Patents
Literature
14970results about "Multiprogramming arrangements" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Apparatus and system for efficient delivery and deployment of an application
InactiveUS6393605B1Digital computer detailsMultiprogramming arrangementsClient-sideApplication software
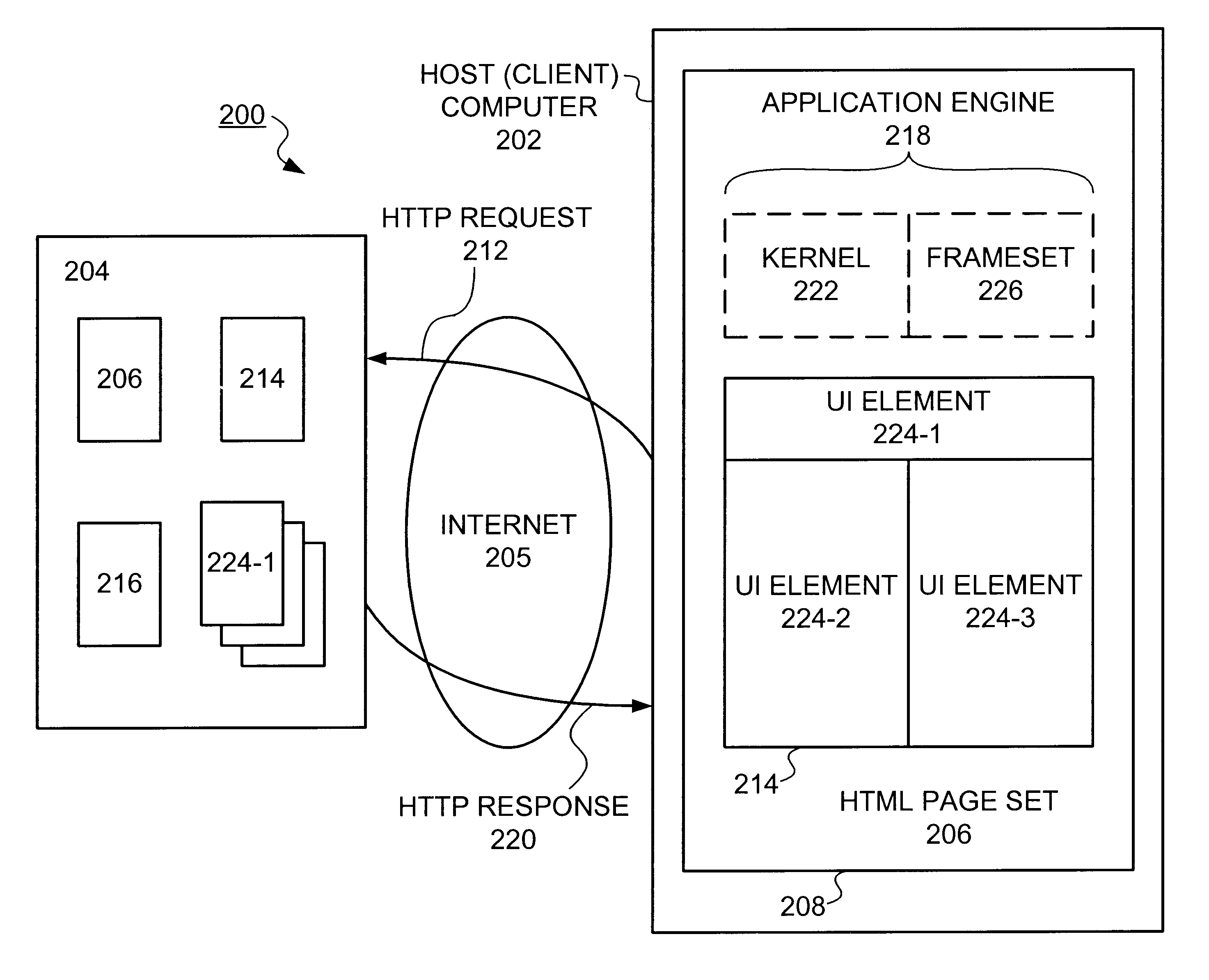
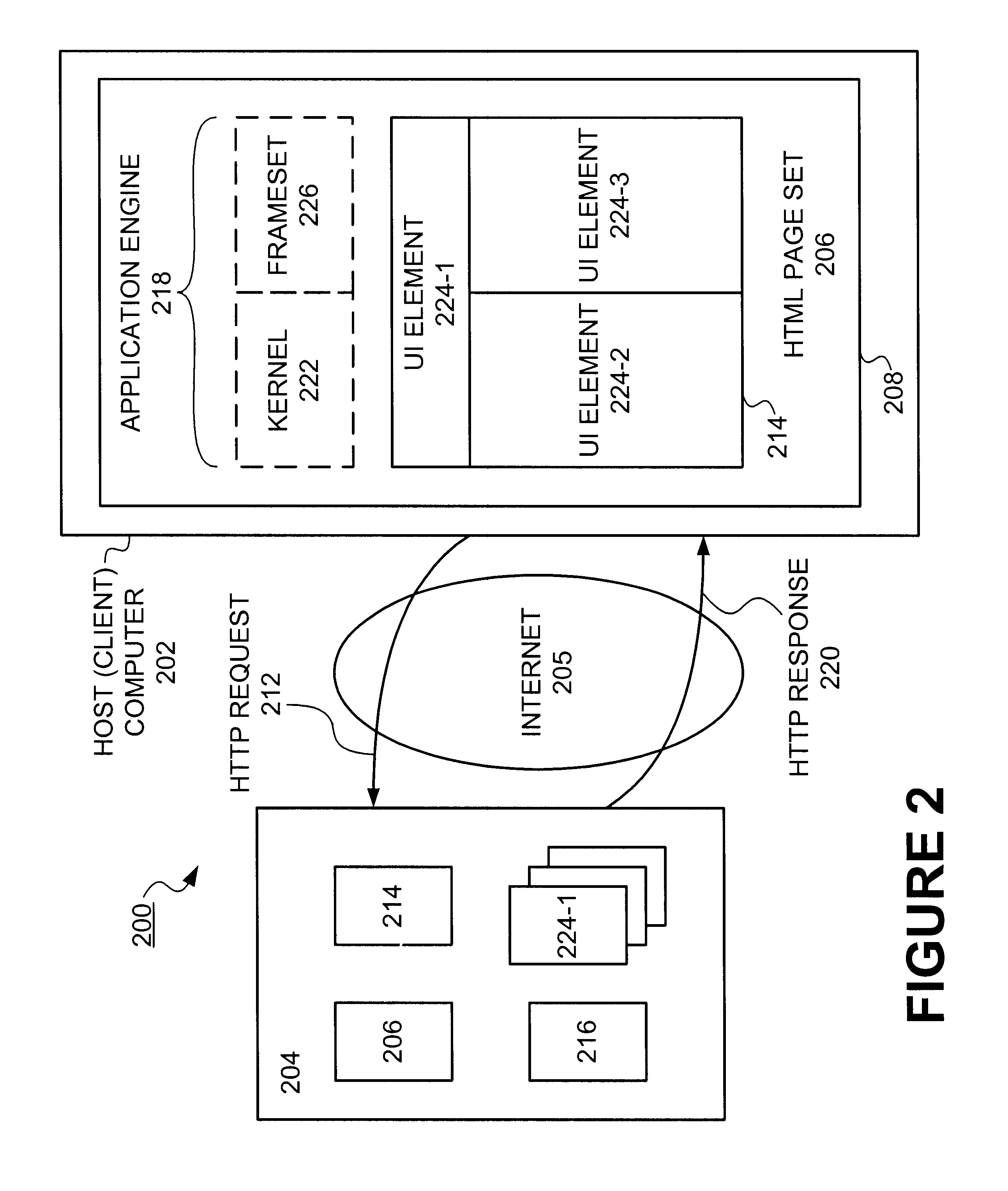
Methods and apparatus for deploying a generic application engine in a browser program executing on a client platform are described. As a method, an application engine kernel is formed in the browser program that is independent of the client platform and the browser program concurrently with loading user interface (UI) components and corresponding data components associated with the application engine. A minimum required subset of application engine components are then loaded by the kernel in order to process any initial user requests.
Owner:ORACLE INT CORP
Adaptive pattern recognition based control system and method
InactiveUS6400996B1Minimize timeEasy to implementError preventionFrequency-division multiplex detailsData streamSmart house
An adaptive interface for a programmable system, for predicting a desired user function, based on user history, as well as machine internal status and context. The apparatus receives an input from the user and other data. A predicted input is presented for confirmation by the user, and the predictive mechanism is updated based on this feedback. Also provided is a pattern recognition system for a multimedia device, wherein a user input is matched to a video stream on a conceptual basis, allowing inexact programming of a multimedia device. The system analyzes a data stream for correspondence with a data pattern for processing and storage. The data stream is subjected to adaptive pattern recognition to extract features of interest to provide a highly compressed representation that may be efficiently processed to determine correspondence. Applications of the interface and system include a video cassette recorder (VCR), medical device, vehicle control system, audio device, environmental control system, securities trading terminal, and smart house. The system optionally includes an actuator for effecting the environment of operation, allowing closed-loop feedback operation and automated learning.
Owner:BLANDING HOVENWEEP
Methods and apparatus for interpreting user selections in the context of a relation distributed as a set of orthogonalized sub-relations
Owner:ORACLE INT CORP
Dynamically matching users for group communications based on a threshold degree of matching of sender and recipient predetermined acceptance criteria
InactiveUS6480885B1Quality of communicationReduce in quantitySpecial service provision for substationMultiprogramming arrangementsPersonalizationWeb service
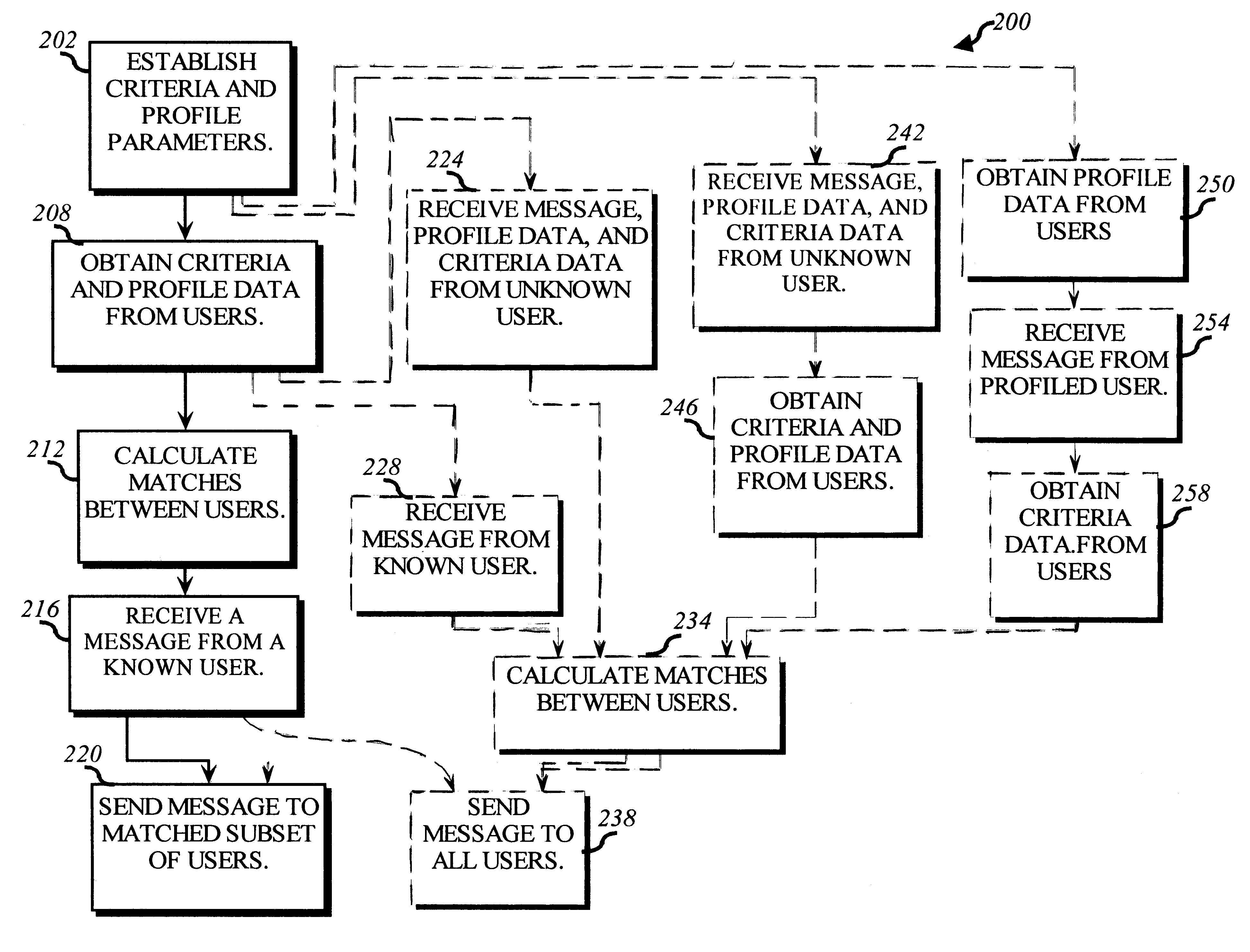
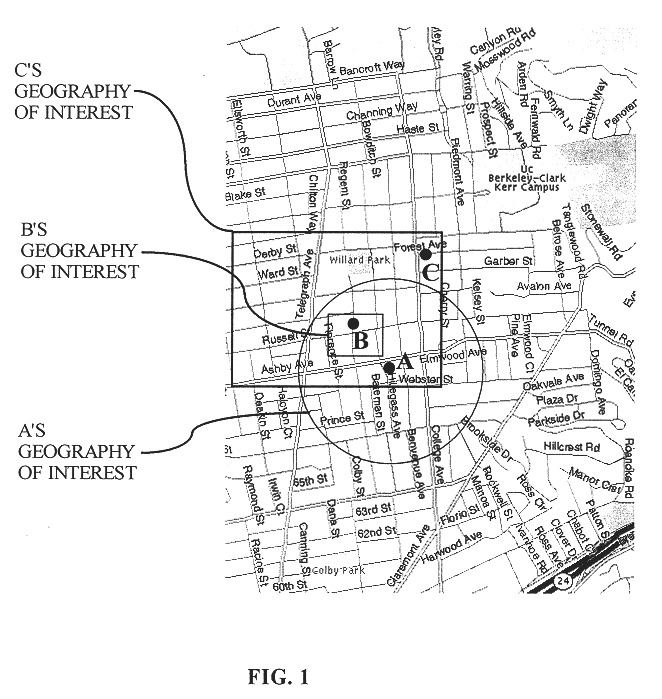
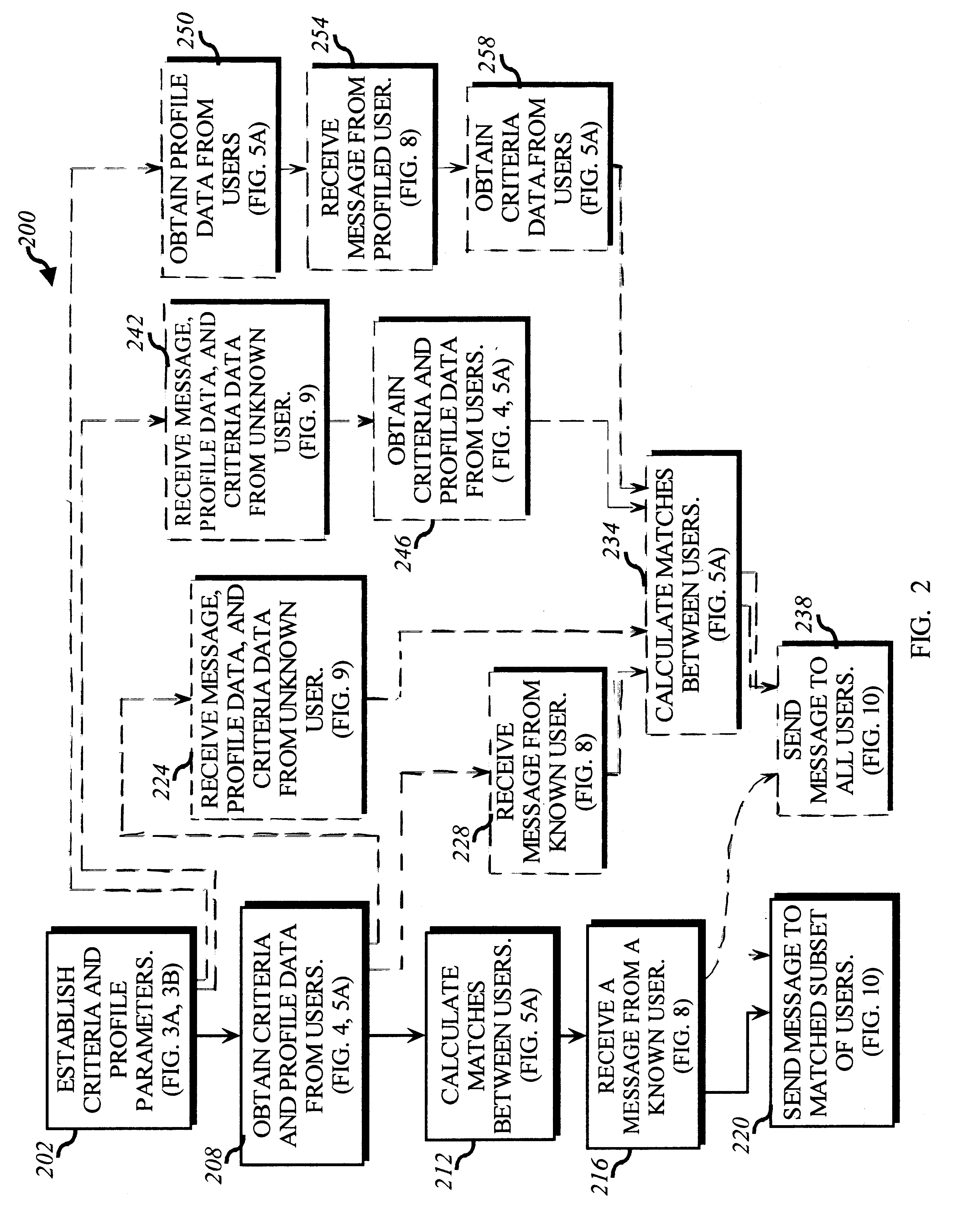
A method for enabling users to exchange group electronic mail by establishing individual profiles and criteria, for determining personalized subsets within a group. Users establish subscriptions to an electronic mailing list by specifying user profile data and acceptance criteria data to screen other users. When a user subscribes, a web server establishes and stores an individualized recipient list including each matching subscriber and their degree of one-way or mutual match with the user. When the user then sends a message to the mailing list, an email server retrieves 100% her matches and then optionally filters her recipient list down to a message distribution list using each recipient's message criteria. The message is then distributed to matching users. Additionally, email archives and information contributions from users are stored in a database. A web server creates an individualized set of web pages for a user from the database, containing contributions only from users in his recipient list. In other embodiments, users apply one-way or mutual criteria matching and message profile criteria to other group forums, such as web-based discussion boards, chat, online clubs, USENET newsgroups, voicemail, instant messaging, web browsing side channel communities, and online gaming rendezvous.
