Patents
Literature
12993results about How to "Avoid problems" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
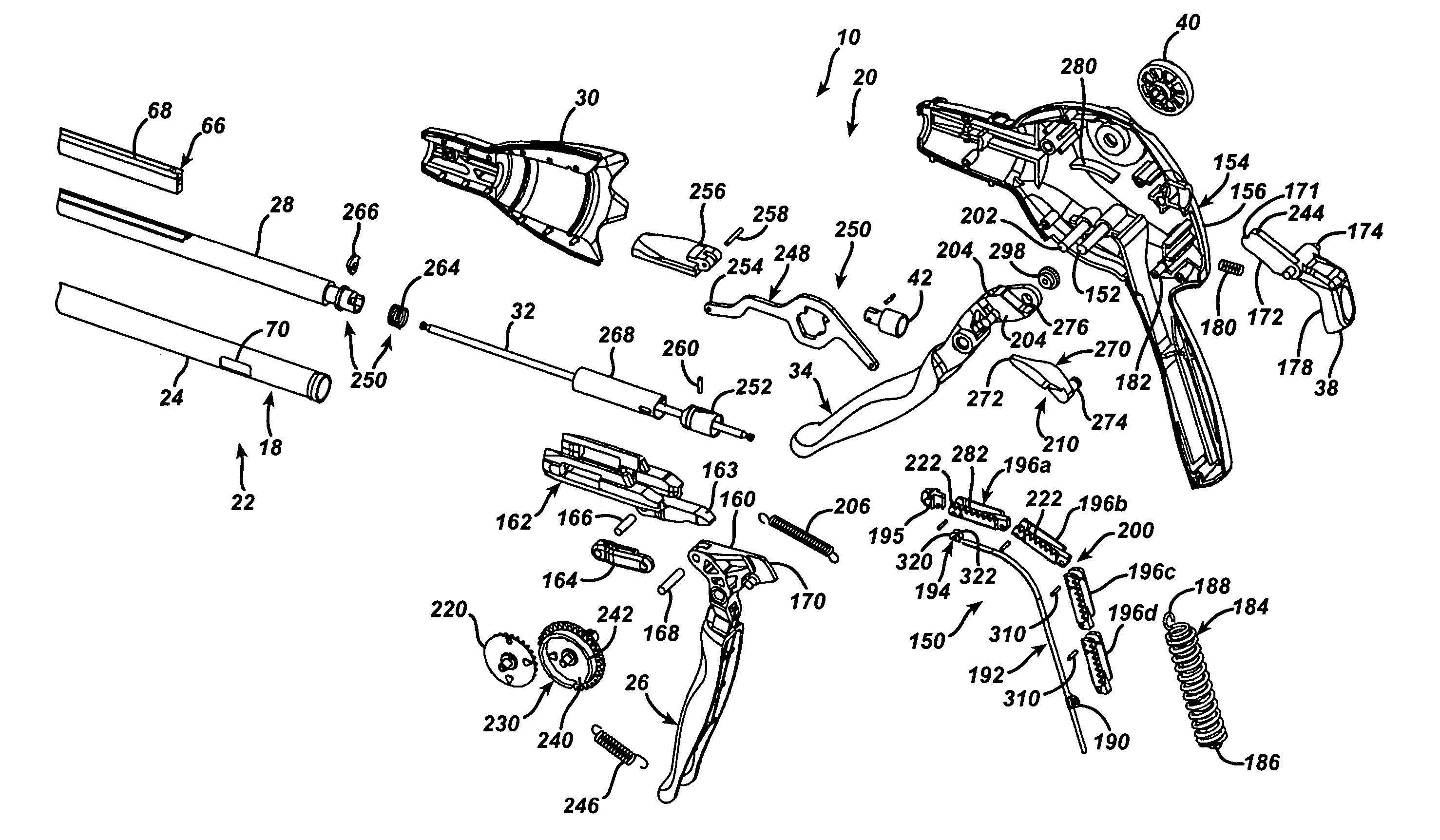
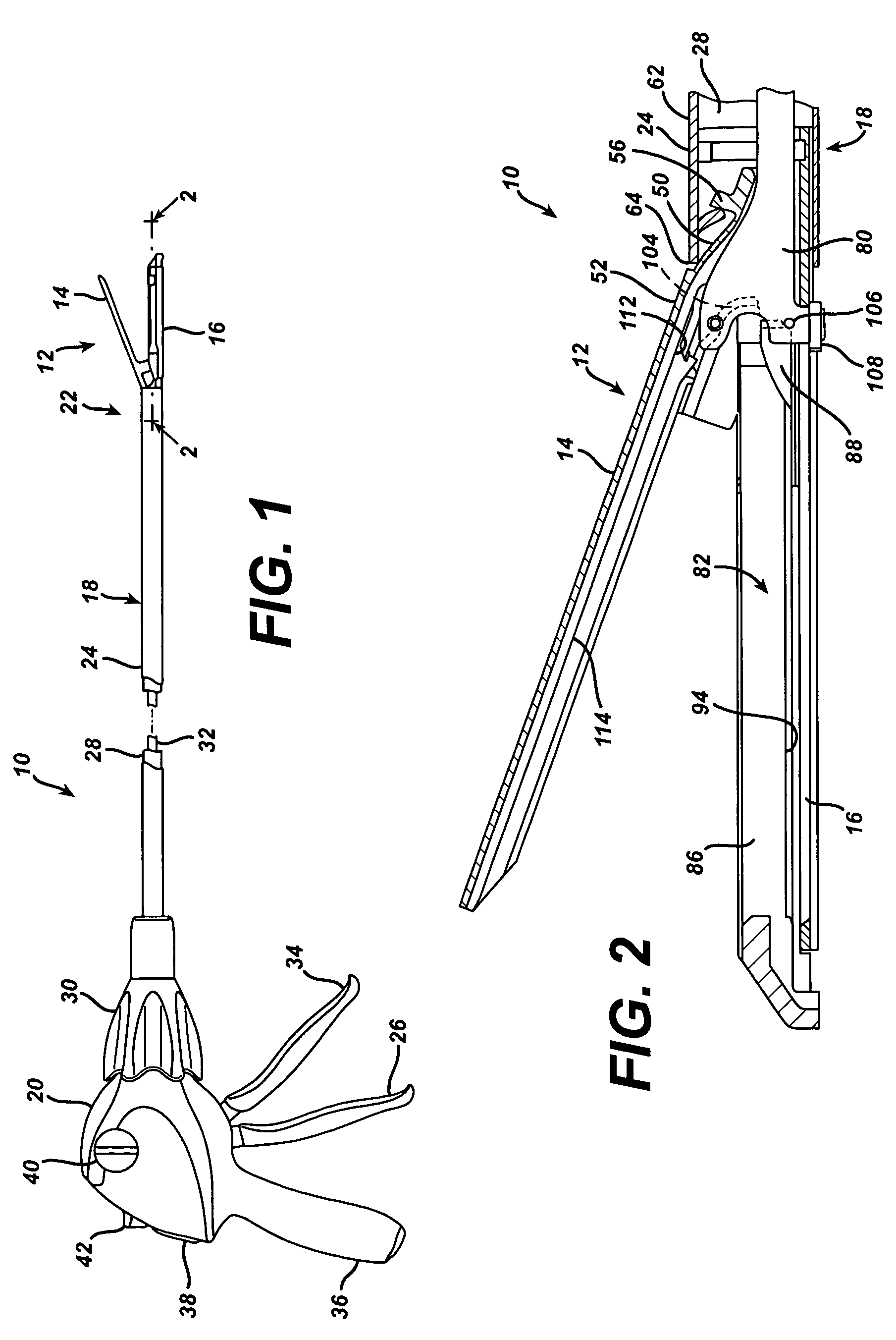
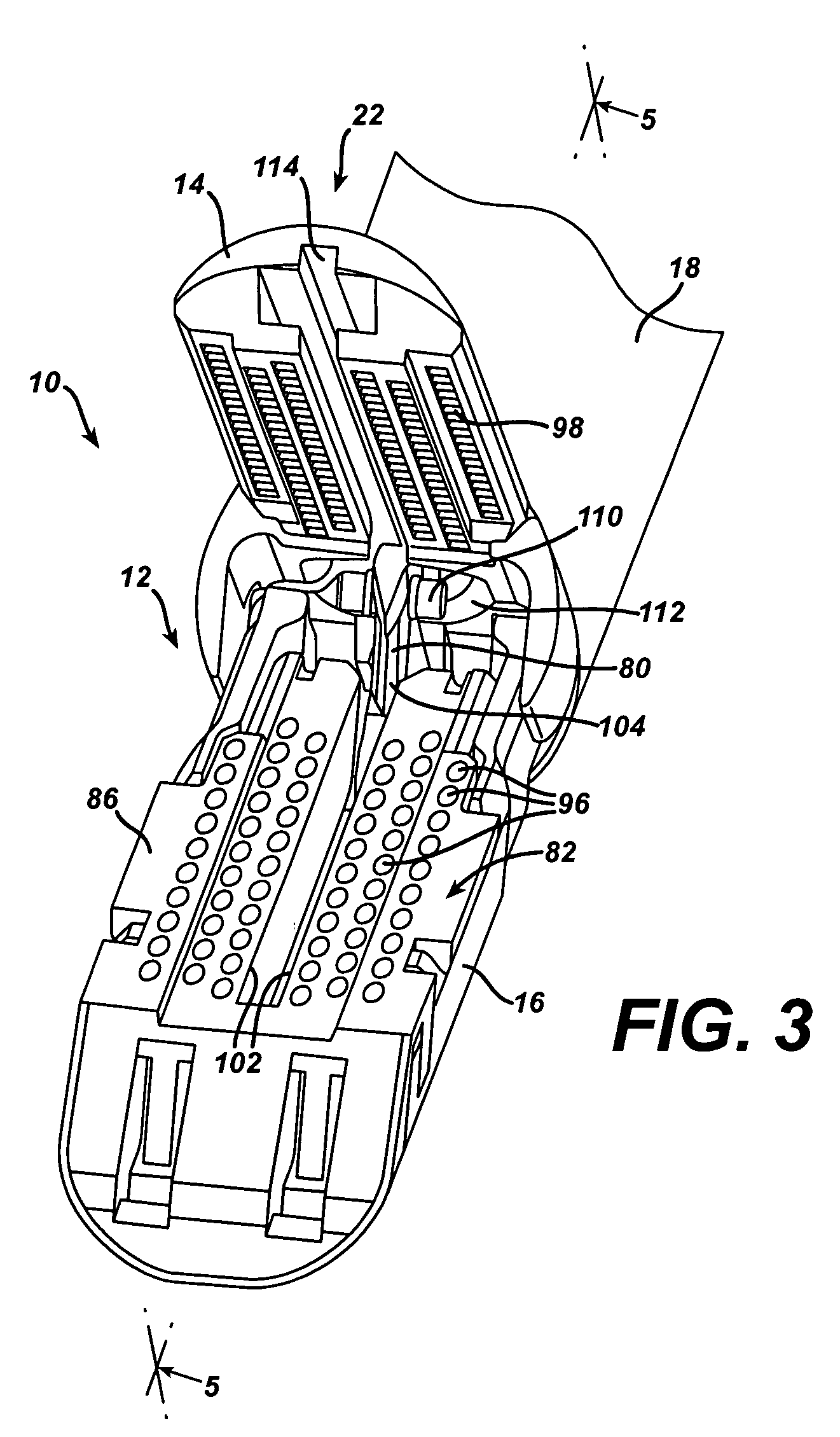
Surgical stapling instrument having multistroke firing incorporating a traction-biased ratcheting mechanism
A surgical stapling and severing instrument particularly suited to endoscopic procedures incorporates a handle that produces separate closing and firing motions to actuate an end effector. In particular, the handle produces multiple firing strokes in order to reduce the required amount of force required to fire (i.e., staple and sever) the end effector. A linked transmission reduces the required handle longitudinal length, yet achieves a rigid, strong configuration when straightened for firing. A traction biased firing mechanism avoids binding in driving this straightened linked rack in cooperation with an anti-backup mechanism, with a lockout mechanism that prevents releasing the closure trigger during firing. Furthermore, an external indicator gives feedback to the surgeon as to how far firing has progressed, as well as providing a manual retraction capability.
Owner:CILAG GMBH INT
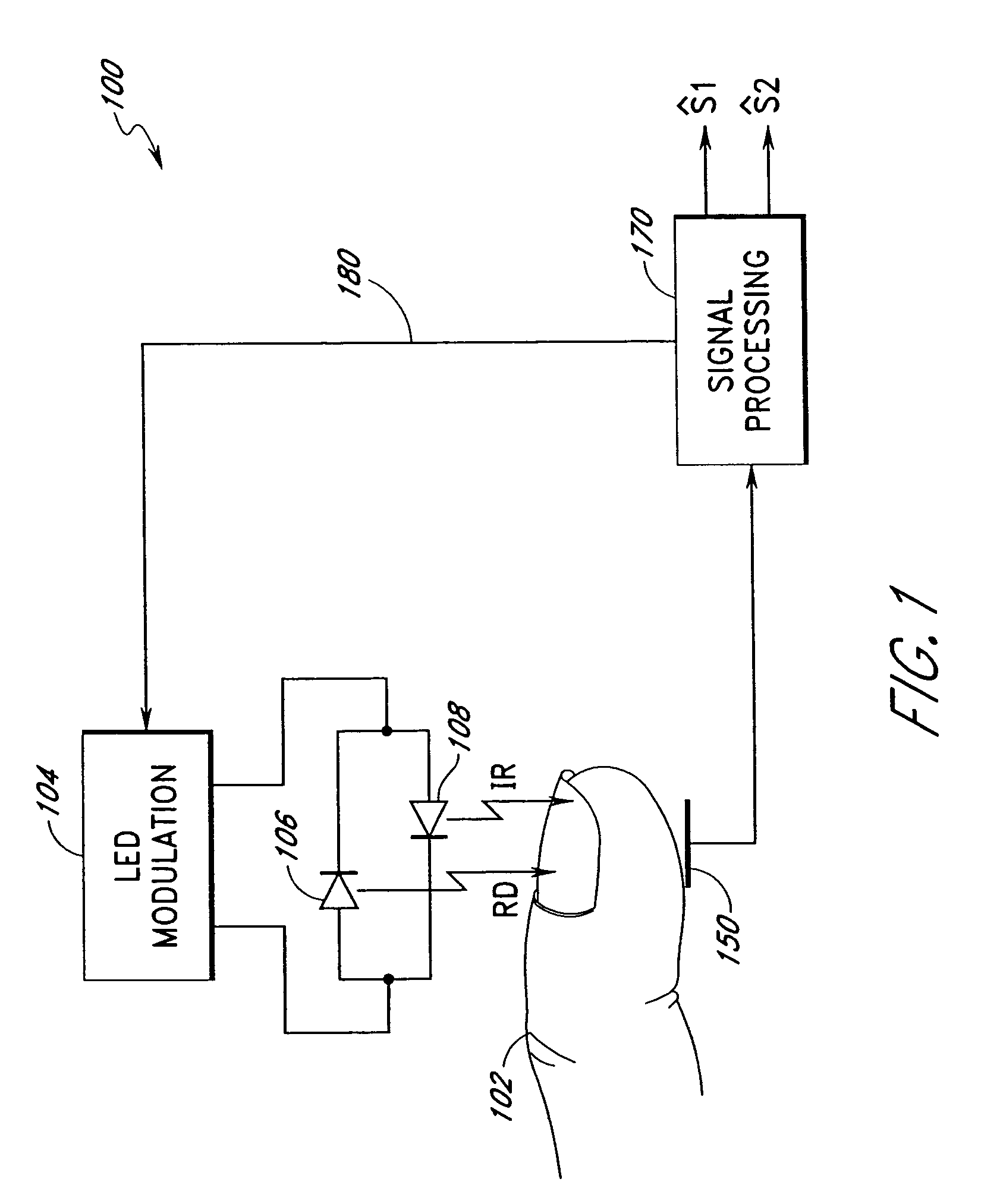
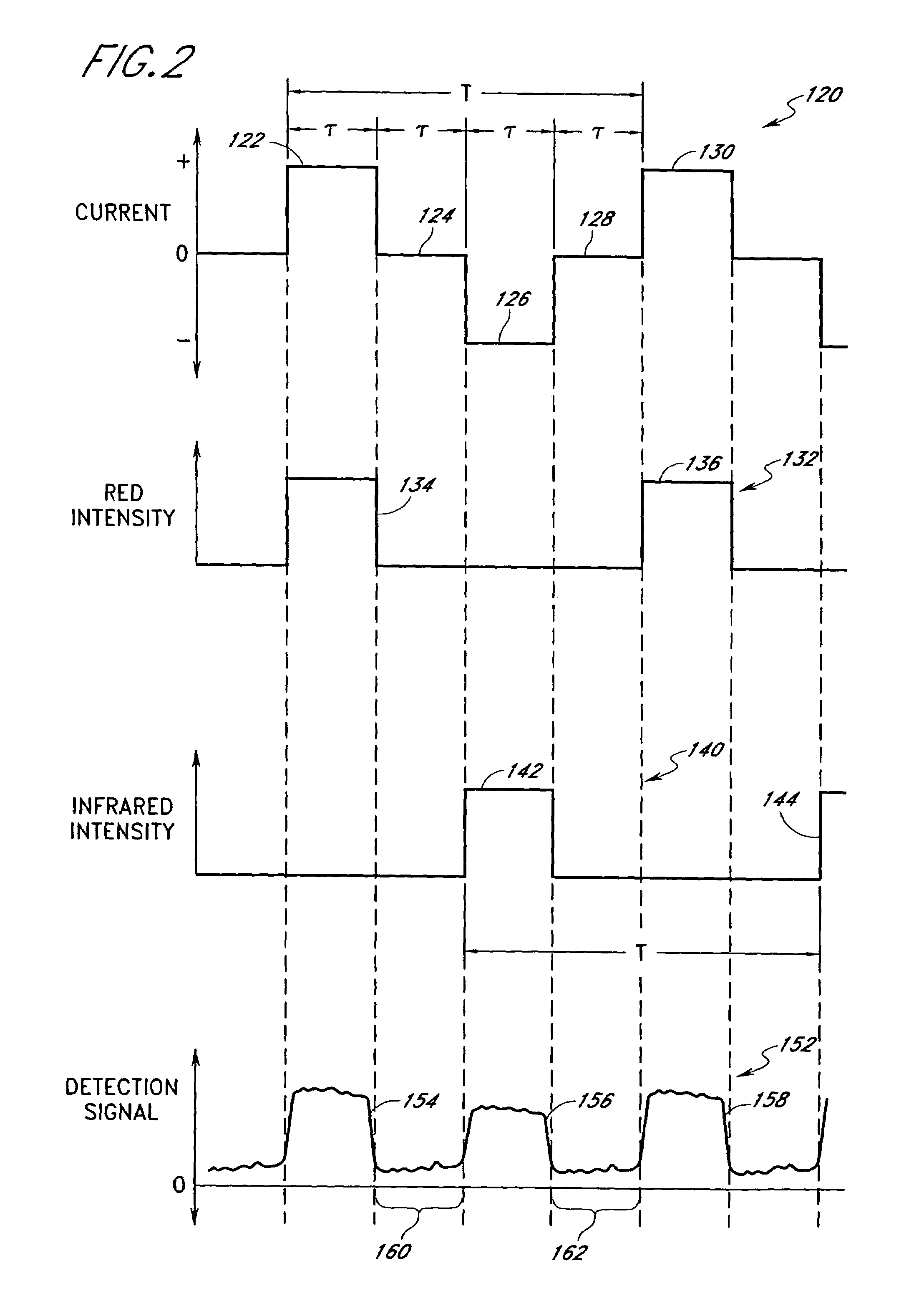
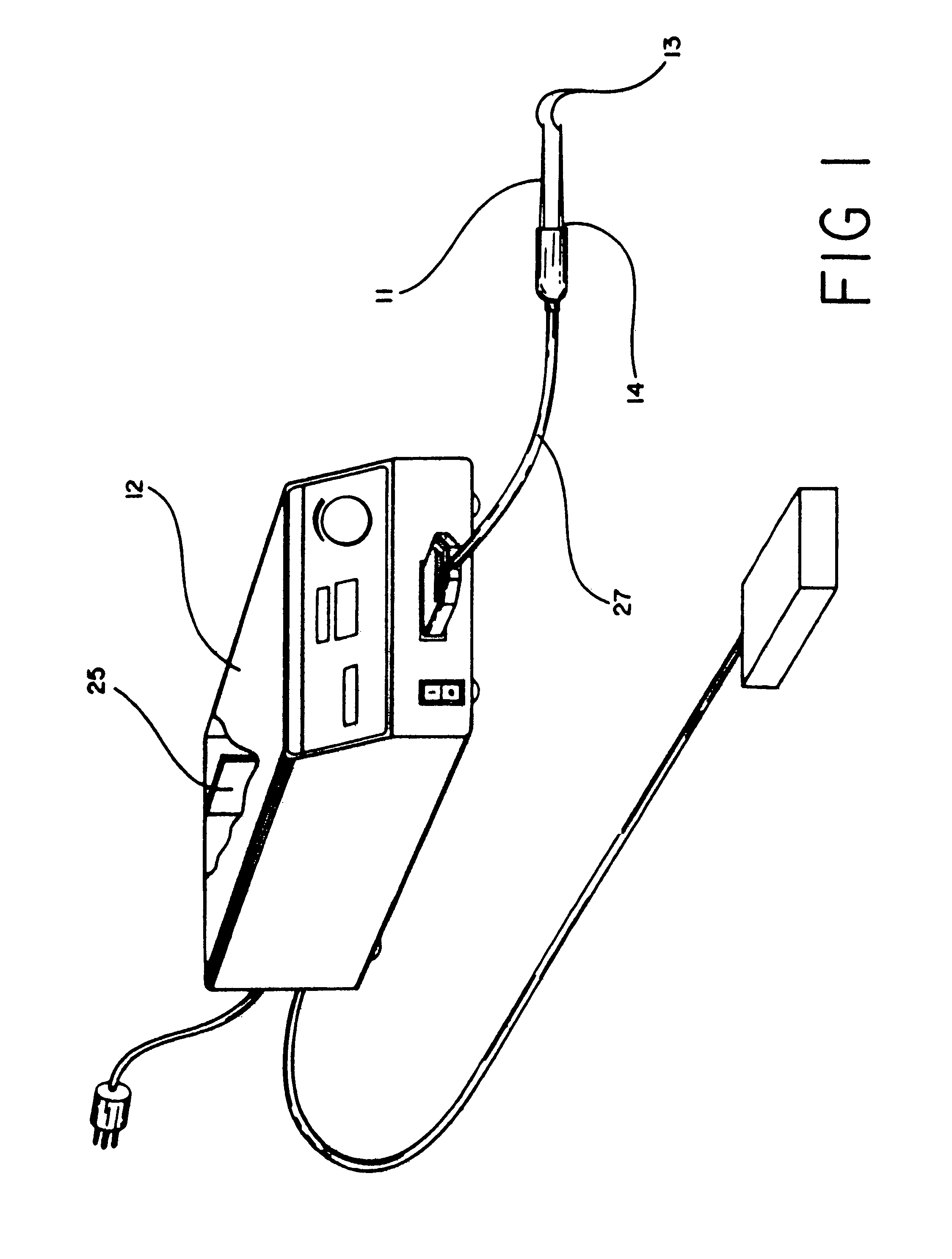
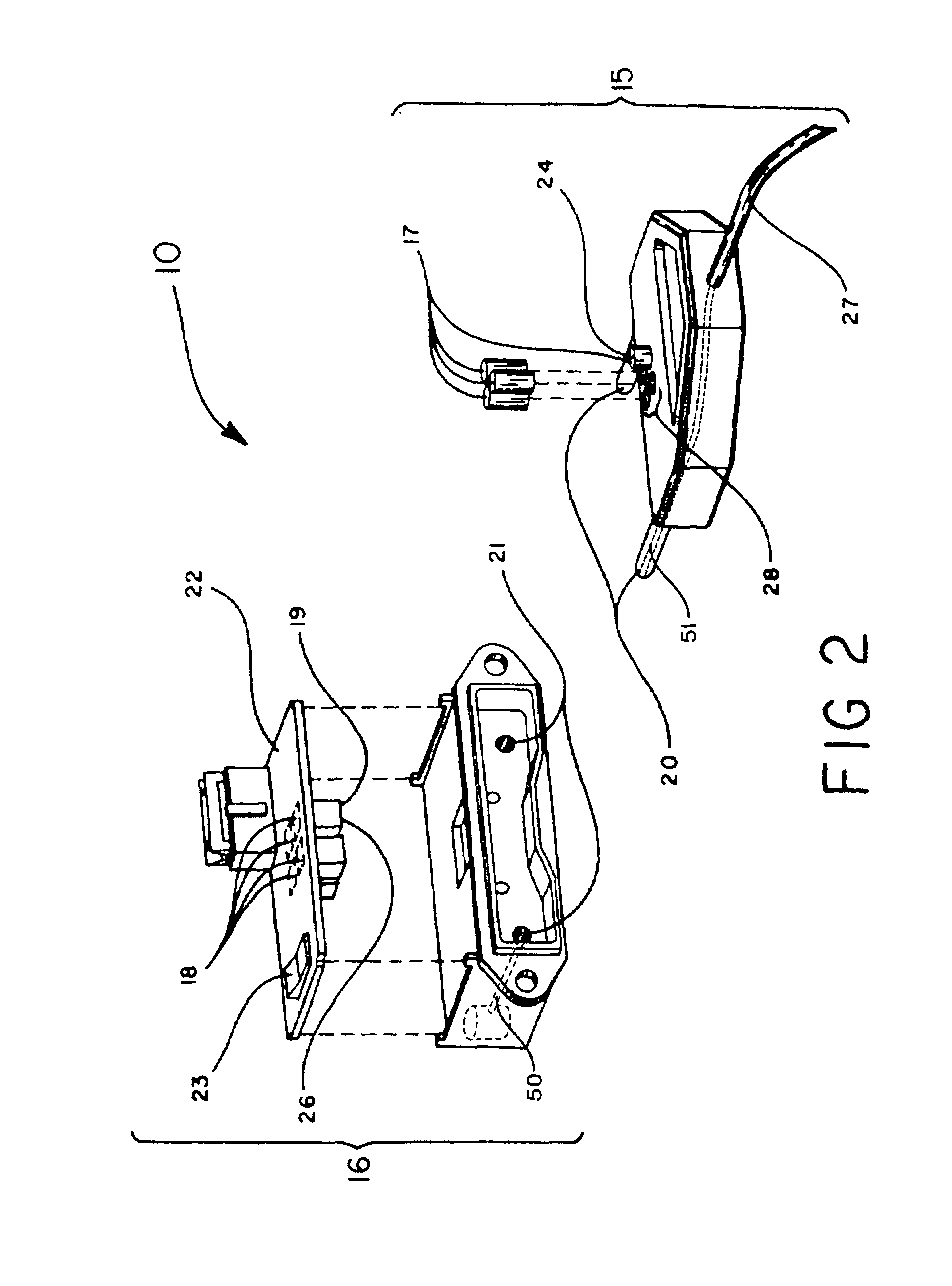
Method and apparatus for demodulating signals in a pulse oximetry system
InactiveUS7003339B2Reduce distractionsHigh resolutionTime-division optical multiplex systemsTime-division multiplexHarmonicBlood oxygenation
A method and an apparatus measure blood oxygenation in a subject. A first signal source applies a first input signal during a first time interval. A second signal source applies a second input signal during a second time interval. A detector detects a first parametric signal responsive to the first input signal passing through a portion of the subject having blood therein. The detector also detects a second parametric signal responsive to the second input signal passing through the portion of the subject. The detector generates a detector output signal responsive to the first and second parametric signals. A signal processor receives the detector output signal and demodulates the detector output signal by applying a first demodulation signal to a signal responsive to the detector output signal to generate a first output signal responsive to the first parametric signal. The signal processor applies a second demodulation signal to the signal responsive to the detector output signal to generate a second output signal responsive to the second parametric signal. The first demodulation signal and the second demodulation signal both include at least a first component having a first frequency and a first amplitude and a second component having a second frequency and a second amplitude. The second frequency is a harmonic of the first frequency. The second amplitude is related to the first amplitude to minimize crosstalk from the first parametric signal to the second output signal and to minimize crosstalk from the second parametric signal to the first output signal.
