Patents
Literature
100 results about "Os kernel" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
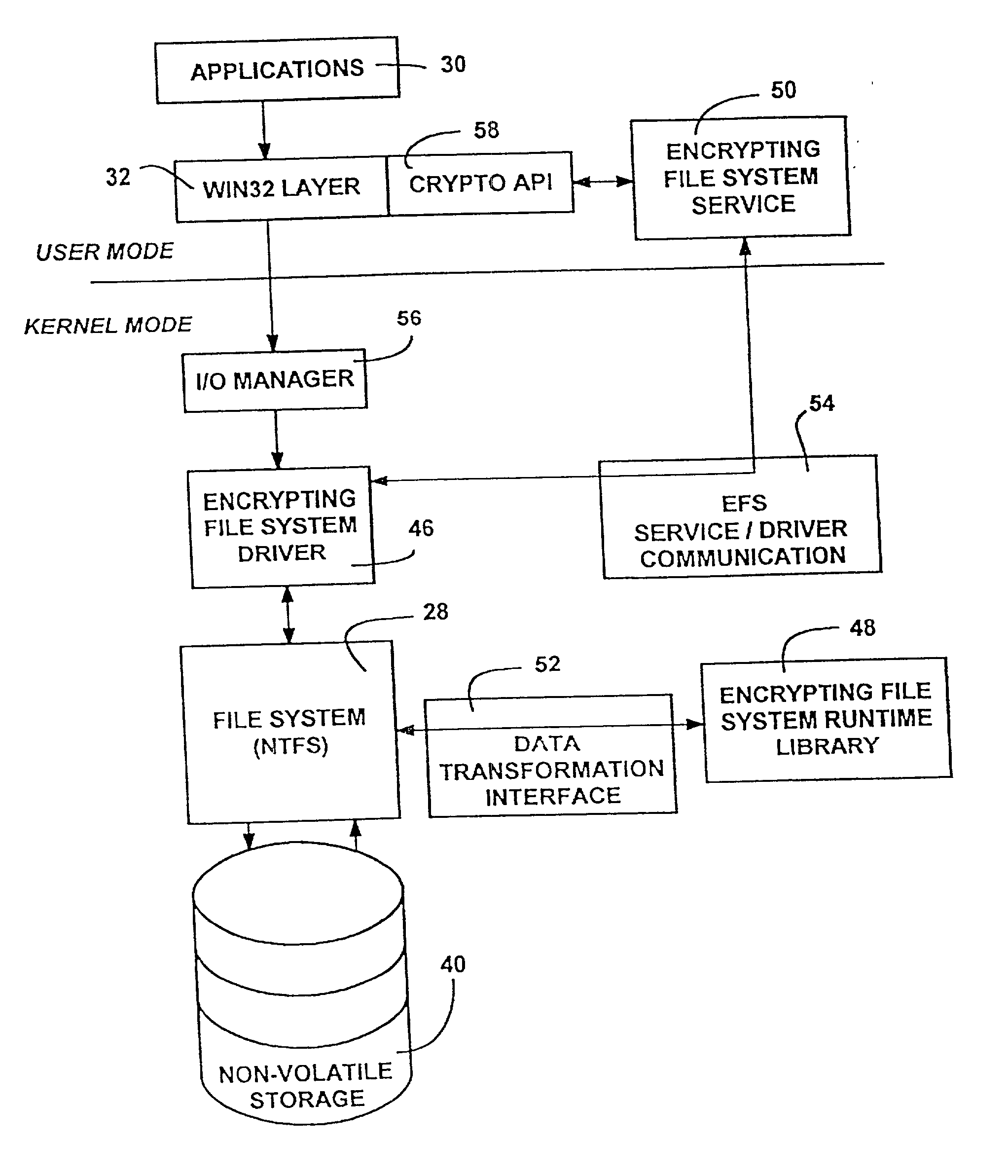
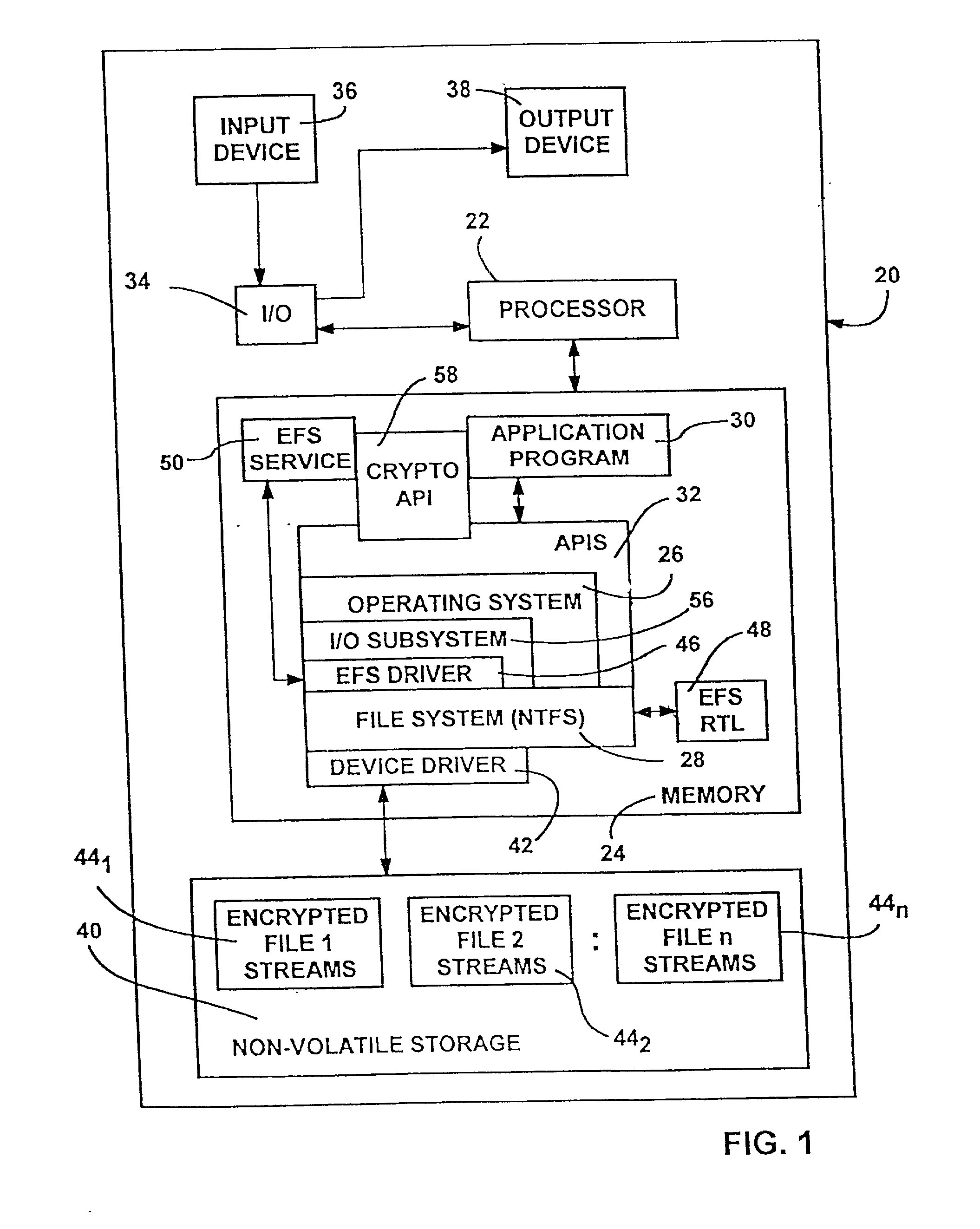
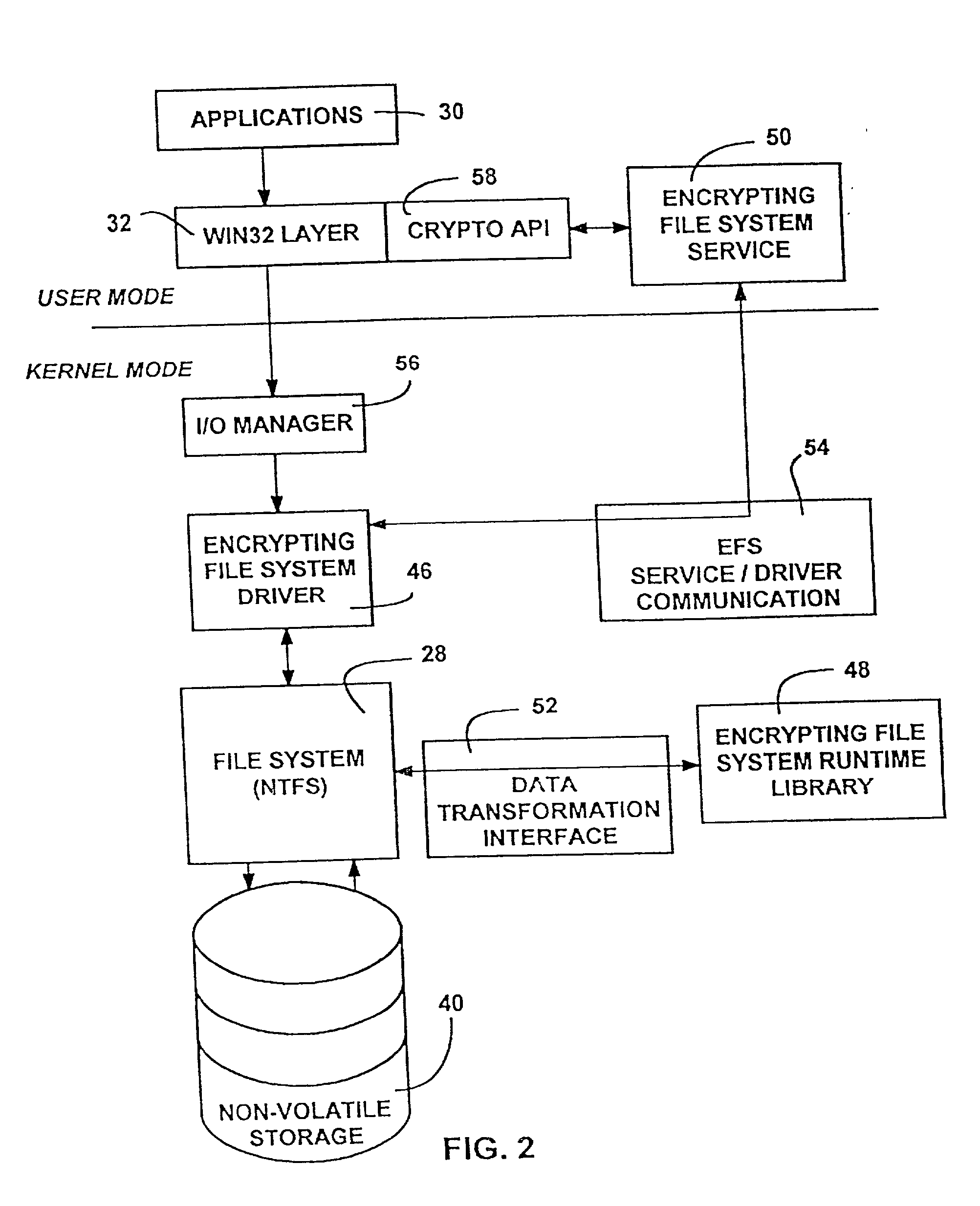
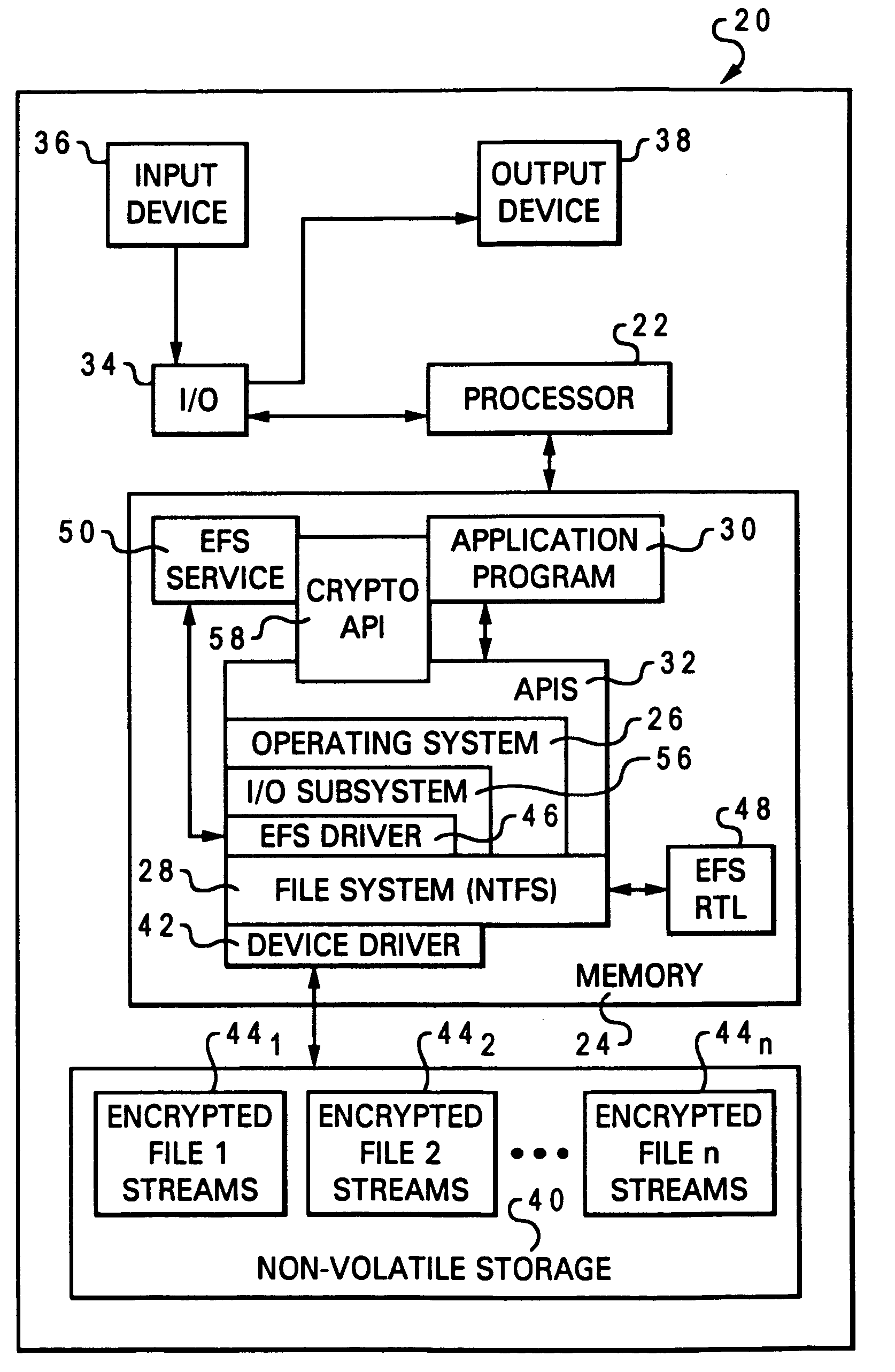
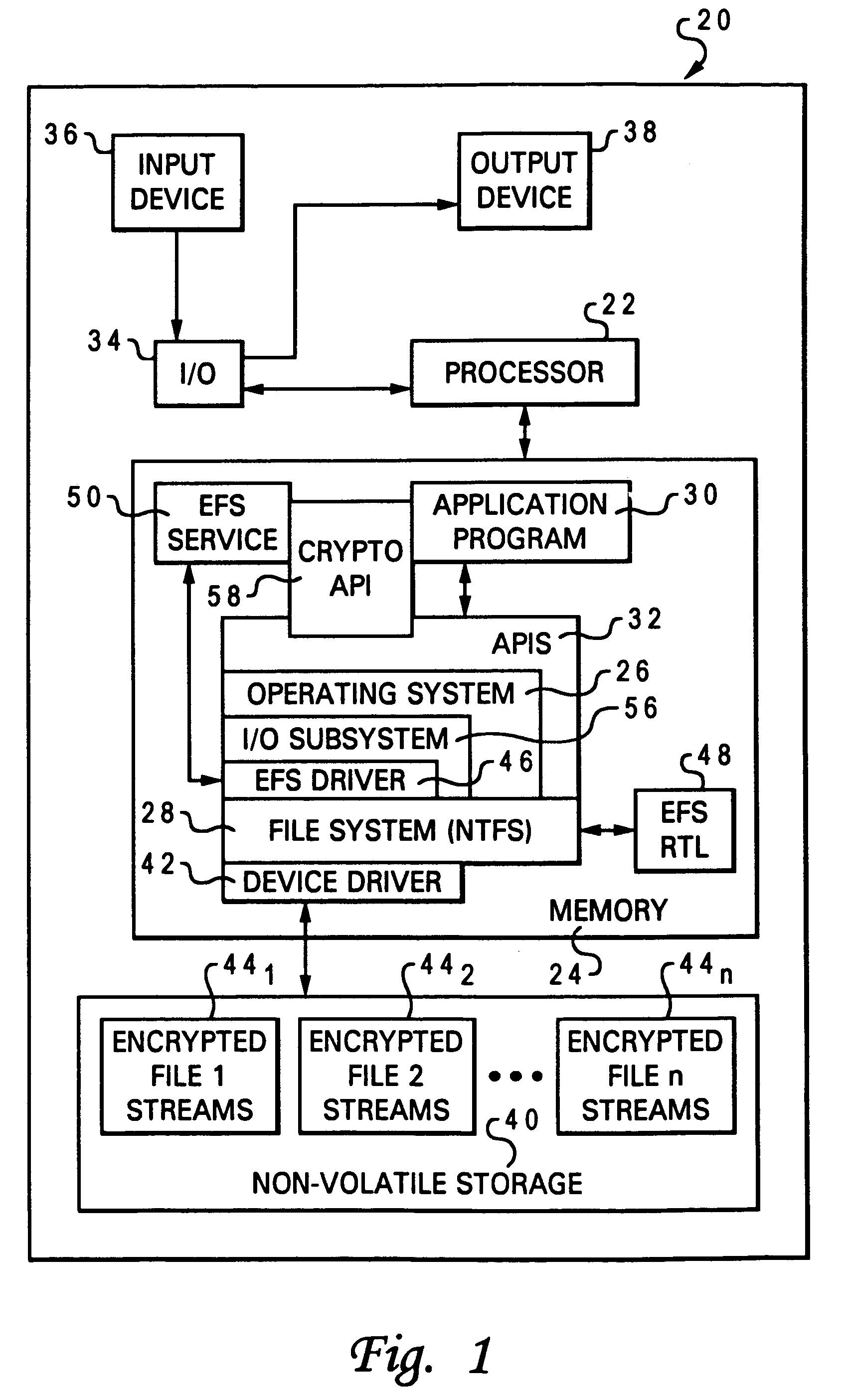
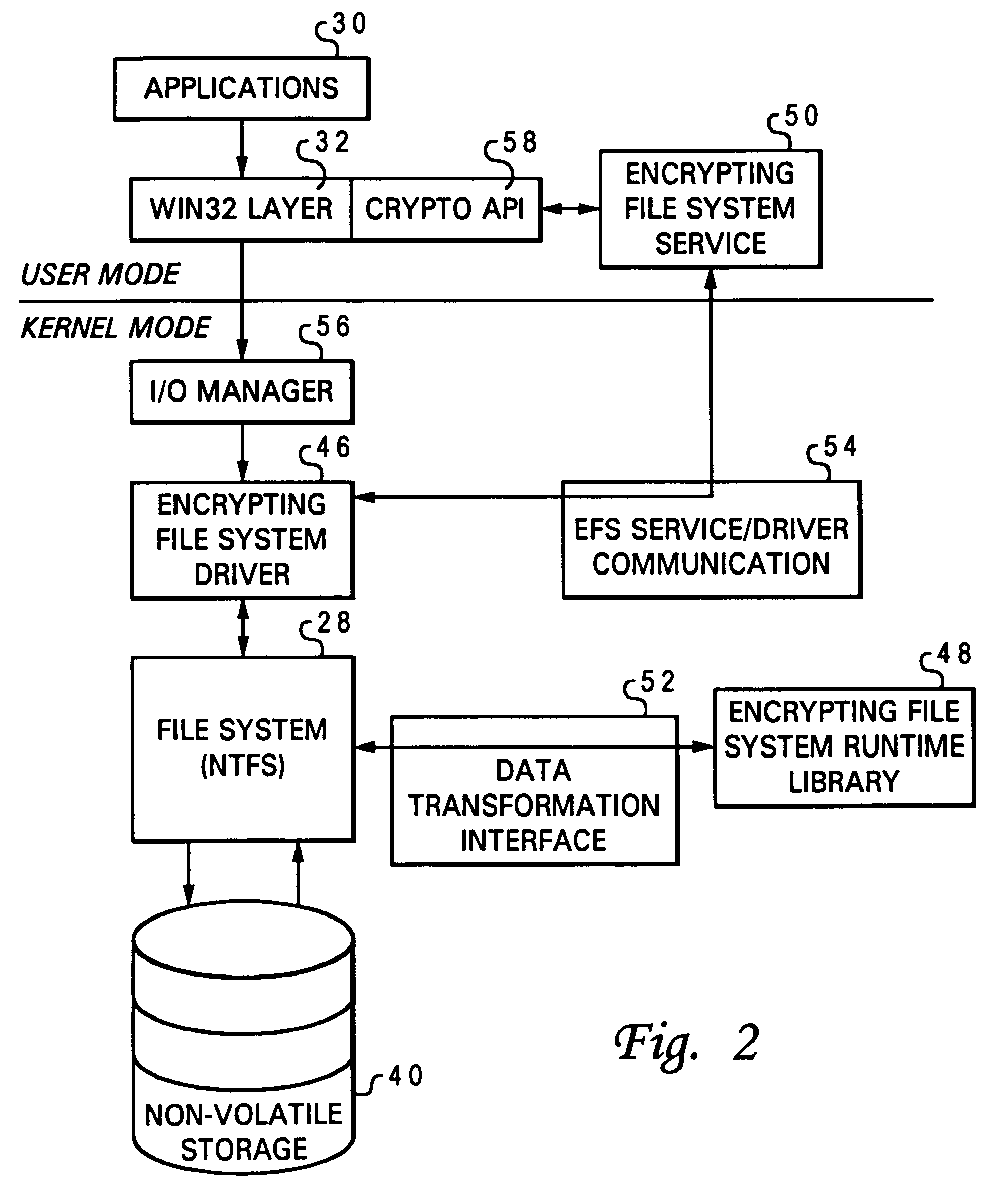
Encrypted file system using TCPA
ActiveUS20030188179A1Digital data processing detailsUser identity/authority verificationComputerized systemControl register
A method for restricting access to an encryption key of an encrypted file system (EFS), whereby access is provided only when a computer system is booted in a trusted state. The EFS encrypts the files within a TPM chip according to TCPA specifications and simultaneously creates the encryption key, which is also stored in the TPM. The key is sealed to one or more platform control register (PCR) states (i.e., the TPM will export the key only when the PCRs are in a pre-defined state.). The original PCR states are modified during boot up of the computer system via a secure hashing algorithm, which extends a value of one PCR to a next PCR at each stage of the boot process and then hashes the value with the remaining content of the next PCR. When the system boot process is completed and before control passes to the user, the values within the PCRs are compared to values stored in a PCR table within the TPM, and the encryption key is exported to the OS kernel only when the PCR values match the table values. The control code of the TPM chip decrypts and exports the key only if the value of each and every PCR matches its corresponding table value. A complete match indicates that the computer system has completed a trusted boot sequence.
Owner:LENOVO PC INT
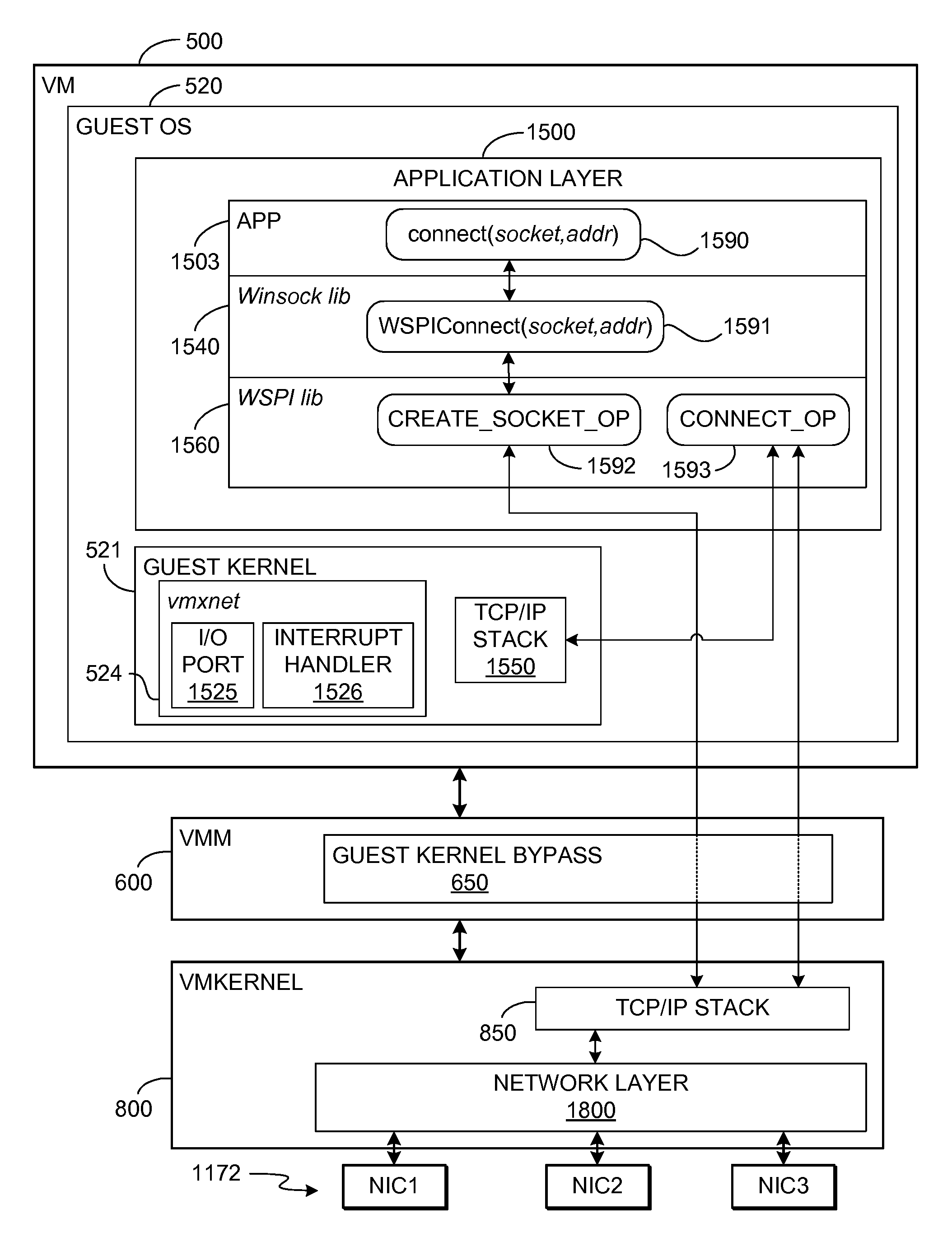
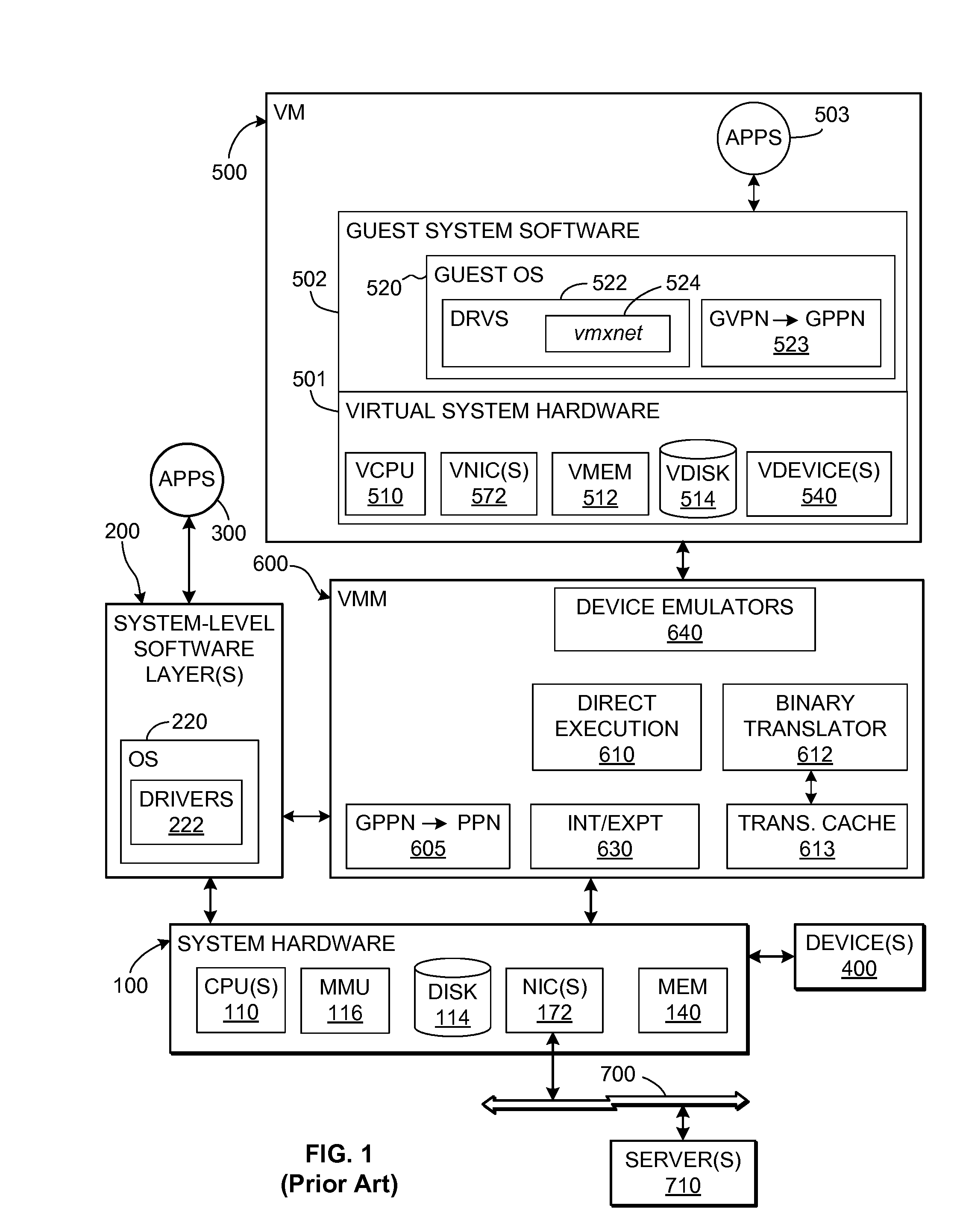
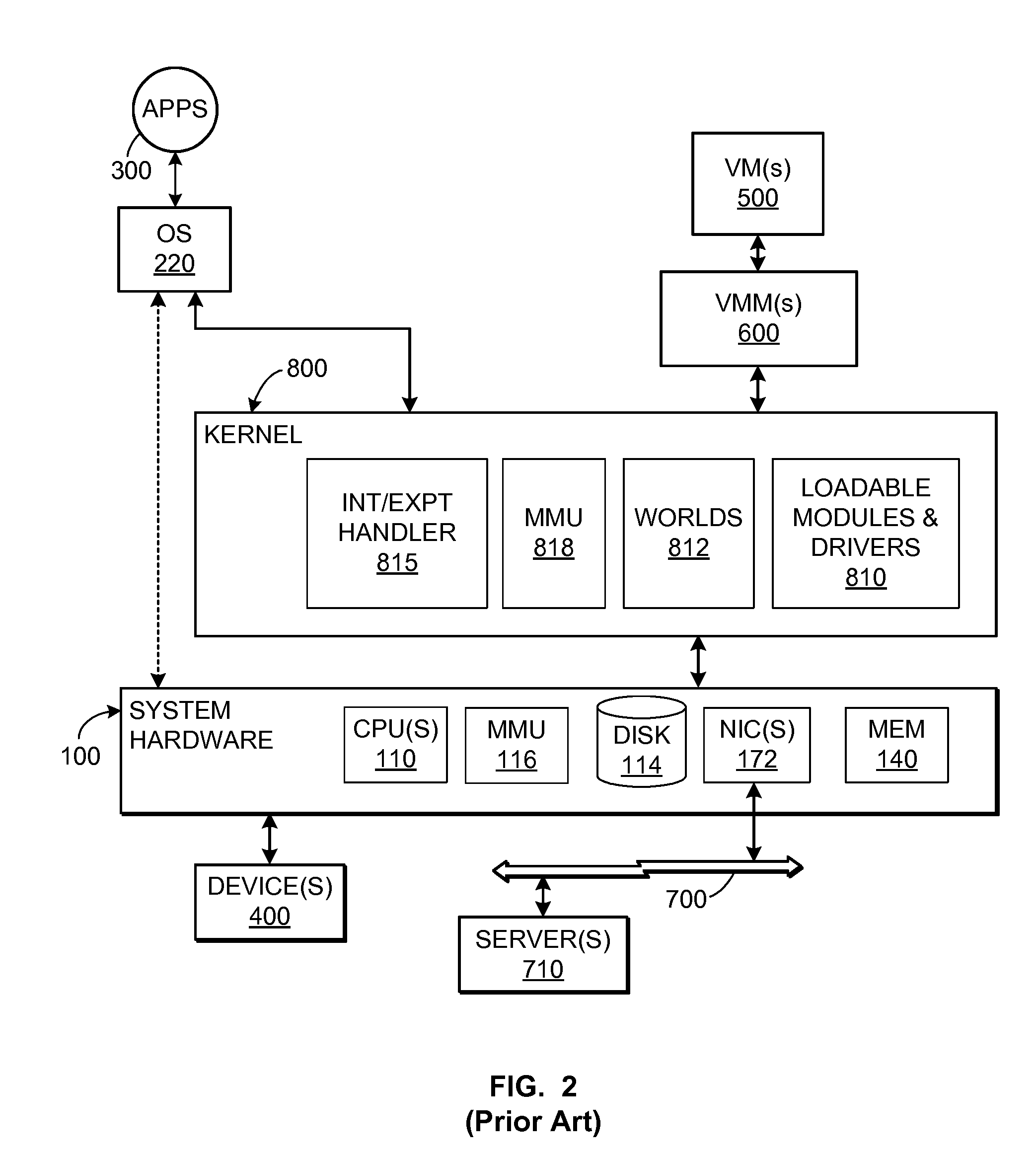
TCP/IP offloading for virtual machines
An engine (TOE) is provided in a virtualized computer system for offloading I / O tasks using any defined protocol such as TCP / IP. The system includes a virtual machine (VM), which has a guest operating system (OS) that runs via a virtual machine monitor (VMM) on a system-level software platform (vmkernel), which also forms the software interface layer to at least one physical network connection device. A TCP / IP stack is included in vmkernel. During normal I / O operation, for sockets associated with TOE, processes in an application layer in the guest OS are able to communicate directly with vmkernel's TCP / IP stack, thereby bypassing the guest OS kernel.
