Patents
Literature
596 results about "Data entity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
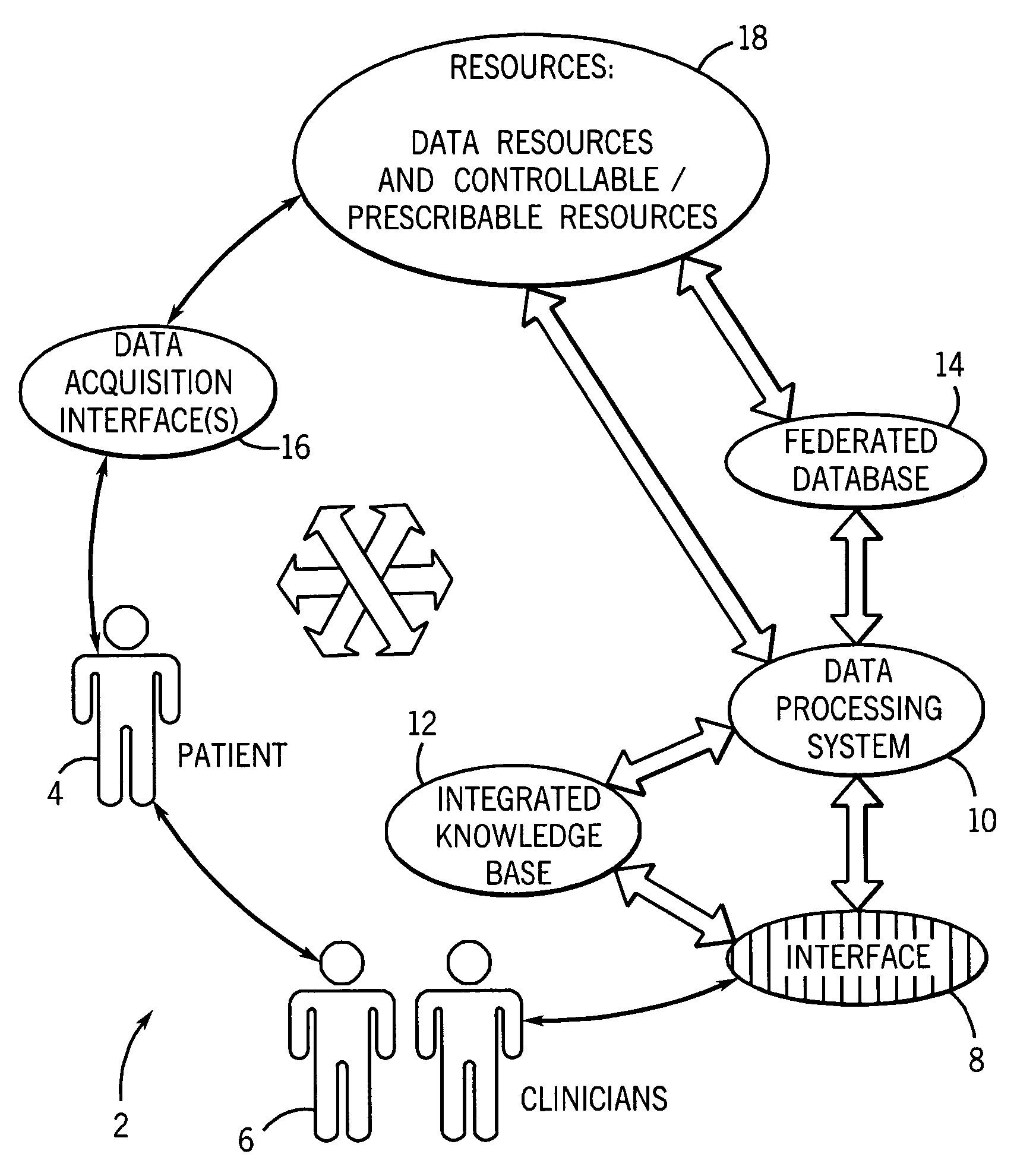
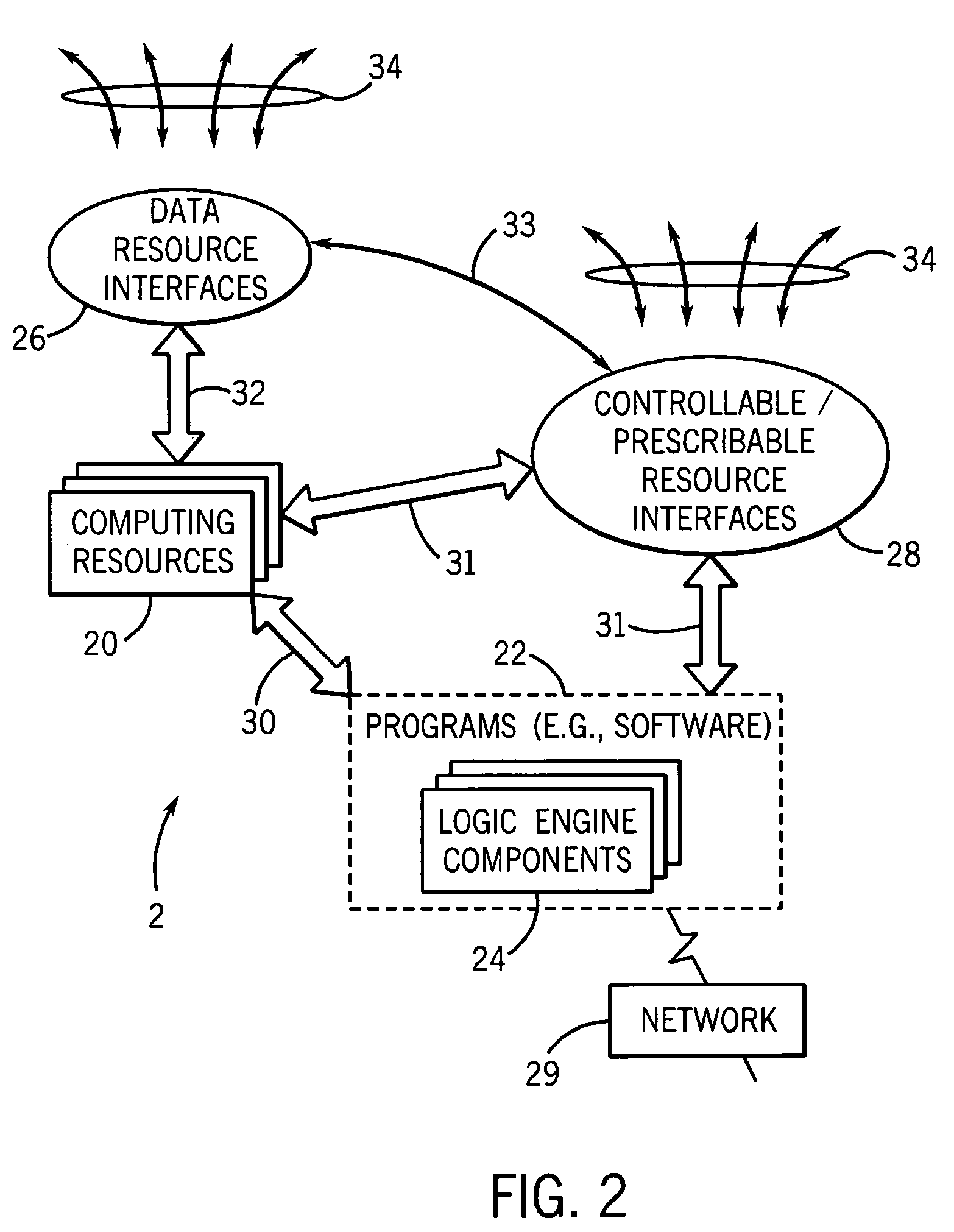
System and method for integrated learning and understanding of healthcare informatics
InactiveUS20070118399A1Data processing applicationsPatient personal data managementCrowdsData entity
An informatics system permits data entities from a wide range of data sources to be accessed and evaluated. The sources of the data entities may be simply data sources, such as for articles and other non-patient or population specific information, as well as controllable and prescribable sources, such diagnostic imaging, clinical and other sources forming part of the patient care path. The entities are organized, analyzed in accordance with a domain framework, which may be altered by a user to focus on factors and informational components of interest. Holistic and integrated understanding of such factors are there fore available, and refinement of healthcare processes can be made to provide improved care in a more time and cost effective manner.
Owner:GENERAL ELECTRIC CO
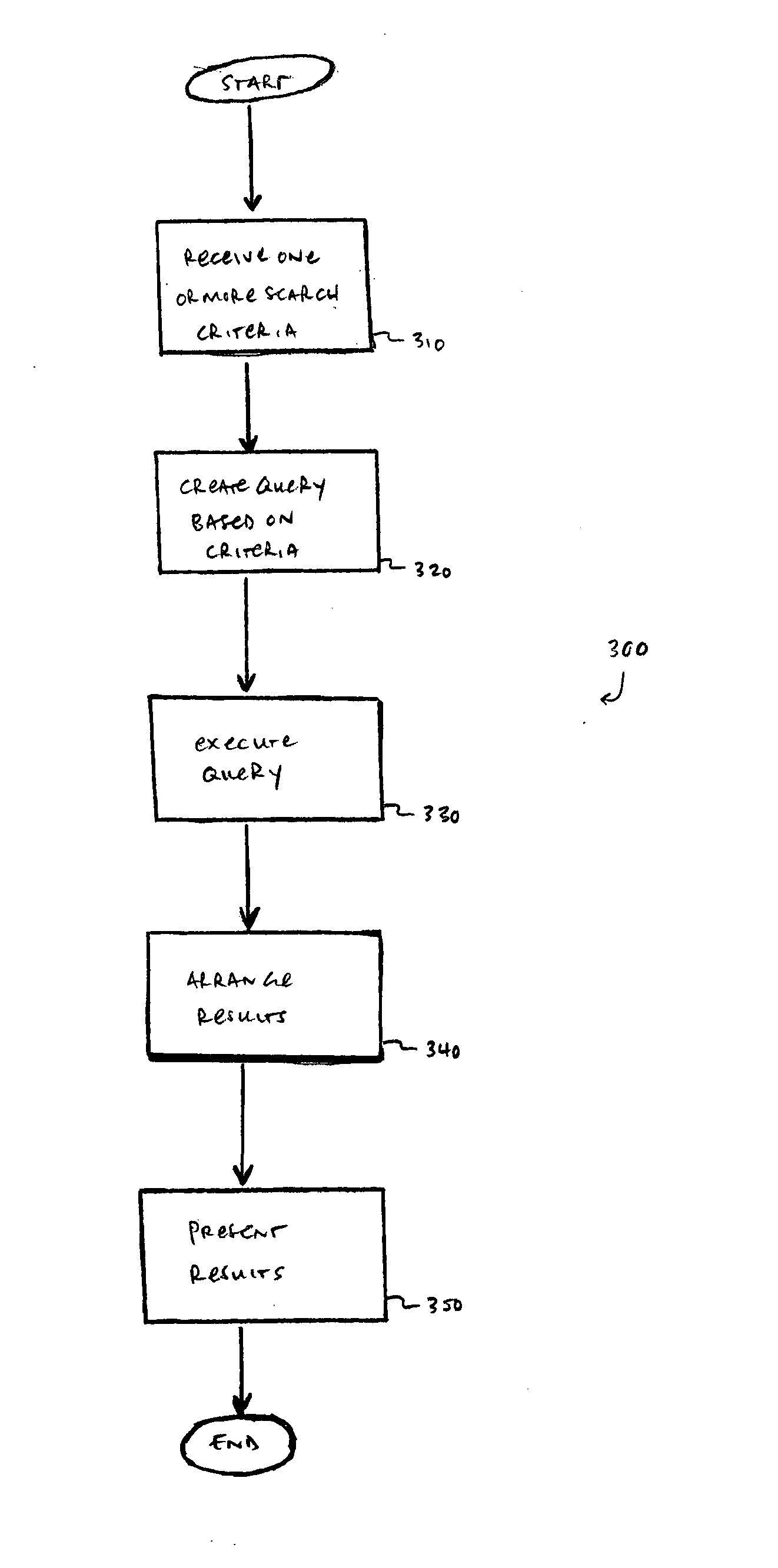
Method and apparatus for improved relevance of search results
A method and system for information retrieval are provided whereby at least one search criterion is received from a user; a query is created based on the at least one search criterion; the query is executed to generate results, each of the results corresponding to a respective data entity which satisfies the at least one search criterion; the results are arranged into an order, the order being determined at least in part by a characteristic of the data entity corresponding to each result and a previous act by a user with respect to the data entity corresponding to each result; and the results are displayed to the user.
Owner:IRON MOUNTAIN INCORPORATED
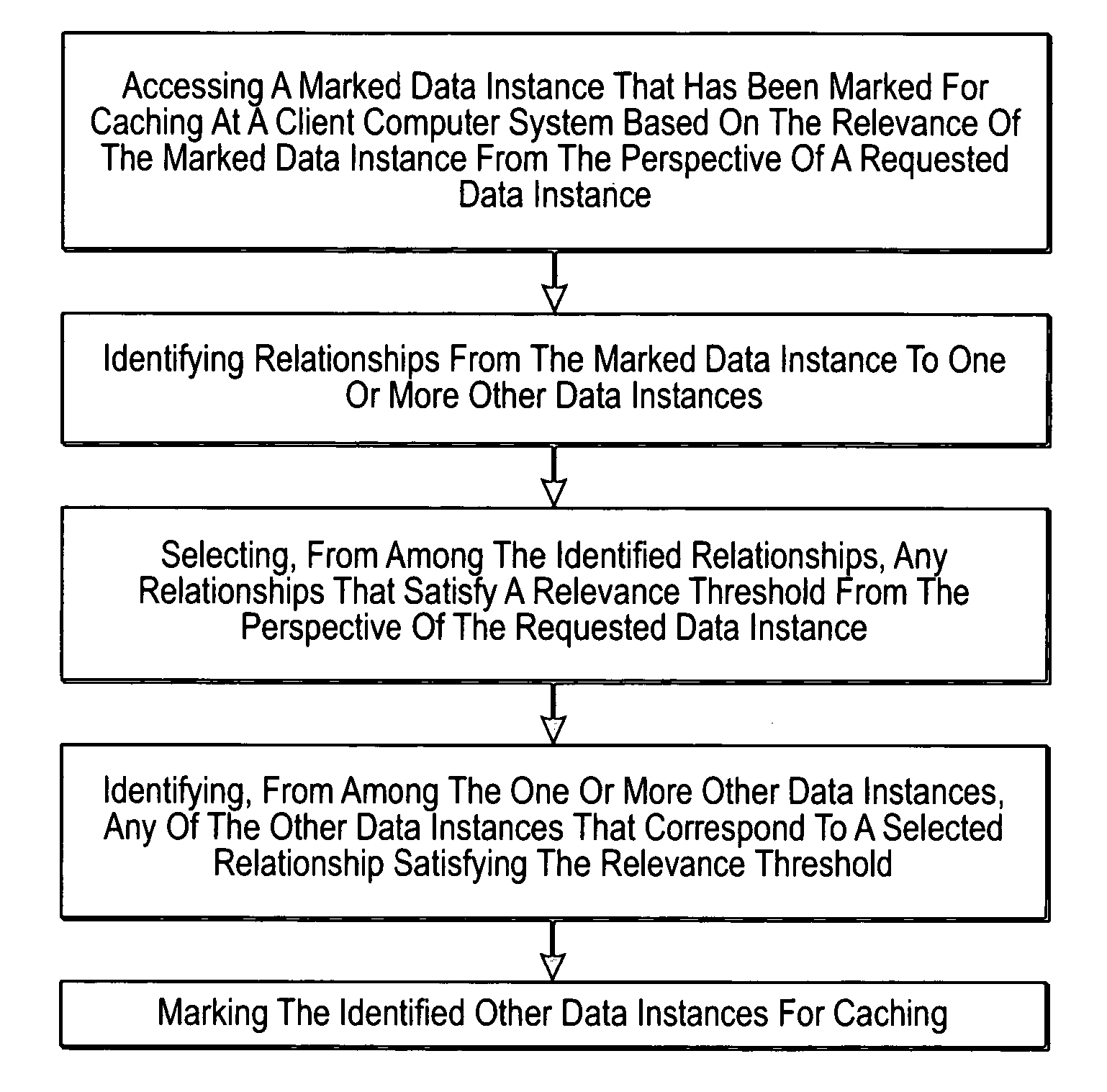
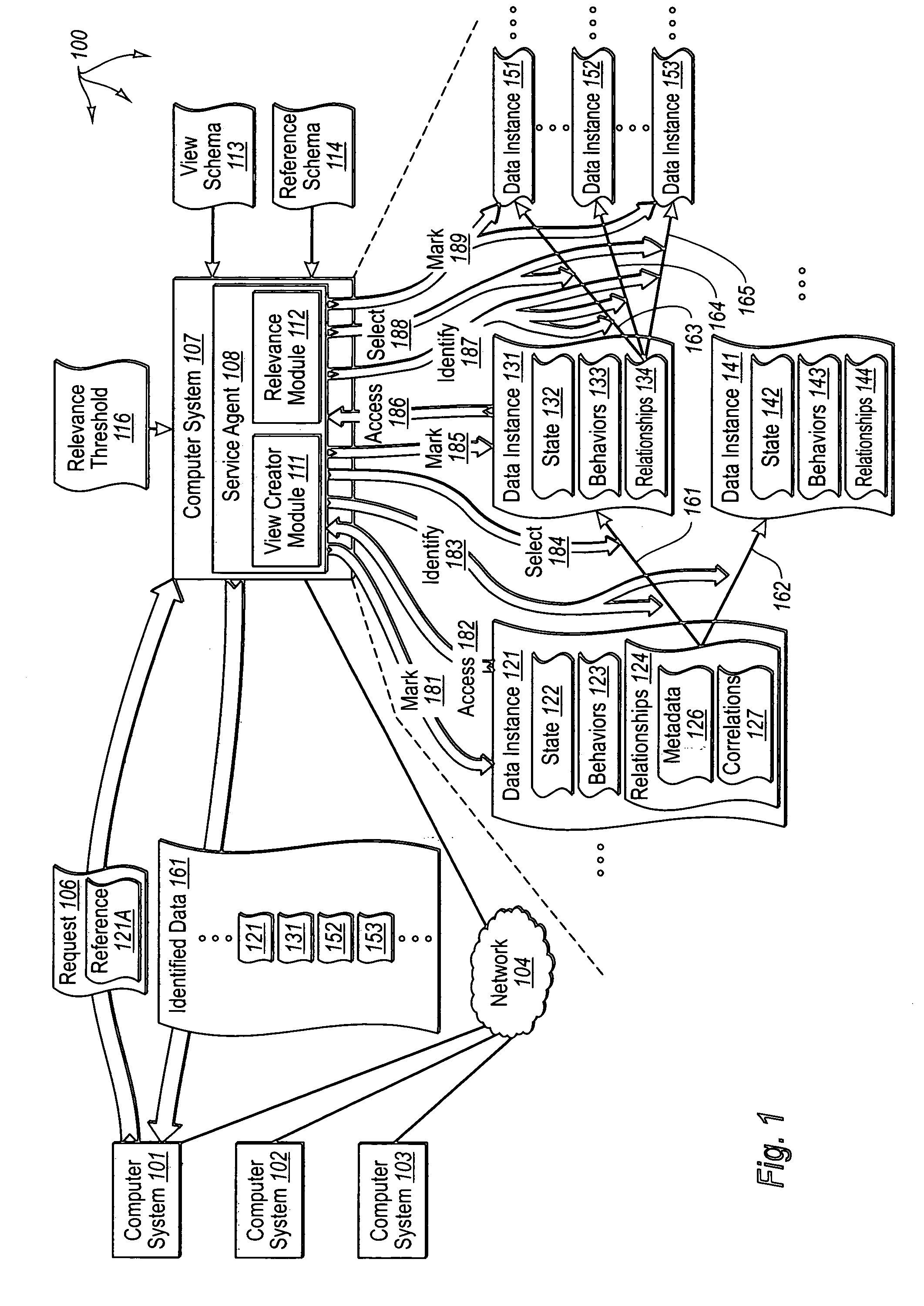
Identifying relevant data to cache
InactiveUS20070005892A1Digital data information retrievalSpecial data processing applicationsRelevant informationClient-side
The present invention extends to methods, systems, and computer program products for identifying relevant information to cache. A computer system accesses a marked data entity that has been marked for caching at a client computer system. The marked data entry is marked for caching based on the relevance of the marked data entity from the perspective of a requested data entity. The computer system identifies relationships from the marked data entity to one or more other data entities. The computer system selects, from among the identified relationships, any relationships that satisfy a relevance threshold from the perspective of the requested data entity. The computer system identifies, from among the one or more other data entities, any of the other data entities that correspond to a selected relationship satisfying the relevance threshold. The computer system marks the identified other data entities for caching.
Owner:MICROSOFT TECH LICENSING LLC
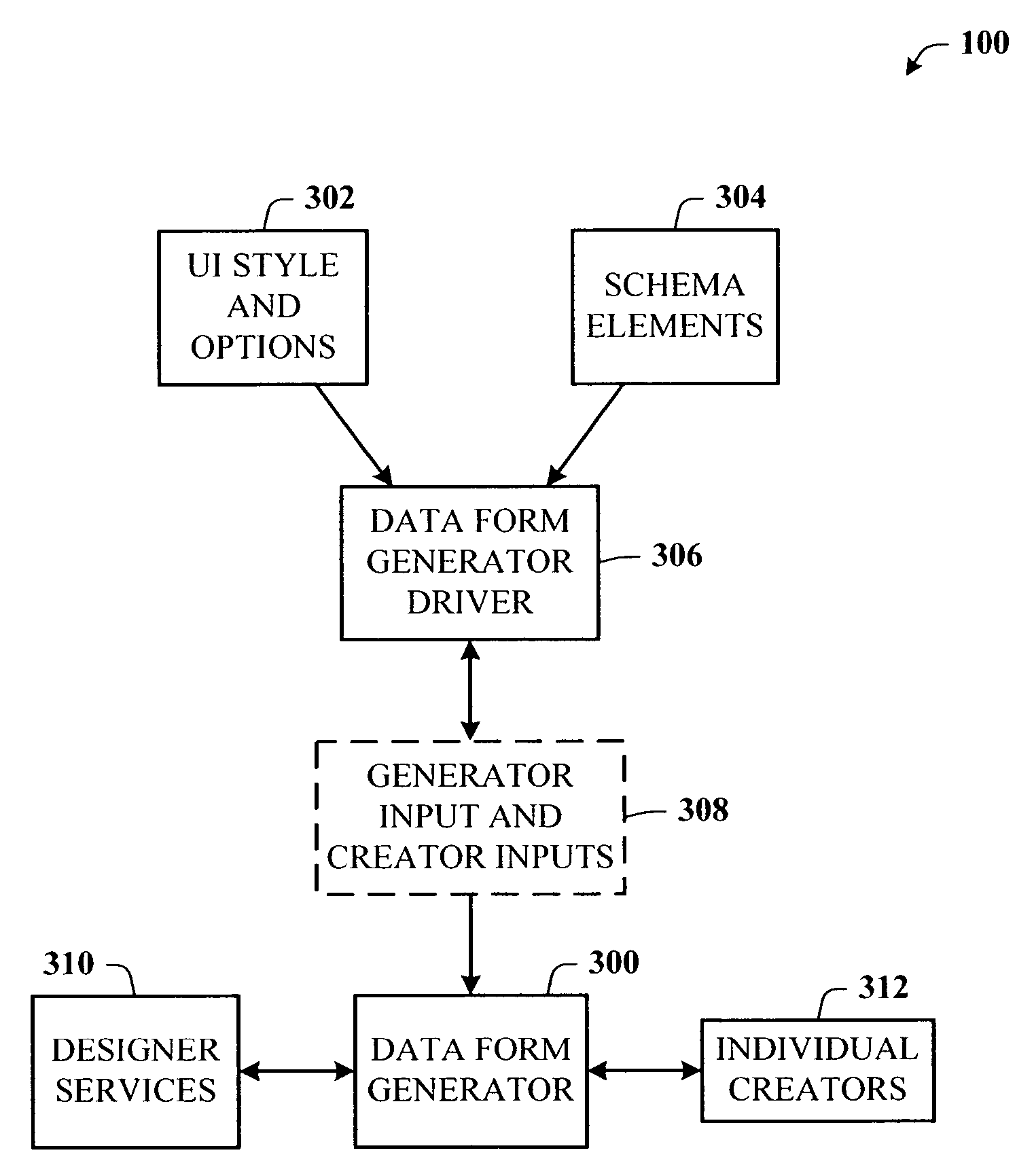
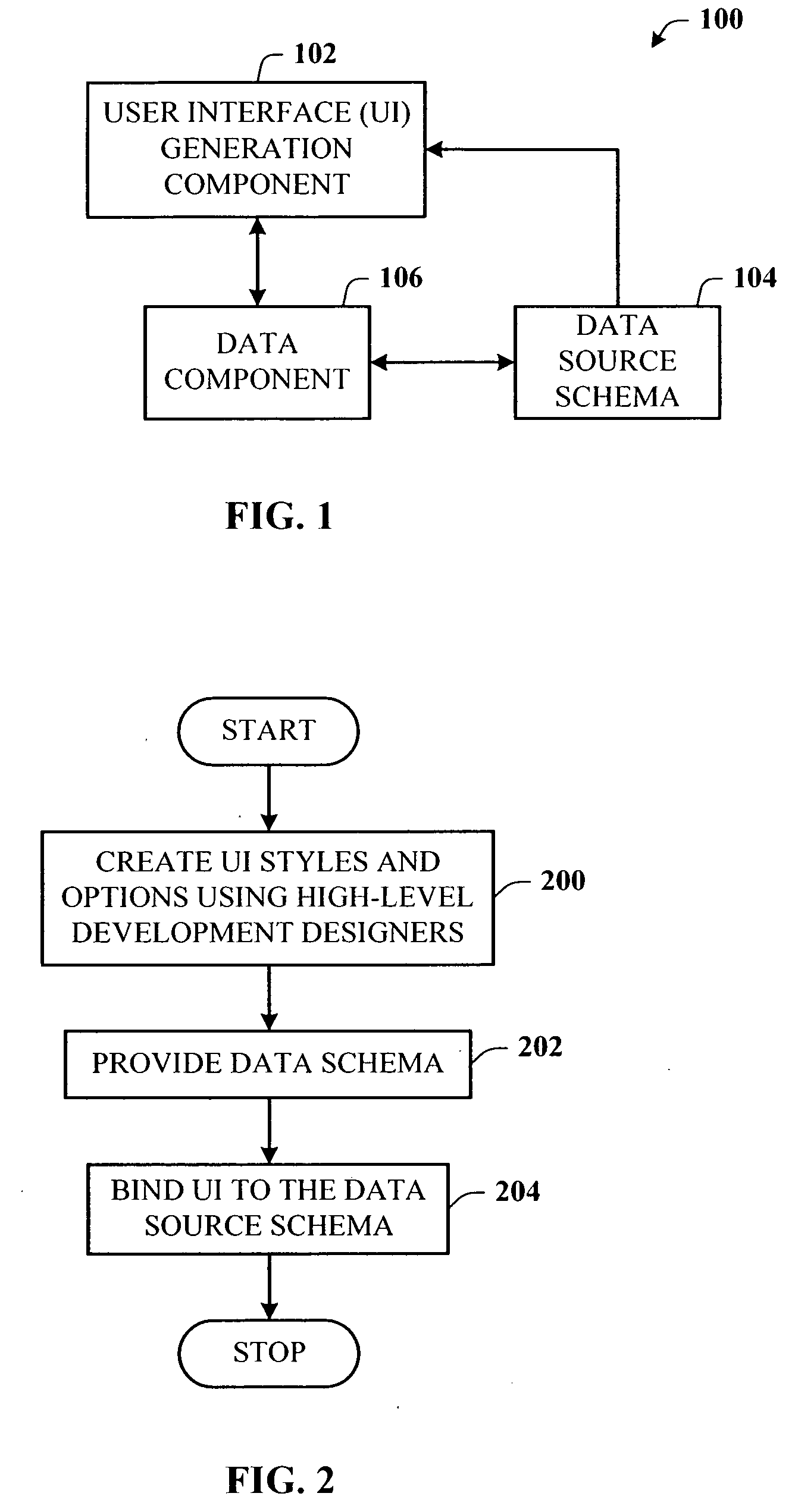
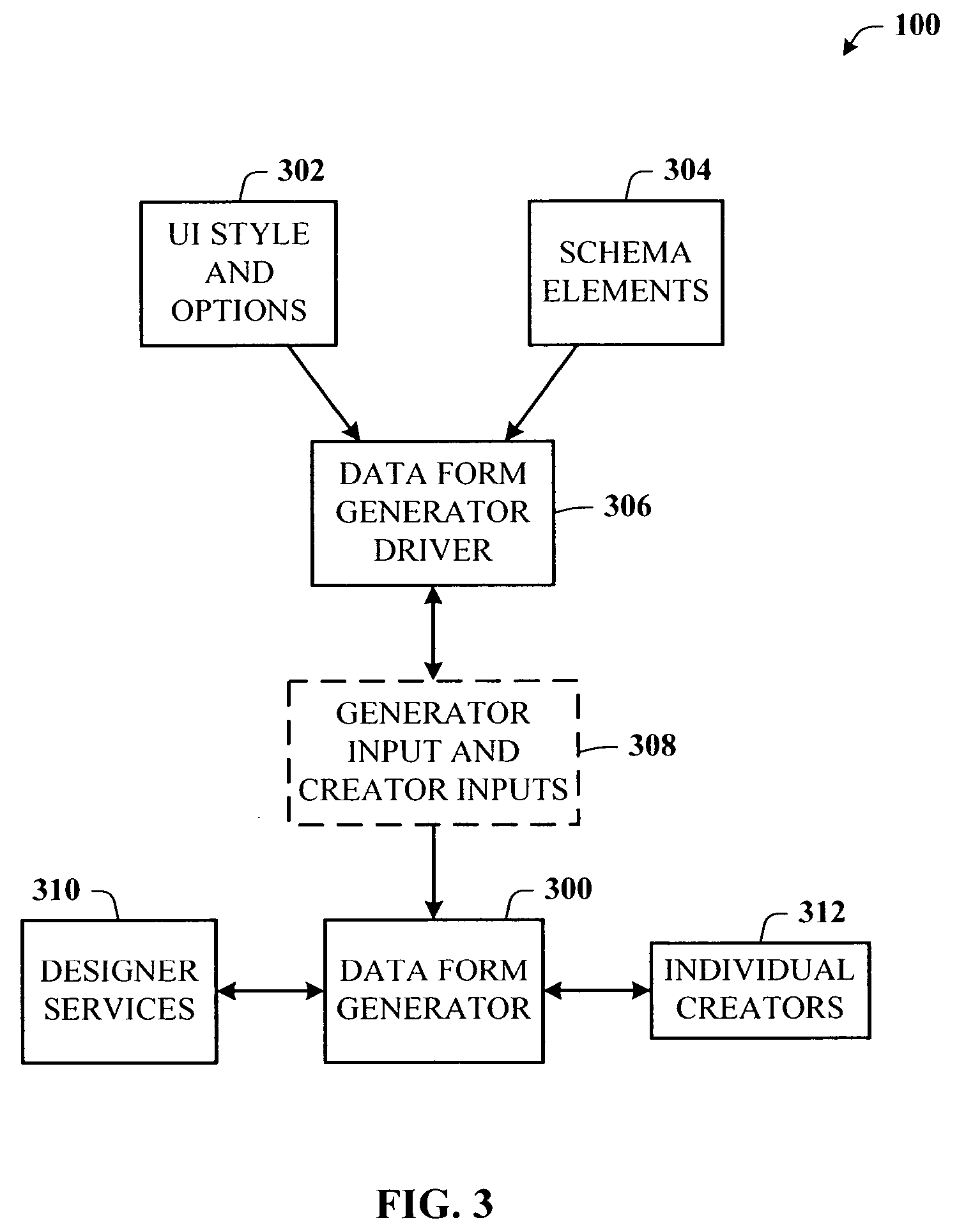
Architecture for creating a user interface using a data schema
InactiveUS20050172261A1Easy to createFast dataSoftware engineeringSpecific program execution arrangementsGraphicsDrag and drop
A rich user interface (UI) development framework that uses the schema of a data source to which it is relevant. The developer is able to rapidly create a data bound UI using a number of familiar gestures, including drag and drop, from the schema in a data tool window, using a designer tasks, or using a data form creation wizard. The system includes a UI generation component that allows a developer to input a number of different controls into the interface using associated control graphics. A data source object, type, or file can be passed to the UI generation component as an input. The developer chooses the desired controls and associates (or binds) the data entity of the data source with the control by any number of gestures.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for content repository with versioning and data modeling
InactiveUS6904454B2Lower requirementData processing applicationsDigital computer detailsData modelingData entity
The present invention is related to method and apparatus for versioning. Versioning information is stored as metadata associated with data entities. A hierarchical relationship between the entities allows the definition of an editorial sequence and separate revisions within that sequence as well as relationships between sequences in a self-contained format.
