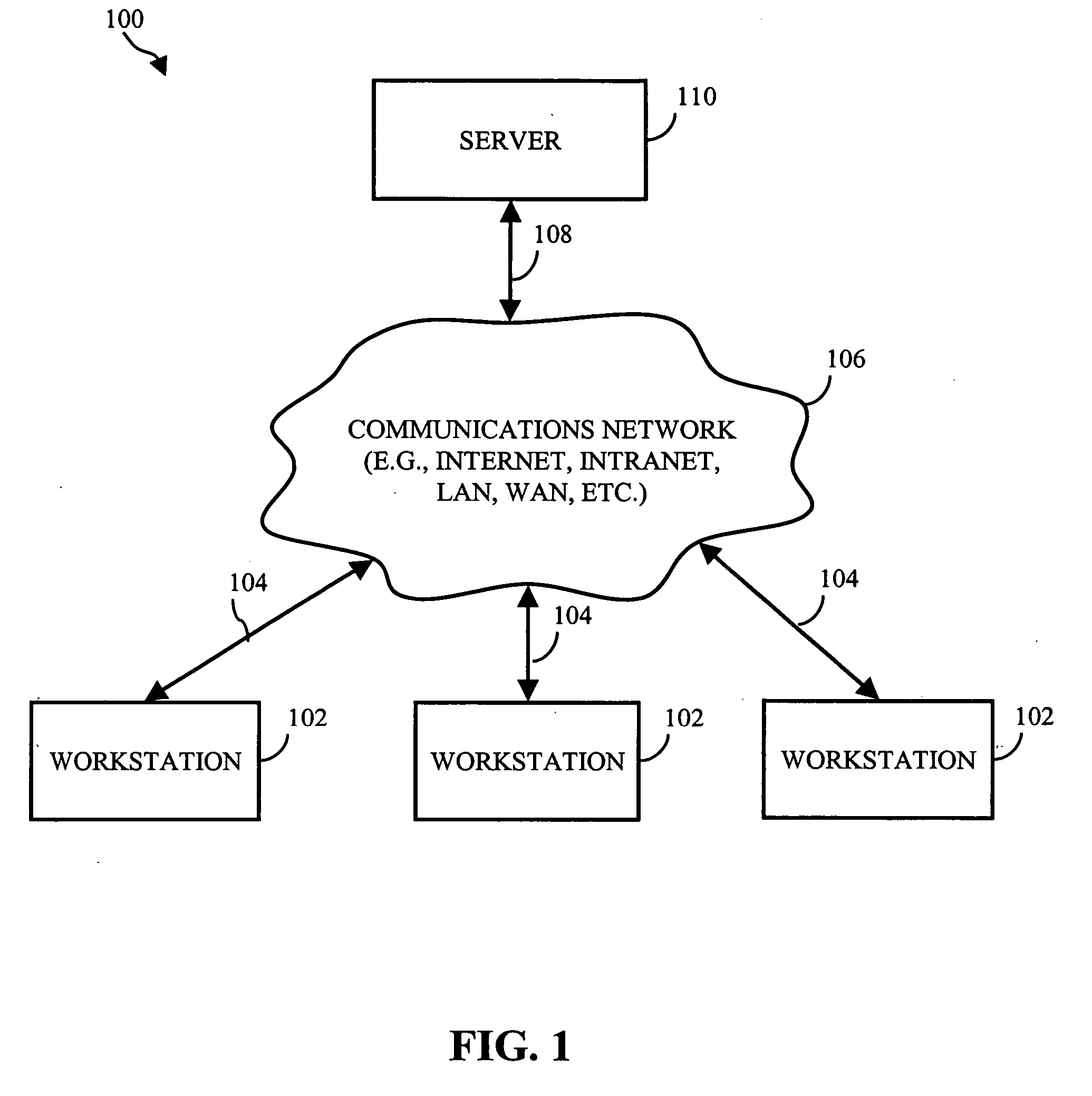
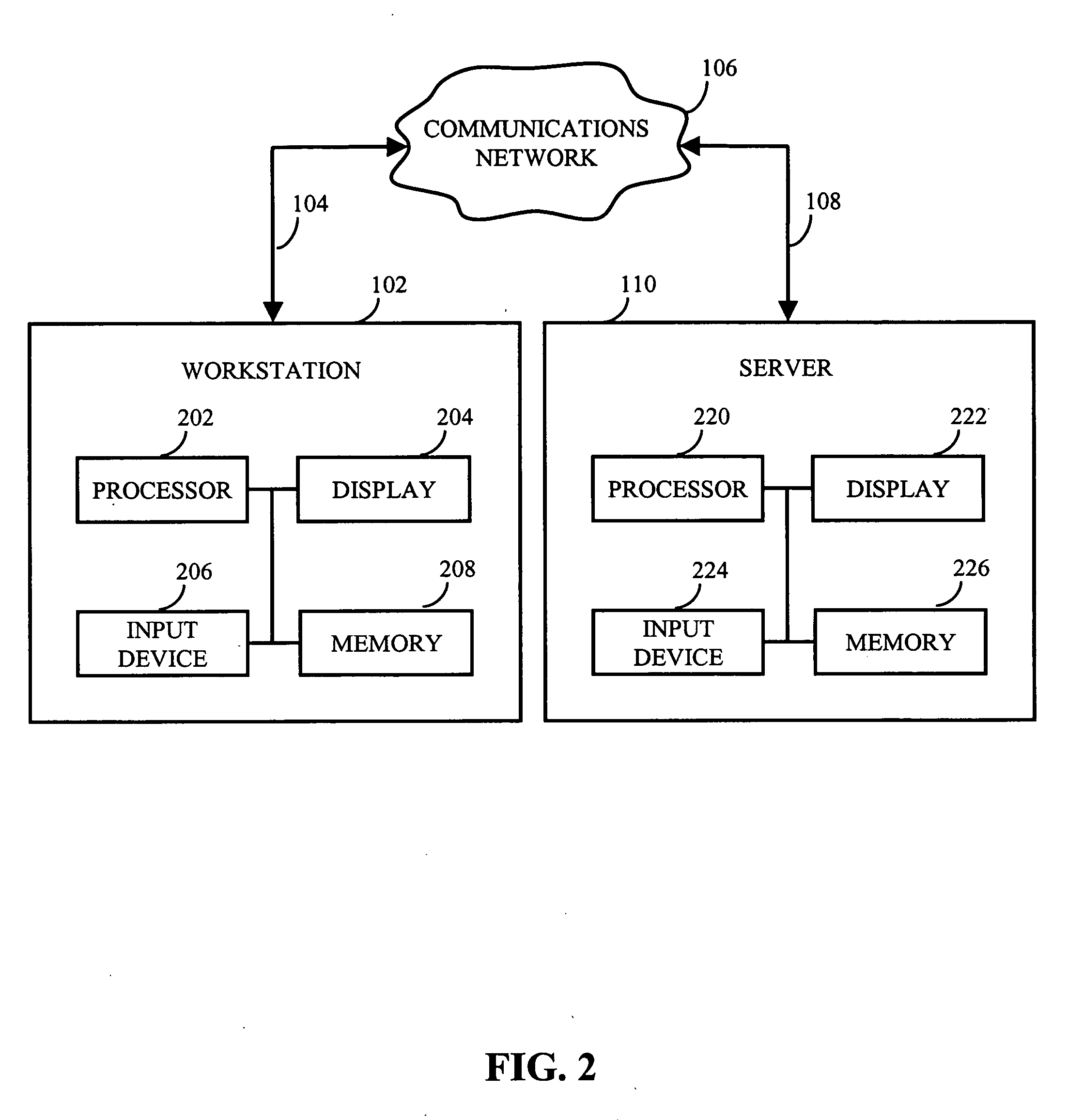
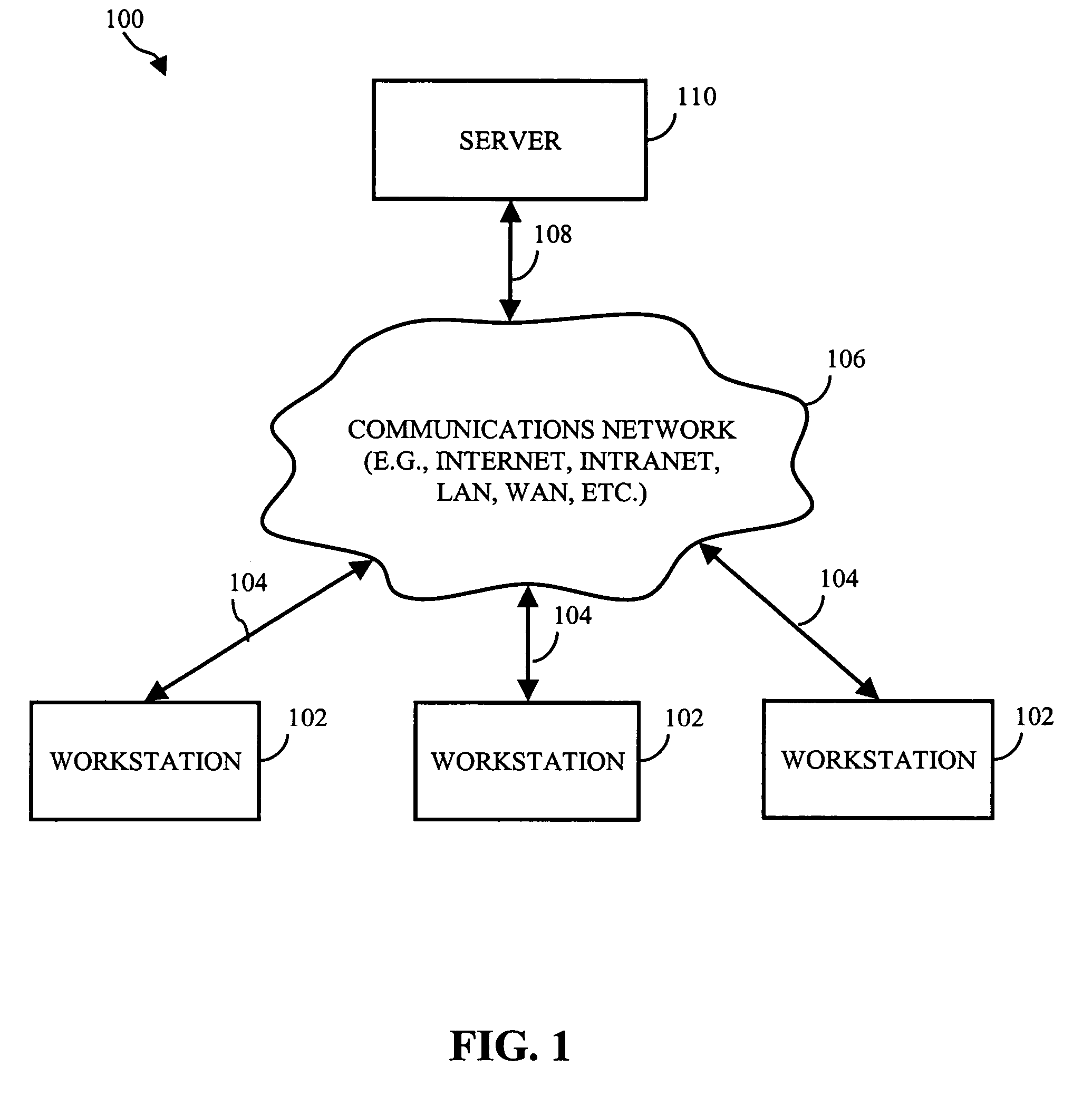
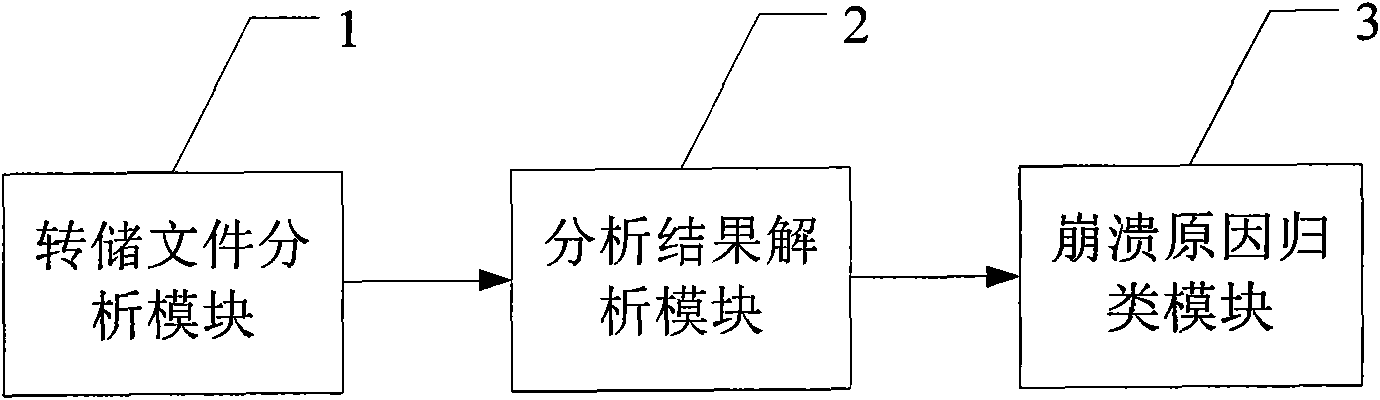
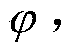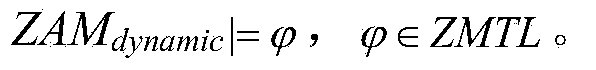Patents
Literature
212 results about "Software failure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
What is Software Failure. 1. A failure that occurs when the user perceives that the software has ceased to deliver the expected result with respect to the specification input values. The user may need to identify the severity of the levels of failures such as catastrophic, critical, major or minor, depending on their impact on the systems.
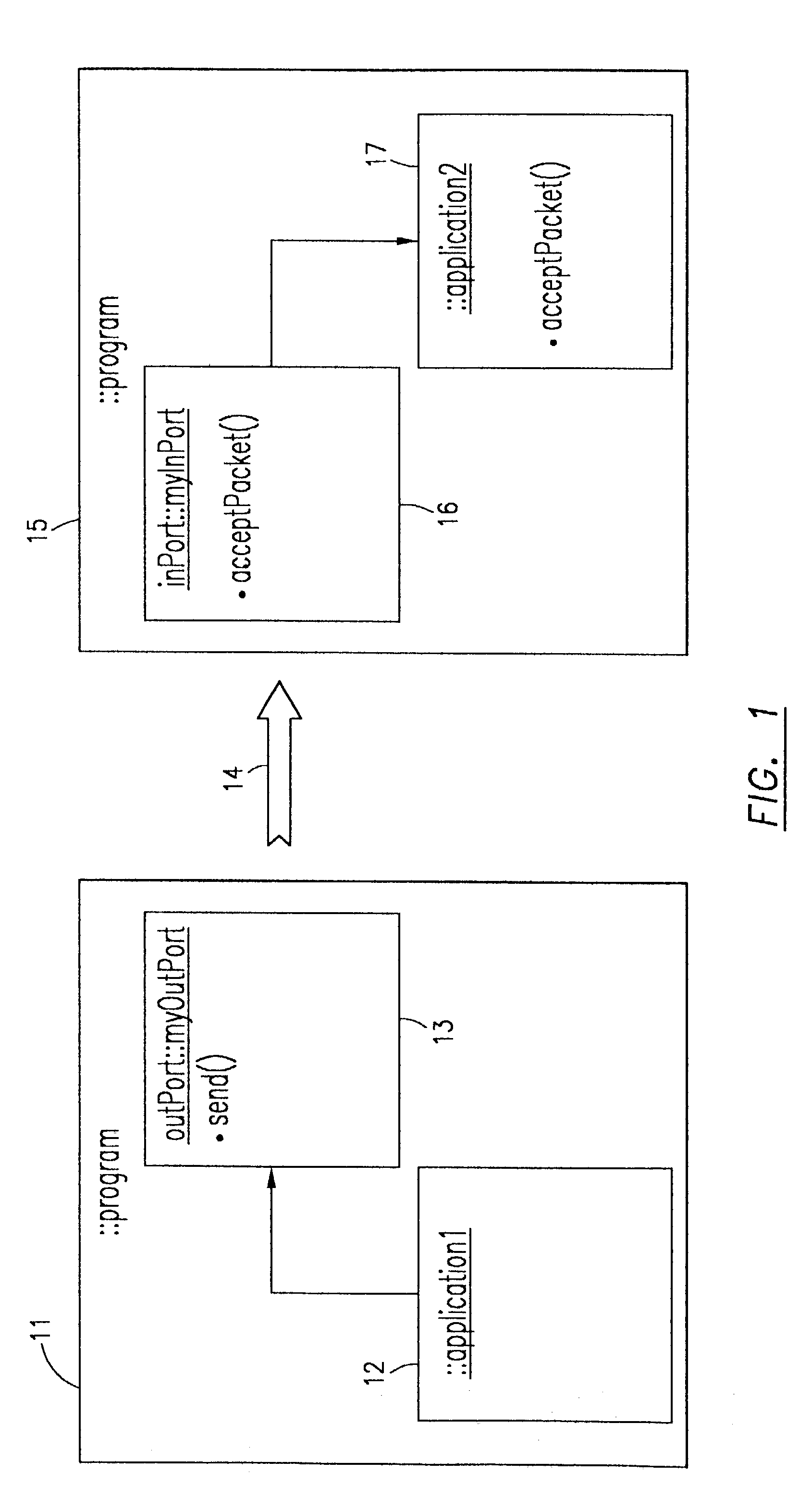
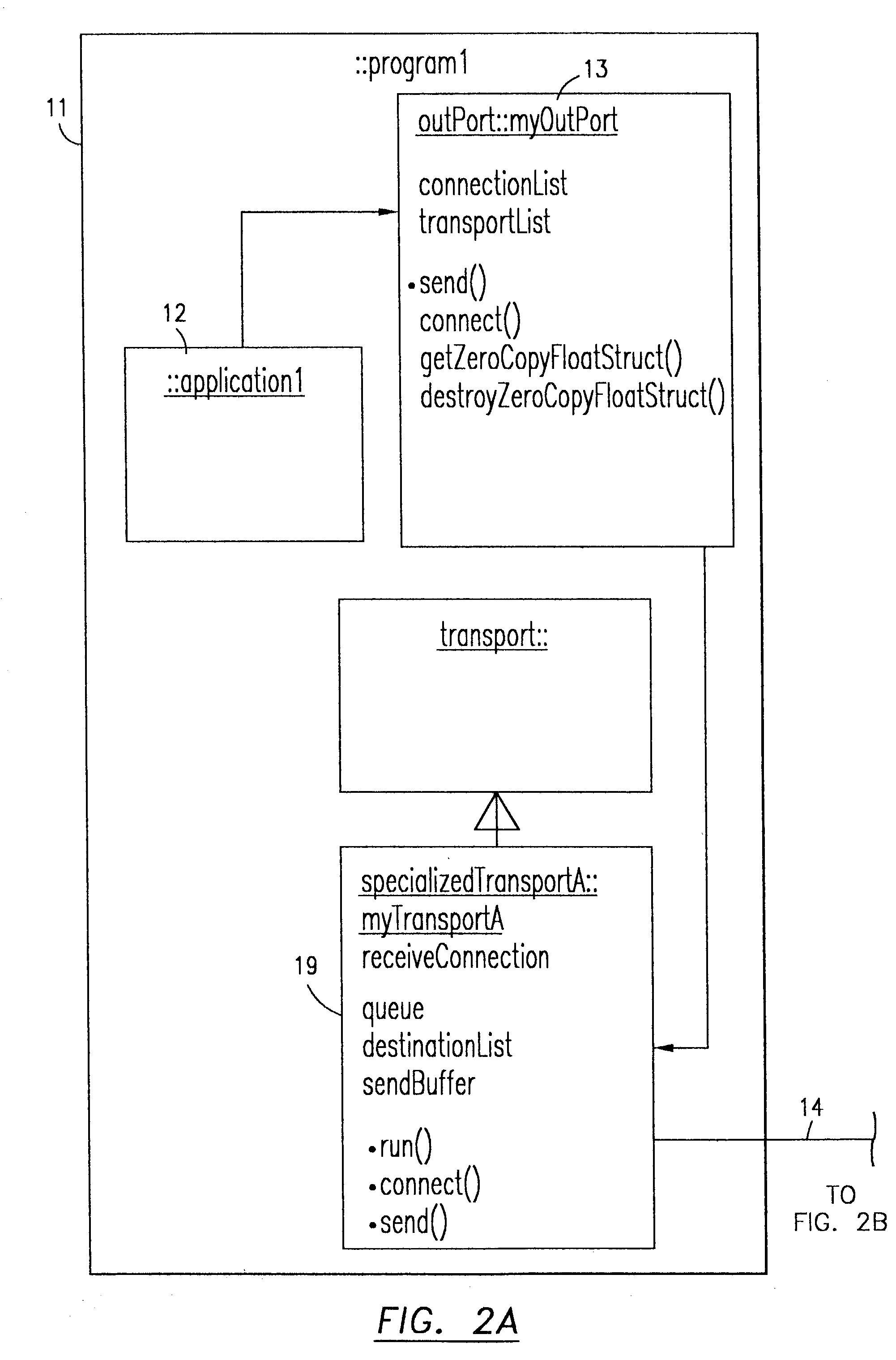
Method and apparatus for executing applications on a distributed computer system
ActiveUS20050005200A1Simplify the management processEasy to manageError detection/correctionDigital data processing detailsControl systemSoftware failure
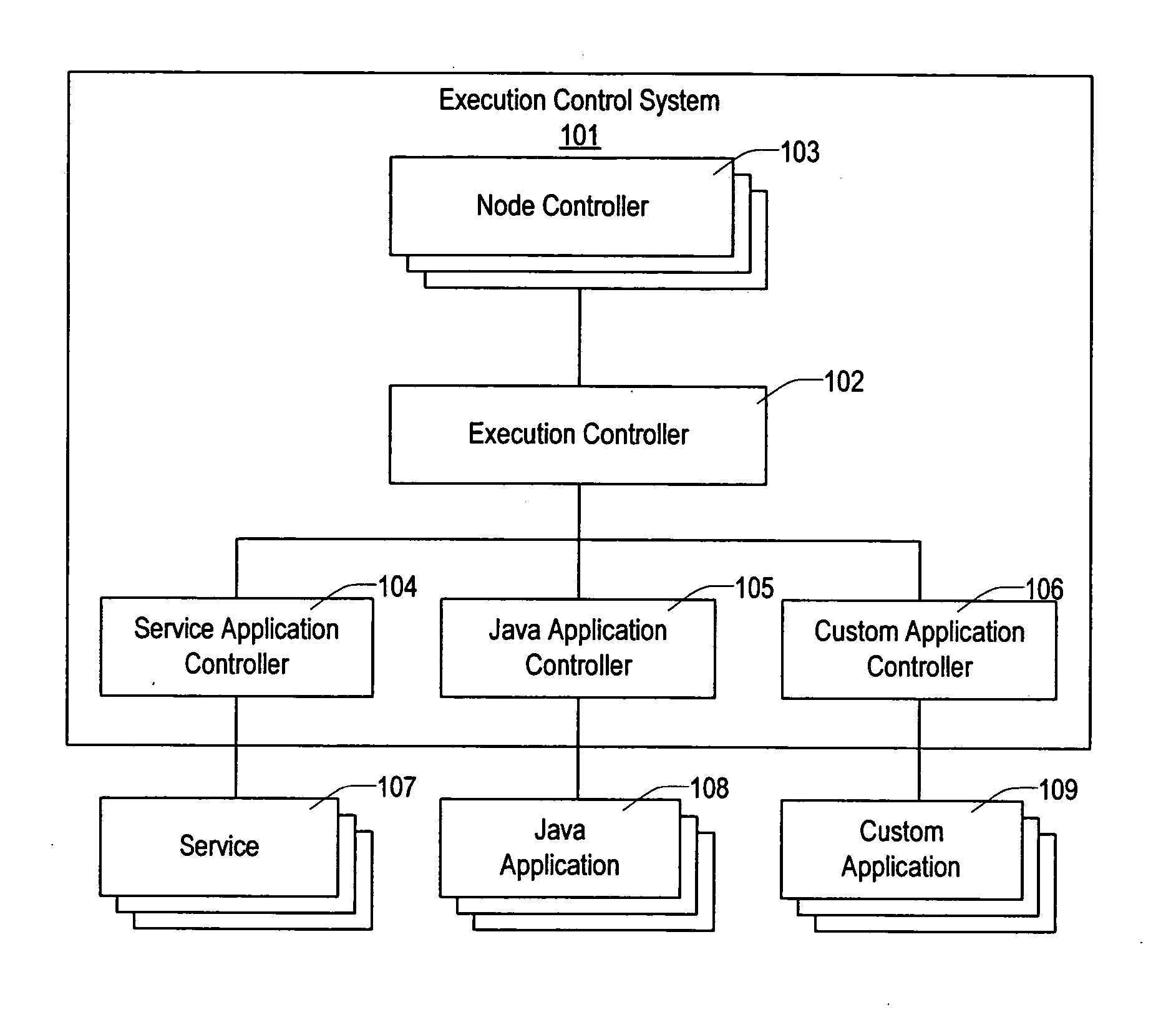
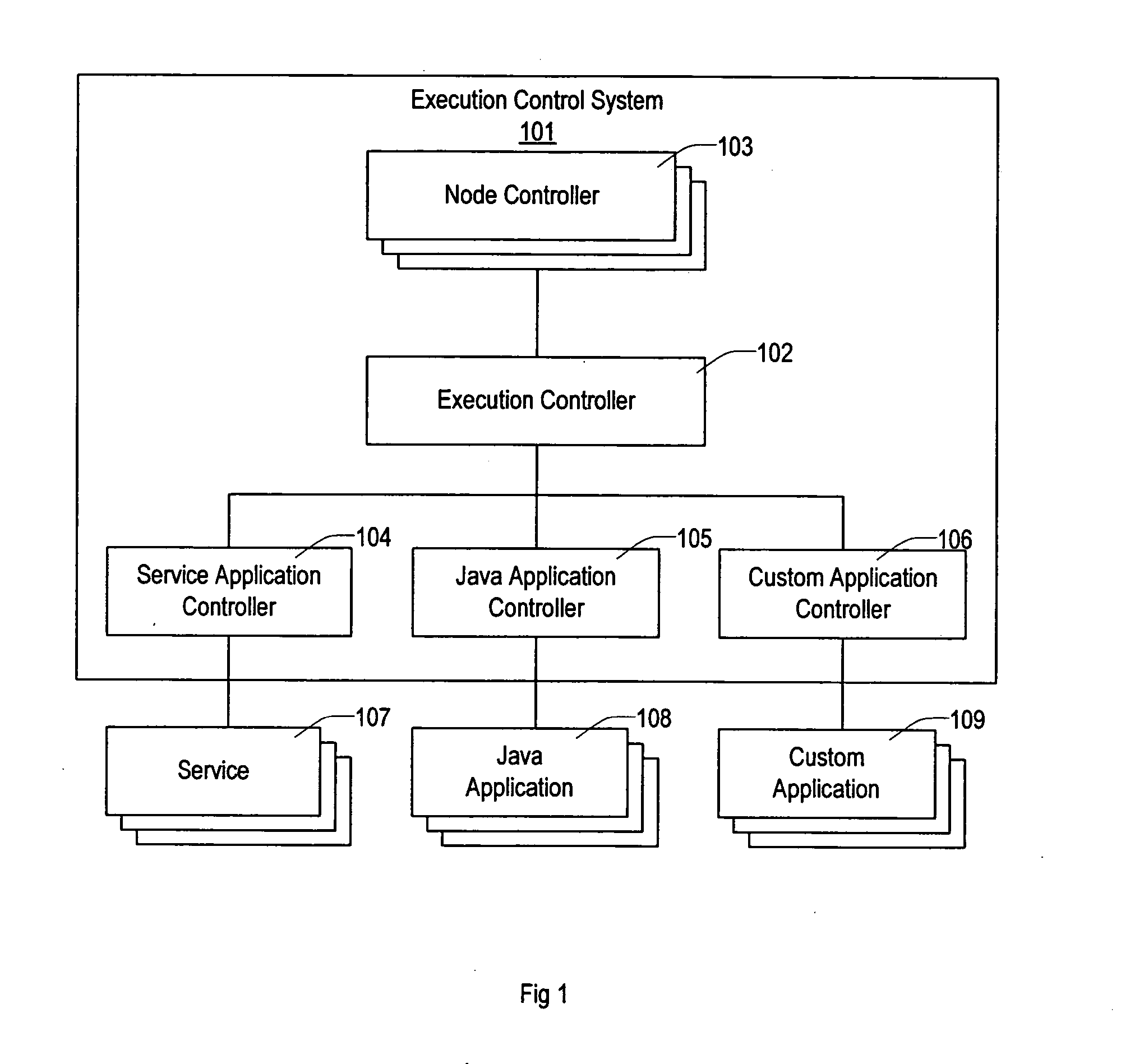
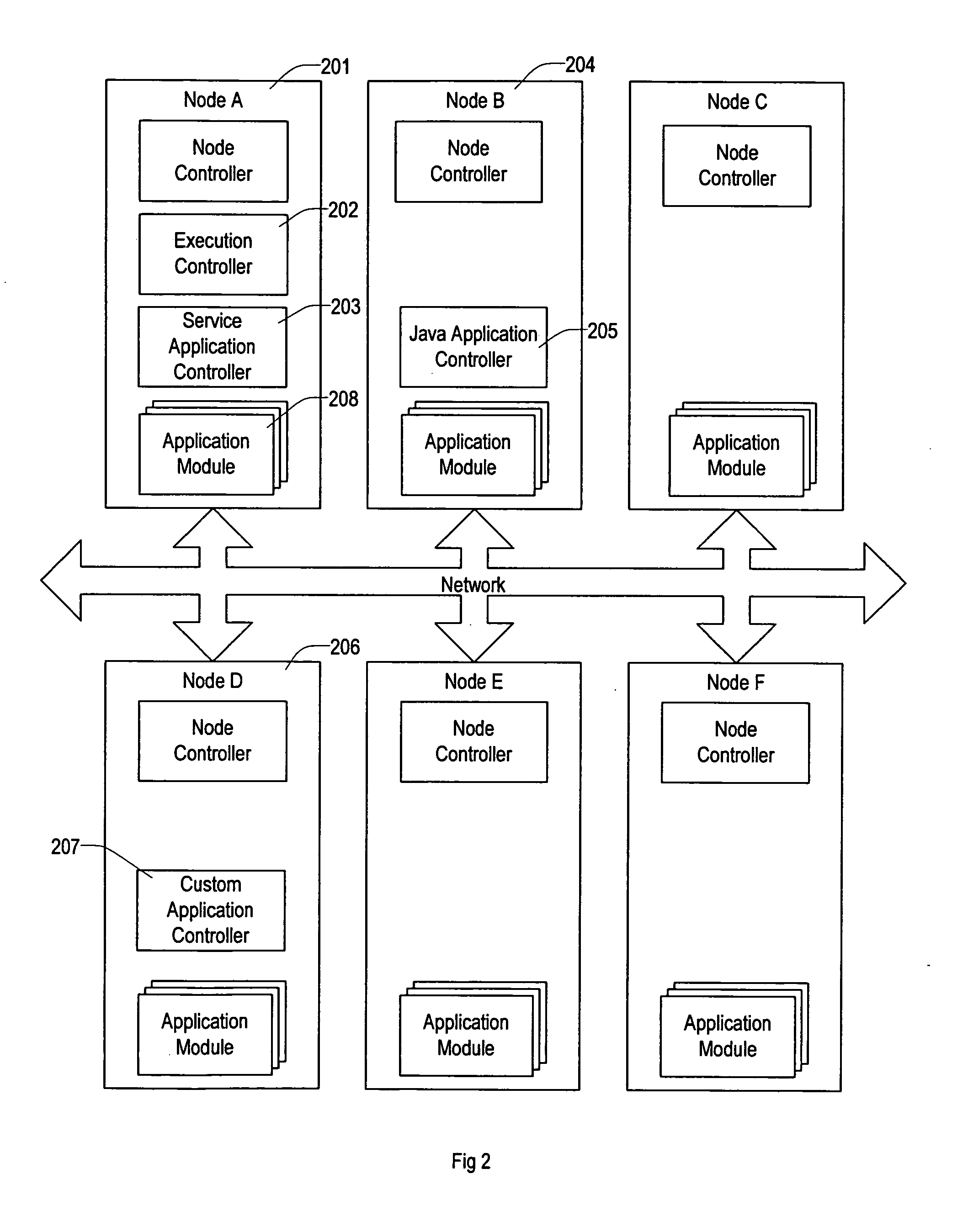
The present invention provides a flexible and extensible execution control system for distributed computer systems including multiple nodes interconnected through a network. Distributed computer systems that include an execution control system consistent with the present invention can be used for more types of applications than systems using prior art. The applications running on a distributed computer system that includes an execution control system consistent with the present invention can achieve better protection from hardware and software failures than systems using prior art systems and methods.