Owner:VMWARE INC
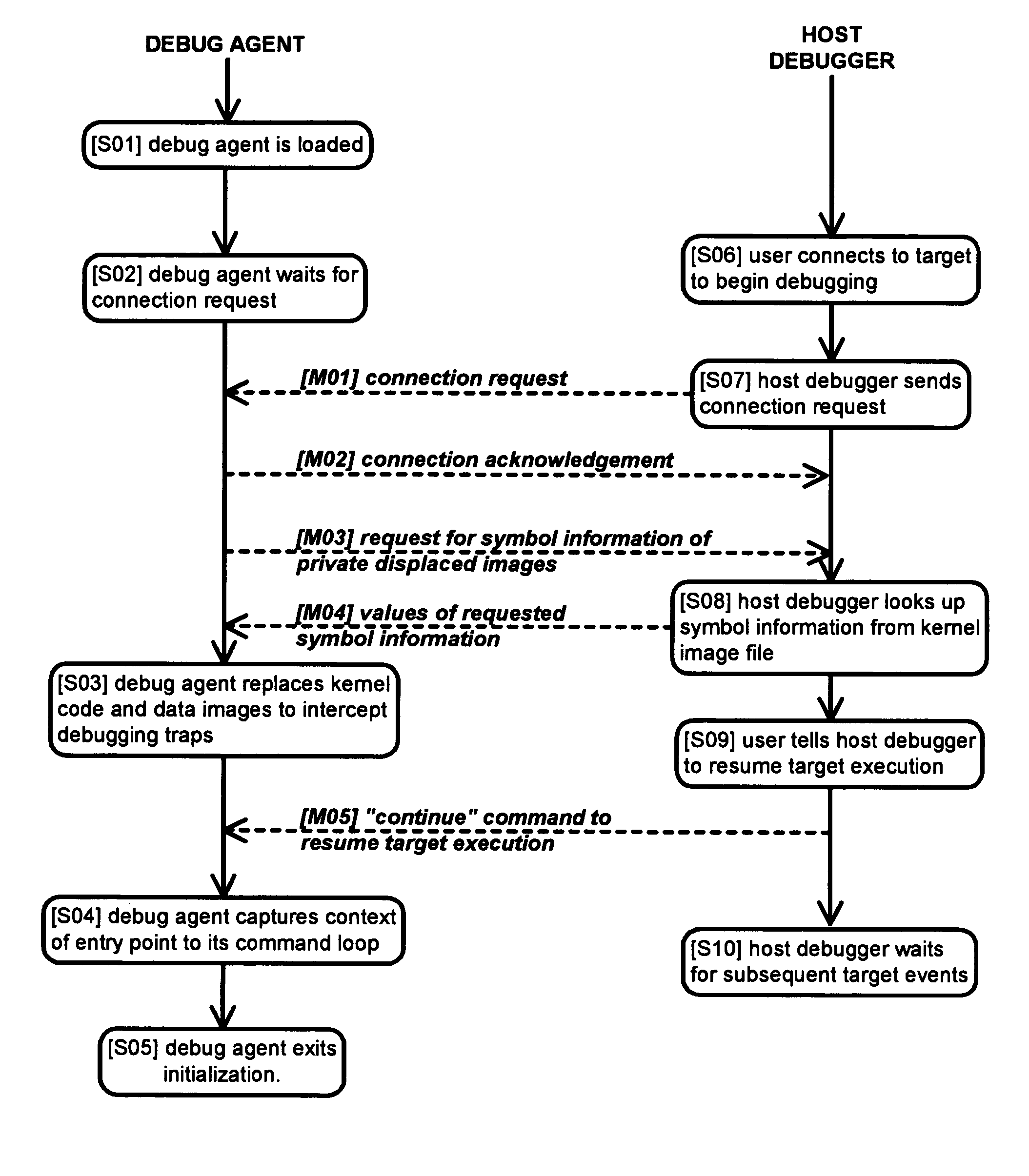
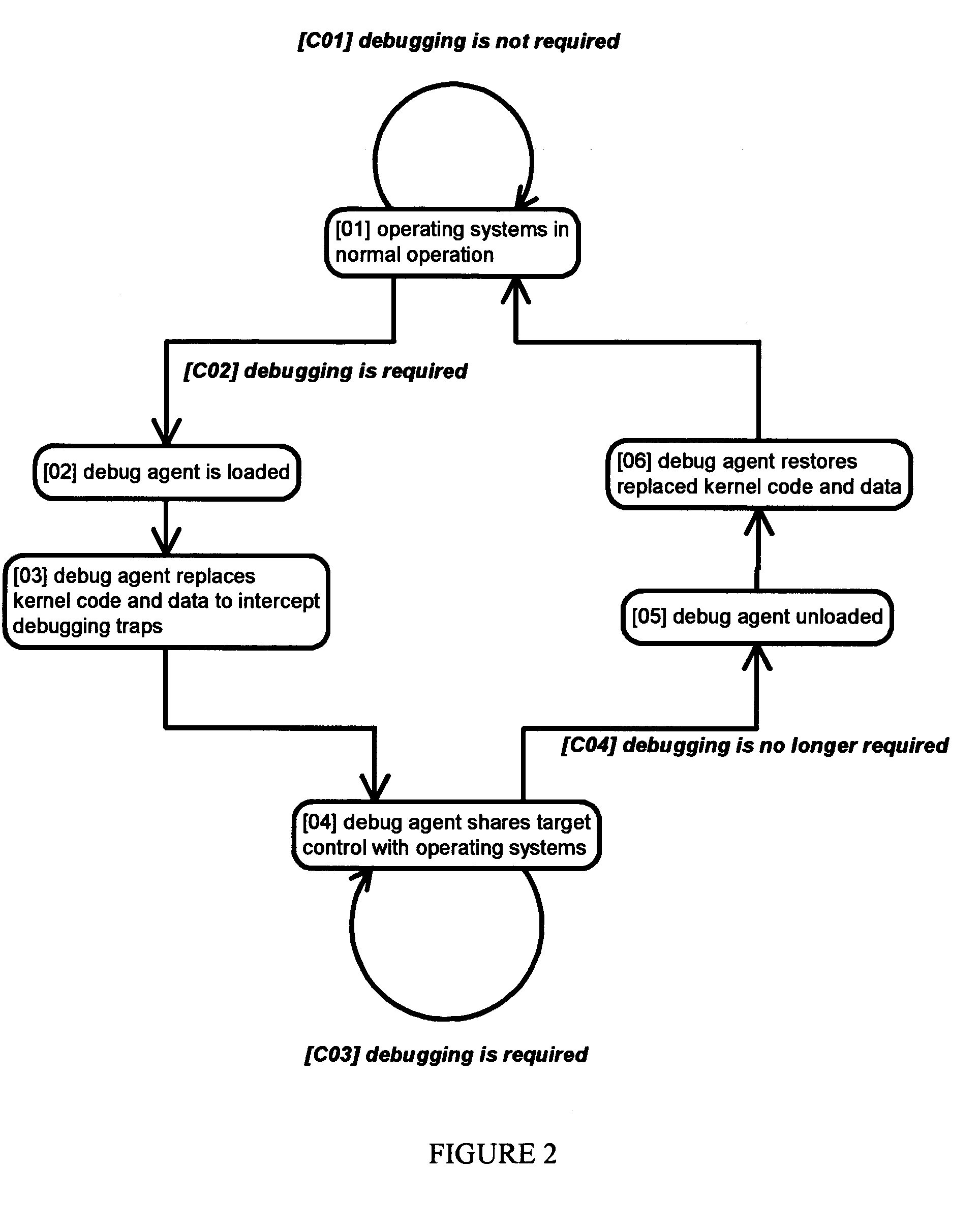
Method and apparatus for remote debugging of kernel and application software
InactiveUS20050216895A1Modified dynamicallyError detection/correctionSpecific program execution arrangementsOperational systemSystem call
A method and apparatus for debugging of OS kernel and applications software that does not require use of a hardware probe; can debug both user-mode programs and a significant body of the OS kernel code; allows the OS to continue servicing exceptions while debugging; leverages OS built-in device drivers for communicating devices to communicate with the host debugger; and can debug a production version of the OS kernel. When debugging is required, the running OS kernel dynamically loads a software-based debug agent on demand whereby such debug agent dynamically modifies the running production OS kernel code and data to intercept debugging traps and provide run-control. To provide debugging of loadable module, the debug agent implement techniques to intercept the OS module loading system call; set breakpoints in the loaded module initialization function; calculate the start address of the debugged module in memory; and asynchronously put the system under debug. By structuring command loop to execute in non-exception mode, and devising a process to transfer execution from the debug agent exception handler to the debug agent command loop and back, the debug agent can communicate with the host debugger using interrupt-driven input / output devices as well as allowing the system to service interrupts while under debug.
Owner:TRAN HIEU TRUNG
Methods and architecture for enhanced computer performance
InactiveUS20160378545A1Reducing mode switchingReduce limitationsProgram initiation/switchingHardware monitoringOperational systemComputer performance
Methods and systems for enhanced computer performance improve software application execution in a computer system using, for example, a symmetrical multi-processing operating system including OS kernel services in kernel space of main memory, by using groups of related applications isolated areas in user space, such as containers, and using a reduced set of application group specific set of resource management services stored with each application group in user space, rather than the OS kernel facilities in kernel space, to manage shared resources during execution of an application, process or thread from that group. The reduced sets of resource management services may be optimized for the group stored therewith. Execution of each group may be exclusive to a different core of a multi-core processor and multiple groups may therefore execute separately and simultaneously on the different cores.
Owner:APL SOFTWARE INC
Method and computing system for transparence computing on the computer network
ActiveUS20060117172A1Improve performanceImprove availabilityDigital computer detailsData resettingOperational systemTransparent computing
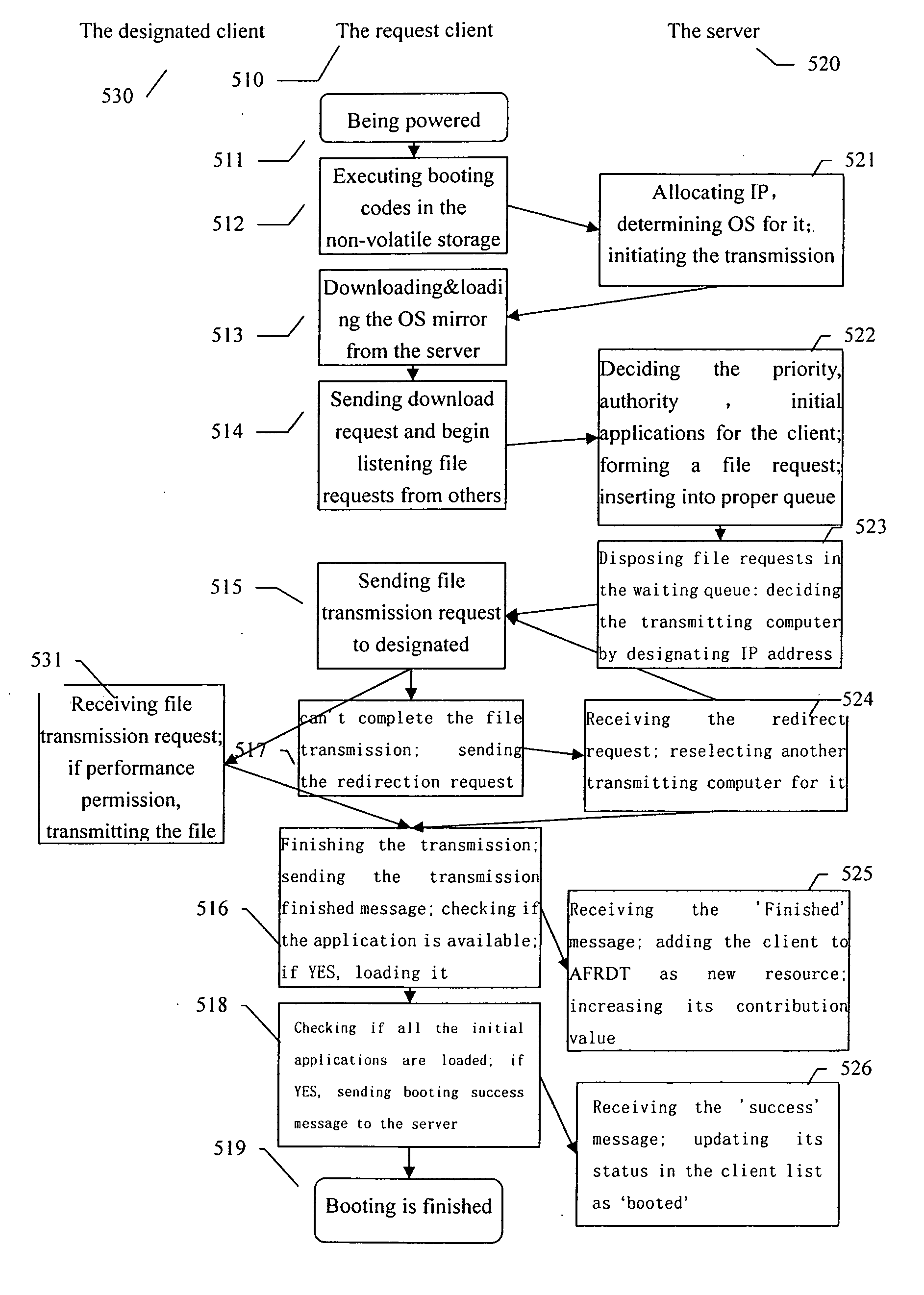
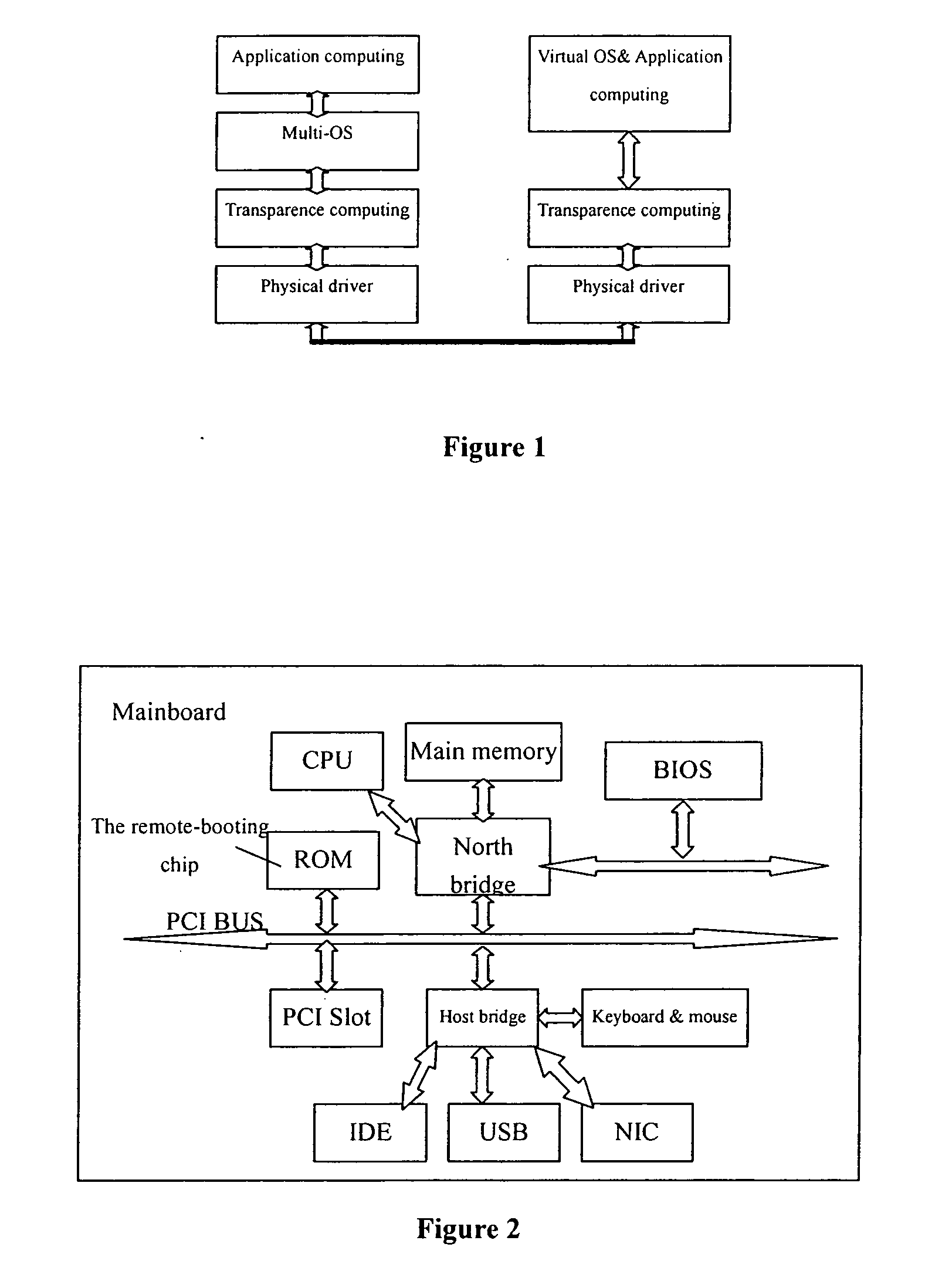
A computing system based on Transparence Computing consists of clients and a server. There is no disk and no preinstalled OS on the client; a remote booting chip is set on the client's mainboard for downloading and loading the OS. Boot-supporting services, OS kernel mirrors, and applications are preset on the server; After being powered, the client broadcasts the boot request to the network and the server allocates network parameters for it. The client downloads an OS-selecting script from the server. After the user selects the needed OS, the client downloads and loads the selected OS from the server. Hence, the client fulfills the user's computing requirements just as a normal PC. The computing work is implemented on the client-side, during which the client can acquire corresponding resources such as applications, data, and documents from the server on demand. The client can be provided with private storage across the network by presetting a service in the mirror for creating virtual disks on the server, and thus data generated during or after the computing can be persistently stored on the server's storage.
Owner:TSINGHUA UNIV
High performance wireless networks using distributed control
ActiveUS20090040989A1Cost effectiveLower latencyNetwork traffic/resource managementNetwork topologiesSecure communicationOperational system
A design and proof of concept of a new type of WLAN, complete with simulation and results from the simulation has been described. Each AP Node is implemented as a self-contained embedded OS unit, with all algorithms resident in its Operating system. The normal day-to-day functioning of the AP node is based entirely on resident control algorithms. Upgrades are possible through a simple secure communications interface supported by the OS kernel for each AP node. Benefits provided by a wireless network, as proposed in this invention, are that: it installs out of the box; the network is self-configuring; the network is redundant in that mesh network formalism is supported, ensuring multiple paths; load balancing is supported; there is no single point of failure; allows for decentralized execution; there is a central control; it is network application aware; there is application awareness; there is automatic channel allocation to manage and curtail RF interference, maximize non interference bandwidth and enable seamless roaming between adjoining wireless sub networks (BSS) and it supports the wireless equivalent for switching—for seamless roaming requirements.
