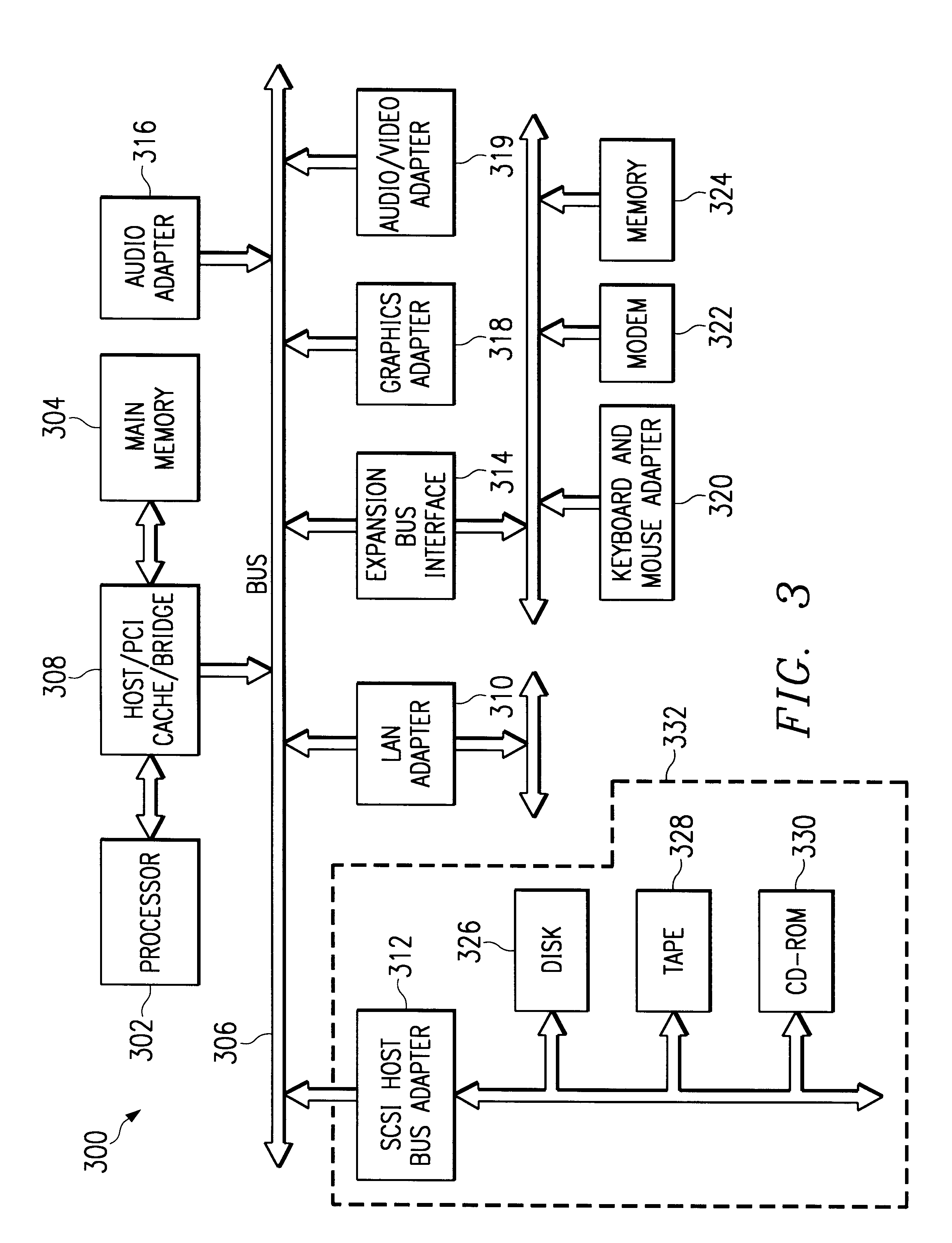
Patents
Literature
2093 results about "Booting" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, booting is the process of starting a computer. It can be initiated by hardware such as a button press, or by a software command. After it is switched on, a computer's central processing unit (CPU) has no software in its main memory, so some process must load software into memory before it can be executed. This may be done by hardware or firmware in the CPU, or by a separate processor in the computer system.
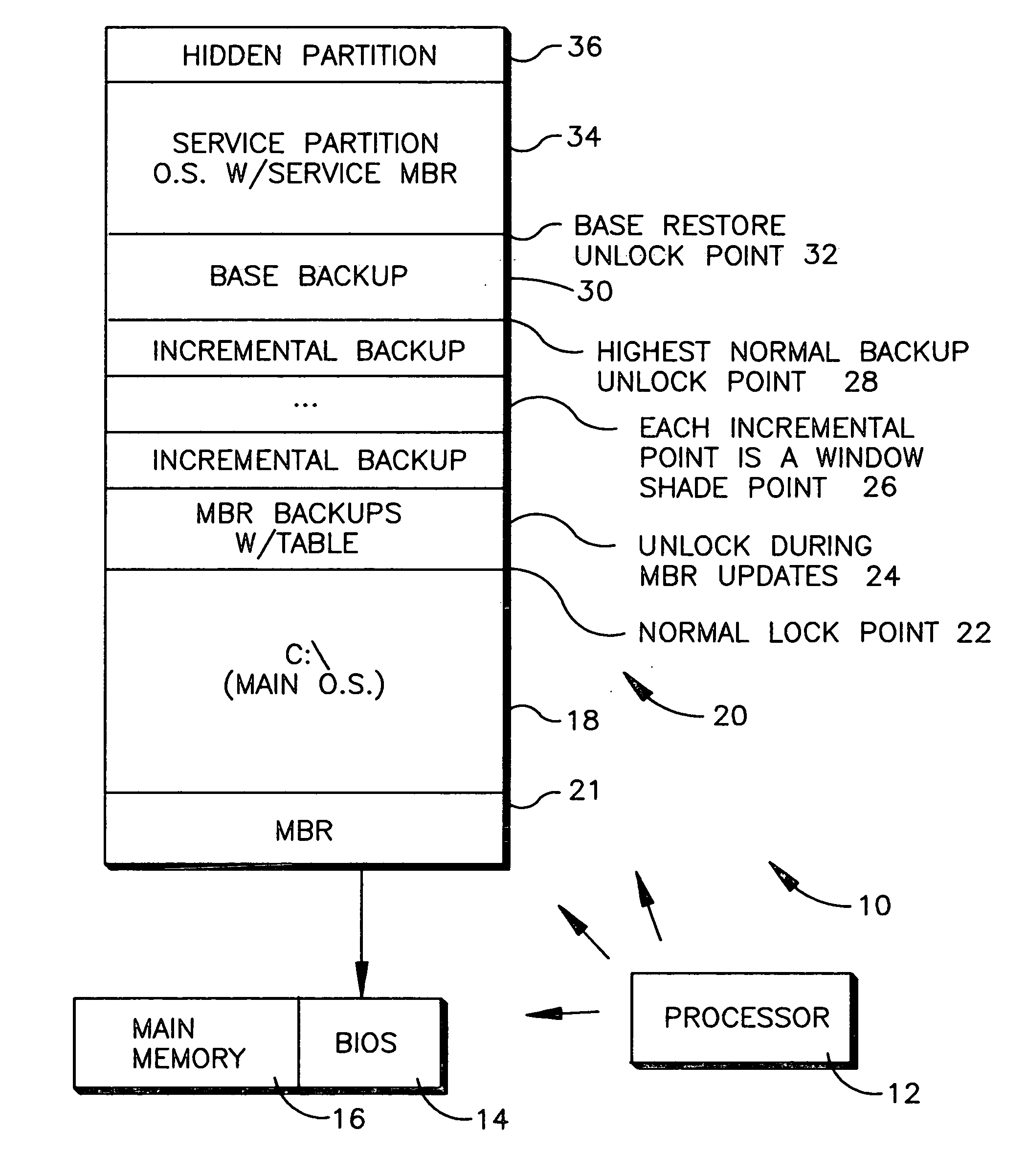
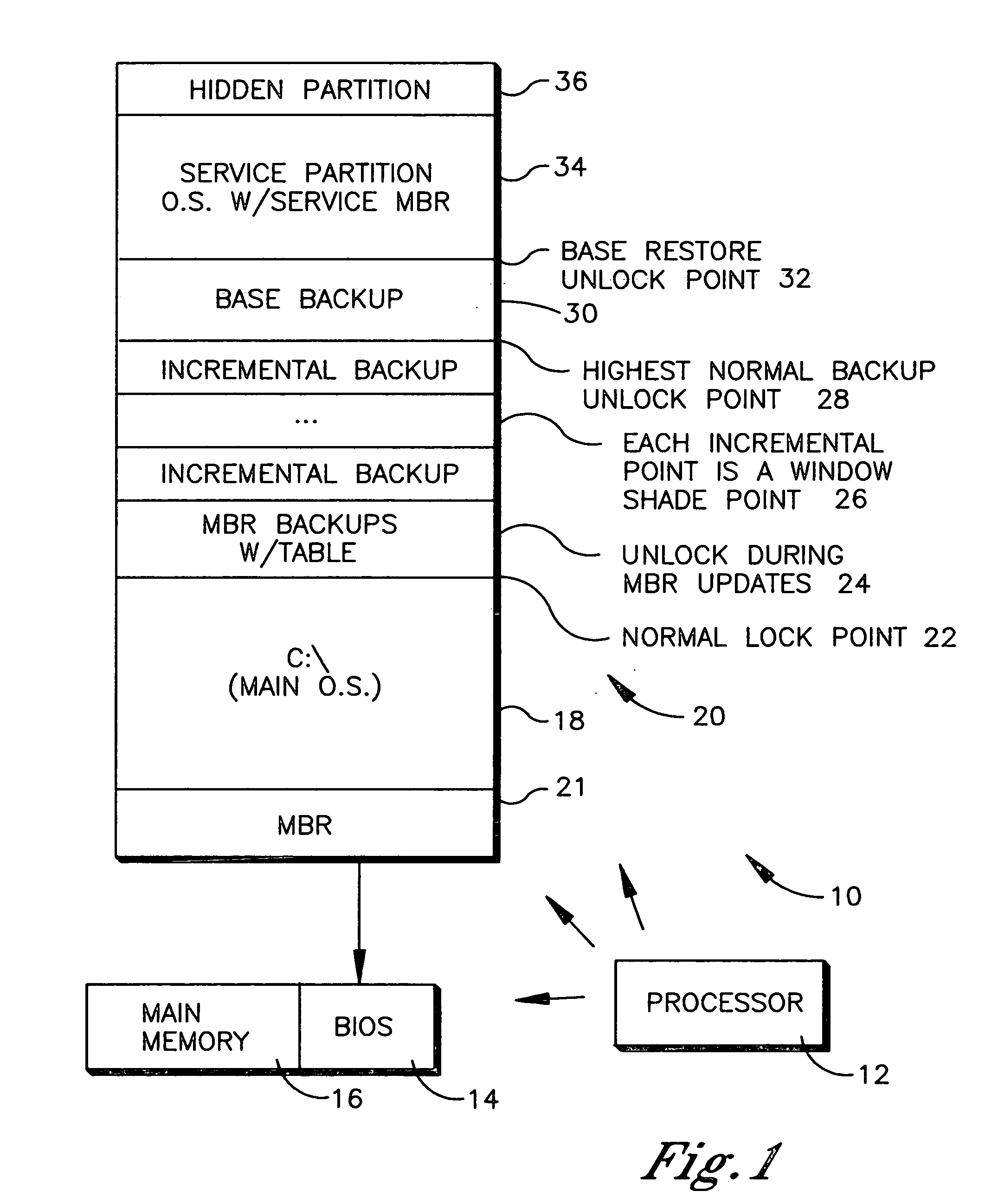
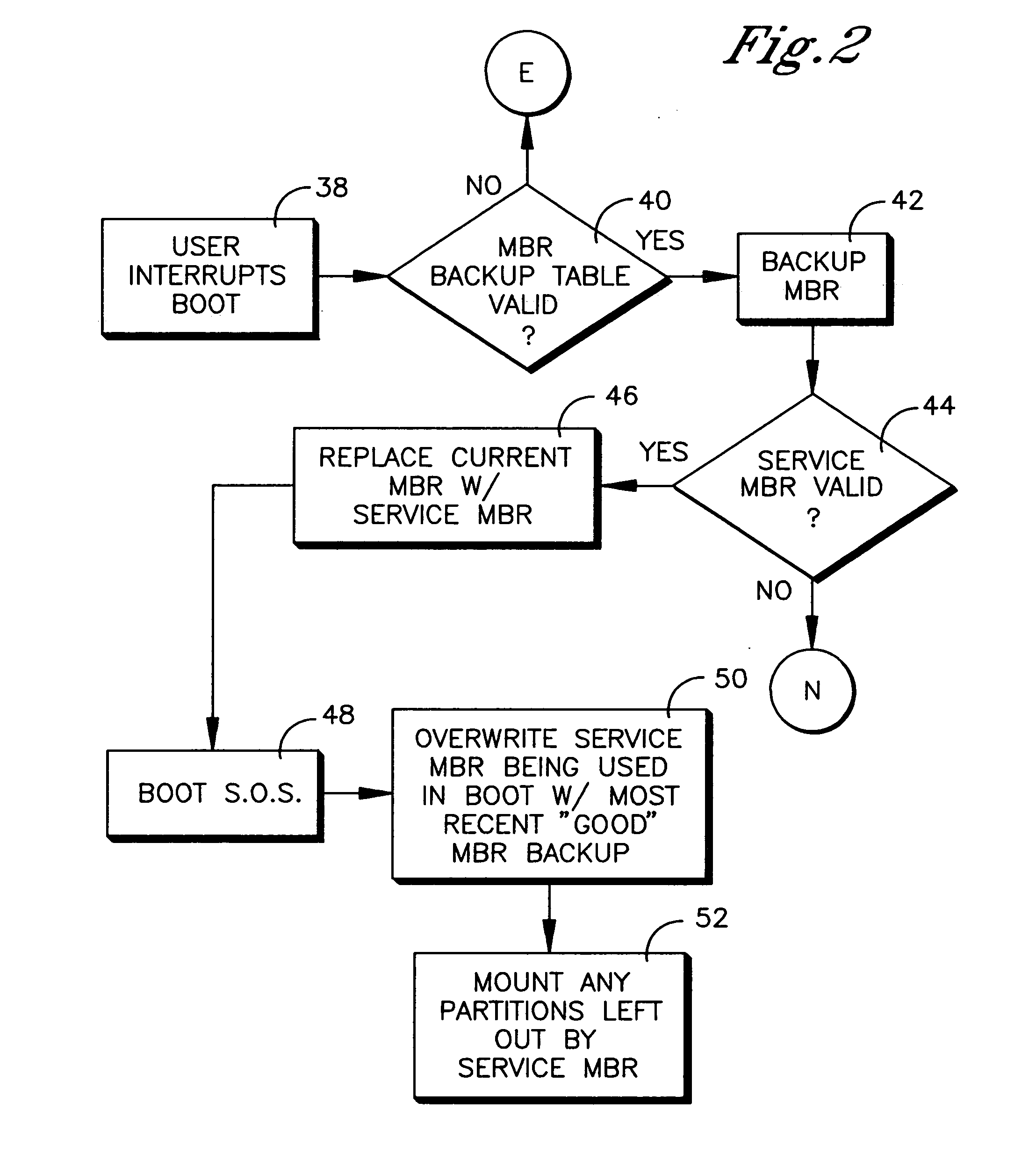
System and method for booting alternate MBR in event of virus attack
ActiveUS20080046781A1Digital computer detailsPlatform integrity maintainanceHard disc driveOperational system
In the event of a virally infected MBR on a hard disk drive that might prevent booting, a service MBR in a hidden protected area (HPA) can be used to boot a service O.S., and then the service MBR can be replaced with a previously backed-up MBR, also in the HPA, to mount any missing partitions.
Owner:LENOVO PC INT
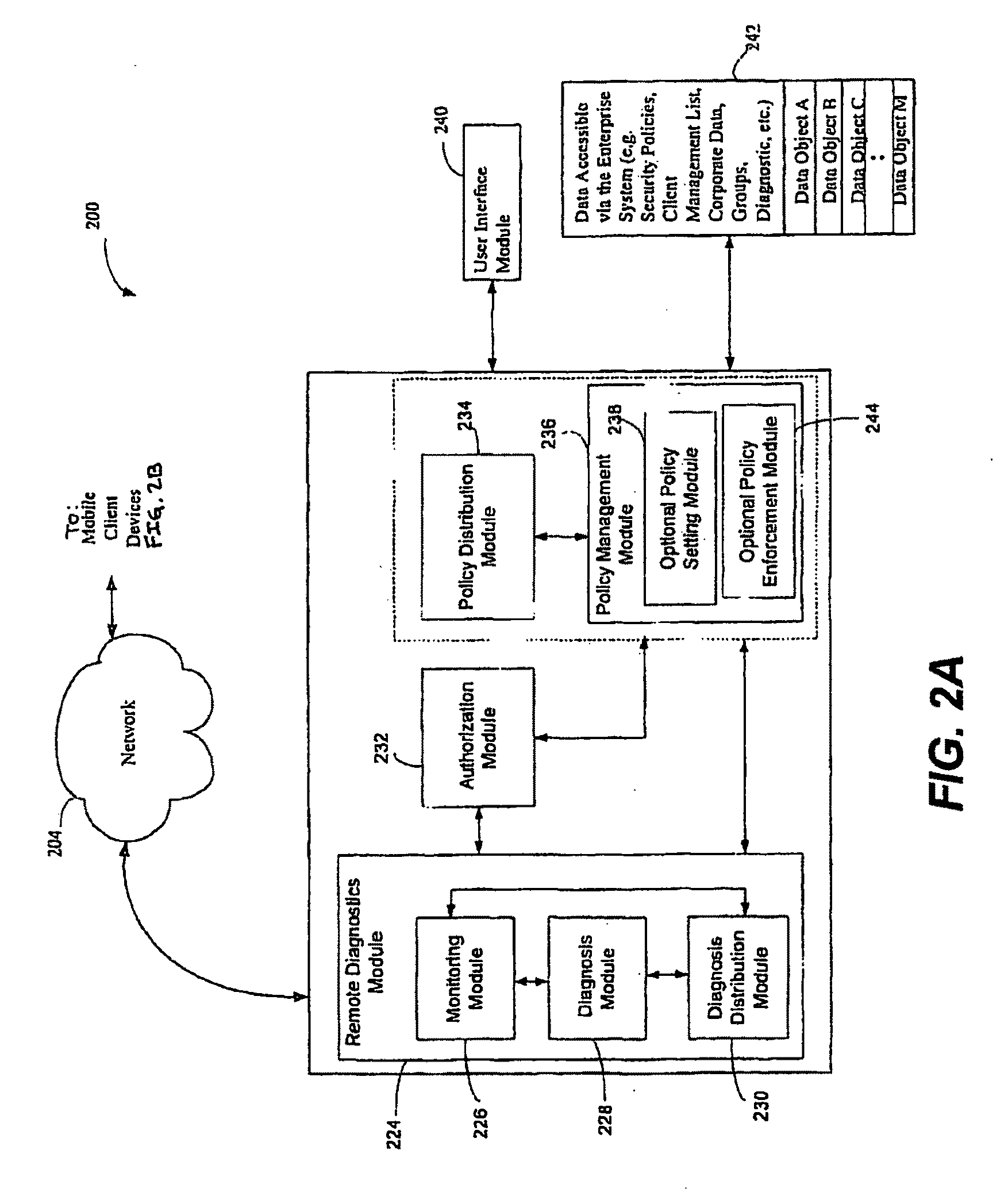
Pre-boot securing of operating system (OS) for endpoint evaluation
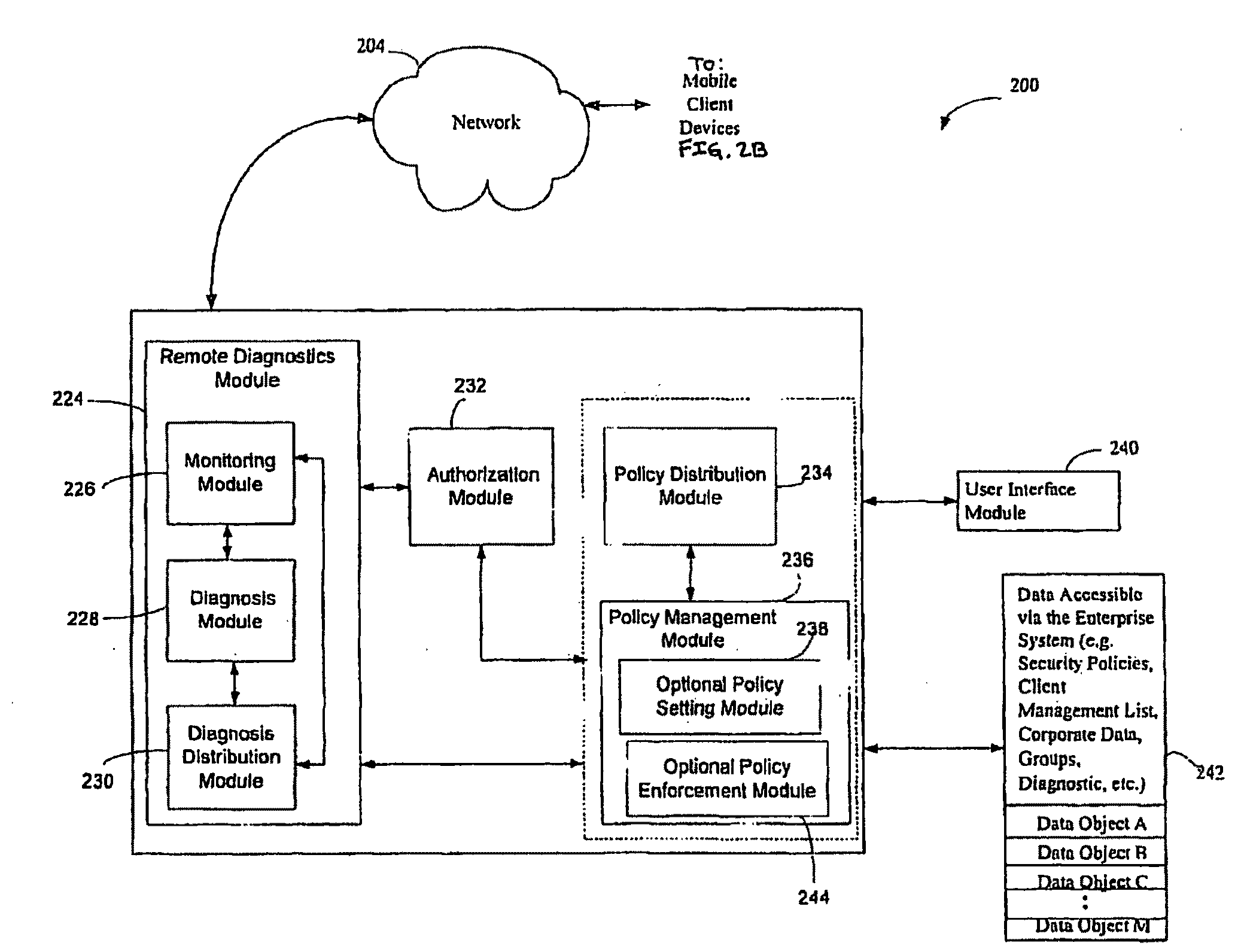
Methods and apparatus involve evaluating endpoint computing assets. The endpoint has both a traditional operating system for applications, and the like, and another operating system during a pre-boot phase of operation. During use, the traditional operating system identifies a last evaluation status of the computing device at a time just prior to shutting down. Upon a next booting, the pre-boot operating system loads and examines [reads] the last evaluation status. If the last evaluation status requires any completion action in order to comply with a predetermined computing policy, either or both the operating systems attend to its effectuation, including communication / handoff by way of one or more security agents. In a variety of ways, effectuation occurs by: determining a present location of the computing device, quarantining the computing device from certain network traffic; VPN enforcement; patching applications; firewall involvement; etc. Computer program products are also disclosed.
Owner:MICRO FOCUS SOFTWARE INC
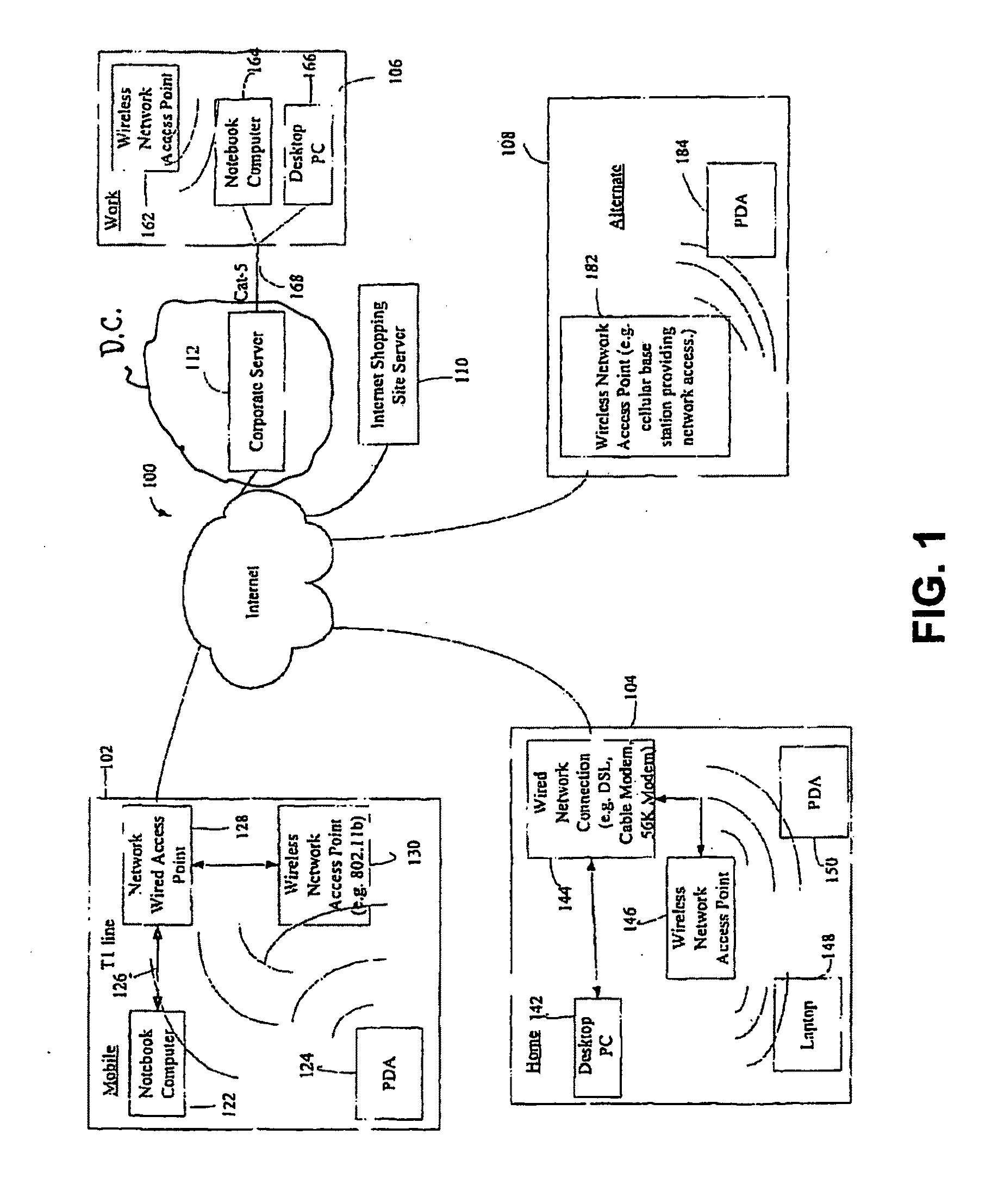
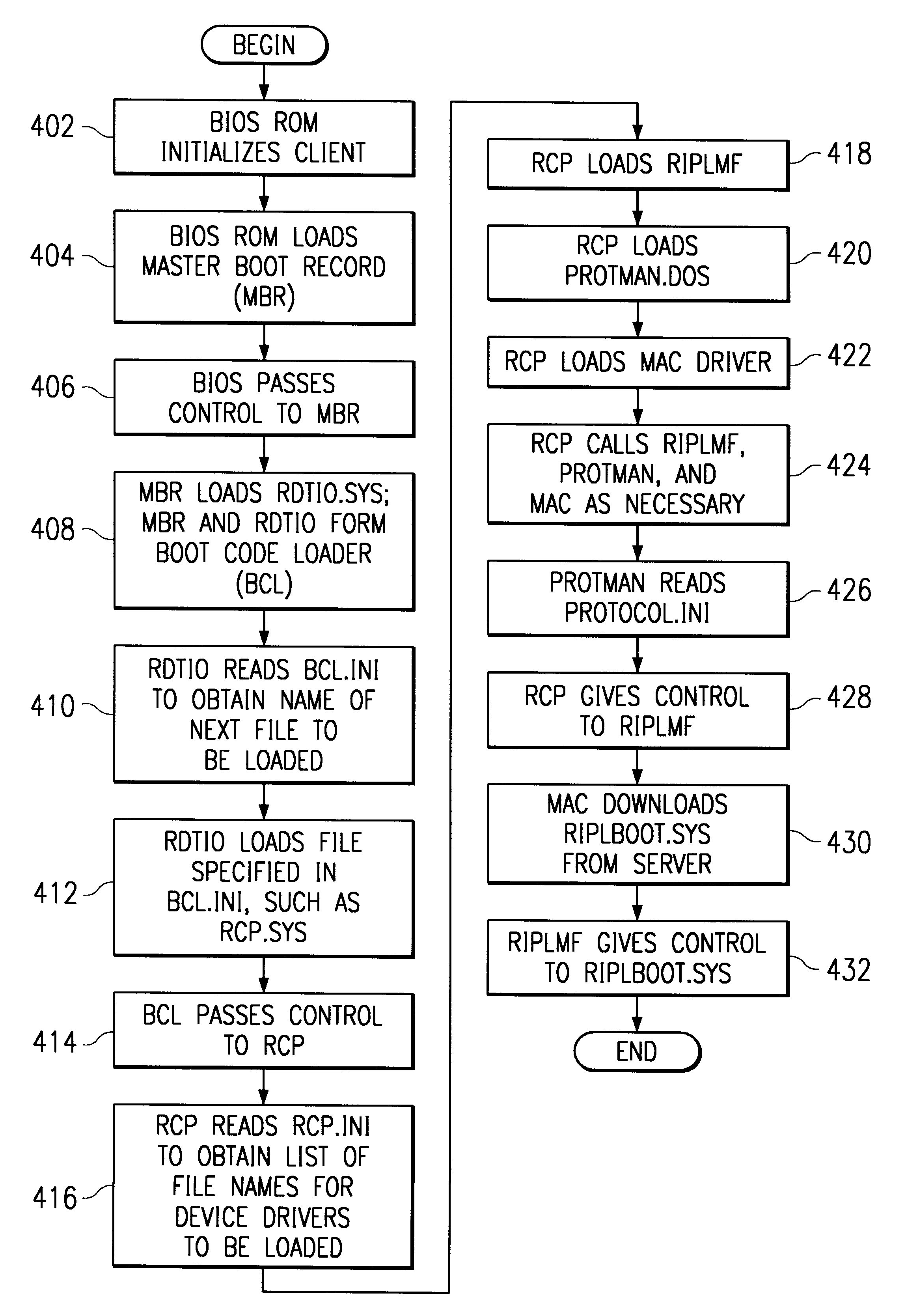
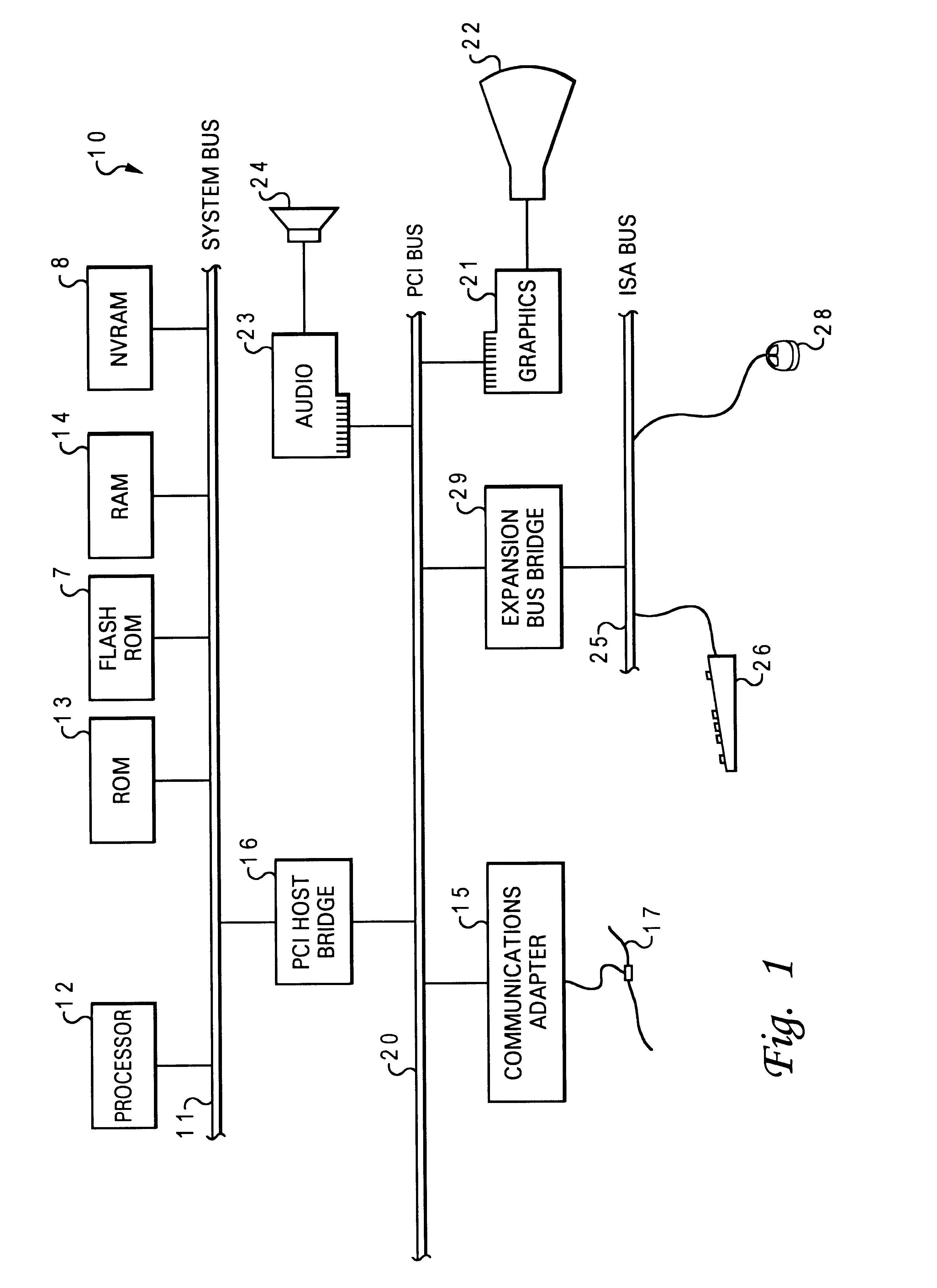
Method and apparatus for remotely booting a client computer from a network by emulating remote boot chips
A method and apparatus for booting a client computer connected to a network without a boot ROM and without an operating system is provided. Instructions from a BIOS ROM are executed to load a boot code loader from a nonvolatile, read / write memory, such as a diskette or hard disk. The boot code loader executes to load a control program from the diskette, and the control program executes to load a set of programs and / or device drivers from the diskette without loading an operating system. The set of programs and / or device drivers communicate with a network server to retrieve a boot program from the network server, and the boot program executes to complete the boot process of the client, such as downloading an operating system from the server.
