Patents
Literature
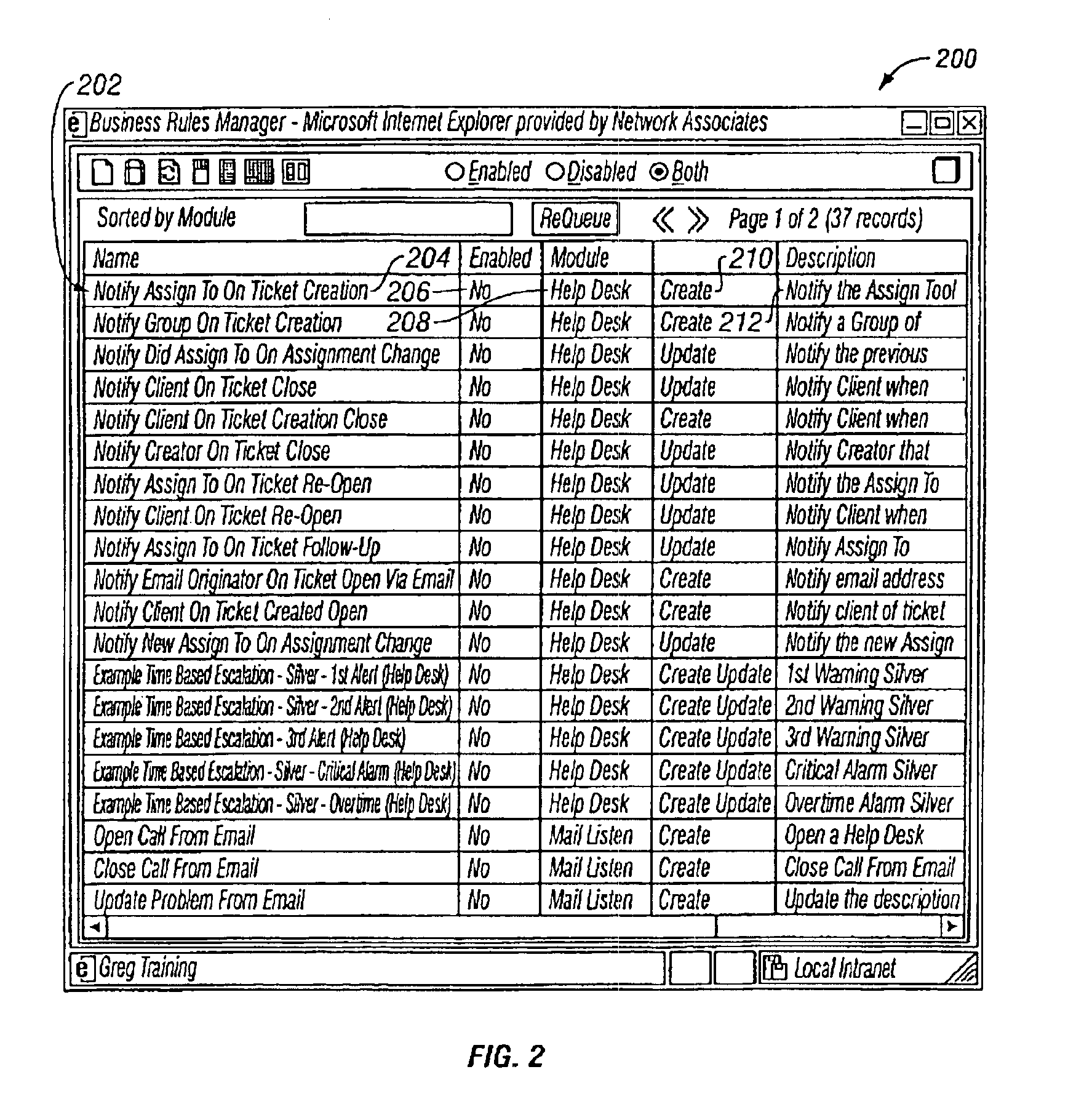
4876 results about "Business logic" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer software, business logic or domain logic is the part of the program that encodes the real-world business rules that determine how data can be created, stored, and changed. It is contrasted with the remainder of the software that might be concerned with lower-level details of managing a database or displaying the user interface, system infrastructure, or generally connecting various parts of the program.
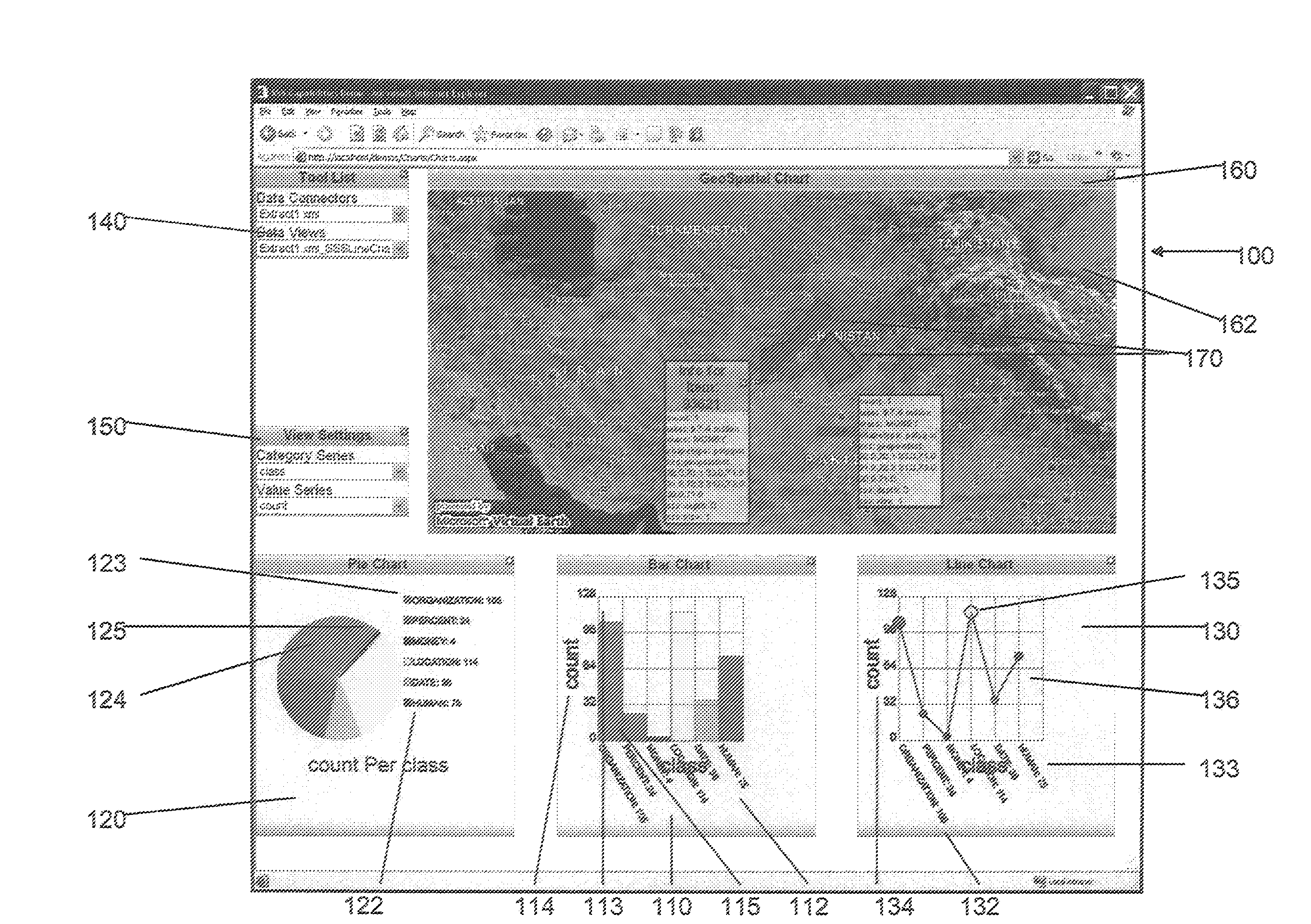
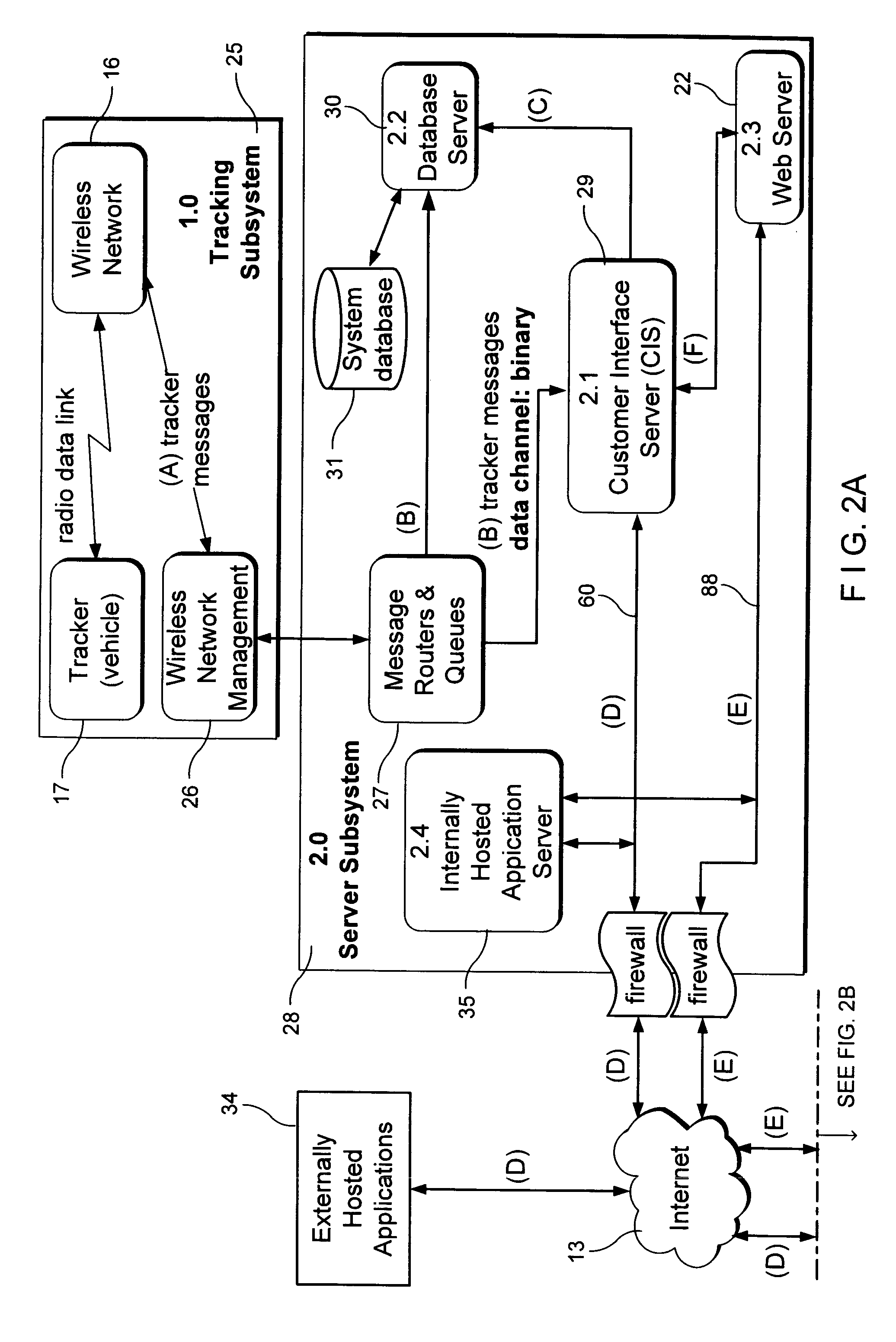
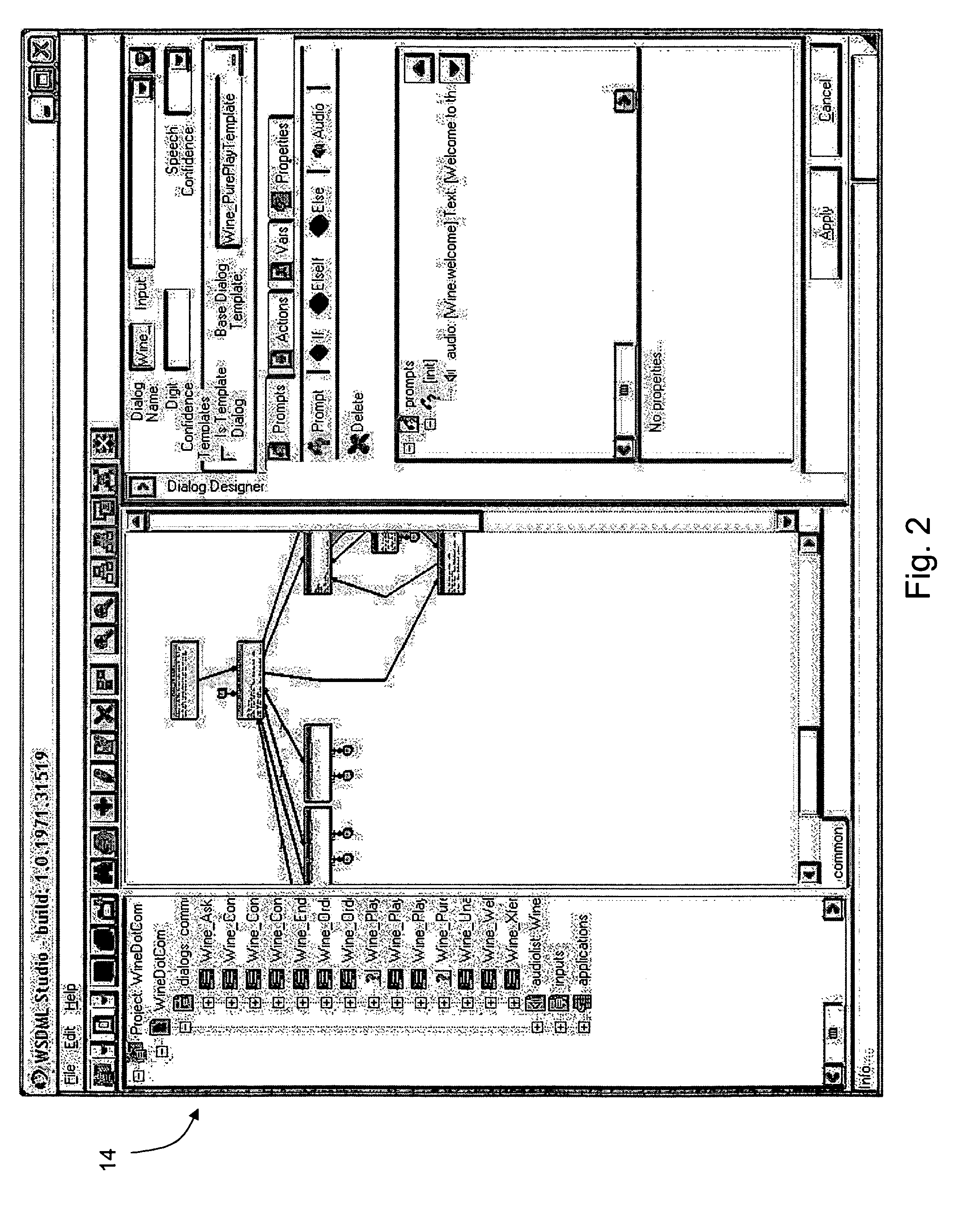
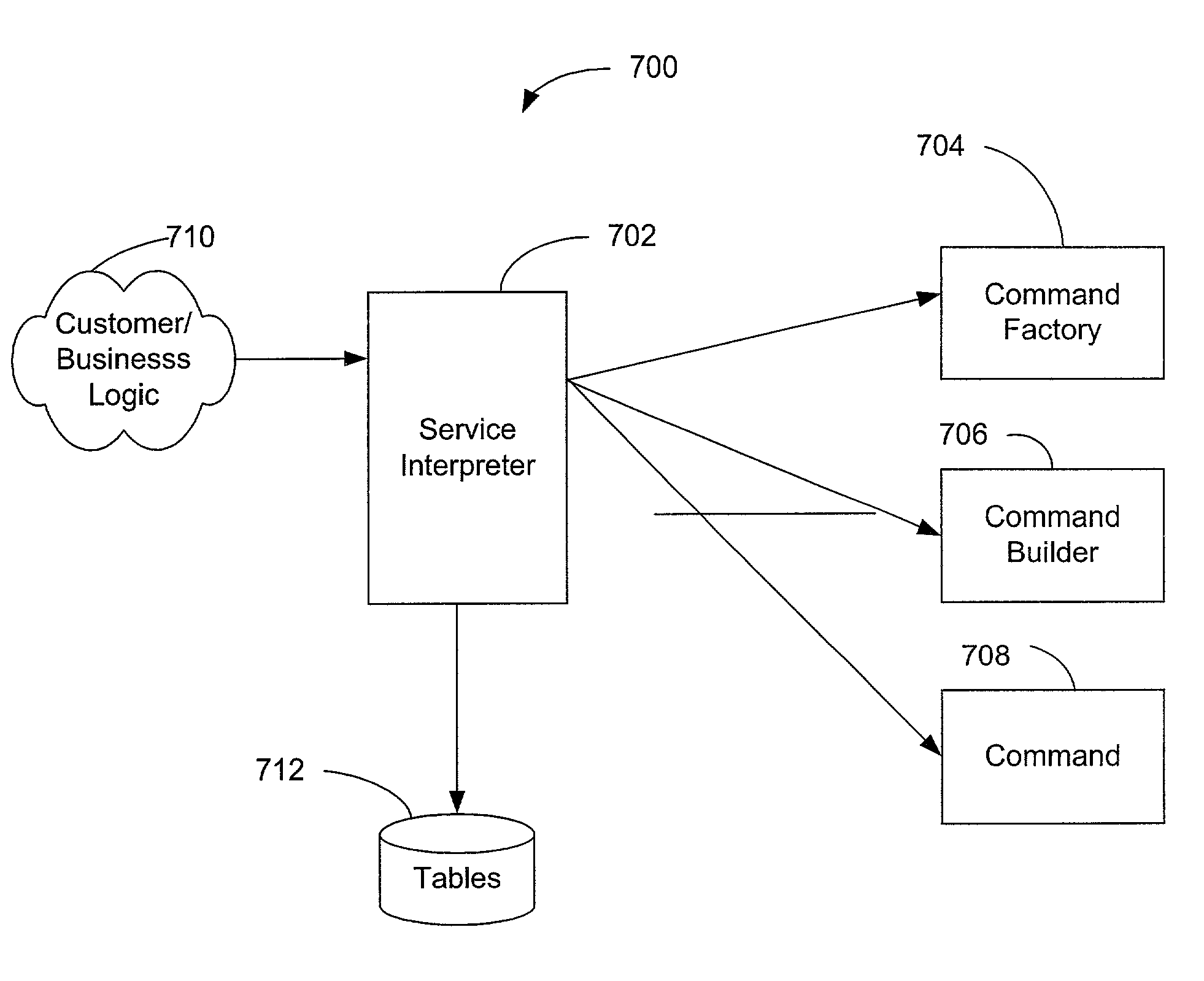
Server-based systems and methods for enabling interactive, collabortive thin- and no-client image-based applications
InactiveUS20070226314A1Eliminates start-stop-start-stop natureDirect operation2D-image generationMultiple digital computer combinationsGraphicsAnalysis data
A server receives image, graphic and / or analytic data and processes and asynchronously outputs that data to a thin / no client. The server inputs image data in a variety of different formats and renders a normalized format that can be streamed to the thin / no client using light-weight protocol(s). The server updates the image, feature and / or analytic data in real time. The server inputs feature, analytic, business logic and other data and process it into various format(s) that can be streamed to the thin / no client and overlaid on the image data. The server provides application services, which can include collaboration, tracking, alerting, business, workflow and / or other desired services. The server can receive collaboration data from one thin / no client and stream that collaboration data to other thin / no clients to enable shared situational awareness between the thin / no clients. The server includes a programming environment for programming thin / no clients contained within server-based web pages.
Owner:VISTRACKS
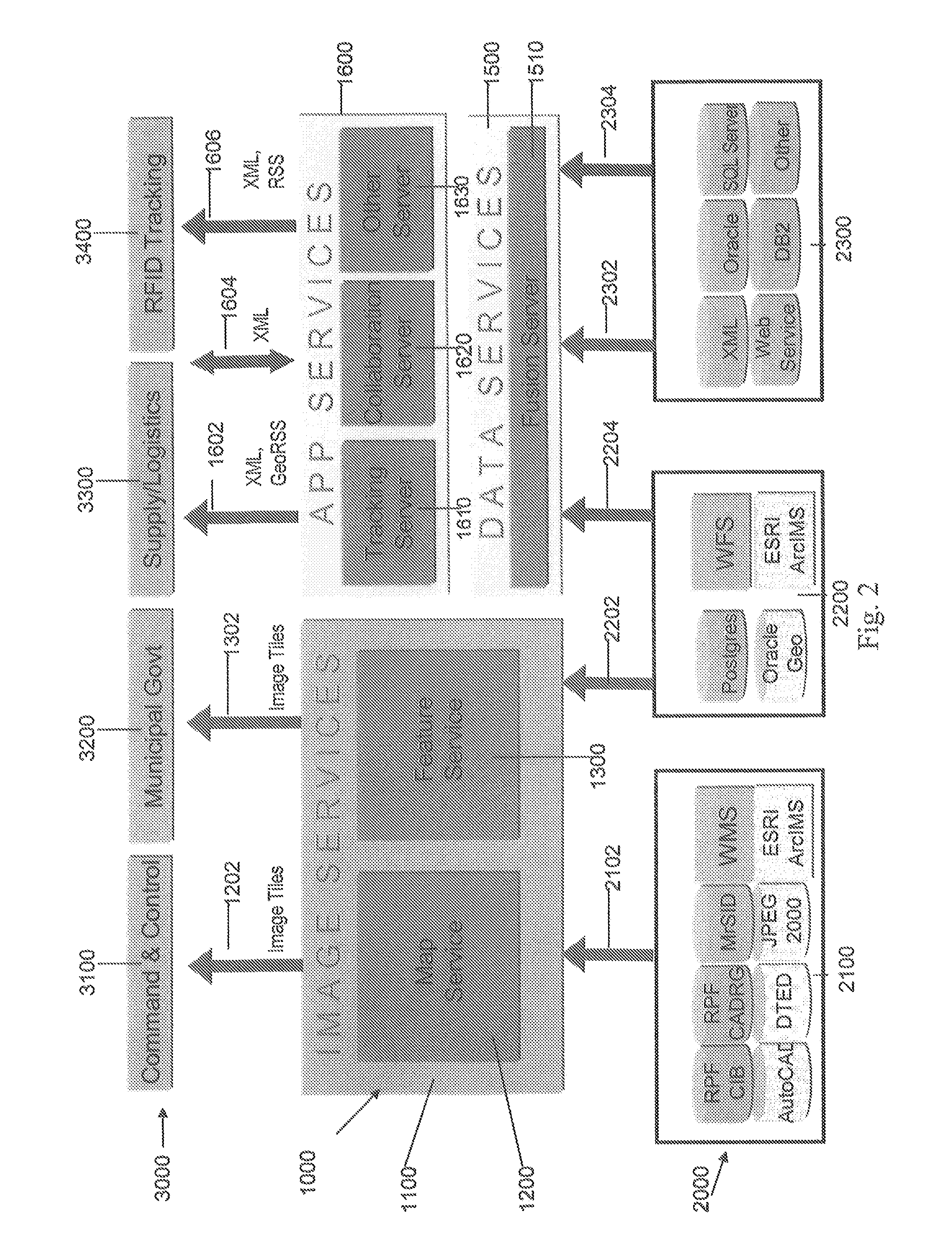
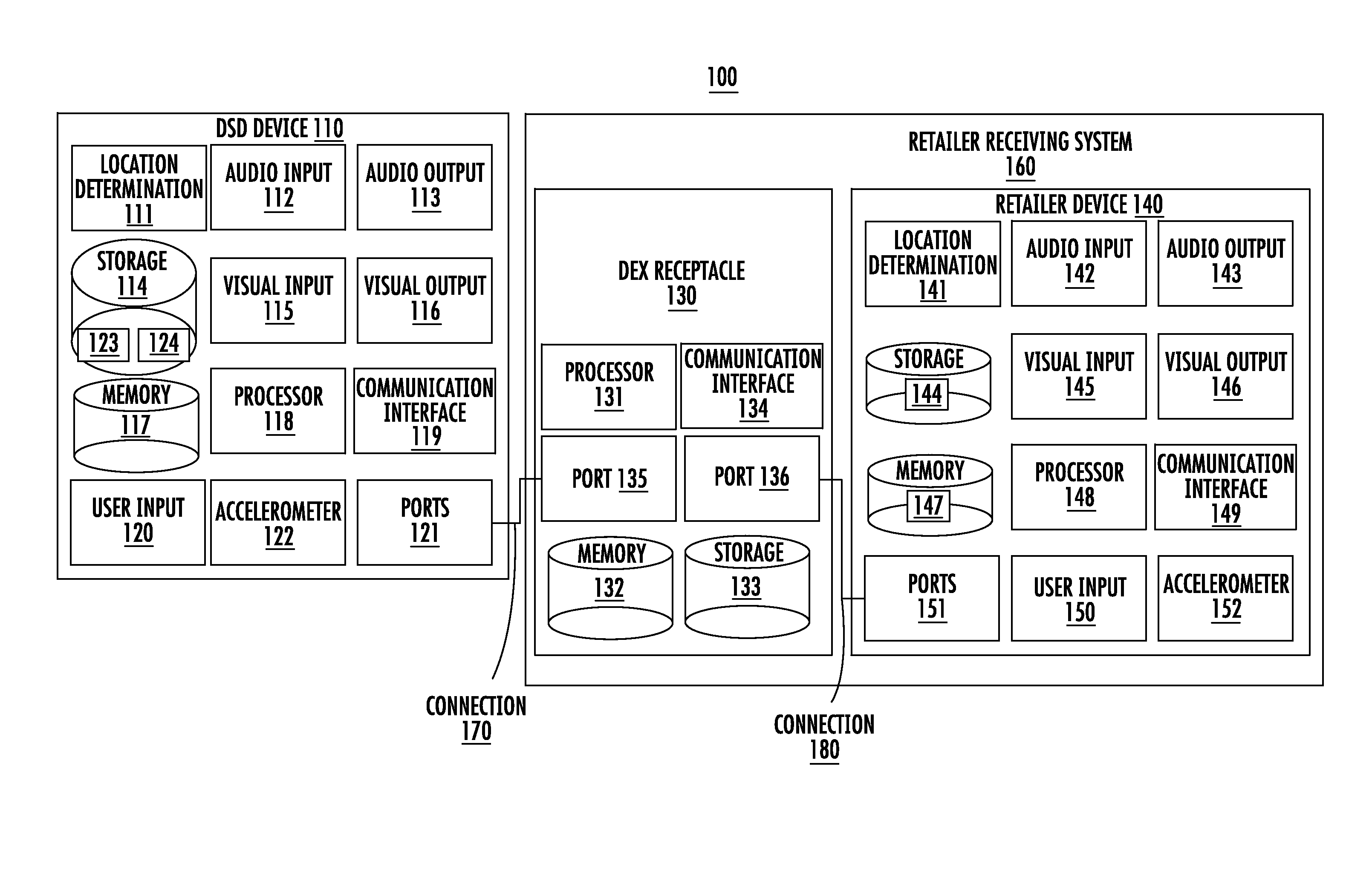
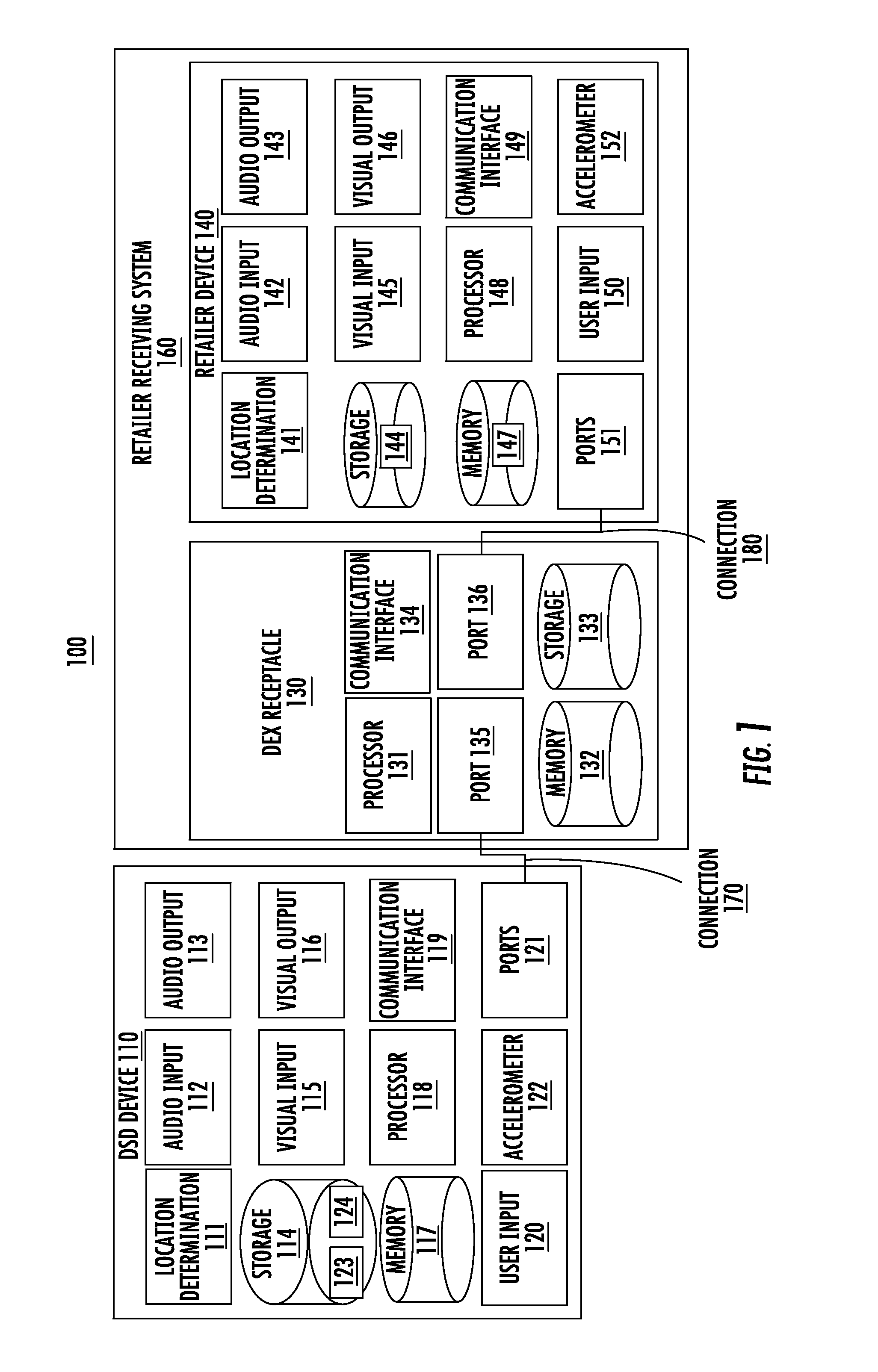
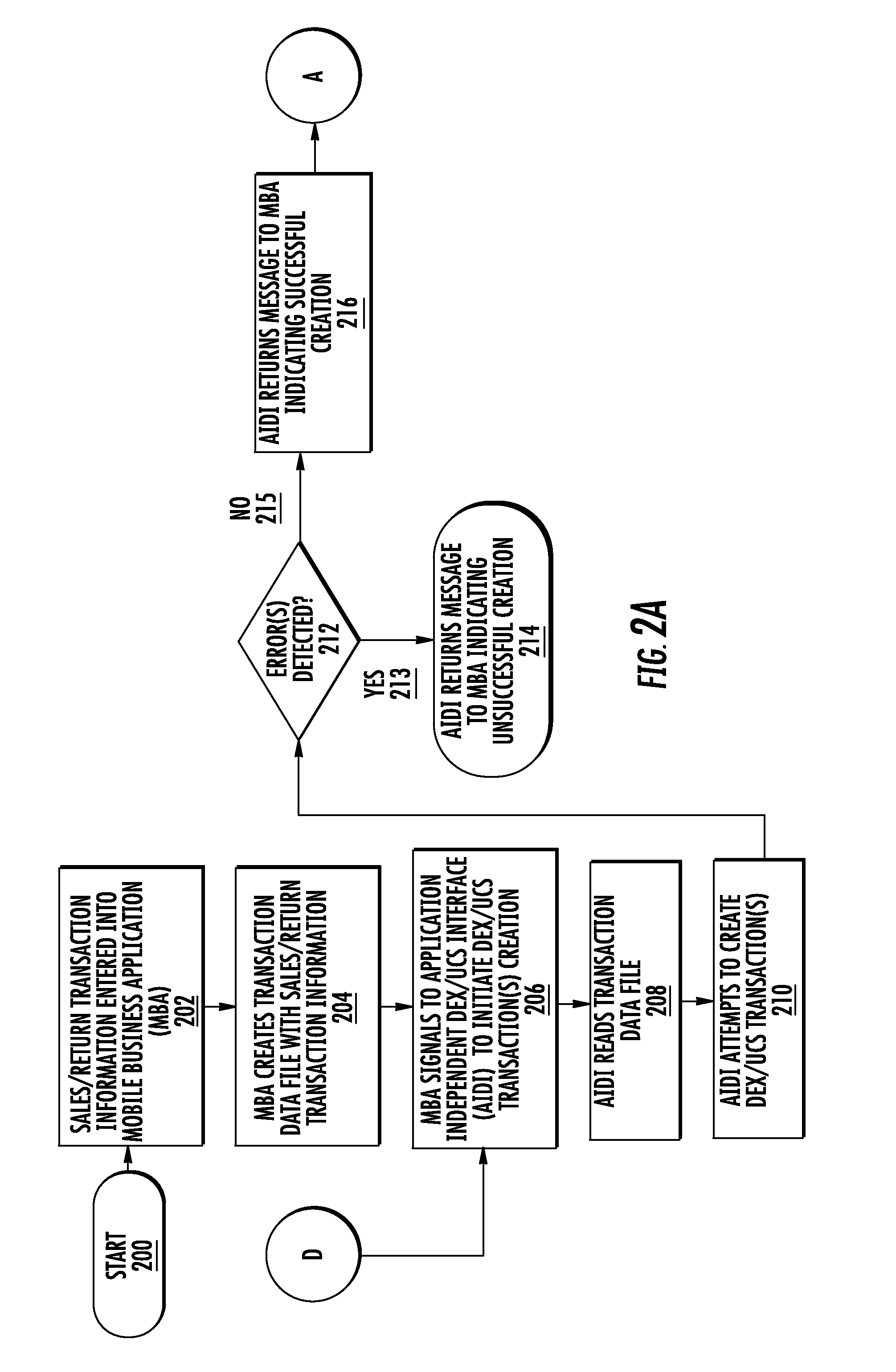
Application independent dex/ucs interface
ActiveUS20160328762A1Digital data information retrievalMultiple digital computer combinationsSERCOS interfacePlug and play
Systems, methods, and devices are described for an application independent DEX / UCS interface (AIDI). The AIDI is a “plug and play” DEX / UCS solution that removes the requirement for developers to know the structure, function, and format of DEX / UCS transaction sets and to make the DEX / UCS process independent from the existing business logic of many mobile applications.
