Patents
Literature
237 results about "Single entity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
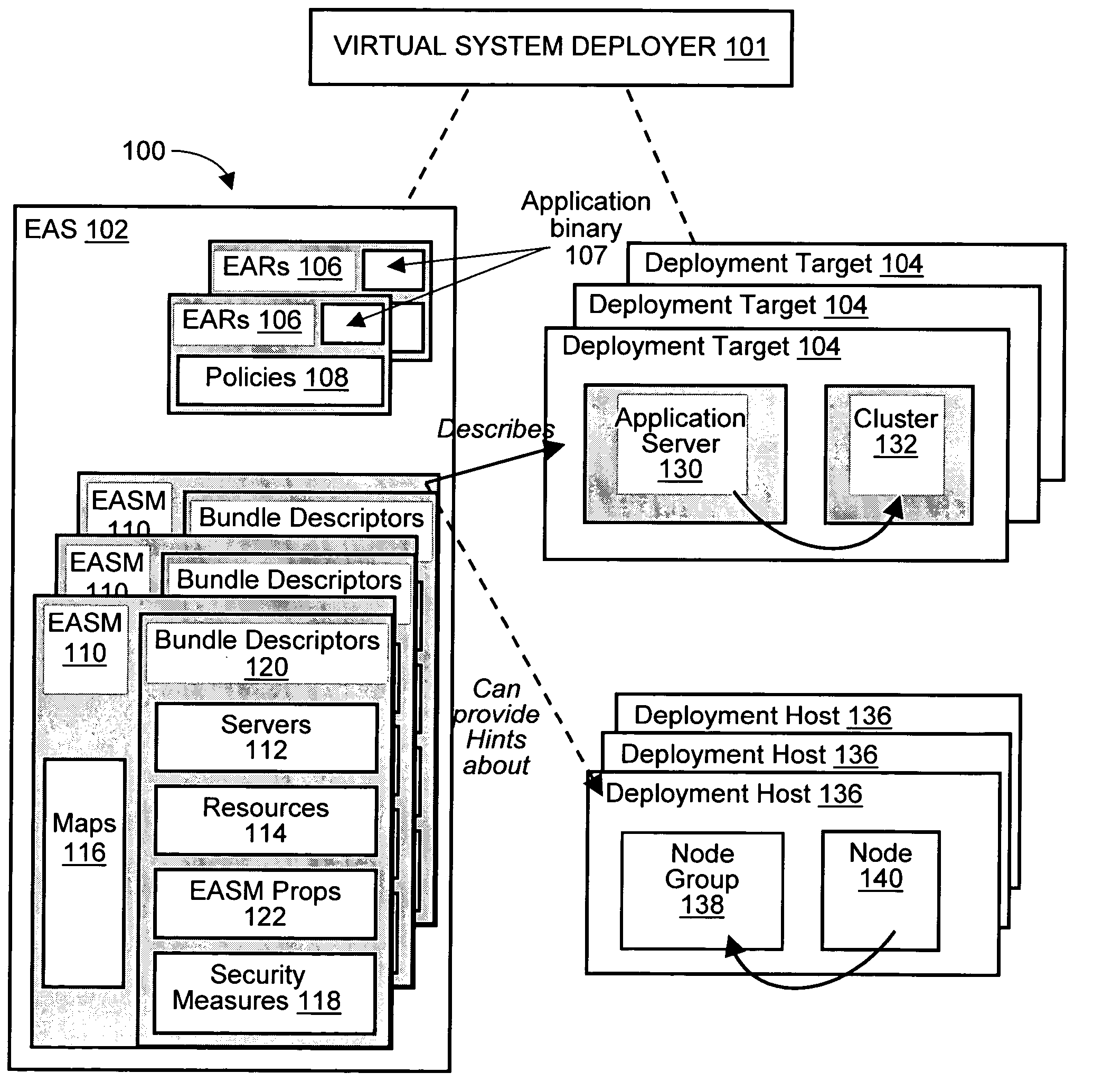
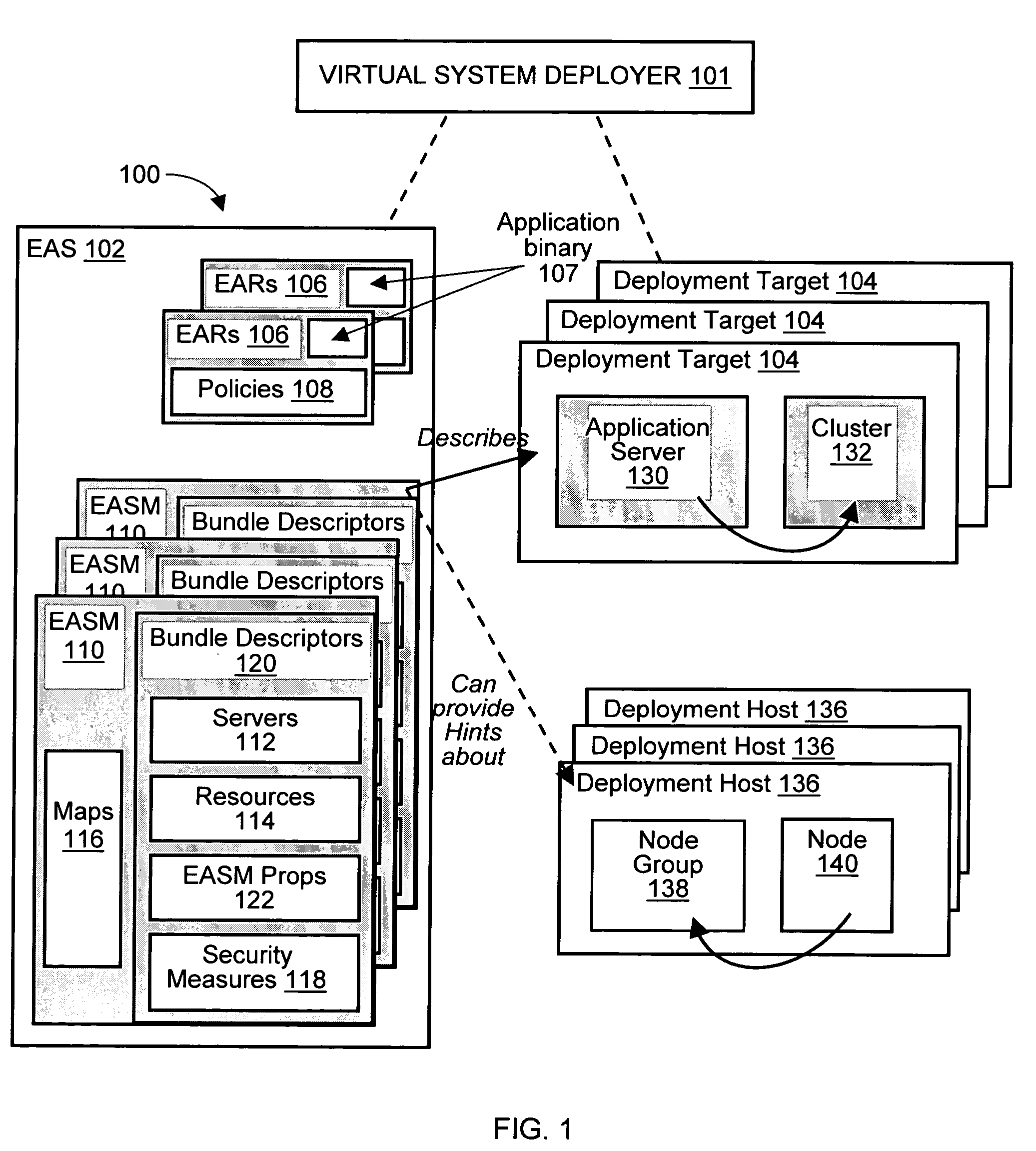
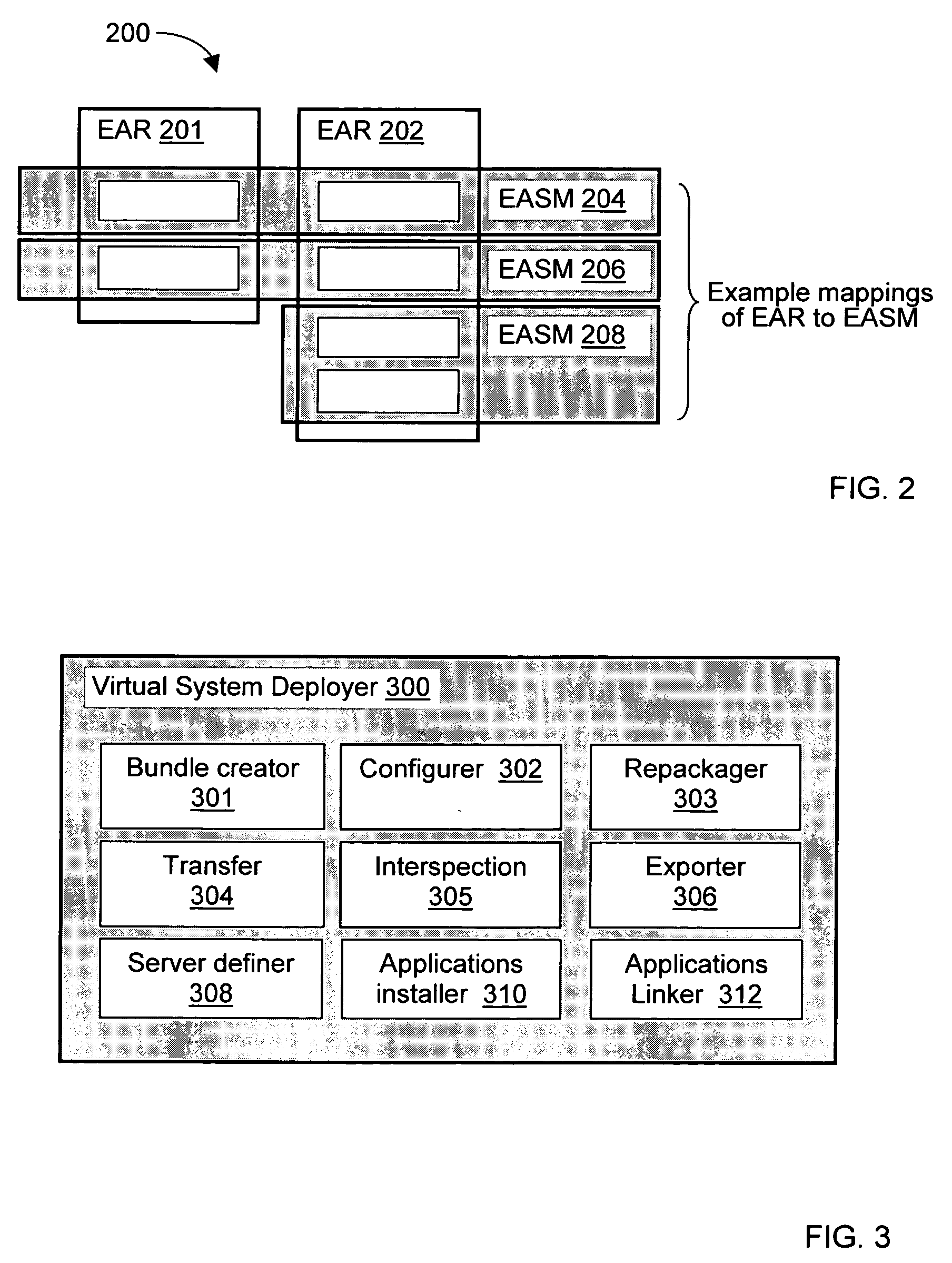
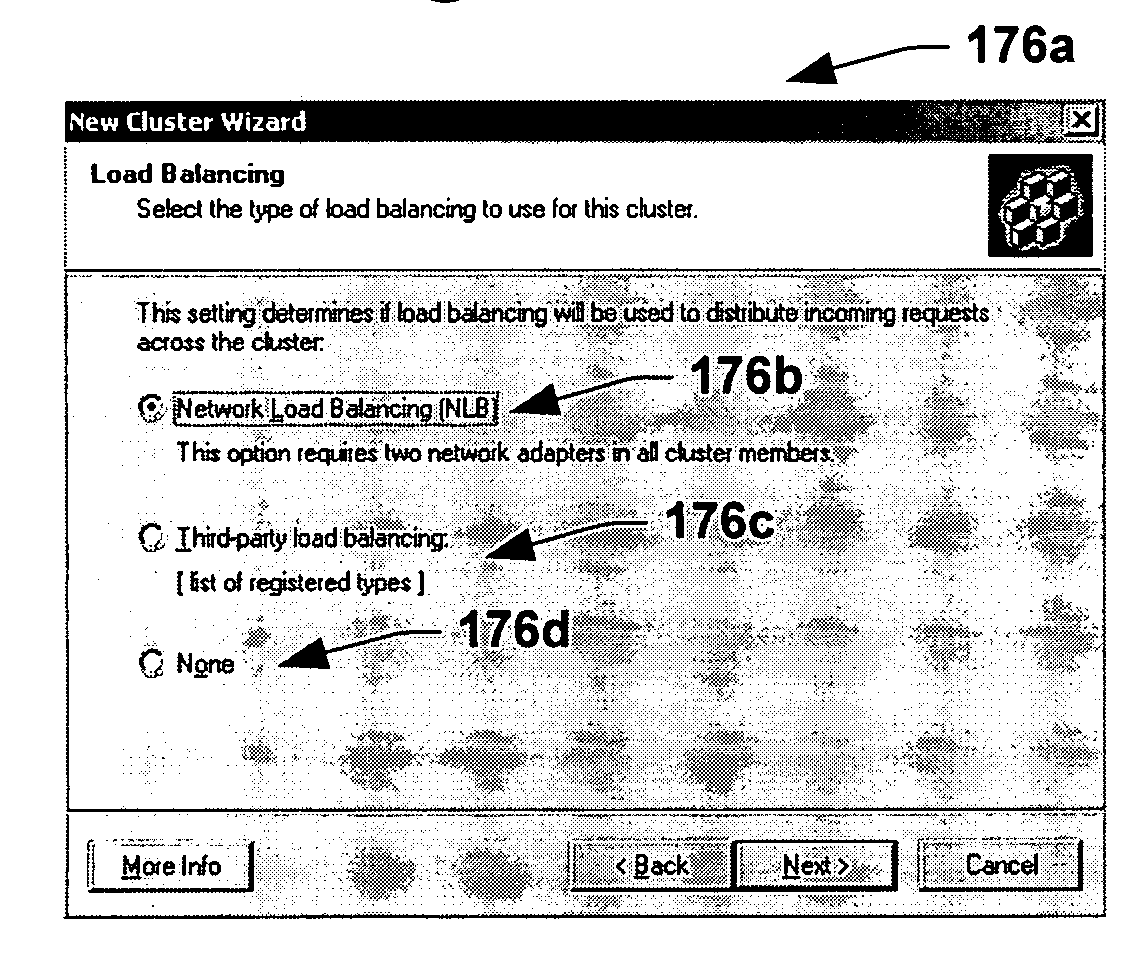
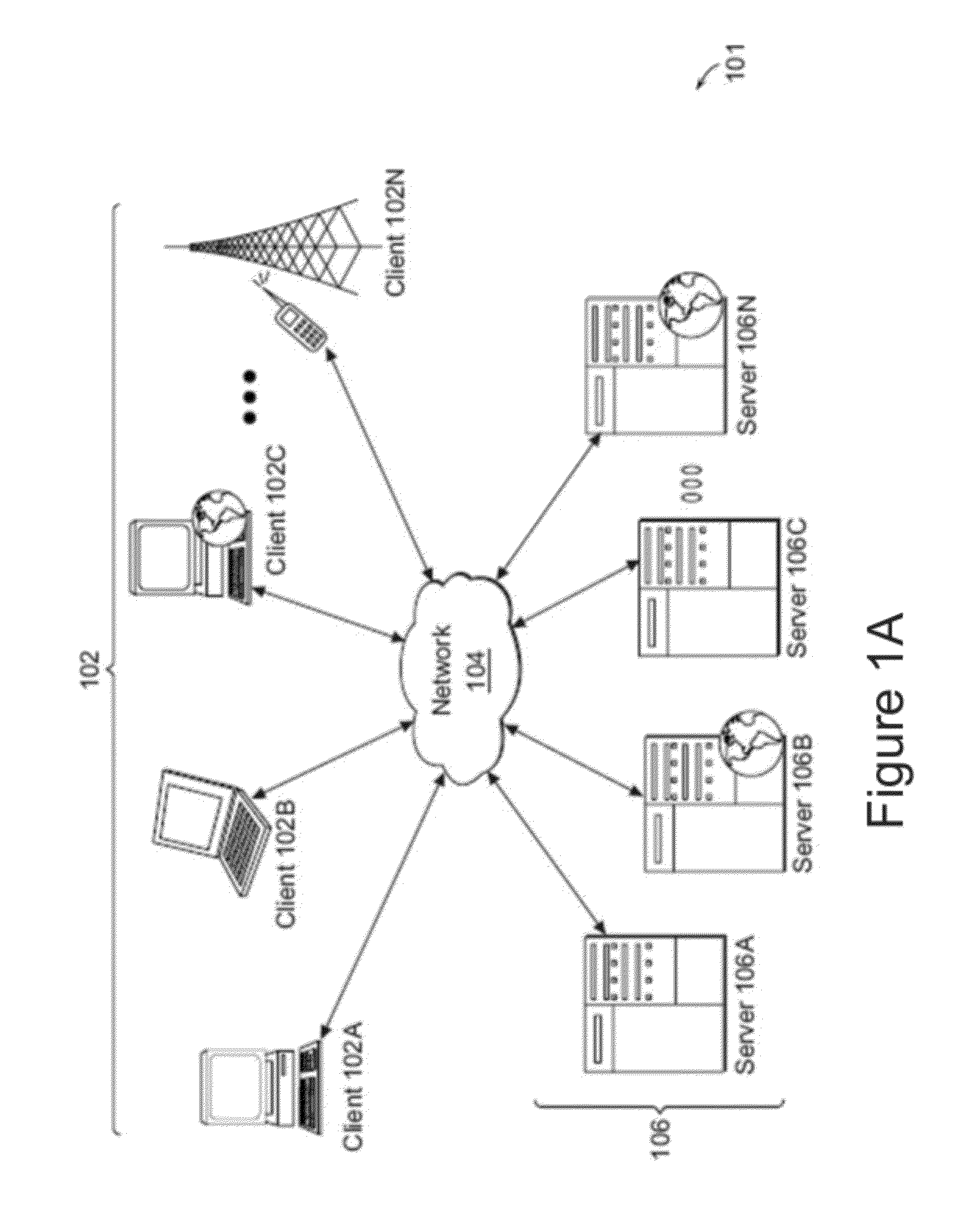
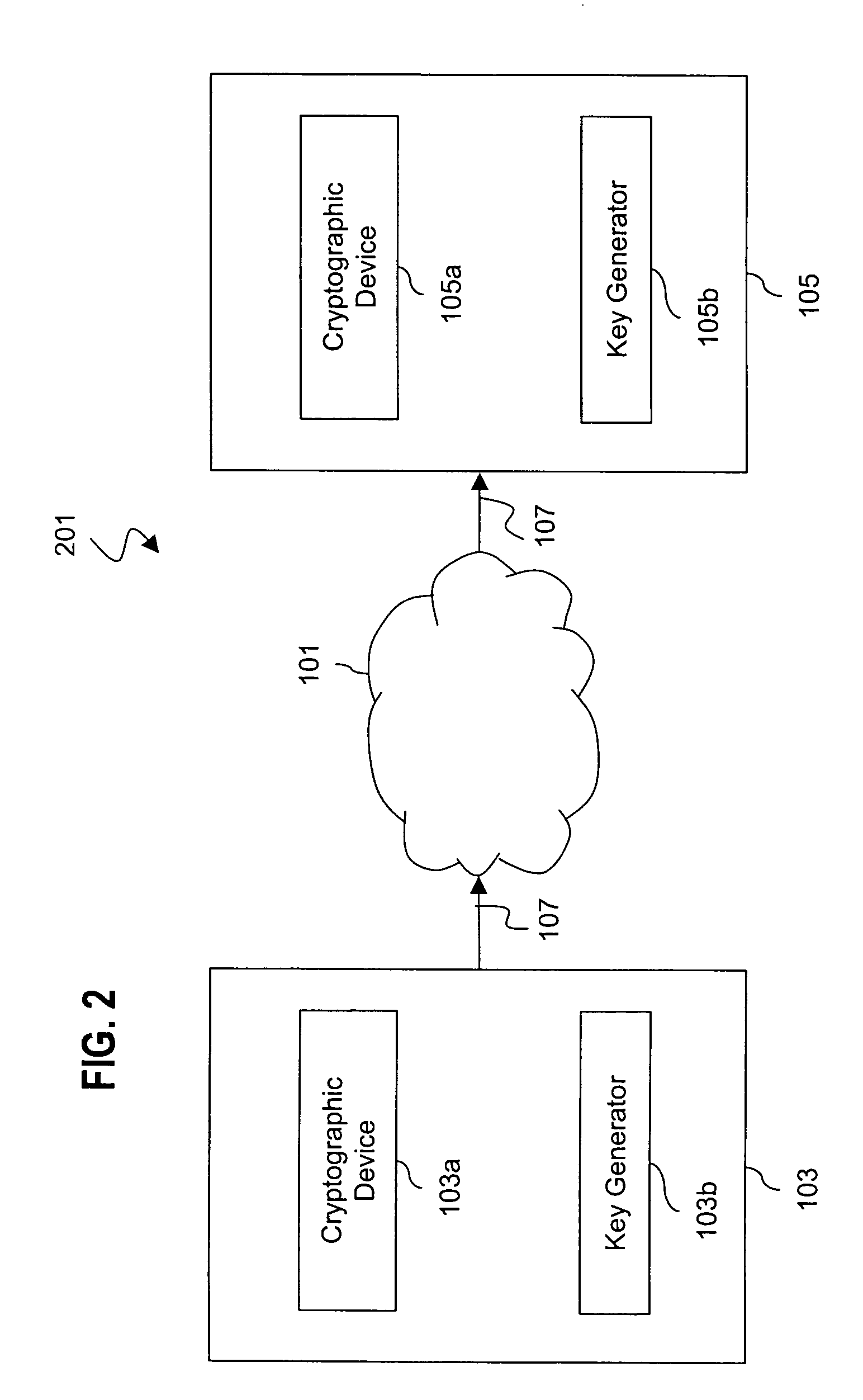
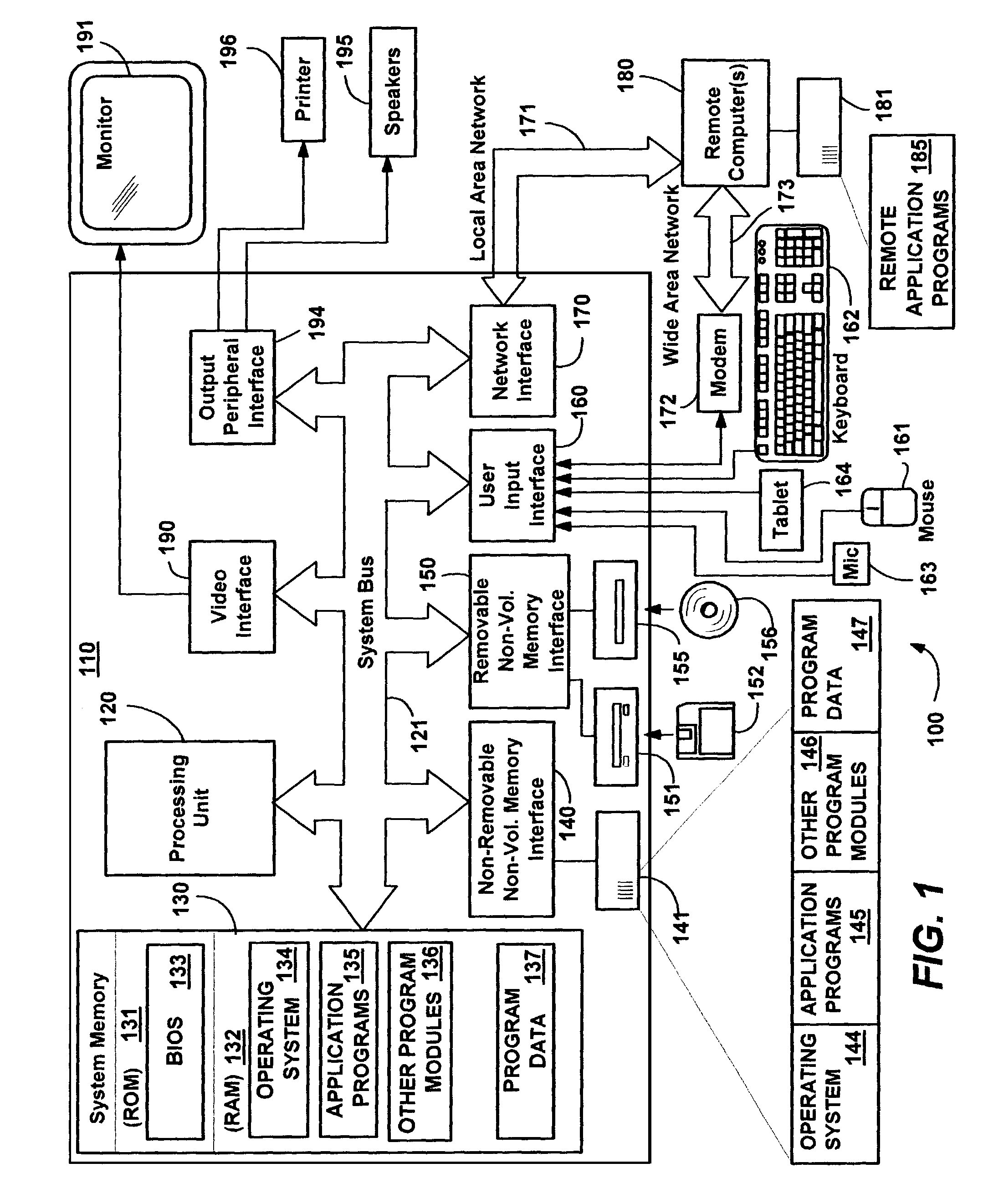
Deploying an application software on a virtual deployment target
InactiveUS20050289538A1Program loading/initiatingMemory systemsApplication program softwareRelevant information
Methods and arrangements to propagate application software to a virtual deployment target are contemplated. More specifically, a user may create multiple virtual deployment targets in a software system such as WebSphere™ and deploy applications to multiple the virtual deployment targets without having to manually fit policy-driven applications into each virtual deployment target. Embodiments are particularly advantageous when the application software is a business solution that needs to be deployed multiple times such as during the development and testing of the business solution. For example, application software of a business solution typically includes a group of applications designed to cooperatively function as a single entity. An application bundle such as an Enterprise Application Solution (EAS) file describes the application software and includes pertinent information about the application software, application configuration data, and runtime configuration data to implement the business solution. Then, the application bundle can be deployed automatically or substantially automatically.