Owner:III HLDG 3
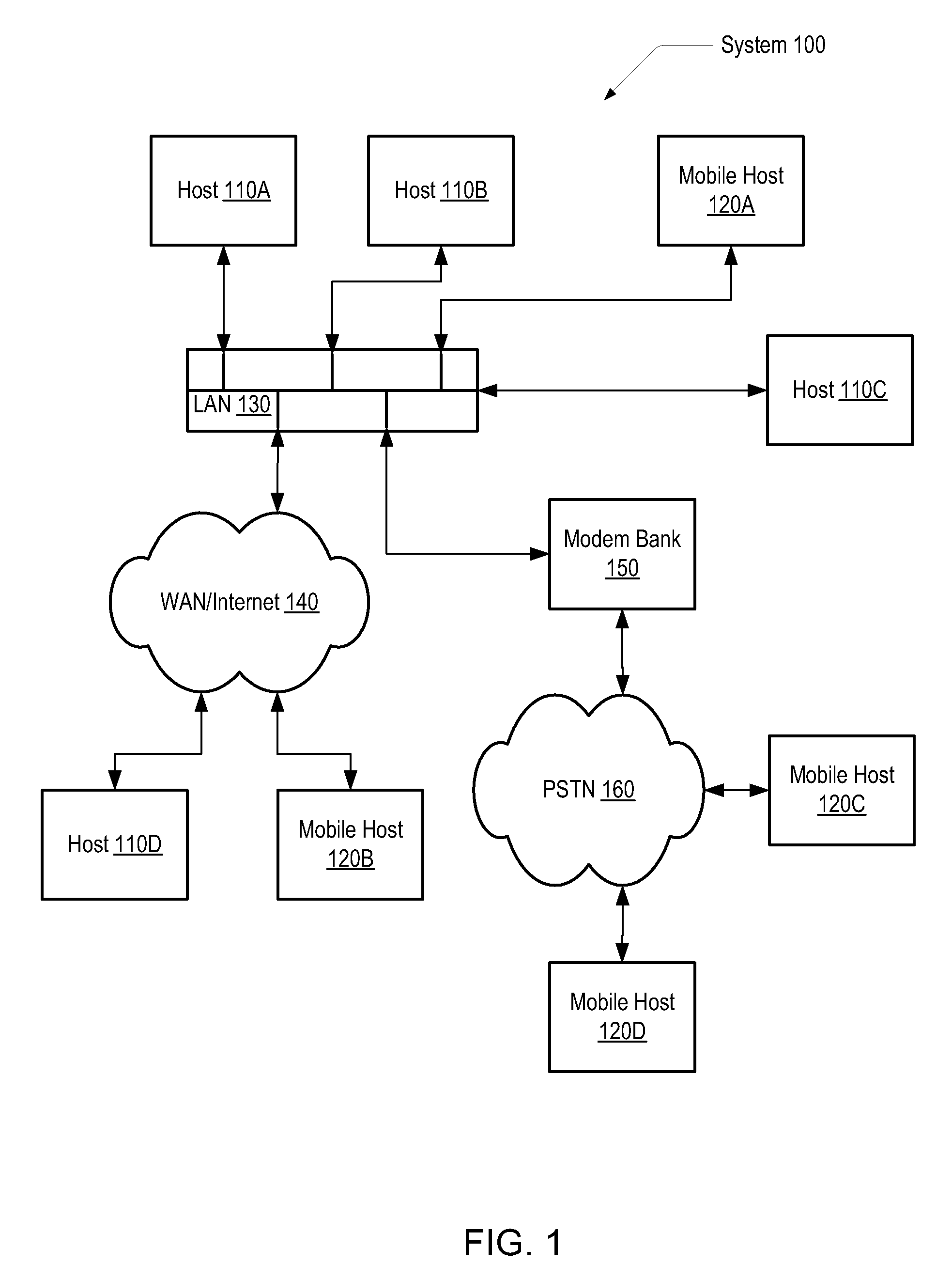
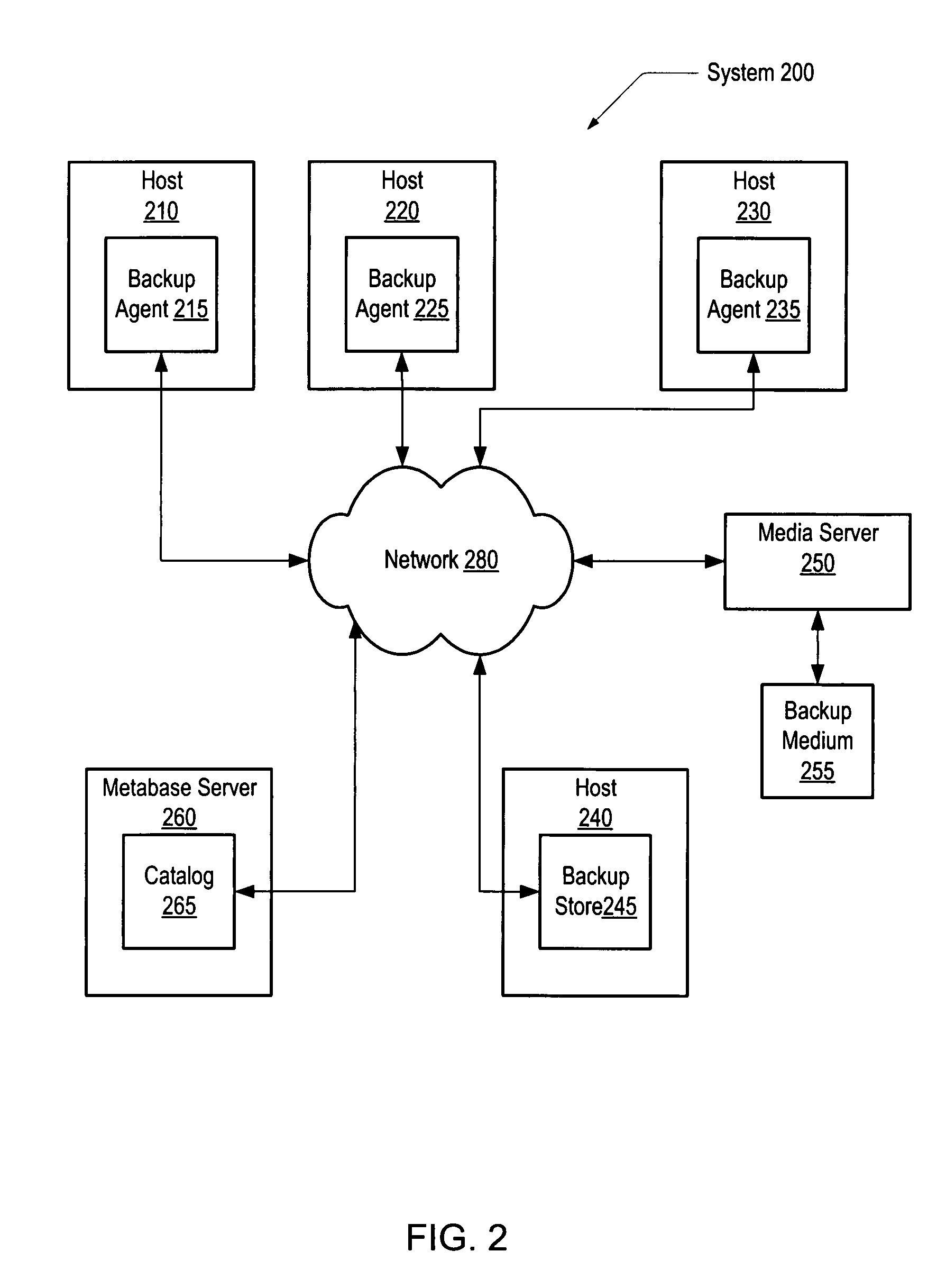
Implementing read/write, multi-versioned file system on top of backup data
ActiveUS20080243953A1Digital data information retrievalError detection/correctionData segmentFile system
Various embodiments of a computer system and methods are disclosed. In one embodiment, a computer system includes hosts coupled to a backup medium. The backup medium stores data segments and objects, each object referencing one or more segments. A second host conveys a write request to a first host identifying a data entity comprising segments referenced by a first object. The first host restores a copy of the data entity and creates a second object referencing the segments that were referenced by the first object in response to receiving the write request. The first host adds segment references to the second object in response to receiving a change that adds data to the copy or deletes a portion of a segment from the copy. The first host removes a segment reference from the second object if a change deletes all of a segment from the copy.
Owner:VERITAS TECH
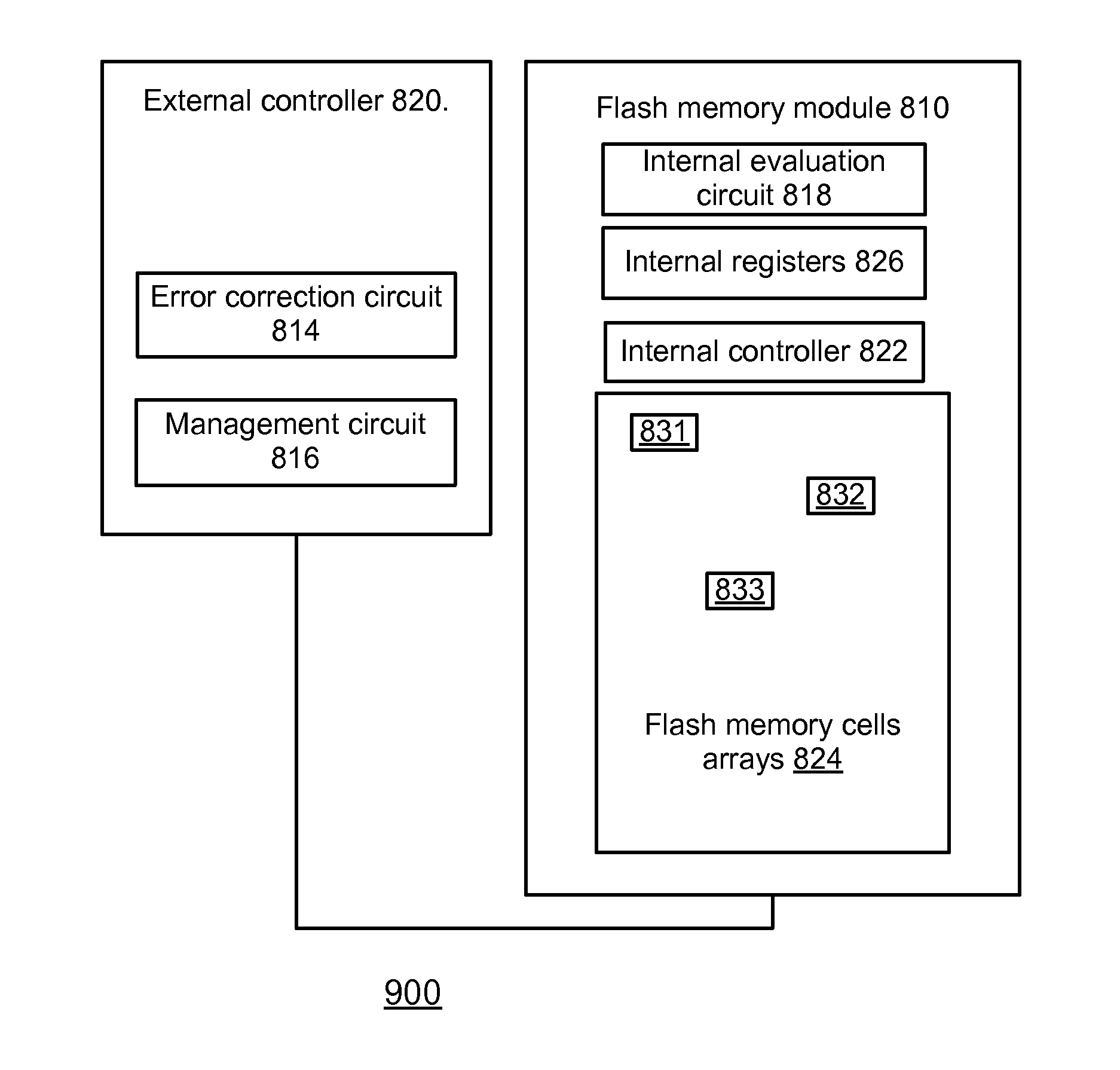
Meethod, system and computer readable medium for copy back
ActiveUS20120110250A1Compensating for such errorMore reliableError detection/correctionRead-only memoriesSoftware engineeringData entity
Systems, computer readable media and methods for updating a flash memory device involve procedures for transferring, from a flash memory device to an external controller, only a portion of a data entity; and determining, by the external controller, based upon the portion of the data entity, whether to complete a copy back operation of the data entity or to correct errors of the data entity. If it is determined to correct errors of the data entity, then the procedure includes (a) completing a transfer of the data entity to the external controller; (b) error correcting the data entity to provide an amended data entity; and (c) writing the amended data entity to the flash memory device. If, however, it is determined to complete the copy back operation then the procedures includes completing the copy back operation of the data entity by transferring the data entity within the flash memory device.
Owner:AVAGO TECH INT SALES PTE LTD
Hidden link dynamic key manager for use in computer systems with database structure for storage of encrypted data and method for storage and retrieval of encrypted data
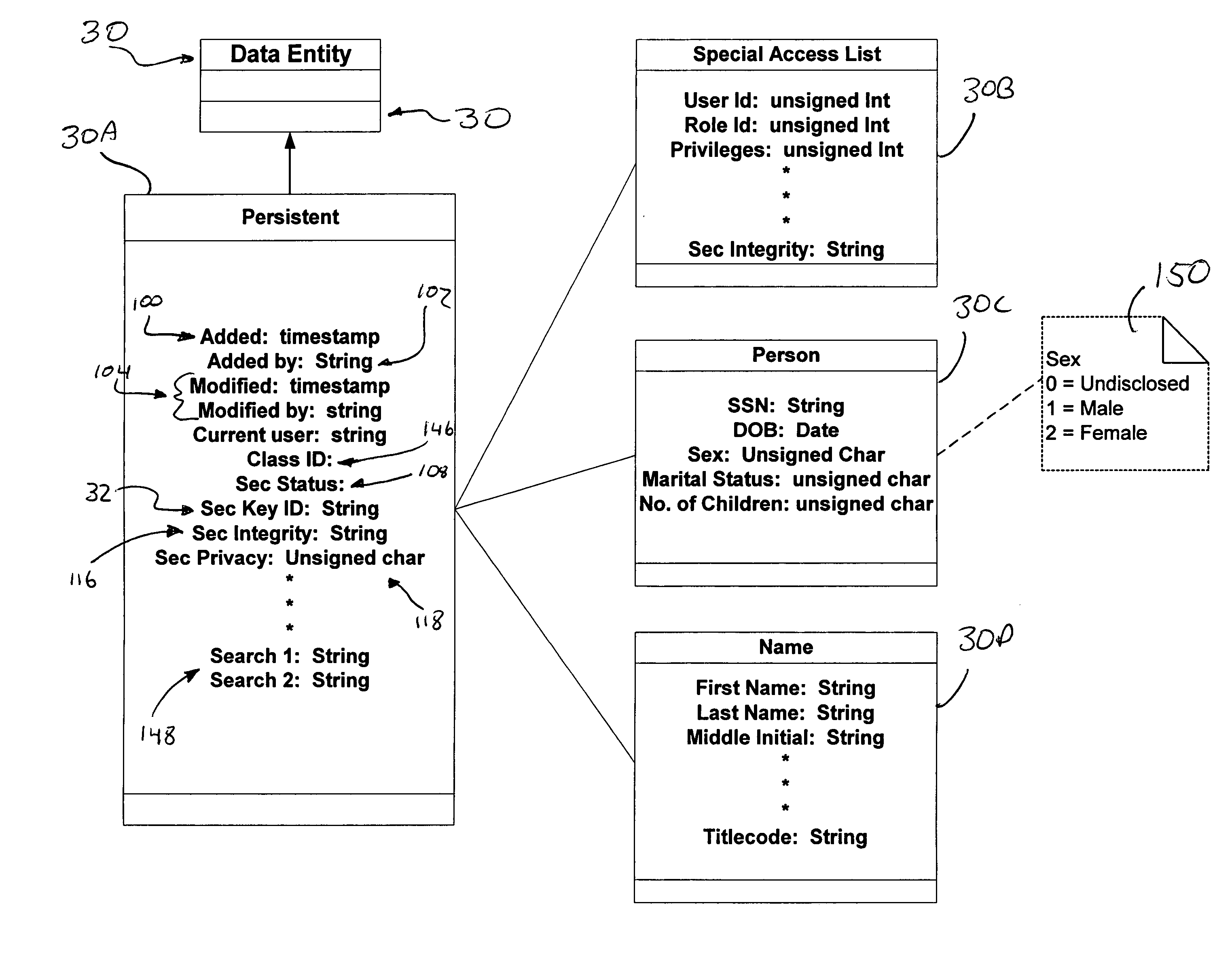
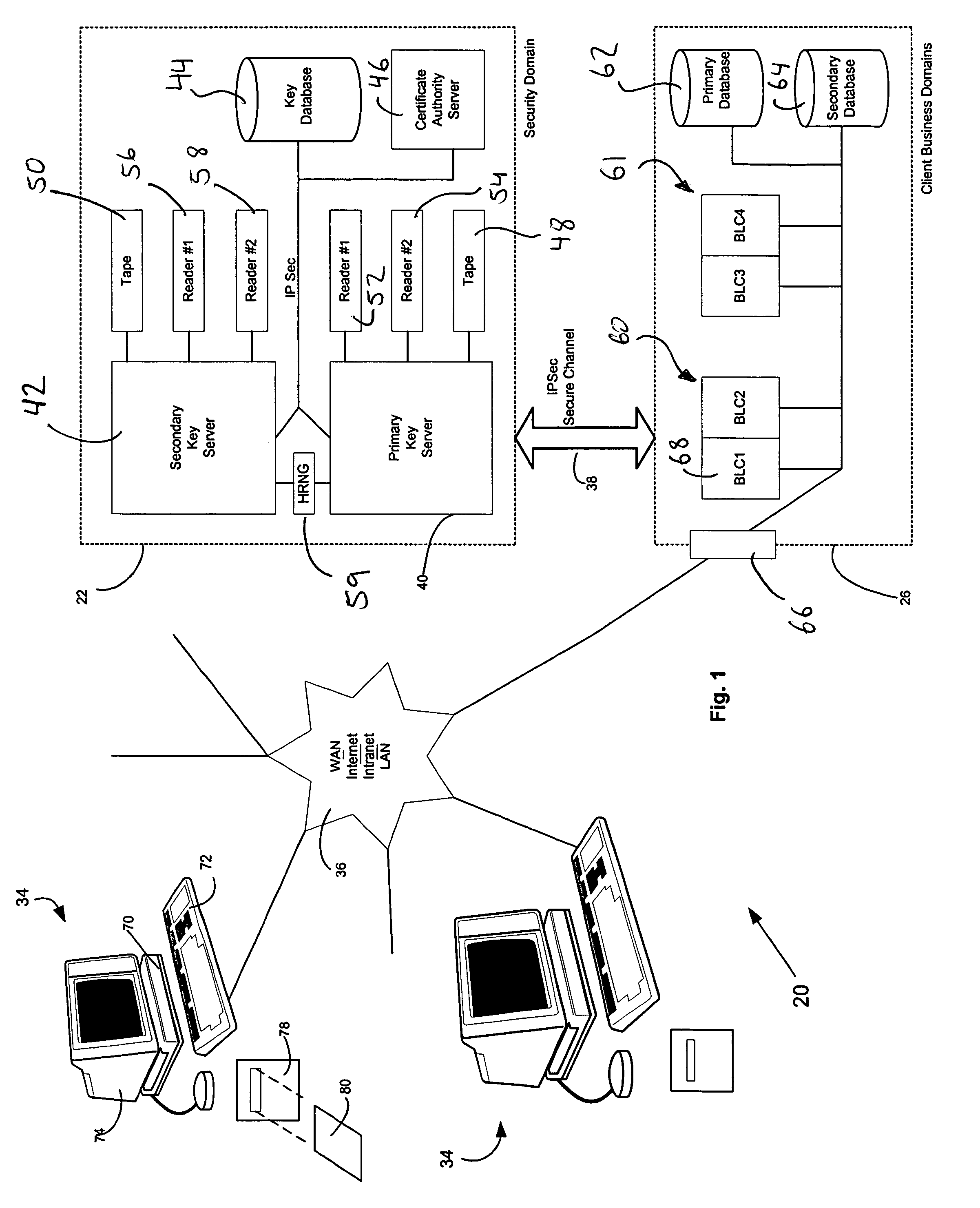
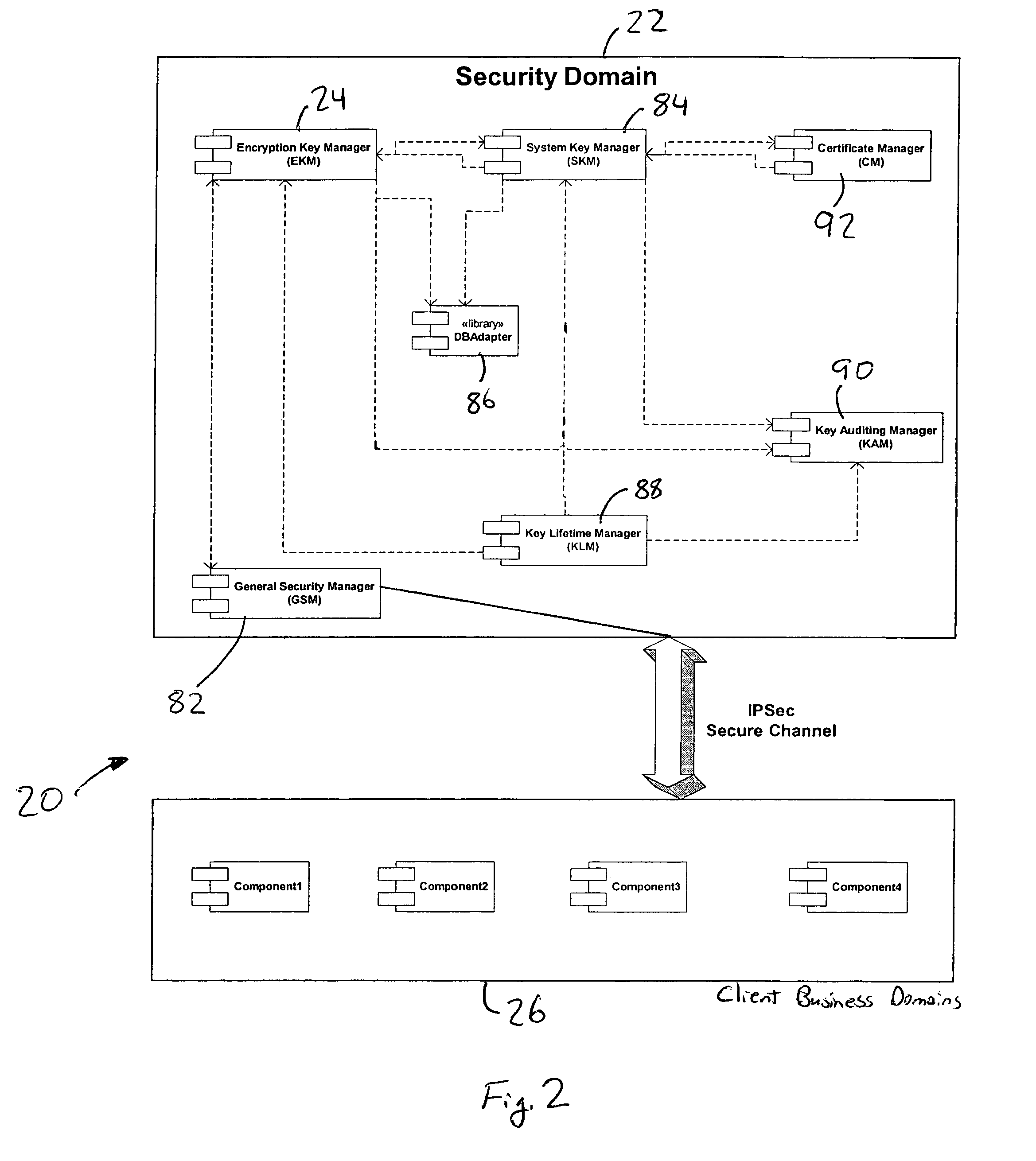
InactiveUS7362868B2Improve securityOpportunities decreaseMultiple keys/algorithms usageComputer security arrangementsCommon nameSecurity domain
A computer system (20) having a security domain (22), at least one client business domain (26), and a plurality of client terminals (34) utilizes a hidden link dynamic key manager (24, 84) and a database structure that includes encrypted data entities (30C, 30D) and a security identification attribute (32) for storage of encrypted data. Methods for encrypting data and for storing, decrypting, and retrieving encrypted data operate on the computer system (20), which also includes an information database (62) and a key database (44). The key database (44) is isolated from the information database (62). The hidden link key manager is stored in the security domain (22) and includes a system key manager (84) operable to generate system keys with system key common names and an encryption key manager (24) operable to generate encryption keys having encryption key identifications. The key managers (24, 84) operate on a key server (40), which is mirrored by a secondary key server (42). A general security manager (82) also operates on the key server (40) to control access to the security domain (22). The security information attribute (32) is stored with a persistent data entity (30A) that is associated with the other encrypted data entities (30C, 30D) by a database schema. The encryption key identification (112) for the encryption key used to encrypt the data entities (30C, 30D) is encrypted by a system key and then stored as part of the security information attribute (32). The system key common name hash value (114) is also stored in the security information attribute (32). The information data entities (30) are stored on the information database (62), but the encryption key identification (153), encryption key (154), system key common name hash value (156, 157), and system key common name (158) are stored in the key database (44) inside the security domain (22). The system key itself is stored on a Smart Card reader (56) inside the security domain.
Owner:FARRUKH ABDALLAH DR +1
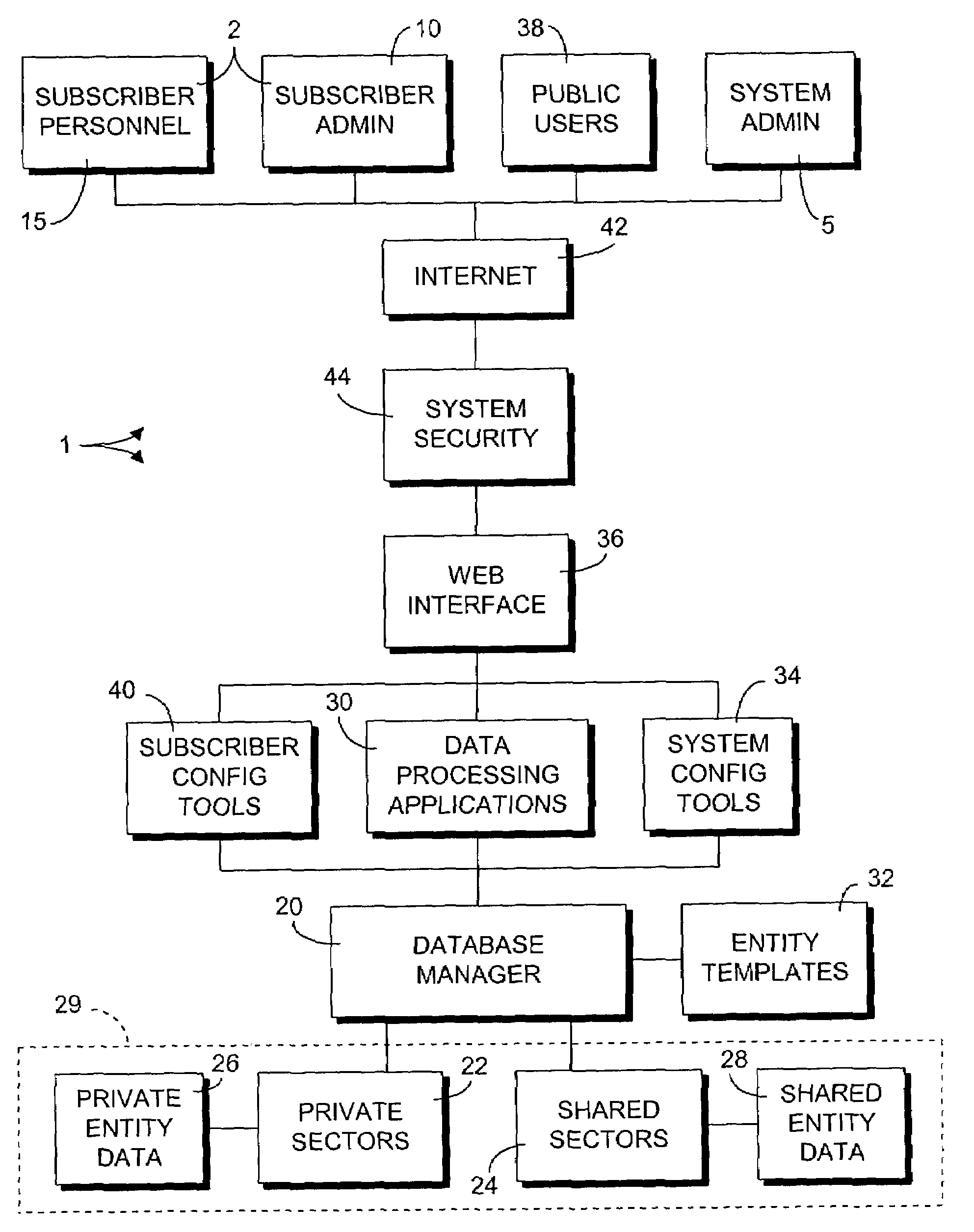
Multi-organizational project management system
InactiveUS7305392B1Effectively use such informationEasy to operateDigital data processing detailsOffice automationGraphicsGraphical user interface
A multi-organizational project management system provides for full lifecycle tracking of business activities of a complex mix of governmental entities and business organizations by maintaining a secure database of data entities or records to track such activities. The system provides for secure sharing of information among the governments and organizations by controlling access to data entities based on organizational membership and assigned role of system users. The system provides flexible structural relationships among the various data entities. A graphic, web-based user interface of the system enables efficient access to the data entities for entry and update of specific data.