Owner:HAND HELD PRODS
System and method for customizing and processing business logic rules in a business process system
Systems and methods for customizing business logic rules within a business process automation system and for processing business logic rules in a business process automation system are disclosed. The method for customizing business rules of a business logic application generally comprises serving a content page to a client browser of a client by a server that allows entering and modifying of data relating to a business logic rule, generating data by the server according to a predefined format such as a predefined XML format from information received via the content page, and automatically committing the generated data in the predefined format into a database. Preferably, a verification process such as by using DTDs (Document Type Definitions) is performed by the server prior to committing the data. The database stores data including data relating to business logic rules for implementing business logic as entries in the database and the generated data is committed into a corresponding entry in the database. Upon committing, the committed database business rule entry is ready for execution by the business logic application.
Owner:MCAFEE LLC
System and method for developing and deploying computer applications over a network
InactiveUS20050155027A1Reduce bandwidth costsReduce maintenance costsNatural language data processingProgram loading/initiatingVisual BasicOperational system
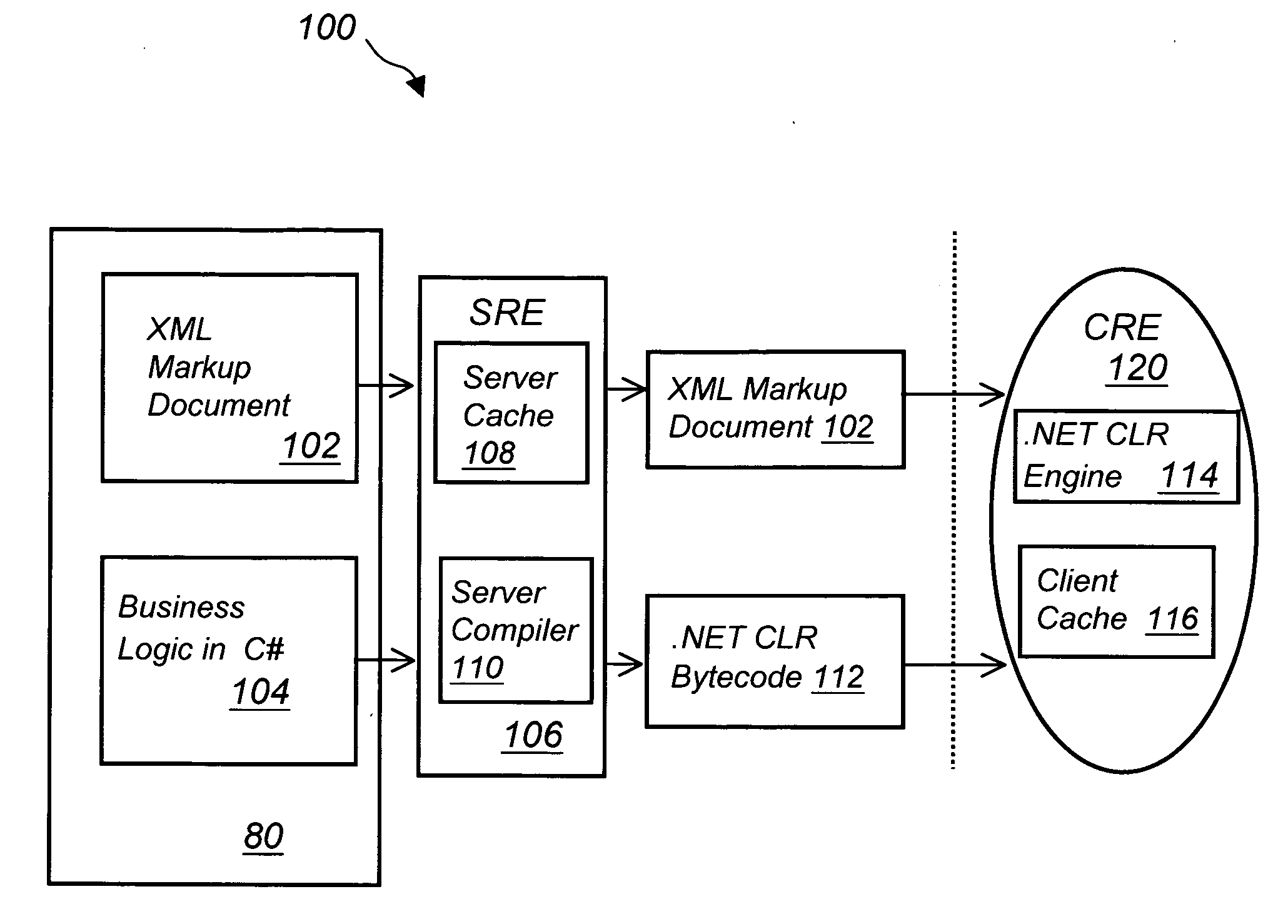
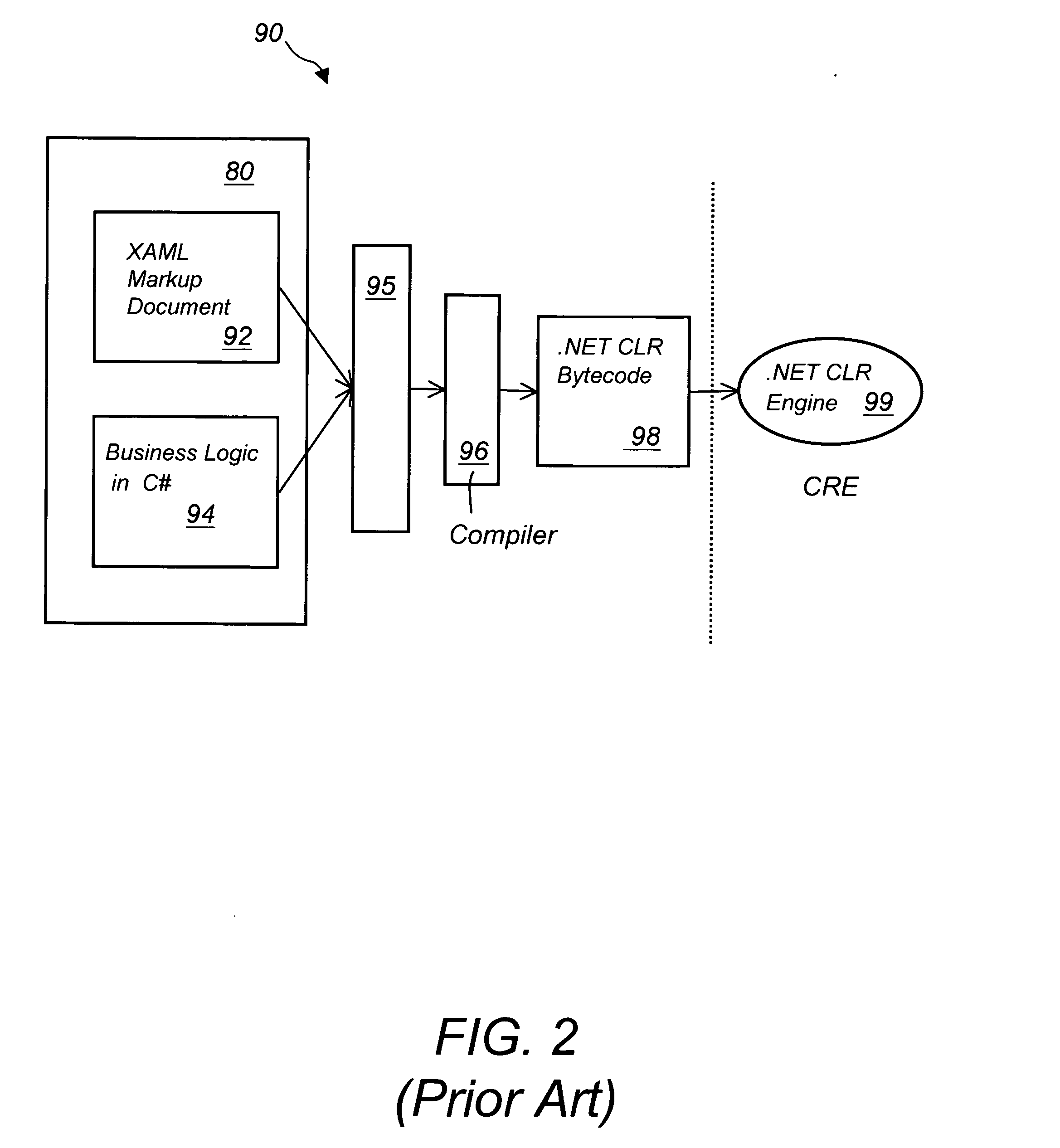
A method of developing a computer application by coding a markup document in an XML markup language, coding a business logic component using any programming language, compiling the business logic component into a specific executable code, converting the XML document into a specific markup language document and deploying the converted markup document and the executable code to a client machine running a specific operating system via a network connection. The XML markup document can be converted in any markup language including XUL, SVG, Xforms, XML related languages, HTML, HTML related languages, text, and combinations thereof. The business logic component can be written using any programming language including Java, JavaScript, J#, C#, C, C++, Visual Basic, ActionScript, XSL, XQuery, and XPath, among others. The computer application can run in any operating system including next generation Windows Longhorn, Windows 2000, Linux, Unix, Apple or Palm operating systems, among others.
Owner:NEXAWEB
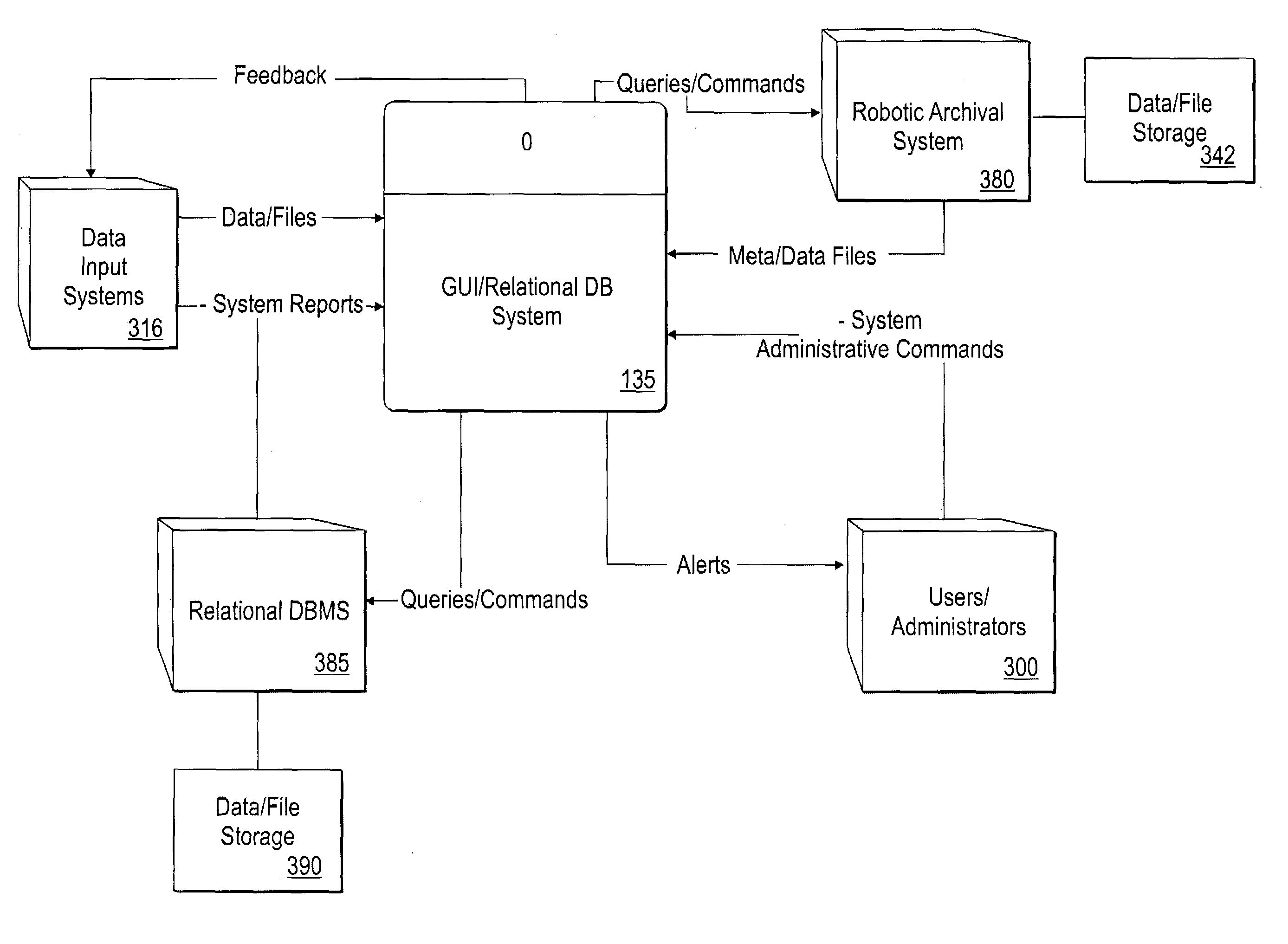
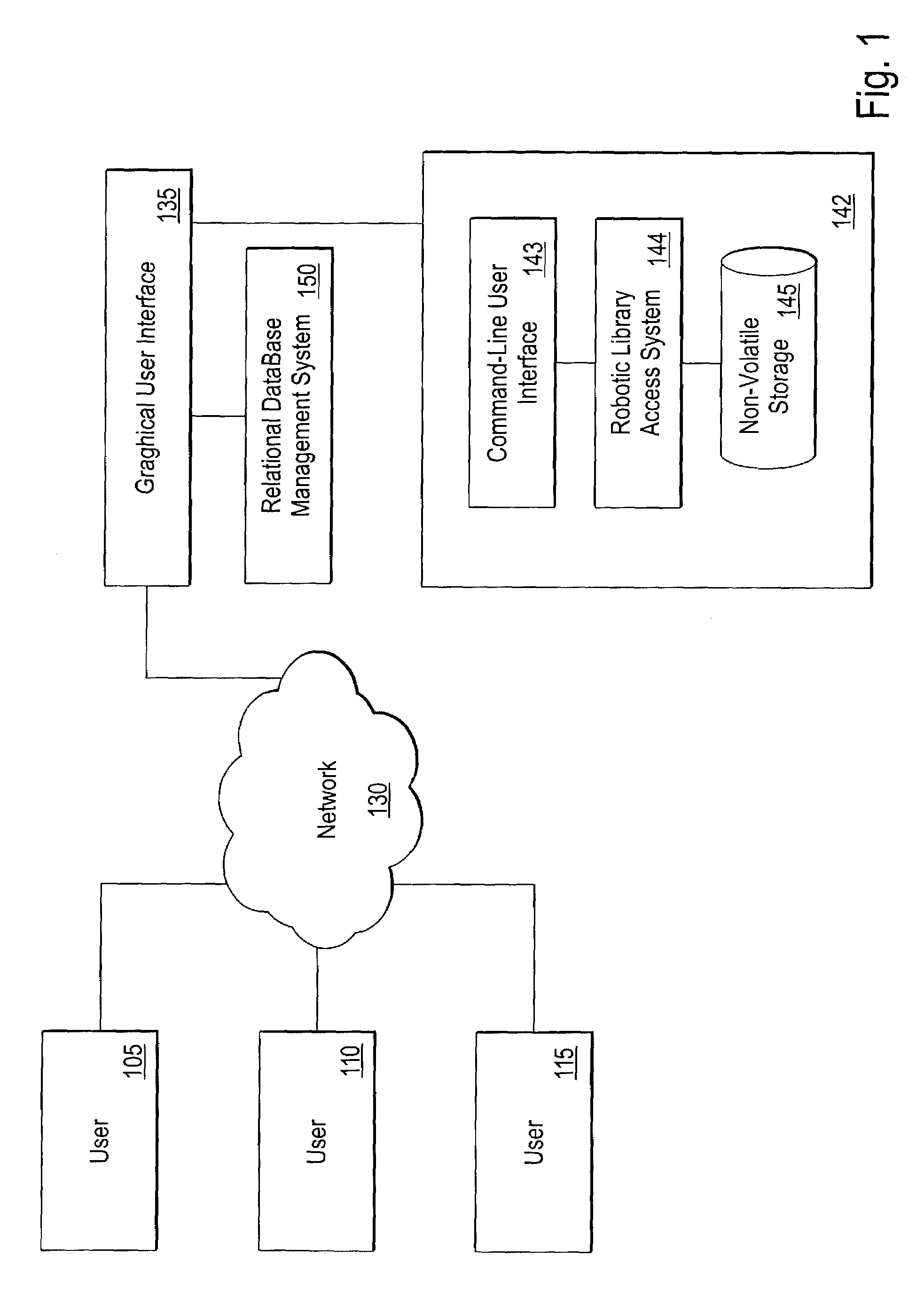
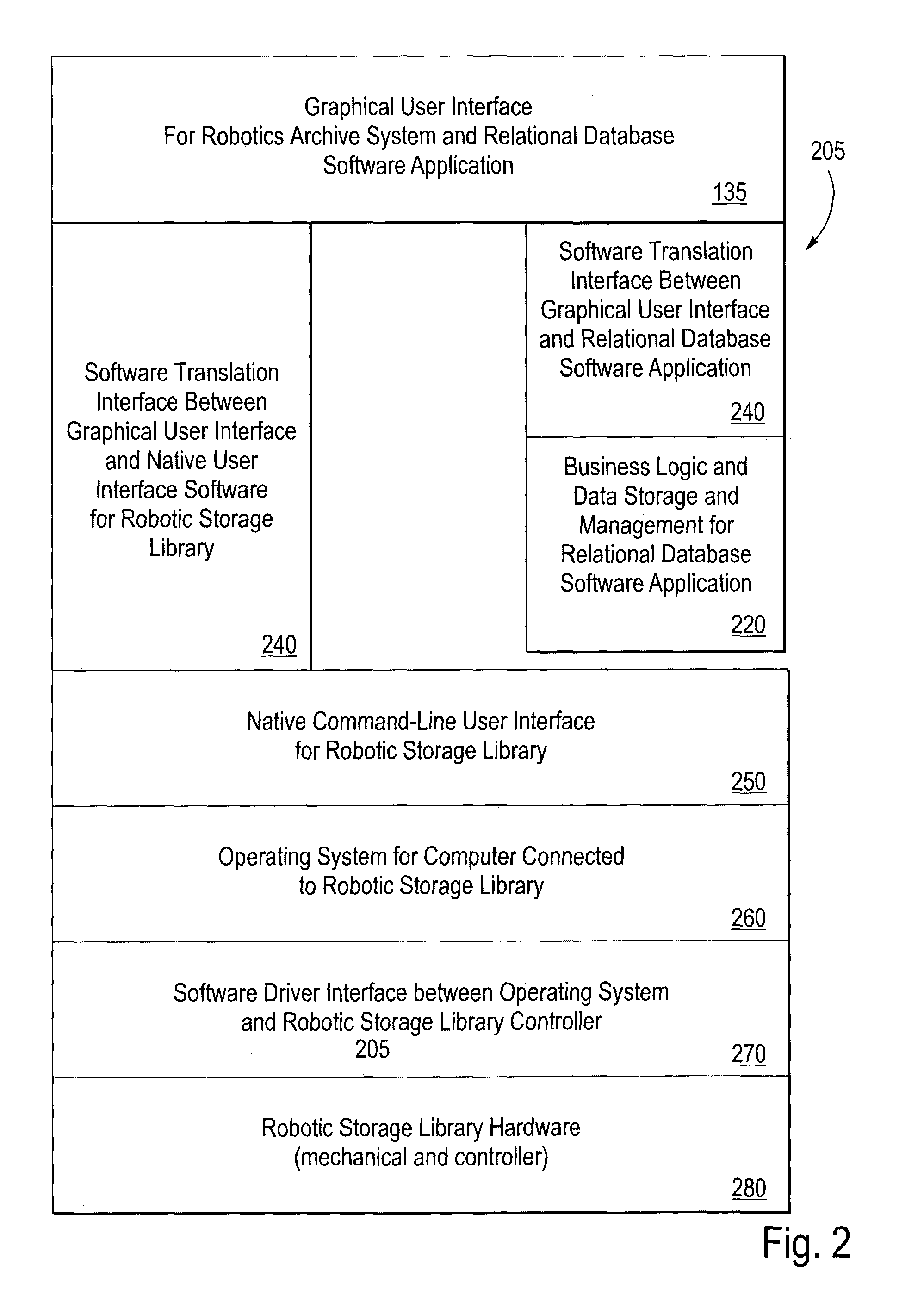
Graphical user interface-relational database access system for a robotic archive
InactiveUS6980987B2Shorten the timeData processing applicationsDigital data processing detailsRelational databaseNetwork connection
The invention includes a system for data file archival management including: a robotic data storage system having multiple non-volatile storage media, input and output means for reading and writing to the storage media, adapted and configured for storing data files, and having a command-line software code portion adapted and configured to provide a command-line user interface to control the robotic tape data storage system; a server; a business logic software code portion resident in memory on the server, configured and adapted for adding and searching metadata about the data files, where the metadata is organized as a relational database; a plurality of personal computers or workstation clients connected to the server computer over a network; a GUI software code portion resident in the memory of the personal computers, workstations, or of a server in communication with the personal computers or workstations, configured and adapted for providing a graphical user interface to at least a portion of the business logic software code portion; and a translation software code portion resident in the memory of the database server adapted and configured for translating adding, deleting, updating, and searching messages from a format compatible with the business logic code portion into and from a format compatible with the command-line code portion.
Owner:ALTO TECH RESOURCES
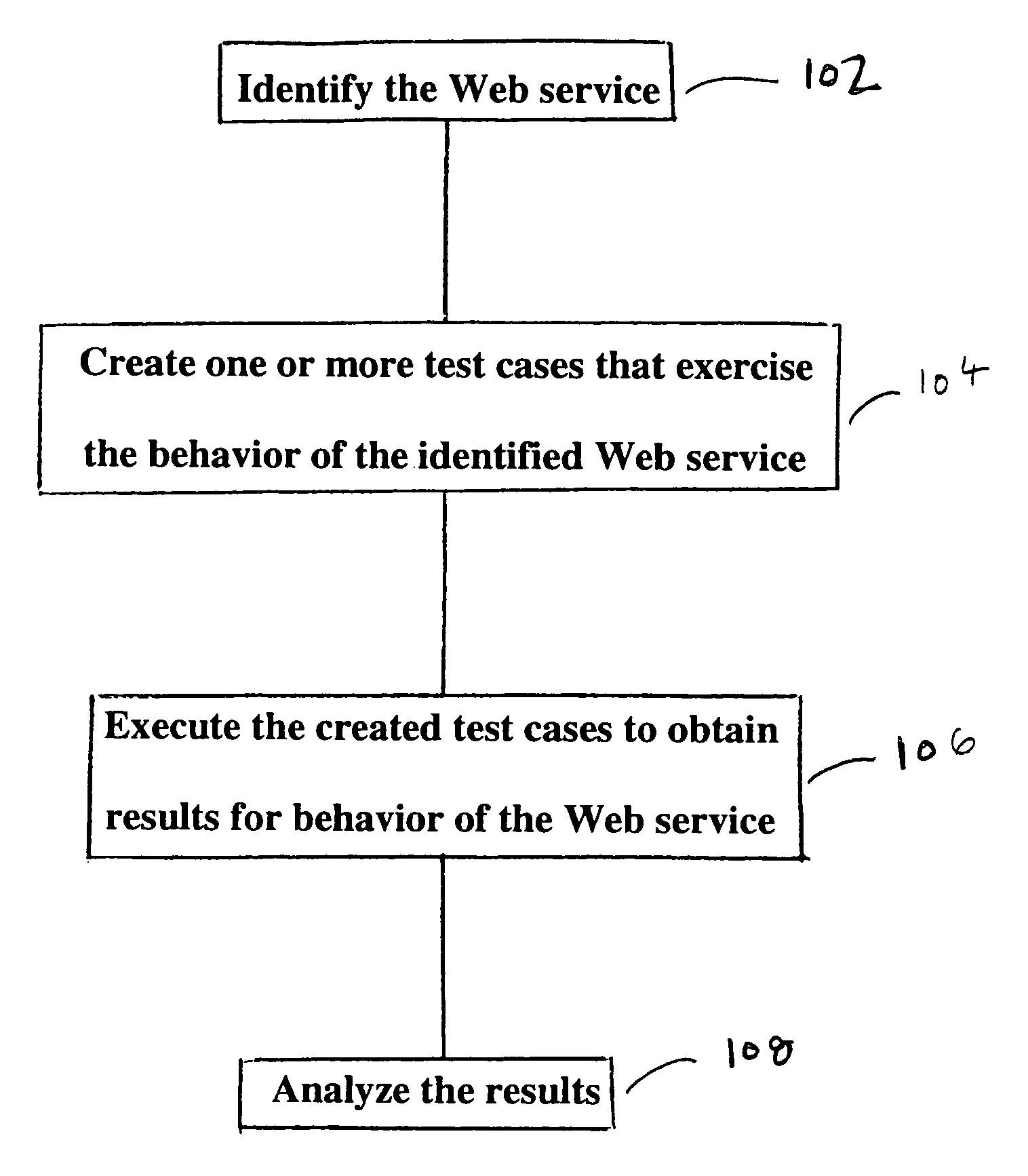
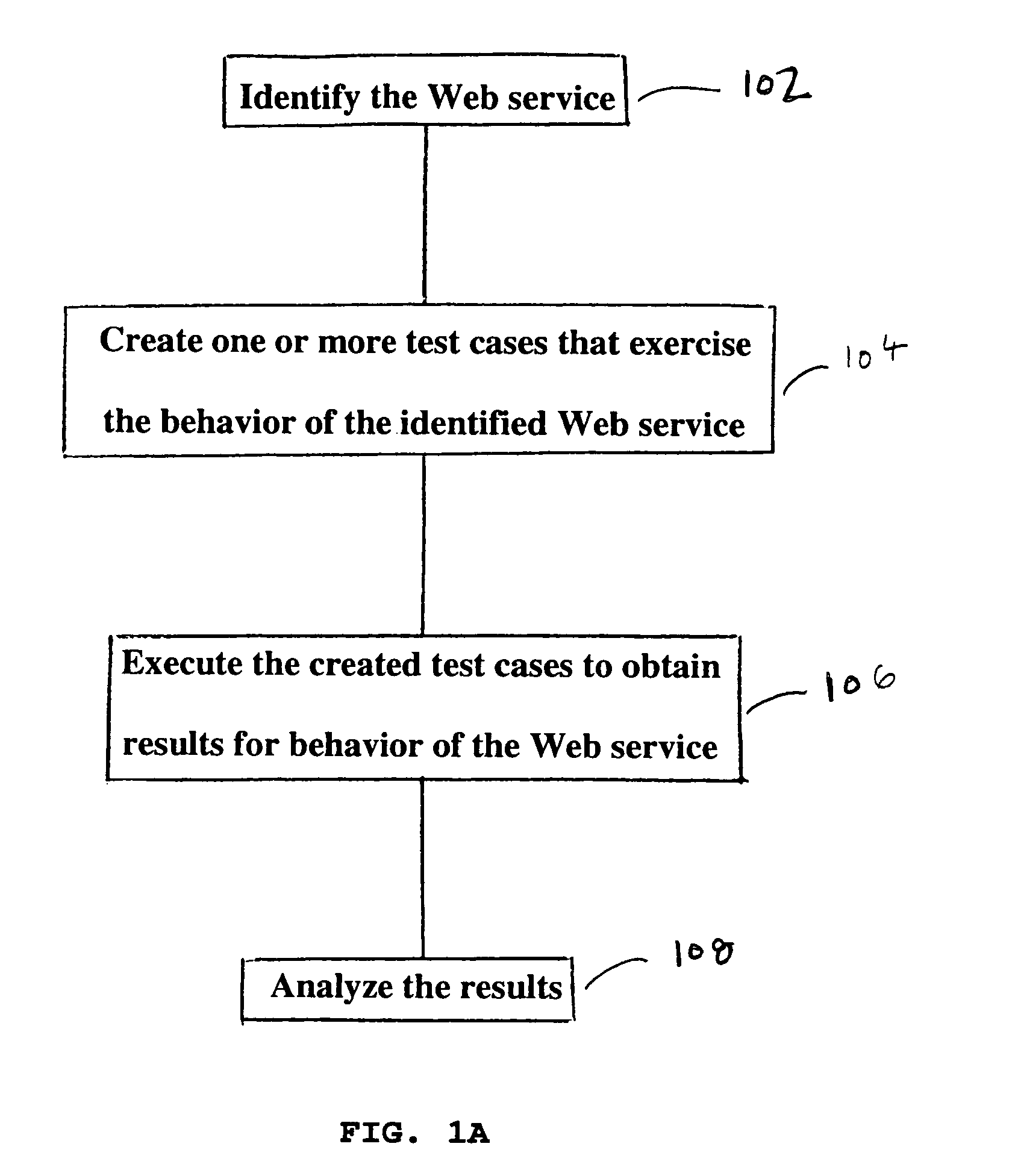
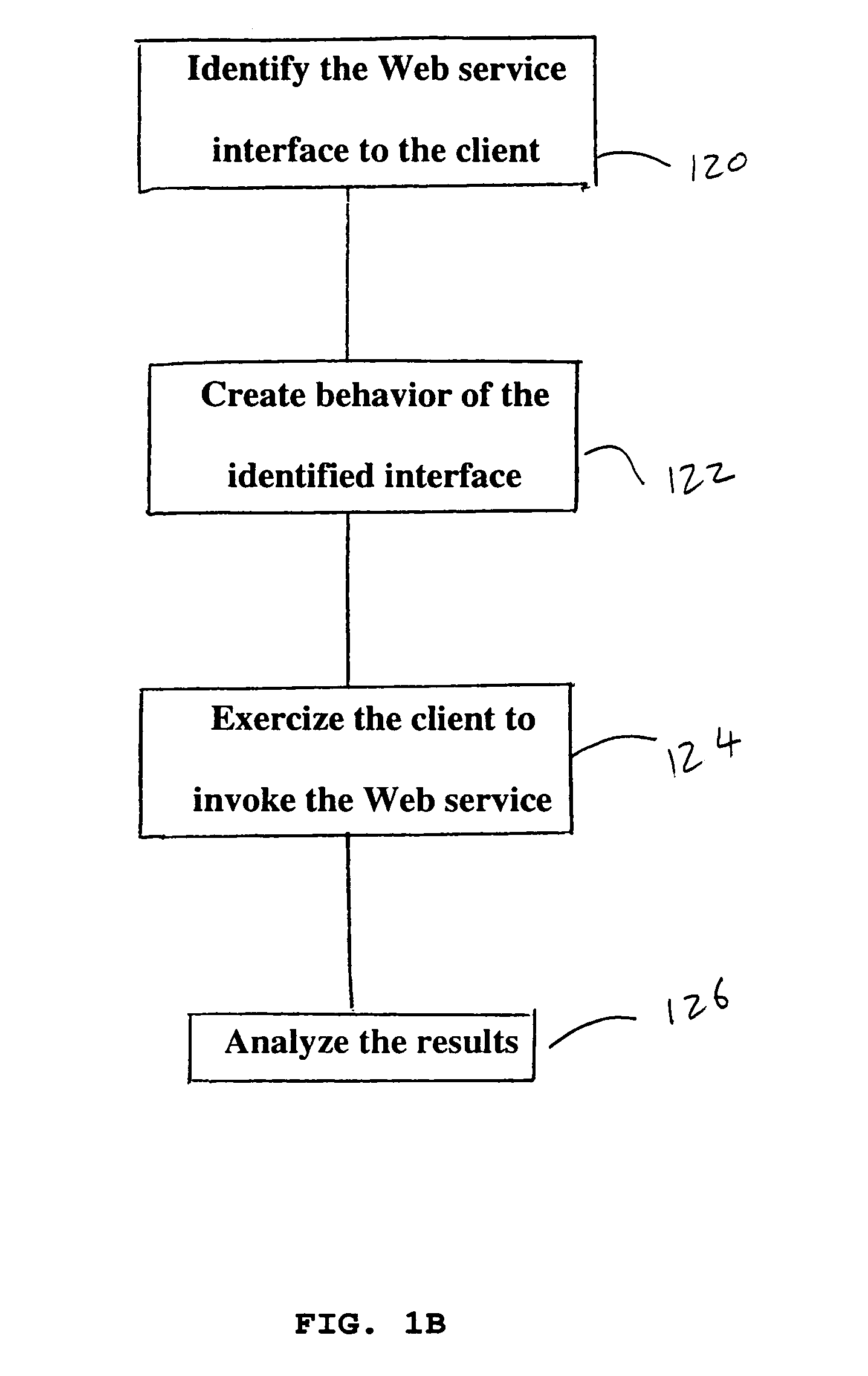
System and method for testing of web services
ActiveUS7028223B1Overcome problemsIncrease exerciseError detection/correctionData switching networksXML schemaRegression testing
The present invention is a module testing tool for Web services. In one embodiment, the present invention automates the testing of Web services that use SOAP as a wire protocol and HTTP as a transport protocol. The invention provides an easy interface for exercising Web services and testing their functionality. The invention helps users confirm the responses to SOAP messages with such features as fault detection, textual comparisons, XML validation by DTDs or XML Schemas, and the ability to express and flag complex patterns in XML. The invention lets the users validate responses that require application-specific verification (such as business logic validation) by plugging in their own code. It also provides the capability to perform regression testing of web services. The invention can automatically creates regression test controls from SOAP Client responses, or users can create their own regression tests.