Owner:IBM CORP
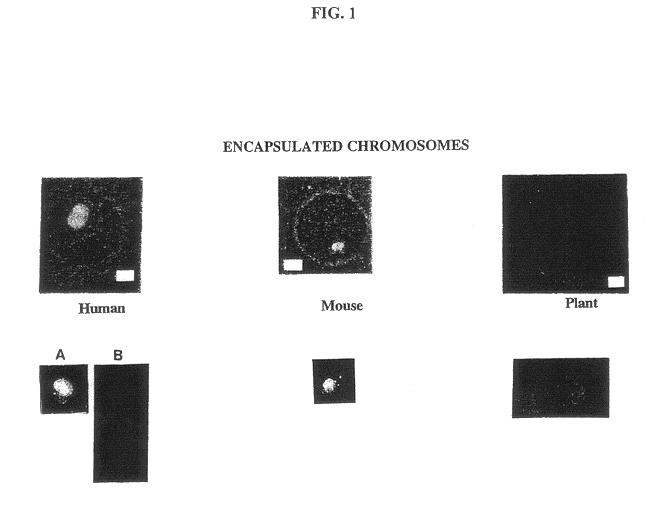
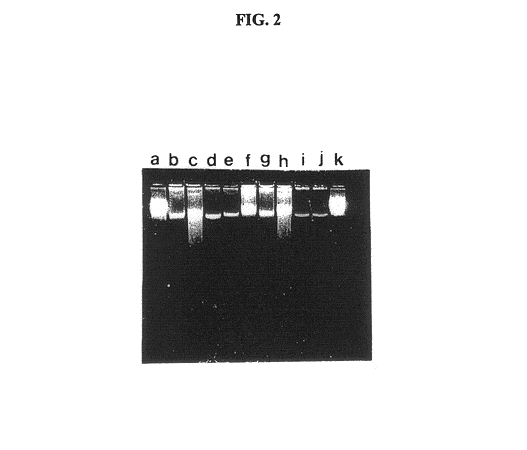
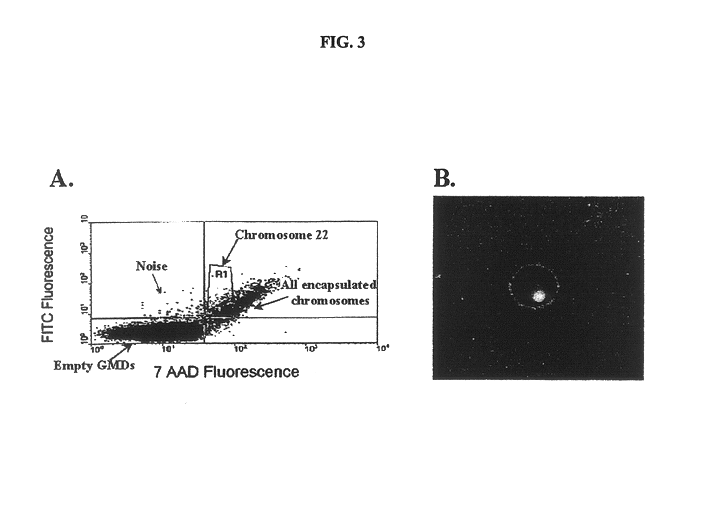
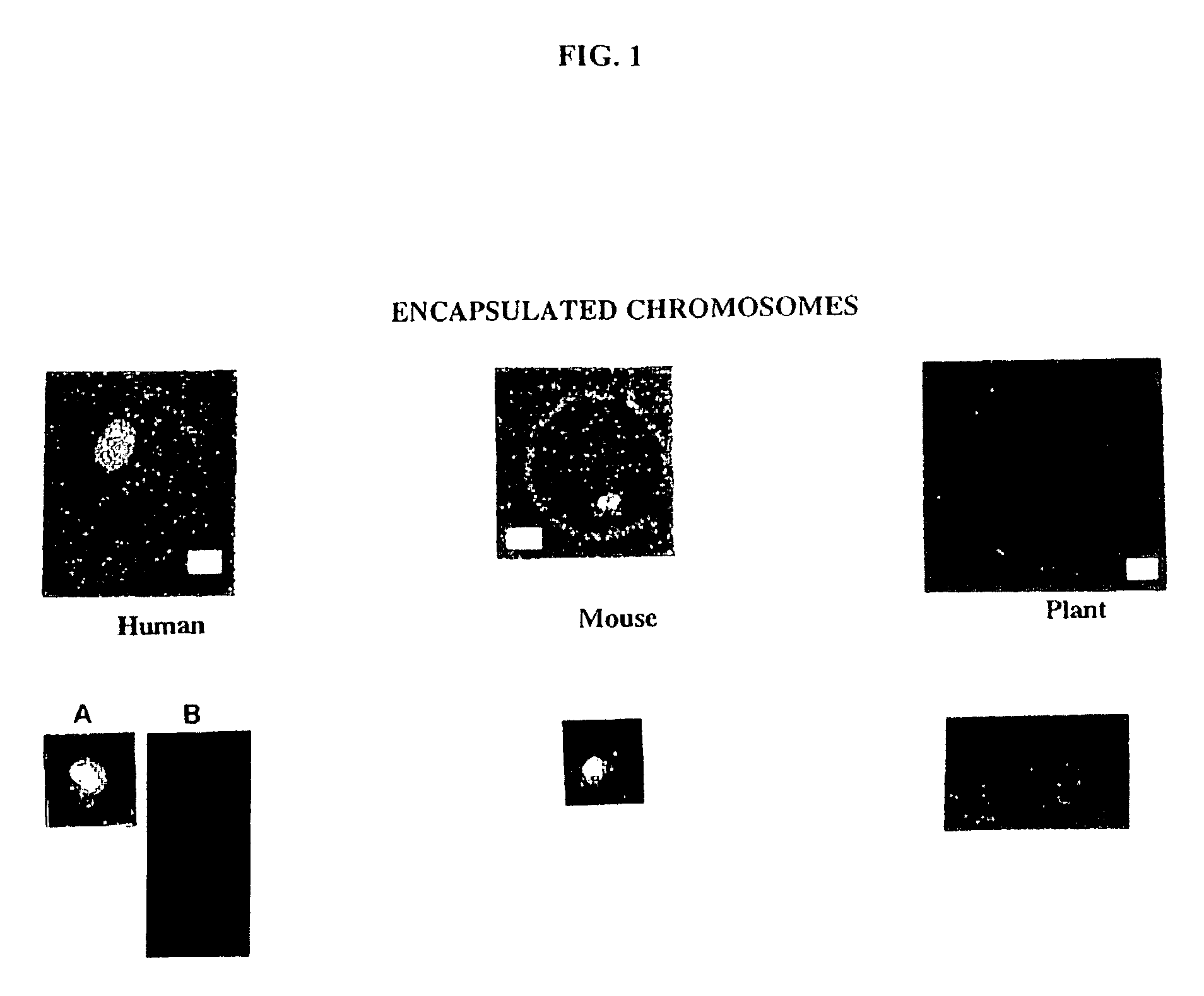
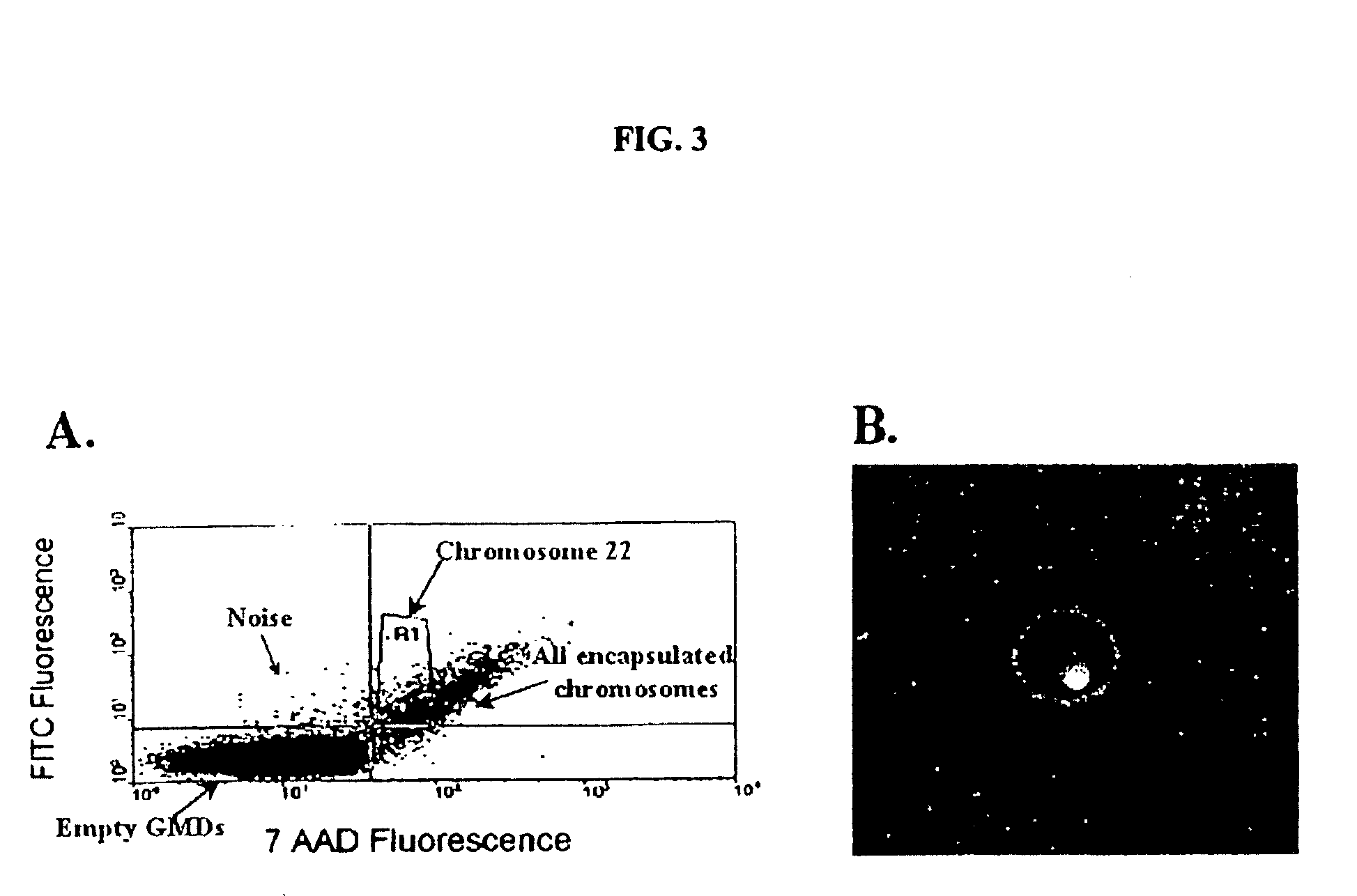
Gel microdrops in genetic analysis
InactiveUS6586176B1Bioreactor/fermenter combinationsBiological substance pretreatmentsSingle entityVirus
The invention provides methods of nucleic acid analysis. Such methods entail forming a population of gel microdrops encapsulating a population of biological entities, each entity comprising a nucleic acid, whereby at least some microdrops in the population each encapsulate a single entity. The population of gel microdrops is then contacted with a probe under conditions whereby the probe specifically hybridizes to at least one complementary sequence in the nucleic acid in at least one gel microdrop. At least one gel microdrop is then analyzed or detected. The biological entities can be cells, viruses, nuclei and chromosomes.
Owner:CELLAY
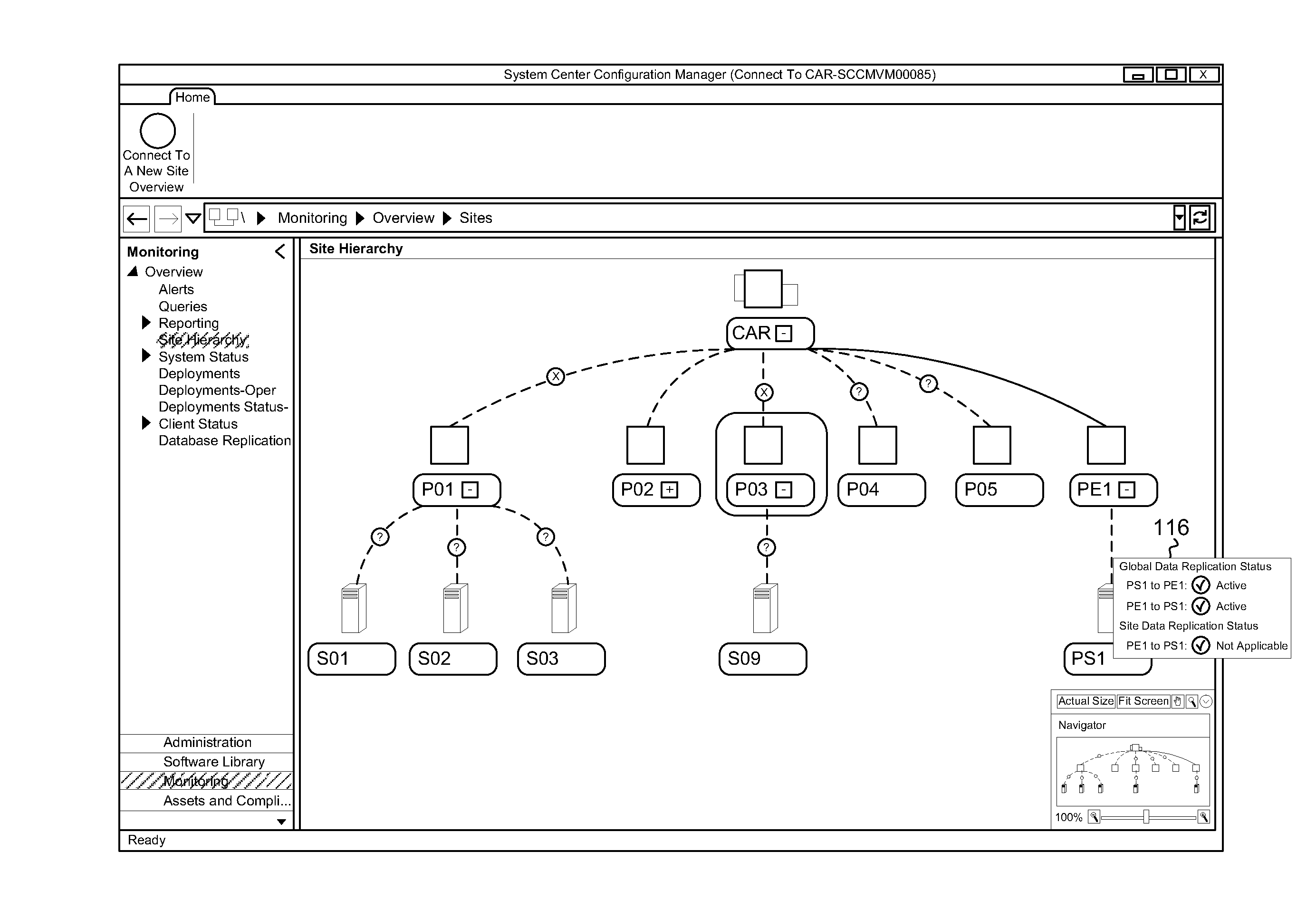
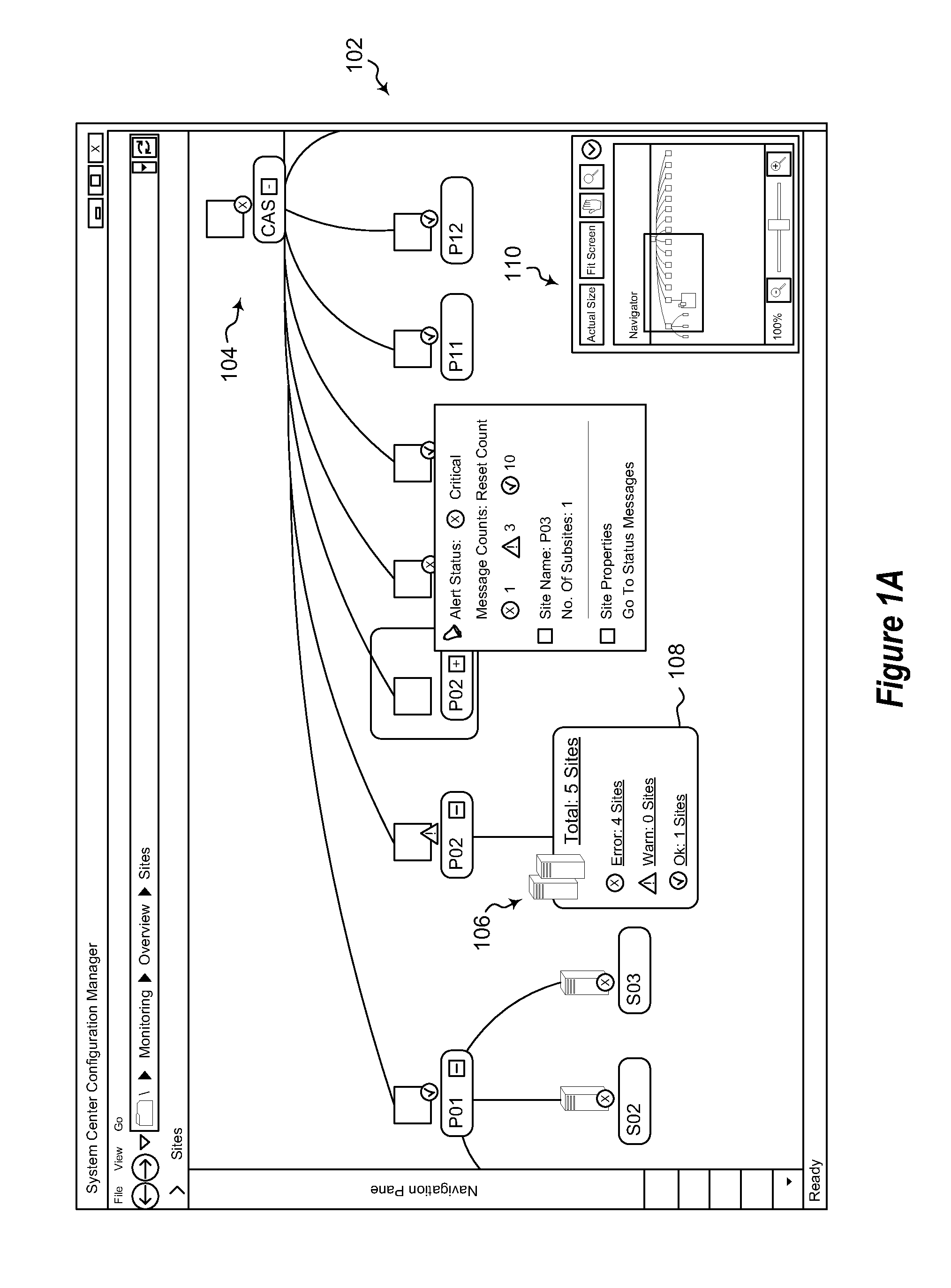
Relationship visualization and graphical interaction model in it client management
ActiveUS20120036484A1TransmissionInput/output processes for data processingGraphicsGraphical user interface
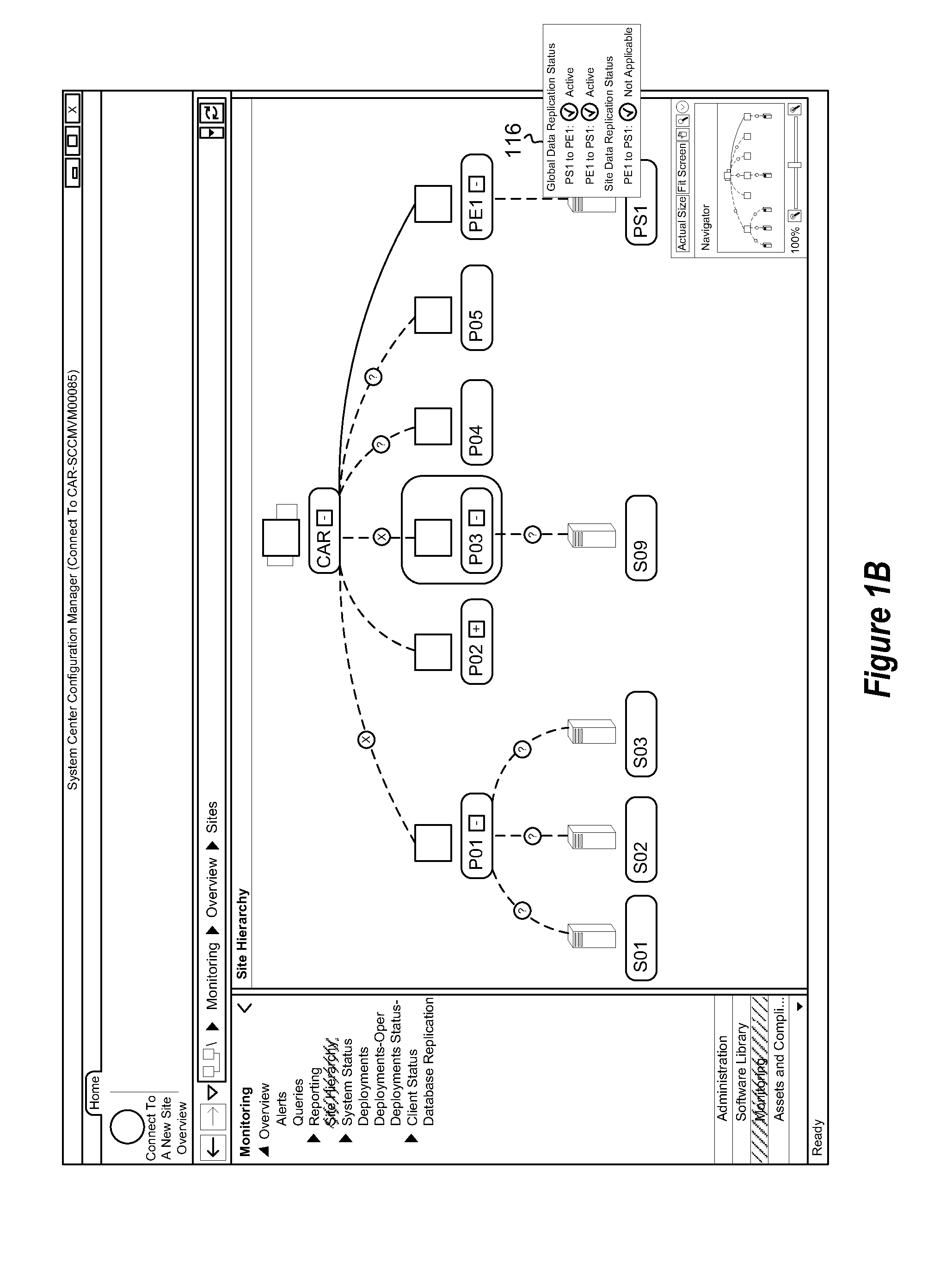
Displaying a hierarchy. A method includes identifying a set of nodes representing sites in a hierarchy. The set of nodes share one or more common characteristics not shared by any other nodes in the hierarchy. The method further includes determining that the set of nodes, as a set, meet a predetermined condition. As a result of the nodes sharing the one or more common characteristics not shared by any other nodes in the hierarchy and as a result of the set meeting the predetermined condition, the method further includes aggregating at least a portion of the set of nodes. The method further includes displaying in a graphical user interface a representation of the hierarchy including displaying the aggregated portion as a single entity in the hierarchy.
Owner:MICROSOFT TECH LICENSING LLC
User interface to display and manage an entity and associated resources
InactiveUS20050081157A1Easy to configureReduce decreaseError detection/correctionMultiple digital computer combinationsSingle entityUser interface
A user interface to display and manage a plurality of entities as if a single entity is provided. The user interface includes a representation of the collection of entities as a whole, and a representation of members associated with the entity. If an action is performed on the representation of the entities as a whole, then the action is propagated to the collection of entities, if the action is performed on the representation of the member associated with the entity, then the action is directed to the member.
Owner:MICROSOFT TECH LICENSING LLC
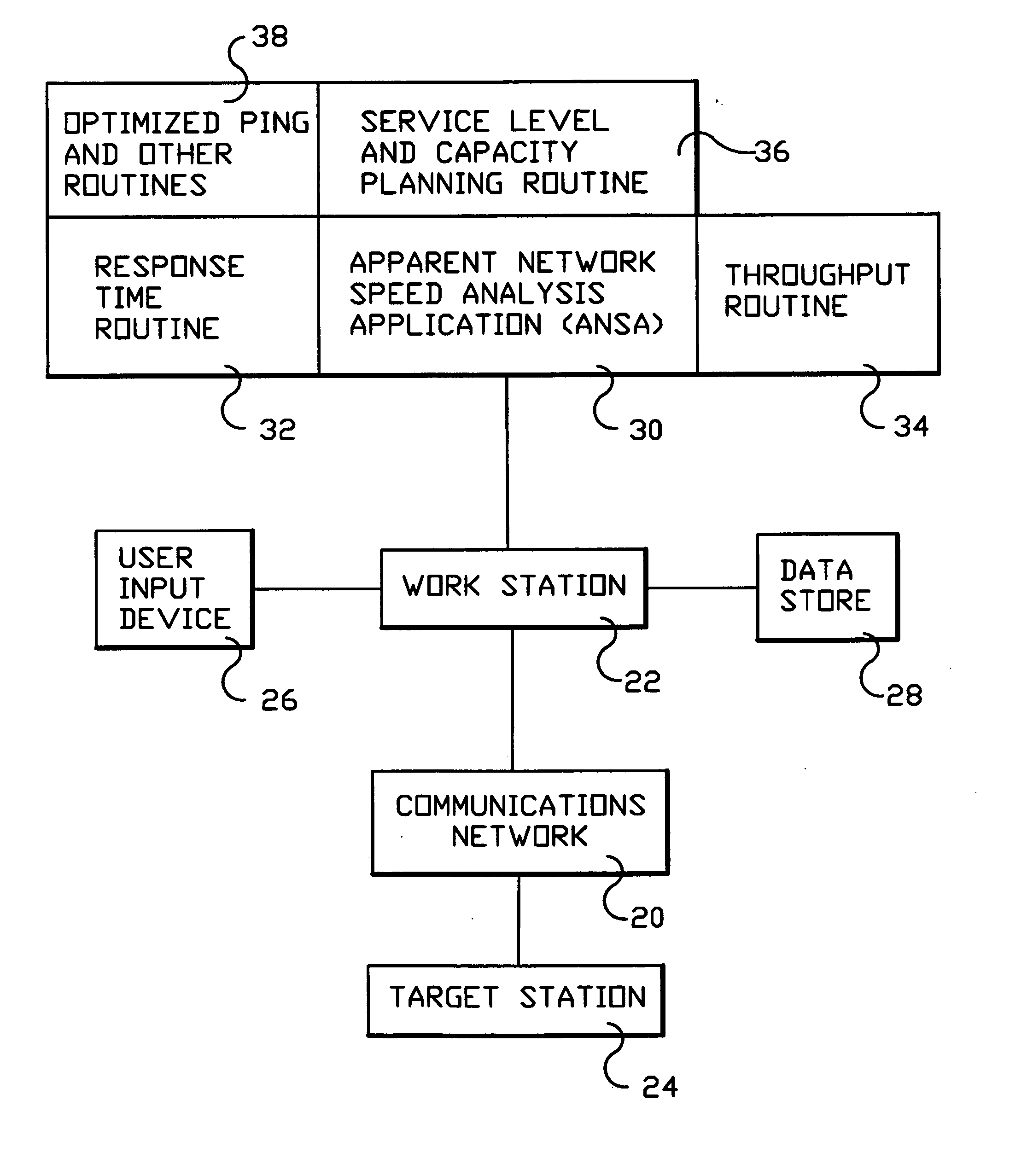
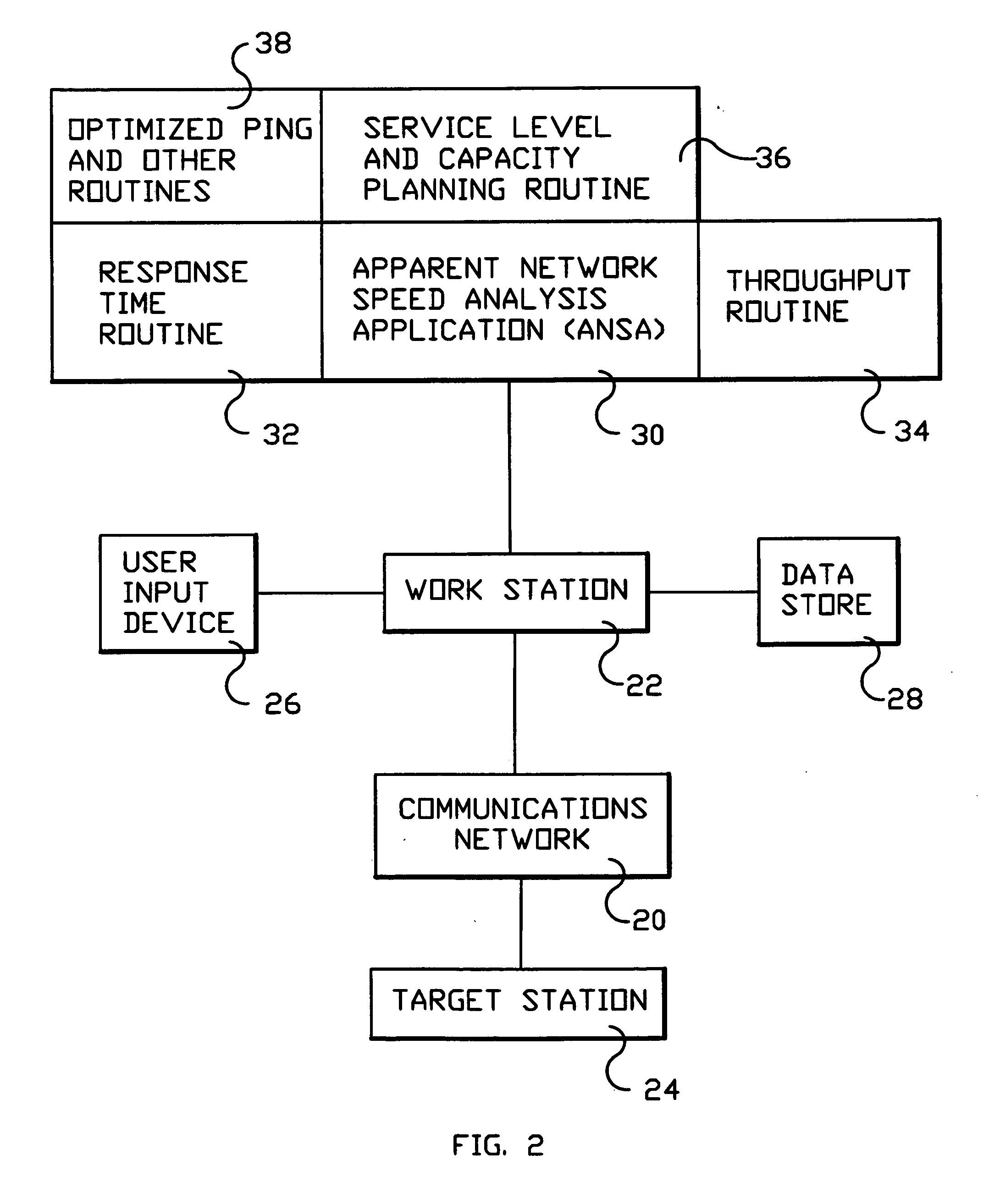
System and method for monitoring performance, analyzing capacity and utilization, and planning capacity for networks and intelligent, network connected processes
InactiveUS20050018611A1Error preventionFrequency-division multiplex detailsTotal responseTest sample
Analysis of networks and testing and analyzing intelligent, network connected devices. An instantaneous network utilization value is assigned for the worst surviving ping instance of between 90% and 99% (determined proportionately from the ratio of dropped test samples to surviving test samples), and then used to solve for average network message size and average utilization of the network. A plurality transactions of different types are transmitted across the network to intelligent end systems and the results mathematically evaluated to determine the portion of the total response time contributed by the network and by the end processors; the utilization of the end processor processing subsystems and of the end processor I / O subsystems; and the utilization of the end system as a whole; and of the network and end processors considered as a unitary entity. Steps include determining utilization of the network when test packets are dropped by the network; utilization of intelligent processor and other devices attached to the network when test transactions are dropped, and when not dropped; and response time for remote processes at both the network and processor level.