Owner:APEX INNOVATIONS
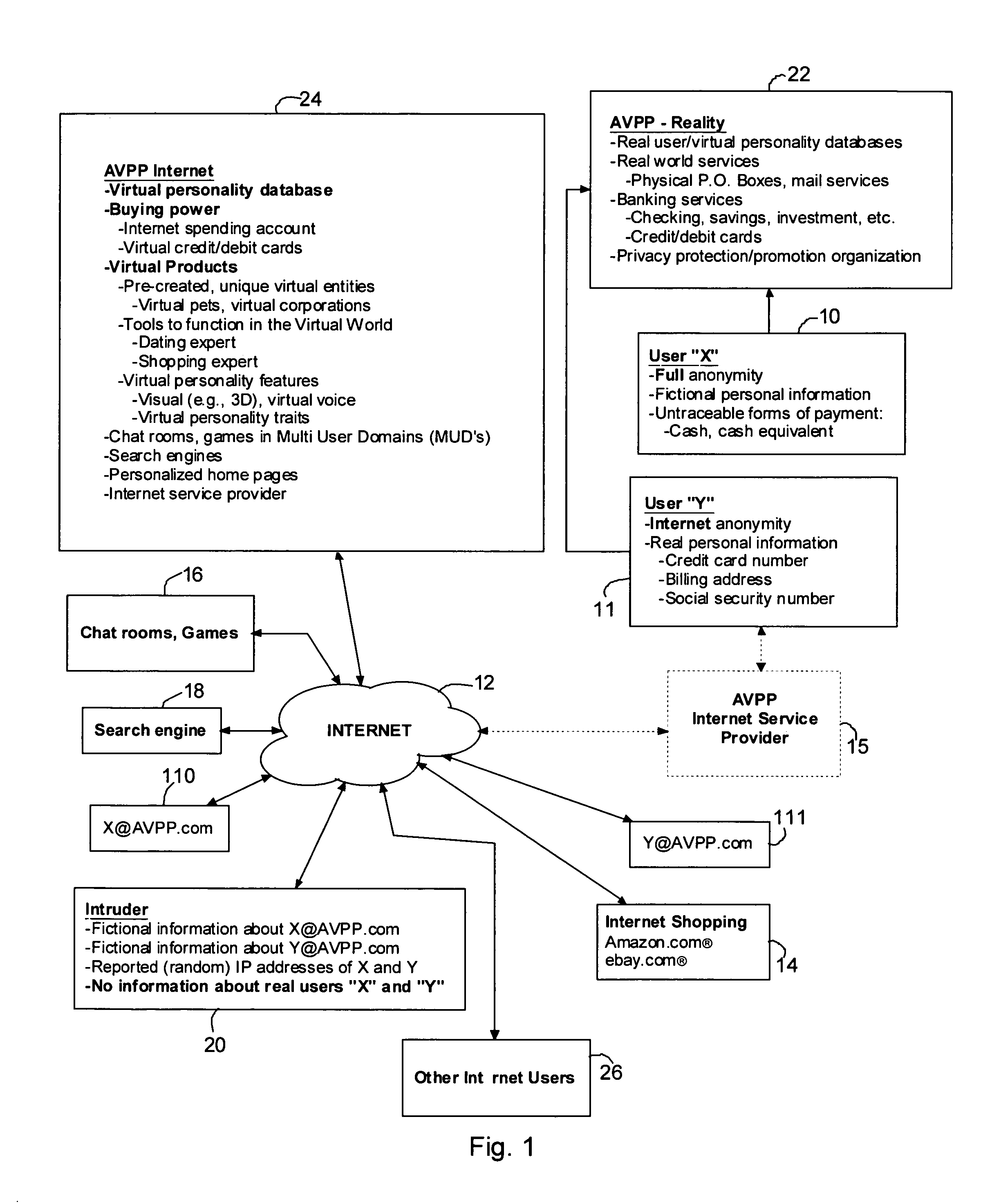
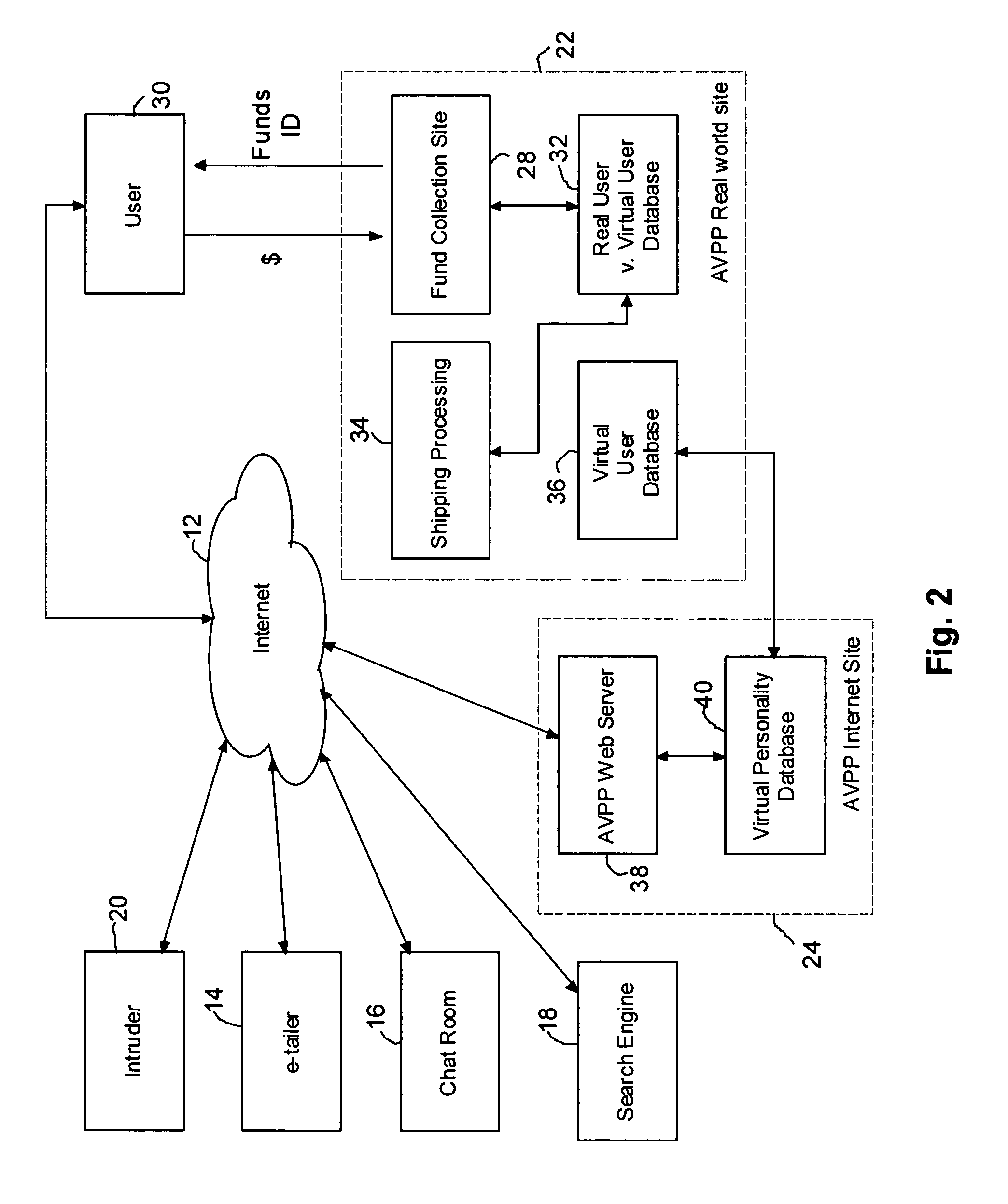
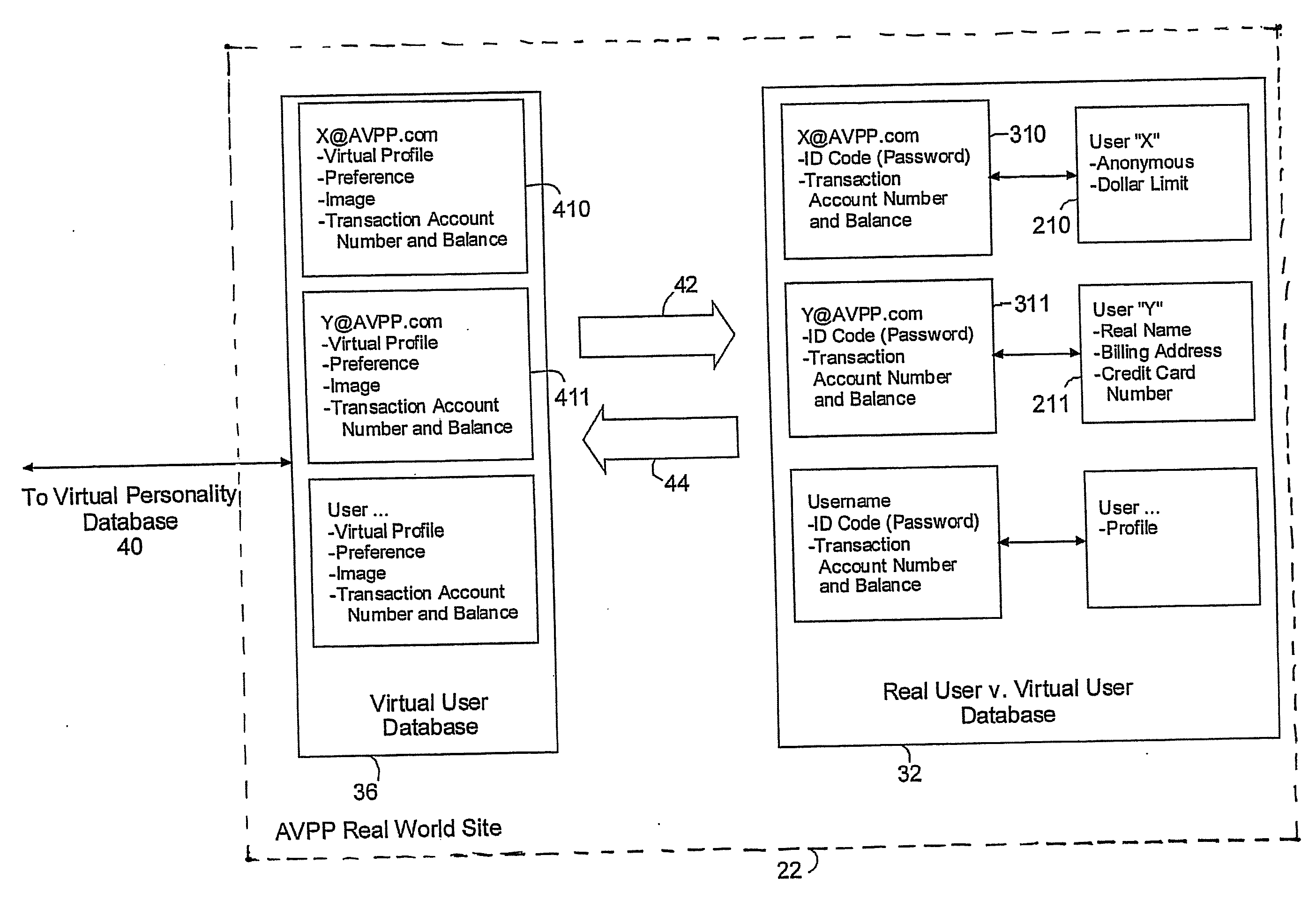
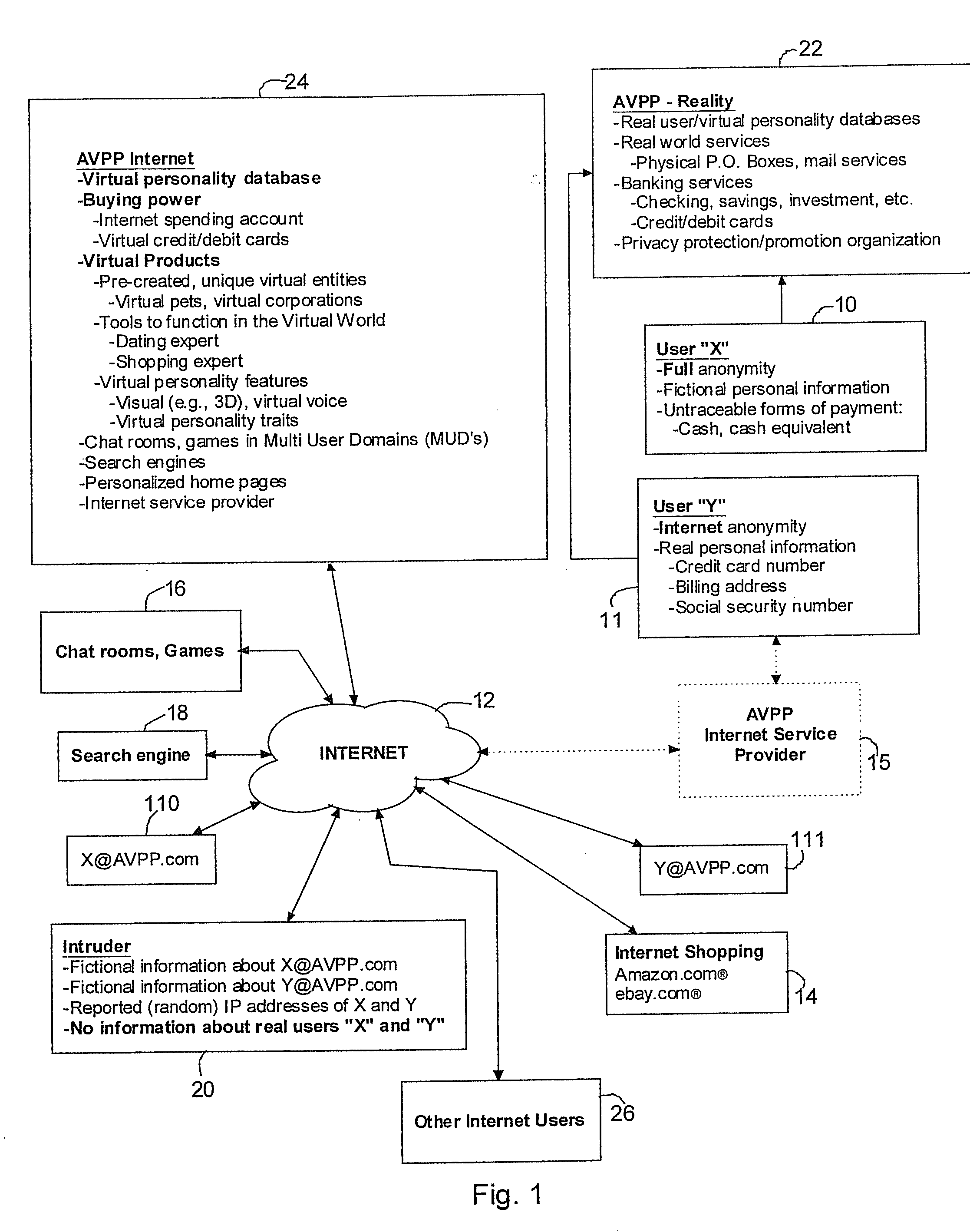
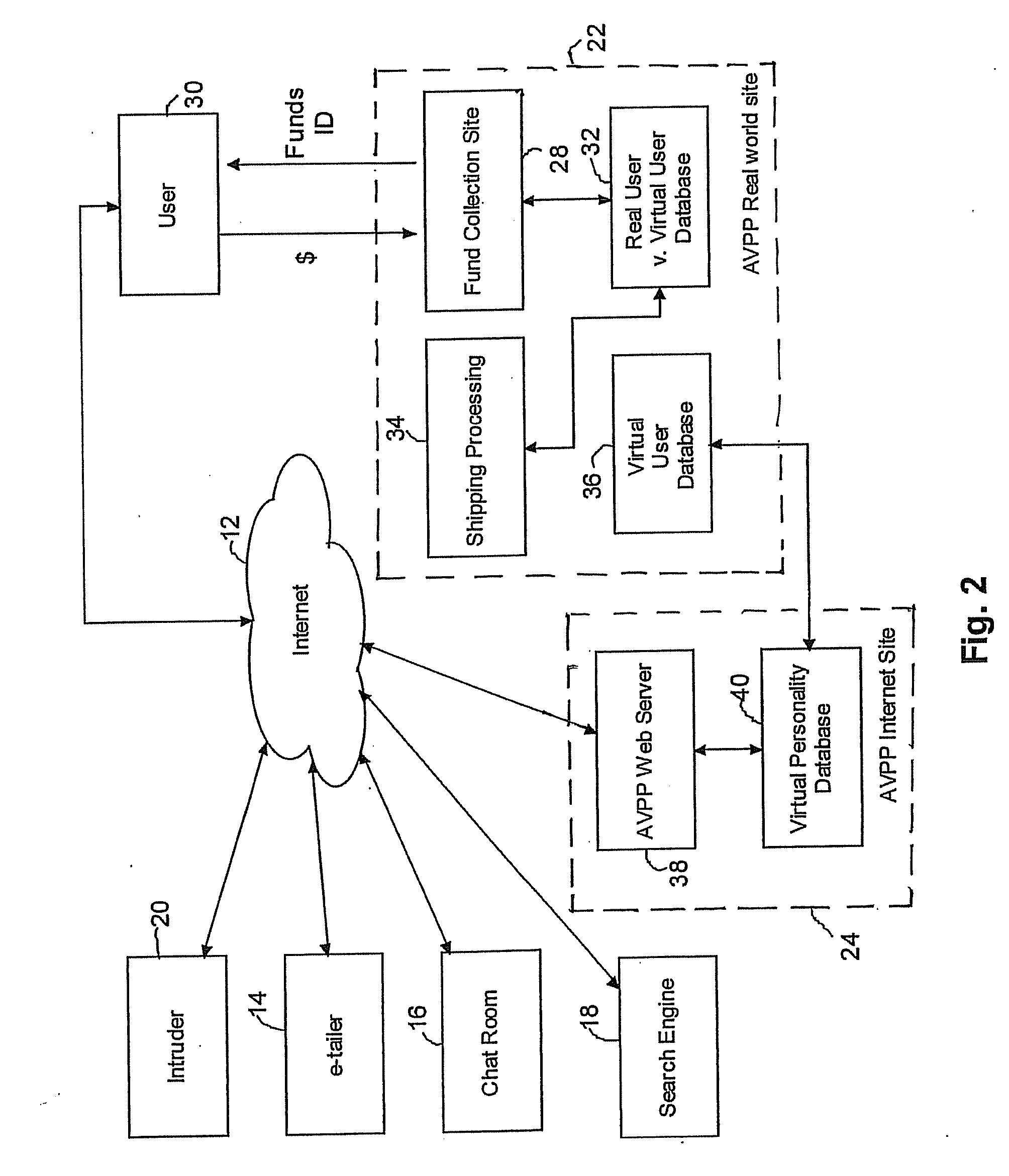
Method and system for securing user identities and creating virtual users to enhance privacy on a communication network
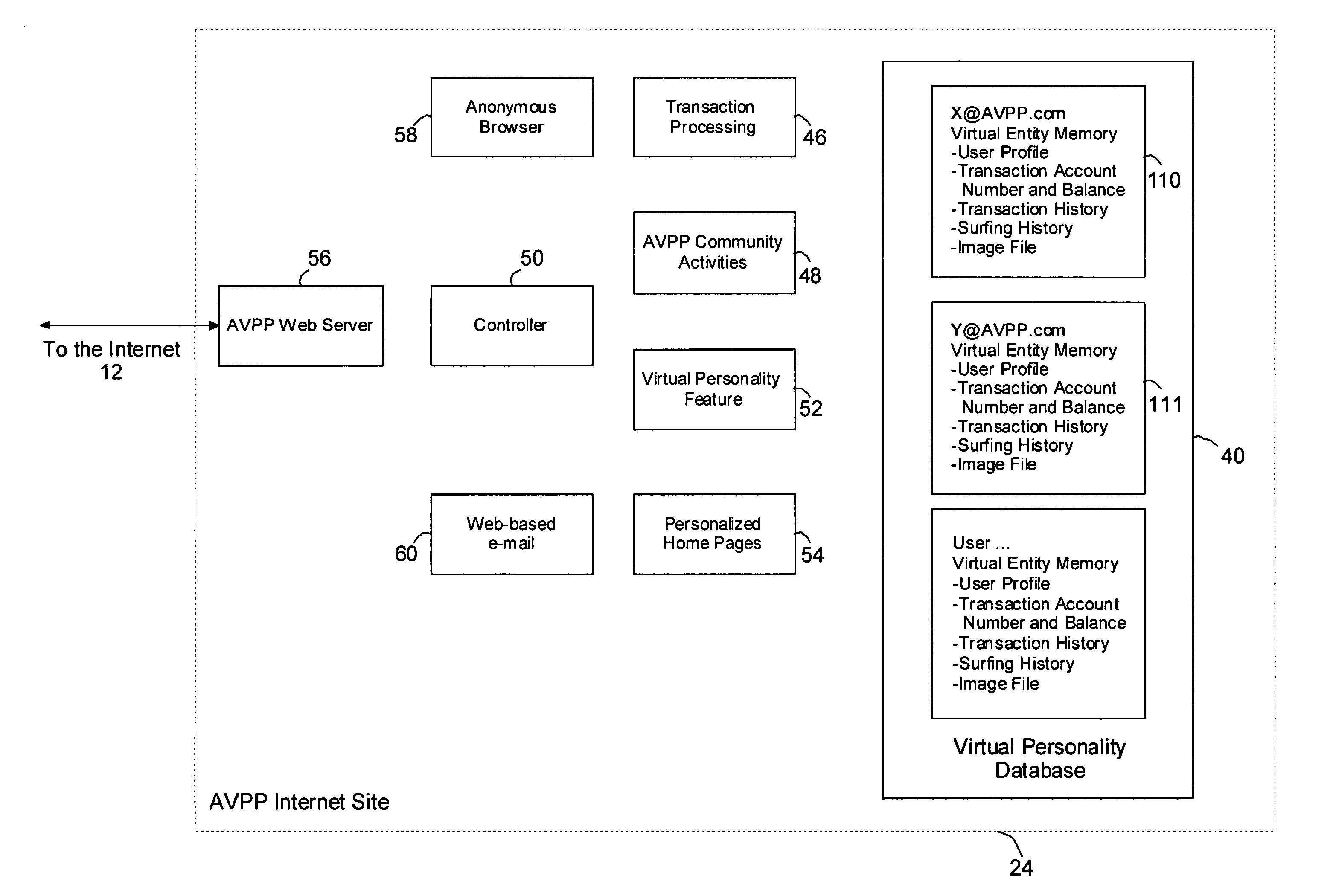
InactiveUS7412422B2Effective distributionMinimize shipping timeComplete banking machinesFinanceVirtual userVirtual entity
A method of enabling a real entity to access a service on a communication network using a virtual entity, the method including the steps of establishing a user account including at least first data corresponding to the identity of the real entity and second data corresponding to the virtual entity and not identifying the real entity, storing the first and second data in a first database, linking between the first and second data in the first database, storing the second data at a second database, associating the second database with a communication network site, connecting the communication network site to the communication network, receiving the second data from an unidentified user on the communication network site, identifying the unidentified user as the virtual entity based on receiving the second data, and allowing the virtual entity to access the service.
Owner:SHILOH DEKEL
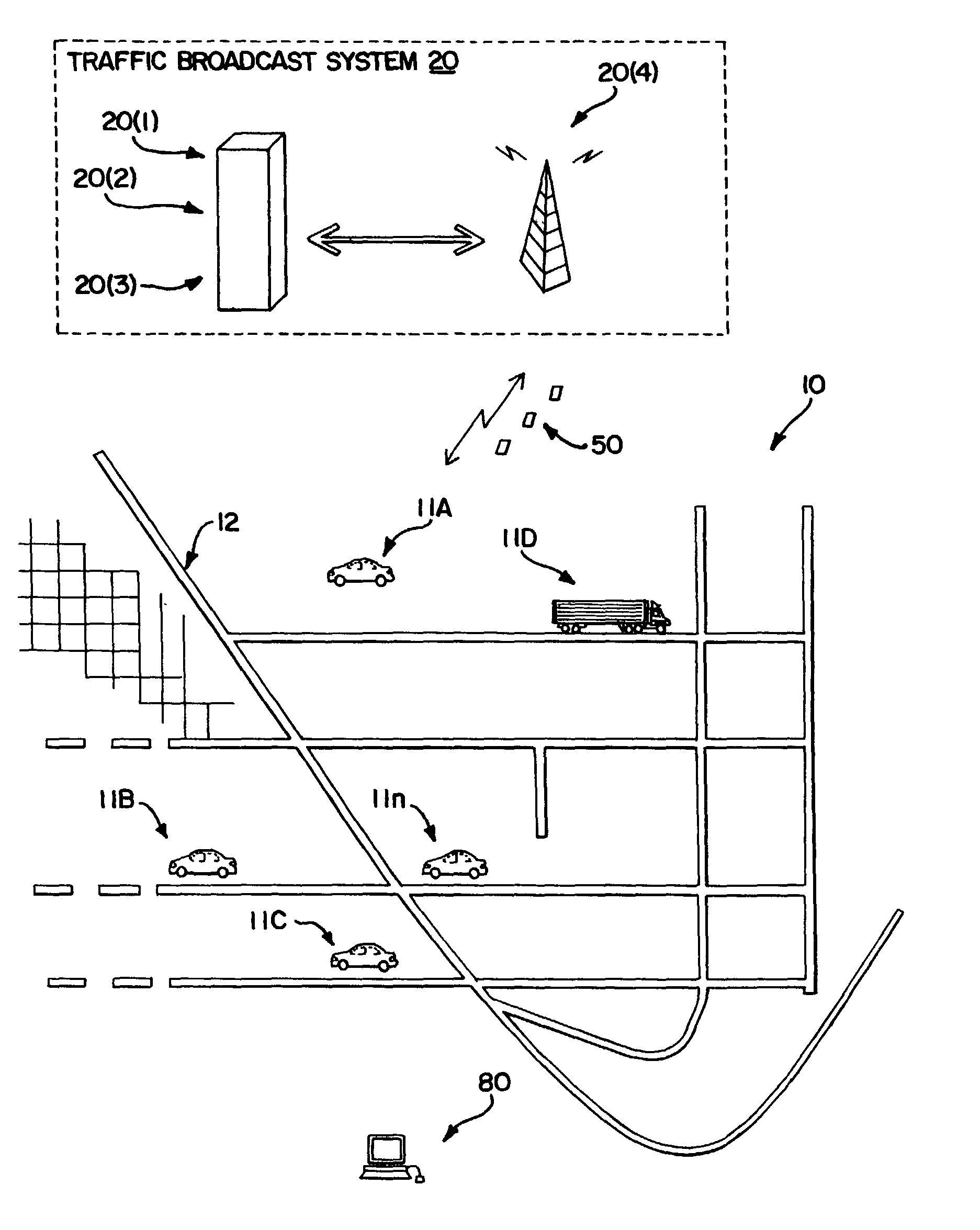
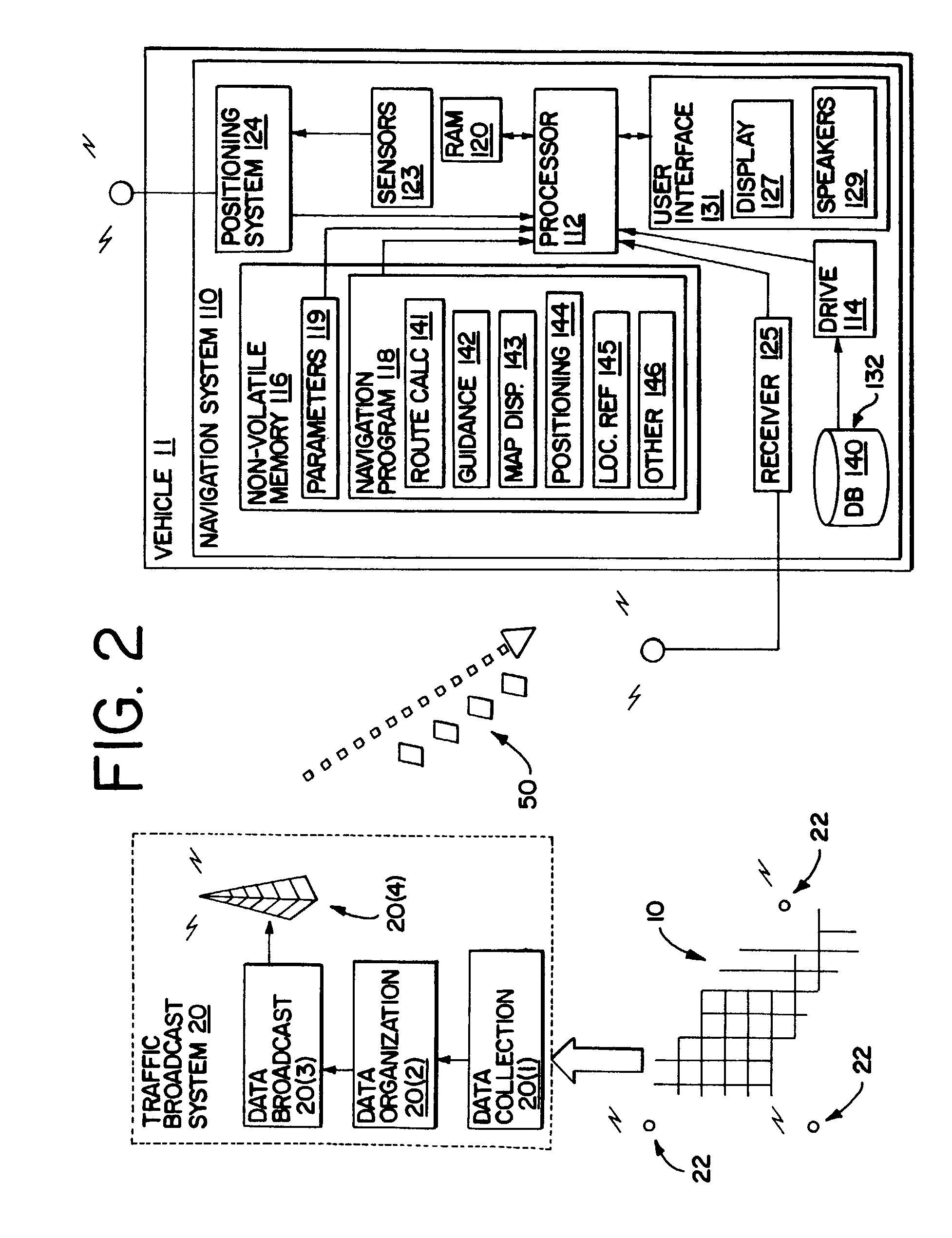
Method and system for using real-time traffic broadcasts with navigation systems
InactiveUS7031983B2Analogue computers for vehiclesInstruments for road network navigationTelecommunications linkGeographic feature
Owner:HERE GLOBAL BV
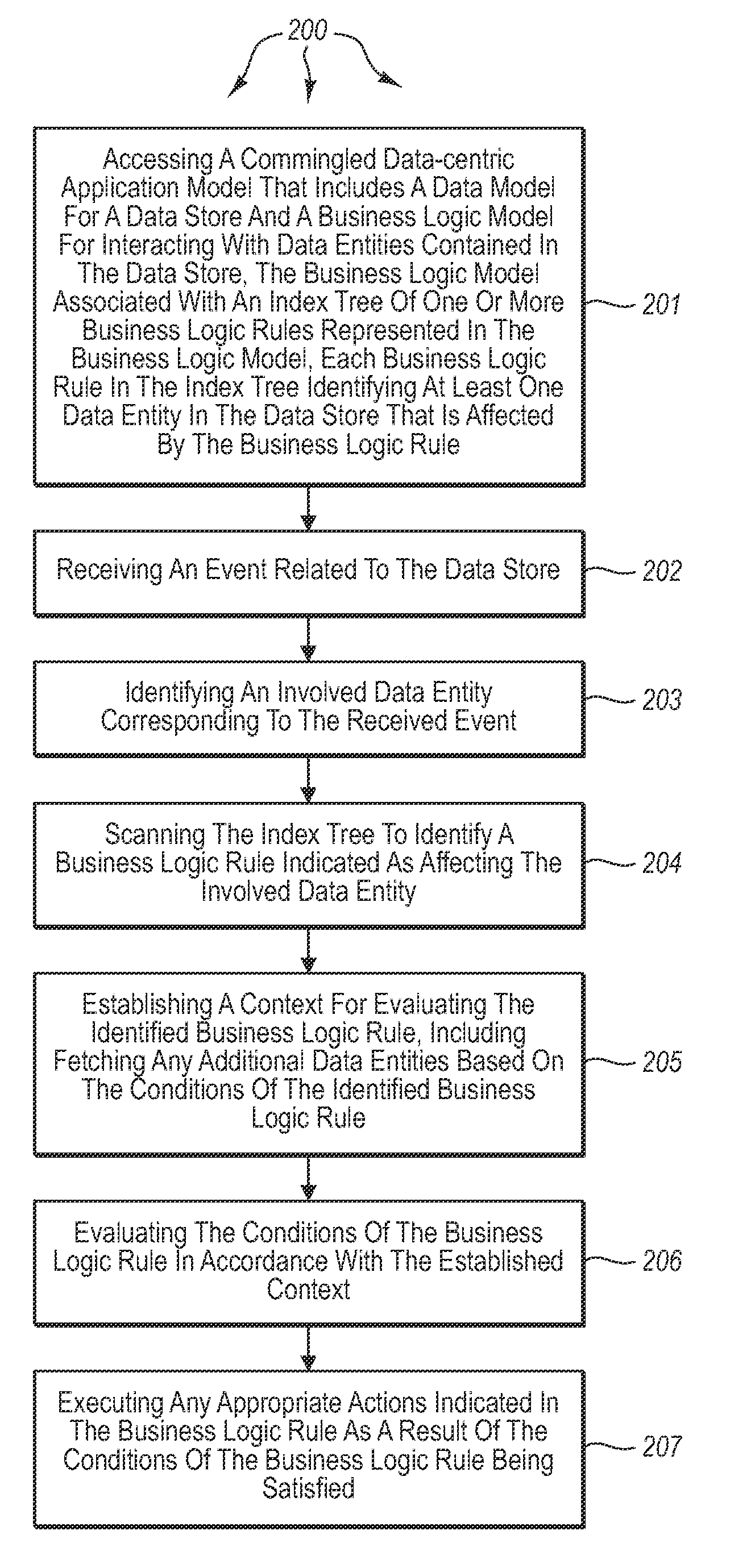
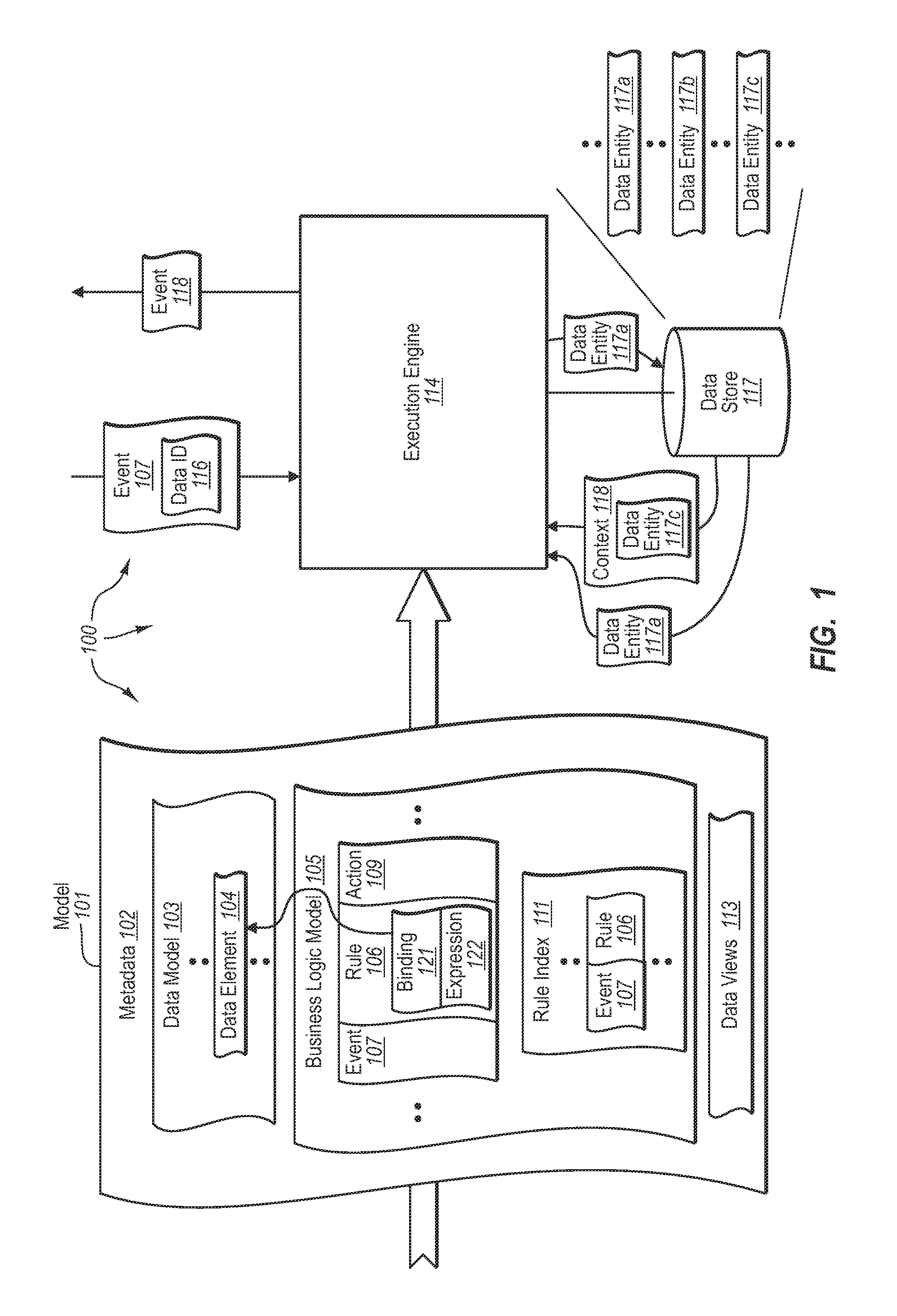
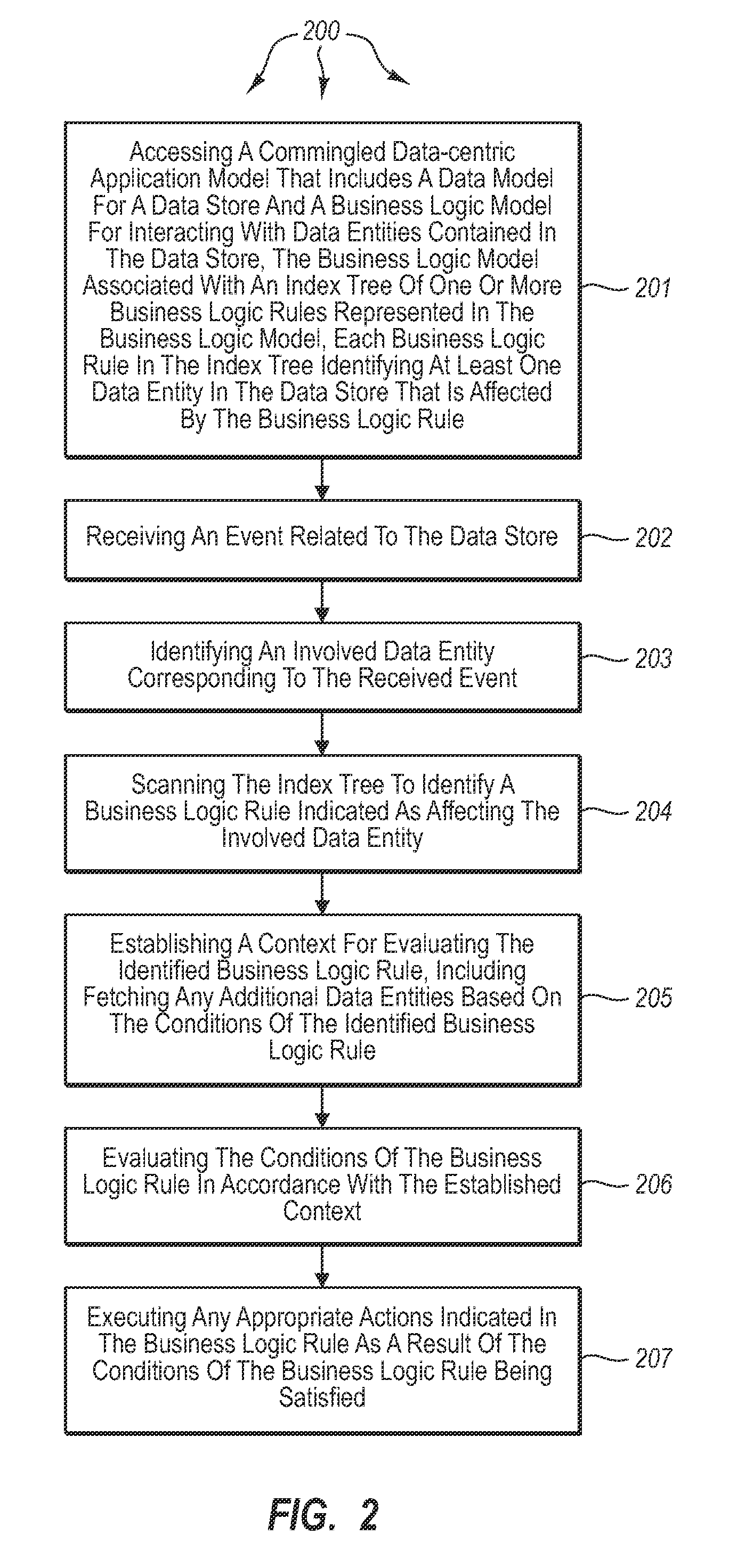
Processing data-centric business models
ActiveUS7599901B2Knowledge representationSpecial data processing applicationsApplication softwareData store
The present invention extends to methods, systems, and computer program products for processing data-centric business models. An execution engine accesses a commingled data-centric application model that includes a data model for a data store and a business logic model for interacting with data entities contained in the data store. The execution engine receives an event related to the data store and identifies an involved data entity corresponding to the received event. The execution engine identifies a business logic rule indicated as affecting the involved data entity. The execution engine establishes a context for evaluating the identified business logic rule. The execution engine evaluates the conditions of the business logic rule in accordance with the established context. The execution engine executes any appropriate actions indicated in the business logic rule as a result of the conditions of the business logic rule being satisfied.