Owner:PARASOFT
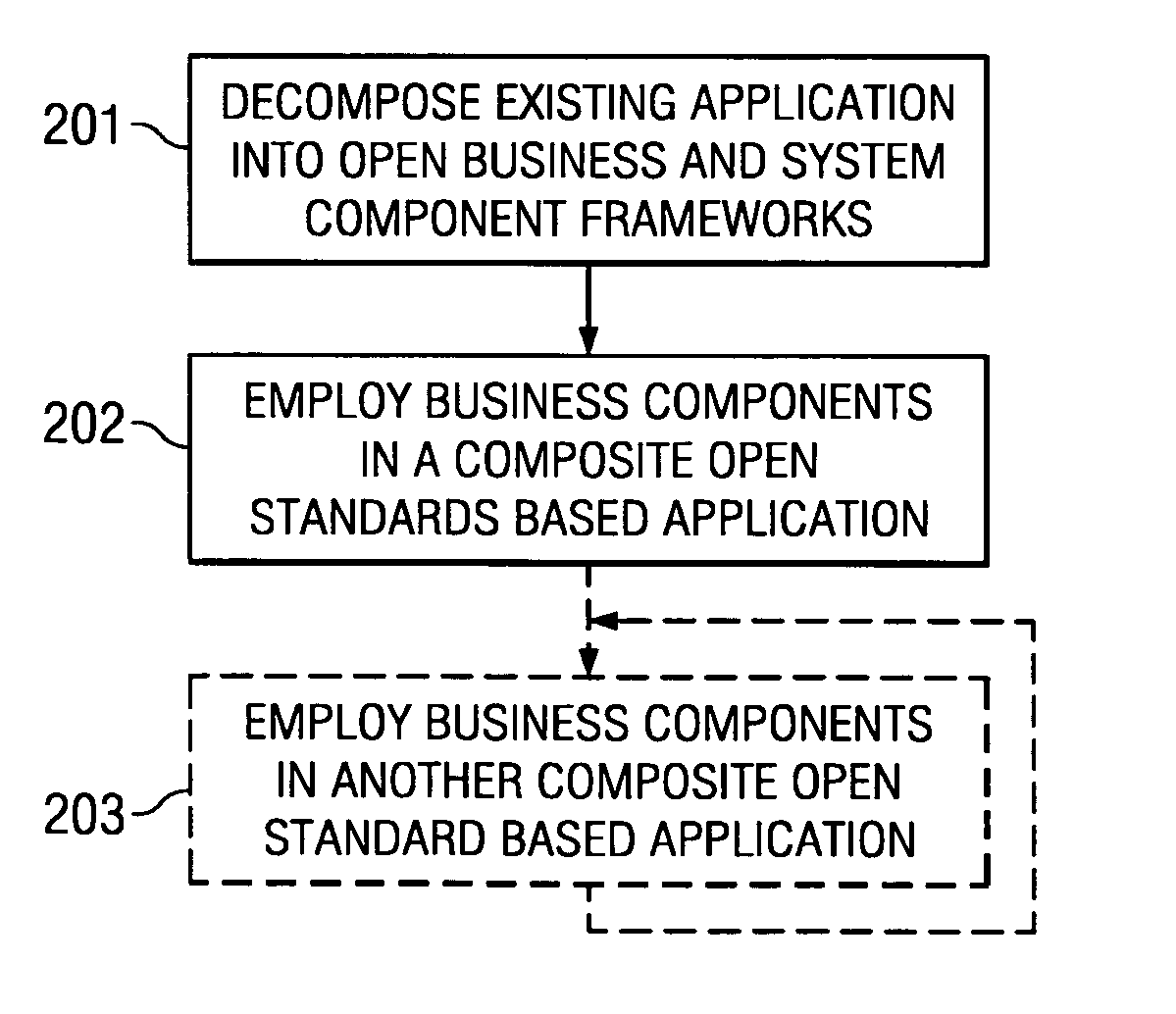
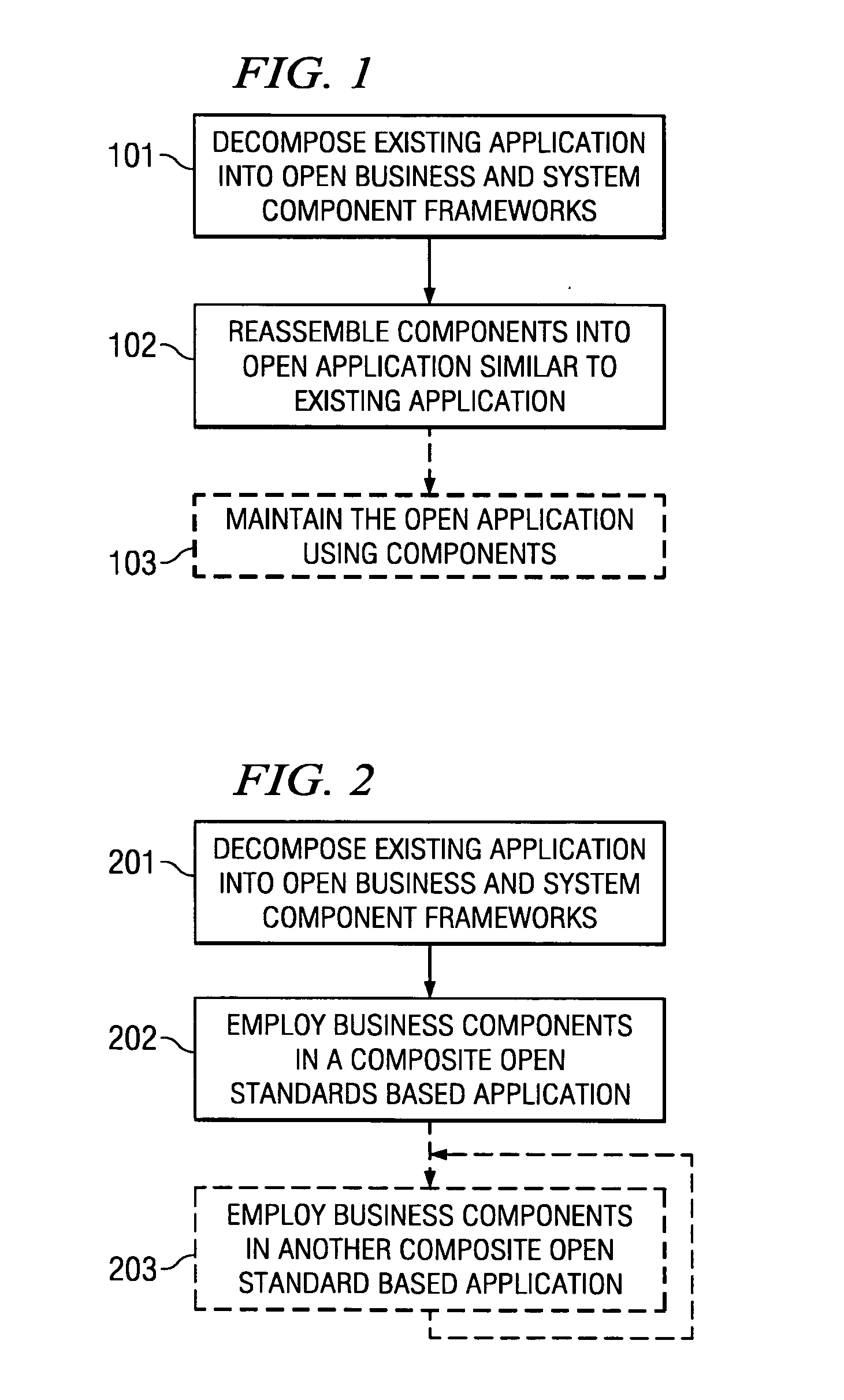
Systems and methods for modeling and generating reusable application component frameworks, and automated assembly of service-oriented applications from existing applications
InactiveUS20050144226A1Effective and meaningful supportLower barrierSoftware maintainance/managementMultiple digital computer combinationsService oriented applicationsBusiness process
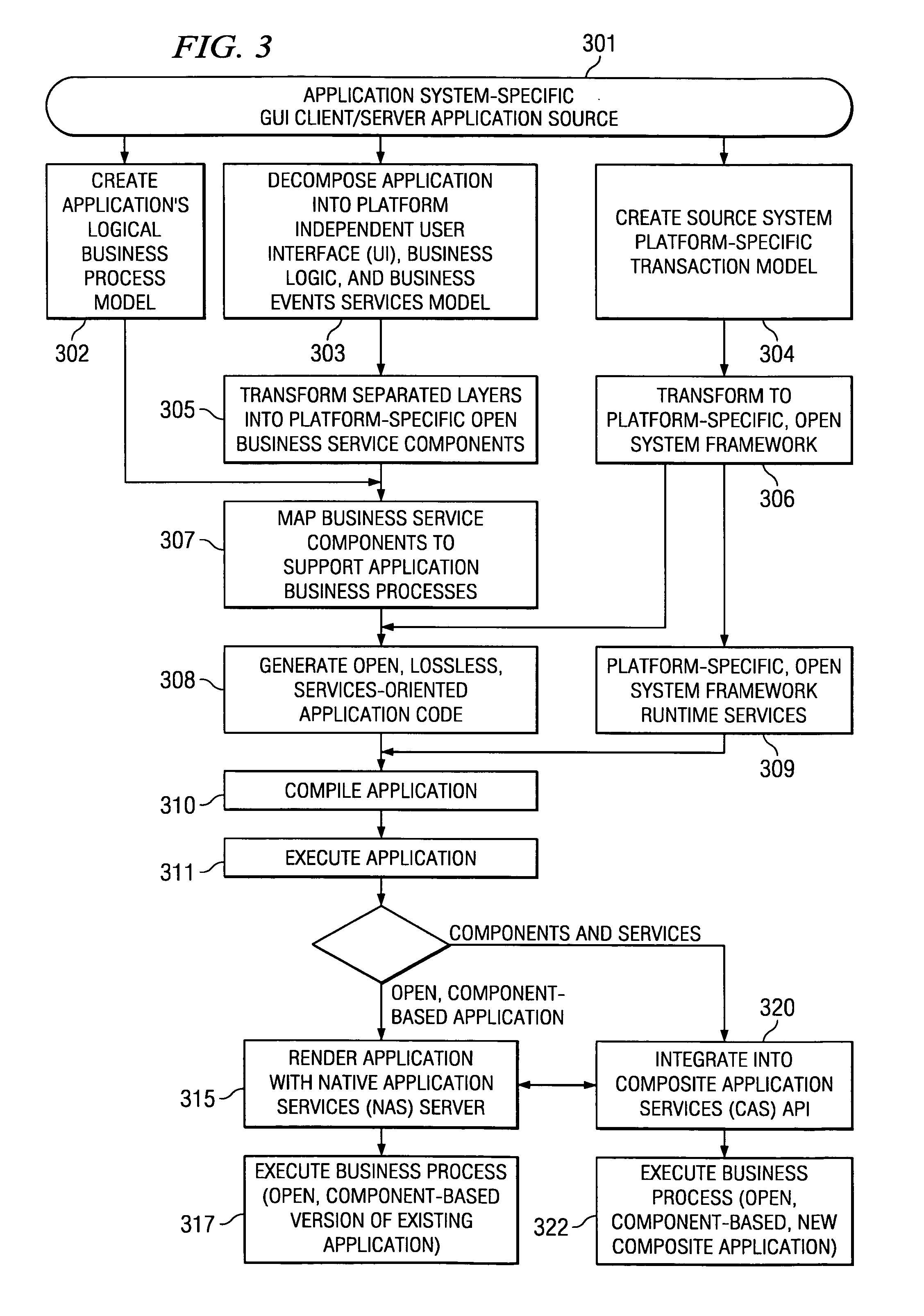
Embodiments of systems and methods model and generate open reusable, business components for Service Oriented Architectures (SOAs) from existing client / server applications. Applications are decomposed into business component frameworks with separate user interface, business logic, and event management layers to enable service-oriented development of new enterprise applications. Such layers are re-assembled through an open standards-based, Native Application Services (NAS) to render similar or near identical transactional functionality within a new application on an open platform, without breaking former production code, and without requiring a change in an end-user's business processes and / or user experience. In addition, the same separated layers may form re-usable business components at any desired level of granularity for re-use in external composite applications through industry-standard interfaces, regardless of usage, context, or complexity in the former Client / Server application.
Owner:SAP AG
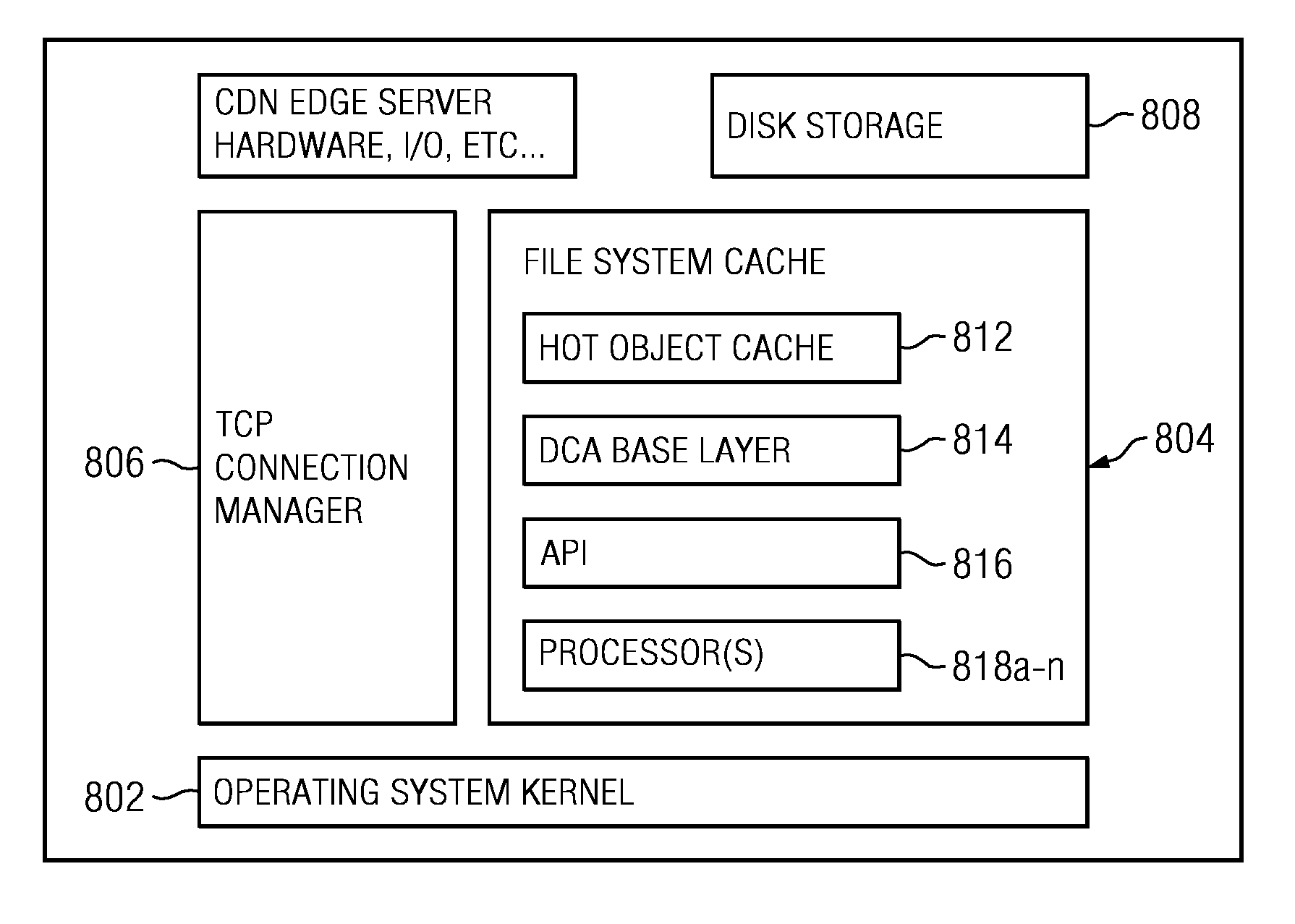
Dynamic content assembly on edge-of-network servers in a content delivery network
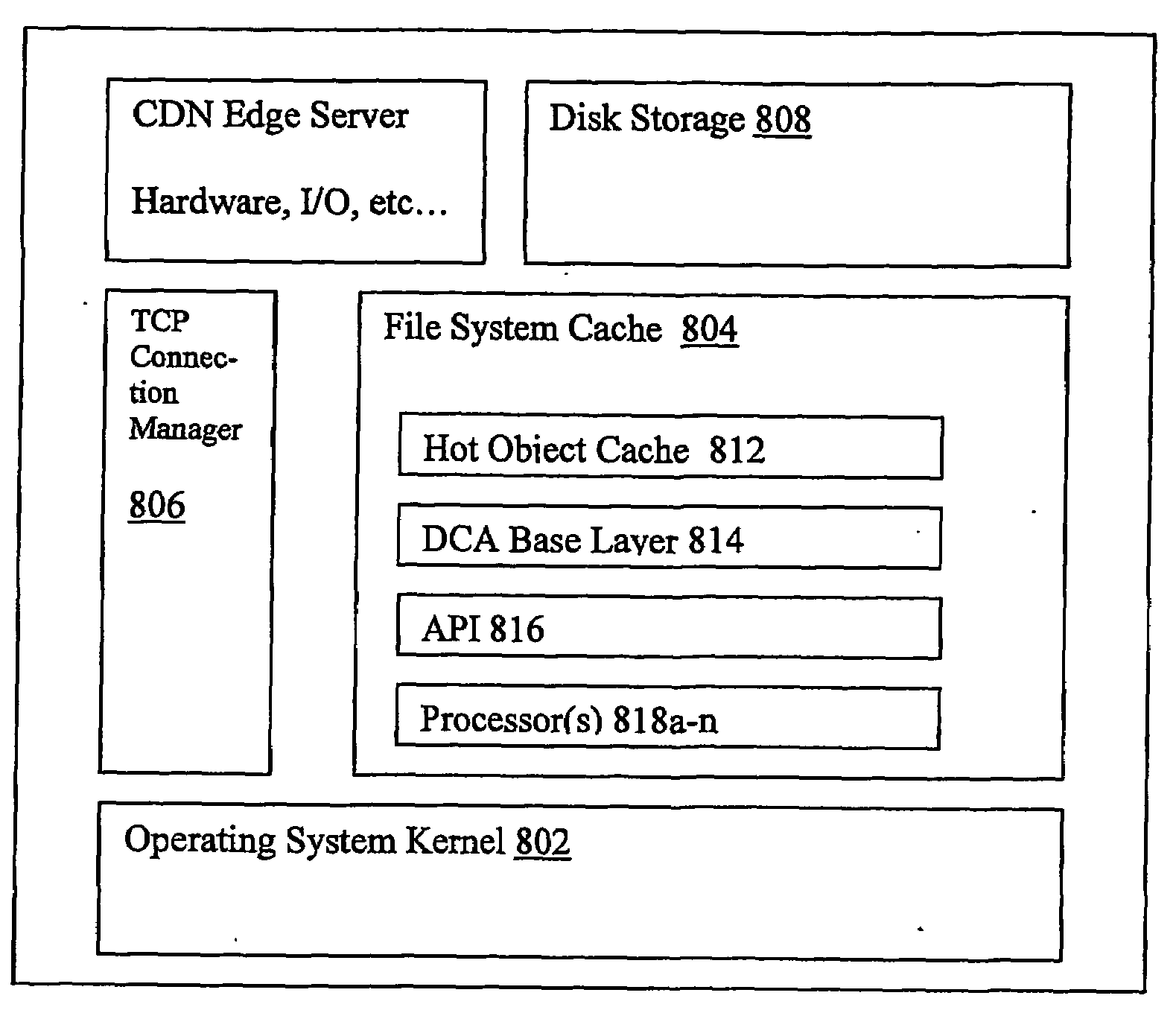
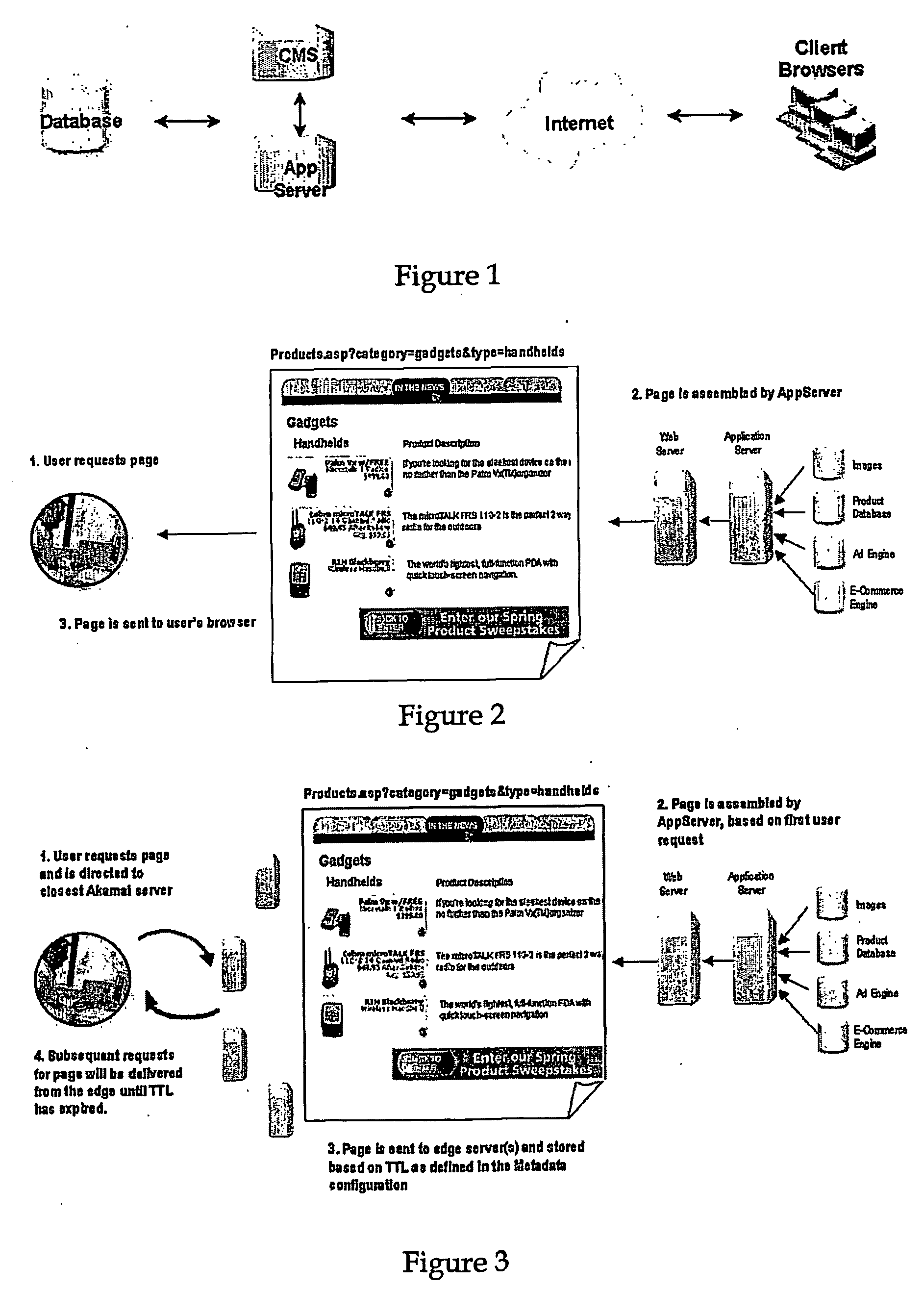
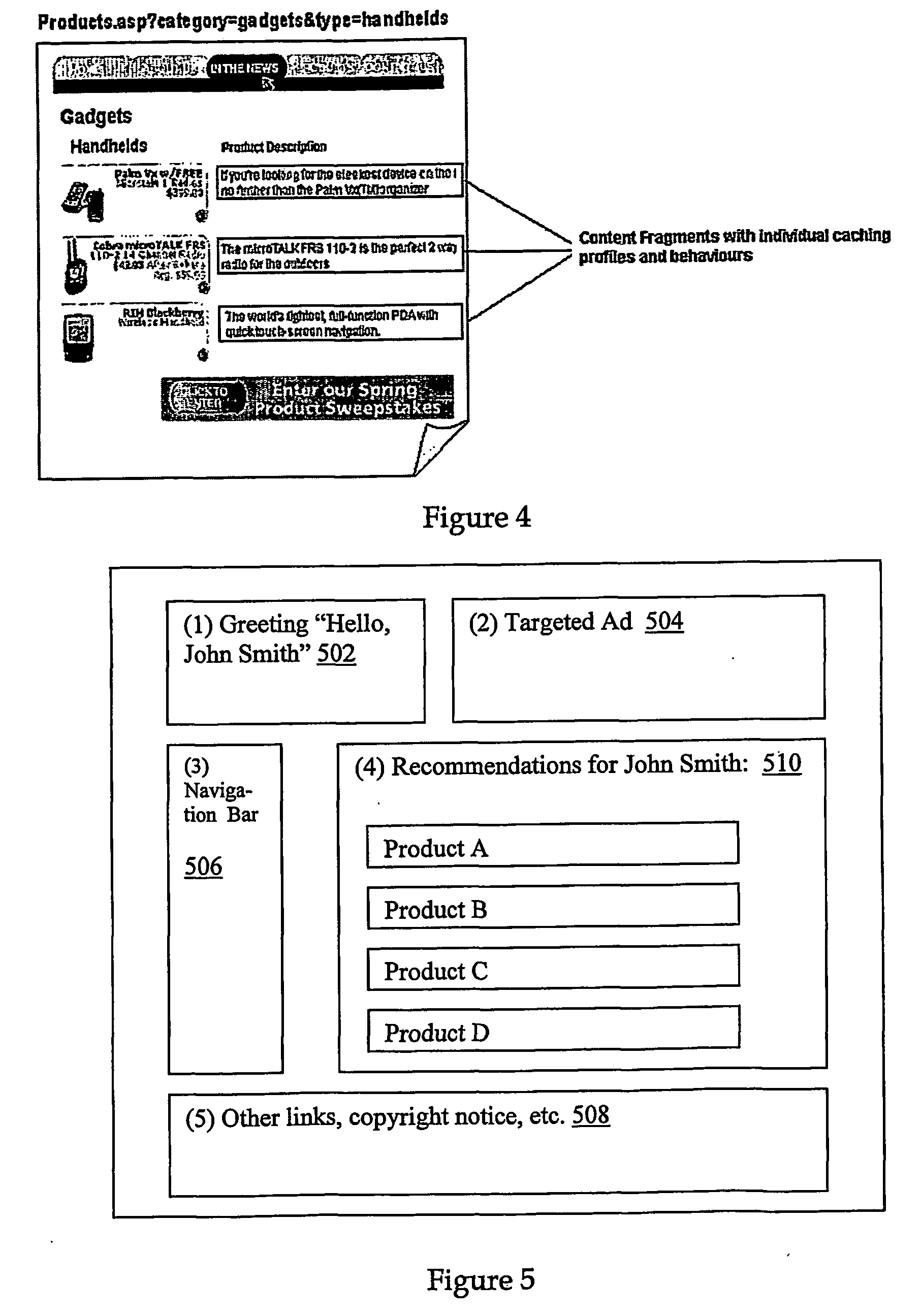
ActiveUS20090150518A1Improve site performanceImprove performanceDigital data information retrievalInterprogram communicationEdge serverWeb service
The present invention enables a content provider to dynamically assemble content at the edge of the Internet, preferably on content delivery network (CDN) edge servers. Preferably, the content provider leverages an “edge side include” (ESI) markup language that is used to define Web page fragments for dynamic assembly at the edge. Dynamic assembly improves site performance by catching the objects that comprise dynamically generated pages at the edge of the Internet, close to the end user. The content provider designs and develops the business logic to form and assemble the pages, for example, by using the ESI language within its development environment. Instead of being assembled by an application / web server in a centralized data center, the application / web server sends a page template and content fragments to a CDN edge server where the page is assembled. Each content fragment can have its own cacheability profile to manage the “freshness” of the content. Once a user requests a page (template), the edge server examines its cache for the included fragments and assembles the page on-the-fly.
Owner:AKAMAI TECH INC
Support for multiple data stores
ActiveUS20020143943A1Complete banking machinesDigital data information retrievalData accessData storing
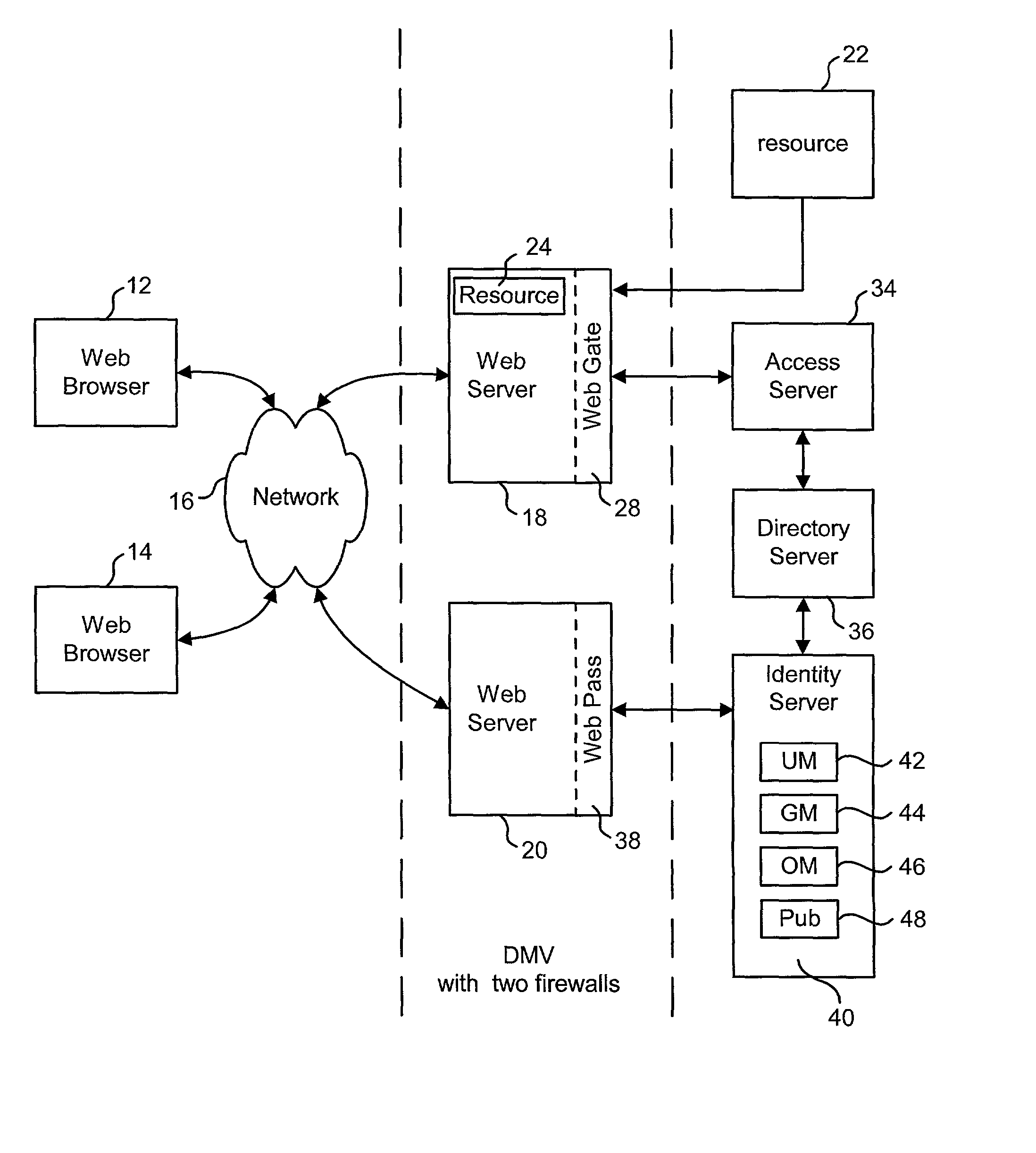
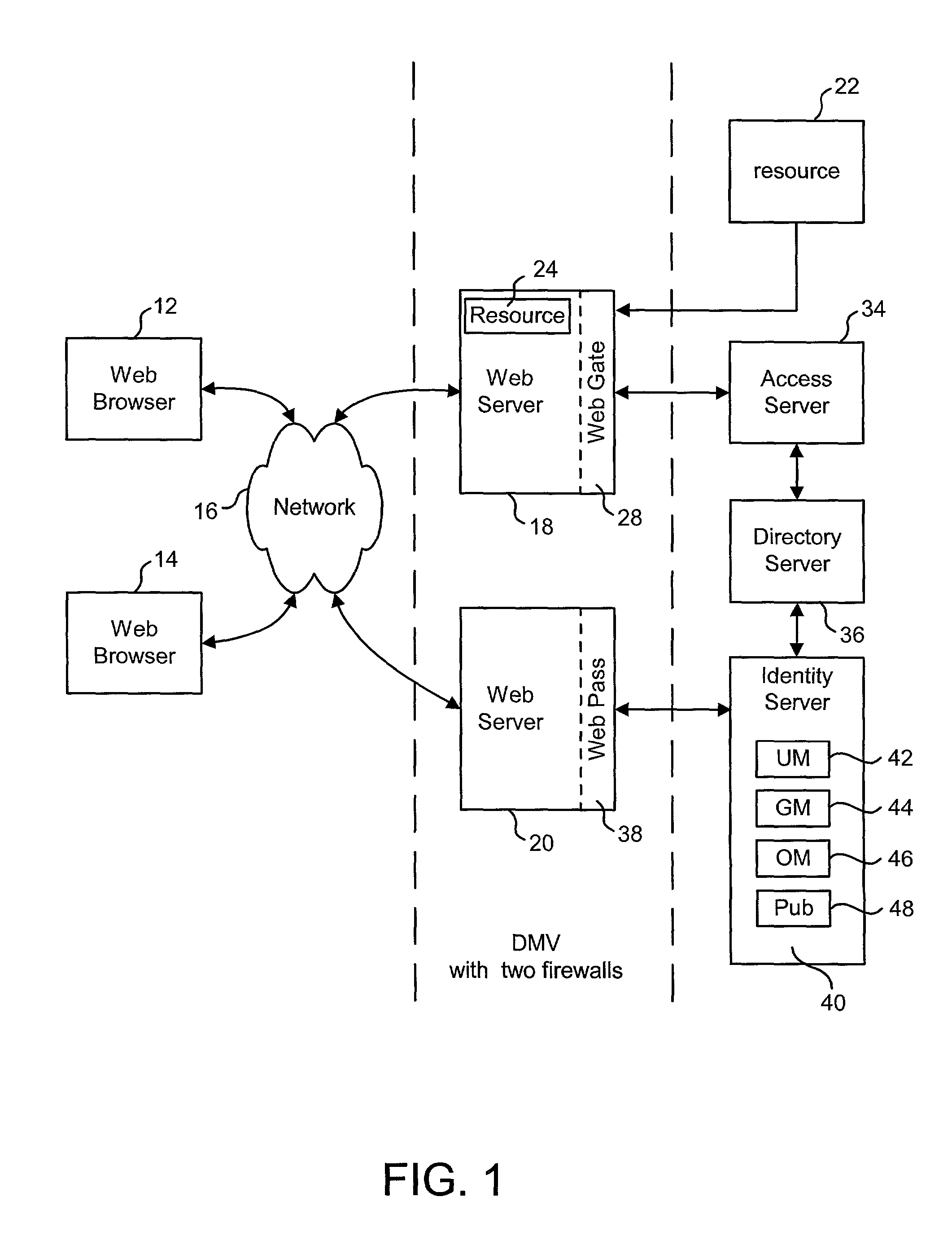
Technology is disclosed for supporting multiple data stores. The set of data stores can be of a uniform type, or the various data stores can be different types (e.g. LDAP, SQL, etc.). One implementation of the disclosed technology is with an Identity System. Another implementation is with an integrated Identity System and Access System. Various embodiments of the present invention utilize different means to separate the business logic of a system from the data access logic so that different types of data stores can be used without changing the business logic.
