Patents
Literature
443 results about "Call stack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
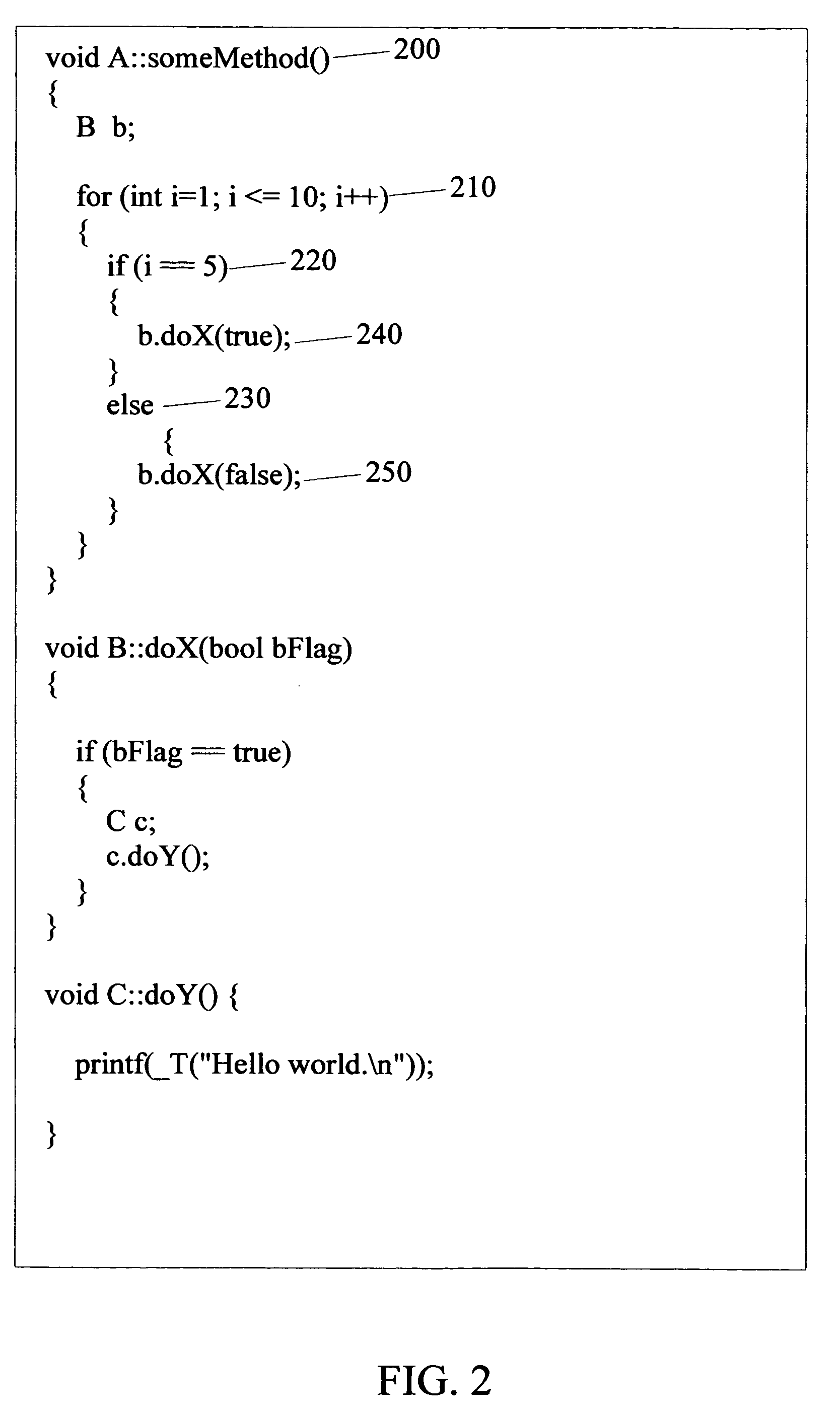
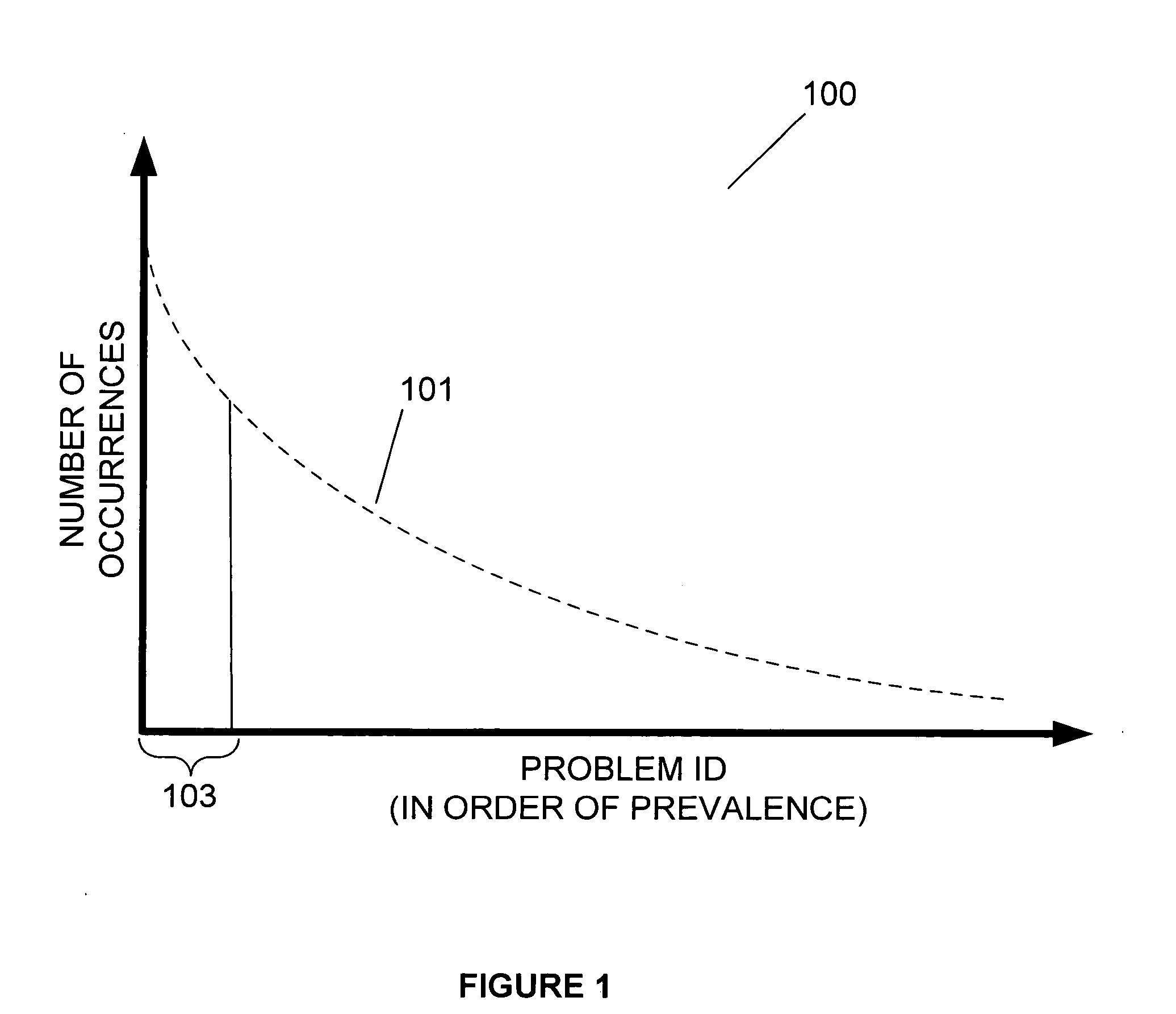
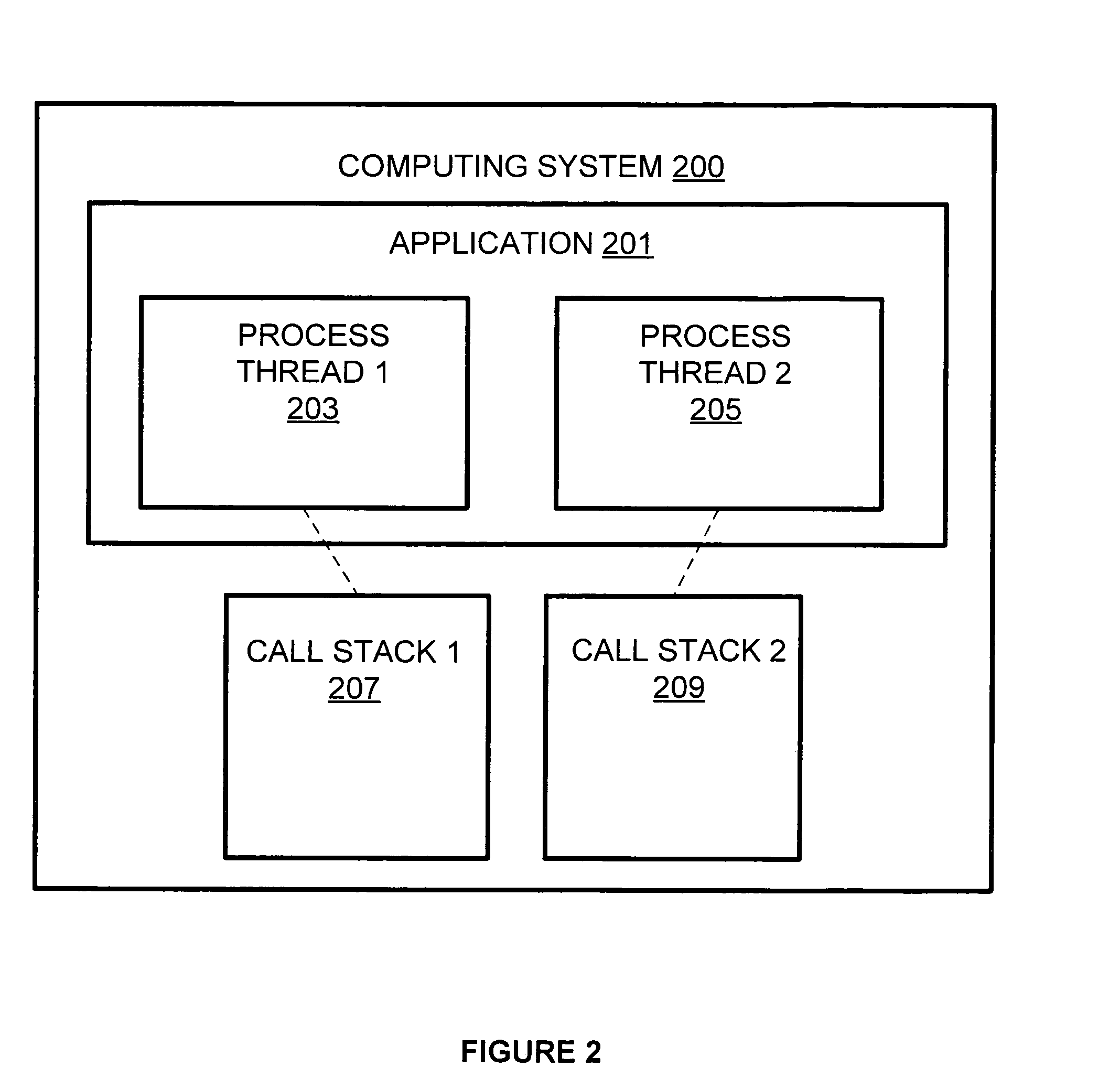
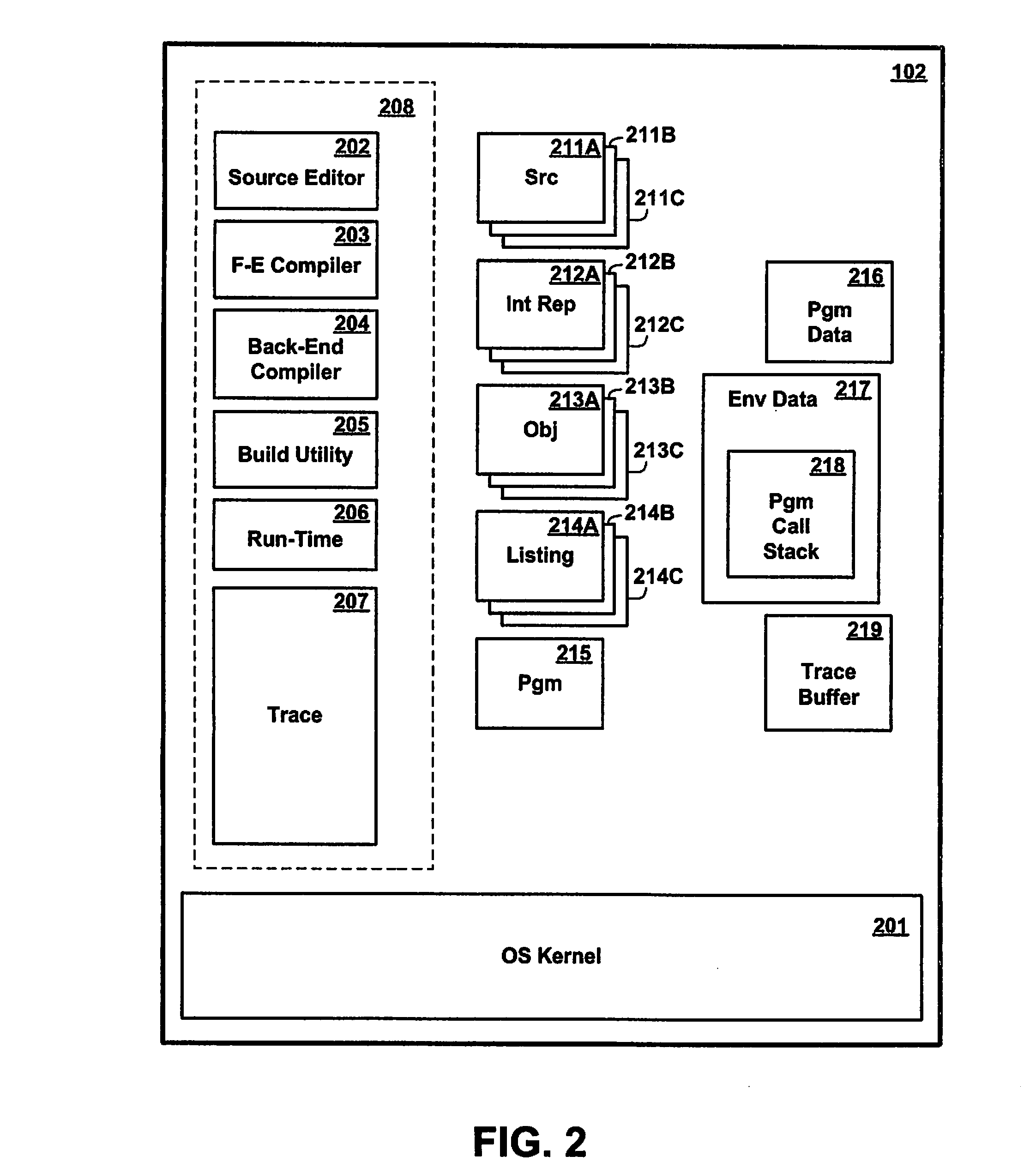
In computer science, a call stack is a stack data structure that stores information about the active subroutines of a computer program. This kind of stack is also known as an execution stack, program stack, control stack, run-time stack, or machine stack, and is often shortened to just "the stack". Although maintenance of the call stack is important for the proper functioning of most software, the details are normally hidden and automatic in high-level programming languages. Many computer instruction sets provide special instructions for manipulating stacks.
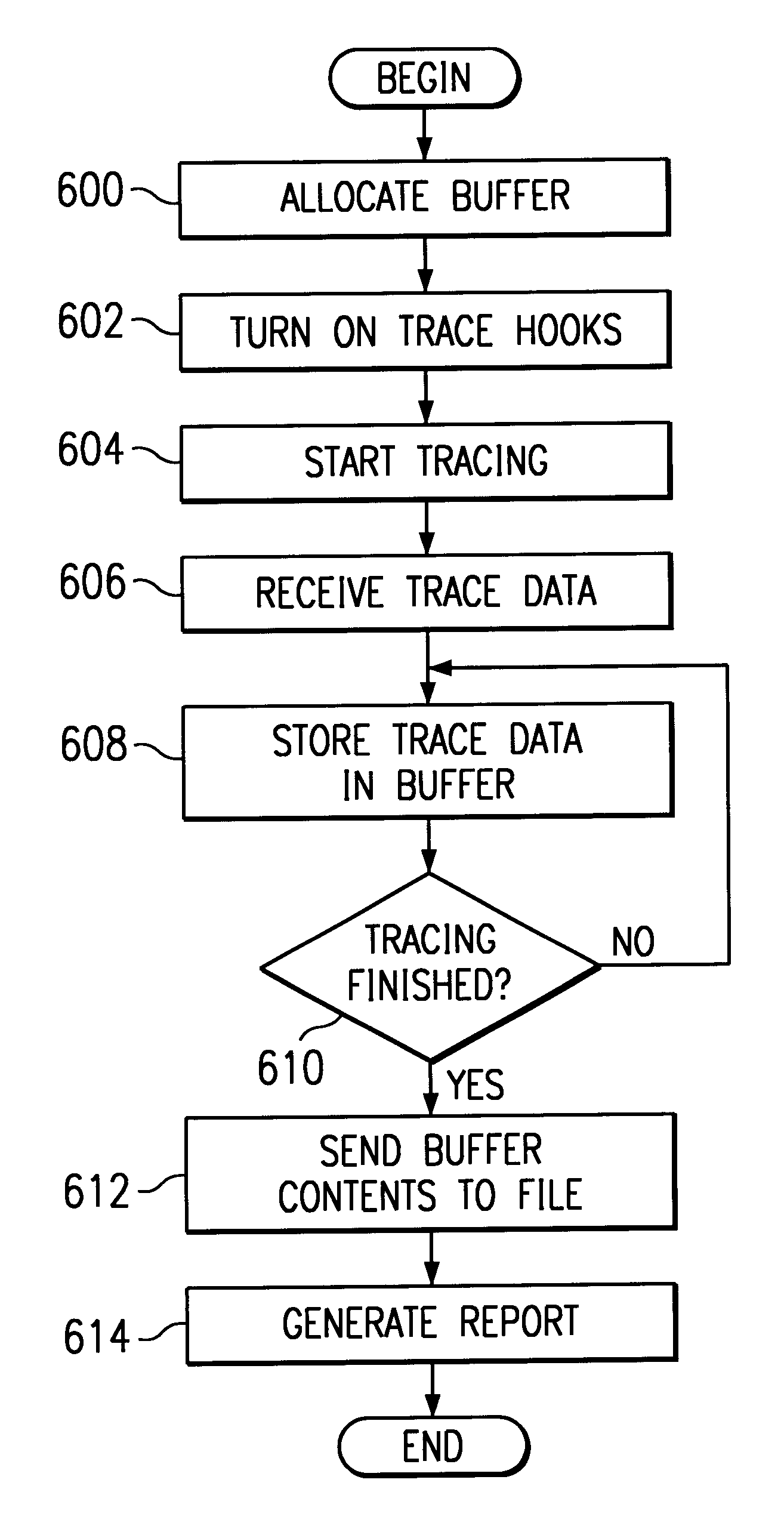
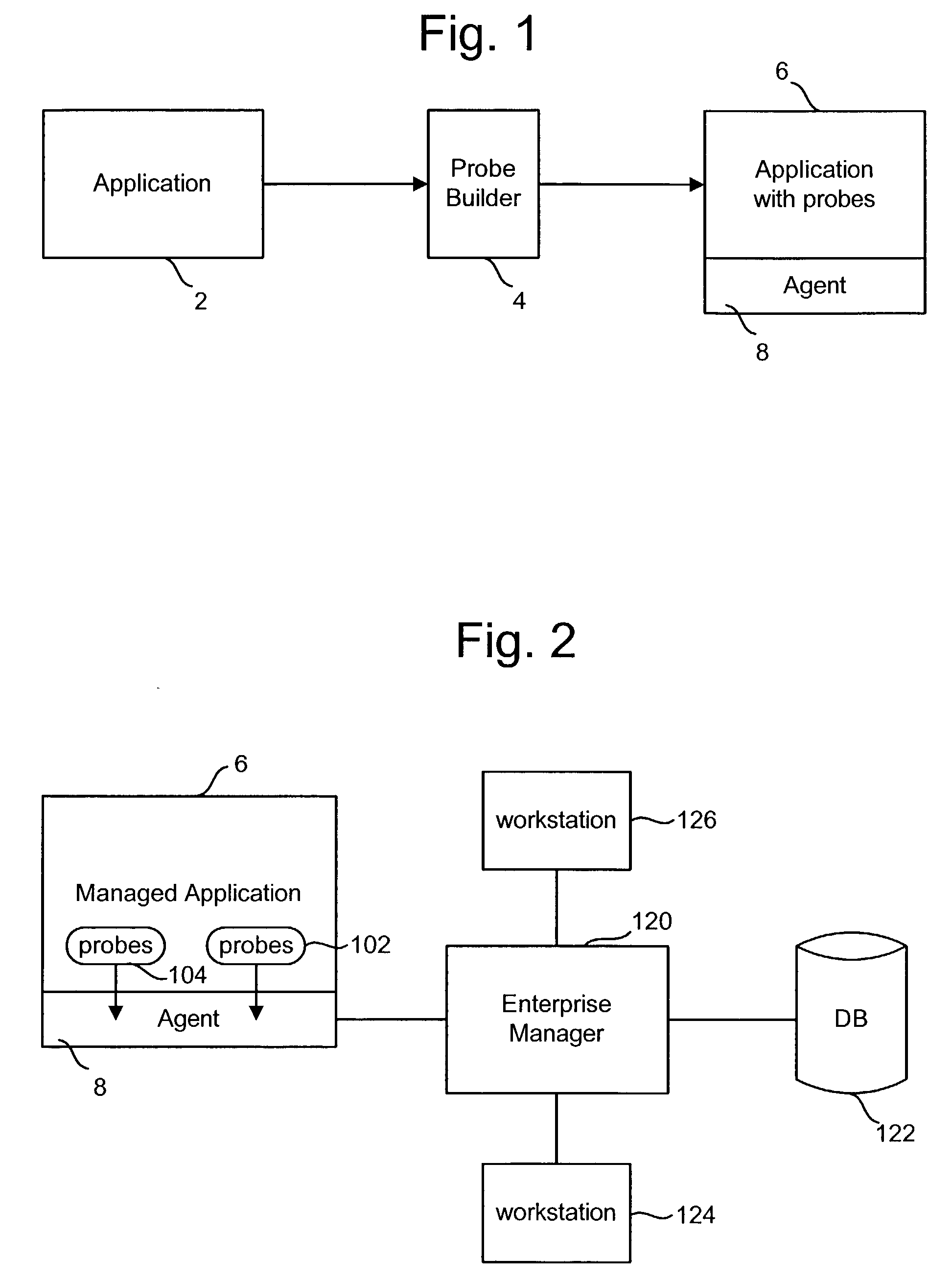
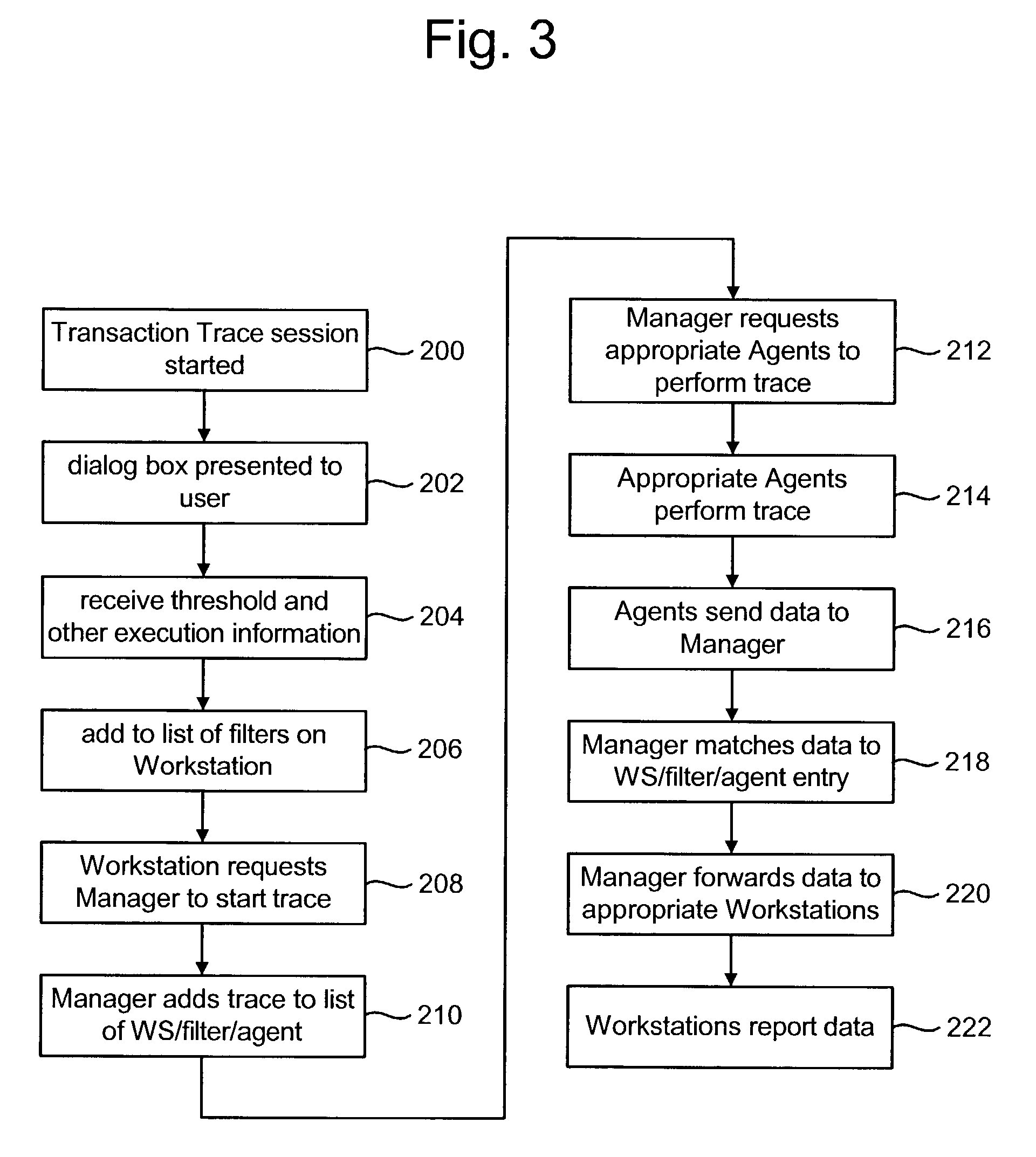
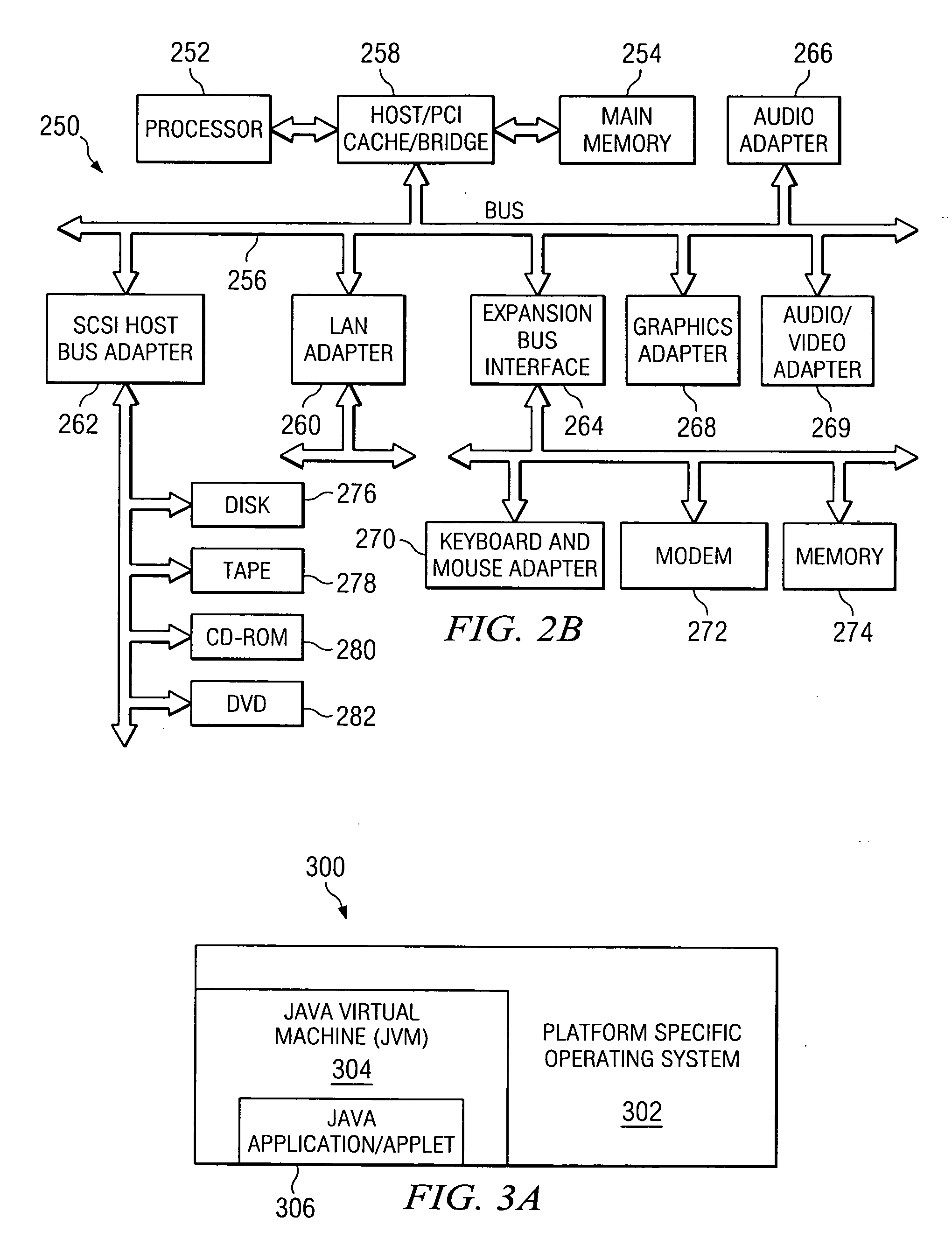
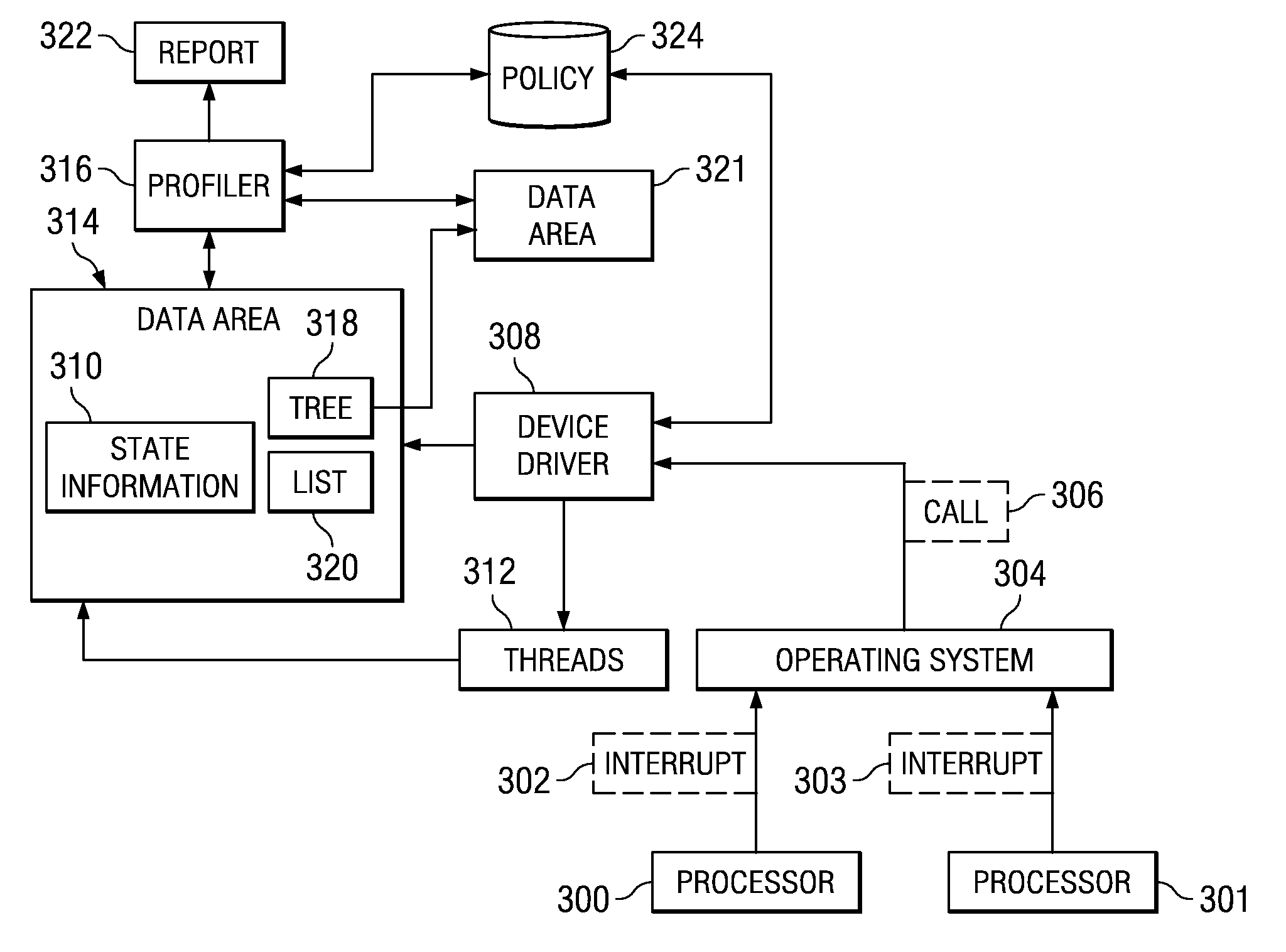
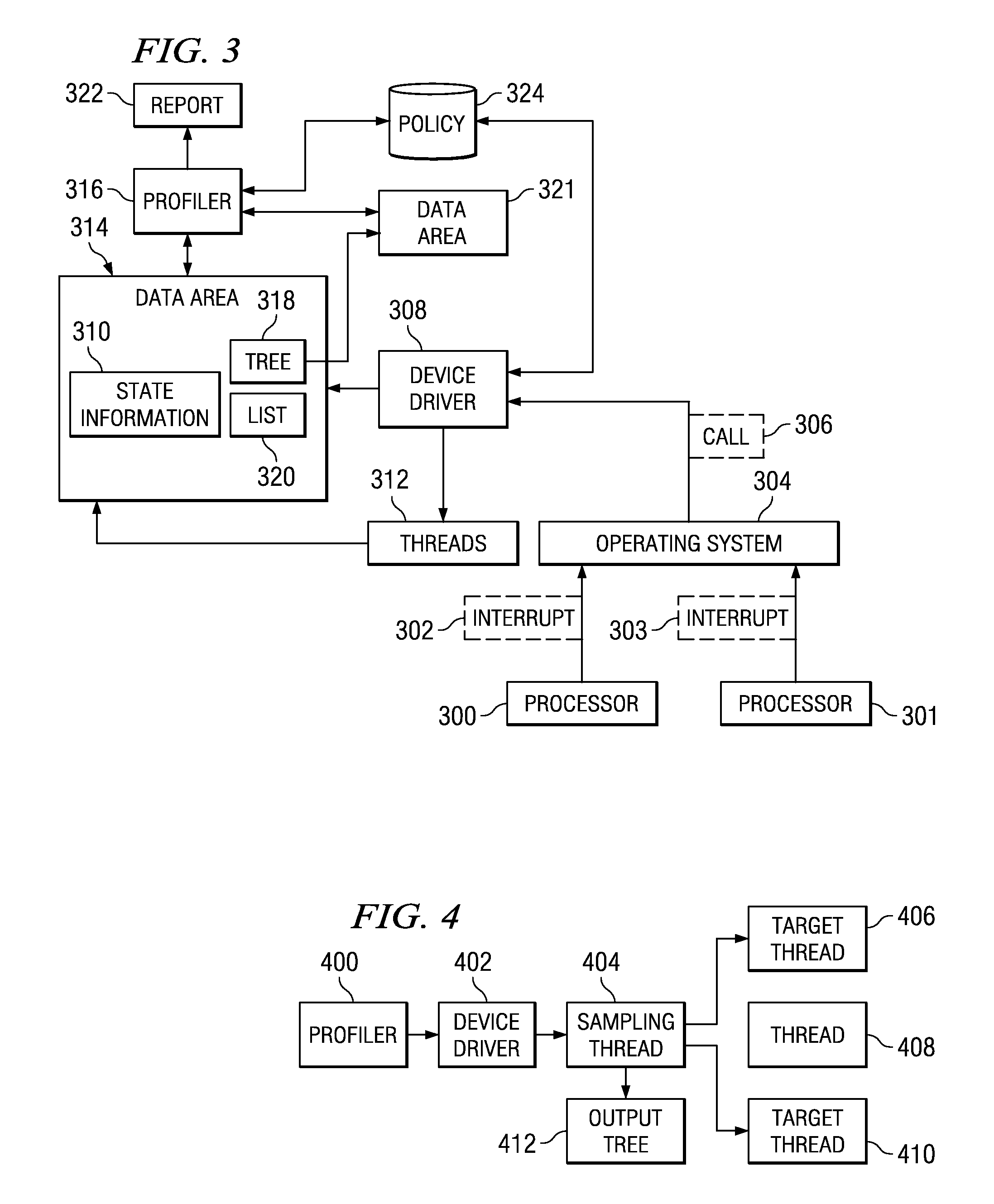
Method and system for merging event-based data and sampled data into postprocessed trace output
InactiveUS6513155B1Hardware monitoringSpecial data processing applicationsData processing systemCall stack
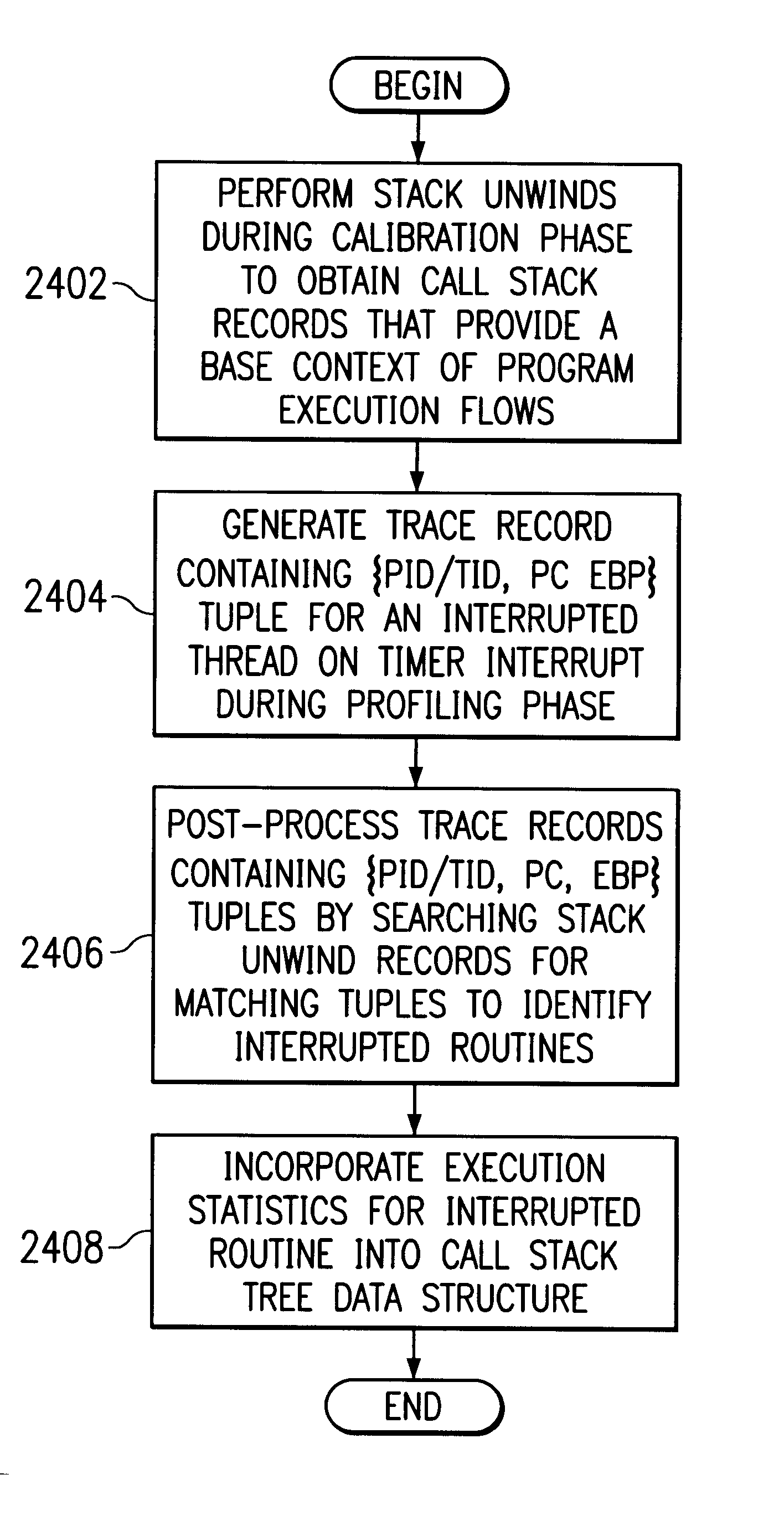
A process and system for profiling code executing on a data processing system is provided. Event-based trace data is recorded in response to selected events, and the event-based trace data includes an indication which code is being interrupted. The trace data may be processed to identify a thread or method that was executing during the event. A periodically occurring event is also detected, and a call stack associated with the profiled code is identified in response to detection of the periodically occurring event, such as a timer interrupt. The call stack is examined to identify each routine that is currently executing during the periodically occurring event, and the trace data is recorded with the call stack information. The trace data from the recorded events and the trace data from the call stacks are processed to generate a tree structure in which the nodes indicate the call structure of the routine information from both the trace events and the call stacks.