Owner:MICROSOFT TECH LICENSING LLC
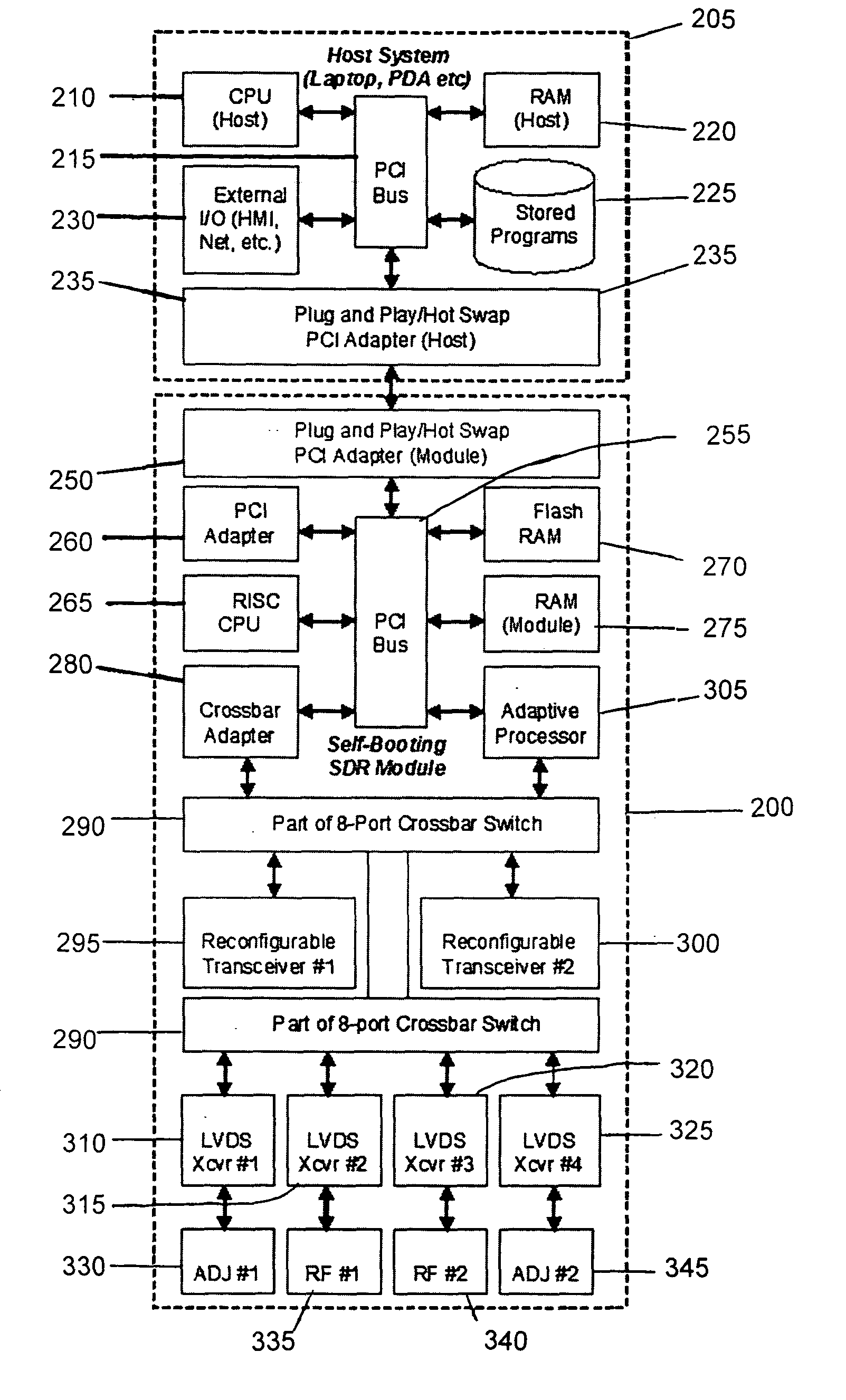
Self-booting software defined radio module
ActiveUS20060015674A1Performance characteristicDigital computer detailsTelephonic communicationSoftware define radioNetworking protocol
The invention in the simplest form is a self-booting software defined radio (SDR) module which may be embodied as a PCMCIA, Compact Flash, or other plug in form factor module. The performance characteristics of the module, may include the radio frequency (RF) carrier frequency, instantaneous RF bandwidth, carrier modulation and demodulation, symbol coding and decoding, security, and network protocol that can be altered and saved by means of computer software transferred to the module from a host device such as a cellular telephone, personal digital assistant, lap top computer or other programming device
Owner:TECNICA
Method and computing system for transparence computing on the computer network
ActiveUS20060117172A1Improve performanceImprove availabilityDigital computer detailsData resettingOperational systemTransparent computing
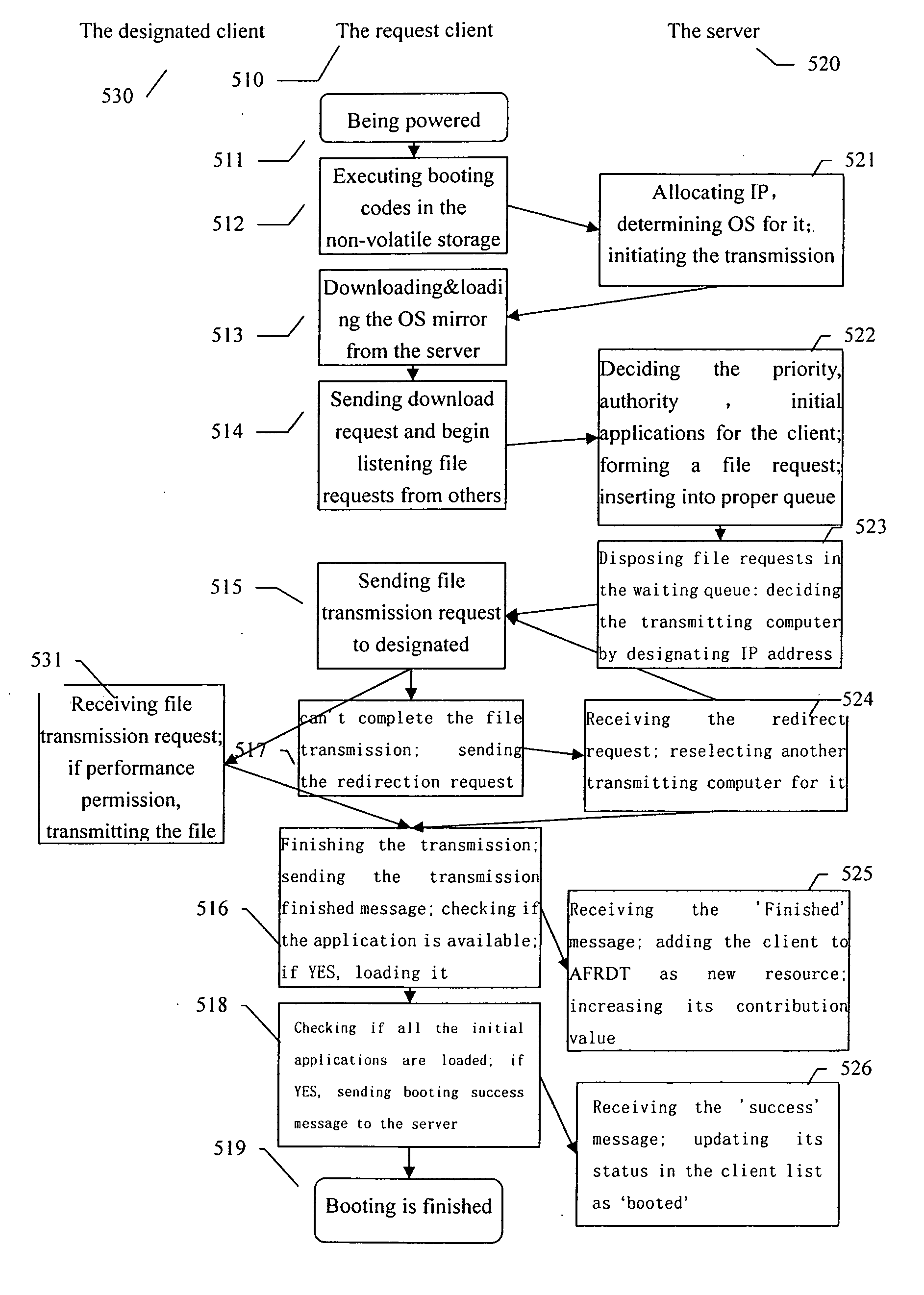
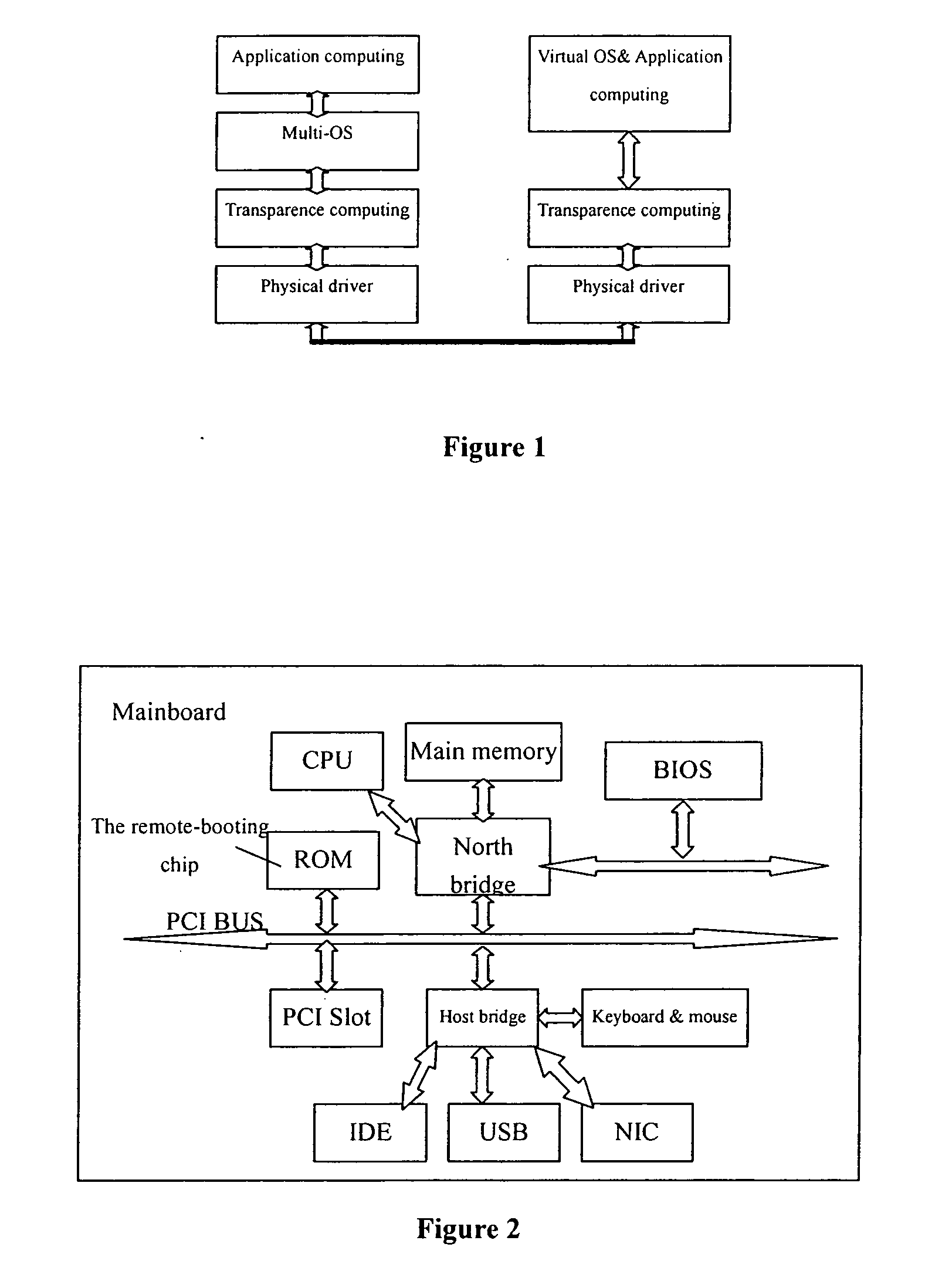
A computing system based on Transparence Computing consists of clients and a server. There is no disk and no preinstalled OS on the client; a remote booting chip is set on the client's mainboard for downloading and loading the OS. Boot-supporting services, OS kernel mirrors, and applications are preset on the server; After being powered, the client broadcasts the boot request to the network and the server allocates network parameters for it. The client downloads an OS-selecting script from the server. After the user selects the needed OS, the client downloads and loads the selected OS from the server. Hence, the client fulfills the user's computing requirements just as a normal PC. The computing work is implemented on the client-side, during which the client can acquire corresponding resources such as applications, data, and documents from the server on demand. The client can be provided with private storage across the network by presetting a service in the mirror for creating virtual disks on the server, and thus data generated during or after the computing can be persistently stored on the server's storage.
Owner:TSINGHUA UNIV
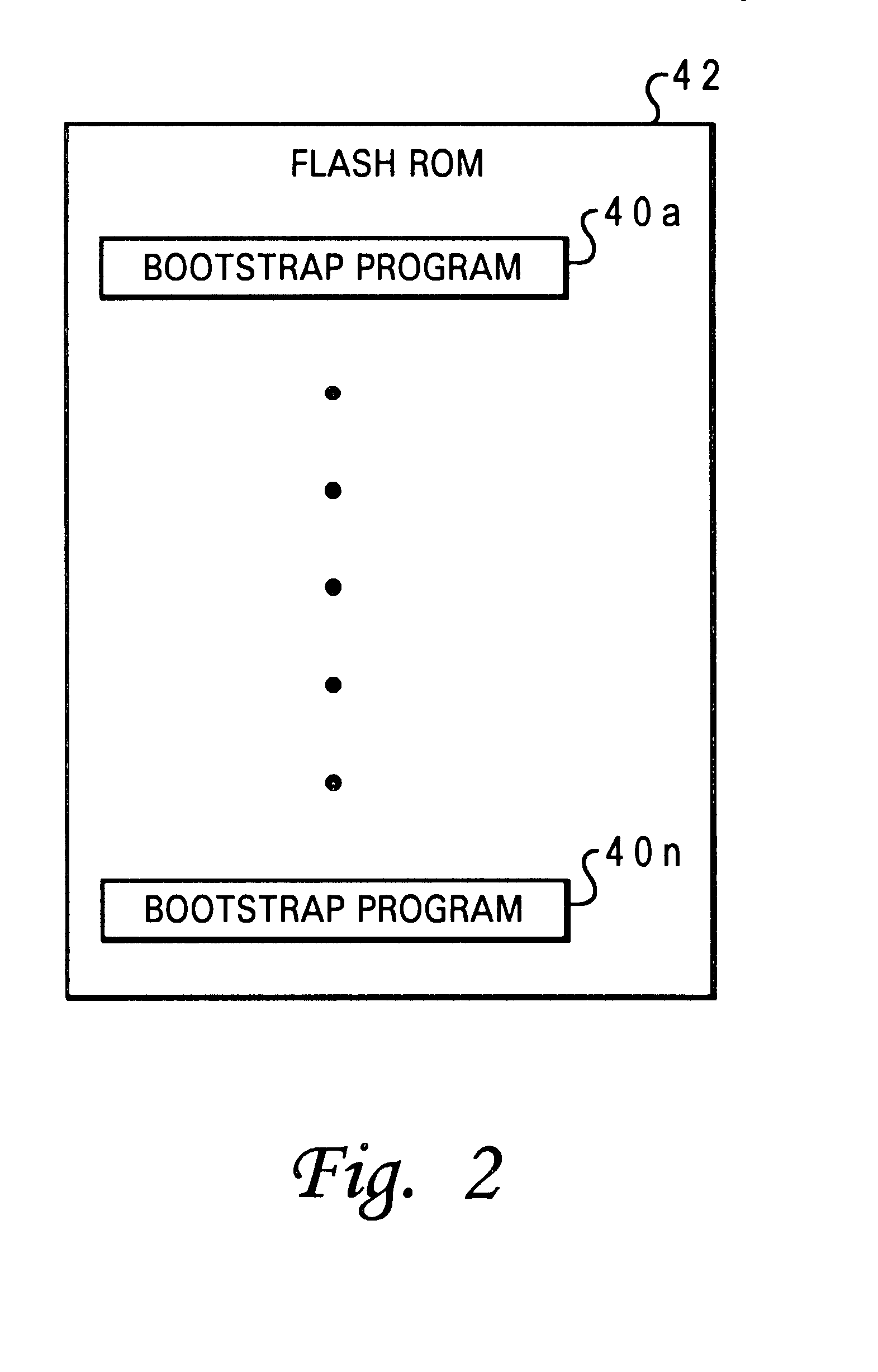
Method and system for automatically configuring the boot process of a computer having multiple bootstrap programs within a network computer system
InactiveUS6490677B1Automatically configuring the boot process of a network computerDigital computer detailsProgram loading/initiatingAuto-configurationProcess configuration
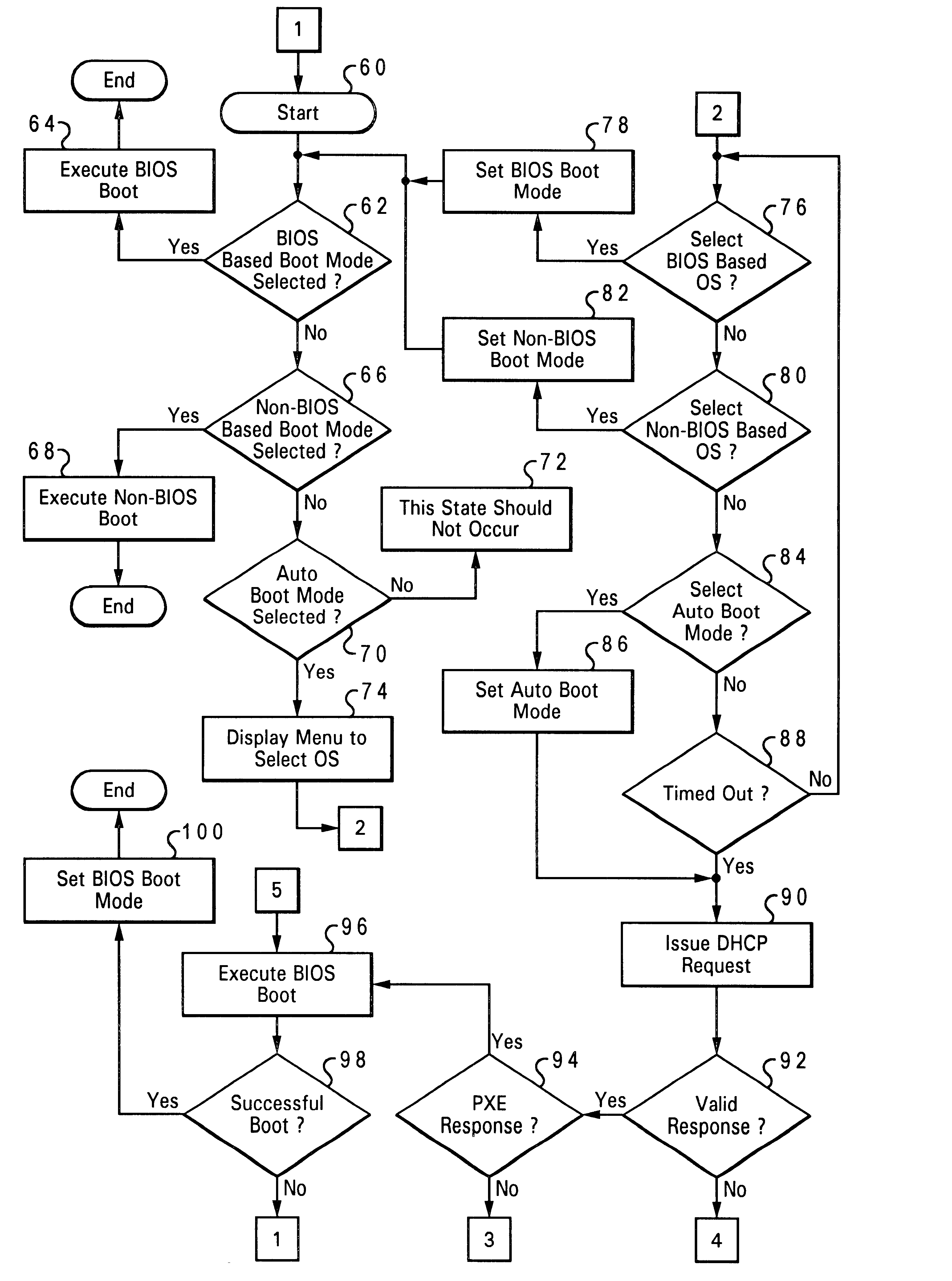
A method and system for automatically configuring a boot process of a network computer initially connected within a network comprising at least one server. A request is broadcast from a network computer to a network for an available server, upon a first initiation of the network computer within the network. Responses from the broadcast are gathered which indicate whether a server is available. A selected boot program is then executed from among multiple boot programs available in the network computer. The selected boot program and the identity of an available server are stored as boot process configuration settings in a nonvolatile storage of the network computer, in response to successful execution of the boot program, such that a subsequent boot process of a network computer is automatically configured.
Owner:LENOVO PC INT
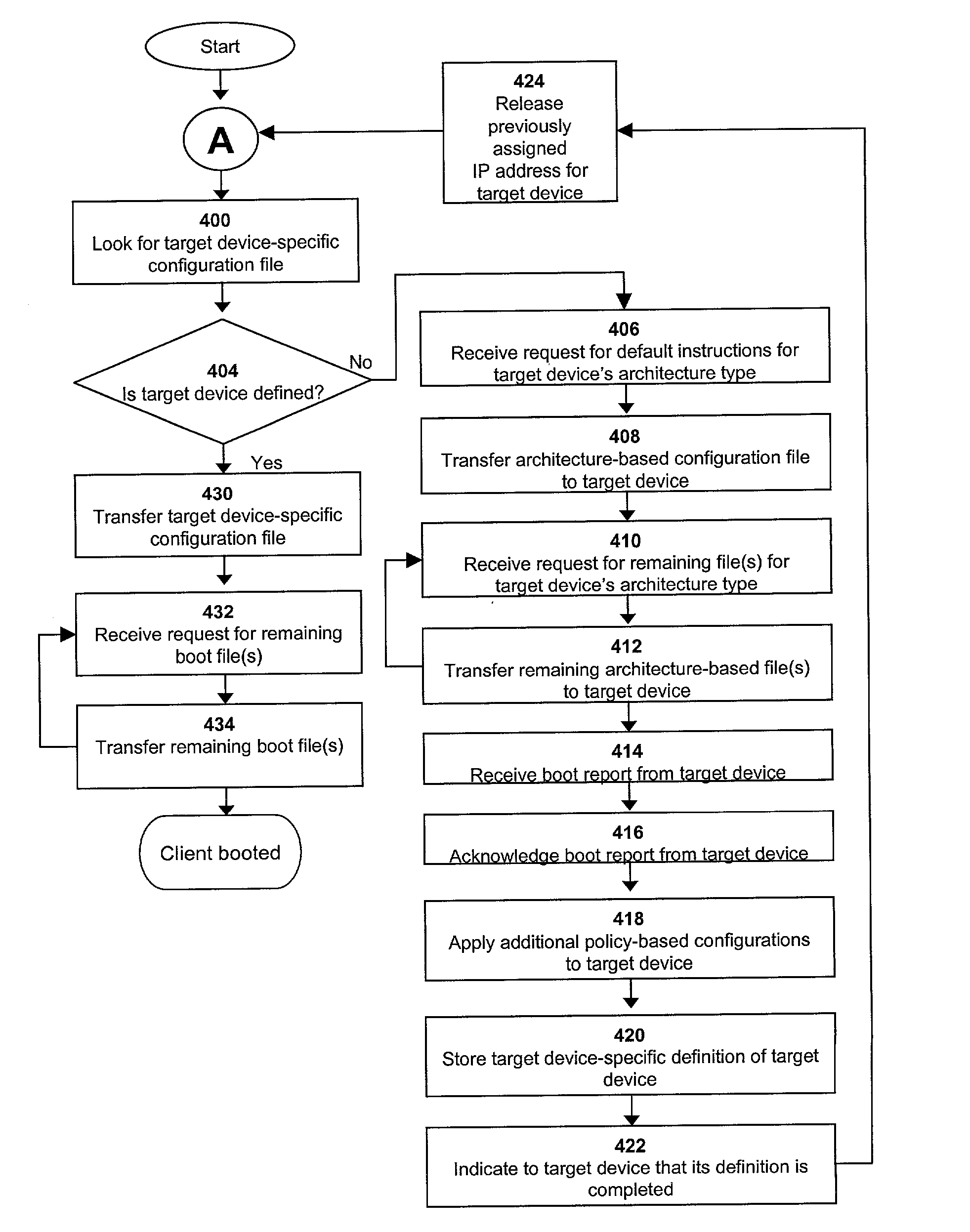
Method and system for booting of a target device in a network environment based on automatic client discovery and scan
A method of booting a plurality of target devices in communication with a network based on at least one target device definition is provided. A server in communication with the plurality of target devices receives a request for a boot file from at least one target device. A boot server in communication with the plurality of target devices is contacted. The boot server determines if the target device is defined. If the target device is not defined, the target device definition for the target device is created at the boot server. A bootstrap is executed at the target device, the bootstrap corresponding to the target definition. Systems and programs for using the method are also provided.
Owner:IBM CORP
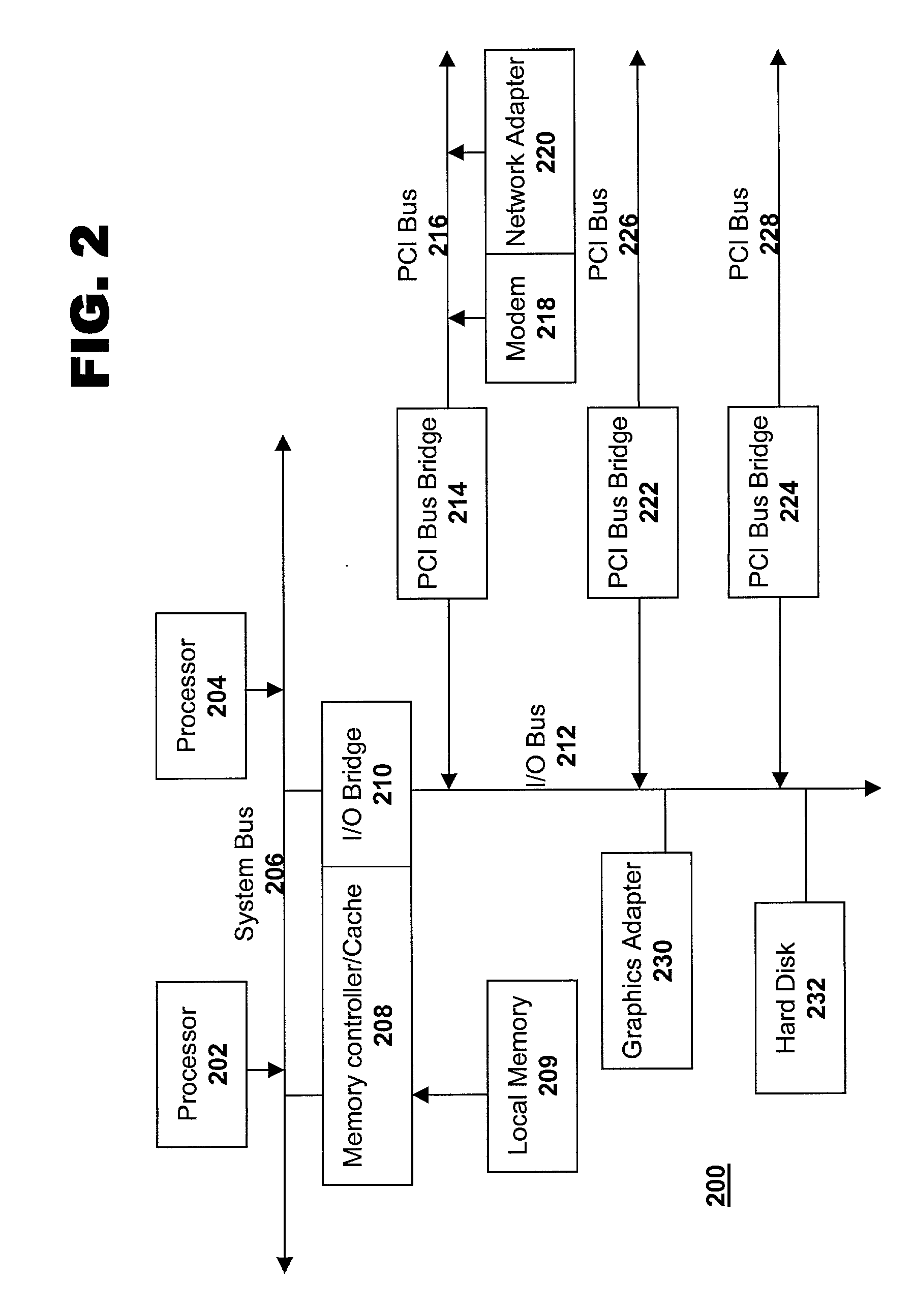
Systems and method for booting devices in a multiple-card computing system
A method for booting devices in a multi-card computing system comprising a plurality of cards connected to a shared backplane may include: dynamically generating a Media Access Control (MAC) addresses for at least some of the devices in the computing system, the dynamically generated MAC address for each device including information regarding the location of that device within the multi-card computing system; a boot management system receiving a boot-related information request from a particular device in the multi-card system, the boot-related information request comprising a request for particular boot-related information for facilitating a boot process for the requesting device, and including the MAC address of the requesting device; and the boot management system determining whether to send a response to the requesting device with the requested boot-related information based at least on the information in the MAC address regarding the location of the requesting device within the multi-card computing system.