Owner:ORACLE INT CORP
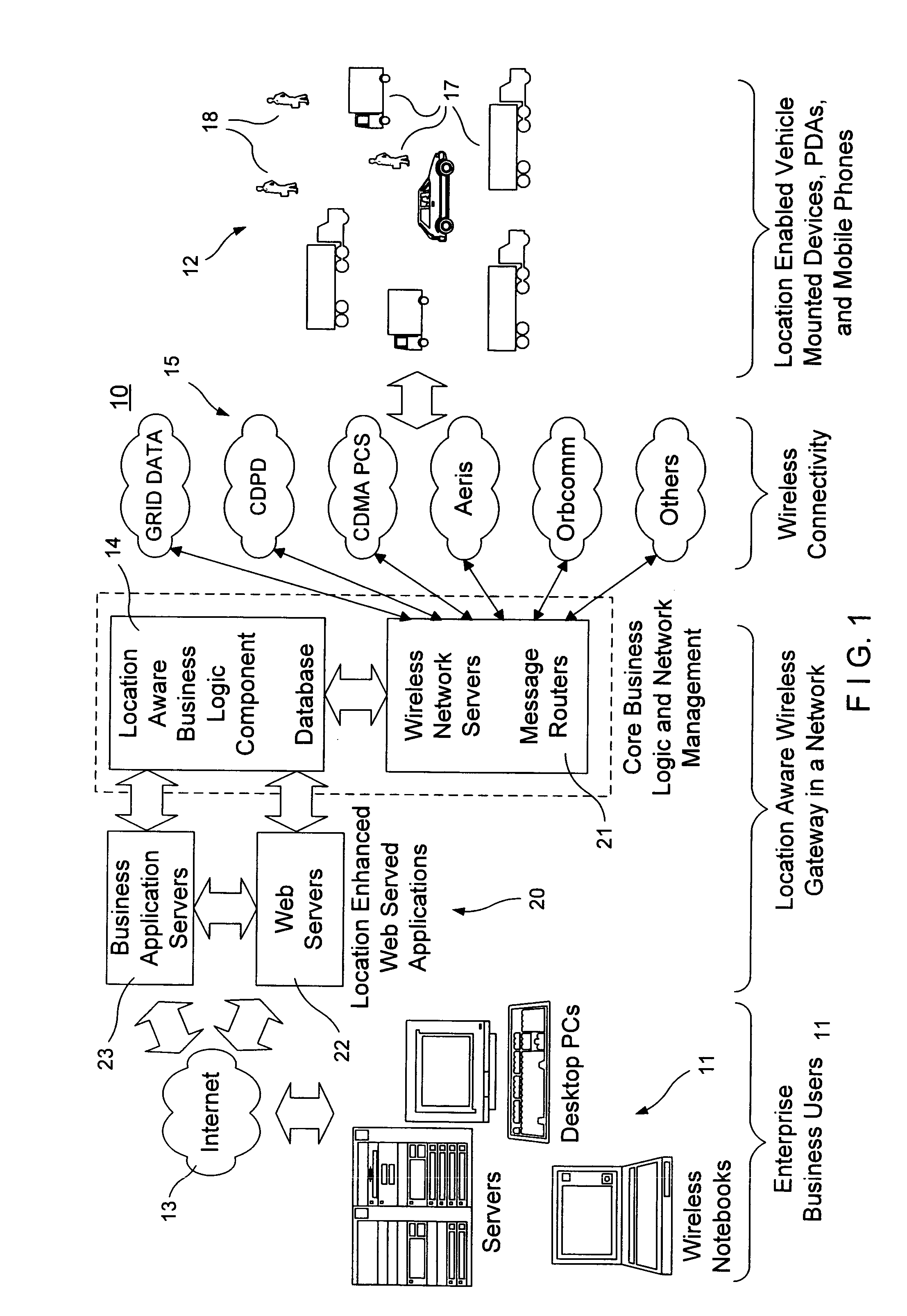
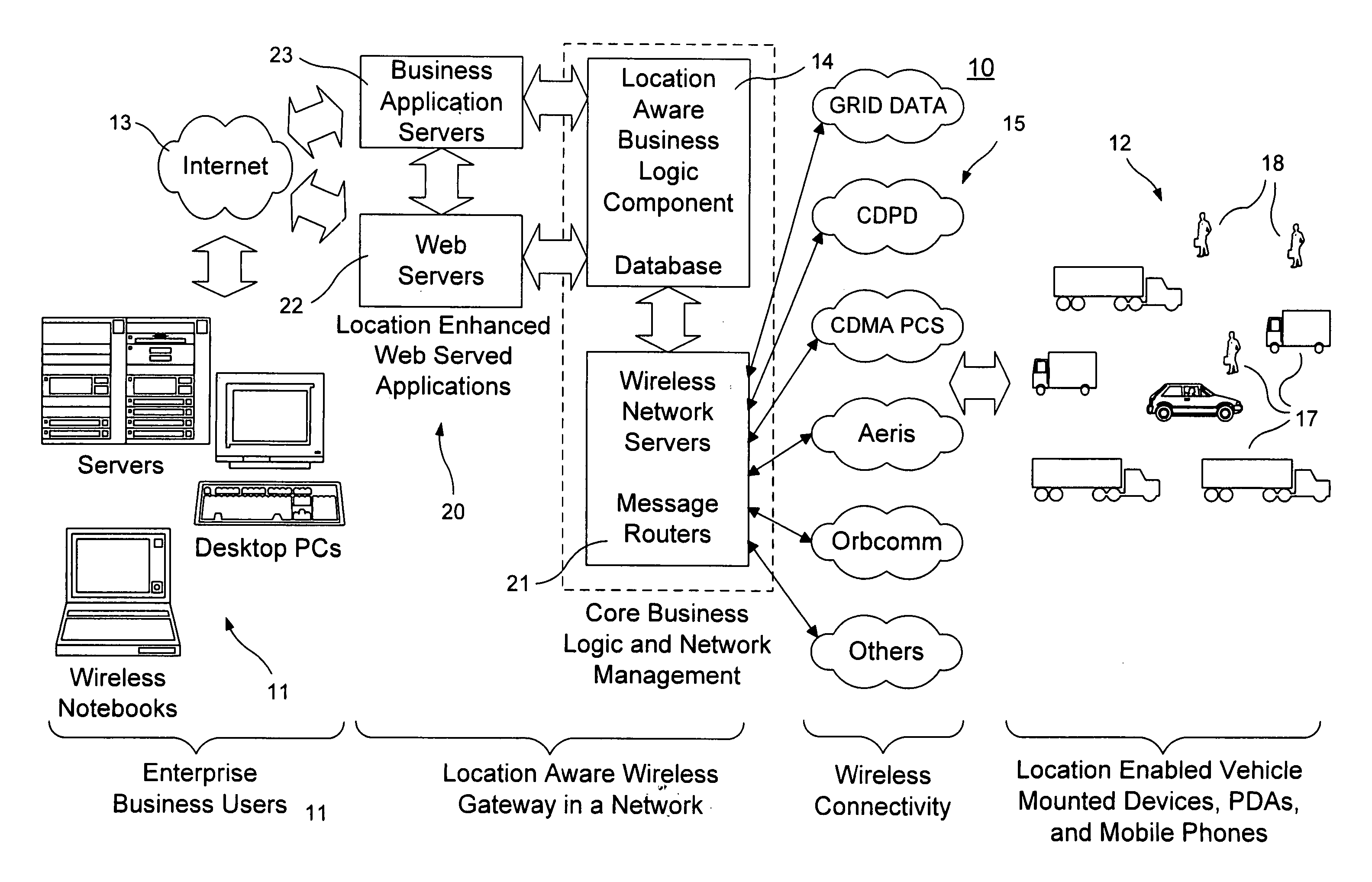
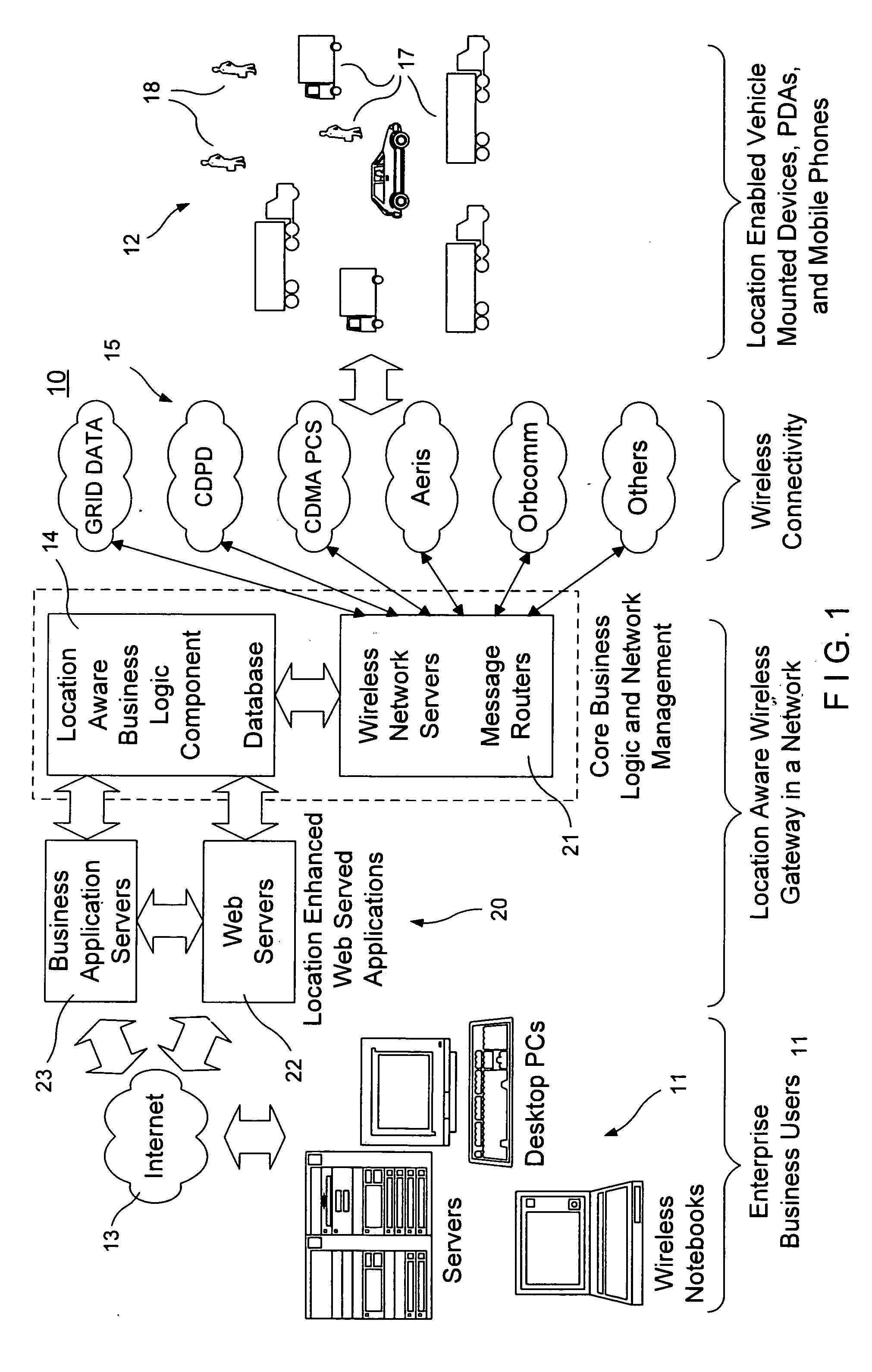
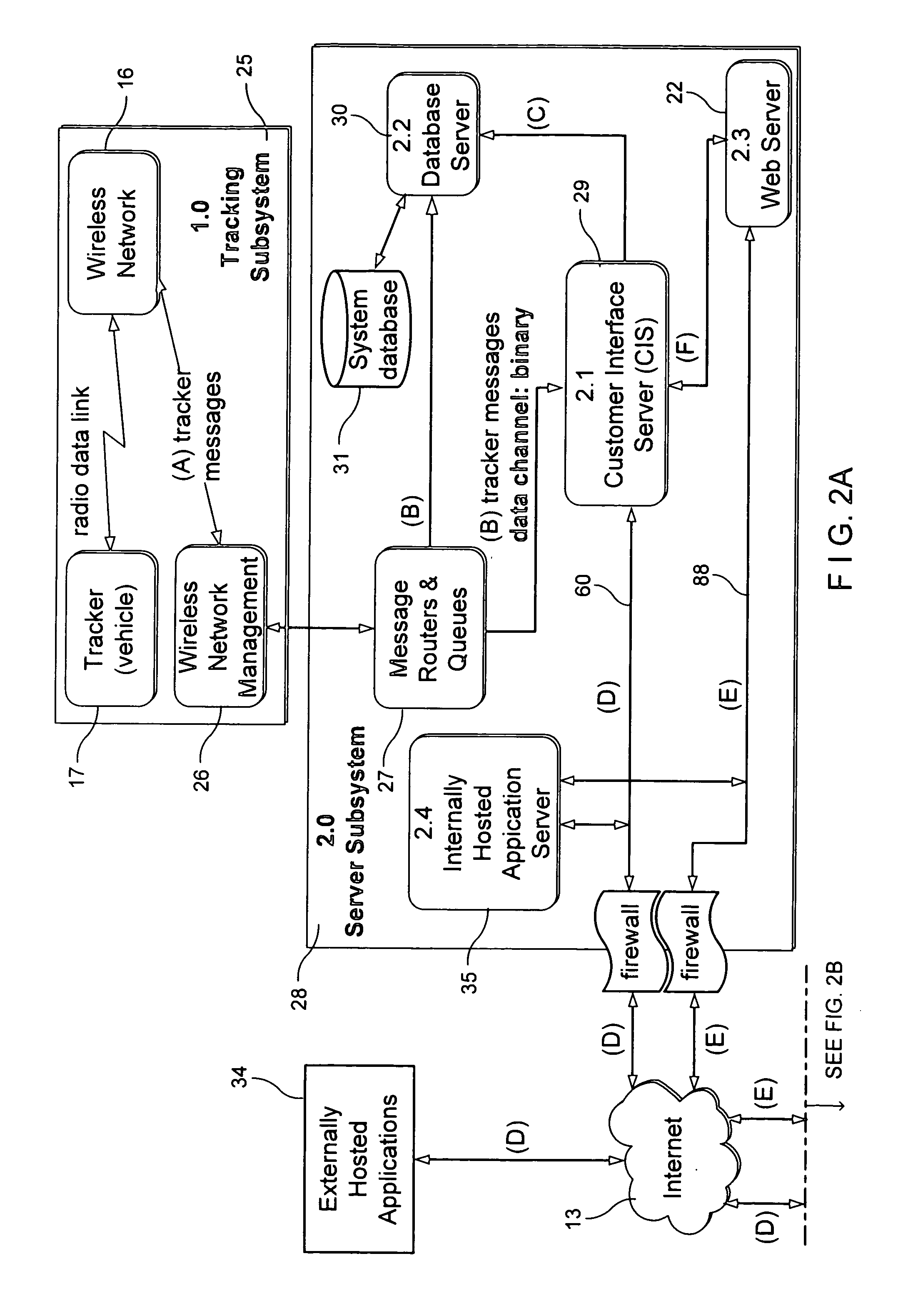
Location aware wireless data gateway
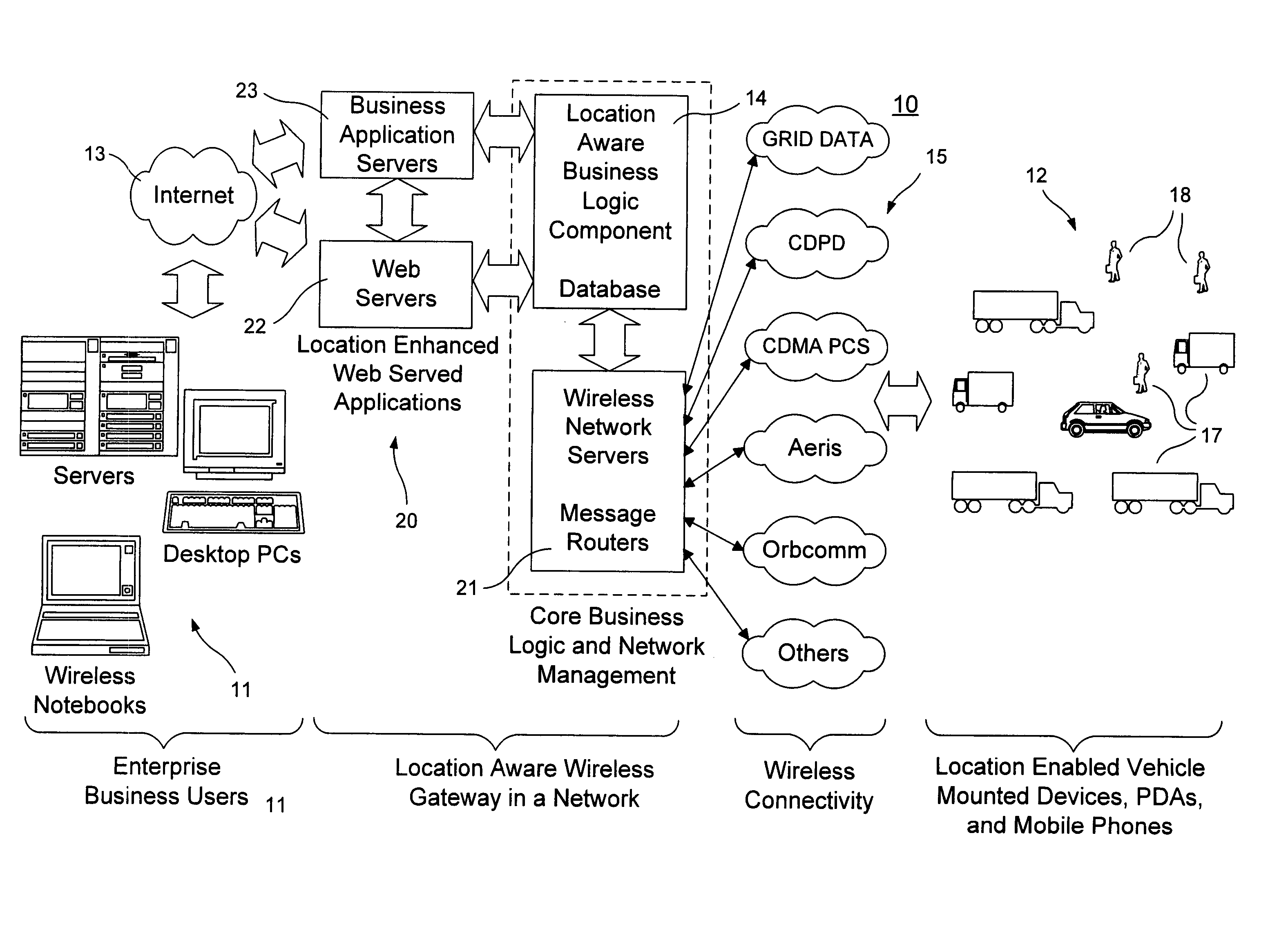
InactiveUS20060129691A1Fast and interactiveIntuitive imageMultiple digital computer combinationsTransmissionBusiness enterpriseThe Internet
A wireless gateway is provided that connects mobile and remote assets or employees to business enterprise users through multiple wireless networks and the Internet by using web served applications. The central core of the gateway is a location aware business component that sends and receives location based information to and from remote and mobile assets and applies business logic to the location data to enhance and automate business applications run by the enterprise user. This functionality considerably exceeds that of a traditional wireless gateway, which simply manages messages passed through multiple wireless networks but does nothing with the content of the messages. The business logic component provides a common interface and protocol for handling location information and allows applications that follow the protocol to interface with the gateway to take advantage of location information by using location data to trigger events or to tag events, messages, or other data.
Owner:GRID DATA
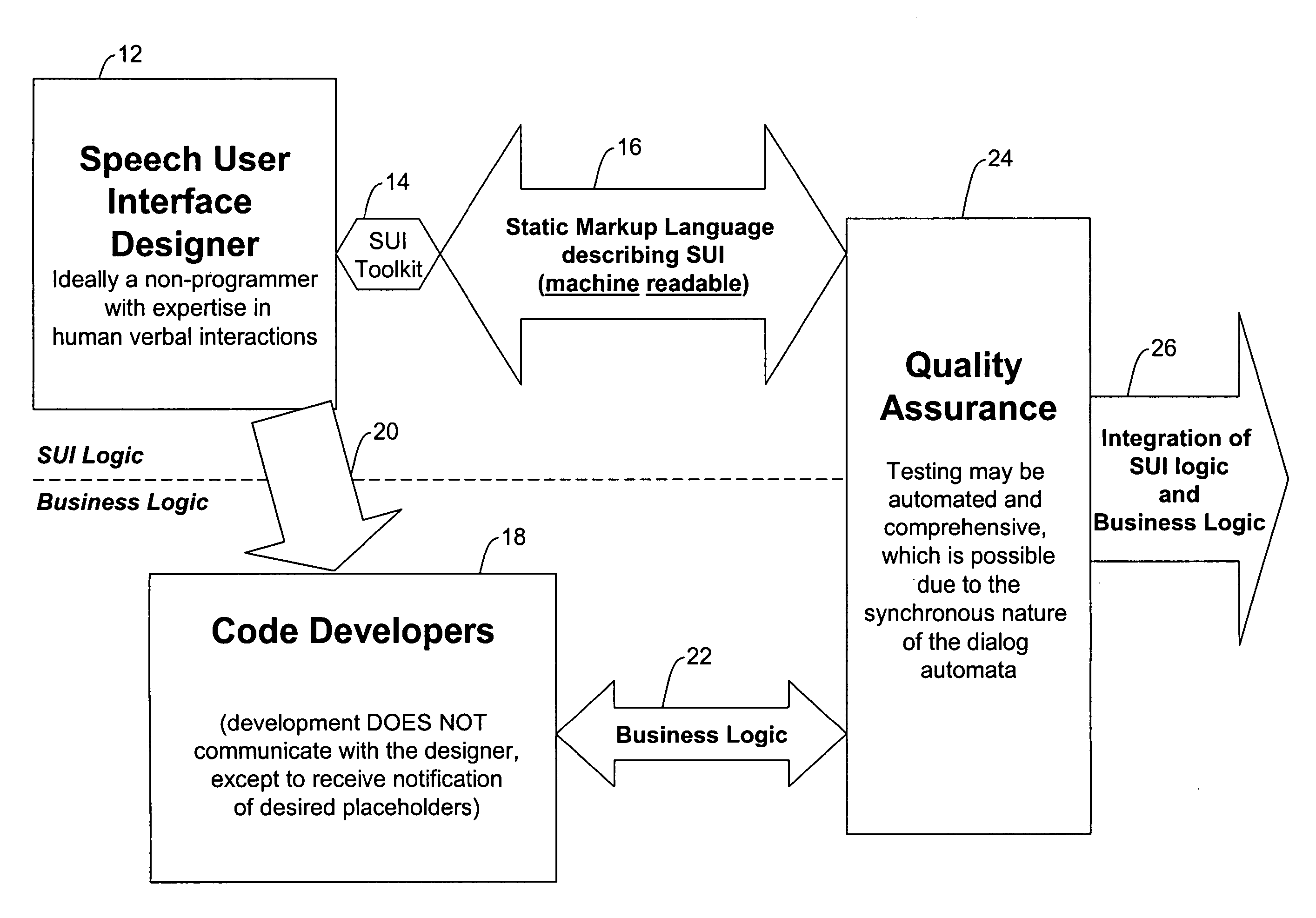
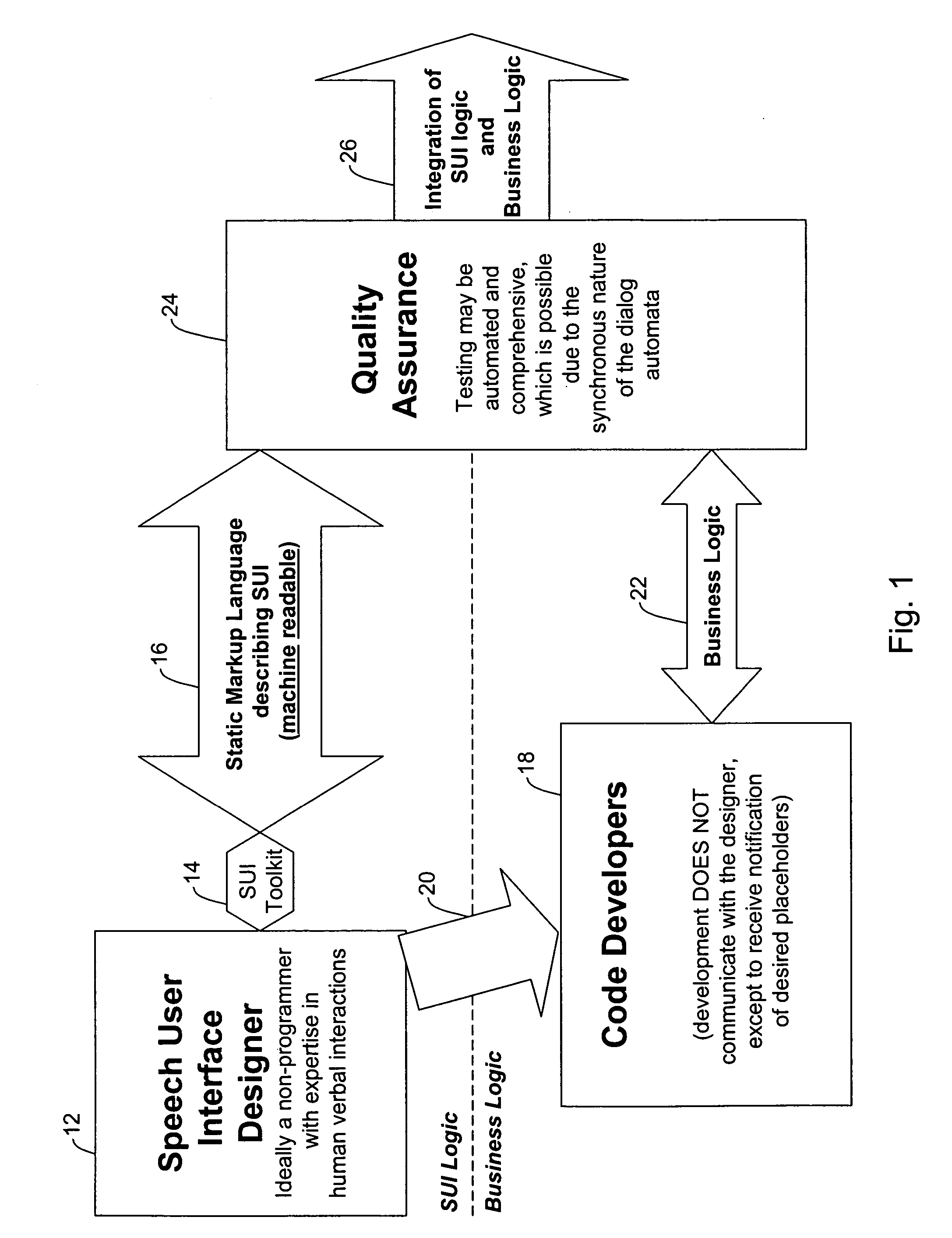
Methods and systems for developing and testing speech applications
InactiveUS20060230410A1Simple and intuitive designEliminate requirementsMultiprogramming arrangementsAutomatic exchangesSpeech applicationsSpeech sound
A system and method for facilitating the efficient development, testing and implementation of speech applications is disclosed which separates the speech user interface from the business logic. A speech user interface description is created devoid of business logic in the form of a machine readable markup language directly executable by the runtime environment based on business requirements. At least one business logic component is created separately for the speech user interface, the at least one business logic component being accessible by the runtime environment.