Owner:IBM CORP
User interface for viewing performance information about transactions
Data about a transaction is accessed. The transaction has a set of components. A graphical representation of the components of the transaction is displayed such that the graphical representation includes a time axis and a call stack position axis. In one embodiment, the time axis depicts time left to right and the call stack position axis depicts call stack position top to bottom. Additionally, the user interface can receive a selection of one of the components, access data for the selected component and display additional details about that selected component.
Owner:CA TECH INC
Minimizing profiling-related perturbation using periodic contextual information
InactiveUS6662358B1Digital data information retrievalError detection/correctionCall stackProgram counter
A method and system for monitoring performance of a program is provided. A trace record containing a call stack associated with the program is periodically generated. An occurrence of a selected event or a timer interrupt is detected, and in response, an execution context sample is obtained that contains a process identifier, a thread identifier, a program counter, and a stack pointer. A trace record containing the execution context sample data is generated. During post-processing, the execution context samples are compared with a call stack to identify the routine associated with the execution sample data.
Owner:IBM CORP
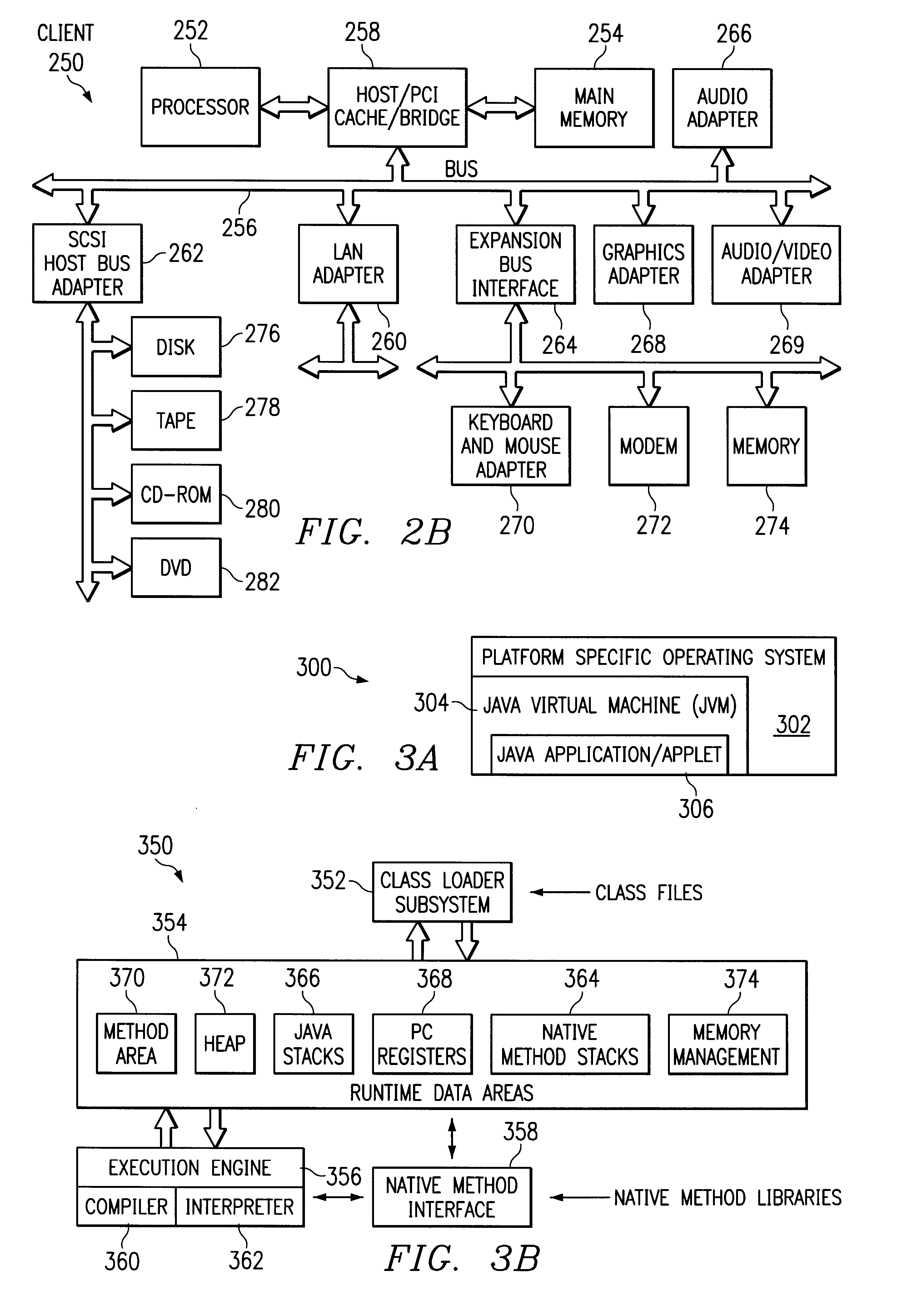
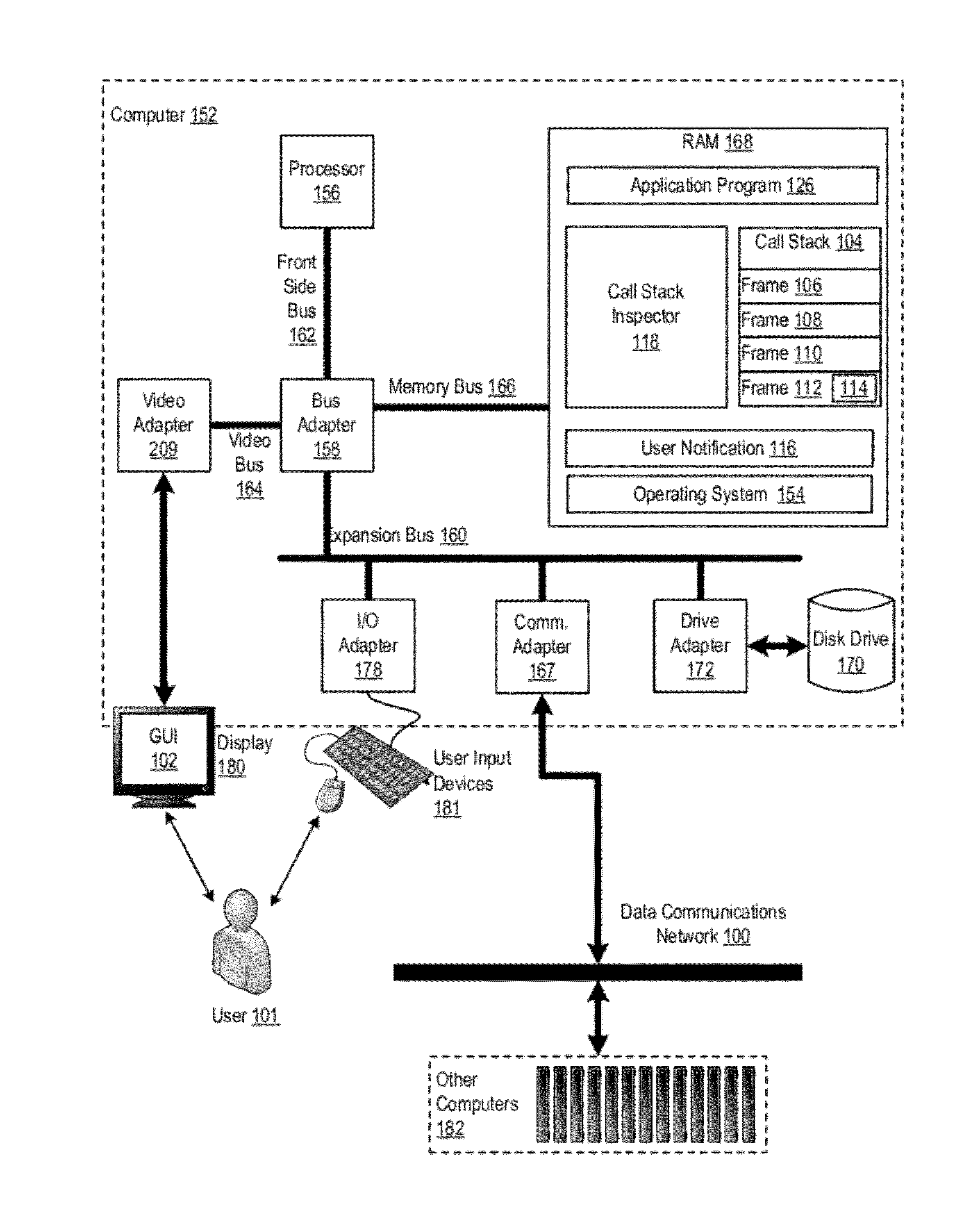
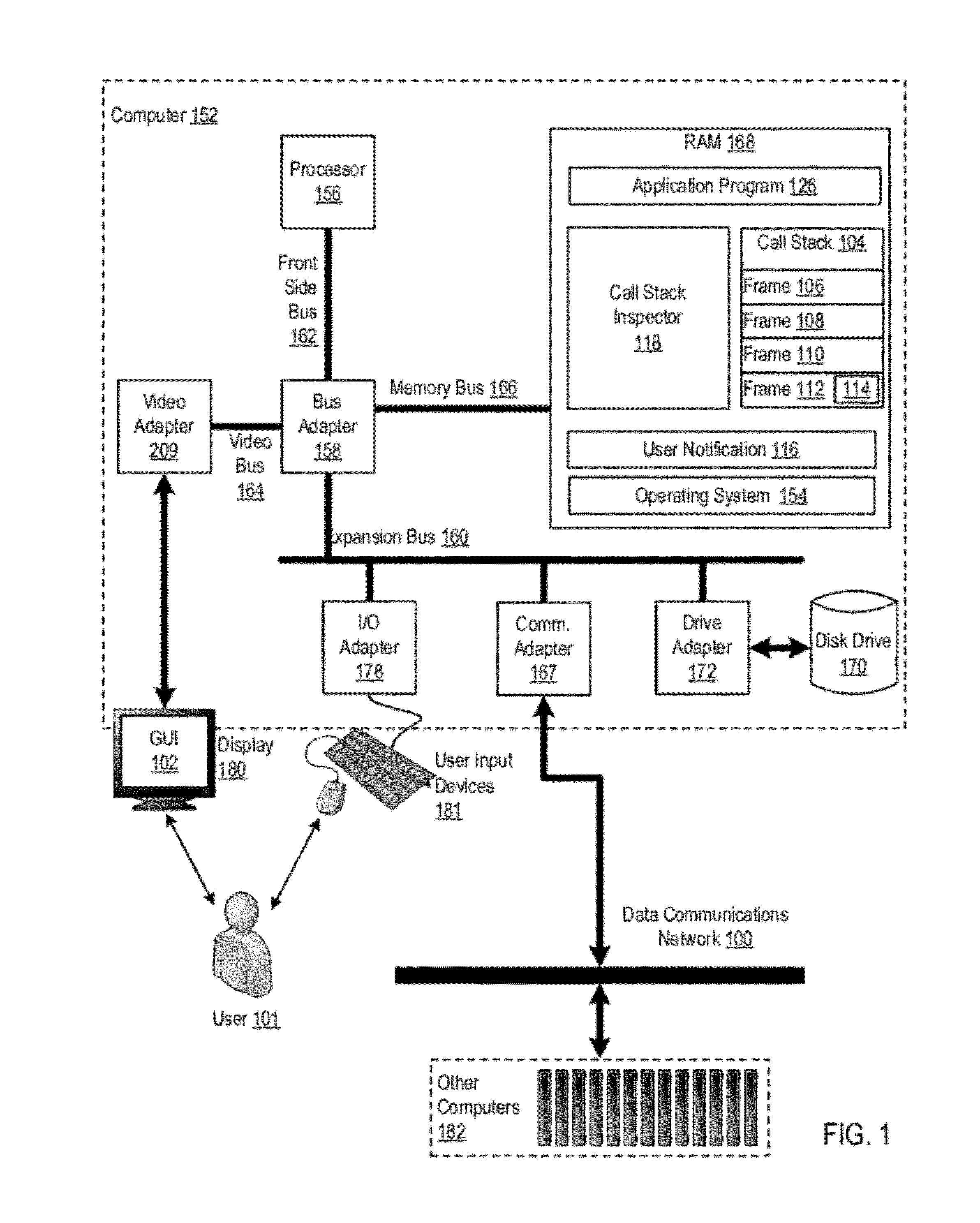
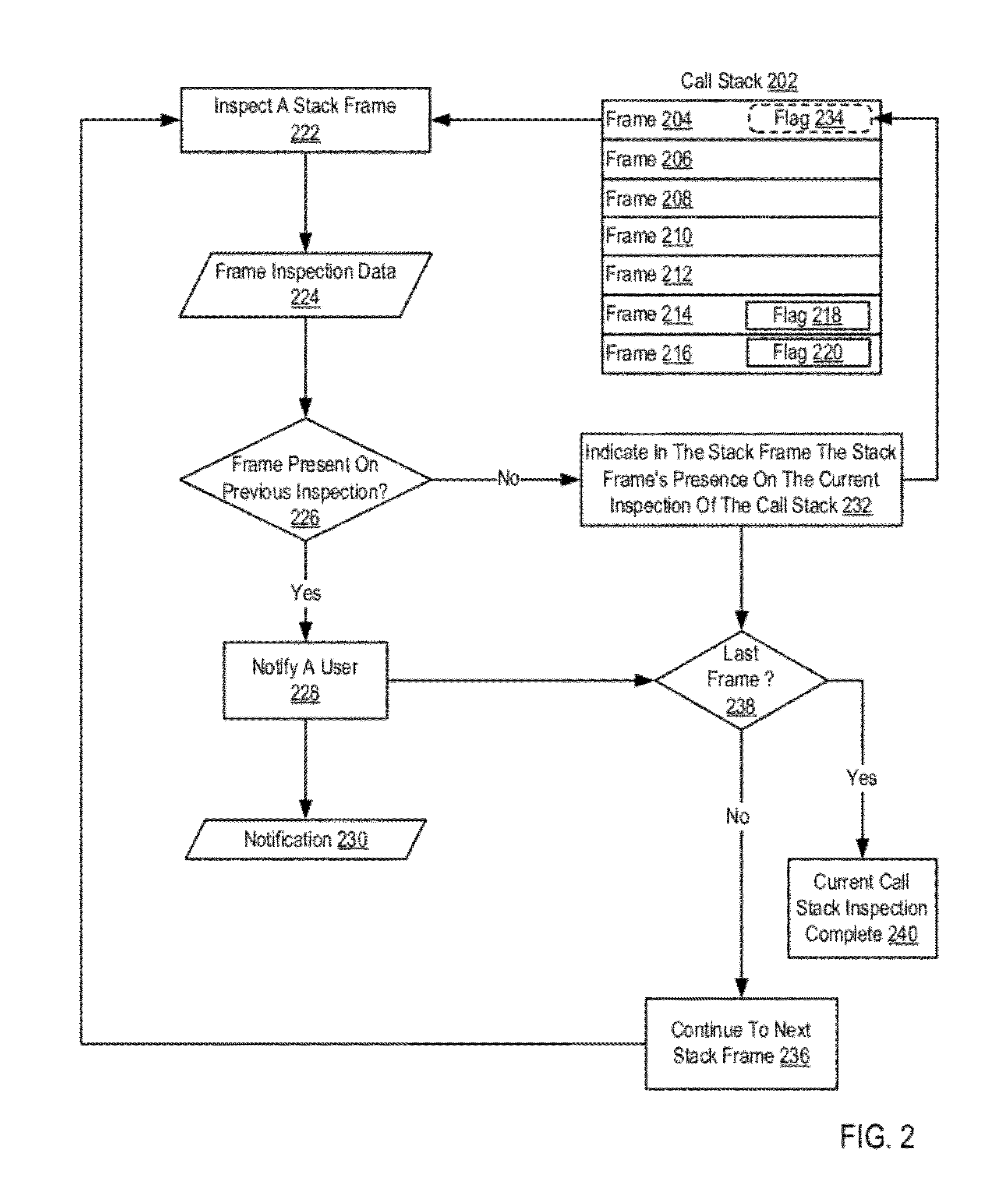
Call Stack Inspection For A Thread Of Execution
Call stack inspection for a thread of execution, including, for each stack frame in the call stack, beginning with the stack frame at the top of the call stack: inspecting the stack frame; determining whether the stack frame was present in the call stack on a previous inspection of the call stack; if the stack frame was not present on a previous inspection, indicating in the stack frame the stack frame's presence on the current inspection of the call stack; and if the stack frame was present on a previous inspection, notifying a user.