Owner:DYNAMIC MESH NETWORKS
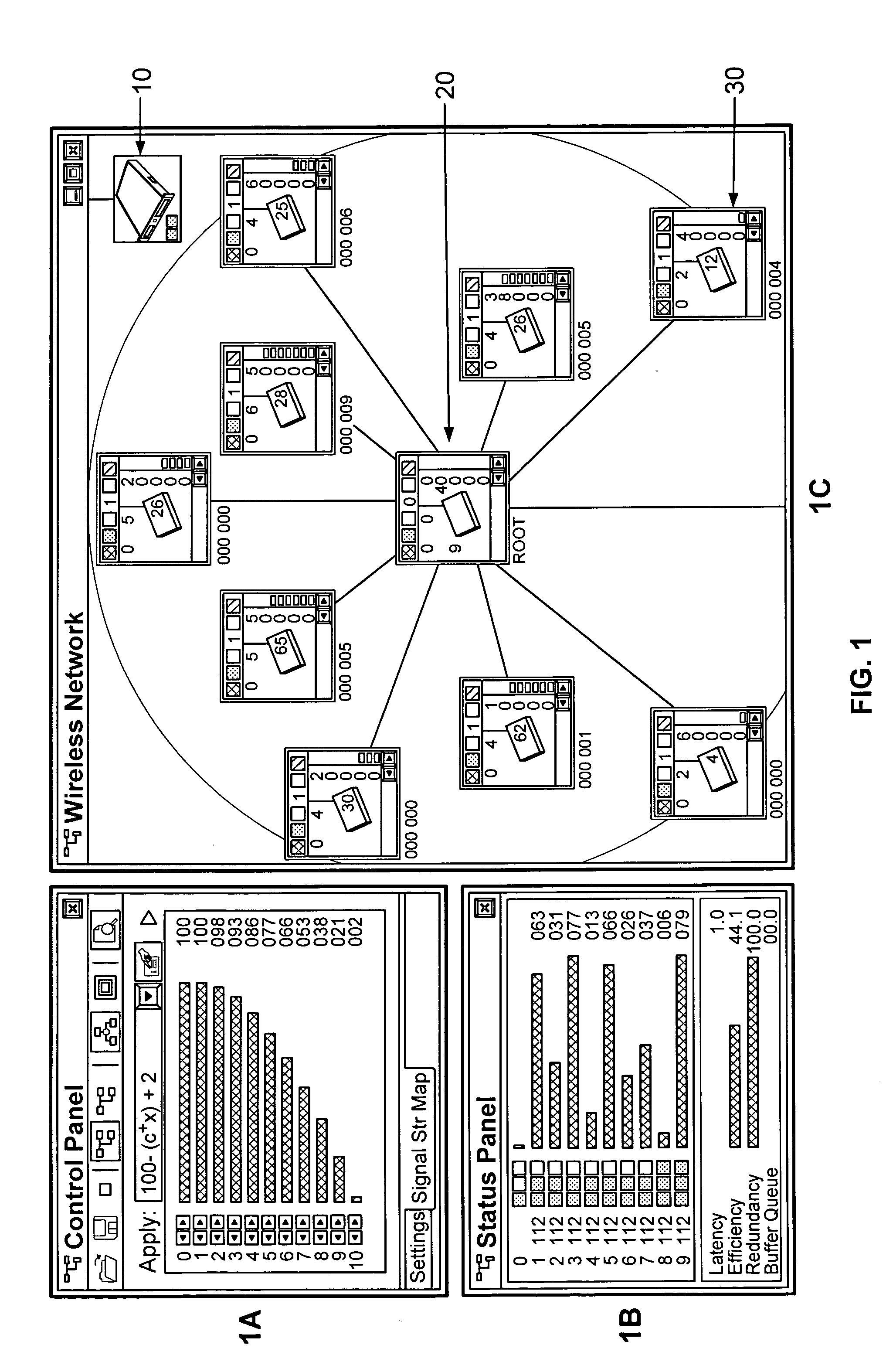
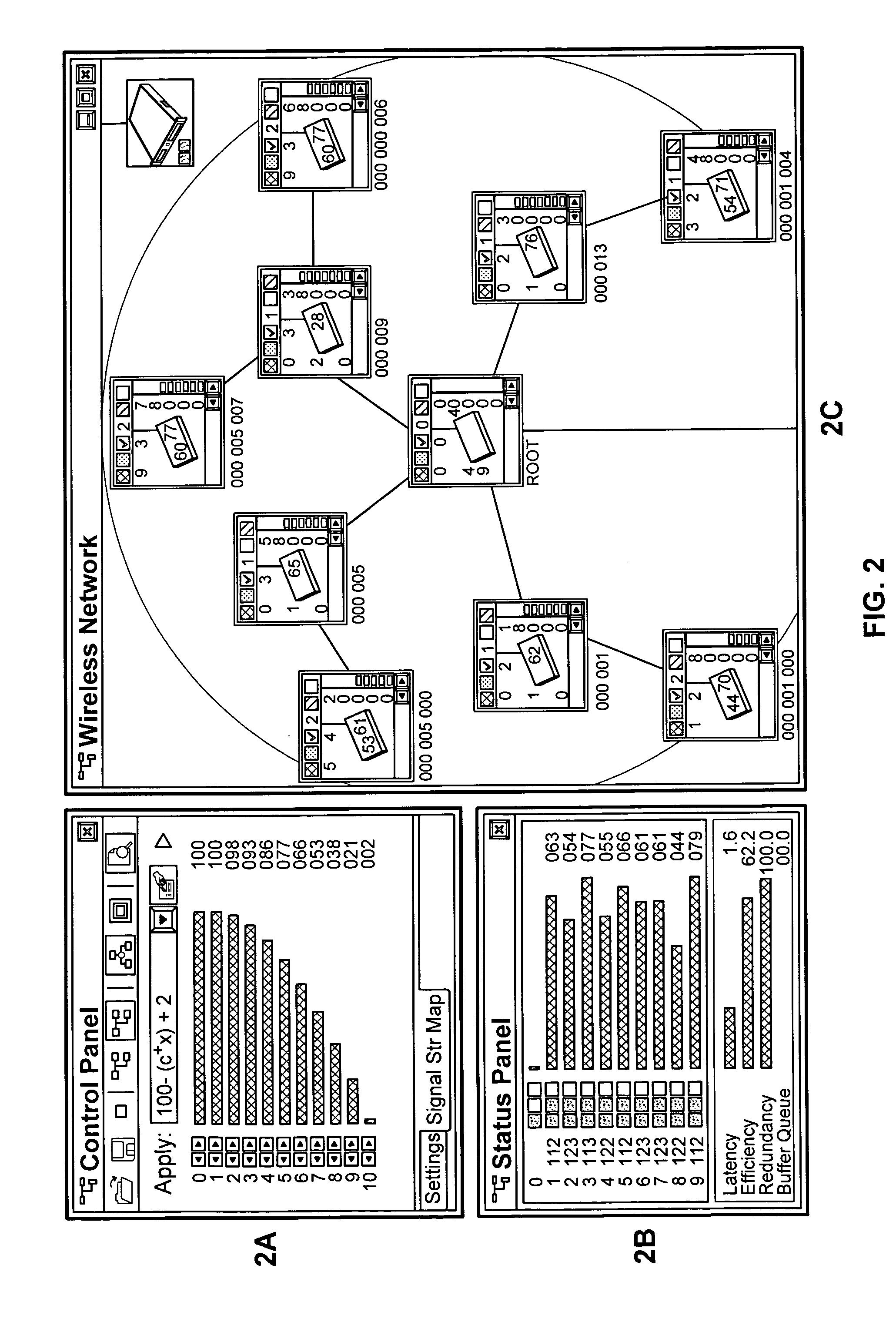
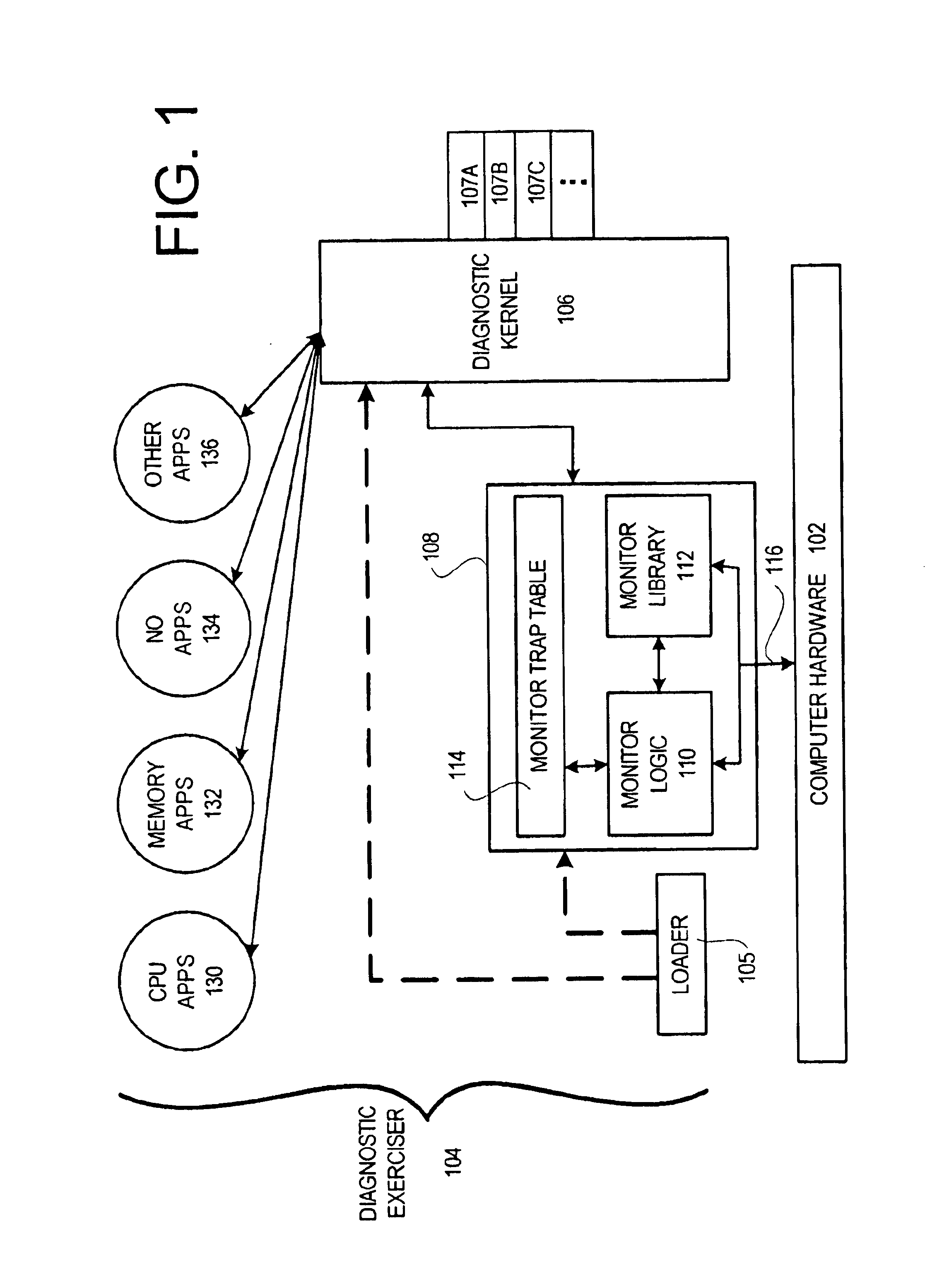
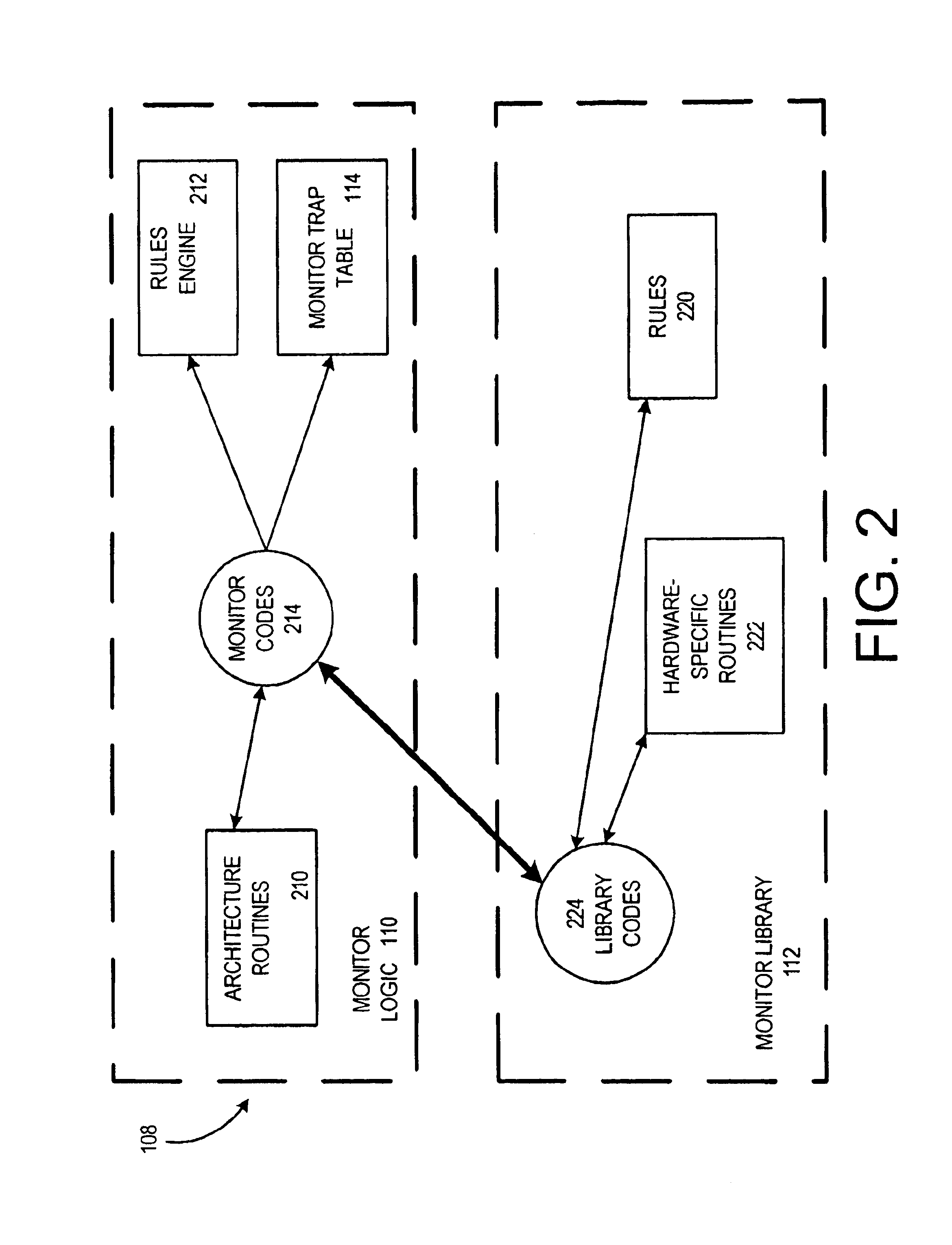
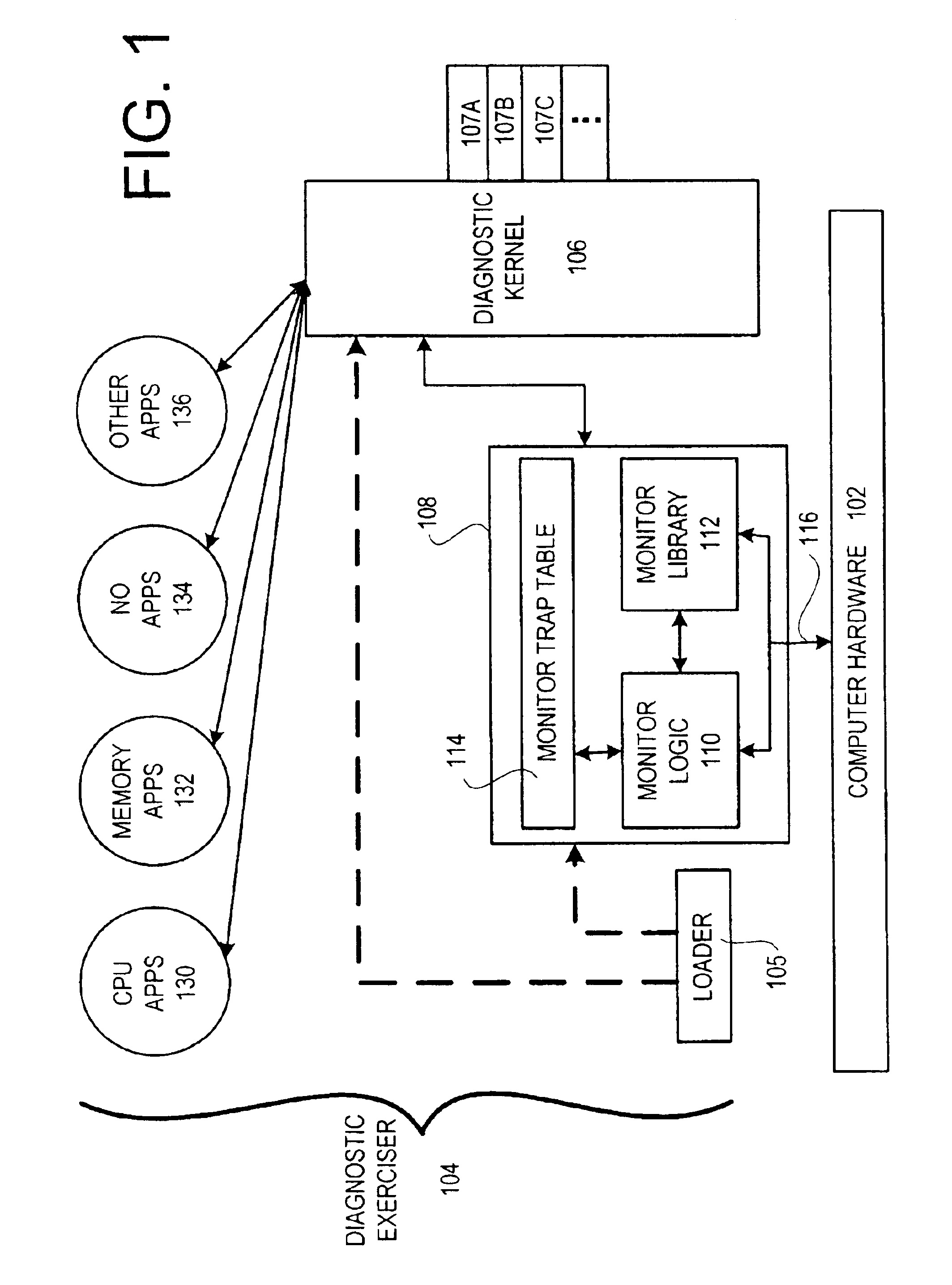
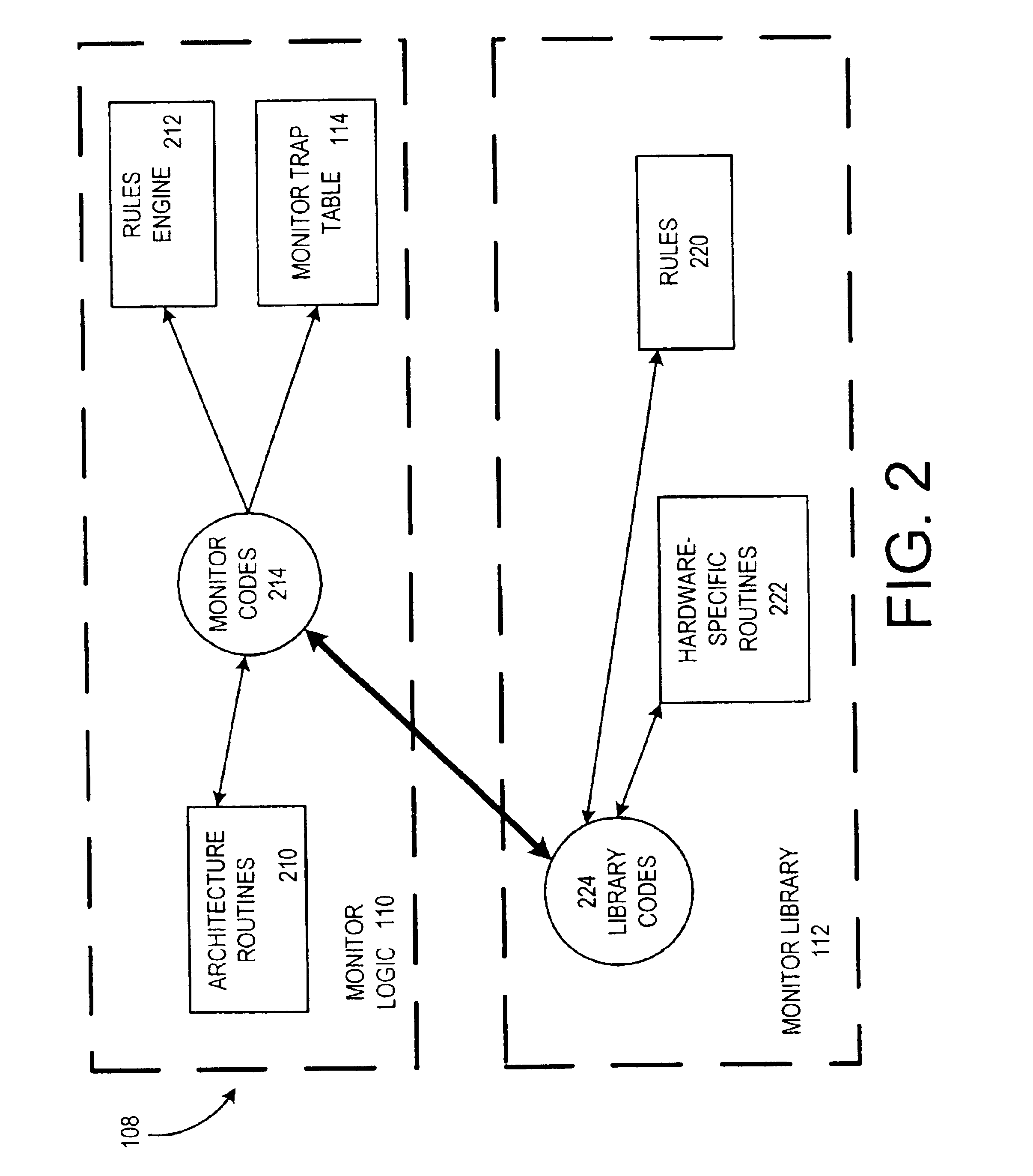
Diagnostic exerciser and methods therefor
InactiveUS6889167B2Program initiation/switchingDigital computer detailsOperational systemComputerized system
A computer-implemented method for diagnosing the performance of a computer system using a diagnostic application. The method includes providing a diagnostic application and providing an operating system (OS) kernel, the diagnostic application being configured to execute under the OS kernel in the computer system, the OS kernel having a kernel trap arrangement. The method also includes providing a diagnostic monitor, the diagnostic monitor being configured to execute cooperatively with the OS kernel, the diagnostic monitor having a monitor trap arrangement. The method additionally includes ascertaining, using the diagnostic monitor, whether a trap encountered during execution of the diagnostic application is to be handled by the OS kernel or the diagnostic monitor. Furthermore, the method includes passing, if the trap is to be handled by the OS kernel, the trap to the OS kernel for handling.
Owner:VALTRUS INNOVATIONS LTD +1
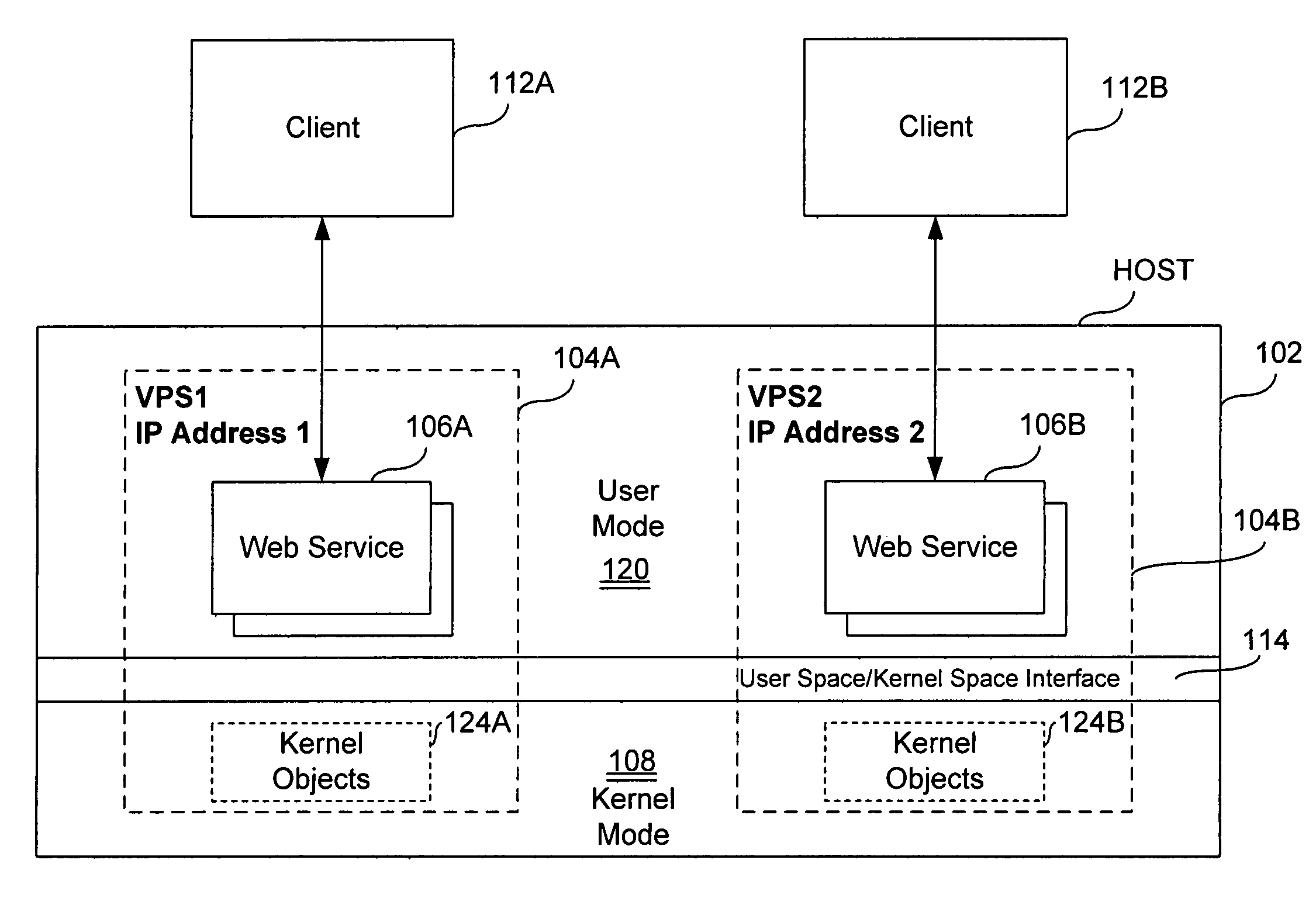
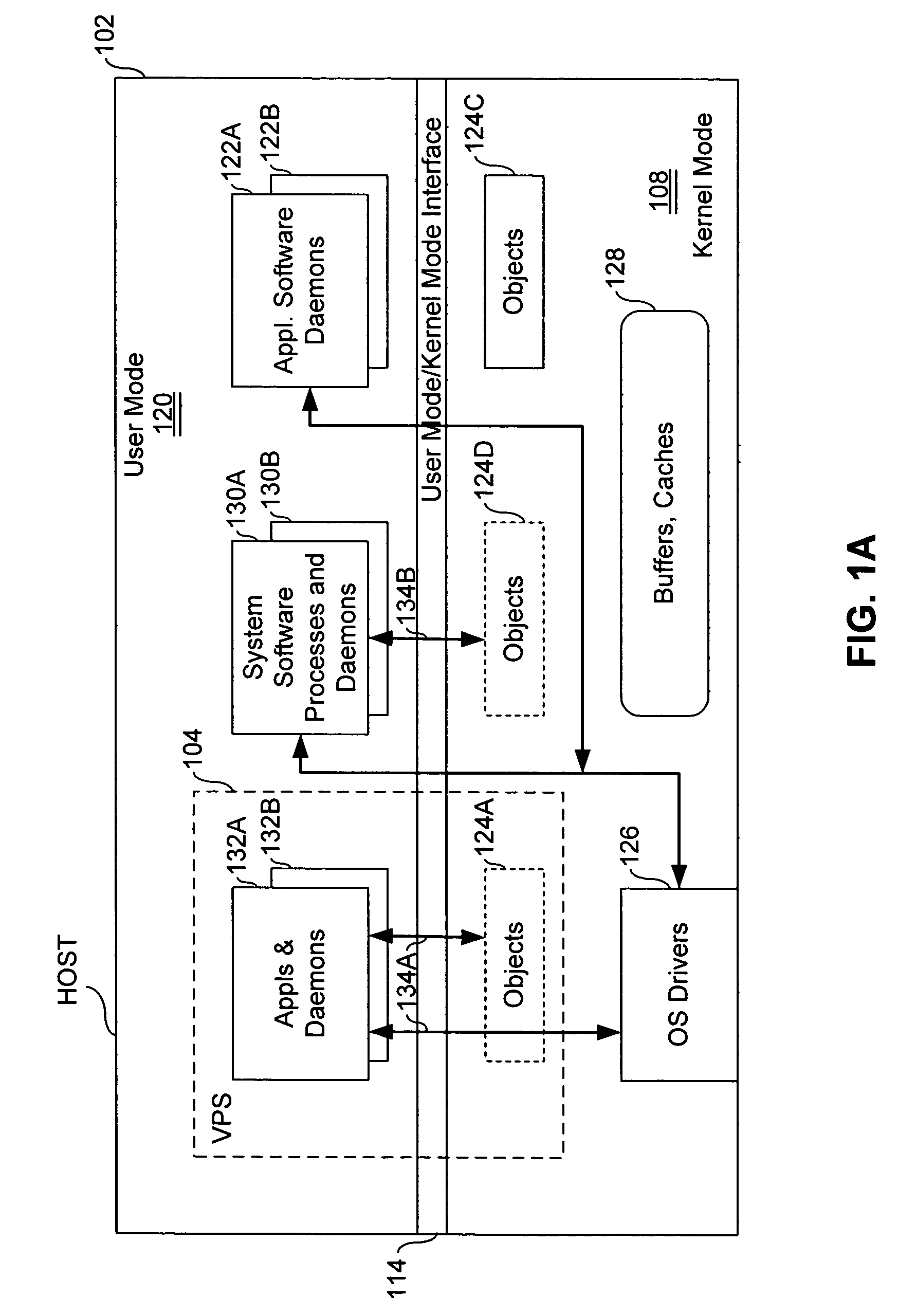
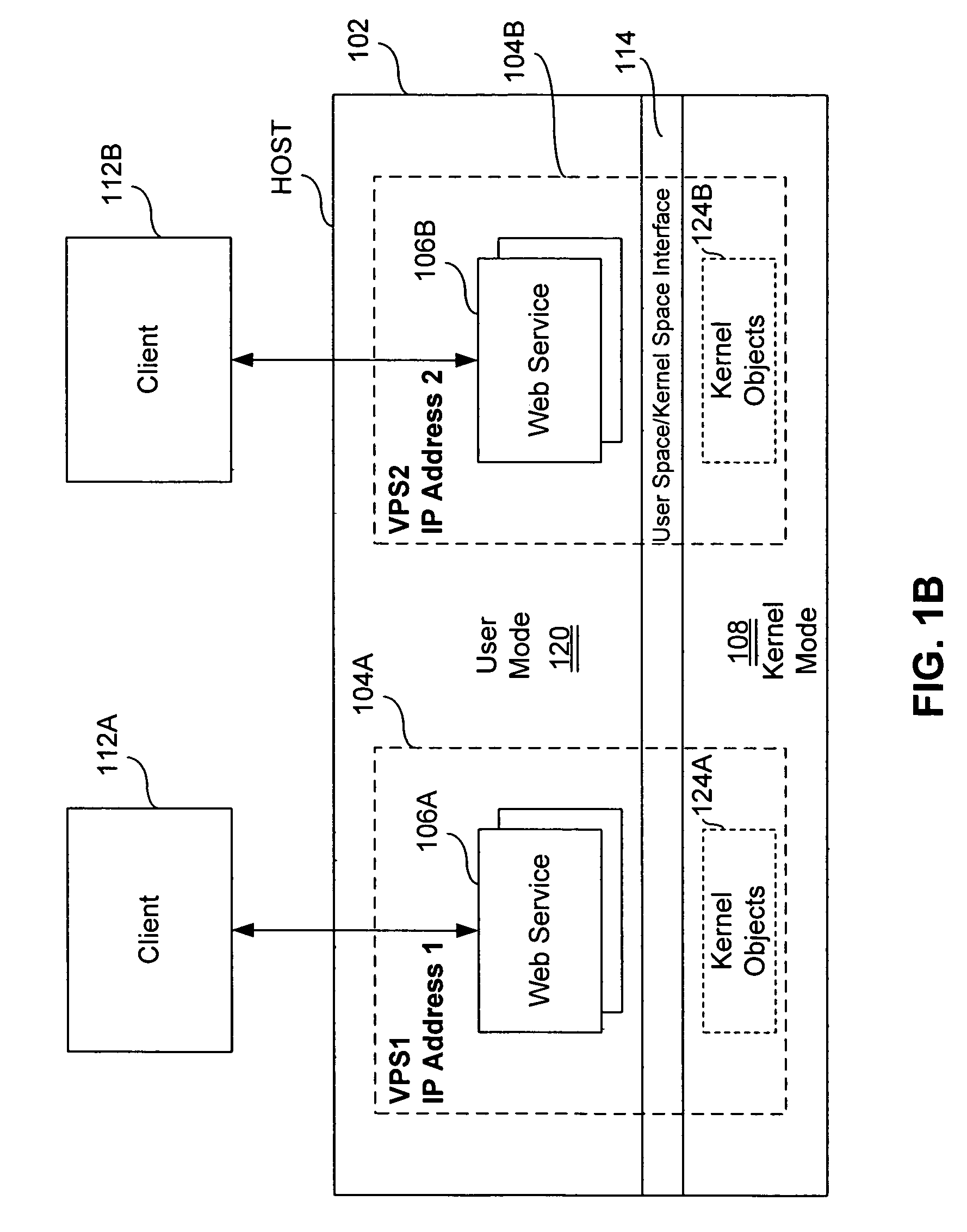
Virtual private server with isolation of system components
ActiveUS7461148B1Eliminate disadvantagesMultiprogramming arrangementsMultiple digital computer combinationsOperational systemUnique identifier
A server includes a host running an operating system kernel. Isolated virtual private servers (VPSs) are supported within the kernel. At least one application is available to users of the VPS. A plurality of interfaces give the users access to the application. Each VPS has its own set of addresses. Each object of each VPS has a unique identifier in a context of the operating system kernel. Each VPS is isolated from objects and processes of another VPS. Each VPS includes isolation of address space of each user from address space of a user on any other VPS, isolation of server resources for each VPS, and failure isolation. The server includes a capability of allocating (or reallocating) system resources to a designated VPS, allocating (or reallocating) system resources to a VPS in current need of such resources, dynamically allocating (or reallocating) VPS resources to a VPS when additional resources are available, and compensating a particular VPS in a later period for a period of under-use or over-use of server resources by the particular VPS in a current period. VPS resources are allocated for each time cycle. All the VPSs are supported within the same OS kernel.
Owner:VIRTUOZZO INT GMBH
High performance wireless networks using distributed control
ActiveUS7420952B2Cost-effective distributed sensingCost-effective controlError preventionFrequency-division multiplex detailsWireless mesh networkOperational system
A design and proof of concept of a new type of WLAN, complete with simulation and results from the simulation has been described. Each AP Node is implemented as a self-contained embedded OS unit, with all algorithms resident in its Operating system. The normal day-to-day functioning of the AP node is based entirely on resident control algorithms. Upgrades are possible through a simple secure communications interface supported by the OS kernel for each AP node. Benefits provided by a wireless network, as proposed in this invention, are that: it installs out of the box; the network is self-configuring; the network is redundant in that mesh network formalism is supported, ensuring multiple paths; load balancing is supported; there is no single point of failure; allows for decentralized execution; there is a central control; it is network application aware; there is application awareness; there is automatic channel allocation to manage and curtail RF interference, maximize non interference bandwidth and enable seamless roaming between adjoining wireless sub networks (BSS) and it supports the wireless equivalent for switching—for seamless roaming requirements.