Owner:JPMORGAN CHASE BANK NA
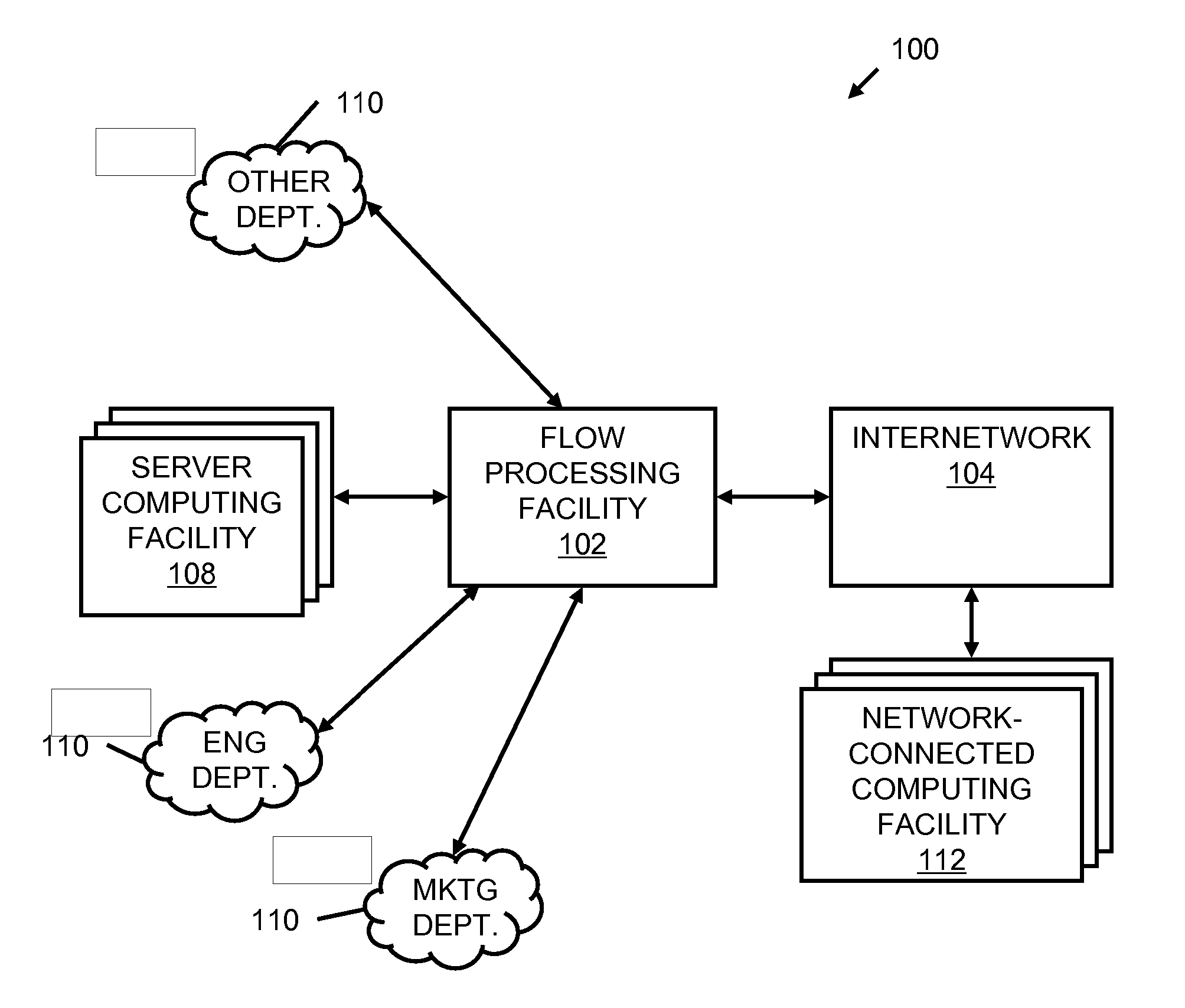
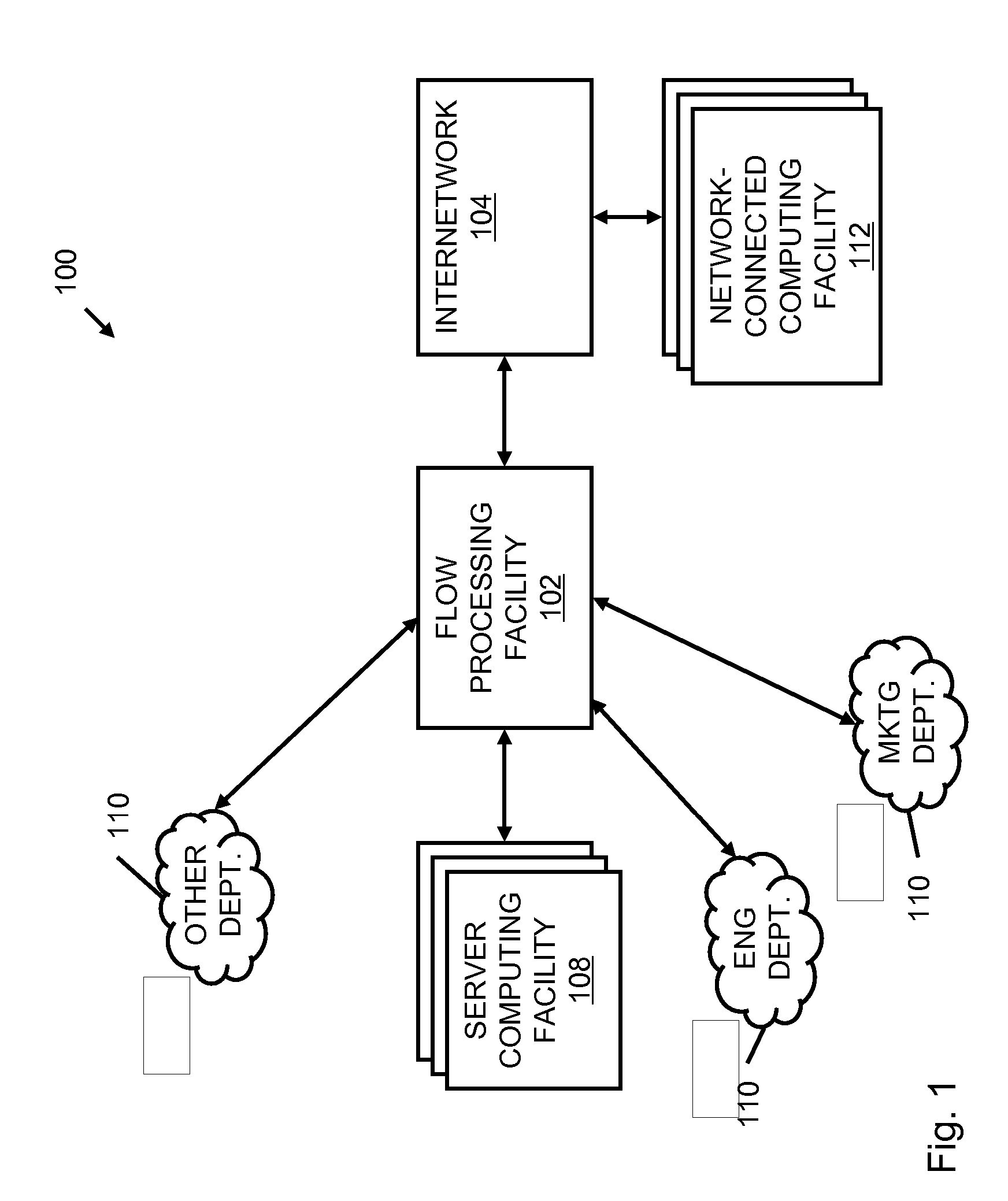
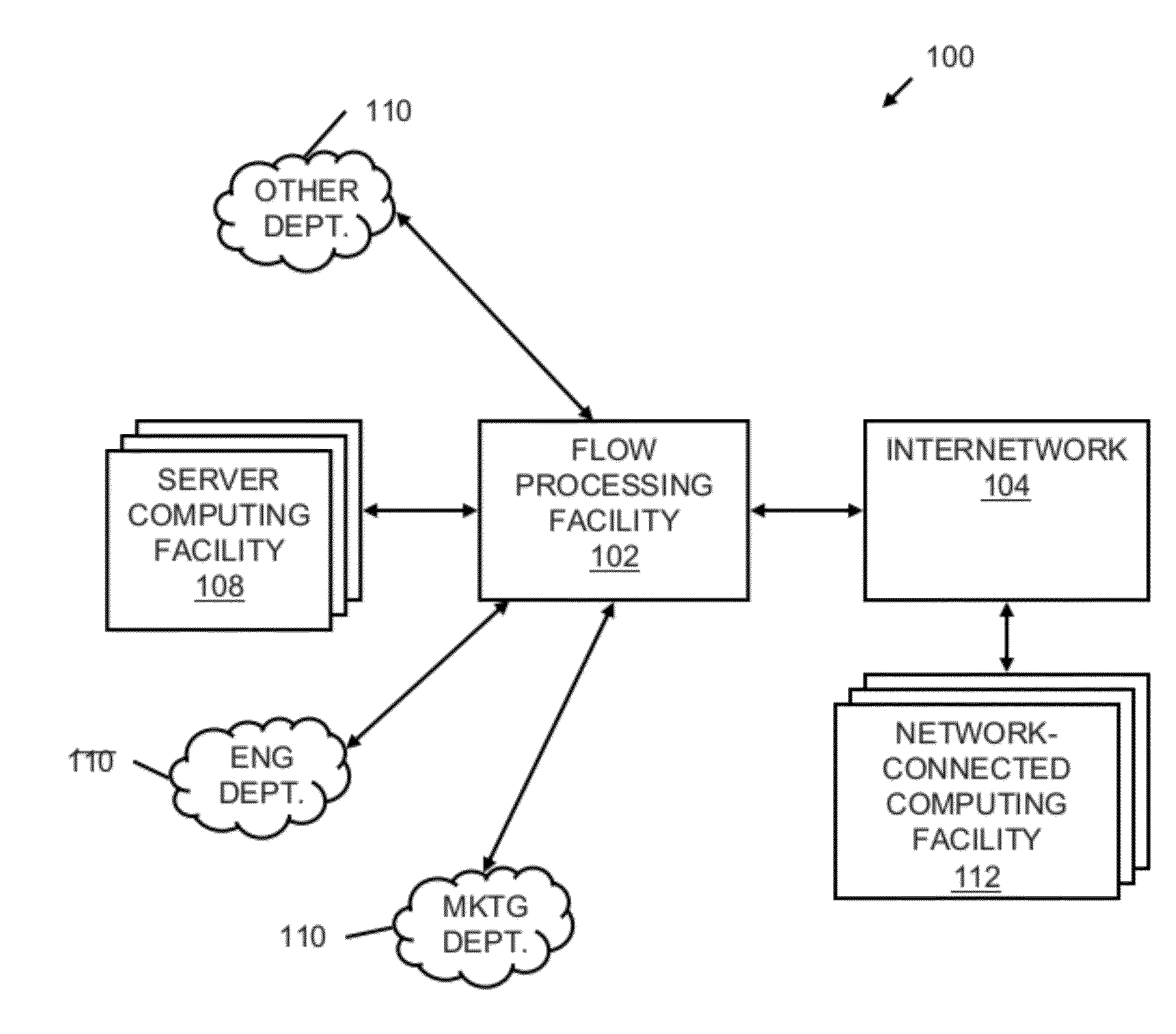
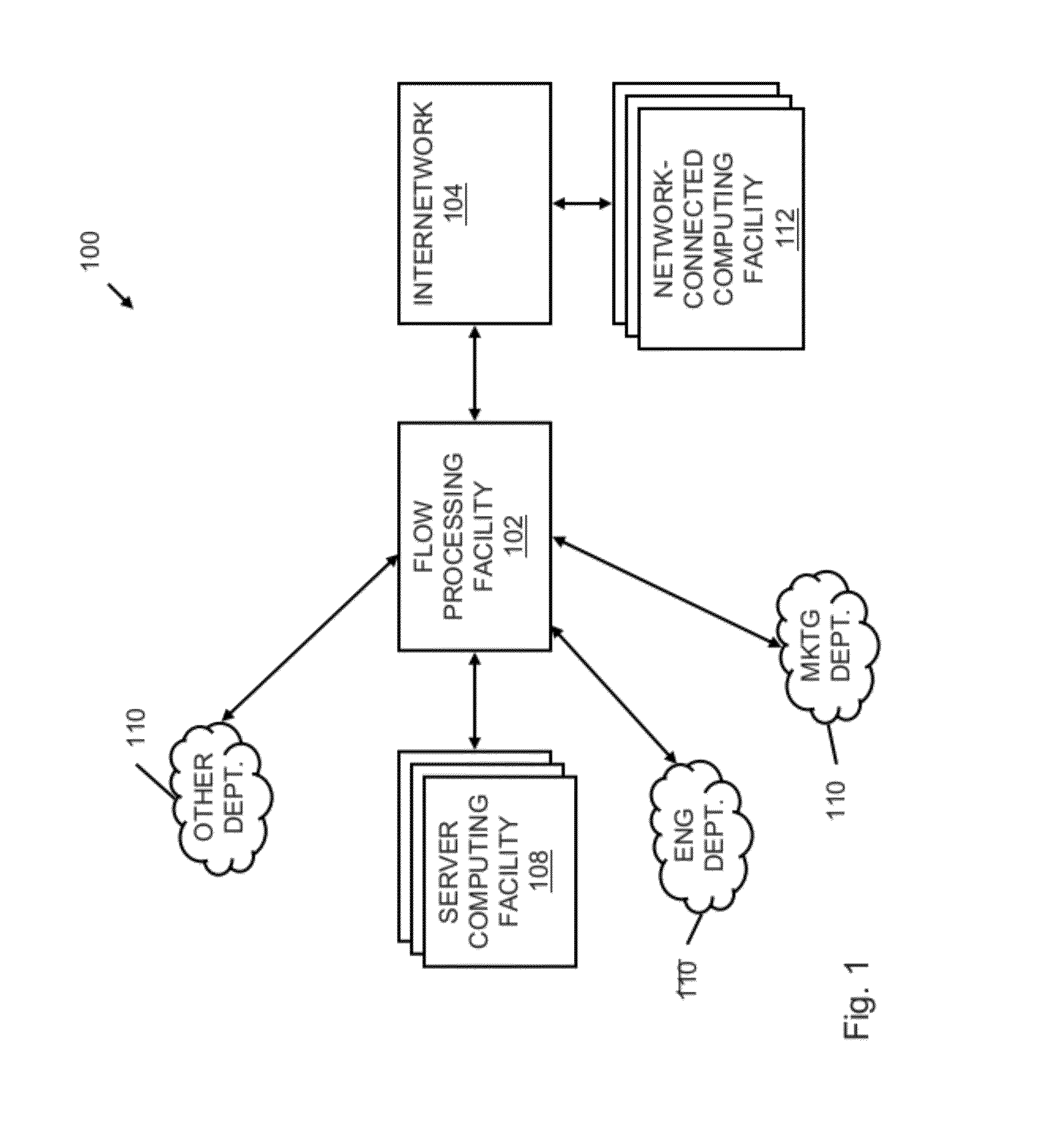
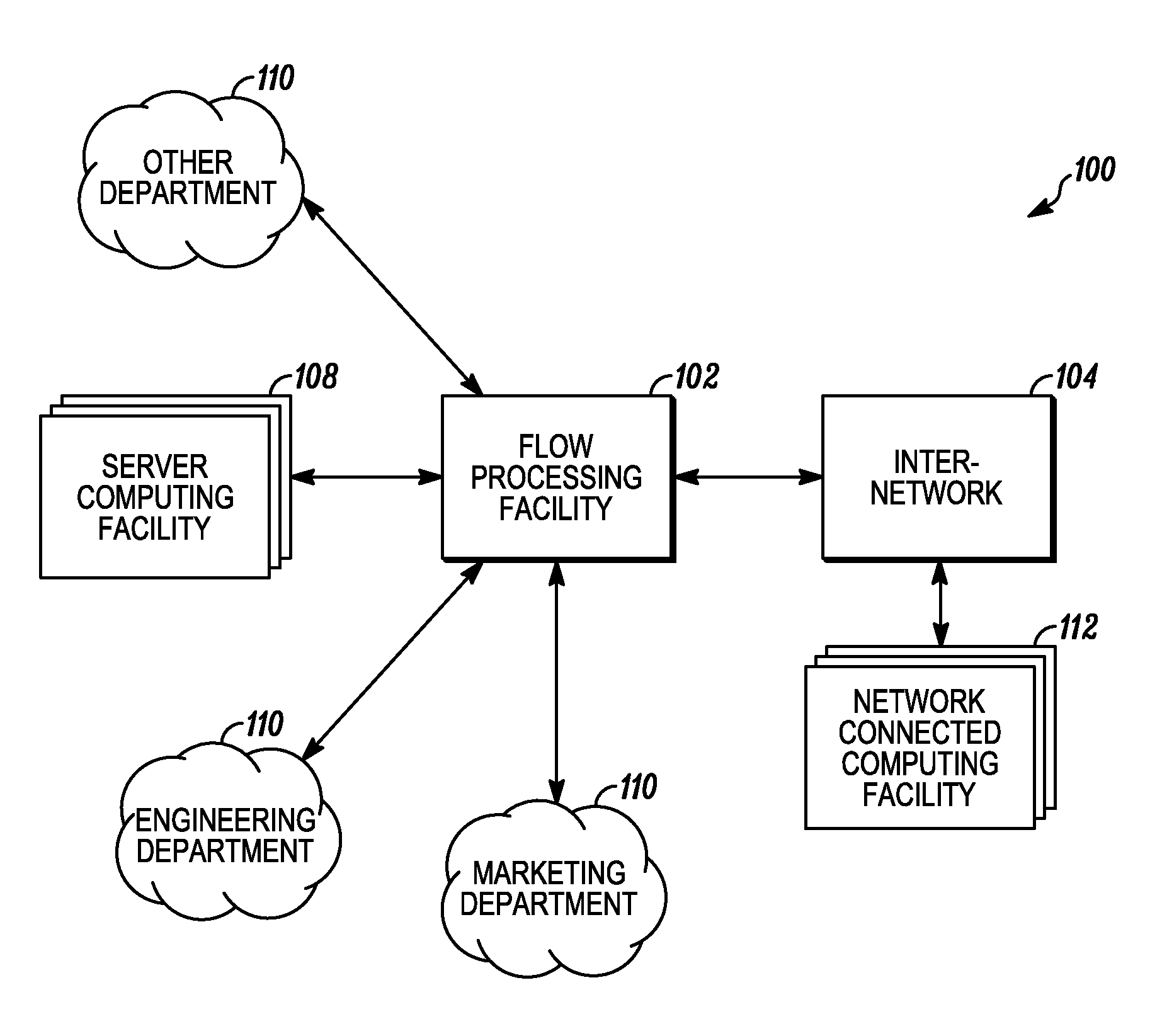
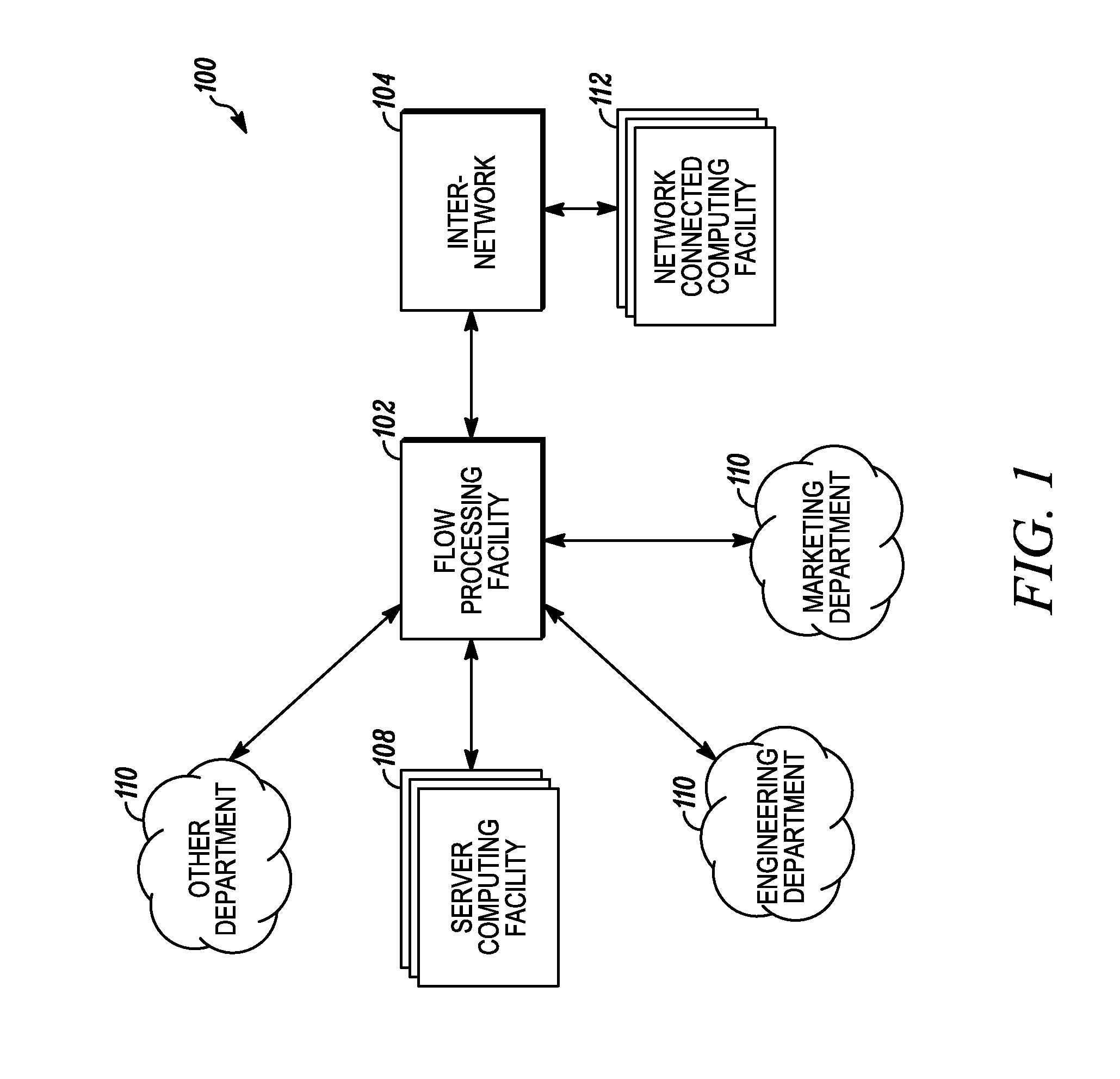
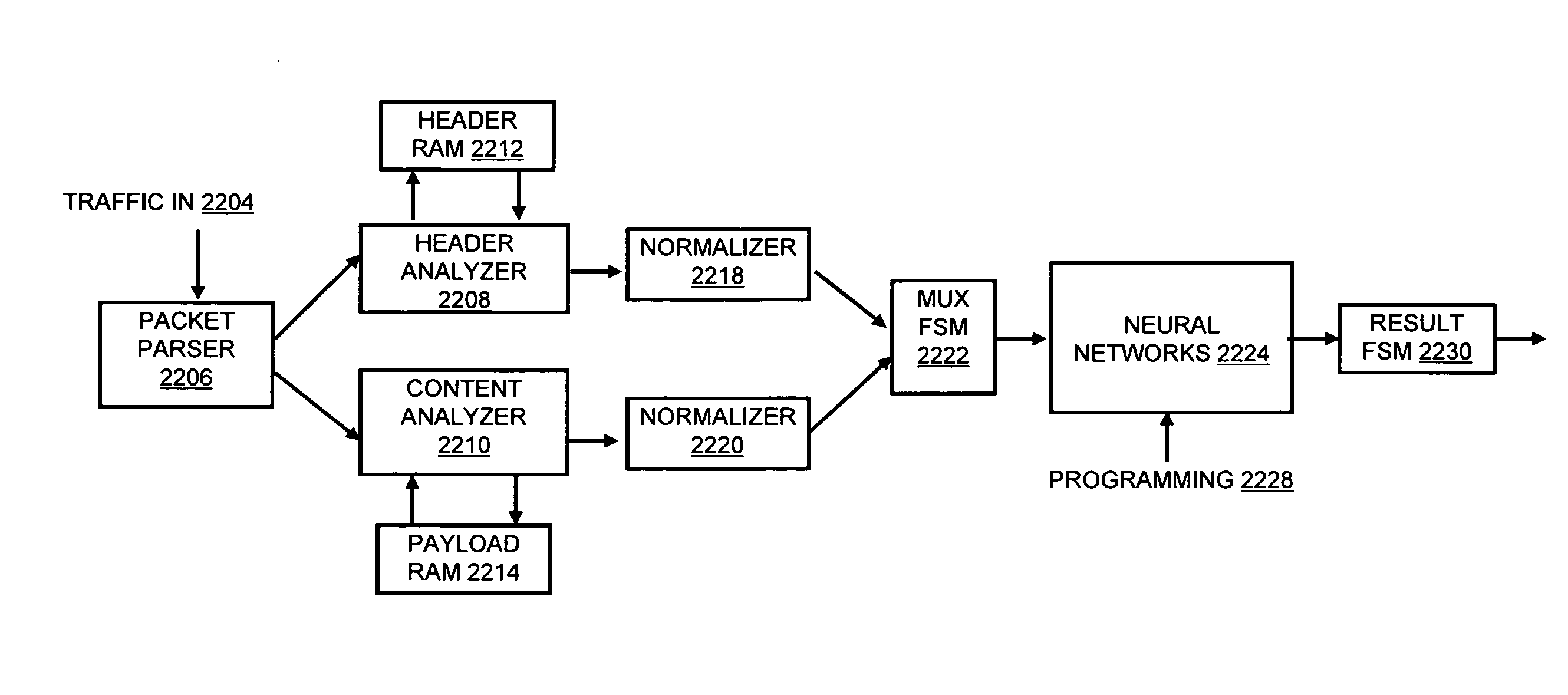
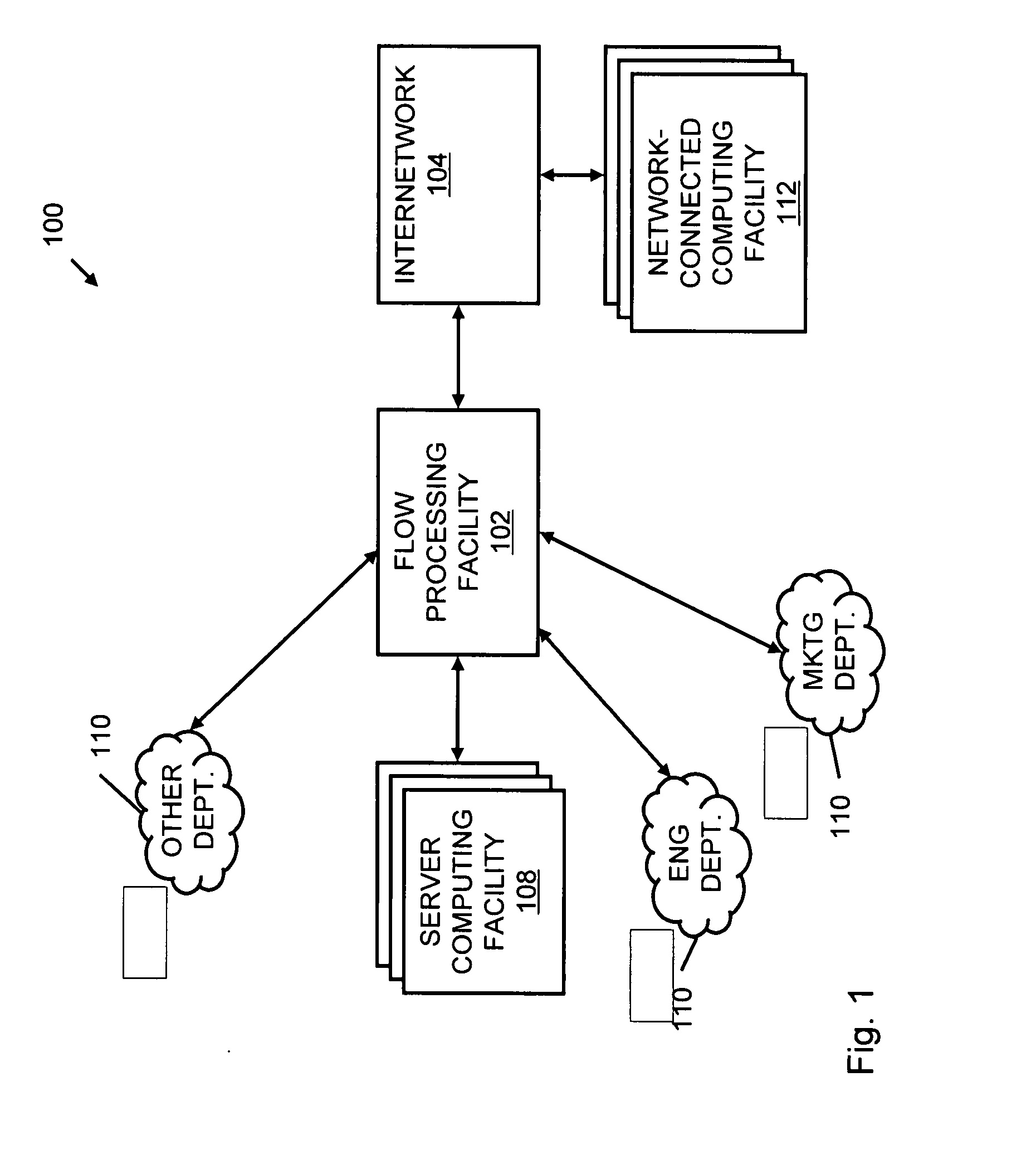
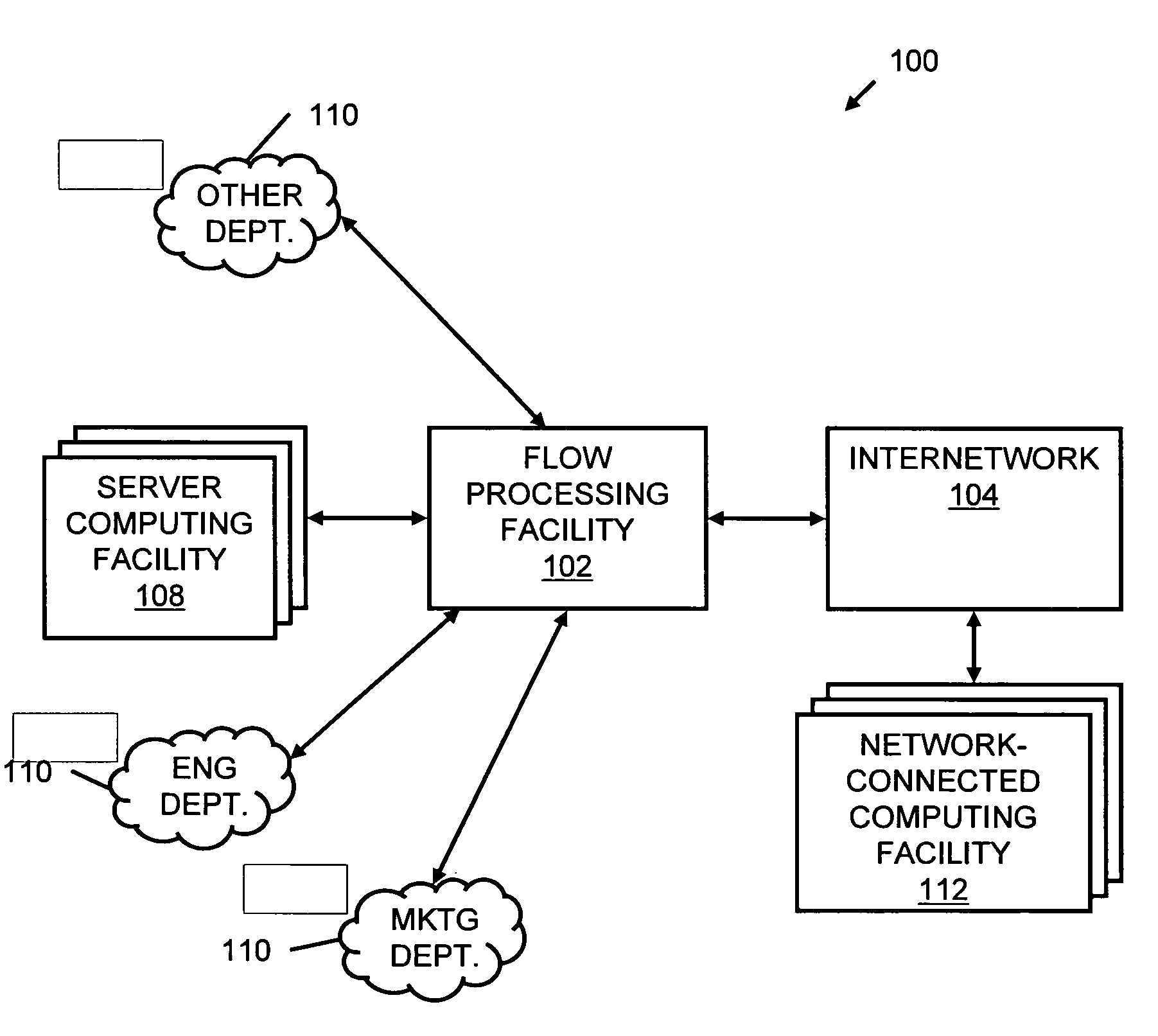
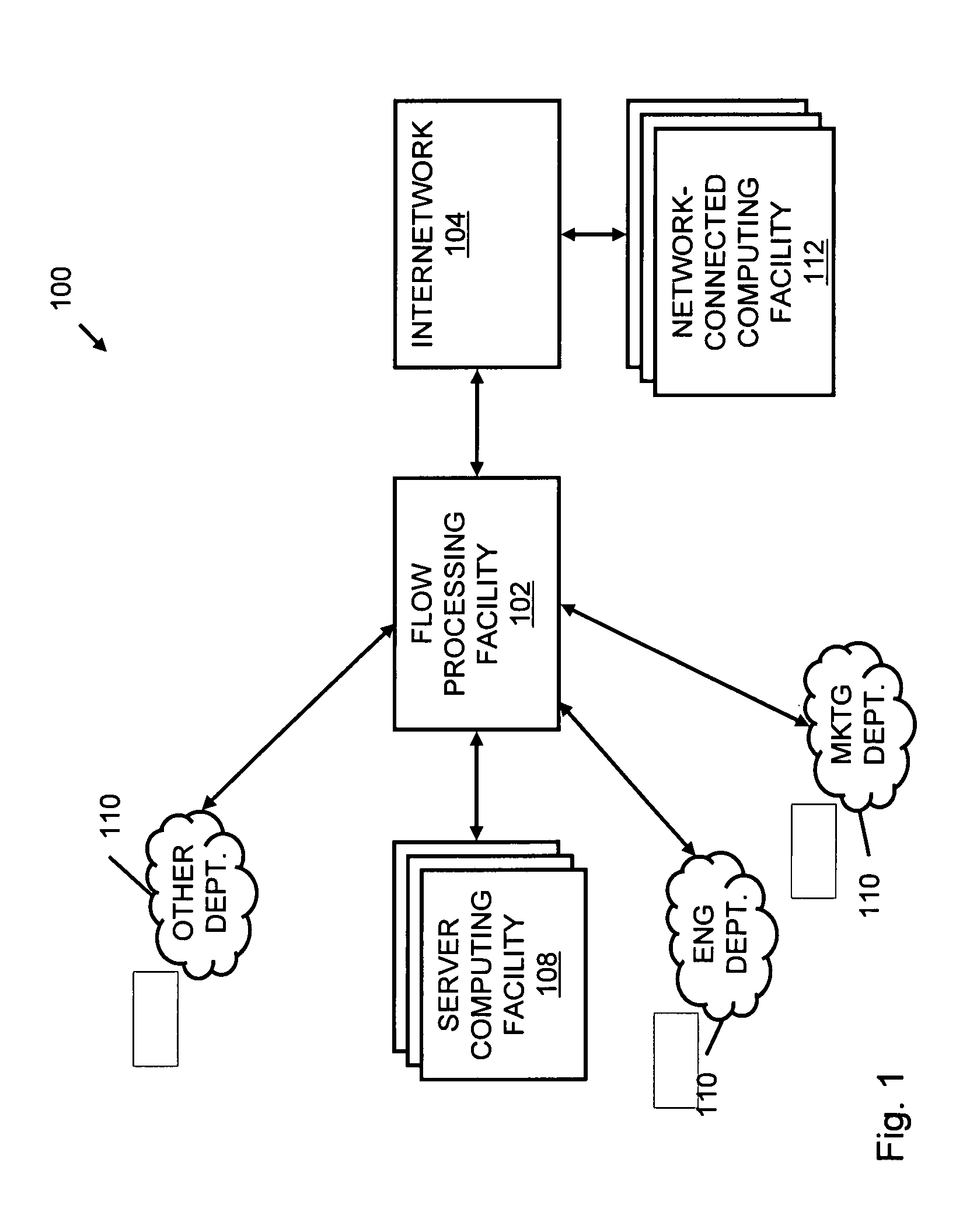
Systems and methods for processing data flows
InactiveUS20070192863A1Increased complexitySignificant expenseMemory loss protectionError detection/correctionData packData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Systems and methods for processing data flows
ActiveUS20120240185A1Facilitate detectionIncreased complexityComputer security arrangementsTransmissionPacket payloadUnified threat management
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
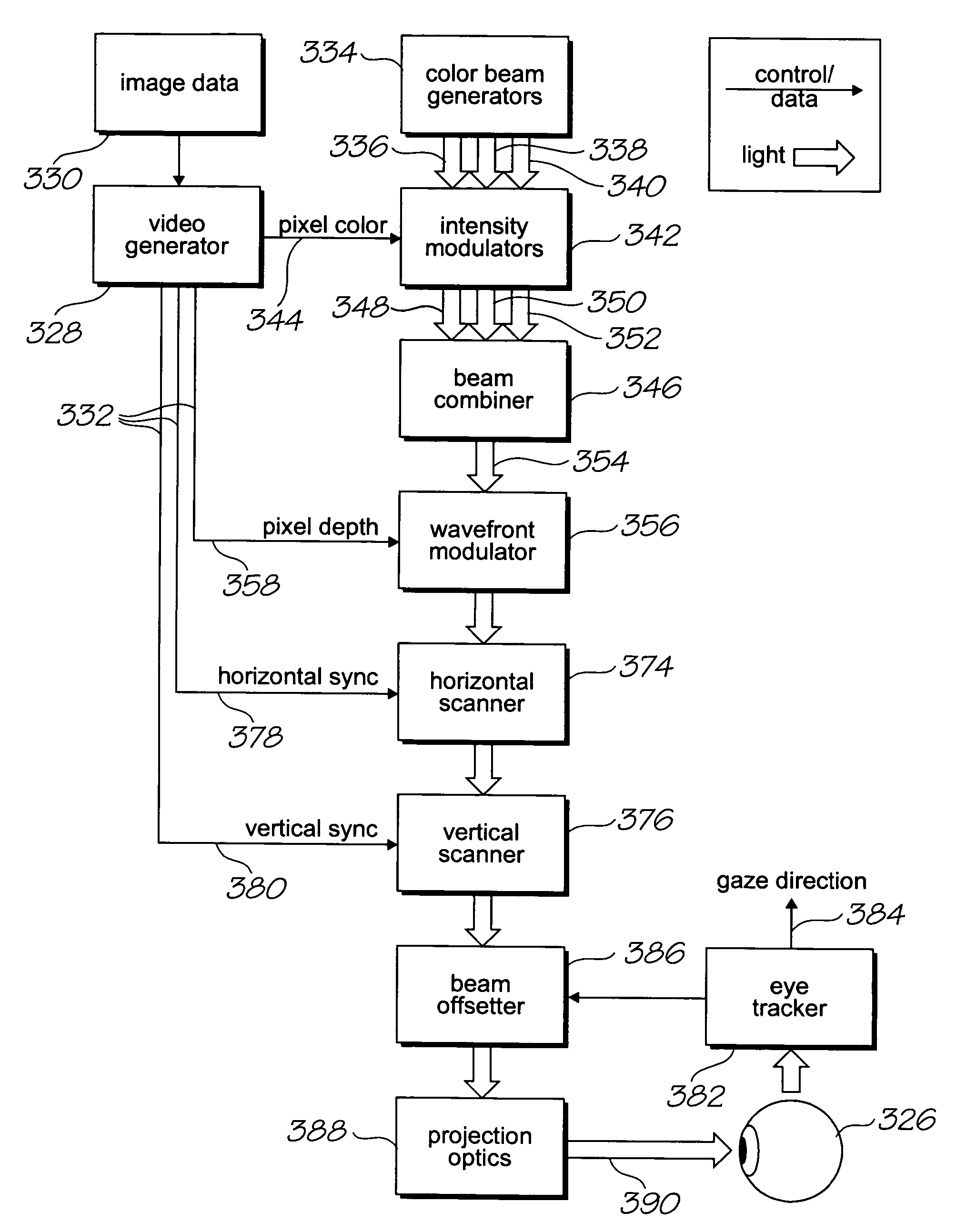
Head mounted display with wave front modulator
InactiveUS20060028400A1Precise positioningAvoid problemsCathode-ray tube indicatorsSteroscopic systemsDisplay deviceSee-through display
An augmented reality device for inserting virtual imagery into a user's view of their physical environment, the device comprising: a display device through which the user can view the physical environment; an optical sensing device for sensing at least one surface in the physical environment; and, a controller for projecting the virtual imagery via the display device; wherein during use, the controller uses wave front modulation to match the curvature of the wave fronts of light reflected from the display device to the user's eyes with the curvature of the wave fronts of light that would be transmitted through the device display if the virtual imagery were situated at a predetermined position relative to the surface, such that the user sees the virtual imagery at the predetermined position regardless of changes in position of the user's eyes with respect to the see-through display.