Owner:TUMBLEWEED HLDG LLC
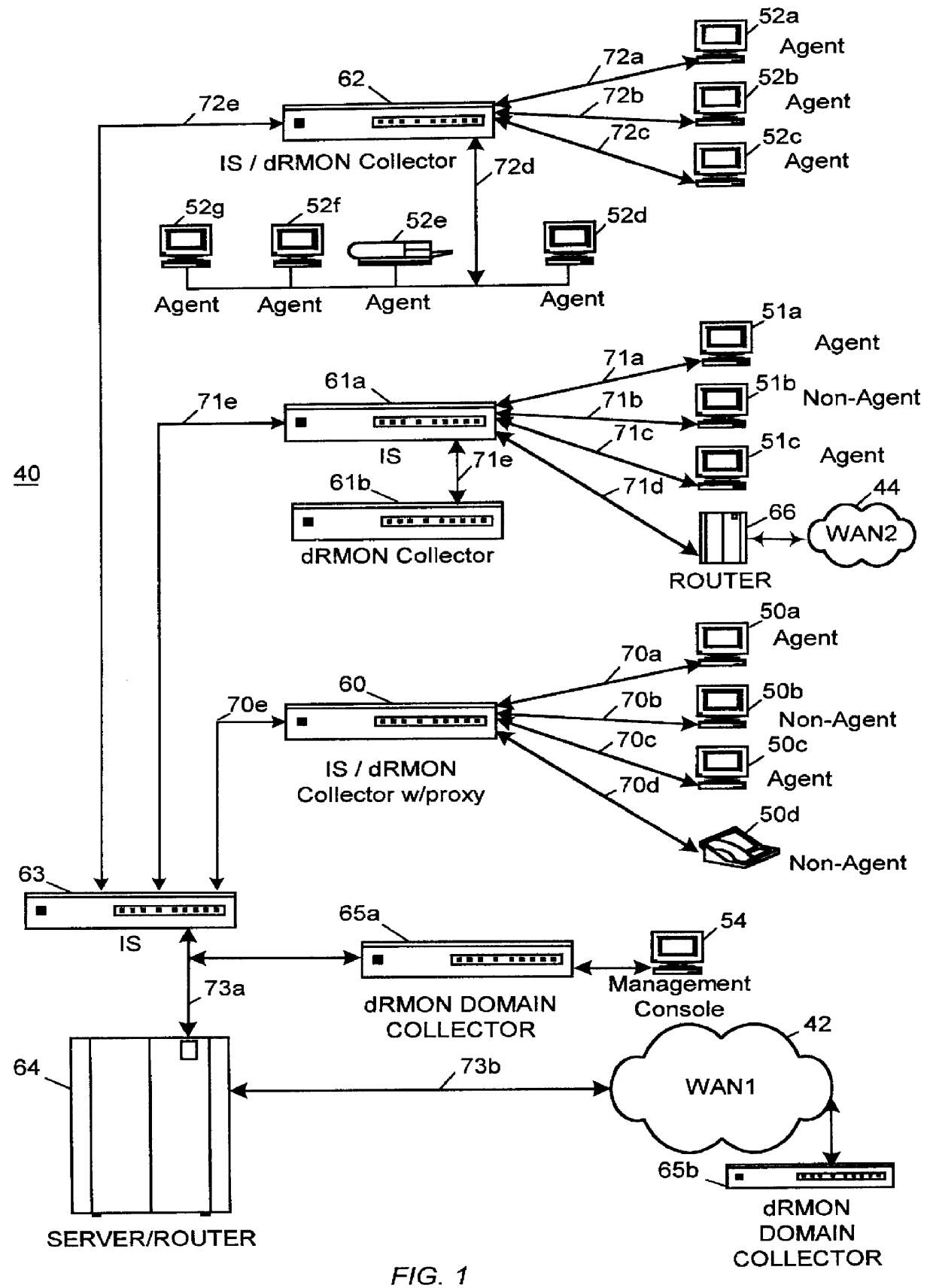
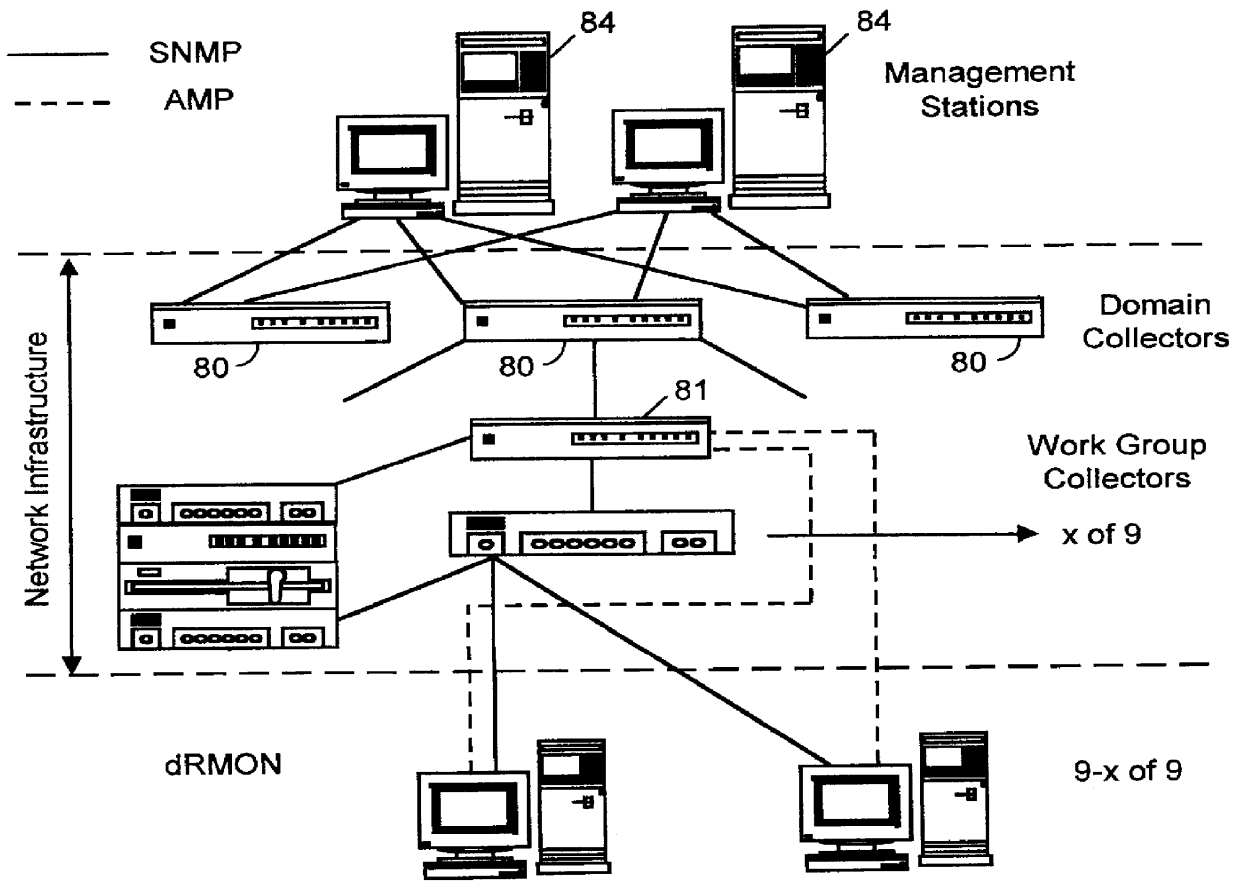
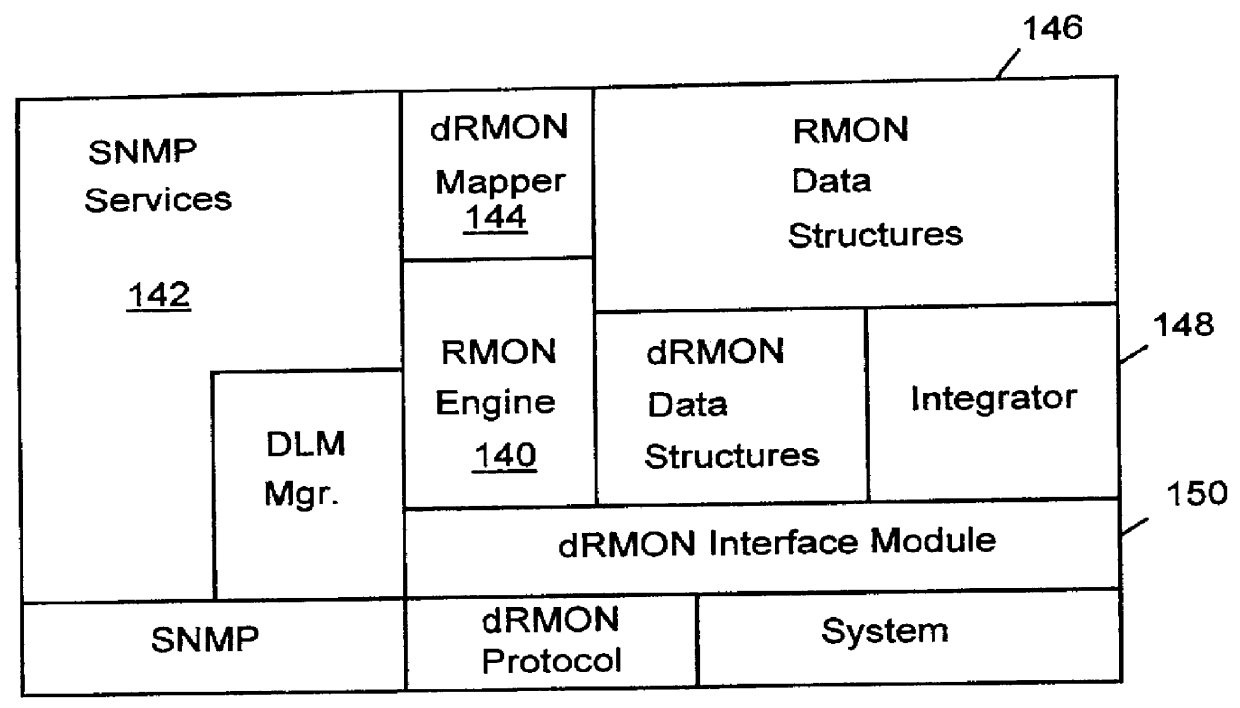
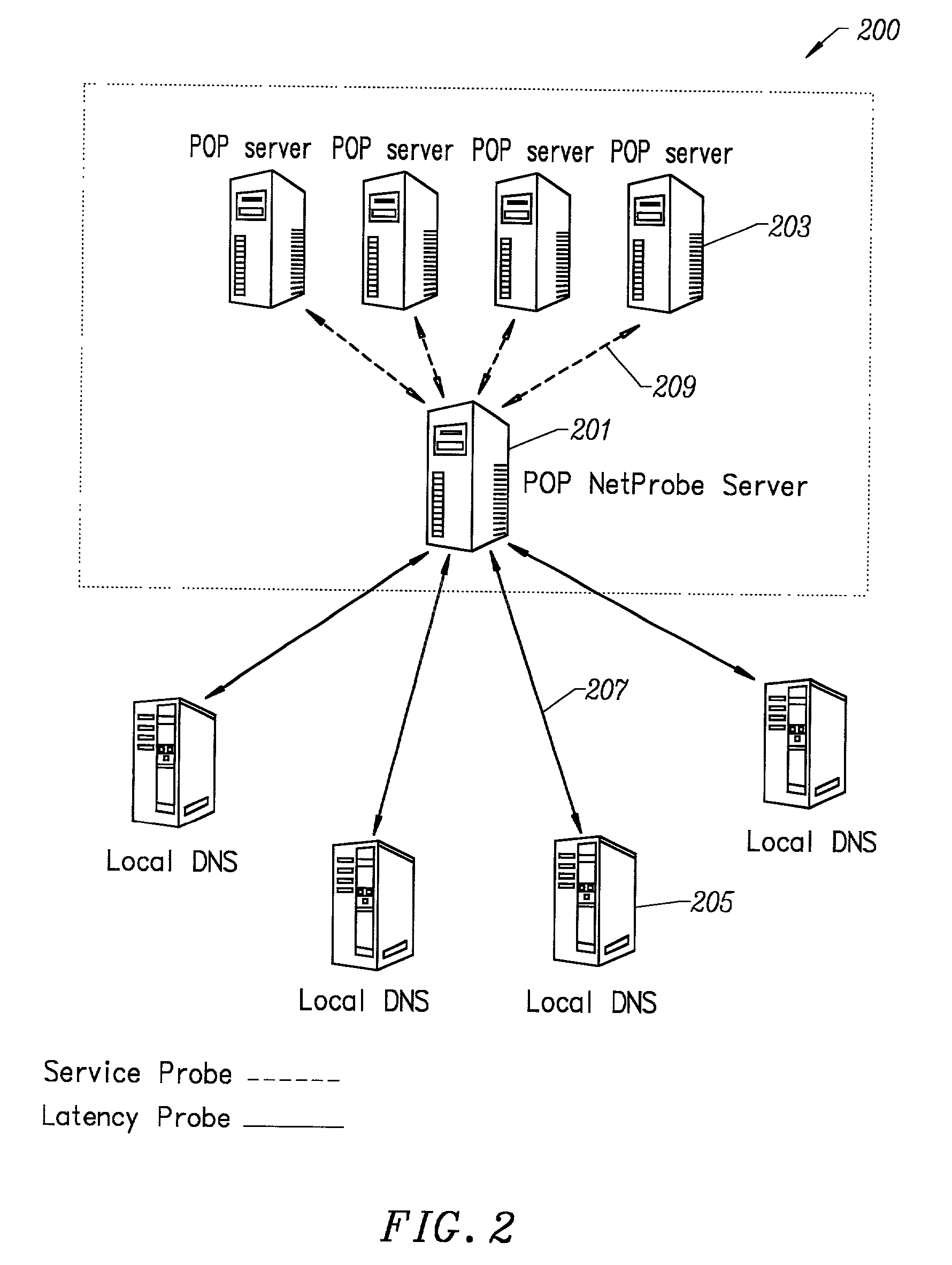
Distributed remote monitoring (dRMON) for networks
InactiveUS6108782AError preventionFrequency-division multiplex detailsNetwork operating systemOperational system
Distributed remote monitoring (dRMON) of network traffic and performance uses distributed nodes to collect traffic statistics at distributed points in the network. These statistics are forwarded to collectors which compile the statistics to create combined views of network performance. A collector may mimic a prior art, non-distributed, network probe and may interact with network management software as though it were a stand alone network probe thereby simplifying a user's interaction with the distributed system. The invention is designed to work in accordance with a variety of standard network management protocols including SNMP, RMON, and RMON2 but is not limited to those environments. The invention has applications in a variety of communication system environments including local area networks, cable television distribution systems, ATM systems, and advanced telephony systems. A specific embodiment of the invention solves is particularly optimized to work in LAN environments with end systems running under Windows-compatible network operating systems.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
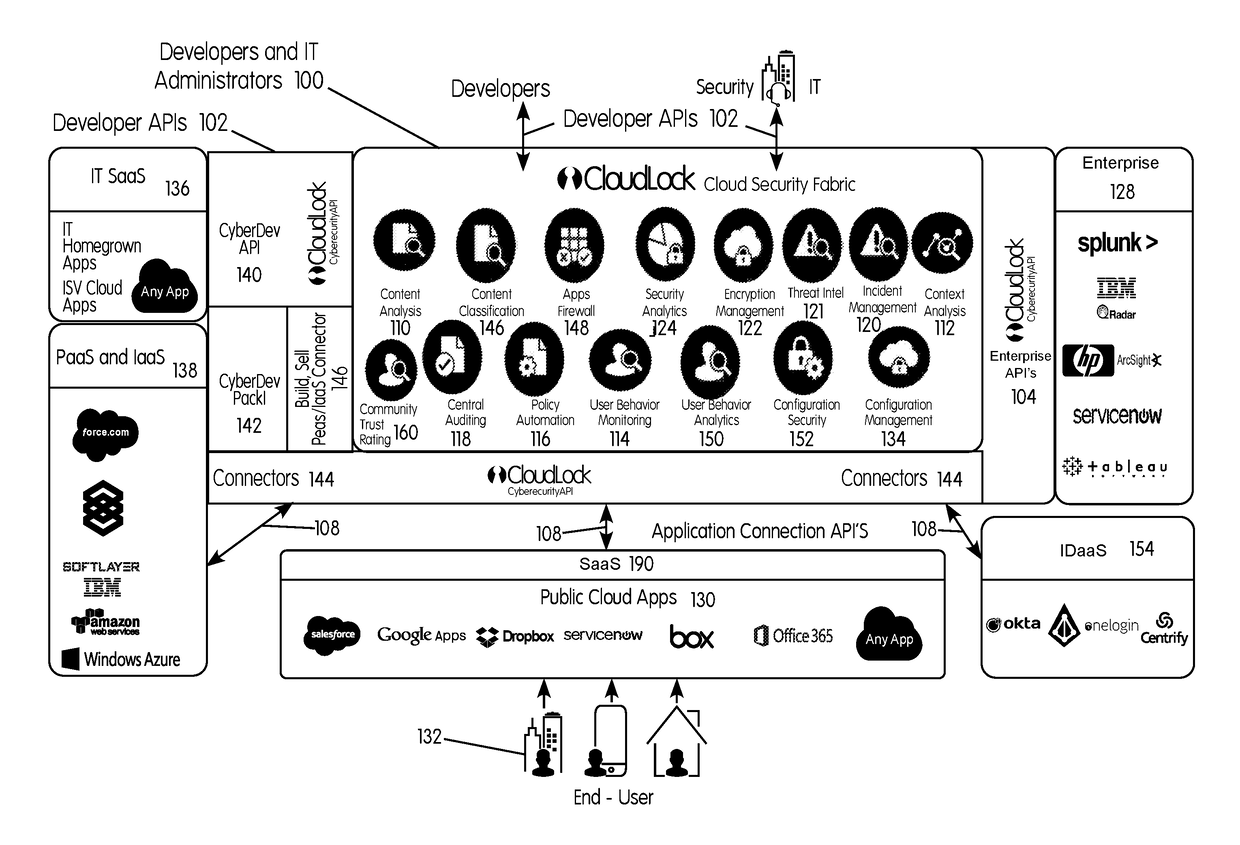
System and method for securing an enterprise computing environment
InactiveUS20180027006A1Process safetyKeep Content SafeMultiprogramming arrangementsComputer security arrangementsInternet privacyEnterprise computing
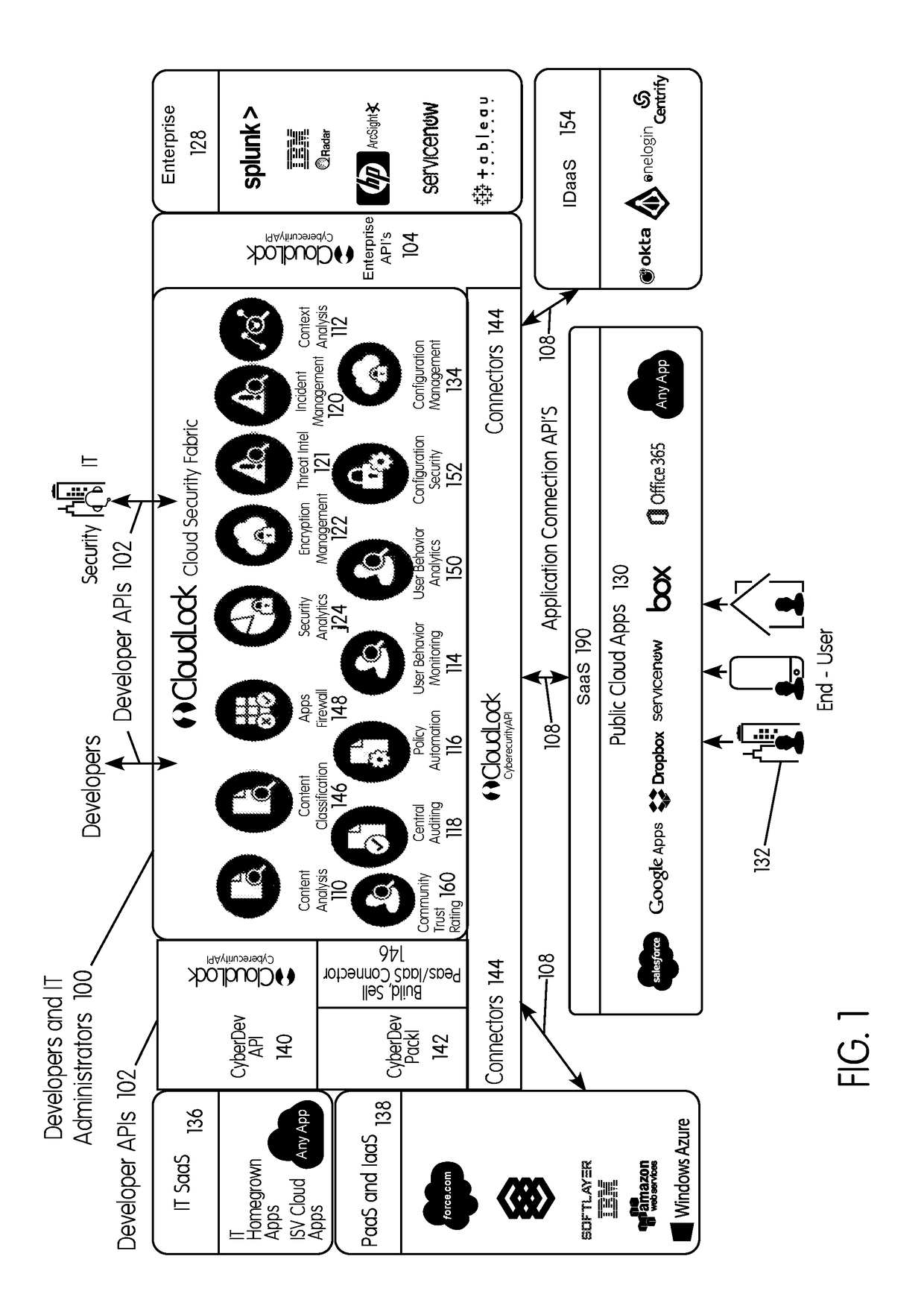
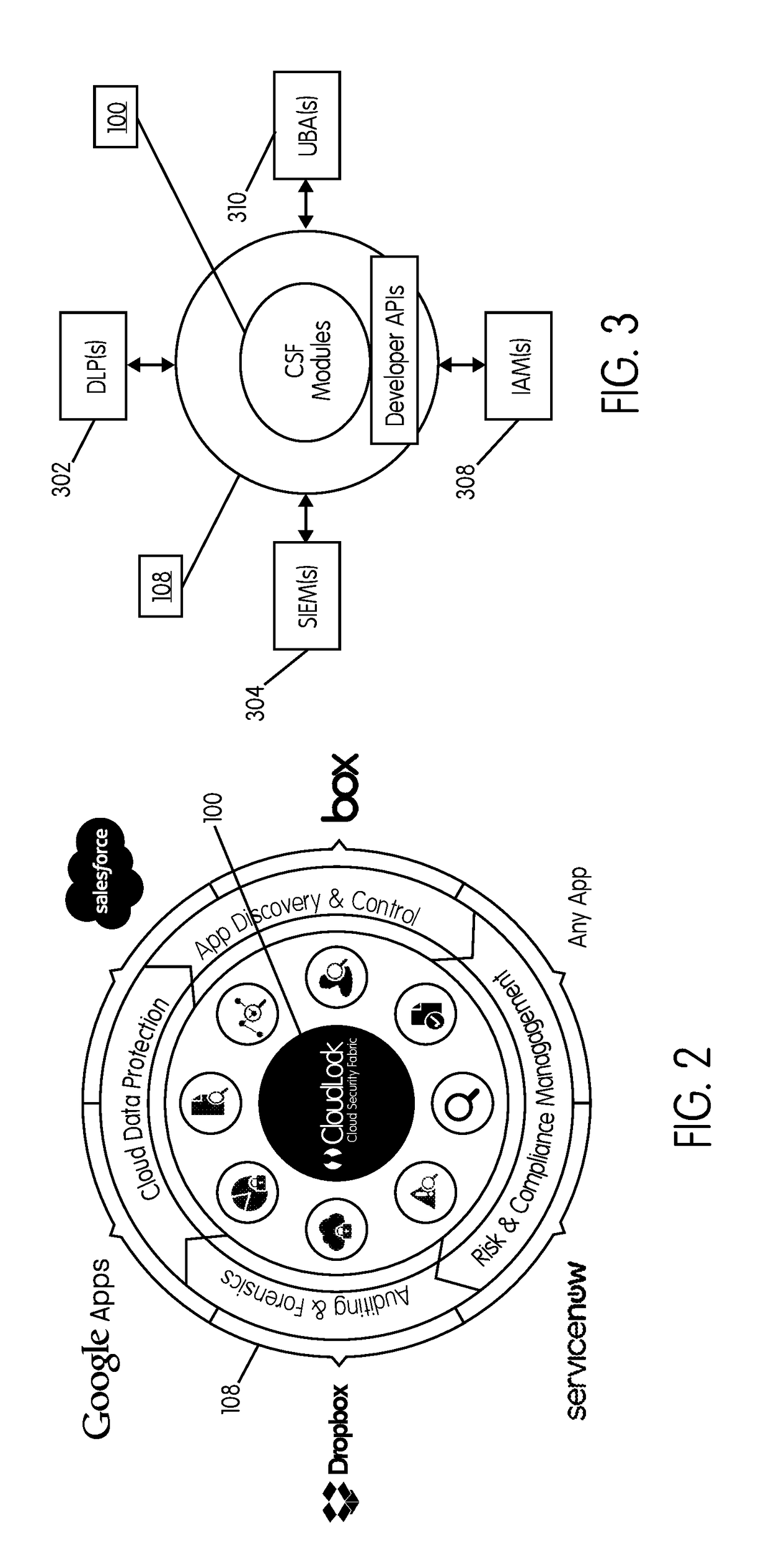
Methods and systems provided herein include a cyber intelligence system, a unified application firewall, and a cloud security fabric that has enterprise APIs for connecting to the information technology infrastructure of an enterprise, developer APIs 102 for enabling developers to access capabilities of the fabric and connector APIs by which the fabric may discover information about entities relevant to the information security of the enterprise (such as events involving users, applications, and data of the enterprise occurring on a plurality of cloud-enabled platforms, including PaaS / IaaS platforms), with various modules that comprise services deployed in the cloud security fabric, such as a selective encryption module, a policy creation and automation module, a content classification as a service module, and user and entity behavior analytics modules.