Owner:DYNAMIC MESH NETWORKS
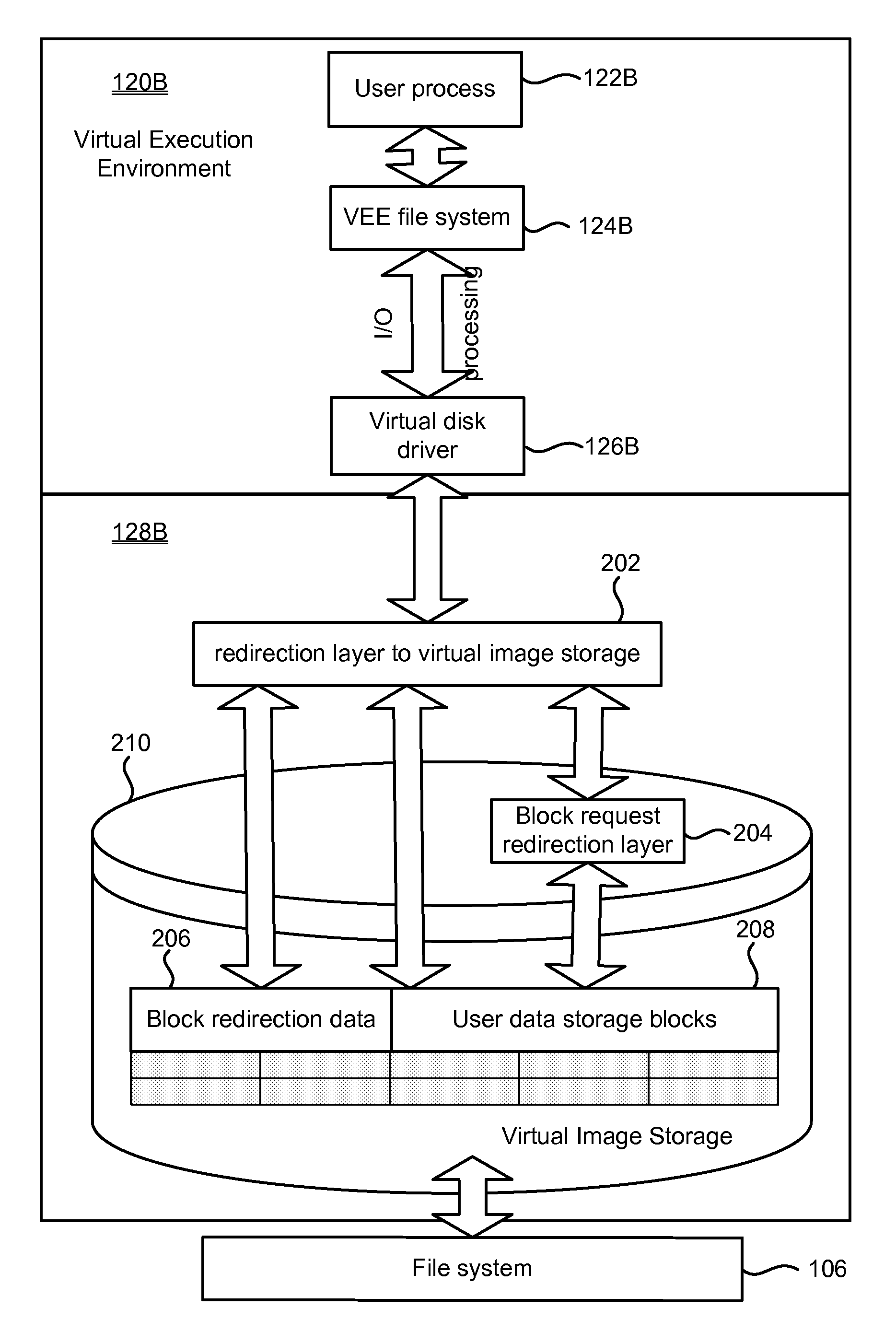
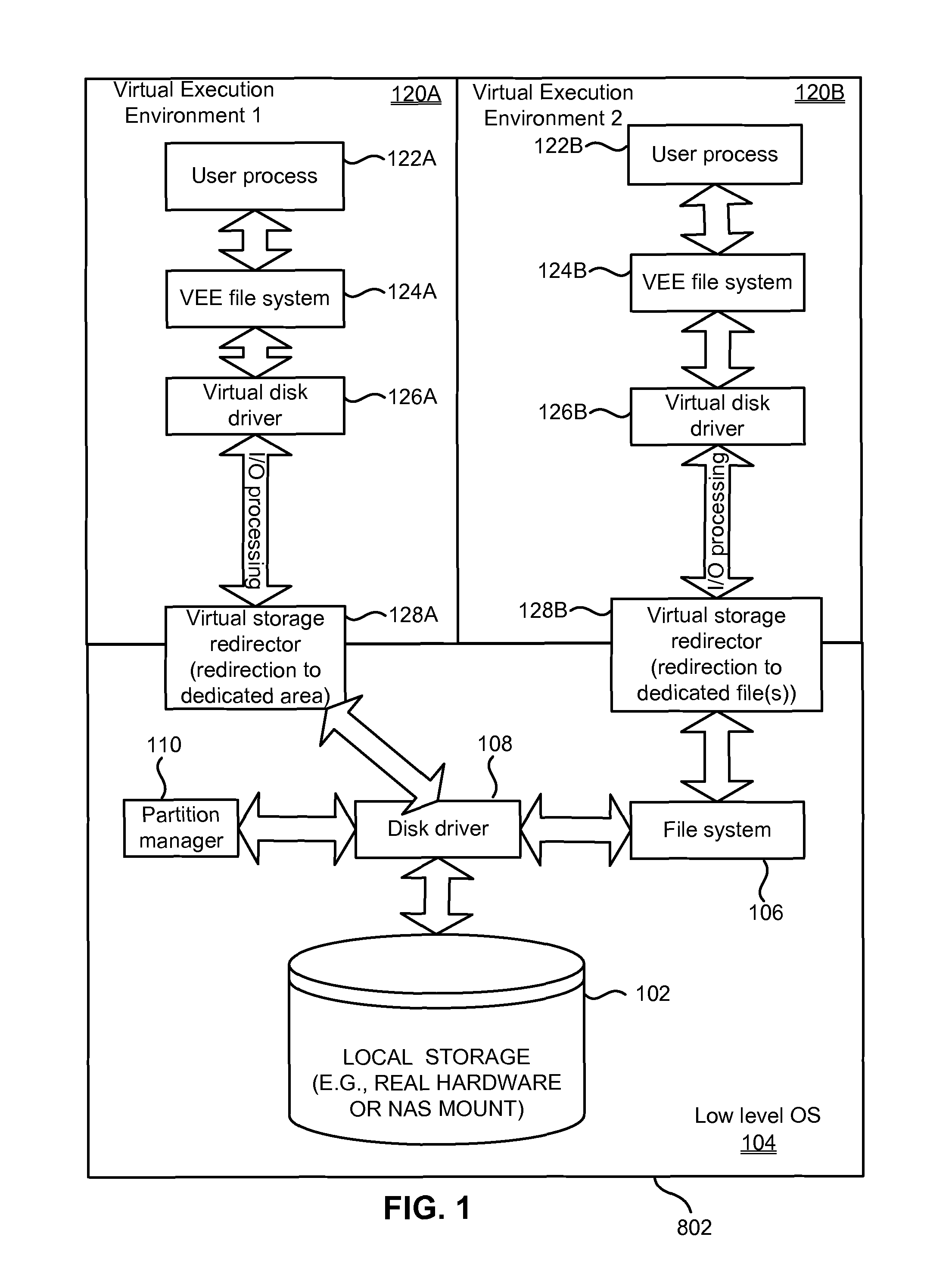
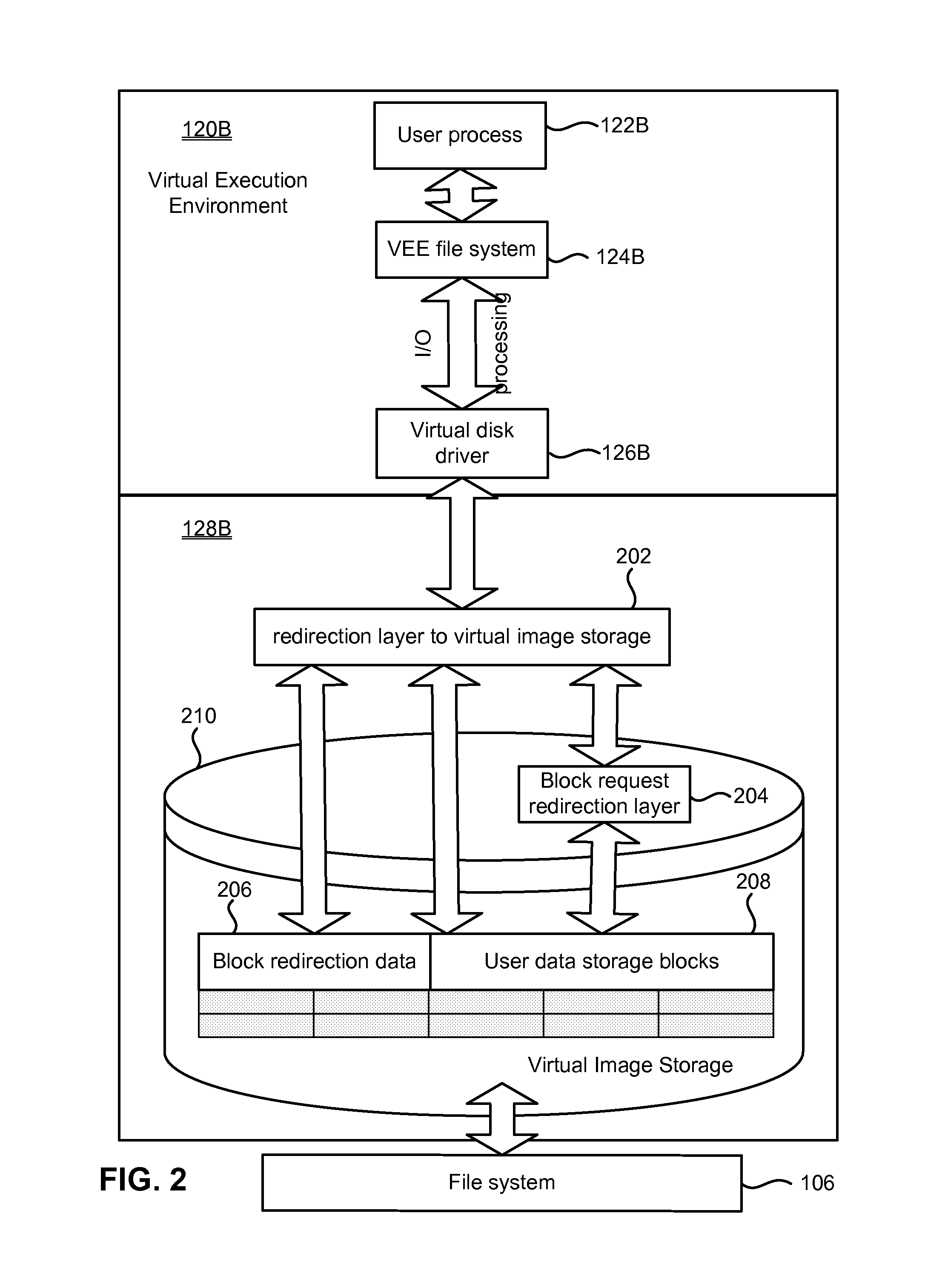
System and method for management of virtual execution environment disk storage
ActiveUS8539137B1Eliminate disadvantagesMultiprogramming arrangementsComputer security arrangementsVirtualizationFile system
A method, system and computer program product for storing data of a Virtual Execution Environment (VEE), such as a Virtual Private Server (VPS) or a Virtual Machine, including starting an operating system running a computing system; starting a Virtual Machine Monitor under control of the operating system, wherein the VMM virtualizes the computing system and has privileges as high as the operating system; creating isolated Virtual Machines (VMs), running on the computing system simultaneously, wherein each VM executes its own OS kernel and each VM runs under the control of the VMM; starting a storage device driver and a file system driver in the operating system; mounting a virtual disk drive; starting VM-specific file system drivers in the VM, the VM specific file system driver together with the common storage device drivers support virtual disk drives, the virtual disk drive is represented on the storage device as a disk image, the disk image data are stored on the storage device as at least one file that includes user data storage blocks and redirection blocks, the redirection blocks point to user data storage blocks, the redirection blocks have a multilevel hierarchy, and the internal structure is used by the VM-specific file system driver.
Owner:VIRTUOZZO INT GMBH
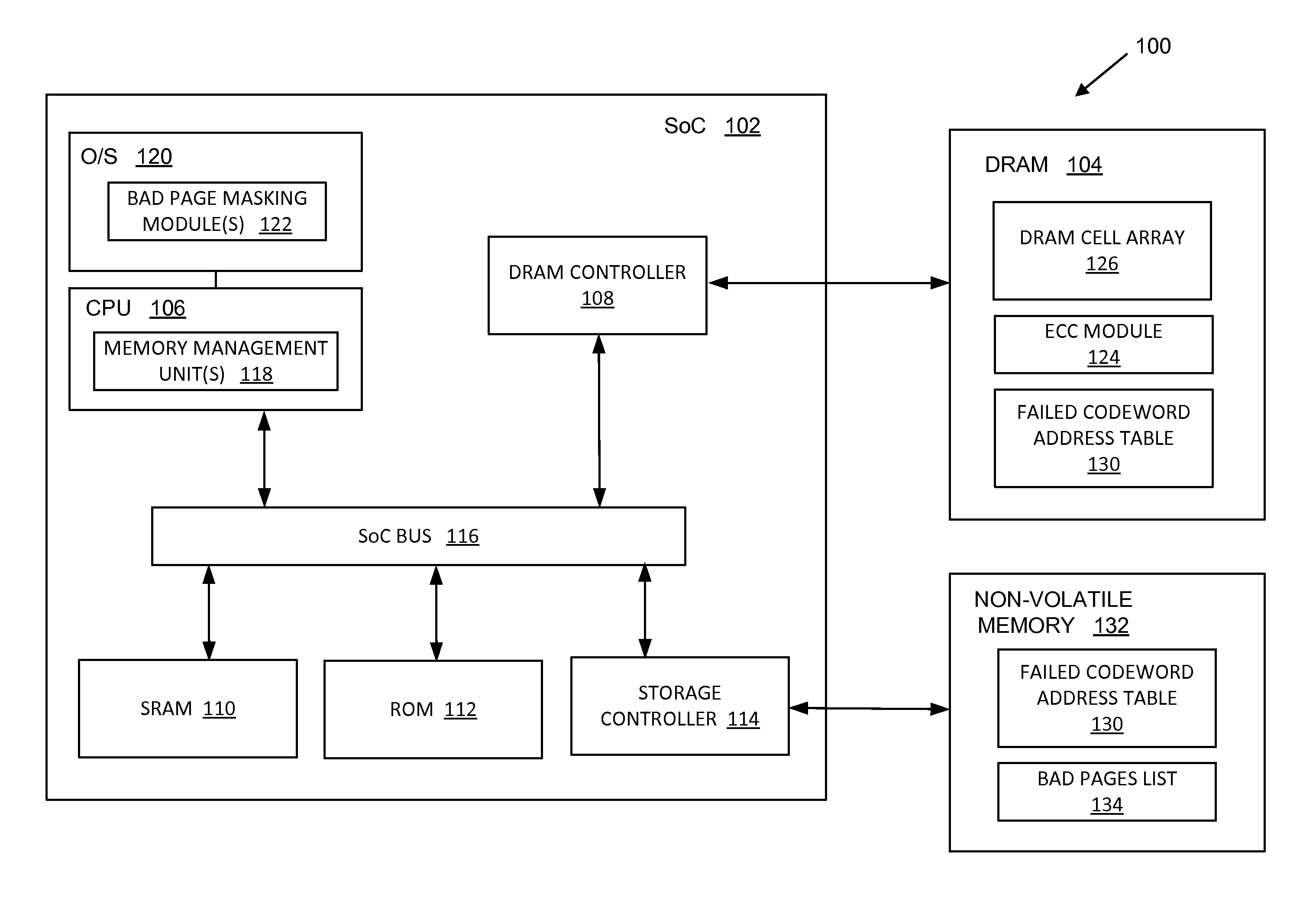
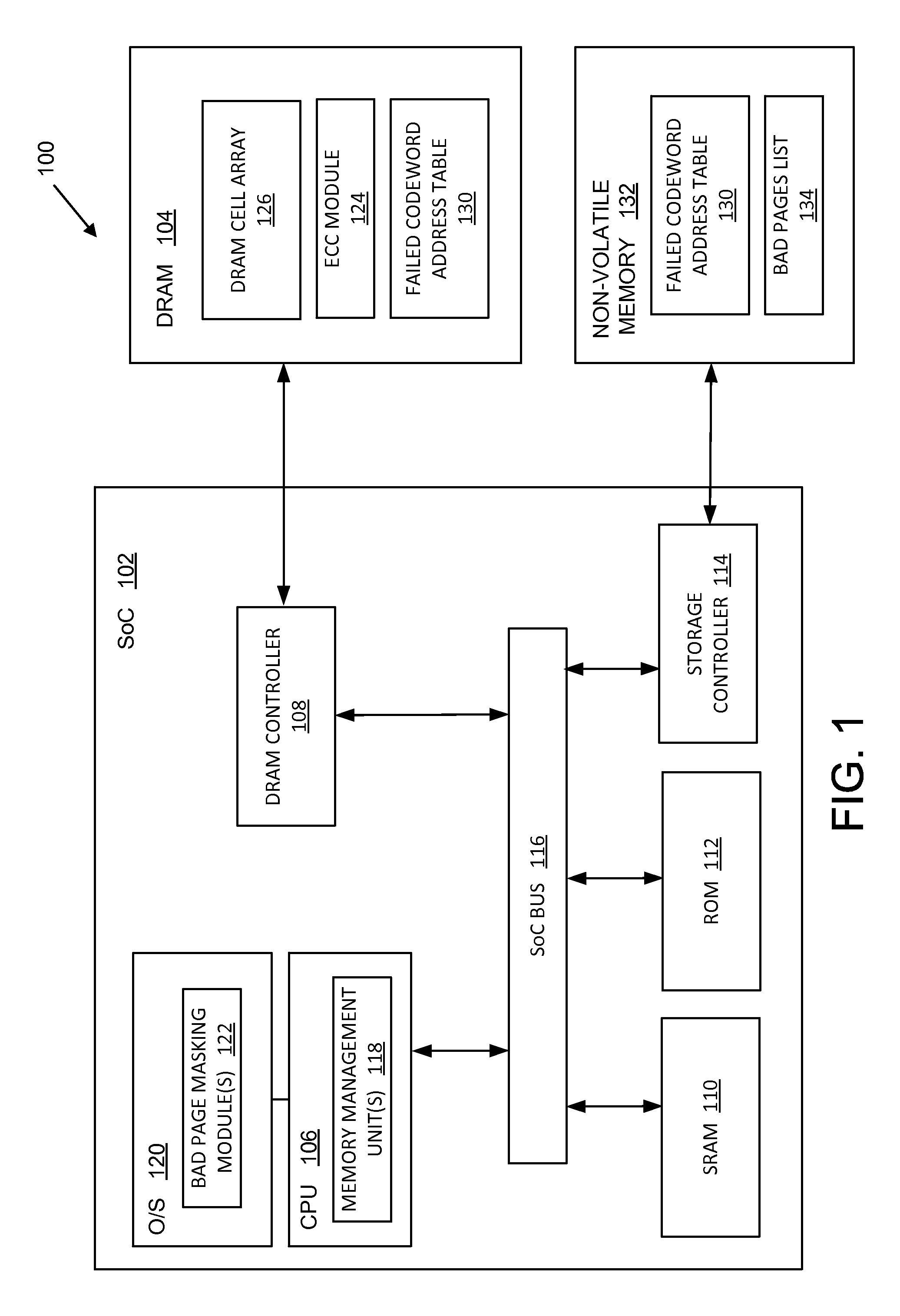
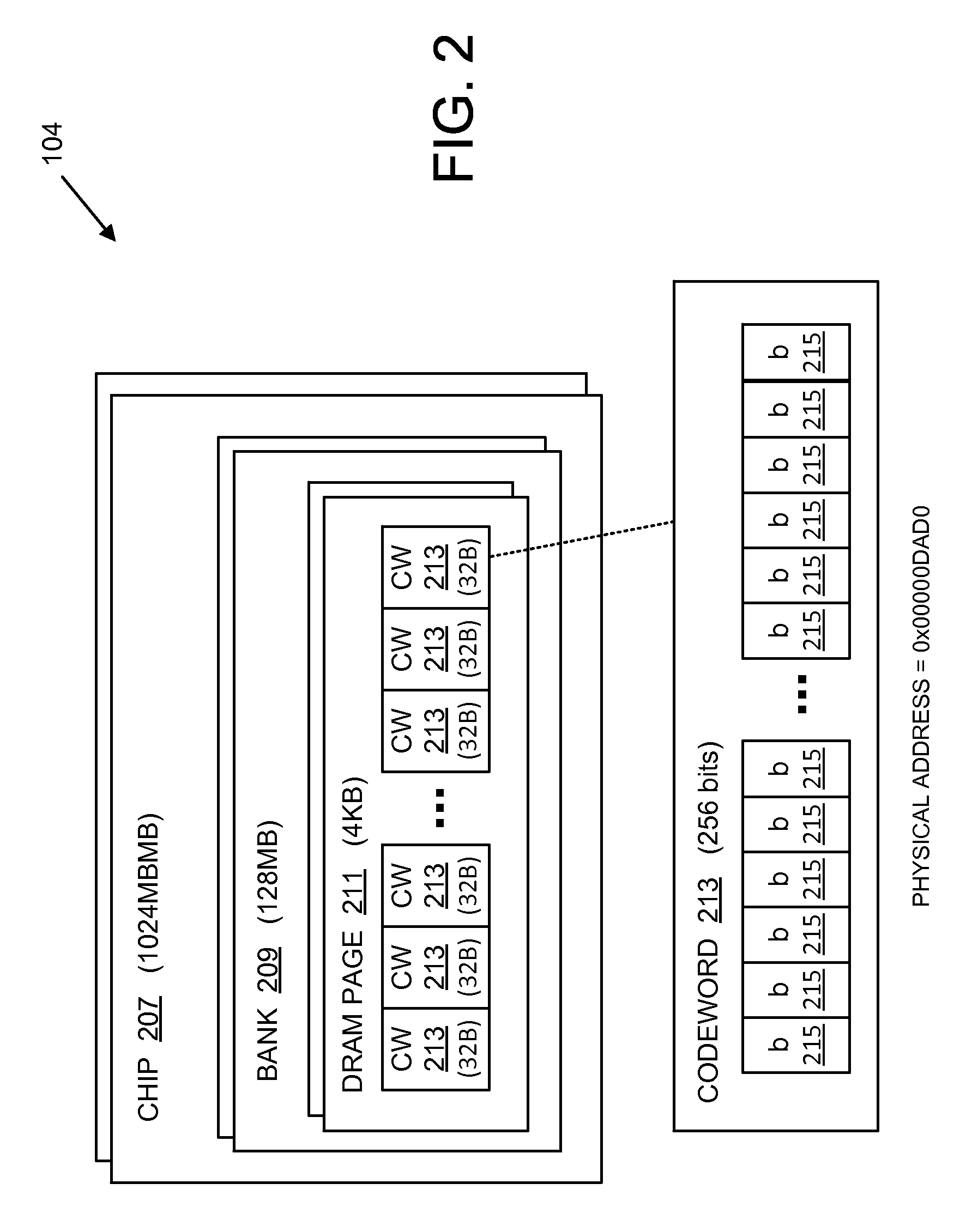
Kernel masking of DRAM defects
ActiveUS9299457B2Memory architecture accessing/allocationMemory adressing/allocation/relocationStatic random-access memoryRandom access memory
Systems, methods, and computer programs are disclosed for kernel masking dynamic random access memory (DRAM) defects. One such method comprises: detecting and correcting a single-bit error associated with a physical address in a dynamic random access memory (DRAM); receiving error data associated with the physical address from the DRAM; storing the received error data in a failed address table located in a non-volatile memory; and retiring a kernel page corresponding to the physical address if a number of errors associated with the physical address exceeds an error count threshold.
Owner:QUALCOMM INC
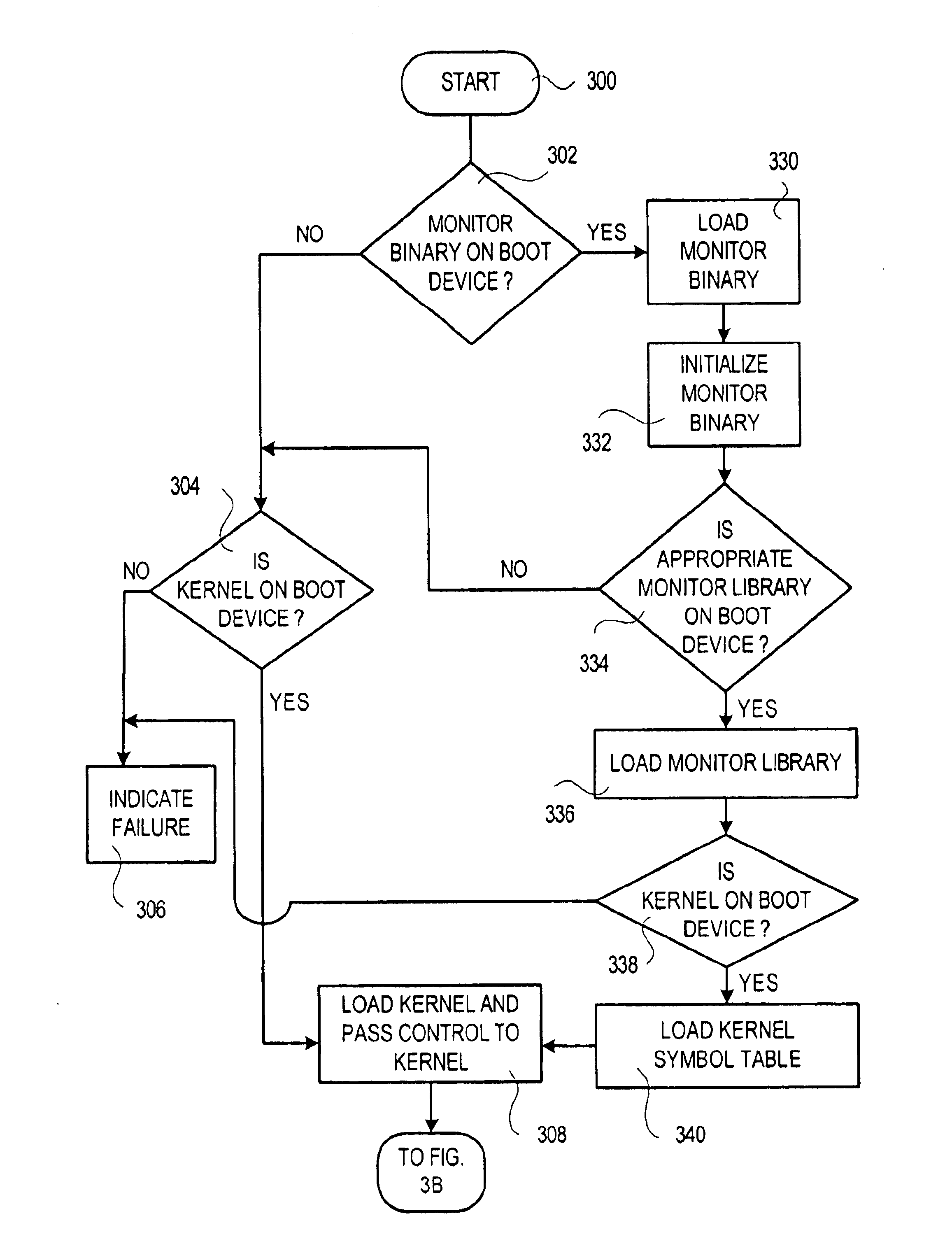
Diagnostic monitor for use with an operating system and methods therefor
InactiveUS6959262B2Program initiation/switchingNuclear monitoringOperational systemComputerized system
A computer-implemented method for monitoring a computer system when the computer system executes a user application using a production operating system (OS) is disclosed. The method includes providing a diagnostic monitor, the diagnostic monitor being configured to be capable of executing even if the OS kernel fails to execute, the diagnostic monitor having a monitor trap arrangement. If a trap is encountered during execution of the user application, the method includes ascertaining using the diagnostic monitor whether the trap is to be handled by the OS kernel or the diagnostic monitor. If the trap is to be handled by the OS kernel, the method includes passing the trap to the OS kernel for handling.
Owner:HEWLETT PACKARD DEV CO LP
Encrypted file system using TCPA
InactiveUS7343493B2Without worrying about compromising the security of the EFSDigital data processing detailsUnauthorized memory use protectionControl registerComputerized system
A method for restricting access to an encryption key of an encrypted file system (EFS), whereby access is provided only when a computer system is booted in a trusted state. The EFS encrypts the files within a TPM chip according to TCPA specifications and simultaneously creates the encryption key, which is also stored in the TPM. The key is sealed to one or more platform control register (PCR) states (i.e., the TPM will export the key only when the PCRs are in a pre-defined state.). The original PCR states are modified during boot up of the computer system via a secure hashing algorithm, which extends a value of one PCR to a next PCR at each stage of the boot process and then hashes the value with the remaining content of the next PCR. When the system boot process is completed and before control passes to the user, the values within the PCRs are compared to values stored in a PCR table within the TPM, and the encryption key is exported to the OS kernel only when the PCR values match the table values. The control code of the TPM chip decrypts and exports the key only if the value of each and every PCR matches its corresponding table value. A complete match indicates that the computer system has completed a trusted boot sequence.