Owner:IBM CORP
Method and apparatus for determining computer program flows autonomically using hardware assisted thread stack tracking and cataloged symbolic data
InactiveUS20050210454A1Error detection/correctionDigital computer detailsCall stackOperational system
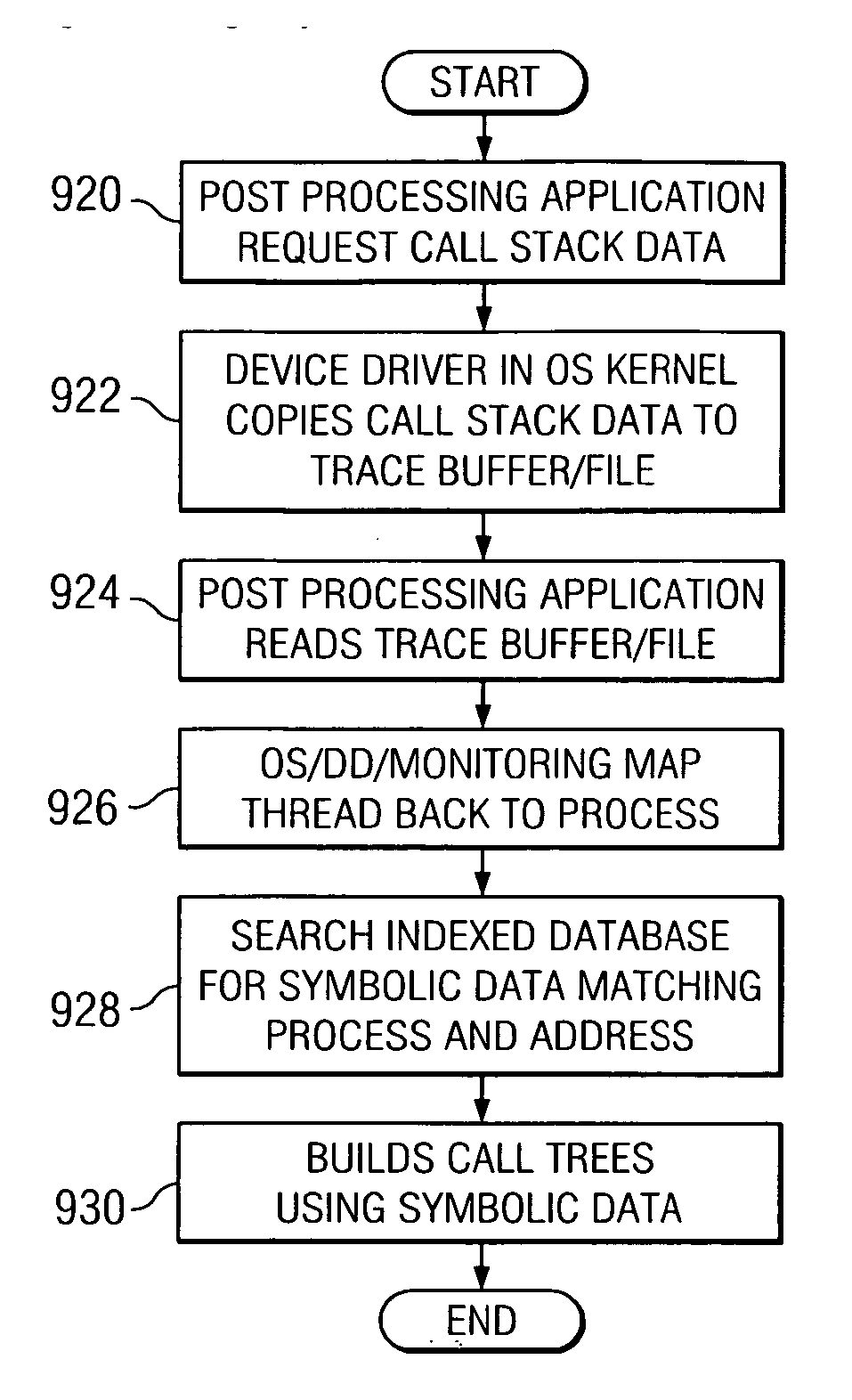
A method, apparatus, and computer instructions for determining computer flows autonomically using hardware assisted thread stack and cataloged symbolic data. When a new thread is spawned during execution of a computer program, new thread work area is allocated by the operating system in memory for storage of call stack information for the new thread. Hardware registers are set with values corresponding to the new thread work area. Upon context switch, values of the registers are saved in a context save area for future restoration. When call stack data is post-processed, the operating system or a device driver copies call stack data from the thread work areas to a consolidated buffer and each thread is mapped to a process. Symbolic data may be obtained based on the process identifier and address of the method / routine that was called / returned in the thread. Corresponding program flow is determined using retrieved symbolic data and call stack data.
Owner:IBM CORP
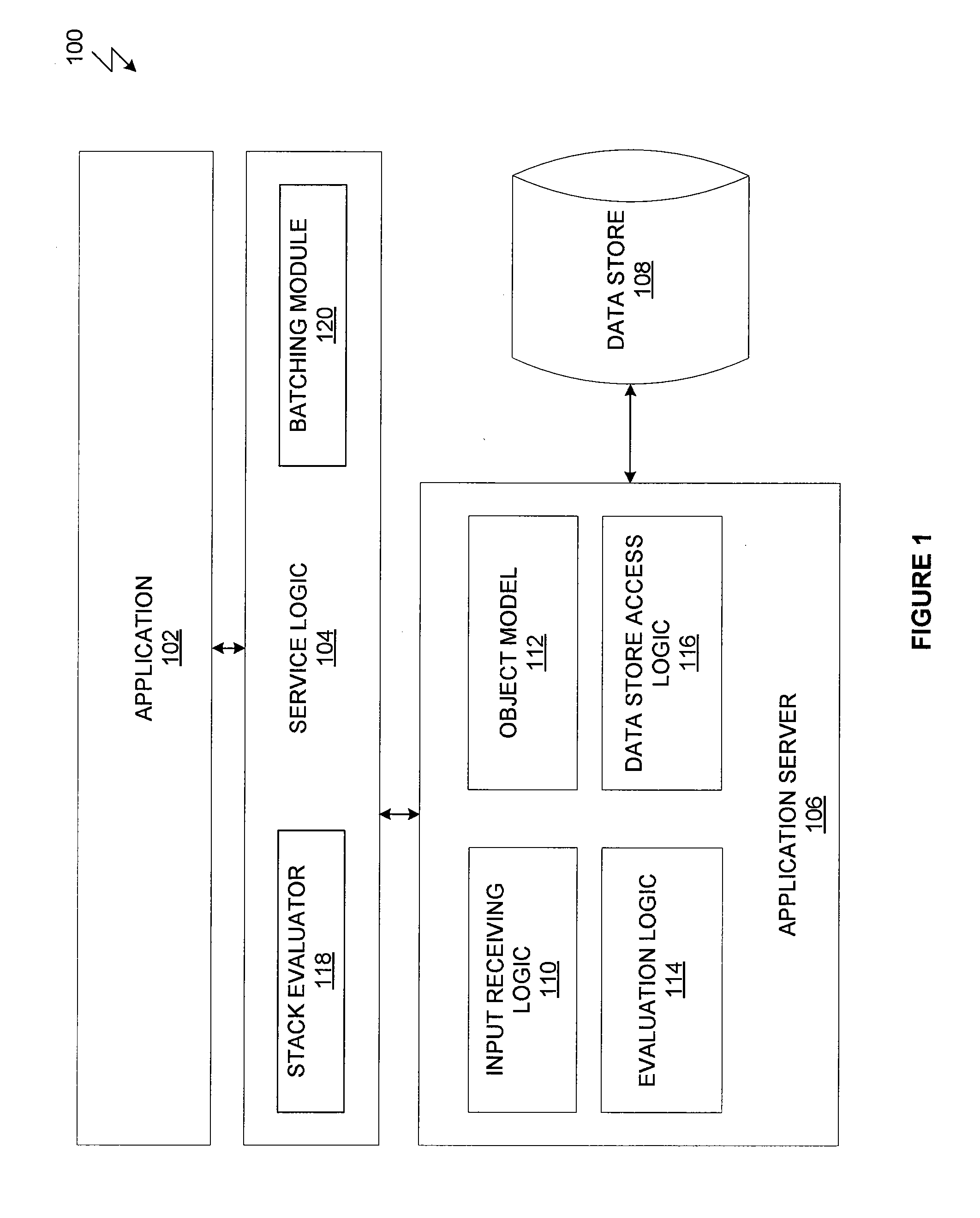
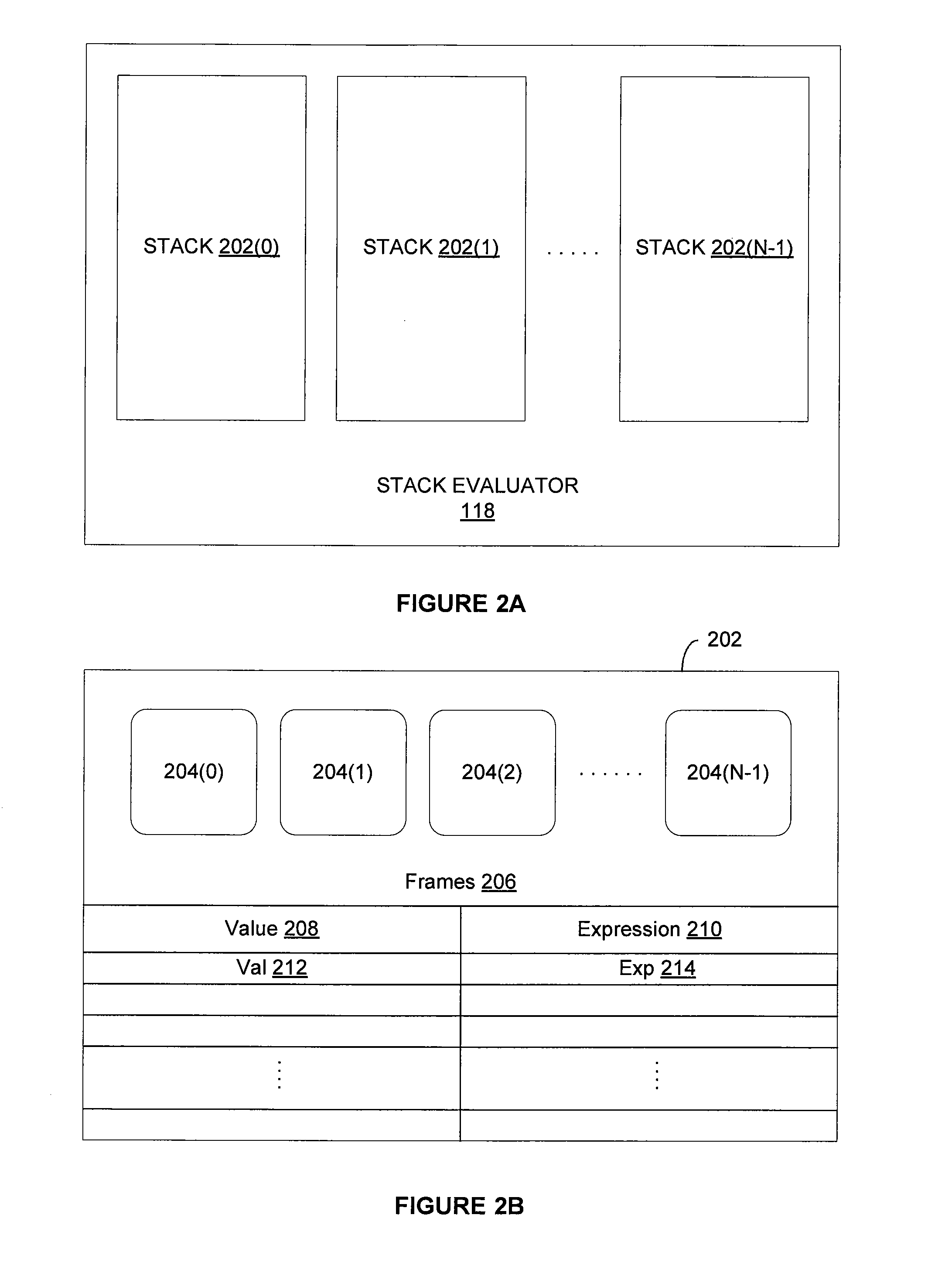
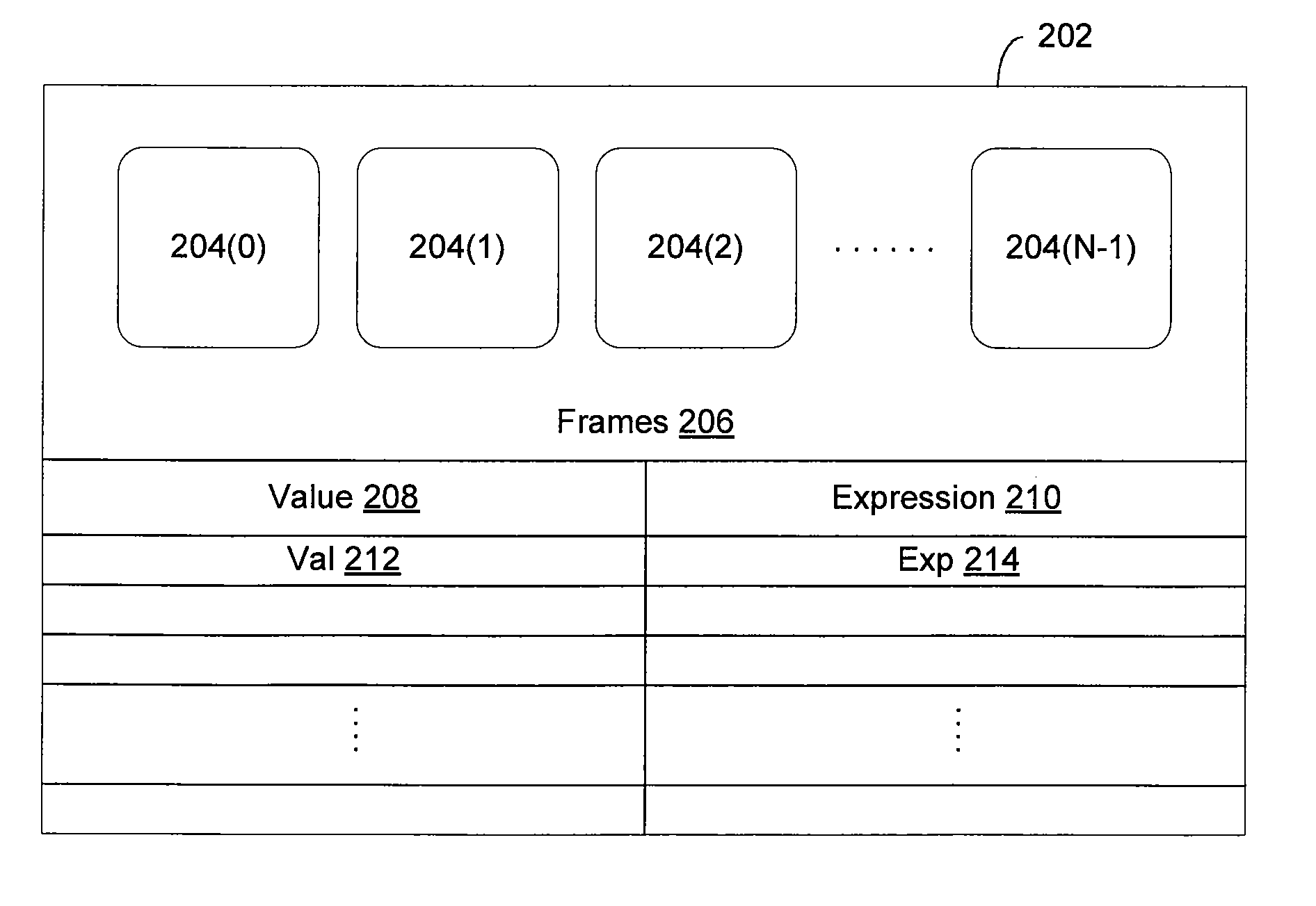
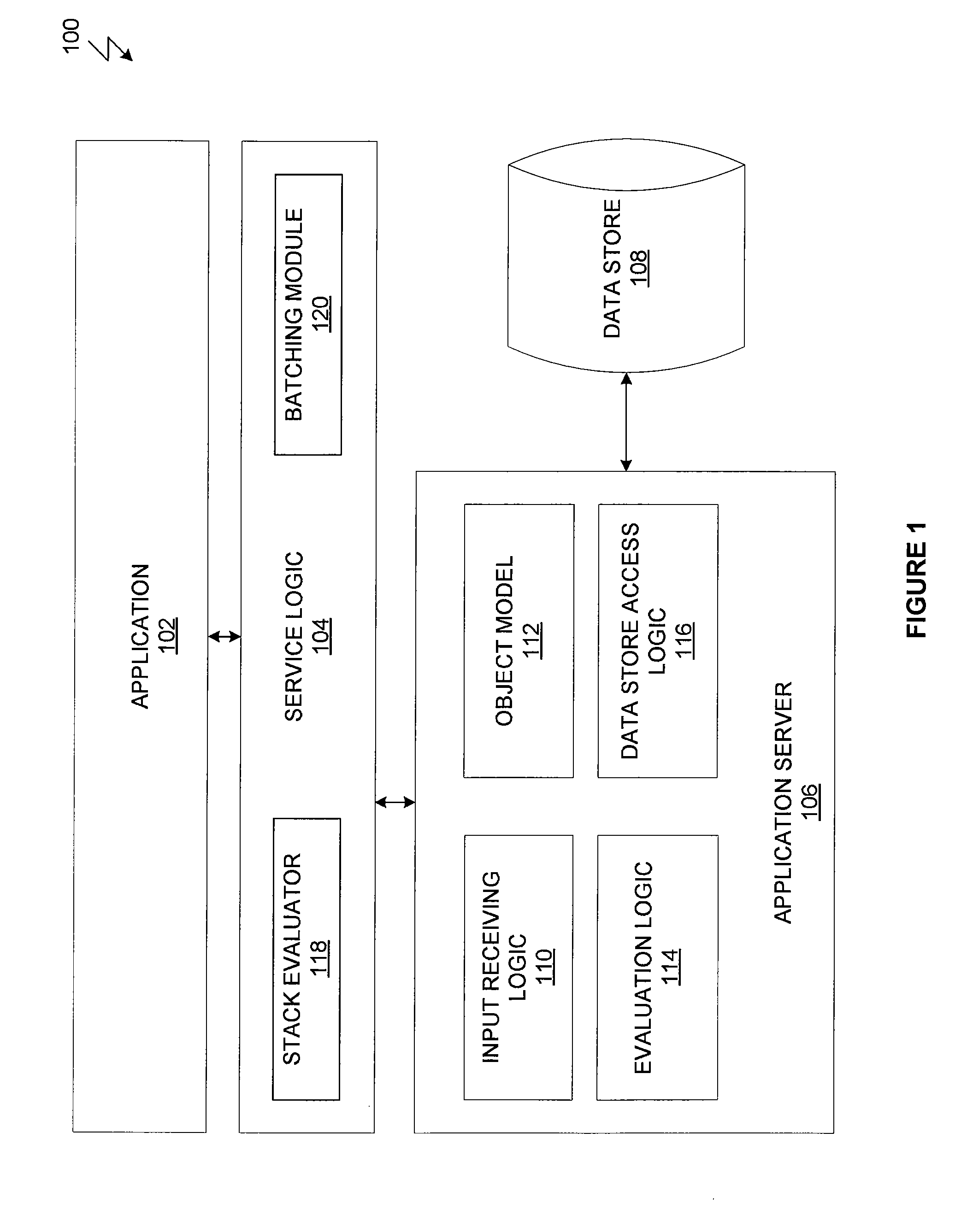
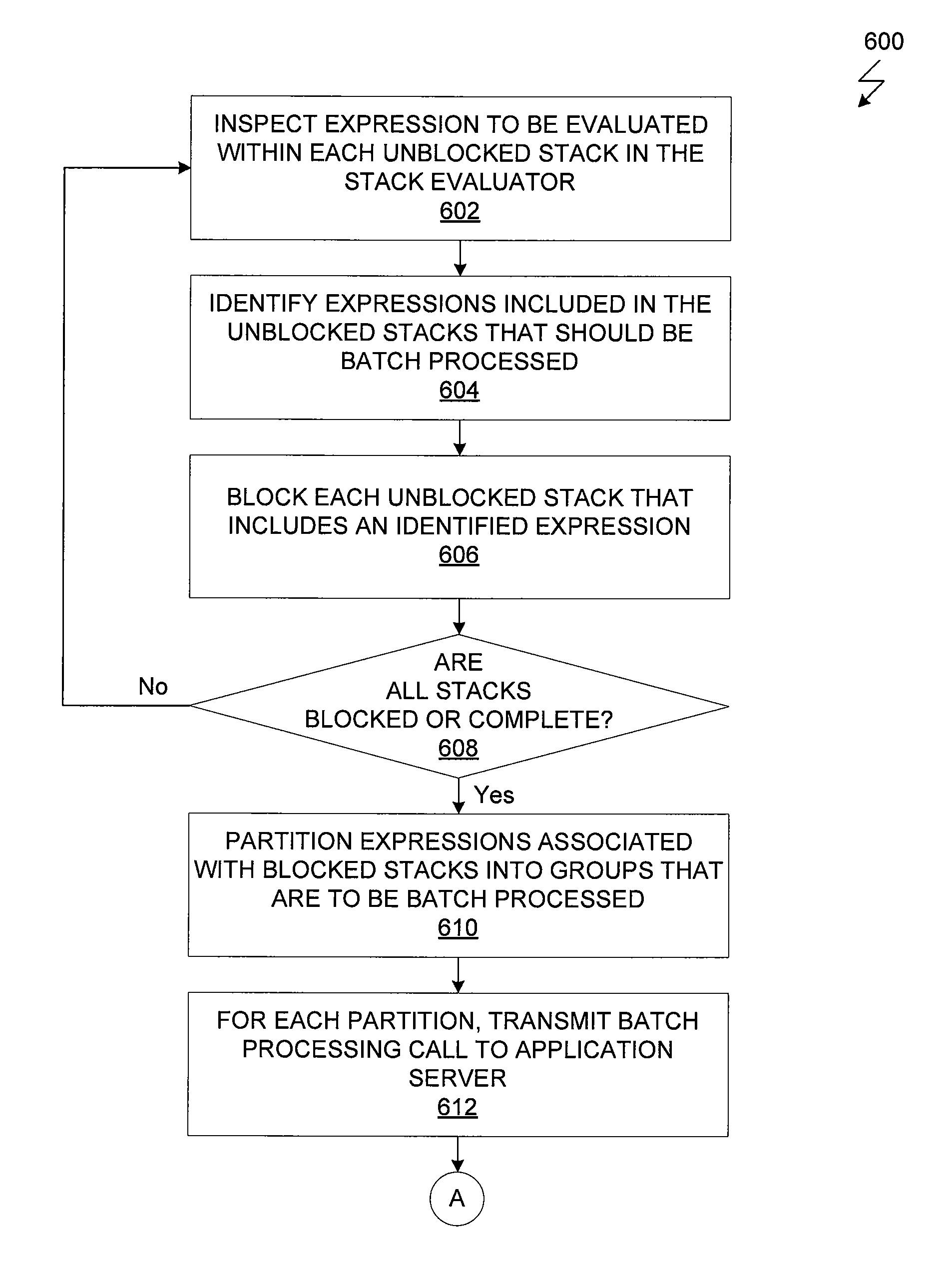
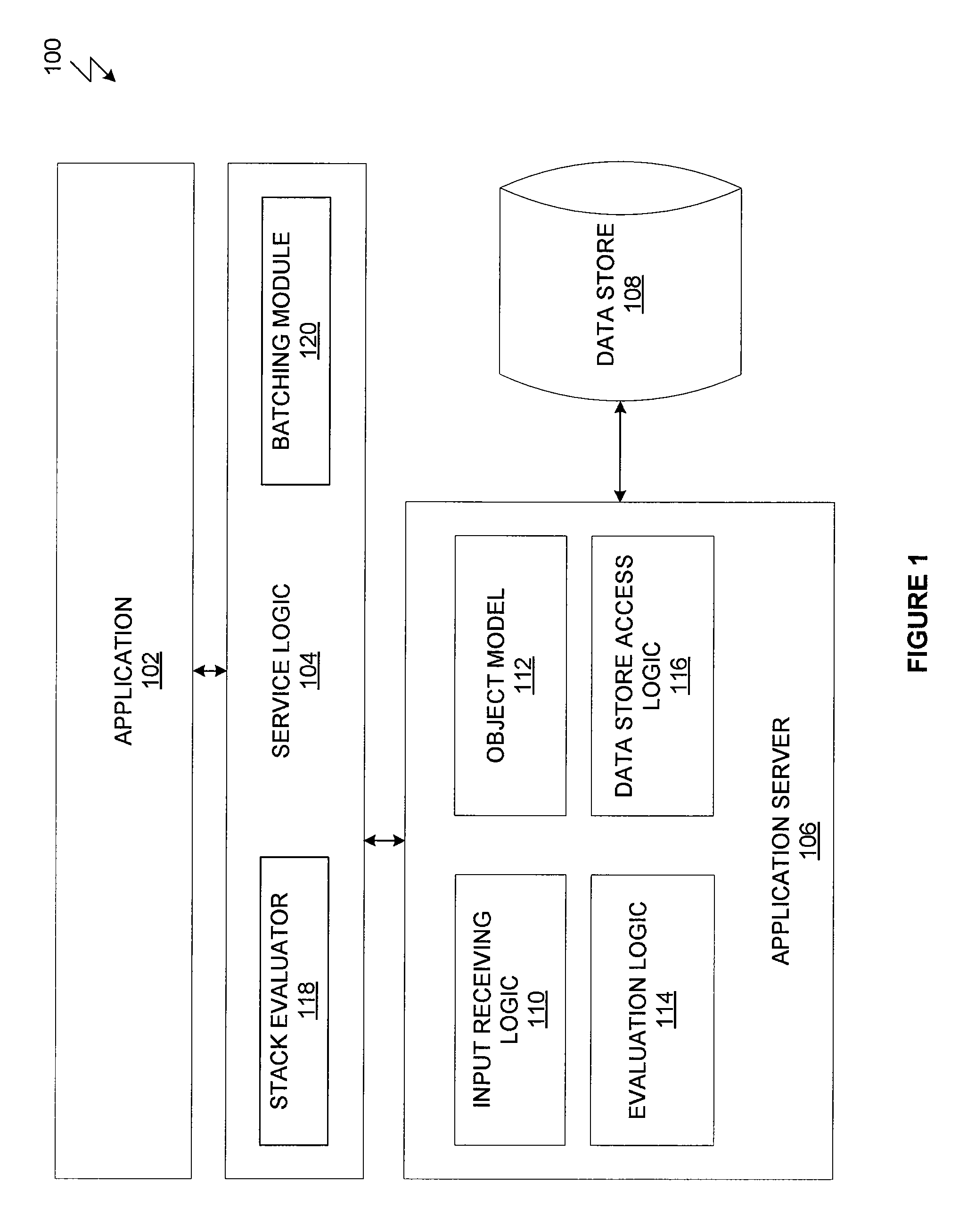
System and method for batch evaluation programs
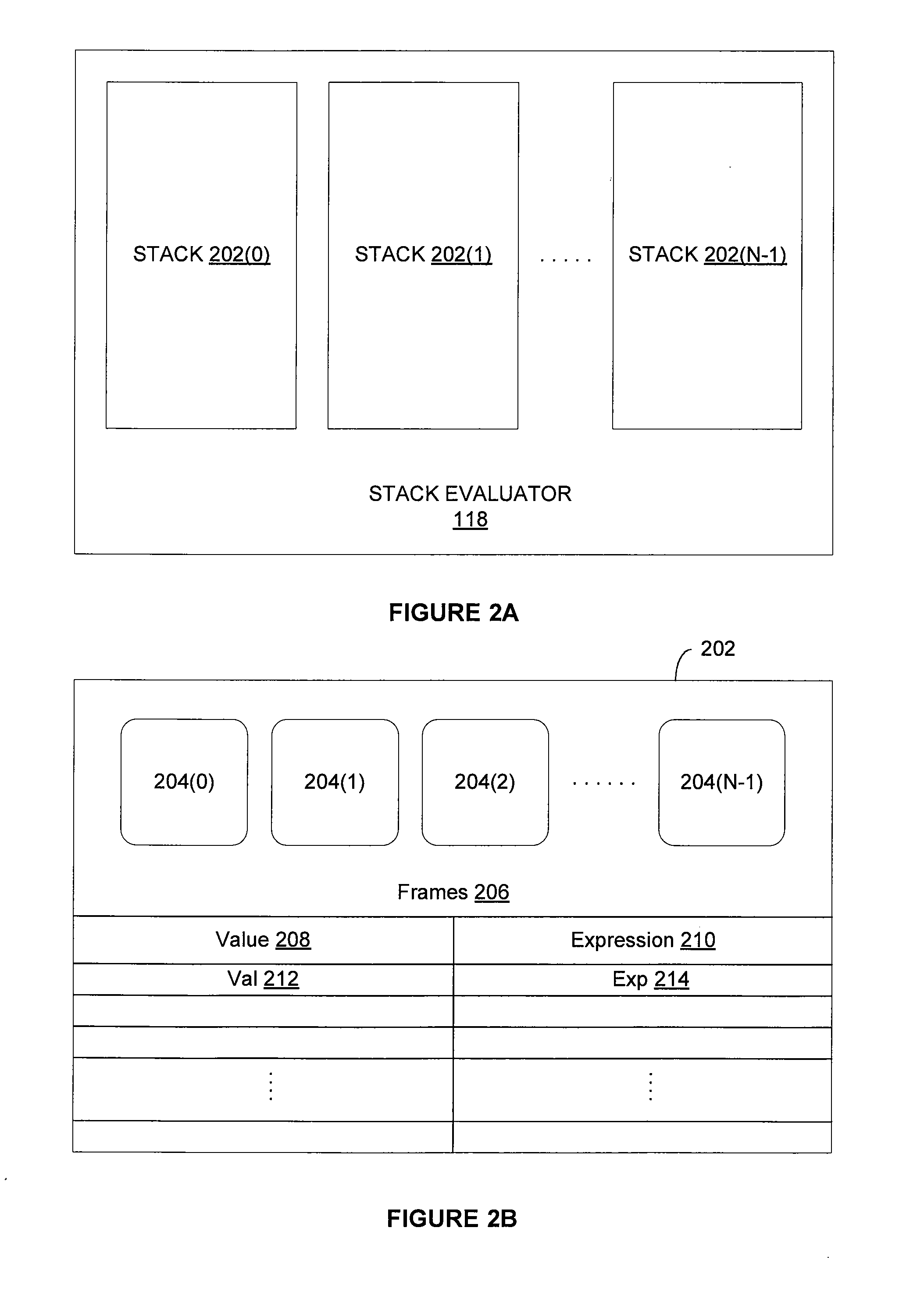
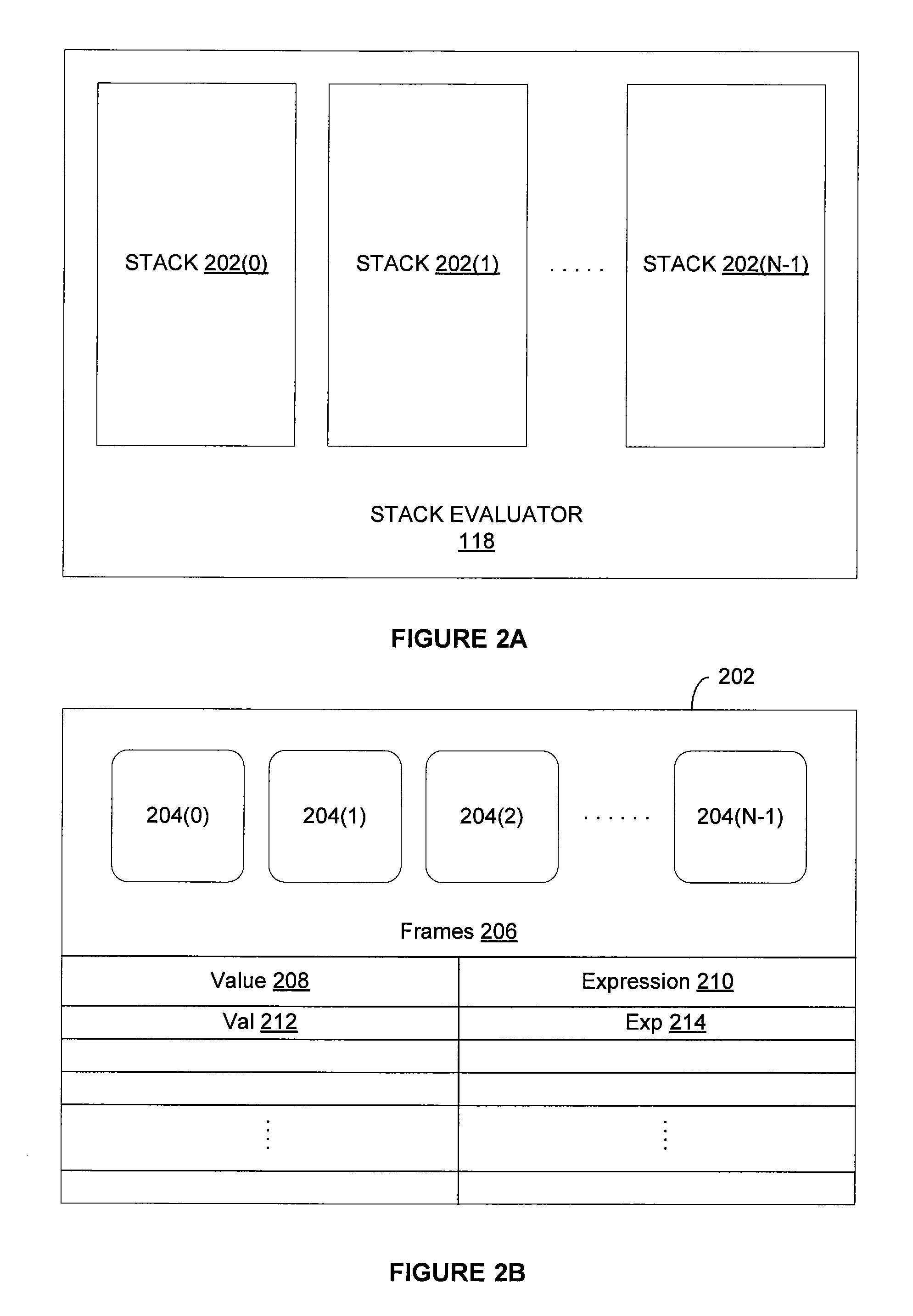
ActiveUS20140115610A1Reduce the number of processesImprove application efficiencyInterprogram communicationObject oriented databasesCall stackBatch processing
A batching module that inspects call stacks within a stack evaluator to identify current expressions that can be evaluated in batch with other expressions. If such expressions are identified, the corresponding stacks are blocked from further processing and a batch processing request for processing the expressions is transmitted to the application server. The application server processes the expressions in batch and generates a value for each of the expressions. The blocked stacks are then populated with the values for the expressions.