Owner:CLOUDLOCK
Multi-object fetch component
InactiveUS6529948B1Digital data processing detailsMultiprogramming arrangementsBusiness objectSoftware engineering
A system, method, and article of manufacture are provided for retrieving multiple business objects across a network in one access operation. A business object and a plurality of remaining objects are provided on a persistent store. Upon receiving a request for the business object, it is established which of the remaining objects are related to the business object. The related objects and the business object are retrieved from the persistent store in one operation and it is determined how the retrieved related objects relate to the business object and each other. A graph of relationships of the business and related objects is instantiated in memory.
Owner:ACCENTURE GLOBAL SERVICES LTD
Relay peers for extending peer availability in a peer-to-peer networking environment
ActiveUS20020143855A1Multiprogramming arrangementsMultiple digital computer combinationsDistributed computingPeer-to-peer
A system and method for allowing peers to exchange messages with other peers independently of their network location in a peer-to-peer environment. Messages may be transparently routed, potentially traversing partitions (e.g. firewalls and NATs), and using different protocols to reach the destination peers. In one embodiment, any peer node may serve as a relay peer that allows peers inside a partition to have a presence outside the partition and provides a mechanism for peers outside partitions to discover and communicate with peers inside the partitions. In one embodiment, a relay peer may maintain information on routes to other peers and assist in relaying messages to other peers. In one embodiment, any peer may query a relay peer for route information. In one embodiment, messages may include routing information as part of their payloads.
Owner:ORACLE INT CORP
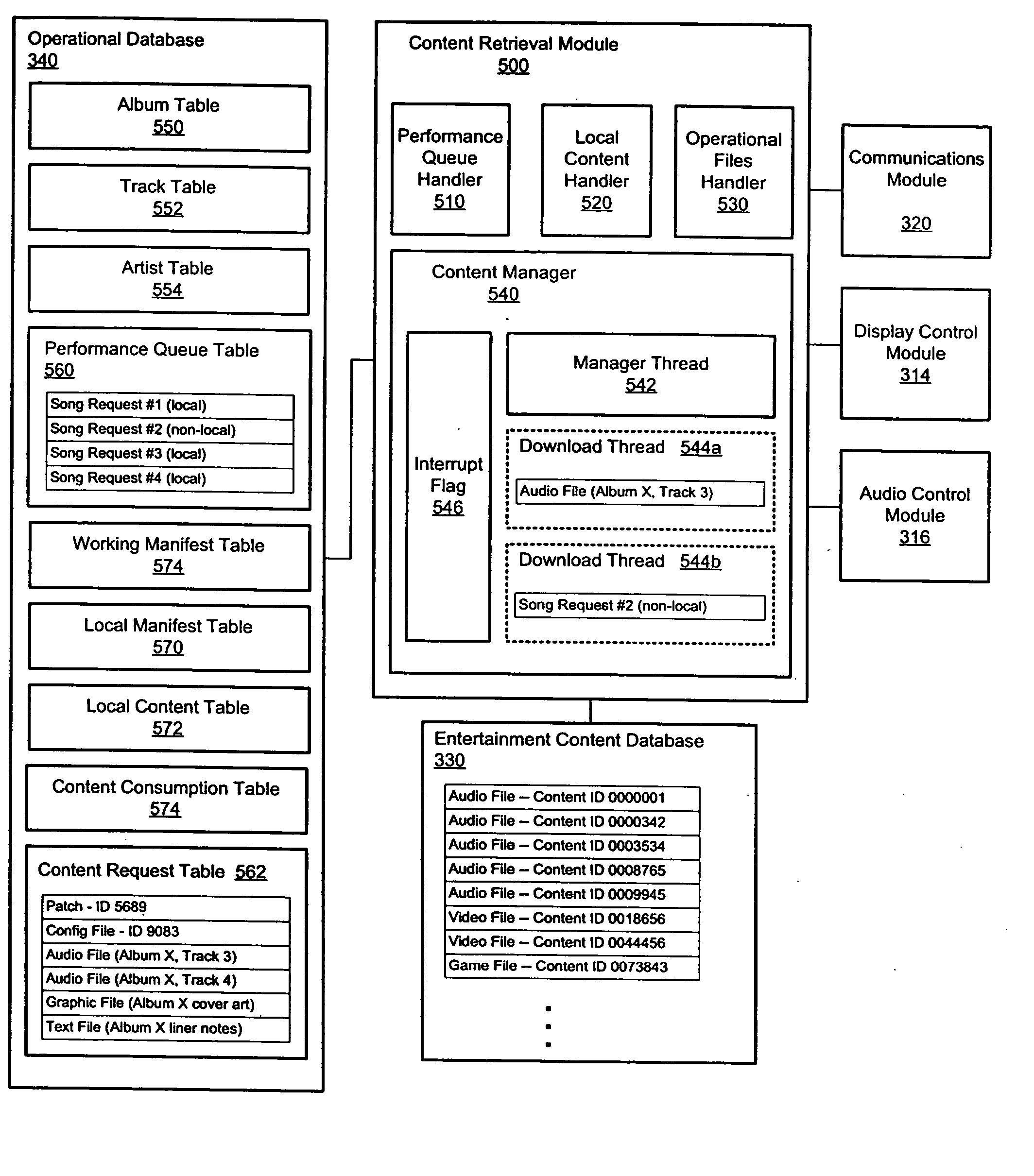
Prioritized content download for an entertainment device
ActiveUS20060074750A1Multiprogramming arrangementsCash registersContent retrievalDistributed computing
Priority-based content retrieval mechanisms for digital entertainment devices are provided. In various embodiments, the download prioritizations may be interrupt-based, sequence-based, or a combination of the two. In interrupt-based prioritizations, a higher priority download request will interrupt a lower-priority download that is already in progress. In sequence-based prioritizations, a plurality of file download requests may be ordered in a download queue depending on the priority of the request, with higher priority requests being positioned towards the top of the queue and lower priority requests being positioned towards the bottom of the queue.
Owner:AMI ENTERTAINMENT NETWORK
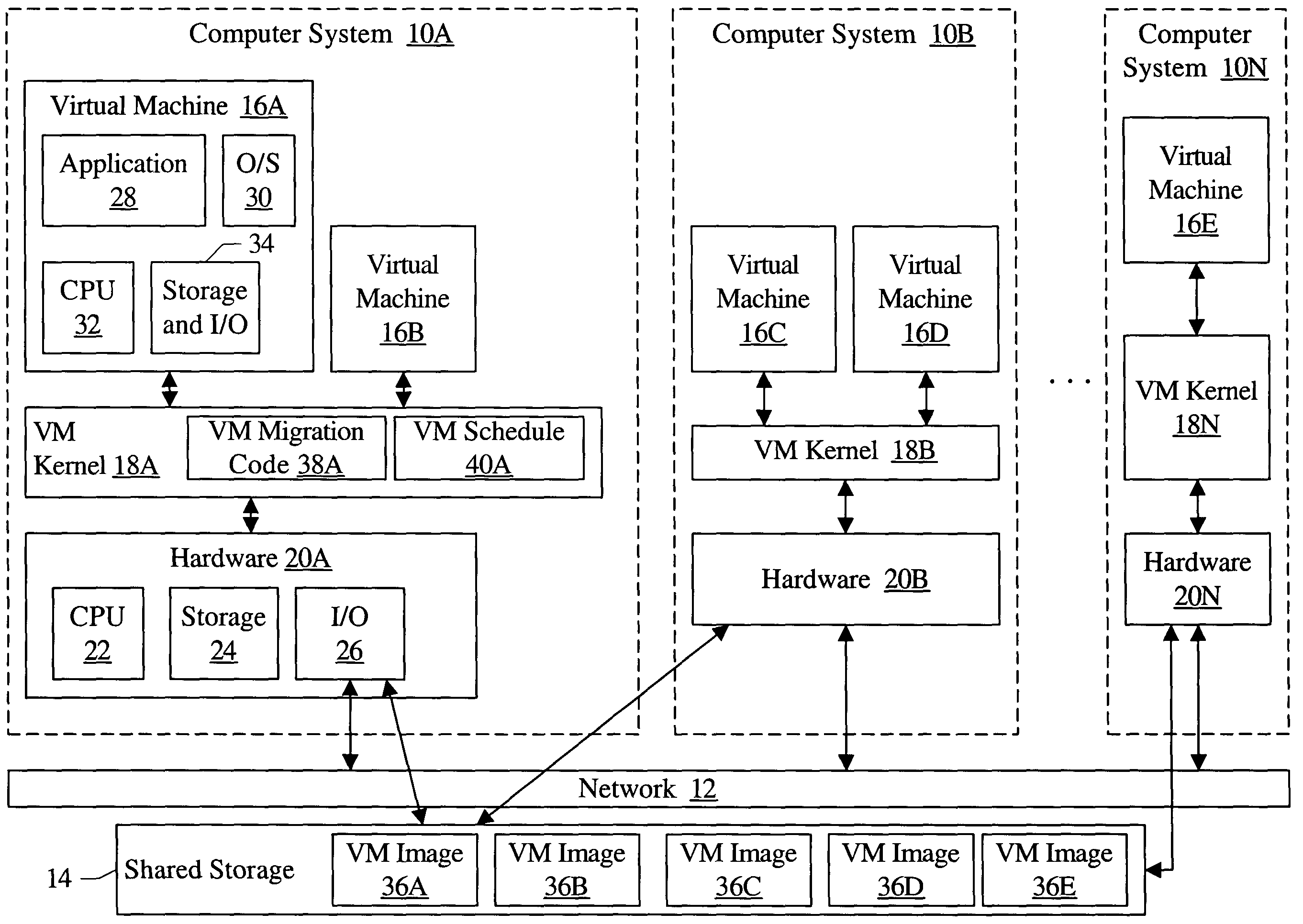
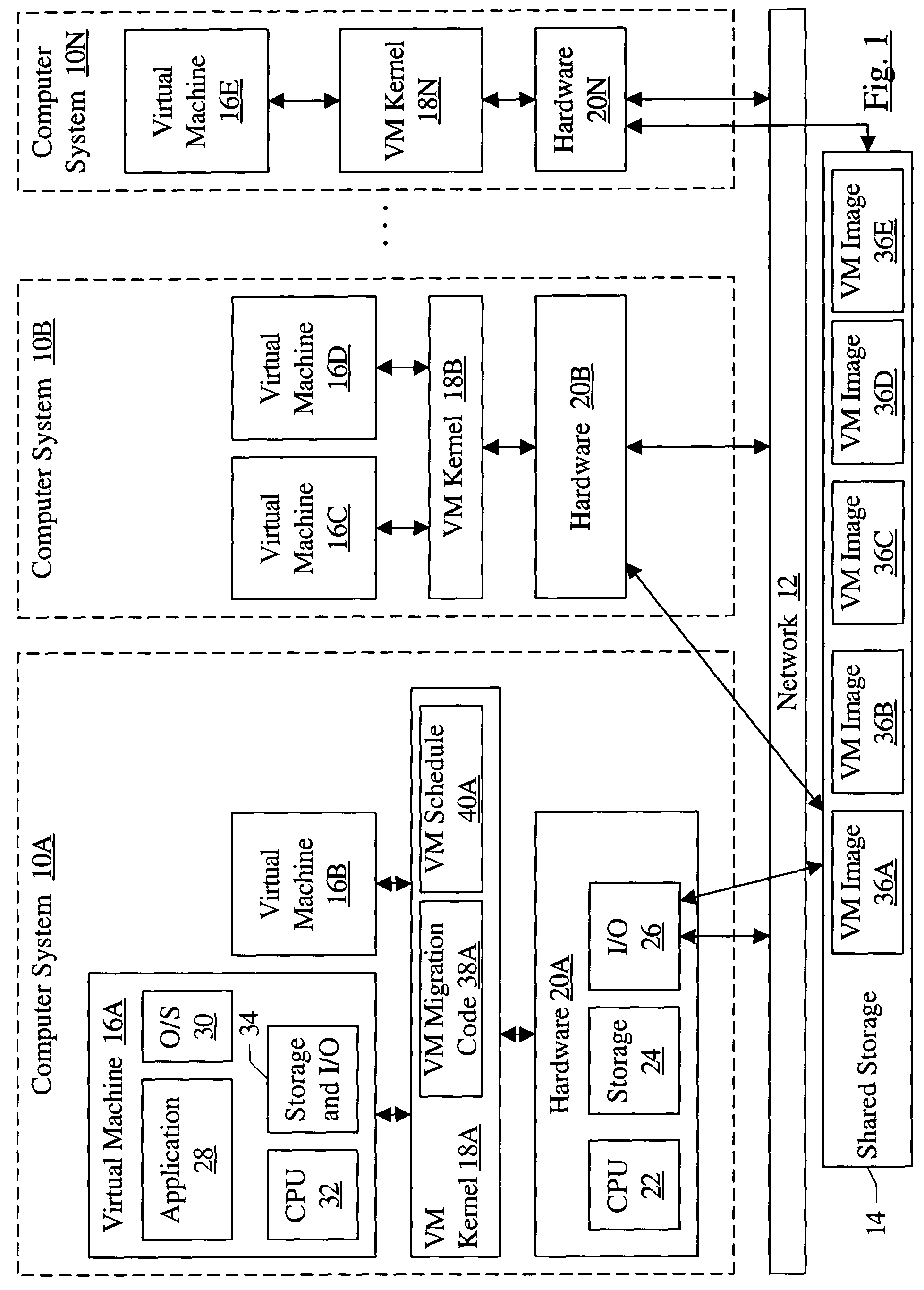
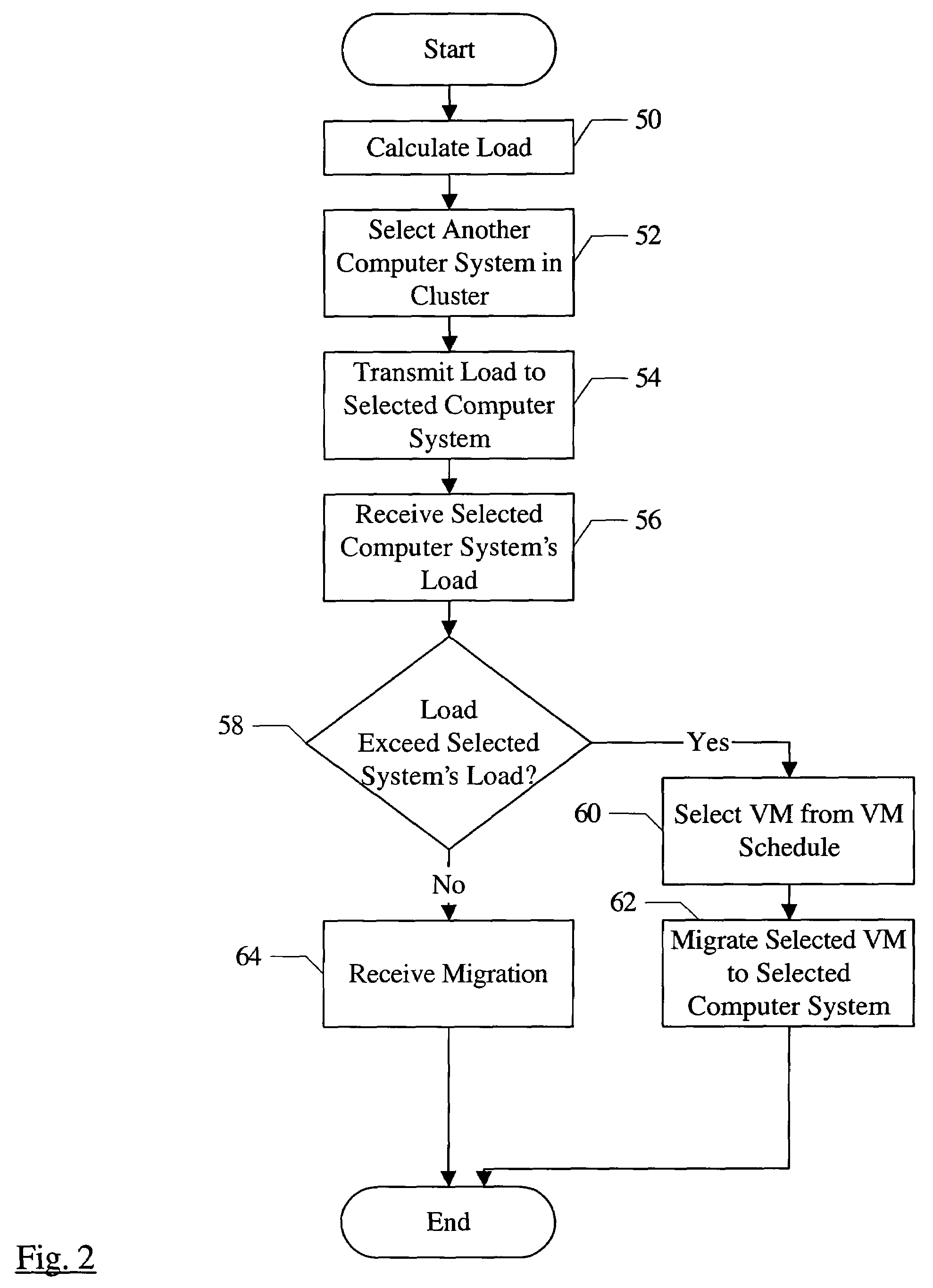
Migrating virtual machines among computer systems to balance load caused by virtual machines
InactiveUS7203944B1Multiprogramming arrangementsSoftware simulation/interpretation/emulationComputerized systemVirtual machine
A cluster comprises a plurality of computer systems, wherein each of the plurality of computer systems is configured to execute one or more virtual machines. Each of the plurality of computer systems comprises hardware and a plurality of instructions. The plurality of instructions, when executed on the hardware, migrates at least a first virtual machine executing on a first computer system of the plurality of computer systems to a second computer system of the plurality of computer systems. The plurality of instructions migrates the first virtual machine responsive to a first load of the first computer system prior to the migration exceeding a second load of the second computer system prior to the migration.
