Patents
Literature
1924 results about "Simulation based" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
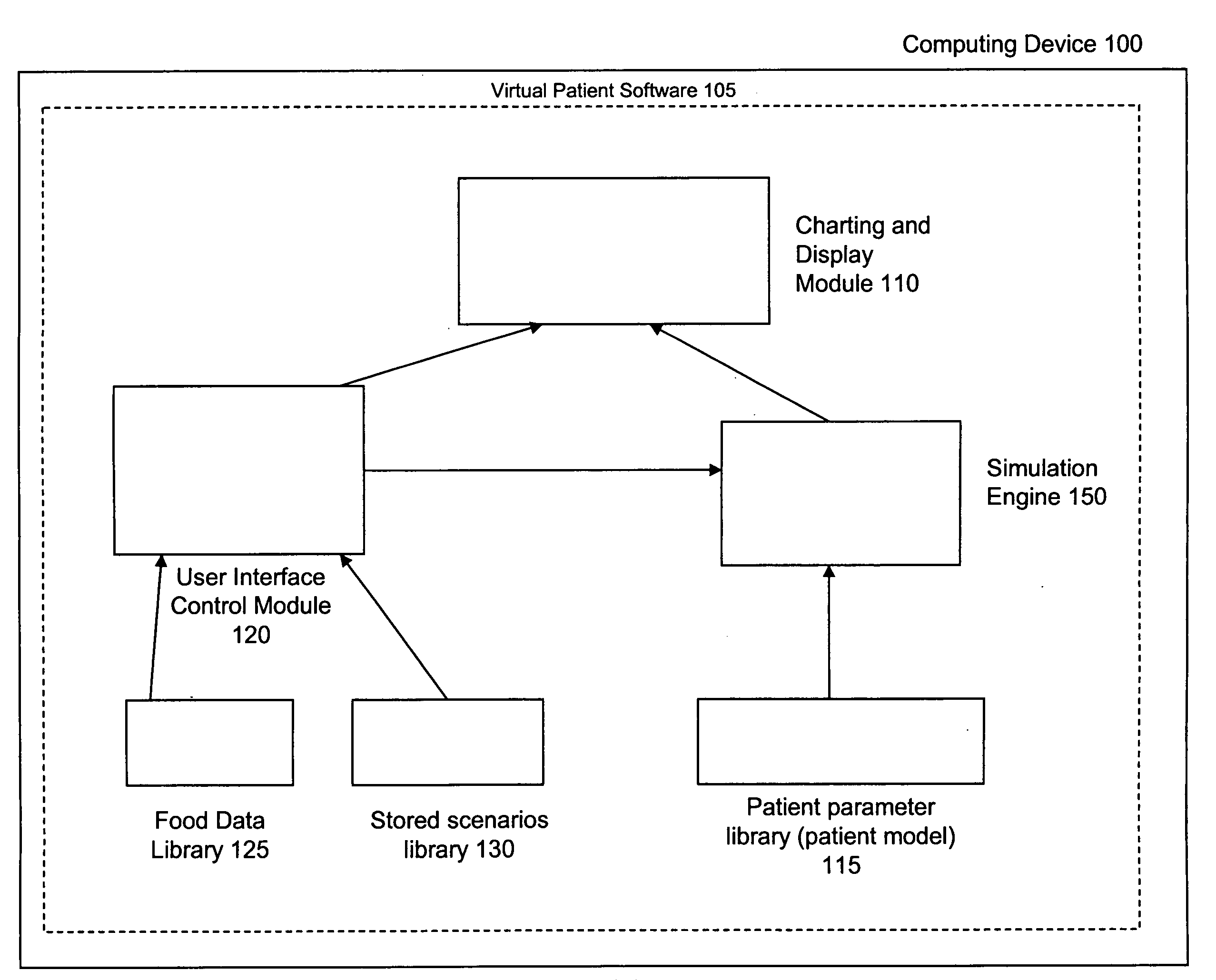
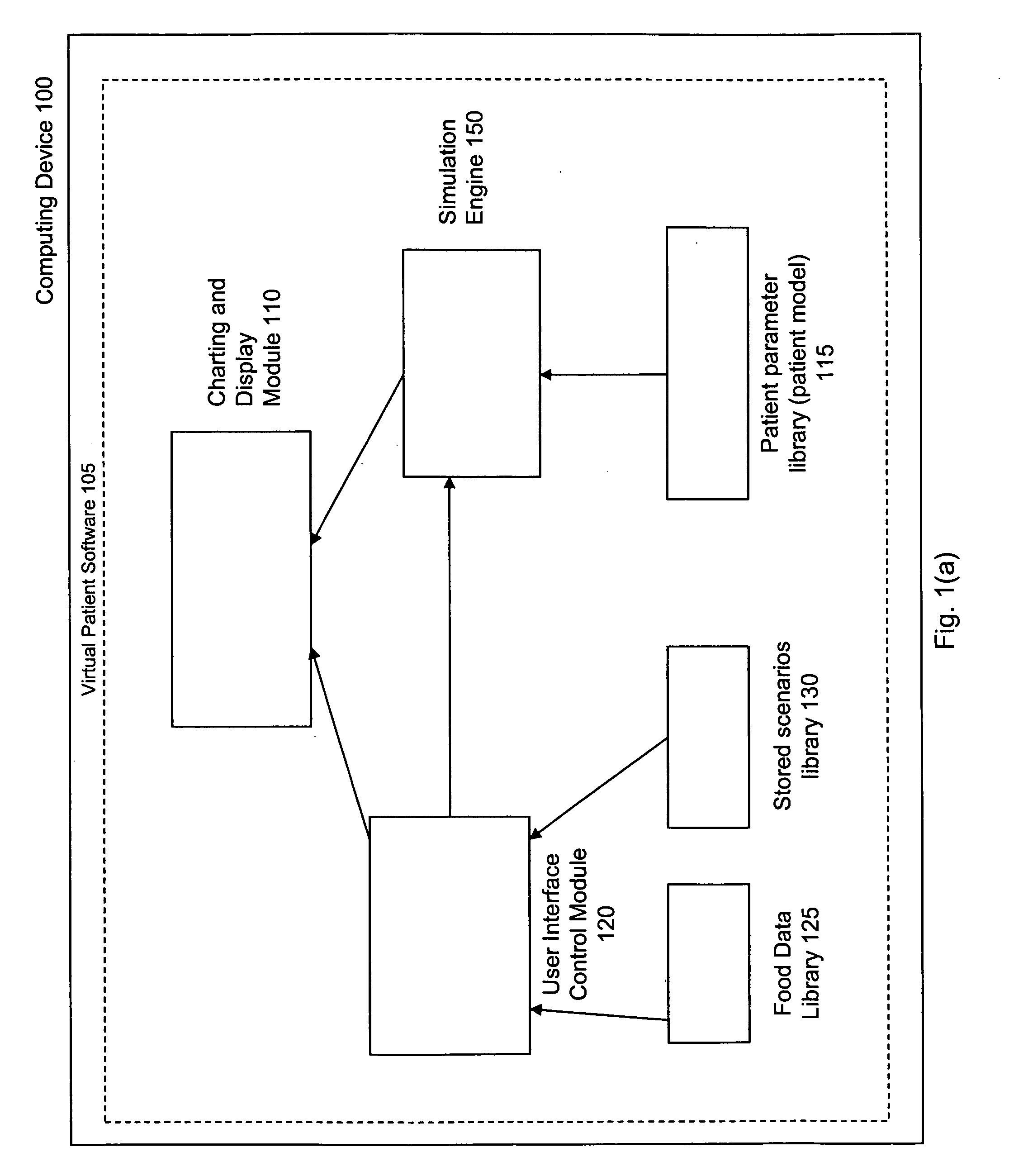
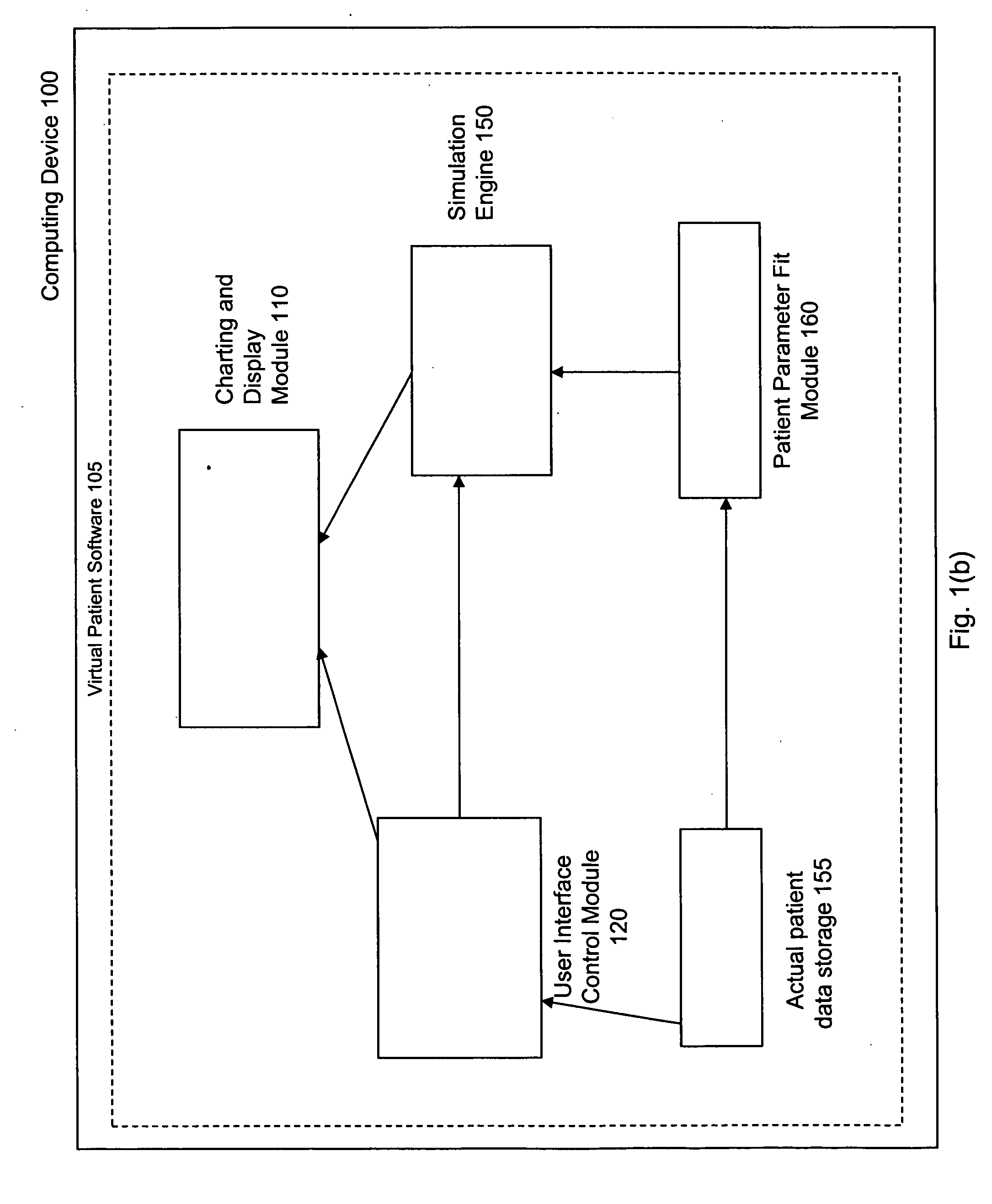
Virtual patient software system for educating and treating individuals with diabetes
A system to assist an individual in developing a therapy in diabetes treatment of a patient includes a user interface control module, a simulation engine, a charting and display module. The user interface control module receives an input related to the patient and captures a current time of the simulation. The simulation engine receives the input, generates a plurality of blood glucose readings for the patient up to the current time of the simulation based on the input, and to transfers the plurality of blood glucose readings. The charting and display module receives the plurality of blood glucose readings and display the plurality of blood glucose readings. The simulation engine receives patient parameters from a patient parameter library based on a selected patient model.
Owner:MEDTRONIC MIMIMED INC
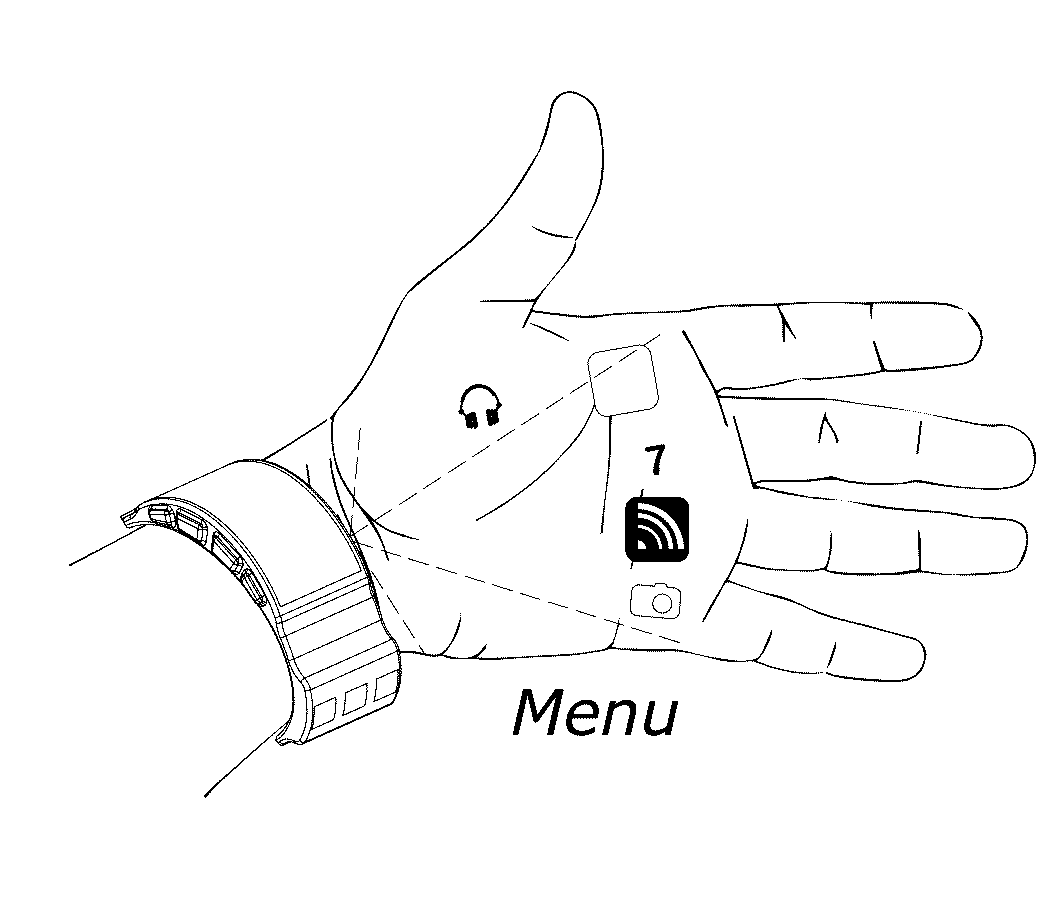
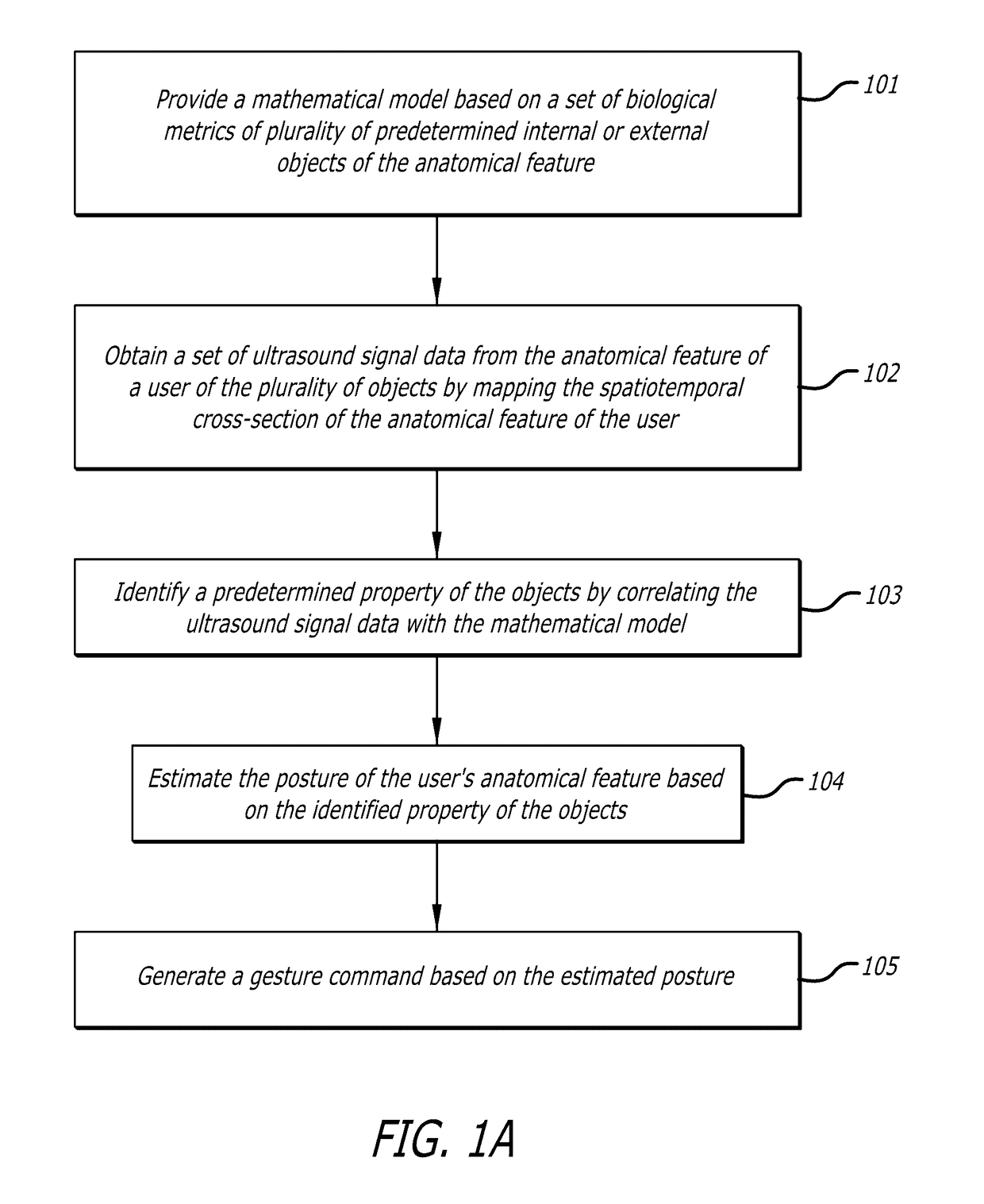
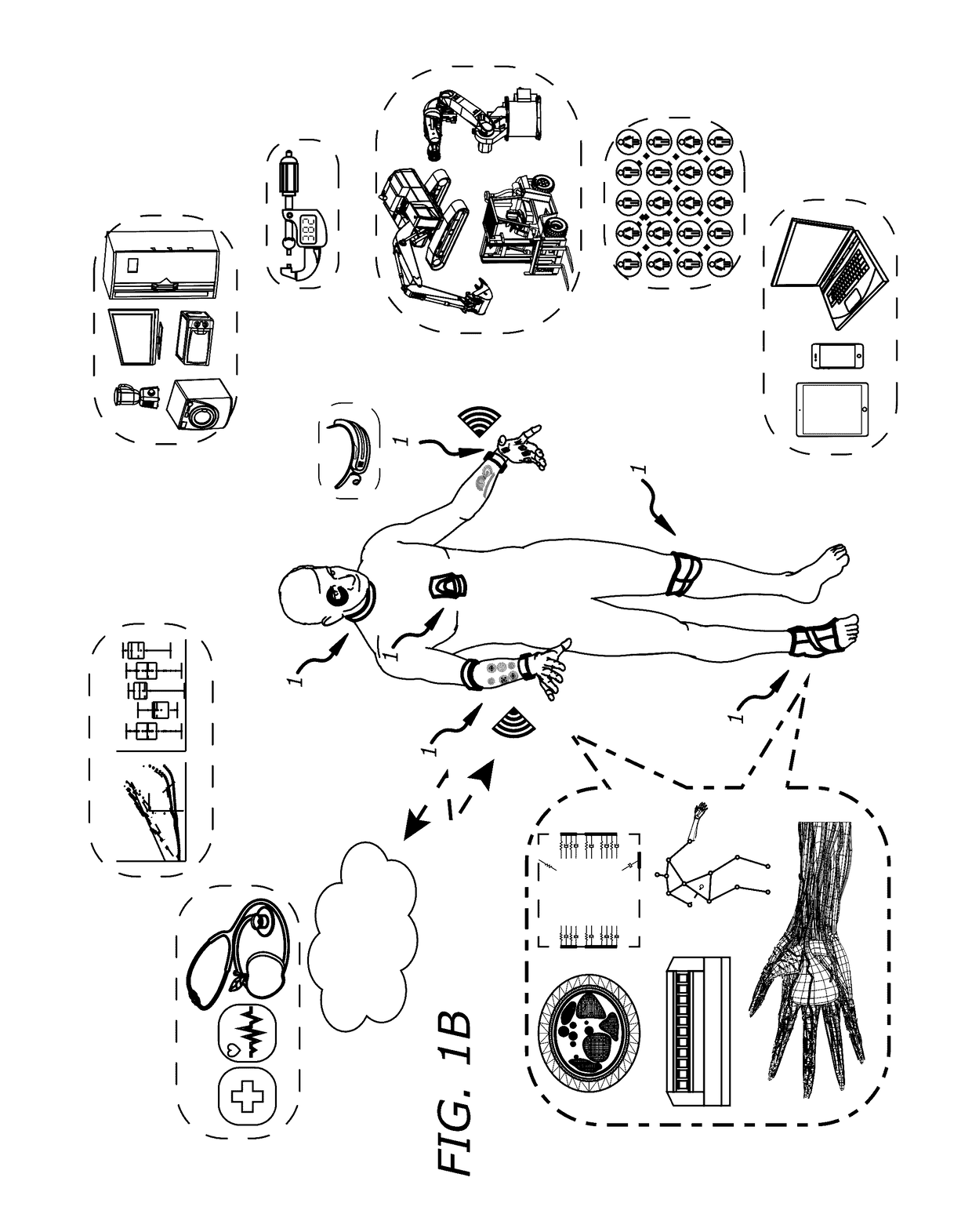
System and methods for on-body gestural interfaces and projection displays
ActiveUS20170123487A1Input/output for user-computer interactionDetails for portable computersSonificationTransceiver
A wearable system with a gestural interface for wearing on, for instance, the wrist of a user. The system comprises an ultrasonic transceiver array structure and may comprise a pico projector display element for displaying an image on a surface. User anatomical feature inputs are received in the form of ultrasound signals representative of a spatio-temporal cross-section of the wrist of the user by articulating wrist, finger and hand postures, which articulations are translated into gestures. Inputs from inertial and other sensors are used by the system as part of the anatomical feature posture identification method and device. Gestures are recognized using a mathematically-modeled, simulation-based set of biological metrics of tissue objects, which gestures are converted to executable computer instructions. Embodiments of the system disclosed herein may also be used to monitor biometric and health data over computer networks or using onboard systems.
Owner:OSTENDO TECH INC
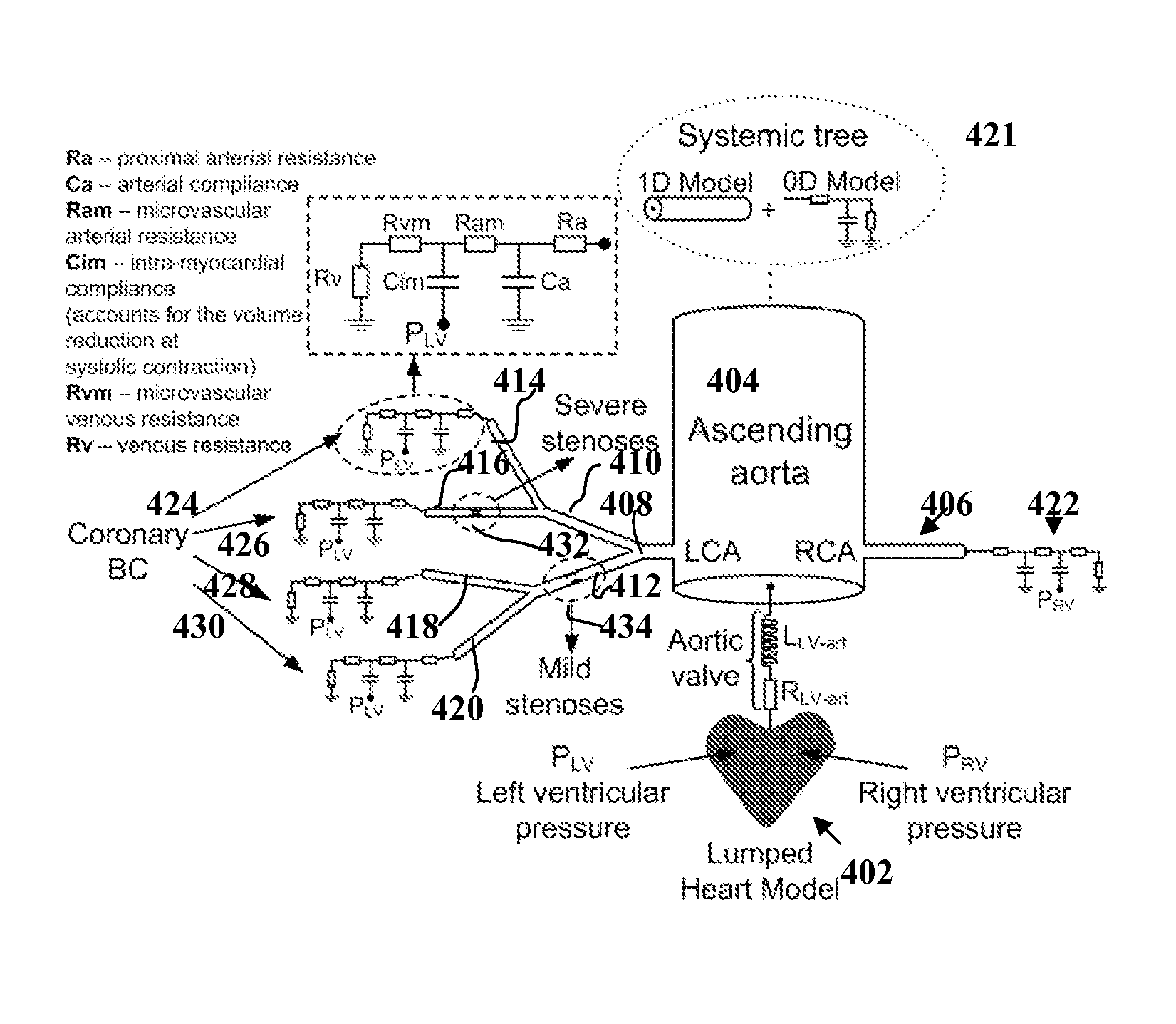
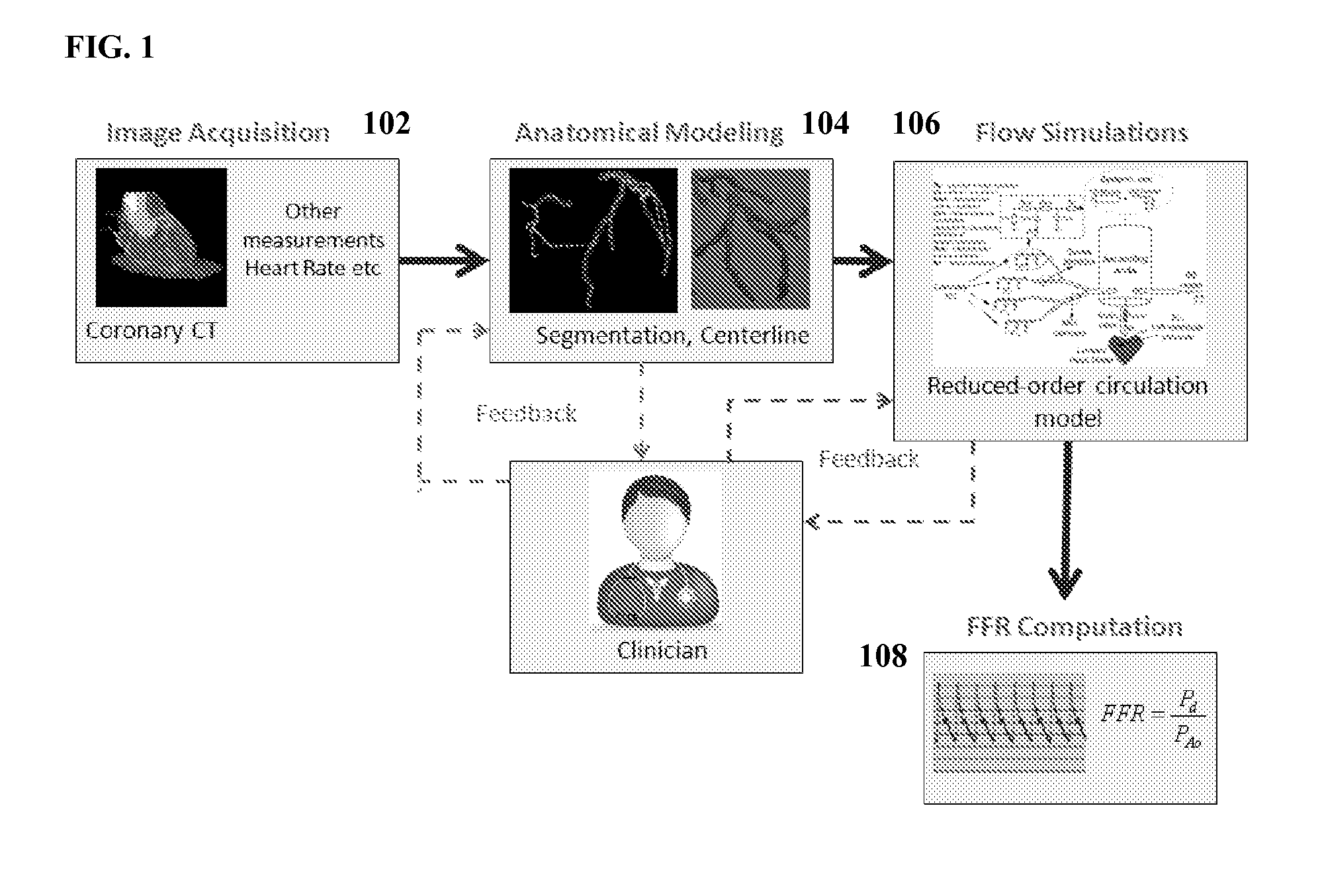
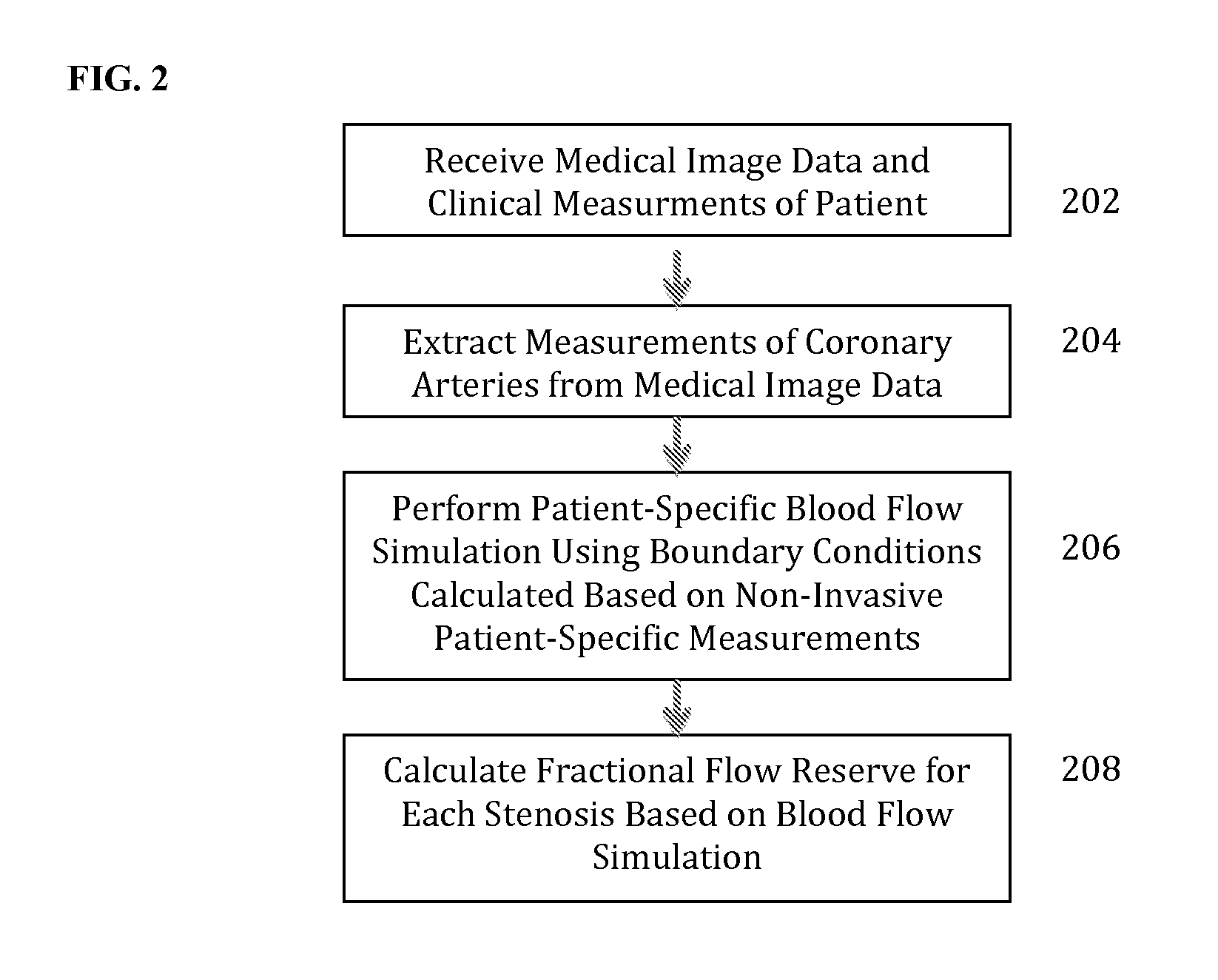
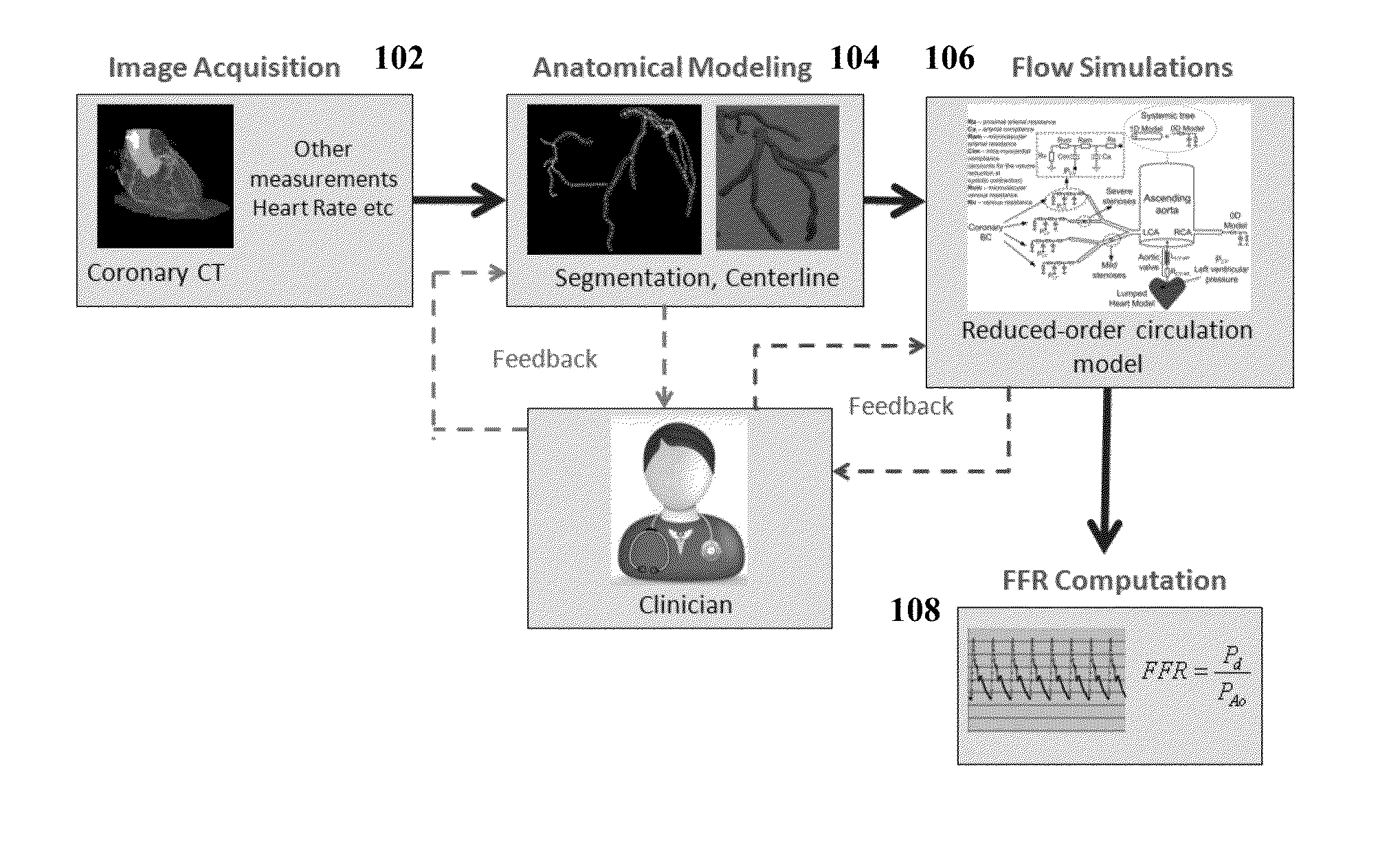
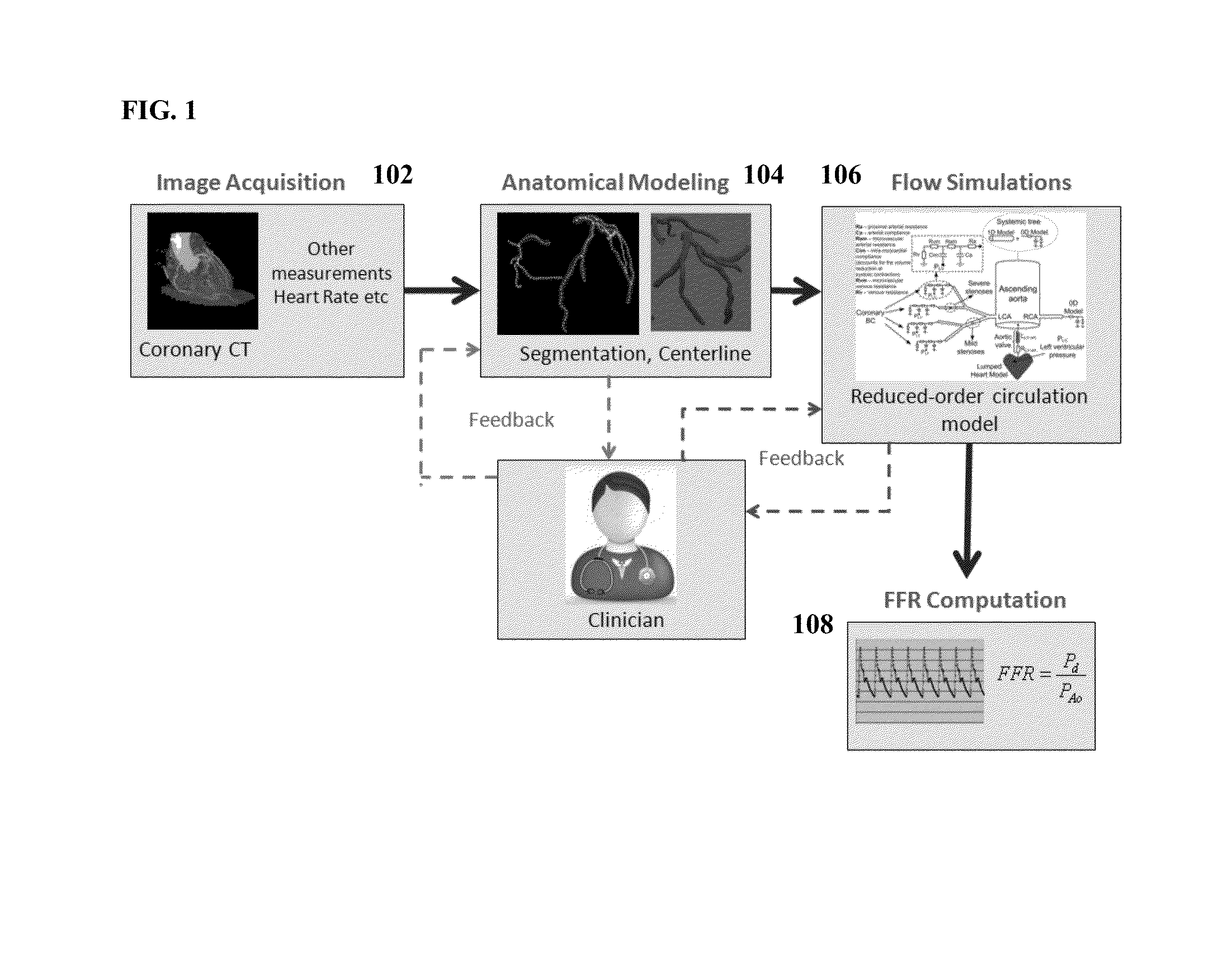
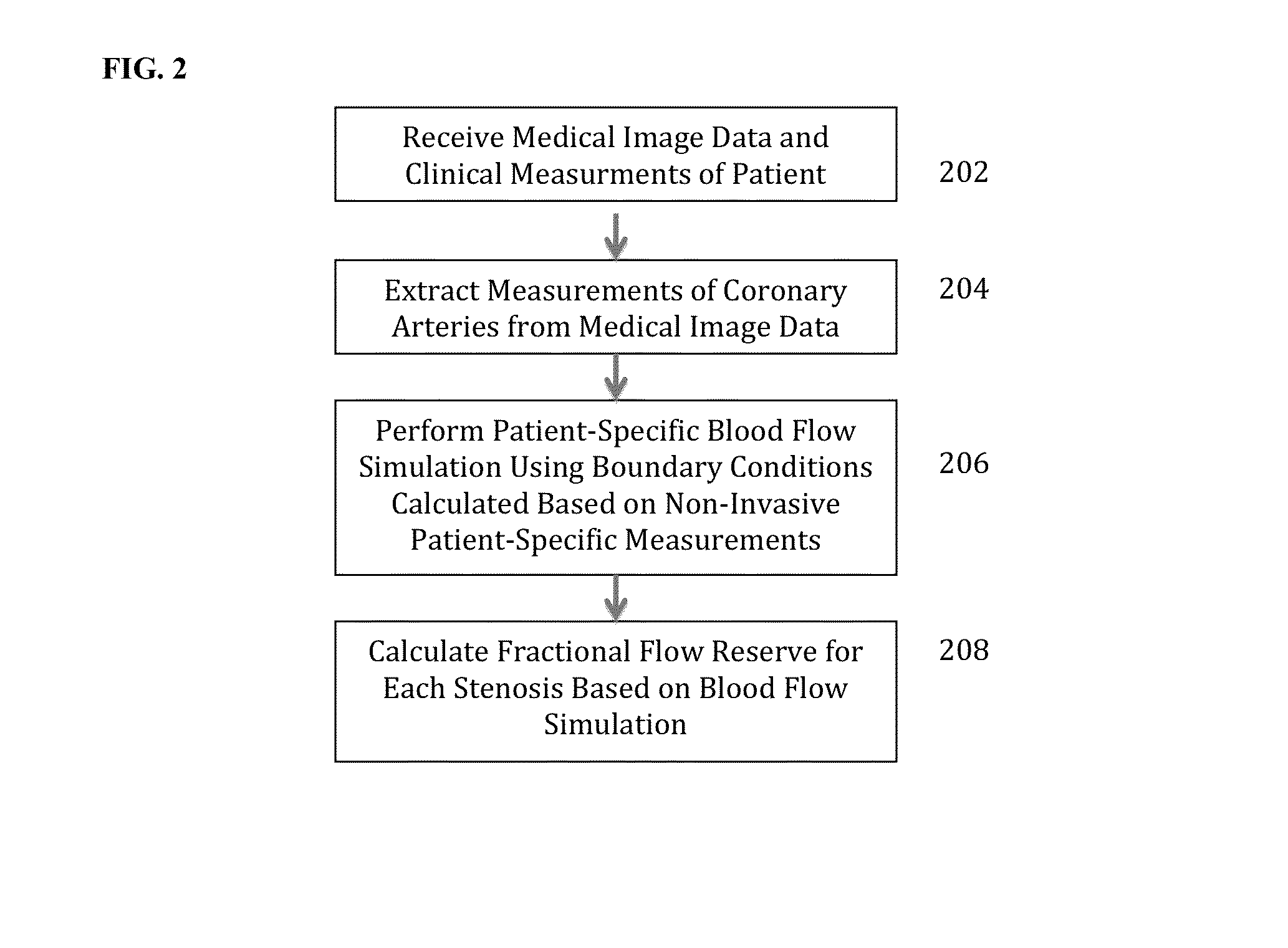
Method and System for Non-Invasive Functional Assessment of Coronary Artery Stenosis
InactiveUS20130246034A1Non-invasive functional assessmentMedical simulationMedical imagingCoronary arteriesAnatomical measurement
