Patents
Literature
48 results about "Core dump" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
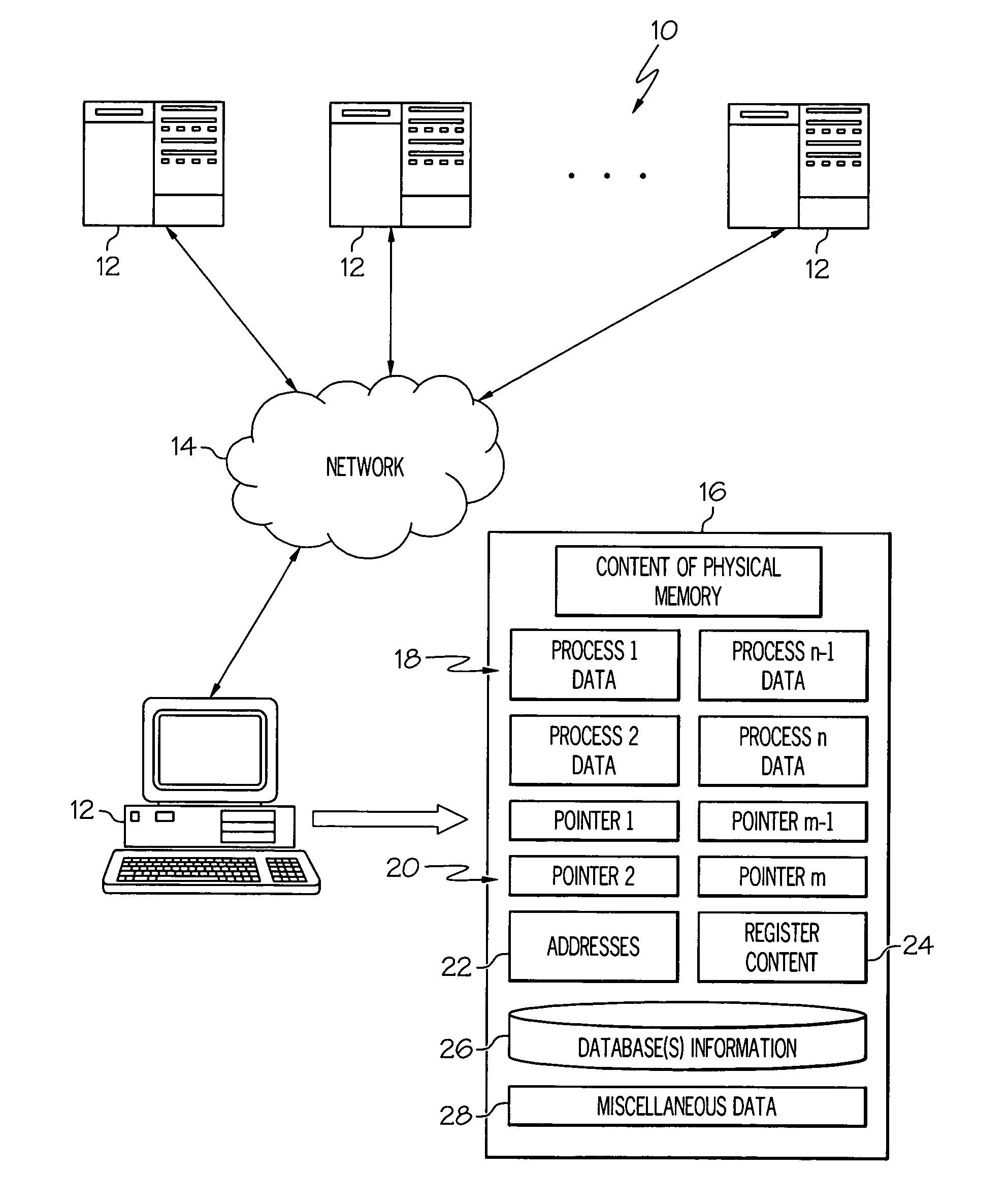
In computing, a core dump, crash dump, memory dump, or system dump consists of the recorded state of the working memory of a computer program at a specific time, generally when the program has crashed or otherwise terminated abnormally. In practice, other key pieces of program state are usually dumped at the same time, including the processor registers, which may include the program counter and stack pointer, memory management information, and other processor and operating system flags and information. A snapshot dump (or snap dump) is a memory dump requested by the computer operator or by the running program, after which the program is able to continue. Core dumps are often used to assist in diagnosing and debugging errors in computer programs.
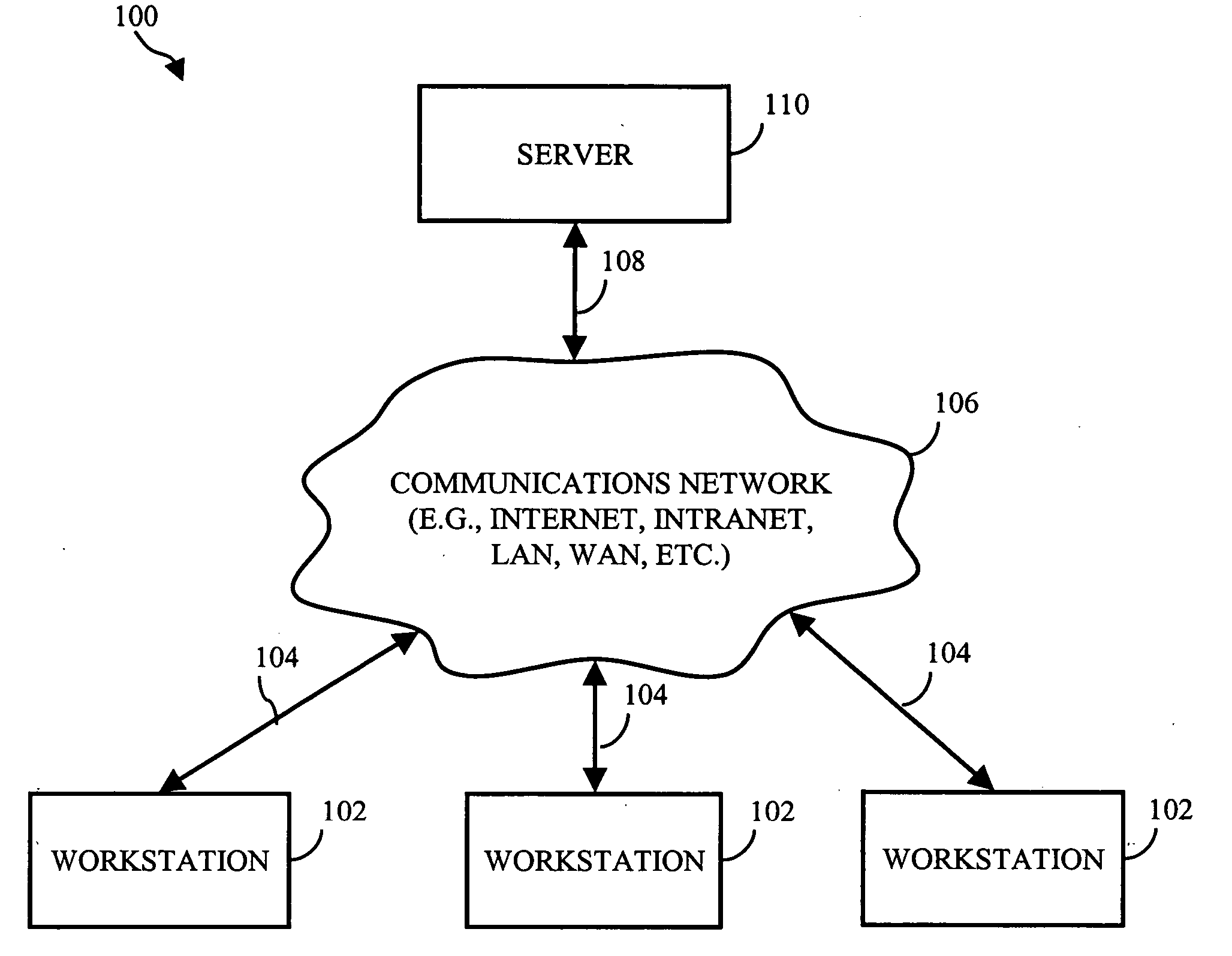
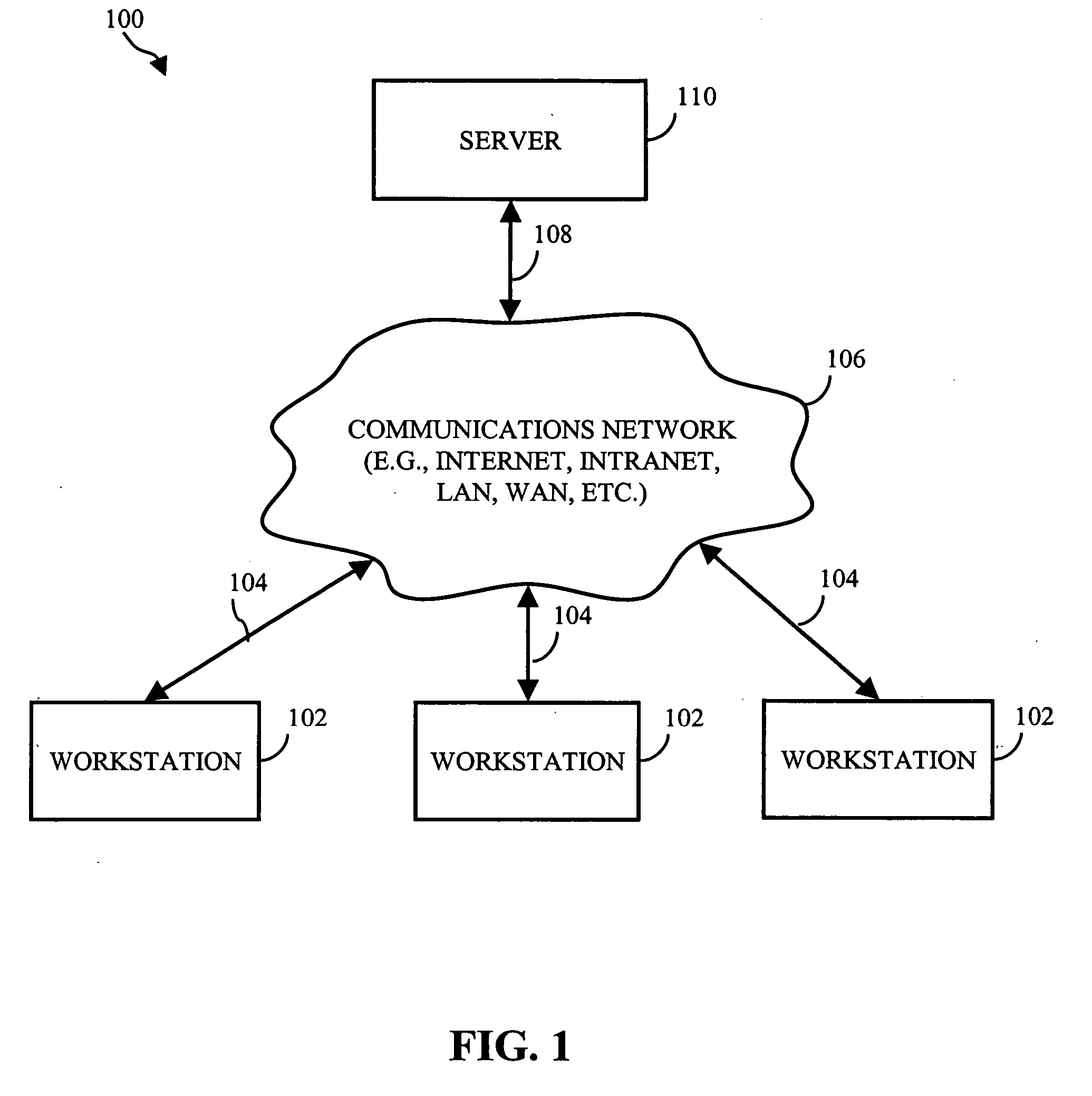
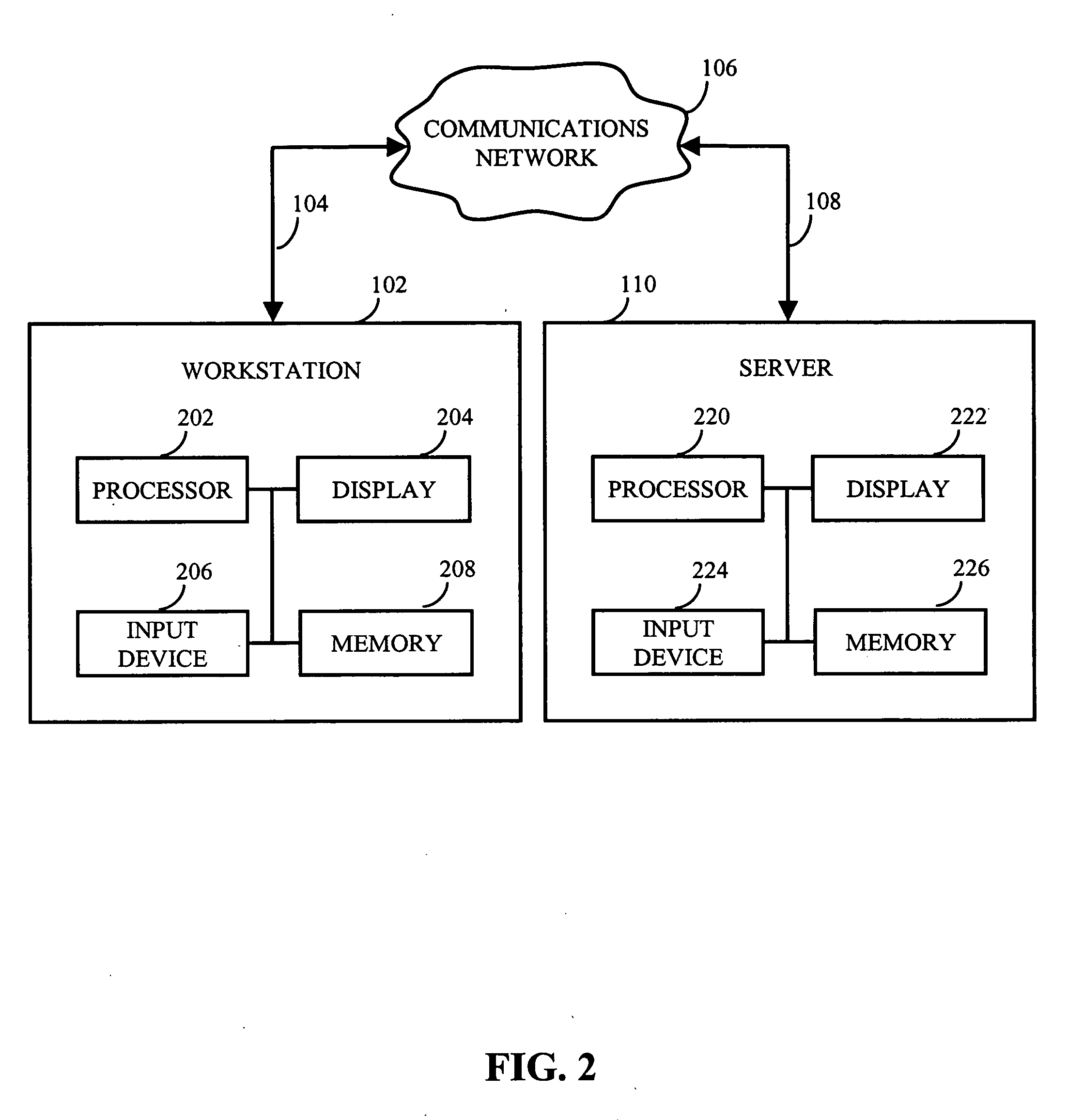
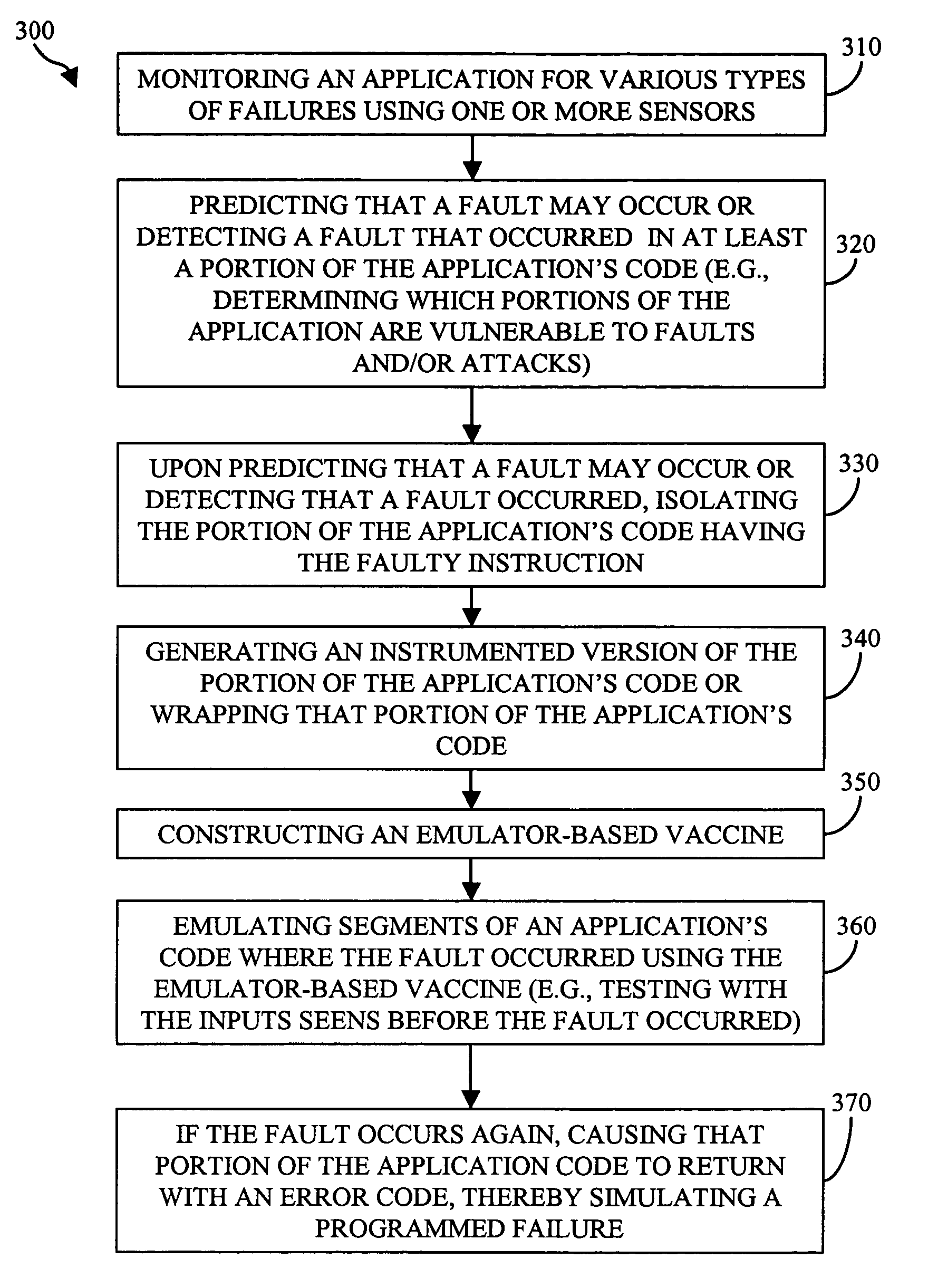
Methods and systems for repairing applications
ActiveUS20060195745A1Improve usabilityEasy to useElectronic circuit testingNon-redundant fault processingCore dumpSoftware failure
In accordance with the present invention, computer implemented methods and systems are provided that allow an application to automatically recover from software failures and attacks. Using one or more sensors, failures may be detected in the application. In response to detecting the failure, the portion of the application's code that caused the failure is isolated. Using the input vectors that caused the failure, information regarding the failure (e.g., the type of failure), a core dump file (e.g., stack trace), etc., an emulator-based vaccine that repairs the failure is constructed. In response to verifying that the vaccine repaired the failure, the application is automatically updated with the emulator-based vaccine without user intervention. Application community features that efficiently use the resources available in software monoculture is also provided. An application community may be defined that includes a plurality of devices and the application's code may be divided into smaller portions of code, which are assigned to each of the plurality of devices for monitoring. Each device also notifies the other devices of the failure.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
Methods and systems for repairing applications
ActiveUS7490268B2Easy to useProvide protectionNon-redundant fault processingPlatform integrity maintainanceCore dumpSoftware failure
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
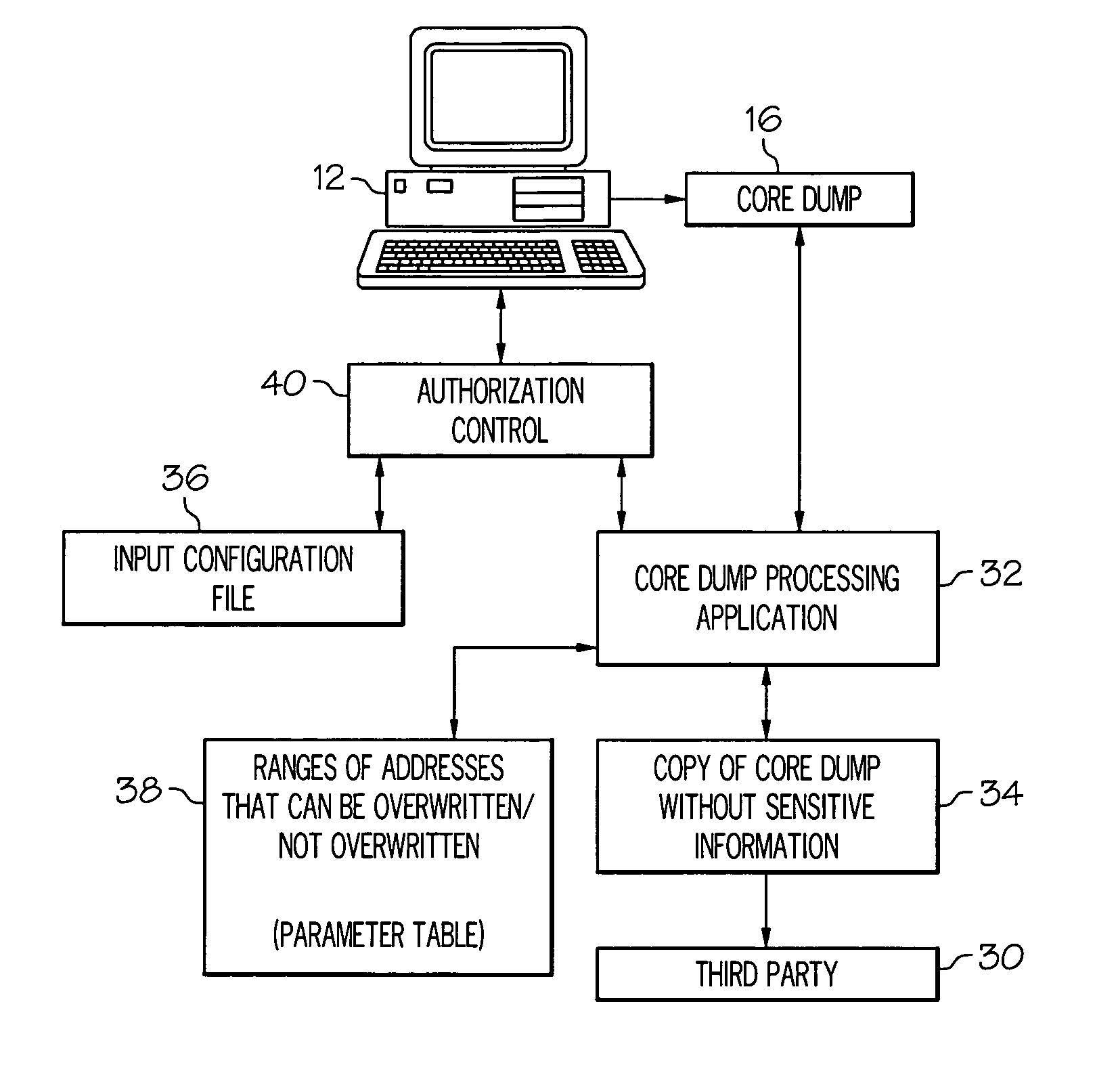
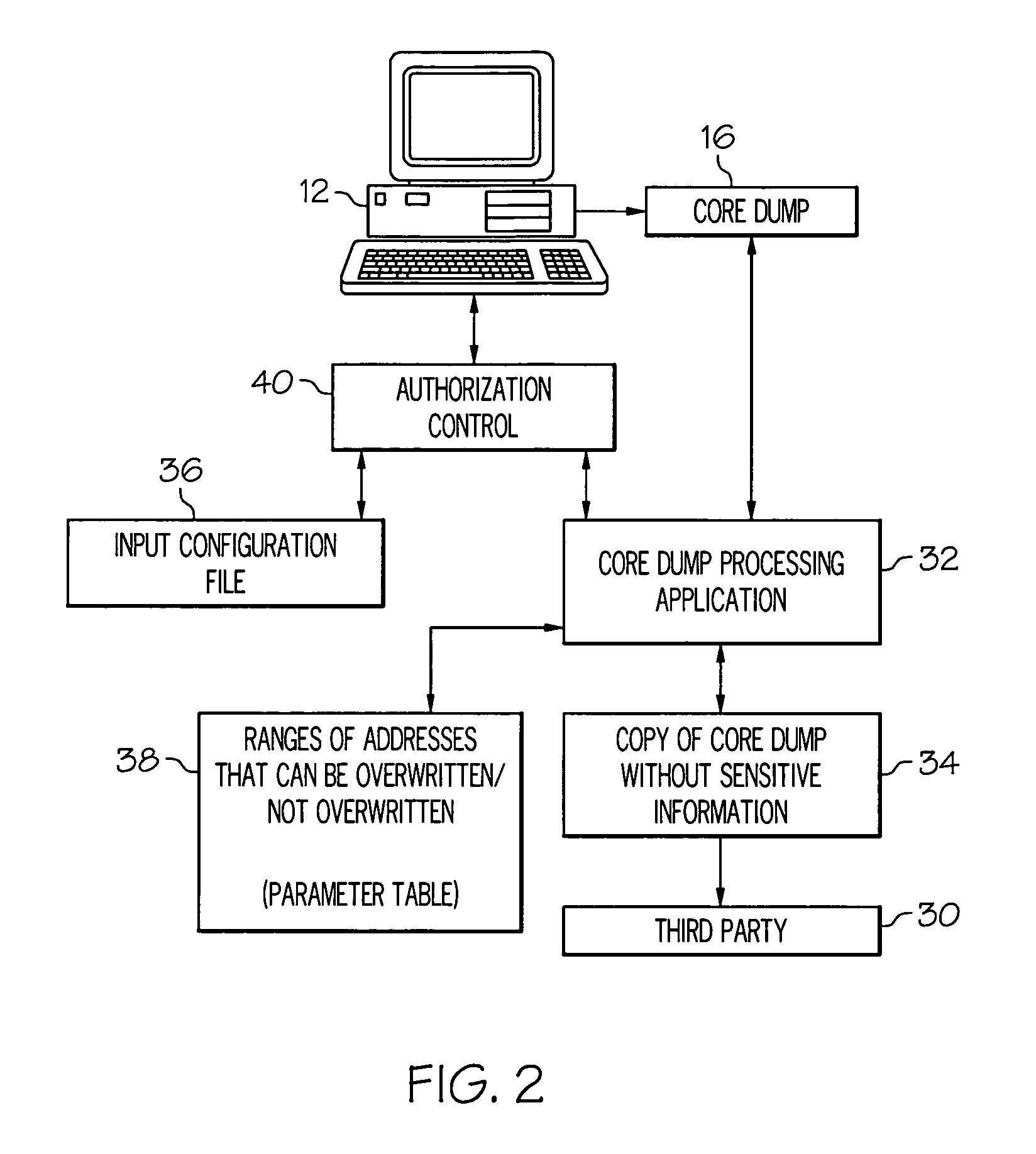
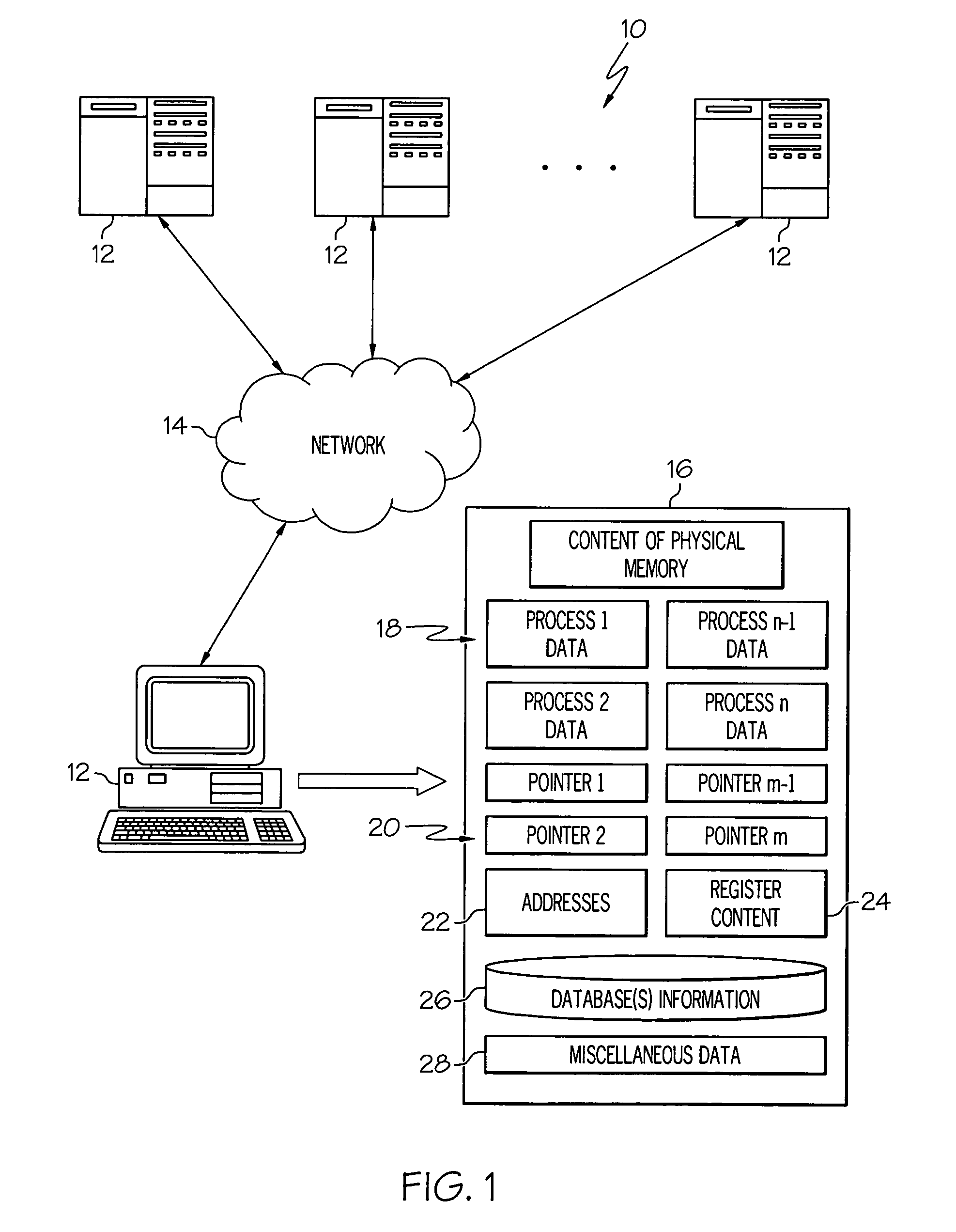
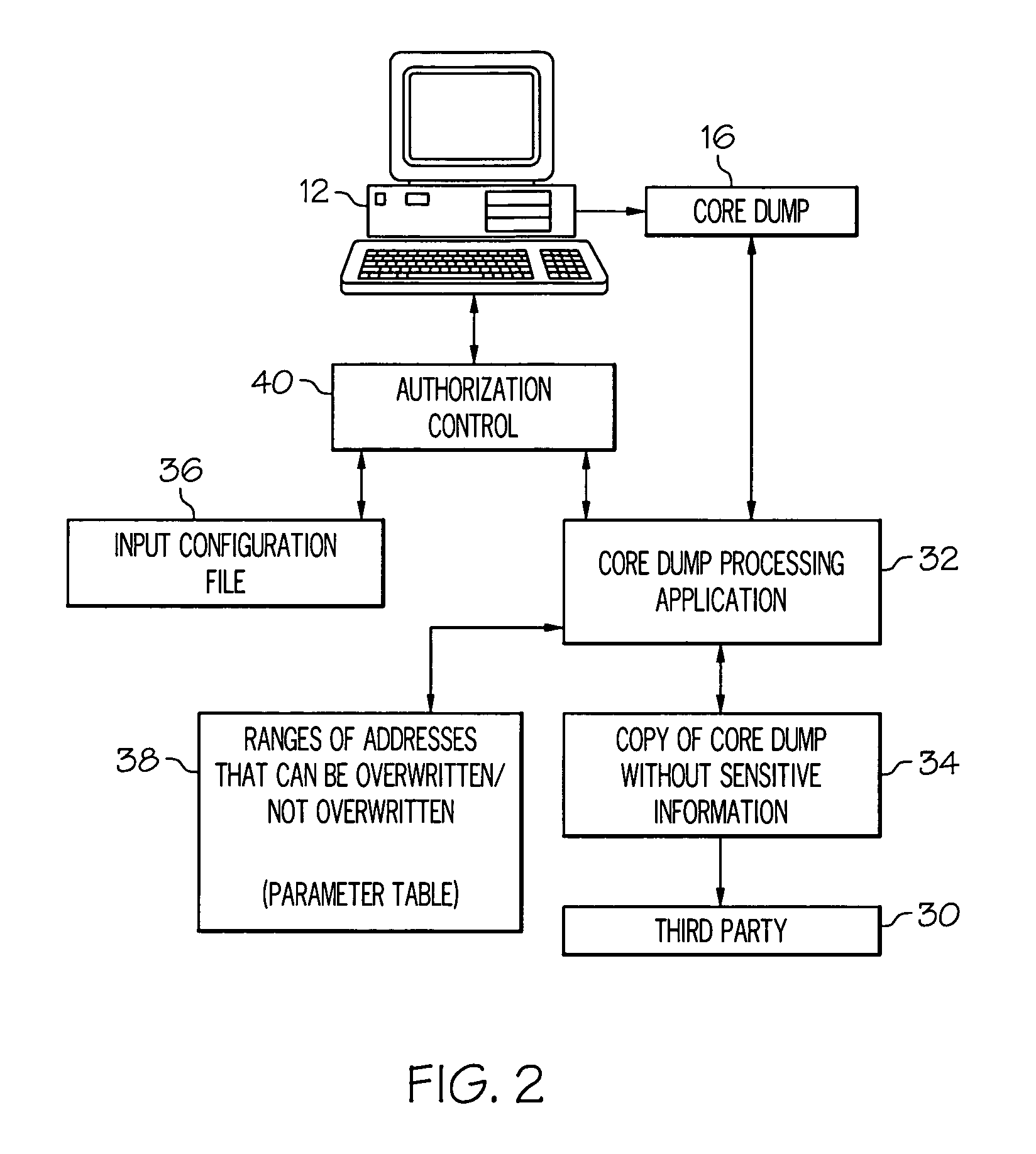
Locating and altering sensitive information in core dumps
ActiveUS20080126301A1Error detection/correctionSpecial data processing applicationsCore dumpProcessing core
A core dump is processed to locate and optionally alter sensitive information. A core dump copy is created from at least a portion of an original core dump. Also, at least one input parameter is provided that corresponds to select information to be identified in the core dump copy and address information associated with the core dump copy is defined that corresponds to at least one of addresses where the select information can be altered and addresses where the select information should not be altered. Each occurrence of the select information located within the core dump copy is identified and optionally replaced with predetermined replacement data if the occurrence of the select information is within the addresses where the select information can be altered.
