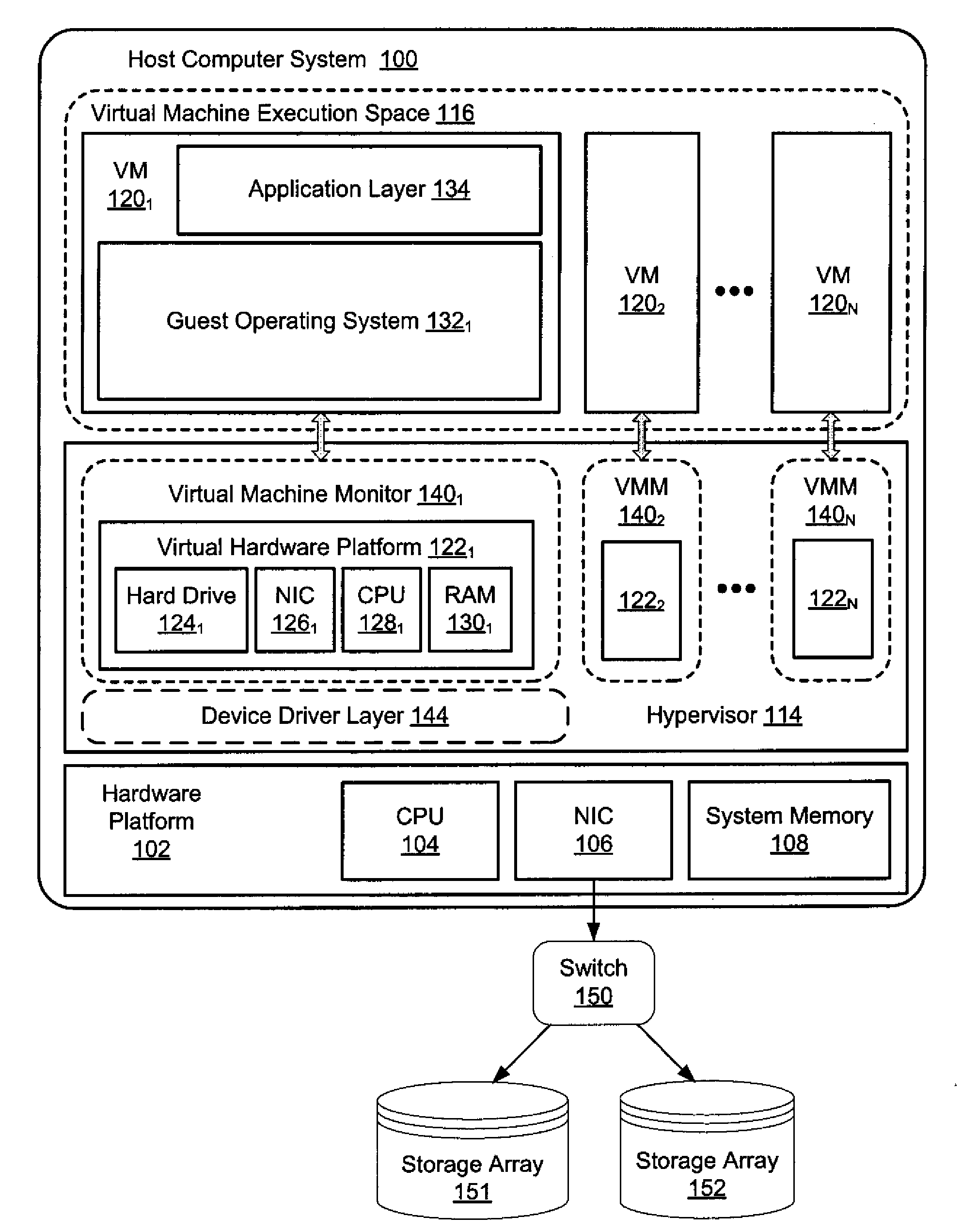
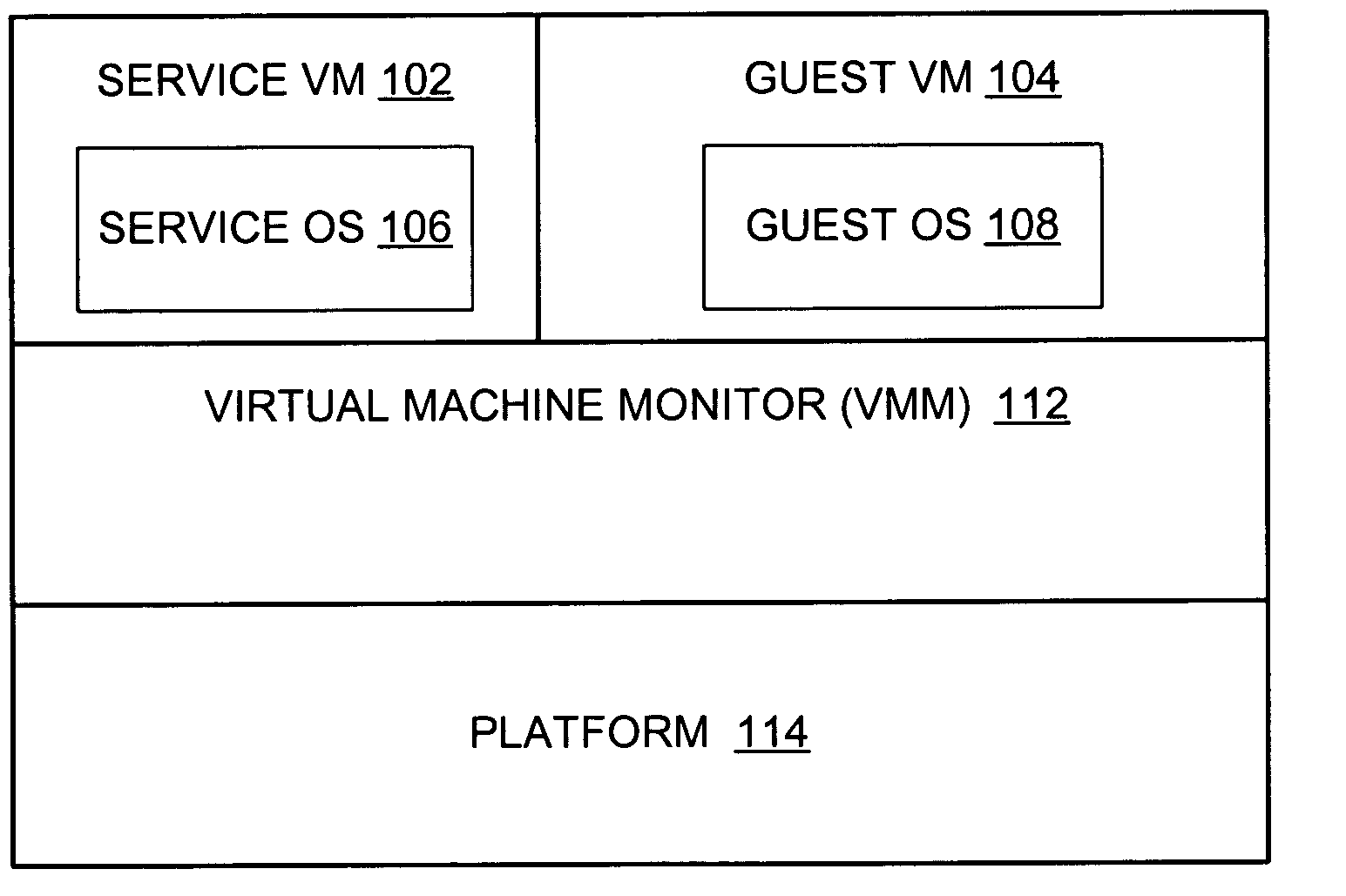
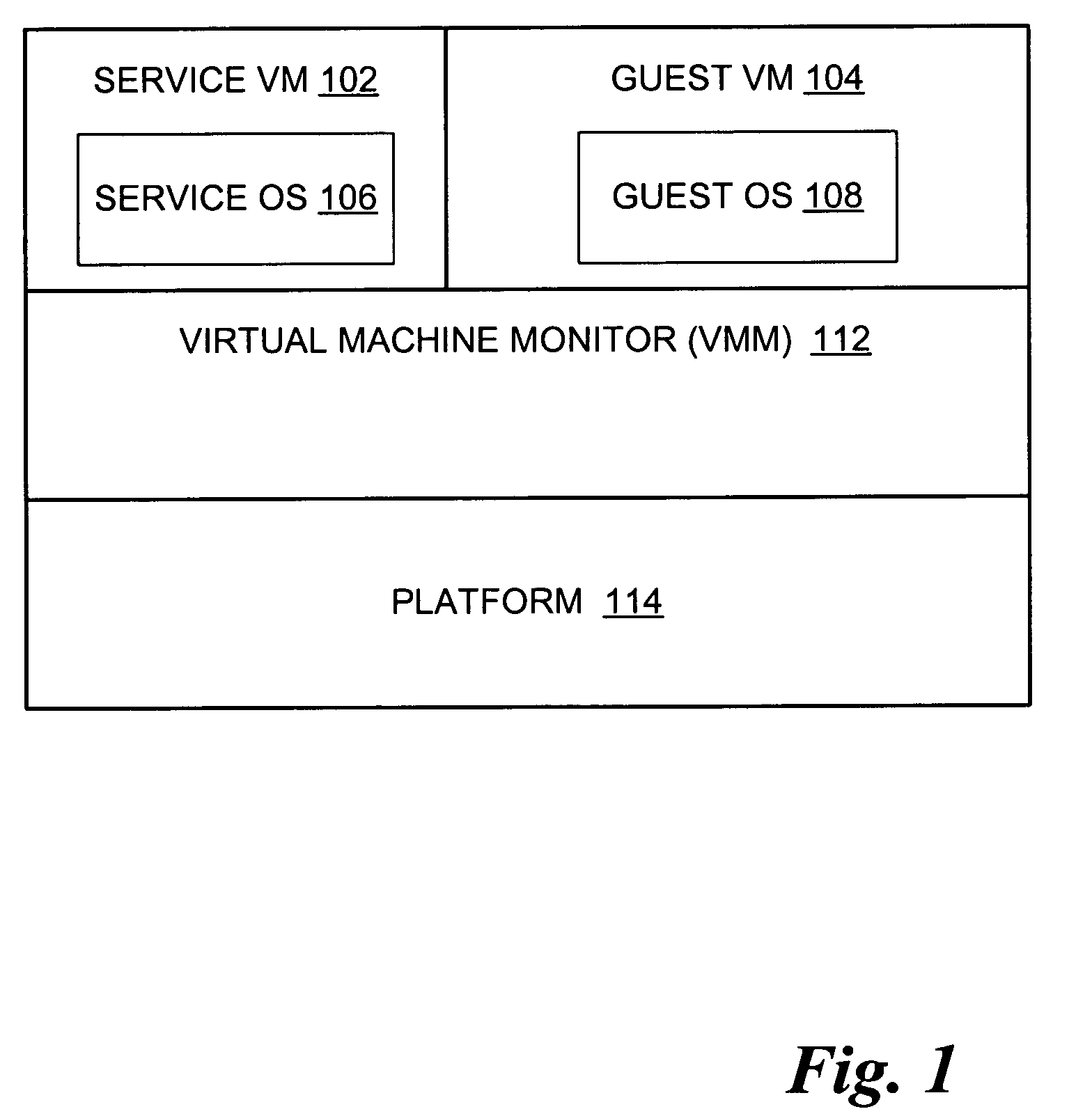
Switching between a service virtual machine and a guest virtual machine in a virtual machine monitor environment
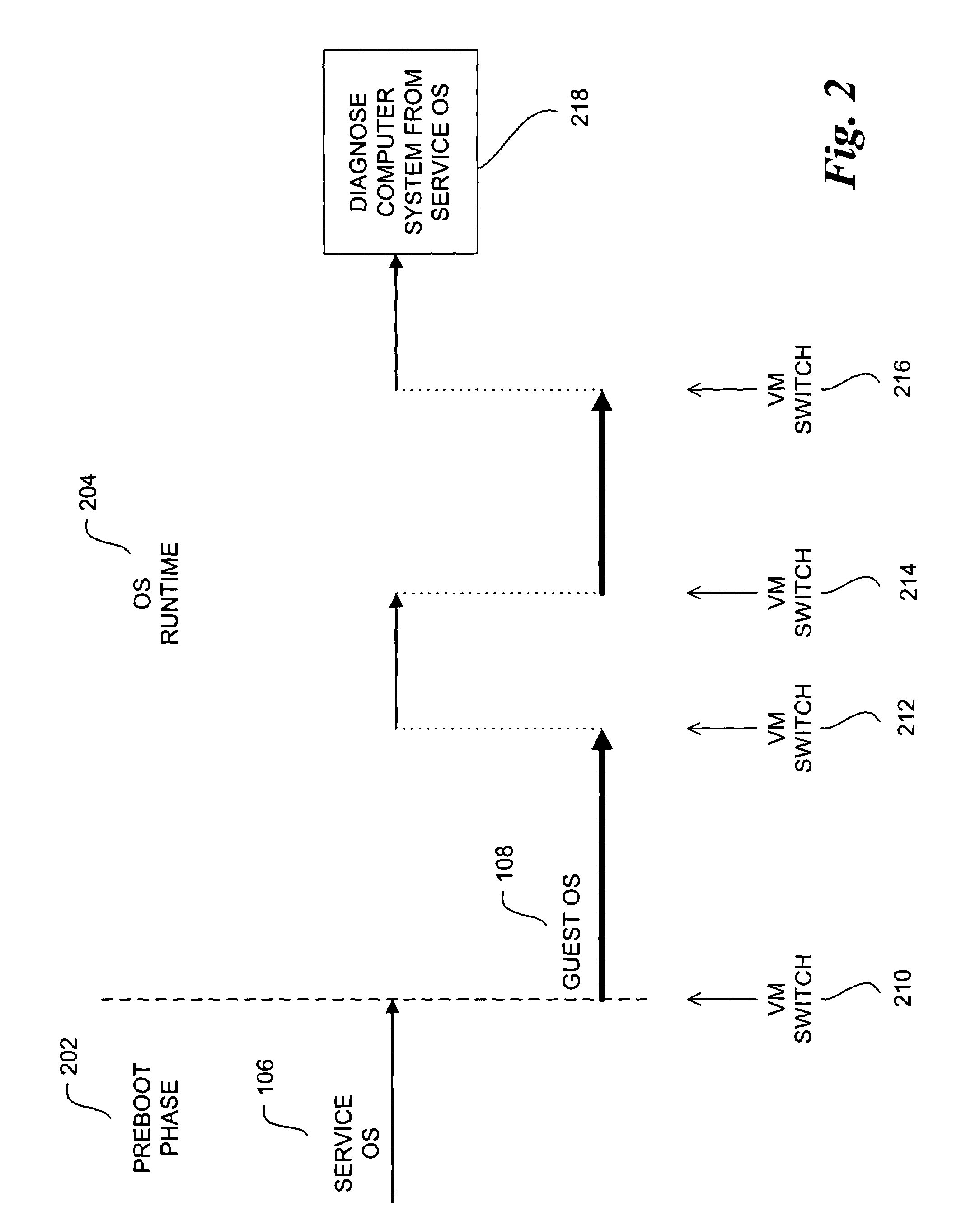
ActiveUS7370324B2Error detection/correctionMultiprogramming arrangementsOperational systemComputerized system
A method and system to switch between a Service virtual machine (VM) and a Guest VM in a virtual machine monitor (VMM) of a computer system. The VMM is loaded on the computer system to support a Service VM and a Guest VM. The Service OS is booted in the Service VM during the pre-boot phase. The Guest OS is booted in the Guest VM of the computer system. During OS runtime of the Guest OS, a VM switch is performed from the Guest VM to the Service VM without rebooting the computer system. The Service OS includes diagnostic tools to analyze the Guest OS. In one embodiment, the VM switch is performed by firmware of the computer system. In another embodiment, the VMM operates in accordance with an Extensible Firmware Interface (EFI) framework standard.