A method and system for non-invasive assessment of coronary artery stenosis is disclosed. Patient-specific anatomical measurements of the coronary arteries are extracted from medical image data of a patient acquired during rest state. Patient-specific rest state boundary conditions of a model of coronary circulation representing the coronary arteries are calculated based on the patient-specific anatomical measurements and non-invasive clinical measurements of the patient at rest. Patient-specific rest state boundary conditions of the model of coronary circulation representing the coronary arteries are calculated based on the patient-specific anatomical measurements and non-invasive clinical measurements of the patient at rest. Hyperemic blood flow and pressure across at least one stenosis region of the coronary arteries are simulated using the model of coronary circulation and the patient-specific hyperemic boundary conditions. Fractional flow reserve (FFR) is calculated for the at least one stenosis region based on the simulated hyperemic blood flow and pressure.
Owner:SIEMENS HEALTHCARE GMBH
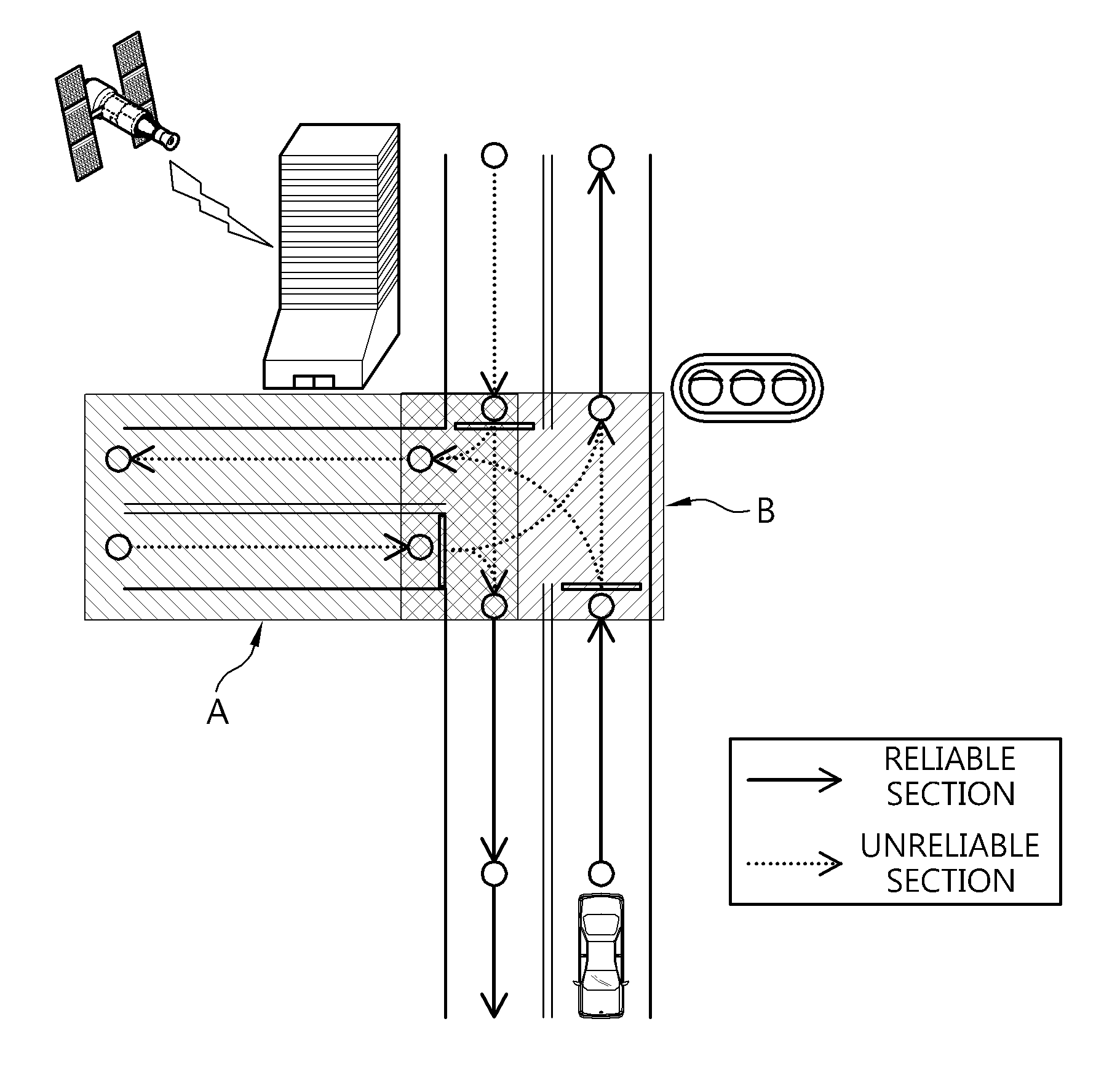
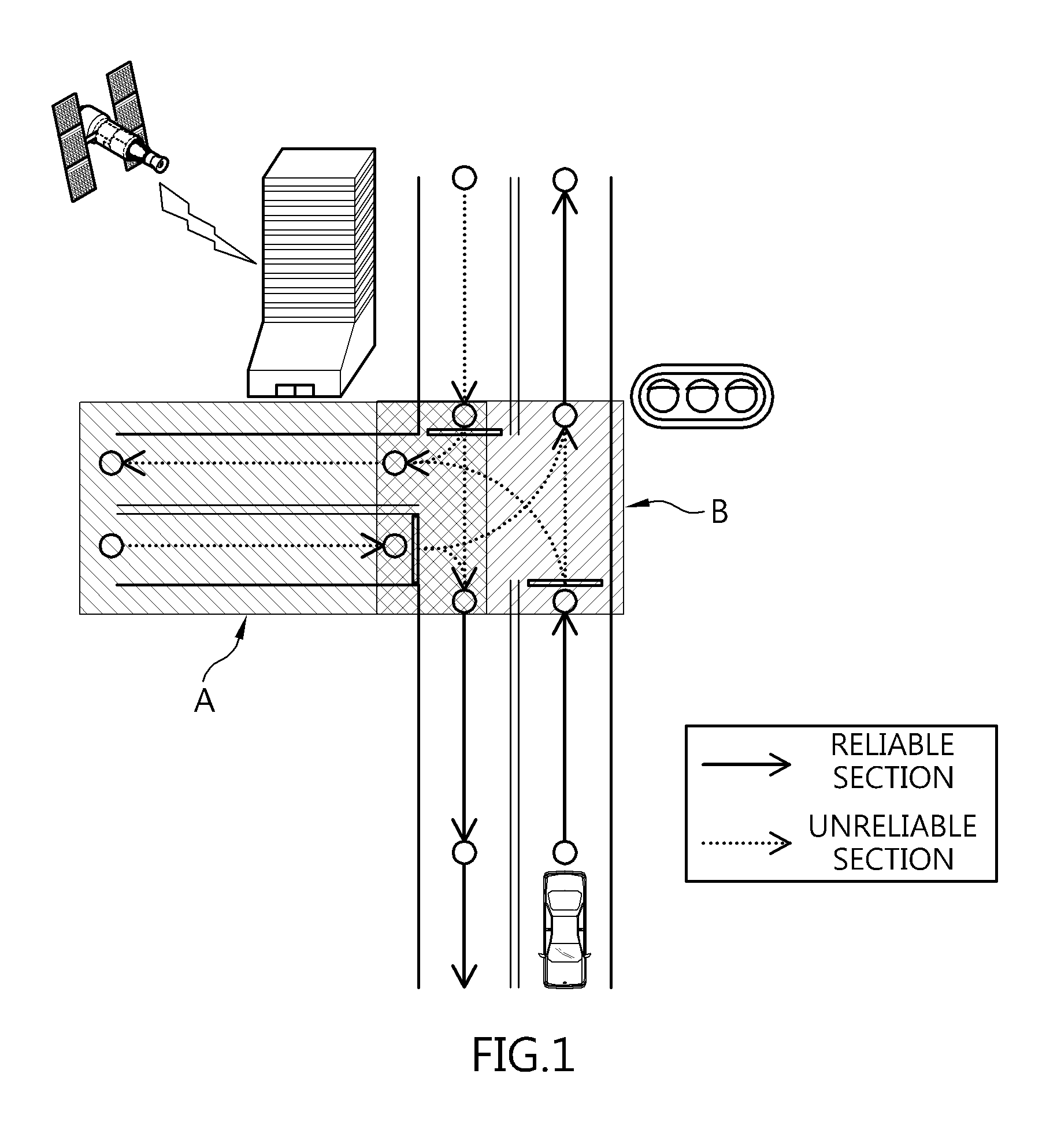
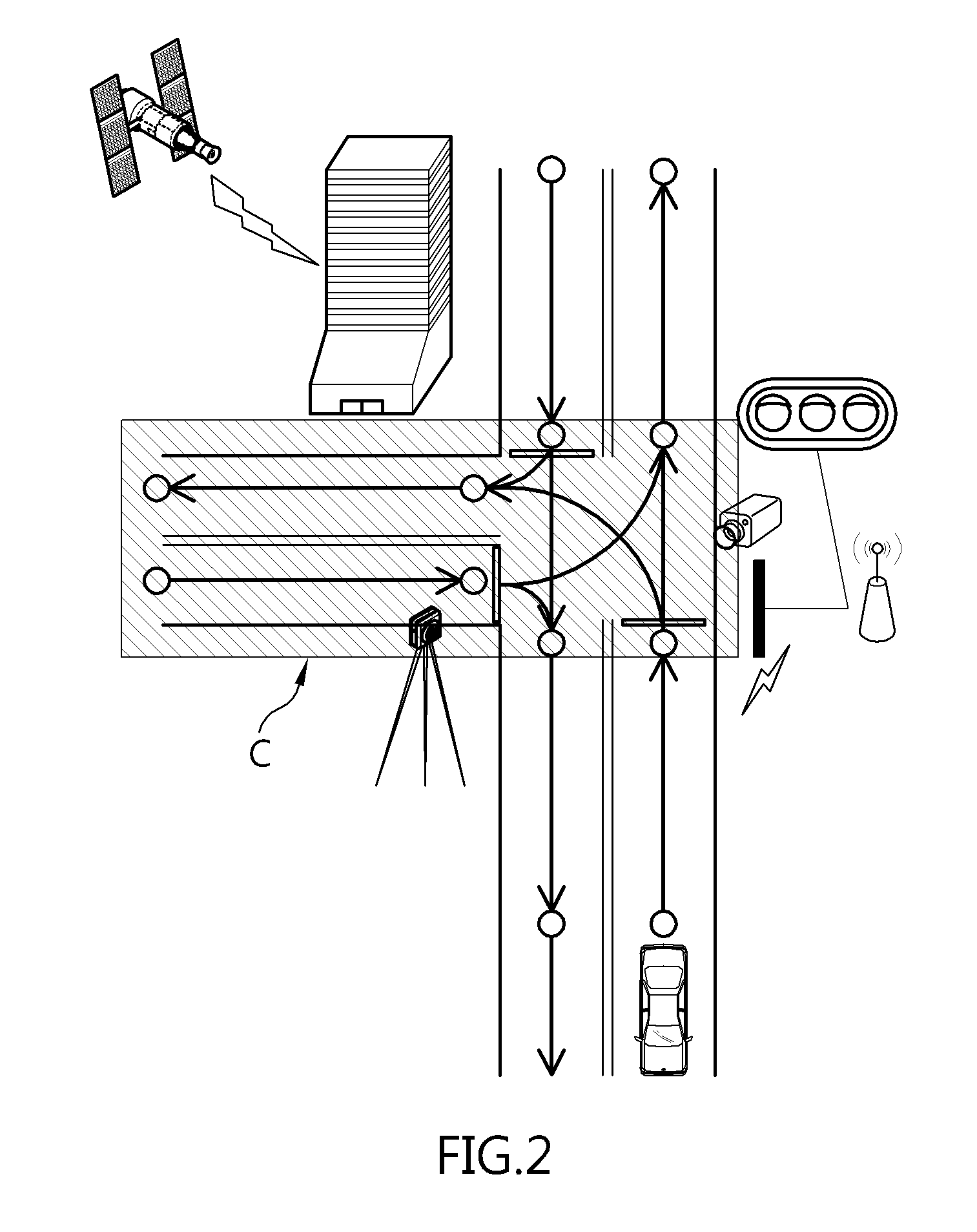
Autonomous driving apparatus and method for vehicle
Disclosed herein are an autonomous driving apparatus and method for a vehicle. The autonomous driving apparatus includes an autonomous driving context data processing unit, a simulator unit, a section determination unit, a path planning unit, and a context determination main control unit. The autonomous driving context data processing unit gathers autonomous driving context data. The simulator unit simulates autonomous driving based on the gathered autonomous driving context data. The section determination unit determines a reliable section or an unreliable section based on results of the simulation. The path planning unit searches for at least one global path to a set destination based on results of the determination, and searches the at least one global path for a local path along which the autonomous driving is possible. The context determination main control unit controls the autonomous driving of the vehicle along the local path.
Owner:ELECTRONICS & TELECOMM RES INST
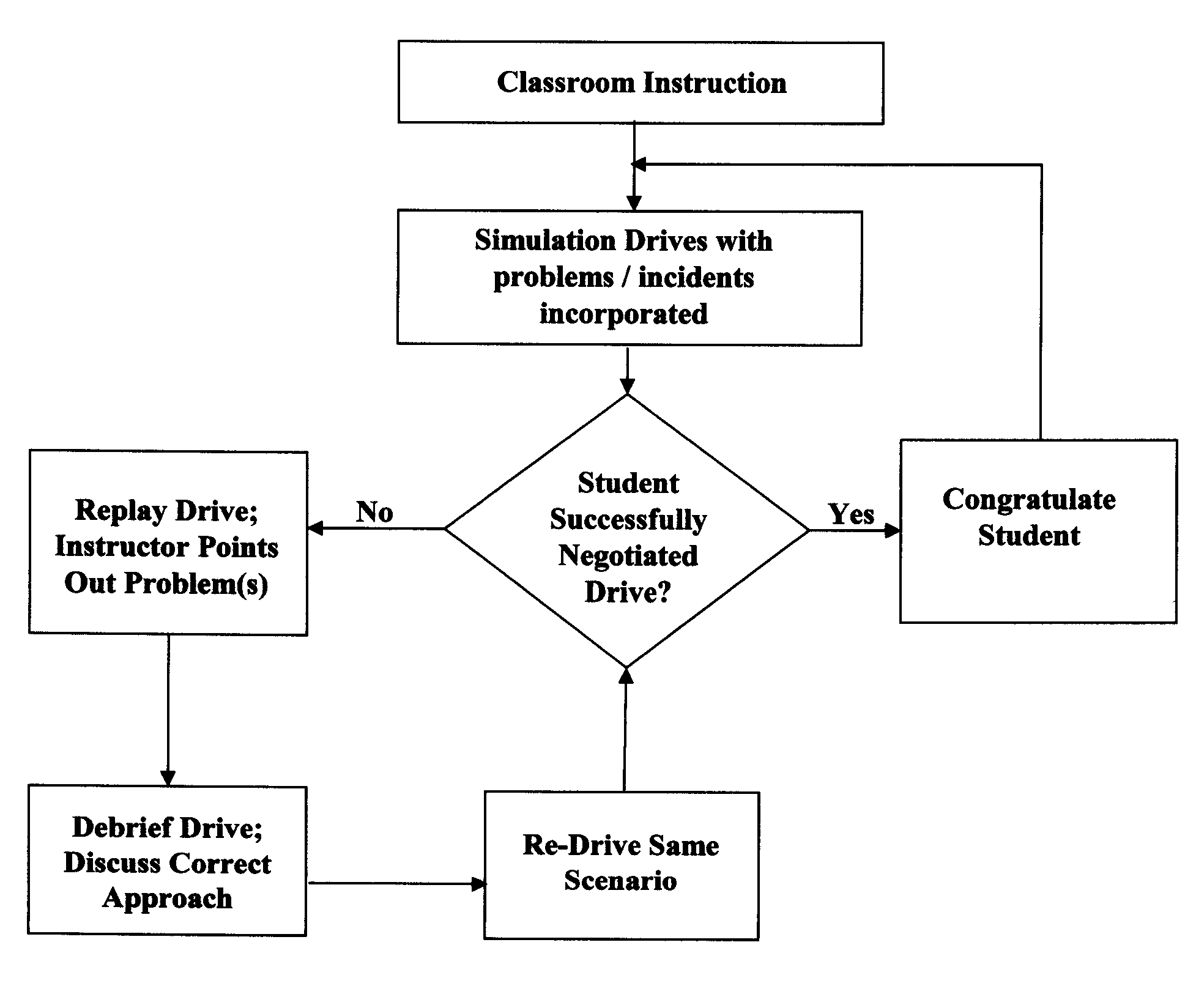
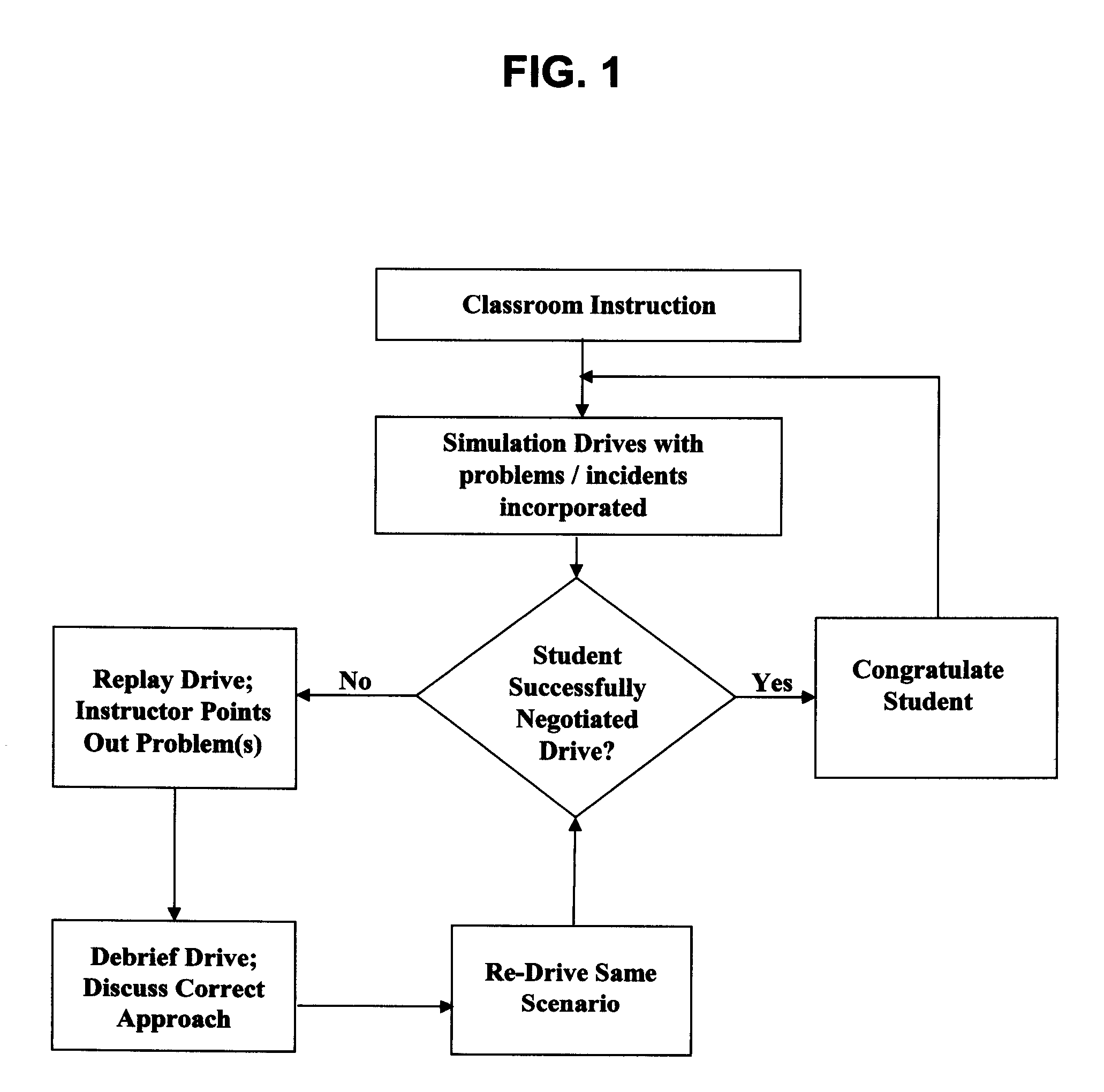
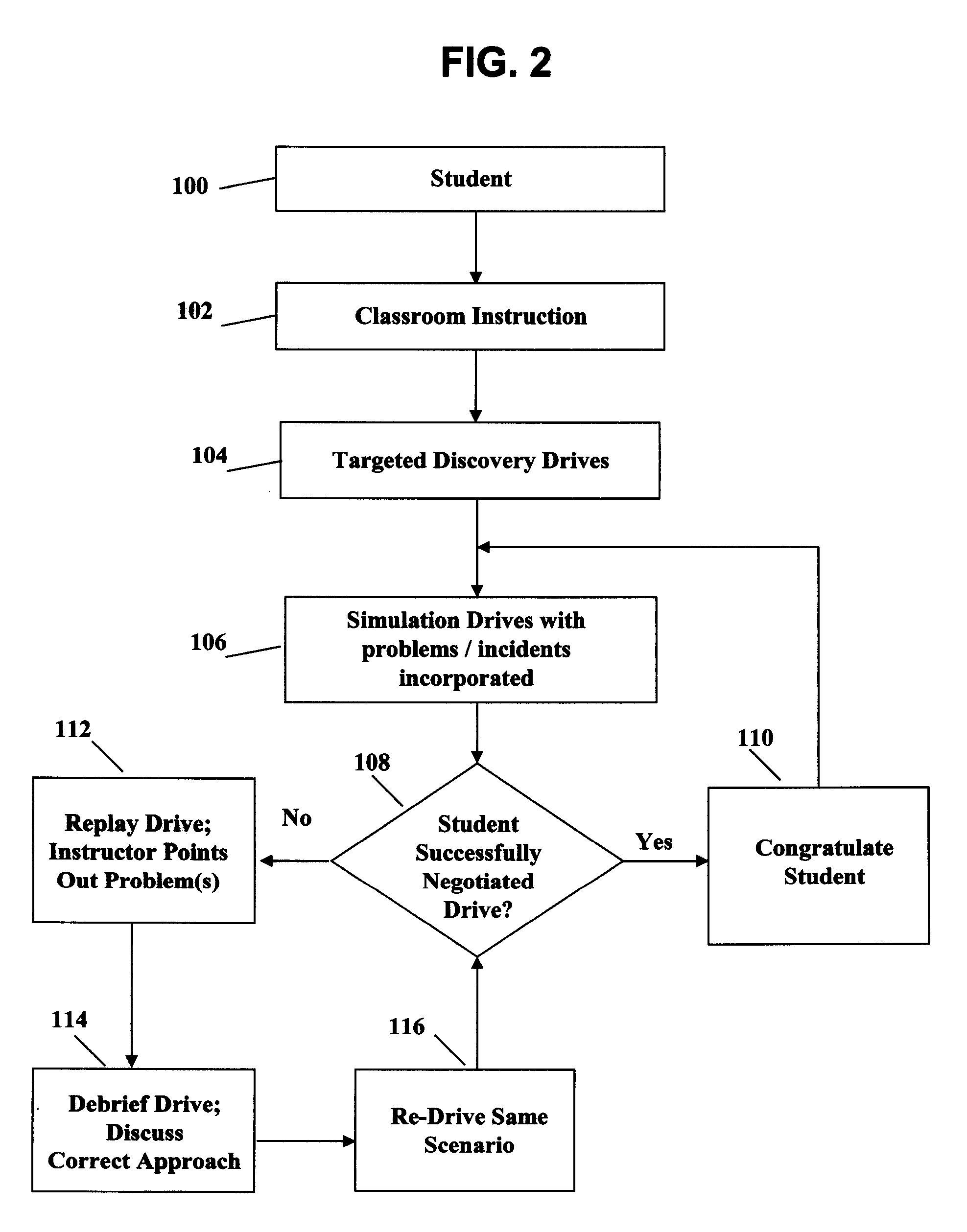
Simulation-based novice driver instruction system and method
InactiveUS20080064014A1Cosmonautic condition simulationsSimulatorsDriver/operatorProgram instruction
The present invention provides for a simulation-based system and method for driver instruction using a highly sophisticated physical and computer-based simulation system combined with a novel simulation-based instruction methodology that allows a novice driver to learn driving fundamentals and advanced defensive driving skills in the safety of the simulator environment. The novelty of the present invention lies in the driving simulation aspect of the driver instruction disclosed herein combined with the novel method of instruction disclosed herein. The simulation-based system and method provides numerous advantages over any other driving instruction system or method currently in use or known in the art.