Owner:VLADIMIR MATENA +1
Methods and systems for repairing applications
ActiveUS20060195745A1Improve usabilityEasy to useElectronic circuit testingNon-redundant fault processingCore dumpSoftware failure
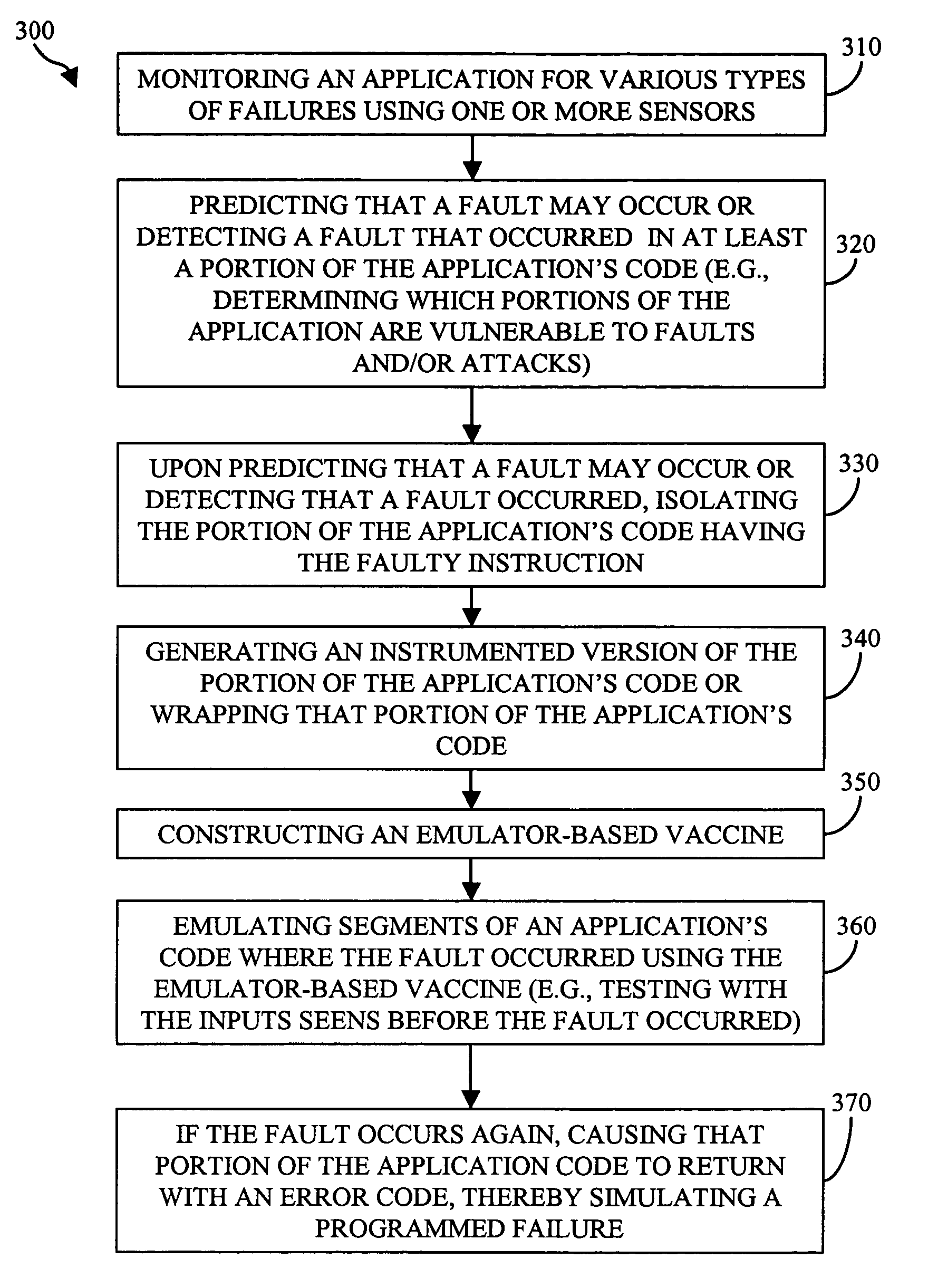
In accordance with the present invention, computer implemented methods and systems are provided that allow an application to automatically recover from software failures and attacks. Using one or more sensors, failures may be detected in the application. In response to detecting the failure, the portion of the application's code that caused the failure is isolated. Using the input vectors that caused the failure, information regarding the failure (e.g., the type of failure), a core dump file (e.g., stack trace), etc., an emulator-based vaccine that repairs the failure is constructed. In response to verifying that the vaccine repaired the failure, the application is automatically updated with the emulator-based vaccine without user intervention. Application community features that efficiently use the resources available in software monoculture is also provided. An application community may be defined that includes a plurality of devices and the application's code may be divided into smaller portions of code, which are assigned to each of the plurality of devices for monitoring. Each device also notifies the other devices of the failure.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
Methods and systems for repairing applications
ActiveUS7490268B2Easy to useProvide protectionNon-redundant fault processingPlatform integrity maintainanceCore dumpSoftware failure
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
Method for determining field software reliability metrics
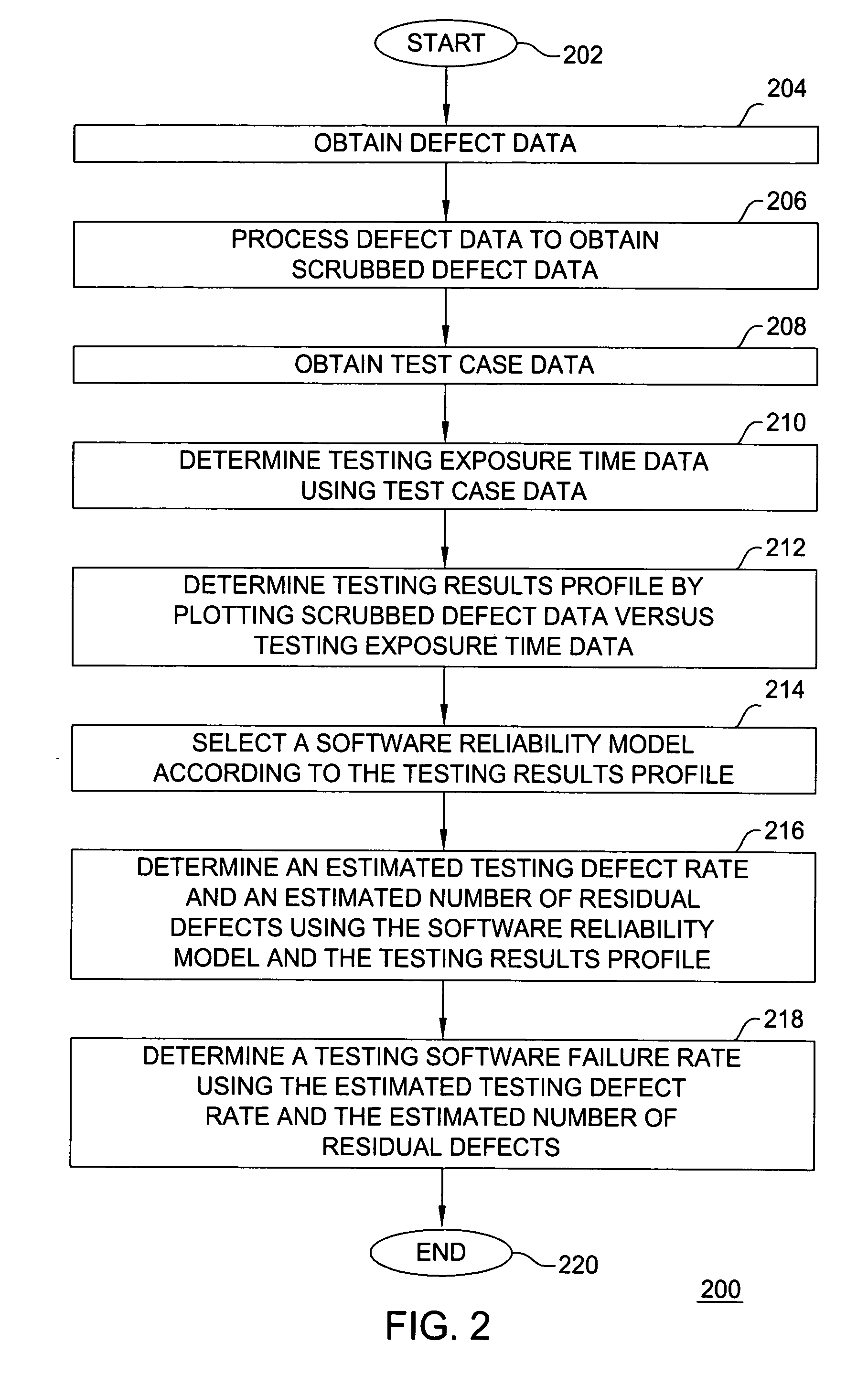
The invention includes a method for determining a software reliability metric, including obtaining testing defect data, obtaining test case data, determining testing exposure time data using the test case data, and computing the software reliability metric using testing defect data and testing exposure time data. The defect data includes software defect records. The test case data includes test case execution time data. A testing results profile is determined using testing defect data and testing exposure time data. A software reliability model is selected according to the testing results profile. A testing defect rate and a number of residual defects are determined by using the software reliability model and the testing results profile. A testing software failure rate is determined using the testing defect rate and the number of residual defects. A field software availability metric is determined using the field software failure rate determined using the testing software failure rate.
Owner:LUCENT TECH INC
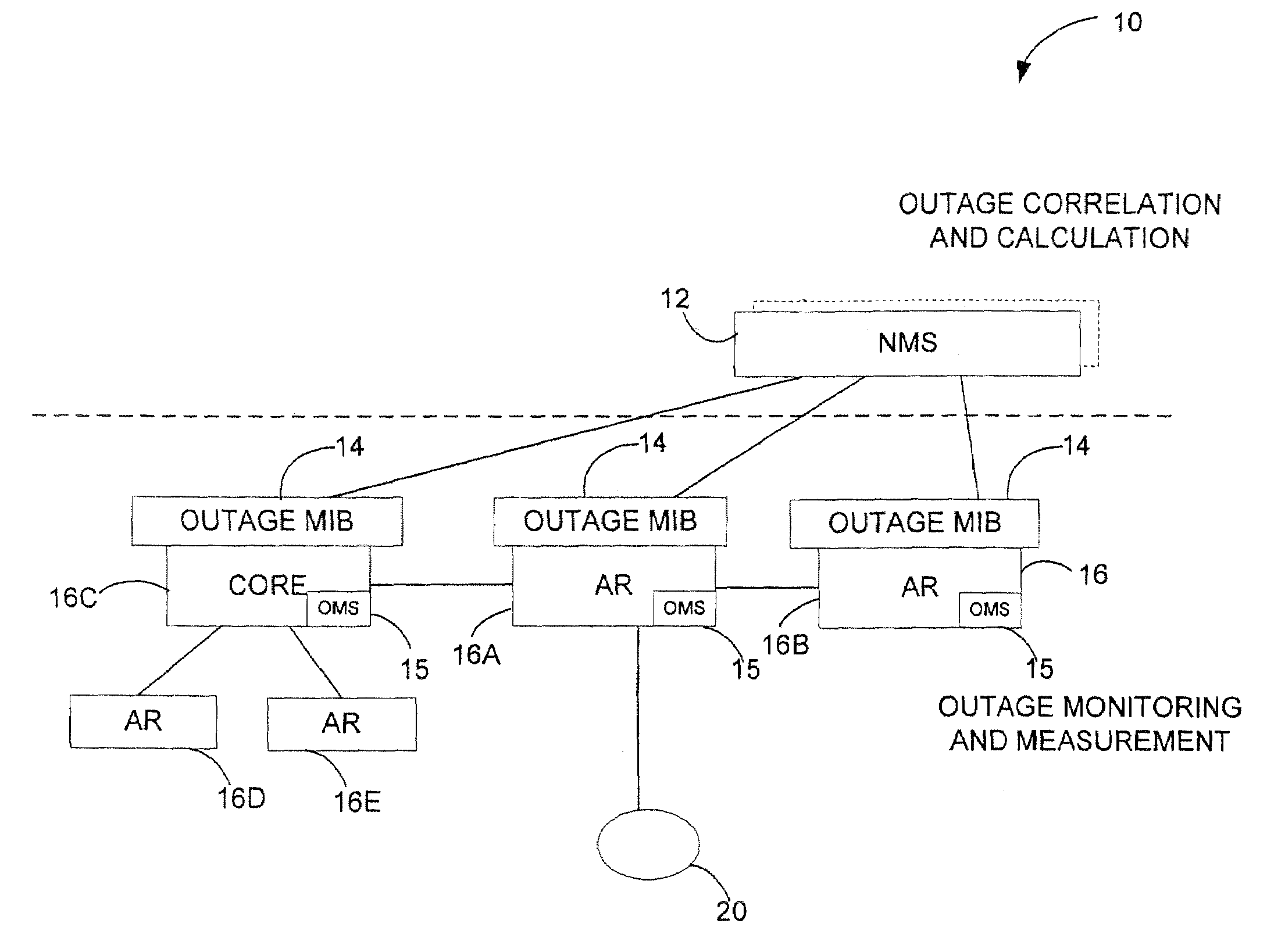
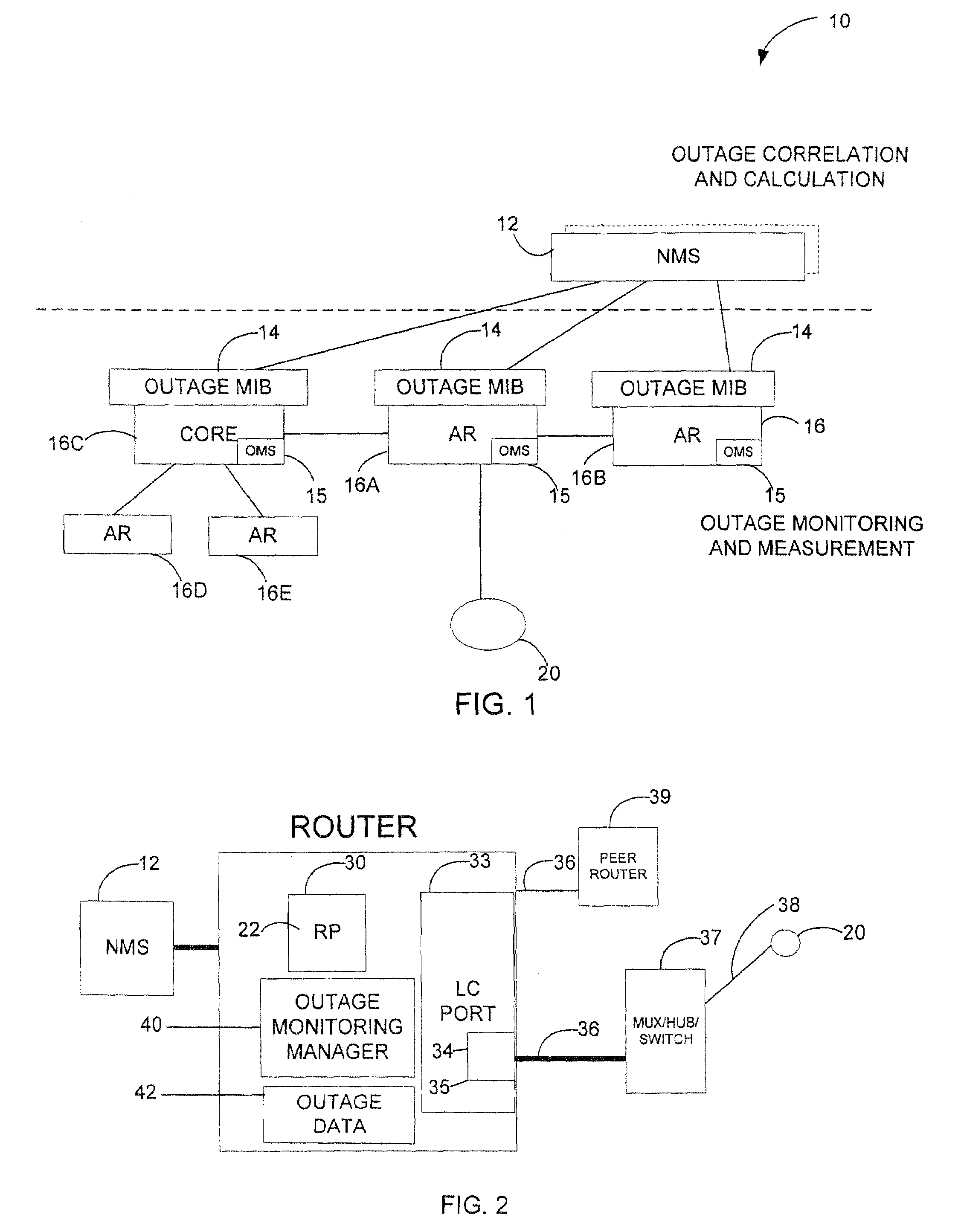
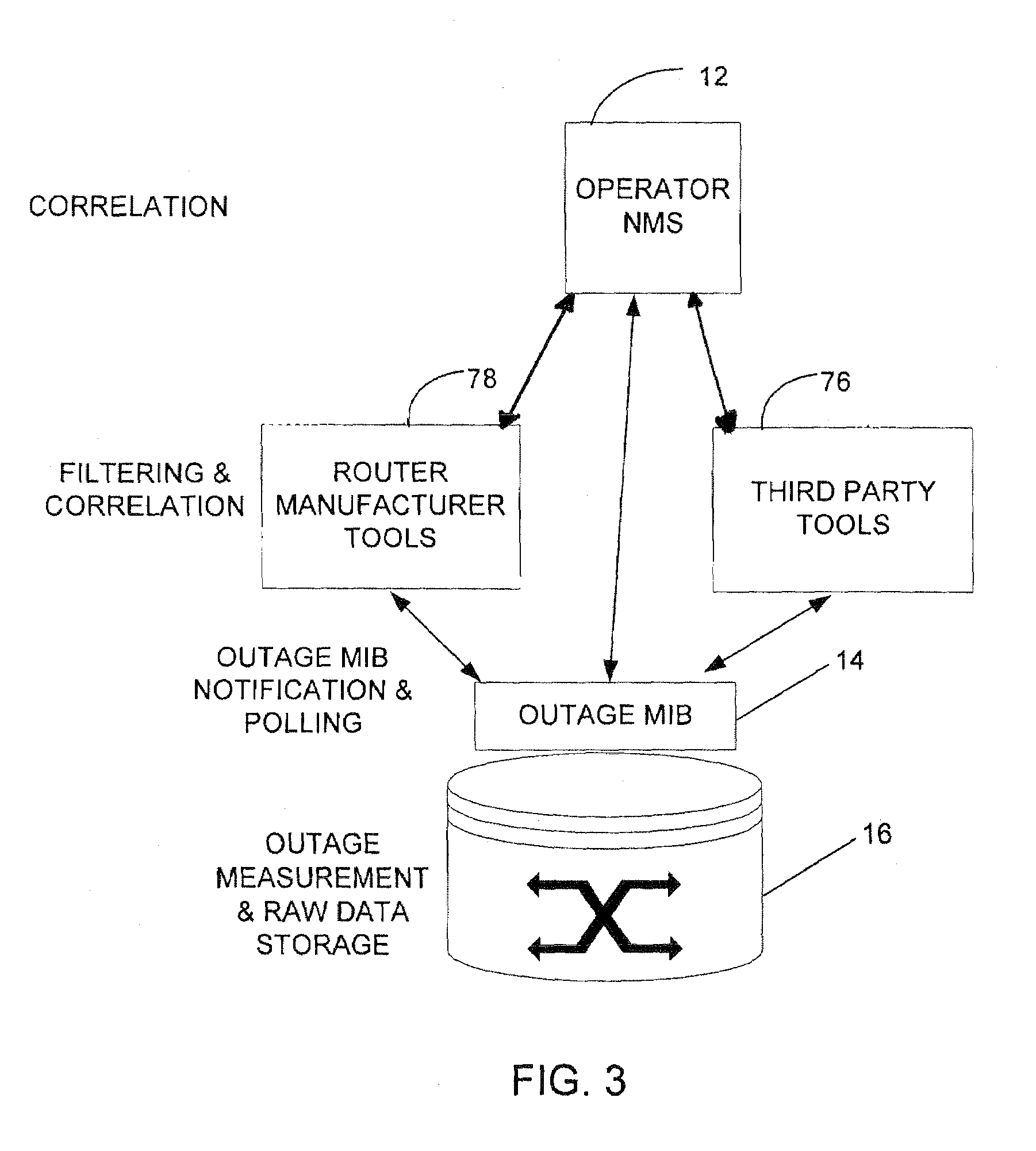
Automated and embedded software reliability measurement and classification in network elements
ActiveUS7213179B2Digital computer detailsReliability/availability analysisSoftware failureEmbedded software
The present invention provides automated kernel software outage measurement and classification. System failures are categorized into software-caused failures and hardware-caused failures. Software failures are further classified as unplanned outages and operational outages. The operational outages are then classified as unplanned operational outages and planned operational outages.