Owner:LENOVO PC INT
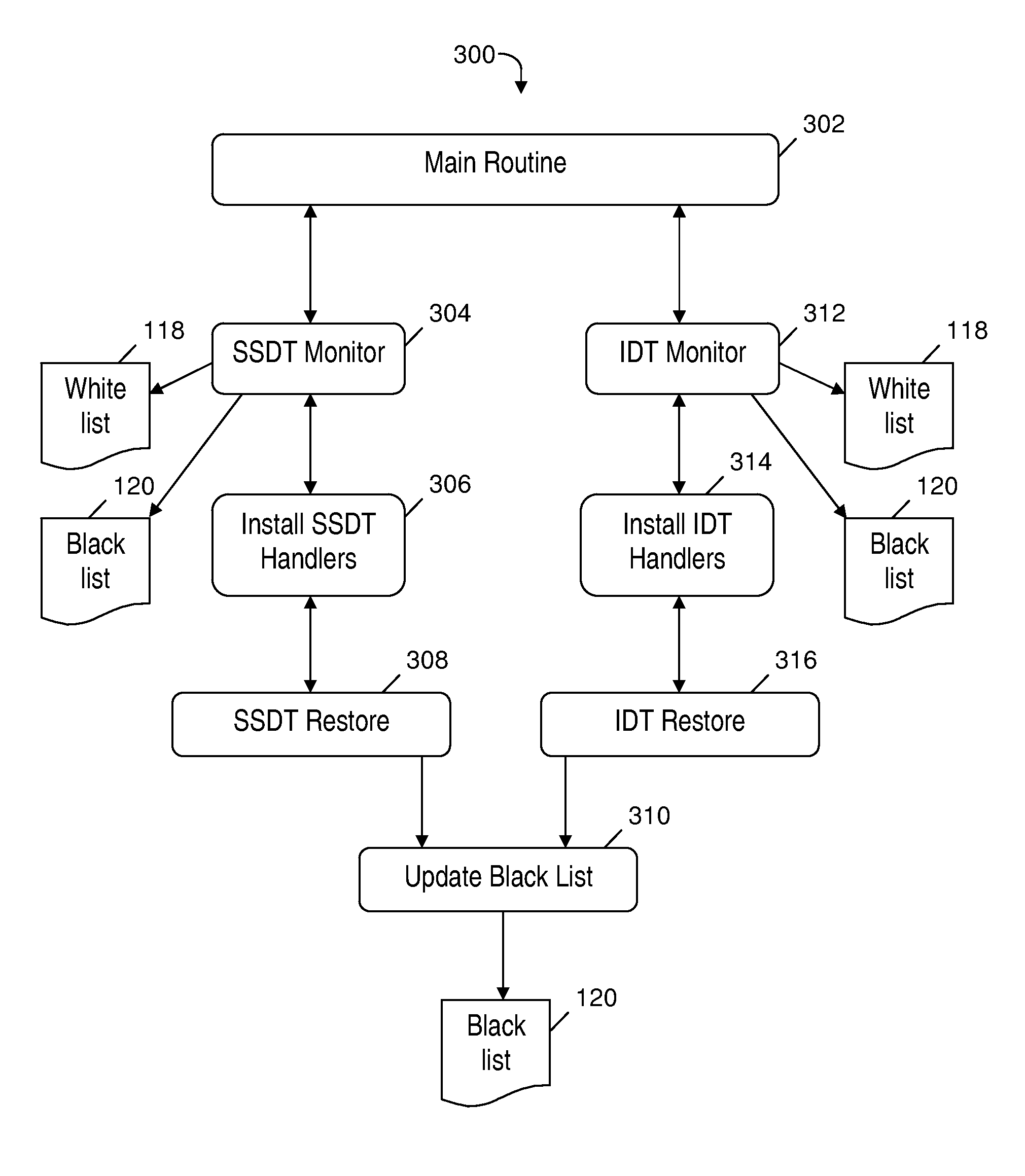
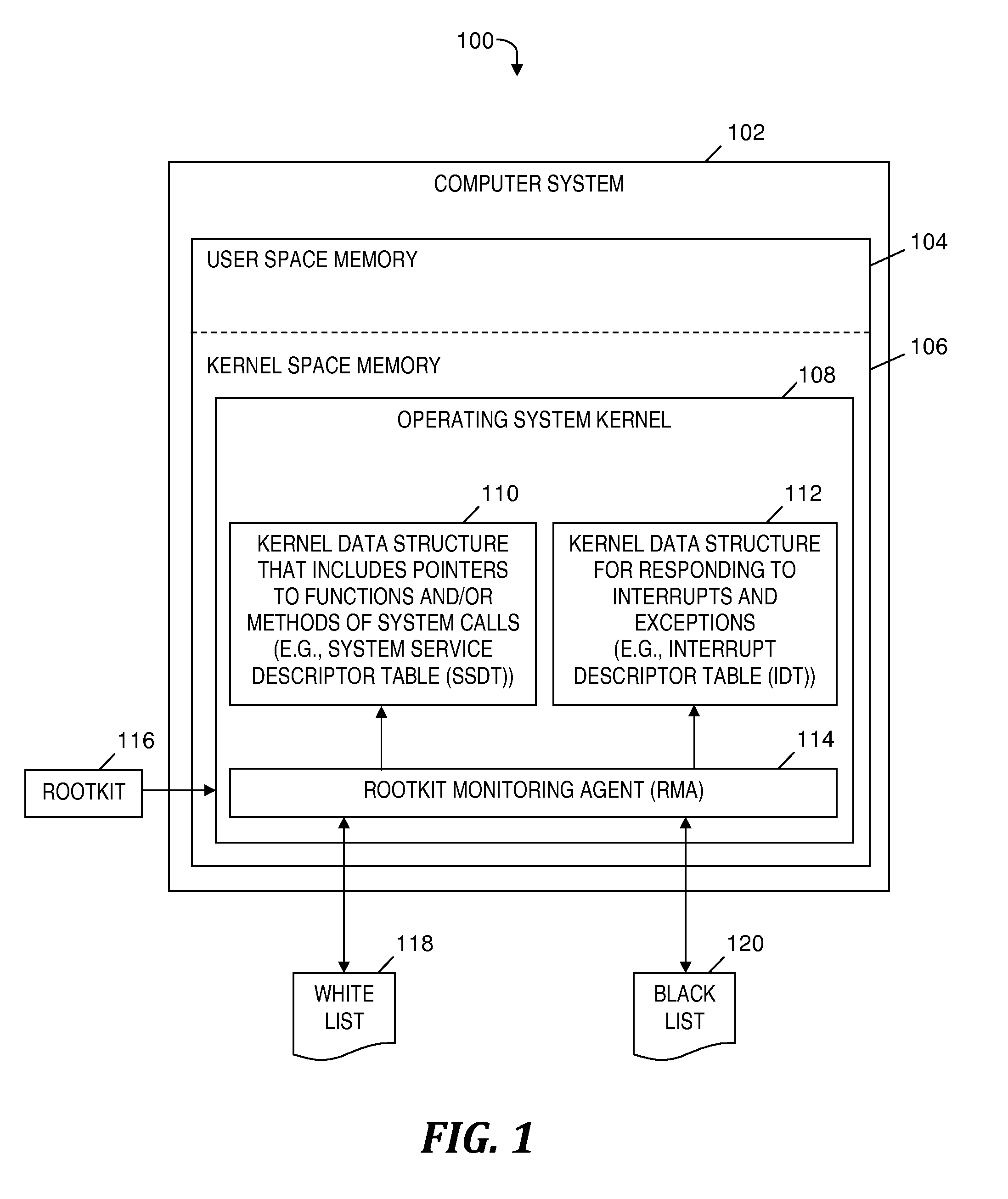
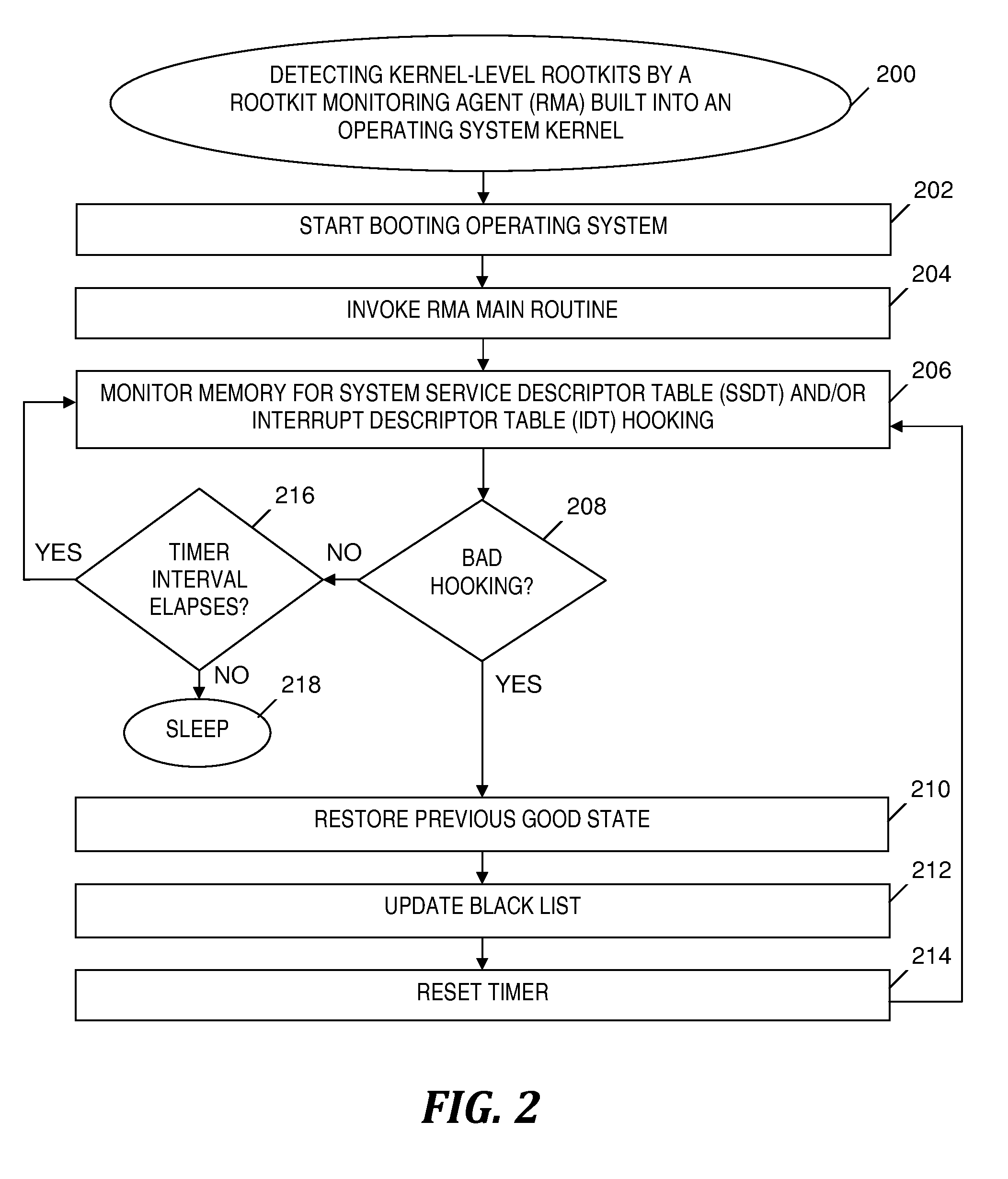
Rootkit monitoring agent built into an operating system kernel
InactiveUS8539584B2Avoid negative effectsMemory loss protectionUnauthorized memory use protectionOperational systemWhitelist
A rootkit monitoring agent (RMA) built into an operating system (OS) kernel for detecting a kernel-based rootkit and preventing subsequent effects of the rootkit. The RMA is activated as a kernel process subsequent to the OS initialization and stores a good state of OS kernel data structures including the System Service Descriptor Table (SSDT) and Interrupt Descriptor Table (IDT). The RMA monitors the SSDT and IDT and detects that a hook previously stored in the good state is changed by an installation of suspect software. The RMA determines the suspect software is a kernel-based rootkit by determining a whitelist does not indicate the changed hook. The RMA restores the changed hook to its good state. The RMA updates a blacklist to reference the changed hook.
Owner:INT BUSINESS MASCH CORP
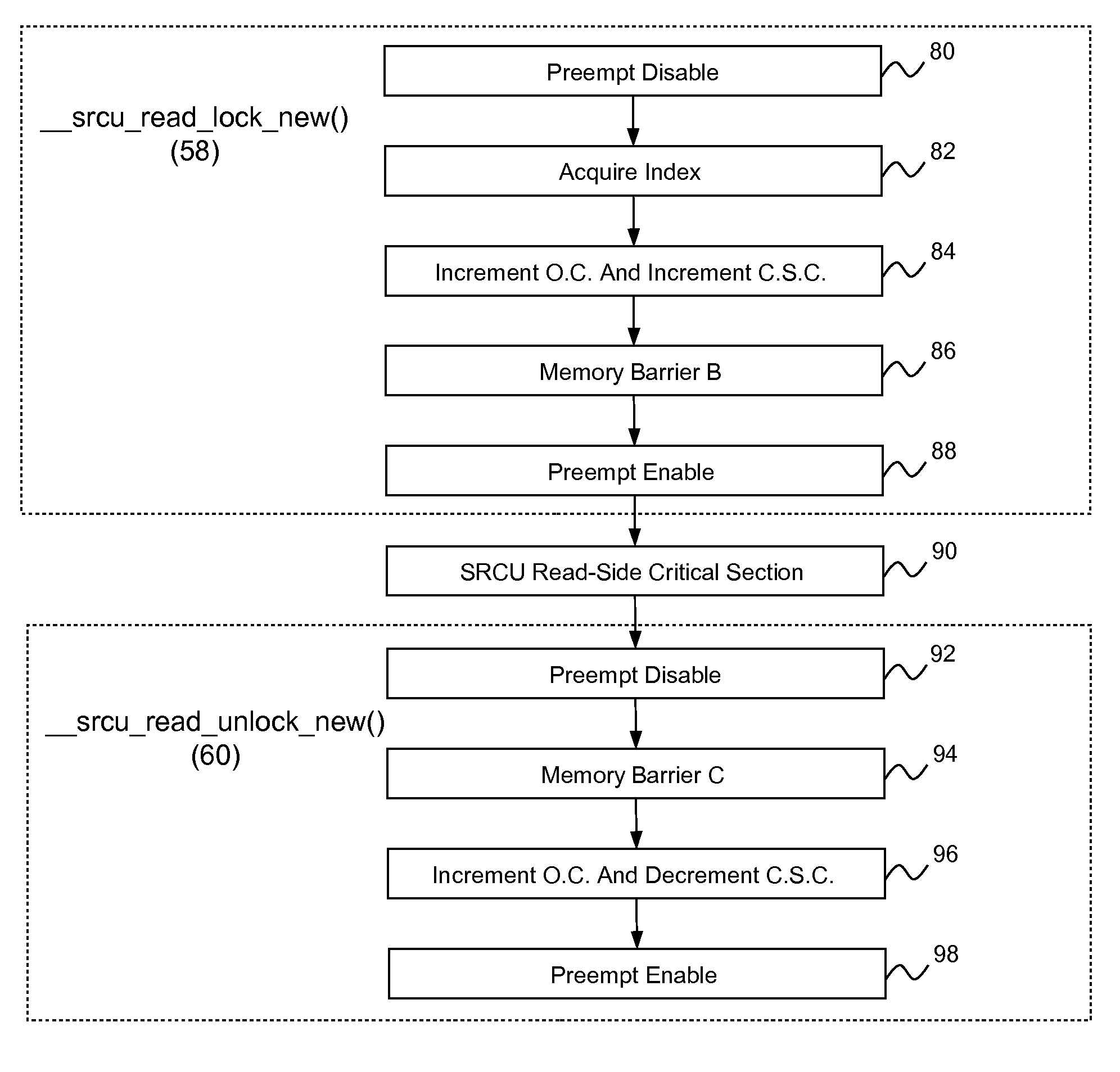
In-kernel SRCU implementation with reduced OS jitter
A technique for implementing SRCU with reduced OS jitter may include: (1) providing a pair of critical section counters for each CPU; (2) when entering an SRCU read-side critical section, incrementing one of the critical section counters associated with a first grace period; (3) when exiting an SRCU read-side critical section, decrementing one of the critical section counters associated with the first grace period; (4) when performing a data update, initiating the second grace period and performing a counter summation operation that sums the critical section counters associated with the first grace period to generate a critical section counter sum; (5) storing a snapshot value for each critical section counter during the summing; and (6) if the critical section counter sum indicates there are no active SRCU read-side critical sections for the first grace period, rechecking by comparing the snapshot values to current values of the critical section counters.
Owner:INT BUSINESS MASCH CORP
Method for creating allocation-on-demand incremental volume
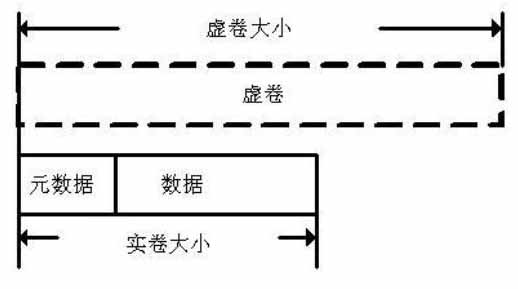
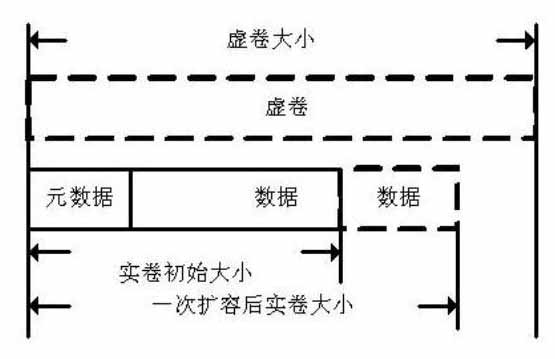
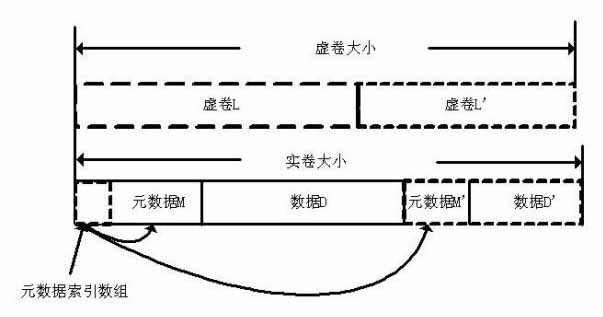
InactiveCN102073464AImprove space utilizationEasy to acceptInput/output to record carriersShardPhysical space
The invention belongs to the technical field of network storage, and discloses a method for creating an allocation-on-demand incremental volume. The volume has a two-layer volume structure, and realizes separation of a physical space and a logical space. The creating method comprises that: a user state interface participates in a new parameter (N) in a user state command lvcreate of a logical volume manger (LVM). The real volume of the bottom layer is a common logical volume, and the virtual volume of the upper layer is a data structure in a Linux kernel. The physical space of the real volume is allocated according to the actual requirement, so the utilization rate of a disk space is improved. Real-time monitoring of the physical space of the real volume and automatic capacity expansion of the actual space effectively avoid overflow of the spaces. A user can randomly designate capacity expansion increment magnitude as required to perform capacity expansion of the virtual volume. The volume processes the write request by adopting a mode of additional write. Moreover, the volume processes garbage fragments by adopting a quick and effective garbage reclamation algorithm.
Owner:NANKAI UNIV
Method and apparatus for managing thread execution in a multithread application
InactiveUS20040139432A1Easy to useBetter conformsProgram initiation/switchingMemory systemsOperational systemApplication software
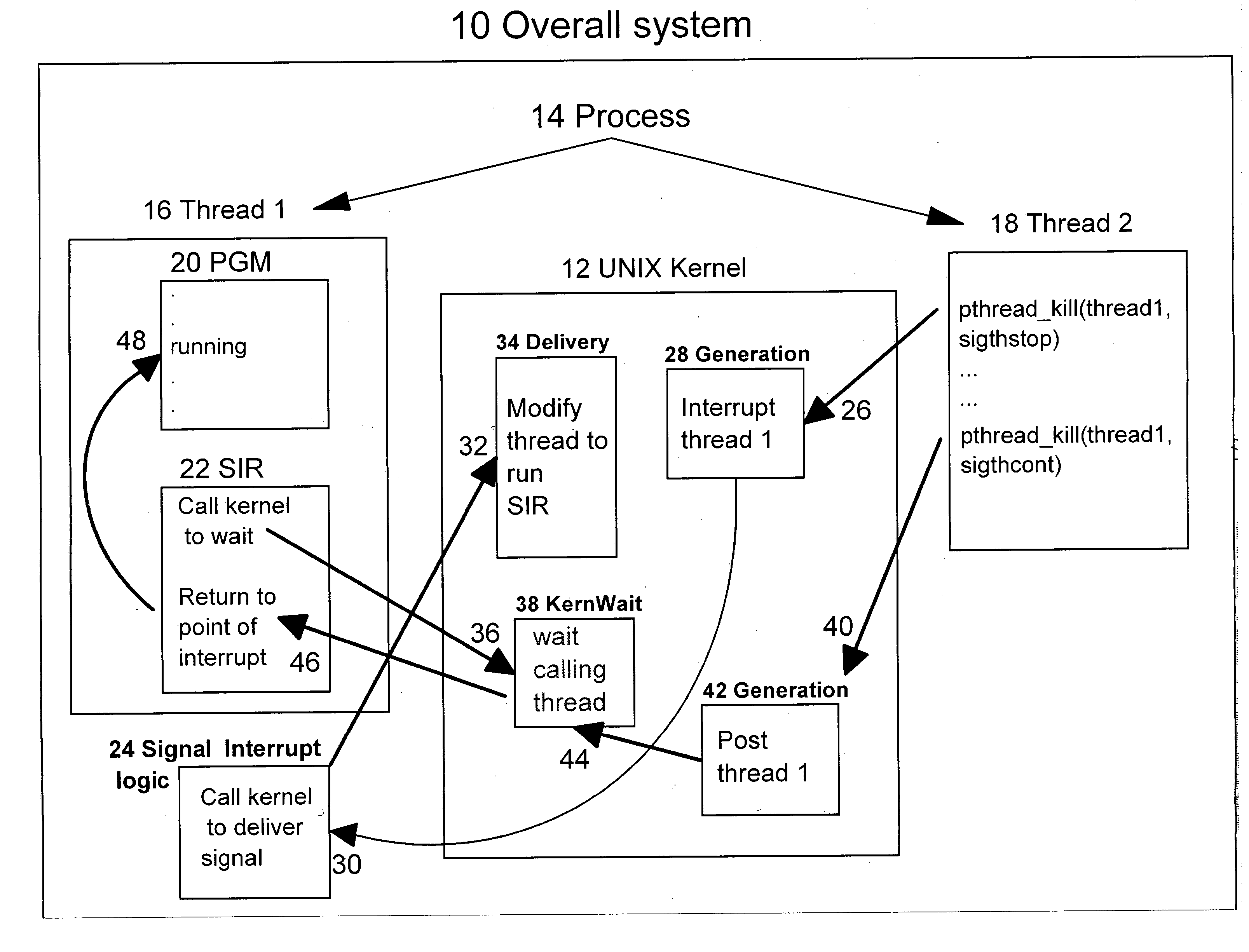
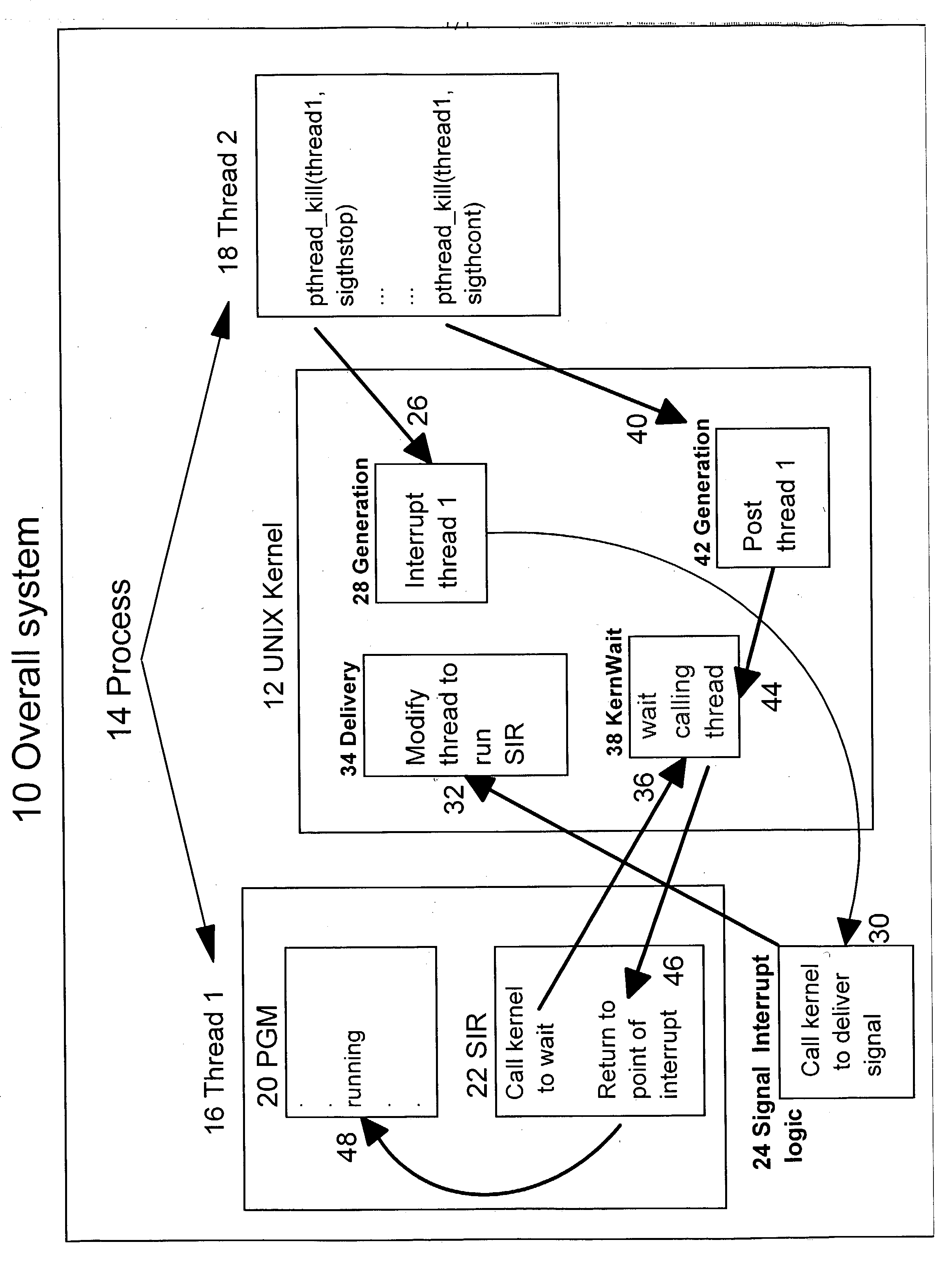
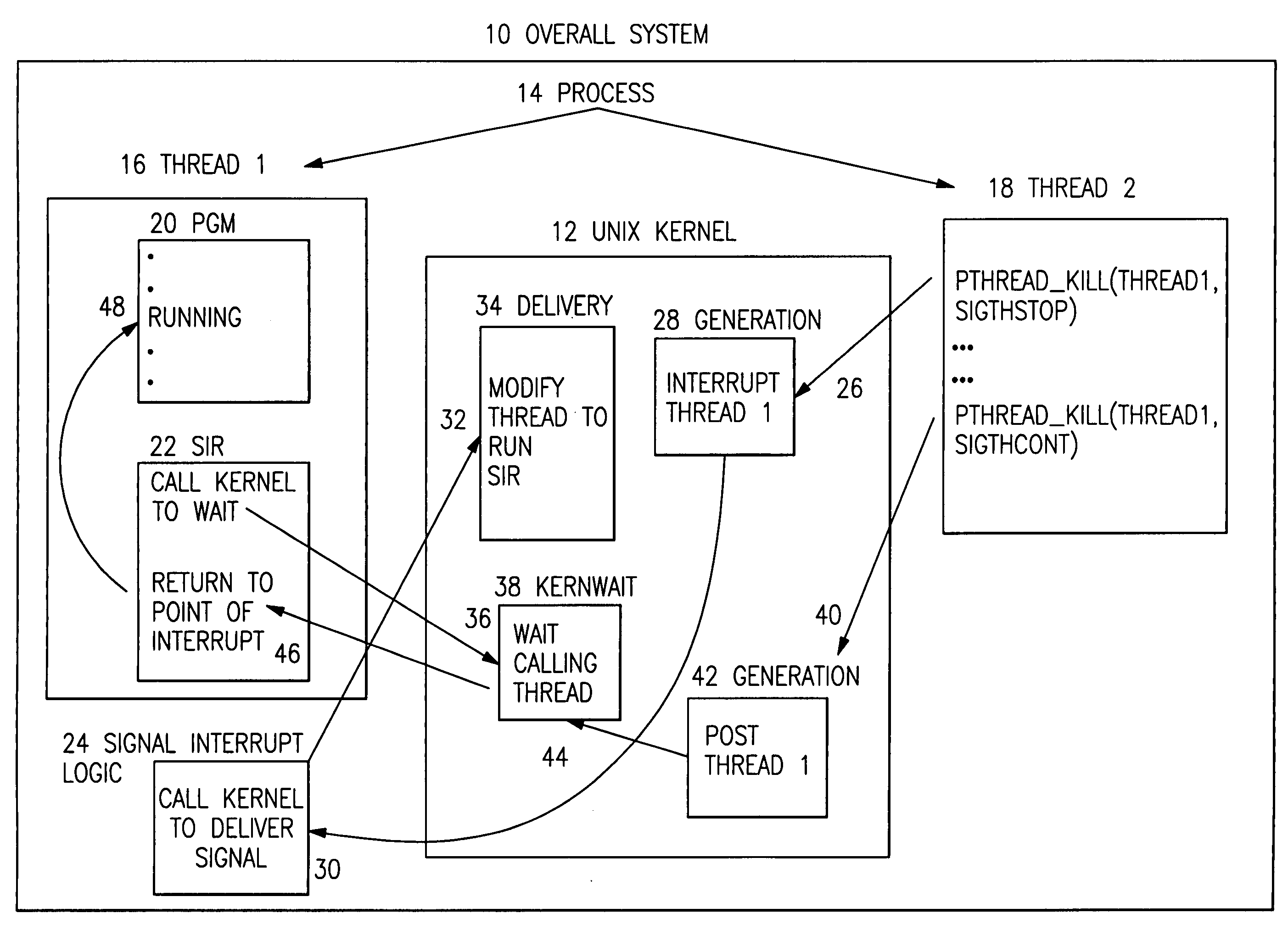
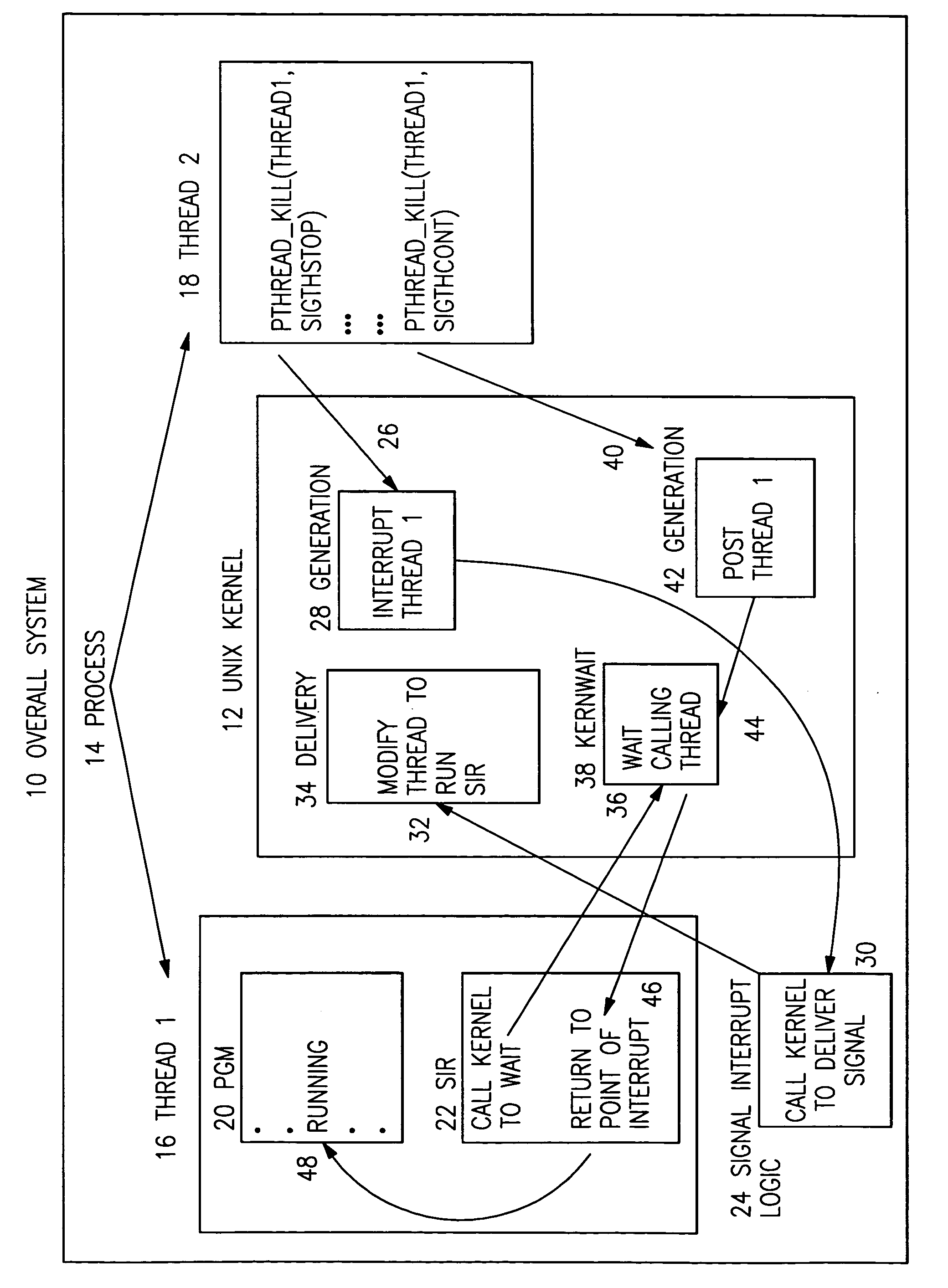
A method for managing the suspension and resumption of threads on an individual basis in an information handling system having an operating system (OS) kernel and a user process having multiple threads of execution. An originating thread issues a pthread_kill( ) service request to the OS kernel to send a specified signal (thread-stop or thread-continue) to a specified target thread within the same process to suspend or resume execution of the target thread. More particularly, in response to a request from a thread to suspend the execution of the target thread, the OS kernel sends a thread-stop signal (SIGTHSTOP) to the target thread, transferring control within the target thread from a normally executing program portion to a signal interrupt routine. Upon gaining control, the signal interrupt routine issues a service request to the kernel to stop the target thread. In response to a request from a thread to resume execution of the target thread, the OS kernel sends a thread-continue signal (SIGTHCONT) to the target thread to post the waiting target thread and return control to the signal interrupt routine. Upon regaining control, the signal interrupt routine returns control to the program at the point of interrupt.