Owner:DRIVINGMBA
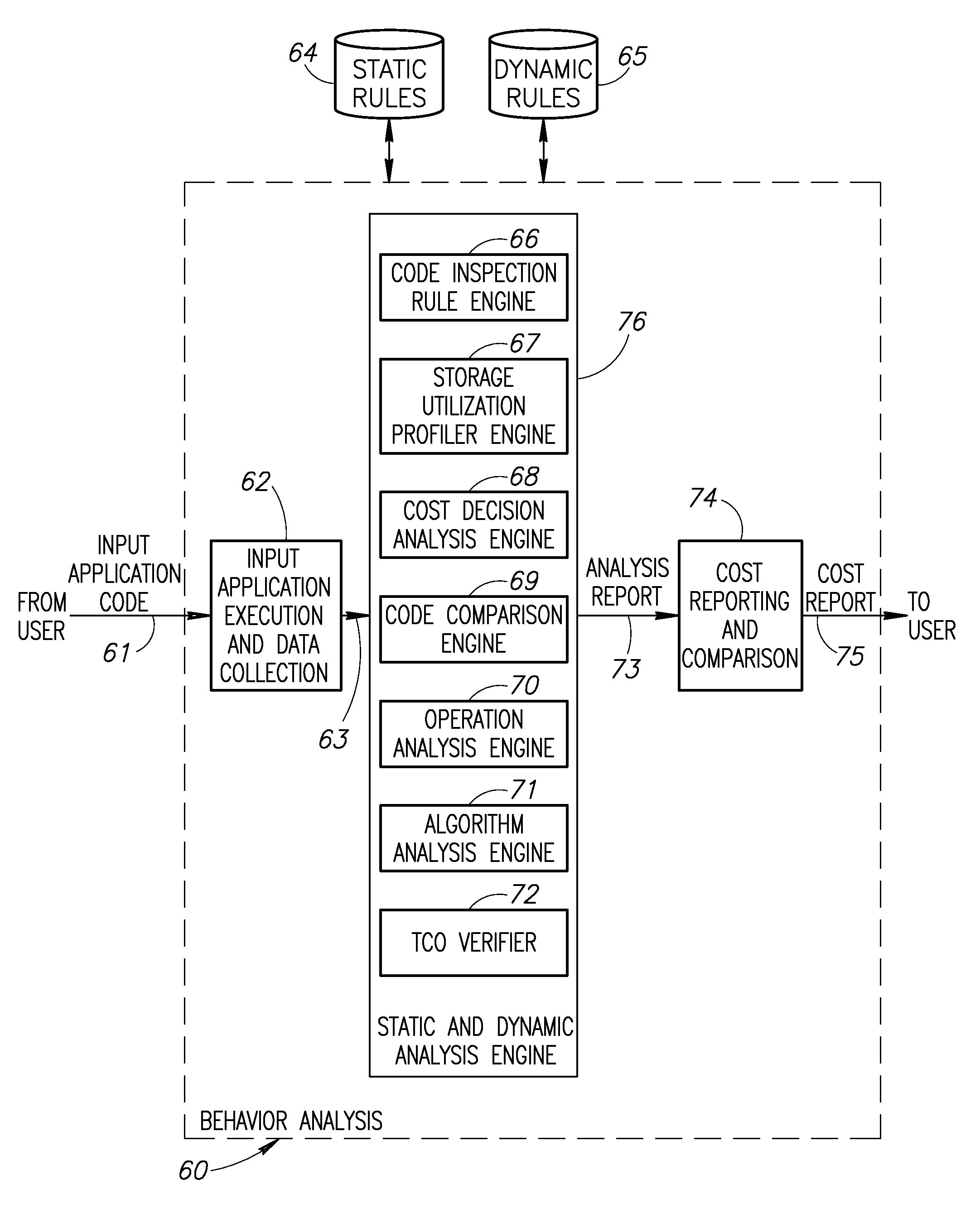
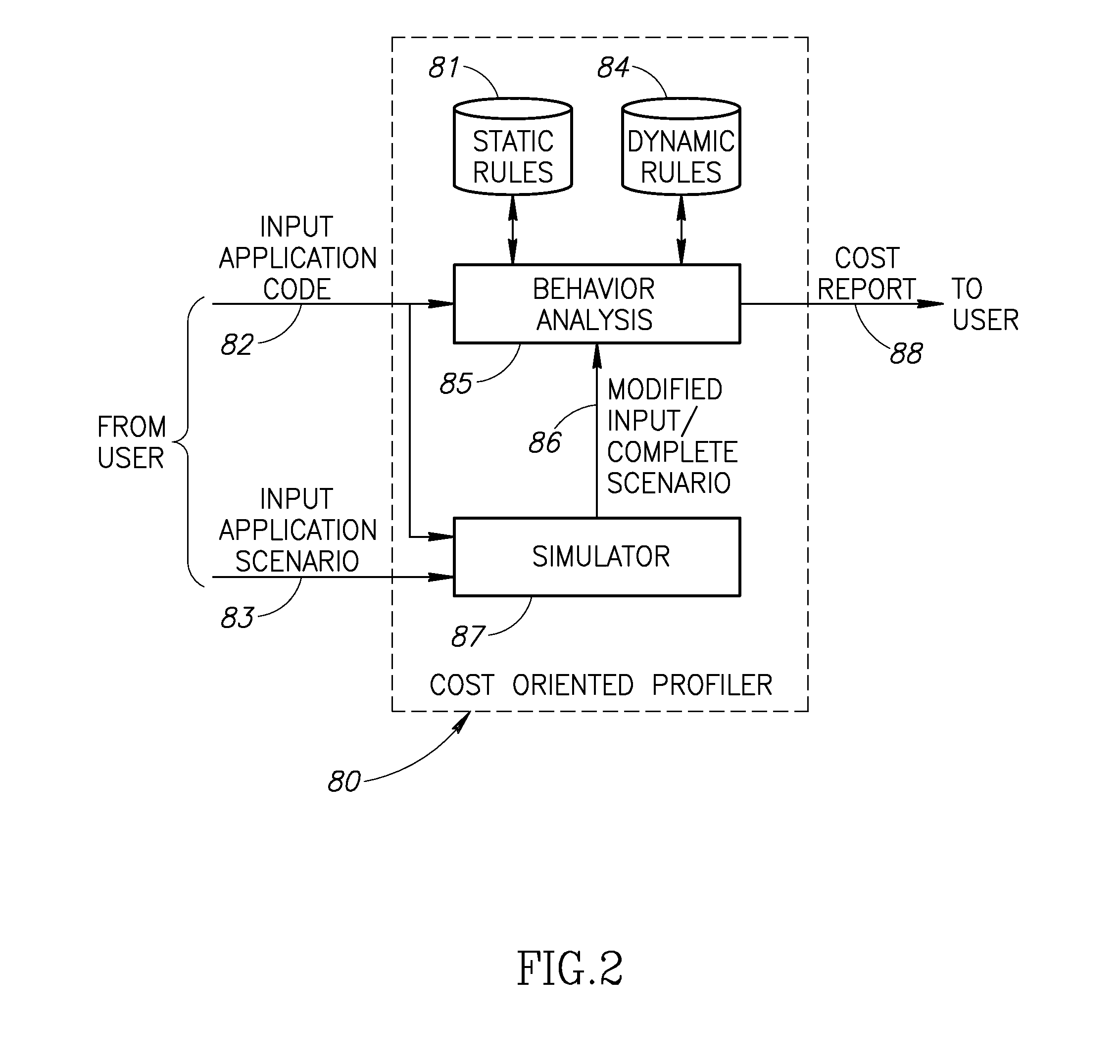
System and method of cost oriented software profiling
ActiveUS20120060142A1Reduce software costsLow costError detection/correctionSoftware maintainance/managementCost analysisSimulation based
A cost oriented profiler (COP) mechanism that analyzes the behavior of input application source code with regard to the software total cost of ownership (TCO). The cost analysis tool provided by the mechanism analyzes the behavior of the source code and generates a cost report with indications as to the portions of the source code that have the most impact on the TCO of the application. Based on simulations and by comparing multiple versions of the source code, the COP mechanism determines if a particular change to the source code will increase or decrease software TCO. Behavior analysis, including static and dynamic analysis of the source code, is used to generate one or more code recommendations to reduce the TCO.
Owner:CODE VALUE
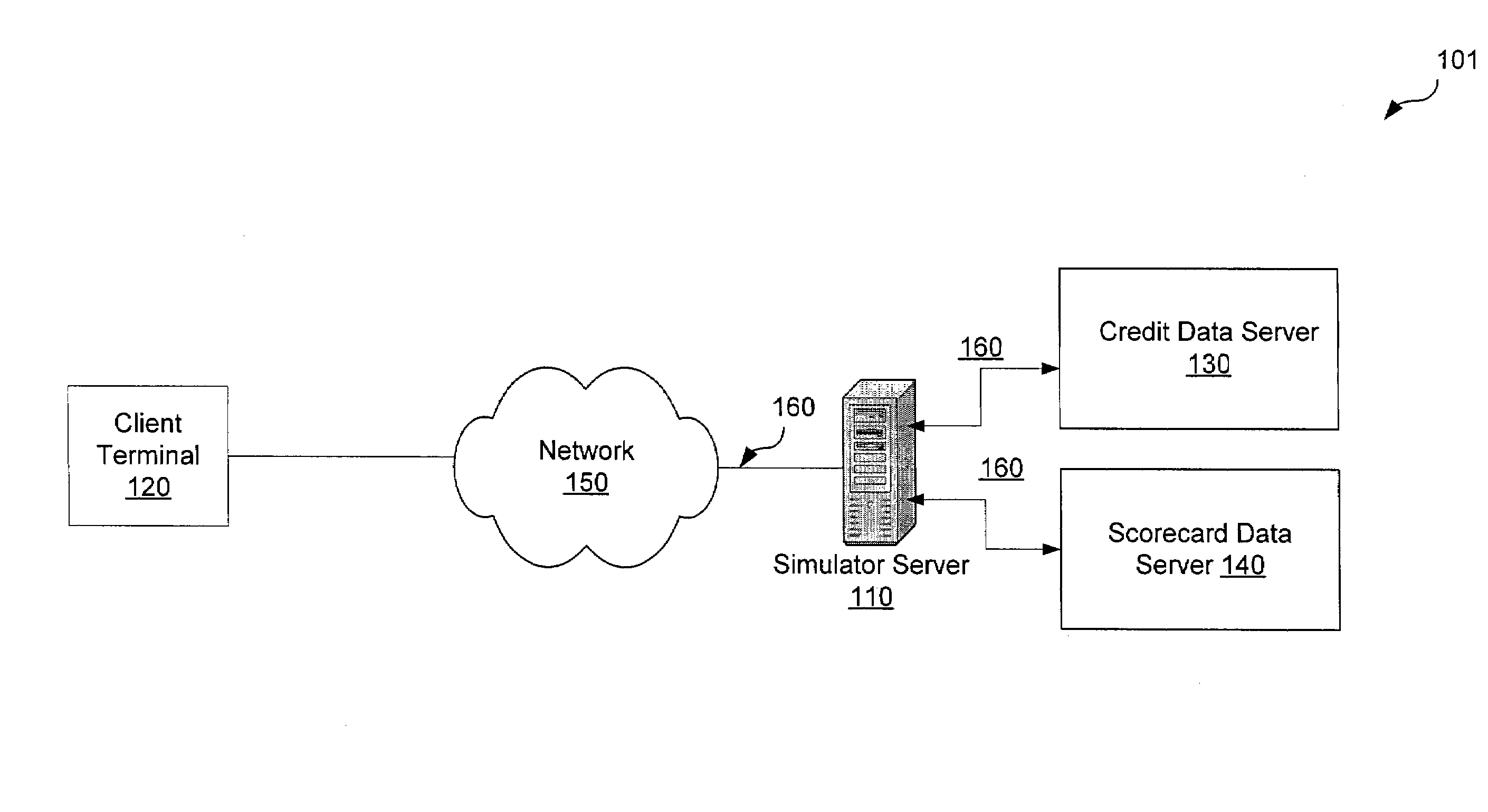
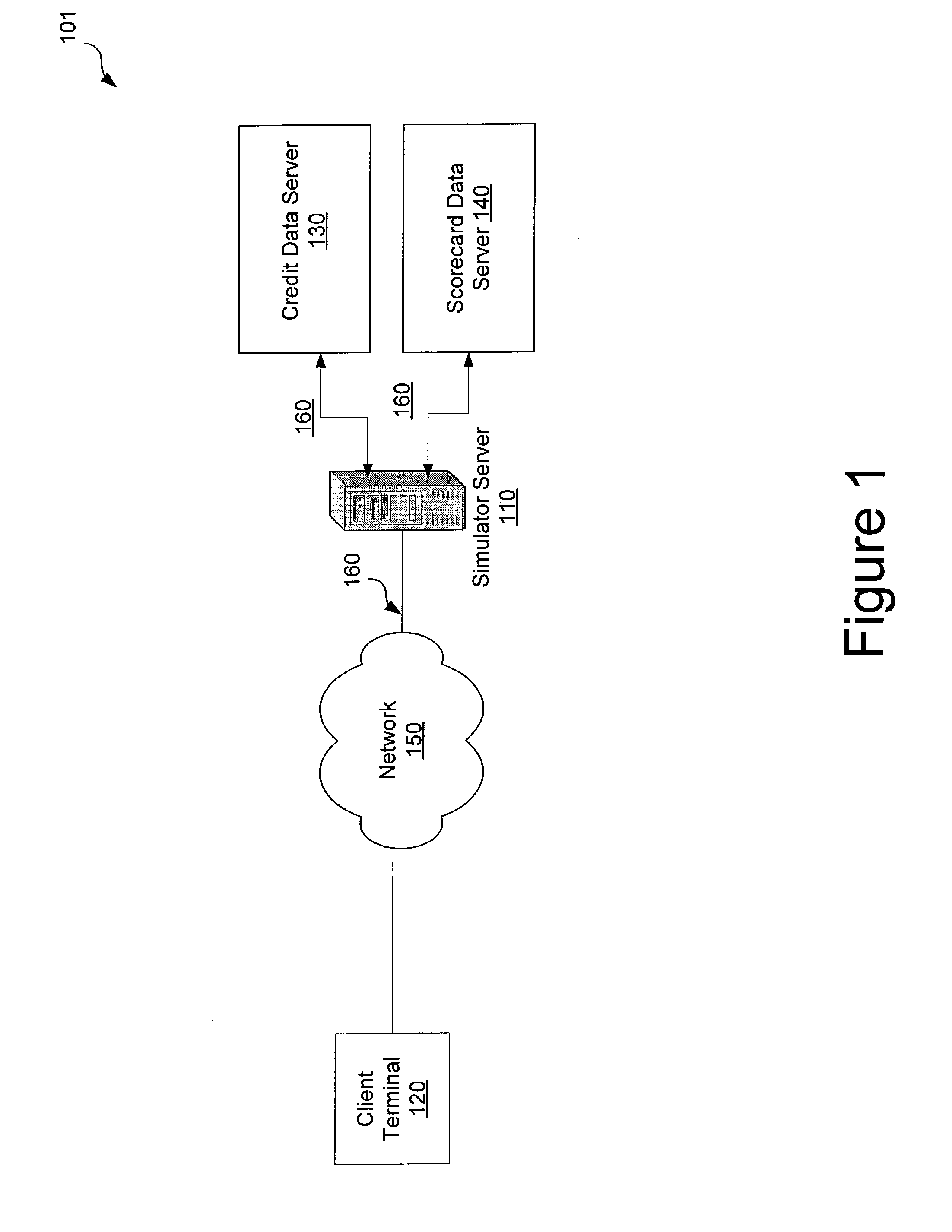
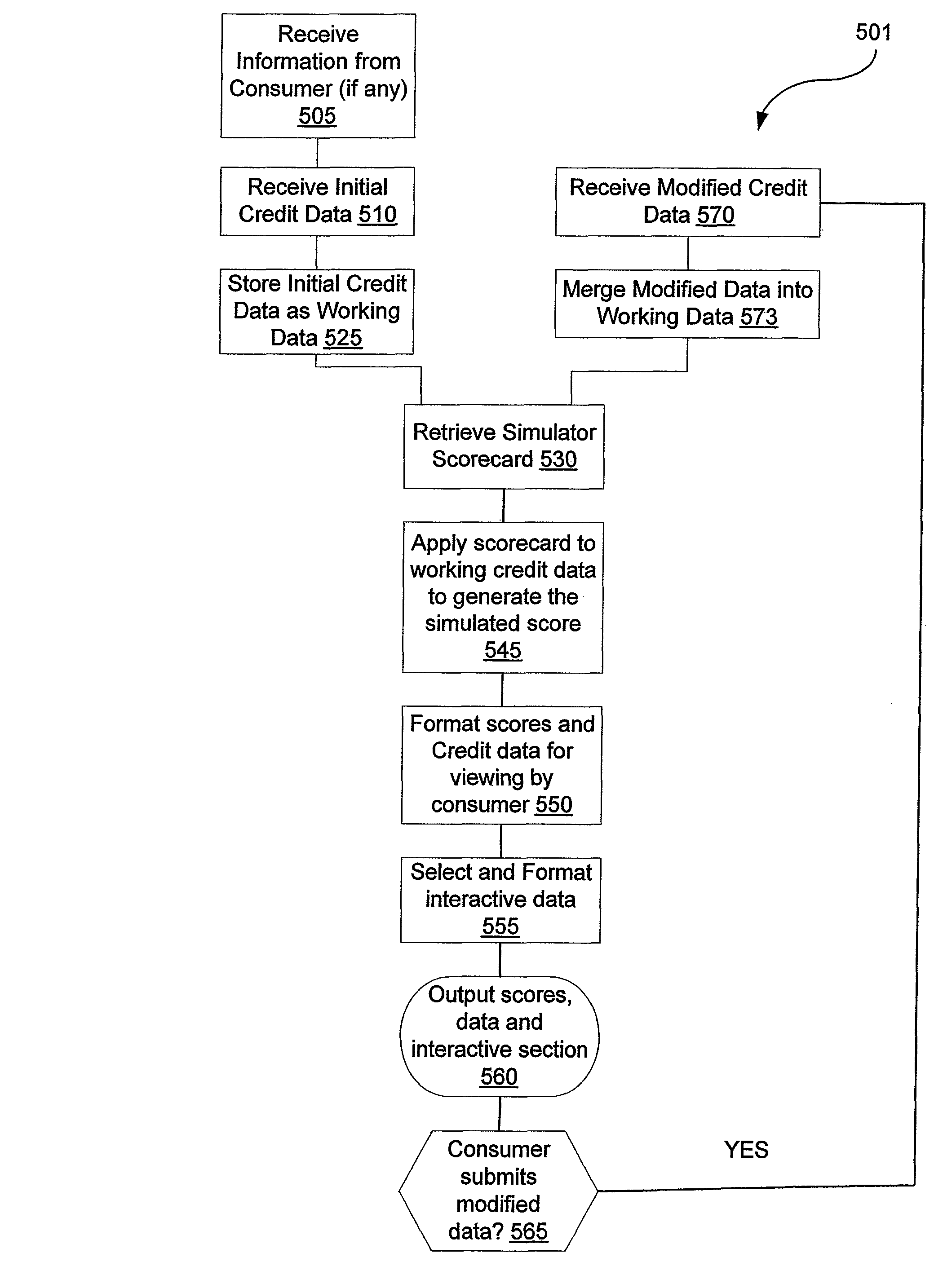
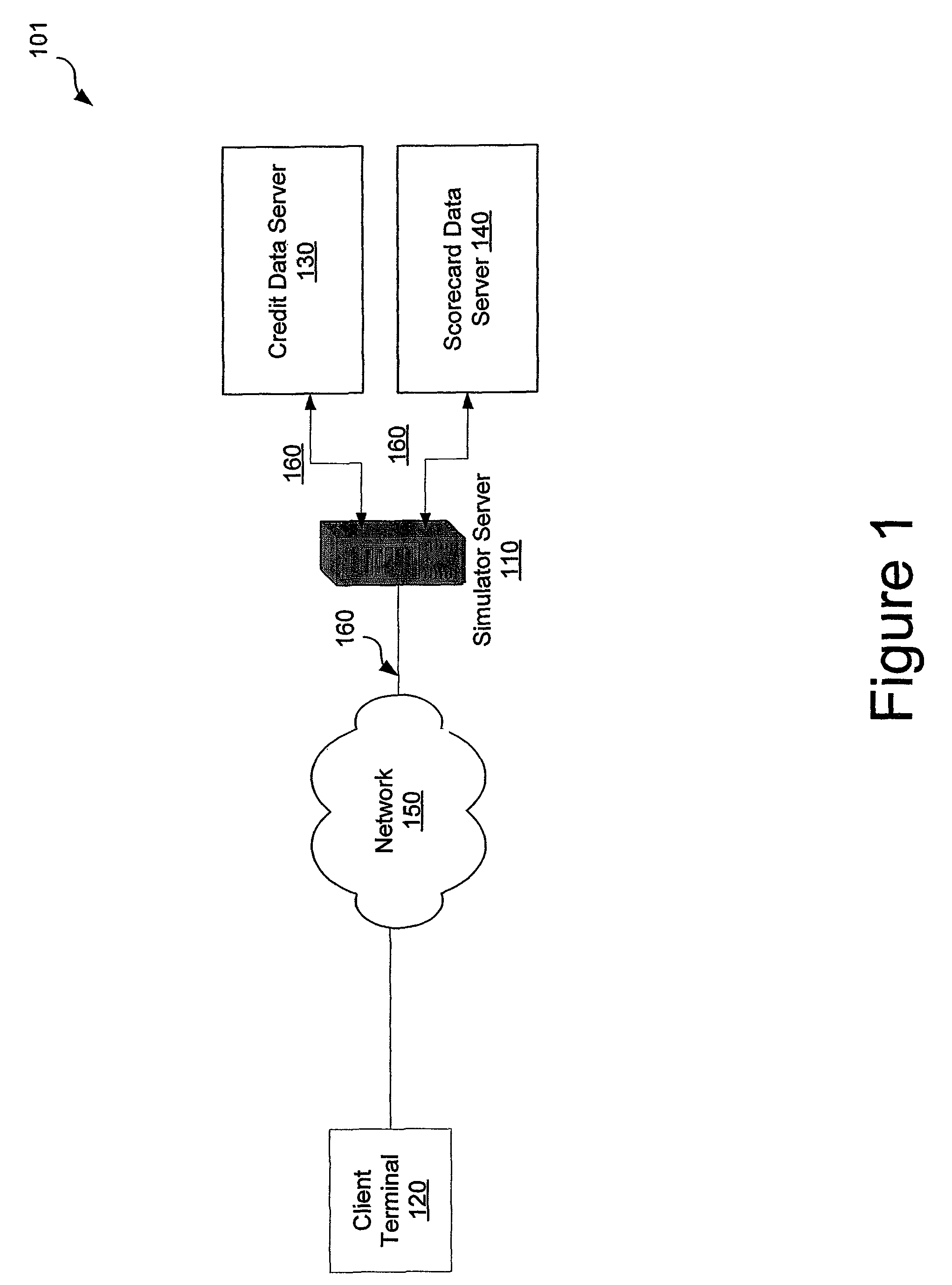
System and method for interactively simulating a credit-worthiness score
ActiveUS7610229B1Quick responseSimple interfaceFinancePayment architectureWeb serviceSimulation based
A system and method is provided to allow a consumer to interactively explore his credit score by submitting hypothetical values based on his actual credit data. The system uses the consumer's real credit data and the submitted hypothetical values to calculate a simulated credit score based on a simulator scorecard. The consumer may then observe the changes in the resultant scores. The system and the scorecard may utilize fewer data elements than a complete credit-worthiness scorecard and may instead focus on the key elements affecting a consumer's credit score. The system may be implemented in part on a web server or as a stand-alone application. The system may also update the score dynamically as the consumer adjusts the hypothetical values or may require the consumer to affirmatively submit the new hypothetical data.
Owner:CONSUMERINFO COM
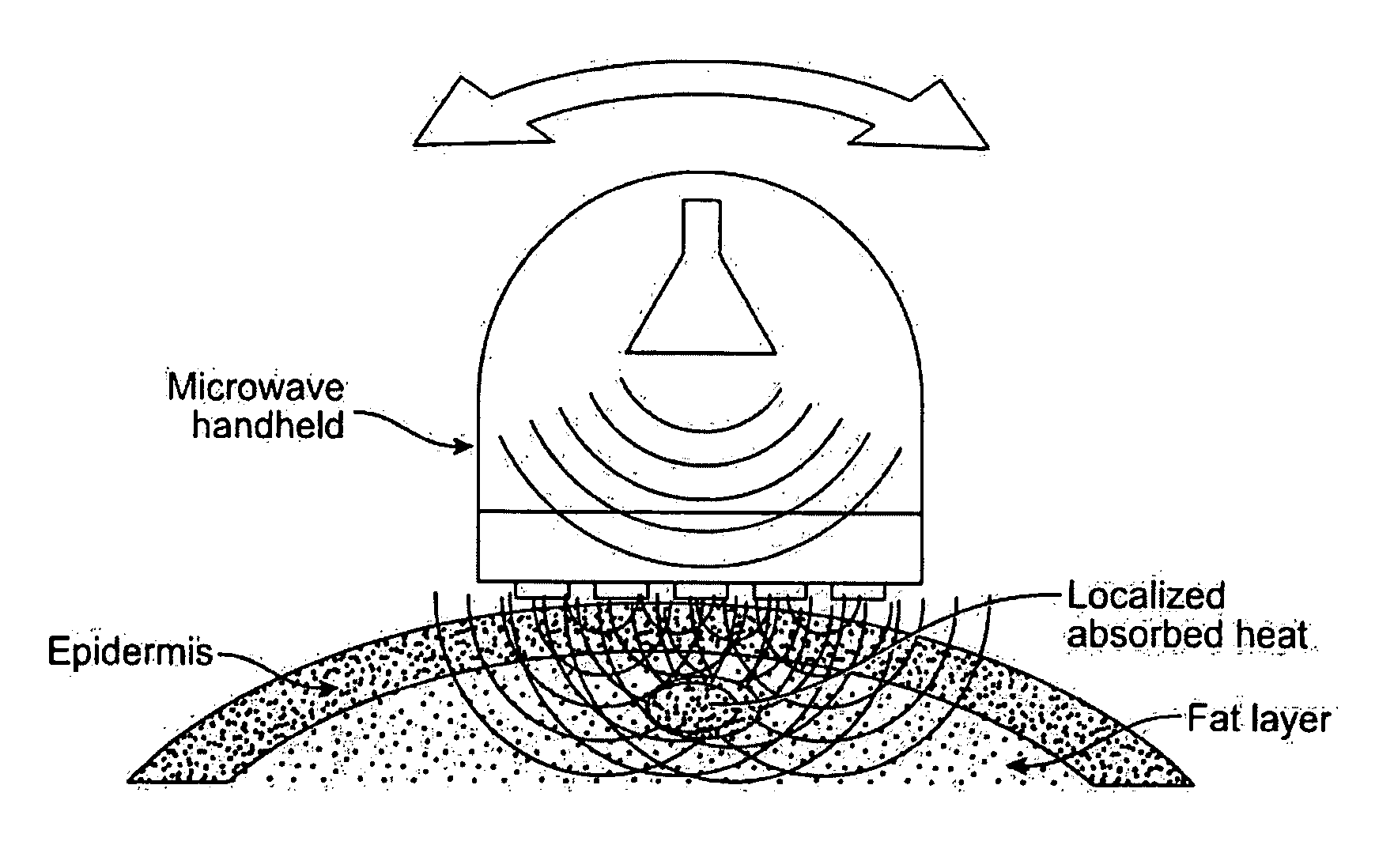
Thermal Ablation Design and Planning Methods
InactiveUS20090221999A1Improve efficiencyHigh success rateDiagnosticsSurgical systems user interfaceSimulation basedEngineering
Methods for simulation of heat transport phenomena applicable to the design of a near-field microwave ablation device, the design of such a device based on simulation and a patient planning and monitoring station using simulated thermal ablation of tissue are provided.
Owner:CALIFORNIA INST OF COMP ASSISTED SURGERY
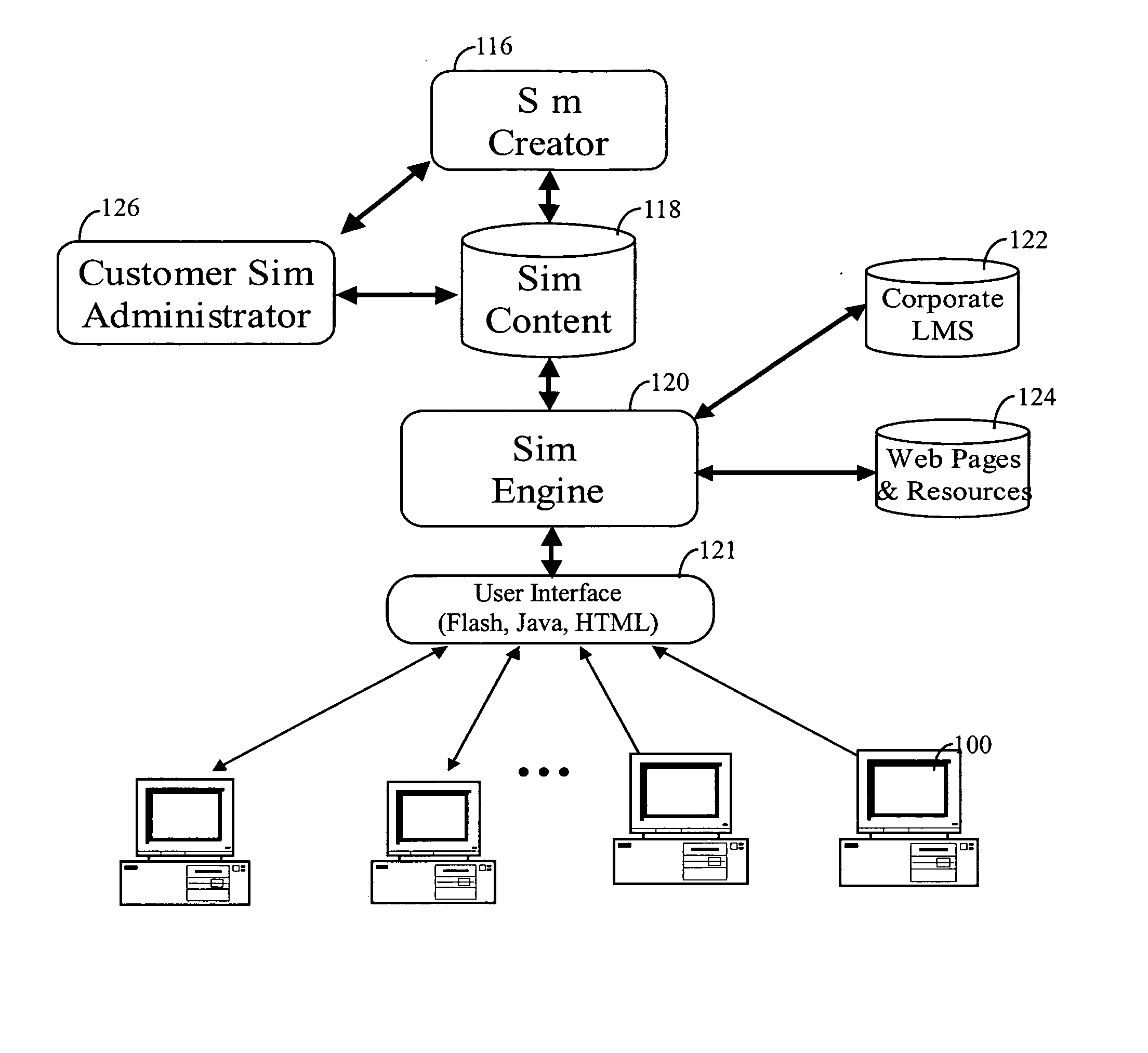
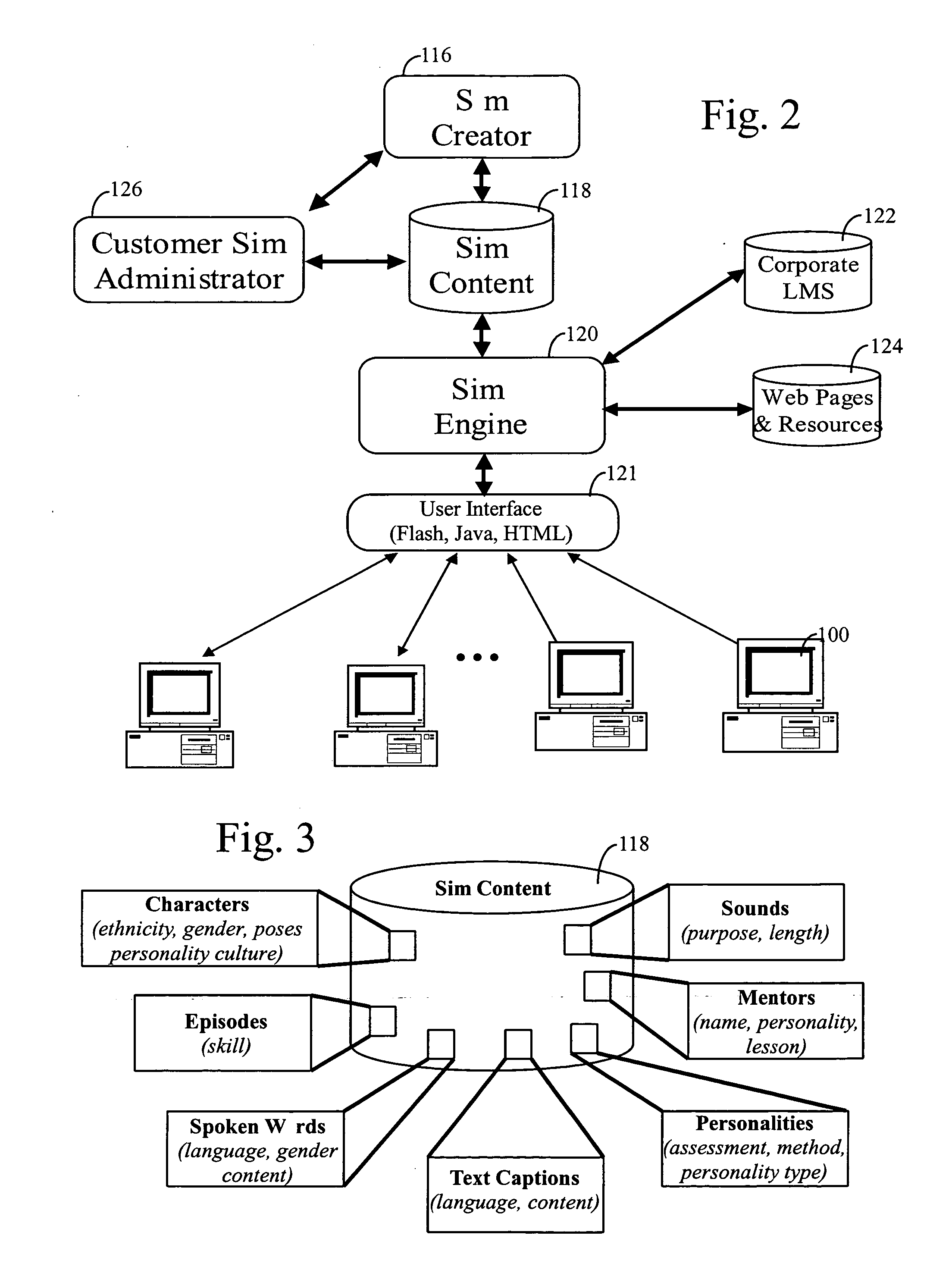
Integrated multi-tiered simulation, mentoring and collaboration E-learning platform and its software
InactiveUS20050095569A1Improve retentionElectrical appliancesMechanical appliancesSkill setsSimulation based
A multi-tiered e-learning software platform and its software is disclosed including educational simulations, real-time and stored mentoring based on simulation performance and peer collaboration using the skill sets learned in the simulations and mentoring sessions.