Owner:IBM CORP
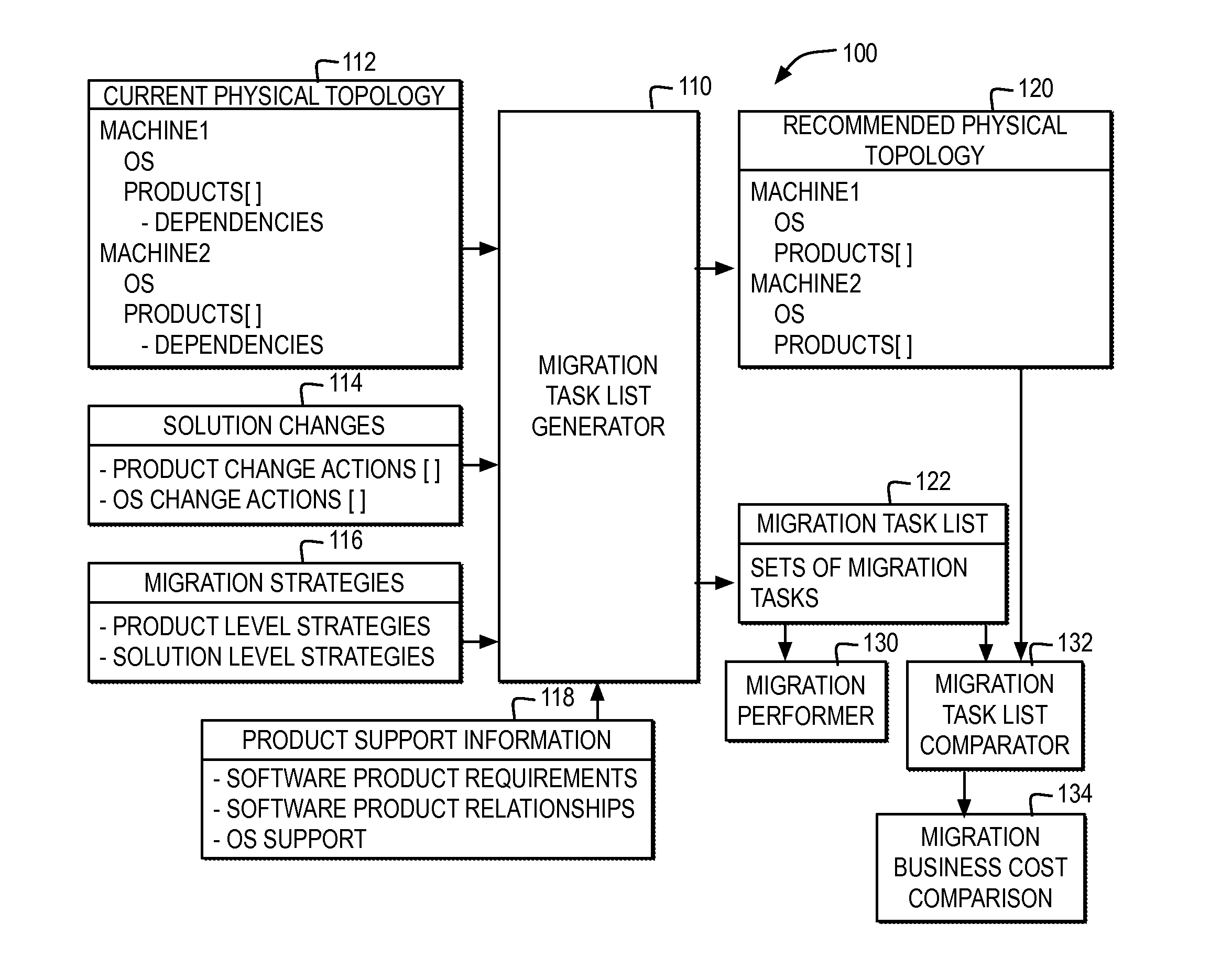
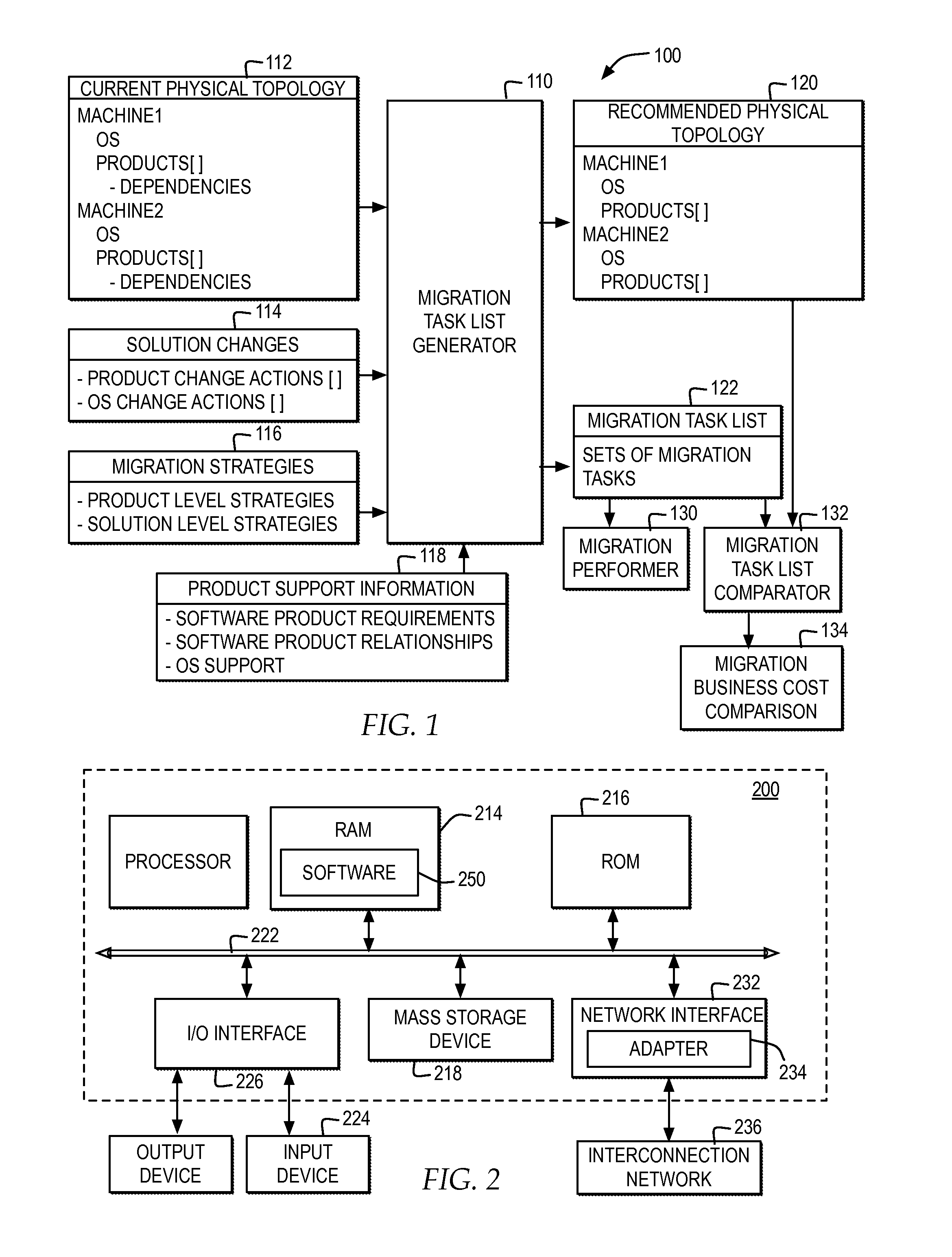
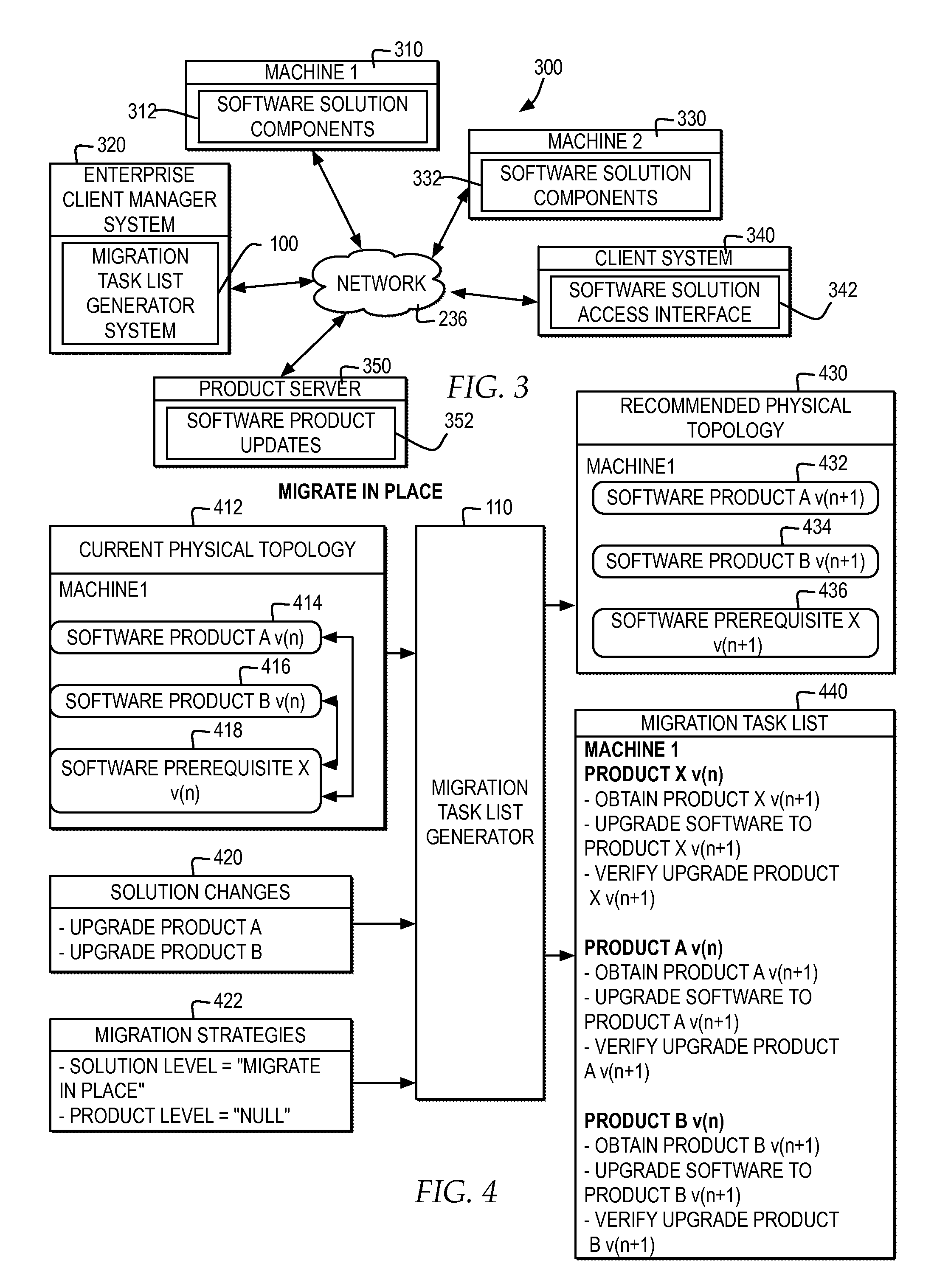
Generating a customized set of tasks for migration of a deployed software solution
A migration set list generator specifies a physical topology of a deployed software solution, wherein the software solution comprises a plurality of software components and data associated with said plurality of software components integrated into a single entity. The migration set list generator specifies at least one solution change to the deployed software solution to meet at least one business requirement and specifies at least one migration strategy for migrating the deployed software solution, wherein the at least one migration strategy comprises at least one of a product level strategy specified for a particular software component of the plurality of software components and at least one solution level strategy specified for the plurality of software components, wherein the product level strategy overrides the solution level strategy for the particular software component. The migration set list generator generates a plurality of migration tasks for making the at least one solution change to the deployed software solution specified in the physical topology based on the at least one migration strategy and generates a recommended physical topology yielded for the software solution if the physical topology is updated according to the plurality of migration tasks.
Owner:IBM CORP
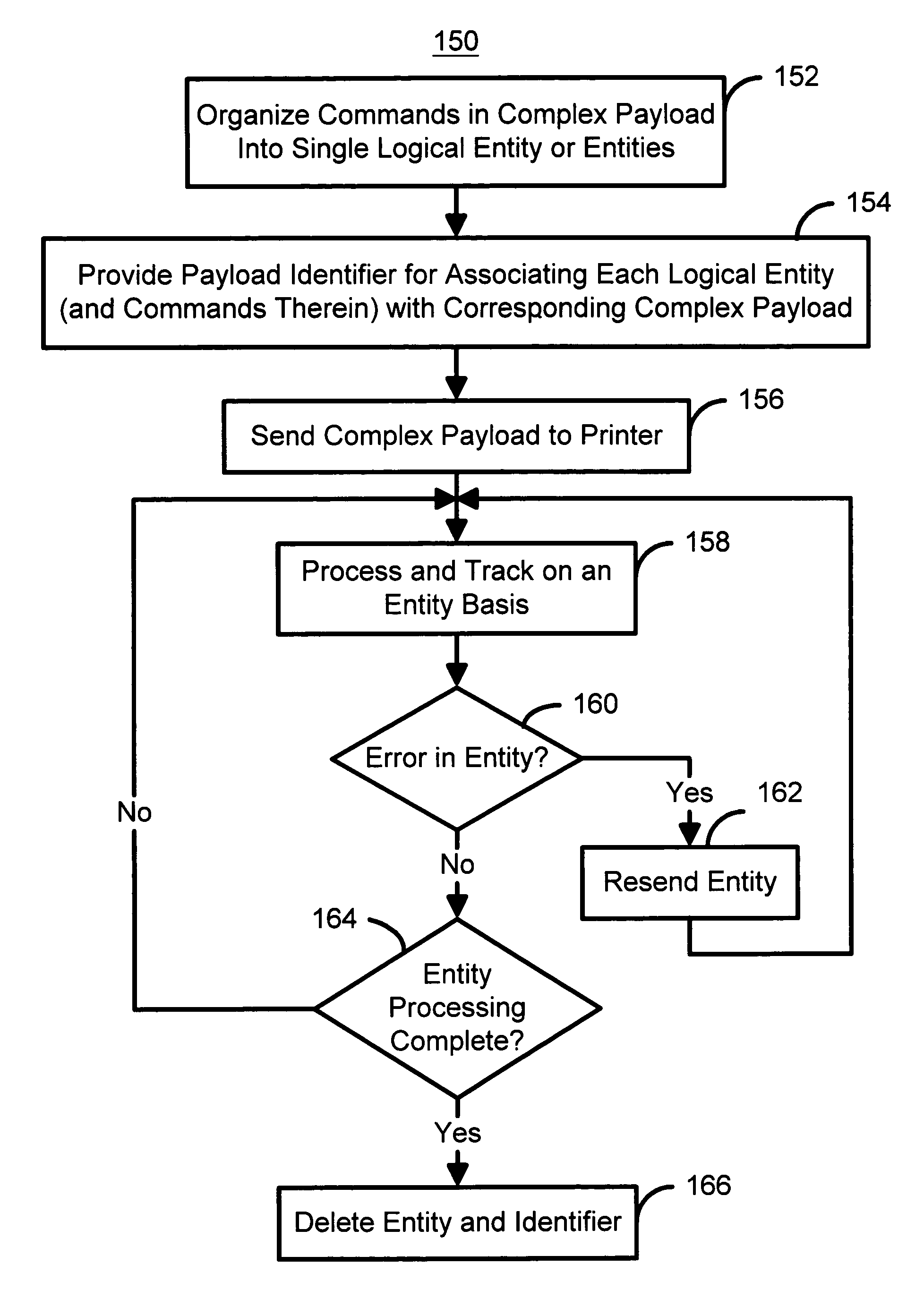
Method for more efficiently managing complex payloads in a point of sale system
ActiveUS7889384B2Easy to operateEfficient managementDigitally marking record carriersVisual presentation using printersSingle entityPoint of sale
Owner:TOSHIBA GLOBAL COMMERCE SOLUTIONS HLDG
Gel microdroplets in genetic analysis
InactiveUS20030207260A1Bioreactor/fermenter combinationsBiological substance pretreatmentsVirusSingle entity
Owner:ONE CELL SYST
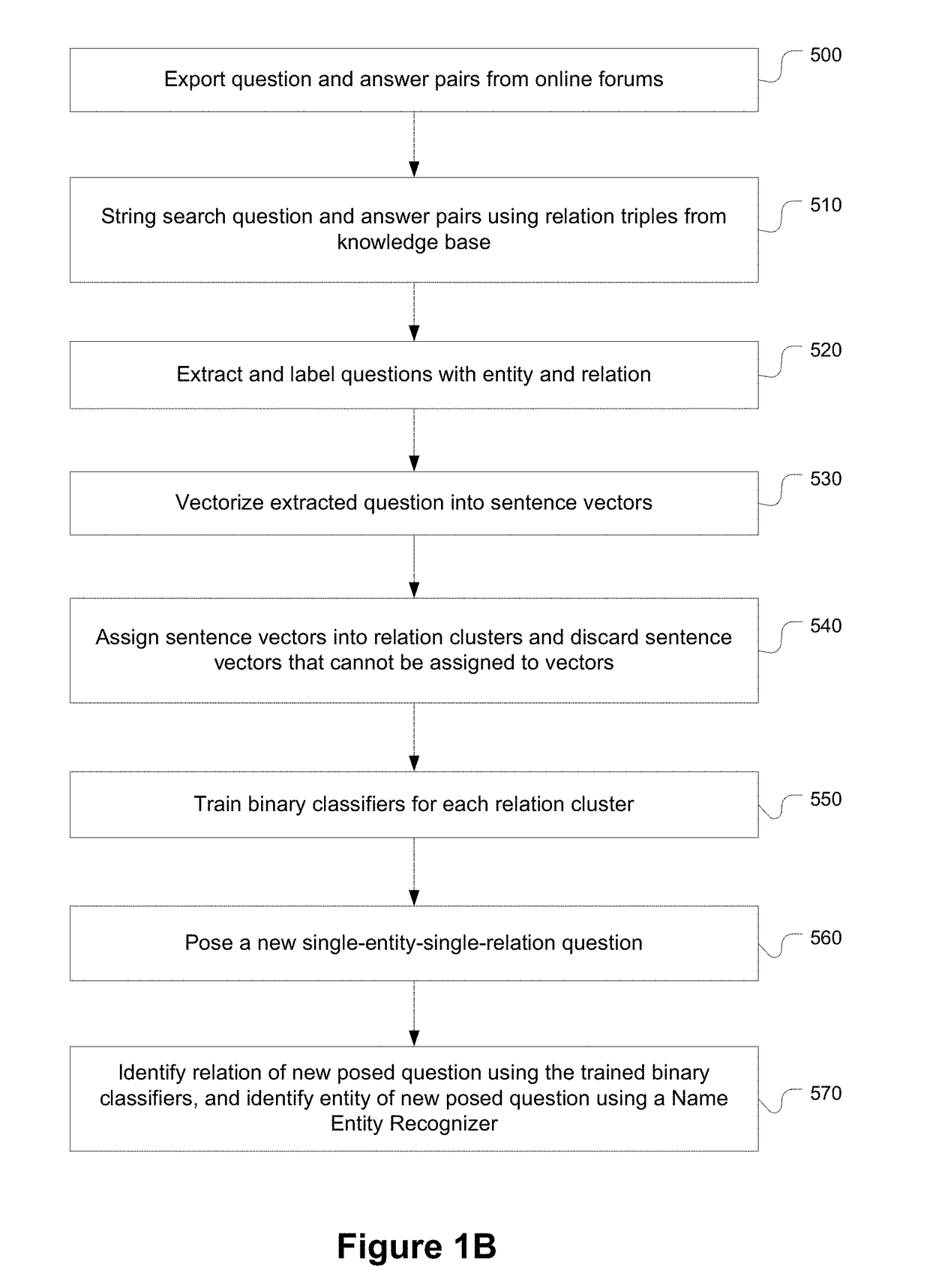
Single-entity-single-relation question answering systems, and methods
ActiveUS20190065576A1Accurate answerRelational databasesSpecial data processing applicationsQuestions and answersLabeled data
Provided are systems and methods related to converting unlabeled data into structured and labeled data for answering one or more single-entity-single-relation questions. The systems and methods automates the labeling of data to generate training data for machine learning. The systems and methods identify and import question and answer pairs from an user generated discussion platform and access a knowledge base questions to extract questions by supervised extraction. The extracted questions are further filtered to remove mislabeled questions. When a question is posed, it is parsed for entity and relation, and an answer is identified by searching through the knowledge base.
Owner:RSVP TECH
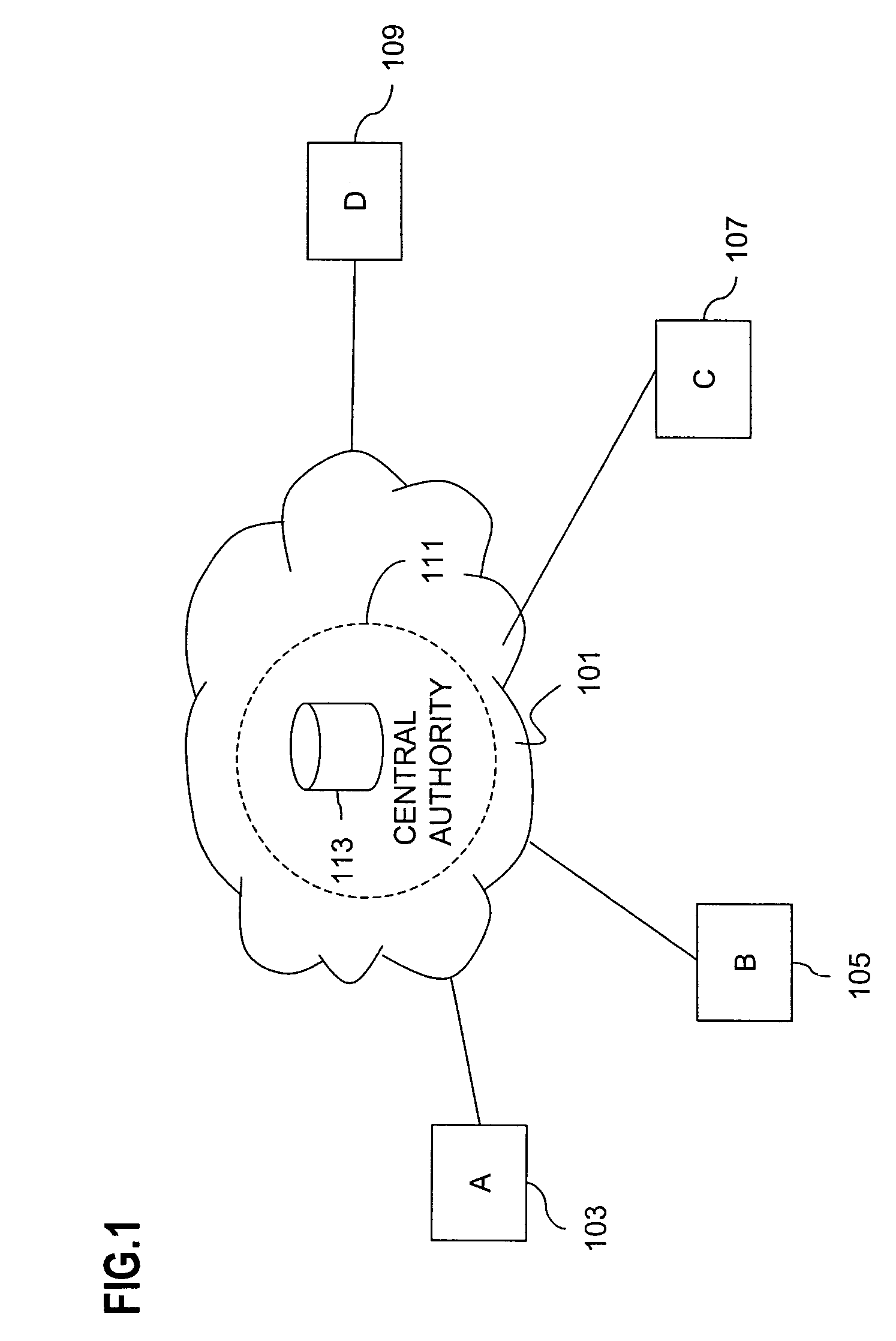
Certificate-based encryption and public key infrastructure
InactiveUS20050246533A1Key distribution for secure communicationPublic key for secure communicationCryptosystemSingle entity
The present invention provides methods for sending a digital message from a sender (606) to a recipient (608) in a public-key based cryptosystem comprising an authorizer (606). The authorizer can be a single entity (606) or comprise a hierarchical or distributed entity (602, 604a-604b). The present invention allows communication of messages by an efficient protocol, not involving key status queries or key escrow, where a message recipient (608) can decrypt a message from a message sender (606) only if the recipient (608) possesses up-to-date authority from the authorizer. The invention allows such communication in a system comprising a large number (e.g. millions) of users.