Owner:IBM CORP
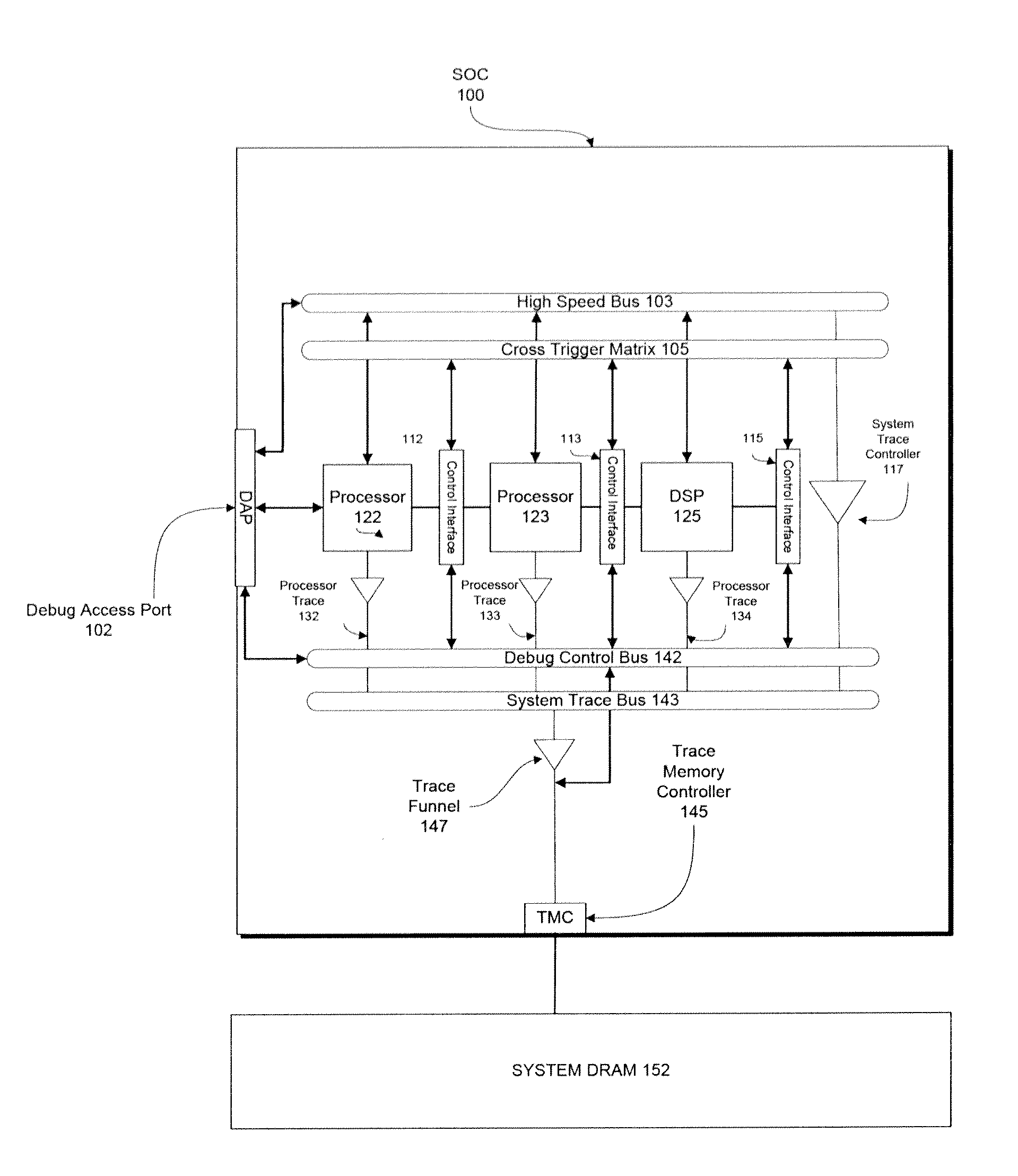
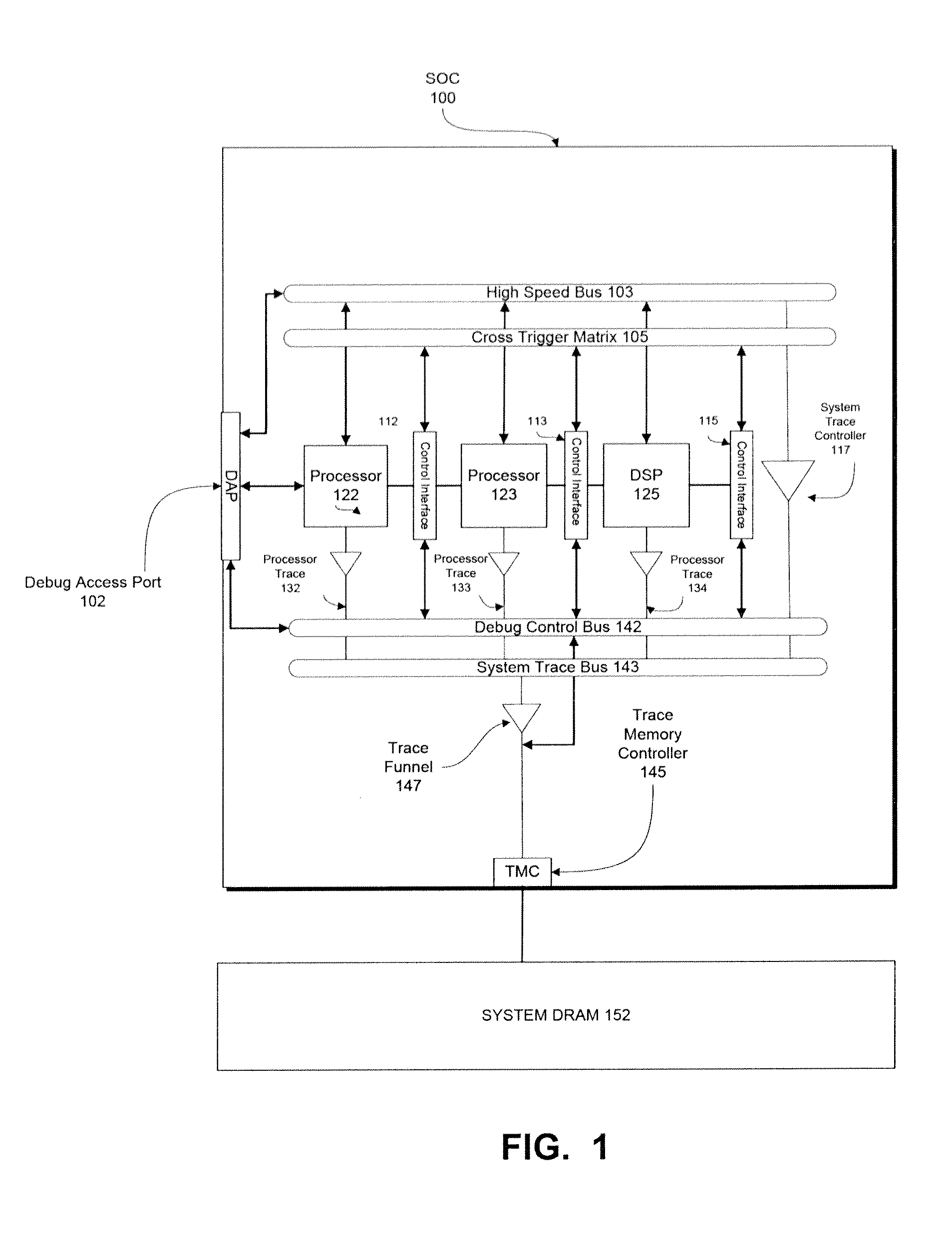
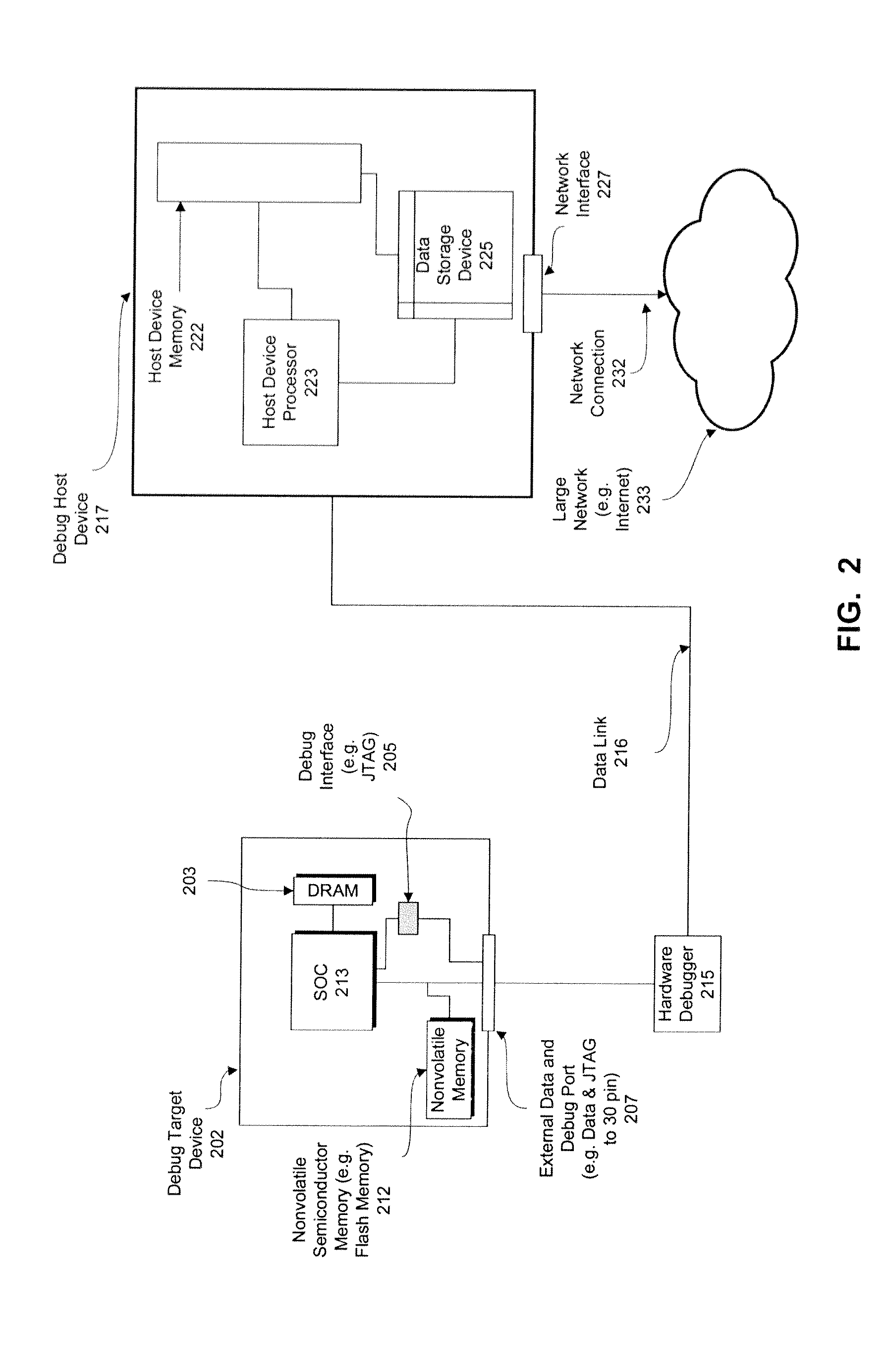
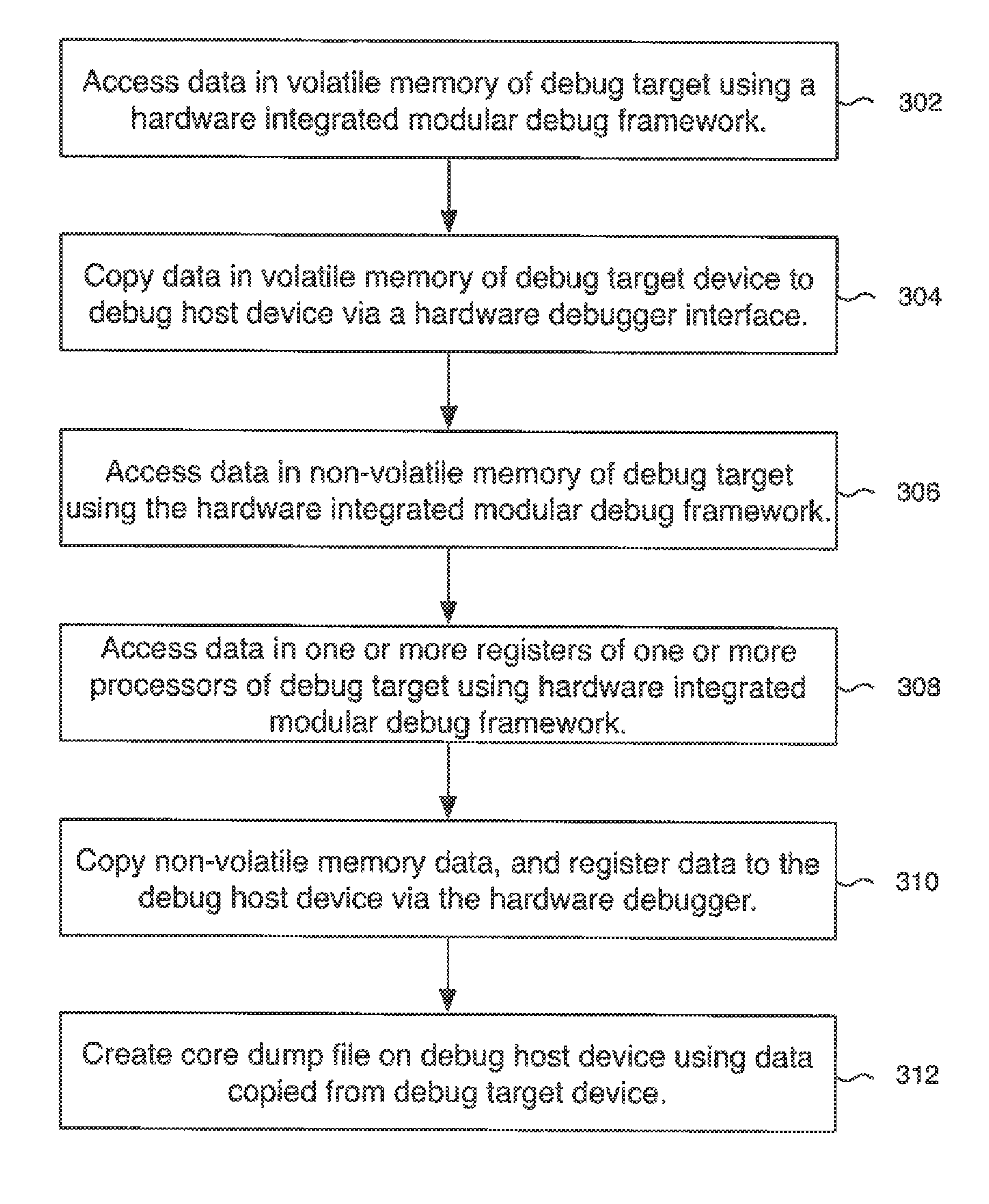
Enhanced debugging for embedded devices
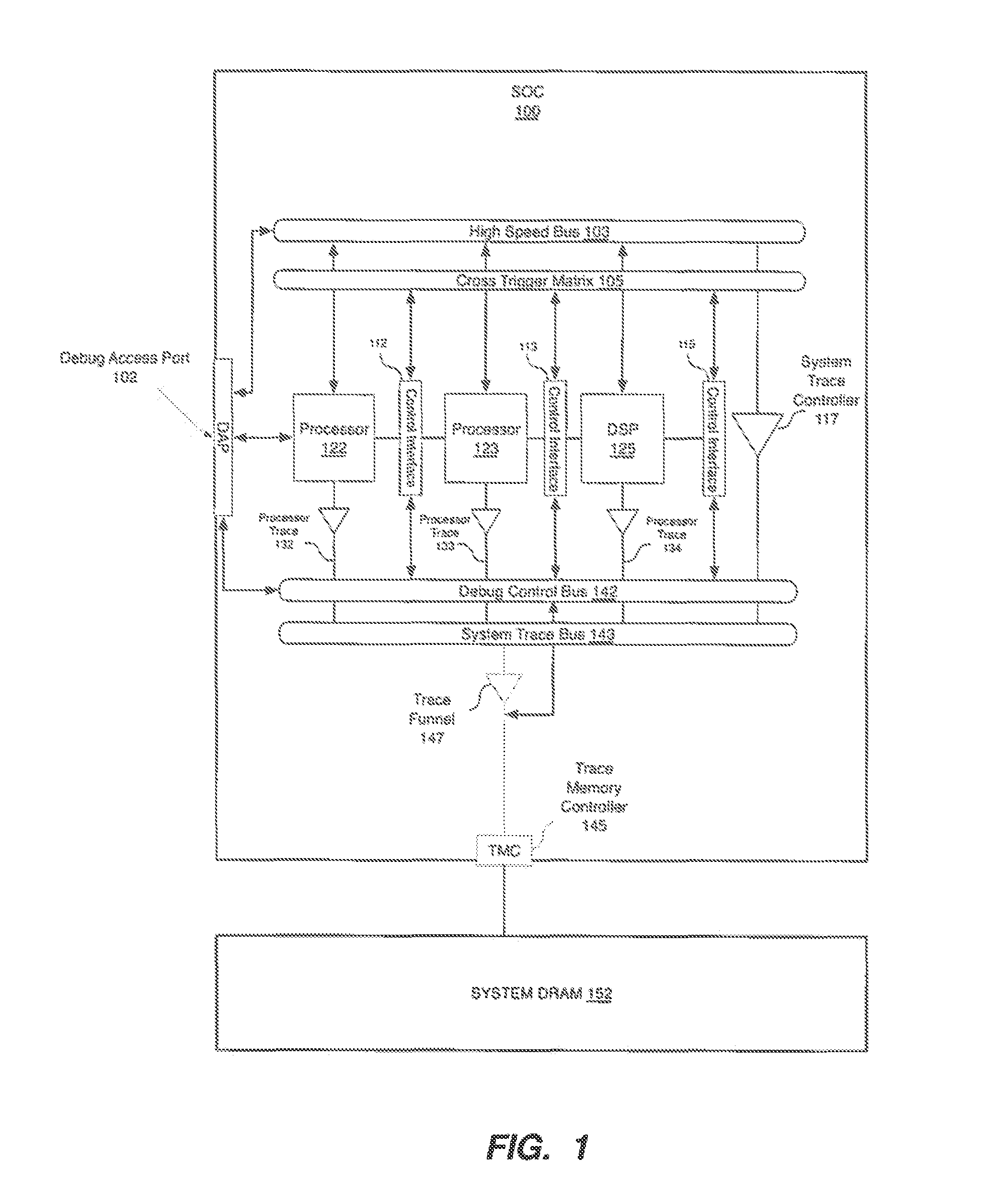
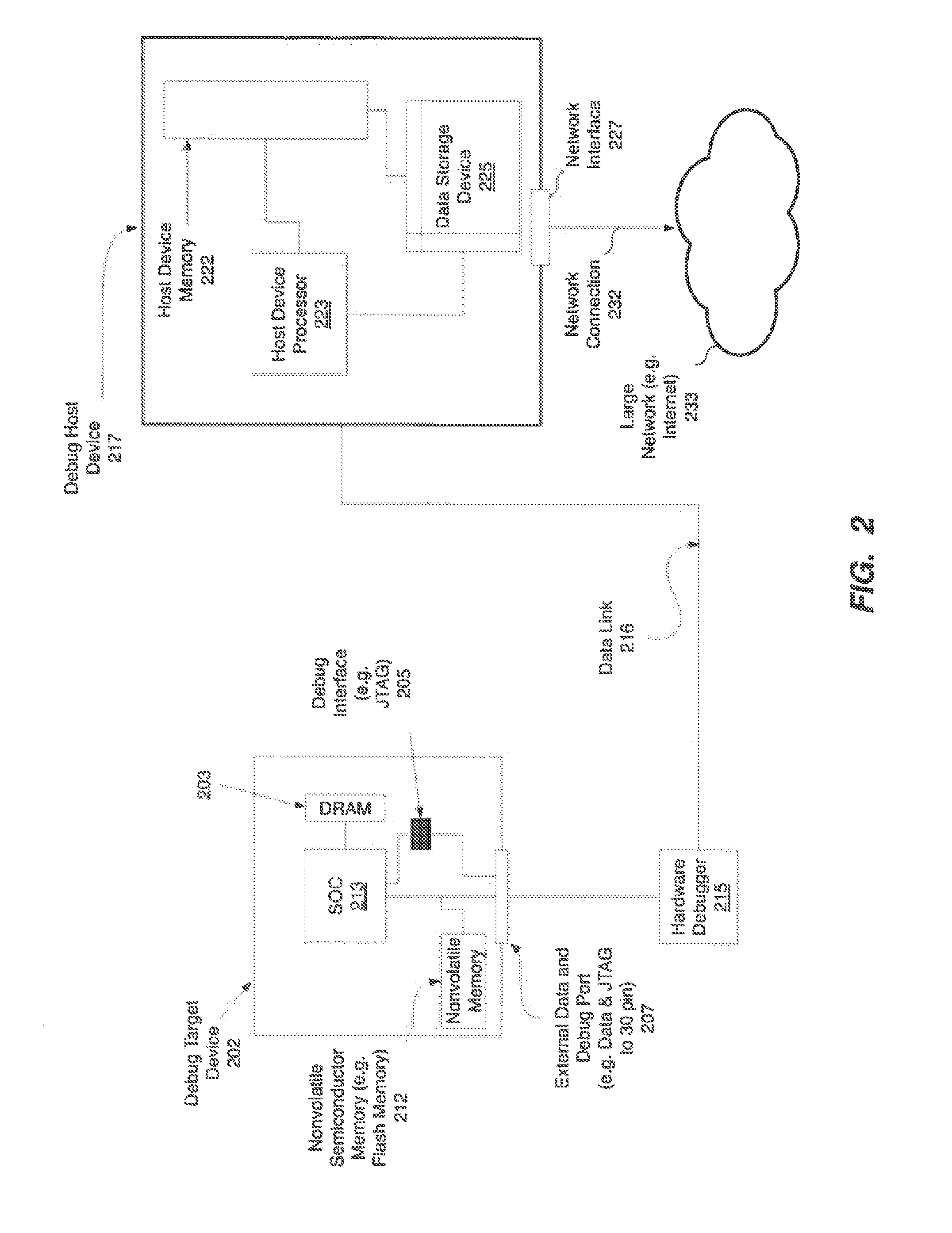
Methods, machine-readable tangible storage media, and data processing systems that enable a debug host device to acquire memory dump information from a debug target device after the target device suffers an unrecoverable system malfunction are disclosed. In one embodiment, data in the volatile memory on a debug target device is accessed via a hardware integrated debug framework, which is also used to access data on a nonvolatile electronically erasable semiconductor memory of a debug target device, and one or more registers of one or more processors on a debug target device, and a core dump is created on the debug host device.