Owner:MICROSOFT TECH LICENSING LLC
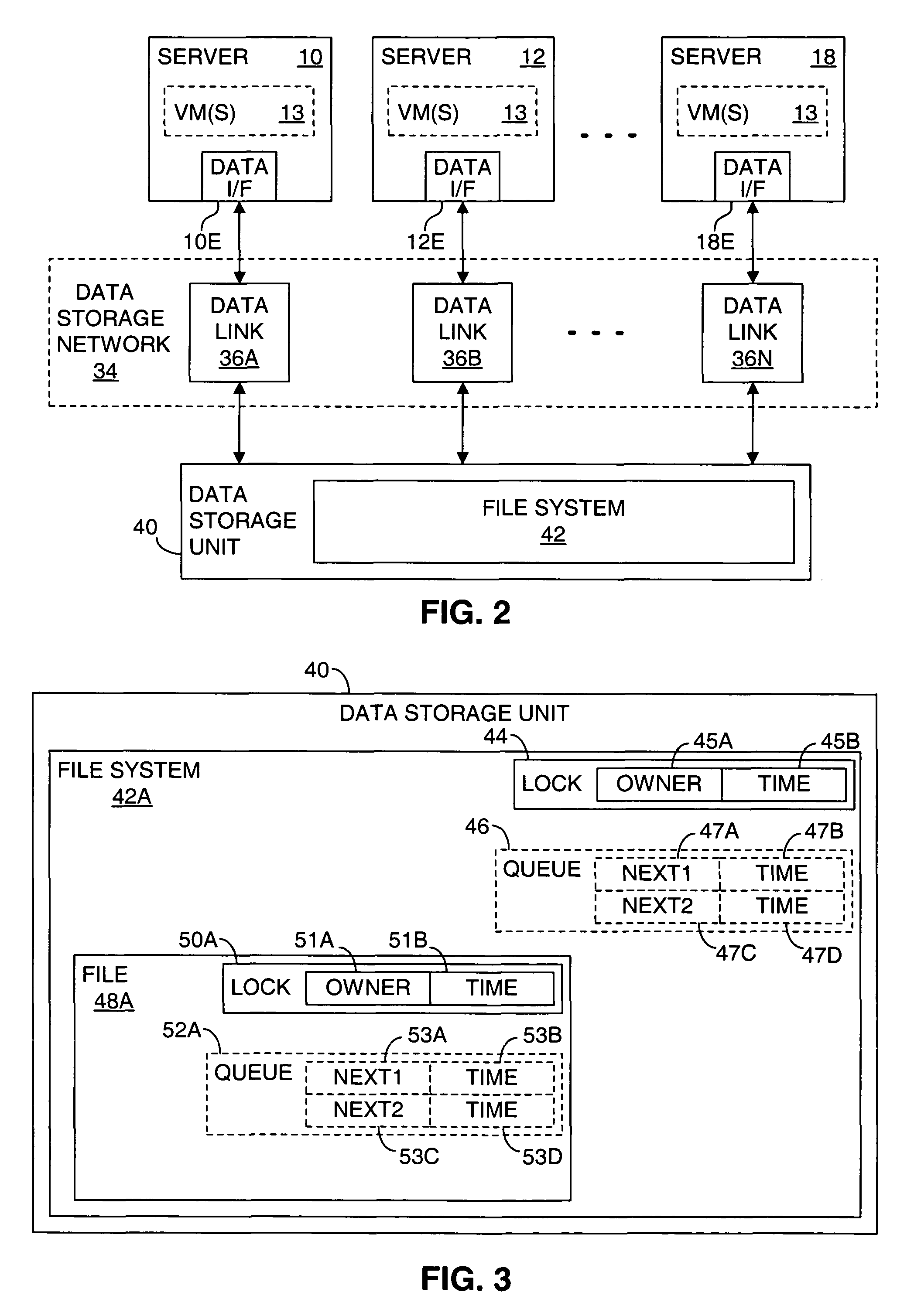
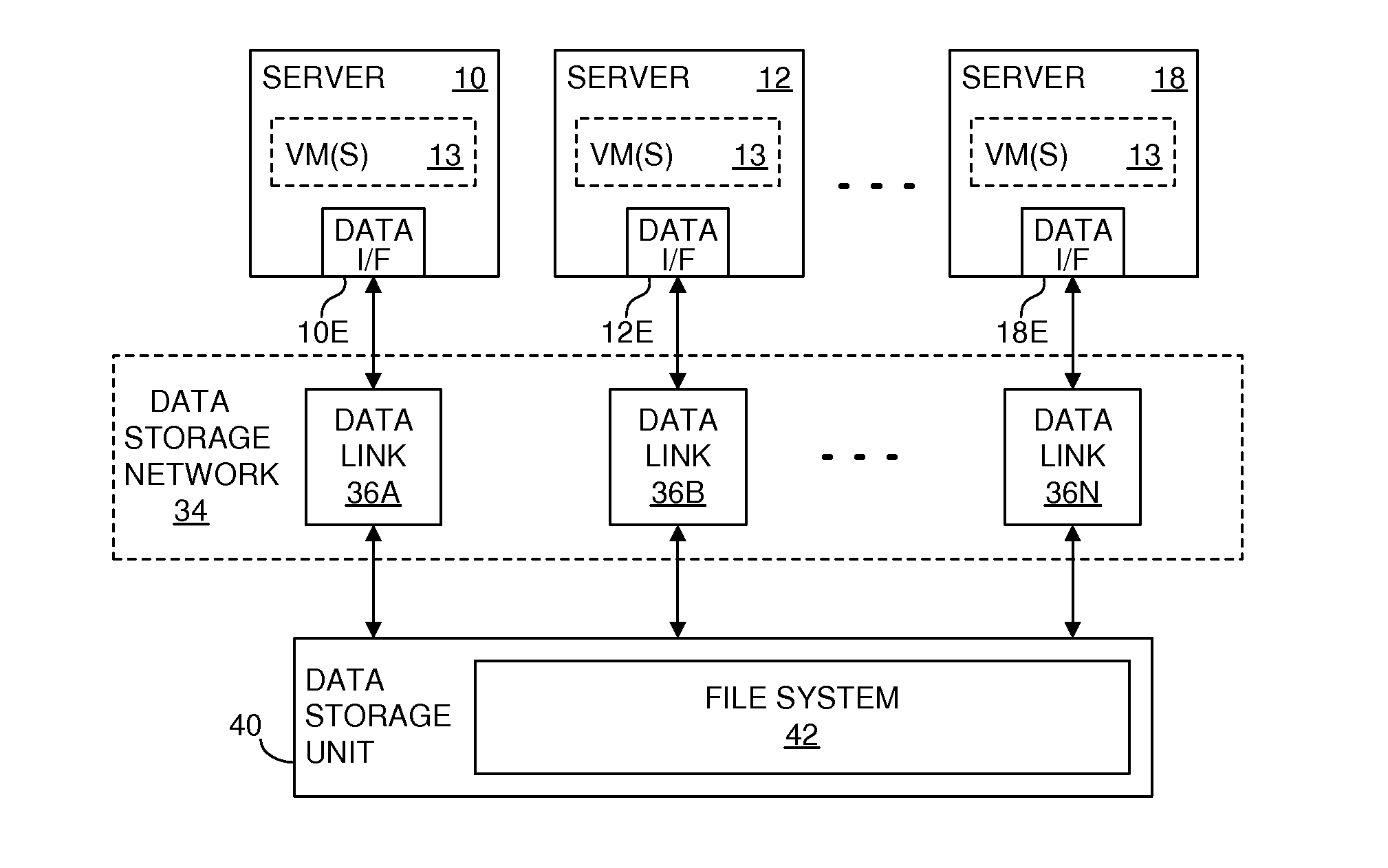
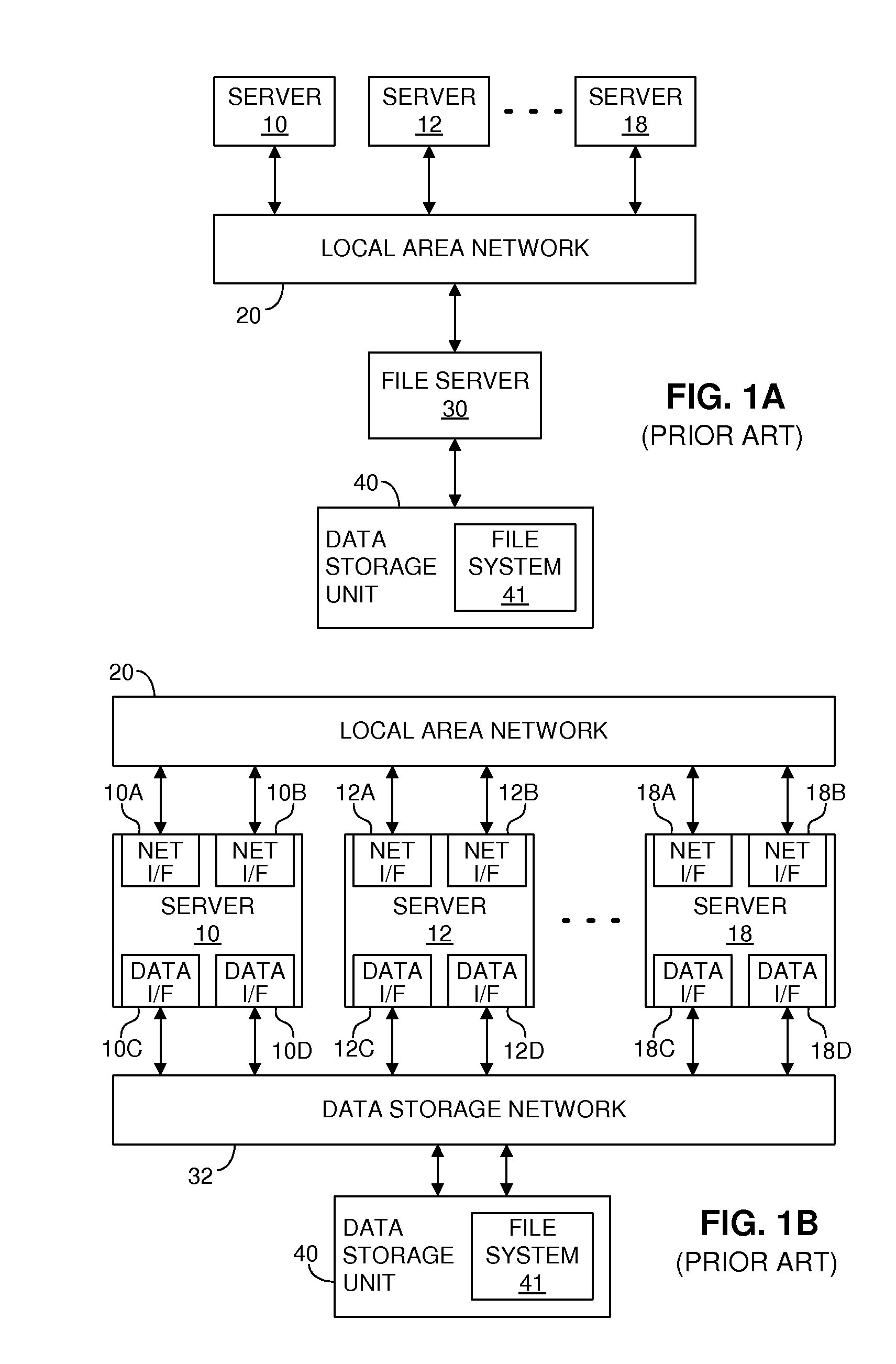
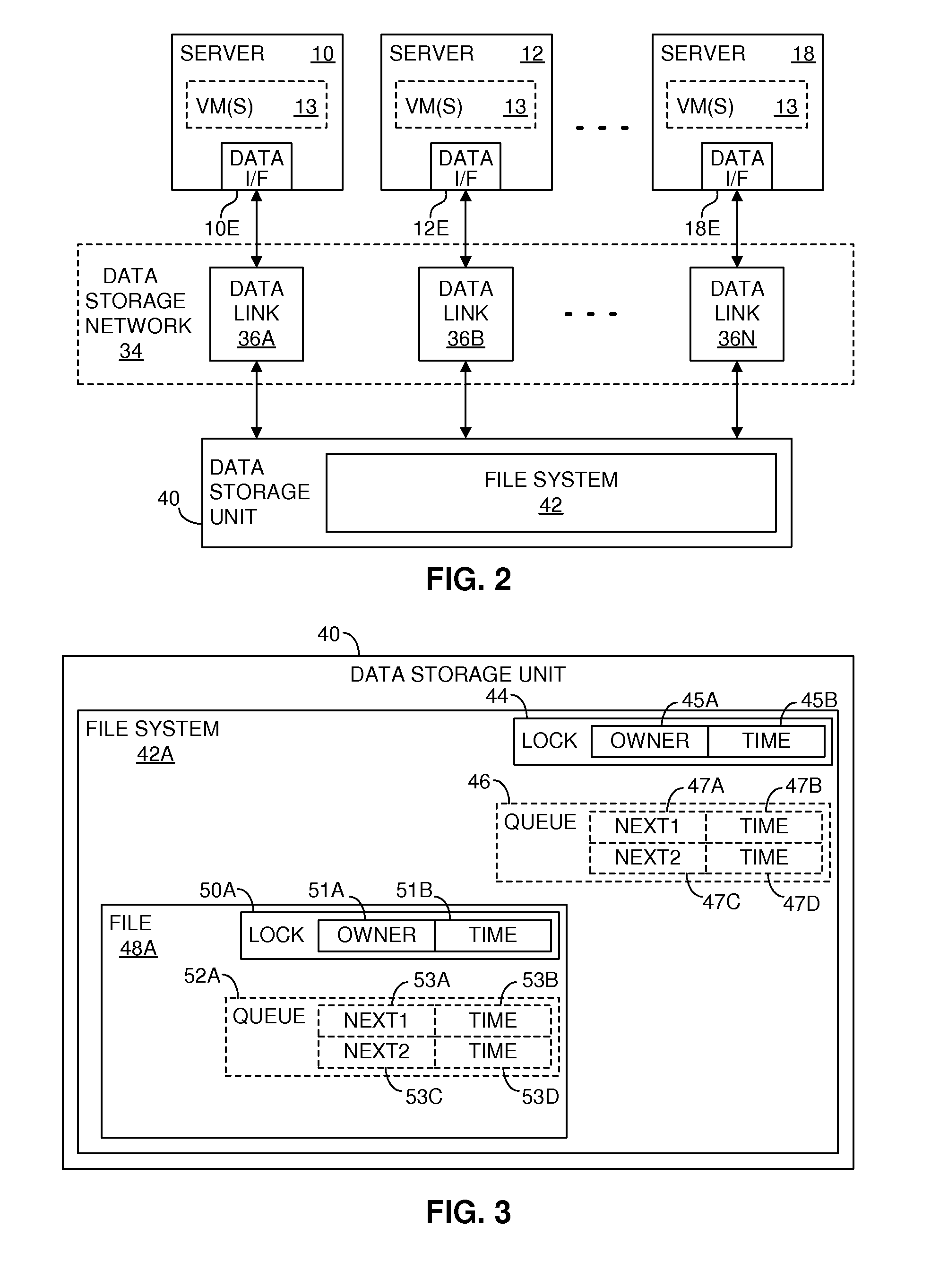
Providing multiple concurrent access to a file system
ActiveUS7849098B1Digital data processing detailsComputer security arrangementsFile systemExclusive or
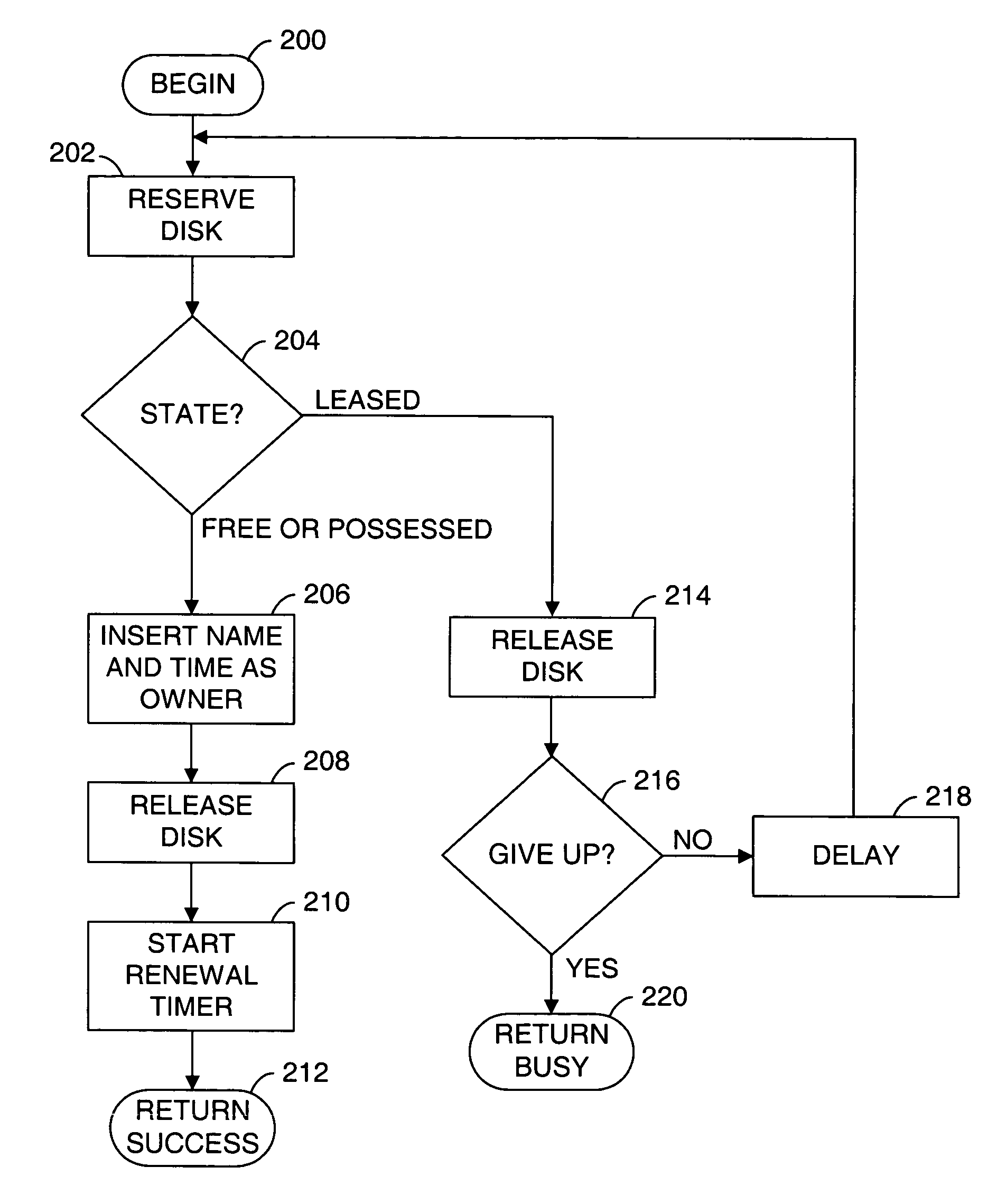
Multiple computers are connected to a data storage unit that includes a file system, which further includes multiple data entities, including files, directories and the file system itself. The file system also includes, for each data entity, an owner field for indicating which computer, if any, has exclusive or shared access to the data entity, along with a time field for indicating when a lease of the data entity began. When a computer wants to lease a data entity, the computer uses a disk reservation capability to temporarily lock the data storage unit, and, if the data entity is not currently leased, the computer writes its own identification value into the owner field and a current time into the time field for the data entity, to claim the data entity for a renewable lease period. If a prior lease of a data entity has expired, another computer may break the lease and claim ownership for itself.
Owner:VMWARE INC
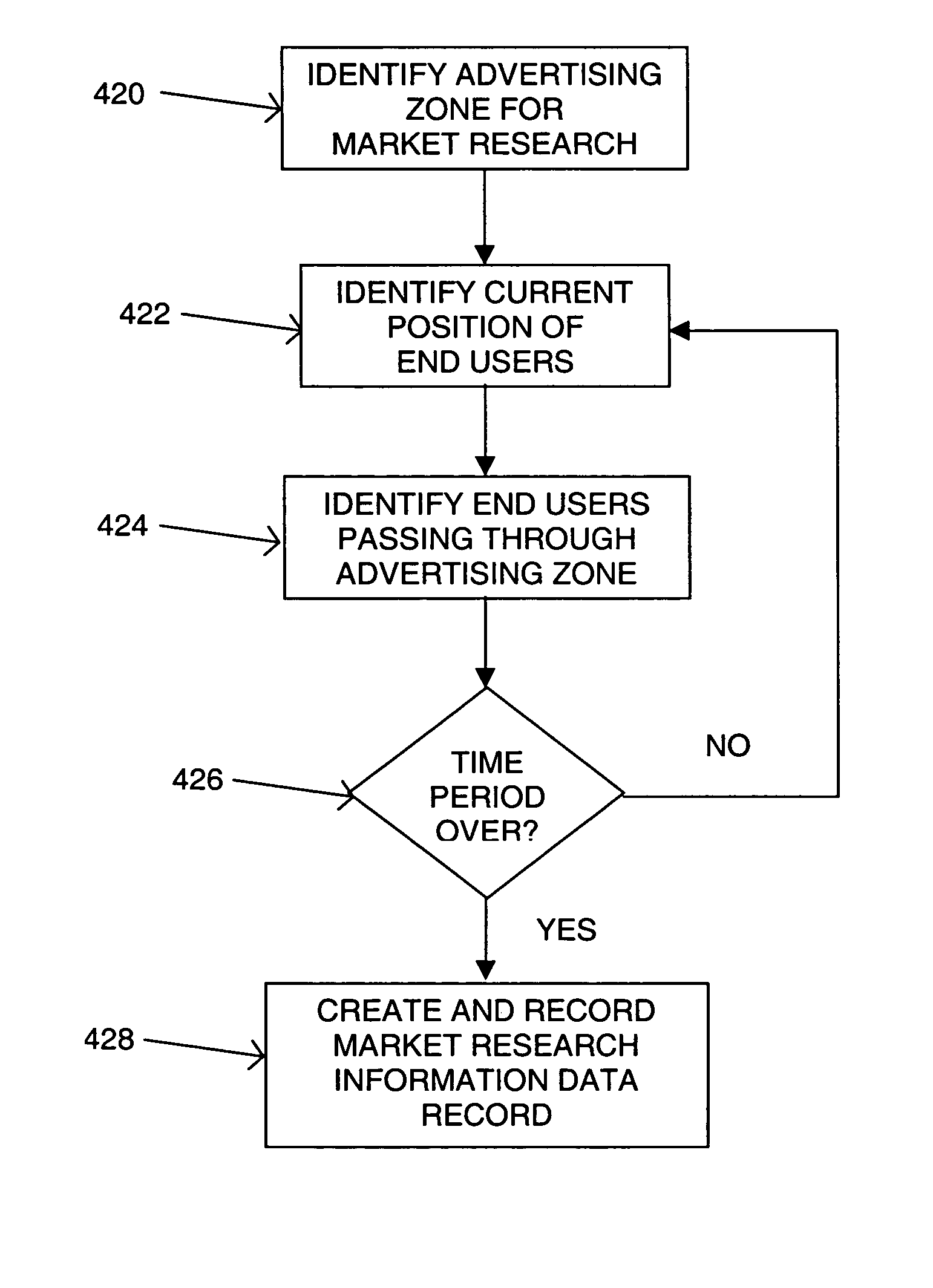
Method of collecting market research information
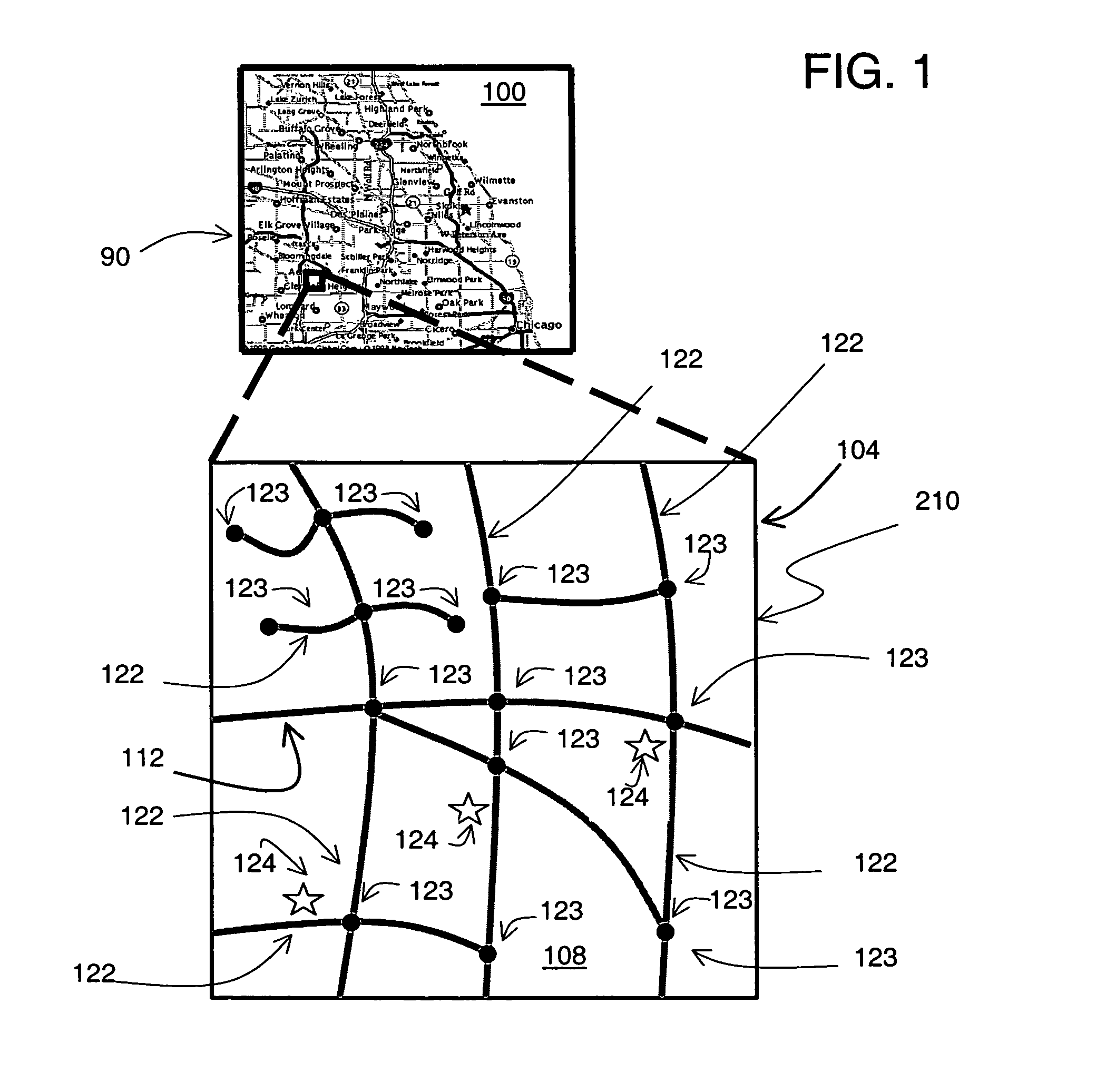
InactiveUS7092964B1Digital data processing detailsLocation information based serviceGeographic featureGeographic regions
A method of collecting market research information is disclosed. A geographic database contains data entities that represent geographic features, such as roads, located in a geographic region. Advertising zones are defined within the geographic region. Users of mobile computing platforms are provided with geographically-related services that use the geographic database. As users of the mobile computing platforms travel in the geographic region, the locations of the mobile computing platforms are determined. Demographic information of the mobile computing platform is associated with the position of the mobile computing platform. A market research record identifies which of the mobile computing platforms are located within or passing through one of the advertising zones.