Owner:SILVERBROOK RES PTY LTD
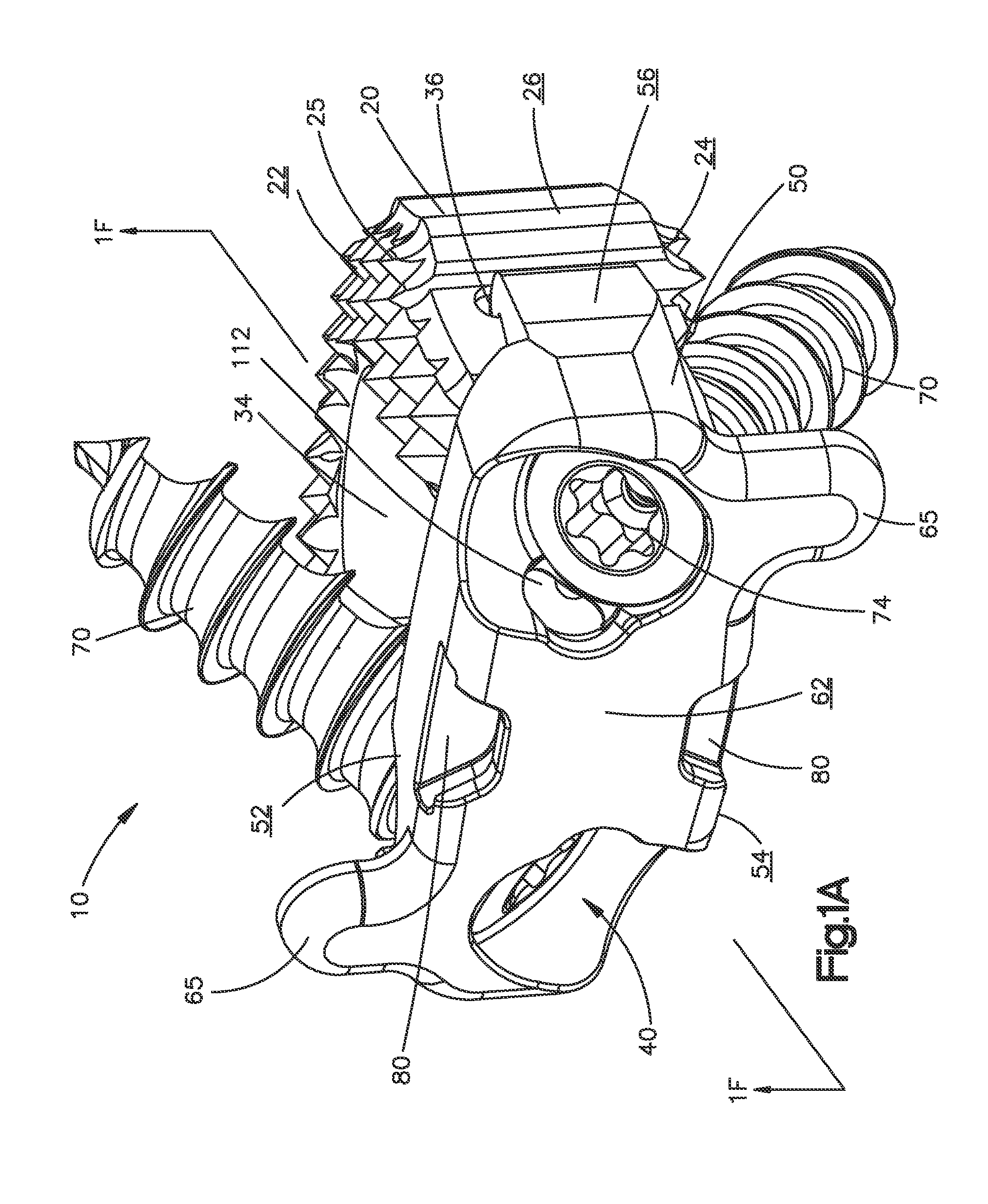
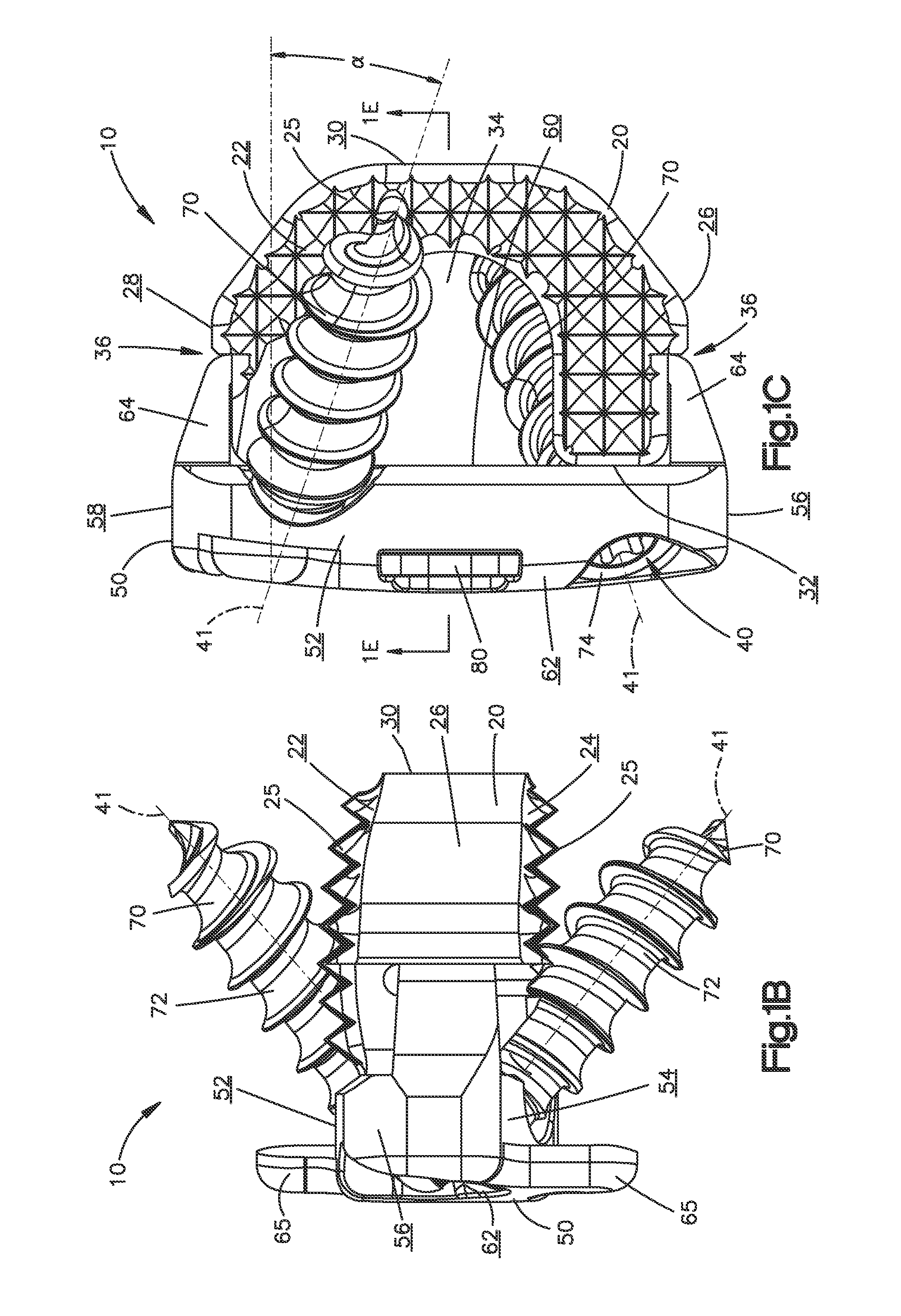
Smart recognition apparatus and method
InactiveUS7044949B2Avoid problemsTight optical and mechanical toleranceDiagnosticsClose-range type systemsProximateElectrosurgery
A qualifying connection for an instrument attaches to a source of electrosurgery energy and to the instrument and has first and second parts coupled to the instrument and the source, respectively. Optical couplings on the connection transmit invisible energy to identify the instrument and are proximate on the first and second parts. A light modifier on the first part is proximal to the second part for modification of radiation in the infrared wavelengths so infrared transmitters encode signals and non-contact coded proximity detectors on the second part are the coupled detectors. Mechanical attachments include conjugating male and female portions which physically extend between the parts and matingly engage. An identifying circuit couples to the second part and responds to invisible light optically communicated across the couplings for verifying the type of instrument connected by the cable to the source. A method of using the connection has steps including juxtaposing and conjugating the parts with attachments and couplings for transmitting invisible optical energy to identify the instrument. The method includes modifying the invisible optical energy with geographically disposed proximate couplings of the parts when the attachments engage and the couplings are proximate. Passing and assessing signals of the modified energy are transmitted through the connection and to an identifying circuit in the source.
Owner:COVIDIEN AG
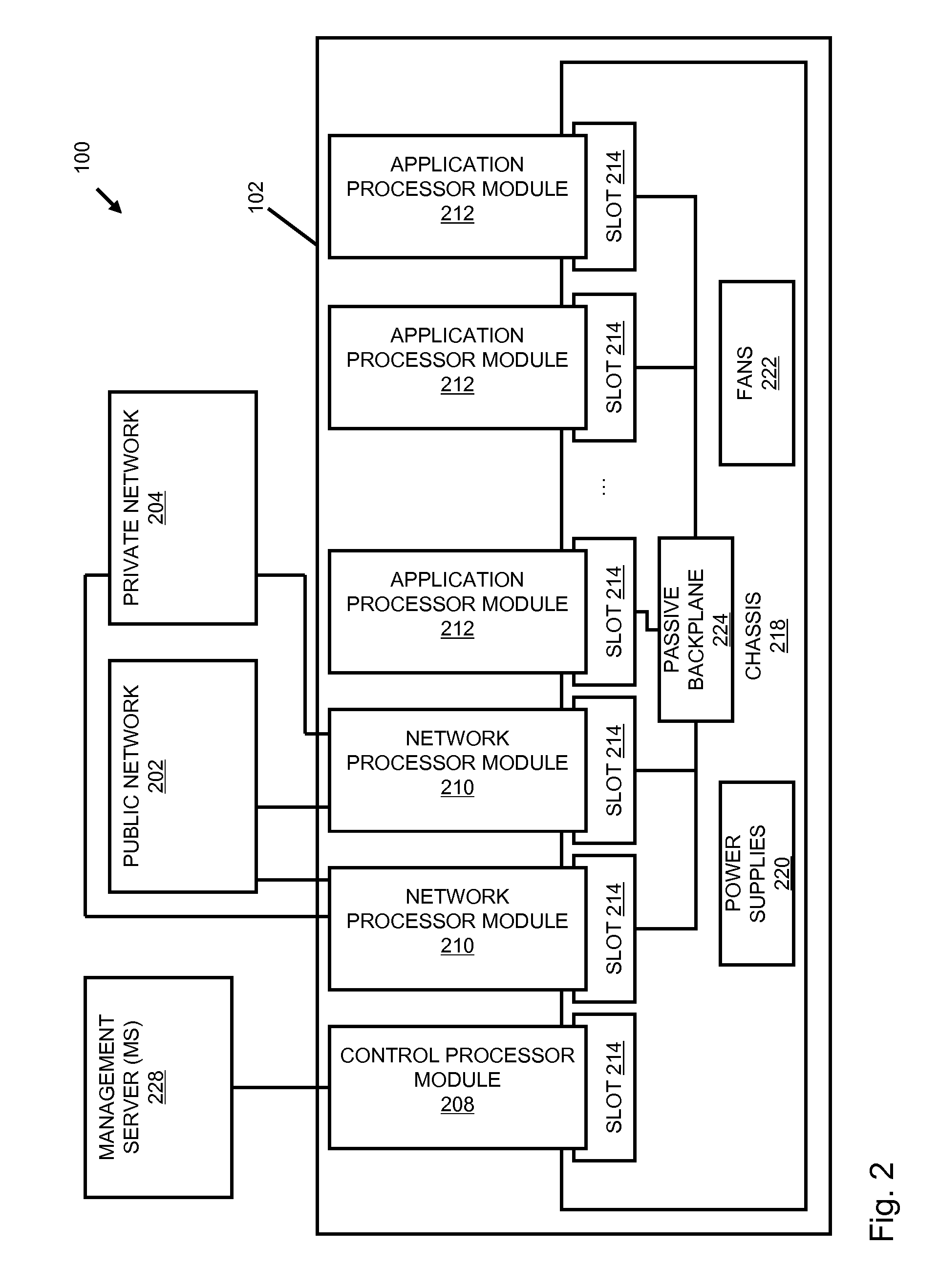
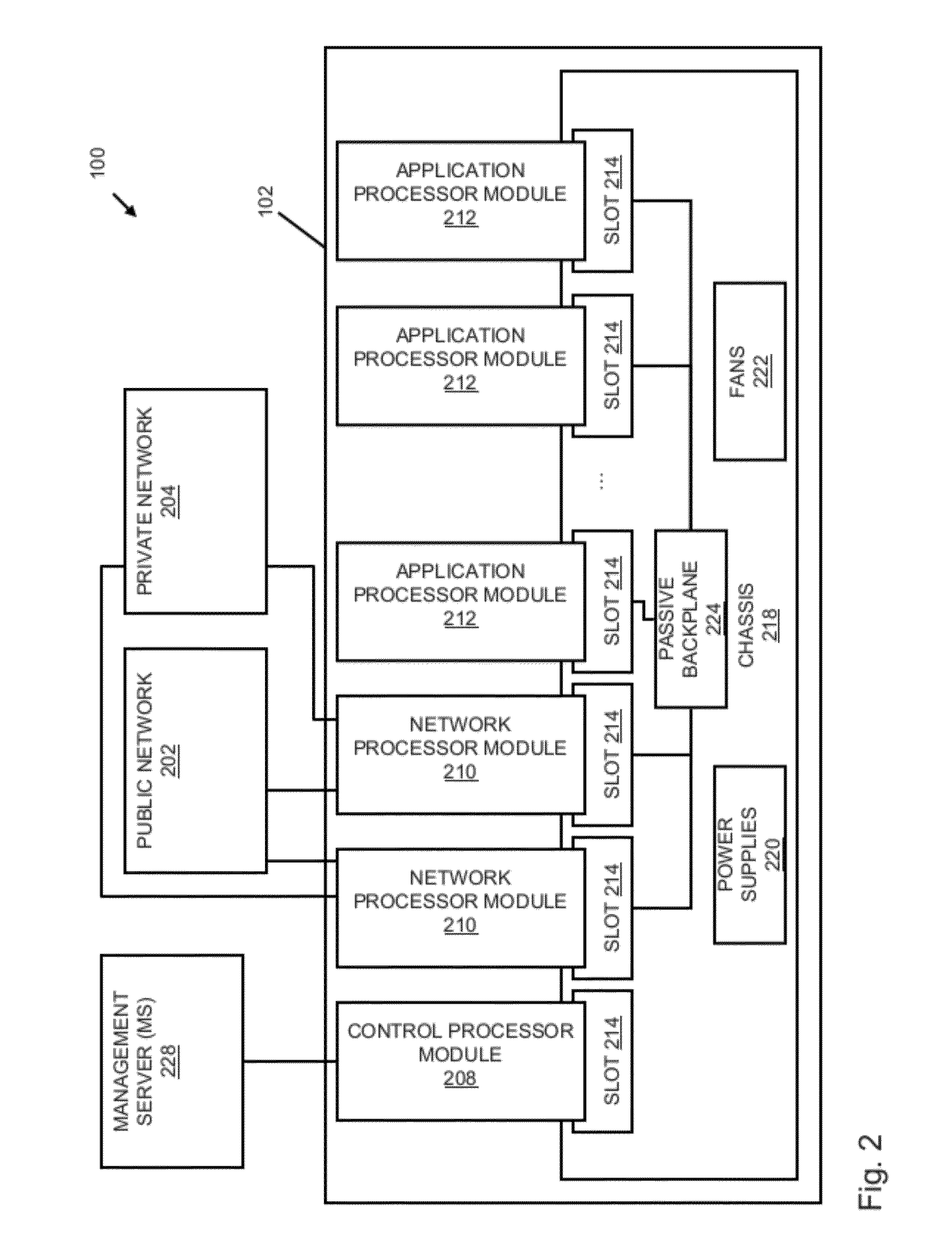
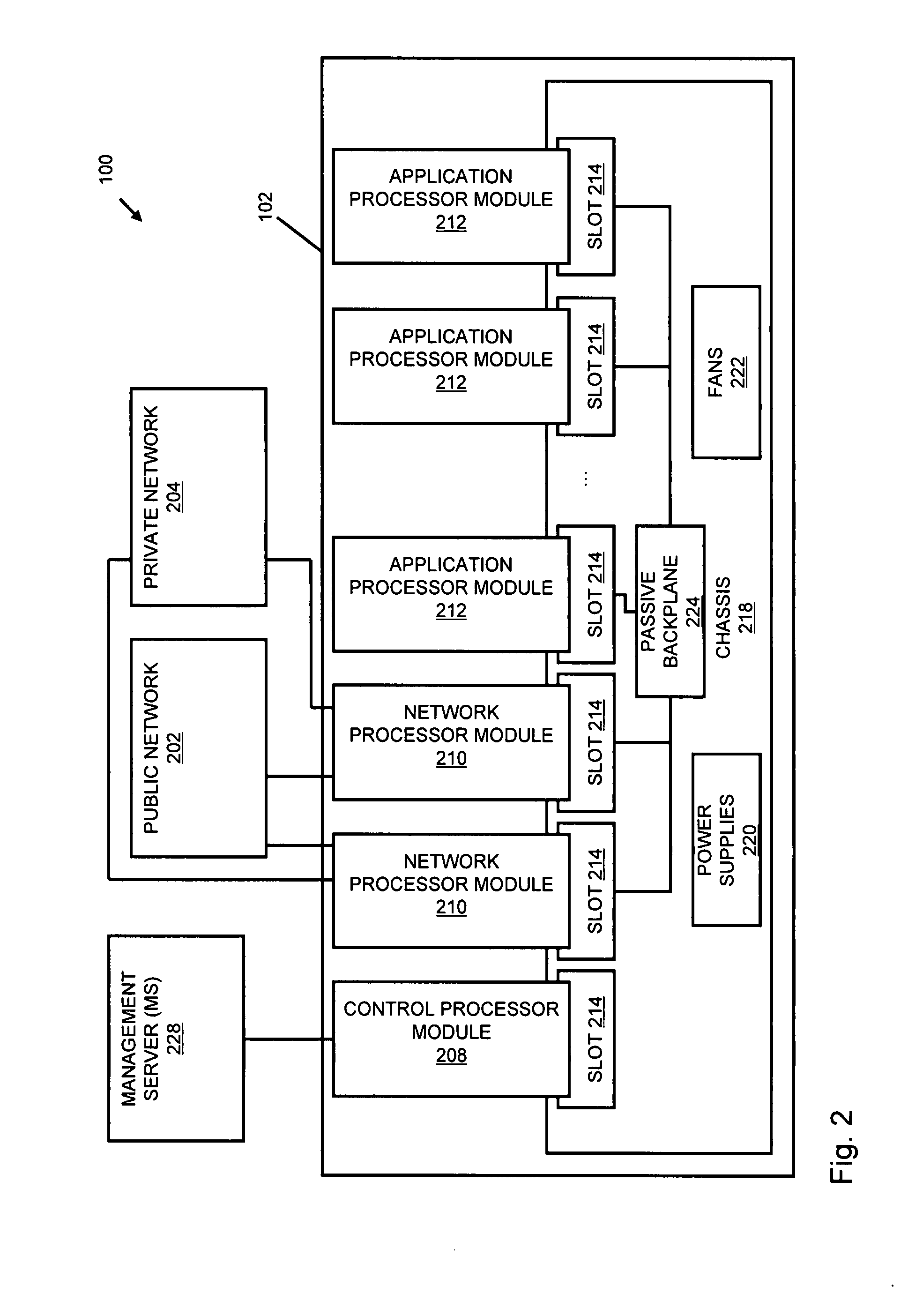
Processing data flows with a data flow processor
InactiveUS20110238855A1Increased complexityAvoid problemsMultiple digital computer combinationsPlatform integrity maintainanceData controlConfigfs
An apparatus and method to distribute applications and services in and throughout a network and to secure the network includes the functionality of a switch with the ability to apply applications and services to received data according to respective subscriber profiles. Front-end processors, or Network Processor Modules (NPMs), receive and recognize data flows from subscribers, extract profile information for the respective subscribers, utilize flow scheduling techniques to forward the data to applications processors, or Flow Processor Modules (FPMs). The FPMs utilize resident applications to process data received from the NPMs. A Control Processor Module (CPM) facilitates applications processing and maintains connections to the NPMs, FPMs, local and remote storage devices, and a Management Server (MS) module that can monitor the health and maintenance of the various modules.
Owner:BLUE COAT SYSTEMS
Systems and methods for forming metal oxides using alcohols
InactiveUS7041609B2Reduce decreaseAvoid problemsTransistorSolid-state devicesAlcoholDeposition process
A method of forming (and an apparatus for forming) a metal oxide layer on a substrate, particularly a semiconductor substrate or substrate assembly, using a vapor deposition process, one or more alcohols, and one or more metal-containing precursor compounds.