Owner:APPLE INC
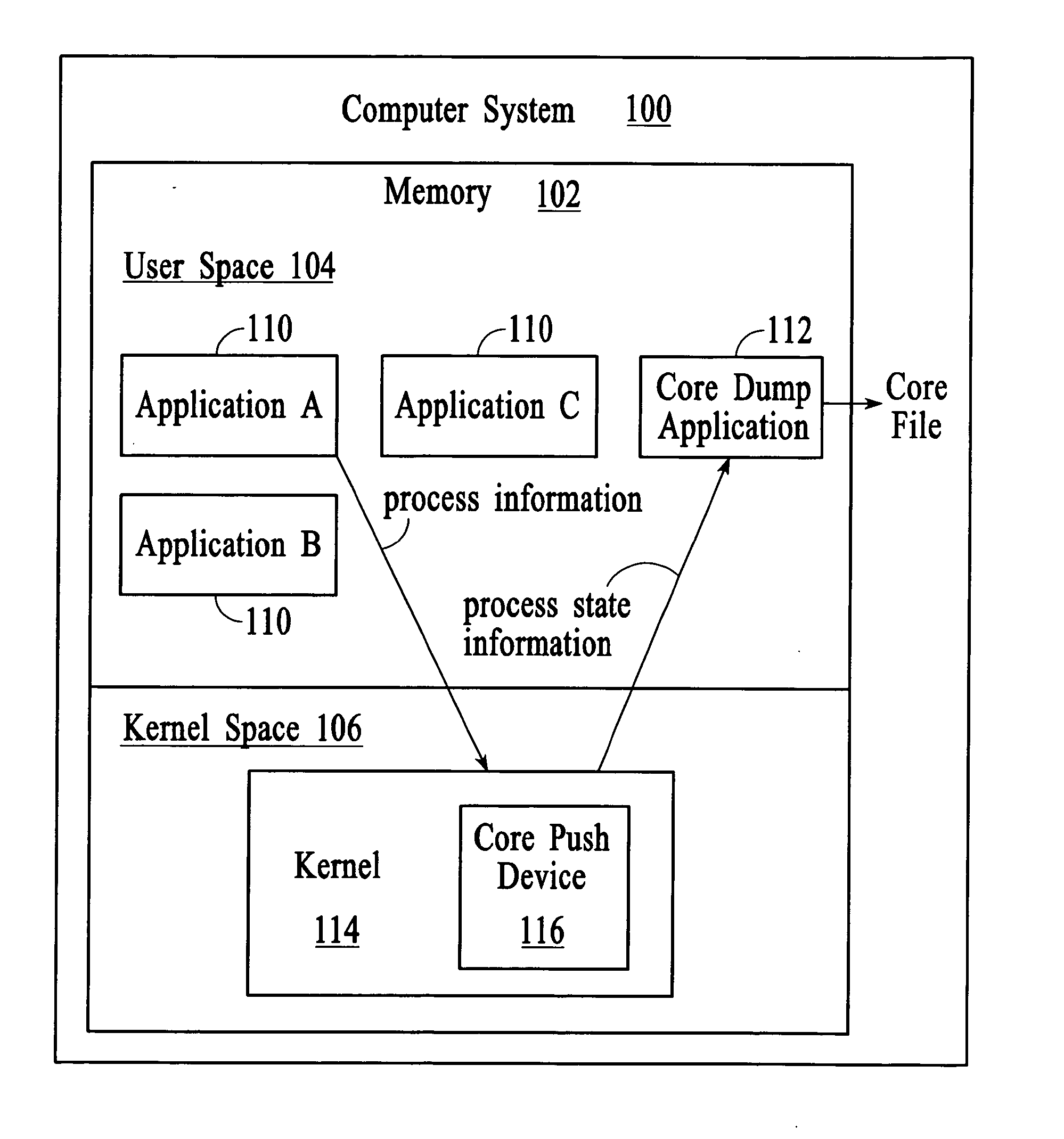
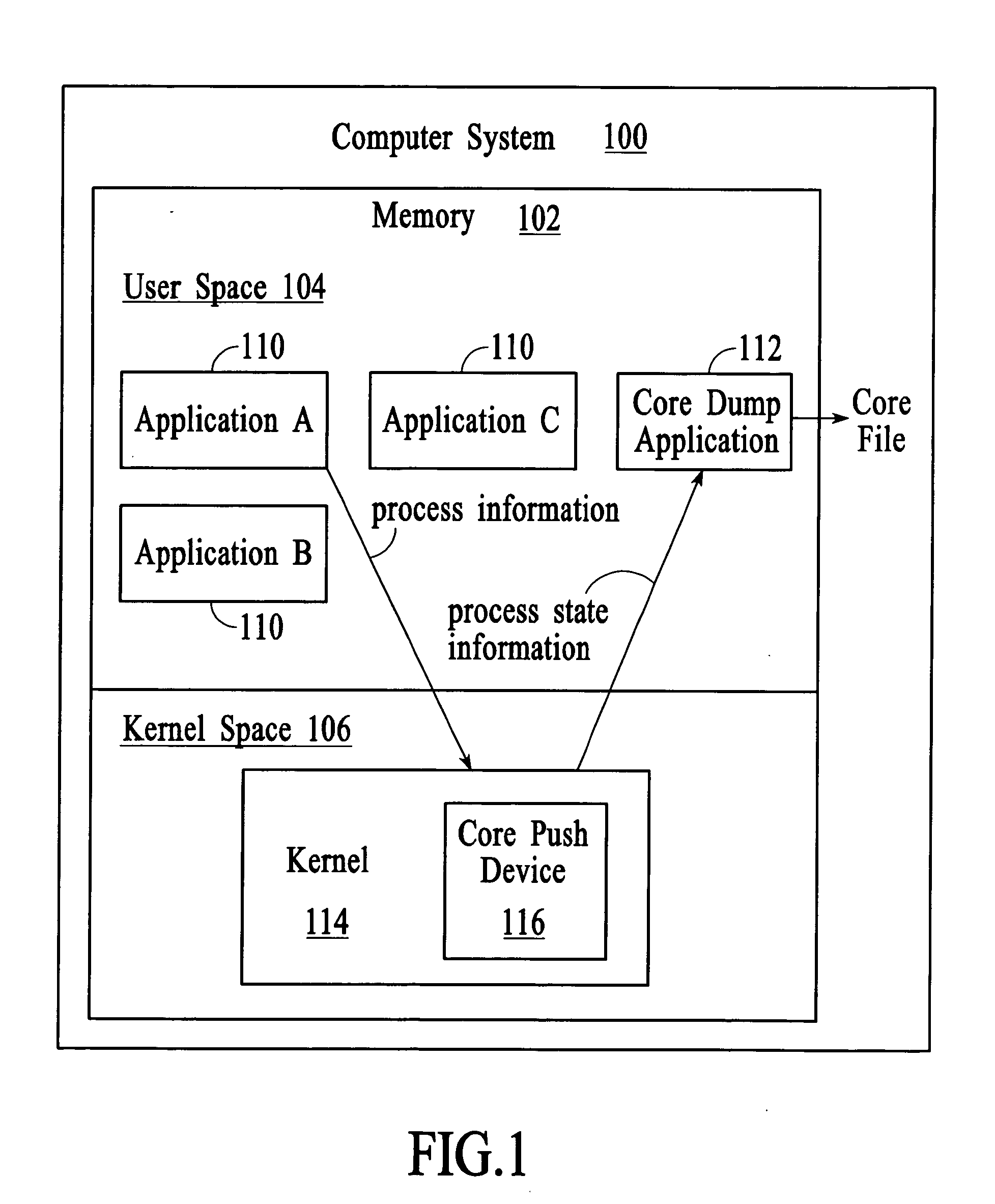
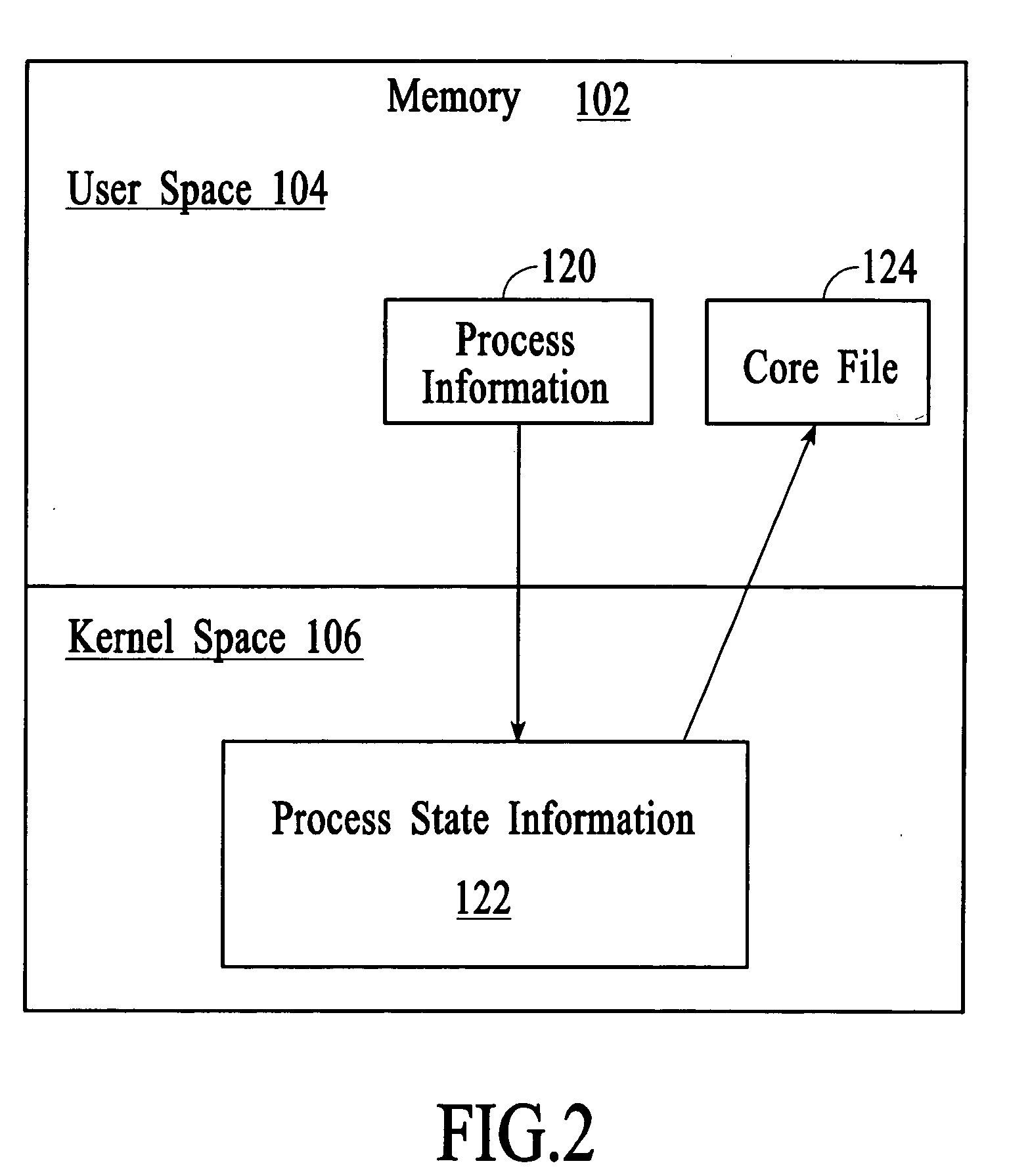
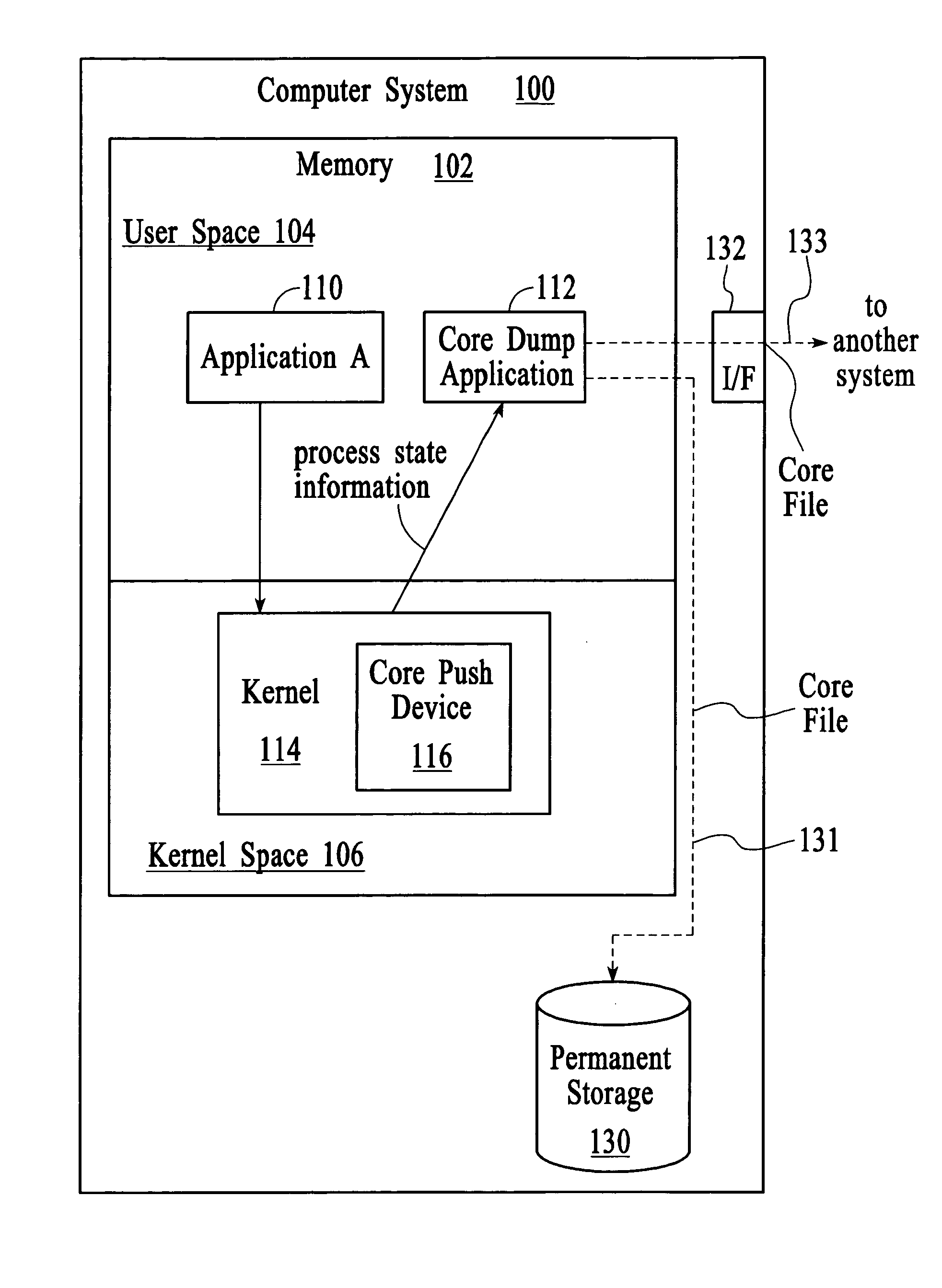
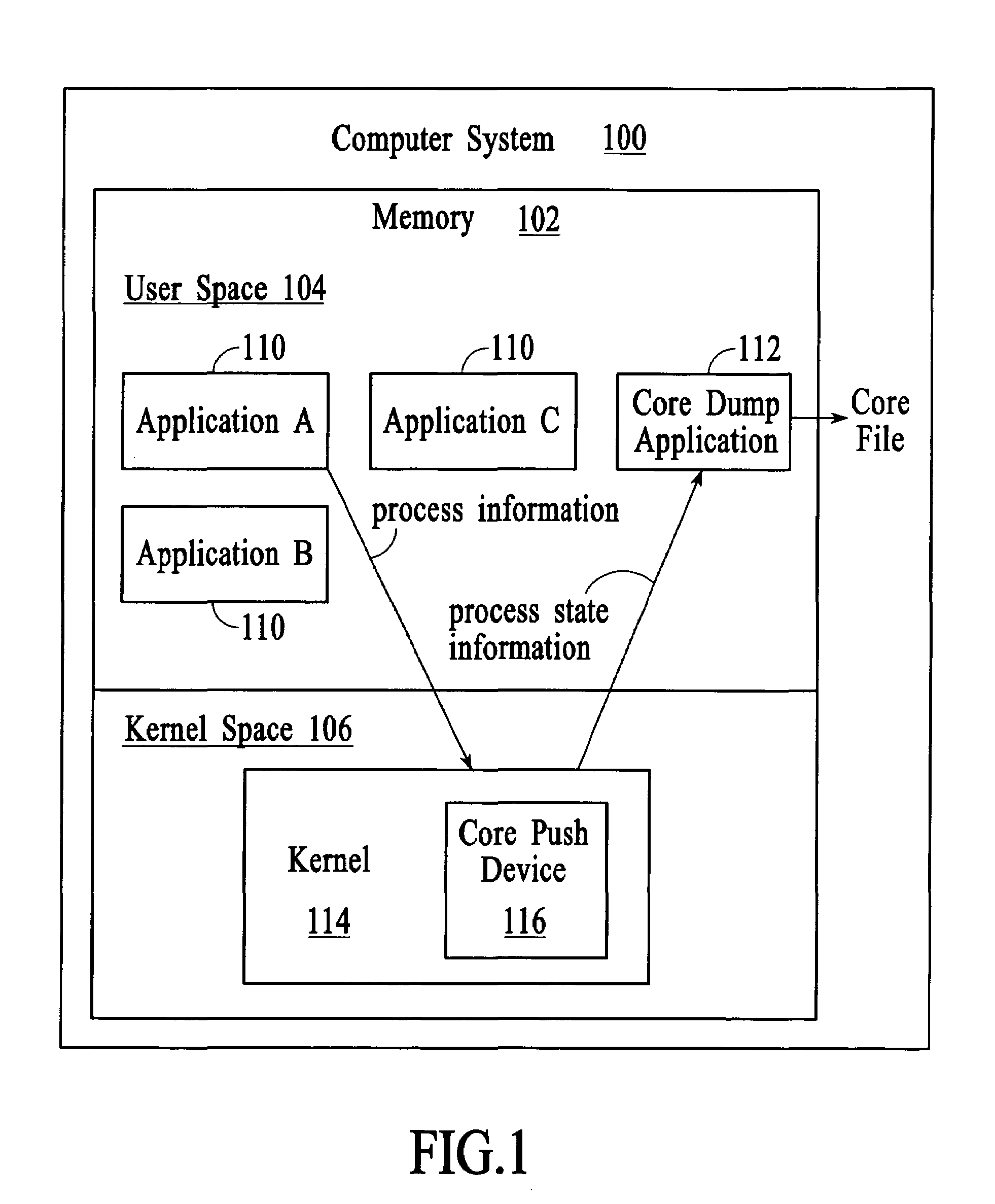
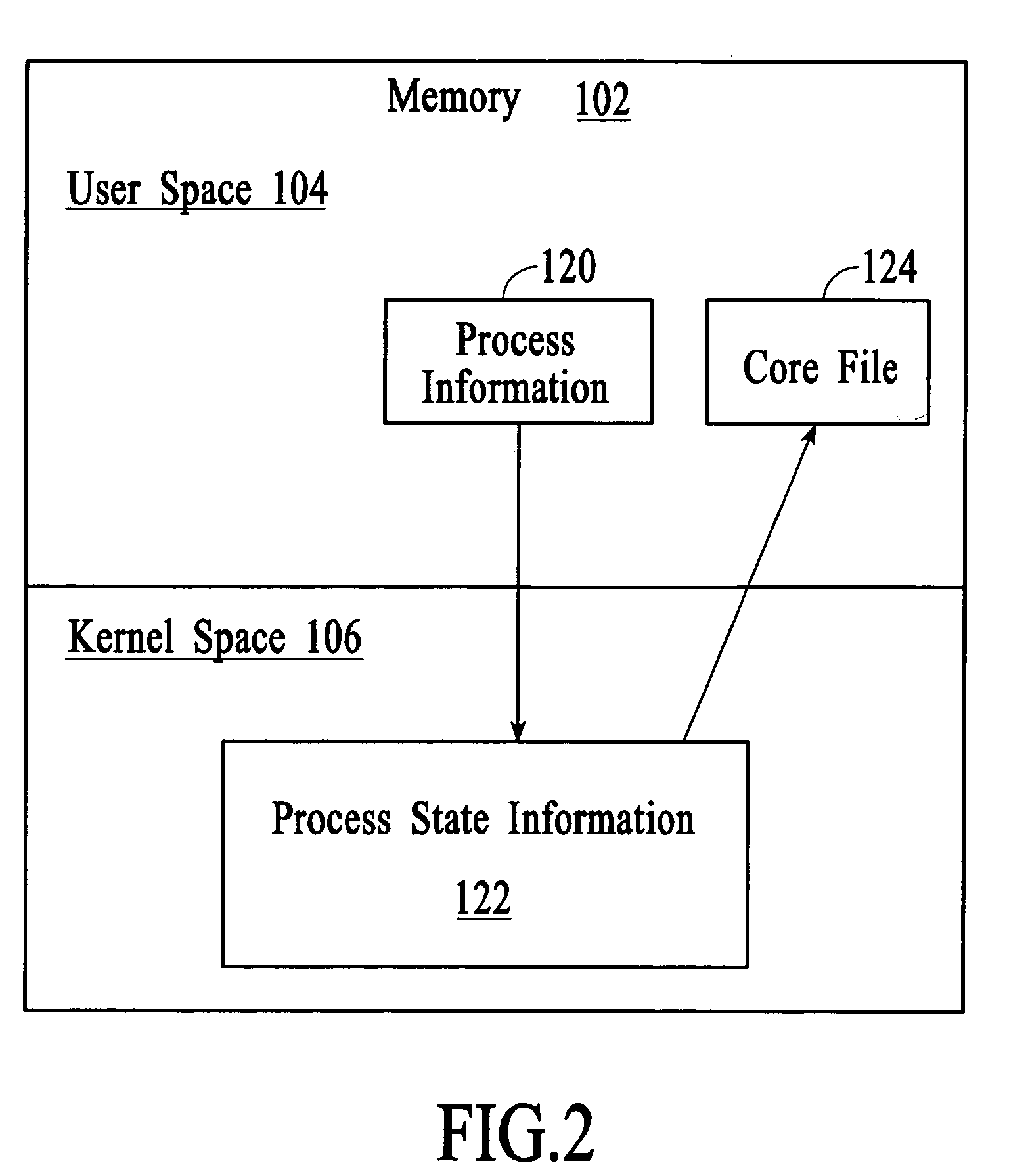
Managing process state information in an operating system environment
InactiveUS20050210077A1Excessively generatedNon-redundant fault processingProgram controlCore dumpOperational system
A technique for managing process state information involves pushing process state information from the kernel space to the user space in the event of an application crash and generating a core file at the user level instead of at the kernel level. Handling the process state information at the user level instead of at the kernel level provides more flexibility in the generation and management of a core file as compared to systems that use kernel code to generate and manage the core file. A core dump application at the user level can be programmed to forward the core file to another system that has permanent storage capacity available. Additionally, the core dump application can be programmed to compress the process state information and / or to extract only certain information from the process state information while generating the core file.
Owner:LUCENT TECH INC
Enhanced debugging for embedded devices
Methods, machine-readable tangible storage media, and data processing systems that enable a debug host device to acquire memory dump information from a debug target device after the target device suffers an unrecoverable system malfunction are disclosed. In one embodiment, data in the volatile memory on a debug target device is accessed via a hardware integrated debug framework, which is also used to access data on a nonvolatile electronically erasable semiconductor memory of a debug target device, and one or more registers of one or more processors on a debug target device, and a core dump is created on the debug host device.
Owner:APPLE INC
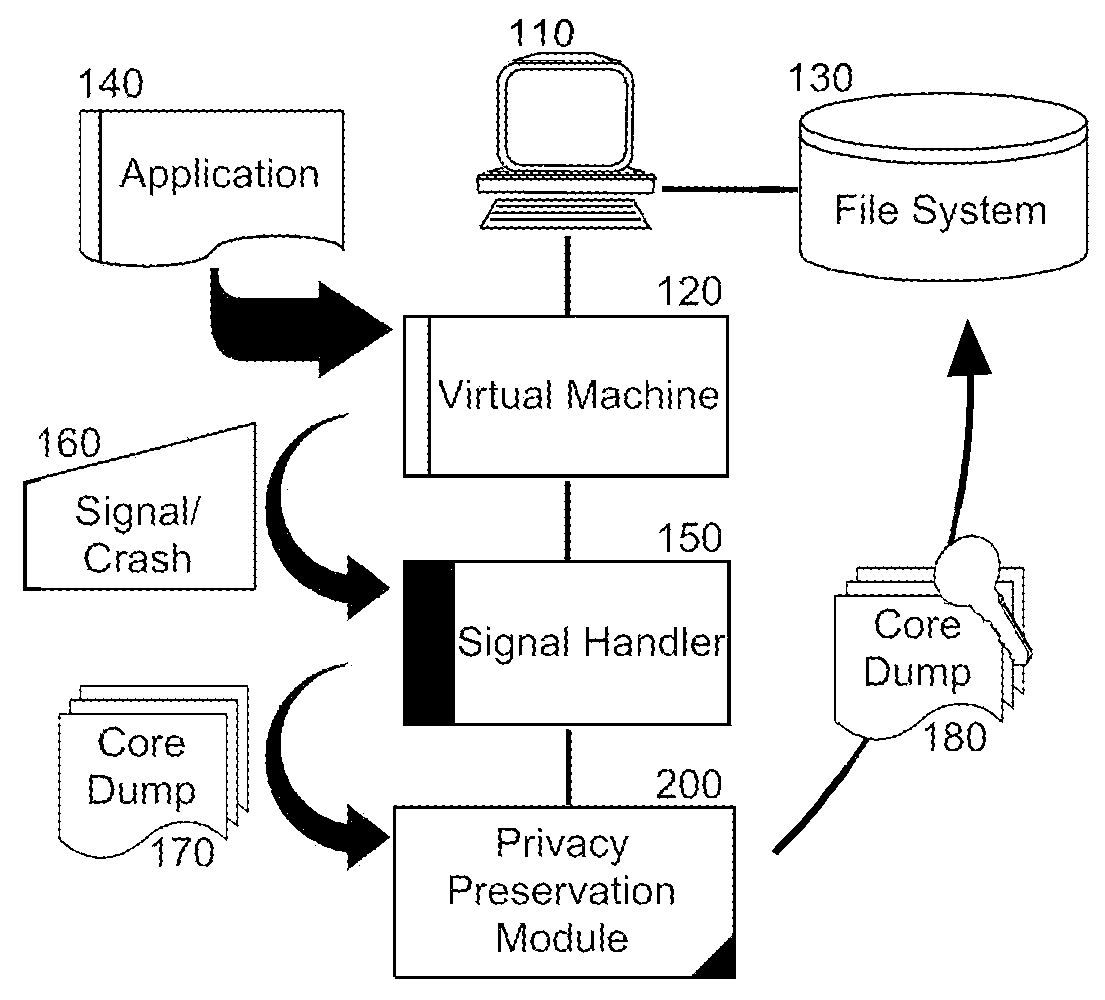
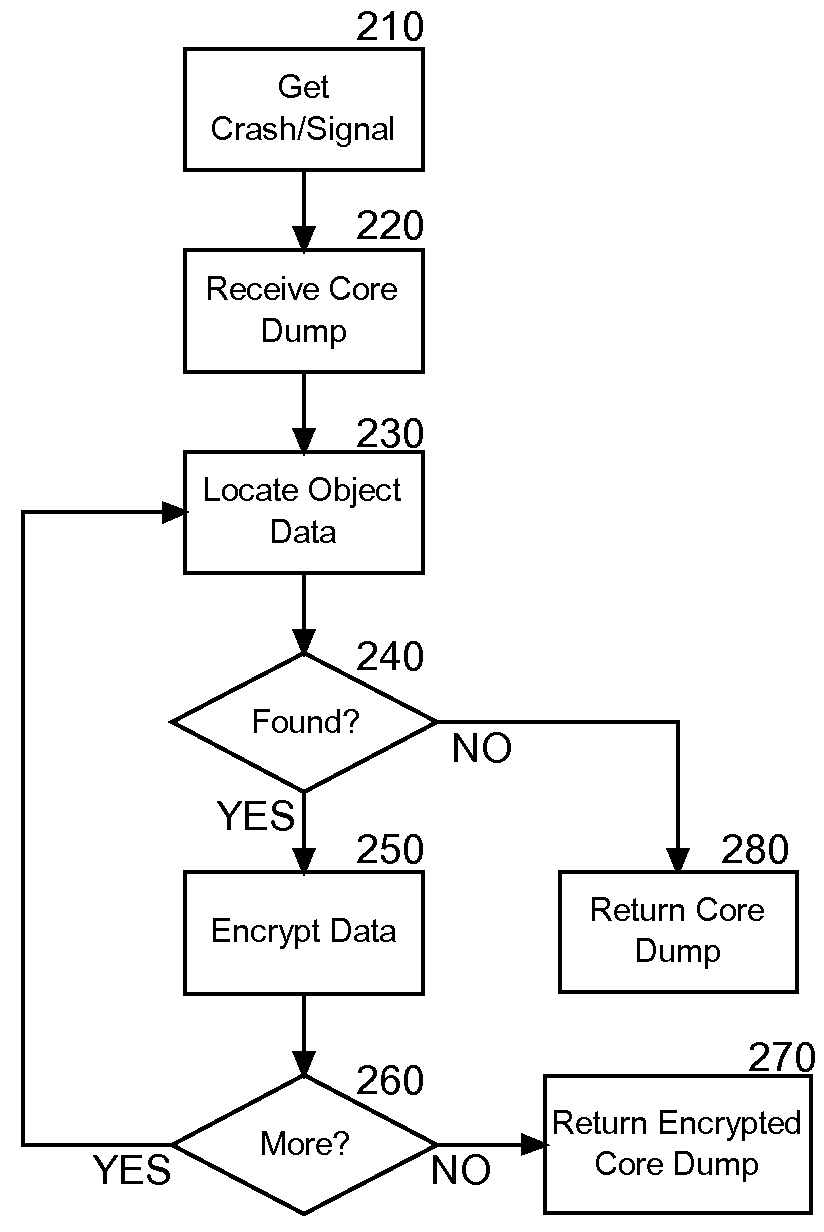
Core dump privacy during application failure
InactiveUS20090172409A1Privacy protectionUnauthorized memory use protectionHardware monitoringCore dumpInternet privacy
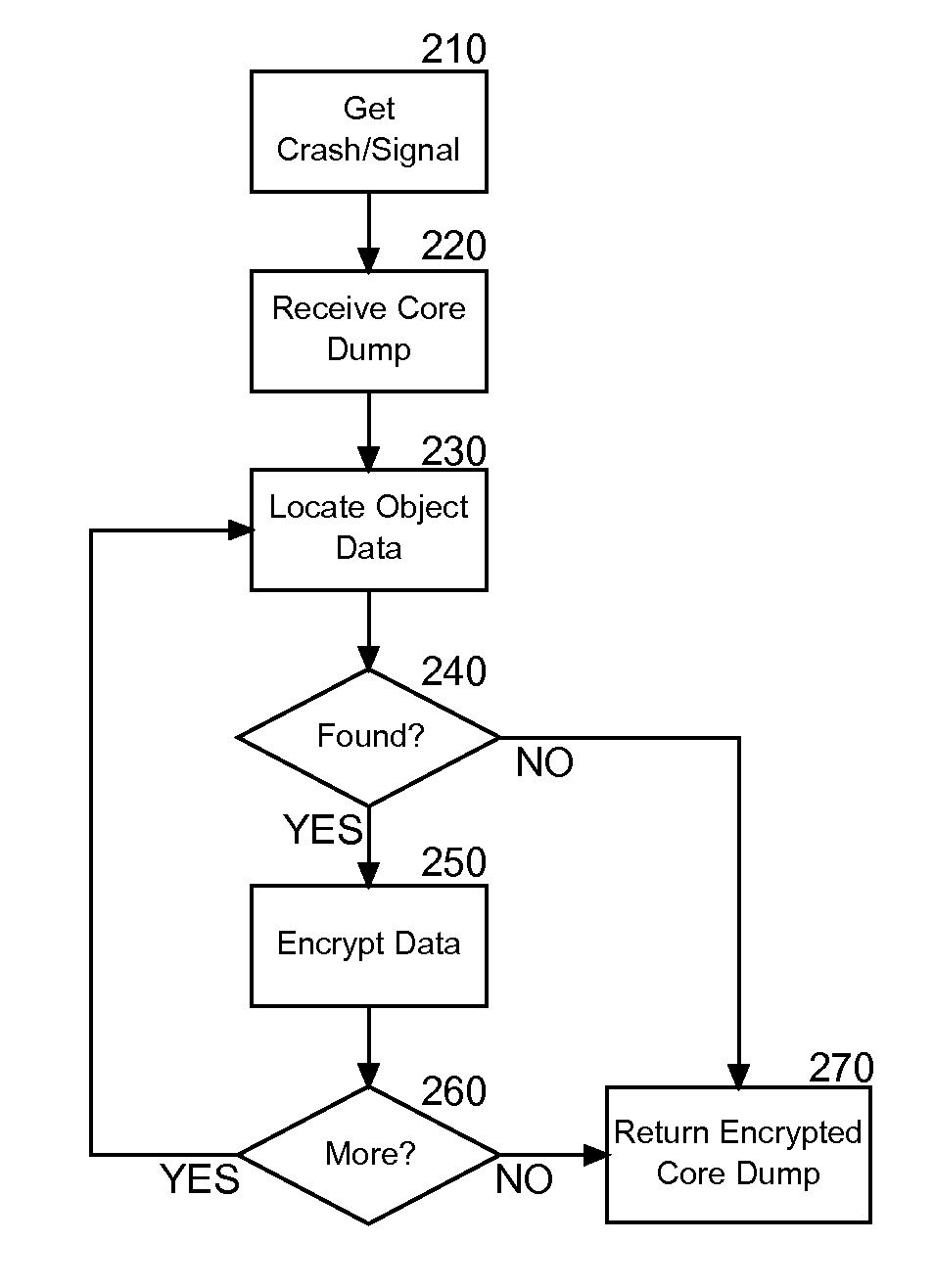
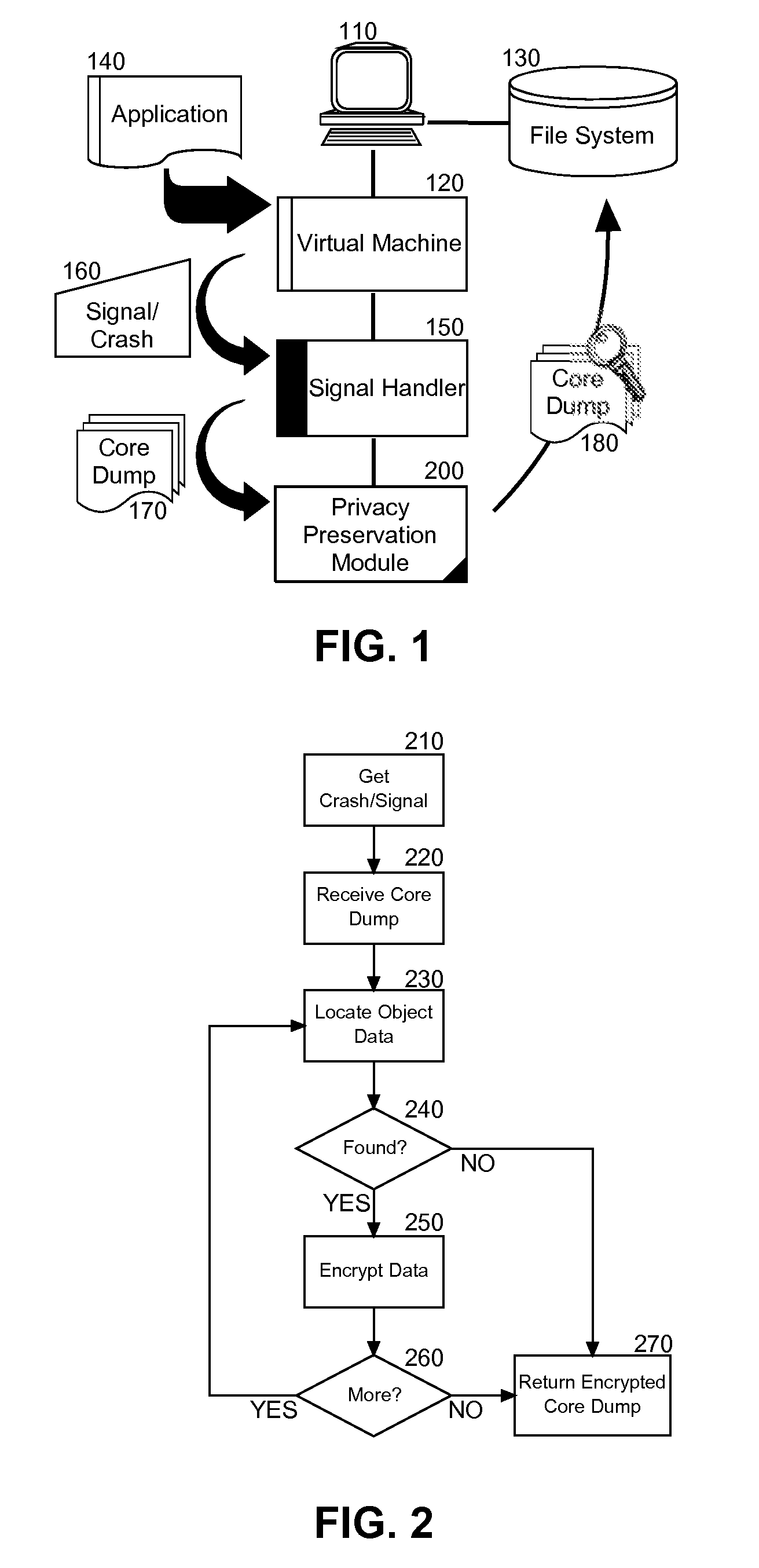
Embodiments of the present invention address deficiencies of the art in respect to core dump generation during application fault handling and provide a method, system and computer program product for privacy preservation of core dump data during application fault handling. In an embodiment of the invention, a method for privacy preservation of core dump data during application fault handling can be provided. The method can include receiving a crash signal for an application and generating a core dump with object data for the application. The method further can include obfuscating the object data in the core dump and writing the core dump with obfuscated object data to a file. In this way, the privacy of the object data in the core dump can be preserved.