Owner:IBM CORP
Trusted safe mobile storage device
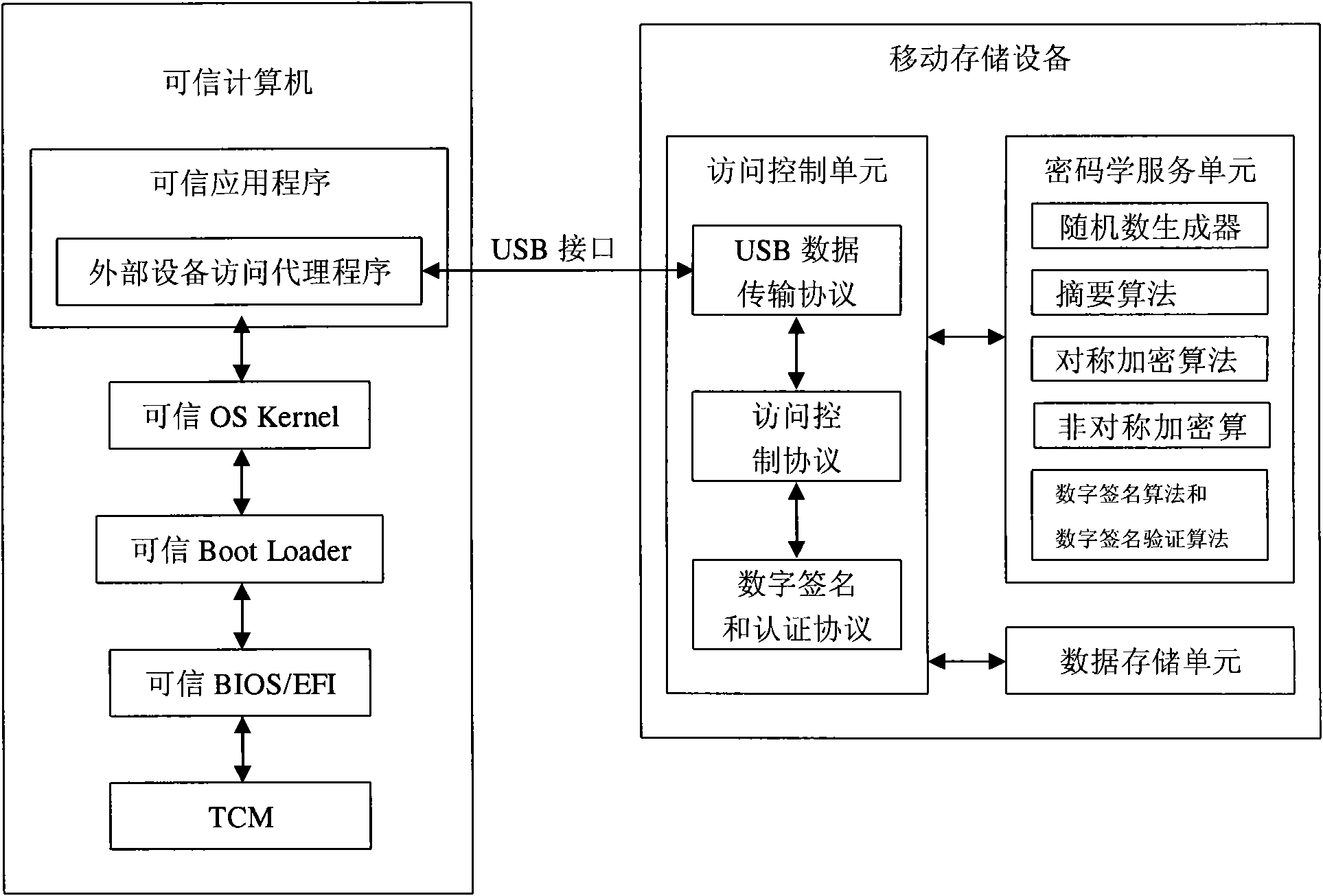
ActiveCN101881997AWith mobility in mindTake security into considerationDigital data processing detailsUser identity/authority verificationApplication softwareBIOS
The invention relates to a trusted safe mobile storage device, belonging to the technical field of information security. The device comprises a mobile storage device and a trusted computing device connected with the mobile storage device. The mobile storage device comprises an access control unit, a cryptography service unit, a data storage unit and a USB interface. The identity of the mobile storage device is bound with the identity of the trusted computing device in a way of digital signature and signature verification. The trusted computing device comprises a trusted application program, a trusted OS Kernel, a trusted Boot Loader, a trusted BIOS / EFI and a trusted crypto module (TCM) which are connected with each other. The trusted crypto module (TCM) is used as the trusted root of the trusted computing device and a trusted computing environment is constructed based on the trusted root. Compared with the prior art, through binding the identity of the mobile storage device with the identity of the trusted computing device, the invention has the advantages that data in the mobile storage device can flow only in a local range and the data leakage is effectively avoided.
Owner:TSINGHUA TONGFANG CO LTD
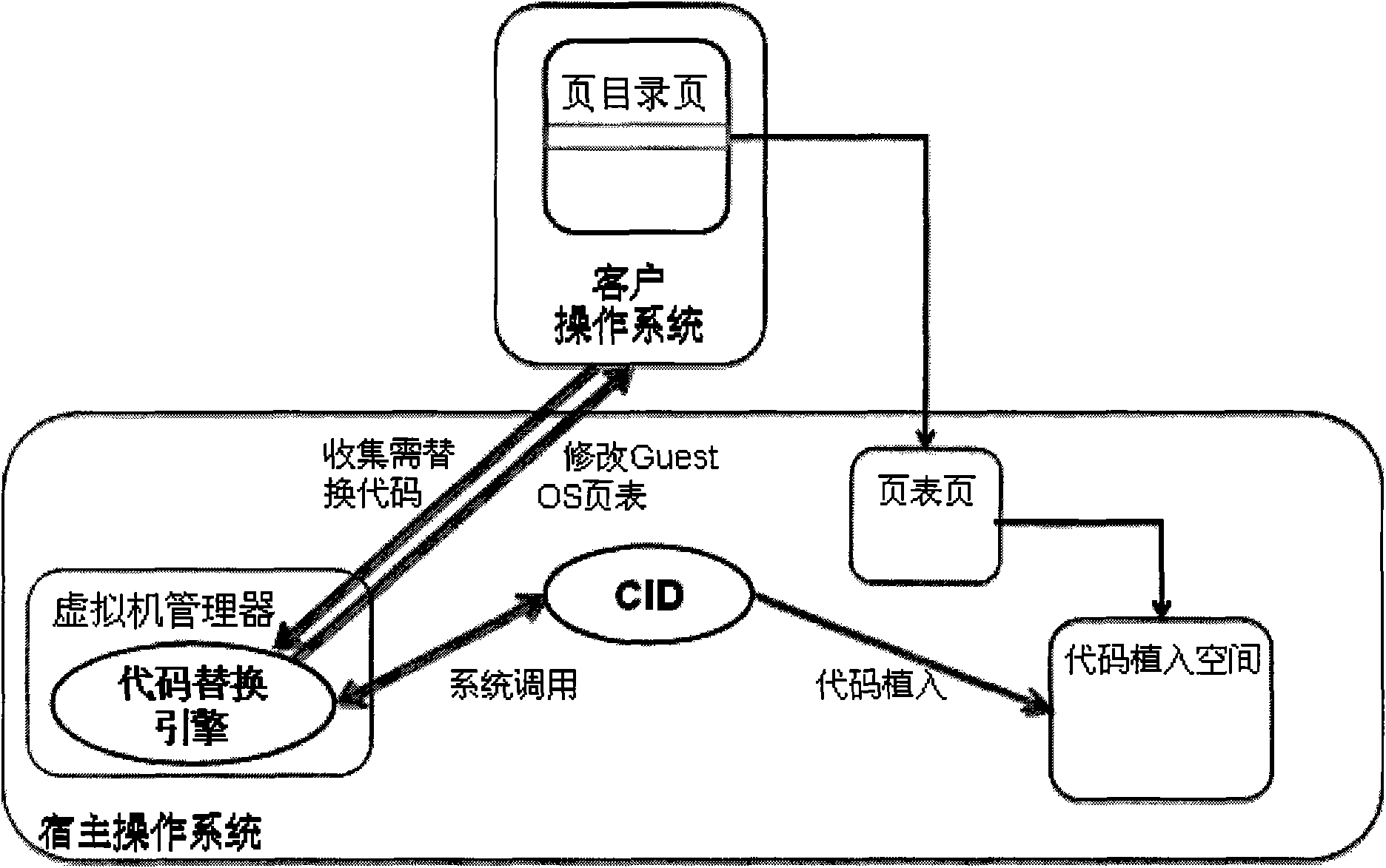
Client operating system nucleus code dynamic replacement method of virtual machine manager
InactiveCN101539868AOvercome limitationsDynamic replacement automaticMultiprogramming arrangementsSoftware simulation/interpretation/emulationCall stackOperational system
The invention discloses a client operating system nucleus code dynamic replacement method of a virtual machine manager, belonging to the software technical field. The method is as follows: (1) a host operating system is internally added with a CID process, assigned with an implantation space so as to contain implanted alternate codes, and then VMM maps the implantation space to a kernel process space of Guest OS; (2) the VMM counts codesnippet needed to be replaced; (3) the CID appoints a section of replacing codes according to the statistical results; (4) the appointed replacing codes are read into the implantation space, and a call stack in which the replacing codes locate is obtained; (5) the CID finds out calling points of the replacing codes in the Guest OS; the VMM changes skip addresses of the call points into the offset address of the appointed replacing address. The invention makes the advantages of the half virtualization method being blended into the full virtualization technology possible and does dynamic replacement for Guest OS kernel in a binary system bedding surface.
Owner:PEKING UNIV
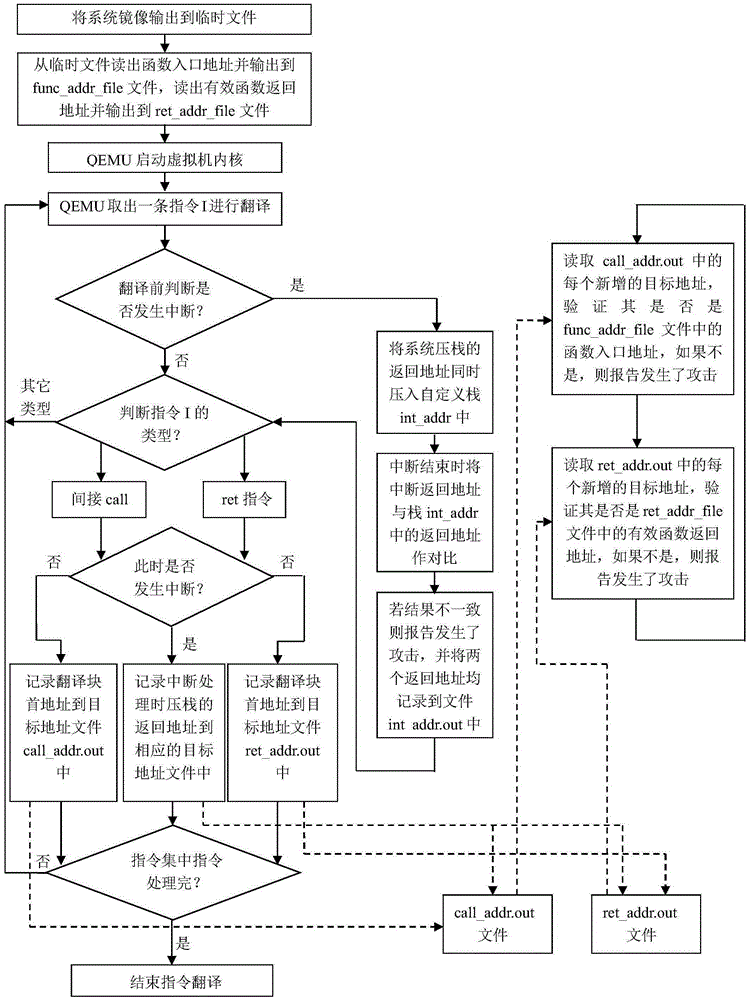
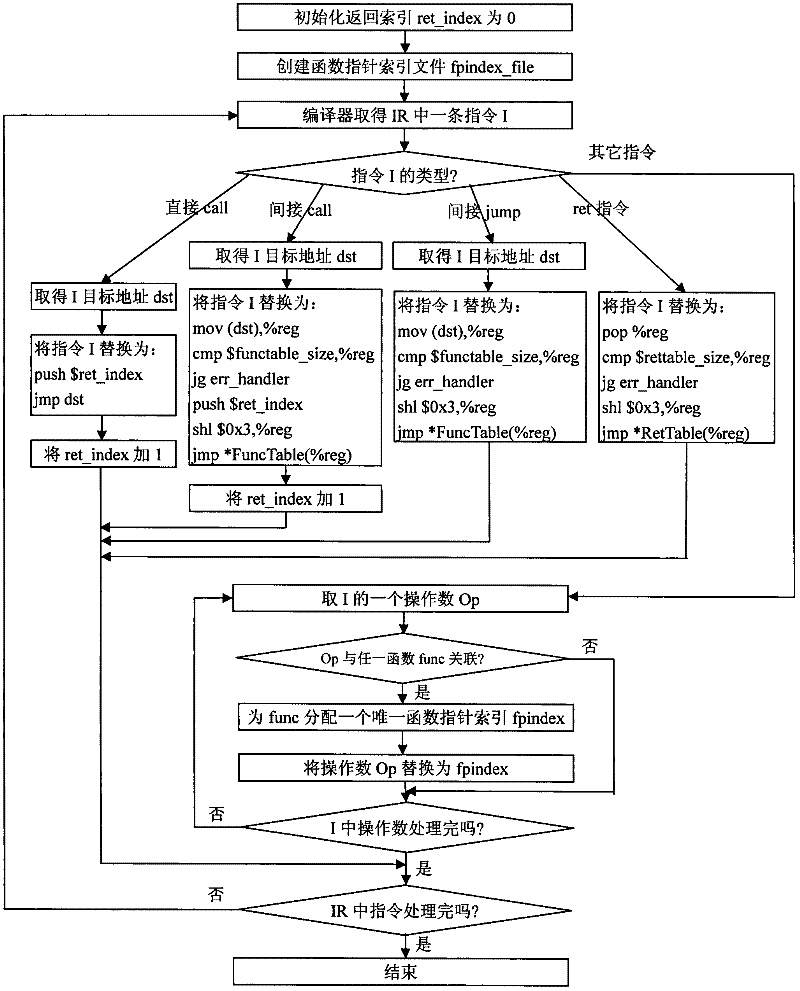
Kernel-level code reuse type attack detection method based on QEMU
ActiveCN105260659AProtection securityLow costPlatform integrity maintainanceControl flowOperational system
The invention discloses a kernel-level code reuse type attack detection method based on QEMU. The method mainly solves the problem of relying on hardware or need of modifying kernel source code in the prior art. According to the method, a function module of a QEMU virtual machine manager is expanded; each instruction which operates on the function module and in an operating system kernel is traversed and detected; jumping instructions relevant to the control flow process are recognized from the instructions, wherein the jumping instructions include ret and indirect call instructions; the jumping target addresses of the instructions are recorded; then, the target addresses are compared with legal target addresses in the system normal execution flow process for detecting whether a system is normally executed or not; and meanwhile, the interruption return addresses pushed into a stack during the interruption occurrence and the return addresses used during interruption actual return are subjected to comparison verification, so that whether attack occurs or not is judged. The kernel-level code reuse type attack detection method has the advantages that by aiming at the characteristic that the system original execution flow process needs to be changed for the code reuse type attack, the attack can be effectively discovered by monitoring the kernel execution flow process change instructions (and positions), and the kernel-level code reuse type attack detection method can be used for protecting the security of an operating system.
Owner:XIDIAN UNIV
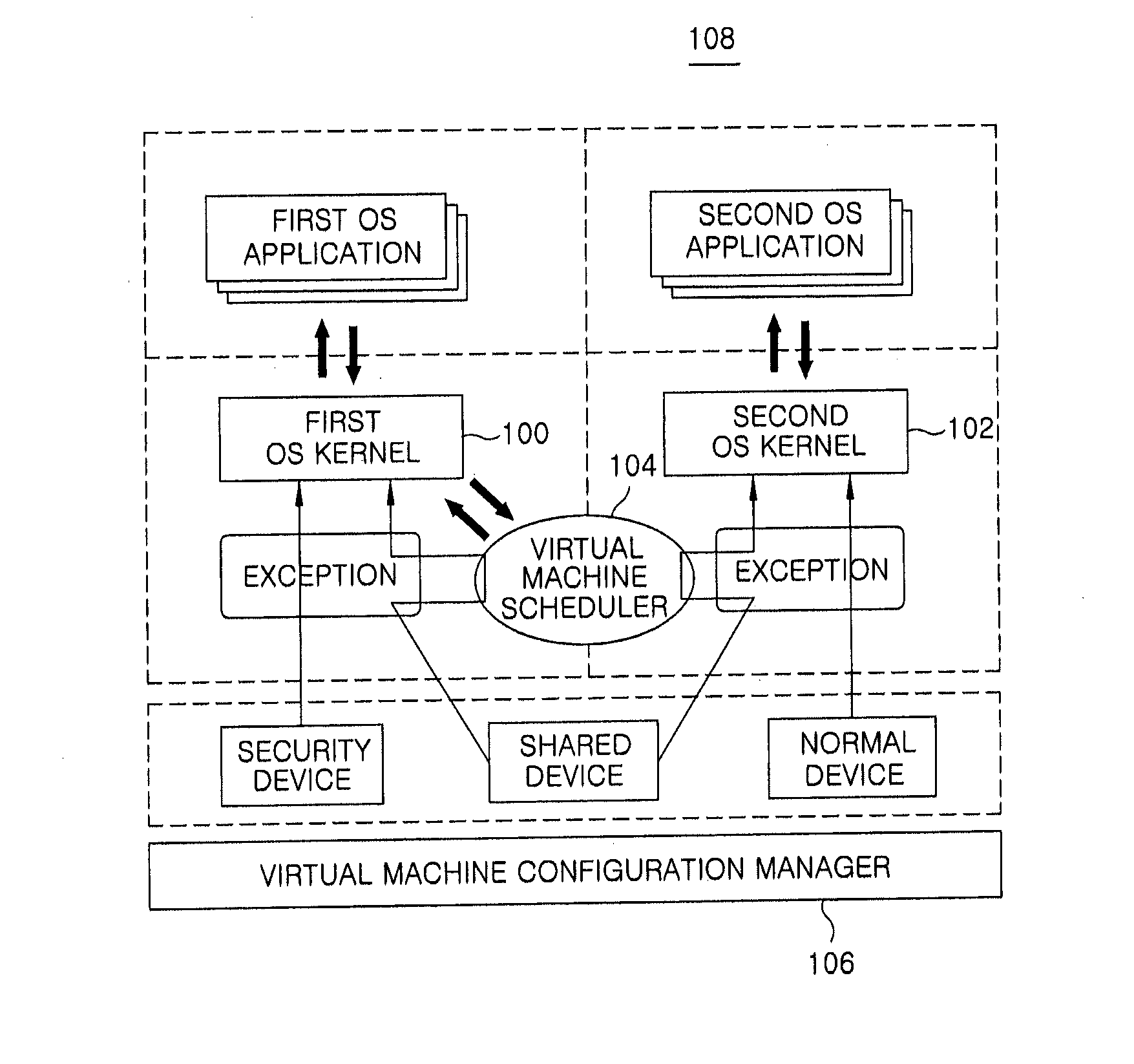
Virtual machine management apparatus and virtualization method for virtualization-supporting terminal platform
InactiveUS20110219373A1Minimized in sizeImprove performanceSoftware simulation/interpretation/emulationMemory systemsVirtualizationComputer terminal
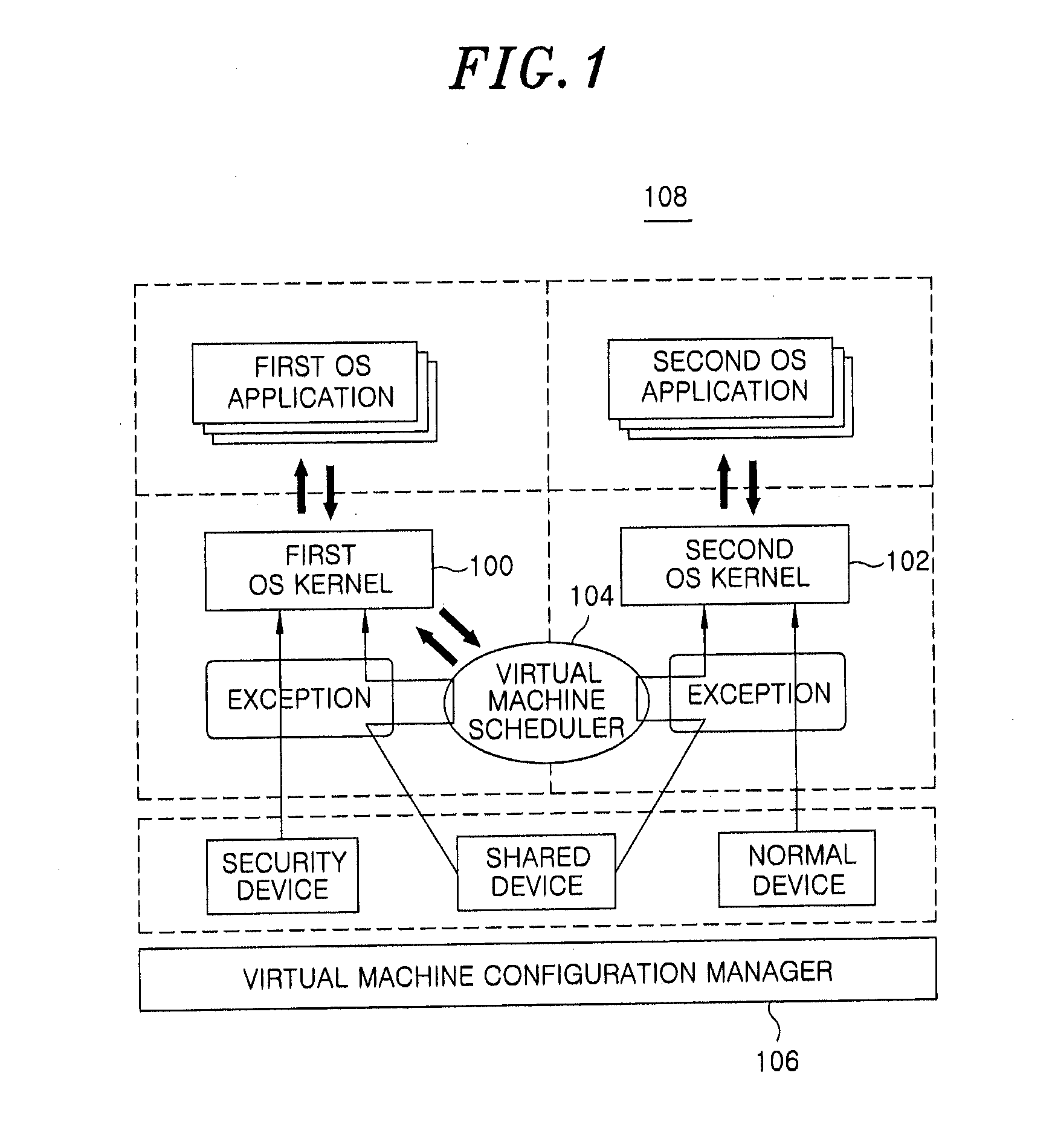
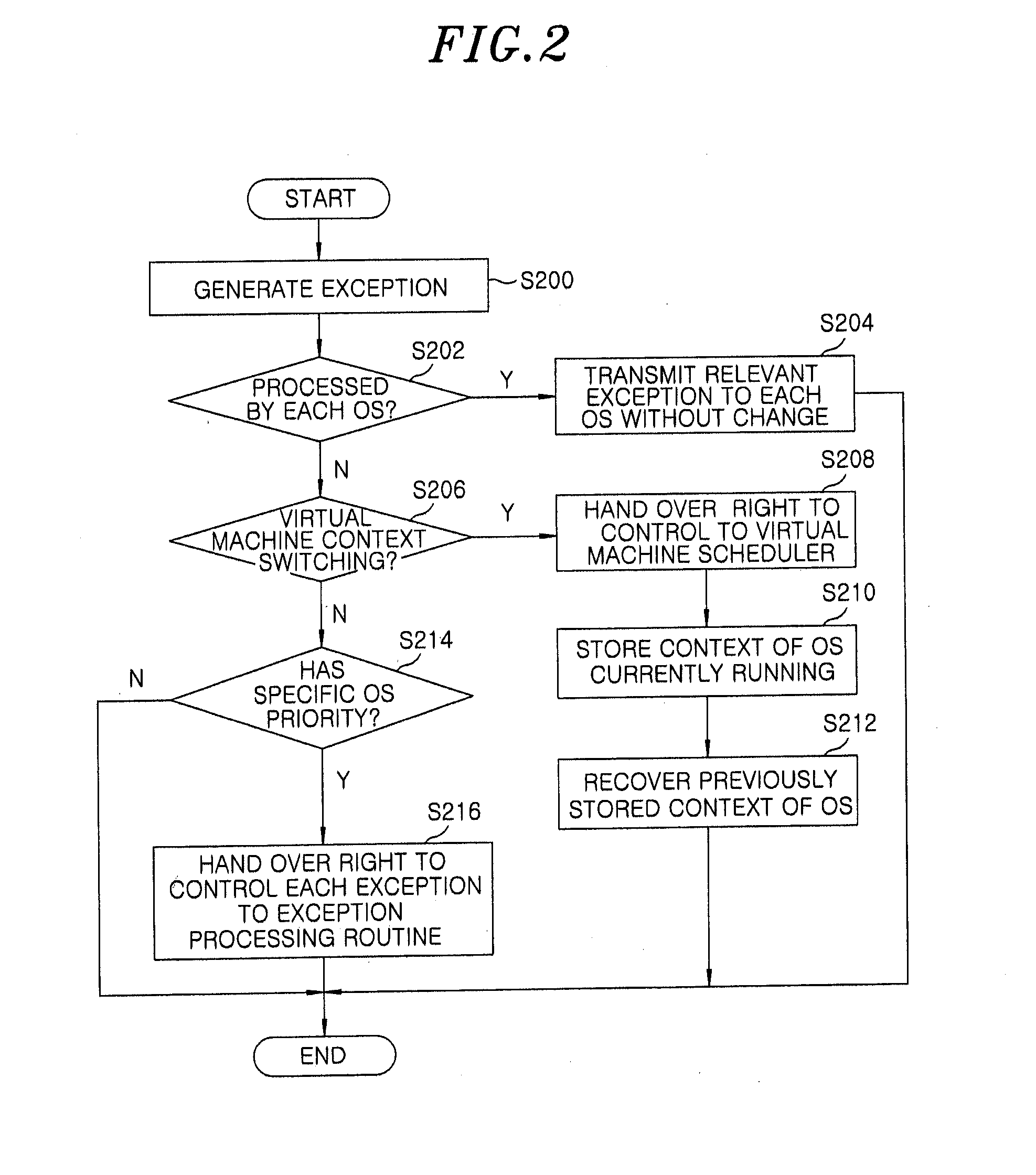
A virtual machine management apparatus includes a first Operating System (OS) kernel for supporting a first OS that runs on a virtualization-supporting terminal platform; and a second OS kernel for supporting a second OS that runs on the terminal platform. Further, the virtual machine management apparatus includes a virtual machine configuration manager for, when an exception task is requested based on the first OS or the second OS of the terminal platform, controlling processing of the exception task in compliance with a preset policy.
