Patents
Literature
397results about How to "Effective way" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
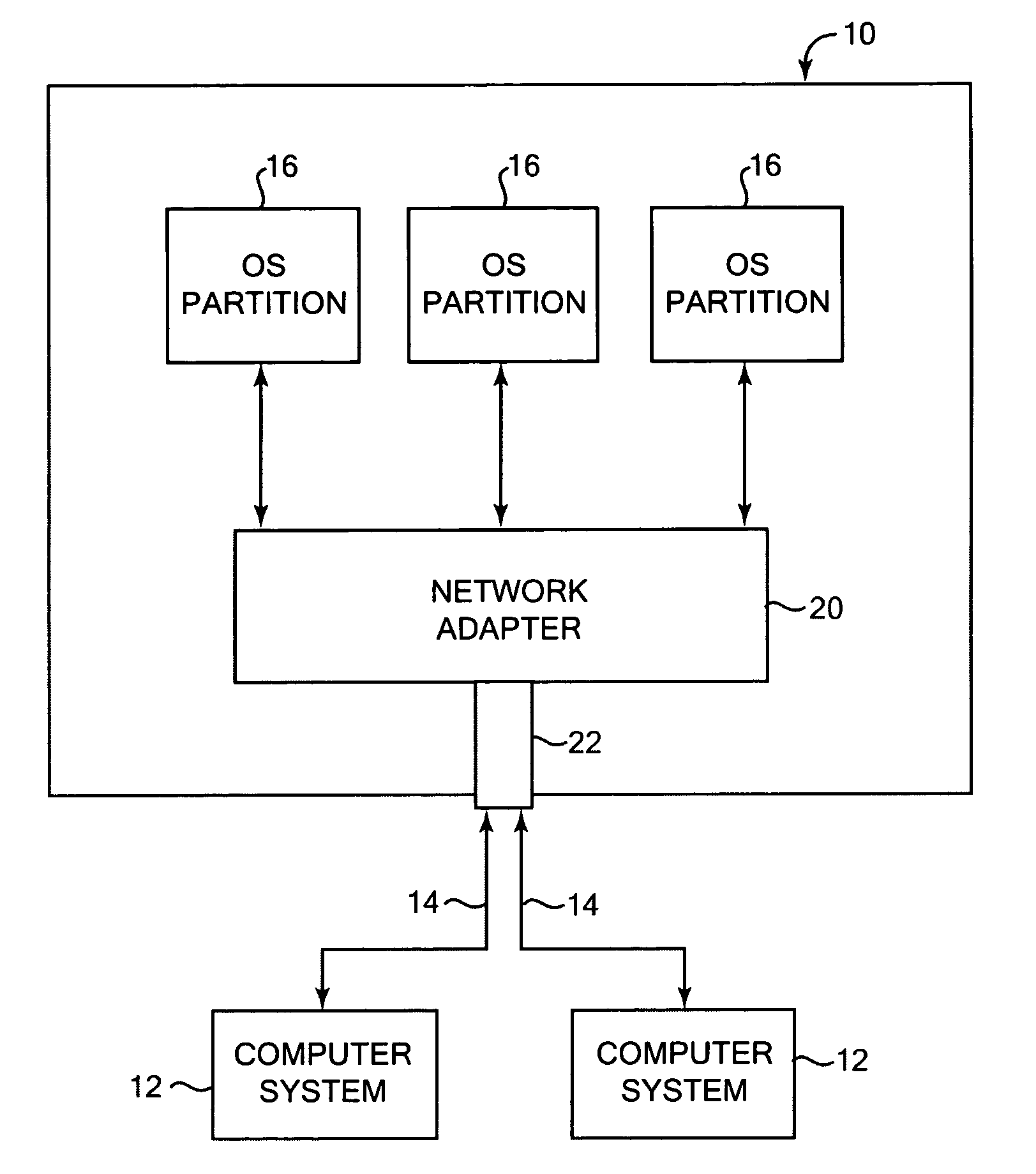
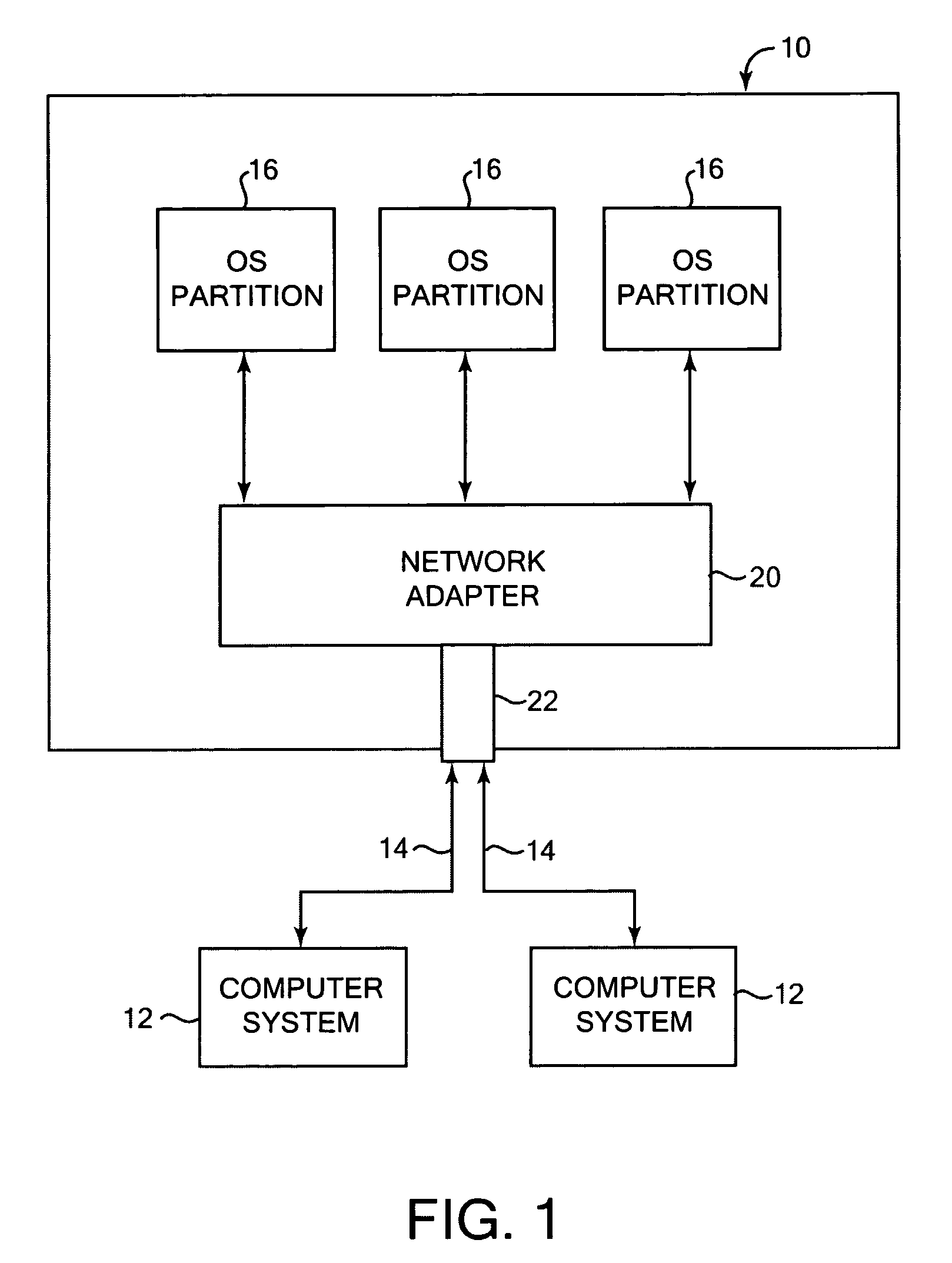
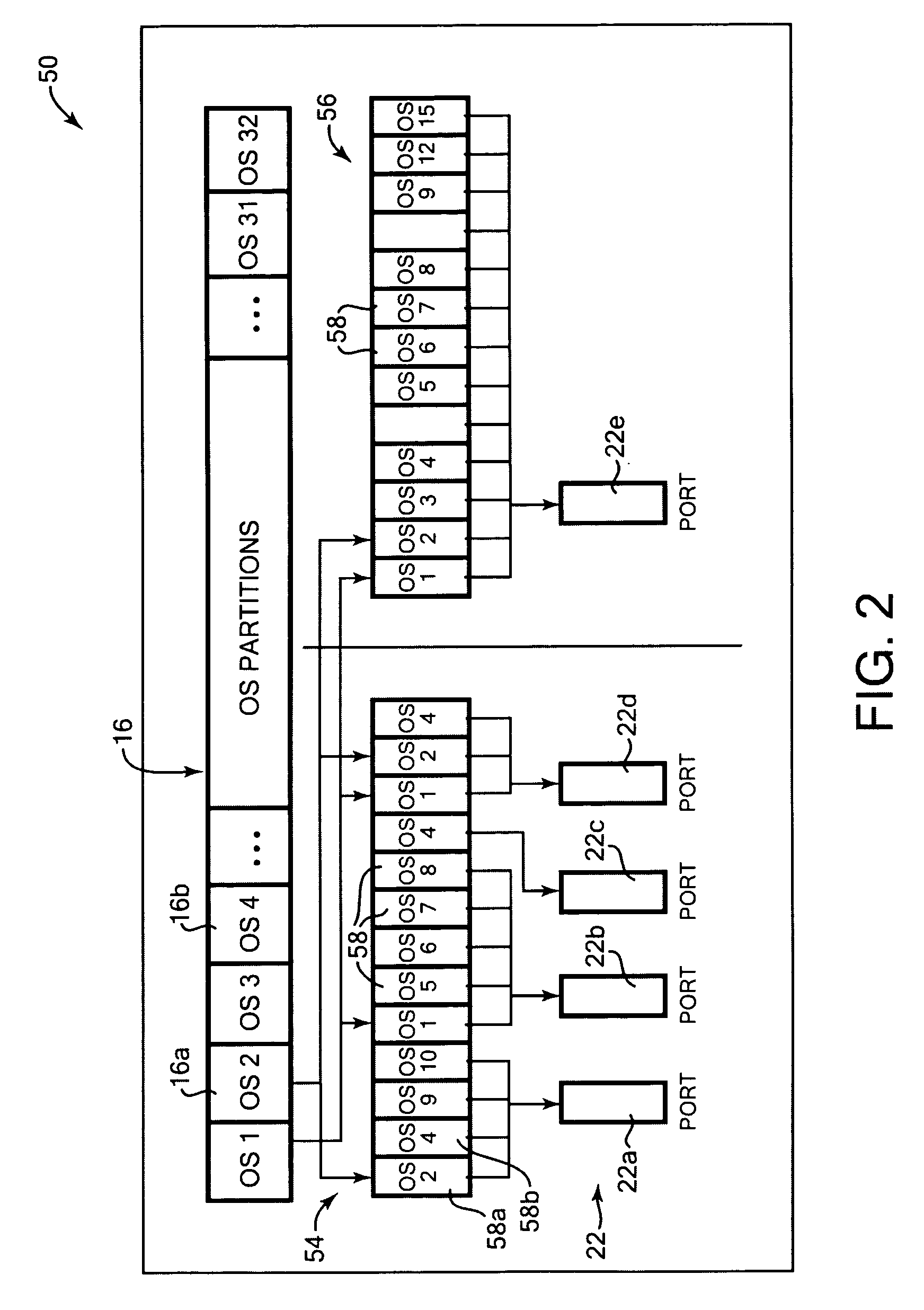
Network communications for operating system partitions
ActiveUS20060221961A1Fast and efficient communicationEfficiently provideData switching by path configurationSecuring communicationOperational systemNetwork packet
Providing communications between operating system partitions and a computer network. In one aspect, an apparatus for distributing network communications among multiple operating system partitions includes a physical port allowing communications between the network and the computer system, and logical ports associated with the physical port, where each logical port is associated with one of the operating system partitions. Each of the logical ports enables communication between a physical port and the associated operating system partition and allows configurability of network resources of the system. Other aspects include a logical switch for logical and physical ports, and packet queues for each connection and for each logical port.
Owner:IBM CORP
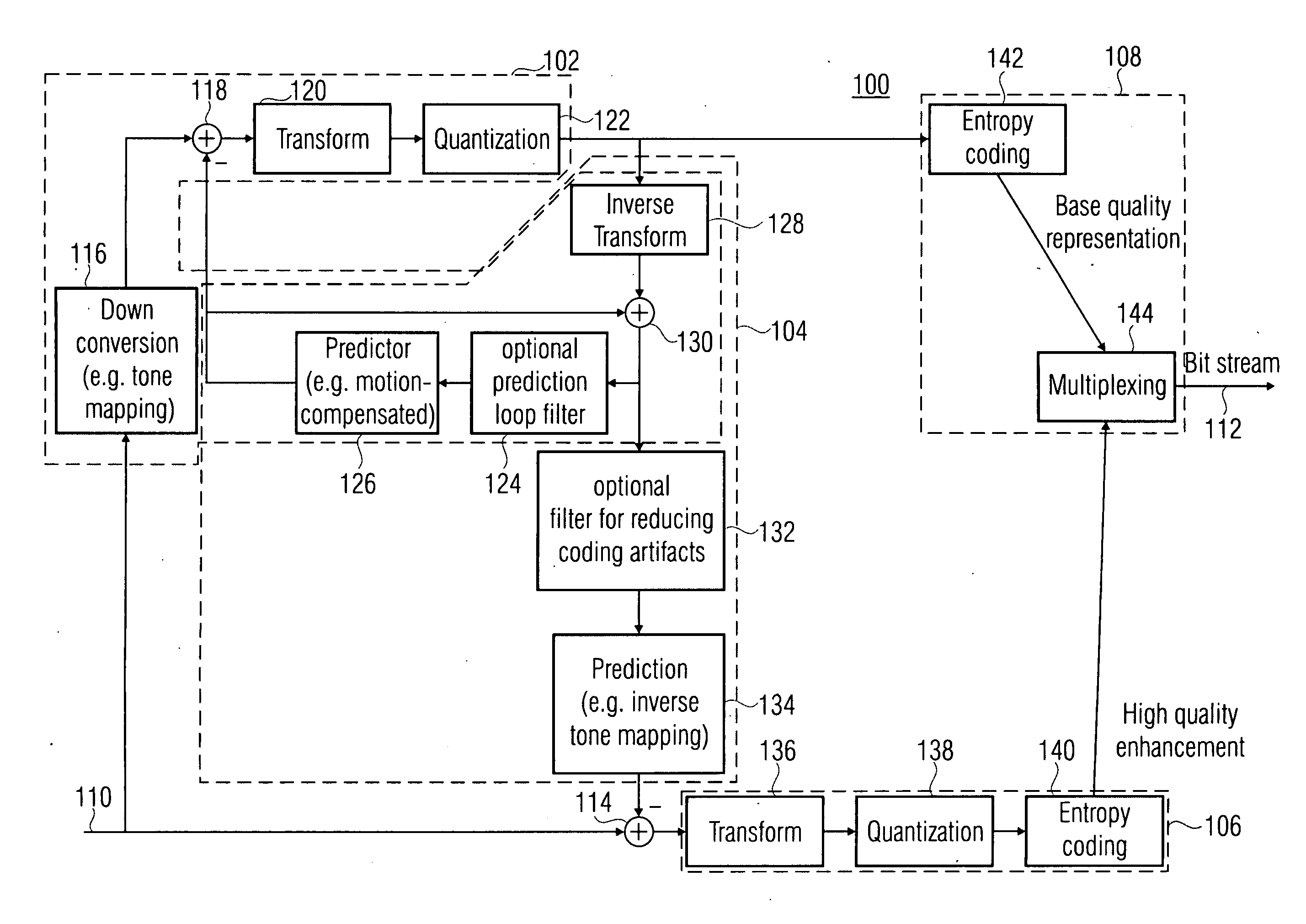
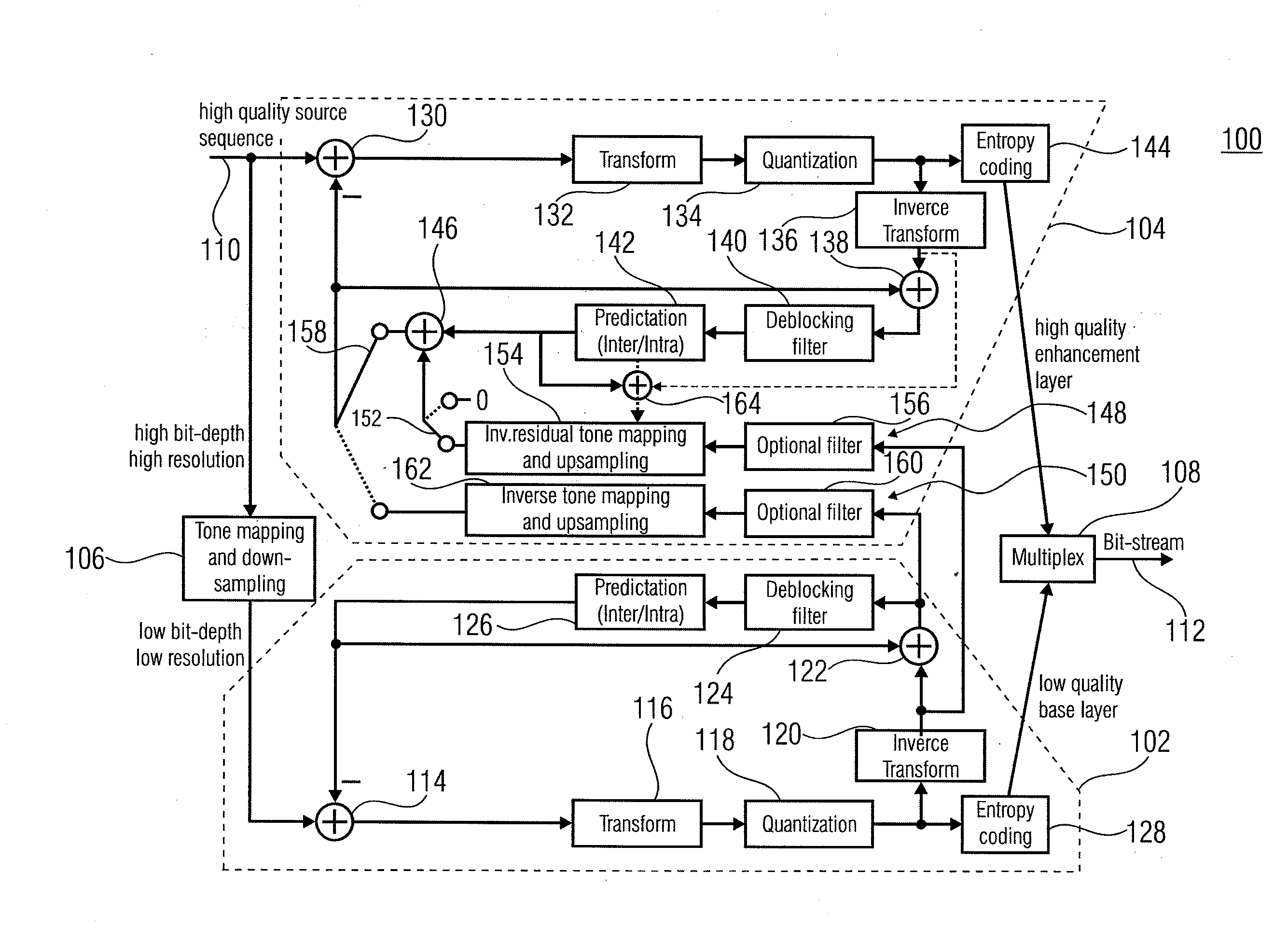
Quality scalable coding
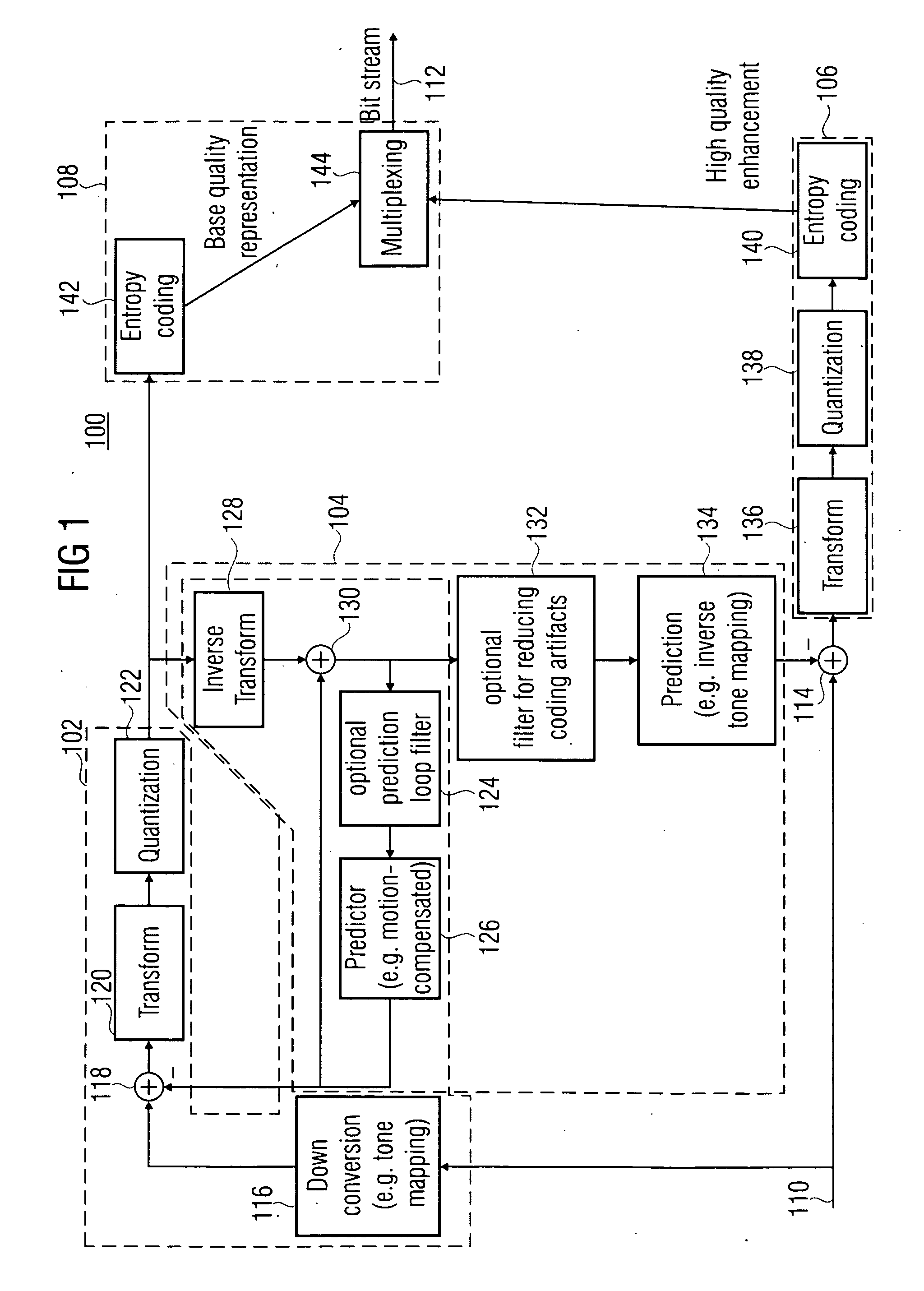
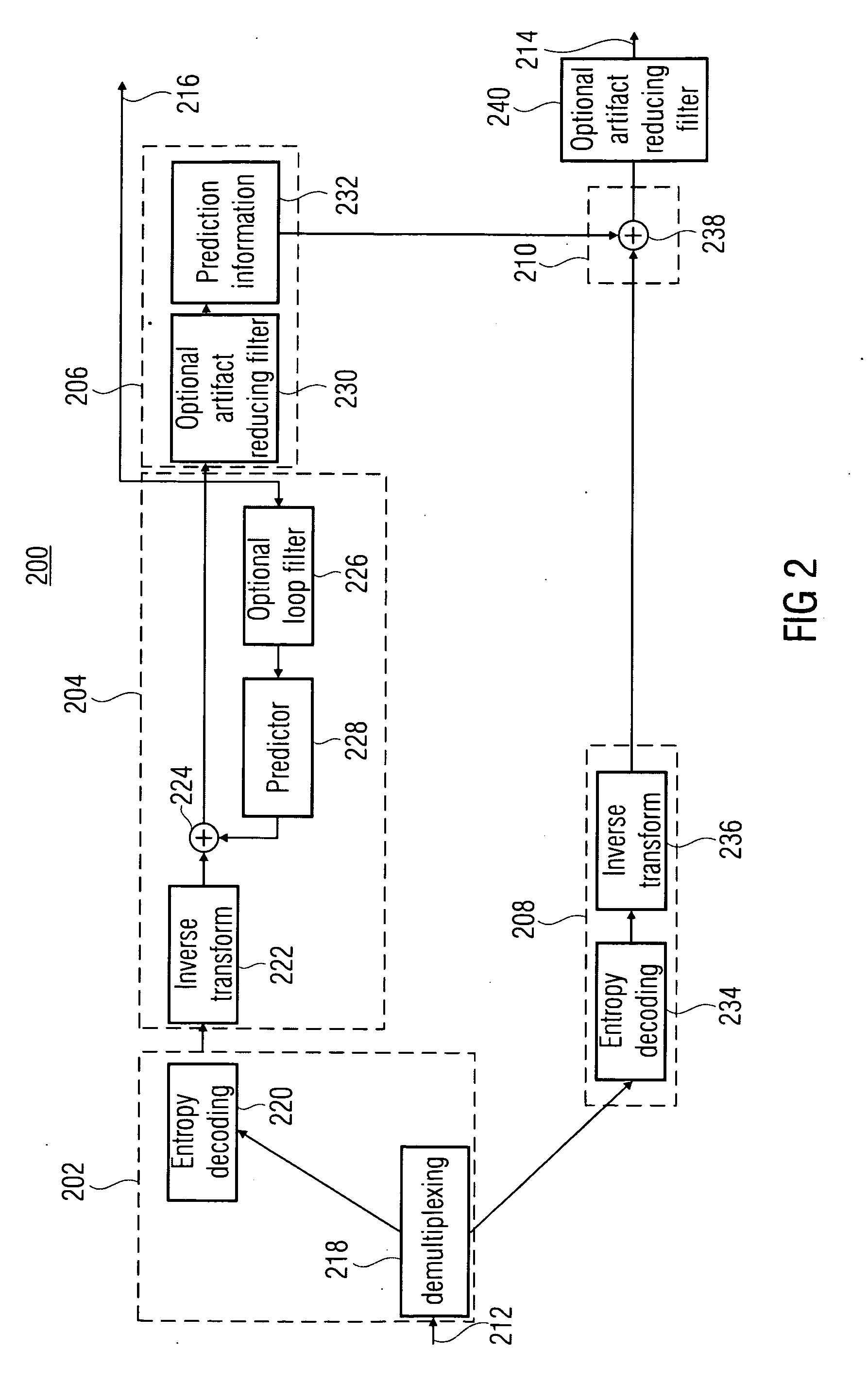
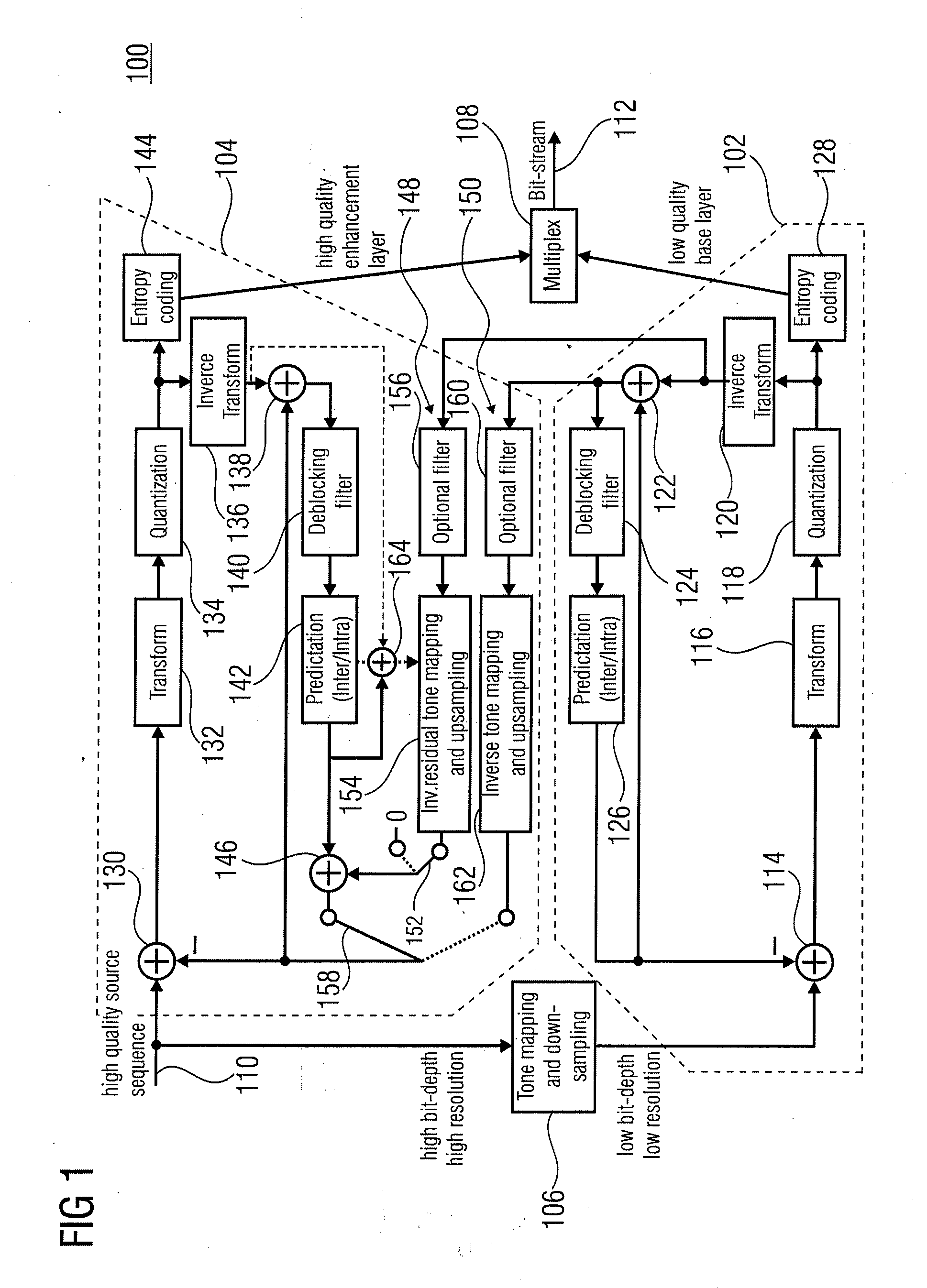
ActiveUS20100020866A1Effective wayHigh bit-depthColor television with pulse code modulationColor television with bandwidth reductionPattern recognitionData stream
A more efficient way of addressing different bit-depths, or different bit-depths and chroma sampling format requirements is achieved by using a low bit-depth and / or low-chroma resolution representation for providing a respective base layer data stream representing this low bit-depth and / or low-chroma resolution representation as well as for providing a higher bit-depth and / or higher chroma resolution representation so that a respective prediction residual may be encoded in order to obtain a higher bit-depth and / or higher chroma resolution representation. By this measure, an encoder is enabled to store a base-quality representation of a picture or a video sequence, which can be decoded by any legacy decoder or video decoder, together with an enhancement signal for higher bit-depth and / or reduced chroma sub-sampling, which may be ignored by legacy decoders or video decoders.
Owner:GE VIDEO COMPRESSION LLC
Distributed cell balancing
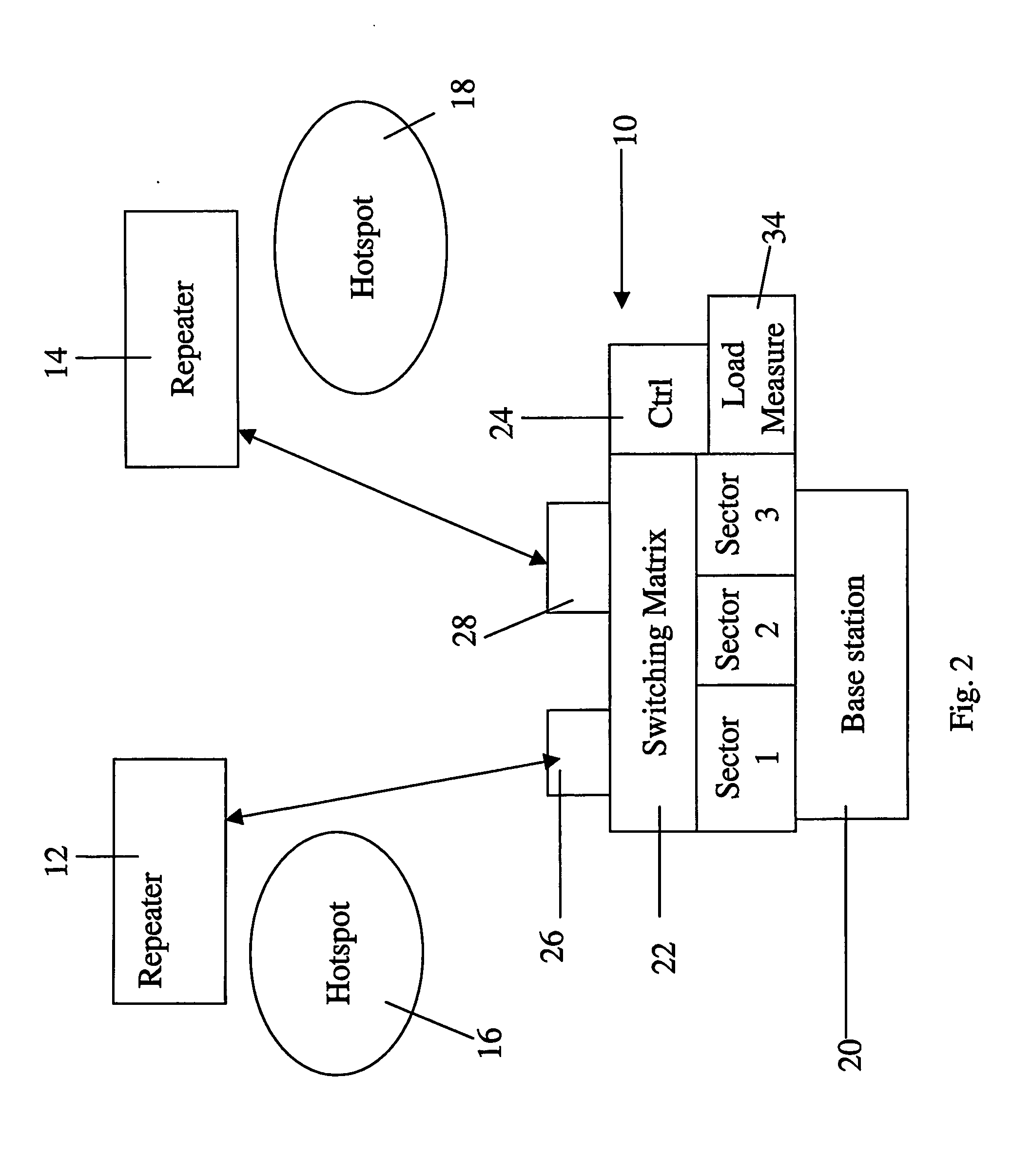
InactiveUS20070129071A1Avoid problemsEffective wayRadio/inductive link selection arrangementsWireless commuication servicesRepeaterDynamic equilibrium
A load balancing system for dynamic balancing of load between sectors of a sectored cellular base station, comprises a plurality of repeaters with local coverage in the sectors, and a switching matrix, for associating between the repeaters and the base station, and for allowing the repeaters to be switched between different sectors. If the system uses the base station assigned frequency band for communication with the repeaters then the system can be provided with minimal interference as an add-on to a legacy base station. An add-on may also be provided using microwave frequency and dedicated antennas.