Owner:CISCO TECH INC
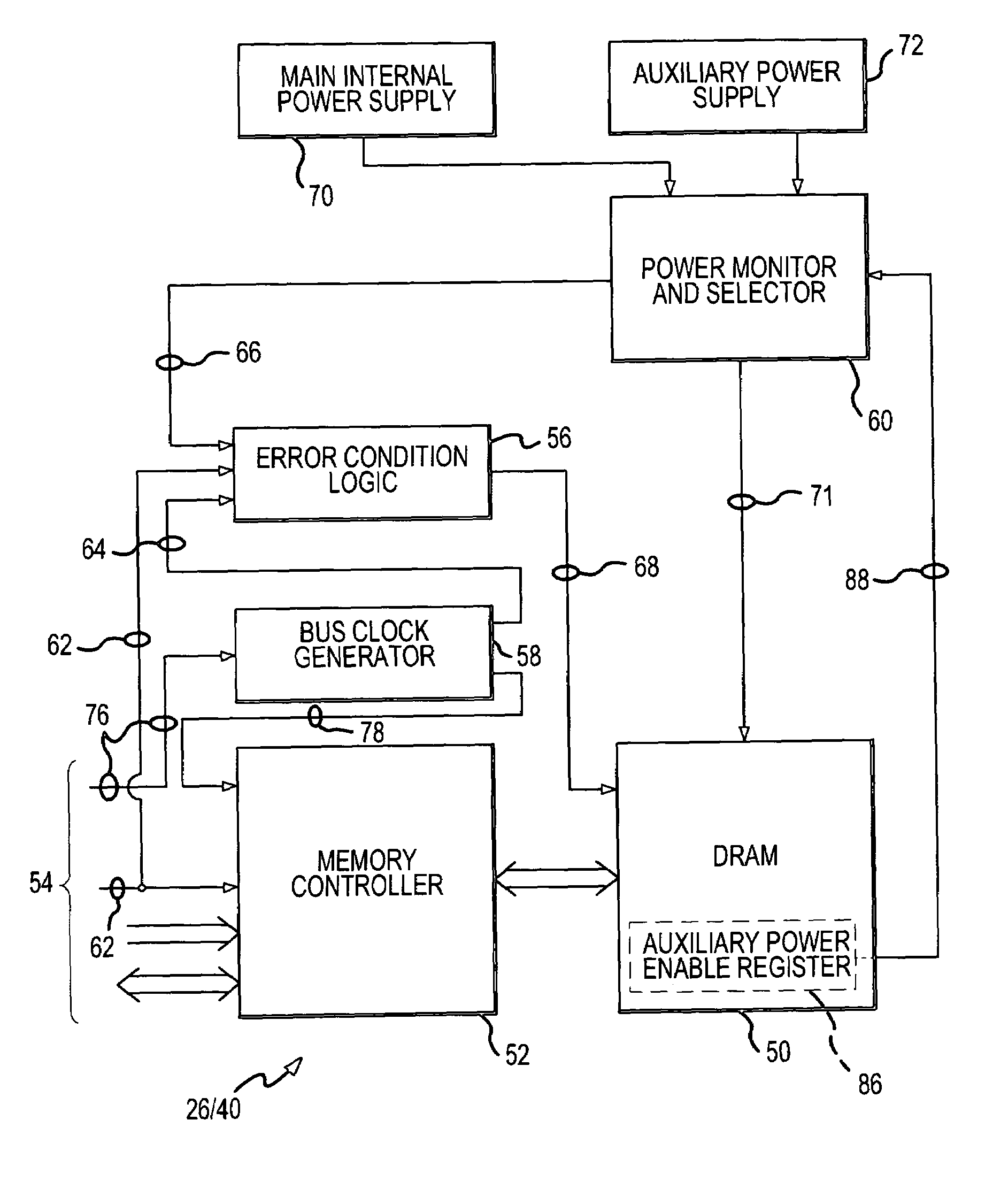
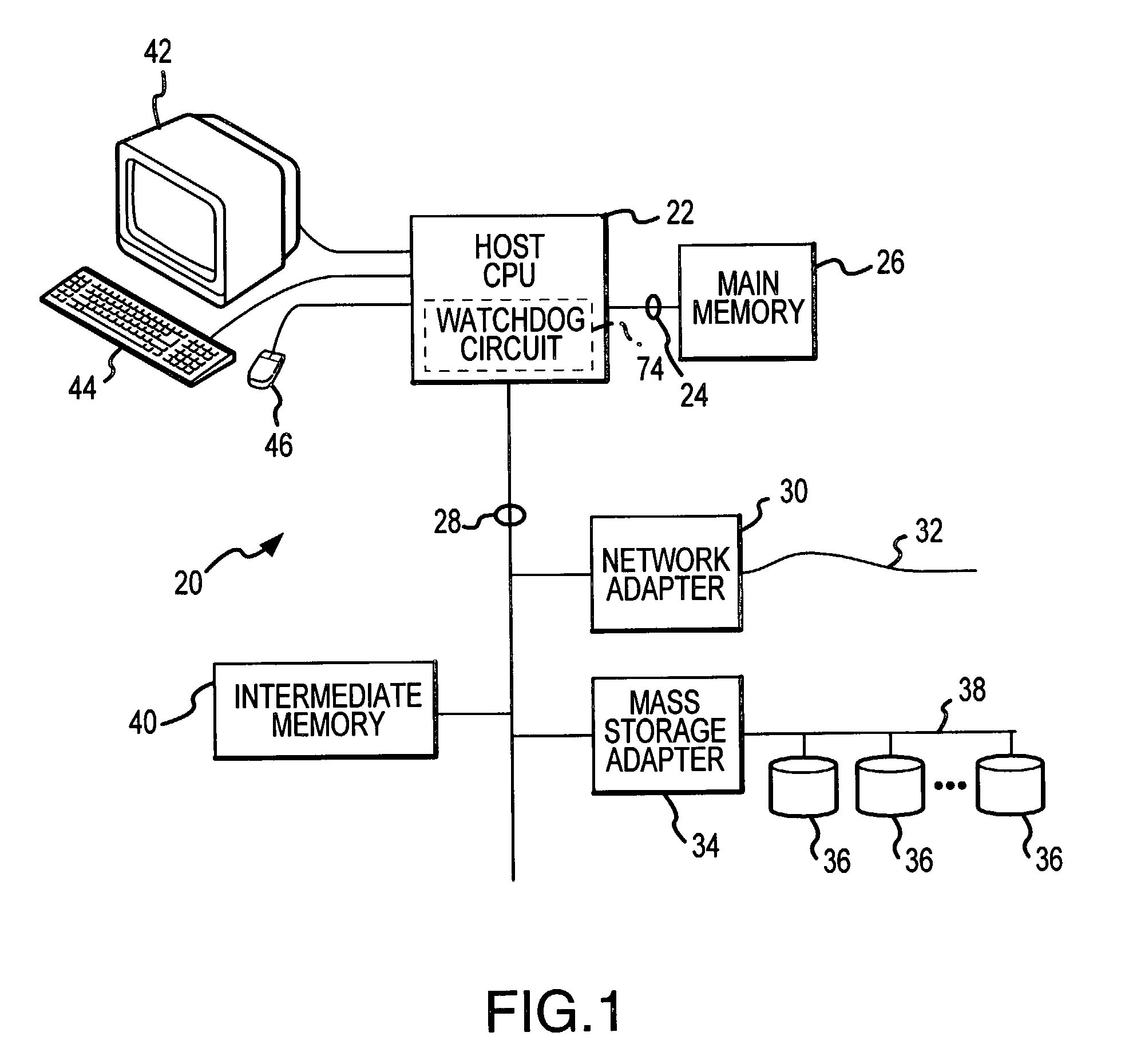
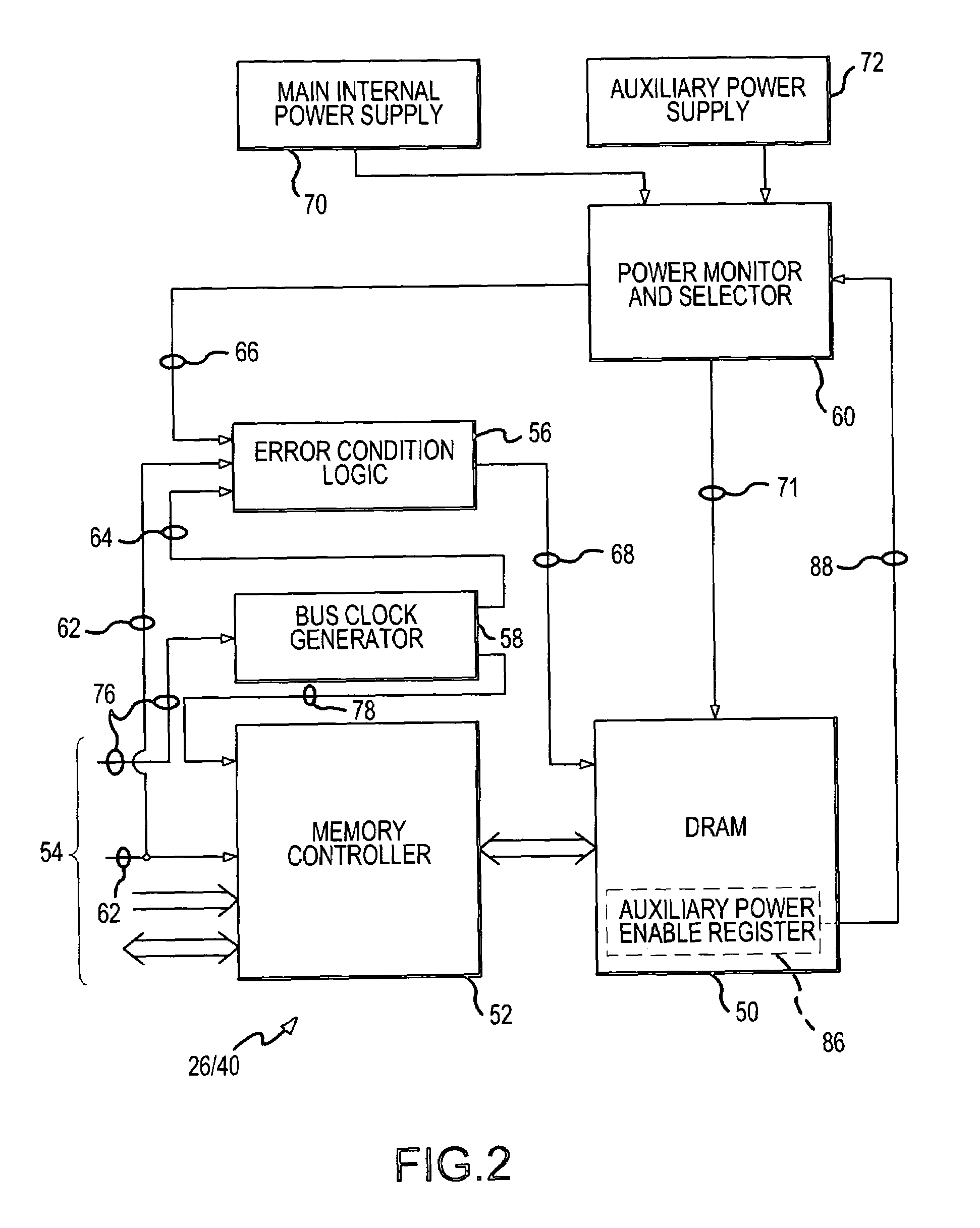
Method and apparatus to establish safe state in a volatile computer memory under multiple hardware and software malfunction conditions
ActiveUS7139937B1Avoid data lossImprove abilitiesError detection/correctionDigital data processing detailsSignal onSoftware failure
Volatile memory is placed into a data-preserving safe state in a computer system in response to any one of a reduction in power applied to the volatile memory, a bus reset signal on a data communication bus of the computer system, and an absence of a bus clock signal on the bus. The volatile memory is powered from an auxiliary uninterruptible power supply in response to the reduction in power. The volatile memory is also placed into the data-preserving safe state in response to a cessation in executing software instructions by a CPU of the computer system. Placing the volatile memory into the safe state in response to and under these conditions enhances the opportunity to preserve data in response to error and malfunction conditions.
Owner:NETWORK APPLIANCE INC
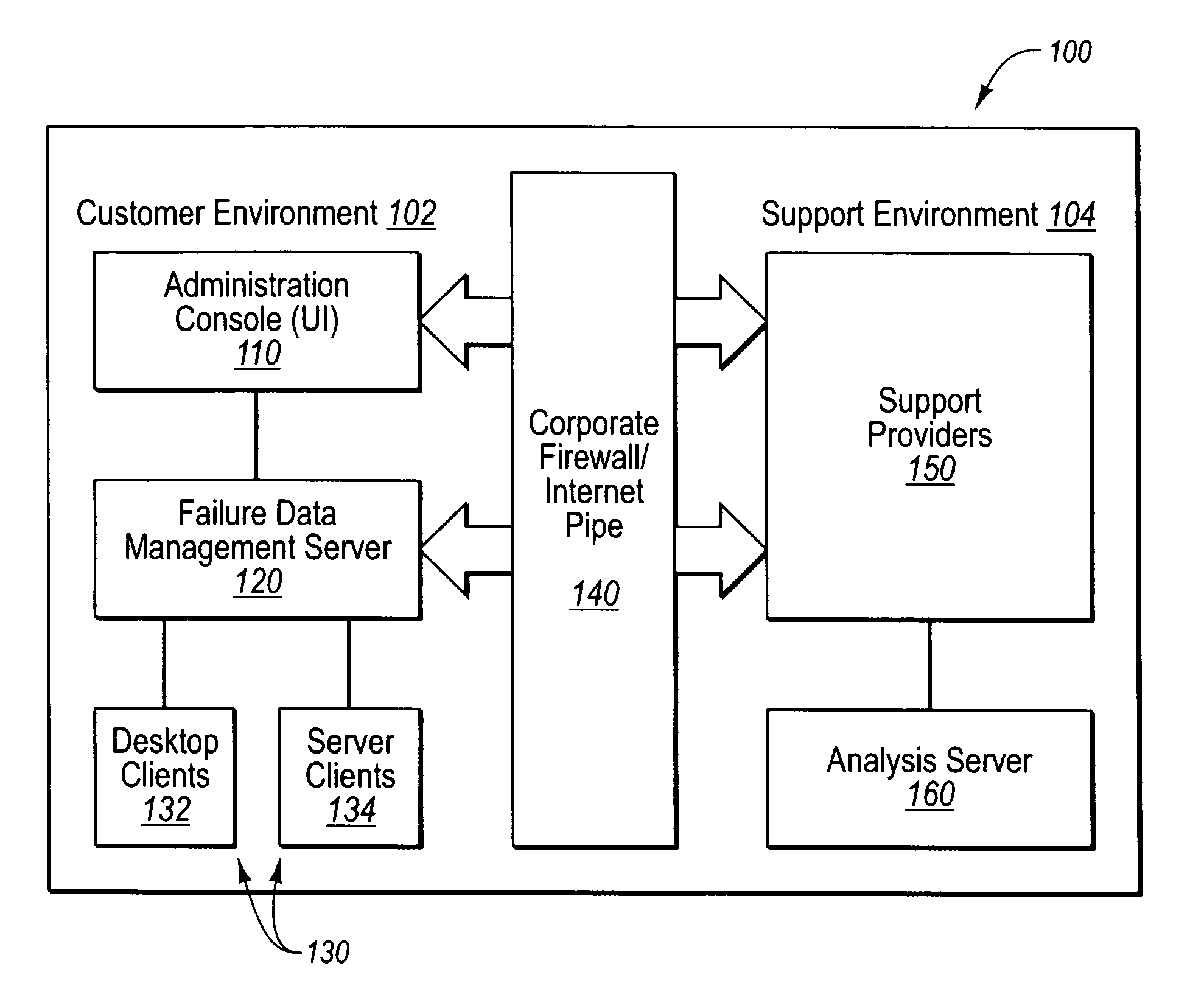
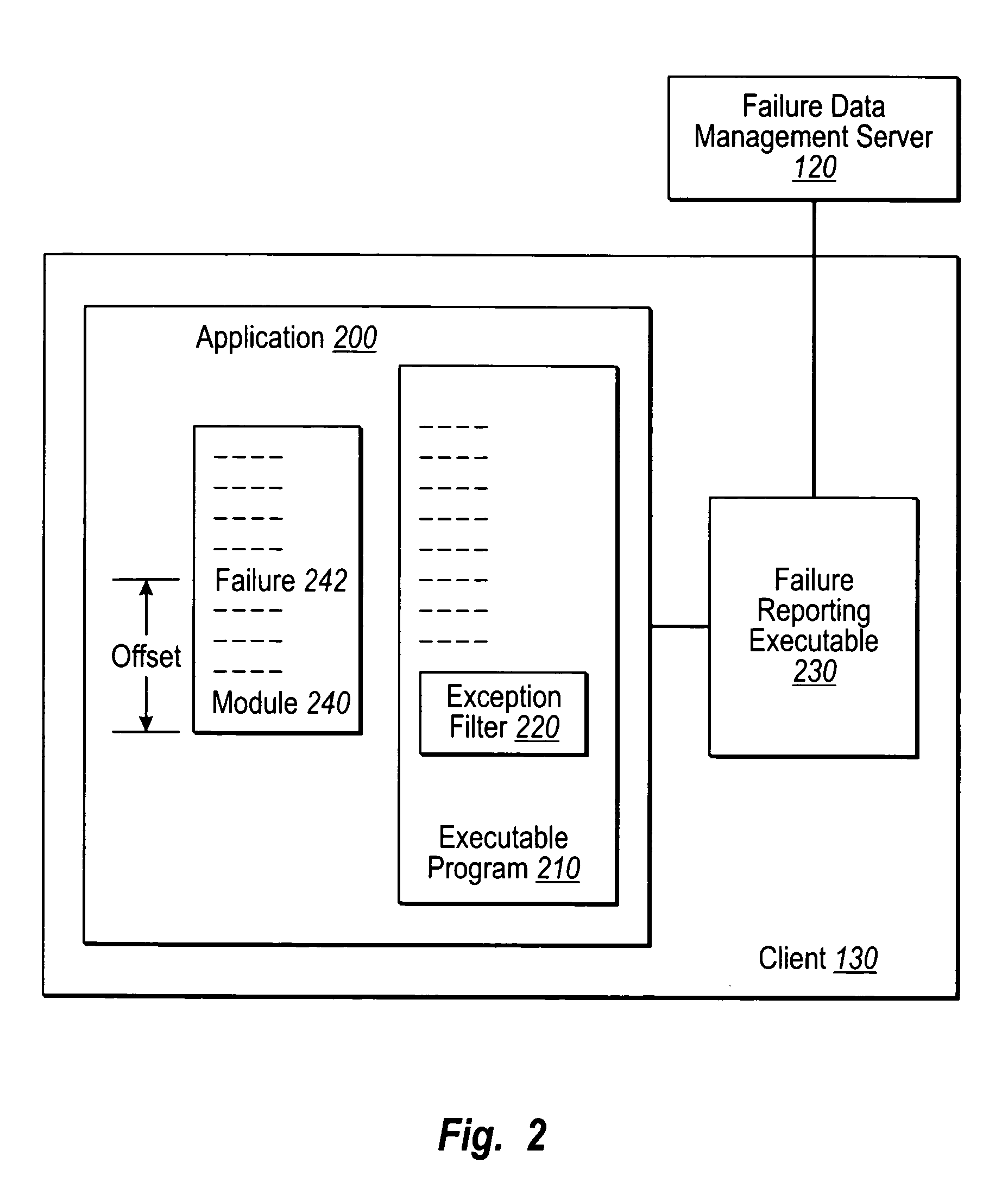
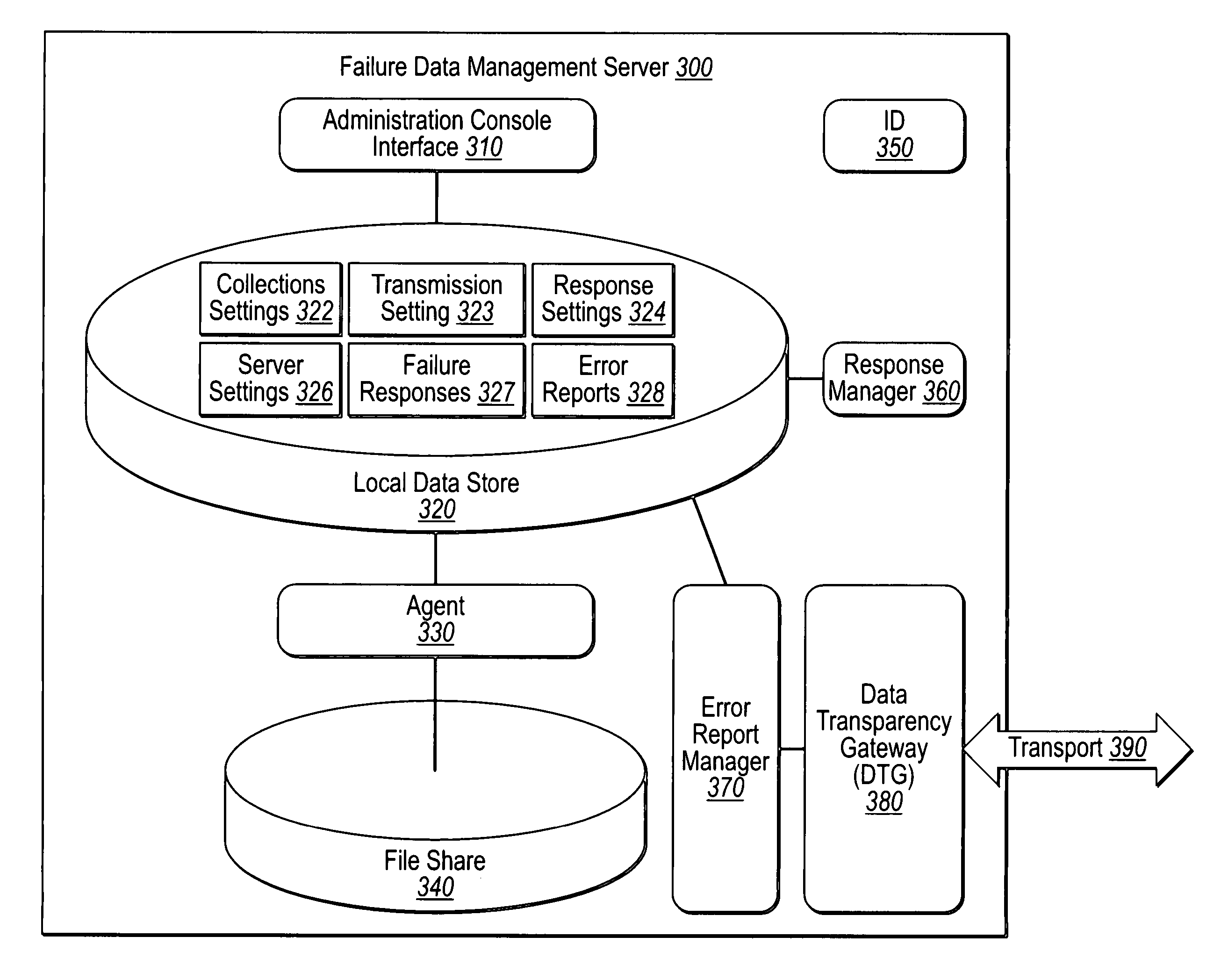
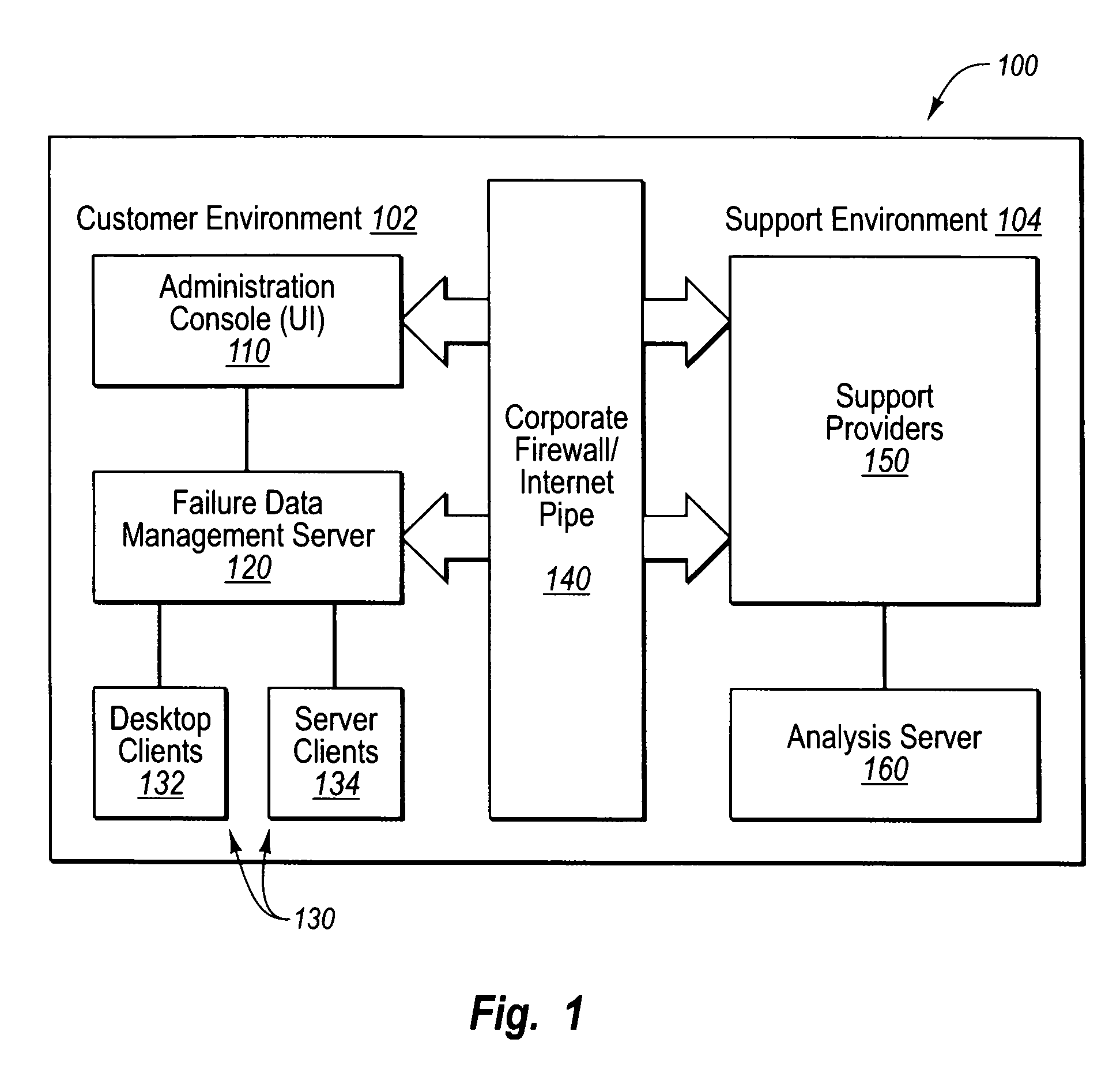
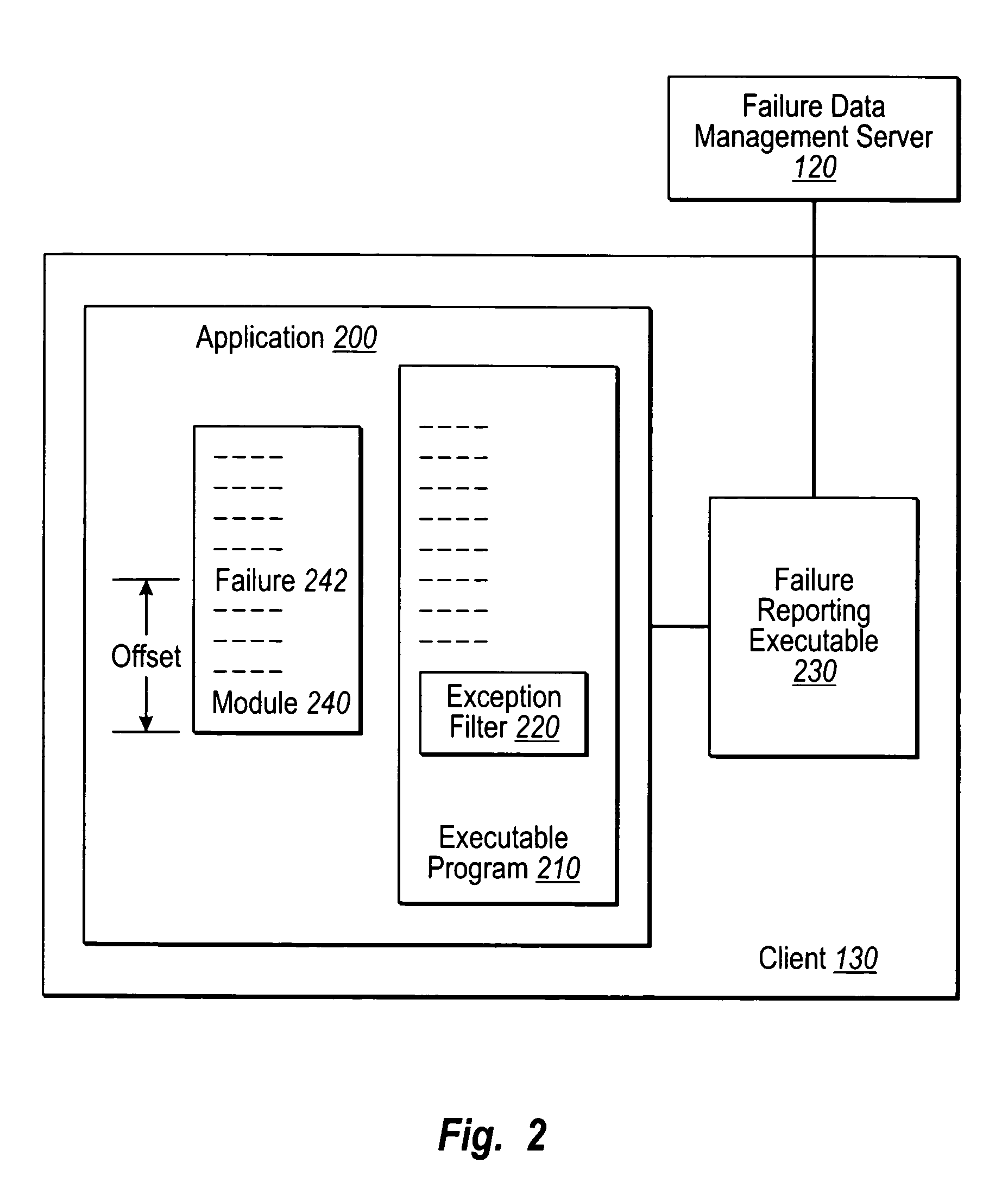
Controlling software failure data reporting and responses
User input defines transmission filter rules to be met when sending an error report to a support provider. User input also defines collection filter rules to be met when including failure data within an error report. Error reports corresponding to crash failures at clients are filtered with the transmission filter rules to determine which of the error reports to send to the support provider, and each error report to be sent to the support provider is further filtered to remove any failure data that fails to satisfy the collection filter rules. Each error report that satisfies the transmission filter rules, along with the failure data satisfying the collection filter rules, is sent to the support provider for analysis. Standard and or custom failure responses corresponding to the failures at the clients may be retrieved and sent to the clients in accordance with the collection filter rules.