Owner:TAHOE RES LTD
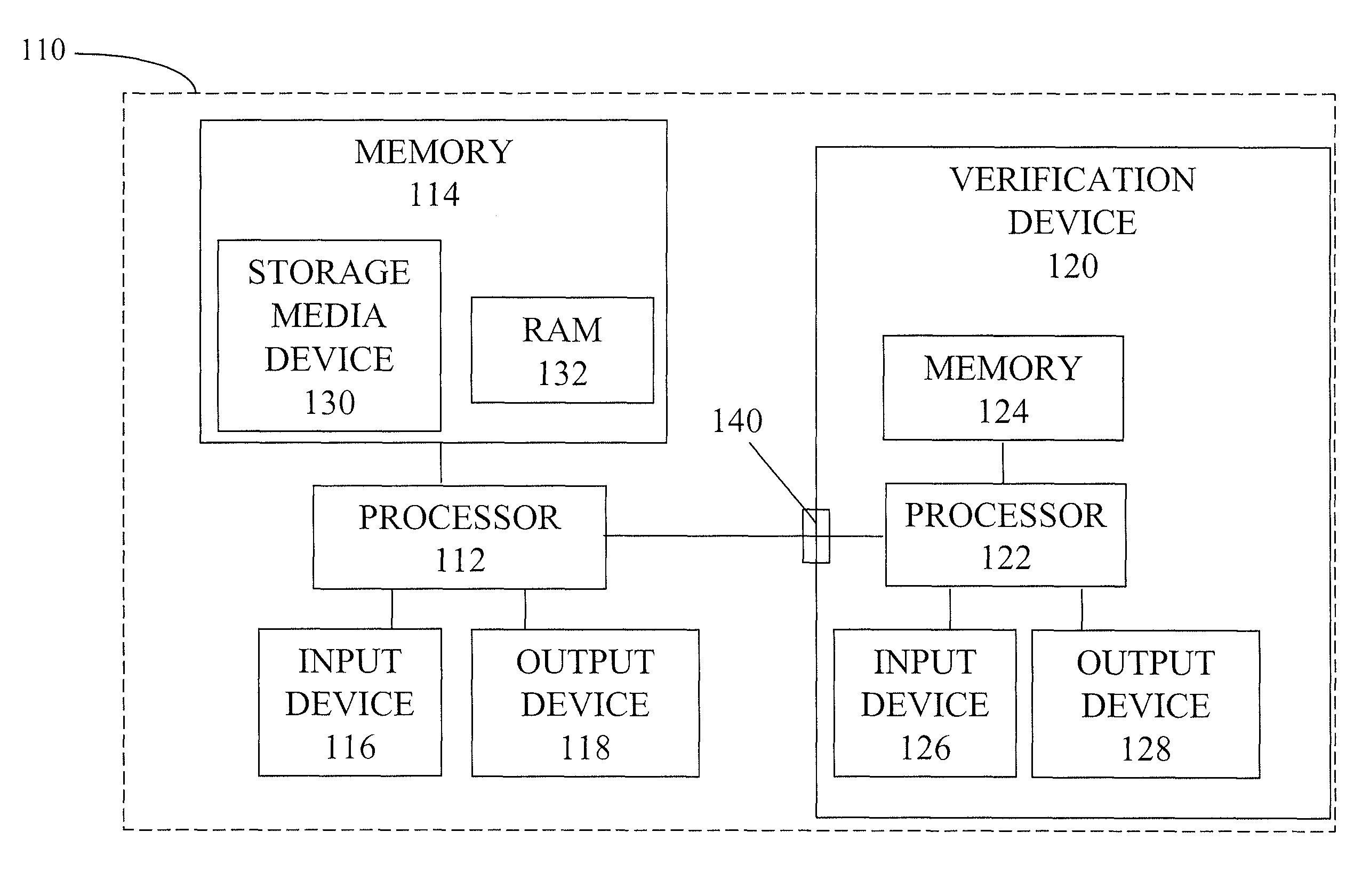
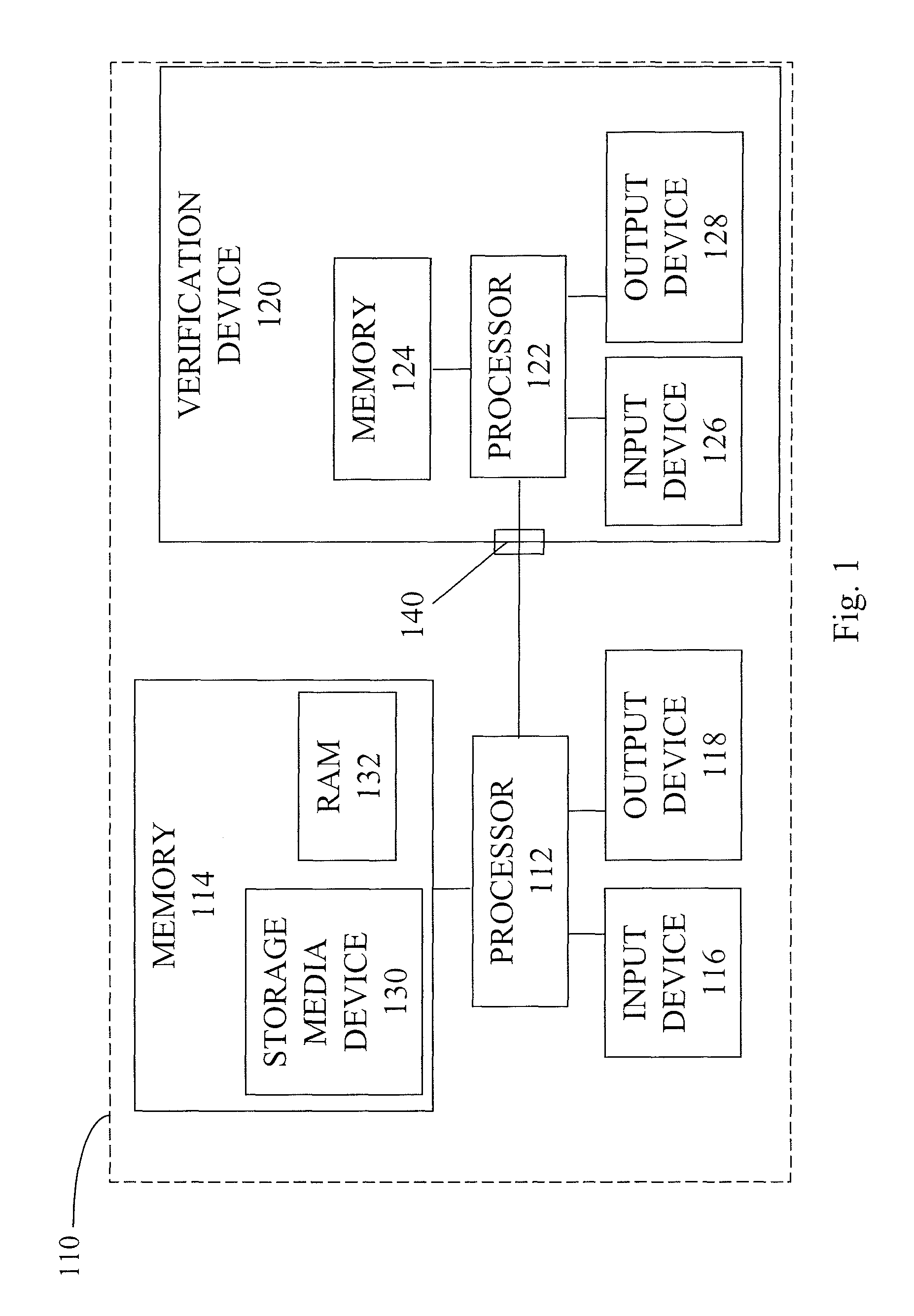
Methods and apparatuses for user-verifiable execution of security-sensitive code
ActiveUS8627414B1Accurate operationPreventing executionMemory loss protectionError detection/correctionRebootHypervisor
A computer including a processor and a verification device. The processor in the computer performs the steps of authenticating a secure connection between a hypervisor and the verification device, measuring the identity of at least a portion of a select guest before the select guest executes any instruction, and sending a measurement of the identity of the select guest to the verification device. The verification device compares the policy stored in the verification device with the measurement of the select guest received by the verification device. The steps of authenticating, measuring, sending, and comparing are performed after receiving a signal indicative of a request to execute the select guest and without rebooting the computer.