Owner:KEYSIGHT TECH SINGAPORE (SALES) PTE LTD
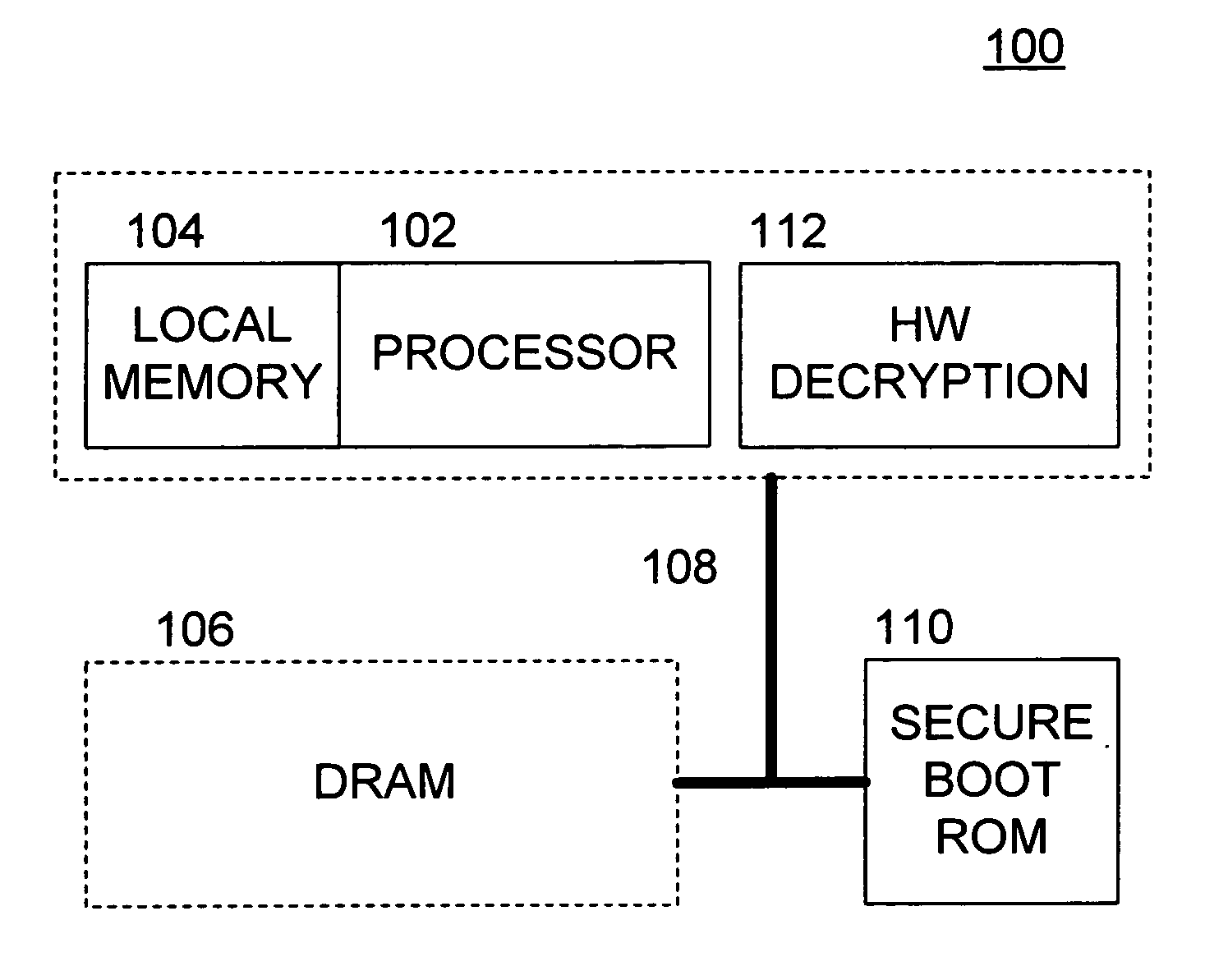
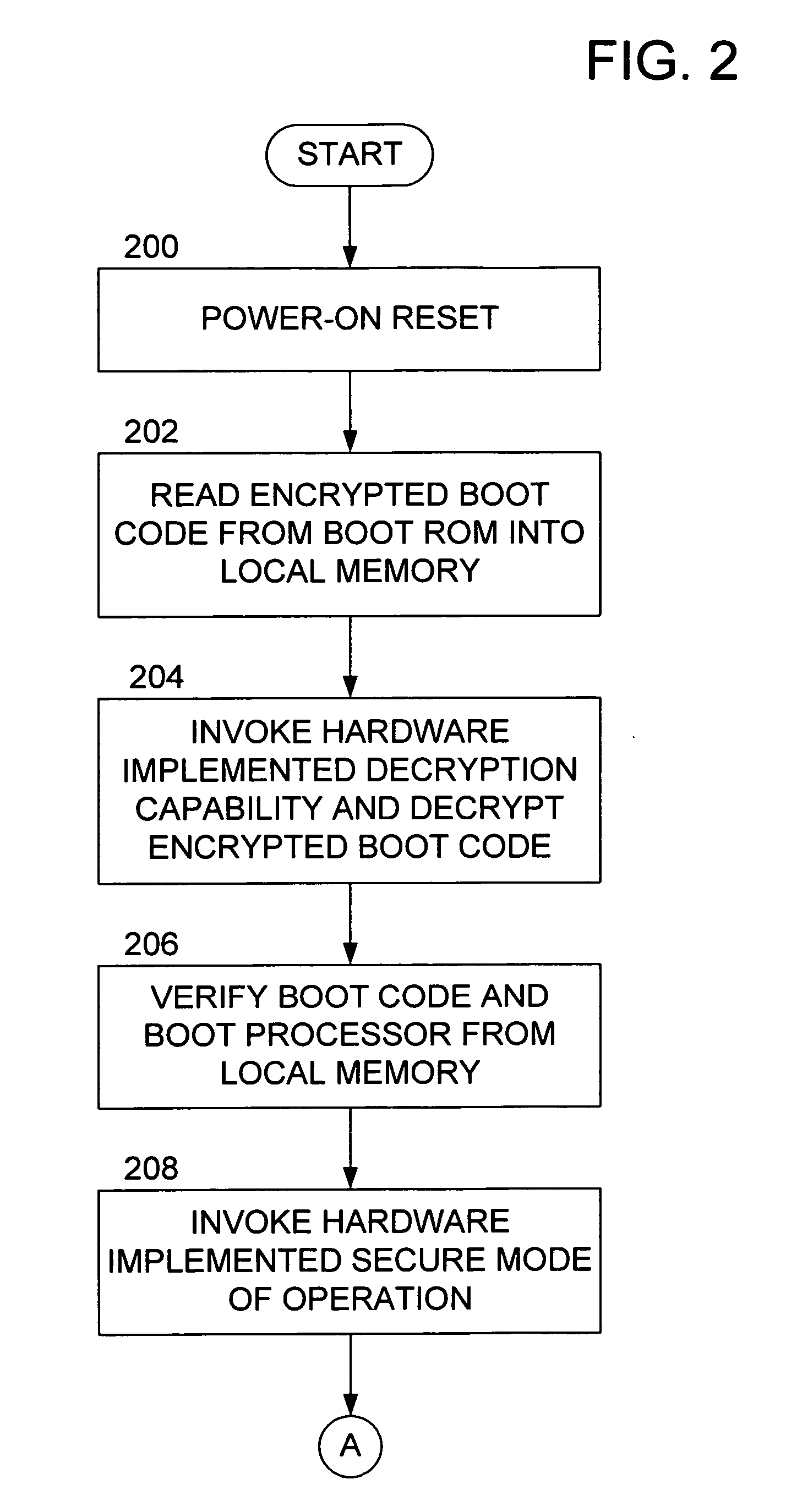
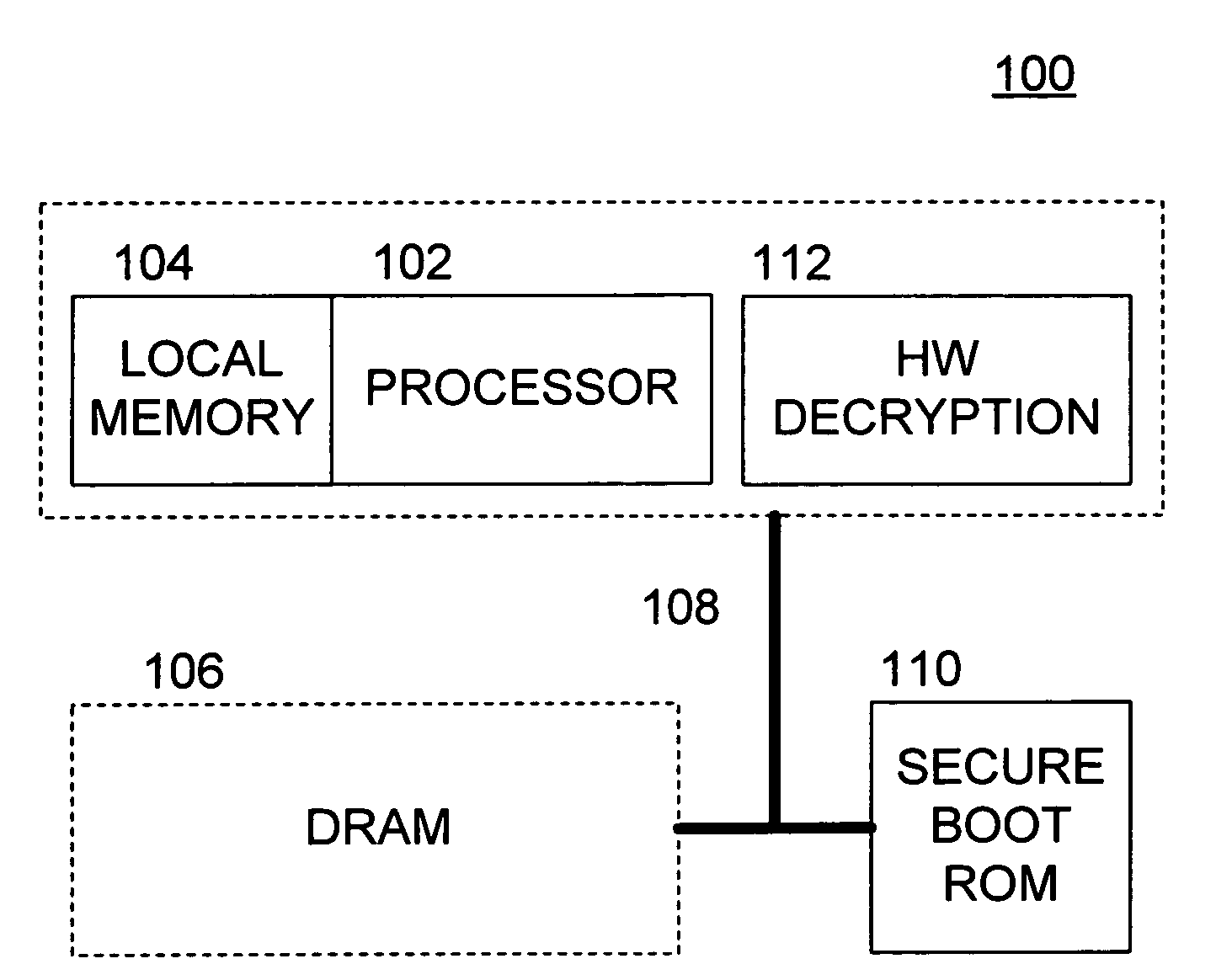
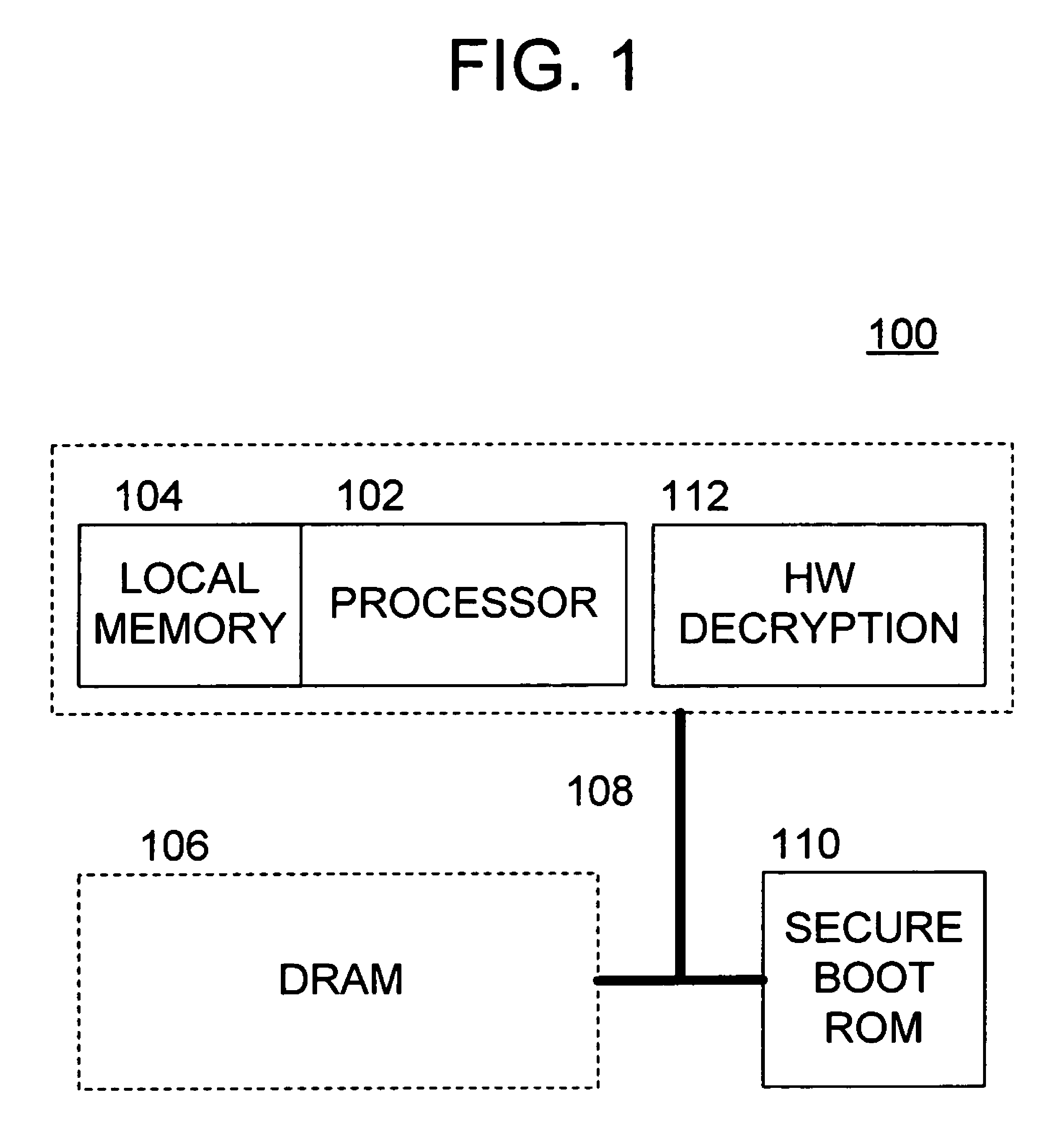
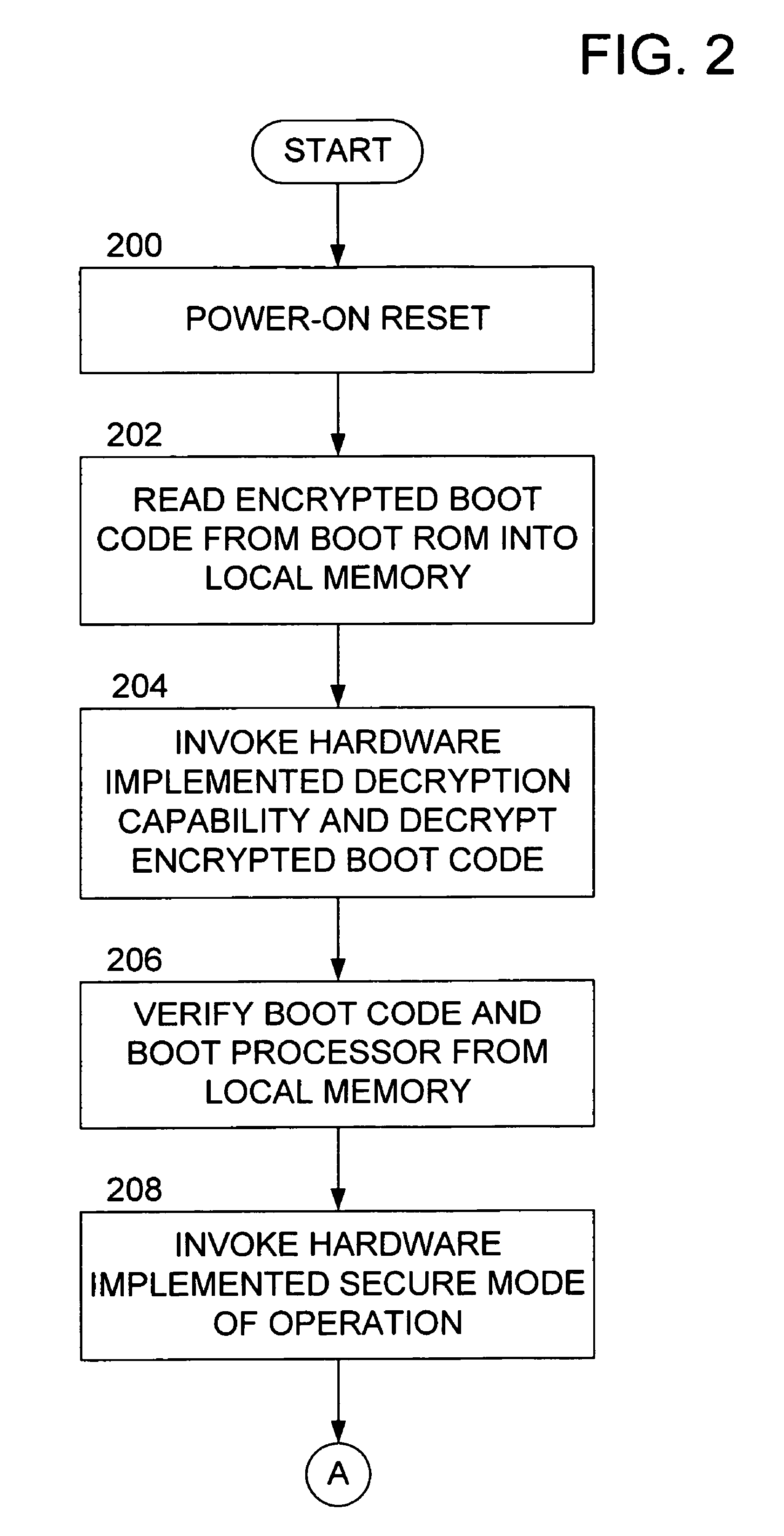
Methods and apparatus for providing a secure booting sequence in a processor
ActiveUS20060179302A1User identity/authority verificationUnauthorized memory use protectionLocal memoriesBooting
Methods and apparatus provide for: reading encrypted boot code from a storage medium into a local memory associated with a first of a plurality of processors; decrypting the encrypted boot code using a trusted decryption function of the first processor such that the boot code is verified as being authentic; booting the first processor using the boot code from the local memory; and authenticating boot code for one or more of the other processors in the first processor prior to the one or more other processors booting up.
Owner:SONY COMPUTER ENTERTAINMENT INC
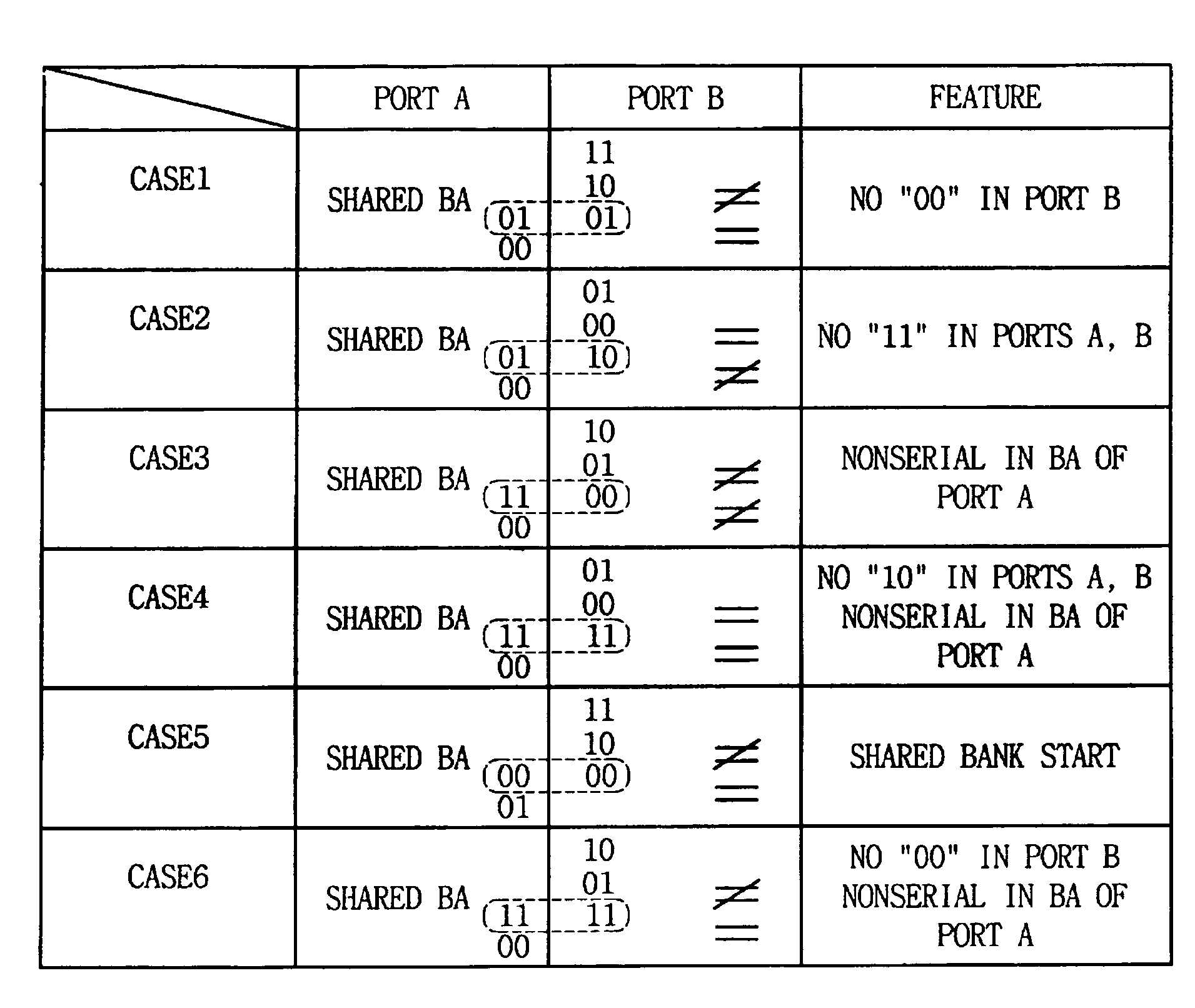
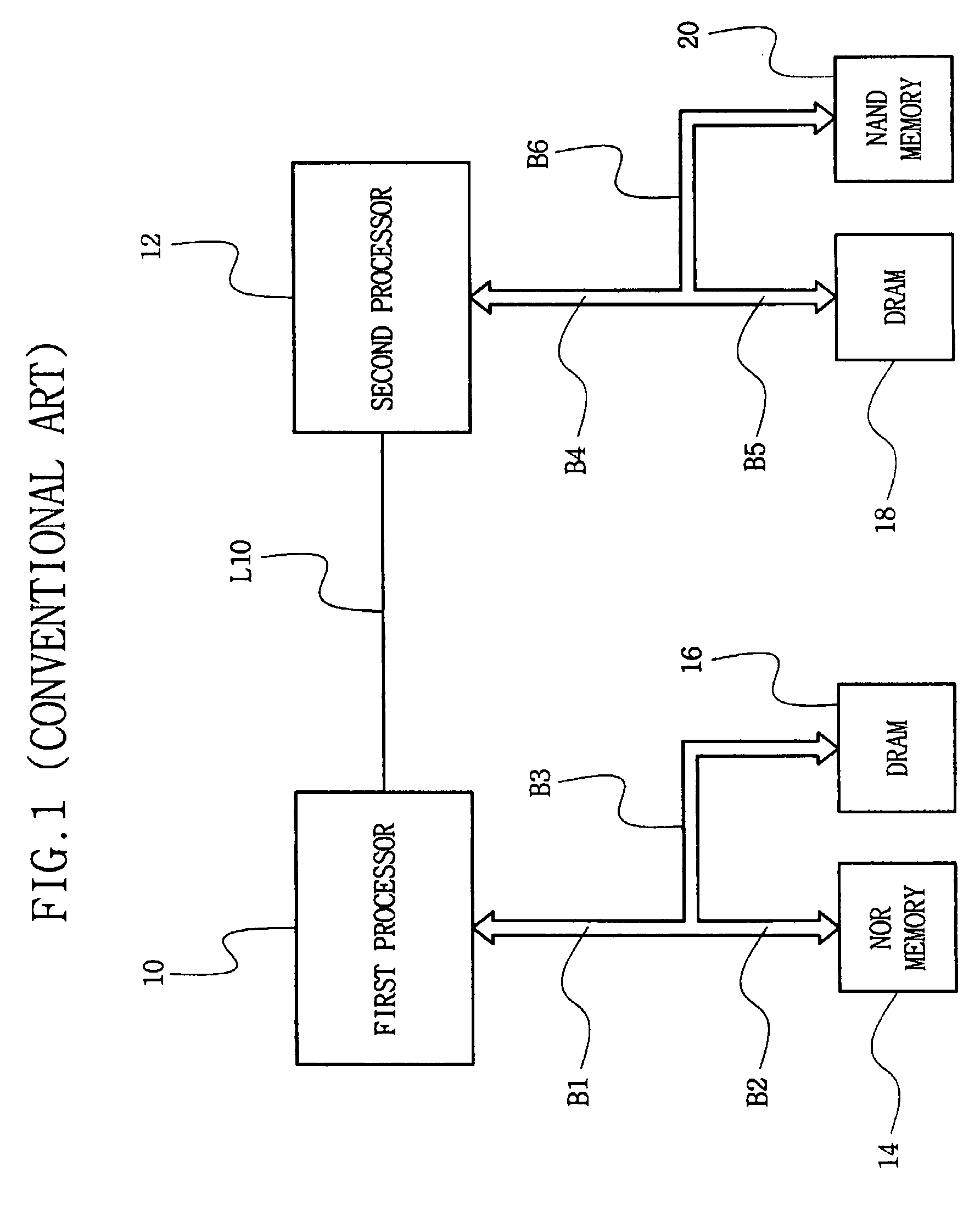
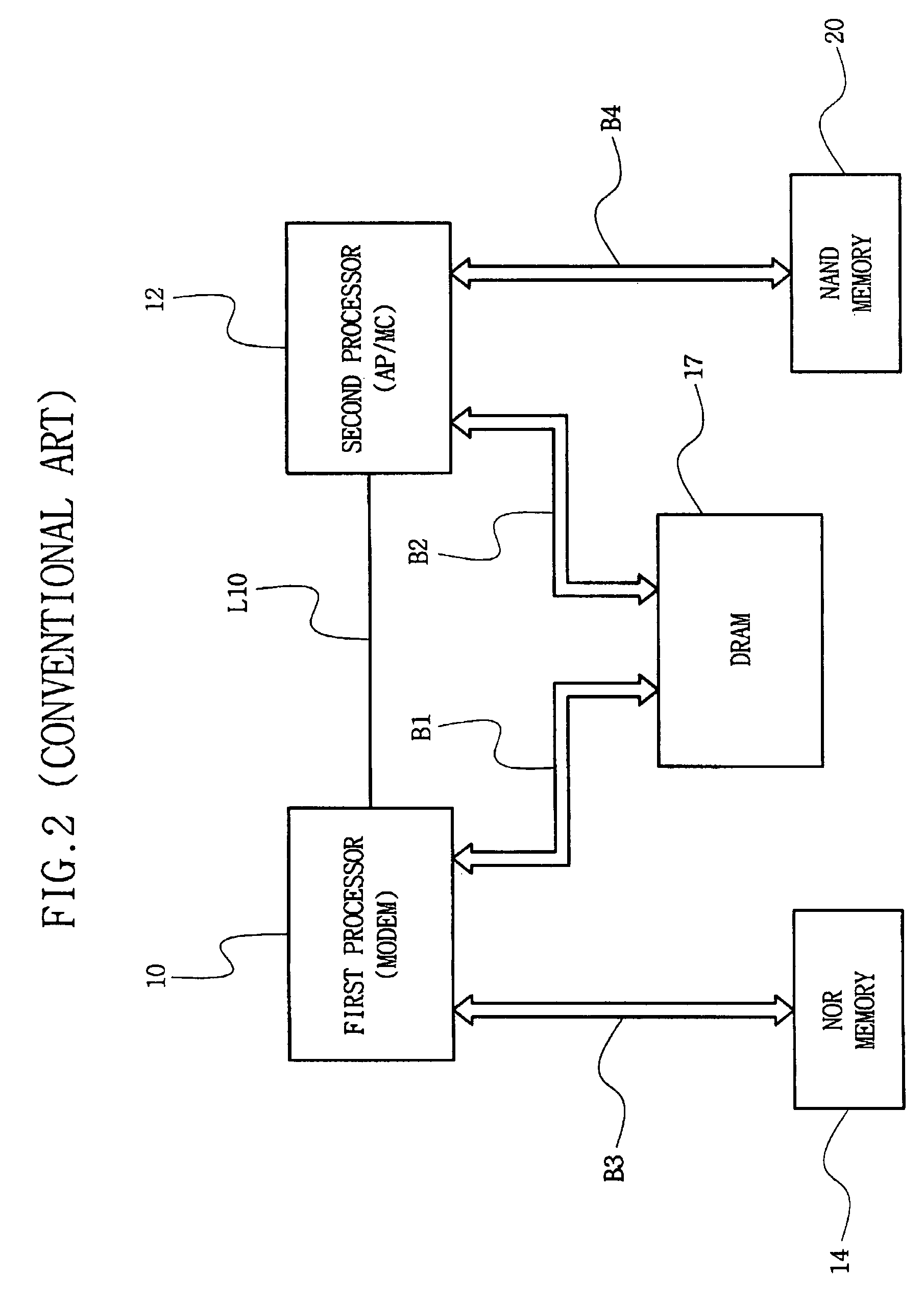
Multiprocessor system and method thereof
A multiprocessor system and method thereof are provided. The example multiprocessor system may include first and second processors, a dynamic random access memory having a memory cell array, the memory cell array including a first memory bank coupled to the first processor through a first port, second and fourth memory banks coupled to the second processor through a second port, and a third memory bank shared and connected with the first and second processors through the first and second ports, and a bank address assigning unit for assigning bank addresses to select individually the first and second memory banks, as the same bank address through the first and second ports, so that starting addresses for the first and second memory banks become equal in booting, and assigning bank addresses to select the third memory bank, as different bank addresses through the first and second ports, and assigning, through the second port, bank addresses to select the fourth memory bank, as the same bank address as a bank address to select the third memory bank through the first port.