Owner:PALANTIR TECHNOLOGIES
System and method for batch evaluation programs
ActiveUS20140115589A1Reduce the number of processesImprove application efficiencyMemory systemsTransaction processingCall stackBatch processing
A batching module that inspects call stacks within a stack evaluator to identify current expressions that can be evaluated in batch with other expressions. If such expressions are identified, the corresponding stacks are blocked from further processing and a batch processing request for processing the expressions is transmitted to the application server. The application server processes the expressions in batch and generates a value for each of the expressions. The blocked stacks are then populated with the values for the expressions.
Owner:PALANTIR TECHNOLOGIES
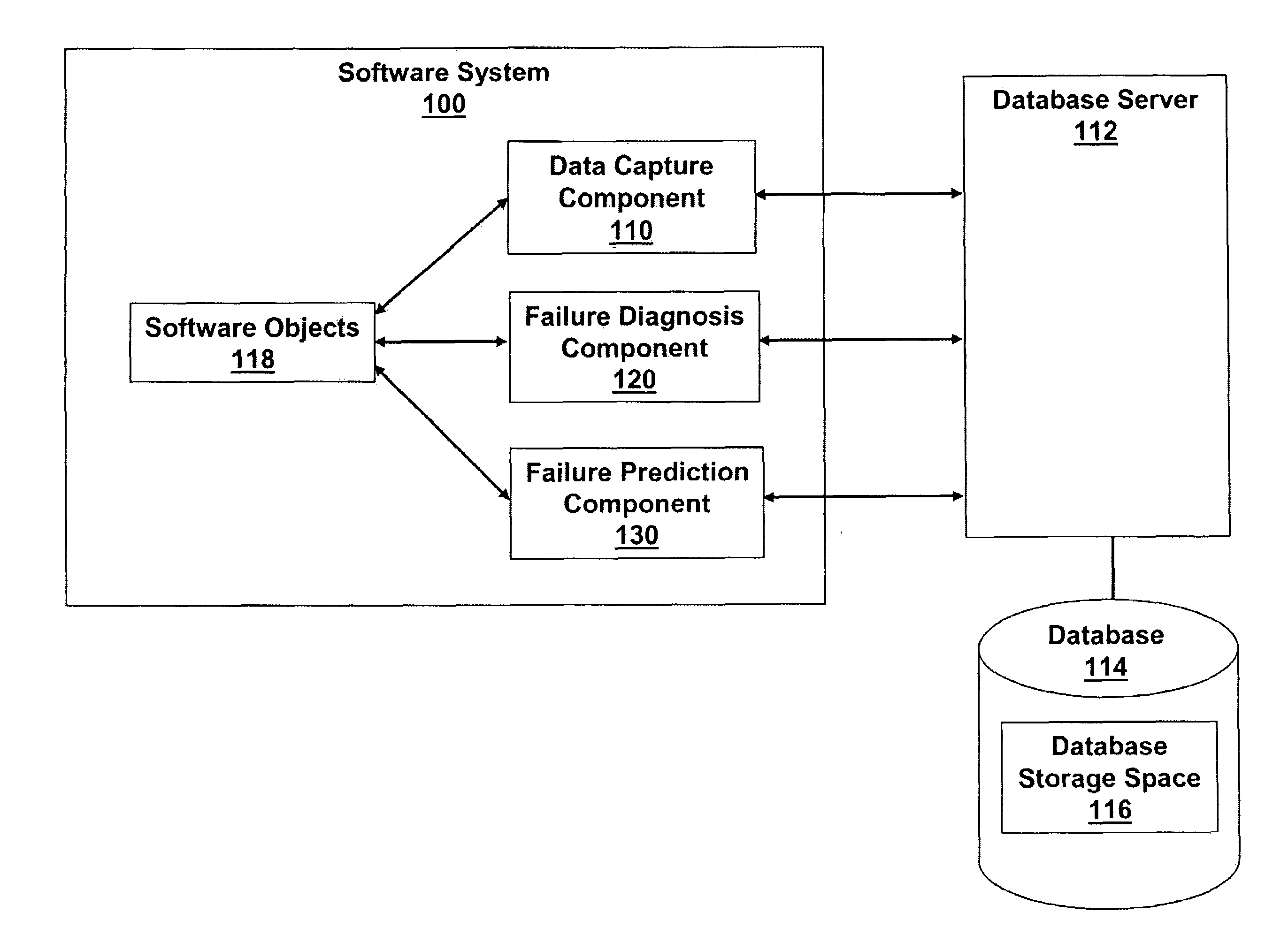
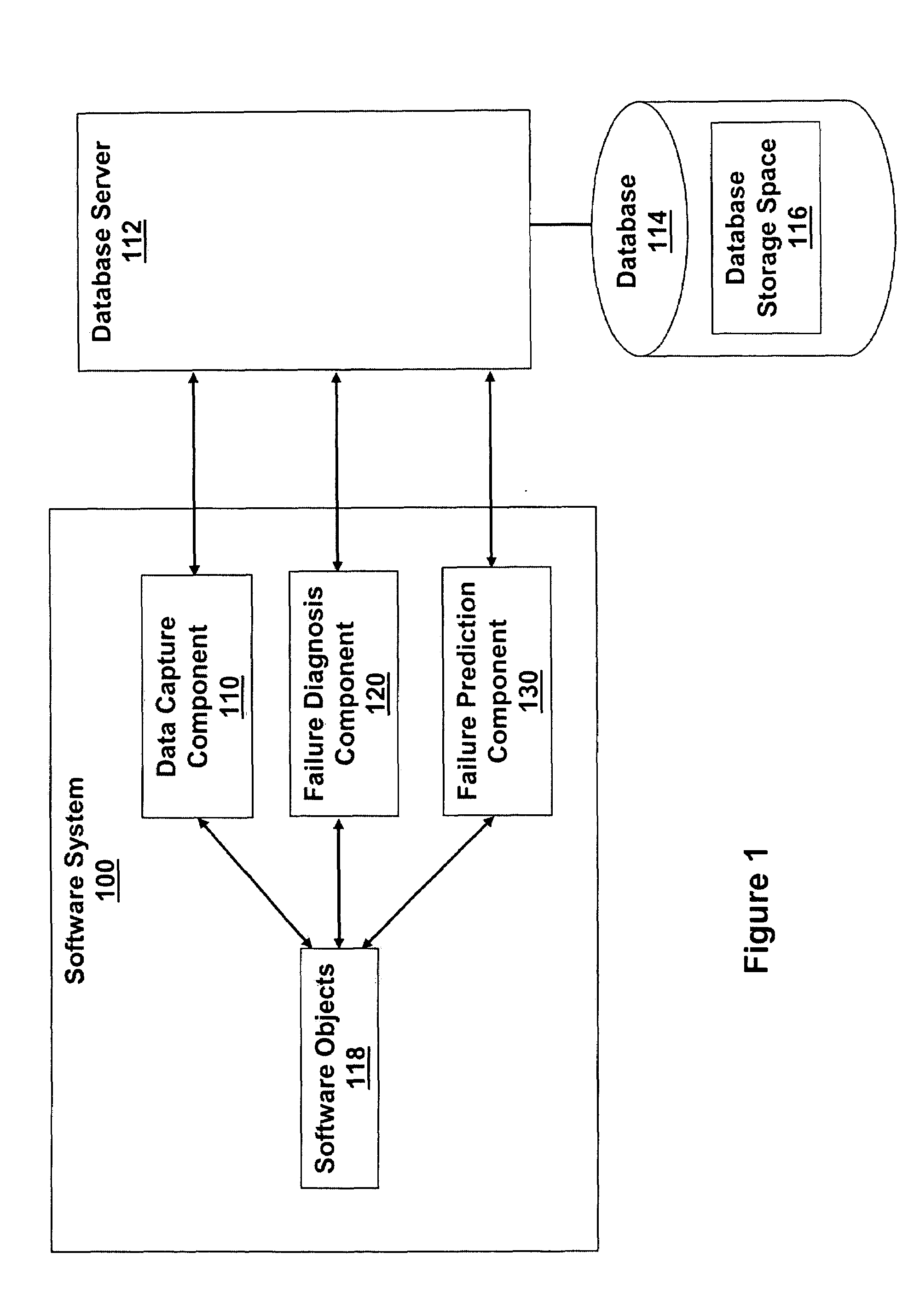
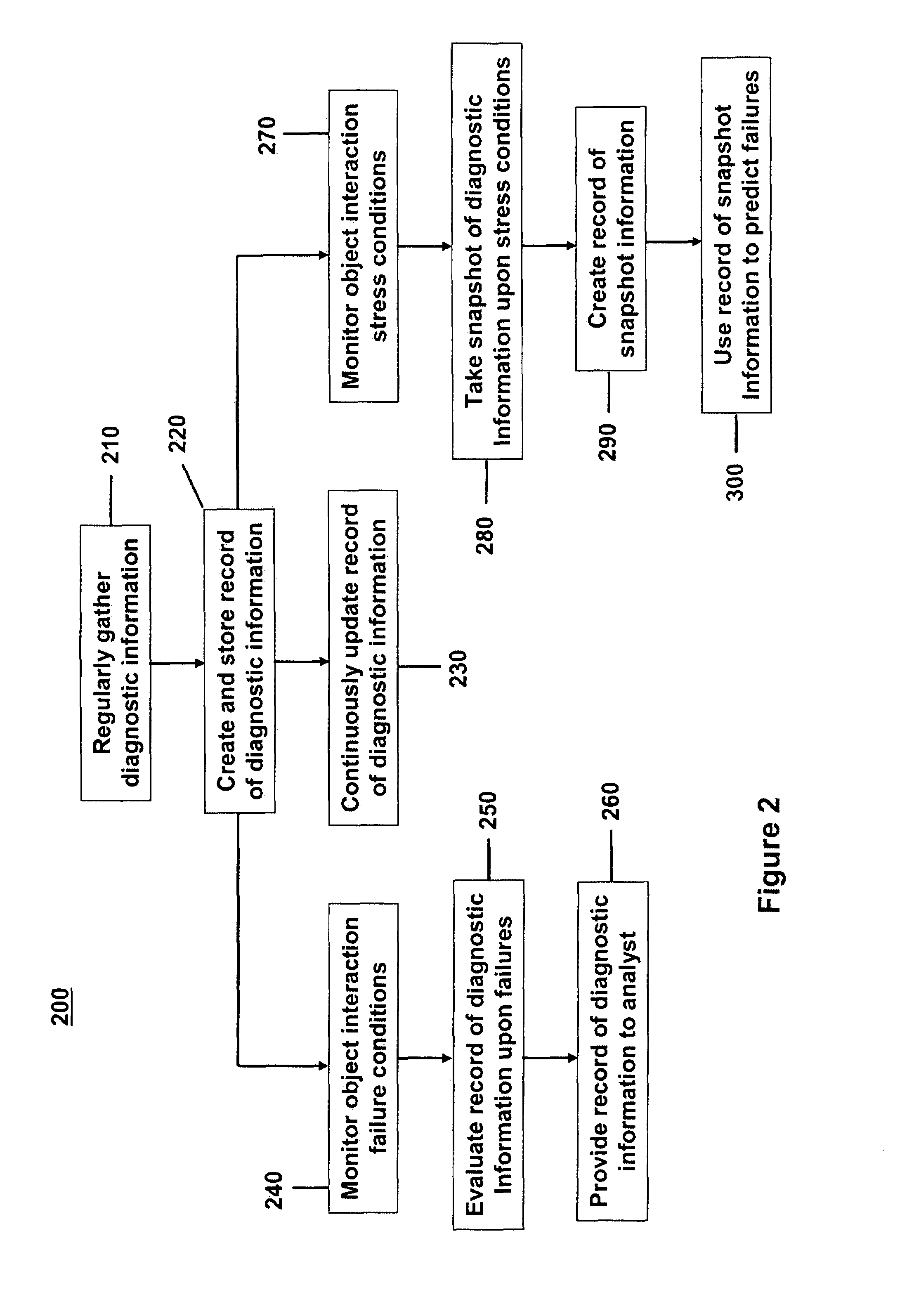
System and method of fault detection, diagnosis and prevention for complex computing systems
A method is provided for diagnosing failures in an object-oriented software system. The method comprises collecting runtime diagnostic information; maintaining a record of the diagnostic information in a storage buffer; and dynamically updating the record of the diagnostic information to include a group of the diagnostic information collected over a most recent occurrence of a predetermined interval. The diagnostic information includes at least one set of call stack information for at least one currently running application and at least one set of other information. Each of the at least one set of other information is selected from a set of memory access information, a set of data access information, and a set of paging information for each currently executing process.
Owner:IBM CORP
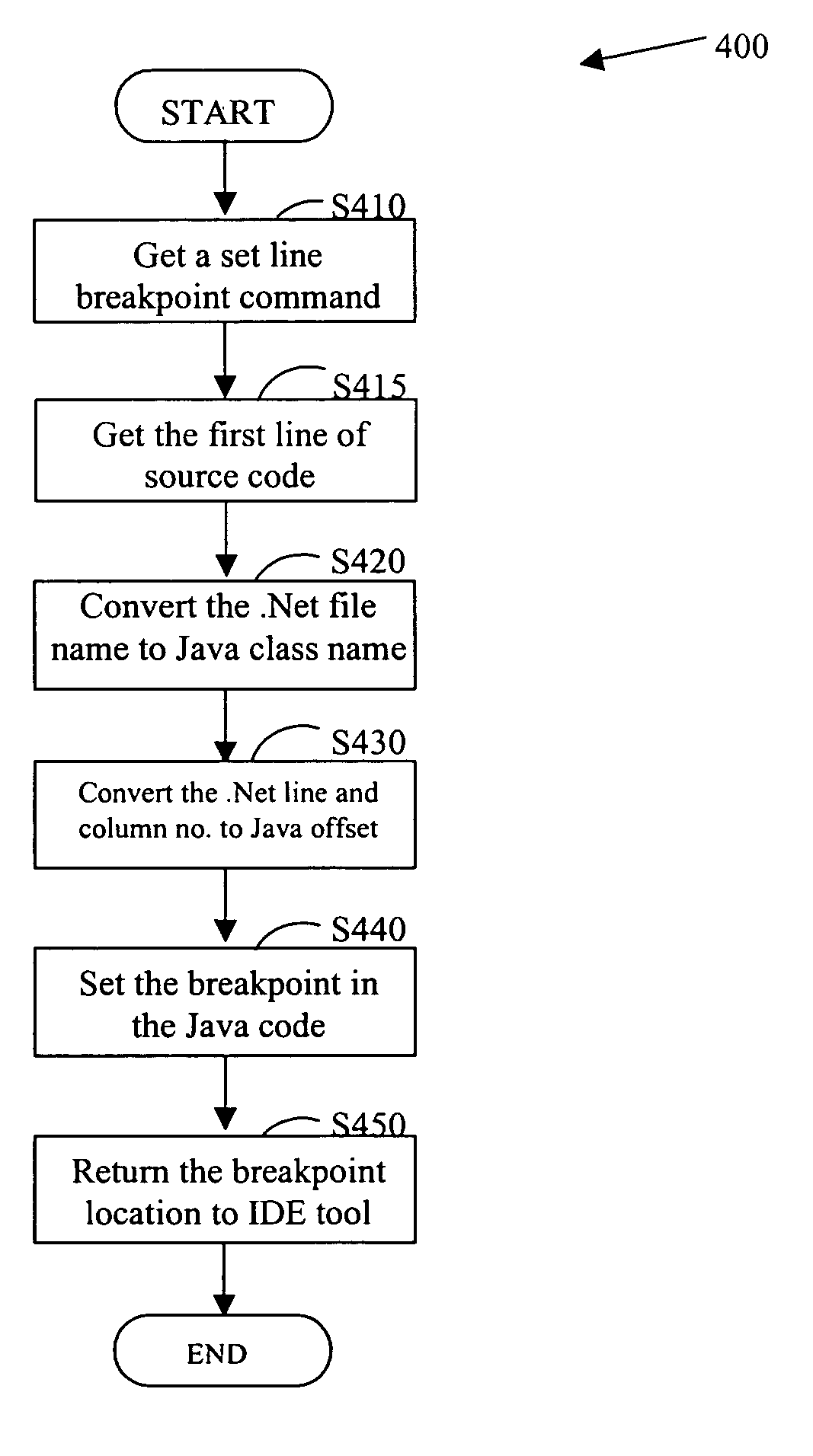
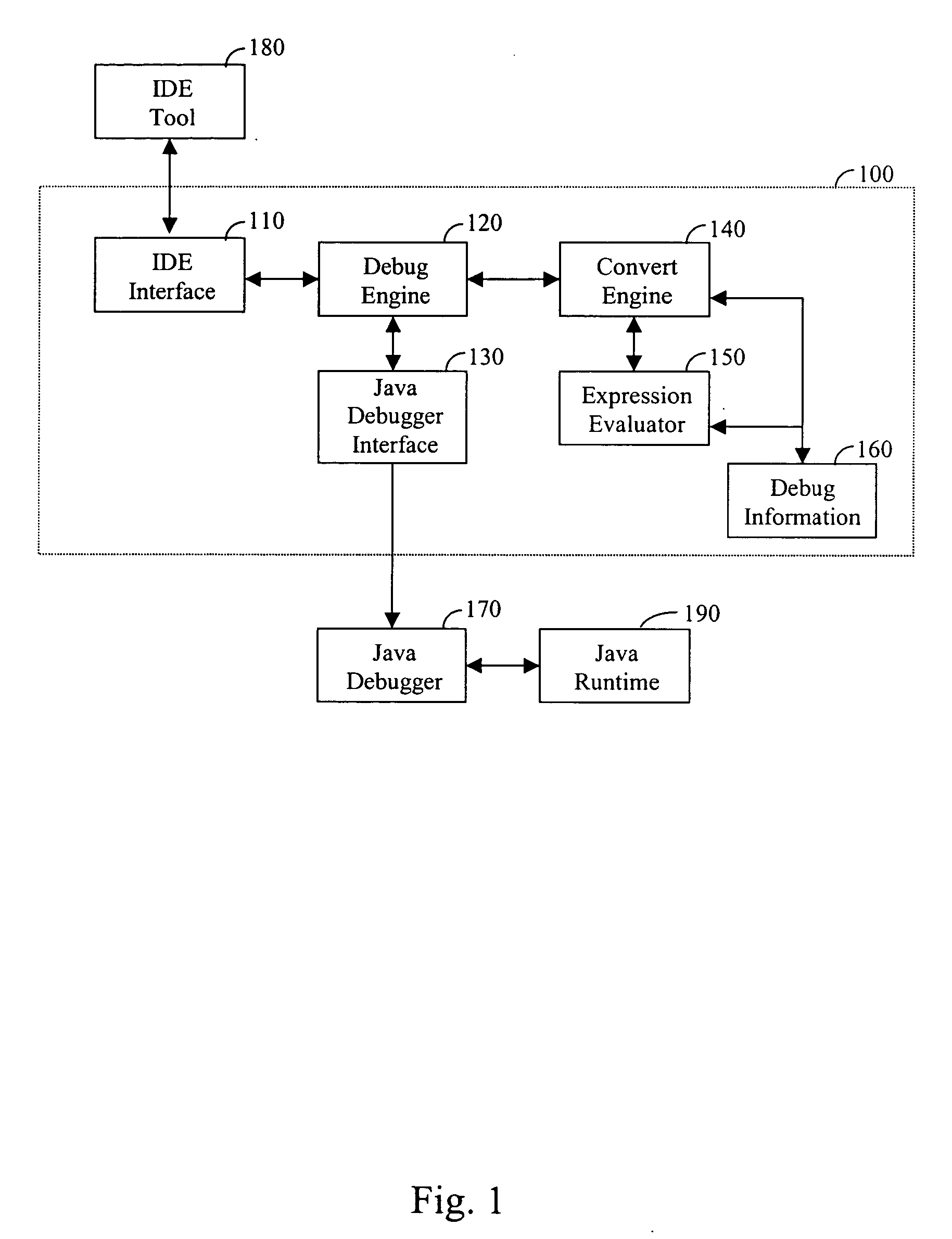
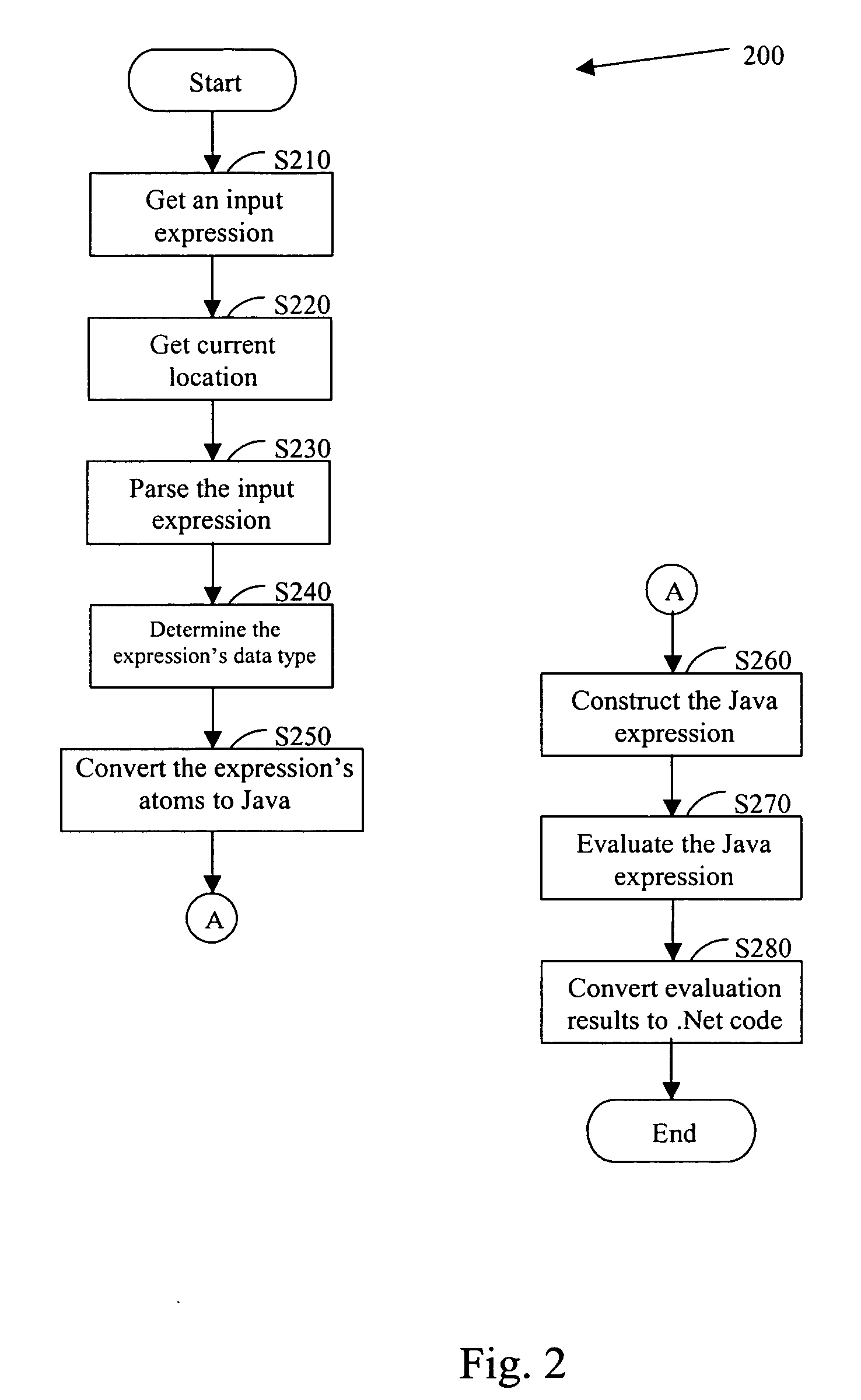
Debugger and method for debugging computer programs across multiple programming languages
InactiveUS20060064677A1Error detection/correctionSpecific program execution arrangementsCall stackSoftware development
A debugger and method for debugging computer programs across multiple programming languages are provided. The debugging is performed at a source level of a computer program written in any programming language supported by the .Net® platform, while the program is executed over a Java runtime environment. The debugger disclosed provides a call stack display and an expression evaluator. Furthermore, the debugger allows software developers to step through Java source code and follow the execution flow of the Java program. One exemplary embodiment of the disclosed debugger is an extension of the Microsoft® Visual Studio .Net®.