Owner:CARNEGIE MELLON UNIV
Module and method for automatic restoring BIOS device
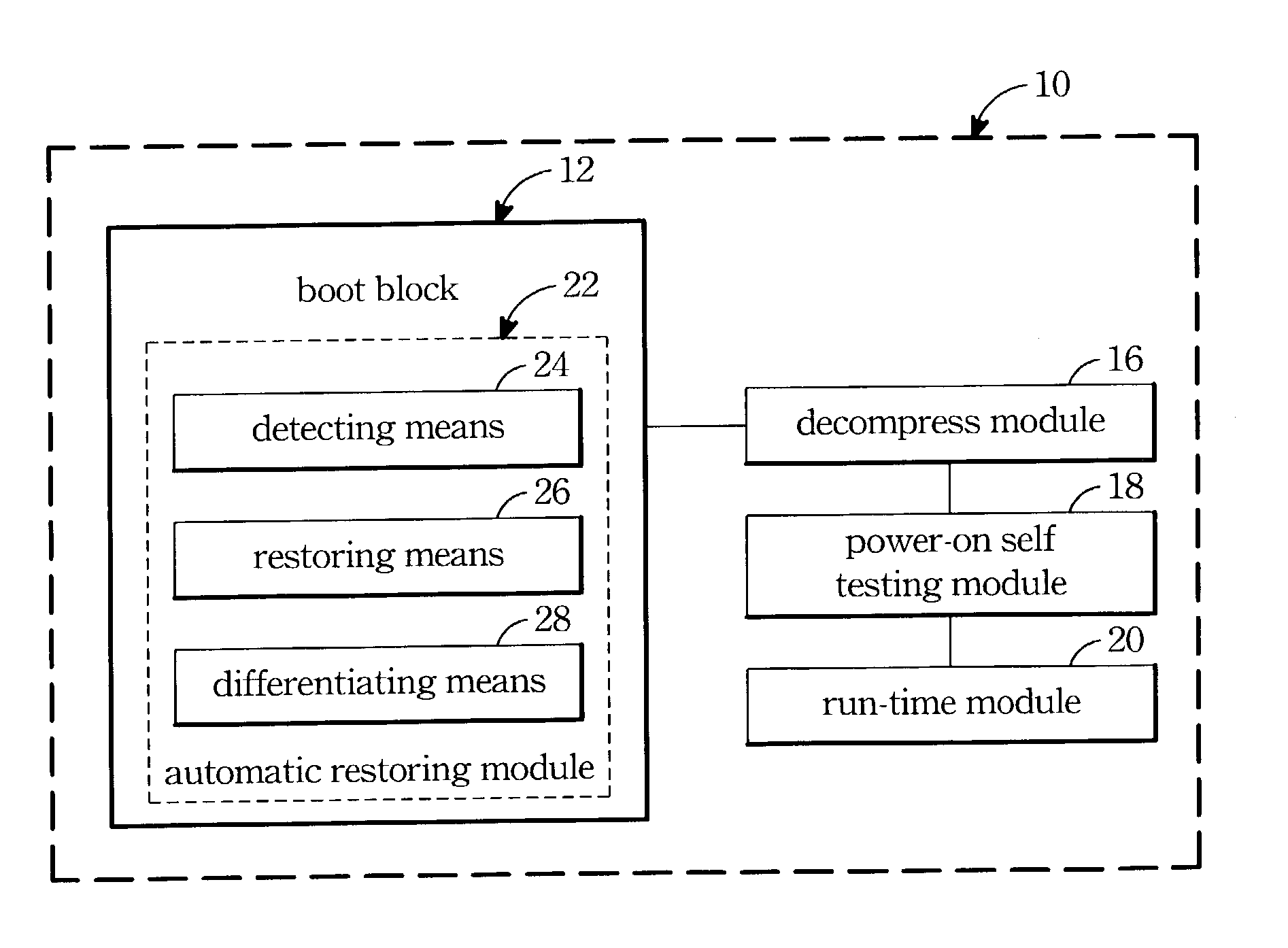
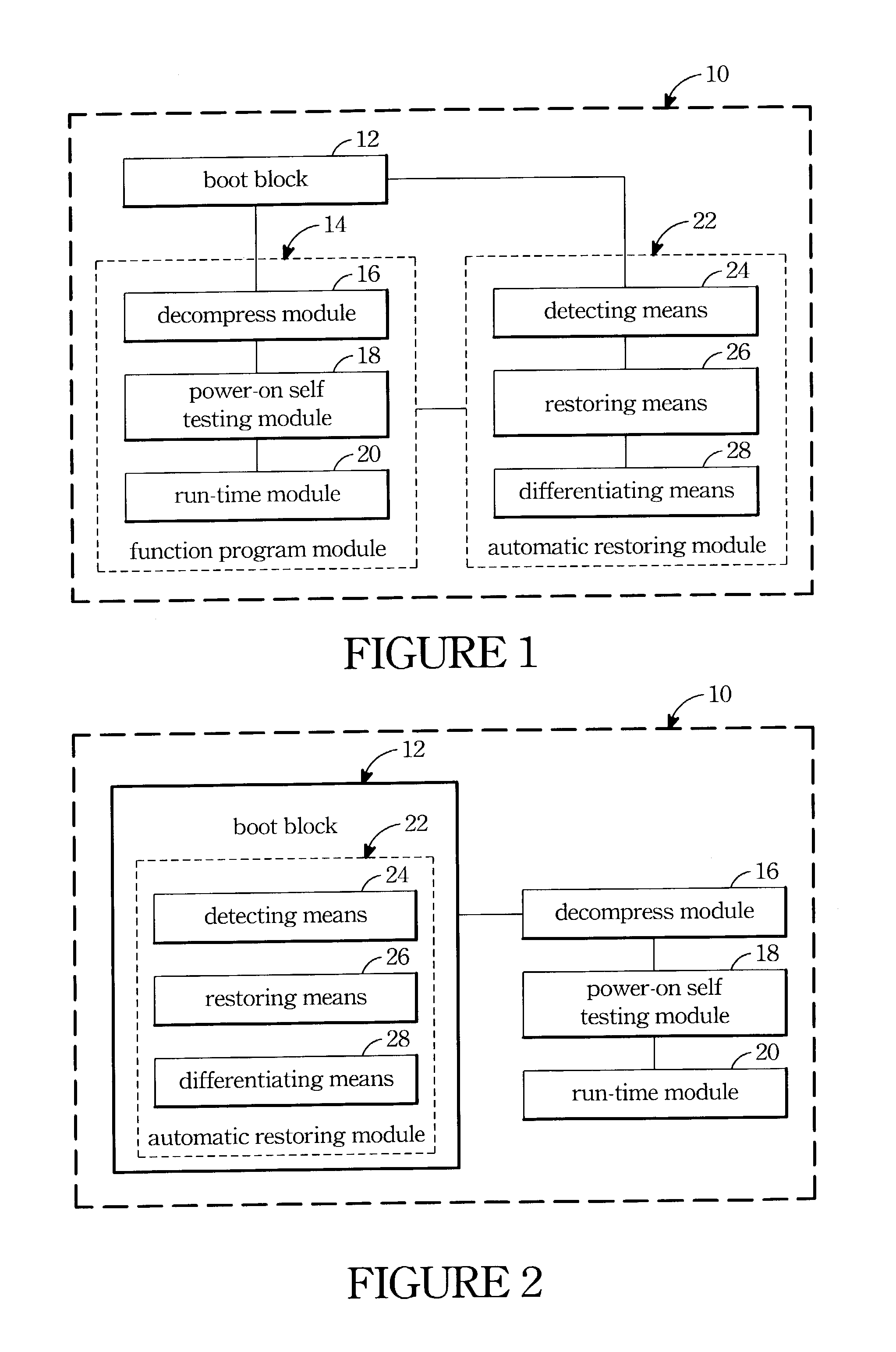
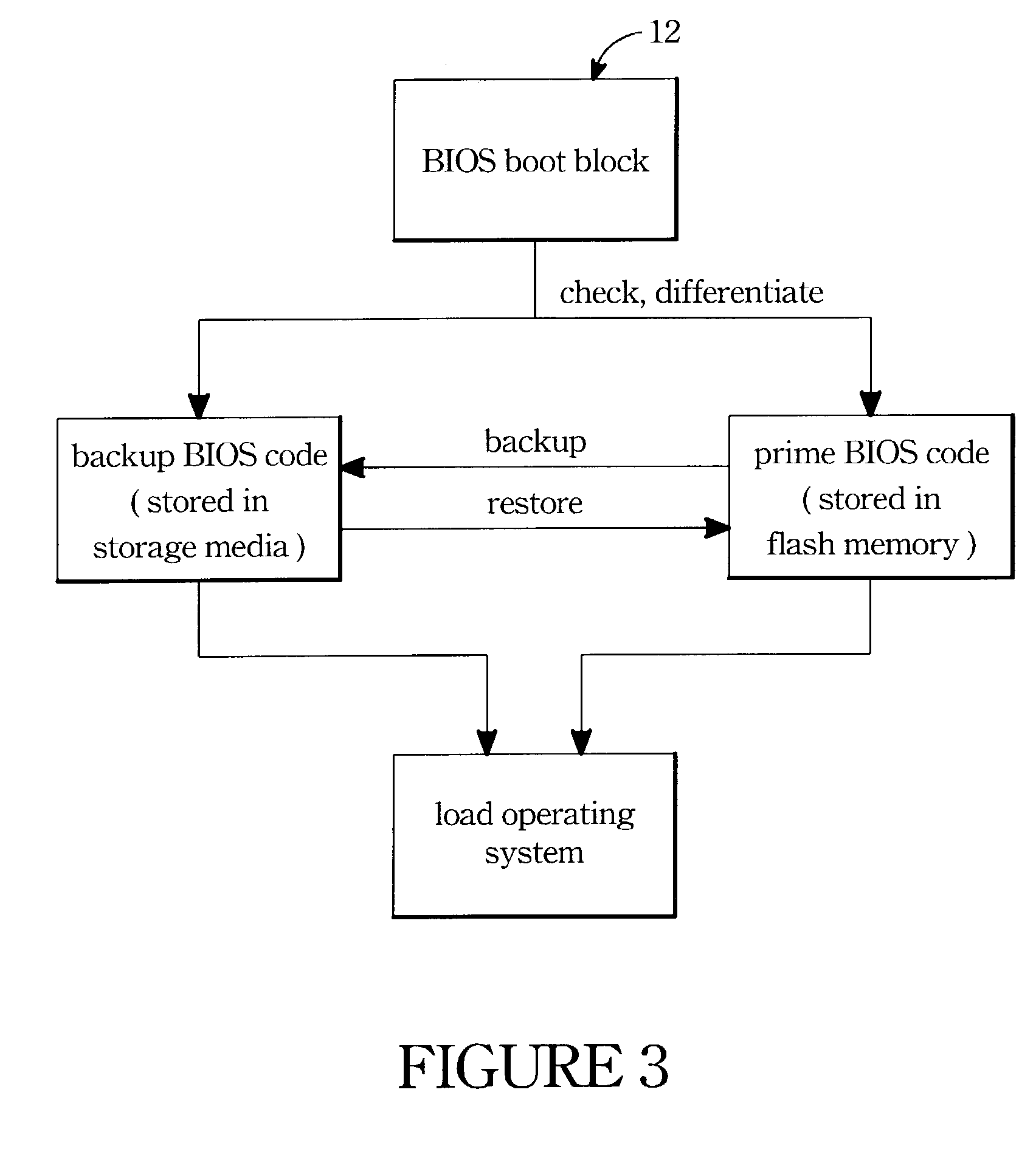
A BIOS module for automatic restoring and the related method are provided. The BIOS module has a BIOS memory and a prime BIOS code embedded therein. When the contents of a BIOS memory is damaged, a backup BIOS code can be loaded from other storage media for rebooting the computer system. The BIOS code comprises a BIOS function program module having a compressed function program, a detecting means for detecting the correctness of the BIOS function program module, a restoring module responsive to the detecting means for automatic rebooting the computer when the decompressing procedure has errors to load and execute the BIOS backup code from other