Owner:IBM CORP
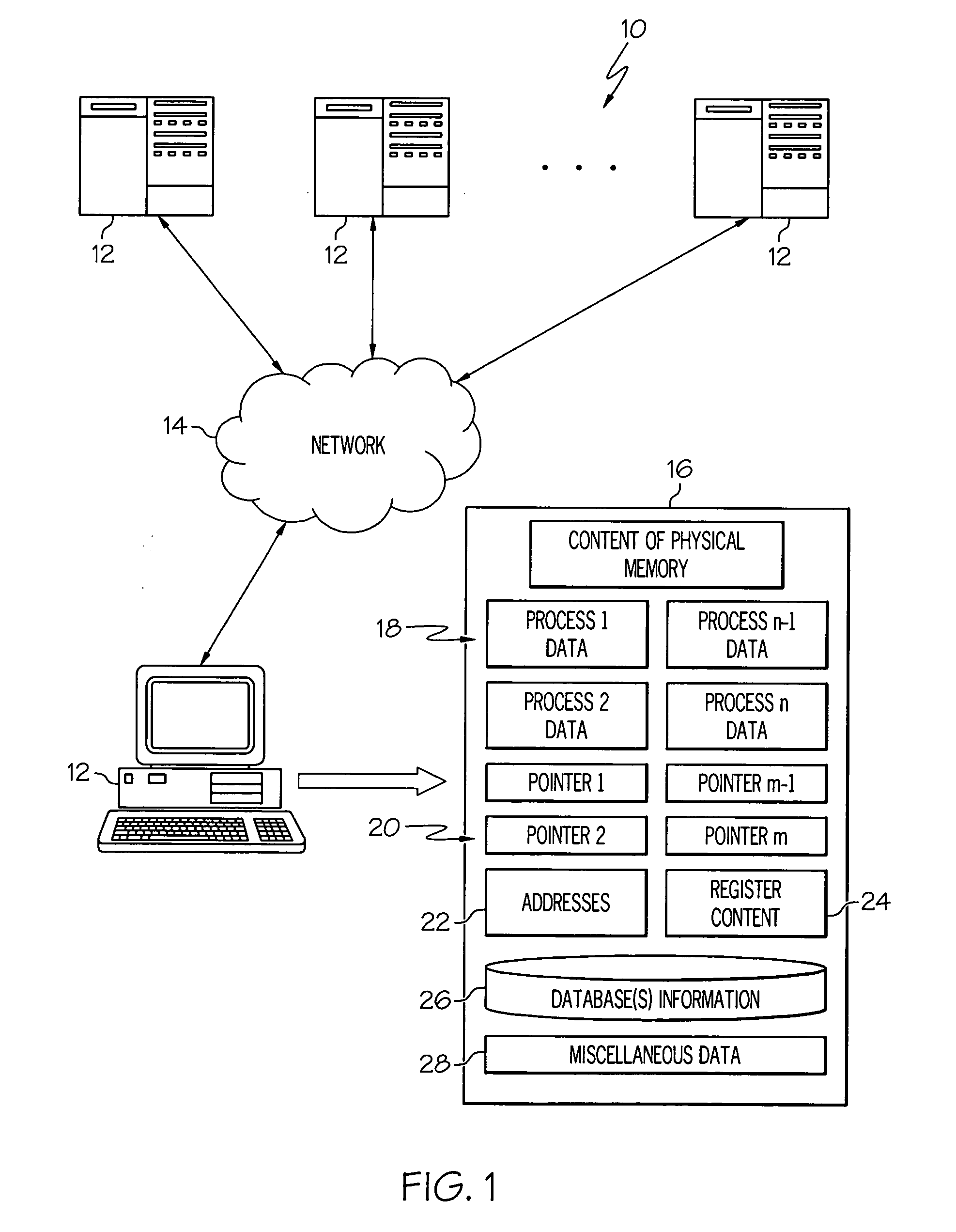
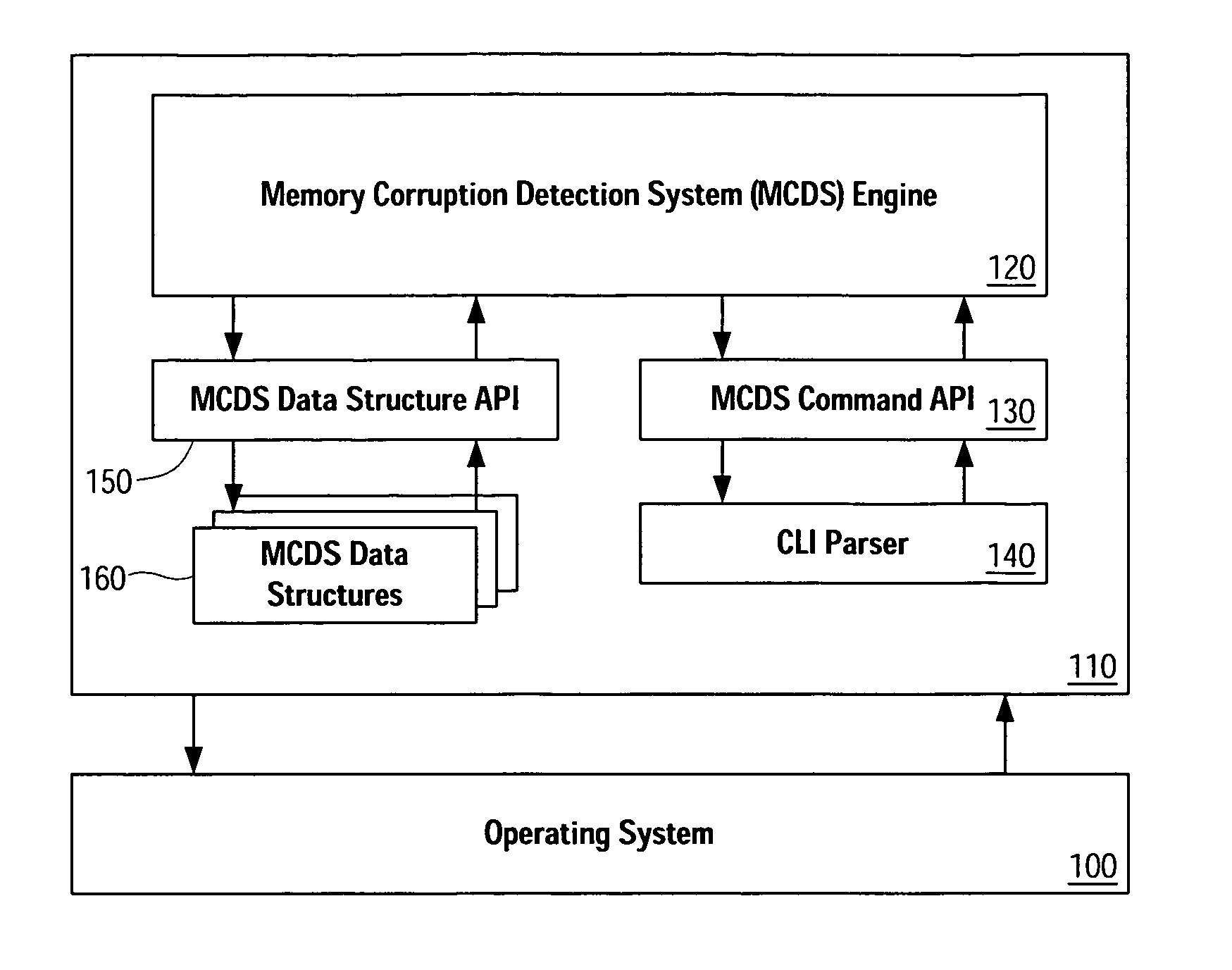
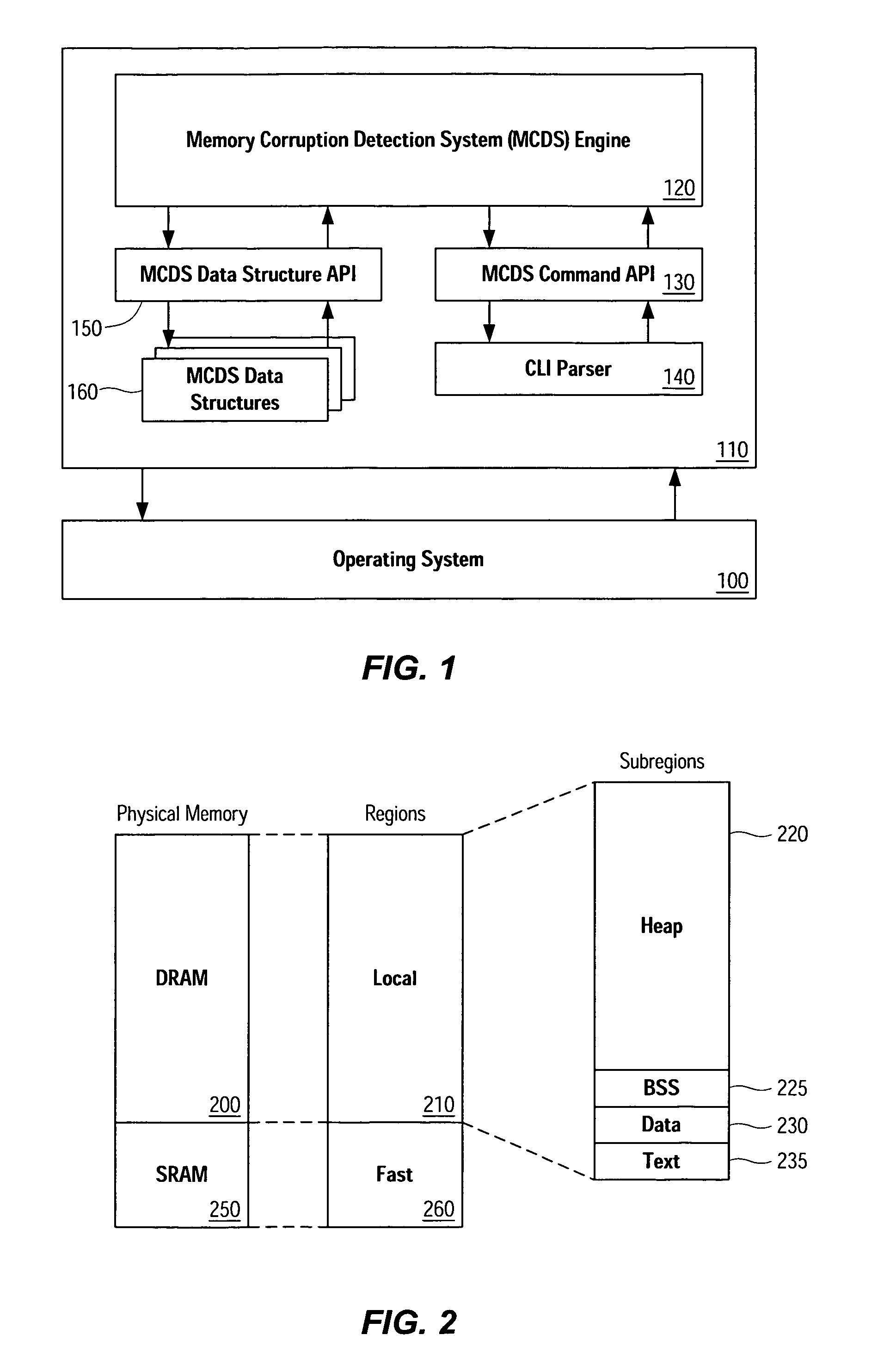
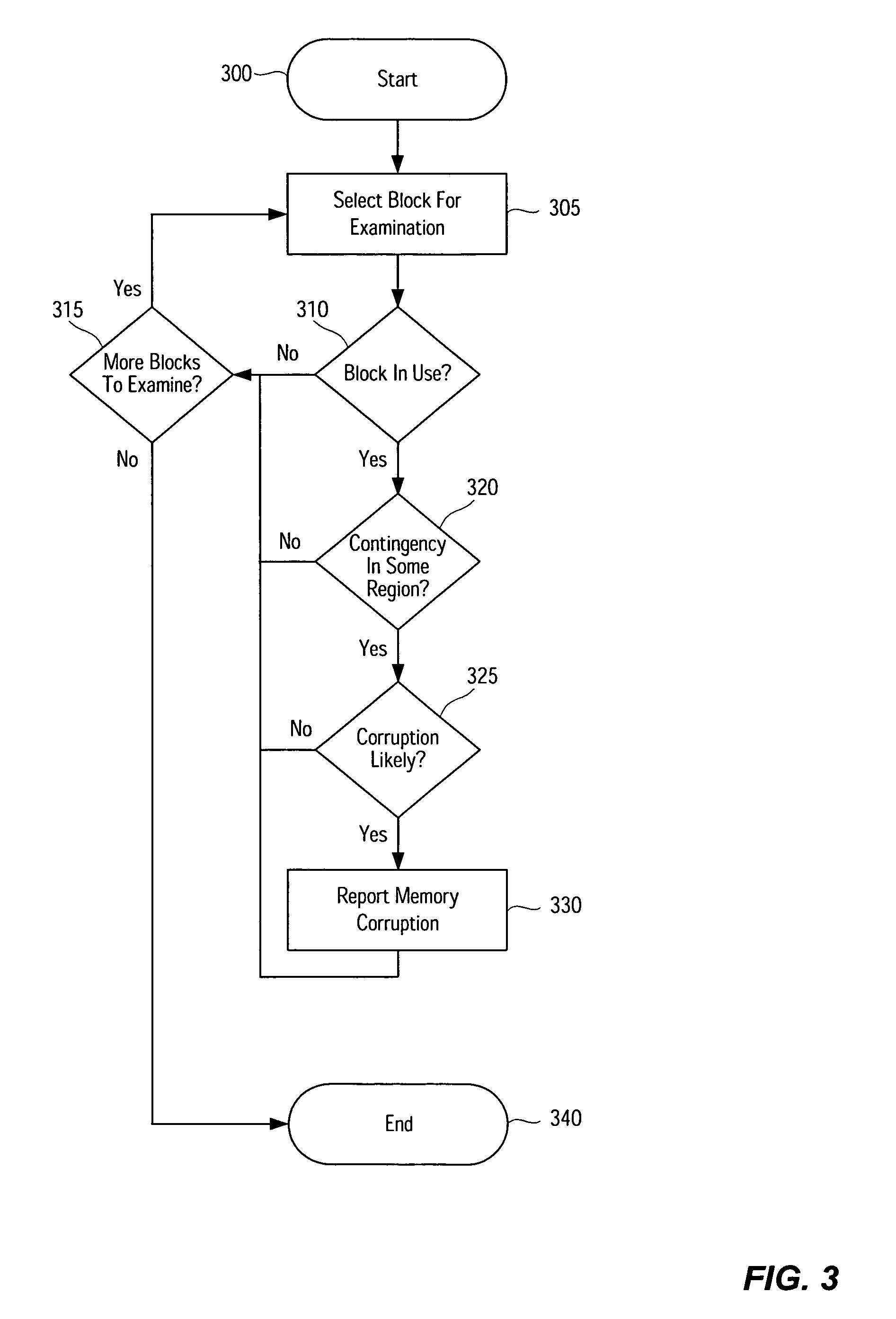
Memory corruption detection system and method using contingency analysis regulation
Systems, methods, apparatus and software can be implemented to detect possible instances of memory corruption. By analyzing memory blocks stored in a memory, provided in a snapshot file, or provided in a core dump, implicit and / or explicit contingency chains can be obtained. Analysis of these contingency chains identifies potential memory corruption sites, and subsequent verification provides greater confidence in the identification.
Owner:CISCO TECH INC
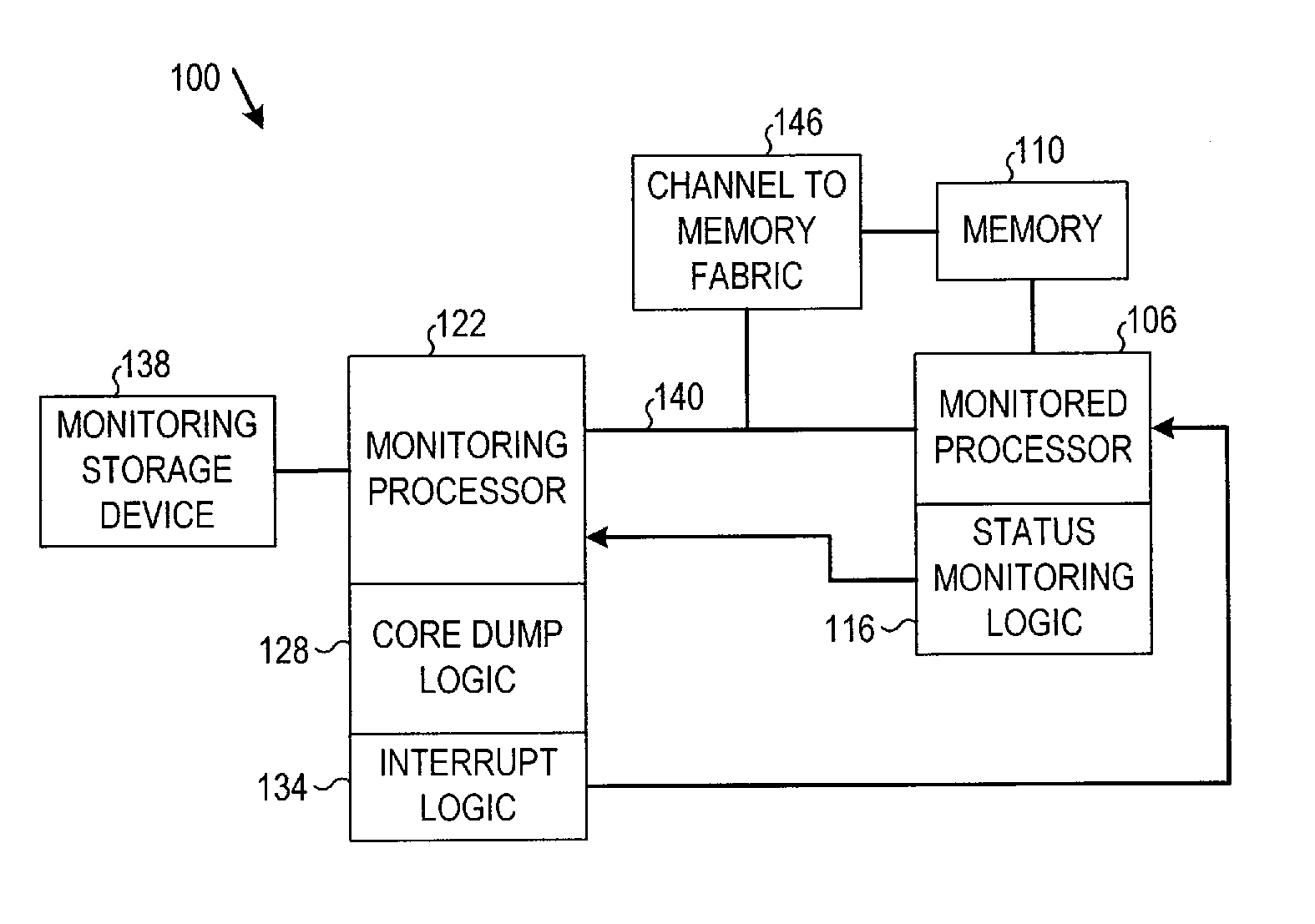
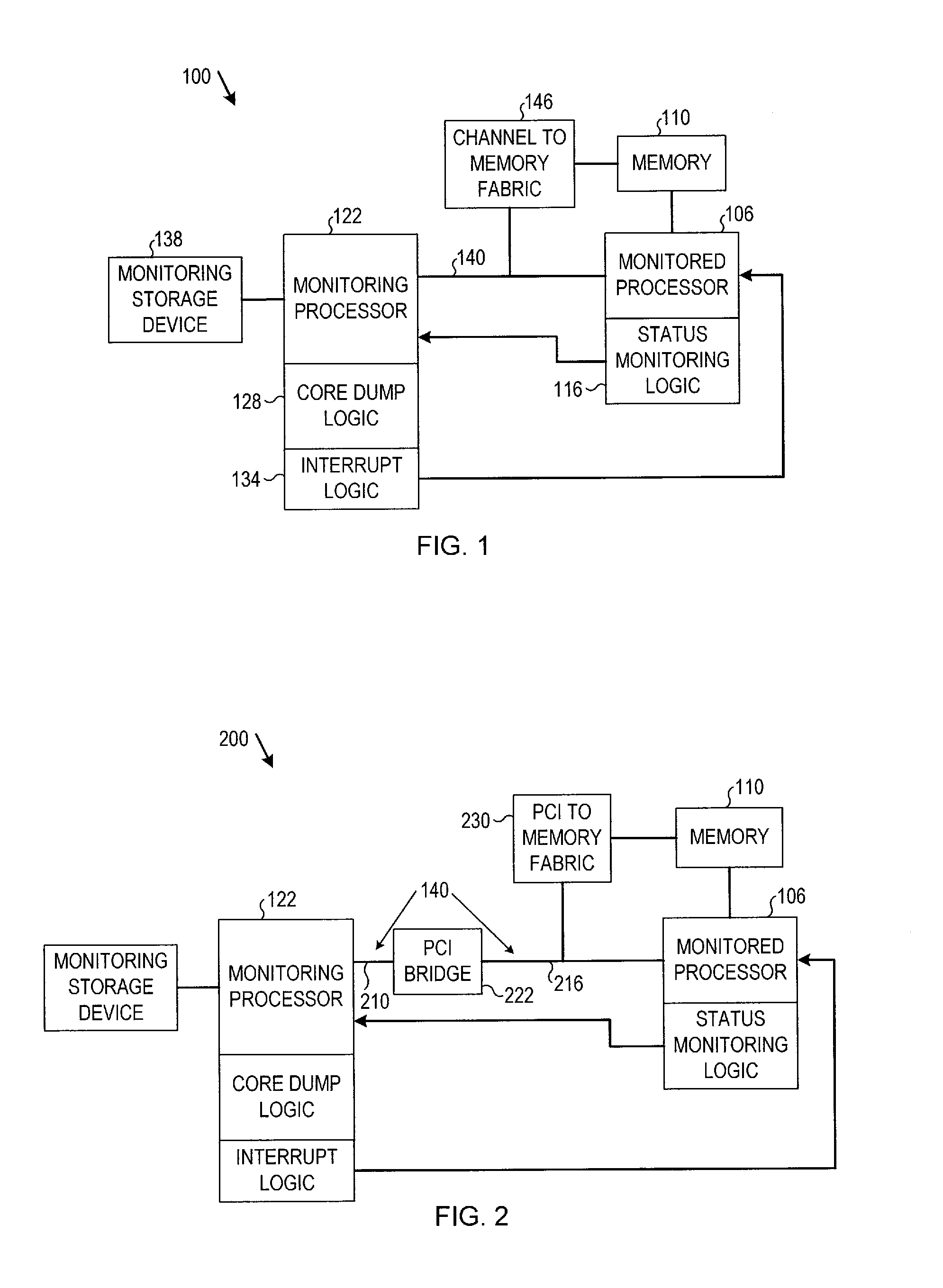
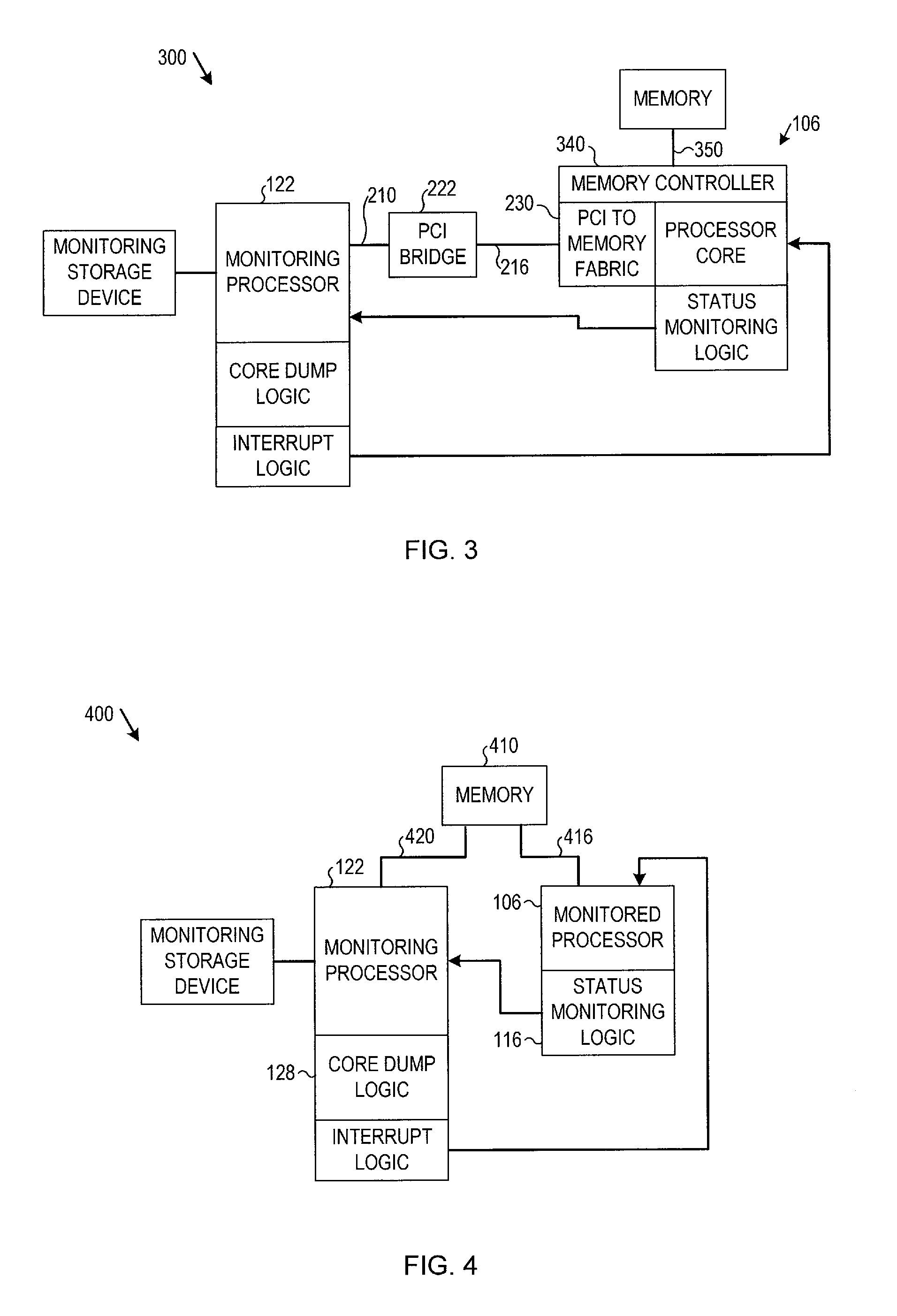
Multiprocessor core dump retrieval
In particular embodiments, a monitoring processor may receive an interrupt from status monitoring logic associated with a monitored processor that has experienced an error. Interrupt logic at the monitoring processor may interrupt the monitored processor to initiate a standby mode of operation in the monitored processor. Core dump logic at the monitoring processor may retrieve a core dump from a memory associated with the monitored processor via a communication channel connecting the monitoring processor to the monitored processor or to the memory. Other embodiments are disclosed and claimed.