Owner:FRLIN PATRICIA
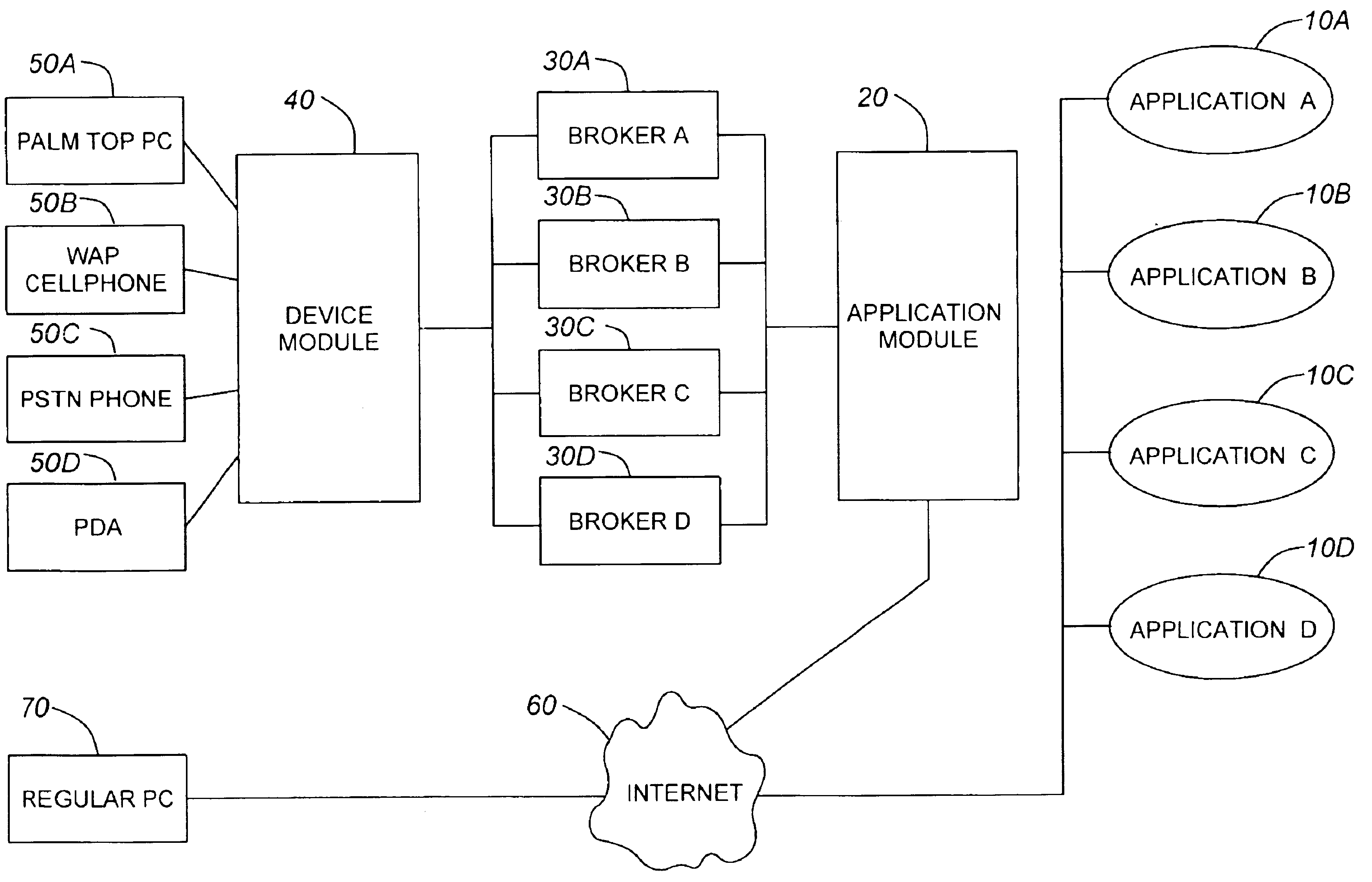
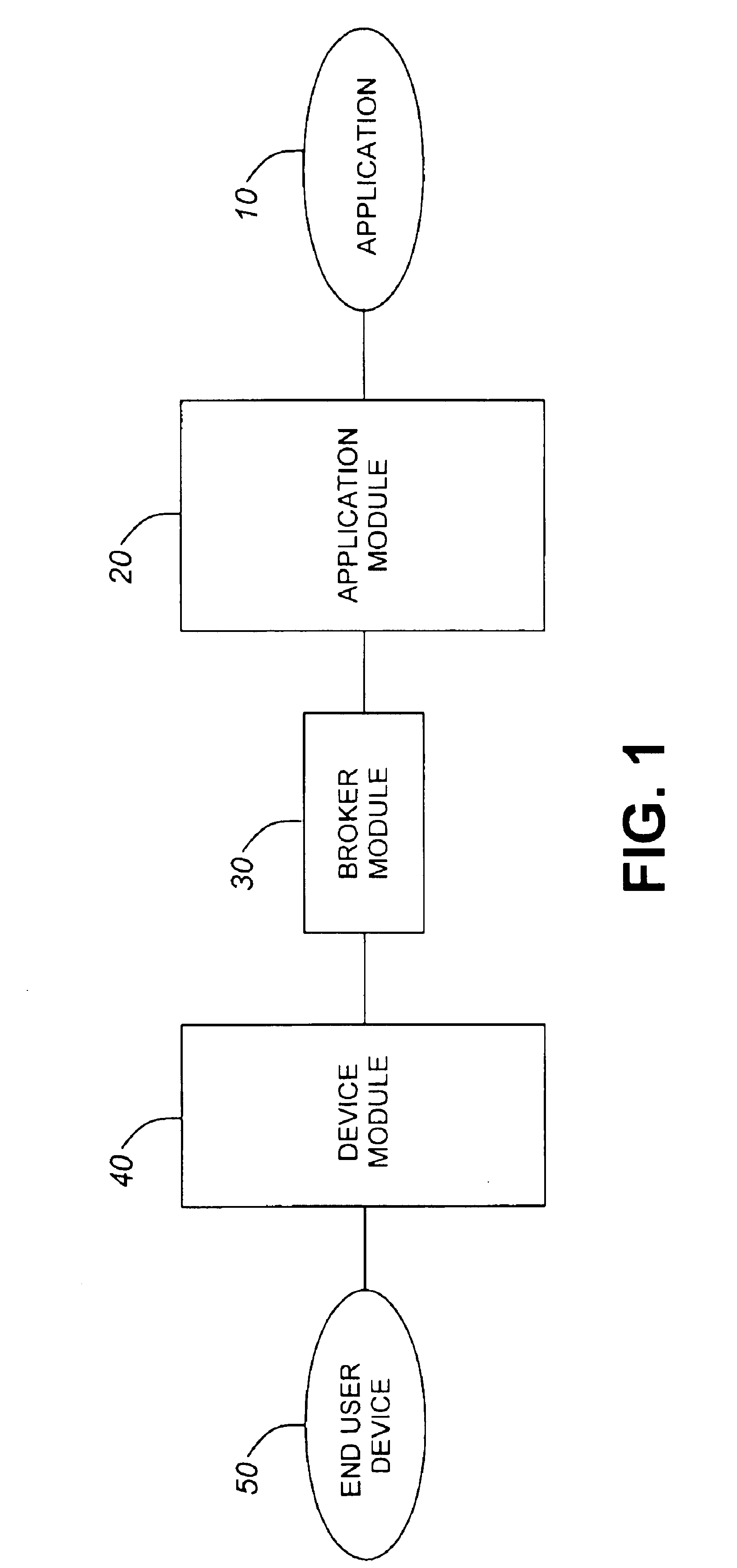
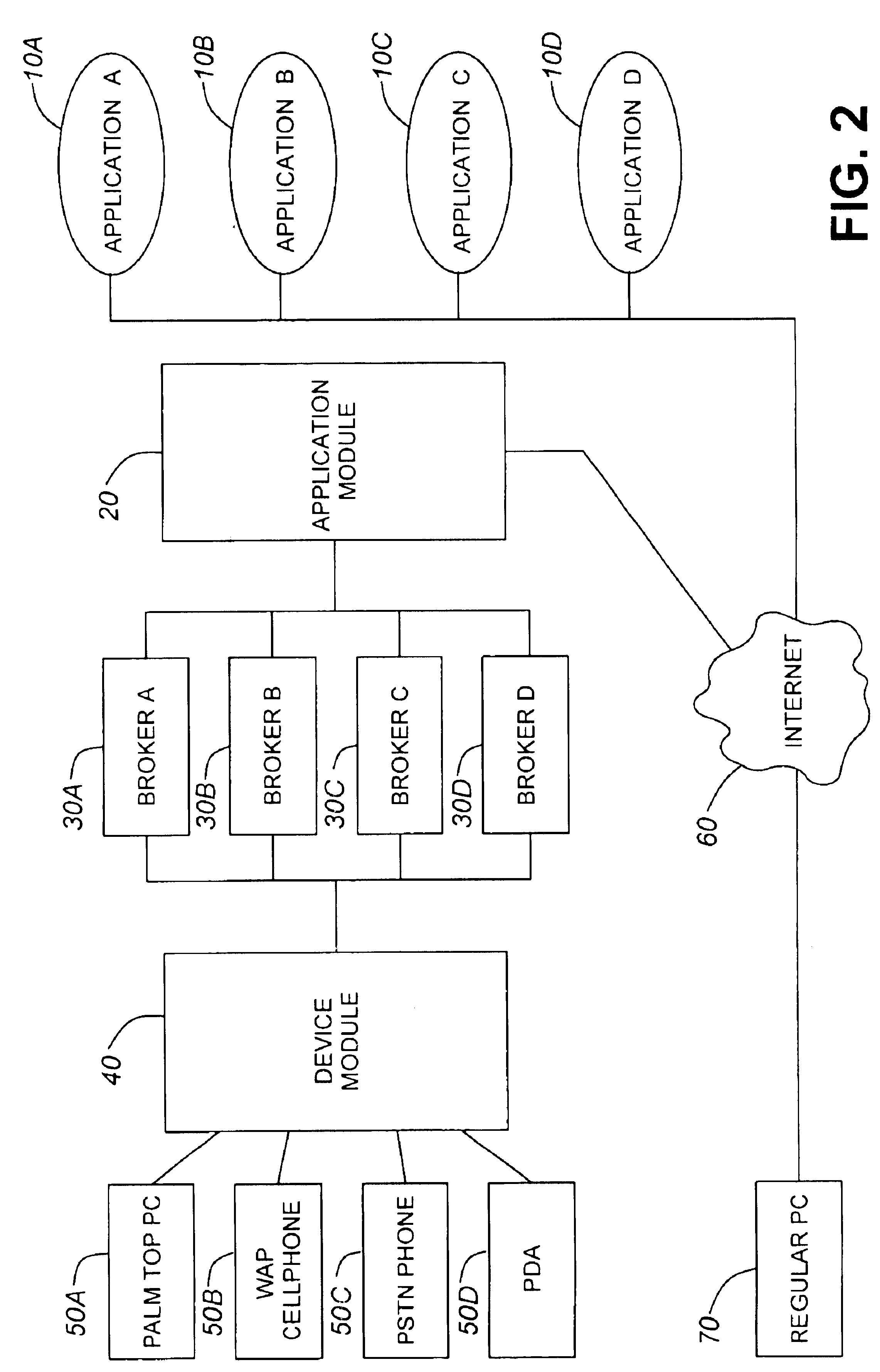
Architecture for multiple channel access to applications
InactiveUS6961776B1Multiprogramming arrangementsMultiple digital computer combinationsOriginal dataSimulation based
A system for enabling multiple types of end user devices to access an Internet-based application, the system comprising: an AMI component communicating with the application; a DMI component communicating with the devices; a broker module communicating with the DMI component and with the AMI component, wherein the DMI component converts end data received from the broker module into a format suitable for the devices; the DMI component transmits replies to prompts from the broker module based on an end user's input into the devices; the broker module emulates a sequence of events and decisions followed by the application; the broker module requests application data from the AMI component based on the broker module emulating the application; the AMI component receives requests from the broker module and transmits replies to the requests to the broker module based on original data from the application, the broker module transmits end date to the DMI component, the end data being based on at least one factor chosen from the group comprising: the broker module's emulation of the application; and application data received from the AMI component.
Owner:RPX CLEARINGHOUSE
Method and System for Non-Invasive Functional Assessment of Coronary Artery Stenosis
ActiveUS20140058715A1Non-invasive functional assessmentMedical simulationMedical imagingCoronary arteriesAnatomical measurement
A method and system for non-invasive assessment of coronary artery stenosis is disclosed. Patient-specific anatomical measurements of the coronary arteries are extracted from medical image data of a patient acquired during rest state. Patient-specific rest state boundary conditions of a model of coronary circulation representing the coronary arteries are calculated based on the patient-specific anatomical measurements and non-invasive clinical measurements of the patient at rest. Patient-specific rest state boundary conditions of the model of coronary circulation representing the coronary arteries are calculated based on the patient-specific anatomical measurements and non-invasive clinical measurements of the patient at rest. Hyperemic blood flow and pressure across at least one stenosis region of the coronary arteries are simulated using the model of coronary circulation and the patient-specific hyperemic boundary conditions. Fractional flow reserve (FFR) is calculated for the at least one stenosis region based on the simulated hyperemic blood flow and pressure.
Owner:SIEMENS HEALTHCARE GMBH
Methods and systems for repairing applications
ActiveUS20060195745A1Improve usabilityEasy to useElectronic circuit testingNon-redundant fault processingCore dumpSoftware failure
In accordance with the present invention, computer implemented methods and systems are provided that allow an application to automatically recover from software failures and attacks. Using one or more sensors, failures may be detected in the application. In response to detecting the failure, the portion of the application's code that caused the failure is isolated. Using the input vectors that caused the failure, information regarding the failure (e.g., the type of failure), a core dump file (e.g., stack trace), etc., an emulator-based vaccine that repairs the failure is constructed. In response to verifying that the vaccine repaired the failure, the application is automatically updated with the emulator-based vaccine without user intervention. Application community features that efficiently use the resources available in software monoculture is also provided. An application community may be defined that includes a plurality of devices and the application's code may be divided into smaller portions of code, which are assigned to each of the plurality of devices for monitoring. Each device also notifies the other devices of the failure.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
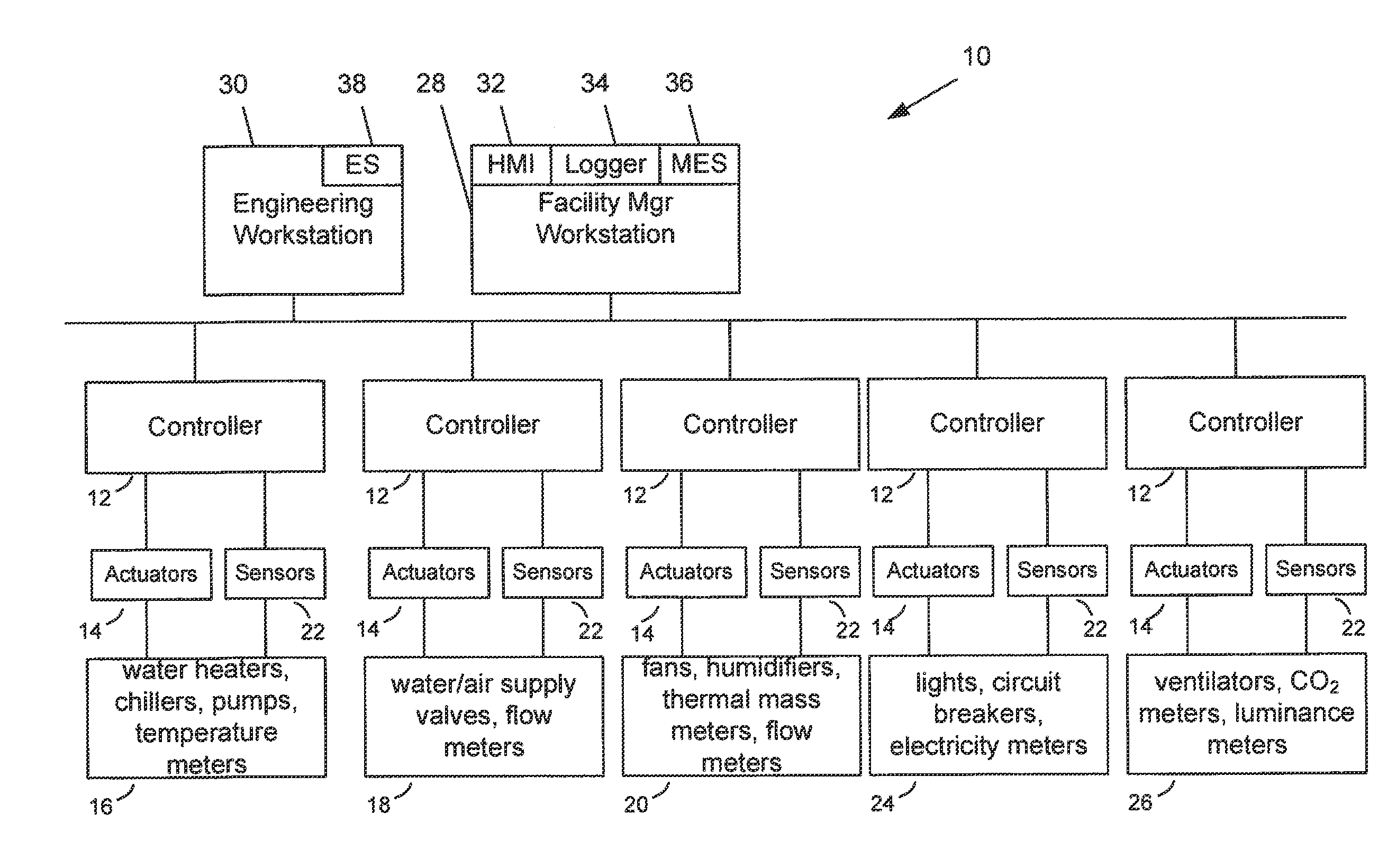
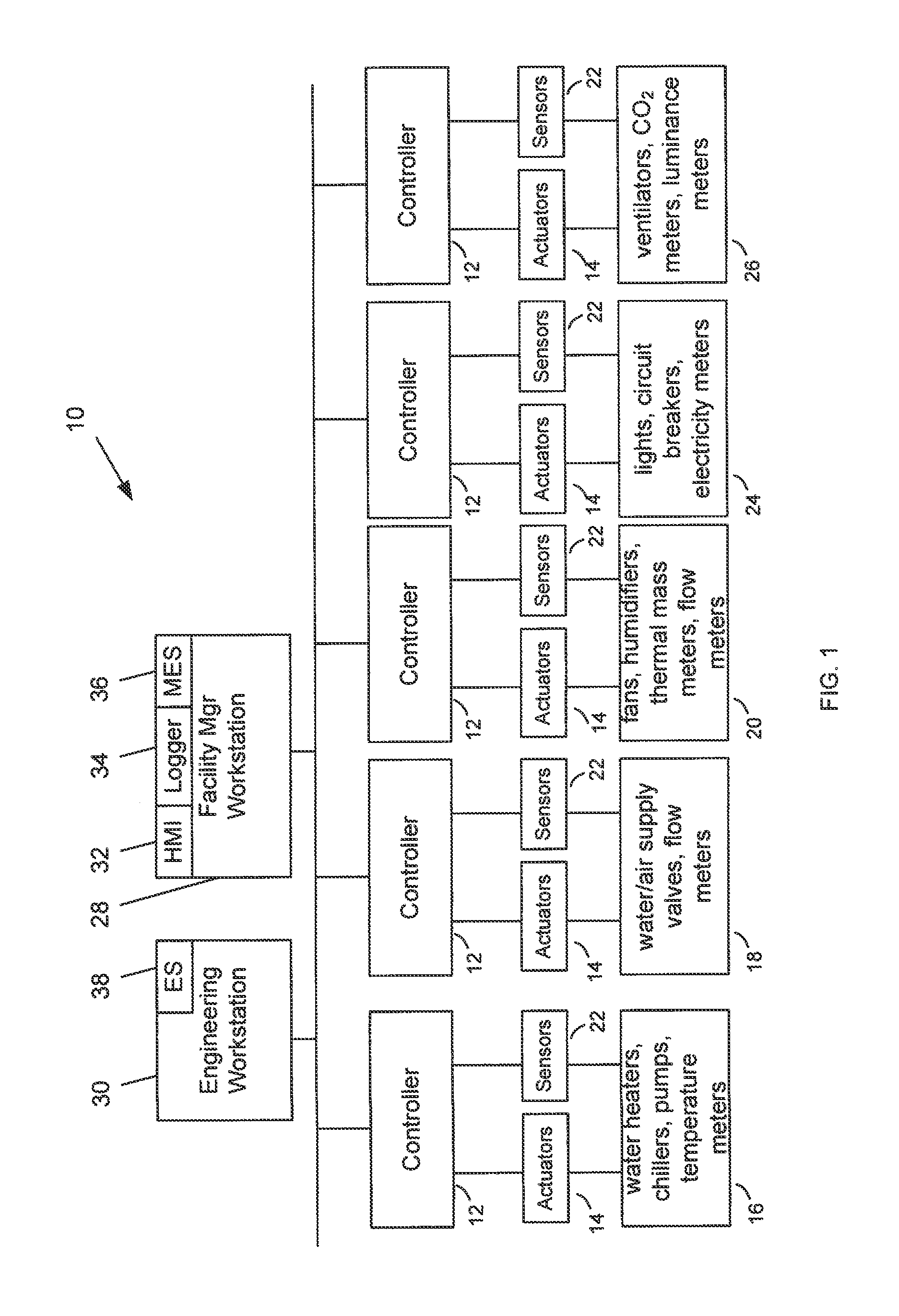
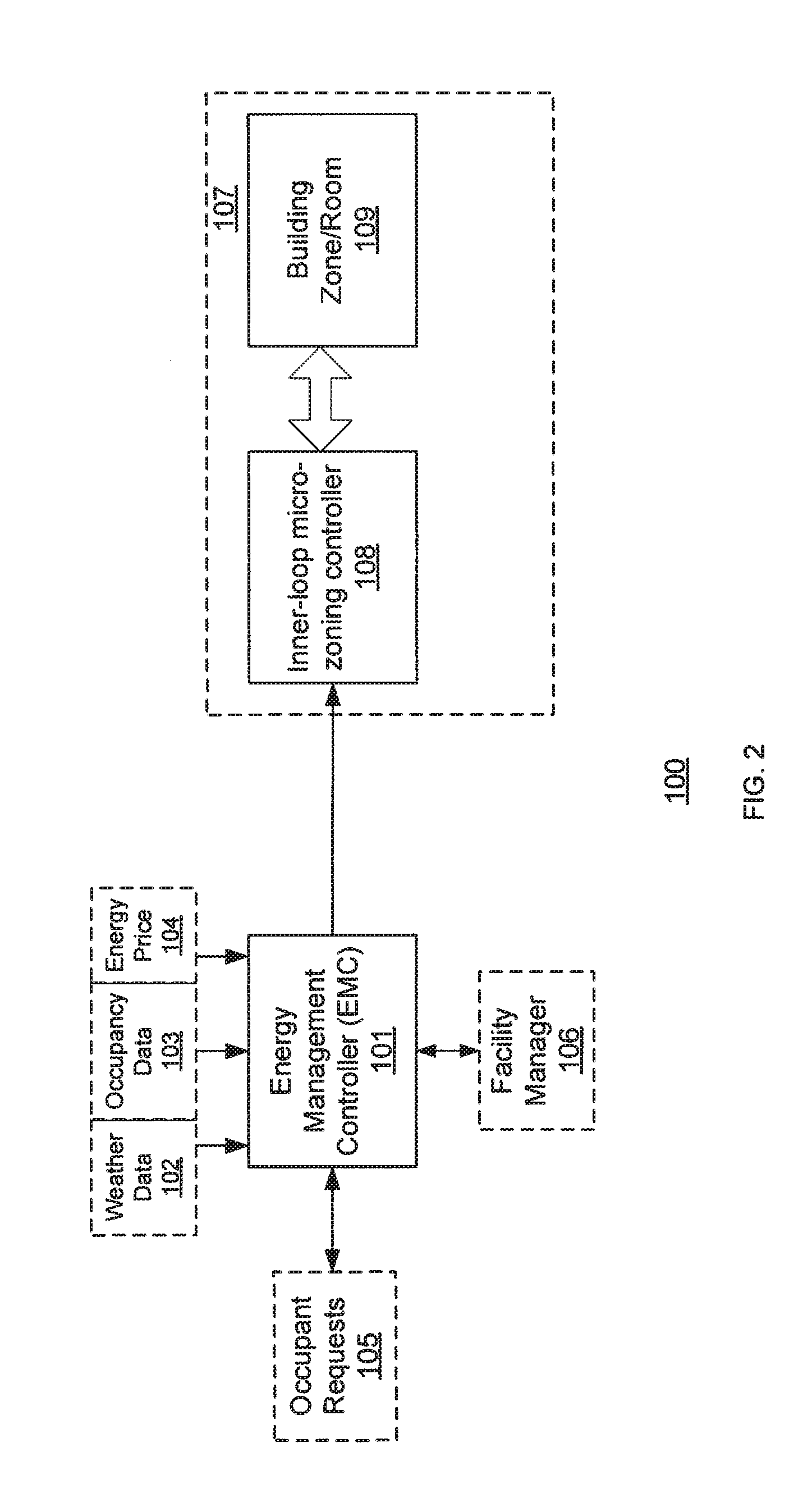
Cloud enabled building automation system
ActiveUS20130274940A1Optimize energy useLow costMechanical power/torque controlData processing applicationsControl signalOperating energy
A method of controlling energy consumption in a building. The method includes receiving occupant request data comprising a plurality of requests, wherein each of the plurality of requests corresponds to one of a plurality of zones in the building wherein the occupant request data is received via a cloud computing resource. The method also includes receiving weather data comprising at least one of current weather measurement data and weather forecast data wherein the weather data is received via a cloud computing resource. In addition, a facility management rule is received via a cloud computing resource. Further, the method includes generating a plurality of output control signals via cloud computing resource, wherein each of the plurality of output control signals is based on one of a plurality of requests and predicted occupant schedules, energy price data and the facility management rule. The control signals are generated by using simulation-based model predictive control method to determine a set of optimized control signals based on optimized energy use or optimized energy cost. The optimized control signals are transmitted to controllers.