Owner:CELLETRA
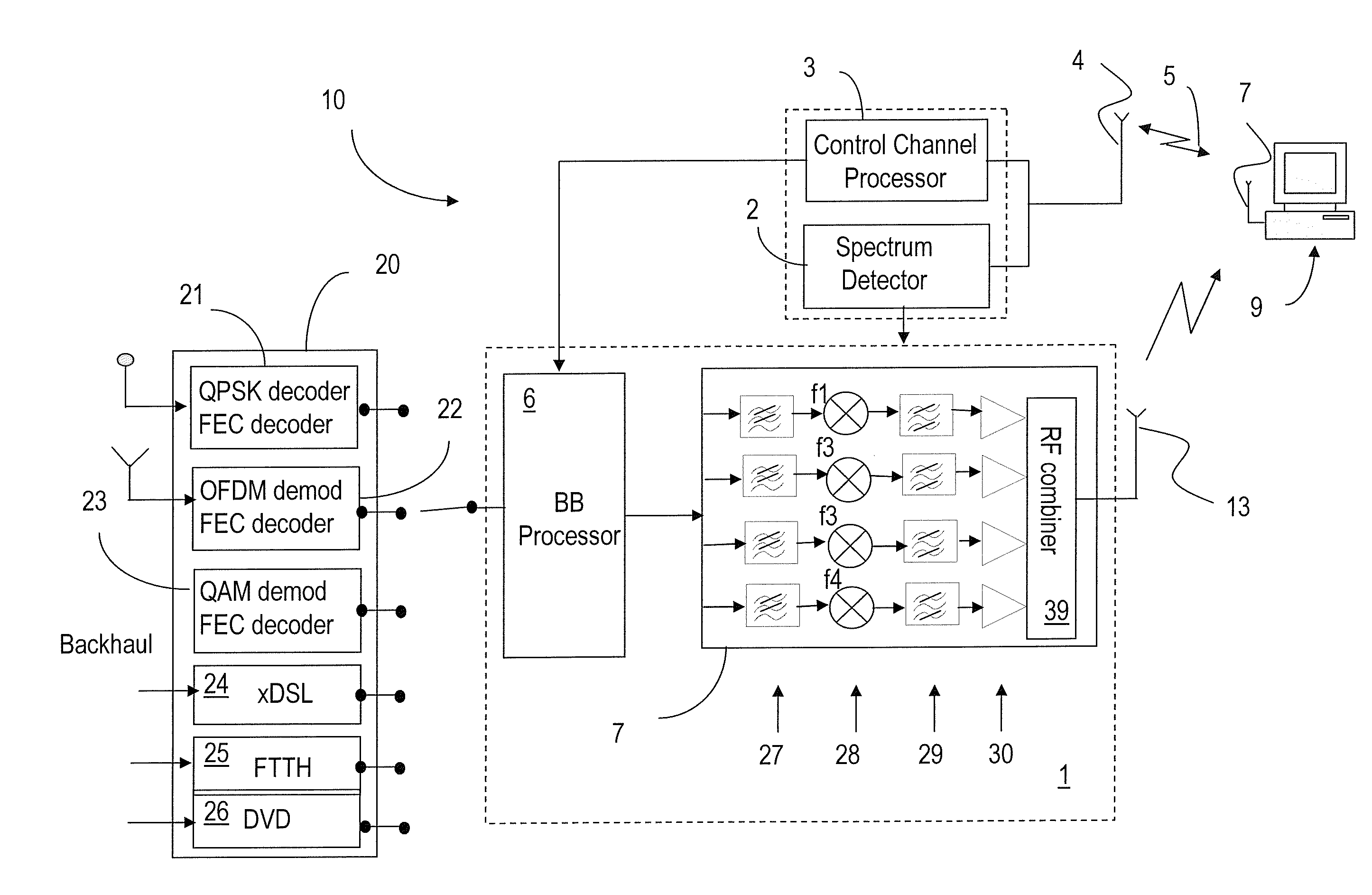
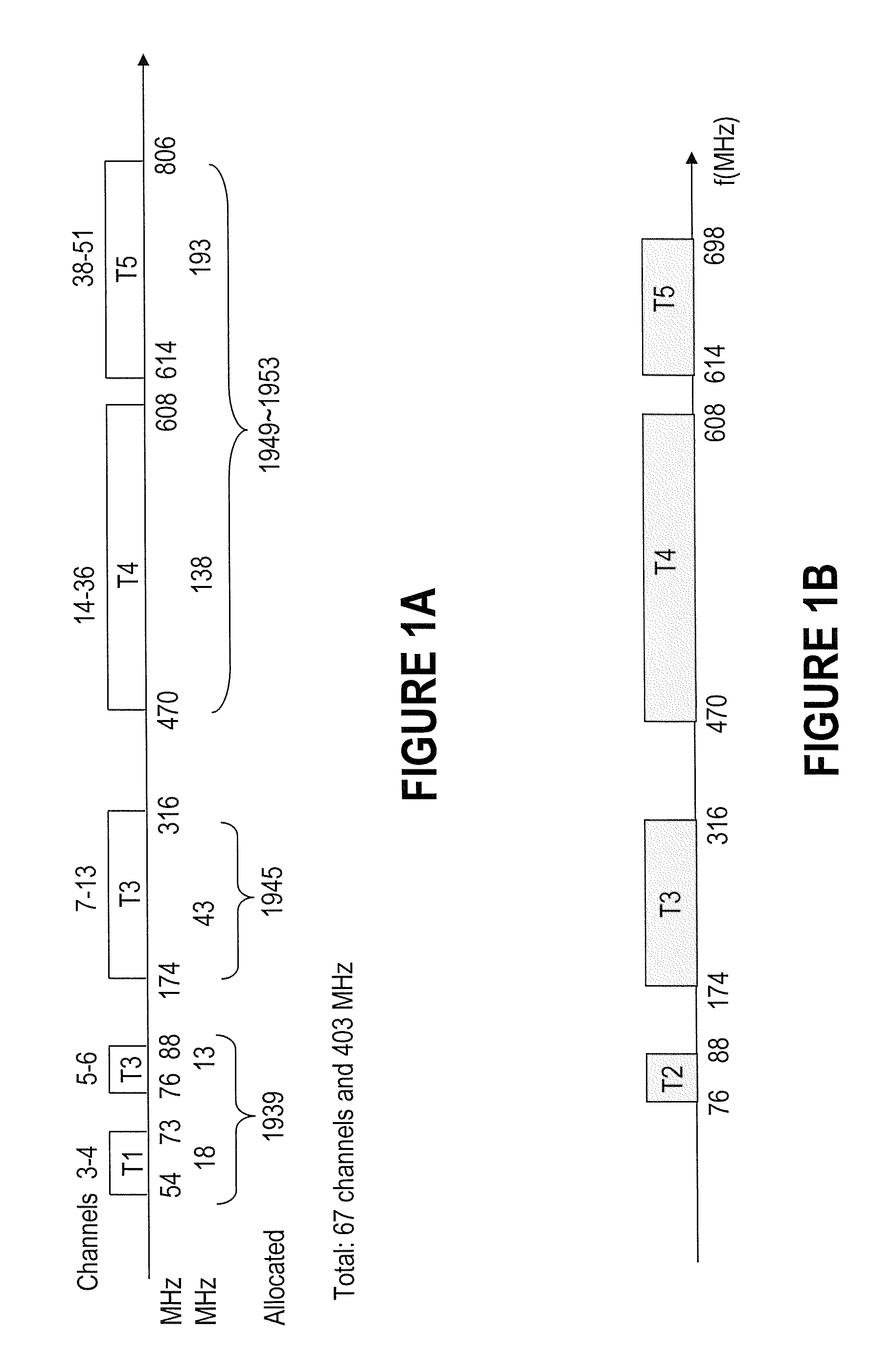
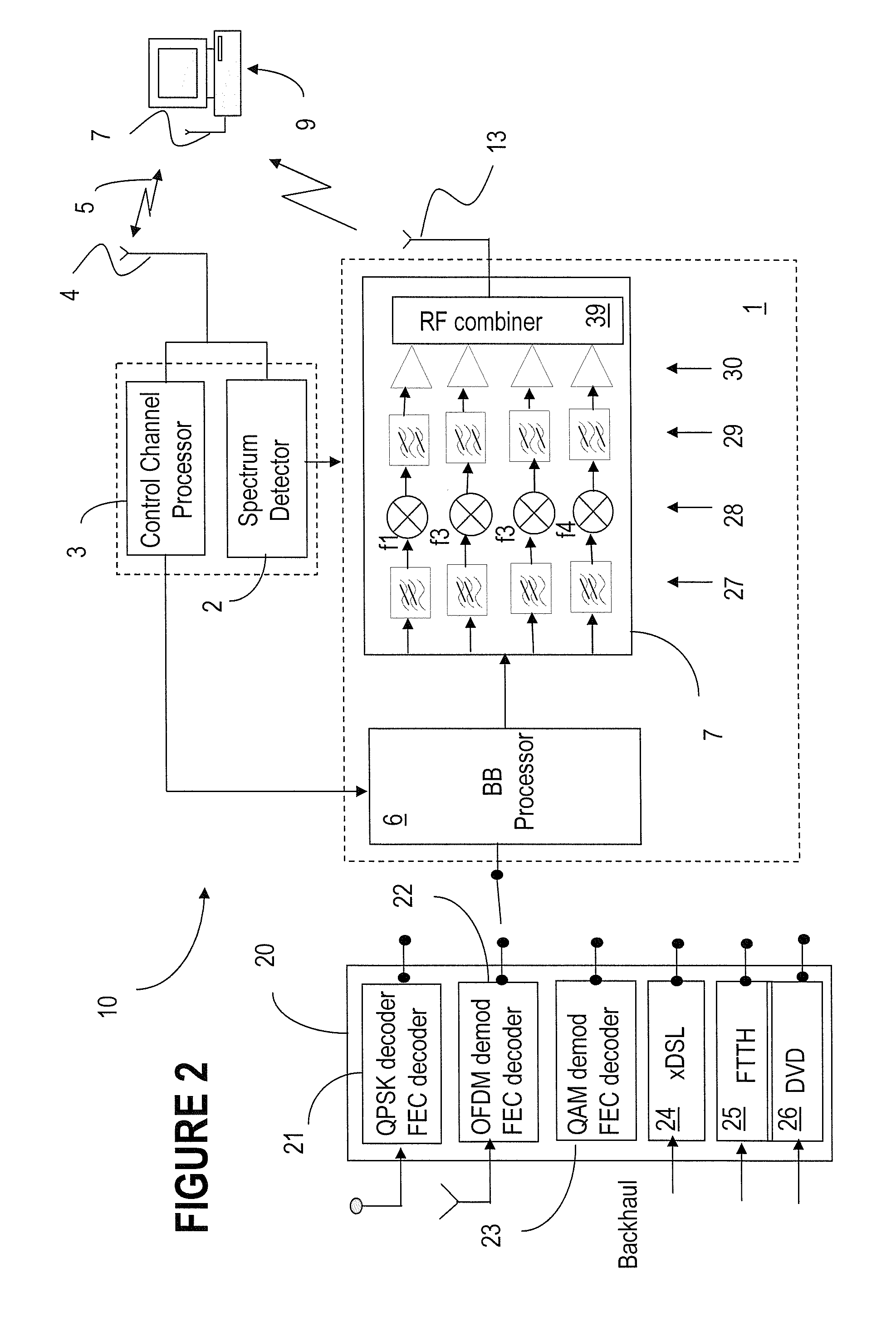
Systems and etiquette for home gateways using white space
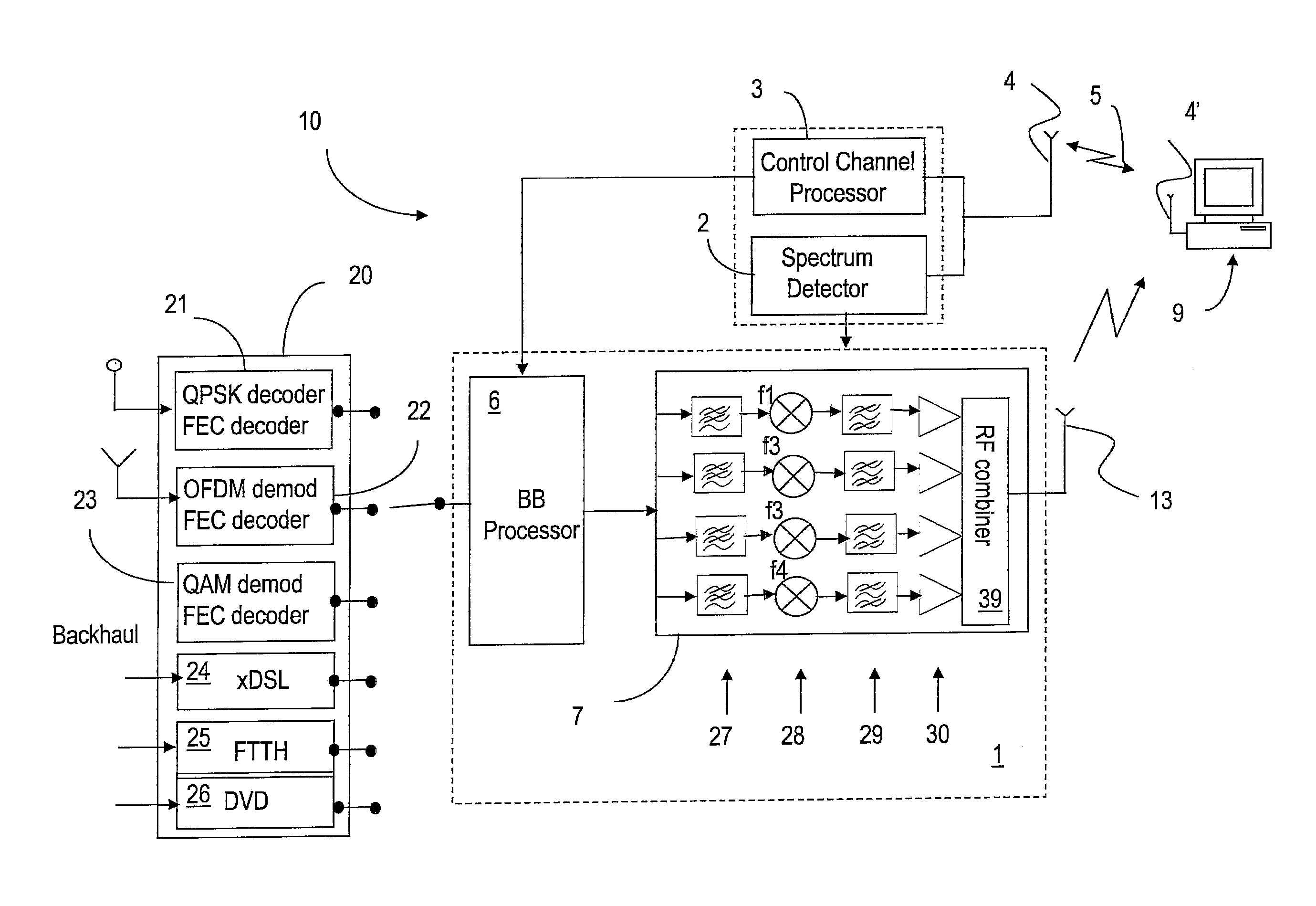
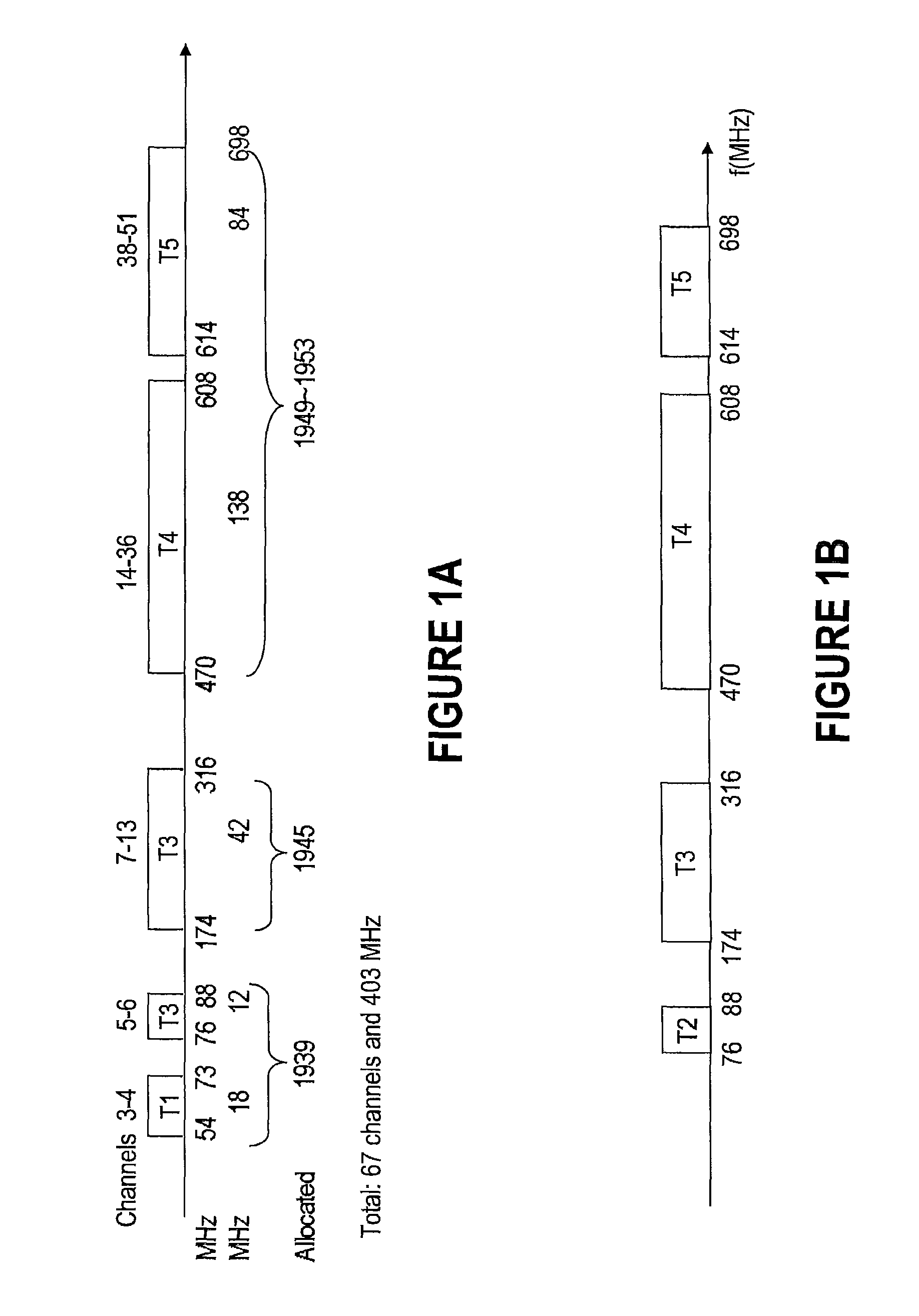
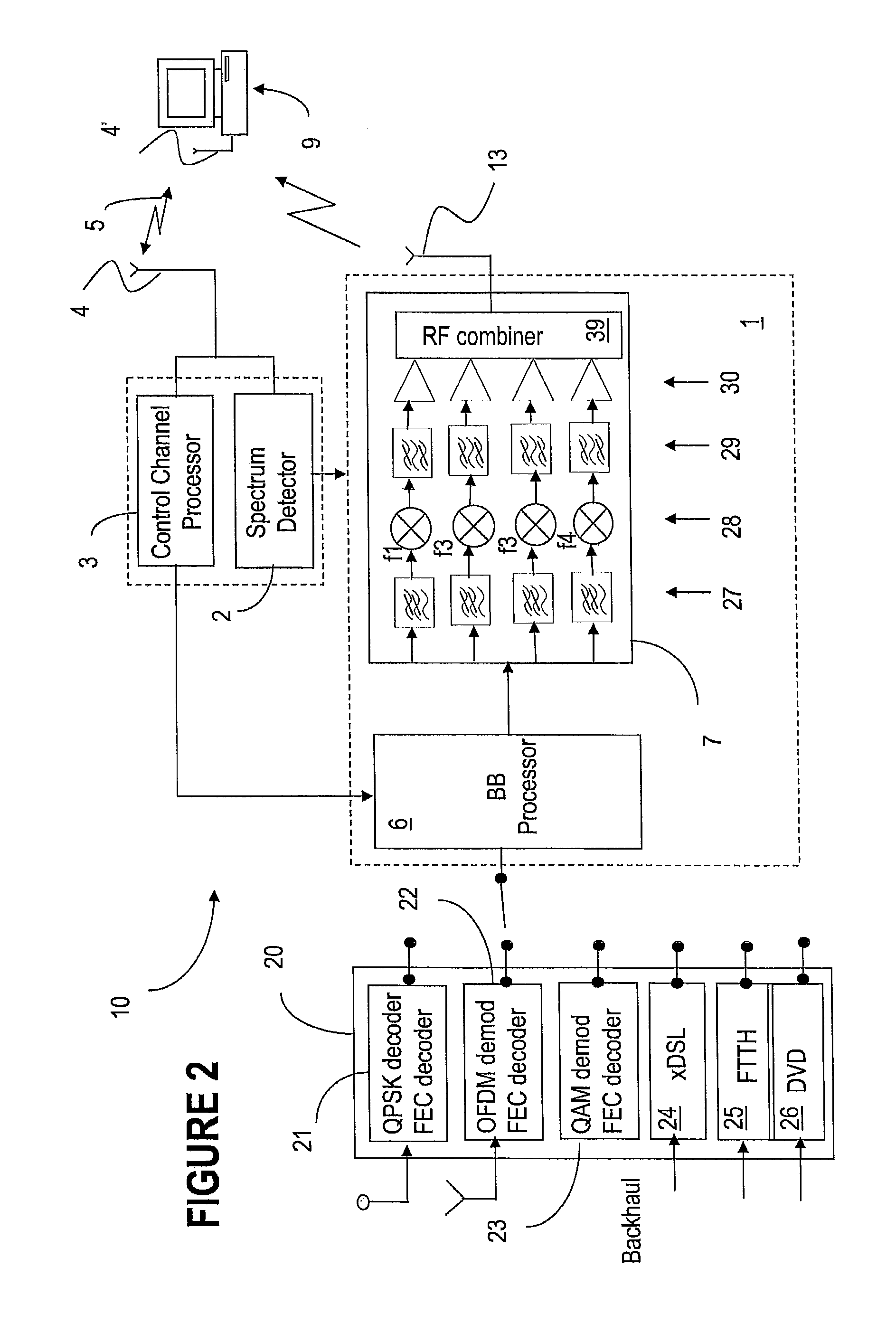
InactiveUS8107391B2Effective wayWithout degrading qualityError preventionFrequency-division multiplex detailsFrequency spectrumService sharing
Owner:TAIWAN SEMICON MFG CO LTD
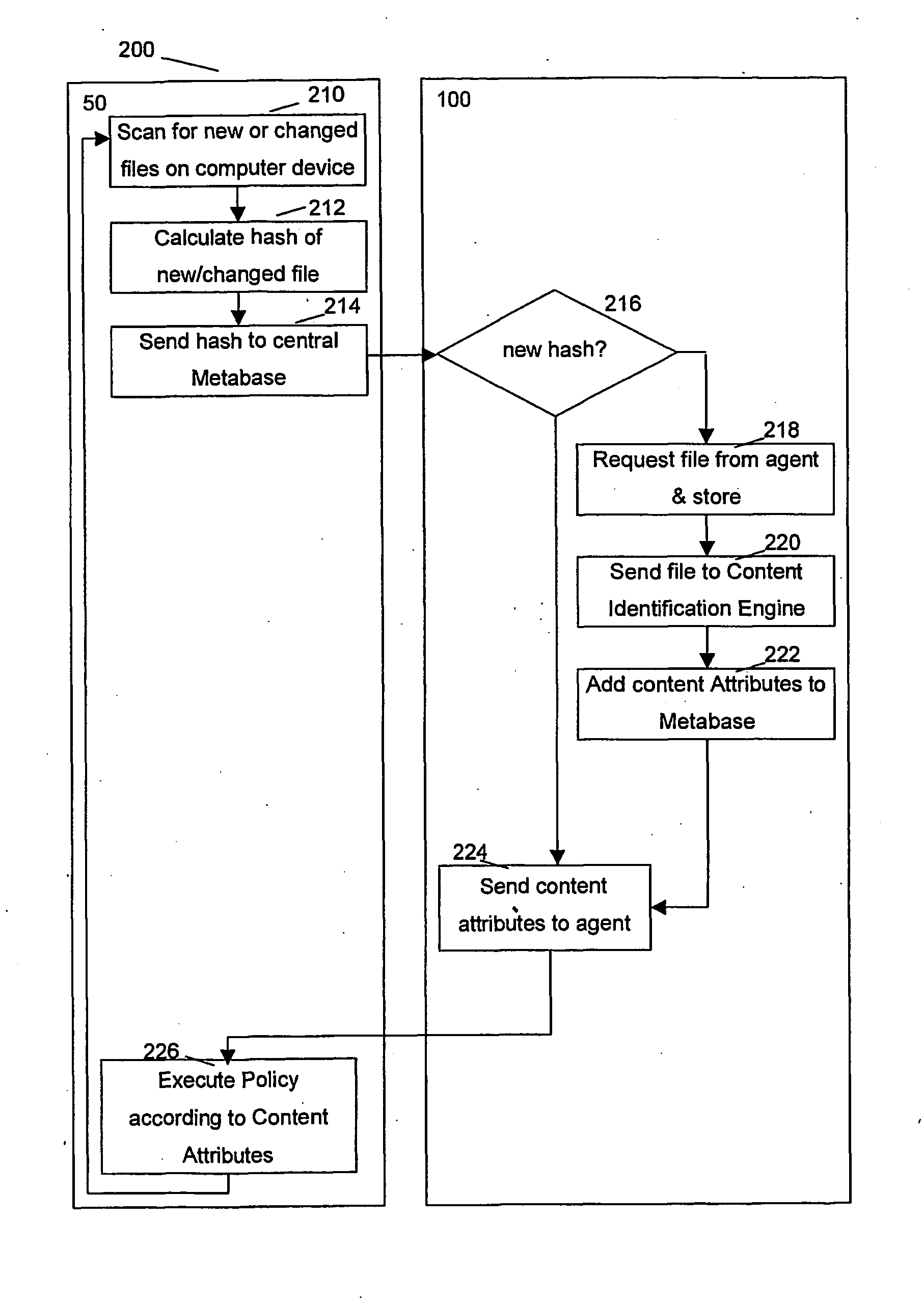
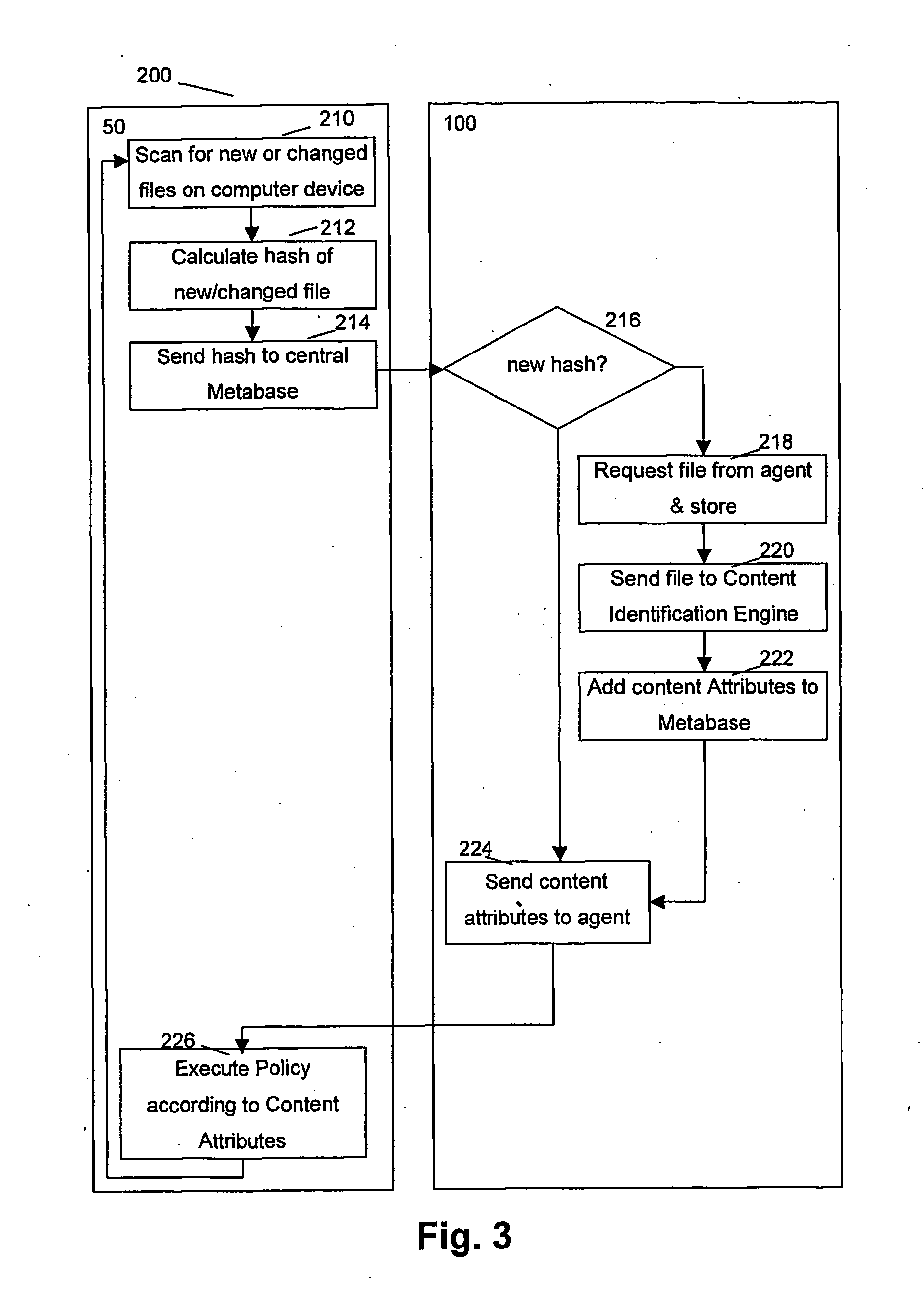
Method and system for identifying the content of files in a network
InactiveUS20070150948A1Improve security levelTimely processingMemory loss protectionError detection/correctionOperating systemData bank
A method and system for performing securing and controlling of a network using content identification of files in a network having a central infrastructure and local computing devices is presented. The method comprises calculating a hash value of a new file created or received on a local computing device, transmitting the hash value to the central infrastructure, comparing the hash value with a previously determined hash value stored in a database on the central infrastructure to determine whether the file is new to the network and if the file is new to the network, checking the file content with a content identifying engine, installed and updated on the central infrastructure. Content attributes are determined for the files which allow to perform appropriate actions on the local computing devices according to policy rules.