Owner:PARUS HLDG
Dynamic content assembly on edge-of-network servers in a content delivery network
ActiveUS7752258B2Improve performanceFast loadingDigital data information retrievalMultiple digital computer combinationsEdge serverData center
Owner:AKAMAI TECH INC
Method and system for evaluating network safety situation
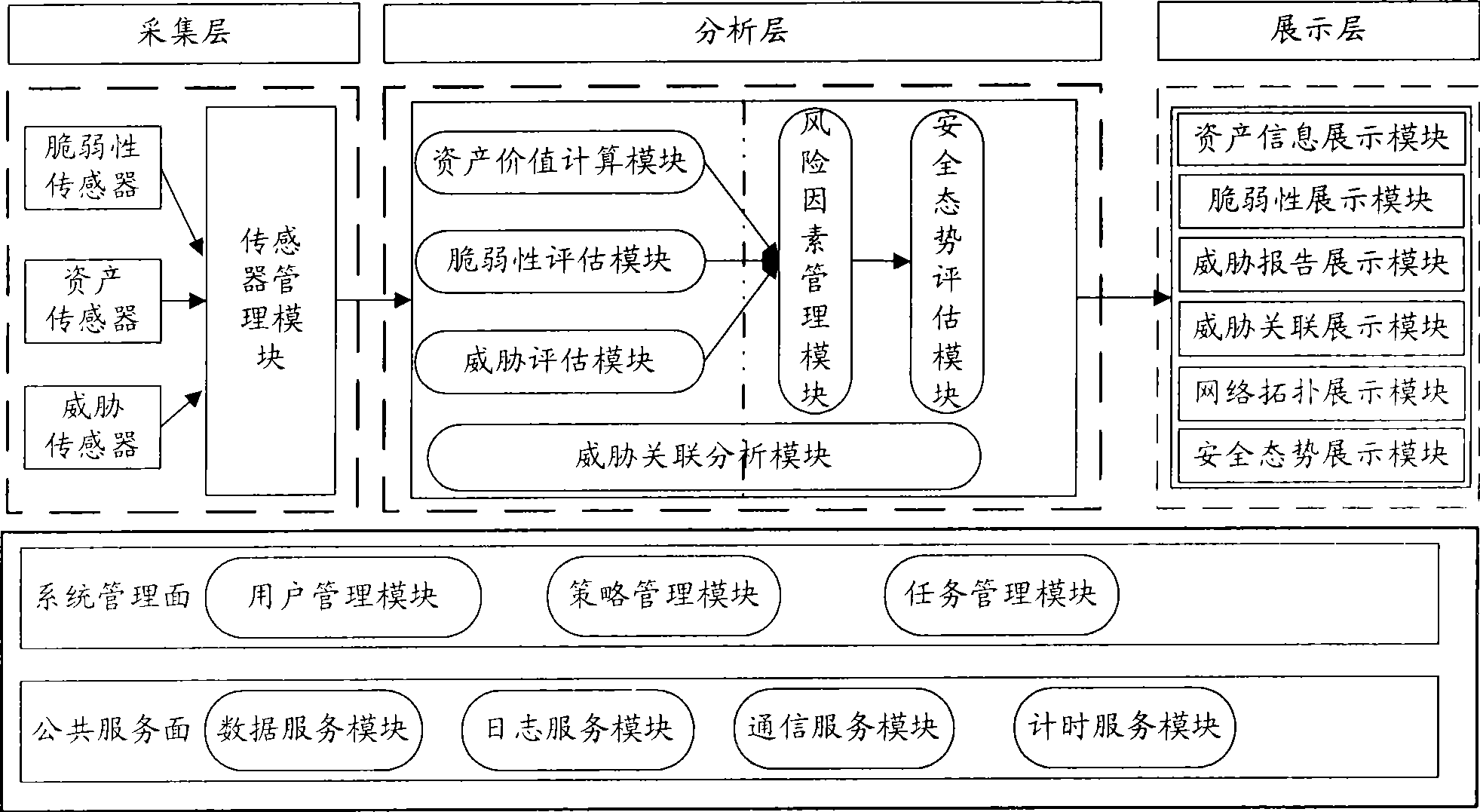
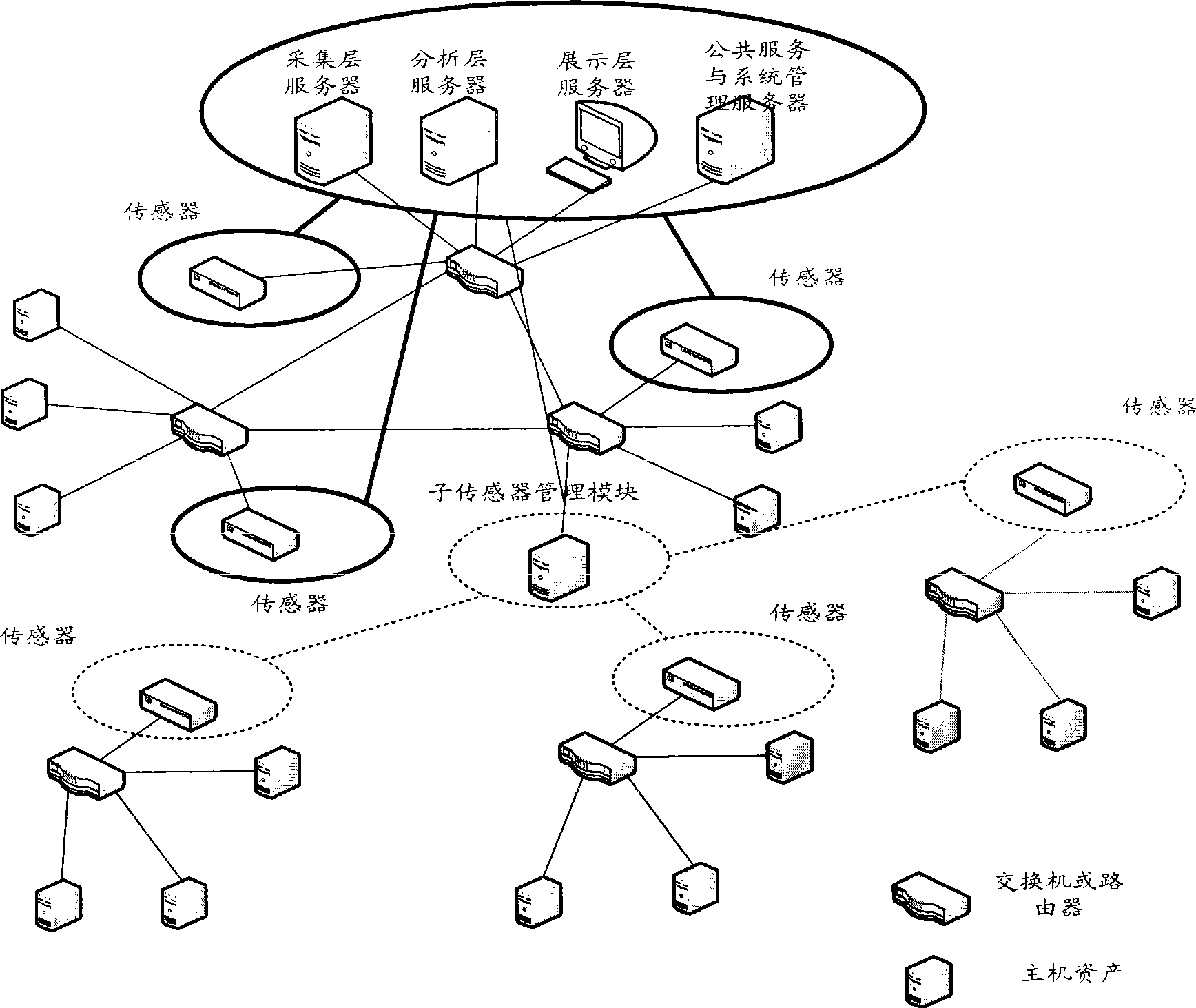
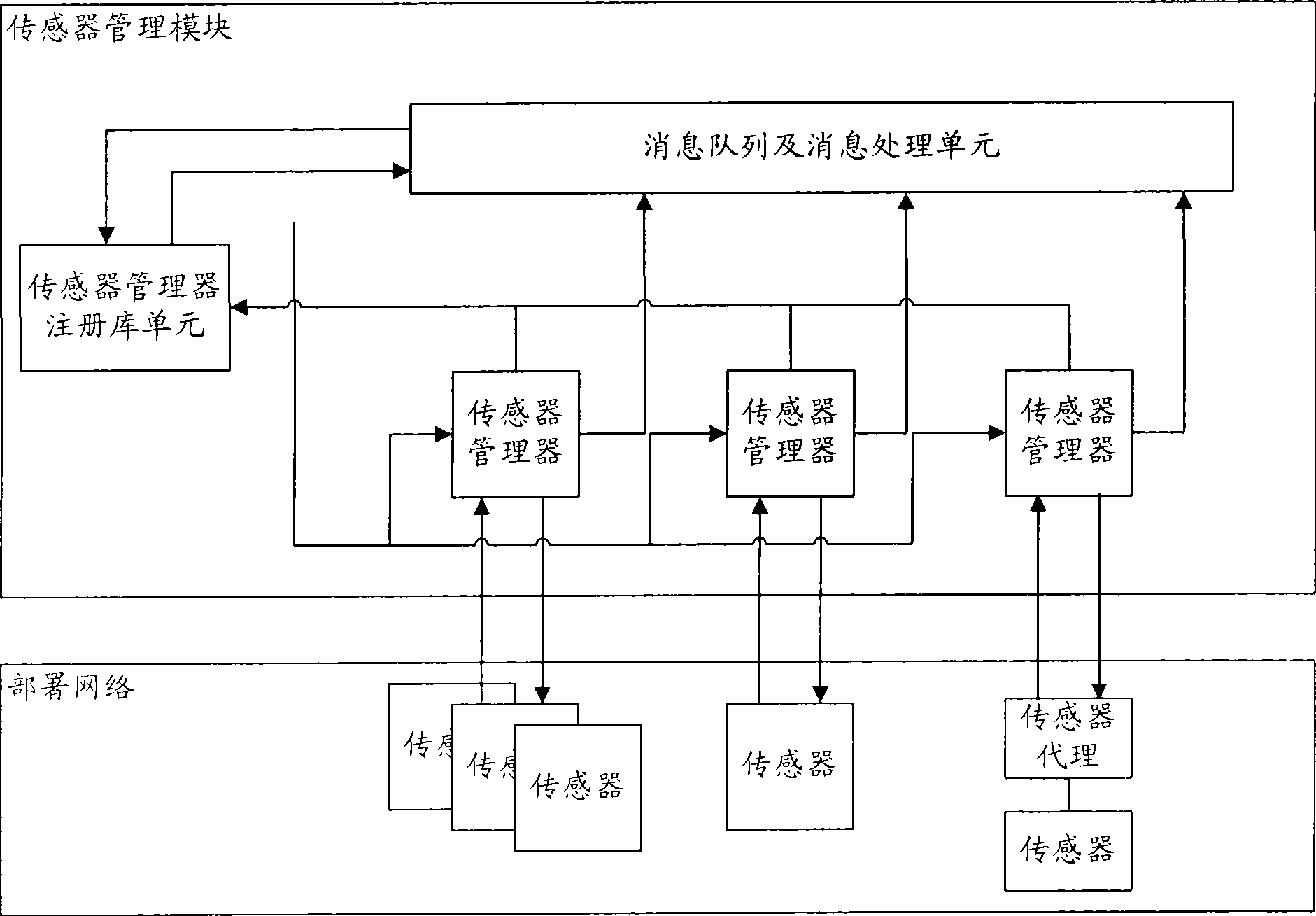
InactiveCN101436967AEasy to operateImprove securityData switching networksThree levelSecurity solution
The invention relates to a method for evaluating the security situation of a network and a system thereof. The system has a two-surface three-level framework and is provided with a public service surface and a service management surface for executing uniform coordinated management on each functional module of the system; according to a service logic processing flow, the system is divided into three levels: an acquisition level, an analysis level and an exhibition level for completing four evaluating operations of assets, frangibility, threat and security situation; the invention is based on the characteristic of service operation in the network, combines the prior risk evaluation method, the prior flow and the prior security detection tool and provides a set of a novel dynamic real-time evaluation method. The system can analyze the assets and service of the network and the risk of the whole network and carries out the evaluation of the security situation. The system can provide the security state of the whole network in macroscopy, can deepen to specific service and assets and know the specific security problem, thereby effectively helping network security personnel to analyze the root of the security problem and assisting to provide a security solution proposal and implement a defense measure.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Location aware wireless data gateway
InactiveUS20060182055A1Fast and interactiveIntuitive imageData switching by path configurationRadio/inductive link selection arrangementsBusiness enterpriseThe Internet
A wireless gateway is provided that connects mobile and remote assets or employees to business enterprise users through multiple wireless networks and the Internet by using web served applications. The central core of the gateway is a location aware business component that sends and receives location based information to and from remote and mobile assets and applies business logic to the location data to enhance and automate business applications run by the enterprise user. This functionality considerably exceeds that of a traditional wireless gateway, which simply manages messages passed through multiple wireless networks but does nothing with the content of the messages. The business logic component provides a common interface and protocol for handling location information and allows applications that follow the protocol to interface with the gateway to take advantage of location information by using location data to trigger events or to tag events, messages, or other data.
Owner:COFFEE JOHN R +9
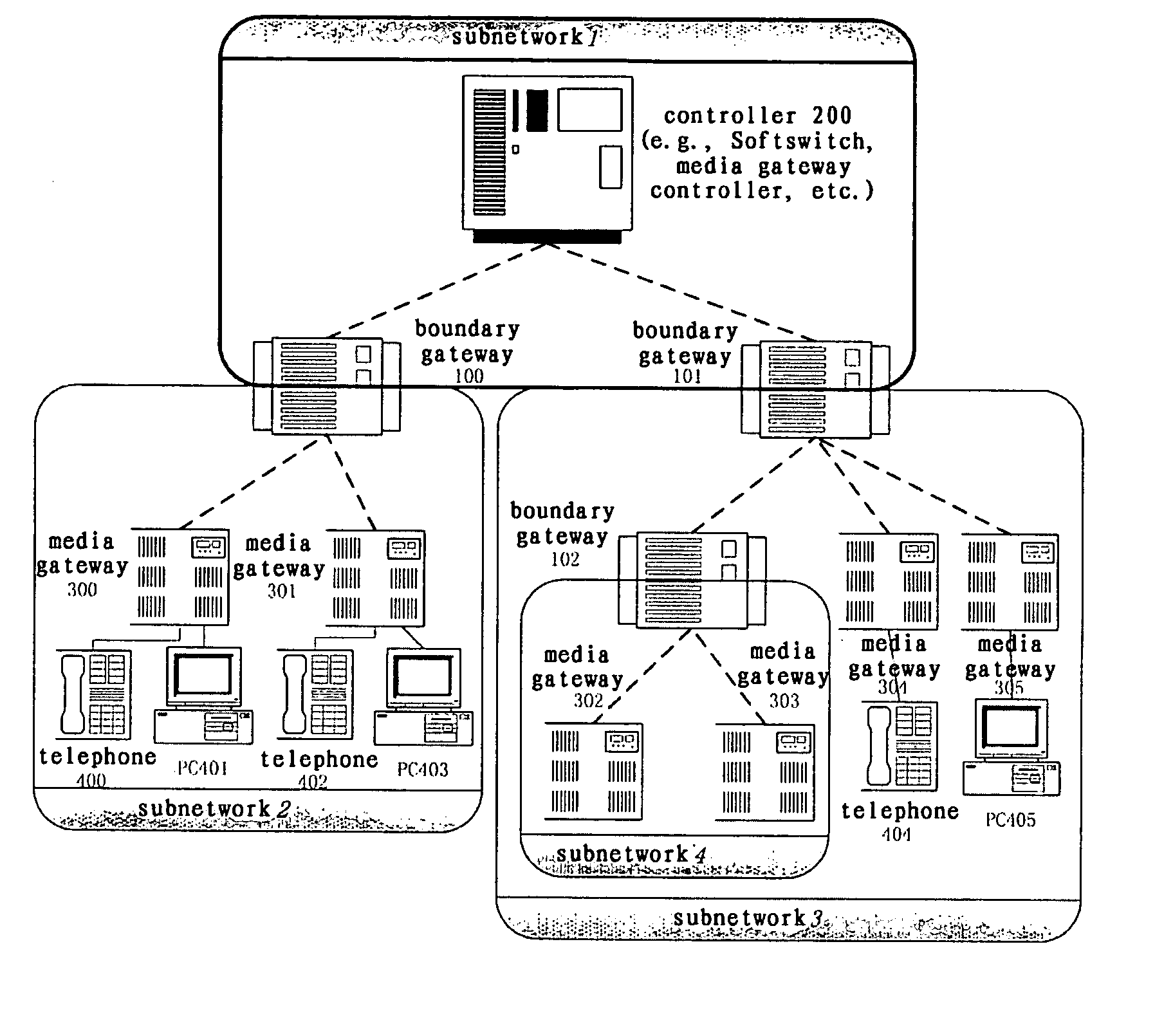
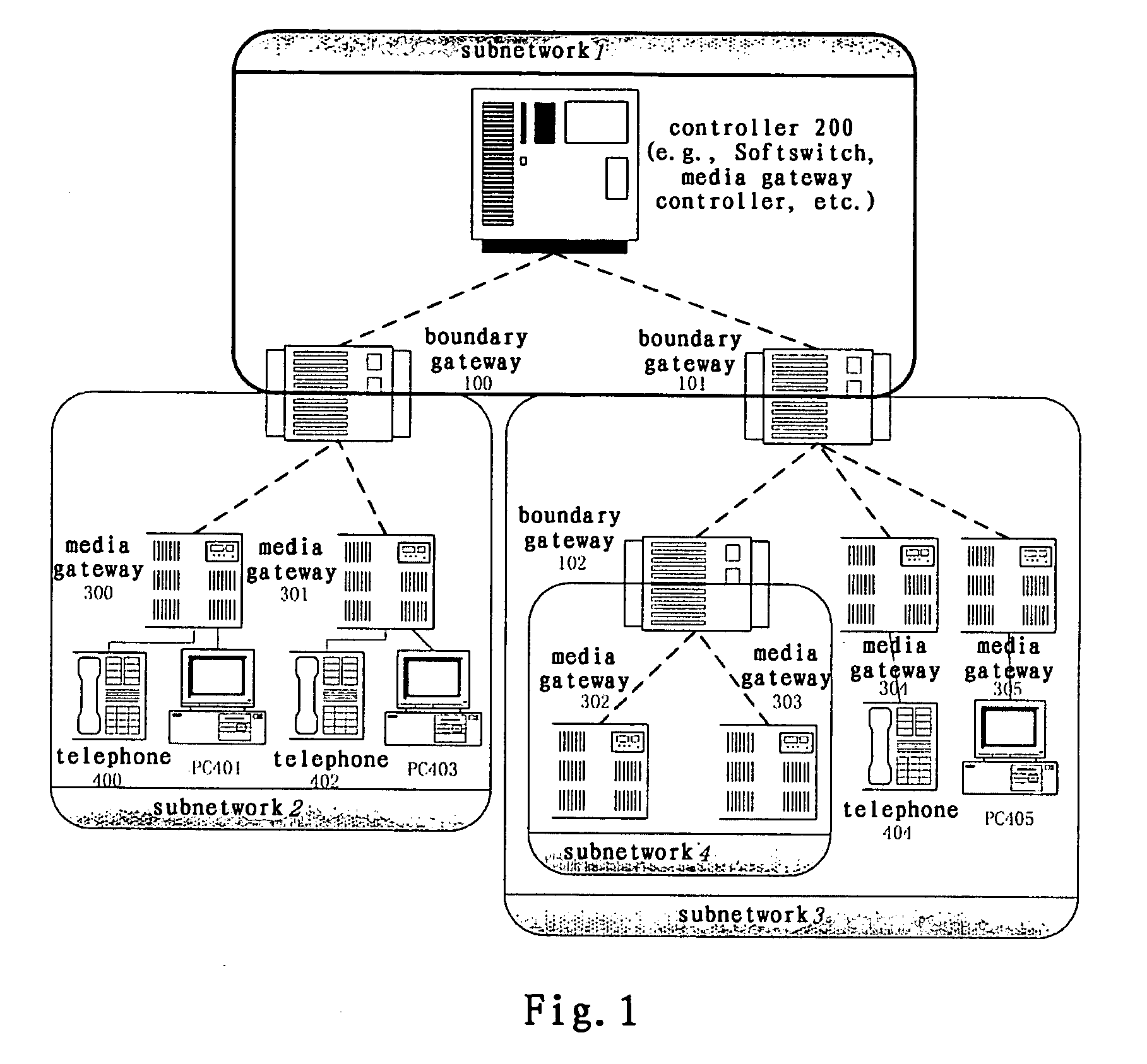
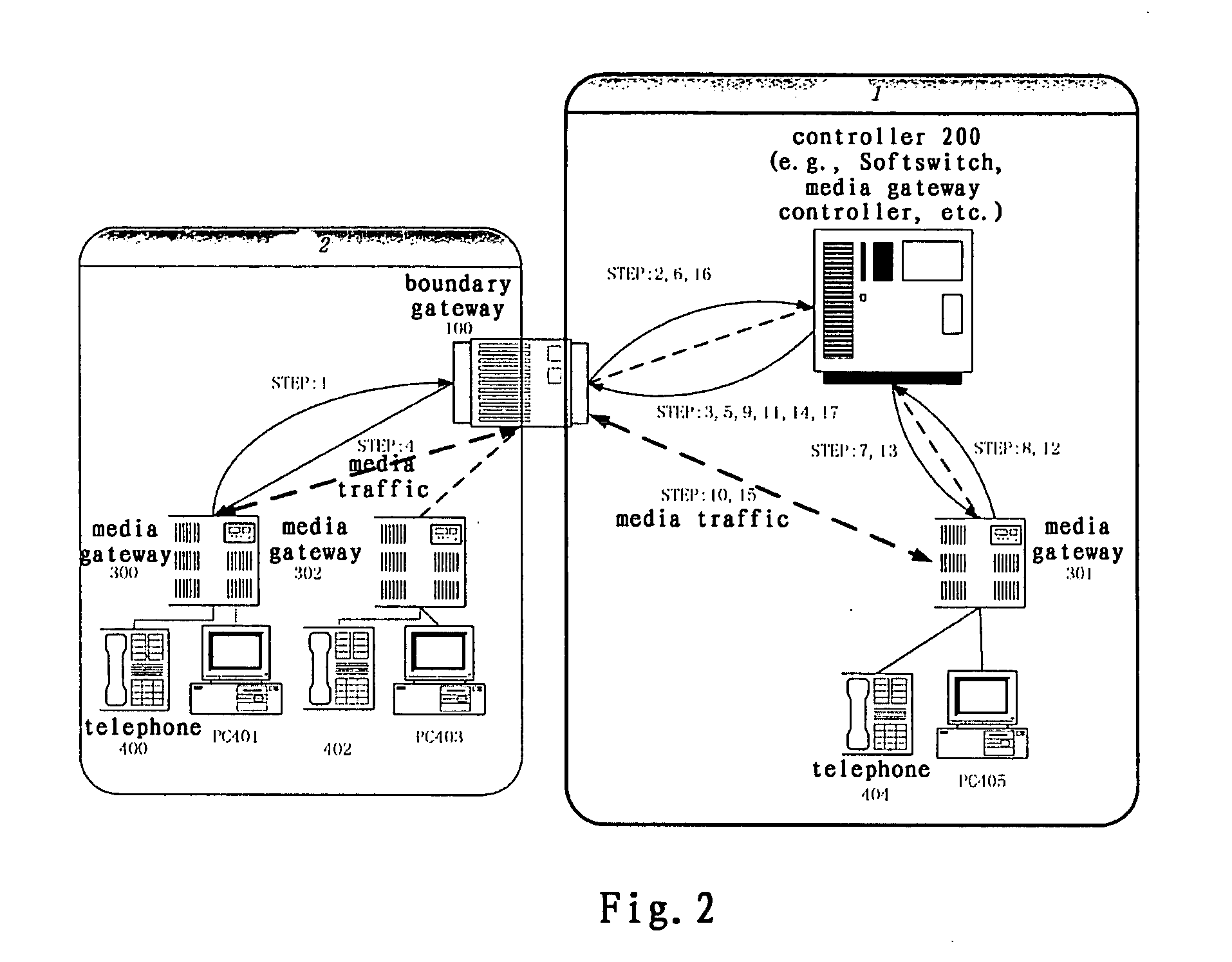
System and method for implementing multimedia calls across a private network boundary
ActiveUS20070140267A1Integrity guaranteedData switching by path configurationWireless commuication servicesInformation processingPrivate network
A system and method of the present invention for implementing multimedia calls across a private network boundary is provided, the system comprising a public network and at least one private network, and at least the following hardware components: at least one media gateway for connecting with multimedia terminals of various protocols; at least one boundary gateway for connecting the private network and the public network and performing the translation of a private network address and a public network address between each other, wherein each boundary gateway is provide with an unique subnetwork ID to correspond to the private network connected therewith; a call controller for establishing calls and controlling service logics, in which is recorded the correspondence relationship information of all said boundary gateways and the subnetwork IDs; wherein, the call controller processes a call concerning a private network according to the subnetwork ID information. The system and method of the present invention is simple to implement, has high efficiency and wide application range; saves the boundary gateway resources, does not modify the signaling content and retain its integrity; is applicable to the media gateways of various protocols, and has a high adaptability.
Owner:ZTE CORP
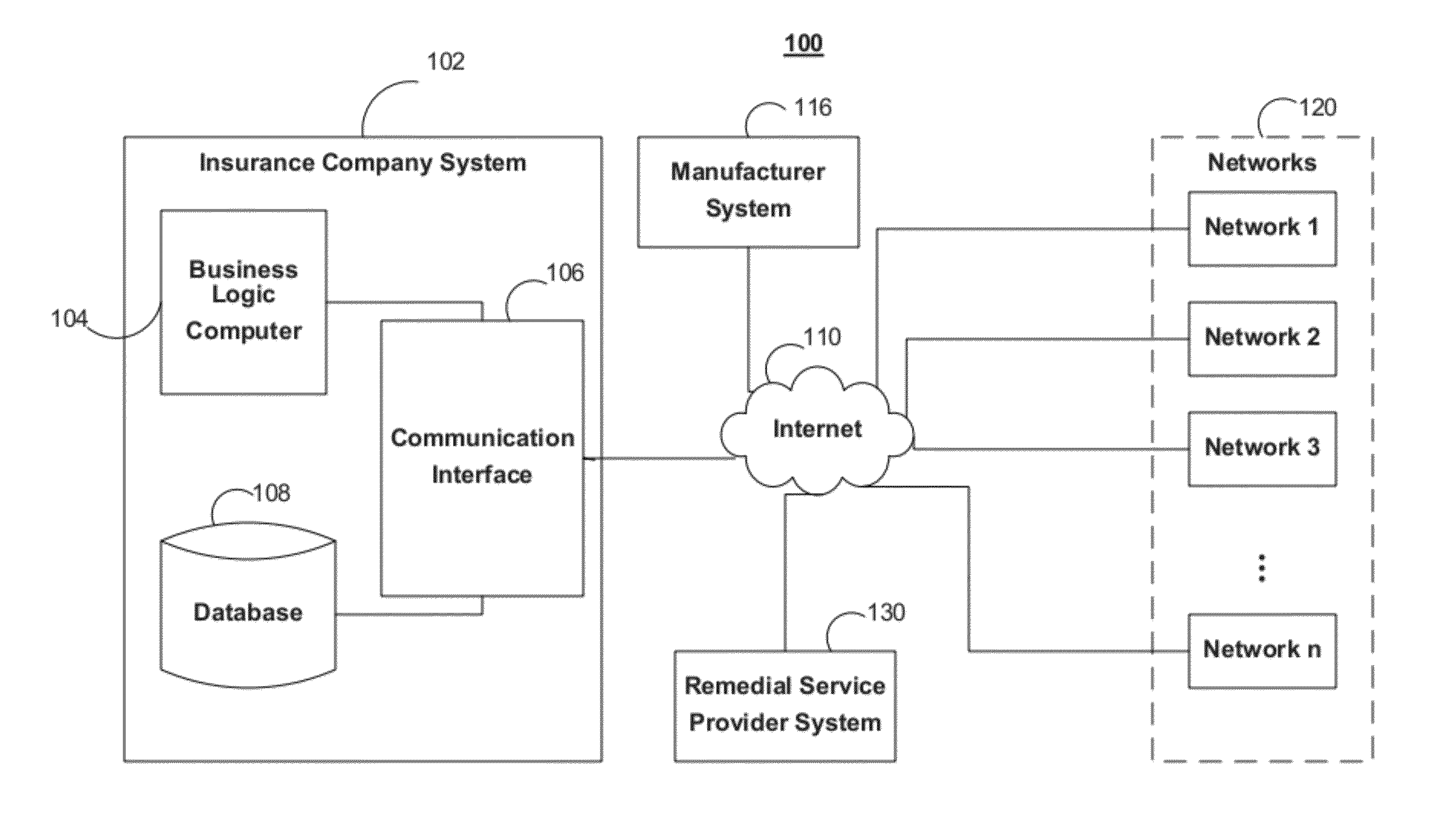
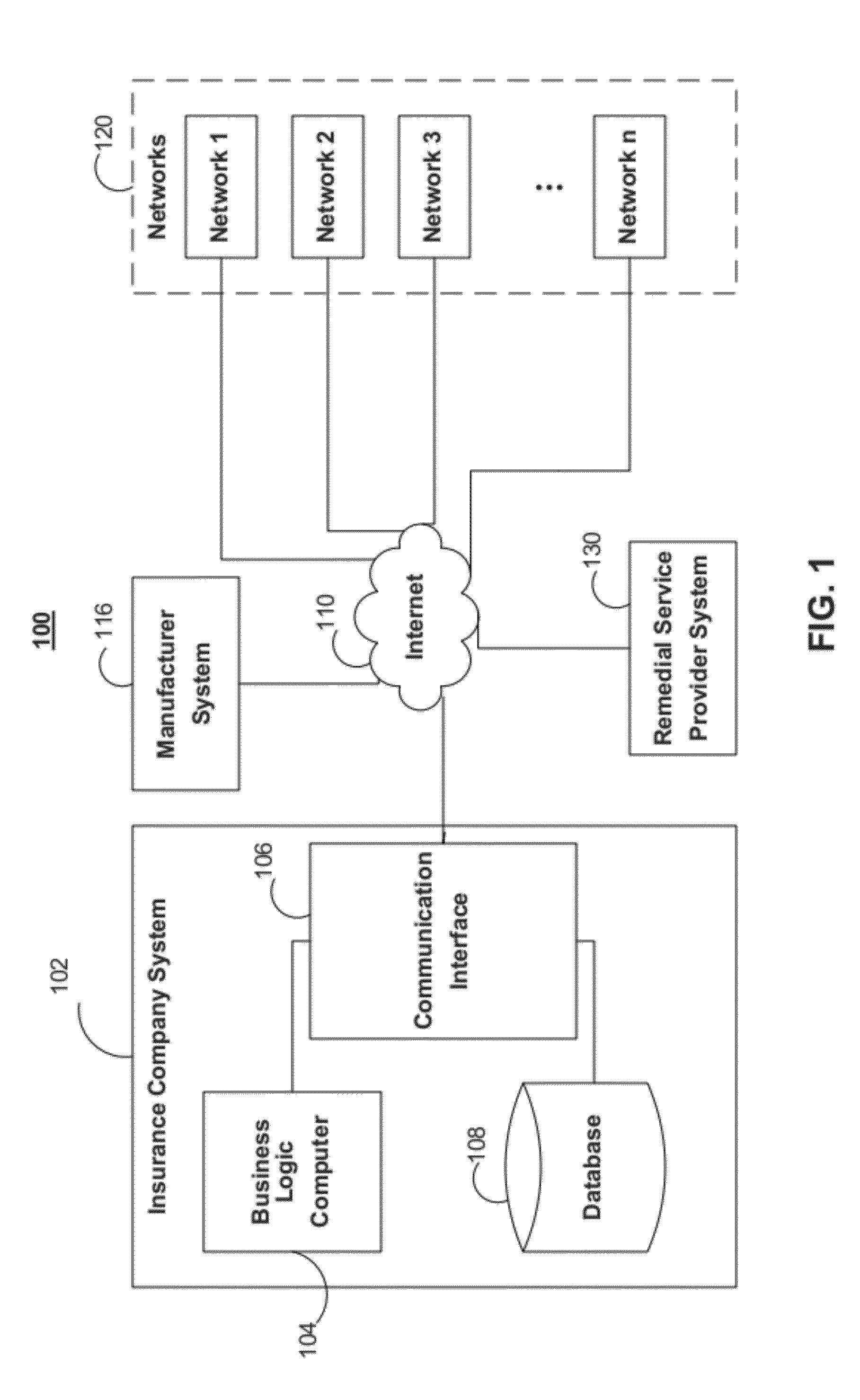
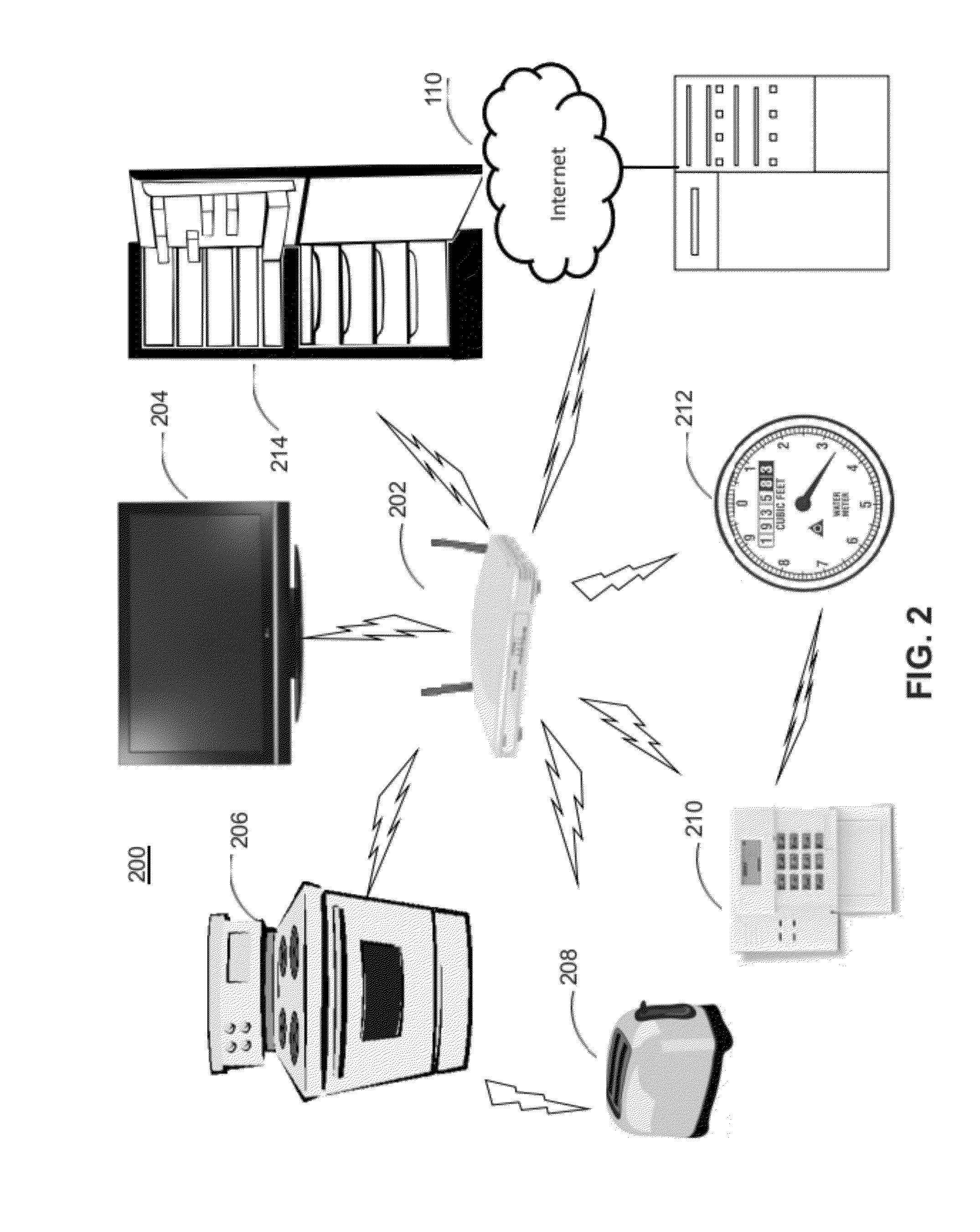
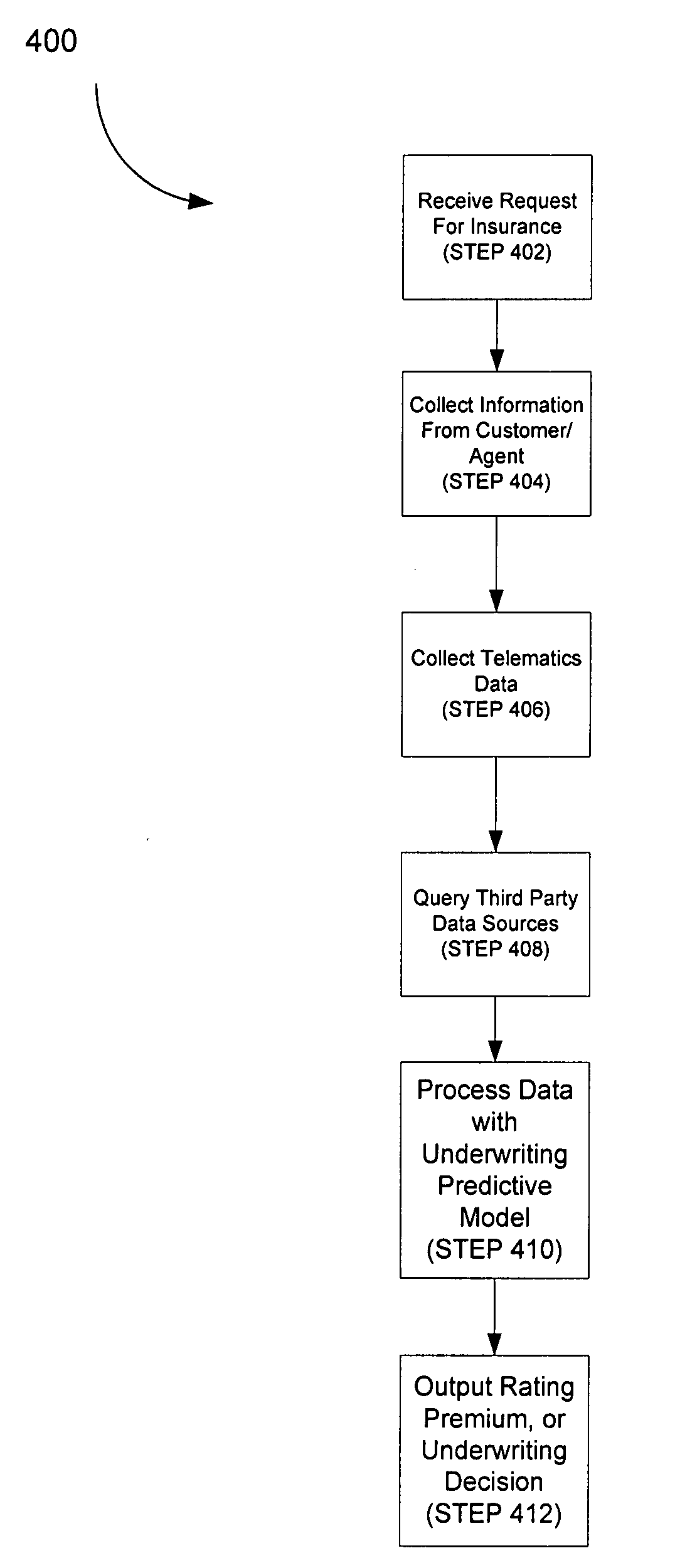
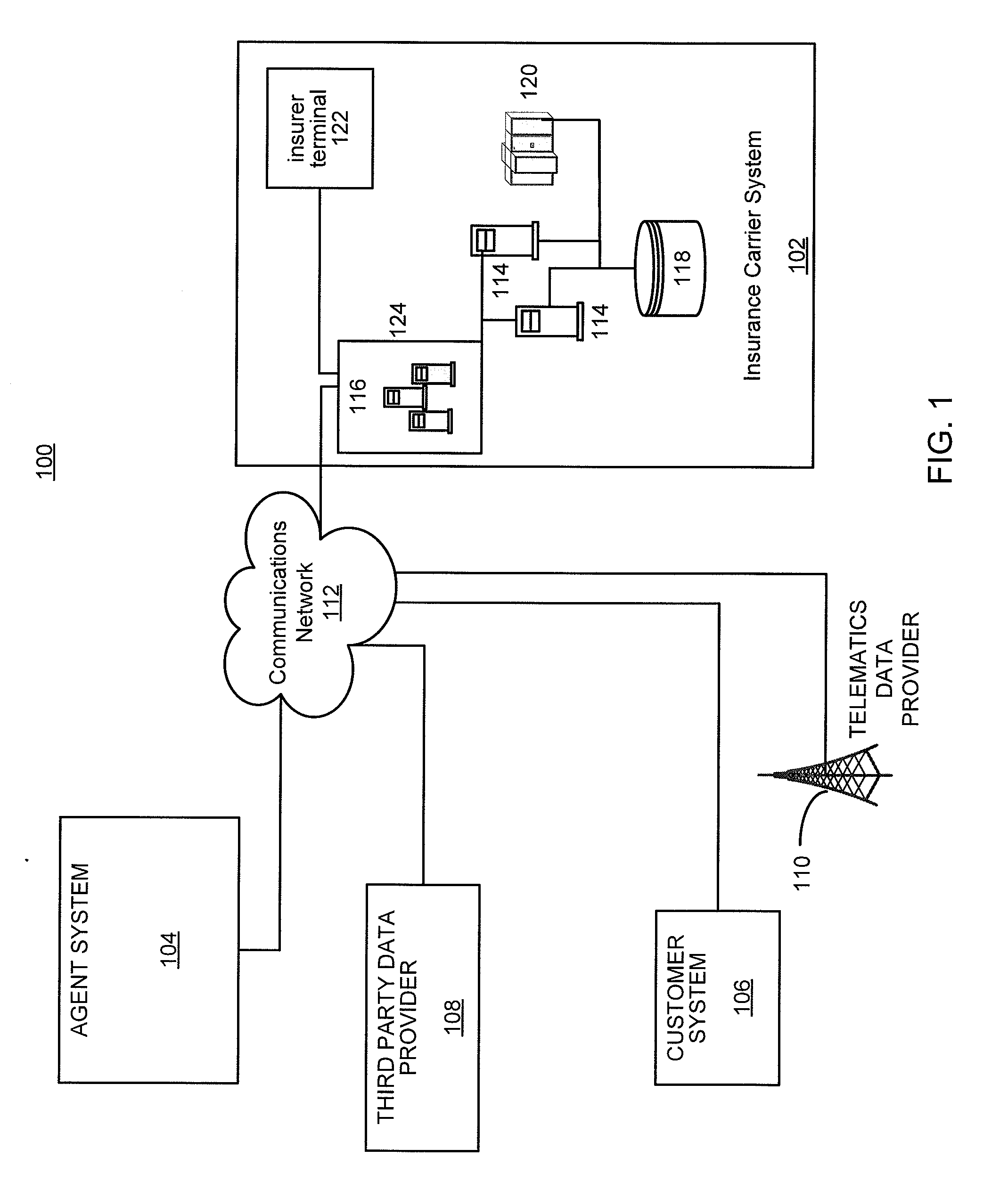
System and method for active insurance underwriting using intelligent ip-addressable devices
A system and method are disclosed herein for maintaining an inventory of assets located at an insured property covered under an insurance policy based on data received from IP-addressable devices located at the property. The system includes an inventory database for storing inventory information about assets located at an insured property, a communication interface for receiving registration and operational data associated with an IP-addressable device, and a business logic computer. The business logic computer creates a data structure for storing inventory information about assets located at the insured property in the inventory database for each insured property. The business logic computer determines, for the insured property, the inventory information about the insured property's assets based on registration and operational data received from its IP-addressable devices located at the property. The business logic computer stores the insured property's inventory information in its associated data structure in the inventory database.
