Certificate-based encryption and public key infrastructure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
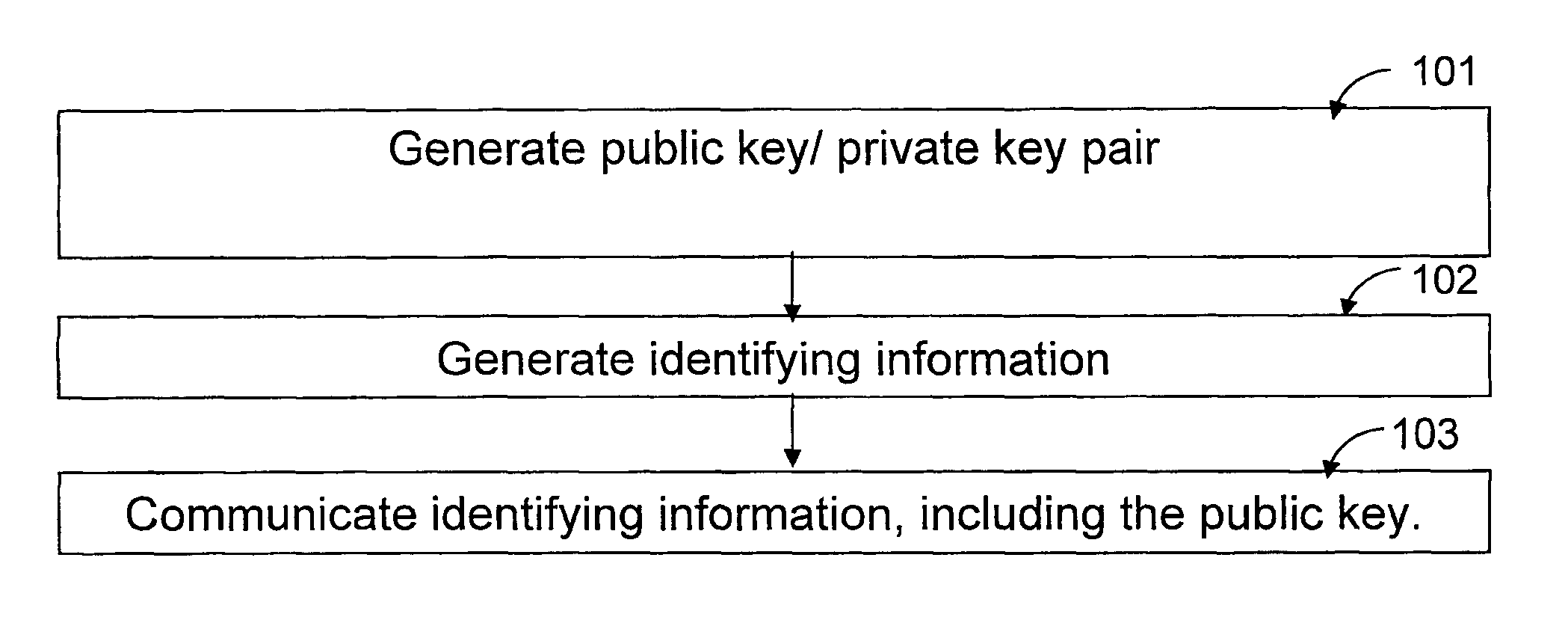