Owner:SYMANTEC CORP
Scalable video coding supporting pixel value refinement scalability
ActiveUS20100260260A1Improve rate-distortion performanceReduce complexityColor television with pulse code modulationColor television with bandwidth reductionVideo encodingAlgorithm
A more efficient way of enabling scalability in terms of pixel value resolution is achieved by temporally predicting a first and a second representation of a video material separately to each other with the first representation being of a lower pixel value resolution than the second representation, with mapping the first prediction residual or a reconstructed version thereof from the first pixel value resolution to the second pixel value resolution dependent on the second prediction signal obtained from temporally predicting the second representation, and by coding a second prediction residual being of the second pixel value resolution as representing a deviation between a combination of the second and third prediction signals and the second representation.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
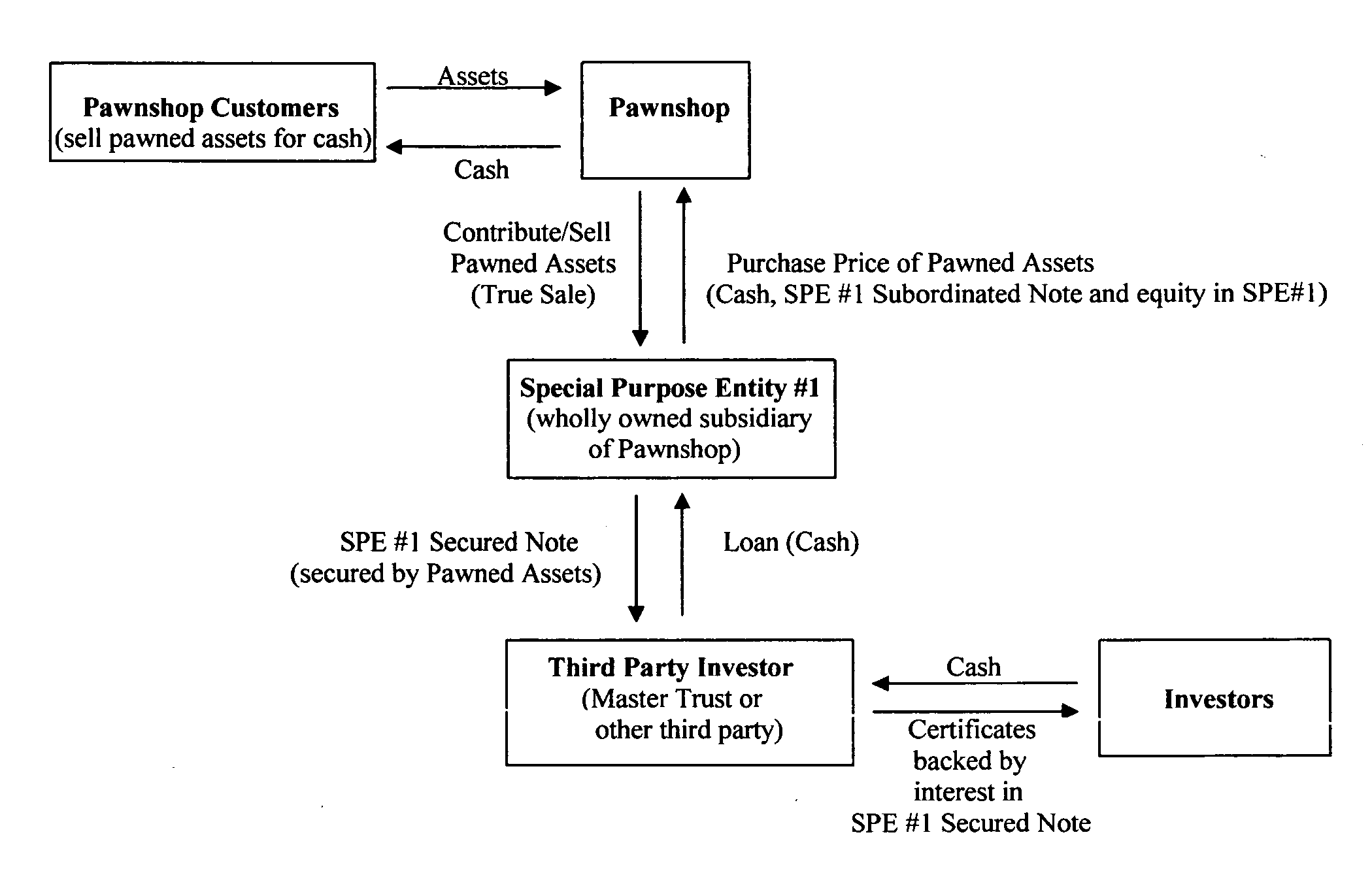
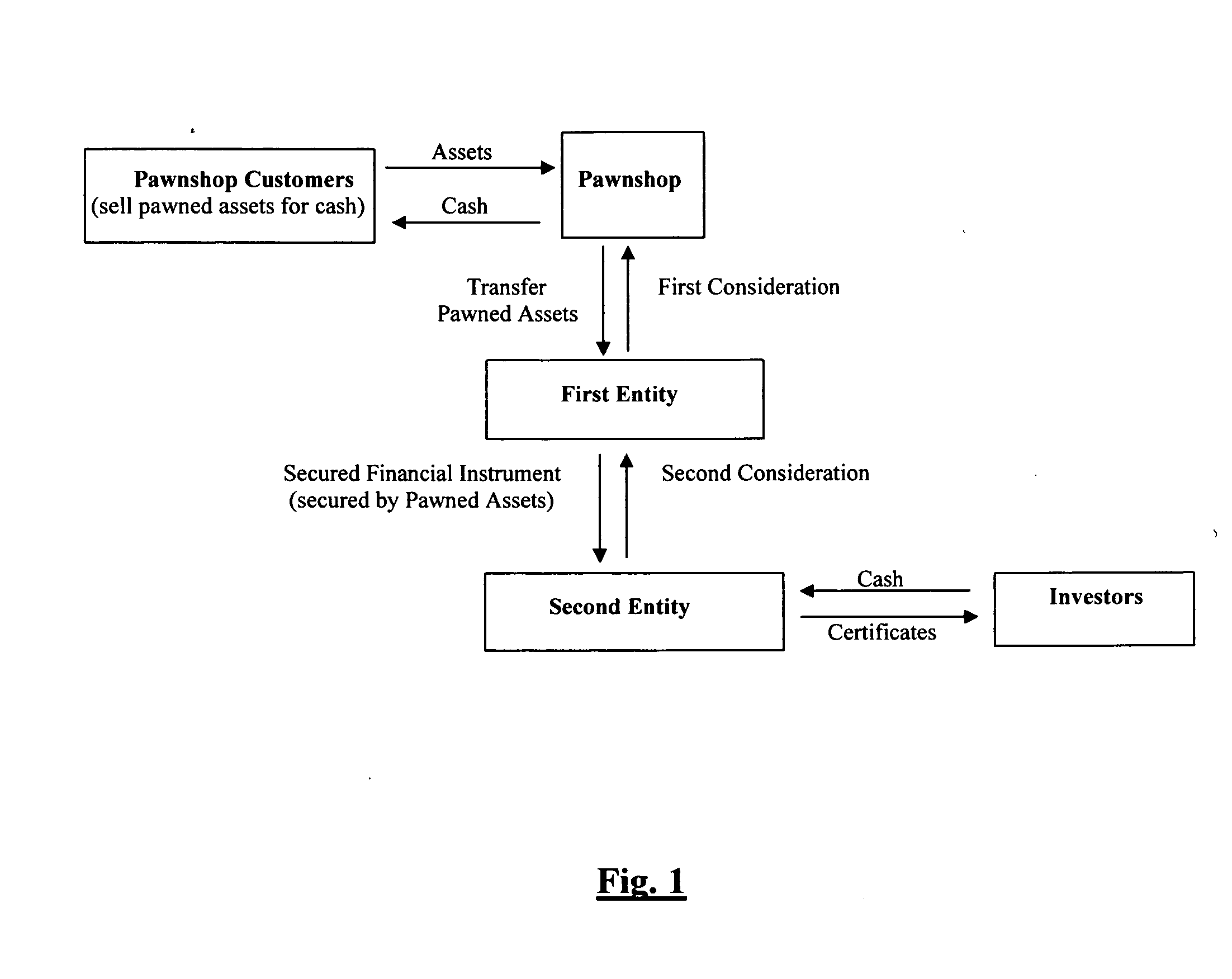
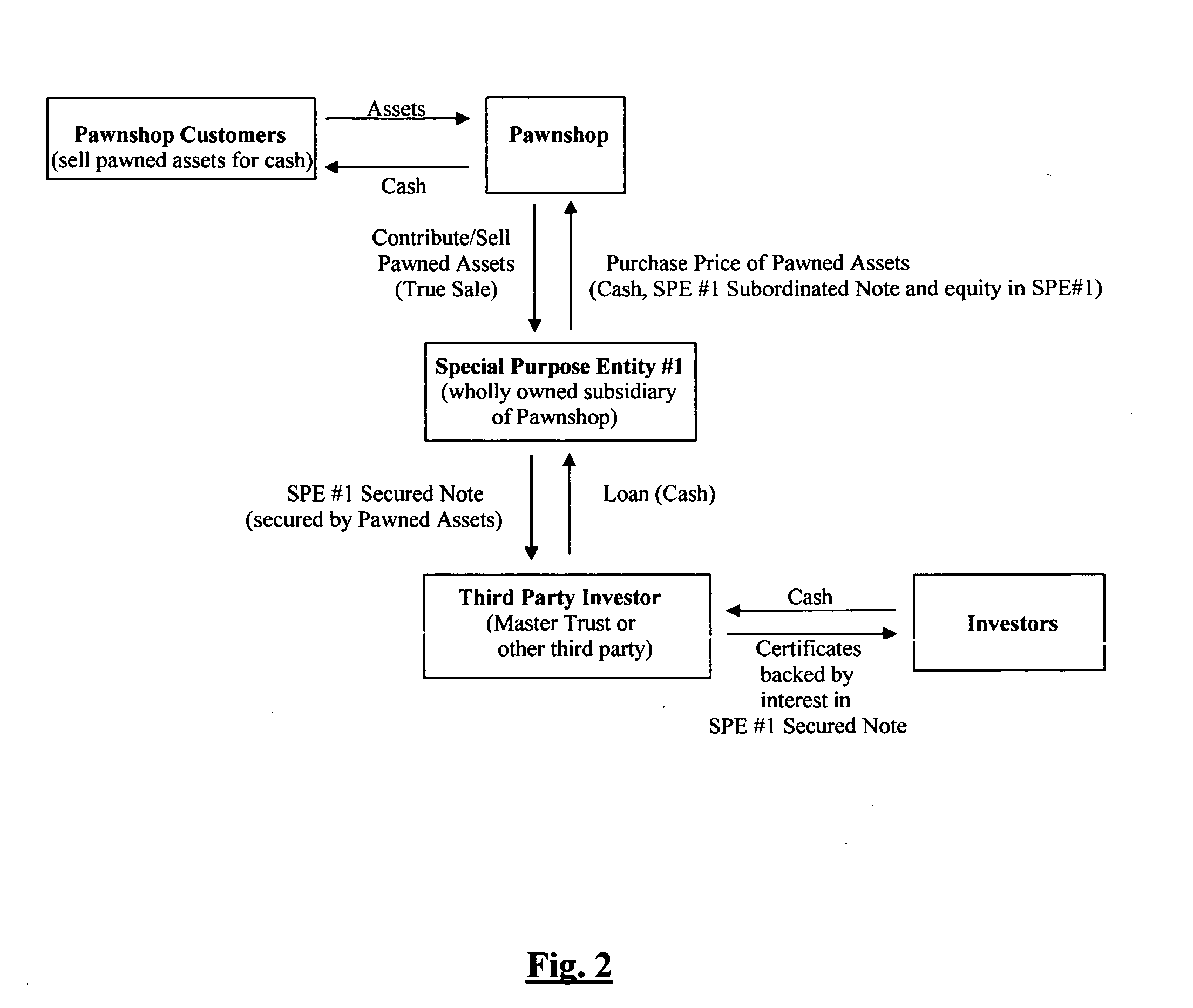
System and method for securitizing tangible assets in the alternative financial services industry
InactiveUS20060293985A1Significant comprehensive benefitsAvoids conflicting lenderFinanceComputer scienceFinancial transaction
Owner:SECURITIZATION GROUP
Systems and etiquette for home gatways using white space
InactiveUS20100124254A1Easy to operateEfficient identificationModulated-carrier systemsTransmission path divisionFrequency spectrumComputer science
Methods and systems for sharing white space with primary services and other emerging services are provided. Signal distribution within a specified location, such as a dwelling, is performed using a home gateway that identifies unused white space, reserves such white space spectrum, and delivers data to one or more devices at the respective location using the reserved spectrum. Signalling between the devices and the gateway is performed over a shared signalling channel, which enables the gateway to advise the devices from where and when to receive data. The gateway also uses a common spectrum reservation OFDM symbol to advise the neighbouring gateways of the local spectrum reservation.
Owner:TAIWAN SEMICON MFG CO LTD
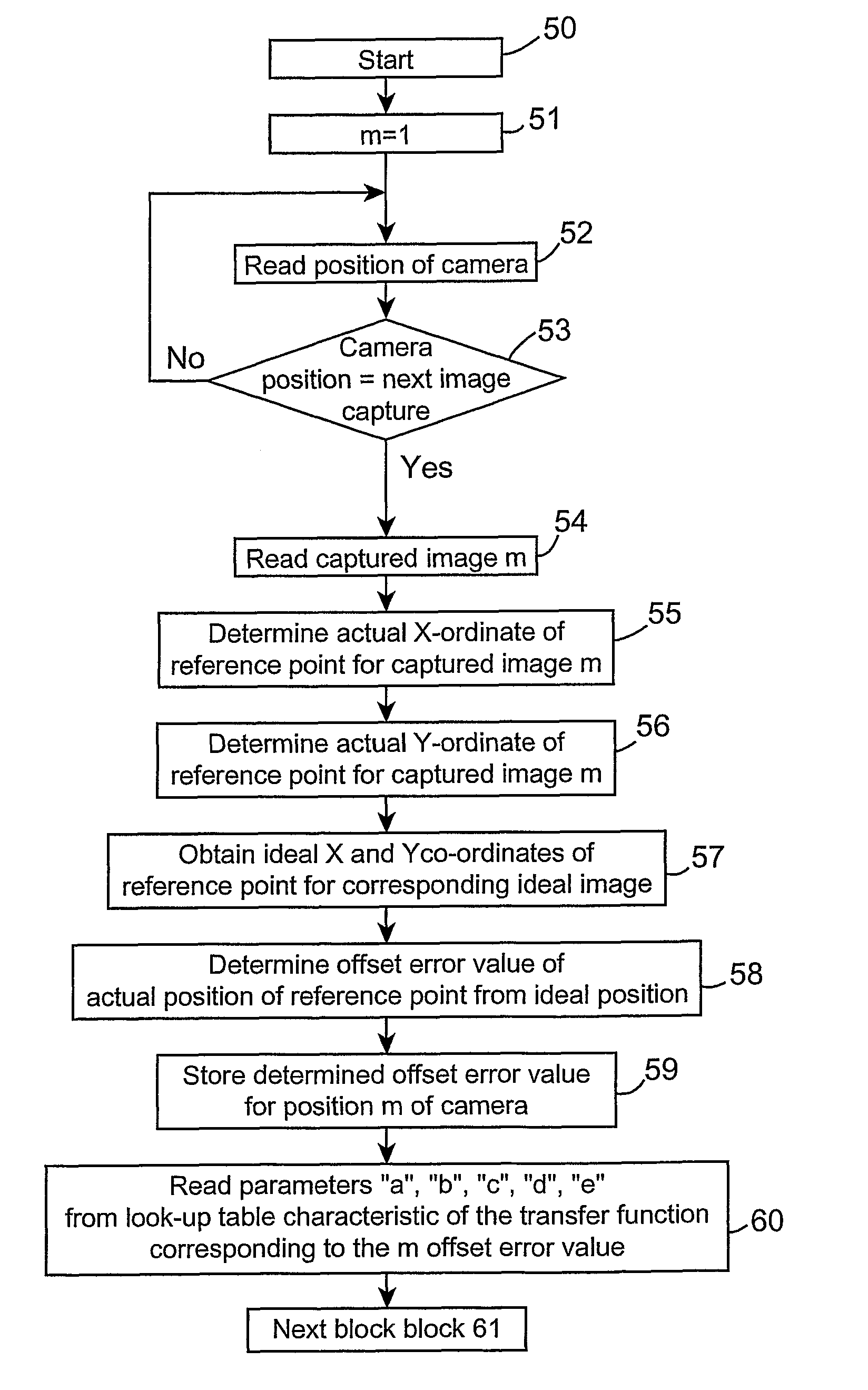
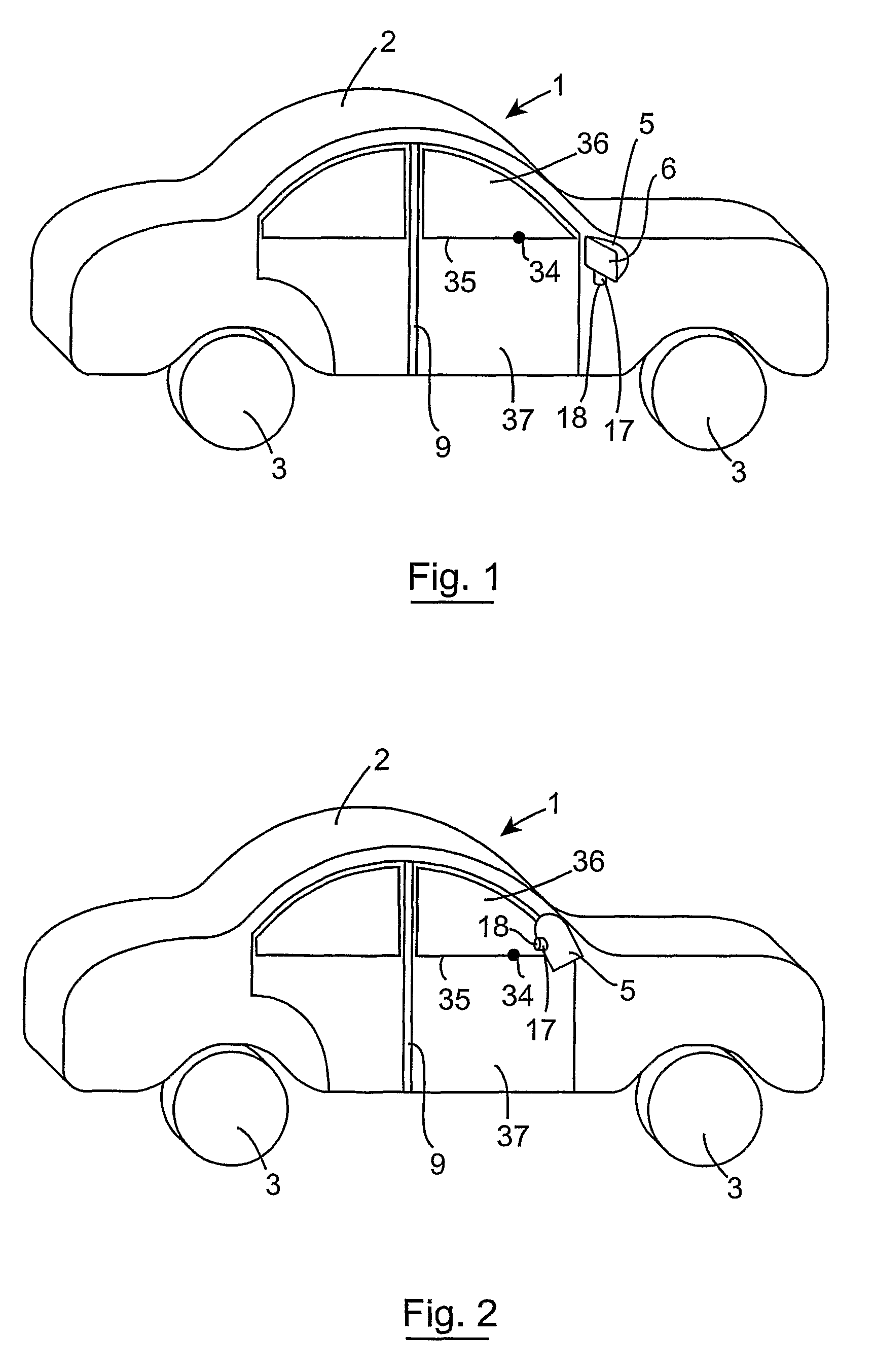
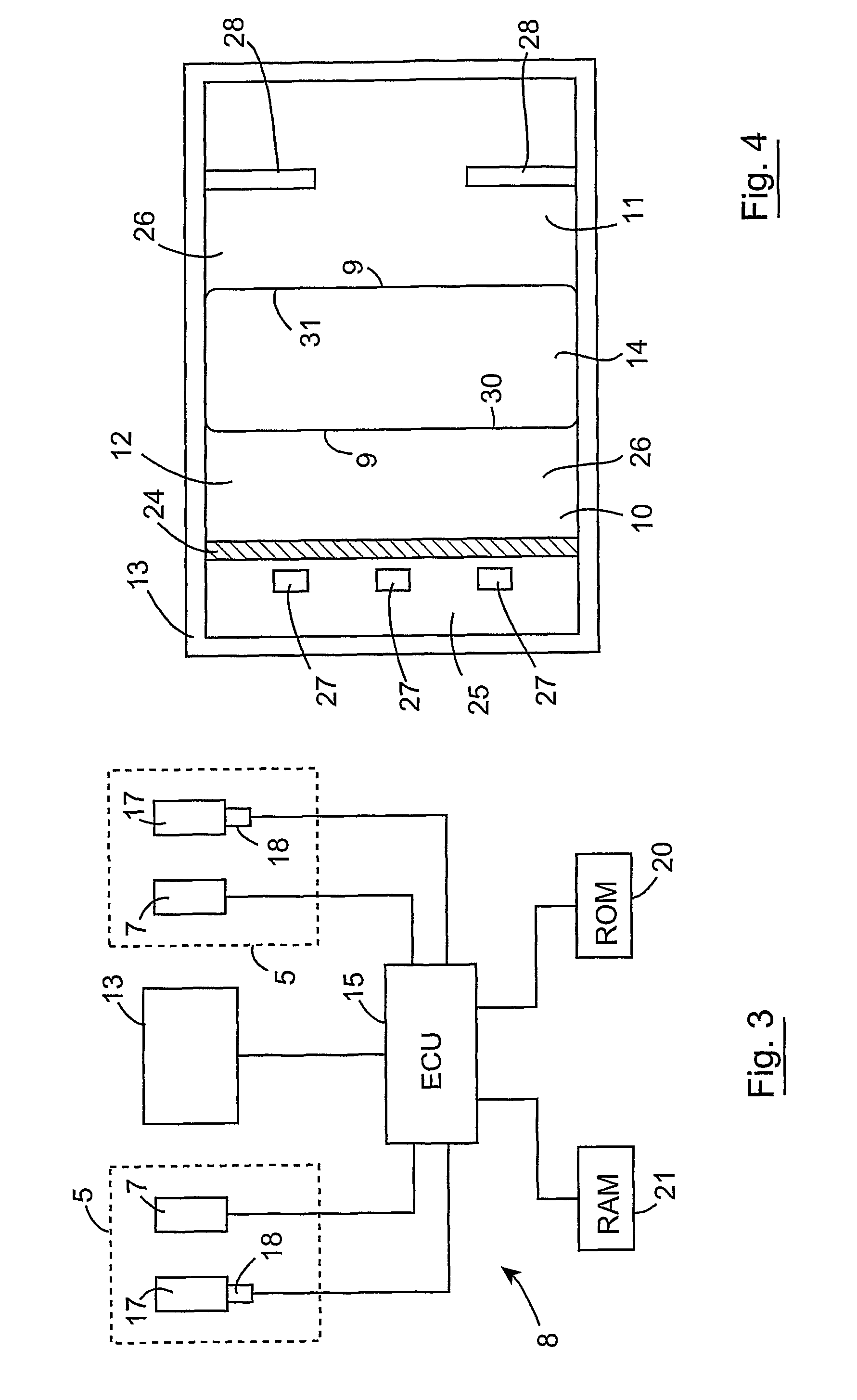
Method and apparatus for calibrating an image capturing device, and a method and apparatus for outputting image frames from sequentially captured image frames with compensation for image capture device offset
ActiveUS7949486B2Accurate CalibrationAutomatically calibratingTelevision system detailsImage enhancementRest positionIn vehicle
A camera (17) mounted on a rear view minor housing (5) of a vehicle (1), which captures a plan view image of the ground on one side of the vehicle for display on an in-vehicle visual display unit (13) is calibrated to correct for offset of the camera (17) from an ideal position. During calibration an image of a reference point (34) on the vehicle (1) is captured as the mirror housing (5) is swiveled from a rest position to an operative position. The offset of the actual position of the image of the reference point in the captured image from its ideal position is computed, and a look-up table is prepared, which indicates the position at which pixels of subsequently captured image frames should be located to produce image frames with offset correction.
Owner:CONNAUGHT ELECTRONICS
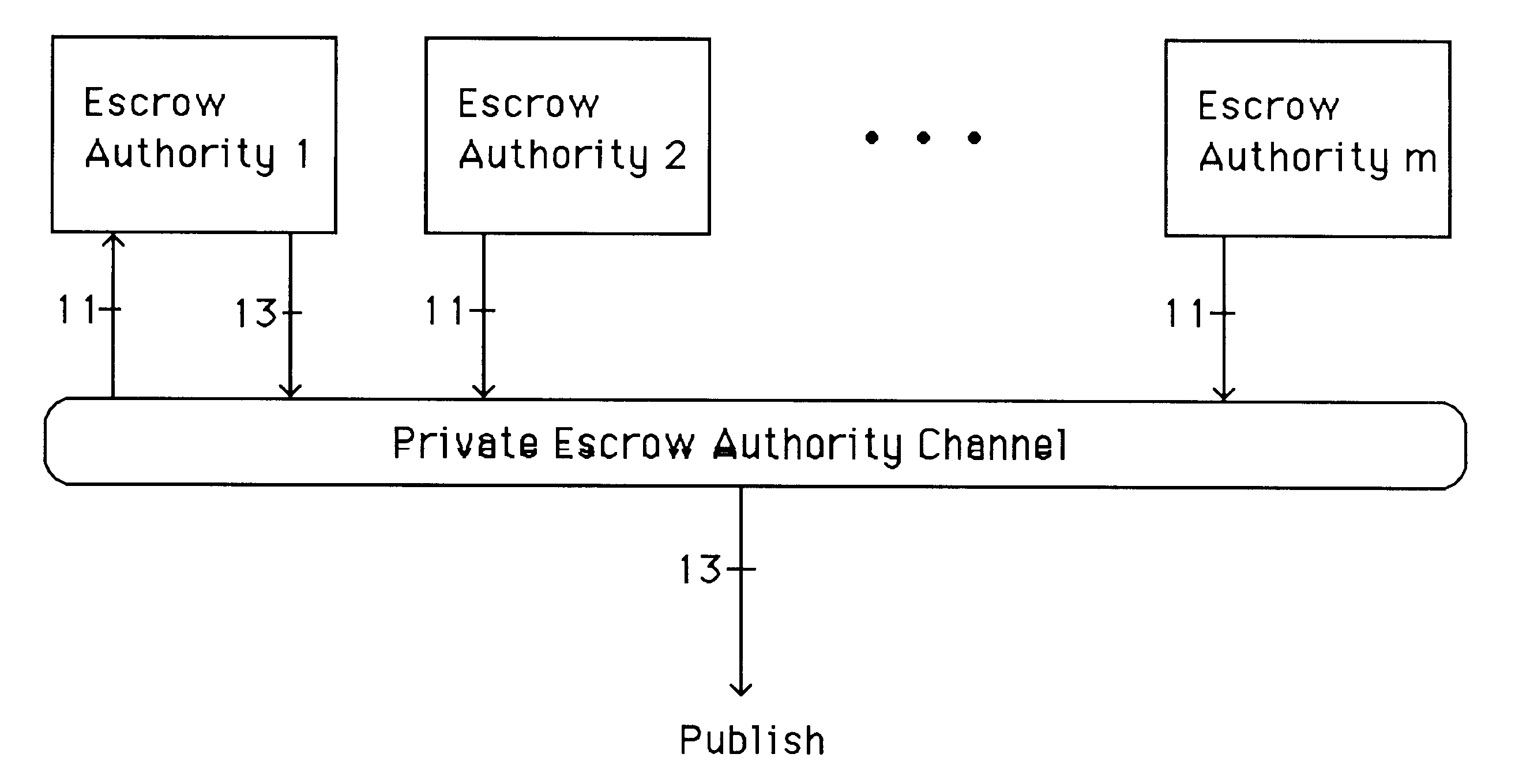
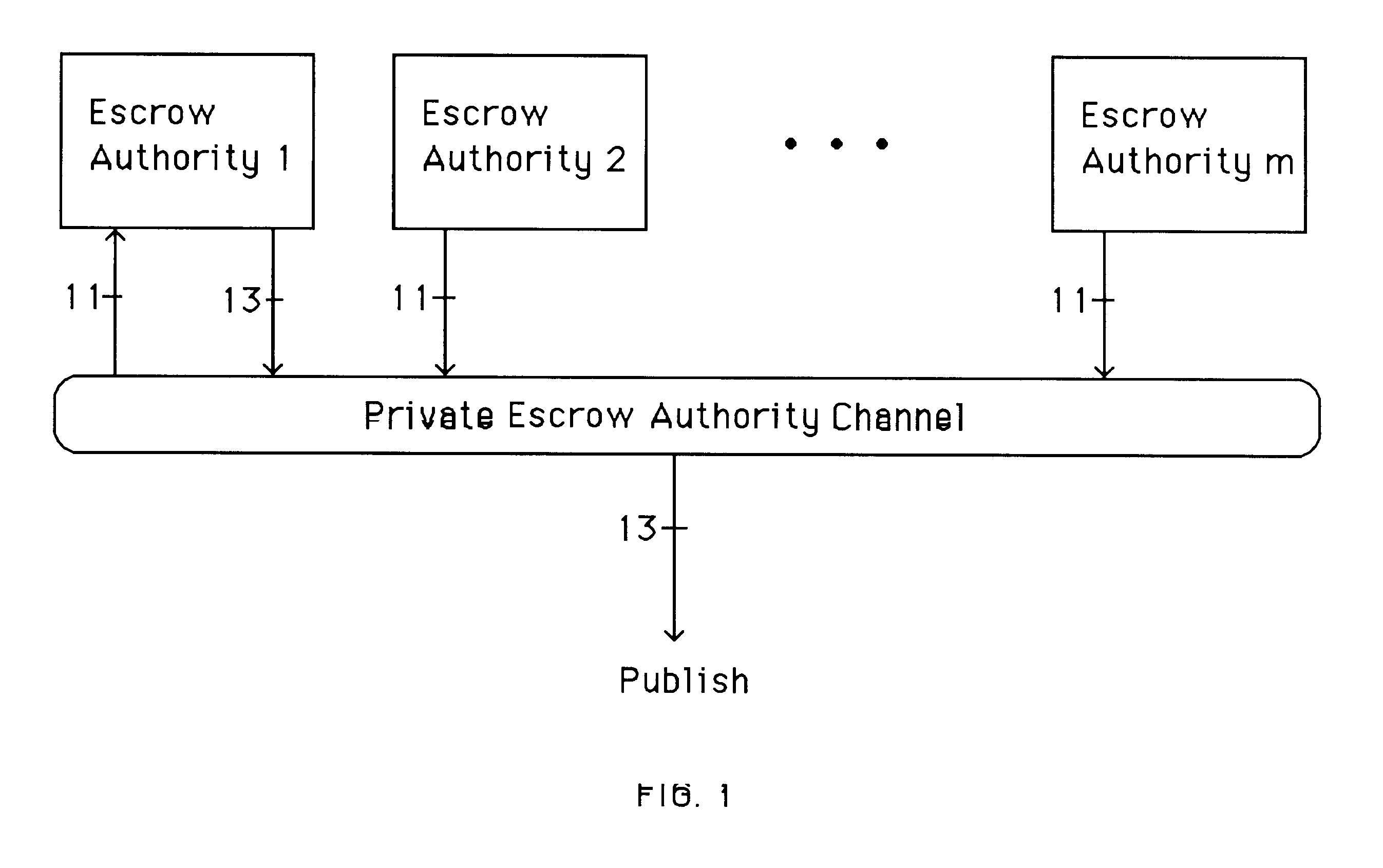
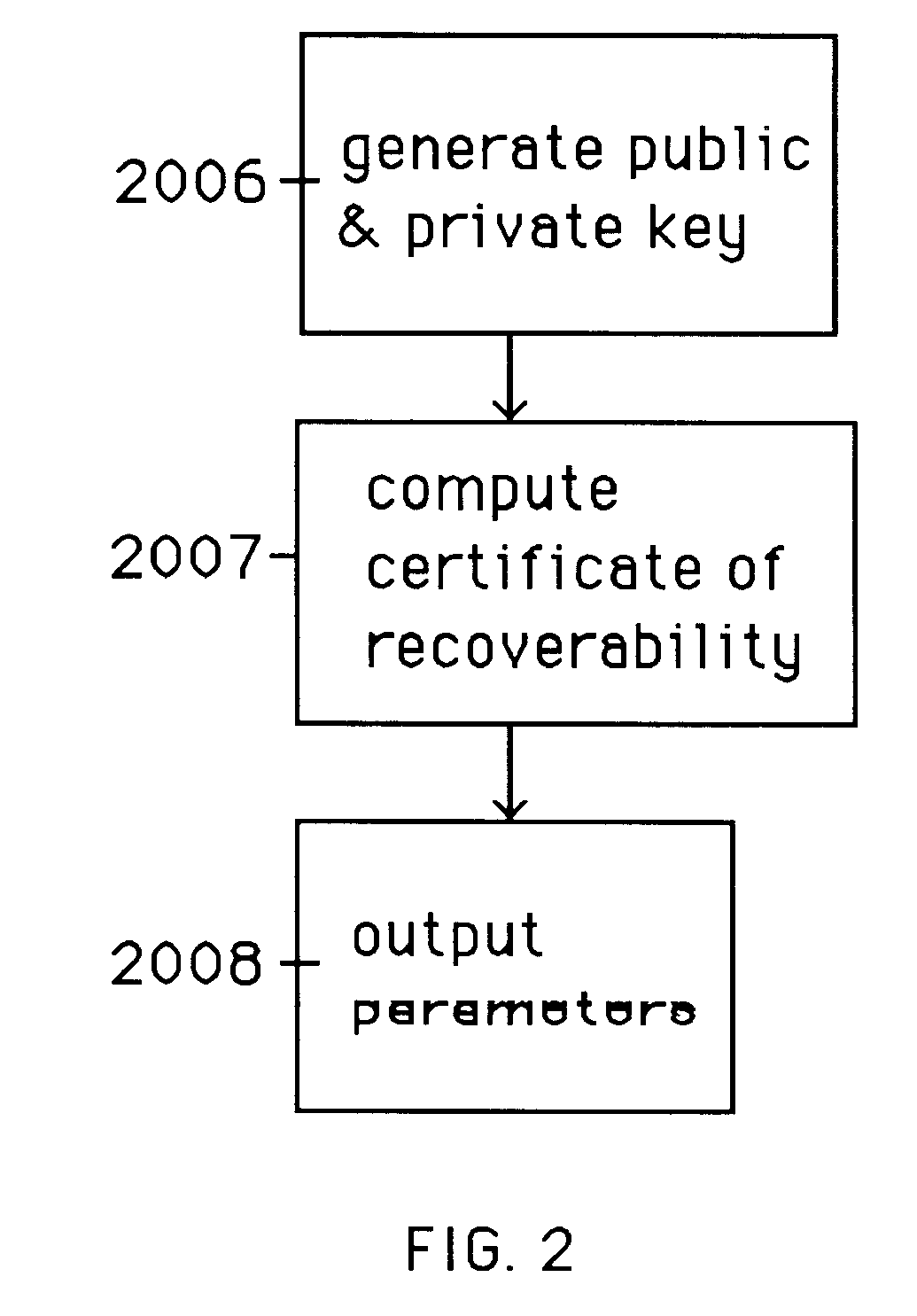