Owner:HARMON IE R&D
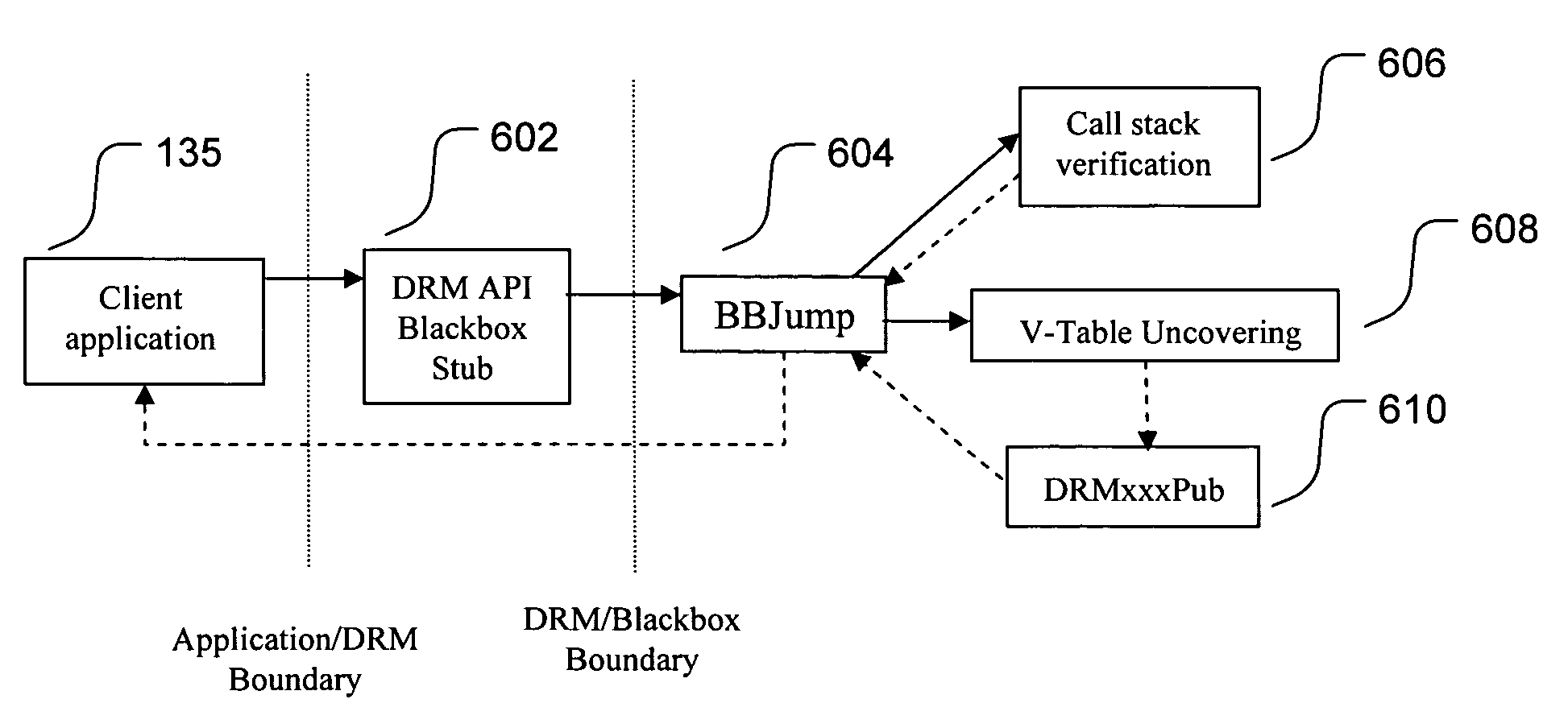
Run-time call stack verification
InactiveUS7546587B2Efficient identificationProgram/content distribution protectionSpecific program execution arrangementsCode moduleCall stack
Owner:MICROSOFT TECH LICENSING LLC
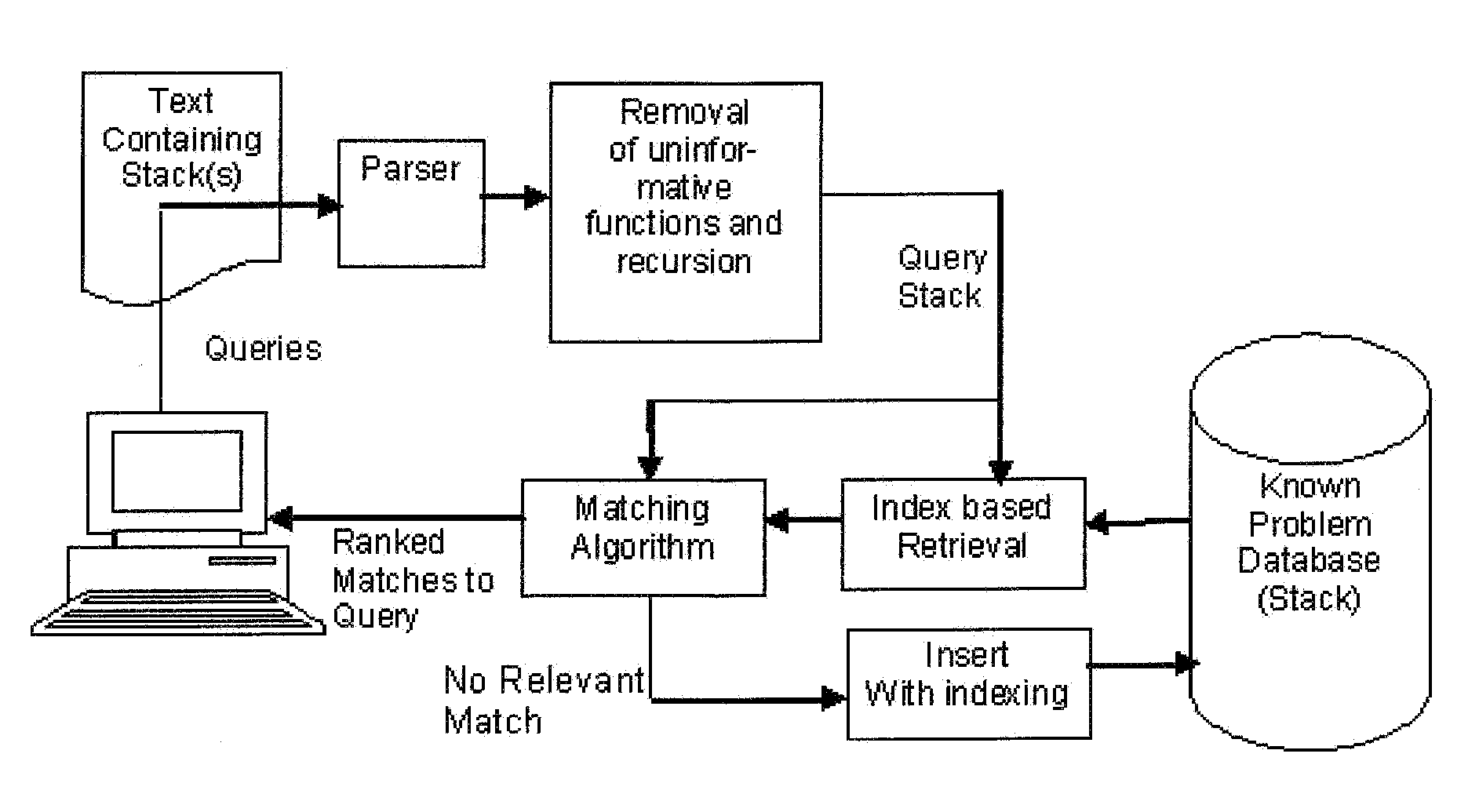
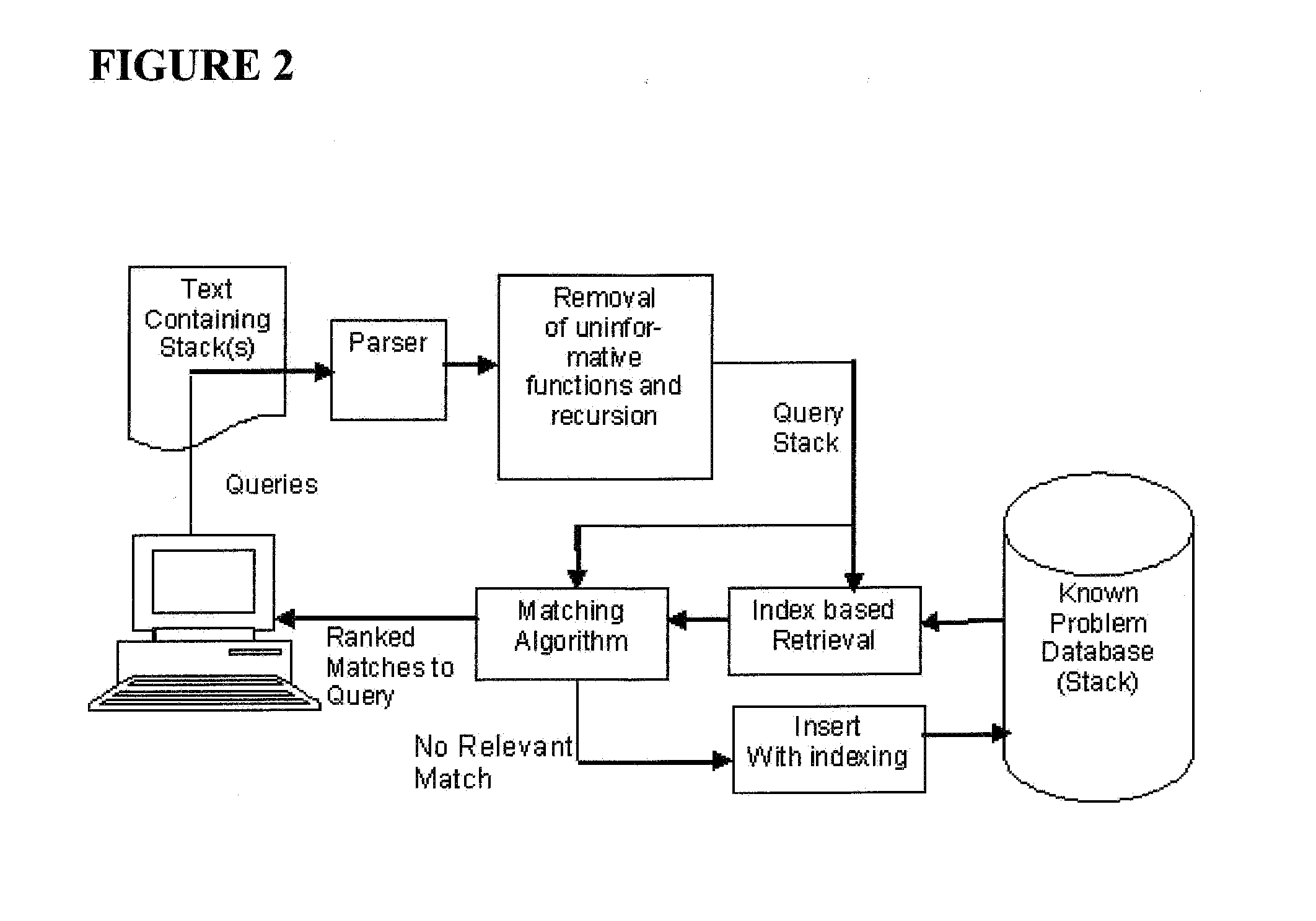
System and method for matching a plurality of ordered sequences with applications to call stack analysis to identify known software problems
InactiveUS20070283338A1Reduce searchHigh precisionSoftware testing/debuggingSpecific program execution arrangementsCall stackSoftware Problem
The invention finds matches in ordered sequences, e.g. program function call stacks from anomalous software program executions for discovering related or identical software flaws and possible known solutions. Call stacks are matched after removing recursive and uninformative subpatterns, e.g. names of common error handling routines, to see if they were generated due to the same possibly known problem. Sequences statistically unlikely to be matches are pruned from the search. Matches found earlier in the sequences may be weighted differently, e.g. to be more important in call stacks, than other matches. Sequences are indexed so that those relevant to a query are identified automatically without detailed exhaustive search. Maximum matches are found by optimizing a cost function based on weighted sequence similarity.
Owner:LINKEDIN
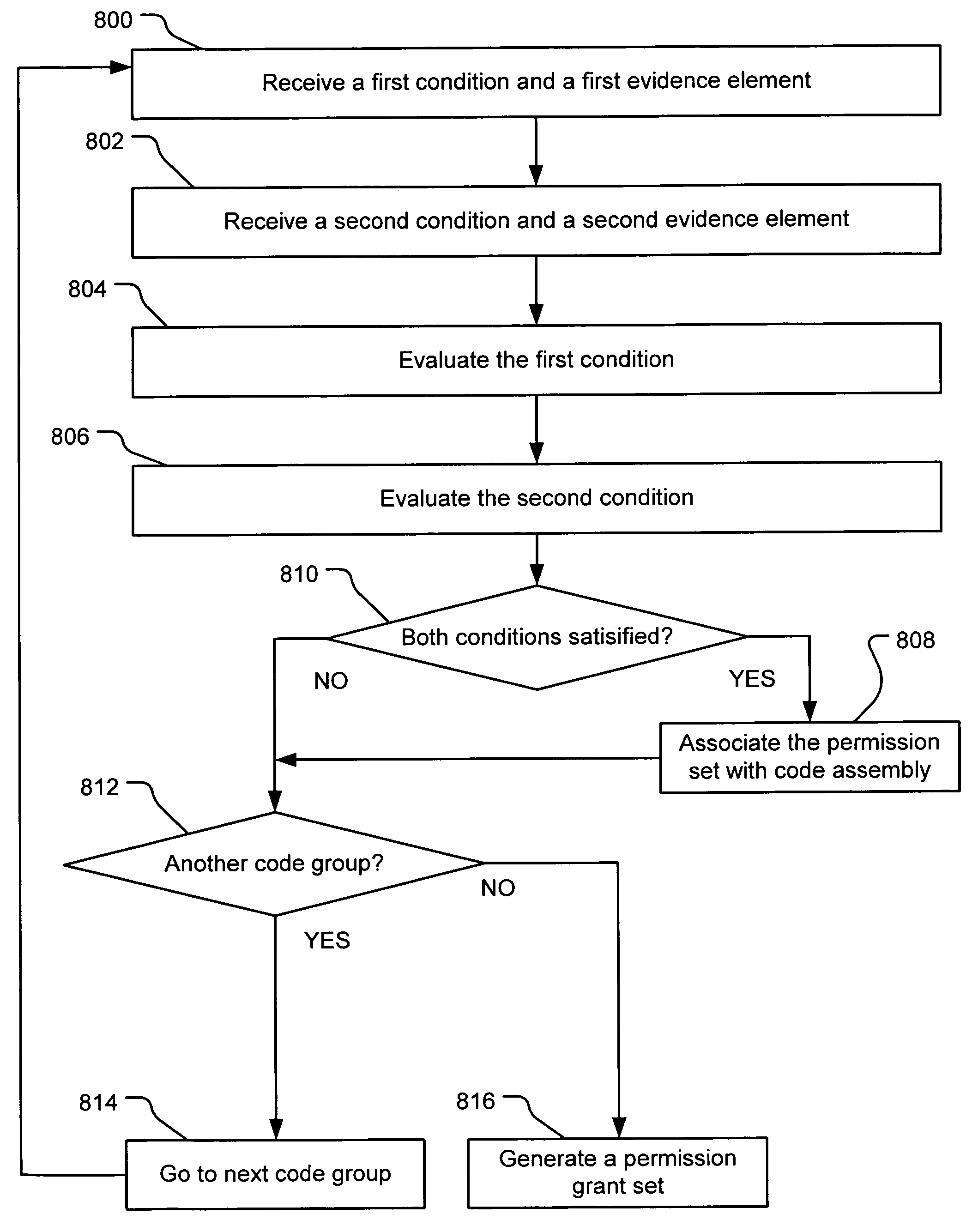
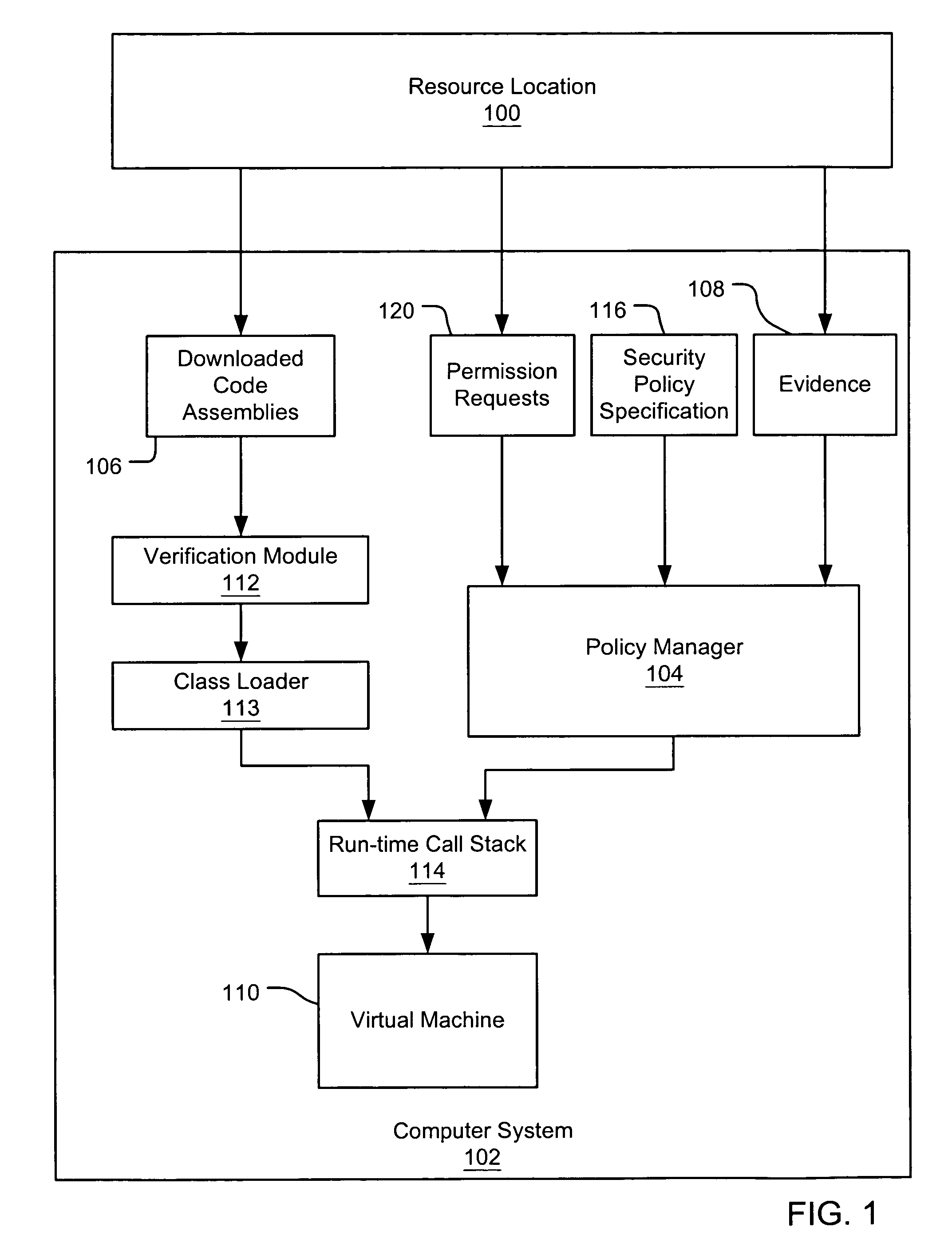
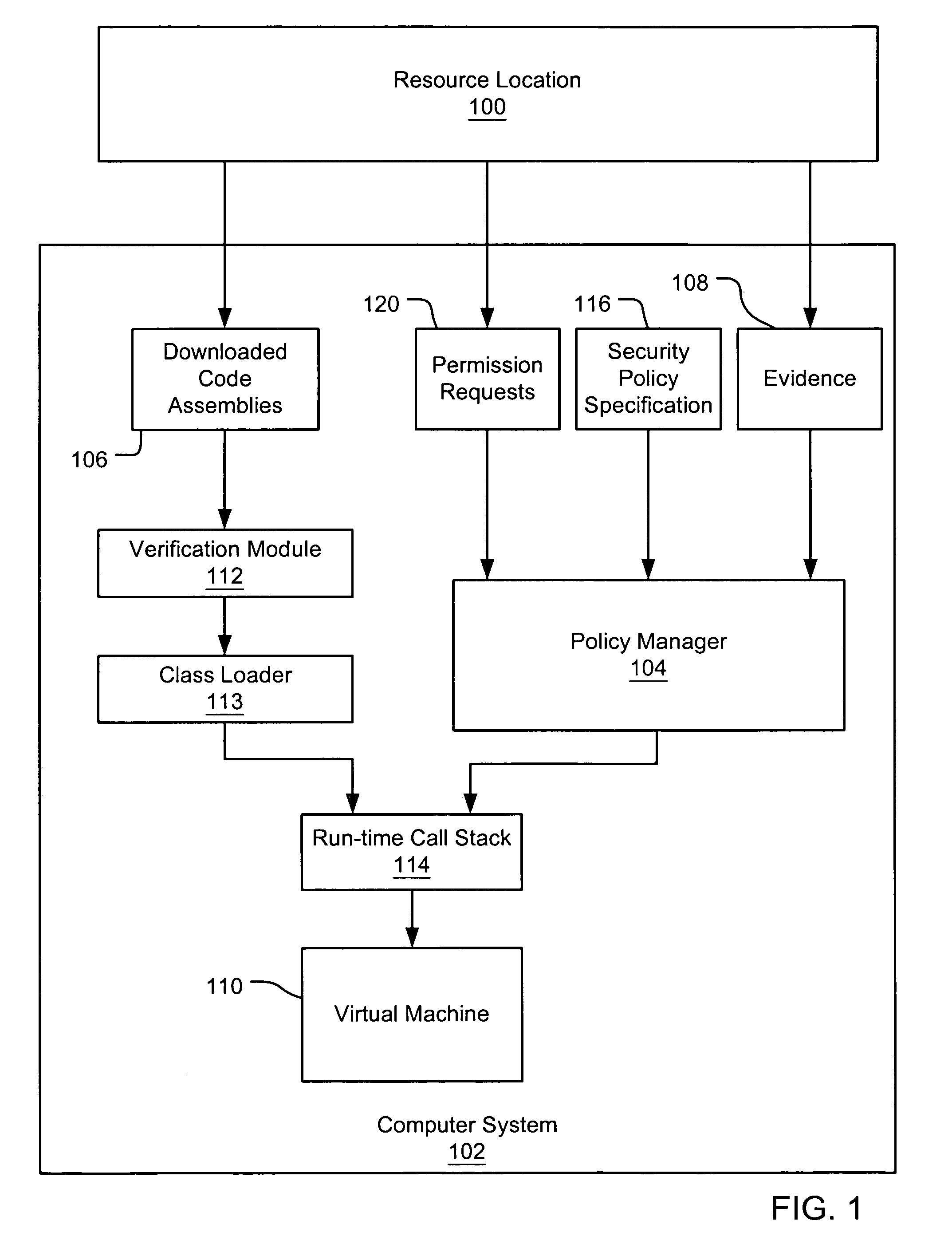
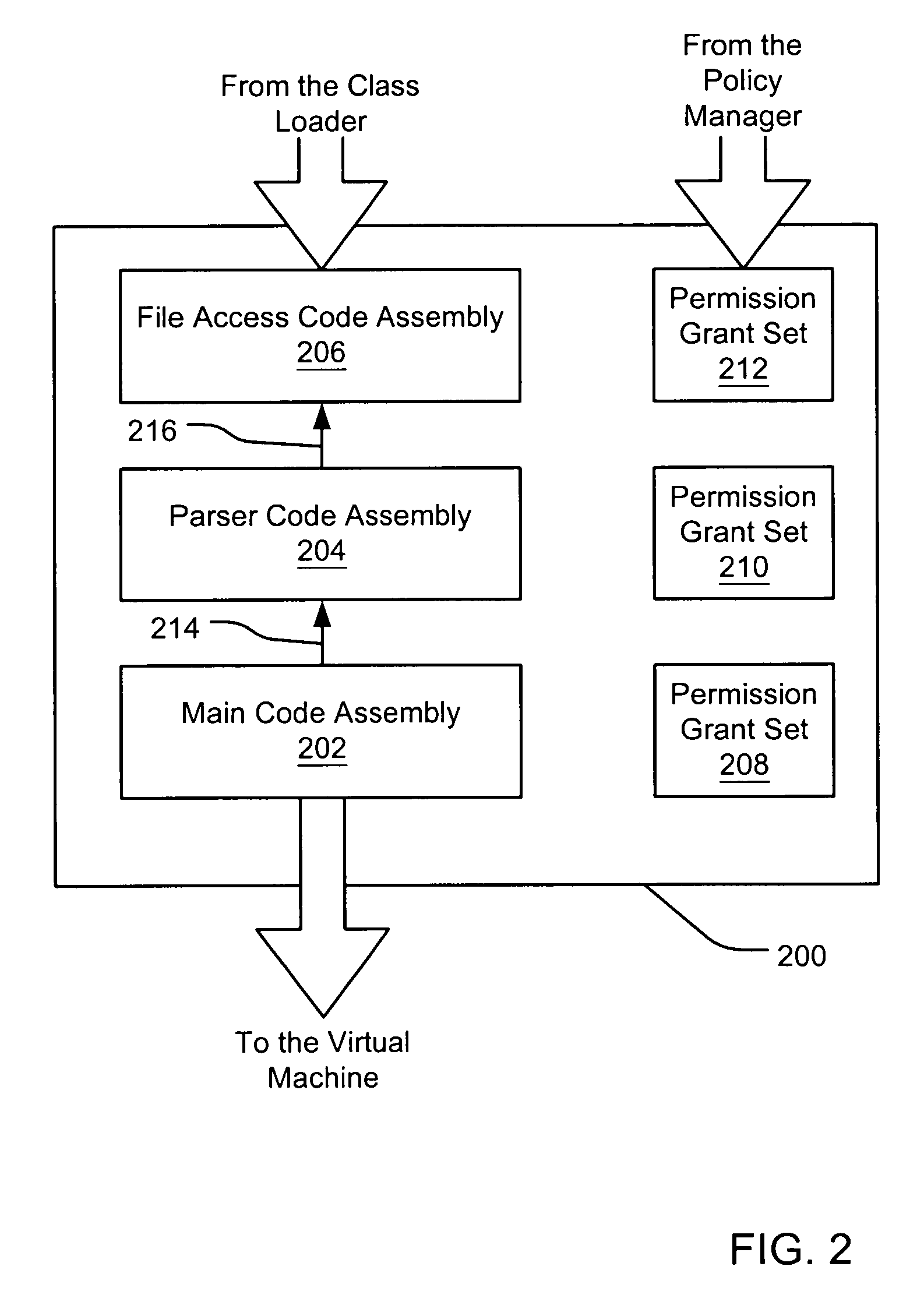
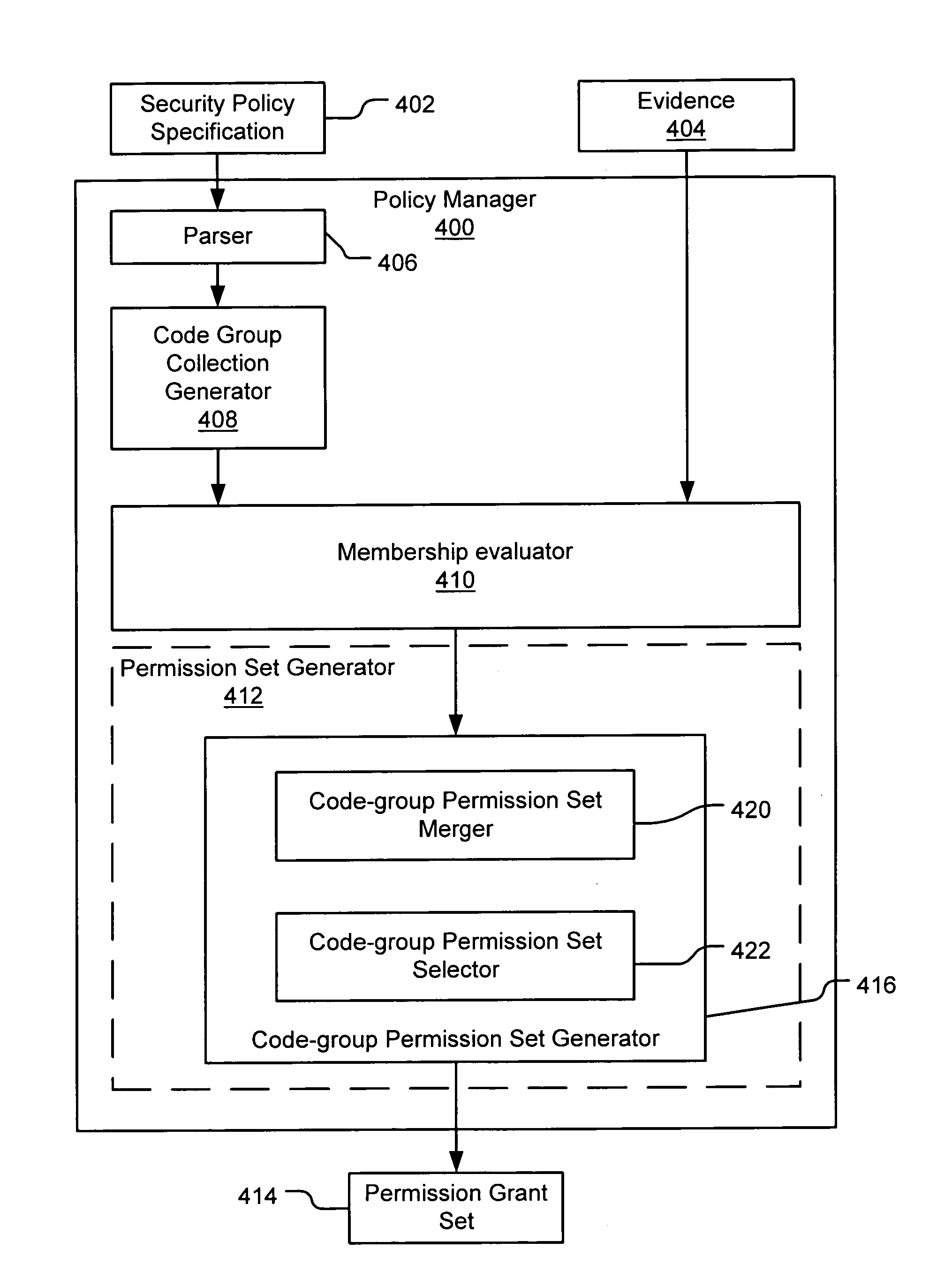
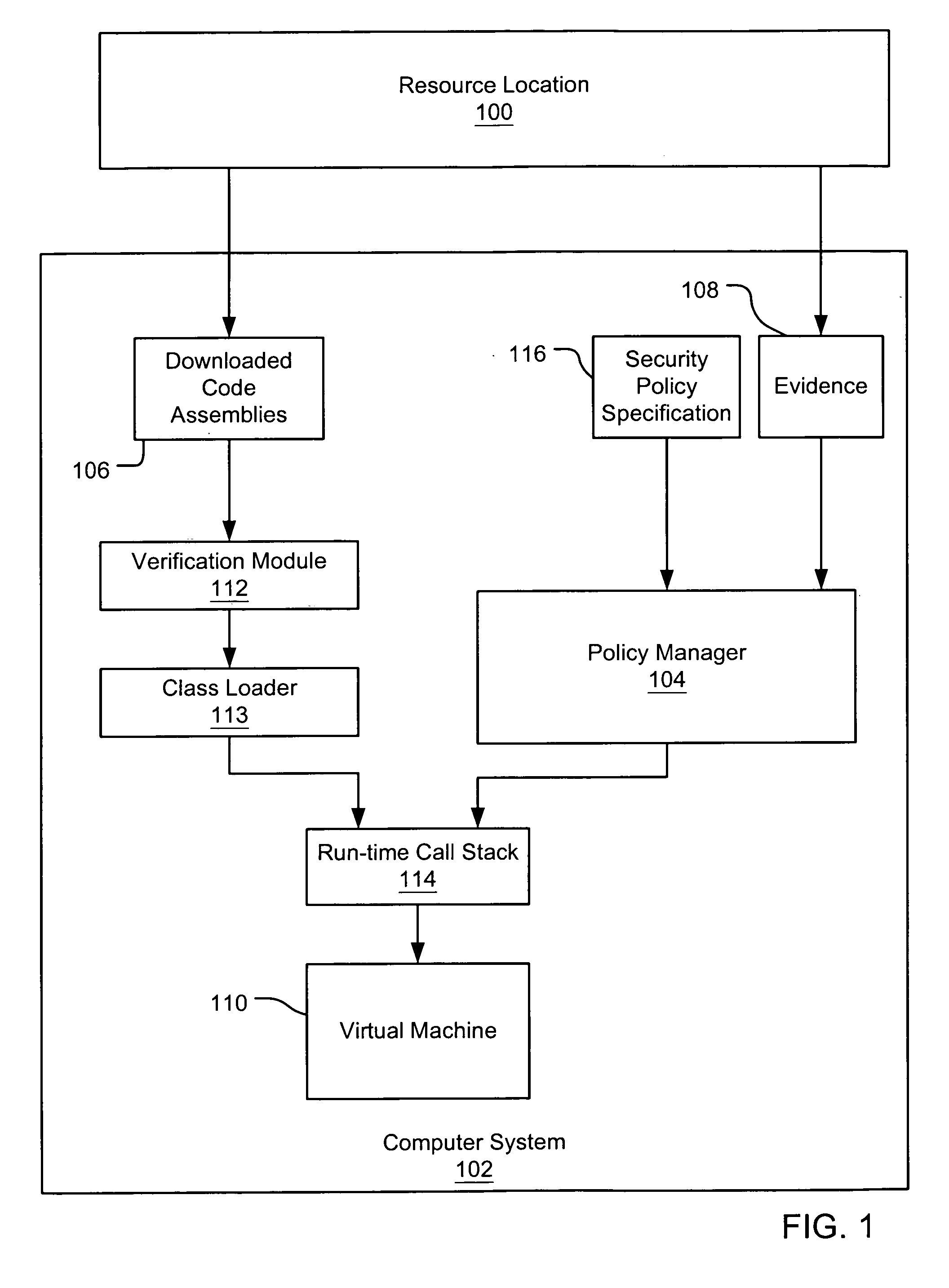
Evaluating initially untrusted evidence in an evidence-based security policy manager
InactiveUS7131143B1Digital data processing detailsAnalogue secracy/subscription systemsCall stackTrust level
An evidence-based policy manager generates a permission grant set for a code assembly received from a resource location. The policy manager executes in a computer system (e.g., a Web client or server) in combination with the verification module and class loader of the run-time environment. The permission grant set generated for a code assembly is applied in the run-time call stack to help the system determine whether a given system operation by the code assembly is authorized. Both code assemblies and evidence may be received from a local origin or from a remote resource location via a network (e.g., the Internet). Evidence having different levels of trust may be evaluated in combination so that a permission grant set is associated only with trusted code assemblies. The policy manager may comprise execution modules for parsing a security policy specification, generating one or more code hierarchies, evaluating membership of the received code assembly in one or more code groups, and generating a permission grant set based upon this membership evaluation.