Owner:SAMSUNG ELECTRONICS CO LTD
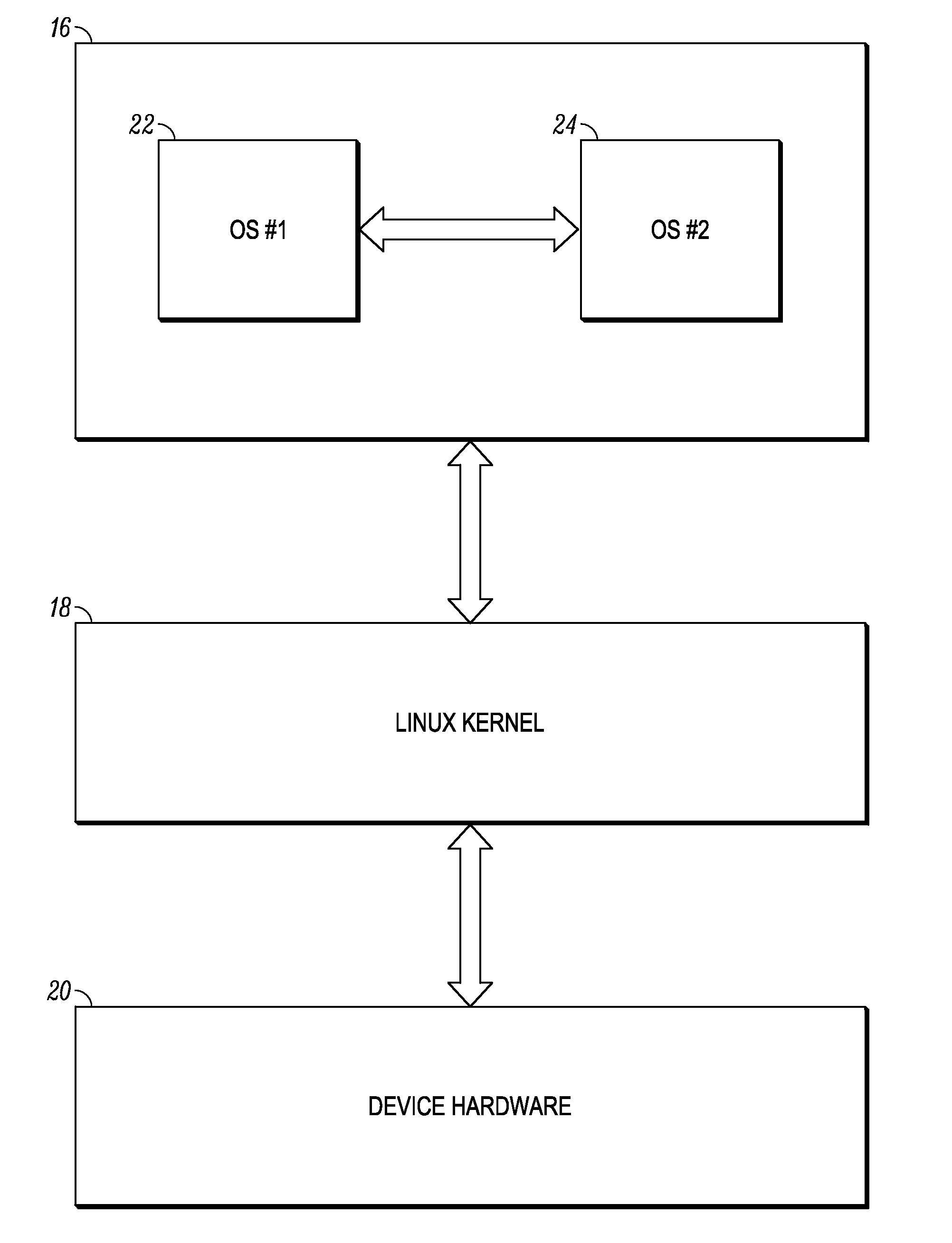
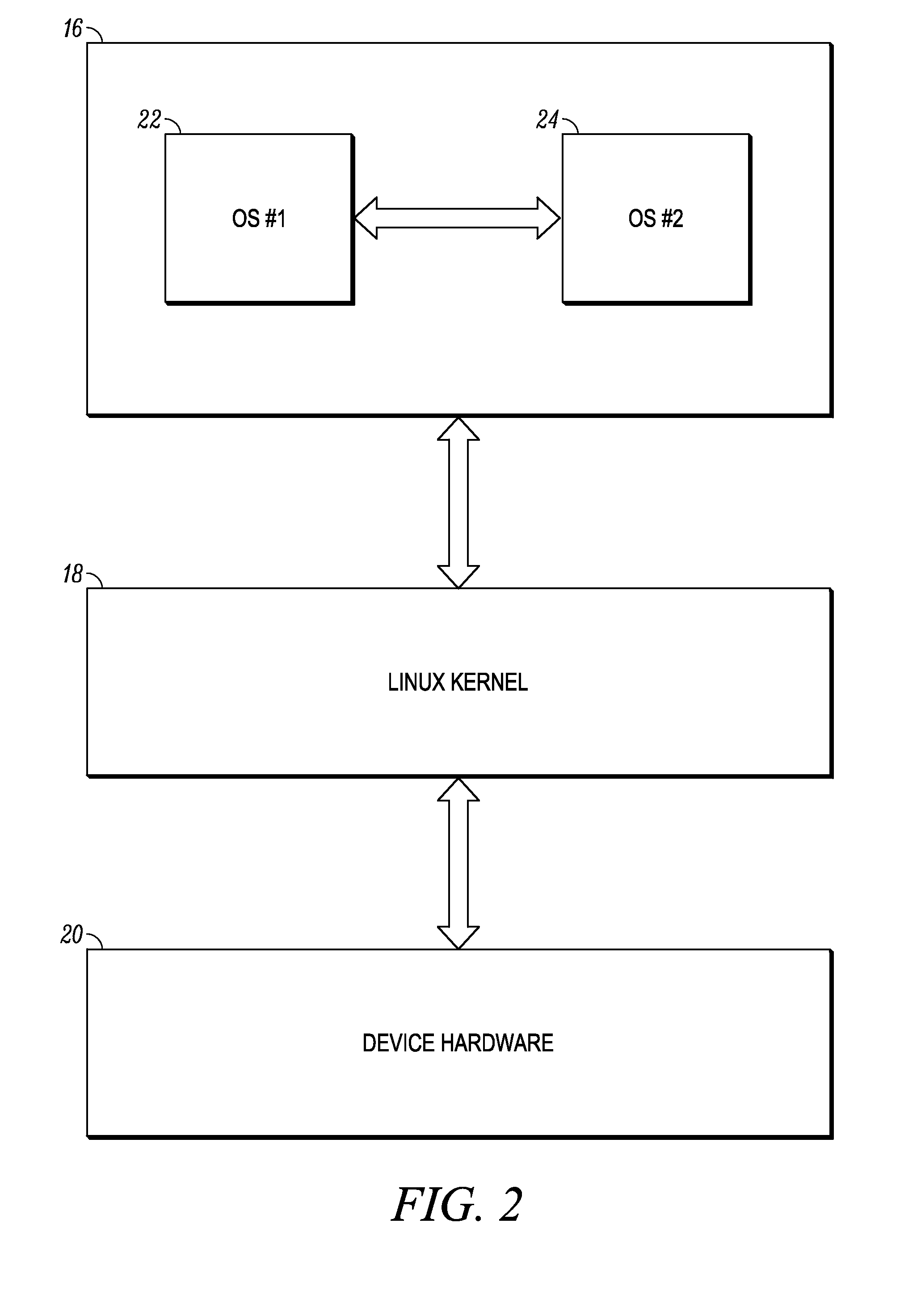
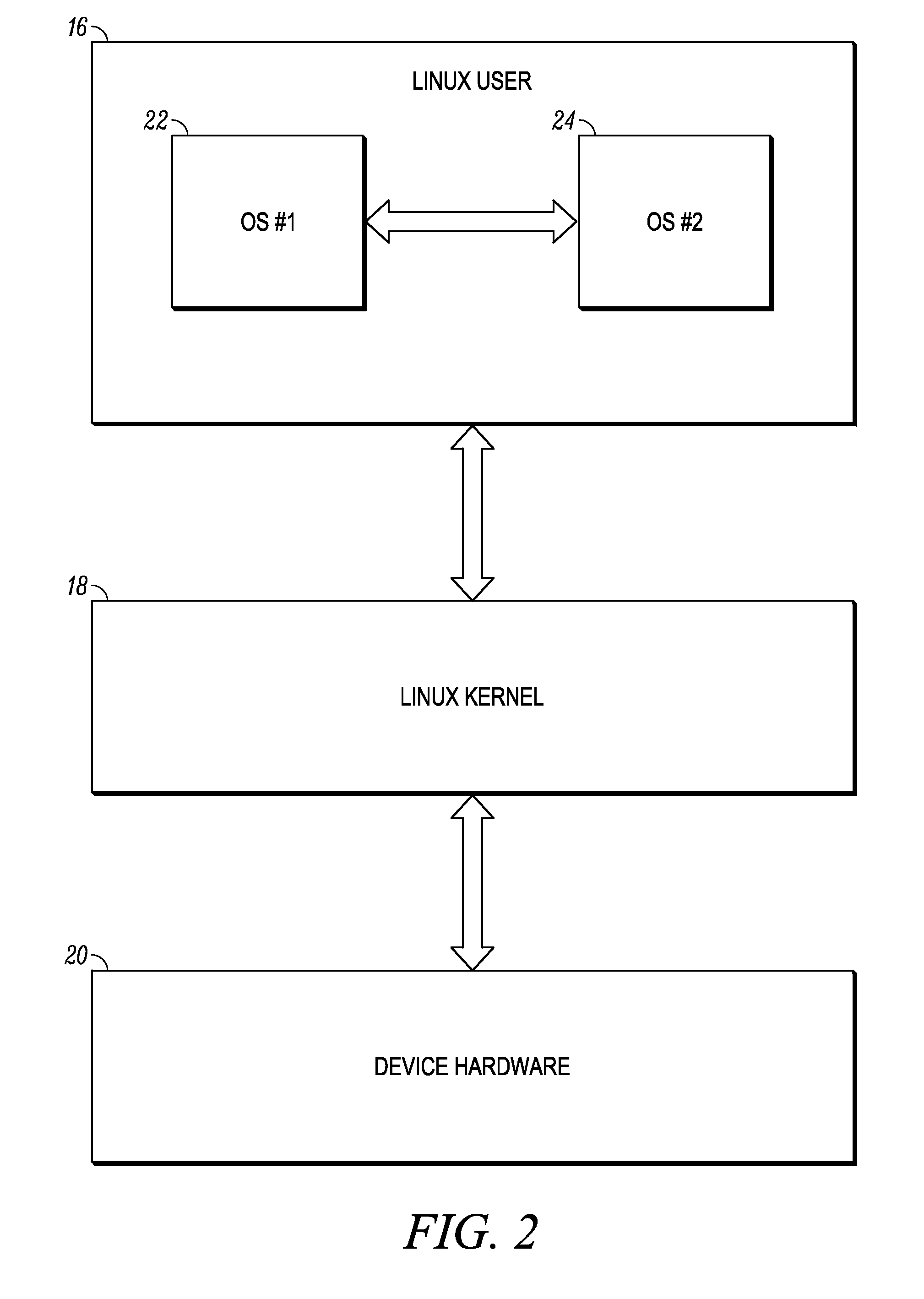
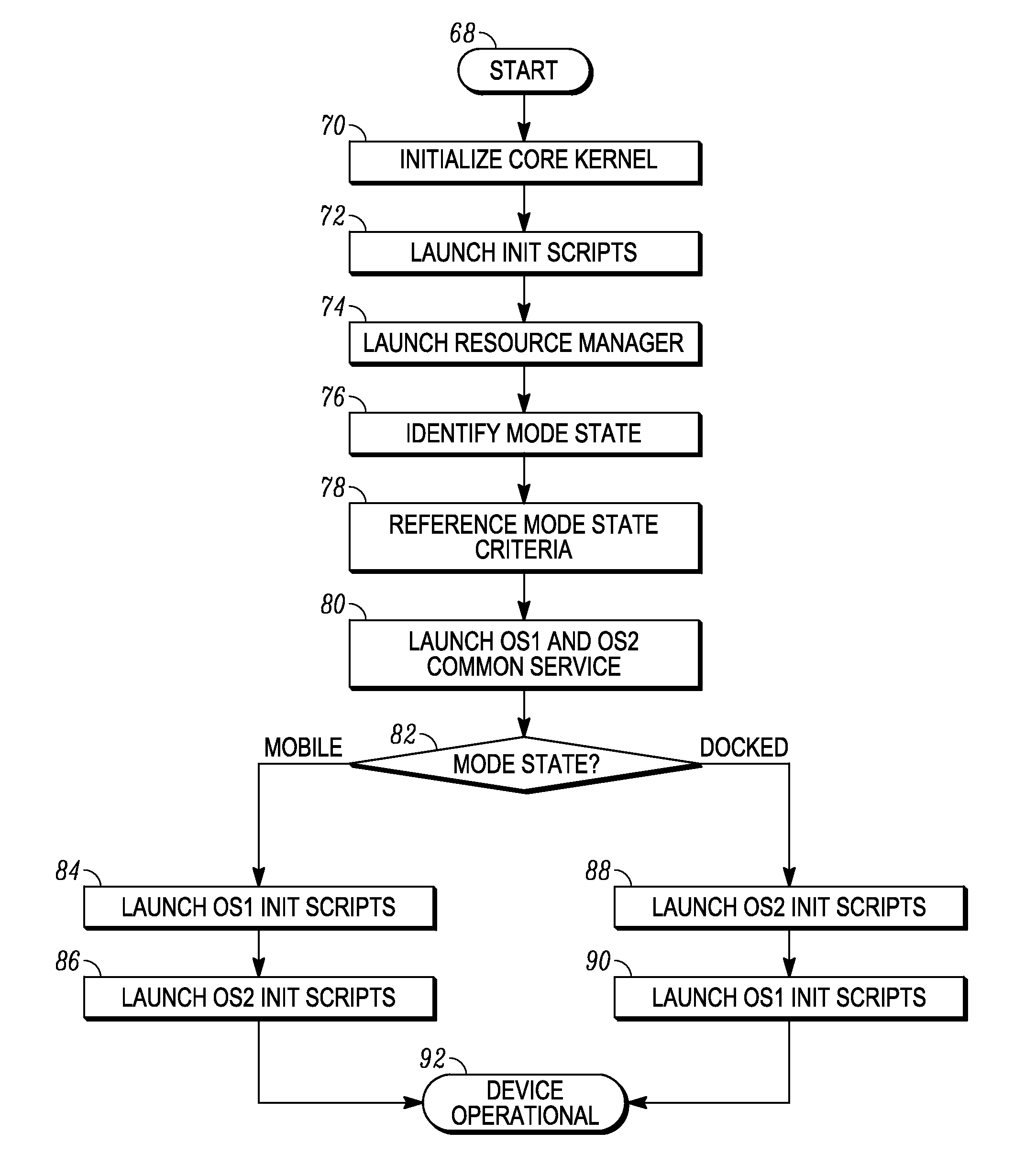
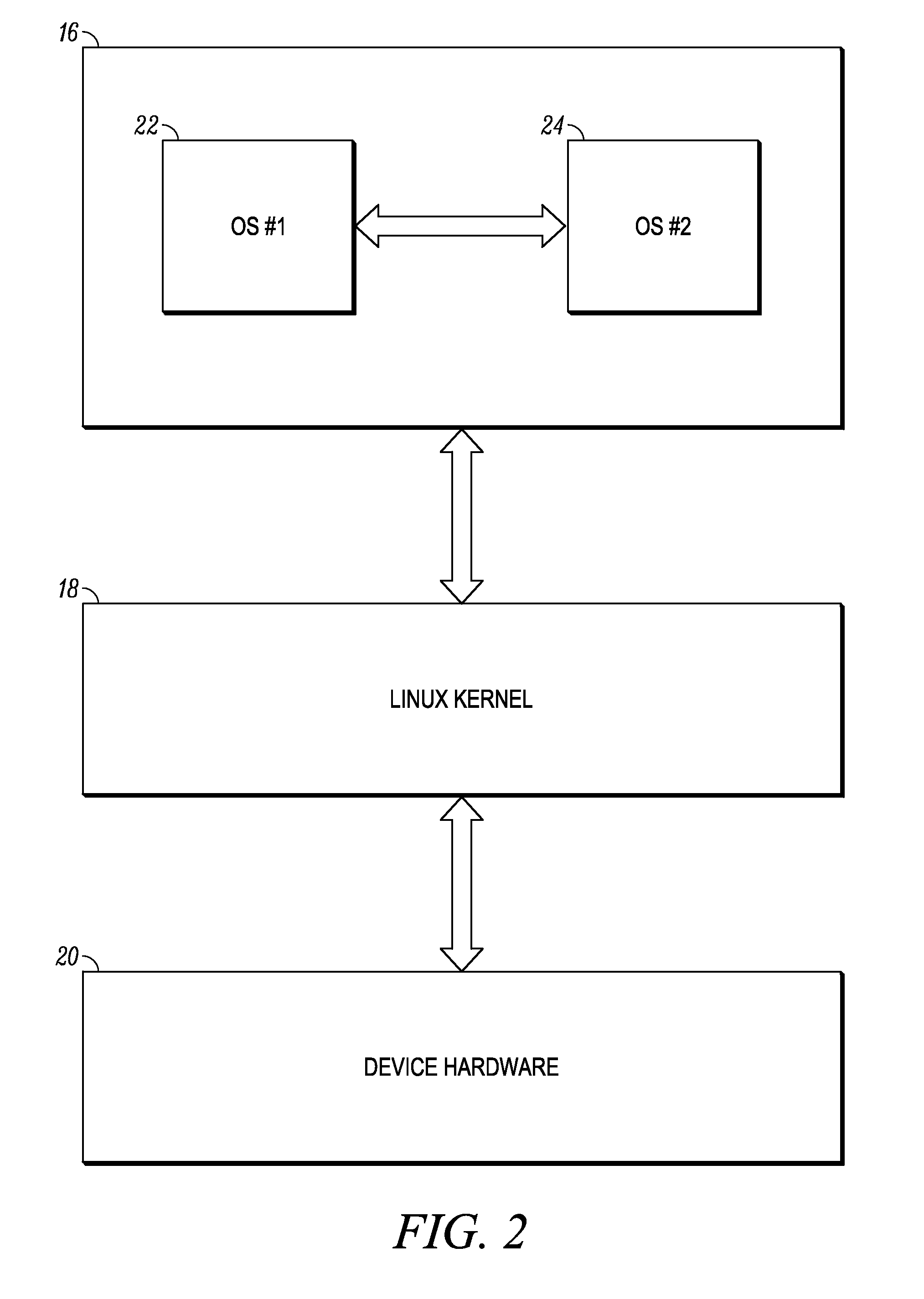
Multi-environment operating system
ActiveUS20110016299A1Program initiation/switchingDigital computer detailsOperational systemEngineering
Various embodiments of the present invention provide a mobile computing device that operates multiple, co-existing and independent operating system environments on a common kernel. A booting process for initiating a multiple operating system environment is also provided. Additionally, various embodiments of the present invention include processes for managing a switch between one operating system environment to a second operating system environment.
Owner:GOOGLE TECH HLDG LLC
Methods and apparatus for providing a secure booting sequence in a processor
ActiveUS7831839B2User identity/authority verificationUnauthorized memory use protectionLocal memoriesBooting
Owner:SONY COMPUTER ENTERTAINMENT INC
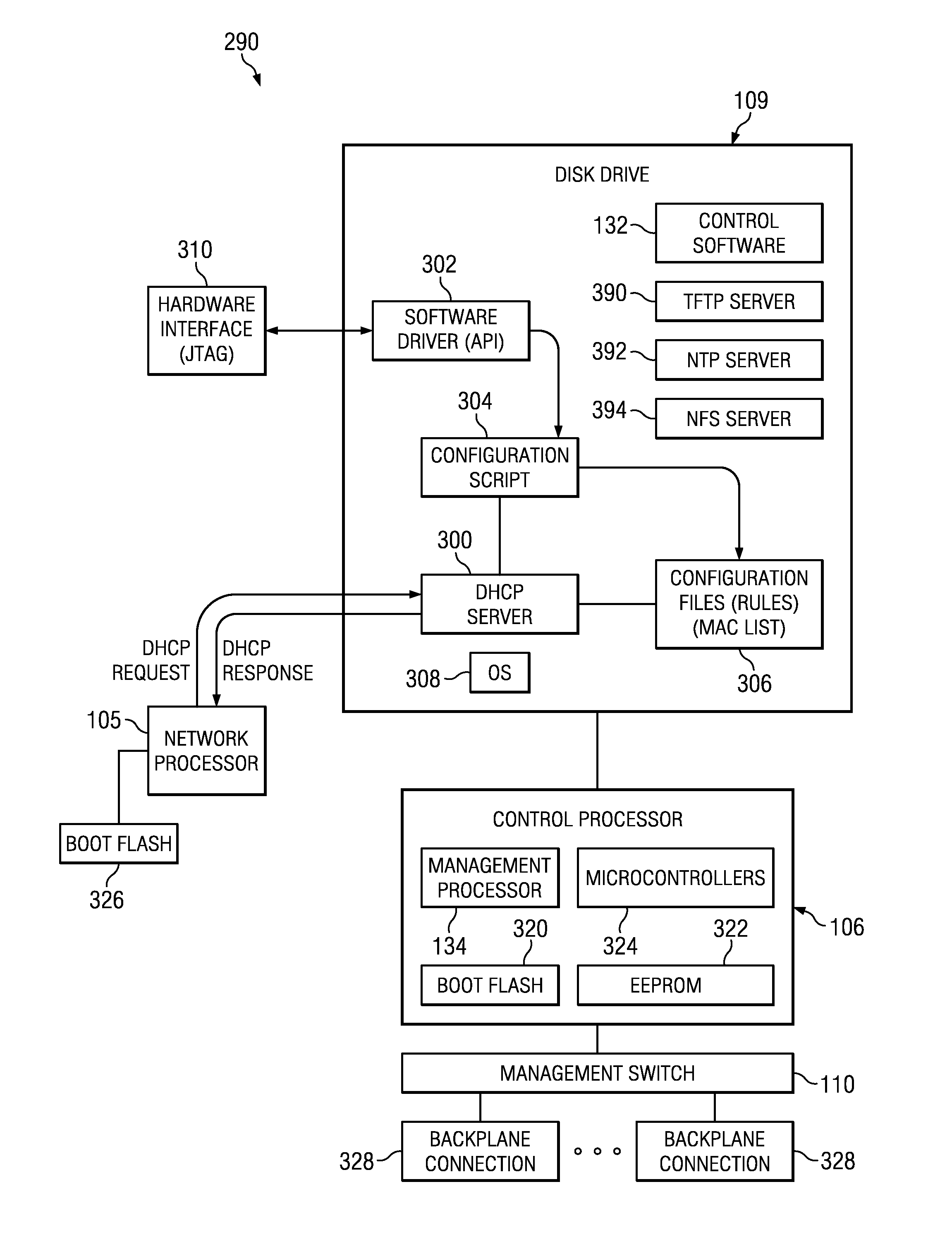
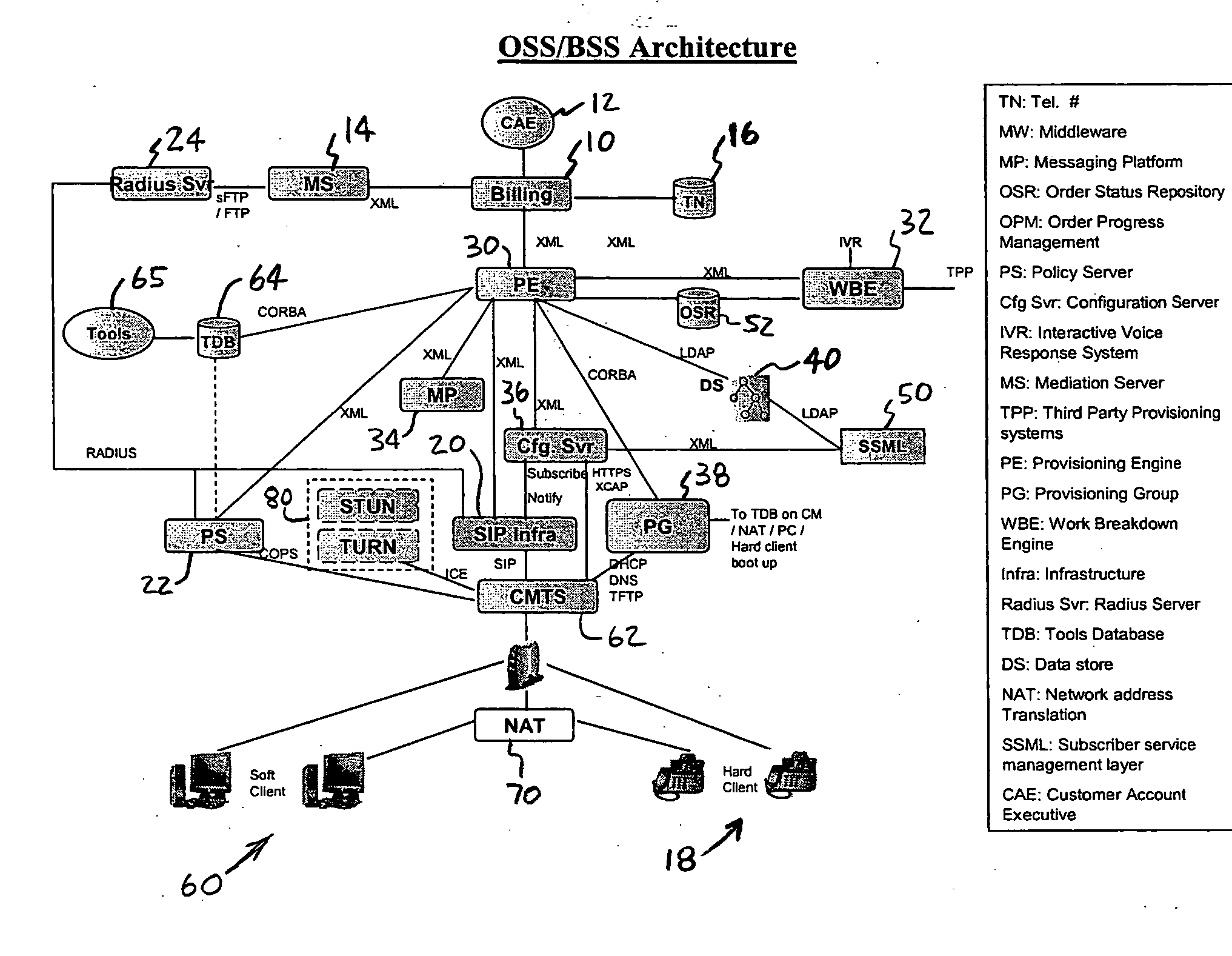
Method and system for booting, provisioning and activating hardware and software clients
ActiveUS20070058792A1Interconnection arrangementsAutomatic call-answering/message-recording/conversation-recordingClient-sideProxy server
Automated booting of a client for a subscriber is provided for clients that are for use in interactive user sessions that involve multimedia. A subscribe message is sent from the client to a proxy server. The proxy server authenticates the subscribe message, and sends the subscribe message to the configuration server. A notify message is sent to the client from the configuration server. The notify message is sent through the proxy server, and contains a location of a profile for the client. The profile is downloaded to the clients. This arrangement allows the persistence of profiles in a centralized place.
Owner:COMCAST CABLE COMM LLC
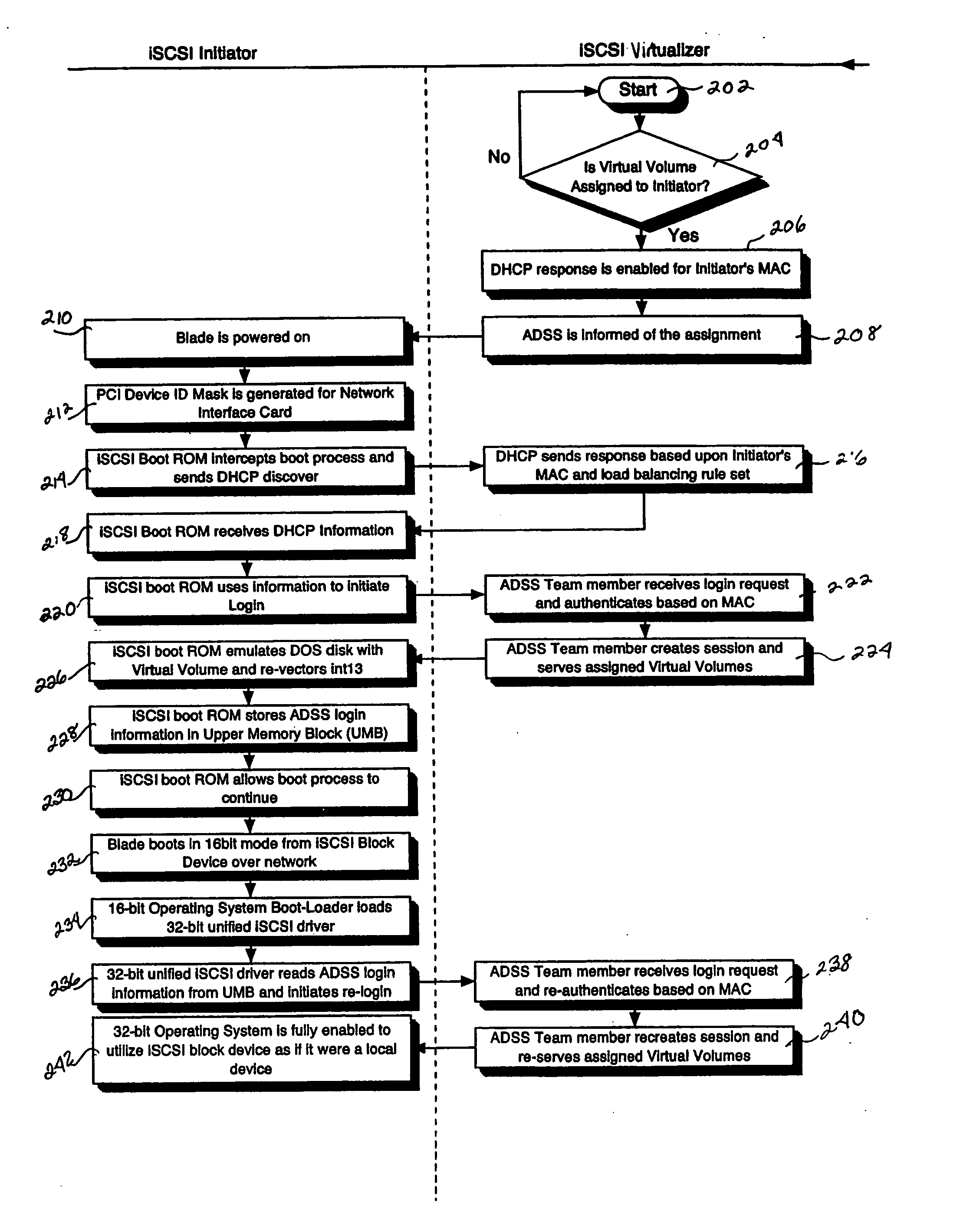
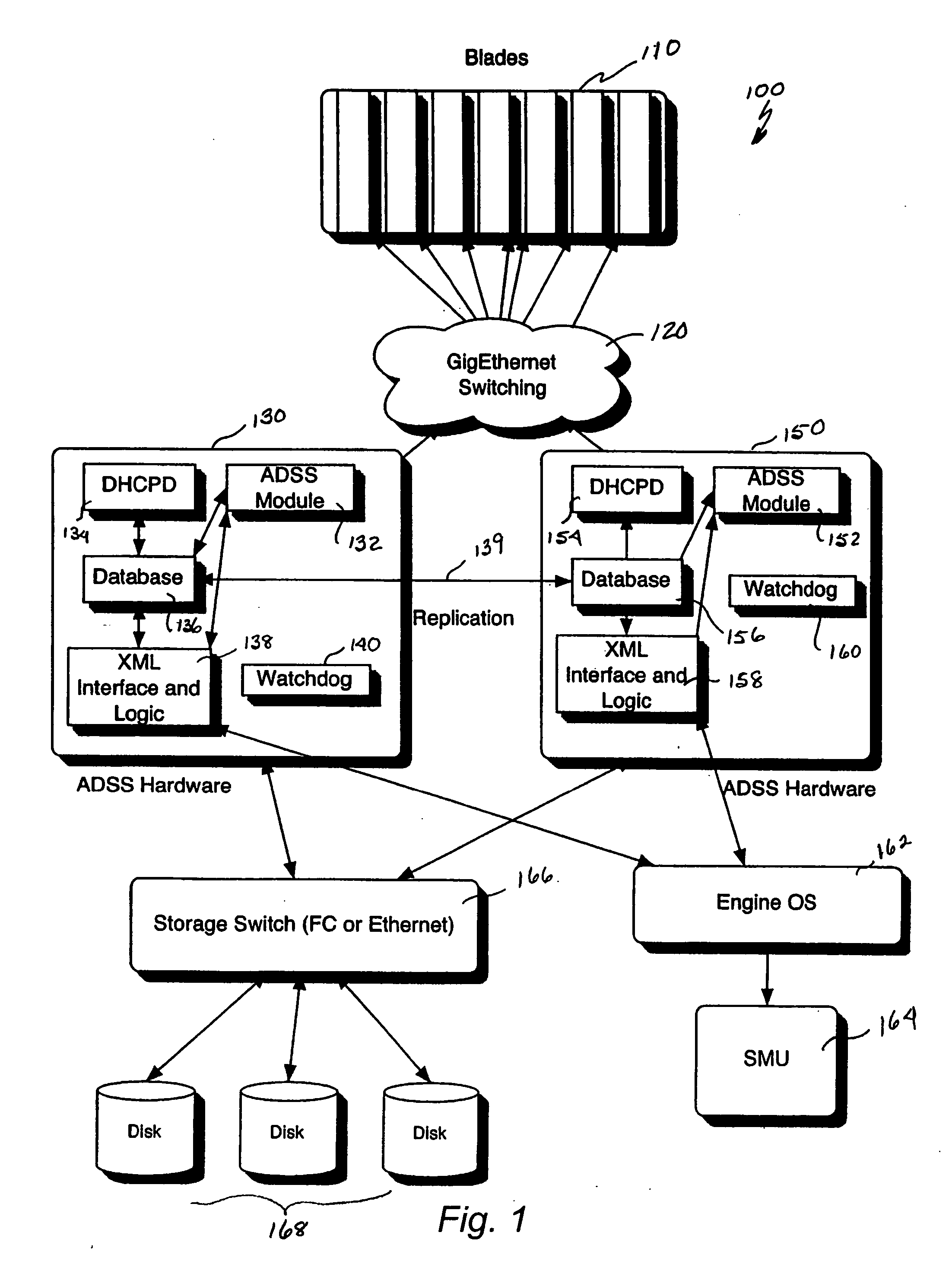
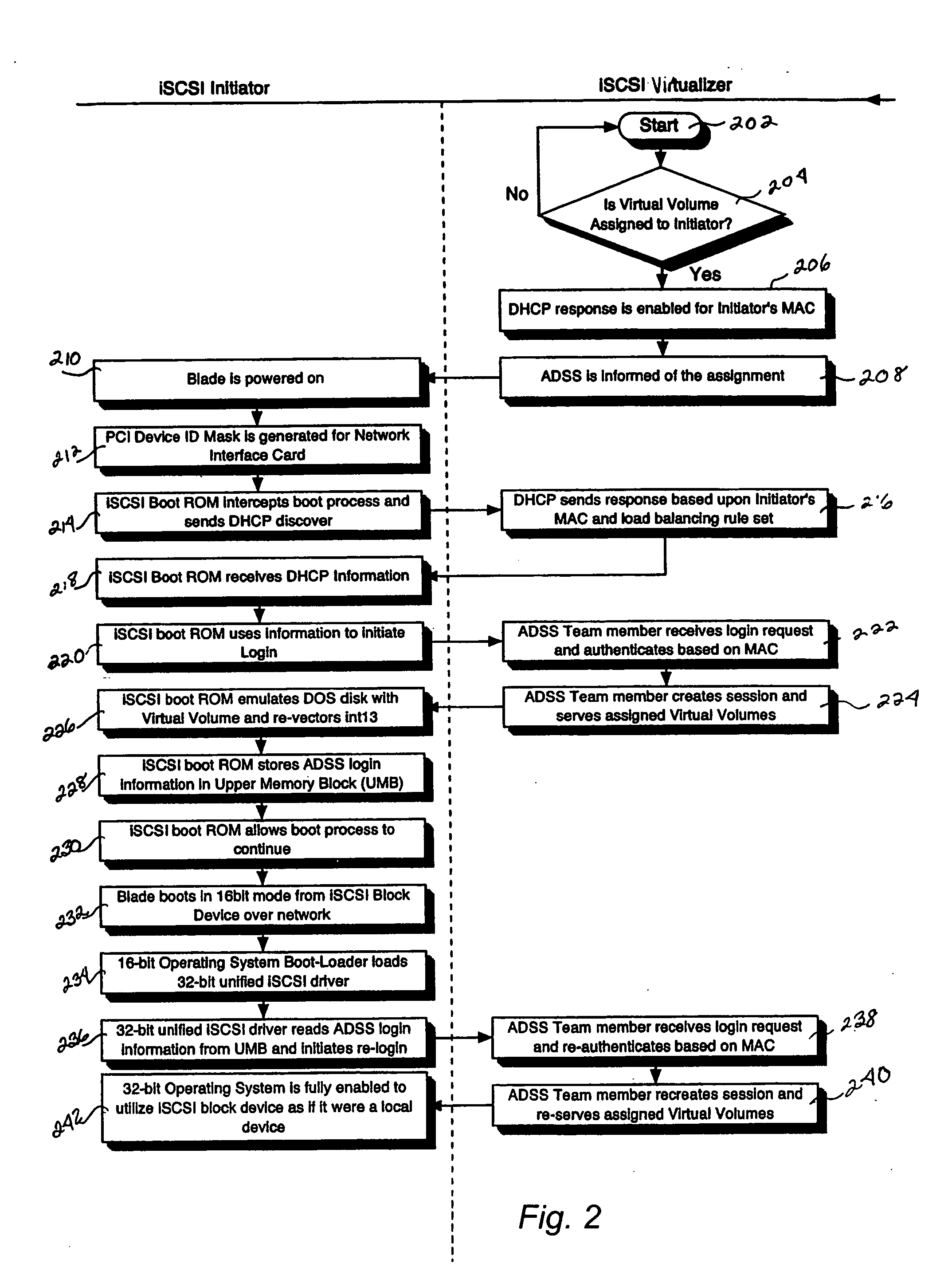
iSCSI boot drive system and method for a scalable internet engine
InactiveUS20050138346A1Digital computer detailsProgram loading/initiatingOperational systemThe Internet
A system for remote booting of a server generally includes a client initiator, an iSCSI virtualizer, and an iSCSI initiator. The client initiator requests access to the server and the iSCSI virtualizer receives the access request. Then, the iSCSI initiator acts upon the request received by the iSCSI virtualizer to initiate login to the server through use of an iSCSI Boot ROM on the server and to emulate a disk operating system through use of the iSCSI Boot ROM, which enables the server to boot. The server boots in both an 8-bit and a subsequent 32-bit mode. The iSCSI Boot ROM appears as a local device upon the completion of the server boot. The iSCSI virtualizer authenticates the login at least twice. The iSCSI virtualizer includes a pair of replicated active directory service servers (ADSS).