Owner:NTT DOCOMO INC
Flexible rate split method for MIMO transmission
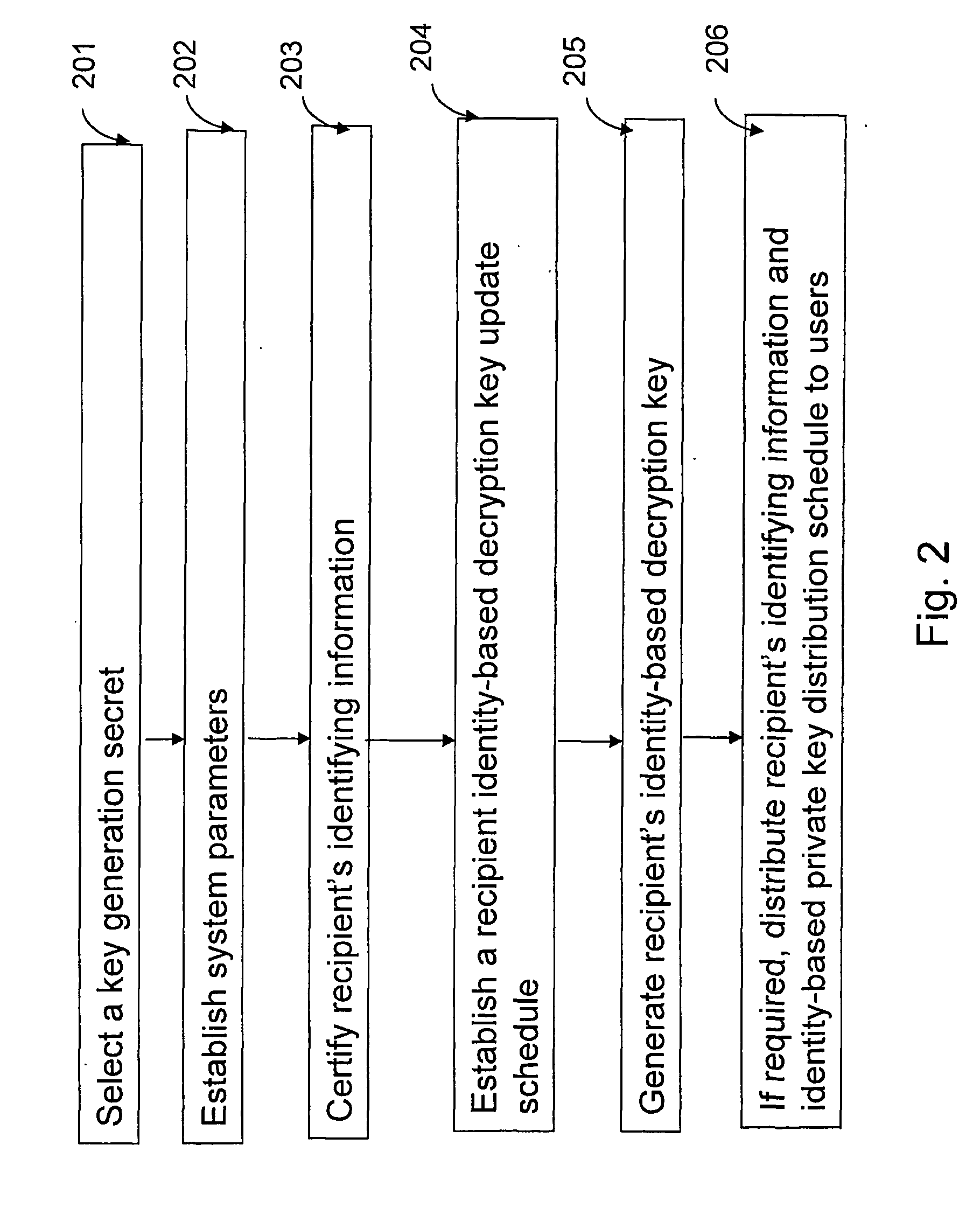
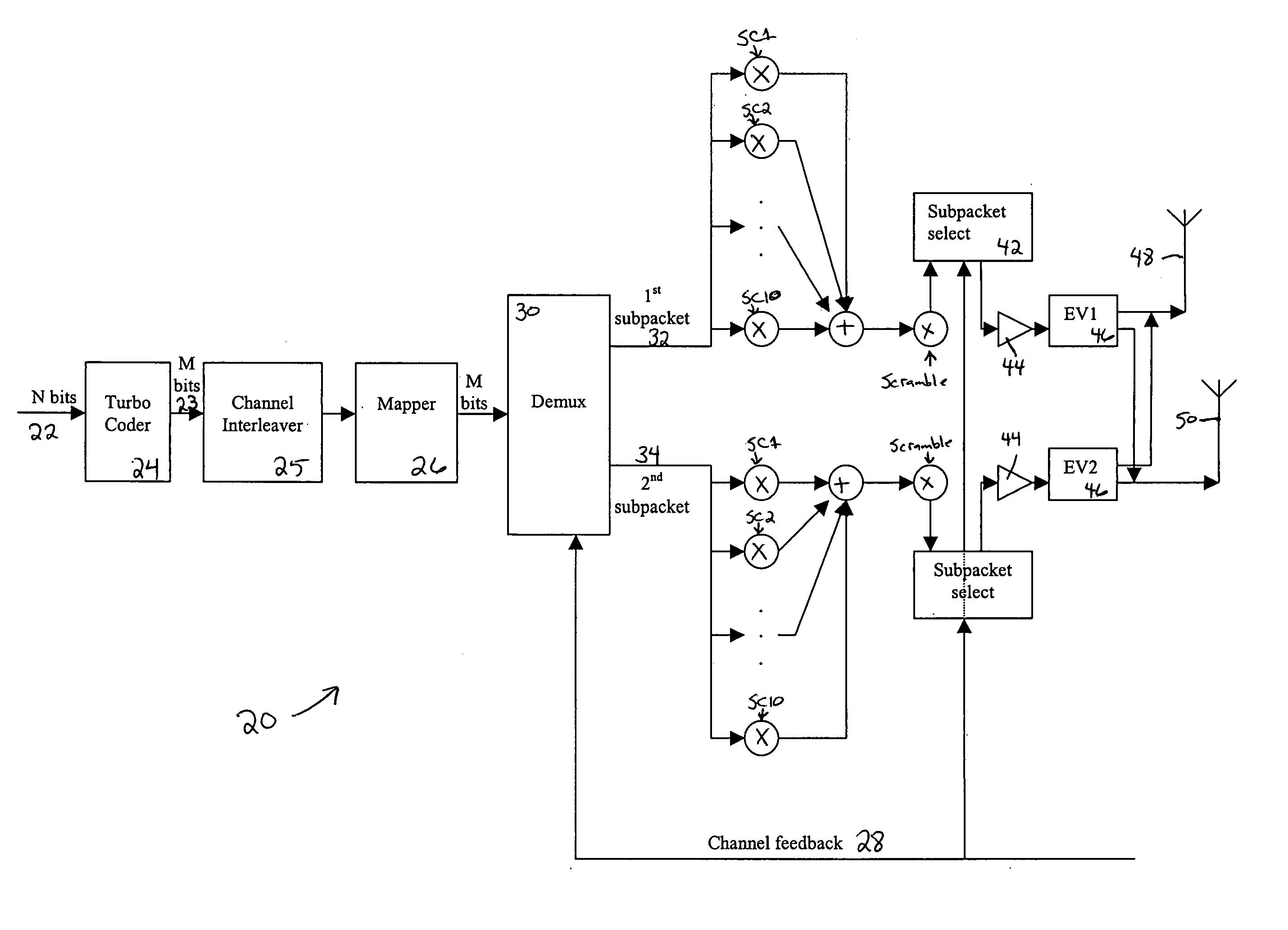
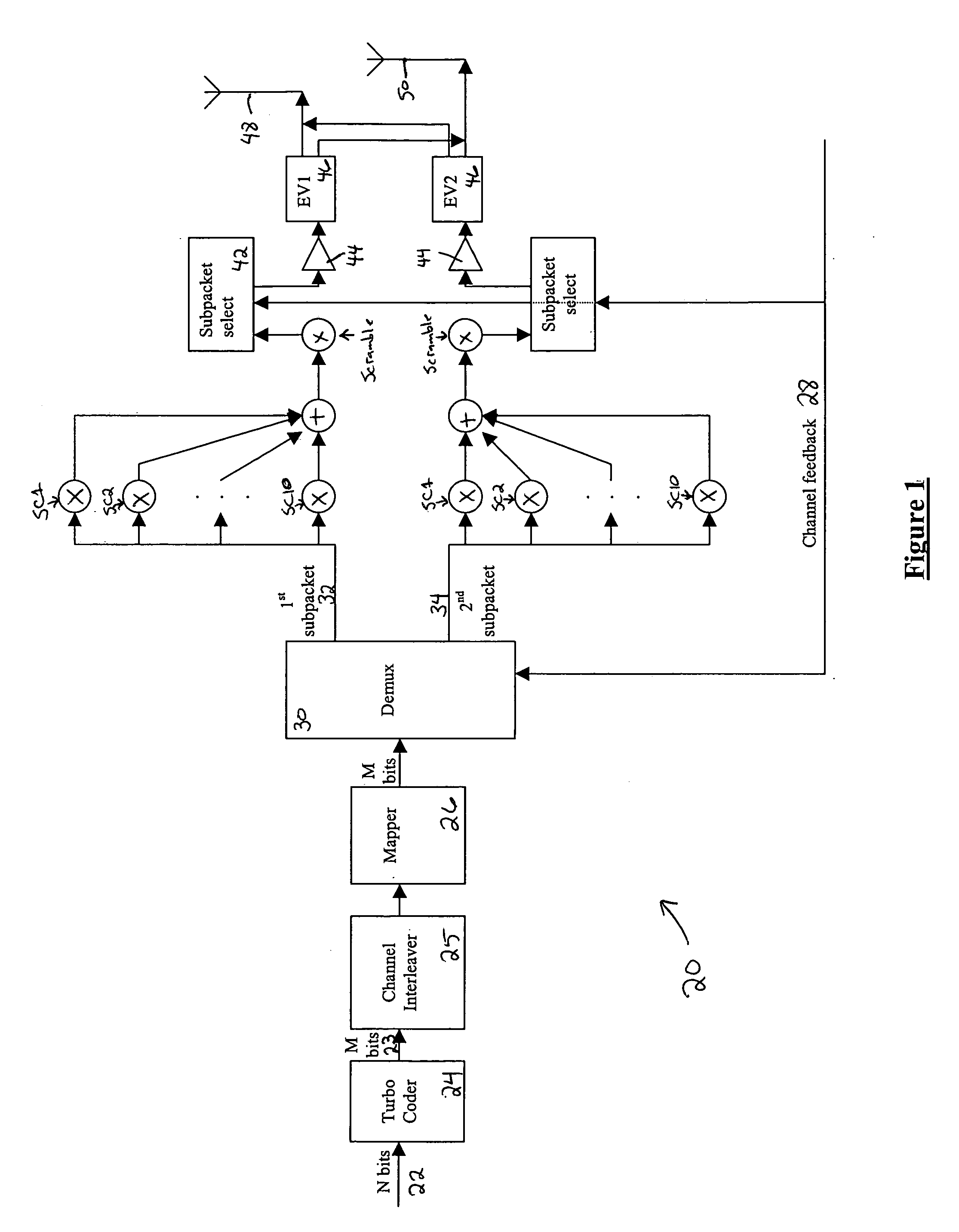
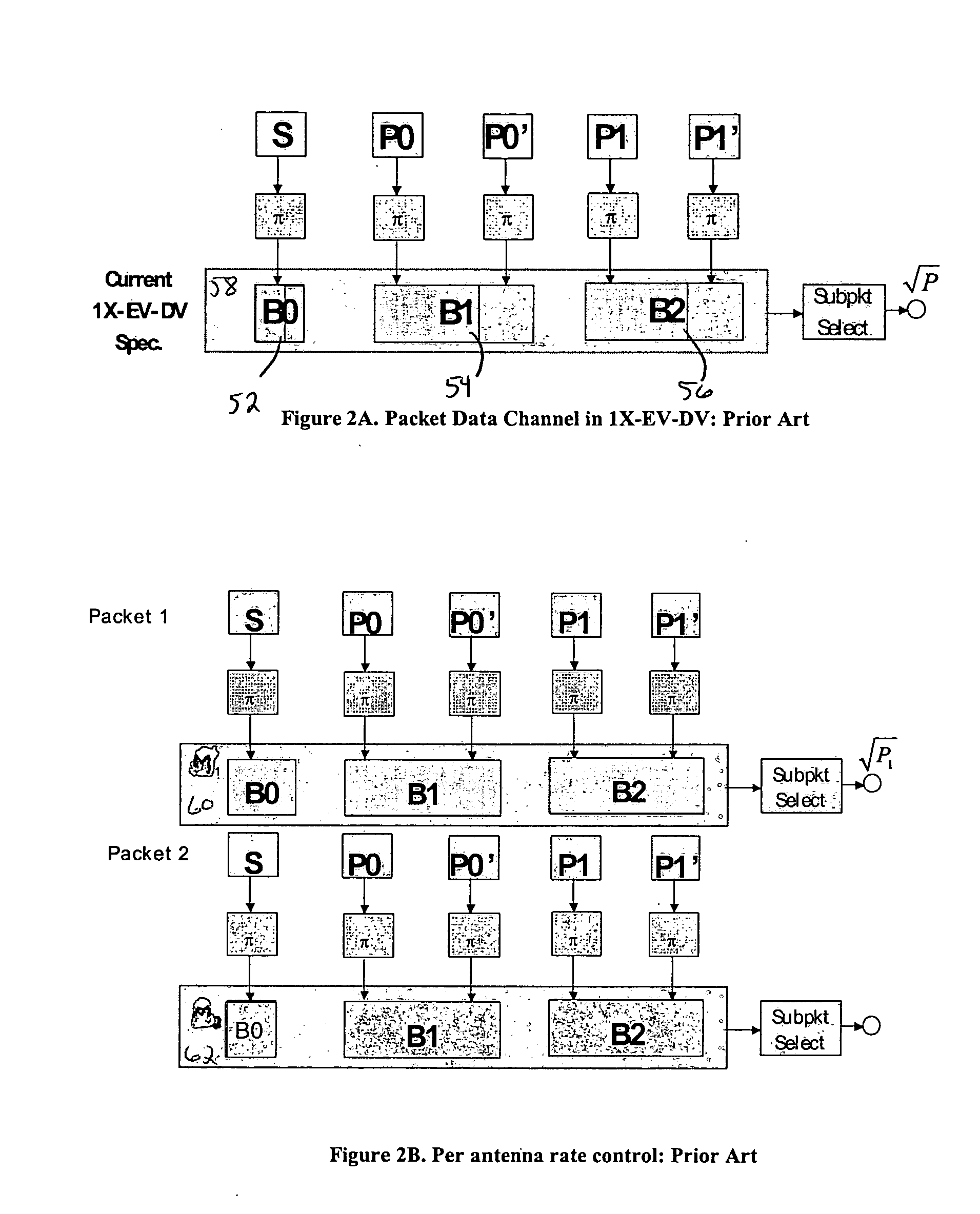
InactiveUS20050111376A1Wide diversityReduce error rateSpatial transmit diversityFrequency-division multiplex detailsMimo transmissionSelection system
A method for transmitting a packet of N input bits includes encoding all of the N bits as a single entity, such as with an interleaver of length N within a turbo coder, outputting M encoded bits, channel interleaving the M bits, splitting the M encoded bits into a parallel first and second portion, and transmitting them over separate channels to achieve spatial diversity. The size of the first and second portion is determined based on a closed feedback loop that provides some knowledge of the channel, preferably a measure of channel capacity. The feedback loop may also provide channel knowledge to a subpacket selector associated with each transmit antenna, which determines an appropriate rate for that channel and selects subpackets to fill a transmission packet for that channel. The subpacket selectors choose a subpacket of systematic bits and fill the remaining transmission packet size with subpackets of parity bits. Eigenvectors may be employed to transmit each transmission packet over more than one channel with a power disparity between the channels. A transmitter according to the present invention is also described.
Owner:NOKIA CORP
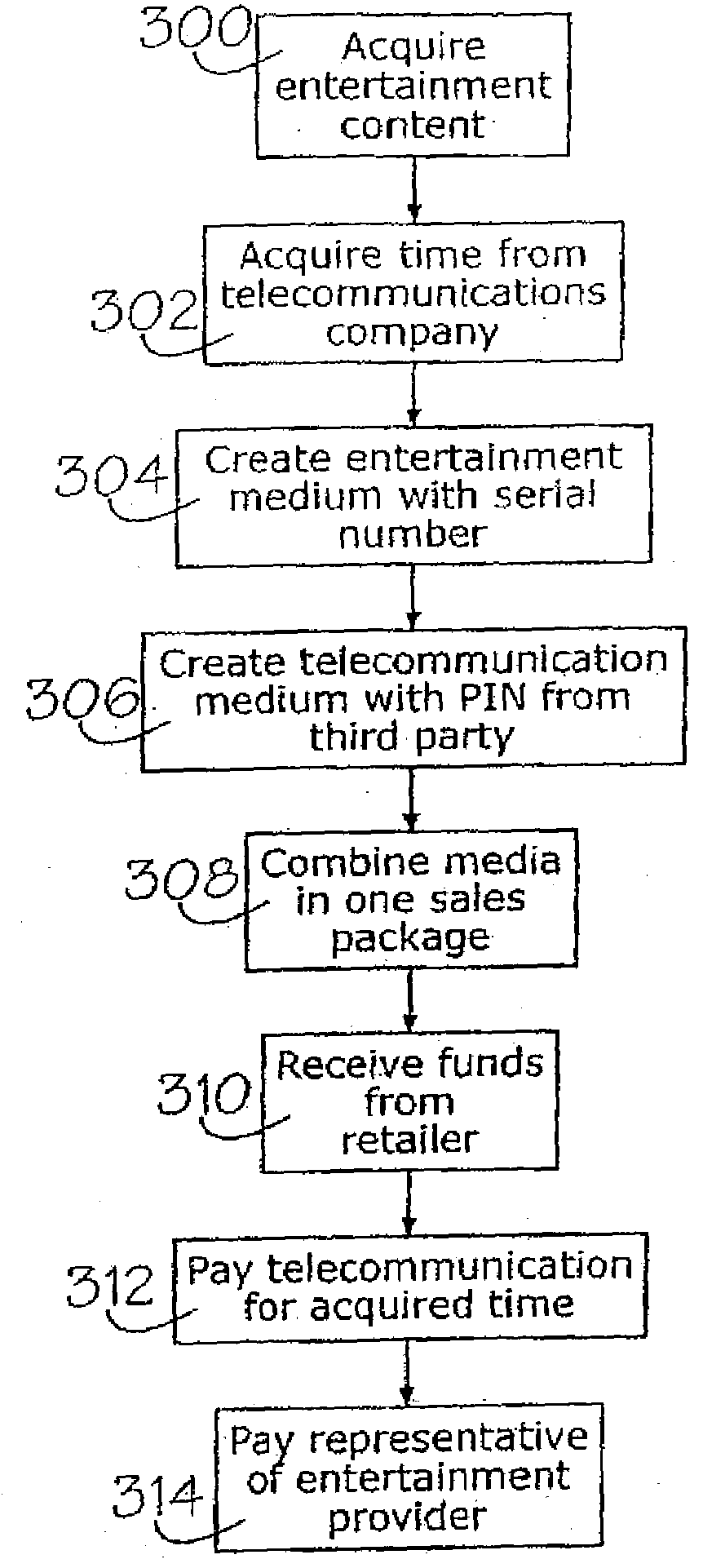
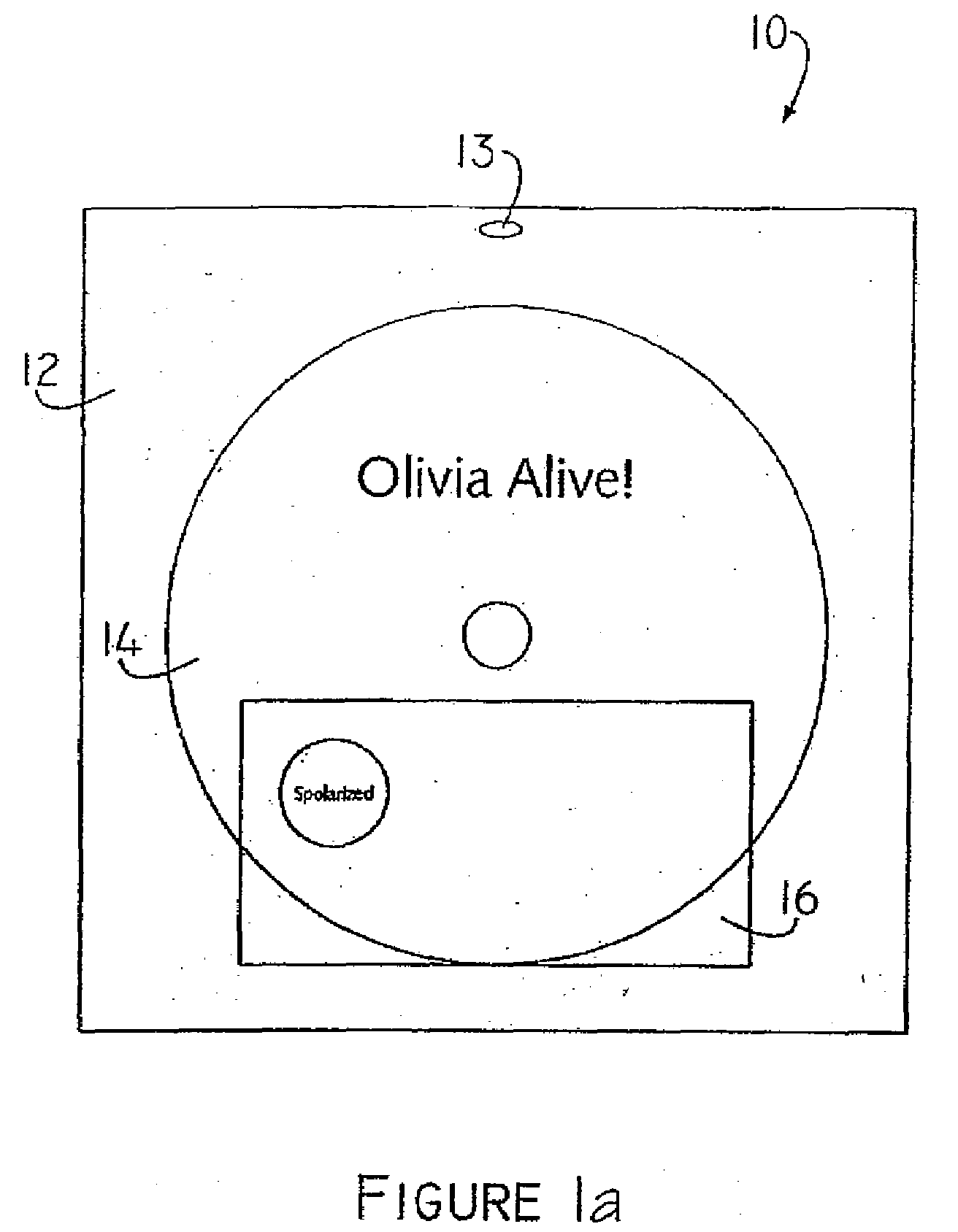
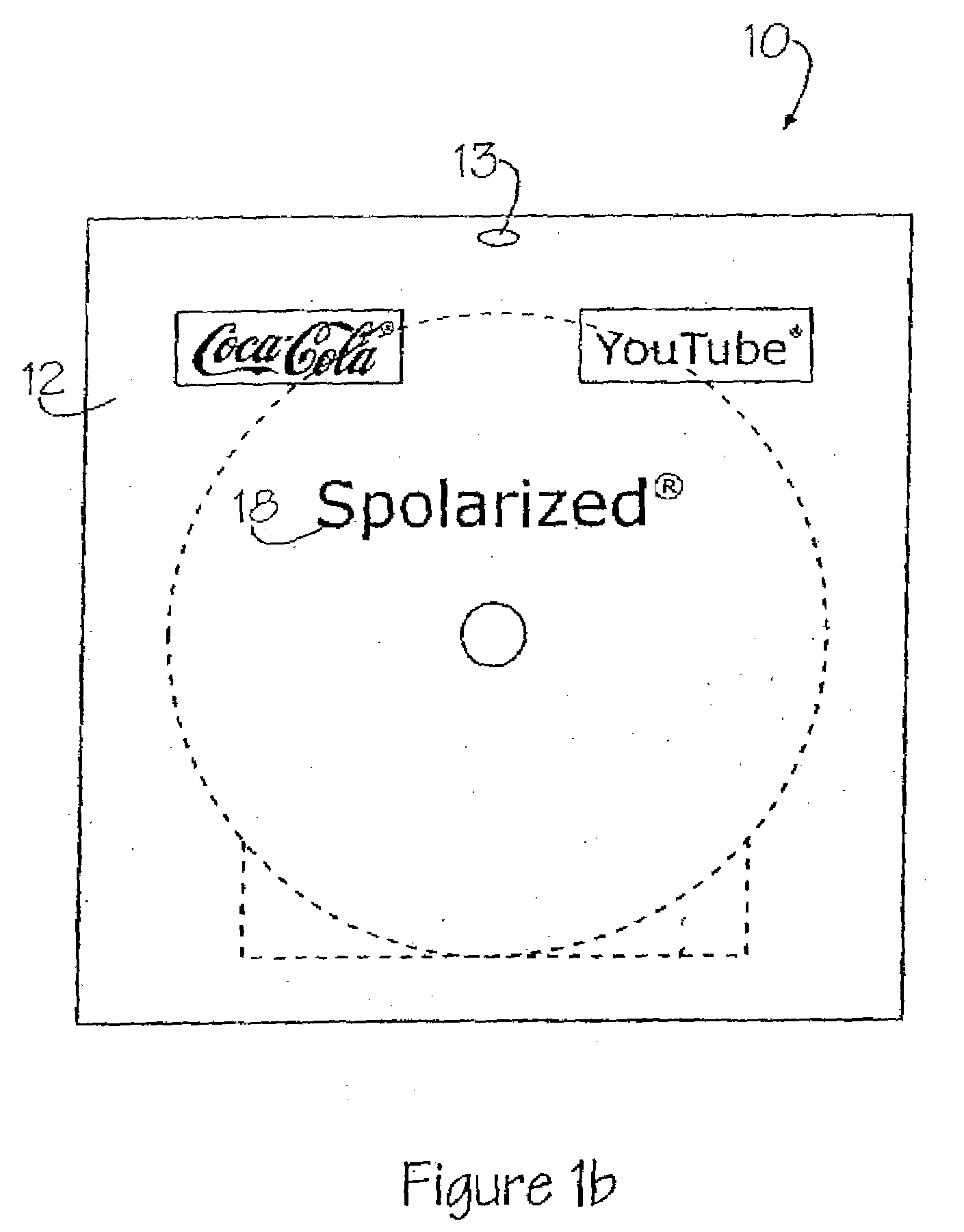
System for combining and bundling commercial products, items having monetary value, business transactions, and entertainment
InactiveUS20100114783A1Payment architectureBuying/selling/leasing transactionsSingle entityMonetary value
A method for acquiring and distributing entertainment items, information representative of monetary funds, and / or commercial products, some or all which maybe combined or bundled in a single package. Goods and services are first identified. Advertising is provided for at least one commercial product. The advertising includes a predetermined code associated with the commercial product. The commercial product is sold and, upon acceptance of the predetermined code, a second commercial product or an entertainment item or a medium containing information representative of monetary funds is provided as a single entity or transaction.
Owner:SPOLAR MARGARET M
User interface to display and manage an entity and associated resources
InactiveUS20050081156A1Easy to manageEasy to navigateError detection/correctionMultiple digital computer combinationsSingle entityUser interface
A user interface to display and manage a plurality of entities as if a single entity is provided. The user interface includes a representation of the collection of entities as a whole, and a representation of members associated with the entity. If an action is performed on the representation of the entities as a whole, then the action is propagated to the collection of entities, if the action is performed on the representation of the member associated with the entity, then the action is directed to the member.
Owner:MICROSOFT TECH LICENSING LLC
Virtual mimo communication system
ActiveUS7508798B2Create efficientlySite diversitySpatial transmit diversityTelecommunicationsMimo transmission
The present invention provides an effective way to create a virtual MIMO transmission system using mobile terminals that have only one transmit path and antenna. This is accomplished by assigning mobile terminals to a group and assigning certain shared resources and user-specific resources to those mobile terminals in the group. In a synchronized fashion, the mobile terminals will provide uplink transmission in concert, as if they were a single entity having multiple transmission paths and antennas. Preferably, the shared resources bear on how the data is transmitted, and the user-specific resources relate to pilot signals. The data transmitted may be encoded in any number of ways, and in one embodiment, the mobile terminals may relay their information to each other, such that uplink transmissions can incorporate STTD decoding or other space-time codes. The invention is applicable to virtually any multiple access technology, including OFDM, TDMA, and CDMA, preferably synchronous CDMA.
Owner:MALIKIE INNOVATIONS LTD
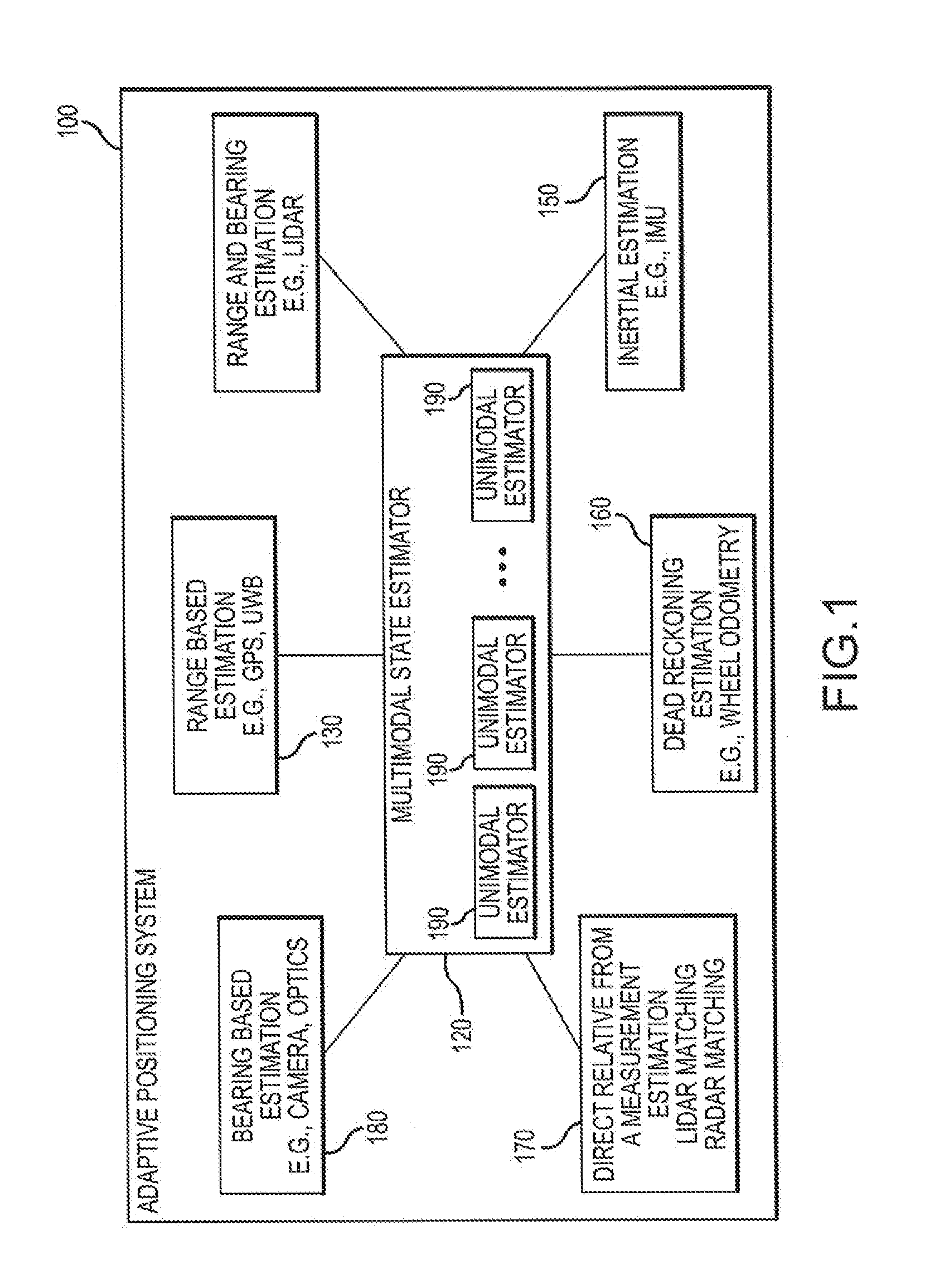
Adaptive positioning system
InactiveUS20170023659A1Reduce odometric driftReduce errorsRegistering/indicating working of vehiclesPosition fixationMobile vehicleMultiple sensor
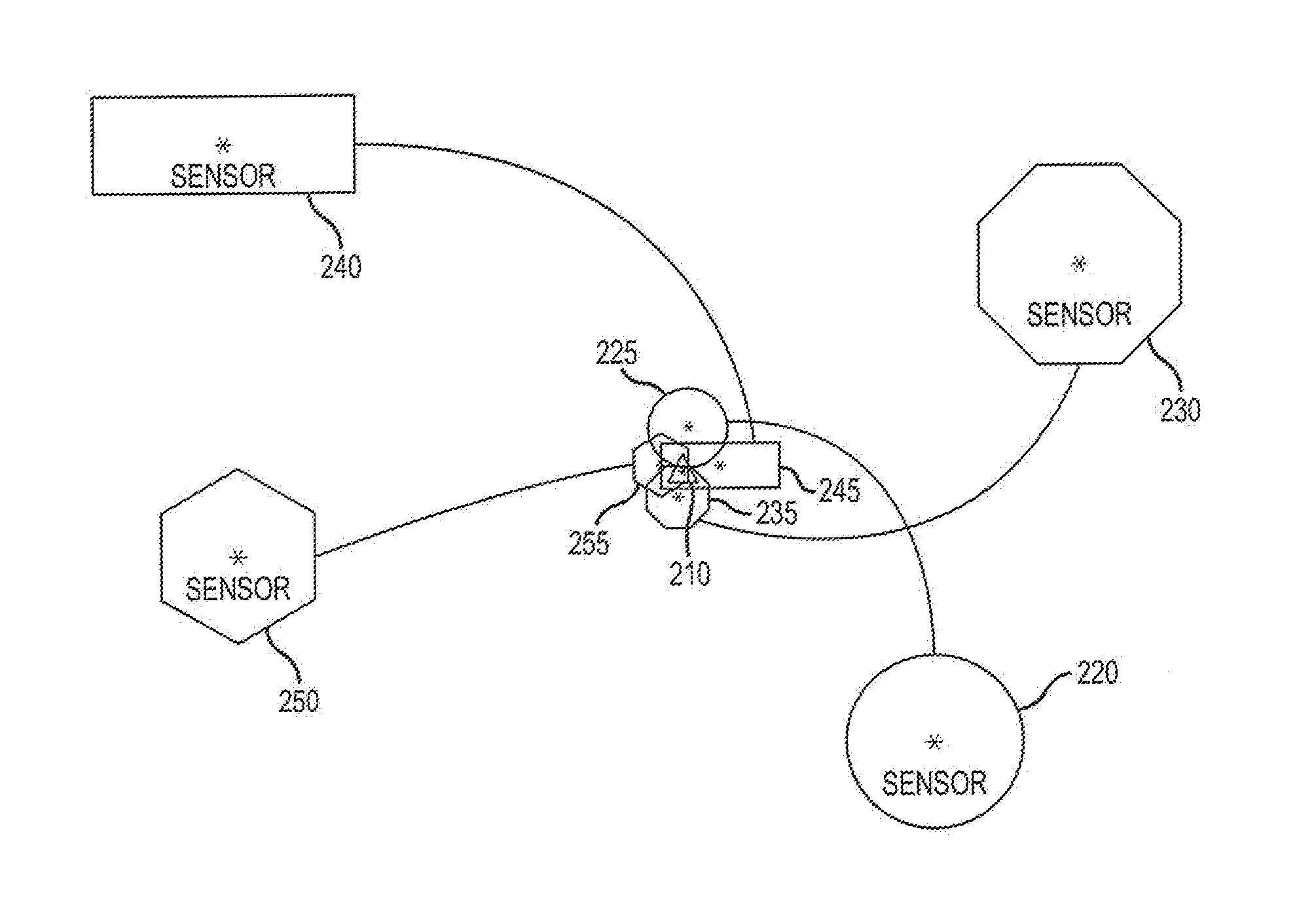
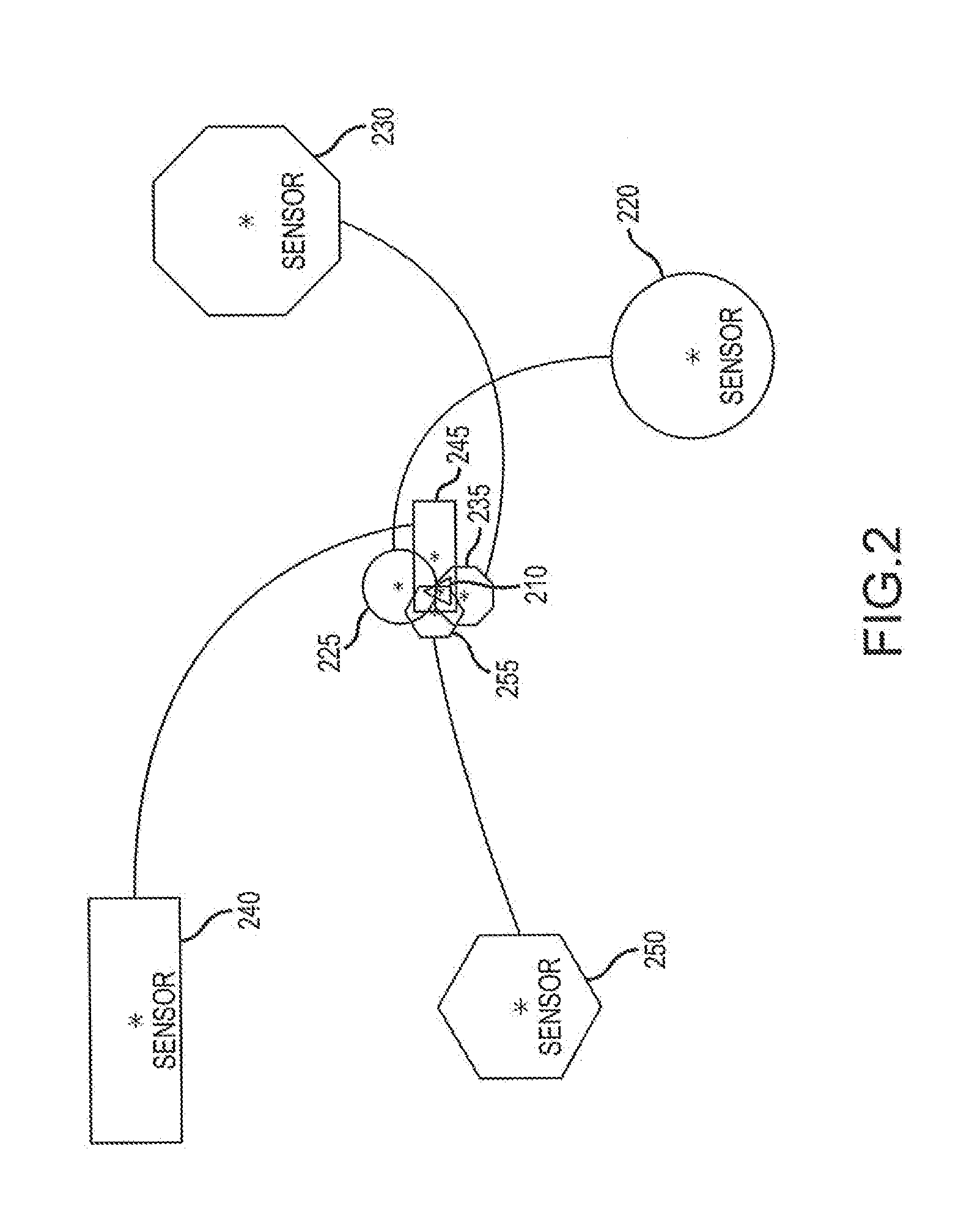
An Adaptive Positioning System provides a method for directing and tracking position, motion and orientation of mobile vehicles, people and other entities using multiple complementary positioning components to provide seamless positioning and behavior across a spectrum of indoor and outdoor environments. The Adaptive Positioning System (APS) provides for complementary use of peer to peer ranging together with map matching to alleviate the need for active tags throughout an environment. Moreover, the APS evaluates the validity and improves the effective accuracy of each sensor by comparing each sensor to a collaborative model of the positional environment. The APS is applicable for use with multiple sensors on a single entity (i.e. a single robot) or across multiple entities (i.e. multiple robots) and even types of entities (i.e. robots, humans, cell phones, cars, trucks, drones, etc.).
