Patents
Literature
2168results about How to "Provide protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
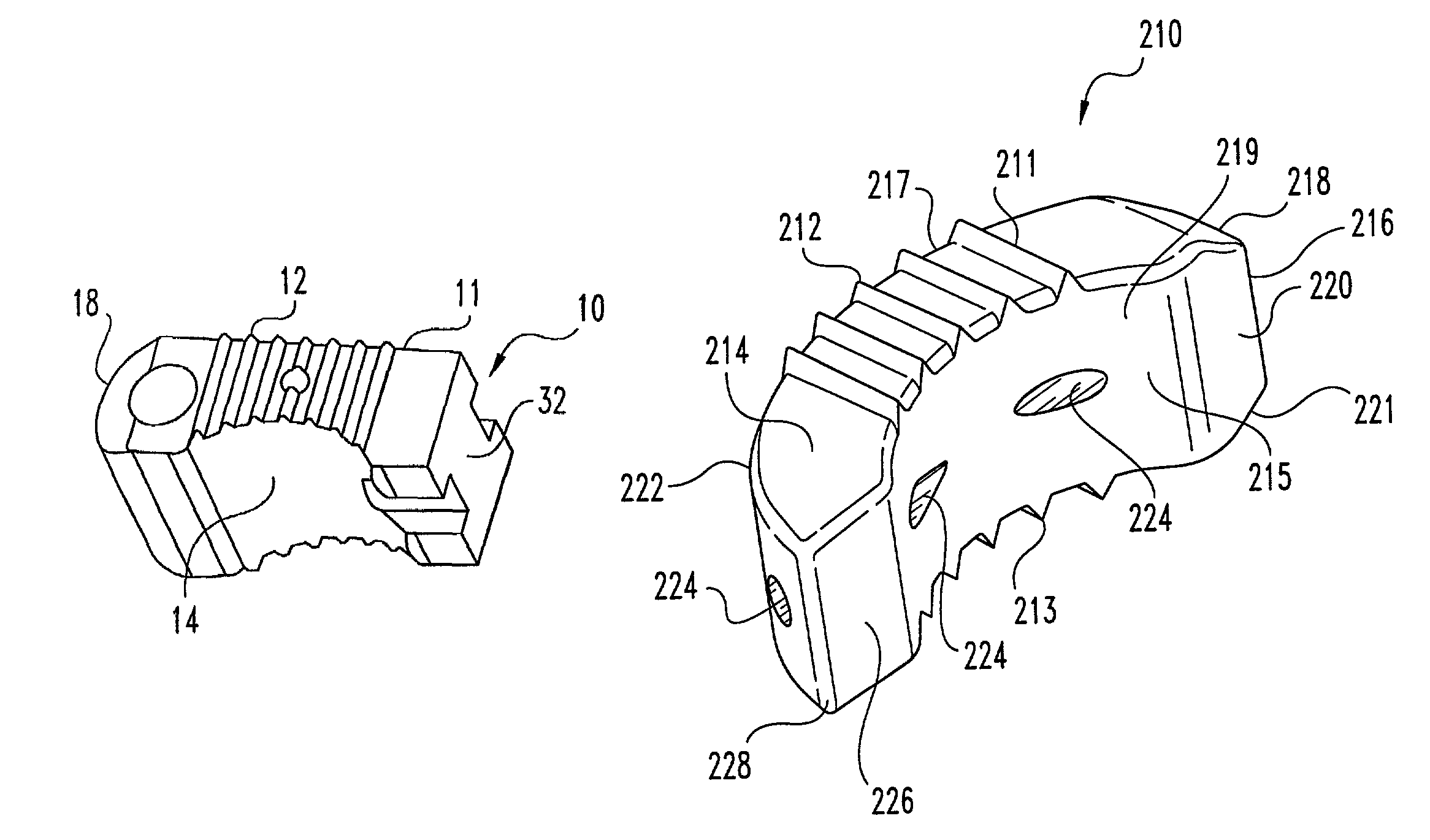
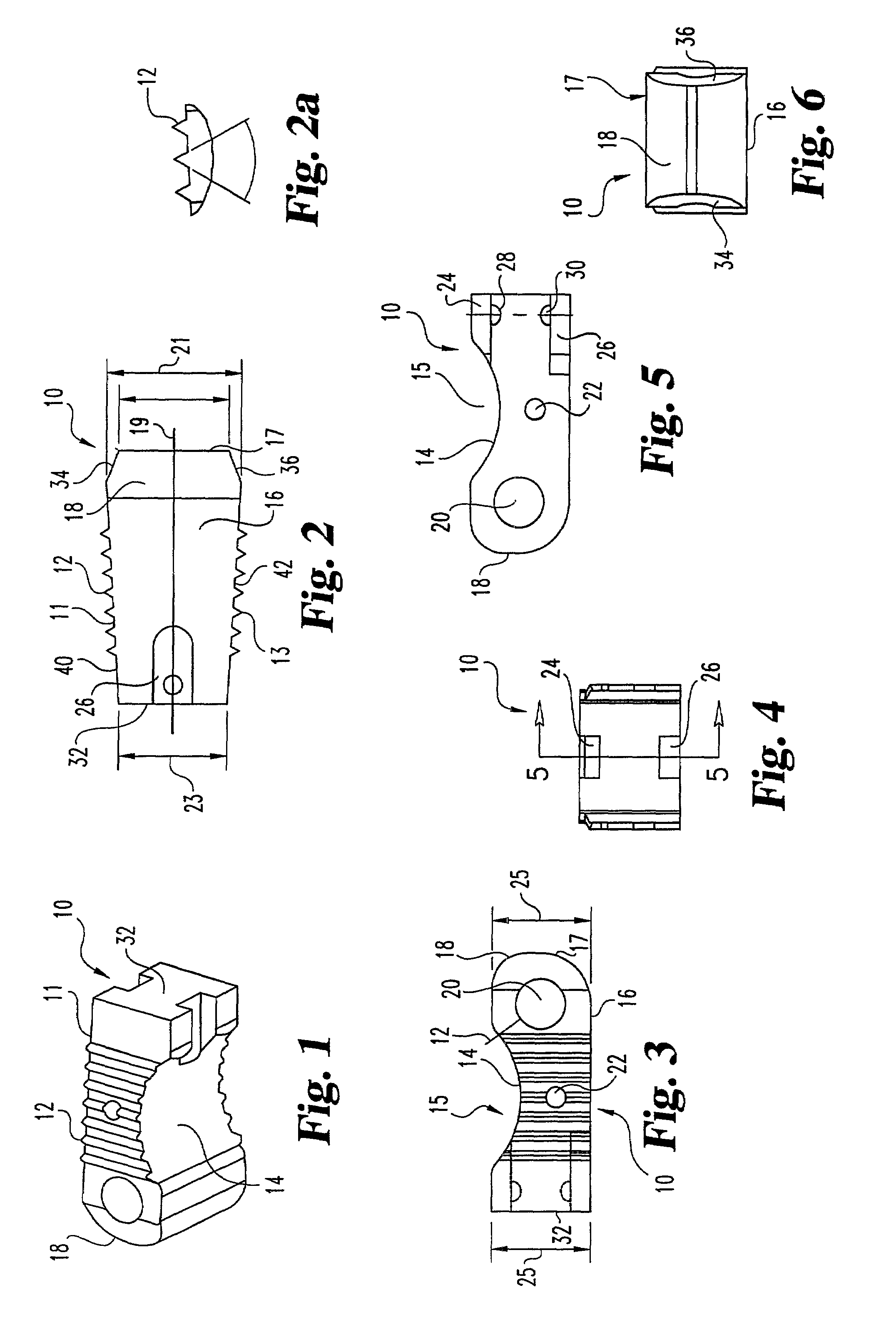
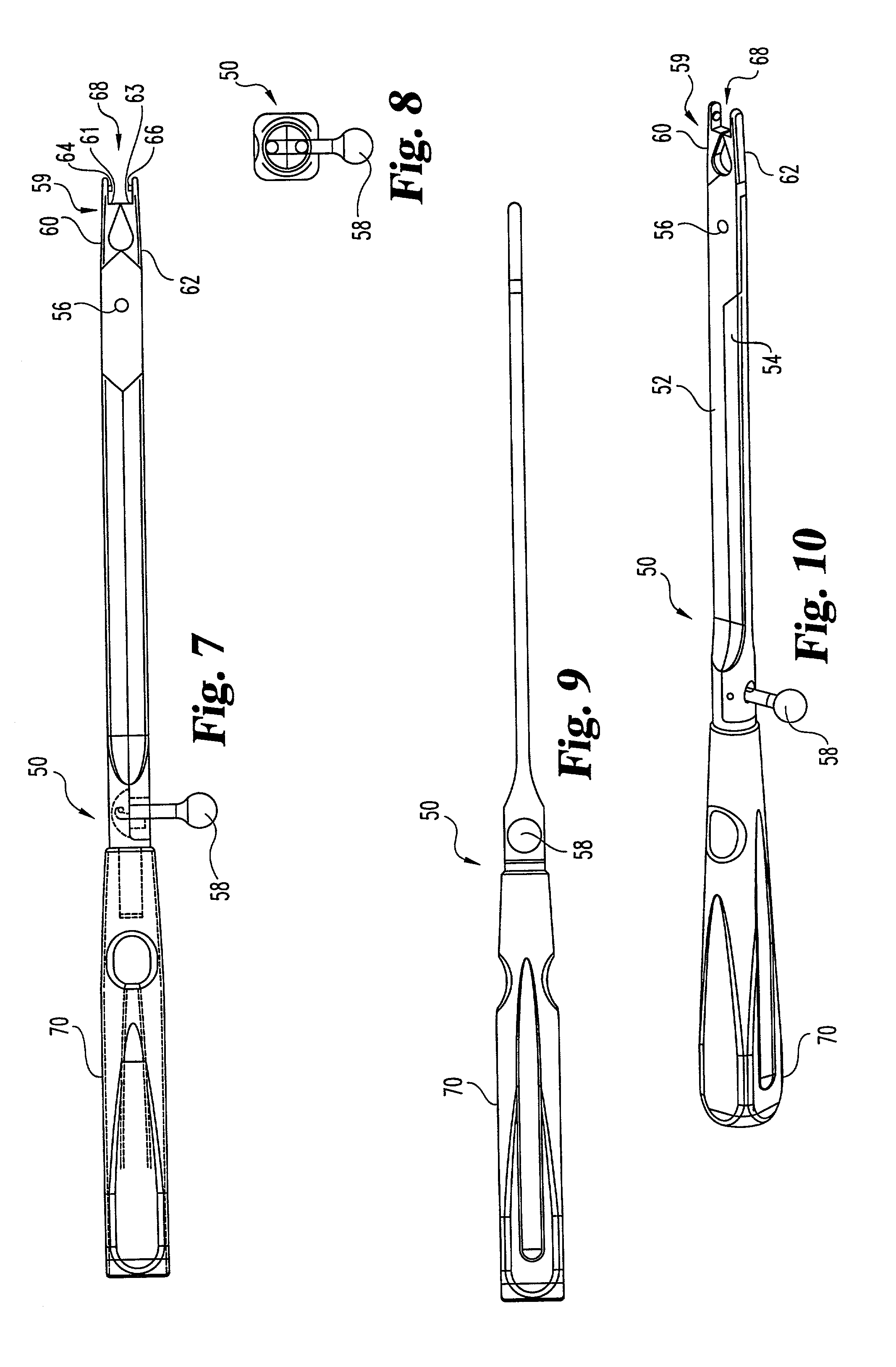
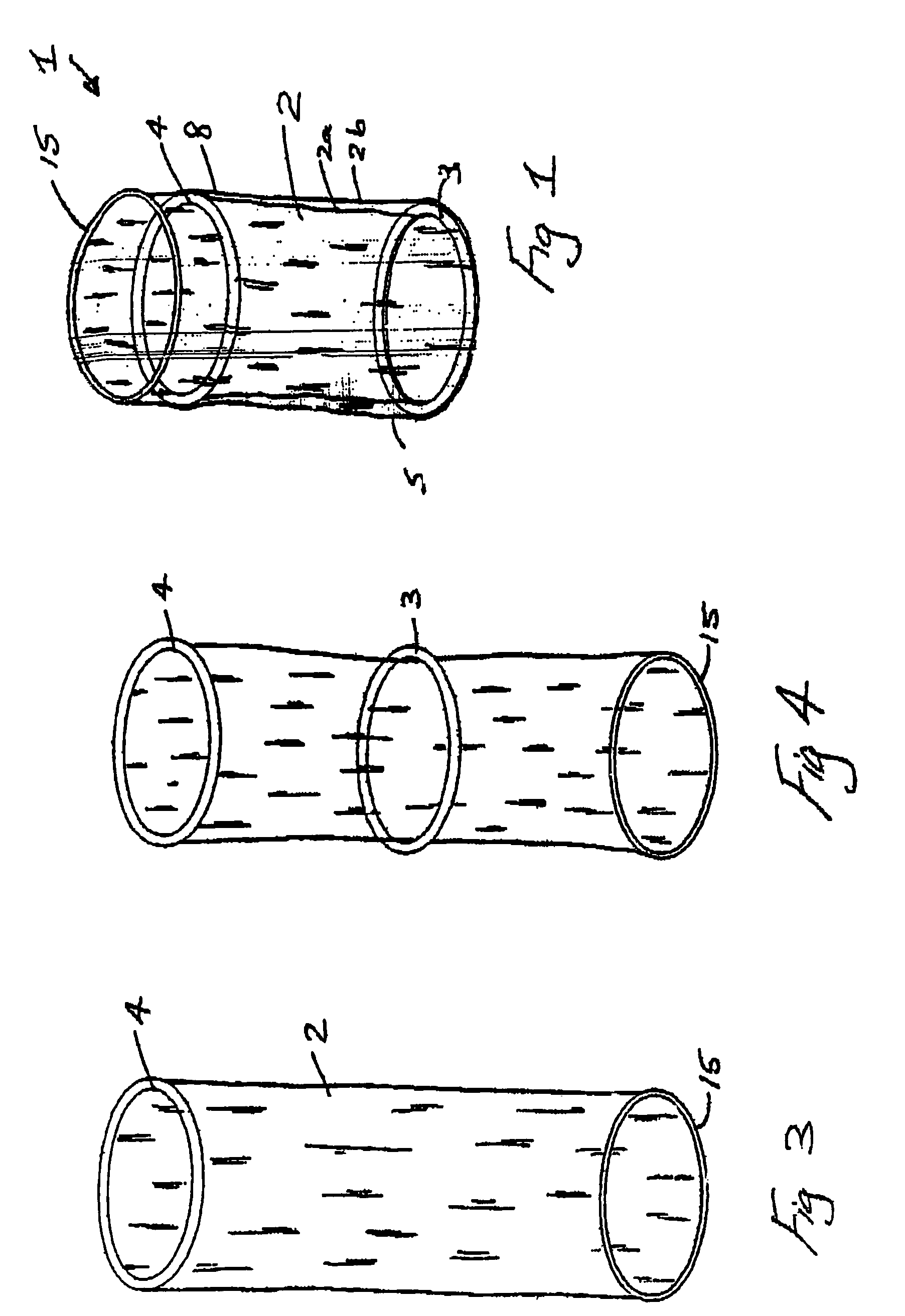
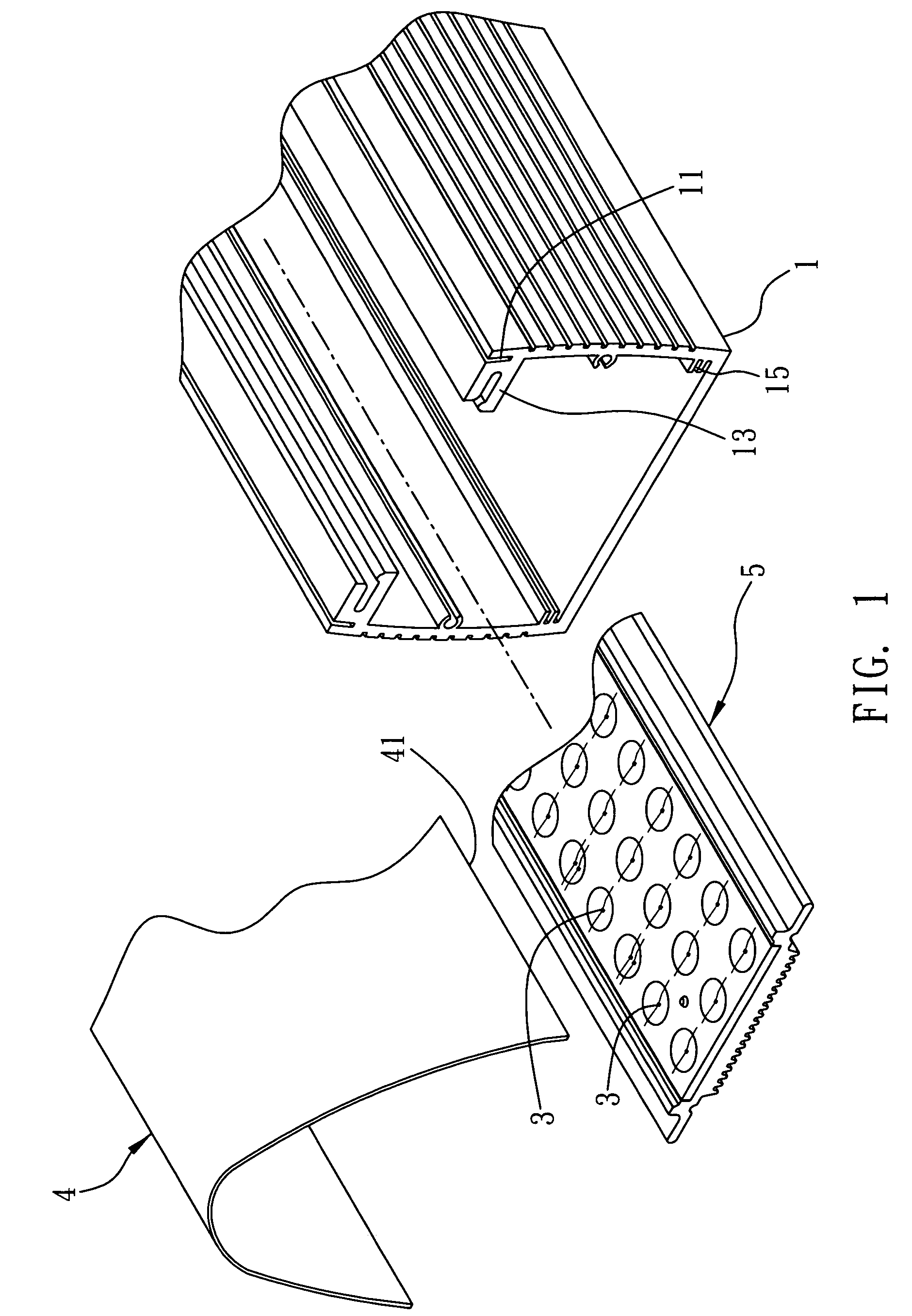
Interbody fusion grafts and instrumentation
InactiveUS7479160B2Maintain disc heightMaintain distractionInternal osteosythesisBone implantMedicineDonor bone
This invention relates to implants formed from donor bone for use in lumbar interbody fusion procedures and instruments for performing such procedures. The implants are formed to include a concave surface formed from a portion of the medullary canal of a long bone. The concaved surface defines a recess in the implant that serves as a depot for osteogenic material. Specific instruments for inserting the implants prepared according to this invention and for preparing the intervertebral space to receive the implants are also provided.
Owner:WARSAW ORTHOPEDIC INC
Wound retractor
InactiveUS7540839B2Facilitate localised releaseReduce coefficient of frictionCannulasSurgical needlesWound retractorGeneral surgery
A surgical wound retractor comprises a retracting member for insertion into a wound opening and a proximal member for location externally of a wound opening A clamp is used to clamp the retracting member to the proximal member.
Owner:ATROPOS LTD
Microfluidic system
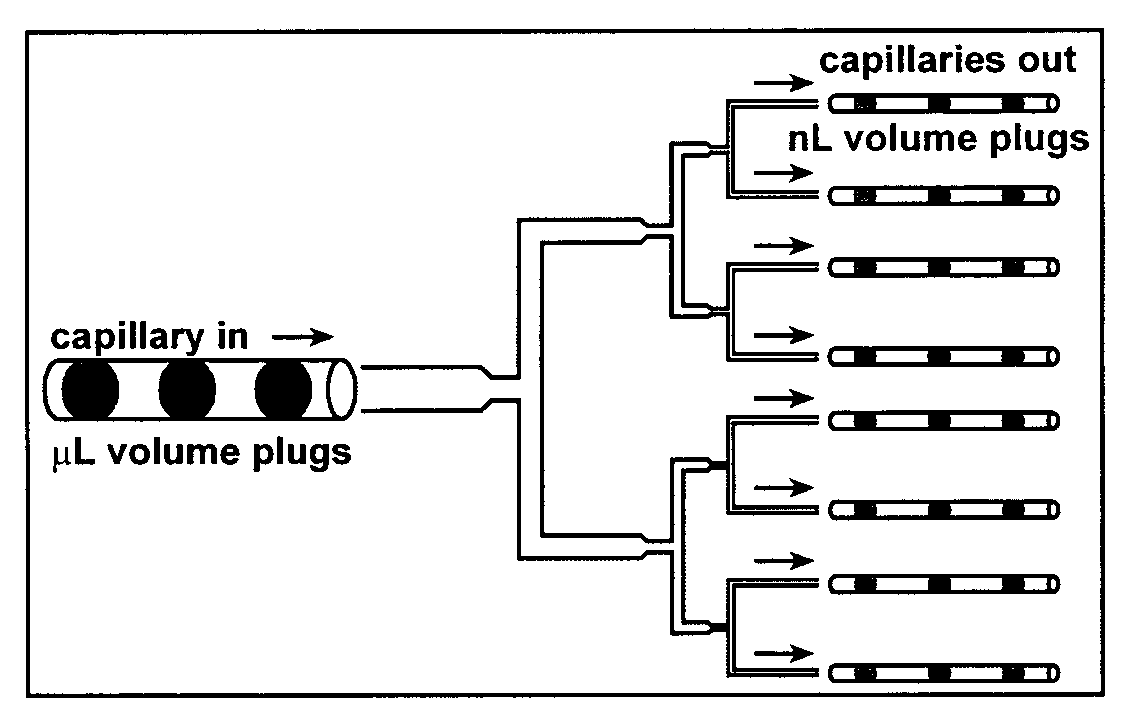
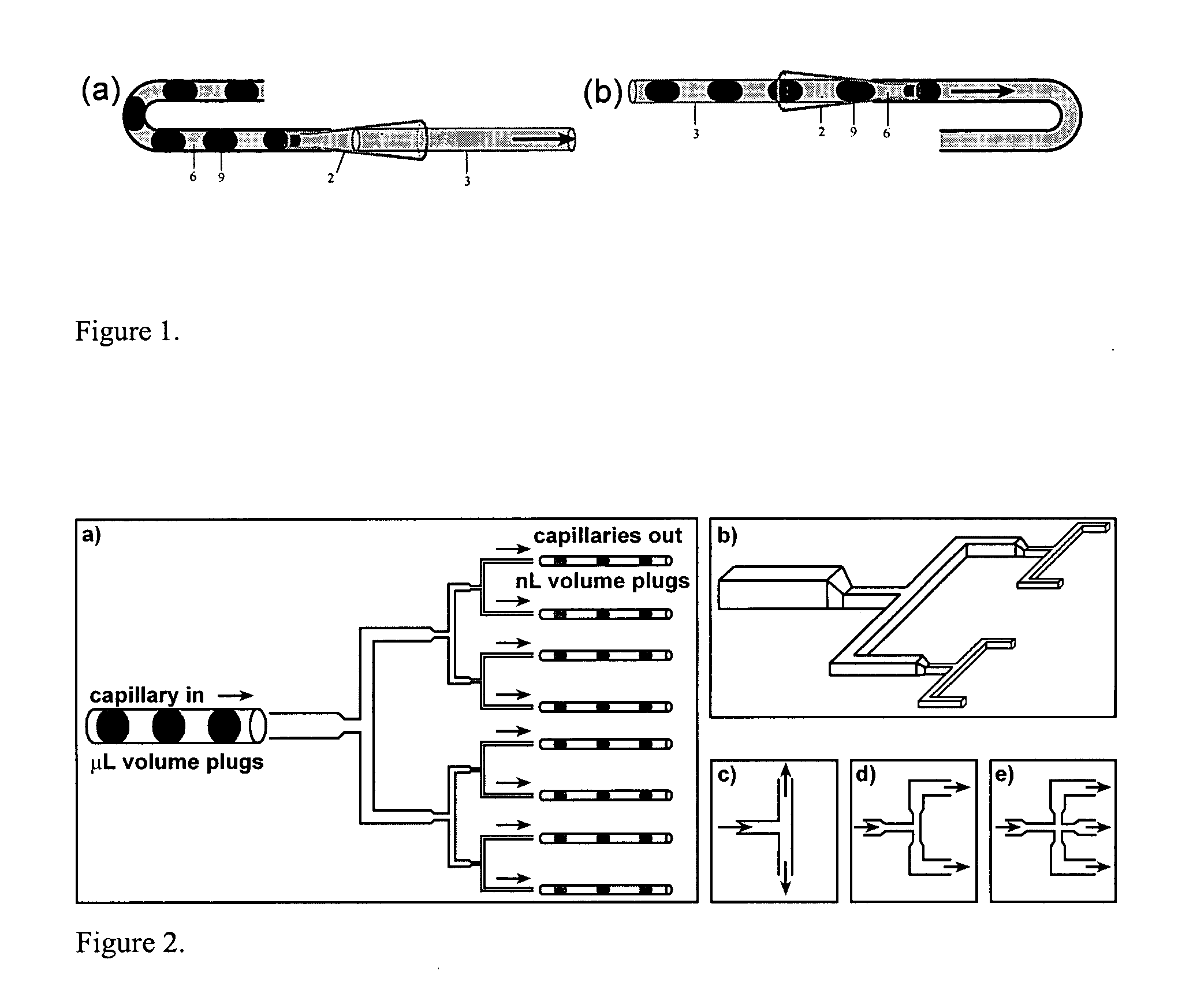
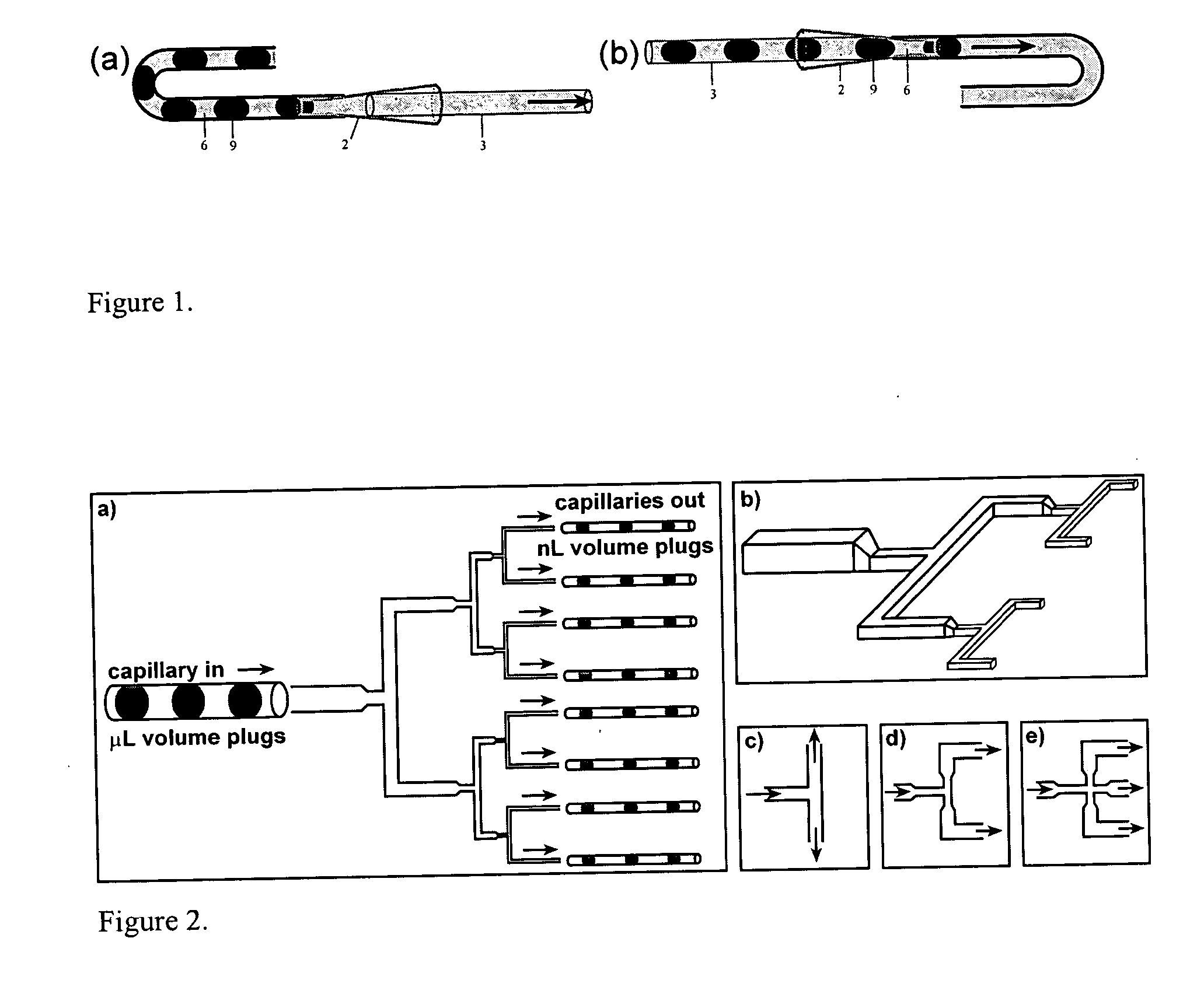
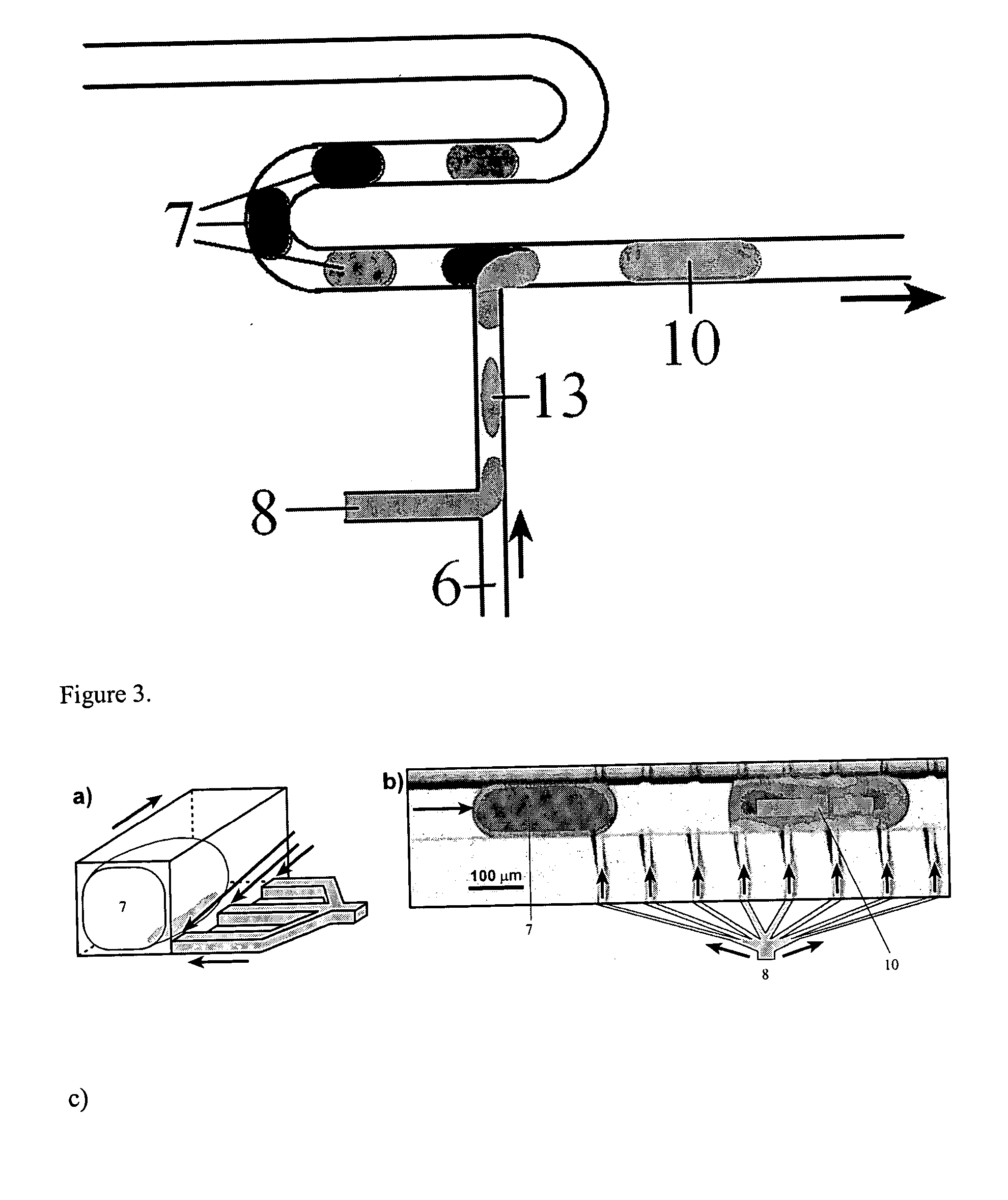
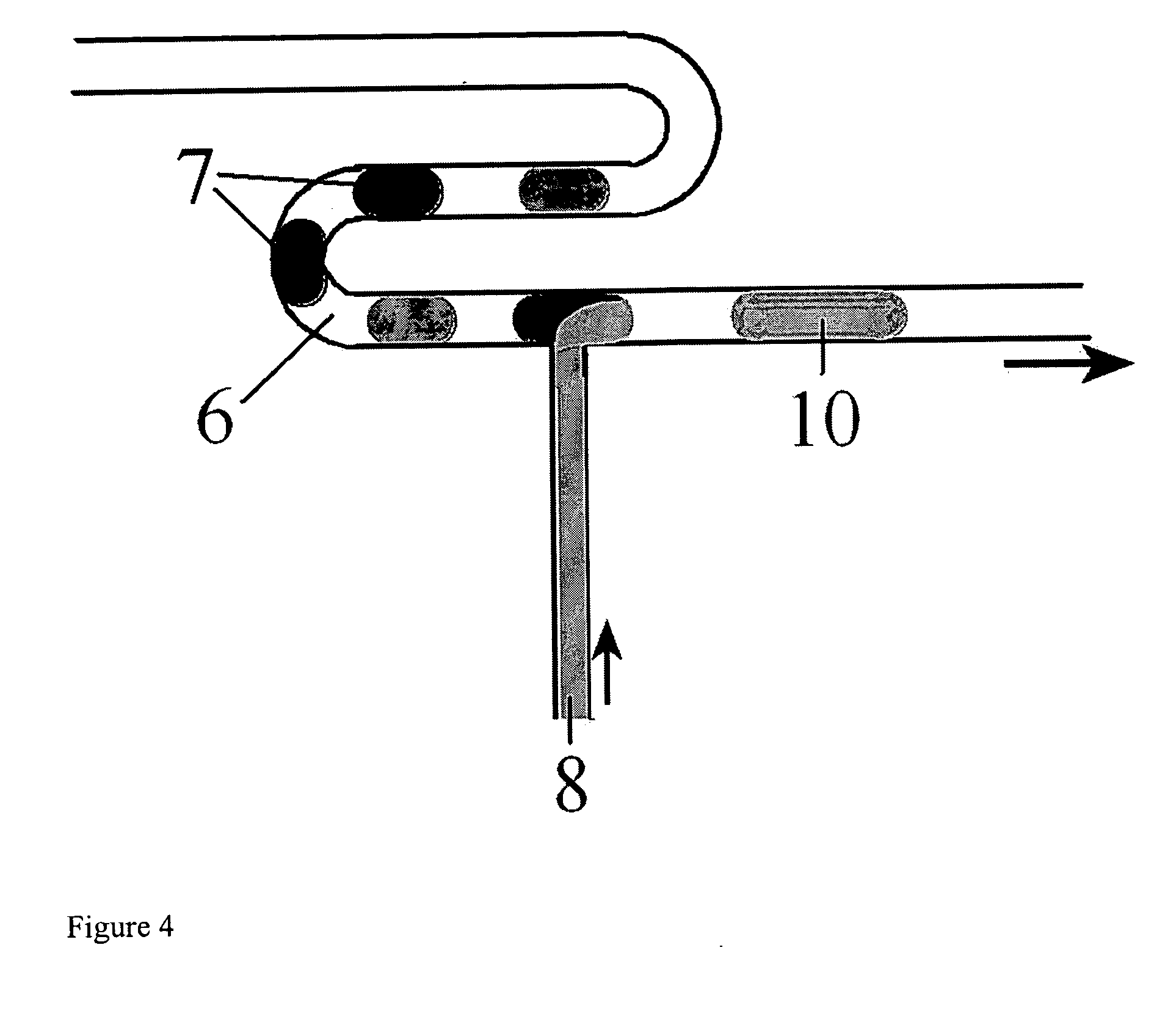
ActiveUS20060094119A1Rapid and economical reactionIncrease rangePolycrystalline material growthAnalysis using chemical indicatorsFemtoliterEngineering
Owner:CHICAGO UNIV OF
Method and apparatus for per-service fault protection and restoration in a packet network
InactiveUS20060013210A1Quickly and efficiently restoredLower Level RequirementsError preventionTransmission systemsService flowTraffic capacity
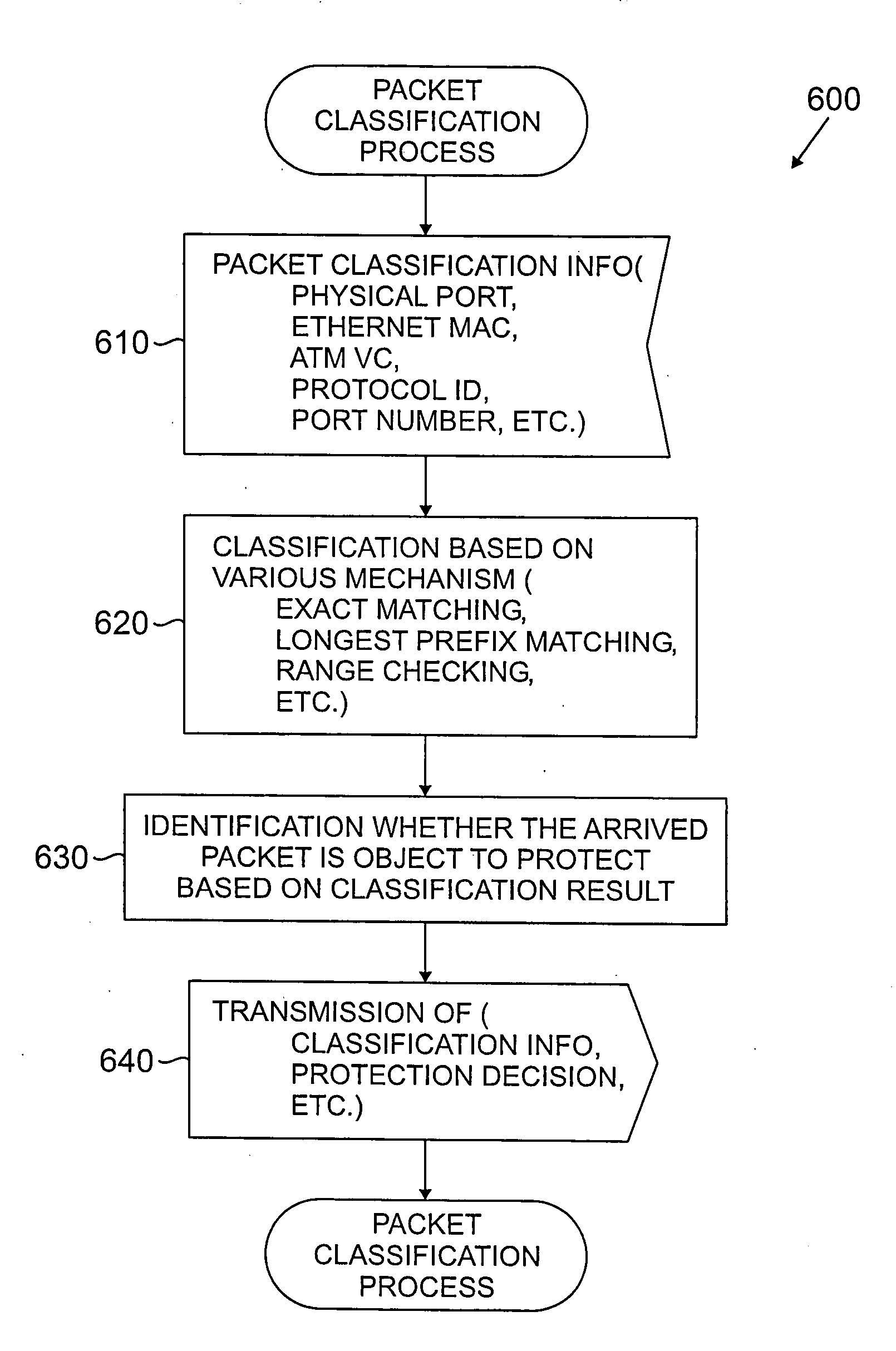