Owner:HERE GLOBAL BV
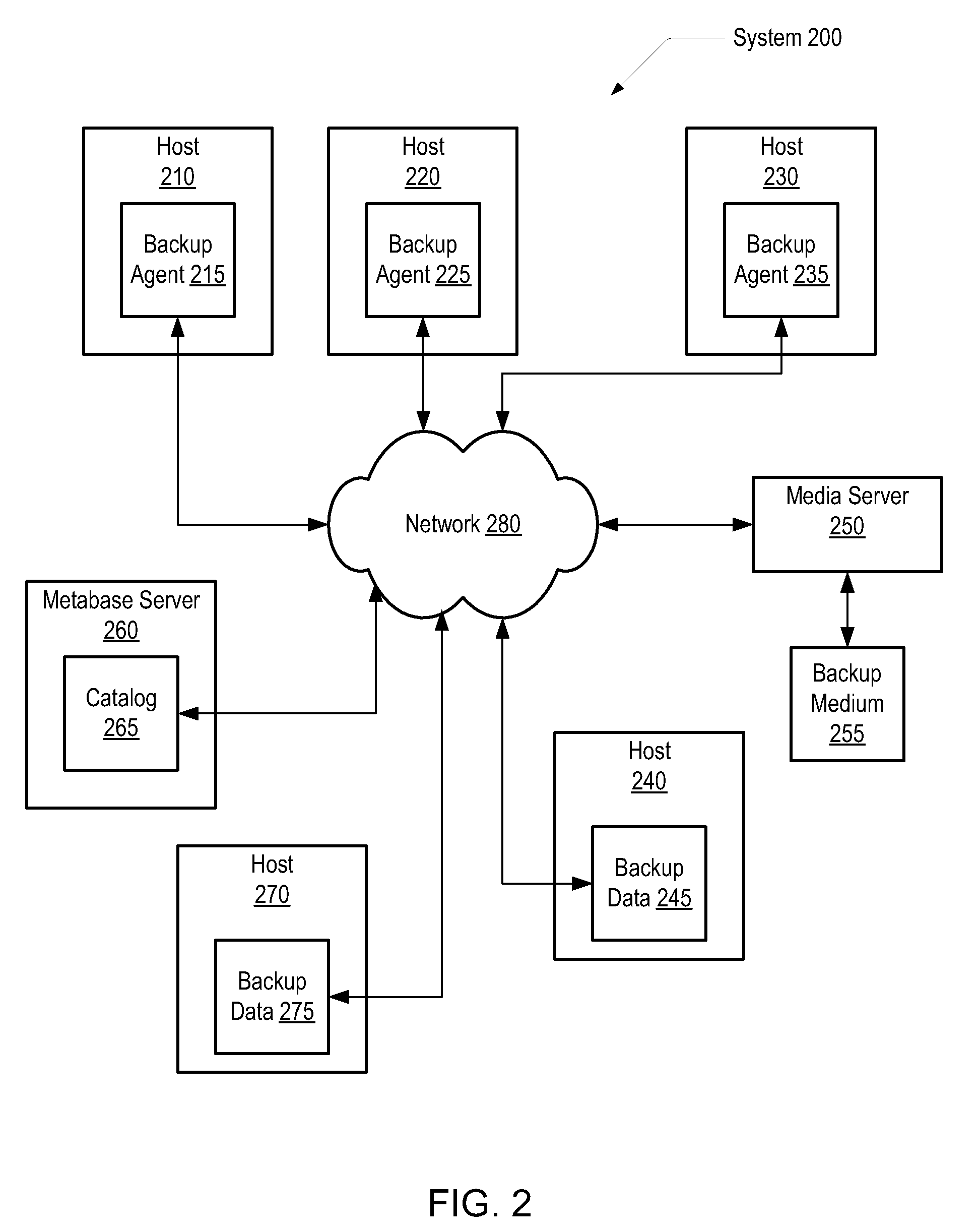
Application aware storage appliance archiving
ActiveUS7827150B1Digital data information retrievalDigital data processing detailsData setMagnetic tape
Various embodiments of a computer system and methods are disclosed. In one embodiment, a computer system includes a host coupled to a backup store. The host backs up a dataset to the backup store. The dataset comprises data entities and application-specific metadata describing the data entities. The application-specific metadata enables an application to use the data entities. The host: mounts the backup store for read / write access by the application, accesses the backup store with the application, selects a data entity, and performs an operation on the data entity in the backup store using the application. The operation may comprise verifying that the data entity is valid and usable in the context of the application or creating an archival backup of the data entity on a backup medium. The backup store may be a disk-based backup store and the backup medium may be a tape-based backup medium.
Owner:VERITAS TECH
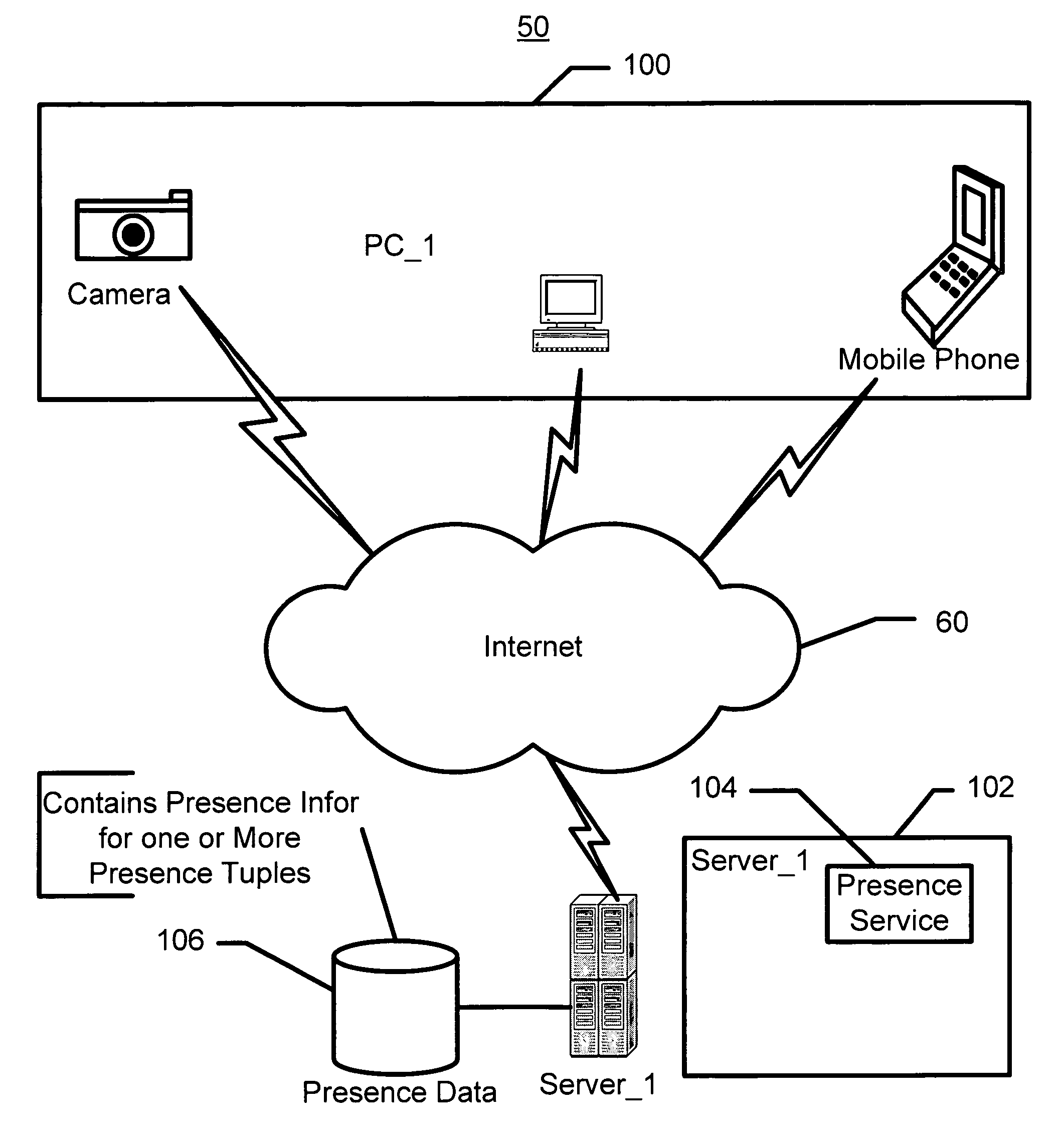
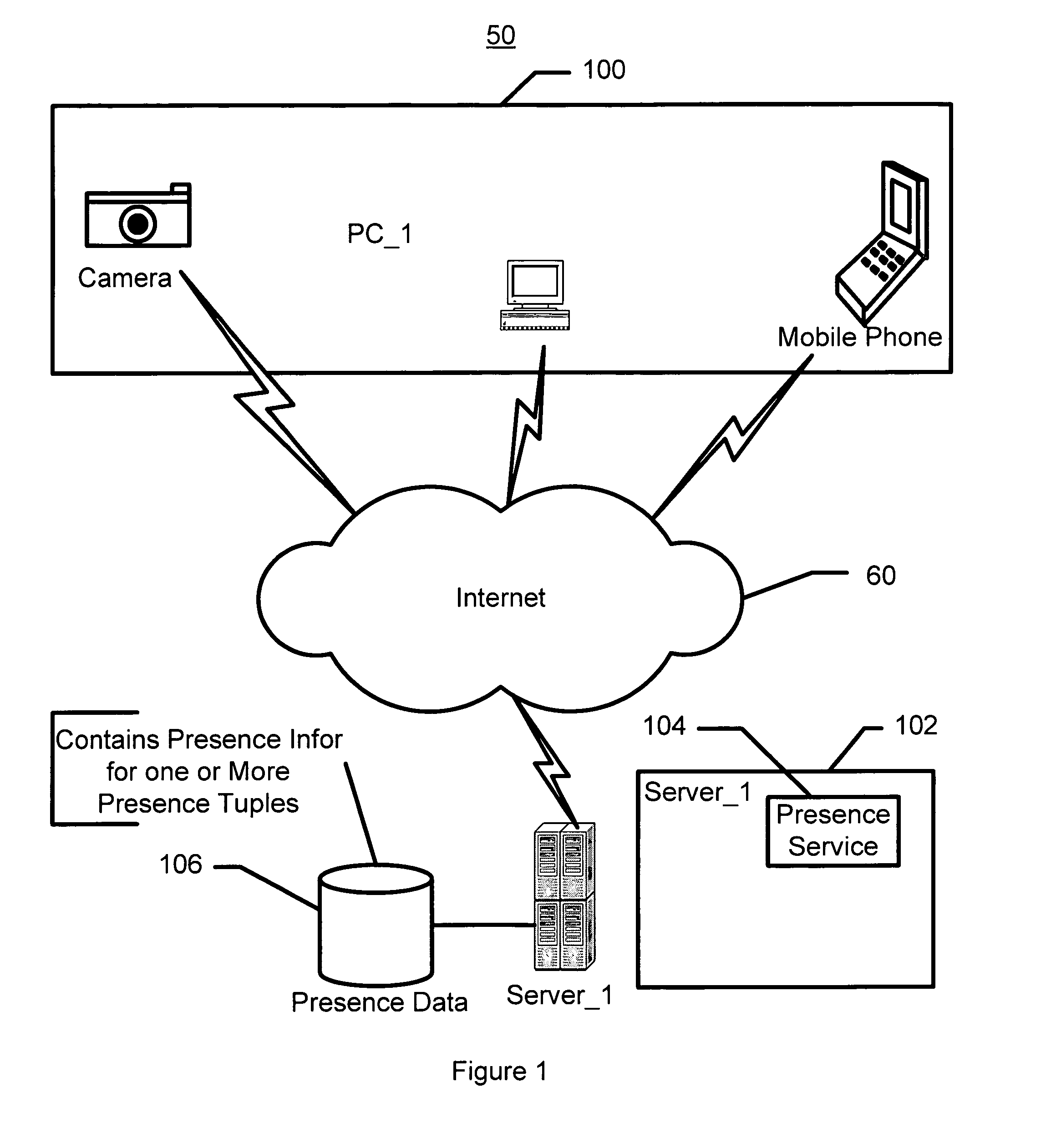
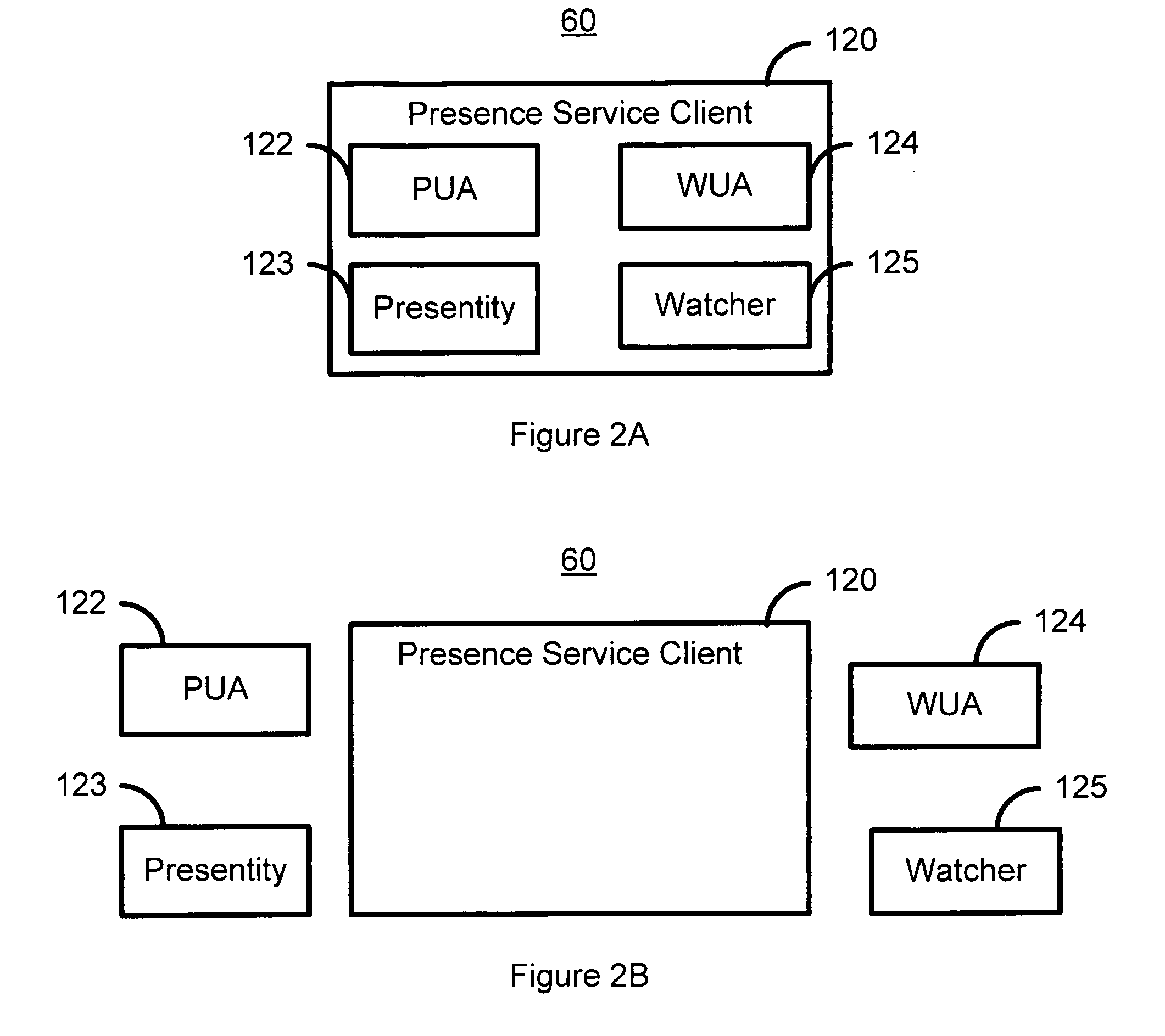
System and method for utilizing contact information, presence information and device activity
InactiveUS20070198725A1Multiple digital computer combinationsOffice automationPresence serviceClient-side
A method and system utilizes presence information for a plurality of presence service clients is disclosed. In one aspect, the method and system include determining the presence information for the presence service clients, individually tailoring the presence information for presentation to each of a portion of the presence service clients, and presenting the tailored presence information to the portion of the presence service clients. In another aspect, the method and system include associating a component or a data entity of a device with presence information such that the component or the data entity corresponds to a first of the presence service clients. In this aspect, the method and system also include providing a presentity for the first presence service client. A second of the presence service clients corresponds to a user. Each presentity communicates with a presence service on behalf of the first and second presence service clients.
Owner:SCENERA TECH
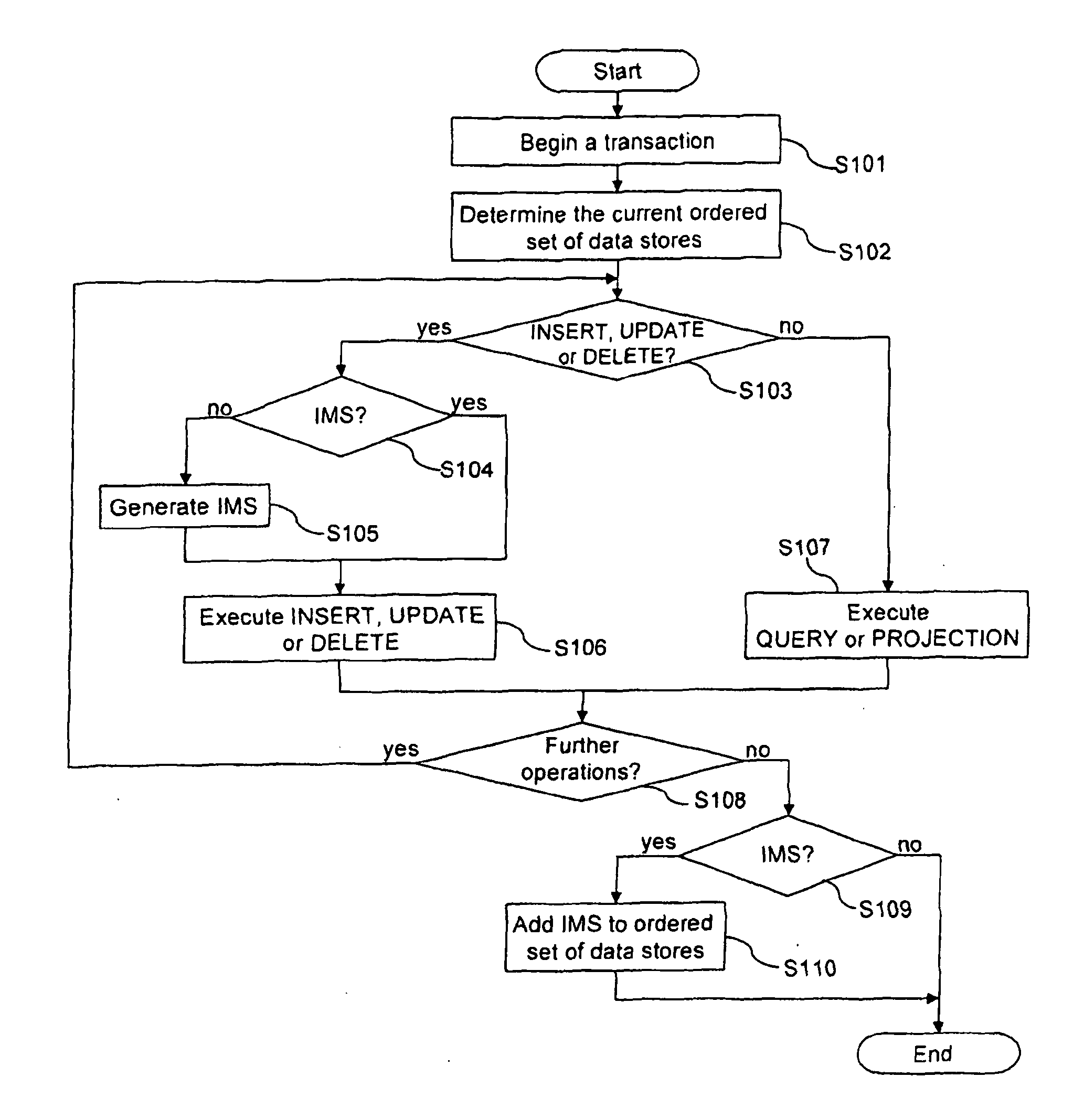
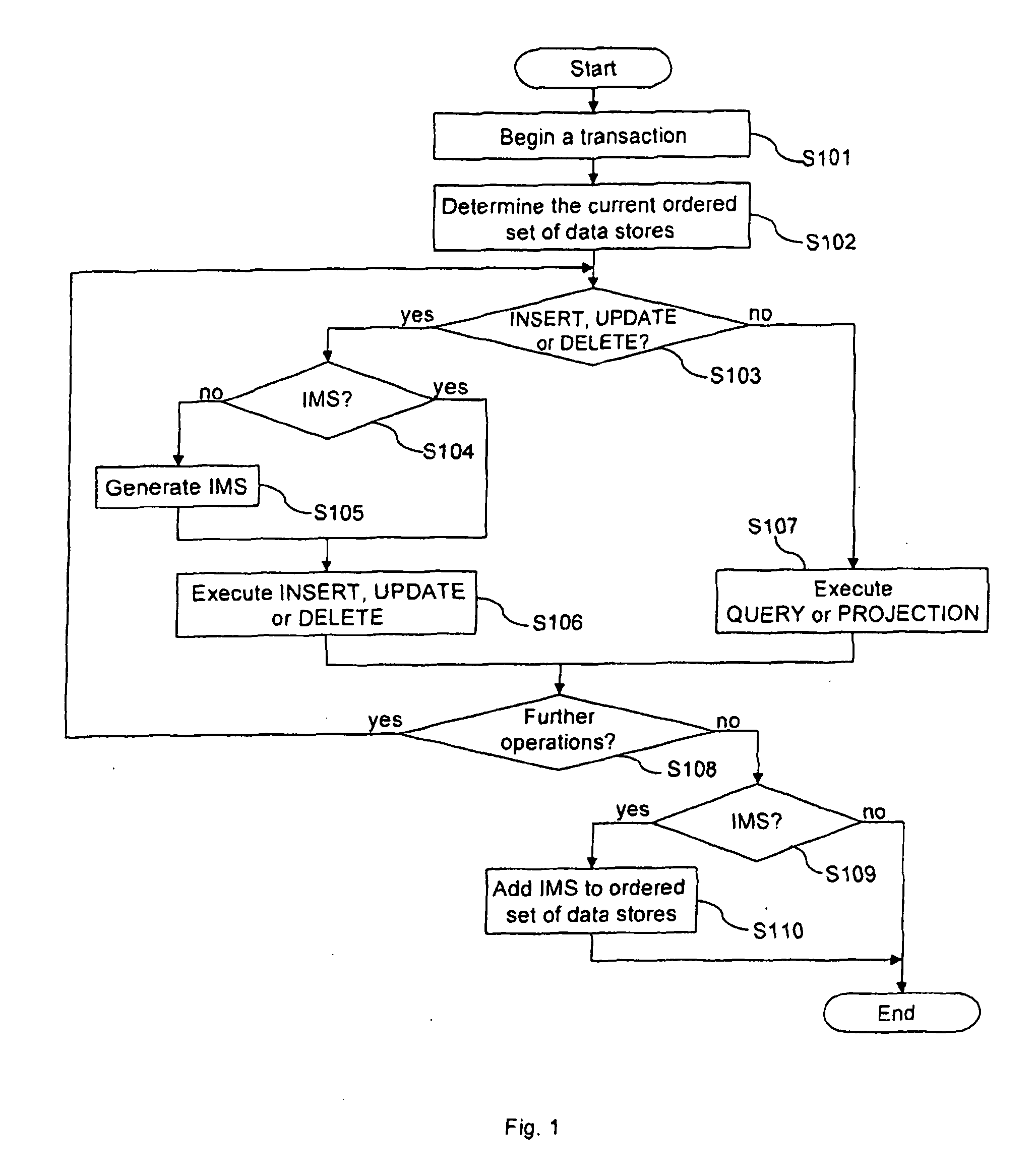
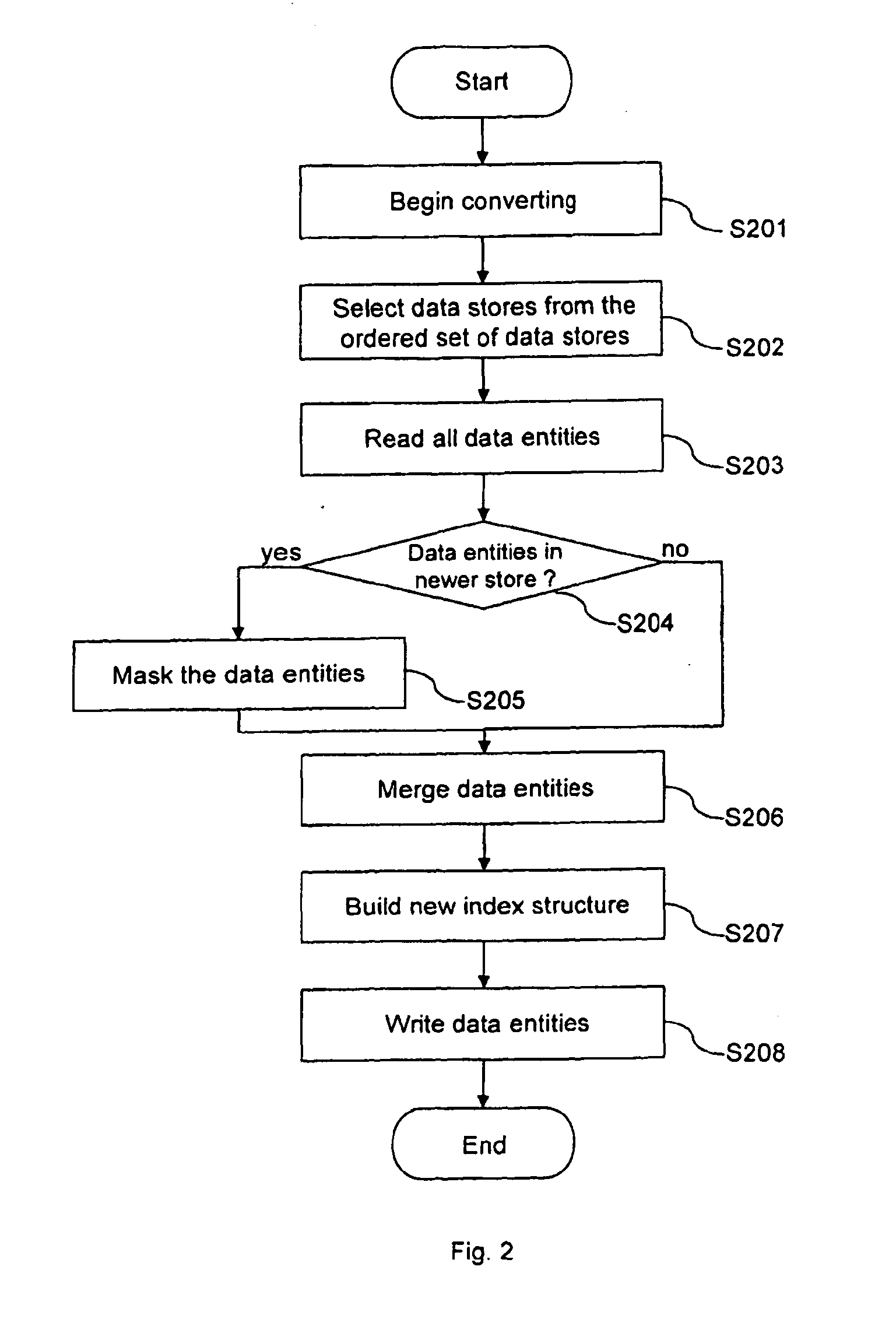
Method for performing transactions on data and a transactional database
ActiveUS20130110766A1Improve performanceLow costDigital data information retrievalDigital data processing detailsData storingOrder set
The present invention provides a method for performing transactions on data entities in a database and a transactional database. The database comprises an ordered set of data stores with at least one static data store, wherein said static data store uses an index structure based on a non-updatable representation of an ordered set of integers according to the principle of compressed inverted indices. The method allows to generate a modifiable data store when the performed transaction comprises an insert, update or delete operation, to execute operations of the transaction on the ordered set being present at the time when the transaction has been started and, if present, on the modifiable data store and to convert data stores to a new static data store, The insert, update or delete operation are executed on the modifiable data store which is the only data store modifiable for the transaction.
Owner:OPEN TEXT SA ULC
Method and system for securing user identities and creating virtual users to enhance privacy on a communication network
InactiveUS20090024636A1High activityEffective interactionDigital data processing detailsAnalogue secracy/subscription systemsVirtual userVirtual entity
A method of enabling a real entity to access a service on a communication network using a virtual entity, the method including the steps of establishing a user account including at least first data corresponding to the identity of the real entity and second data corresponding to the virtual entity and not identifying the real entity, storing the first and second data in a first database, linking between the first and second data in the first database, storing the second data at a second database, associating the second database with a communication network site, connecting the communication network site to the communication network, receiving the second data from an unidentified user on the communication network site, identifying the unidentified user as the virtual entity based on receiving the second data, and allowing the virtual entity to access the service.