Owner:HUMATICS CORP
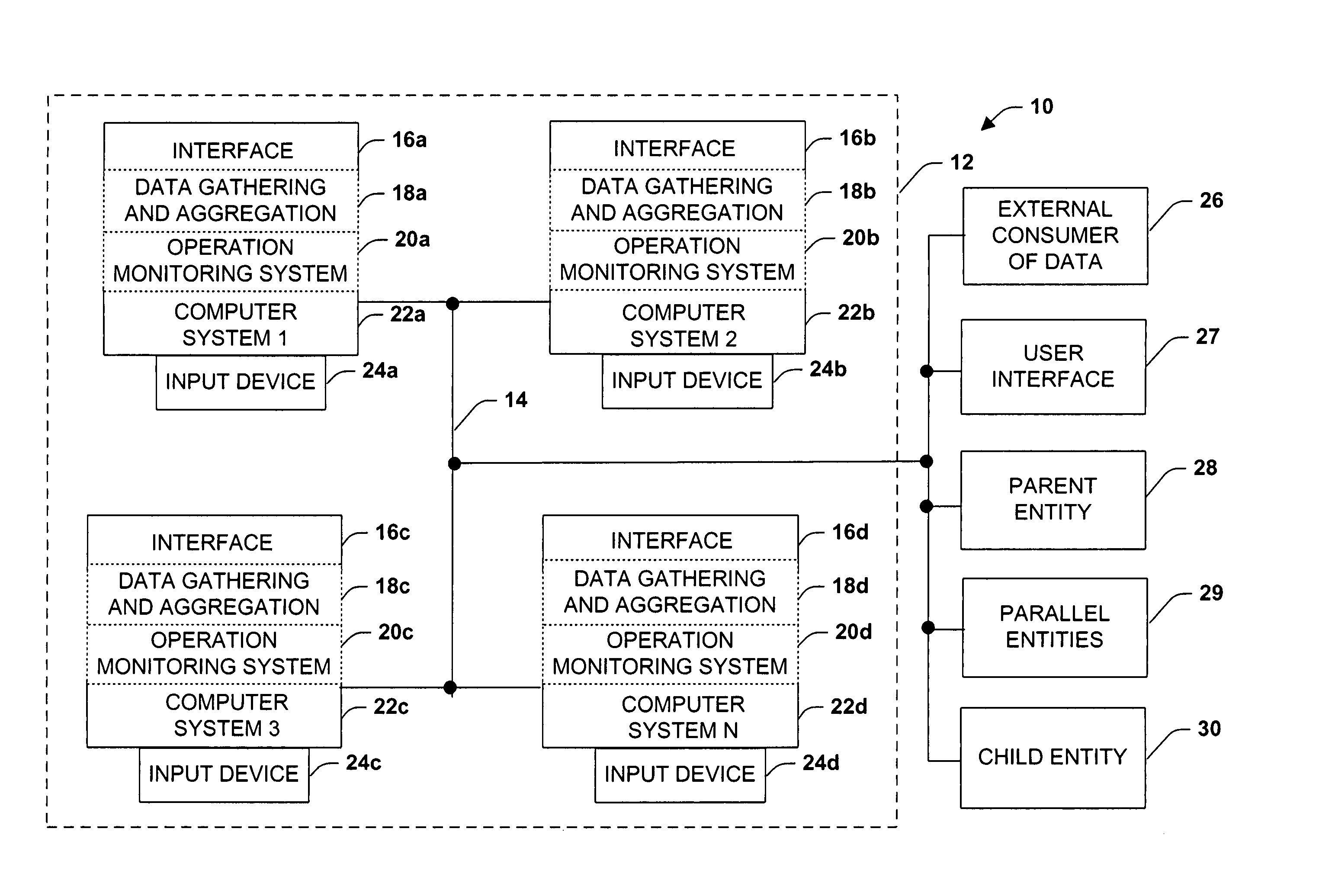
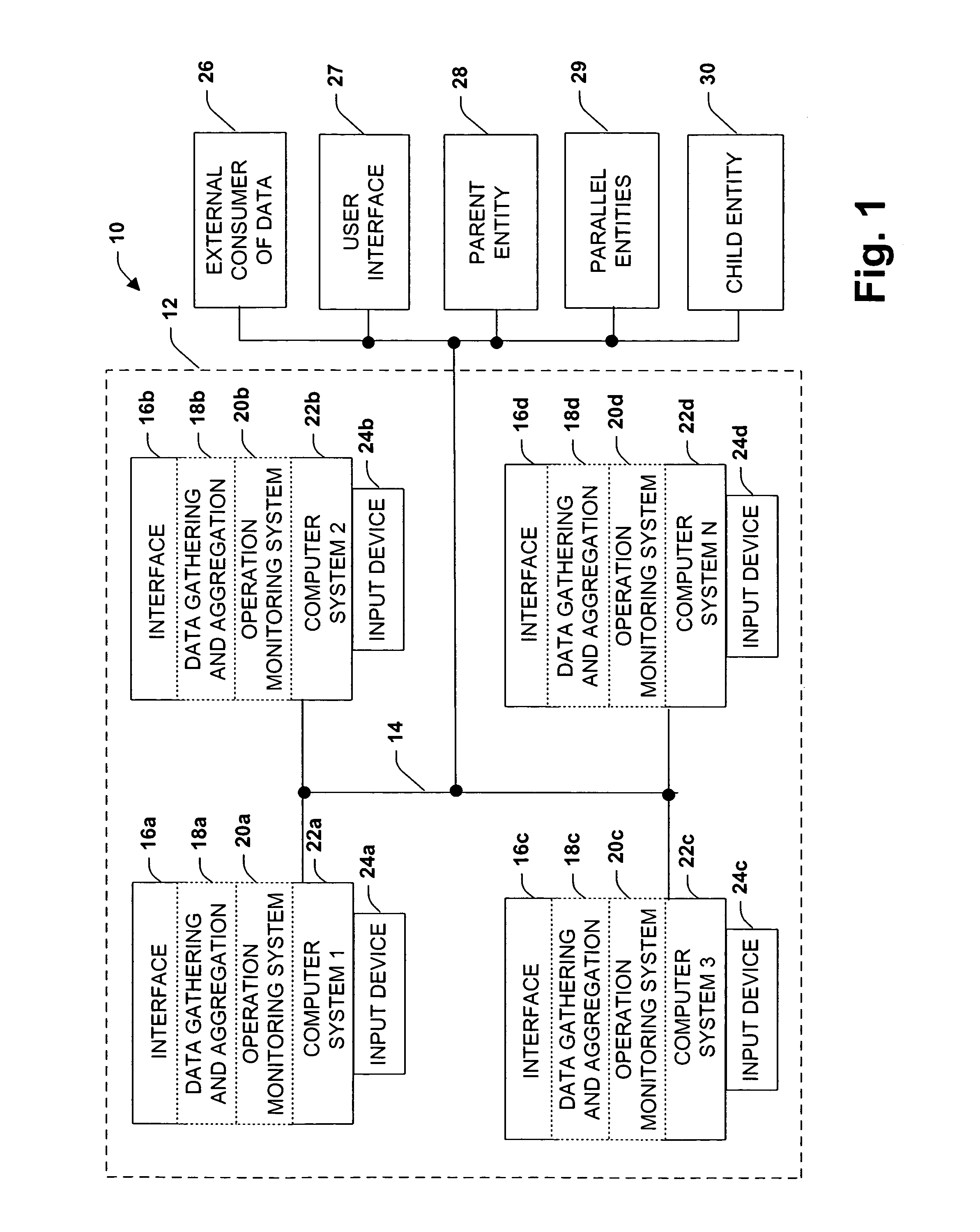
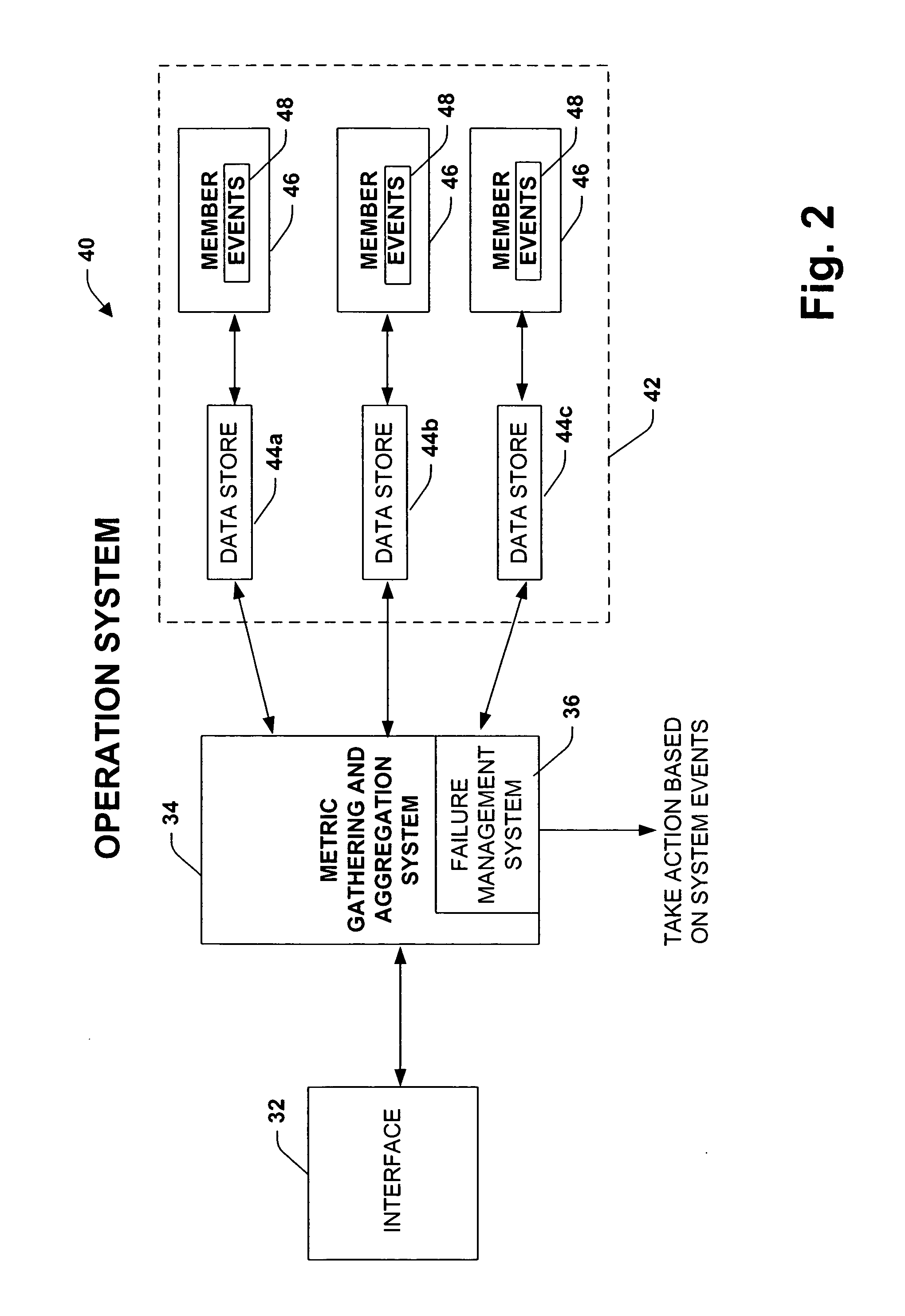
Distributed data gathering and aggregation agent
InactiveUS20050021748A1Reduced manageable blockReduced portionData processing applicationsError detection/correctionResult setSingle entity
A system and method is provided for gathering and aggregating operational metrics (e.g., performance metrics, process events, health monitor state, server state) for a plurality of members as a single entity and for a plurality of entities as a singular entity. The system and method provides for operational metrics of members and entities to be aggregated and retrieved as a single result set, such that entity wide operational metrics can be acquired, monitored and displayed as a single entity.
Owner:MICROSOFT TECH LICENSING LLC
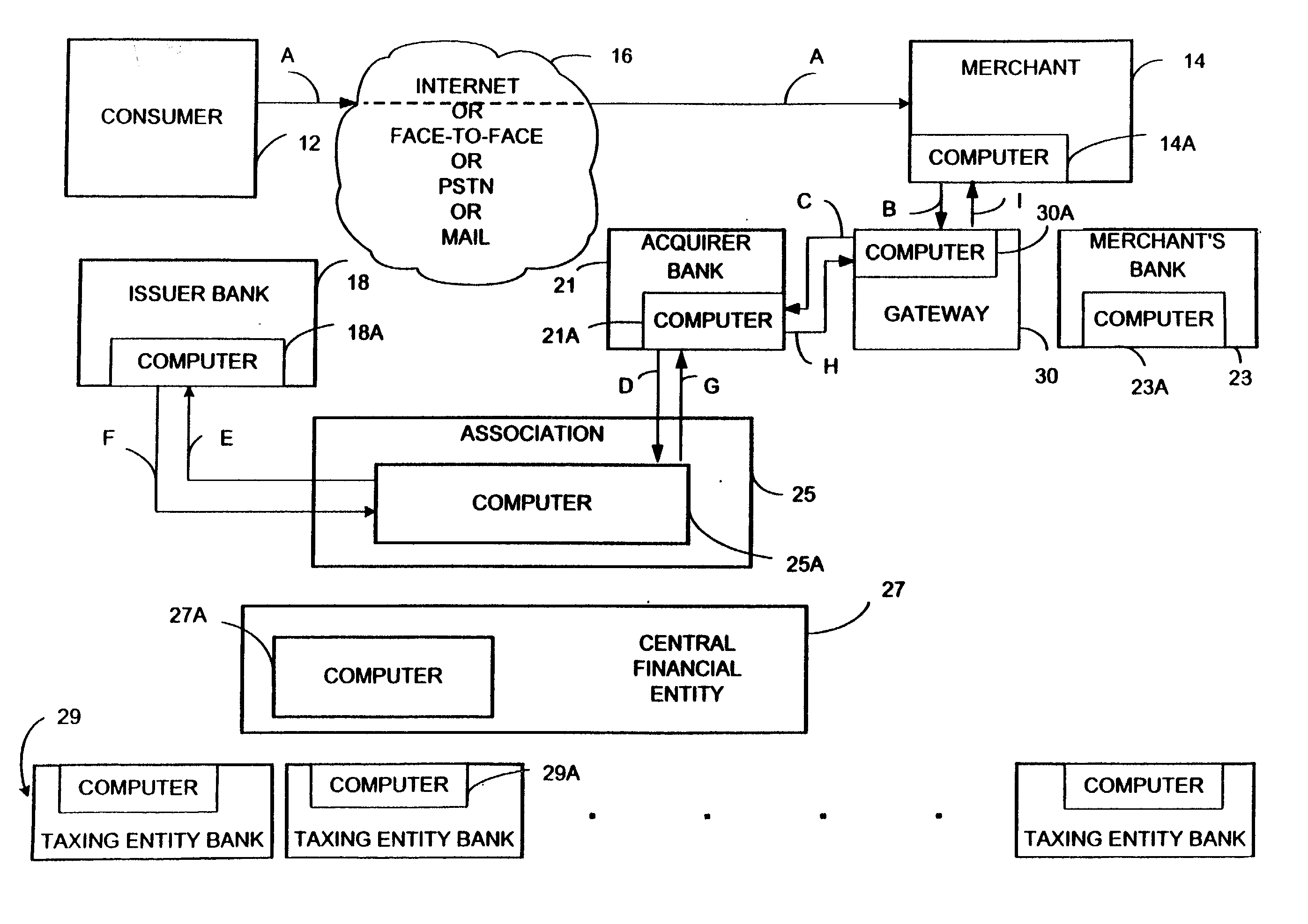
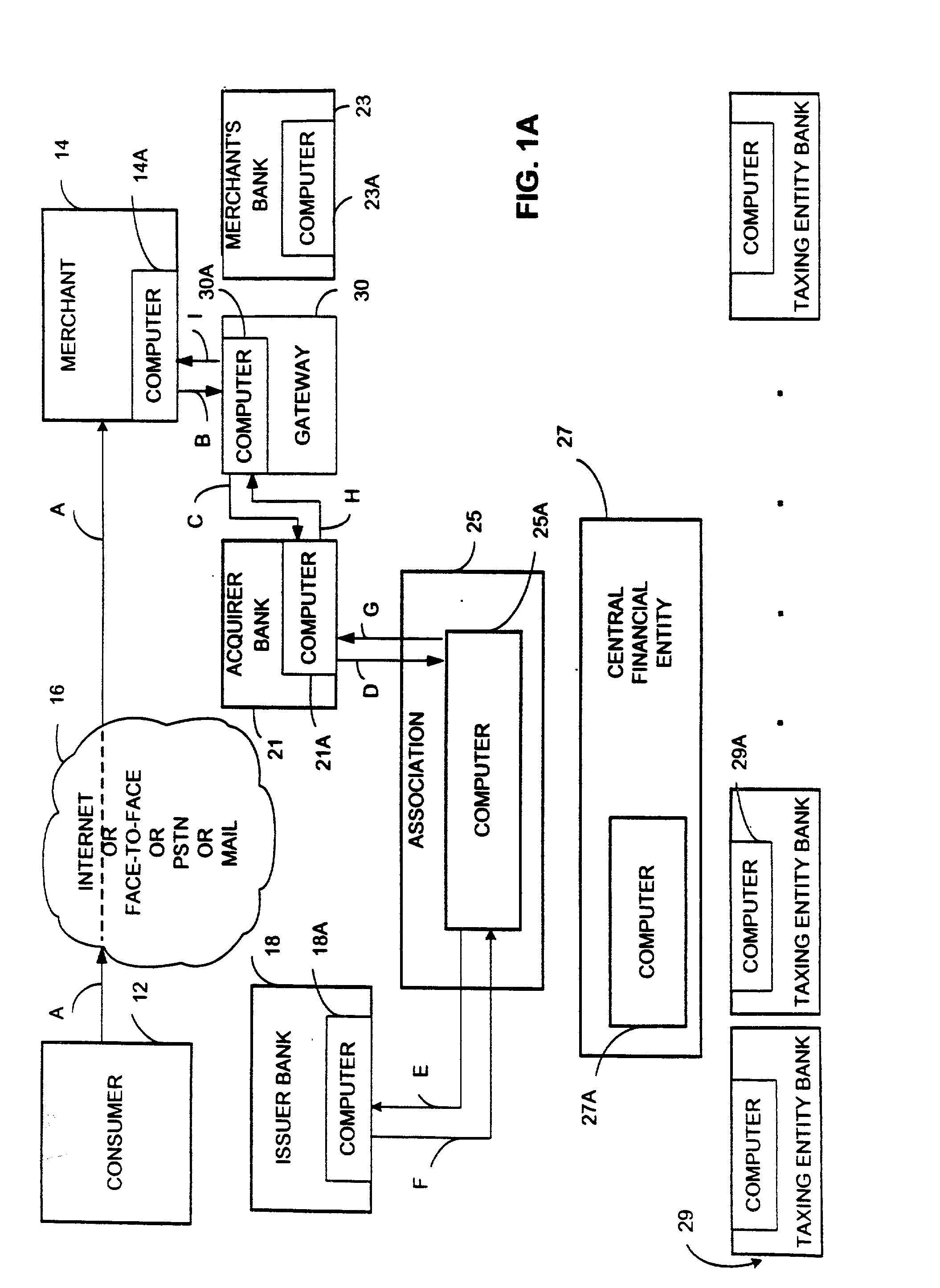
System for and method of rapid collection of income taxes
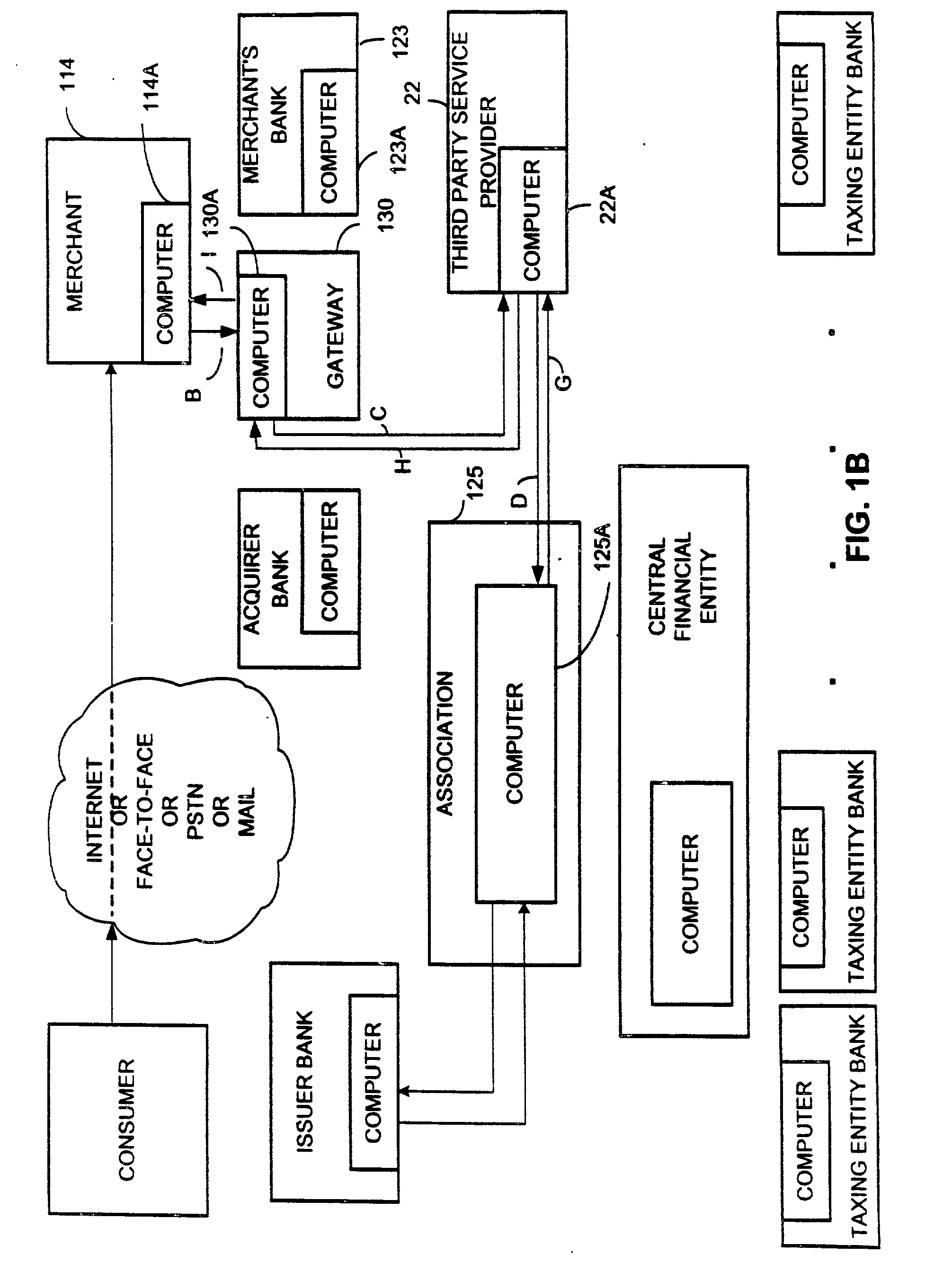
Preferred examples of a system and method for rapid collection and distribution of taxes are disclosed. The disclosed embodiments of the present invention provide a system and a method for point-of-sale collection and distribution of sales taxes on a frequent, regular basis, such as daily or weekly, or other periodic time intervals, that can be used for face-to-face, e-commerce, telephone or other transactions. The disclosed embodiments provide a system and a method for transferring funds from numerous merchants to numerous taxing authorities in an efficient manner, with each merchant seeking to transfer funds to perhaps several taxing authorities and each taxing authority seeking to receive funds from many merchants. According to other examples of the invention, a centralized distribution feature allows the merchants and the taxing authorities to each communicate with a single entity or other in transferring the funds. Therefore, efficient tax collection and distribution may be achieved without overburdening either individual merchants or individual taxing authorities
Owner:FAIRSHARE
Extensible multi-dimensional framework
InactiveUS20080040364A1Easy to implementEasy to modifyOffice automationSpecial data processing applicationsDevelopment teamMulti dimensional
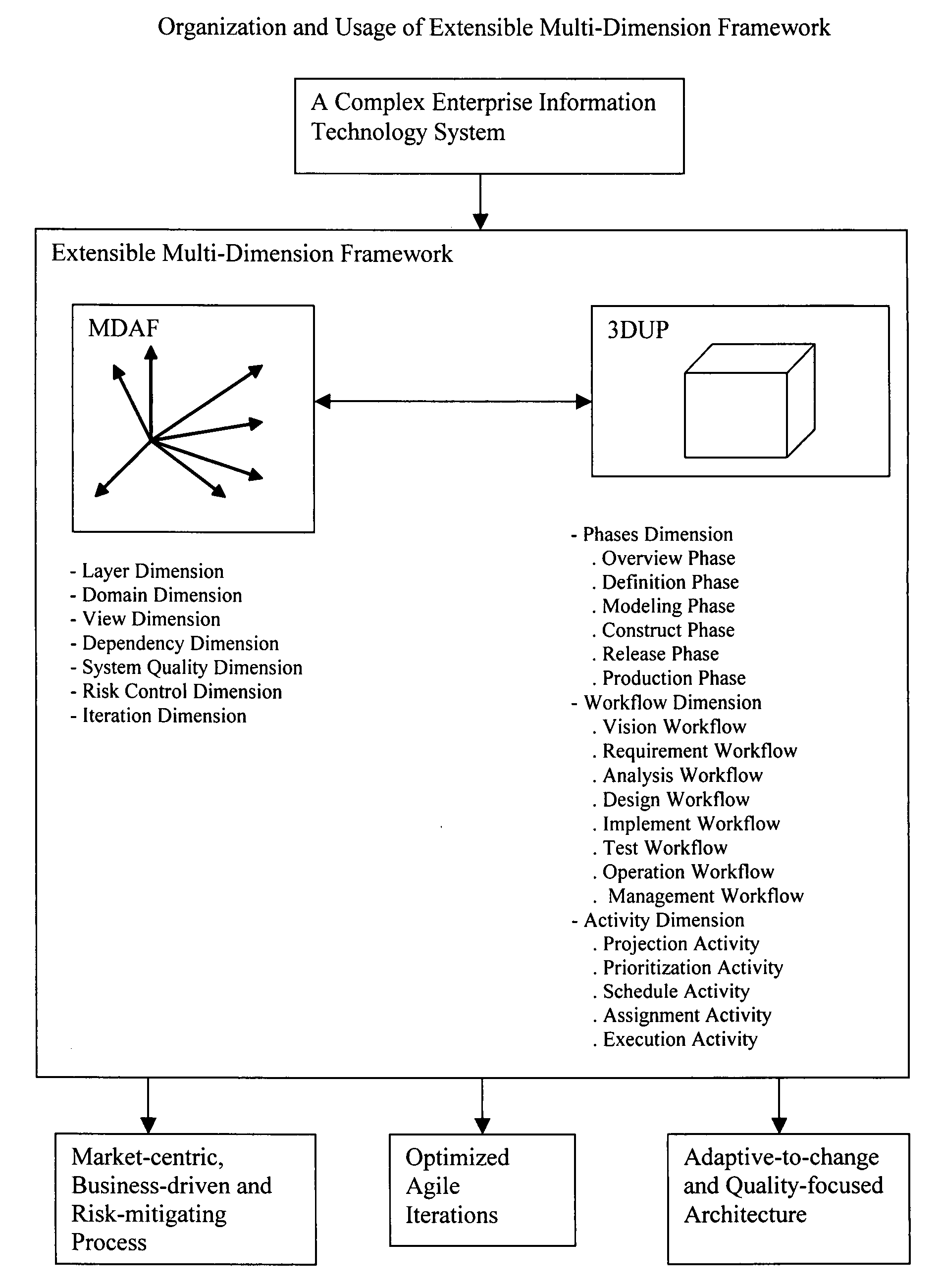
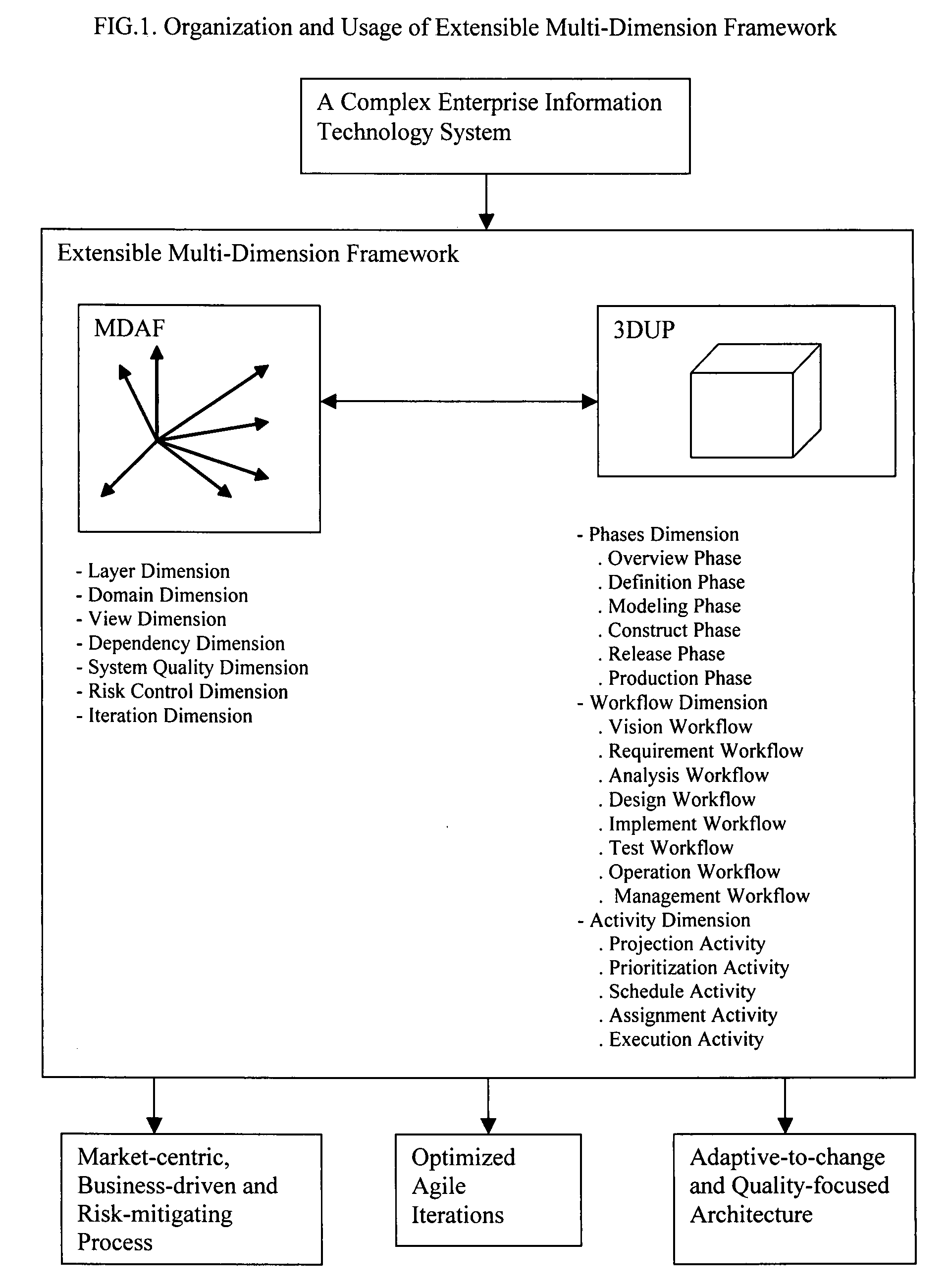
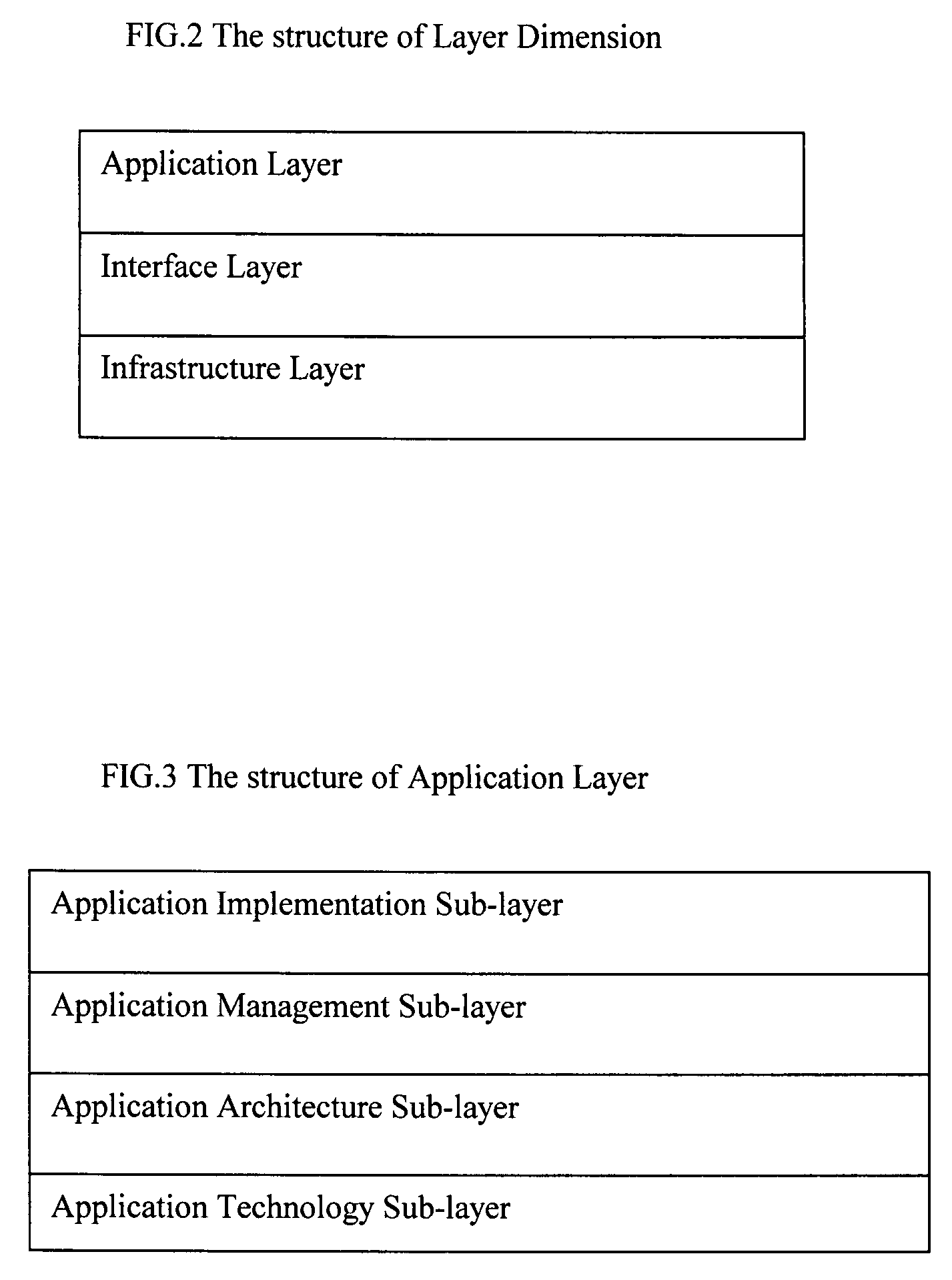
Extensible Multi-Dimensional Framework (EMDF) is a system engineering framework for designing, developing and managing enterprise information technology systems. It includes two parts: multi-dimensional architecture framework (MDAF) and three-dimensional unified process (3DUP). MDAF includes comprehensive concepts for modeling an enterprise information technology system. 3DUP provides an iterative system development process. EMDF addresses an enterprise information technology system as a single entity. By projecting this entity on intertwined MDAF dimensions through the 3DUP lifecycle, all logical or physical elements encompassed in the entity will be exposed and captured in well-organized artifacts defined in MDAF. These elements are then prioritized and scheduled in a set of agile iterations. The iterations will be planned in parallel projects implemented by multiple development teams. During a long-term system development lifecycle, some elements may change. The dimensions included in MDAF provide a flexible framework to adjust system architectures, iterations and projects in order to adapt to such changes. The key deliverables of EMDF include an adaptive-to-change quality-focused architecture, optimistic agile iterations, and a market-centric business-driven risk-mitigating process.