Owner:MICRON TECH INC
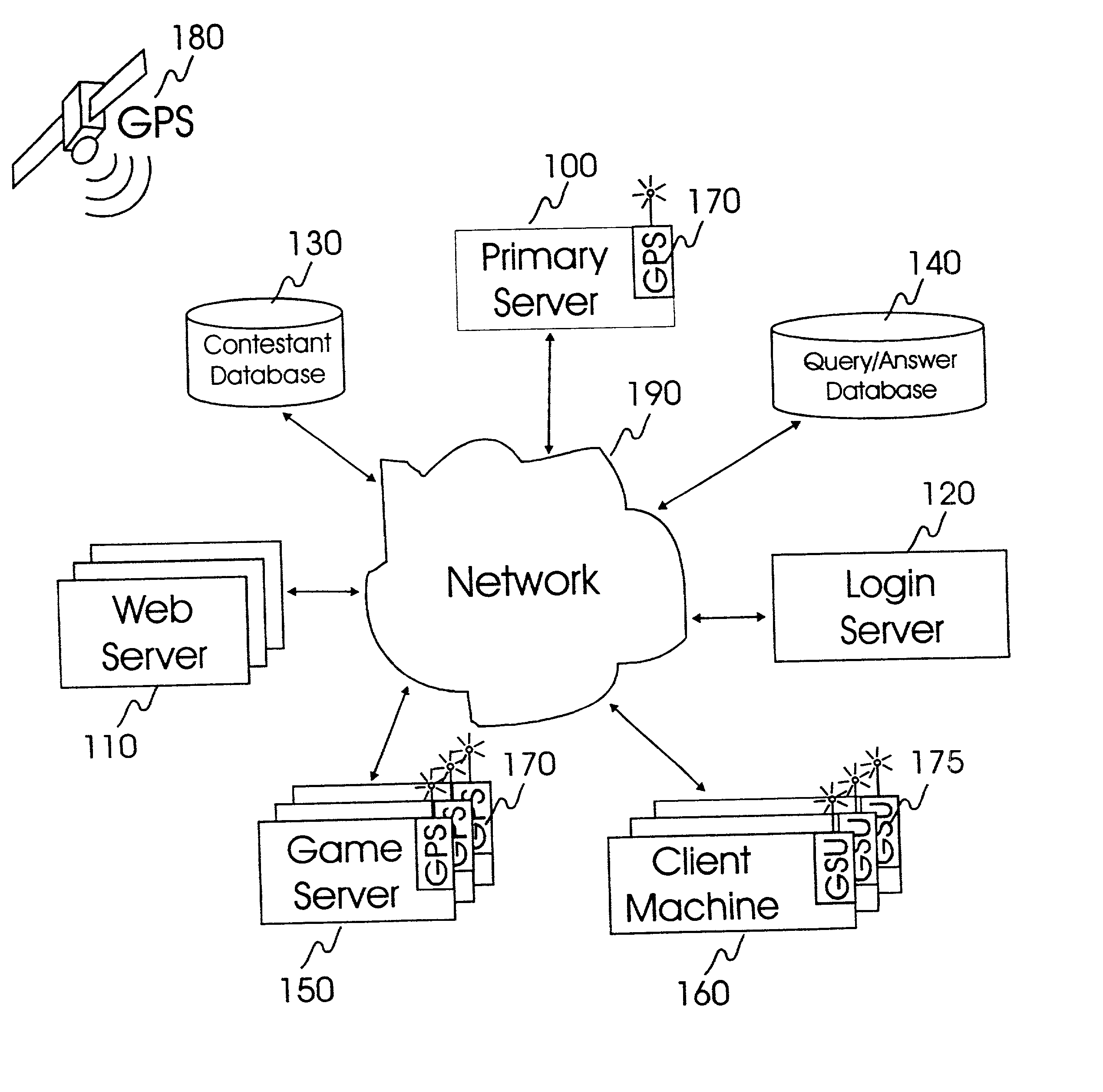
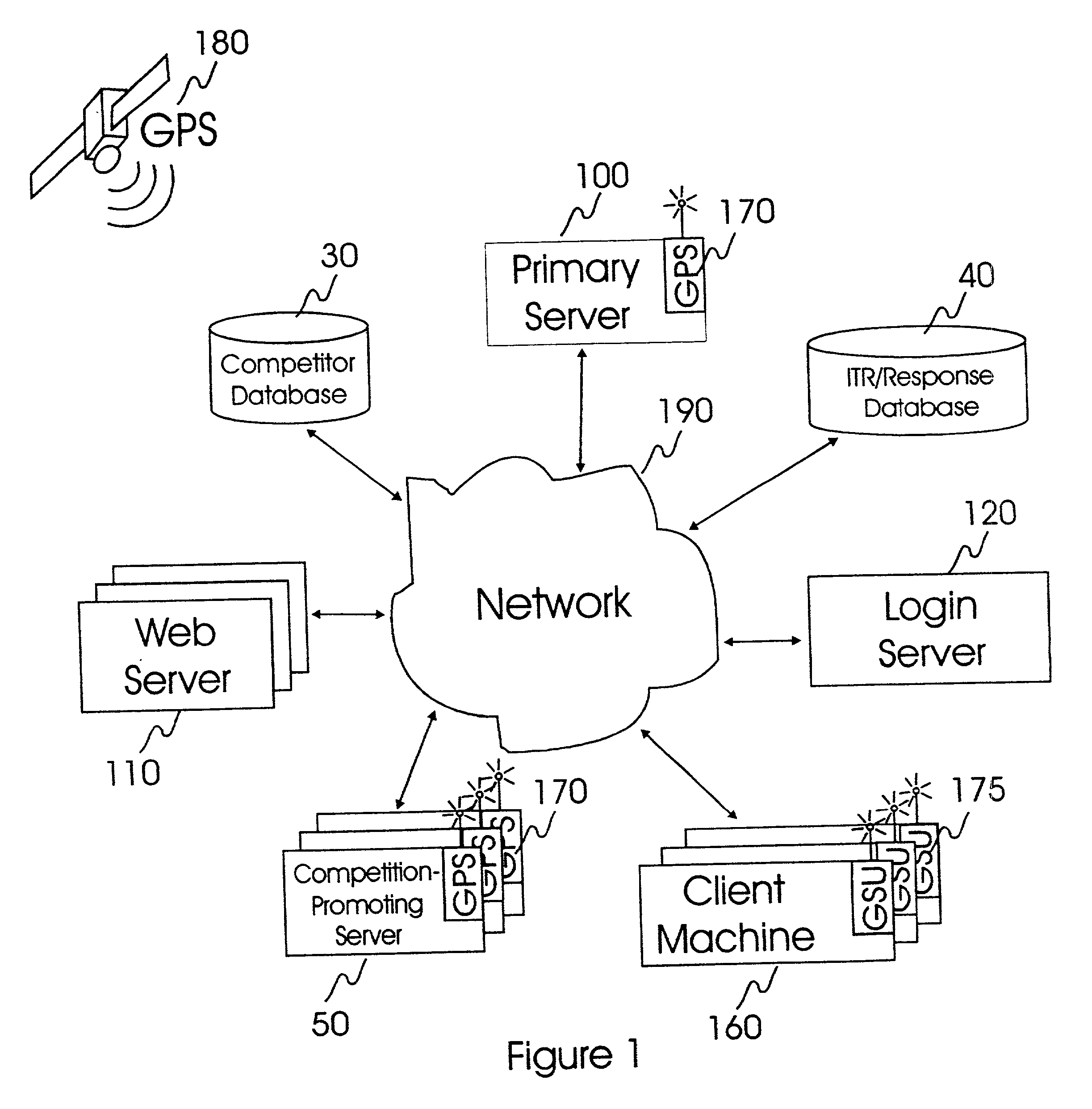
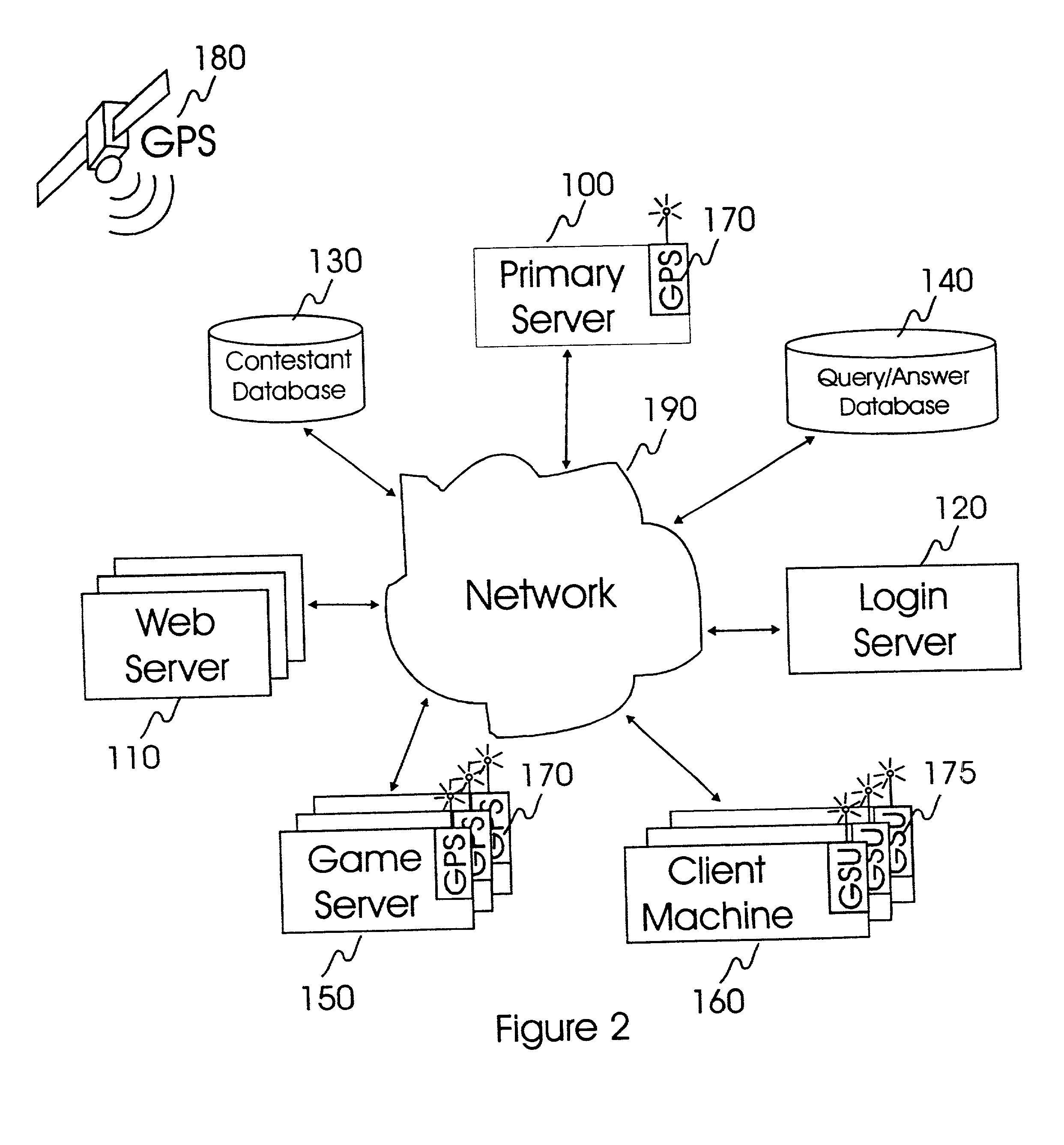
Internet-based system and method for fairly and securely enabling timed-constrained competition using globally time-sychronized client subsystems and information servers having microsecond client-event resolution
InactiveUS20020026321A1Avoiding shortcoming and drawbackBetterment of human societyBuying/selling/leasing transactionsVideo gamesTime responseTTEthernet
An improved system and method of fairly and securely enabling timed-constrained competitions over the Internet among millions of competitors while compensating for the variable network communication latencies experienced by client machines used by the competitors. The system employs globally time-synchronized Internet information servers and client machines in order to synchronize the initial display of each invitation to respond (e.g. stock price to buy or sell, query to answer, or problem to solve) on a client machine so each competitor can respond to the invitation at substantially the same time, regardless of his or her location on the planet, or the type of Internet-connection used by his or her client machine. Also, by using globally time-synchronized client machines, each competitor's response is securely time and space stamped at the client machine to ensure that competitor responses are resolved within microsecond accuracy.
Owner:REVEO
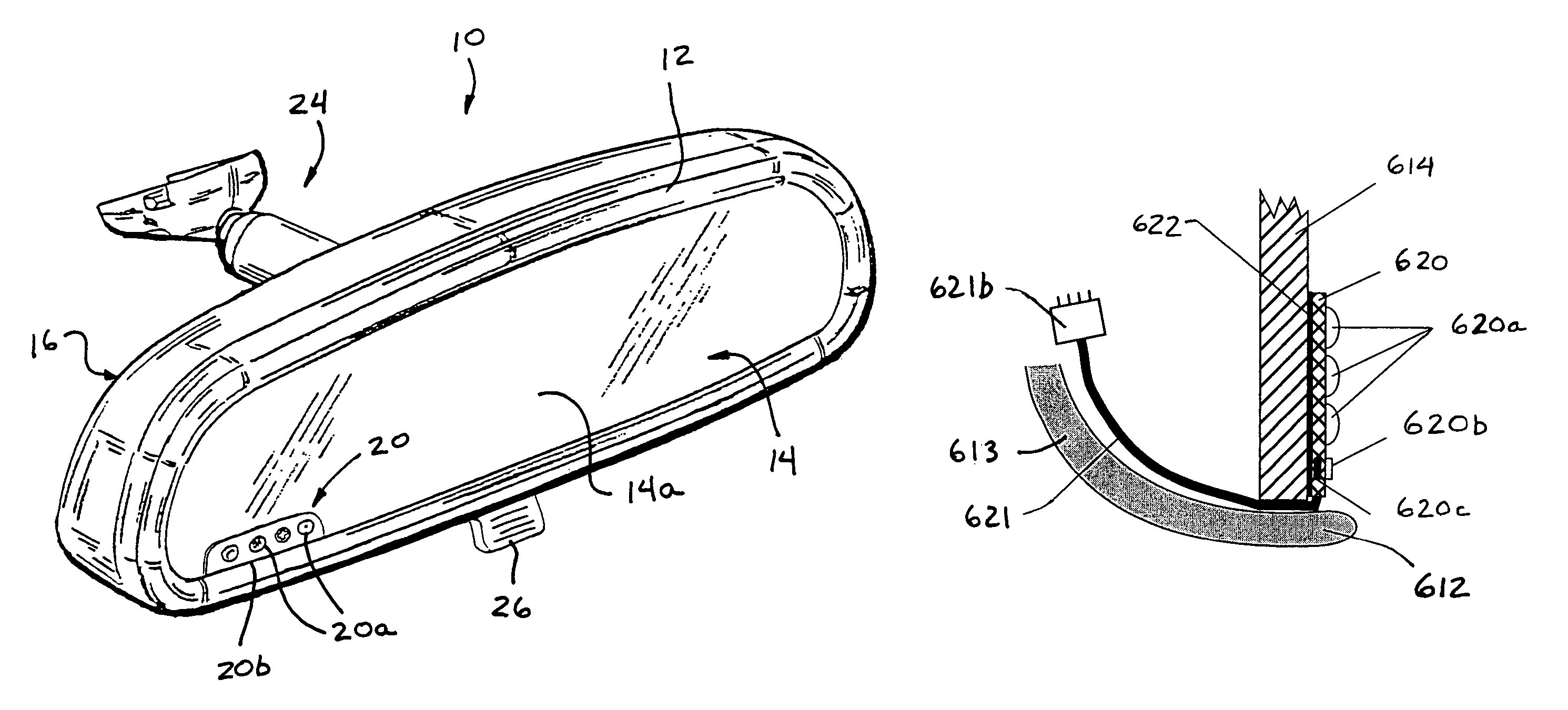
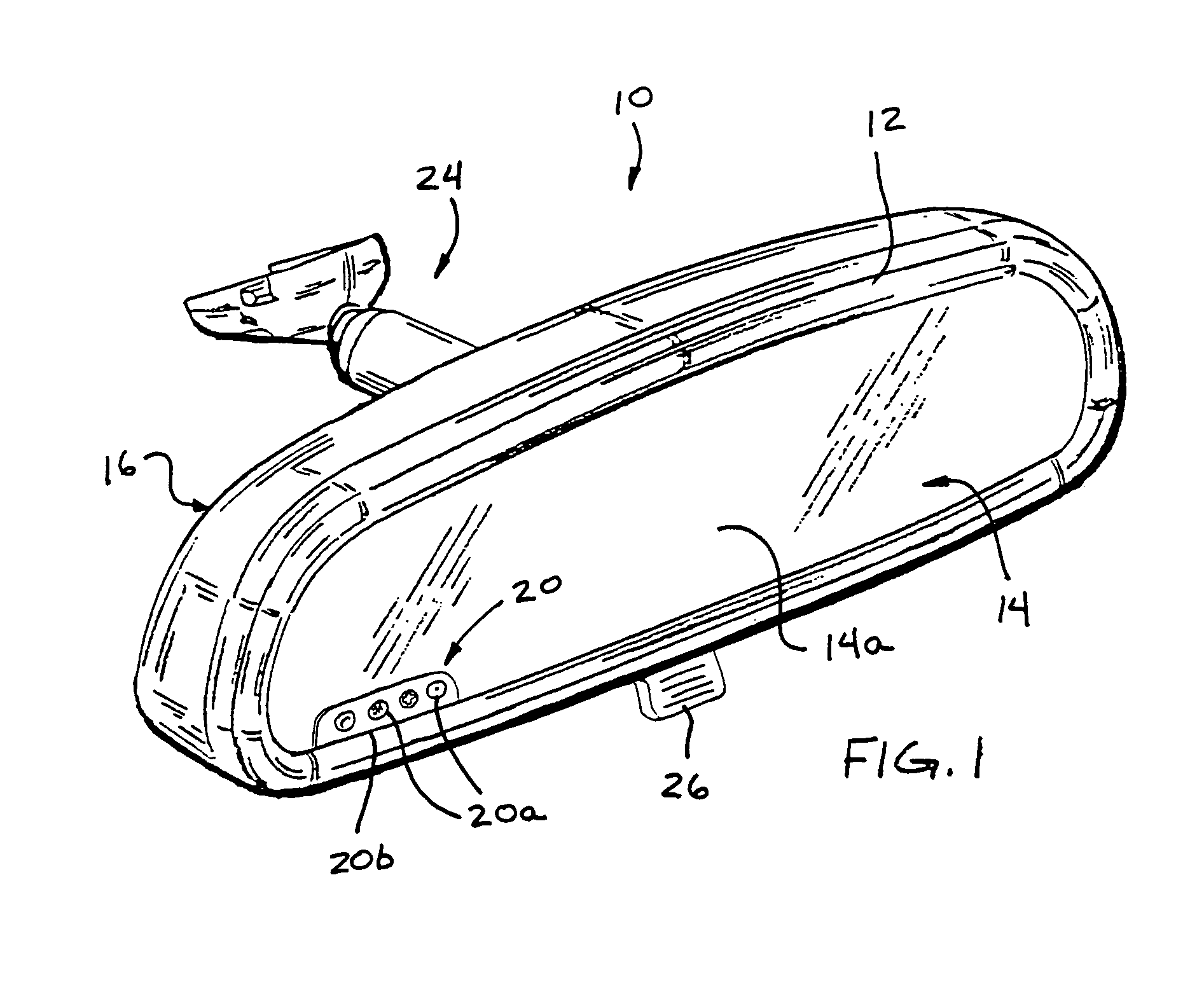
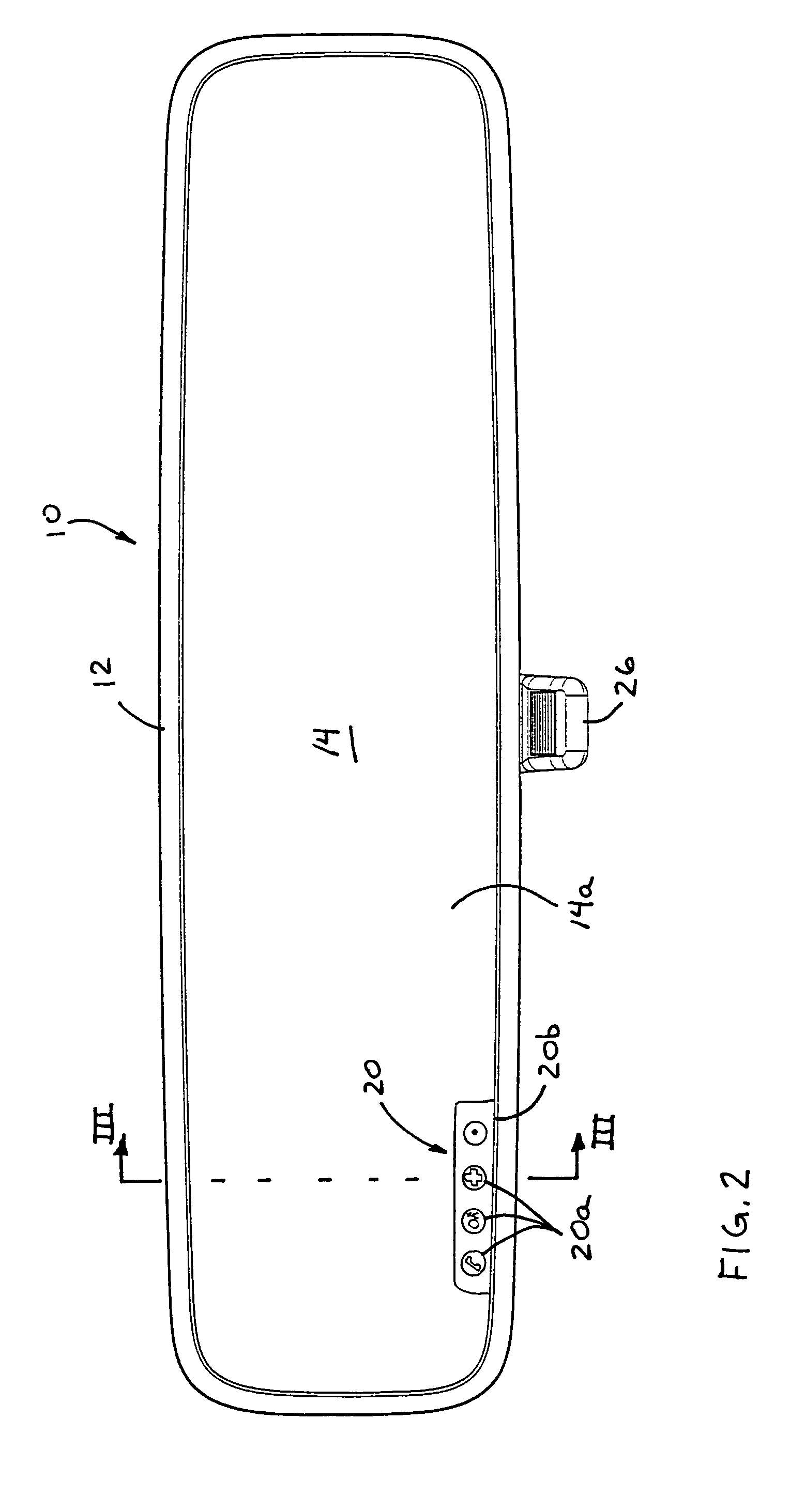
Mirror assembly for vehicle
InactiveUS7360932B2Facilitate customization and personalizationEasy to viewMirrorsElectric devicesDriver/operatorUser input
Owner:DONNELLY CORP
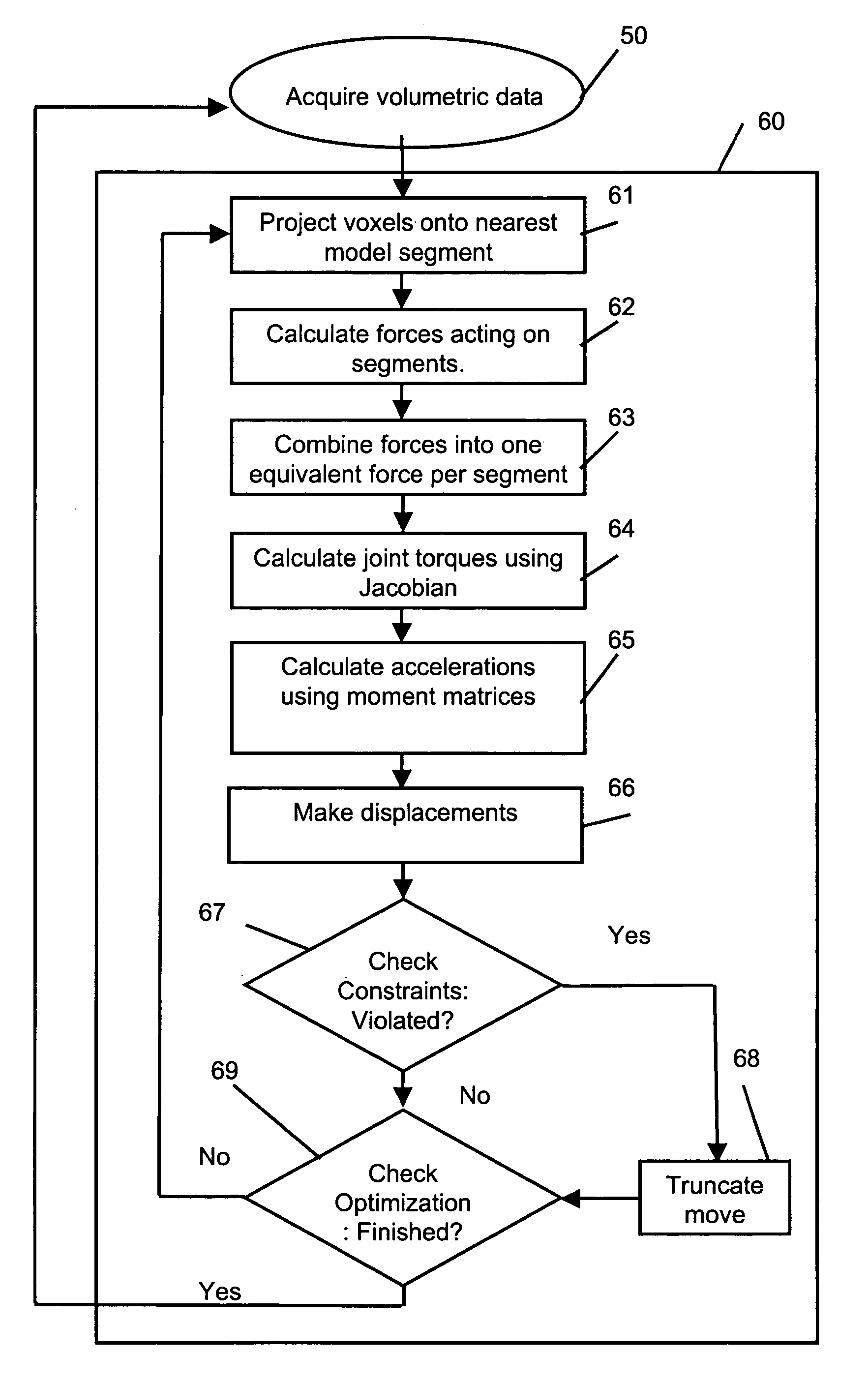
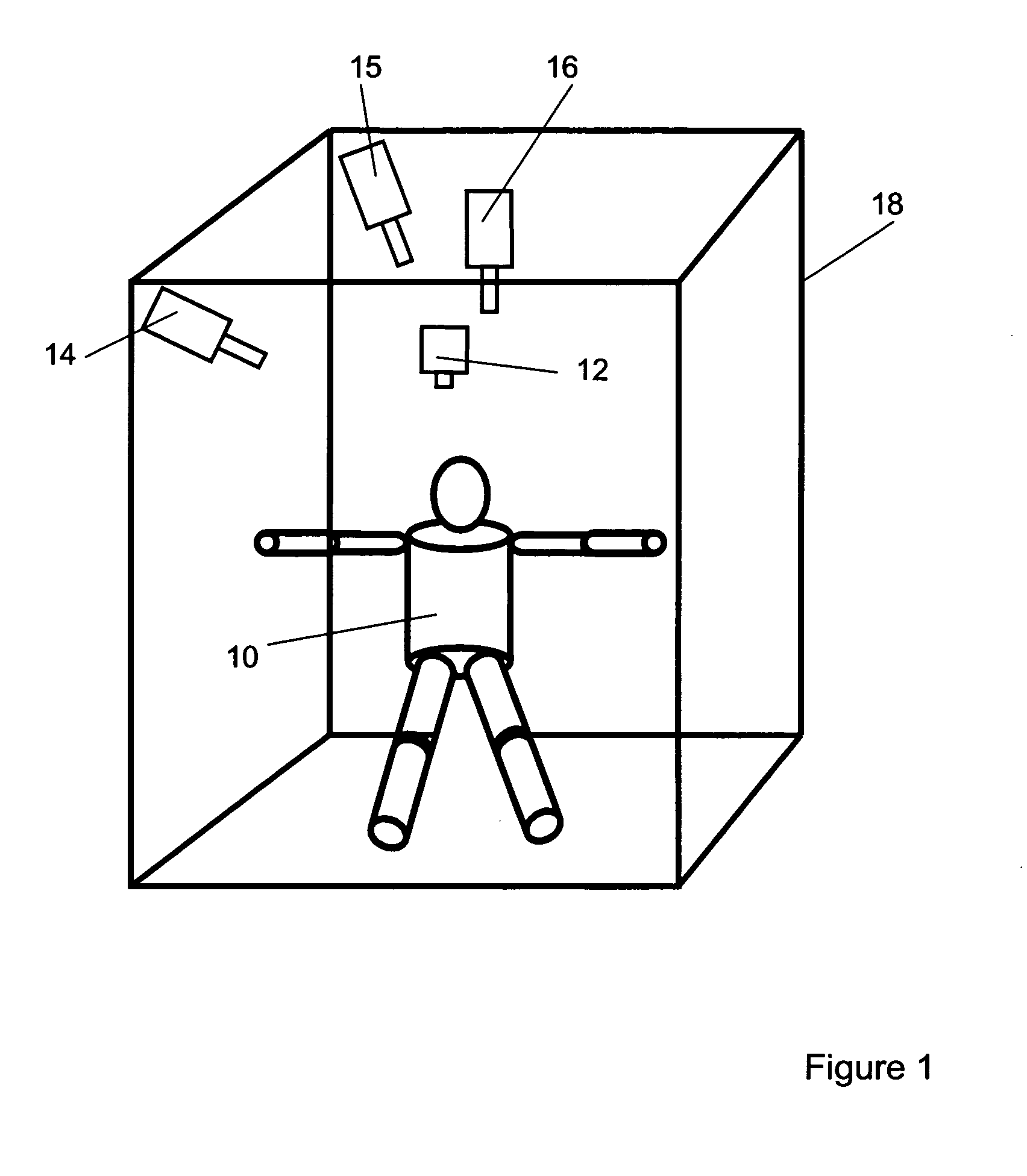
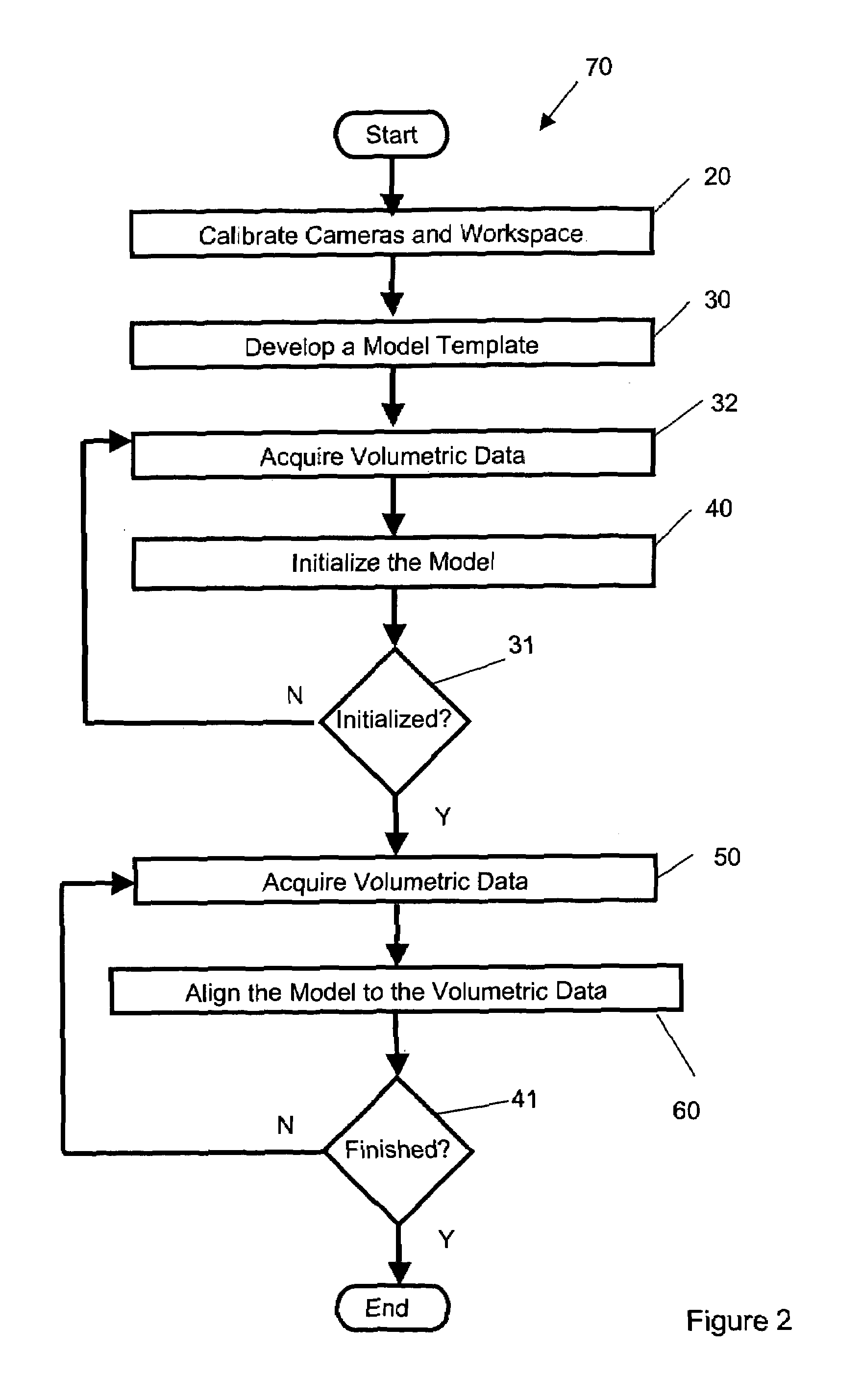
Real time markerless motion tracking using linked kinematic chains
A markerless method is described for tracking the motion of subjects in a three dimensional environment using a model based on linked kinematic chains. The invention is suitable for tracking robotic, animal or human subjects in real-time using a single computer with inexpensive video equipment, and does not require the use of markers or specialized clothing. A simple model of rigid linked segments is constructed of the subject and tracked using three dimensional volumetric data collected by a multiple camera video imaging system. A physics based method is then used to compute forces to align the model with subsequent volumetric data sets in real-time. The method is able to handle occlusion of segments and accommodates joint limits, velocity constraints, and collision constraints and provides for error recovery. The method further provides for elimination of singularities in Jacobian based calculations, which has been problematic in alternative methods.
Owner:NAT TECH & ENG SOLUTIONS OF SANDIA LLC
Total disc implant
InactiveUS6994727B2Impressive mechanicalImpressive tribologicalInternal osteosythesisJoint implantsHuman patientIntervertebral disk
A total disc implant (TDI) is provided for total replacement of a spinal disc or discs in a human patient or other mammal, wherein the TDI is designed to maintain a substantially full range of natural motion (ROM) following implantation. The TDI generally comprises, in one preferred form, upper and lower end plates for affixation to adjacent vertebral bodies, with an intervening insert disposed therebetween. The end plates each include elongated part-cylindrical surfaces oriented generally perpendicular to each other, with one of said surfaces extending in an anterior-posterior direction and the other extending in a medial-lateral direction. The intervening insert defines concave upper and lower part-cylindrical seats oriented for respectively engaging these part-cylindrical surfaces, wherein these part-cylindrical seats are defined by offset radii to include a somewhat flattened central base region merging smoothly with upwardly curving radiused sides.