Owner:HARTFORD FIRE INSURANCE
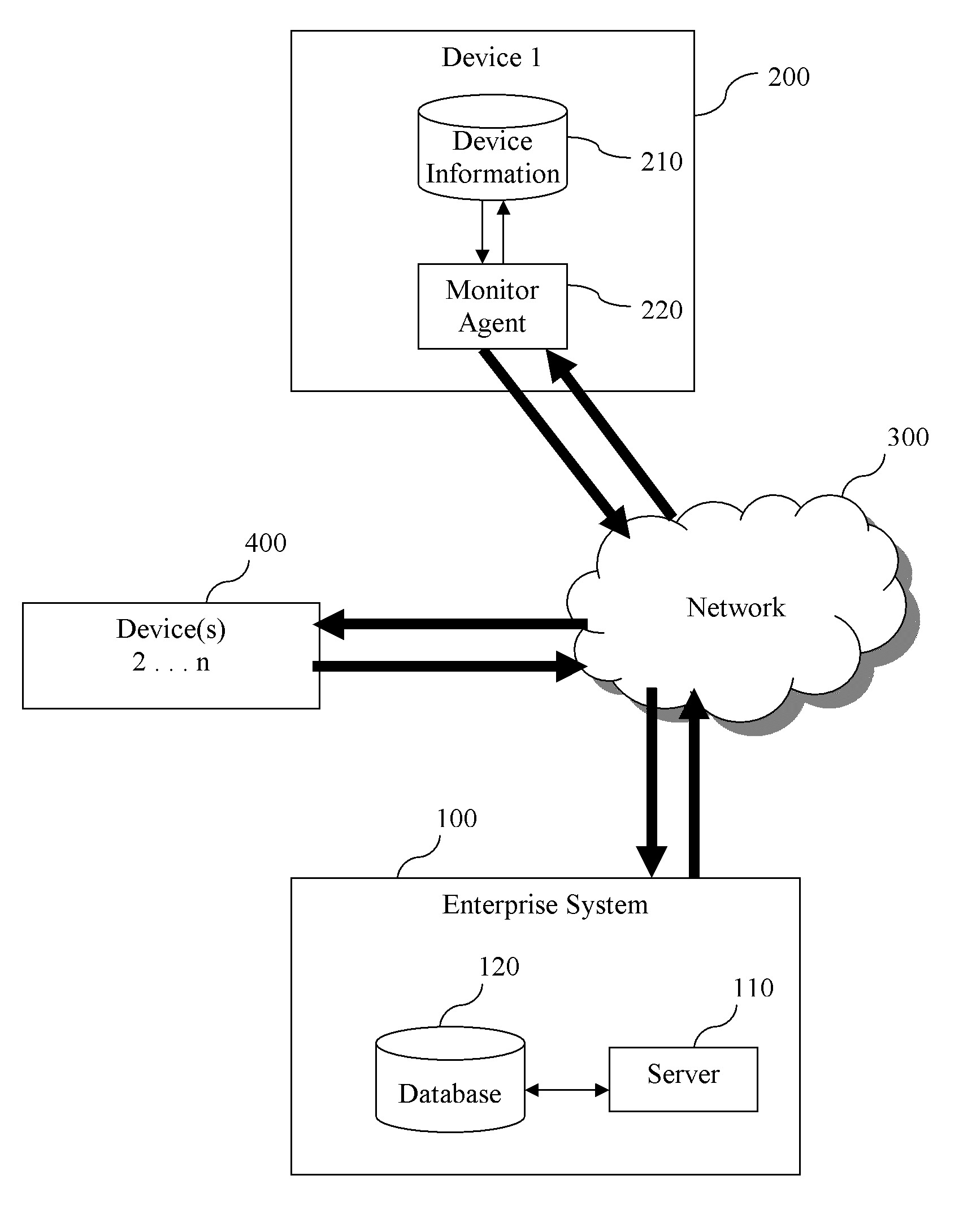
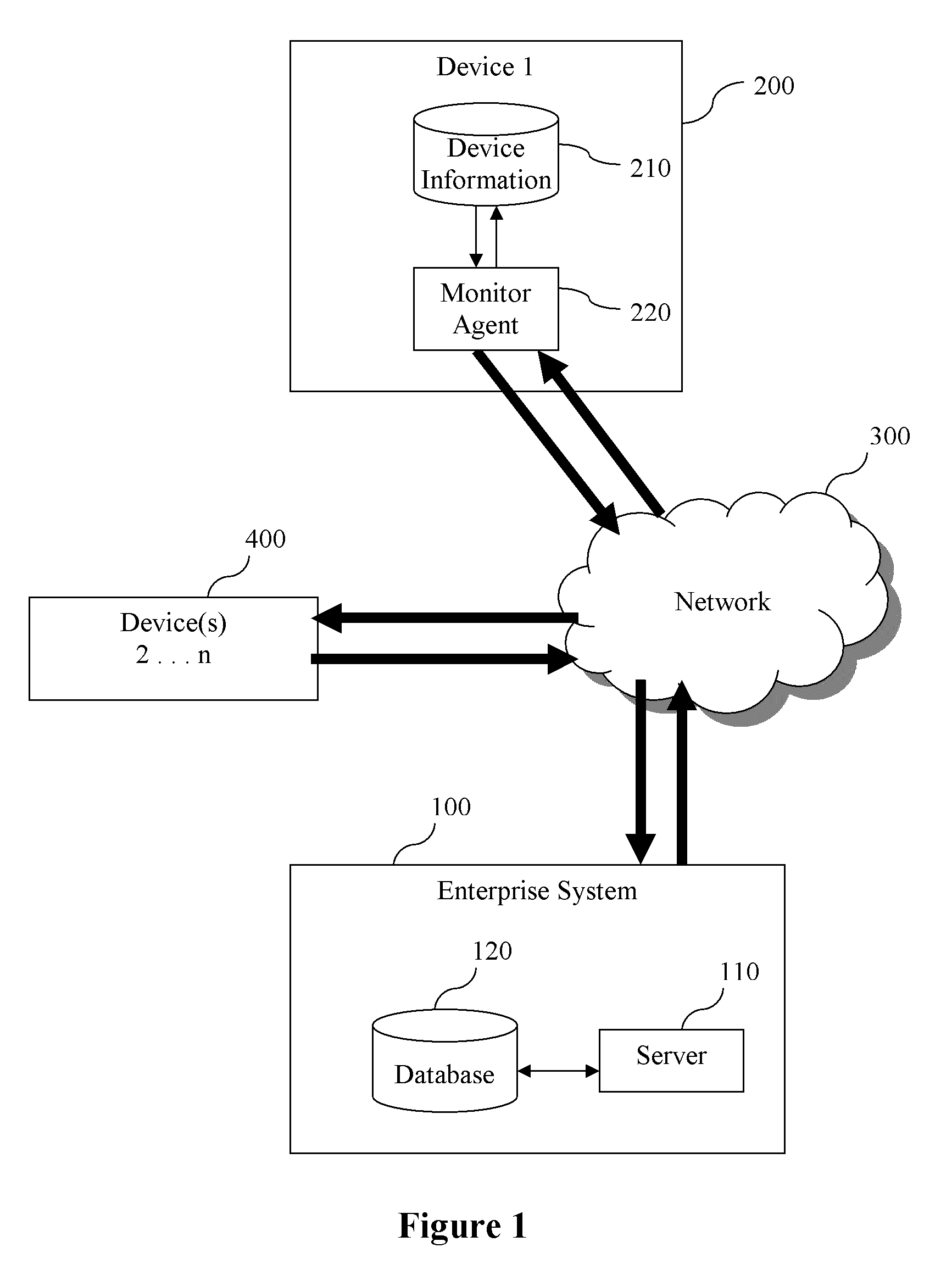
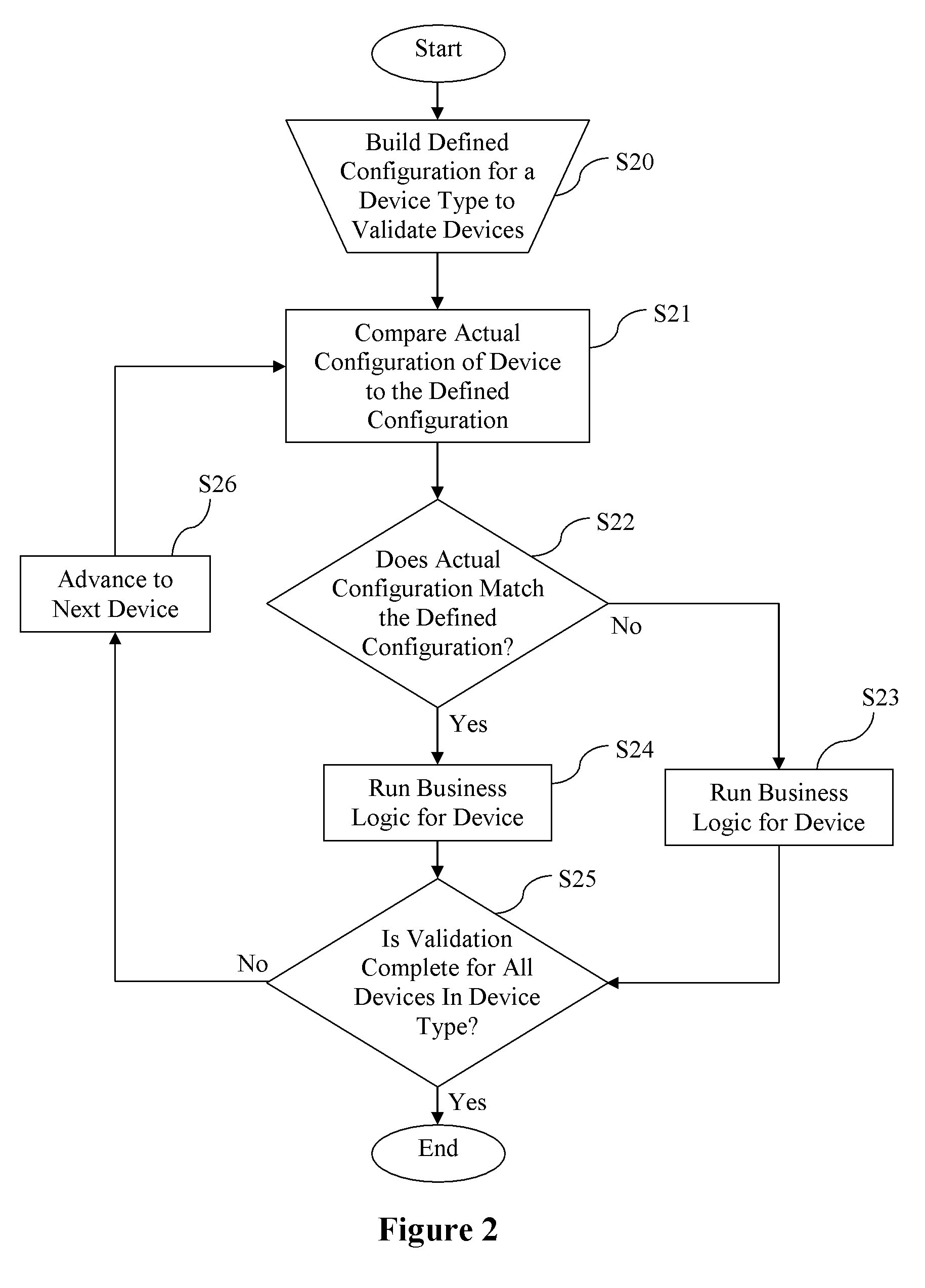
Managing configurations of distributed devices
A method manages configurations of devices in a system that communicates information between a device type. The method includes building a defined configuration for a device type. The defined configuration includes a set of value requirements. An actual configuration having values associated with the device is compared to the defined configurations. The actual configuration and defined configuration are stored in a database of the enterprise. The method also includes determining, in the enterprise, if the values of actual configuration match the corresponding value requirements of the defined configurations. The method runs business logic associated with the device based on a result from the step of determining if the values of the actual configuration match the corresponding values of the defined configurations. The matched configurations are stored for subsequent use.
Owner:PARAMETRIC TECH CORP
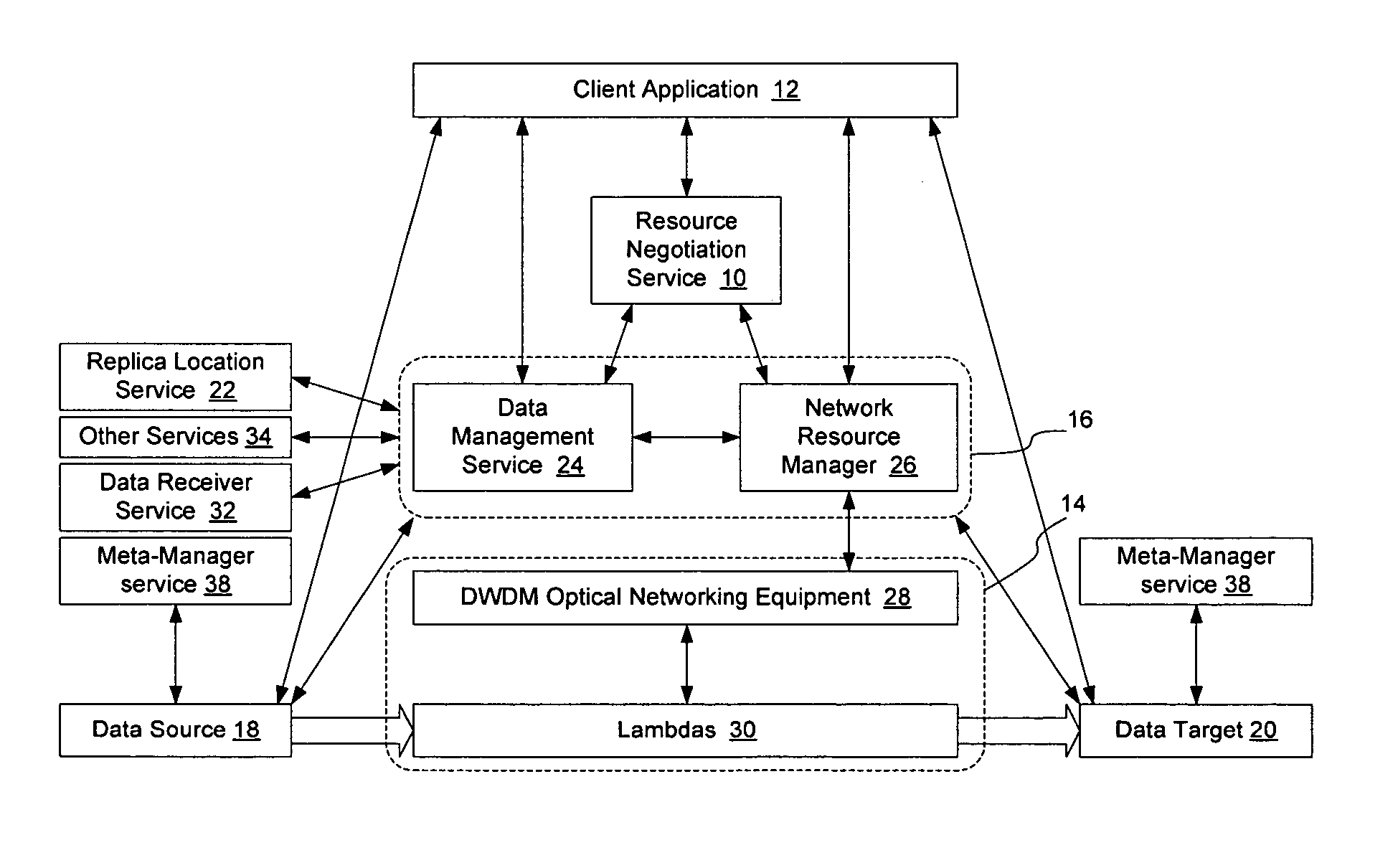
Method and apparatus for automated negotiation for resources on a switched underlay network
A resource negotiation service is provided to enable business logic decisions to be made when obtaining switched underlay network resources, to interface business logic with network conditions and schedules. The resource negotiation service may be implemented as a web service or other network service to enable business logic to be used in the selection of available network resources. This may allow policy to be used on both the subscriber side and the network provider side to optimize network resource allocations for a proposed transfer. The policy may include subscriber policy, network policy, and other factors such as current and expected network conditions. The resource negotiation service may include an interface to enable existing subscribers and new customers to obtain switched underlay resources.
Owner:NORTEL NETWORKS LTD
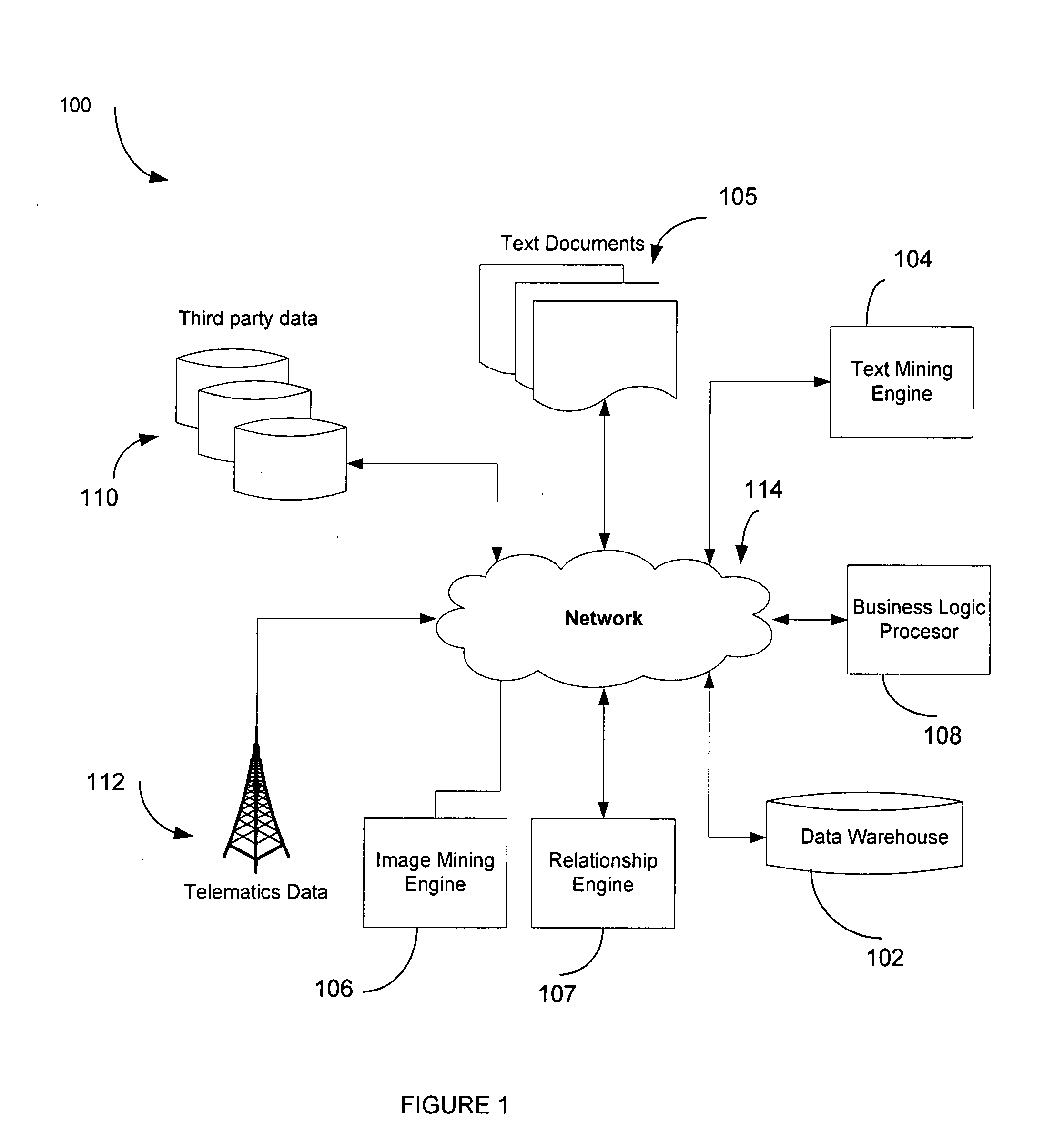
System for synergistic data processing
InactiveUS20080077451A1Improve reliabilityThe result is accurateFinanceData miningThird partyText mining
A data analysis system that includes an information mining engine for extracting structured data from unstructured data, a data store for storing the extracted structured data, data received from third party data sources, and data received from sensors monitoring insured property is described. The system also includes a business logic processor that synergistically analyzes the structured data extracted by the text mining engine, the data received from the sensor, and the data received from the third party data source to make an insurance evaluation.
Owner:HARTFORD FIRE INSURANCE
System and method for an automated validation system
System and method are disclosed herein for an automated validation system for validating whether a property of a policyholder receiving at least one insurance benefit is currently receiving remote monitoring services, as claimed by the policyholder. The system comprises an application server, a trusted third party server, and a business logic computer. The application server requests the trusted third party server to validate whether the property of the policyholder is presently receiving remote monitoring services from a service provider. A business logic computer can adjust the policyholder's insurance policy based on the received validation results.
Owner:HARTFORD FIRE INSURANCE
Rule-based filtering and alerting
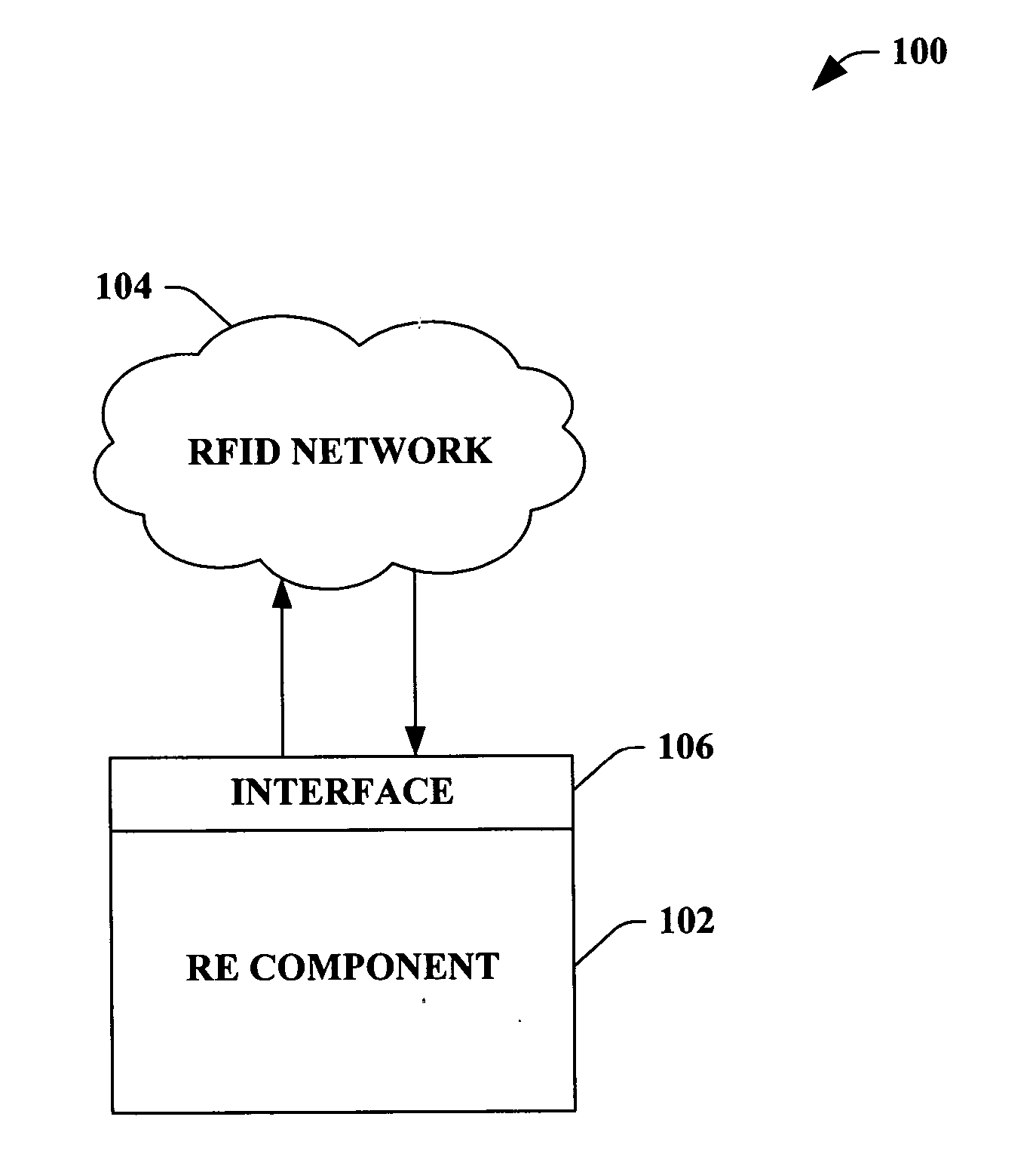
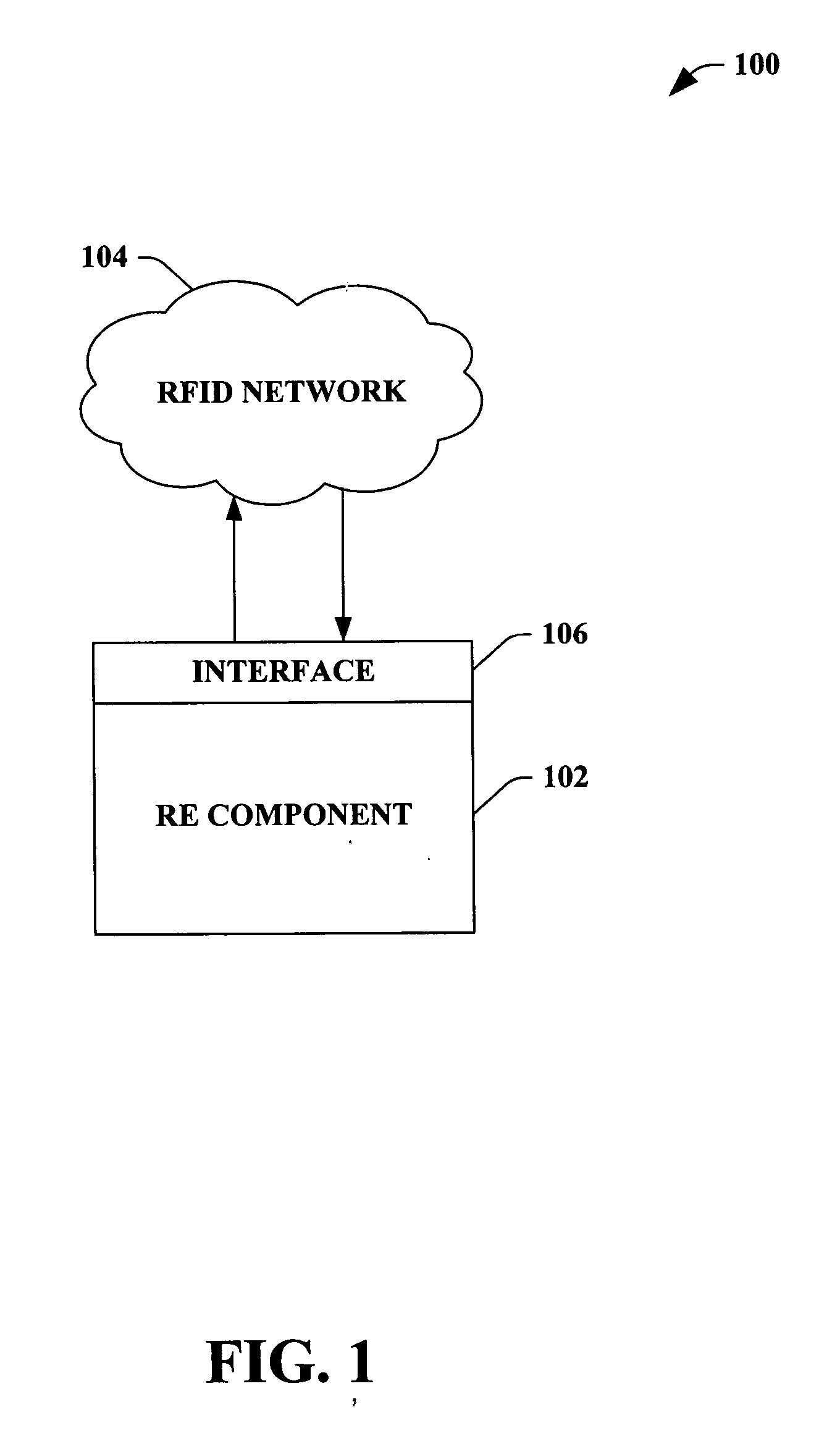
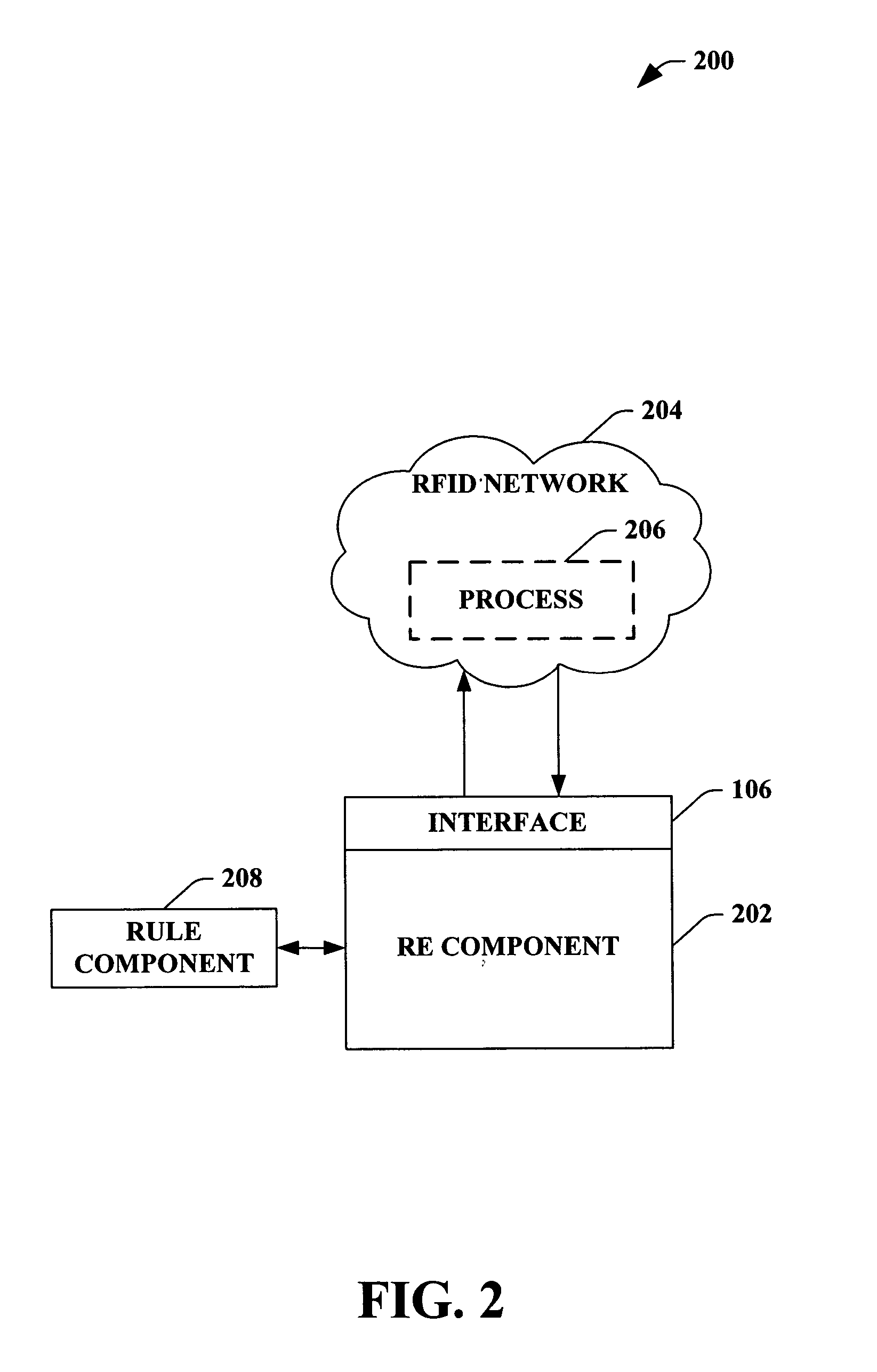
ActiveUS20060047789A1Convenience to mergeElectric signal transmission systemsDigital data processing detailsSubject matterBusiness logic
The claimed subject matter provides a system and / or a method that facilitates utilizing rule-based technology with radio frequency identification (RFID) network. An interface can receive real-time RFID data from a process comprising at least one device collection in the RFID network, wherein a rules engine (RE) component can employ a declarative event policy associated with the RFID network as rules. The RE allows dynamic updates of business logic associated with applications in real-time without the re-start and / or stop the applications. The system and / or method further comprises a vocabulary component that provides terms that defines at least one of the rule, rule condition, and action based at least in part upon an industry specific nomenclature.