Owner:RPX CORP
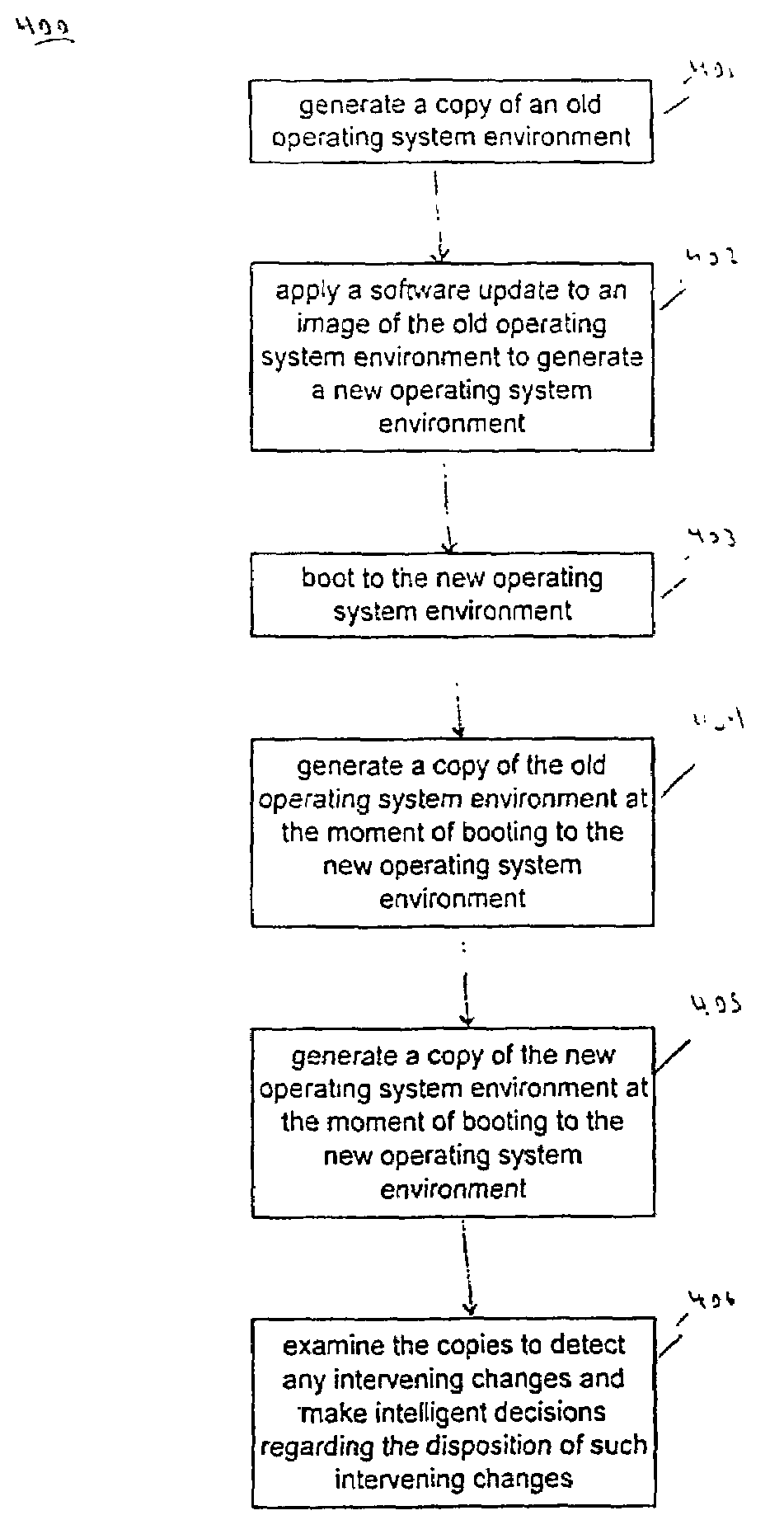
Method and system for live operating environment upgrades
ActiveUS7000229B2Safe recoveryData processing applicationsError preventionOperational systemComputerized system
A method and system for implementing a live operating system upgrade of a computer system. The method includes generating a first copy of a previous operating system environment of the computer system. The computer system is then booted to a subsequent operating system environment. A second copy of the previous operating system environment at the time of the booting is then generated. Additionally, a third copy of the subsequent operating system environment, at the time of the booting is generated. The copies function by ensuring the subsequent operating system environment is synchronized with the previous operating system environment by comparing the first copy, the second copy, and the third copy to detect any intervening changes and allow decisions to be made regarding such changes.
Owner:ORACLE INT CORP
Advanced parking management system
ActiveUS20140218527A1Ticket-issuing apparatusIndication of parksing free spacesPaymentDriver/operator
A parking management system that facilitates motorist guidance, payment, violation detection, and enforcement using highly accurate space occupancy detection, unique vehicle identification, guidance displays, payment acceptance, violation detection, enforcement data generation, electronic booting, and towing management is described. The system enables reduced time to find parking, congestion mitigation, accurate violation detection, and easier enforcement, and increased payment and enforcement revenues to cities.
Owner:SUBRAMANYA BALU
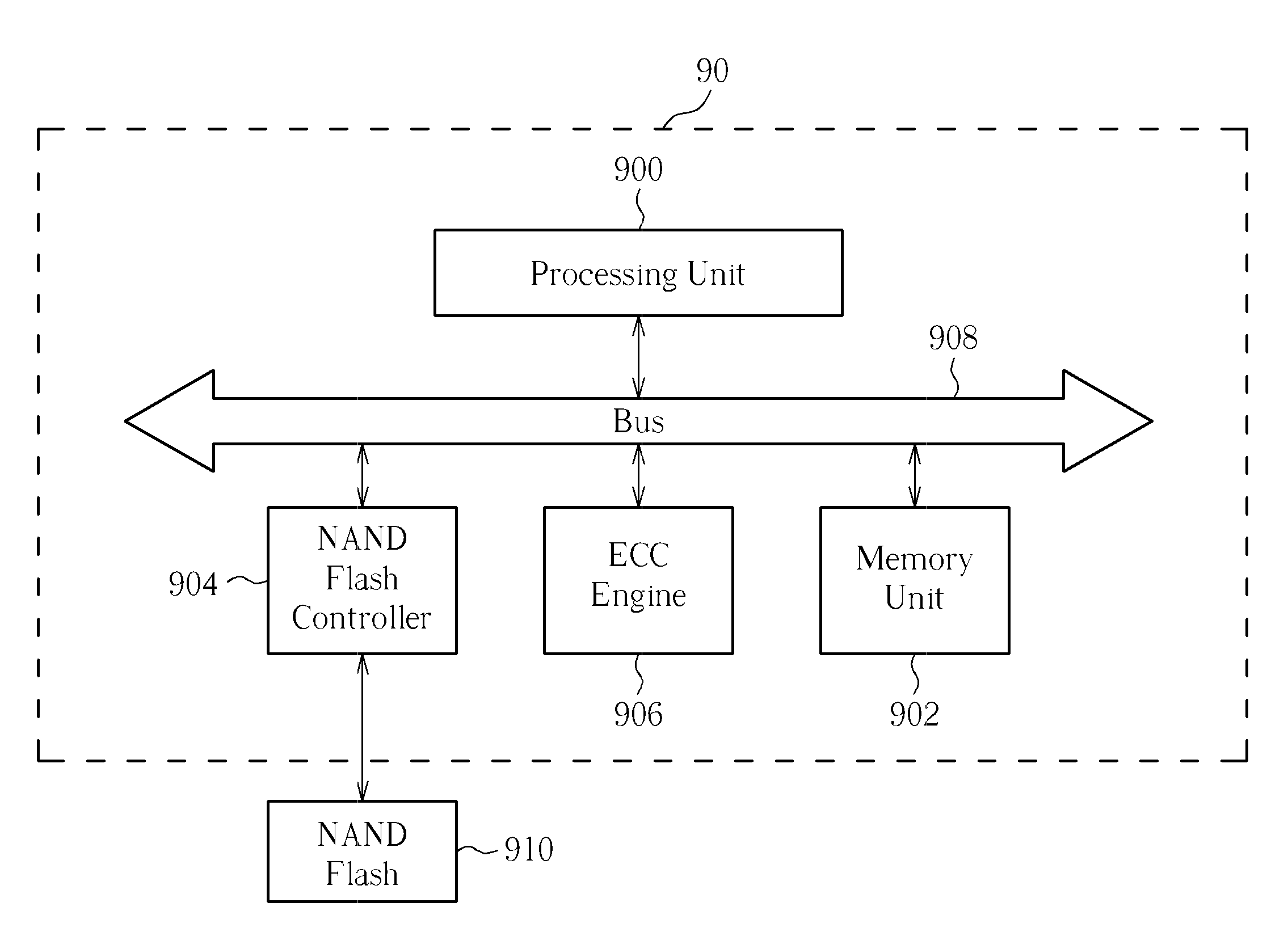
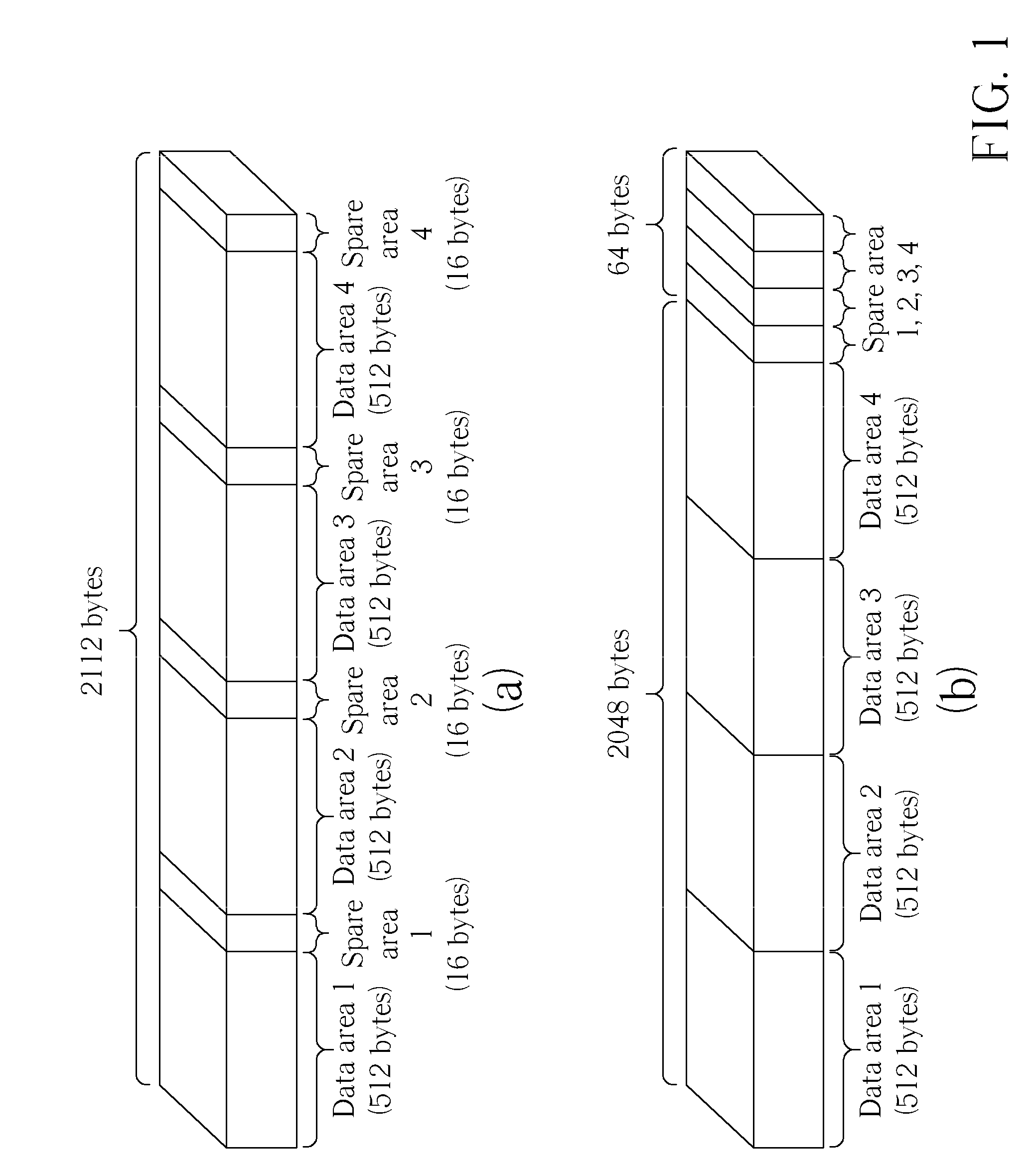
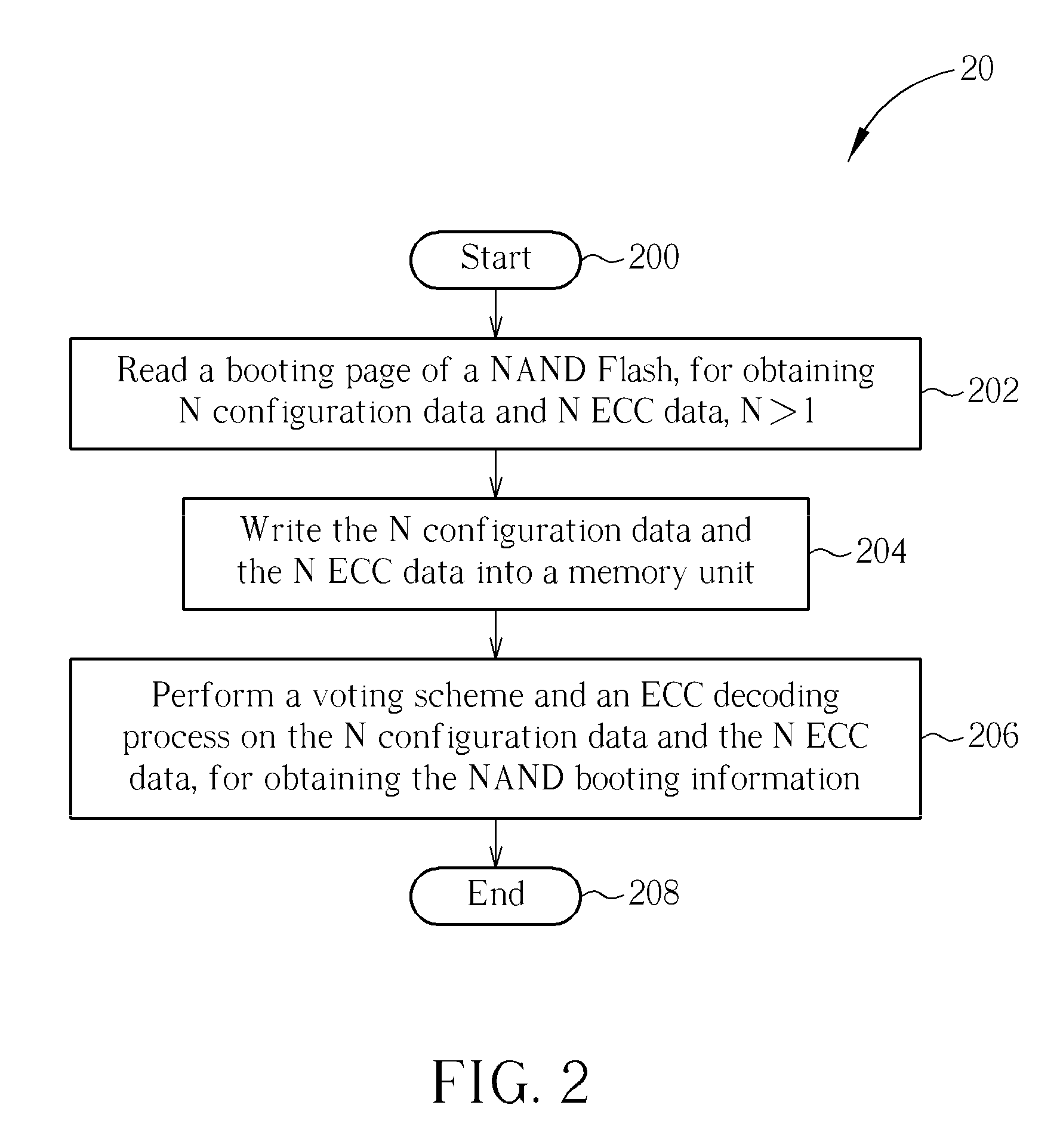
Decoding/encoding method for booting from a NAND flash and system thereof
InactiveUS8175012B2Error detection/correctionTransmission control/equalisingDecoding methodsBit numbering
A decoding method for booting from a NAND Flash including a booting page storing a plurality of copies of NAND booting information and a plurality of corresponding parities, each parity generated by an predetermined error correction code (ECC) bit number. The decoding method includes reading the booting page, for obtaining a plurality of configuration data and a plurality of ECC data, and performing a voting scheme and an ECC decoding process on the plurality of configuration data and the plurality of ECC data, for obtaining the NAND booting information. Besides, an encoding method for encoding such booting information is disclosed the same.
Owner:MEDIATEK INC
System and method for switching between environments in a multi-environment operating system
Various embodiments of the present invention provide a mobile computing device that operates multiple, co-existing and independent operating system environments on a common kernel. A booting process for initiating a multiple operating system environment is also provided. Additionally, various embodiments of the present invention include processes for managing a switch between one operating system environment to a second operating system environment.
Owner:GOOGLE TECH HLDG LLC
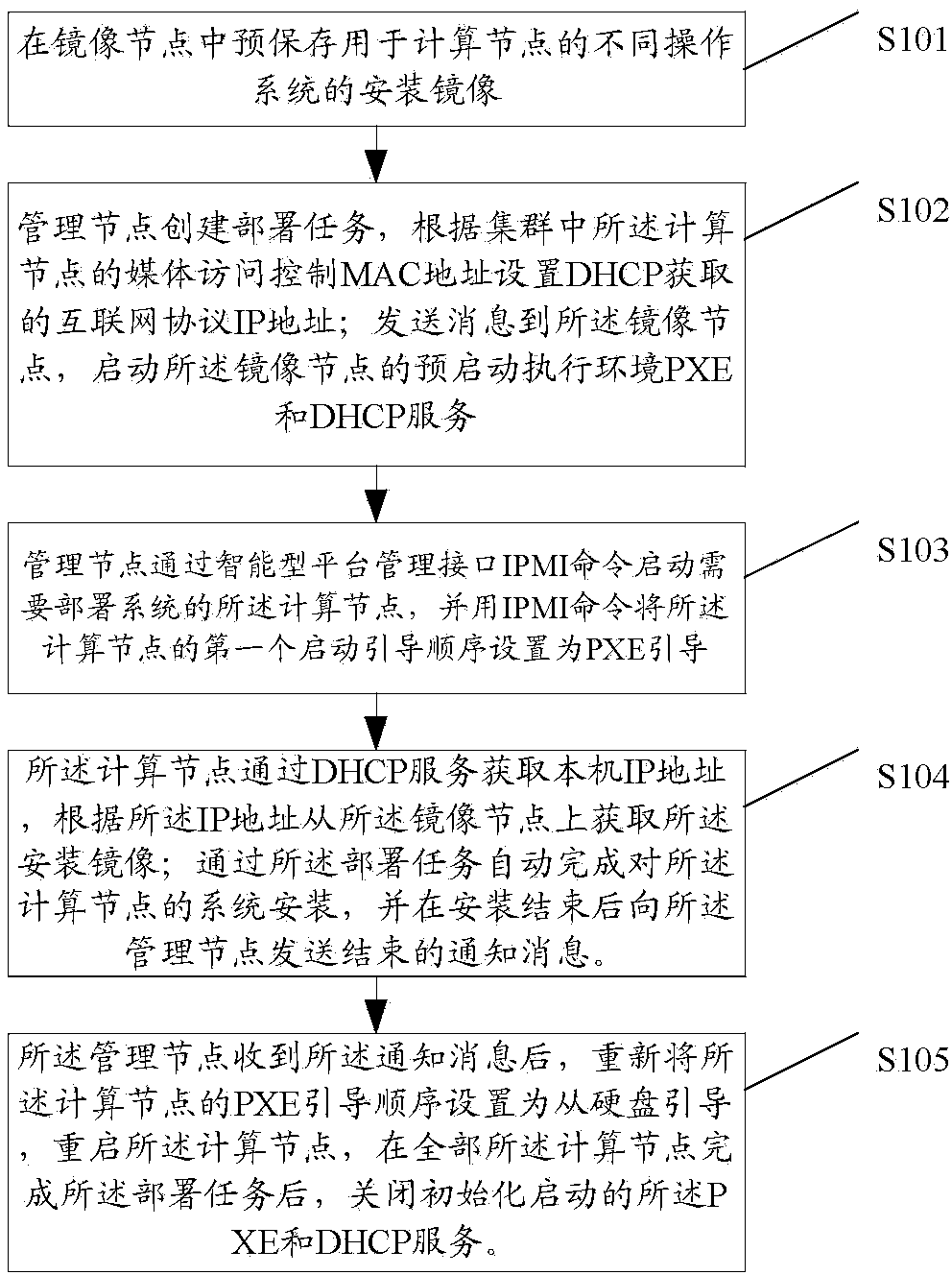
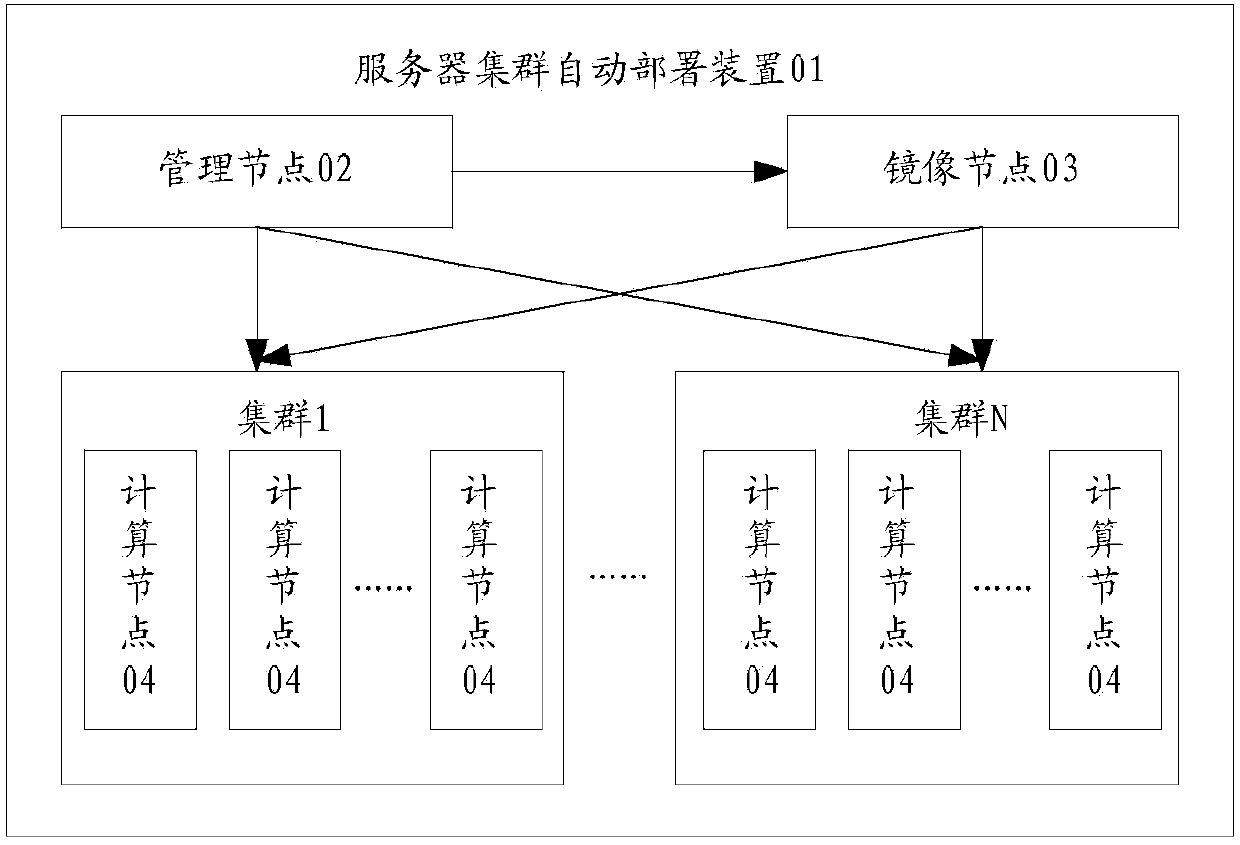
Automatic server cluster deploying method and device
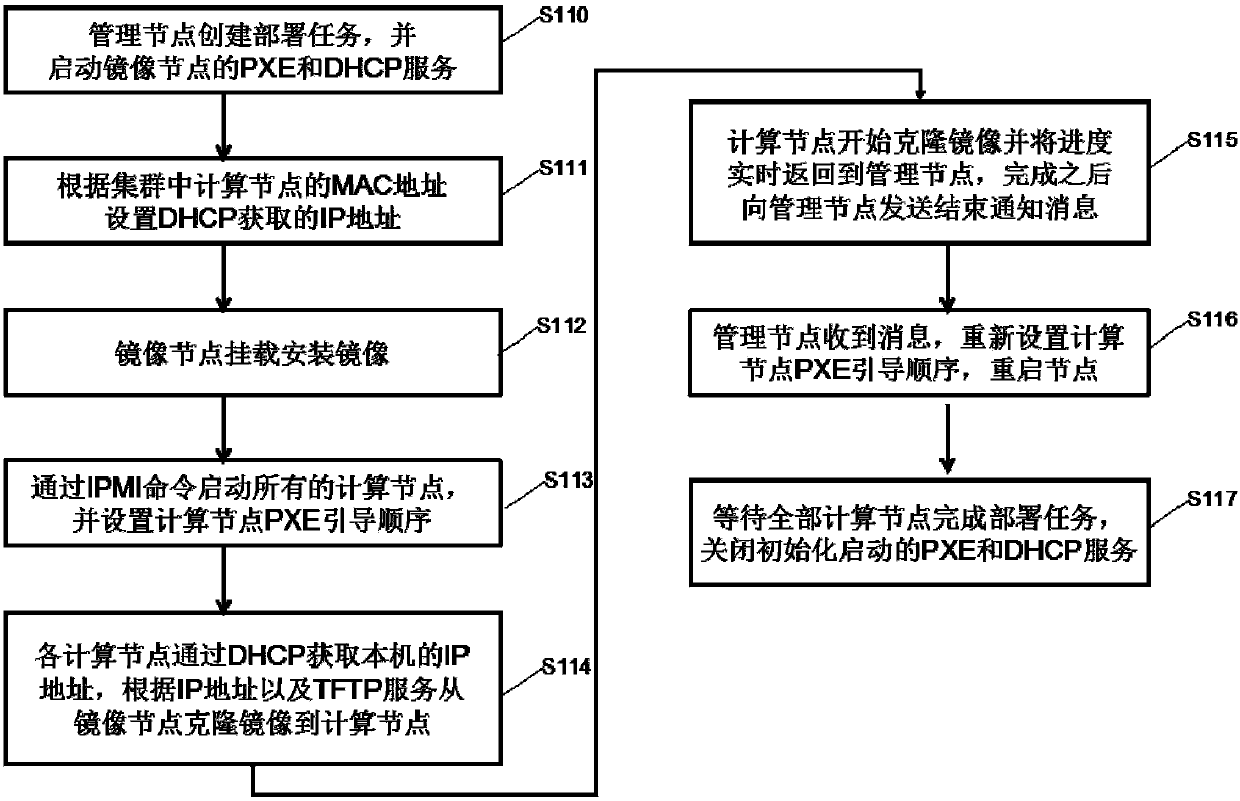
InactiveCN104219099AQuick configurationSimplify the configuration processData switching networksOperational systemIp address
The invention provides an automatic server cluster deploying method and device. The automatic server cluster deploying method comprises the steps of pre-storing installation images of different operating systems of computational nodes in image nodes; managing the nodes and establishing deployment tasks, setting internet protocol (IP) addresses of the computational nodes and booting pre-boot execution environments (PXE) and dynamic host configuration protocol (DHCP) service of the image nodes; booting the computational nodes needing deployment systems and setting the first booting guide sequence as a PXE guide; enabling the computational nodes to obtain local IP addresses through the DHCP service, and accordingly obtaining the installation images from the image nodes; automatically completing system installation of the computational nodes. By means of the automatic server cluster deploying method and device, automatic allocation of large-scale cluster nodes in the cloud computing cluster environment deployment process is achieved, quick allocation of the large-scale cluster nodes is achieved, the allocation process is simplified, and the allocation efficiency is improved.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
Method of safe and recoverable firmware update and device using the same
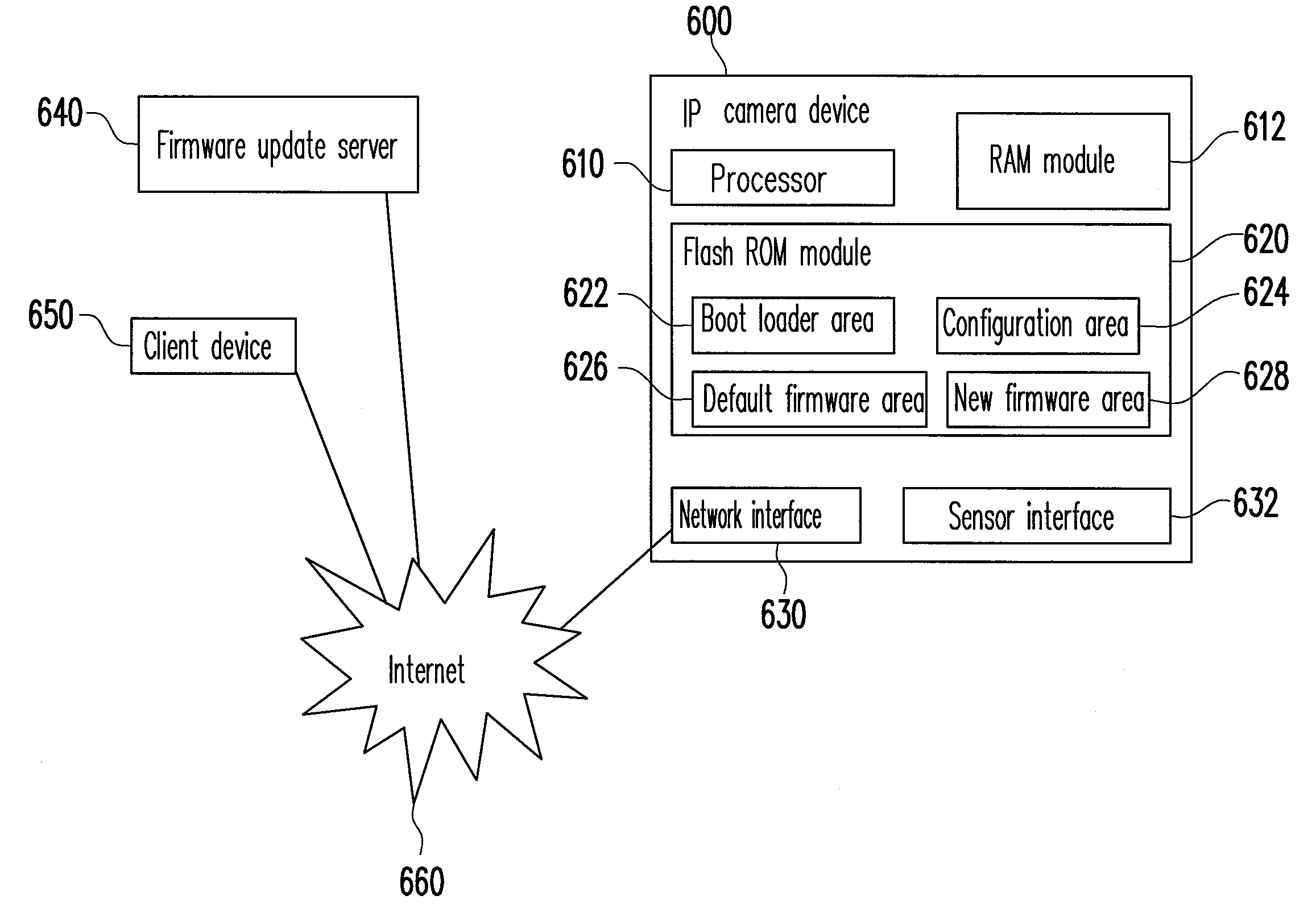
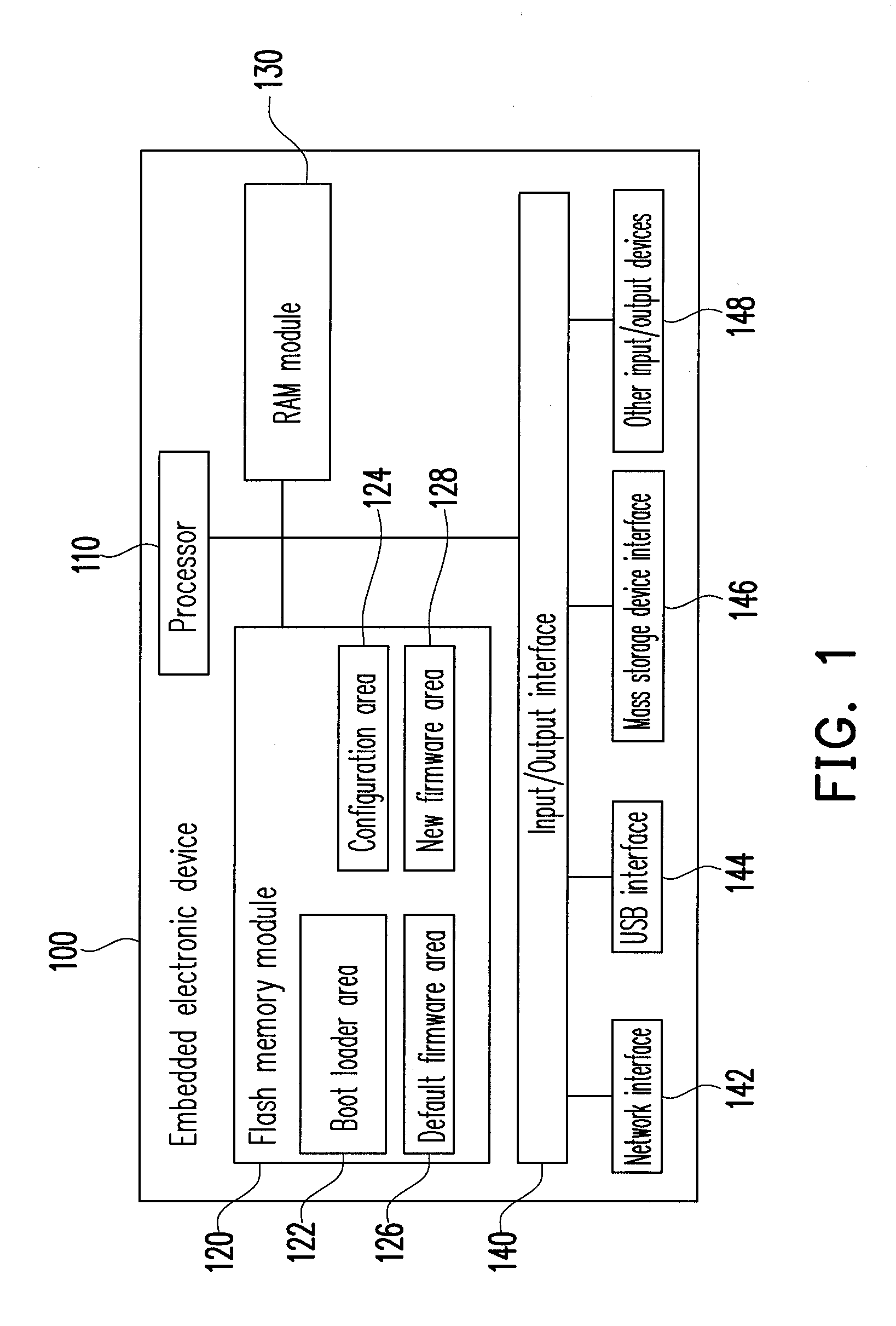
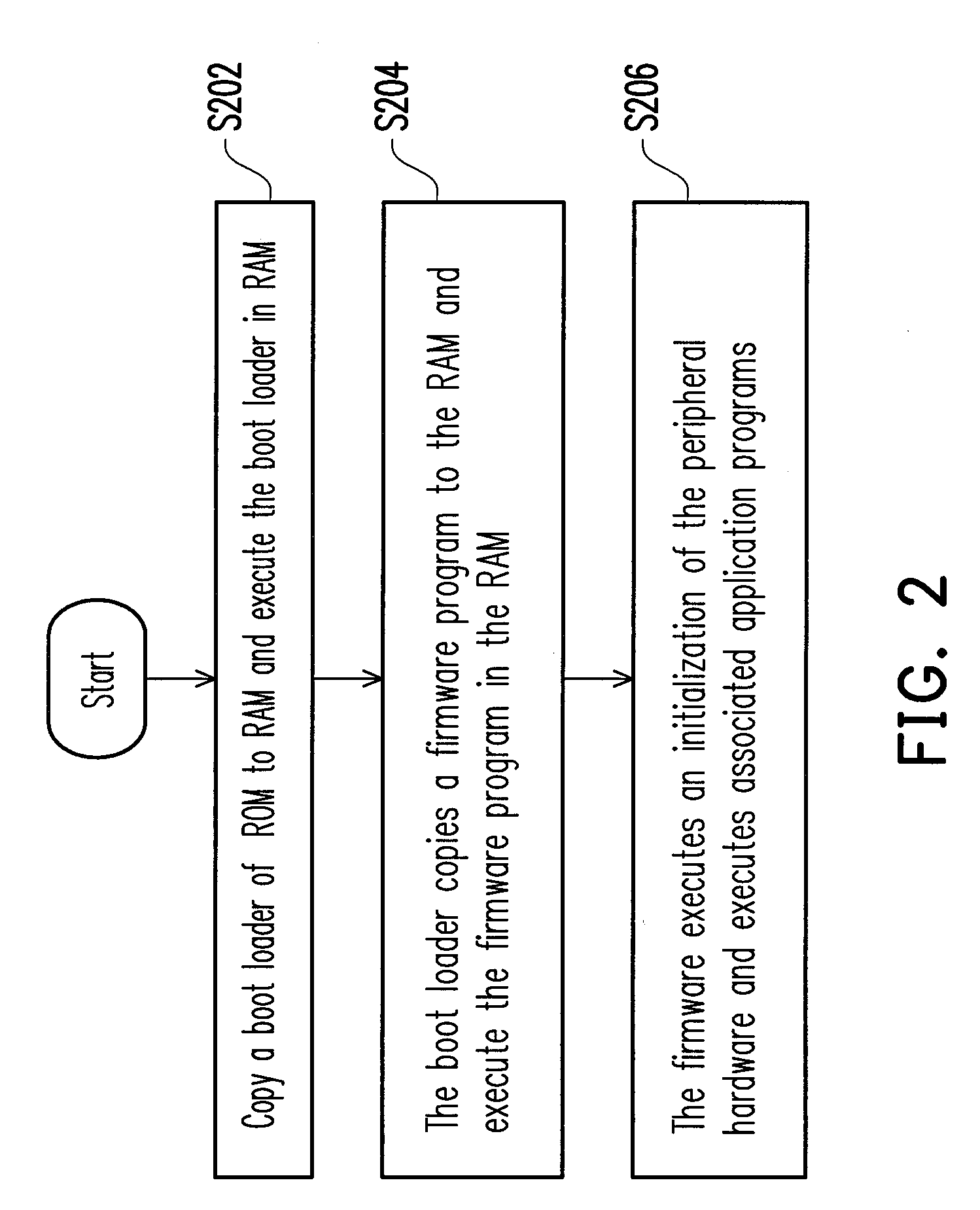
ActiveUS20100199078A1Maintain abilityMemory adressing/allocation/relocationDigital computer detailsValidation methodsEmbedded electronics
A safe and recoverable firmware update method which for a remote embedded electronic device and the device thereof. The method includes reading an update status in a flash memory, and determining the update status. If the update status is “DEFAULT”, a default firmware is executed. If the update status is not “DEFAULT”, the update status is further determined if it is “UPDATED”. If the update status is “UPDATED”, a configuration area is set as “BOOTING” and a new firmware is executed. If the update status is not “UPDATED”, the update status is determined if it is “RUNNEW”. If the update status is “RUNNEW”, a new firmware and an update validation method are executed. If the update validation method gets an update completion validation message, the update status is set as “RUNNEW”. If the update status is not “RUNNEW”, a default firmware is executed.