A method and apparatus are disclosed for per-service flow protection and restoration of data in one or more packet networks. The disclosed protection and restoration techniques allow traffic to be prioritized and protected from the aggregate level down to a micro-flow level. Thus, protection can be limited to those services that are fault sensitive. Protected data is duplicated over a primary path and one or more backup data paths. Following a link failure, protected data can be quickly and efficiently restored without significant service interruption. A received packet is classified at each end point based on information in a header portion of the packet, using one or more rules that determine whether the received packet should be protected. At an ingress node, if the packet classification determines that the received packet should be protected, then the received packet is transmitted on at least two paths. At an egress node, if the packet classification determines that the received packet is protected, then multiple versions of the received packet are expected and only one version of the received packet is transmitted.
Owner:AGERE SYST INC
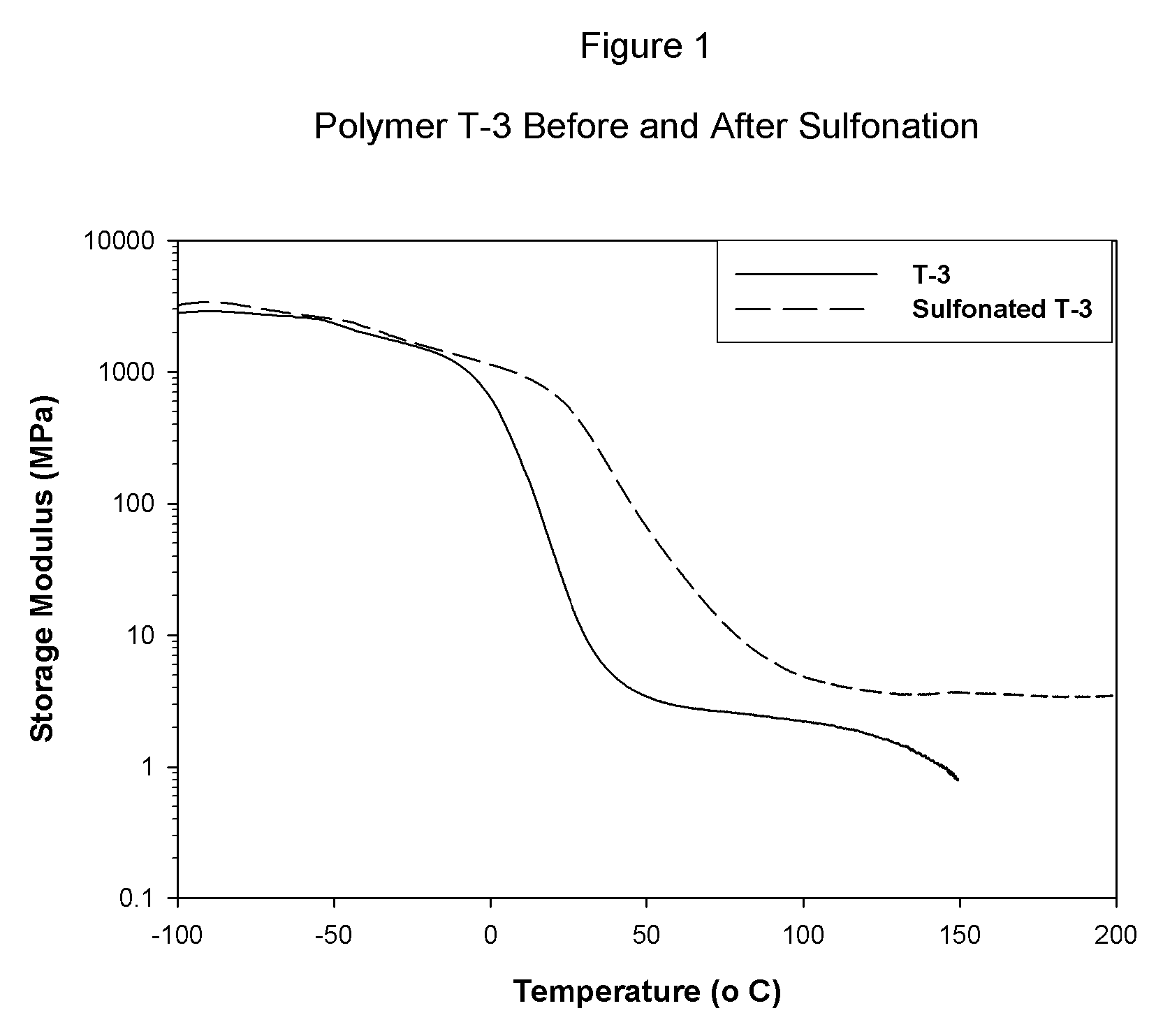
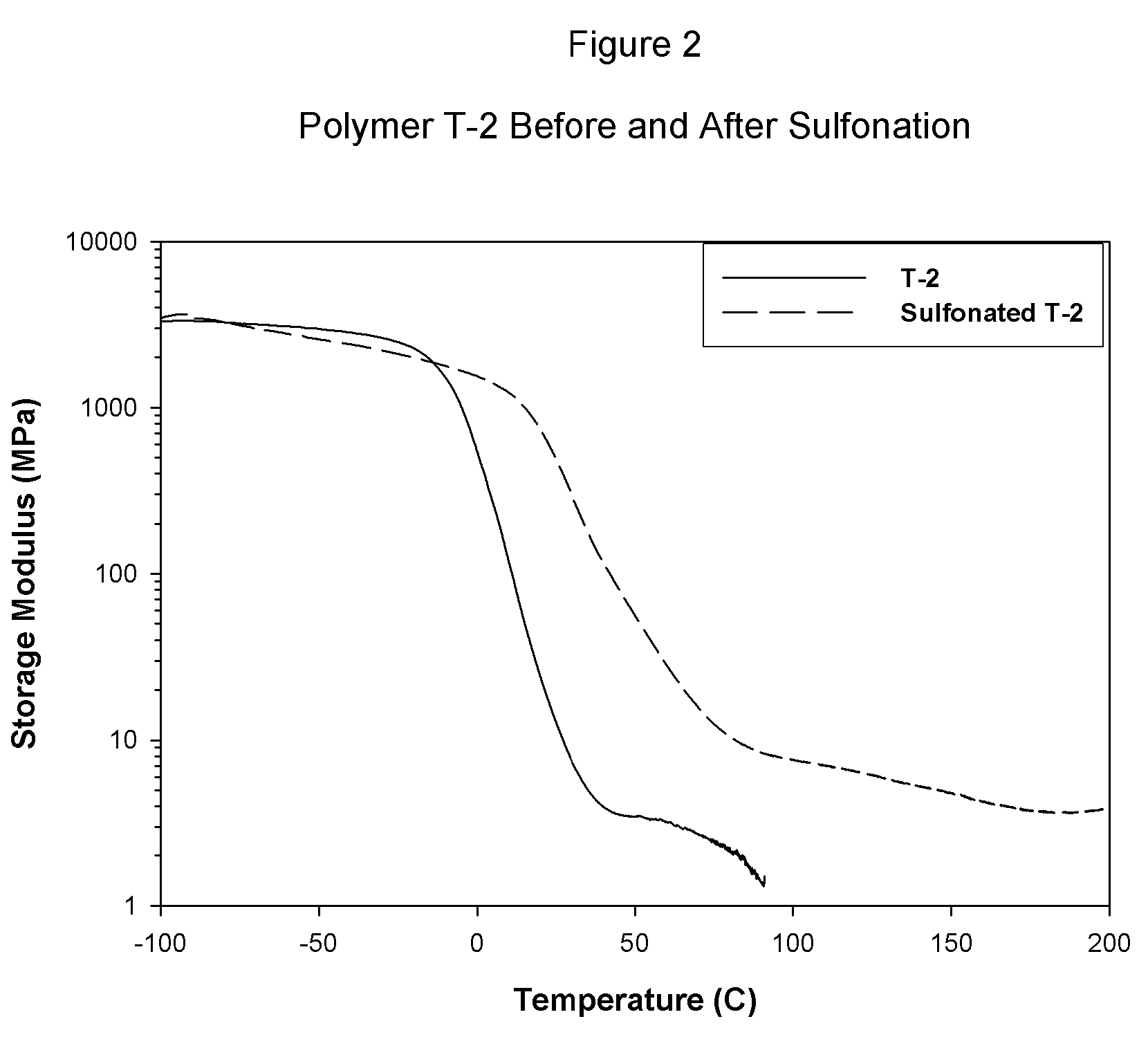
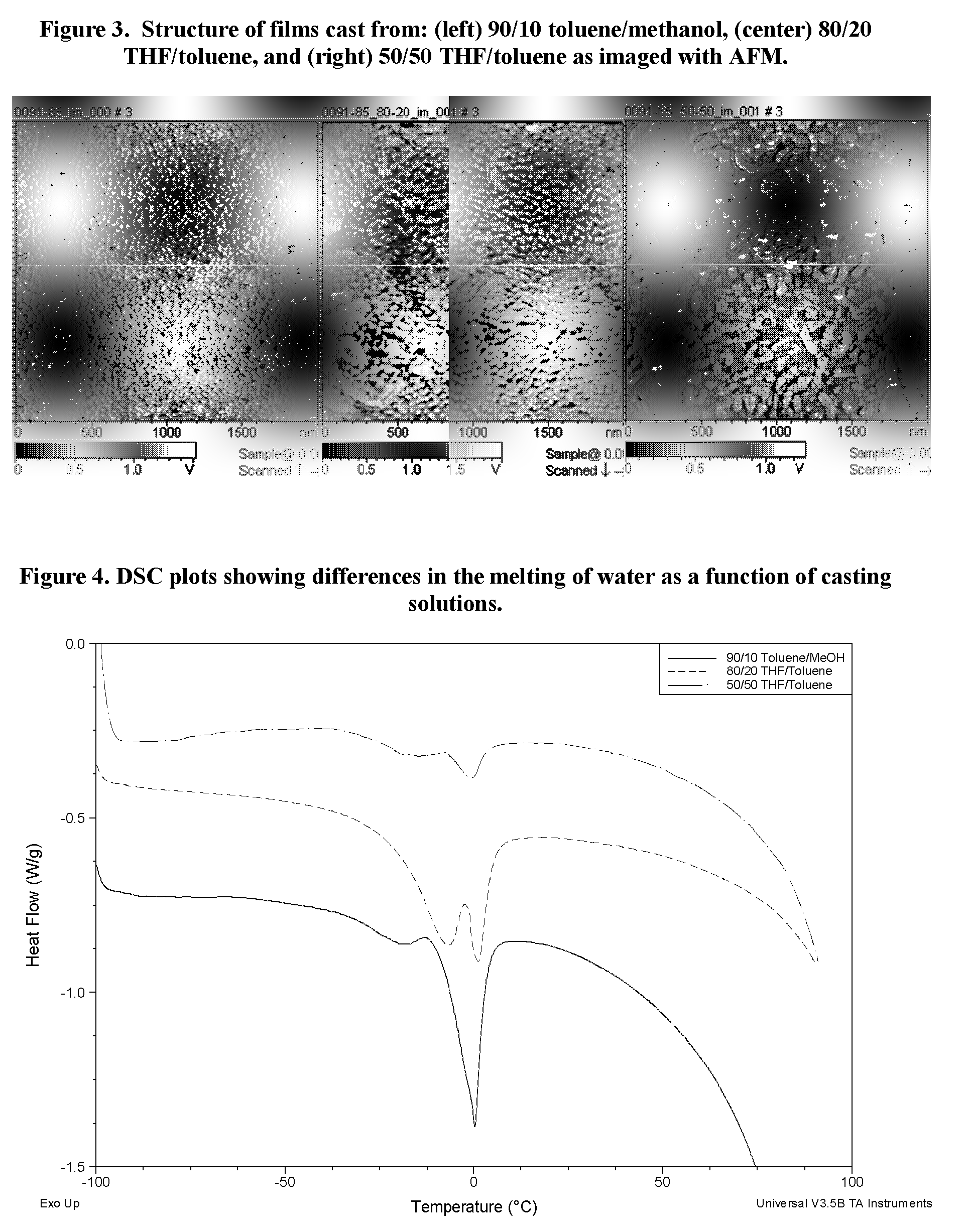
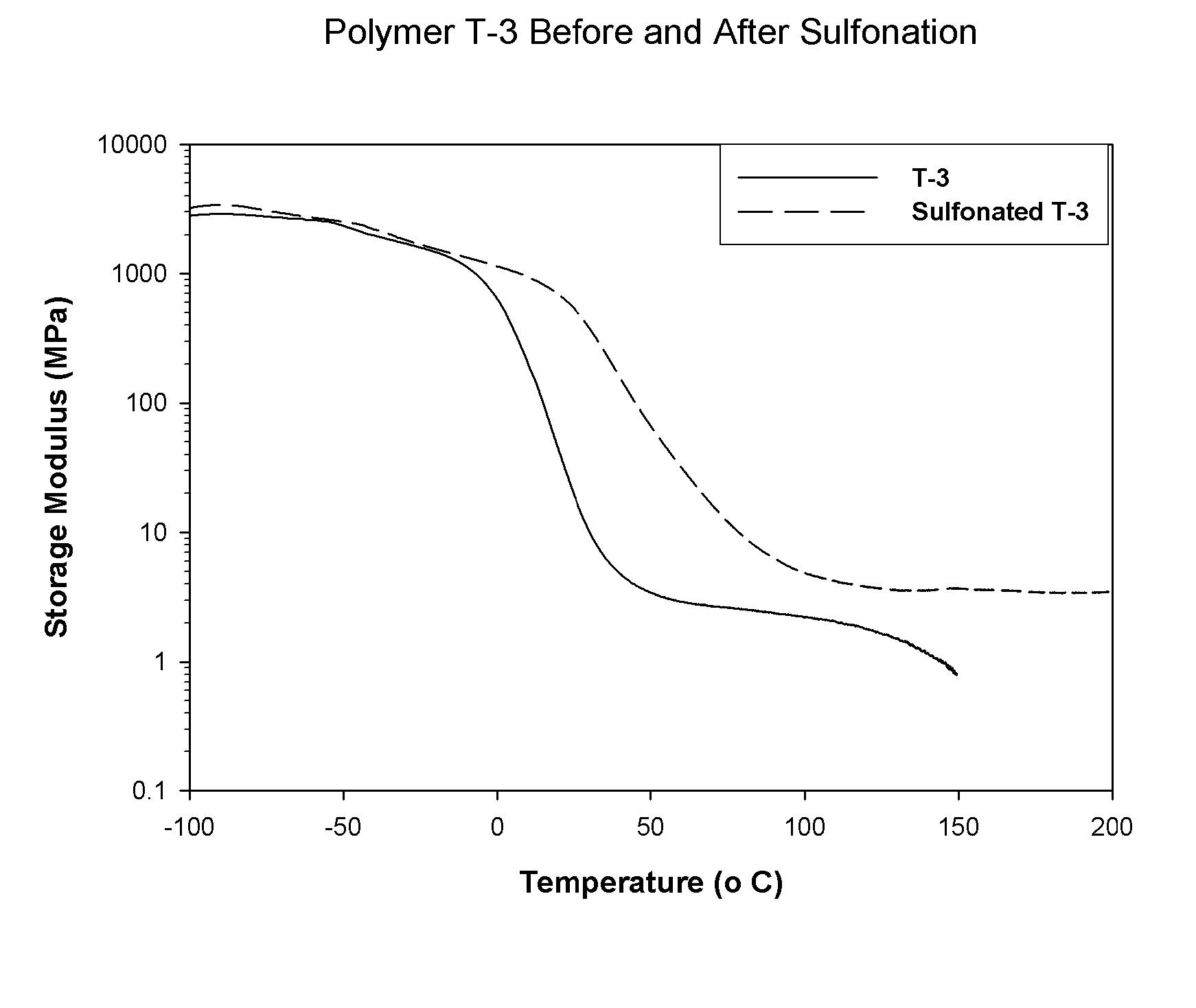
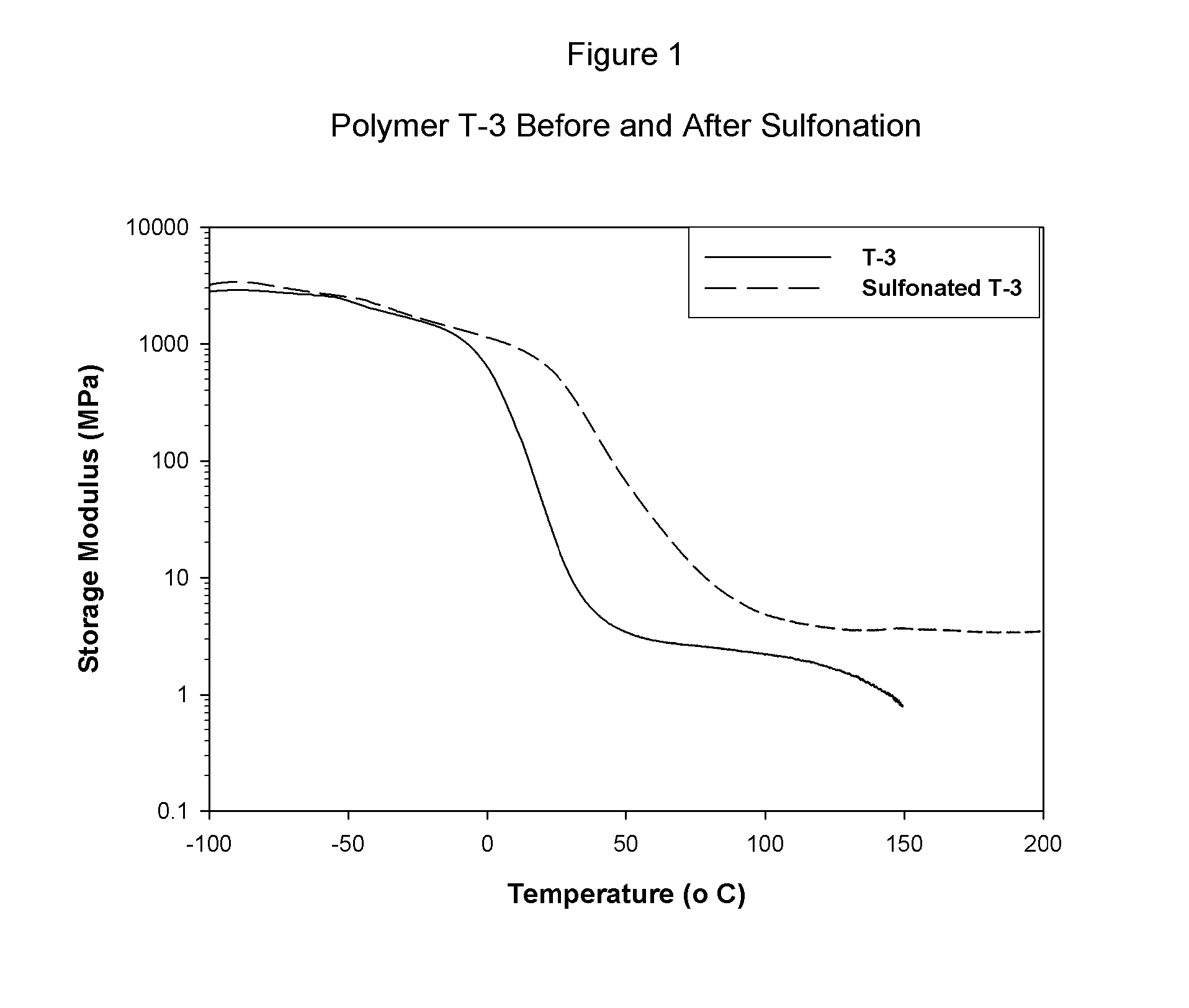
Sulfonated block copolymers, method for making same, and various uses for such block copolymers
ActiveUS7737224B2Reduced responseHigh propertySemi-permeable membranesNegative electrodesMethacrylatePolymer science
The present invention is a, solid block copolymer comprising at least two polymer end blocks A and at least one polymer interior block B wherein each A block is a polymer block resistant to sulfonation and each B block is a polymer block susceptible to sulfonation, and wherein said A and B blocks do not contain any significant levels of olefinic unsaturation. Preferably, each A block comprising one or more segments selected from polymerized (i) para-substituted styrene monomers, (ii) ethylene, (iii) alpha olefins of 3 to 18 carbon atoms; (iv) hydrogenated 1,3-cyclodiene monomers, (v) hydrogenated monomers of conjugated dienes having a vinyl content less than 35 mol percent prior to hydrogenation, (vi) acrylic esters, (vii) methacrylic esters, and (viii) mixtures thereof; and each B block comprising segments of one or more polymerized vinyl aromatic monomers selected from (i) unsubstituted styrene monomers, (ii) ortho-substituted styrene monomers, (iii) meta-substituted styrene monomers, (iv) alpha-methylstyrene, (v) 1,1-diphenylethylene, (vi) 1,2-diphenylethylene and (vii) mixtures thereof. Also claimed are processes for making such block copolymers, and the various end uses and applications for such block copolymers.