Owner:SYMANTEC OPERATING CORP
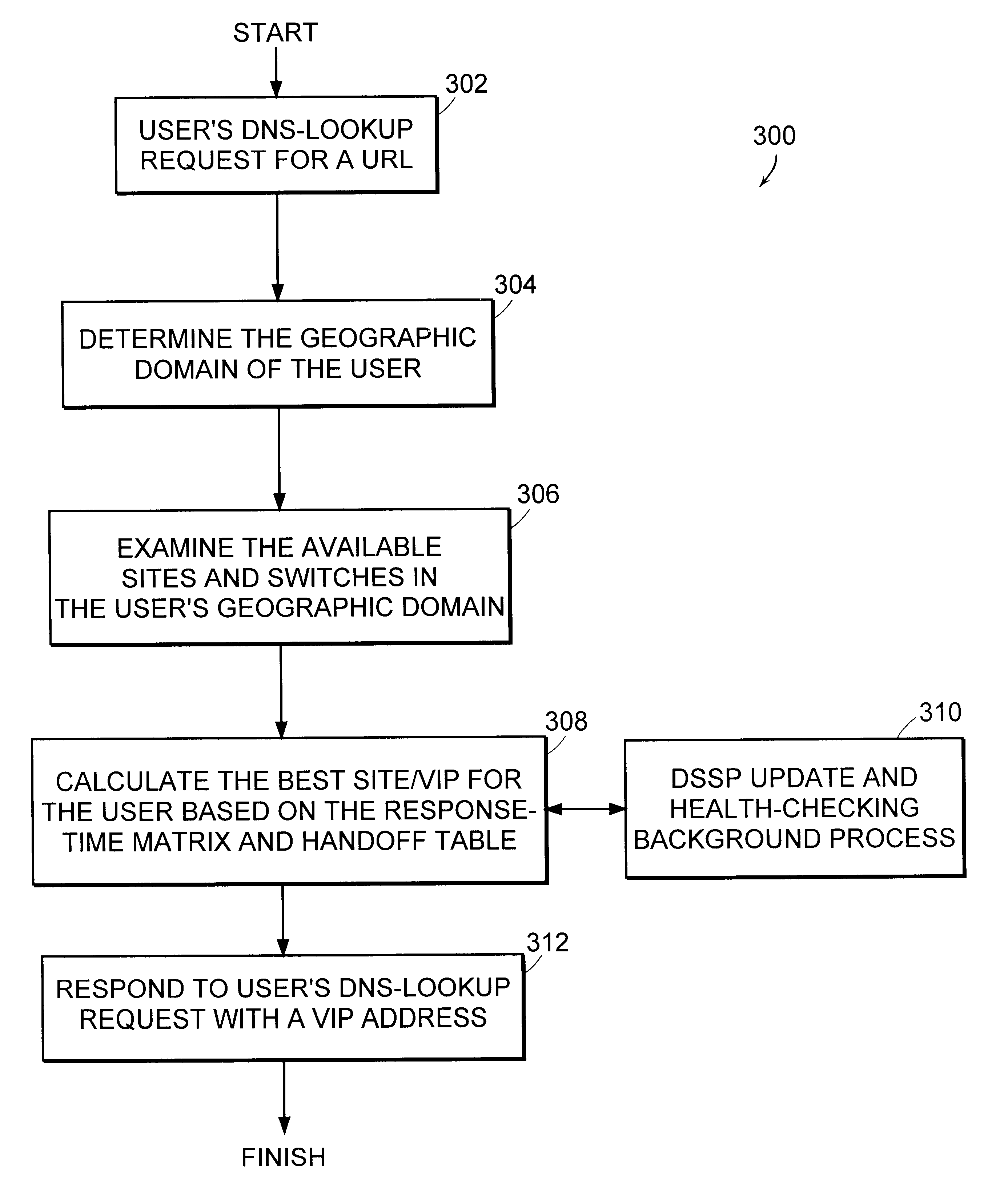
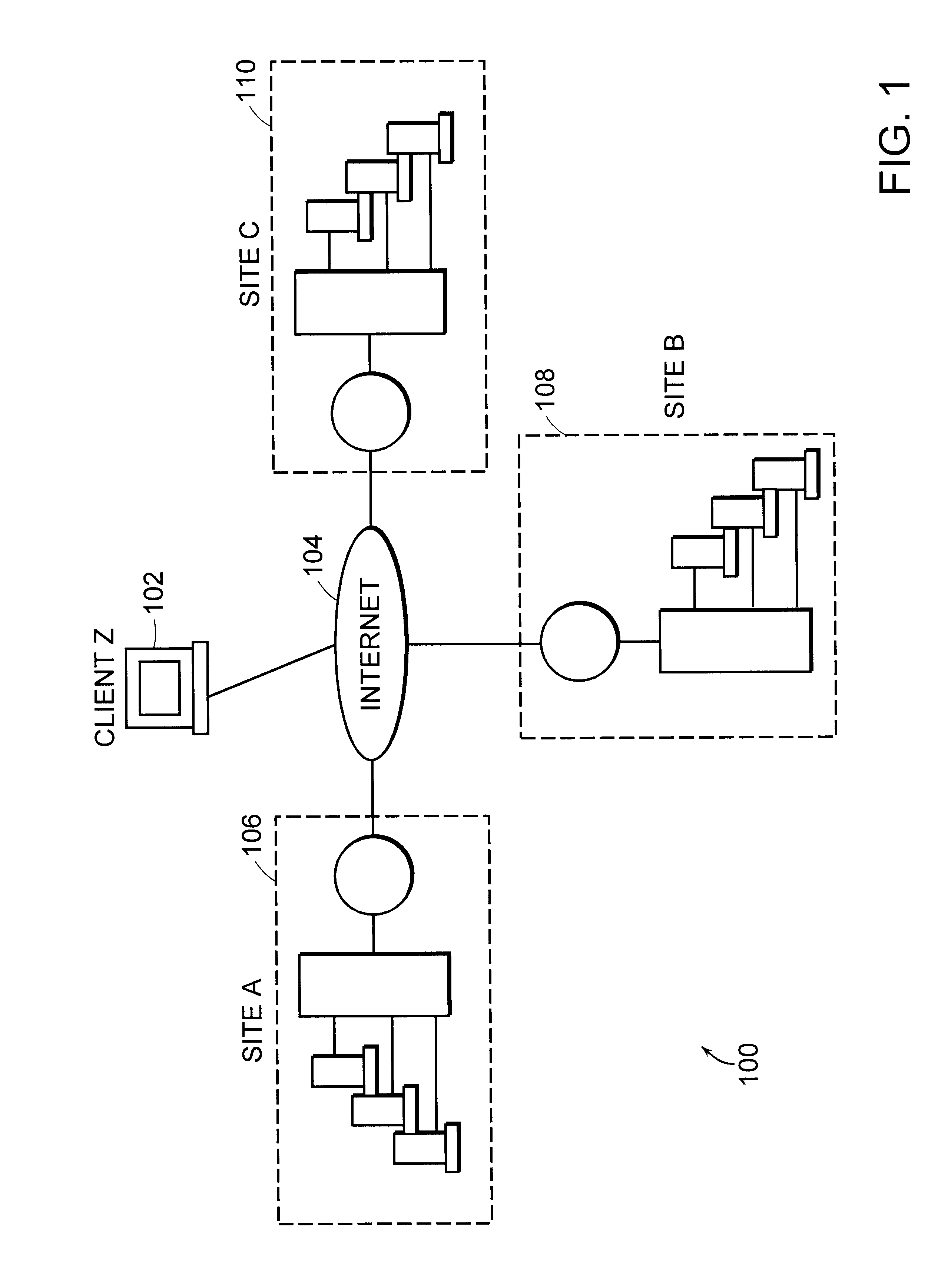
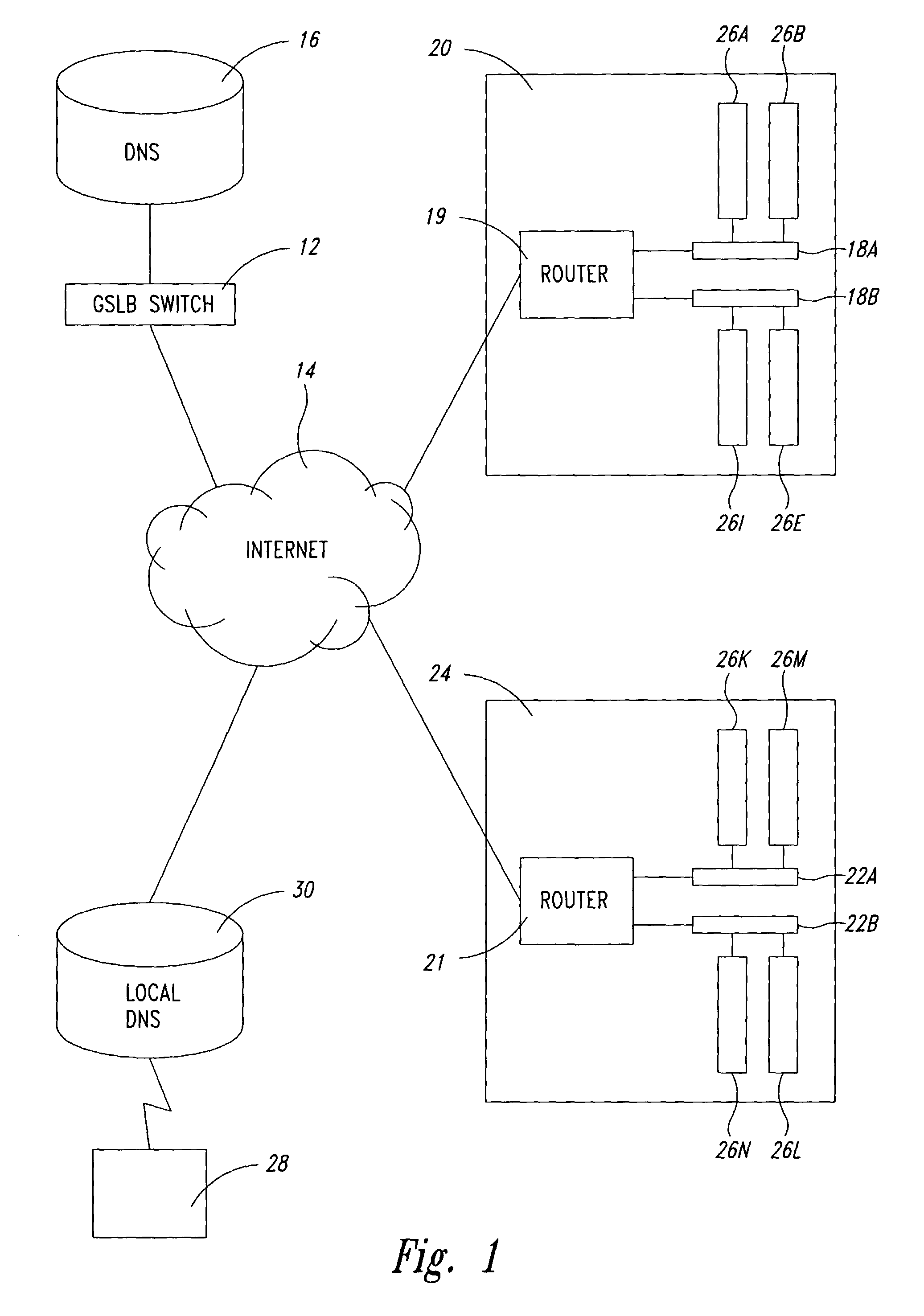
Distributed load-balancing internet servers
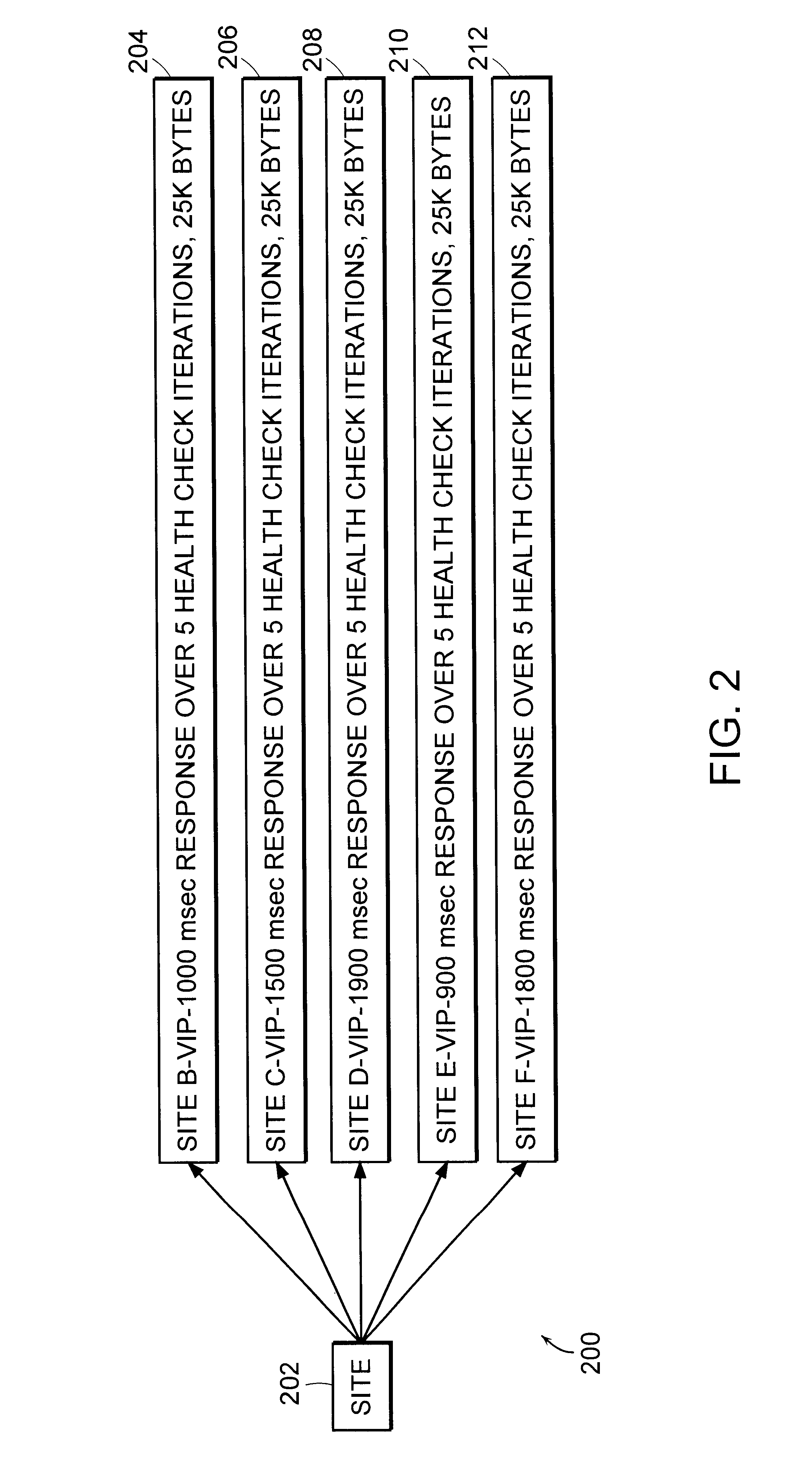
The actual site that serves the Web pages to a client in response to a URL domain name is automatically and transparently selected from a list of many switches each having identical data storage. In a peer hand-off process, a switch receives domain name server lookup request for a particular virtual Internet protocol (VIP) domain name. The switch examines the source IP-address for the domain name server request, examines the user's IP-address, and determines if there is server site that is geographically close to that user. The switch examines an ordered hand-off table corresponding to the domain. The switch chooses a next remote server (or its own VIP) in line based on, (a) the remote server location compared to domain name server request source, (b) the remote servers' weights, and (c) the remote server that experienced the previous hand-off. The switch then sends the domain name server response back to client domain name server with the IP-addresses in an ordered list.
Owner:RADWARE
Dynamic selection of memory virtualization techniques
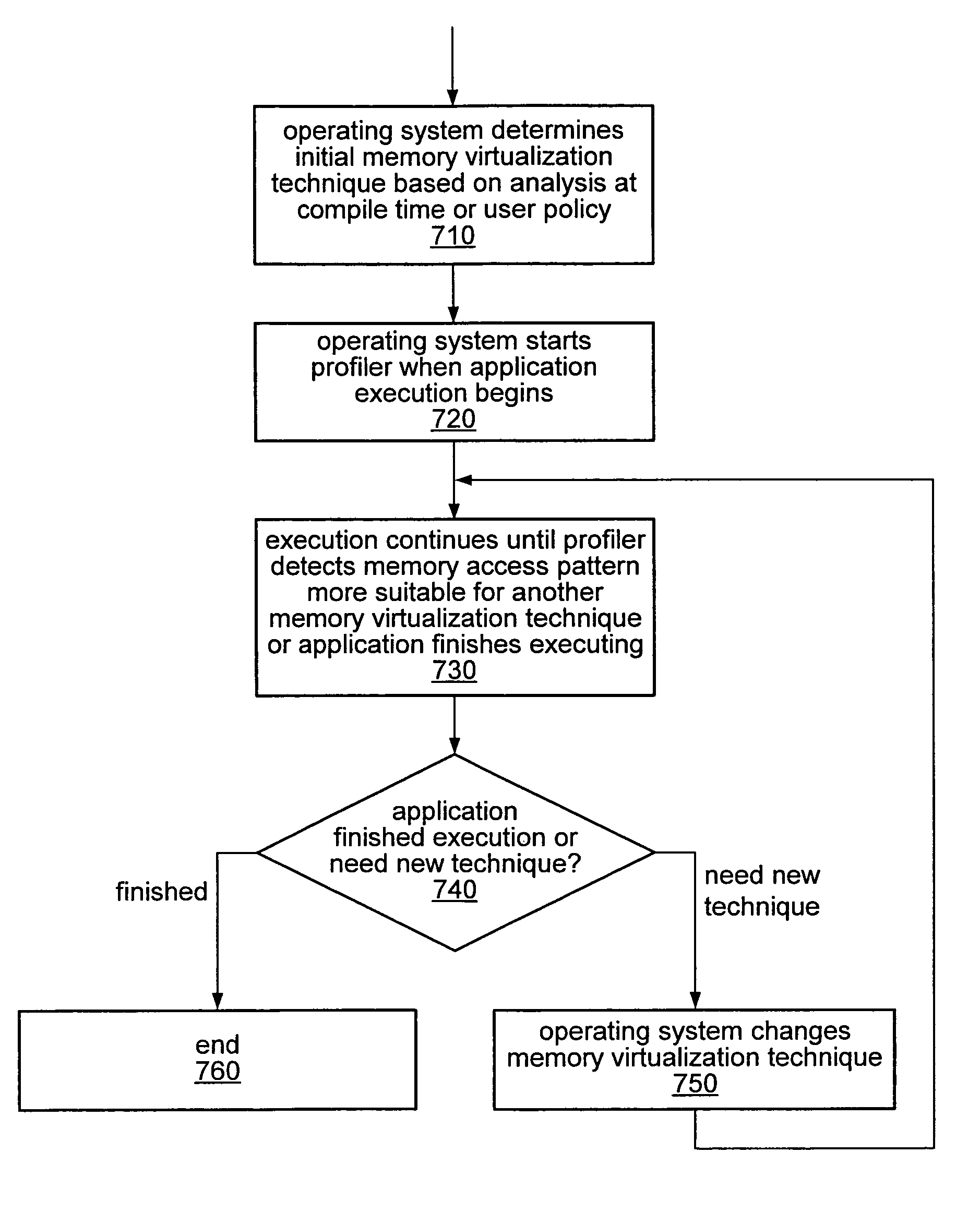
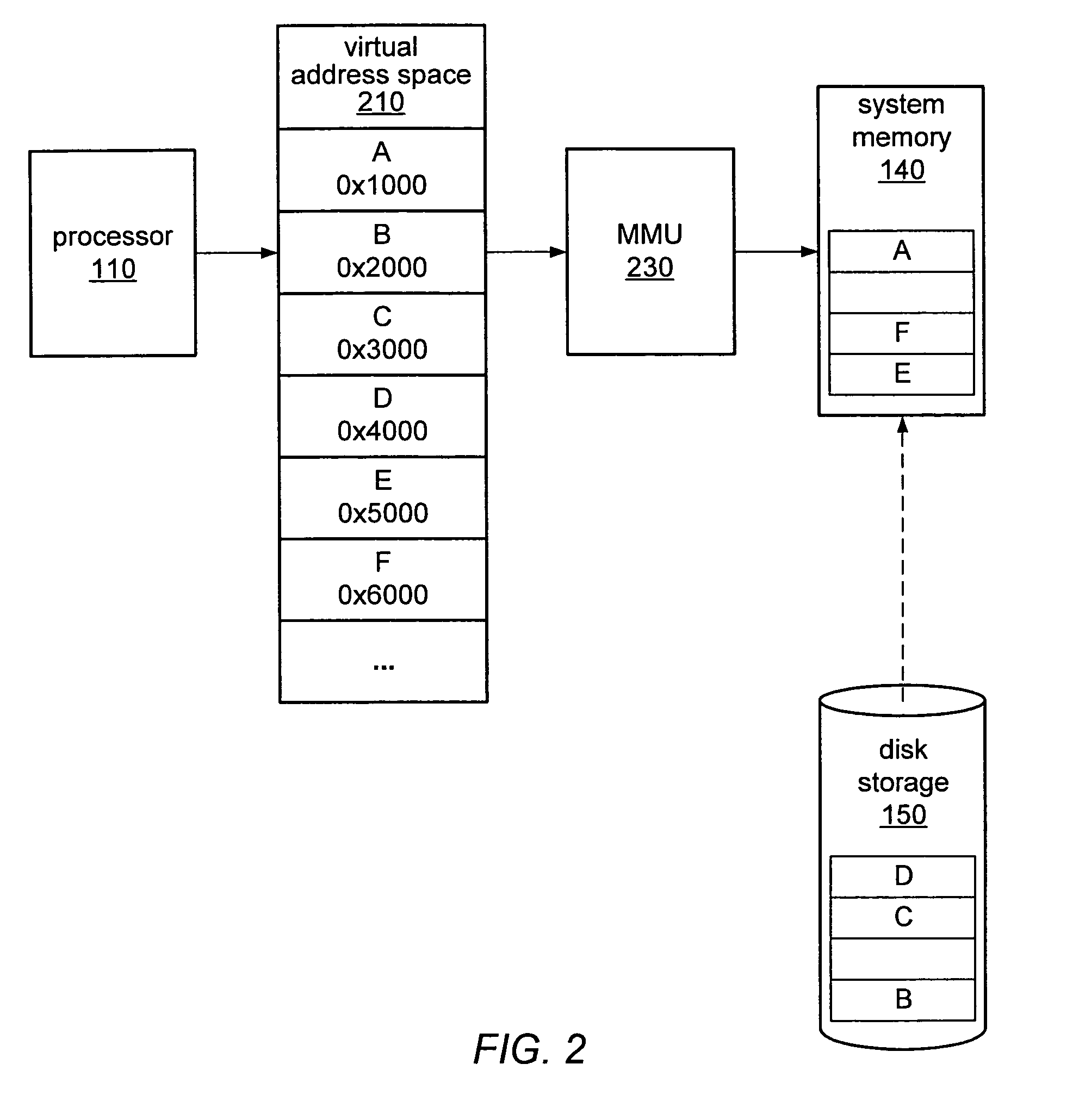
ActiveUS7752417B2Error detection/correctionMemory adressing/allocation/relocationVirtualizationComputerized system
A computer system may be configured to dynamically select a memory virtualization and corresponding virtual-to-physical address translation technique during execution of an application and to dynamically employ the selected technique in place of a current technique without re-initializing the application. The computer system may be configured to determine that a current address translation technique incurs a high overhead for the application's current workload and may be configured to select a different technique dependent on various performance criteria and / or a user policy. Dynamically employing the selected technique may include reorganizing a memory, reorganizing a translation table, allocating a different block of memory to the application, changing a page or segment size, or moving to or from a page-based, segment-based, or function-based address translation technique. A selected translation technique may be dynamically employed for the application independent of a translation technique employed for a different application.