Owner:MICROSOFT TECH LICENSING LLC
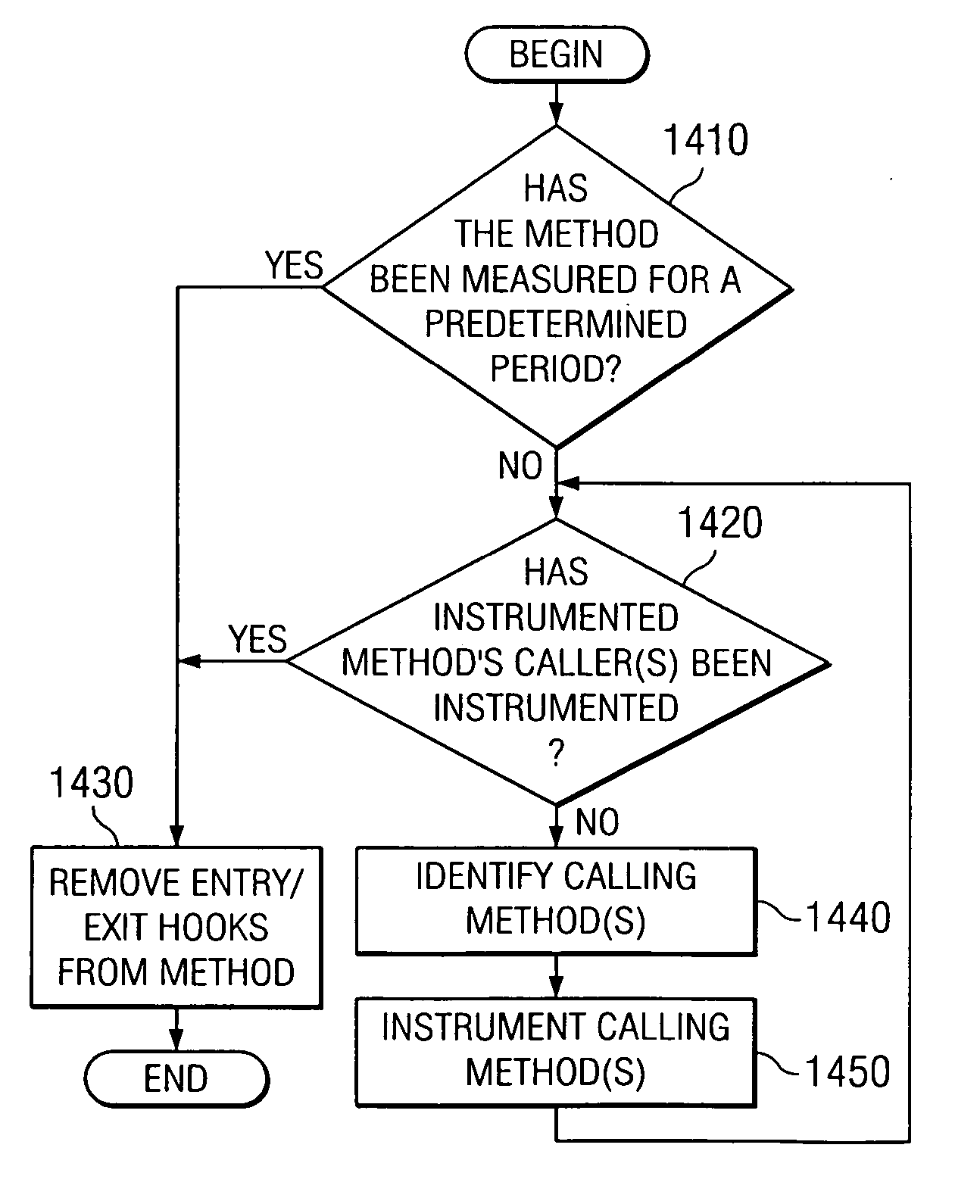
Apparatus and method for dynamic instrumenting of code to minimize system perturbation
InactiveUS20070006168A1Minimize the numberError detection/correctionSpecific program execution arrangementsCall stackDynamic instrumentation
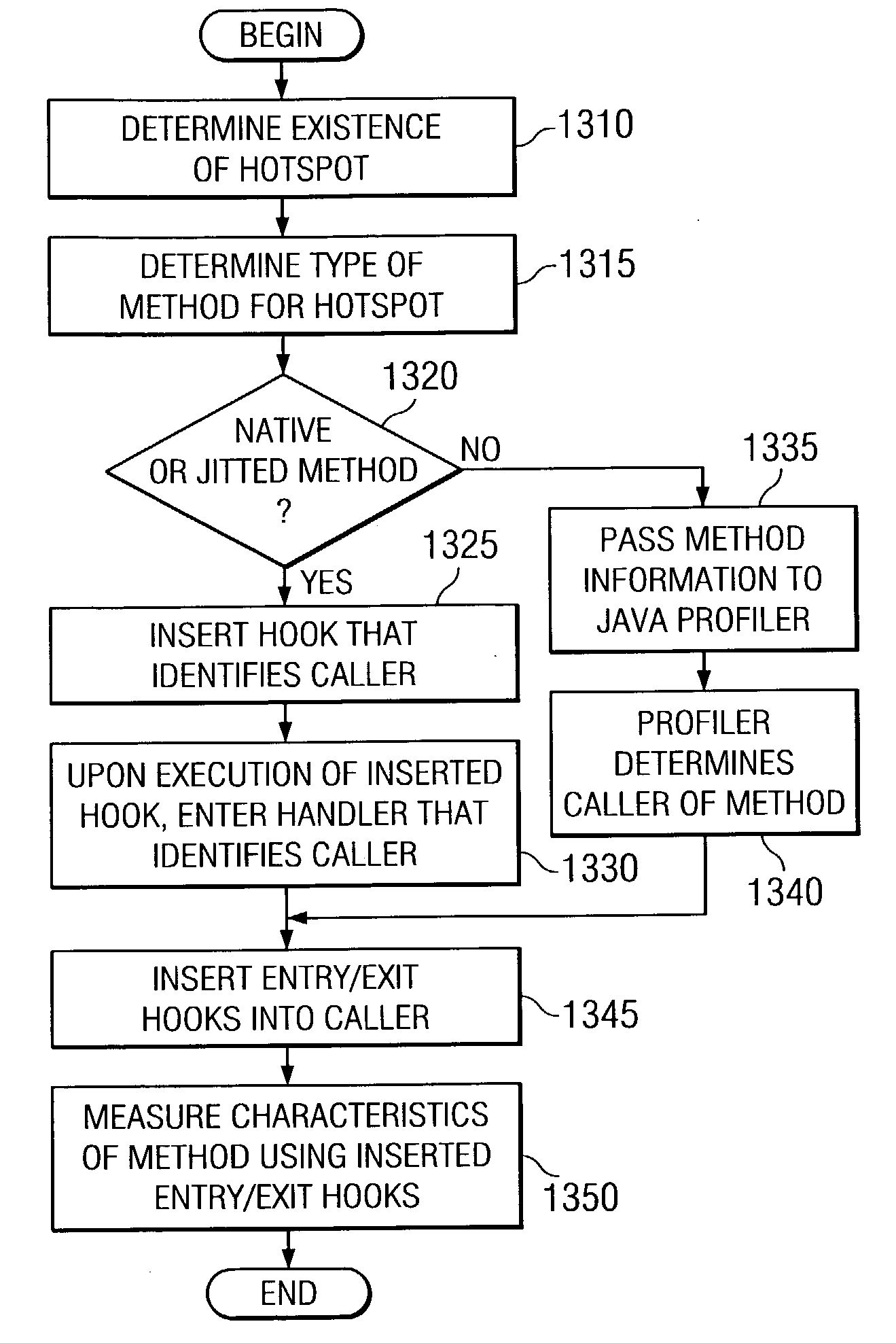
An apparatus and method are provided for the dynamic instrumentation of code to minimize system perturbation during tracing of the execution of the code. With the apparatus and method, “hot spots” in the execution of the code are dynamically determined during tracing of the execution of the code. These “hot spots” are dynamically instrumented, i.e. an event hook is inserted, to cause control to be passed to a handler that determines a caller of the “hot spot” method. The method that called the “hot spot” method, or “caller” method, is identified from a call stack and is dynamically instrumented for an appropriate metric so that the next time the calling method is executed, the dynamically inserted hooks are executed. The execution of the hooks in the caller method is continued for a predetermined period, e.g., number of invocations, to get an understanding of the caller method's characteristics. A list of callers of instrumented methods is maintained and used to determine one or more calling methods of the instrumented caller method. One or more of these calling methods may be instrumented and the hooks inserted in the instrumented caller method (called by the one or more calling methods), are removed. In this way, the call graph of the hot spots of a program execution is “walked up” and characterized over time.
Owner:IBM CORP
Method and apparatus for call stack sampling to obtain information for analyzing idle states in a data processing system
ActiveUS20080148240A1Error detection/correctionSpecific program execution arrangementsCall stackData processing system
A computer implemented method, apparatus, and computer usable program code for sampling call stack information. Monitoring for an event is performed during an execution of a plurality of threads by a set of processors. A portion of the plurality of threads is identified based on a policy to form a set of identified threads in response to an occurrence of the event. Call stack information is collected for the set of identified threads using an under utilized processor in a set of processors in response to identifying the portion of the plurality of threads, wherein the call stack information is used to profile a processor in the set of processors.
Owner:IBM CORP
Apparatus and method for dynamic instrumenting of code to minimize system perturbation
InactiveUS7114150B2Minimize the numberError detection/correctionSpecific program execution arrangementsTime scheduleCall stack
An apparatus and method are provided for the dynamic instrumentation of code to minimize system perturbation during tracing of the execution of the code. With the apparatus and method, “hot spots” in the execution of the code are dynamically determined during tracing of the execution of the code. These “hot spots” are dynamically instrumented, i.e. an event hook is inserted, to cause control to be passed to a handler that determines a caller of the “hot spot” method. The method that called the “hot spot” method, or “caller” method, is identified from a call stack and is dynamically instrumented for an appropriate metric so that the next time the calling method is executed, the dynamically inserted hooks are executed. The execution of the hooks in the caller method is continued for a predetermined period, e.g., number of invocations, to get an understanding of the caller method's characteristics. A list of callers of instrumented methods is maintained and used to determine one or more calling methods of the instrumented caller method. One or more of these calling methods may be instrumented and the hooks inserted in the instrumented caller method (called by the one or more calling methods), are removed. In this way, the call graph of the hot spots of a program execution is “walked up” and characterized over time.
Owner:IBM CORP
Methods, systems, and computer program products for summarizing operational behavior of a computer program
InactiveUS20050273757A1Simple processSmall artifacts (whichError detection/correctionReverse engineeringCall stackOperational behavior
Methods, systems, and computer program products for summarizing operational behavior of a computer program are disclosed. A method for summarizing the operational behavior of a computer program may include executing a computer program in a mode that allows control over execution of the computer program. Execution of the program is paused at predetermined locations corresponding to each instruction in the computer program. For each location, contents of a call stack containing function calls made by the program that have not yet returned are recorded. For each function call in the call stack, information regarding conditions under which the function was called are recorded. Execution of the program is resumed until the next pause location is encountered.
Owner:ANDERSON CRAIG D
Apparatus and method for call stack profiling for a software application
InactiveUS20060130001A1Error detection/correctionSpecific program execution arrangementsCall stackParallel computing
A method and apparatus for monitoring the performance of a computer system with one or more active programs. A periodic sampling of the call stack is obtained. The sampled call stack is examined to infer the system performance similar to that obtained using prior art event based profiling. Embodiments also are directed to a combination approach to describing the system performance using a historical sampling to infer additional detail to fill in the gaps of the sampled data.
Owner:IBM CORP
Method and Apparatus for Call Stack Sampling Using a Virtual Machine
InactiveUS20090178036A1Error detection/correctionSoftware simulation/interpretation/emulationCall stackMemory working
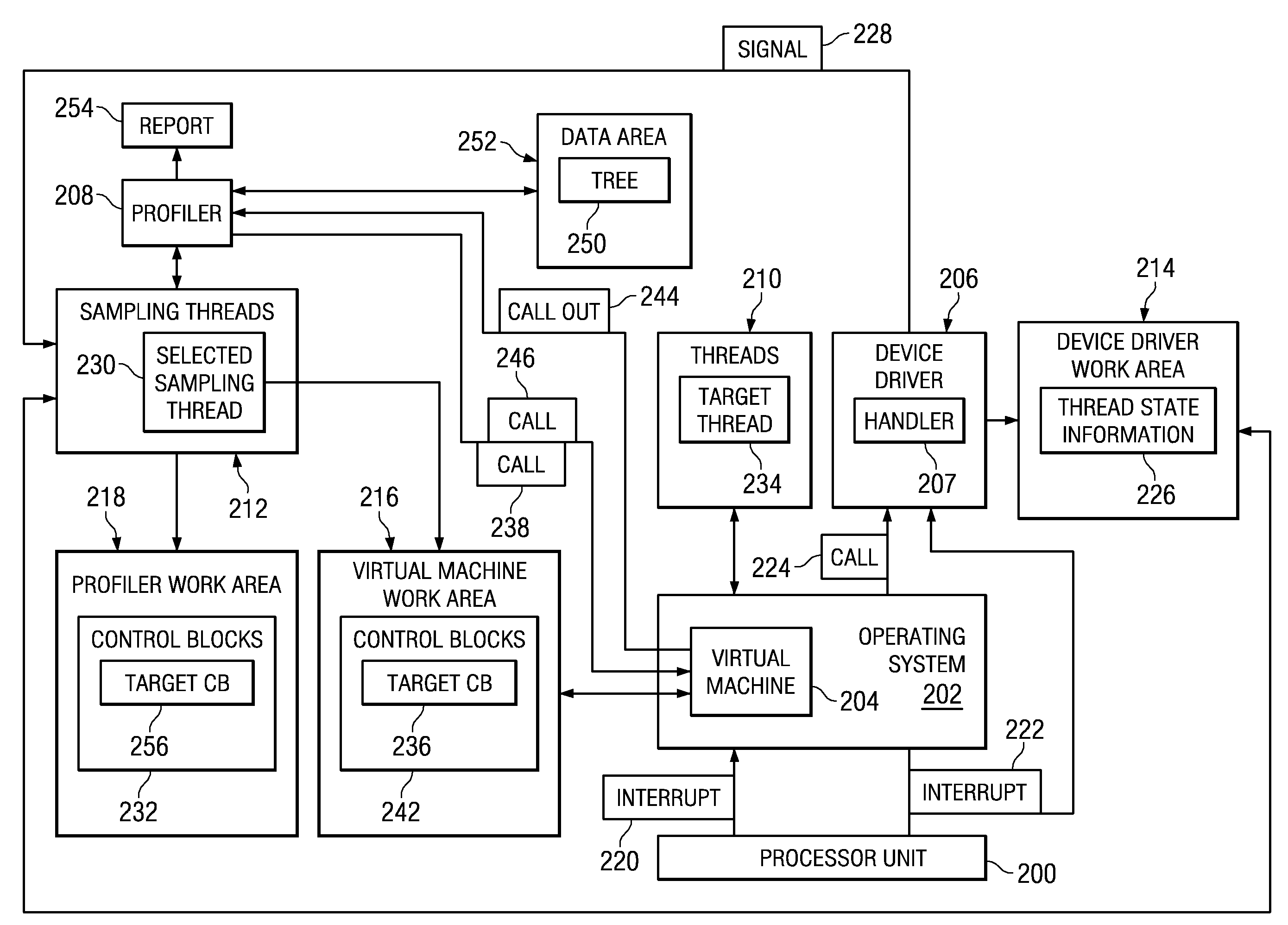
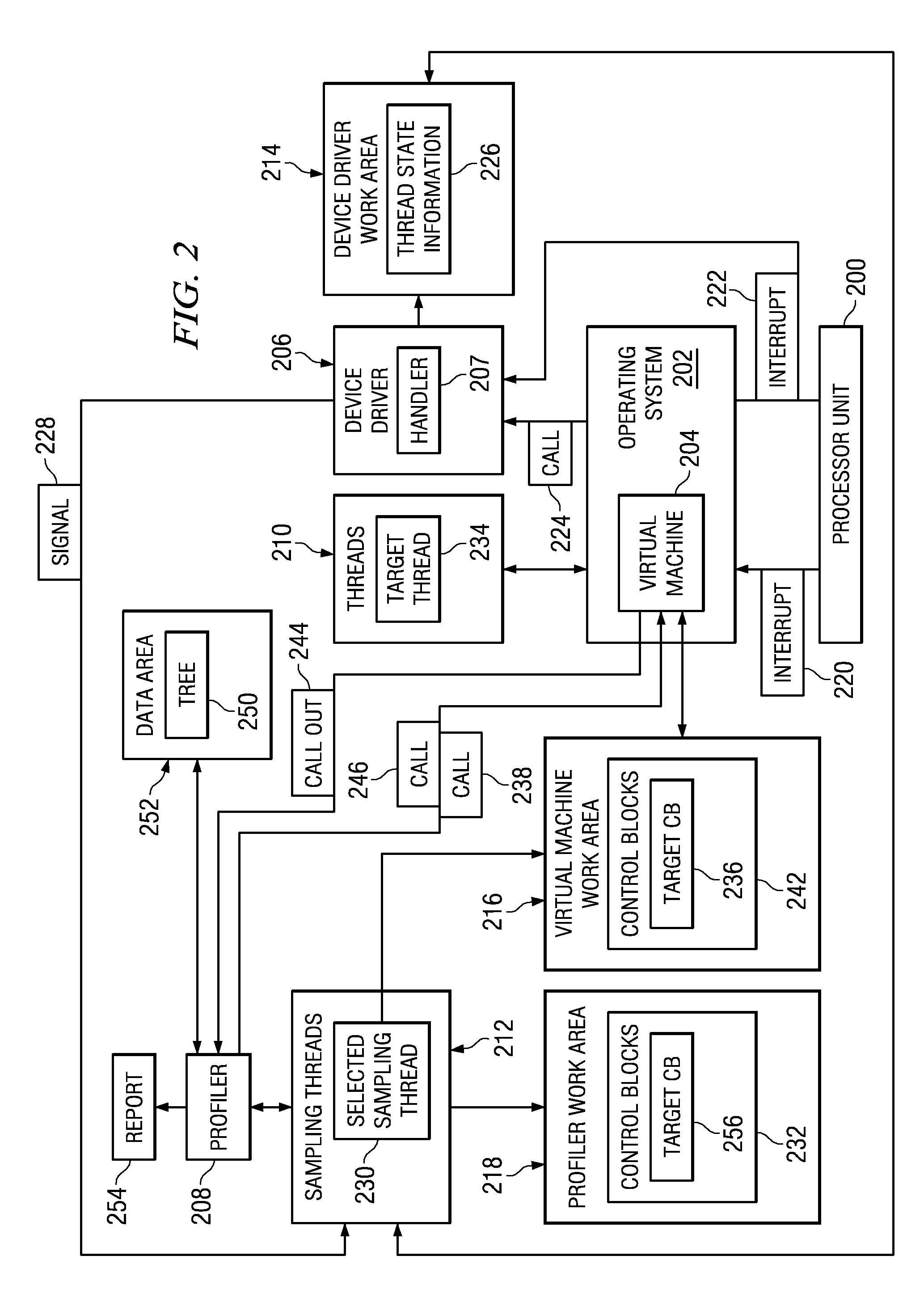
A computer implemented method, apparatus, and computer usable program code for sampling call stack information. A flag associated with a target thread is set in a memory work area associated with a virtual machine in response to an interrupt. Monitoring for an event during execution of a plurality of threads created by the virtual machine. A determination is made as to whether the flag is set in response to an occurrence of the event. If the flag is set, the virtual machine makes a call out to a profiler which initiates sampling of the call stack information in response to the flag being set.
Owner:IBM CORP
Apparatus and method for autonomic hardware assisted thread stack tracking
InactiveUS20050102673A1Not affectProgram control using stored programsError detection/correctionCall stackOperational system
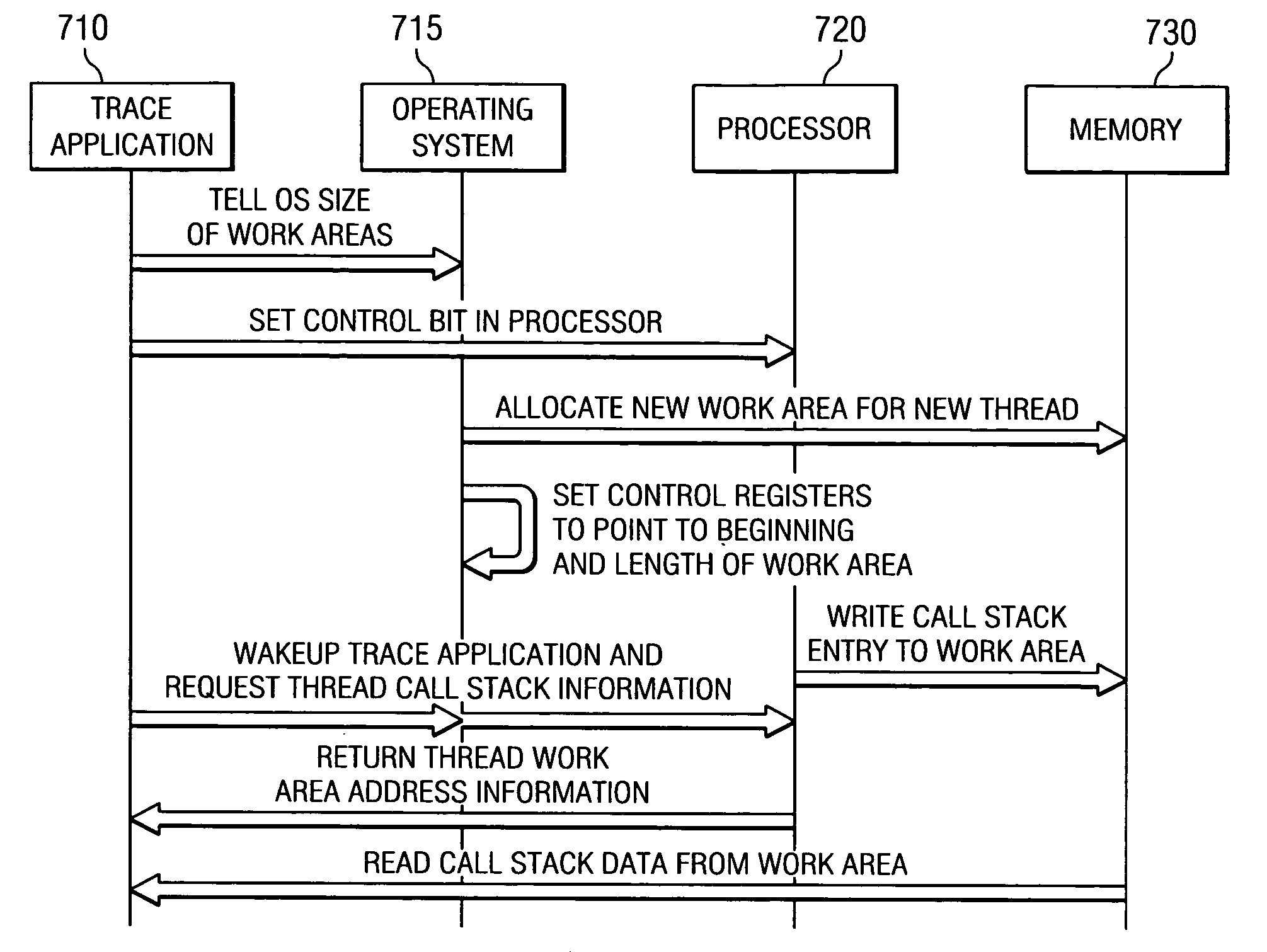
A method and apparatus for providing an autonomic mechanism for tracking thread stacks during a trace of a computer program. The method and apparatus include hardware assistance mechanisms that allow the processor to autonomically maintain a work area for each thread where a call stack is stored. With the apparatus and method, the operating system of the computing device informs the operating system of the size of the data area to allocate to a particular thread work area. In addition, when a trace of a computer program is to be performed, the trace software, via the operating system, informs the processor to begin maintaining the thread call stack information in the thread work area. For each thread in the computer program execution, the processor maintains a work area having a size that is determined based on the size communicated by the operating system. The work area is designated by address and length information stored in control registers of the processor. The processor contains microcode that is used to cause the processor to automatically store thread tracking information in the work areas designated by the control registers of the processor when the control bit is set.