Owner:MICROSOFT TECH LICENSING LLC
Methods, apparatuses, systems, and articles for determining and implementing an efficient computer network architecture
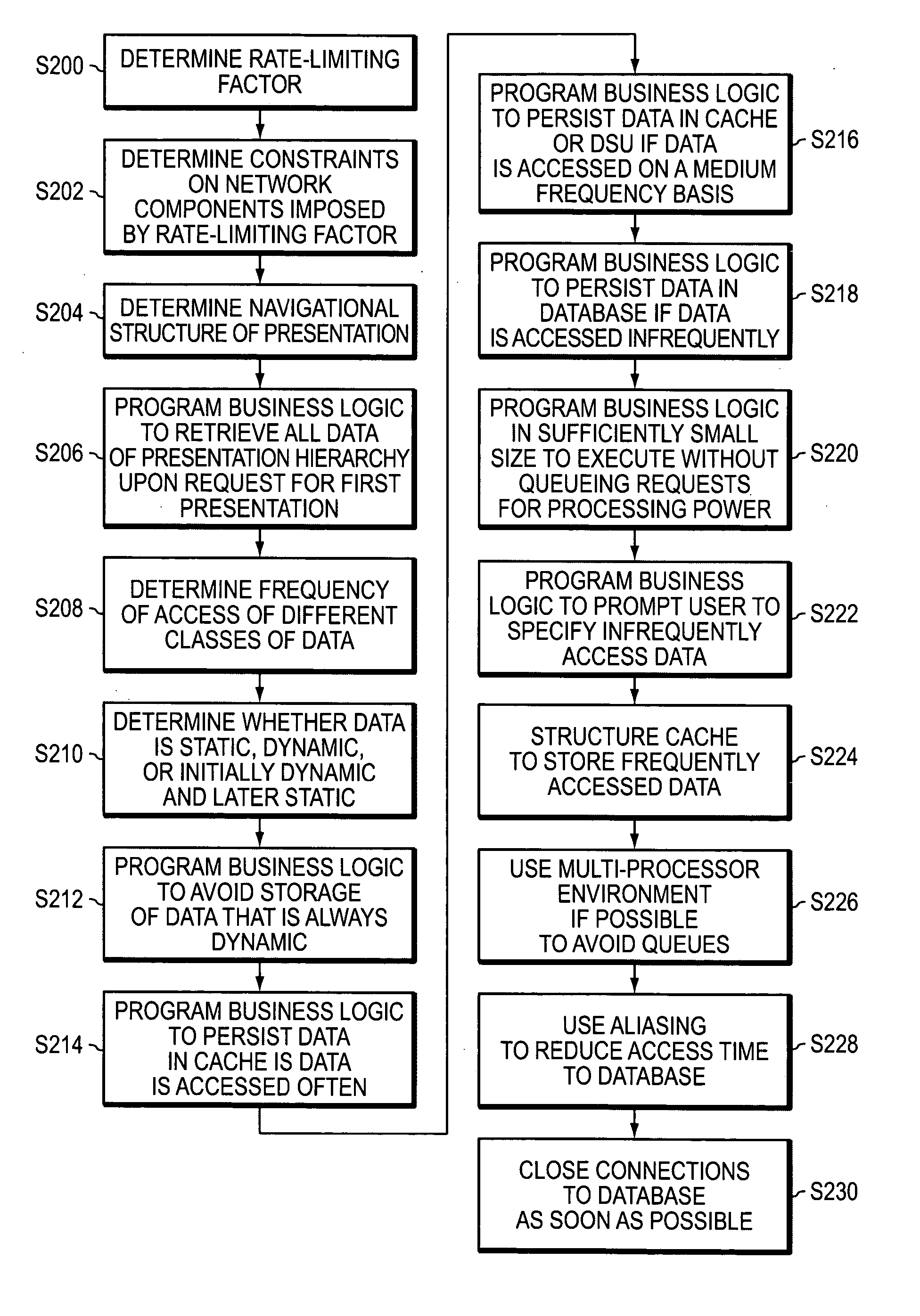
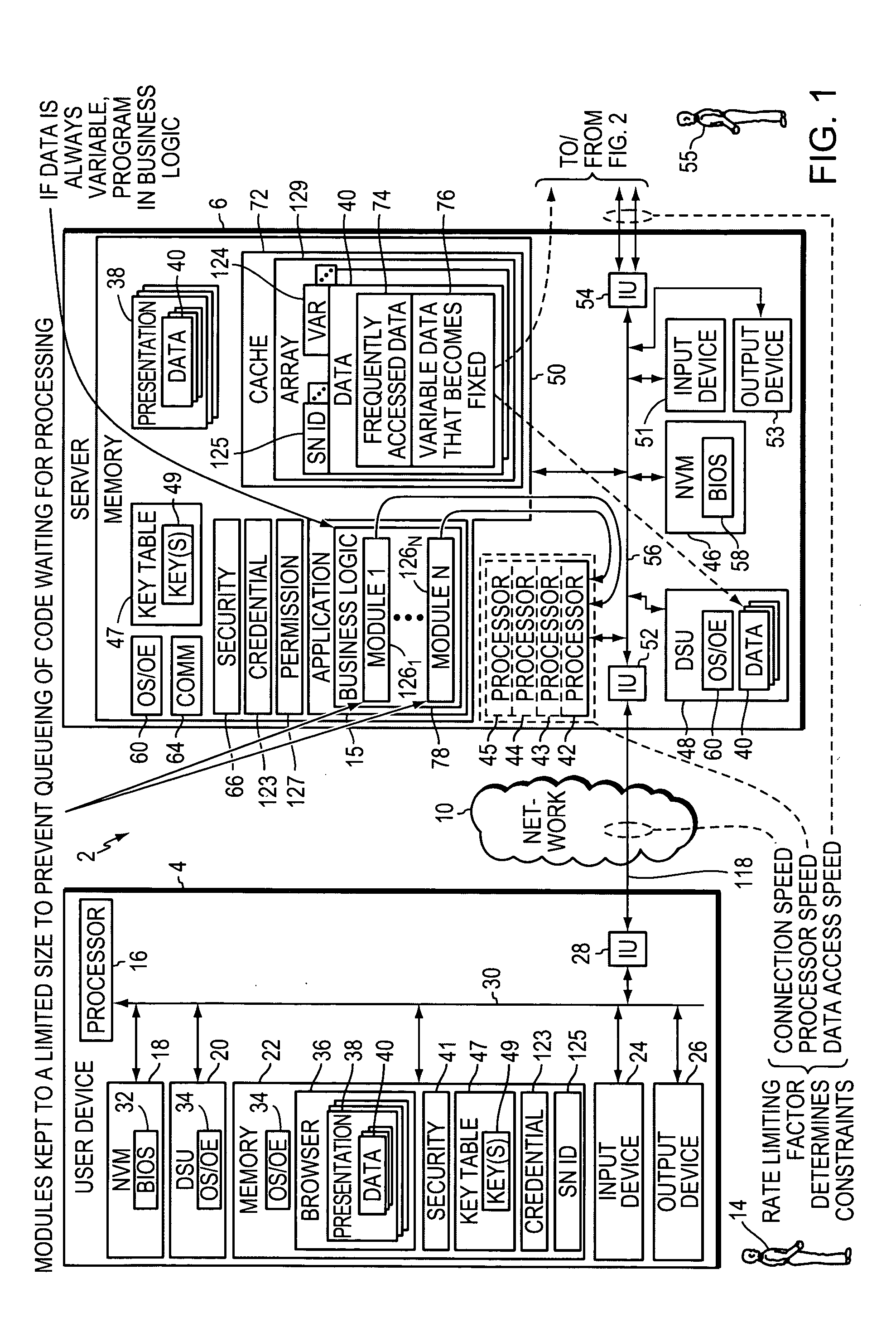
InactiveUS20050138198A1Reduce system performanceAvoid queuingMultiple digital computer combinationsTransmissionRate limitingNetwork architecture
Methods, apparatuses, systems, and articles of the invention are used to enhance the efficiency of a computing environment, and to improve its responsiveness to one or more users. In the invention, queuing of data or computer instructions is avoided since this would detract from best case performance for a network environment. The rate-limiting factor for the network is determined, and all constraints imposed by the rate-limiting factor are determined. Business logic is programmed in modules sufficiently small to avoid queuing of instructions. Data is stored by frequency of access and persistence to increase responsiveness to user requests. Requests for data from a data storage device are fulfilled not only with the requested data, but also additional data which is likely to be requested in the navigational hierarchy of presentations to which the requested data belongs.
Owner:IT WORKS
System and method for operating modules of a claims adjudication engine
InactiveUS20060149784A1High errorHigh omissionFinanceOffice automationFinancial transactionLine item
A system and method for configuring an adjudication system to adjudicate a claim transaction. The system and method comprise: receiving the claim transaction containing line items describing an insured service for a recipient to be financed by a payer for the insured service; providing an adjudication engine for coordinating the adjudication processing of the received claim transaction; representing the claim transaction as a plurality of business objects coupled to a database such that the business objects are selected from a set of available business objects, the business objects coupled to the adjudication engine and configured for containing data instances of the claim transaction; and selecting a plurality of adjudication modules for coupling to the plurality of business objects, the plurality of adjudication modules selected from a set of available adjudication modules, the selected adjudication modules configured for providing business logic applied to the business objects during the adjudication processing to manipulate the data instances of the business objects; wherein the configured adjudication system adjudicates the data instances of the business objects according to the business logic of the selected adjudication modules for determining an adjudication status of the claim transaction.
Owner:EMERGIS INC
System and method for populating HTML forms using relational database agents
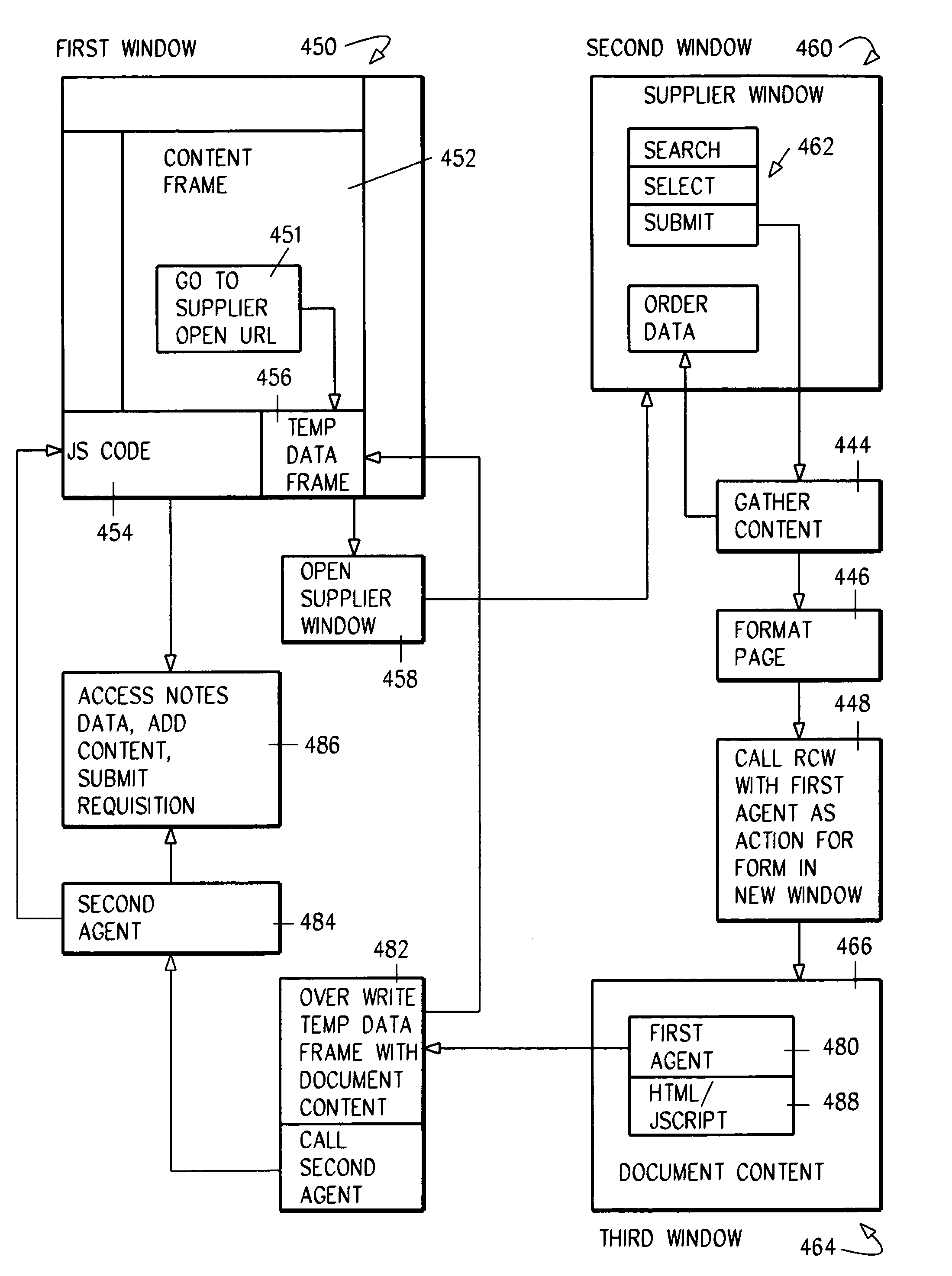
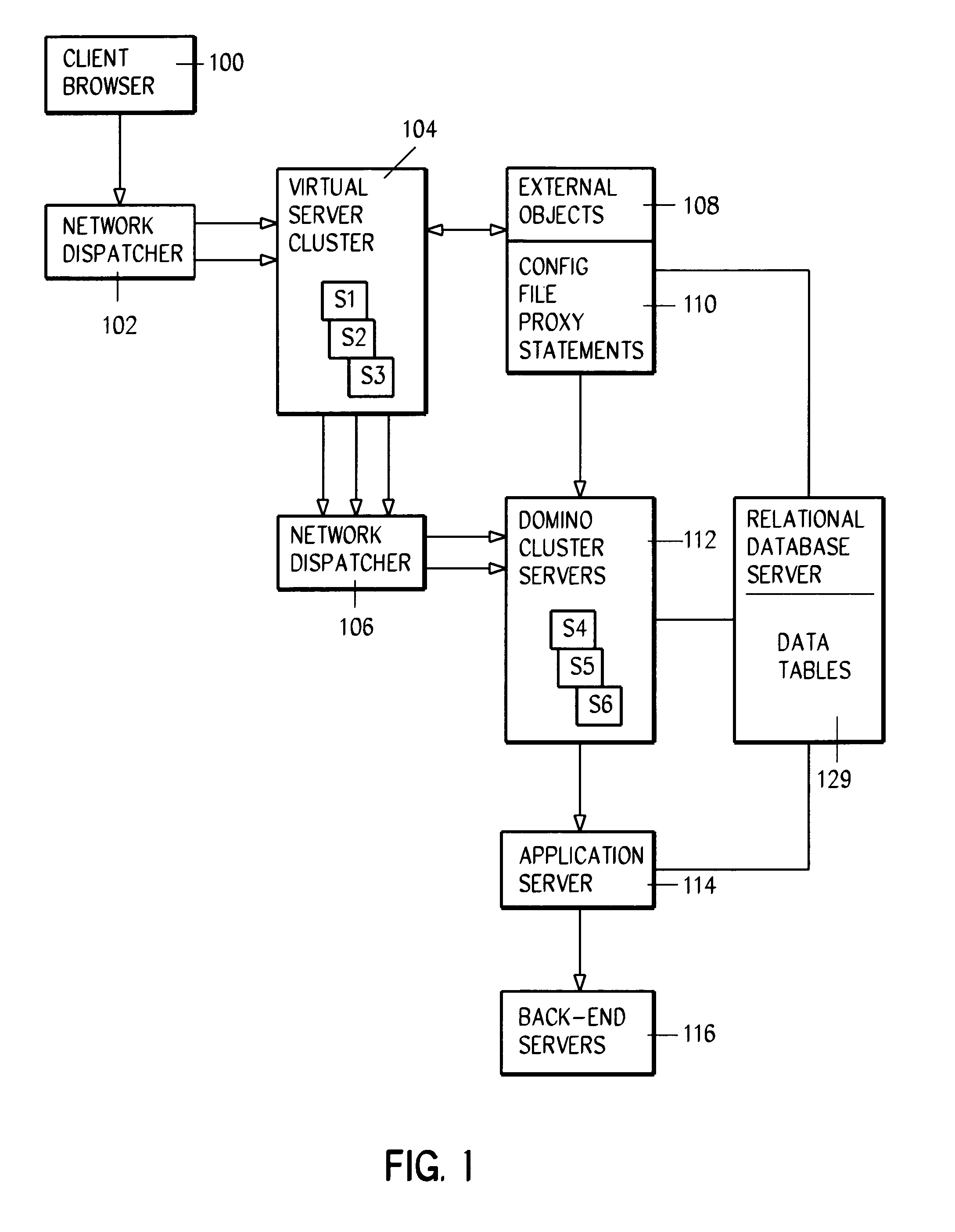
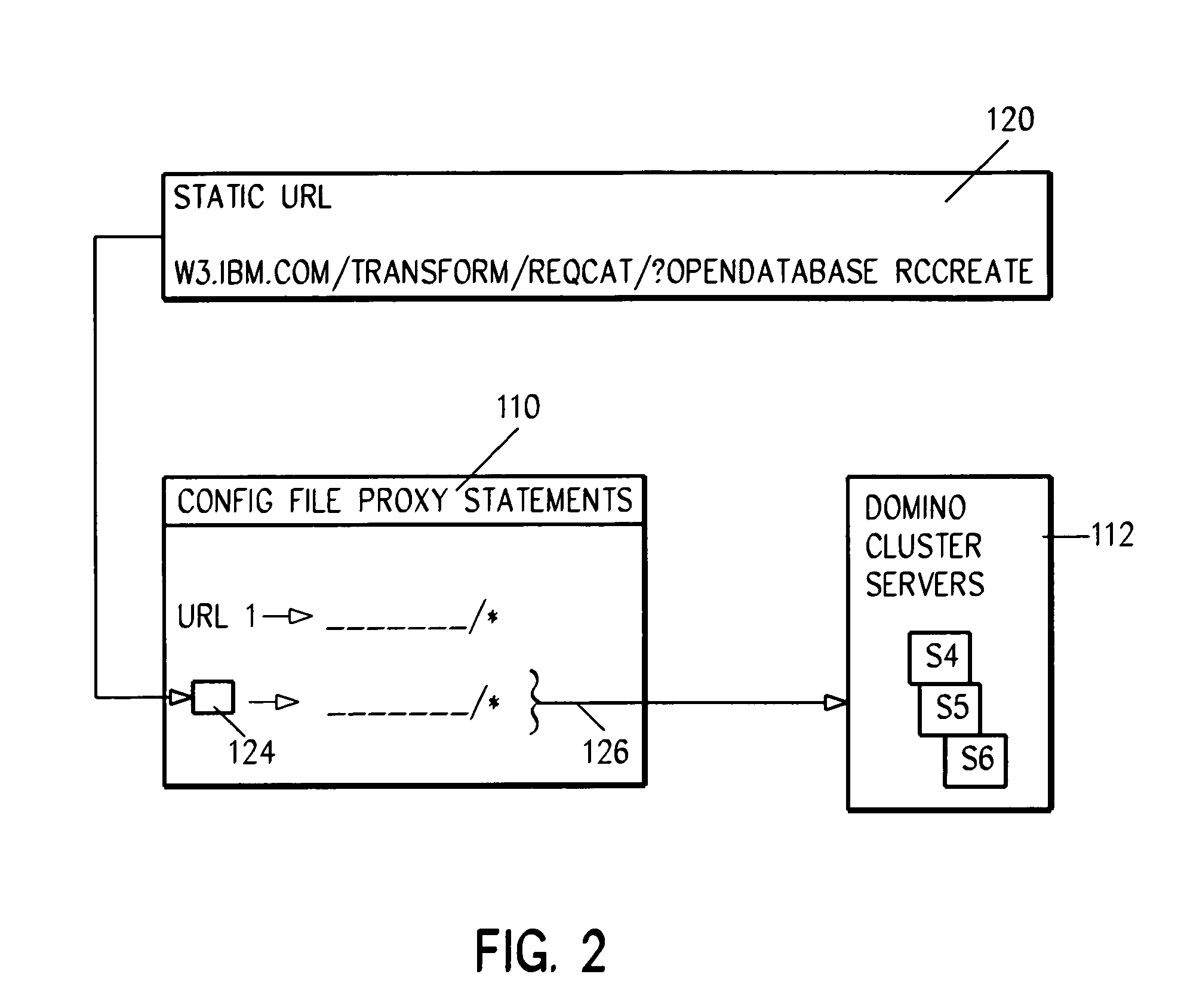
A hybird Notes / DB2 environment provides a requisition catalog on the Web. Client browsers are connected to a GWA infrastructure including a first network dispatcher and a virtual cluster of Domino.Go servers. The network dispatcher sprays out browser requests among configured .nsf servers in virtual server cluster. Communications from this virtual server cluster are, in turn, dispatched by a second network dispatcher servers in a Domino cluster. External objects, primarily for a GUI, are served in a .dfs and include graphic files, Java files, HTML images and net.data macros. The catalog is built from supplier provided flat files. A front end is provided for business logic and validation, as also is a relation database backend. HTML forms are populated using relational database agents. A role table is used for controlling access both to Notes code and DB2 data. Large amounts of data is quickly transferred using an intermediate agent and window.
Owner:KYNDRYL INC
Processing data-centric business models
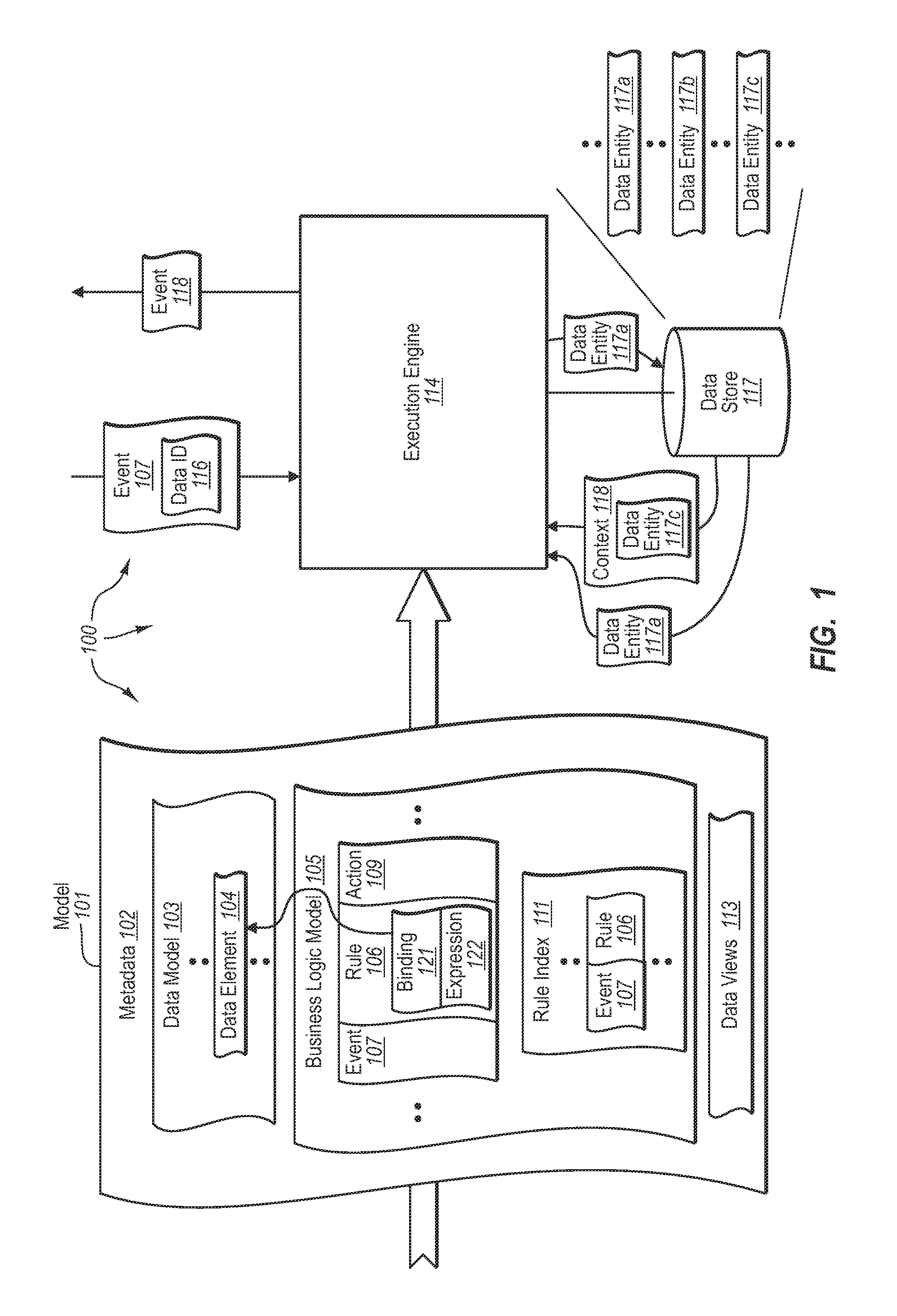
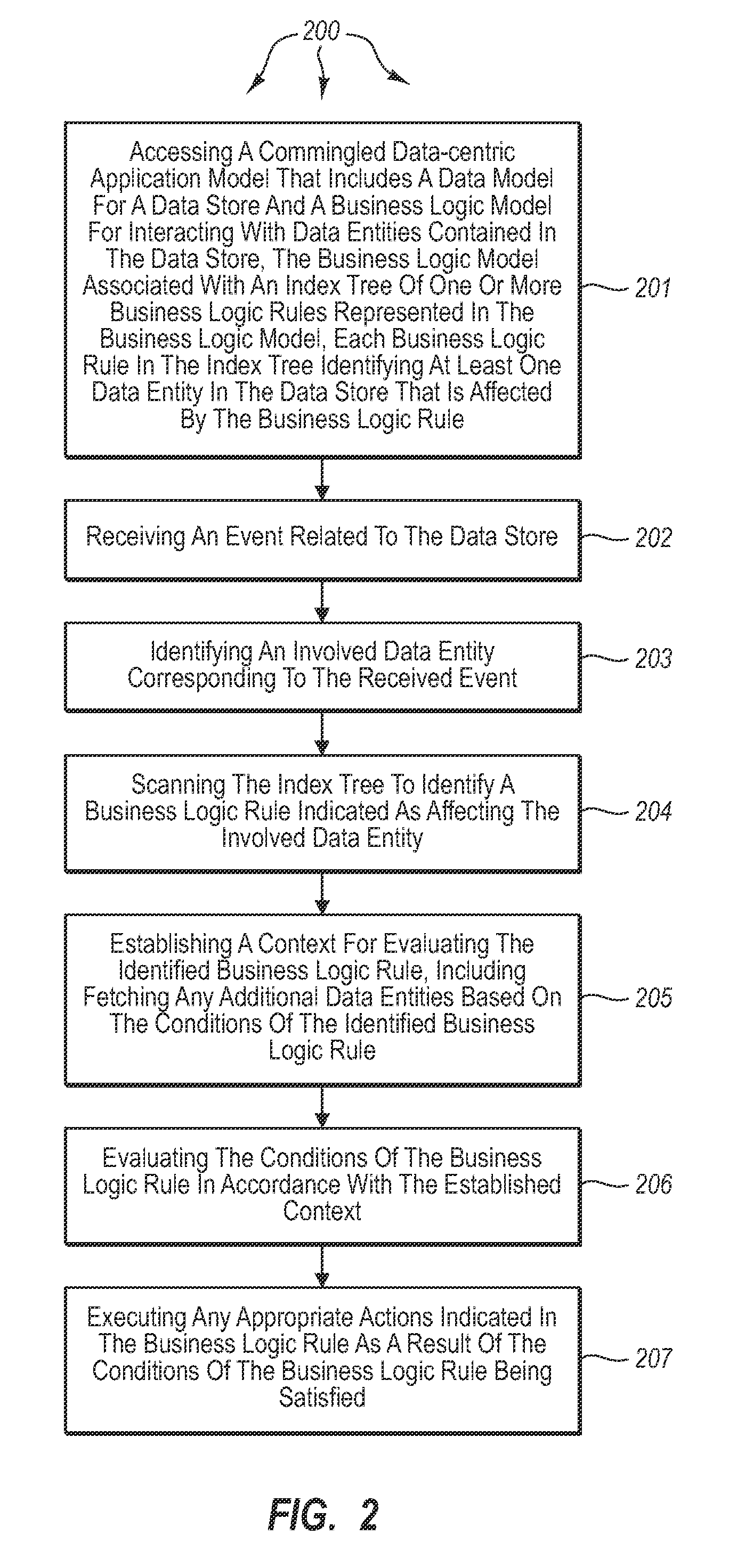
ActiveUS7599901B2Knowledge representationSpecial data processing applicationsApplication softwareData store
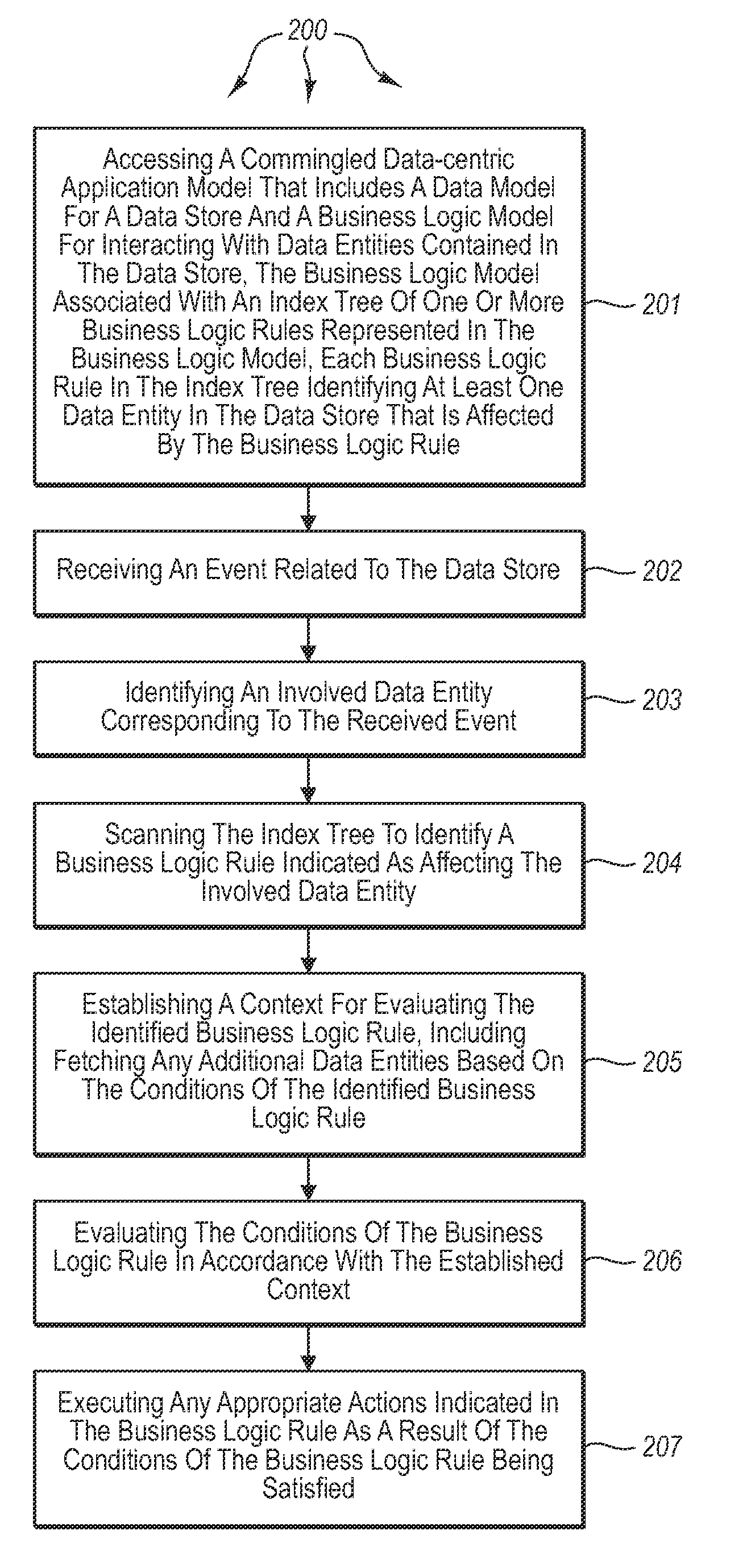
The present invention extends to methods, systems, and computer program products for processing data-centric business models. An execution engine accesses a commingled data-centric application model that includes a data model for a data store and a business logic model for interacting with data entities contained in the data store. The execution engine receives an event related to the data store and identifies an involved data entity corresponding to the received event. The execution engine identifies a business logic rule indicated as affecting the involved data entity. The execution engine establishes a context for evaluating the identified business logic rule. The execution engine evaluates the conditions of the business logic rule in accordance with the established context. The execution engine executes any appropriate actions indicated in the business logic rule as a result of the conditions of the business logic rule being satisfied.