Owner:CISCO TECH INC
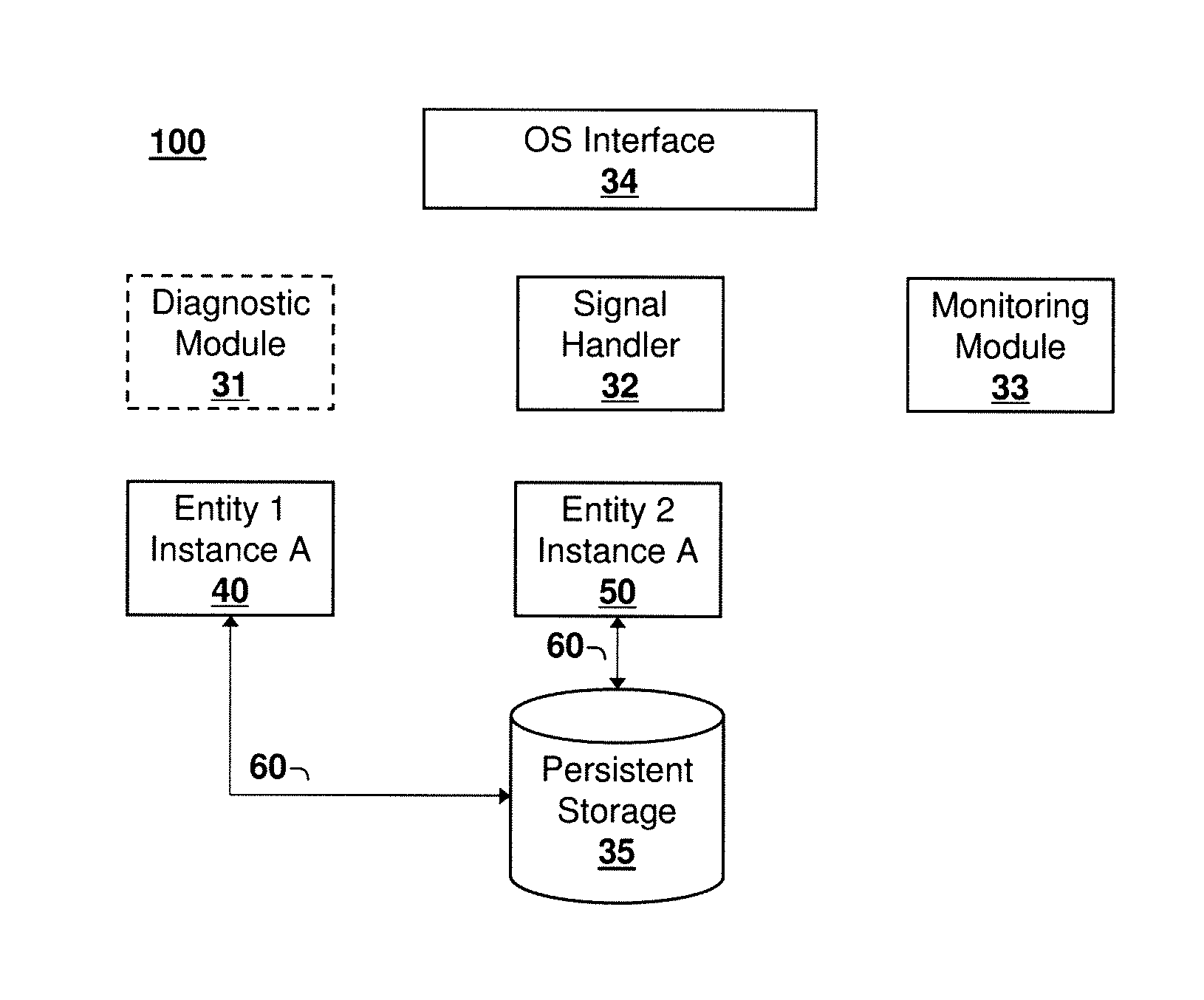
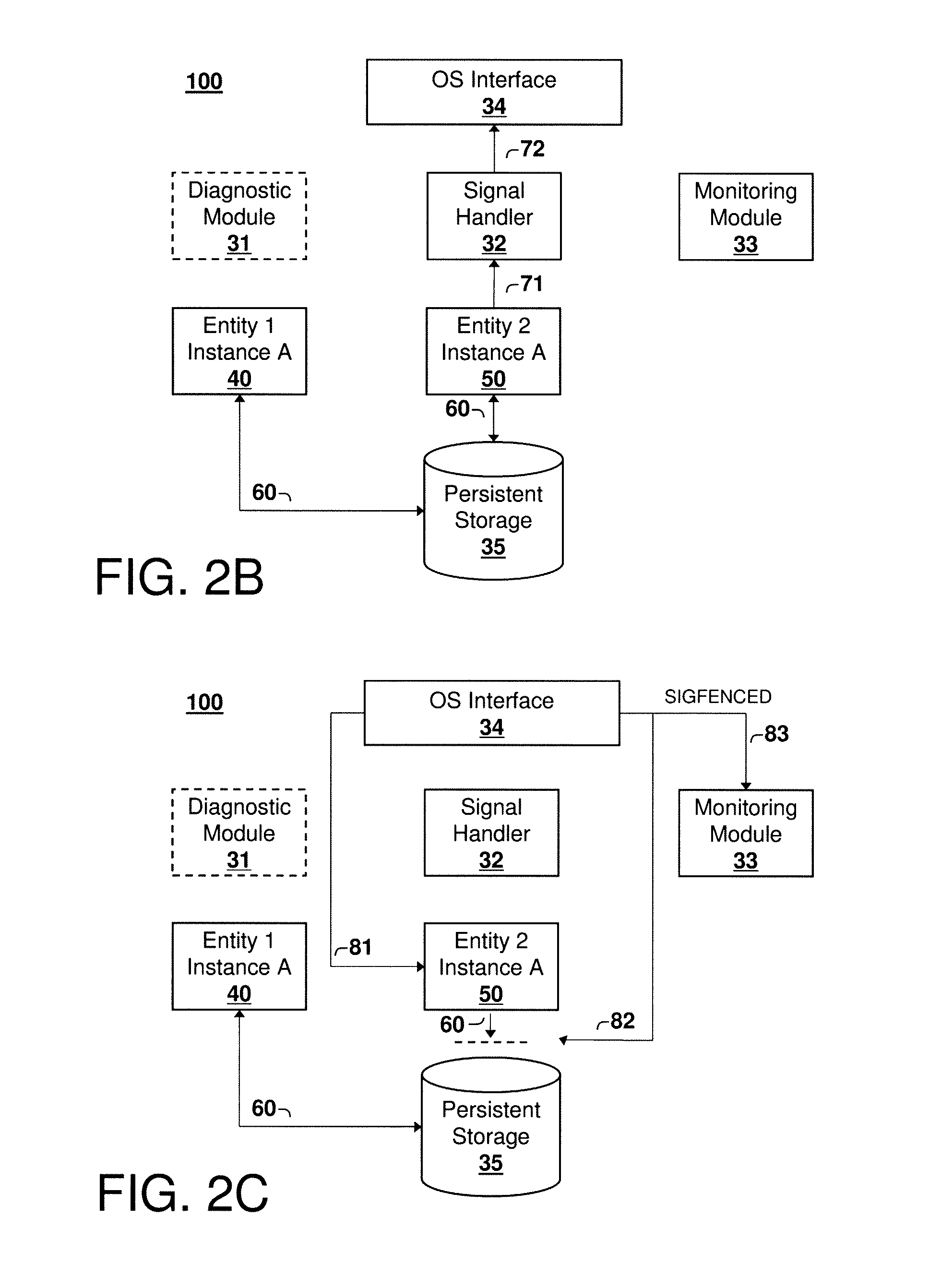
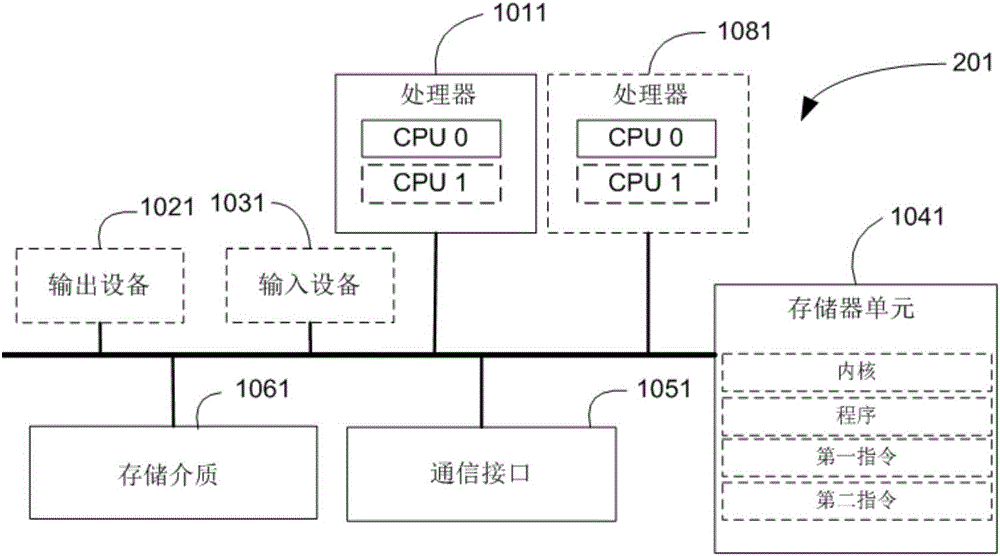
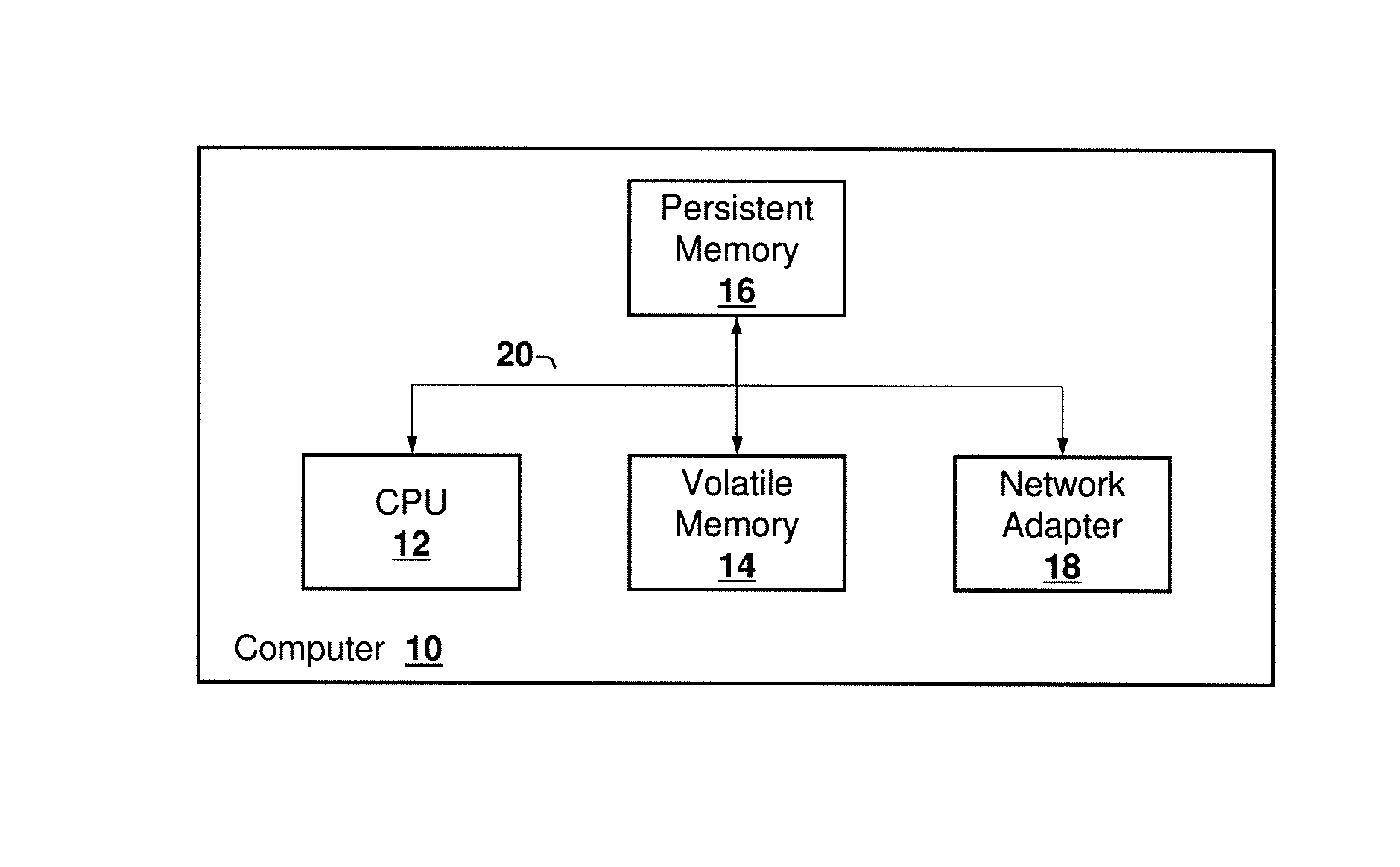
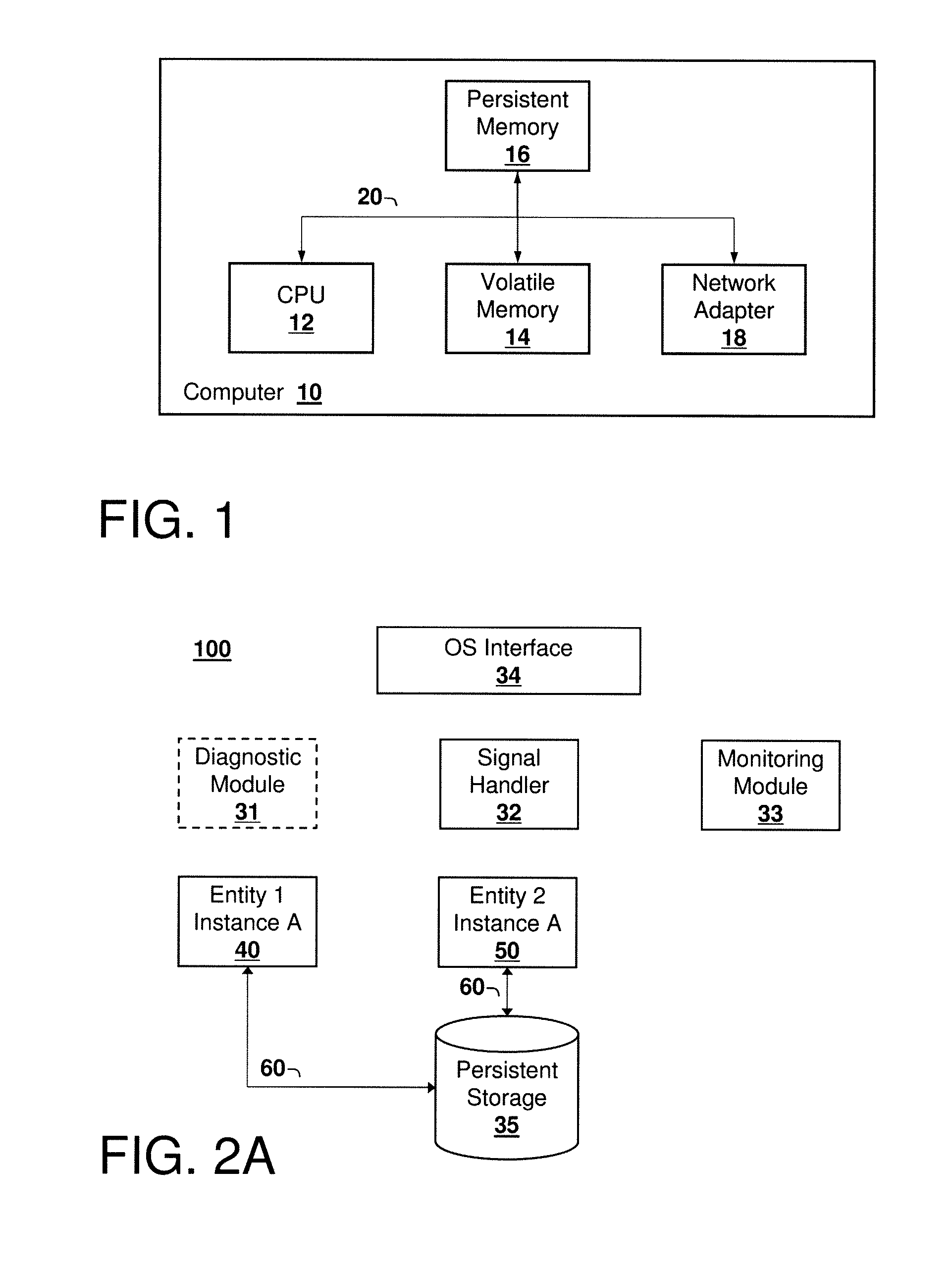
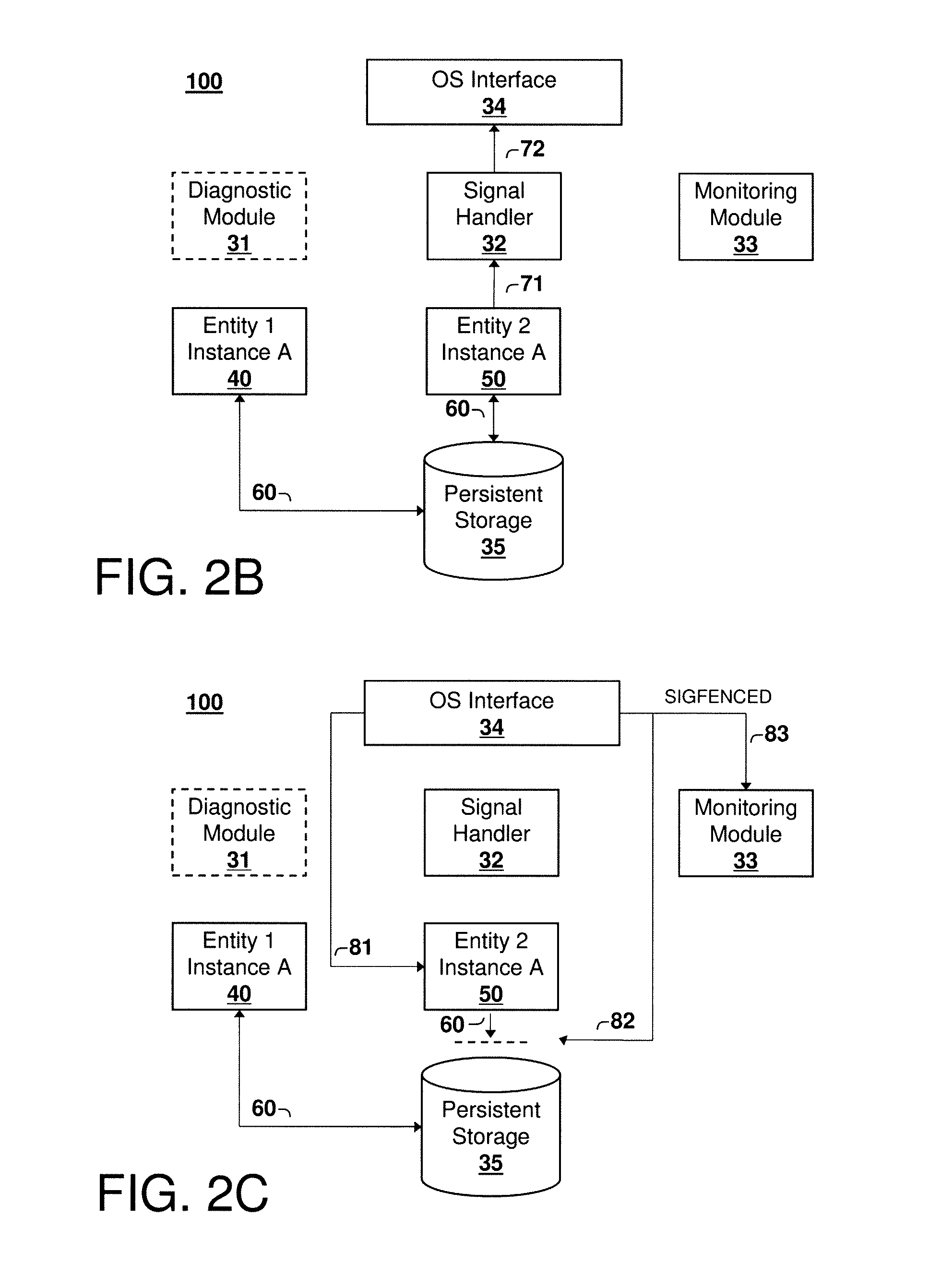
Failure Detection and Fencing in a Computing System
A method, computer program product, and system for detecting and fencing off a failed entity instance so that failover time in the computing system is reduced. Upon detection of a failed entity, for example a failed process, a signal handler invokes an operating system interface to fence off the failed instance from modifying its persistent state, so that the entity may be re-instantiated prior to termination of the failed instance. This approach reduces failover time and eliminates split-brain problems without compromising access to the failed instance to obtain diagnostic information, core dumps, and the like.
Owner:IBM CORP
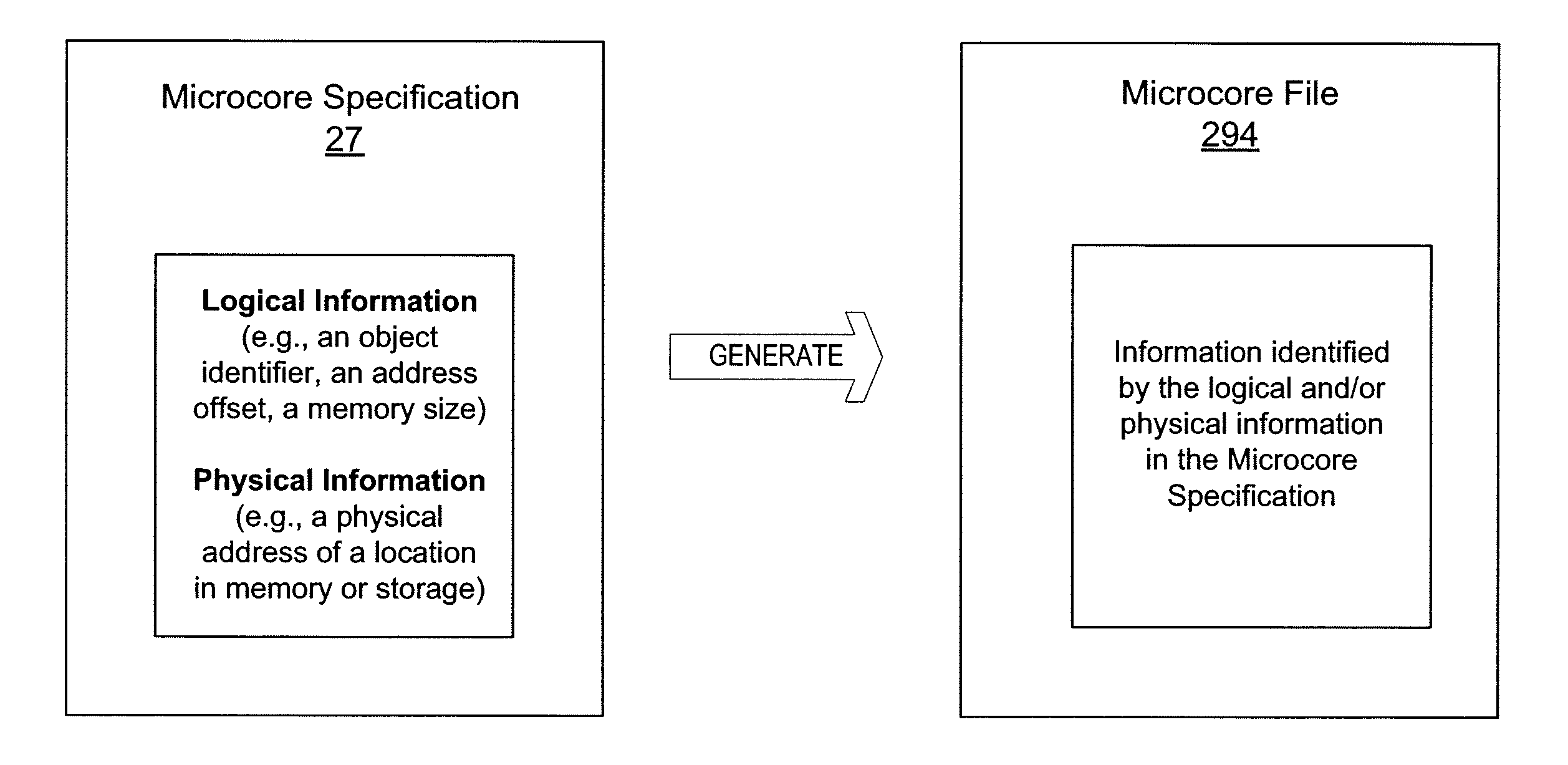
Method and apparatus for generating dynamic microcores
ActiveUS7783932B1Easy transferQuick identificationError detection/correctionCore dumpComputer architecture
A method of generating a microcore file, which is a subset of a full core dump, for a networked storage system includes generating a microcore file according to a microcore specification, and dynamically defining the microcore specification at runtime of the network storage system. The microcore specification is dynamically defined with information provided by results of an event that triggers the generation of the microcore file. After the microcore specification is defined, a region of a system memory is identified according to the microcore specification. The method further includes dumping the data from the region of the system memory into the microcore file.
Owner:NETWORK APPLIANCE INC
Managing process state information in an operating system environment
InactiveUS7240240B2Excessively generatedNon-redundant fault processingProgram controlCore dumpOperational system
A technique for managing process state information involves pushing process state information from the kernel space to the user space in the event of an application crash and generating a core file at the user level instead of at the kernel level. Handling the process state information at the user level instead of at the kernel level provides more flexibility in the generation and management of a core file as compared to systems that use kernel code to generate and manage the core file. A core dump application at the user level can be programmed to forward the core file to another system that has permanent storage capacity available. Additionally, the core dump application can be programmed to compress the process state information and / or to extract only certain information from the process state information while generating the core file.
Owner:LUCENT TECH INC
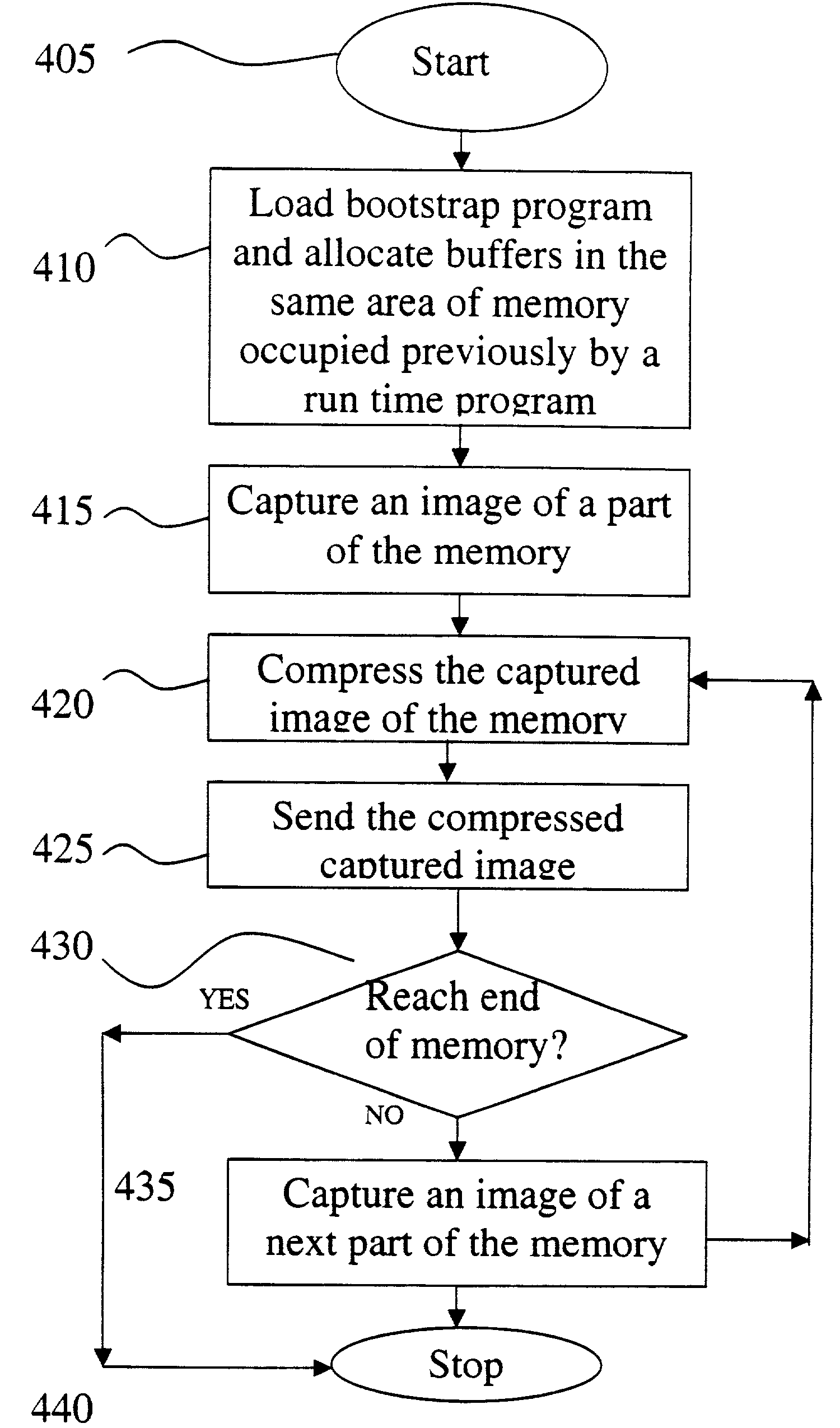
Method for capturing core dump of a service module
A bootstrap program is loaded into an area of memory previously occupied by a run time program in a service module. The bootstrap program is loaded after the service module is reset due to an error. The service module does not have a persistent storage. The bootstrap program captures a memory image of the memory. The captured memory image of the memory is compressed and transferred to a control module to be stored in a persistent storage of the control module. The control module receives captured memory images from one or more service modules.
Owner:CISCO TECH INC
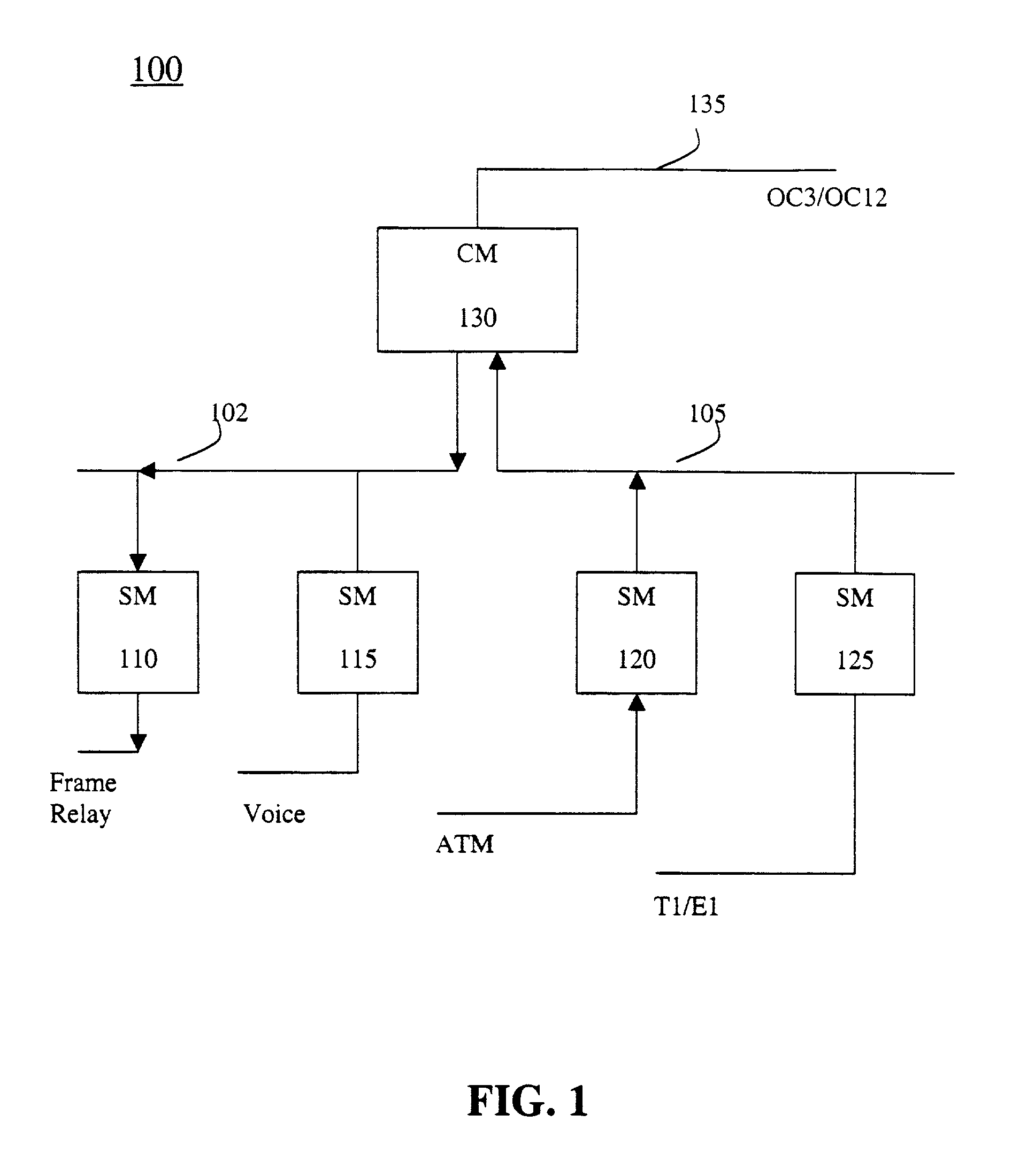
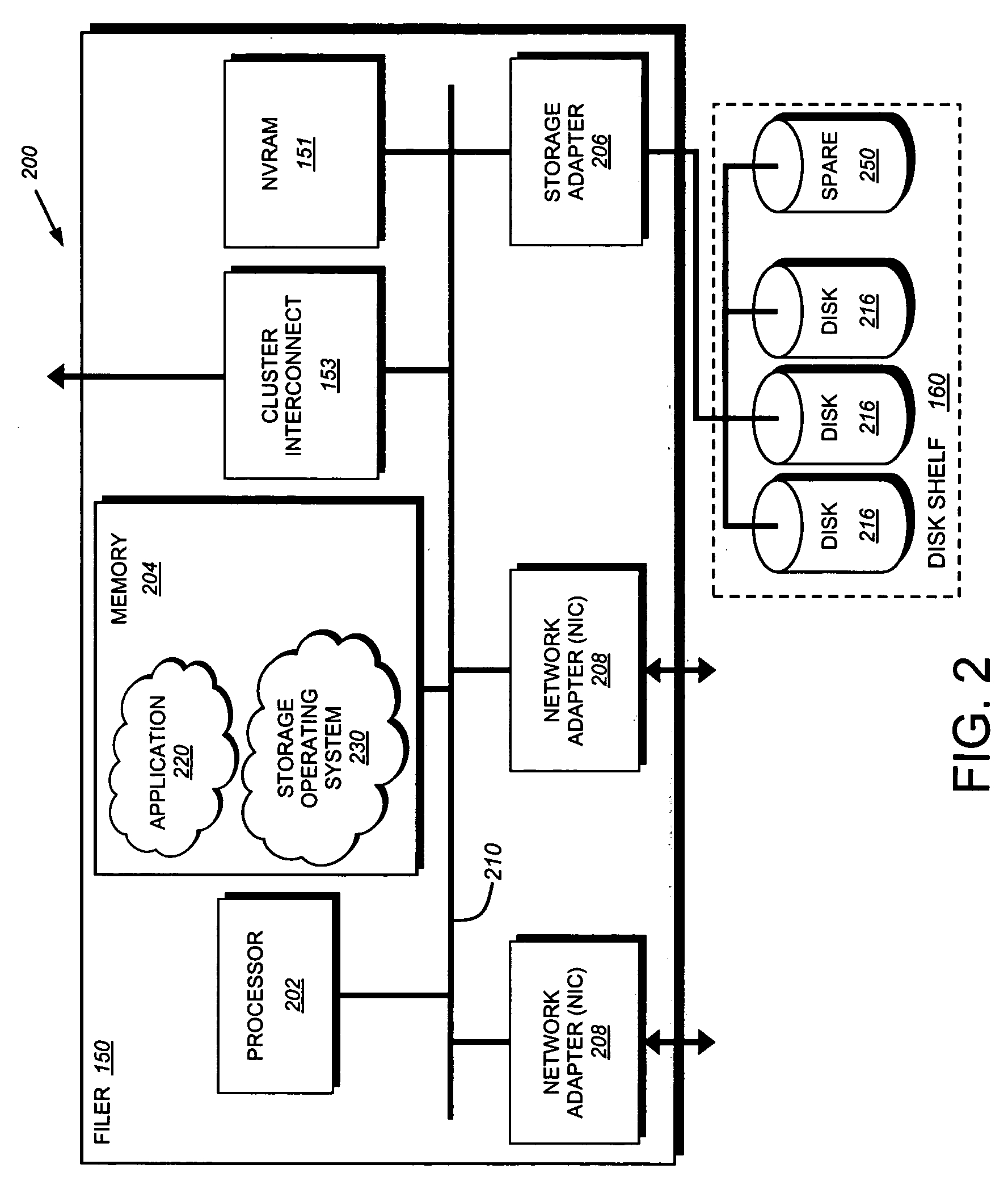
System and method of selection and communication of a disk for storage of a coredump
ActiveUS20050177764A1Reduce wasteRapidly takeNon-redundant fault processingRedundant hardware error correctionCore dumpFile server
This invention provides a system and method for selecting and communicating a single disk (a “coredump disk”) for use in a coredump procedure by a failed file server (or filer). A selection method on the failed filer determines the “best candidate” coredump disk according to a predetermined set of criteria. For example, the available disks that can receive coredump data are located and ordered so as to prefer disks that best match the coredump data size requirement, are least likely to be needed for normal service by the server; and require the least preparation to receive coredump data. Appropriate attributes on the selected coredump disk are written to indicate that a coredump is in progress, and the location of the coredump data. Upon reboot of the failed filer (or takeover by a cluster partner), the coredump disk is identified and the coredump data recovered by reading back appropriate attributes.