Owner:ORACLE INT CORP
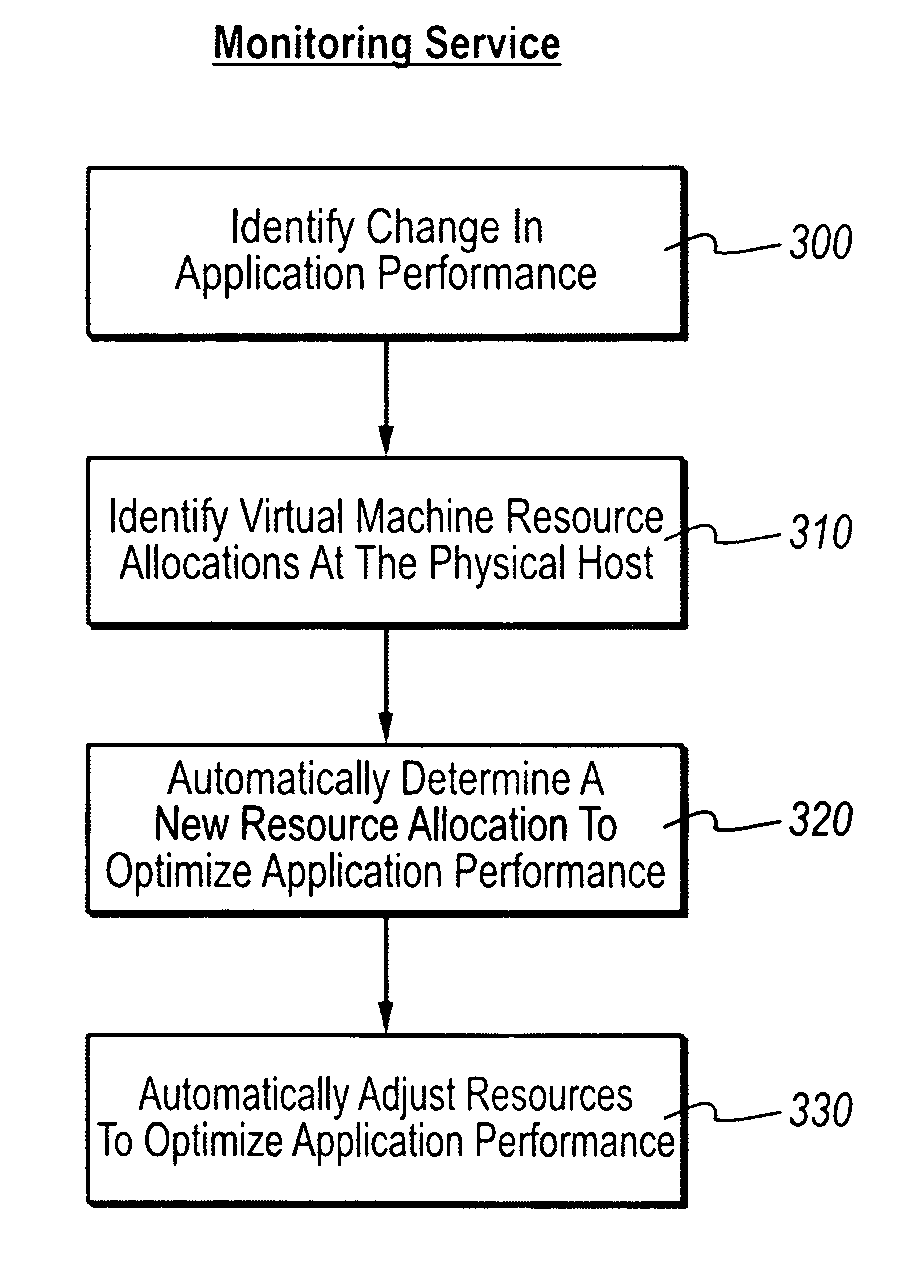
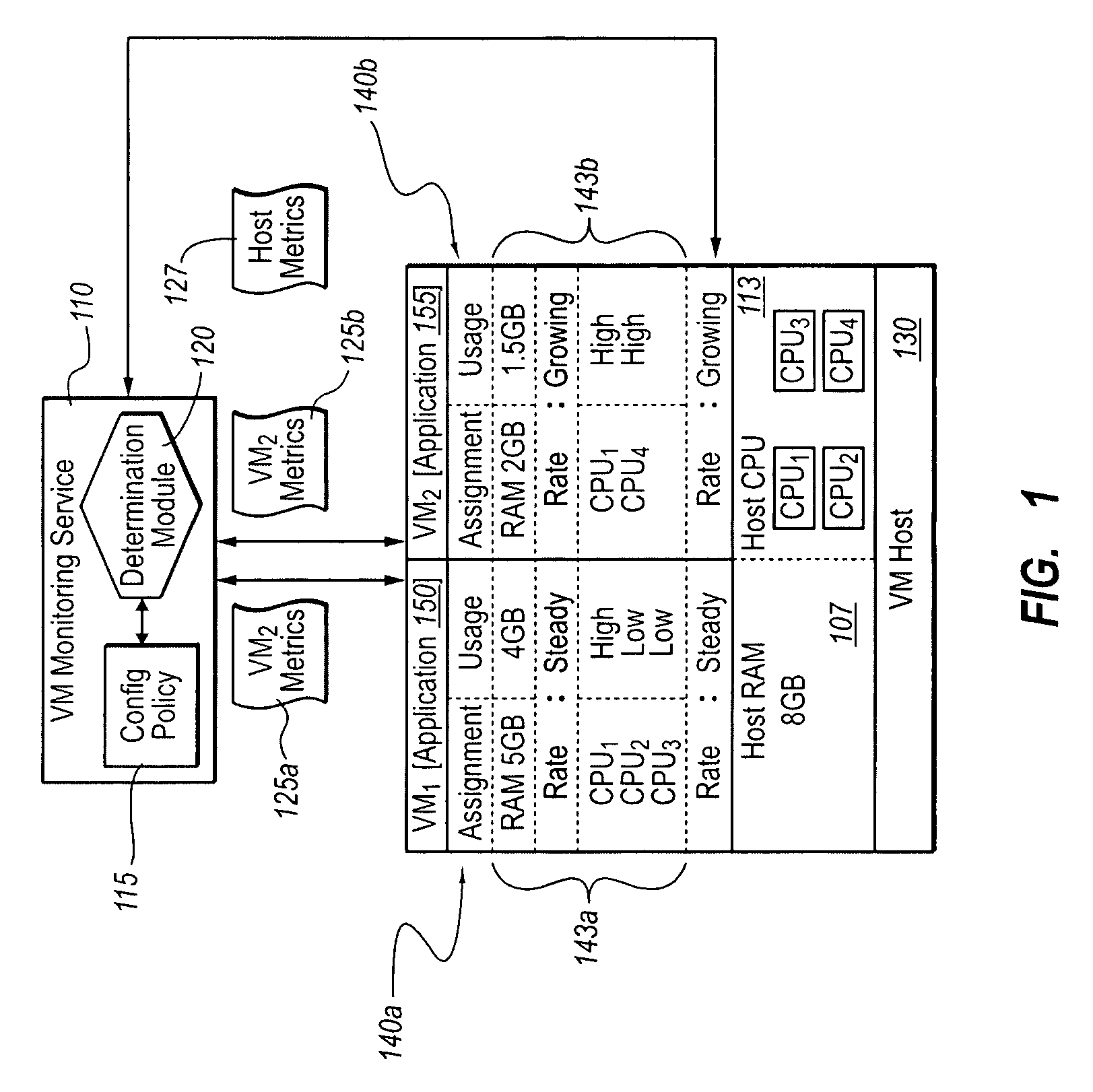
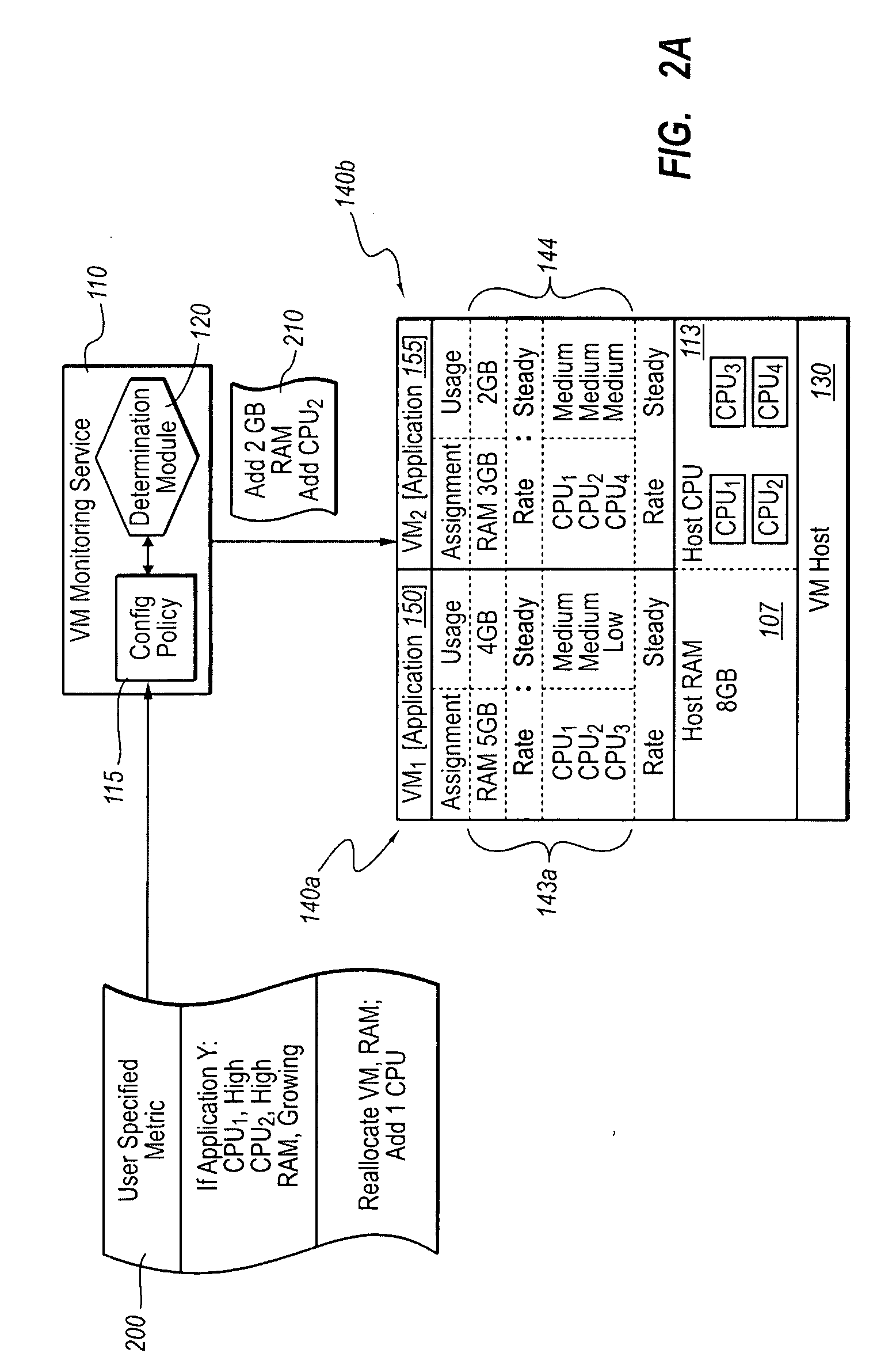
Optimizing application performance on virtual machines automatically with end-user preferences
InactiveUS20090265707A1Improve performanceError detection/correctionMultiprogramming arrangementsUser inputResource utilization
A virtual machine management / monitoring service can be configured to automatically monitor and implement user-defined (e.g., administrator-defined) configuration policies with respect to virtual machine and application resource utilization. In one implementation, the monitoring service can be extended to provide user-customized alerts based on various particularly defined events that occur (e.g., some memory or processing threshold) during operation of the virtual machines and / or application execution. The user can also specify particularly tailored solutions, which can include automatically reallocating physical host resources without additional user input on a given physical host, or moving / adding virtual machines on other physical hosts. For example, the monitoring service can be configured so that, upon identifying that a virtual machine's memory and processing resources are maxed out and / or growing, the monitoring service adds memory or processing resources for the virtual machine, or adds a new virtual machine to handle the load for the application program.
Owner:MICROSOFT TECH LICENSING LLC
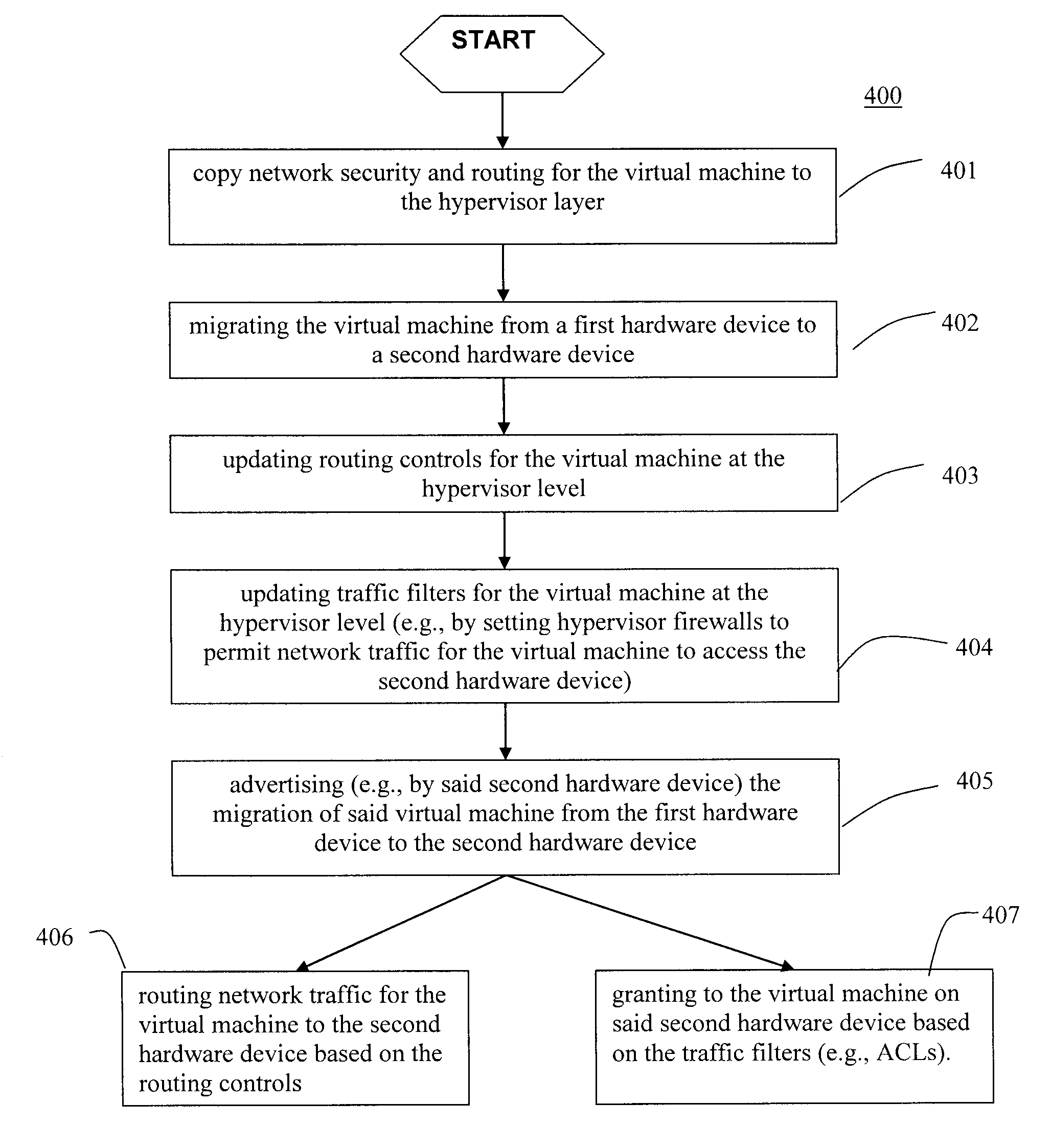
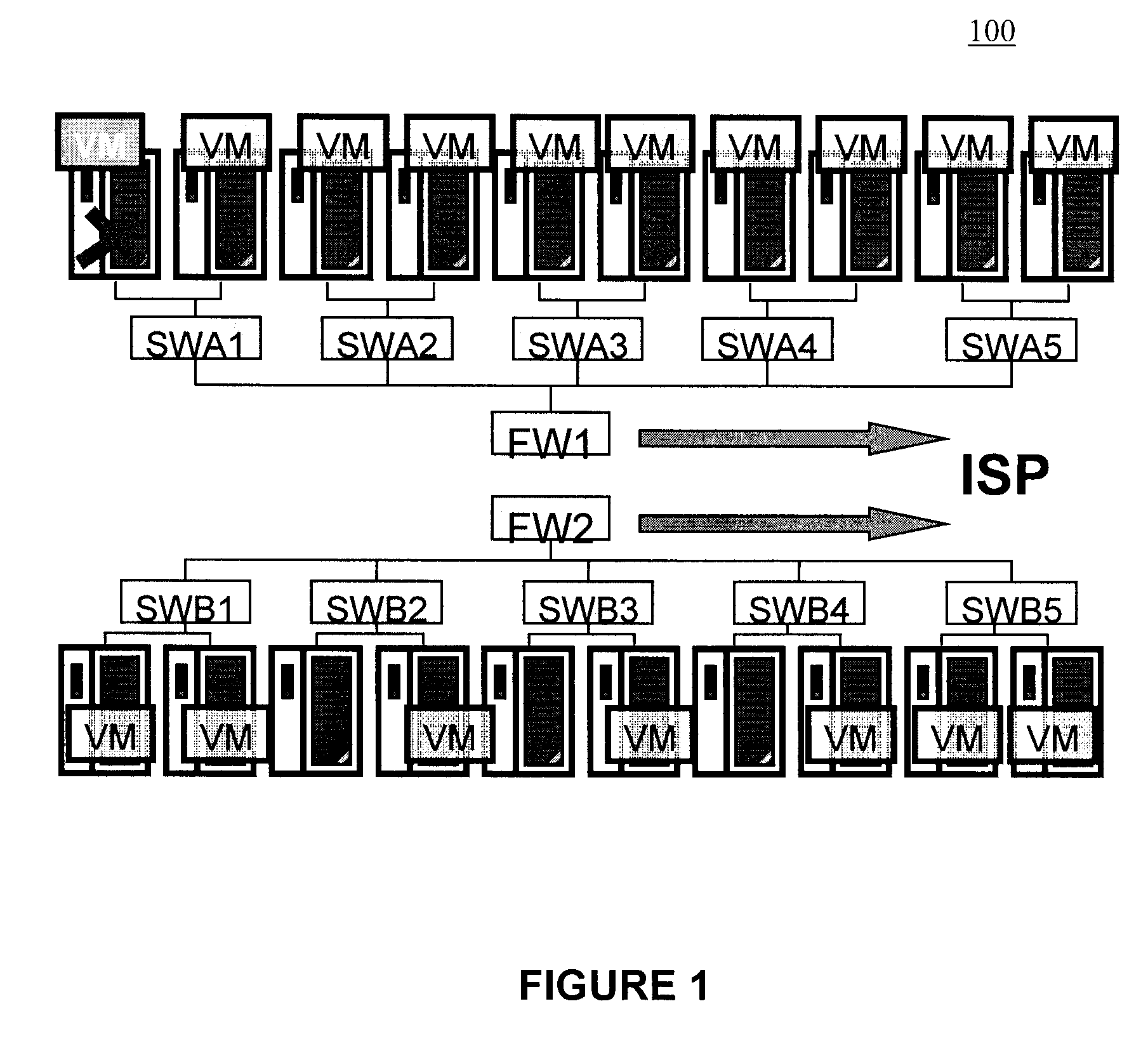
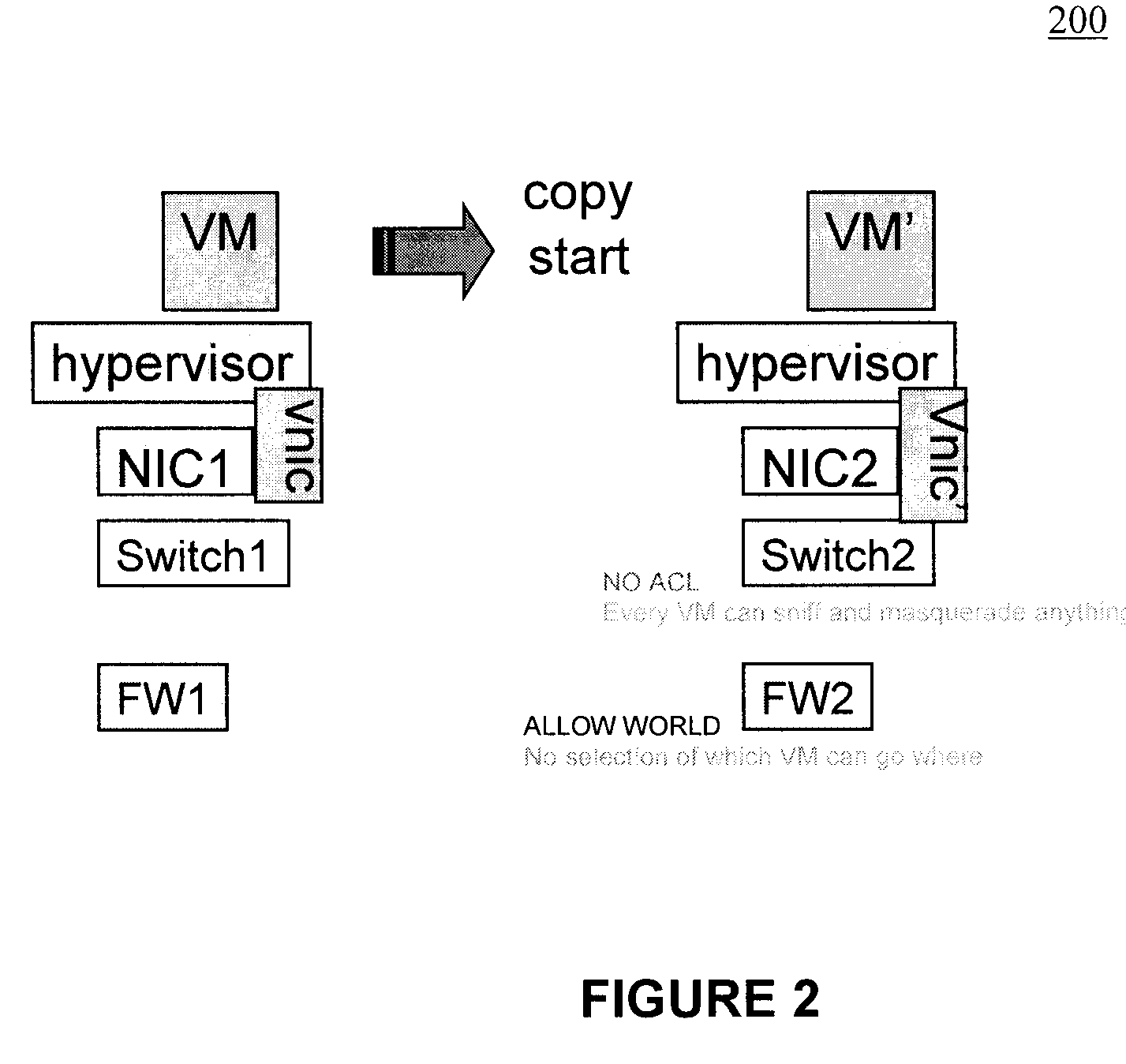
Moveable access control list (ACL) mechanisms for hypervisors and virtual machines and virtual port firewalls
ActiveUS20080163207A1Efficient responseRapid deploymentSemiconductor electrostatic transducersMicrophone structural associationVLAN access control listAccess control list
A method (and system) which provides virtual machine migration with filtered network connectivity and control of network security of a virtual machine by enforcing network security and routing at a hypervisor layer at which the virtual machine partition is executed, and which is independent of guest operating systems.