Owner:KRATON POLYMERS US LLC
Wound retractor device
InactiveUS7559893B2Extensive exposureProvide protectionCannulasSurgical needlesBiomedical engineeringWound retractor
A wound protector and retractor device comprising a longitudinal axis, a distal member, a proximal member, and a sleeve extending at least between the distal member and the proximal member. The sleeve has a proximal gripping portion for pulling the sleeve upwardly to shorten an axial extent located between the distal member and the proximal member.
Owner:ATROPOS LTD
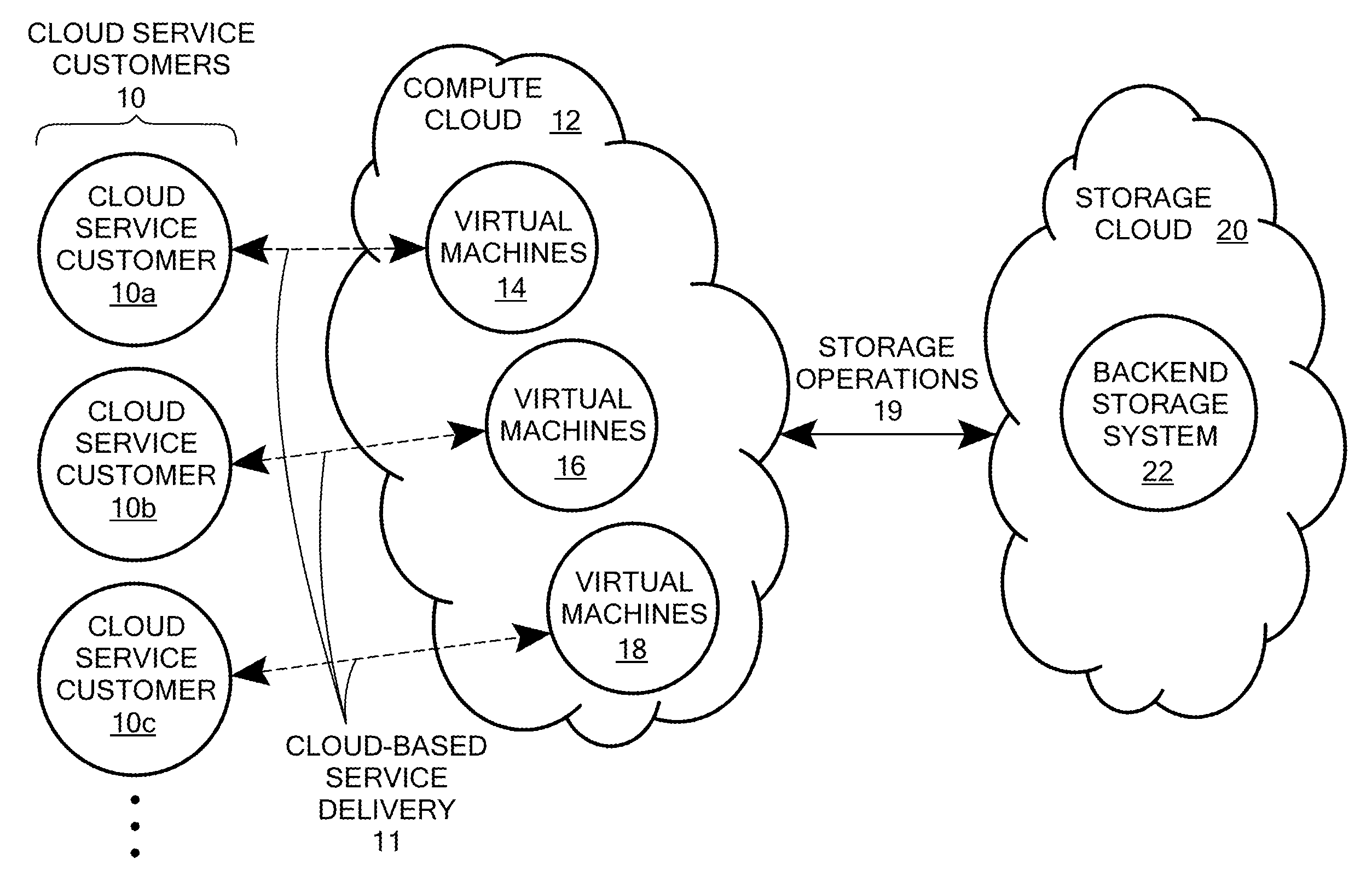
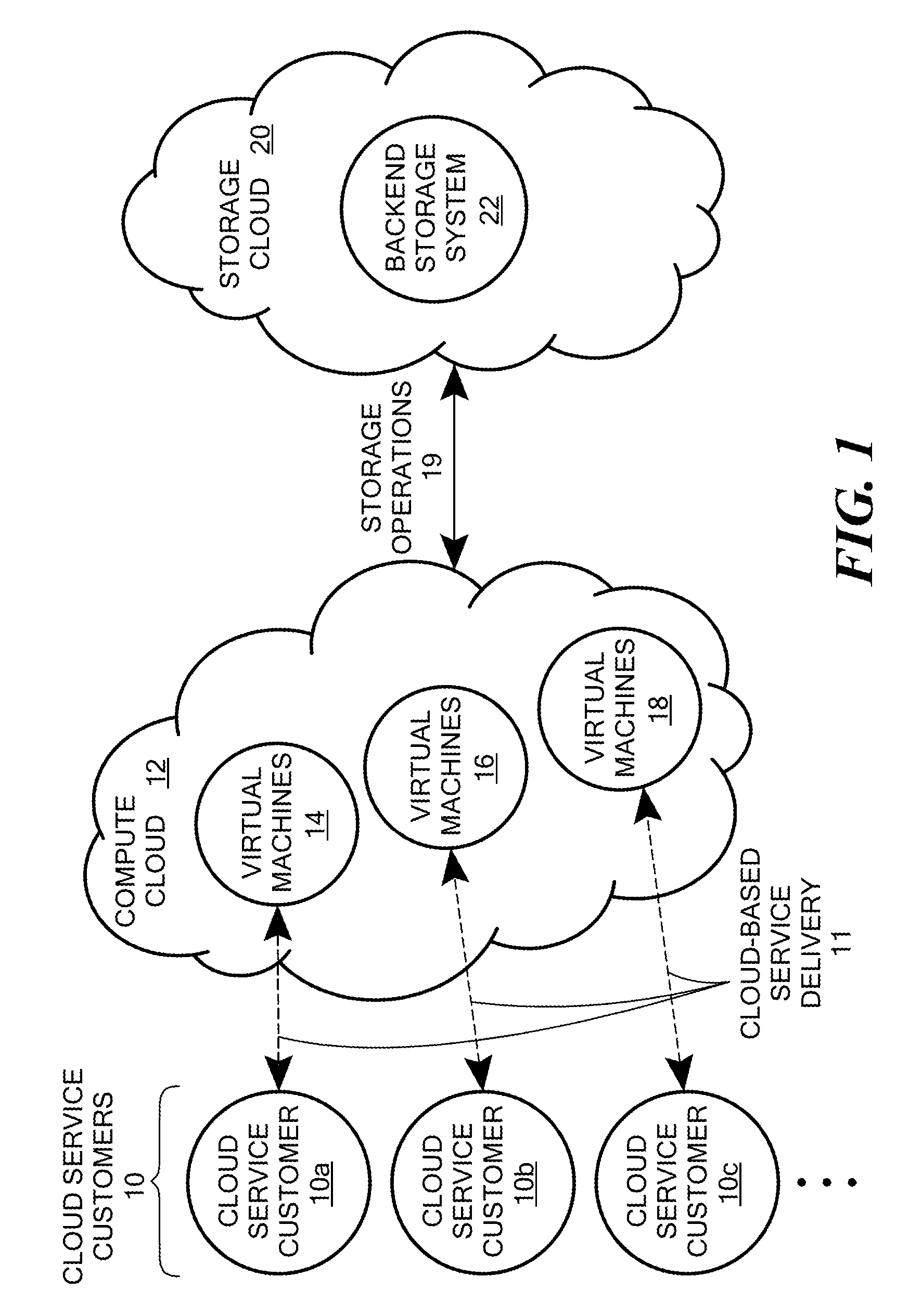
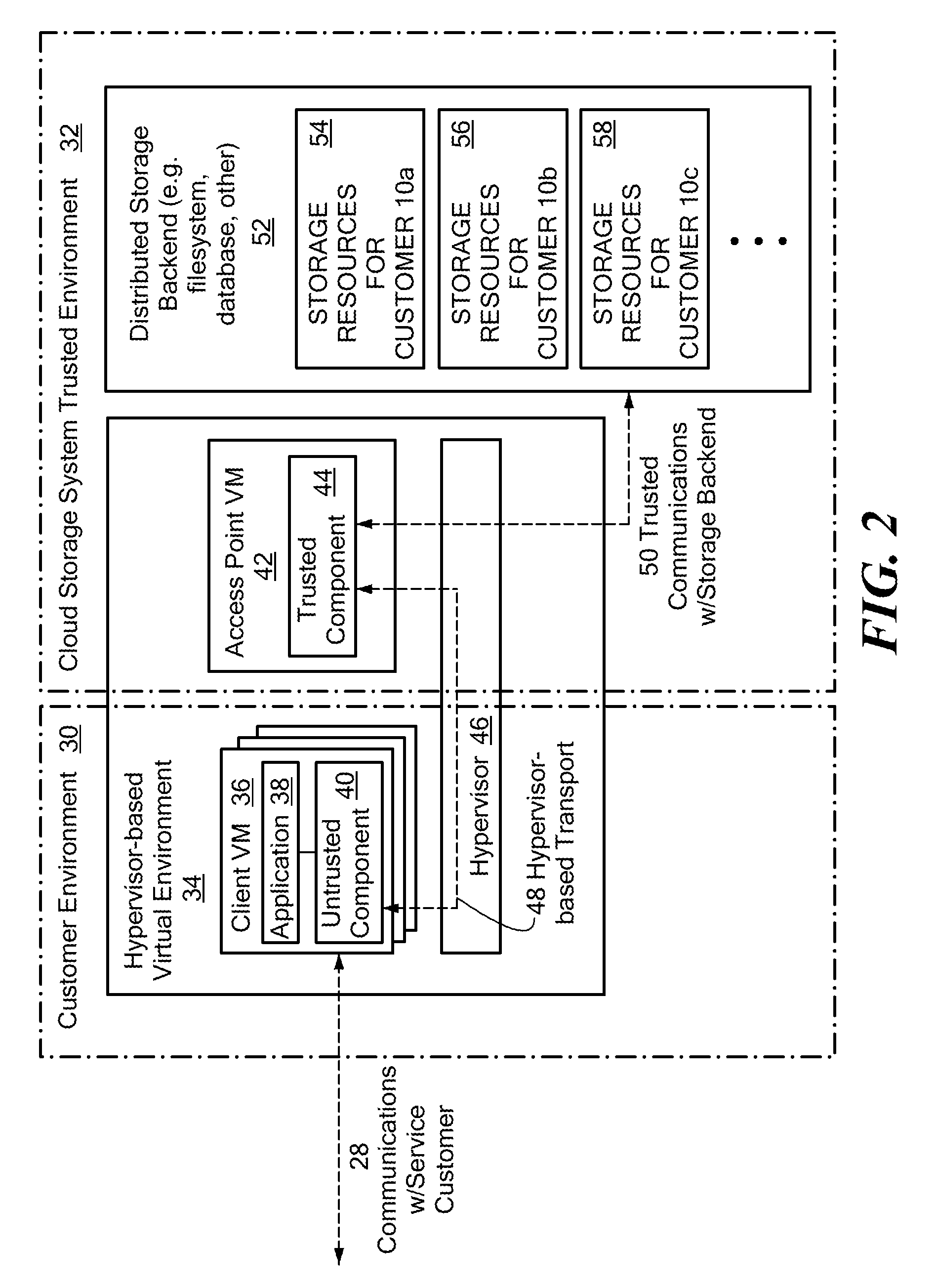
Scalable and secure high-level storage access for cloud computing platforms
ActiveUS8352941B1Effective segmentationImprove the level ofMultiprogramming arrangementsSoftware simulation/interpretation/emulationTrusted componentsTrust relationship
An untrusted component exposing a high level storage object interface within an untrusted client virtual machine accepts application level storage object operations. Responsive to a storage object operation, the untrusted component passes a message through the underlying hypervisor to an associated trusted component. The trusted component processes the message by authenticating the client virtual machine and locating an internal mapping between the client virtual machine and an associated customer-specific set of backend storage resources to which the requested storage object operation is to be applied. The trusted component uses a trust relationship with the backend storage system to securely communicate the storage object operation to the backend storage system, and passes the operation results through the hypervisor back to the untrusted component in the source client virtual machine from which the storage object request originated.
Owner:EMC IP HLDG CO LLC
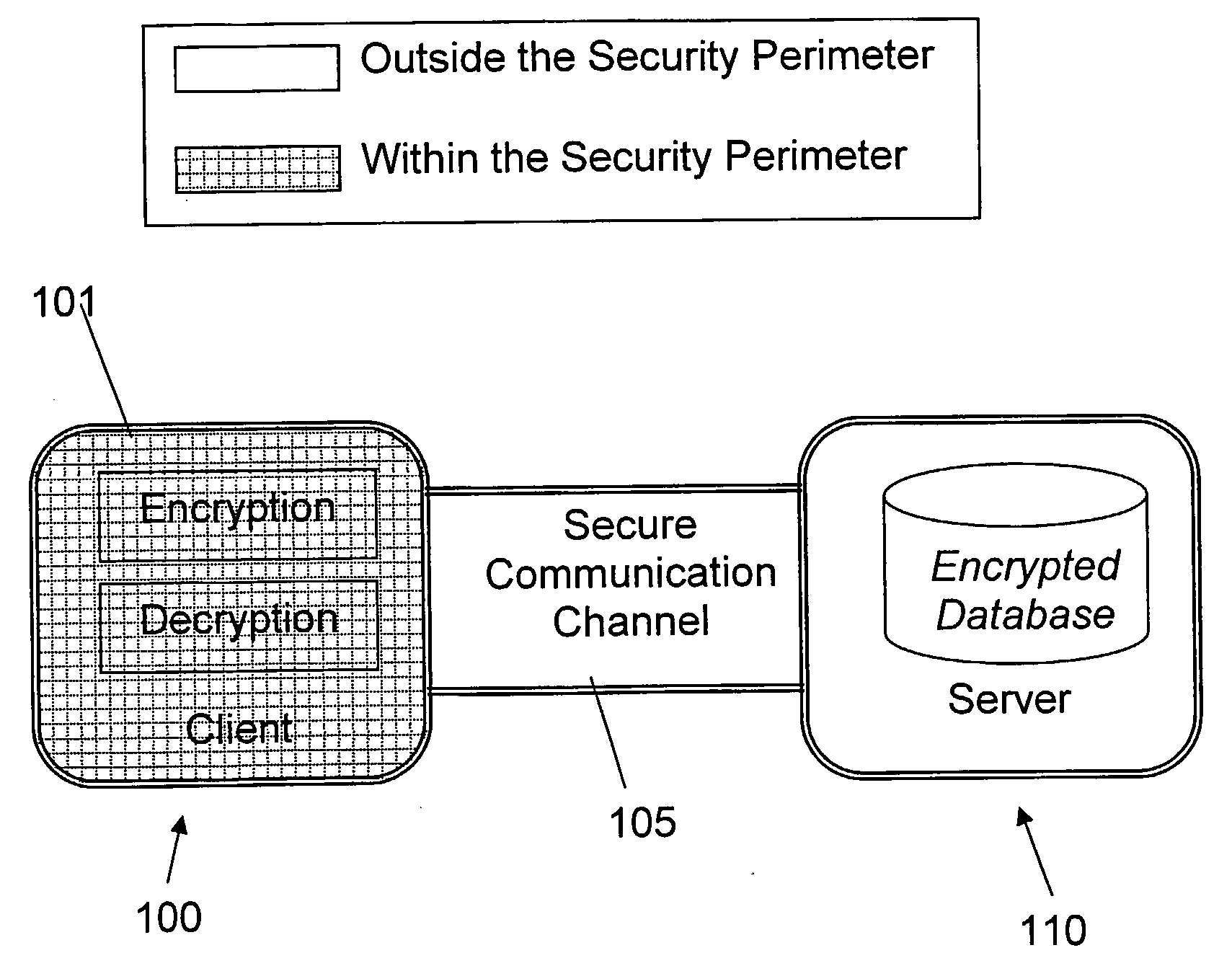
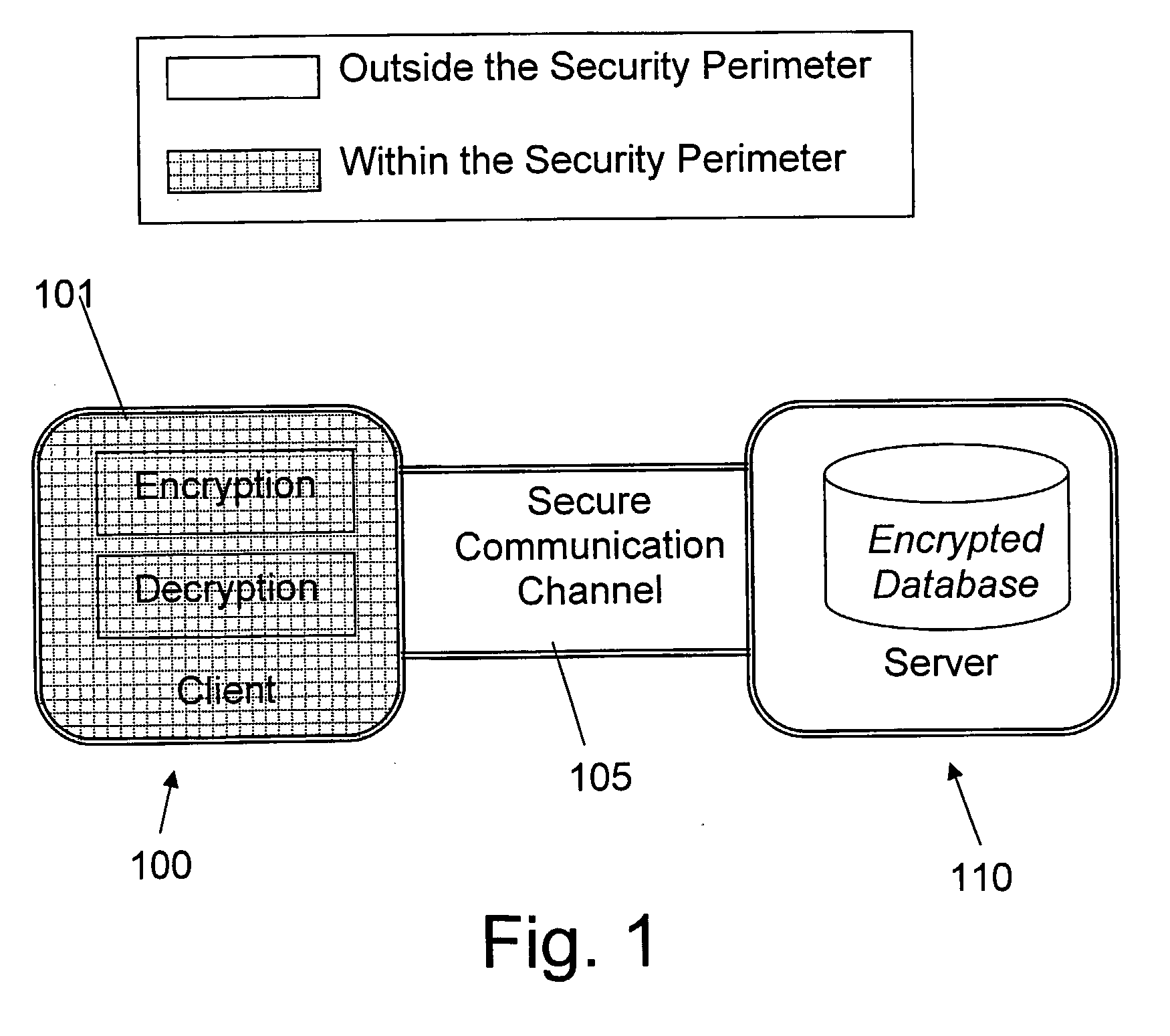
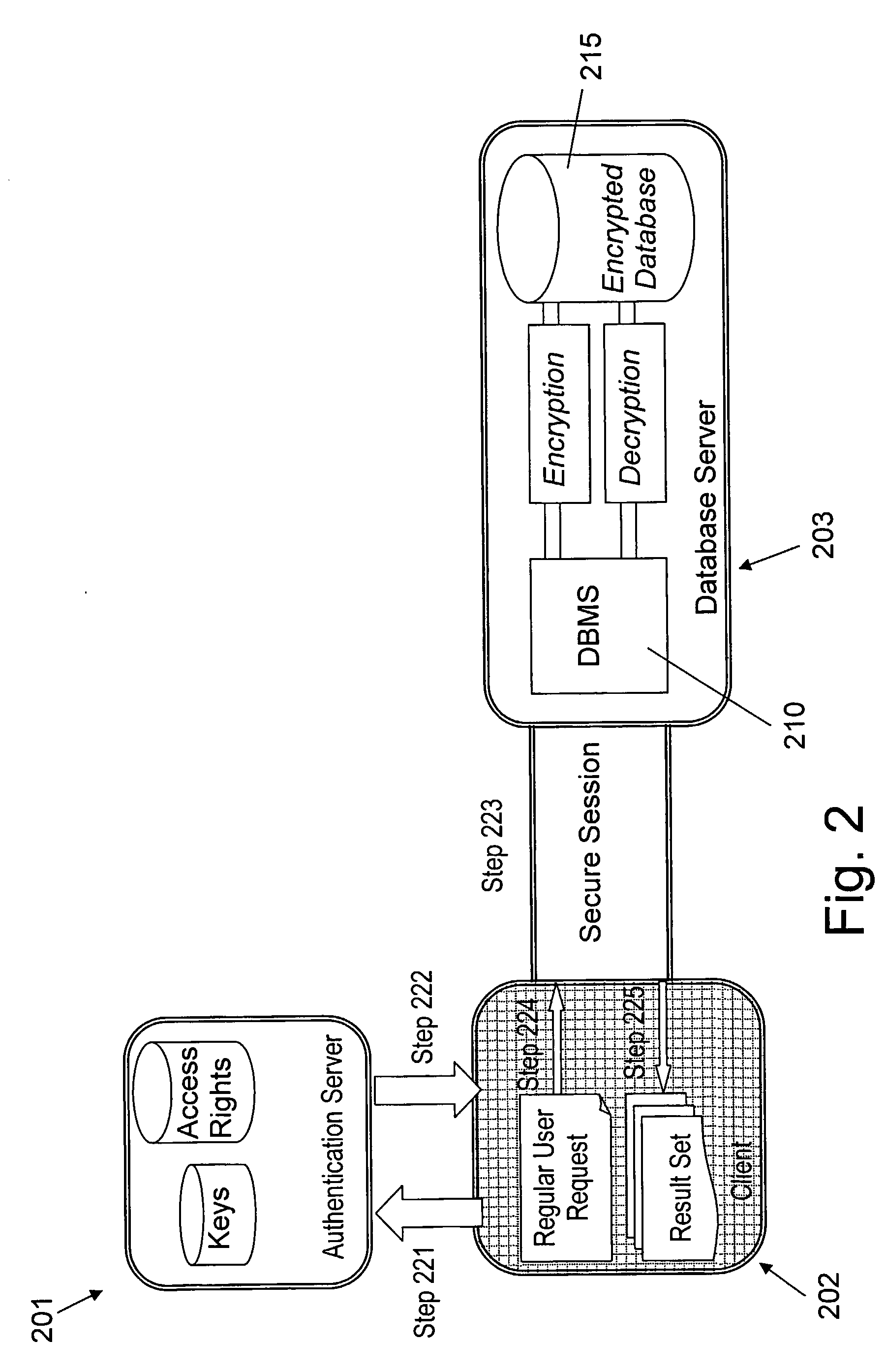
Structure Preserving Database Encryption Method and System
ActiveUS20080133935A1Easy accessAvoid contactKey distribution for secure communicationMultiple keys/algorithms usageDatabase indexMulti user environment
A database encryption system and method, the Structure Preserving Database Encryption (SPDE), is presented. In the SPDE method, each database cell is encrypted with its unique position. The SPDE method permits to convert a conventional database index into a secure one, so that the time complexity of all queries is maintained. No one with access to the encrypted database can learn anything about its content without the encryption key. Also a secure index for an encrypted database is provided. Furthermore, secure database indexing system and method are described, providing protection against information leakage and unauthorized modifications by using encryption, dummy values and pooling, and supporting discretionary access control in a multi-user environment.