Owner:ELECTRONICS & TELECOMM RES INST
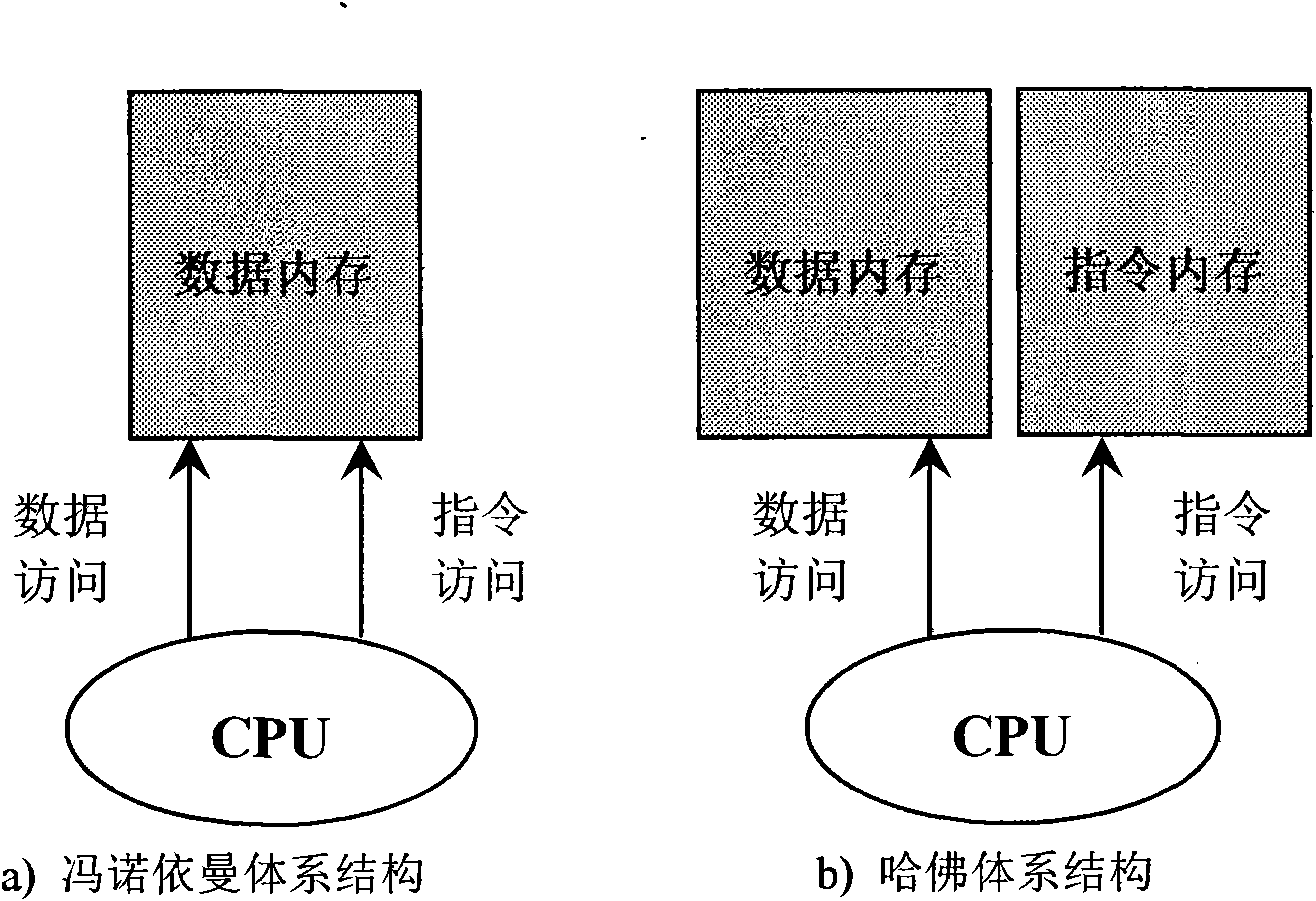
Kernel code protection method based on Harvard architecture
The invention belongs to the field of computer security, and provides a kernel code protection method by using the virtualized Harvard memory architecture by combining the research of virtualization technology in order to overcome the shortage of the kernel code protection of the prior operating system. The method realizes the virtualized Harvard memory architecture on a computer based on the vonNeumann architecture by a kernel patch form and separates an instruction operation and a data operation in a memory area of the kernel code so as to basically prevent the probability of distortion forthe kernel code. The invention can well prevent the threat of the kernel grade Rootkit on the kernel code, record information associated with illegal operations while ensuring the integrality of thekernel code, and provide clue for analyzing attacks; in the aspect of performance, the method fully utilizes an instruction TLB (Translation Lookaside Buffer, namely branch translation buffer or pagetable buffer) and data TLB without remarkably influencing the performance of the operating system.
Owner:HUNAN UNIV
System and method for executing convolution in a neural network
ActiveUS20200218978A1Improve executionReduce in quantityKernel methodsNeural learning methodsAlgorithmTheoretical computer science
A system and method of executing a convolution layer of a neural network may include: (a) selecting an output spatial position (OSP) of an output matrix data element of the convolution layer; (b) selecting, based on the selected OSP, a non-zero input element of an input matrix data element; (c) producing, based on the selected OSP, a vector of kernel elements from a kernel matrix data element; (d) performing a vectoral multiplication operation of the selected non-zero input element and the vector of kernel elements, and accumulating a product of the vectoral multiplication in a vector register of a processor; (e) repeating (c) and (d) with subsequent non-zero input elements and corresponding vectors of kernel elements to obtain an outcome of the convolution of the selected OSP; and (f) repeating (a) through (e) with subsequent selection of OSPs, to obtain an outcome of the convolution layer.
Owner:NEURALMAGIC INC
Creditability detection method of computer
ActiveCN102214278AImprove securityIncrease flexibilityPlatform integrity maintainanceComputerized systemChain of trust
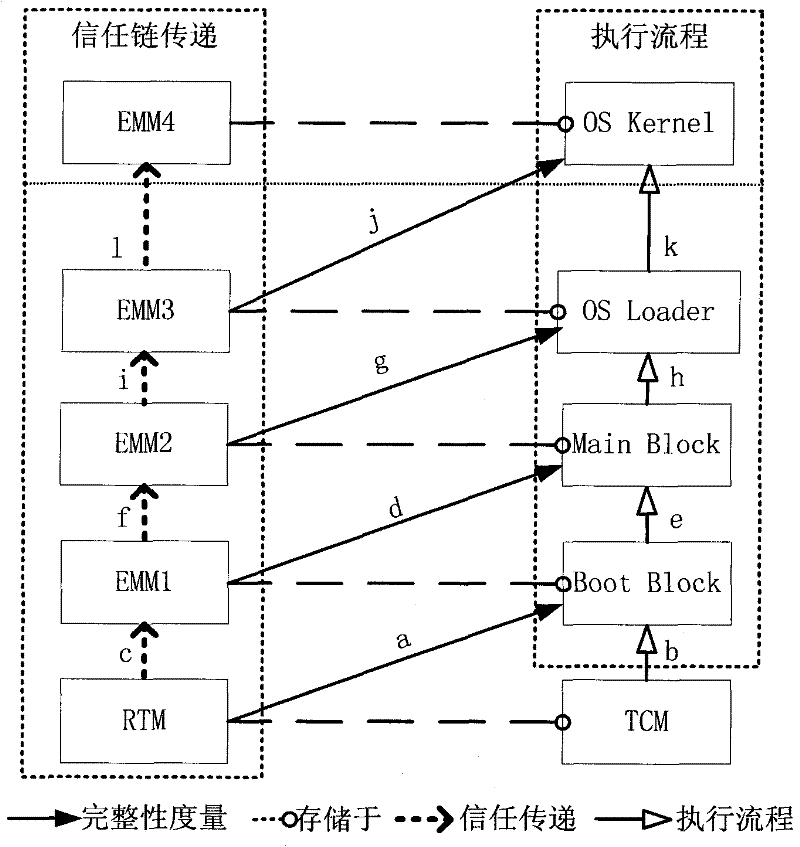
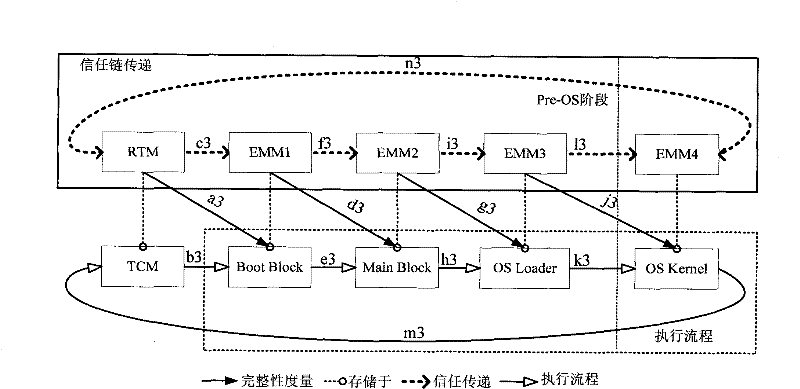
The invention relates to a creditability detection method of a computer. The method comprises the following steps of: building an annular trust chain, wherein the annular trust chain has end points which sequentially are a trusted cryptography module (TCM), a boot block of a basic input output system (BIOS), a main block, an operating system (OS) loader and an OS kernel; initializing integrity measurement from any one of the end points on the annular trust chain, and sequentially carrying out the integrity measurement along a clockwise direction or an anticlockwise direction of the annular trust chain until the measurement of all end points on the annular trust chain is finished; and after the measurement of the last end point which is subjected to the integrity measurement is finished, transmitting trust to the TCM, and finishing a final creditability report of a computer platform by the TCM. By the creditability detection method of the computer, the safety and validation flexibilityof the computer platform are improved, the maintenance updating cost of a computer system is reduced, and the expansion of the computer system can be facilitated.
Owner:NATIONZ TECH INC
Method and apparatus for managing thread execution in a multithread application
InactiveUS7216346B2Easy to useBetter conformsProgram initiation/switchingMemory systemsOperational systemApplication software
A method for managing the suspension and resumption of threads on an individual basis in an information handling system having an operating system (OS) kernel and a user process having multiple threads of execution. An originating thread issues a pthread_kill( ) service request to the OS kernel to send a specified signal (thread-stop or thread-continue) to a specified target thread within the same process to suspend or resume execution of the target thread. More particularly, in response to a request from a thread to suspend the execution of the target thread, the OS kernel sends a thread-stop signal (SIGTHSTOP) to the target thread, transferring control within the target thread from a normally executing program portion to a signal interrupt routine. Upon gaining control, the signal interrupt routine issues a service request to the kernel to stop the target thread. In response to a request from a thread to resume execution of the target thread, the OS kernel sends a thread-continue signal (SIGTHCONT) to the target thread to post the waiting target thread and return control to the signal interrupt routine. Upon regaining control, the signal interrupt routine returns control to the program at the point of interrupt.
Owner:INT BUSINESS MASCH CORP
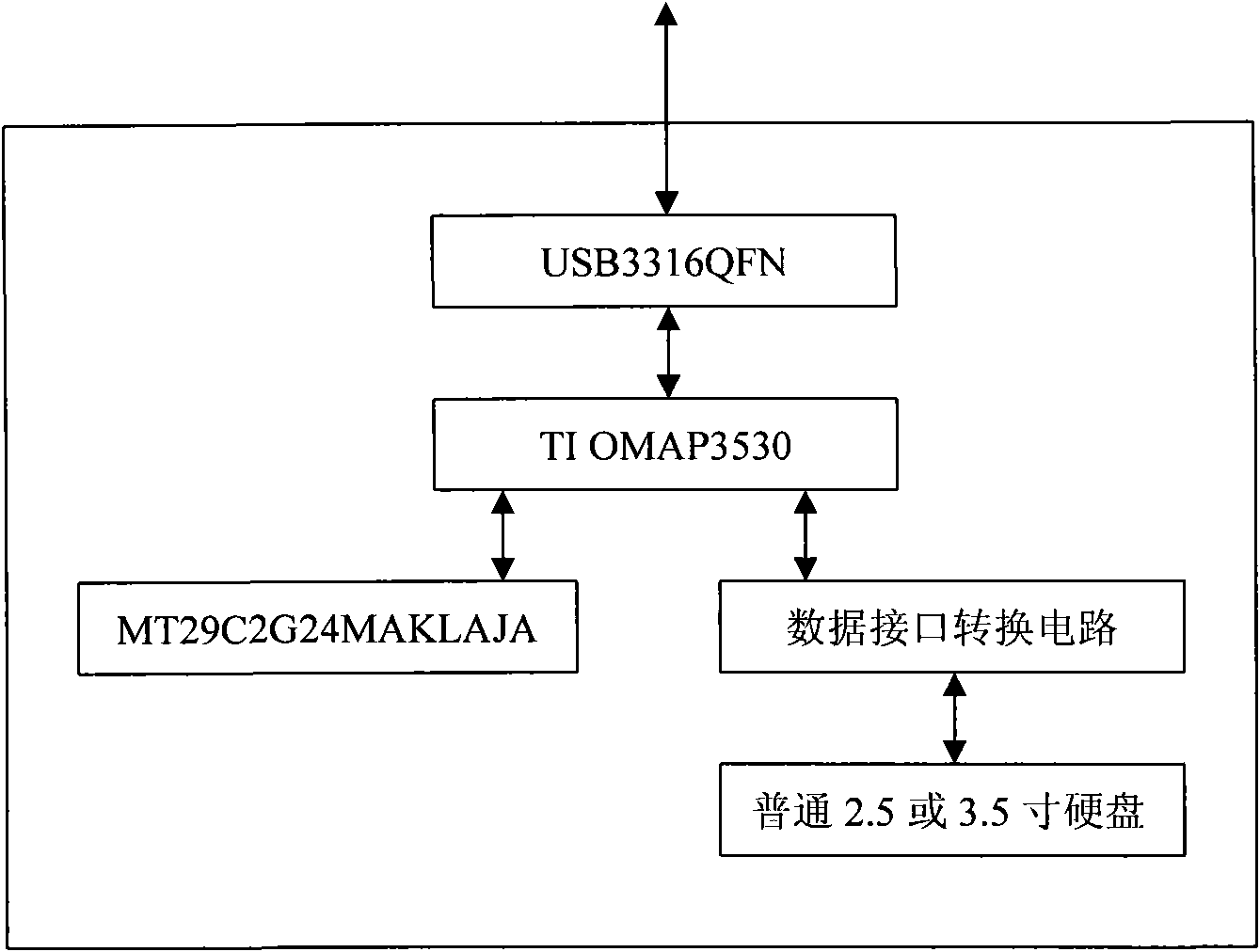
A method for hardware drive program of intelligent loading mobile phone
InactiveCN1964526AOvercome the problem of limited storage space resourcesEasy loadingRadio/inductive link selection arrangementsSubstation equipmentOperational systemProcessor register
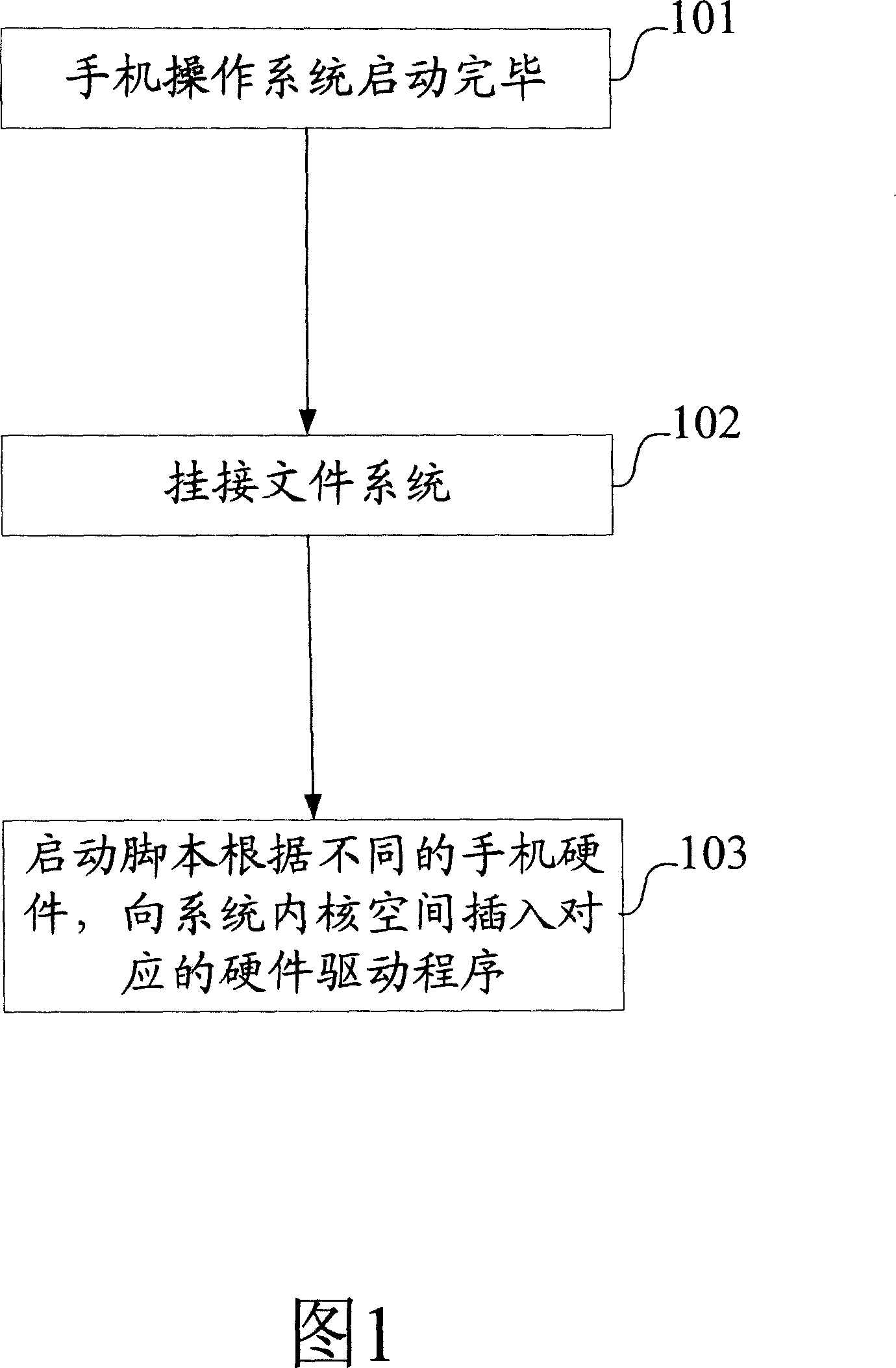
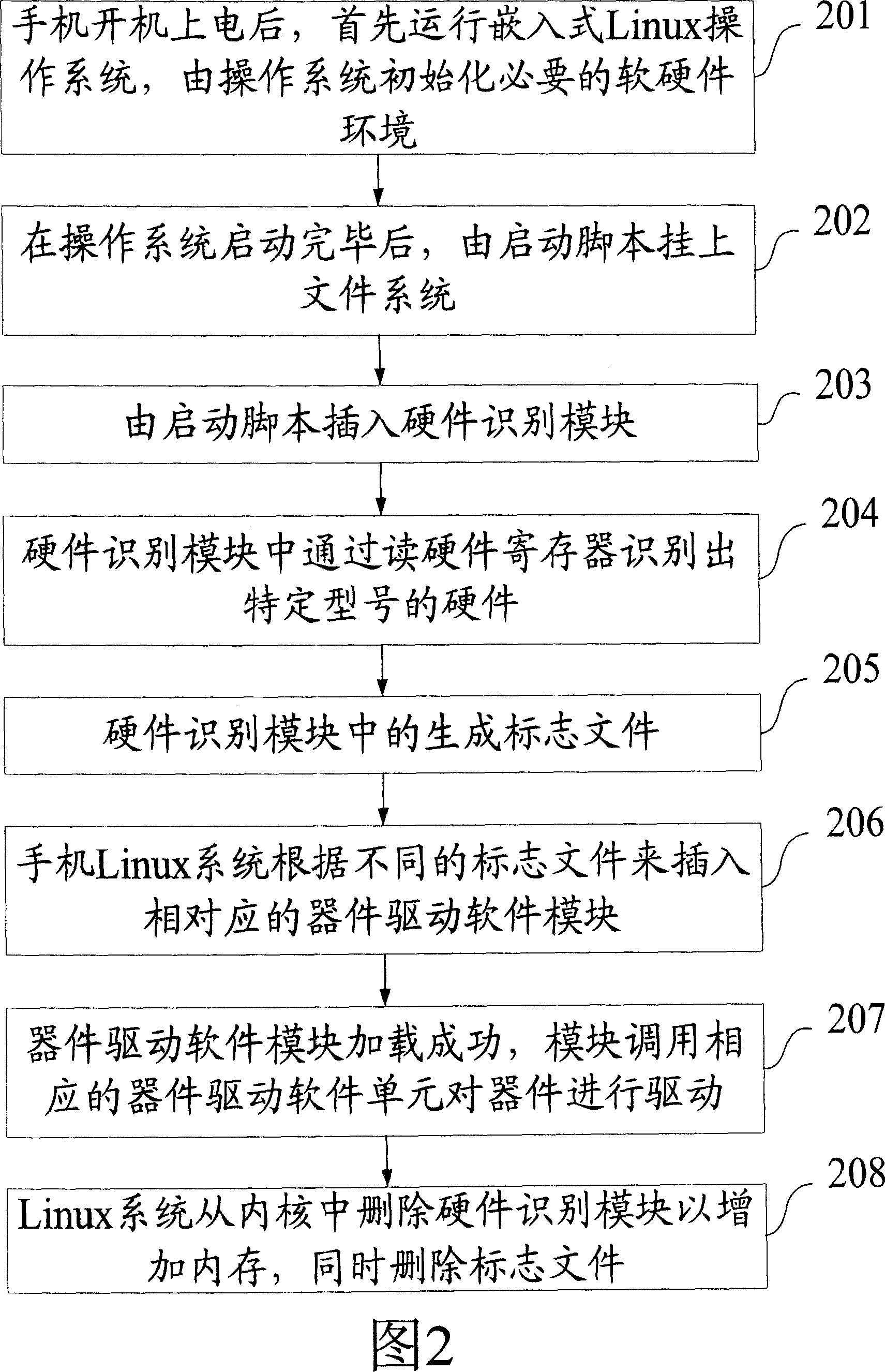
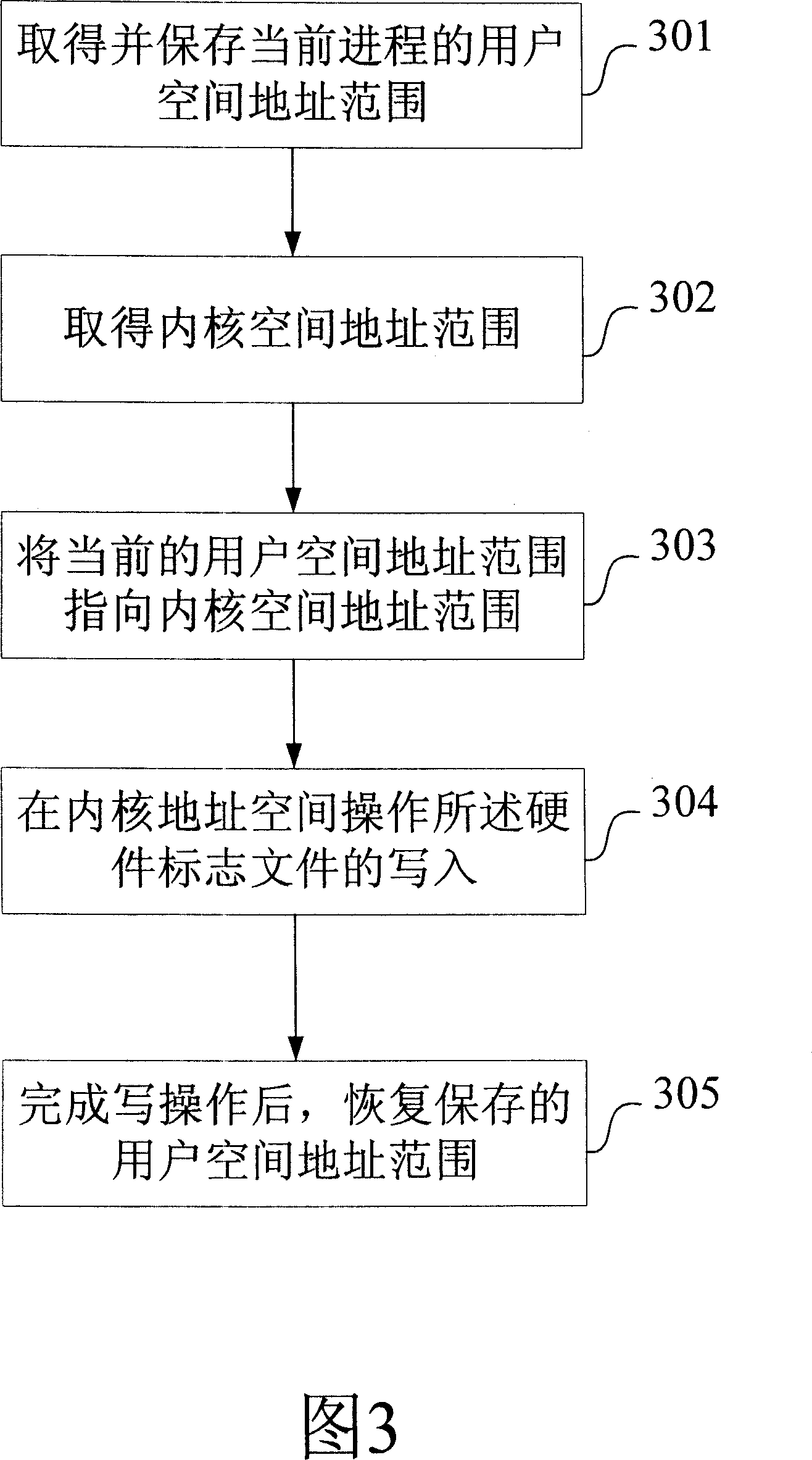
The provided intelligent loading method for mobilephone hardware driver comprises: inserting a hardware recognition module into OS kernel to read hardware register and recognize hardware type, generating hardware mark file; then inserting hardware driver into OS kernel. This invention overcomes defect in prior art, saves cost, and convenient to expand and update.
