Patents
Literature
1334results about "Reverse engineering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
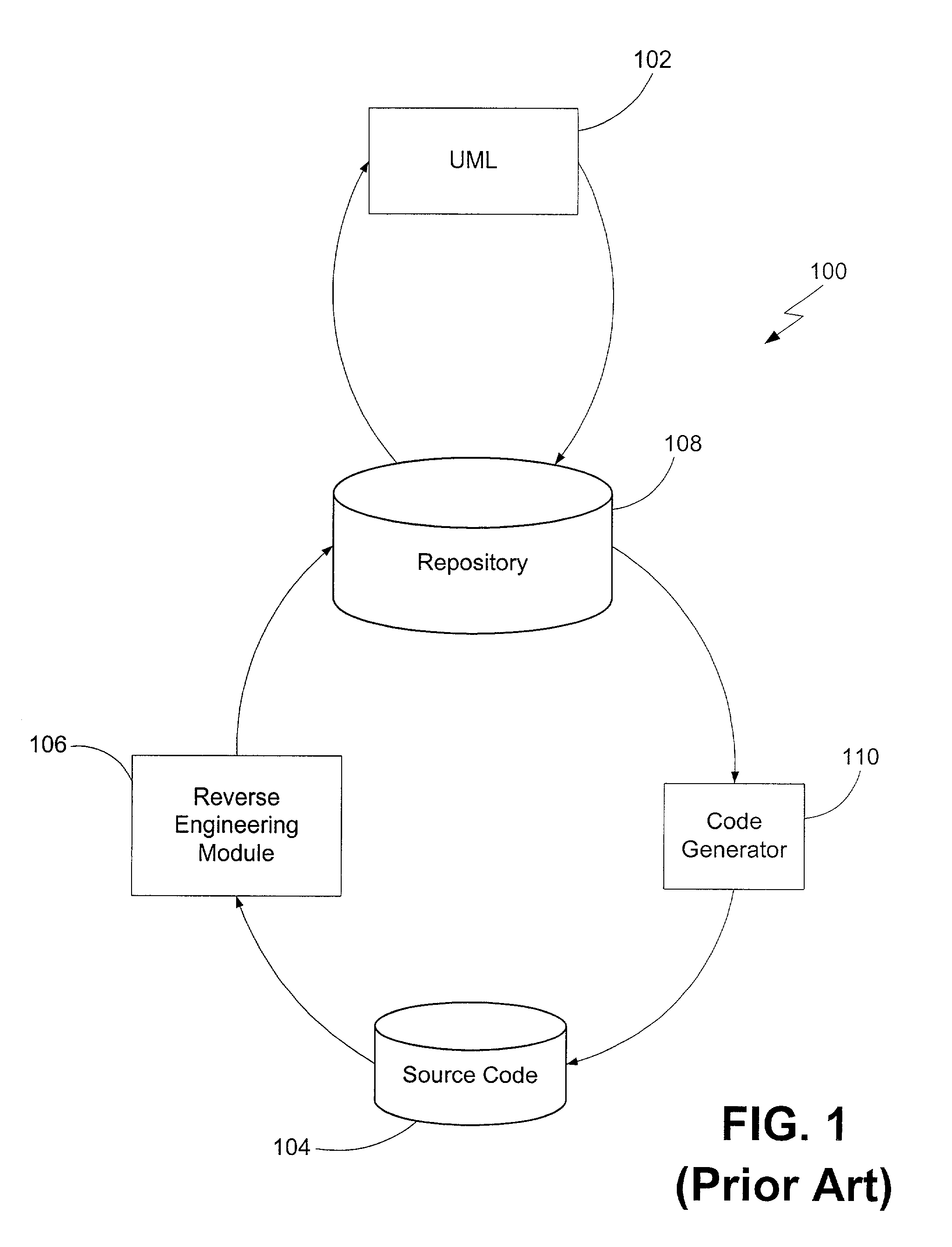
A System for analyzing applications in order to find security and quality issues
InactiveUS20150309813A1Accurate analysisError detection/correctionComputer security arrangementsMachine controlWeb application
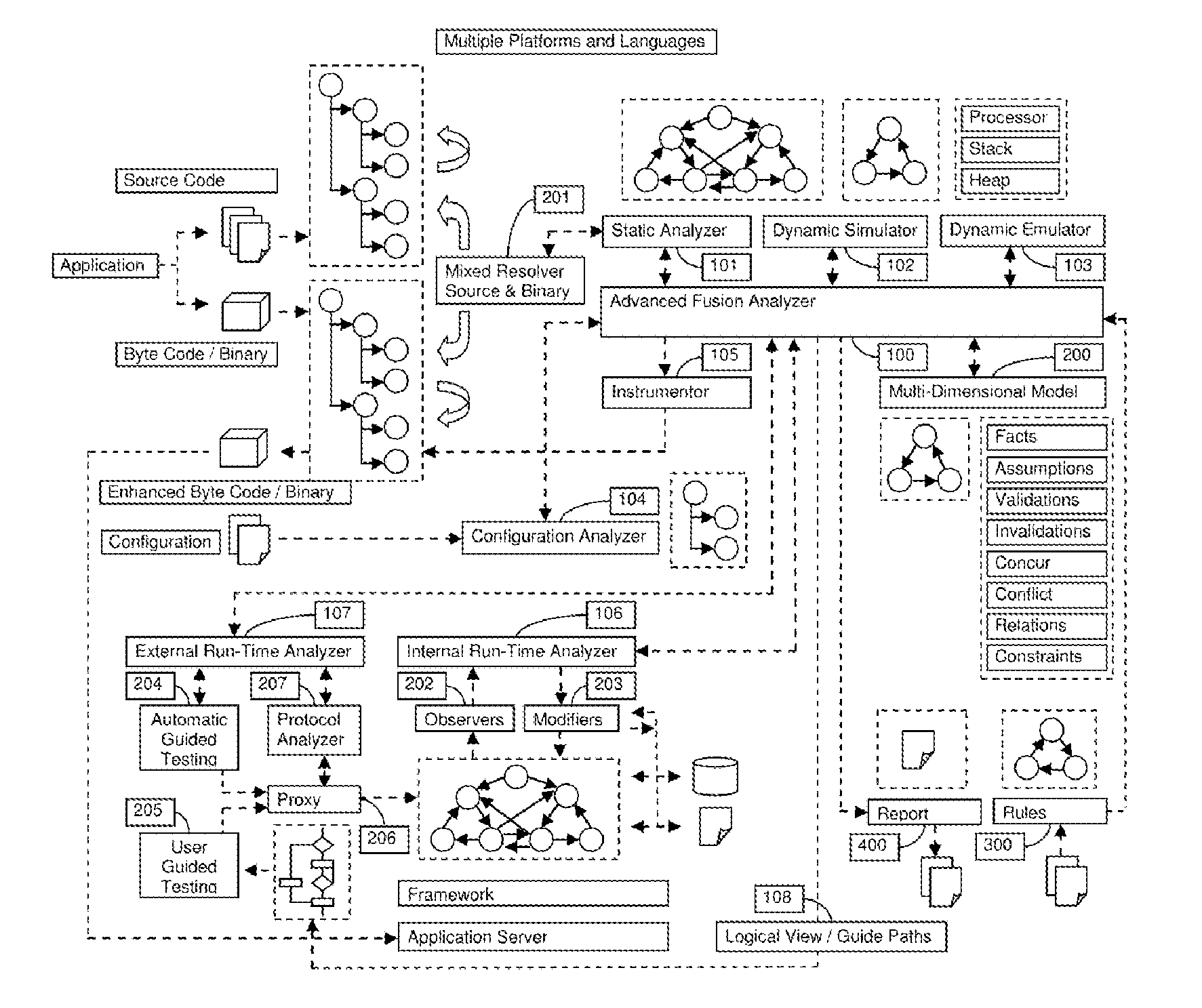
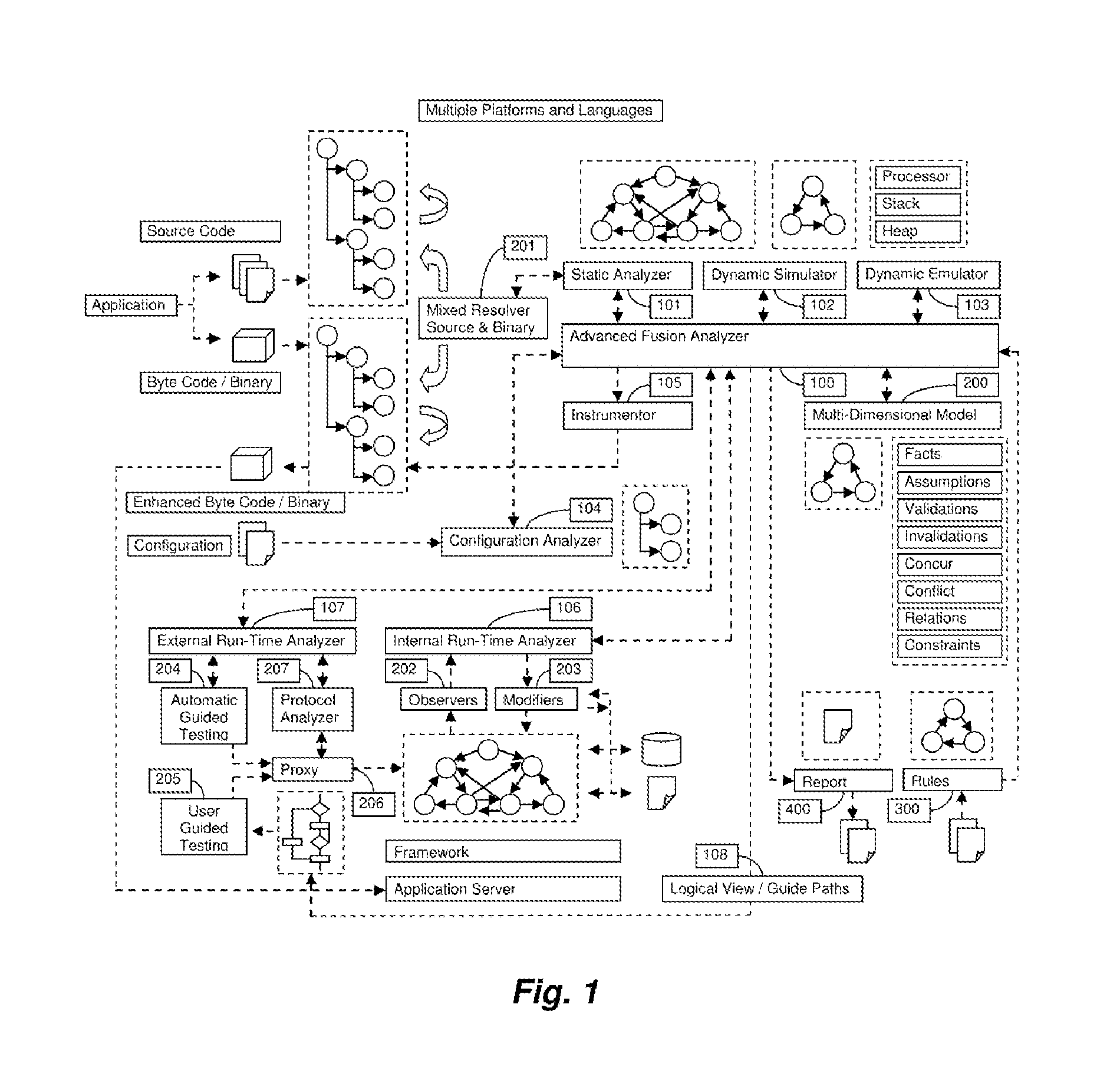
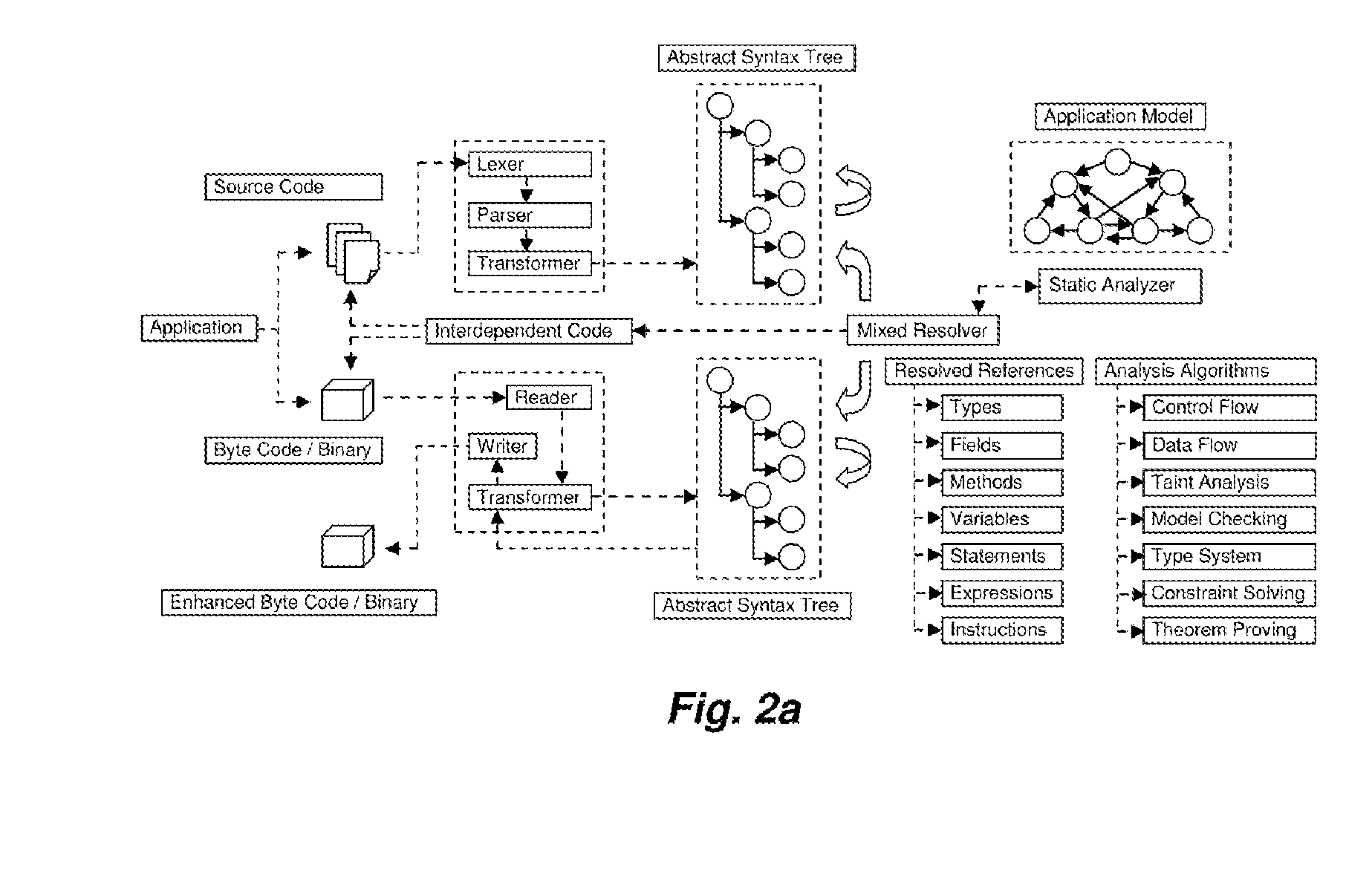
The present invention relates to field of application and more specifically to analysis of applications for determining security and quality issues. The present invention describes an application analysis system providing a platform for analyzing applications which is useful in finding security and quality issues in an application. In particular, the present invention is composed of an advanced fusion analyzer which gains an understanding of the application behavior by using a multi-way coordination and orchestration across components used in the present invention to build an continuously refine a model representing knowledge and behavior of the application as a large network of objects across different dimensions and using reasoning and learning logic on this model along with information and events received from the components to both refine and model further as well as drive the components further by sending information and events to them and again using the information and events received as a result to further trigger the entire process until the system stabilizes. The present invention is useful in analysis of internet / intranet based web applications, desktop applications, mobile applications and also embedded systems as well as for hardware, equipment and machines controlled by software.
Owner:IAPPSECURE SOLUTIONS PVT
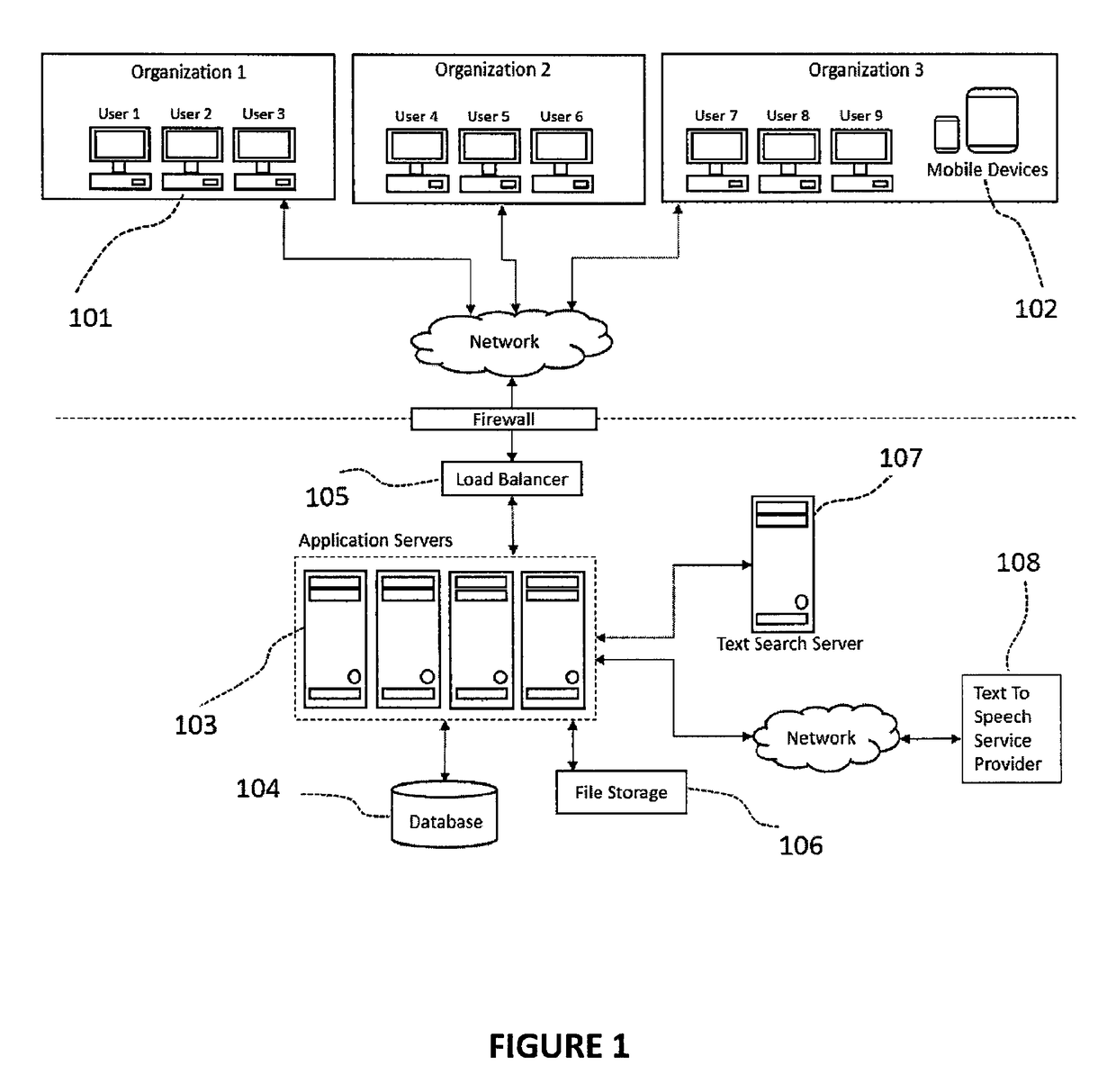
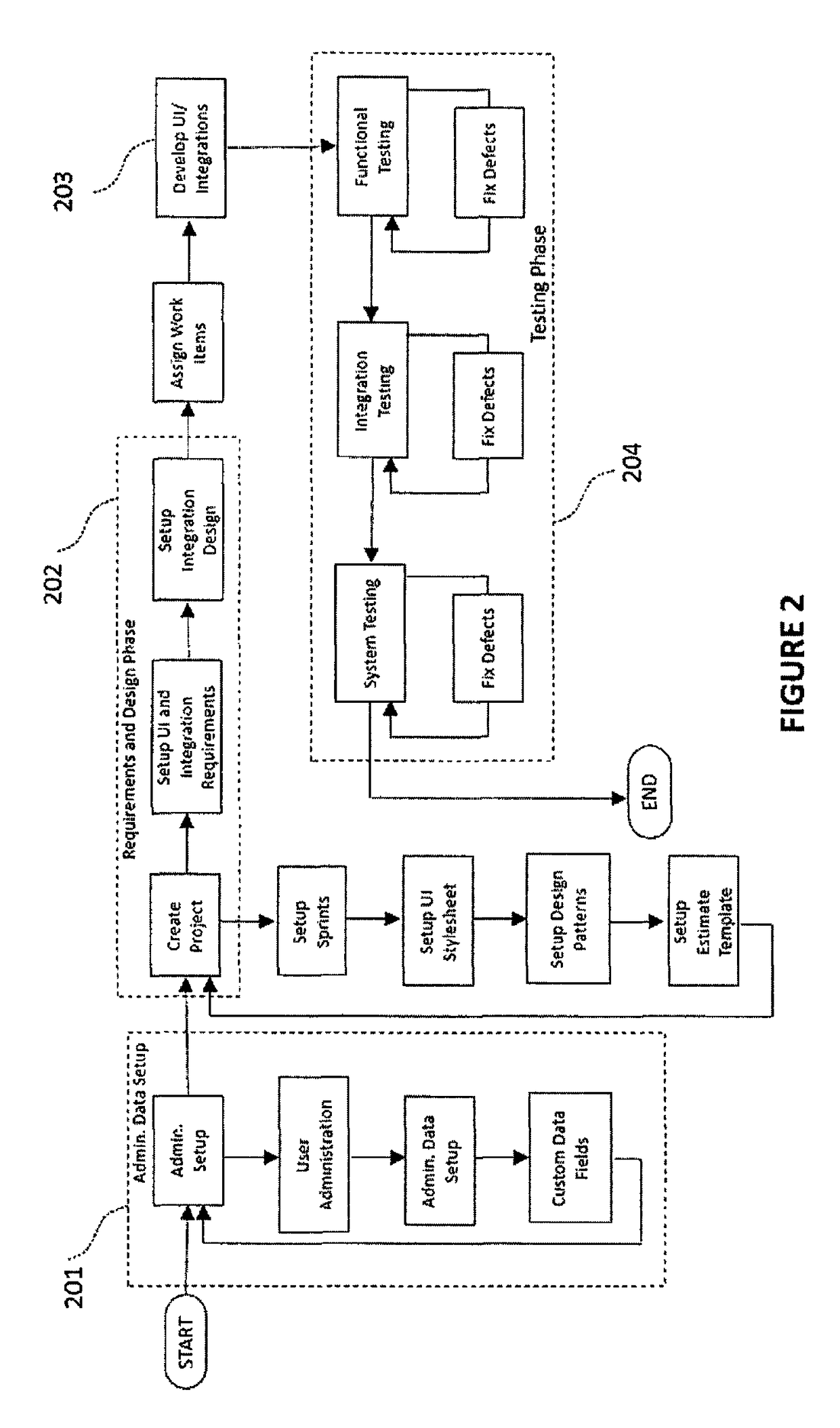
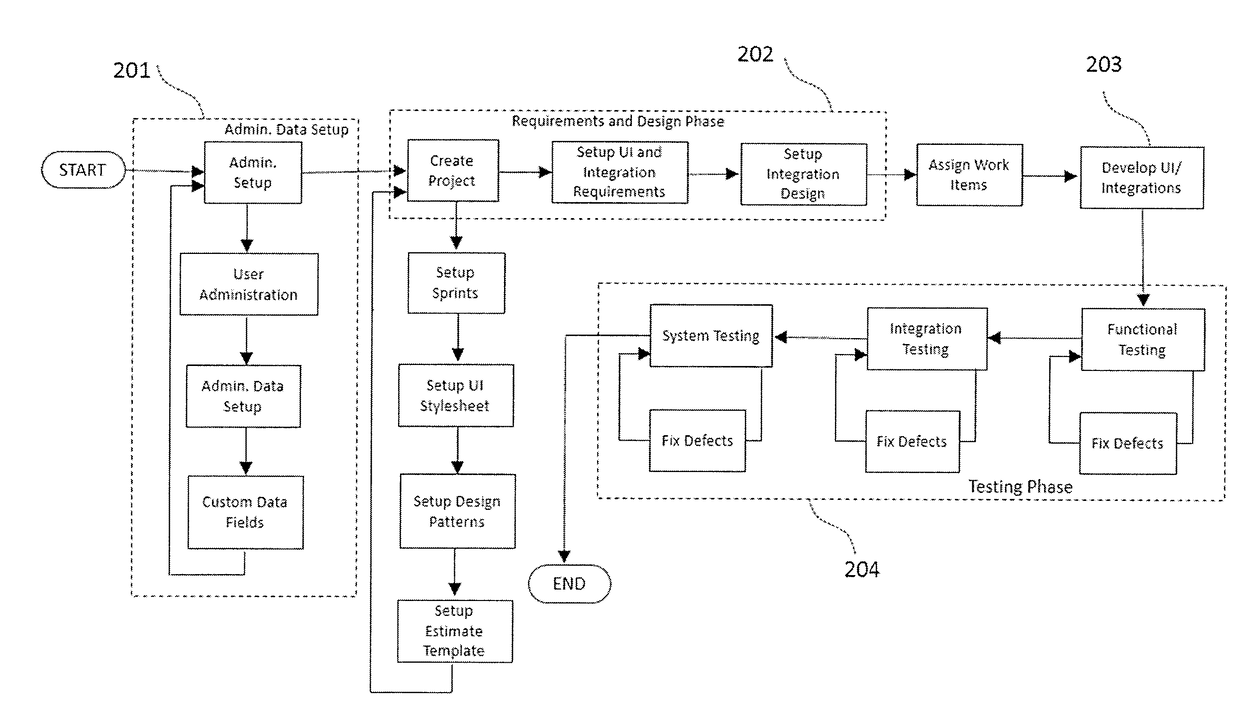
Integrated system for software application development
InactiveUS10001975B2Equally distributedProgram initiation/switchingVersion controlIntegrated softwareProject management
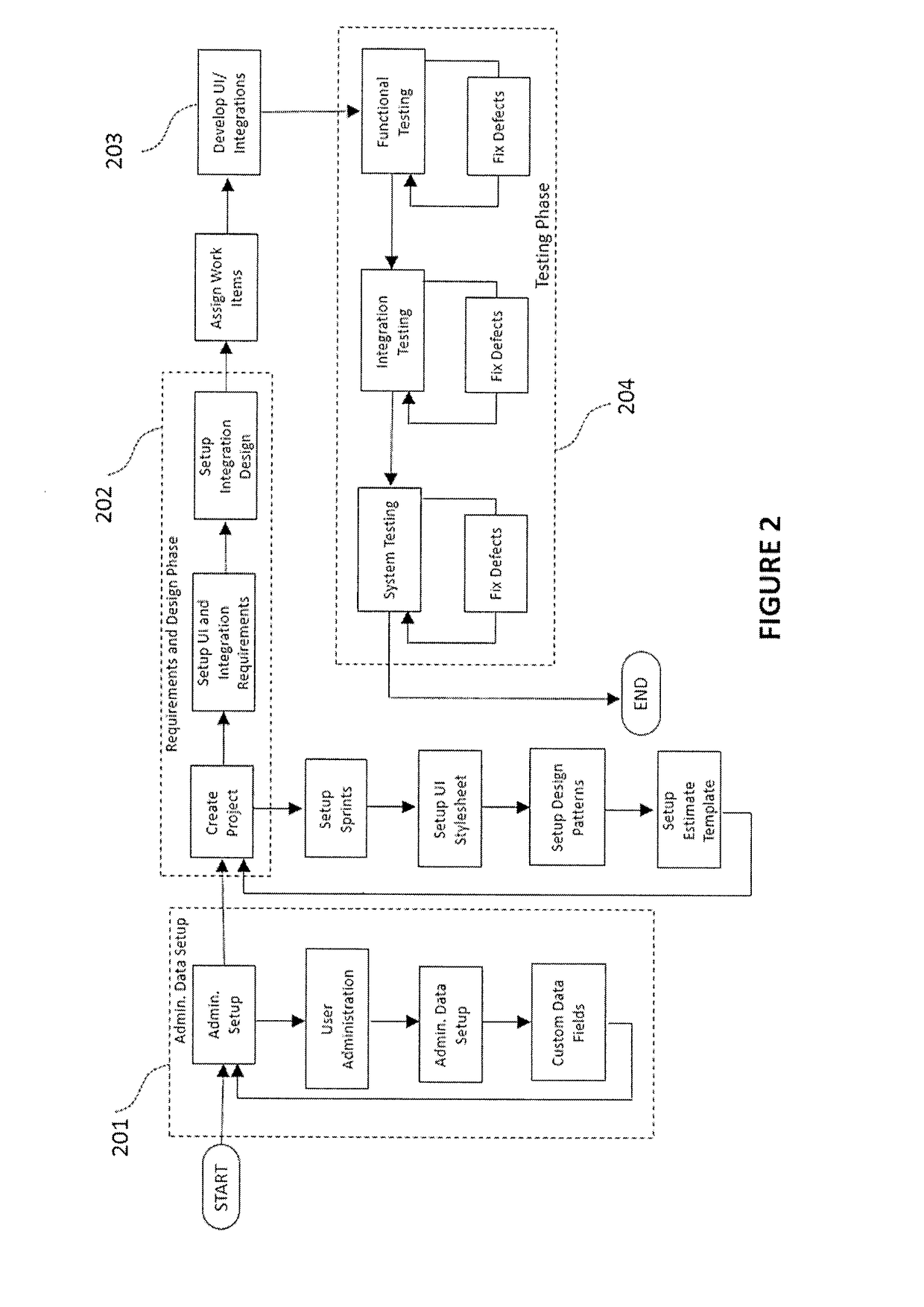
Methods and systems are disclosed for developing a software application through requirements specification, design, effort estimation, assigning and tracking work items, development, testing, collaboration and project management. The system is structured as an integrated software development system allowing for structured, systematic and user friendly set up of requirements specification (including workflow, user interface, business rules and integrations), technical design for UI features and integrations using design patterns, automated effort estimation, automated story card and task creation. The system also provides a novel, audio-video playback capability for workflow visualization. Further, the system provides visual depiction of defects and changed items side-by-side with requirements, as well as predictive modeling of defects that allows for forecasting of defect completion rate. In the preferred embodiment, the system is delivered as a multi-tenant Software as a Service.