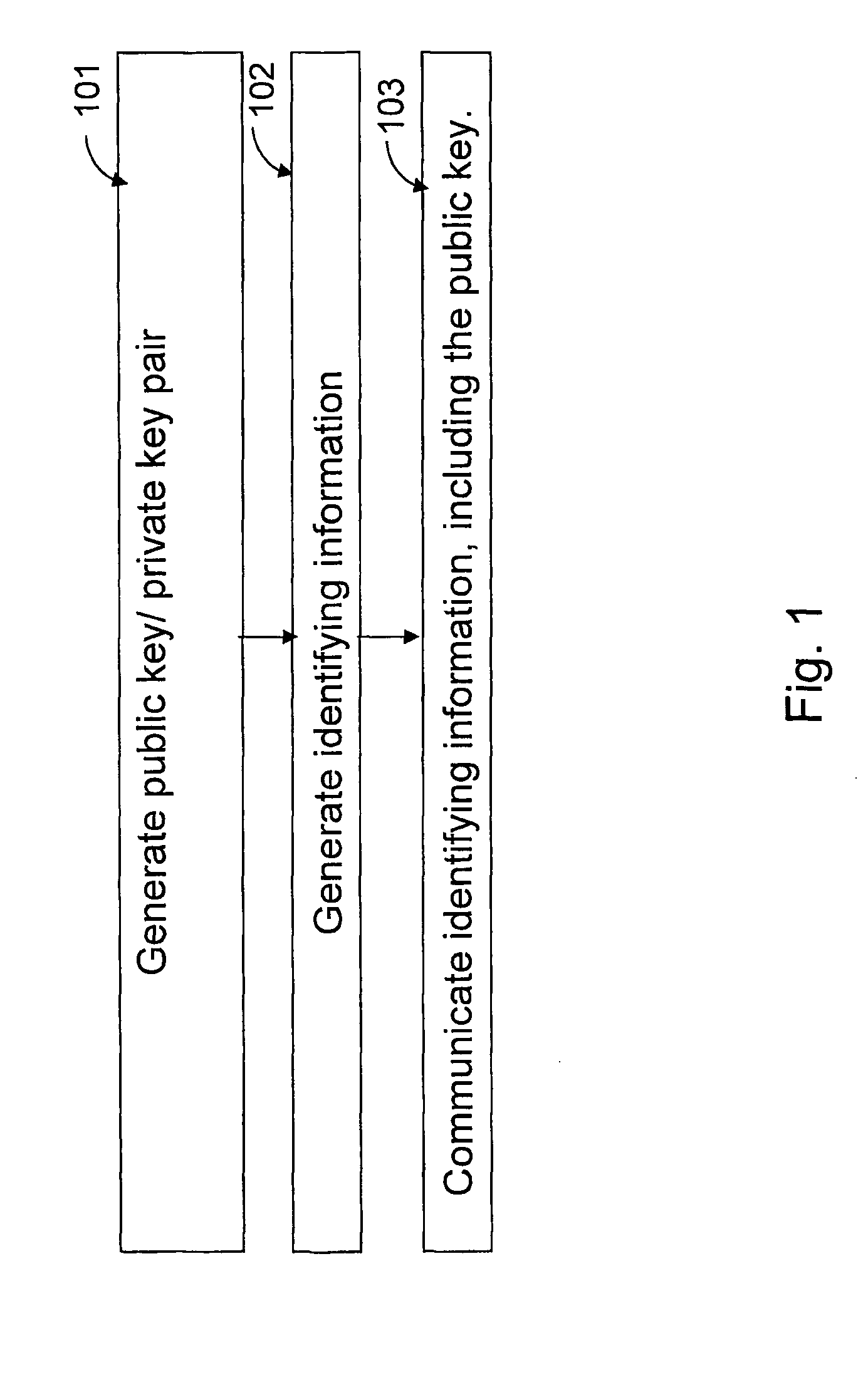
[0017] The present invention provides methods for implementing a secure and practical certificate-based encryption scheme.