Owner:NOVATEK MICROELECTRONICS CORP
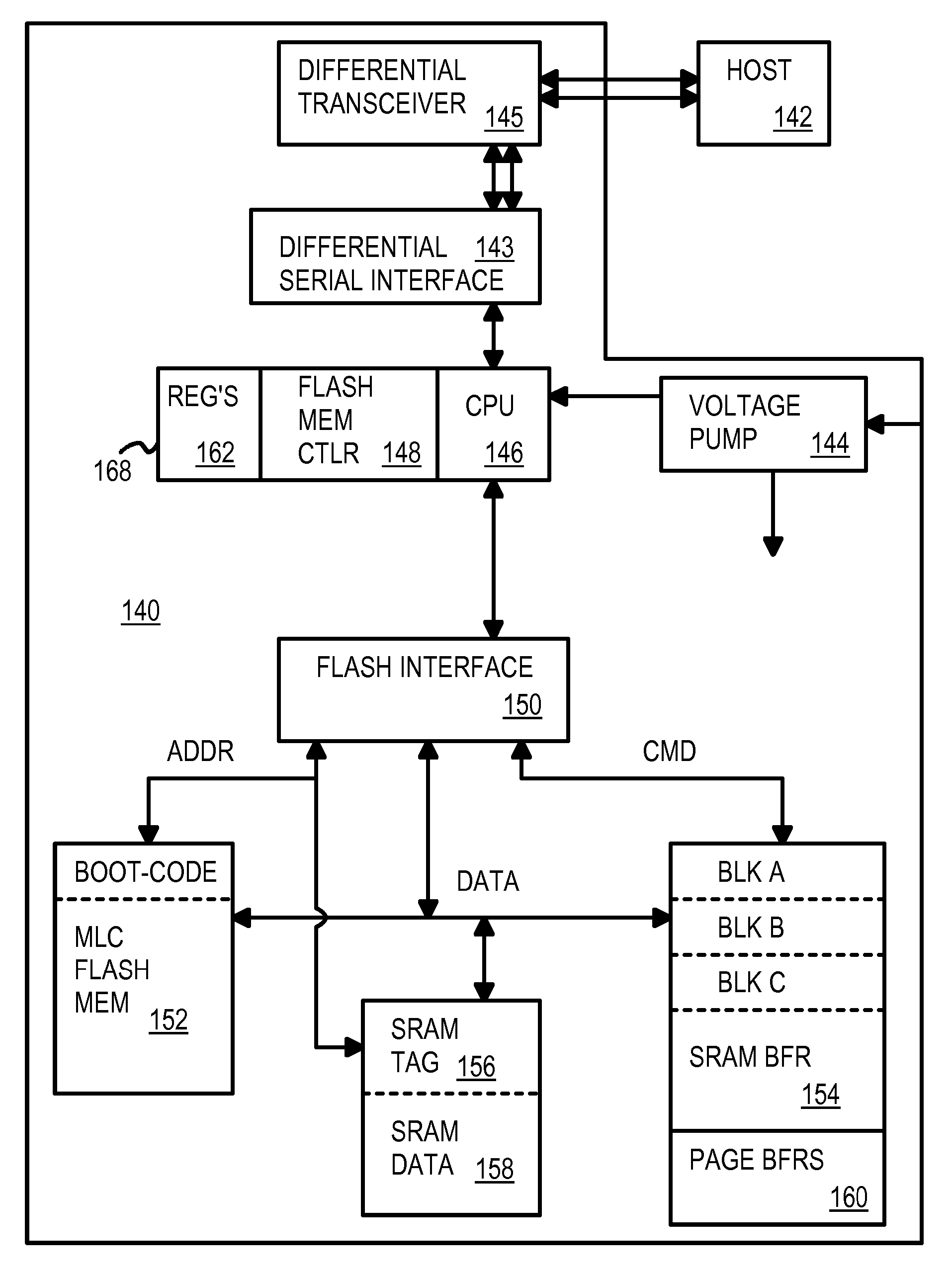
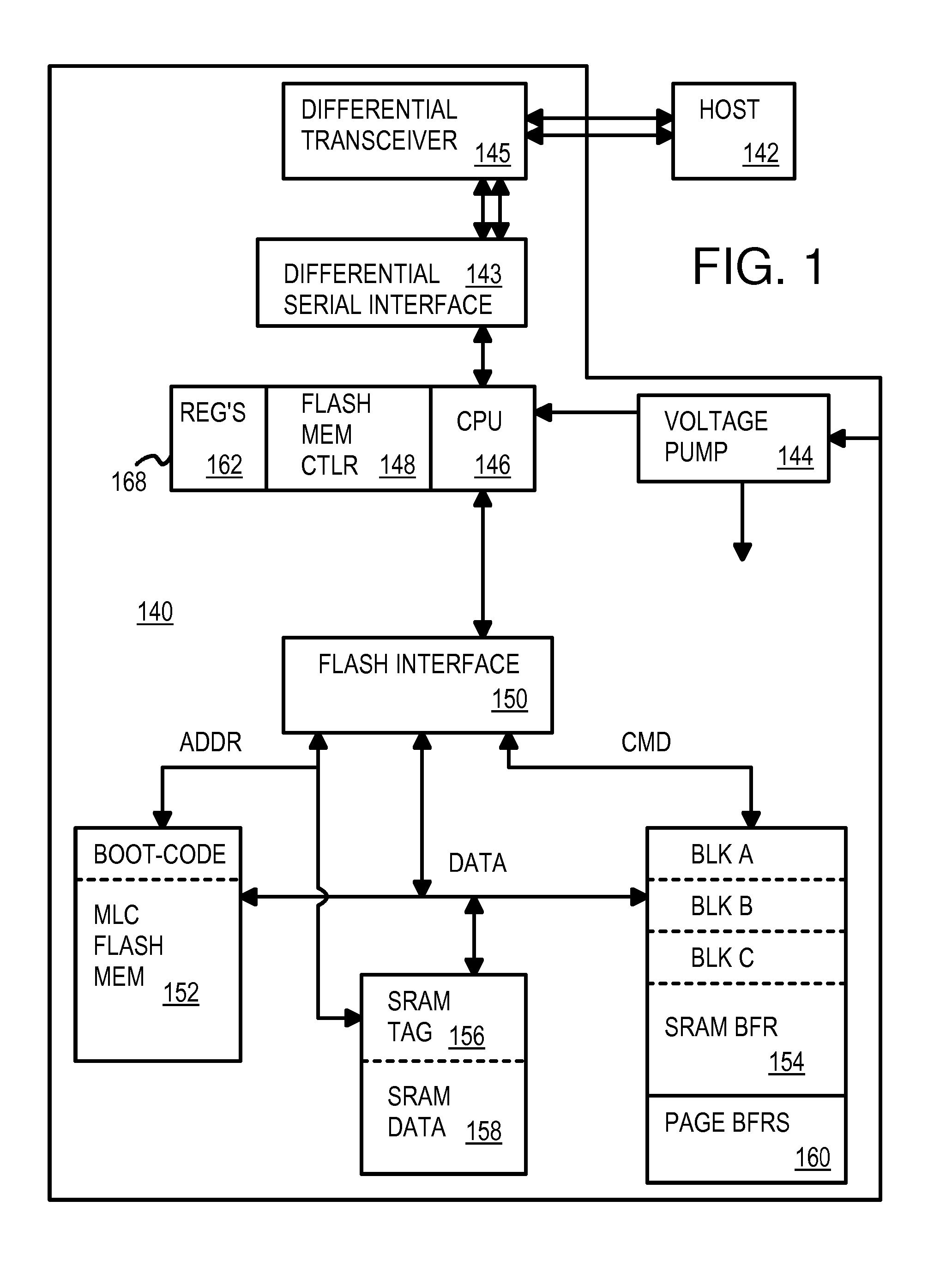
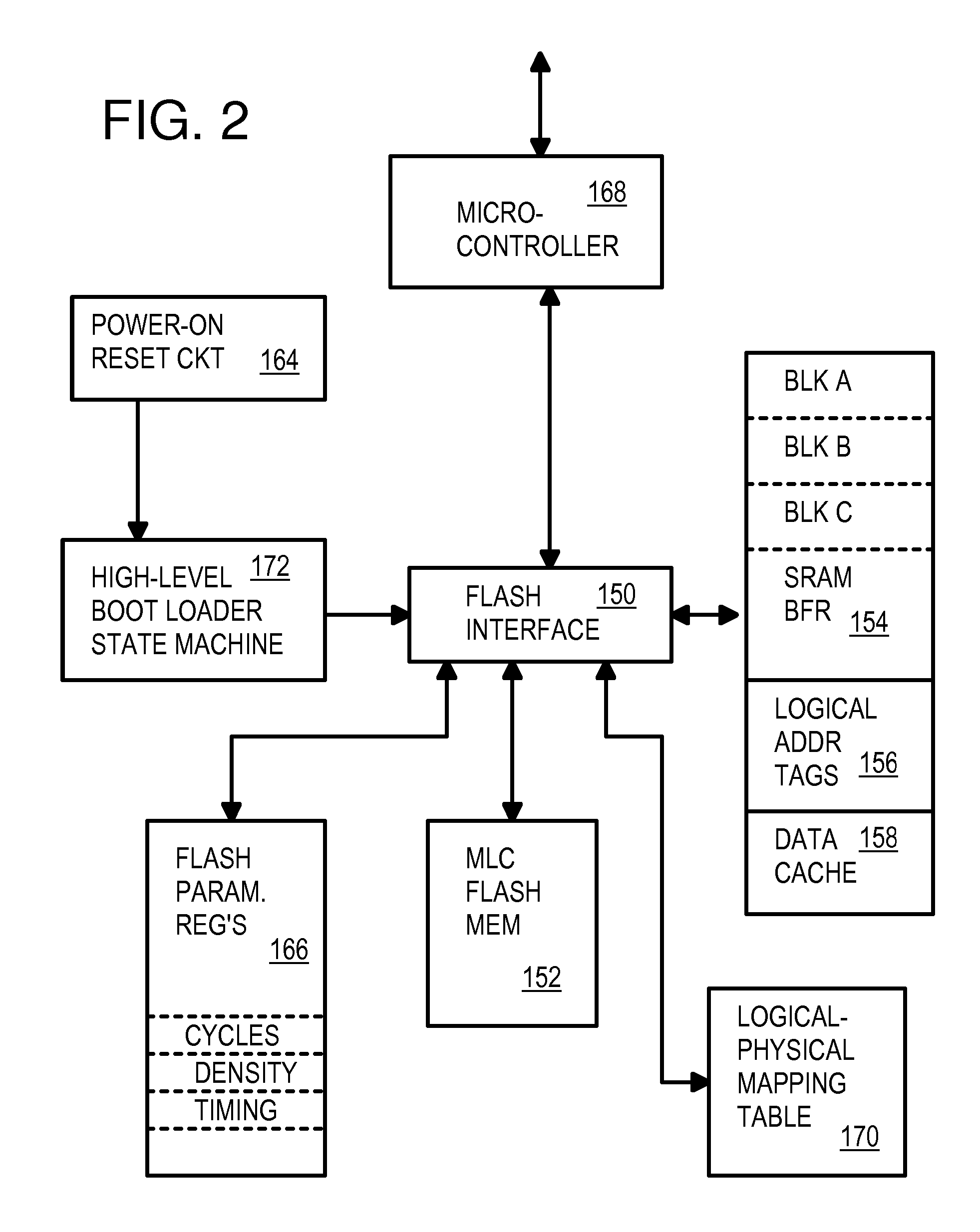
SRAM Cache & Flash Micro-Controller with Differential Packet Interface
InactiveUS20080098164A1Memory architecture accessing/allocationMemory systemsMicrocontrollerTransceiver
A flash microcontroller has a Static Random-Access-Memory (SRAM) buffer that stores several blocks of boot code read from a flash memory. The SRAM buffer also operates as a cache of flash data after booting is complete. Cache read and write hits use the SRAM cache rather than flash memory, while old cache lines and read misses access the flash memory. Both the external host and the microcontroller are booted from boot code buffered in the SRAM buffer. A boot-loader state machine reads the flash ID and programs flash parameter registers with timing parameters for the flash memory. The flash microcontroller uses a differential interface to the external host, with a differential transceiver and a differential serial interface. Frame, packet, and encoded clock processing is also performed by the serial interface.
Owner:SUPER TALENT TECH CORP
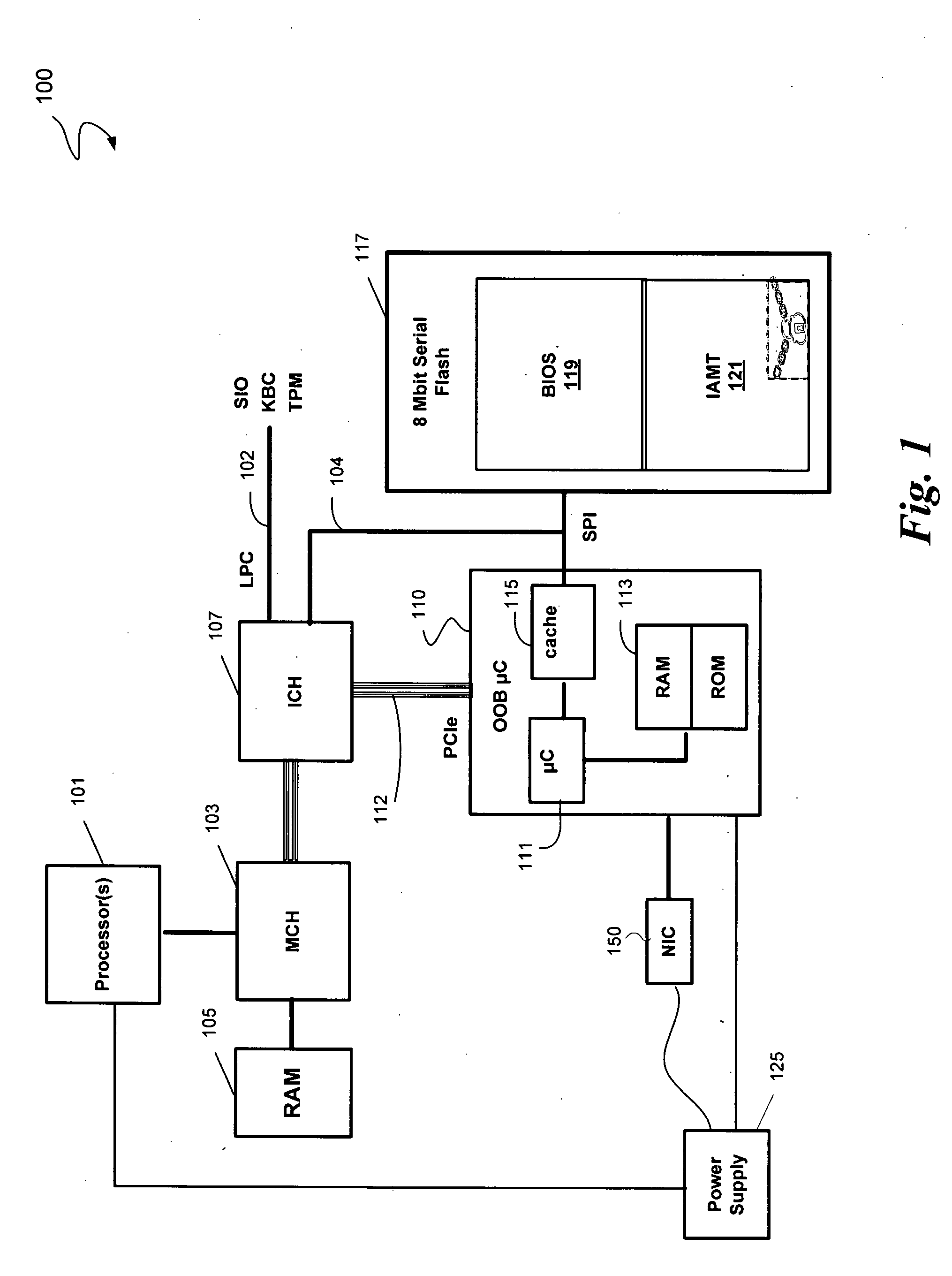
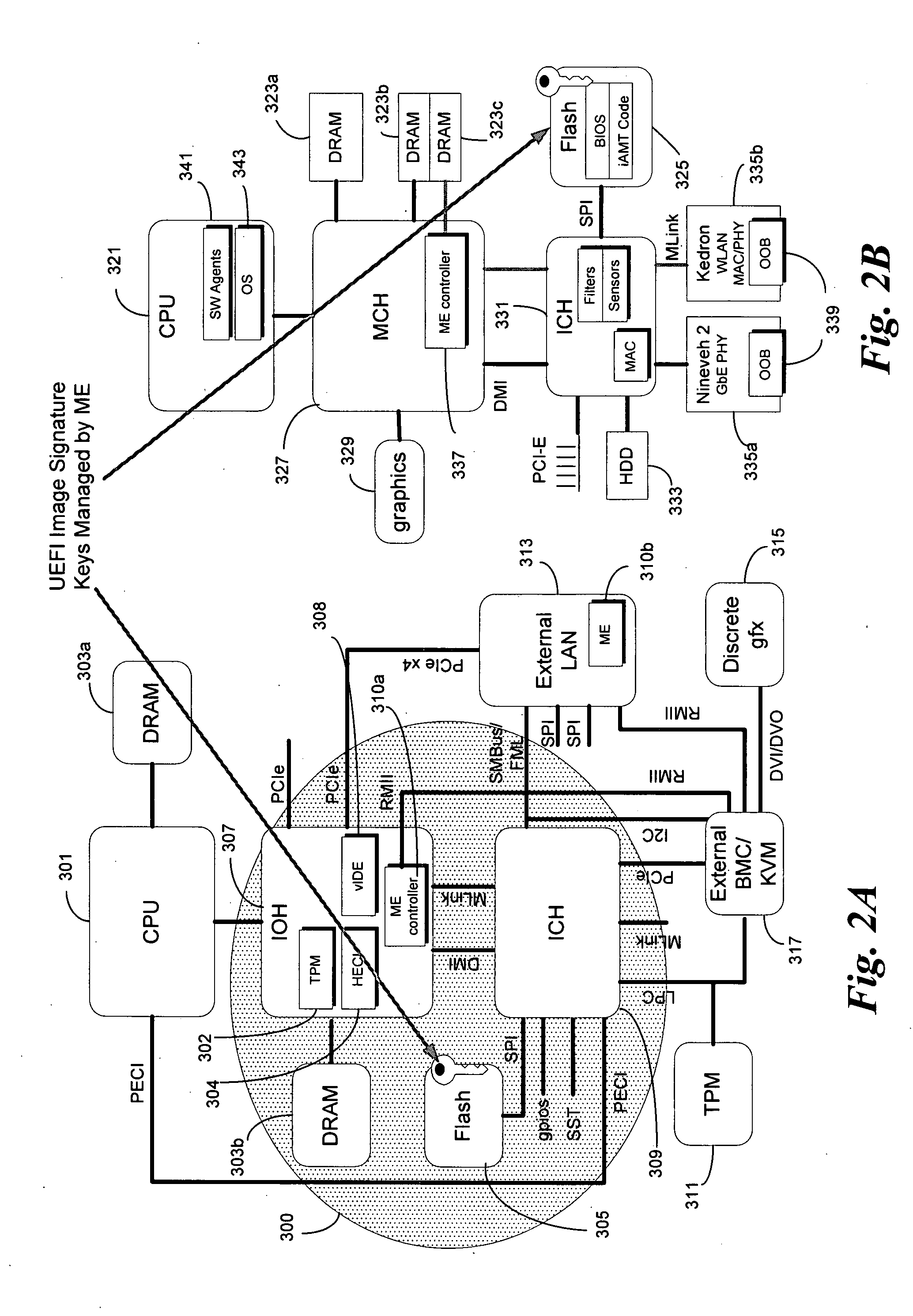
Server active management technology (AMT) assisted secure boot
ActiveUS20080244257A1Digital computer detailsComputer security arrangementsMicrocontrollerMaster processor
In some embodiments, the invention involves a system and method relating to secure booting of a platform. In at least one embodiment, the present invention is intended to securely boot a platform using one or more signature keys stored in a secure location on the platform, where access to the signature is by a microcontroller on the platform and the host processor has no direct access to alter the signature key. Other embodiments are described and claimed.
Owner:INTEL CORP
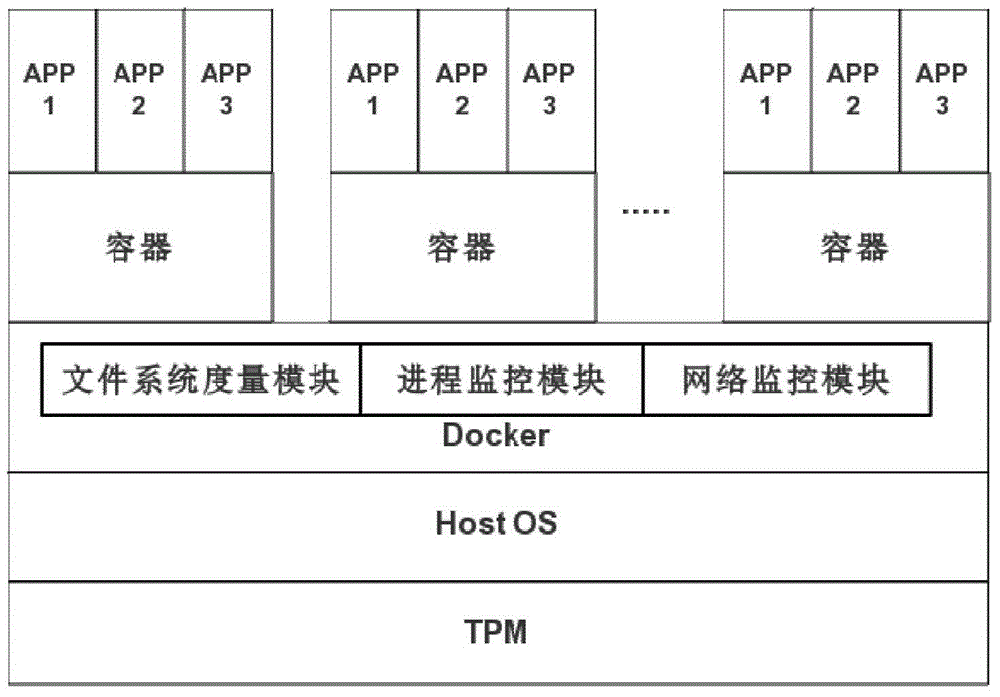
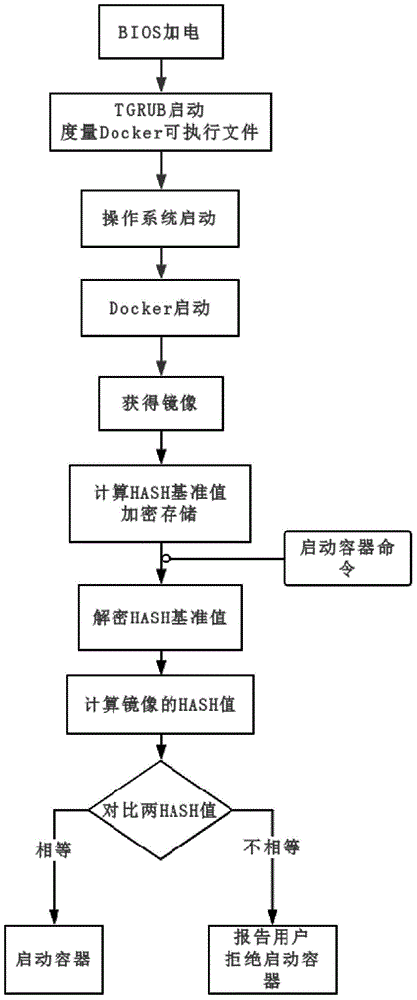
Security reinforcement method for credible container based on Docker
ActiveCN105069353ATrusted bootGuaranteed normal startupPlatform integrity maintainanceNetwork communicationMirror image
The invention discloses a security reinforcement method for a credible container based on Docker used for performing security reinforcement on a Docker container system, and realizes the credible container based on the Docker, as well is applied to a server cluster based on the Docker. The credible container based on the Docker comprises a container program Docker, a container credible measurement module, a progress monitoring module and a network communication monitoring module, wherein the container credible measurement module comprises a credible booting sub-module and a file measurement sub-module. The reinforcement method focuses on the credibility of the Docker container; a credible computing and integrity measurement technology is matched with a real-time monitoring module to reinforce the container system based on the Docker, so that the container and a mirror image are prevented from tampering; and meanwhile, a network communication behavior of the container is limited, and an inner progress of the container is monitored, so as to realize the security reinforced credible container.