Owner:BHARTHULWAR SHRIDHAR V
Distributed computing component system with diagrammatic graphical representation of code with separate delineated display area by type
InactiveUS7051316B2Save significant programming development time and costShort amount of timeVersion controlReverse engineeringGraphicsProgramming language
Owner:BORLAND
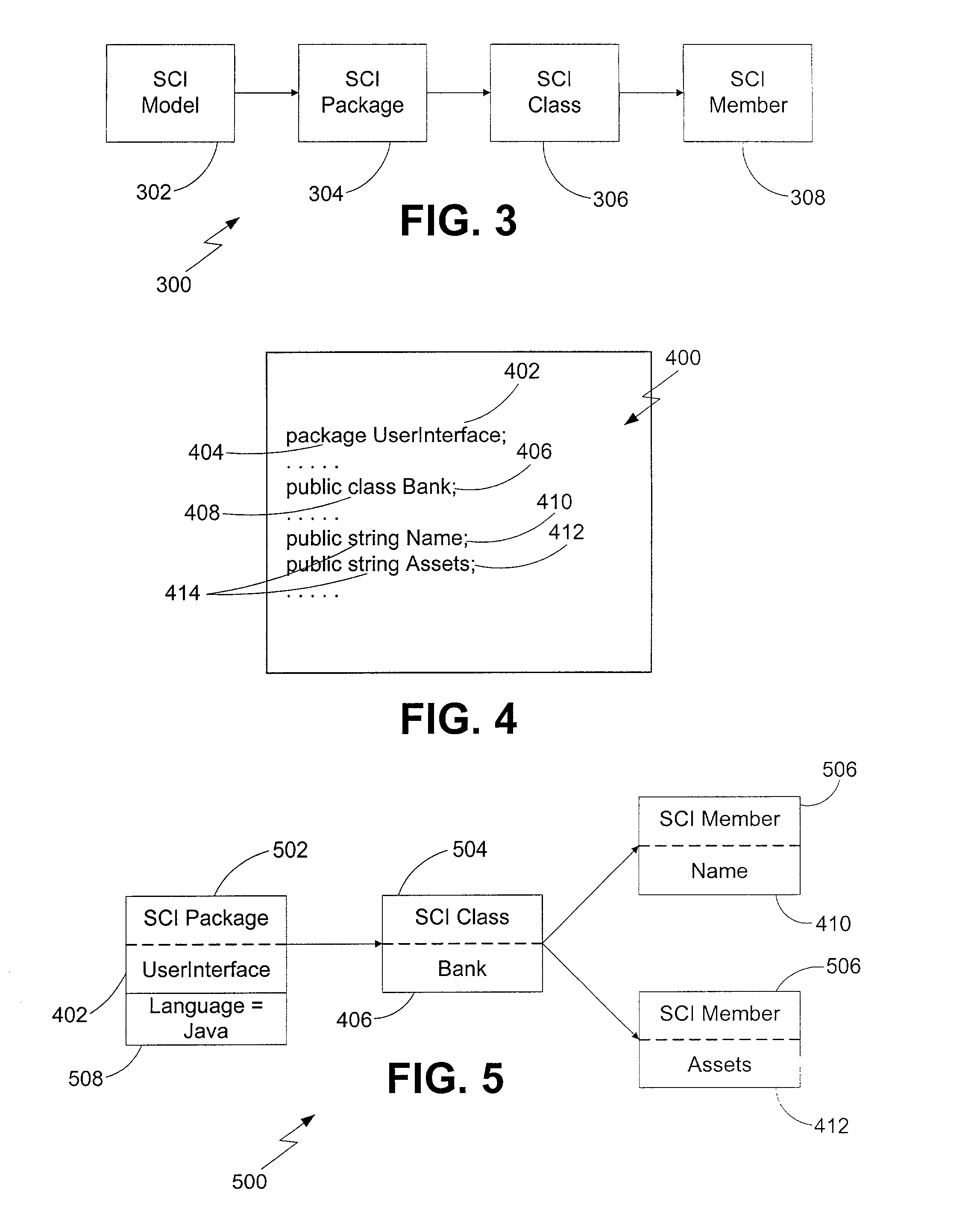
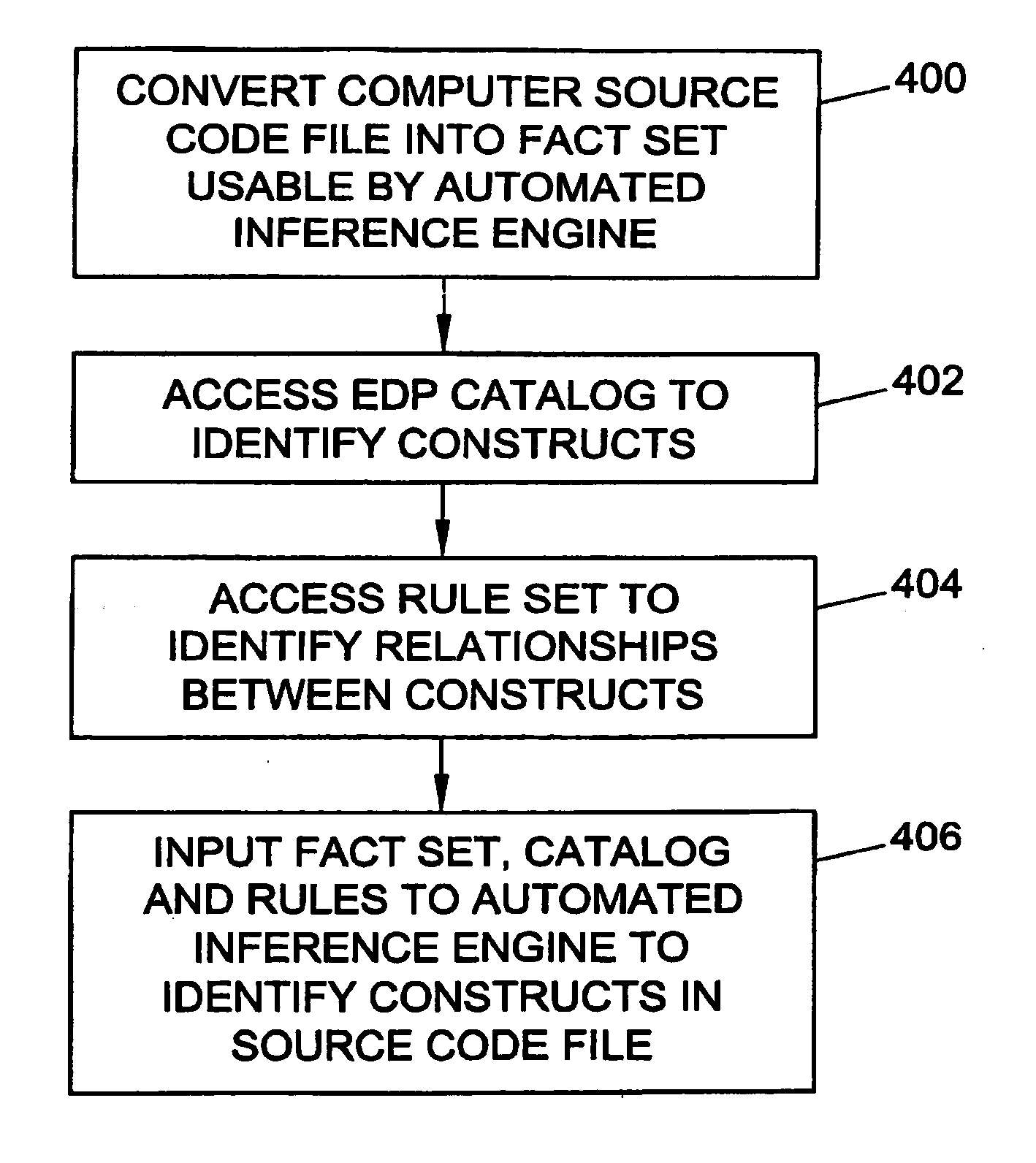
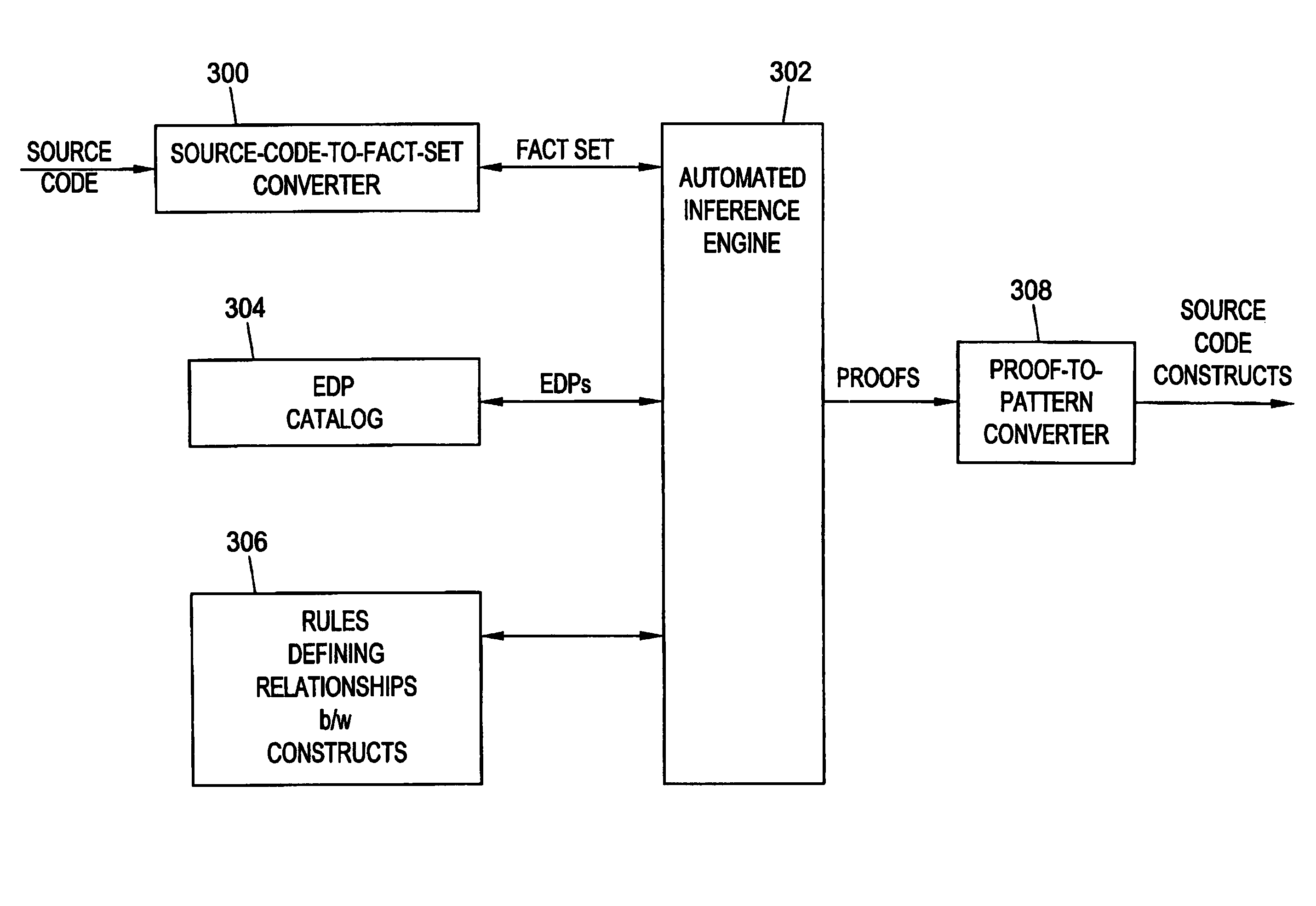
Methods, systems, and computer program products for identifying computer program source code constructs
Methods, systems, and computer program products for identifying computer source code constructs are disclosed. According to one method, computer source code is converted to a format suitable for an automated inference engine. The automated inference engine receives as inputs the converted source code, a set of elemental design patterns defining patterns to be identified, and a set of rules defining relationships between patterns. The automated inference engine outputs proofs indicative of patterns present in the source code. The proofs may be converted to a source code pattern report.
Owner:THE UNIV OF NORTH CAROLINA AT CHAPEL HILL
System and method for automated building of component based applications for visualizing complex data structures
InactiveUS20060236254A1Promote generationSmall sizeReverse engineeringProgram controlGraphicsGraphical user interface
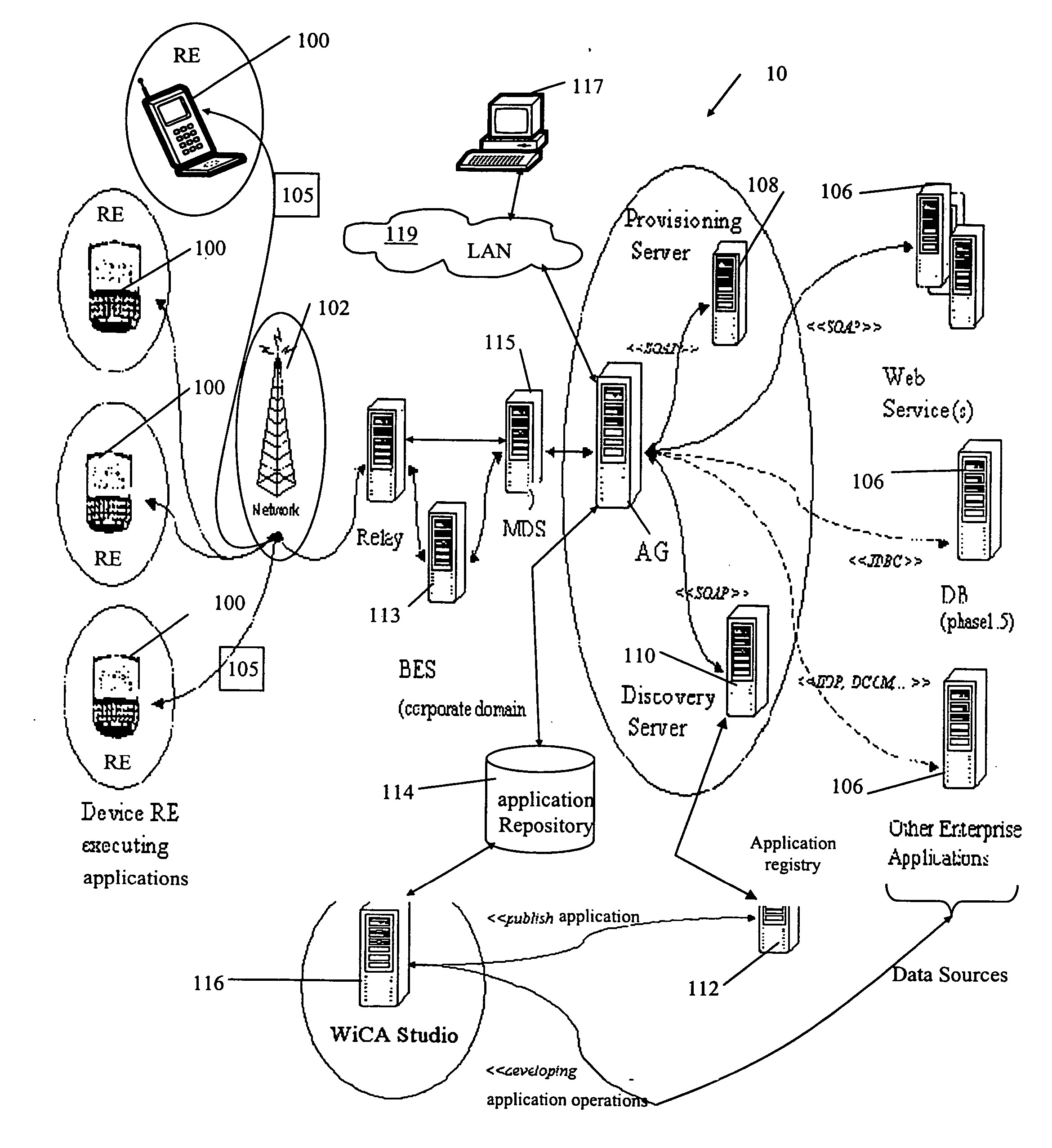
A system and method for generating a screen component configured to visualize a data structure in a displayed screen on a graphical user interface of a device. The screen component for including in an application for execution on the device and having definitions expressed in a structured definition language for defining the visualization of the data structure. The visualized data structure related to data content associated with messages communicated over a network between the device and a data source. The system and method comprises: a parser module for analyzing a set of predefined message and data definitions expressed in a structured definition language to identify corresponding data structure and message details related to the messages, the predefined message and data definitions for including in the application; a screen template for providing a representative example of the screen to be displayed on the graphical user interface; and a screen component generation module for applying the predefined message and data details to the screen template to generate the screen component; wherein the predefined message and data definitions and the screen component are subsequently assembled in to the application.
Owner:BLACKBERRY LTD
Methods and systems for identifying dependencies between object-oriented elements
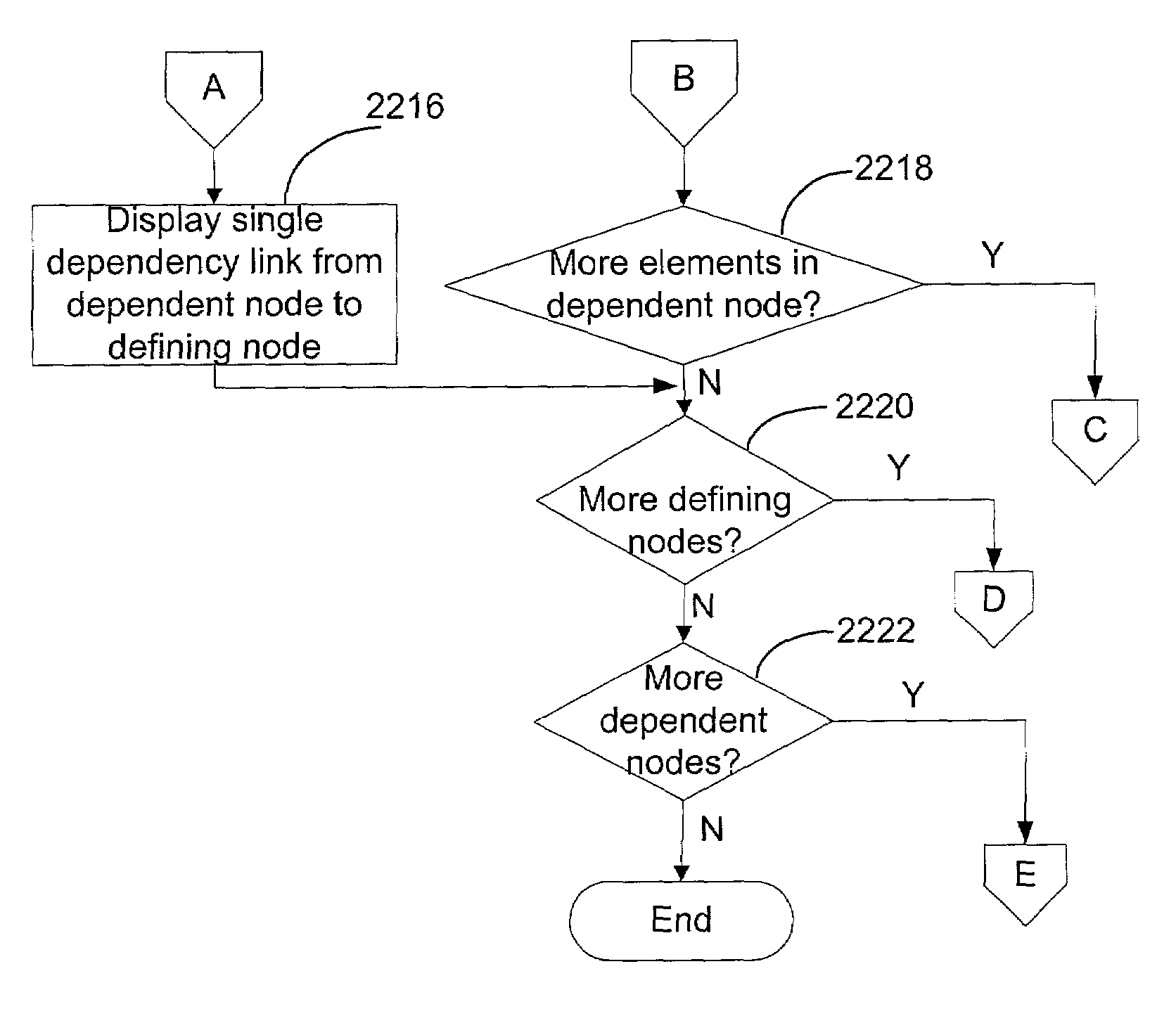
InactiveUS7055130B2Save significant programming development timeAid in productionVersion controlReverse engineeringSoftware developmentDependency relation
Methods and systems consistent with the present invention provide an improved software development tool that represents multiple dependencies between a dependent node and a defining node in a project as a single dependency link. Methods and systems consistent with the present invention also identify and display details regarding each dependency in a project upon request by the user.
Owner:BORLAND
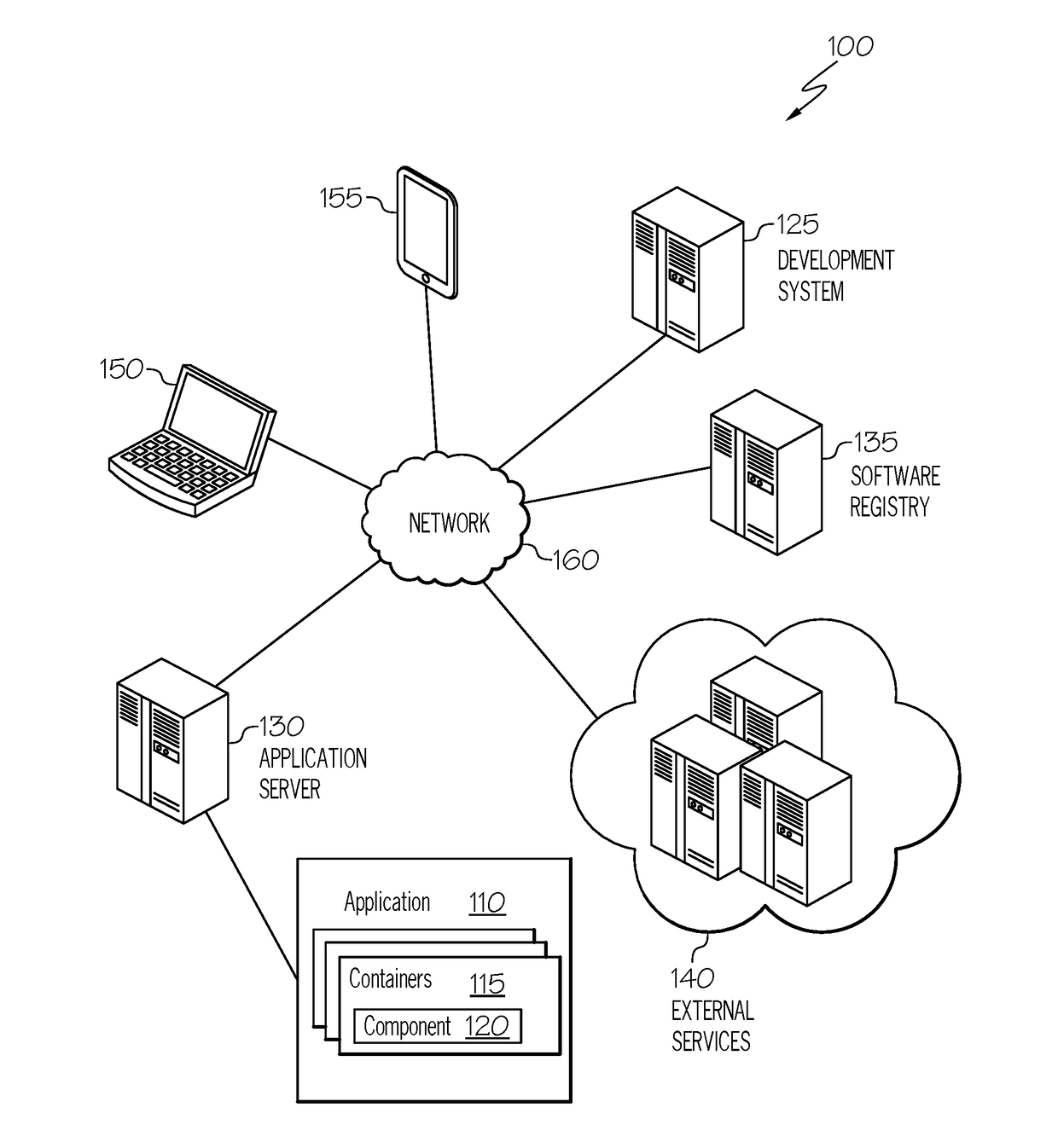
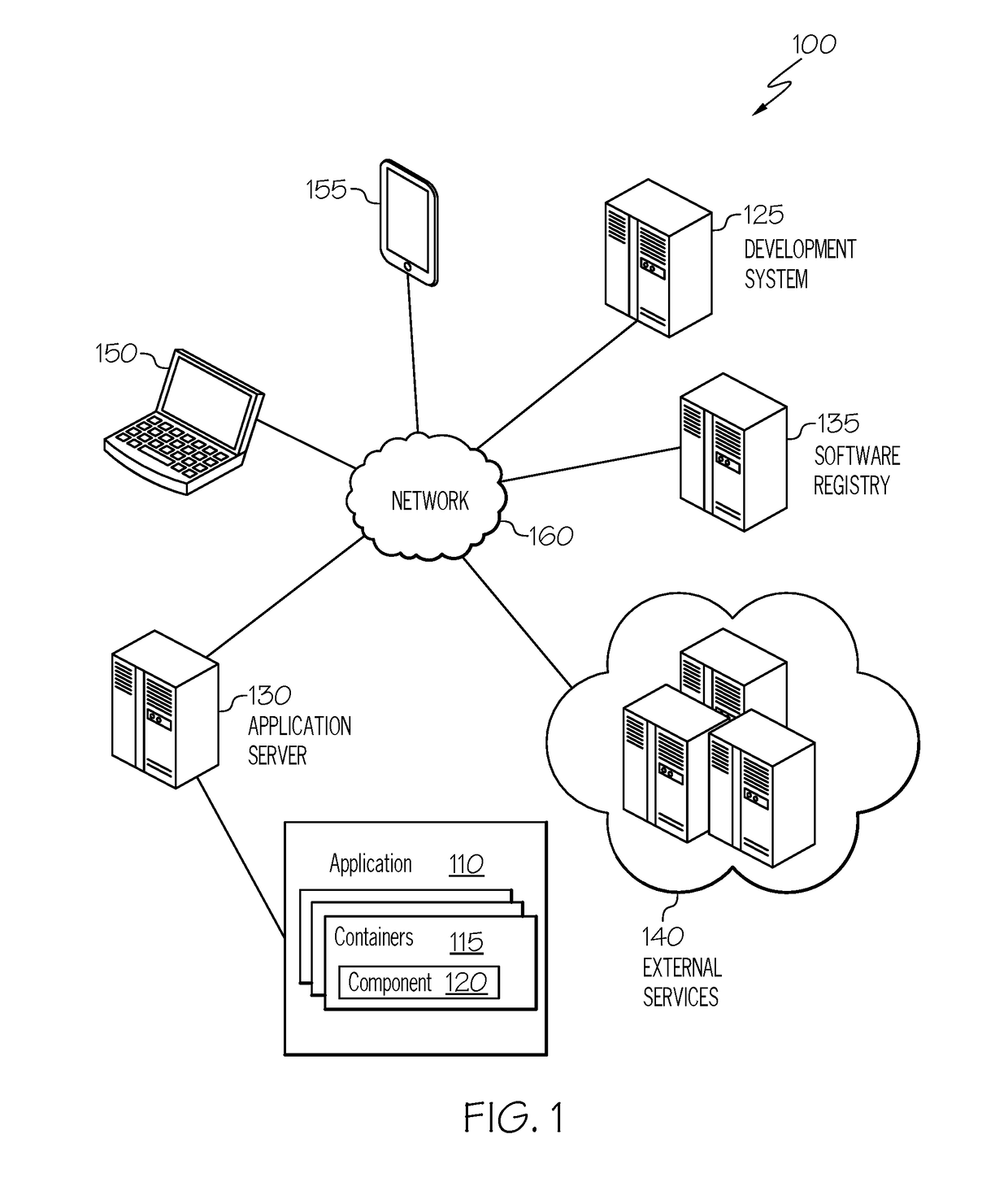
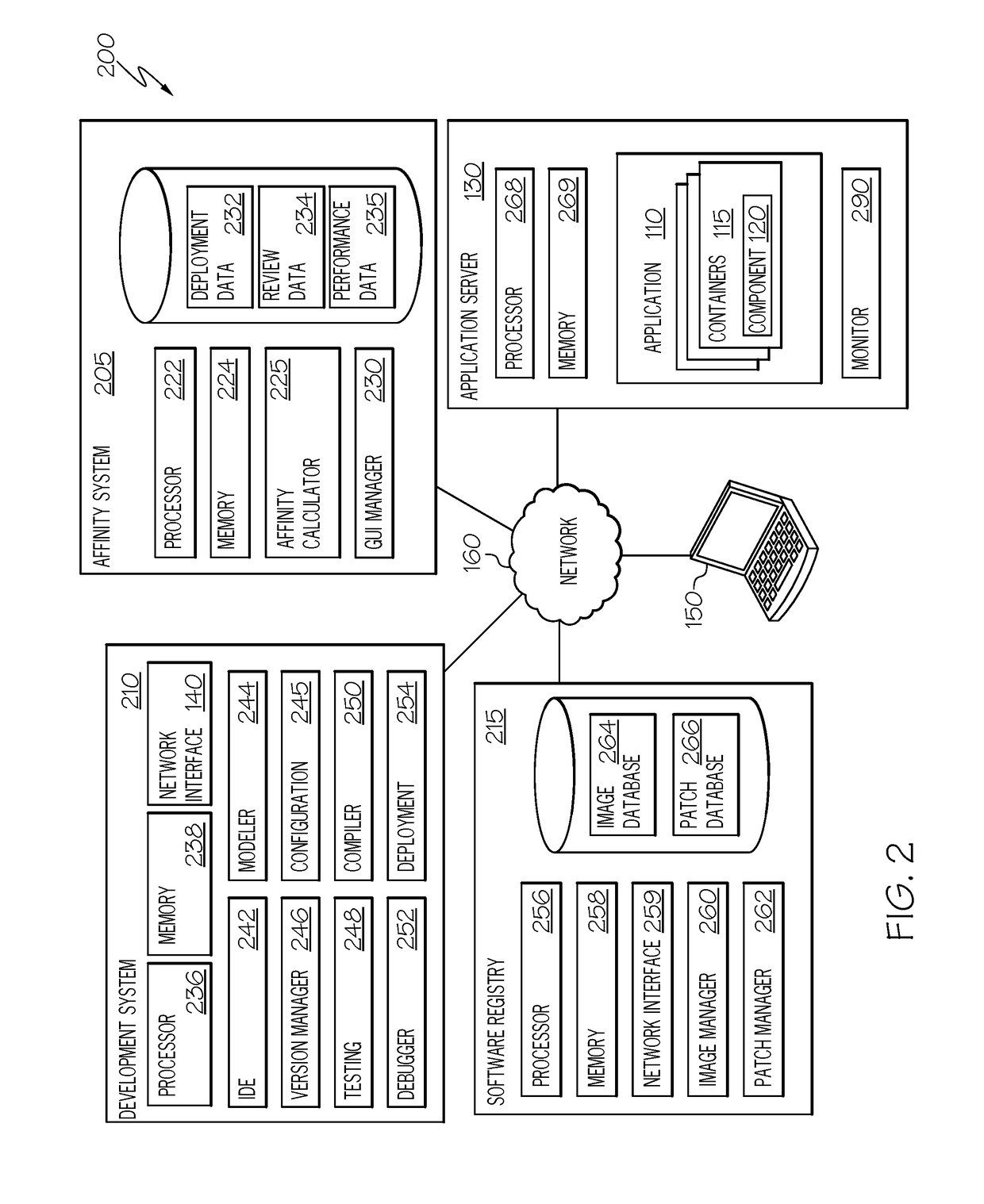
Affinity of microservice containers
A particular software container hosting a particular microservice is identified that is to implement at least a portion of a software program. A set of other containers hosting other microservices are determined to be interoperable with the particular microservice and an affinity value corresponding to the particular container is determined for each other container in the set, each of the affinity values representing a respective degree of correspondence between the particular container and the corresponding other container. A listing of at least a subset of the set of other containers are presented together with an indication of the corresponding affinity value of each of the subset of other containers.