Owner:BEN GURION UNIVERSITY OF THE NEGEV
Microfluidic system
ActiveUS20060003439A1Rapid and economical reactionIncrease rangeBioreactor/fermenter combinationsSequential/parallel process reactionsEngineering
Owner:UNIVERSITY OF CHICAGO
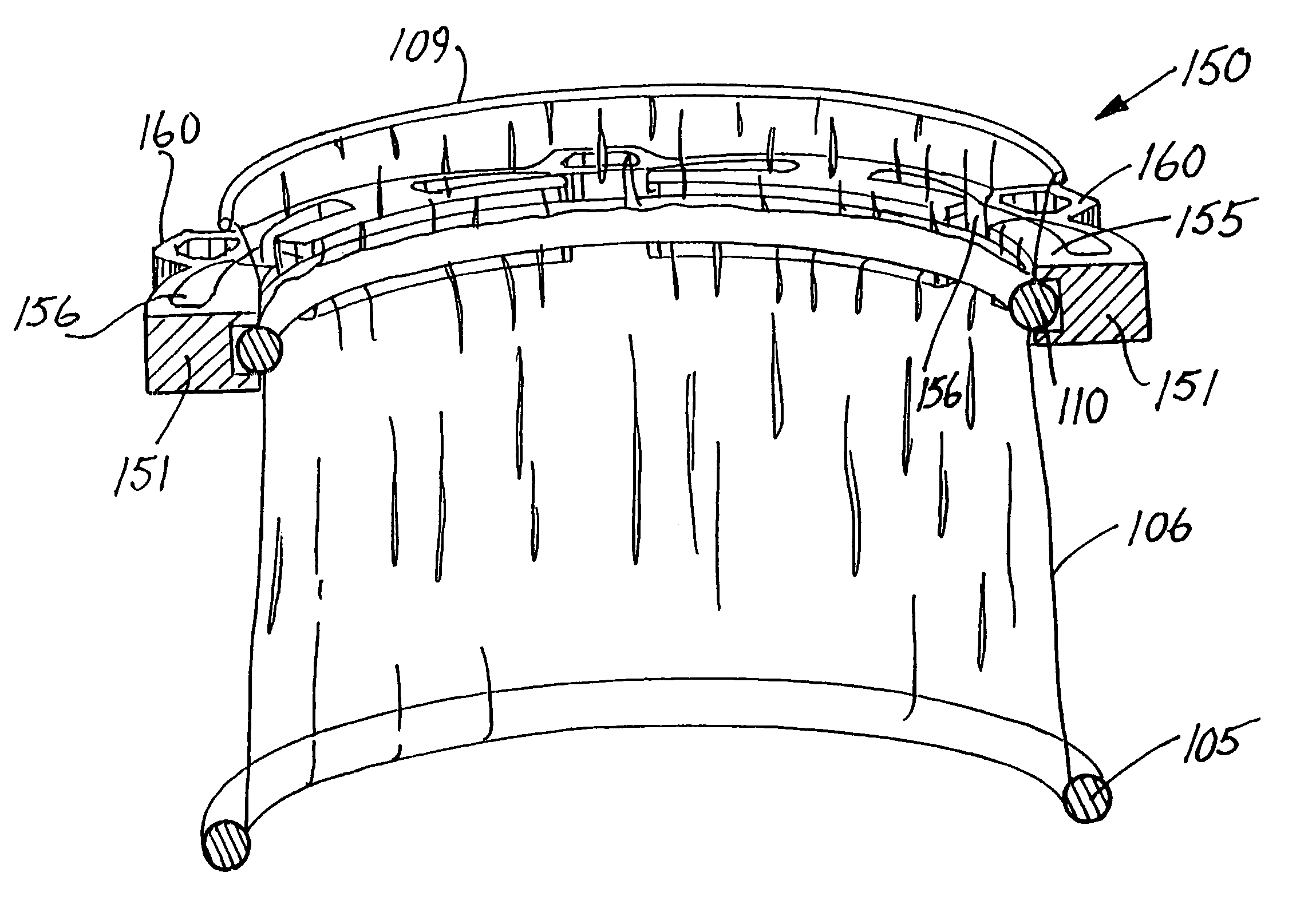
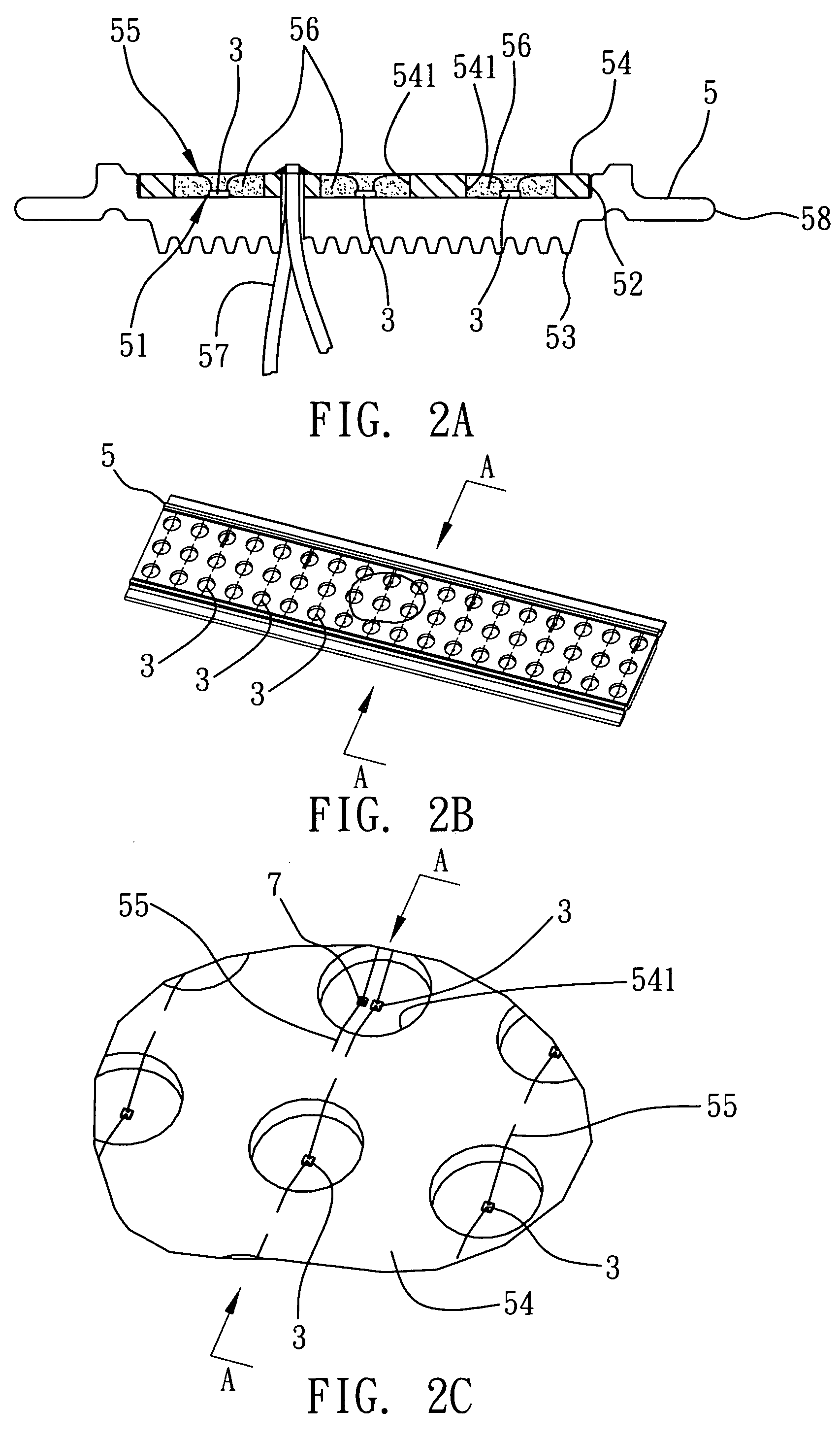
Sheath assembly for spinal stabilization device
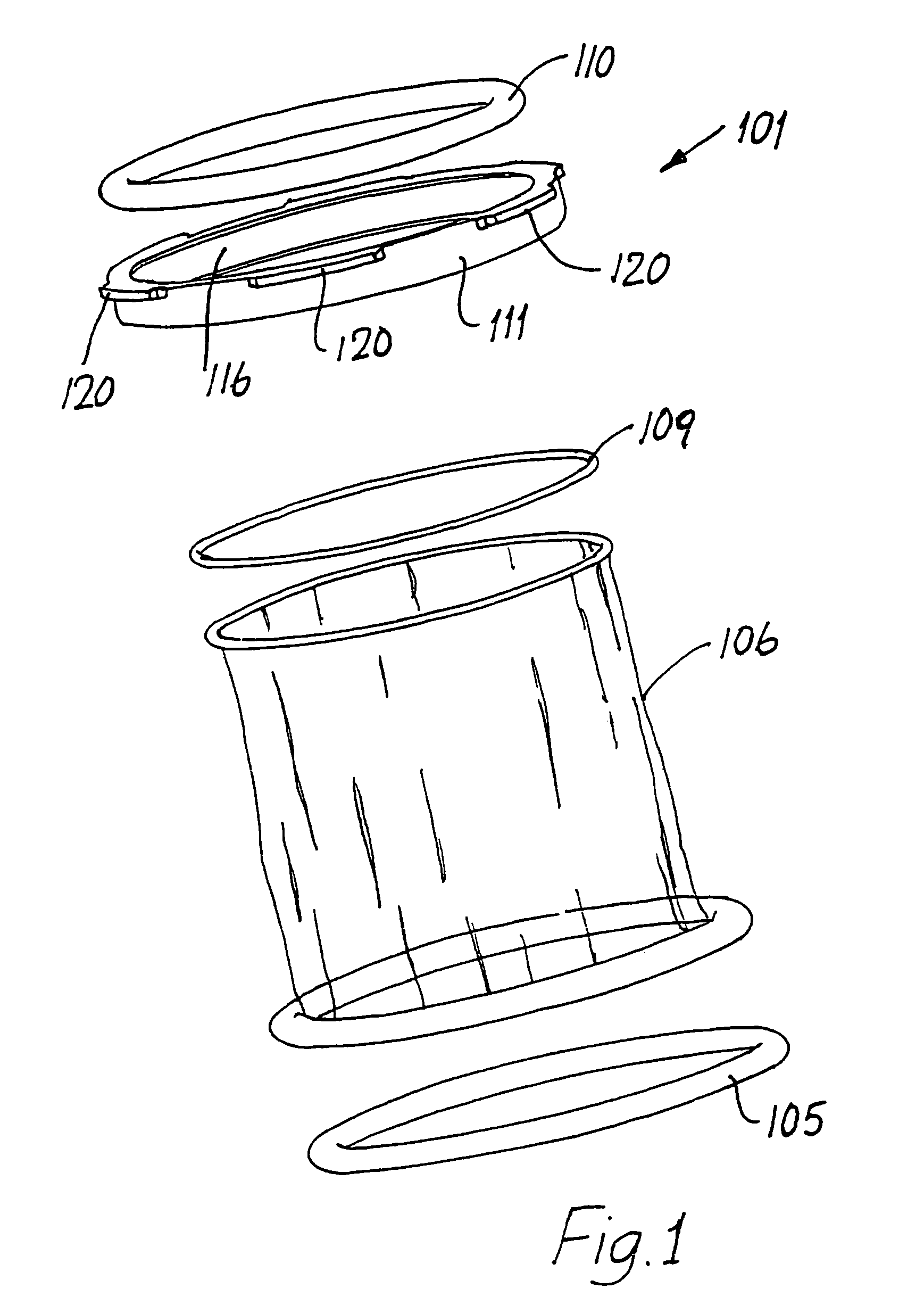
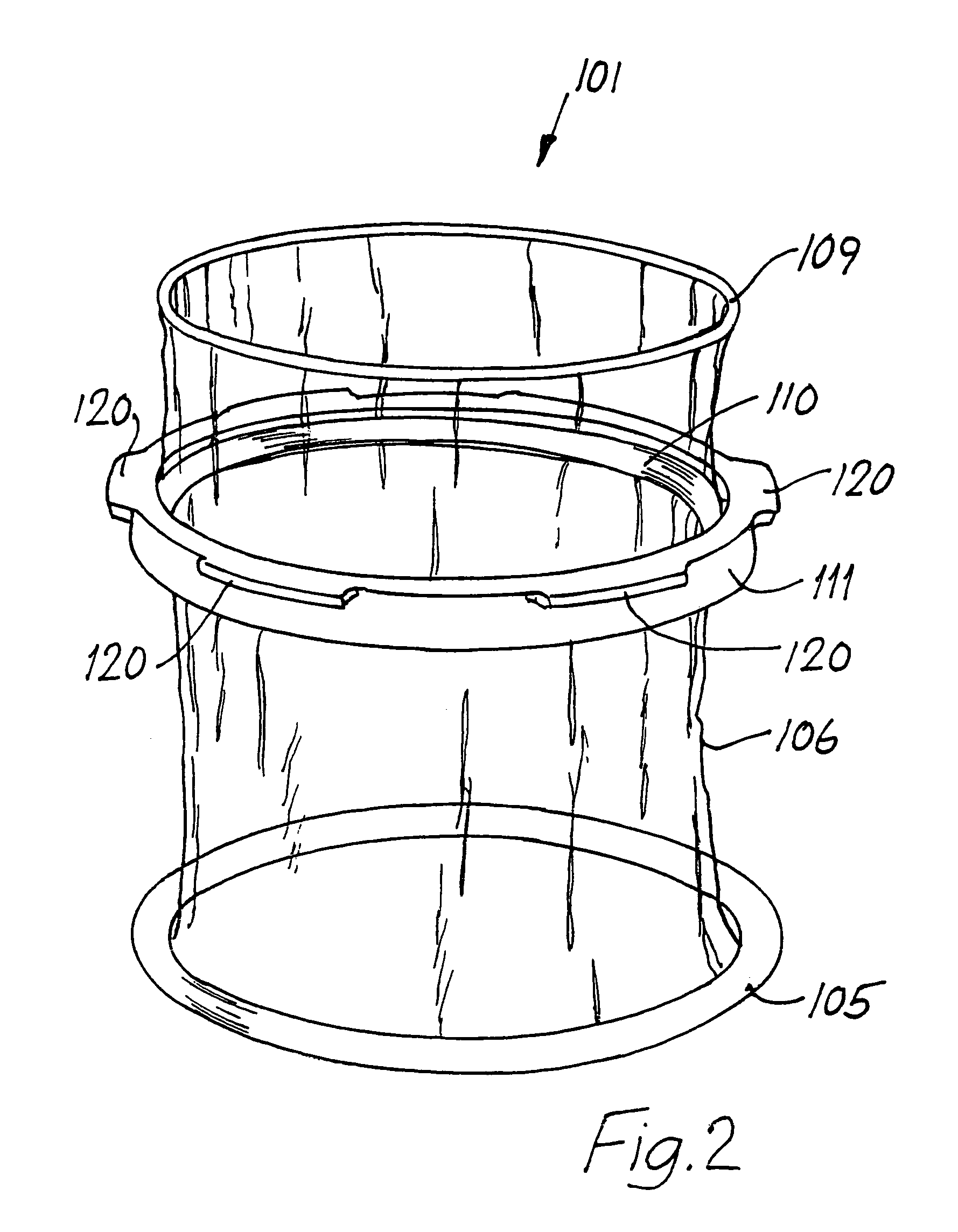
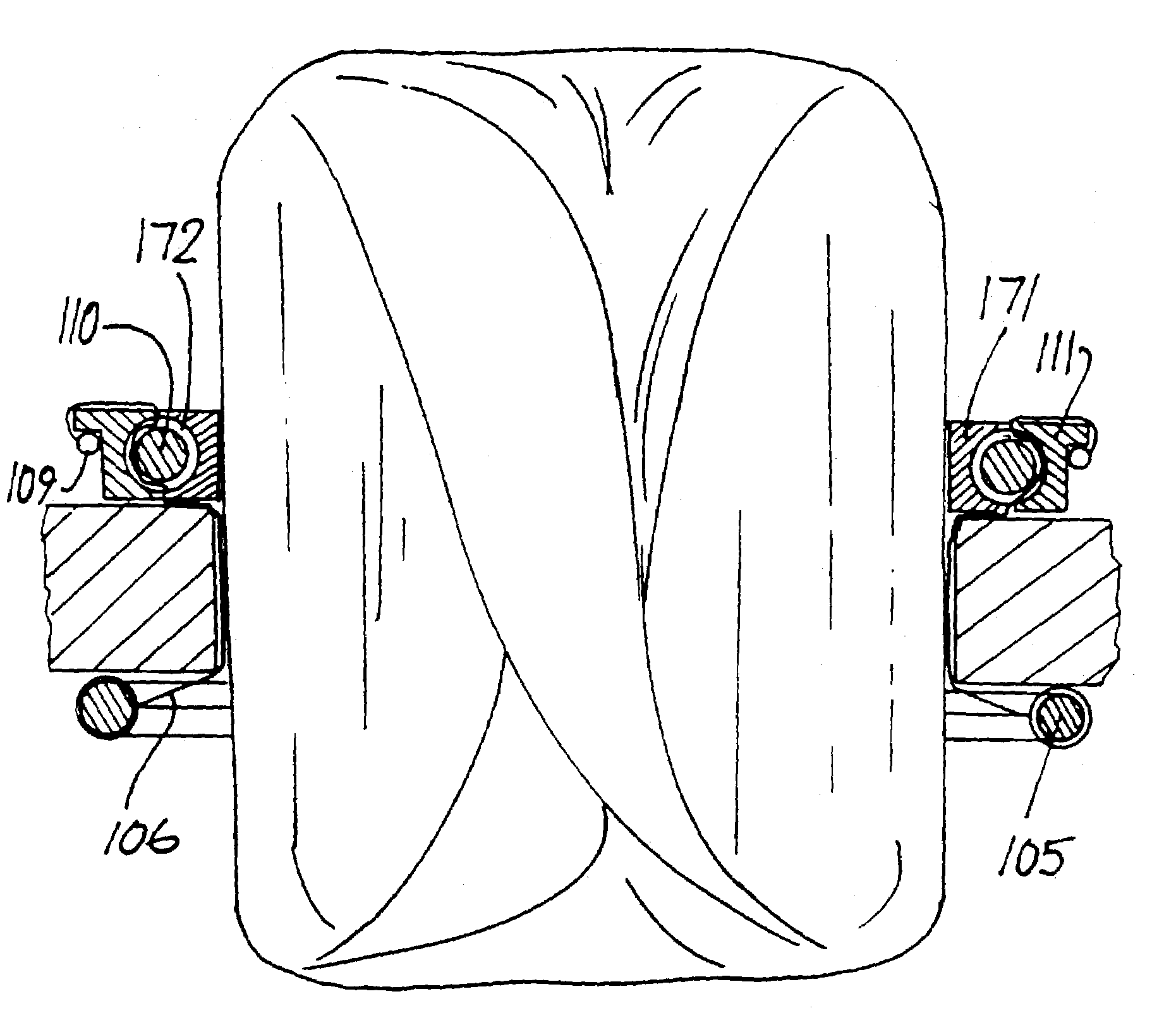
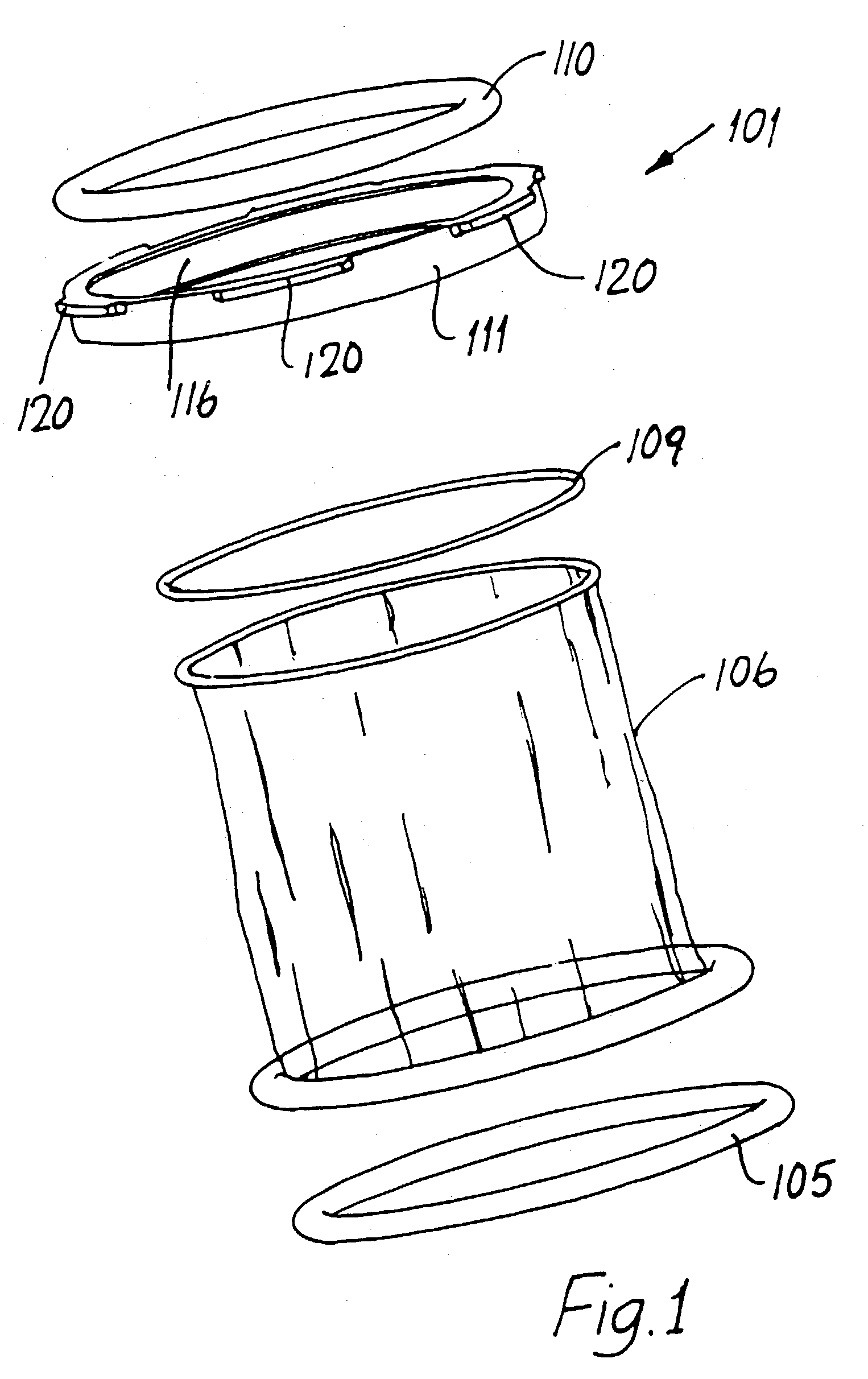
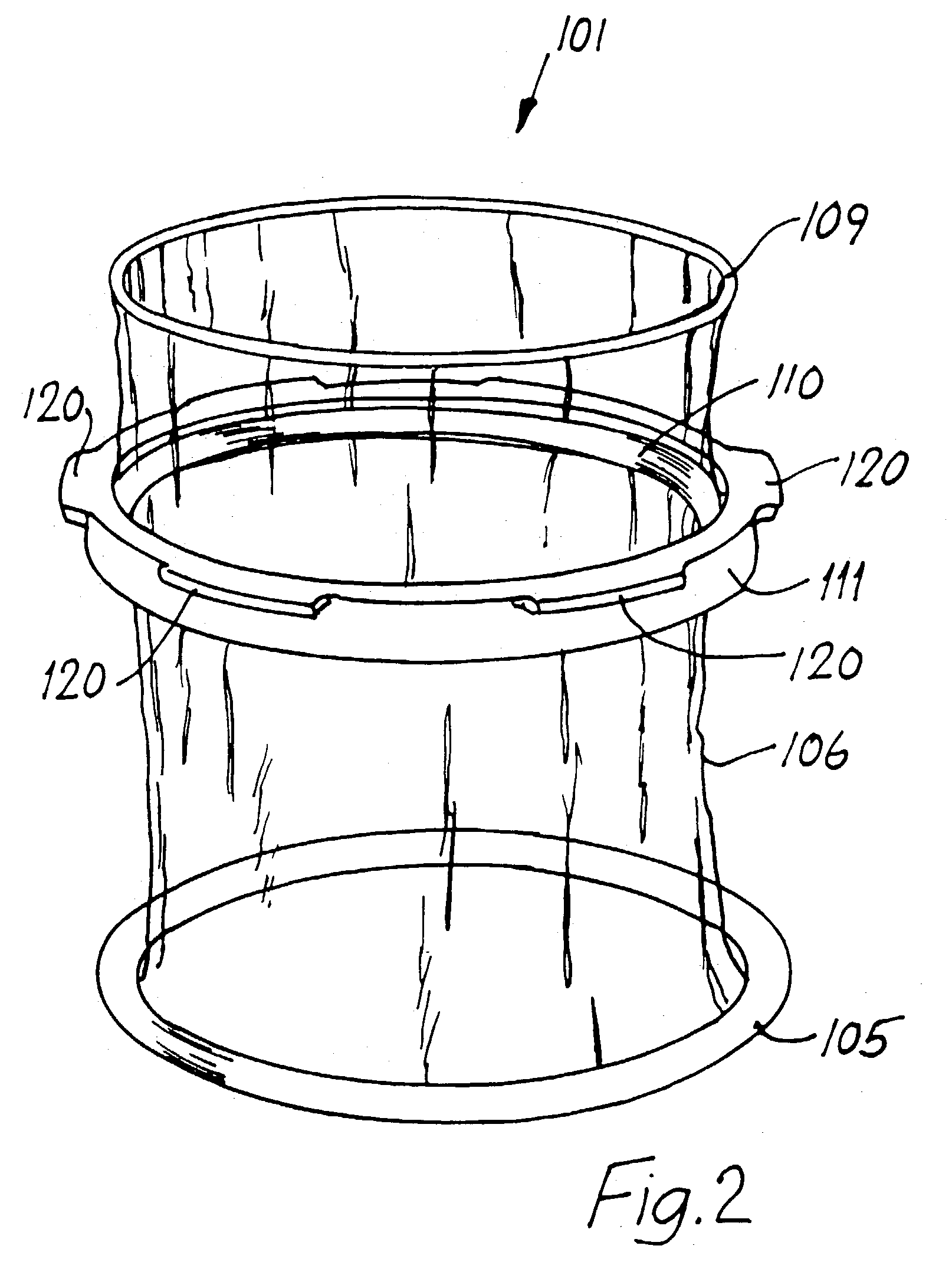
InactiveUS20060229613A1Provide protectionAvoid abrasionsInternal osteosythesisJoint implantsInternal cavityBiomedical engineering
Systems, assemblies and methods for assembling a sheath member with respect to a spinal stabilization device are provided. The disclosed sheath assembly includes at least one connector ring mounted with respect to a sheath member. The connector ring defines an inner wall that shields the sheath member from elements positioned therewithin, e.g., spring members, and generally includes a plurality of radially-spaced notches. The connector ring receives the sheath member within an internal cavity and is secured thereto by crimping, compression or swaging. The sheath assembly may be mounted with respect to a spinal stabilization device by crimping, compressing or swaging the connector ring to an underlying structure, e.g., an end cap or associated flange. The internal cavity of the connector ring is generally defined by an inner face, an outer wall and an intermediate apex region. Methods for assembly are also disclosed.
Owner:APPLIED SPINE TECH
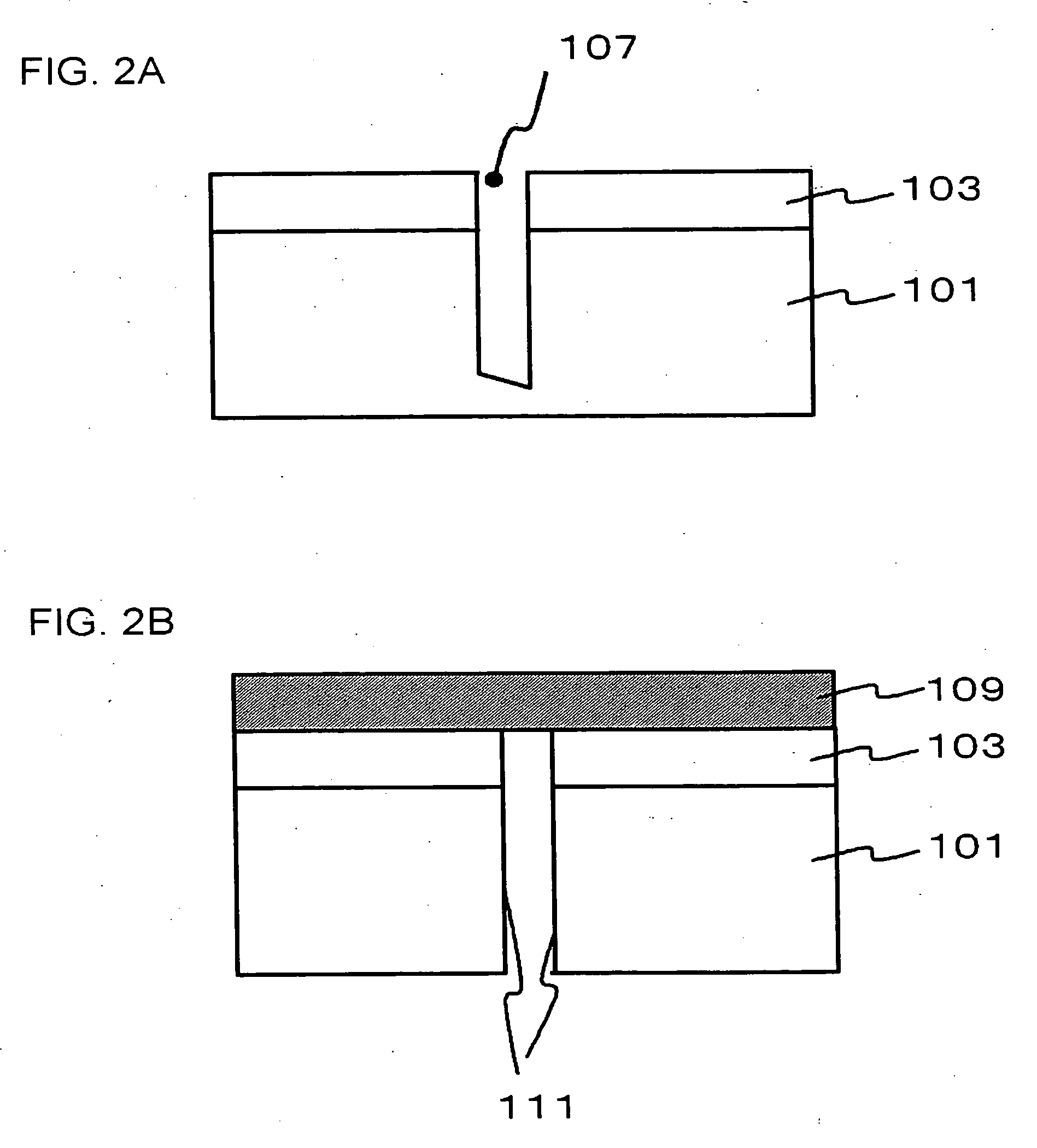
Method for manufacturing semiconductor device
InactiveUS20060205182A1Reduce widthRate of the processing for providing the trenched portion can beSolid-state devicesSemiconductor/solid-state device manufacturingDevice materialDevice form
A method of dicing a semiconductor wafer includes providing an interconnect layer providing a protective film on the interconnect layer on the side of a device-forming surface of a silicon wafer, irradiating the protective film with a laser beam to provide a trenched portion that extends through the interconnect layer from the protective film and reaches to an inside of the silicon wafer, removing a portion of the silicon wafer selectively in a depth direction from a bottom of the trenched portion, after irradiating with the laser beam to provide the trenched portion and dividing the silicon wafer along the portion where the trenched portion is provided into respective pieces of the silicon wafer, after removing a portion of the silicon wafer 101 selectively in the depth direction.
Owner:NEC ELECTRONICS CORP
Dosage form having first and second coats
A dosage form comprising a composition comprising a drug surrounded by a first coat and a second coat with an exit for administering the drug to a patient; and a method of using the dosage form are disclosed for an indicated therapy.