Owner:SIEMENS AG
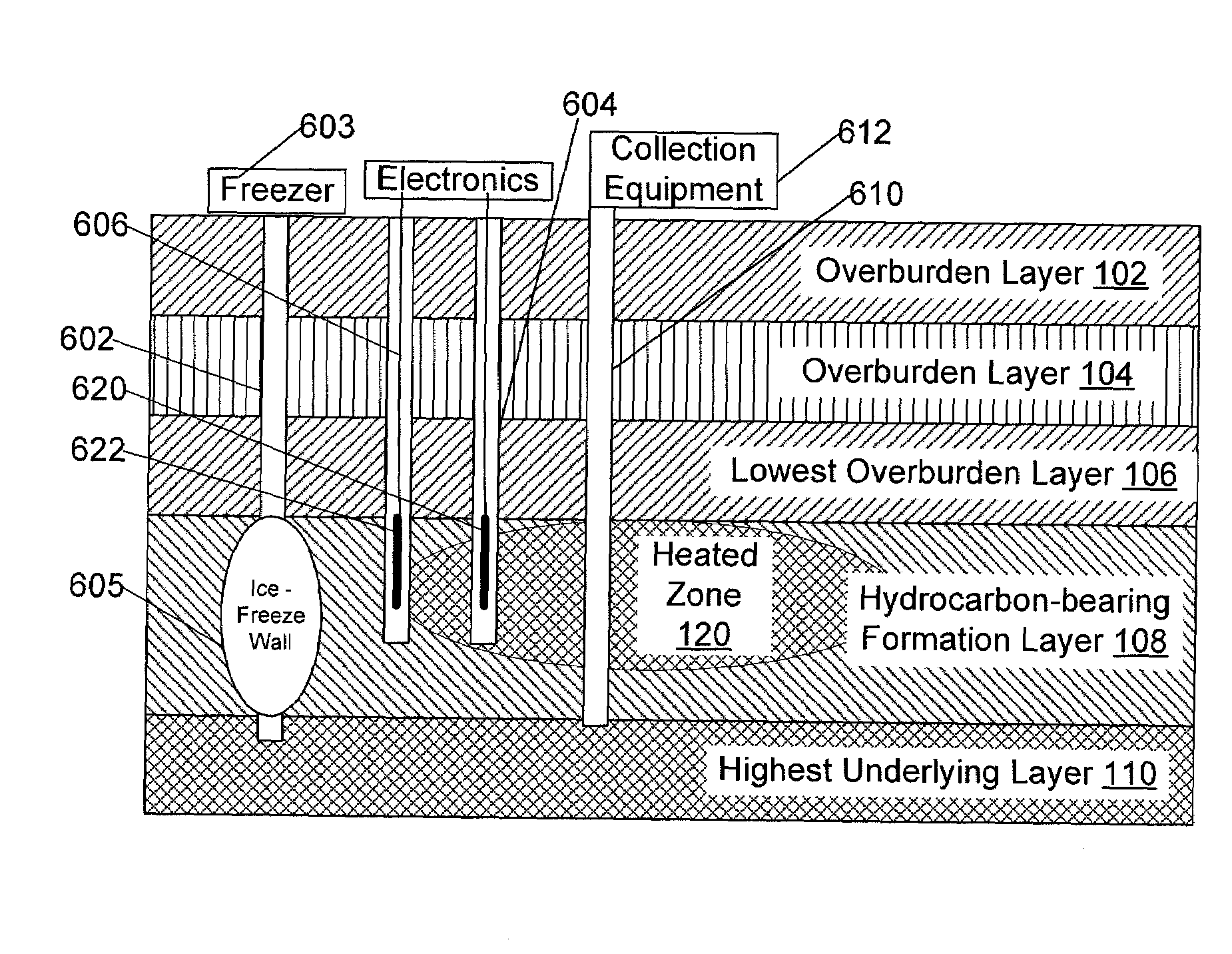
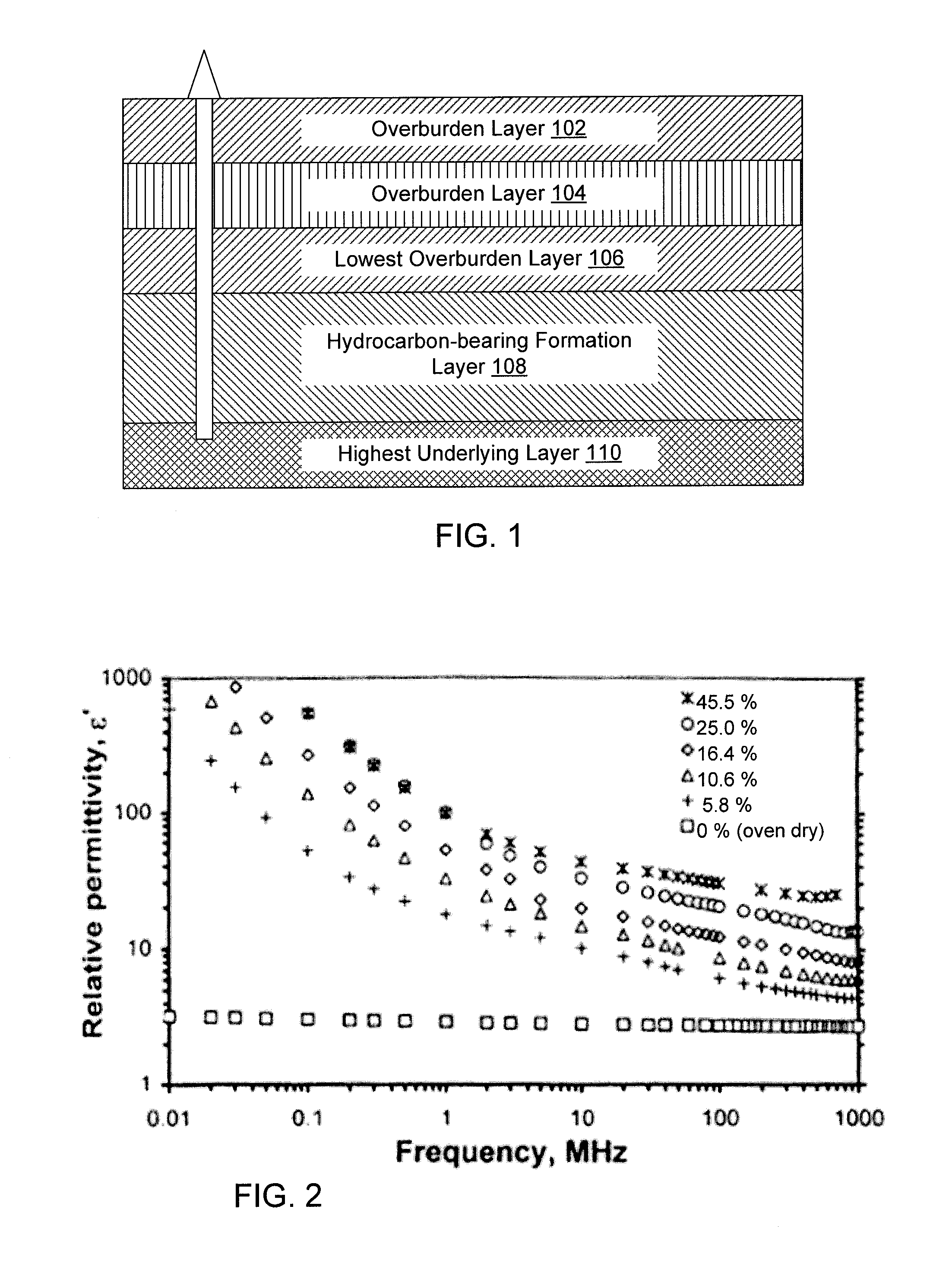
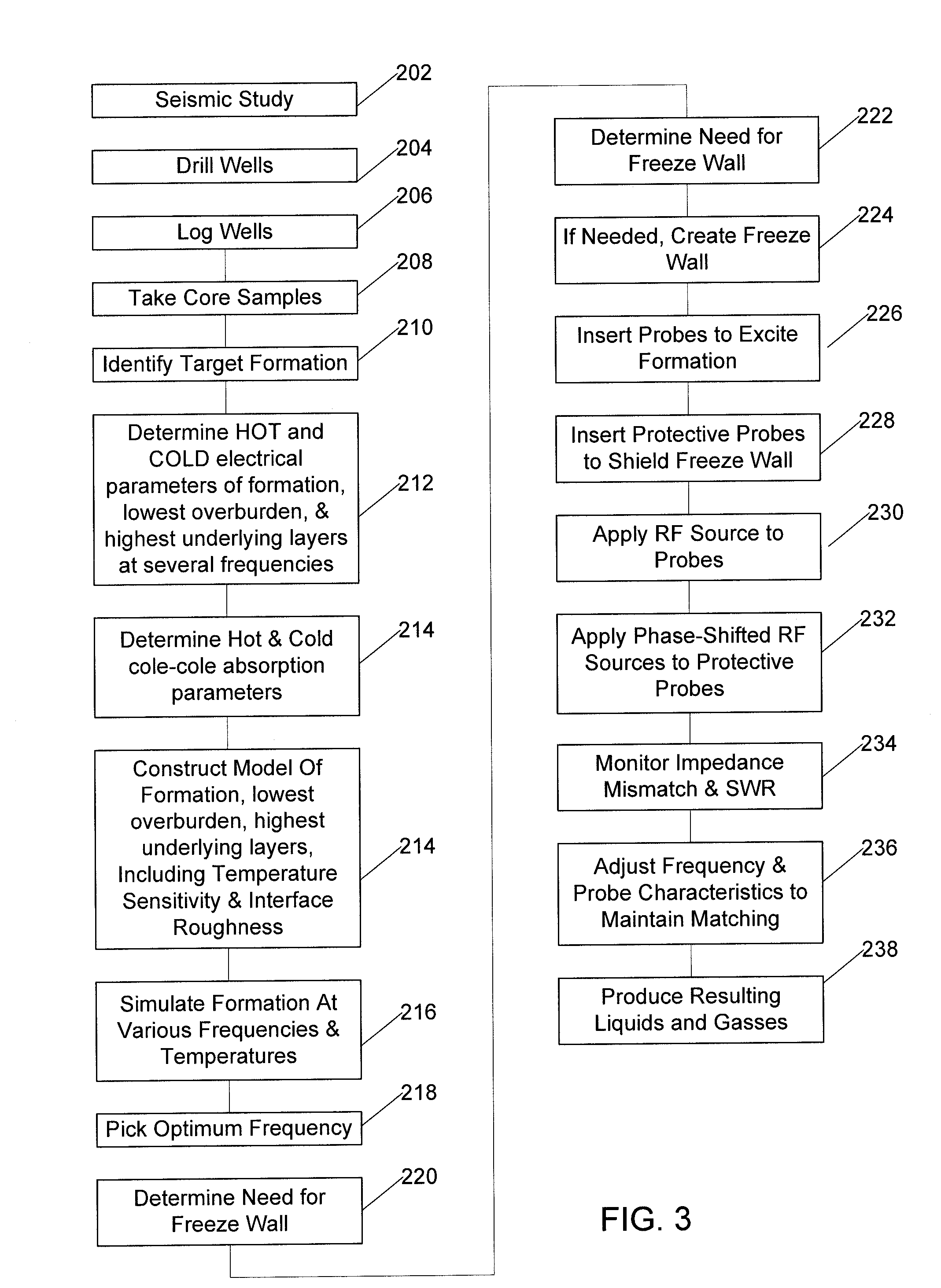
System and method for extraction of hydrocarbons by in-situ radio frequency heating of carbon bearing geological formations
A method of producing liquid hydrocarbons from a hydrocarbon-bearing rock in situ in a geological formation begins with exploring the formation by drilling a plurality of boreholes into the formation and taking core samples of the hydrocarbon-bearing rock and at least one overburden layer. Electrical parameters of the hydrocarbon-bearing rock and the overburden layer are determined, as well as a roughness of a boundary between the hydrocarbon-bearing rock and the at least one overburden layer. These electrical parameters are used to construct a computer model of a portion of the hydrocarbon-bearing rock and at least one overburden layer, the computer model based upon modeling the formation as a rough-walled waveguide. This computer model is used to simulate propagation of radio frequency energy within the hydrocarbon-bearing rock, including simulation of radio frequency wave confinement within the hydrocarbon-bearing rock, at several frequencies and temperatures. A frequency for retorting is selected based upon simulation results. Radio frequency couplers are installed into at least one borehole in the hydrocarbon-bearing rock and driven with radio frequency energy to heat the hydrocarbon-bearing rock. As the rock heats, it releases carbon compounds and these are collected.
Owner:PAO HSUEH YUAN
System and method for interactively simulating a credit-worthiness score
InactiveUS8015107B2Quick responseSimple interfaceFinancePayment architectureWeb serviceSimulation based
A system and method is provided to allow a consumer to interactively explore his credit score by submitting hypothetical values based on his actual credit data. The system uses the consumer's real credit data and the submitted hypothetical values to calculate a simulated credit score based on a simulator scorecard. The consumer may then observe the changes in the resultant scores. The system and the scorecard may utilize fewer data elements than a complete credit-worthiness scorecard and may instead focus on the key elements affecting a consumer's credit score. The system may be implemented in part on a web server or as a stand-alone application. The system may also update the score dynamically as the consumer adjusts the hypothetical values or may require the consumer to affirmatively submit the new hypothetical data.
Owner:CONSUMERINFO COM
Associative Database Scanning and Information Retrieval
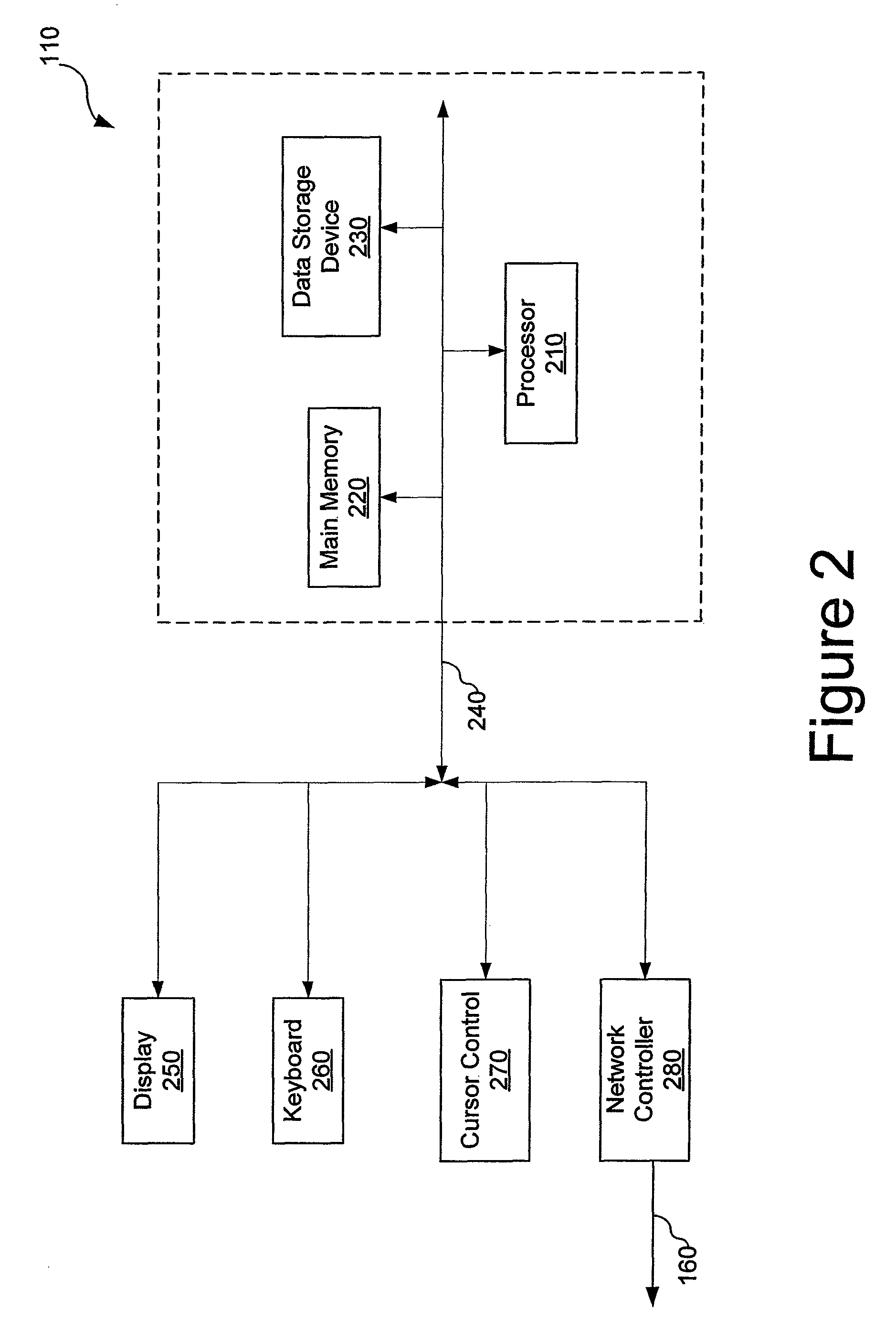
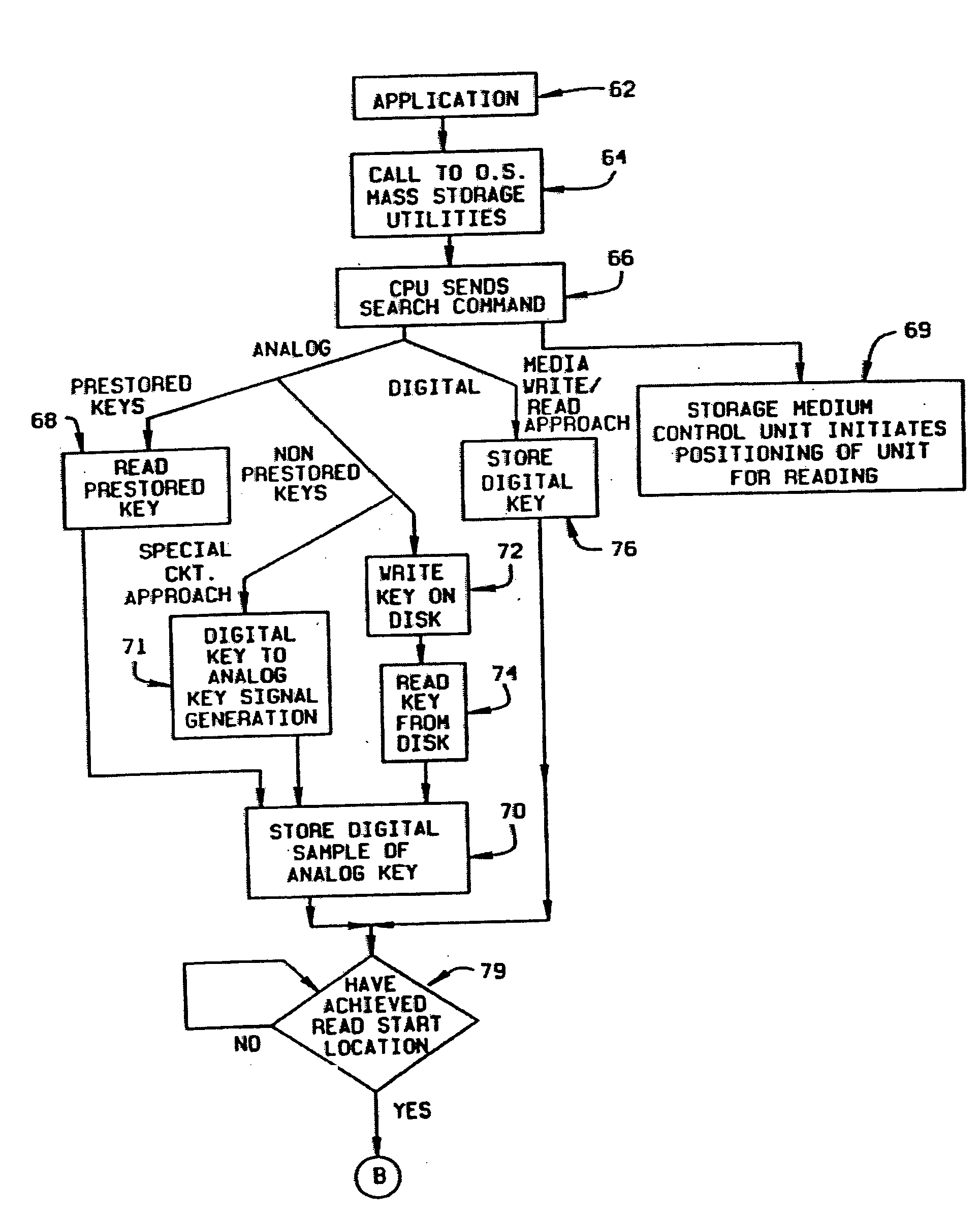
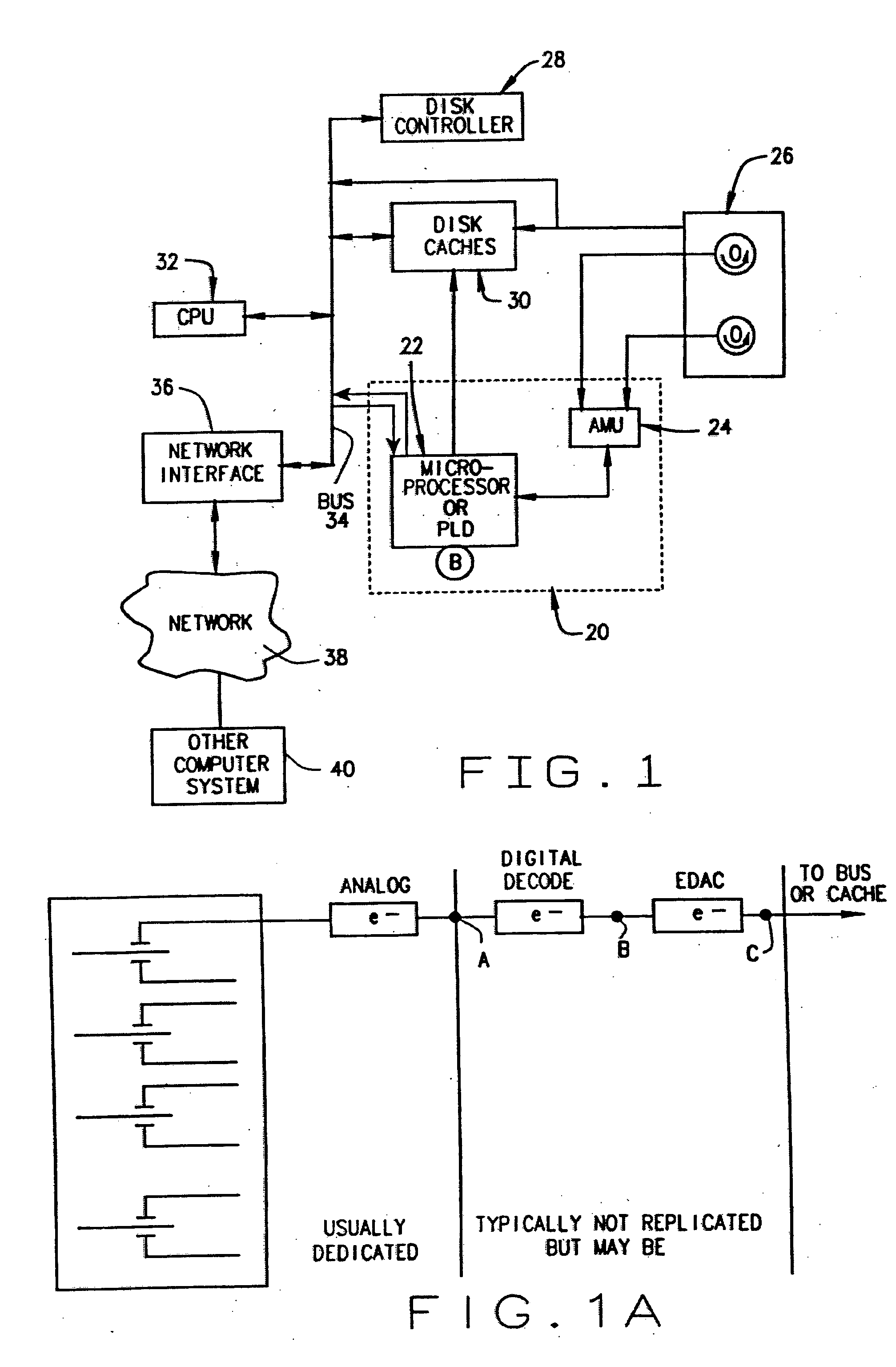
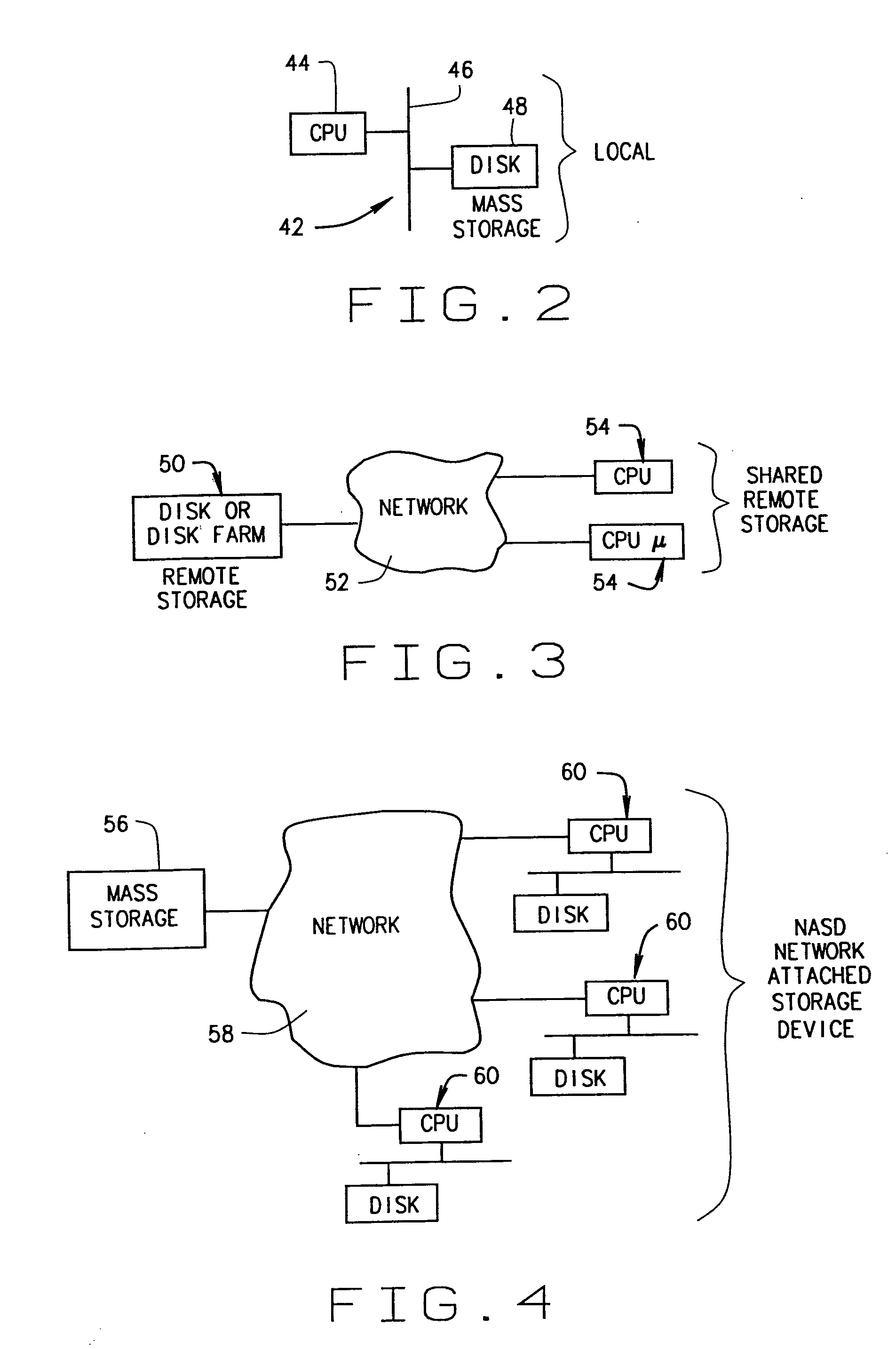
InactiveUS20070118500A1Threshold may be loweredRaise the importanceData processing applicationsInput/output to record carriersMass storagePattern matching
A method and device are disclosed for an associative and approximate, analog or digital scanning of databases that allows for the asynchronous accessing of data from a mass storage medium. The invention includes providing dedicated analog and digital circuitry and decision logic at the mass storage medium level for determining a key identifying the data of interest, continuously comparing the key to a signal generated from a reading of the data from the mass storage medium with an approximate or exact matching circuit to determine a pattern match, determining a correlation value between the key and the data as it is read in a continuous fashion, and determining a match based upon a preselected threshold value for the correlation value. The pattern matching technique eliminates any need to compare data based on its intrinsic structure or value, and instead is based on an analog or digital pattern. The key and data may be either analog or digital. This device and method may be provided as part of a stand-alone computer system, embodied in a network attached storage device, or can otherwise be provided as part of a computer LAN or WAN.
Owner:IP RESERVOIR
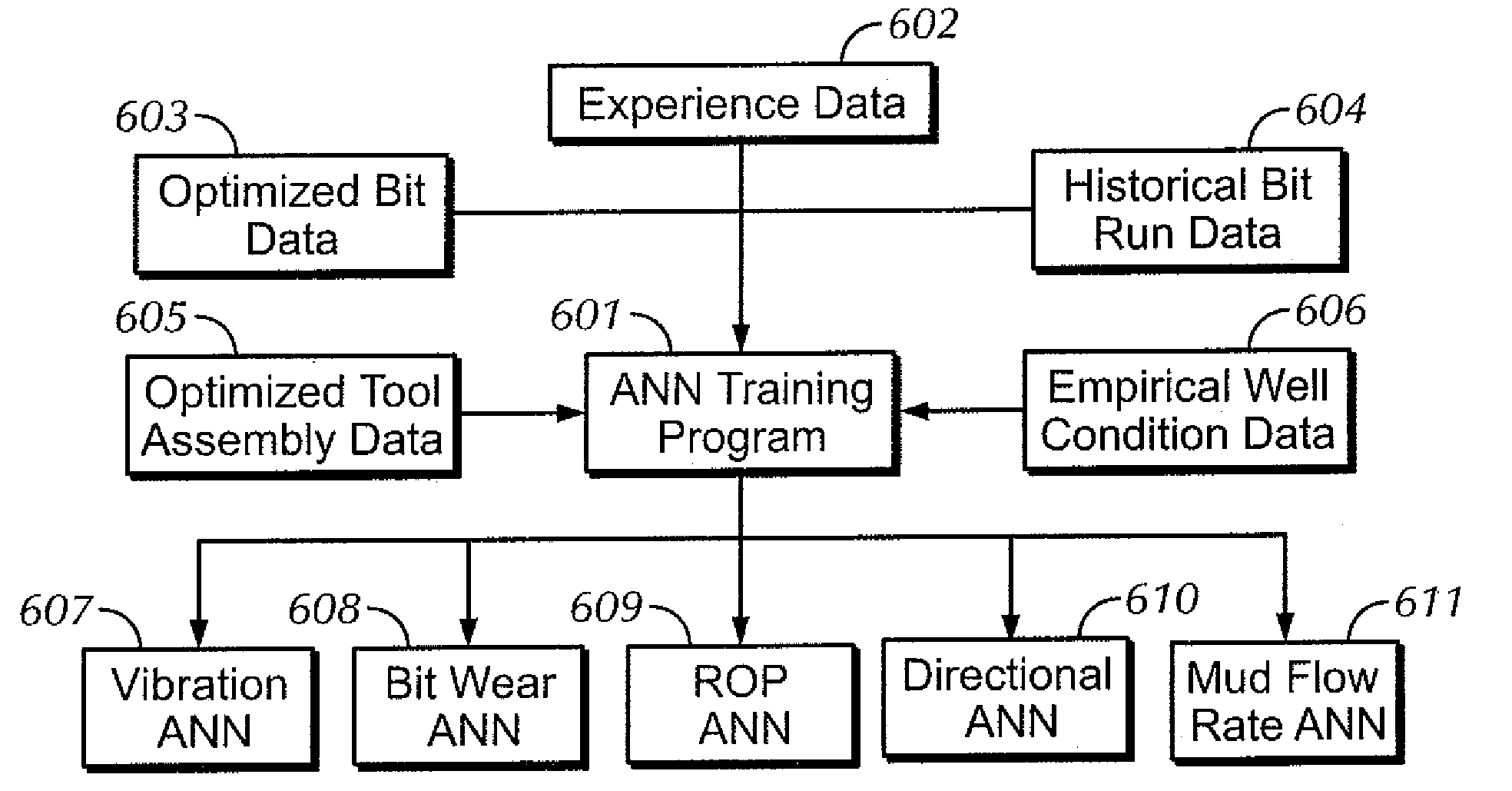
Neural net for use in drilling simulation
A method of optimizing a drilling tool assembly including inputting well data into an optimization system, the optimization system having an experience data set and an artificial neural network. The method further including comparing the well data to the experience data set and developing an initial drilling tool assembly based on the comparing the well data to the experience data, wherein the drilling tool assembly is developed using the artificial neural network. Additionally, the method including simulating the initial drilling tool assembly in the optimization system and creating result data in the optimization system based on the simulating.
Owner:SMITH INT INC
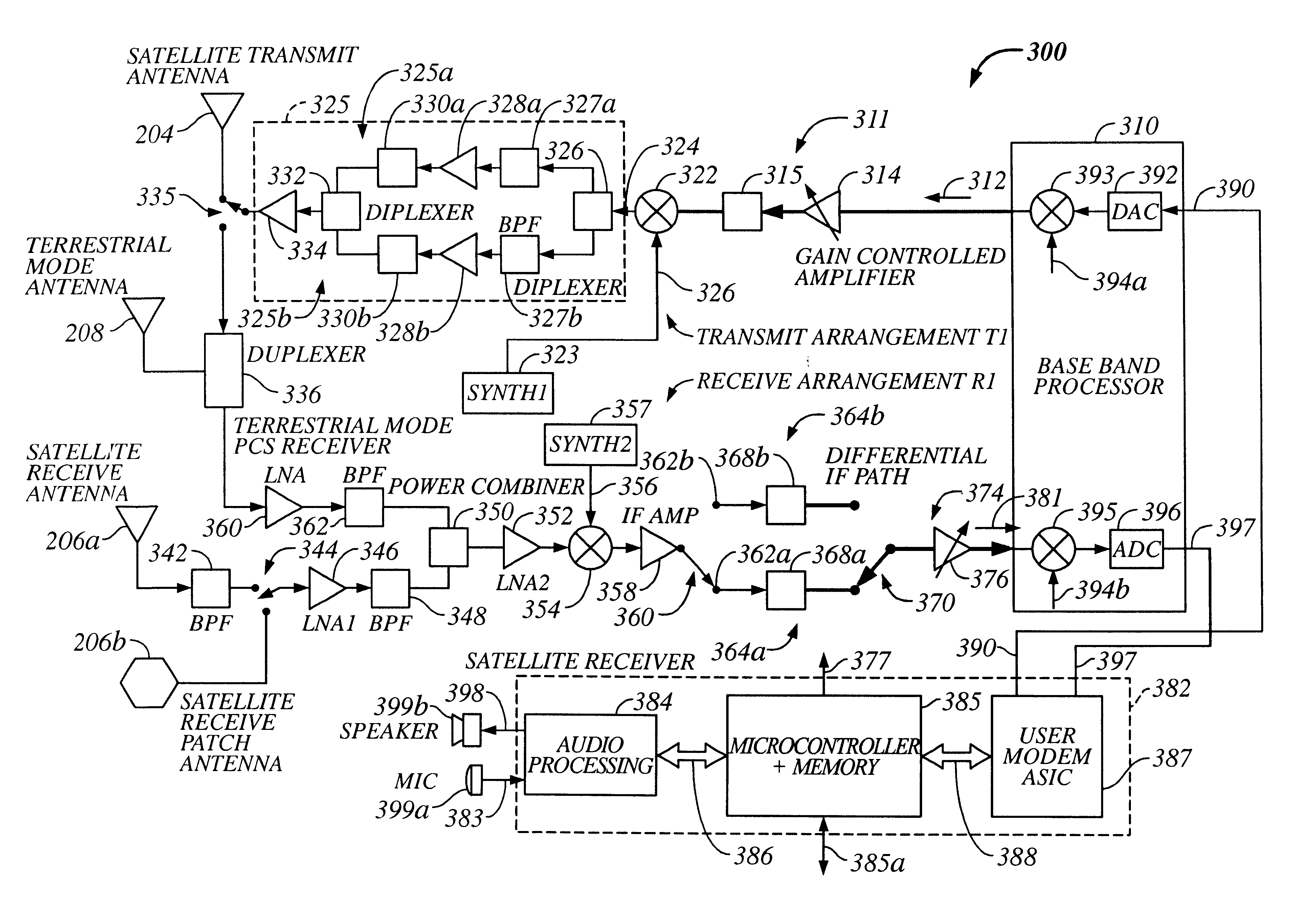
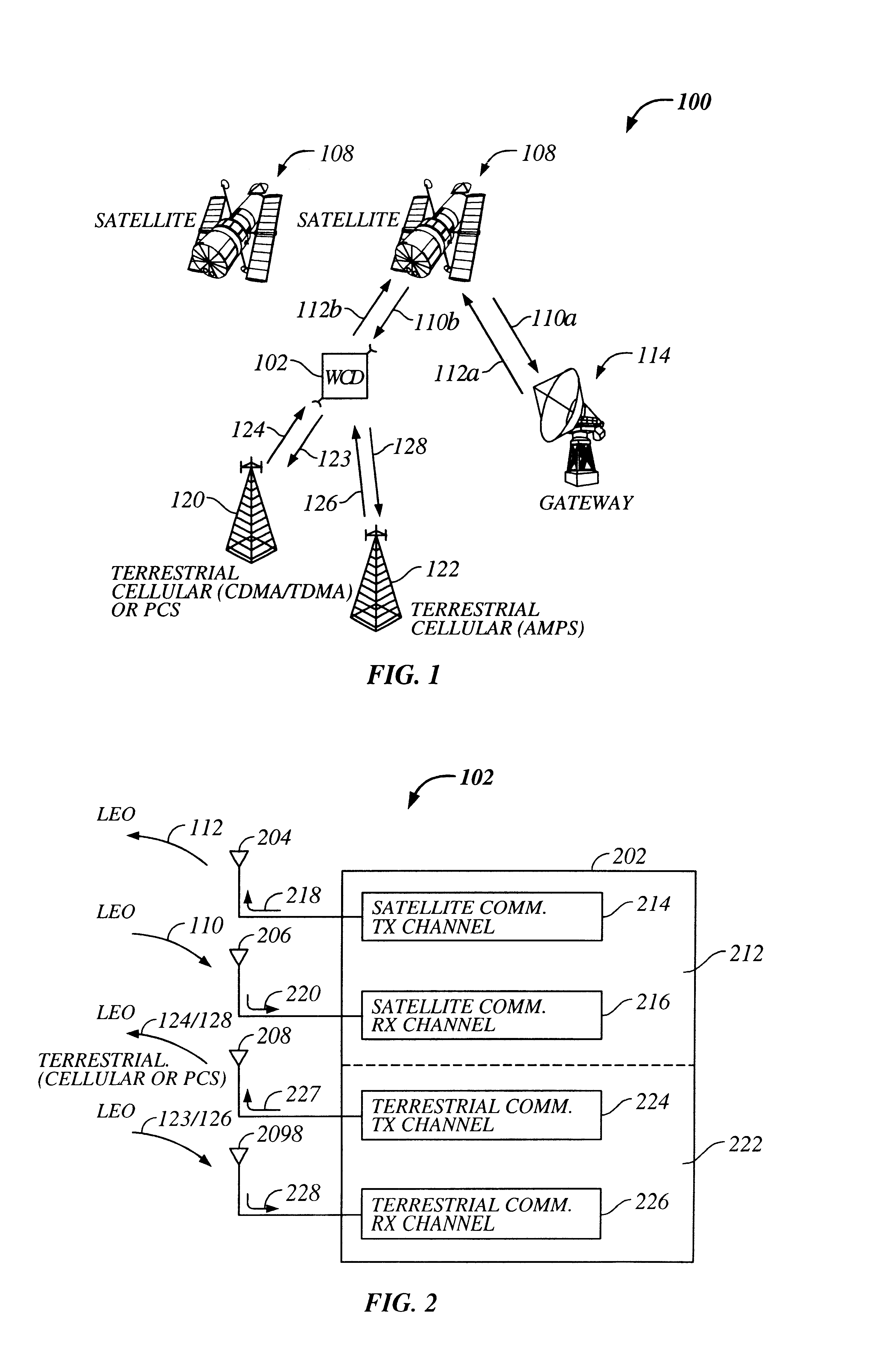
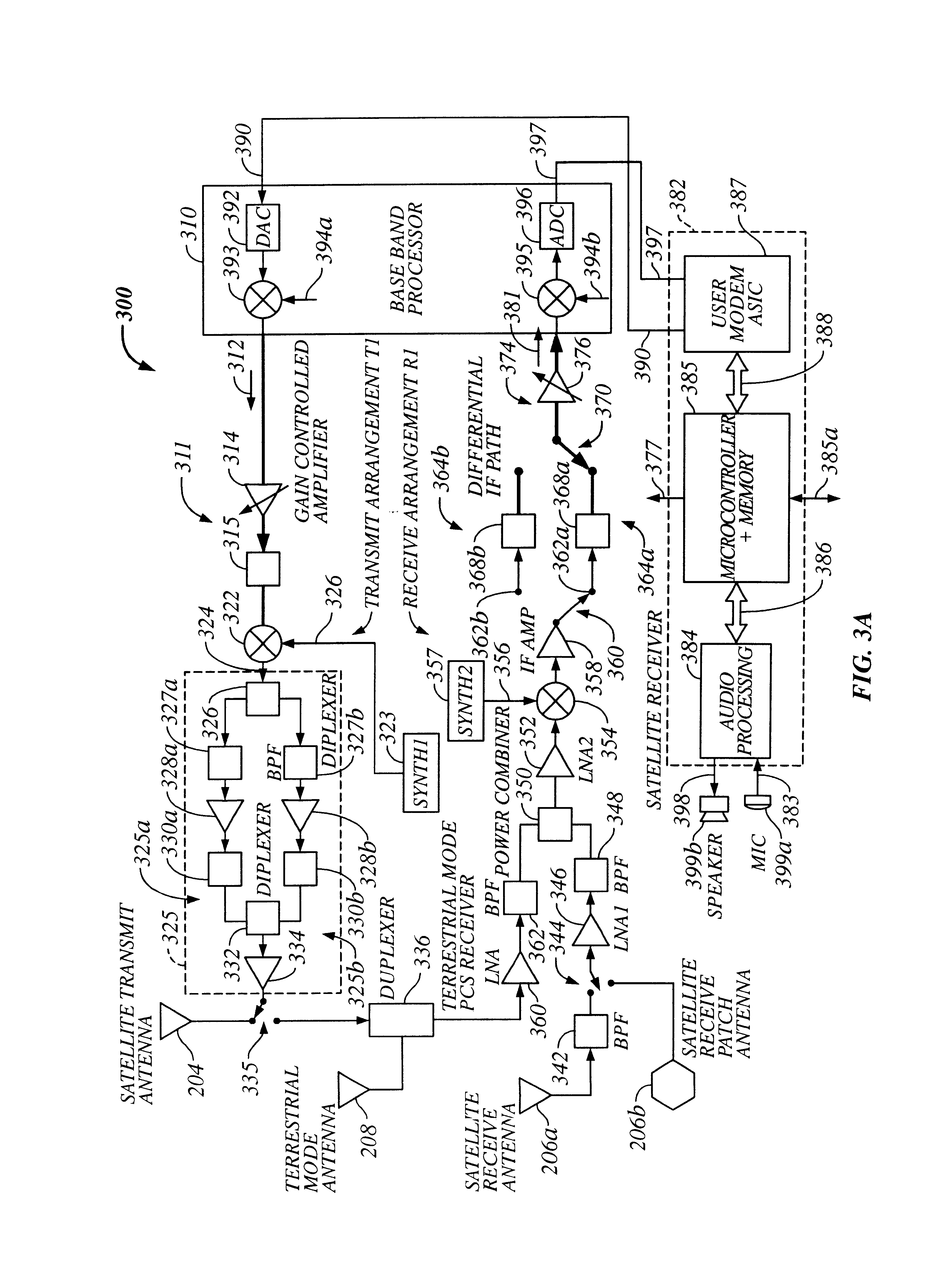
Multi-mode satellite and terrestrial communication device
InactiveUS6714760B2Appropriate performanceBroadcast transmission systemsRadio/inductive link selection arrangementsCommunications systemSimulation based
The present invention provides a multiple band mobile radio (also referred to as a Wireless Communication Device (WCD)) capable of communicating with both a satellite communication system and a terrestrial communication system. The satellite communication system can be, for example, a Low Earth Orbit (LEO) satellite system. The terrestrial communication system can be a Personal Communication System (PCS), or a cellular system, including either an analog or a digitally based cellular system. The cellular analog system can be AMPS. The digitally based cellular system can be a CDMA or a TDMA based communication system. The WCD can concurrently receive signals from the terrestrial communication system and the satellite communication system.