Owner:CA TECH INC
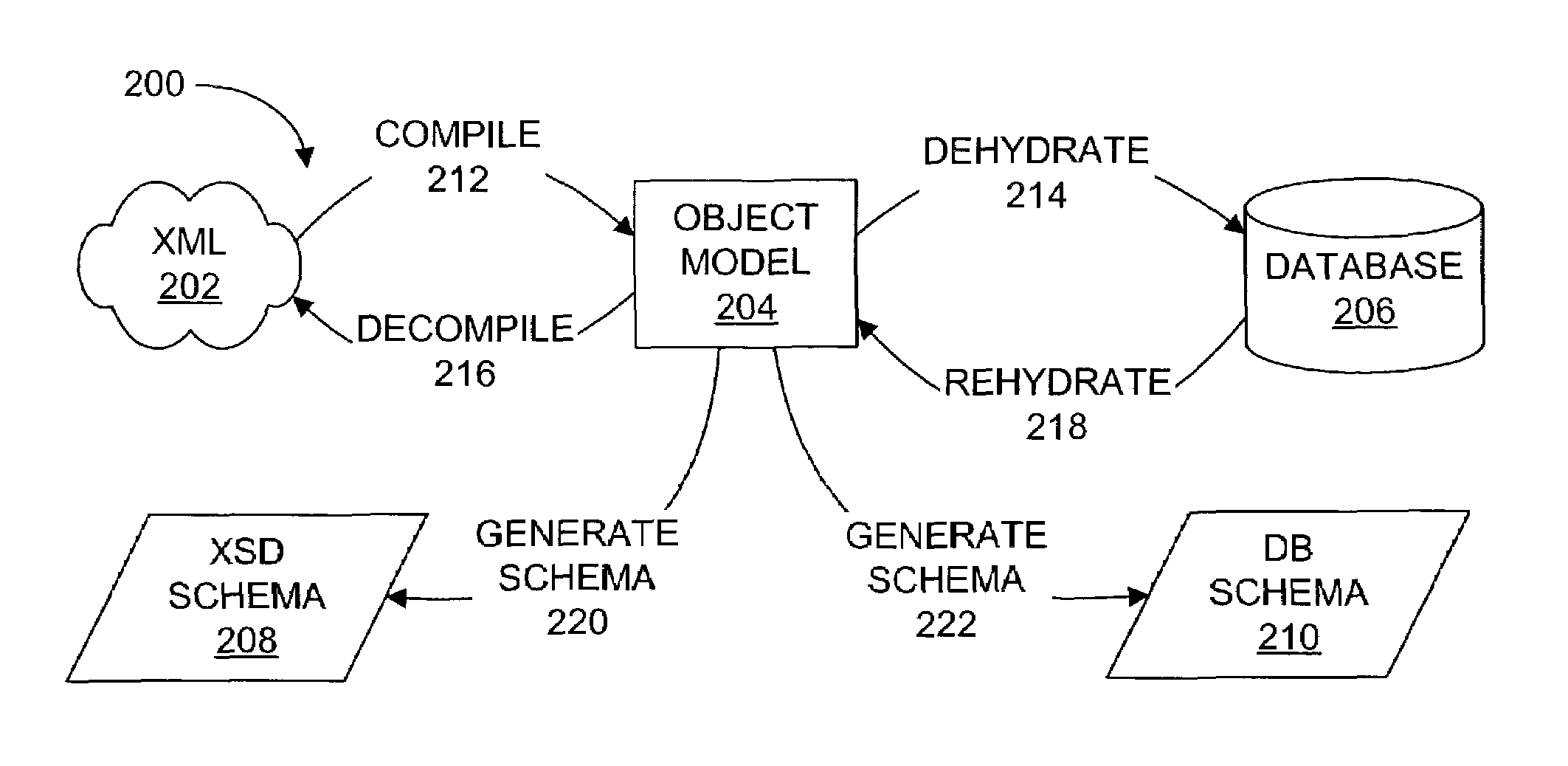
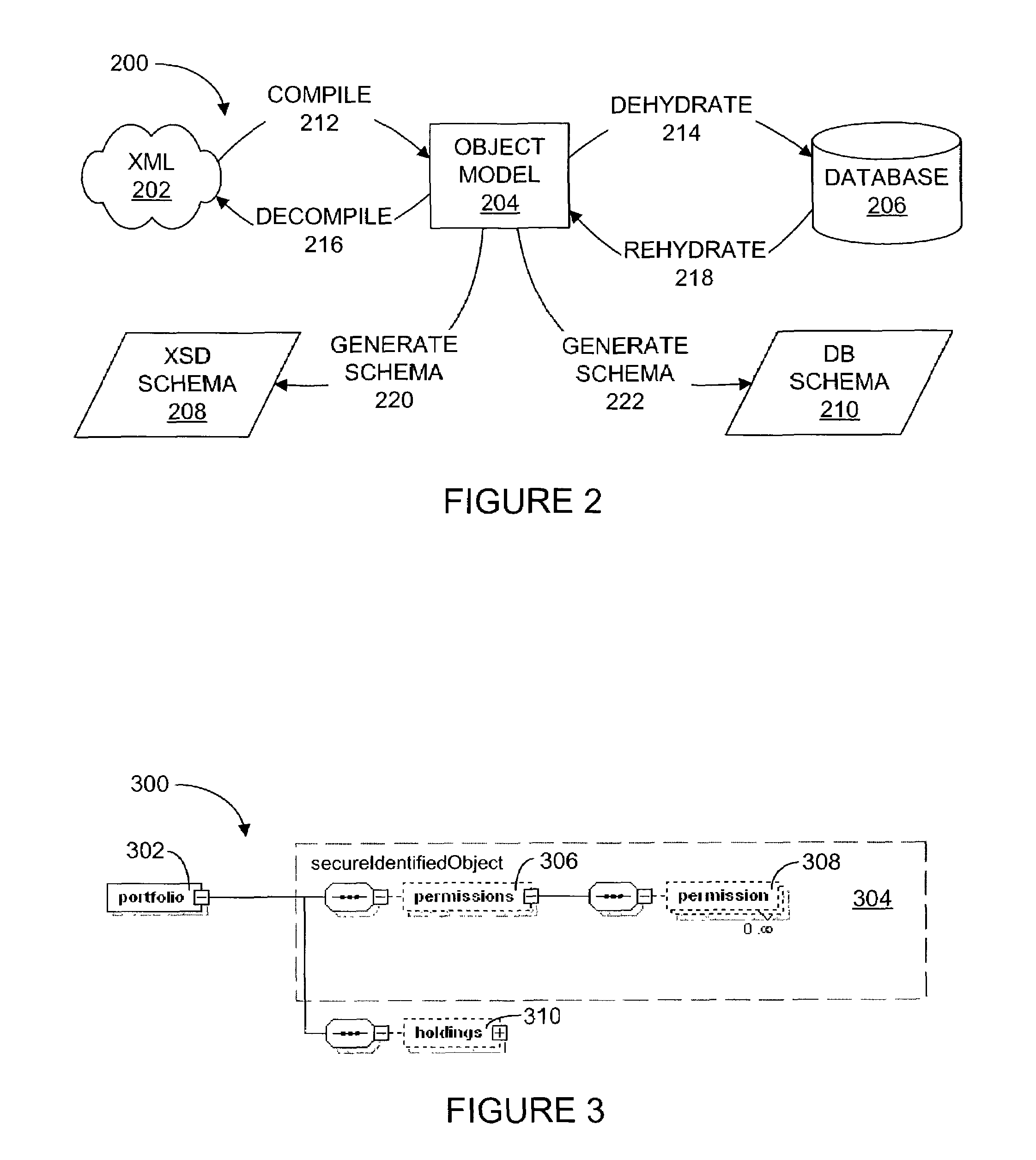
Framework for applying operations to nodes of an object model
InactiveUS6973460B1Convenience to mergeRelievingData processing applicationsDigital data processing detailsRunning timeDatabase
A framework may include an object model and services. The framework may gather information at run-time from metadata within the object model before the framework operates on the classes. For a class within the object model, a subclass may be generated for containing pertinent metadata about the class. Through annotations of class members, the framework may determine the various types of data within the framework. This hierarchy information may specify how objects within the object model relate to one another. An annotation set within the subclass may contain information specifying how members of the class should behave, including, which services of the framework the class member should participate in and how the class member should participate. The annotations may be used for indicating how services of the framework should persist data to various storage units, such as an XML file and / or a database table.
Owner:MICROSOFT TECH LICENSING LLC
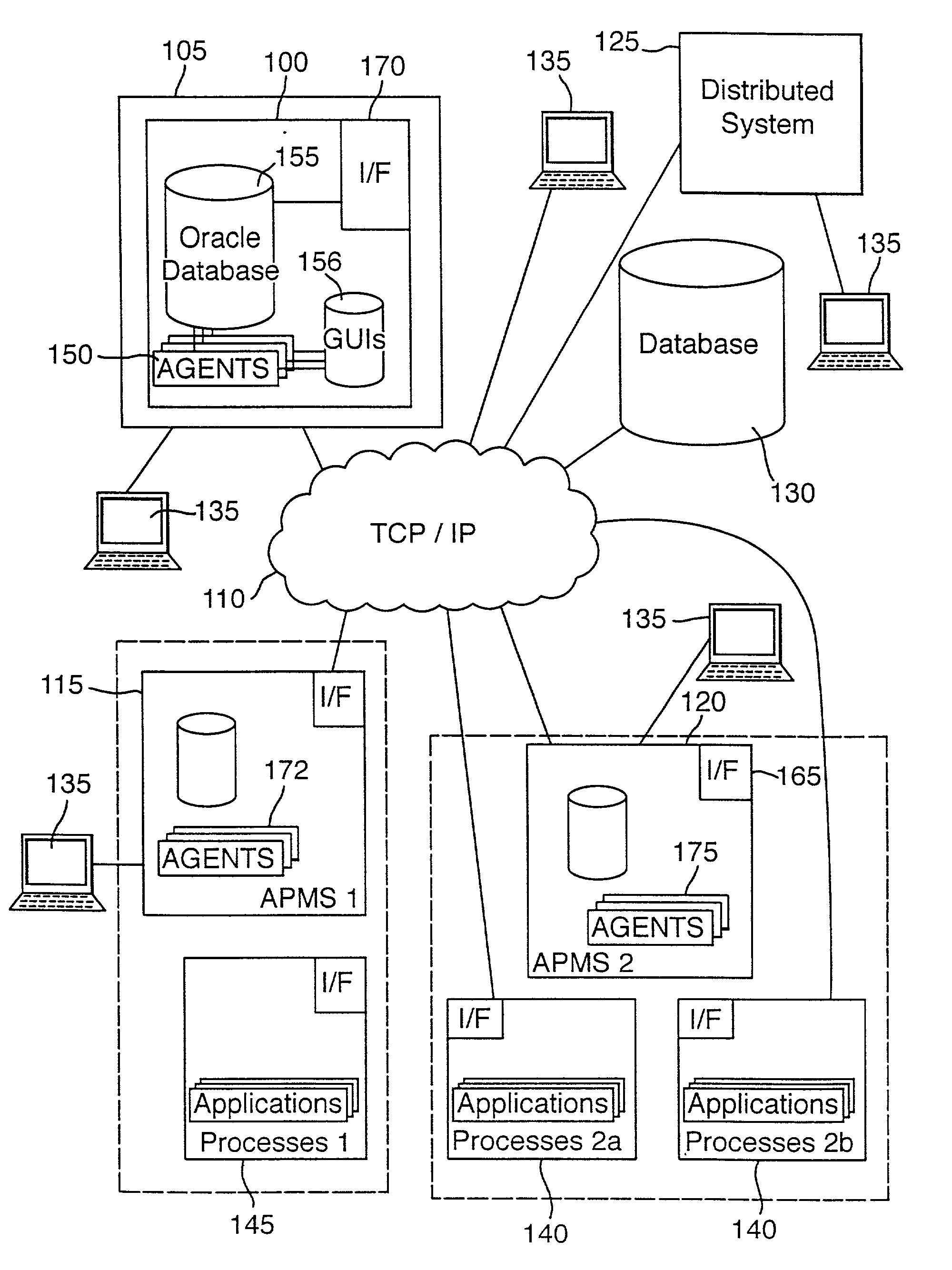
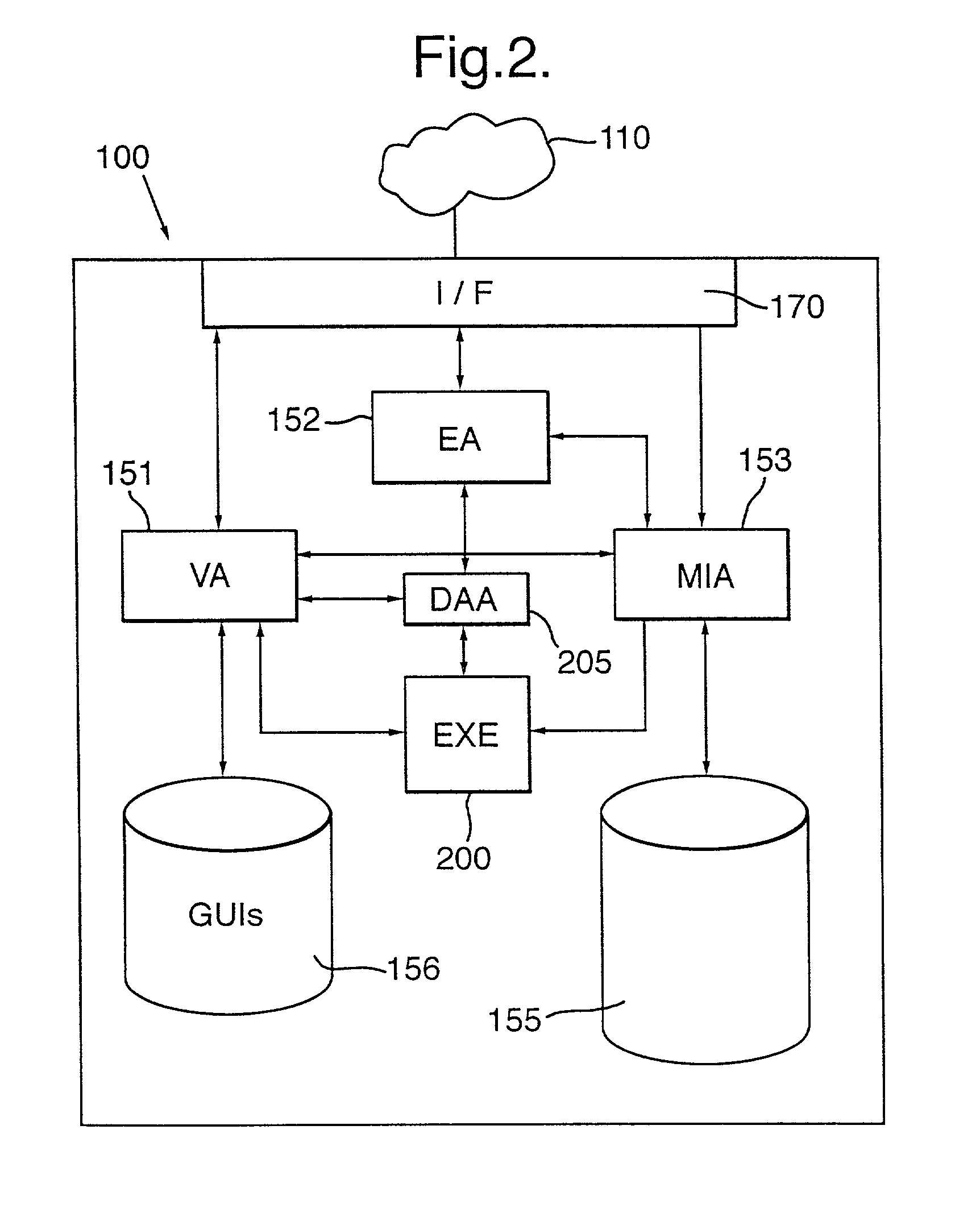
Distributed software system visualization
InactiveUS7155715B1Easy to adaptData processing applicationsDigital data processing detailsGraphicsGraphical user interface
A data management system stores and visualizes data generated during process management. The data management system provides different data management services and definitions of these are stored in a database. Management of data in this database is carried out by a collection of software agents, one of which, the management information agent, can access, update and download data in or from the database. Stored separately are graphical user interfaces which are downloaded to a user in accordance with the relevant service definition stored in the database when the user requests a particular data access service.
Owner:BRITISH TELECOMM PLC
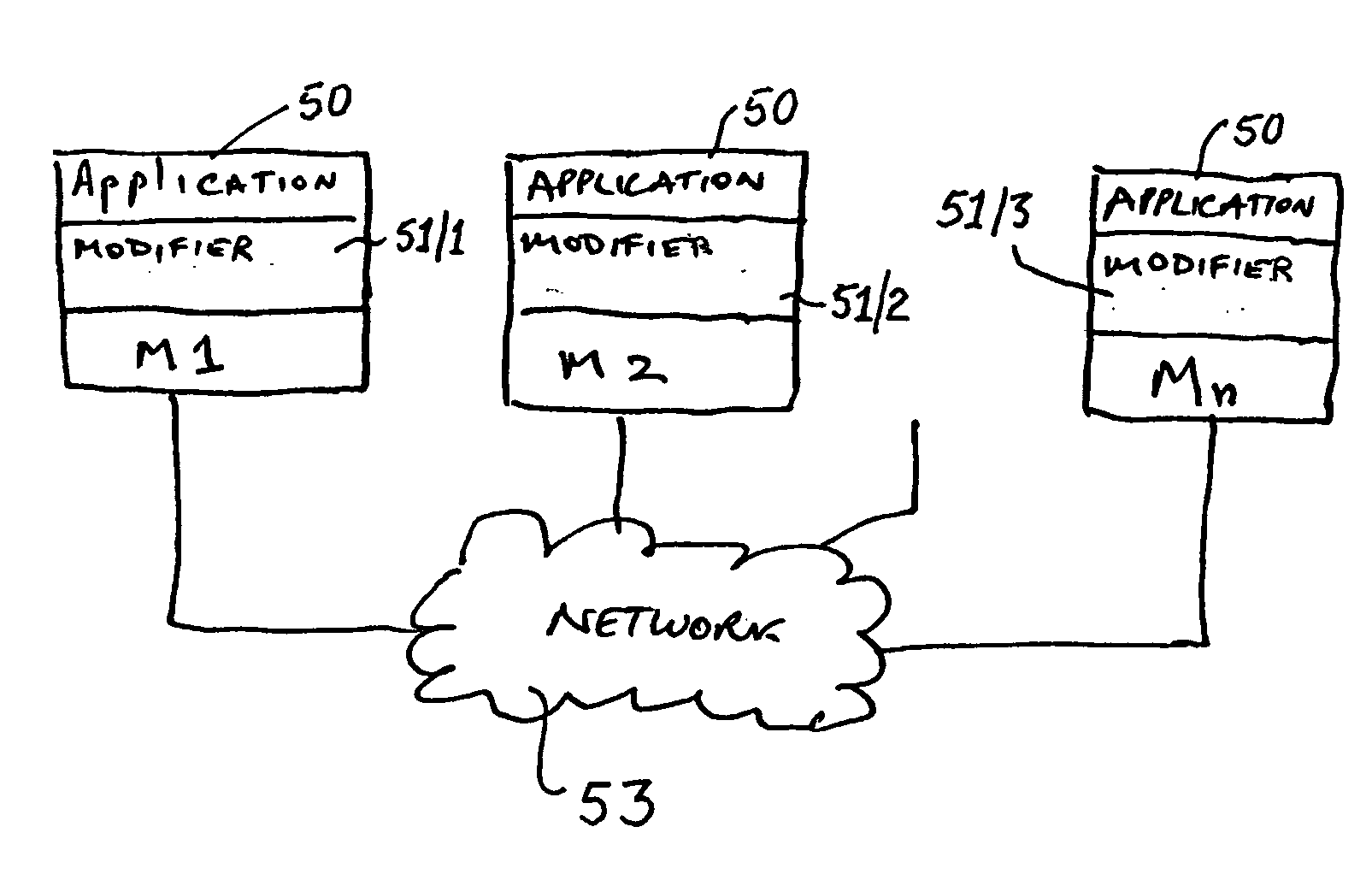
Multiple computer architecture with synchronization
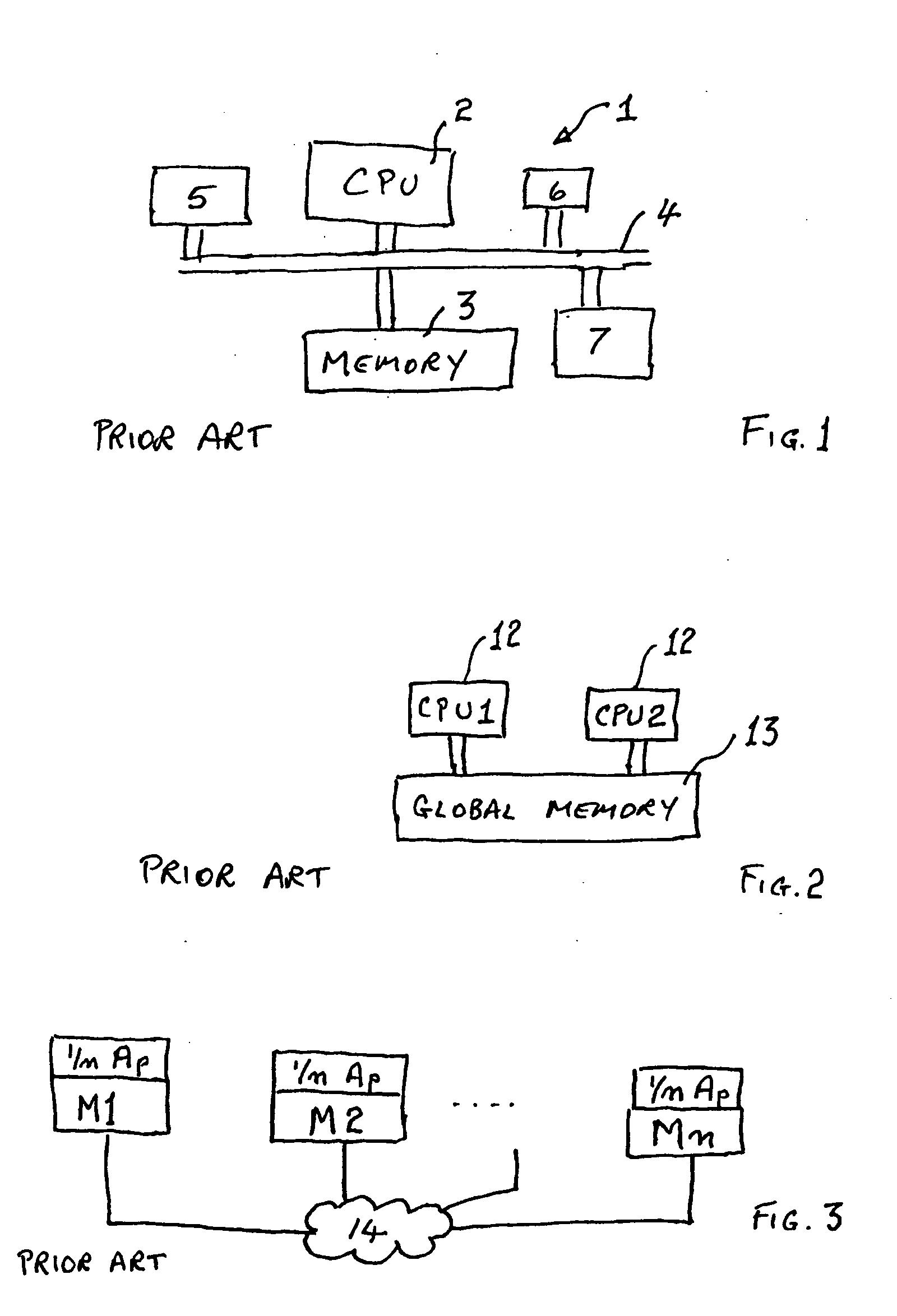
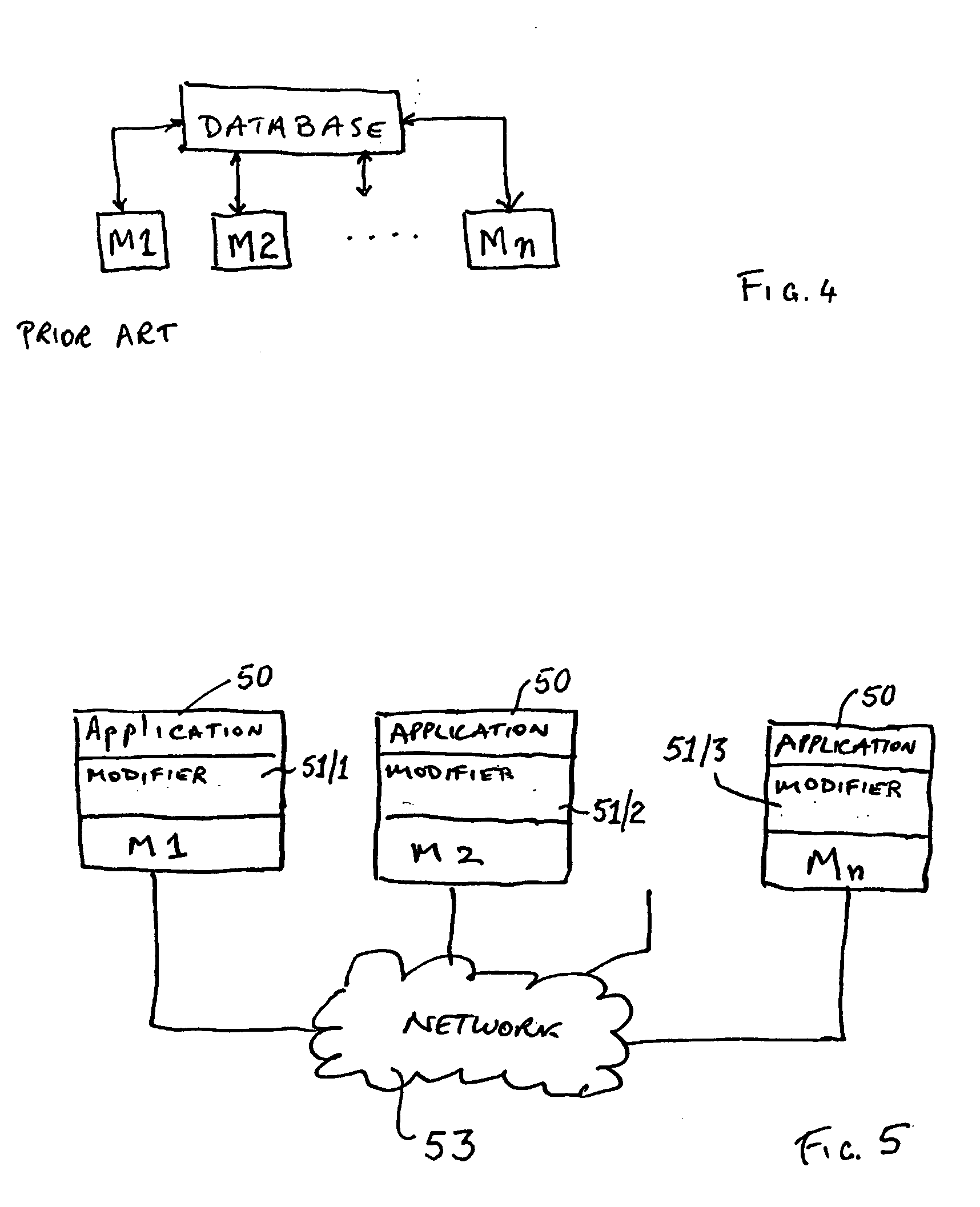
ActiveUS20060020913A1Program synchronisationDigital data processing detailsApplication softwareShared memory
The present invention discloses a modified computer architecture (50, 71, 72) which enables an applications program (50) to be run simultaneously on a plurality of computers (M1, . . . Mn). Shared memory at each computer is updated with amendments and / or overwrites so that all memory read requests are satisfied locally. During initial program loading (75), or similar, instructions which result in the application program (50) acquiring (or releasing) a lock on a particular asset (50A, 50X-50Y) (synchronization) are identified. Additional instructions are inserted (162, 163) to result in a modified synchronization routine with which all computers are updated.
Owner:WARATEK LTD
Systems And Methods For Software Analysis
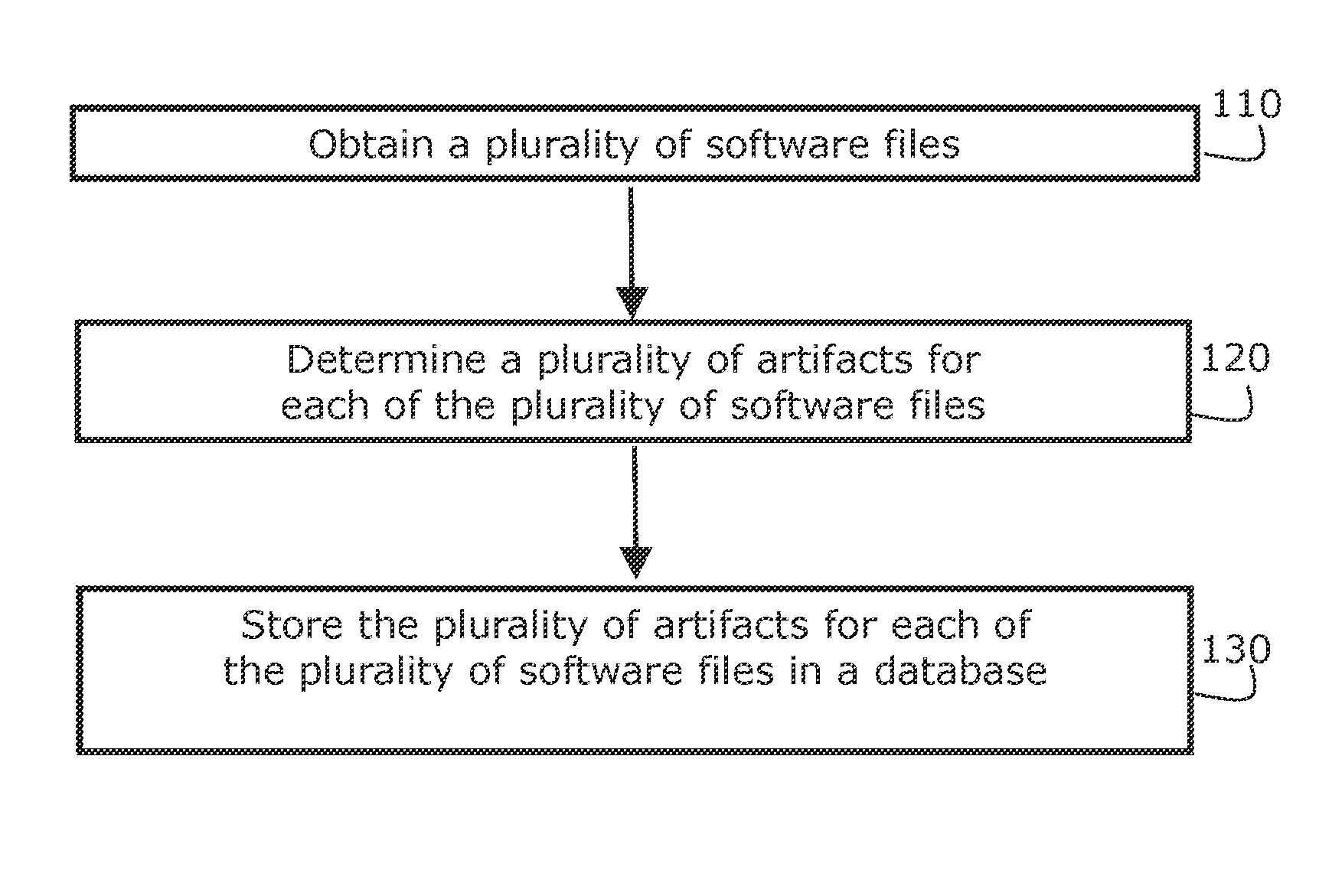
Systems, methods, and computer program products are provided for identifying software files, flaws in code, and program fragments by obtaining a software file, determining a plurality of artifacts, accessing a database which stores a plurality of reference artifacts for reference software files, comparing at least one of the artifacts to at least one of the reference artifacts stored in the database, and identifying the software file by identifying the reference software file having the reference artifacts that correspond to the plurality of artifacts. Certain embodiments can also automatically provide updated versions of files, patches to be applied, or repaired blocks of code to replace flawed blocks. Example embodiments can accept a wide variety of file types, including source code and binary files and can analyze source code or convert files to an intermediate representation (IR) and analyze the IR.