Owner:IBM CORP
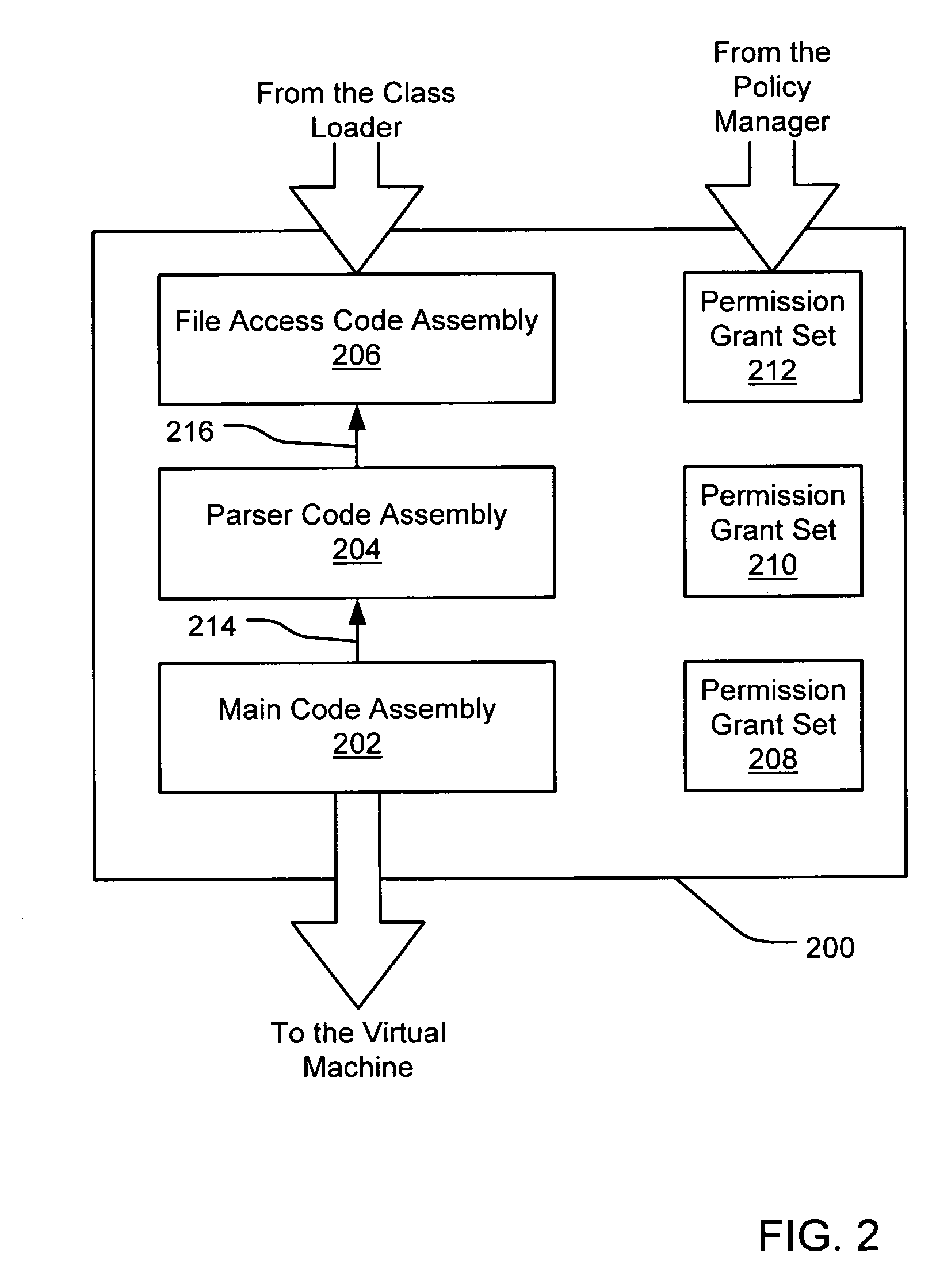
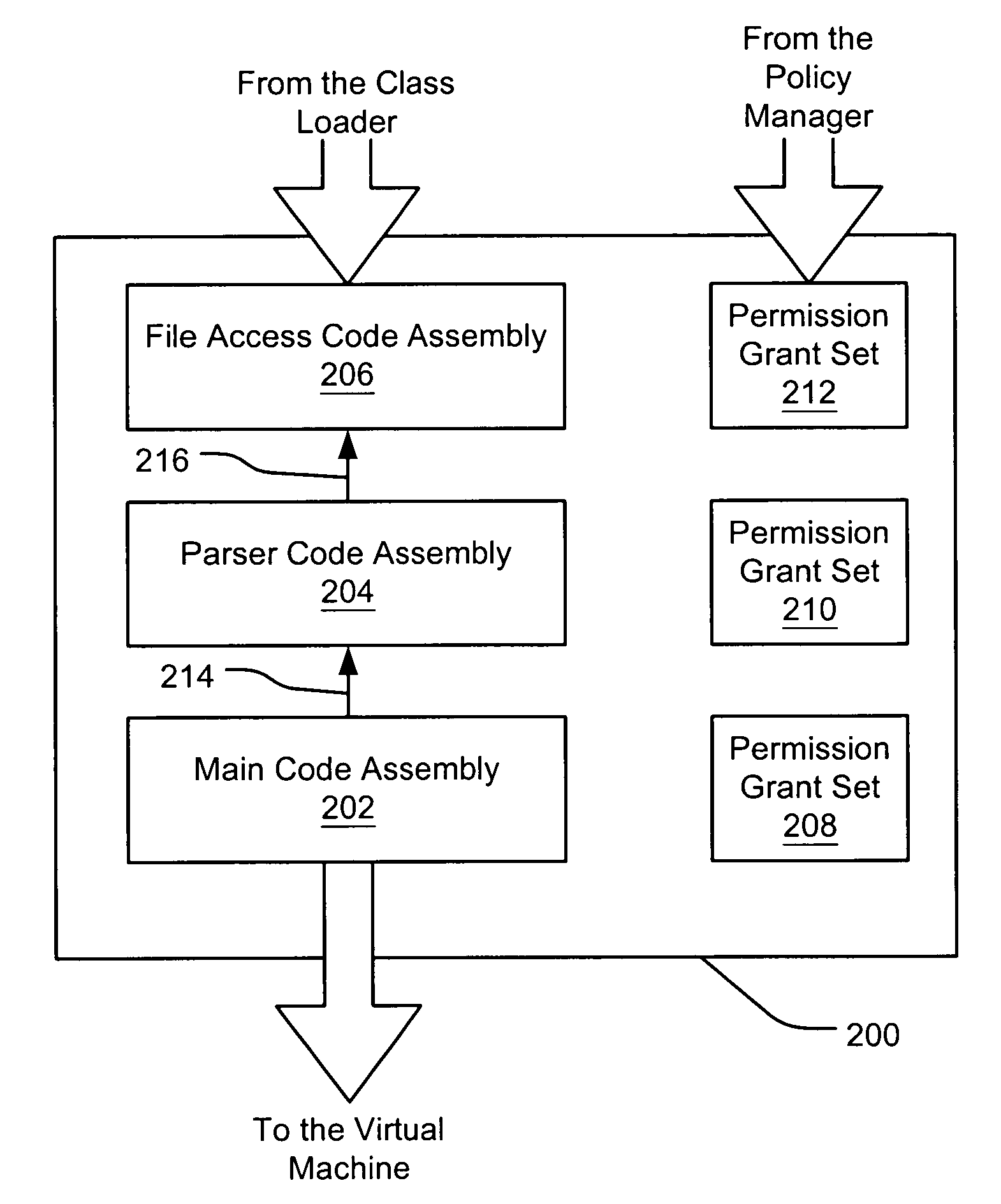
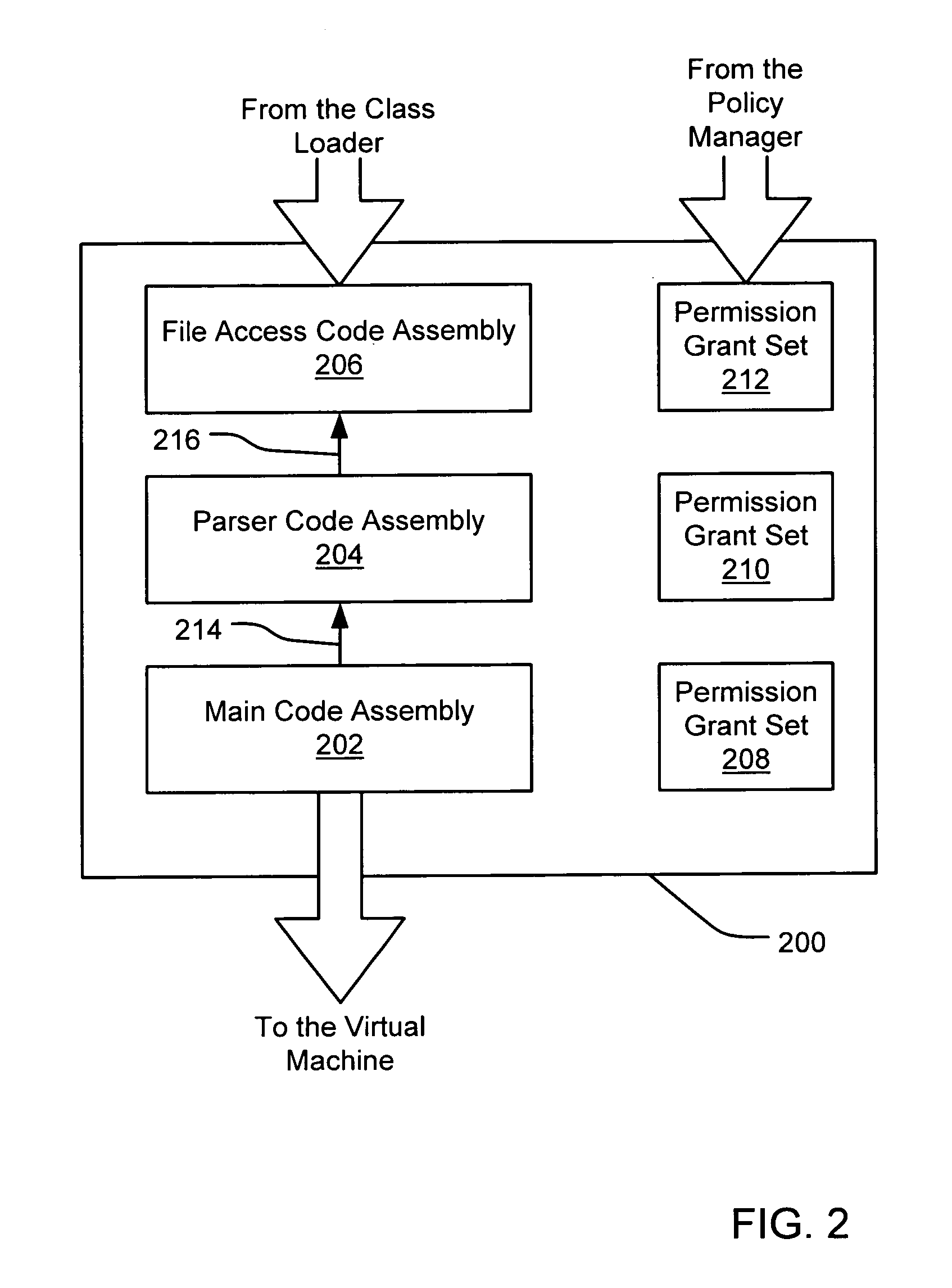
Filtering a permission set using permission requests associated with a code assembly
InactiveUS6981281B1Avoid contactPrevent inadvertent accessDigital data processing detailsUser identity/authority verificationCall stackComputerized system
A security policy manager generates a permission grant set for a code assembly received from a resource location. The policy manager can execute in a computer system (e.g., a Web client) in combination with the verification module and class loader of the run-time environment. The permission grant set generated for a code assembly is applied in the run-time call stack to help the system determine whether a given system operation by the code assembly is authorized. A permission request set may also be received in association with the code assembly. The permission request set may include a minimum request set, specifying permissions required by the code assembly to run properly. The permission request set may also include an optional request set, specifying permissions requested by the code assembly to provide an alternative level of functionality. In addition, the permission request set may include a refuse request set, specifying permissions that are not to be granted to the code assembly. The permission requests are used to filter a permission set to generate a permission grant set.
Owner:MICROSOFT TECH LICENSING LLC
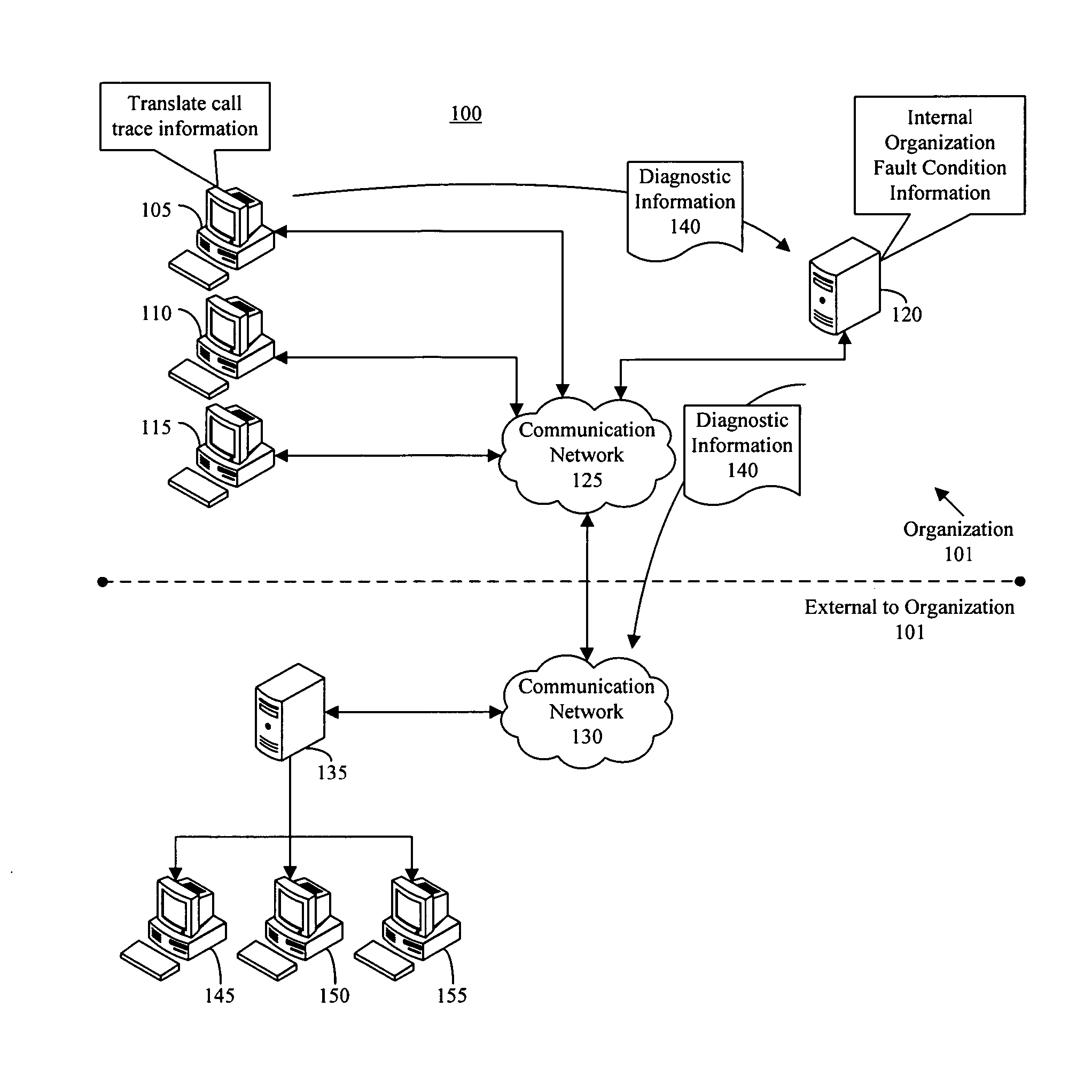
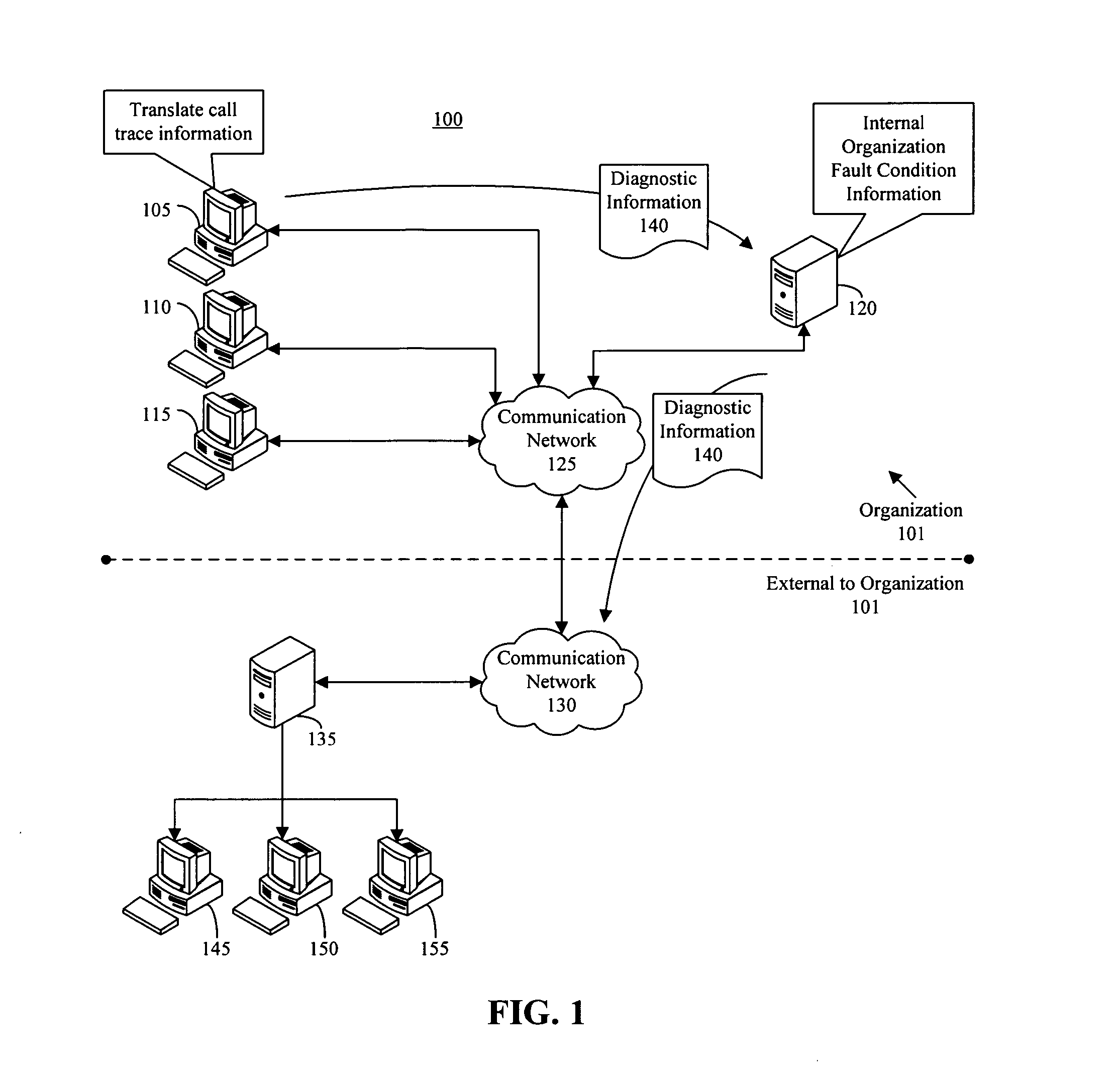
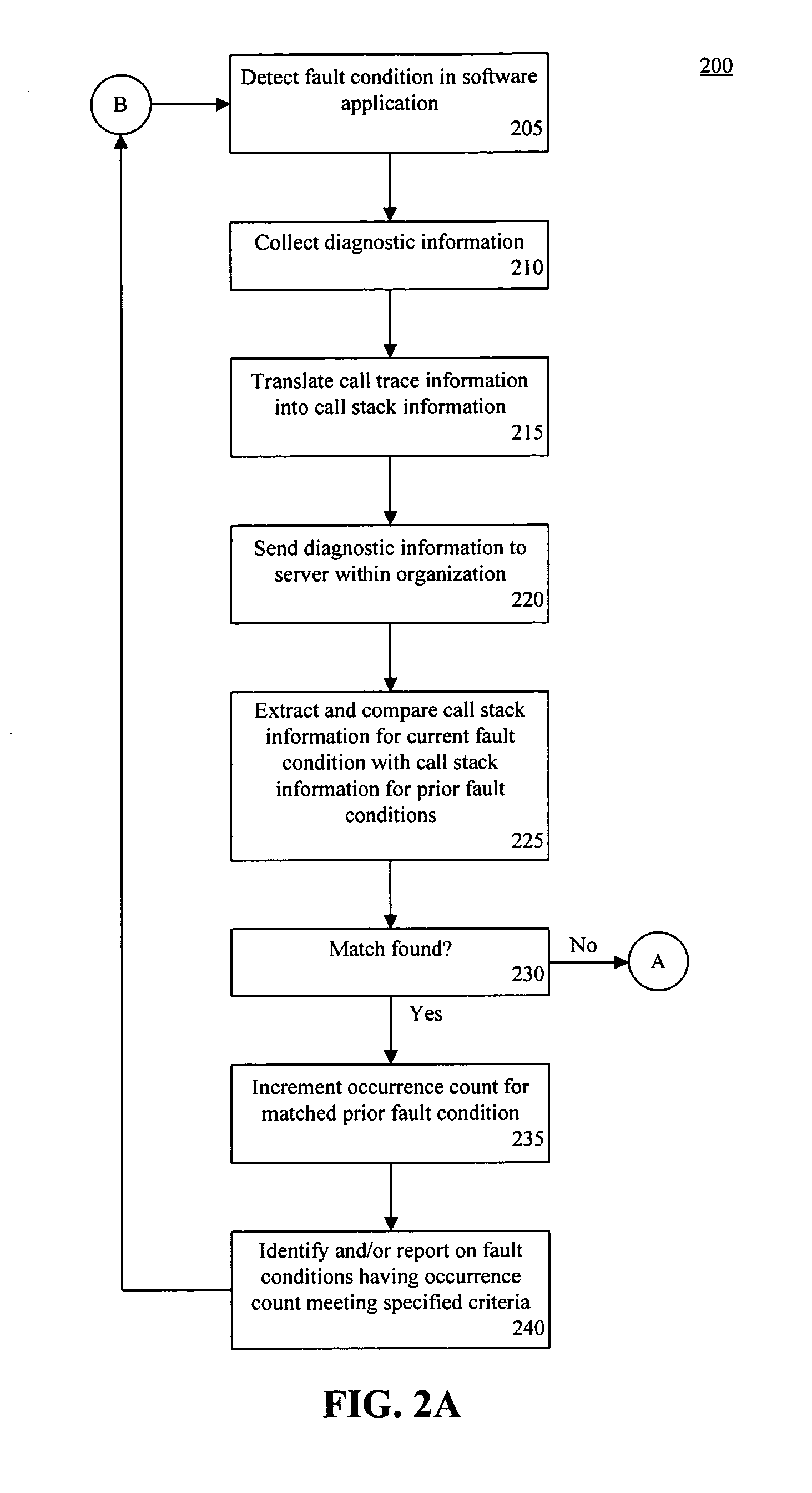
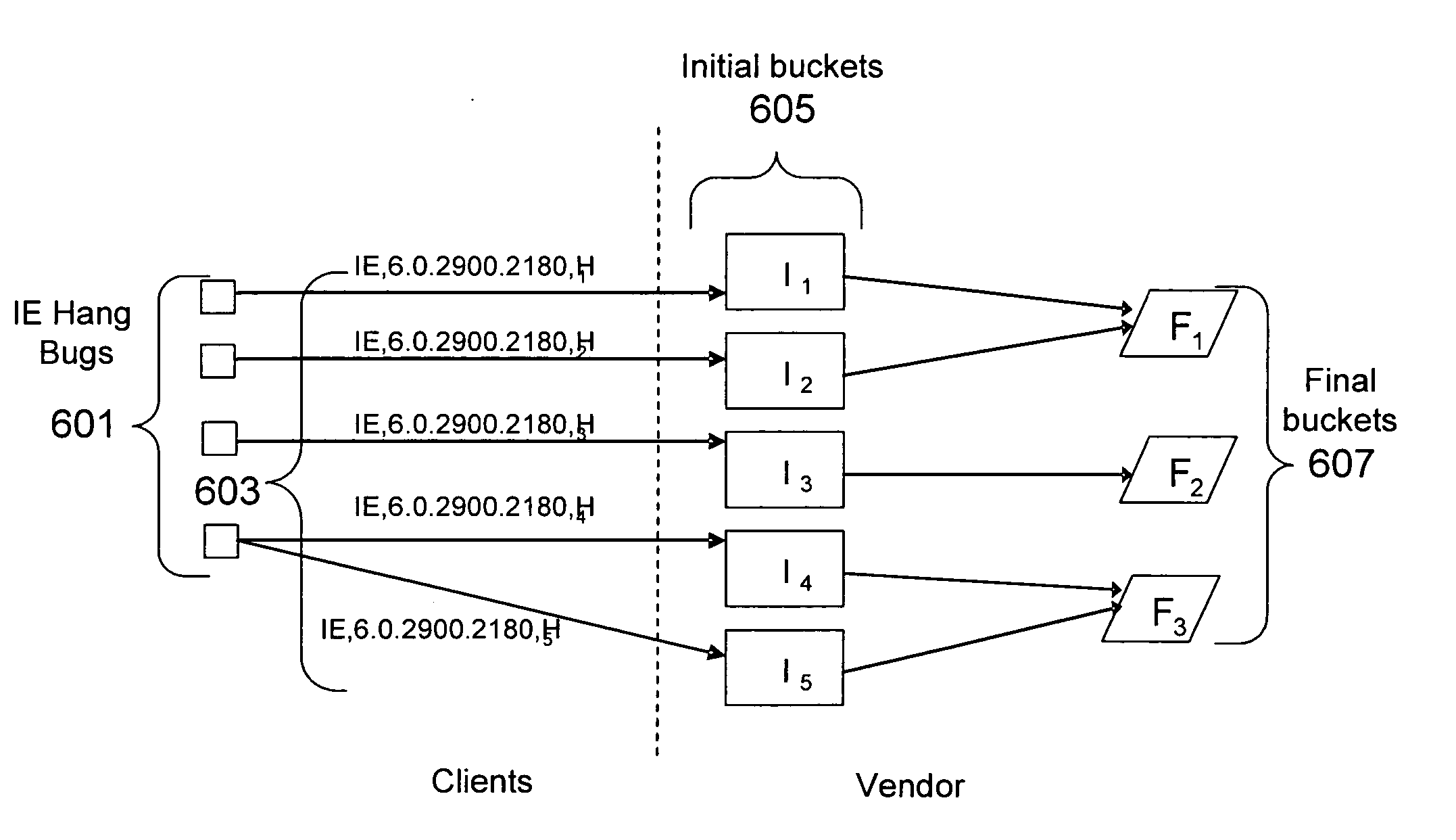
Call-stack pattern matching for problem resolution within software
A method of diagnosing a fault condition within software can include, responsive to a fault condition within a computing system belonging to an organization, automatically sending call-stack information for the fault condition to a first server within the organization. Within the first server, the call-stack information for the fault condition can be compared with call-stack information from prior fault conditions that occurred within the organization to determine whether the call-stack information for the fault condition matches call-stack information from one of the prior fault conditions. The method further can include sending the call-stack information to a second server for comparison with call-stack information from prior fault conditions that occurred within at least one different organization if the call-stack information for the fault condition does not match.