Owner:ALZA CORP
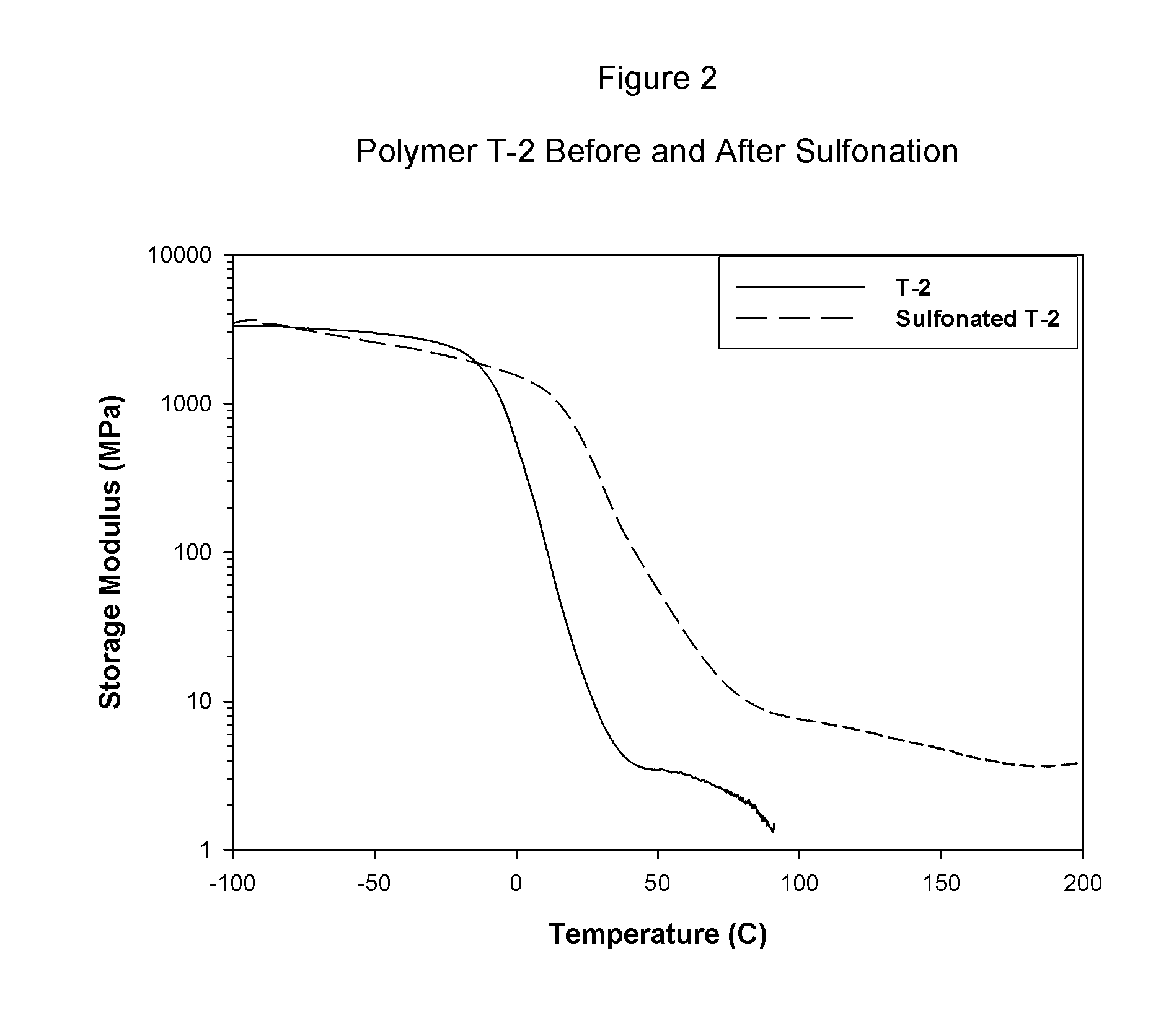
Sulfonated block copolymers, method for making same, and various uses for such block copolymers
ActiveUS20070021569A1High water transport propertyImprove wet strengthSemi-permeable membranesNegative electrodesMethacrylatePolymer science
The present invention is a, solid block copolymer comprising at least two polymer end blocks A and at least one polymer interior block B wherein each A block is a polymer block resistant to sulfonation and each B block is a polymer block susceptible to sulfonation, and wherein said A and B blocks do not contain any significant levels of olefinic unsaturation. Preferably, each A block comprising one or more segments selected from polymerized (i) para-substituted styrene monomers, (ii) ethylene, (iii) alpha olefins of 3 to 18 carbon atoms; (iv) hydrogenated 1,3-cyclodiene monomers, (v) hydrogenated monomers of conjugated dienes having a vinyl content less than 35 mol percent prior to hydrogenation, (vi) acrylic esters, (vii) methacrylic esters, and (viii) mixtures thereof; and each B block comprising segments of one or more polymerized vinyl aromatic monomers selected from (i) unsubstituted styrene monomers, (ii) ortho-substituted styrene monomers, (iii) meta-substituted styrene monomers, (iv) alpha-methylstyrene, (v) 1,1-diphenylethylene, (vi) 1,2-diphenylethylene and (vii) mixtures thereof. Also claimed are processes for making such block copolymers, and the various end uses and applications for such block copolymers.
Owner:KRATON POLYMERS US LLC
Oral care compositions containing combinations of anti-bacterial and host-response modulating agents
InactiveUS20070053849A1Potent anti-inflammatory activityPromote progressAntibacterial agentsCosmetic preparationsWhole bodyOral bacterial infection
The present invention encompasses topical oral care compositions comprising the combination of an anti-bacterial agent with an anti-inflammatory agent in an orally acceptable carrier for effective treatment and prevention of bacteria-mediated diseases and conditions in the oral cavity and for modulating host reaction to bacterial pathogens present in the oral cavity and to the toxins, endotoxins, inflammatory cytokines and mediators released by or prompted by these pathogens. The present invention also encompasses methods of use of these compositions comprising topical application to the oral cavity. The benefits of the present compositions and methods extend beyond treating and preventing oral bacterial infections in the oral cavity to promoting whole body or systemic health.
Owner:THE PROCTER & GAMBLE COMPANY
Retractor
InactiveUS7445597B2Extensive exposureProvide protectionCannulasSurgical needlesBiomedical engineering
Owner:ATROPOS LTD
Fiber optic drop cable slack storage receptacle
ActiveUS20050145522A1Easy to deployEasy to installContainers for annular articlesFilament handlingFiberNetwork interface device
A slack storage receptacle for storing an excess length of a pre-connectorized fiber optic drop cable extending between an optical connection terminal and a network interface device (NID) includes a housing and a storage means disposed within the housing for receiving the drop cable such that the drop cable slack is stored external to the NID. The slack storage receptacle may be secured to an exterior wall of a subscriber premises and the NID mounted thereon. Alternatively, the slack storage receptacle may be positioned around and formed to the NID. Alternatively, the slack storage receptacle may be buried in the ground adjacent the NID. The drop cable slack may be wound onto the storage means after deployment. Alternatively, the slack storage receptacle may be pre-assembled, shipped to the subscriber premises, and the drop cable unwound from the storage means with the drop cable slack remaining wound on the storage means.
Owner:CORNING OPTICAL COMM LLC
Storing and accessing data in a mobile device and a user module
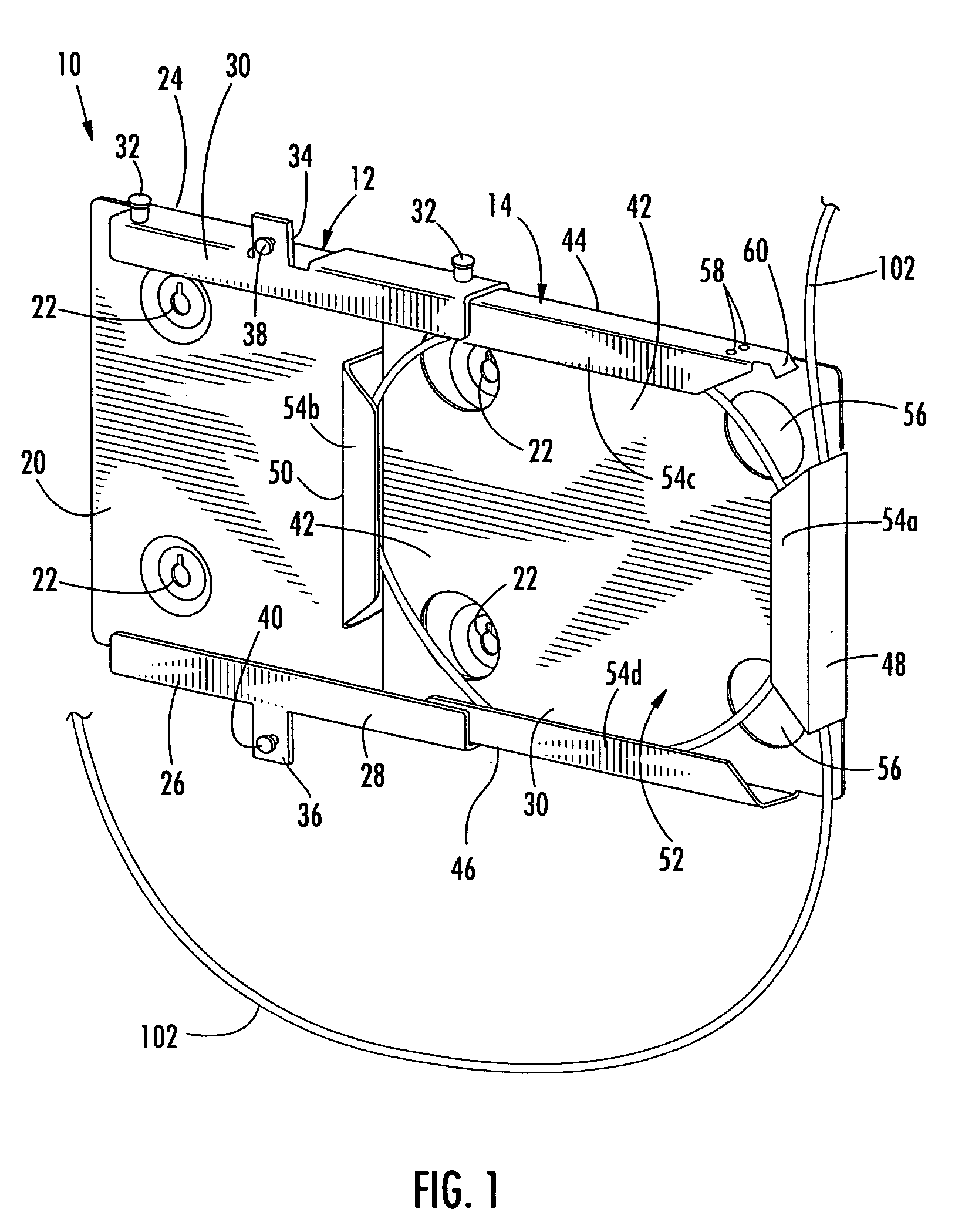
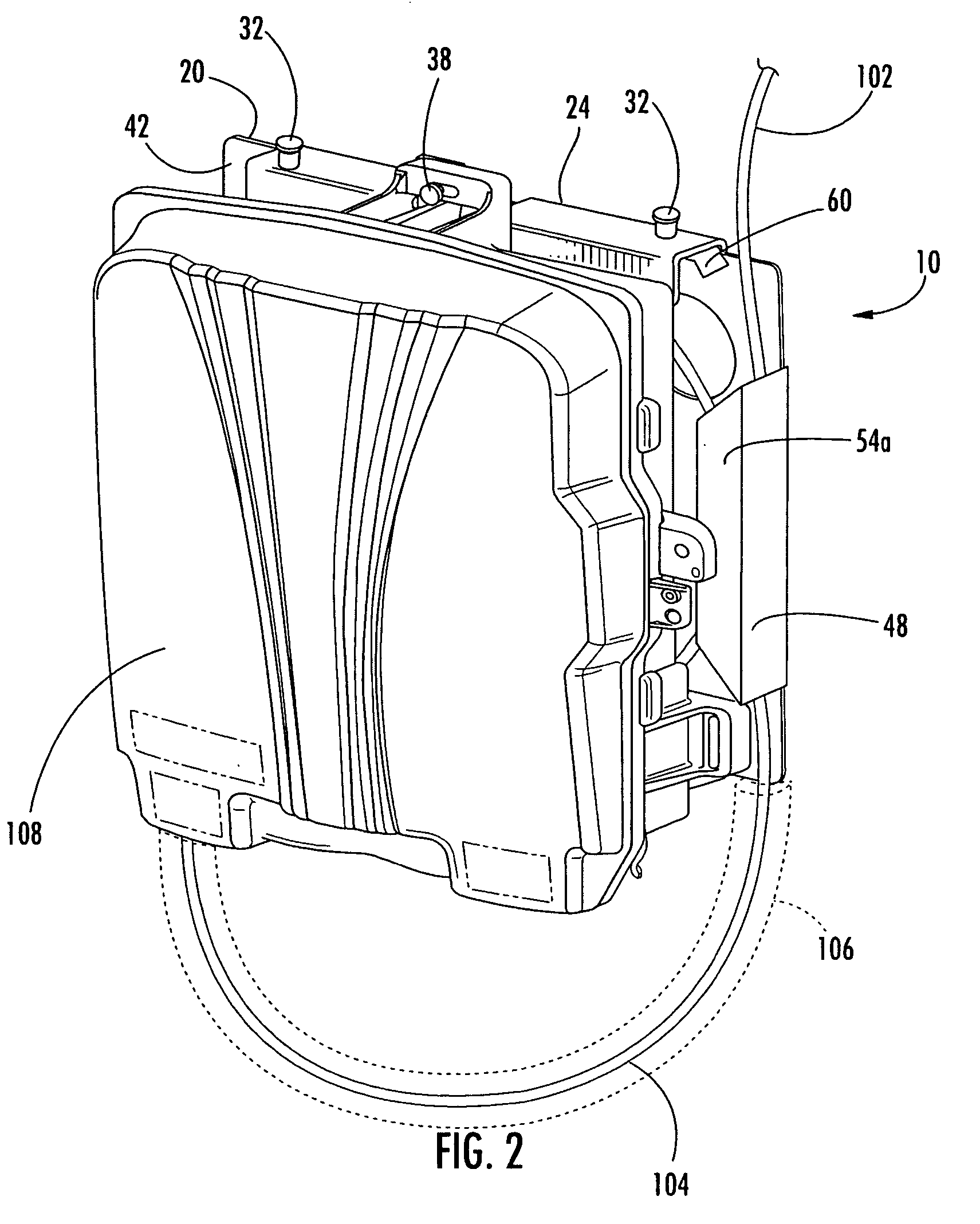
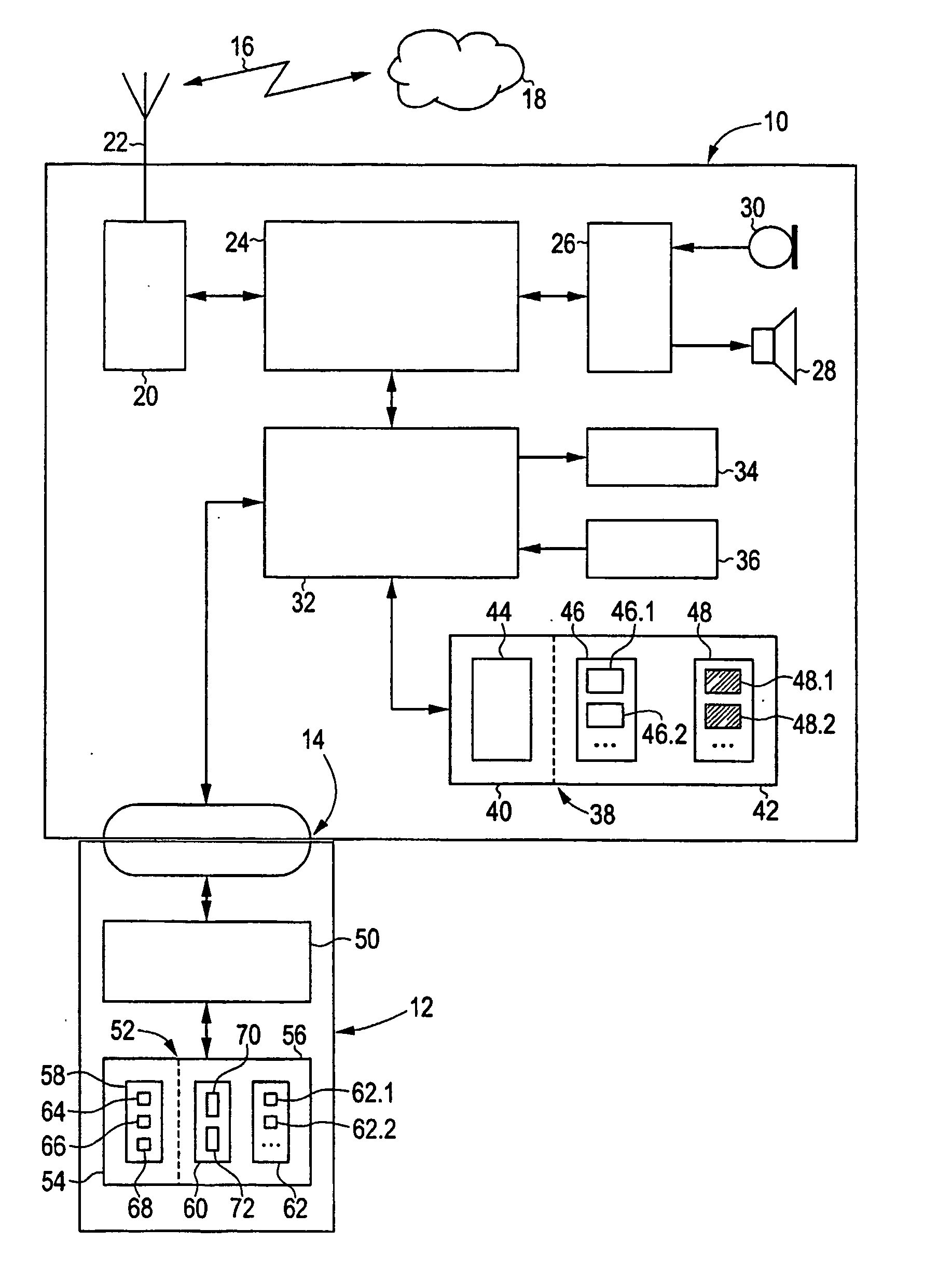
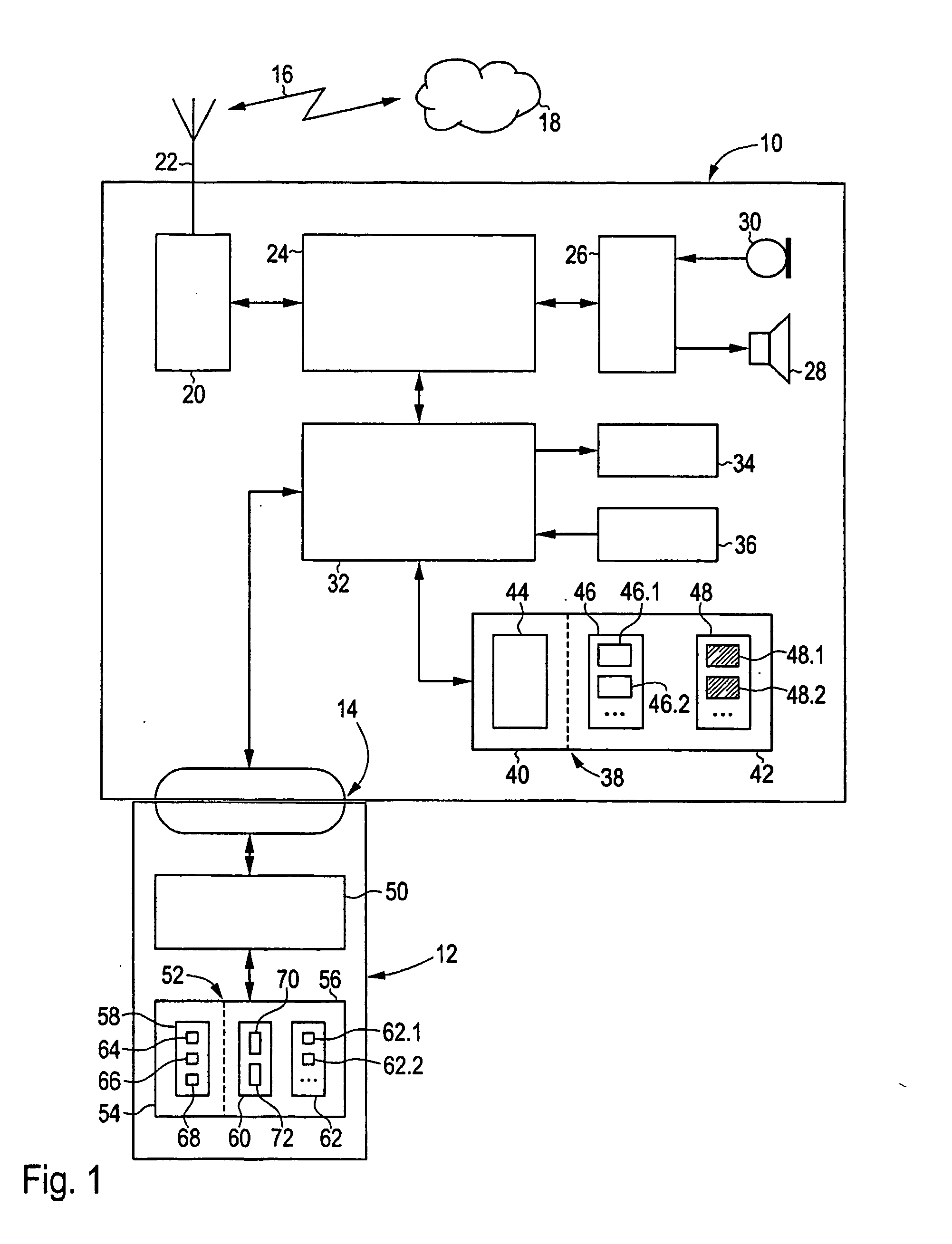
ActiveUS20050120225A1Improve user convenienceImplemented cost-effectivelyAccounting/billing servicesUnauthorized memory use protectionInternet privacyMobile device
The invention relates to methods for storing and accessing user data (48) and configuration data (62) in a mobile device (10) that is connected to a user module (12). According to a first aspect of the invention, the user data (48) is stored in the mobile device (10) at least partially in encrypted form, and is decrypted, in access operations, using a decrypting function (66) of the user module (12). According to a second aspect of the invention, the configuration data (62) is stored in the user module (12). The configuration data (62) indicates whether, or to what extent, an application program (46) is allowed to be executed by the mobile device (10). Security and protection against unauthorised access to user data (48) and application programs (46) in the mobile device (10) are increased by the invention.
Owner:GIESECKE & DEVRIENT MOBILE SECURITY GMBH
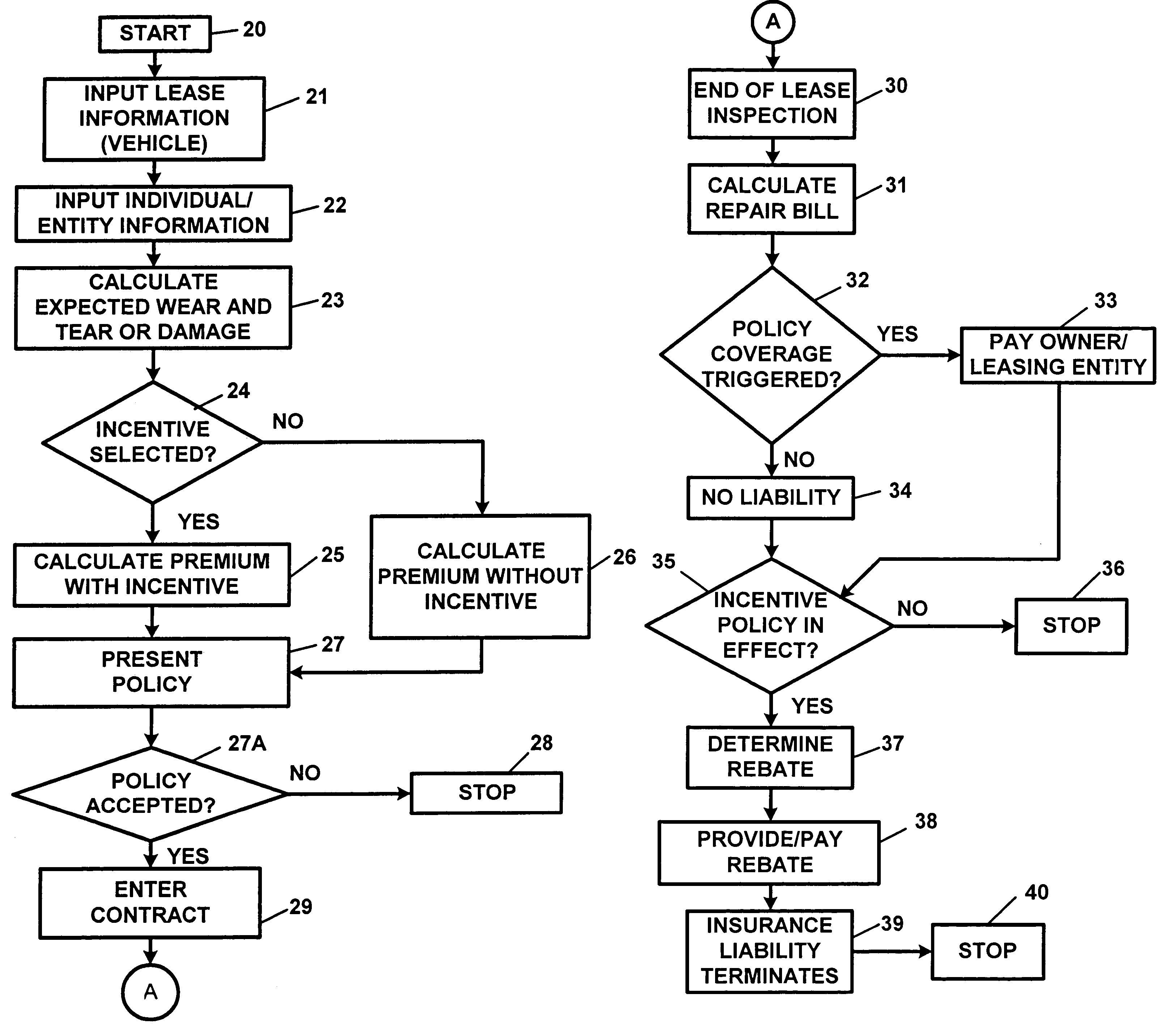
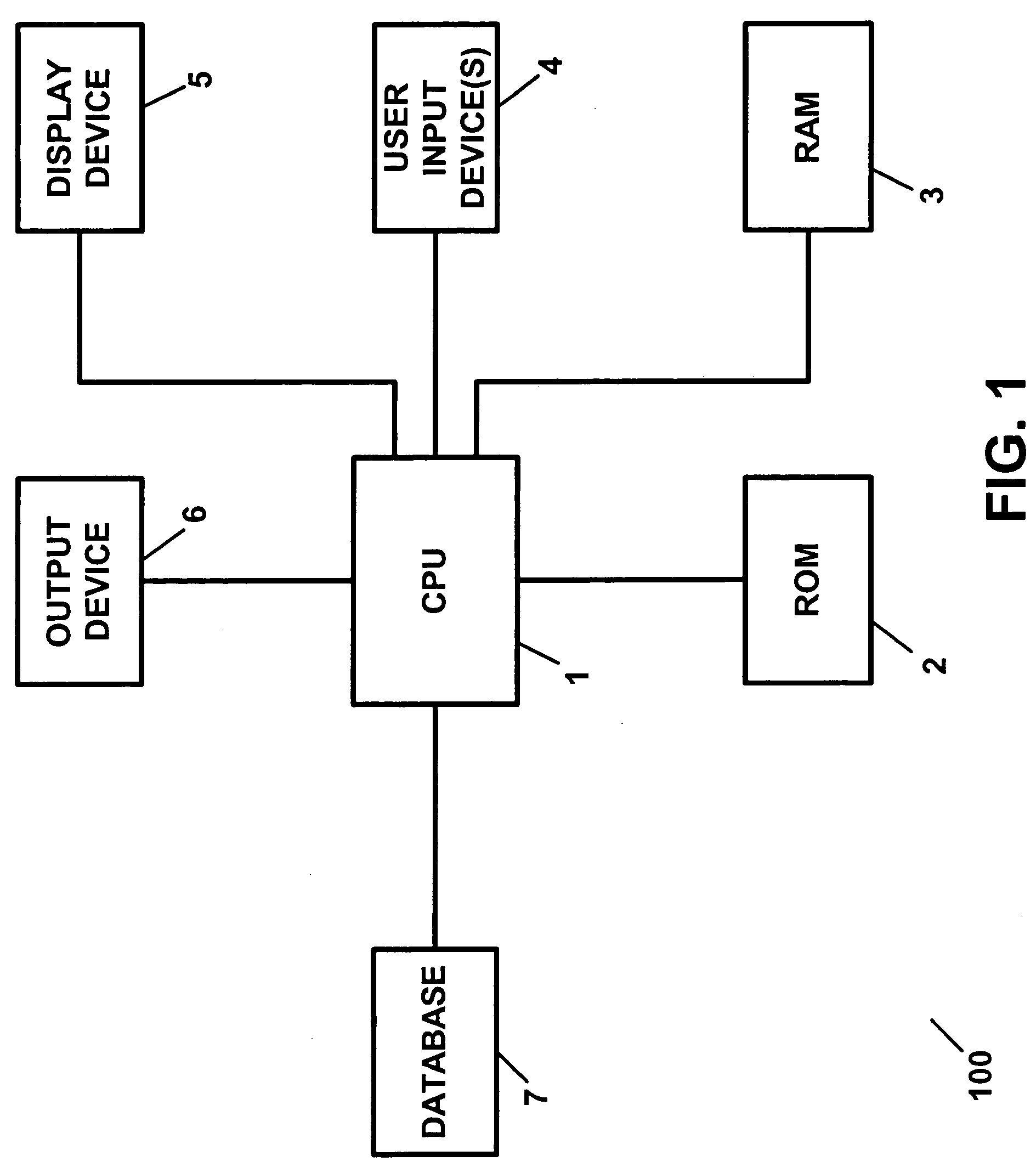
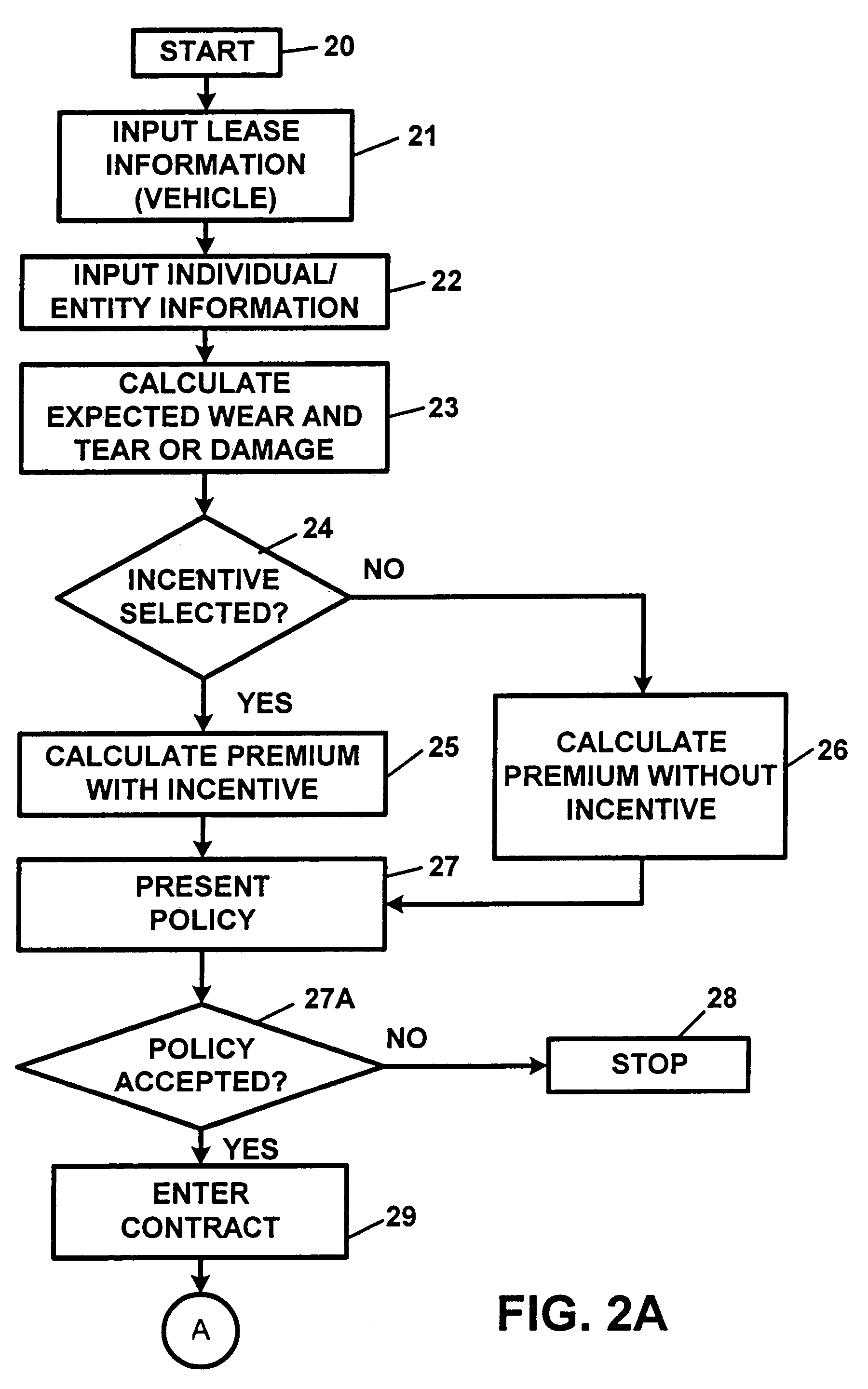
Apparatus and method for processing lease insurance information
InactiveUS7870010B2Provide protectionExcess damageFinanceOffice automationDisplay deviceOutput device
An apparatus and method for processing lease insurance information, including a processor for processing information for generating at least one of an insurance premium and an insurance policy for providing insurance for excess wear or post warranty repairs for a leased entity, wherein the processor generates a information regarding an insurance premium or an insurance policy, wherein the processor generates information regarding at least one of a liability, a potential liability, and a risk of loss, associated with the at least one of an insurance policy and an insurance product, and at least one of a display device and an output device for providing information, the insurance premium, the insurance policy, or the insurance product.