Owner:CHARLES STARK DRAPER LABORATORY
System and method for generating EJB components from reusable business logics in servlet program
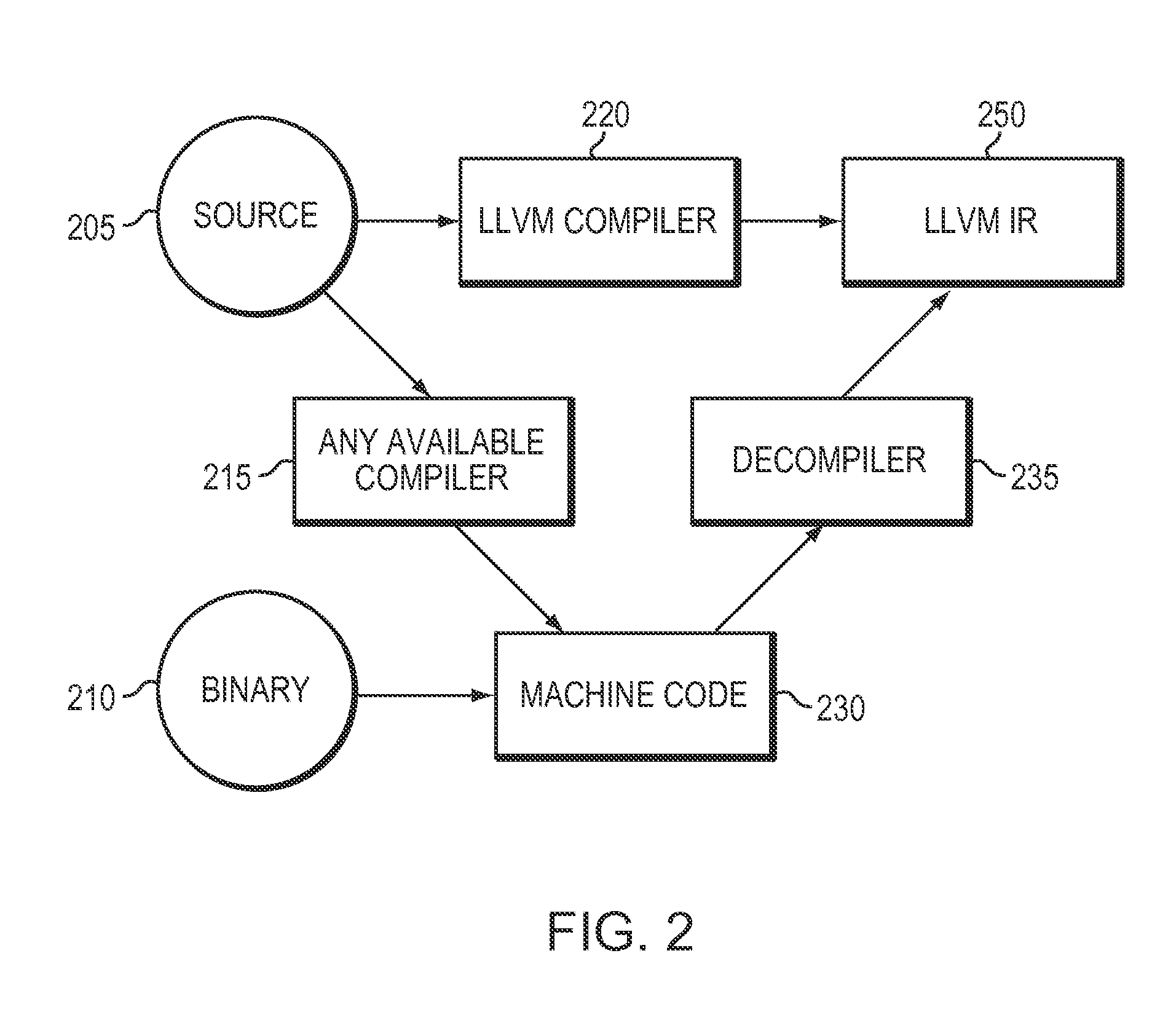
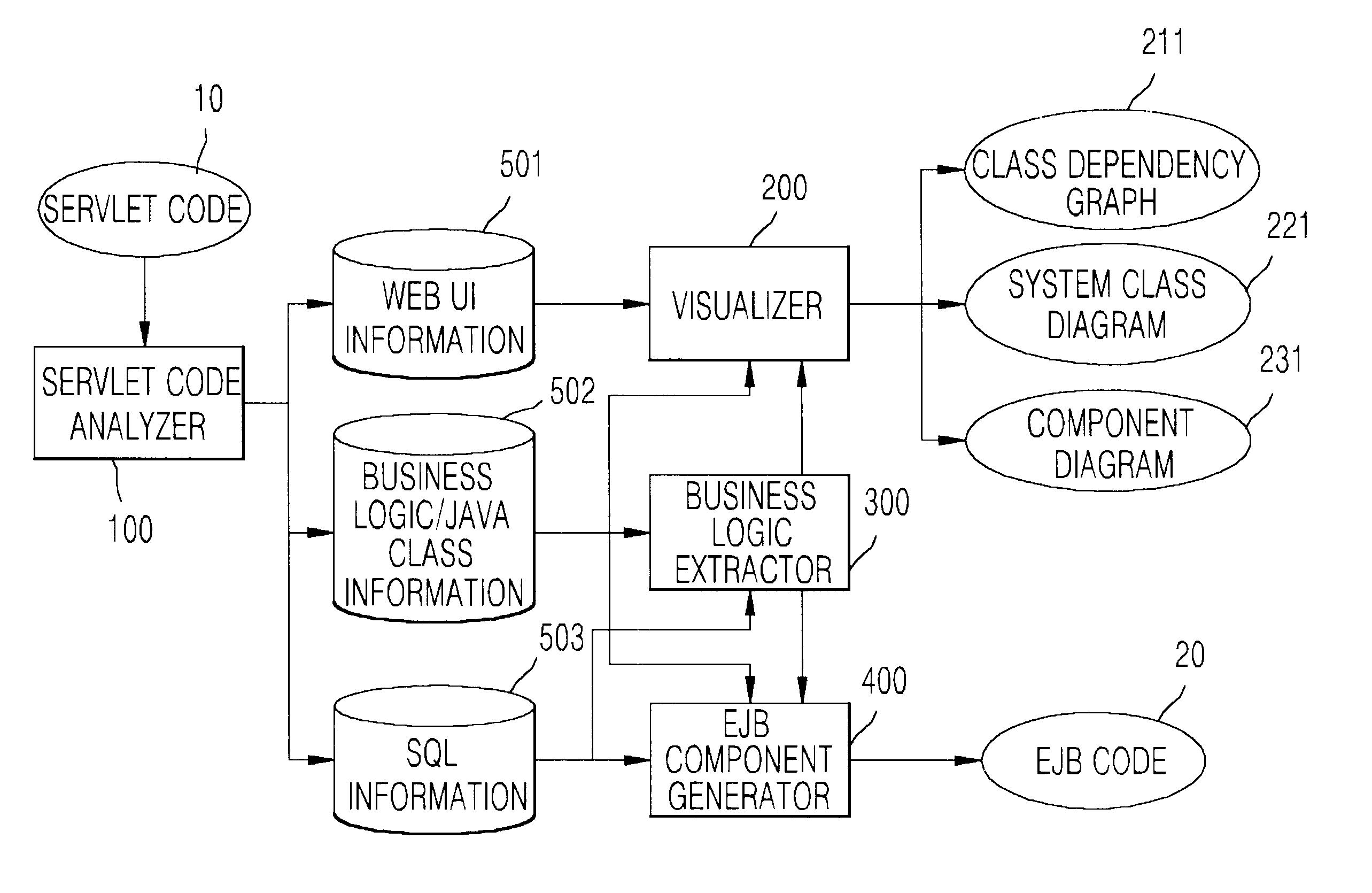
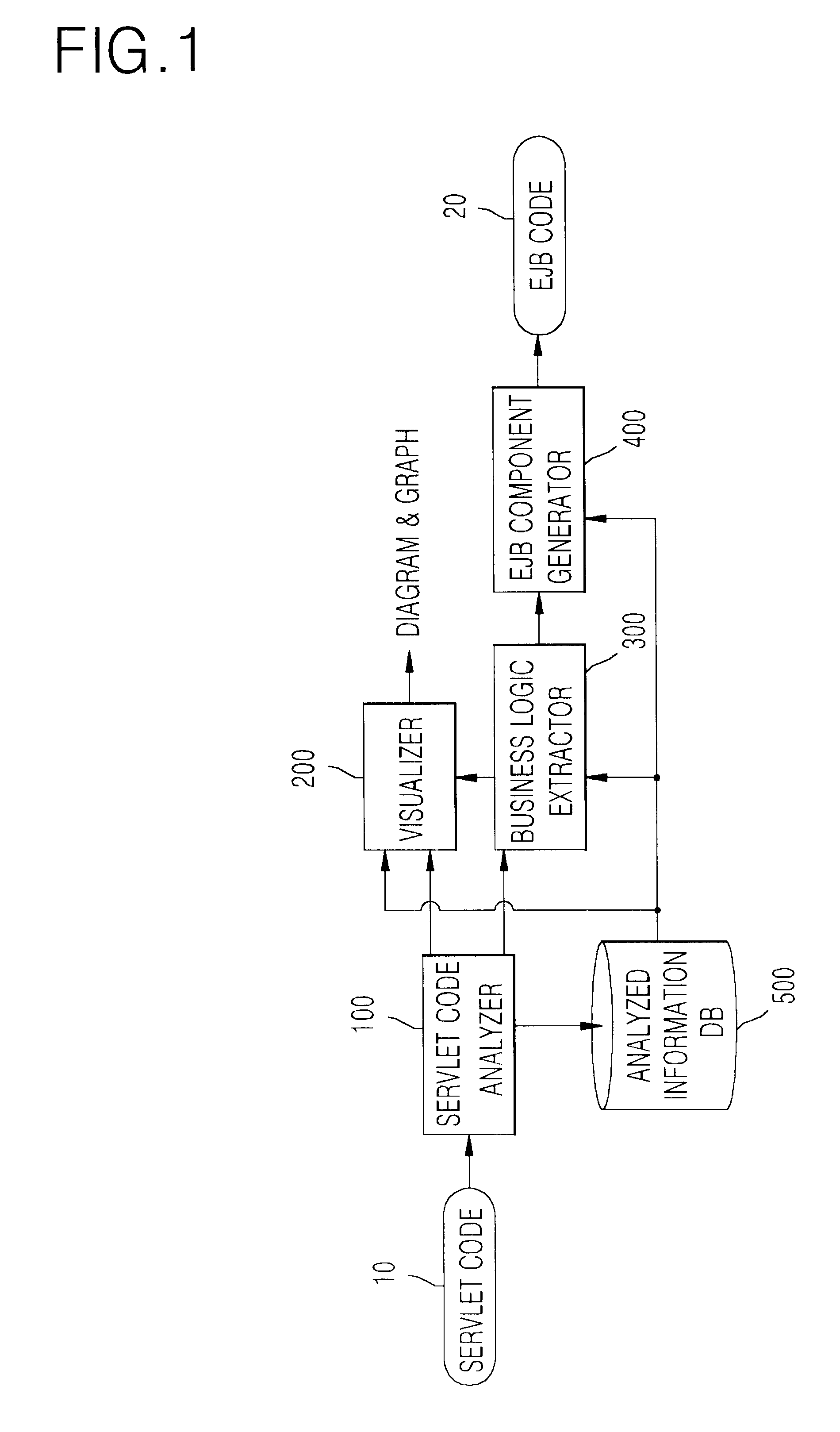
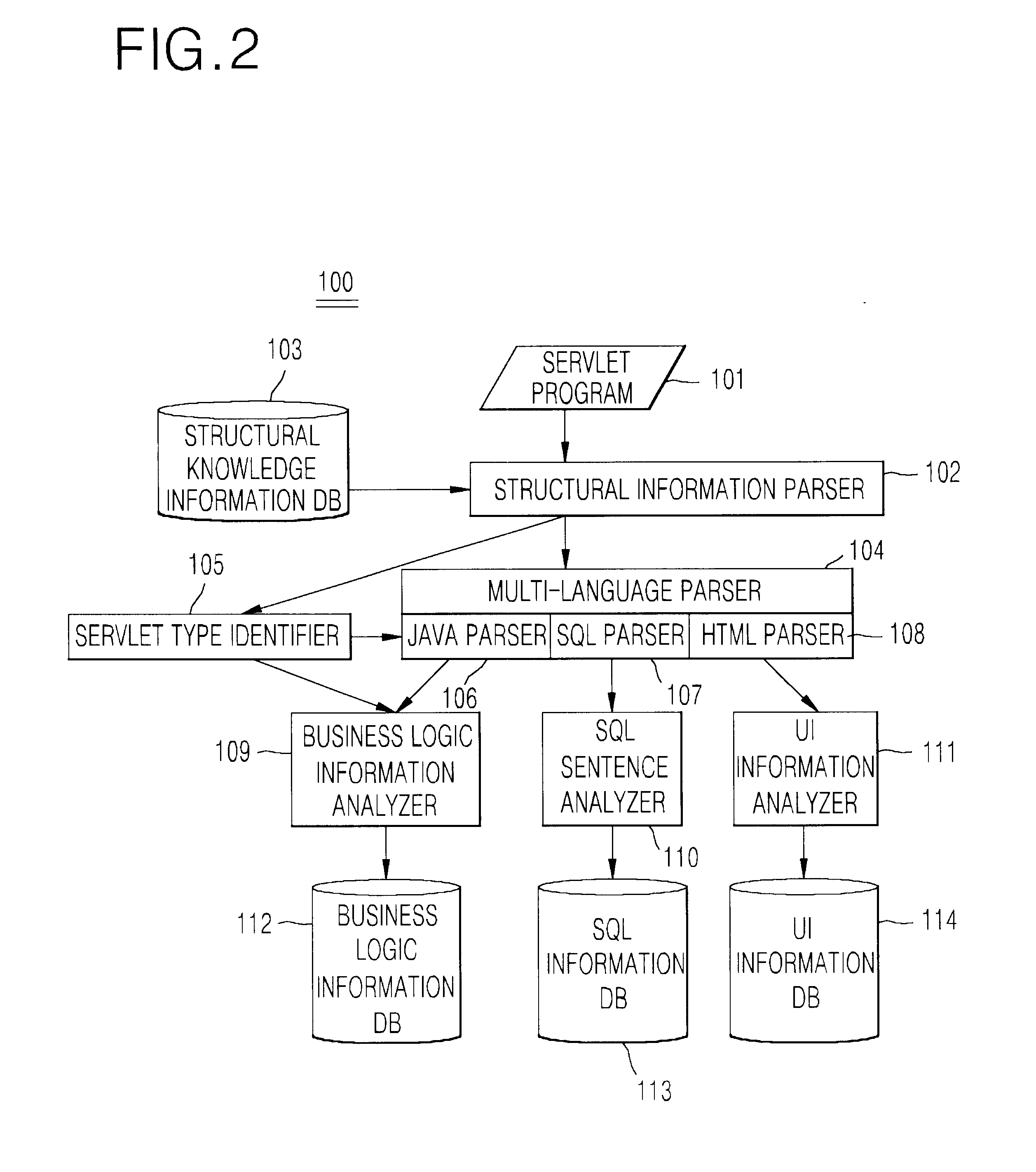
InactiveUS6847981B2Data processing applicationsReverse engineeringMulti languageApplication software
Disclosed is a system and method for generating EJB components by extracting reusable business logic from servlet programs that is one of web program languages used in web-based applications. The system a servlet code analyzer that is a reverse engineering module for analyzing the existing servlet program source, a visualizer for visualizing the analyzed information, a business logic extractor for extracting a reusable business logic, and an EJB component generator for generating the EJB components using the extracted information. The servlet code analyzer considers the flexibility of coding permitted by the servlet program and the use of a multi-language, and the visualizer helps the understanding of the existing legacy program. The business logic extractor extracts the reusable module by extracting the business logic within many user interface related codes, and thus enable the reuse of software. The EJB component generator generates java codes in a jar file that can be deployed.
Owner:ELECTRONICS & TELECOMM RES INST
System and method for evaluating software sustainability
InactiveUS20090138843A1Easier” to sustainEasy to findReverse engineeringSpecific program execution arrangementsSoftware engineeringComputer science
A system and method for evaluating software sustainability are provided. The illustrative embodiments provide code scanning tools for identifying authors of portions of a software product and various attributes about the development, maintenance, and improvement of portions of the software product over time. This information may be correlated with organizational