Owner:WUHAN UNIV
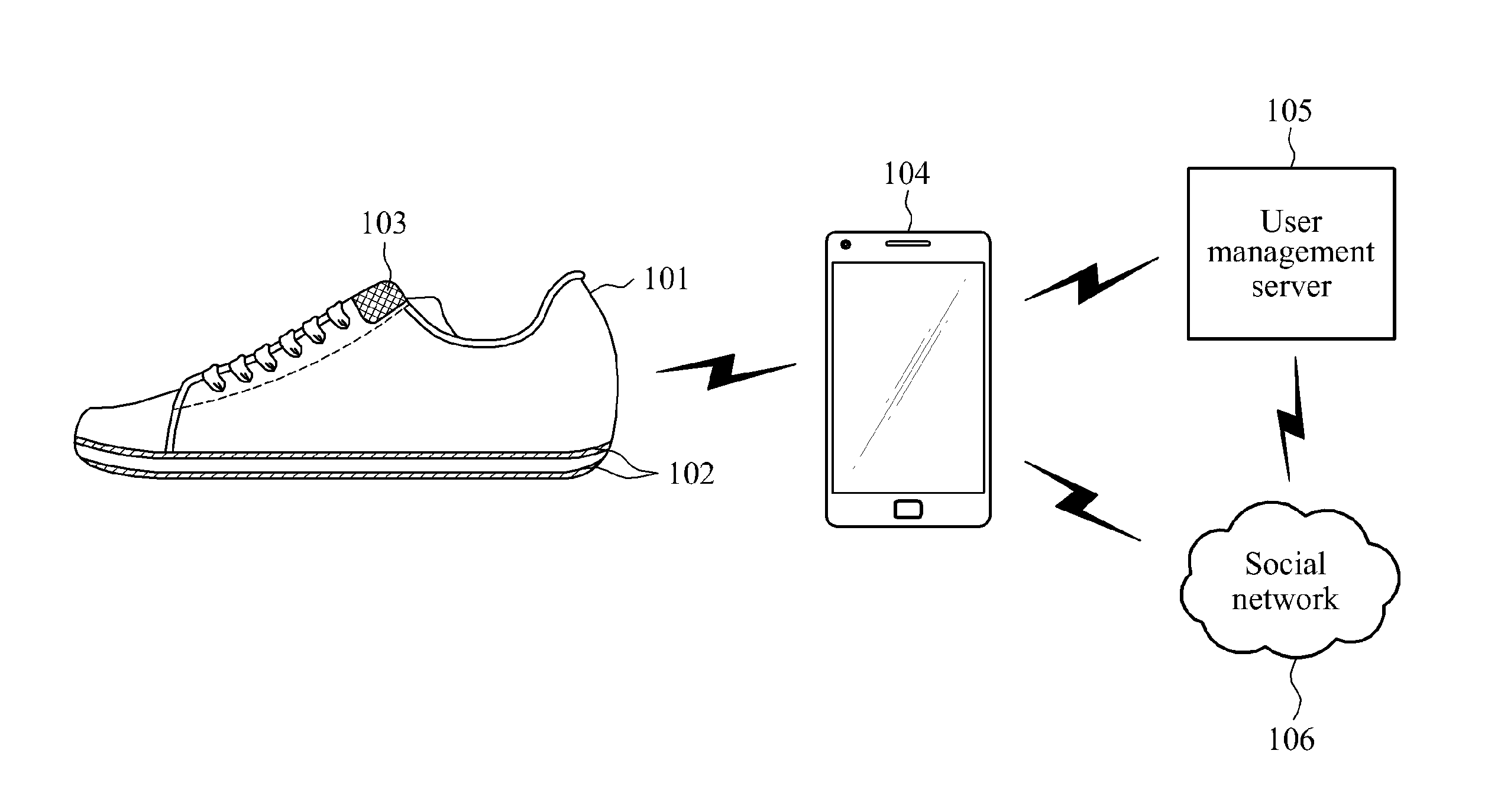
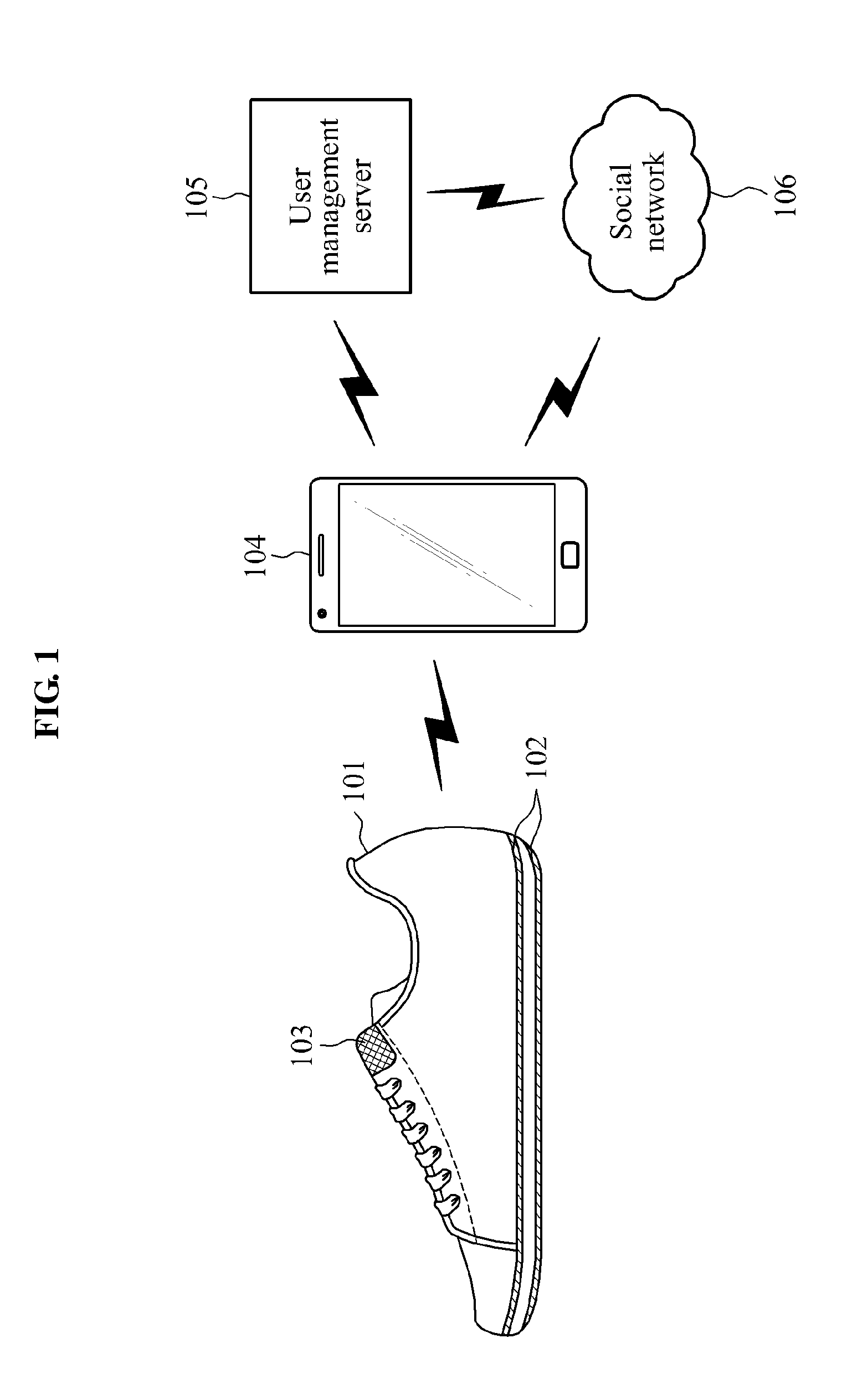
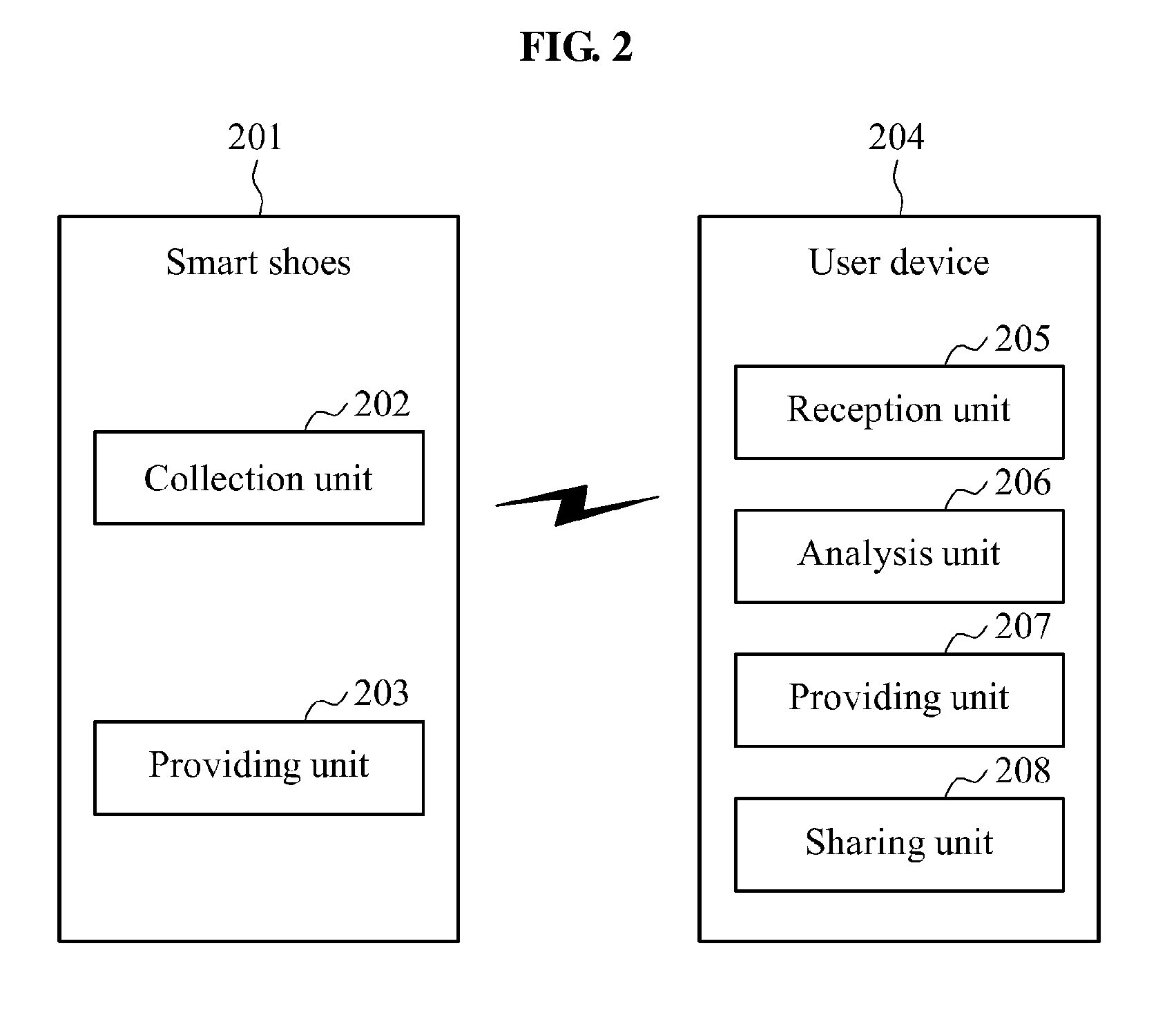
Smart shoes, method of providing sensor information to smart shoes, smart device and method of providing guidance program via smart device
ActiveUS20150182844A1Improve accuracyReliable weight measurementWeighing indication devicesDiagnostic recording/measuringUser deviceBooting
Smart shoes including a sensor unit including at least one sensor of a pressure sensor to sense a pressure in the smart shoes, a temperature sensor to sense a temperature in the smart shoes, an acceleration sensor to sense a movement of the smart shoes and an altitude sensor to sense an altitude, a controller to collect sensor information output by the at least one sensor and process the collected sensor information according to a request from a user device, and a providing unit to provide the processed sensor information to the user device.
Owner:ELECTRONICS & TELECOMM RES INST
Portable, secure enterprise platforms
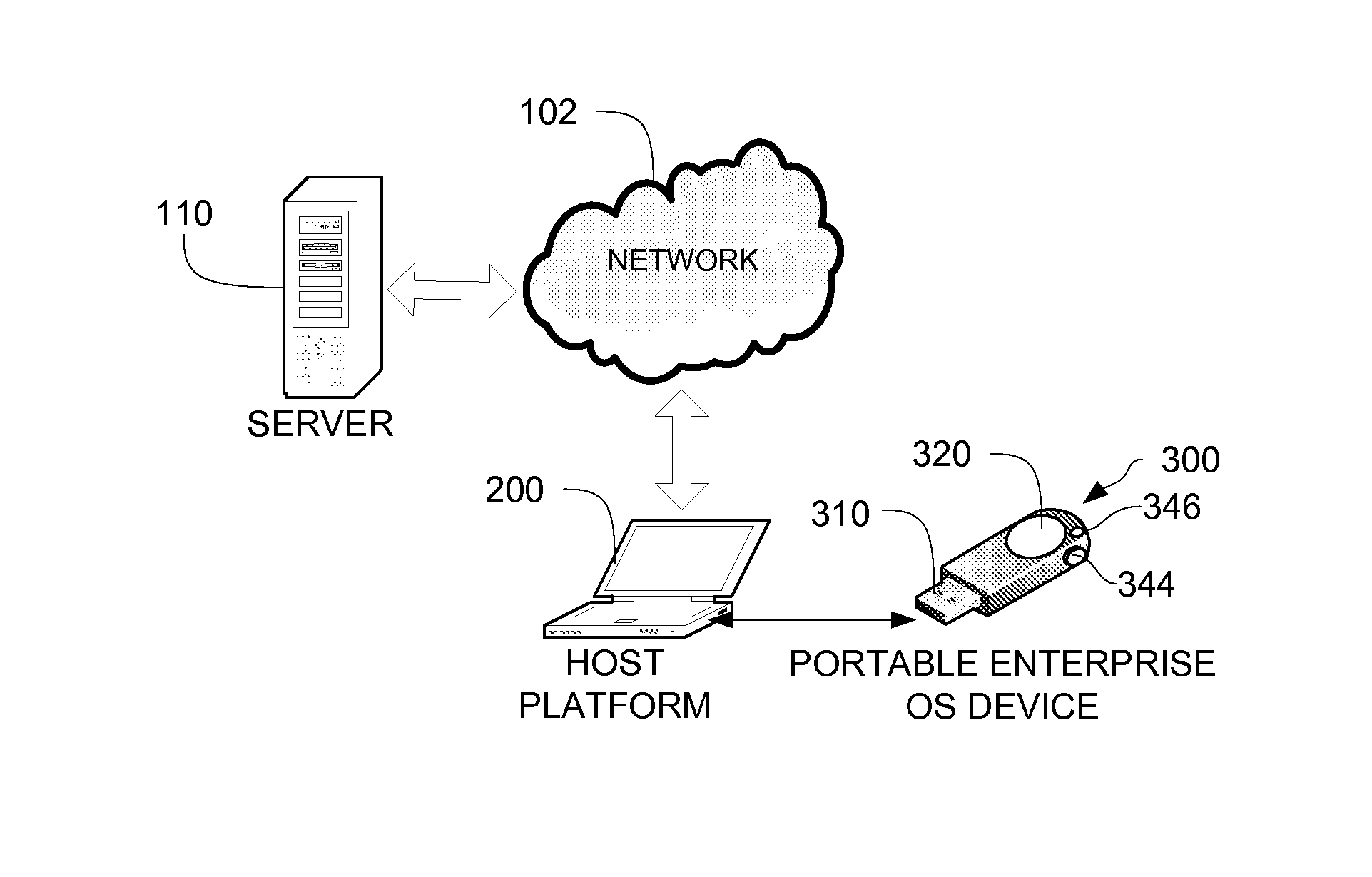
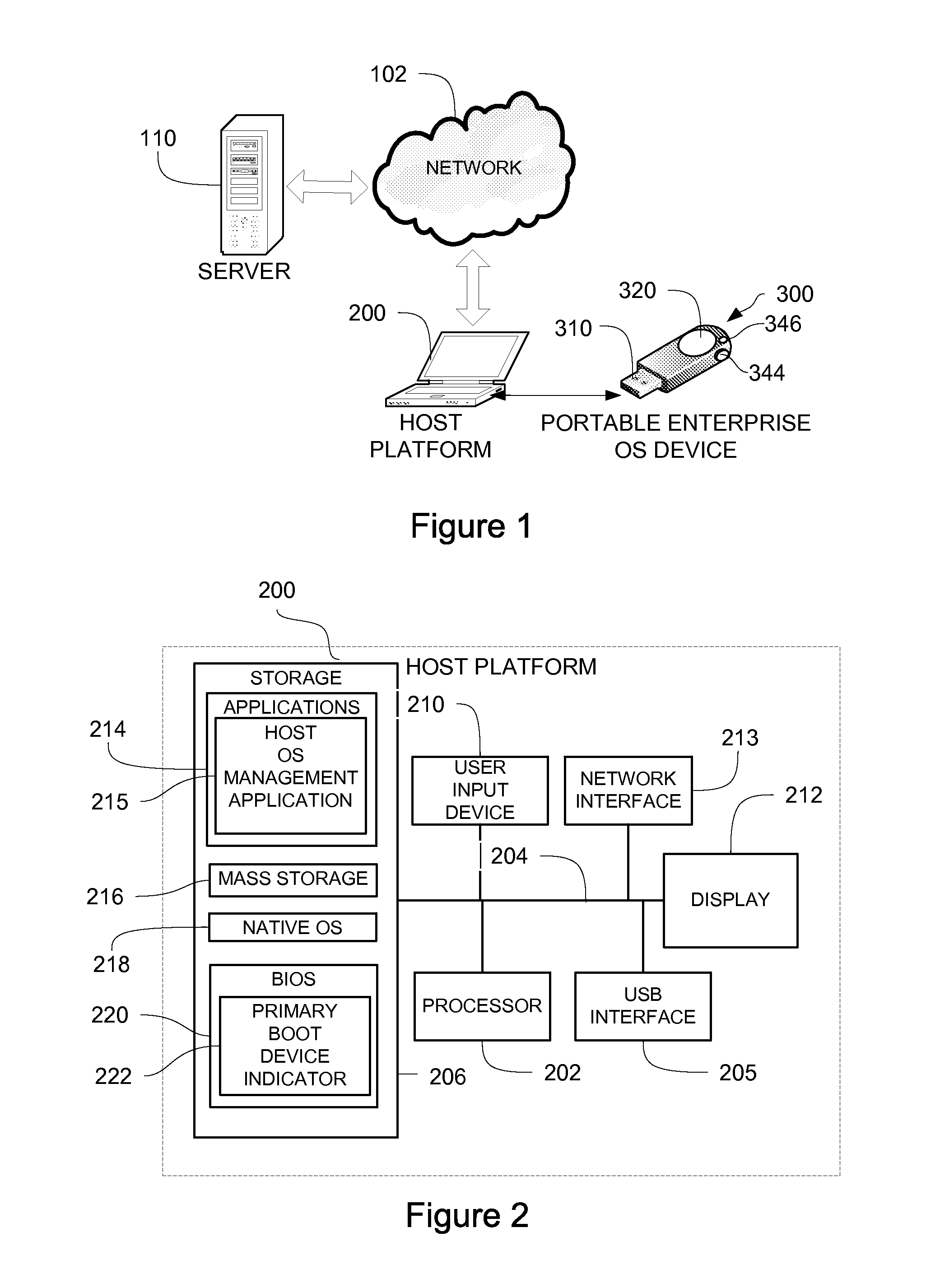
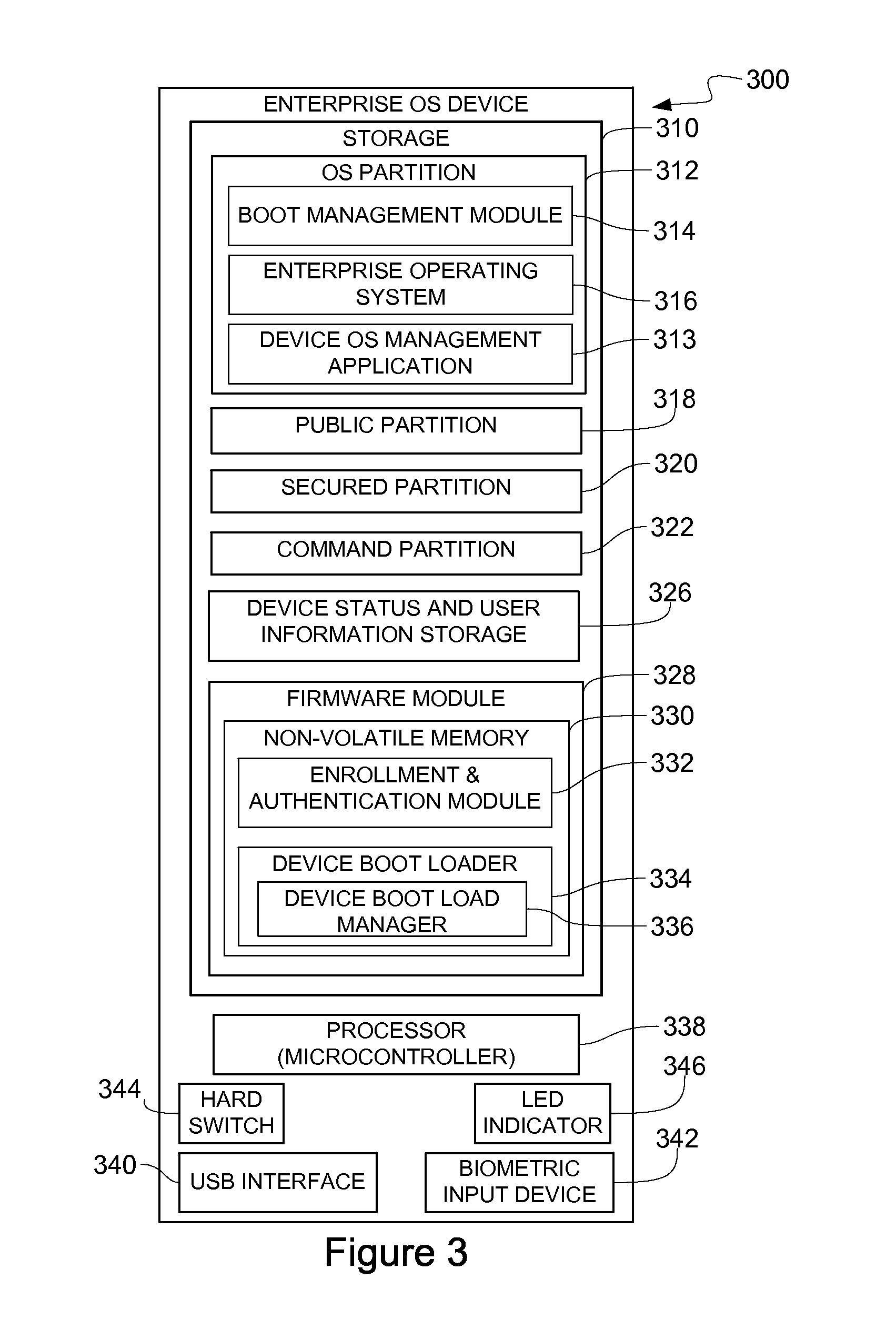
InactiveUS20140101426A1Improve securityPrevent unauthorized accessDigital computer detailsDigital data authenticationProgram managementComputer module
A portable, secure enterprise computing platform is provided by a device having a storage or memory, including a firmware module, a processor and an interface for interfacing with a host platform. The interface may be a USB interface and the device may have the form factor of a USB thumb drive. The storage may include a public partition, secure partition, operating system partition and command partition. A boot load manager in the firmware module causes the processor to load an operating system on the operating system partition and selectively enables access to the operating system by the host platform. The operating system partition may be formatted as a CDFS device such that the host platform recognizes the device as a bootable CD drive. The device provides for secure booting to the operating system partition by the host platform, without risk of corruption or malware from the host platform. A user may select from multiple operating systems. Multiple devices may be managed by a policy management application, which may assign groups of users and applications to one or more devices across an enterprise.
Owner:MSI SECURITY
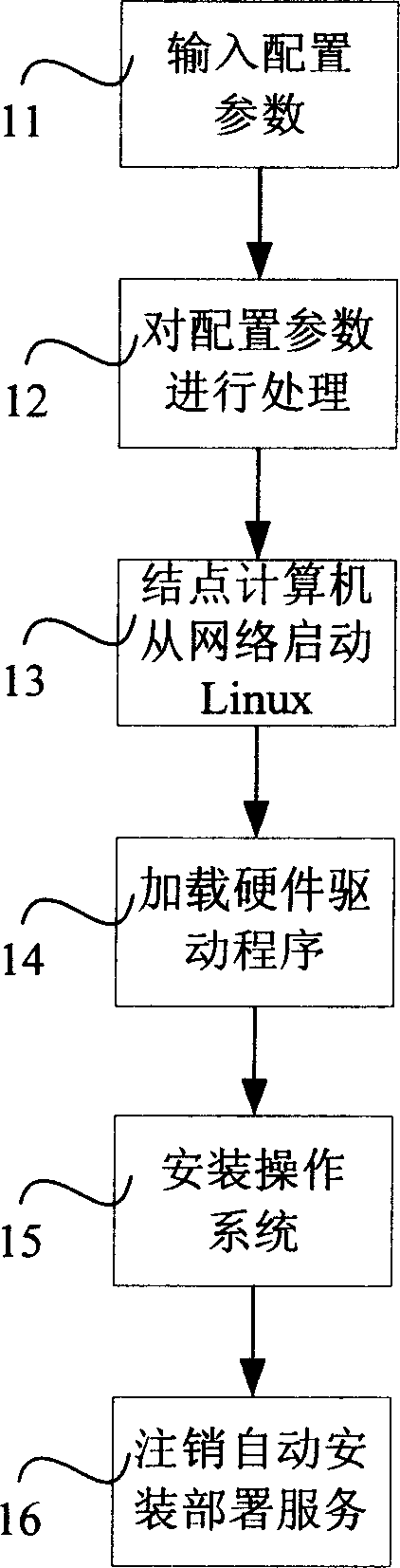
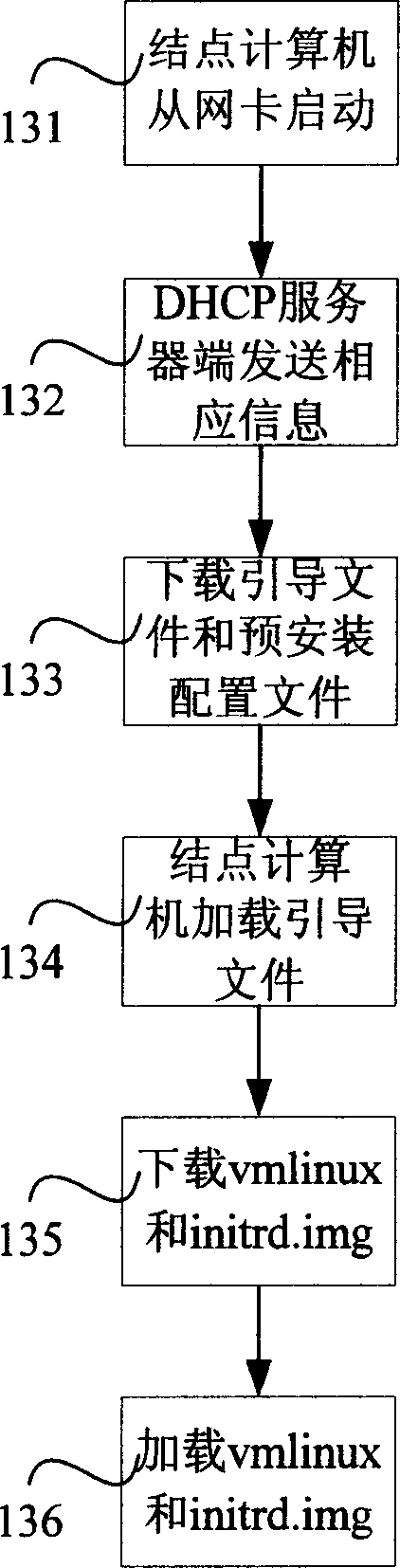
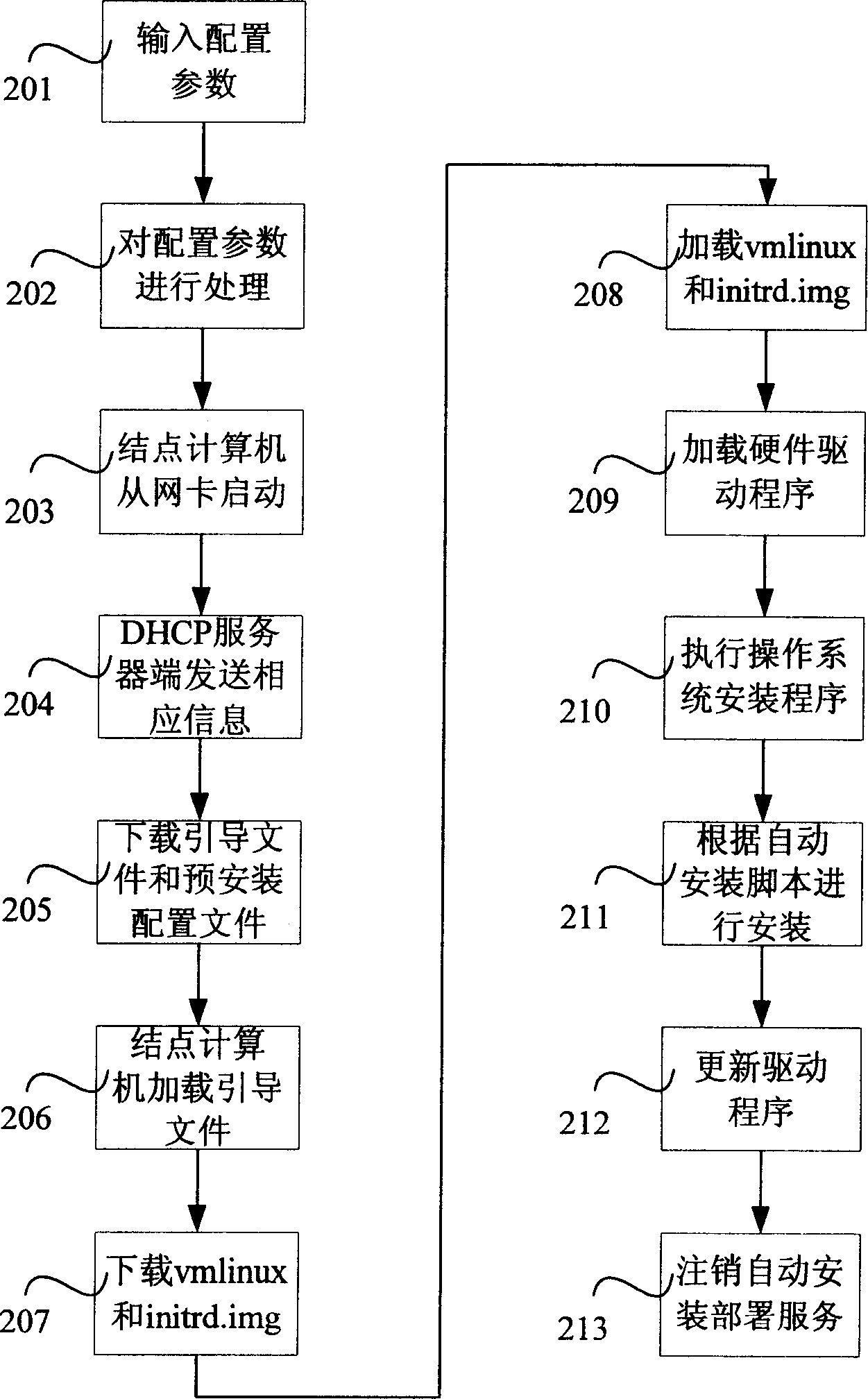
Method for automatic deploying operate system
ActiveCN1916846AQuick installationEasy and fast initializationProgram loading/initiatingHardware structureOperational system
A method for automatically arranging operation system includes using arrangement service end of server to process parameters of operation system and erection to be erected on node computer, downloading lead program and preerection file from network card by node computer and starting up preerection environmental program from network by said lead program, using said environmental program to load driving program of hardware, erecting operation system and erection driving program on node computer by said environmental program, finalizing erection of operation system and canceling automatic erection service.