Owner:GTJ VENTURES
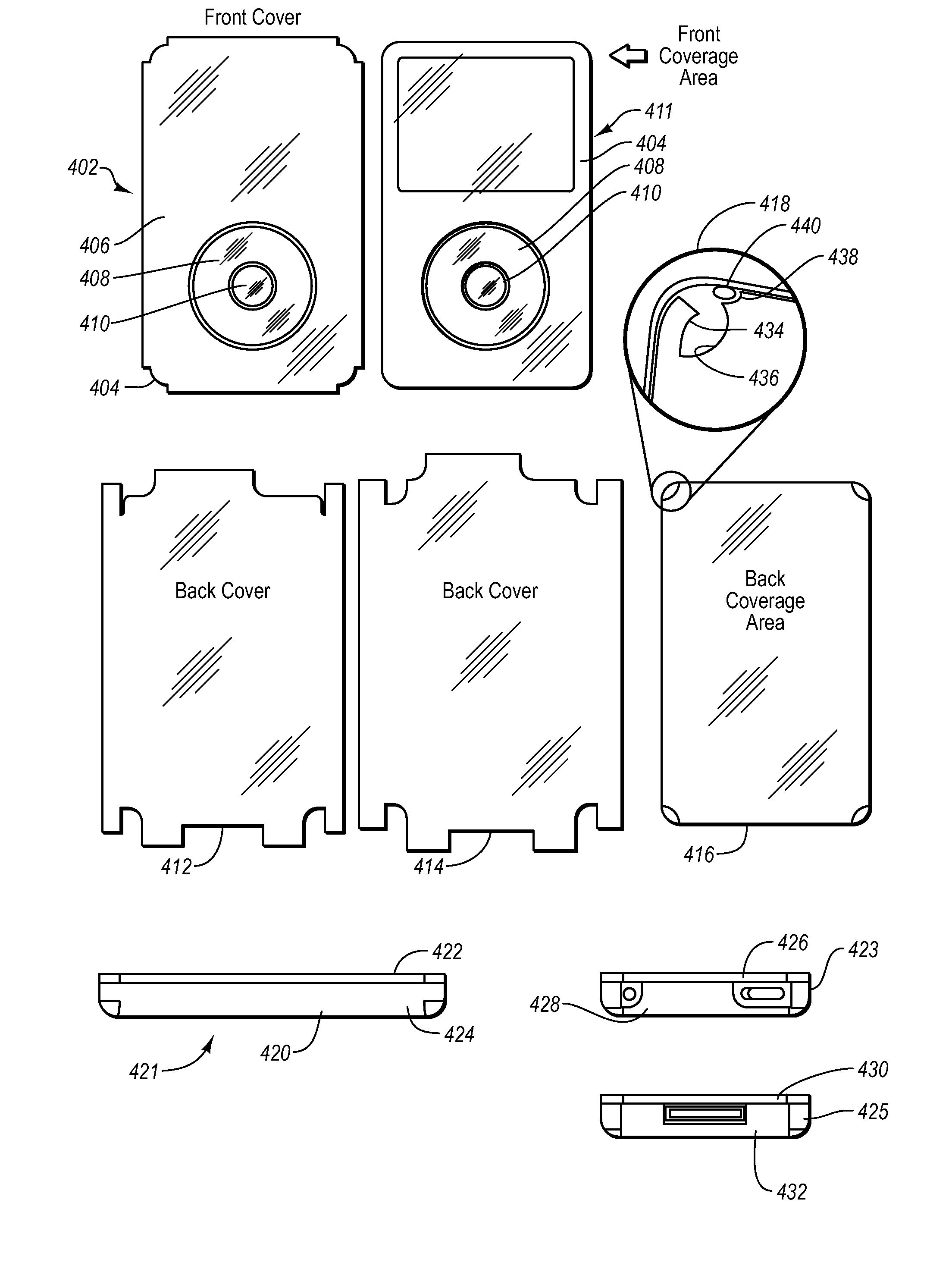
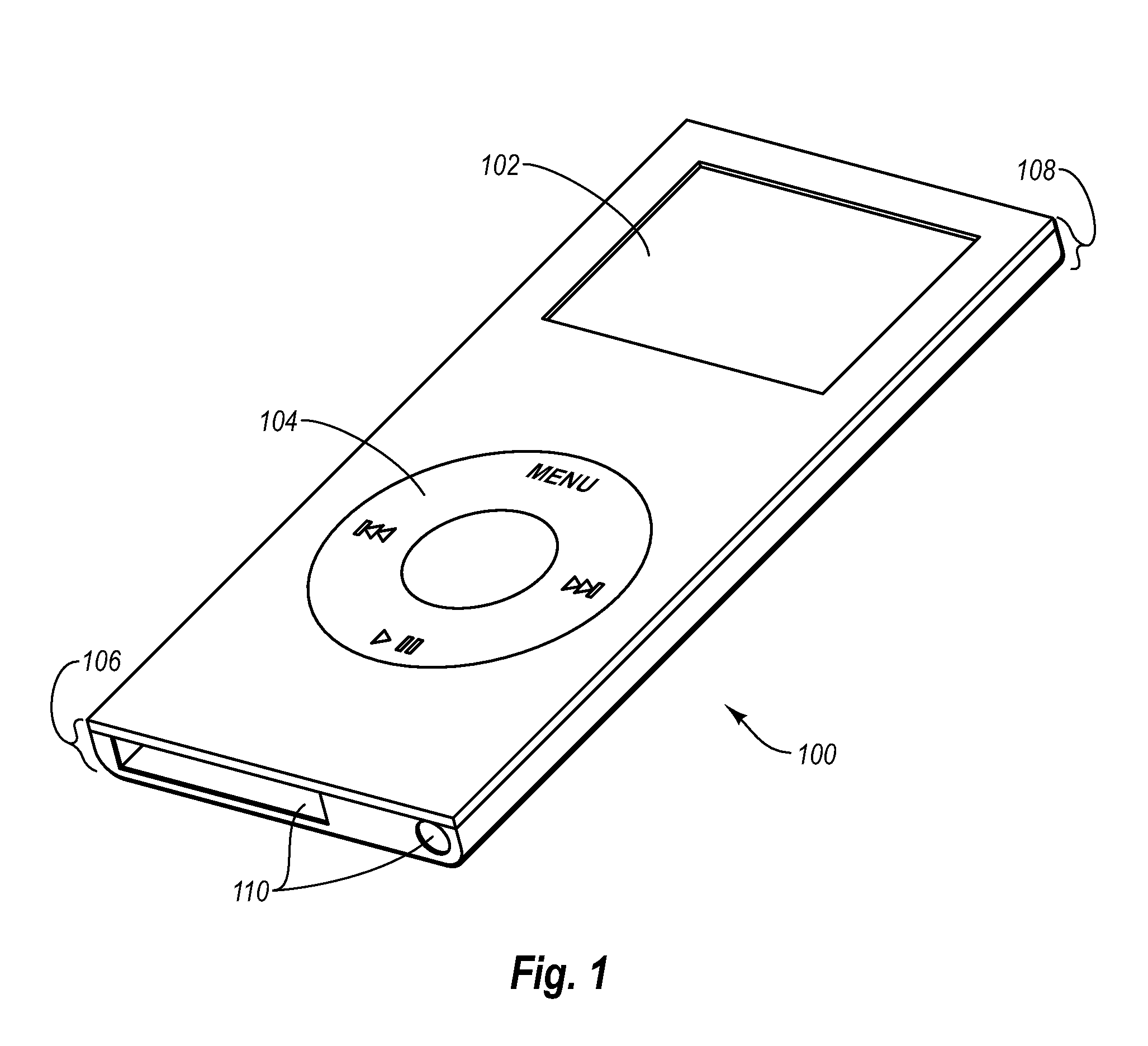
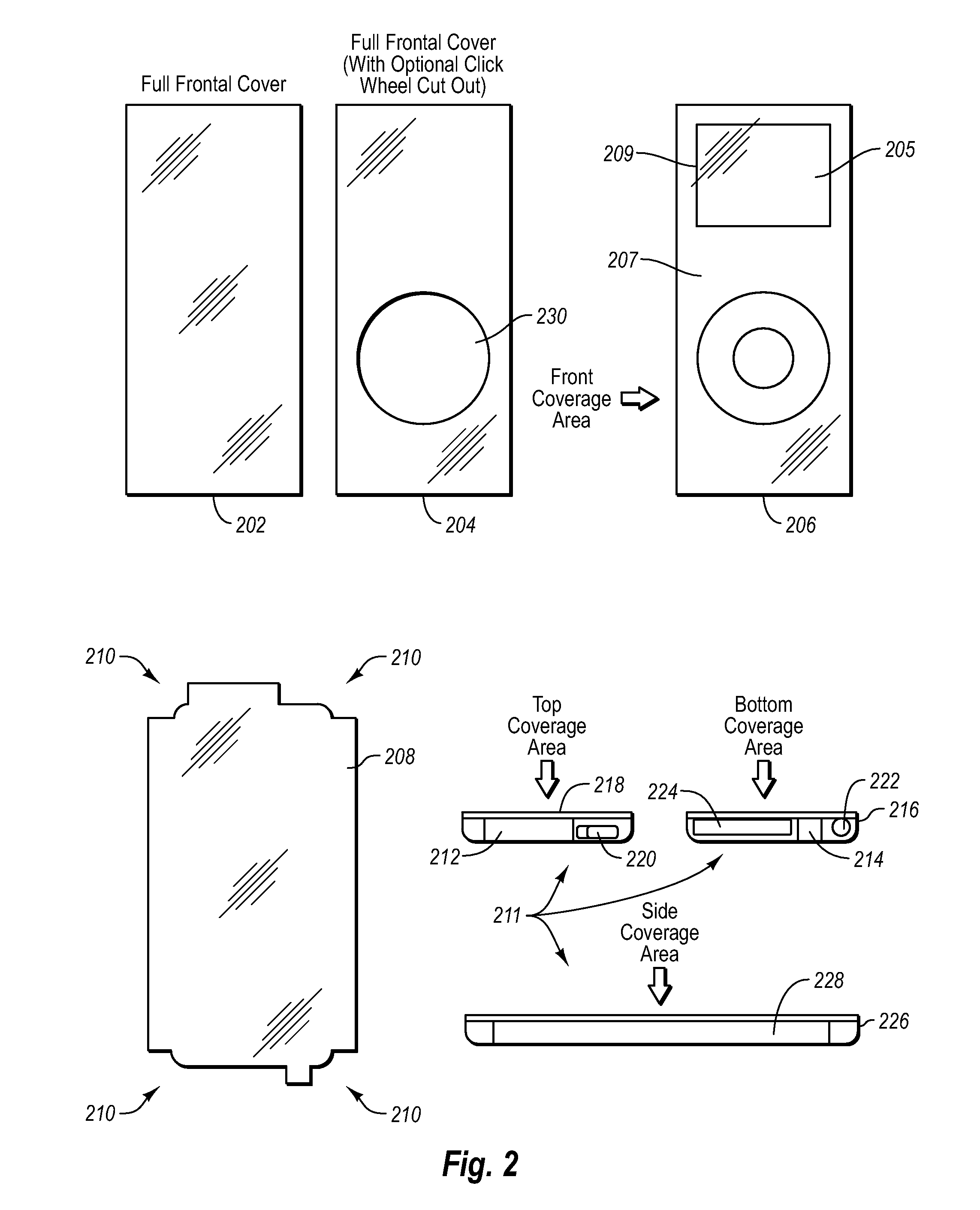
Protective covering for an electronic device
ActiveUS7957524B2Easy to disassemblePrecise positioningInterconnection arrangementsLayered productsElectric equipmentUser interface
A protective cover for electronic devices. A device is examined and a film is prepared. The film may include multiple pieces and may have cutouts for discontinuities in the surfaces of the device or to accommodate a user interface. The corners or other portions of the films are then cut such that the films substantially cover the surface of the device without bunching or creating air pockets.
Owner:ZAGG
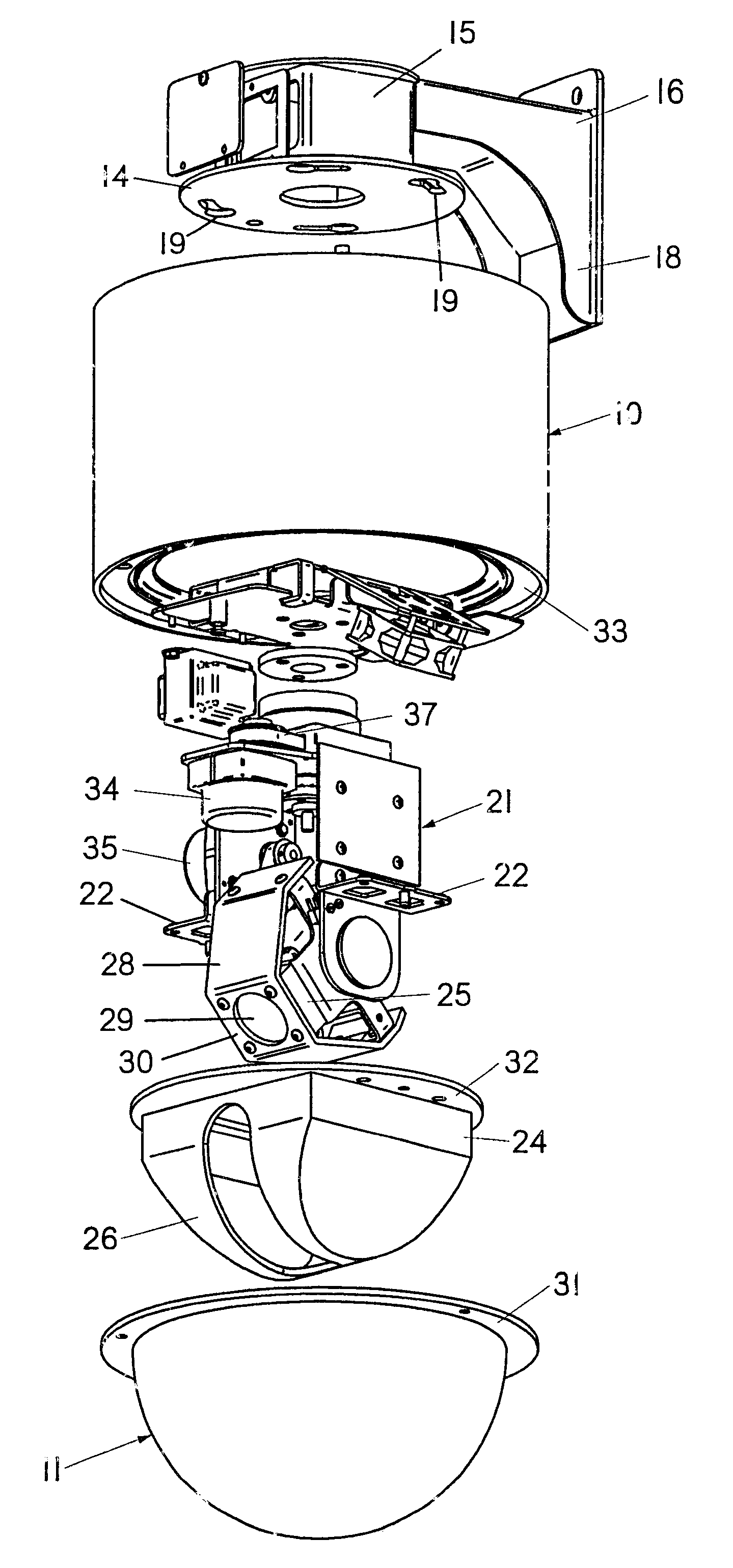
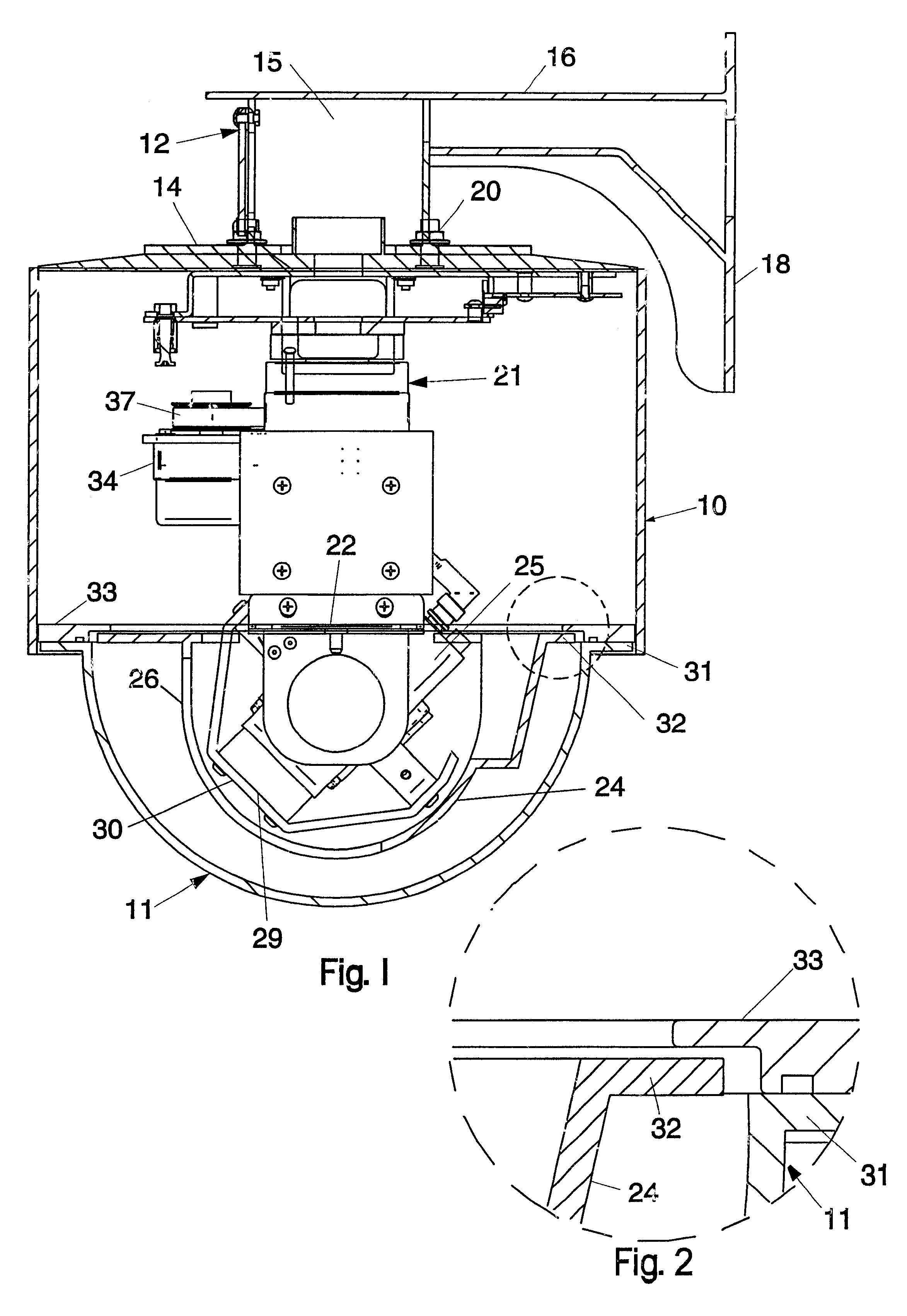
Housing for surveillance camera
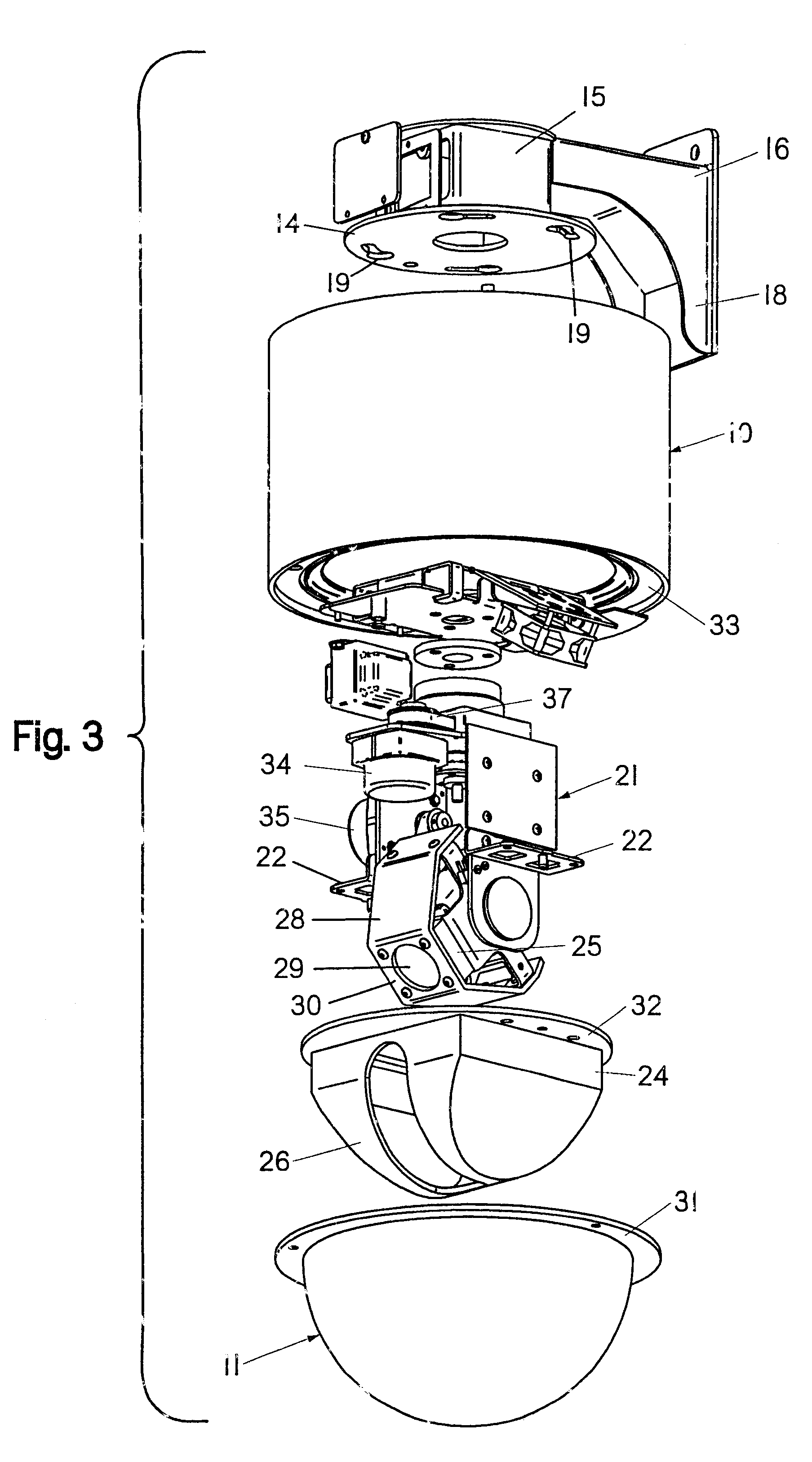
InactiveUS6354749B1Provide protectionColor television detailsClosed circuit television systemsCamera lensSurveillance camera
A housing for a surveillance camera has an upper housing that is cylindrical and made of steel or the like to withstand ballistic attack. The upper housing houses the pan-and-tilt mechanism, which is suspended from the inside of the upper housing. The camera is carried by the pan-and-tilt mechanism, and extends into a lower, transparent, housing. An inner liner is within the lower housing and covers the camera, the inner liner being made of hardened aluminum or the like to withstand ballistic attack. The inner liner covers the camera, except that a slot allows the camera lens to receive images through the lower housing. A shield is fixed to the camera to move with the camera, covering the slot in the inner liner, the shield defining one opening for the camera lens. The inner liner and the shield are dark in color to prevent visual location of the camera lens, and a polymeric guard physically protects the camera lens.
Owner:VIDEOLARM
Fiber optic drop cable slack storage receptacle
ActiveUS7346253B2Provide protectionEasy to deployPackagingOptical light guidesFiberNetwork interface device
A slack storage receptacle for storing an excess length of a pre-connectorized fiber optic drop cable extending between an optical connection terminal and a network interface device (NID) includes a housing and a storage means disposed within the housing for receiving the drop cable such that the drop cable slack is stored external to the NID. The slack storage receptacle may be secured to an exterior wall of a subscriber premises and the NID mounted thereon. Alternatively, the slack storage receptacle may be positioned around and formed to the NID. Alternatively, the slack storage receptacle may be buried in the ground adjacent the NID. The drop cable slack may be wound onto the storage means after deployment. Alternatively, the slack storage receptacle may be pre-assembled, shipped to the subscriber premises, and the drop cable unwound from the storage means with the drop cable slack remaining wound on the storage means.
Owner:CORNING OPTICAL COMM LLC
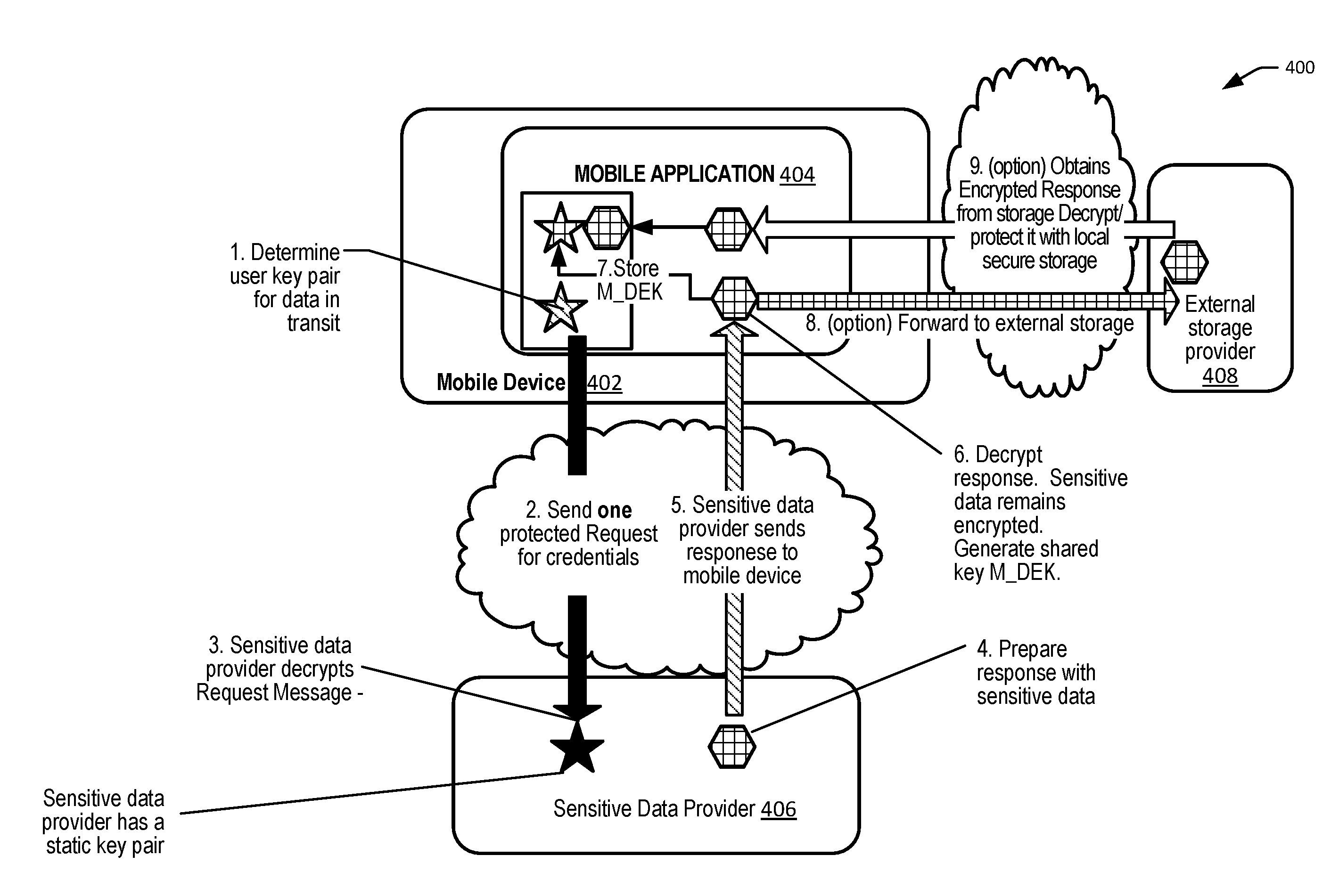
Methods for secure credential provisioning
ActiveUS20160218875A1Minimizing substantially exposure to riskProvide protectionKey distribution for secure communicationMultiple keys/algorithms usageComputer securityUser device
Embodiments can provide methods for securely provisioning sensitive credential data, such as a limited use key (LUK) onto a user device. In some embodiments, the credential data can be encrypted using a separate storage protection key and decrypted only at the time of a transaction to generate a cryptogram for the transaction. Thus, end-to-end protection can be provided during the transit and storage of the credential data, limiting the exposure of the credential data only when the credential data is required, thereby reducing the risk of compromise of the credential data.