Owner:MICROSOFT TECH LICENSING LLC
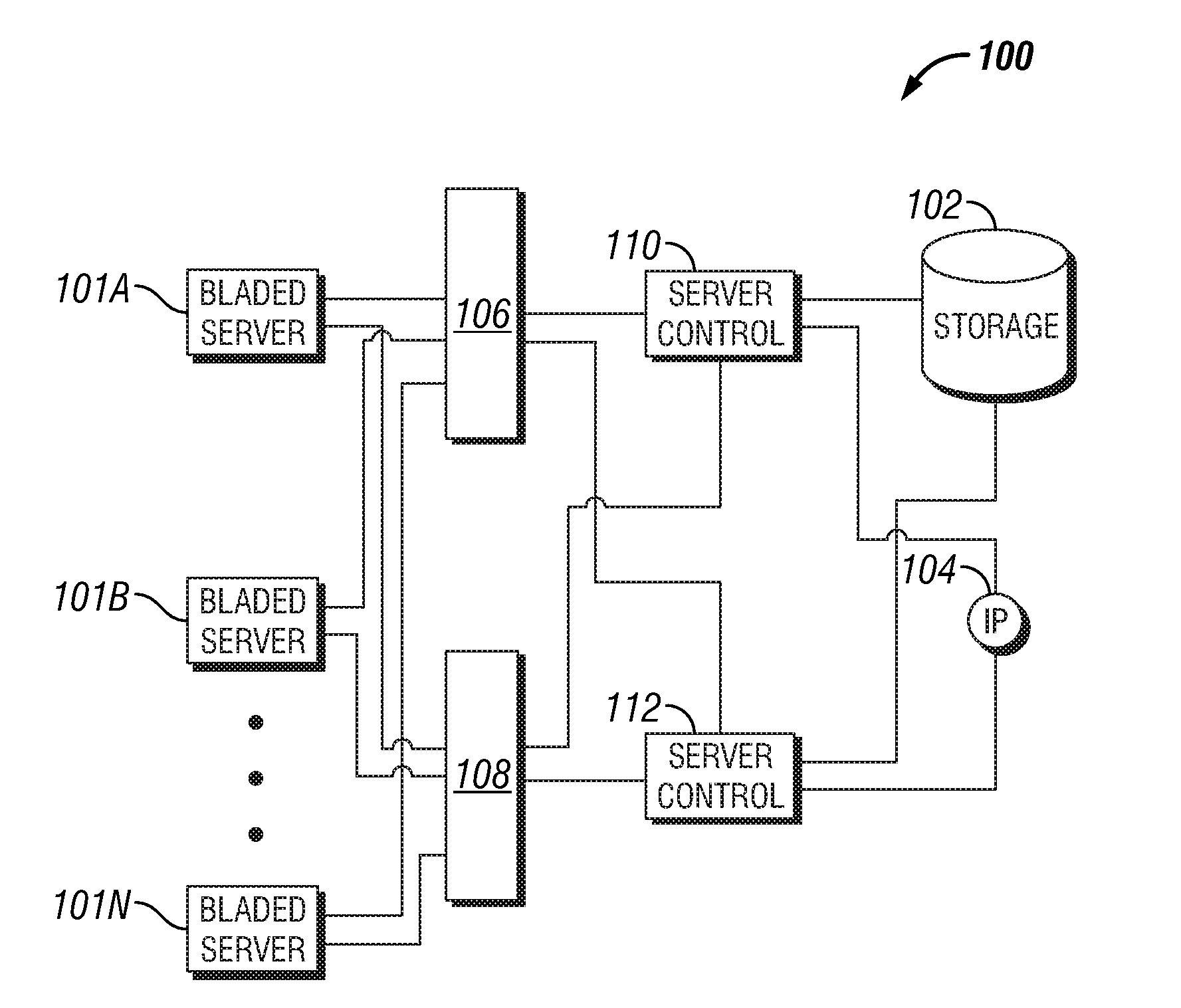
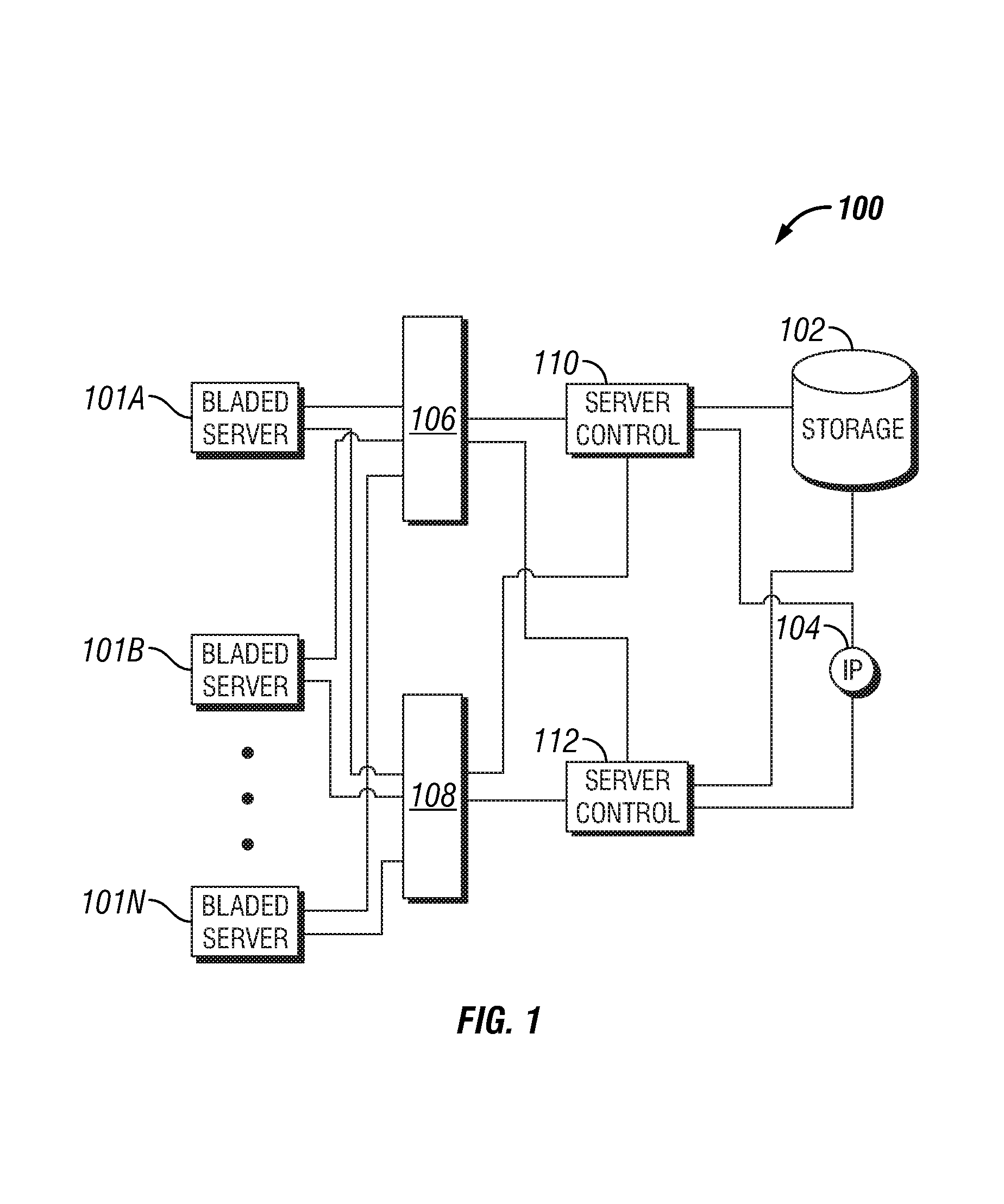
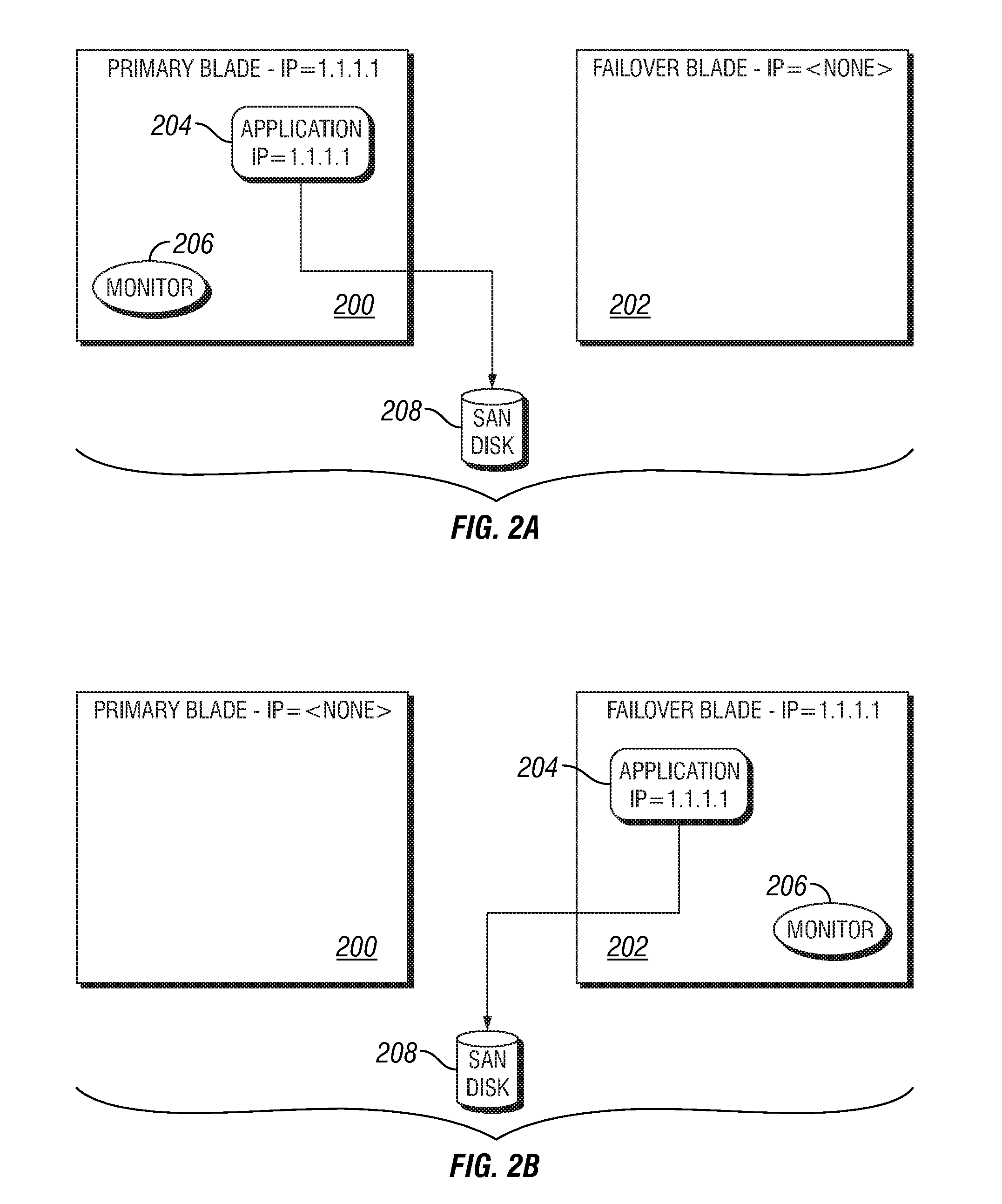
System and method for software failover on a bladed system
ActiveUS7590727B1Multiple digital computer combinationsRedundant hardware error correctionFailoverExternal storage
A system for managing software failover on a bladed server is provided. The system includes a plurality of bladed servers, including a first bladed server and a second failover bladed server. The system includes a server control, a storage device, and software. The server control is in communication with the plurality of bladed servers, and the storage device is accessible by the plurality of bladed servers. The software is stored on the storage device. The system also includes a management component that is operable on the server control. The management component monitors execution of the software on the first bladed server. The management component is operable in response to detecting failure of the software on the first bladed server to promote execution of the software from the external storage device by the second failover bladed server. A method for automated software failover is also provided.
Owner:T MOBILE INNOVATIONS LLC
Methods and arrangements for generating debugging information following software failures
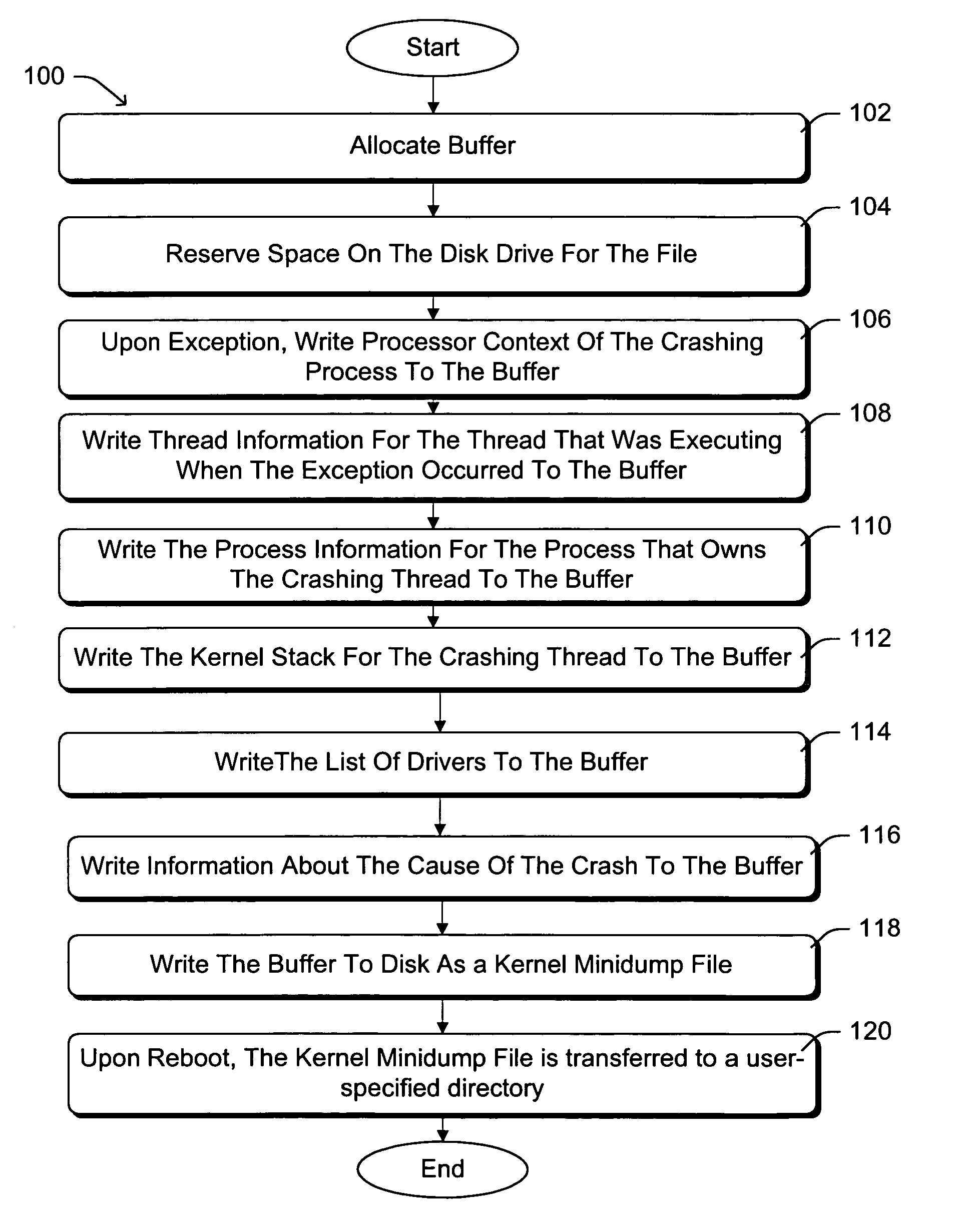
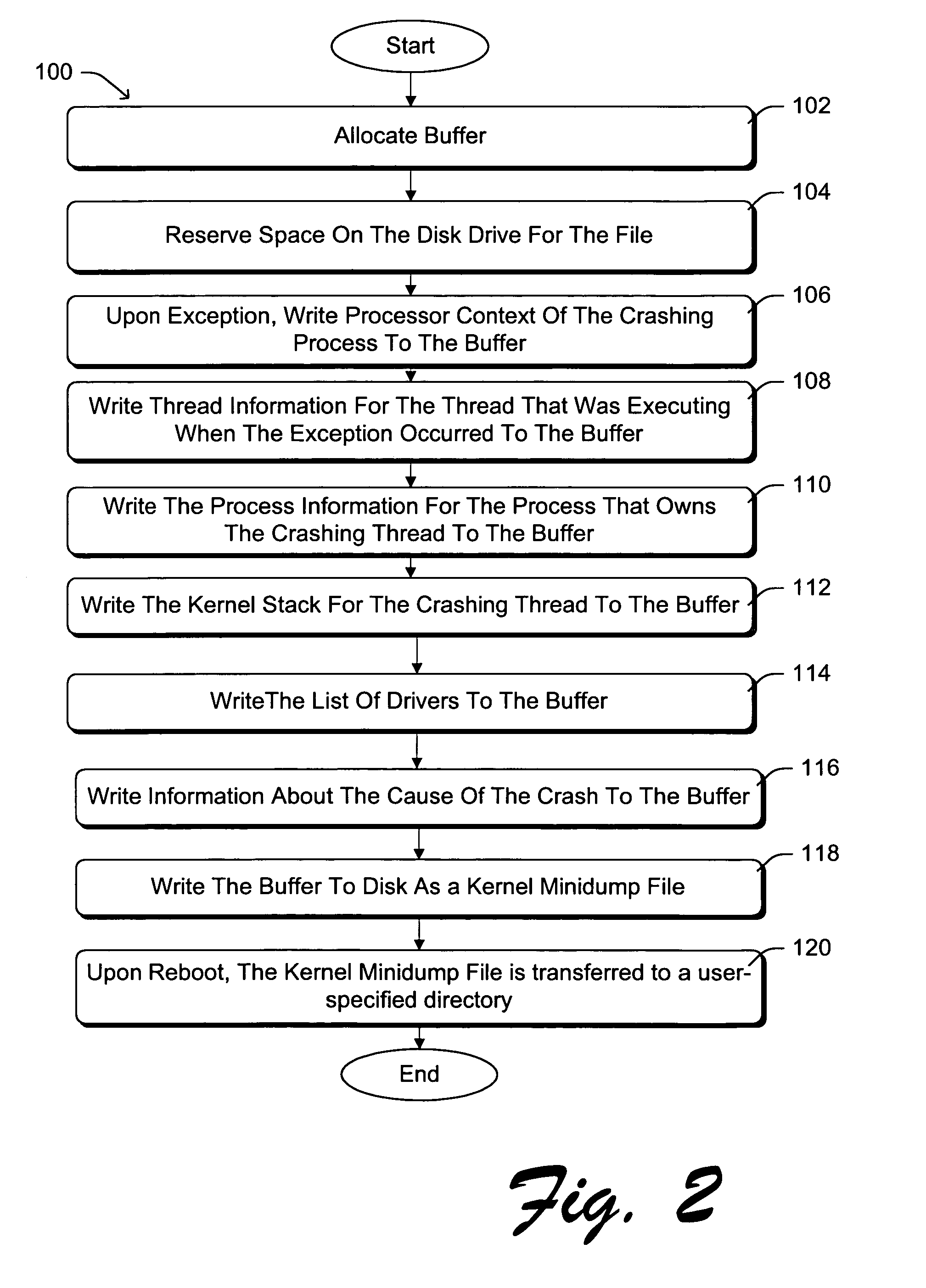
InactiveUS7028056B1Reduce requisite amount of dataRapid online user supportData processing applicationsError detection/correctionComputer failureOperational system
Methods and arrangements are provided that substantially reduce the requisite amount of data required to conduct postmortem analysis following a computer failure. The methods and arrangements can be advantageously configured to allow for rapid online user support for a variety of users, computing devices, operating systems, applications, and the like. One method includes determining when to generate a dump file, and generating a dump file by gathering thread, callstack and thread context information for the running thread, process identifying information associated with the running thread, and information identifying the reason for generating the dump file. The resulting dump file is then stored to a storage medium and accessed during subsequent analysis. The dump file can be a kernel minidump file that is associated with an operating system program failure, in which case the running thread is the single thread that was running when the failure occurred. The kernel minidump file would include the kernel callstack and the process identifying information that would identify the process that initiated the single thread. The method is further applicable to non-operating system programs, wherein a user minidump file is generated by also gathering callstack information for all running threads, thread context information for all running threads, and a listing of all loaded modules for the faulting non-operating system program.
Owner:MICROSOFT TECH LICENSING LLC
Failsafe mechanism for dynamic instrumentation of software using callbacks
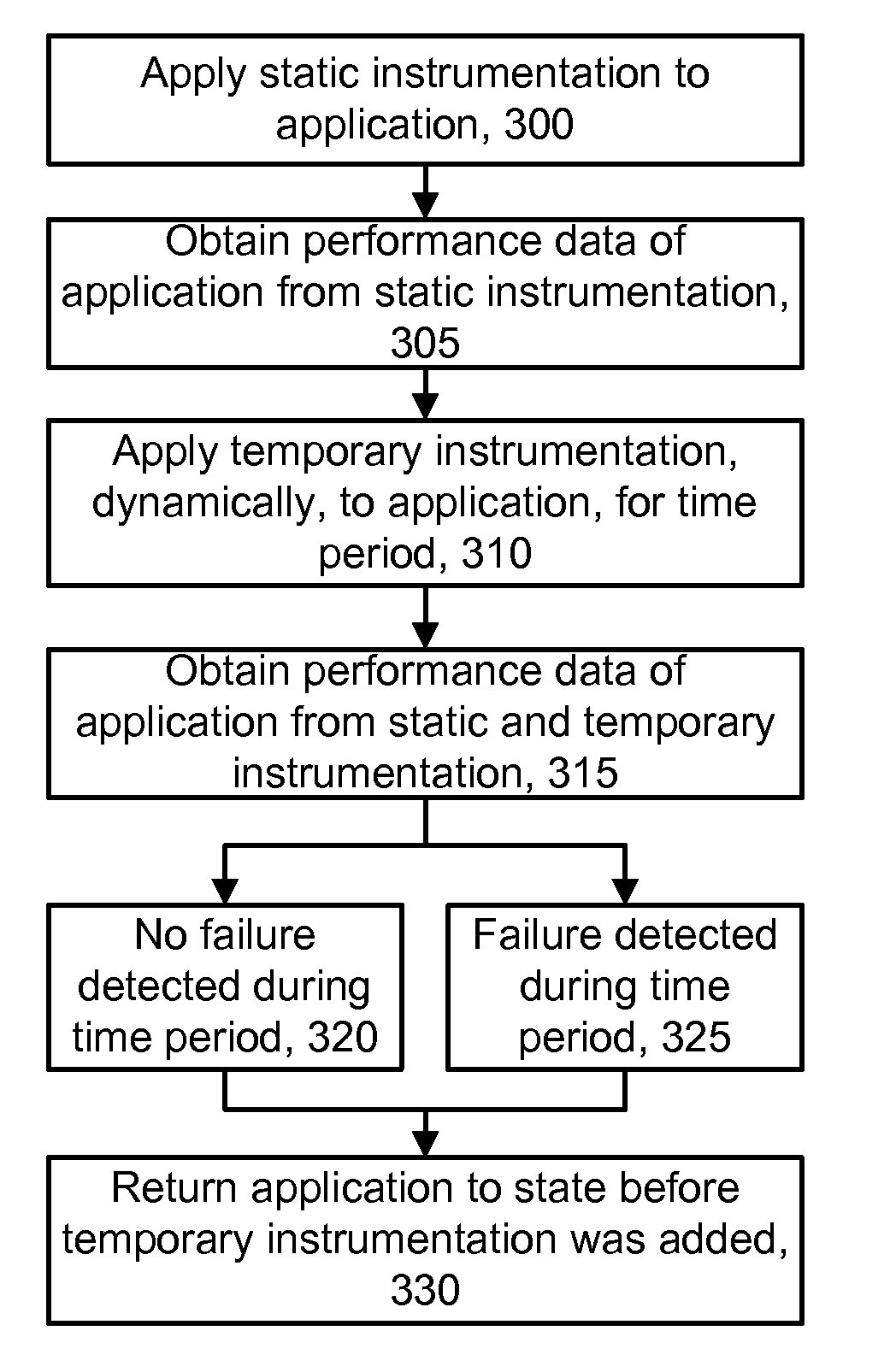
InactiveUS20110283265A1Error detection/correctionSpecific program execution arrangementsSoftware failureDynamic instrumentation
A failsafe mechanism for installing and removing temporary instrumentation during a runtime of an application. Initially, an application is configured with a baseline set of instrumented components such as methods. Additional instrumentation is then deployed in the application, such as to diagnose a performance problem. The failsafe mechanism ensures that the additional instrumentation is automatically removed, even when there is an interruption in a communication link to the application, a computing device failure, a software failure, or some other type of failure, which renders it impossible to manually roll back the instrumentation from a remote user interface. The failsafe mechanism can be provided using callbacks between the computing devices which detect when a connection is unexpectedly lost or closed. Termination of one callback can cascade to one or more other callbacks. The instrumentation rollback can involve reloading un-instrumented byte code of the application.
Owner:CA TECH INC
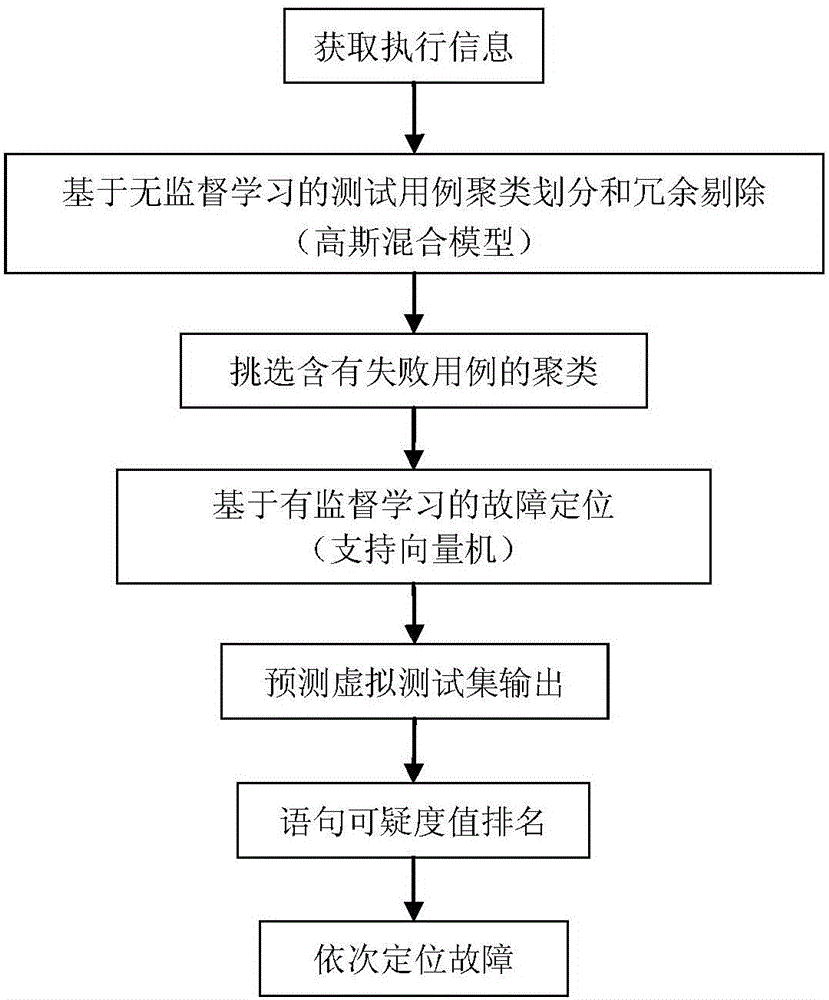
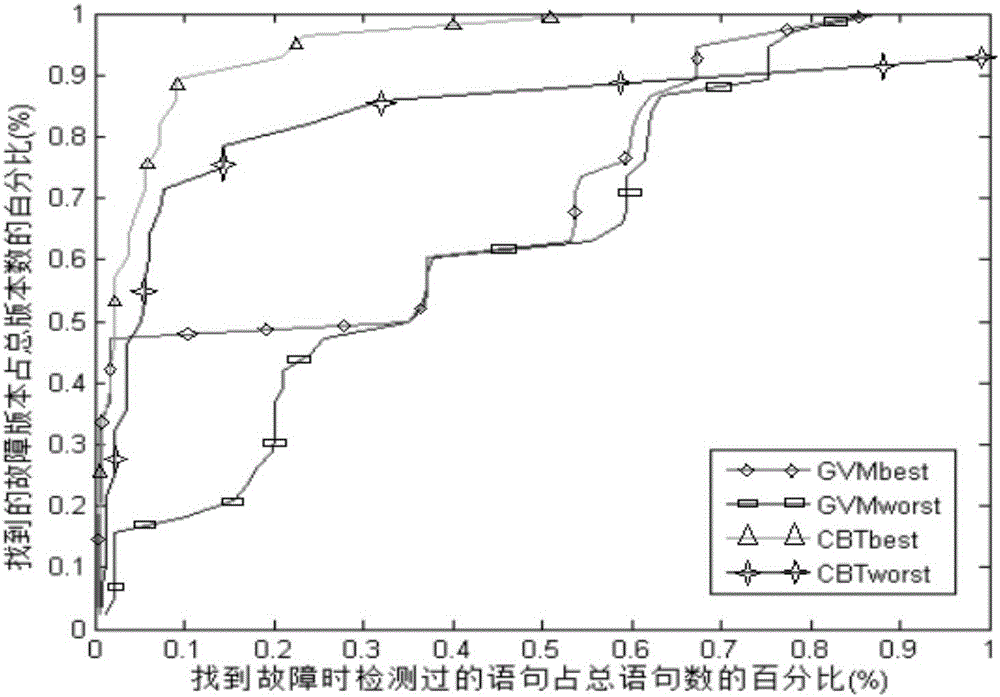
Software failure positioning method based on machine learning algorithm
InactiveCN105893256AReduce adverse effectsImprove fault location efficiencySoftware testing/debuggingSoftware failureGaussian mixture distribution
The invention discloses a software failure positioning method based on machine learning algorithm to solve the technical problem of low positioning efficiency of existing software failure positioning methods. According to the technical scheme, the method comprises the steps of describing failure distribution possibly existing in an actual program based on Gaussian mixture distribution to enable failure distribution in the program to be more definite; removing redundant test samples with a cluster analysis method based on a Gaussian mixture model, and finding a special test set for a specific failure, so that the adverse effect of redundant use cases on positioning precision is reduced; remodifying a support vector machine model to be adapted to an unbalanced data sample, and finding the nonlinear mapping relation between use case coverage information and an execution result by means of the parallel debugging theory, so that machine learning algorithm is free from the local optimal solution problem caused by uneven samples; finally, designing a virtual test suite, placing the virtual test suite in a well trained model for prediction, obtaining a statement equivocation value ranking result, and conducting failure positioning. In this way, software failure positioning efficiency is improved.