Owner:SHILOH DEKEL
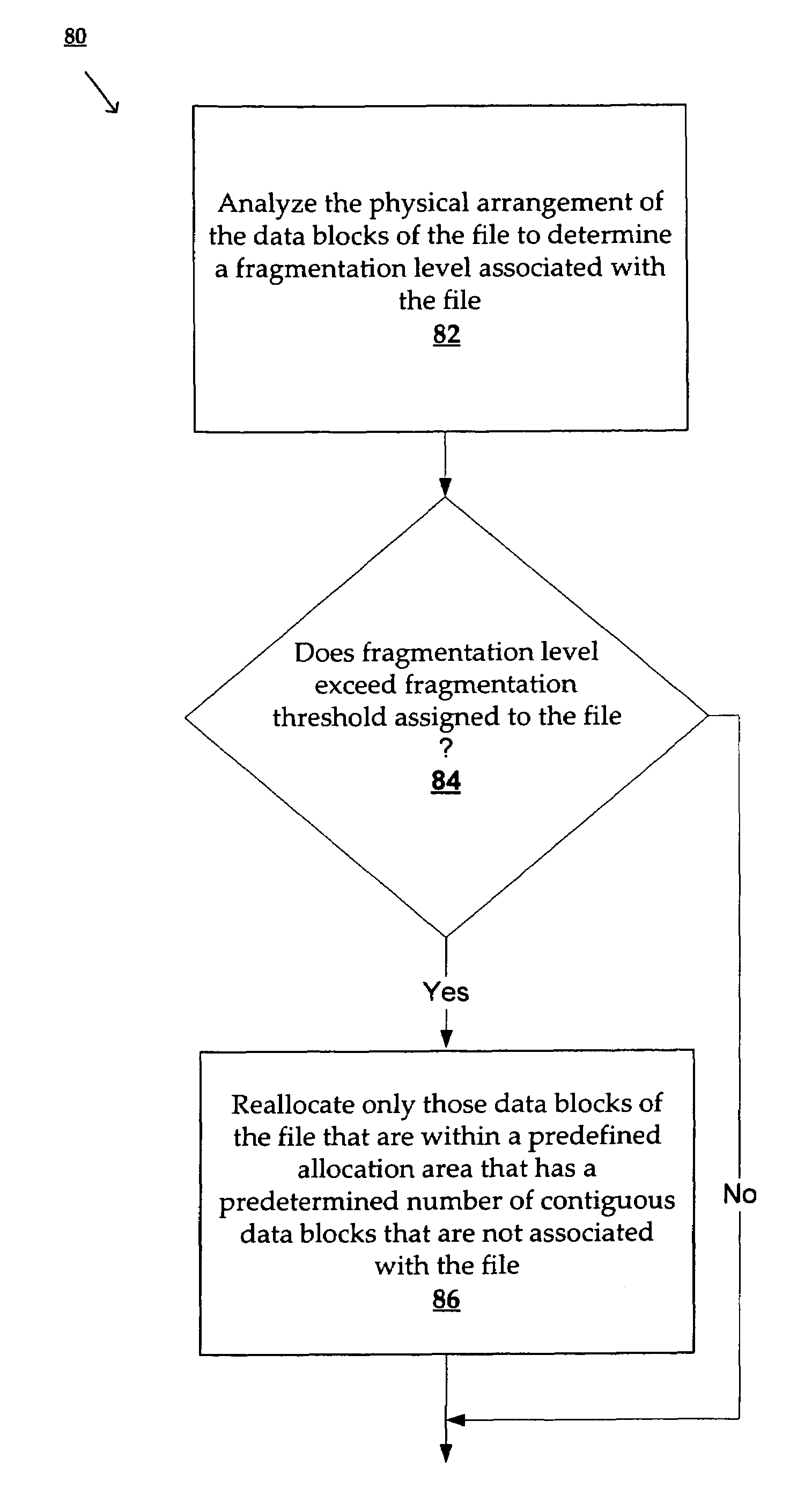
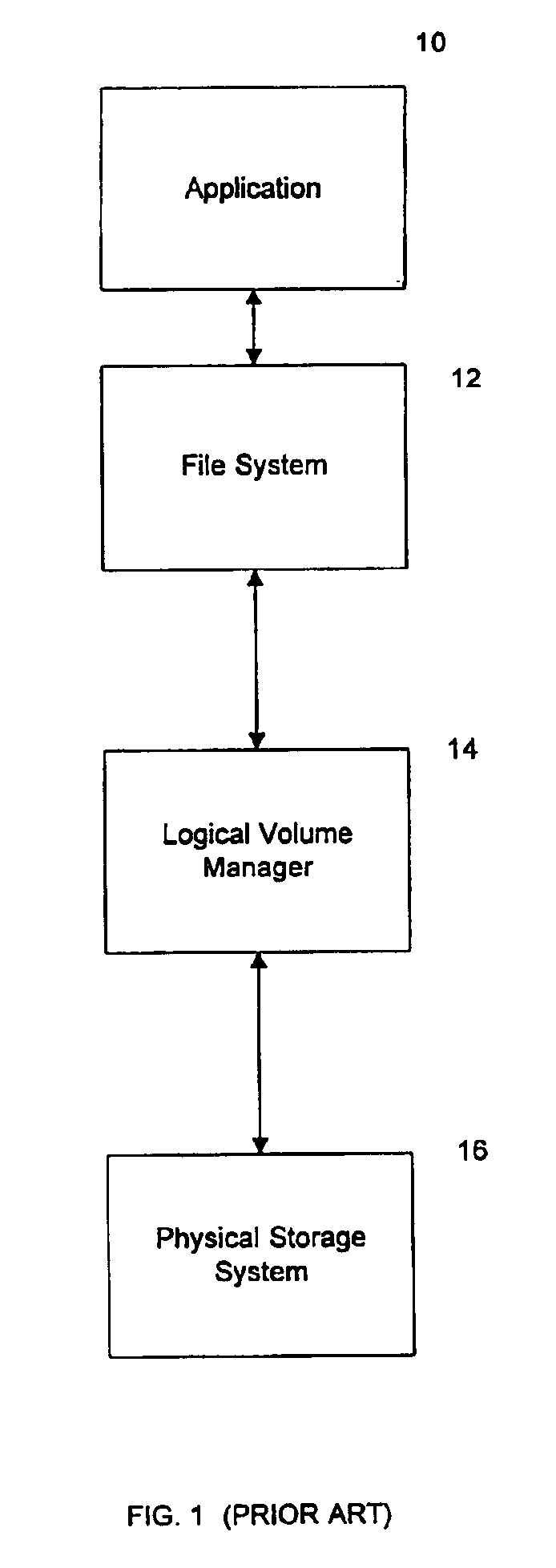
Method and system for reallocating data in a file system
A method and system for reallocating the data blocks of a logical data entity are described. According to one aspect of the invention, the physical arrangement of data blocks of a logical data entity are analyzed to determine a fragmentation level. Next the fragmentation level is compared with a fragmentation threshold previously assigned to the logical data entity. If the fragmentation level exceeds the fragmentation threshold, only those data blocks of the logical data entity that are within a predefined allocation area having a predetermined number of contiguous data blocks that are not associated with the logical data entity are reallocated.
Owner:NETWORK APPLIANCE INC
Method and system for managing event attributes
InactiveUS7111010B2Maintain qualityAnalogue computers for electric apparatusOffice automationData entityData science
Owner:XENOGENIC DEV LLC
Providing multiple concurrent access to a file system
ActiveUS20110055274A1Digital data processing detailsComputer security arrangementsFile systemExclusive or
Multiple computers are connected to a data storage unit that includes a file system, which further includes multiple data entities, including files, directories and the file system itself. The file system also includes, for each data entity, an owner field for indicating which computer, if any, has exclusive or shared access to the data entity, along with a time field for indicating when a lease of the data entity began. When a computer wants to lease a data entity, the computer uses a disk reservation capability to temporarily lock the data storage unit, and, if the data entity is not currently leased, the computer writes its own identification value into the owner field and a current time into the time field for the data entity, to claim the data entity for a renewable lease period. If a prior lease of a data entity has expired, another computer may break the lease and claim ownership for itself.
Owner:VMWARE INC
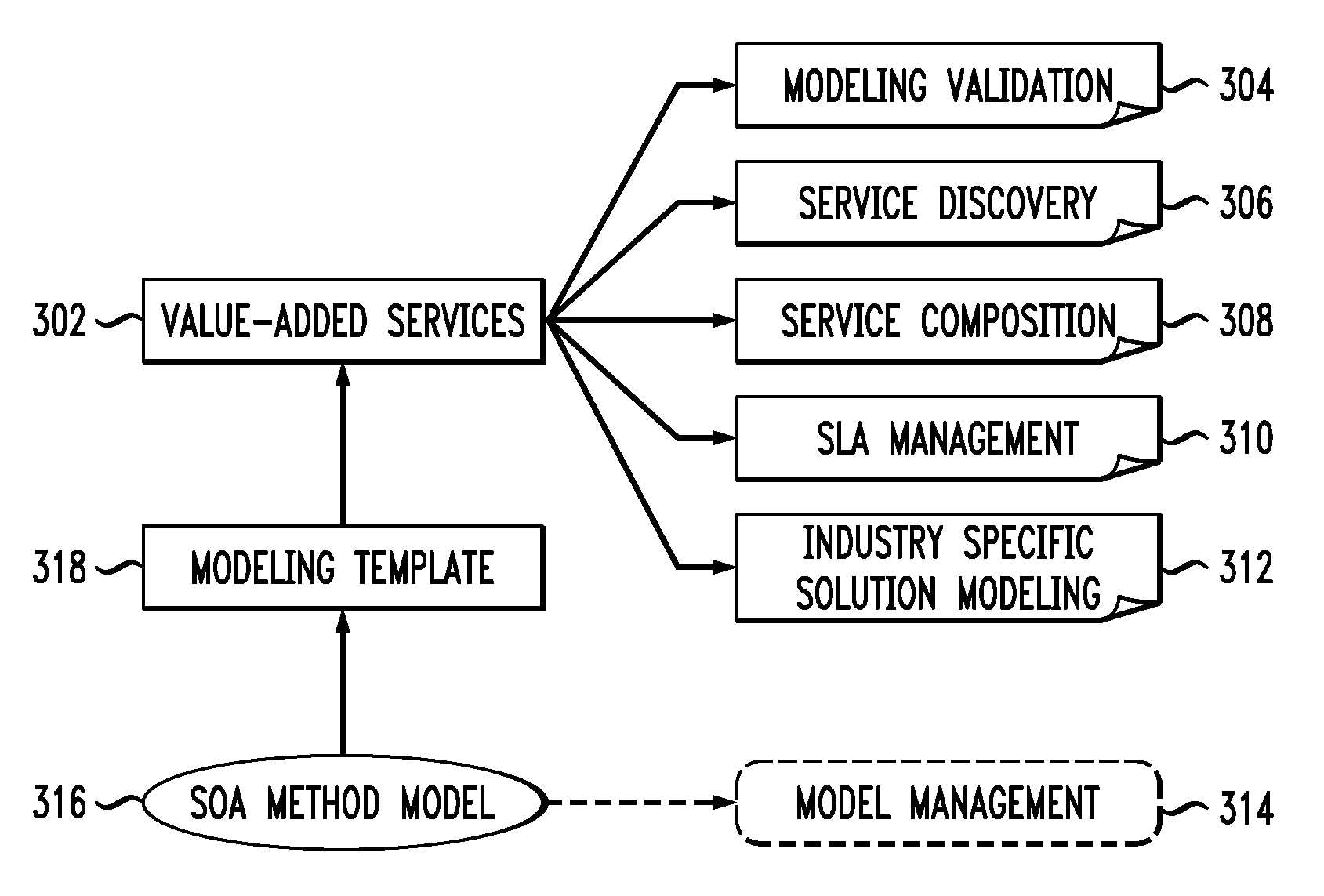
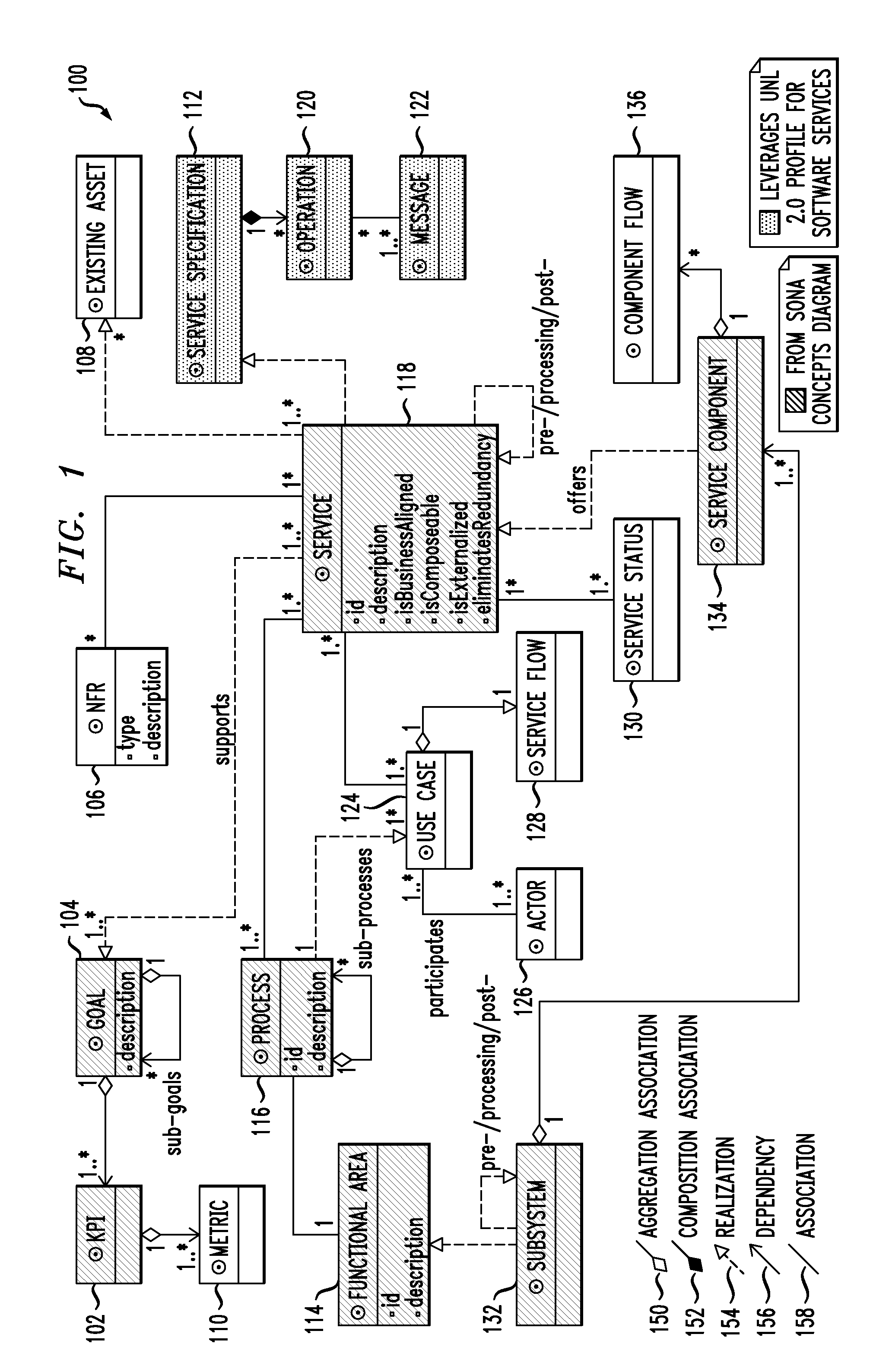
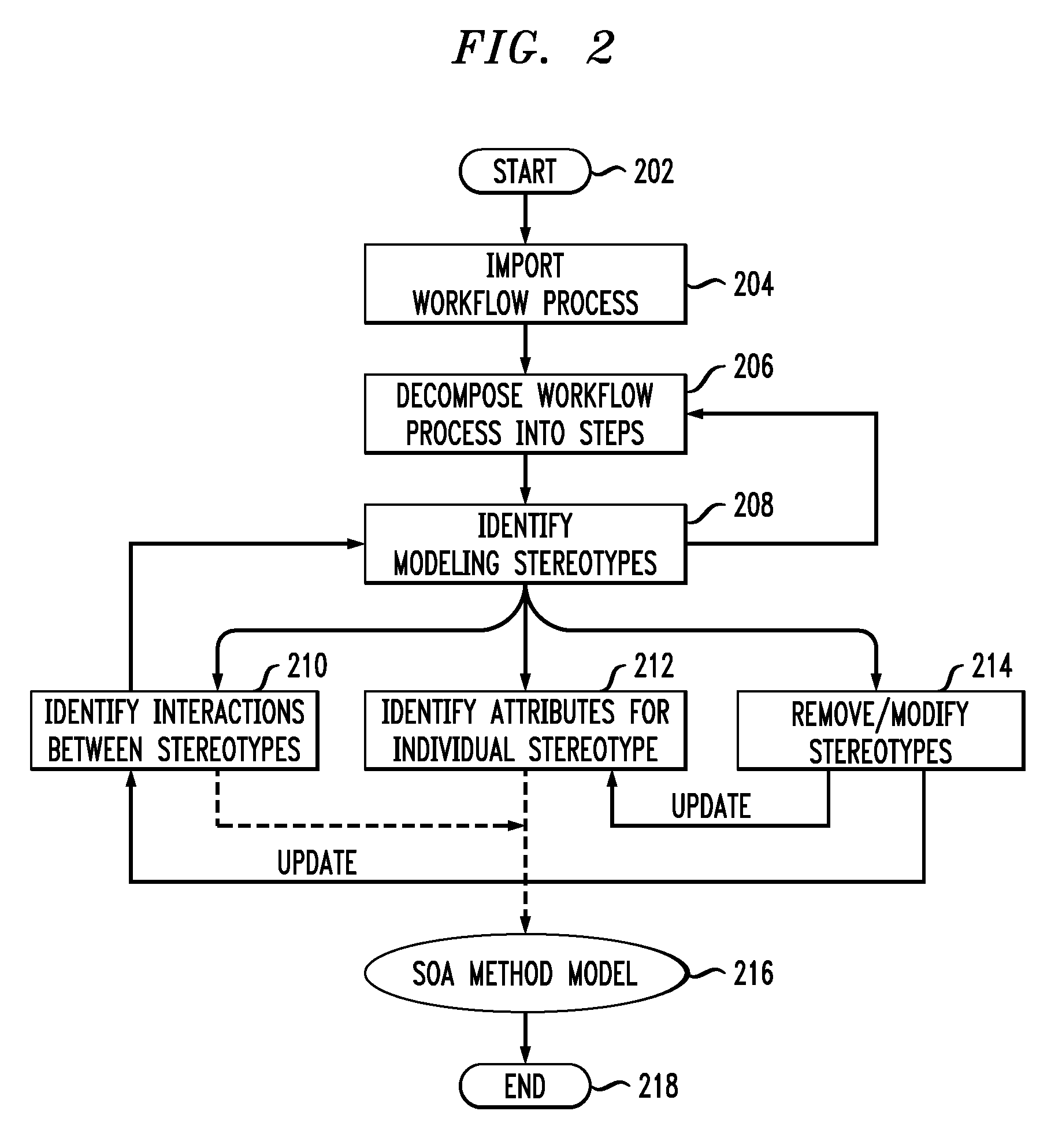
Method and apparatus for service-oriented architecture process decomposition and service modeling
ActiveUS7979840B2Multiple digital computer combinationsResourcesService-oriented architectureData entity
Techniques are provided for service-oriented (SOA) process decomposition and service modeling. In one aspect of the invention, the techniques include identifying meta-data entities, attributes of the meta-data entities and relationships between stereotypes of the meta-data model, managing the meta-data model for creating, modifying and removing modeling artifacts, and creating modeling templates from the meta-data model to facilitate addressing at least one need of industry-specific applications. In another aspect the invention, the techniques include packaging the method for SOA process decomposition and service modeling, facilitating lifecycle management of modeling assets, and facilitating maintenance of the modeling assets.
Owner:IBM CORP
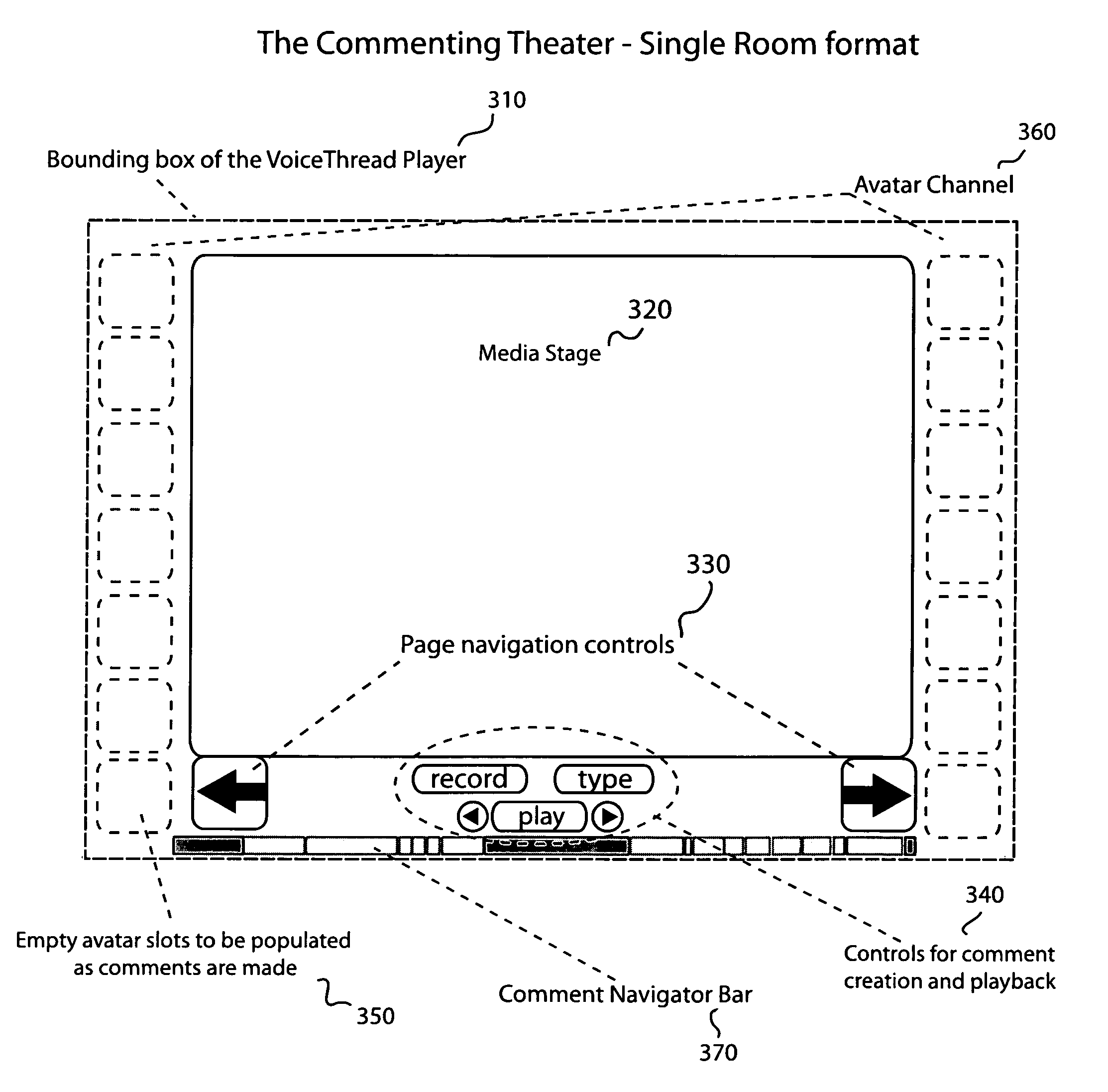
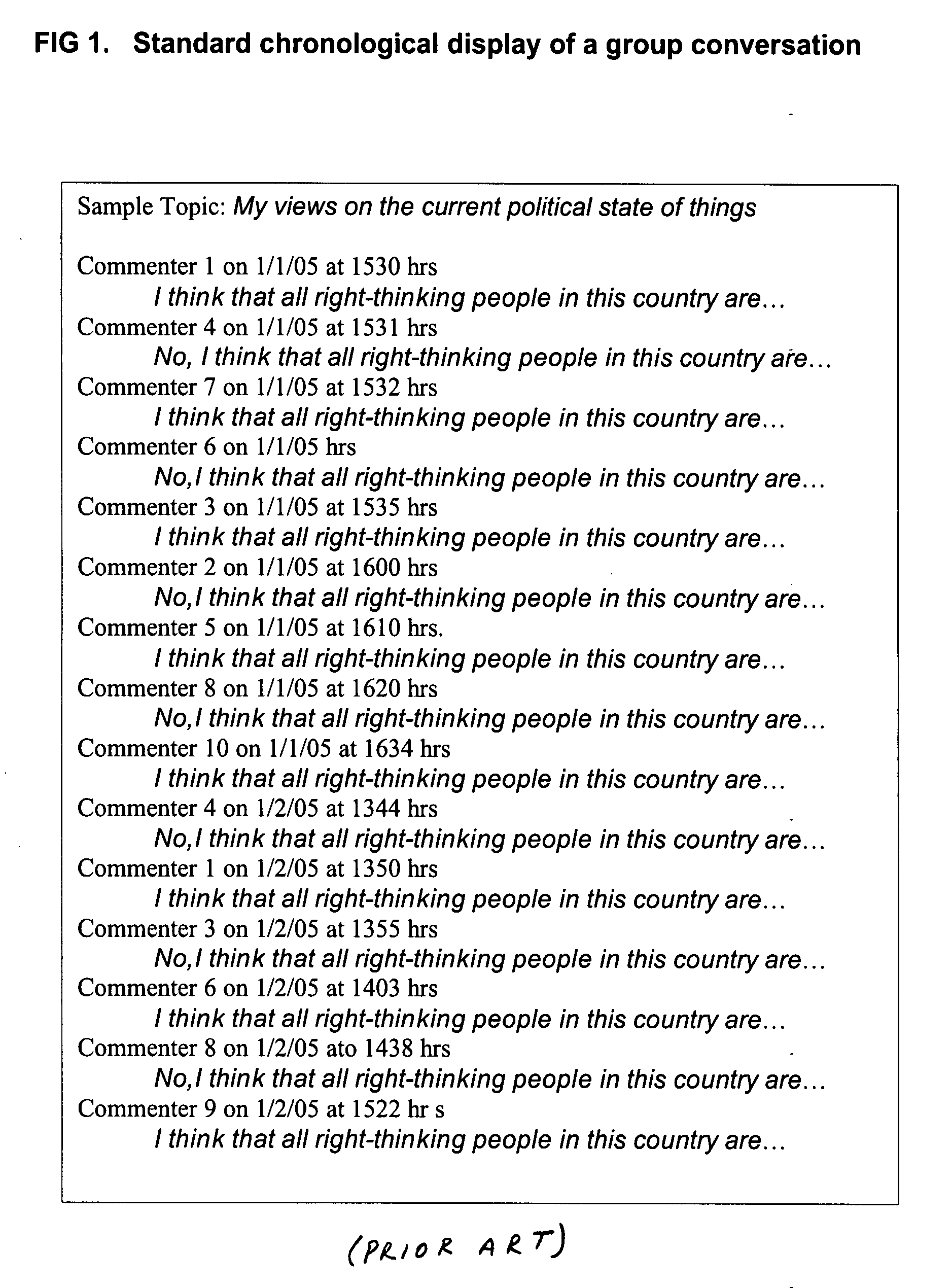
System of archiving and repurposing a complex group conversation referencing networked media
InactiveUS20070271331A1Improve user engagementImprove accessibility and usabilityMultimedia data browsing/visualisationRecord information storageNetwork mediaData entity
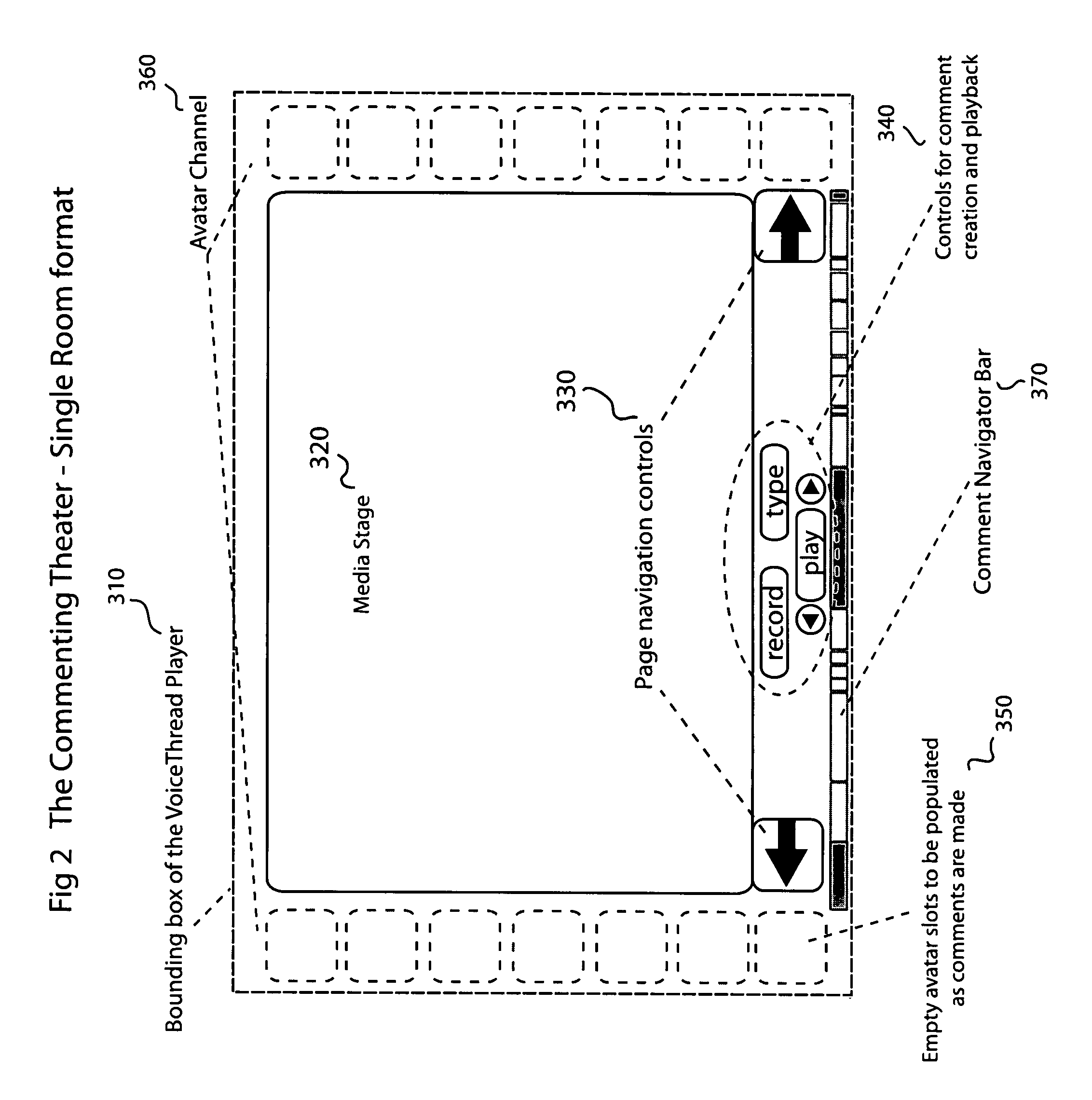
System and method for creating a database of user media and associated user comments wherein the user's comments are collected, collated, stored, and made available to users through a Commenting Theater that allows for the simultaneous representation of and access to the entirety of an archived complex group conversation without reliance upon text. The present invention provides a method for creating electronic collections of media with associated user comments contained and collated into a single entity “VoiceThread Media Player” that has an integral capacity to host a complex electronic conversation and allows content owners to manage a group conversation wherein all of the comments and referenced media remain separate and repurposable data entities and yet both the media content and the resulting conversation are presented in a unified, coherent and casually accessible manner.