information to identify portions of the software product that may be lacking in sustainability by the persons currently associated with the software organization. Moreover, this information may be used to obtain information regarding the relative quality of the composition or conception of portions of the software product, portions of the software product that have required a relatively larger amount of resources to develop over time, a relative indication of which portions of the software product are “harder” or “easier” to sustain and who is associated with those portions of the software product, and the like.
Owner:IBM CORP
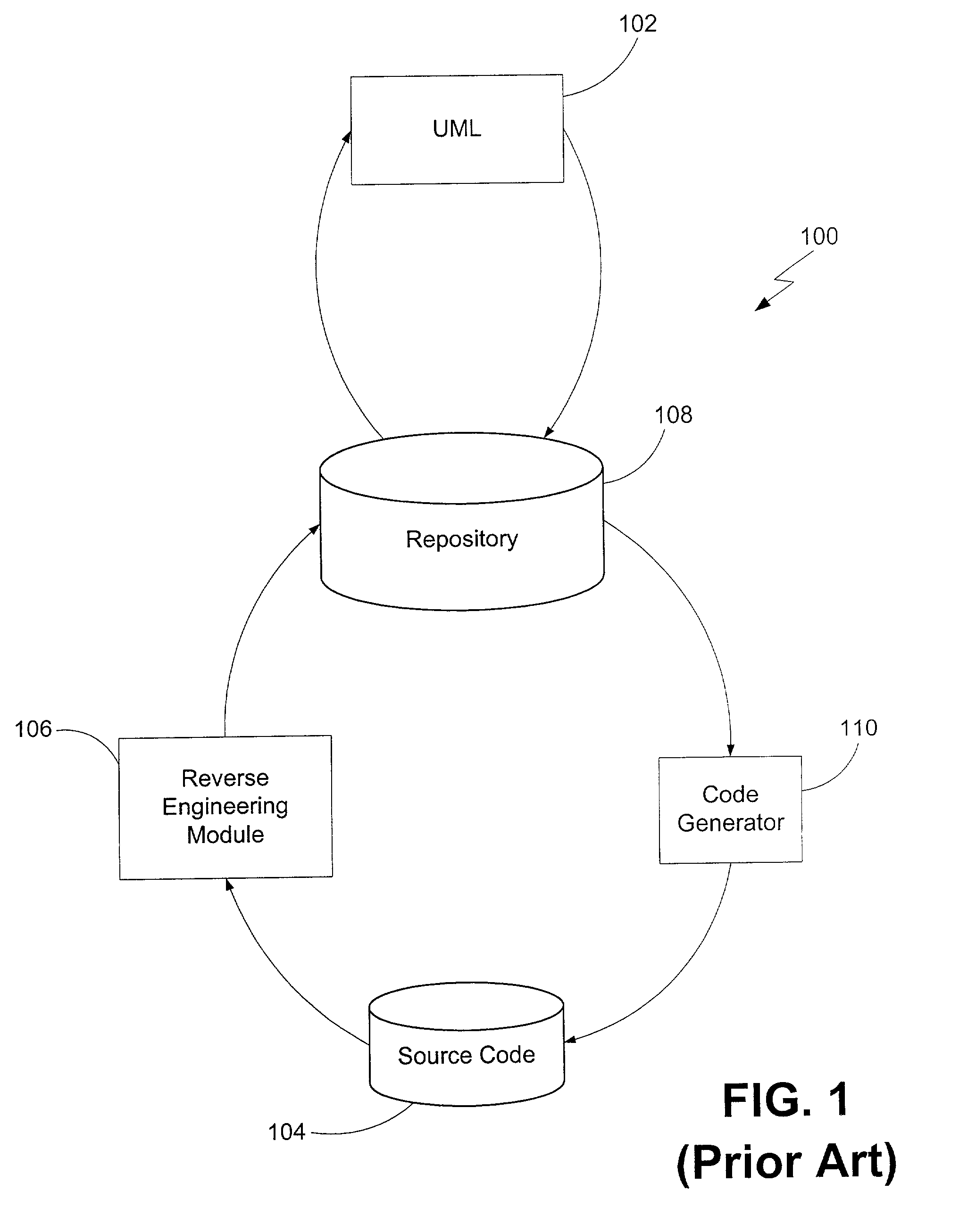
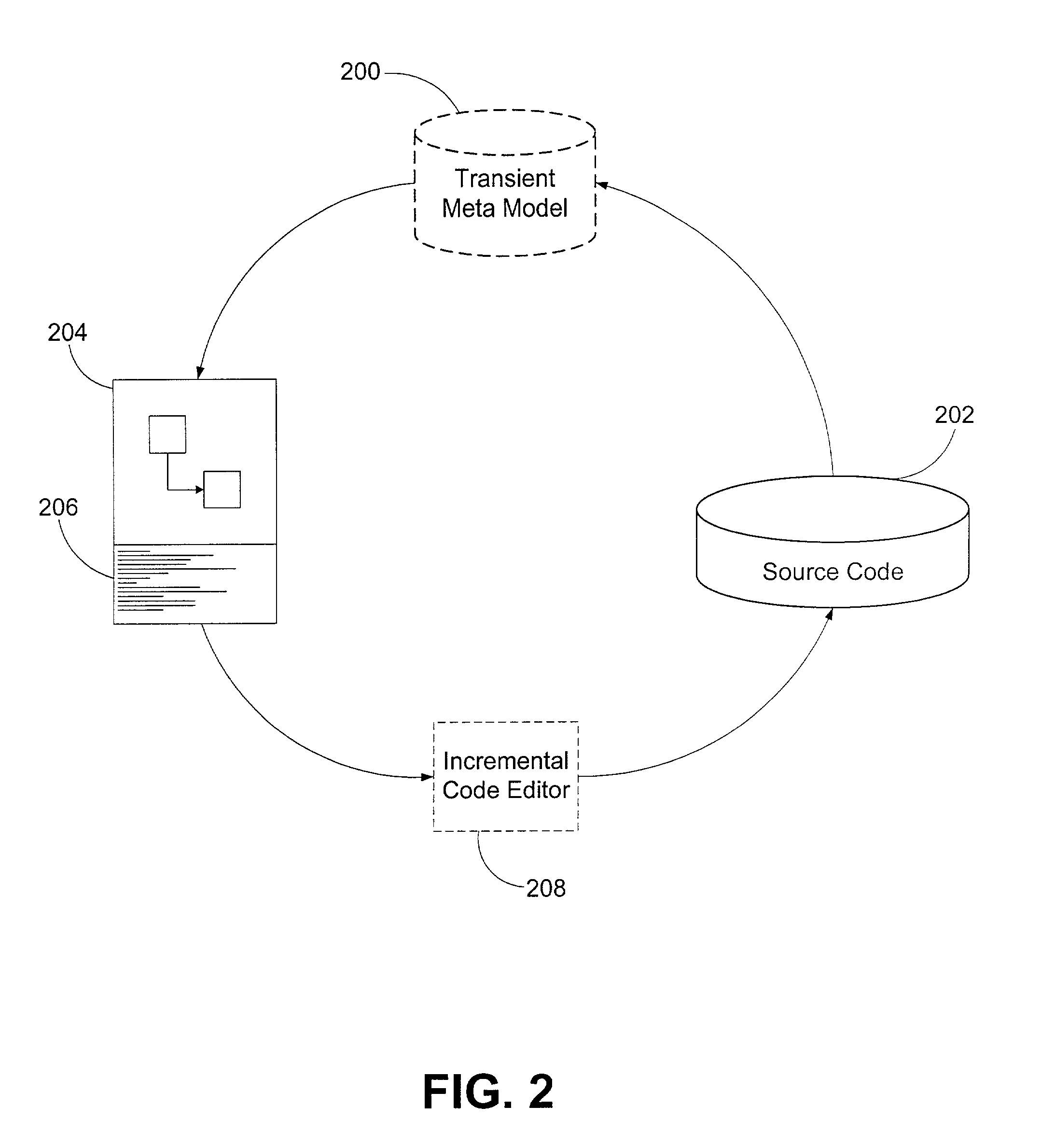
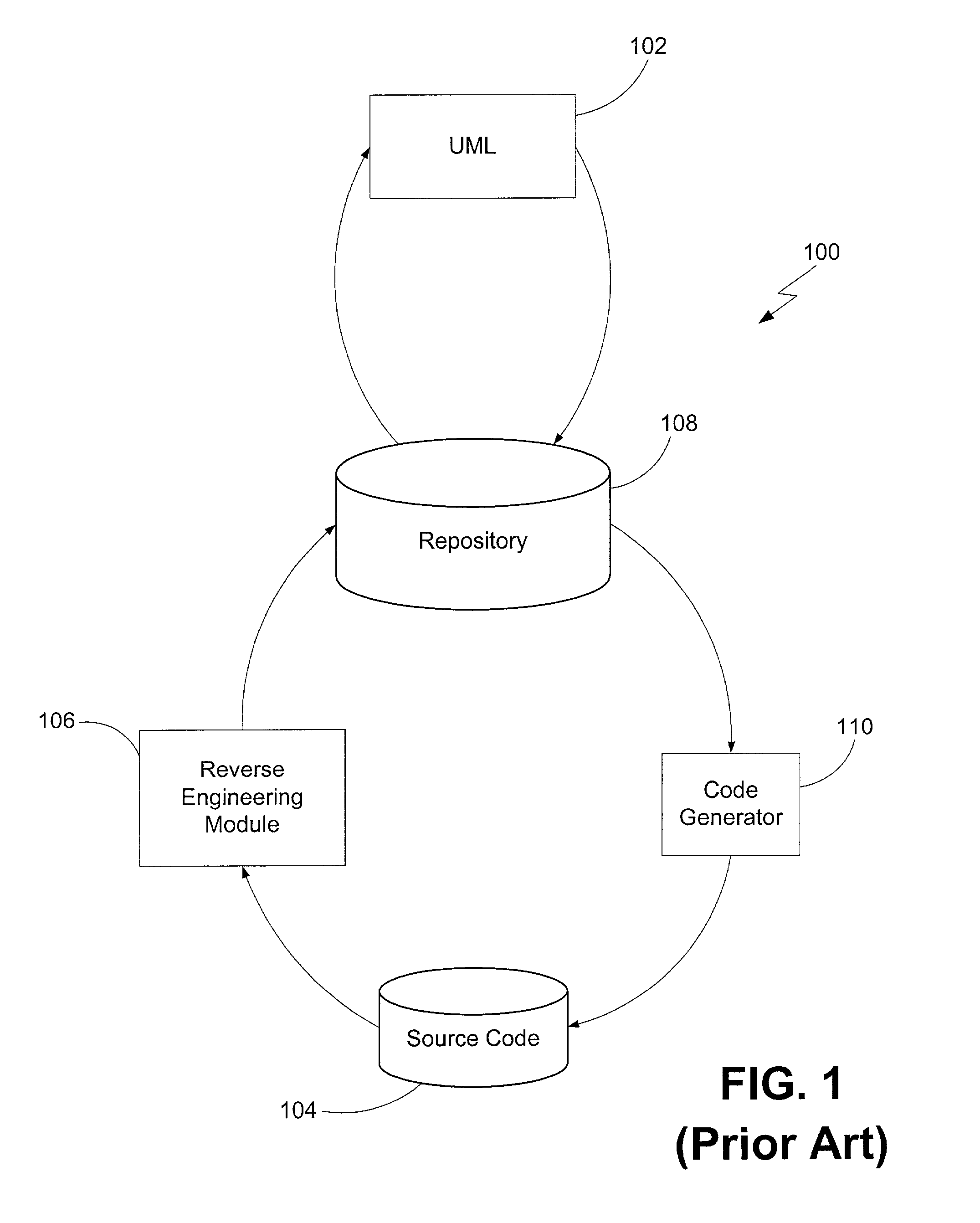
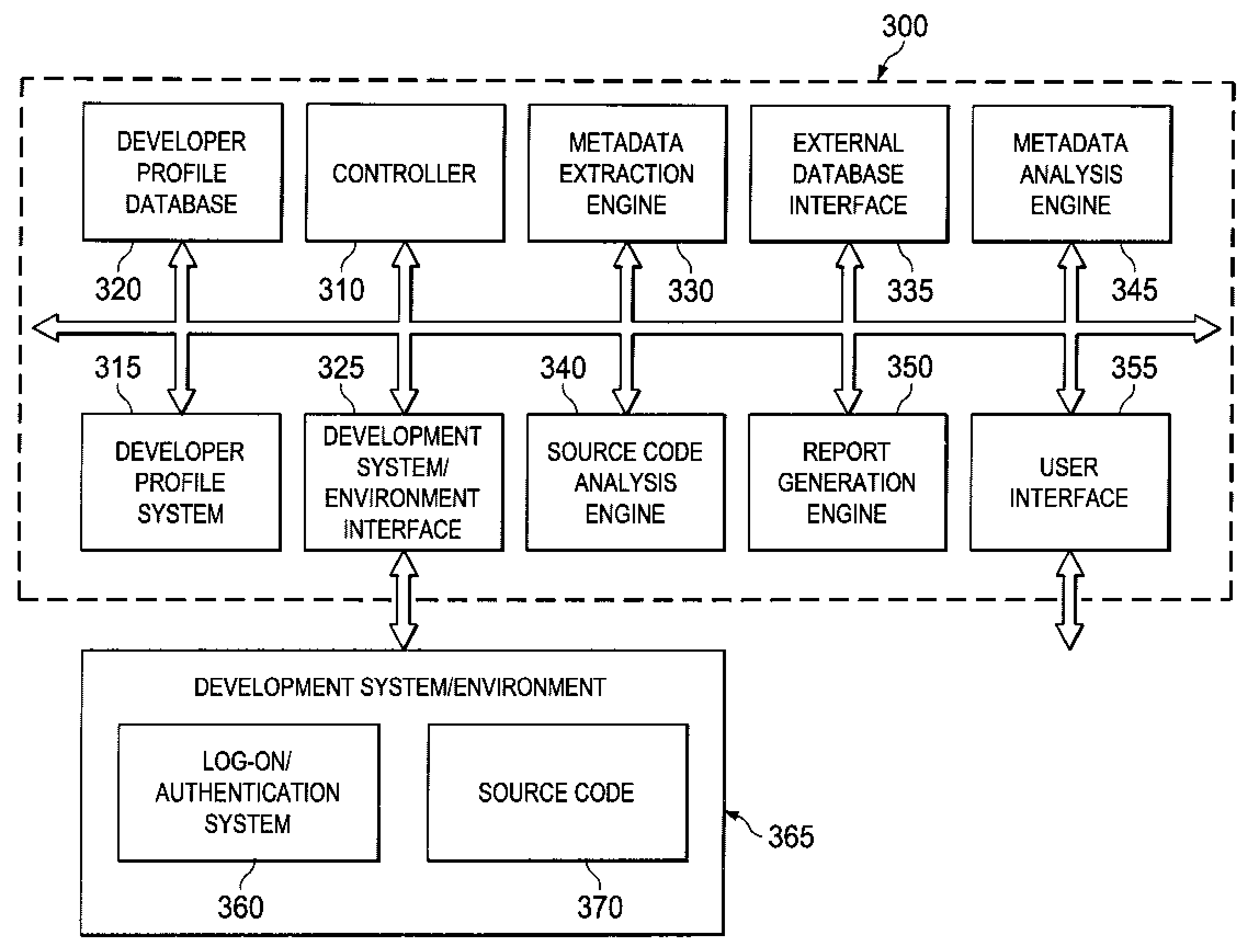
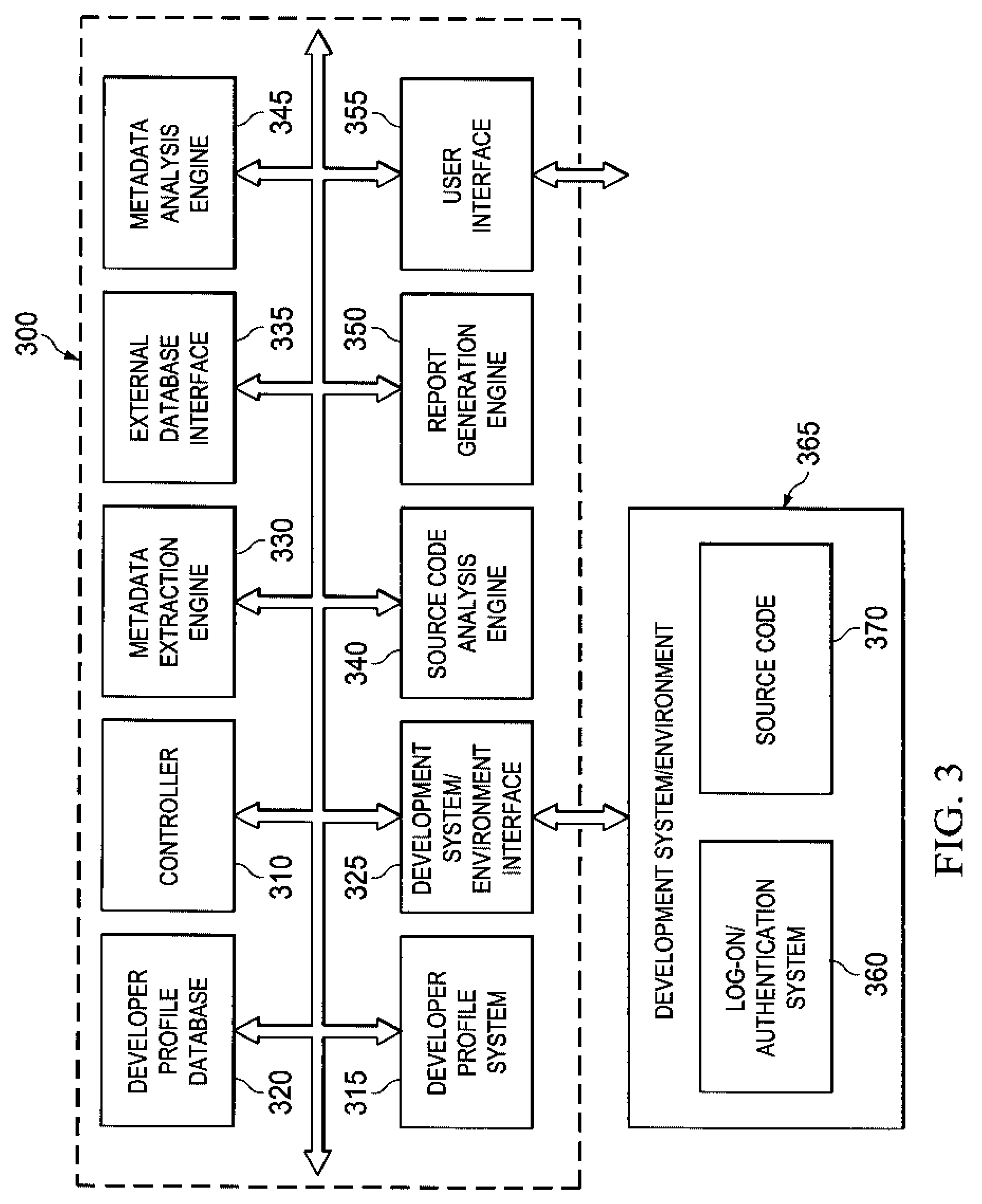
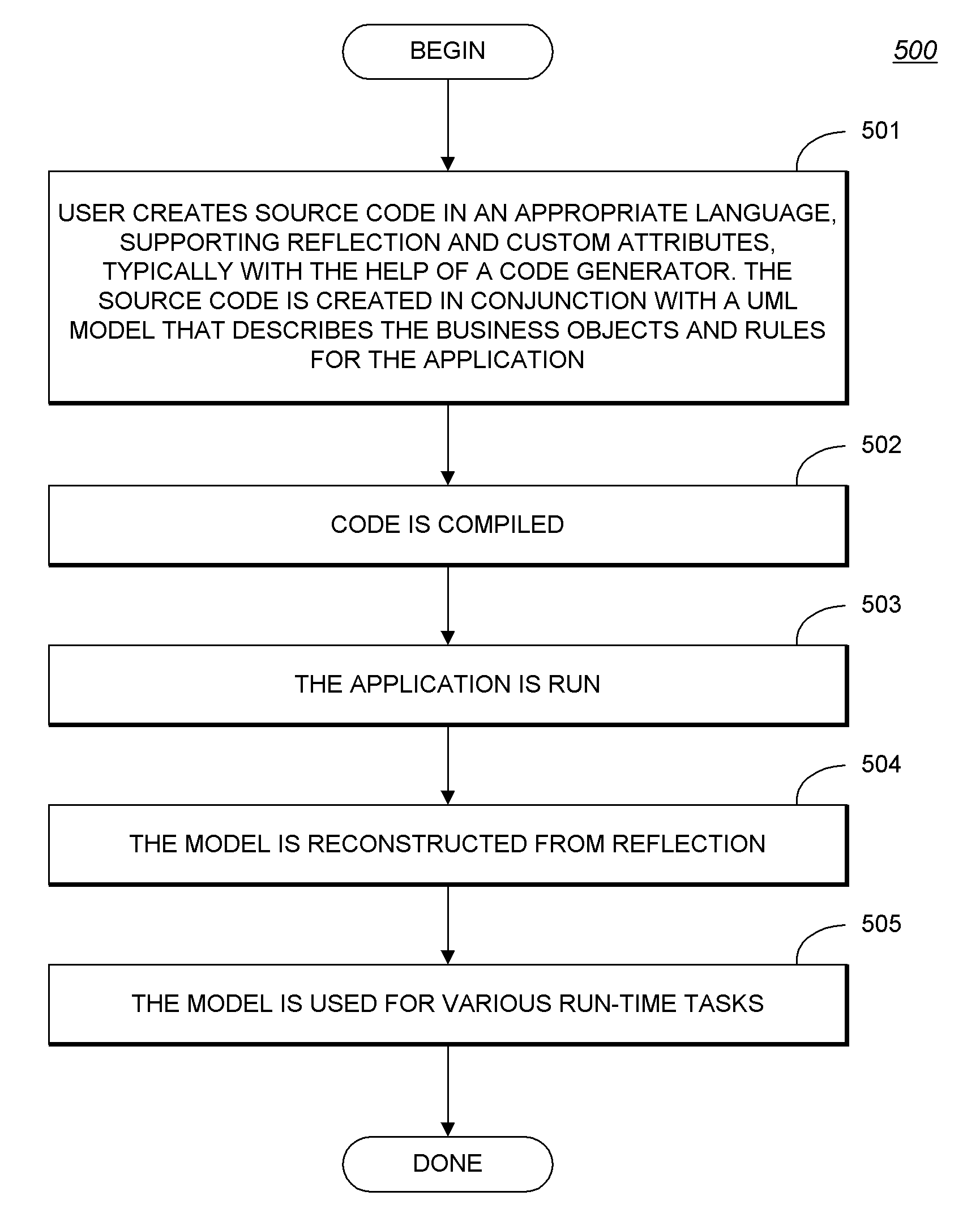
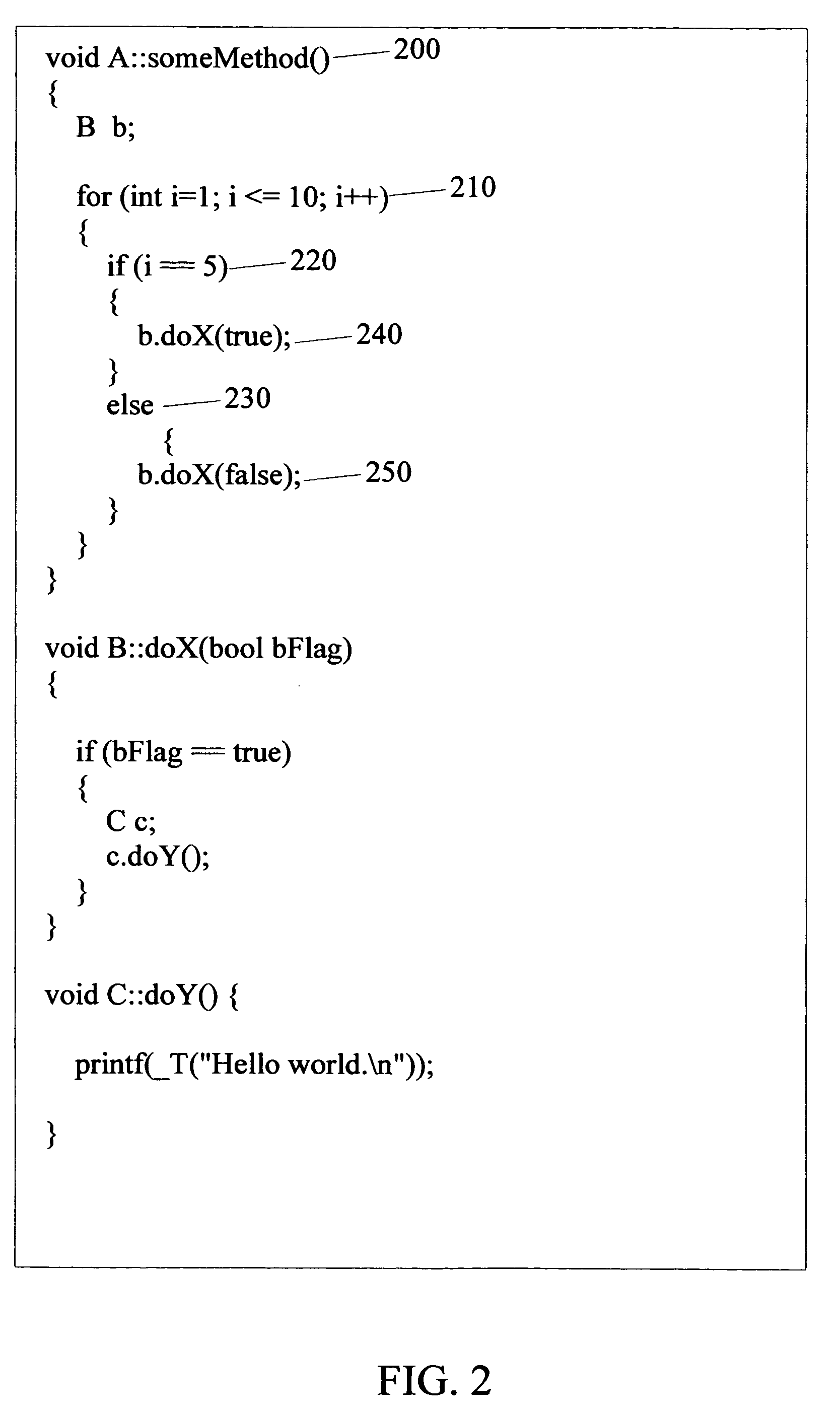
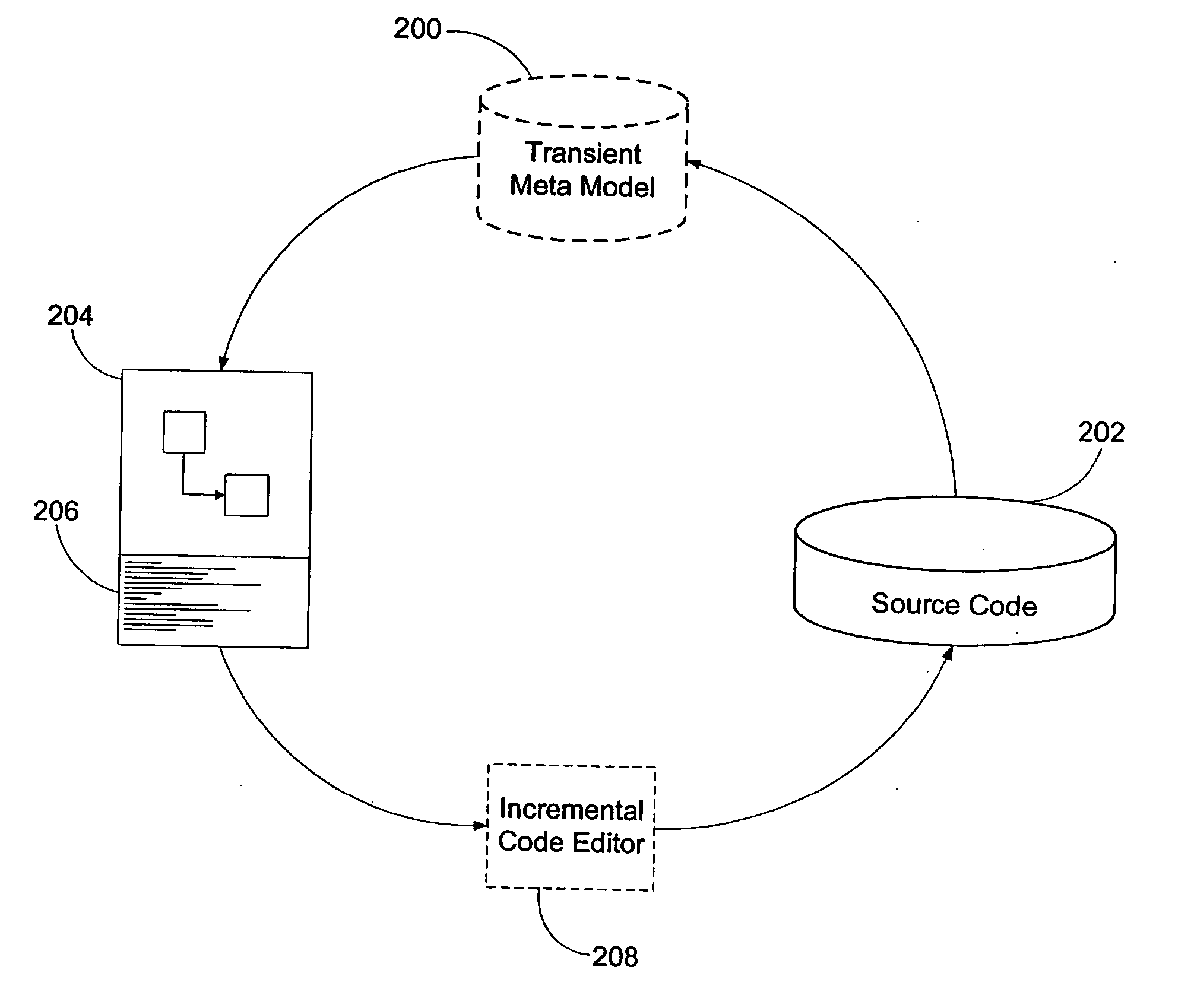
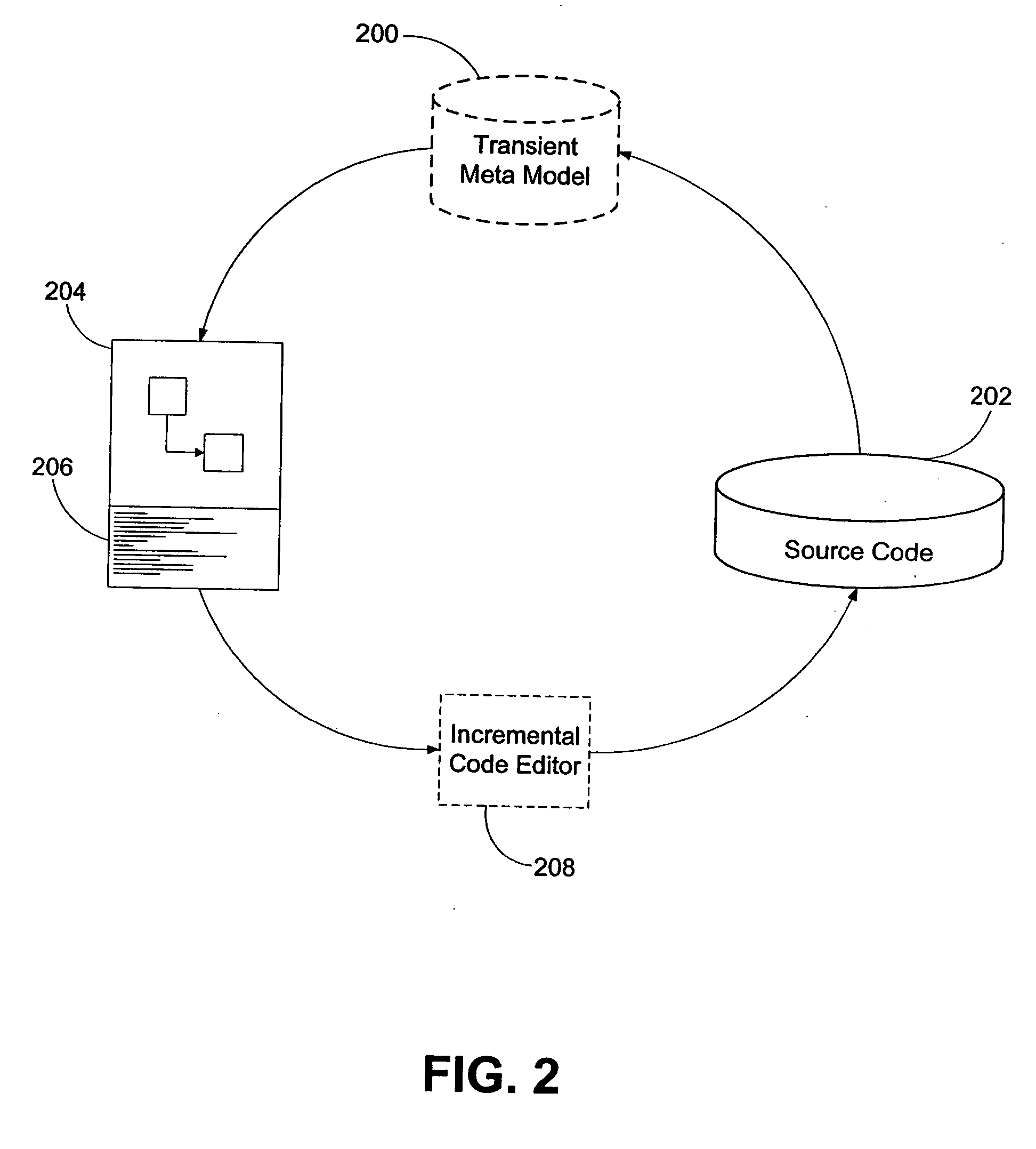
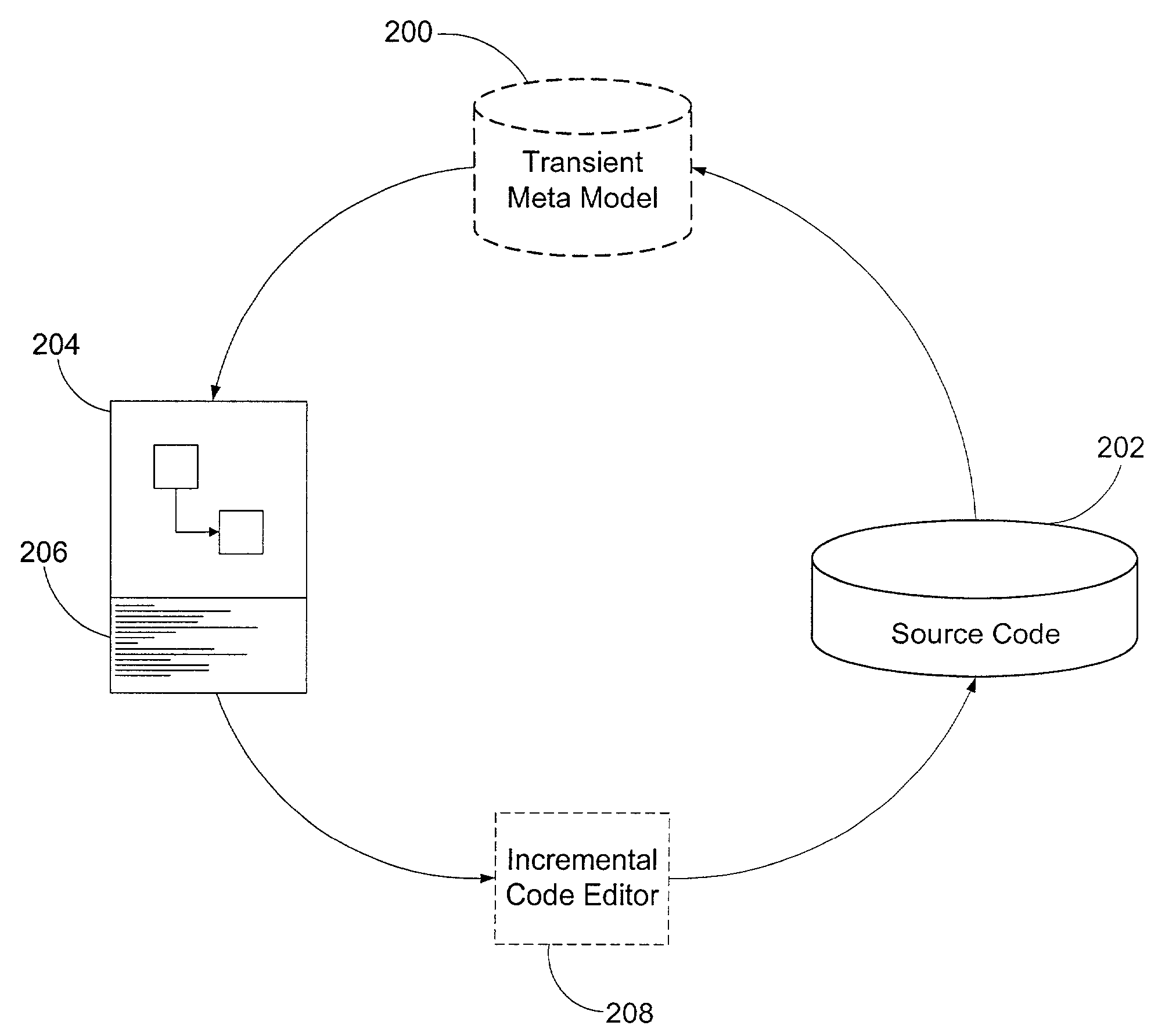
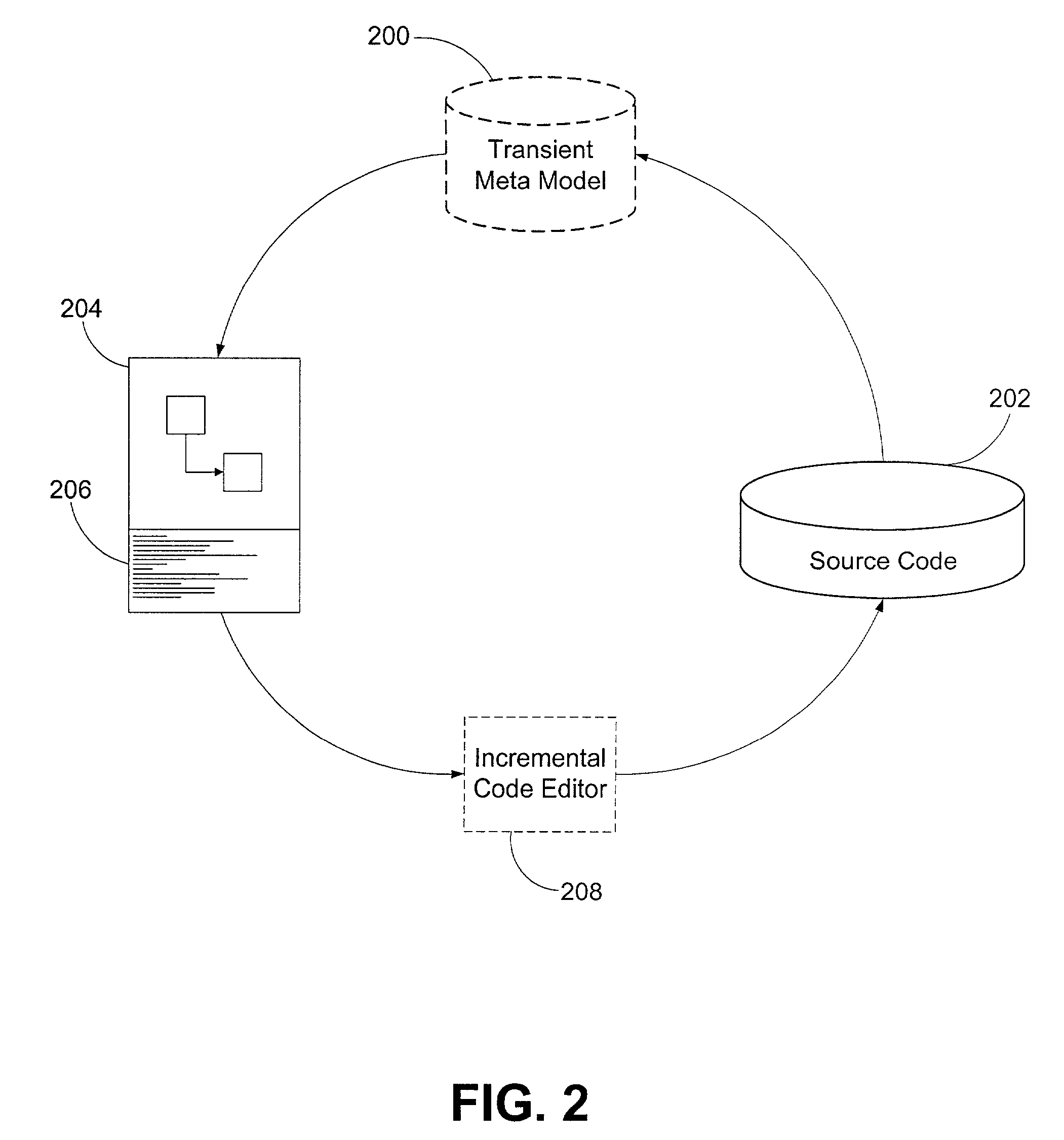
Development system with methodology for run-time restoration of UML model from program code
A development system with methodology for run-time restoration of UML model from program code is described. In one embodiment, for example, in a computer system, an improved method is described for developing and executing an application, the method comprises steps of: creating a model describing business objects and rules of the application; creating source code for the application, including representing the model within the source code itself; compiling the source code into an executable application; running the executable application on a target computer in conjunction with a run-time framework that provides services to the executable application; and while the executable application is running, reconstructing the model from the executable application and making it available to the run-time framework.