Owner:NETWORK APPLIANCE INC
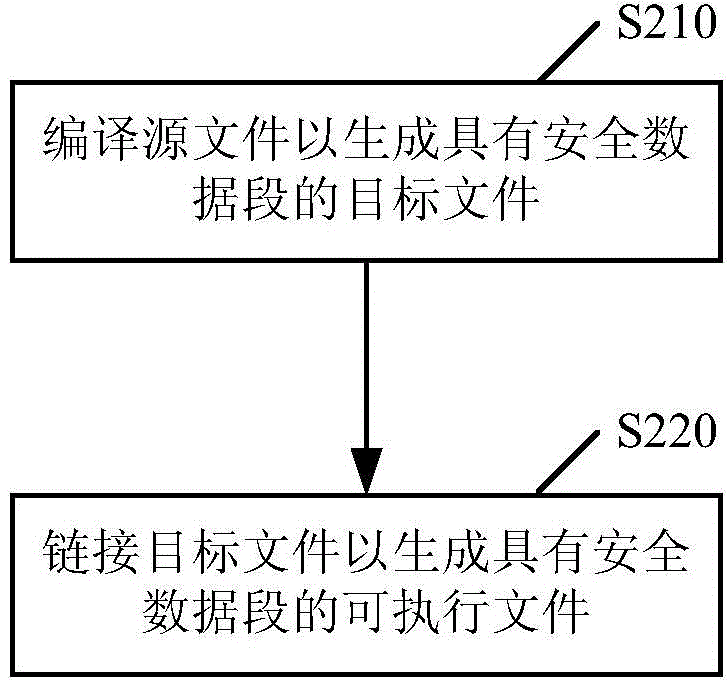
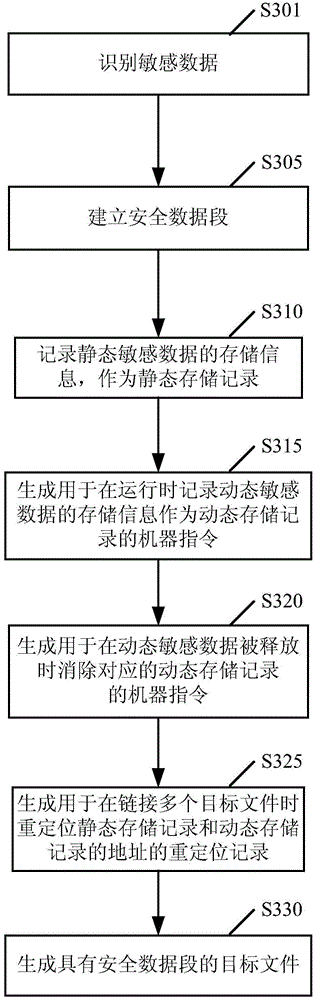
Method and apparatus for protecting sensitive data in software product
ActiveCN104881611APrecise positioningAccurate trackingLink editingDigital data protectionCore dumpRunning time
Sensitive data is protected in a software product. A source file of the software product is compiled to generate an object file, in which the source file includes at least one piece of sensitive data marked with a specific identifier. The object file has a secure data section for saving storage information of the at least one piece of sensitive data at compile-time and run-time. The object file is linked to generate an executable file. The executable file updates the secure data section at run-time. Sensitive data is also protected when a core dump is generated.
Owner:IBM CORP
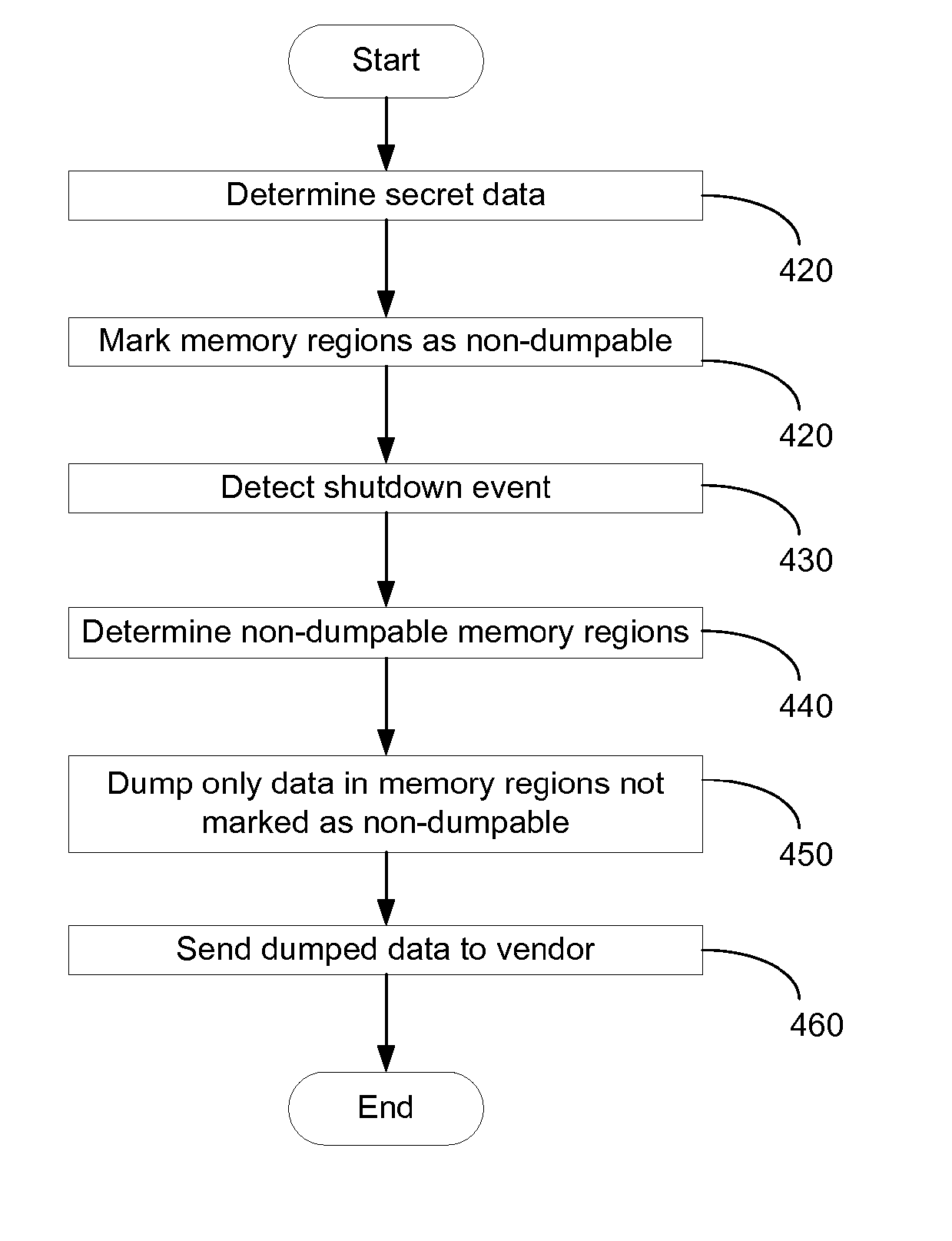
Systems and Methods for Protecting Customer Secrets During Vendor Troubleshooting
InactiveUS20070255912A1Reduce riskComputer security arrangementsMemory systemsCore dumpSystems approaches
Systems, methods, and computer products for protecting information during troubleshooting are provided. A dumping mechanism includes marking at least one of a plurality of memory regions in the computer-readable medium as non-dumpable, initiating a core dump, determining which memory regions of the plurality regions are non-dumpable, and dumping the contents only of memory regions not marked as non-dumpable.
Owner:CA TECH INC
Core dump privacy during application failure
Embodiments of the present invention address deficiencies of the art in respect to core dump generation during application fault handling and provide a method, system and computer program product for privacy preservation of core dump data during application fault handling. In an embodiment of the invention, a method for privacy preservation of core dump data during application fault handling can be provided. The method can include receiving a crash signal for an application and generating a core dump with object data for the application. The method further can include obfuscating the object data in the core dump and writing the core dump with obfuscated object data to a file. In this way, the privacy of the object data in the core dump can be preserved.
Owner:IBM CORP
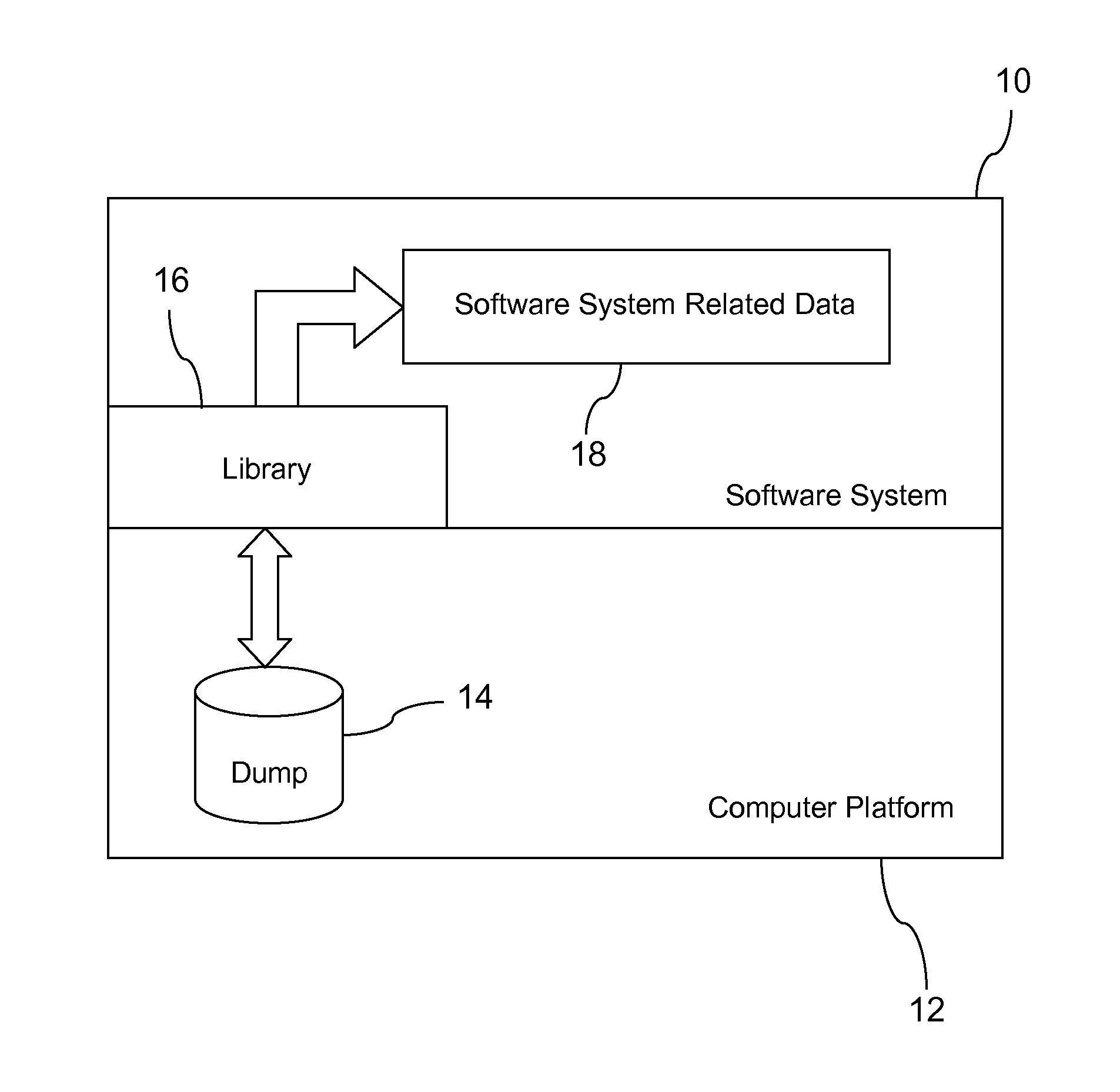
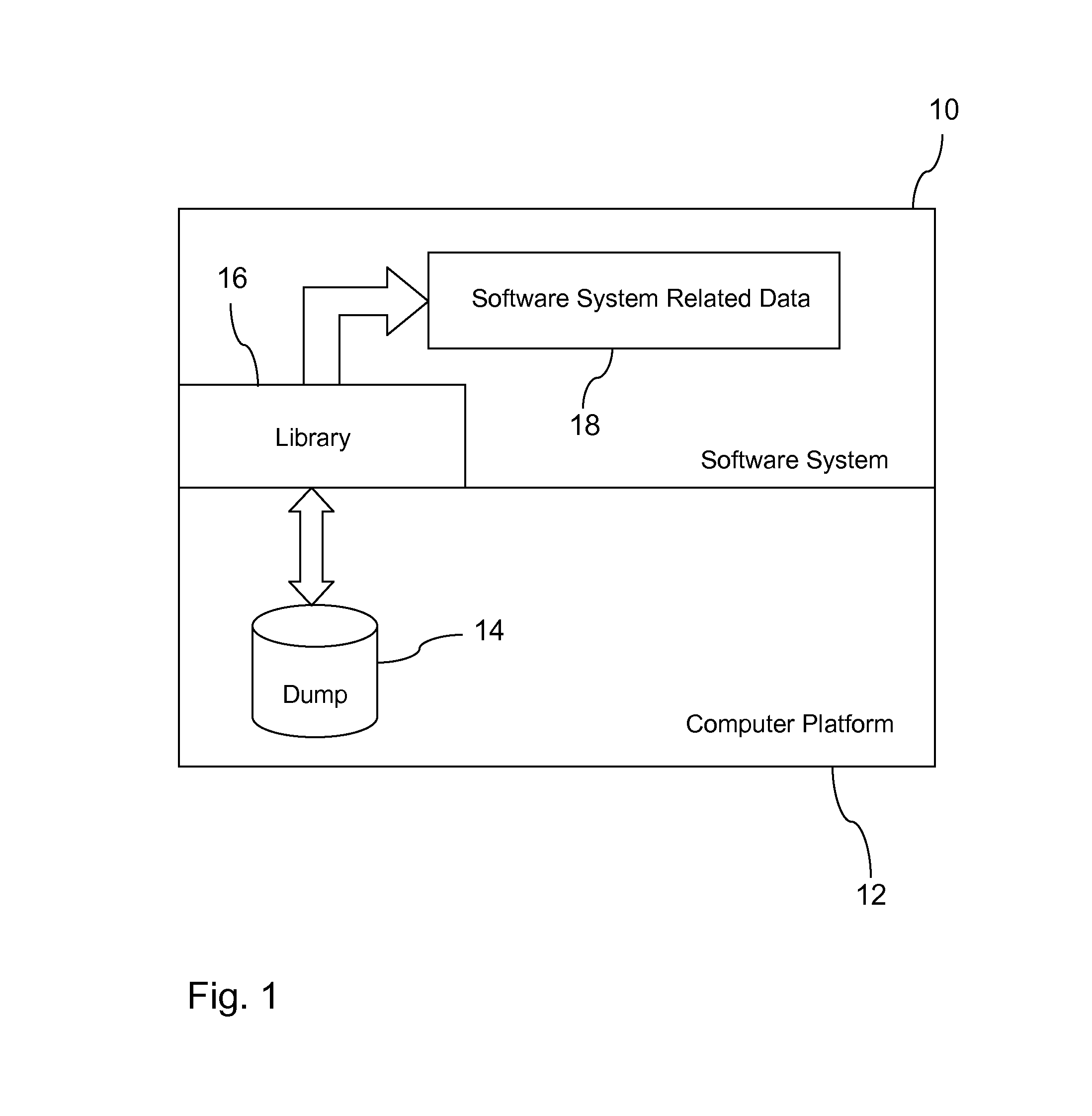
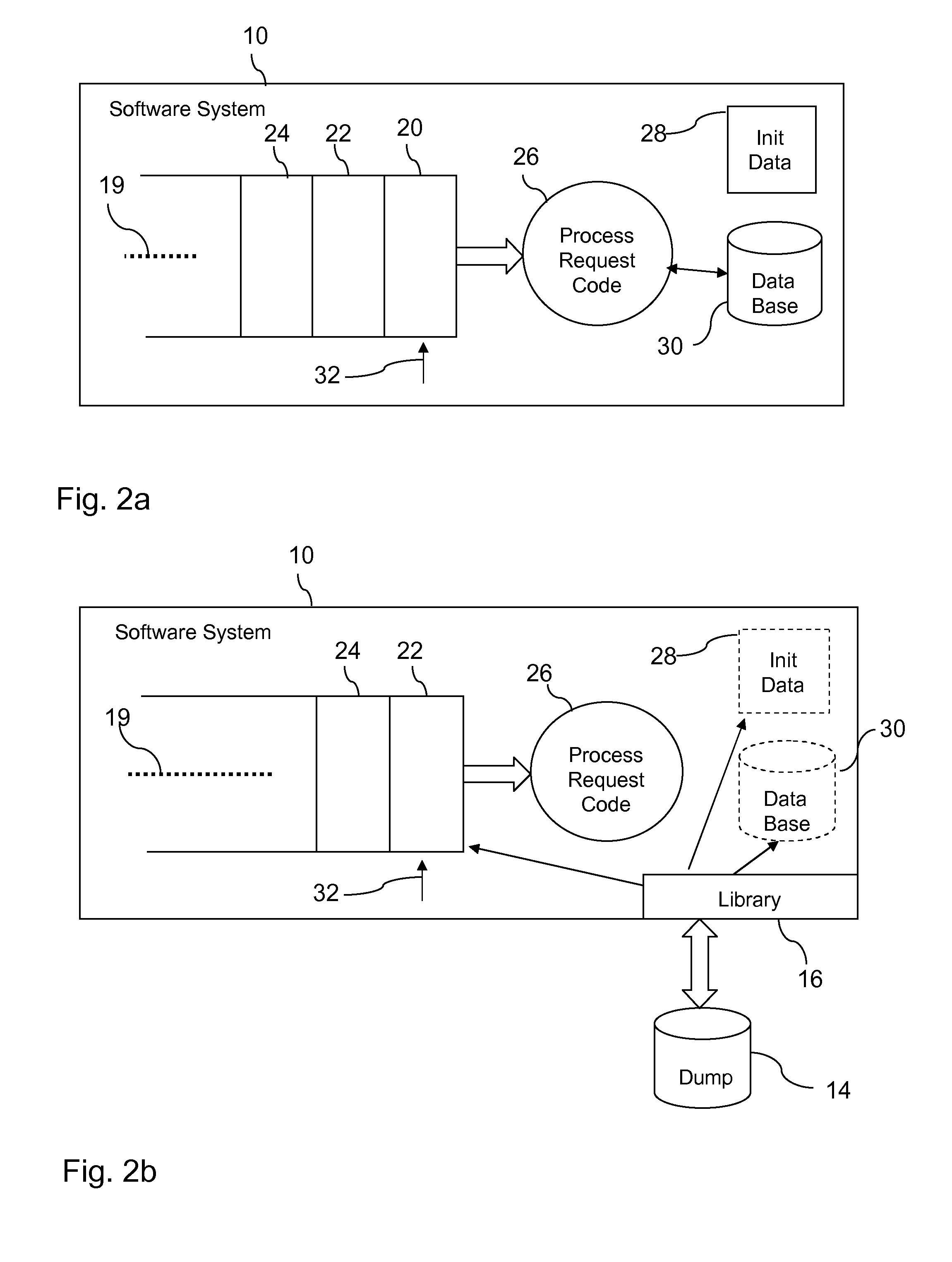
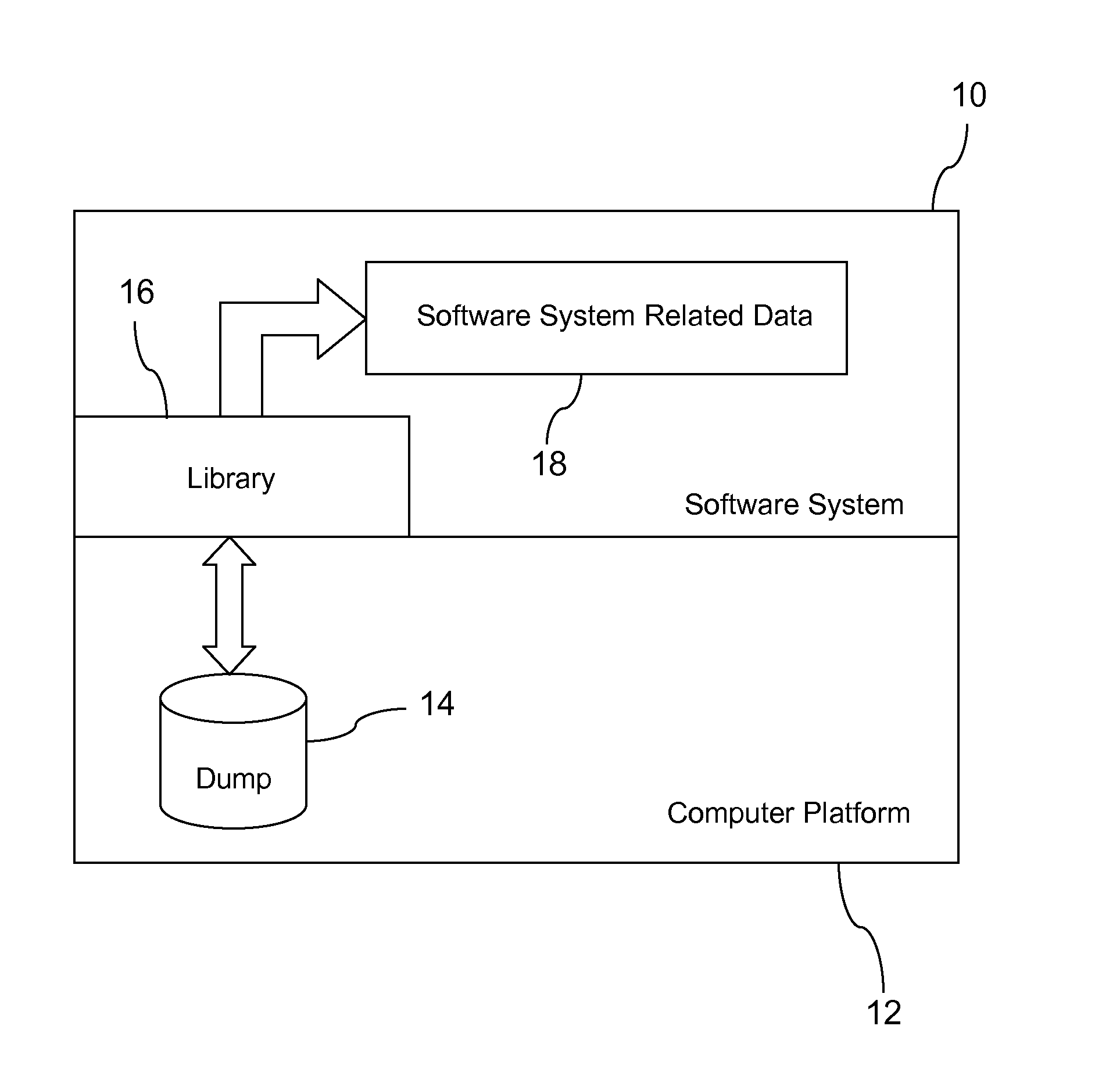
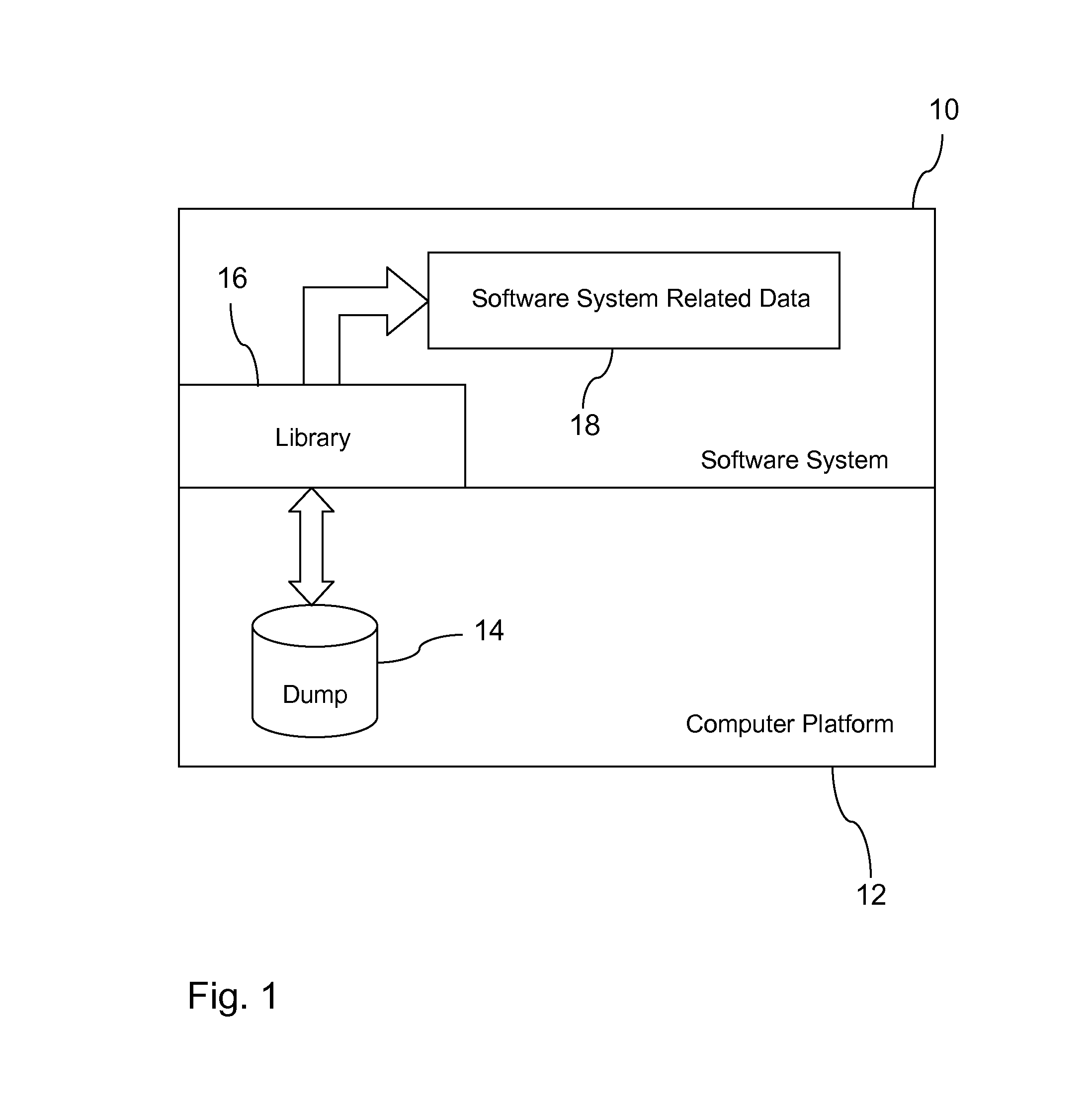
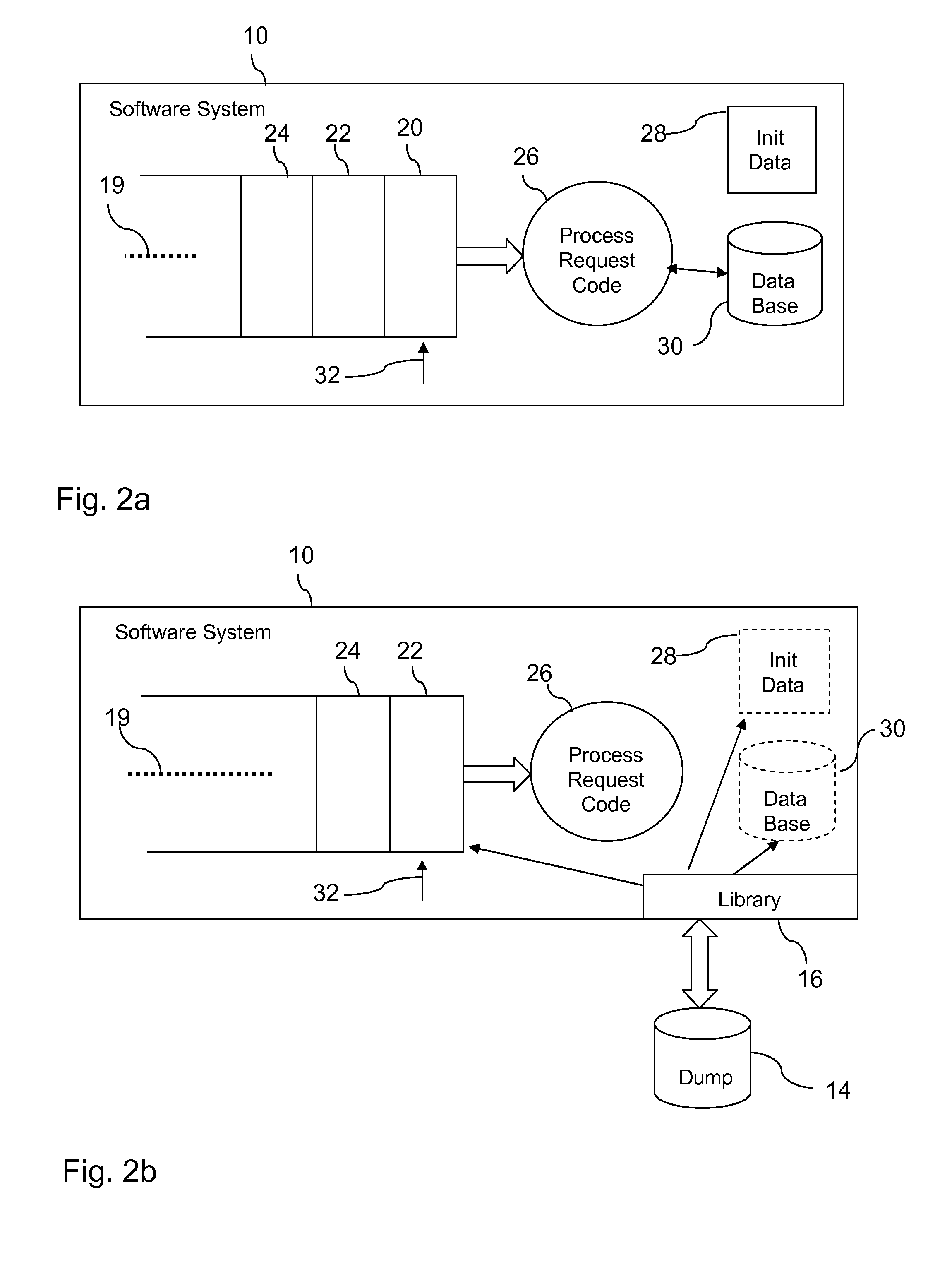
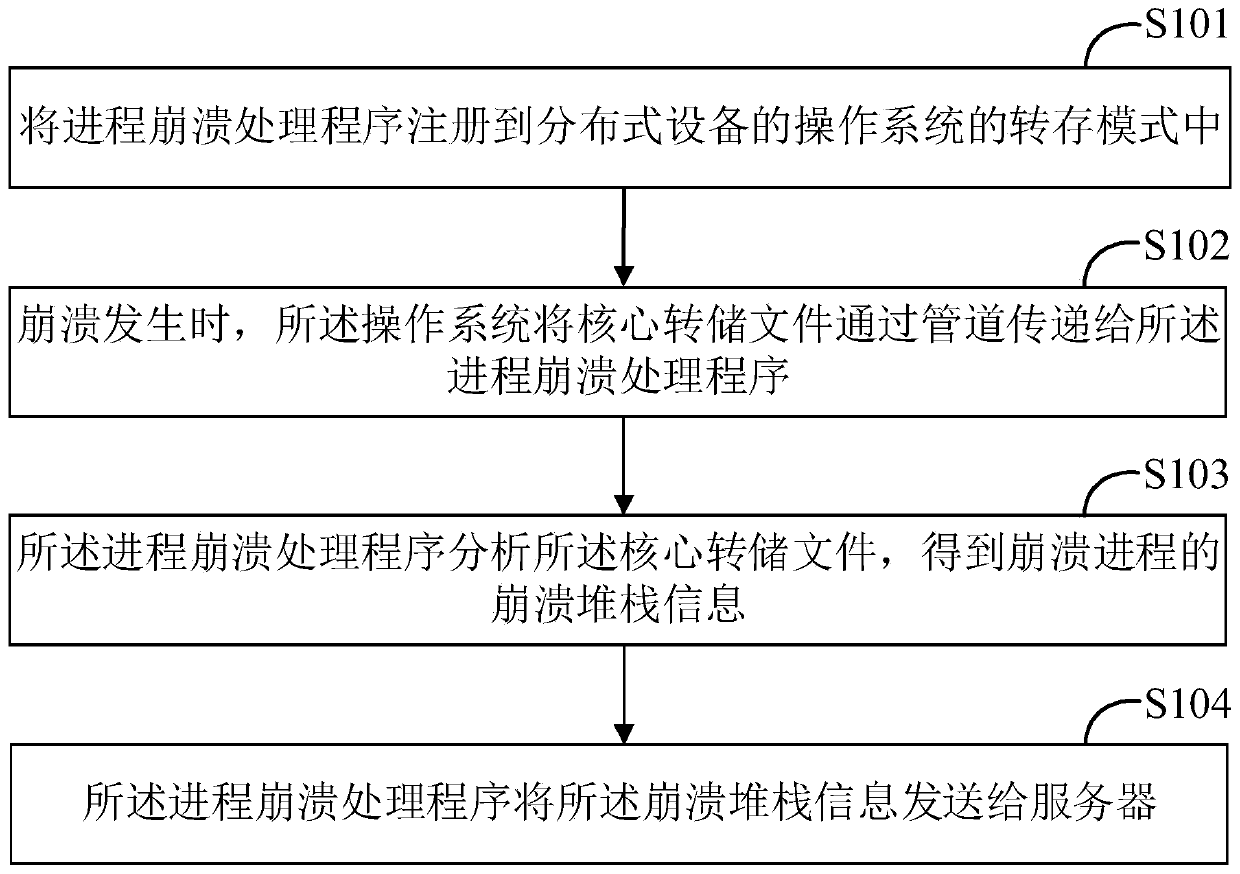
Restarting a software system
In one aspect, a technique for restarting a software system on a computer platform after an unintentional software system shutdown. The technique includes, for instance, generating a core dump file on the computer platform when the software system shuts down unintentionally, restarting the software system, using a library for copying software system related data from the core dump file to the software system, and continuing execution of the software system.