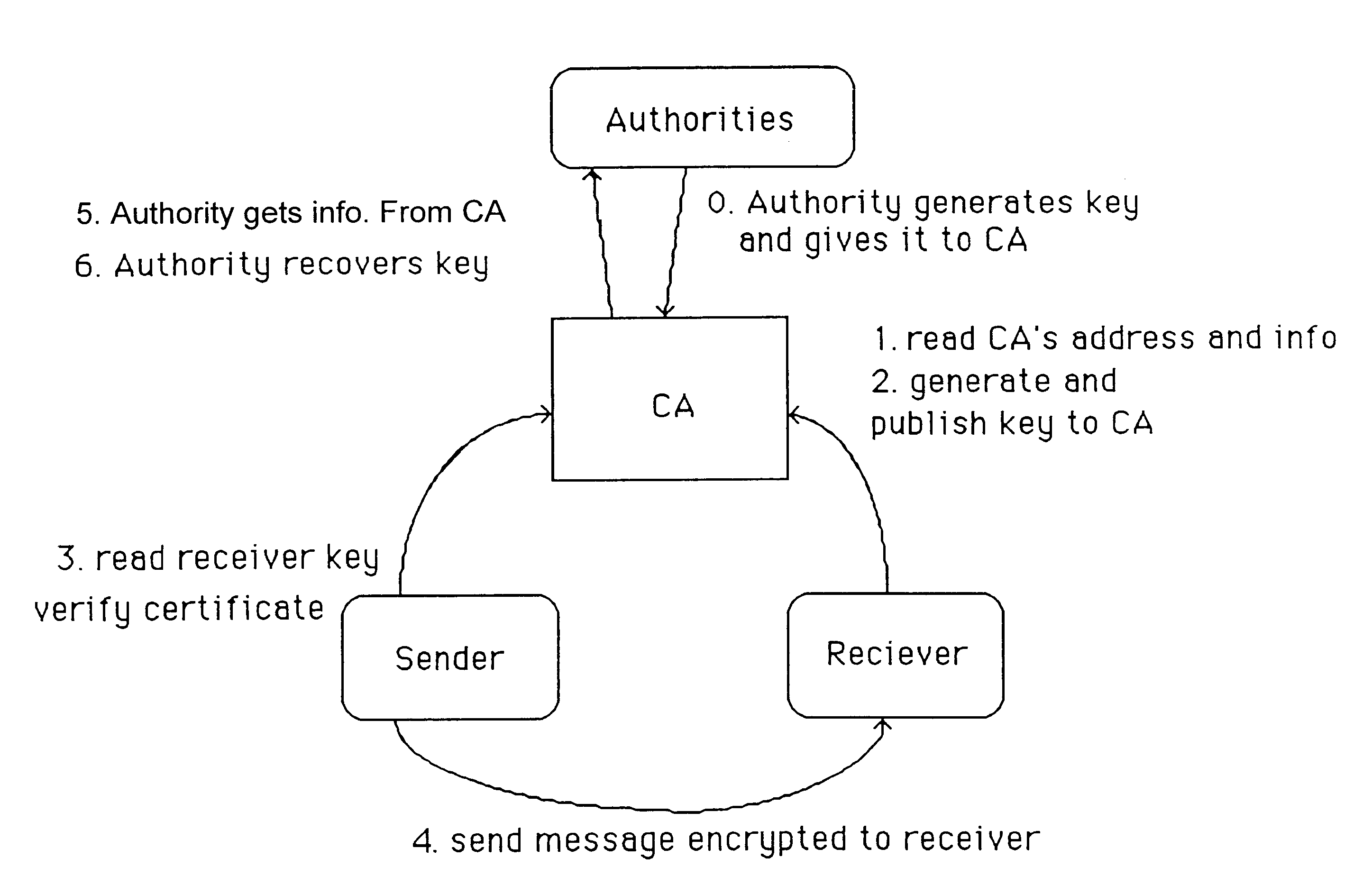
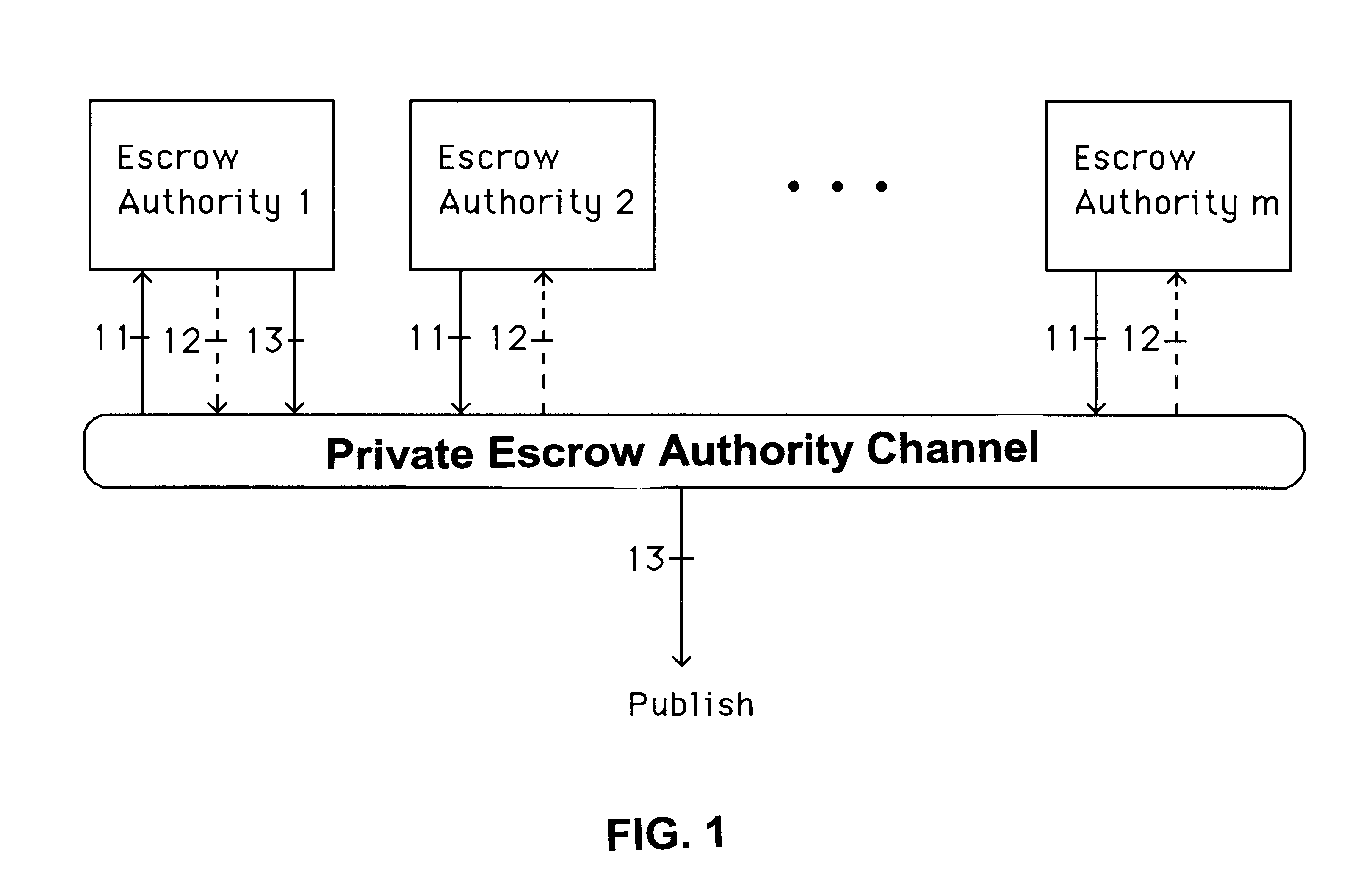
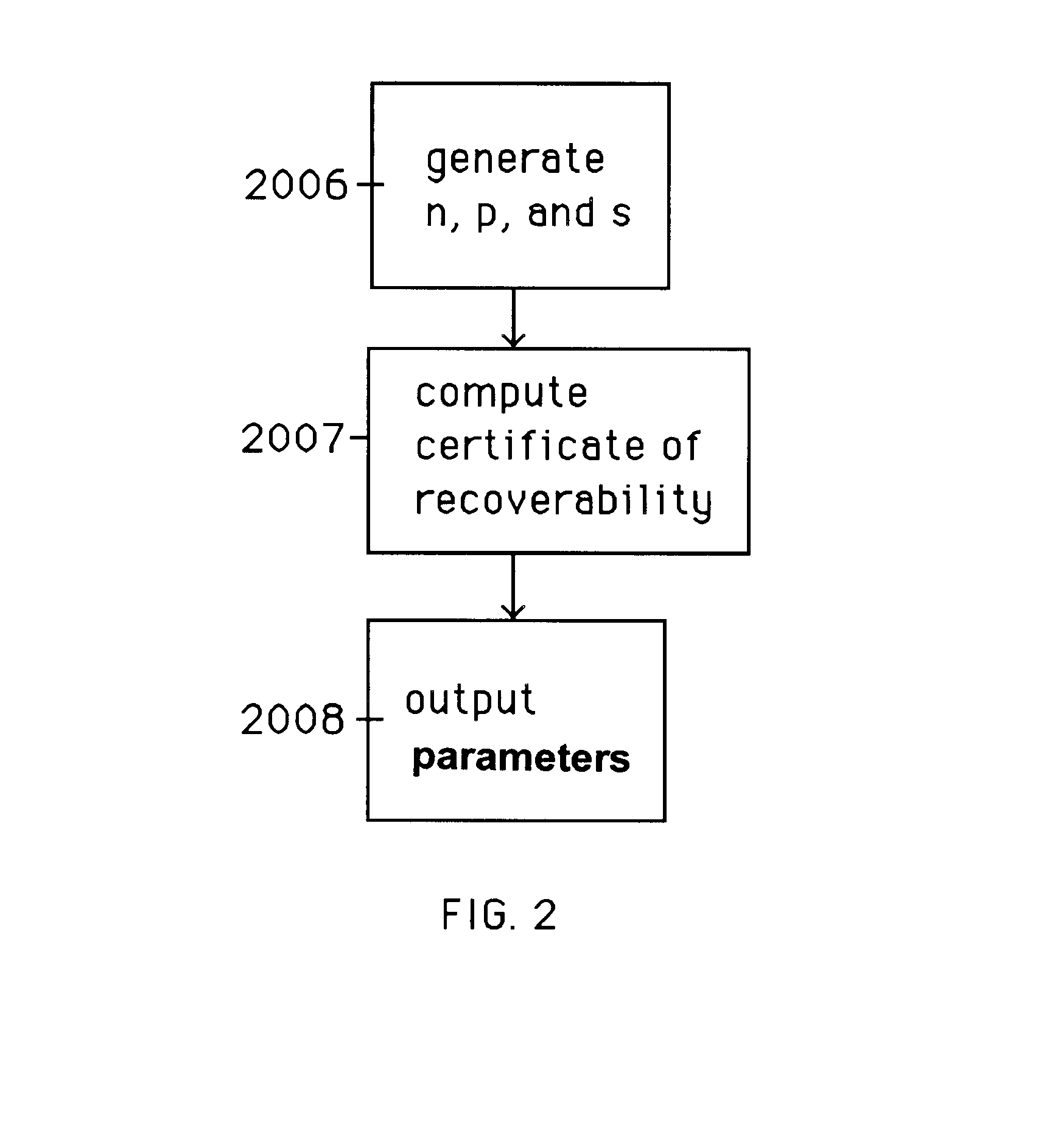
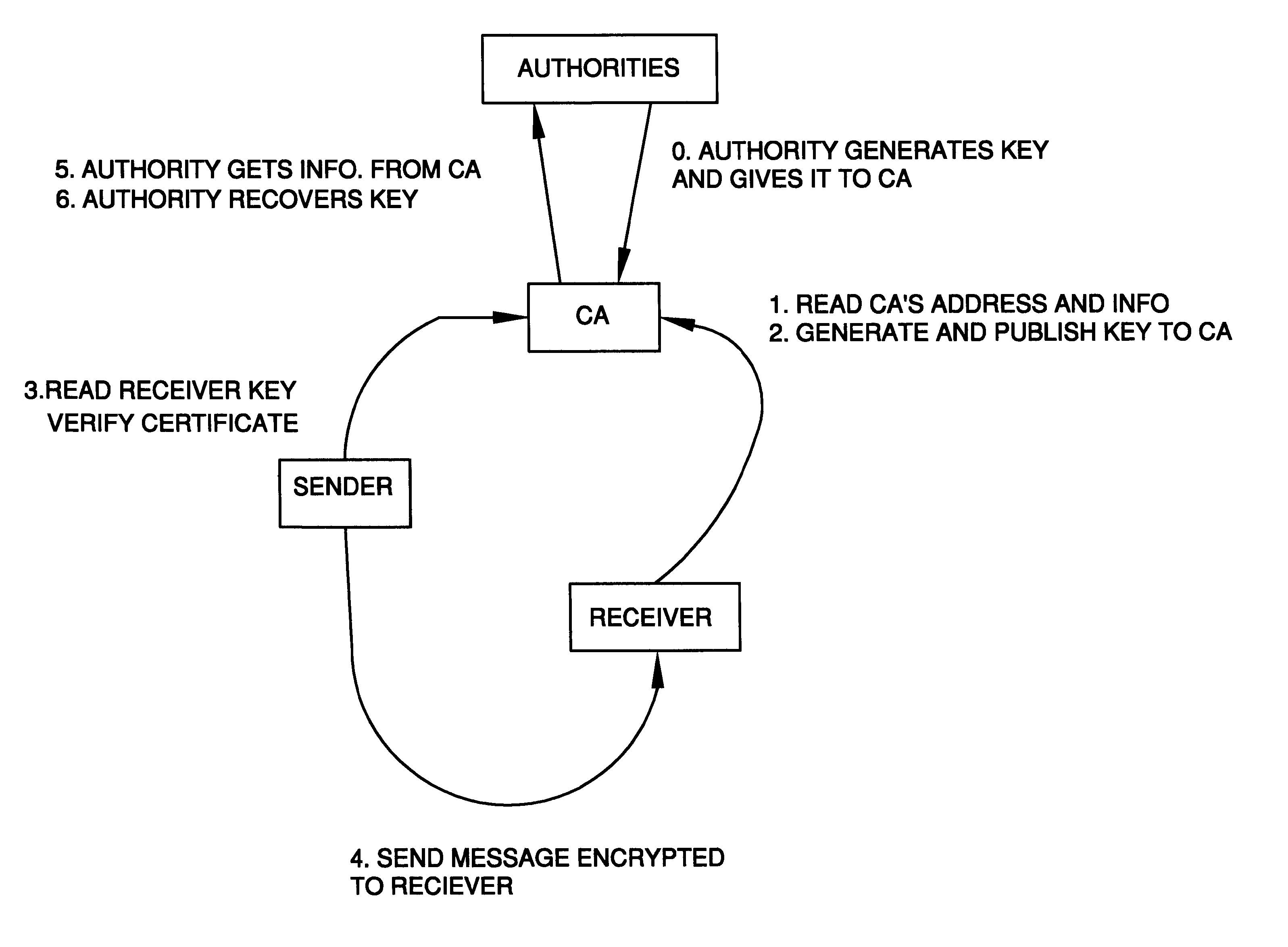
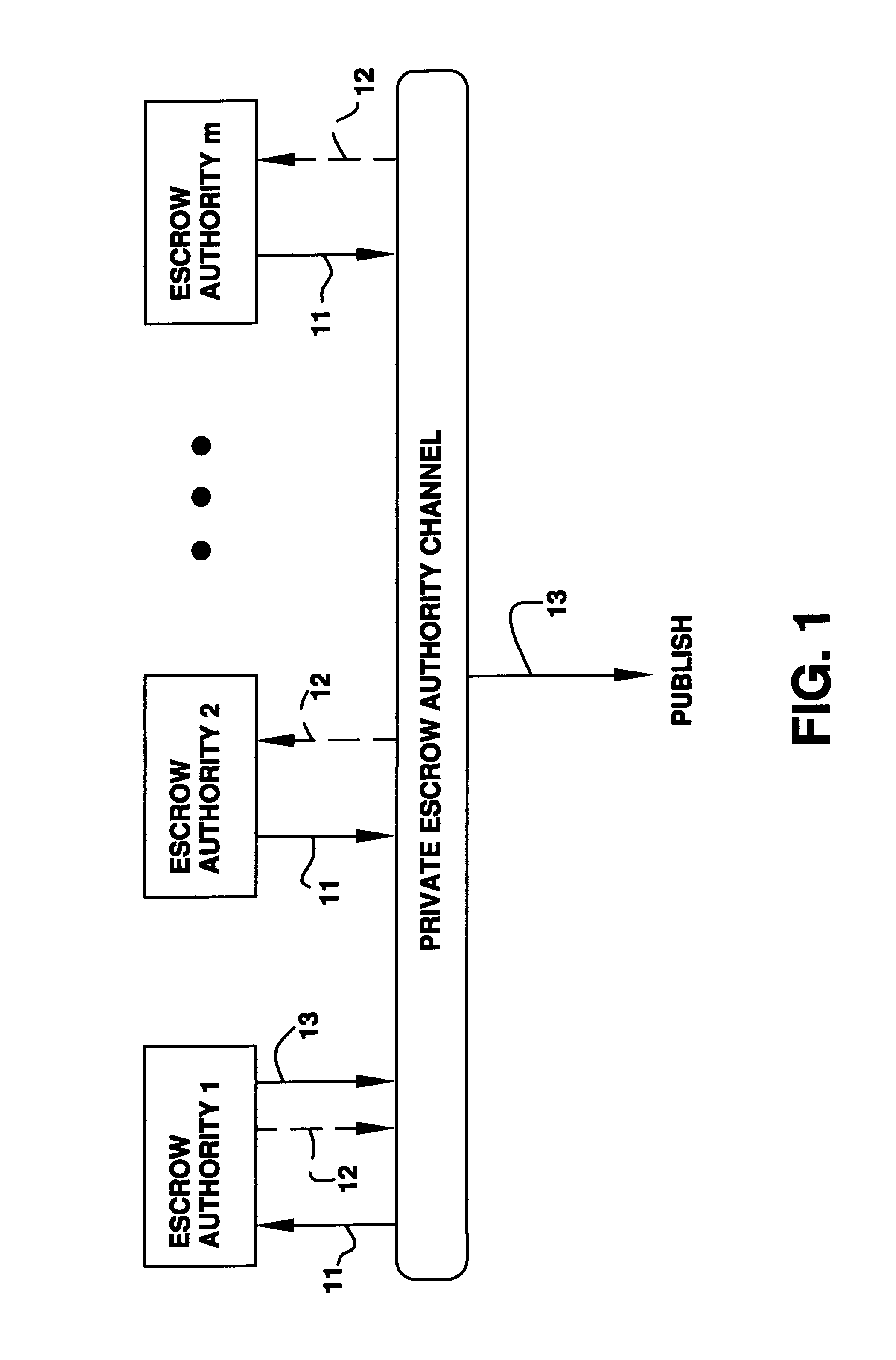
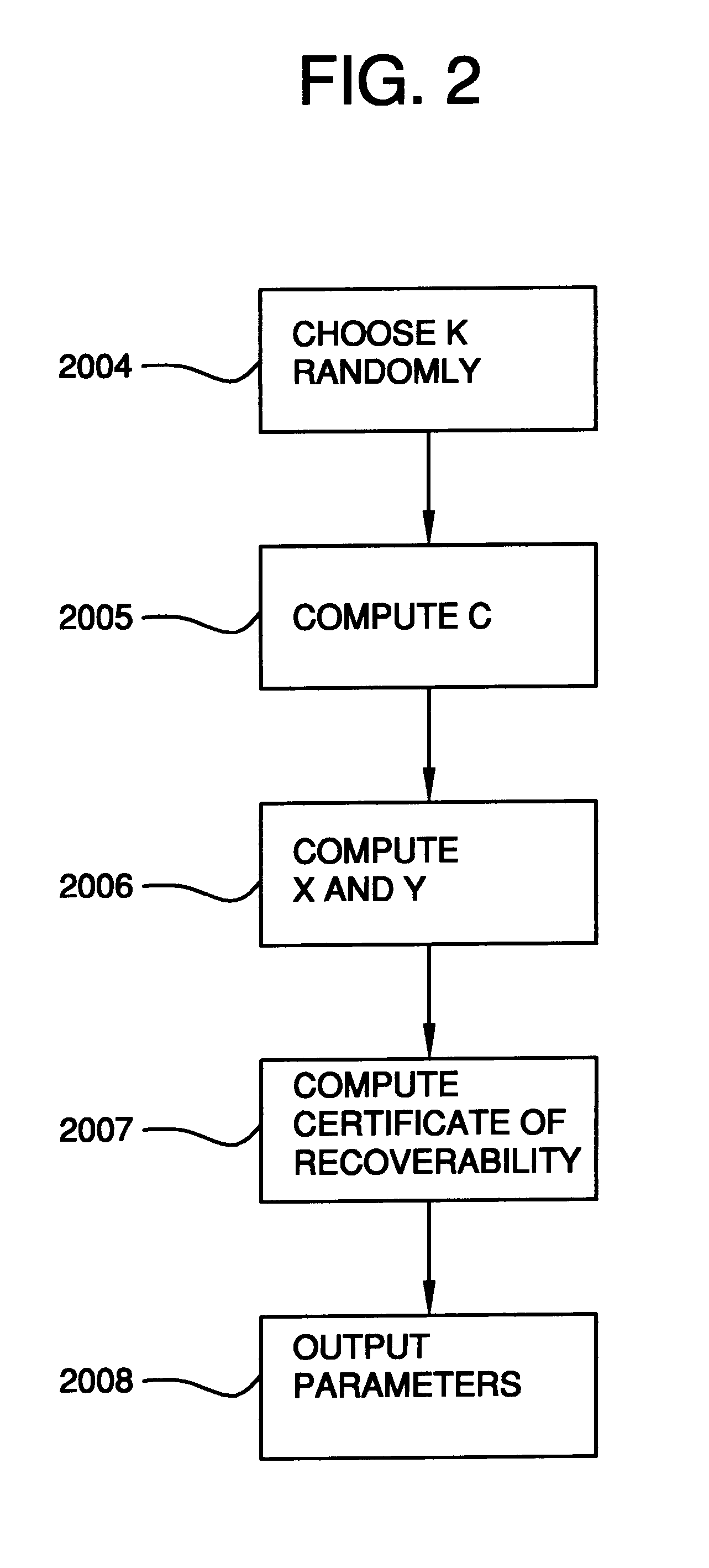
Auto-recoverable and auto-certifiable cryptostem using zero-knowledge proofs for key escrow in general exponential ciphers
InactiveUS6282295B1Fast and easy disseminationEasy to handleKey distribution for secure communicationPublic key for secure communicationTrusted authorityValidation methods
A method is provided for an escrow cryptosystem that is essentially overhead-free, does not require a cryptographic tamper-proof hardware implementation (i.e., can be done in software), is publicly verifiable, and cannot be used subliminally to enable a shadow public key system. A shadow public key system is an unescrowed public key system that is publicly displayed in a covert fashion. The keys generated by the method are auto-recoverable and auto-certifiable (abbrev. ARC). The ARC Cryptosystem is based on a key generation mechanism that outputs a public / private key pair, and a certificate of proof that the key is recoverable by the escrow authorities. Each generated public / private key pair can be verified efficiently to be escrowed properly by anyone. The verification procedure does not use the private key. Hence, the general public has an efficient way of making sure that any given individual's private key is escrowed properly, and the trusted authorities will be able to access the private key if needed. Since the verification can be performed by anyone, there is no need for a special trusted entity, known in the art as a "trusted third party". The proof and verification method involves one party proving to a second party that a third party can gain access to an encrypted value. In addition, the system is designed so that its internals can be made publicly scrutinizable (e.g., it can be distributed in source code form). This differs from many schemes which require that the escrowing device be tamper-proof hardware. The system is efficient and can be implemented as a "drop-in" replacement to an RSA or ElGamal cryptosystem. The system is applicable for lawenforcement, file systems, e-mail systems, certified e-mail systems, and any scenario in which public key cryptography can be employed and where private keys or information encrypted under public keys need to be recoverable. The system security relies solely on the security of cipher systems involved whose security has been extensively studied in the past.
Owner:CRYPTOPEAK SECURITY LLC
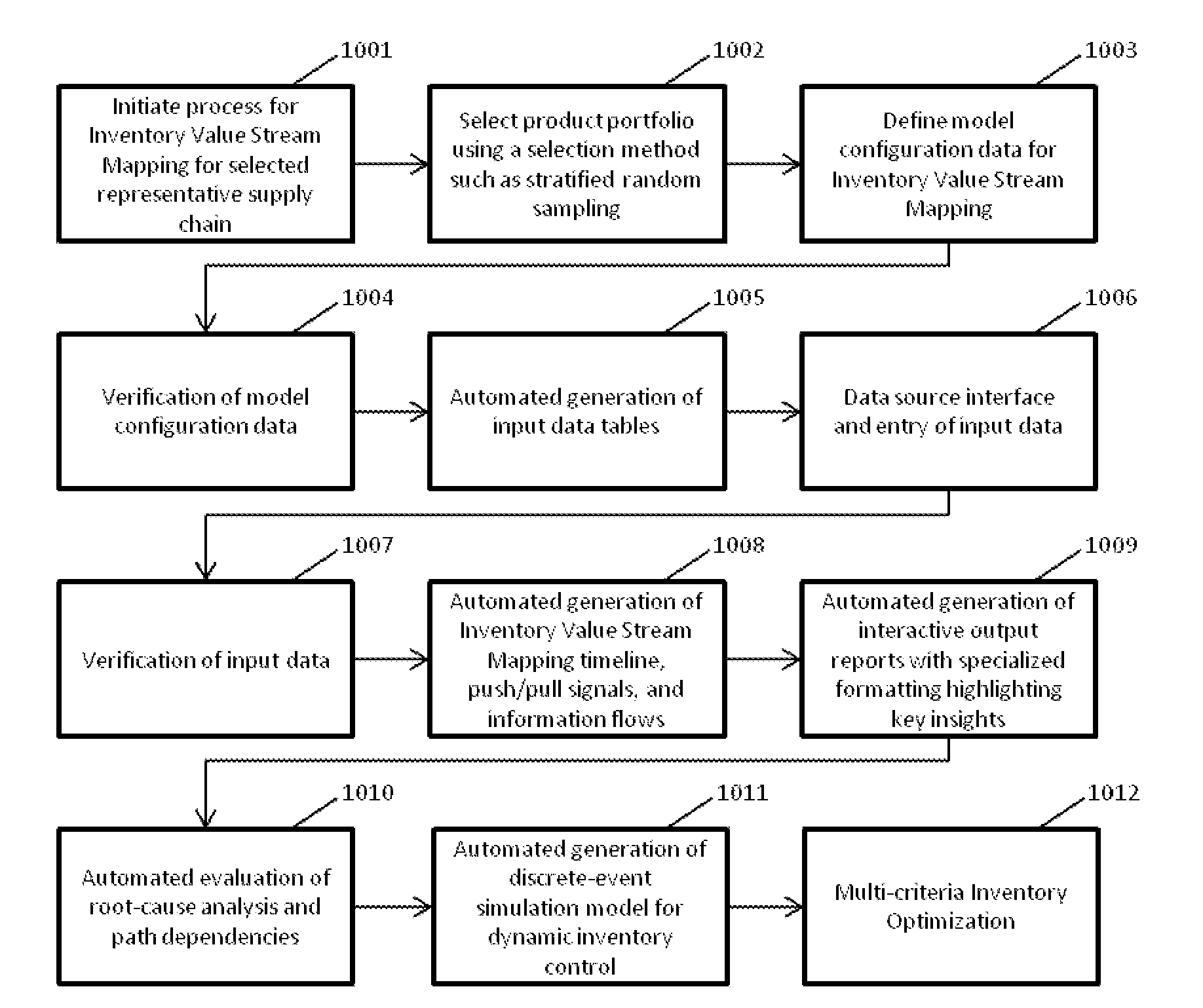
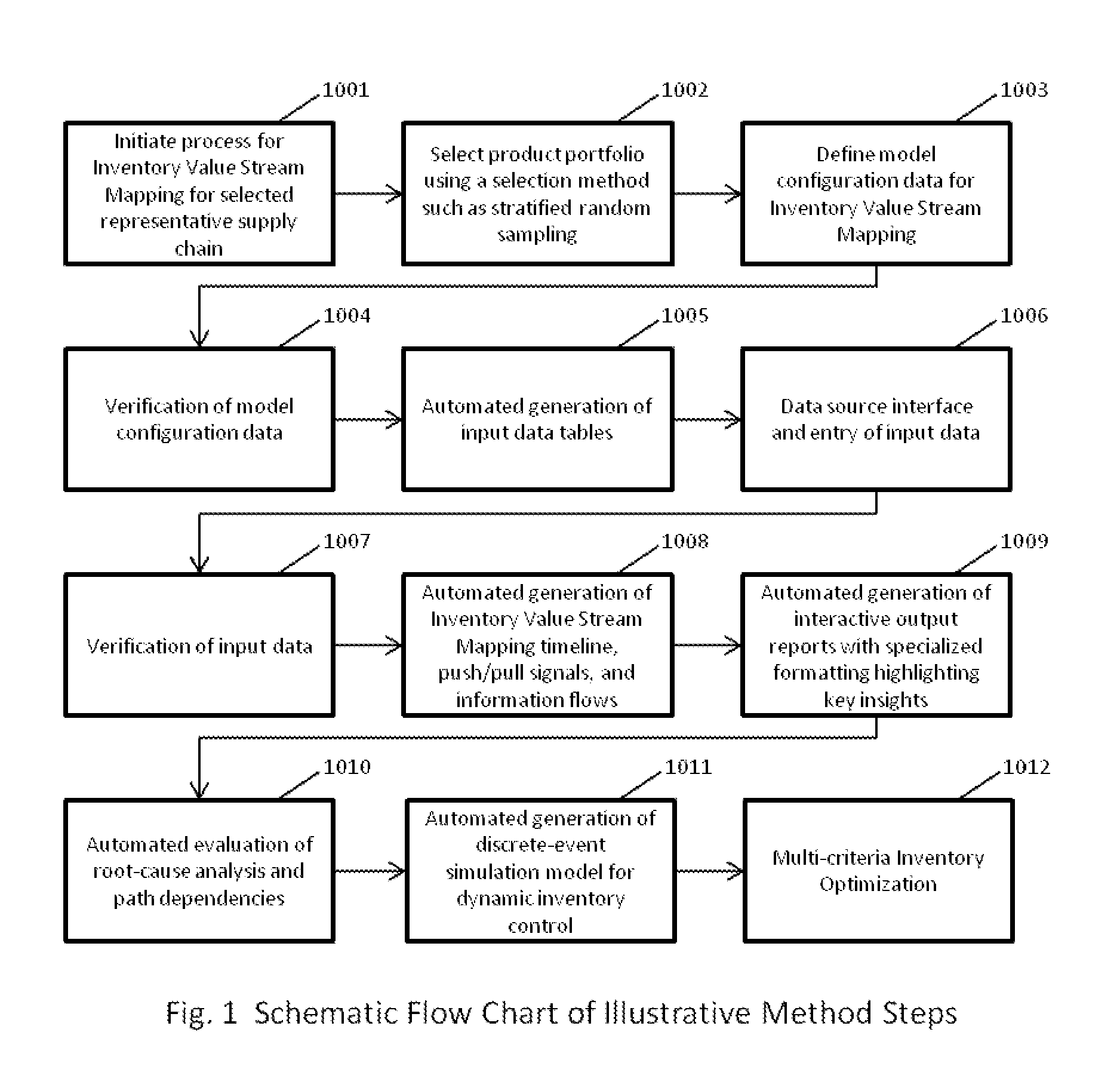
Supply Chain Analysis
InactiveUS20130018696A1Efficient analysisEasy to operateForecastingResourcesComputer scienceInventory optimization
The disclosure relates to analyzing and visualizing flows in a supply chain context for the purpose of inventory optimization. Embodiments disclosed include a method of analyzing a process flow in a supply chain context, the method comprising: inputting (3402) a first set of data to an application residing on a processor, relating to products, locations and supply routes connecting the different locations in the supply chain; the application generating (3403) from the first set of data an input data array; inputting (3404) a second set of data relating to measured and forecast flows of products through the supply chain over a defined time period; the application calculating (3405) from the data a series of measures of operation of the supply chain; and, based on one or more of the measures being outside a predefined range, the application generating (3406) an output indicating recommendations for adjusting operation of the supply chain.