Owner:QUALCOMM INC
Game Simulation Based on Current Events
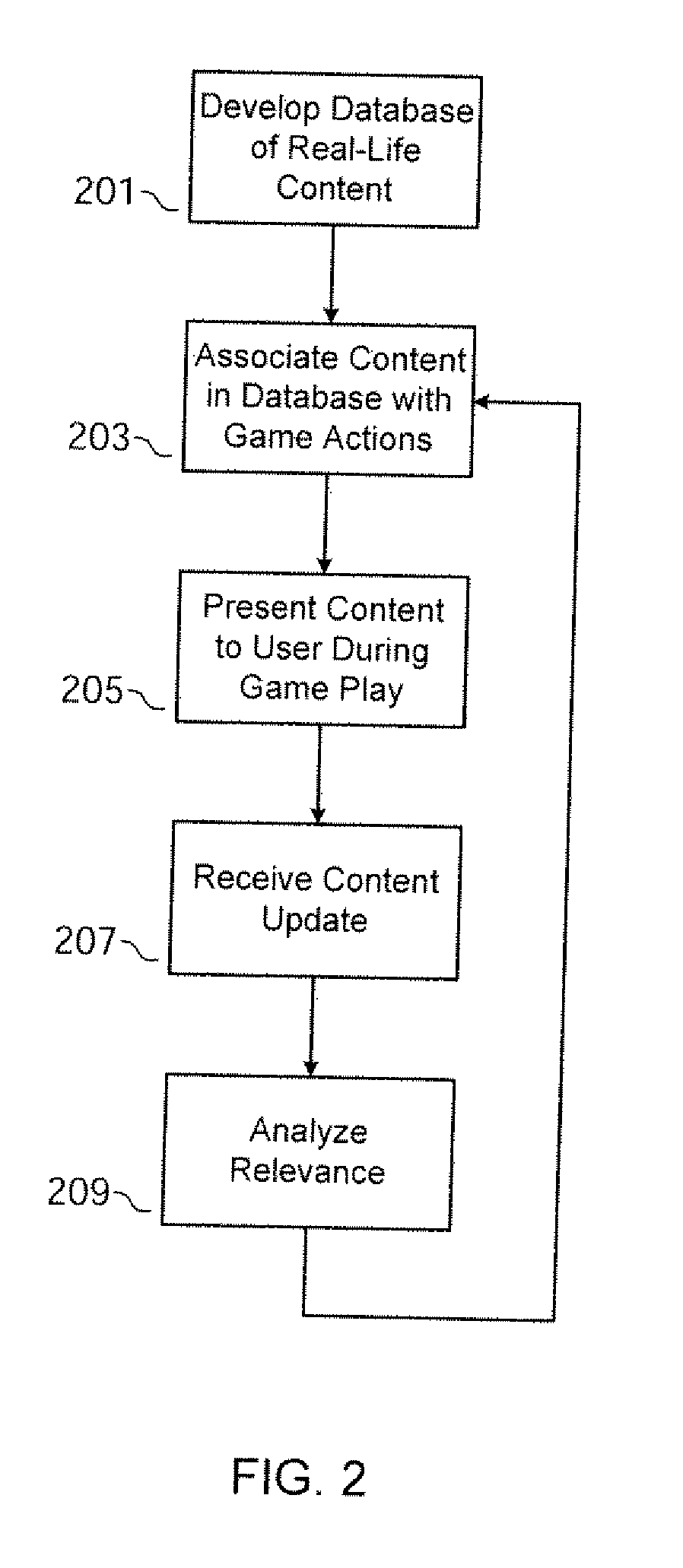
InactiveUS20070207846A1Video gamesSpecial data processing applicationsGraphicsGraphical user interface
A video game includes: (i) a graphic user interface that presents a user a simulation of real-life events; (ii) a content database containing a collection of actual photos and videos of real-life events; (iii) a simulation engine that, presents a plurality of possible actions to the user, receives a selection of at least one of the actions from the user, identifies at least one photo or video in the database that is associated with the user-selected action, and presents the user with a result in response to the selection, wherein the result includes the identified photo or video; (iv) a content update module that receives updated photo or video content from one or more content distributors, creates an association element for the updated content and an available action in the game, and includes the updated content and association element in the content database; and (v) a scoring module.
Owner:HYBRID LEARNING SYST
Innovative satellite scheduling method based on genetic algorithms and simulated annealing and related mission planner
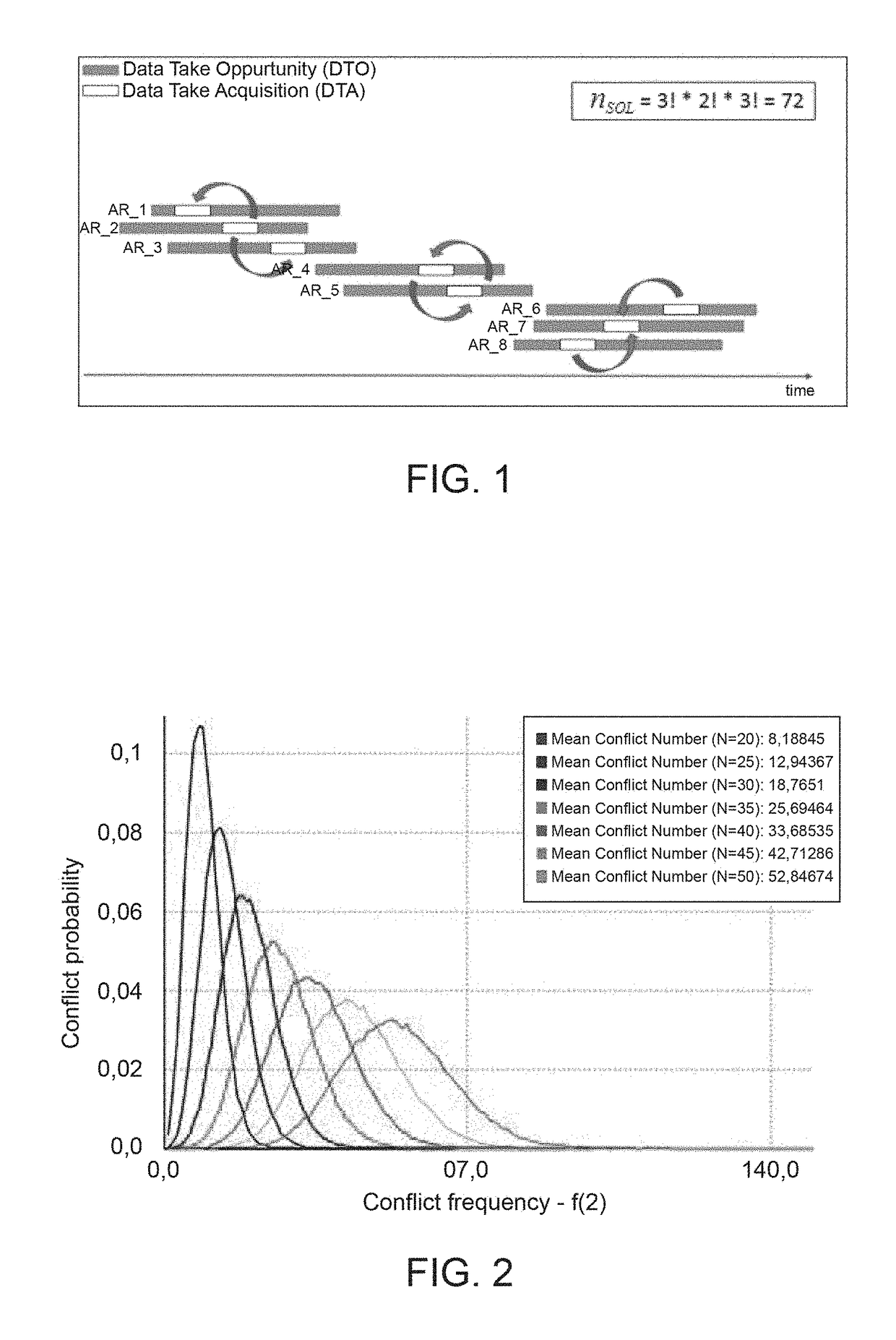
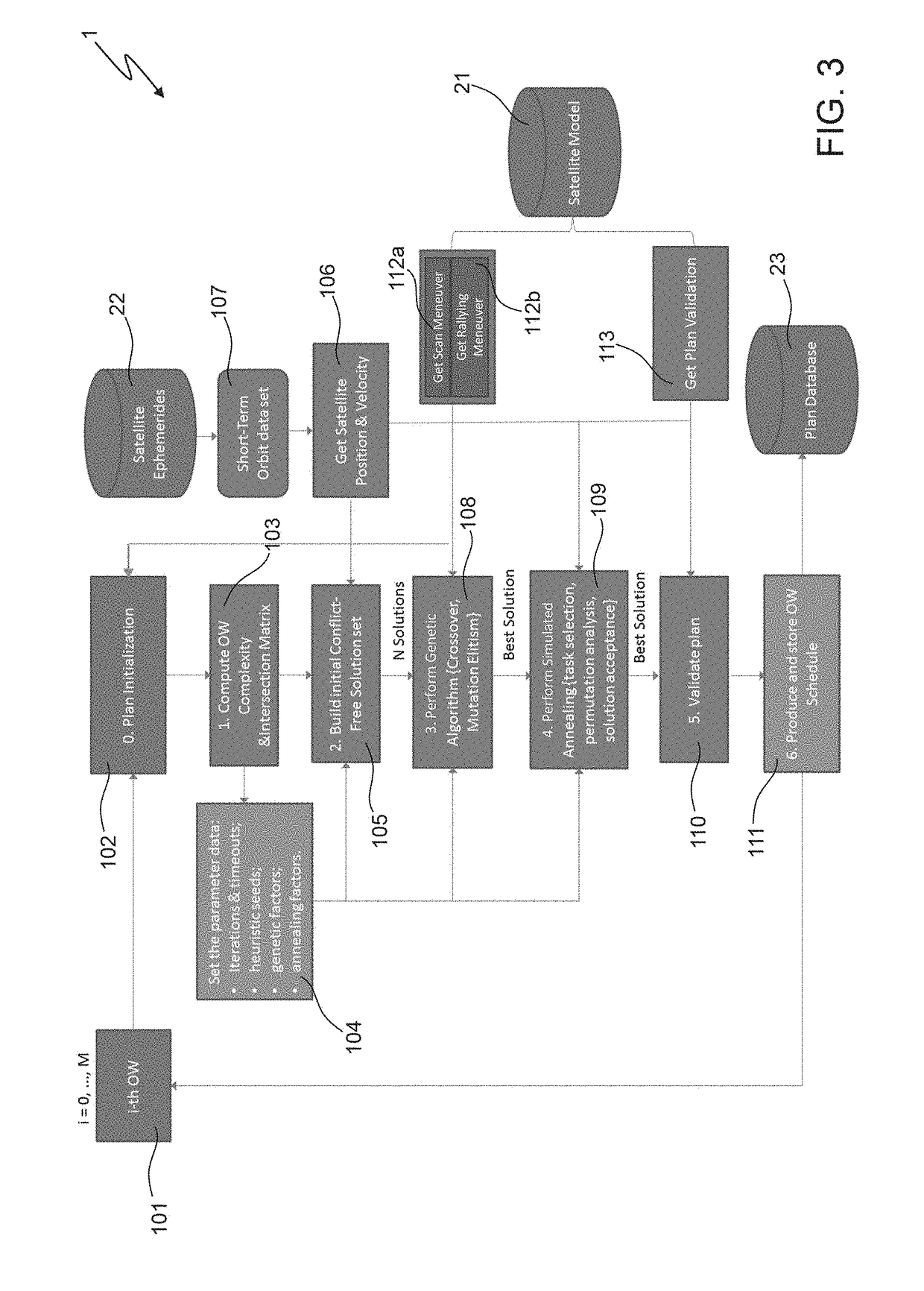
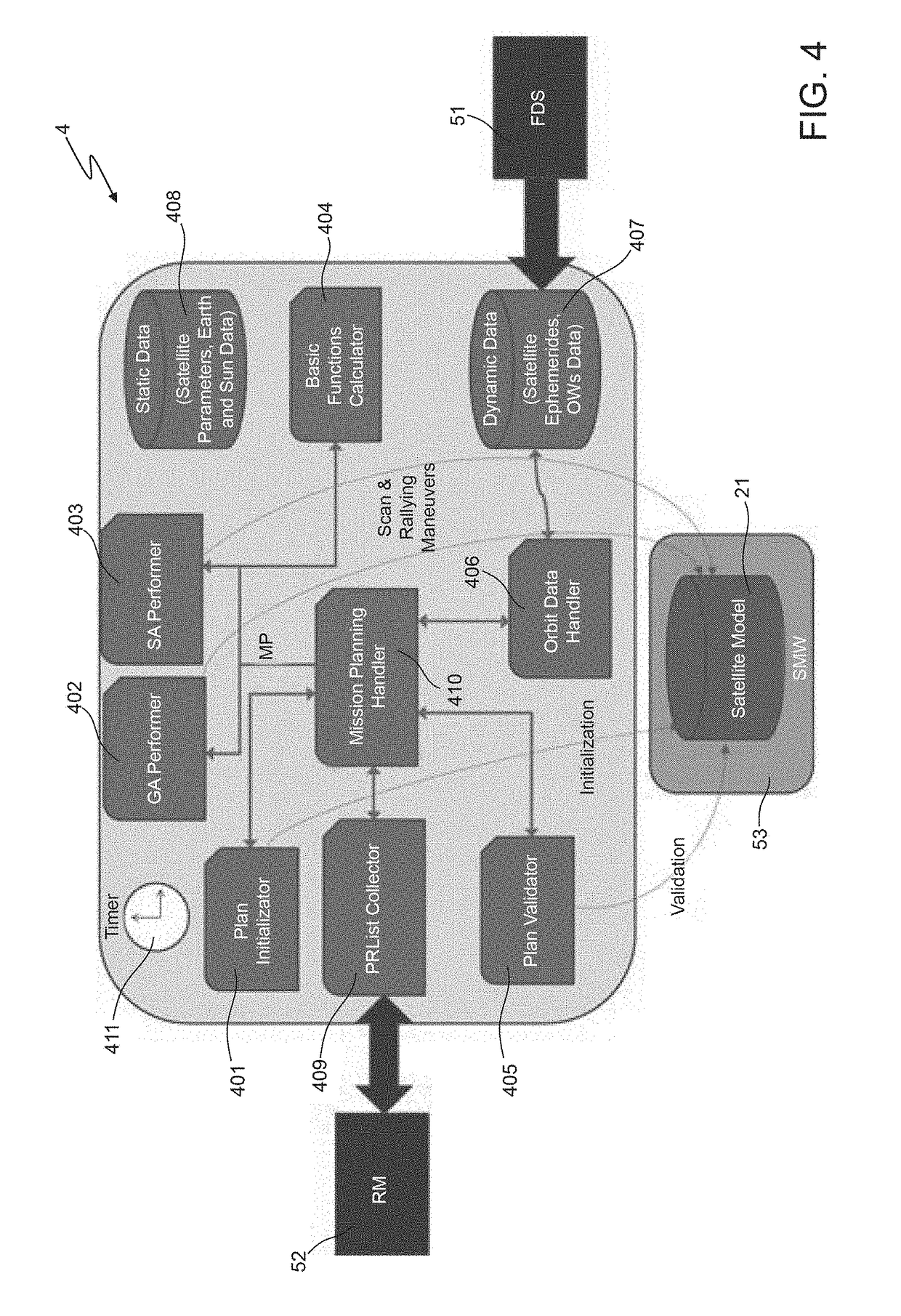
ActiveUS20180341894A1Maximal diversityCosmonautic vehiclesCosmonautic partsSimulation basedGenetic algorithm
A method includes: a) producing initial scheduling plans based on requests related to tasks to be performed within a time period by a remote sensing satellite; wherein each initial scheduling plan schedules respective tasks, which do not conflict with each other in time and in using satellite resources; and each task is scheduled in at least one of the initial scheduling plans; b) applying a genetic-algorithm-based processing to the initial scheduling plans to produce a genetic-algorithm-based scheduling plan which is for mission objectives, and complies with constraints related to the satellite resources, to the tasks, and to the time period; and c) applying a simulated-annealing-based processing to the genetic-algorithm-based scheduling plan to produce a simulated-annealing-based scheduling plan that fits the mission objectives, complies with the constraints, and in which a larger number of tasks is scheduled than in the genetic-algorithm-based scheduling plan.
Owner:TELESPAZIO SPA
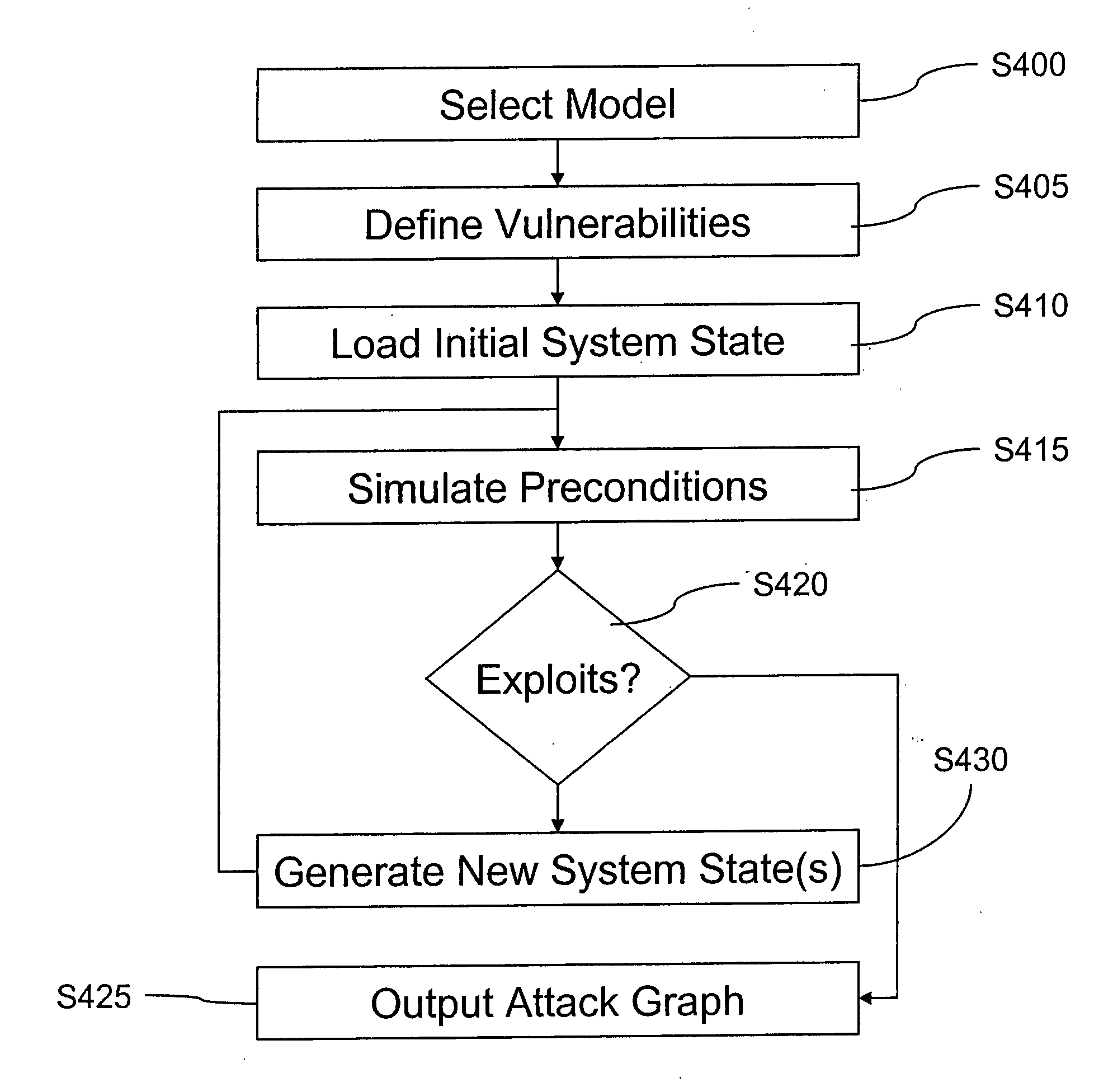
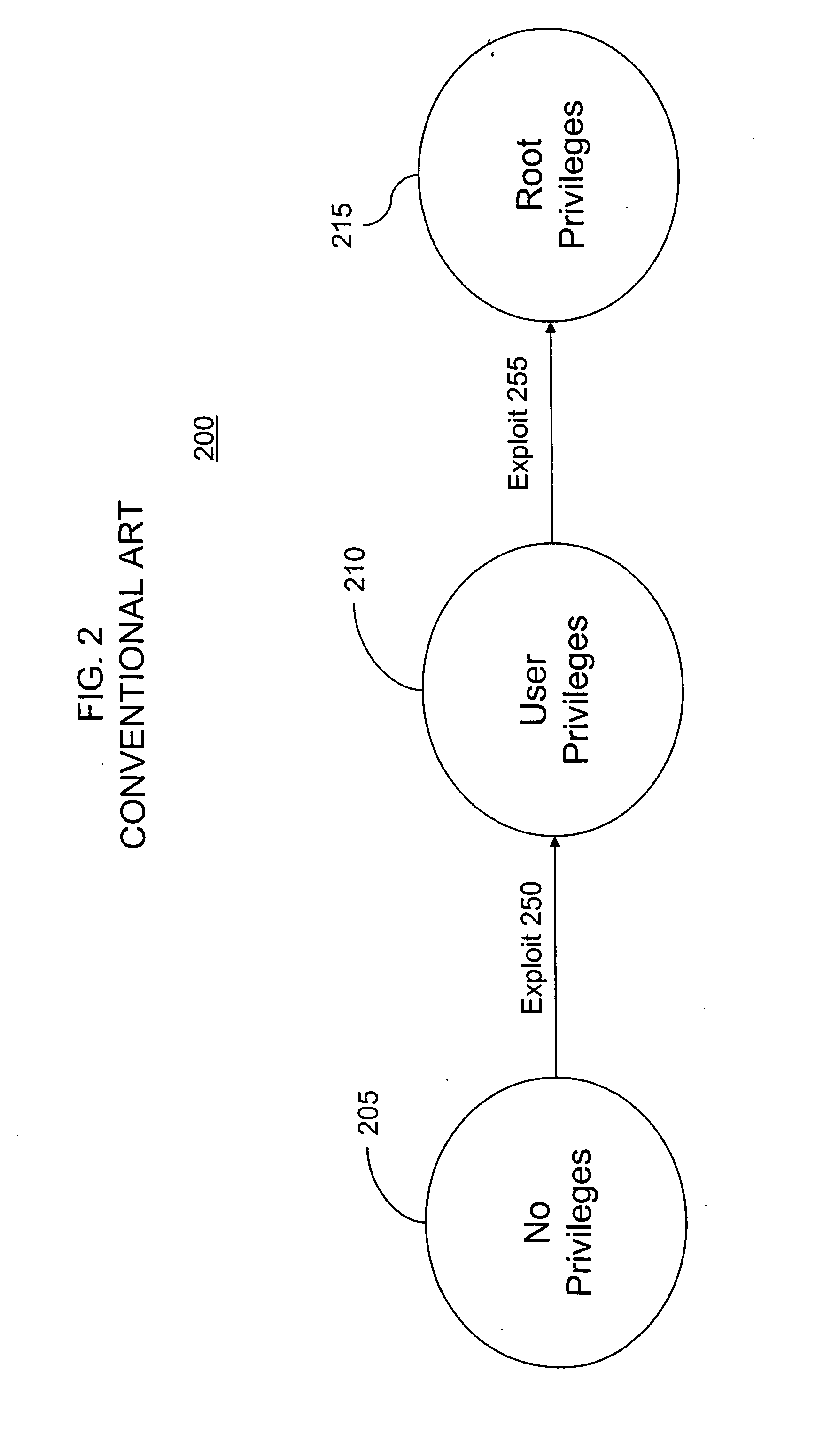
Methods of simulating vulnerability
Methods of simulating vulnerability are provided. In an example, multi-stage vulnerability across multiple systems may be simulated by first simulating a probing of at least one intermediate entity, the at least one intermediate entity connected to a target system, second simulating a probing of the target system if the first simulated probing is successful and generating an attack graph based on the results of the first and second simulating steps. In another example, multi-system vulnerability may be simulated by receiving a plurality of attributes associated with vulnerabilities of a plurality of systems within a network, the plurality of systems including at least one target system and generating an attack graph including one or more attack chains based at least in part on the received plurality of attributes. In another example, system (e.g., single-system) vulnerability may be simulated by first simulating whether vulnerabilities exploited from a first system state cause a transition to a second system state, the second system state having a higher-privilege level than the first system state within a target system and generating an attack graph based at least in part on the results of the simulation.
Owner:LGS INNOVATIONS
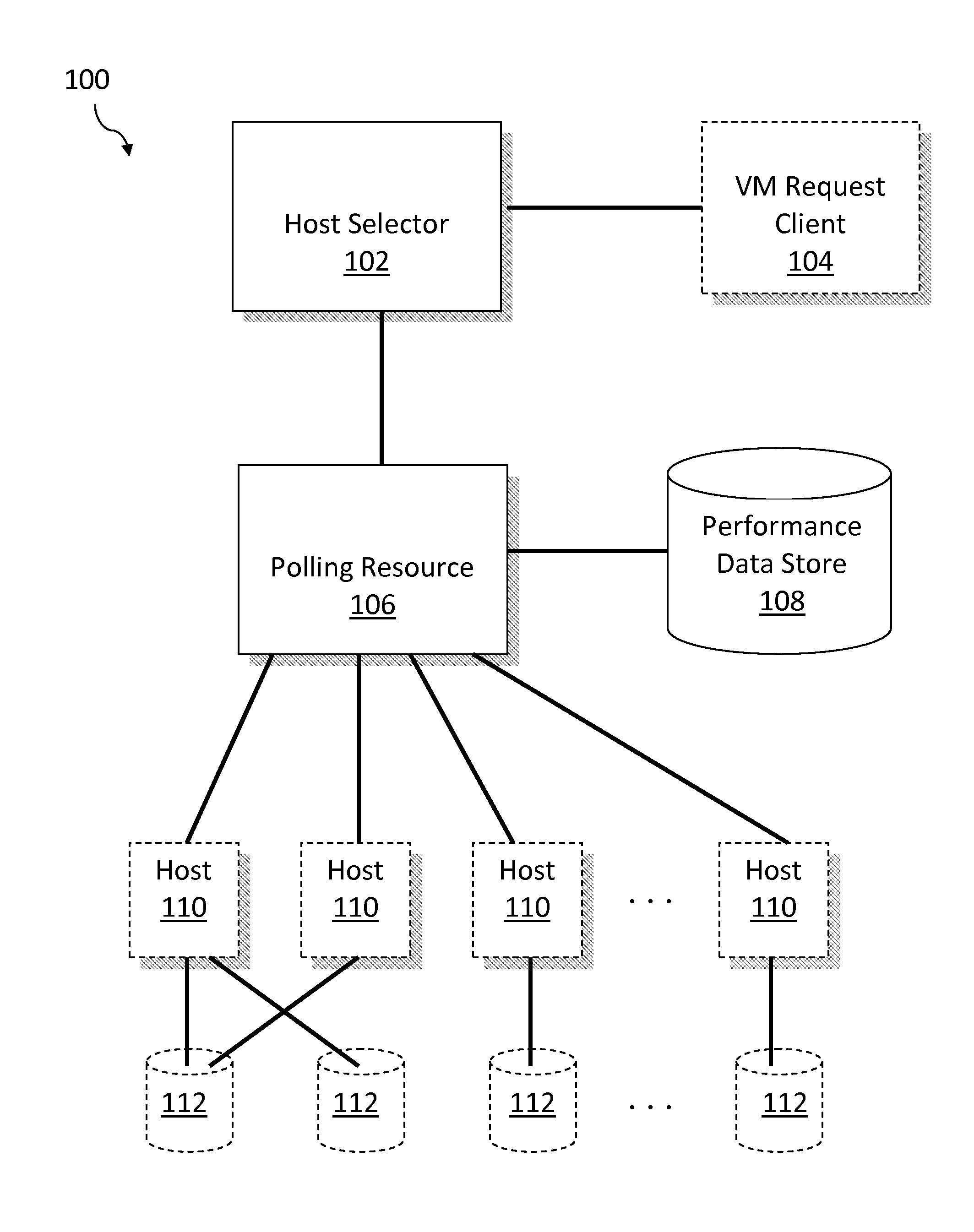
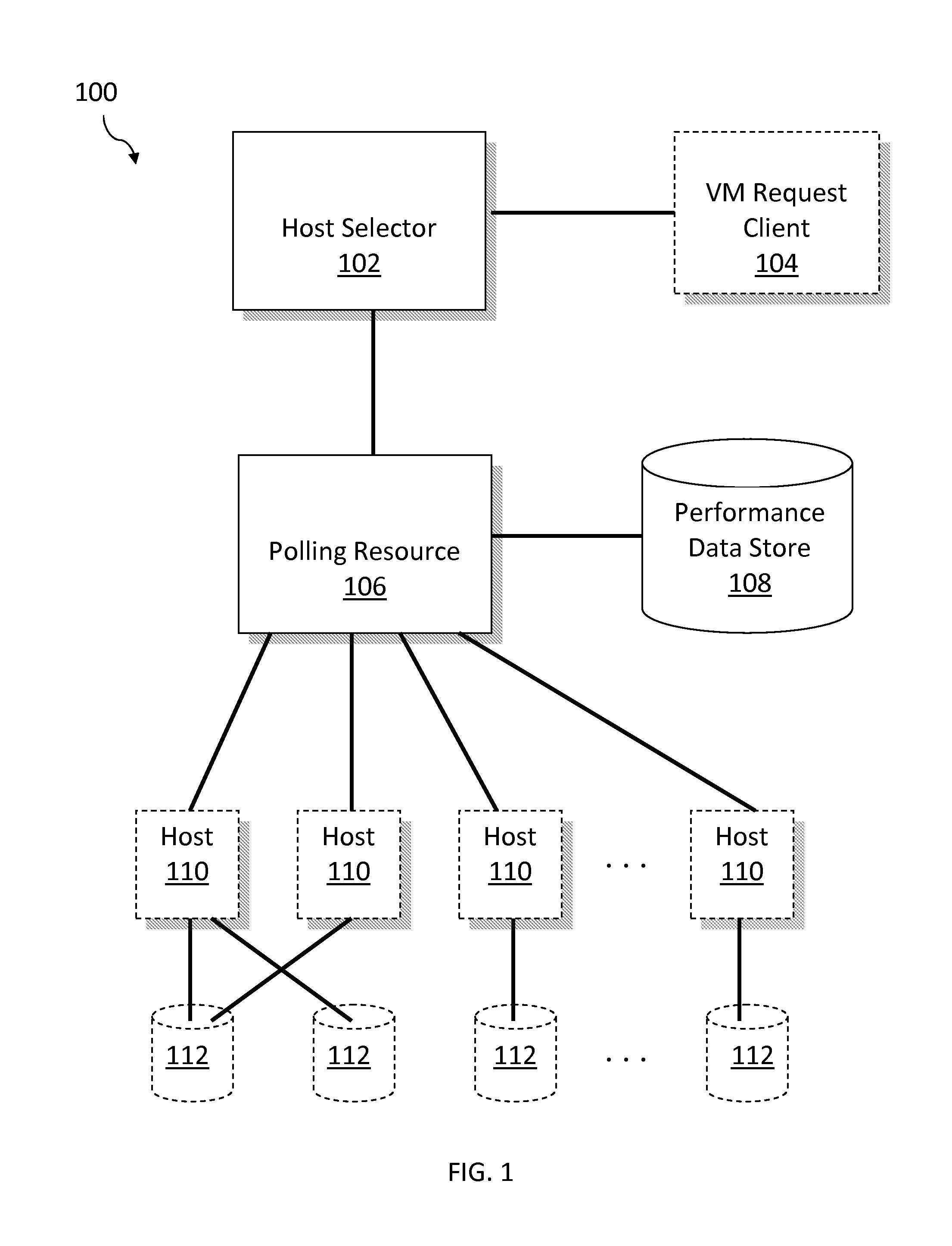
Performant host selection for virtualization centers
InactiveUS20140282540A1Software simulation/interpretation/emulationMemory systemsVirtualizationSimulation based
A host for a virtual machine is selected by first electronically receiving (i) a virtual-machine allocation request for resources in a cluster of servers upon which a plurality of virtual machines are executing and (ii) performance data related to the execution of the plurality of virtual machines. The effect of executing a new virtual machine associated with the request on each server using on the gathered performance data is simulated, and a server is selected based on a result of the simulation; the new virtual machine is caused to execute on the selected server.