Owner:LENOVO (BEIJING) LTD
System and method for initiating a multi-environment operating system
Various embodiments of the present invention provide a mobile computing device that operates multiple, co-existing and independent operating system environments on a common kernel. A booting process for initiating a multiple operating system environment is also provided. Additionally, various embodiments of the present invention include processes for managing a switch between one operating system environment to a second operating system environment.
Owner:GOOGLE TECH HLDG LLC
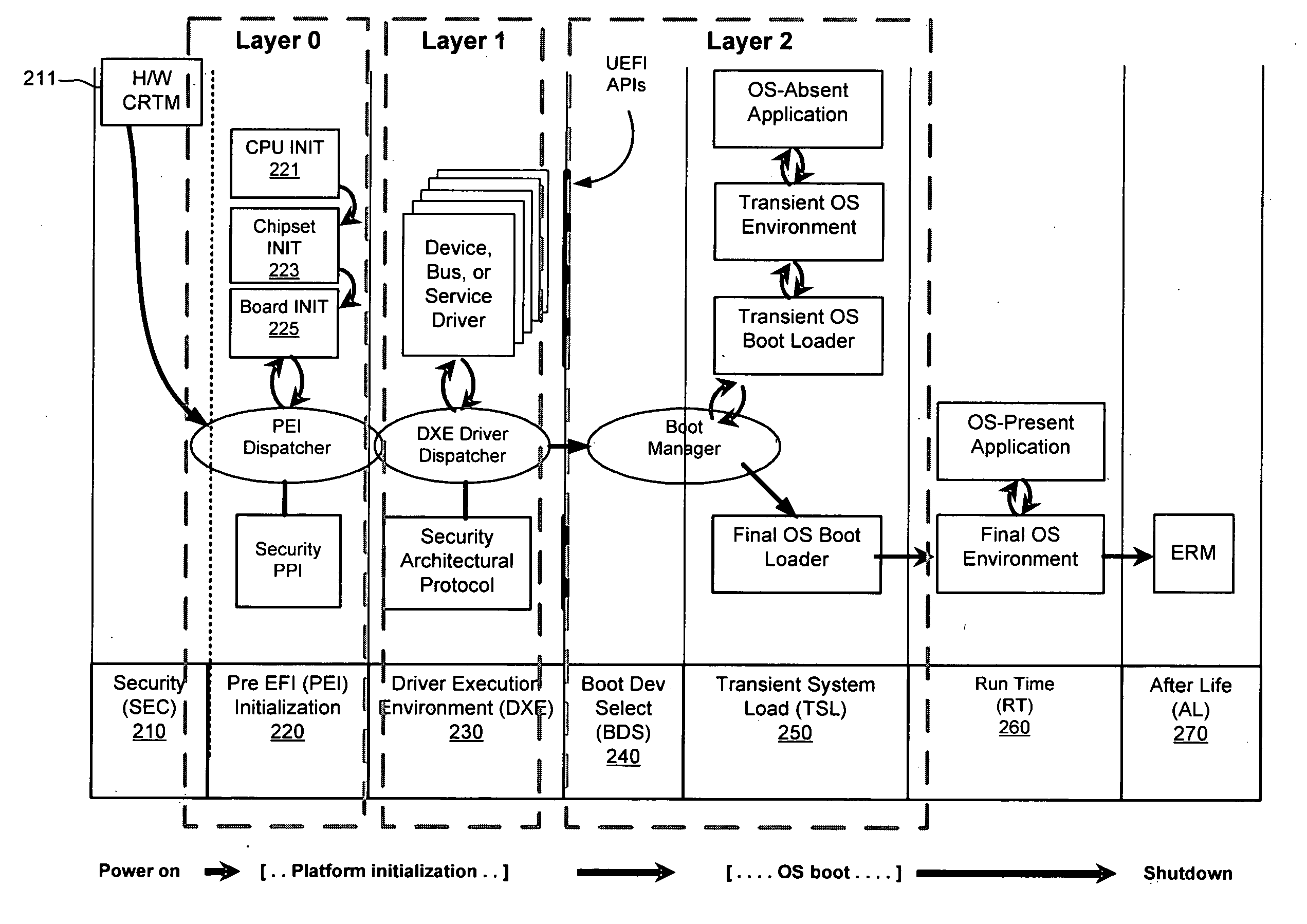
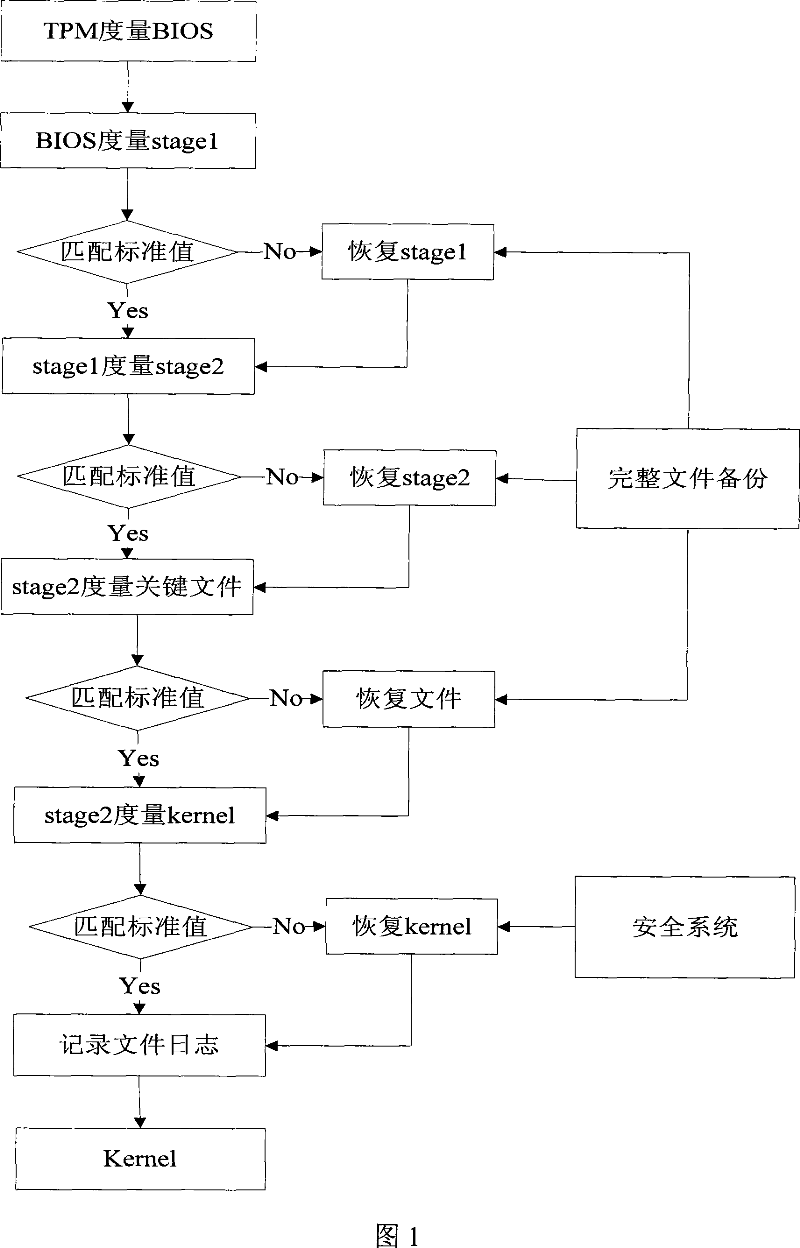
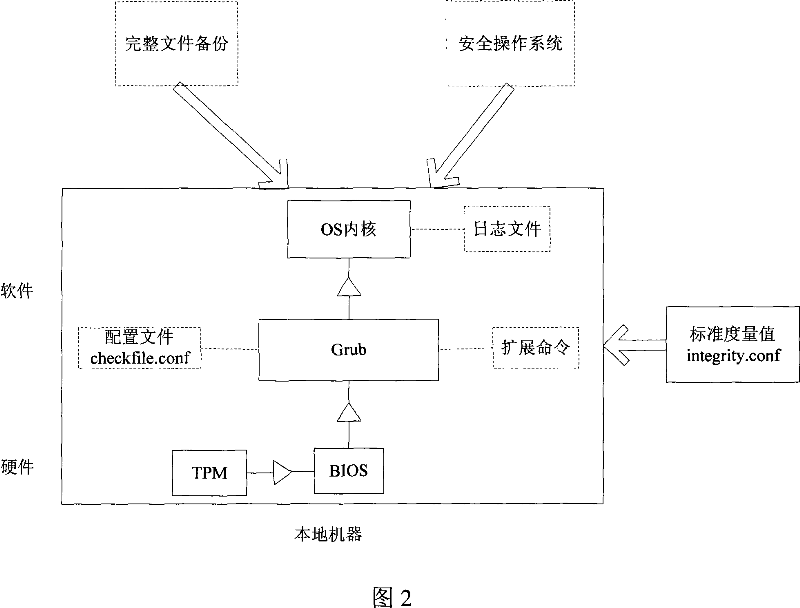
Trusted bootstrap method and system thereof
The invention provides a method and system for improving the system booting process via a trusted platform module, wherein he booting process for starting the internal kernel of the operation system are divided into a plurality of interdependent layers, the integrity of the upper layer is verified by the lower layer by using the trusted platform module as the trust root, the system operation control right is transmitted layer upon layer till to the operation system kernel to form an integral trusted chain, and if the integrity verification fails, a correspondent restore scheme will be provided, the boot log is recorded into the file system before entering the operation system. The invention takes into account of the situations such as integrity verification, verification failure restore, and the interaction of the starting log and the operation system so as to form an integral booting system, the initial circumstance is considered as safe and trusted, and the operation system can also proves the safety of its starting circumstances to other platforms by using the log file of the booting process.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
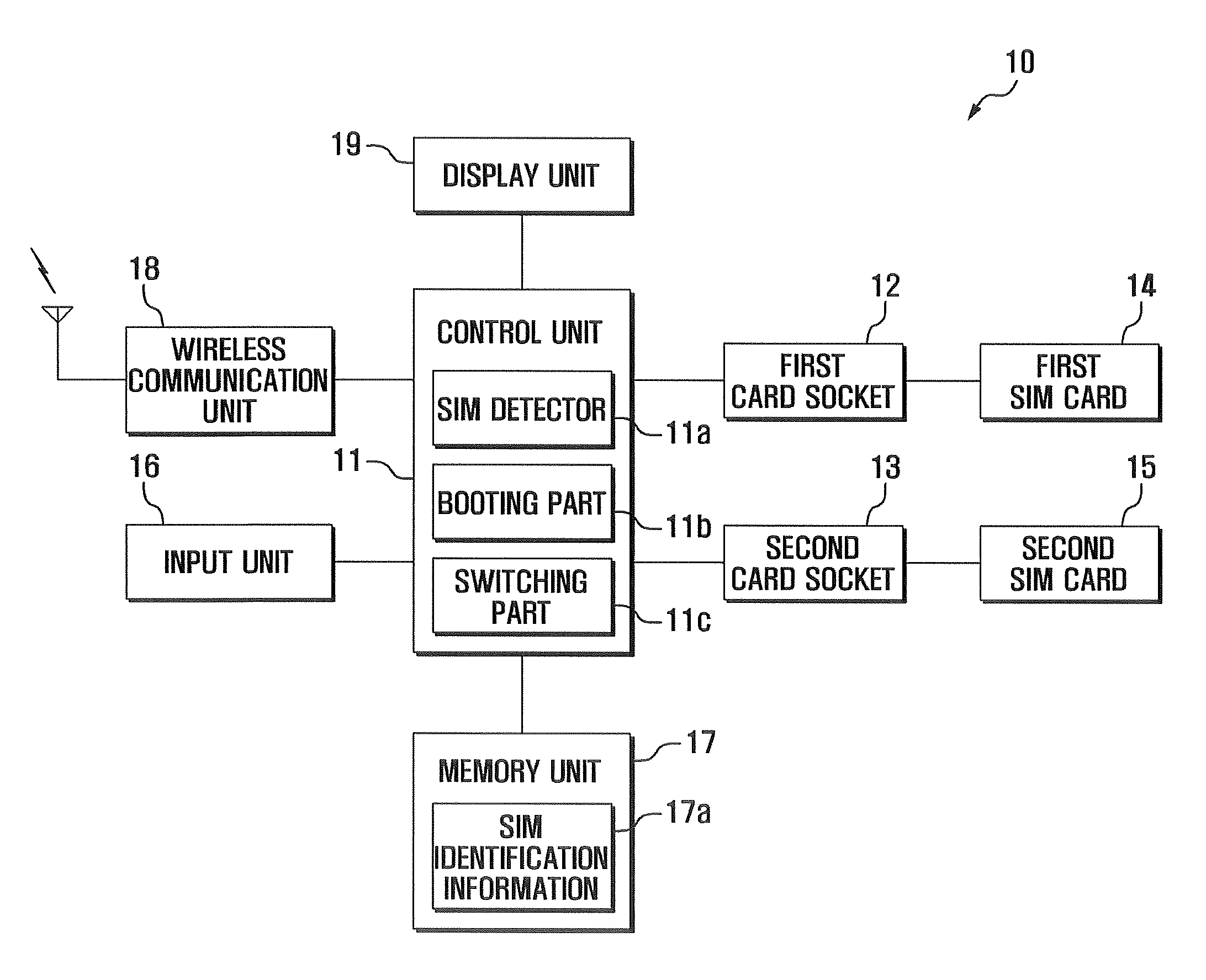
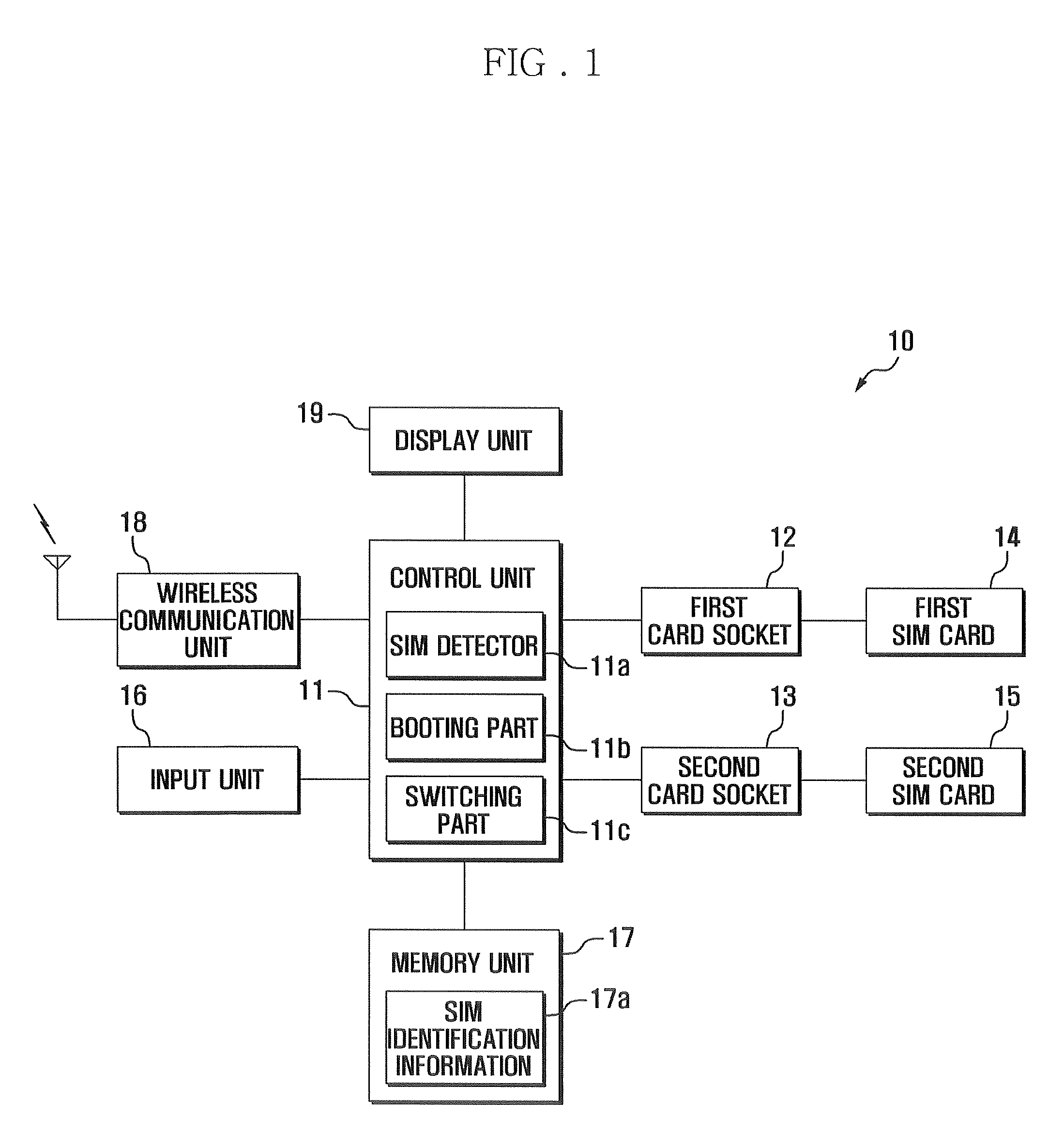
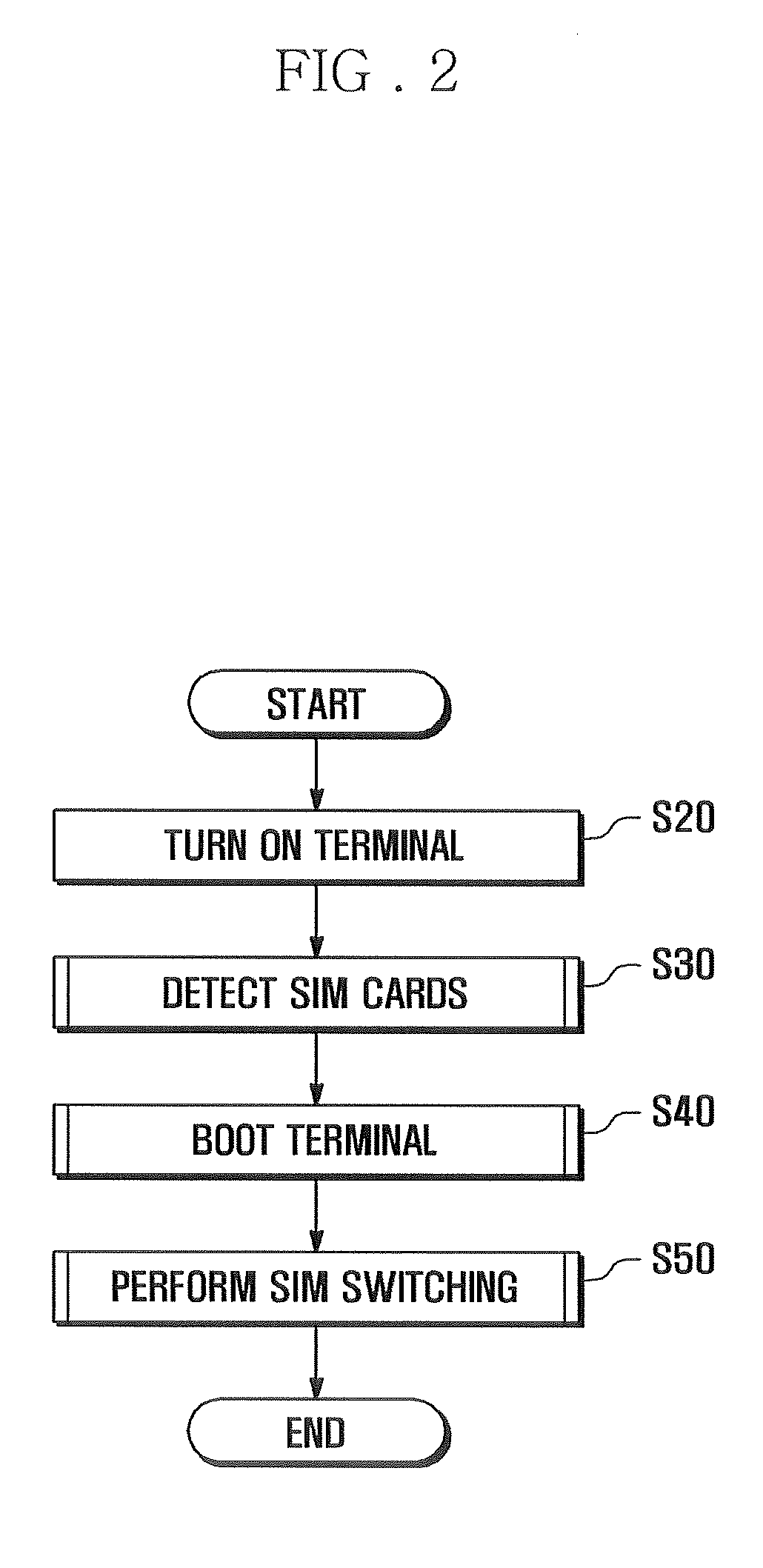
Dual-sim mobile terminal and operation method for the same
A dual-SIM mobile terminal and operation method for the same are disclosed. The dual-SIM mobile terminal checks the number of installed SIM cards during booting, and activates and deactivates the SIM switching mode according to the identified SIM card information. The operation method includes: detecting whether a first SIM card and second SIM card are installed in a first card socket and second card socket; storing SIM identification information regarding the detected SIM card; and performing a boot procedure on the basis of the detected SIM card. In particular, the SIM switching menu is displayed in an activated or deactivated state according to the identified SIM card information. Hence, the user can readily identify the number of installed SIM cards and the availability of SIM card switching through display status of the SIM switching menu.
Owner:SAMSUNG ELECTRONICS CO LTD
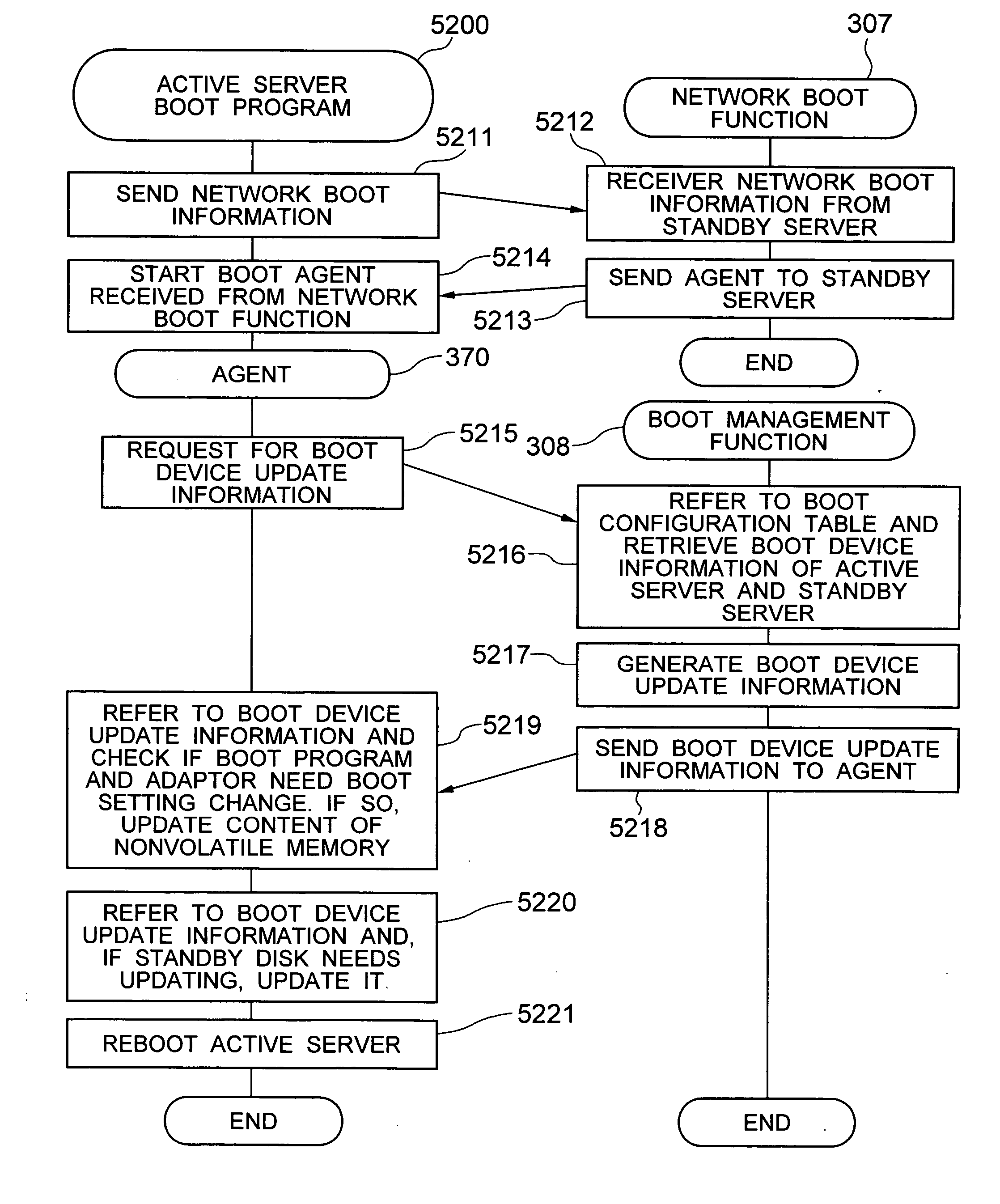
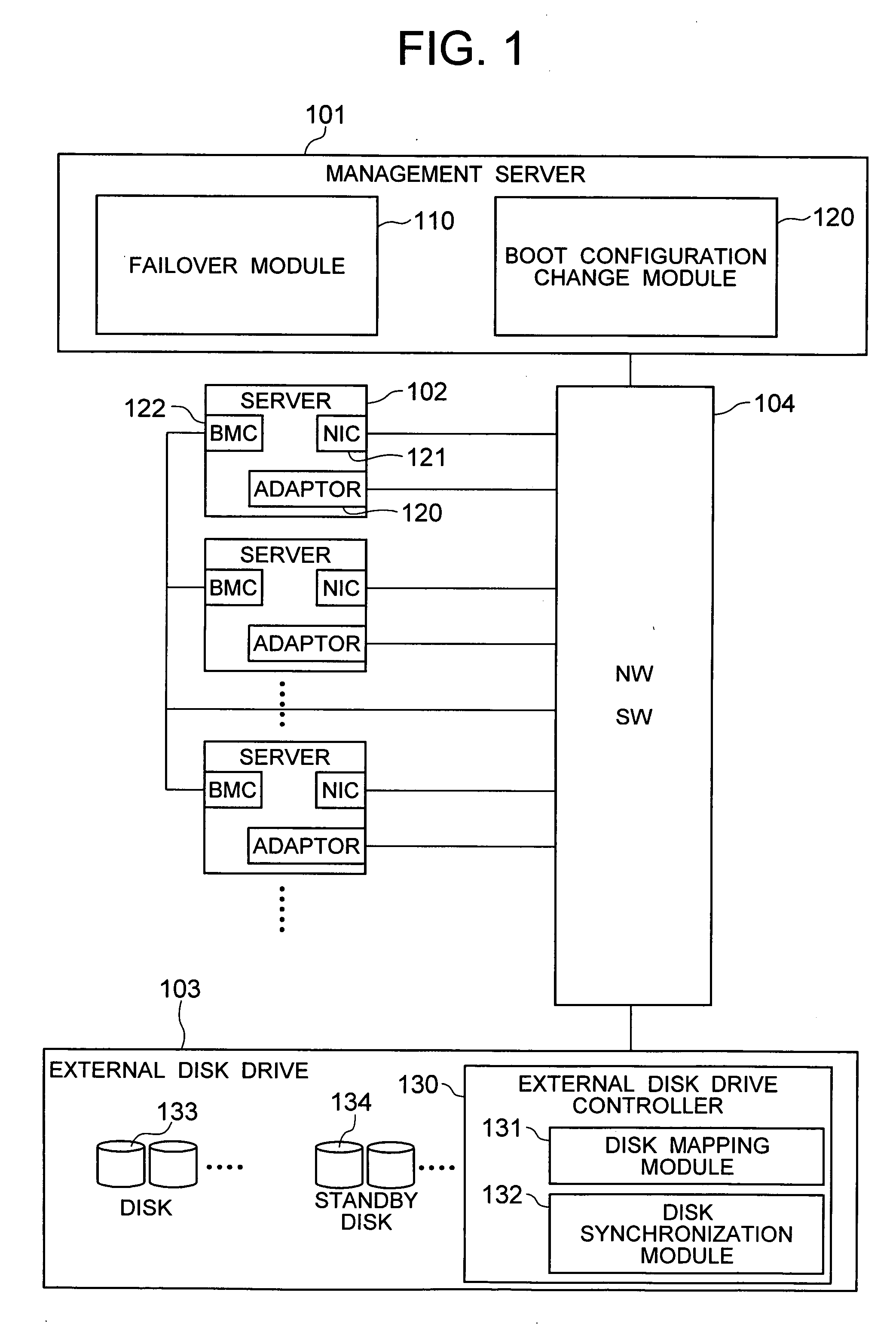
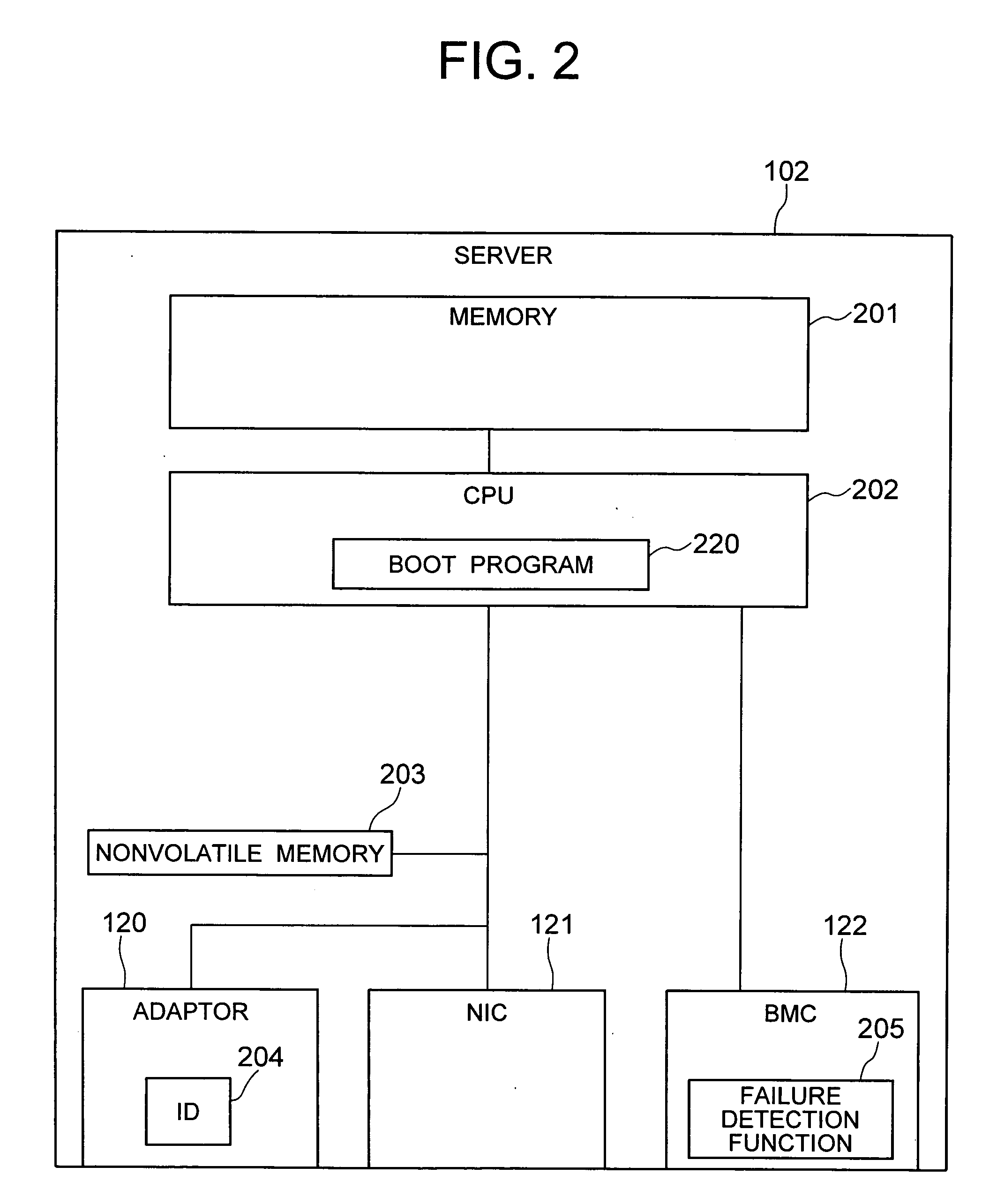
Method for changing booting configuration and computer system capable of booting OS
In a computer system in which a server has, in addition to a disk used for booting, an operation transfer destination disk that has the same content as the boot disk, a method for changing the disk used by the server or another server in the computer system for booting to the operation transfer destination disk is realized by changing the content of the operation transfer destination disk to enable the OS and applications installed in the operation transfer destination disk to be booted from the destination disk and by changing the setting of a boot program of the server to enable booting from the operation transfer destination disk.
Owner:HITACHI LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com