Owner:IBM CORP
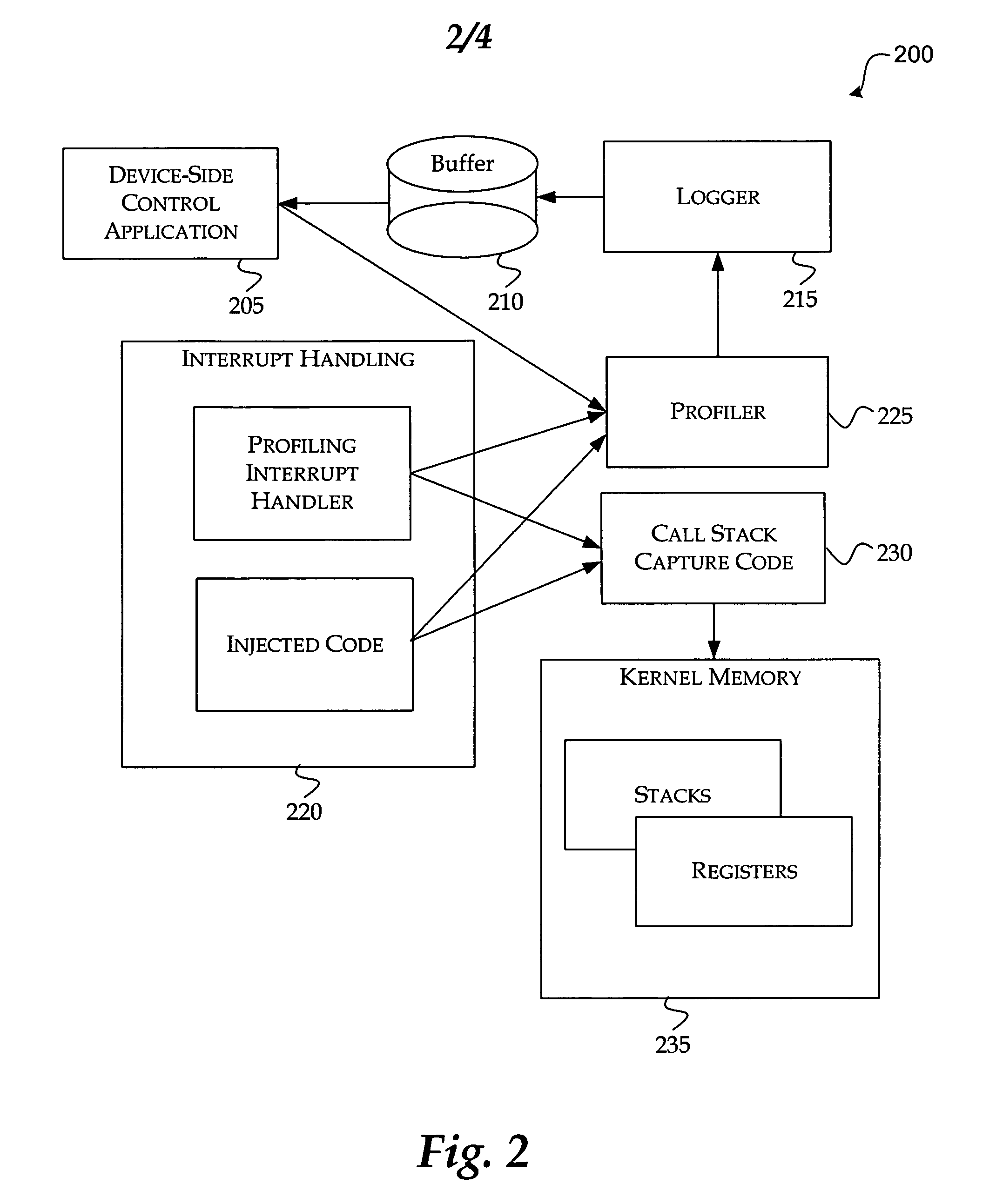
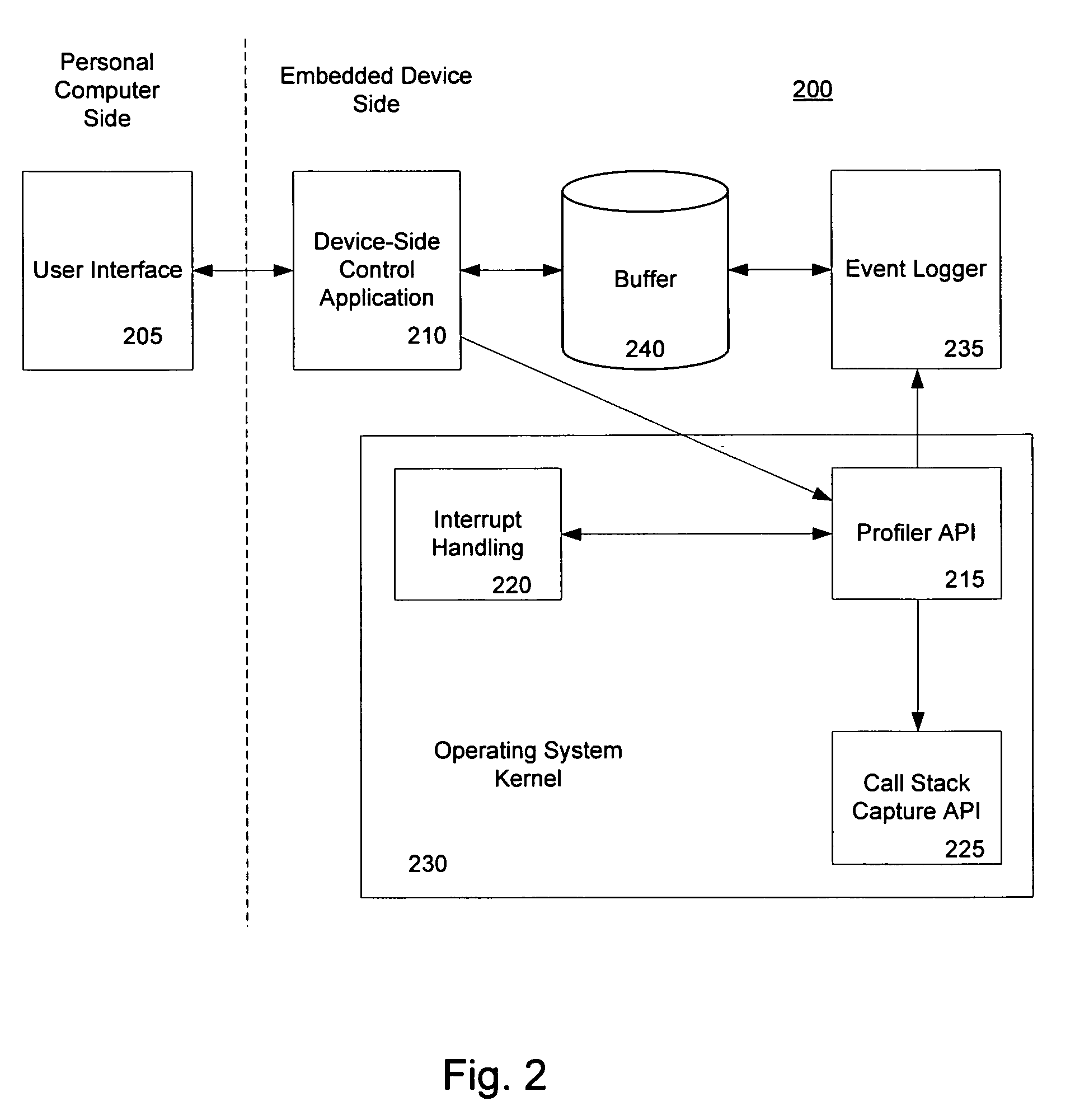
Call stack capture in an interrupt driven architecture
InactiveUS20060059486A1Simplify workError detection/correctionMultiprogramming arrangementsCall stackCpu architecture
The present invention provides a method and system for capturing the call stack of a currently-running thread at the time a profiler interrupt occurs. The thread context of the thread is determined before a full push of the thread context is performed by the CPU architecture. The hardware state at the time of the interrupt is used to aid in determining which portions of memory to search for portions of the thread context. Based on the hardware state and the software state of the thread at the time of the interrupt the thread context is captured. Code may also be injected into a thread to capture a thread's call stack. The state of the thread is altered to induce the thread to invoke the kernel's call stack API itself, using its own context.
Owner:MICROSOFT TECH LICENSING LLC
Using a call stack hash to record the state of a process
InactiveUS20060253837A1Minimal impact performanceRaise privacy concernError detection/correctionSpecific program execution arrangementsCall stackRoot cause
In embodiments of the invention, selected aspects of a process' call stacks are hashed, and the hash is used to capture the execution state of the process in a concise form and with minimal impact on the performance of the process and with no modification to the process code. The hash allows vendors and developers to classify failures in order to associate them with their known root causes to support rapid customer feedback and to maximize efficiency of correction. Further, the hash provides a metric usable to prioritize diagnosis of failures. In an embodiment of the invention, the identities of modules on the call stack are hashed in combination with some but not all offset information to minimize the affect of patches and minor changes to the code, and improve the ability to discriminate different execution paths.
Owner:MICROSOFT TECH LICENSING LLC
System and method for batch evaluation programs
ActiveUS9348677B2Reduce the number of processesImprove application efficiencyProgram initiation/switchingObject oriented databasesCall stackBatch processing
A batching module that inspects call stacks within a stack evaluator to identify current expressions that can be evaluated in batch with other expressions. If such expressions are identified, the corresponding stacks are blocked from further processing and a batch processing request for processing the expressions is transmitted to the application server. The application server processes the expressions in batch and generates a value for each of the expressions. The blocked stacks are then populated with the values for the expressions.
Owner:PALANTIR TECHNOLOGIES
Evidence-based security policy manager
InactiveUS7051366B1Increase flexibilityAddressing slow performanceDigital data processing detailsUser identity/authority verificationCall stackThe Internet
An evidence-based policy manager generates a permission grant set for a code assembly received from a resource location. The policy manager executes in a computer system (e.g., a Web client or server) in combination with the verification module and class loader of the run-time environment. The permission grant set generated for a code assembly is applied in the run-time call stack to help the system determine whether a given system operation by the code assembly is authorized. Both code assemblies and evidence may be received from a local origin or from a remote resource location via a network (e.g., the Internet). The policy manager may comprise execution modules for parsing a security policy specification, generating a one or more code hierarchies, evaluating membership of the received code assembly in one or more code groups, and generating a permission grant set based upon this membership evaluation.
Owner:MICROSOFT TECH LICENSING LLC
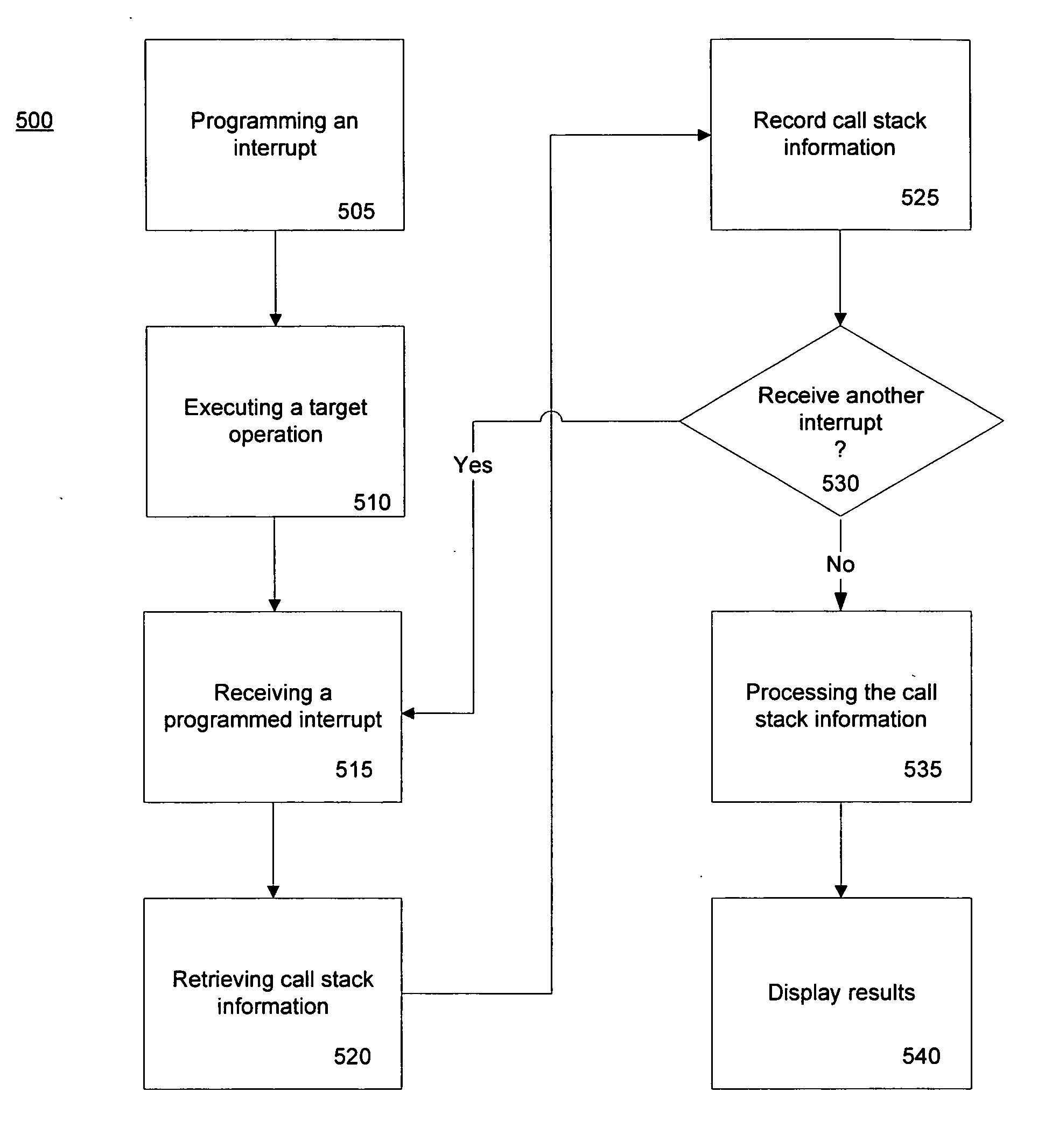
Method and system for a call stack capture
InactiveUS20060075386A1Reduces effect of profilingEliminate the effects ofError detection/correctionSpecific program execution arrangementsCall stackOperational system
A method of acquiring software profile information of a target software application includes receiving a programmed interrupt while executing an application in a computer system, servicing the interrupt such that call stack information is acquired and processing the call stack information to produce statistical information concerning function calls. The call stack information includes program counter and other information which is derived from the target application as well as operating system. Some or all of the call stack information may be recorded. The statistical information includes statistics concerning the number of samples wherein a series of functions calls are included in the call stack information and the number of samples wherein a set of function calls are at the top of the call stack information.
Owner:MICROSOFT TECH LICENSING LLC
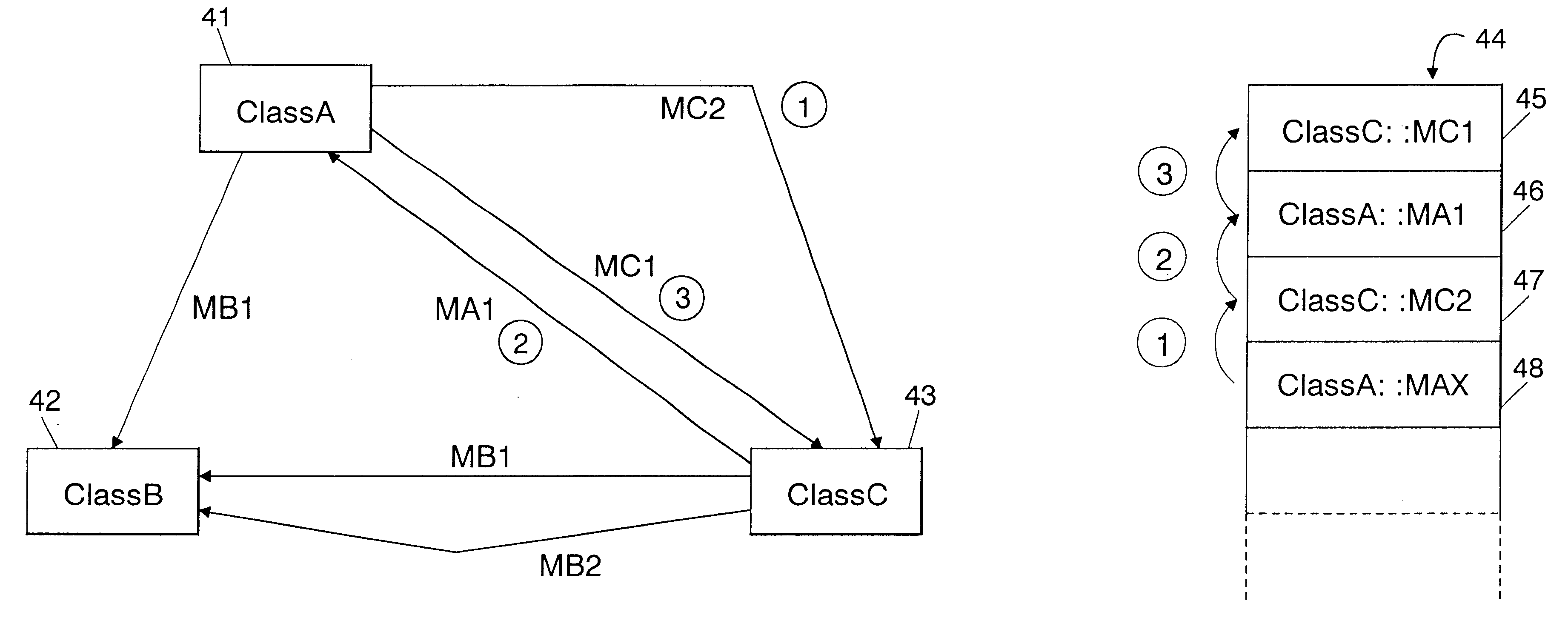
Method and system for analyzing and displaying program information
InactiveUS6240549B1Program control using stored programsMultiprogramming arrangementsCall stackComputer science
Through an operation of a debugger 57, a process with respect to certain assumed collaboration is carried out for each module such that breakpoints may be set up at appropriate locations in a program. Executing the program, call relations up to a setup time of a breakpoint are stacked on a call stack. Using the debugger 57, these call relations are stored into a collaboration repository 51. A builder 52 is a means for controlling an overall development environment. This builder 52 may call a debugger 57 or another function 53 for displaying program information that comprises a collaboration matrix 54, a call graph 55, a class browser 56 and the like.
Owner:IBM CORP
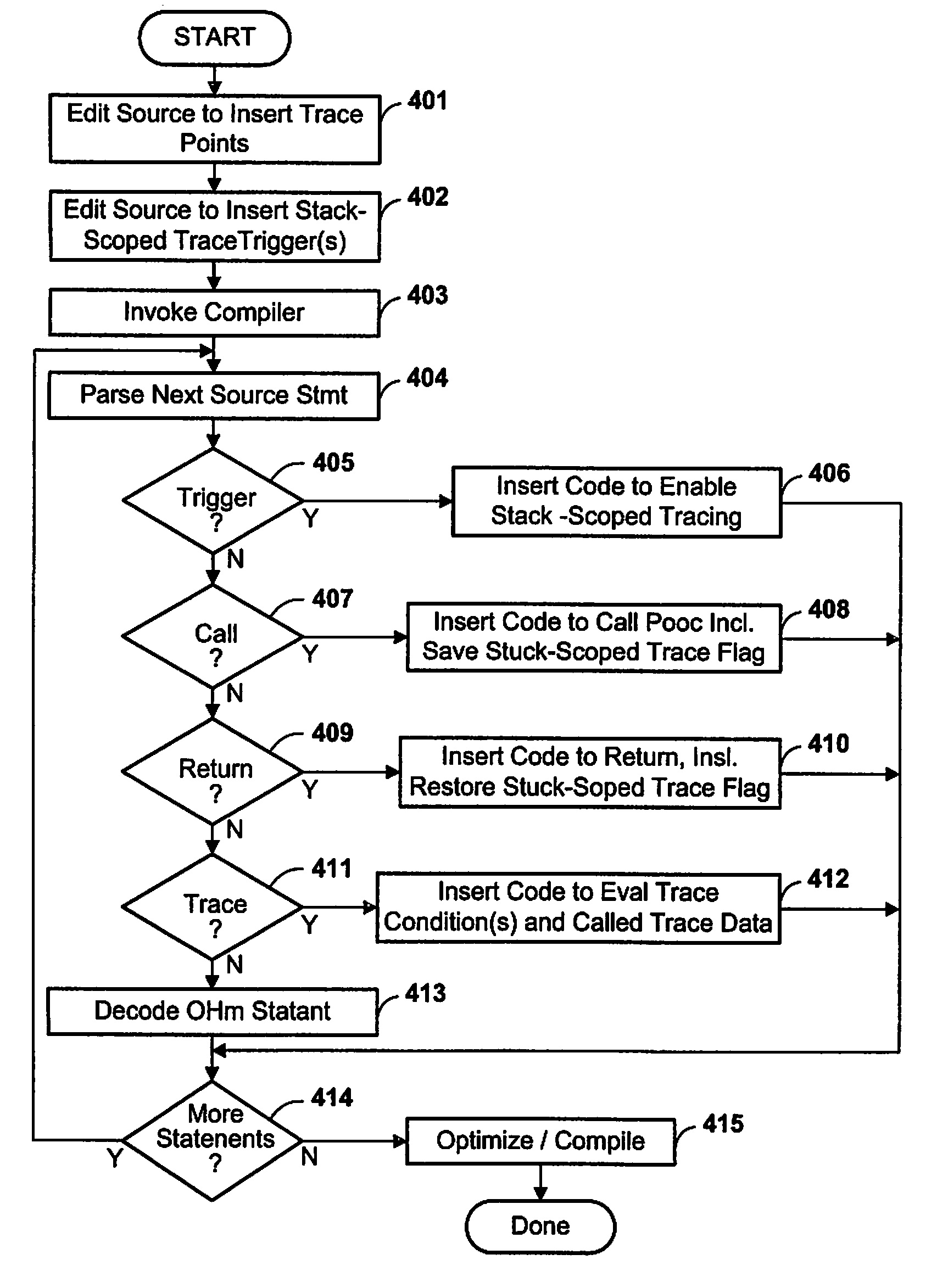
Method and Apparatus for Tracing Execution of Computer Programming Code Using Dynamic Trace Enablement
InactiveUS20080134148A1Lower the volumeMore collectionError detection/correctionSpecific program execution arrangementsCall stackParallel computing
A computer program is traced by associating a trigger with at least one code location, and upon encountering the trigger during execution, selectively enabling trace data collection data at subsequent traceable events. Preferably, collection of trace data is enabled only for procedure instances active (i.e., currently executing or on the call stack) at the time that the trigger is encountered. Preferably, a special environmental flag is set on encountering the trigger, saved in each current stack frame, reset on calling any new procedure, and restored from the stack on return from a procedure. Collection of trace data on a traceable event (such as an explicit trace statement in the code) is conditioned on the state of the special environmental flag.
Owner:IBM CORP
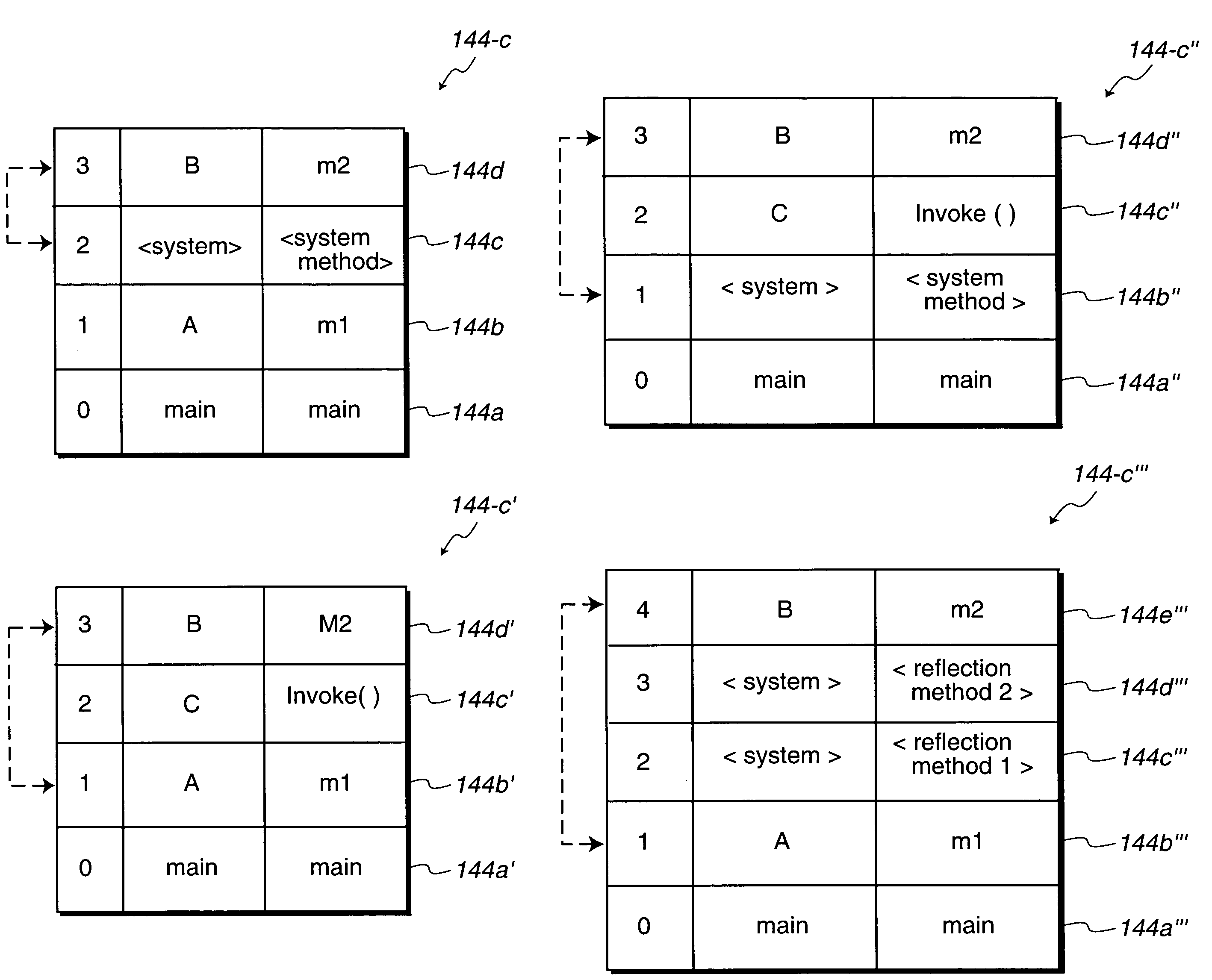
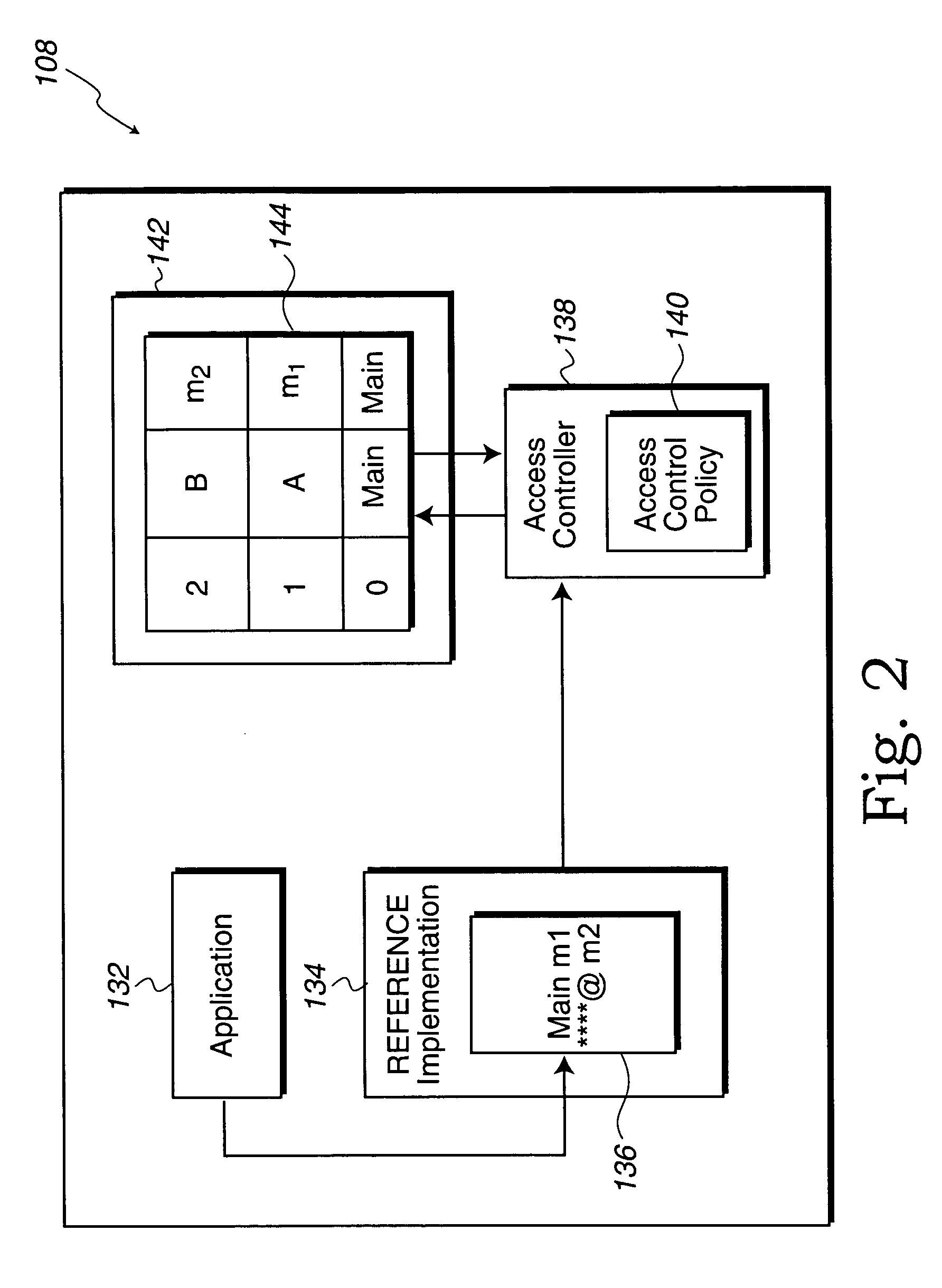
Method and system for detecting deprecated elements during runtime
ActiveUS7320123B2Access be denyInterprogram communicationDigital computer detailsCall stackApplication software
A method for controlling access to deprecated methods of an implementation is provided. The method includes receiving a request to access a method that has been marked as deprecated and building a call stack for the request. Also included is inspecting the call stack to determine if the request is from an application outside of the implementation. The method further includes acting on the request in accordance with a control policy defined by a pluggable policy.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com