Owner:AMEDICA A DELAWARE
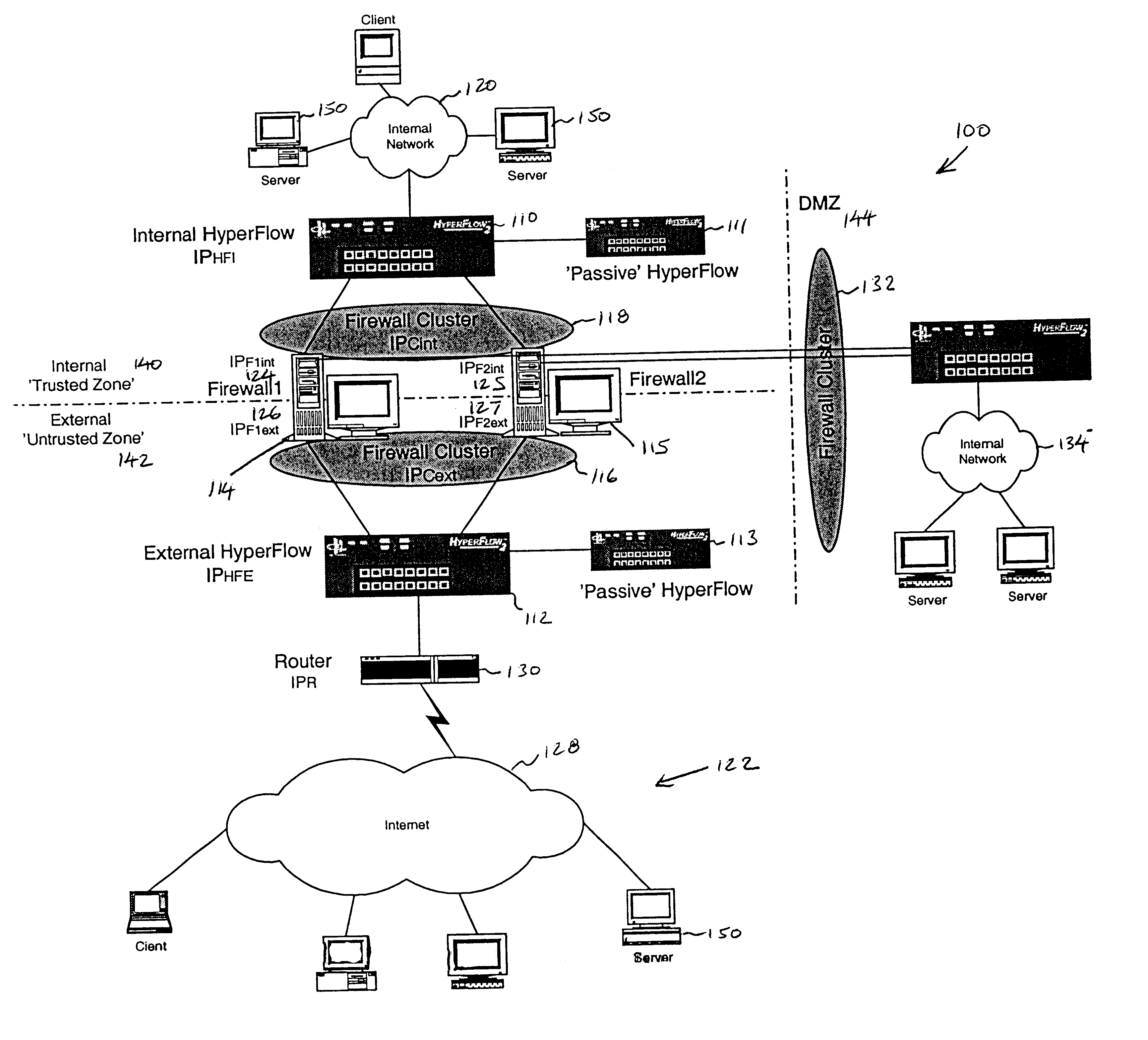
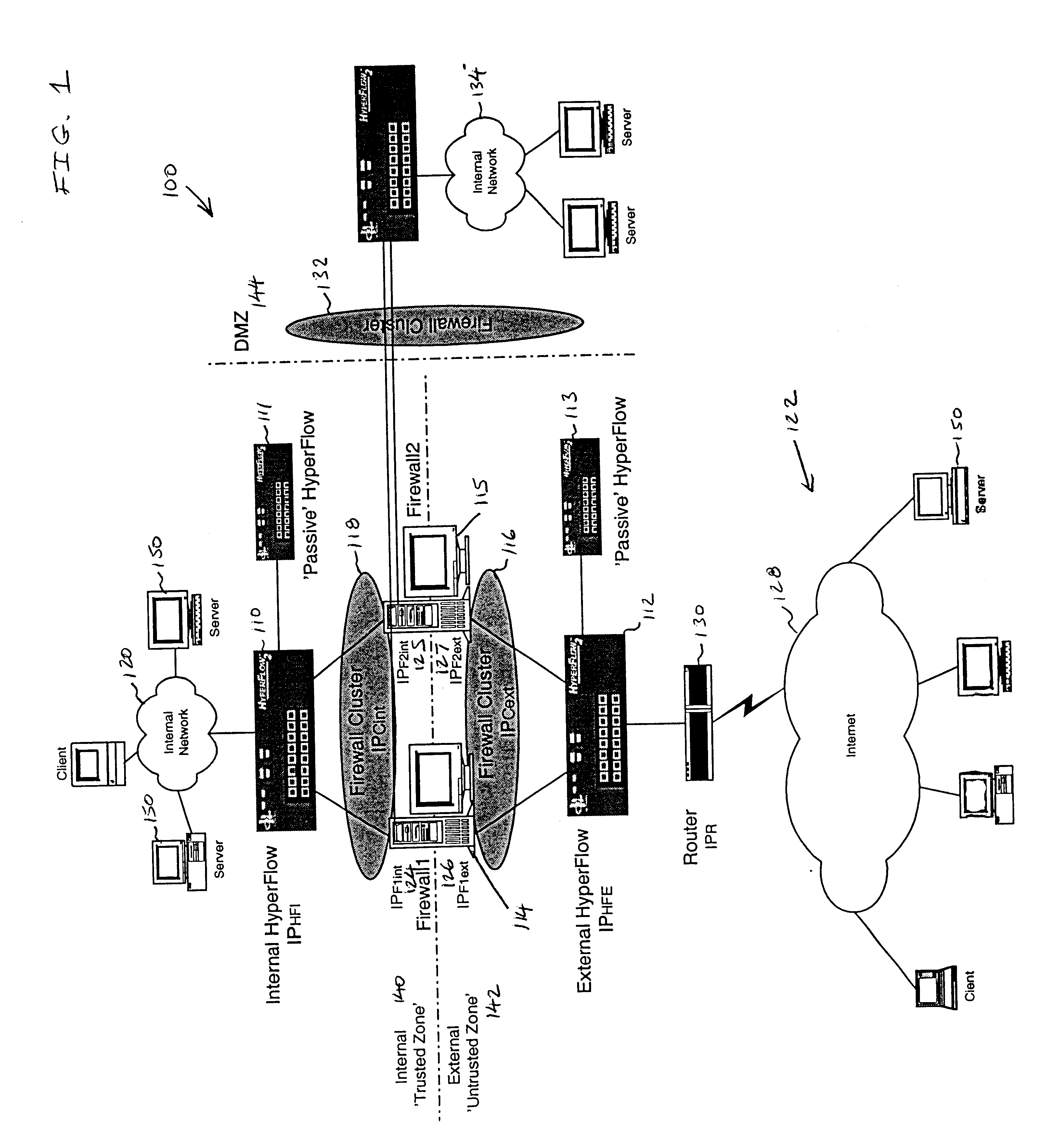
Firewall clustering for multiple network servers
InactiveUS6880089B1Increase capacityReduce calculationMultiple digital computer combinationsProgram controlTraffic capacityExtensibility
A firewall clustering system connects two or more firewalls between an internal network and an external network. The plurality of two or more firewalls are combined to supply high-availability and scaling of processing capacity. Firewalls maintain client-server state information. Flow controllers are connected to the firewalls and placed on both the internal “trusted” side and the external “untrusted” side of the firewalls. Flow controllers are placed on both sides of the firewalls to ensure that traffic for a given client-server session flows through the same firewall in both inbound and outbound directions. The firewalls perform filtering operations and / or network address translation (NAT) services. In both cases, the flow controllers supply high availability, scalability, and traffic distribution for the firewalls in the firewall cluster.
Owner:CITRIX SYST INC
Ablation catheter apparatus with one or more electrodes
InactiveUS20070066972A1Avoid problemsEasy to bendSurgical instruments using microwavesElectrical conductorConductive polymer
A radio frequency (RF) ablation catheter has a flexible distal end portion so that it can be deflected to position an antenna disposed in the distal end portion adjacent a tissue site to be treated. At least one electrical conductor is coupled to the antenna and extends through the catheter to the proximal end of the catheter to a connector at the proximal end of the catheter for connection to a power supply for the RF antenna. At least one electrode is disposed at the distal end portion of the catheter and electrically coupled to the proximal end connector for connection to a monitor. The electrode is of a flexible, electrically conductive material such as conductive polymer material. The electrode may be an electrocardiogram (ECG) electrode.
Owner:MEDWAVE INC
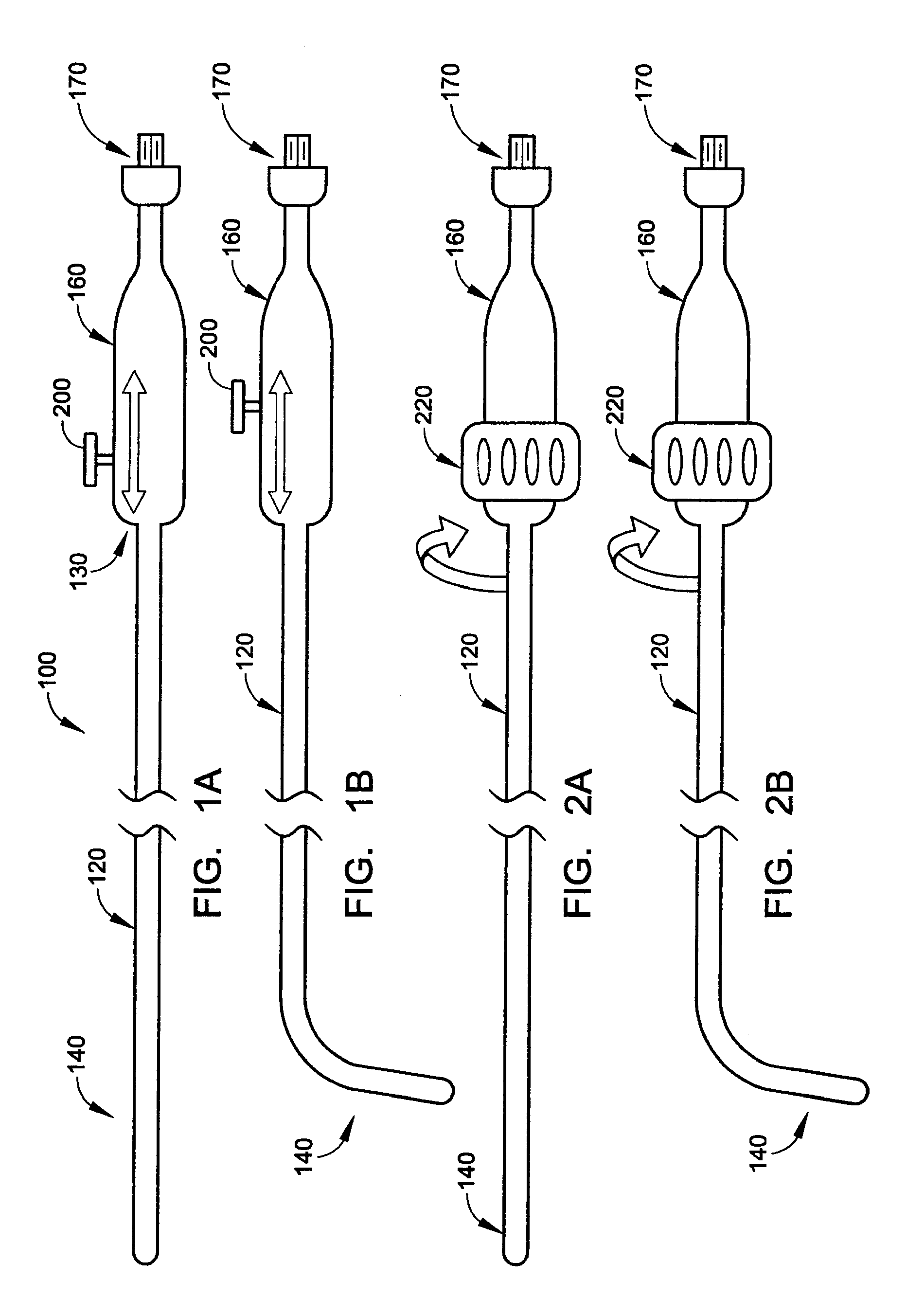
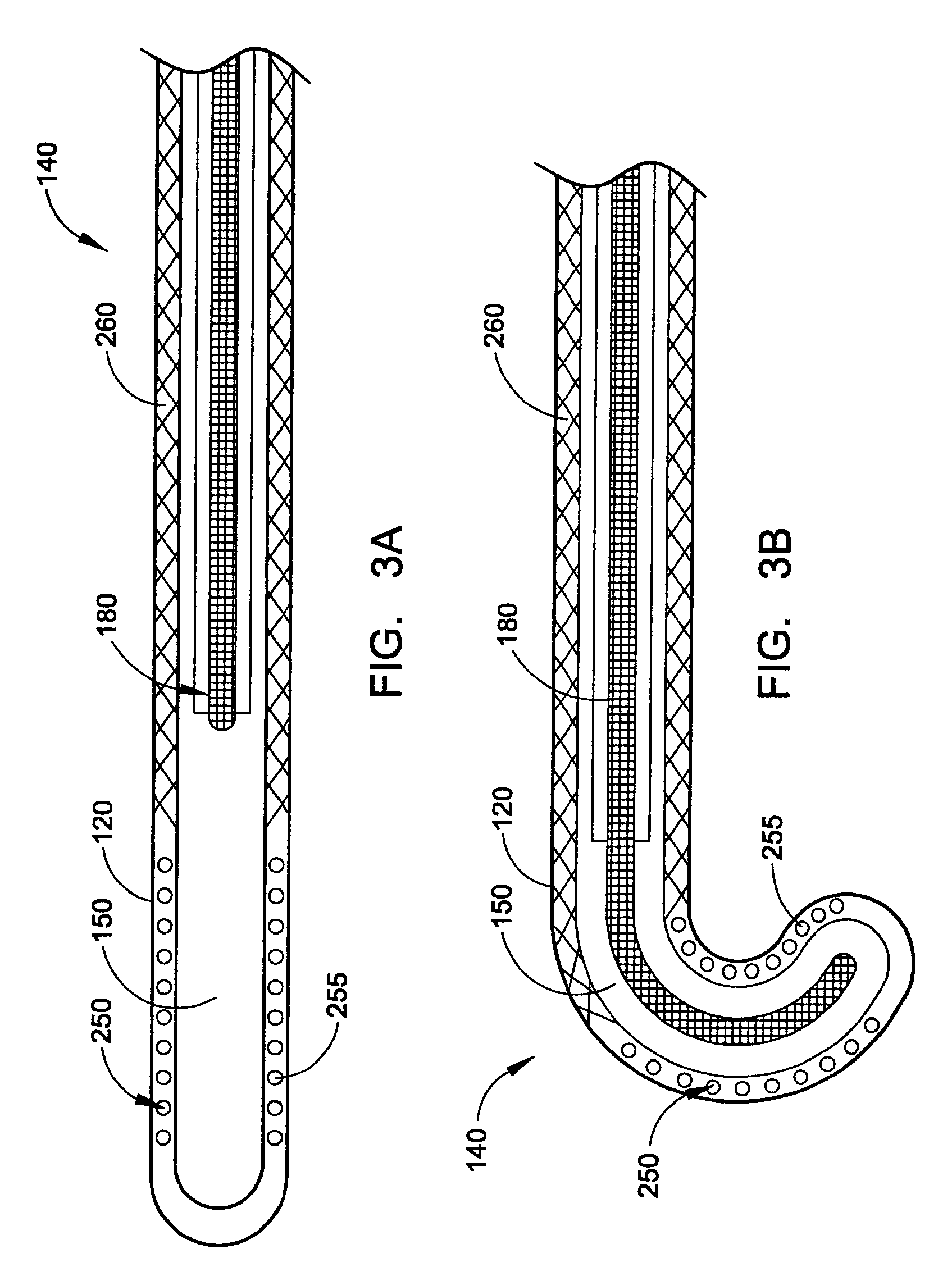
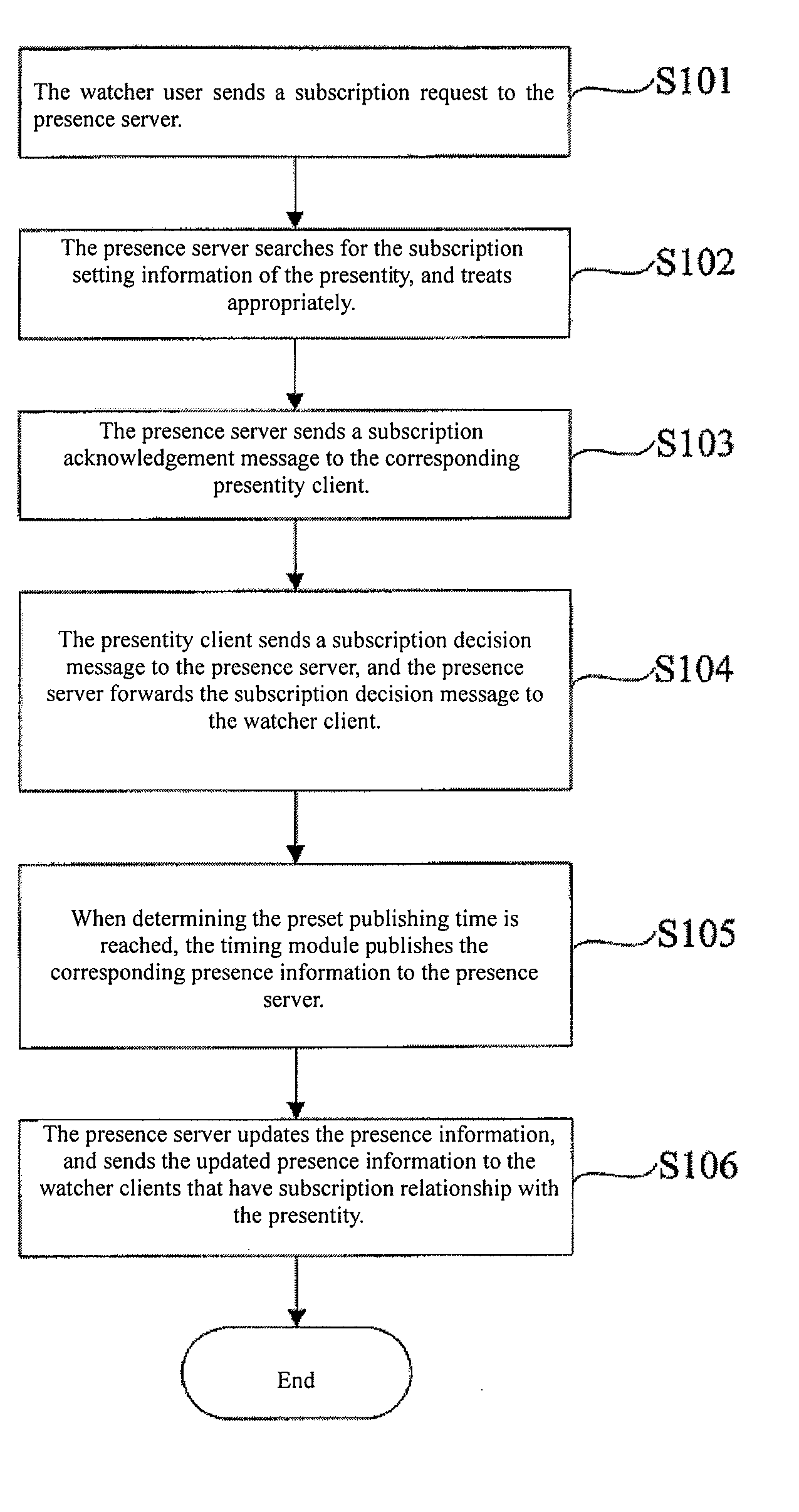
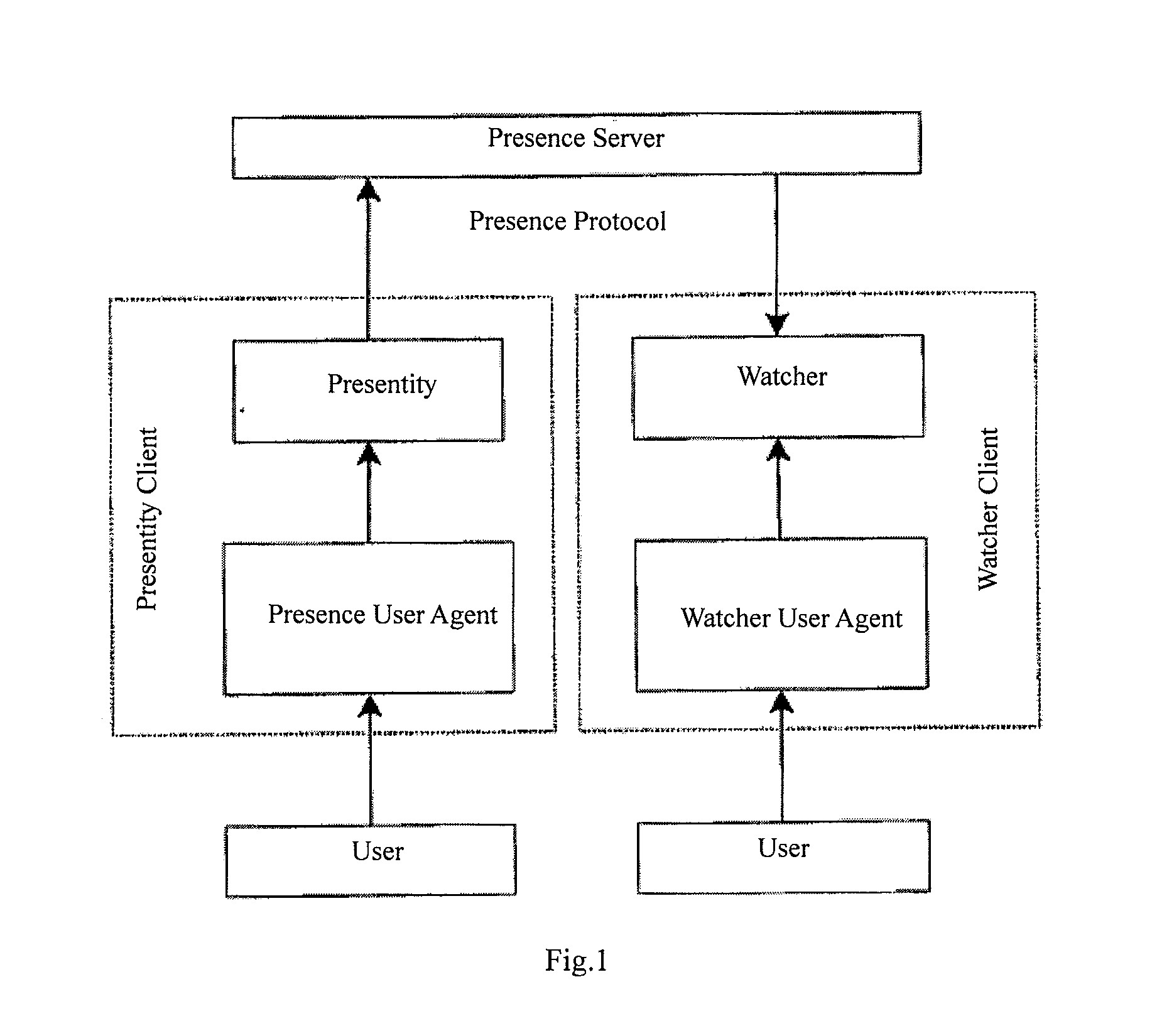
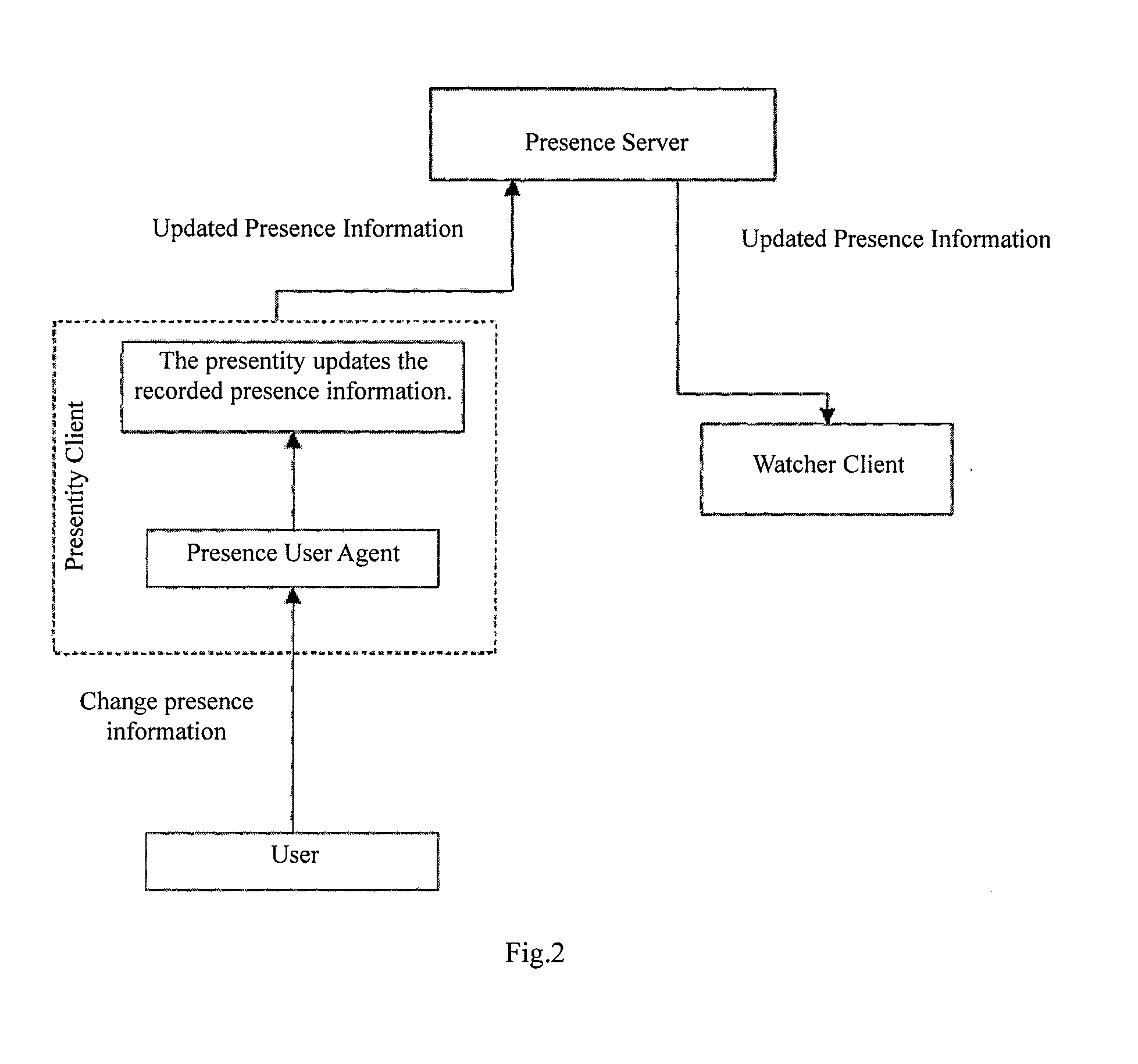
Presence service system and method for publishing presence information
InactiveUS20080120409A1Avoid problemsDigital computer detailsTransmissionPresence serviceComputer science
Owner:HUAWEI TECH CO LTD
Surgical templates
ActiveUS20100191244A1Quick checkShort timeAdditive manufacturing apparatusDiagnosticsProsthesisSurgical template
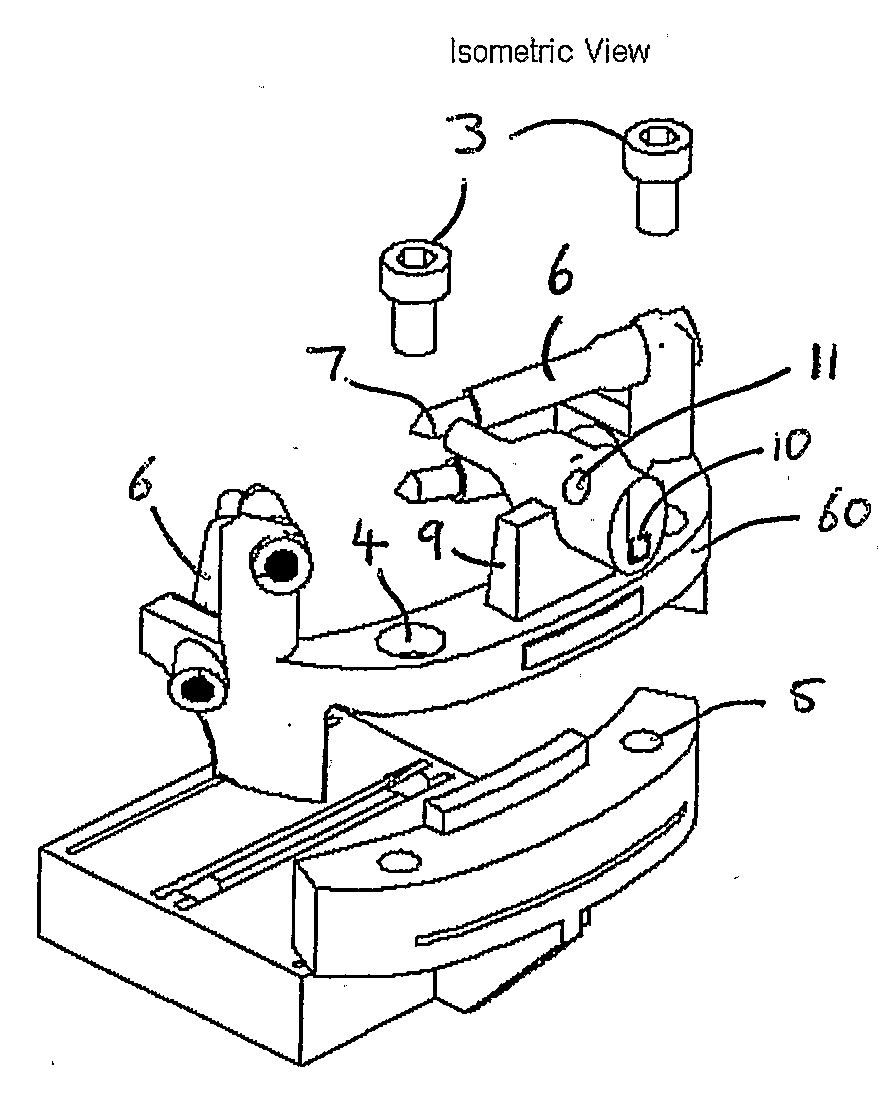
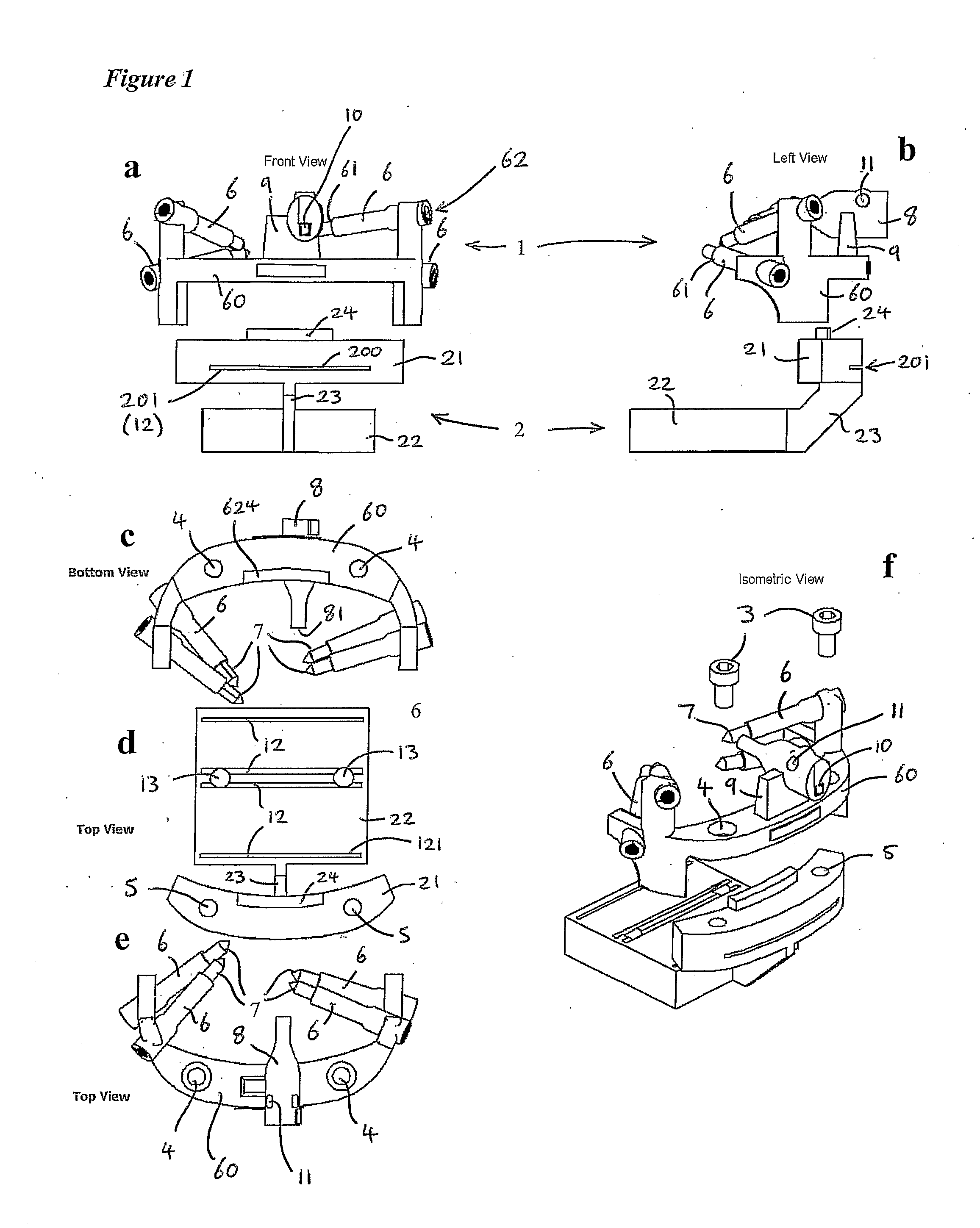
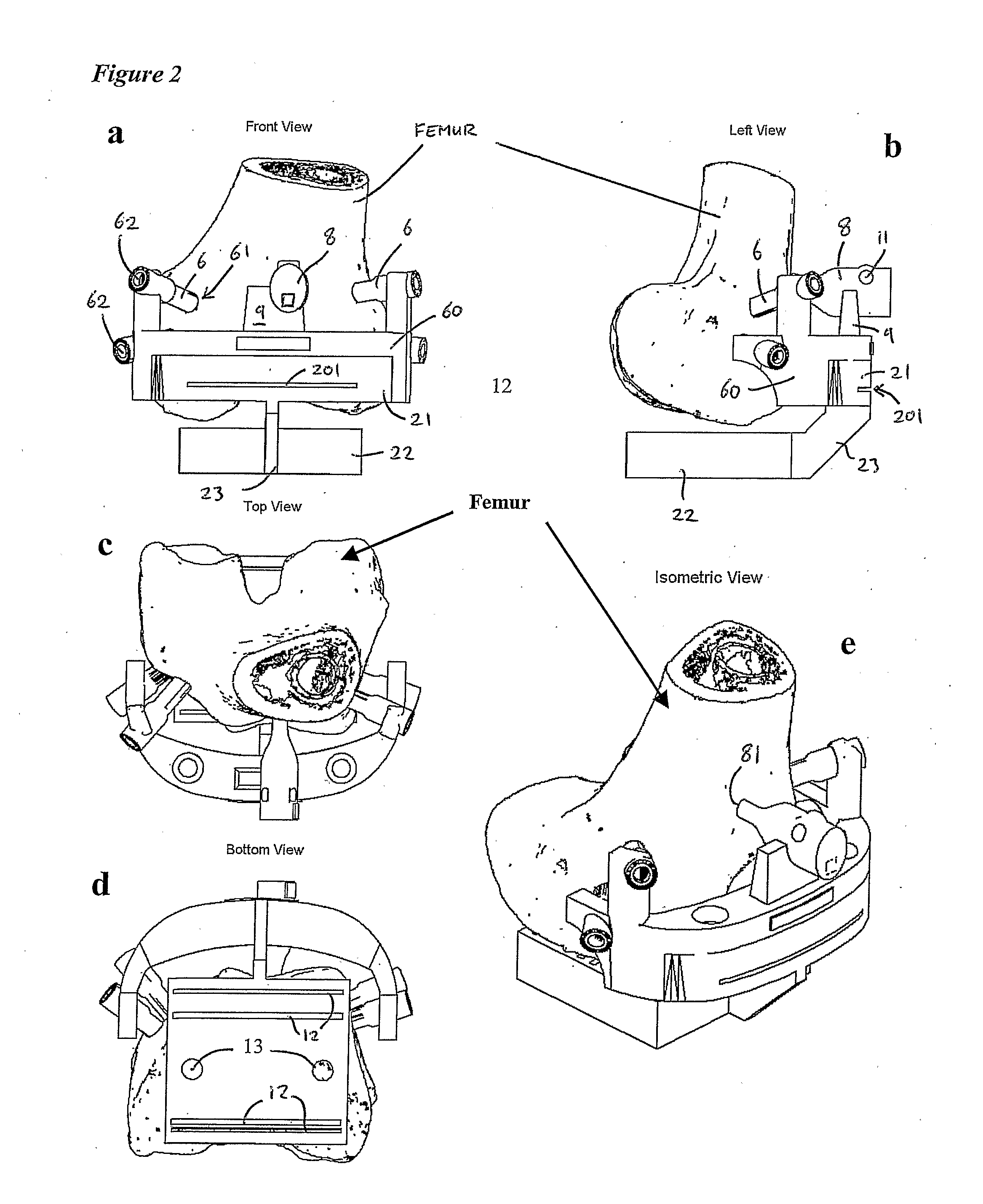
A surgical template system for use in working on a bone comprises: a tool guide block comprising at least one guide aperture for receiving and guiding a tool to work on a bone; locating means comprising a plurality of locating members, each member having a respective end surface for positioning against a surface of the bone; and attachment means for non-adjustably attaching the tool guide block to the locating means such that, when attached, the member end surfaces are secured in fixed position with, respect to each other, for engaging different respective portions of the surface of the bone, and the at least one guide aperture is secured in a fixed position with respect to the end surfaces. Corresponding methods of manufacturing a surgical template system, methods of manufacturing locating means for a surgical template system, methods of fitting a prosthesis to a bone, surgical methods, and surgical apparatus are described.