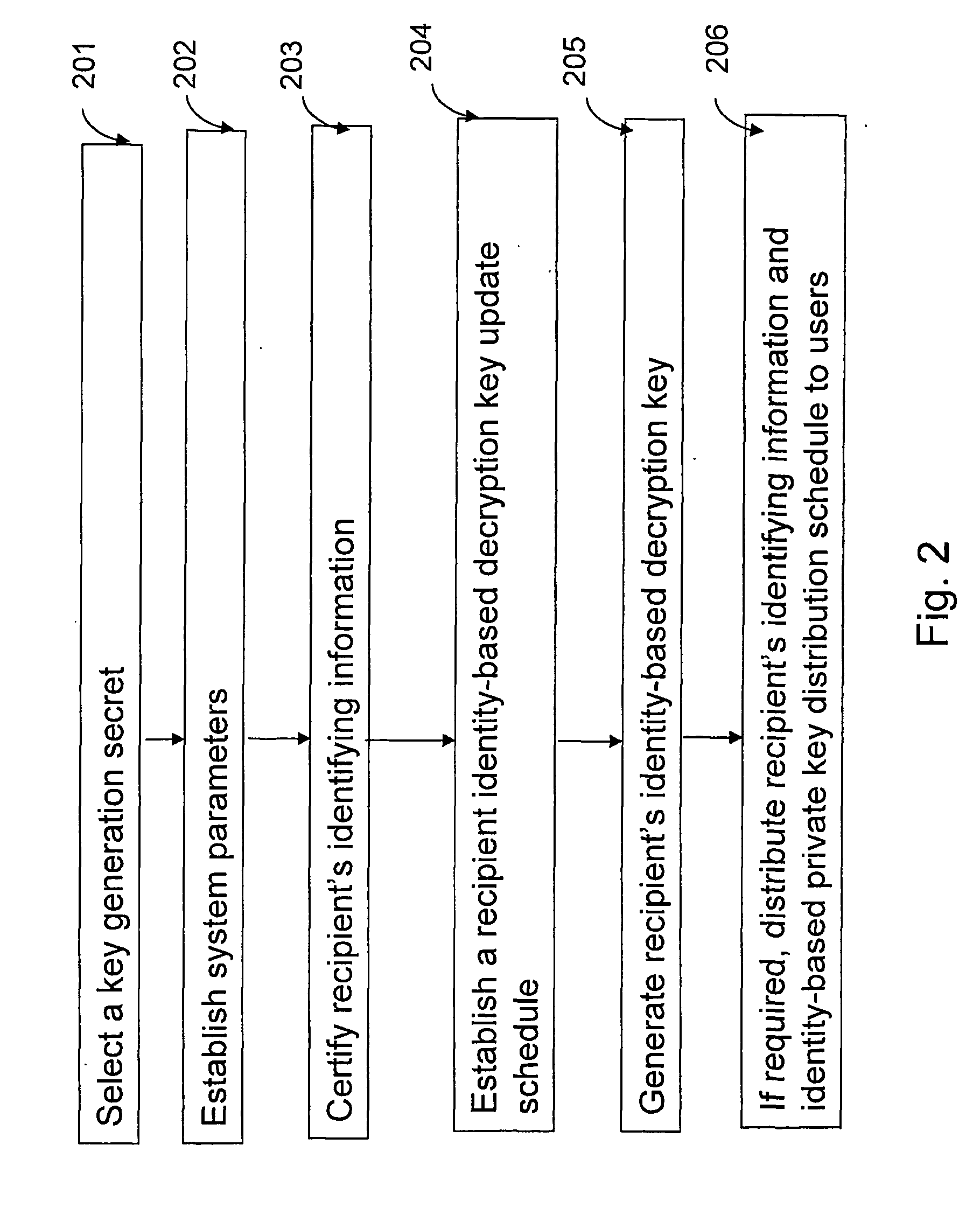
[0018] According to one aspect of the present invention, the method provides for encoding and decoding a digital message between a sender and a recipient in a public-key encryption scheme including the sender, the recipient and an authorizer. The method includes the steps of generating a recipient public key / recipient private key pair and a recipient encryption key. A key generation secret that is a secret of the authorizer is selected. A recipient decryption key is generated using at least the key generation secret and the recipient encryption key where a key formed from the recipient decryption key and a key formed from the recipient encryption key are a public key / private key pair.
[0019] The digital message is encrypted using at least the recipient public key and the recipient encryption key to create an encrypted digital message. The encrypted digital messa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com