Owner:INT BUSINESS MASCH CORP
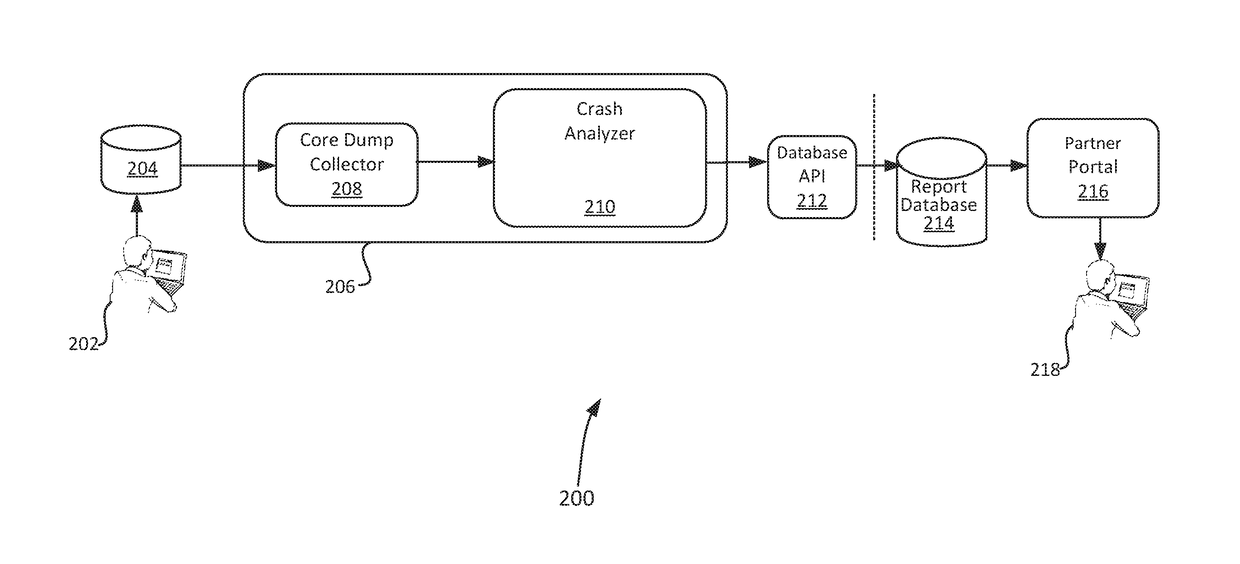
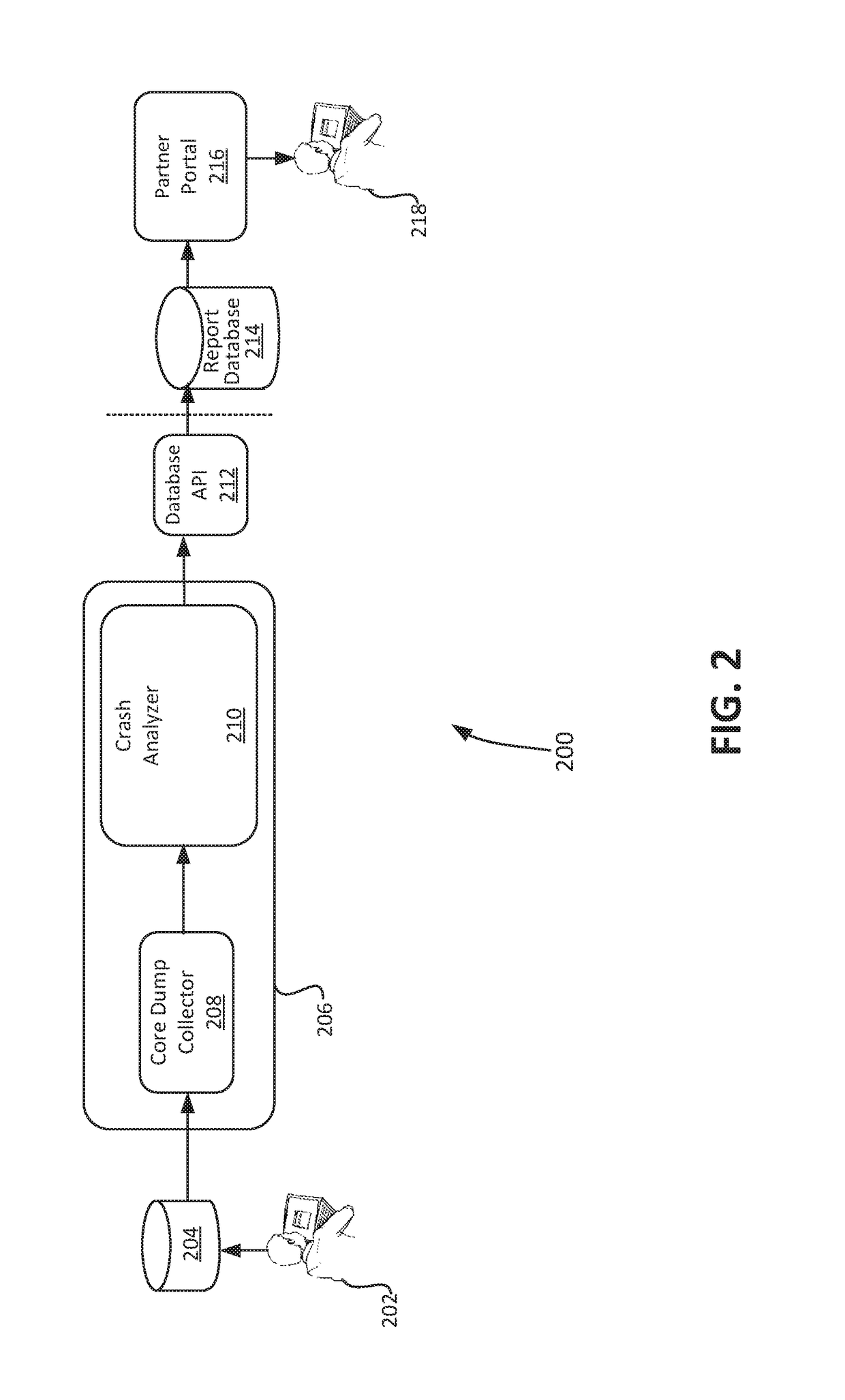
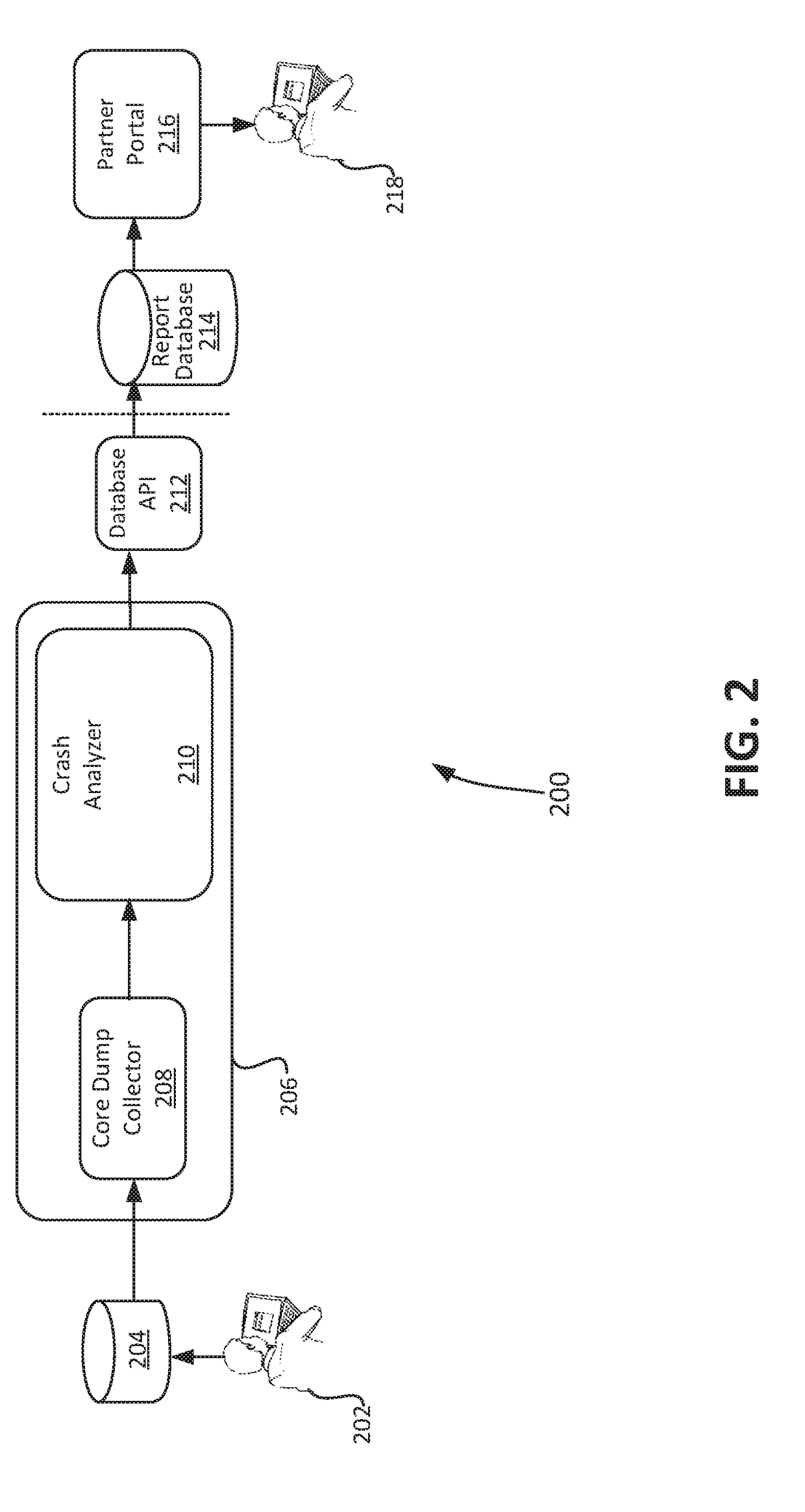
Monitoring of an automated end-to-end crash analysis system
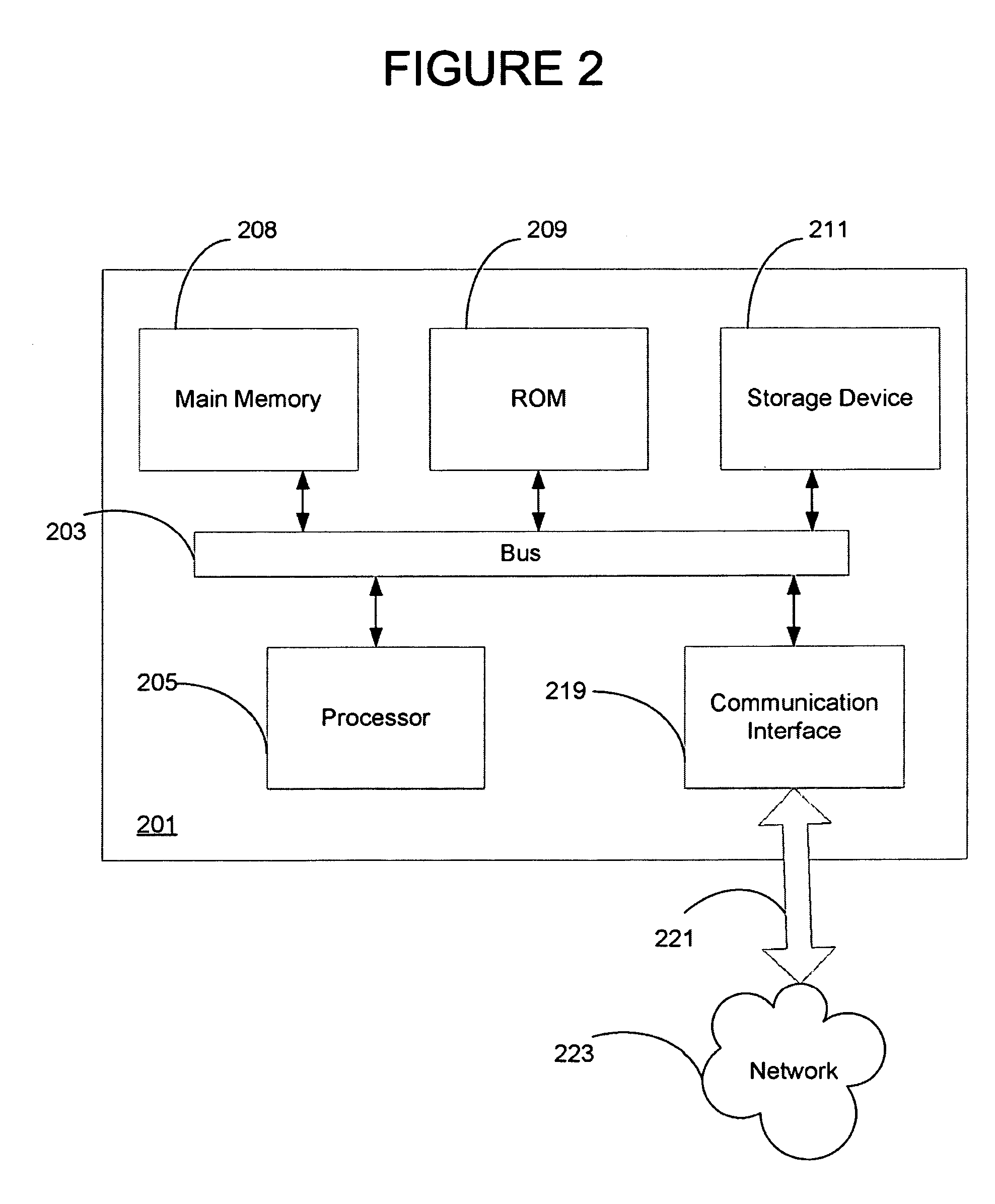
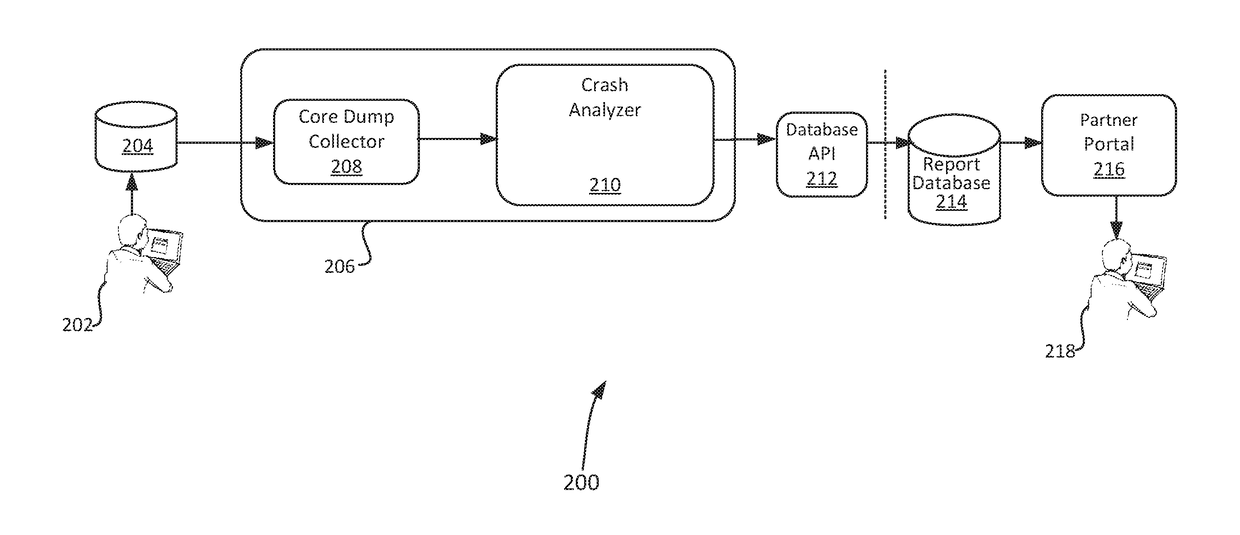
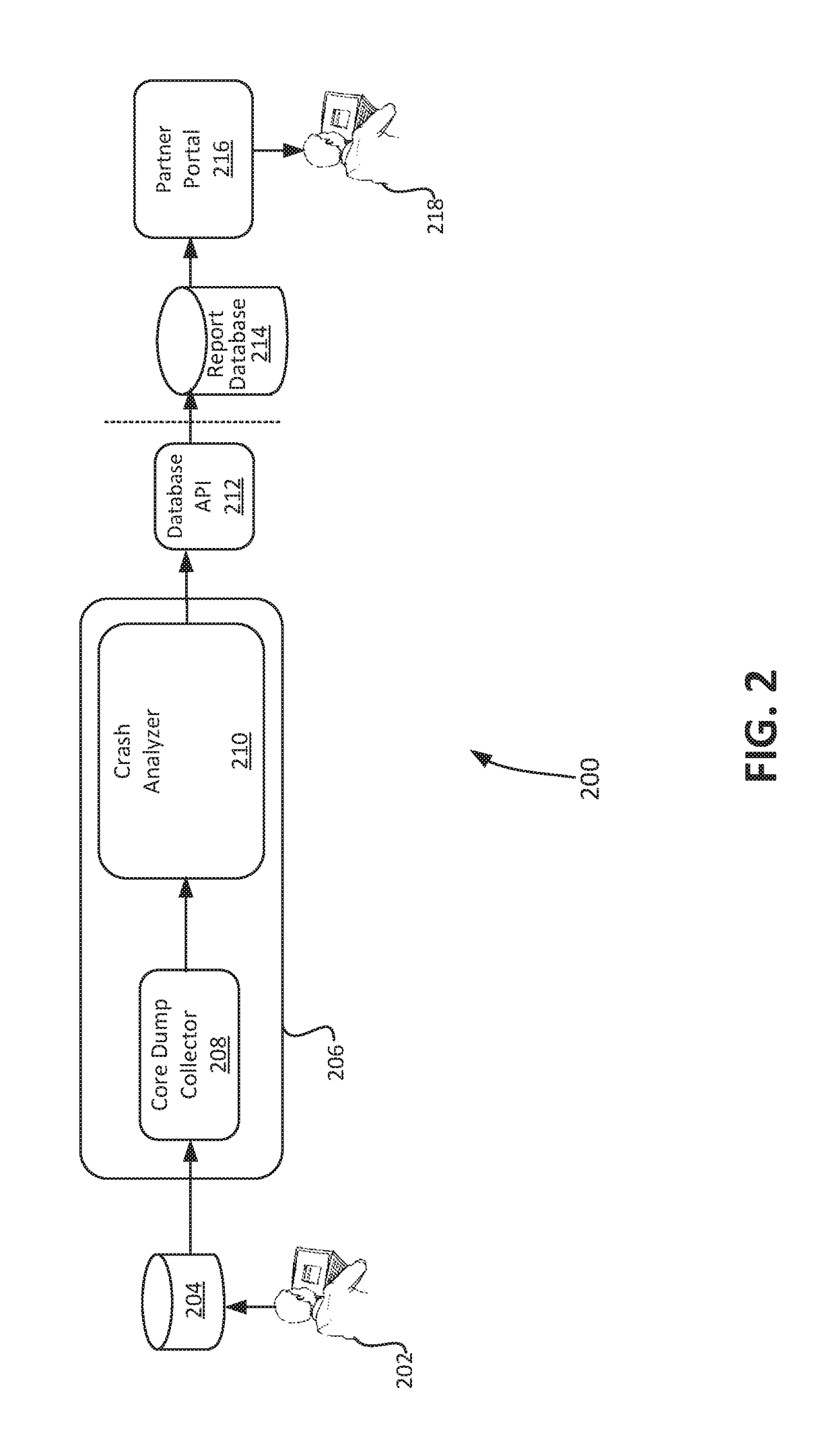
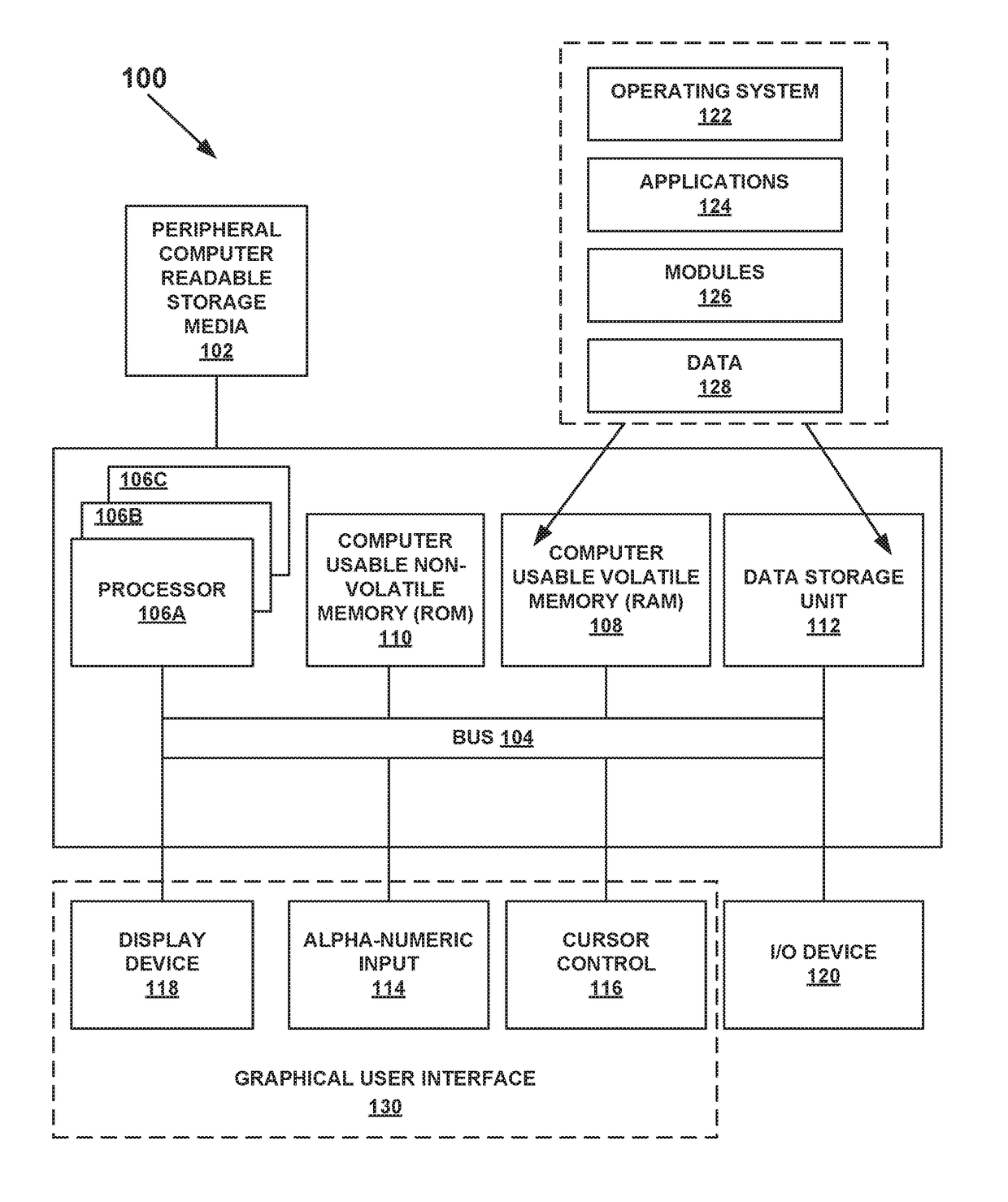
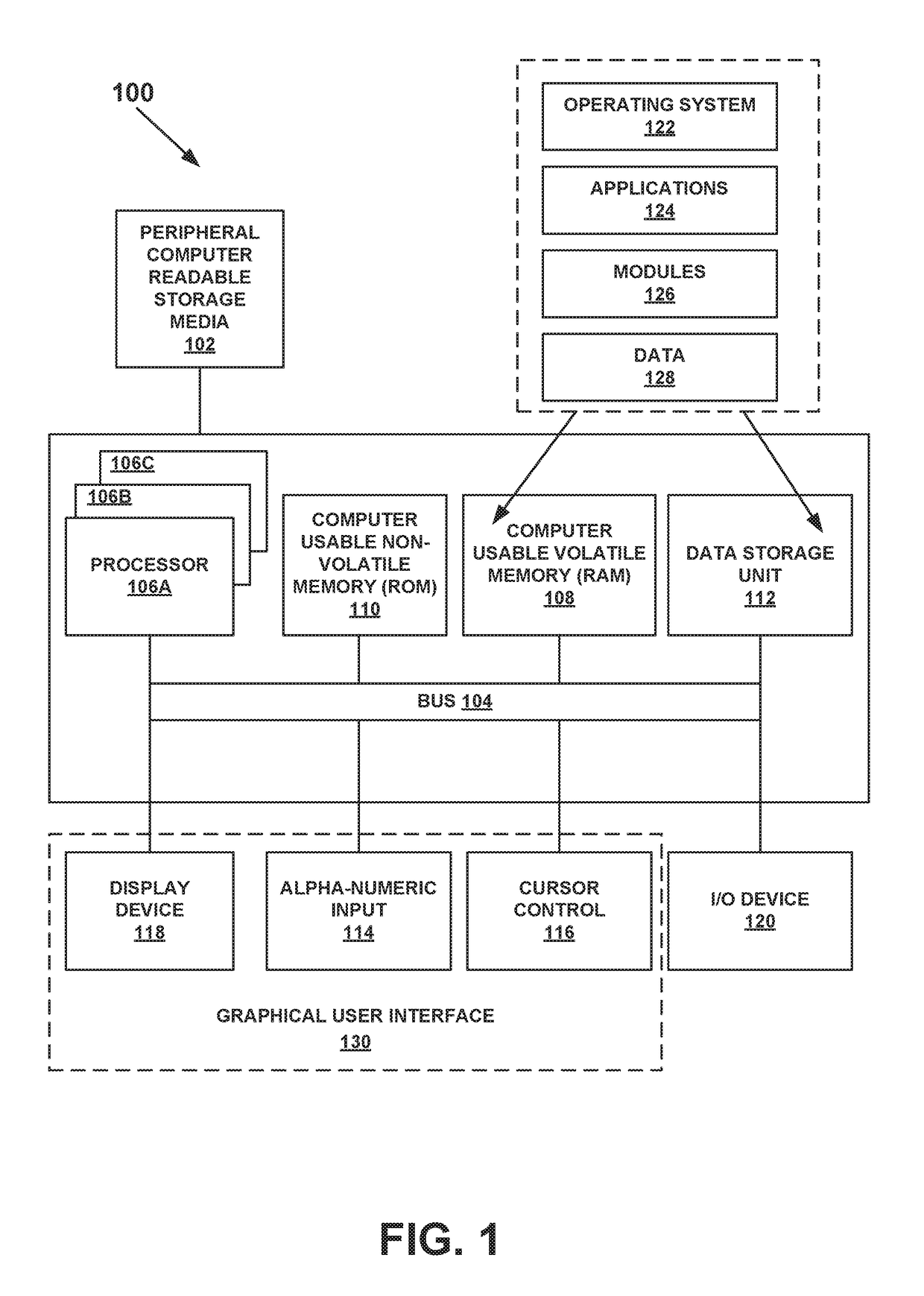
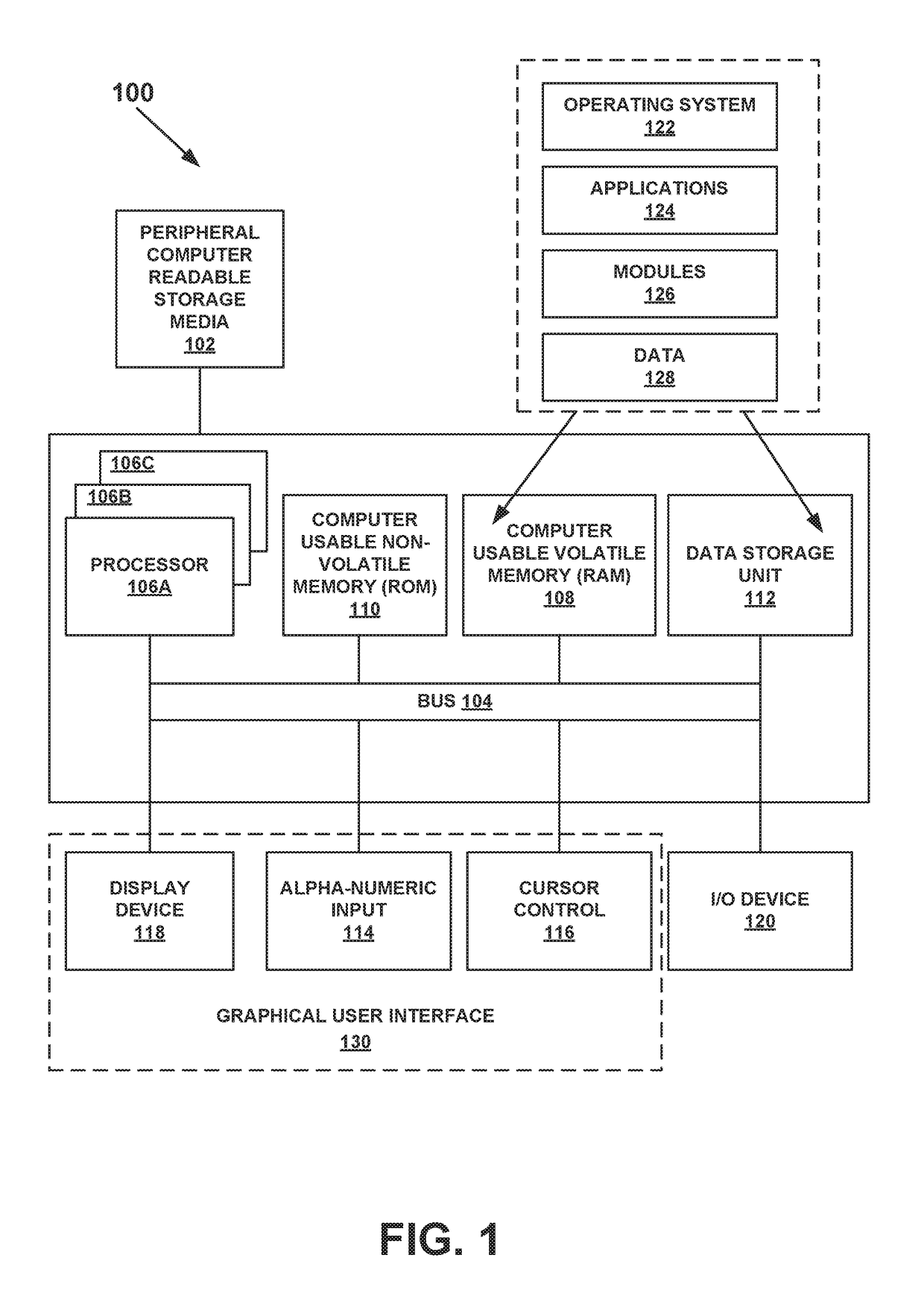
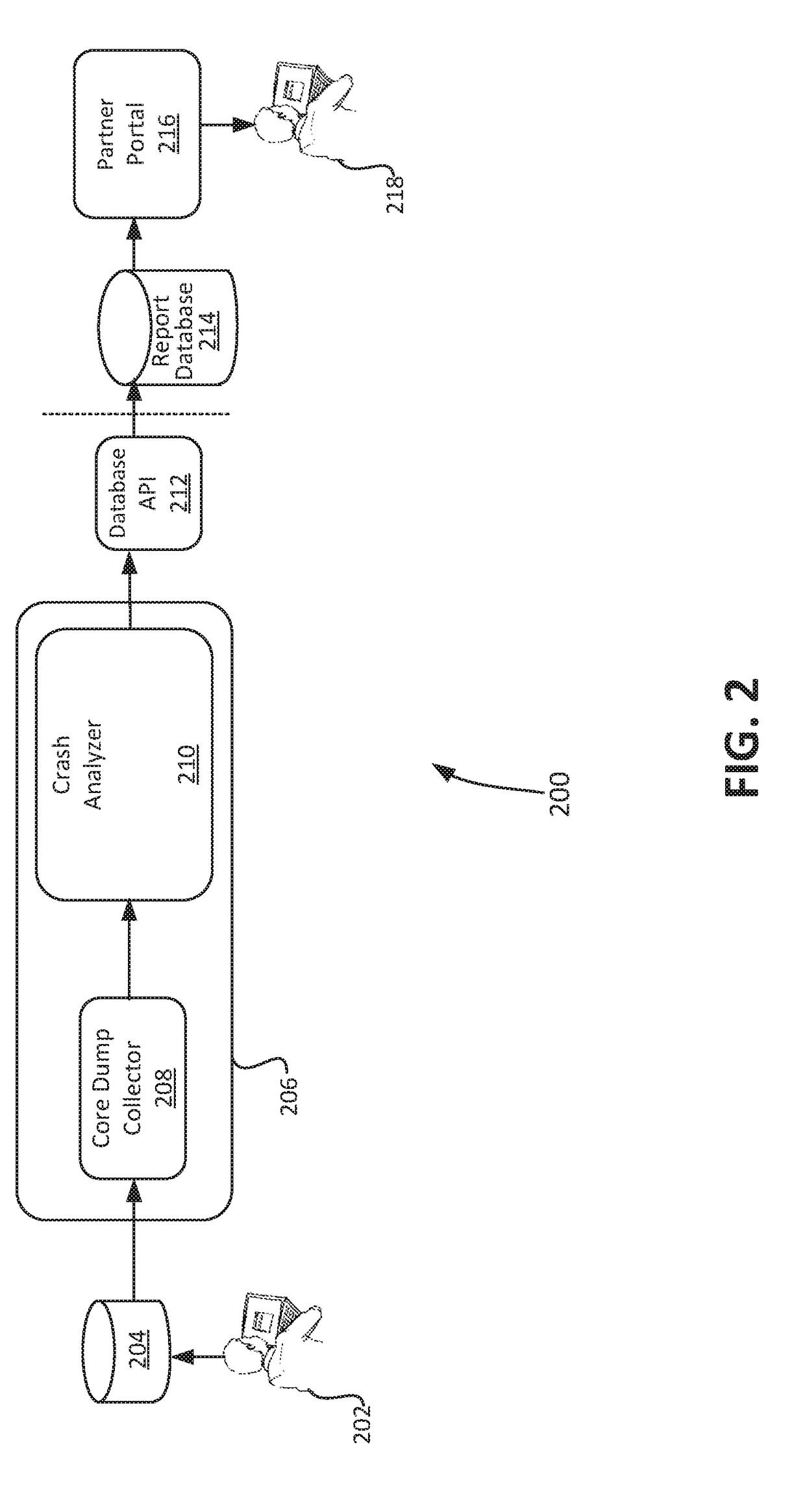
A computer-implemented method for monitoring a crash analysis system is disclosed. Log messages are accessed pertaining to the operation of a crash analysis system for analyzing a core dump. The log messages are analyzed, at a processor, in order to generate operation results data. A graphic user interface for display on a computer is generated. The graphic user interface includes a graphical representation of the operation results data.