Owner:DAEDALUS BLUE LLC
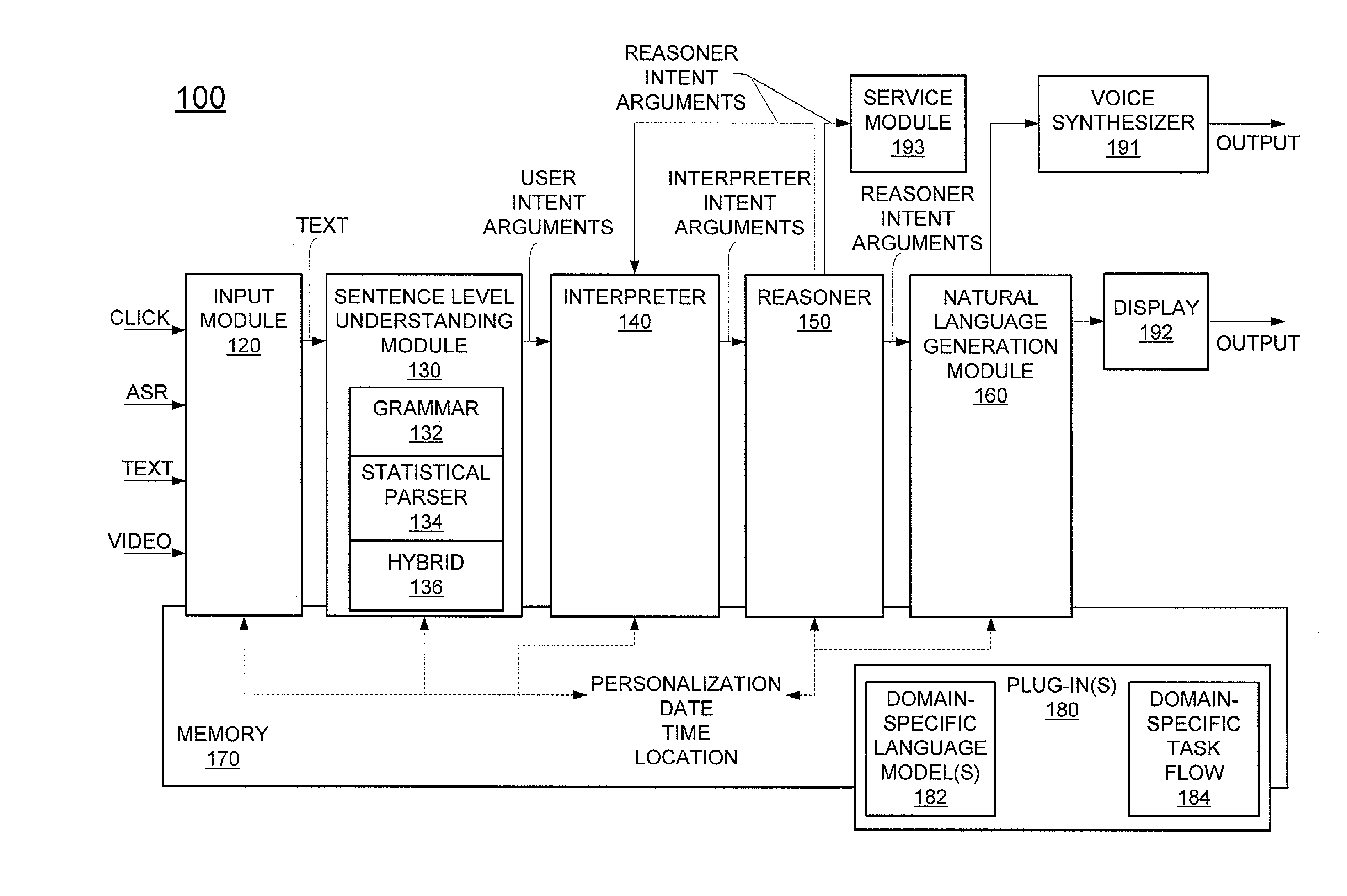
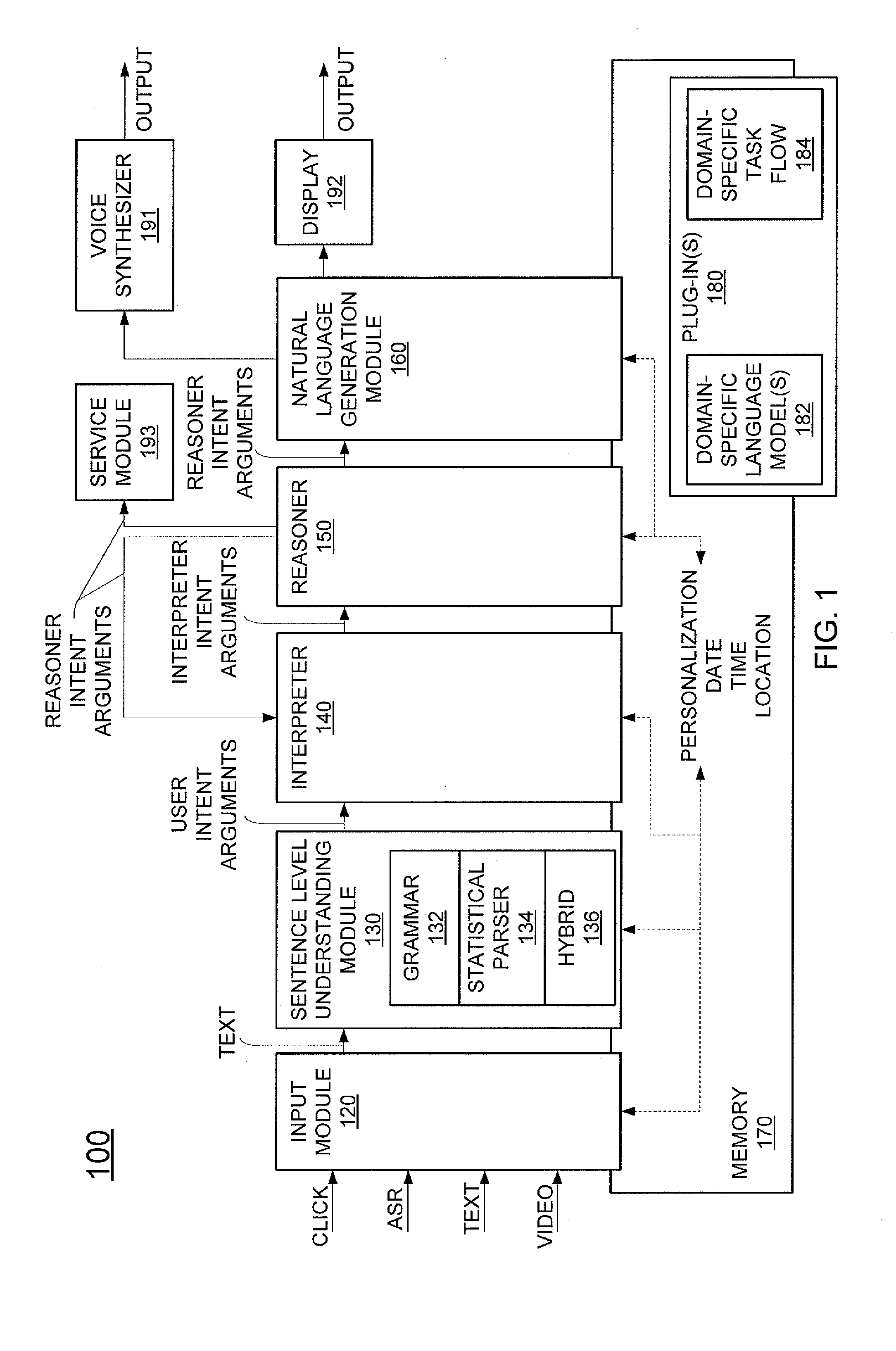
Generic virtual personal assistant platform
ActiveUS20130152092A1Natural language translationMultiprogramming arrangementsLanguage understandingA domain
A method for assisting a user with one or more desired tasks is disclosed. For example, an executable, generic language understanding module and an executable, generic task reasoning module are provided for execution in the computer processing system. A set of run-time specifications is provided to the generic language understanding module and the generic task reasoning module, comprising one or more models specific to a domain. A language input is then received from a user, an intention of the user is determined with respect to one or more desired tasks, and the user is assisted with the one or more desired tasks, in accordance with the intention of the user.
Owner:SRI INTERNATIONAL
Software sequencer for integrated substrate processing system
InactiveUS20080216077A1Programme controlSemiconductor/solid-state device manufacturingProgram planningDistributed computing
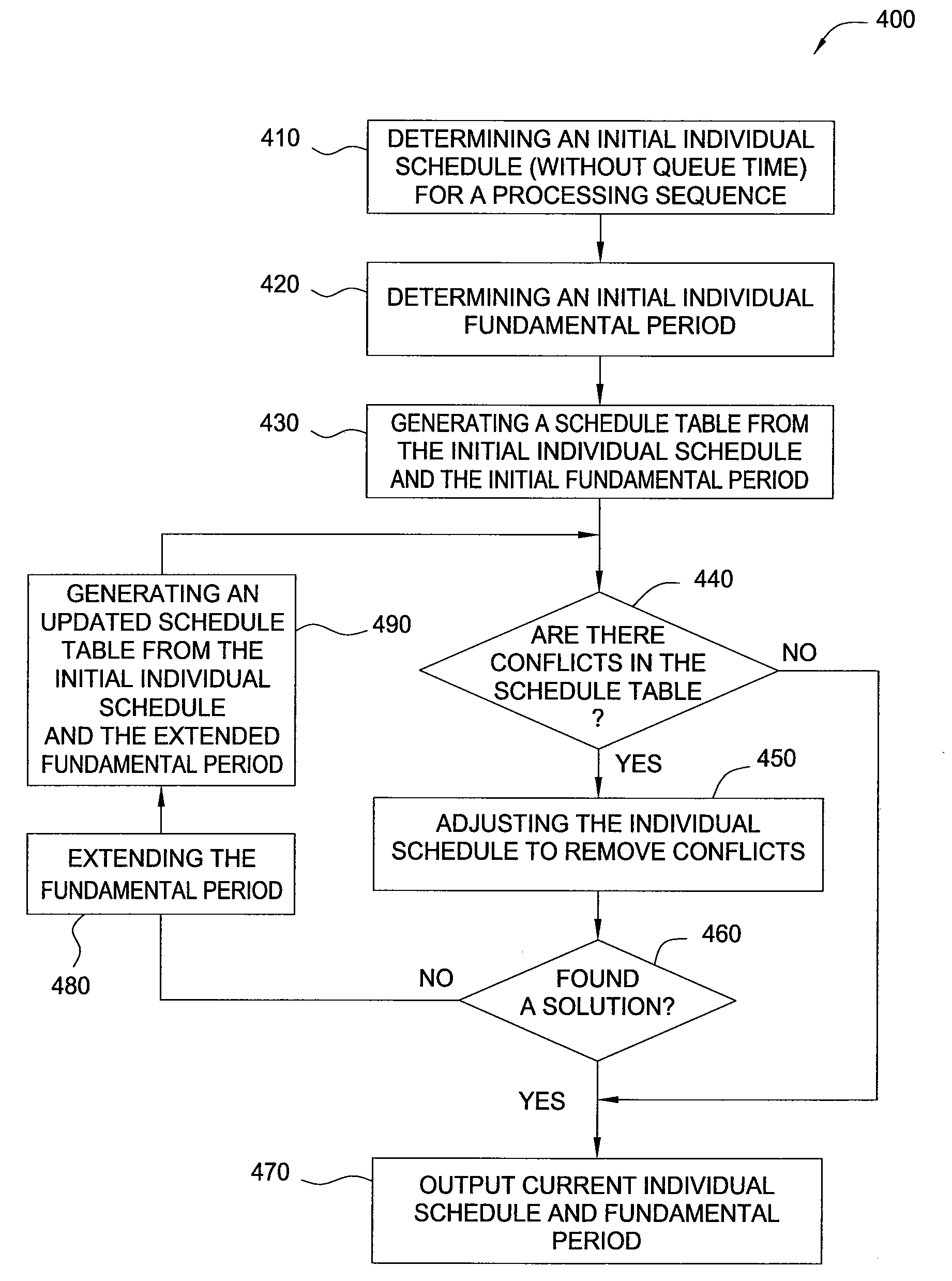
Embodiments of the invention generally provide apparatus and method for scheduling a process sequence to achieve maximum throughput and process consistency in a cluster tool having a set of constraints. One embodiment of the present invention provides a method for scheduling a process sequence comprising determining an initial individual schedule by assigning resources to perform the process sequence, calculating a fundamental period, detecting resource conflicts in a schedule generated from the individual schedule and the fundamental period, and adjusting the individual schedule to remove the resource conflicts.