Owner:EMPIRICA CONSULTING
Umbrella frame and operating system
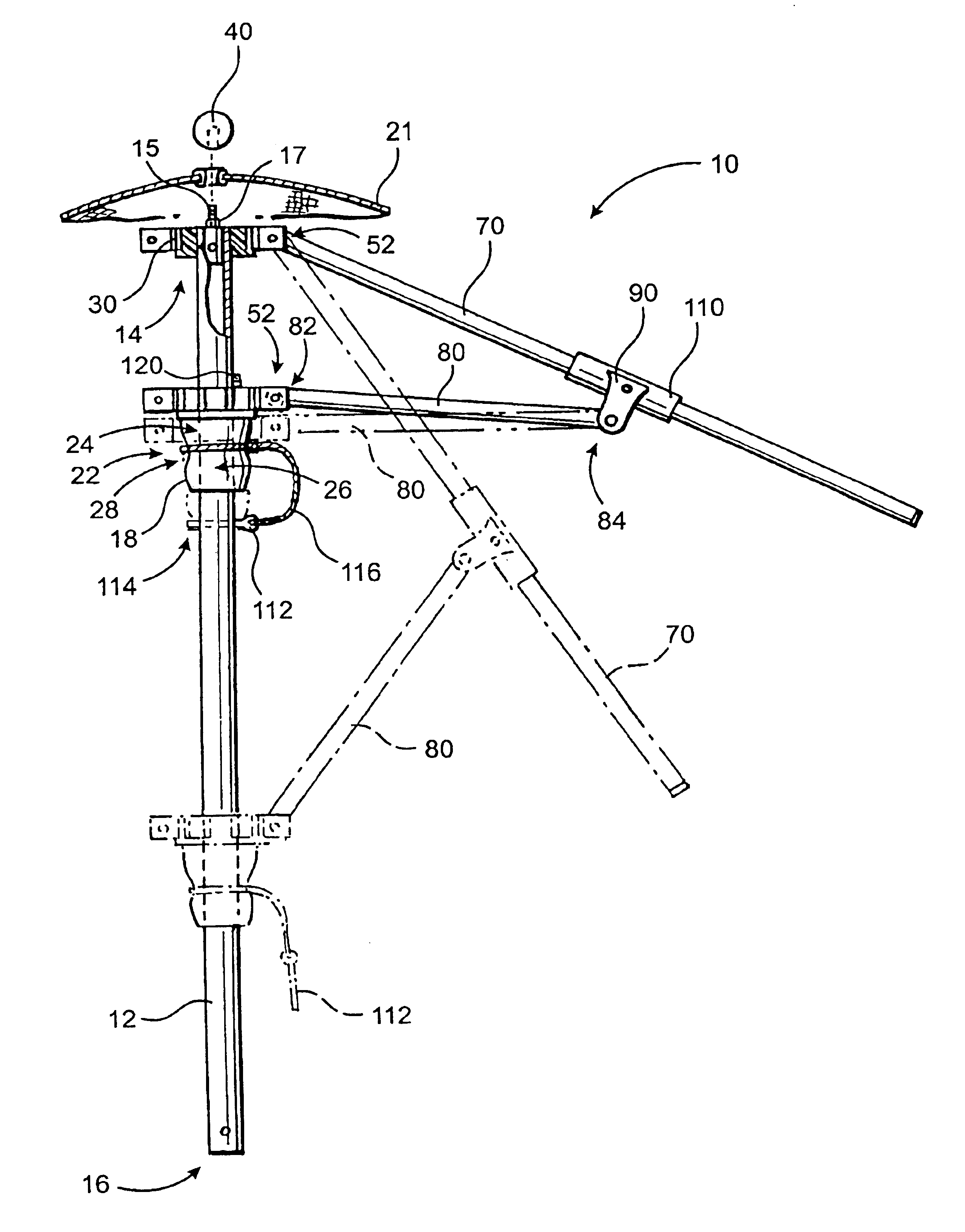
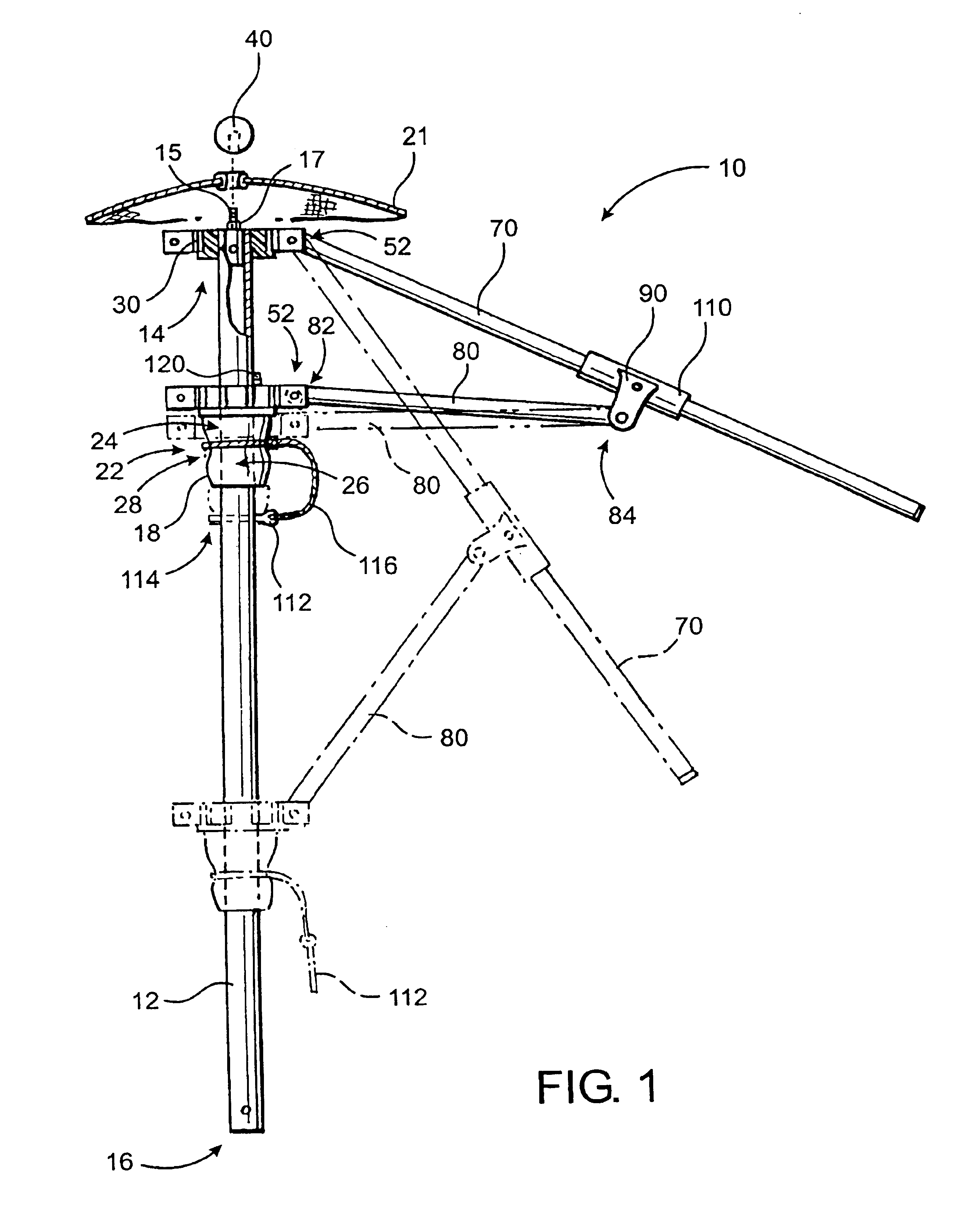
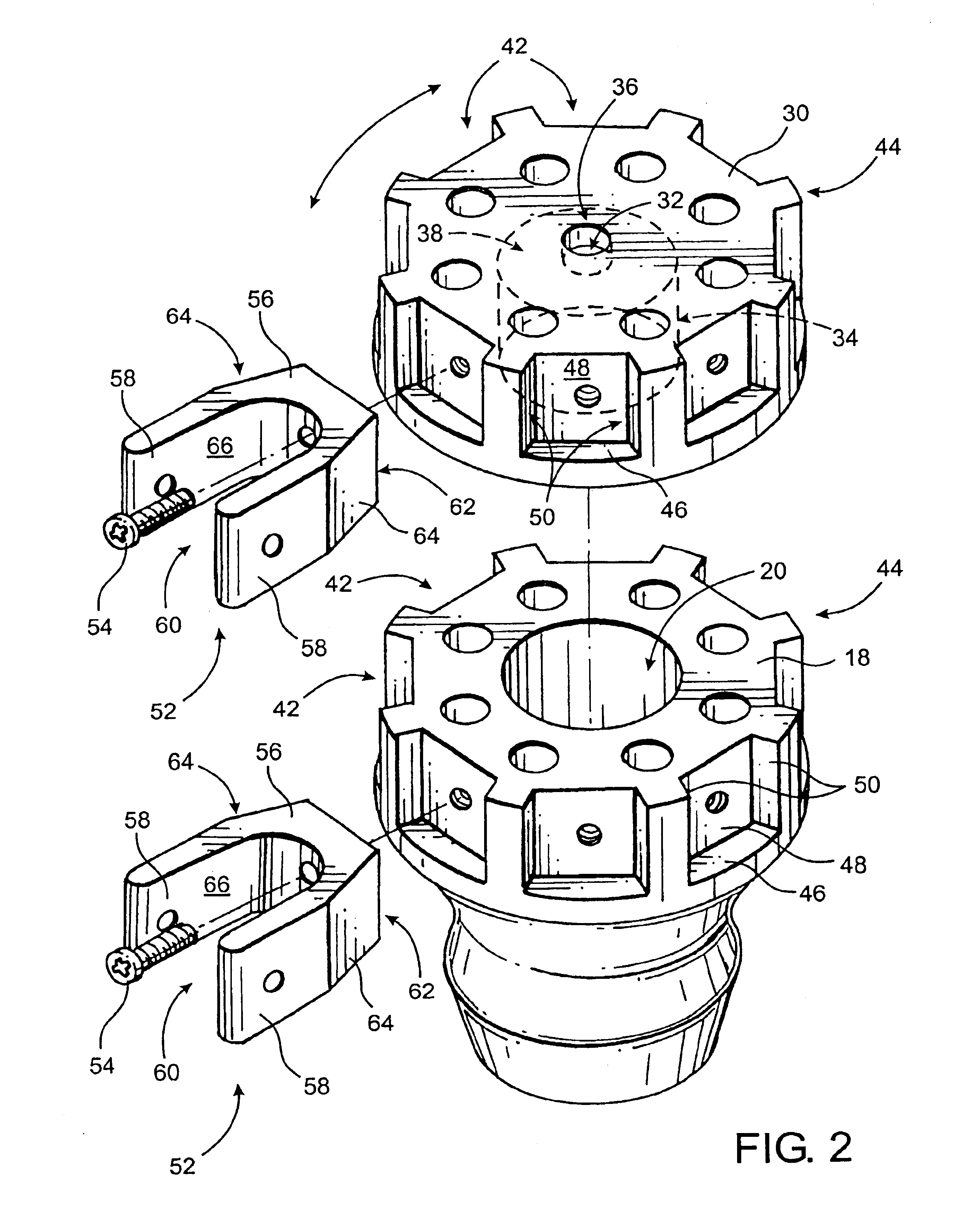
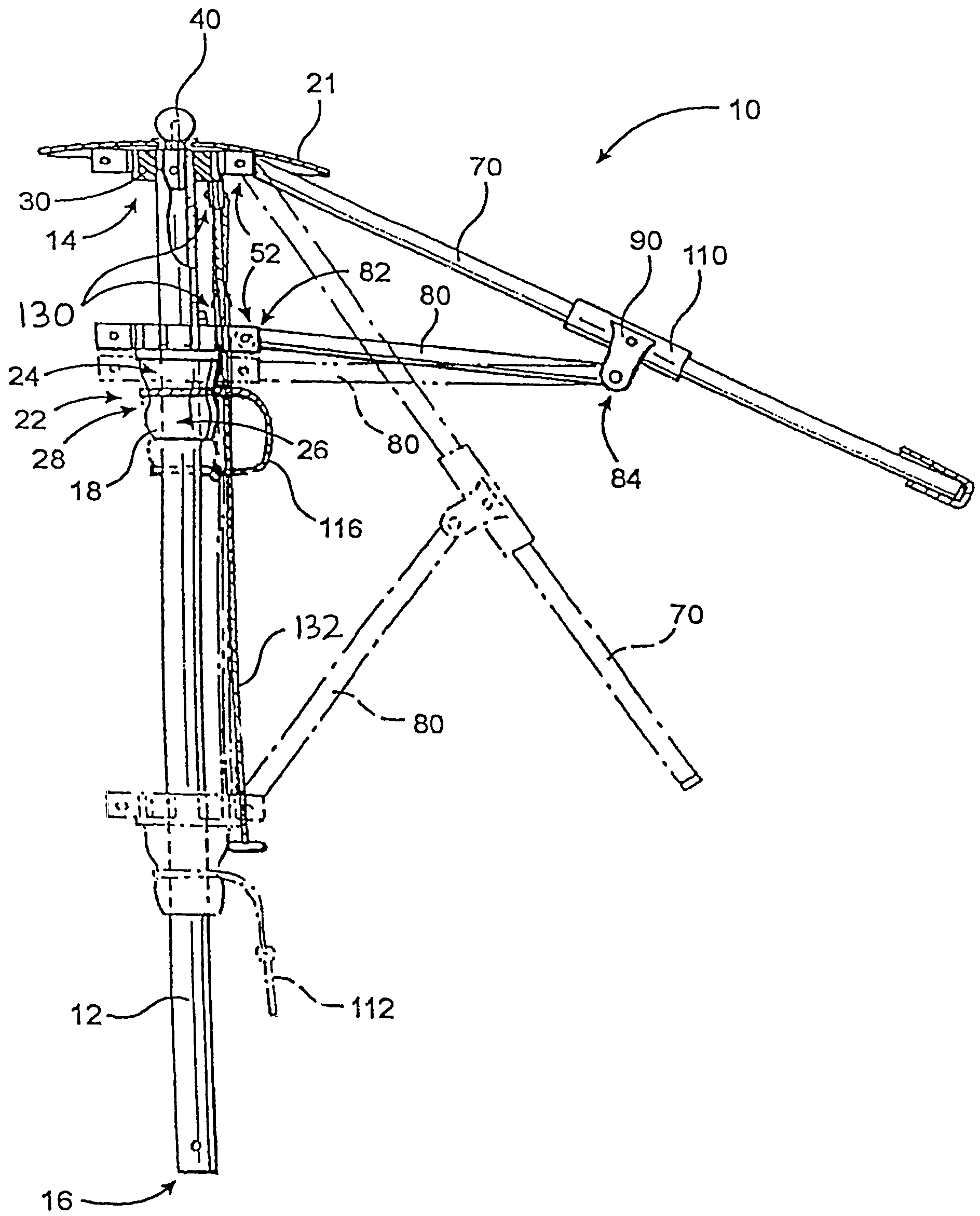
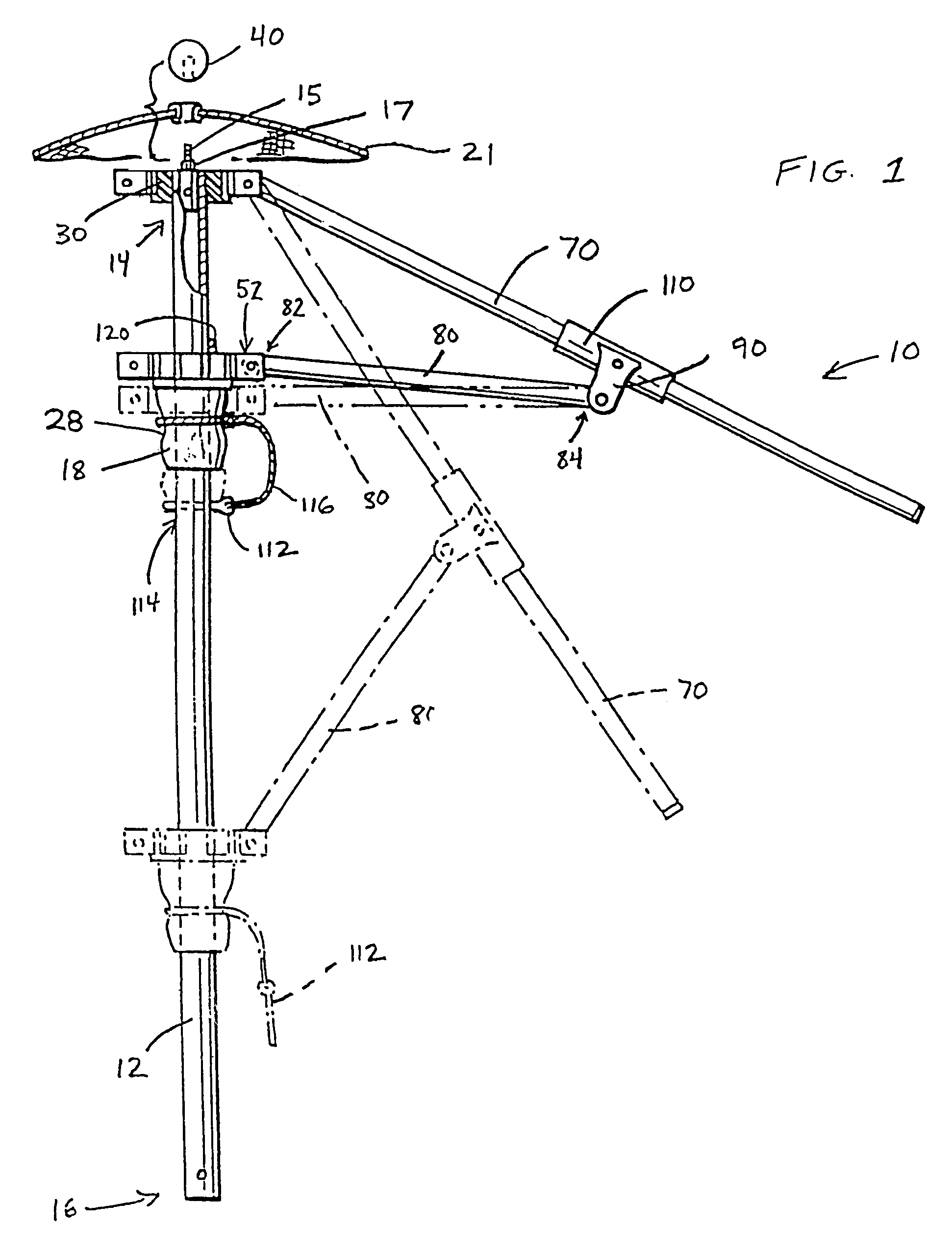
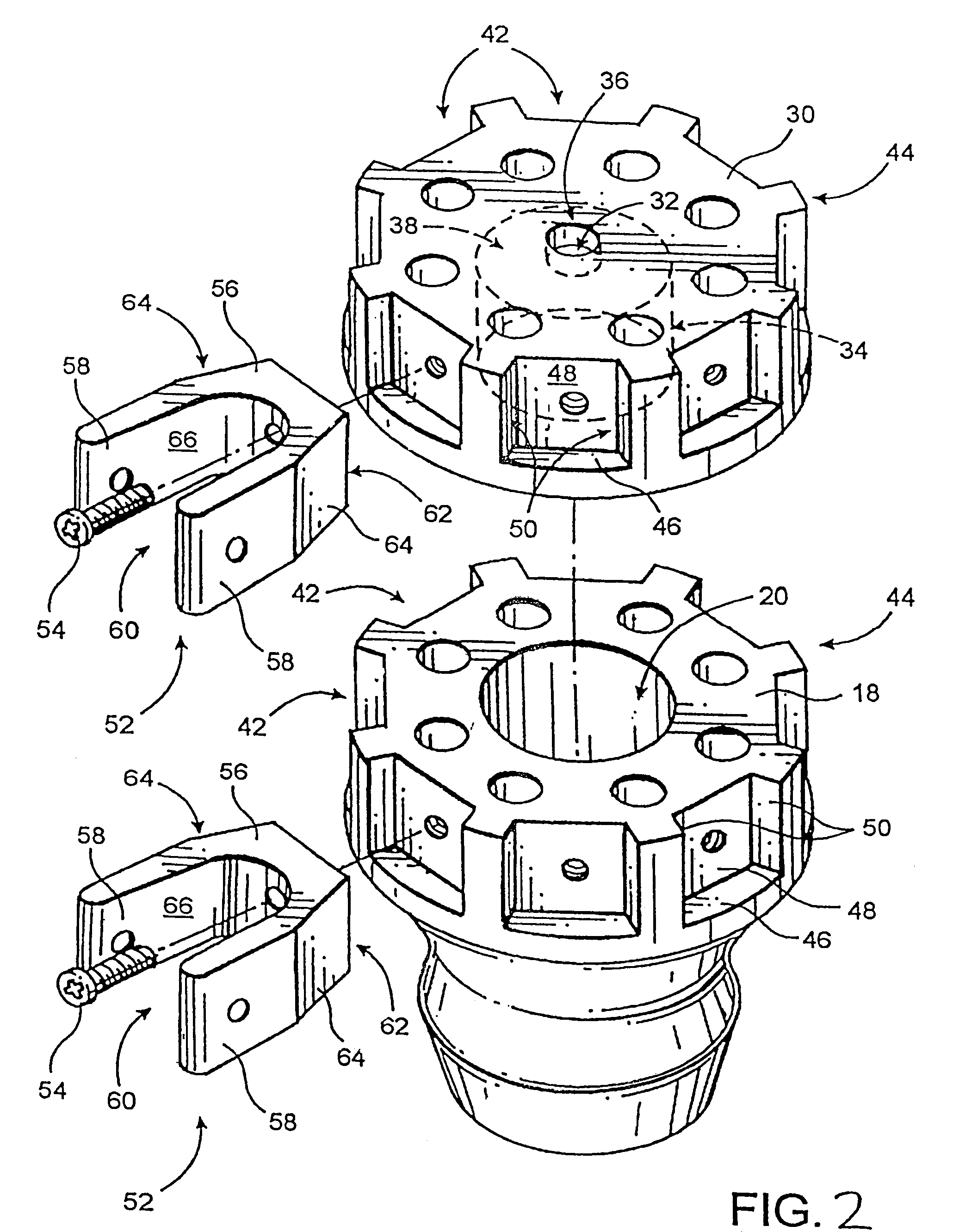
InactiveUS6889699B2Eliminate needQuickly and easily and inexpensively repairedWalking sticksUmbrellasFree rotationEngineering
An improved, durable and versatile umbrella frame assembly is provided to more readily endure abusive weather conditions and that may be quickly, easily and inexpensively repaired. In addition, the assembly is also easily modified to accommodate umbrella canopies of different sizes and shapes. In addition, an improved umbrella operating system is provided to permit simple opening, positioning, and locking of an umbrella while allowing the frame to freely rotate about the pole regardless of the degree to which it is opened, while the pole is held in a stationary position. The assembly includes a pair of hub members mounted about a pole member wherein the main hub member is slidable up and down the pole. A pulley system with a locking cam member may be employed to allow the umbrella to safely and easily open to any desired position. A locking stabilizer arm may be used to secure the main hub member in the fully open position.
Owner:TUUCI WORLDWIDE
Auto-Recoverable and Auto-certifiable cryptosystems with RSA or factoring based keys
InactiveUS6389136B1Fast and easy disseminationEasy to handleKey distribution for secure communicationPublic key for secure communicationTrusted authorityComposite number
A method is provided for an escrow cryptosystem that is essentially overhead-free, does not require a cryptographic tamper-proof hardware implementation (i.e., can be done in software), is publicly verifiable, and cannot be used subliminally to enable a shadow public key system. The keys generated are based on composite numbers (like RSA keys). A shadow public key system is an unescrowed public key system that is publicly displayed in a covert fashion. The keys generated by the method are auto-recoverable and auto-certifiable (abbrev. ARC). The ARC Cryptosystem is based on a key generation mechanism that outputs a public / private key pair, and a certificate of proof that the key is recoverable by the escrow authorities. Each generated public / private key pair can be verified efficiently to be escrowed properly by anyone. The verification procedure does not use the private key. Hence, the general public has an efficient way of making sure that any given individual's private key is escrowed properly, and the trusted authorities will be able to access the private key if needed. Since the verification can be performed by anyone, there is no need for a special trusted entity, known in the art as a "trusted third party". Furthermore, the system is designed so that its internals can be made publicly scrutinizable (e.g., it can be distributed in source code form). This differs from many schemes which require that the escrowing device be tamper-proof hardware. The system is efficient and can be implemented as a "drop-in" replacement to an RSA or Rabin cryptosystem. The system is applicable for law-enforcement, file systems, e-mail systems, certified e-mail systems, and any scenario in which public key cryptography can be employed and where private keys or information encrypted under public keys need to be recoverable. Another aspect of the system is the possibility to organize it in a hierarchical tree structure, where each element in the tree is an escrow authority (or authorities) capable to recover keys and / or information encrypted under these keys within the subtree rooted at the authority (or authorities) and only within this subtree.
Owner:CRYPTOPEAK SECURITY LLC
Auto-escrowable and auto-certifiable cryptosystems
InactiveUS6202150B1Fast and easy disseminationEasy to handleKey distribution for secure communicationUser identity/authority verificationTrusted authorityTamper proof hardware
A method is provided for an escrow cryptosystem that is overhead-free, does not require a cryptographic tamper-proof hardware implementation (i.e., can be done in software), is publicly verifiable, and cannot be used subliminally to enable a shadow public key system. A shadow public key system is an unescrowed public key system that is publicly displayed in a covert fashion. The key generated by the method are auto-recoverable and auto-certifiable (abbrev. ARC). The ARC Cryptosystem is based on a key generation mechanism that outputs a public / private key pair, and a certificate of proof that the key was generated according to the algorithm. Each generated public / private key pair can be verified efficiently to be escrowed properly by anyone. The verification procedure does not use the private key. Hence, the general public has an efficient way of making sure that any given individual's private key is escrowed properly, and the trusted authorities will be able to access the private key if needed. Since the verification can be performed by anyone, there is no need for a special trusted entity, known in the art as a "trusted third party". The cryptosystem is overhead free since there is no additional protocol interaction between the user who generates his or her own key, and the certification authority or the escrow authorities, in comparison to what is required to submit the public key itself in regular certified public key systems. Furthermore, the system is designed so that its internals can be made publicly scrutinizable (e.g., it can be distributed in source code form). This differs from many schemes which require that the escrowing device be tamper-proof hardware.
Owner:CRYPTOPEAK SECURITY LLC
Dry Powder Aerosolized Inhaler
InactiveUS20090025720A1Increase inhalation rateEffective wayRespiratorsLiquid surface applicatorsSide effectInhalation
This invention provides an aerosolized inhaler which enables the drug powder to aerosolize within the inhaler by breathing in the air, comprising the main body (11) and the mouthpiece connector (12) connected thereupon, wherein the inhaler the main body (11) has drug holding opening (1), which connects with the vortex passage, and the vortex passage connects with the mouthpiece (9) on the mouthpiece connector (12). It has many obvious advantages as increasing the inhalation rate, pushing more drug granule to reach to the lower respiratory tract and even into the alveolus; and meanwhile, keeping the drug from being blown out of the inhaler when the users breathes out, preventing from cross inflection and minimizing the side effect of the drug to the whole body, and obviously lightening the burden on the users.
Owner:CHEN QINGTANG +1
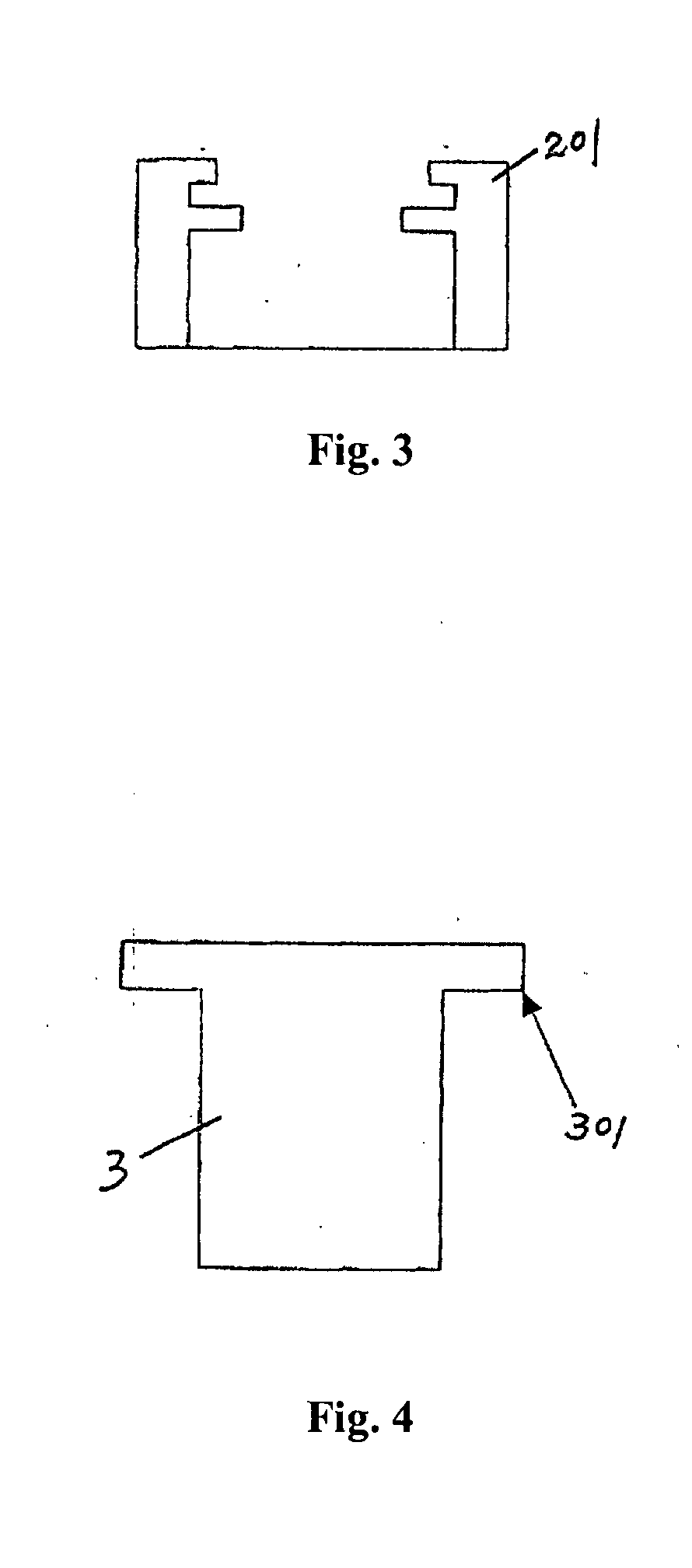
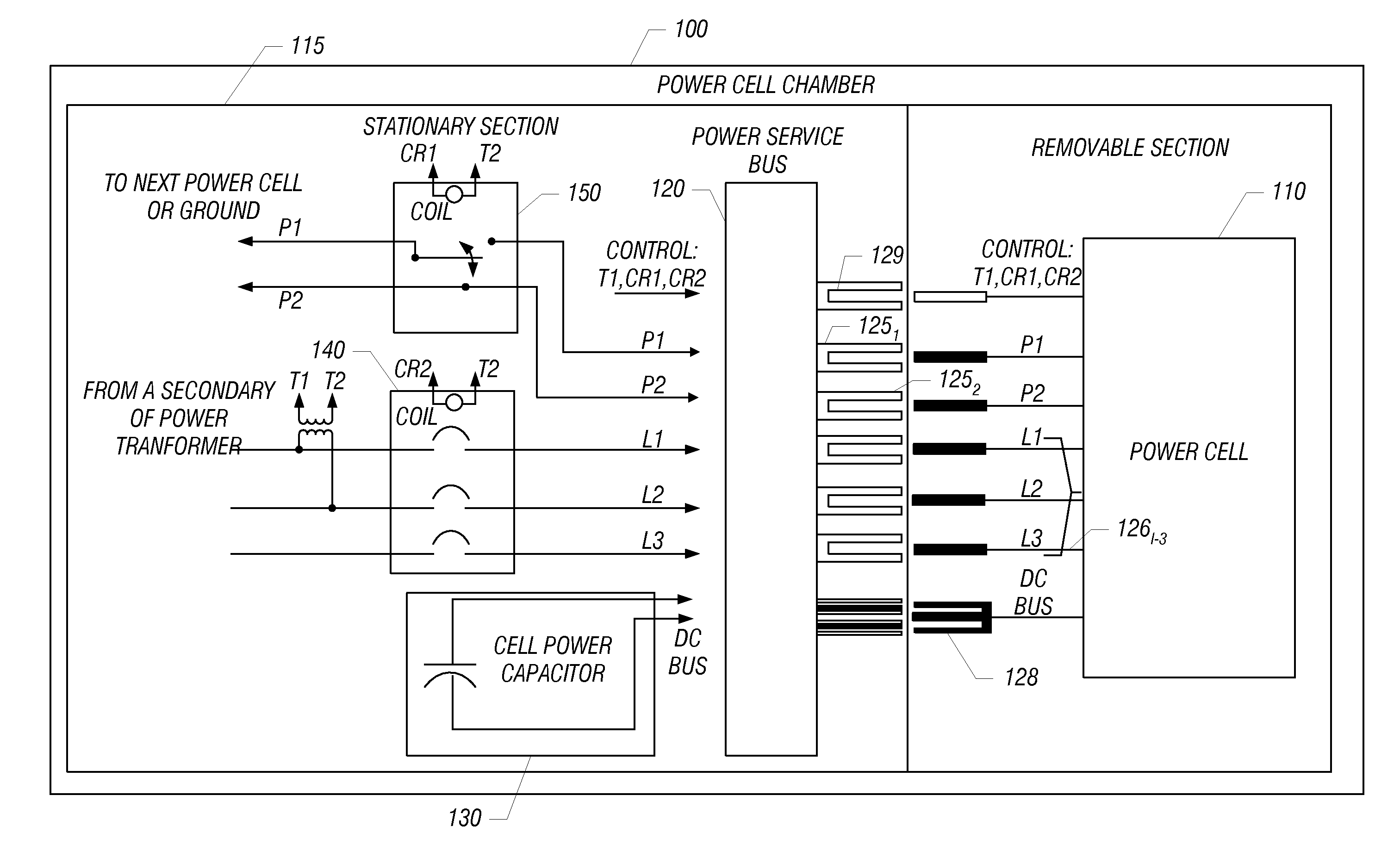
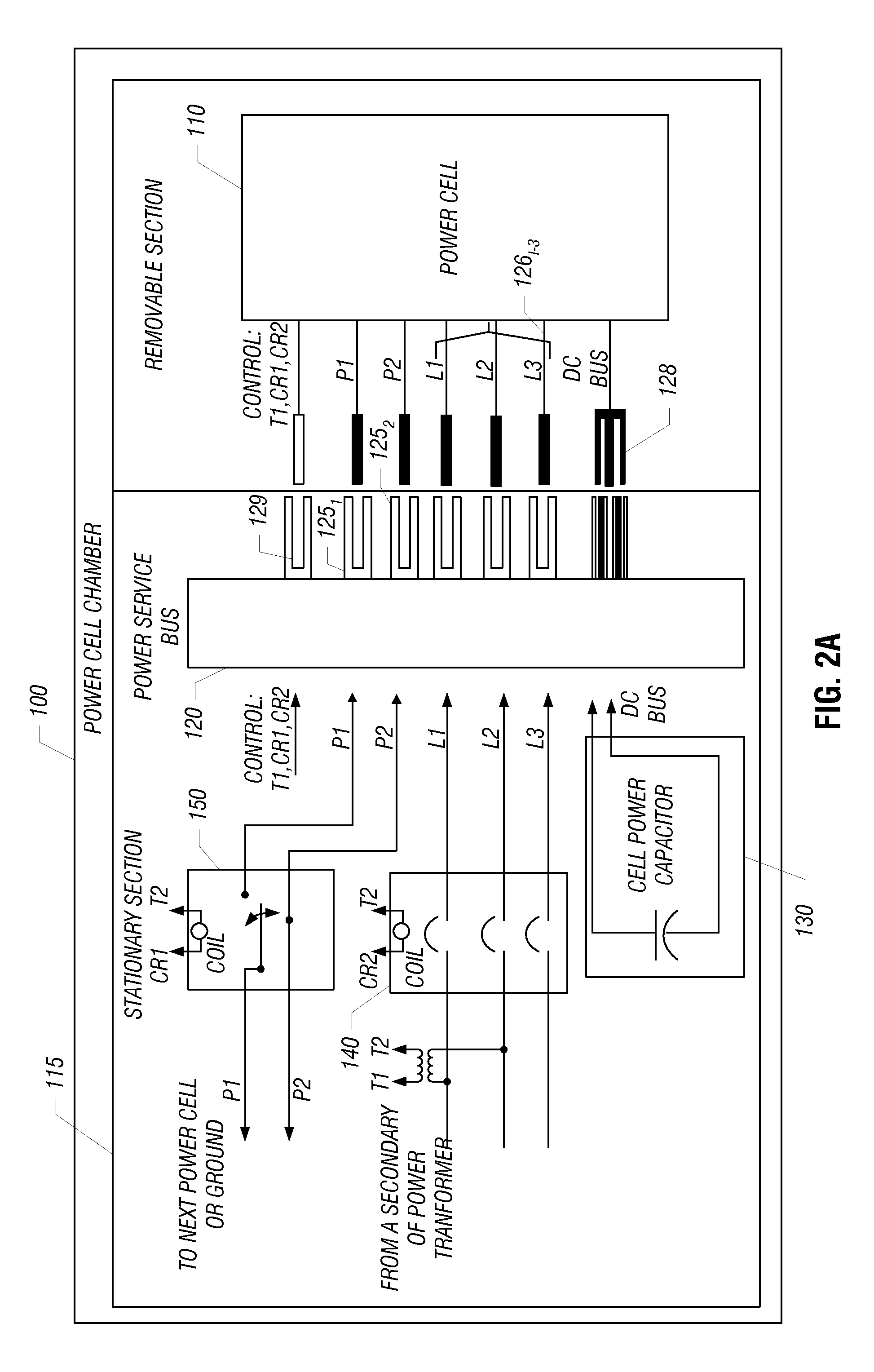
Pluggable Power Cell For An Inverter
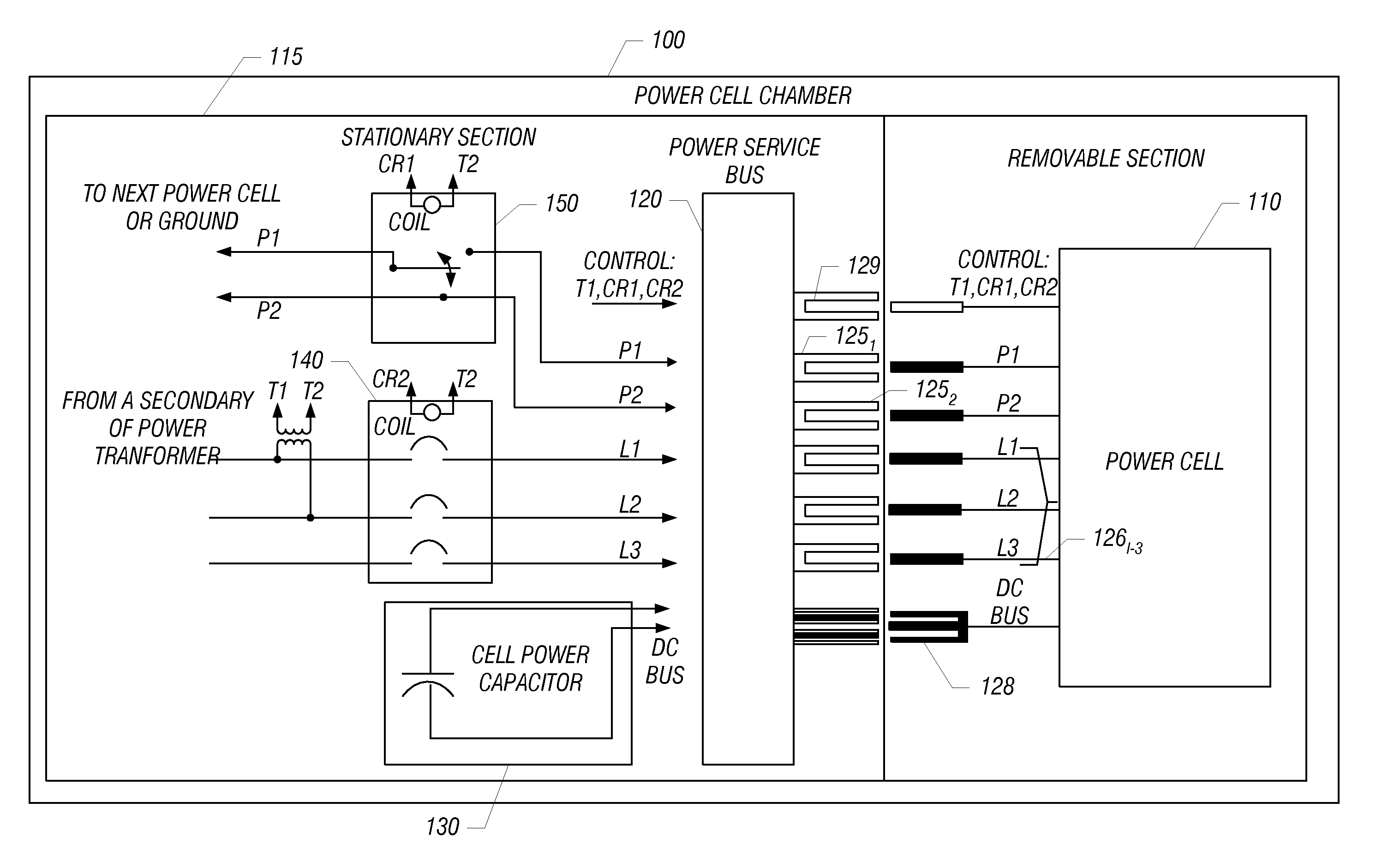
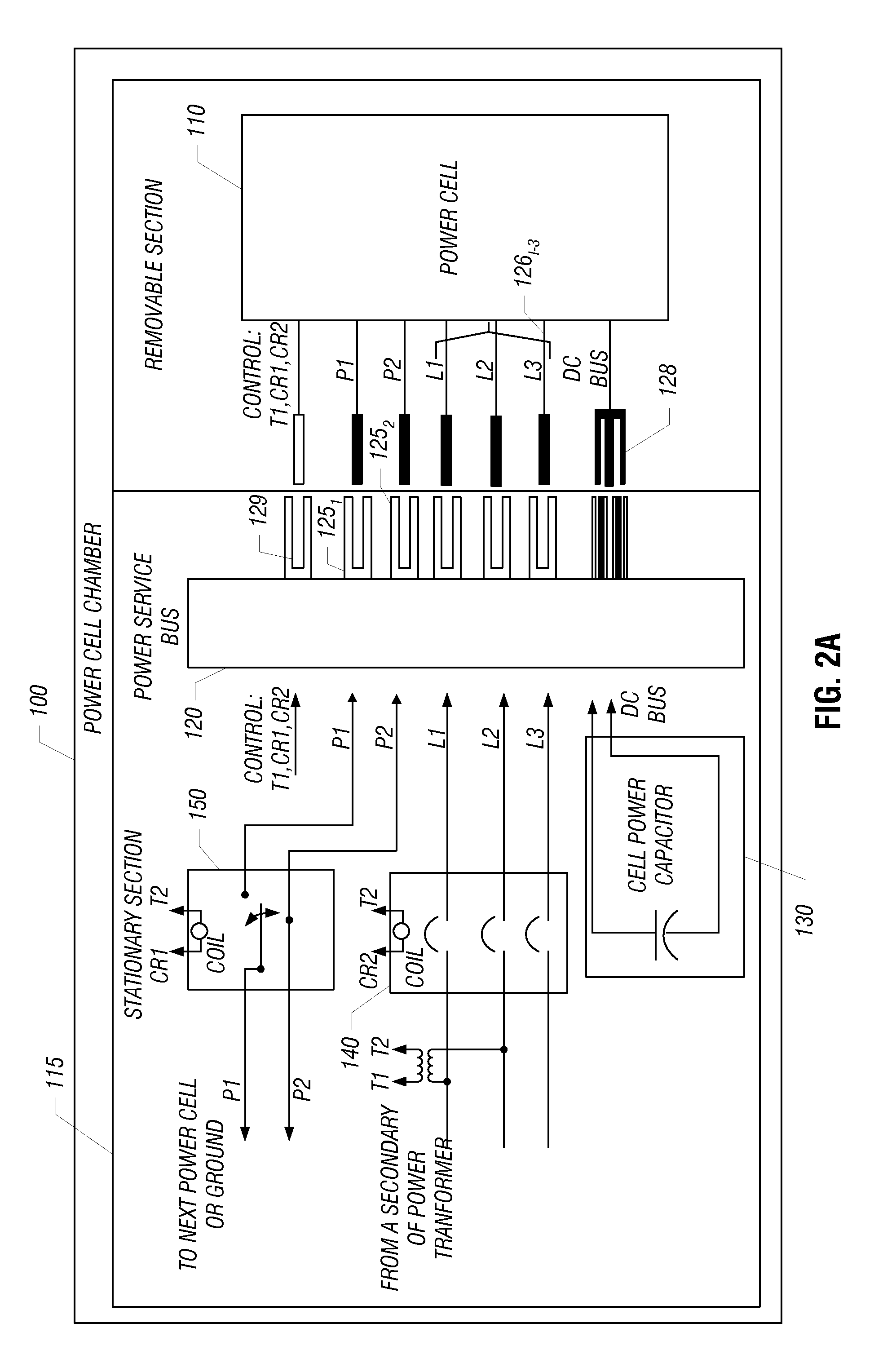
ActiveUS20100328883A1Reduce weightImprove power densityConversion with intermediate conversion to dcConversion constructional detailsTransformerEngineering
In one embodiment, a power cell chamber for a drive system includes moveable and fixed portions. The moveable portion includes a rectifier stage to rectify an input signal received from a secondary winding of a transformer to provide a rectified signal and an inverter stage having a plurality of switching devices to receive a DC signal and output an AC signal. This moveable portion can be slidably adapted within a cabinet of the drive system. In turn, the fixed portion includes a DC link having at least one capacitor to receive the rectified signal and provide the DC signal to the inverter stage.