storing media. And after rebooting the computer system successfully the restoring module also can restore the BIOS backup code into the BIOS memory. Besides, a differentiating means is applied to check the versions of the backup BIOS code and the prime BIOS code. When the prime BIOS code can boot the computer system successfully and the version thereof is latest than that of the backup BIOS code, the prime BIOS code can be backuped to the storage media.
Owner:ASUSTEK COMPUTER INC
Reboot manager usable to change firmware in a high availability single processor system
ActiveUS7188237B2Efficient schedulingError detection/correctionDigital computer detailsDowntimeHigh availability
Owner:AVAGO TECH INT SALES PTE LTD
Persistent snapshot management system
InactiveUS7237080B2Digital data processing detailsMemory adressing/allocation/relocationHard disc drivePrimitive state
Owner:COLUMBIA DATA PRODUCTS
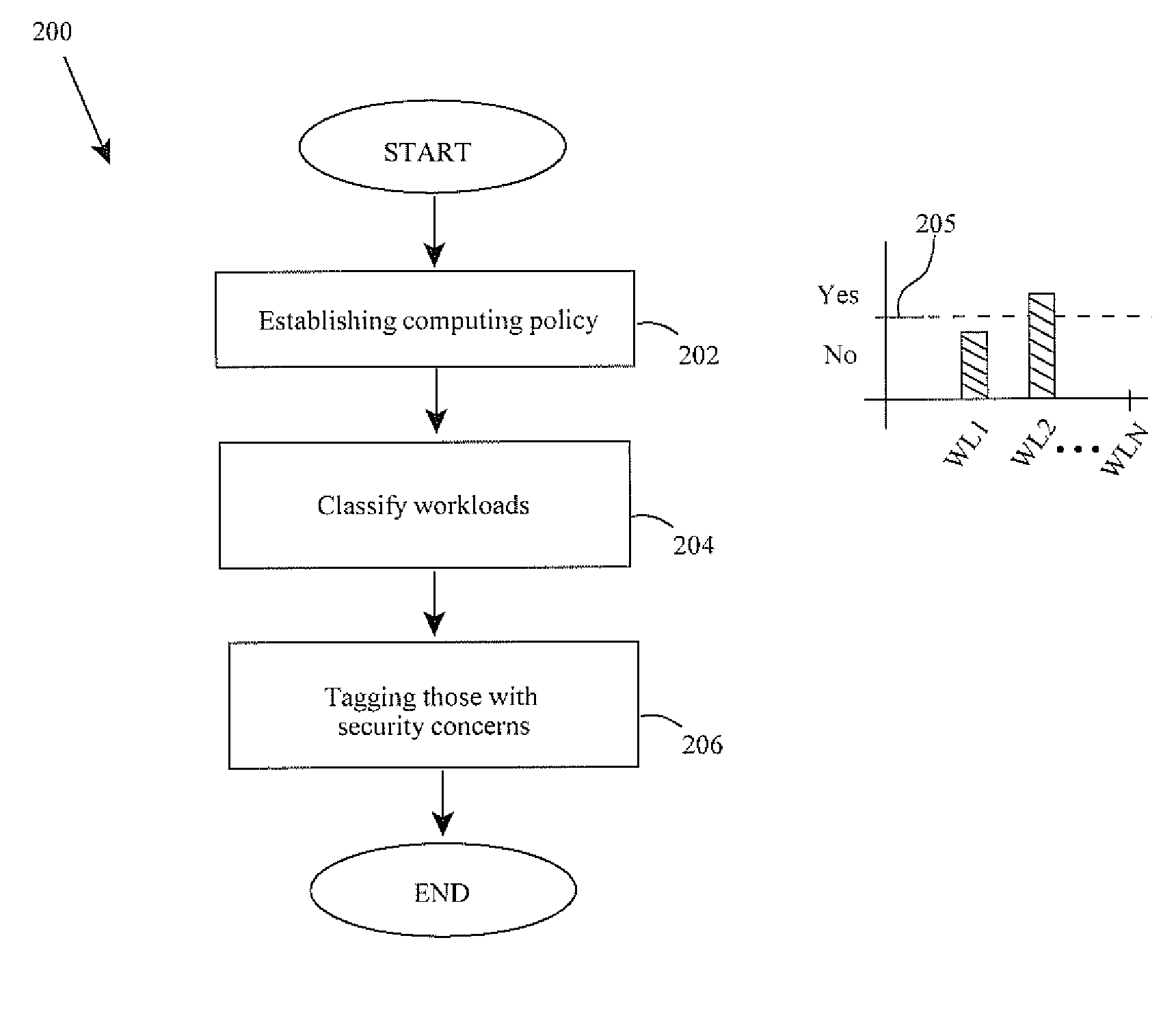
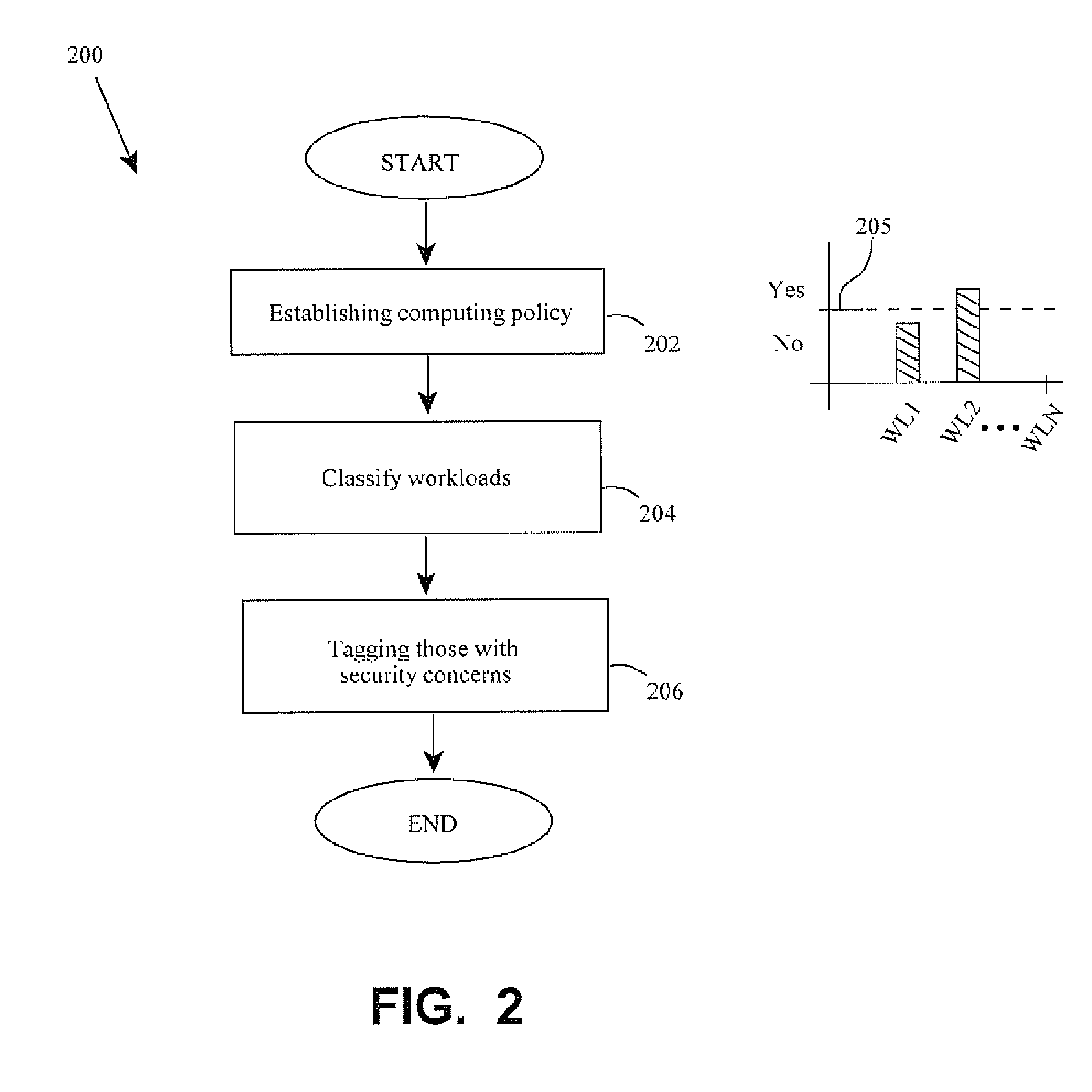
Securely hosting workloads in virtual computing environments
ActiveUS20100275241A1Poor resource utilizationImprove resource utilizationSpecific access rightsDigital data processing detailsSecurity questionWorkload
Methods and apparatus involve securely hosting workloads. Broadly, computing workloads are classified according to security concerns and those with common concerns are deployed together on common hardware platforms. In one instance, security tags are bi-modally attached or not to workloads meeting a predetermined security threshold. Those with tags are deployed on a common machine while those without tags are deployed on other machines. Tags may be embedded in meta data of open virtual machine formats (OVF). Considerations for re-booting computing devices are also contemplated as are multiplexing workloads. Computer program products are further disclosed.
Owner:SUSE LLC
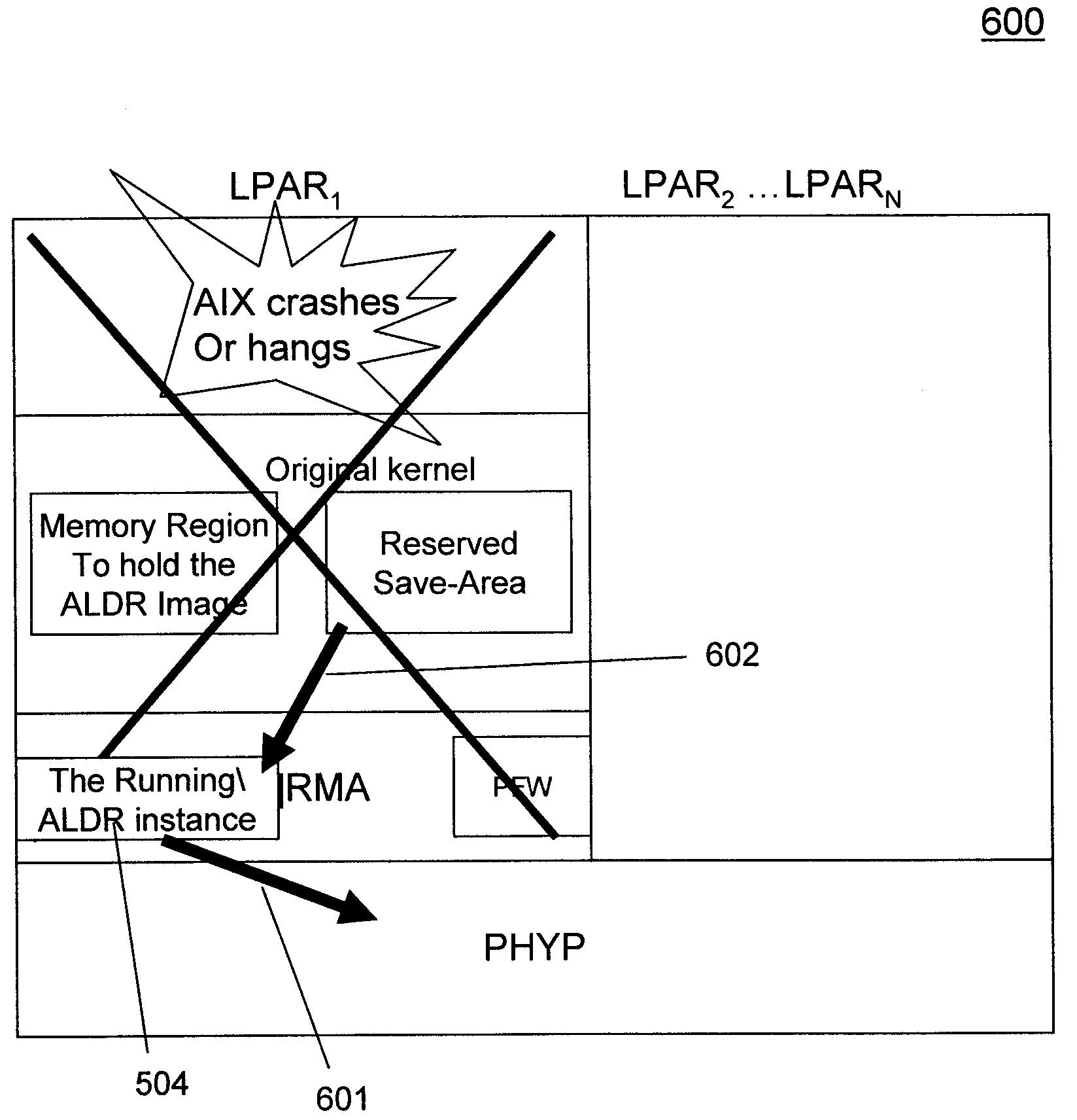
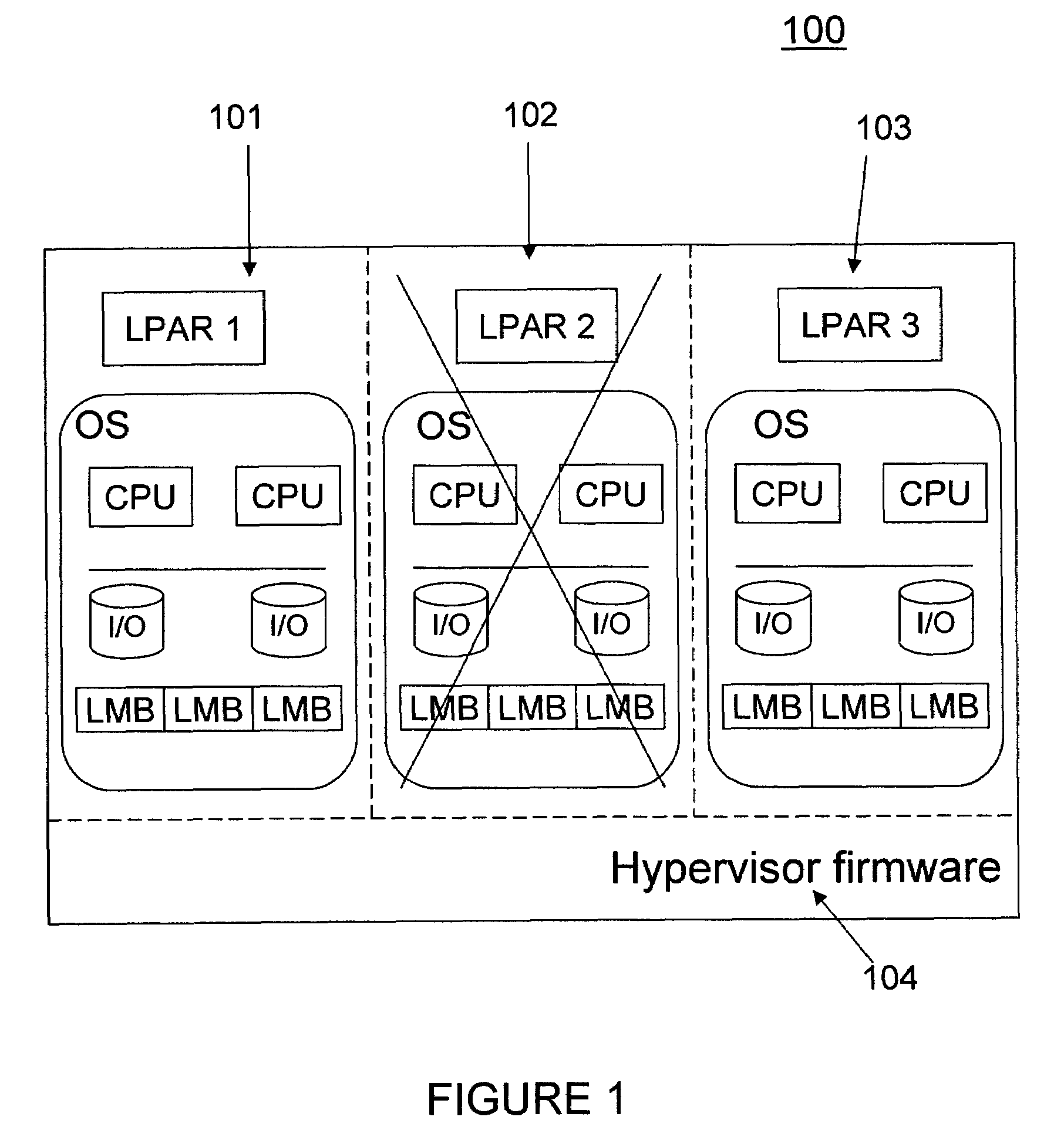
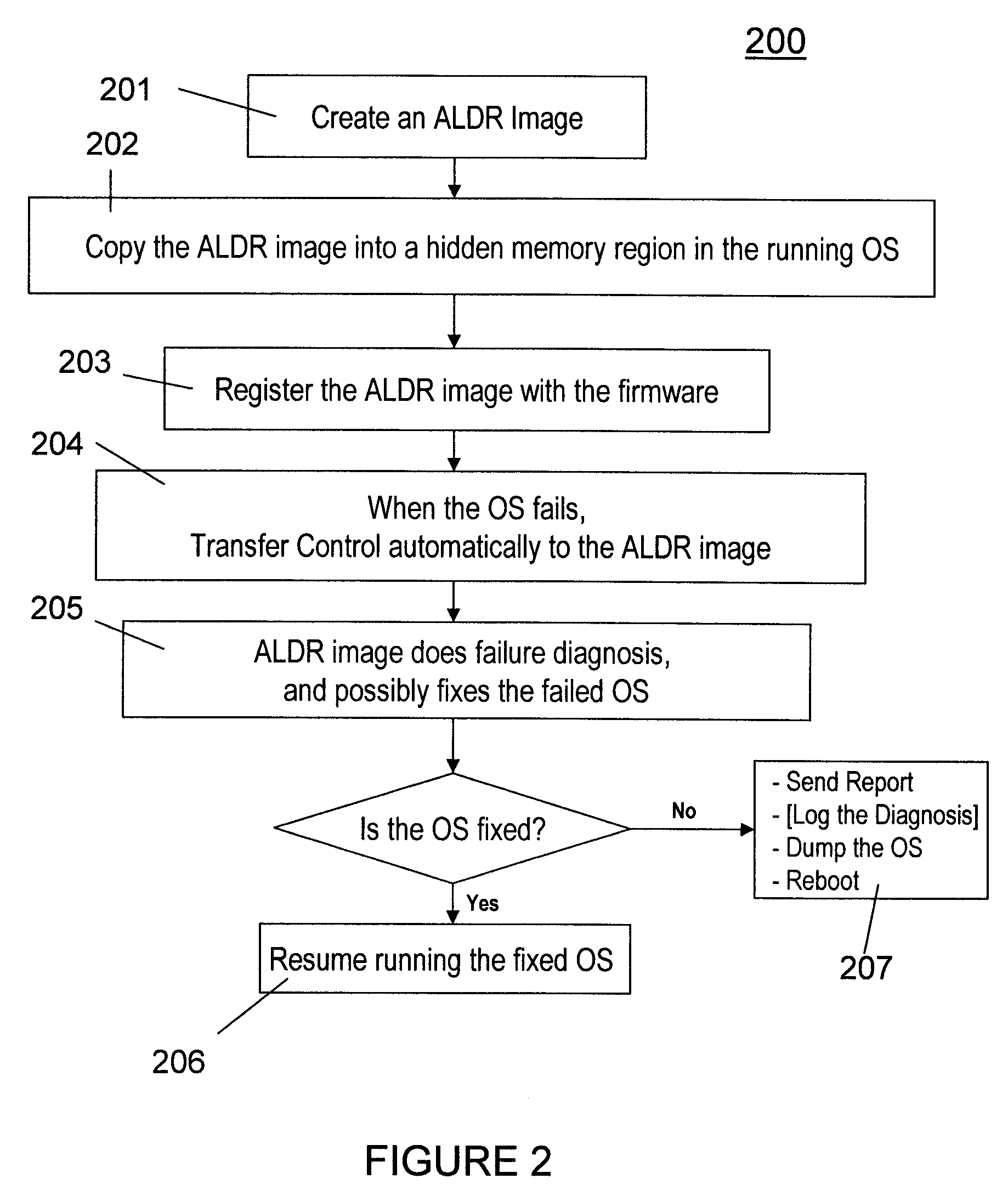
Automated transition to a recovery kernel via firmware-assisted-dump flows providing automated operating system diagnosis and repair
InactiveUS20110035618A1Memory adressing/allocation/relocationNon-redundant fault processingOperational systemSystem diagnosis
A method (and structure) of operating an operating system (OS) on a computer. When a failure of the OS is detected, the computer automatically performs a diagnosis of the OS failure. The computer also attempts to automatically repair / recover the failed OS, based on the diagnosis, without requiring a reboot.