Owner:APPLIED MATERIALS INC
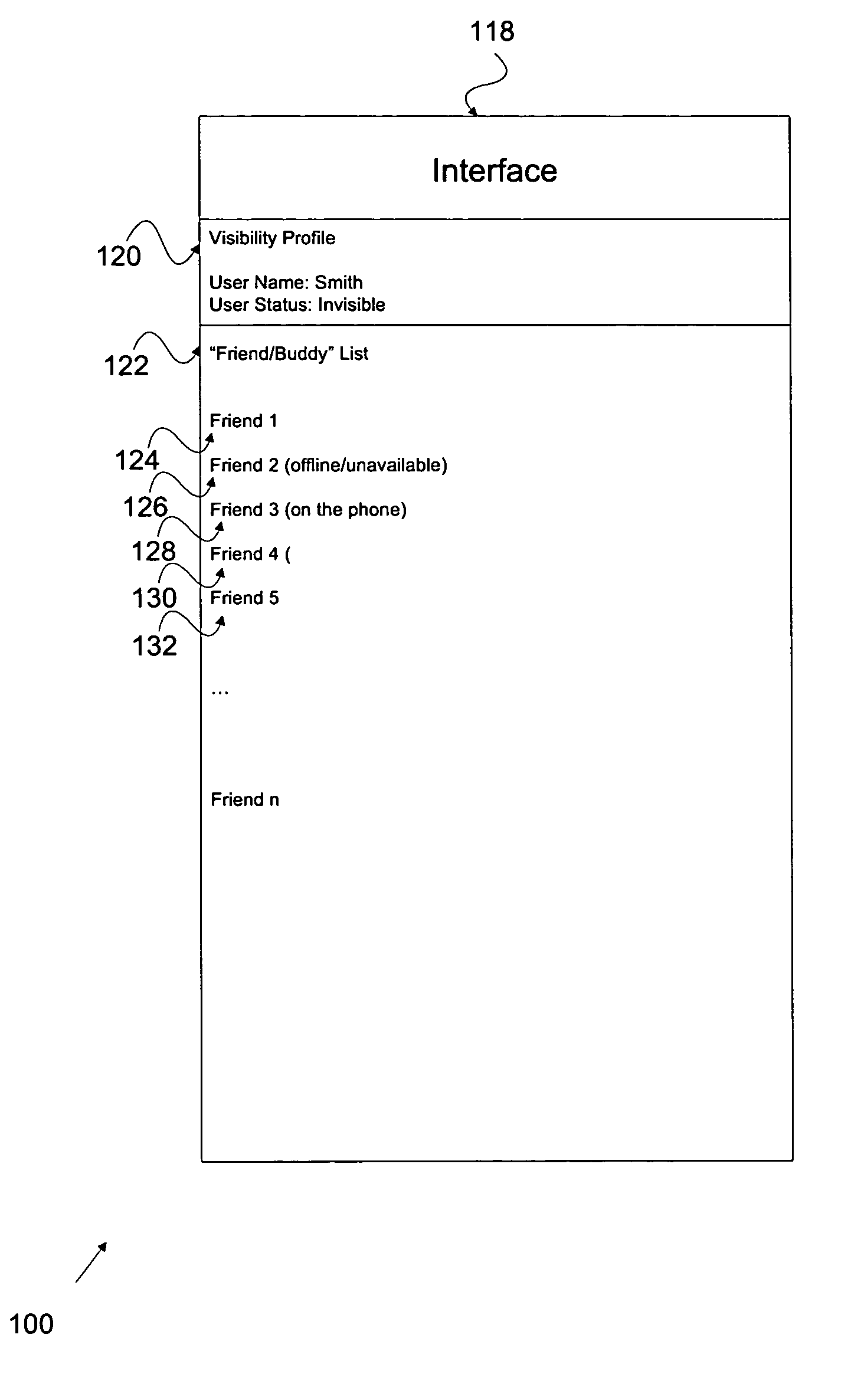
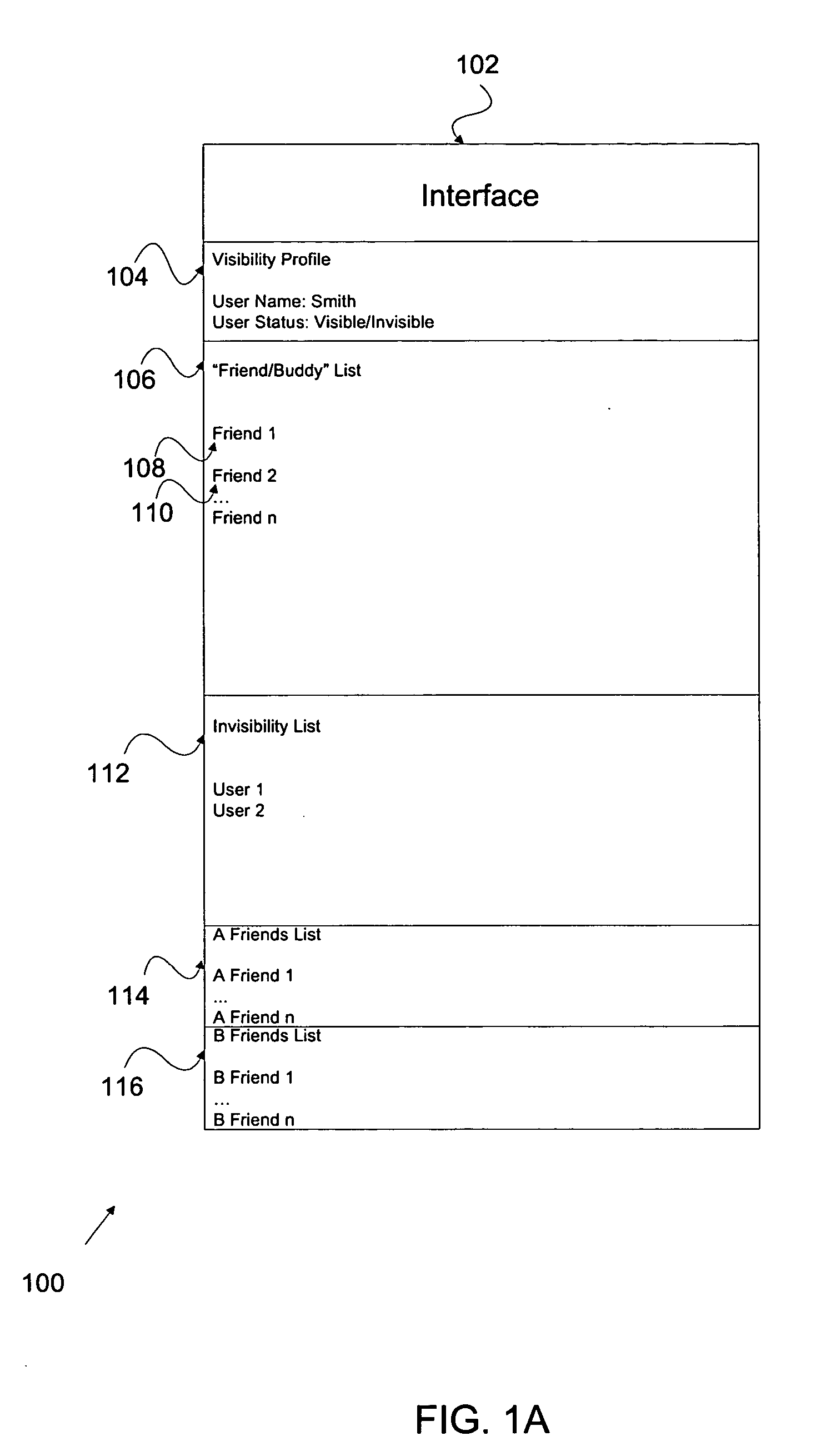
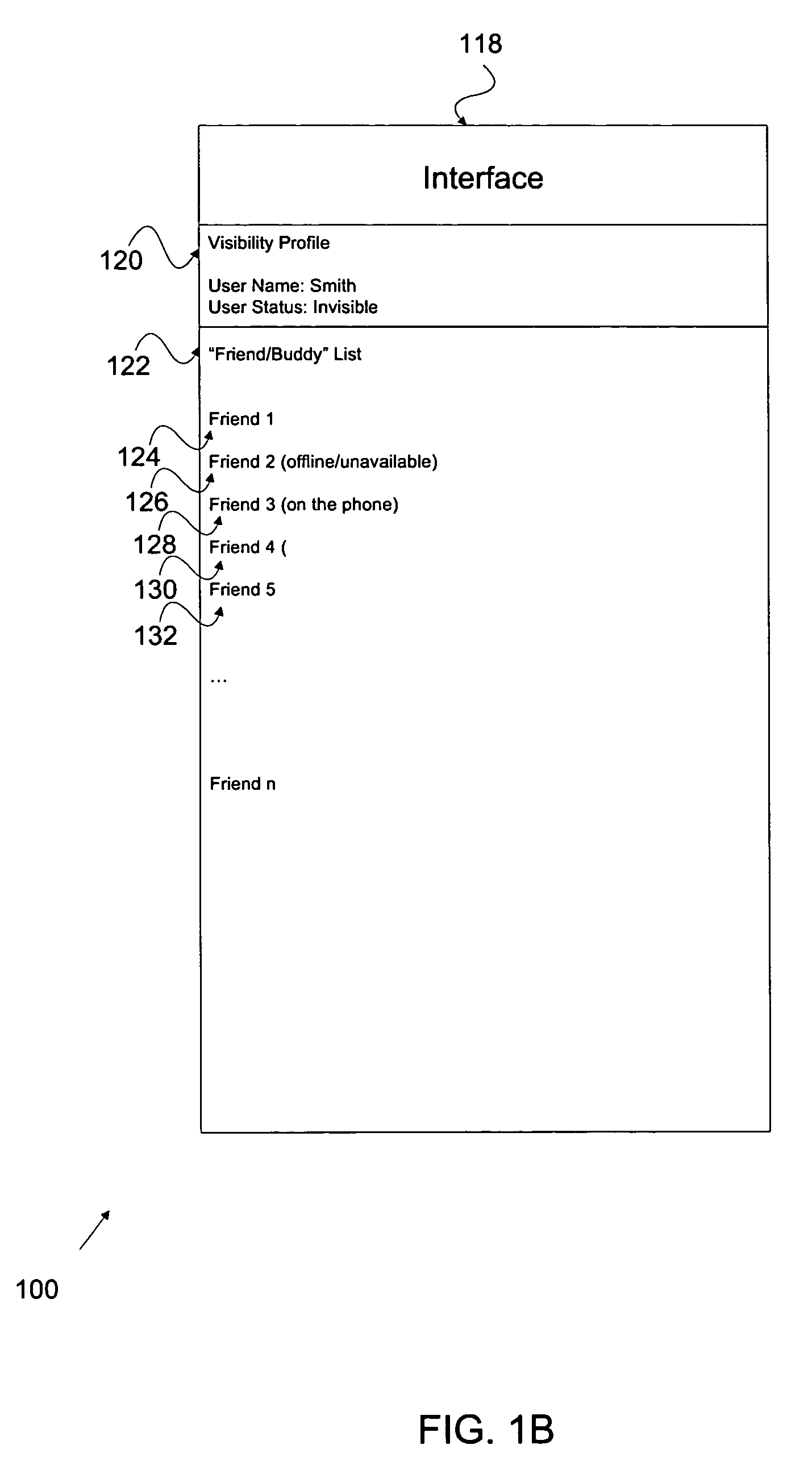
Visibility profile
ActiveUS20050114783A1Multiprogramming arrangementsMultiple digital computer combinationsVisibilityElectronic mail
Visibility profiles associated with a substantially real time messaging environment are disclosed. Additionally, techniques for managing visibility profiles are disclosed, which include automatically associating a first profile with a first situation, automatically associating a second profile with a second situation, and where the first and second profiles are associated with visibility. Visibility profiles may be used to manage the appearance of a user to other users / friends for communication using applications such as instant messaging, electronic mail, web-based mail programs, or other types of data communication exchange applications.
Owner:GOOGLE LLC
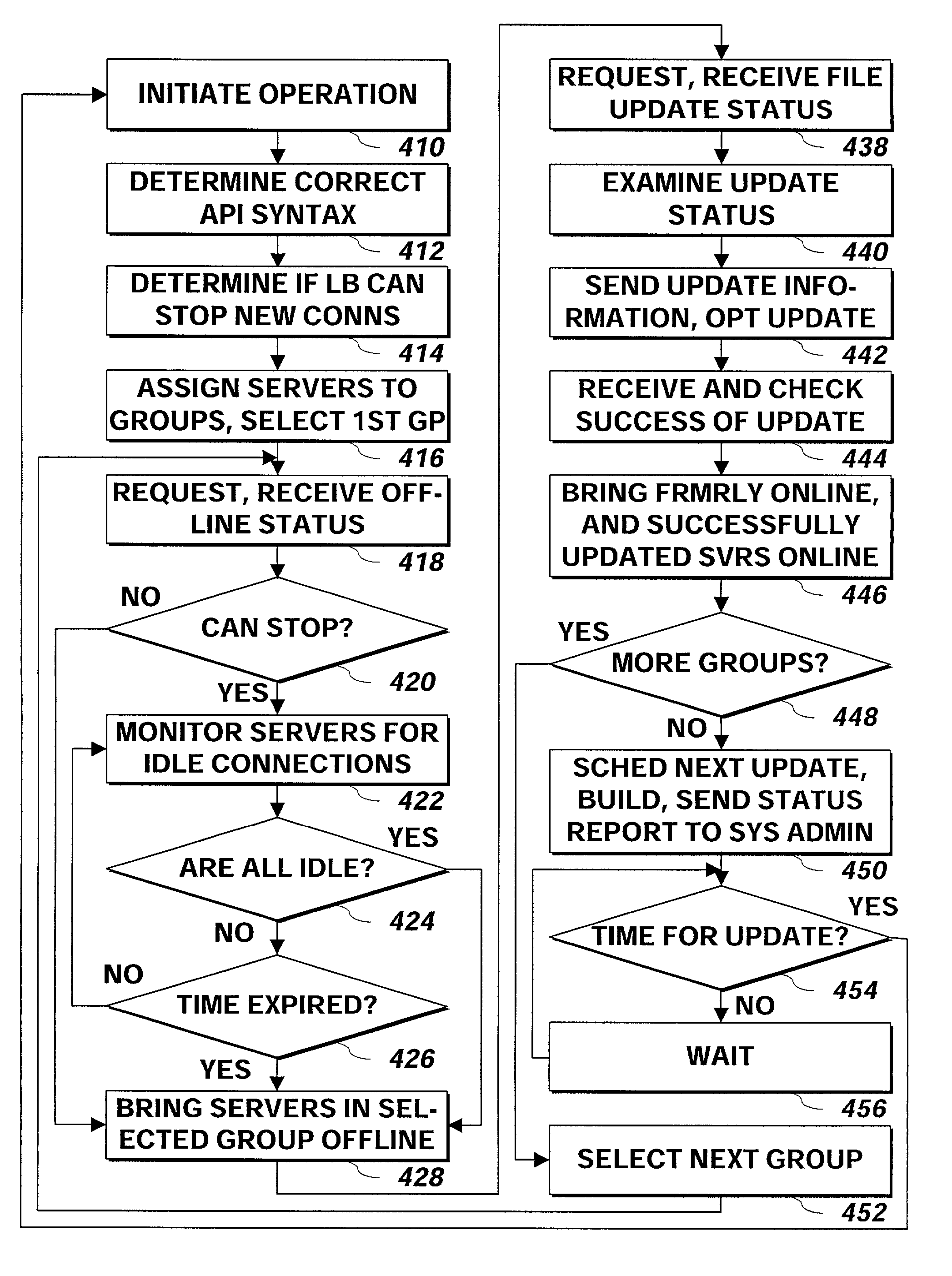
Method and system for automatically updating multiple servers
ActiveUS7020706B2Digital data information retrievalSoftware engineeringMethod selectionOperating system
A system and method updates multiple servers automatically without taking all of the multiple servers off-line at the same time. The system and method selects a group of servers, takes the group off-line, updates the group taken off-line, and then brings on-line those members of the group that were on-line prior to the update and for which the update was installed successfully.
Owner:BMC SOFTWARE
System and method for migrating virtual machines on cluster systems
ActiveUS20060195715A1Satisfactory operationError detection/correctionDigital computer detailsManagement processCluster systems
In one embodiment, a method comprises executing a plurality of virtual machines on a plurality of nodes of a cluster computing system, wherein at least one application is executed within each of the plurality of virtual machines, generating data that is related to performance of applications in the virtual machines, analyzing, by a management process, the data in view of parameters that encode desired performance levels of applications, and migrating, by the management process, a virtual machine on a first node to a second node of the plurality of nodes in response to the analyzing.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Placement of virtual machines based on server cost and network cost
InactiveUS20110225277A1Digital computer detailsMultiprogramming arrangementsInformation processingInformation handling system
A method, information processing system, and computer program product manage server placement of virtual machines in an operating environment. A mapping of each virtual machine in a plurality of virtual machines to at least one server in a set of servers is determined. The mapping substantially satisfies a set of primary constraints associated with the set of servers. A plurality of virtual machine clusters is created. Each virtual machine cluster includes a set of virtual machines from the plurality of virtual machines. A server placement of one virtual machine in a cluster is interchangeable with a server placement of another virtual machine in the same cluster while satisfying the set of primary constraints. A server placement of the set of virtual machines within each virtual machine on at least one mapped server is generated for each cluster. The server placement substantially satisfies a set of secondary constraints.
Owner:IBM CORP
Computer system para-virtualization using a hypervisor that is implemented in a partition of the host system
ActiveUS20070028244A1Improve securityExcessive removalError detection/correctionMemory adressing/allocation/relocationOperational systemSystem call
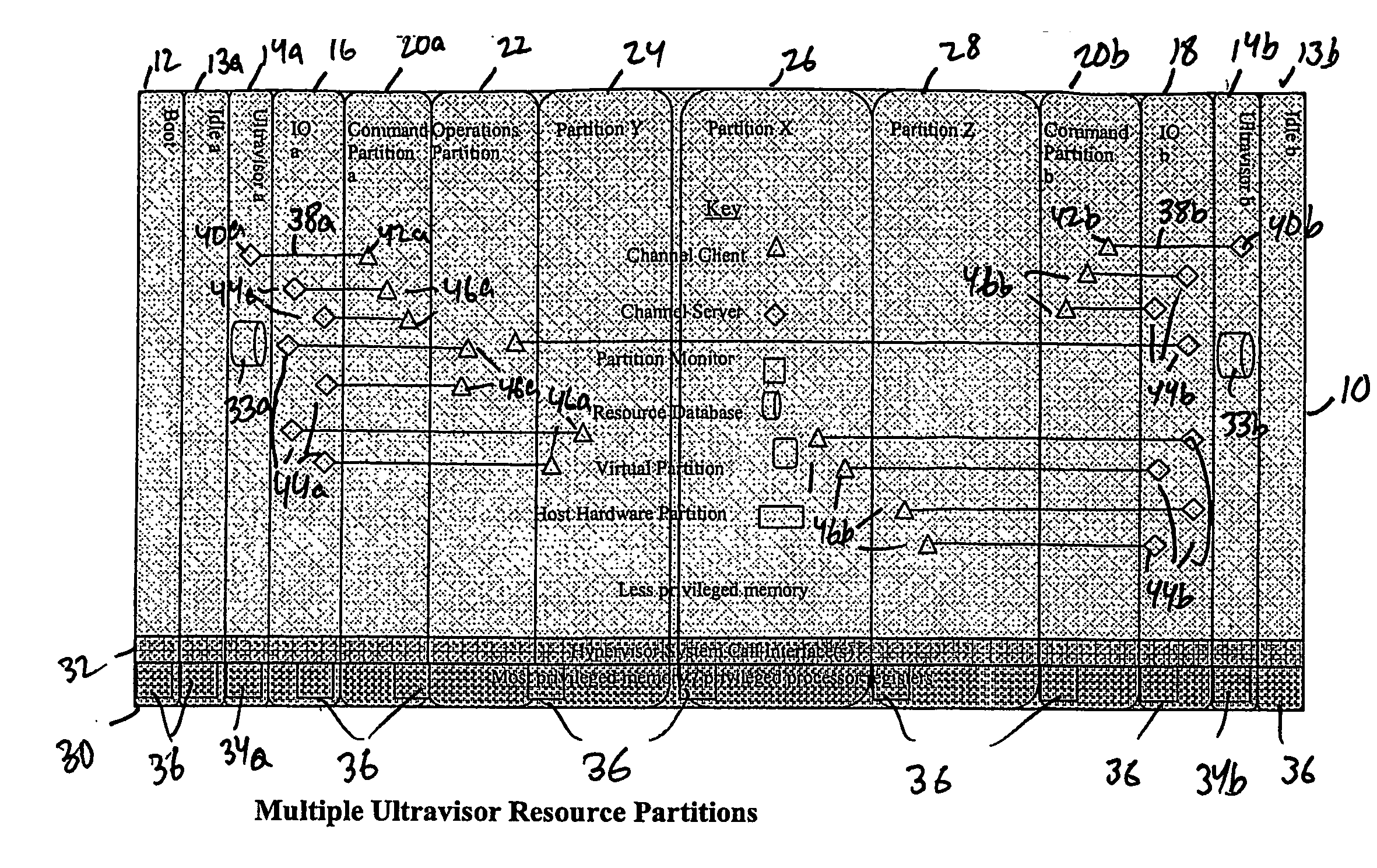
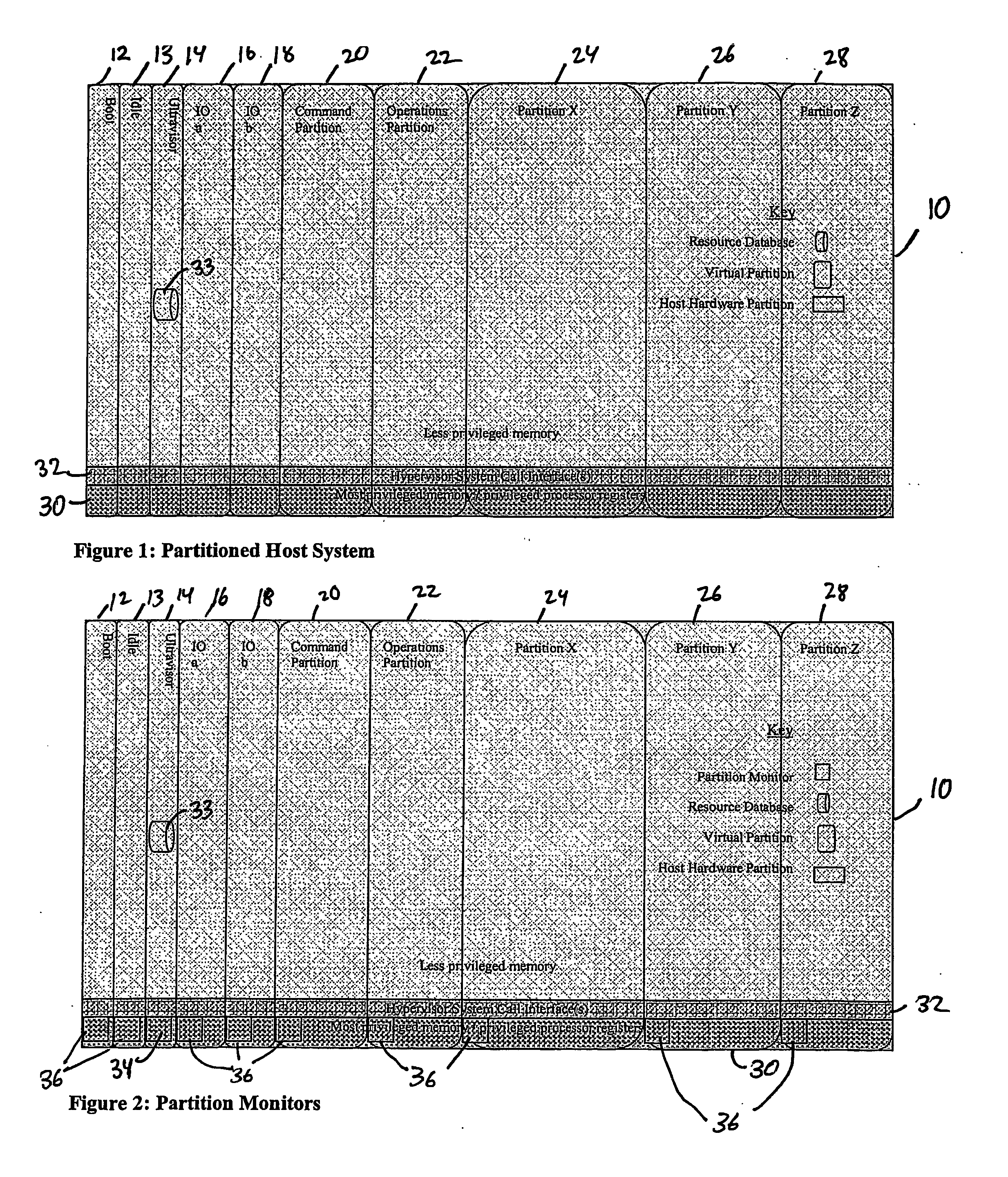
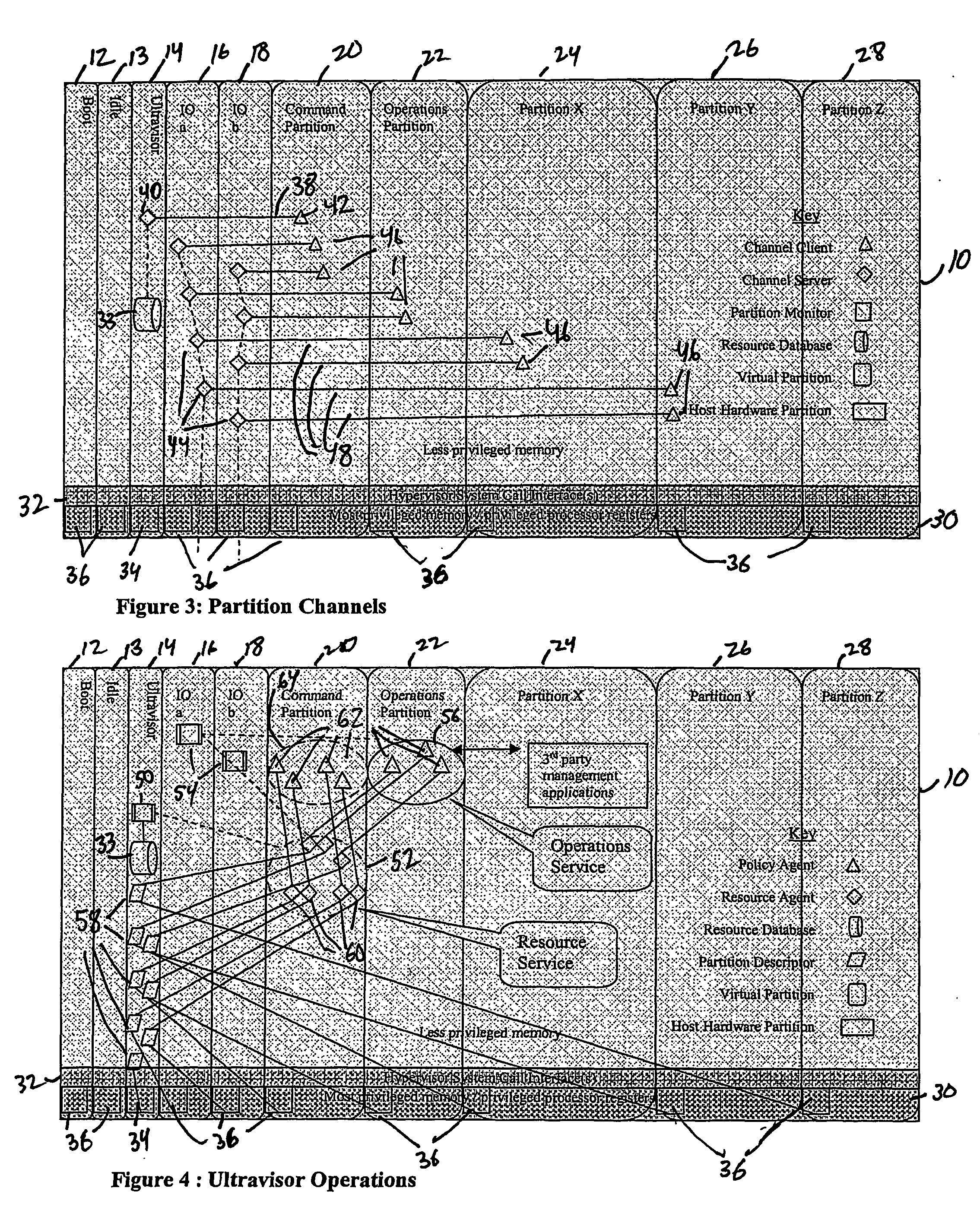
A virtualization infrastructure that allows multiple guest partitions to run within a host hardware partition. The host system is divided into distinct logical or virtual partitions and special infrastructure partitions are implemented to control resource management and to control physical I / O device drivers that are, in turn, used by operating systems in other distinct logical or virtual guest partitions. Host hardware resource management runs as a tracking application in a resource management “ultravisor” partition, while host resource management decisions are performed in a higher level command partition based on policies maintained in a separate operations partition. The conventional hypervisor is reduced to a context switching and containment element (monitor) for the respective partitions, while the system resource management functionality is implemented in the ultravisor partition. The ultravisor partition maintains the master in-memory database of the hardware resource allocations and serves a command channel to accept transactional requests for assignment of resources to partitions. It also provides individual read-only views of individual partitions to the associated partition monitors. Host hardware I / O management is implemented in special redundant I / O partitions. Operating systems in other logical or virtual partitions communicate with the I / O partitions via memory channels established by the ultravisor partition. The guest operating systems in the respective logical or virtual partitions are modified to access monitors that implement a system call interface through which the ultravisor, I / O, and any other special infrastructure partitions may initiate communications with each other and with the respective guest partitions. The guest operating systems are modified so that they do not attempt to use the “broken” instructions in the x86 system that complete virtualization systems must resolve by inserting traps.