Owner:TECO WESTINGHOUSE MOTOR
Umbrella frame and operating system
An improved, durable and versatile umbrella frame assembly is provided to more readily endure abusive weather conditions and that may be quickly, easily and inexpensively repaired. In addition, the assembly is also easily modified to accommodate umbrella canopies of different sizes and shapes. In addition, an improved umbrella operating system is provided to permit simple opening, positioning, and locking of an umbrella while allowing the frame to freely rotate about the pole regardless of the degree to which it is opened, while the pole is held in a stationary position. The assembly includes a pair of hub members mounted about a pole member wherein the main hub member is slidable up and down the pole. A pulley system with a locking cam member may be employed to allow the umbrella to safely and easily open to any desired position. A locking stabilizer arm may be used to secure the main hub member in the fully open position.
Owner:TUUCI WORLDWIDE LLC
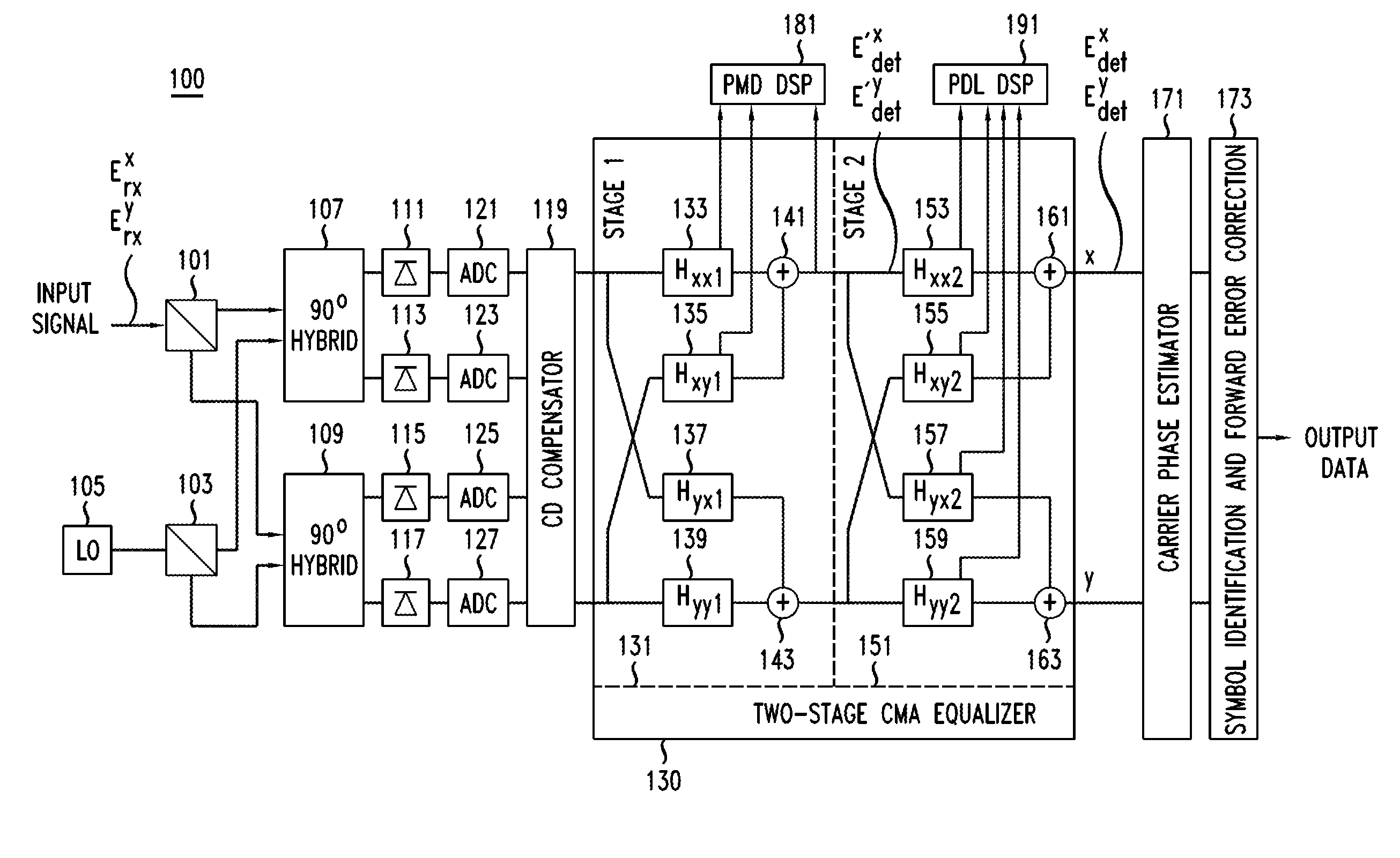
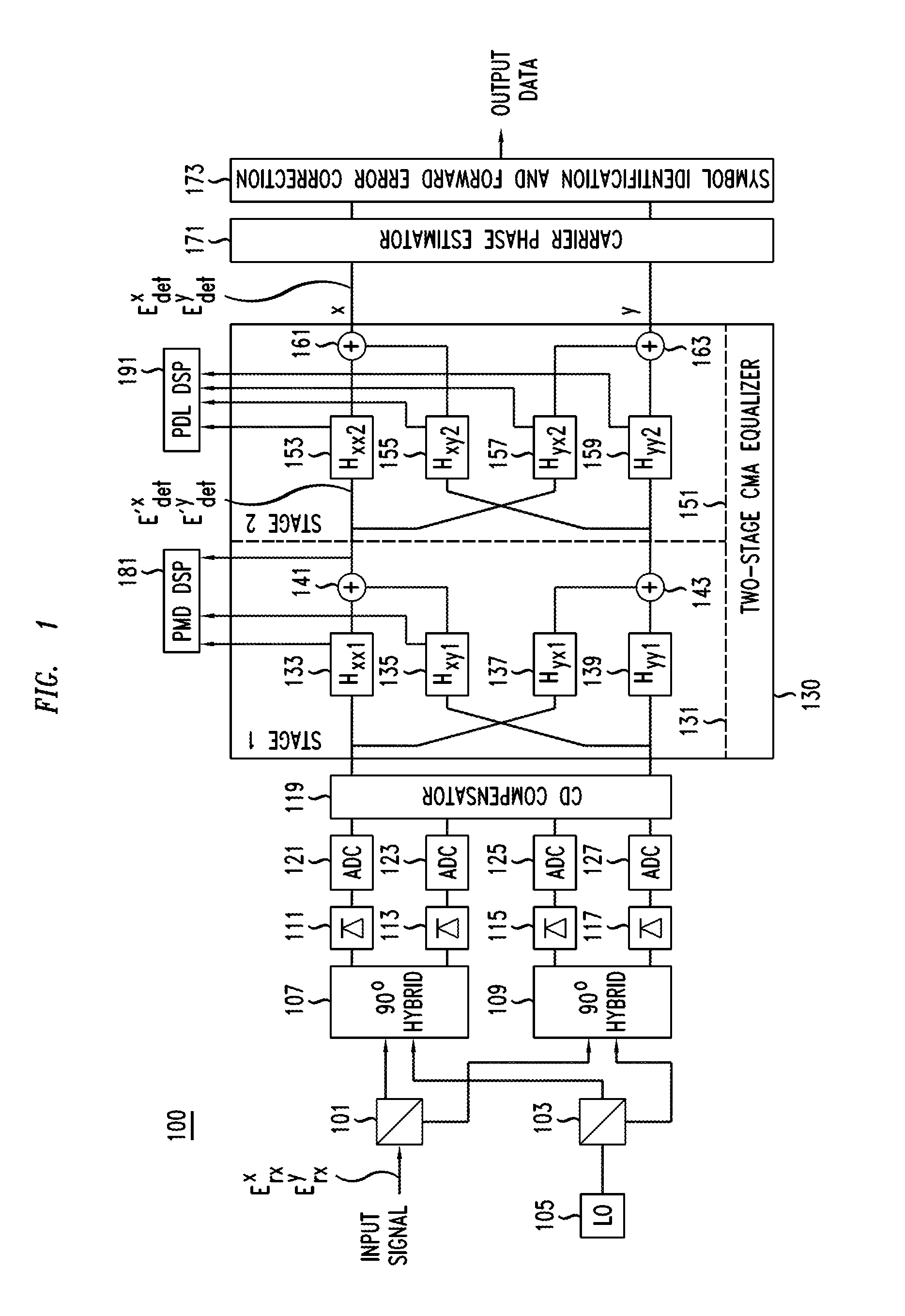
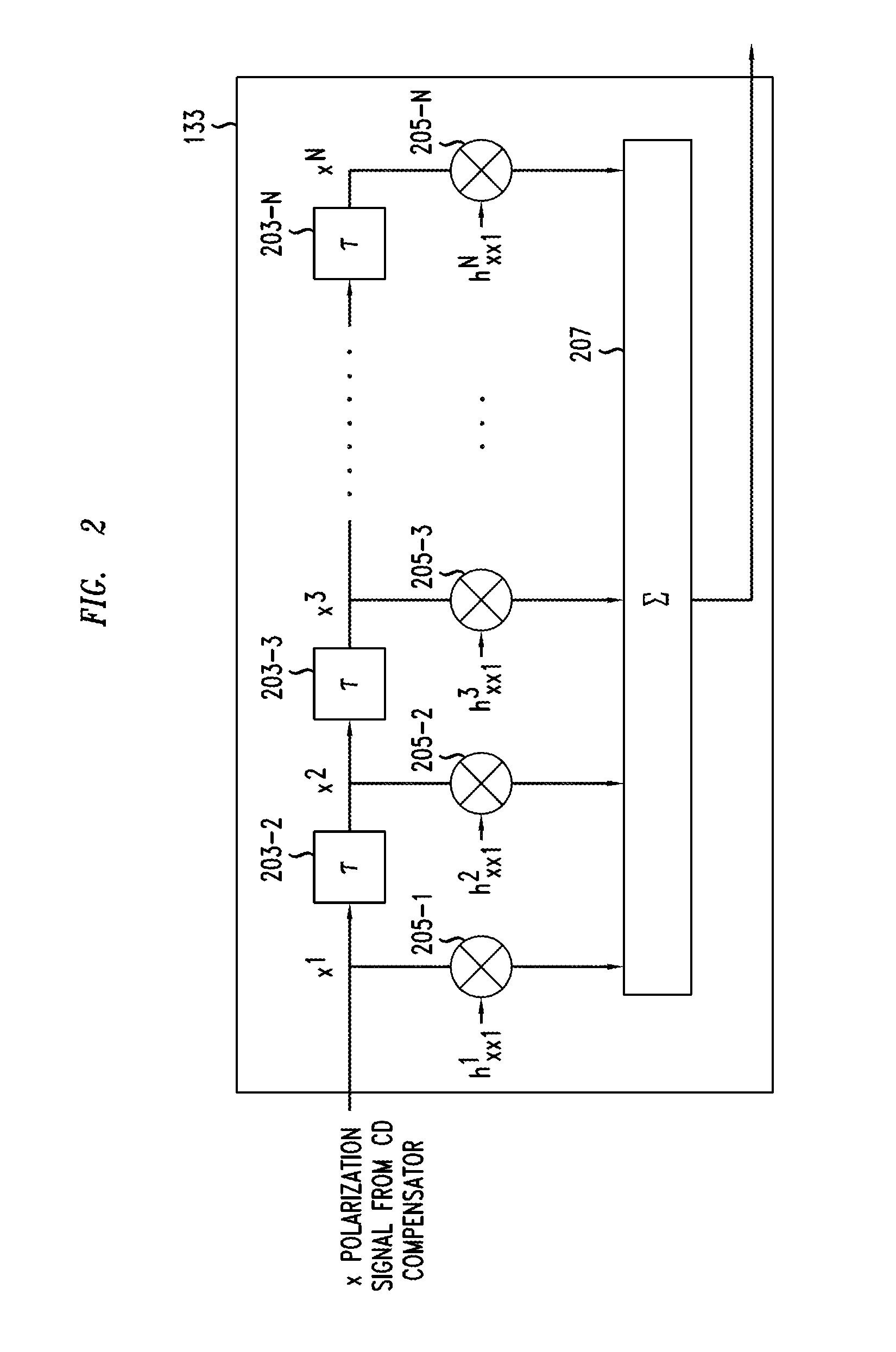
Method And Apparatus For Polarization-Division-Multiplexed Optical Receivers
ActiveUS20120002979A1Effective wayEliminate the problemElectromagnetic receiversEqualizationPolarization mode dispersion
An optical receiver includes a two-stage constant modulus algorithm (CMA) equalizer. The first stage is a modified version of a CMA equalizer and the second stage is a conventional CMA equalizer. The first stage may be made up of four sub-equalizers, of which only two of the sub-equalizers are independent, i.e., uncorrelated to each other. This first stage equalizer compensates for polarization-mode dispersion (PMD). The second stage equalizer is a conventional CMA equalizer made up of four sub-equalizers that are adjusted independently. This second stage equalizer may compensate for polarization-dependent loss (PDL). The receiver includes a first processor that determines PMD information based on a plurality of transfer function parameters of the modified CMA equalization of the first stage equalizer and the modified-equalized output and a second processor that determines PDL based on a plurality of transfer function parameters of the CMA equalization of the second stage equalizer.
Owner:ALCATEL LUCENT SAS
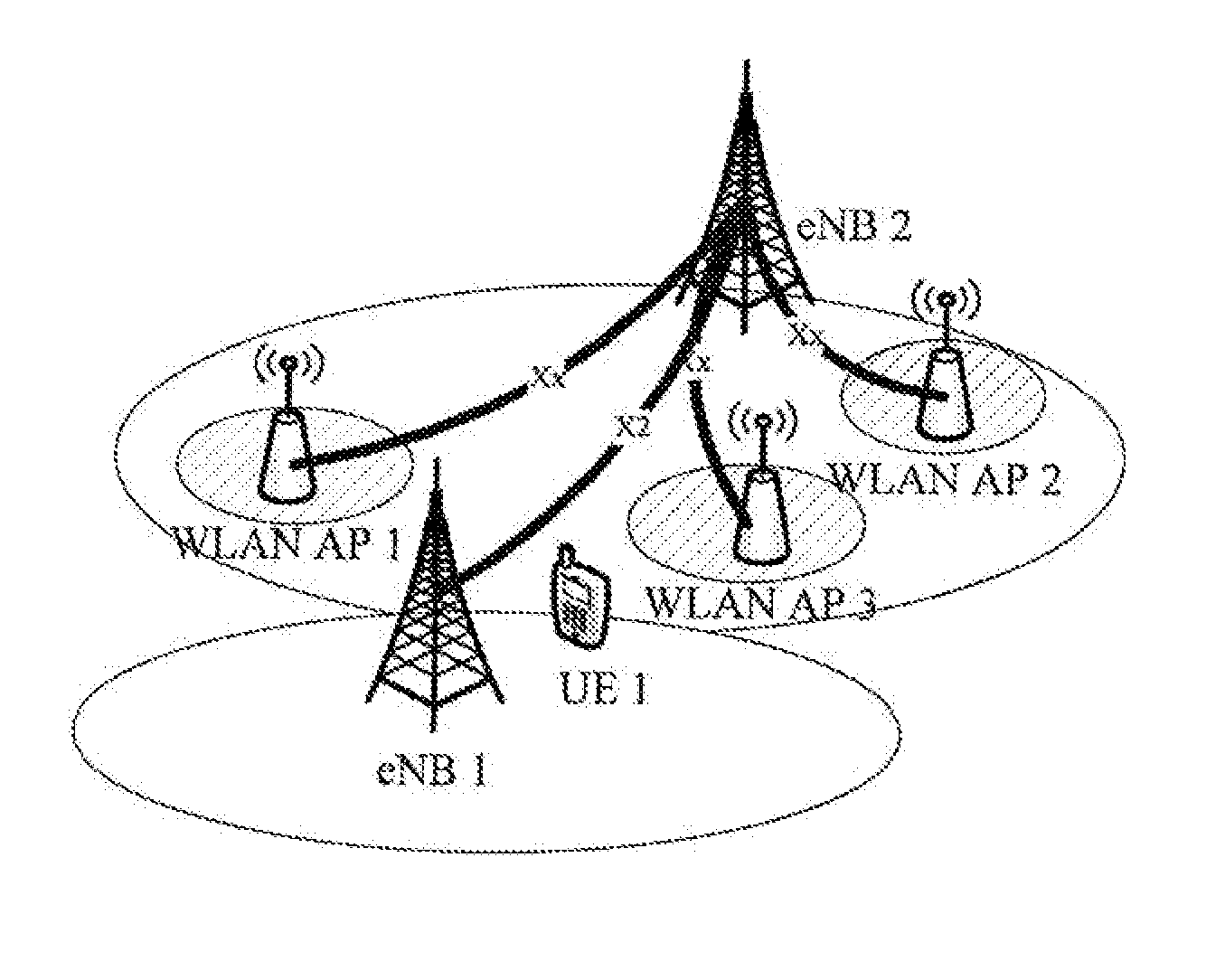
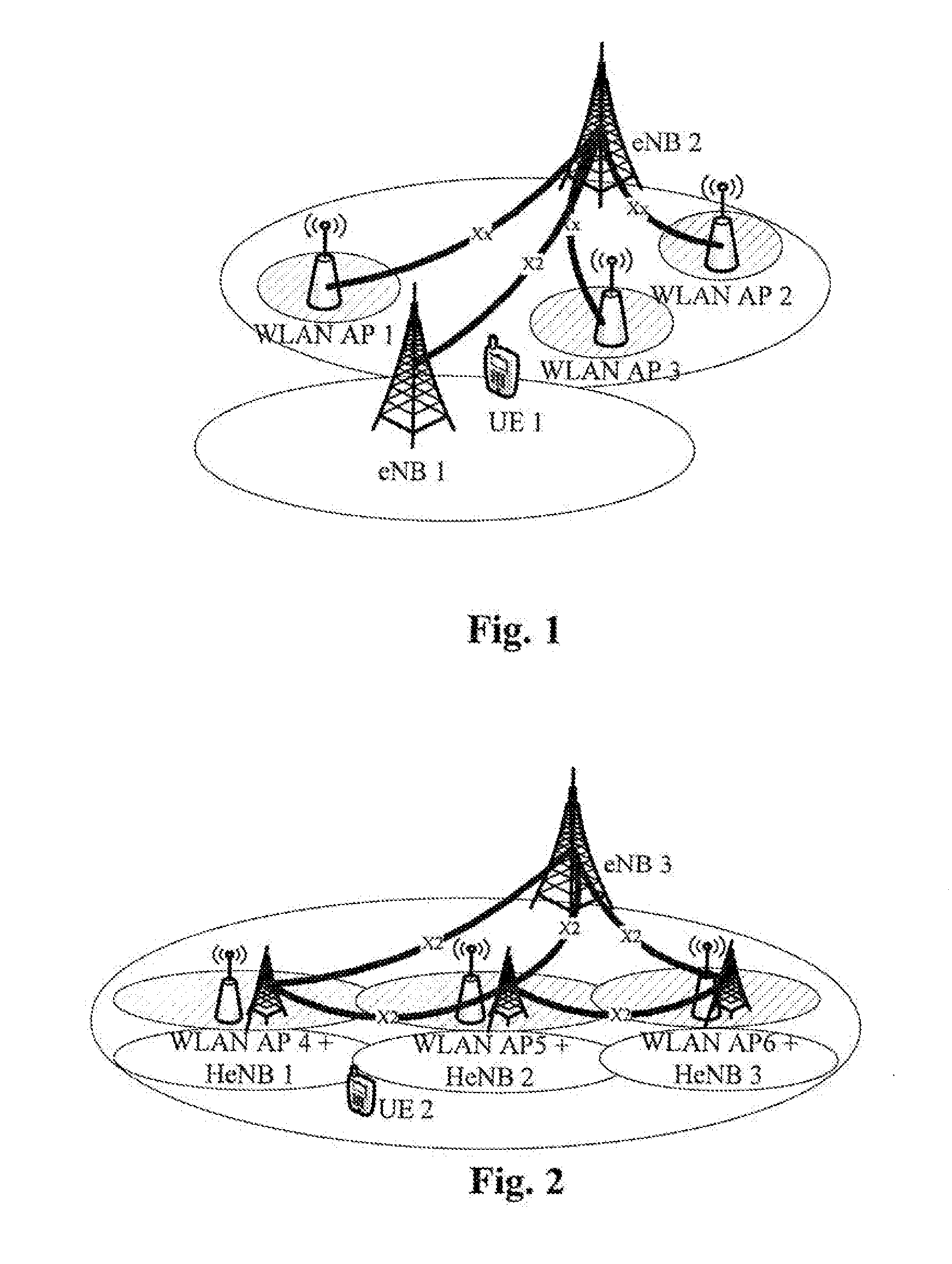
Methods, apparatuses and computer program products for WLAN discovery and handover in coexisted LTE and WLAN networks
InactiveUS20140376515A1Average power consumptionImprove efficiencyAssess restrictionWireless commuication servicesHandover procedureComputer science
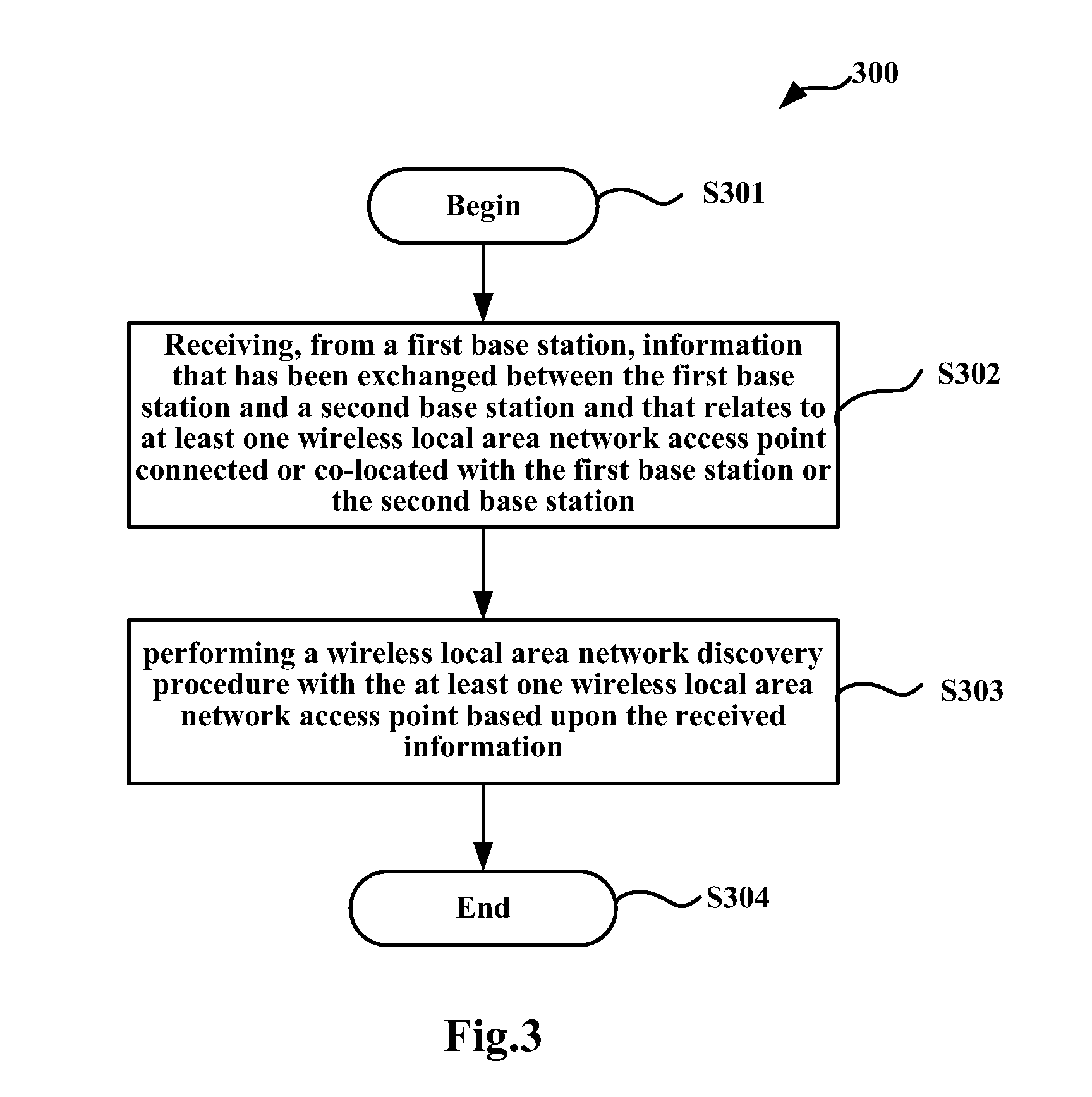
Provided are methods, corresponding apparatuses, and computer program products for triggering WLAN discovery and handover procedures in coexisted LTE and WLAN networks. A method comprises receiving, from a first base station, information that has been exchanged 5 between the first evolve Node B and a second base station and that relates to at least one wireless local area network access point connected or co-located with the first base station or the second base station; and performing a wireless local area network discovery procedure with the at least one wireless local area network access point based upon the received information. With the claimed inventions, signaling cost and power consumption by those unnecessary WLAN 10 discovery procedures could be avoided, acquiring a longer battery life for a user equipment.
Owner:NOKIA TECHNOLOGLES OY
Distributed push-pull information service system
InactiveUS20070288662A1Efficient and less bandwidth consumptionLoad balancingDigital data information retrievalMultiple digital computer combinationsGraphicsUser needs
A distributed push-pull information service system comprises an information service server and at least one client device. The server provides at least a first kind of information in a pushing basis by means of broadcasting and a second kind of information in a pulled basis by means of user demand. The client device can receive the broadcasted first kind of information and send a pulling request to the server for acquiring the second kind of information. The first and second kinds of information are transmitted by means of compressed and encrypted raw data. The client device further comprises a graphic user interface module for transforming at least part of the transmitted raw data into a graphic which is then displayed on the client device. The pulling request includes a search request which contains at least a specific term and a specific time period to be searched. Any information stored in the server meets that specific term during that specific period of time will be transmitted back to the client device as a result of search. The distributed information service system of the present invention also discloses the concept of “Intelligent Pull”, when the user makes a pull request, only the information which is absent in the memory of client device will be pulled, and thus the usage of bandwidth is highly efficient.