Owner:BORLAND
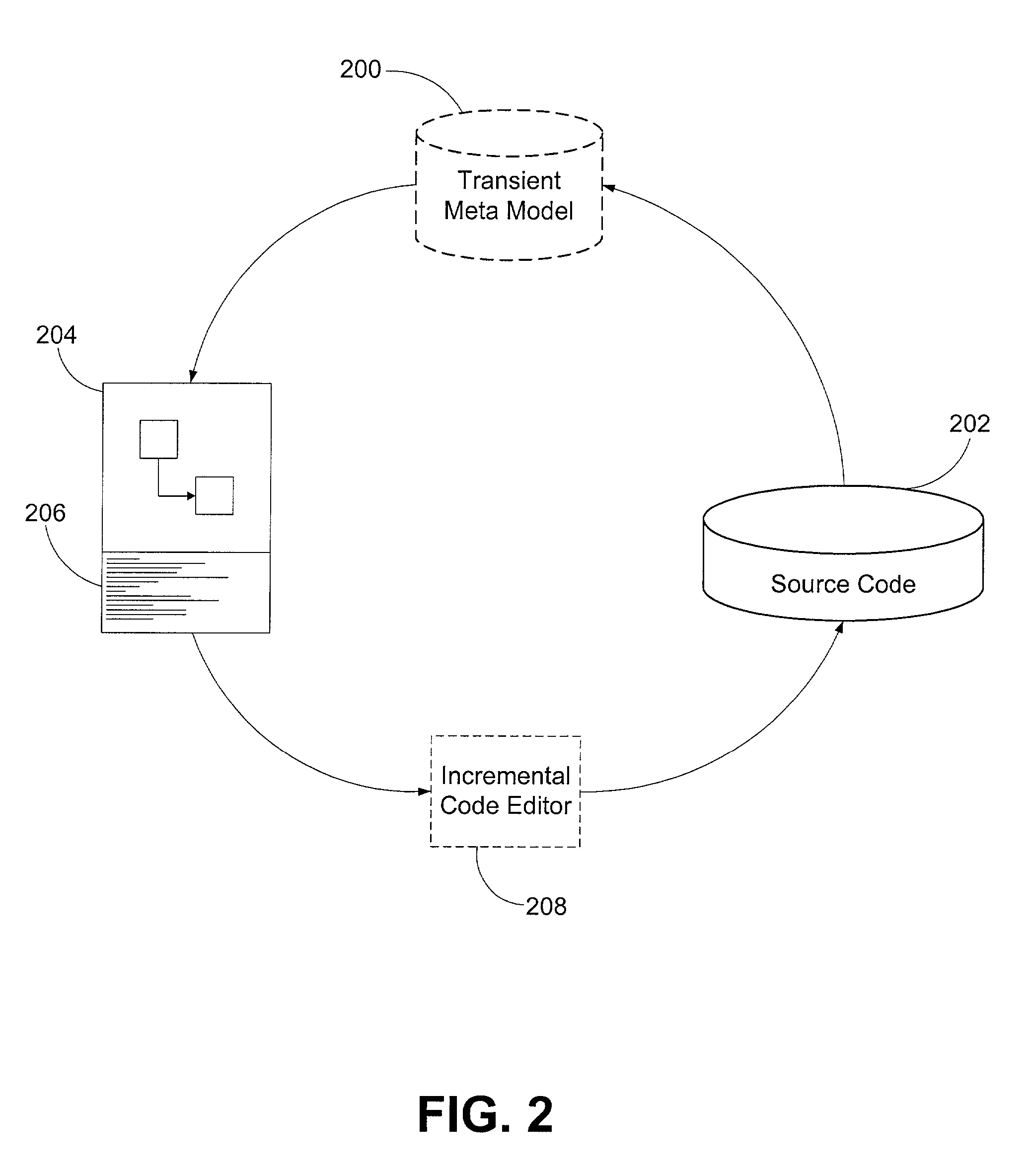
System and method for code migration
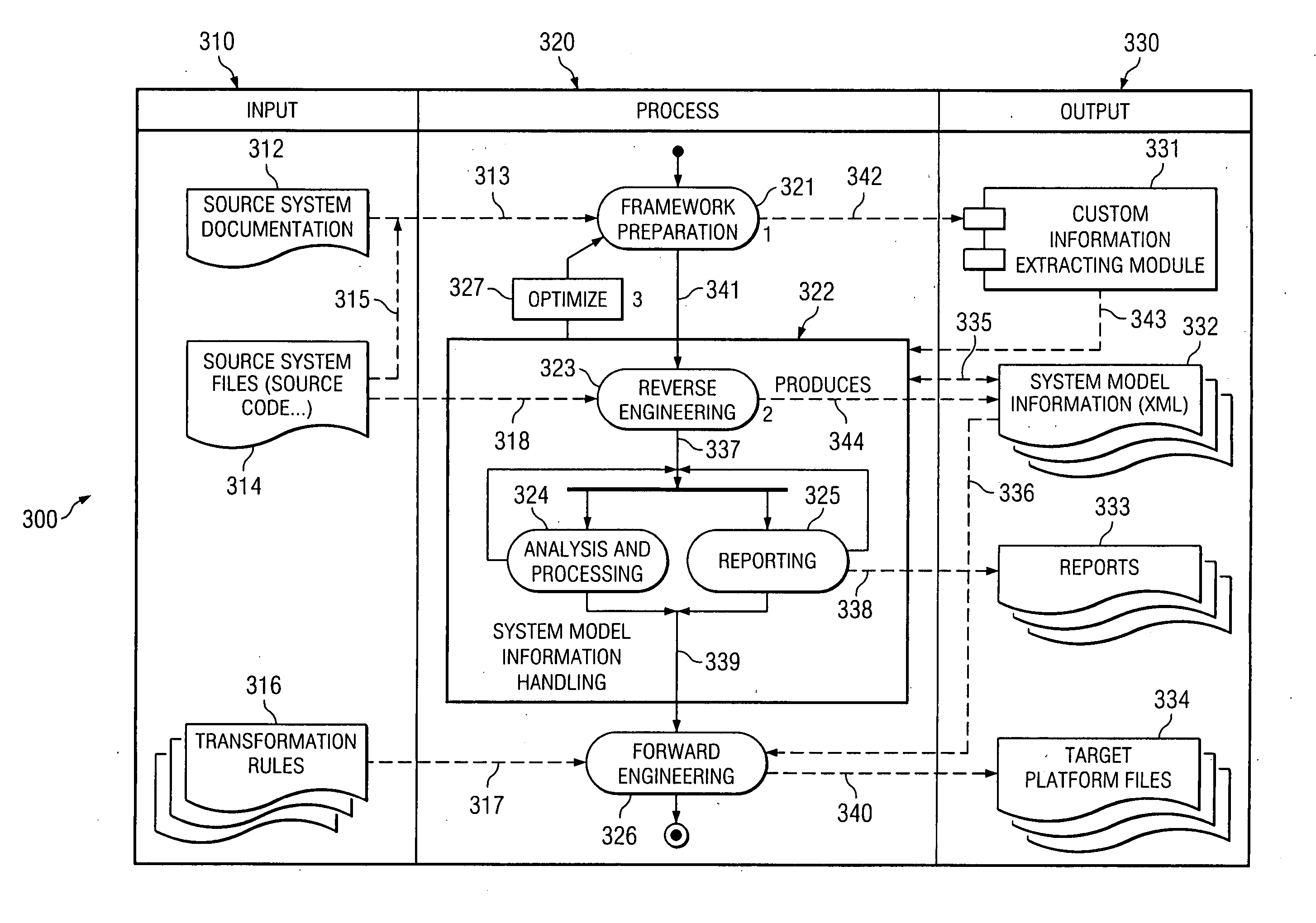
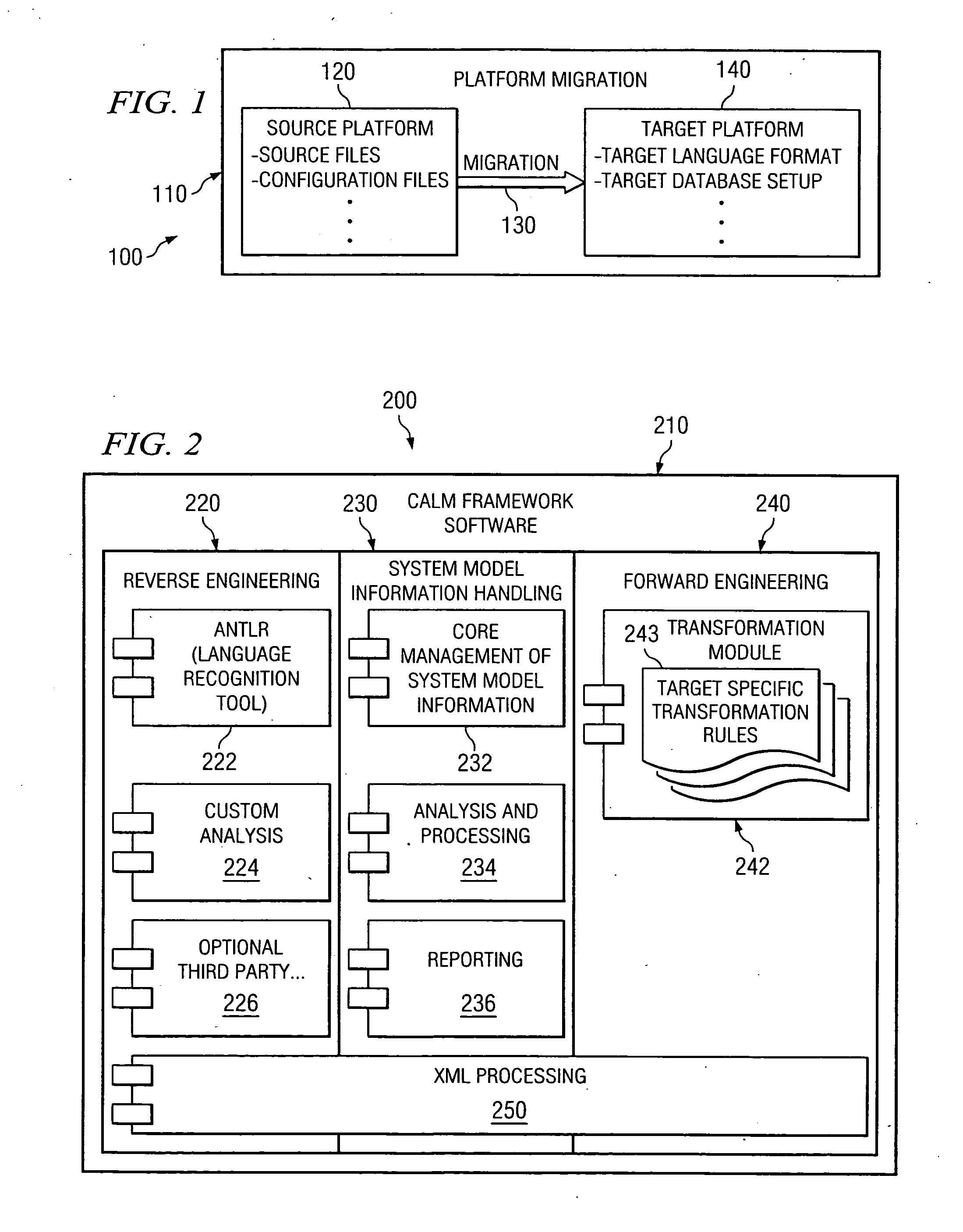
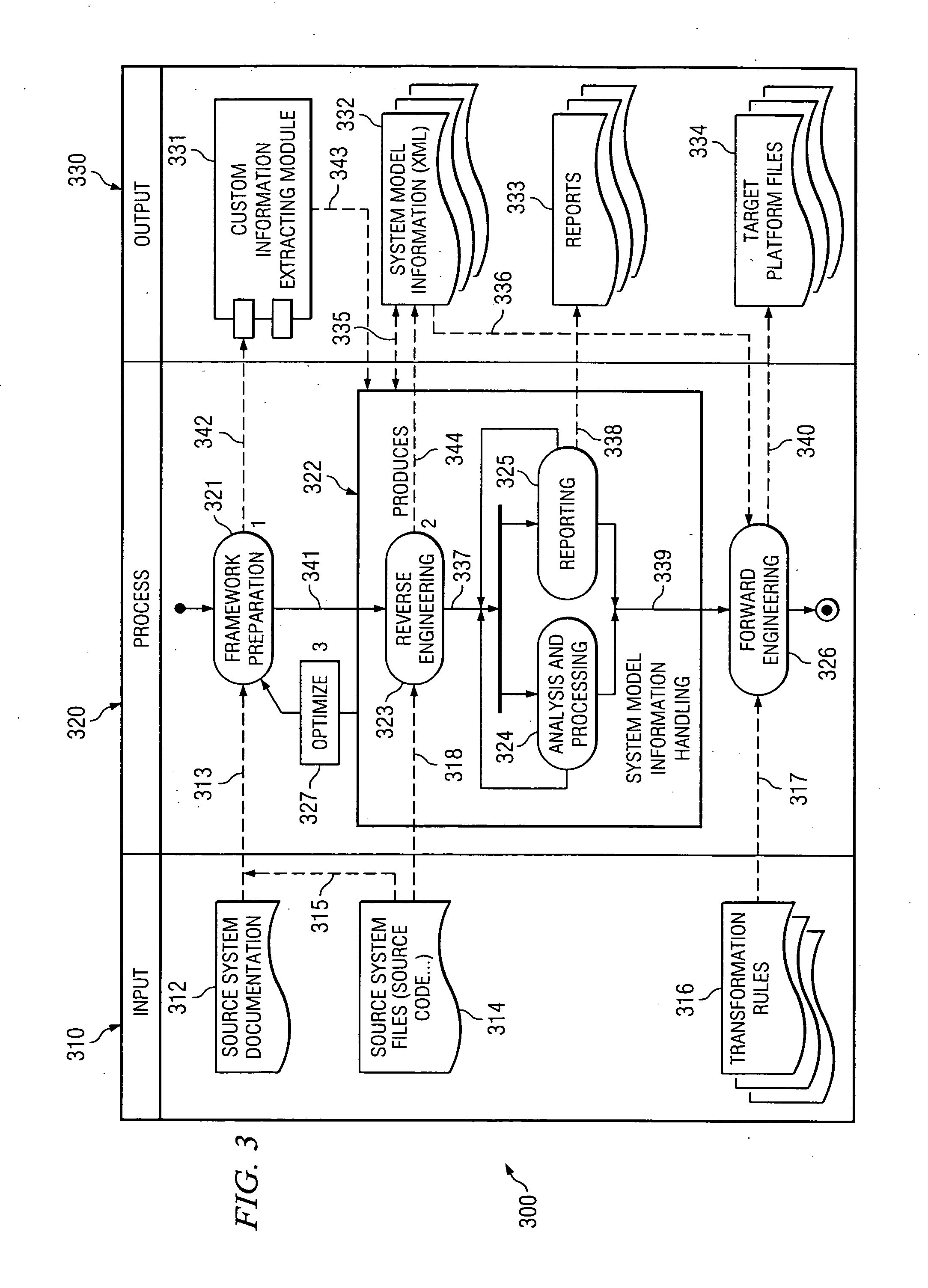
One disclosed method for converting data suitable for use on a source platform into data suitable for use on a target platform comprises analyzing source platform code; extracting information from the analyzed source platform code wherein the extracted information includes at least the logic, flow, user interface description, and data of the source platform code; defining a generic data structure and format for storing the extracted information; storing the extracted information in the defined structure and format; and transforming the extracted information into code suitable for the target platform wherein the transforming step comprises transforming the extracted information into code suitable for the target platform after the extracted information is stored in the defined structure and format.
Owner:HEWLETT PACKARD DEV CO LP
Method and apparatus for executing stored code objects in a database
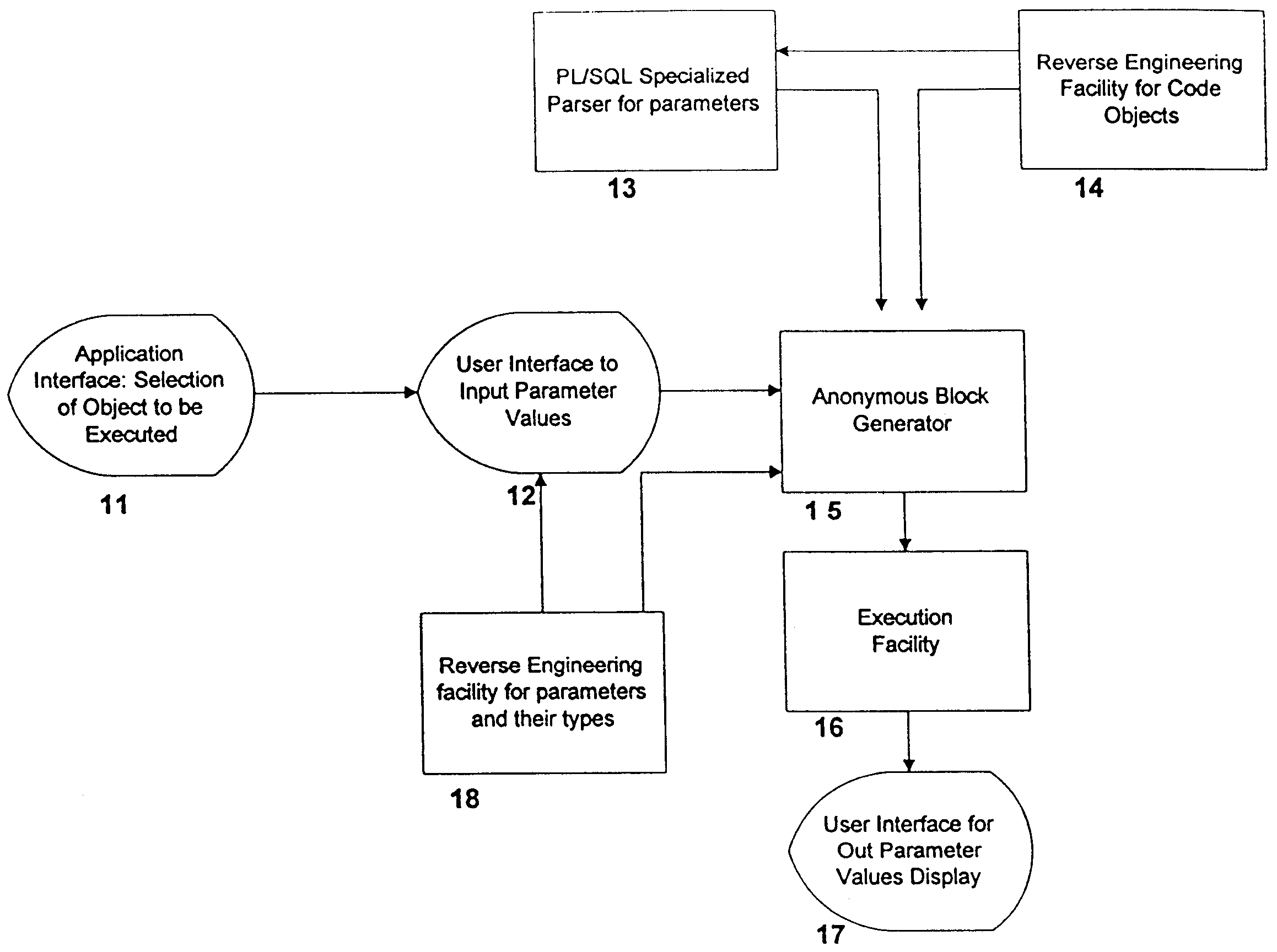
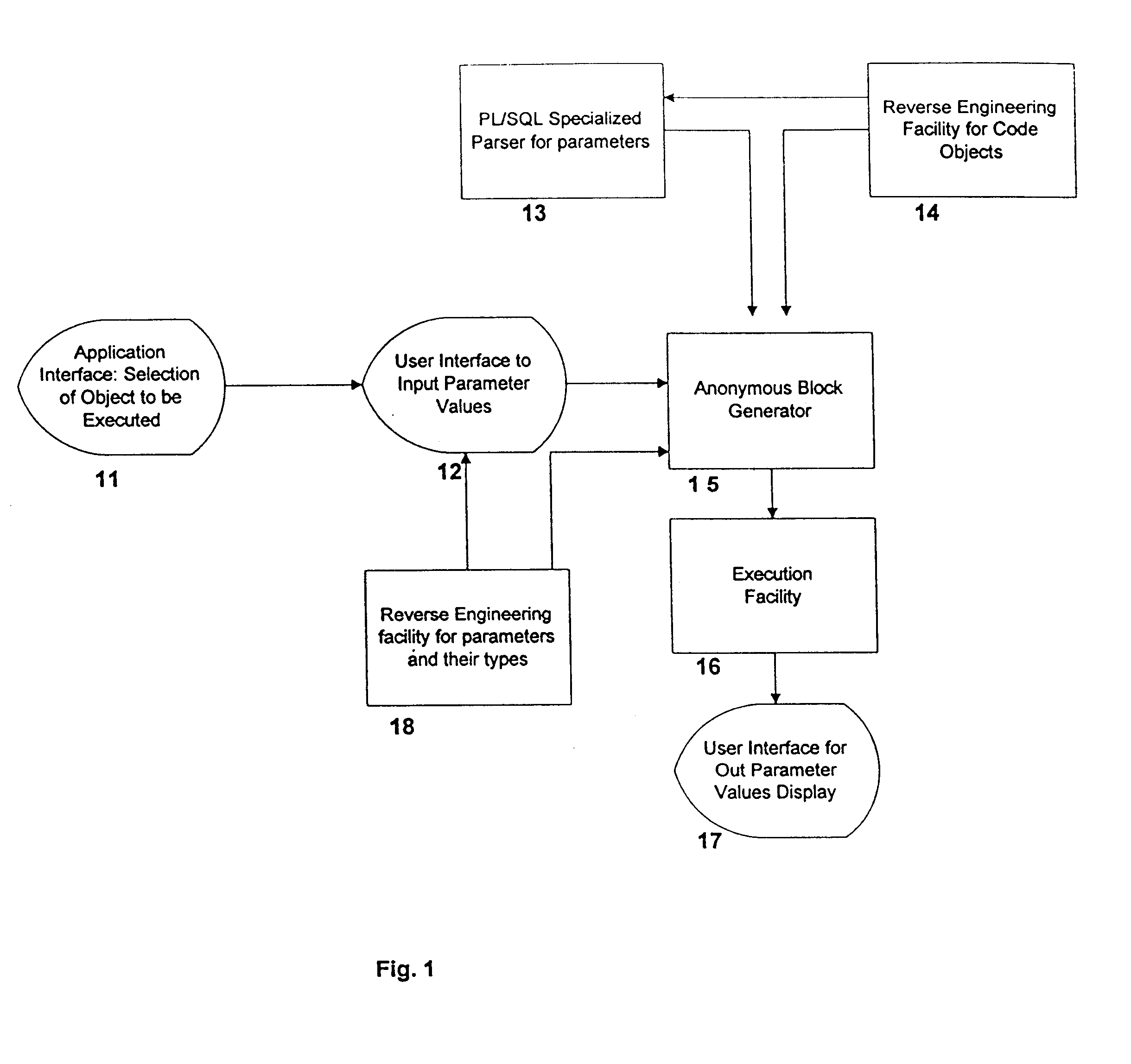
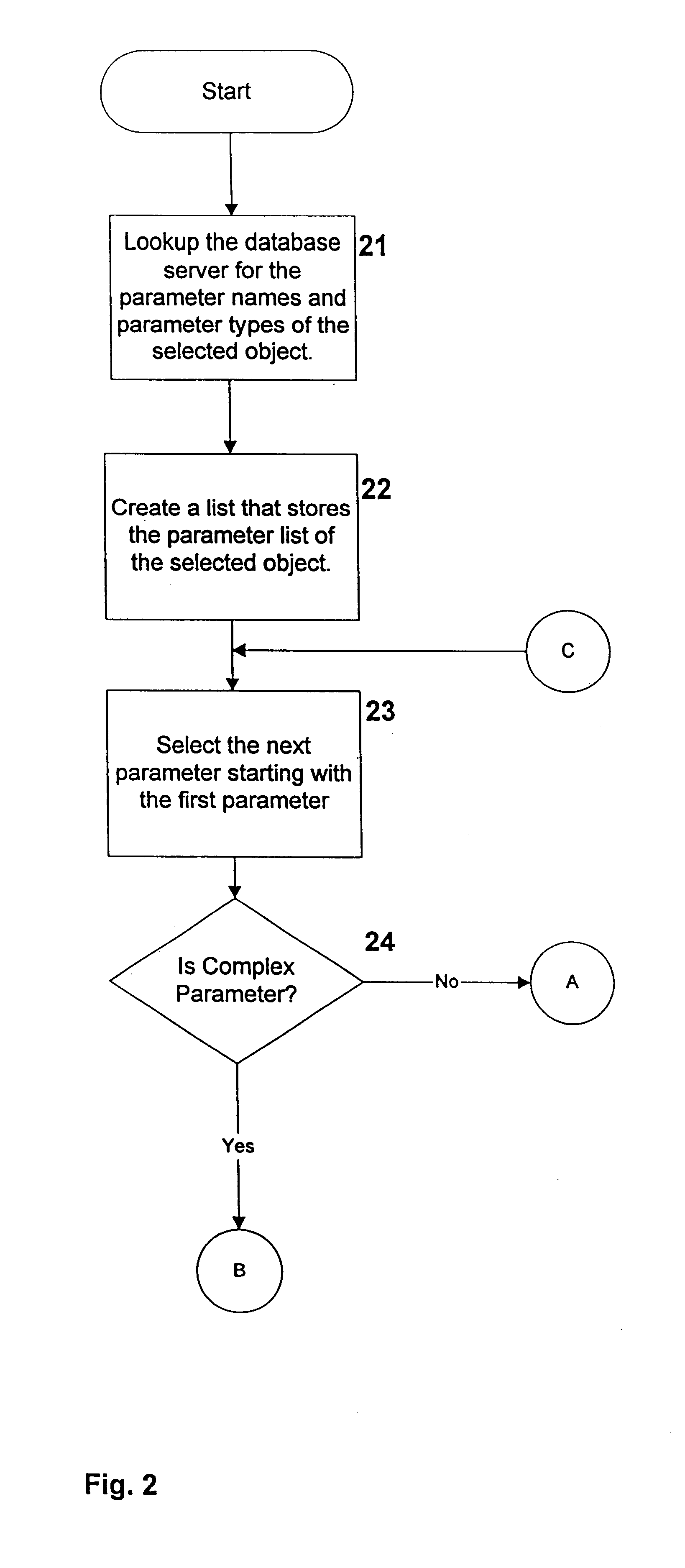
InactiveUS7047249B1Transformation of program codeDigital data information retrievalBase codeSource code
A system, method and database development tool are disclosed for automatically generating parameters for use in executing a stored code object in a data base, by parsing source code derived from existing data base code which represents the stored code object, wherein the parameters may represent complex data types.
Owner:CA TECH INC
Methods, systems, and computer program products for identifying computer program source code constructs
Methods, systems, and computer program products for identifying computer source code constructs are disclosed. According to one method, computer source code is converted to a format suitable for an automated inference engine. The automated inference engine receives as inputs the converted source code, a set of elemental design patterns defining patterns to be identified, and a set of rules defining relationships between patterns. The automated inference engine outputs proofs indicative of patterns present in the source code. The proofs may be converted to a source code pattern report.
Owner:THE UNIV OF NORTH CAROLINA AT CHAPEL HILL
Methods, systems, and computer program products for summarizing operational behavior of a computer program
InactiveUS20050273757A1Simple processSmall artifacts (whichError detection/correctionReverse engineeringCall stackOperational behavior
Methods, systems, and computer program products for summarizing operational behavior of a computer program are disclosed. A method for summarizing the operational behavior of a computer program may include executing a computer program in a mode that allows control over execution of the computer program. Execution of the program is paused at predetermined locations corresponding to each instruction in the computer program. For each location, contents of a call stack containing function calls made by the program that have not yet returned are recorded. For each function call in the call stack, information regarding conditions under which the function was called are recorded. Execution of the program is resumed until the next pause location is encountered.
Owner:ANDERSON CRAIG D
Methods and systems for supporting and deploying distributed computing components
InactiveUS20060053410A1Save significant programming development timeLow costVersion controlReverse engineeringGraphicsSoftware development
Methods and systems consistent with the present invention provide an improved software development tool that generates code corresponding to a distributed computing component that contains methods of a plurality of types and that displays a graphical representation of the code with a separately delineated display area for each type. The improved software development tool also compiles, deploys, and debugs the distributed computing component with a client software component using methods and systems consistent with the present invention.