Owner:MUTH STEVE
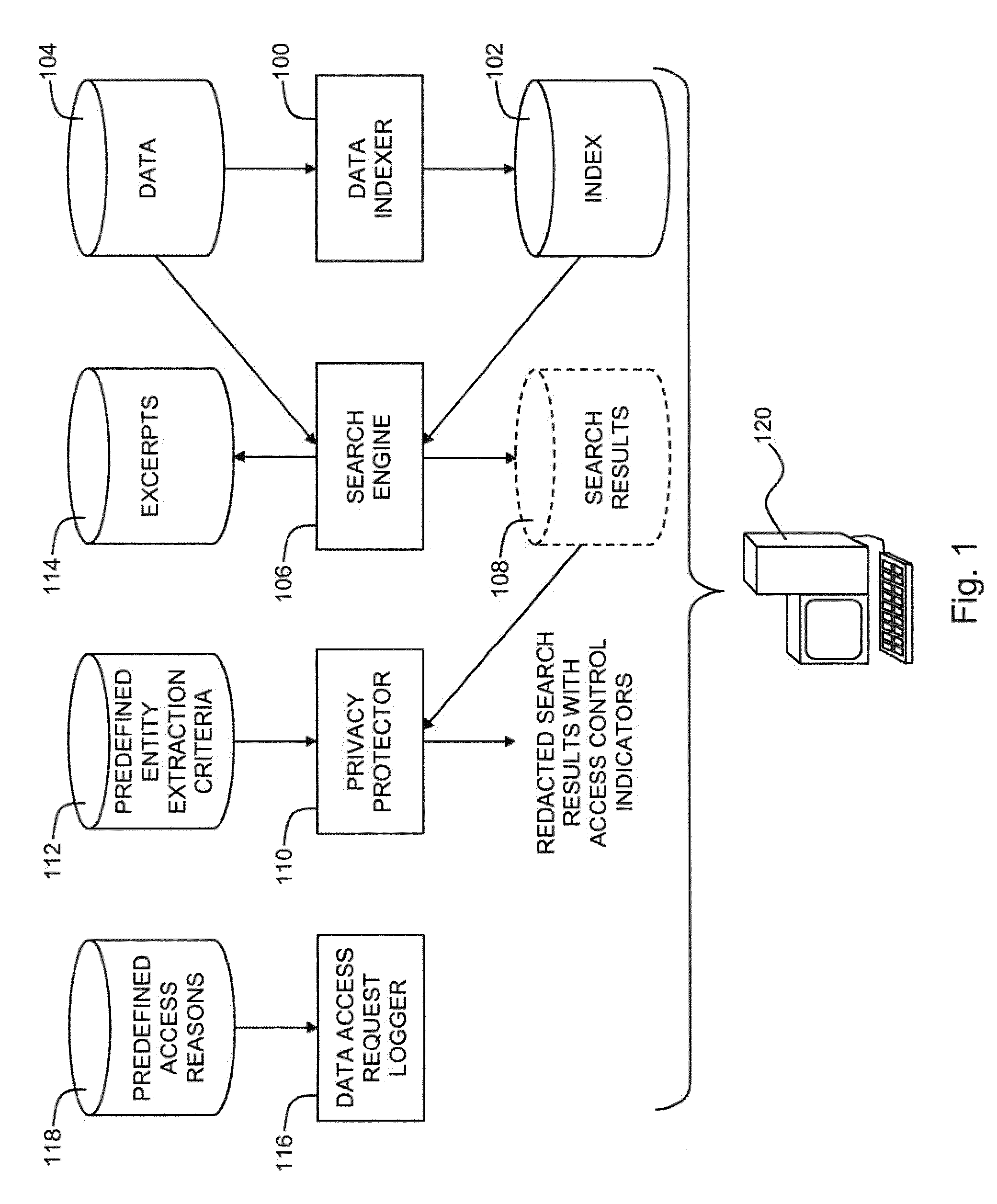
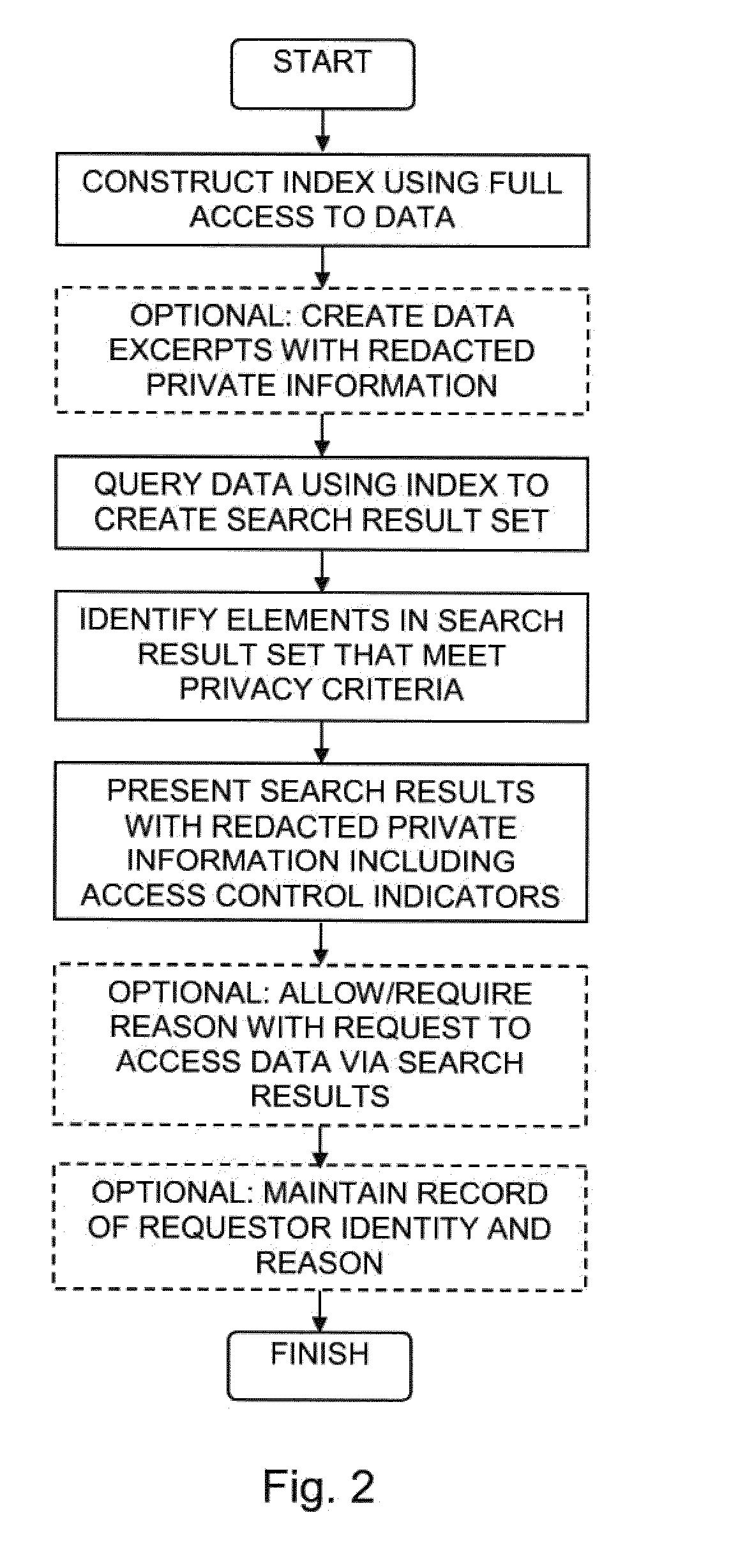
Search engine with privacy protection
ActiveUS20110066606A1Digital data information retrievalDigital data processing detailsPrivacy protectionOutput device
A search engine system with privacy protection, including a data indexer configured to create an index of data, a search engine configured to search the index of the data in response to a query, and create a search result set including excerpts from the data, and a privacy protector configured to identify at least one data entity within at least one excerpt of the search result set that meets at least one predefined entity extraction criterion, redact the search result set by removing the data entity from the excerpt, and present the redacted search result set on a computer output device.
Owner:GREEN MARKET SQUARE LTD
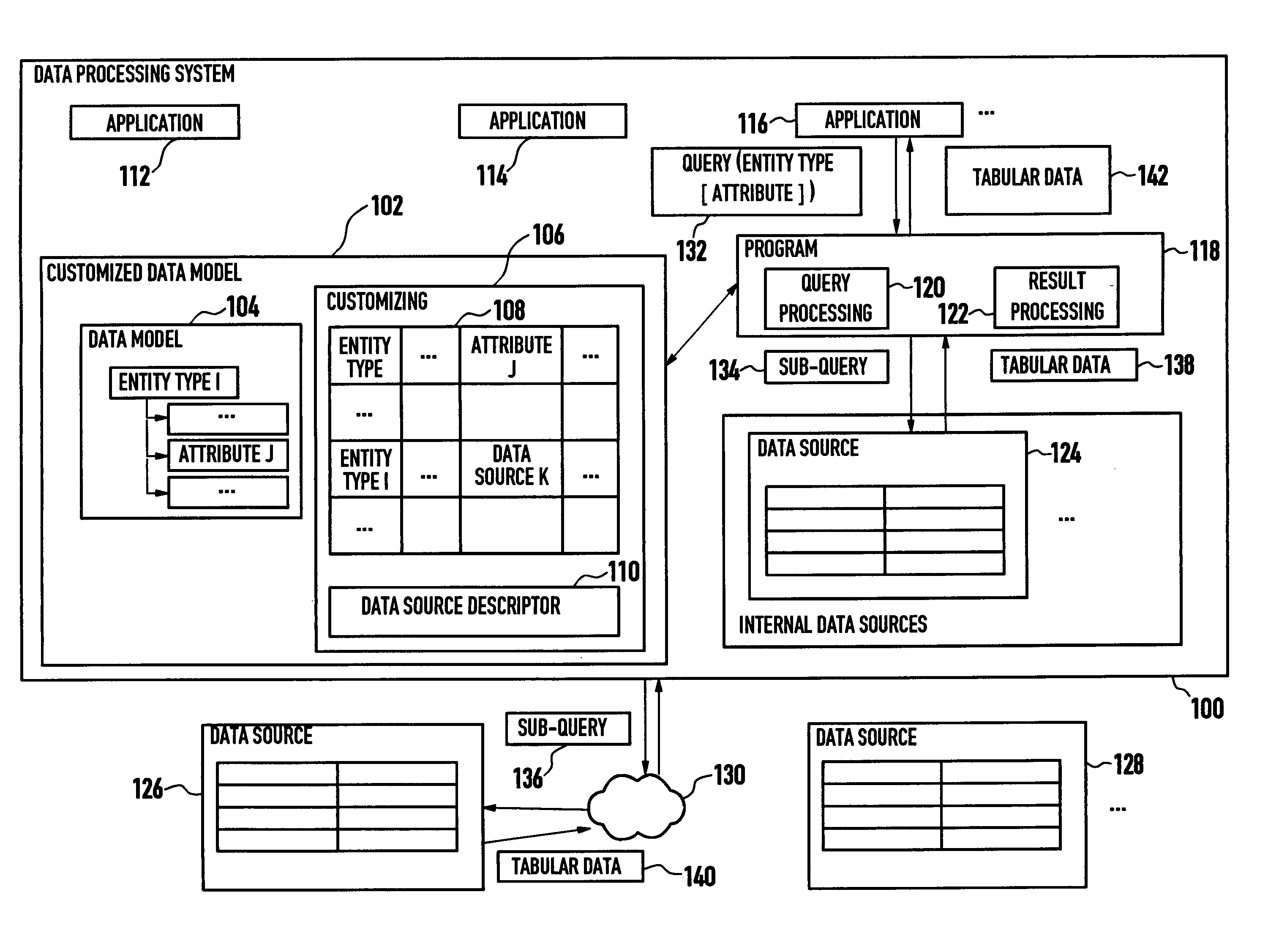
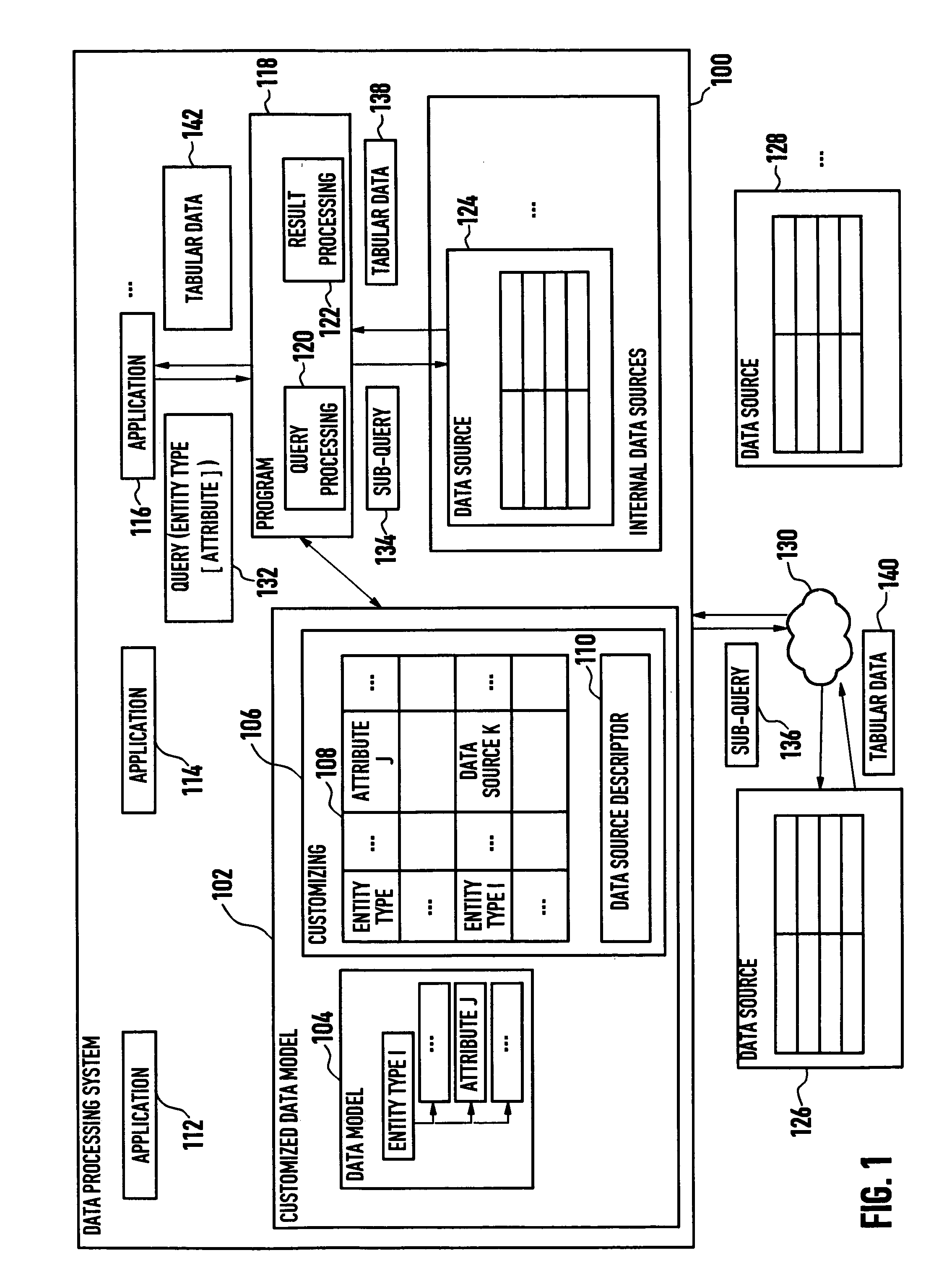
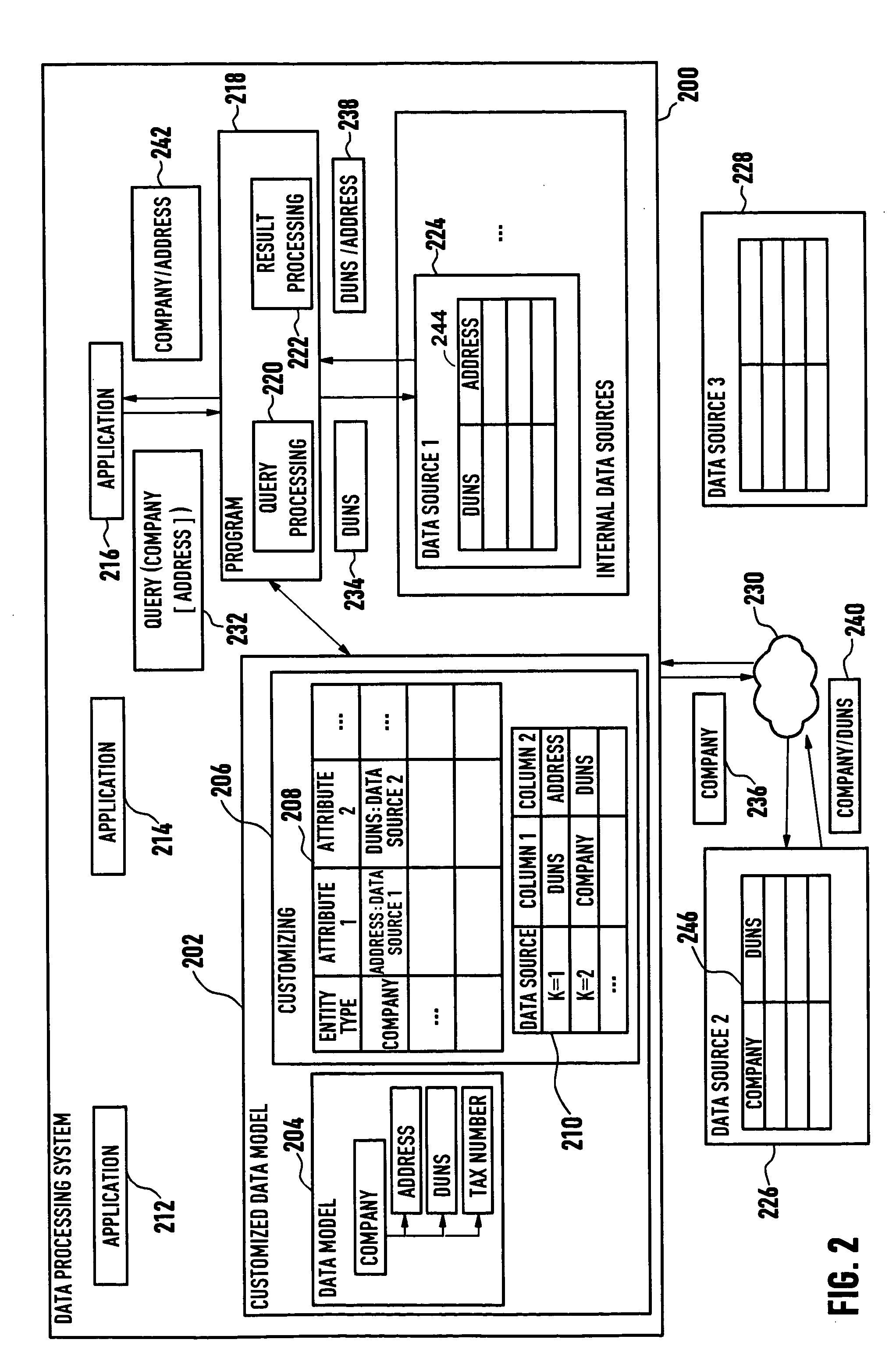
Systems and methods for data processing
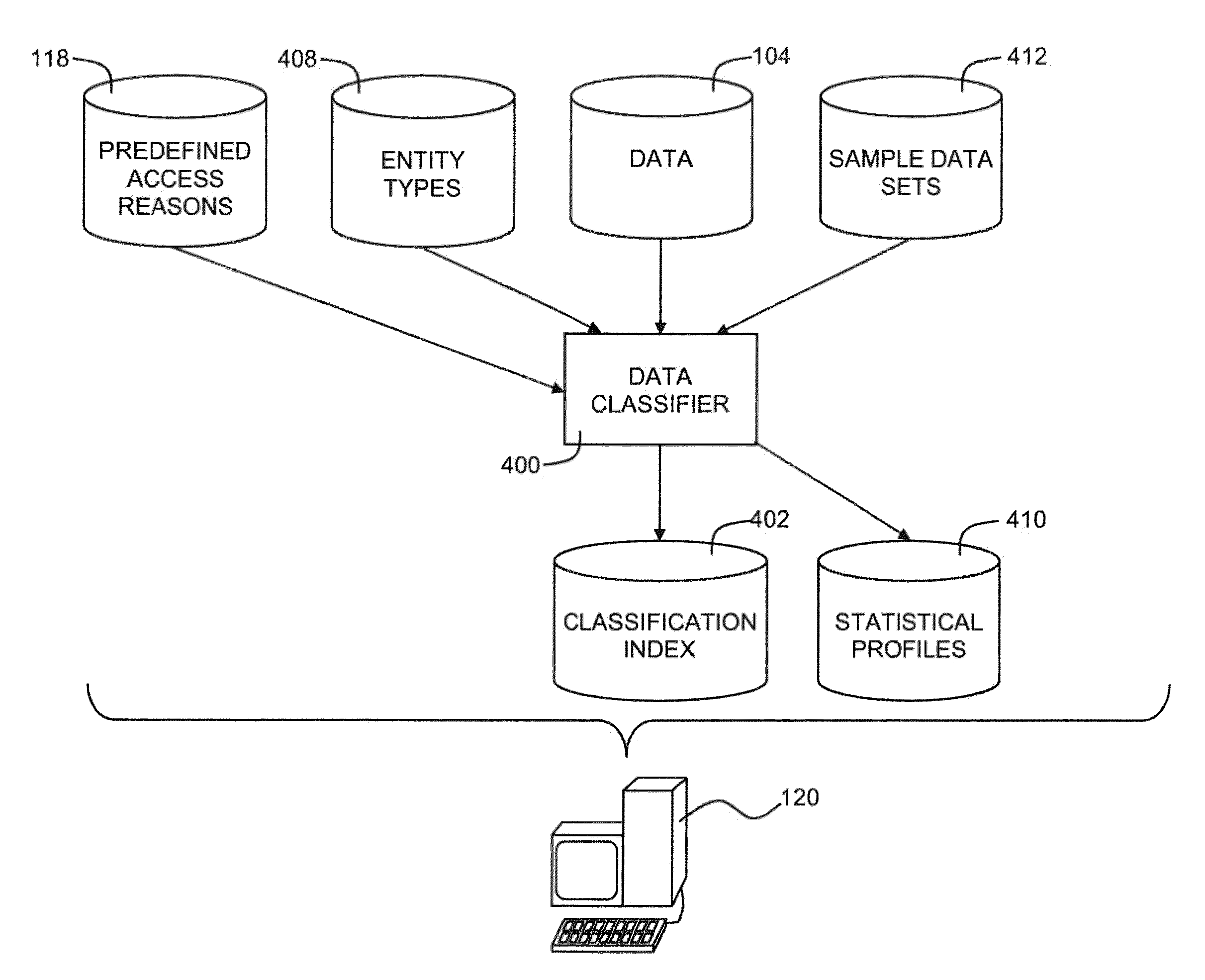
ActiveUS20050027675A1Digital data information retrievalDigital data processing detailsData processing systemEntity type
Systems and methods are provided for data processing. As disclosed herein, such systems and methods may include providing a data model with a set of entity types and set of attributes for each entity type, providing customizing data for the data model, the customizing data indicating data sources for the attributes and describing data structures being provided by the data sources, querying the attribute data for at least a first attribute of the set of attributes of one of the entity types, determining from the customizing data, if a single data source for the first attribute data of the one of the entity types is available, if such a single data source is not available, determining at least first and second ones of the data sources which in combination comprise the first attribute data of the one of the entity types, generating a sub-query for each one of the at least first and second data sources, and combining the results of the sub-queries to provide a query result.
Owner:SERVICENOW INC
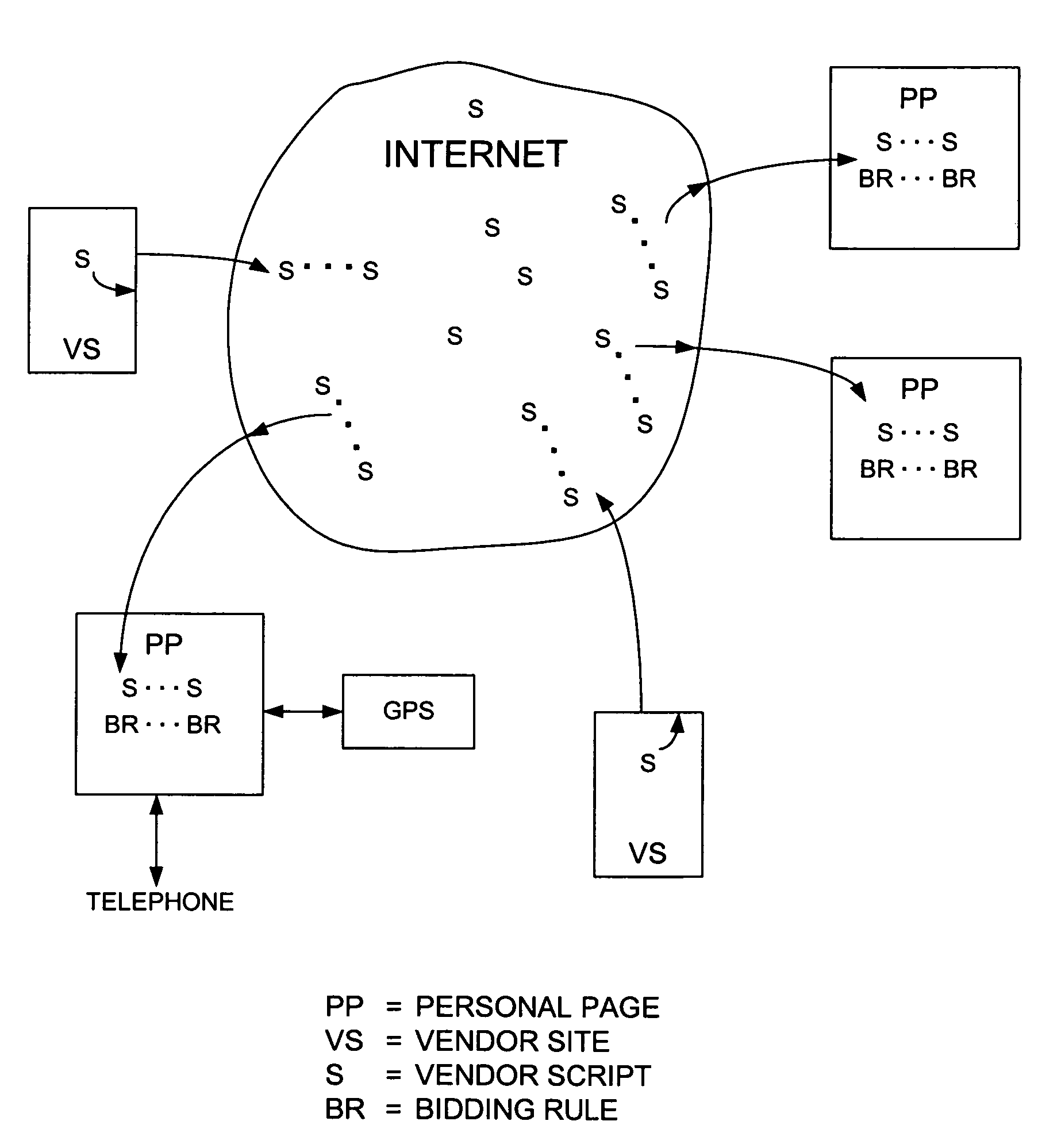
Methods and systems for electronic transactions
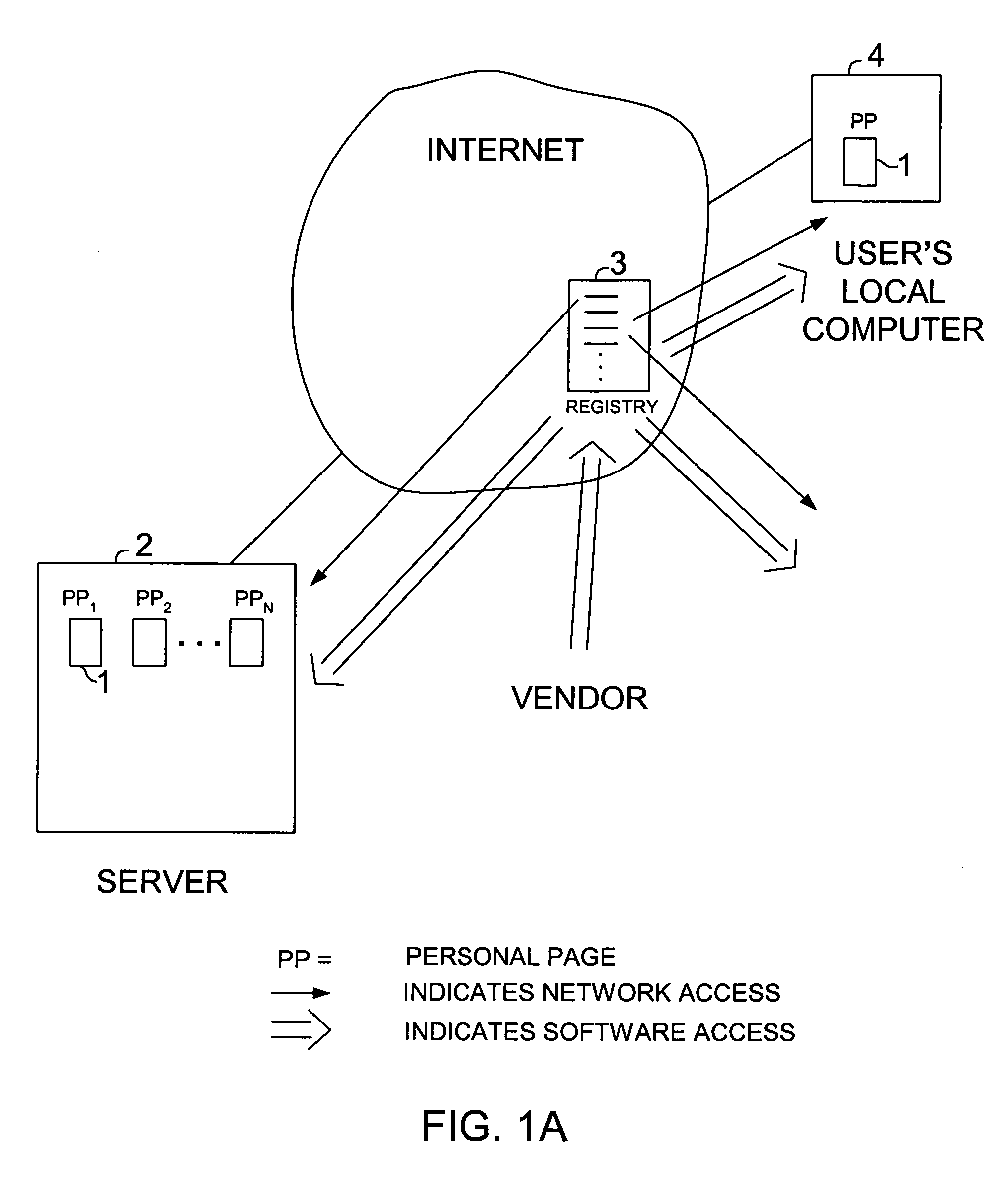
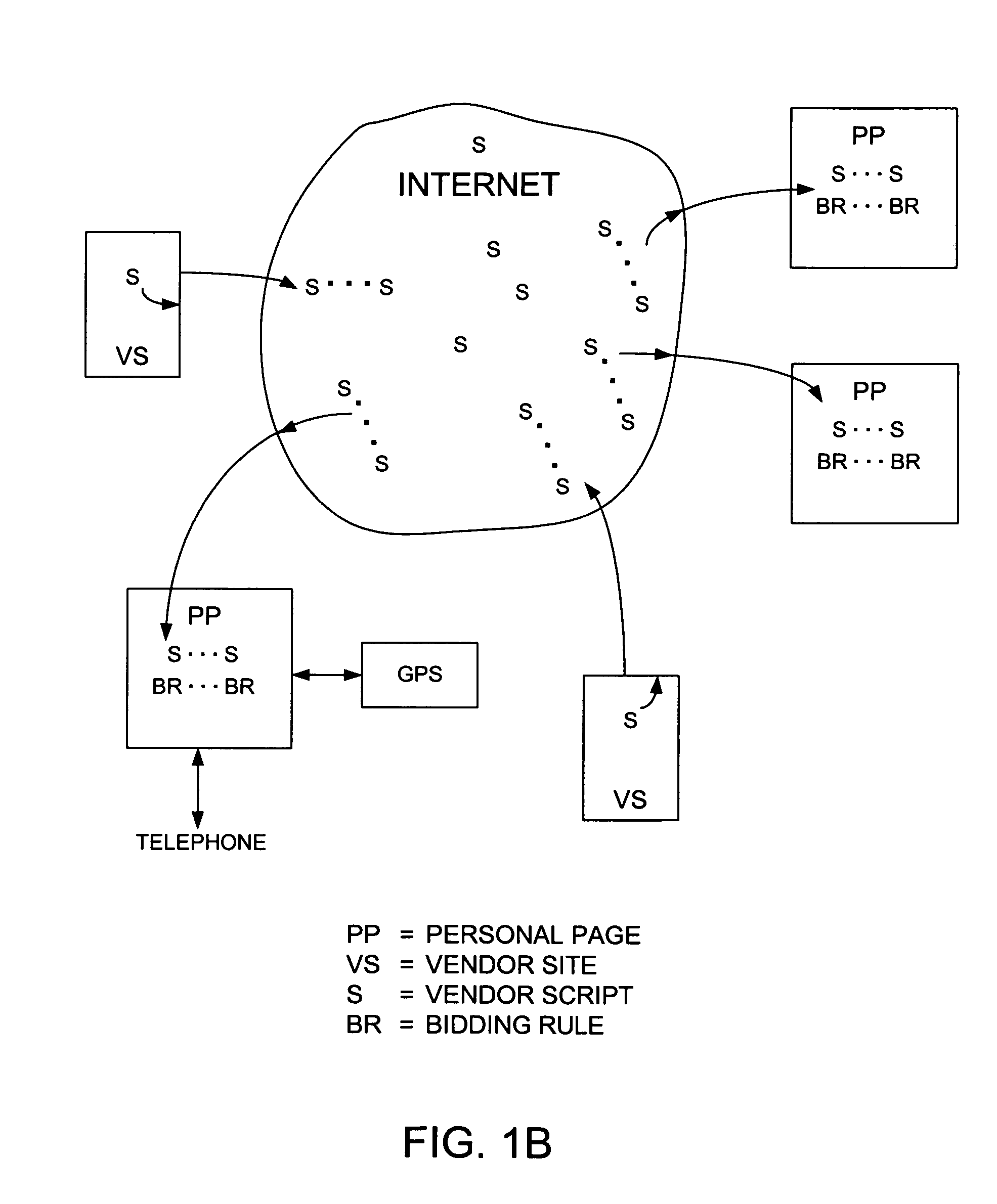
In the preferred computer system, the user is provided with a separate Internet-accessible entity referred to here as the “personal page.” A personal page, preferably, includes memory for storing information related to the user. For example, on his / her personal page the user indicates what he / she wishes to purchase, possibly along with other criteria associated with the purchase, such as, for example, a time that the purchase should take The user is provided with the ability to create personalized bidding rules that vendors that offer goods and services must respect. Vendors have the ability to specify similar criteria, which describe the goods and / or services they offer. Vendors can indicate, for example, the prices of their goods, times and places that their services are available, etc. Preferably, these specifications, called “vendor scripts,” are embodied in active software / data entities (agents) that traverse sites on the Internet visiting sites hosting users' personal pages. Thus, preferably, vendor software / data agents (comprising vendor scripts) are the mobile, active elements in the system and purchasing requirements are stationary and more passive in comparison.