Owner:TELEPAQ TECH
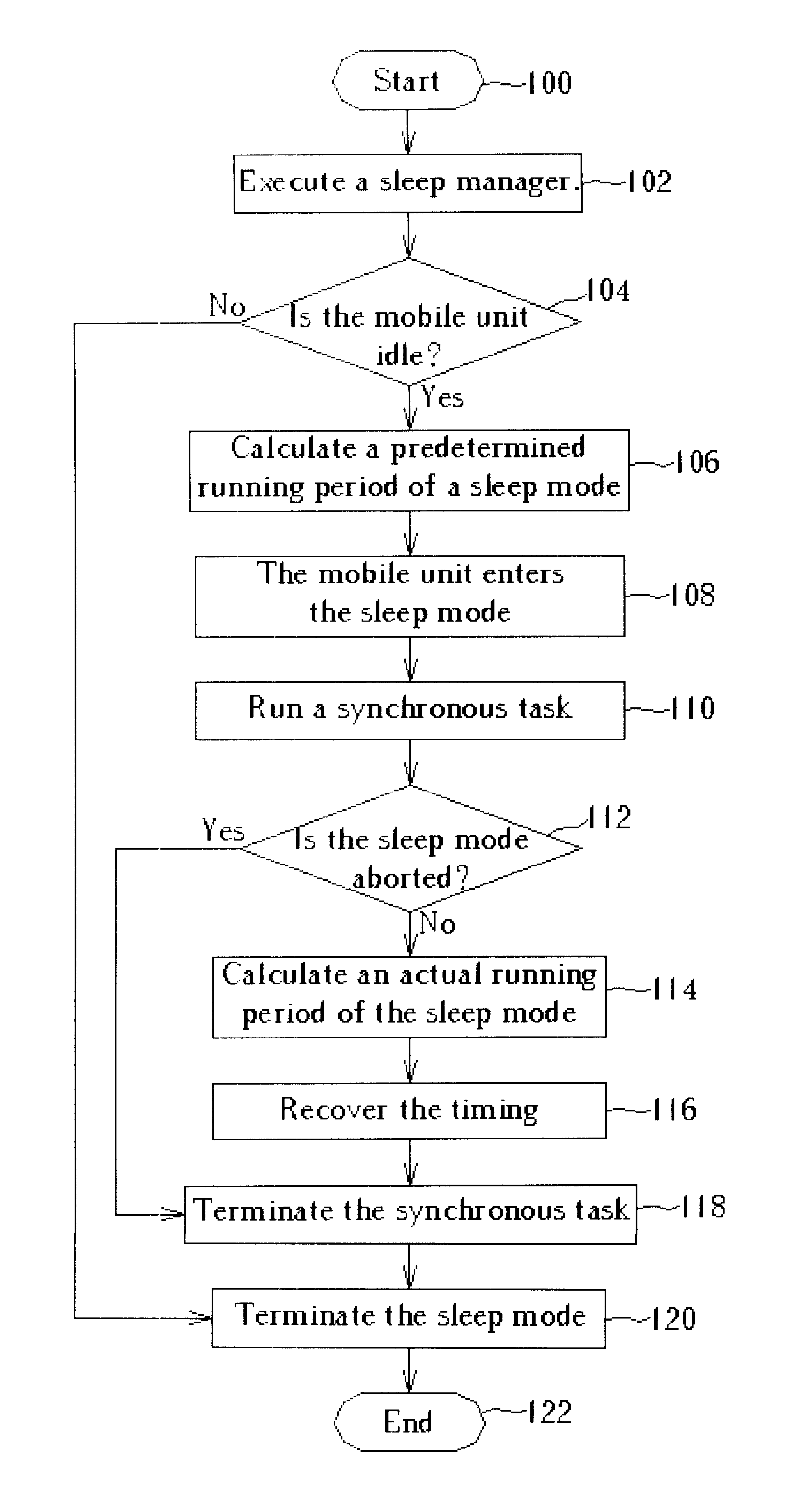
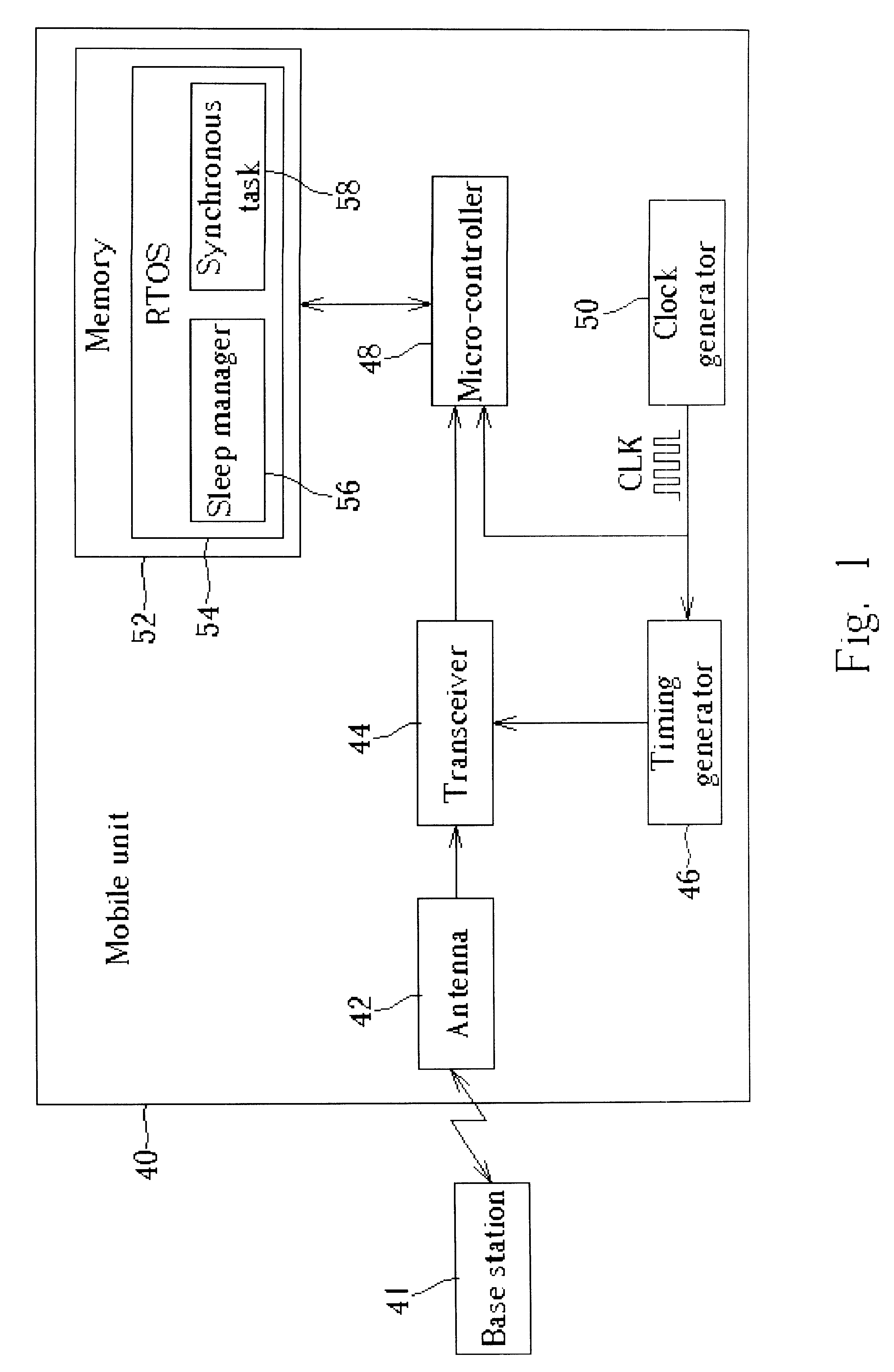
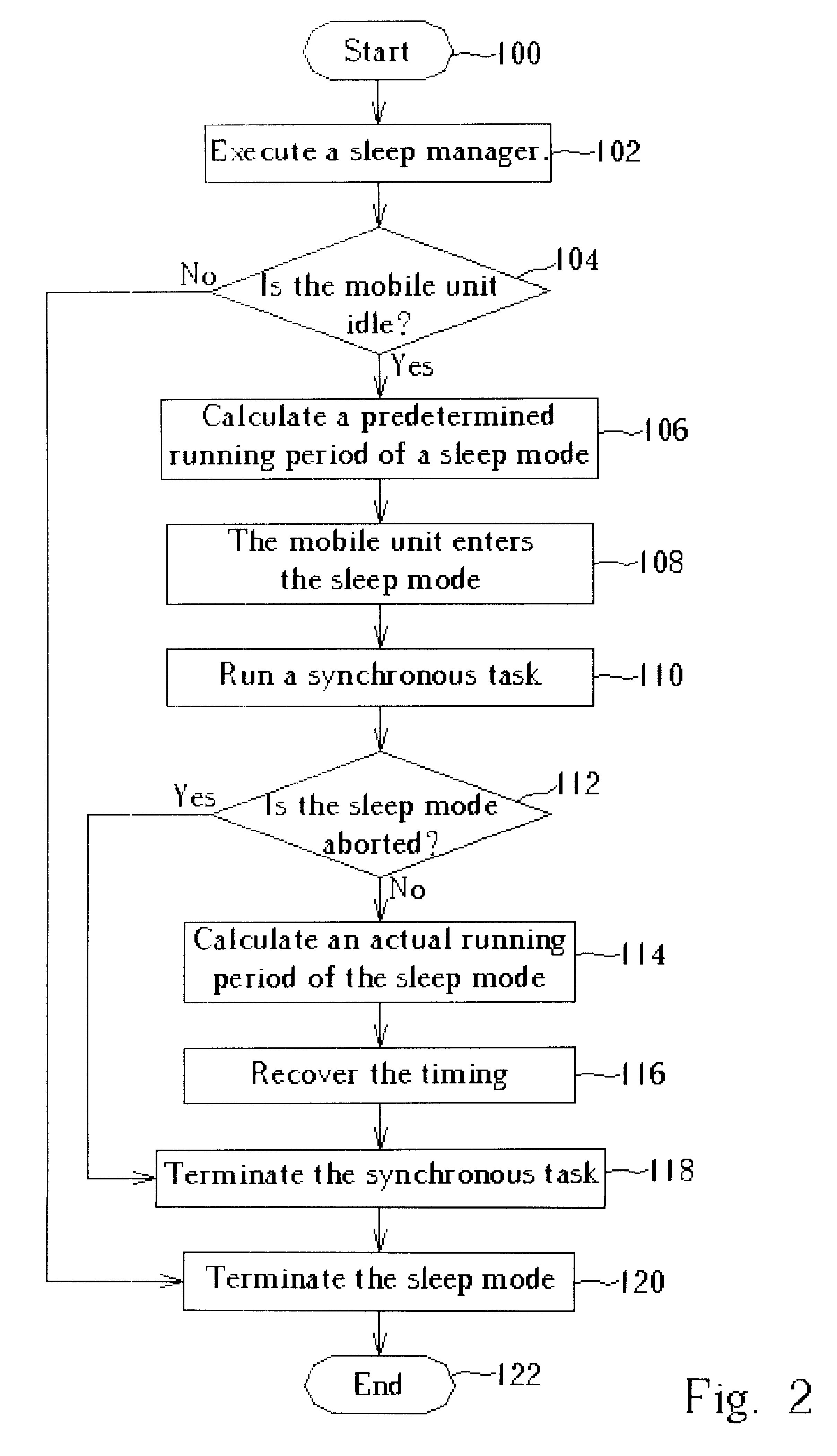
Method for switching a time frame based mobile unit to a sleep mode
InactiveUS7260068B2Reduce power consumptionSimple planEnergy efficient ICTPower managementOperational systemCommunications system
Method for recovering frame timing of a mobile communication device performing a sleep mode. The mobile communication device communicates with a base station through a communication system so that wireless signals are transmitted via frames. The method includes executing a synchronous task for interrupting currently loaded control processes in a real-time operating system and for calculating a predetermined sleep period for the sleep mode, executing the synchronous task for driving the mobile communication device to enter the sleep mode during an actual sleep period, and executing the synchronous task for synchronizing frame timing of the mobile communication with frame timing of the base station according to the actual sleep period.
Owner:MEDIATEK INC
Weight-activated tying shoe
ActiveUS8087188B2Relieve stressEffective wayShoe lace fasteningsHaberdasheryMechanical componentsEngineering
A weight-activated tying shoe wherein user who, upon sliding his foot inside the shoe, will depress a movable inner sole. This activates a side mechanism composed of a winch with a cable system used to close the tongue of the shoe towards the user's foot, thus lacing the shoe. The user simply uses his weight to activate the mechanism. Using his other foot, the user can move a pedal to release the mechanism's tension. Most of the mechanical components are located on both sides of the shoe body.
Owner:POWERLACE TECH
Construction Bracket and Method
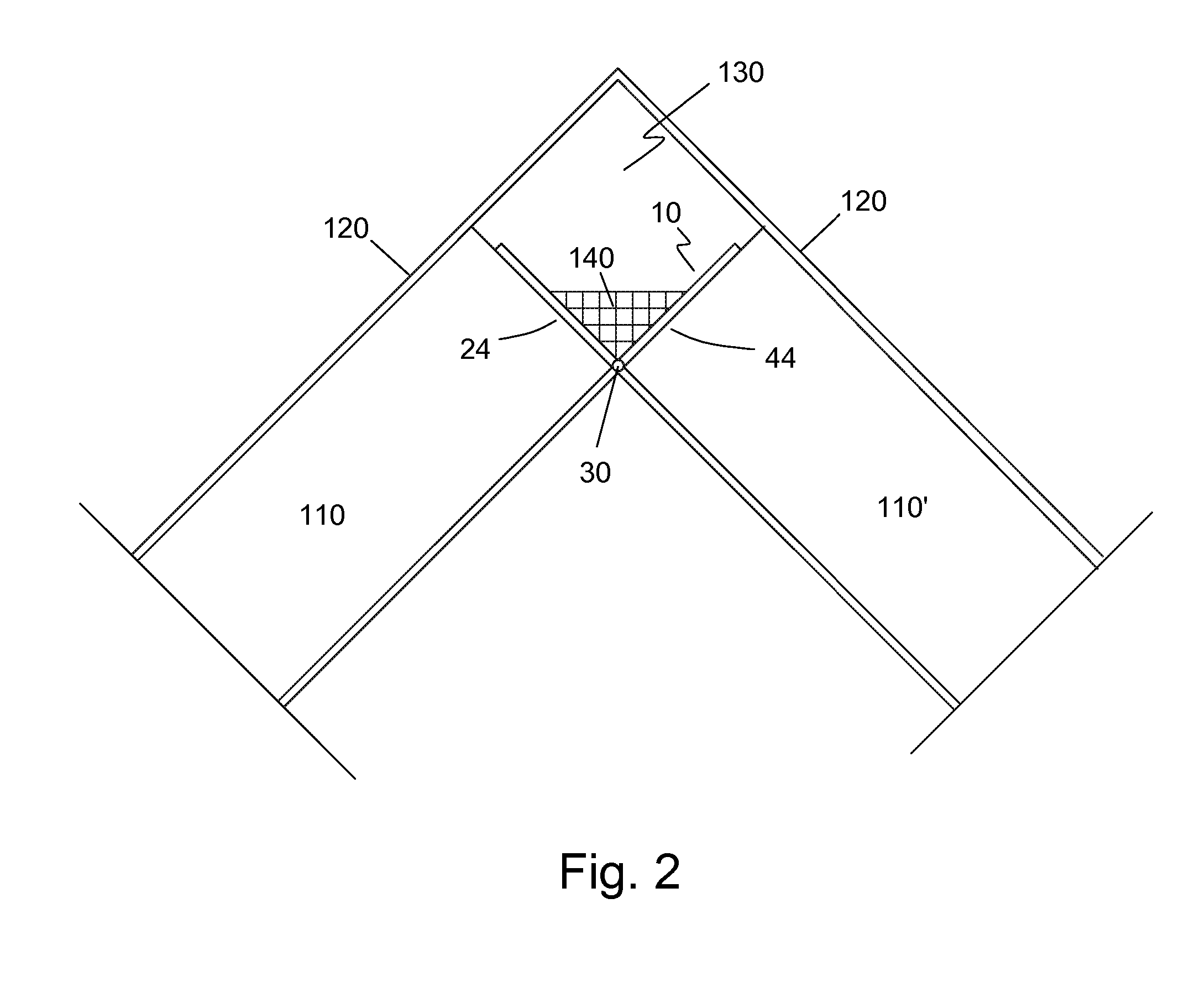
InactiveUS20060254192A1Facilitate rafter construction/assembly processShorten the timeRoof covering using slabs/sheetsBuilding roofsFlangePlenum space
A construction bracket for creating a roof venting space has a first flange having a first flange portion with an first flange outside surface and a first flange side extension that extends away from the first flange outside surface, and a second flange having a second flange portion with a second flange outside surface and a second flange side extension that extends away from the second flange outside surface where the second flange is connected to the first flange forming a predefined angle between the first flange and the second flange.
Owner:FENNELL JR HARRY C
Pluggable power cell for an inverter
ActiveUS8130501B2Reduce weightImprove power densityCoupling device connectionsElectric ignition installationPower inverterTransformer
In one embodiment, a power cell chamber for a drive system includes moveable and fixed portions. The moveable portion includes a rectifier stage to rectify an input signal received from a secondary winding of a transformer to provide a rectified signal and an inverter stage having a plurality of switching devices to receive a DC signal and output an AC signal. This moveable portion can be slidably adapted within a cabinet of the drive system. In turn, the fixed portion includes a DC link having at least one capacitor to receive the rectified signal and provide the DC signal to the inverter stage.
Owner:TECO WESTINGHOUSE MOTOR
Heat Transfer Apparatus and Container
ActiveUS20130059259A1Increase contactIncrease heat transfer rateFurnace componentsClosure with auxillary devicesTemperature controlEngineering
A container for holding liquid is described. The container defines an inner region inside which liquid is adapted to be held and includes one or more walls for facilitating heating or cooling of the liquid therethrough, the one or more walls being adapted for invagination by a temperature control probe such that the temperature control probe extends into the container without directly contacting contents of the inner region of the container.
Owner:KISMET DESIGN
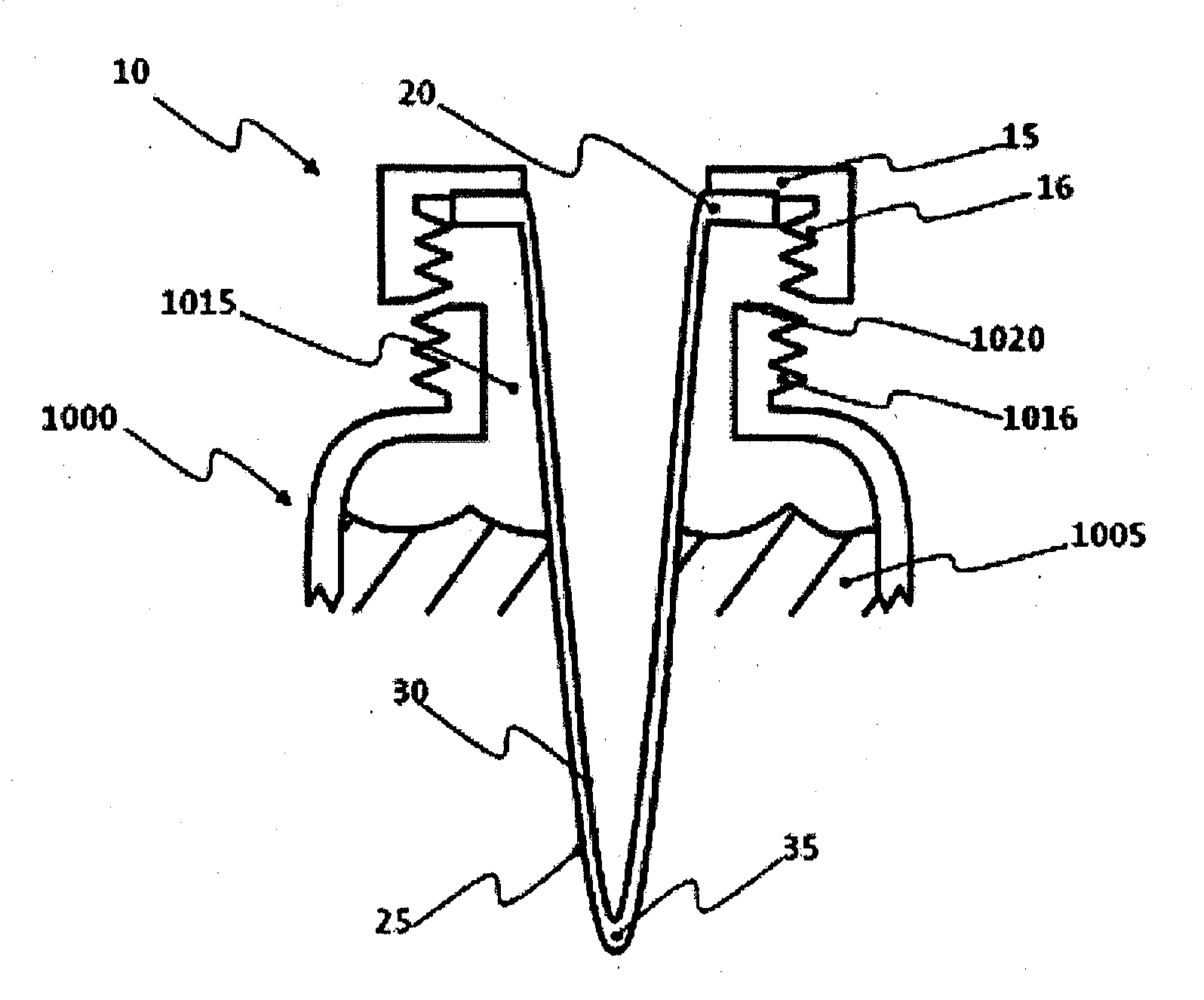
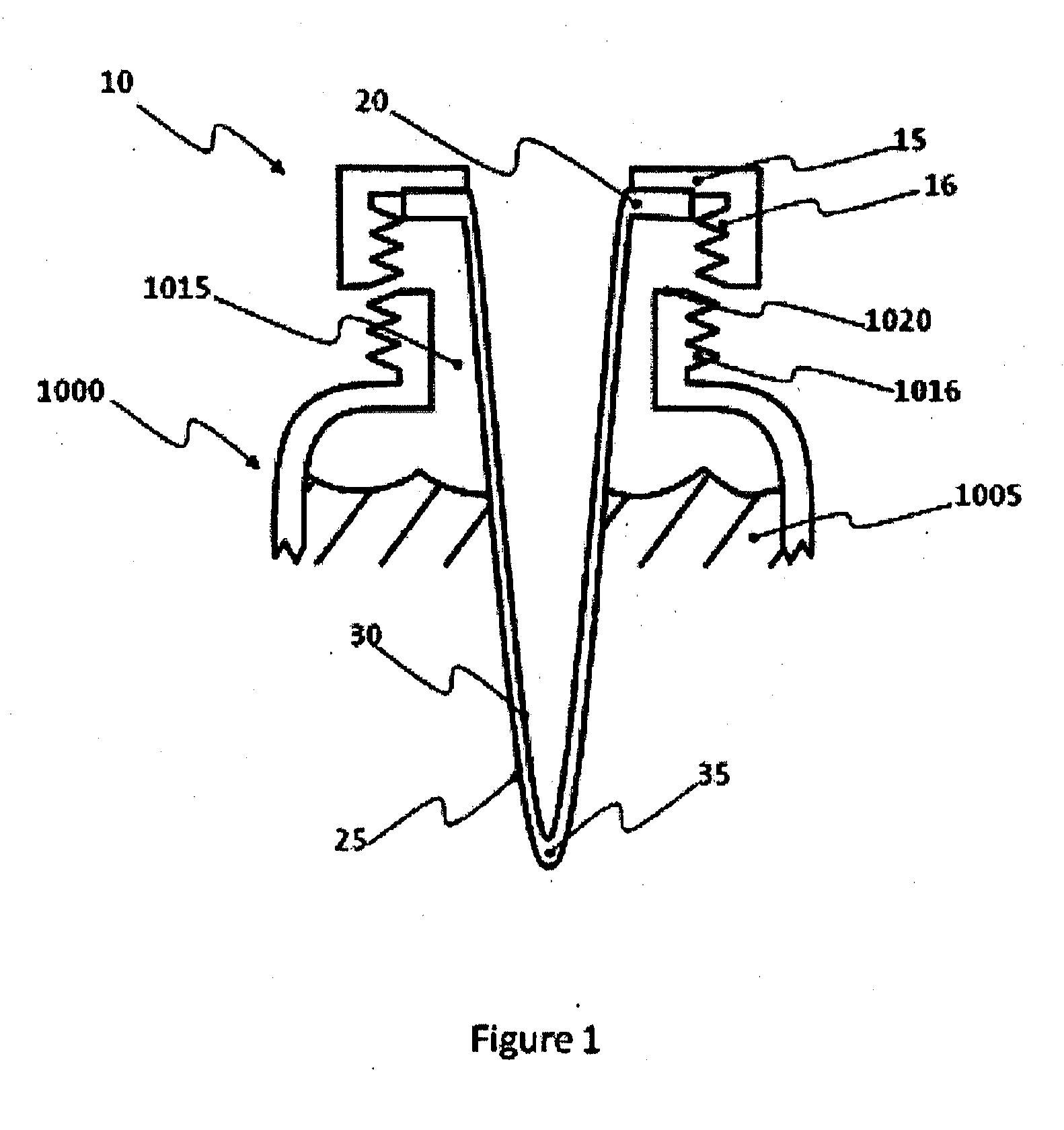
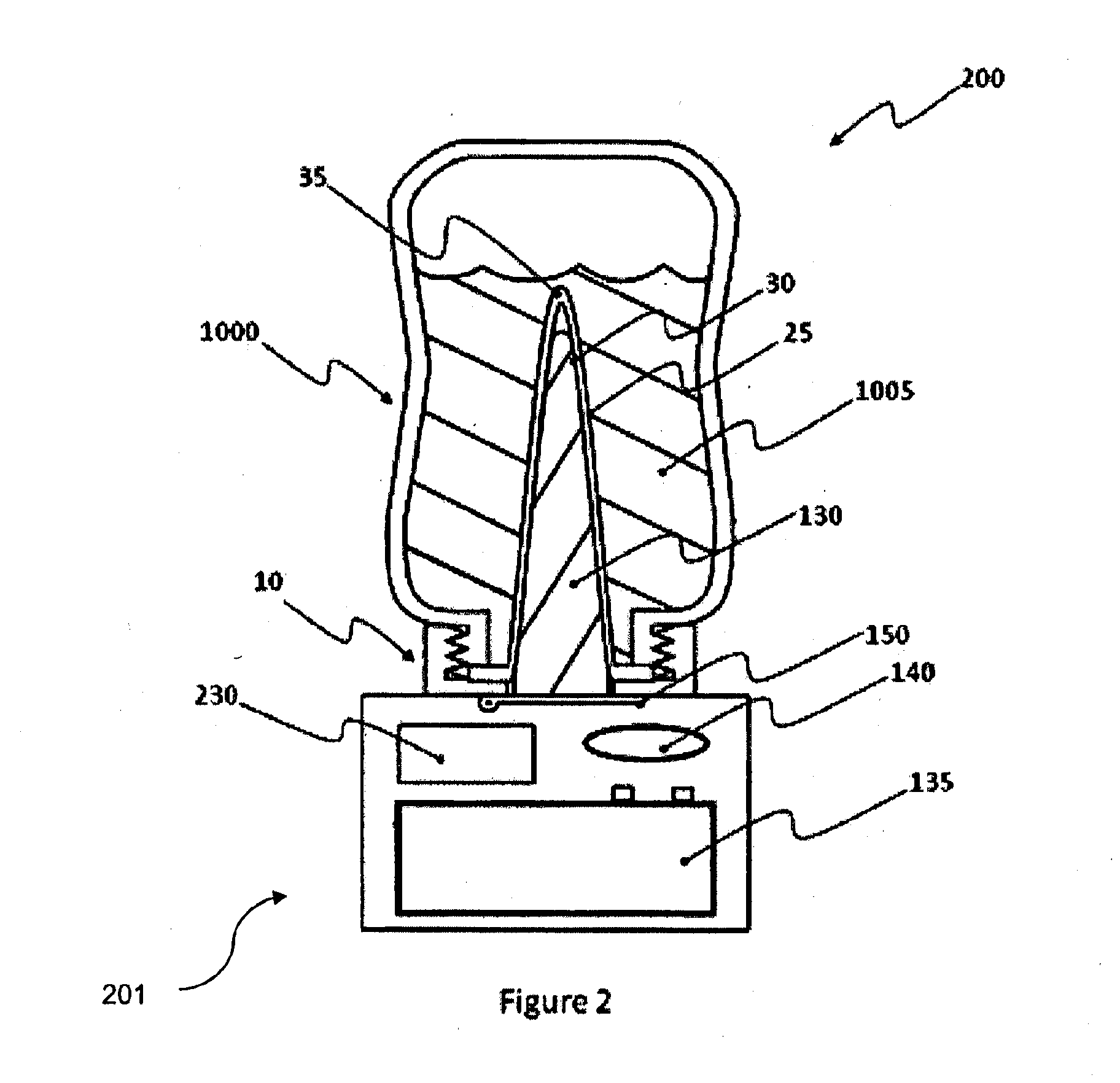
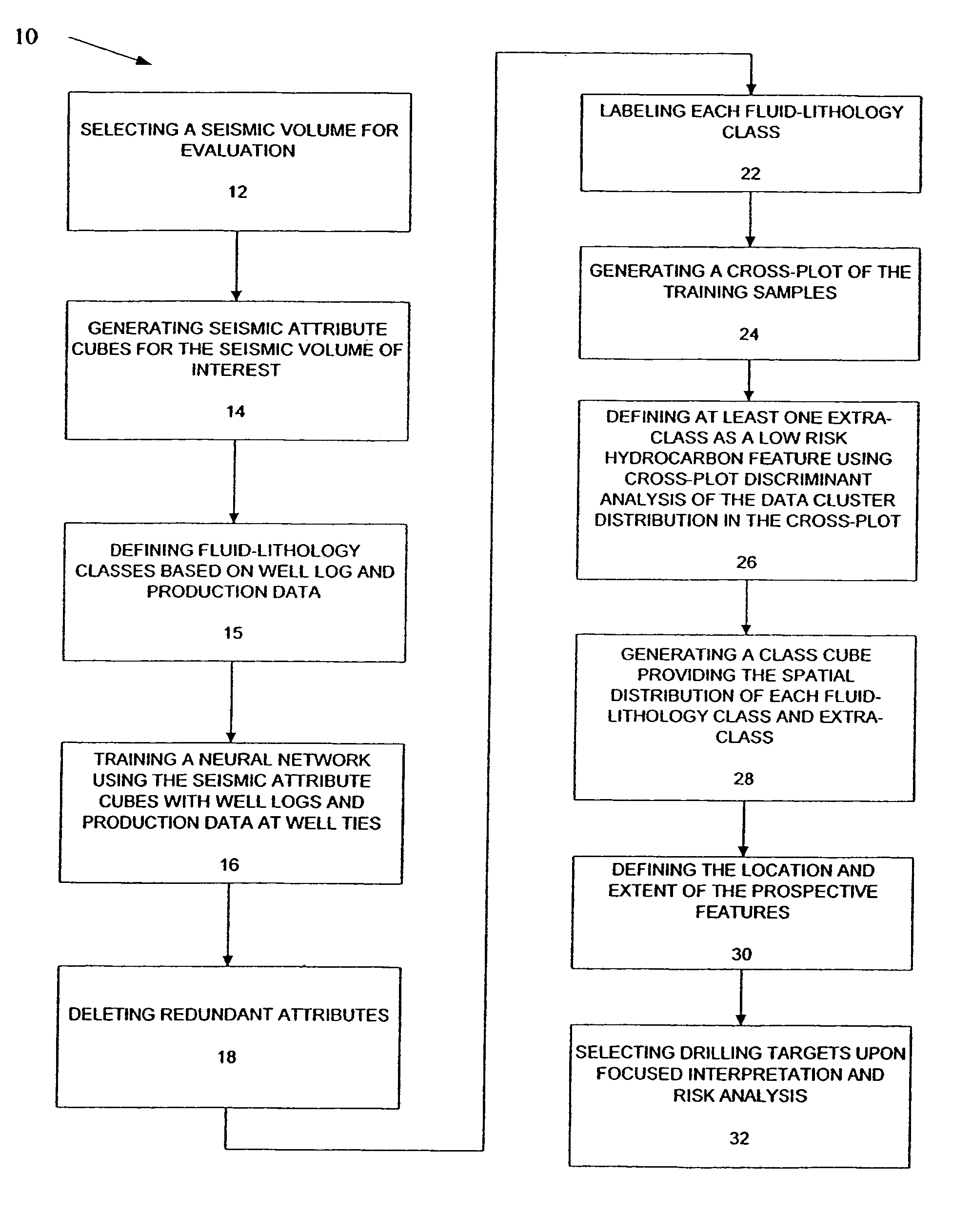
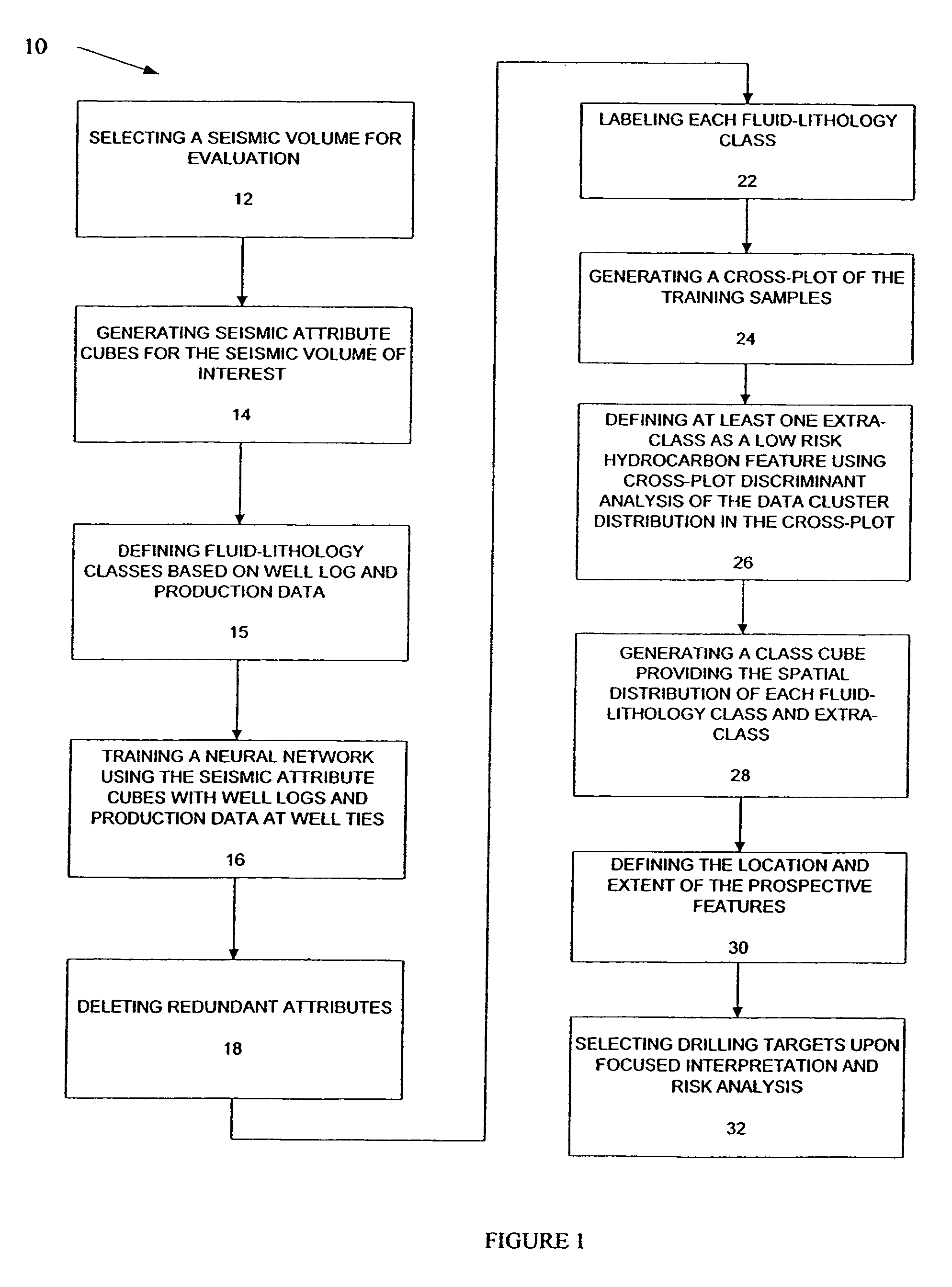
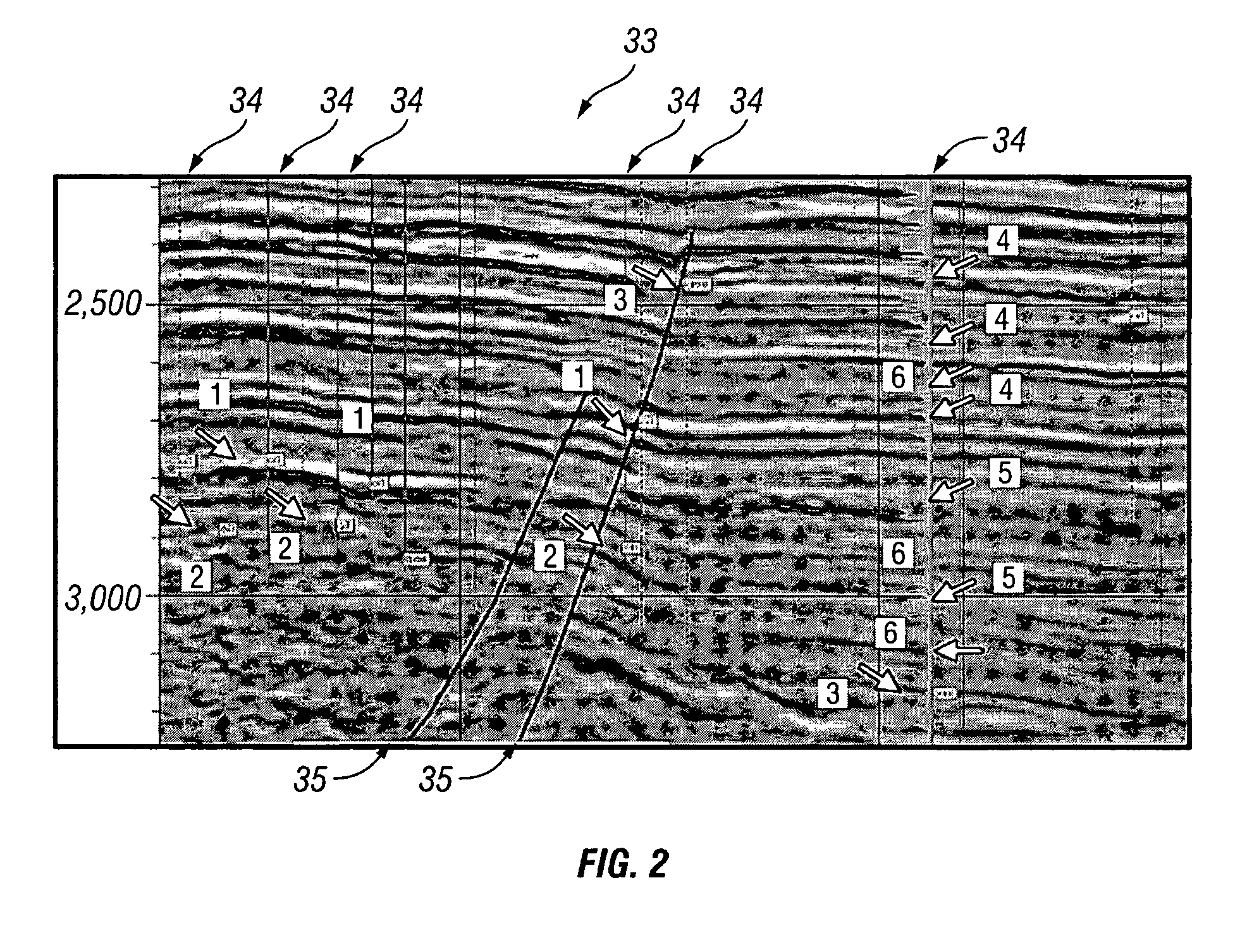
Method for prospect identification in asset evaluation
InactiveUS7113869B2Effective wayPowerful toolElectric/magnetic detection for well-loggingSeismic signal processingLithologyPore fluid
Owner:SCHLUMBERGER TECH CORP
Cable suspended, self leveling tram with self-propelled tractor bogie
A cableway with suspended tram and remote bogie is disclosed. This includes a self-contained motor, traction and support sheaves with provision for adjusting the height of the tram below said cable for limiting vertical acceleration caused by travel along the cantenary curve of the cableway.