Owner:MICROSOFT TECH LICENSING LLC
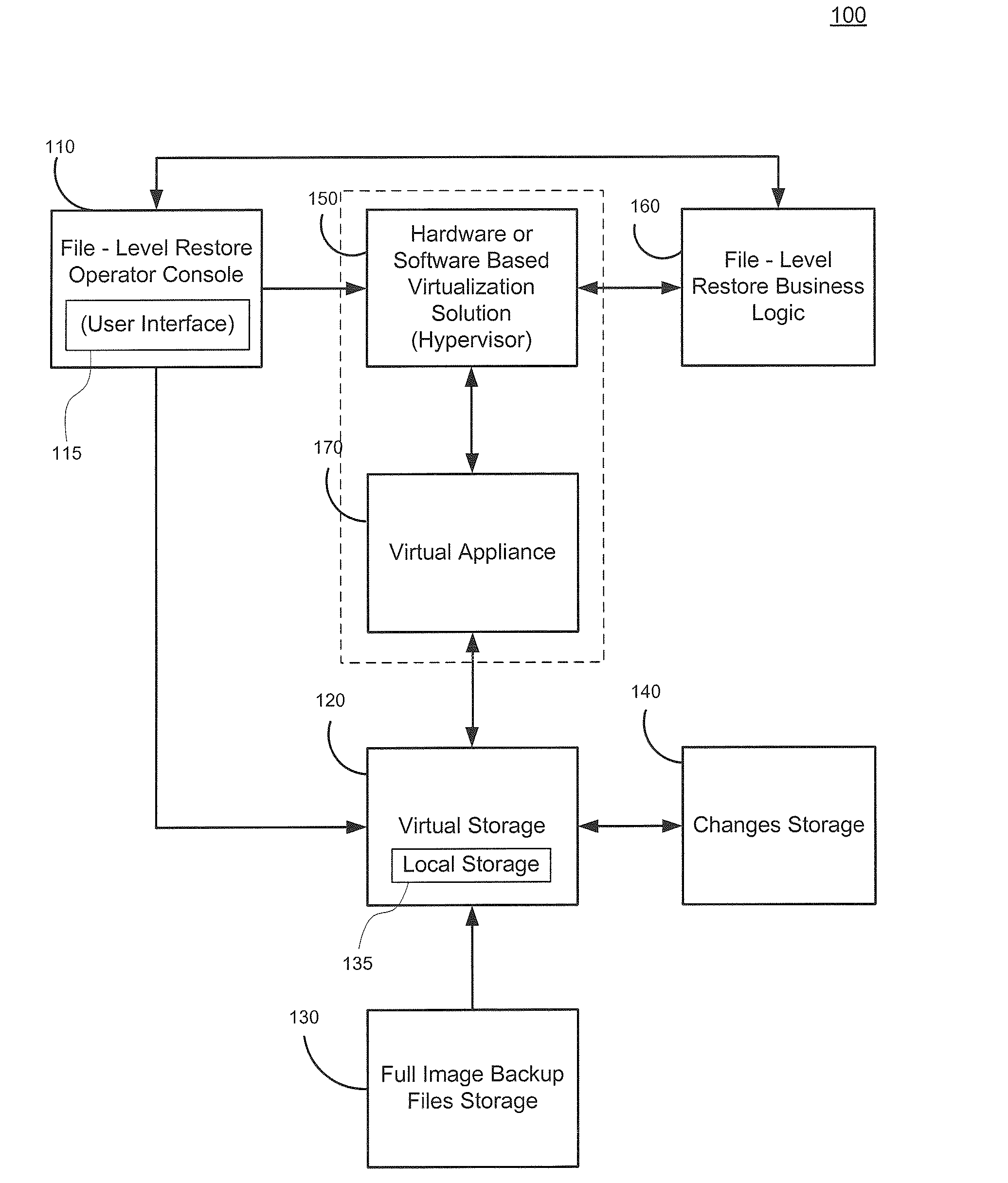
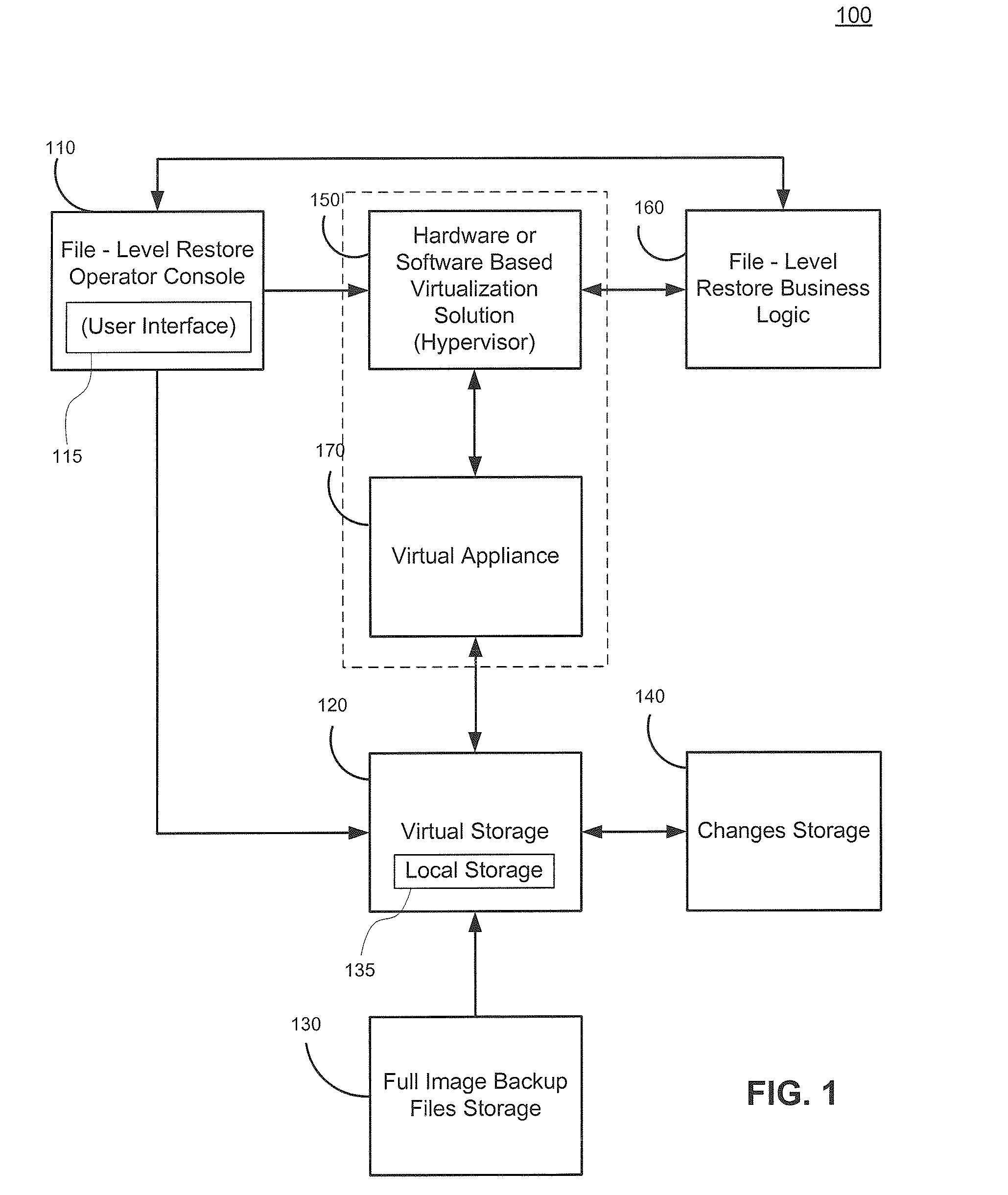
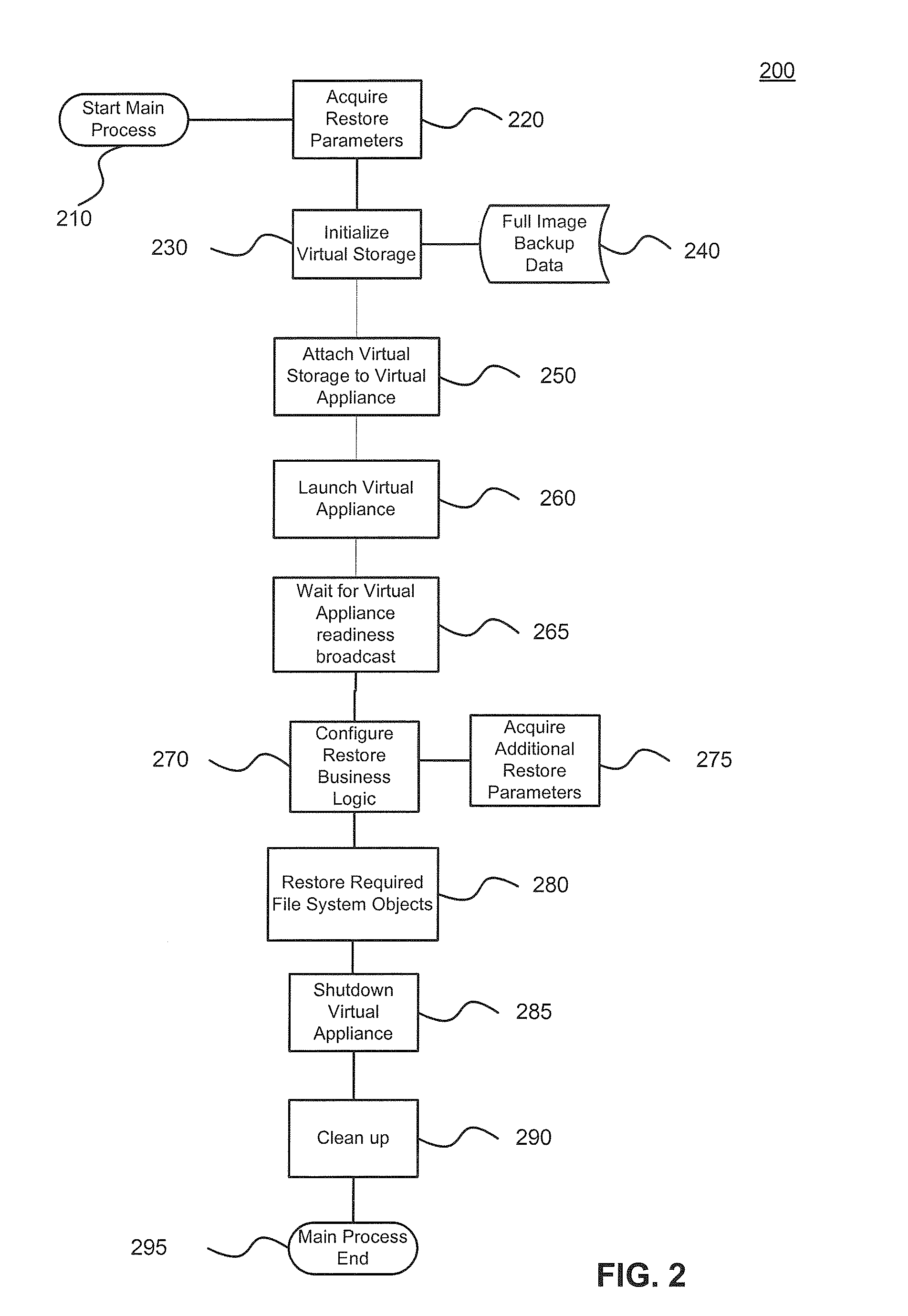
Cross-platform object level restoration from image level backups
ActiveUS20110196842A1Avoid system instabilityReduce developmentDigital data processing detailsError detection/correctionOperational systemFile system
Systems and methods for restoring file system objects from image level backups of servers. The method receives a selection of an image level backup of a source, file system object(s) to be restored, and restoration parameters identifying a destination. The method initializes and attaches a virtual storage to a virtual appliance and an associated hypervisor. The method stores virtual storage data changes resulting from the file system object restoration in changes storage. The method preserves file system object information, wherein the file system object information corresponds to the source operating system (OS) and file system. The method preserves file system object information such as permissions and ownership through business logic that ensures that the file system object information for restored file system object(s) on the destination match file system object information from the source, even when the method operates on a host running a different OS than the source server.
Owner:VEEAM SOFTWARE GROUP GMBH
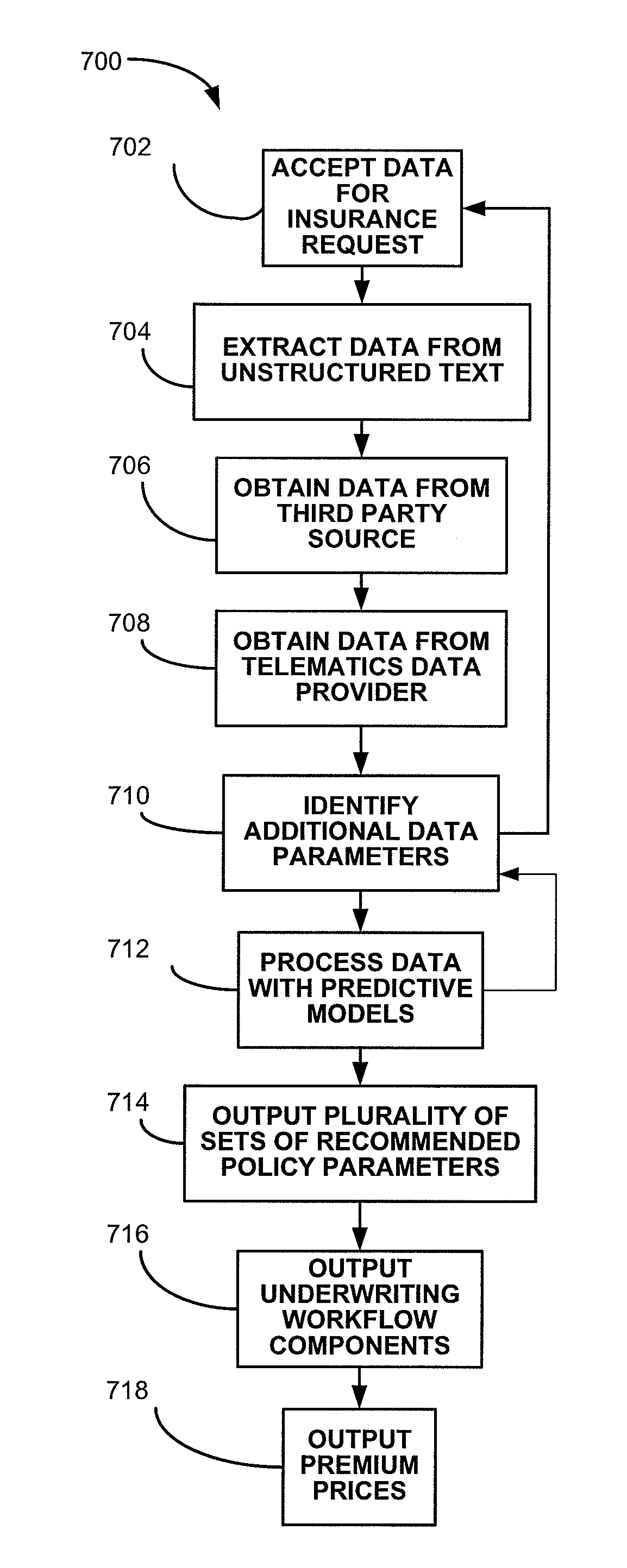
System and method for utilizing interrelated computerized predictive models
The invention relates to a system for handling insurance requests, such as new coverage applications, renewal applications, and insurance quote requests. The system includes at least two computerized predictive models whose outputs each serve as inputs to the other. A business logic module is included in the system to process insurance requests with the predictive models to determine one or more sets of recommended policy parameters for the user and to output the determination to the user via a user interface. In various embodiments, the predictive models also output workflow components (such as underwriting workflow components) and price components (such as premium prices) corresponding to output suggested sets of coverage parameters.
Owner:HARTFORD FIRE INSURANCE
Method and system for separating business and device logic in a computing network system
ActiveUS7688960B1Minimize impactEasy to implementMultiplex system selection arrangementsInterconnection arrangementsGeneration processSource code
The present invention is directed to a method and system for use on a computer for the automated generation of commands or other data to populate tables of a database. The automated generation process of the present invention entails separating business logic from device specific logic, defining the organization of incoming data, identifying and setting default data parameters, defining the format for the output data, and implementing the command generating object oriented classes in program source code, to generate device specific commands.
Owner:T MOBILE INNOVATIONS LLC
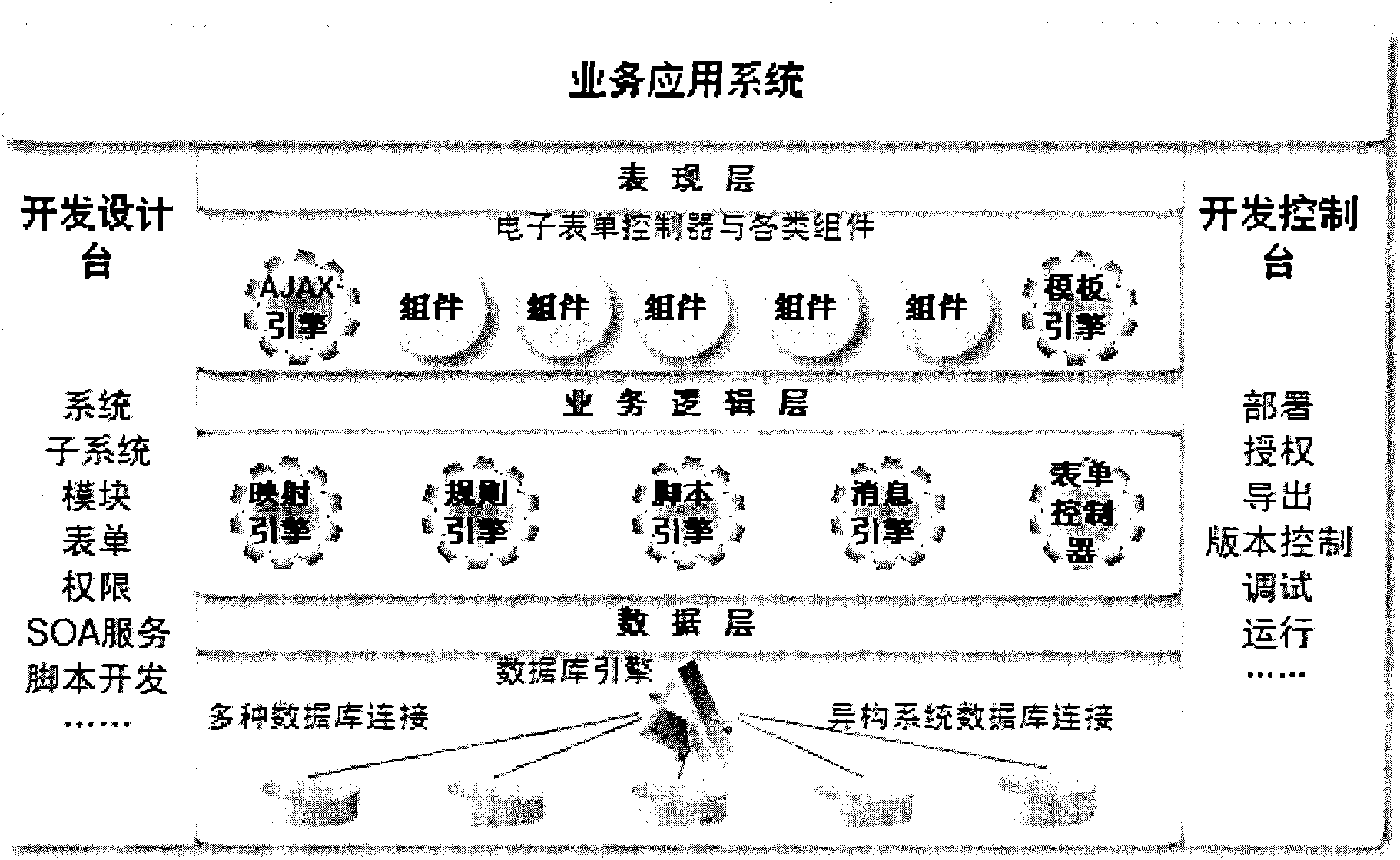
Technical implementation method for application development through electronic form
InactiveCN102063306ARapid Visual DevelopmentReduce the amount of developmentSpecific program execution arrangementsOperational systemElectronic form
The invention discloses a technical implementation method for application development through an electronic form. The electronic form technique integrates data acquisition and presentation functions into a whole; an electronic form system is divided into an interface representation layer, a service logic layer and a data exchange layer; and the electronic form technique reduces the development programming codes by over 90 percent in comparison with the traditional development mode, the development efficiency is improved by one order of magnitude in comparison with the traditional mode, the configured design concept and the development mode are improved, the agility of a service system is greatly promoted, data sharing and application integration are realized by adopting service-oriented architecture (SOA) loose coupling application integration technology, different bottom-layer operating systems and databases can be spanned, and the application system has good compatibility and mobility.
Owner:夏春秋
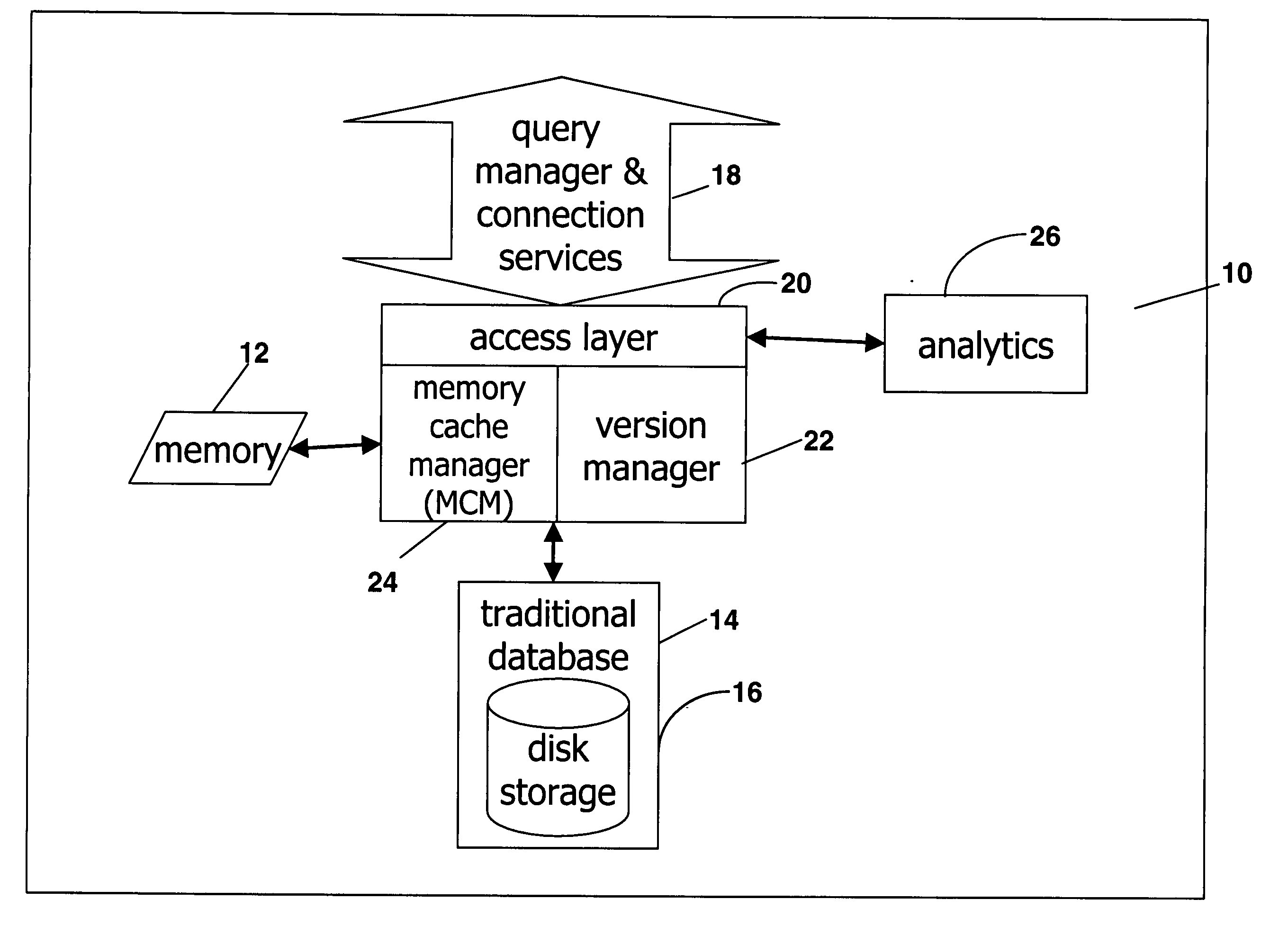
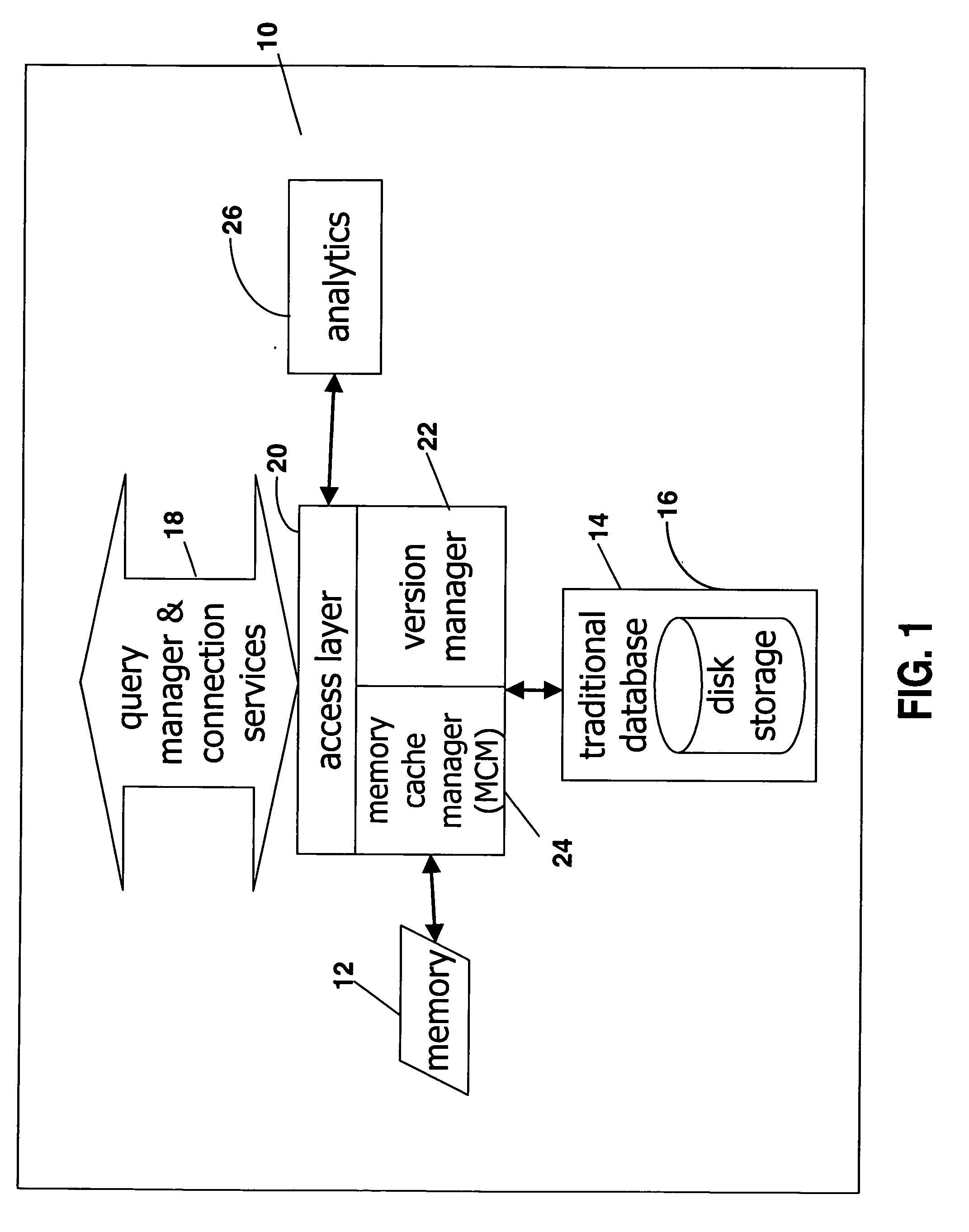
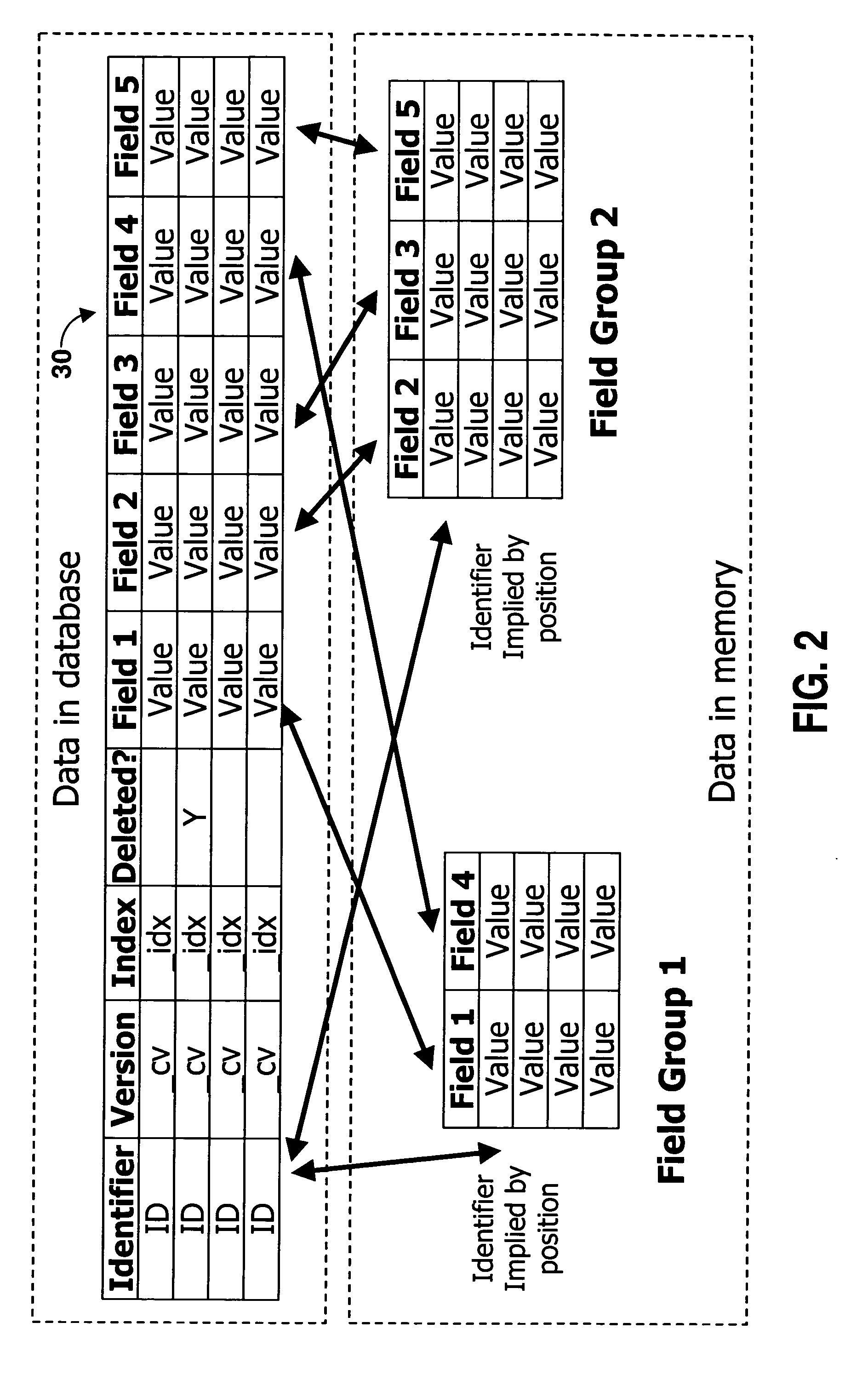
Extended database engine providing versioning and embedded analytics
ActiveUS20050138013A1Increase valueEfficient methodDigital data information retrievalDigital data processing detailsRelational databaseDatabase engine
A system for calculating analytics uses a relational database to store inputs, calculates results, and stores them in cache. The system also includes an access layer that provides a unified view of the data in server. A dynamic access layer is generated at runtime to run an analytic to provide a flexible framework for creating business logic.
Owner:KINAXIS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com