Owner:ELASTICBOX
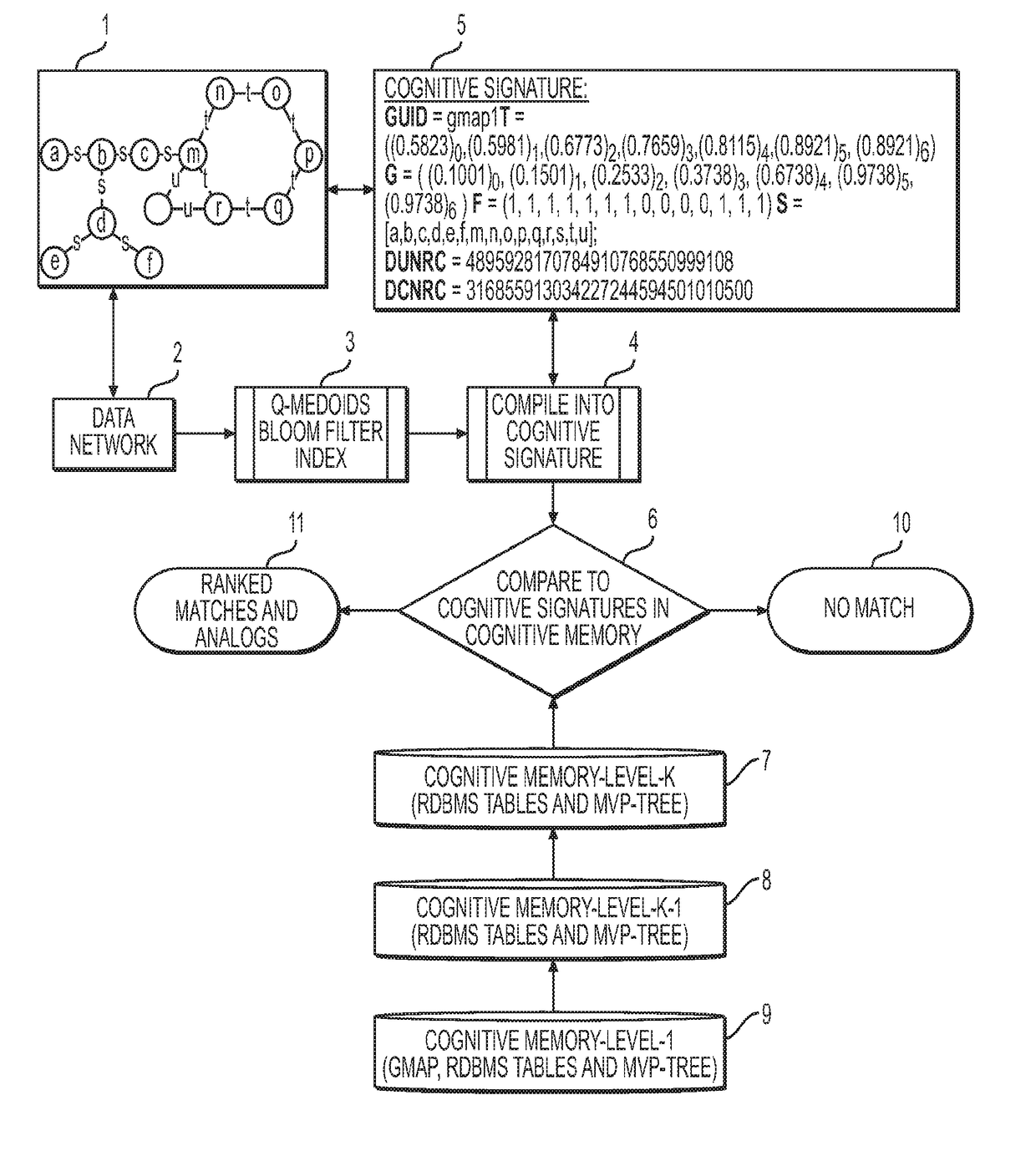
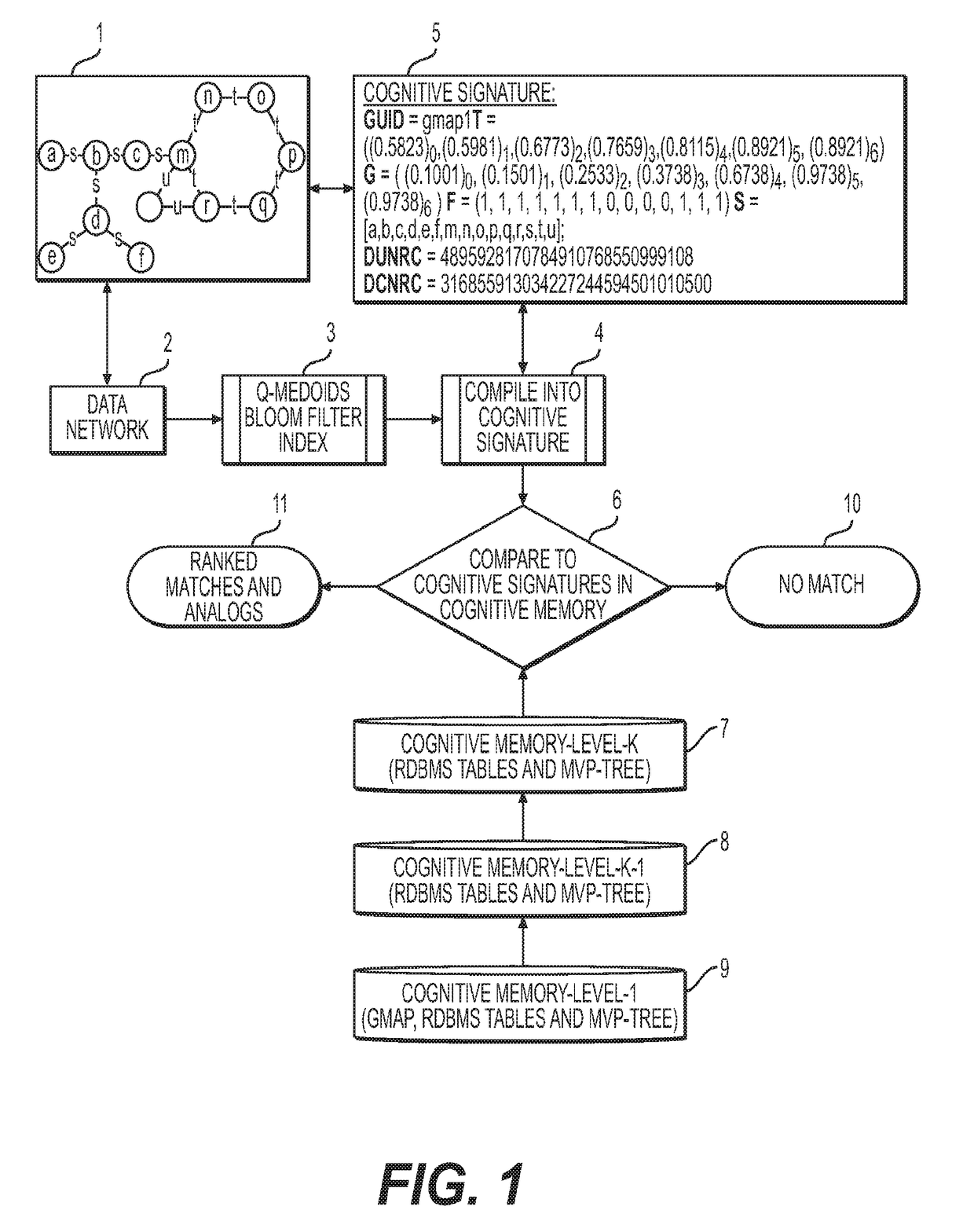
Cognitive memory graph indexing, storage and retrieval
The present disclosure provides a fast approximate as well as exact hierarchical network storage and retrieval system and method for encoding and indexing graphs or networks as well as for identifying substructure matches or analogs within graph data. Cognitive Memory encodes graphs via generalized combinatorial maps and a new quantum-inspired Q-Hashing algorithm to summarize local structures of the graph along with a contraction and graph property calculation to build an index data structure called the Cognitive Signature for property based, analog based or structure or sub-structure based search. The system and method of the present invention is ideally suited to store and index all or parts or substructures or analogs of graphs as well as dynamically changing graphs such as traffic graphs or flows and motion picture sequences of graphs. The system and method has the advantage that properties of the Cognitive Signature of the graph can be used in correlations to the properties of the underlying data making the system ideal for semantic indexing of massive scale graph data sets.
Owner:KYNDI
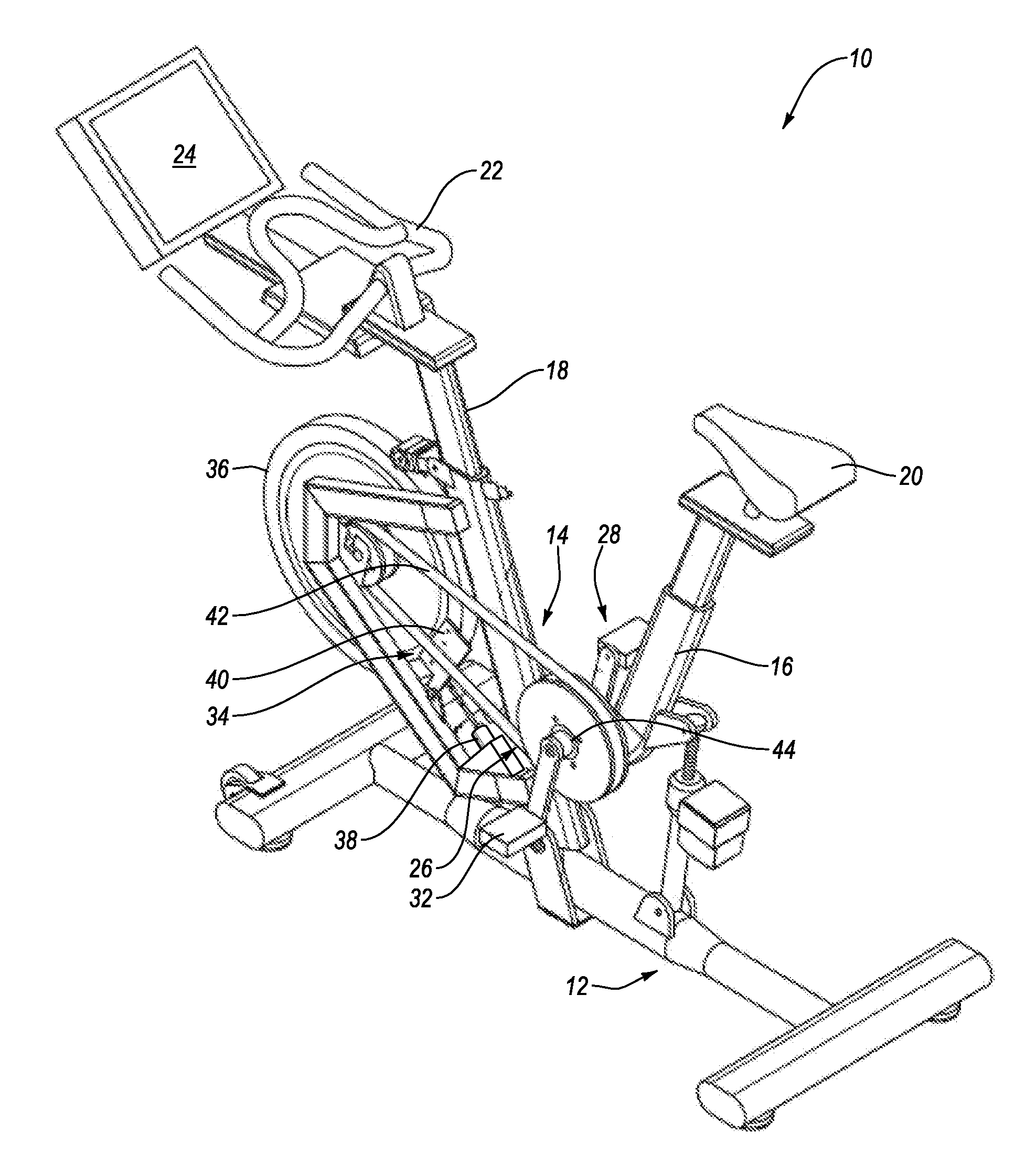
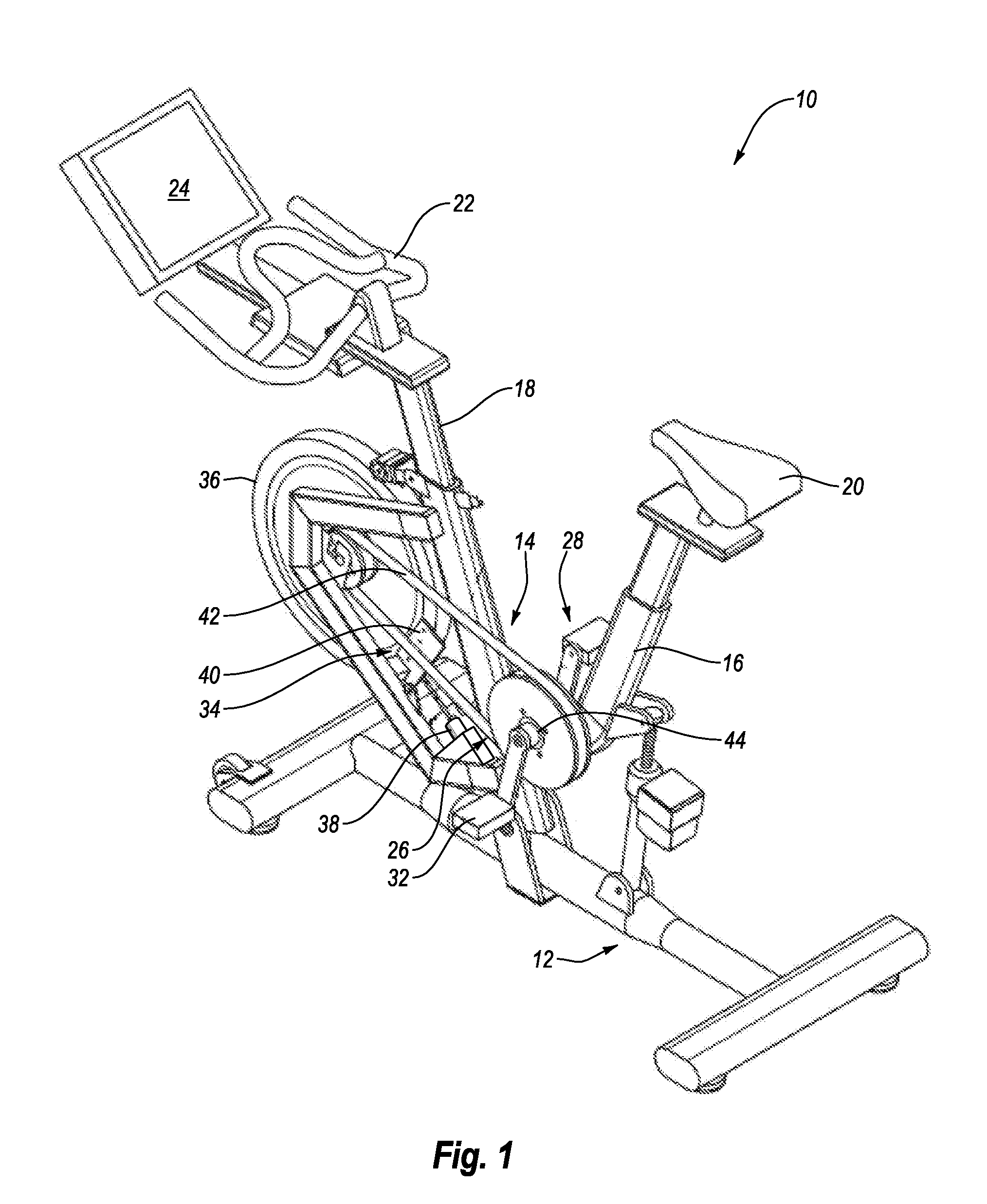
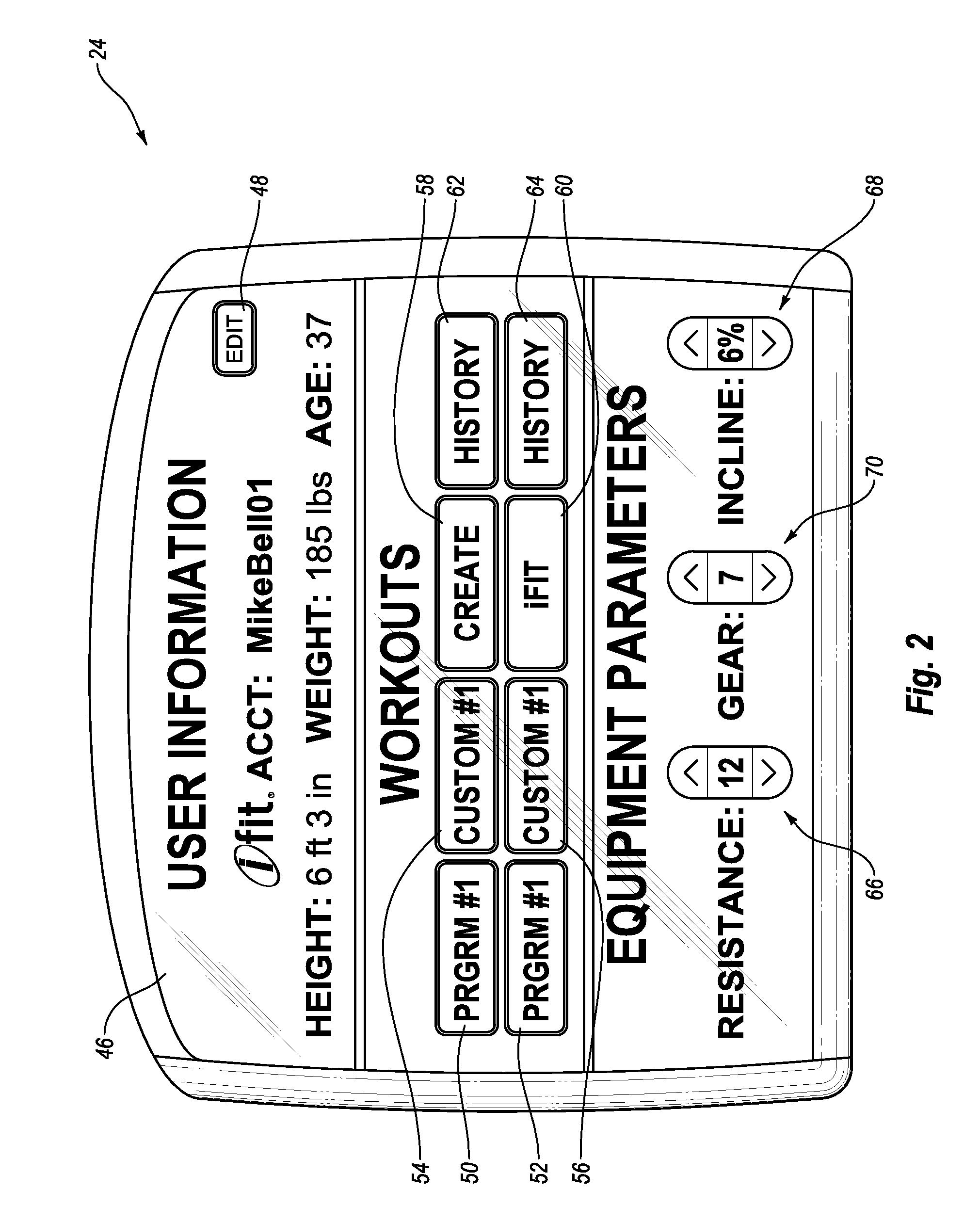
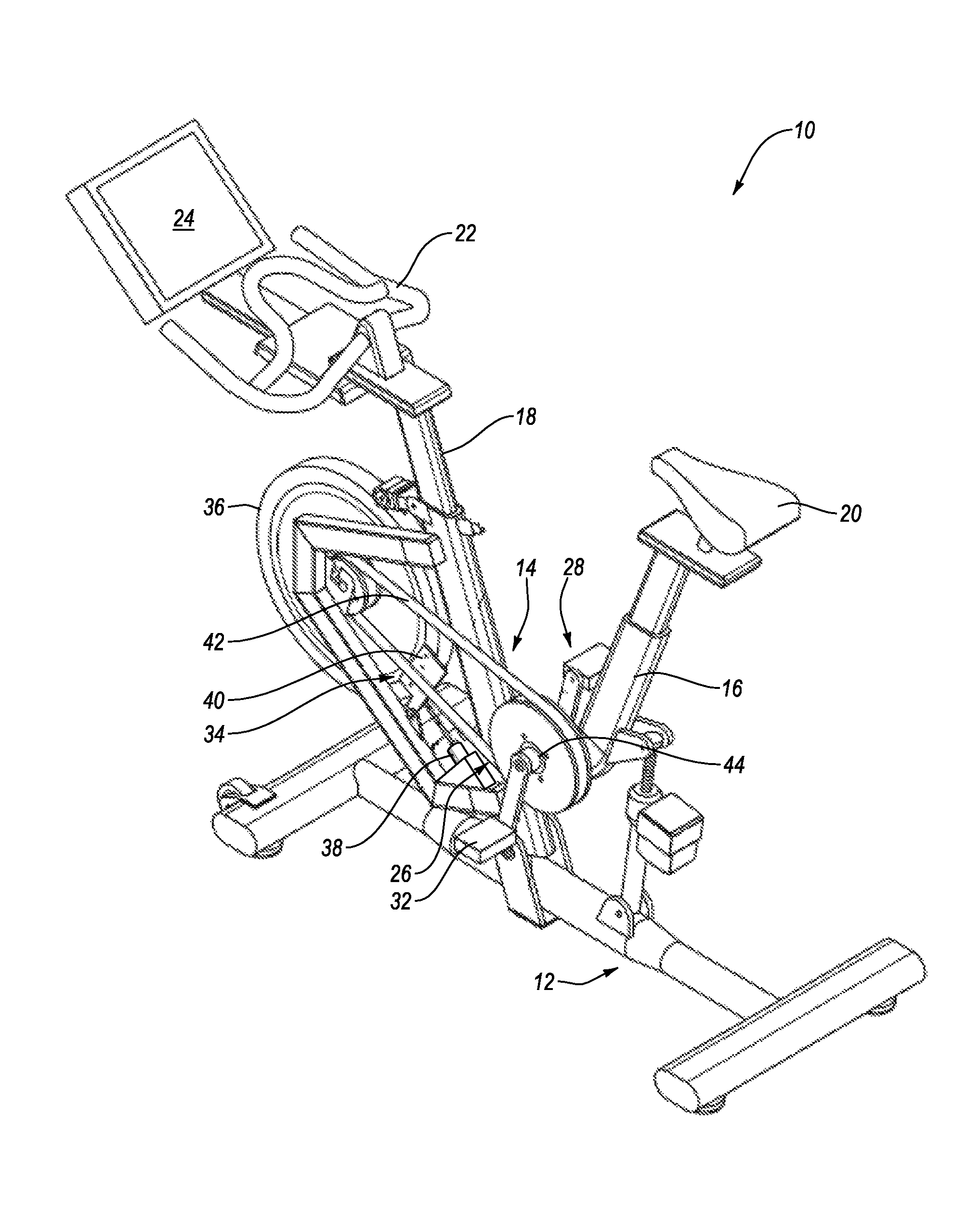
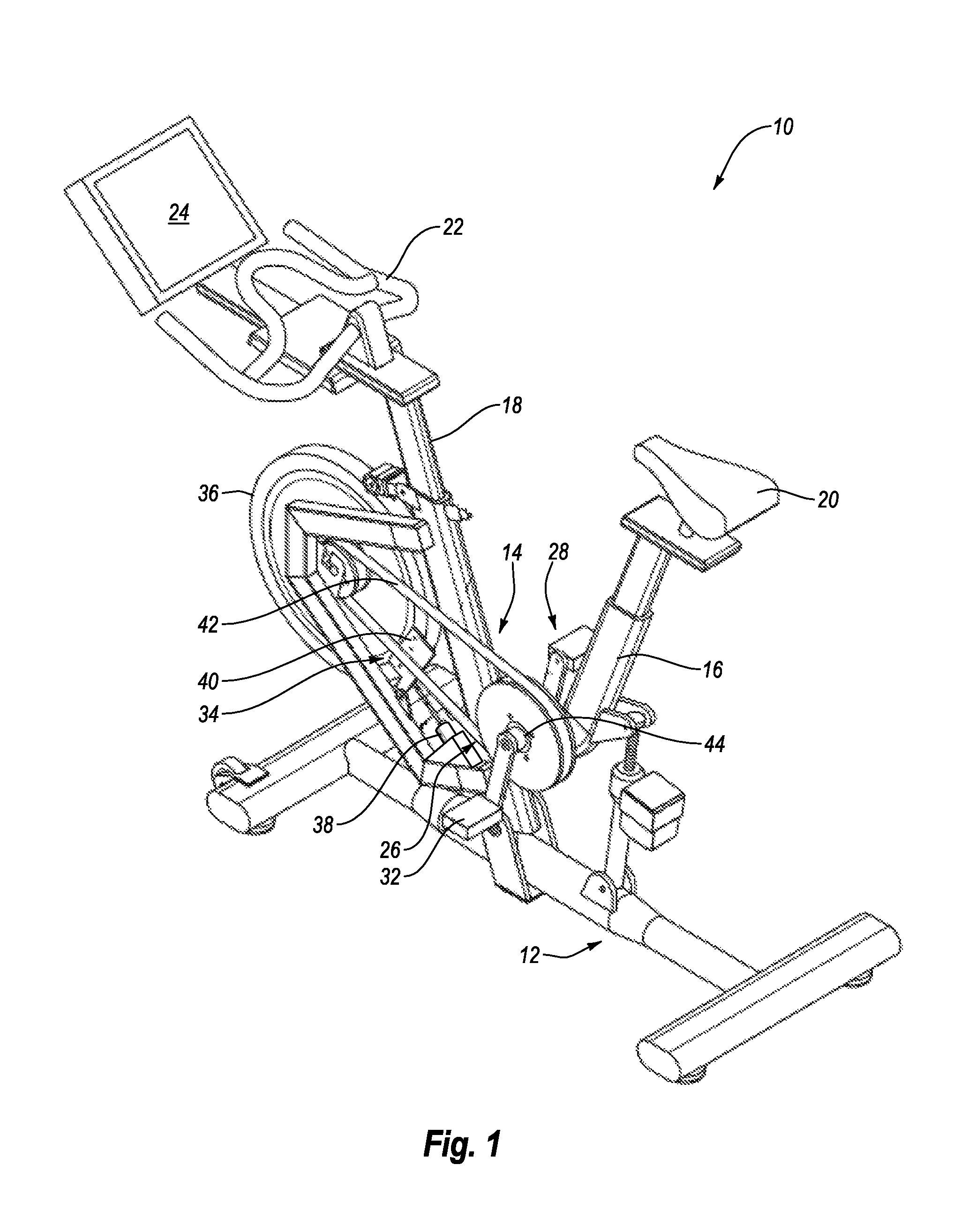
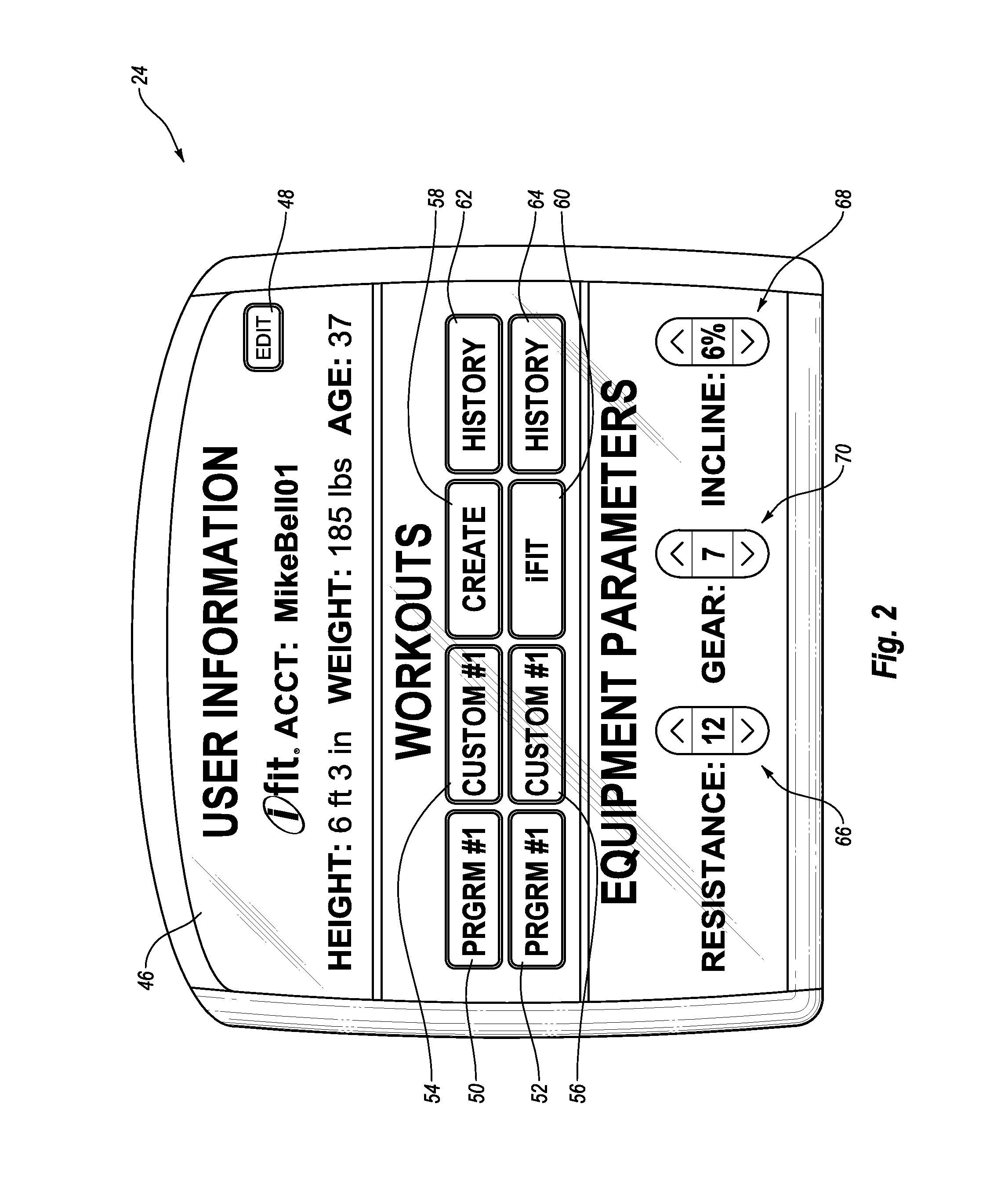
System and Method for Simulating Environmental Conditions on an Exercise Bicycle
A stationary exercise cycle includes a simulation system for simulating real-world terrain based on environmental and other real-world conditions. Using topographical or other data, an actual location can be simulated. The exercise cycle may include a resistance mechanism that is adjusted based on changes in simulated slope, and by amounts simulating actual frictional and gravitational forces. The simulated speed of the rider, as well as speed and direction of a simulated wind, are used to determine a simulated air speed. Based on the simulated air speed, the simulation system determines the simulated air resistance hindering the rider, and changes reflective of the simulated air resistance are made by the resistance mechanism. The stationary exercise cycle takes into account actual or approximate physical information of the user in determining the real-world conditions that are simulated, including the height, weight, shape, and / or rising position of the rider.