Owner:VMWARE INC
Locating and altering sensitive information in core dumps
A core dump is processed to locate and optionally alter sensitive information. A core dump copy is created from at least a portion of an original core dump. Also, at least one input parameter is provided that corresponds to select information to be identified in the core dump copy and address information associated with the core dump copy is defined that corresponds to at least one of addresses where the select information can be altered and addresses where the select information should not be altered. Each occurrence of the select information located within the core dump copy is identified and optionally replaced with predetermined replacement data if the occurrence of the select information is within the addresses where the select information can be altered.
Owner:INT BUSINESS MASCH CORP
Monitoring, analyzing and processing method of core dump problem in progresses
ActiveCN107357731AEfficient and accurate processingReduce overheadSoftware testing/debuggingCore dumpOperational system
The invention provides a monitoring, analyzing and processing method of a core dump problem in progresses. A first service-side monitors and analyzes the core dump problem generated in each progress in service separately, the corresponding progress is restarted, program source code fault information is extracted, and a data library table is stored to a monitoring service system; then a second service-side is entered to achieve alarming. The monitoring, analyzing and processing method of the core dump problem in progresses can be applicable to multiple server operating systems of a linux, an hp-ux or an aix and the like, according to the main method, the path is monitored in real time through a monitoring path method of the first service-side, and then the second service-side conducts alarming.
Owner:福建星瑞格软件有限公司
Systems and methods for protecting customer secrets during vendor troubleshooting
Systems, methods, and computer products for protecting information during troubleshooting are provided. A dumping mechanism includes marking at least one of a plurality of memory regions in the computer-readable medium as non-dumpable, initiating a core dump, determining which memory regions of the plurality regions are non-dumpable, and dumping the contents only of memory regions not marked as non-dumpable.
Owner:CA TECH INC
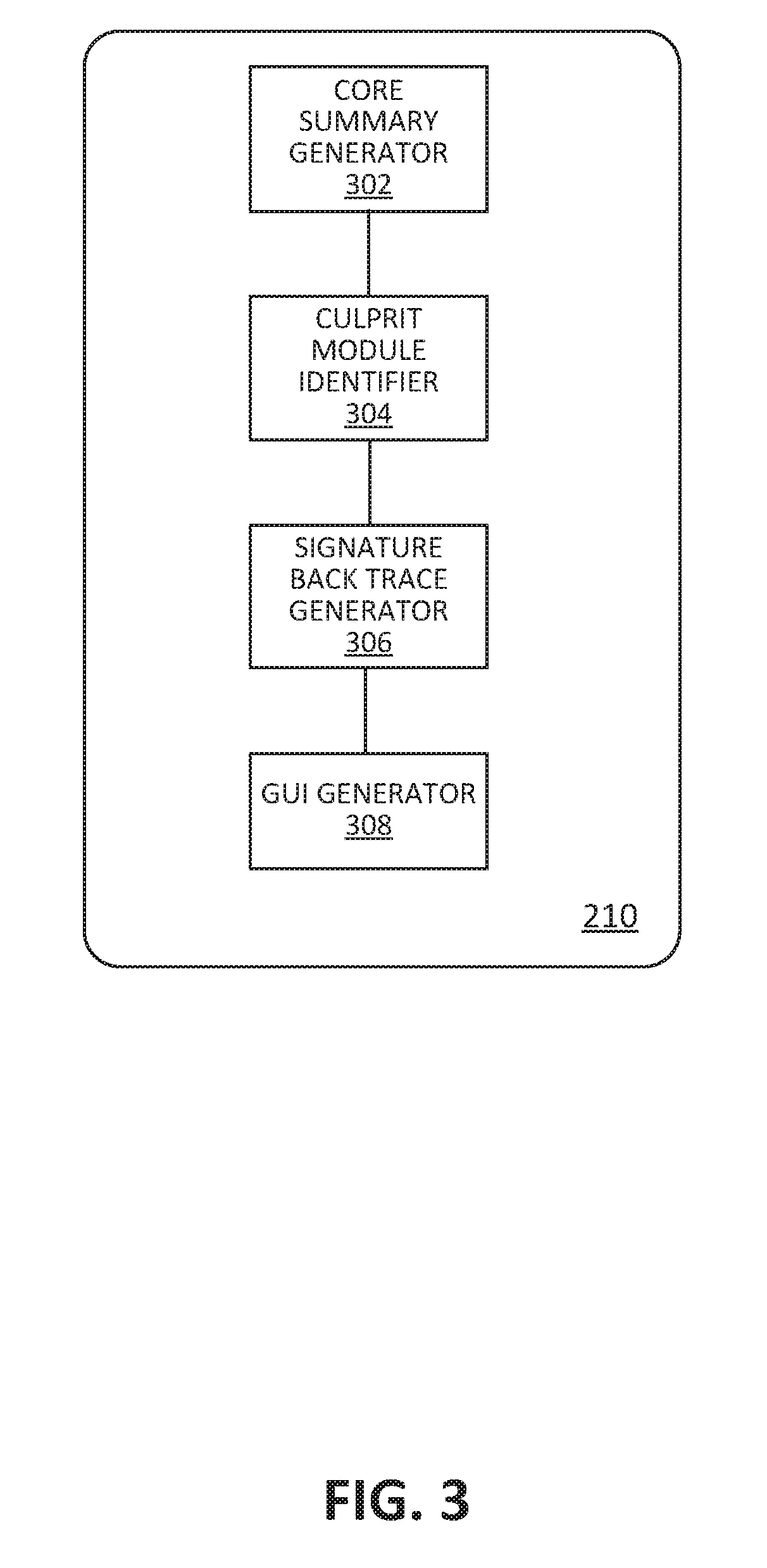
Culprit module detection and signature back trace generation
ActiveUS20170371731A1Software testing/debuggingNon-redundant fault processingCore dumpComputerized system
In a crash analysis system, a method for analyzing a core dump corresponding to a crash of a computer system is disclosed. A core dump is received wherein the core dump corresponds to a crash of a computer system. A culprit module responsible for the crash of the computer system is determined. A signature back trace, which pertains to a symptom of the crash of the computer system is generated.
Owner:VMWARE INC
Automated end-to-end analysis of customer service requests
An automated end-to-end analysis of customer service requests is disclosed. A core dump is received, wherein the core dump corresponds to a customer service request regarding a crash of a computer system. The core dump is automatically analyzed with a processor to generate analysis results. A graphical representation for display on a graphic user interface of a computer is generate, wherein the graphical representation corresponds to the analysis results for the core dump.
Owner:VMWARE INC
Automated end-to-end analysis of customer service requests
An automated end-to-end analysis of customer service requests is disclosed. A core dump is received, wherein the core dump corresponds to a customer service request regarding a crash of a computer system. The core dump is automatically analyzed with a processor to generate analysis results. A graphical representation for display on a graphic user interface of a computer is generate, wherein the graphical representation corresponds to the analysis results for the core dump.
Owner:VMWARE INC
Restarting a software system
In one aspect, a technique for restarting a software system on a computer platform after an unintentional software system shutdown. The technique includes, for instance, generating a core dump file on the computer platform when the software system shuts down unintentionally, restarting the software system, using a library for copying software system related data from the core dump file to the software system, and continuing execution of the software system.
Owner:IBM CORP
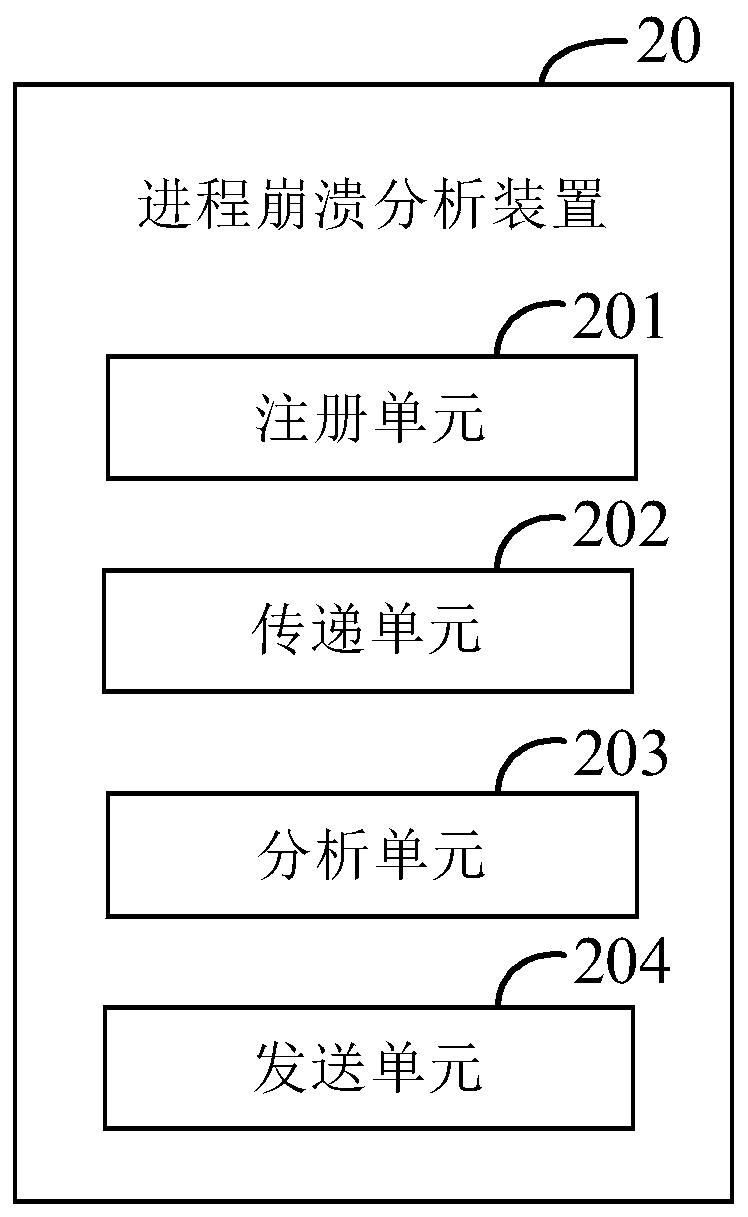
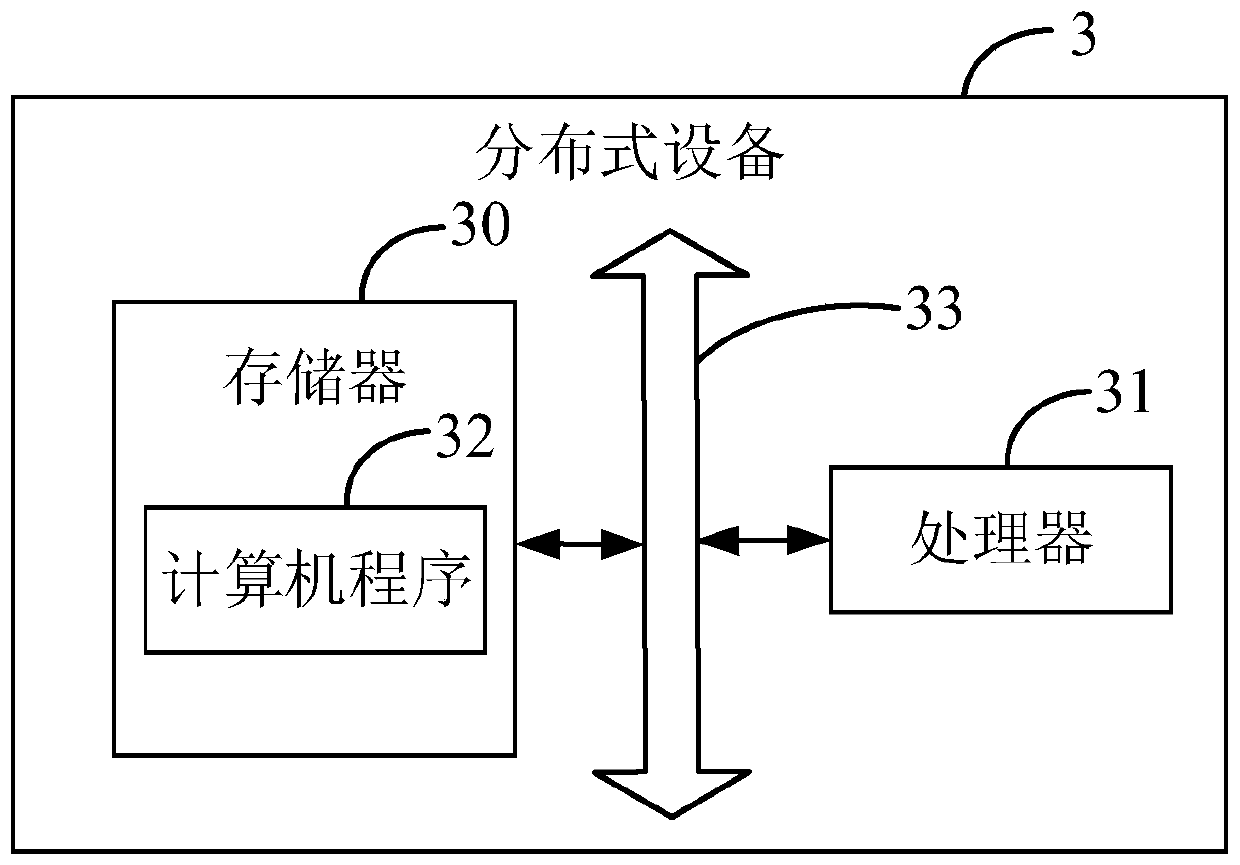
Process crash analysis method and device, distributed device and storage medium
ActiveCN110262918ADatabase distribution/replicationNon-redundant fault processingCore dumpOperational system
The invention provides a process crash analysis method. The method comprises the following steps of registering a process crash processing program into a dump mode of an operating system of a distributed device; when the crash occurs, the operating system transmitting a core dump file of a crash process to the process crash processing program from a kernel of the distributed device through a pipeline; the process crash processing program analyzing the core dump file to obtain the crash stack information of the crash process; and the process crash processing program sending the crash stack information to the server. The invention further provides a process crash analysis device, the distributed device and a storage medium. According to the invention, the crash stack information of the crash process of the distributed device can be acquired and sent to the server, so that the server can perform statistical analysis according to the crash stack information, thereby realizing the process crash analysis under the distributed cloud computing framework.
Owner:SHENZHEN ONETHING TECH CO LTD
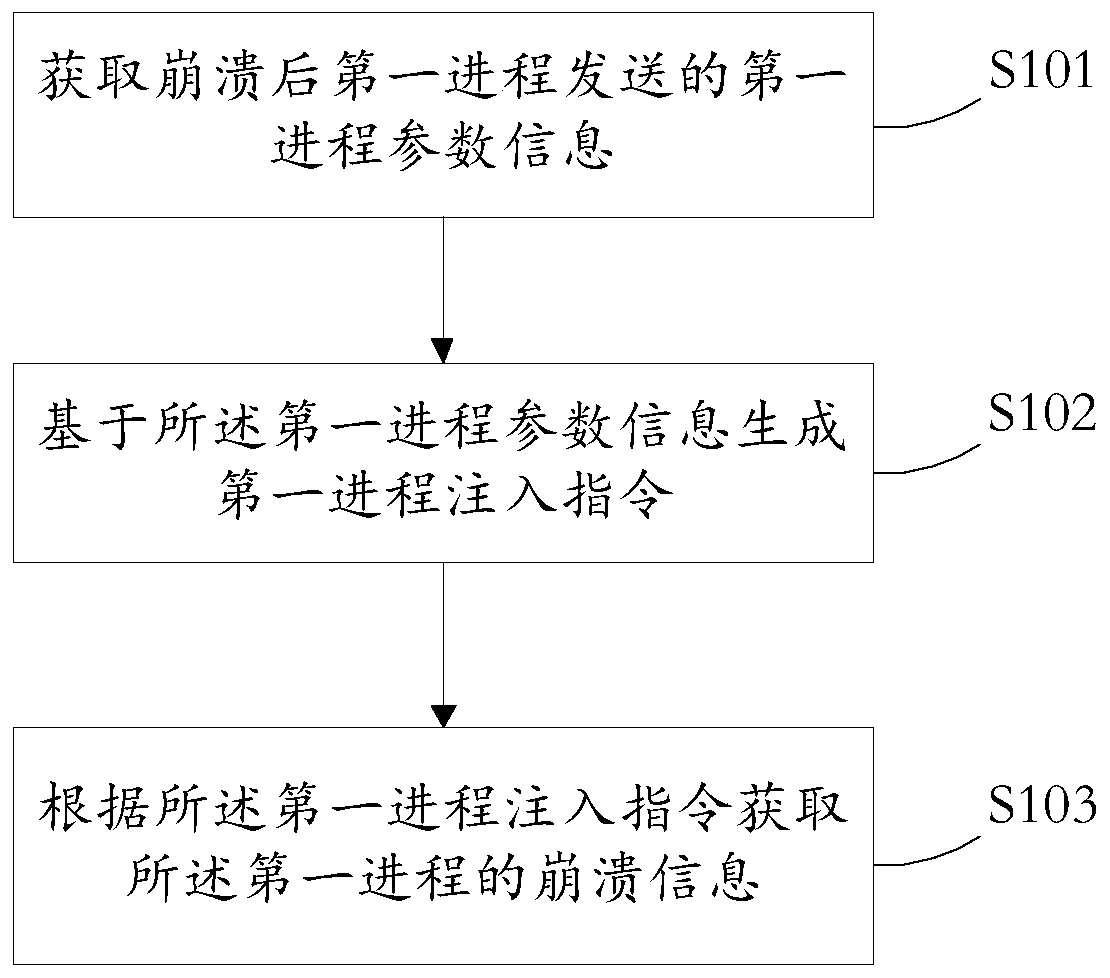
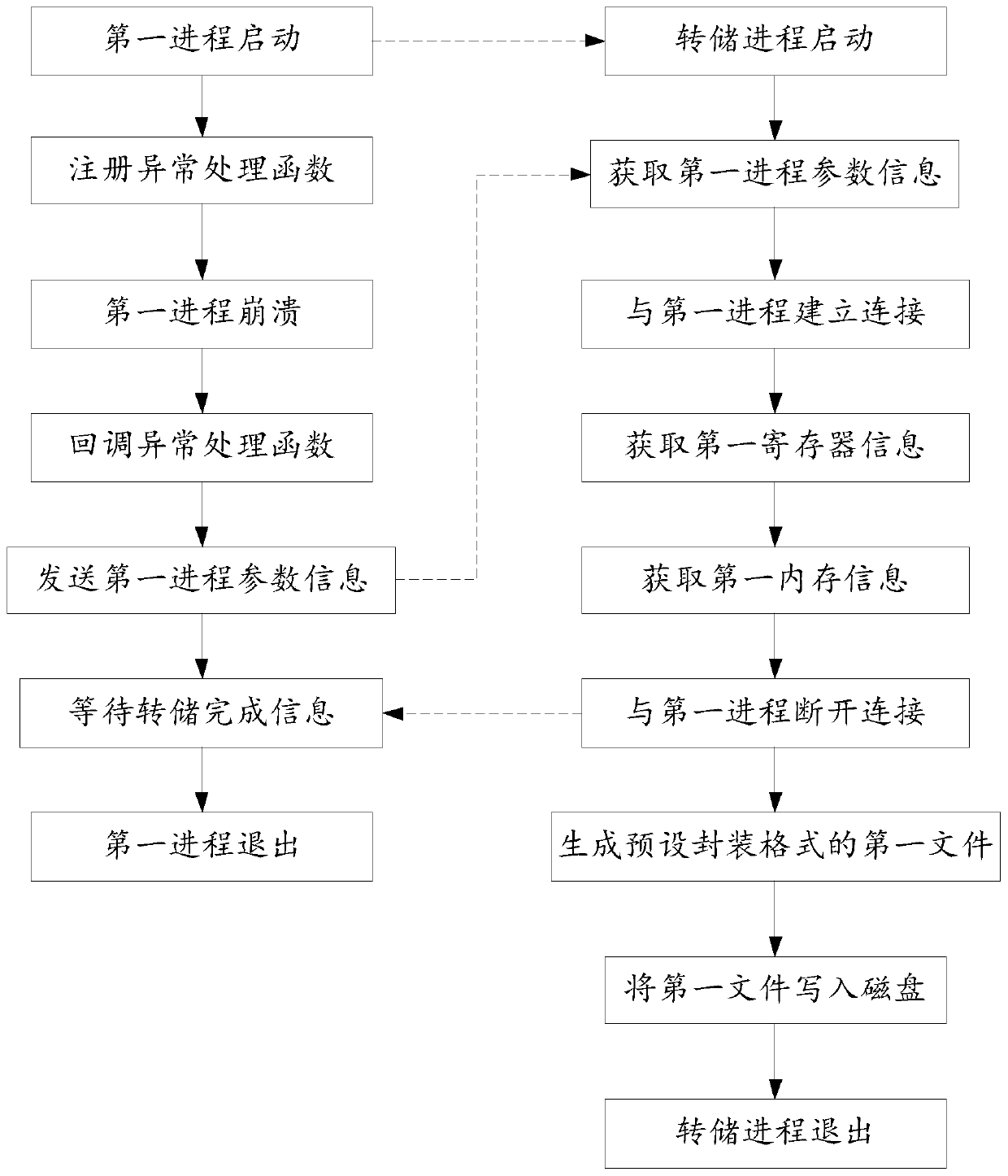
Method and device for obtaining process crash information, medium and electronic equipment
ActiveCN110727566APrecise positioningFix crashHardware monitoringEnergy efficient computingCore dumpSimulation
The invention provides a method and device for obtaining process crash information, a medium and electronic equipment. The method comprises the steps of obtaining first process parameter information sent by a first process after crash; generating a first process injection instruction based on the first process parameter information; and obtaining crash information of the first process according tothe first process injection instruction. According to the method, instruction injection is carried out on the first process through the dump process, and the crash information is obtained, and information before and after process operation when the first process crashes can be obtained from the crash information, and the crash problem is conveniently positioned. By comprehensively analyzing the crash information of the first process, the crash reason of the crash of the first process can be obtained. The problem that process crash cannot be analyzed due to the fact that a core dump mechanismdoes not exist is solved, and the problem of system crash is further solved.
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
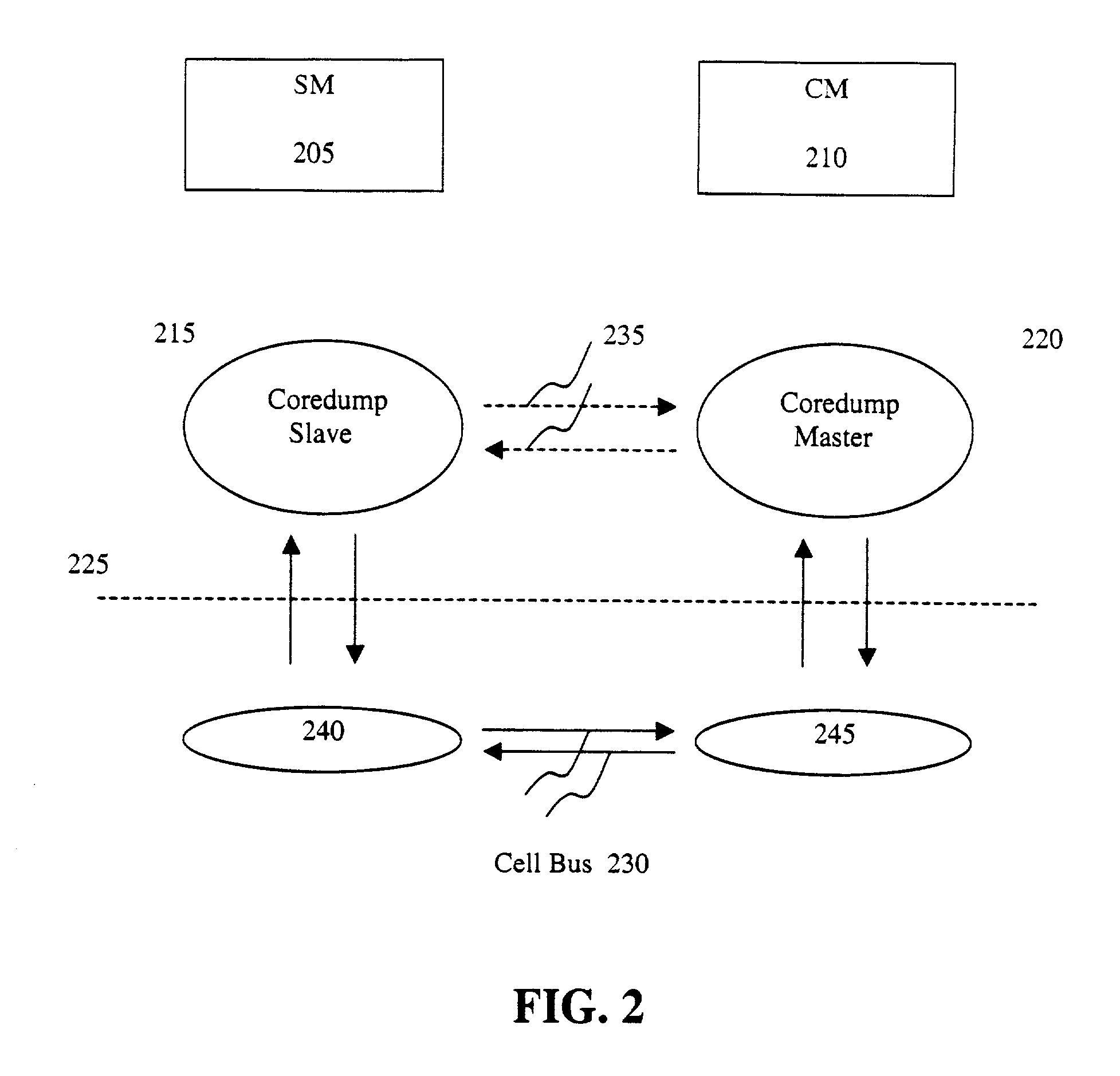
Method for debugging computer program
The invention proposes a debugging method. A computer running a program that generates a master core dump file and one or more slave core dump files in response to a triggering event such as an internal failure. Another computer analyzes the core dump file to debug the program. The master core dump file includes an index list, each entry of the index list corresponds to a slave core dump file of the one or more slave core dump files. The master core dump file may first be transferred to the other computer. Based on the information in the index list, the other computer selectively requests one or more of the generated slave core files for debugging.
Owner:HUAWEI TECH CO LTD
Failure detection and fencing in a computing system
A method, computer program product, and system for detecting and fencing off a failed entity instance so that failover time in the computing system is reduced. Upon detection of a failed entity, for example a failed process, a signal handler invokes an operating system interface to fence off the failed instance from modifying its persistent state, so that the entity may be re-instantiated prior to termination of the failed instance. This approach reduces failover time and eliminates split-brain problems without compromising access to the failed instance to obtain diagnostic information, core dumps, and the like.
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com