Owner:北京京航计算通讯研究所
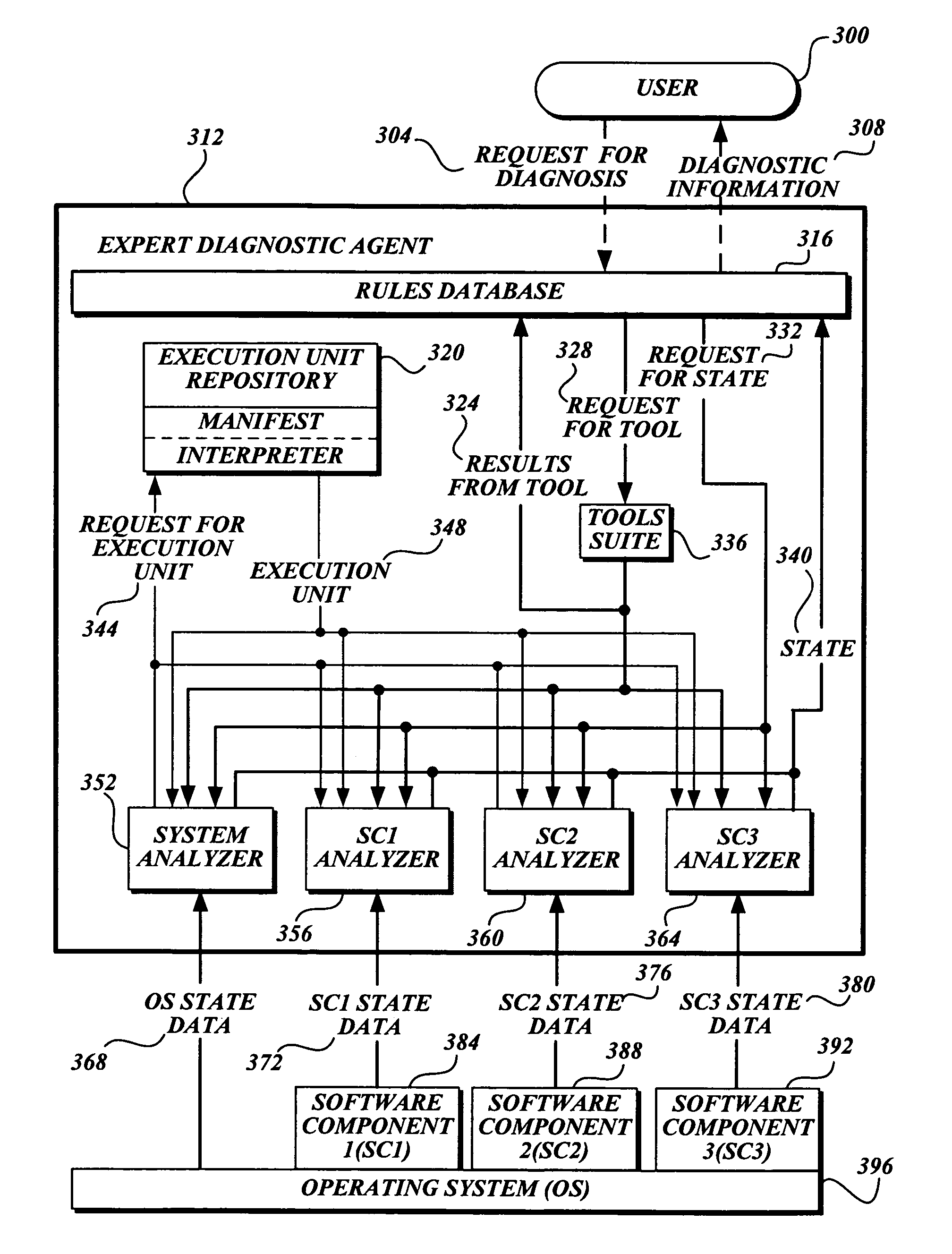
Expert software diagnostic tool
An expert diagnostic agent for use in diagnosing intermittent and / or difficult to reproduce software failures in computing devices is disclosed. The expert diagnostic agent gathers data about the operating system of a computing device and a plurality of software components coupled to the computer operating system; applies rules to the data to identify software failures; invokes tools as needed to attempt to correct the software failures; and reports information about software failures. The expert diagnostic agent may be invoked directly or activated by certain events in computer system.
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods for recoverable workflow
InactiveUS7412520B2Error detection/correctionMultiprogramming arrangementsSoftware failureComputerized system
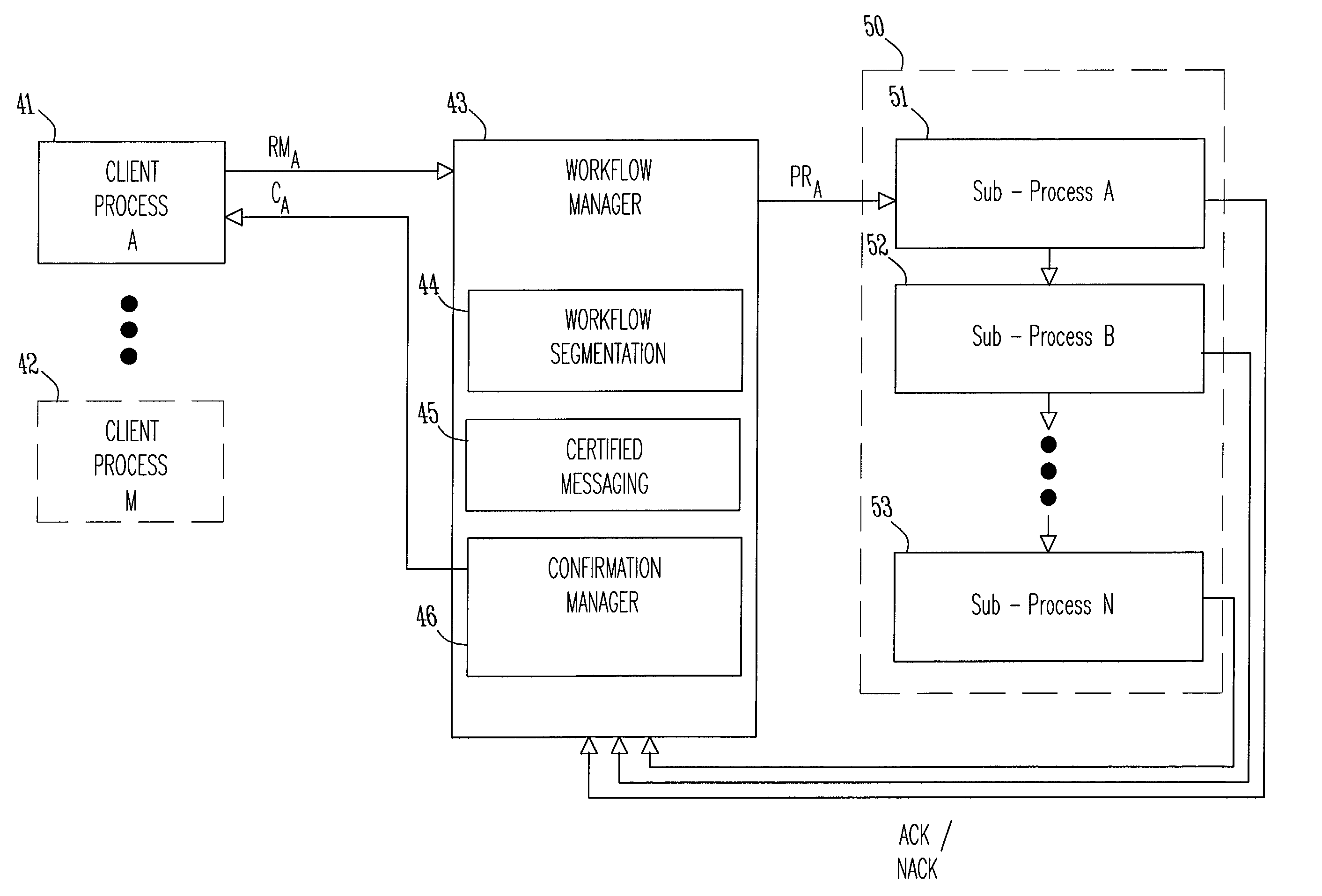
Improved methods for providing recoverable workflow of complex and / or risk-prone workflows in a computer system or computer network include segmenting such workflows into sub-processes, associating a checkpoint with the end of each sub-process, and determining whether processing of each sub-process was successful. If so, a set of parameters is stored at each checkpoint before processing the next sub-process, but otherwise processing of the failed sub-process is retried, using the parameter set stored at the previous checkpoint. In one embodiment, the methods are implemented by a certified messaging capability that guarantees delivery of any message. In the event a hardware or software failure occurs during a sub-process execution, the certified messaging capability returns a failure indication, so that execution of the failed sub-process can be reinitiated. Improved computers and computer networks for providing recoverable workflow are also described.
Owner:INTEL CORP
System and method for replacing underlying connection-based communication mechanisms in real time systems at run-time
InactiveUS6993769B2Lower latencyReduce overhead timeMultiprogramming arrangementsMultiple digital computer combinationsStreaming dataOperational system
Owner:MIND FUSION LLC
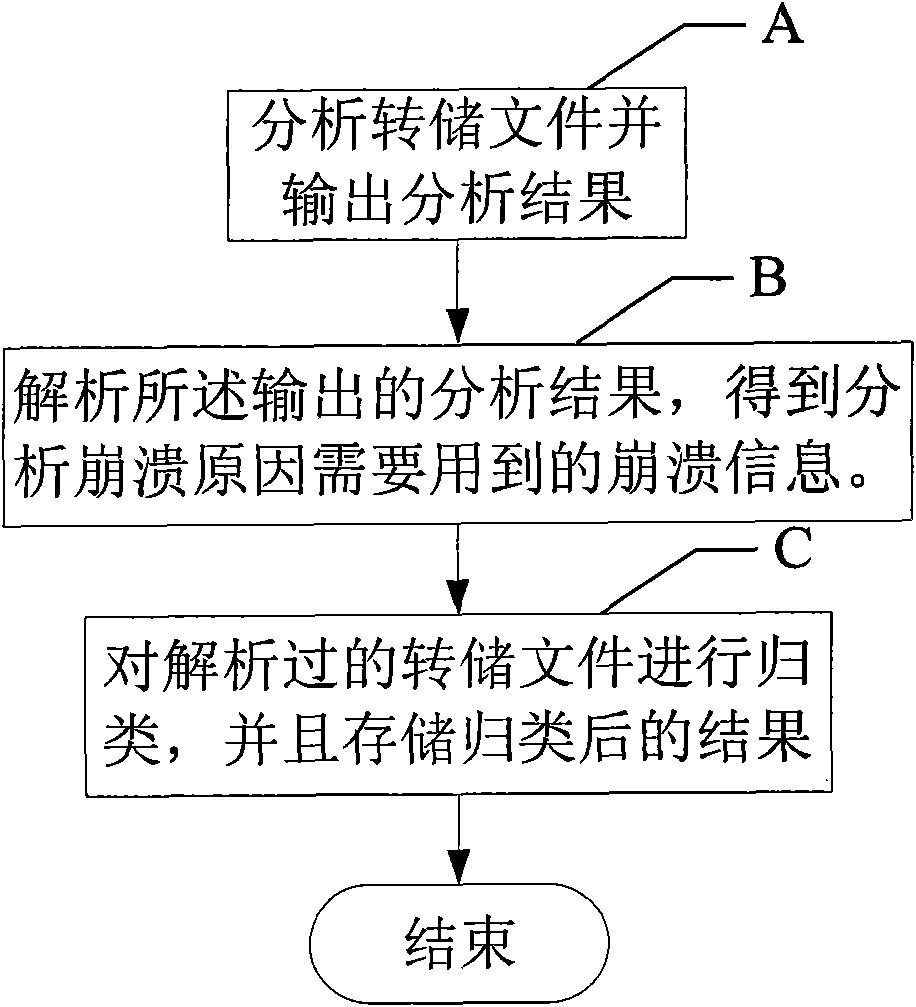
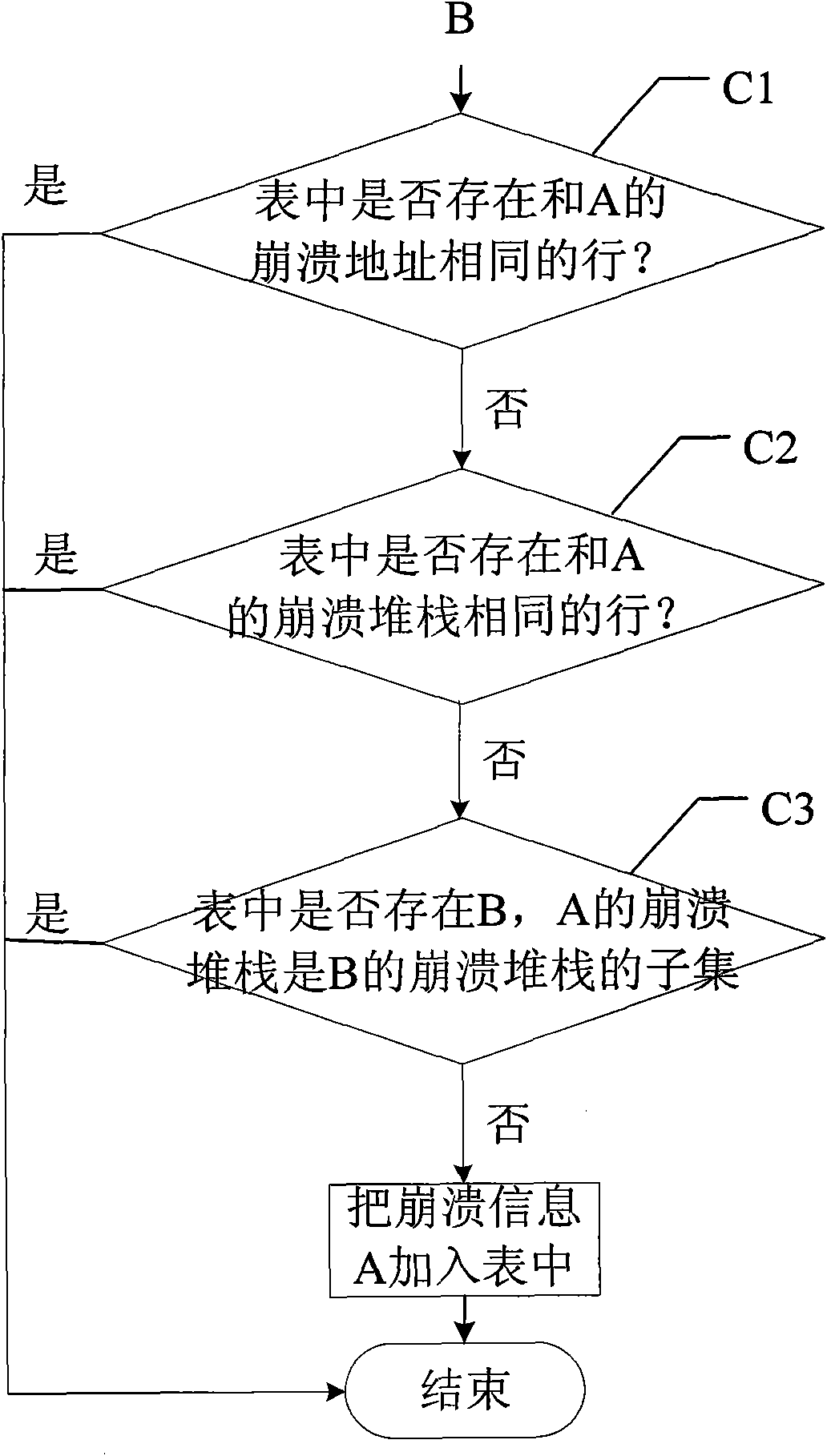
Automatic analysis method and device of crash information of computer software
InactiveCN101944059AAccurate classificationImprove classification accuracyHardware monitoringSoftware failureComputer software
The invention discloses automatic analysis method and device of the crash information of computer software. The method comprises the following steps of: (A) analyzing a dump file and outputting an analysis result; (B) parsing the output analysis result to acquire crash information; and (C) sorting the parsed dump file and storing a sorted result. The invention also discloses the automatic analysis device of the crash information of the computer software. In the invention, the crash dump file is analyzed by automatically calling a debugger provided by a toolkit of Debugging Tools for Windows to acquire the comprehensive and accurate crash information; and the crash information is sorted by using a crash address and a crash stack, therefore, not only the sorting accuracy is improved, but also the redundant information stored in a table is greatly reduced. By applying the invention, calculation staff in the field can accurately acquire the crush reason and provides reference for solving the software failures and optimizing the software.
Owner:ULTRAPOWER SOFTWARE
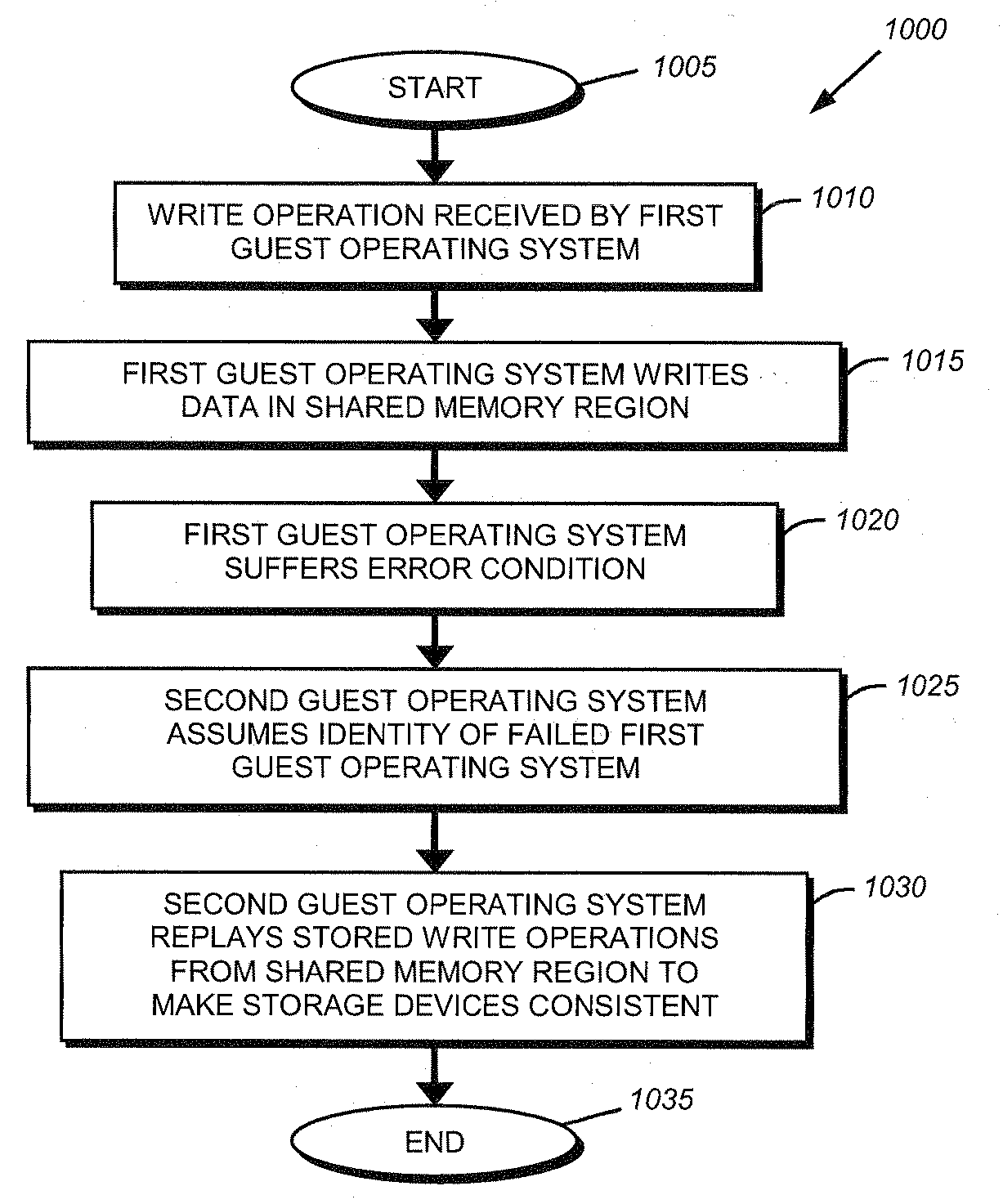
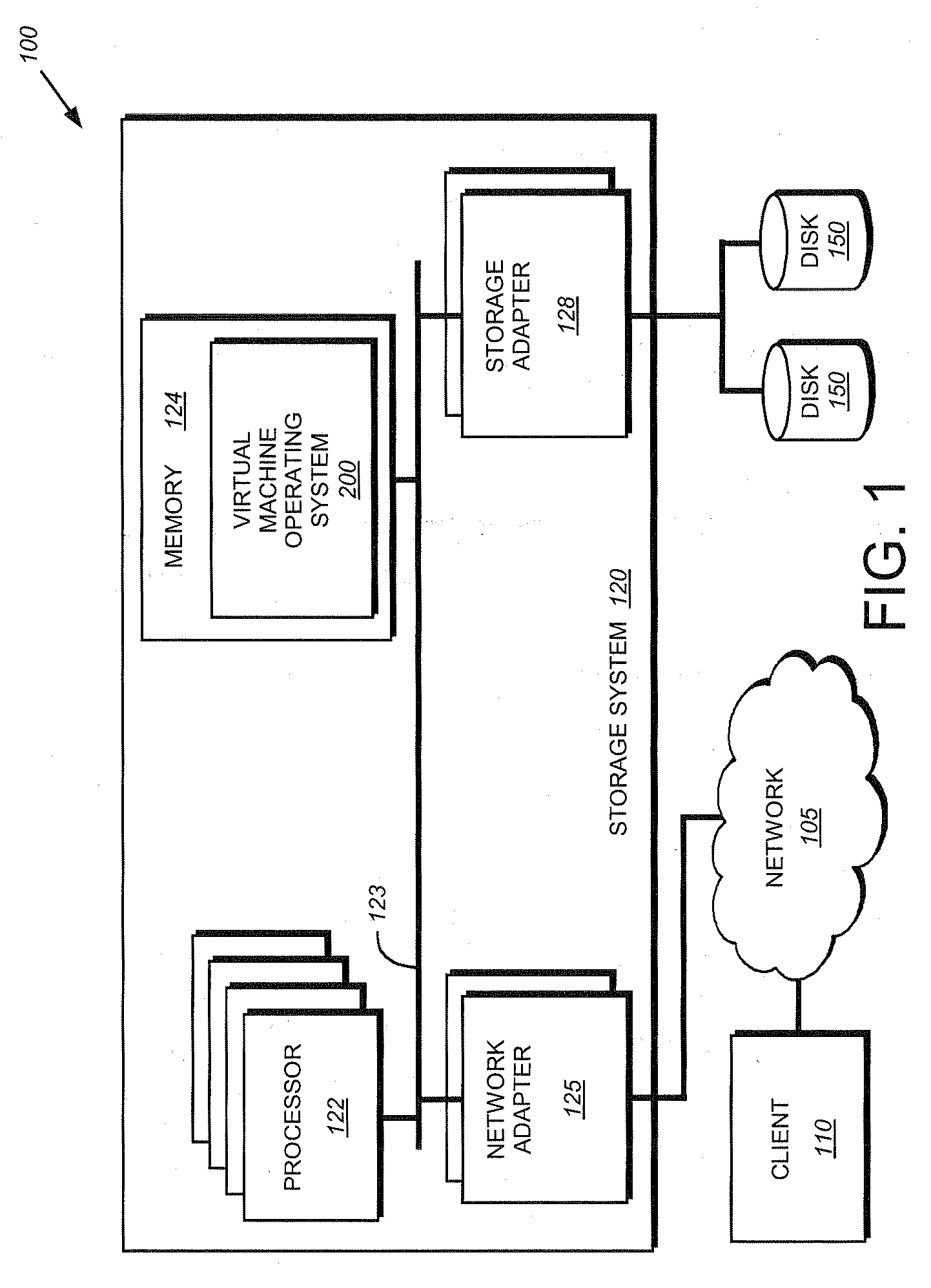
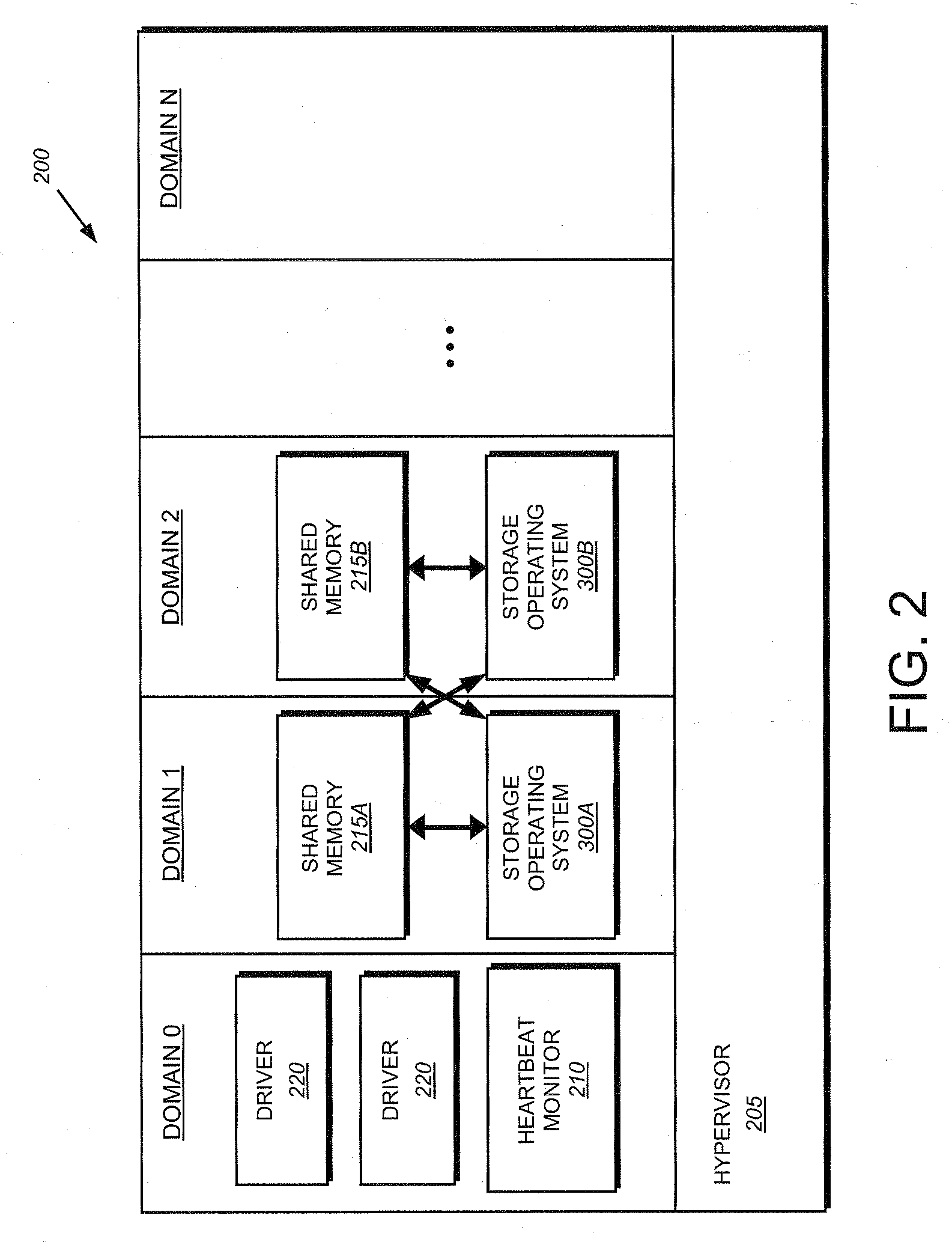
System and method for failover of guest operating systems in a virtual machine environment
A system and method provides for failover of guest operating systems in a virtual machine environment. During initialization of a computer executing a virtual machine operating system, a first guest operating system allocates a first memory region within a first domain and notifies a second guest operating system operating in a second domain of the allocated first memory region. Similarly, the second guest operating system allocates a second region of memory within the second domain and notifies the first operating system of the allocated second memory region. In the event of a software failure affecting one of the guest operating systems, the surviving guest operating system assumes the identity of the failed operating system and utilizes data stored within the shared memory region to replay to storage devices to render them consistent.