Owner:IFIT INC
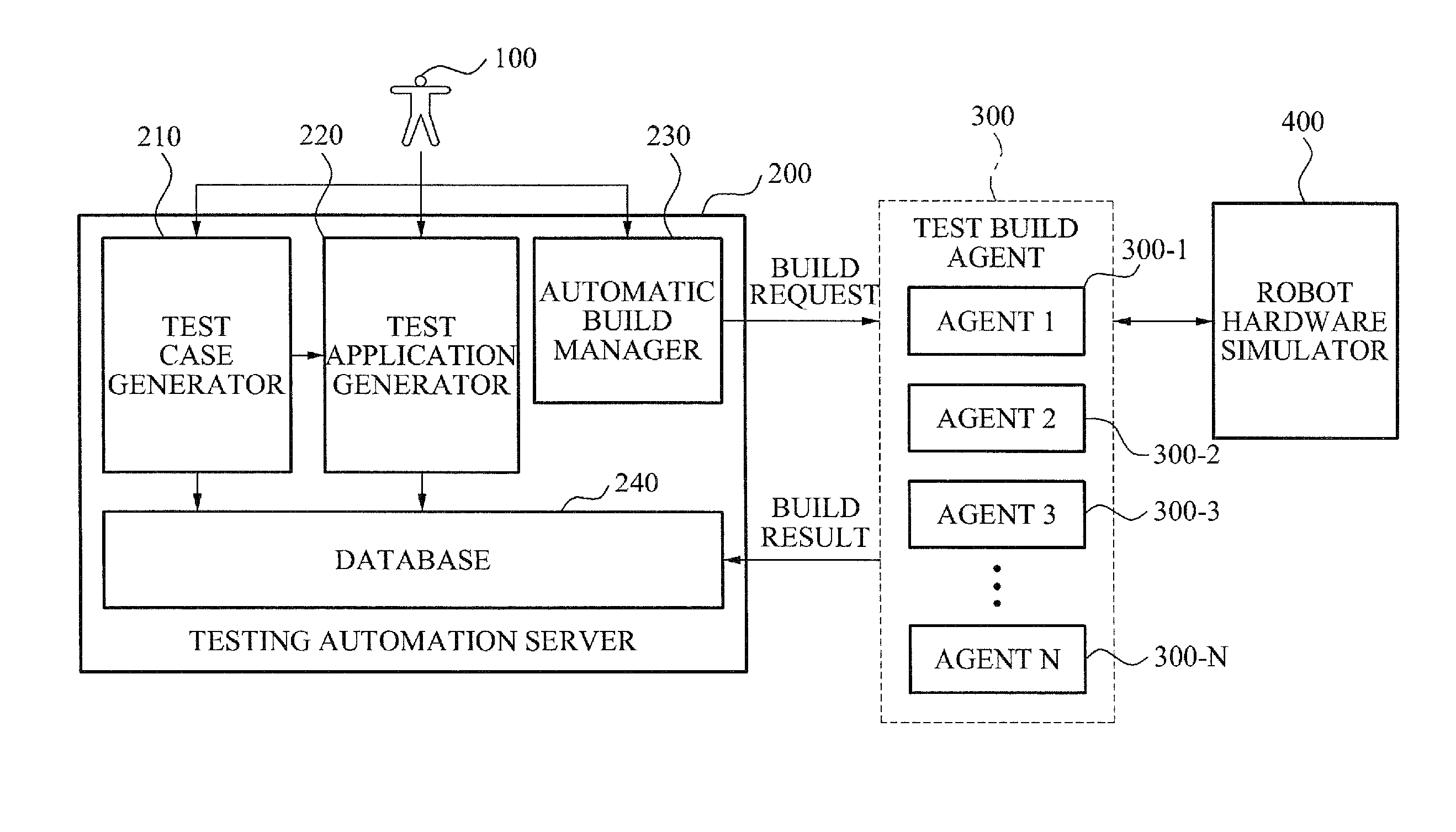
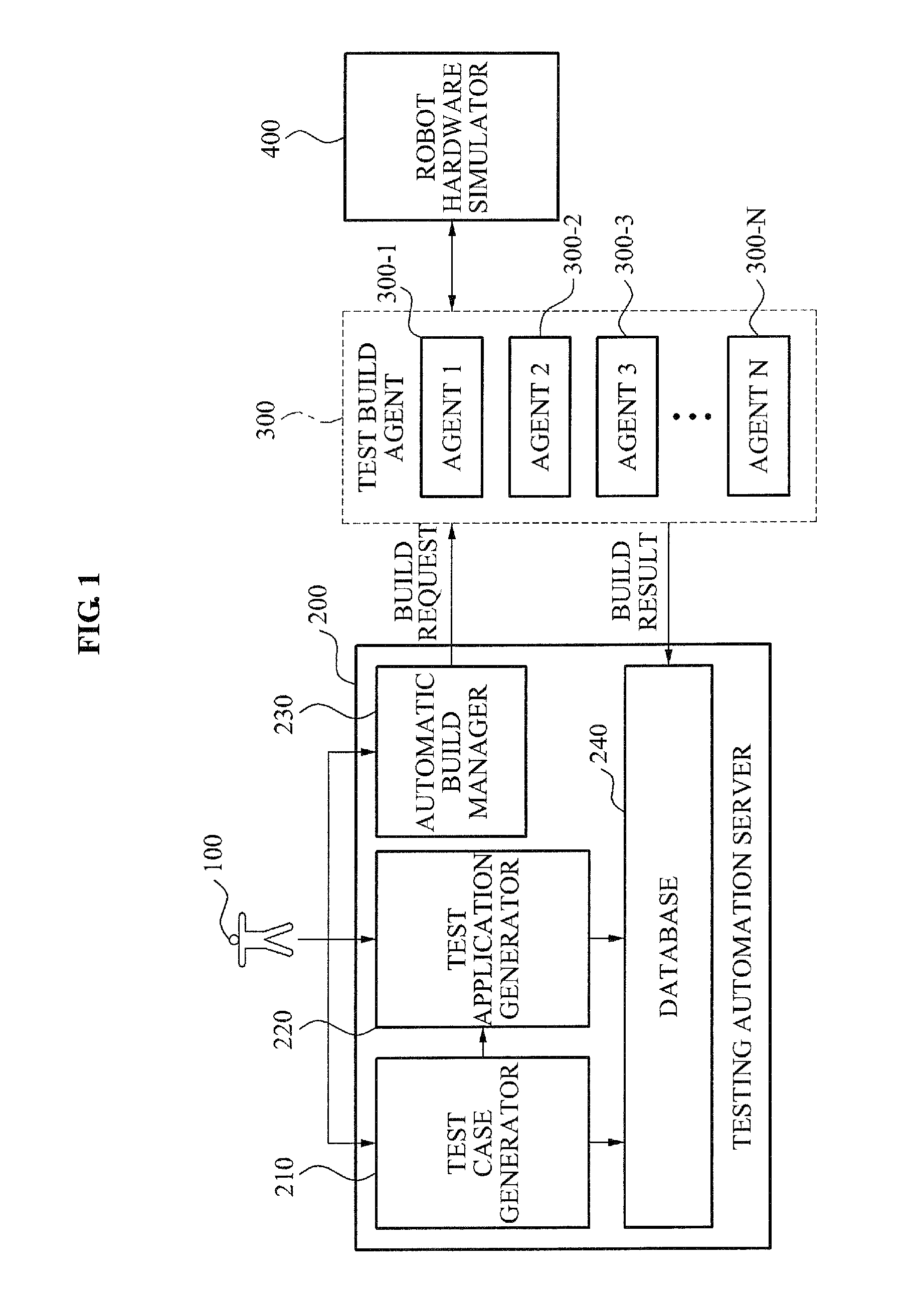
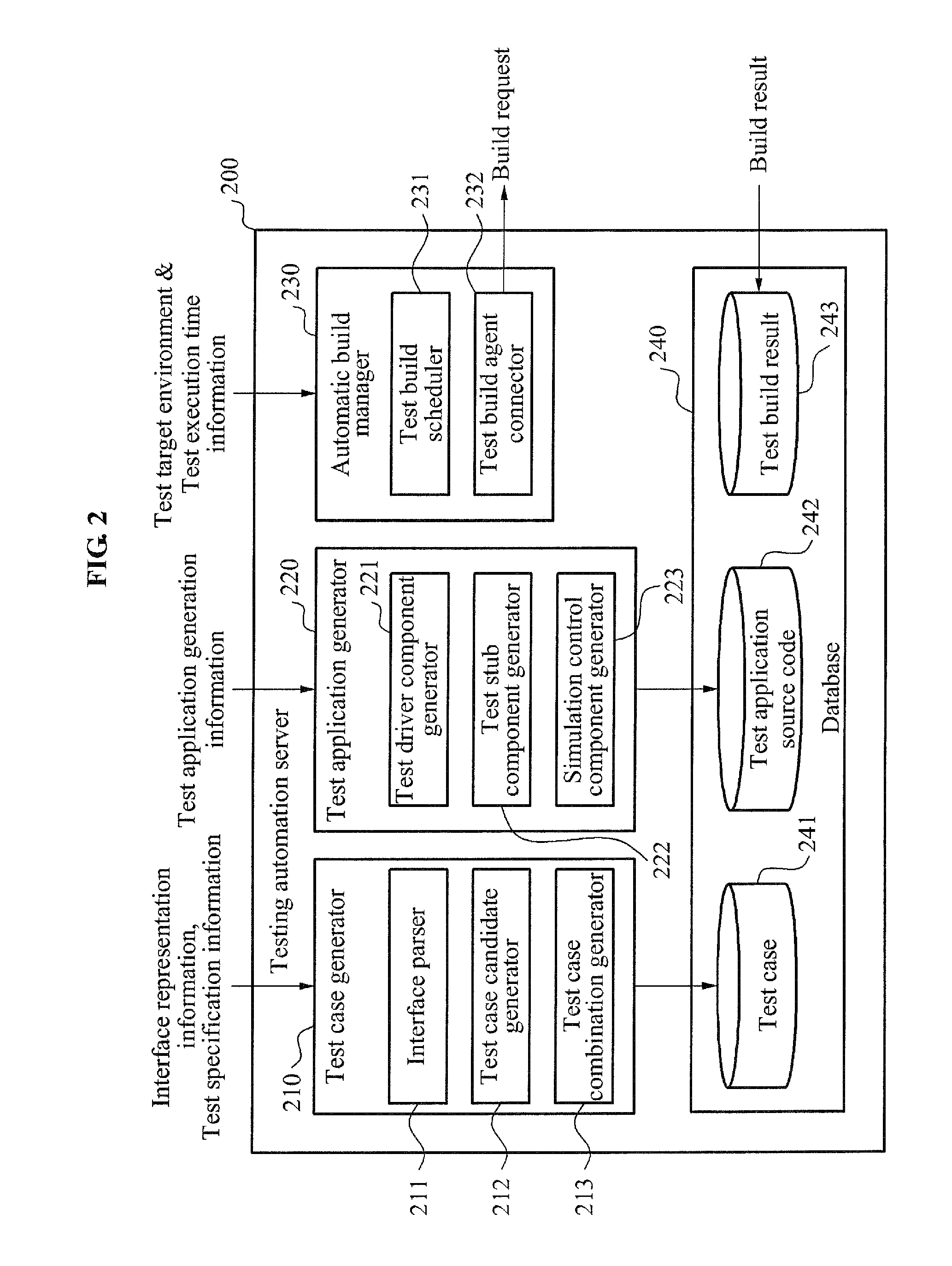
Simulation-based interface testing automation system and method for robot software components
InactiveUS20110307860A1Efficient executionError detection/correctionSpecific program execution arrangementsComputer hardwareSimulation based
A testing tool for verifying a reliability of robot software components is provided, and more particularly, a simulation-based interface testing automation system and method that may automatically perform a test for functions and performance of an interface with respect to robot software components are provided. Thus, it is possible to efficiently perform a test for an interface of robot software components. In particular, it is possible to automatically generate test cases required for testing, to perform a test in various languages, and to perform a test suitable for a robot.
Owner:KNU IND COOPERATION FOUND
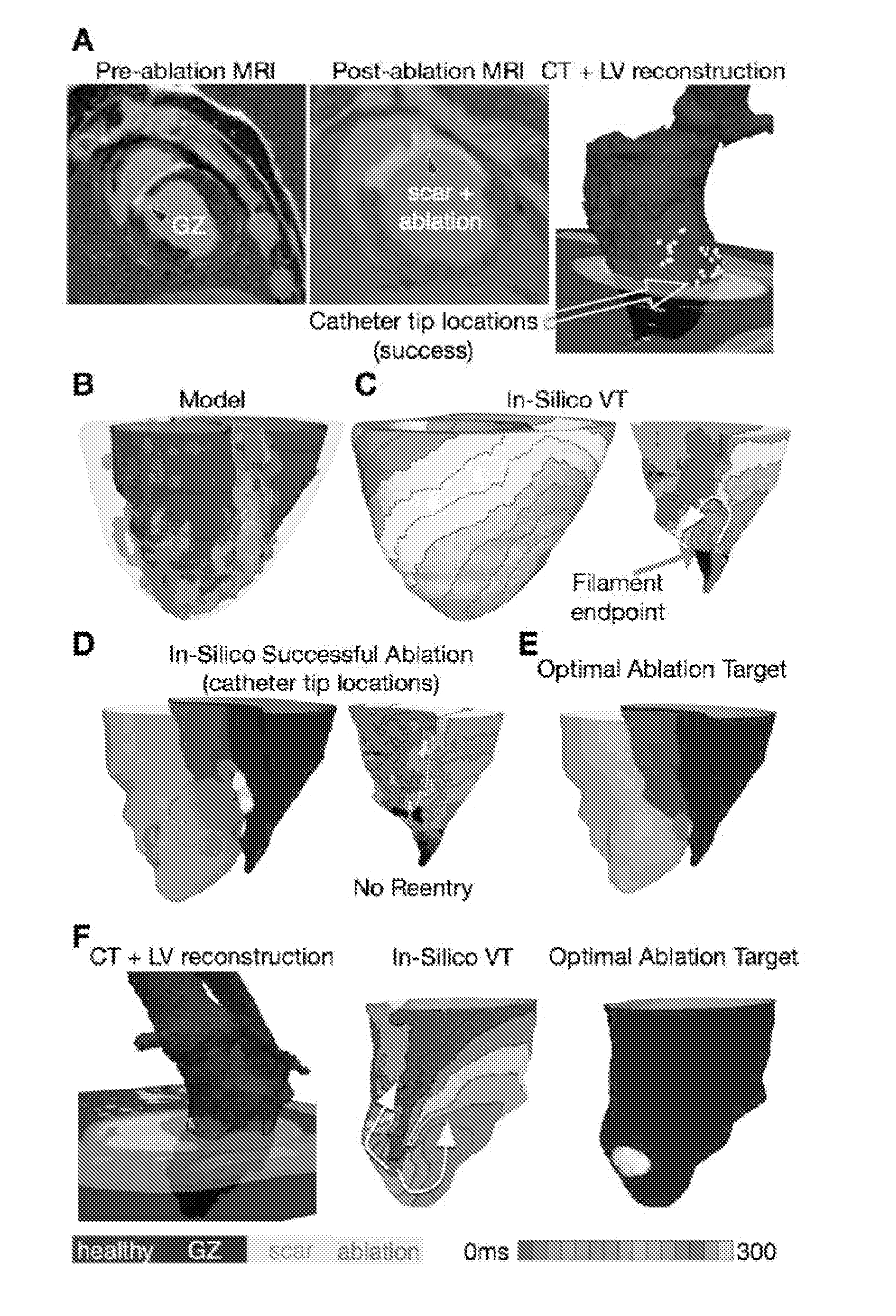
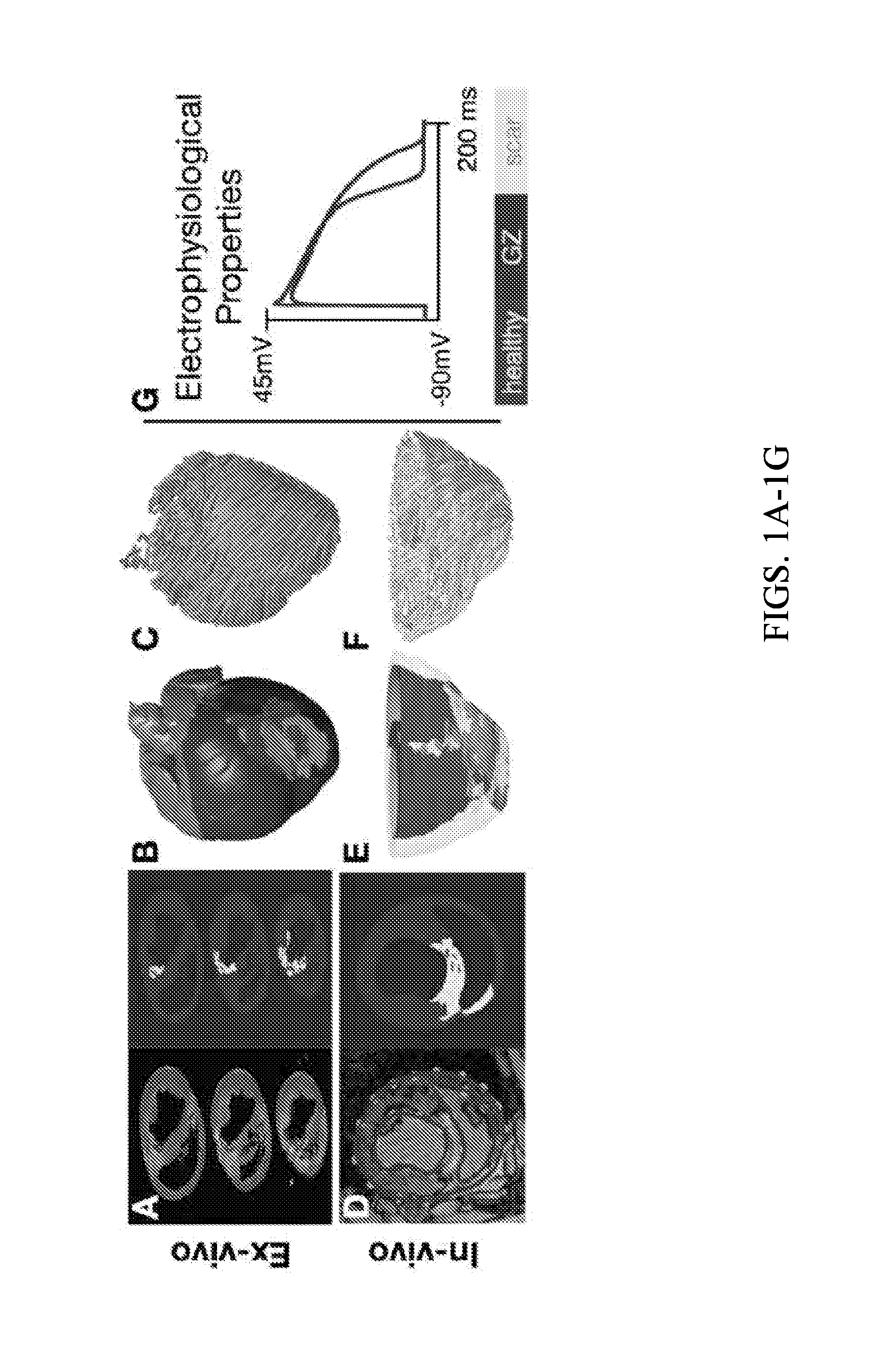
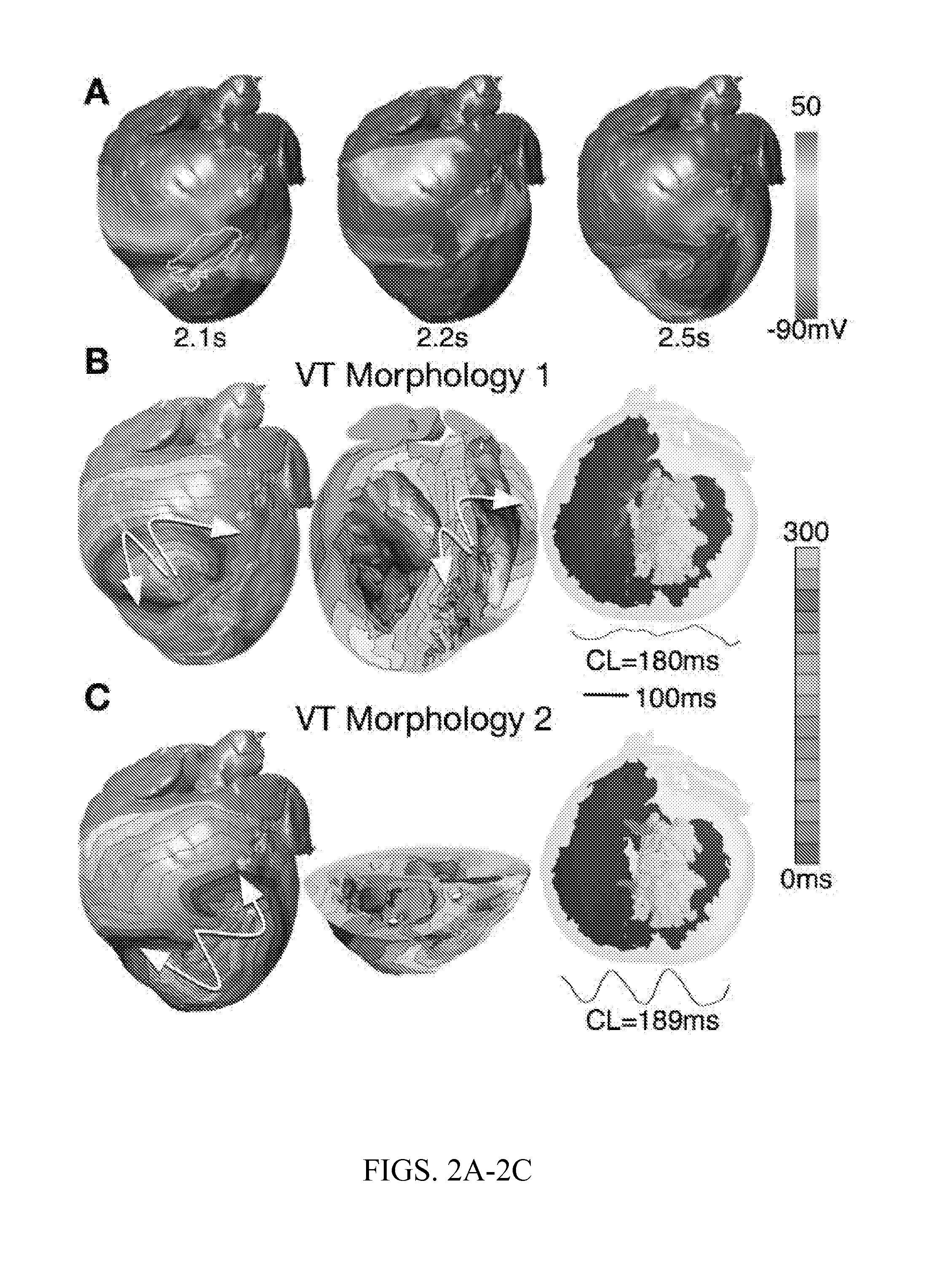
System and method for planning a patient-specific cardiac procedure
ActiveUS20140088943A1Ultrasonic/sonic/infrasonic diagnosticsMedical imagingSimulation basedElectrophysiology
A method of planning a patient-specific cardiac procedure according to an embodiment of the current invention includes receiving three-dimensional imaging data of a patient's heart, simulating at least one of electrophysiological or electromechanical activity of at least a portion of the patient's heart using the three-dimensional imaging data, and planning the patient-specific cardiac procedure based on the simulating. The cardiac procedure is for providing a preselected alteration of at least one of electrophysiological or electromechanical behavior of the patient's heart.
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE
System and method for simulating environmental conditions on an exercise bicycle
A stationary exercise cycle includes a simulation system for simulating real-world terrain based on environmental and other real-world conditions. Using topographical or other data, an actual location can be simulated. The exercise cycle may include a resistance mechanism that is adjusted based on changes in simulated slope, and by amounts simulating actual frictional and gravitational forces. The simulated speed of the rider, as well as speed and direction of a simulated wind, are used to determine a simulated air speed. Based on the simulated air speed, the simulation system determines the simulated air resistance hindering the rider, and changes reflective of the simulated air resistance are made by the resistance mechanism. The stationary exercise cycle takes into account actual or approximate physical information of the user in determining the real-world conditions that are simulated, including the height, weight, shape, and / or rising position of the rider.
Owner:IFIT INC
Simplified modeling software interface and method
InactiveUS6904399B2Reduce complexityReduce of knowledgeDigital data processing detailsAnti-theft devicesModeling softwareSimulation based
Disclosed is a simulation based environment that allows a product based engineer, with a modest understanding of complex software programs, to use complex math models. The system provides an interface by which basic component models can be used within the simulation. Allowances are made for particular variables to be adaptable by the product based engineer.
Owner:TNO MADYMO NORTH AMERICA +1
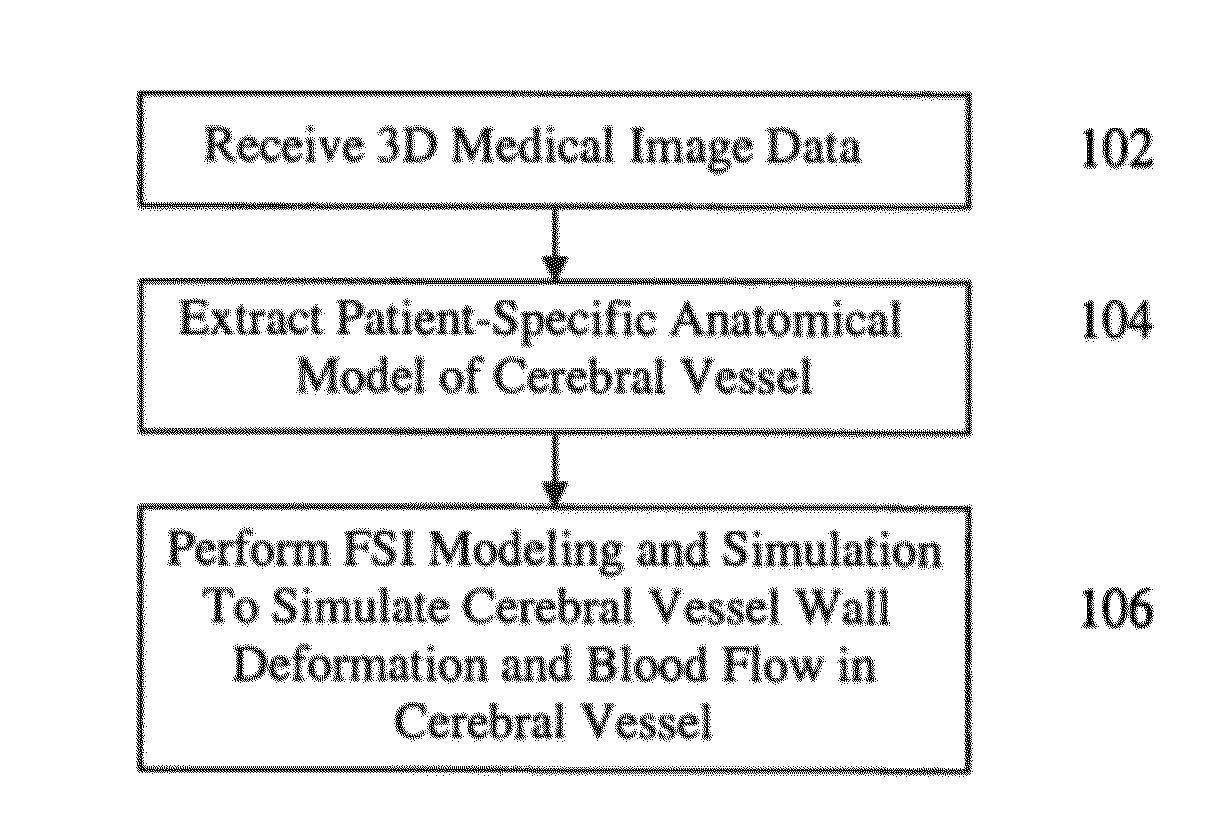
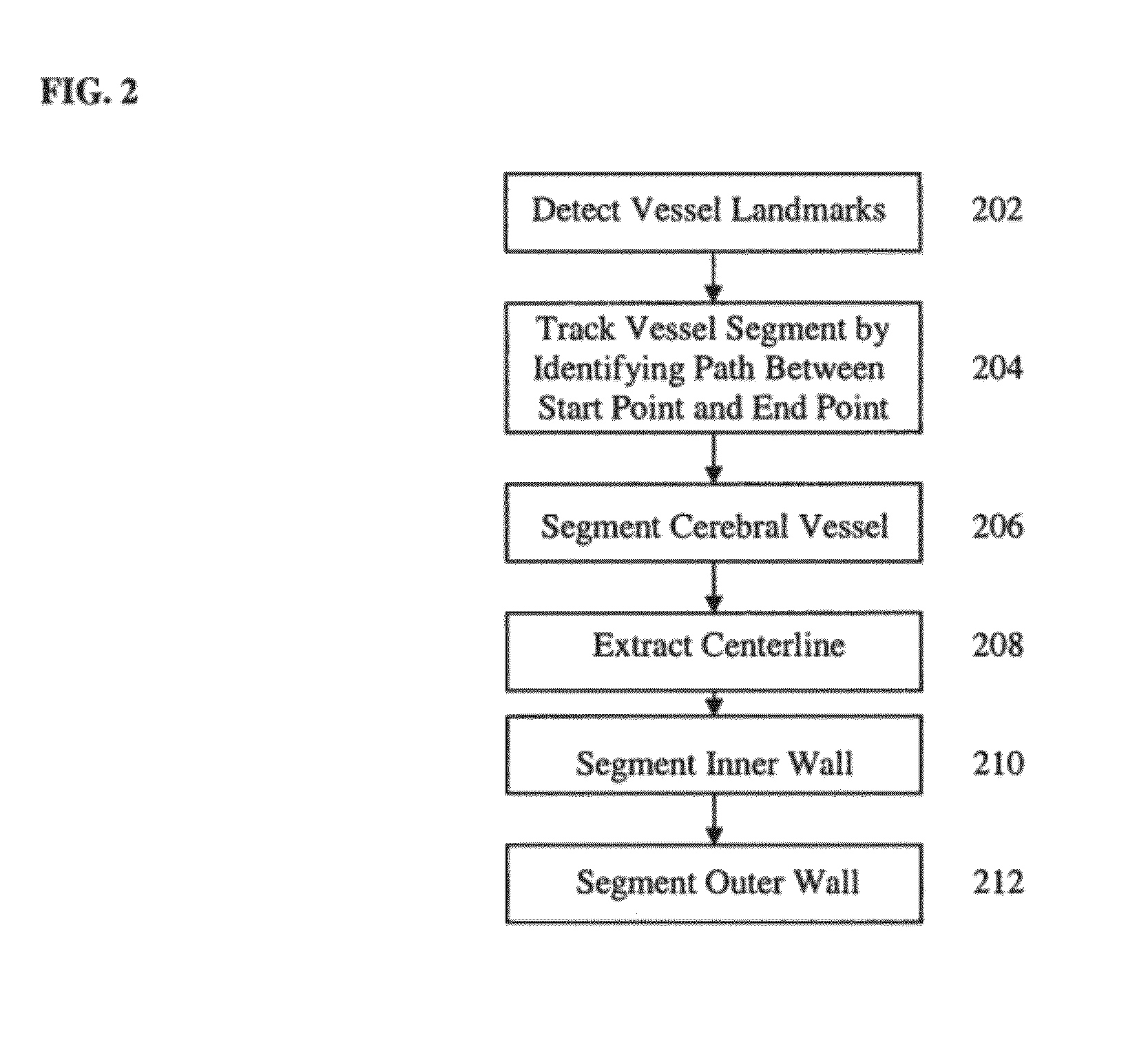
Method and System for Patient-Specific Computational Modeling and Simulation for Coupled Hemodynamic Analysis of Cerebral Vessels
ActiveUS20120203530A1Medical simulationAnalogue computers for distribution networksRadiologySimulation based
A method and system for patient-specific computational modeling and simulation for coupled hemodynamic analysis of cerebral vessels is disclosed. An anatomical model of a cerebral vessel is extracted from 3D medical image data. The anatomical model of the cerebral vessel includes an inner wall and an outer wall of the cerebral vessel. Blood flow in the cerebral vessel and deformation of the cerebral vessel wall are simulated using coupled computational fluid dynamics (CFD) and computational solid mechanics (CSM) simulations based on the anatomical model of the cerebral vessel.
Owner:SIEMENS HEATHCARE GMBH
Simulation-based functional verification of microcircuit designs
InactiveUS7130783B1Shorten the timeConfidenceDetecting faulty computer hardwareAnalogue computers for electric apparatusTest designFormal methods
System, methods, and apparatus for verifying microcircuit designs by interleaving between random and formal simulation techniques to identify input traces useful for driving designs under test into sequences of device states. In a method aspect the invention provides process for beginning random simulation of a sequence of states of a microcircuit design by inputting a sequence of random input vectors to a design under test model in order to obtain a sequence of random simulation states; monitoring a simulation coverage progress metric to determine a preference for switching from random simulation to formal methods of simulating states in the design under test; beginning formal simulation of states in the design under test and monitoring a formal coverage progress metric to determine a preference for resuming random simulation of states of said microcircuit design; and resuming random simulation. Preferably the process of interleaving simulation methods continues until an input vector suitable for driving the design under test model into each of a set of previously-identified goal states has been obtained.
Owner:SYNOPSYS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com