Owner:BORLAND
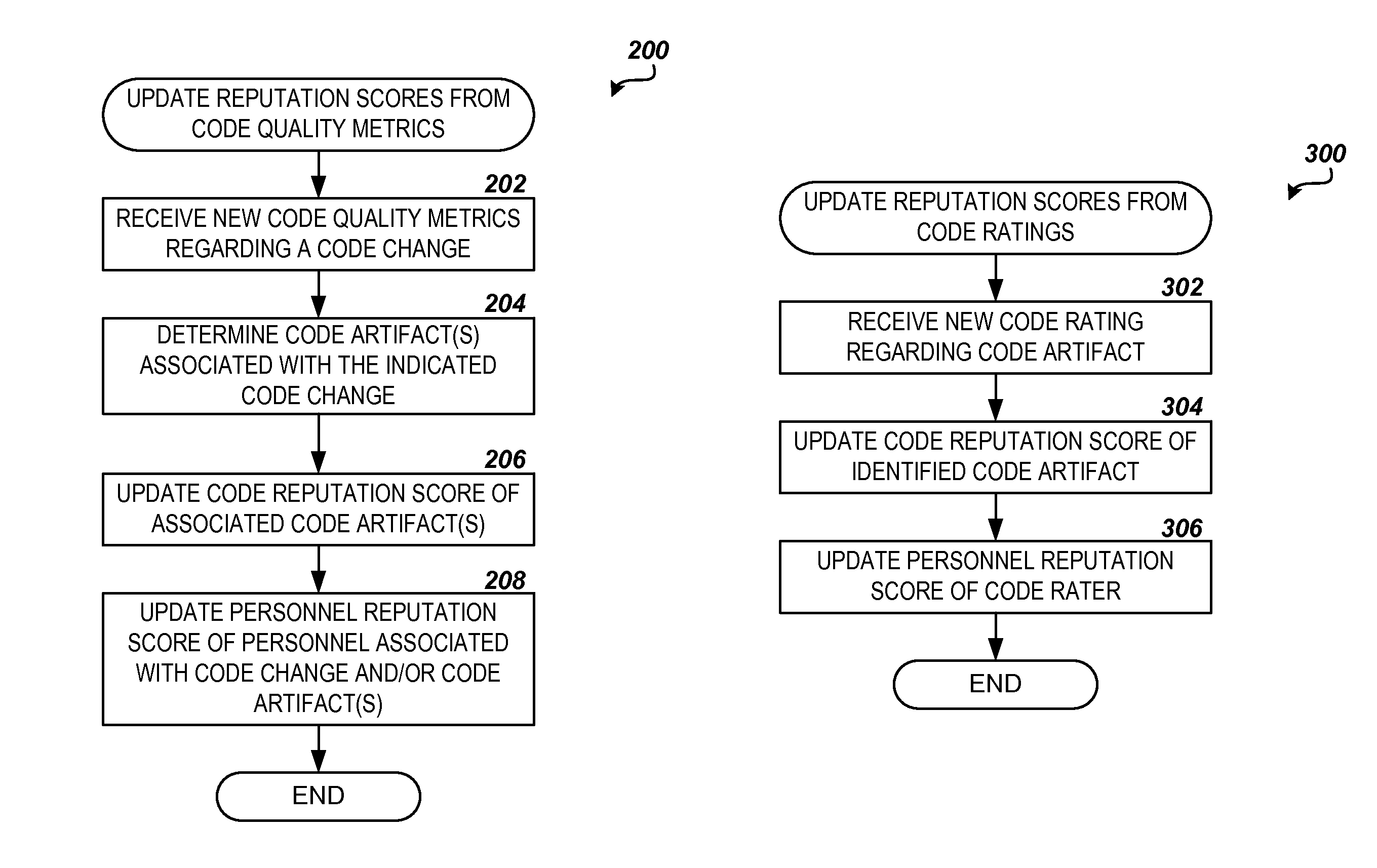
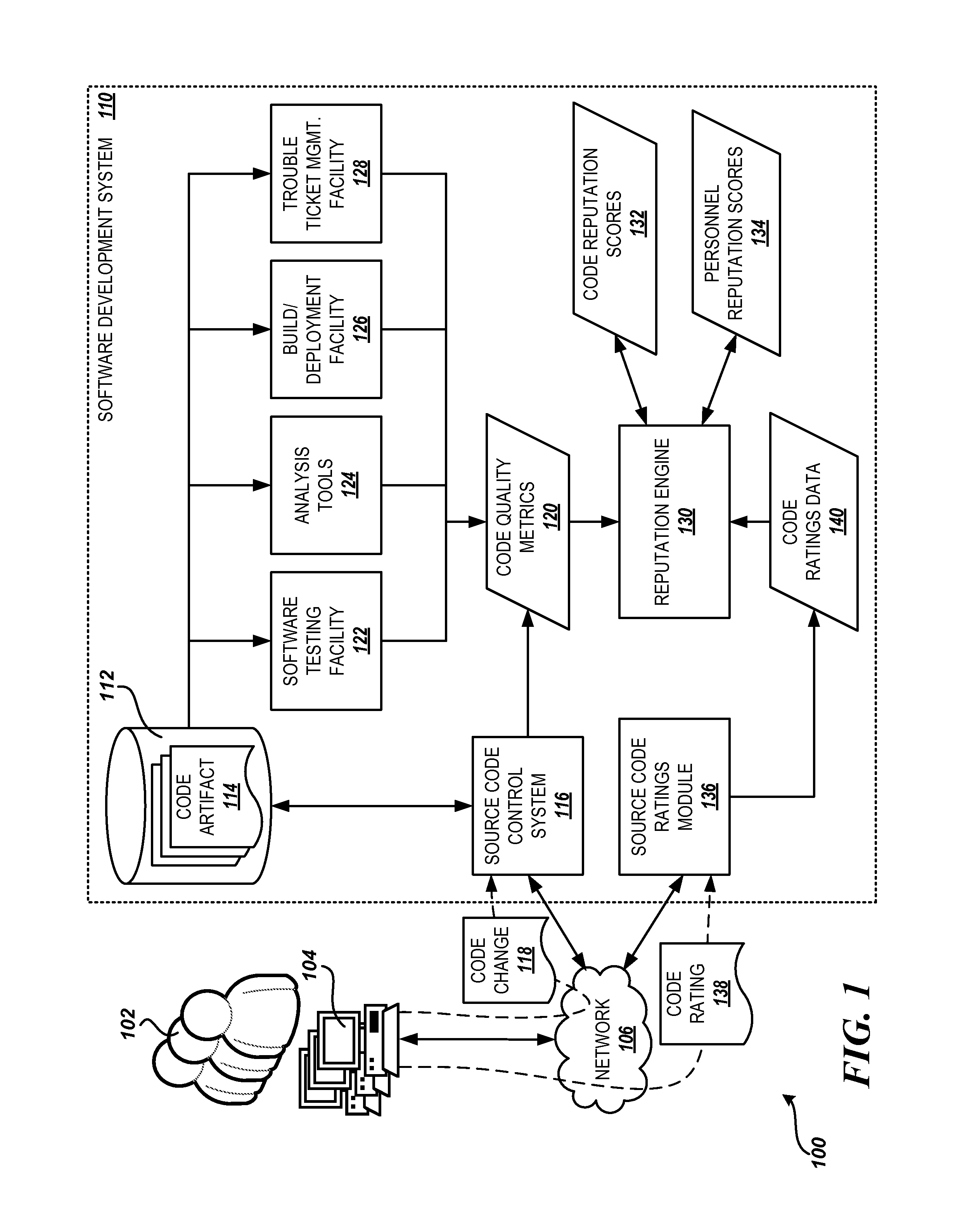
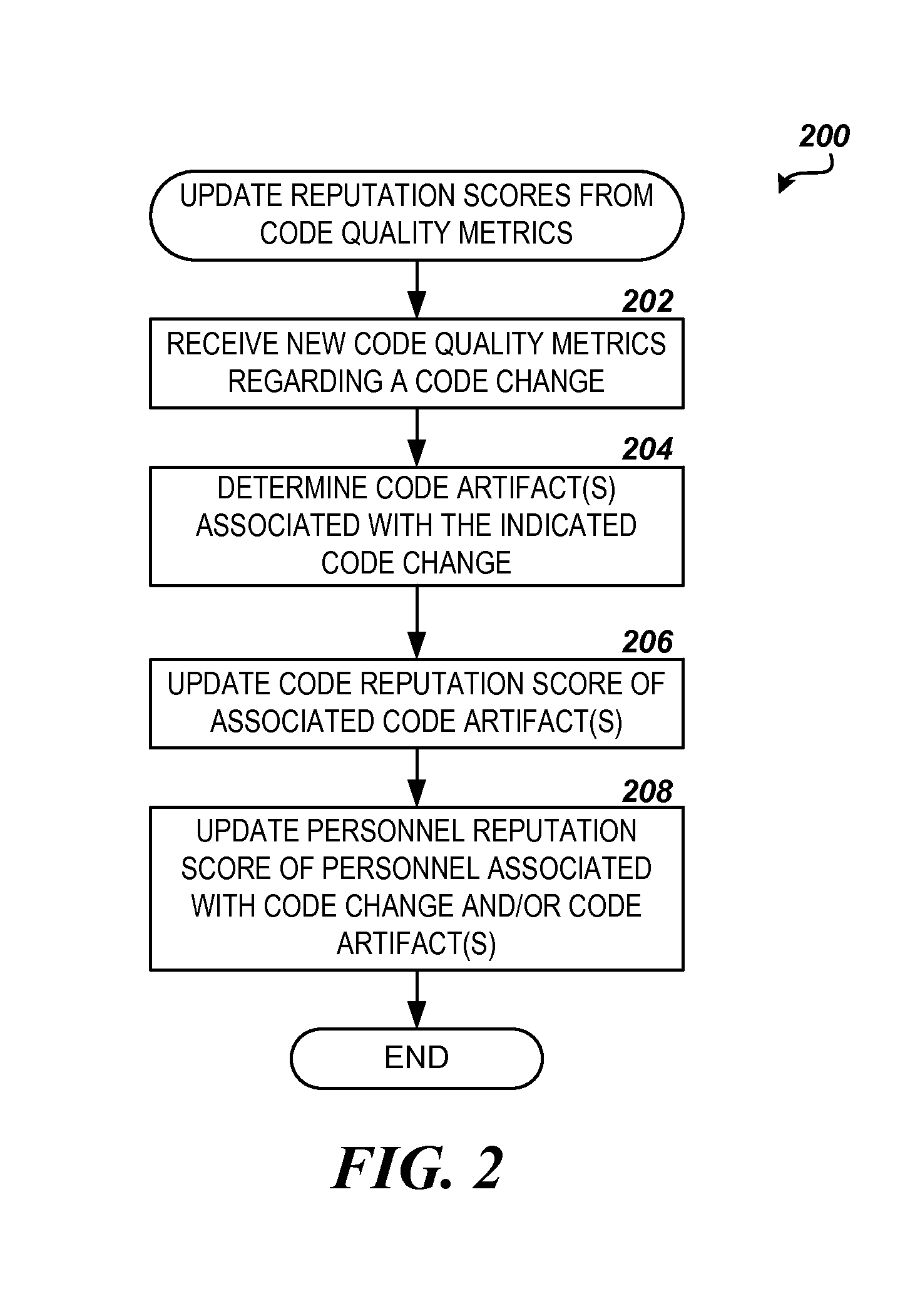
Automated source code and development personnel reputation system
InactiveUS8856725B1Reverse engineeringSpecific program execution arrangementsSoftware development processCoding artifacts
Technologies are described herein for providing an automated reputation system for source code and software development personnel. Code quality metrics regarding code changes associated with a code artifact are automatically generated in response to development lifecycle events in a development environment. The code quality metrics are collected and utilized by a reputation engine to compute a code reputation score for the code artifact. The reputation engine may further utilize the collected code quality metrics to compute personnel reputation scores for one or more development personnel related to the code changes, such as developers, reviewers, testers, and the like. In addition, ratings regarding the code artifact may be received from development personnel in the development environment, and these ratings may be further considered in the computation of the code reputation score for the code artifact and the personnel reputation scores of the related development personnel.
Owner:AMAZON TECH INC
Integrated System for Software Application Development
InactiveUS20170083290A1Equally distributedDigital data information retrievalVersion controlSoftware development processPredictive modelling
Methods and systems are disclosed for developing a software application through requirements specification, design, effort estimation, assigning and tracking work items, development, testing, collaboration and project management. The system is structured as an integrated software development system allowing for structured, systematic and user friendly set up of requirements specification (including workflow, user interface, business rules and integrations), technical design for UI features and integrations using design patterns, automated effort estimation, automated story card and task creation. The system also provides a novel, audio-video playback capability for workflow visualization. Further, the system provides visual depiction of defects and changed items side-by-side with requirements, as well as predictive modeling of defects that allows for forecasting of defect completion rate. In the preferred embodiment, the system is delivered as a multi-tenant Software as a Service.
Owner:BHARTHULWAR SHRIDHAR V
Componentization method for reengineering legacy system
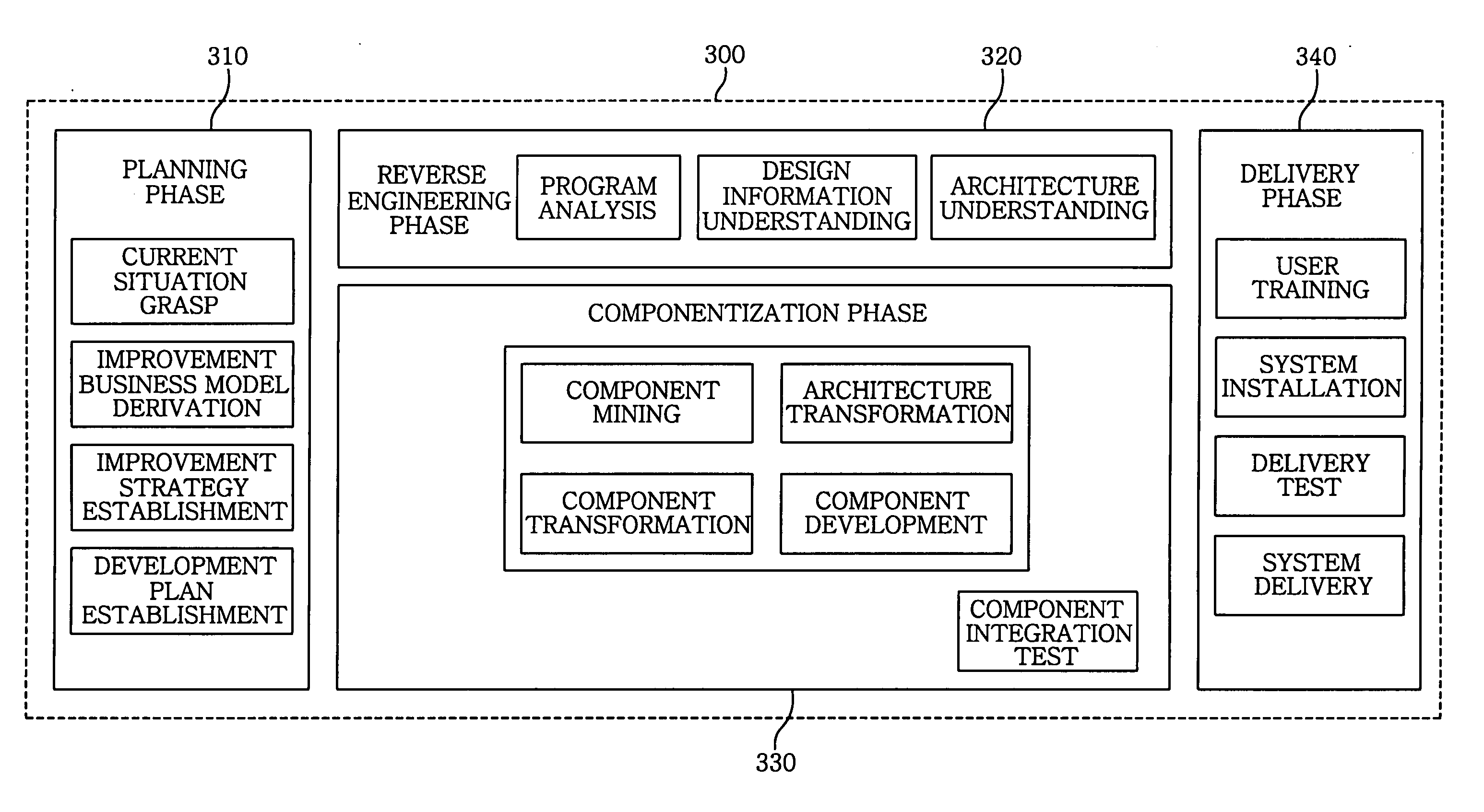
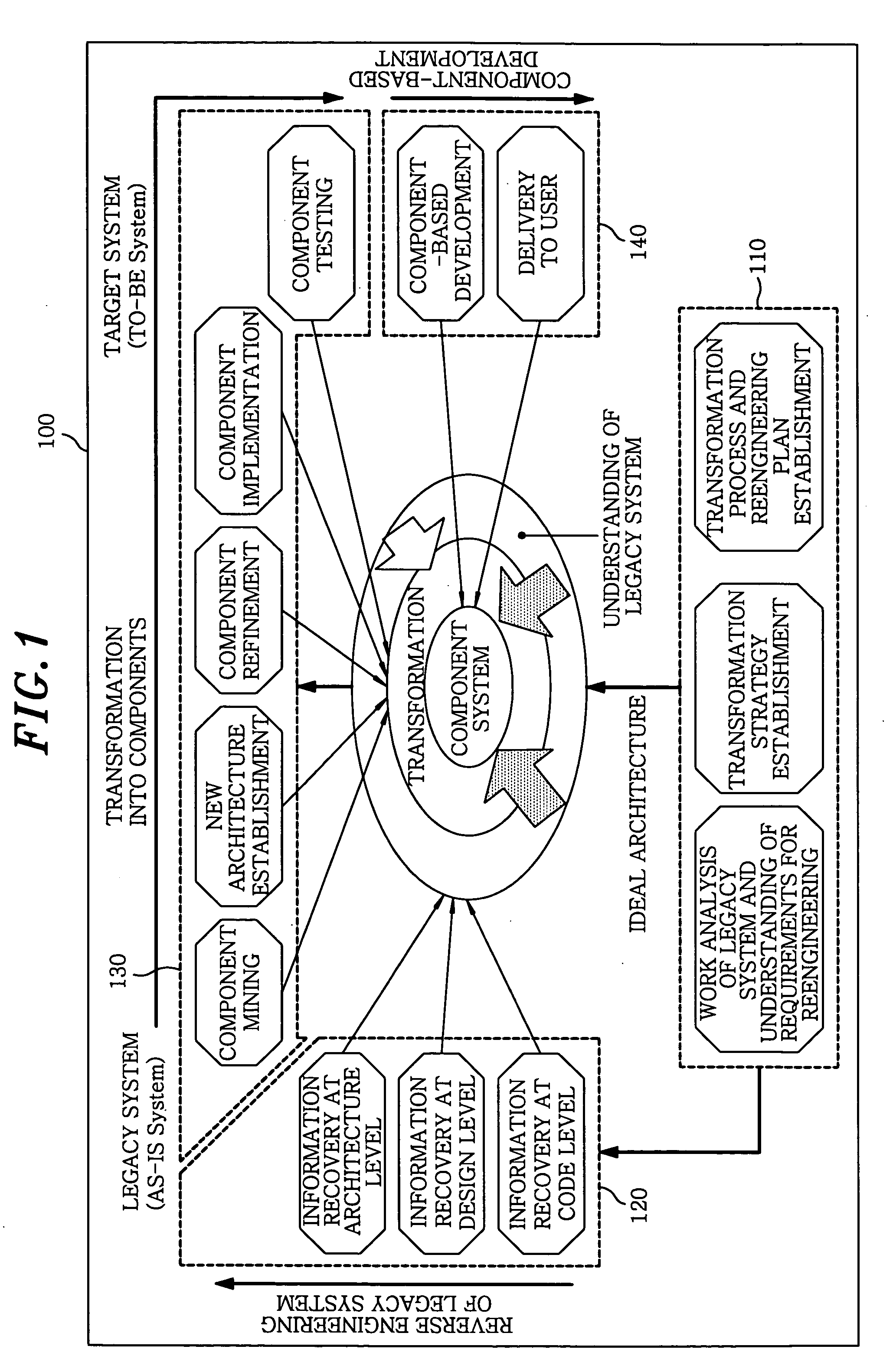
InactiveUS20050138603A1Minimizing semantic differenceIncrease valueDecompilation/disassemblyReverse engineeringProduction rateSoftware engineering
The present invention proposes a Magic and Robust Methodology Integrated-Reengineering (MaRMI-RE), which is a reengineering methodology defining a process including procedures and techniques for a componentization of legacy systems and work products generated during the process. A continuous evolution model for the legacy systems proposed in the present invention enables the legacy systems to be systematically transformed into component systems capable of smoothly complying with new requirements, thus maximizing productivity and efficiency of the legacy systems with respect to potential business and system change requirements.
Owner:ELECTRONICS & TELECOMM RES INST
Methods and systems for finding specific line of source code
Methods and systems consistent with the present invention provide an improved software development tool that allows a developer to locate a portion of source code corresponding to a message from a verification tool. The improved software development tool displays a graphical representation of the portion of the source code corresponding to the message in a visually distinctive manner.
Owner:BORLAND
Methods and systems for relating a data definition file and a data model for distributed computing
InactiveUS7188332B2Overcome limitationsShorten development timeVersion controlReverse engineeringSoftware developmentData element
Methods and systems consistent with the present invention provide an improved software development tool which allows a developer to visually depict an existing data definition file containing data elements and relationships between the data elements by generating an XML structure diagram from the existing data definition file. Using methods and systems consistent with the present invention, the improved software development tool also allows the developer to generate a data definition file from an existing XML structure diagram.
Owner:BORLAND
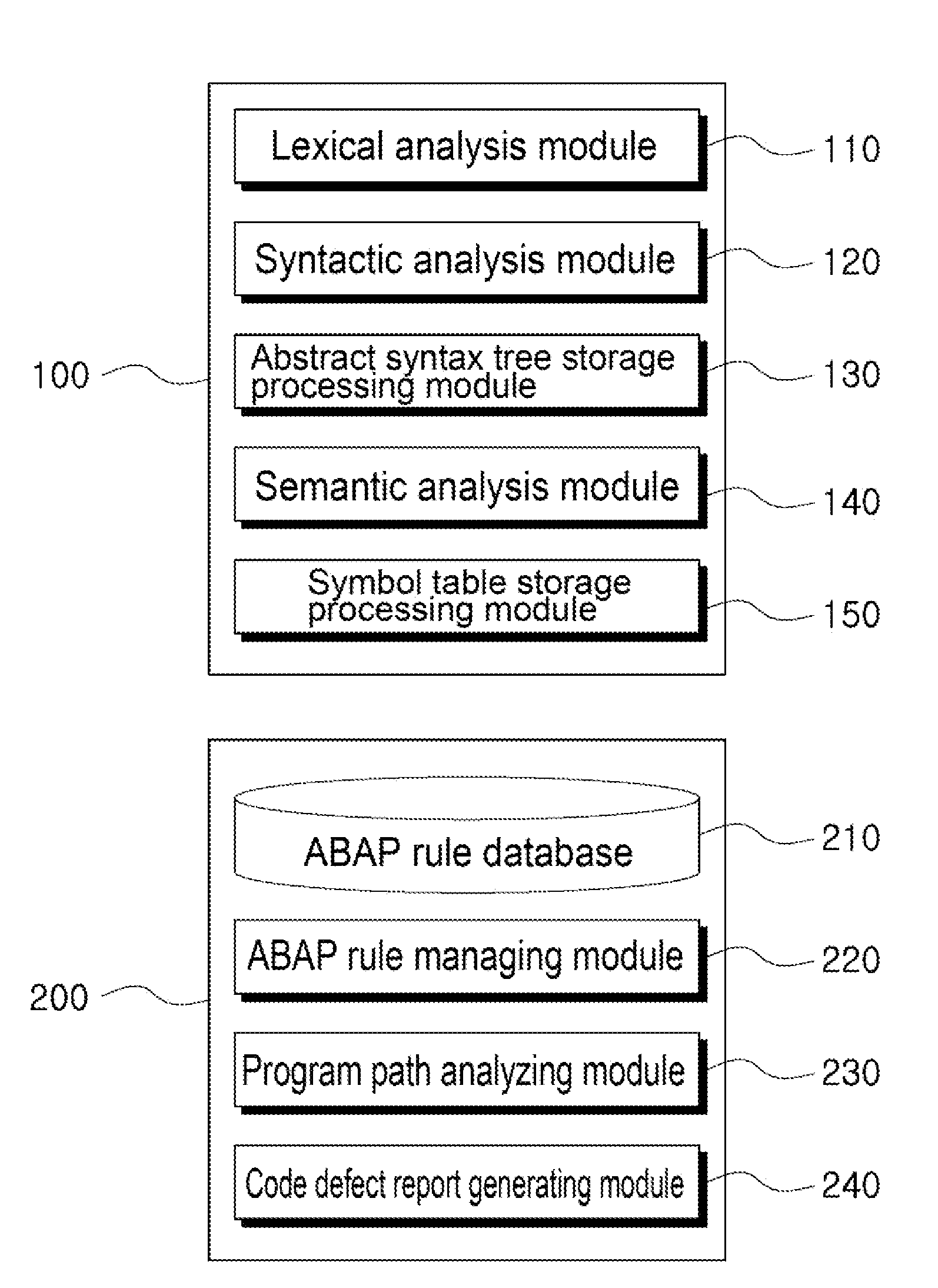
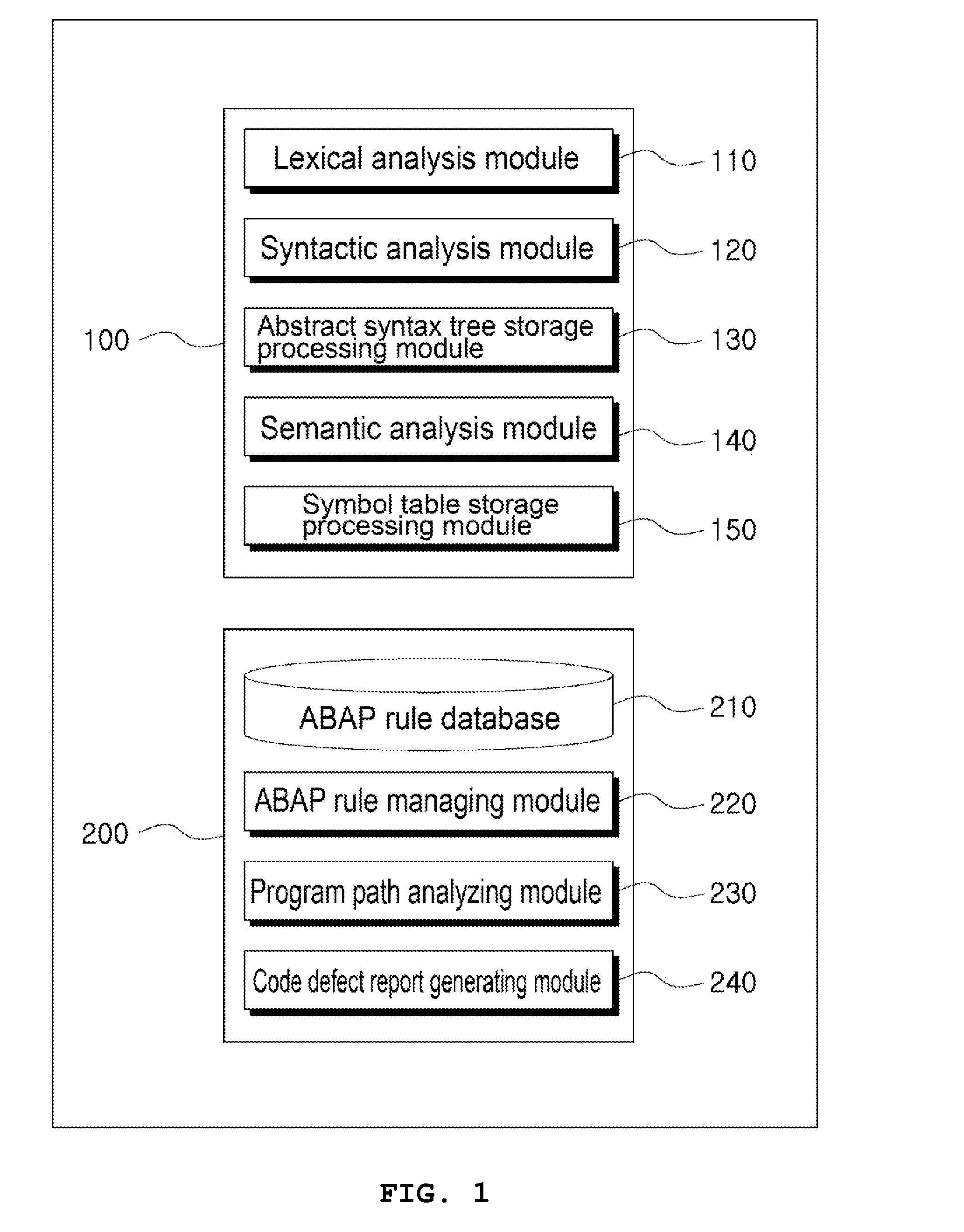
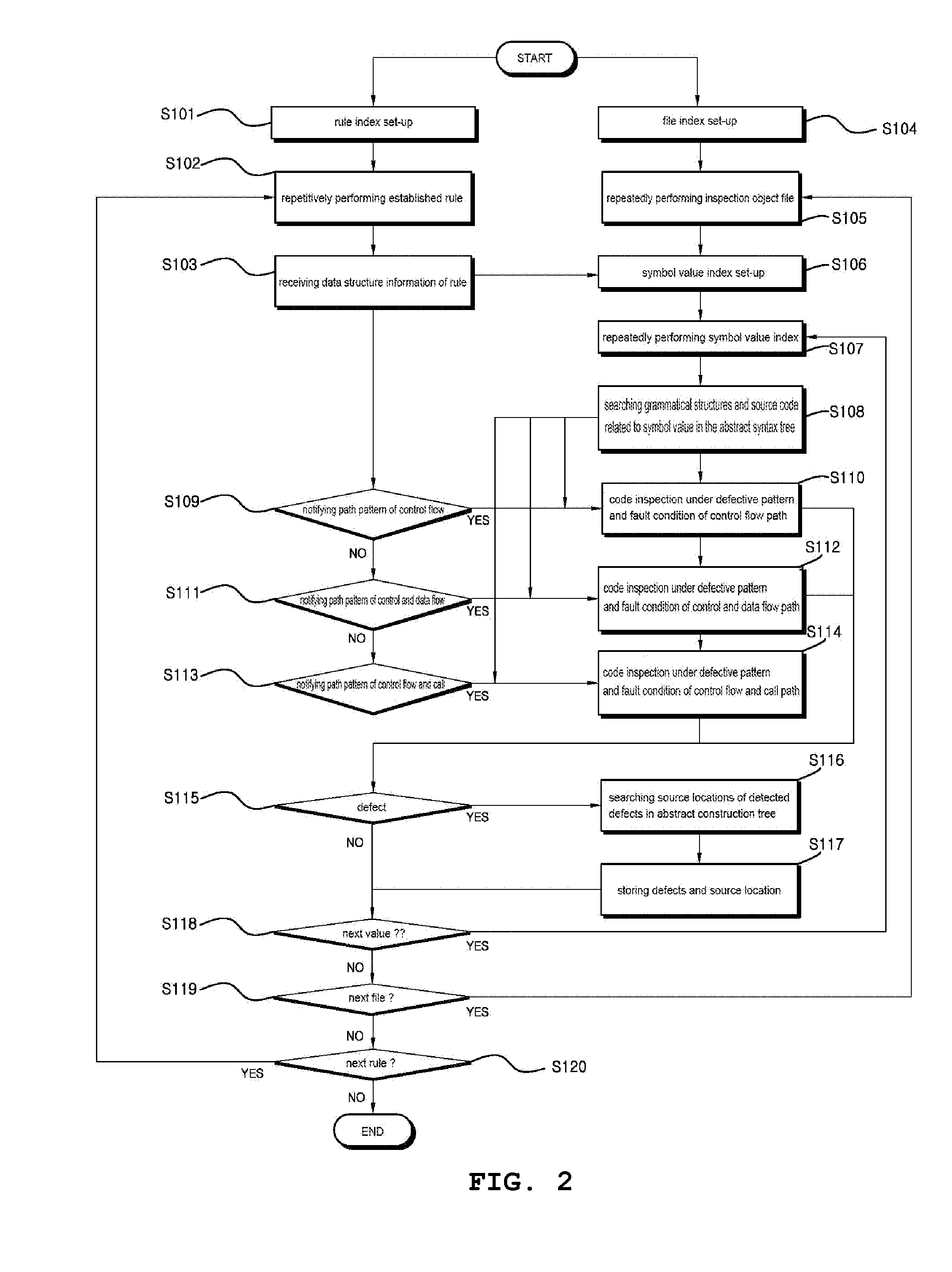
Code inspection executing system for performing a code inspection of ABAP source codes
InactiveUS20130014093A1Improve performanceLow costError detection/correctionReverse engineeringMaintainabilityTheoretical computer science
The present invention relates to a code inspection executing system for performing a code inspection of ABAP source codes, and particularly, to a code inspection executing system for performing a code inspection of ABAP source codes, which provides the reliable maintainability, performance, accuracy, stability, and security of an ABAP application by inspecting coding defects such as system failure and stoppage, data loss and transformation, excessive performance deterioration, erroneous behavior of functions and results thereof, complex code structures, and spelling errors.