Owner:MORRIS RICHARD DAVID
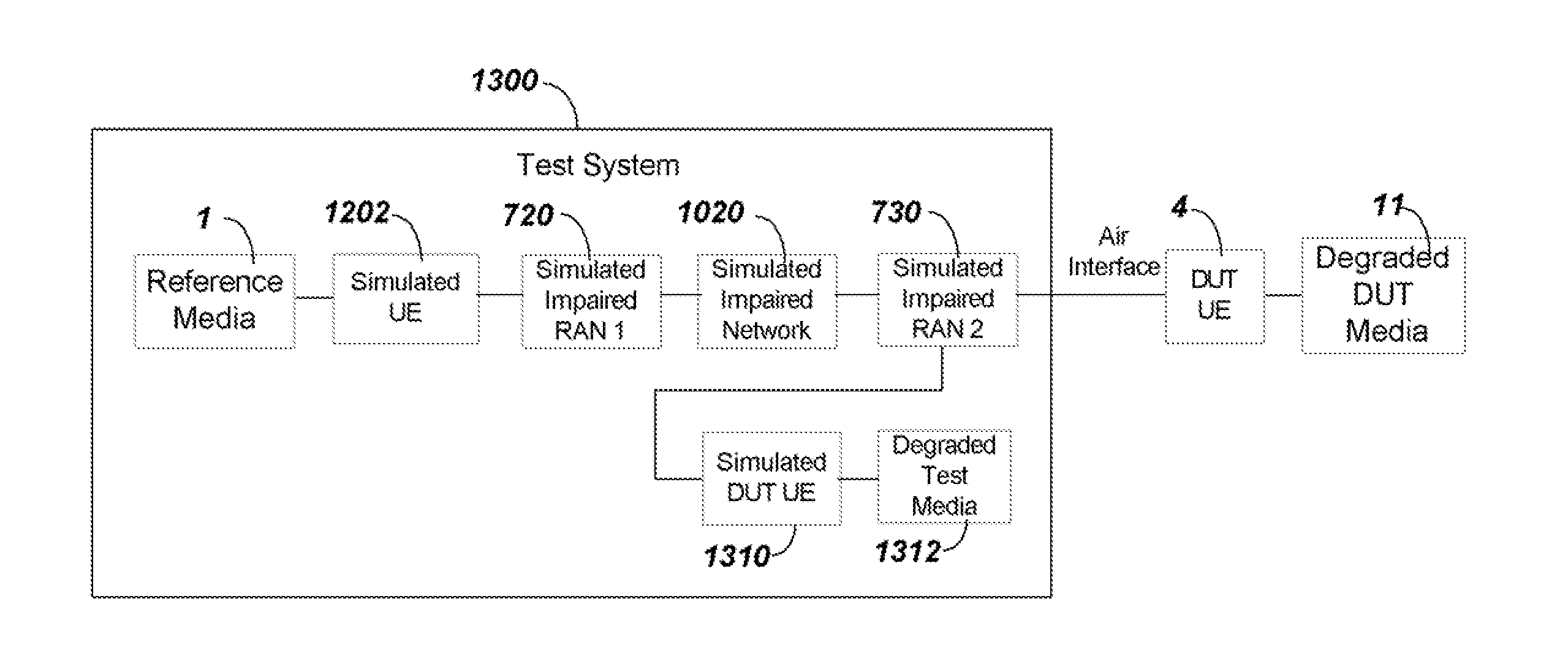
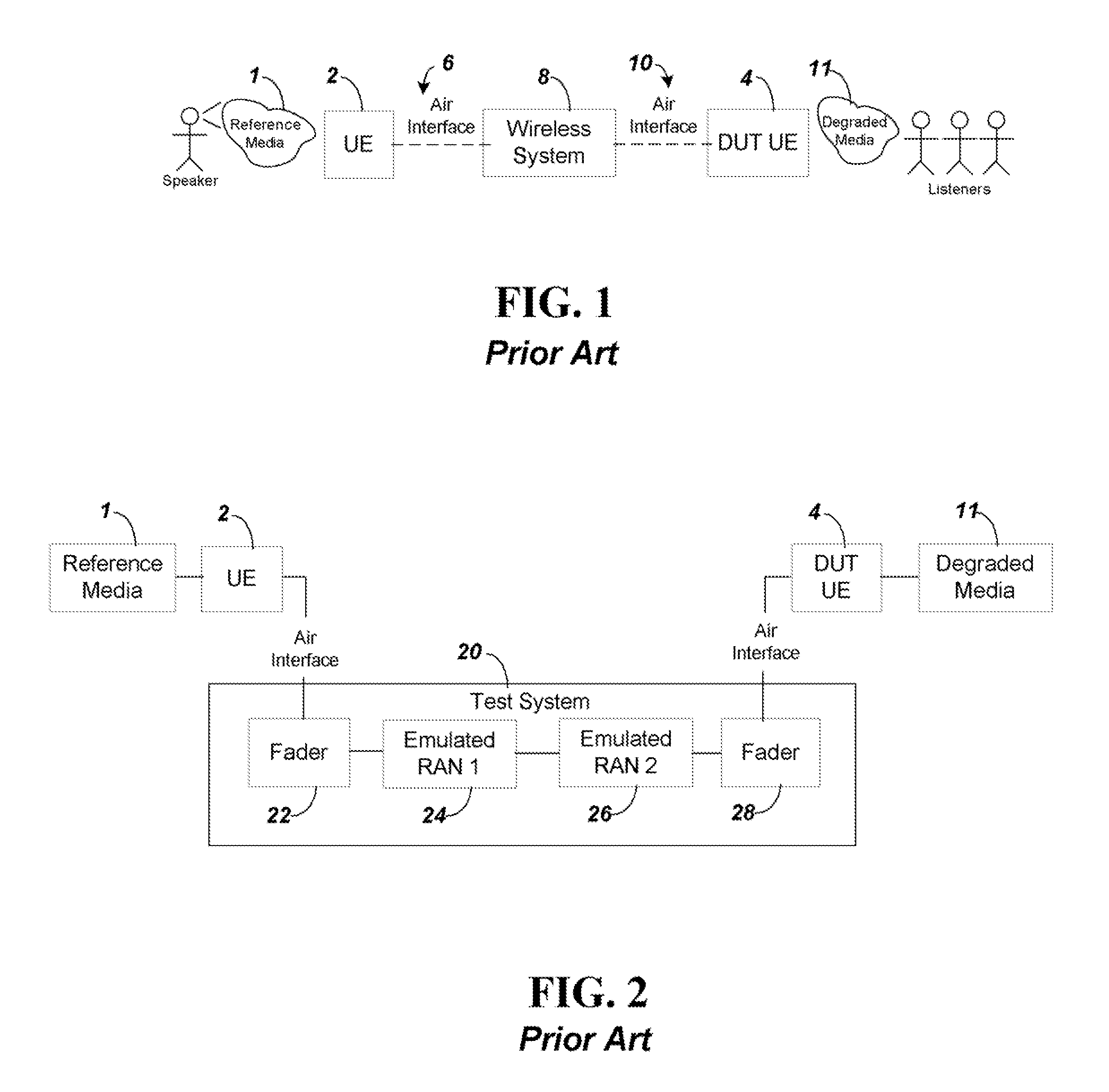
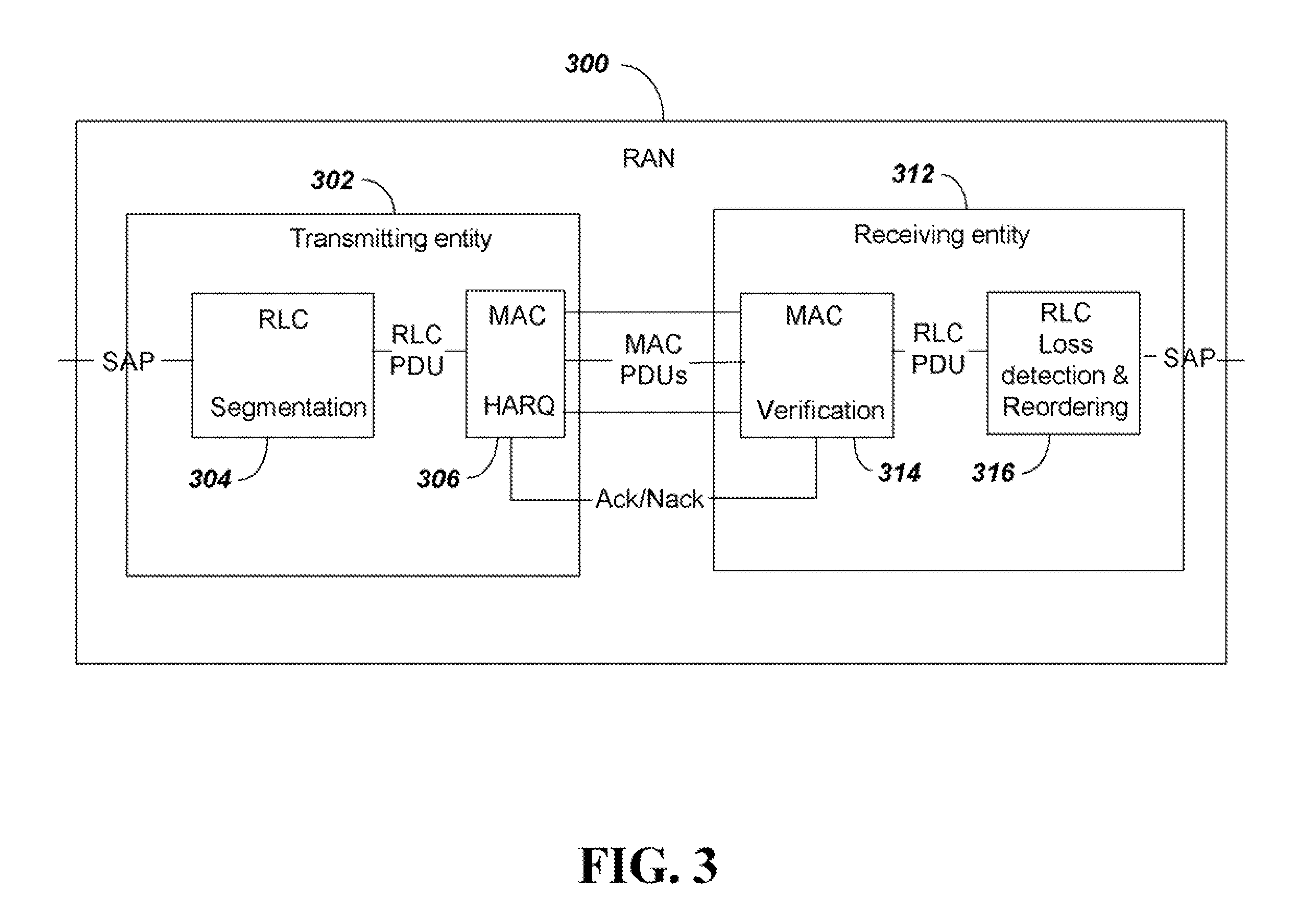
Impairment simulation for network communication to enable voice quality degradation estimation
InactiveUS20130286860A1Low costAvoid signalingError preventionFrequency-division multiplex detailsComputer hardwareRadio access network
An automated method for testing audio signal quality of cell phone transmissions provides a Mean Opinion Score (MOS) output using inexpensive test components. The test system uses a server computer to eliminate the need for expensive faders used in a bench test system. The server computer manipulates data packets from the reference media file to simulate impairments, including losses, errors, noise and jitter, at a much lower cost than using actual faders. Transmission through two separate radio access networks RANs is provided to simulate two parties communicating using separate mobile devices (an end-to-end test solution) with a single cell phone.
Owner:ANRITSU CORP
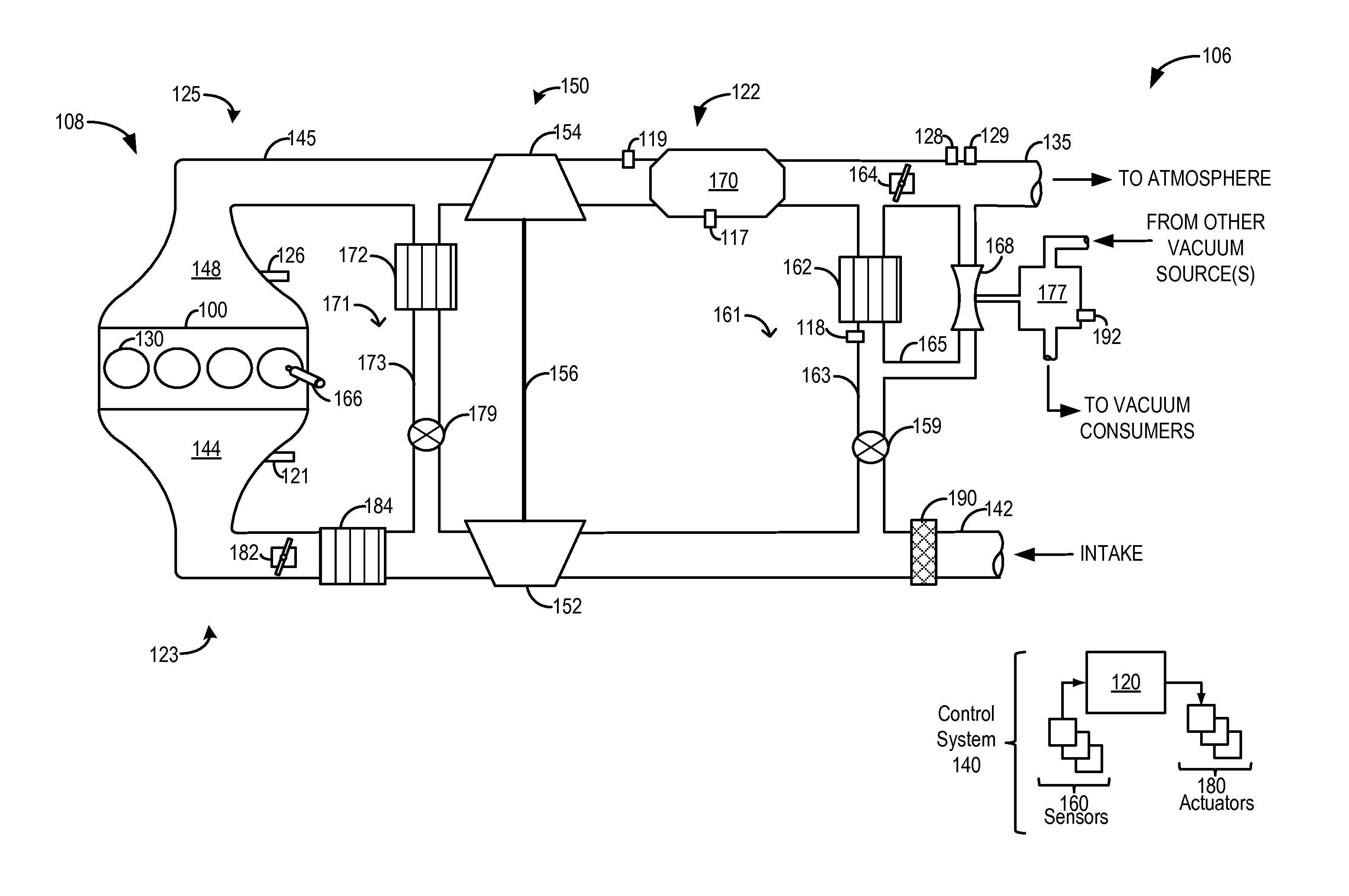
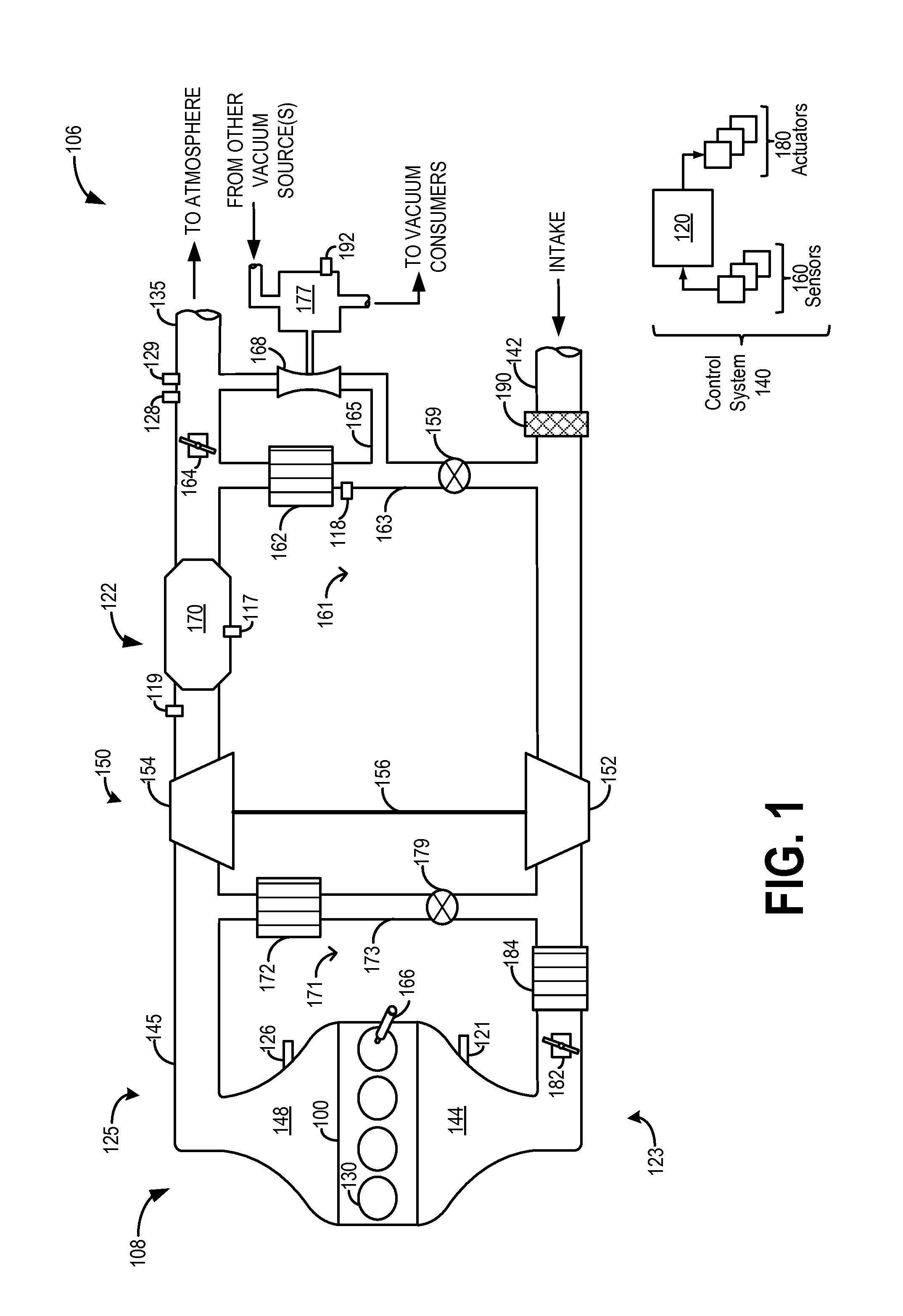
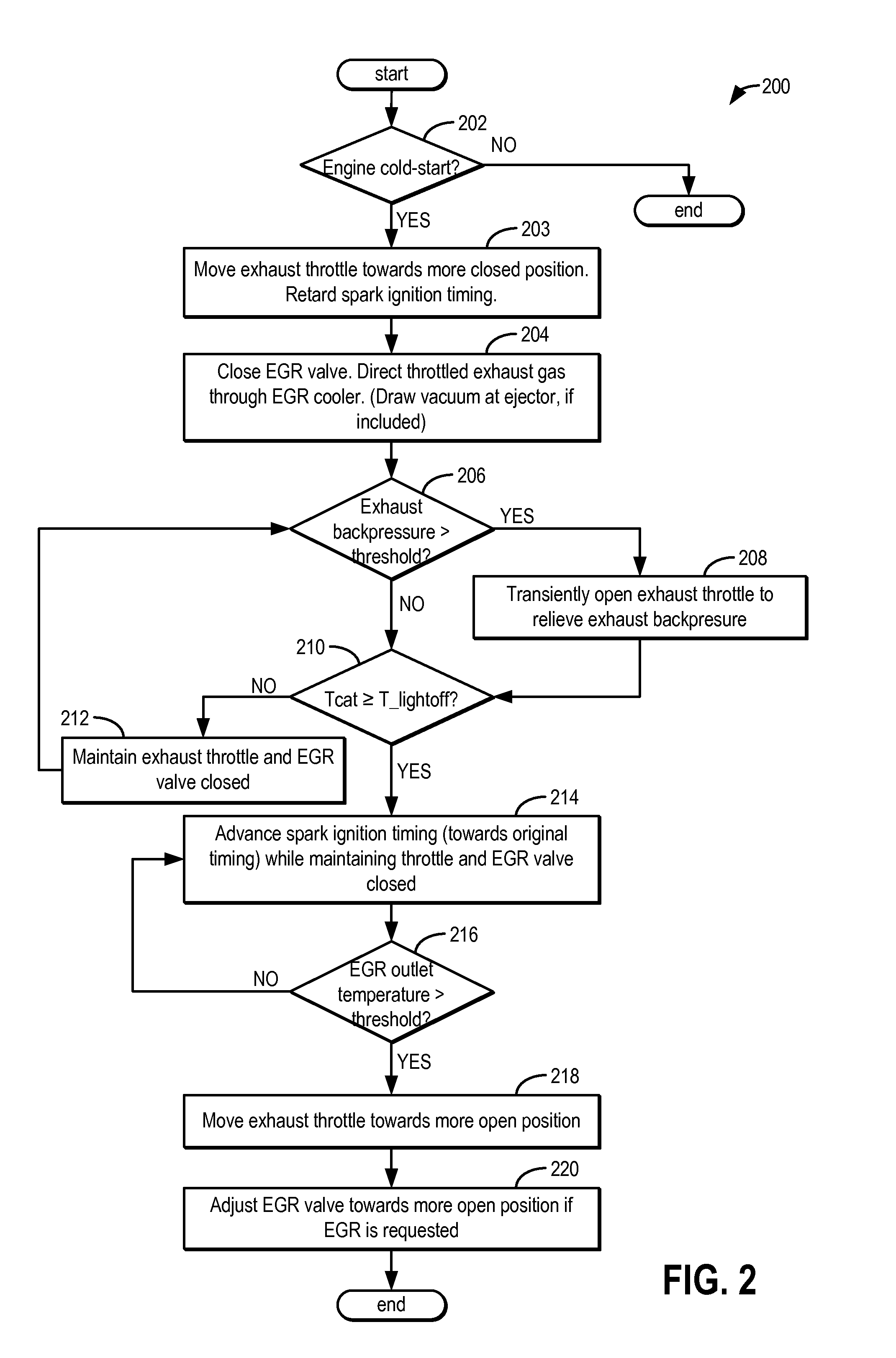
Method and system for catalyst temperature control
ActiveUS20140196454A1Vehicle exhaust qualityQuality improvementElectrical controlInternal combustion piston enginesTemperature controlHeat rejection
Methods and systems are provided for controlling and coordinating control of a post-catalyst exhaust throttle and an EGR valve to expedite catalyst heating. By closing both valves during an engine cold start, an elevated exhaust backpressure and increased heat rejection at an EGR cooler can be synergistically used to warm each of an engine and an exhaust catalyst. The valves may also be controlled to vary an amount of exhaust flowing through an exhaust venturi so as to meet engine vacuum needs while providing a desired amount of engine EGR.
Owner:FORD GLOBAL TECH LLC
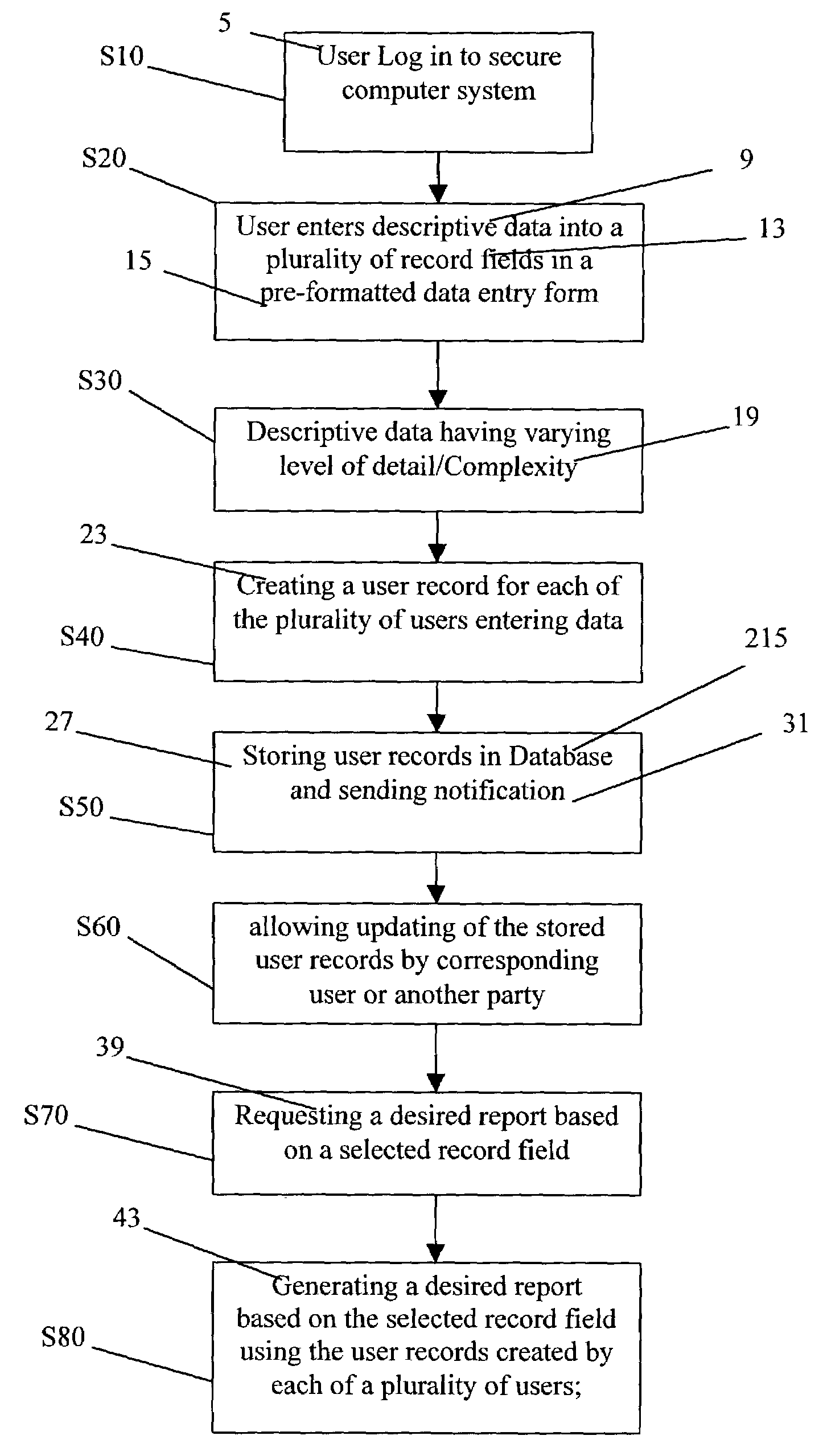
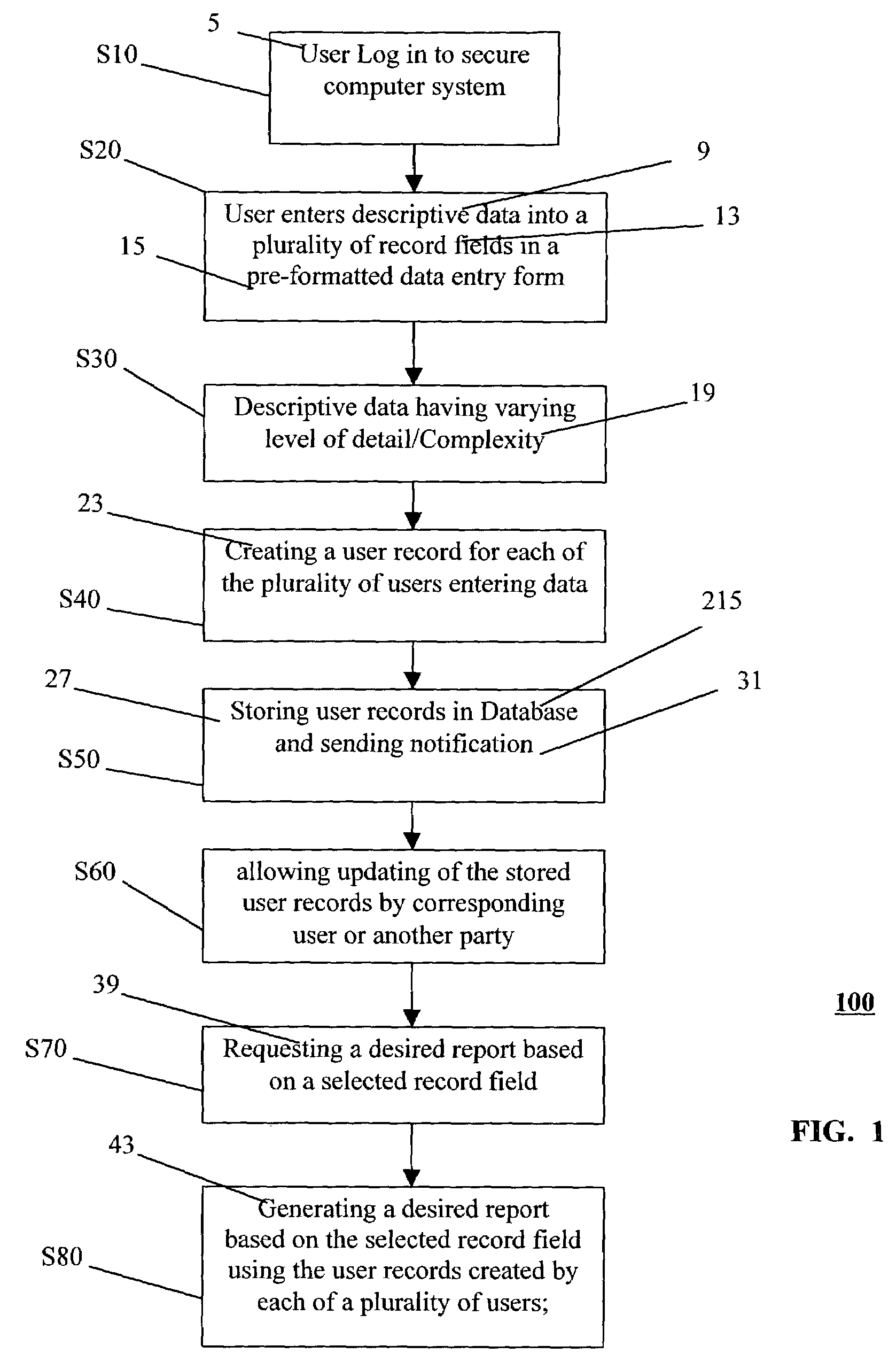
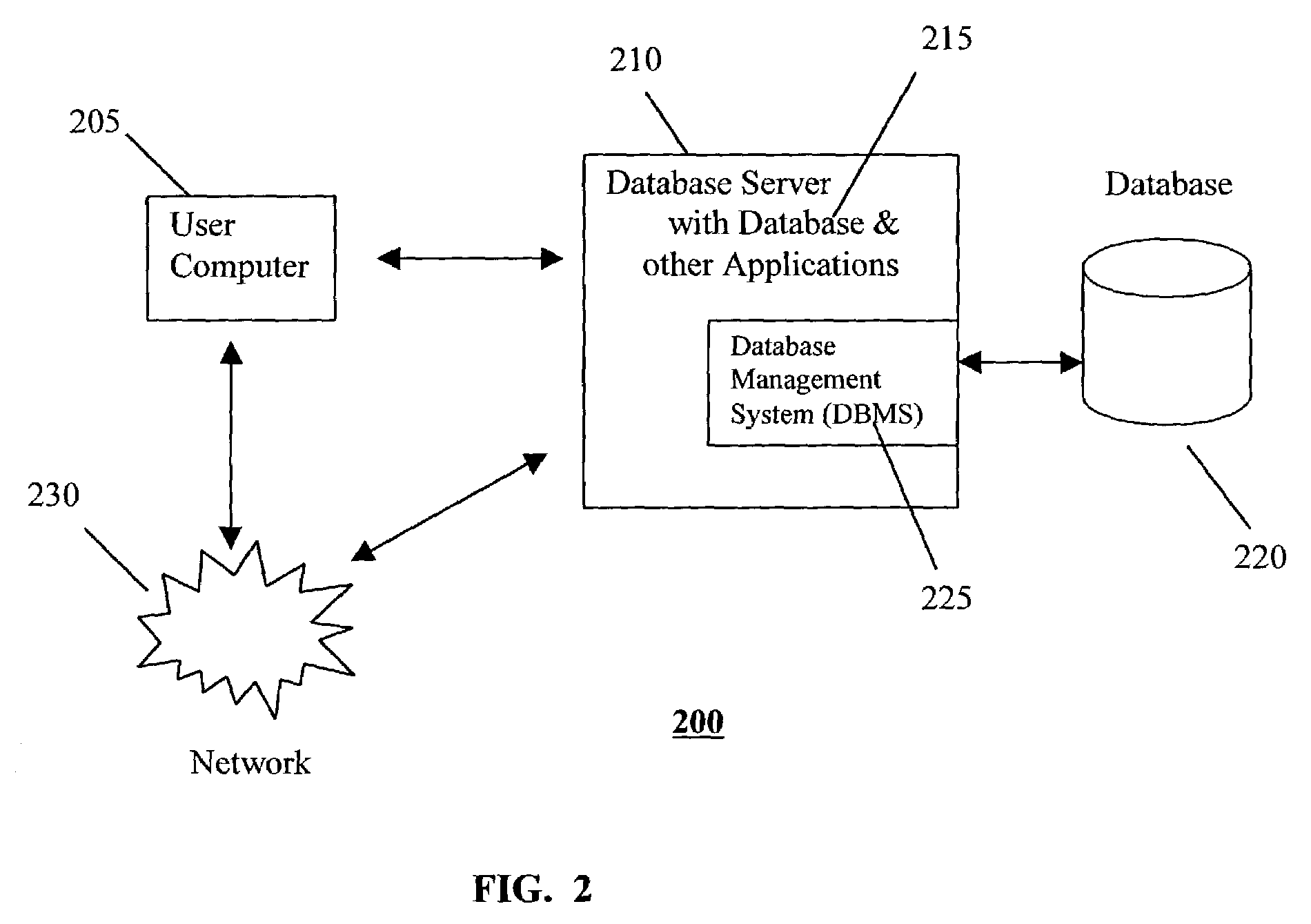
Method and system for automated generation of a requested report in a computer system
InactiveUS7113933B1Generate efficientlyValuable resource timeOffice automationResourcesComputerized systemCentral database
There is provided a method and system for efficiently generating administrative reports in an automated manner and for enabling users, who contributing to the reports, to create and store task, goal, progress and performance related descriptions, of varying complexity and detail, in a central database location from which appropriate task, goal and progress descriptions can be selectively retrieved for use in a desired periodic report for use in workload and performance management. This method and system frees up full time employees from the time consuming work of repeatedly preparing descriptions and information for workload and performance reports and substantially eliminates rework for administrative assistant who often consolidate and compile reports.
Owner:AMERIPRISE FINANCIAL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com