Owner:NETWORK APPLIANCE INC
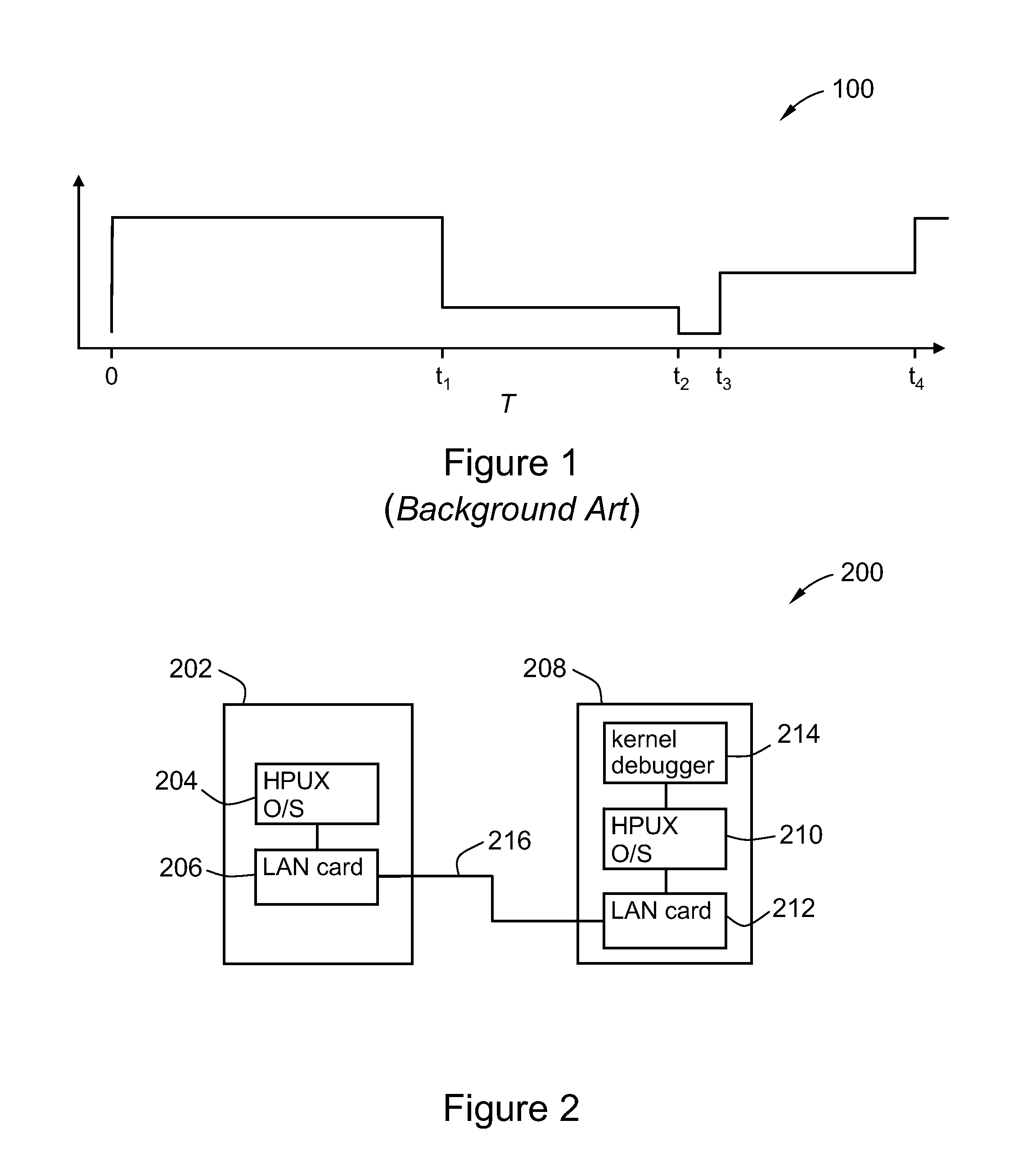
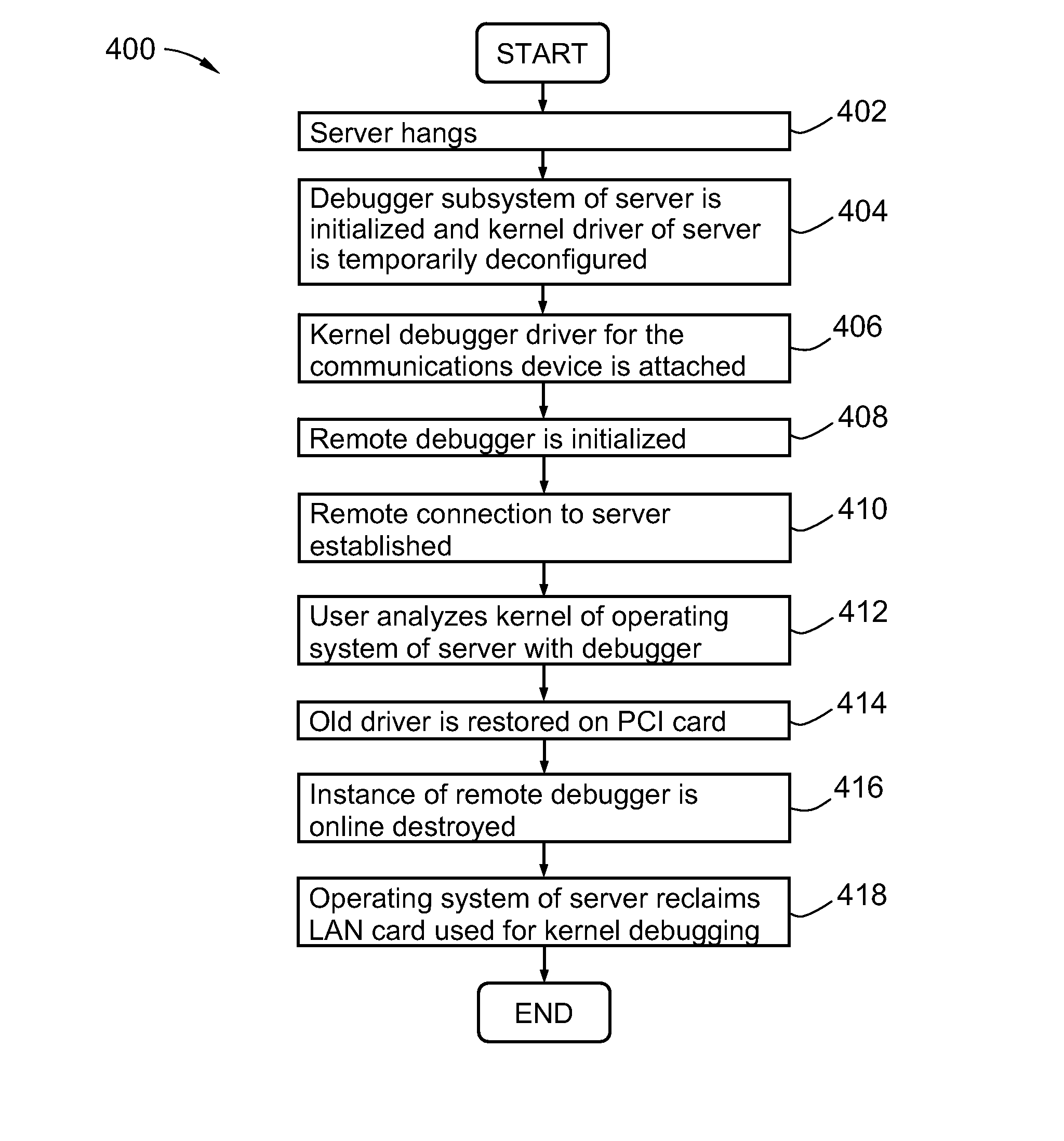
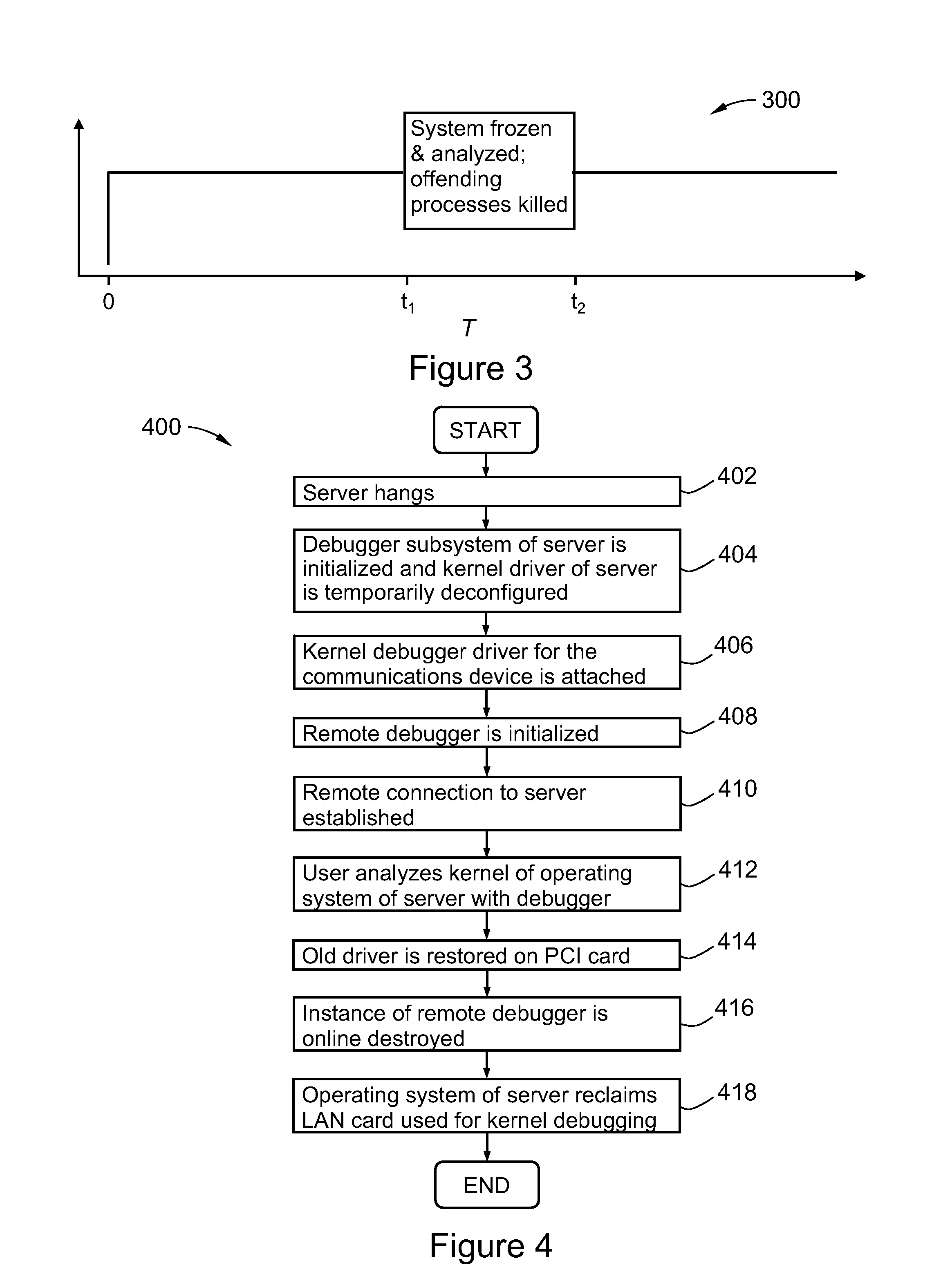
Method and system for remotely debugging a hung or crashed computing system
ActiveUS20080295077A1Error detection/correctionSpecific program execution arrangementsTelecommunications linkSoftware failure
A method and system for debugging a computer upon a kernel hang and / or upon a software failure, the method comprising executing a debugger on a remote computer, connecting the hung or crashed computer to the remote computer with a communications link, and debugging the hung or crashed computer with the debugger without rebooting the system. The method may include deconfiguring any kernel driver of the computer attached to the communication card prior to connecting the remote debugger to the computer.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
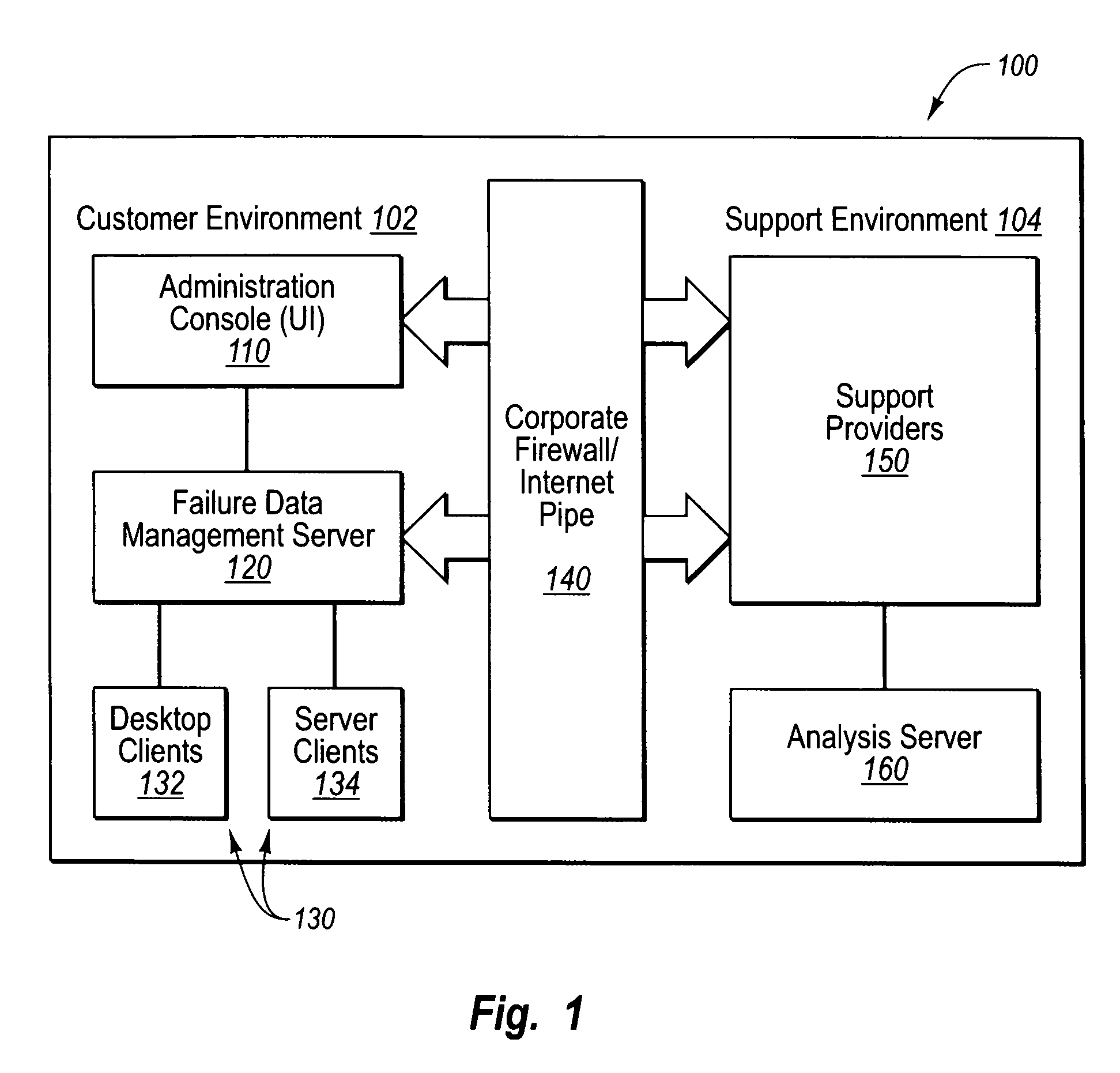
Controlling software failure data reporting and responses
User input defines transmission filter rules to be met when sending an error report to a support provider. User input also defines collection filter rules to be met when including failure data within an error report. Error reports corresponding to crash failures at clients are filtered with the transmission filter rules to determine which of the error reports to send to the support provider, and each error report to be sent to the support provider is further filtered to remove any failure data that fails to satisfy the collection filter rules. Each error report that satisfies the transmission filter rules, along with the failure data satisfying the collection filter rules, is sent to the support provider for analysis. Standard and or custom failure responses corresponding to the failures at the clients may be retrieved and sent to the clients in accordance with the collection filter rules.
Owner:MICROSOFT TECH LICENSING LLC
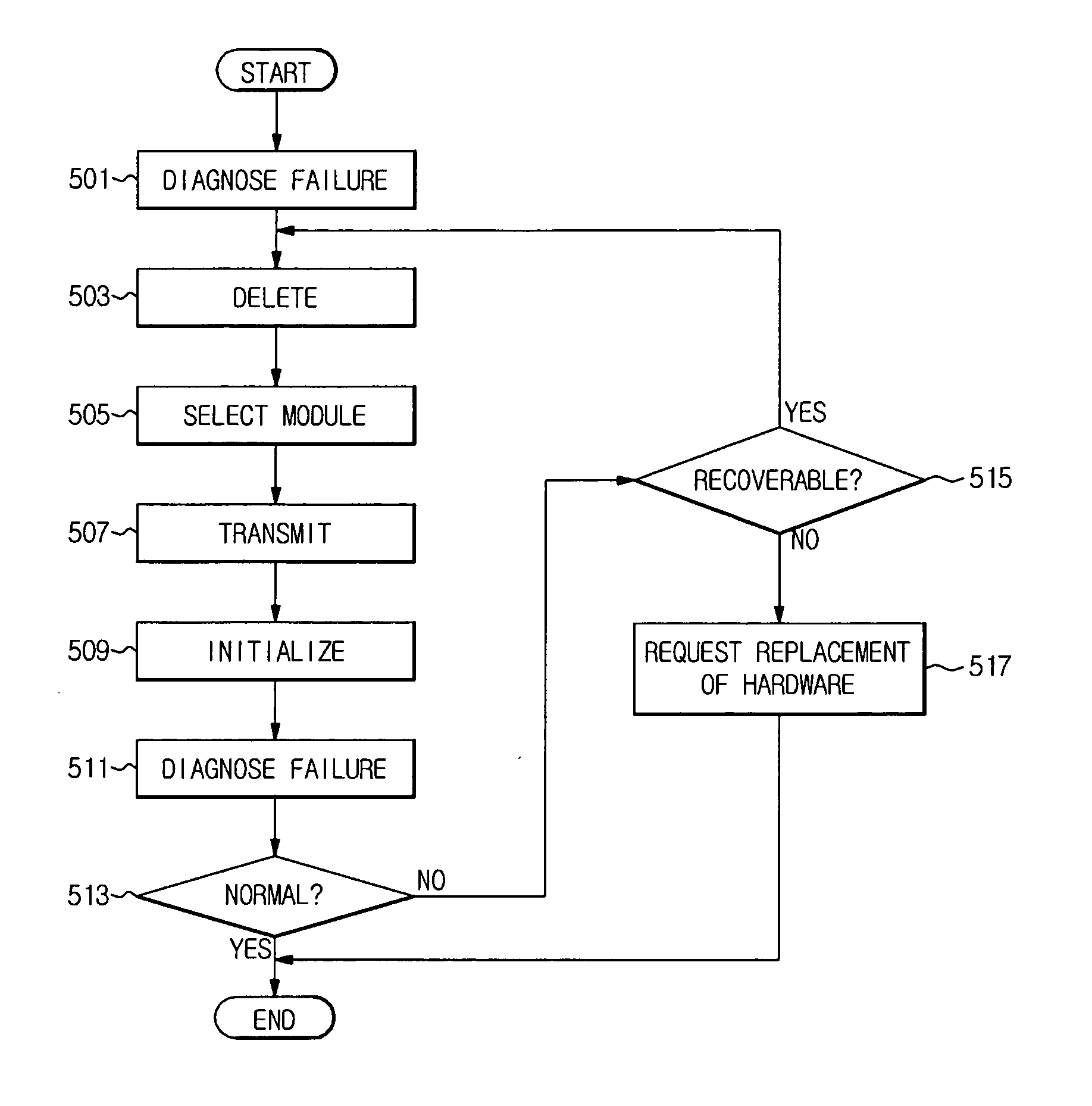
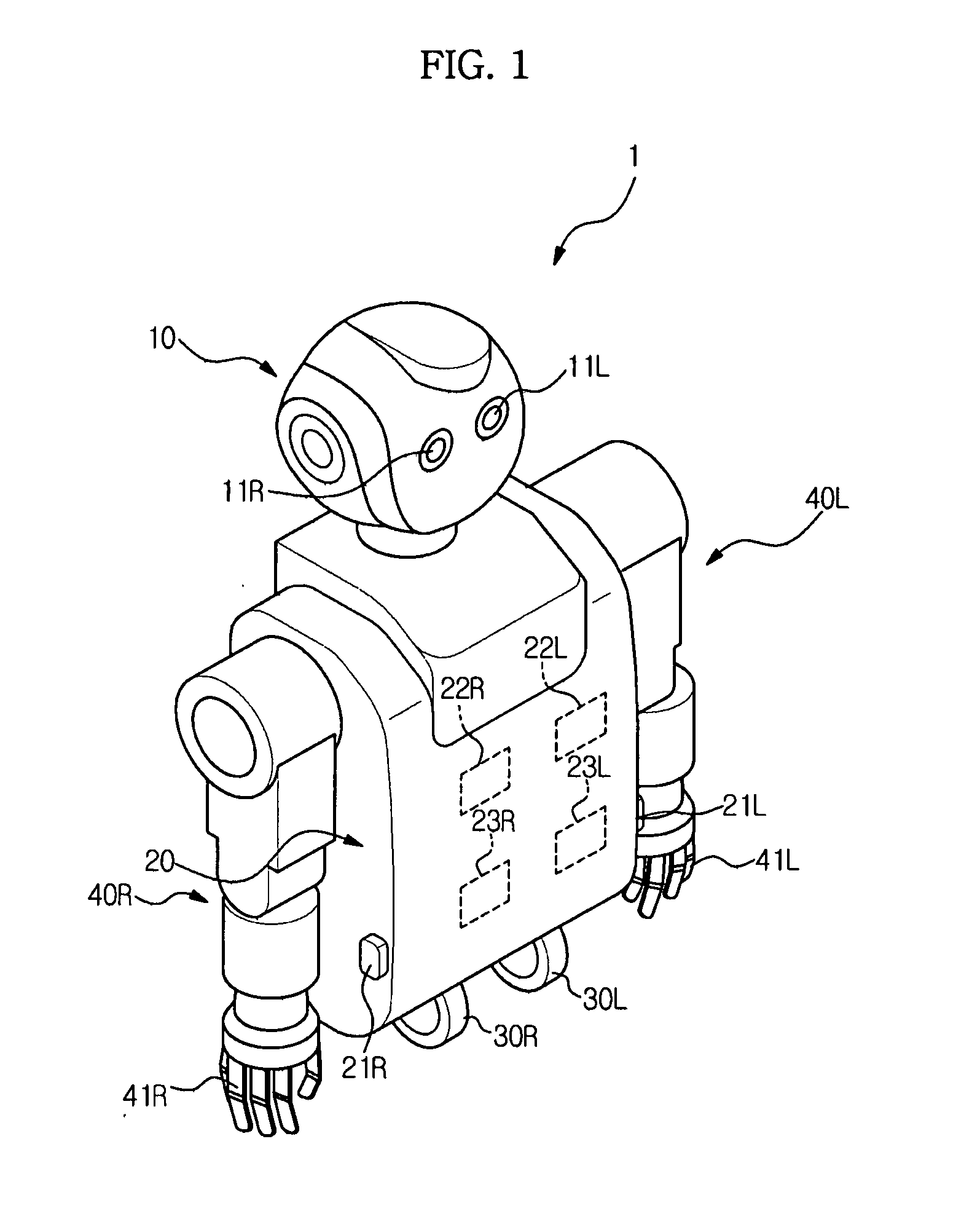
Robot and recovery method thereof
ActiveUS20100152894A1Avoid wasting resourcesProgramme controlProgramme-controlled manipulatorRecovery methodRestoration method
Disclosed herein are a robot capable of recovering from a failure of one of a plurality of symmetrically structured modules, and a recovery method thereof. When a hardware or software failure occurs, the robot recovers by itself by replacing the failed module with another corresponding module. Accordingly, resources of the robot can be more efficiently utilized.