Owner:GLOBALFOUNDRIES INC
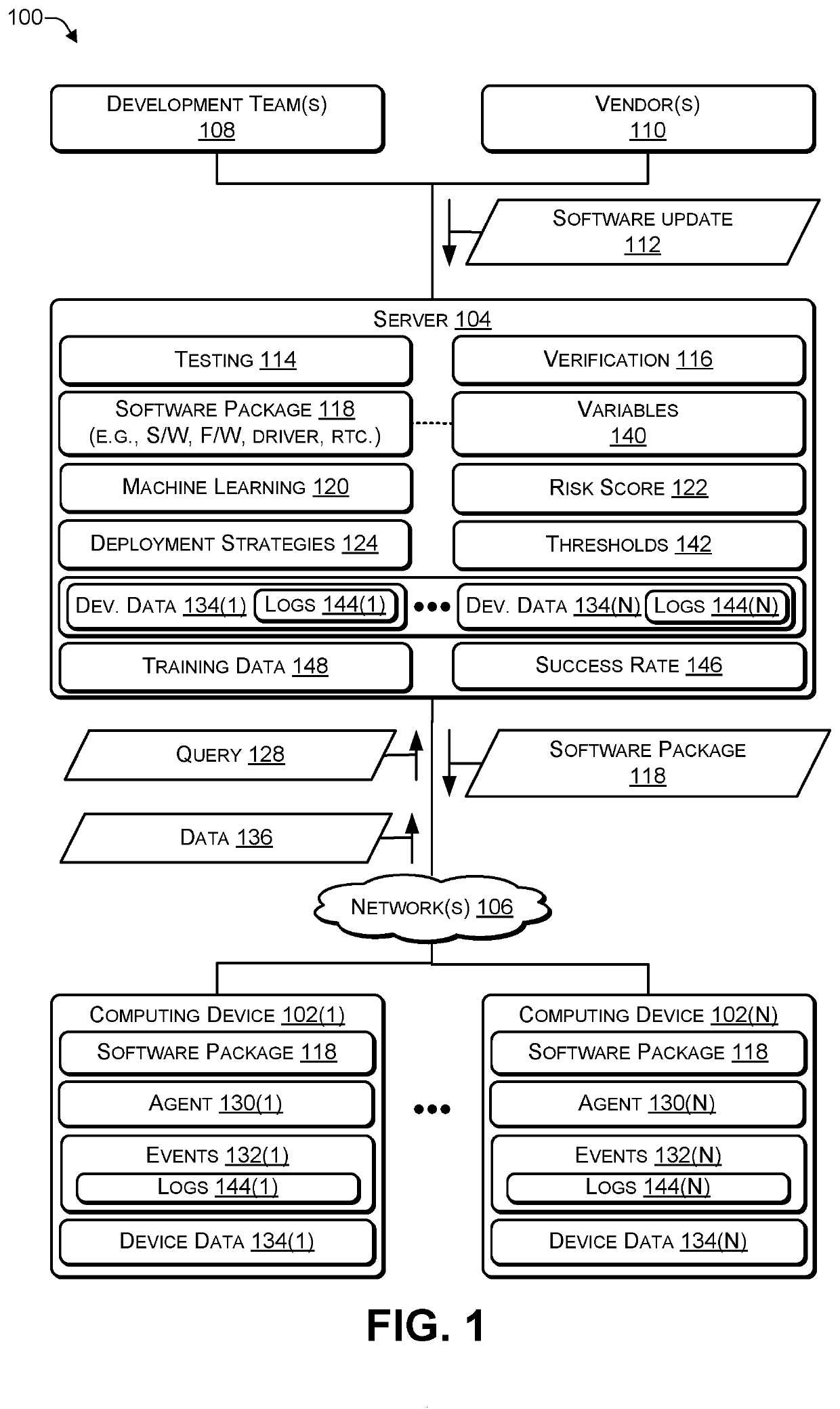
Predicting a success rate of deploying a software bundle
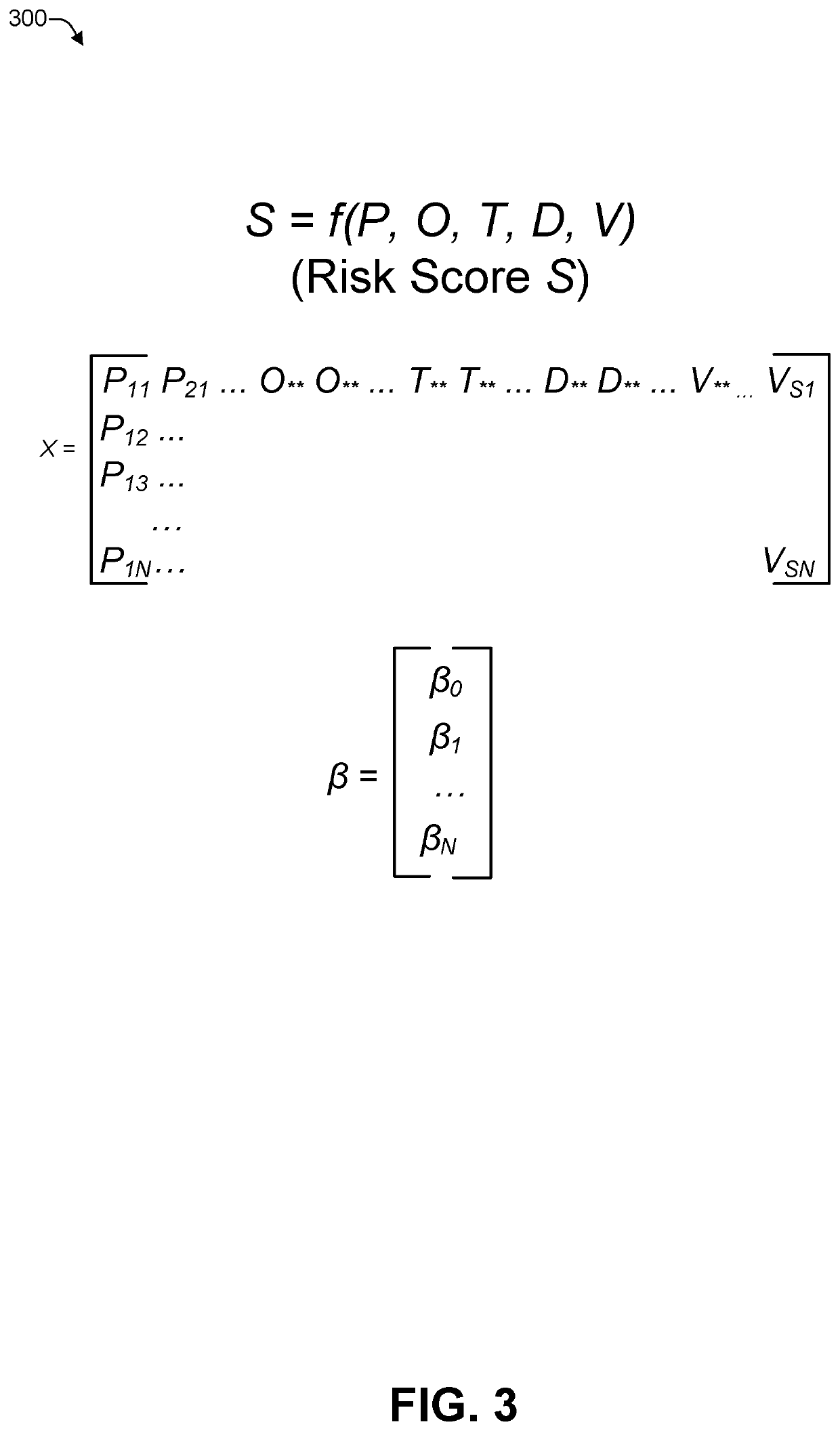
In some examples, a server may determine a plurality of variables associated with a software package. For example, the plurality of variables may include a size of the software package, a reboot variable associated with the software package indicating whether a reboot is to be performed after installing the software package, and an installation type indicating whether the software package is a first install or an upgrade. The server may execute a machine learning model to determine, based on the plurality of variables, a risk score predicting an installation success rate of the software package. The server may select a deployment strategy from a plurality of deployment strategies based at least in part on the risk score and the plurality of variables. The server may provide the software package to a plurality of computing devices in accordance with the deployment strategy.
Owner:DELL PROD LP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com