Owner:ZTE CORP
Multiprocessor system, and method for shared use of devices among operating systems of multiprocessor system
ActiveUS20100325329A1Improve performanceLow costSpecific program execution arrangementsOperational systemMulti processor
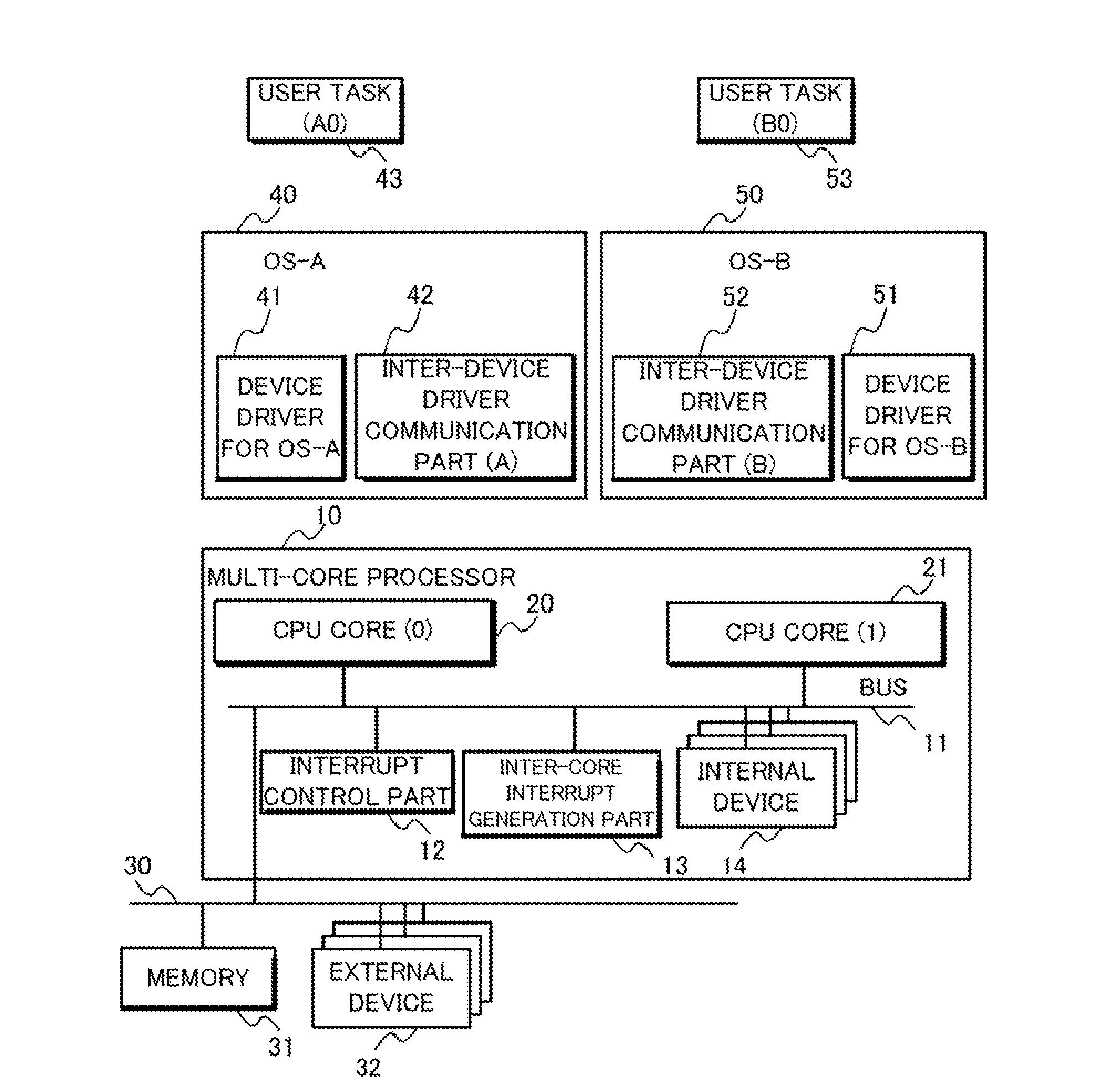
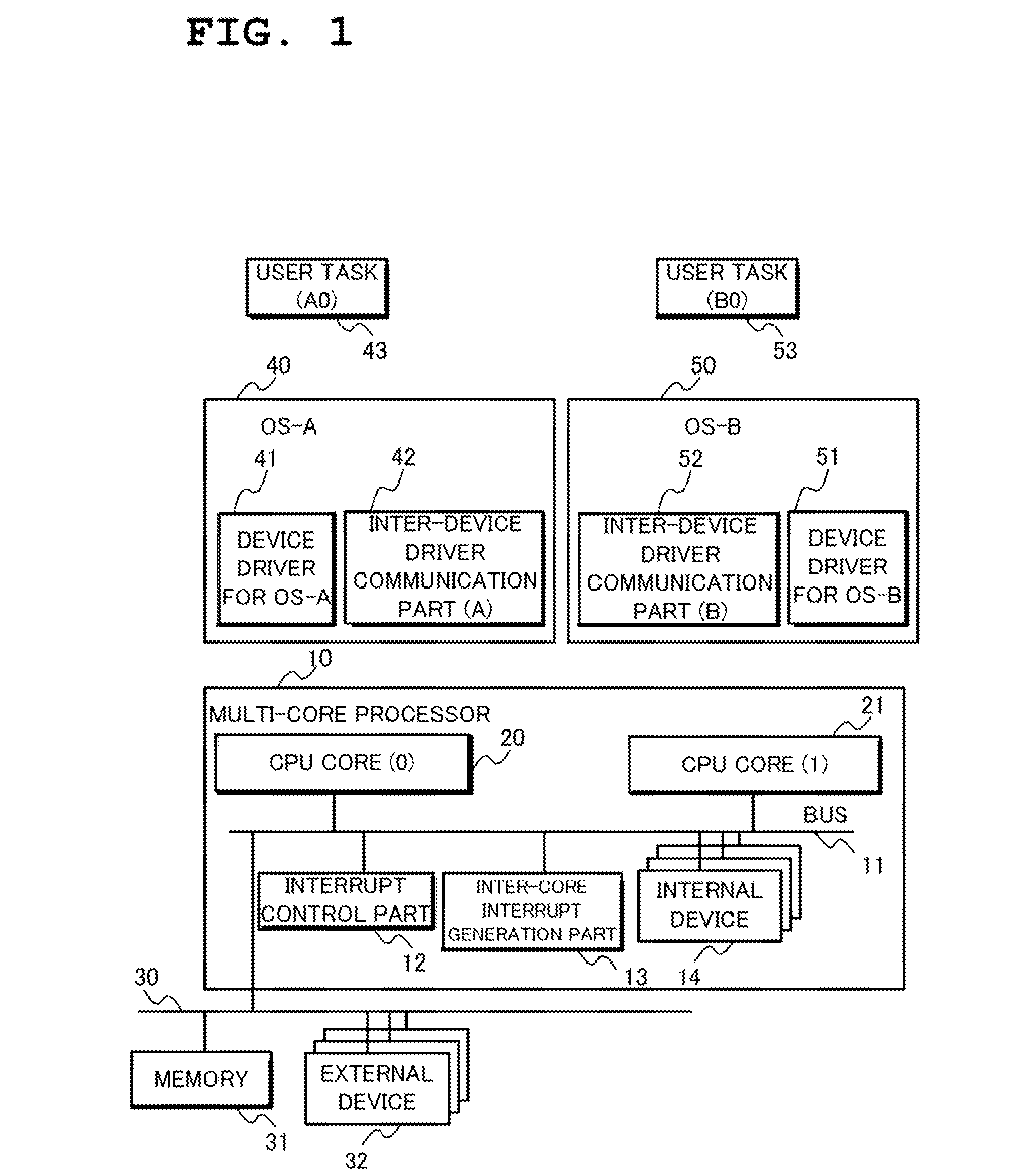
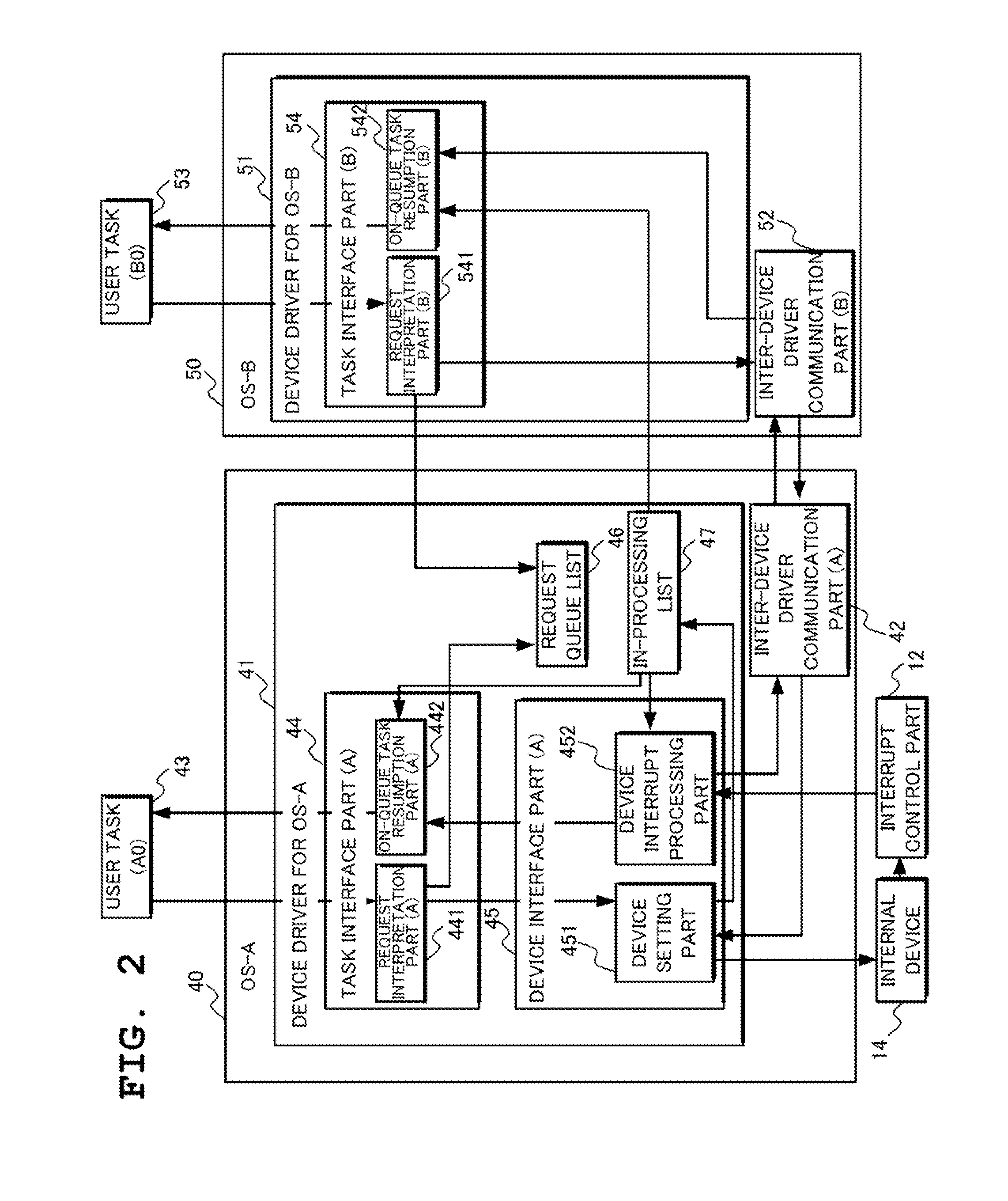
With a system in which a plurality of OSs run on a multi-core processor and which is based on a client-server approach where one OS performs device access on behalf of the other OSs, if a device is to be accessed from tasks on the plurality of OSs, there have been problems of a reduction in performance and an increase in design and manufacturing cost due to the necessity of providing proxy servers.In a multiprocessor system with a plurality of OSs 40, 50 running thereon, each of the plurality of OSs has a device driver 41, 51 which accesses devices for shared use among the OSs, wherein the device driver has at least either of a device interface part 45 or a task interface part 44, 54 which performs inter-OS communication at the OS kernel layer, and wherein the device interface part 45 accesses a device 14 to be operated by the device driver and the task interface part receives a device access request from a task running on each OS and returns a device access result to the task.
Owner:NEC ASIA PACIFIC PTE LTD
Defense method for kernel-level return-oriented rootkits
InactiveCN102375957AFree from harmAchieve the purpose of the attackPlatform integrity maintainanceOperational systemControl data
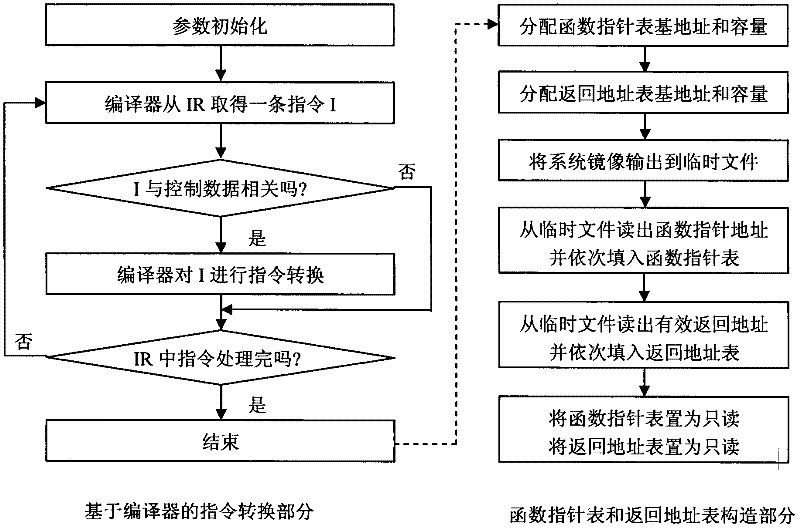
The invention discloses a defense method for kernel-level return-oriented rootkits, which mainly solves the problem of incapability of defending the latest kernel-level return-oriented rootkits attack in the prior art. The method comprises the following implementation steps of: distributing an index for each piece of control data by a compiler and converting a related instruction so as not to directly use the control data during program skip but search a certain skip table by using the index distributed by the compiler to obtain a really effective skip address to indirectly perform; and then collecting all effective skip addresses, namely control data, in a system to a function pointer table and returning to an address table for protection. By adopting the method, a second step of conducting attack cannot be finished by the kernel-level return-oriented rootkits, namely the original execution flow of the system is required to be changed by rewriting a certain piece of control data, and the method can be used for protecting safety of an operating system.
Owner:XIDIAN UNIV
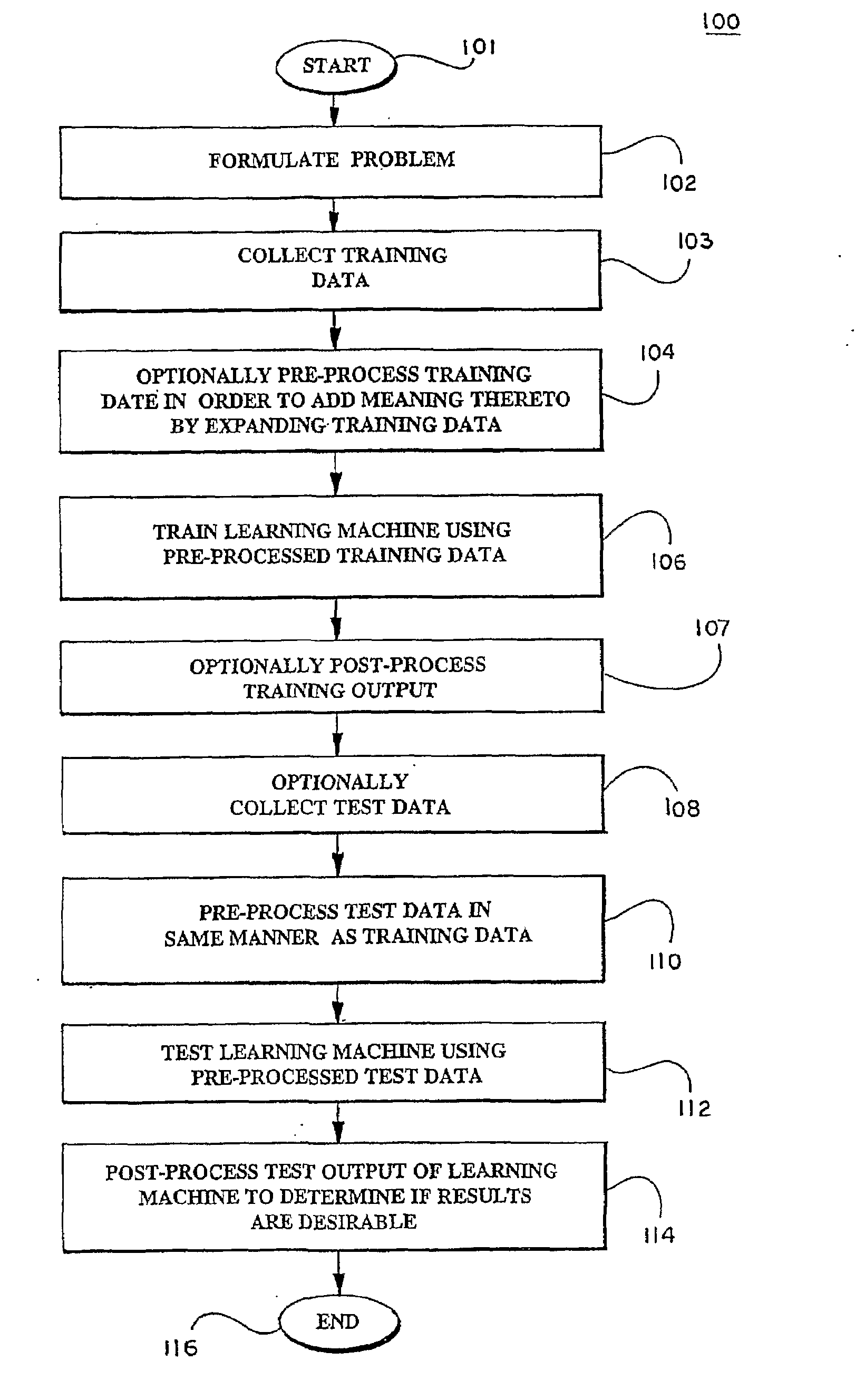
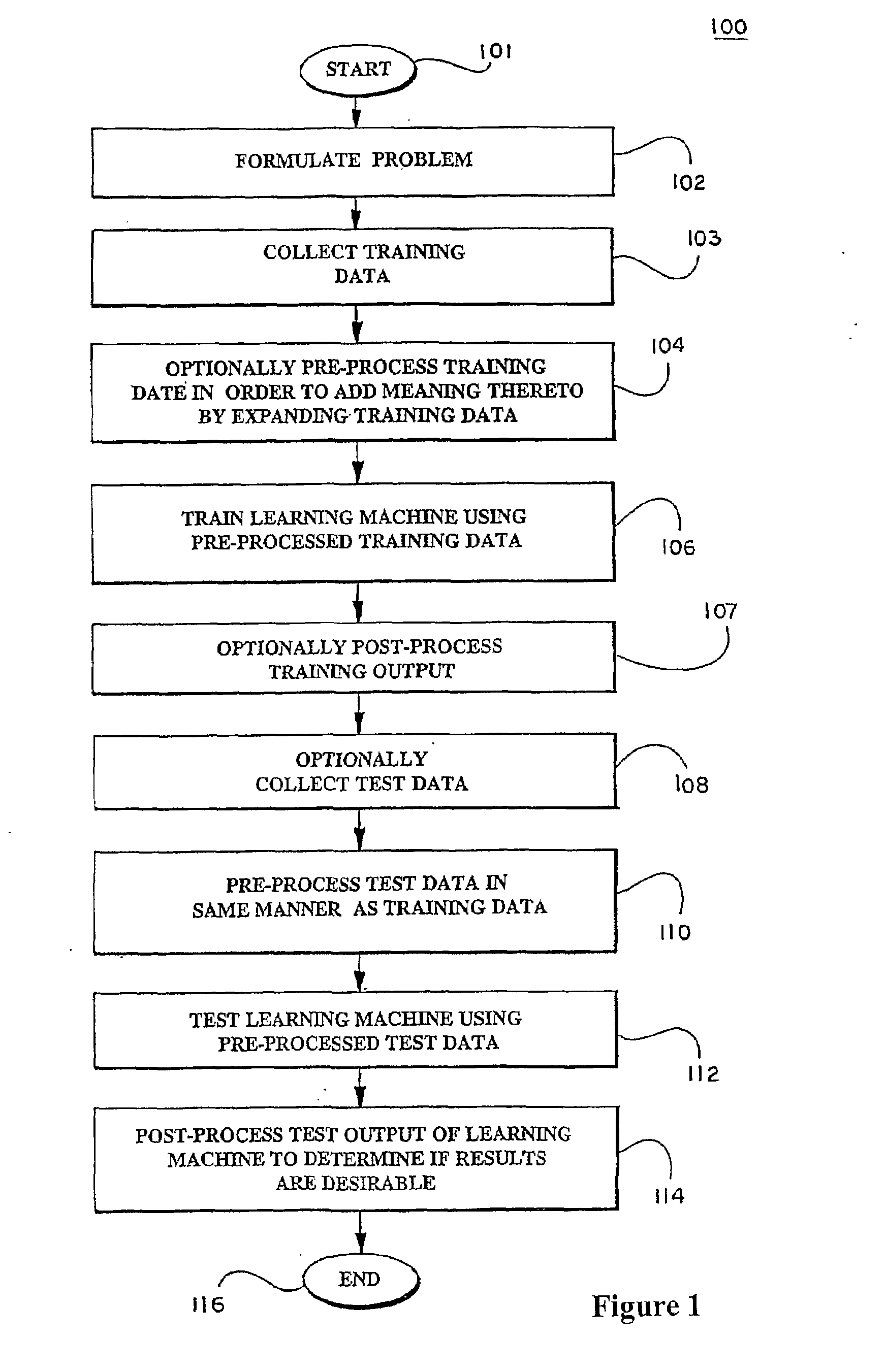
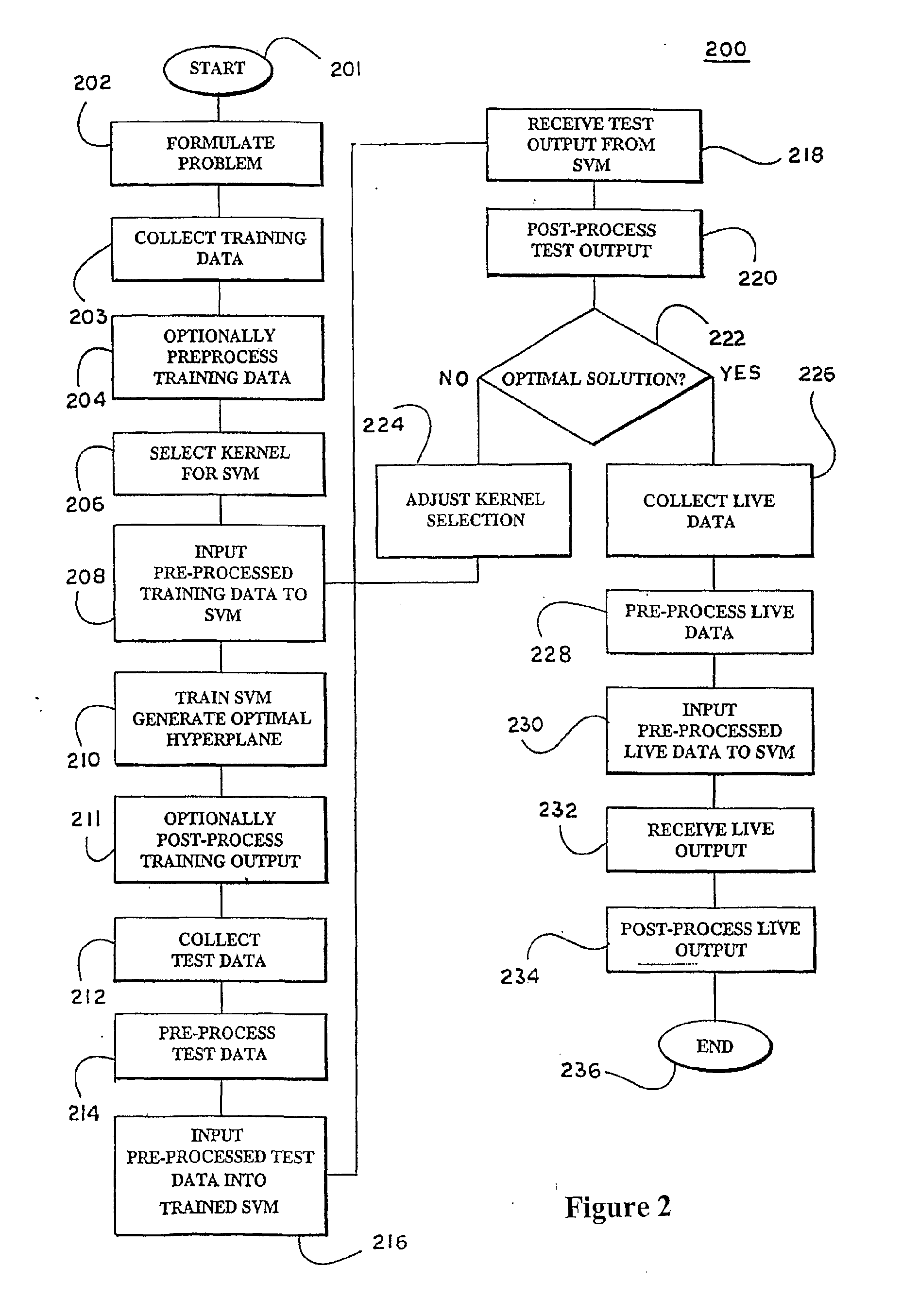
Kernels and methods for selecting kernels for use in learning machines
Learning machines, such as support vector machines, are used to analyze datasets to recognize patterns within the dataset using kernels that are selected according to the nature of the data to be analyzed. Where the datasets possesses structural characteristics, locational kernels can be utilized to provide measures of similarity among data points within the dataset. The locational kernels are then combined to generate a decision function, or kernel, that can be used to analyze the dataset. Where an invariance transformation or noise is present, tangent vectors are defined to identify relationships between the invariance or noise and the data points. A covariance matrix is formed using the tangent vectors, then used in generation of the kernel.
Owner:BIOWULF TECH +1
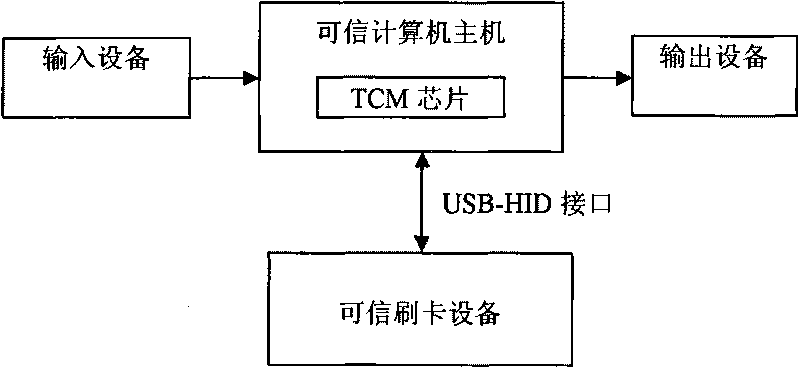
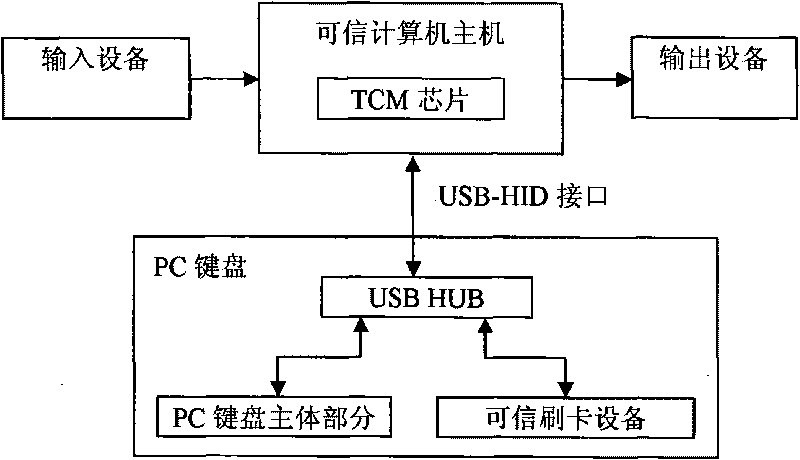
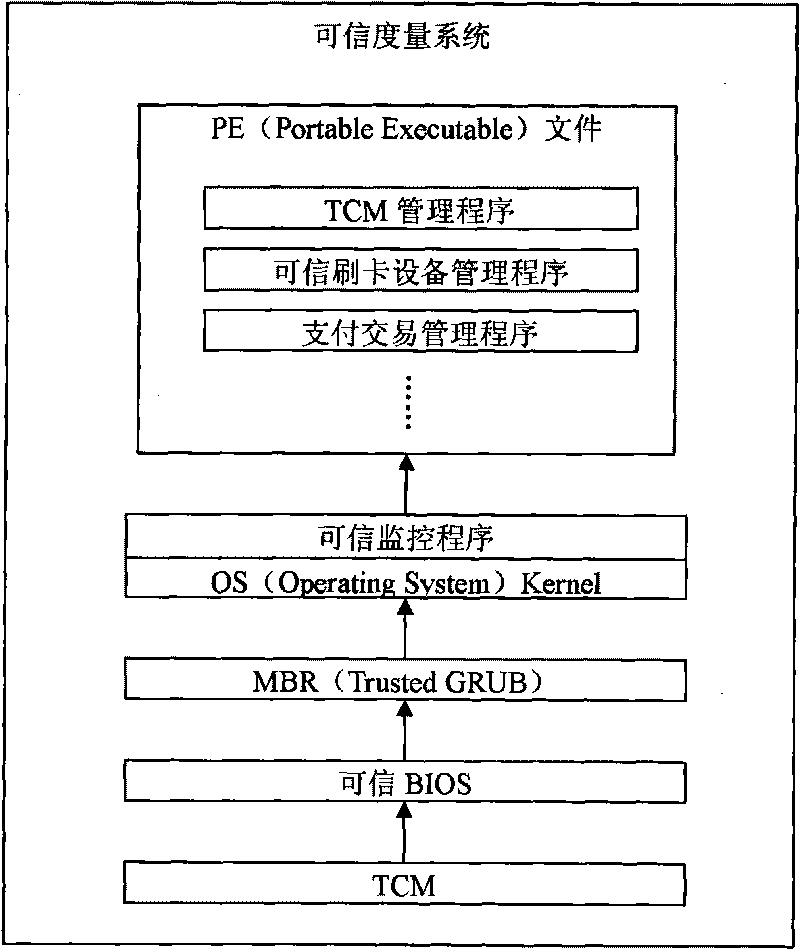
Trusted payment computer system
InactiveCN101739622APrevent forgeryPrevent tamperingPayment architectureCoded identity card or credit card actuationPayment transactionSoftware system
A trusted payment computer system relates to the technical field of information security. The system comprises input equipment, a trusted computer mainframe, output equipment and trusted card reading equipment, wherein the input equipment, the trusted computer mainframe and the output equipment are connected in sequence; and the trusted card reading equipment is connected with the trusted computer mainframe by a USB-HID interface. The input equipment includes a keyboard and a mouse and the output equipment is a display. The system is characterized in that TCM chips are embedded in the trusted computer mainframe to serve as the root of trust for measurement, the root of trust for reporting and the root of trust for storage. A system of trust for measurement inside the trusted computer mainframe completes the following step-by-step measurement: measurement of integrity carried out on trusted BIOS by TCM, measurement of integrity carried out on MBR by trusted BIOS, measurement of integrity carried out on OS Kernel by MBR and measurement of integrity carried out on a PE file by a trusted monitoring program. A software system installed on the trusted computer mainframe contains a TCM management program, a trusted card reading equipment management program and a payment transaction management program. The system is convenient and easy to use and can reliably ensure the security of the whole trusted payment transaction.
Owner:TSINGHUA TONGFANG CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com