Owner:SAMSUNG ELECTRONICS CO LTD
Reliability evaluation system design method based on software fault injection
InactiveCN103473162AReduce distractionsEvaluation is validError detection/correctionSystems designSoftware failure
The invention provides a reliability evaluation system design method based on software fault injection. In the method, a computer system is tested and evaluated specific to reliability serving as an important index for evaluating the performance of the computer system, and the fault-tolerance performance of a fault-tolerance system is tested and estimated by means of fault injection which can contribute to accelerating system failure. The invention introduces a design method of a fault injector oriented to reliability evaluation of the fault-tolerance system on the basis of the thought of software fault injection, and the method has the advantages of diverse fault types and triggering ways, realization of injection faults similar to real faults, easiness in operating, small influence on the system and the like, and can be used for effectively evaluating the system reliability.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
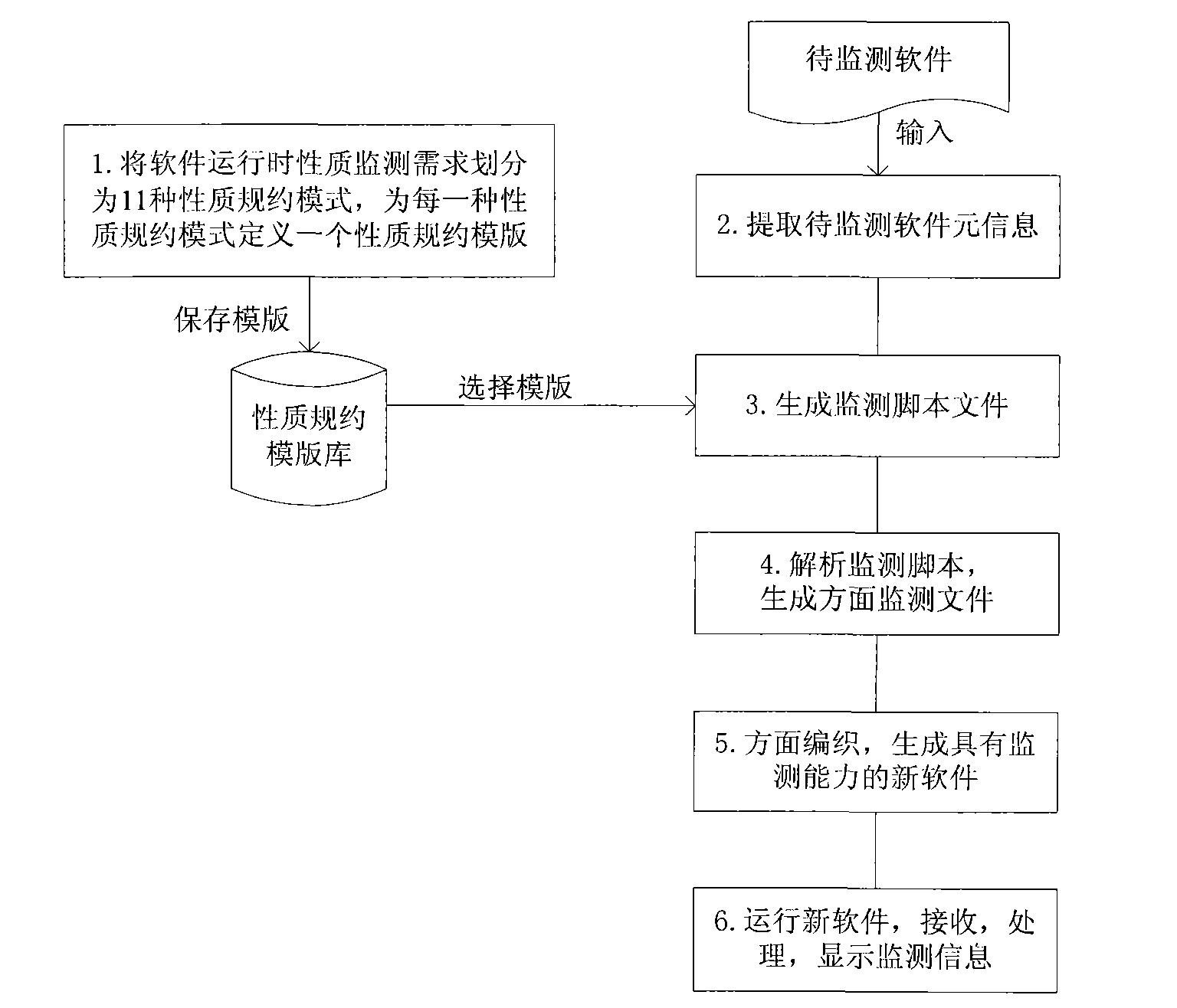
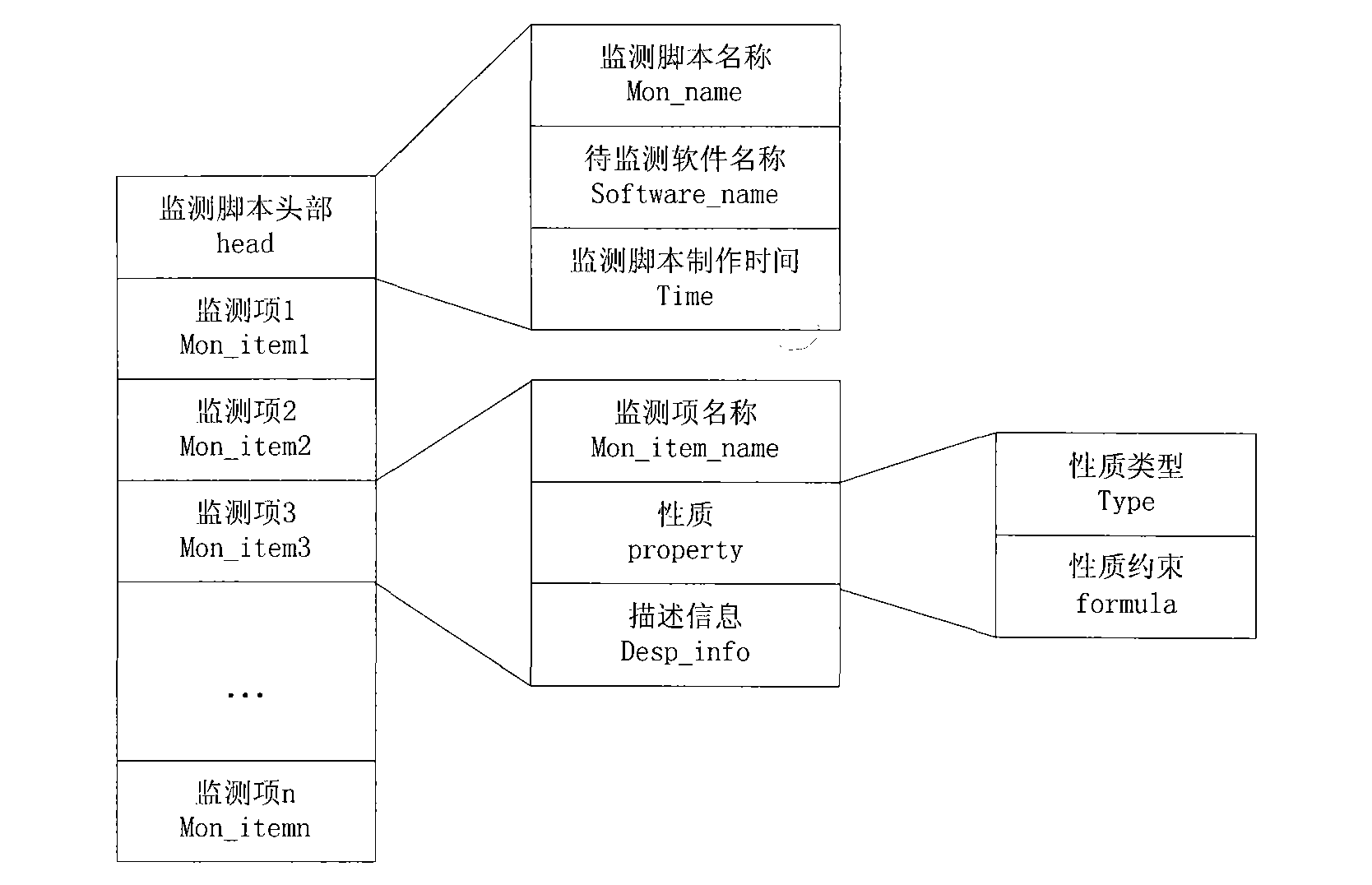
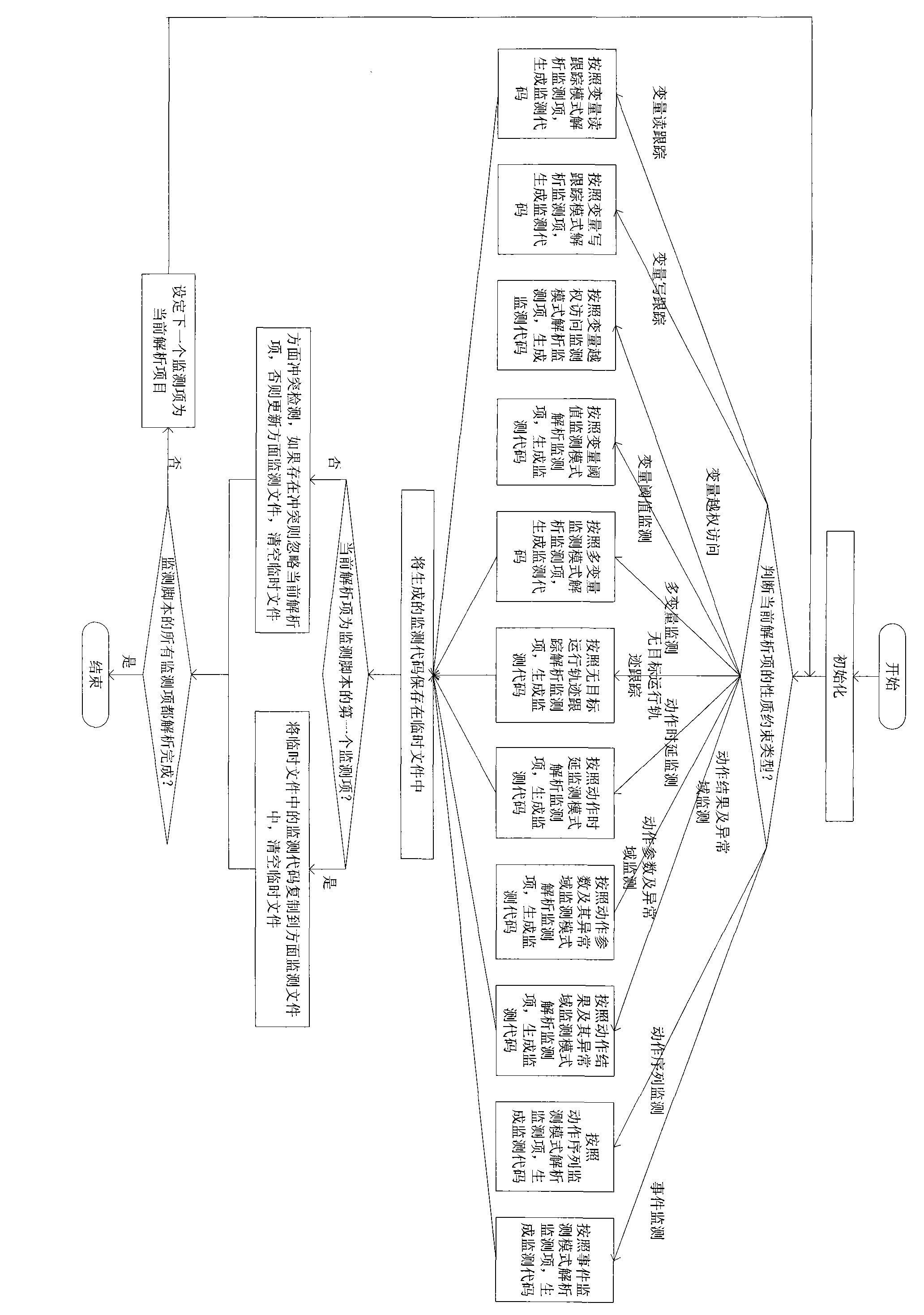
Software run-time property monitoring method based on property specification mode
InactiveCN101794224AEnhanced description abilityRealize generationSpecific program execution arrangementsSoftware failureInformation data
The invention discloses a software run-time property monitoring method based on property specification mode, aiming at providing a software run-time property monitoring method beneficial to fault discovery and diagnosis. The technical scheme includes that software run-time property monitoring requirements are classified into multiple property specification modes, a property specification template is constructed for each property specification mode; meta-information data in software to be monitored is extracted, so as to generate a meta-information file; the property specification template is configured, so as to generate a monitoring script file of the software to be monitored; the monitoring script file is analyzed, so as to generate a monitoring code; the software to be monitored and a comprehensive monitoring file are woven, so as to generate new software with run-time property monitoring capability; and the new software generated by weaving is run, software property is monitored and monitoring result is displayed. By adopting the invention, support can be provided for software fault discovery, diagnosis and defect location, software failure and maintenance cost is reduced, monitoring workload and monitoring difficulty are reduced, and timeliness is improved.
Owner:NAT UNIV OF DEFENSE TECH
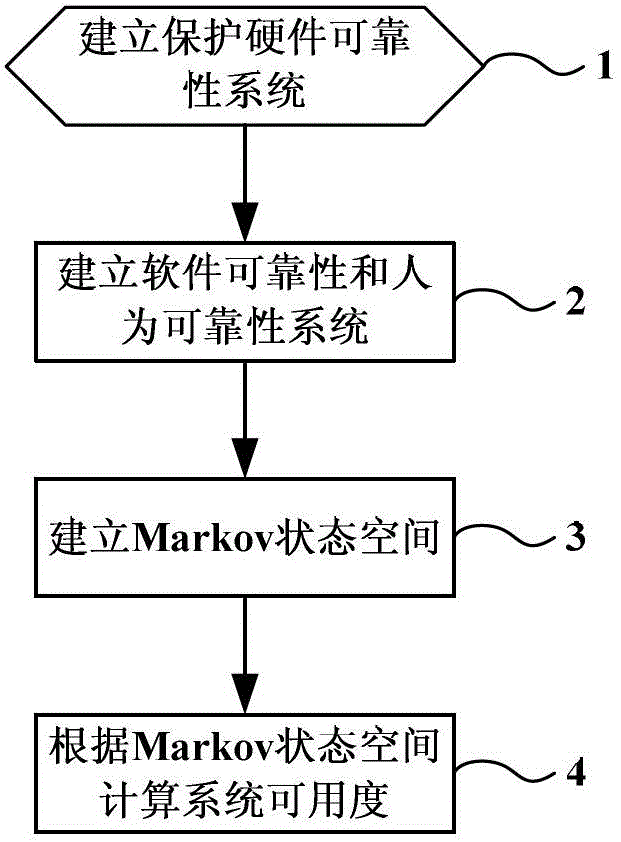
Fully-digital relay protection reliability system based on software failure and human failure, and evaluation method of system
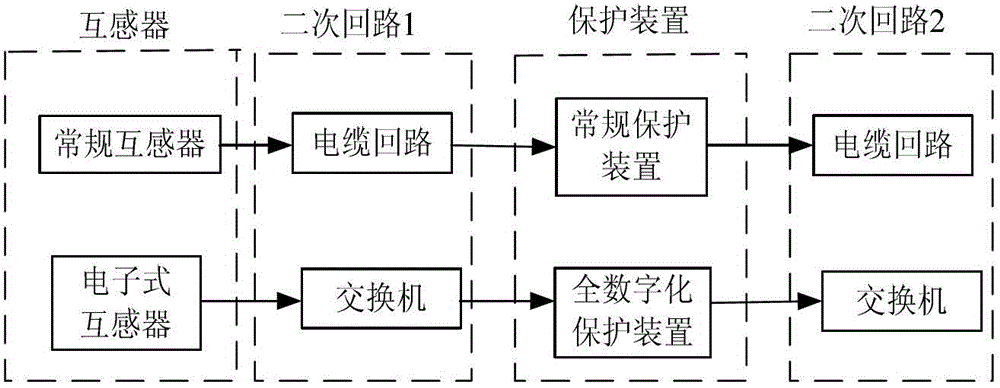
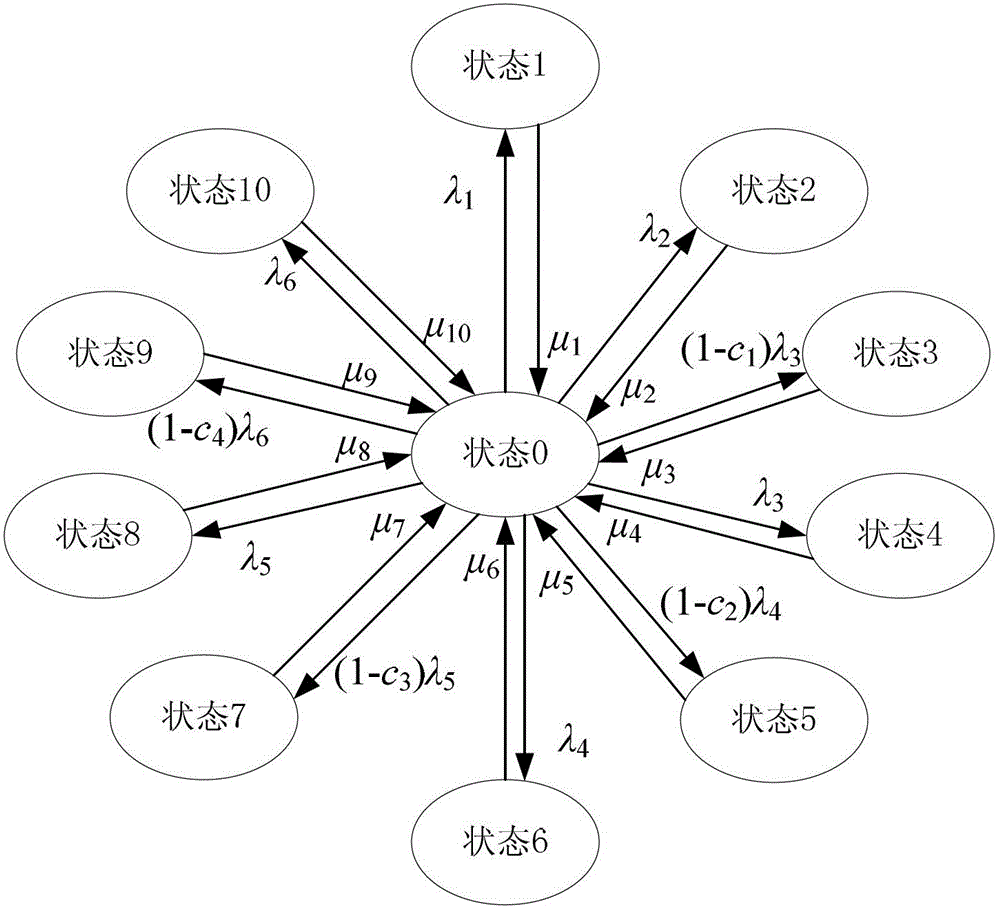
ActiveCN102945315AAvoid failureSpecial data processing applicationsHuman reliabilitySoftware failure
The invention relates to a fully-digital relay protection reliability system based on software failure and human failure, and an evaluation method of the system, and belongs to the field of relay protection reliability of power systems. The fully-digital relay protection reliability system comprises a hardware reliability system, a software reliability system and a human reliability system, and when a failure occurs in any one of the hardware reliability system, the software reliability system and the human reliability system, the fully-digital relay protection reliability system fails to work. The evaluation method comprises the following steps: establishing the hardware reliability system, the software reliability system and the human reliability system for the fully-digital relay protection reliability system; establishing a Markov state space of the fully-digital relay protection reliability system; and calculating the availability of the fully-digital relay protection reliability system according to a Markov system. The sum of the probabilities of steady state of the fully-digital relay protection reliability system in the normal state is the system availability. By considering the software and human failures which influence the relay protection reliability, the relay protection reliability system capable of effectively simulating the condition of state transition of the fully-digital relay protection system, and the evaluation method are established, and the problem that the conventional system considers the hardware failure in protection only from a perspective of the protective device without considering other factors of protection reliability is solved.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
Software system failure diagnosis method, server and system
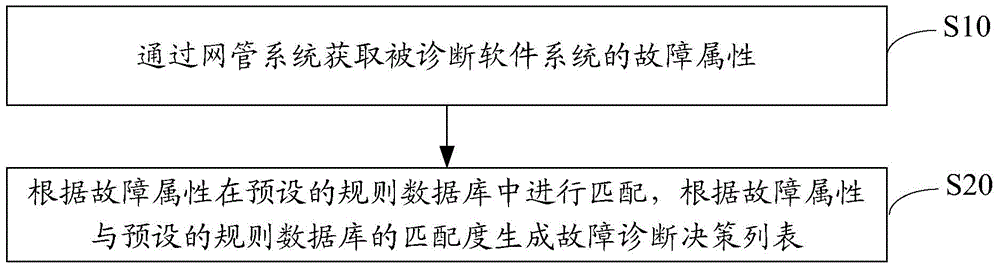
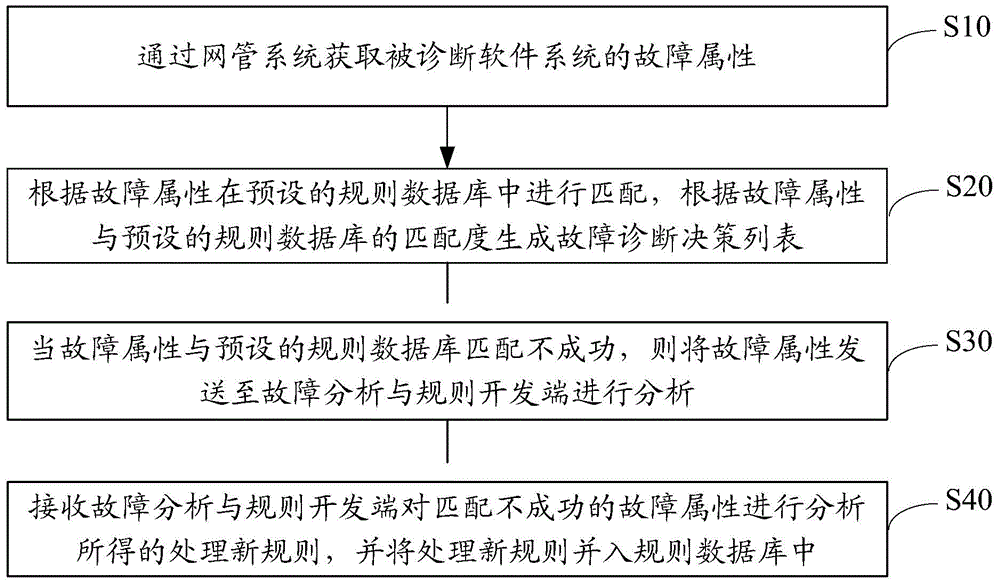
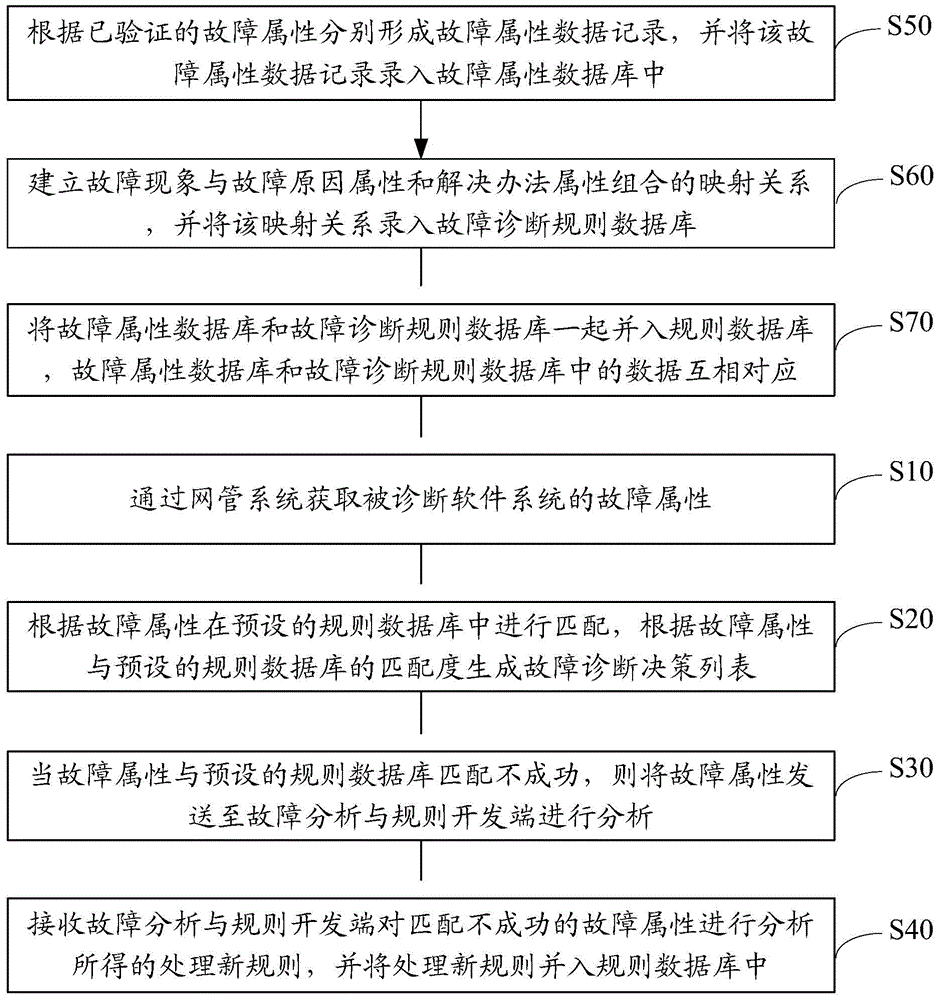
InactiveCN105740140AEasy maintenanceImprove efficiencyHardware monitoringSoftware testing/debuggingSoftware failureSoftware system
The present invention discloses a software system failure diagnosis method. The method comprises: acquiring a failure attribute of a to-be-diagnosed software system by means of a network management system; and performing a match in a preset rule database according to the failure attribute, and generating a failure diagnosis decision list according to a matching degree of the failure attribute and the preset rule database. The present invention further discloses a software system failure diagnosis server and system. According to the software system failure diagnosis method, server and system disclosed by the present invention, intelligent diagnosis and repairing of software system failures, real-time software system failure monitoring and online update of diagnosis rules are achieved, the efficiency and automation degree of software failure diagnosis and repairing are greatly improved, and maintenance and improvement efficiency of the diagnosis system are improved, and thus the technical problems of high learning costs and inconvenience of the existing software system maintenance are solved.
Owner:ZTE CORP
Embedded software trusted attribute modeling and verification method
ActiveCN103488568AAccurately describe credible requirementsEnhanced authenticationSoftware testing/debuggingSoftware failureDynamic models
The invention belongs to the field of trusted computing, and relates to an embedded software trusted attribute modeling and verification method. The method comprises the following steps that (1) a semi-formal model is built; (2) the semi-formal model is converted to a trusted embedded software model ZAM on a finite field, wherein the trusted embedded software model ZAM comprises a time model, a static model and a dynamic model; (3) a ZMTL timing sequence logic formula describing embedded software trusted attributes is given, and trusted attributes of the ZAM model are verified through an FZMCA algorithm. A trusted embedded software modeling and verification frame is divided into a UML / MARTE graphical layer, a model converting layer, a ZAM model layer and a model verification layer. Modeling and verifications can be conducted on the embedded software trusted attributes according to the method to reduce trusted attribute defects of embedded software in the developing process and reduce software failure probability.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Nuclear reactor automatic depressurization system
ActiveUS20120155597A1Inhibition of activationPower plant safety arrangementNuclear energy generationNuclear reactorReactor system
A blocking device for preventing the actuation of an automatic depressurization system in a pressurized nuclear reactor system due to spurious signals resulting from a software failure. The blocking signal is removed when the coolant level within the core makeup tanks drop below a predetermined level.
Owner:WESTINGHOUSE ELECTRIC CORP
Method and system for remotely debugging a hung or crashed computing system
ActiveUS8069371B2Error detection/correctionSpecific program execution arrangementsTelecommunications linkSoftware failure
A method and system for debugging a computer upon a kernel hang and / or upon a software failure, the method comprising executing a debugger on a remote computer, connecting the hung or crashed computer to the remote computer with a communications link, and debugging the hung or crashed computer with the debugger without rebooting the system. The method may include deconfiguring any kernel driver of the computer attached to the communication card prior to connecting the remote debugger to the computer.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
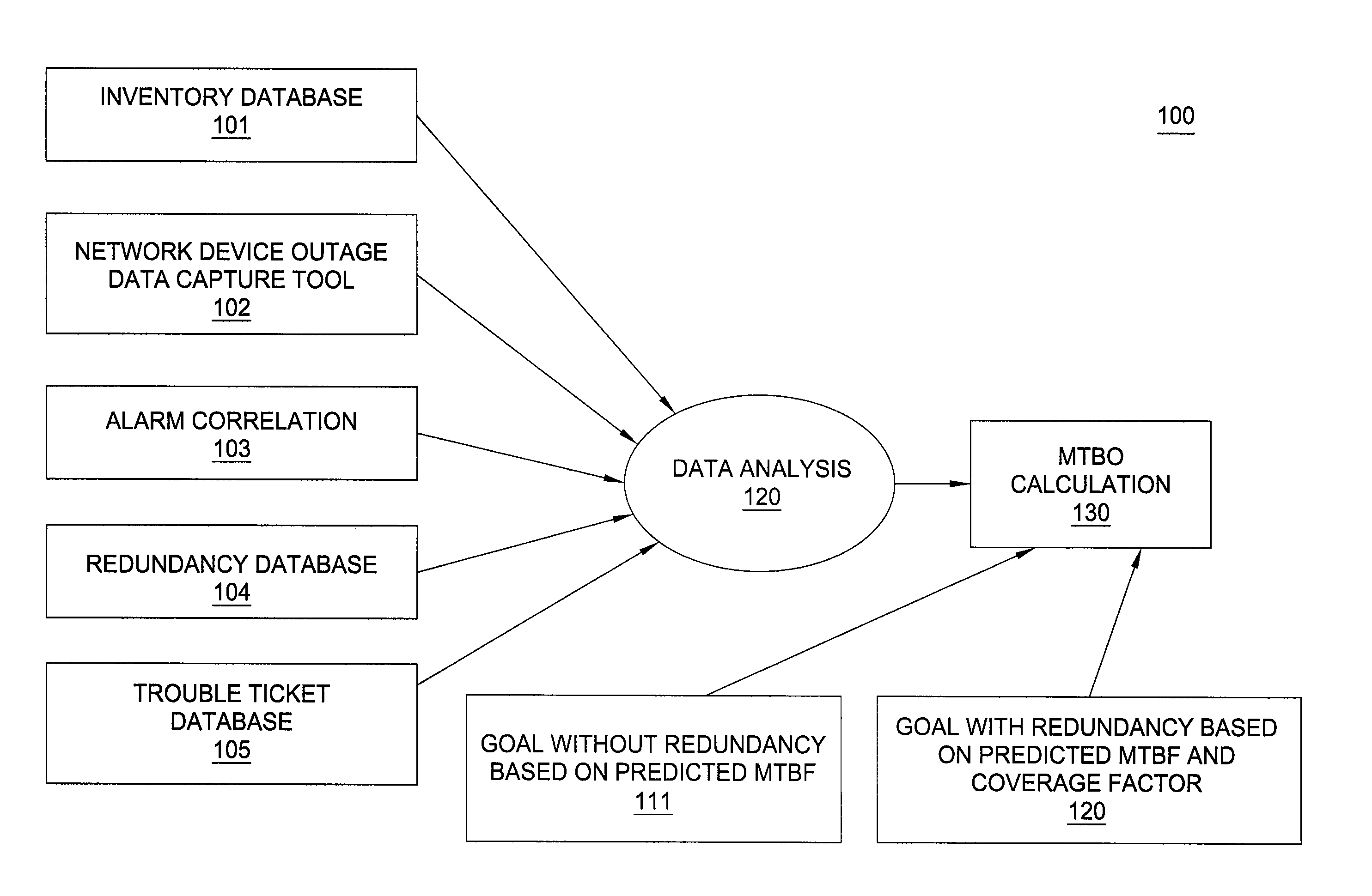
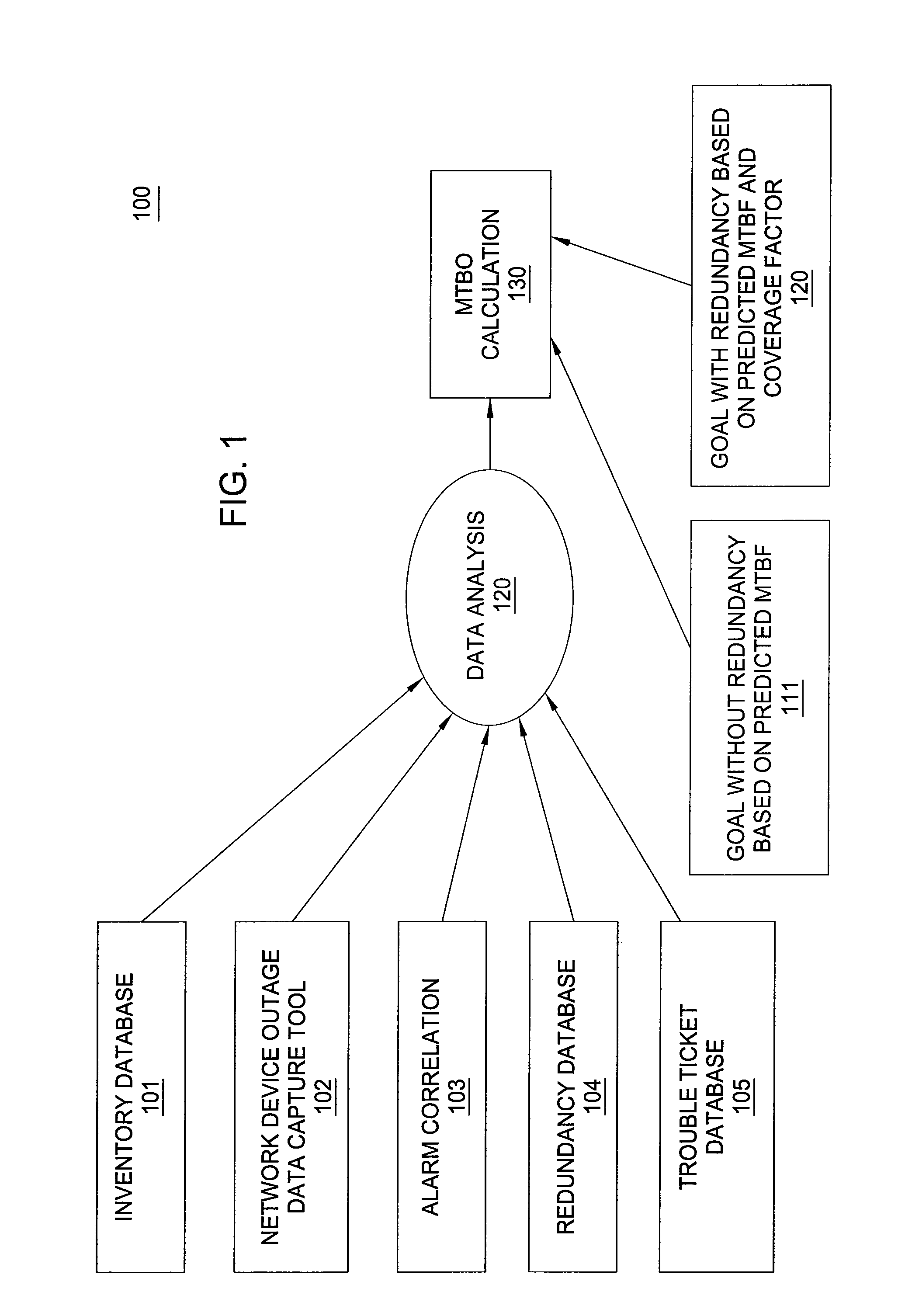
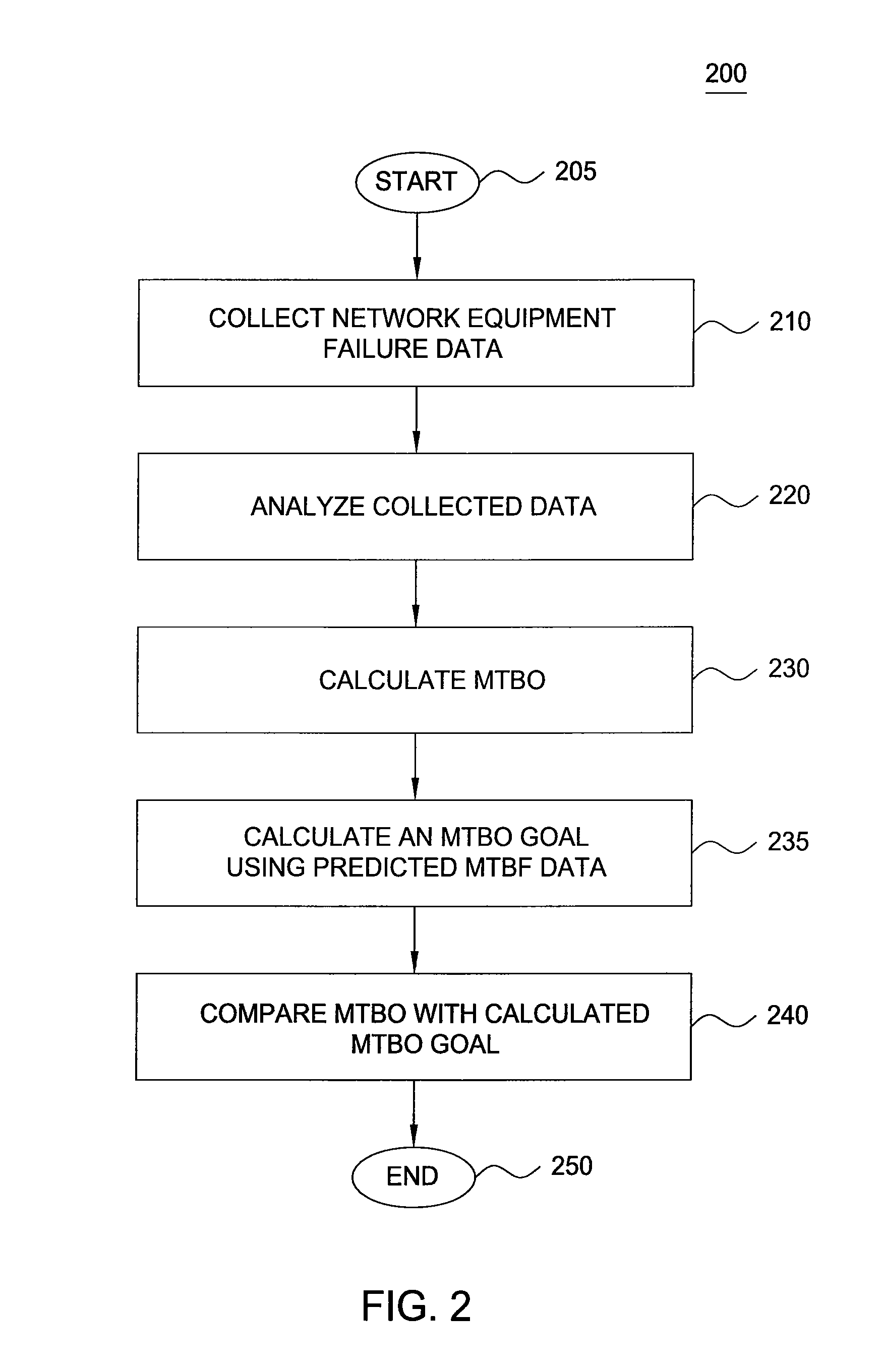
Method and apparatus for measuring customer impacting failure rate in communication networks
ActiveUS20100125745A1Reliability/availability analysisTransmissionFailure rateMean time between outages
A method and system for measuring a customer impacting failure rate in a communication network are disclosed. For example, the method collects a plurality of customer impacting network failure events, where the plurality of customer impacting network failure events comprises both hardware failure events and software failure events associated with a particular type of router or switch, or a particular type of component of the router or the switch. The method computes a Mean Time Between Outage (MTBO) metric from the plurality of customer impacting network failure events and compares the MTBO metric with a MTBO goal metric, wherein the MTBO goal metric is calculated in accordance with a predicted Mean Time Between Failure (MTBF) metric.