Owner:VISA INT SERVICE ASSOC
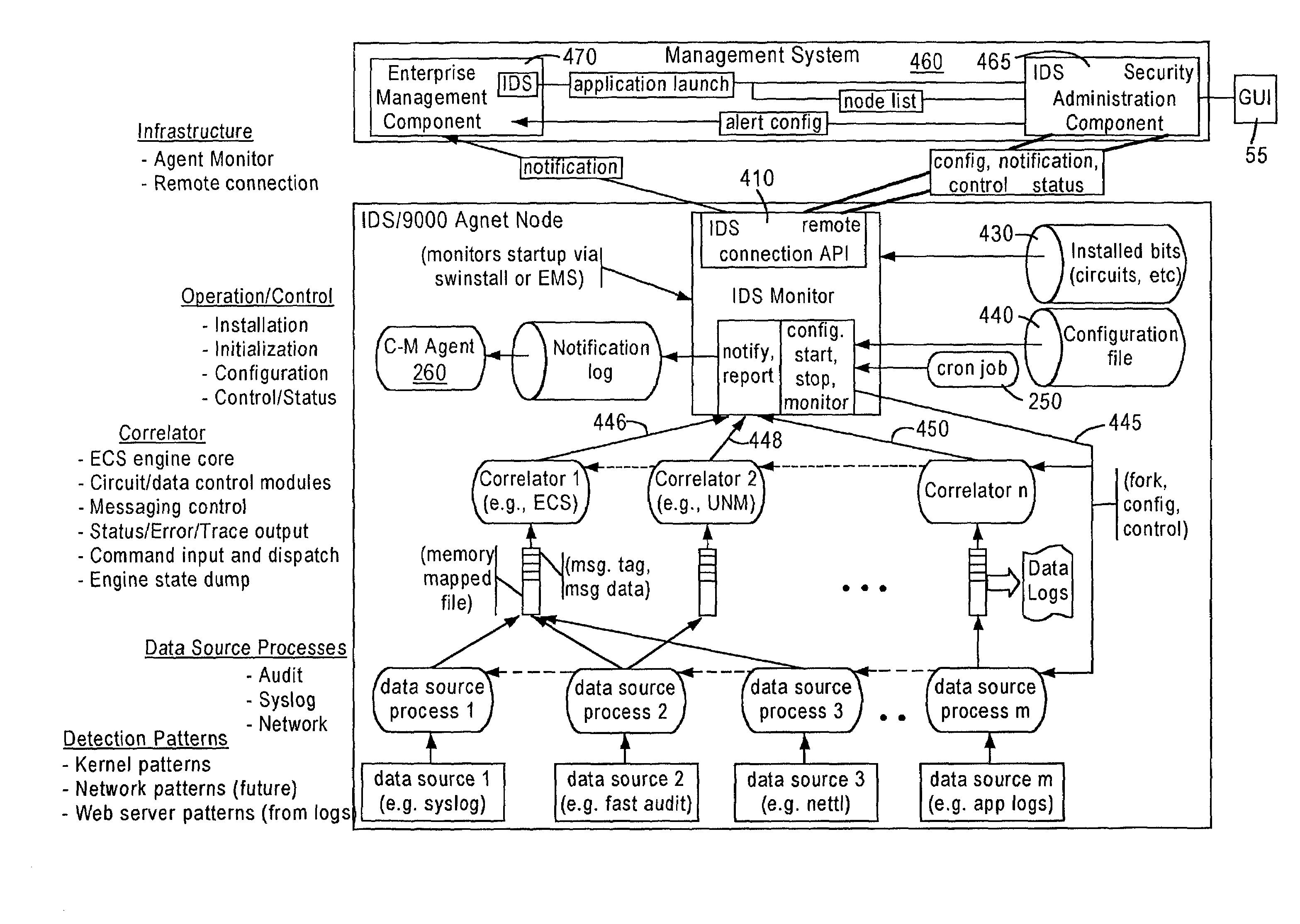
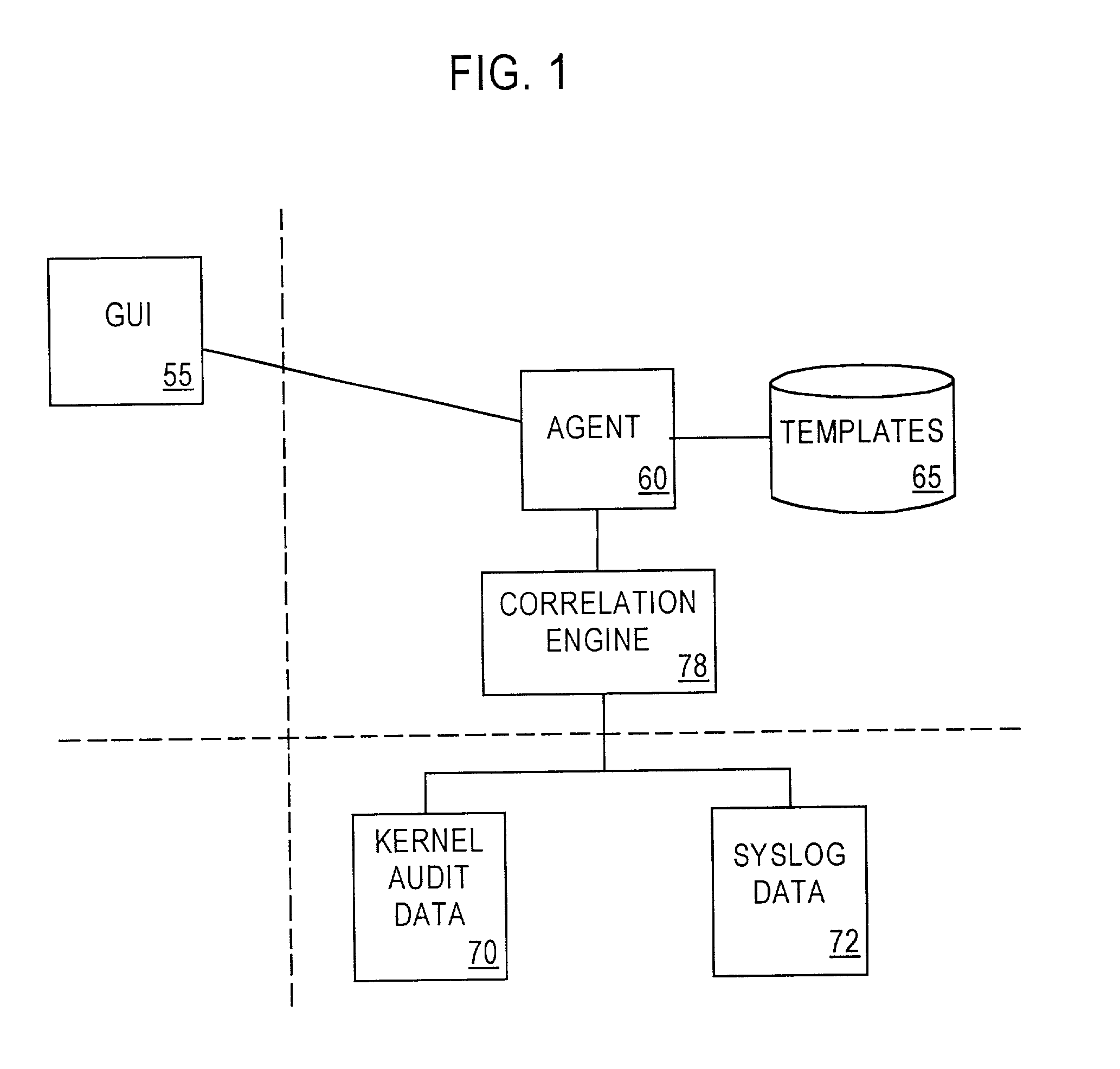
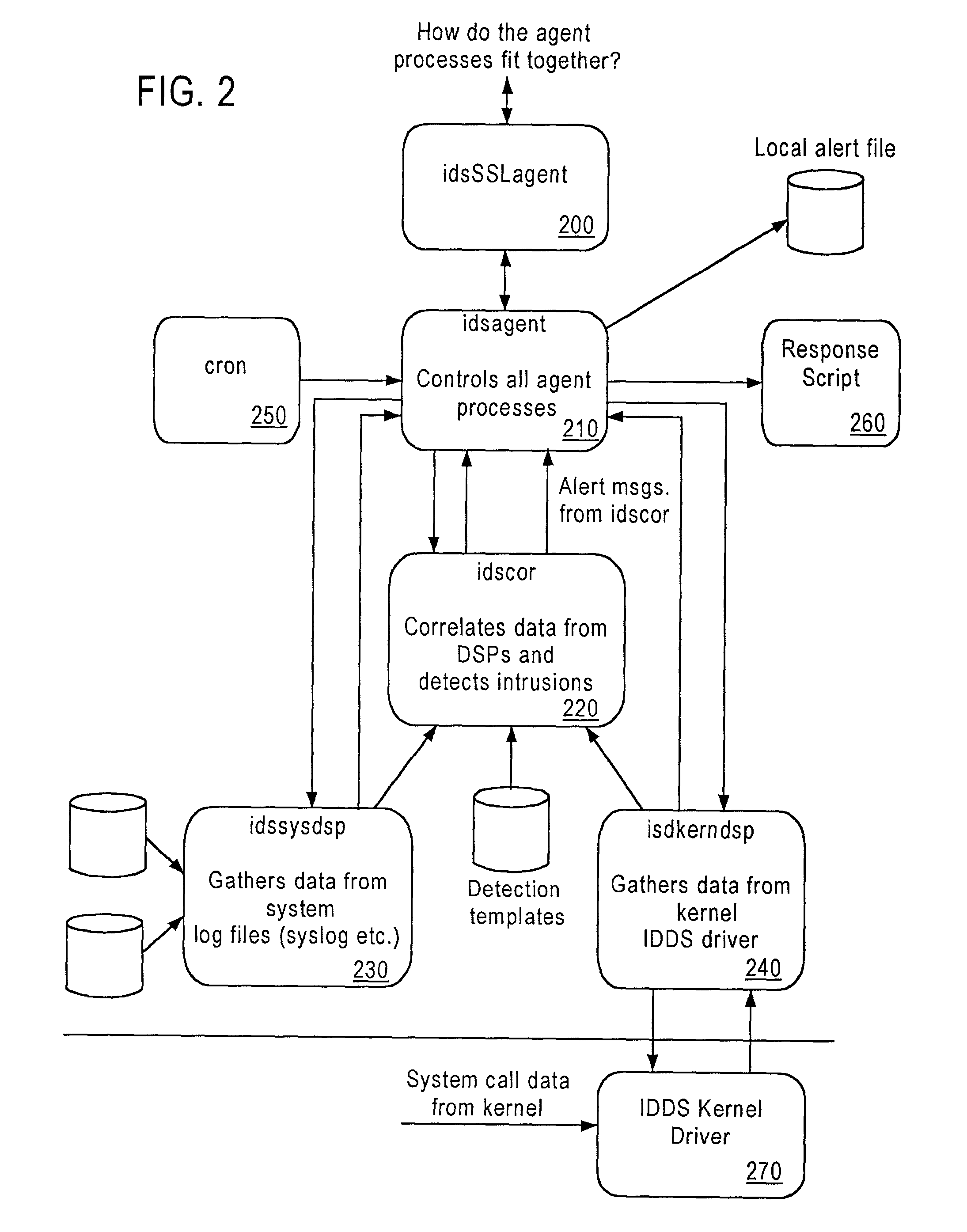
Computer architecture for an intrusion detection system
InactiveUS7007301B2Provide protectionAccurate measurementData processing applicationsMemory loss protectionOperational systemCritical system
The present application is directed to a host-based IDS on an HP-UX intrusion detection system that enhances local host-level security within the network. It should be understood that the present invention is also usable on, for example, Eglinux, solaris, aix windows 2000 operating systems. It does this by automatically monitoring each configured host system within the network for possible signs of unwanted and potentially damaging intrusions. If successful, such intrusions could lead to the loss of availability of key systems or could compromise system integrity.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
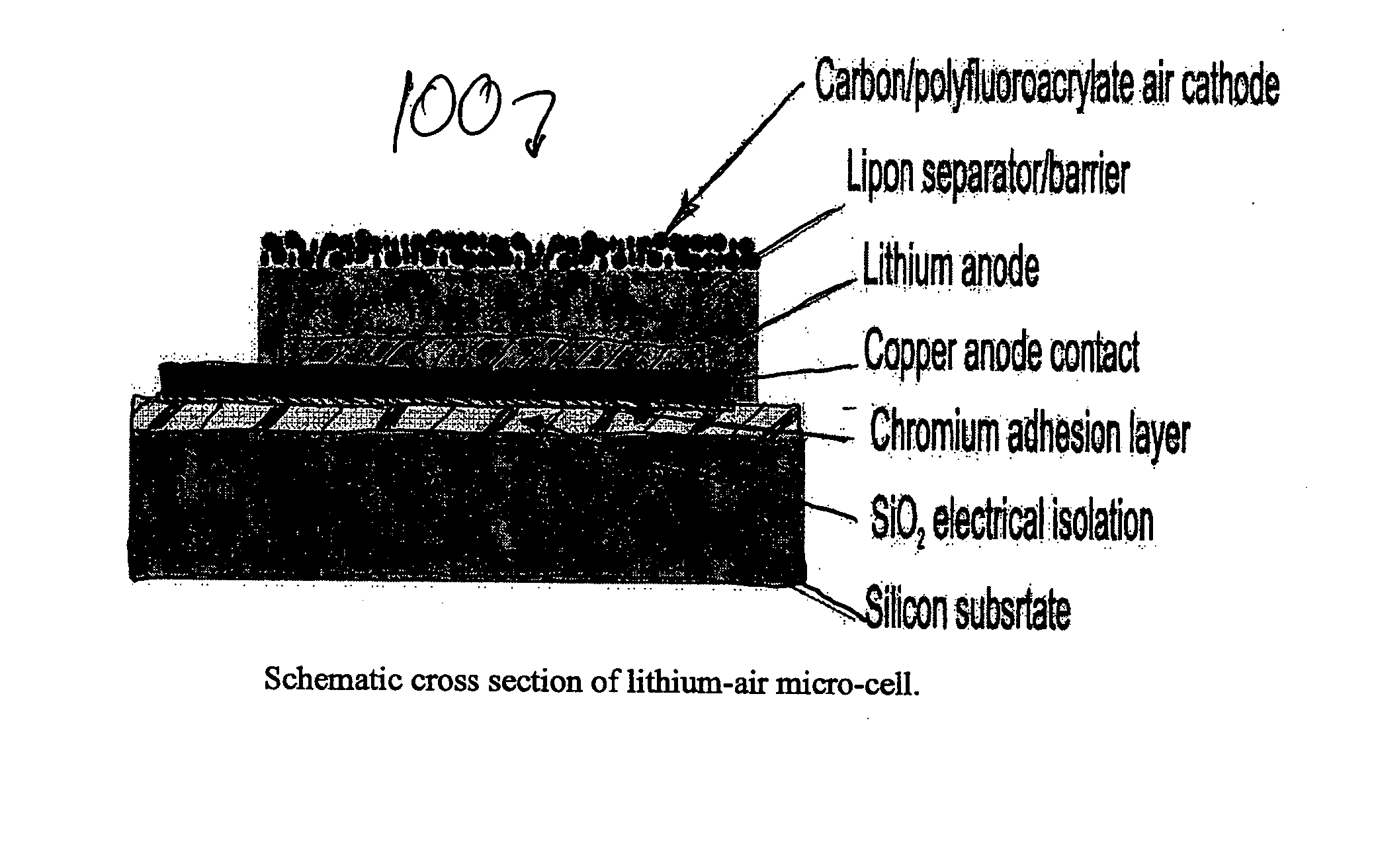
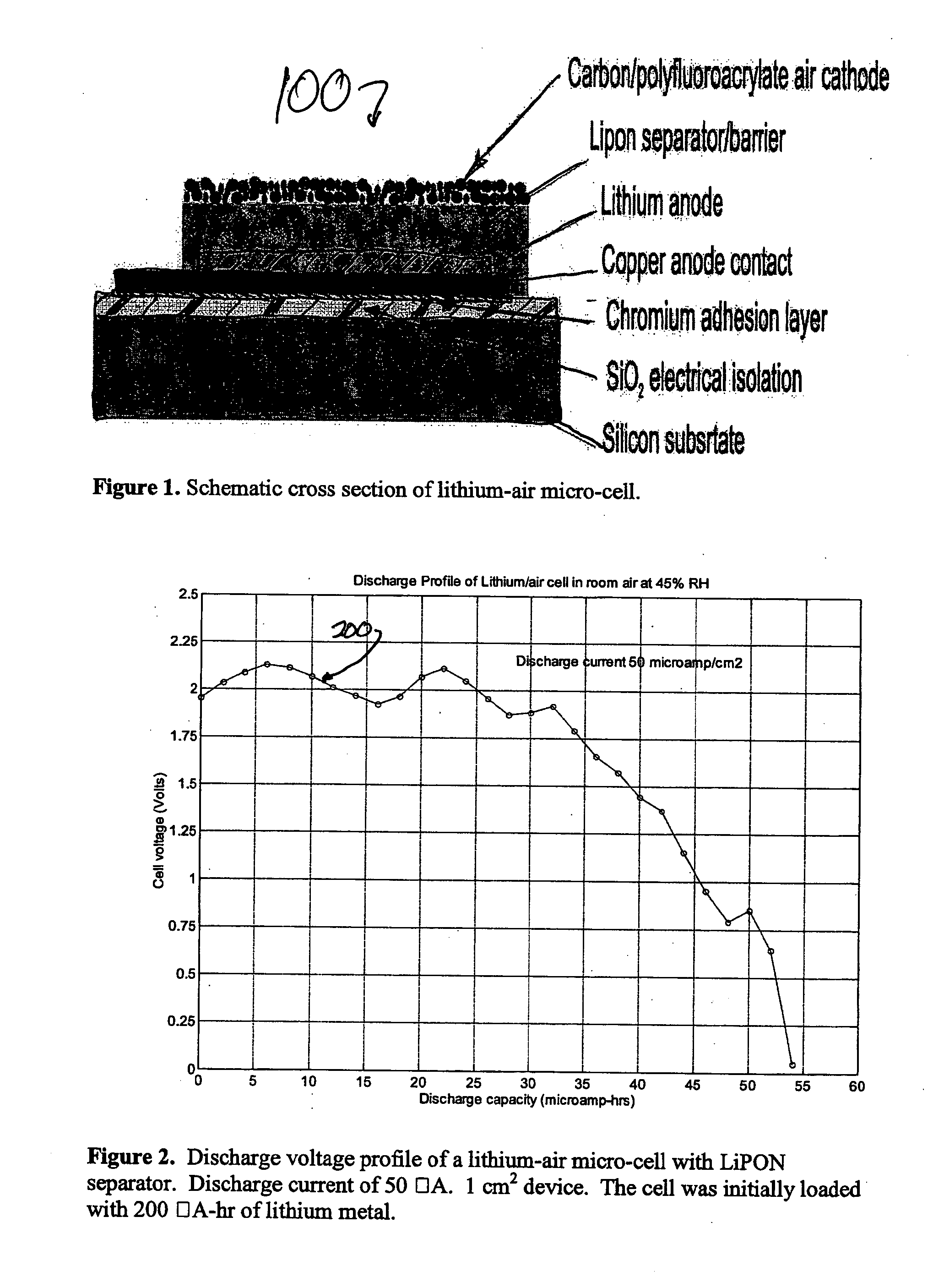
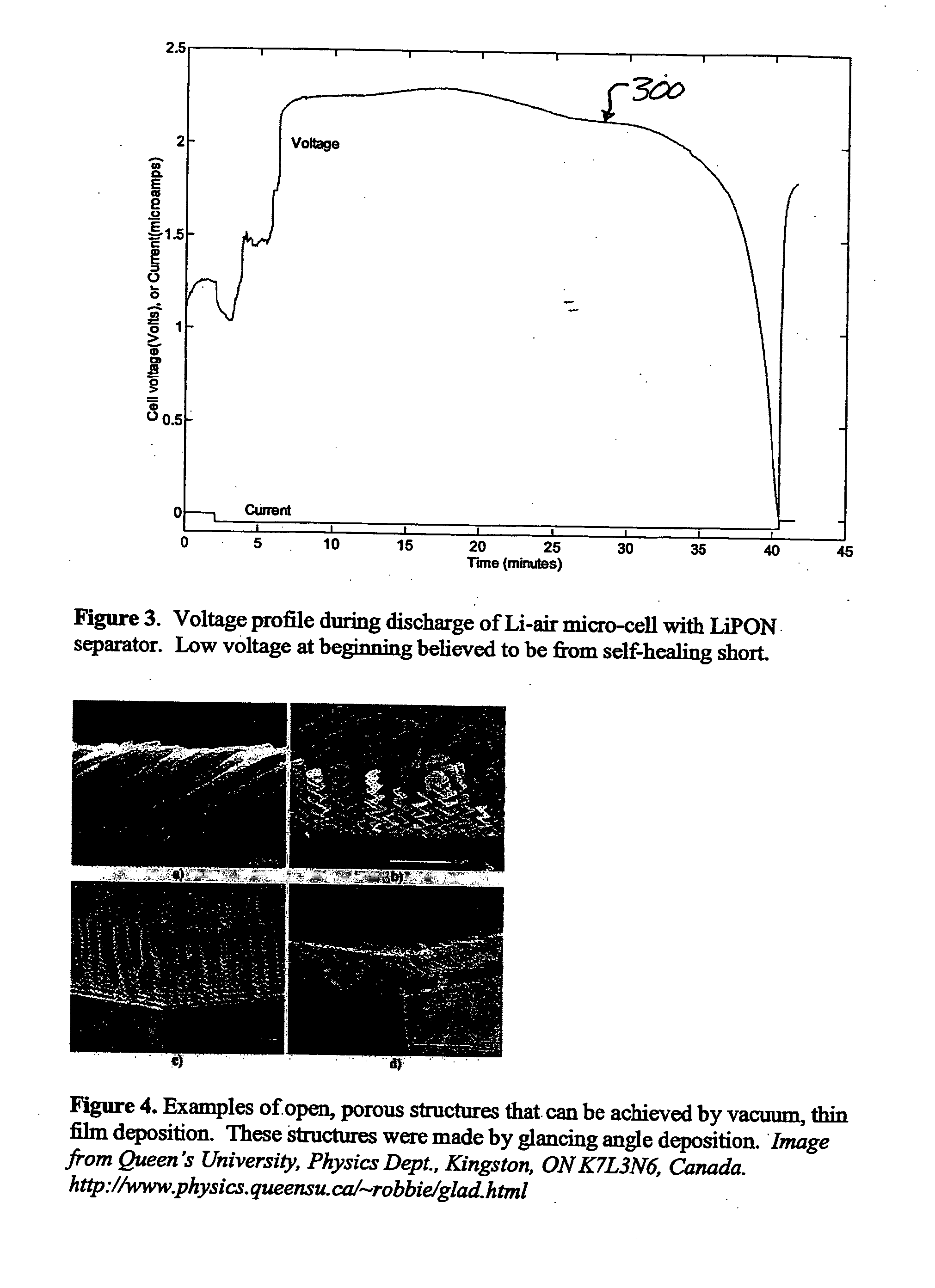
Lithium/air batteries with LiPON as separator and protective barrier and method
InactiveUS20050095506A1Extended shelf lifeProvide protectionFuel and primary cellsElectrode carriers/collectorsProtective barrierLithium–air battery
A method and apparatus for making lithium / air batteries with LiPON as separator and protective barrier, and the resulting cell(s) and / or battery(s). Some embodiments include an apparatus that includes a lithium anode; a polymer-air cathode; and a LiPON separator between the anode and cathode. In some embodiments, the polymer-air cathode includes a carbon-polyfluoroacrylate material. In some embodiments, the anode overlays a copper anode contact.
Owner:CYMBET CORP
Radiation detectable and protective articles
InactiveUS20050211930A1Attribute be easilyPresence be easilyNuclear engineering problemsNuclear engineering solutionsEmulsionCompound (substance)
Compositions and processes for forming radiopaque polymeric articles are disclosed. In one embodiment, radiation inspection apparatuses and methods are then used to determine the presence and attributes of such radiopaque polymeric articles. A radiopaque polymeric article of the present invention can be created by mixing a radiopaque material, such as barium, bismuth, tungsten or their compounds, with a powdered polymer, pelletized polymer or liquid solution, emulsion or suspension of a polymer in solvent or water. In addition to creating radiation detectable objects, the radiopaque polymeric materials of the present invention can be used to create radiation protective articles, such as radiation protective garments and bomb containment vessels. Enhanced radiation protection can also be achieved through the use of nano-materials. The principals of the present invention can be used to provide protection against other types of hazards, including fire, chemical, biological and projectile hazards.