Owner:TAMIRAS PER PTE LTD LLC
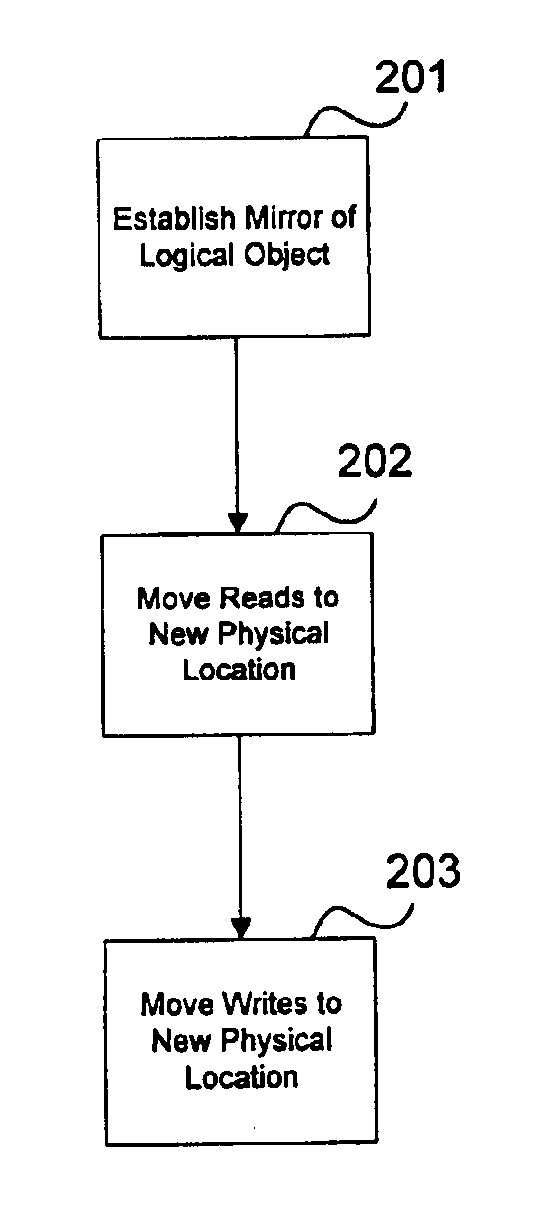
Method and apparatus for controlling read and write accesses to a logical entity
InactiveUS6978324B1Data processing applicationsInput/output to record carriersData entityOperating system
Method and apparatus are disclosed for moving logical data entities from one storage element to another storage element in a computer storage system, when more than one user or host computer may access the logical entity. According to one embodiment of the method, all of the read requests for the logical entity are moved to a new copy of the logical entity, before writes for logical entity are moved to the new copy.
Owner:EMC IP HLDG CO LLC
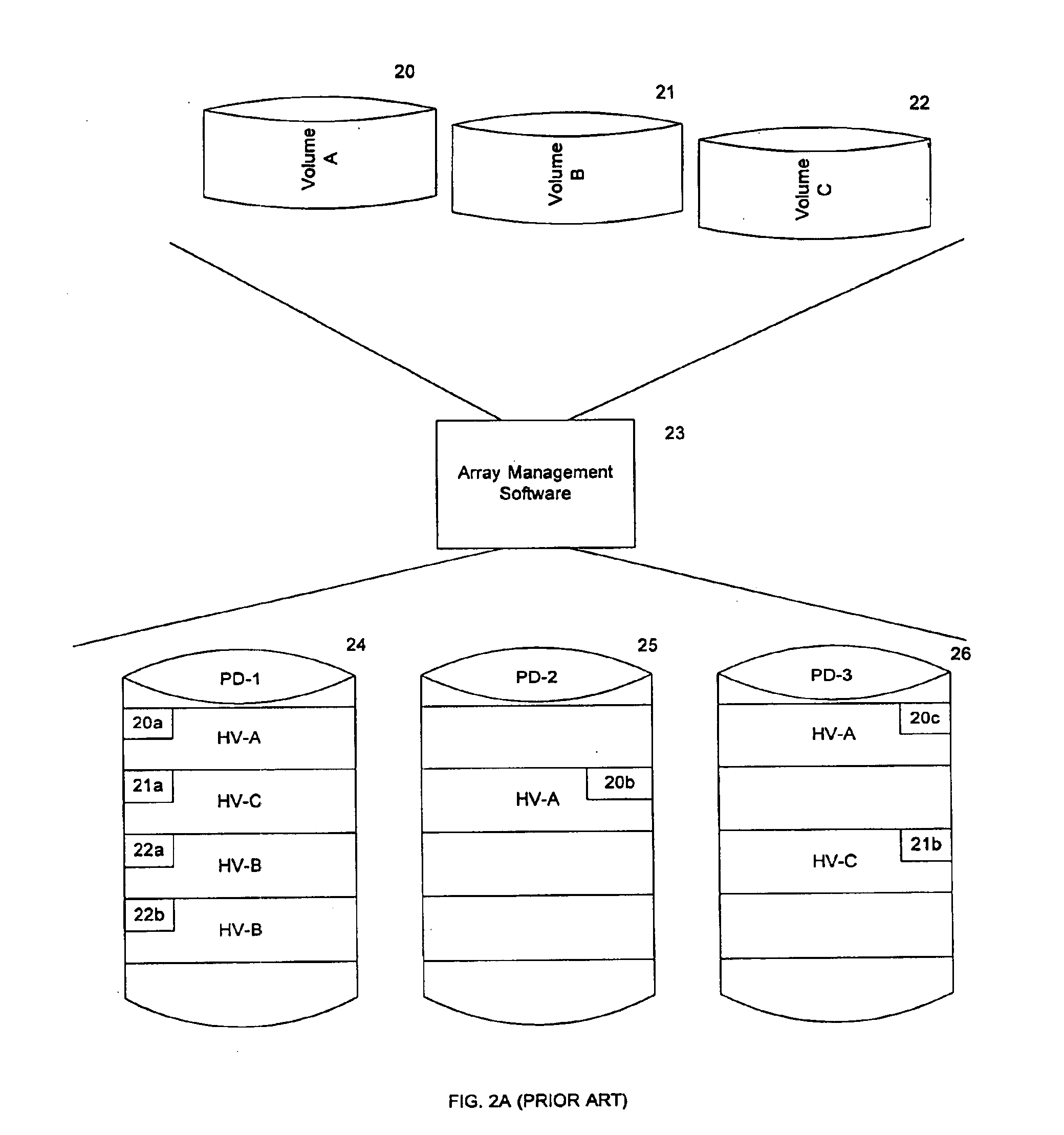
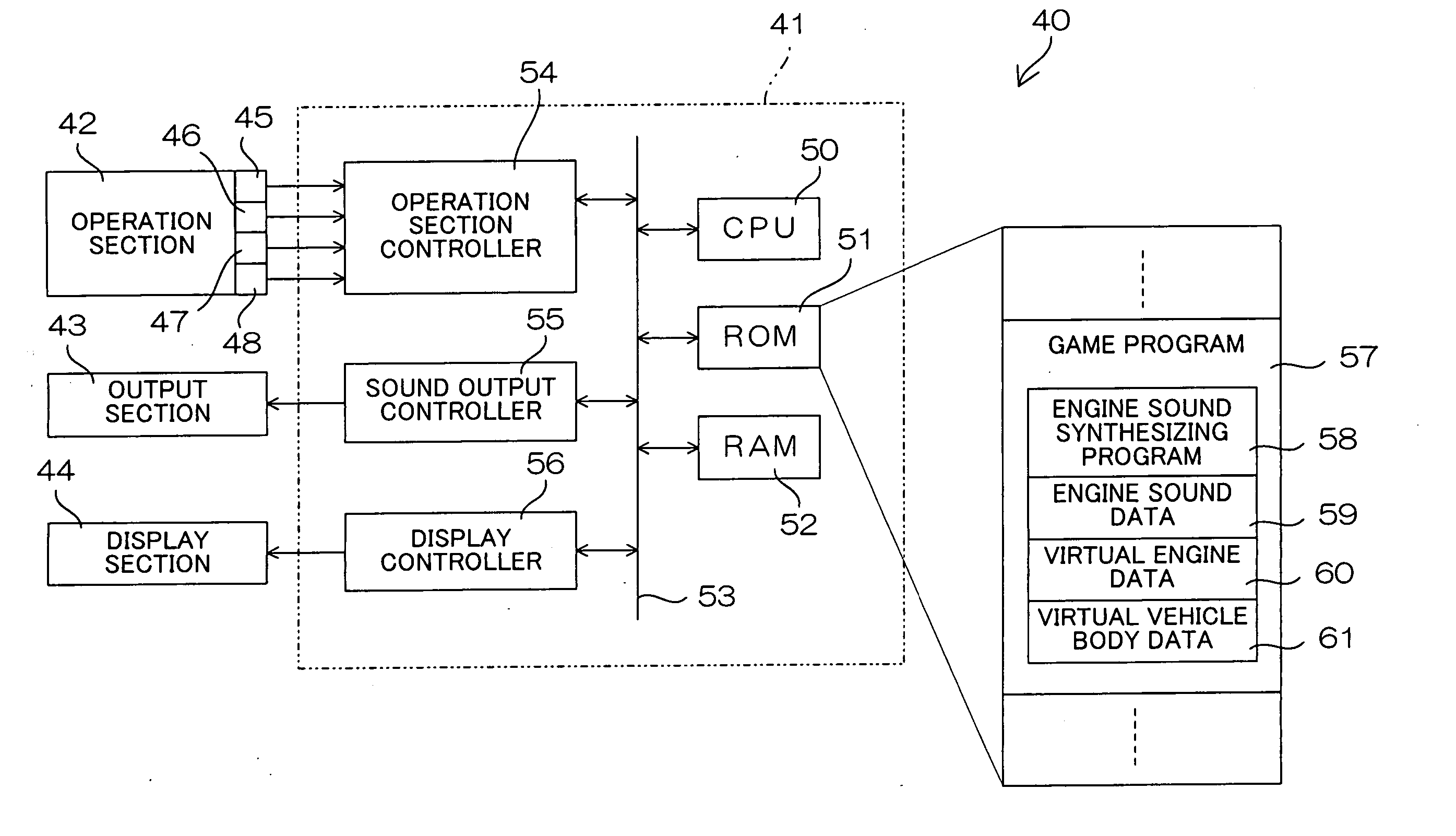
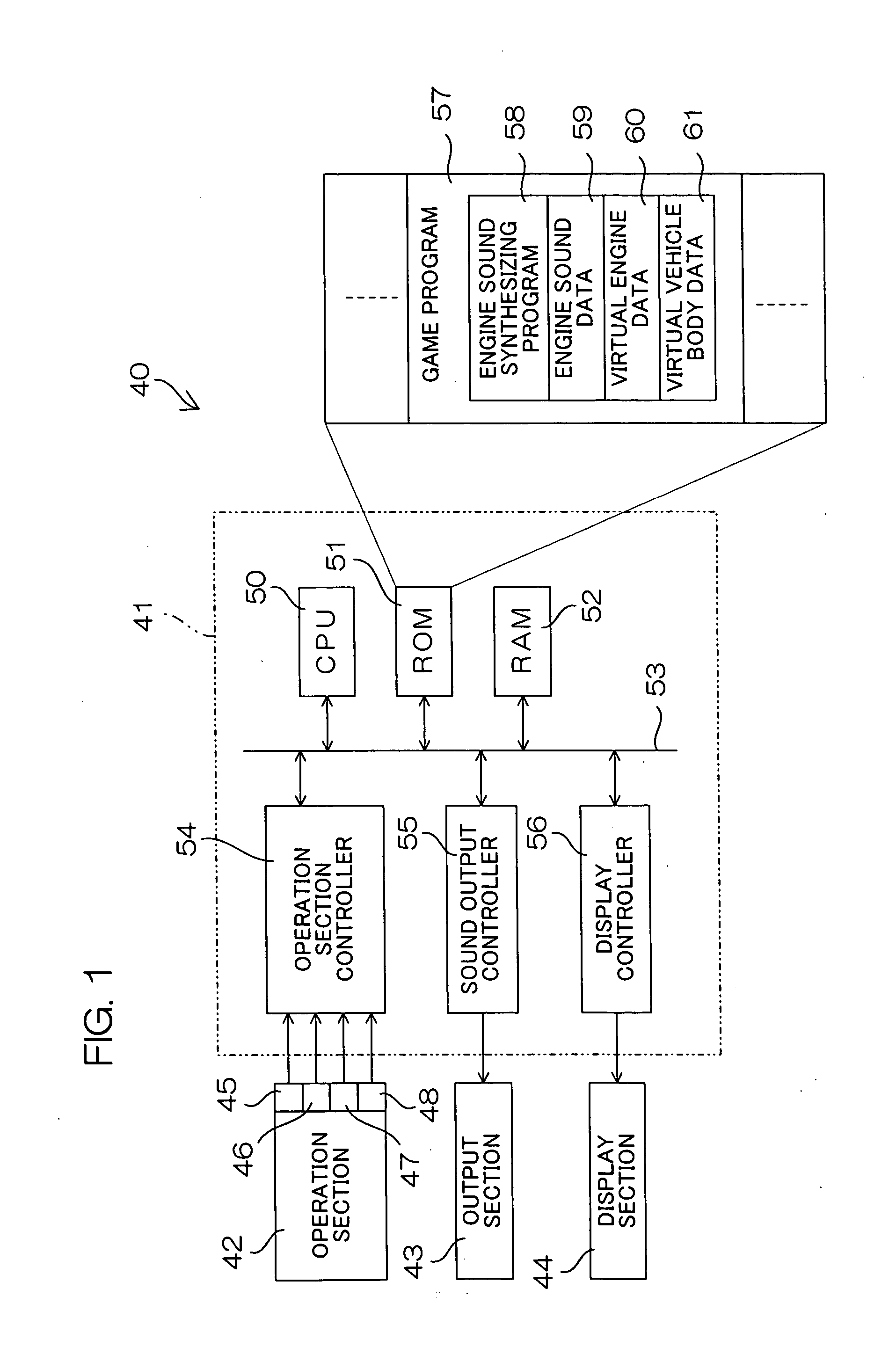
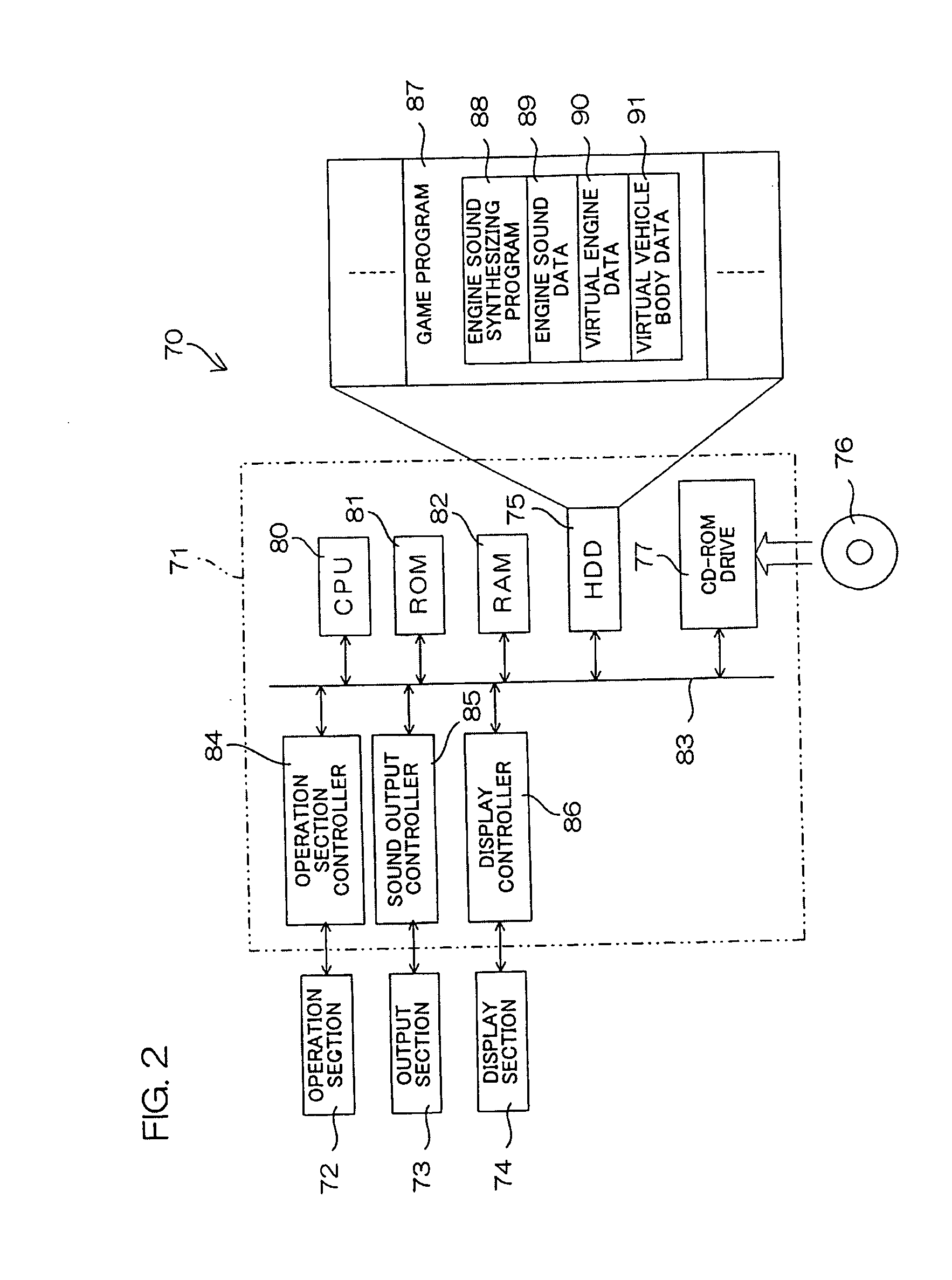
Engine sound synthesizer, motor vehicle and game machine employing the engine sound synthesizer, engine sound synthesizing method, computer program for engine sound synthesis, game program incorporating the computer program, and recording medium containing the computer program for engine sound synthesis
ActiveUS20050113168A1Enhancing verisimilitude provided by the gameGain controlElectric vehiclesData storingThrottle opening
An engine sound synthesizer includes an engine sound storing section, and a synthetic engine sound data generating section which generates synthetic engine sound data on the basis of engine sound data stored in the engine sound storing section. The engine sound storing section stores therein plural groups of plural entities of engine sound data recorded in different driving states, the plural groups of plural engine sound data entities being stored therein in correspondence with predetermined plural driving state ranges. The synthetic engine sound data generating section generates the synthetic engine sound data by selectively reading out of the engine sound storing section plural engine sound data entities in a group corresponding to one of the driving state ranges specified by externally input driving state specification information and selectively combining the read engine sound data entities. The driving states are each defined, for example, by a throttle opening degree and an engine rotation speed.
Owner:YAMAHA MOTOR CO LTD
System and method for presentation of wireless application data using repetitive UI layouts
InactiveUS20050193361A1Reduced executable codeDegree of flexibility and efficiencyProgram loading/initiatingExecution for user interfacesObject definitionData field
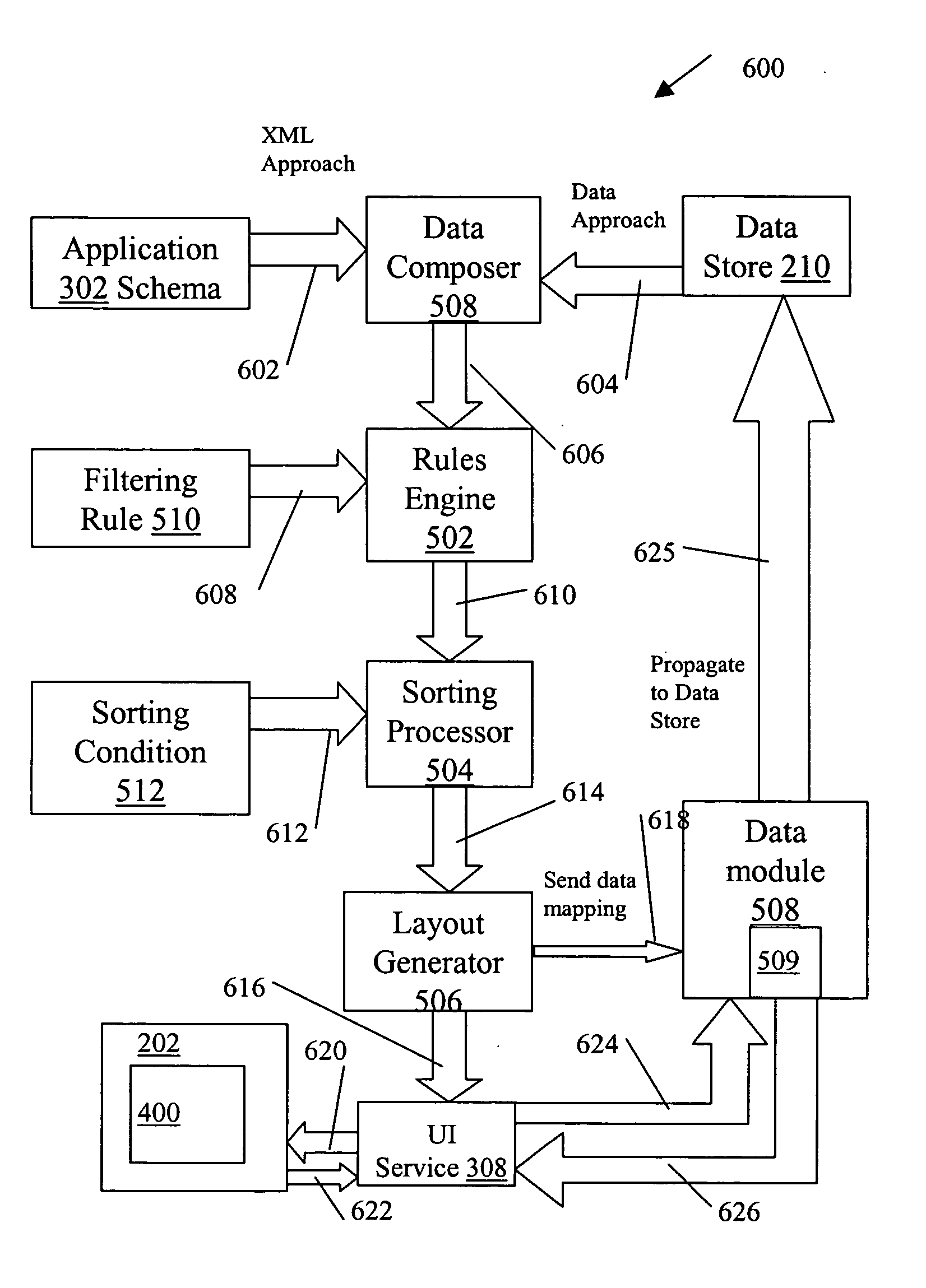
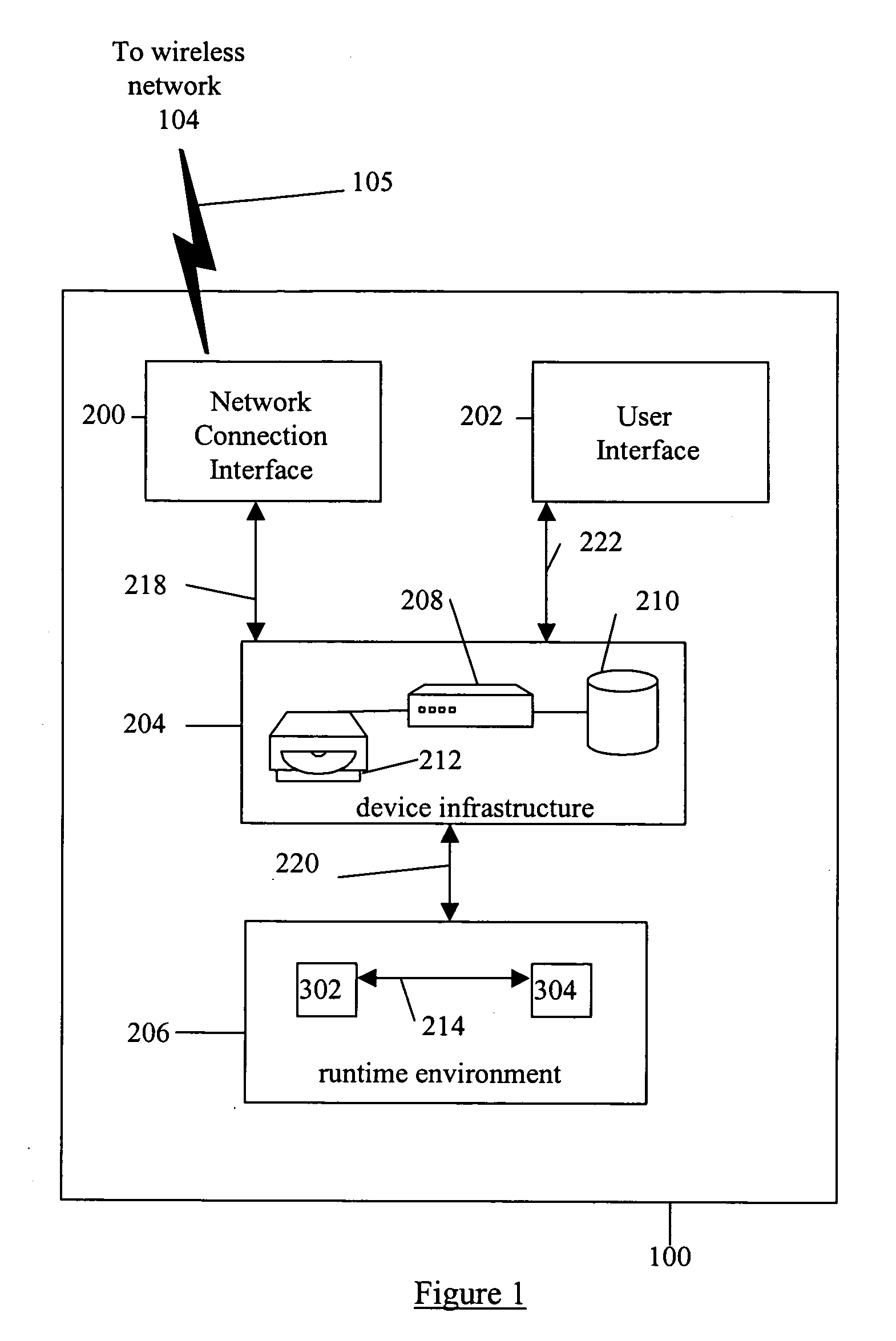
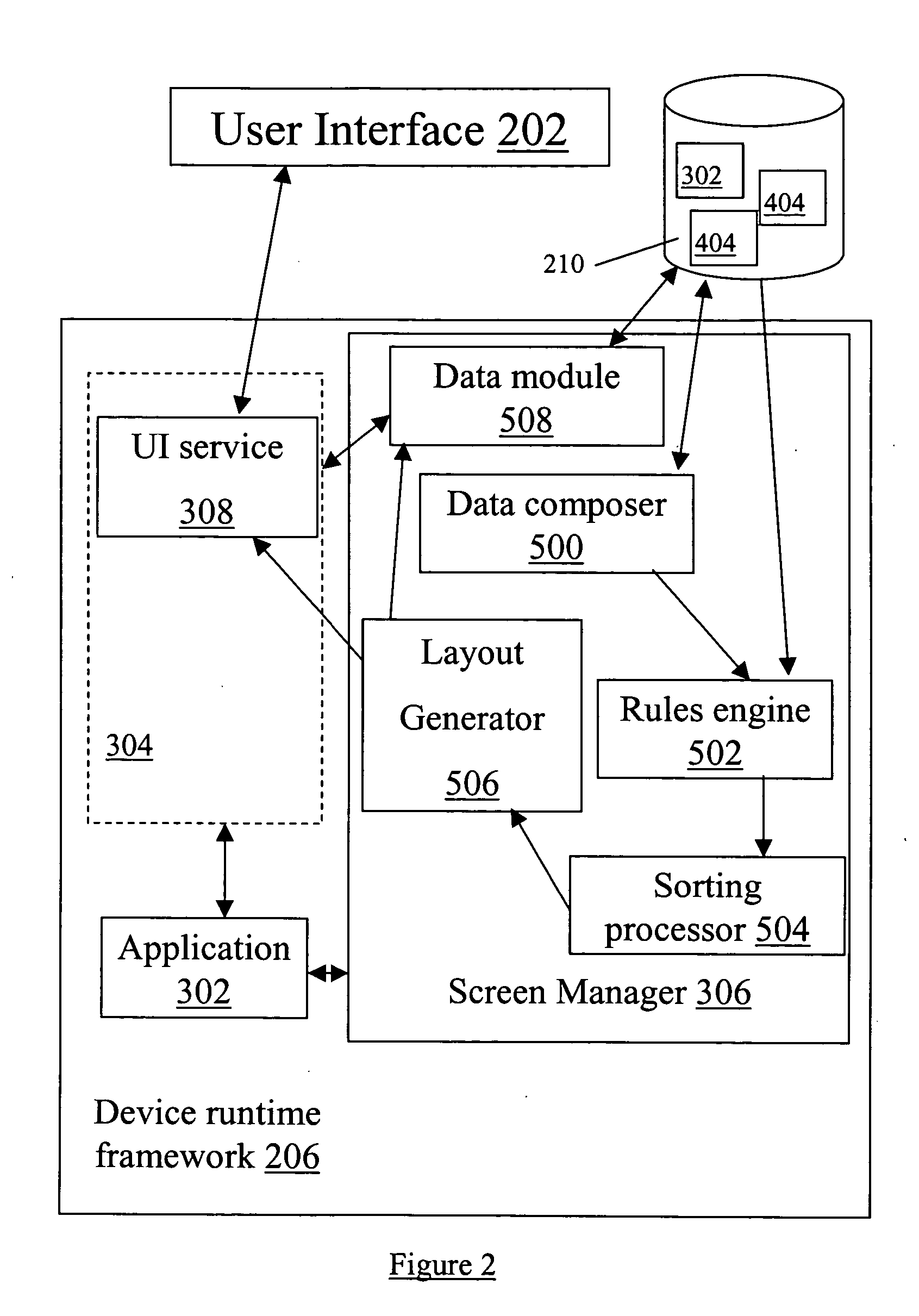
A Repetitive Layout scheme is provided that operates on a collection of data objects, such that each data object accords to the same data object definition (data model) expressed in a structured definition language. The Repetitive Layout consists of one UI section repeated for every object in the collection. Each UI section is composed of a set of UI controls or sub-layouts. The UI controls in each section are associated with the data fields of the corresponding data object. A user of a wireless application interacting with the data objects can select UI sections and edit the controls within them via the user interface of the wireless device executing the application. Any modifications are propagated to the data objects mapped to the respective UI sections. Similarly, all modifications (driven by the application logic or incoming server messages) to the data objects are reflected in the UI section mapped to these objects. The generation and application of the repetitive layout scheme can include the steps: dynamic data entity generation (Data Composer stage); determining the collection of data objects that need to be presented by the user interface (Rules Engine stage); sorting the collection of data objects (Sorting Processor stage); generating the UI Layout (Layout Generator stage); propagating UI changes back to the Data Model having the definitions of the data objects (Data Dispatcher stage); propagating data changes to the Repetitive Layout; and propagating changes to nodes of the data model.
Owner:BLACKBERRY LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com