Owner:AT&T INTPROP I L P +1
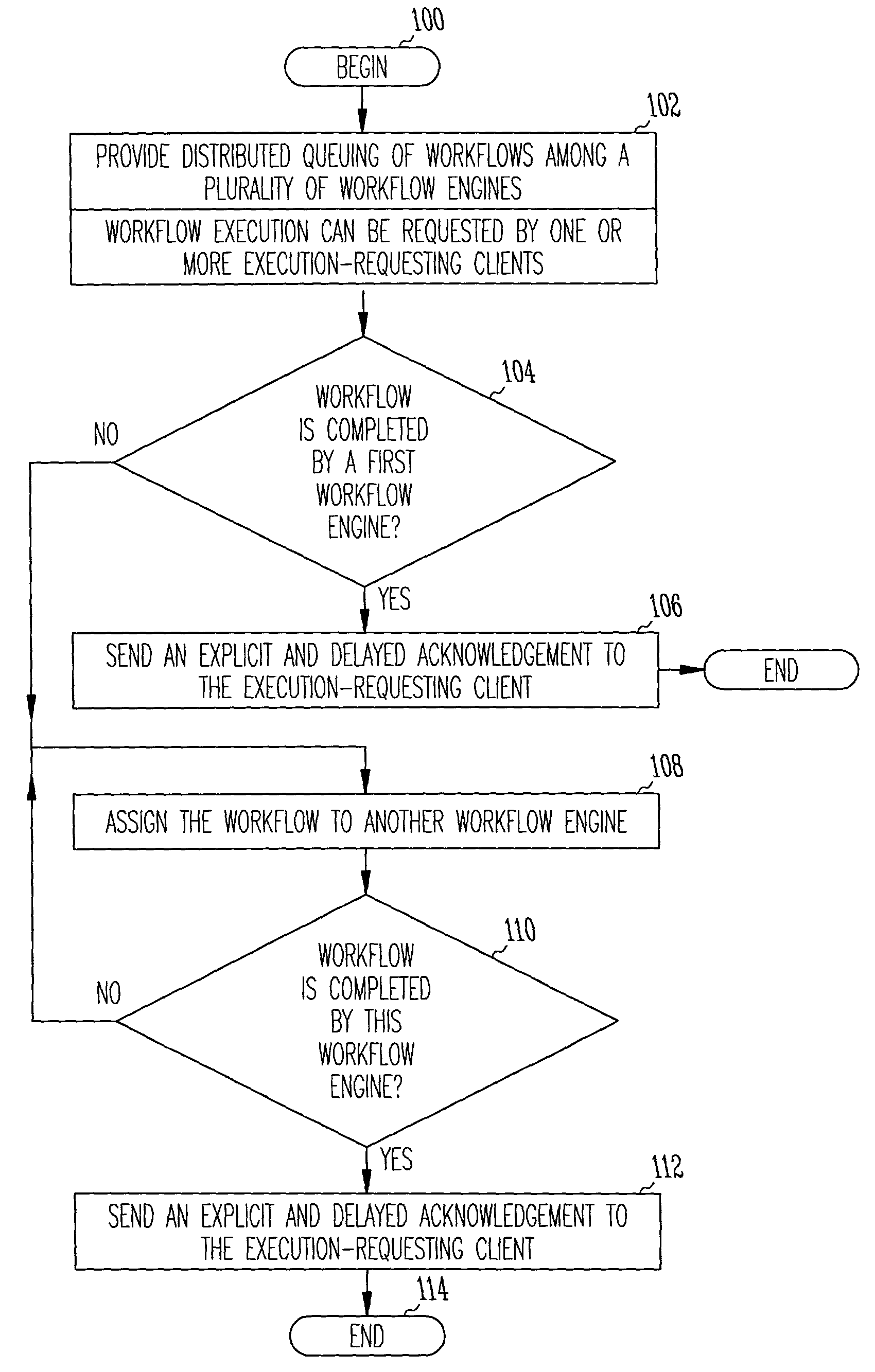
Fault-tolerant system and methods with trusted message acknowledgement
InactiveUS7454751B2Program initiation/switchingError detection/correctionFault toleranceSoftware failure
Improved methods for providing fault tolerance in a distributed computer system utilize an explicit, delayed acknowledgement message protocol to send an acknowledgement message to a workflow-requesting entity, such as a load manager and / or a requesting client, only upon completion of a workflow. The system includes workflow engines operating as a distributed queue group to load-balance processing requests from clients. The system also has a certified messaging capability that guarantees delivery of any message sent by a certified message sender by maintaining a persistent record of the message until an acknowledgement message is received back from the certified message receiver. In the event a hardware or software failure occurs during a workflow execution, the workflow is reassigned to a different workflow engine. Improved fault-tolerant computers and computer networks are also described.
Owner:INTEL CORP
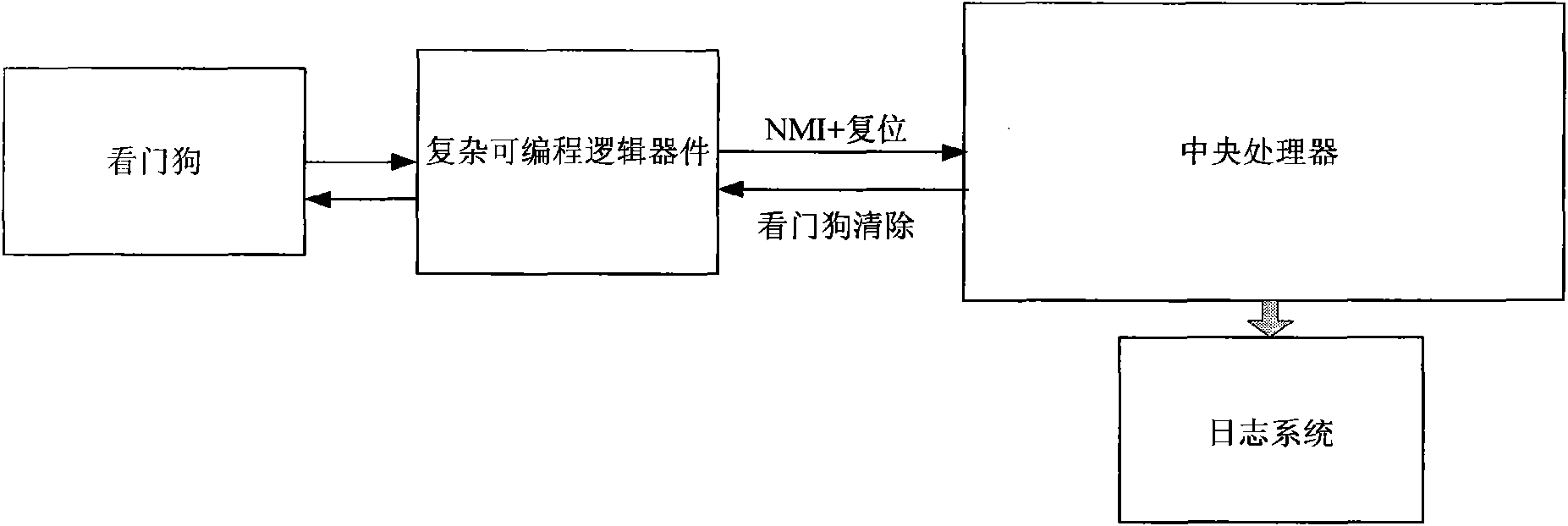
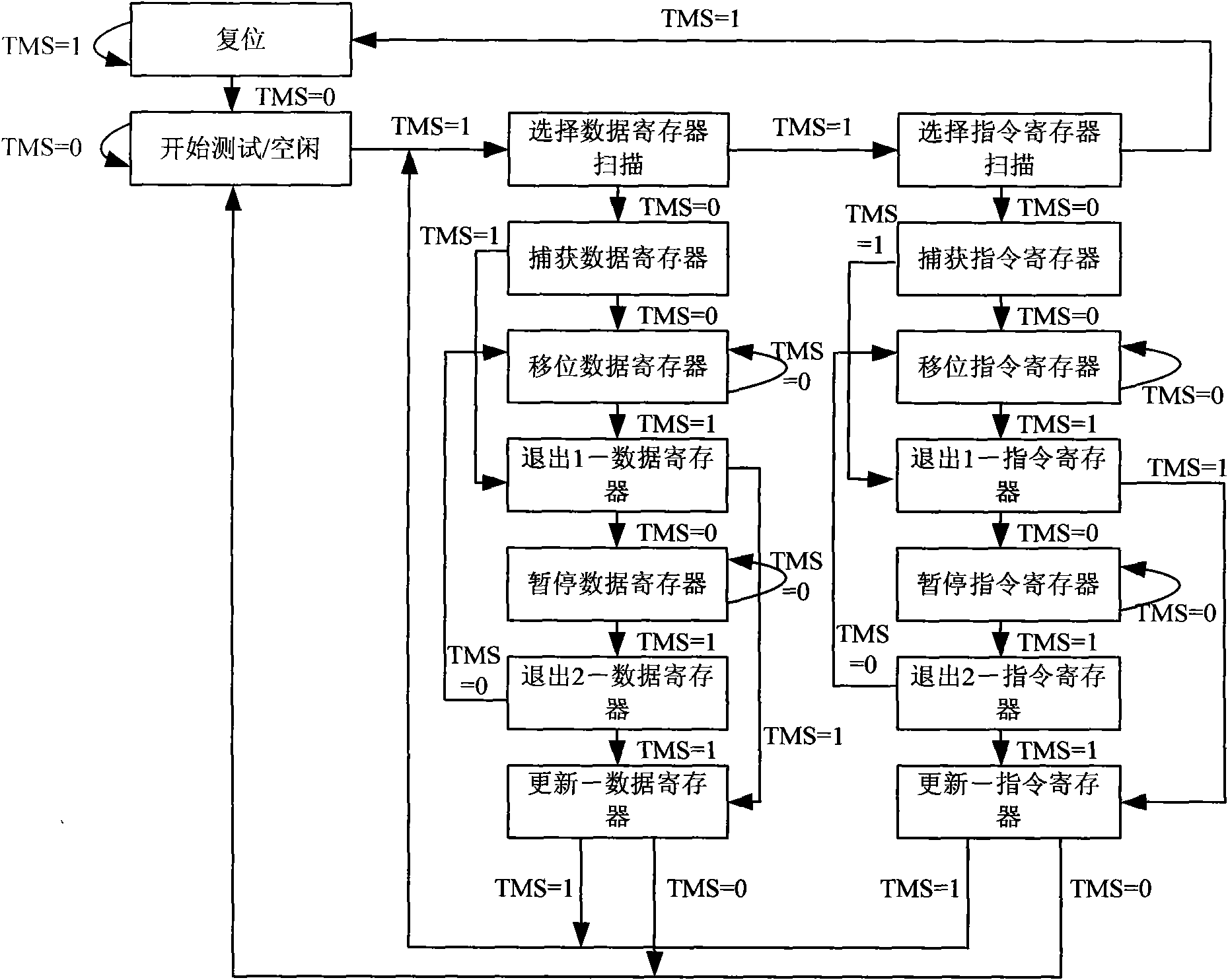
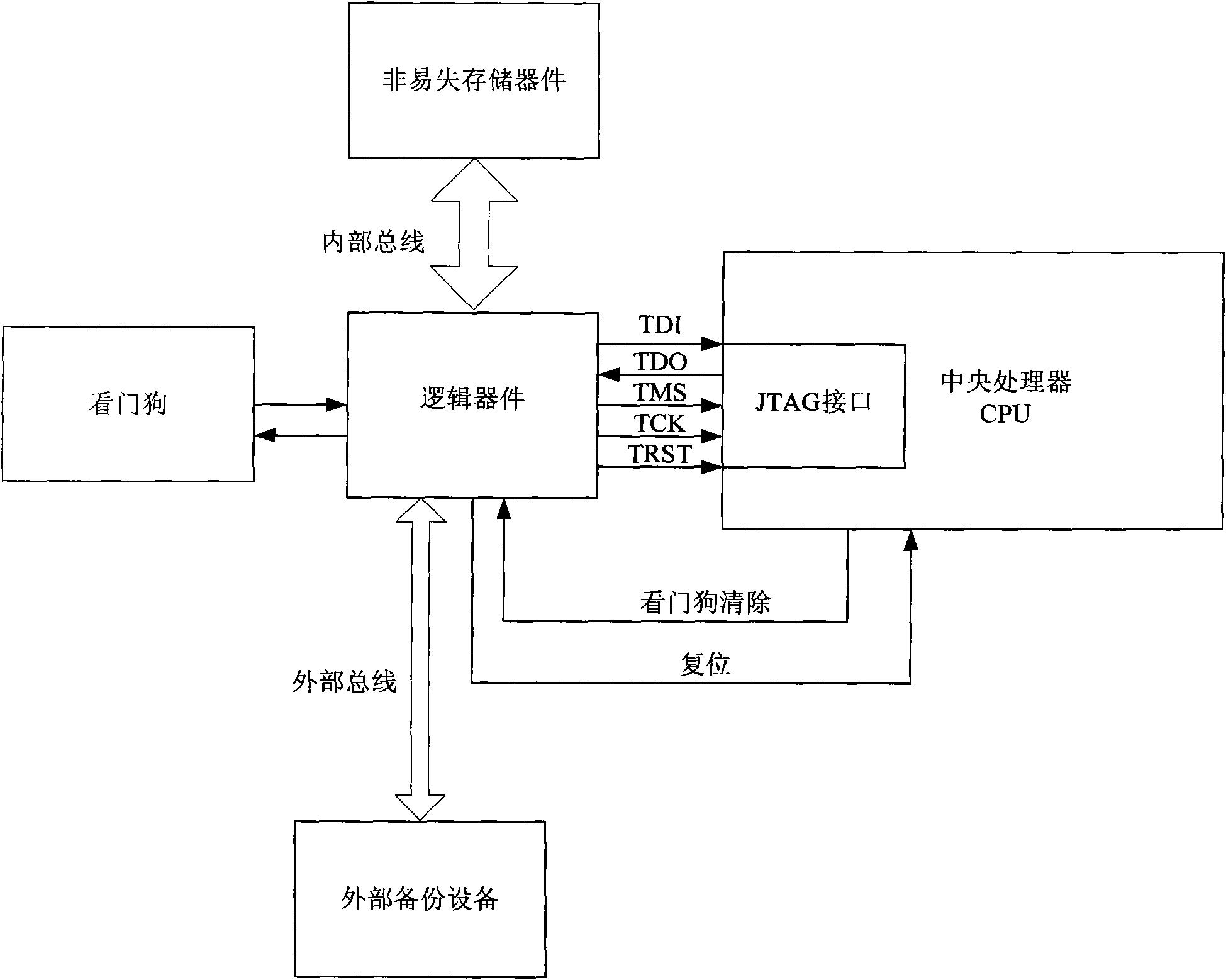
Hardware acquisition system and method for equipment failure log
ActiveCN101556551AUnlimited degree of failureEasy accessHardware monitoringSoftware failureSoftware system
The invention relates to a hardware acquisition system and a method for equipment failure log. A logic device is connected with a watchdog device and the JTAG interfaces of CPU, respectively and is used for receiving trigger from the watchdog device when overtime overflow occurs; boundary scanning is executed for a selected unit in CPU by the JTAG interface according to preset boundary scanning logic and the equipment failure log is generated according to the obtained boundary scan result; in addition, the CPU reset is triggered after the boundary scanning is completed. The hardware acquisition system and the method for equipment failure log is not limited by the software failure degree of the equipment and can still ensure the acquisition of key information even when the failure of the equipment software system is very serious.
Owner:NEW H3C TECH CO LTD
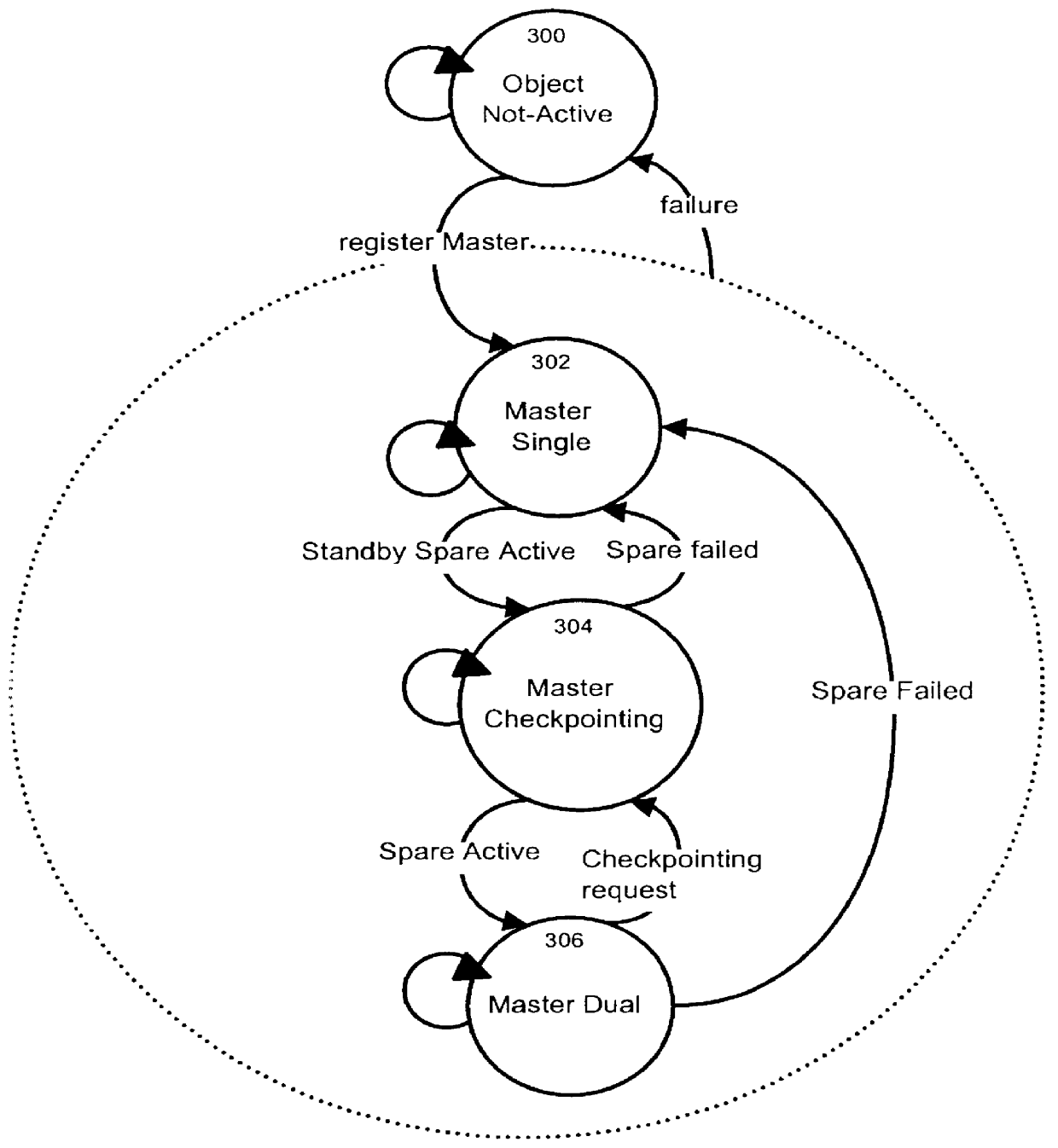
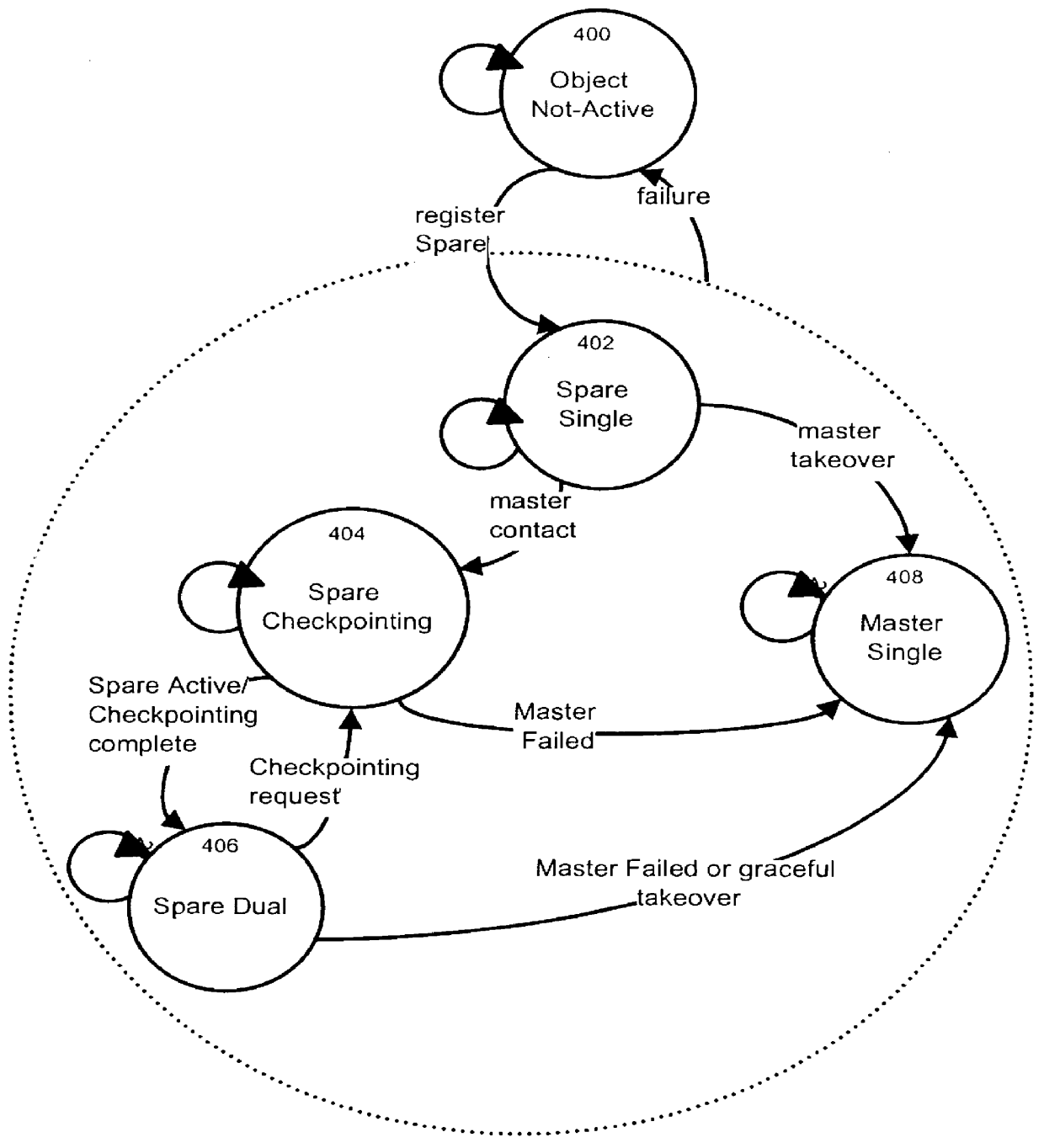
Process and apparatus for reducing software failures using sparing in distributed systems
A software sparing process and apparatus to reduce the likelihood of software failures is provided. Software sparing provides software entities, called spares, which take over and provide similar functionality as the failed system to the clients of the failed entity. They also permit the introduction of new software versions with no loss in service during the switch over period. These spare entities, which may be located on different nodes in a system, communicate using a standard interface protocol. Sparing is done at the software "chunk" level instead of at the hardware box level, which is the common practice, resulting in lower costs and improved reliability. A computer readable storage medium containing a program element to direct a processor of a computer to implement the software sparing process described earlier is also provided.
Owner:AVAYA INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com