Owner:LI DI
User interface to display and manage an entity and associated resources
InactiveUS7278103B1Easy to configureReduce decreaseError detection/correctionMultiple digital computer combinationsSingle entityUser interface
A user interface to display and manage a plurality of entities as if a single entity is provided. The user interface includes a representation of the collection of entities as a whole, and a representation of members associated with the entity. If an action is performed on the representation of the entities as a whole, then the action is propagated to the collection of entities, if the action is performed on the representation of the member associated with the entity, then the action is directed to the member.
Owner:MICROSOFT TECH LICENSING LLC
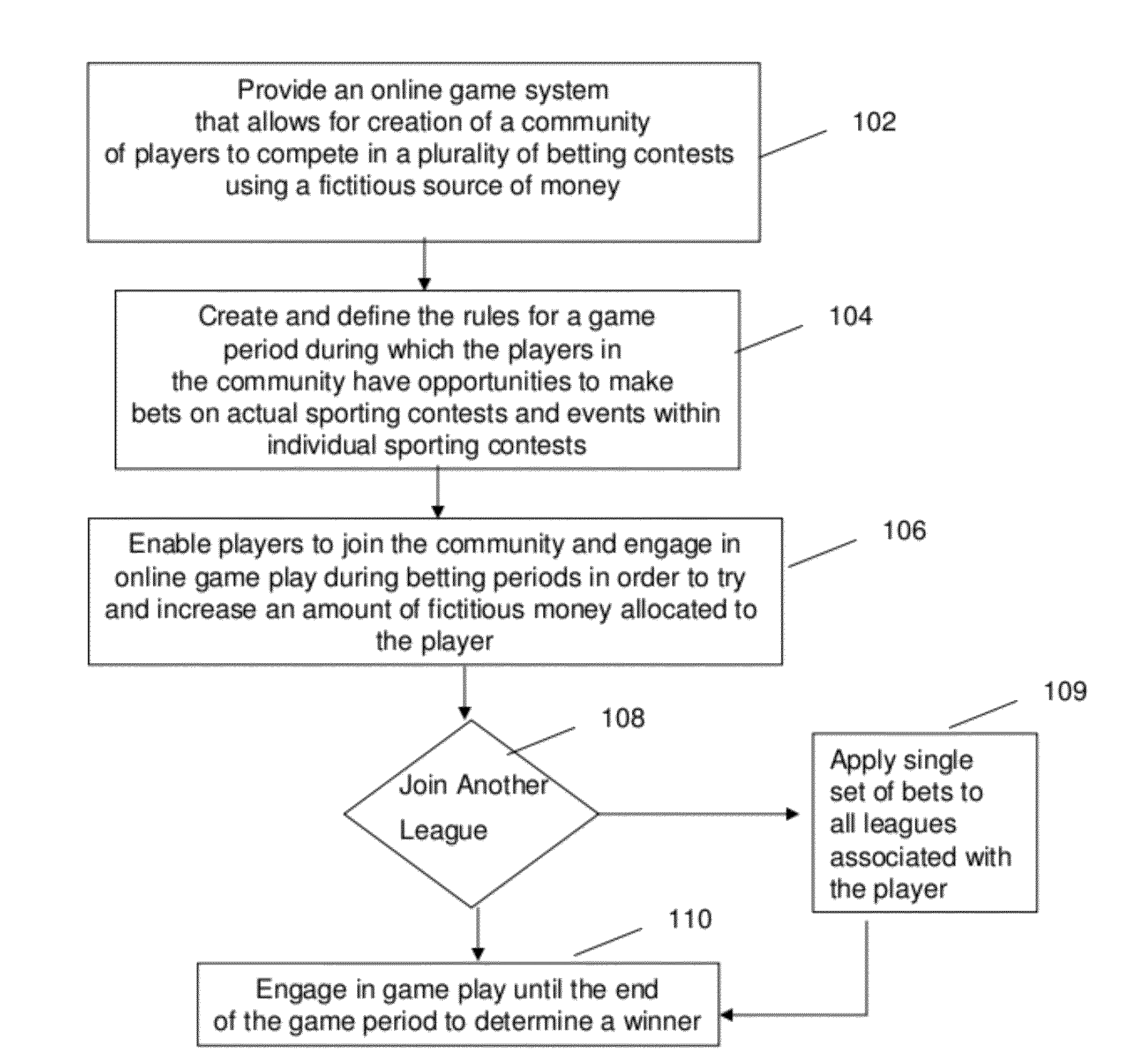
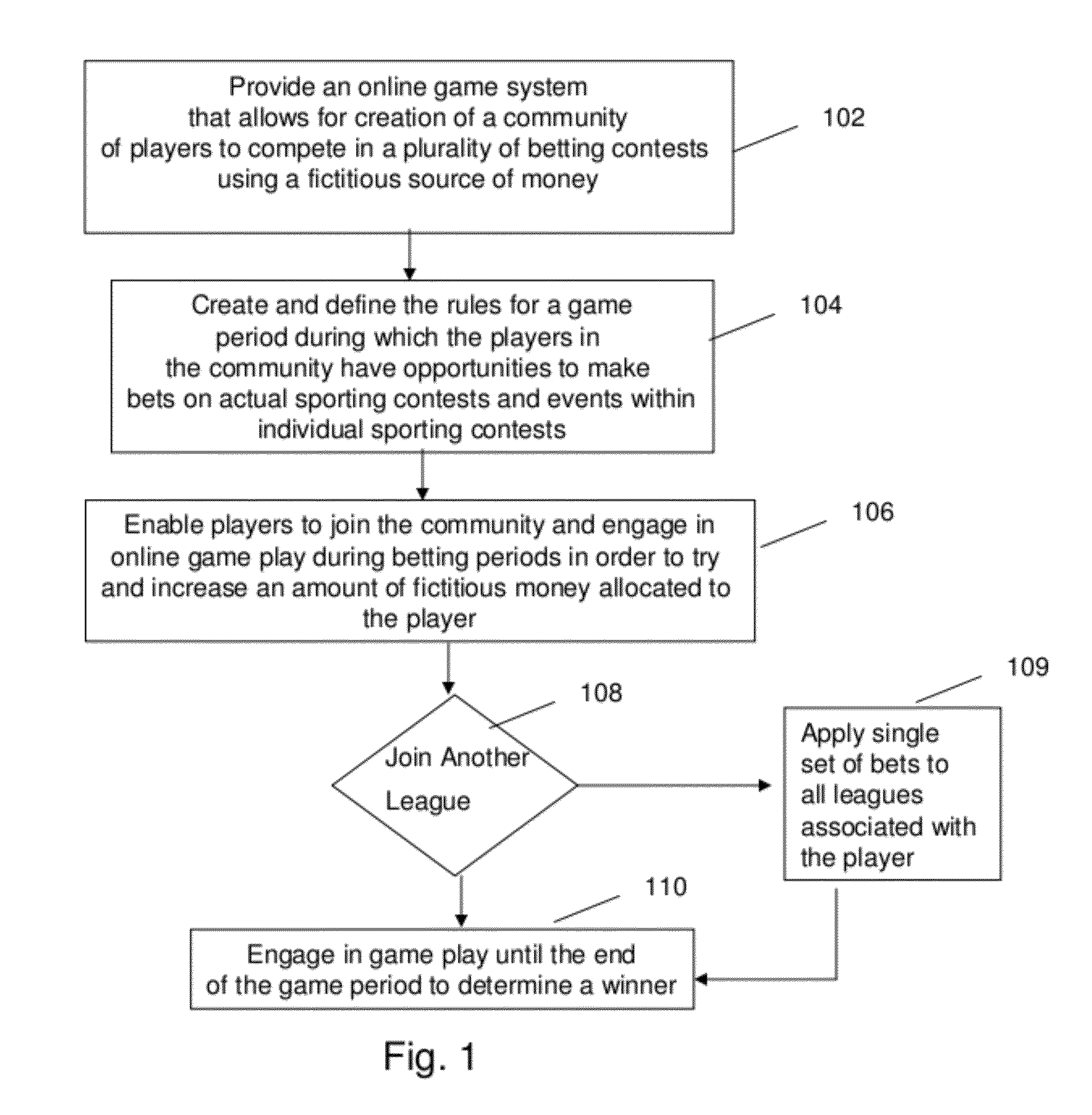
System and Method for Fantasy Sports Gambling
ActiveUS20120115585A1Apparatus for meter-controlled dispensingVideo gamesUser participationSingle entity
A method and system for providing an interactive gaming system is disclosed. At least one interactive social gaming community allows a plurality of users to engage in a wagering contest against a single entity. An initial amount of gaming units associated with an initial user investment is allocated to each user. A payout table is dynamically generated and includes at least one threshold amount of gaming units associated with rewards available to the user. A bet request signal received from a user is automatically reconciled with an outcome of at least one type of contest occurring during an active gaming period. A user account is updated by modifying an amount of gaming units in a user account based on a result of the at least one type of contest and determines if user has earned the reward associated with the at least one threshold.
Owner:PADDY POWER
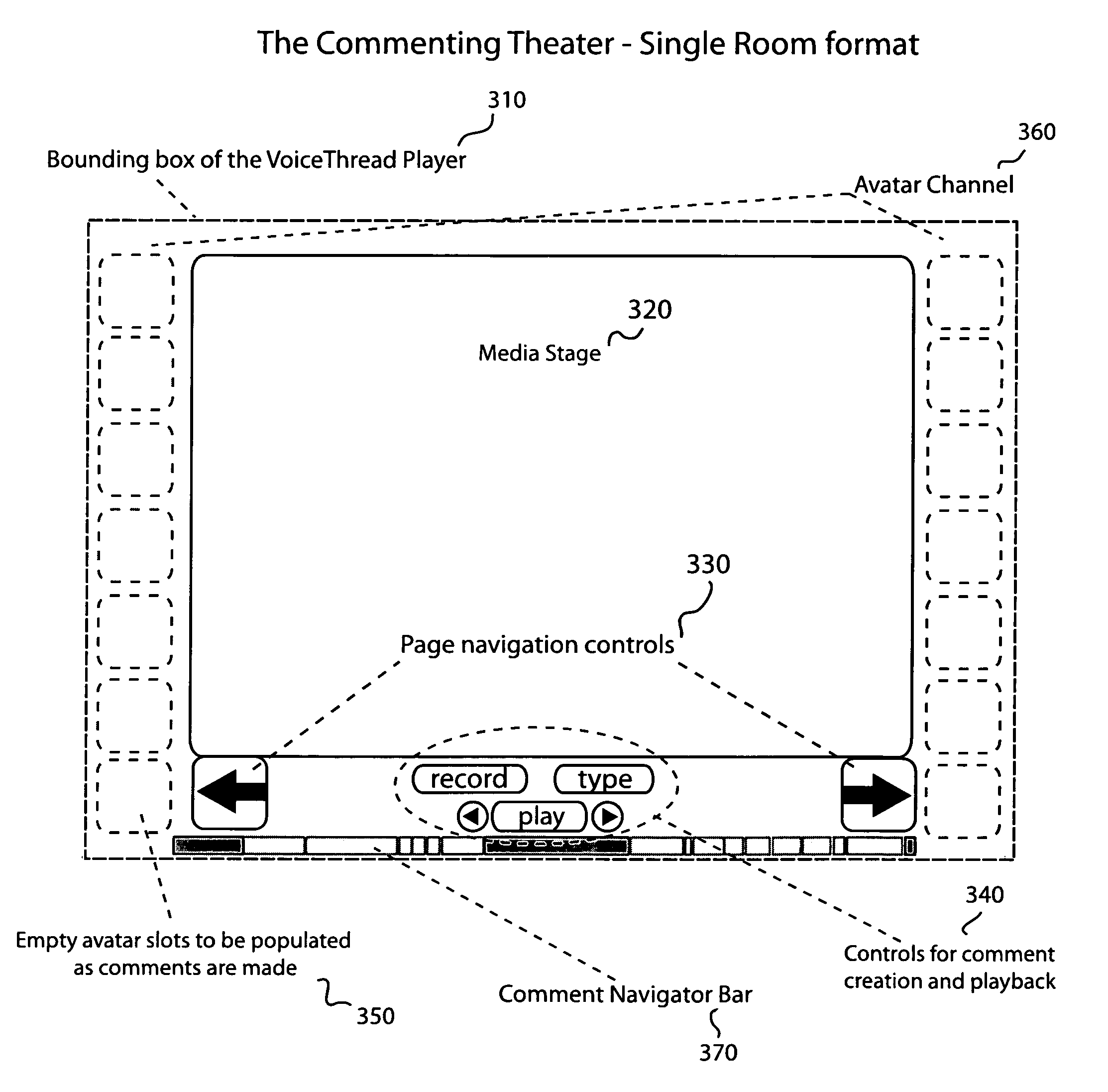
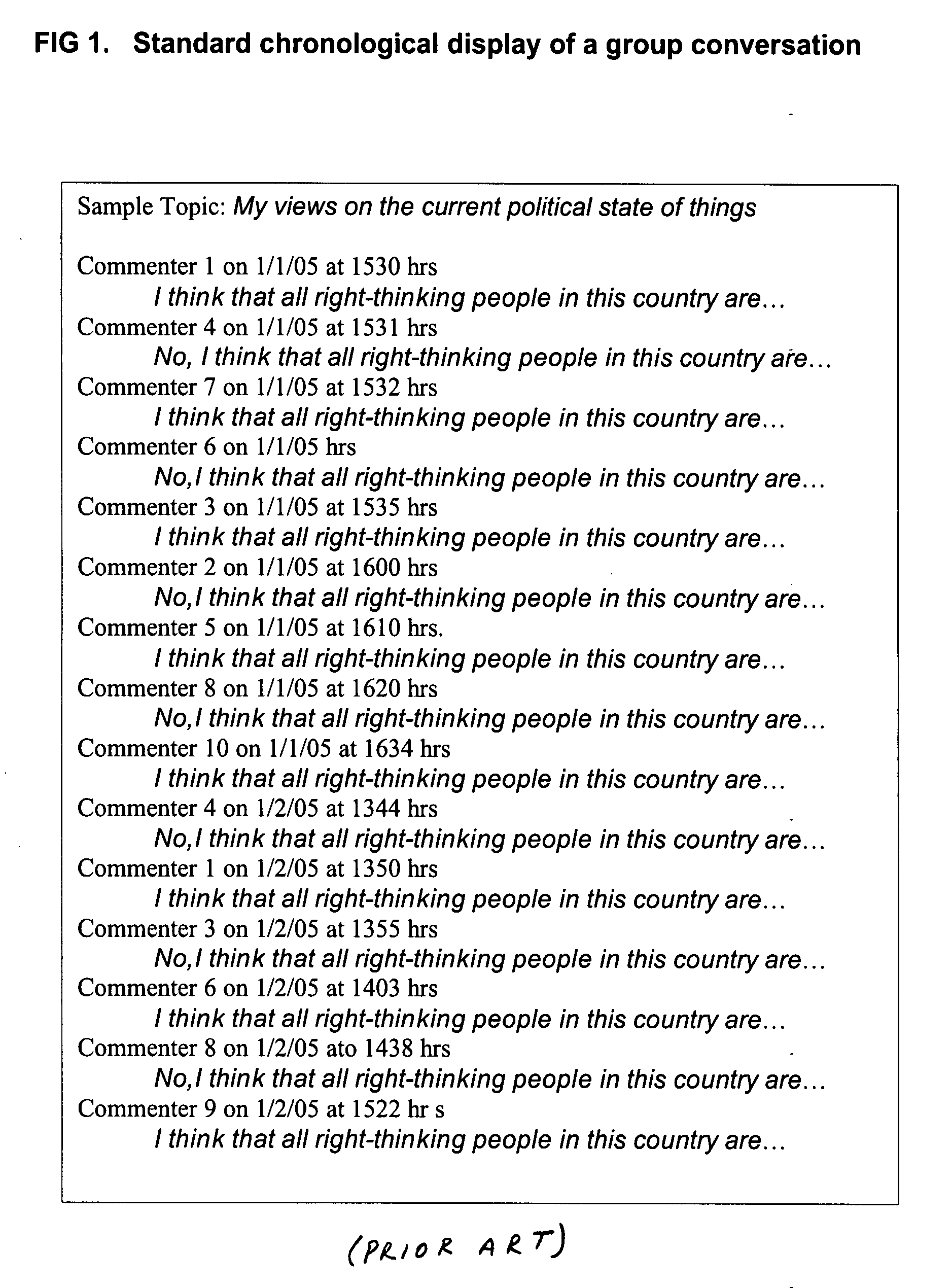
System of archiving and repurposing a complex group conversation referencing networked media
InactiveUS20070271331A1Improve user engagementImprove accessibility and usabilityMultimedia data browsing/visualisationRecord information storageNetwork mediaData entity
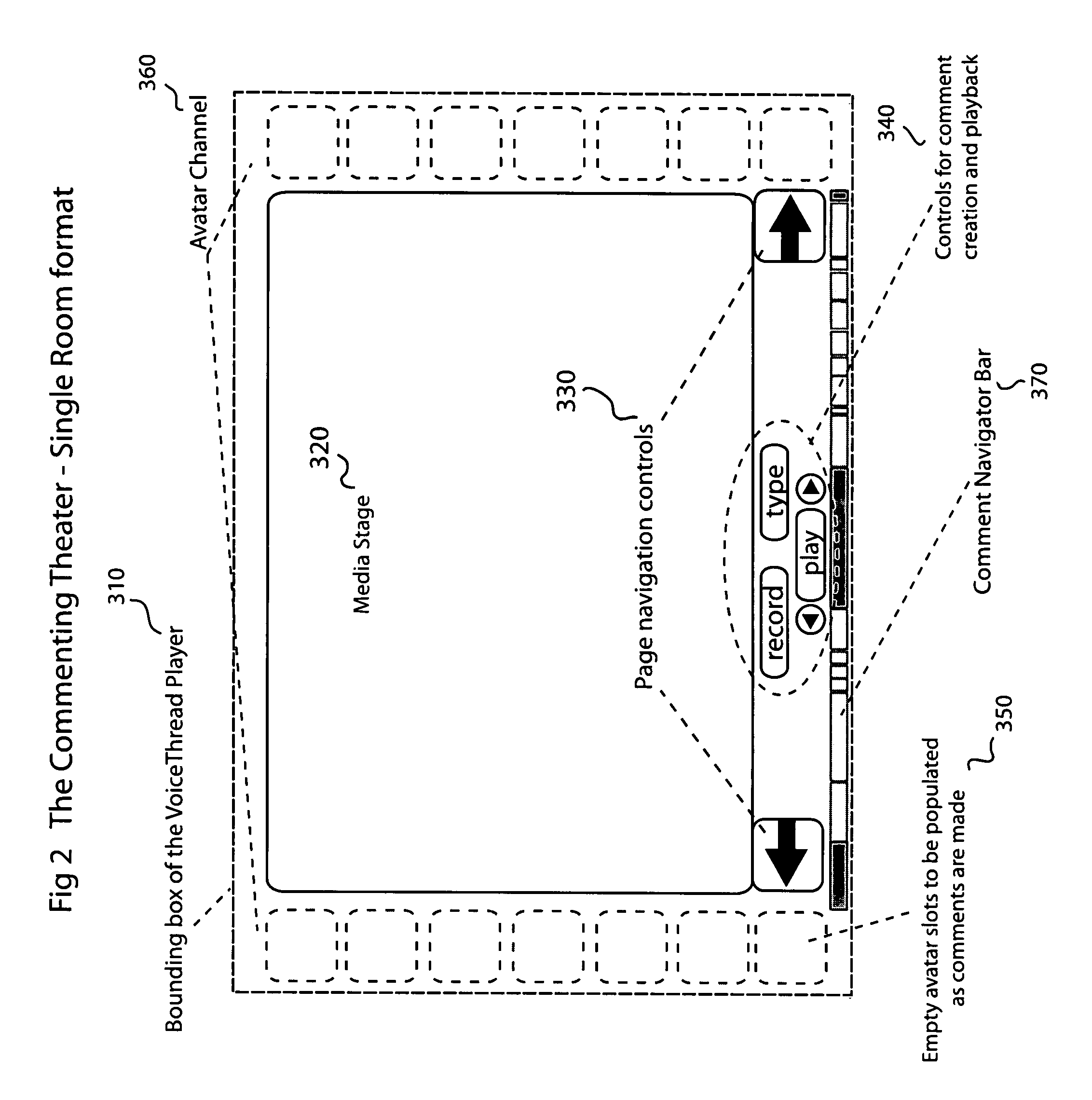
System and method for creating a database of user media and associated user comments wherein the user's comments are collected, collated, stored, and made available to users through a Commenting Theater that allows for the simultaneous representation of and access to the entirety of an archived complex group conversation without reliance upon text. The present invention provides a method for creating electronic collections of media with associated user comments contained and collated into a single entity “VoiceThread Media Player” that has an integral capacity to host a complex electronic conversation and allows content owners to manage a group conversation wherein all of the comments and referenced media remain separate and repurposable data entities and yet both the media content and the resulting conversation are presented in a unified, coherent and casually accessible manner.