Owner:XIROS
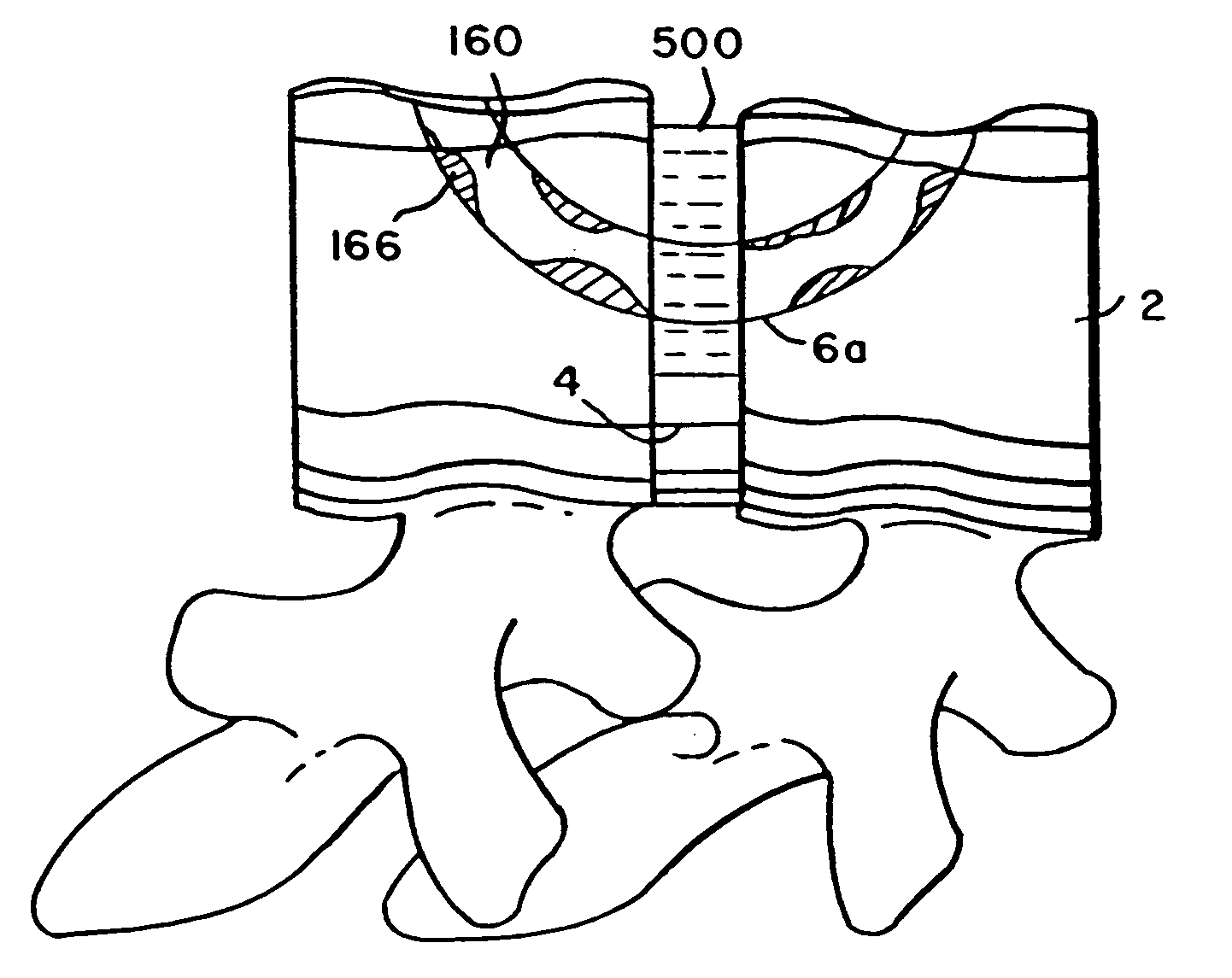
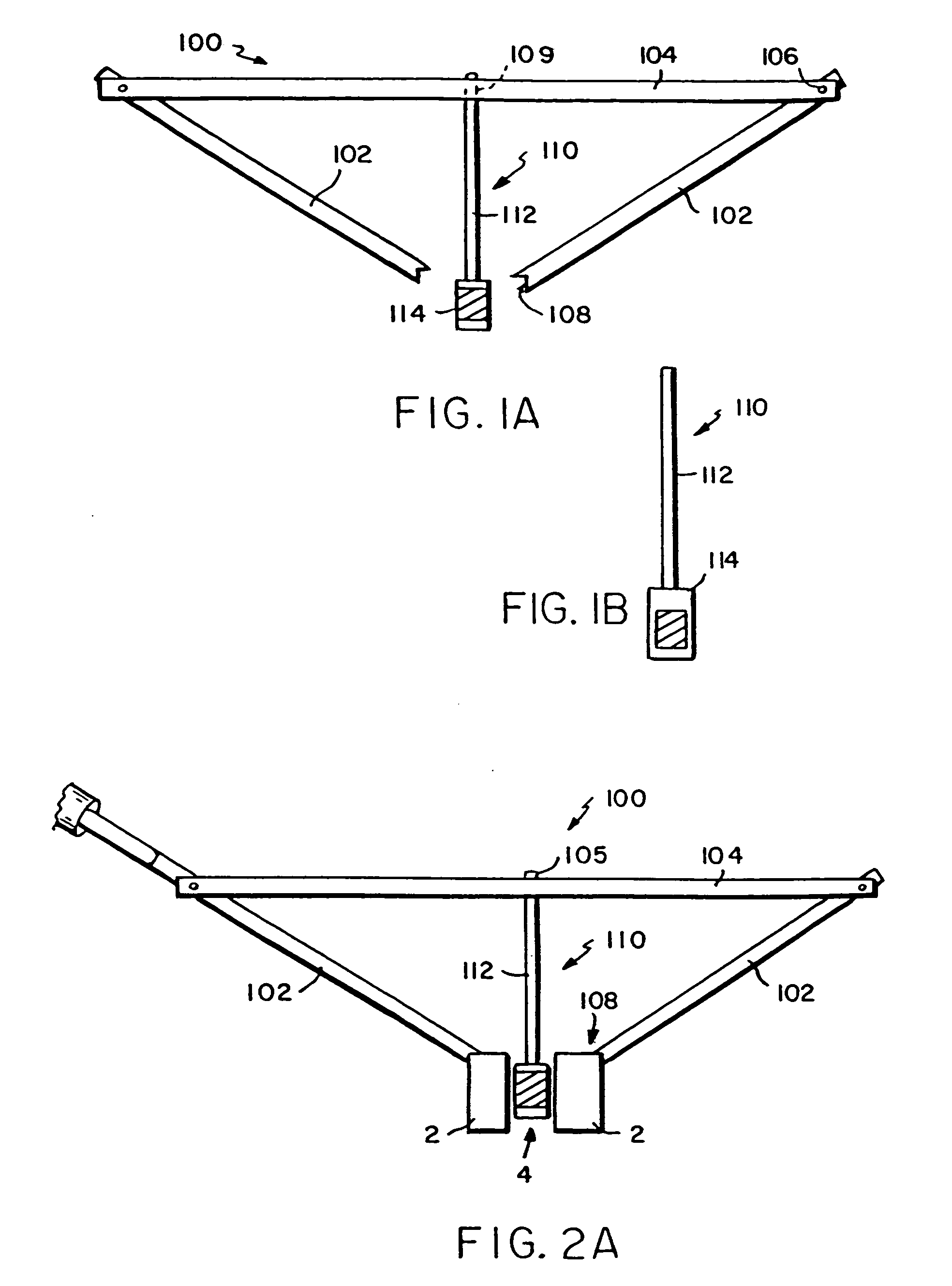
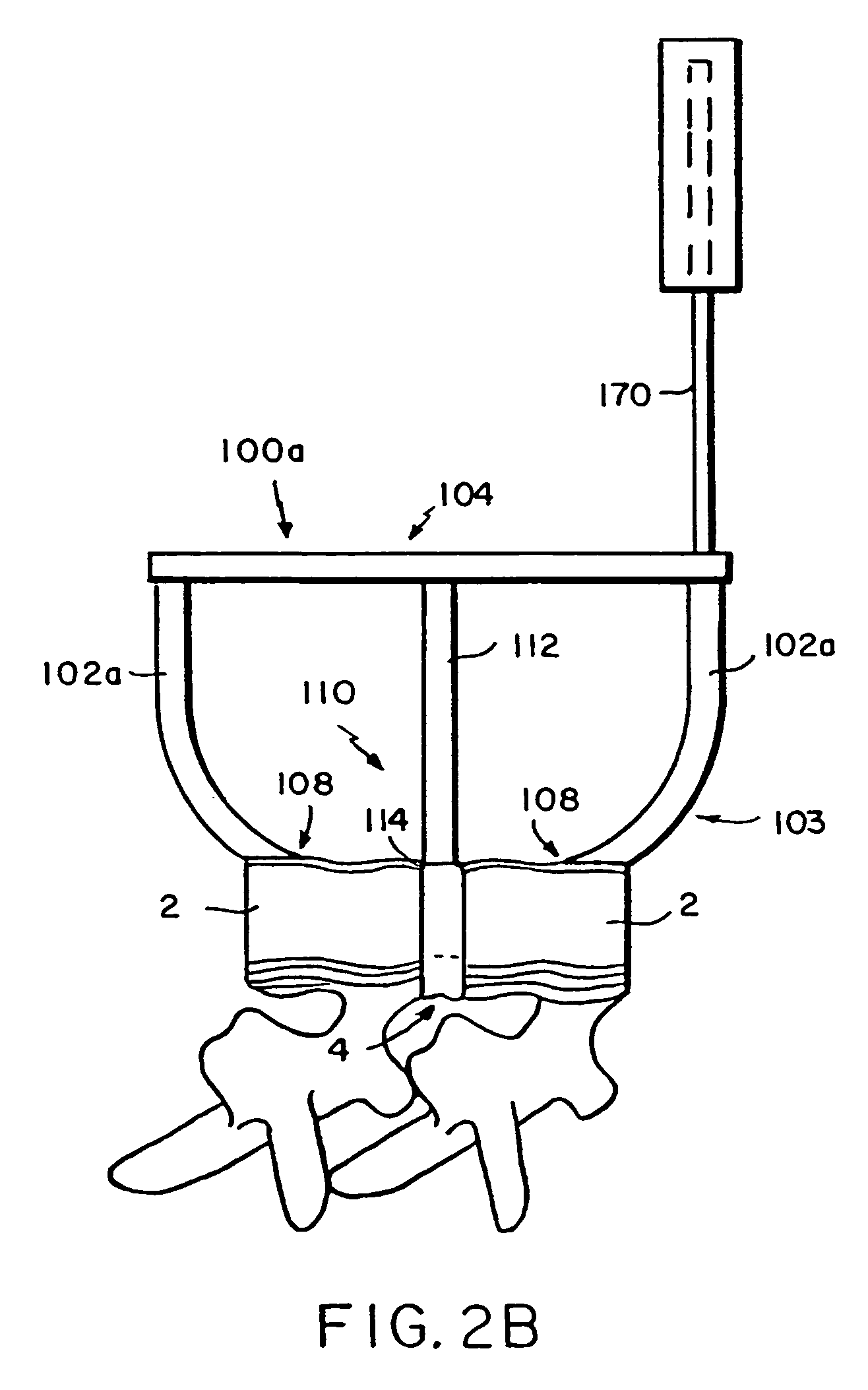
Systems and methods for spinal fixation
InactiveUS6923811B1Maintain alignmentProvide protectionInternal osteosythesisDiagnosticsScrew systemIntervertebral space
Featured are a method and apparatus for fixing adjacent vertebrate of a spine that avoids the need and associated problems with prior cage or straight rod and screw systems. Methods and apparatus of the invention utilize a new implant member, which preferably is arcuate. Preferred methods of the invention for stabilizing adjacent vertebrae of the spine, include steps of providing a positioning apparatus including two guide sleeves, each guide sleeve having a long axis and locating the two guide sleeves with respect to the adjacent vertebrae such that a vertex formed by the long axis of each guide sleeve is located in the intervertebral space for the adjacent vertebrae. The method further includes forming an aperture in each of the adjacent vertebrae using the guide sleeves and inserting an implant into the apertures formed in each of the adjacent vertebrae so that the implant extends between the adjacent vertebrae and through the intervertebral space. In an alternative method a cutting fixture including a pivot arm is secured to the adjacent vertebrae and a cutting device is secured to the pivot arm. The pivot arm and cutting device are configured and arranged so that rotation of the pivot arm about a particularly located pivot point allows the cutting device to form the aperture in each of the adjacent vertebrae. Another alternative method for fixing adjacent vertebrate of a spine includes the step of forming a common channel in and between the adjacent vertebrae and inserting a biscuit implant in the common so as to bridge between the adjacent vertebrae.
Owner:K2M
Systems and methods for processing data flows
InactiveUS20080262991A1Easy to detectPreventing data flowDigital computer detailsBiological neural network modelsData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
Systems and methods for processing data flows
InactiveUS20080134330A1Increased complexityAvoid problemsMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
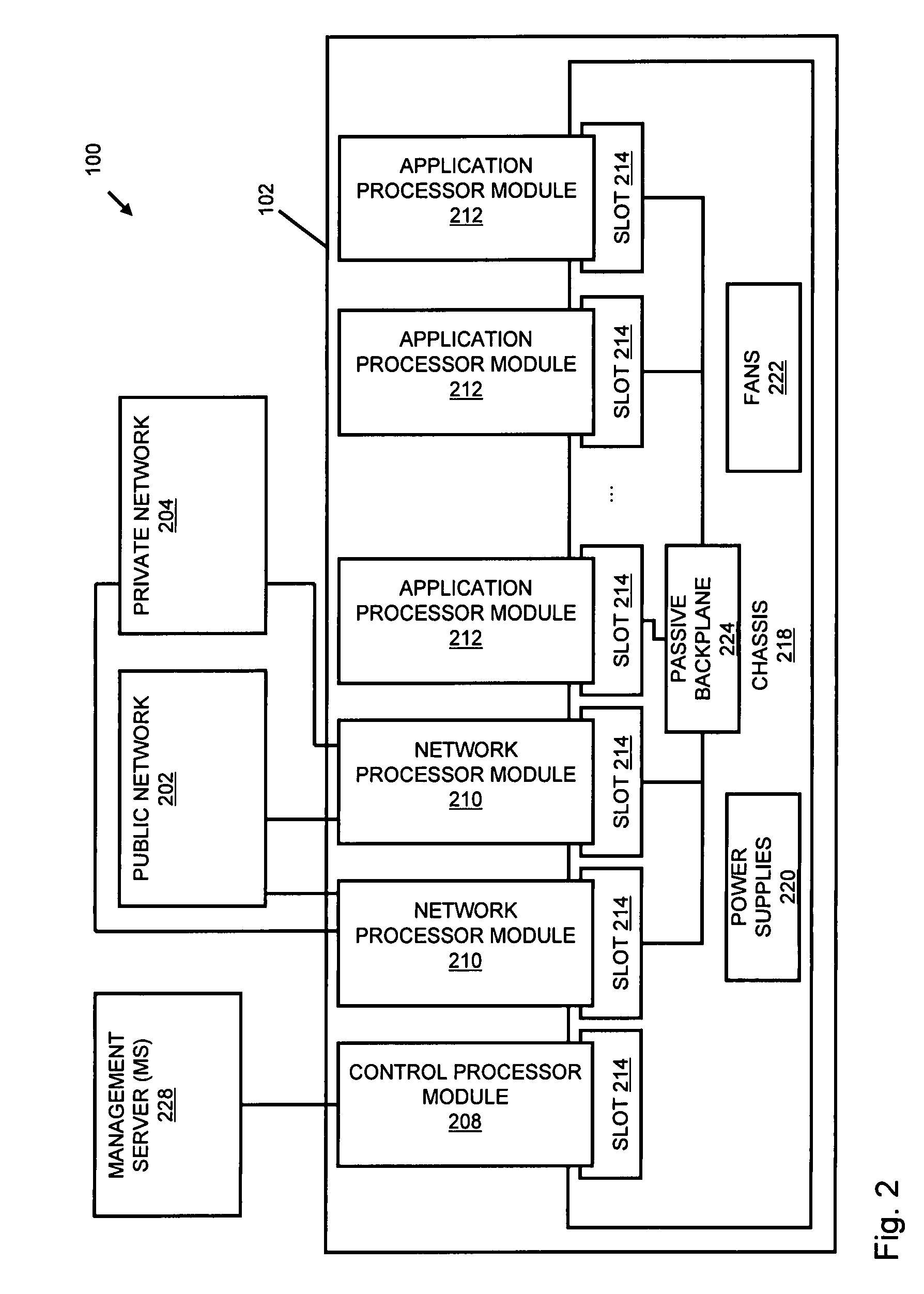
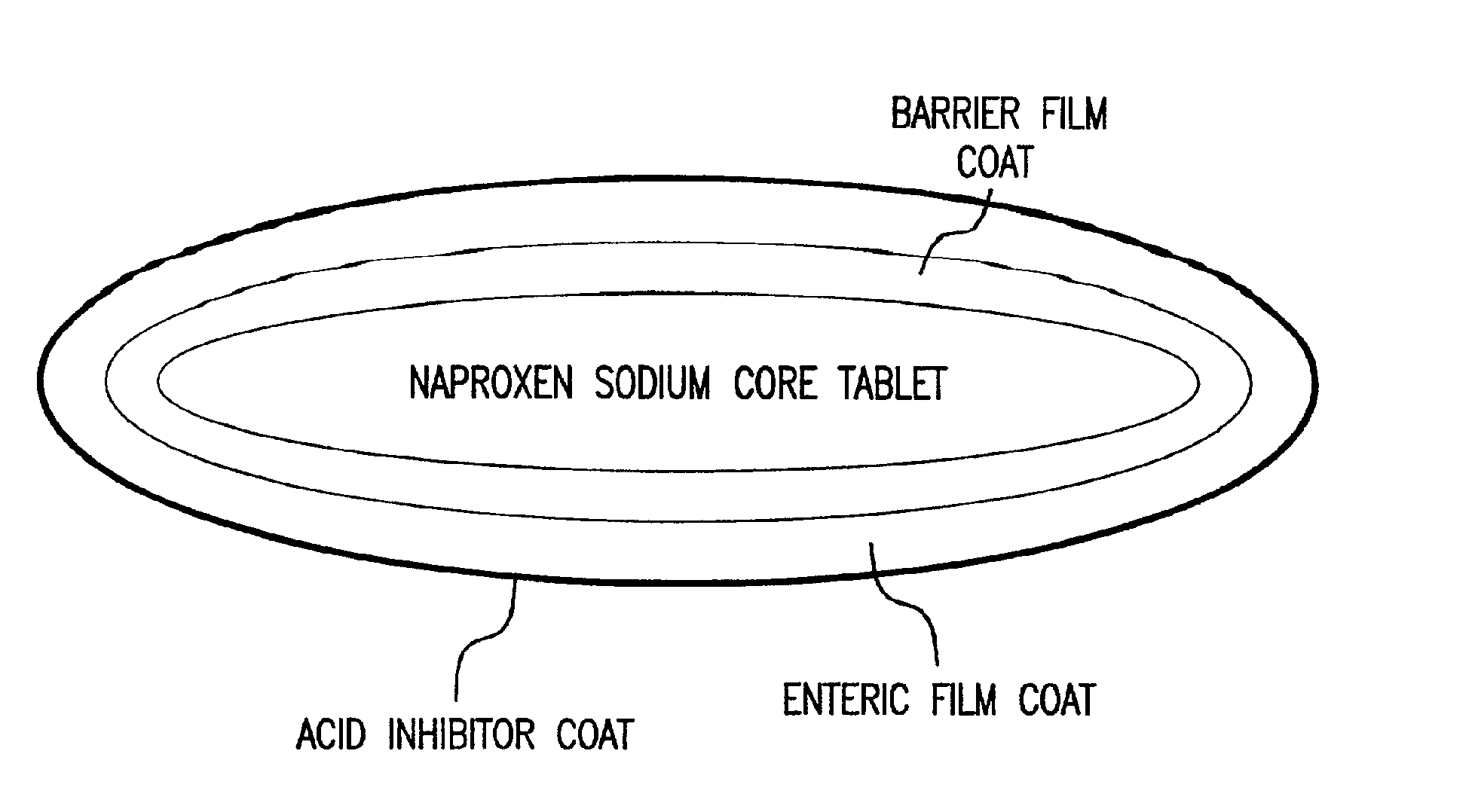
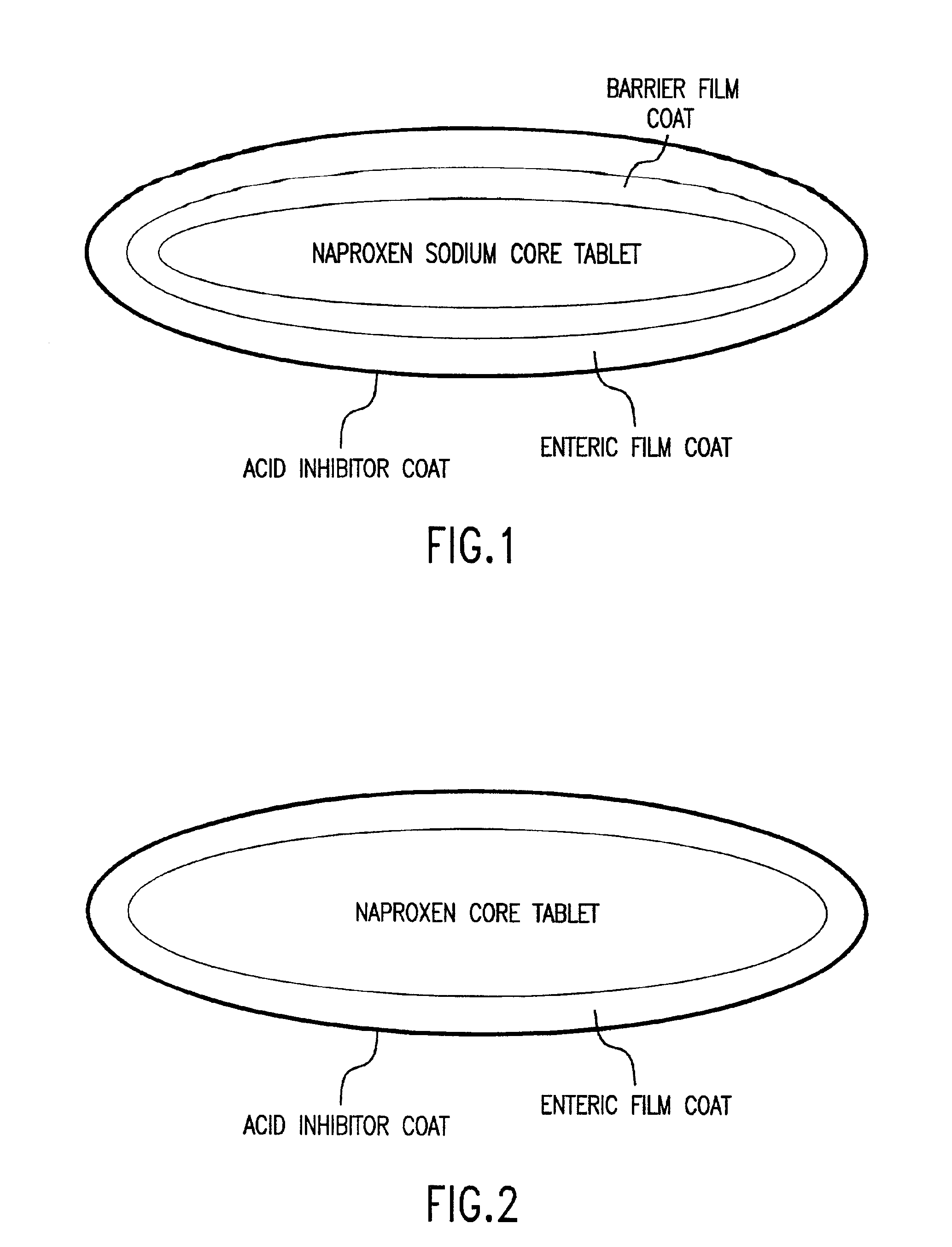
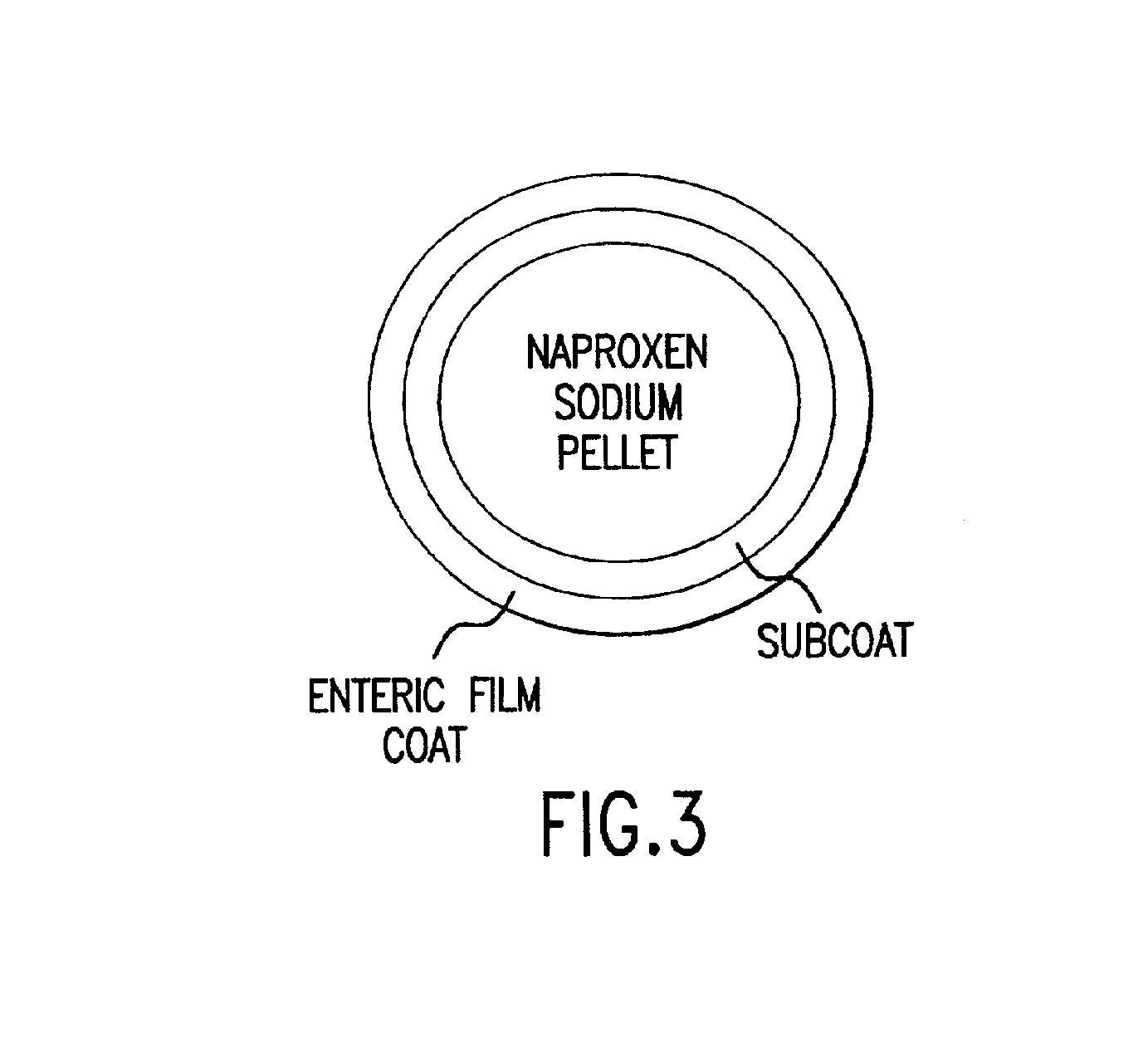
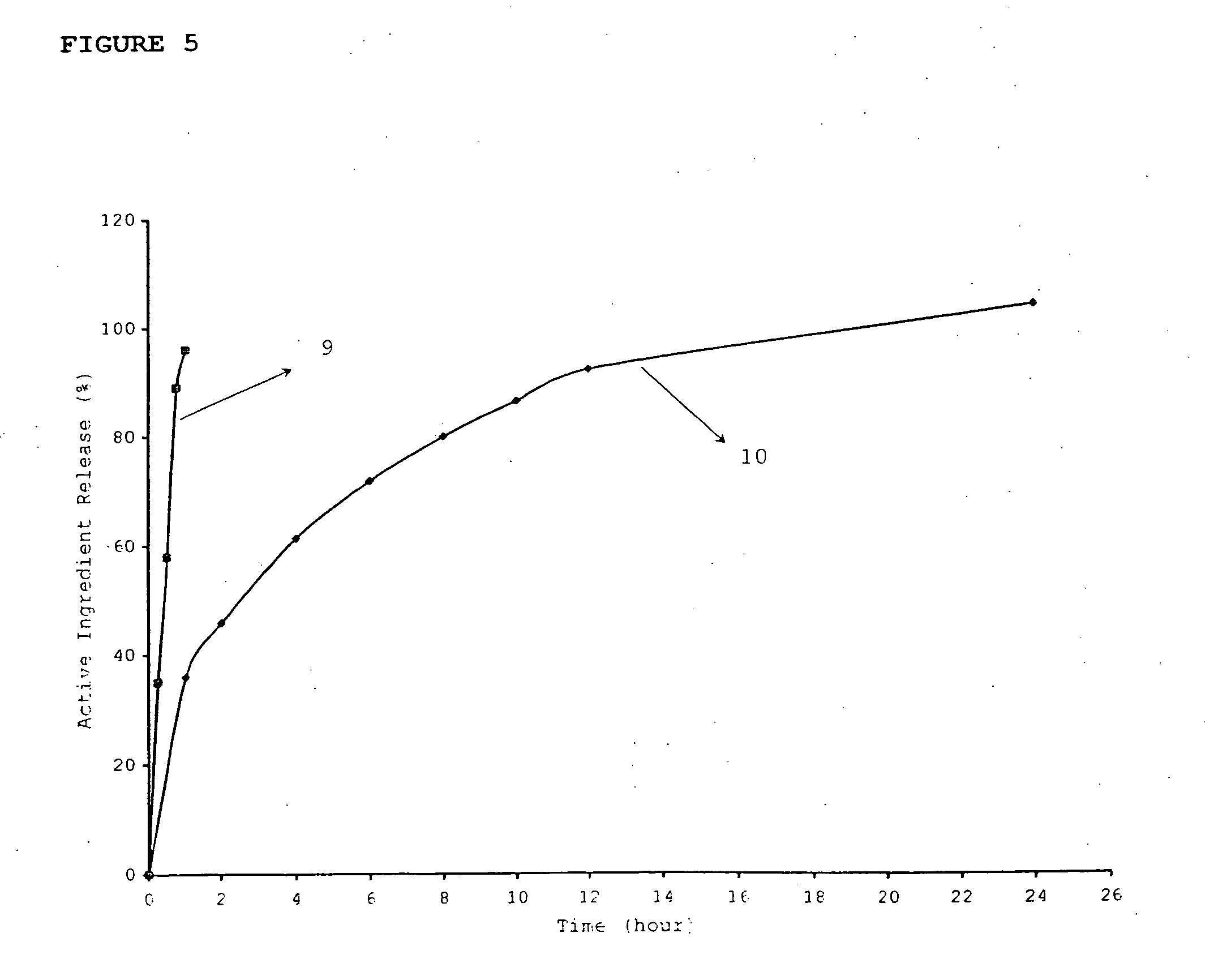
Pharmaceutical compositions for the coordinated delivery of NSAIDs
The present invention is directed to drug dosage forms that release an agent that raises the pH of a patient's gastrointestinal tract, followed by a non-steroidal anti-inflammatory drug. The dosage form is designed so that the NSAID is not released until the intragastric pH has been raised to a safe level. The invention also encompasses methods of treating patients by administering this coordinated release, gastroprotective, antiarthritic / analgesic combination unit dosage form to achieve pain and symptom relief with a reduced risk of developing gastrointestinal damage such as ulcers, erosions and hemorrhages.