Owner:MERIDIAN RES & DEV
Cellular communication system, network controller and method for obtaining feedback from subscriber communication units
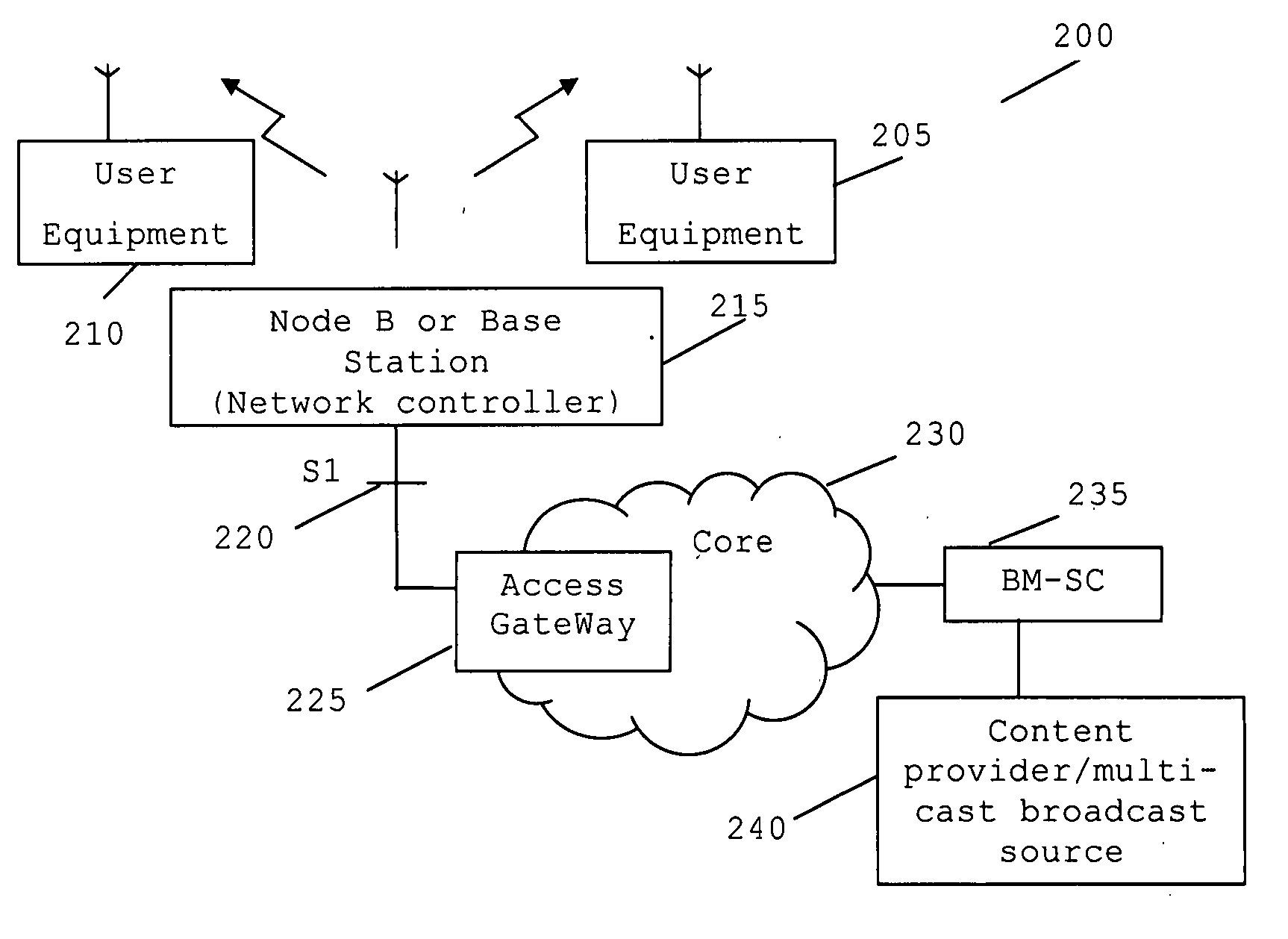
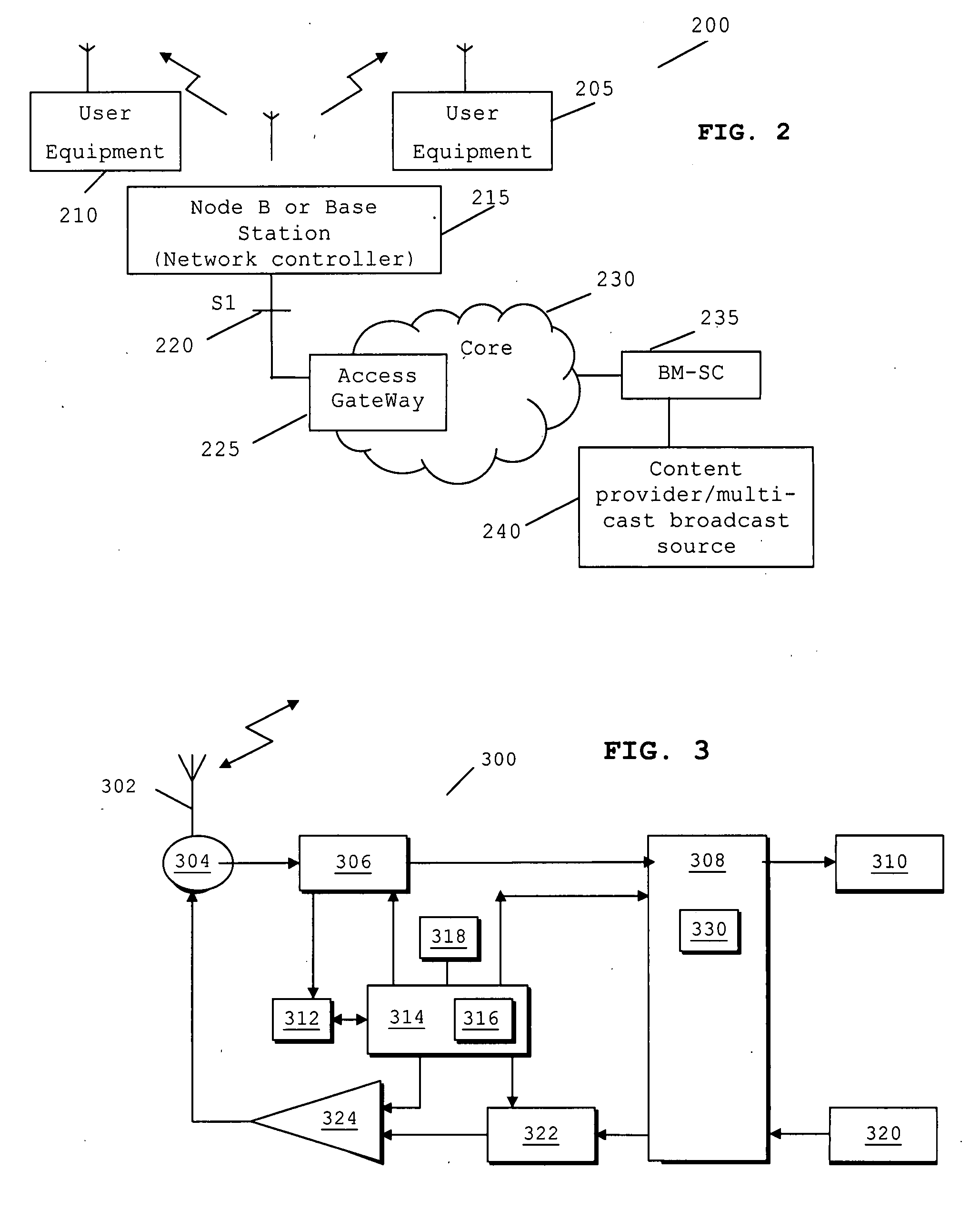
InactiveUS20080043658A1Simple low complexity procedureMore radio resourceReceivers monitoringBroadcast transmission systemsCommunications systemCommunication unit
A method for obtaining feedback from one or more wireless subscriber communication unit(s) related to a broadcast service in a wireless communication system comprising at least one communication cell. The method comprises transmitting a request message by a network controller to one or more wireless subscriber communication unit(s); receiving and processing the request message by a wireless subscriber communication unit; transmitting a layer-1 response signal by the wireless subscriber communication unit in response to the request message; and detecting by the network controller the layer-1 response signal in a particular communication cell, and in response thereto, performs one of the following: (i) entering a point-to-multipoint broadcast mode of operation; (ii) modifying a delivery of the broadcast service in that communication cell.
Owner:SONY CORP
Light-emitting device
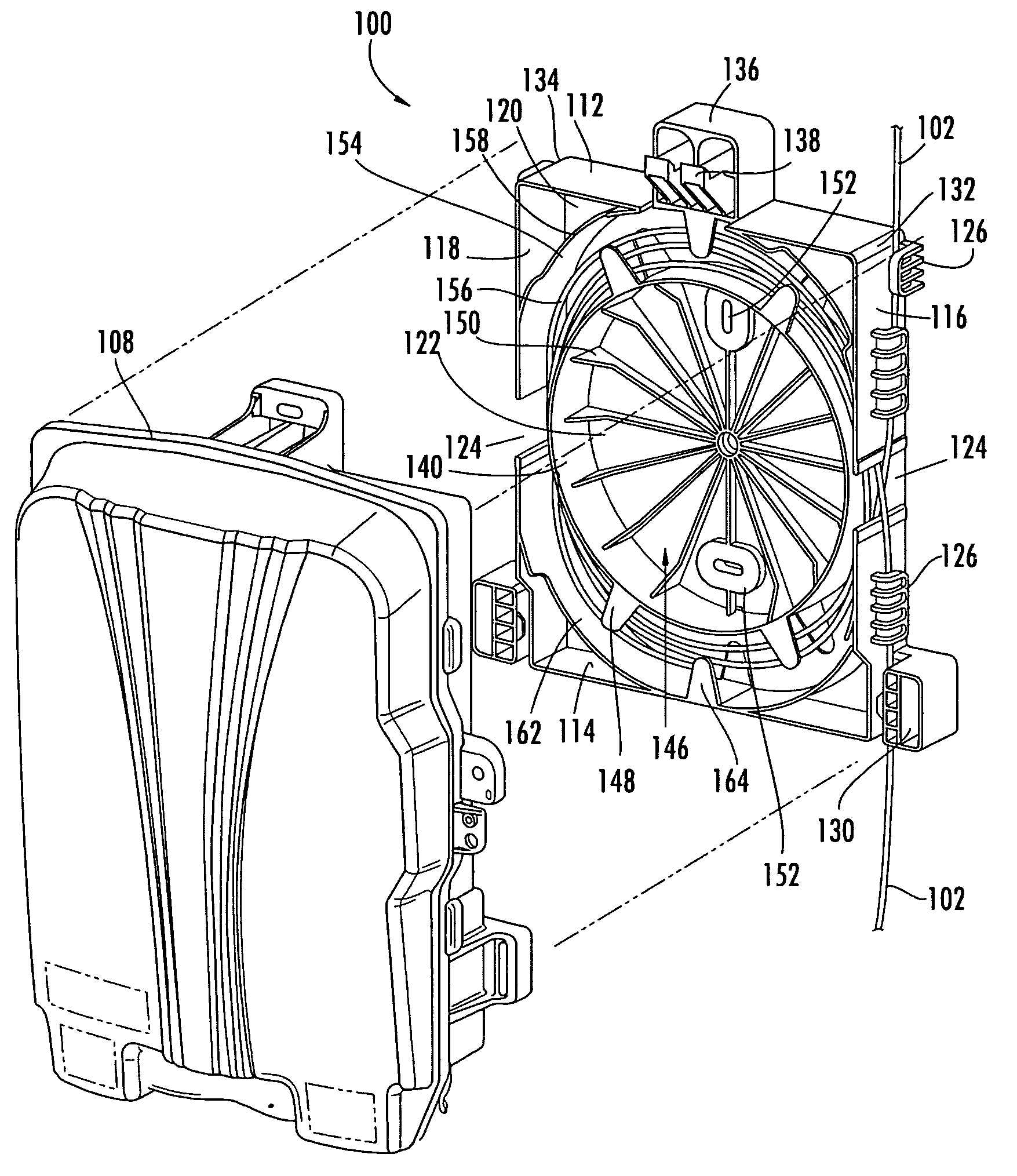
InactiveUS7331689B2Large throughputReduce heat dissipationPlanar light sourcesLighting support devicesOptical processingLight emission
A light emitting device is disclosed, in which a body is provided with a first joining portion, light-emitting elements located at a side of the body having the first joining portion for emitting light and an optical processing element disposed at a side of the light-emitting elements having a second joining portion corresponding to the first joining portion for processing light emitted from each light-emitting element, such that even light emission is obtained.
Owner:GRAND HALO TECH
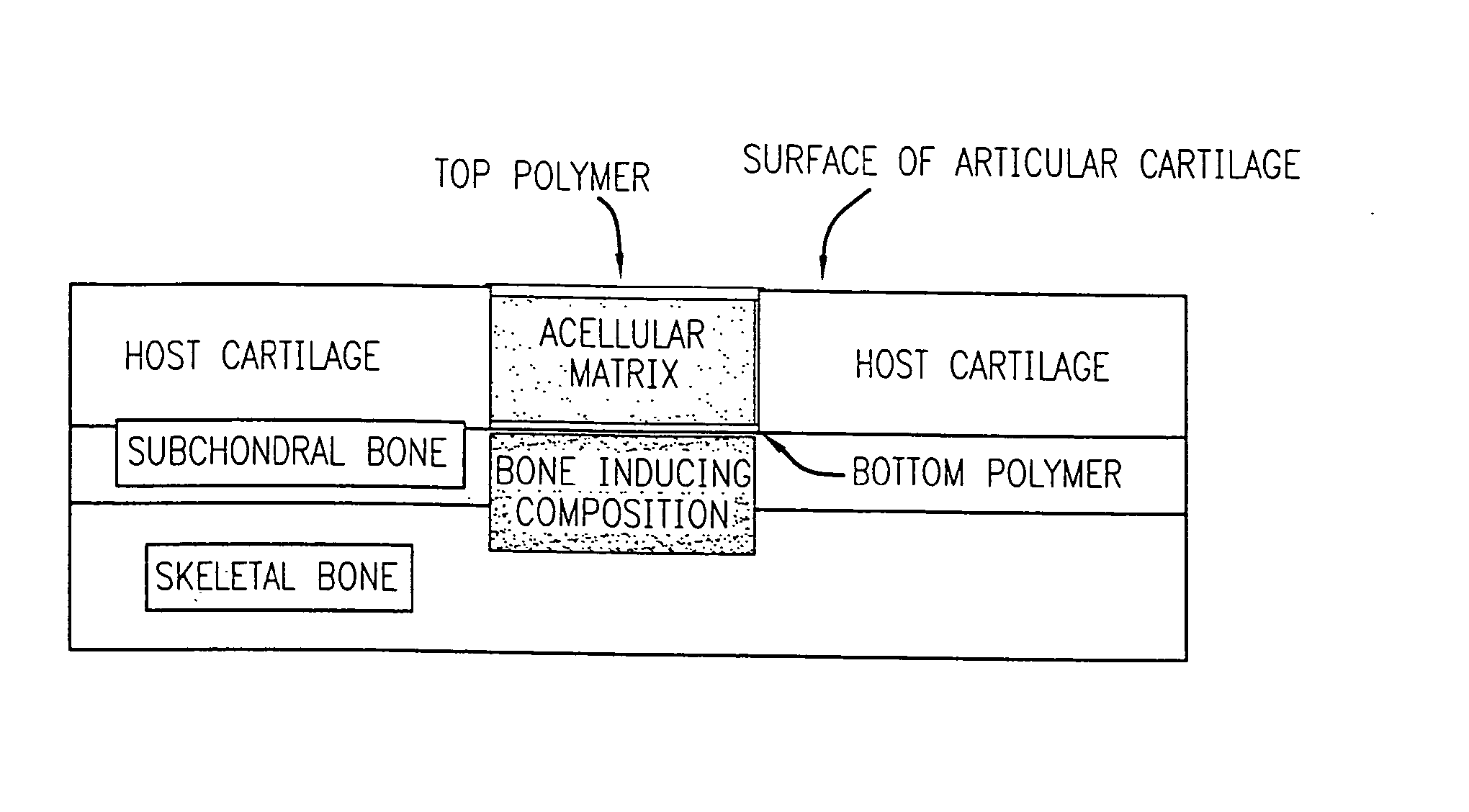
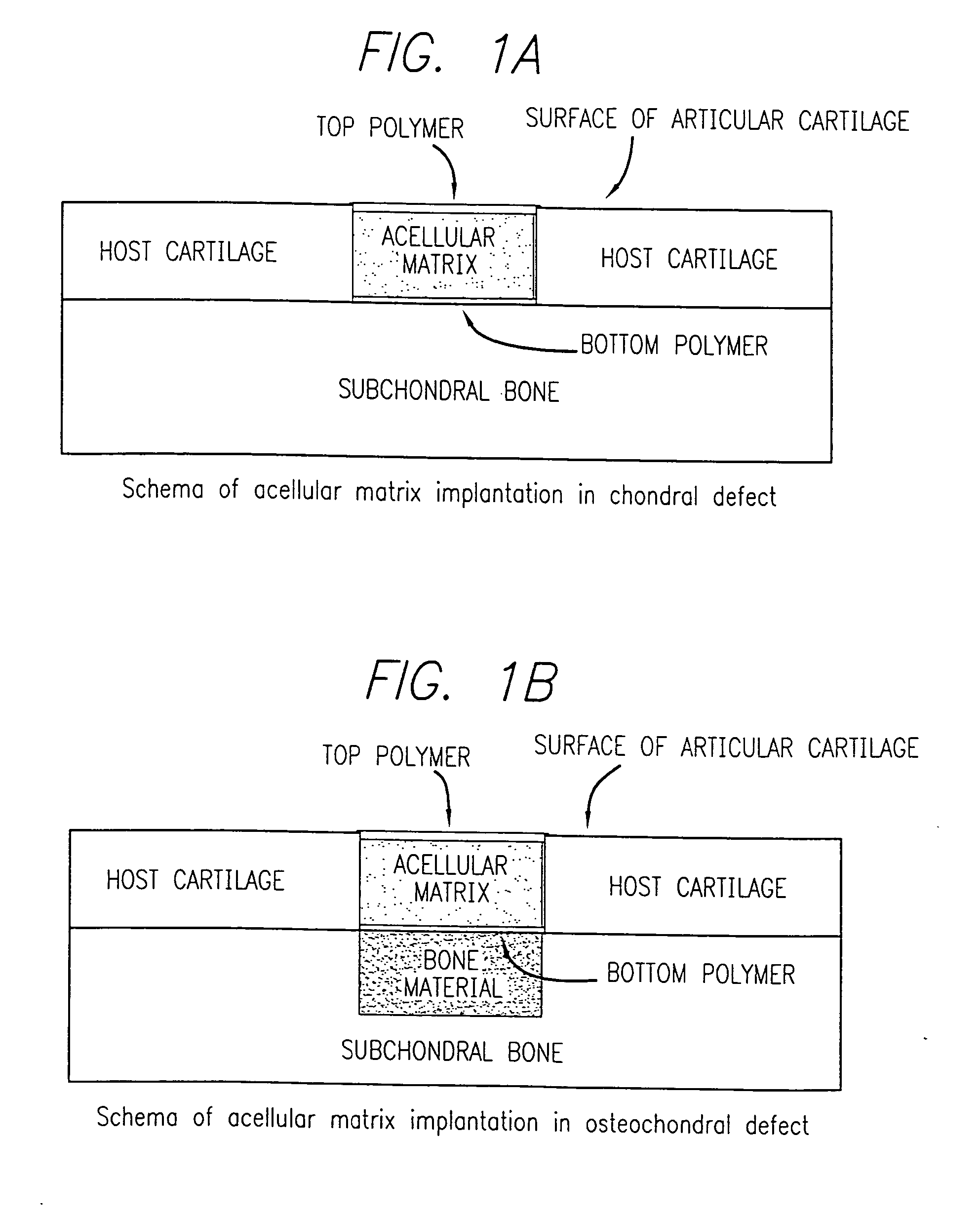
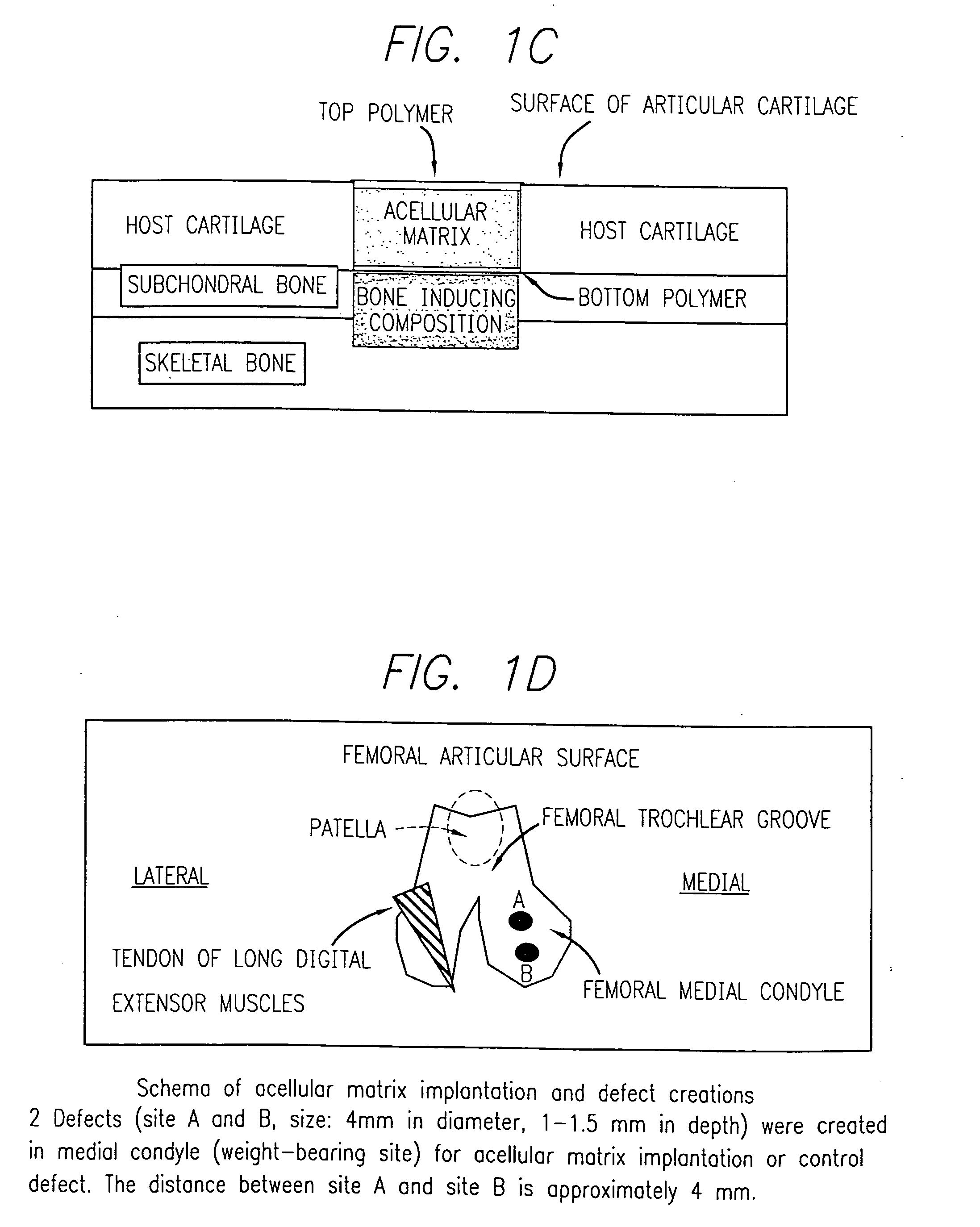
Acellular matrix implanted into an articular cartilage or osteochondral lesion protected with a biodegradable polymer modified to have extended polymerization time and methods for preparation and use thereof
Acellular matrix implants for implantation into an articular cartilage or osteochondral lesion and a method for fabrication thereof. A protective biodegradable polymer barrier having extended polymerization time and a method for preparation thereof. Bone-inducing compositions. A method for treatment of articular cartilage or osteochondral injuries.
Owner:HISTOGENICS
Methods, devices, and systems for unobtrusive mobile device user recognition
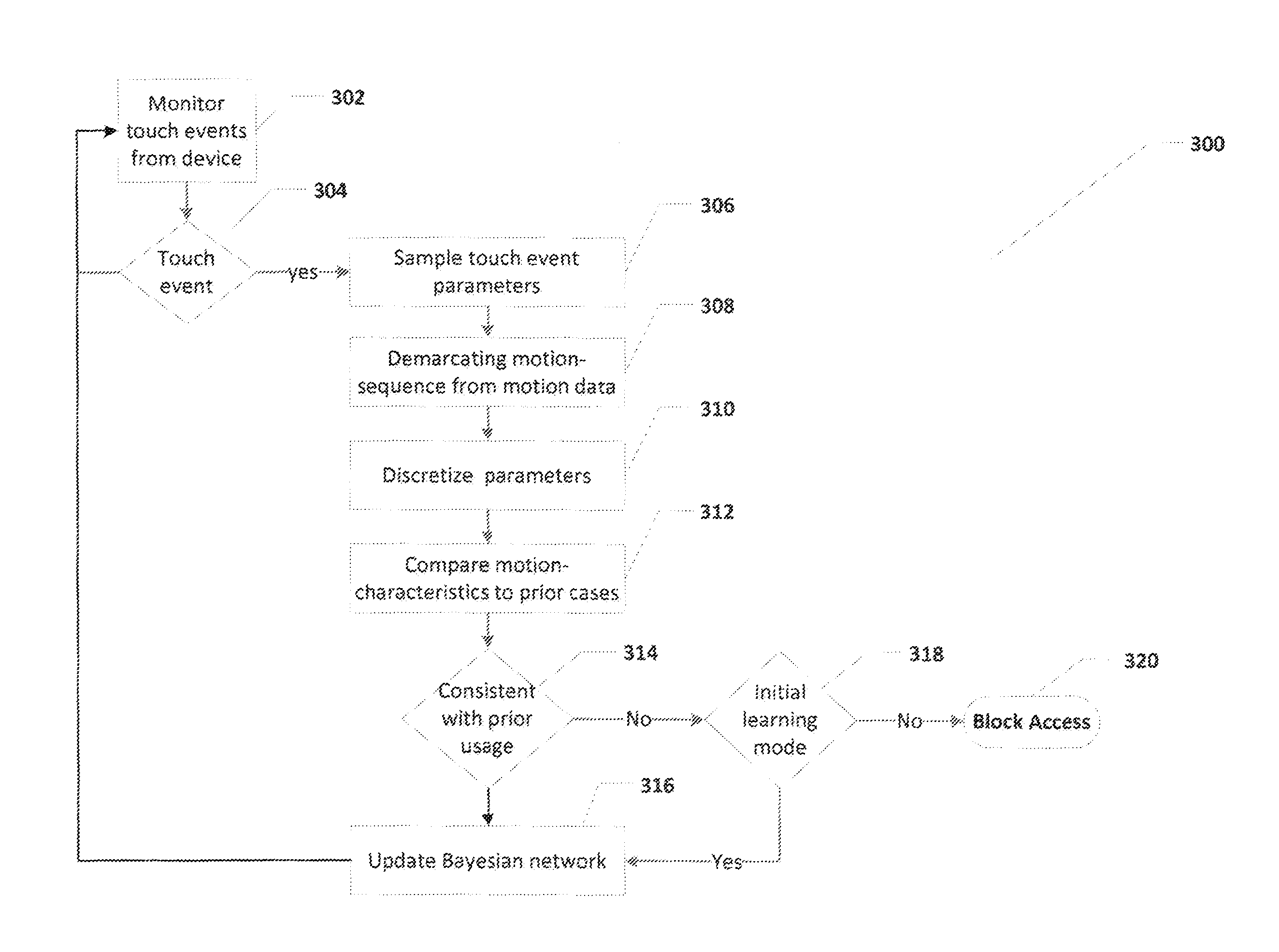
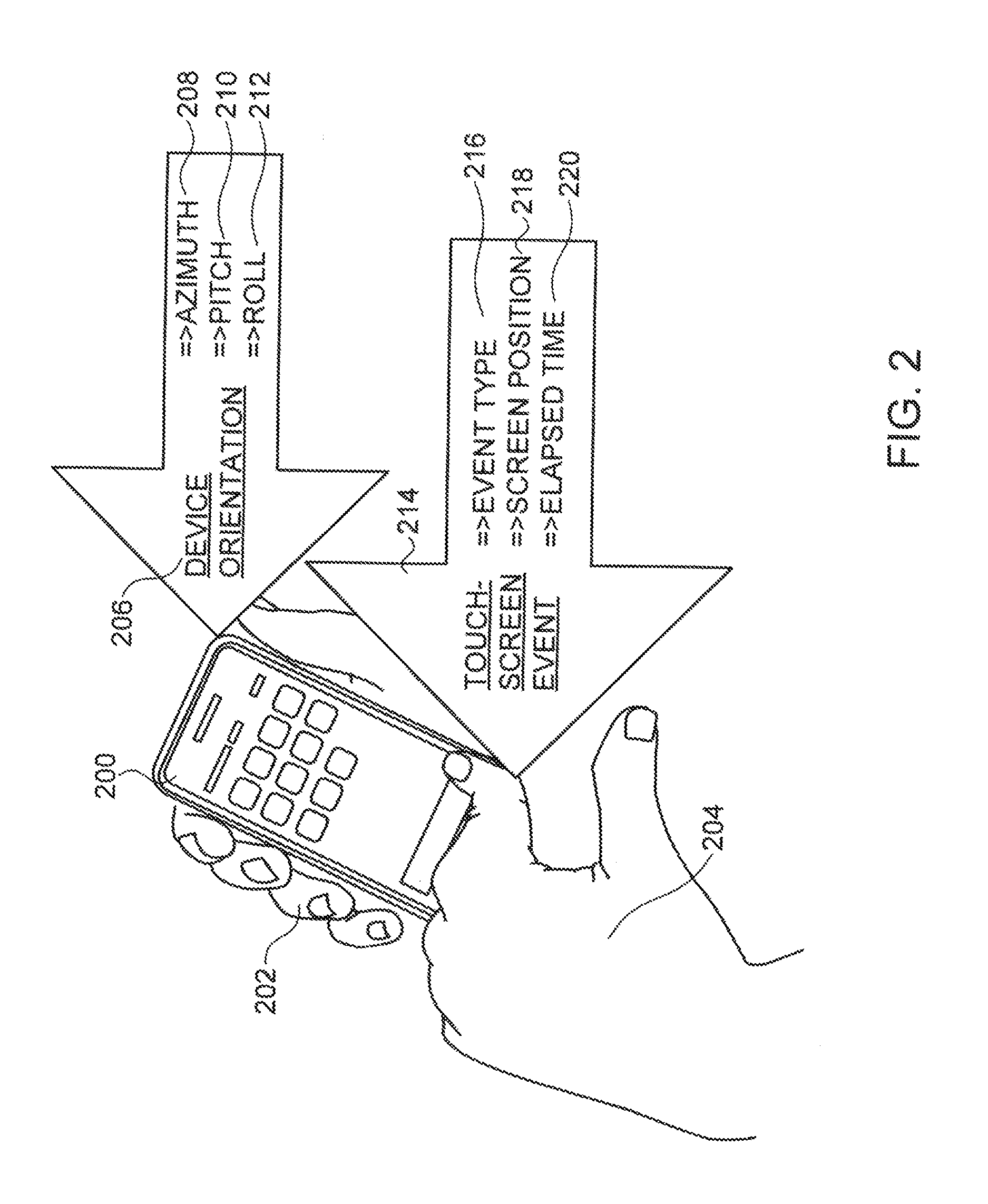
ActiveUS20130191908A1Improve performanceMaximize accuracyError detection/correctionDigital data processing detailsMobile deviceDevice Usage
The present invention discloses methods, devices, and systems for unobtrusively recognizing a user of a mobile device. Methods including the steps of: unobtrusively collecting motion data from the mobile device during normal device usage by monitoring standard authorized-user interaction with the device, without any form of challenge or device-specified action; demarcating the motion data into user motion-sequences based on changes in a motion-state or an elapsed time-period without an occurrence of the changes, wherein the motion-state refers to a placement and speed of the mobile device at a point in time; calculating user motion-characteristics from the user motion-sequences; and generating a motion-repertoire from the user motion-characteristics, whereby the motion-repertoire enables unobtrusive recognition of the user. Preferably, the method further includes the step of: detecting unidentified motion-characteristics that are not associated with the motion-repertoire, thereby enabling unobtrusive recognition of unidentified usage.
Owner:SEAL MOBILE ID
Methods and systems for repairing applications
ActiveUS20060195745A1Improve usabilityEasy to useElectronic circuit testingNon-redundant fault processingCore dumpSoftware failure
In accordance with the present invention, computer implemented methods and systems are provided that allow an application to automatically recover from software failures and attacks. Using one or more sensors, failures may be detected in the application. In response to detecting the failure, the portion of the application's code that caused the failure is isolated. Using the input vectors that caused the failure, information regarding the failure (e.g., the type of failure), a core dump file (e.g., stack trace), etc., an emulator-based vaccine that repairs the failure is constructed. In response to verifying that the vaccine repaired the failure, the application is automatically updated with the emulator-based vaccine without user intervention. Application community features that efficiently use the resources available in software monoculture is also provided. An application community may be defined that includes a plurality of devices and the application's code may be divided into smaller portions of code, which are assigned to each of the plurality of devices for monitoring. Each device also notifies the other devices of the failure.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com