Owner:MUTH STEVE
Network fabric management via adjunct processor inter-fabric service link
ActiveUS20030142628A1Large capacityCooperate wellMultiplex system selection arrangementsError preventionTelecommunicationsNetwork structure
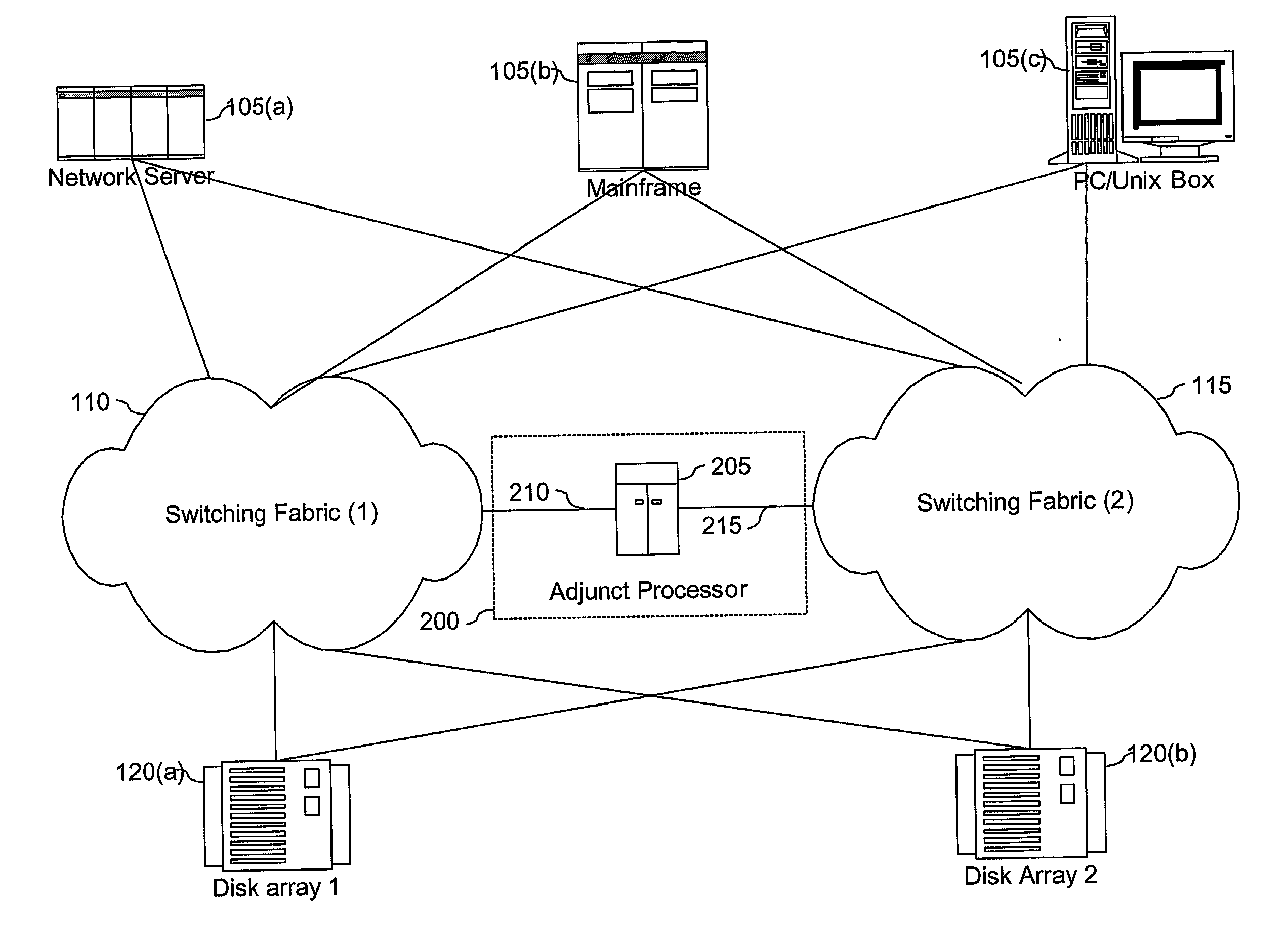
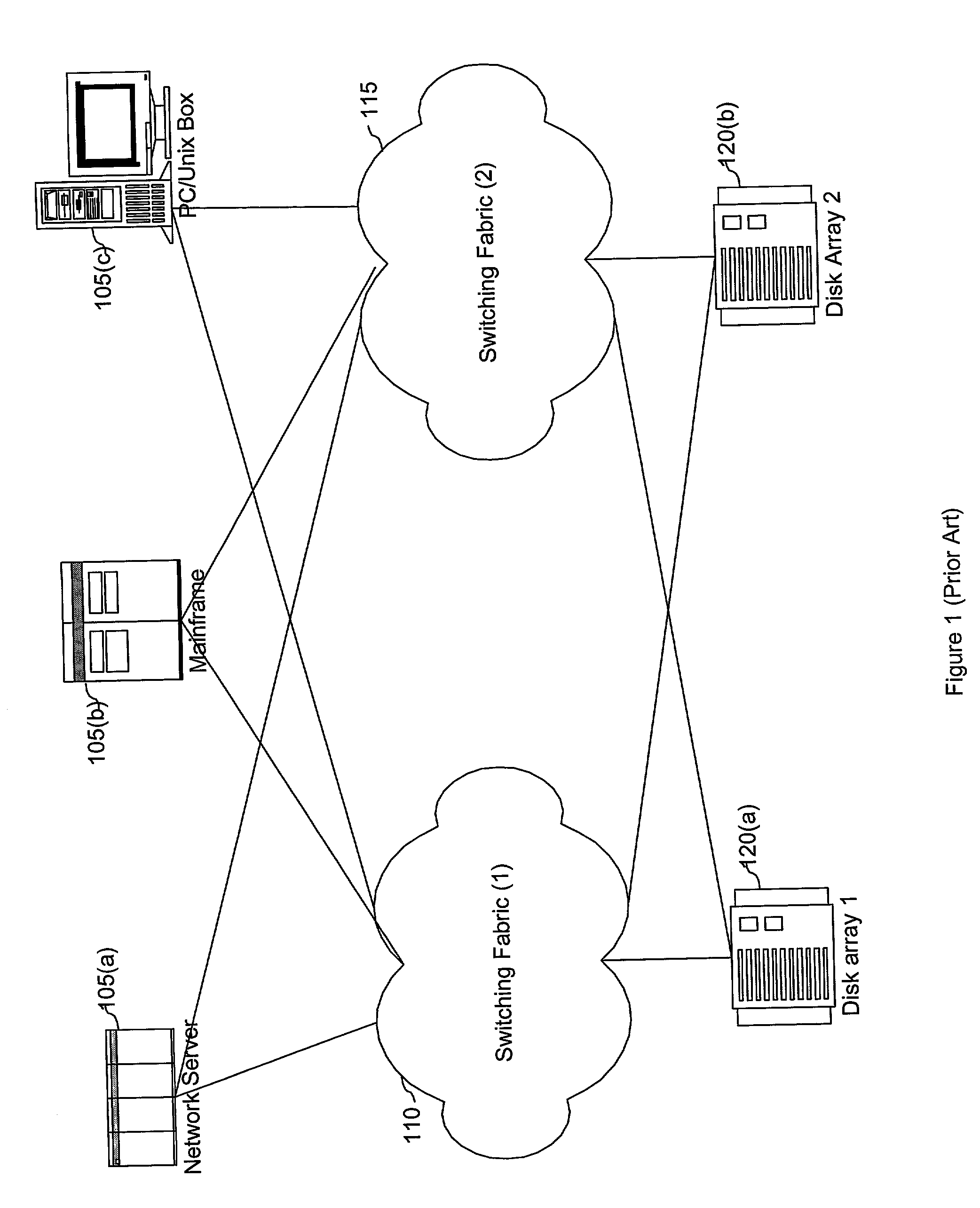
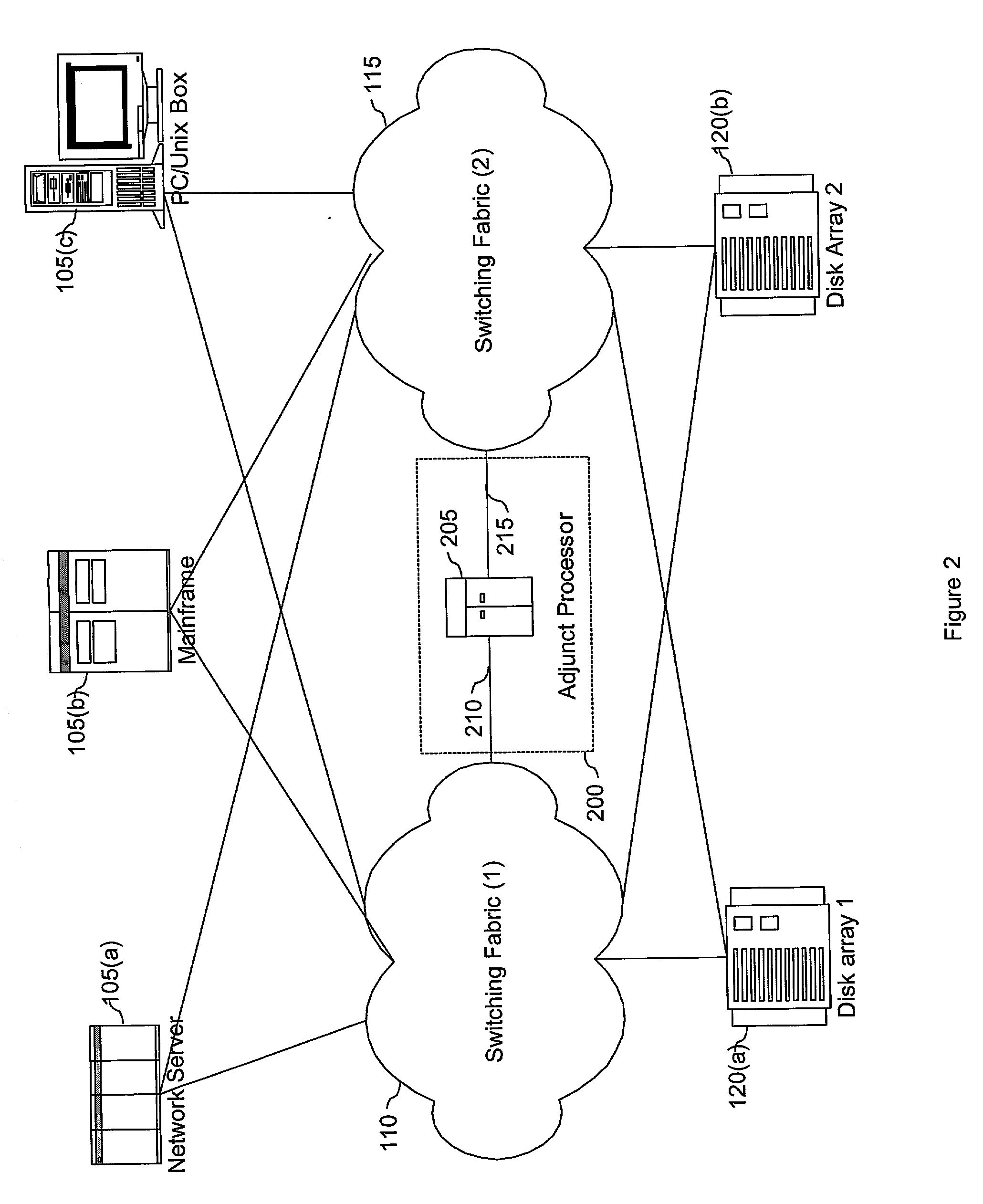
An adjunct processor controls an inter-fabric service link (IFSL) coupled to at least two independent SAN switching networks. The inter-fabric service link is coupled between multiple switching fabrics to allow the attached switching fabrics to be logically managed as a single entity while still being physically independent of each other. The IFSL does not transmit nor receive data being transmitted from a storage device to a host; rather, only management data is transmitted along the IFSL. The IFSL includes an inter-fabric adjunct processor, and a plurality of connections to the attached switching fabrics on which the IFSL communicates with IFSL agents operating on various switching elements within the attached switching fabrics. IFSL agents generate management data corresponding to the particular switching element on which the agent operates. This management data is intermittently transmitted to the IFSL for processing. Upon receipt of this management data, the IFSL updates a fabric map containing the corresponding switching element according to the received management data. As a result, the IFSL has a current snapshot of the status and functionability of each of the switching elements within the attached switching fabrics. Additionally, the IFSL may respond to the received management data by transmitting operation requests to a switching element.
Owner:AVAGO TECH INT SALES PTE LTD
System And Method For Establishing And Managing Social Wireless Network
InactiveUS20110307380A1Easy to useFinanceMultiple digital computer combinationsComputer moduleProtocol for Carrying Authentication for Network Access
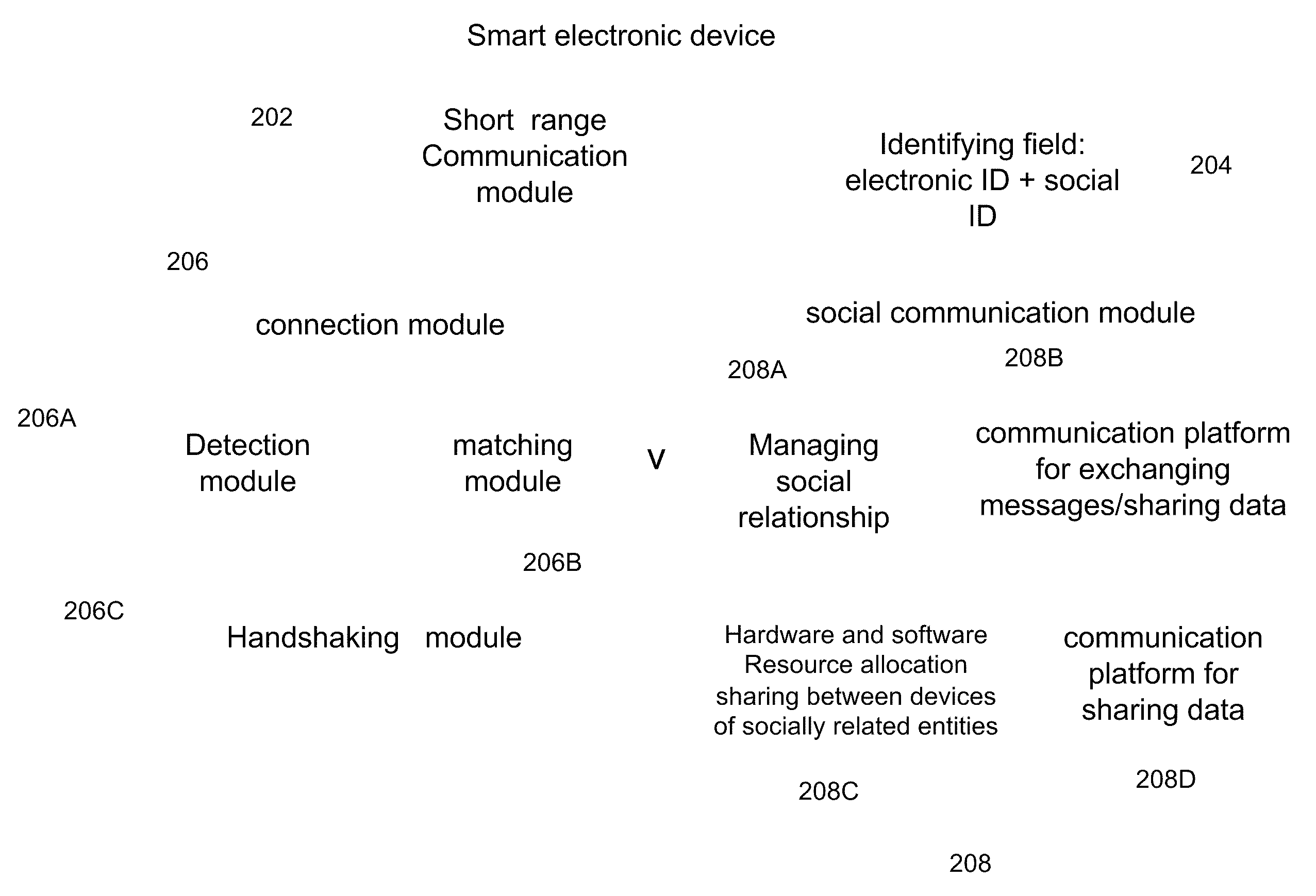
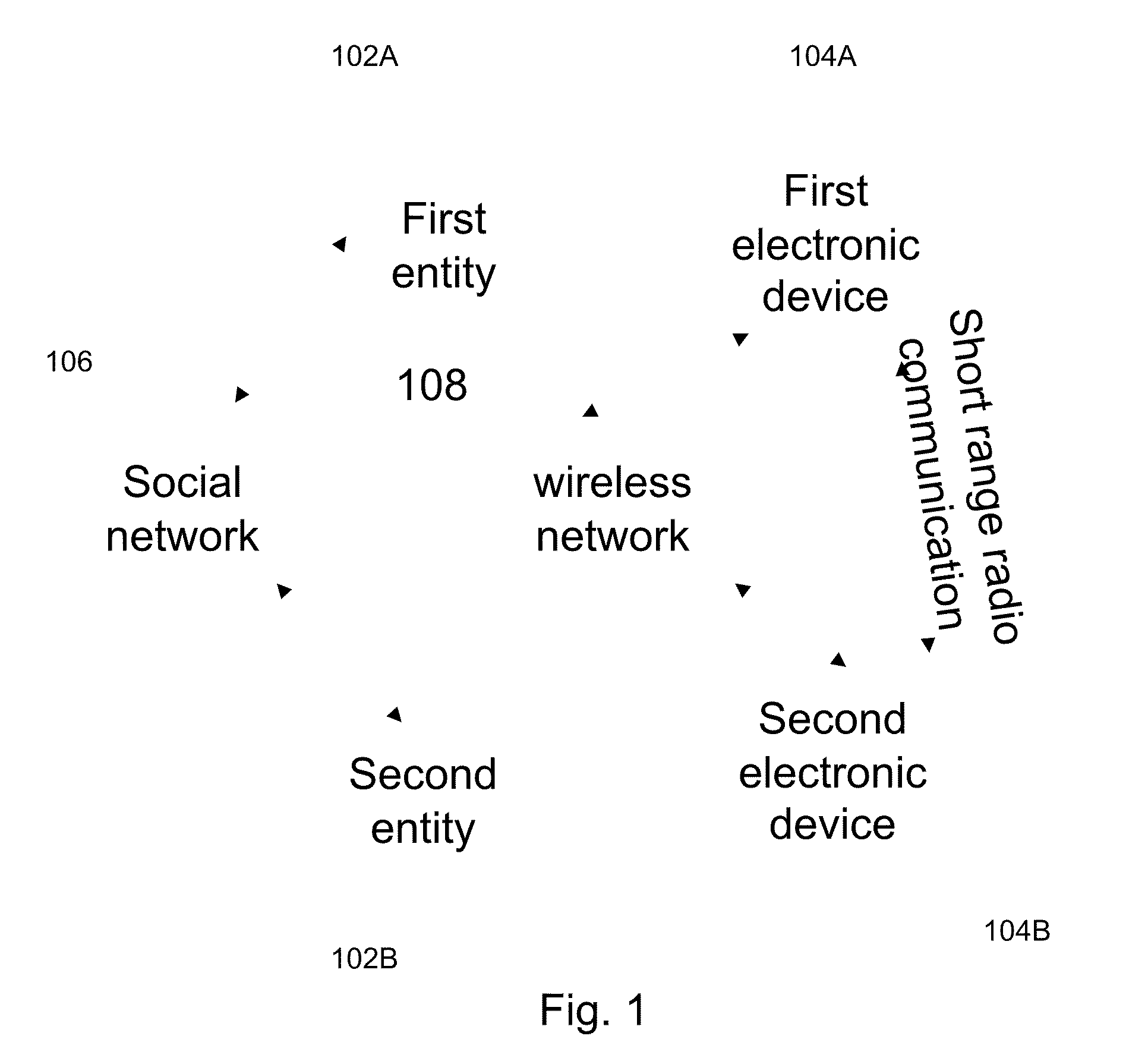
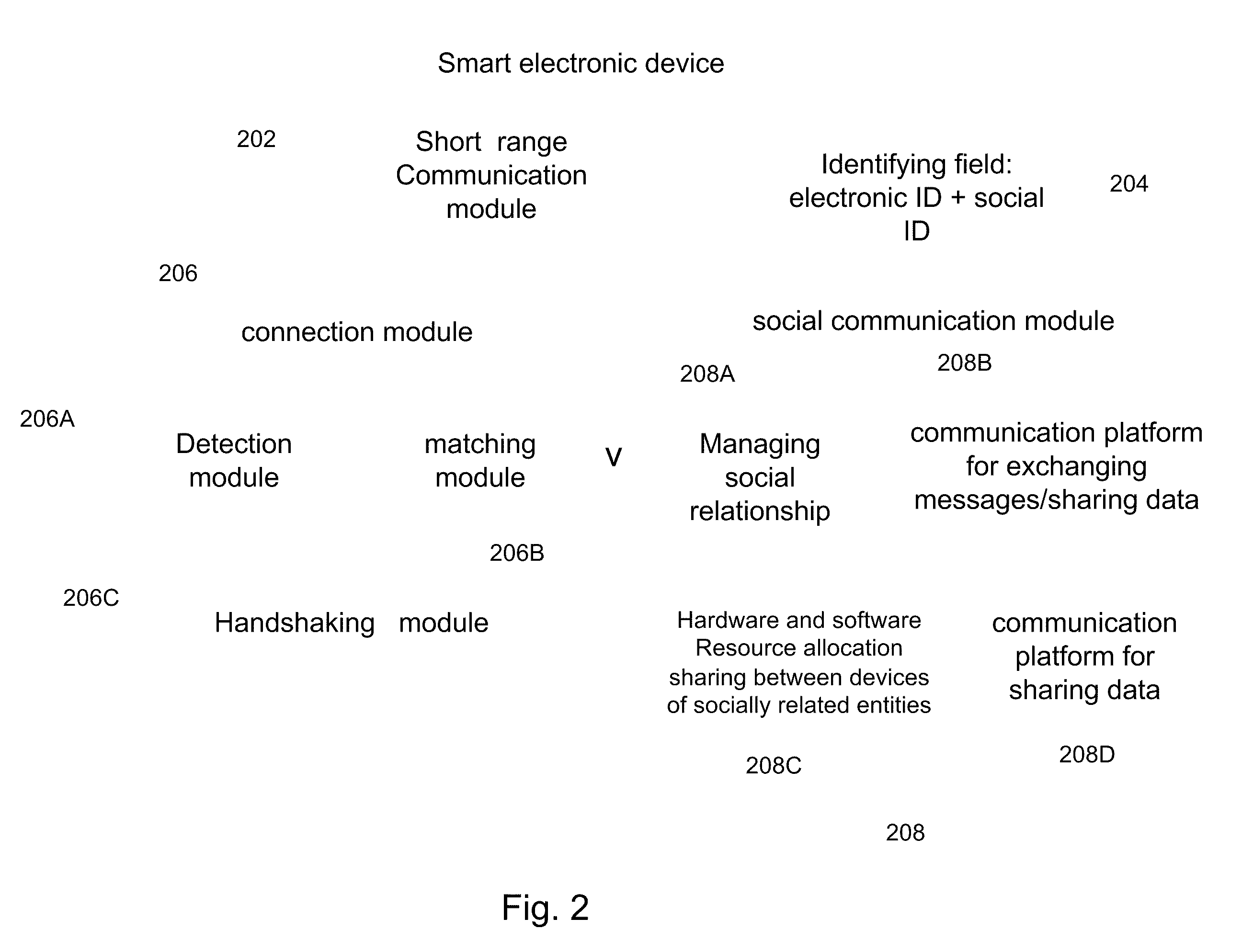
A system for establishing connection between at least two electronic devices, through wireless communication data network, wherein each electronic device is associated with a single entity and at least one of the entities is a human user which participates in at least one social network. The system includes: a connection module supported by a short range communication protocol, integrated within at least one electronic device, wherein the module includes an identifying field uniquely associated with said electronic device and associated entity, the identification field is exposed as BT identity to other electronic devices located at proximity to said first device, wherein the identification field includes at least one unique code corresponding to said electronic device and at least one code associated with ID number of the entity in a social network, at least one repository of a cellular social network members, each member record including the identifying field, user profile and user connections to other entities, and wherein the connection module support handling the handshaking process of establishing social connection between two entities.
Owner:IDO LIEBERMAN
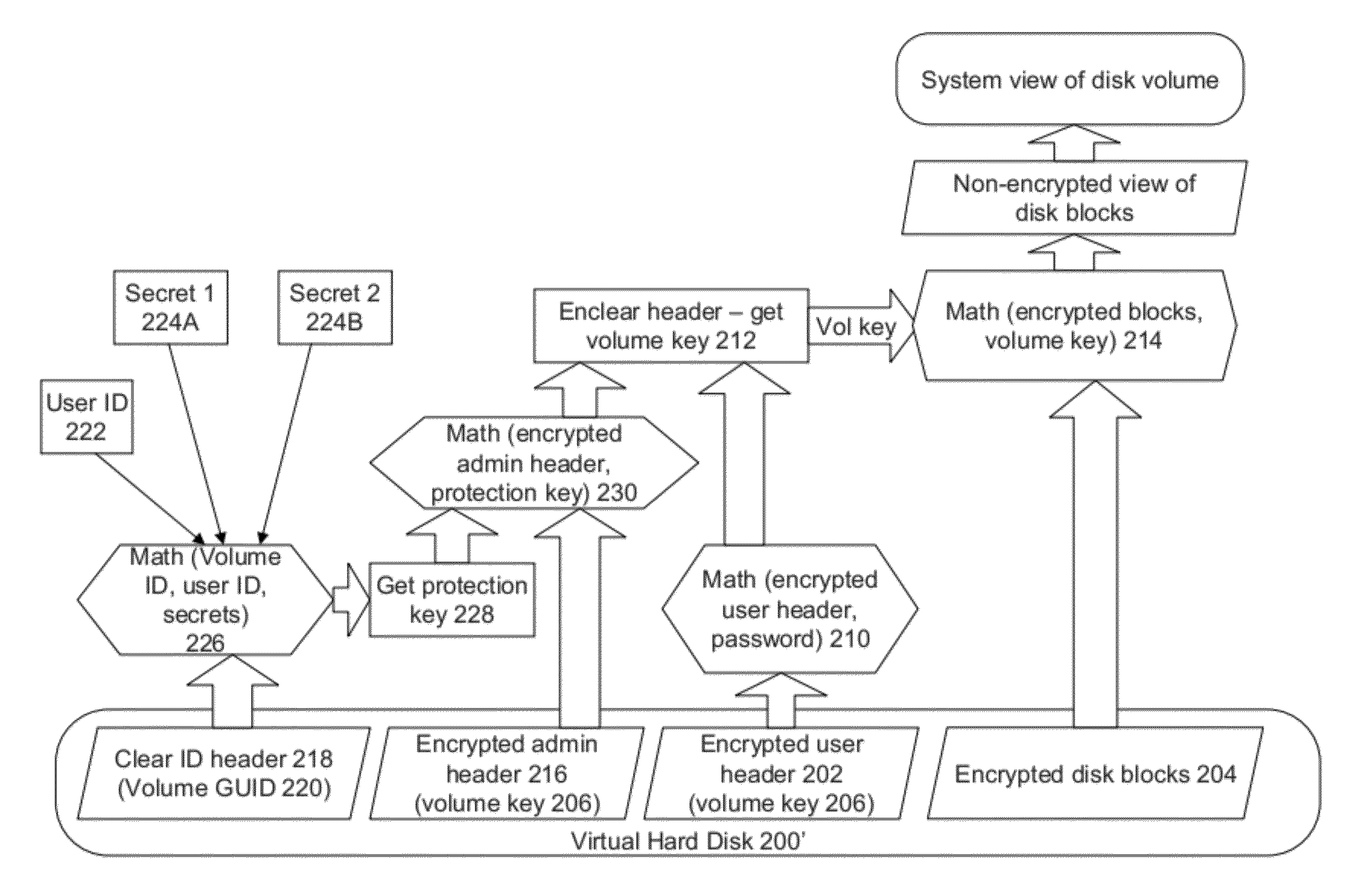
Securing Encrypted Virtual Hard Disks
ActiveUS20120297206A1Multiple keys/algorithms usageUnauthorized memory use protectionCryptographic nonceUser identifier
Owner:CITRIX SYST INC
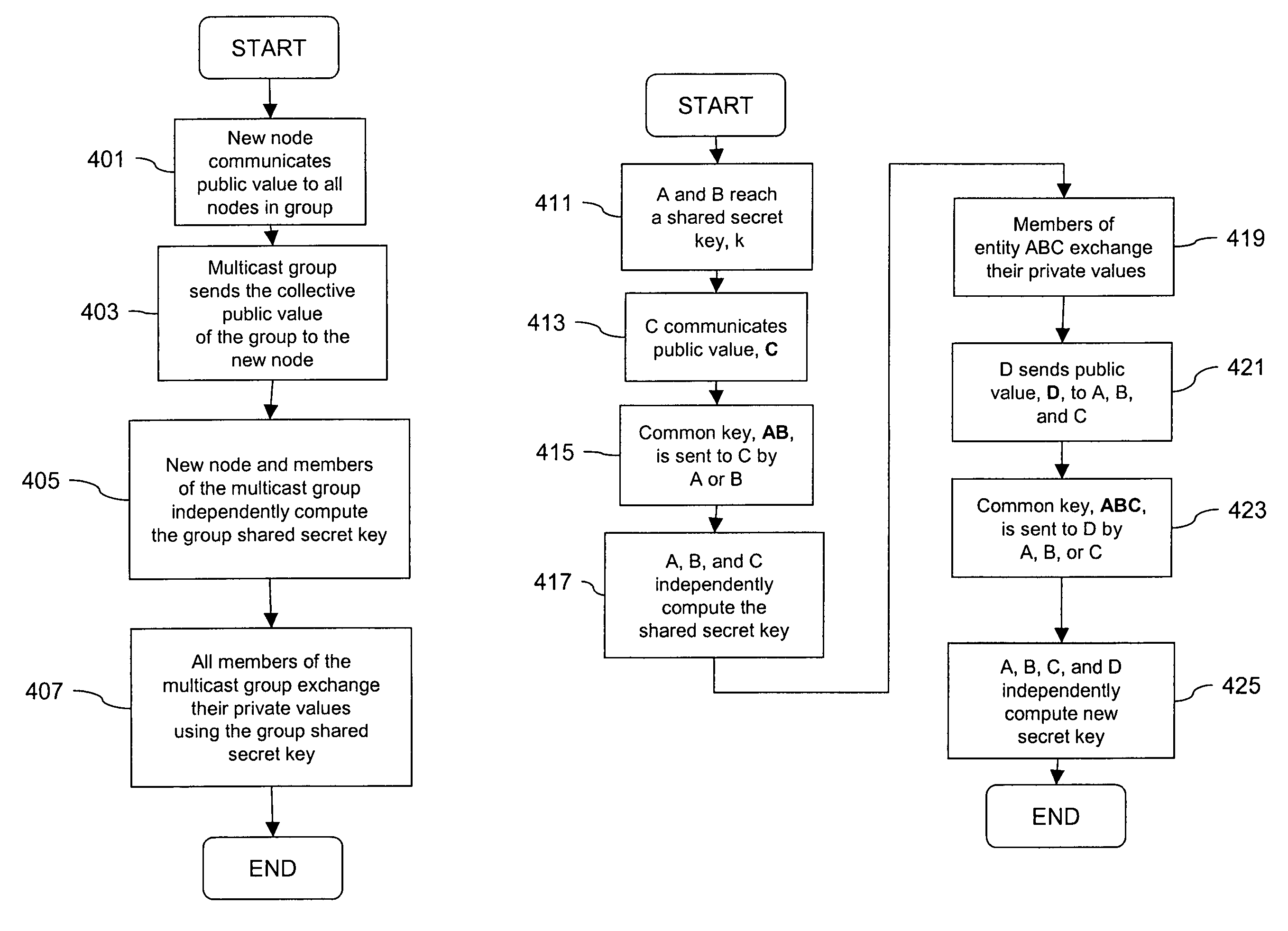
Processing method for key exchange among broadcast or multicast groups that provides a more efficient substitute for Diffie-Hellman key exchange
InactiveUS7181014B1Communication securityKey distribution for secure communicationUser identity/authority verificationDiffie–Hellman key exchangeBroadcasting
Owner:CISCO TECH INC
Method for Analyzing Activities Over Information Networks
InactiveUS20080162397A1Knowledge representationData switching networksLawful interceptionInformation networks
The present invention is a method for analyzing large volumes of network information for the purpose of identifying particular patterns of behavior in a plurality of connections. It enables identifying unique digital fingerprints of particular users, be it individuals, groups or organizations, and tracks their activities in large scale information networks such as corporate wide area networks or the public internet despite attempts on the part of the users to hide their identity. By recognizing unique identifiers and distinguishing patterns of behavior the method may differentiate between different users all using a single connection, or identify a single entity across multiple connections. The method may be applicable for tracking hostile entities inside an organizational network. Advertisers may uniquely and anonymously track the activities of users. The method may also be used to track and identify suspicious activities by law enforcement agencies via lawful interception of network data.