Owner:NUVO PHARMA IRELAND DESIGNATED ACTIVITY CO
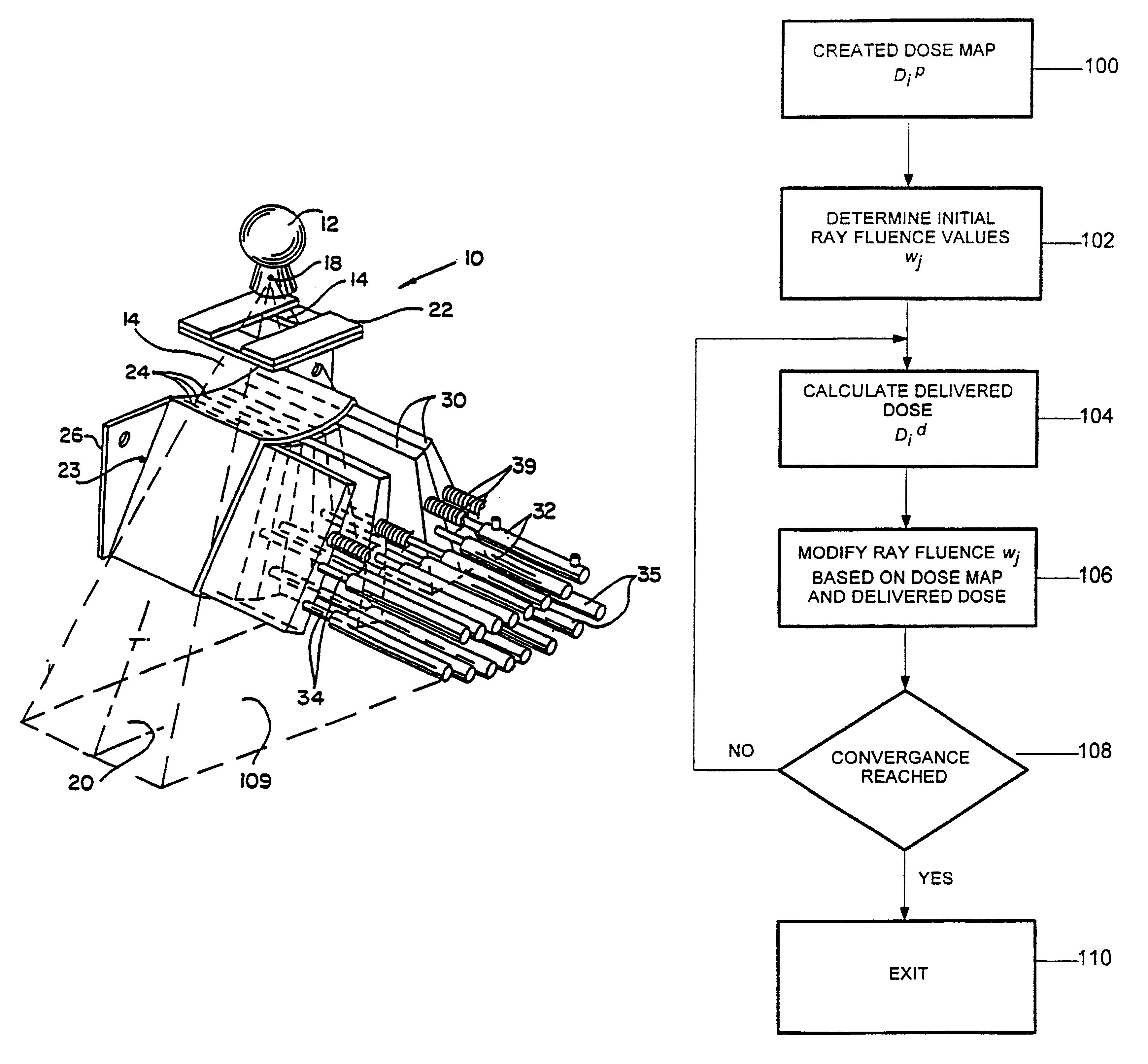
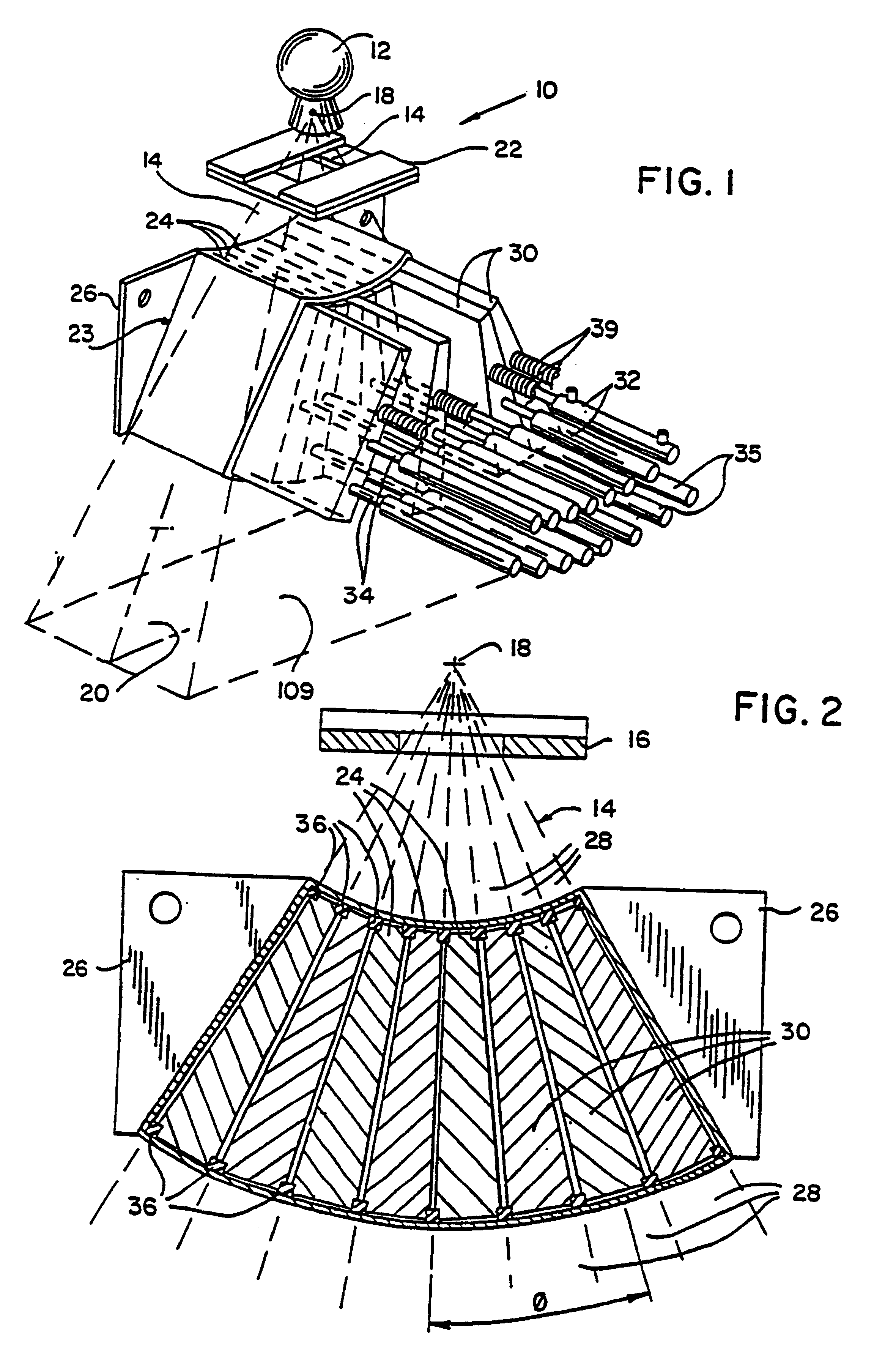
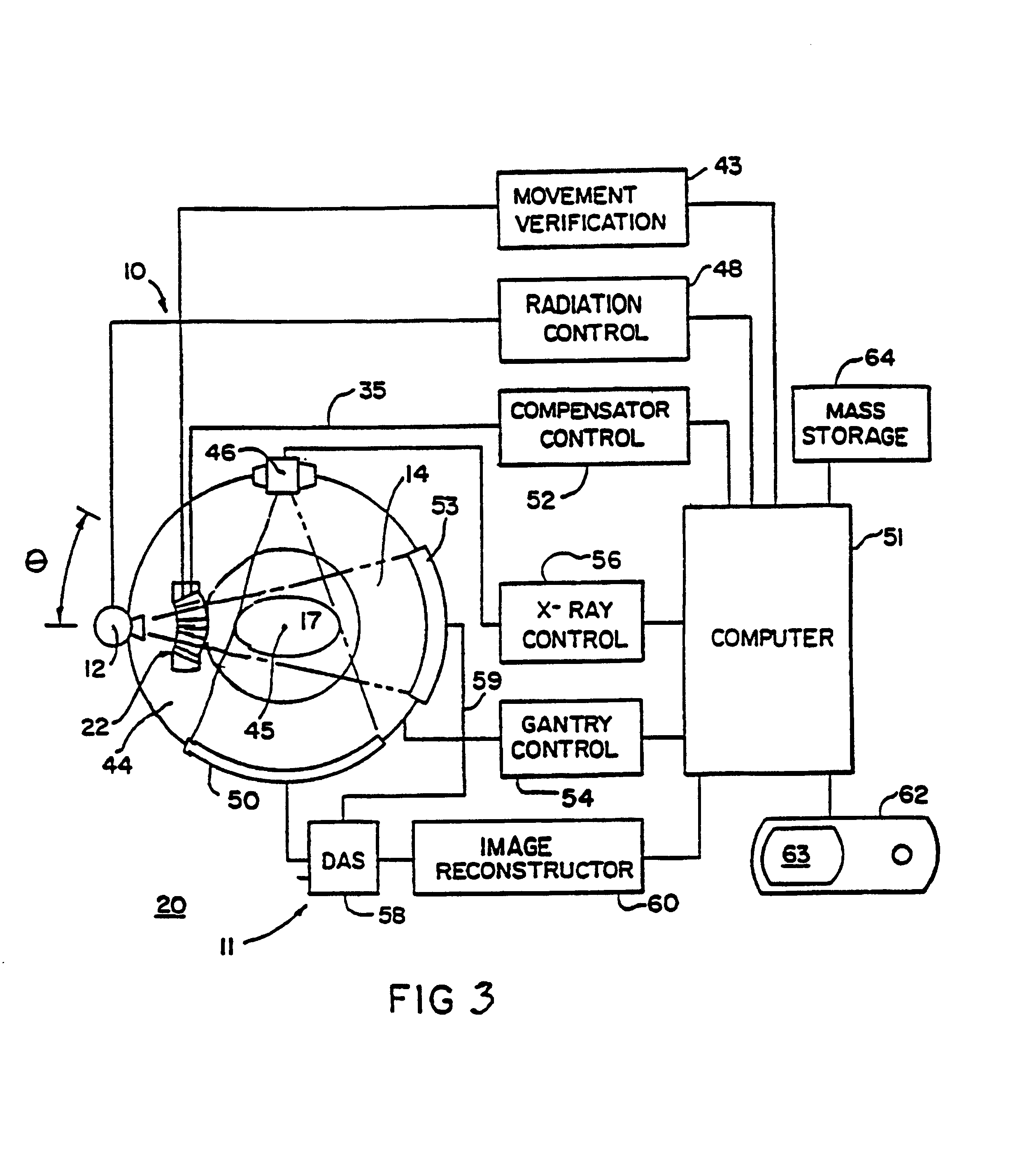
Method for preparing a radiation therapy plan
InactiveUS6560311B1Simple calculationFast executionMechanical/radiation/invasive therapiesComputer-assisted treatment prescription/deliveryDose profileIndividual dose
A method for determining a radiation treatment plan for a radiotherapy system providing multiple individual rays of intensity modulated radiation iteratively optimized the fluence of an initial set of such rays by a function that requires knowledge of only the prescribed dose and the dose resulting from the particular ray fluences. In this way, the need to store individual dose distributions of each ray are eliminated.
Owner:WISCONSIN ALUMNI RES FOUND
Organically-functionalized monodisperse nanocrystals of metals
InactiveUS6103868AHigh selectivityAvoid problemsPolycrystalline material growthLiquid surface applicatorsNanocrystalReducing agent
PCT No. PCT / US96 / 20402 Sec. 371 Date Jun. 18, 1998 Sec. 102(e) Date Jun. 18, 1998 PCT Filed Dec. 27, 1996 PCT Pub. No. WO97 / 24224 PCT Pub. Date Jul. 10, 1997Organically functionalized metal nanoparticles are produced by mixing a metal precursor with an organic surface passivant and reacting the resulting mixture with a reducing agent to generate free metal while binding the passivant to the surface of the free metal to produce organically functionalized metal particles.
Owner:RGT UNIV OF CALIFORNIA
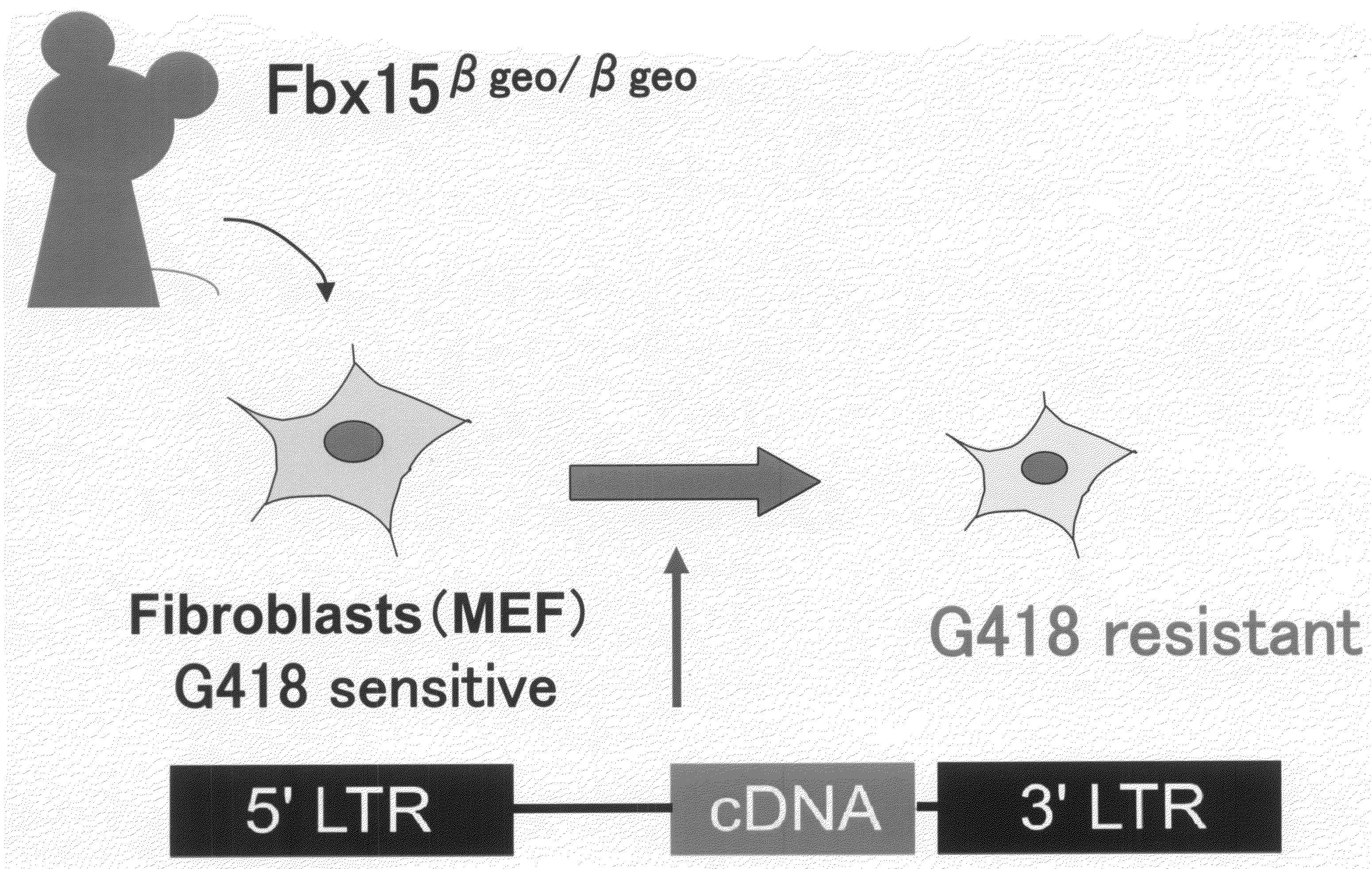
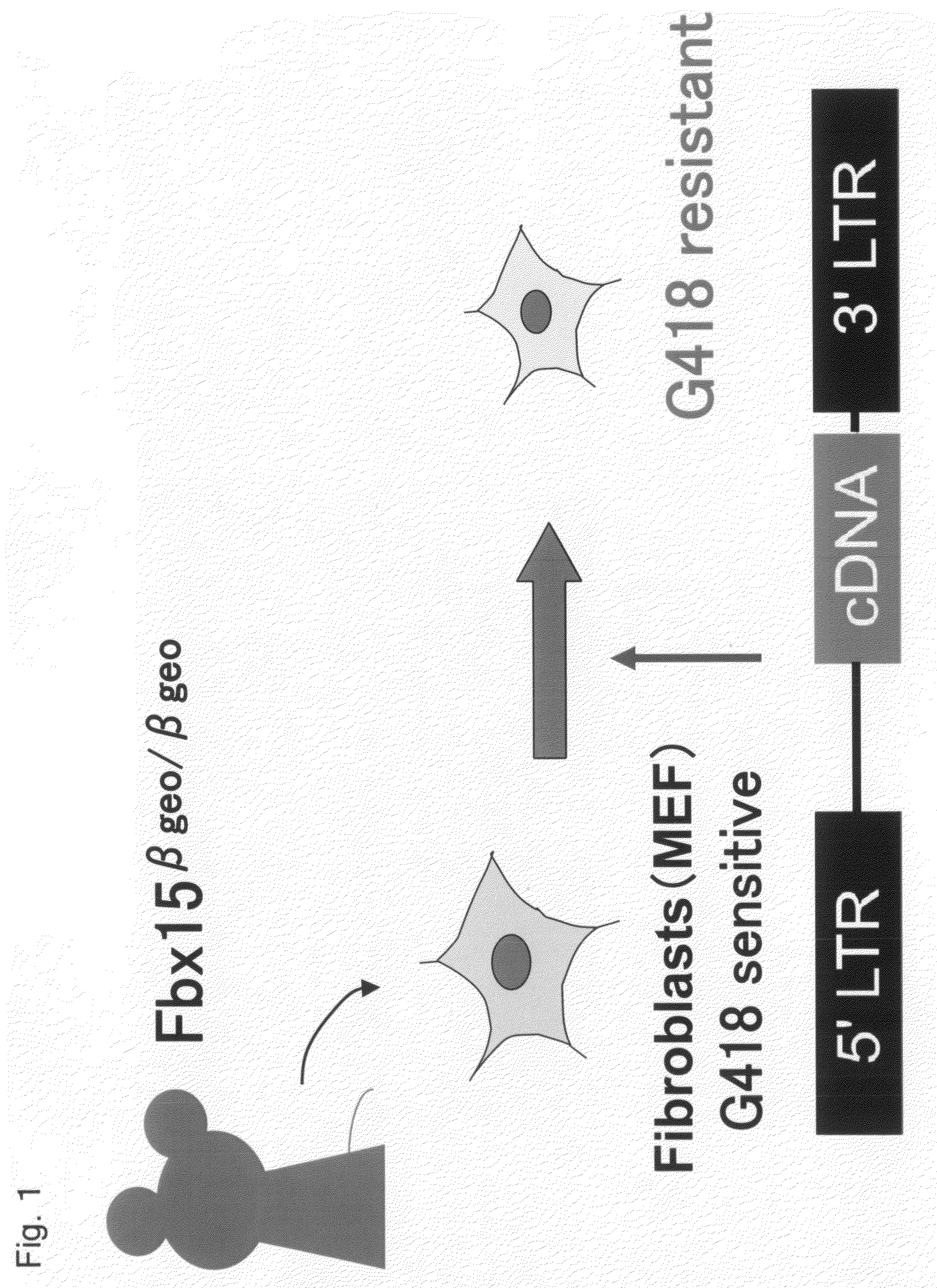
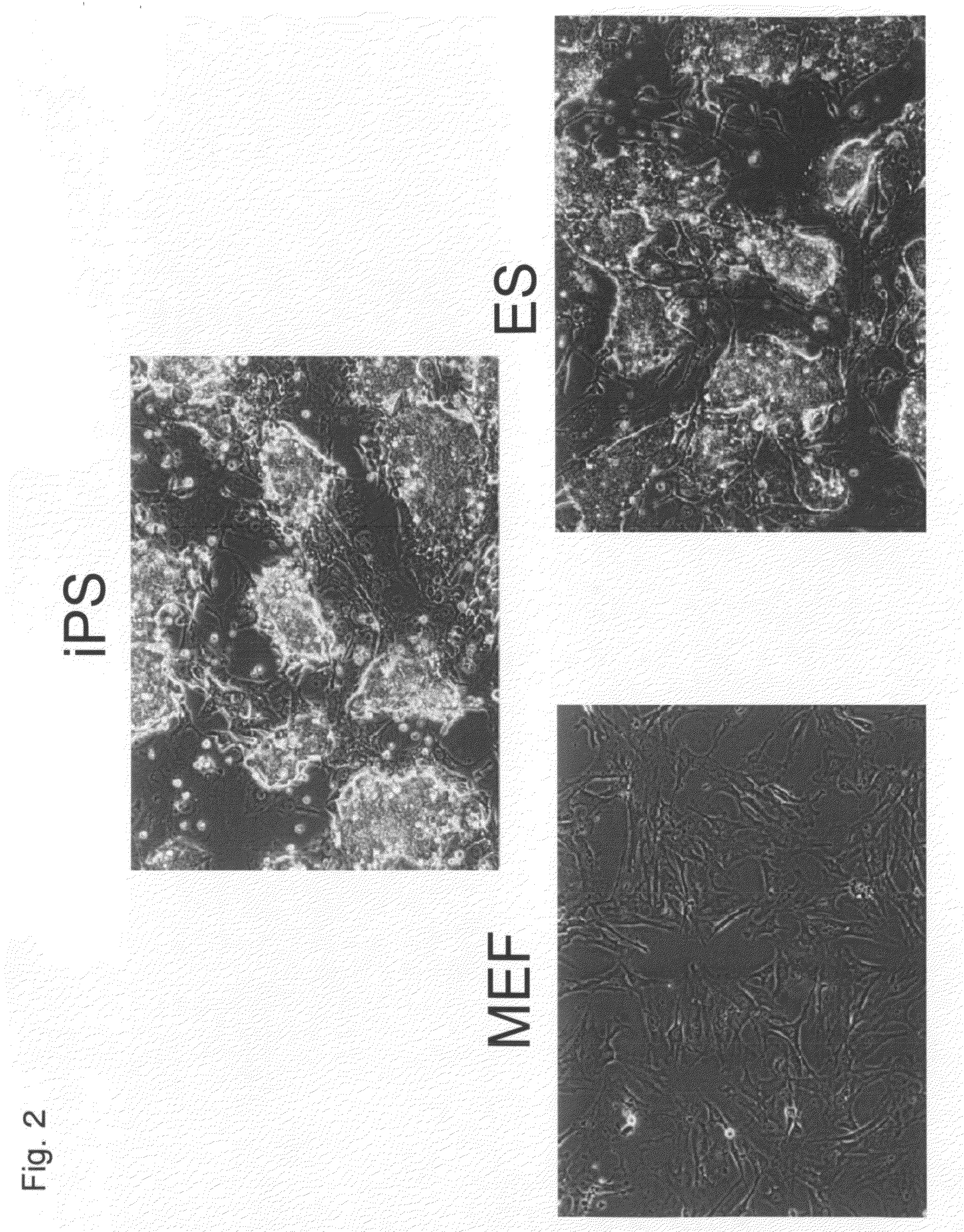
Nuclear Reprogramming Factor
There is provided a nuclear reprogramming factor for a somatic cell, which comprises a gene product of each of the following three kinds of genes: an Oct family gene, a Klf family gene, and a Myc family gene, as a means for inducing reprogramming of a differentiated cell to conveniently and highly reproducibly establish an induced pluripotent stem cell having pluripotency and growth ability similar to those of ES cells without using embryo or ES cell.
Owner:KYOTO UNIV
Novel dosage form
ActiveUS20060024365A1Effectively control release rateReduce sizePill deliveryEster active ingredientsHigh dosesSolubility
A dosage form comprising of a high dose, high solubility active ingredient as modified release and a low dose active ingredient as immediate release where the weight ratio of immediate release active ingredient and modified release active ingredient is from 1:10 to 1:15000 and the weight of modified release active ingredient per unit is from 500 mg to 1500 mg; a process for preparing the dosage form.