Owner:SOFT4SOFT
Configurable pattern detection method and apparatus
InactiveUS7890923B2Easily and accurately reportReverse engineeringSpecific program execution arrangementsAlgorithmPattern detection
Owner:INT BUSINESS MASCH CORP
System, method, and computer readable medium for universal software testing
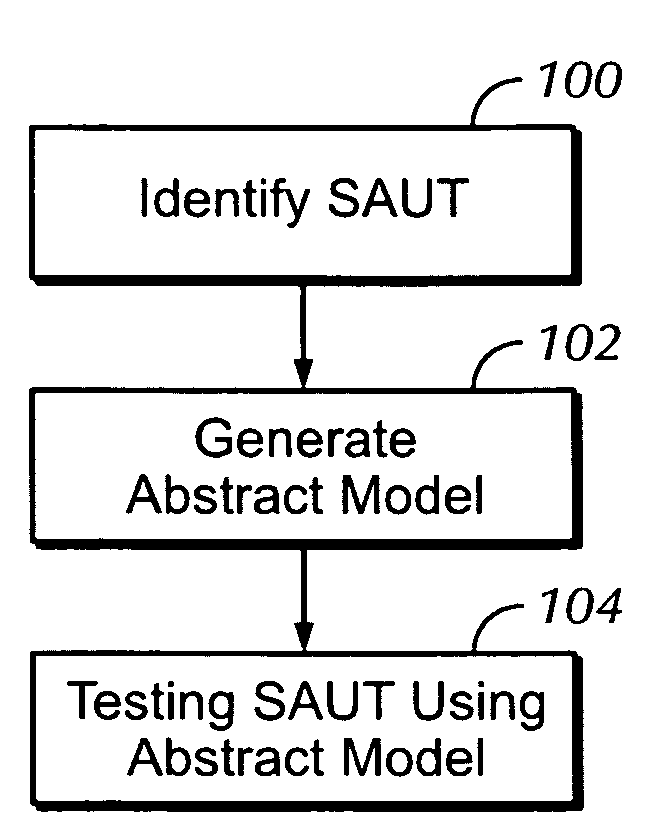
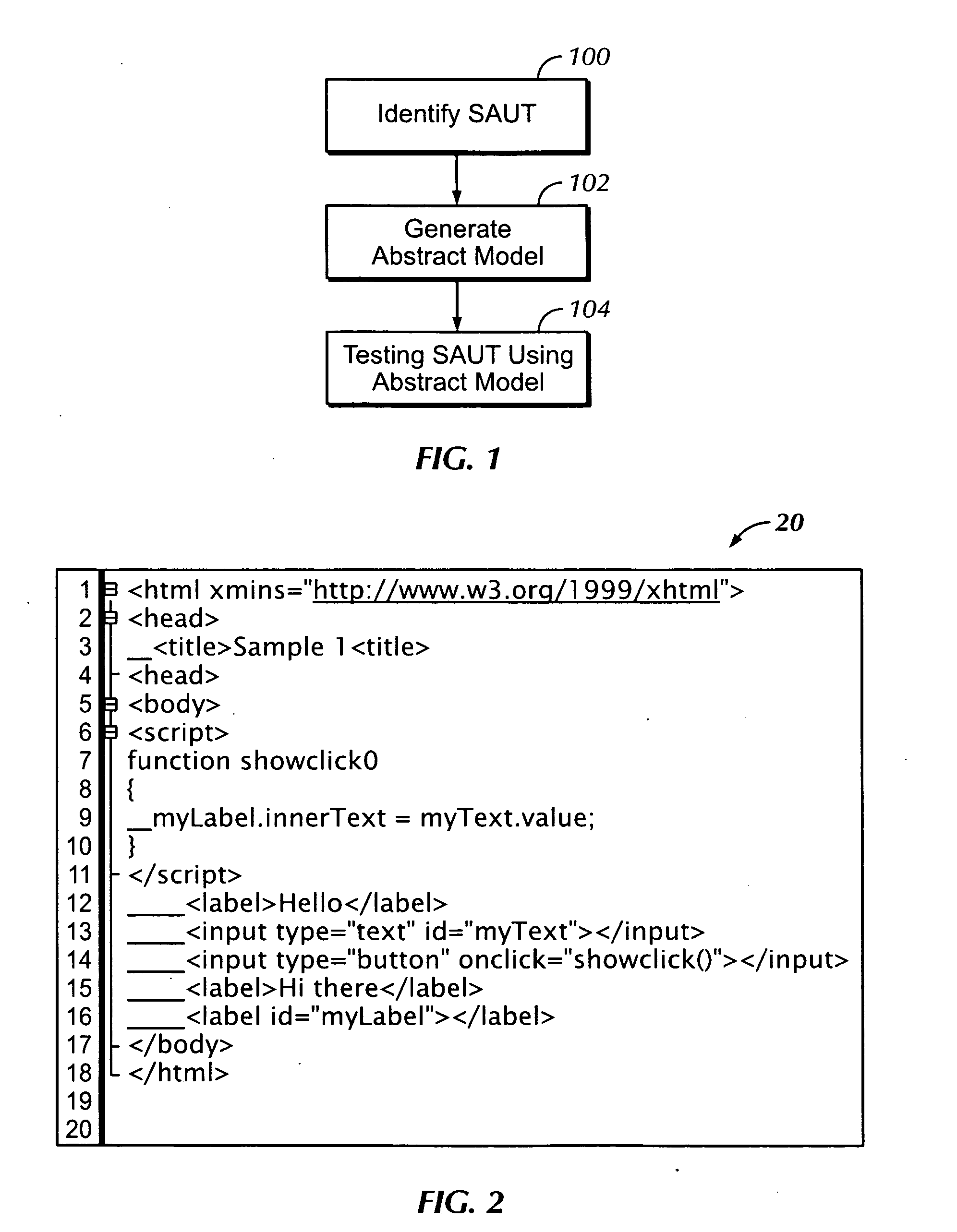
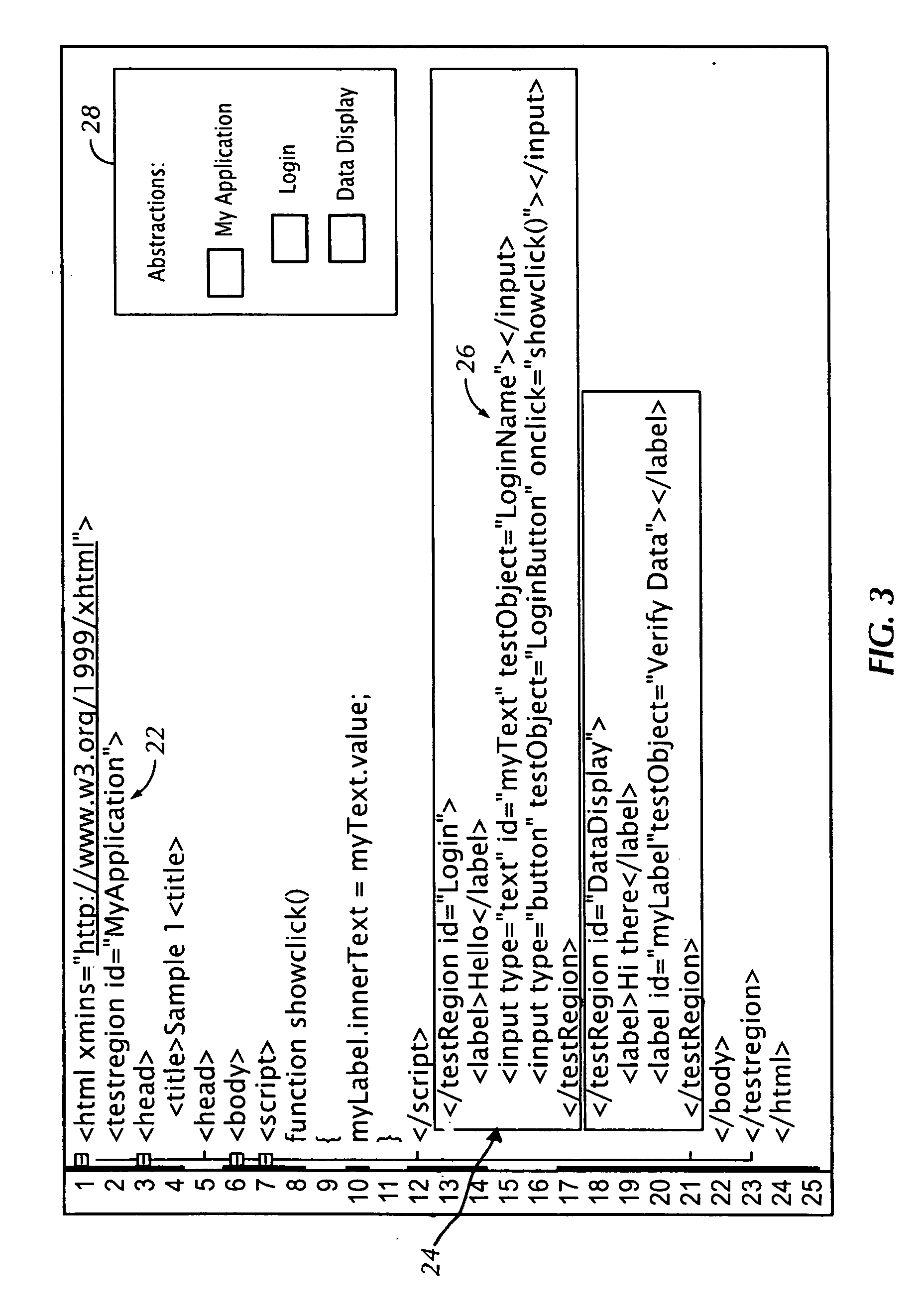
ActiveUS20080092119A1Maximum level of easeLow costError detection/correctionReverse engineeringTest scriptSoftware engineering
An automated software testing and validation system allows testing of a software application under test (SAUT) regardless of the dynamic nature of the SAUT. An abstracted set of hierarchal or linear objects model certain regions of the SAUT. Automated test scripts utilize theses regions to intuitively navigate and identify potions of the SAUT to automate. The scripts can also access specific SAUT elements contain within each defined region. These elements can then be used to invoke actions or verify outputs there from. The system uses a set of rich identification rules embodied in the system which allow the user to configure the identification of any element within the abstracted region. The rules are customizable to allow the user to configure the desired level of loose coupling between the automated scripts and the target element to adapt the scripts to the nature of the SAUT.
Owner:PROGRESS SOFTWARE
System and method for computer-aided graph-based dependency analysis
The present invention is directed to a system and methods for analyzing dependencies. The dependencies that may be analyzed include, for example, dependencies among methods or procedures in software source code, or in system configuration or deployment. A layered system is provided, comprising a back-end layer, abstraction layer and user interface layer are used to derive dependency information from third-party tools, and present the information through uniform interfaces to a user-interface layer. The system maintains a dependency model as a hierarchical graph structure in computer memory, and provides a plurality of user views which may be manipulated actively or passively by the user. Active manipulations are propogated through the back-end layer to modify the system analyzed, and passive manipulations affect the user views without changing the analyzed system. The system provides advantages to users seeking to understand complex systems with many dependencies.
Owner:HEADWAY RES
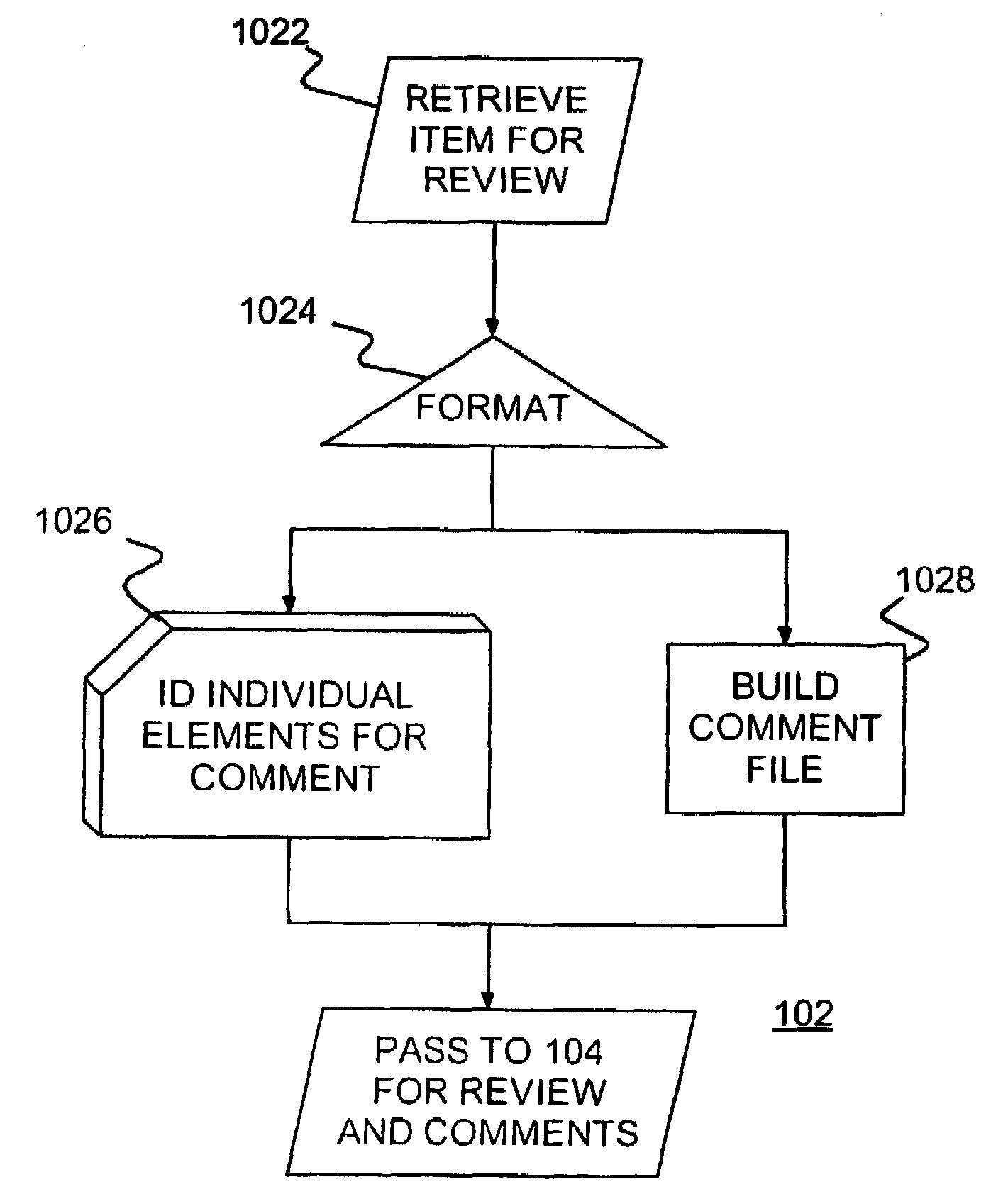
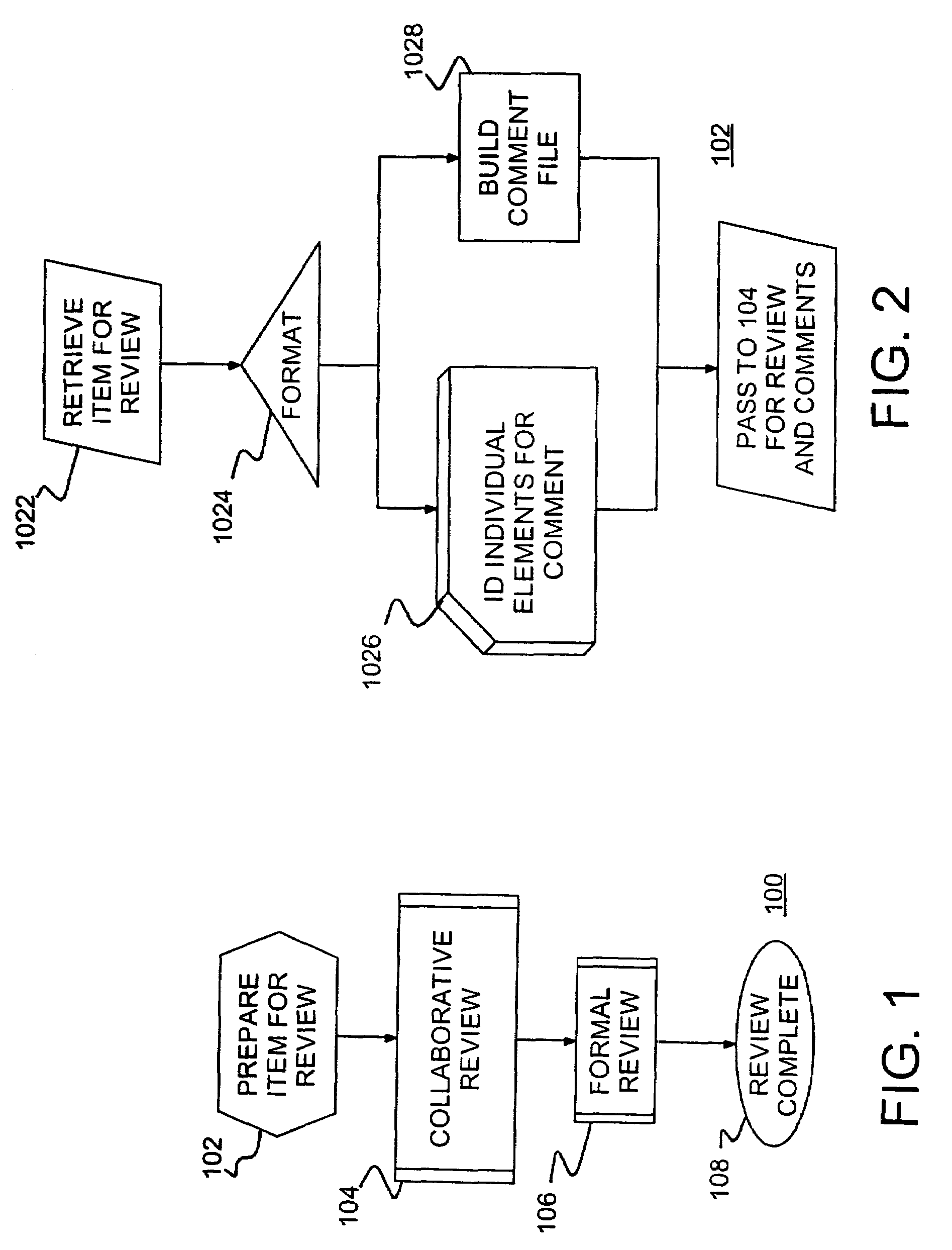
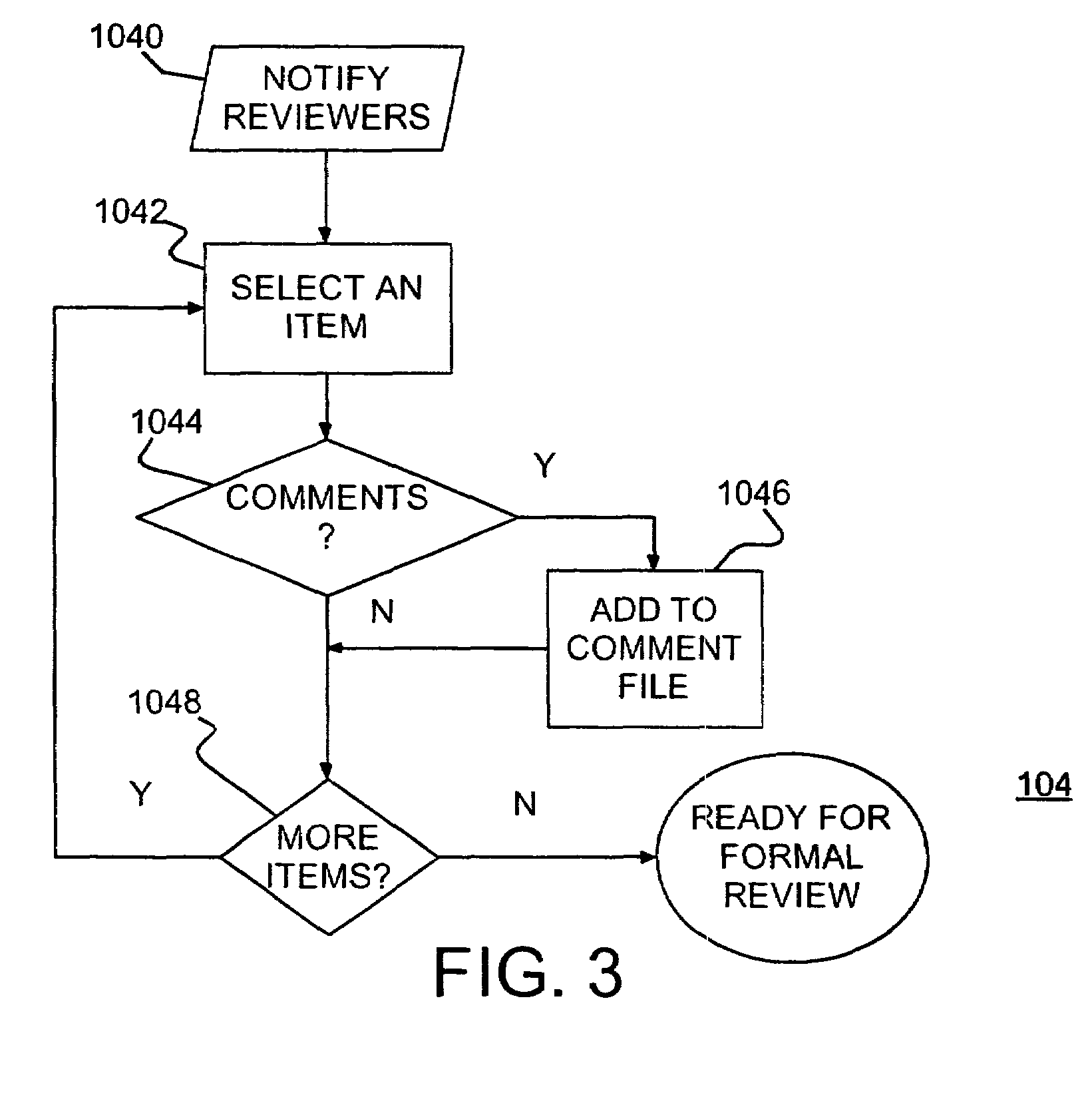
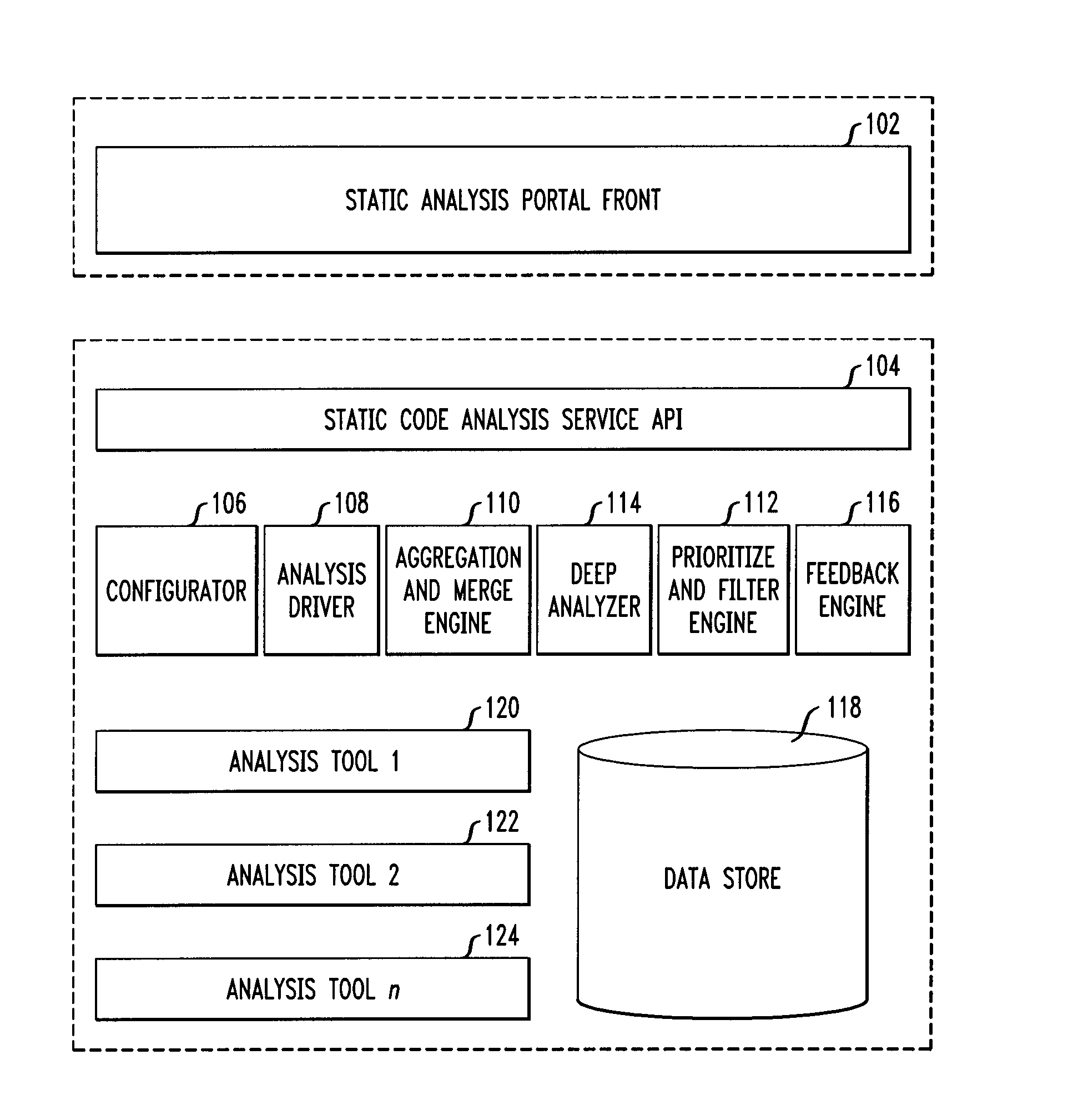
Interactive collaborative facility for inspection and review of software products
InactiveUS7386831B2Shorten the timeReverse engineeringMultiple digital computer combinationsCollaboration toolWeb page
A review facility and review method for interactively reviewing an item, such as a block of code, by a group of reviewers and collecting comments from the reviewers. An author provides the item as text for preparation for interactive review. The text is prepared, tagging each line and making the tagged text available to reviewers, e.g., as links on a web page. Reviewers interactively comment on individual lines and review previously entered comments. An abbreviated formal review may follow the interactive review.
Owner:UNIFY INC
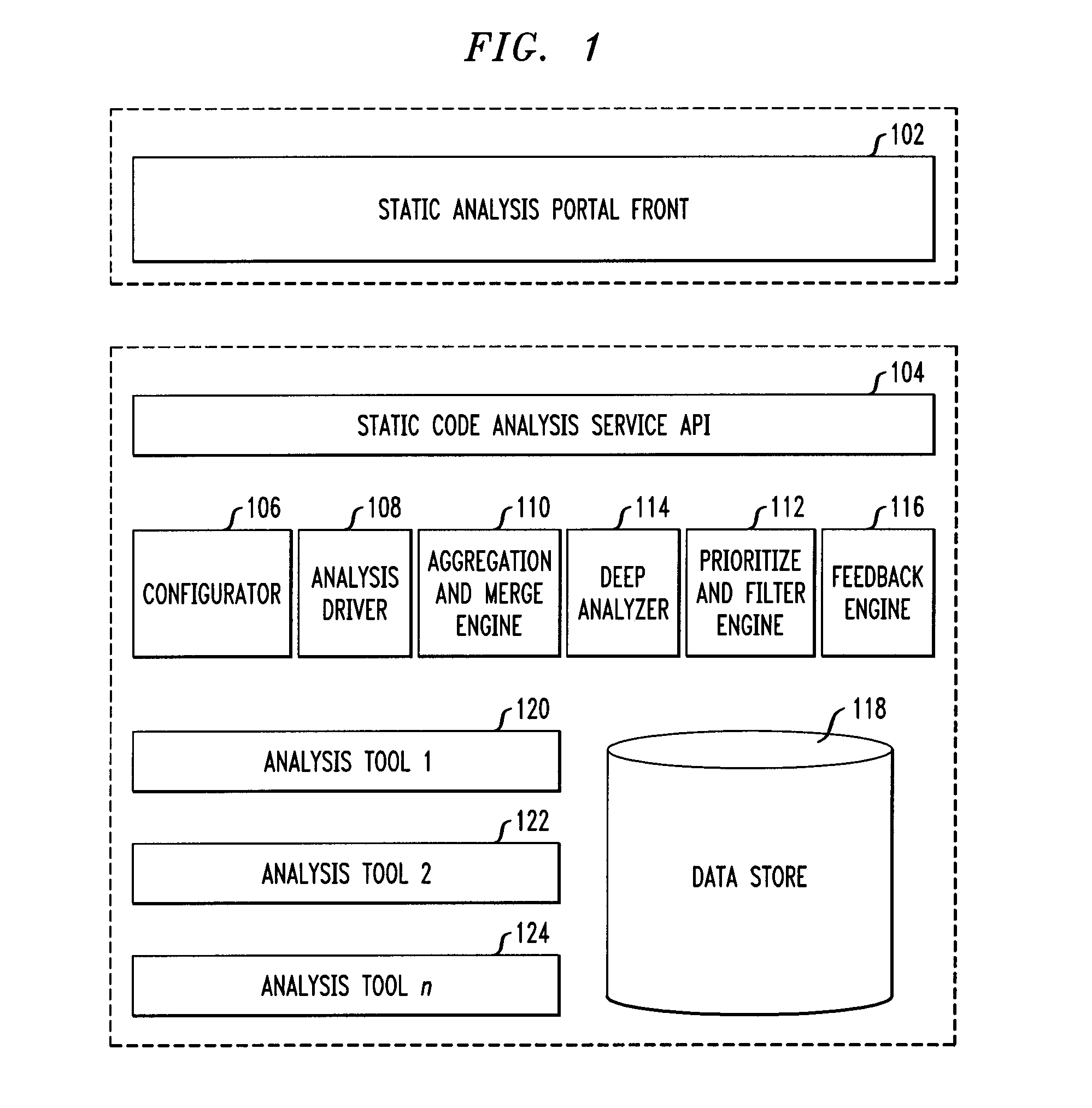
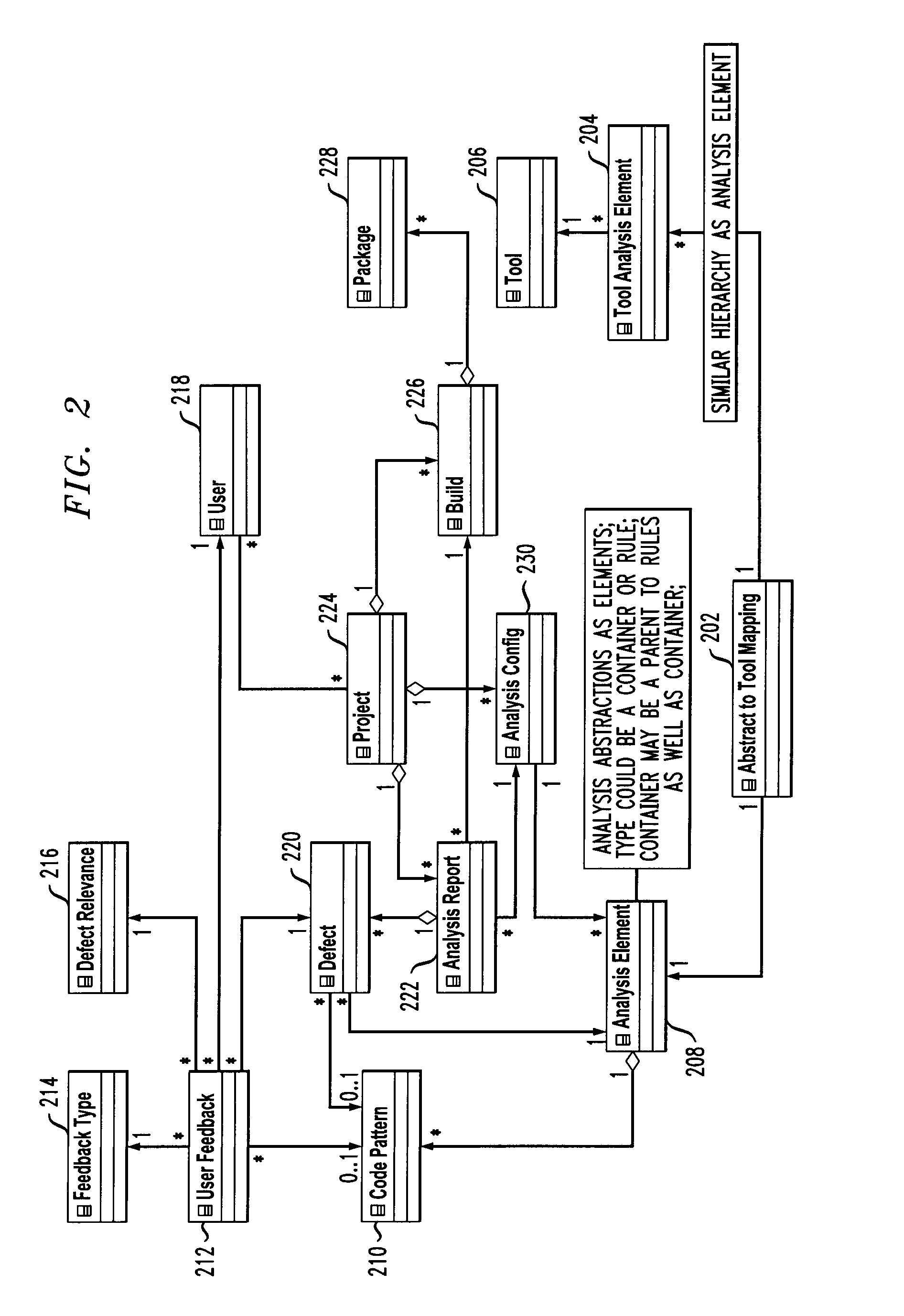
Static code analysis
InactiveUS20100333069A1Reverse engineeringSpecific program execution arrangementsAnalysis toolsStatics
Techniques for static code analysis are provided. The techniques include routing a code analysis request to a set of one or more static code analysis tools based on a context of the request, merging one or more tool-specific outputs of the code analysis, wherein merging the one or more tool-specific outputs comprises using one or more tool-specific mappings to one or more static code analysis abstractions and one or more source linkages of one or more static code analysis defects, performing a deep analysis on a set of one or more defect categories, and combining results of the merging with the deep analysis to filter out one or more false-positives and to add one or more new true positives to create an optimal set of defects.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com