Owner:ZALTZMAN ORI
Process for delivering a menu of media and computer options potentially at no cost to consumers in exchange for viewing interactive advertisements
InactiveUS20060053049A1No out of pocket costEliminate requirementsAdvertisementsElectrical cable transmission adaptationCrowdsSingle entity
A structure for creating a facilitator organization to deliver a menu of media and Internet options potentially at no cost to consumers in exchange for viewing interactive advertisements with the steps of: creating the facilitator organization, by which a single entity is created offering the media and Internet services via any and all available means to the consumer, offering the commercial businesses the advertising services, offering the media and the Internet services to deliver the services to the consumer, offering the interactive advertising to the consumers, collecting and distributing revenue by the advertising viewed by the consumers on the Internet services and the television, by which the data is collected and analyzed, by which the advertiser is satisfied that the advertising has reached the demographic and numerical population that the advertiser has contracted with the facilitator for.
Owner:NOLAN BRIAN ARDLE
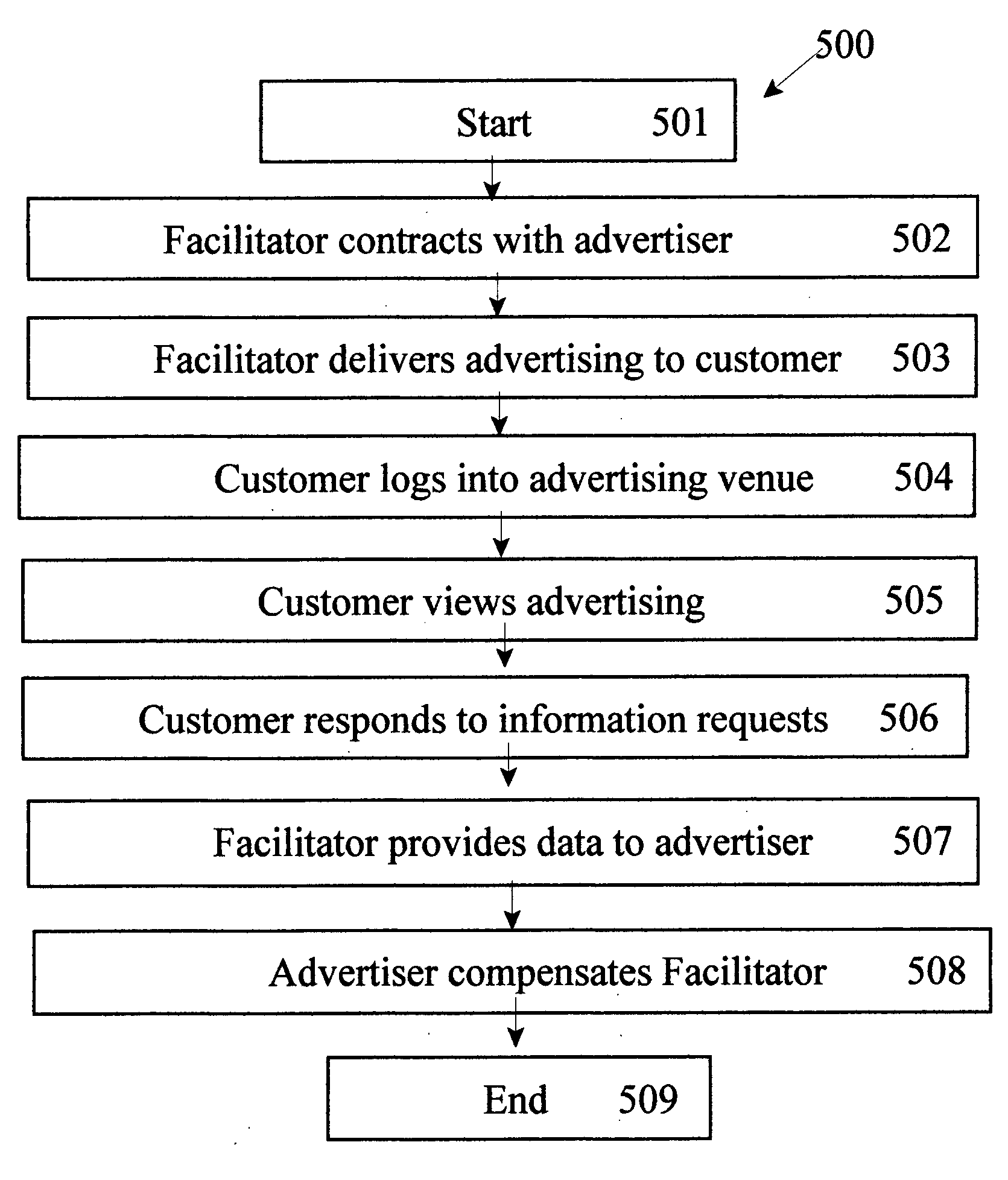
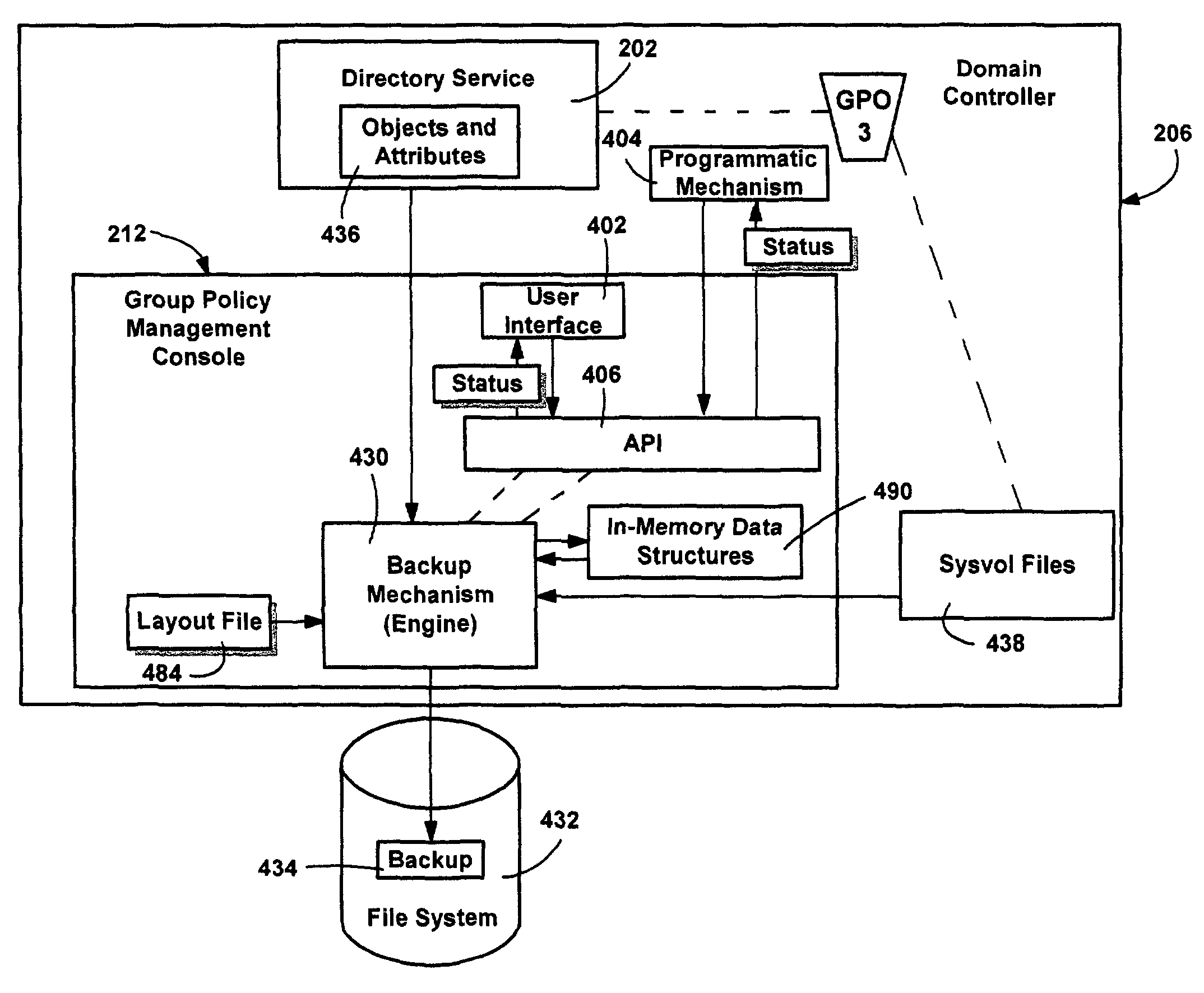
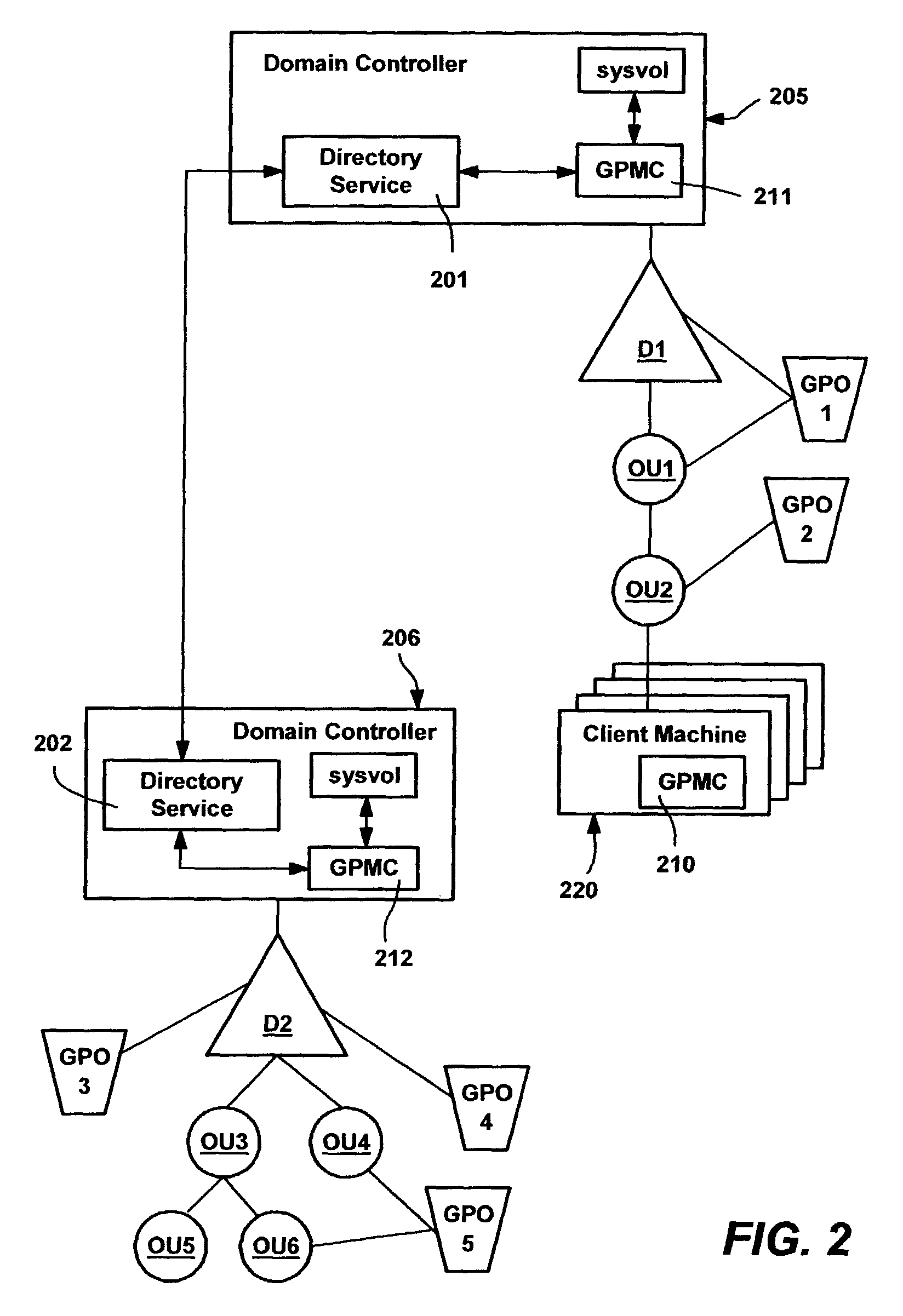
Method and system for implementing group policy operations
ActiveUS8244841B2Facilitates their access and their ability can be foundDigital data processing detailsDigital computer detailsFile systemApplication software
A system and method for performing various operations on group policy objects, by manipulating group policy objects as a single entity to perform backup, restore, import and copy operations. The backup operation transfers the various subparts of a selected group policy object to a file system. A restore operation restores a backed-up group policy object to its domain, in the same state as when the backup was performed. An import operation transfers the settings within a backed-up source group policy object to a destination group policy object, erasing its previous settings. A copy operation transfers the settings from a source group policy object to a new group policy object. Copy and import operations can be cross-domain, and a migration table can be used to convert security group and UNC pathnames as appropriate for the destination domain. Backup management, rollback of incomplete operations, and support for application deployment are also provided.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for logging privilege use in a distributed computing environment
ActiveUS20090319527A1Facilitates tracking privilege useEasily audit privileged operationDigital data processing detailsComputer security arrangementsDistributed Computing EnvironmentClient-side
One embodiment of the present invention provides a system that logs the use of privileges in a distributed computing environment. The distributed computing environment includes a database system, one or more client applications, and a unified security management layer between the database system and the one or more client applications. During operation, the system receives a request from a client application to execute a business function in the distributed computing environment. The system determines a privilege associated with the requested business function, and logs that the request is associated with the privilege. The system then checks, in the unified security management layer, whether a user associated with the request is associated with a role that has the privilege. If the user is associated with a role that has the privilege, the system performs the requested business function. By checking and logging privilege access in the unified security management layer, the system facilitates tracking privilege use for the database system and the client applications in a single entity, thereby enabling security managers to more easily audit privileged operations in the distributed computing environment.
Owner:ORACLE INT CORP
Business vocabulary data retrieval using alternative forms
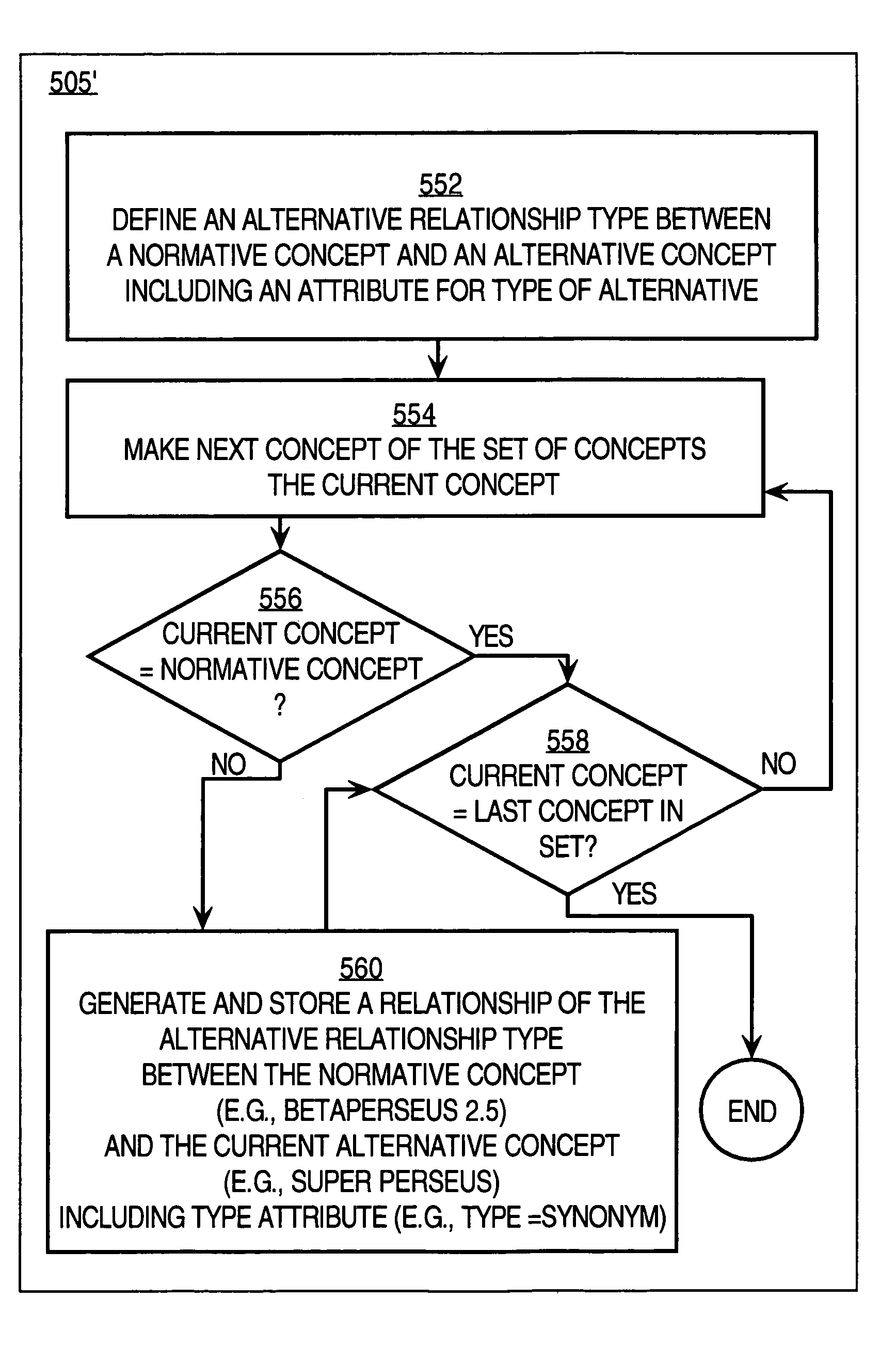
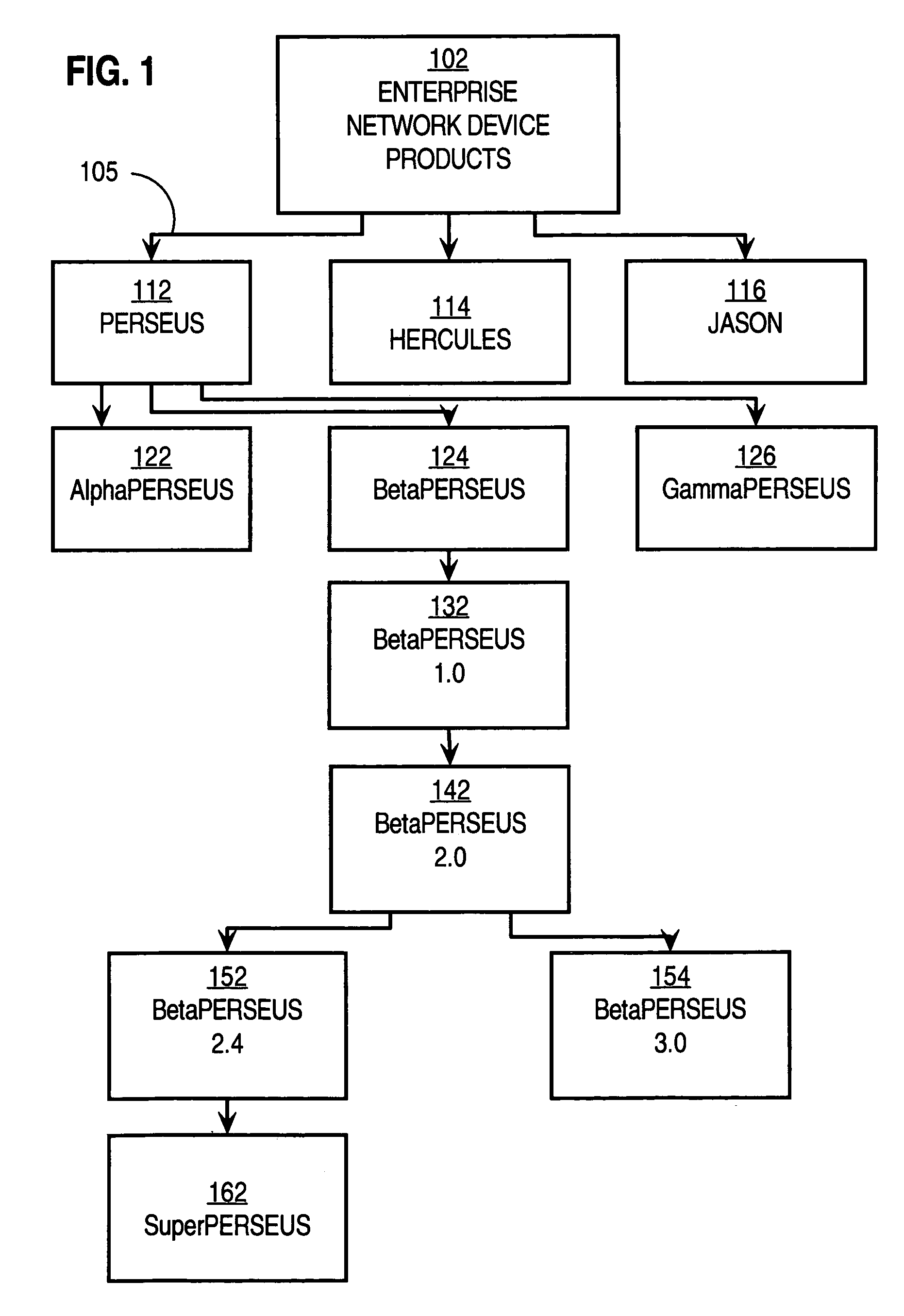
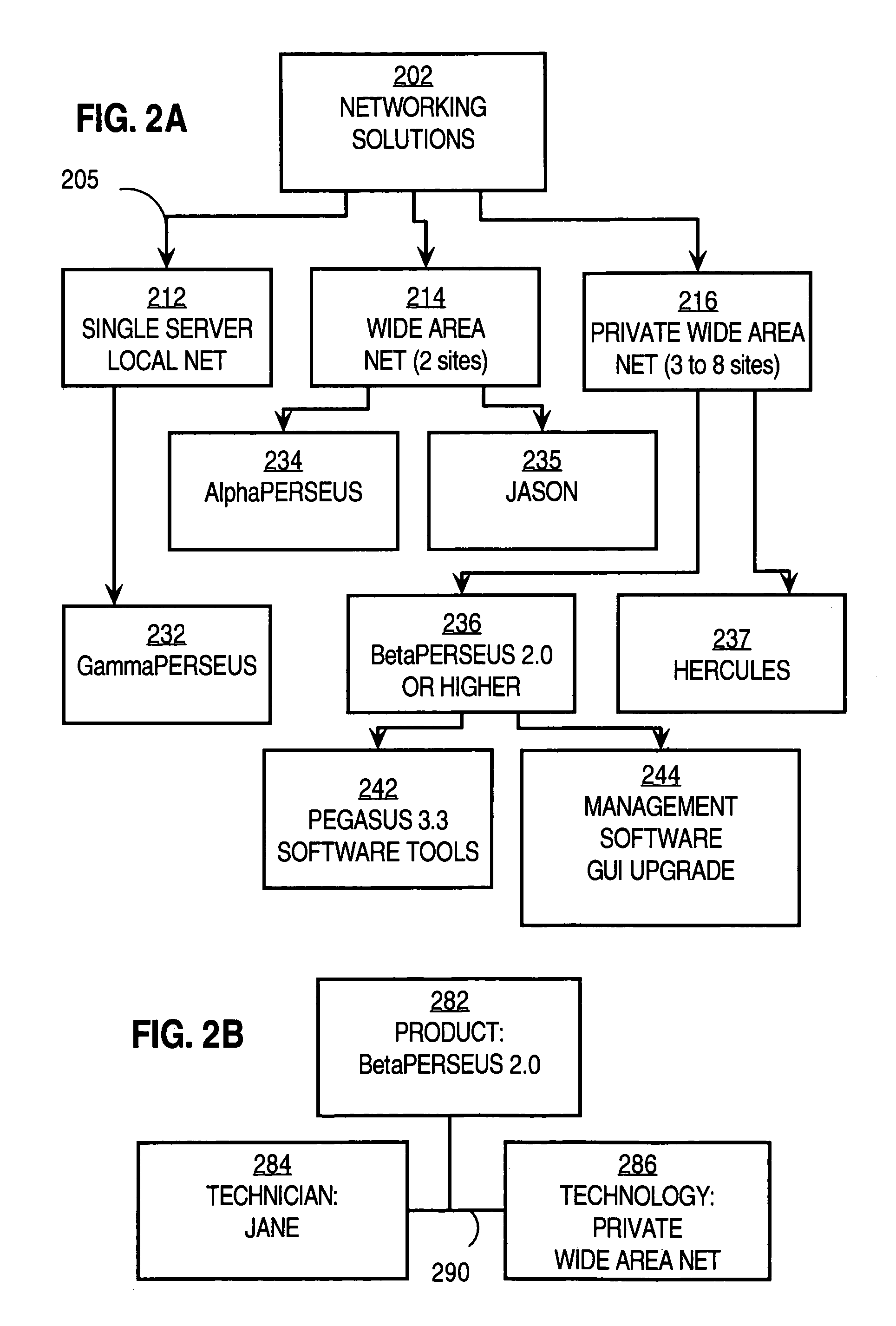
InactiveUS7103607B1Data processing applicationsSpecial data processing applicationsData retrievalSingle entity
Techniques for responding to a request for data about an enterprise include storing a set of names for a single entity associated with the enterprise as a first set of corresponding concepts in a database. The database stores descriptions of entities associated with the enterprise as concepts and relationships among concepts. A first concept of the set of corresponding concepts is indicated. When a request including data indicating a particular name of the set of names is received, a response is sent that includes information associated in the database with the first concept. This invention yields alternative concepts related to a first, official or “normative” concept for each entity associated with the enterprise in all forms, e.g., languages. Entities include descriptions of products, services and activities of the enterprise. Relating alternative concepts to normative concepts allows a customer to issue a “wrong” query using any of the alternative terms and yet still retrieve the correct information associated with the normative term.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com