Owner:TORRENT PHARMA LTD
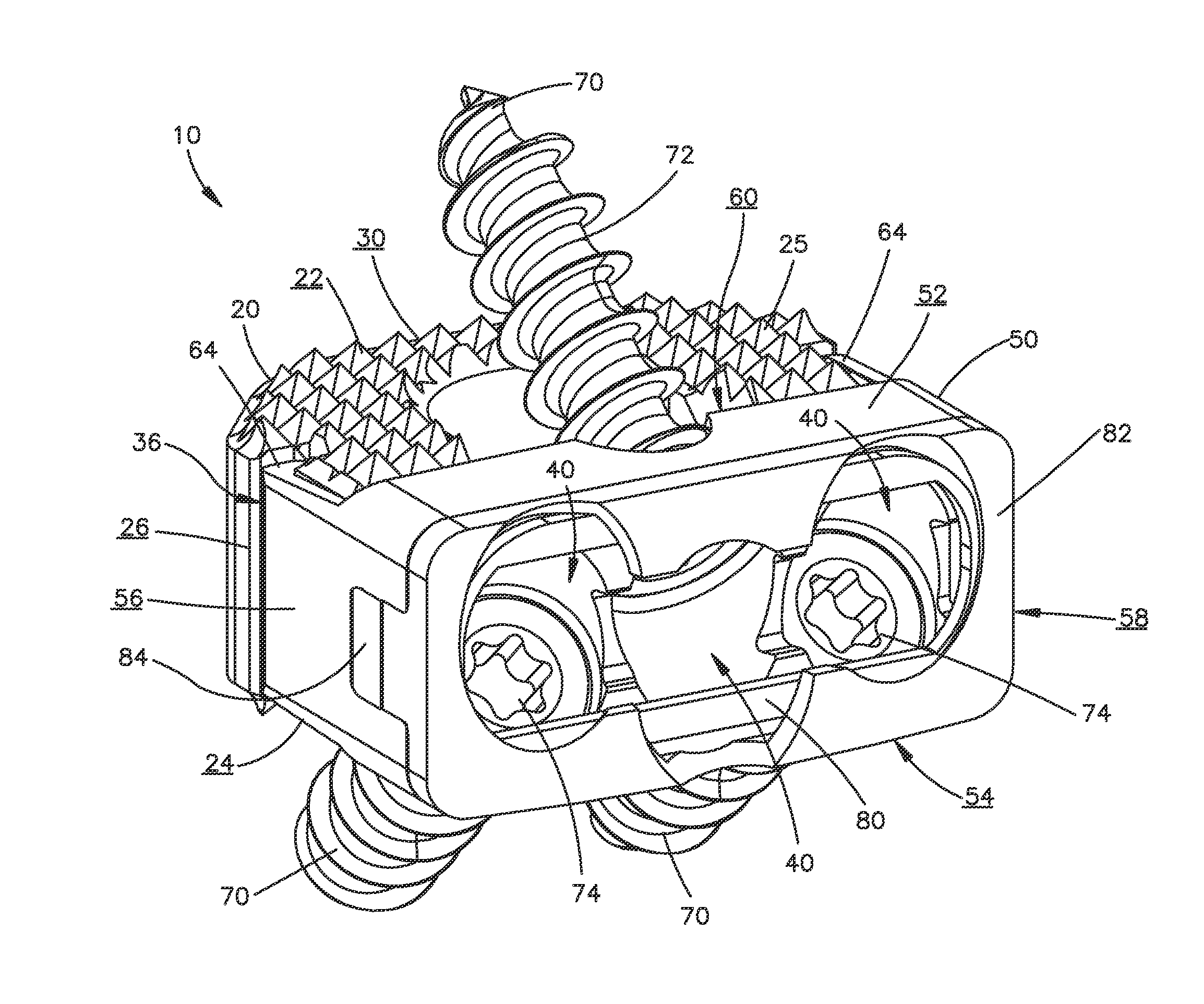
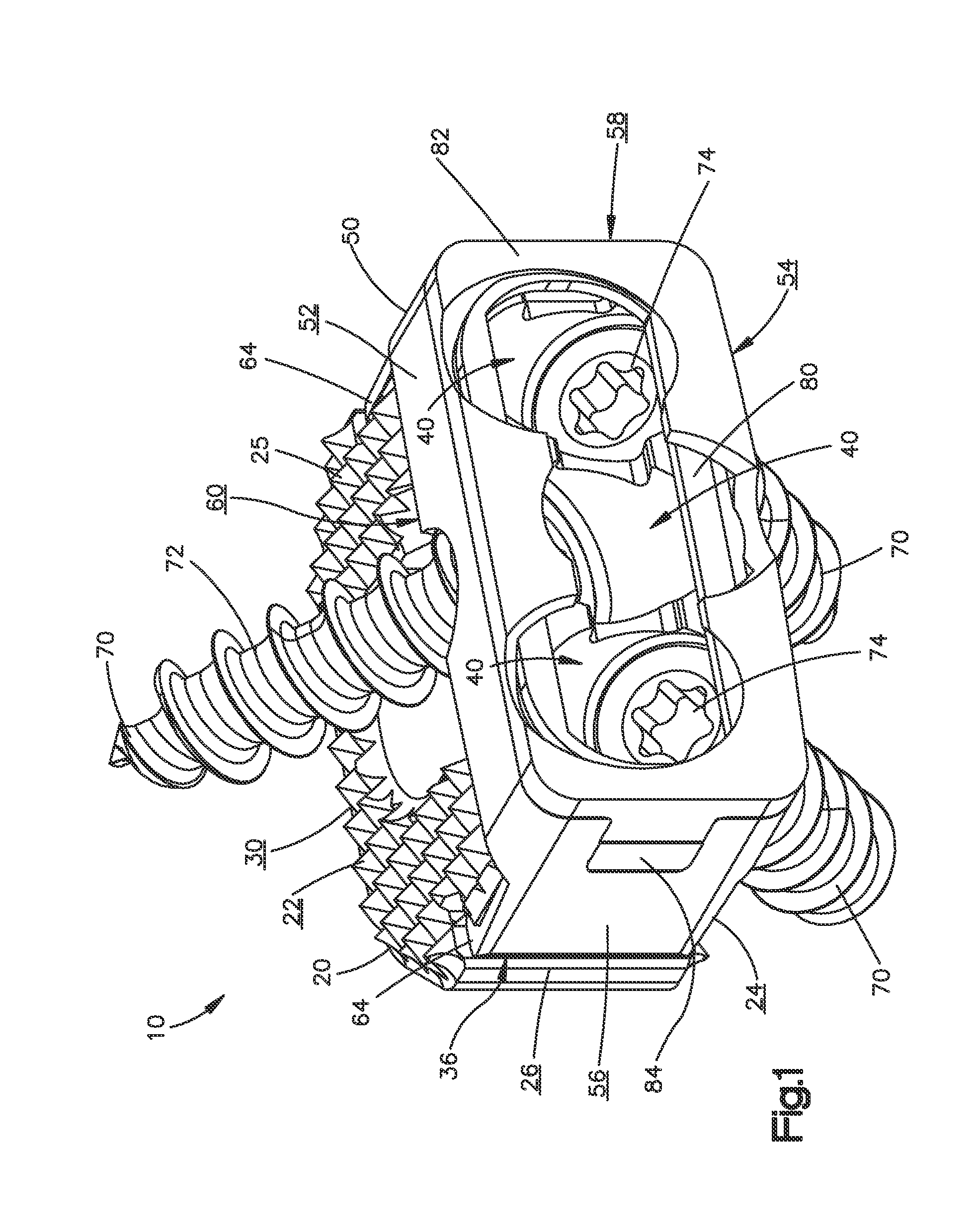
Zero-profile interbody spacer and coupled plate assembly
InactiveUS20100145460A1Avoid problemsPrevent over-insertionInternal osteosythesisSpinal implantsIntervertebral diskBiomedical engineering
An implant for insertion into the disc space between vertebrae. The implant including a spacer portion, a plate portion coupled to the spacer portion, a plurality of bone fixation elements for engaging the vertebrae and a retention mechanism for preventing the bone fixation elements from postoperatively uncoupling from the implant.
Owner:DEPUY SYNTHES PROD INC
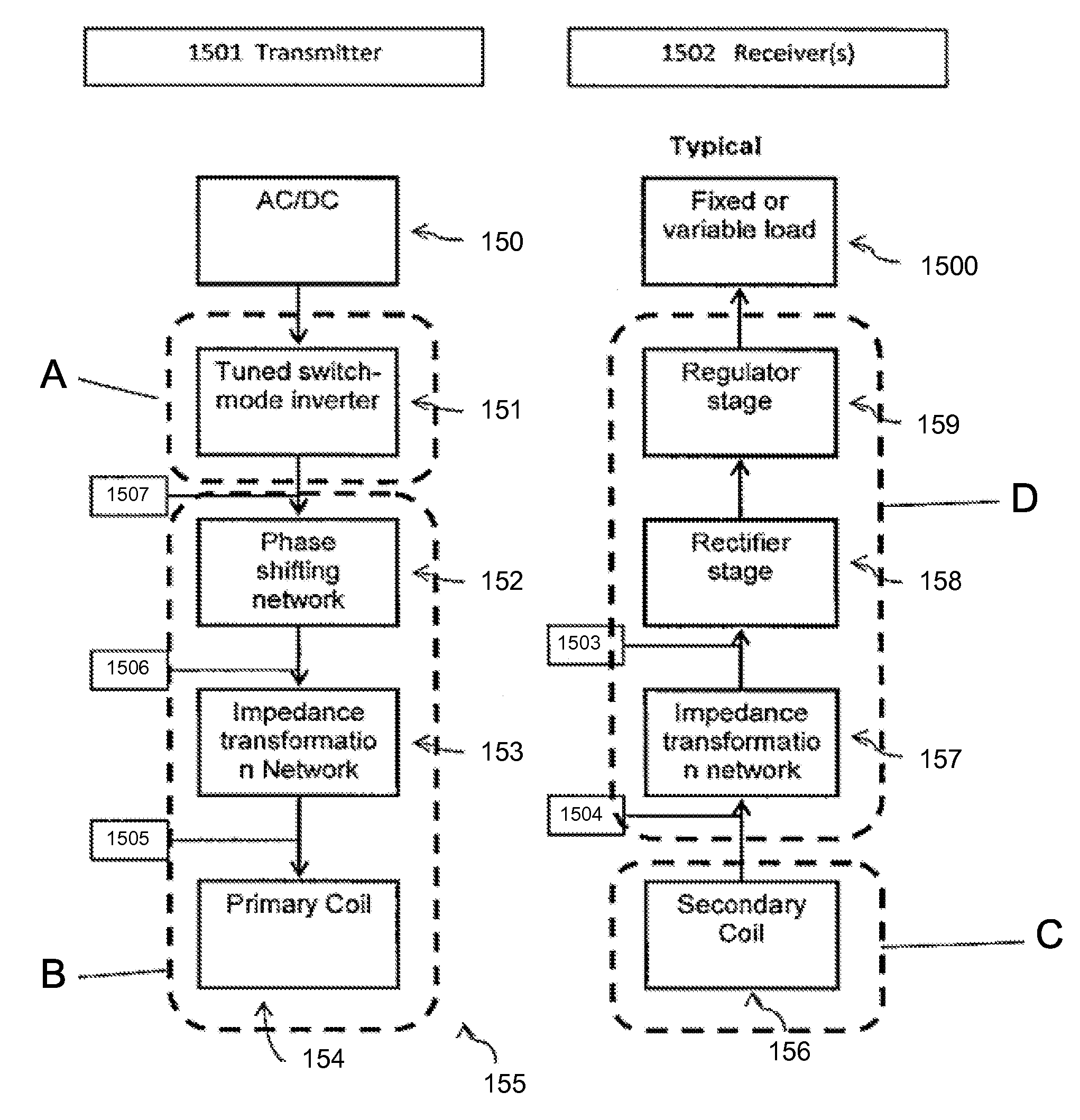
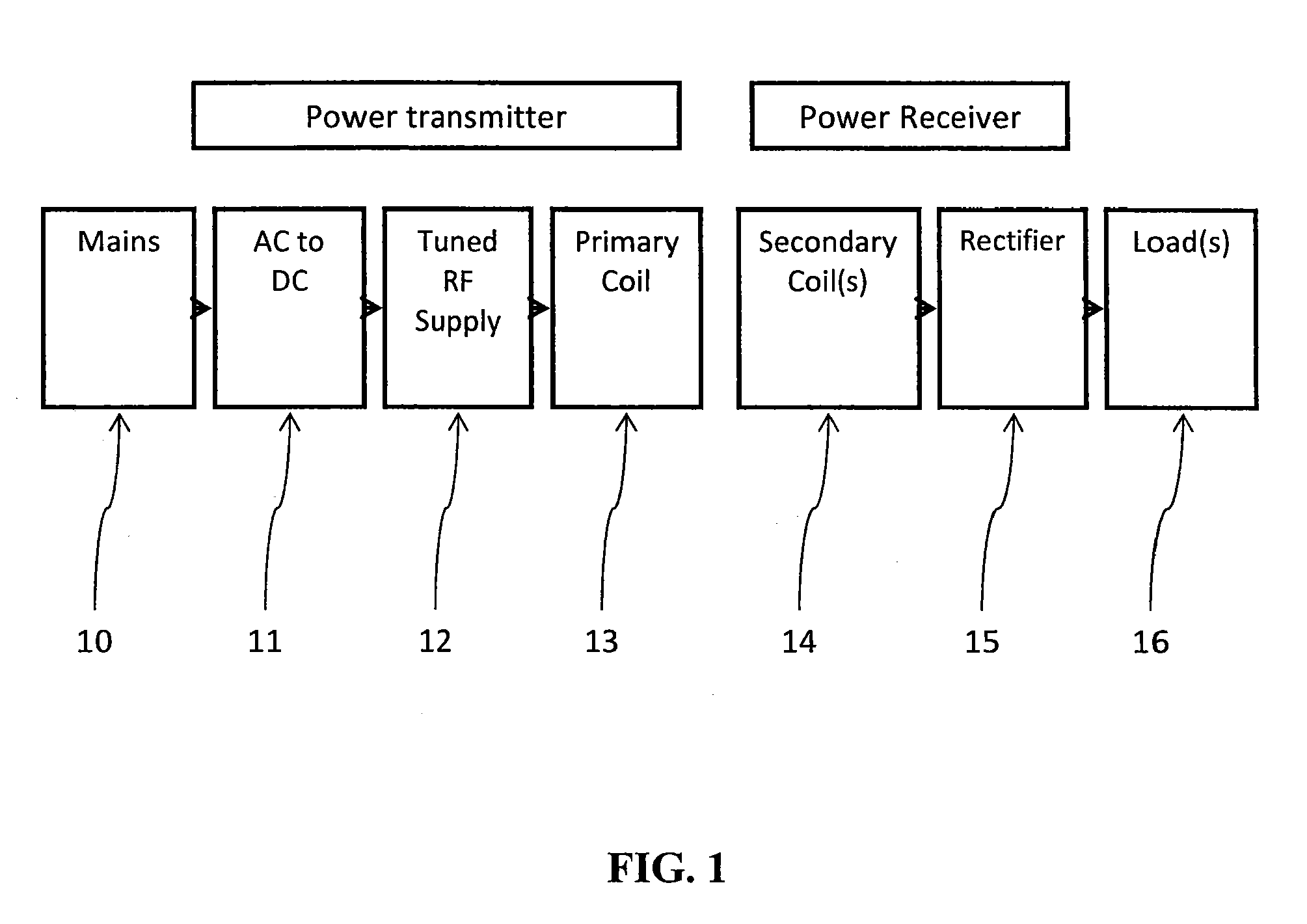
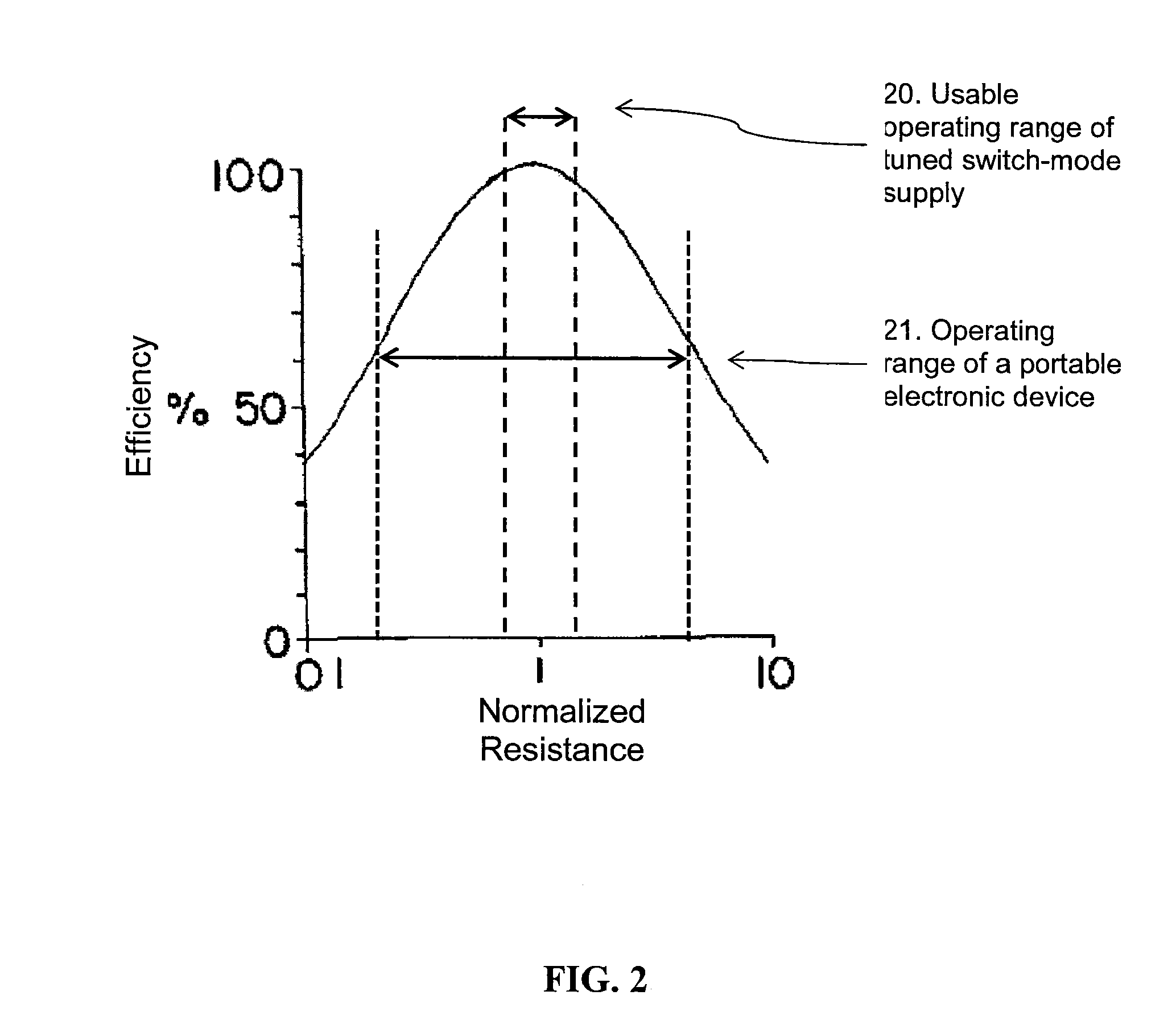
Method and apparatus for contactless power transfer
ActiveUS8674551B2Improve system performanceEasy to controlCircuit monitoring/indicationTransformersElectric power transmissionEngineering
Embodiments of the subject invention pertain to a method and apparatus for contactless power transfer. A specific embodiment relates to an impedance transformation network, a new class of load network for application to a contactless power system. Embodiments of the impedance transformation network enable a contactless power system to operate without encountering the common problems of: 1) over-voltage and / or under-voltage conditions; 2) over-power and / or under-power conditions; 3) power oscillations; and 4) high heat dissipation.
Owner:UNIV OF FLORIDA RES FOUNDATION INC
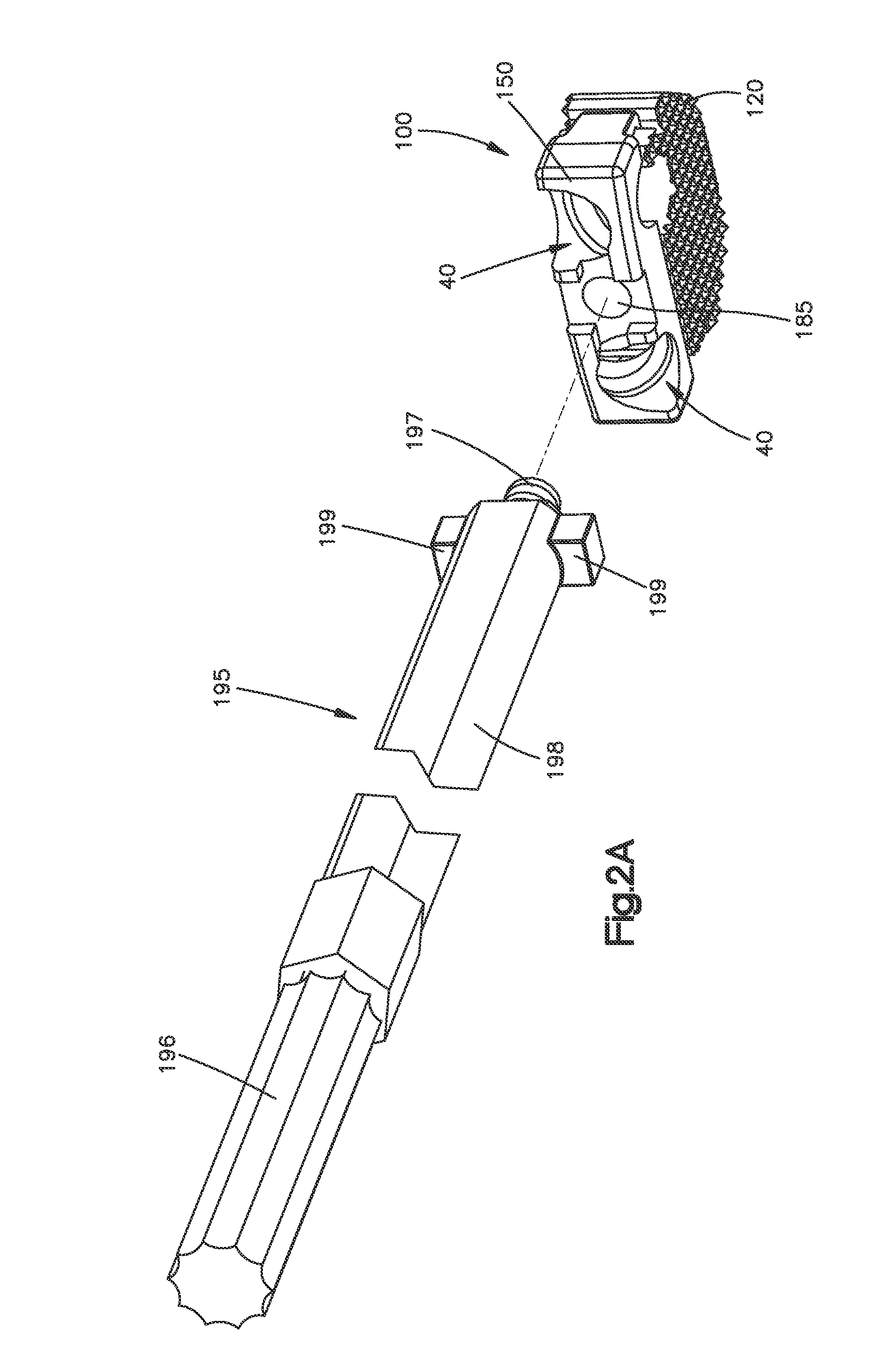
Zero-profile interbody spacer and coupled plate assembly
ActiveUS20100145459A1Prevent over insertionPrevent insertionInternal osteosythesisSpinal implantsPropellerIntervertebral disk
An implant for insertion into a disc space between vertebrae, wherein the implant includes a spacer portion, a plate portion coupled to the spacer portion, two bone fixation elements for engaging the vertebrae and a retention mechanism for preventing the bone fixation elements from postoperatively backing-out of the plate portion. The retention mechanism may be in the form of a spring biased snapper element that is biased into communication with the bone fixation elements so that once the bone fixation element advances past the snapper element, the snapper element is biased back to its initial position in which the snapper element interfaces with the bone fixation elements. Alternatively, the retention mechanism may be in the form of a propeller rotatable between a first position in which the bone fixation elements are insertable to a second position where the bone fixation elements are prevented from backing-out.
Owner:DEPUY SYNTHES PROD INC
Electronic pipe personal vaporizer with concealed removable atomizer/ cartomizer
InactiveUS20130087160A1Avoid accidental activationAvoid problemsTobacco pipesTobacco devicesCircular discControl power
A porous ceramic atomized cartridge contains a heating element, a porous ceramic wick, and the liquid to be vaporized removably concealed within the body of an electronic simulated smoking pipe. Adjustment of the spacing of a circular disc heating element relative to the porous ceramic wick adjusts the level of atomization. All components are easily removable and replaceable and cleaned. A bowl of the pipe is used as an open battery chamber to allow any battery fumes to escape and allow easy removal and replacement of the battery. A conductive contact arm pivots between contact with the battery and the pipe body to control power. Vapor is activated by a manual push button switch or an automatic sound activated switch responsive to the puffing sound of a user.
Owner:GHERGHE ALEXANDRU
Horn antenna for a radar device
A horn antenna for a radar device comprising a metal body having a tubular hollow waveguide section opening into a hollow horn section, a dielectric filling body filling up the inner space of the horn section, and a dielectric cover, wherein the horn antenna is configured to protrude in a measurement environment, protected from highly aggressive process environments and is usable over a wide temperature range.
Owner:SIEMENS AG
Computer and method providing for illumination of keyboard
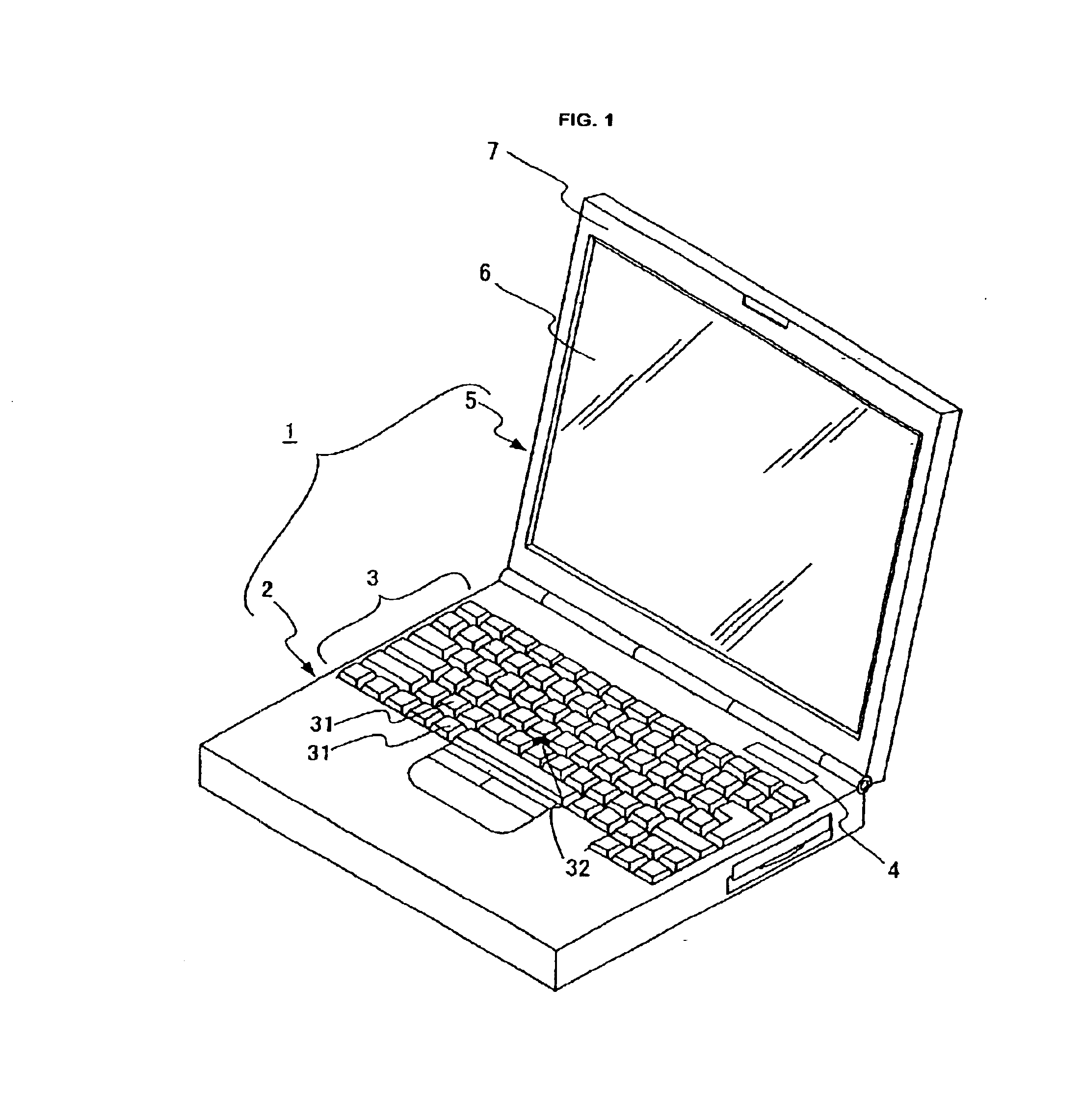
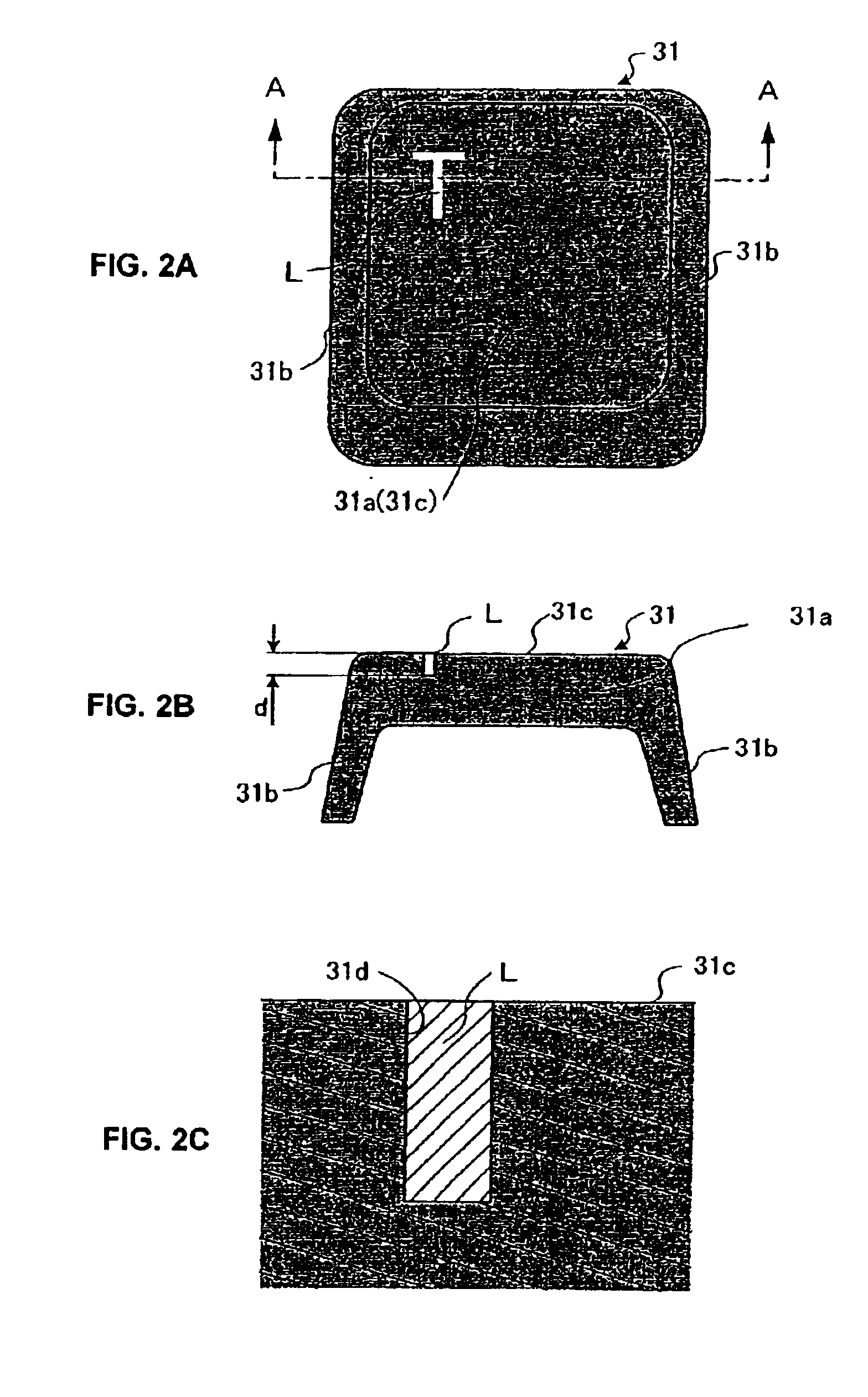
InactiveUS6911971B2Avoid problemsAvoids any increase in the workloadInput/output for user-computer interactionLegendsComputer hardwareComputer graphics (images)
The computer of the present invention is provided with a main body on which keys to be operated by the user are disposed and a display unit that displays an image in accordance with each operation executed for the main body. Each key disposed on the main body is composed of its body having a key top and a light accumulator recess opened in the key top. The light accumulator recess is formed in a manner indicative of the character or symbol associated with such key. The light accumulator recess has embedded in it a light accumulating material such that the character or symbol associated with the key is illuminated by the residual light emission of the light accumulating material when the computer is operated in a location with little or no ambient light.
Owner:LENOVO (SINGAPORE) PTE LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com