Owner:UNISYS CORP
Double-proxy remote data access system
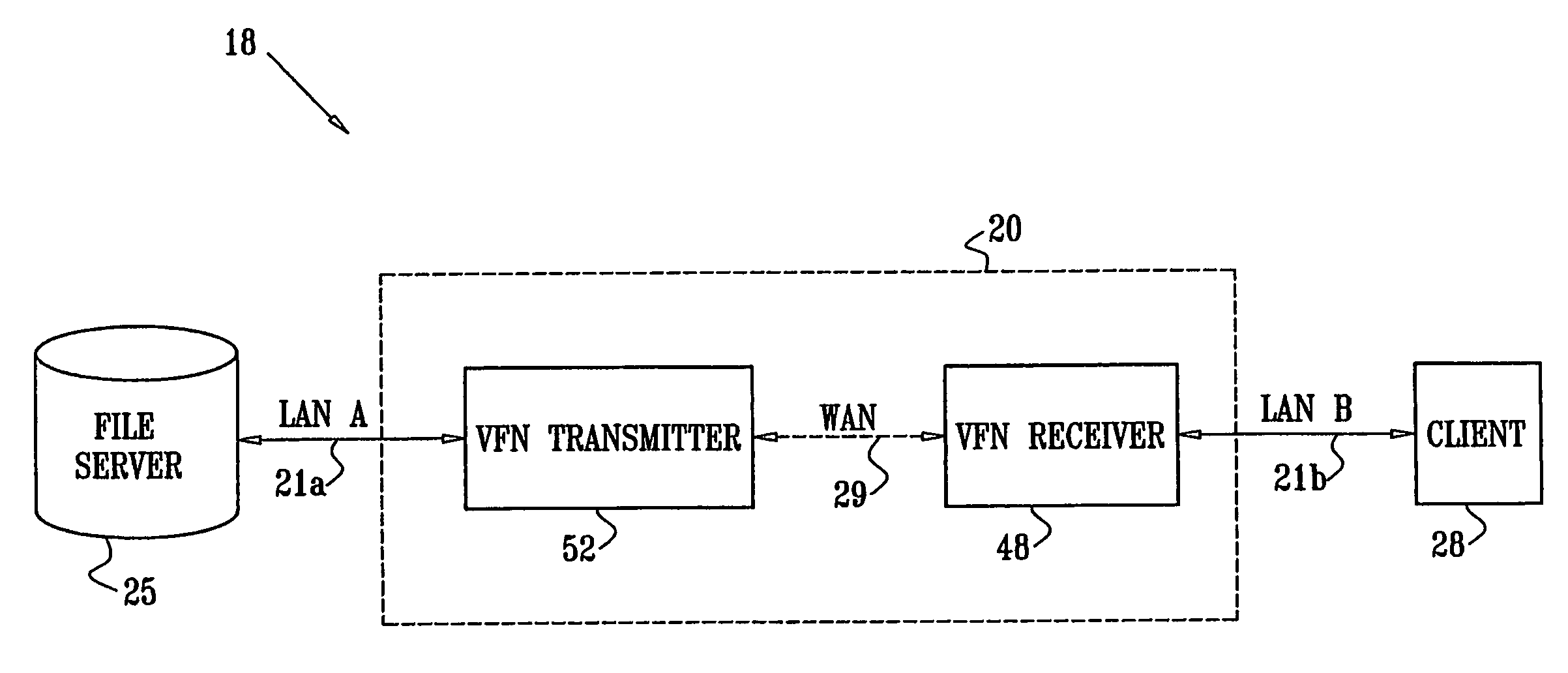
InactiveUS7139811B2Digital data information retrievalData processing applicationsData accessClient-side
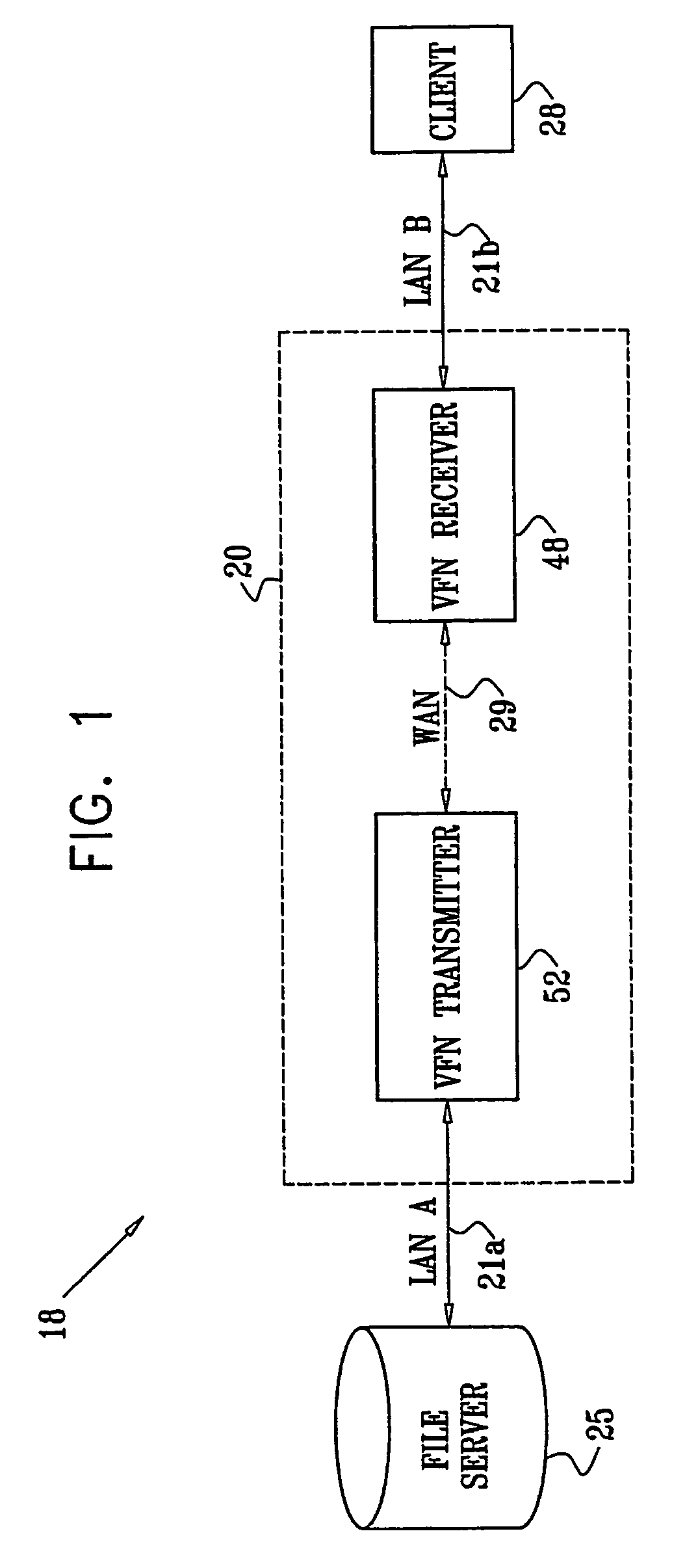
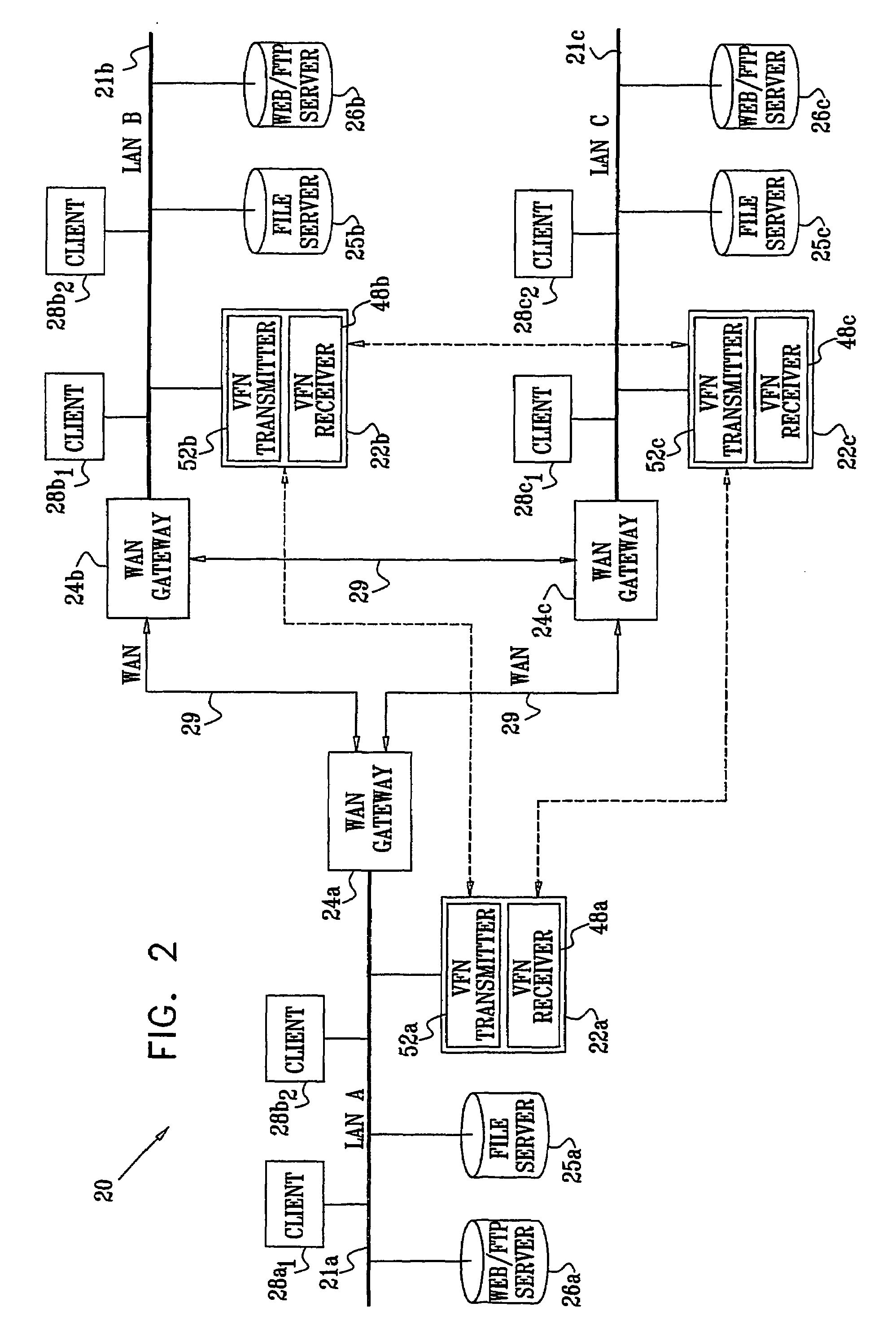
A method for enabling access to a data resource, which is held on a file server (25) on a first local area network (LAN) (21a), by a client (28) on a second LAN (21b). A proxy receiver (48) on the second LAN (21b) intercepts a request for the data resource submitted by the client (28) and transmits a message via a wide area network (WAN) (29) to a proxy transmitter (52) on the first LAN (21a), requesting the data resource. The proxy transmitter (52) retrieves a replica of the data resource from the file server (25) and conveys the replica of the data resource over the WAN (29) to the proxy receiver (48), which serves the replica of the data resource from the proxy receiver (48) to the client (28) over the second LAN (21b).
Owner:CISCO TECH INC
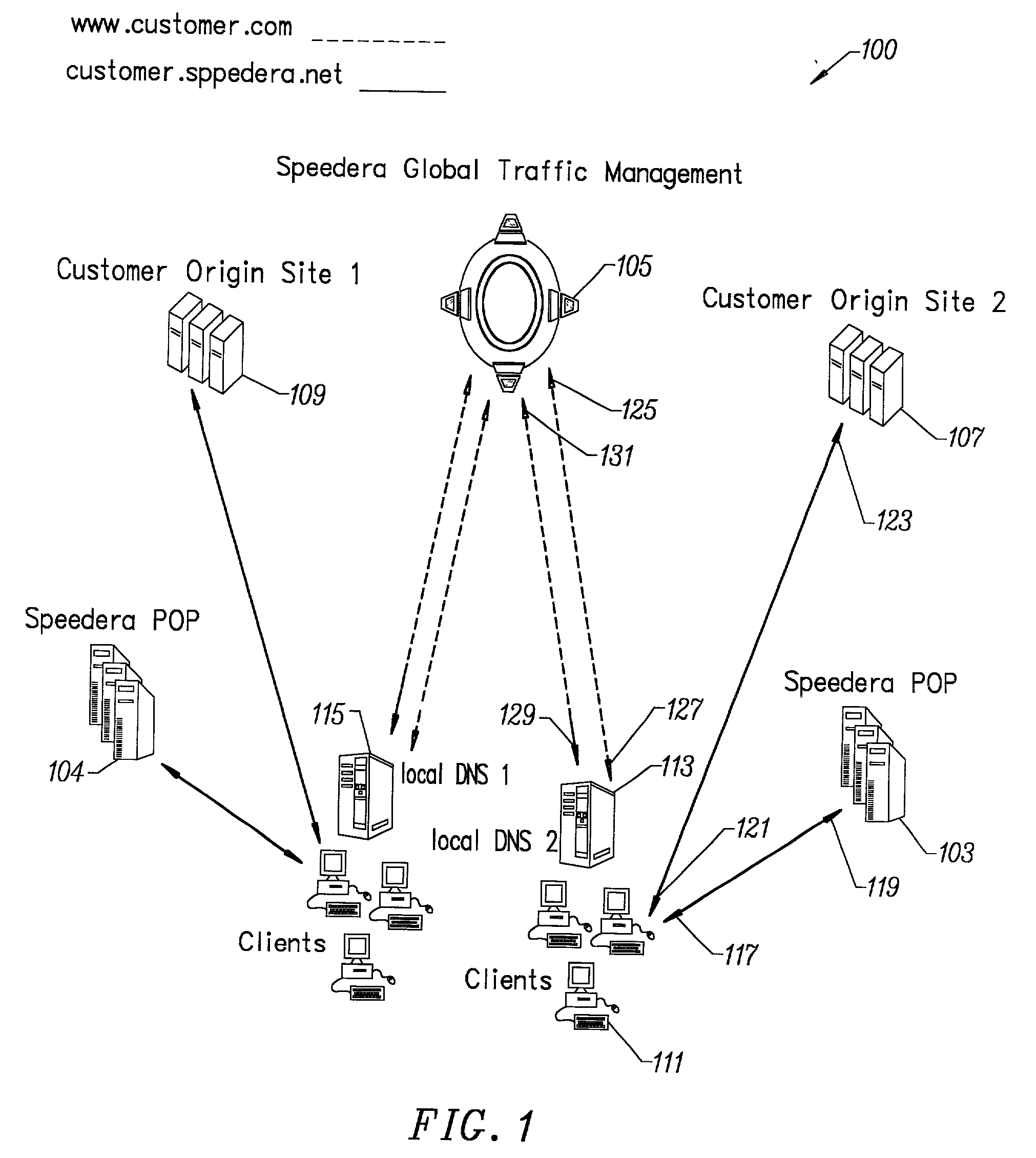
Content delivery and global traffic management network system
InactiveUS20020052942A1Meet cutting requirementsReduce trafficMetering/charging/biilling arrangementsError preventionWeb serviceCache server
Owner:AKAMAI TECH INC
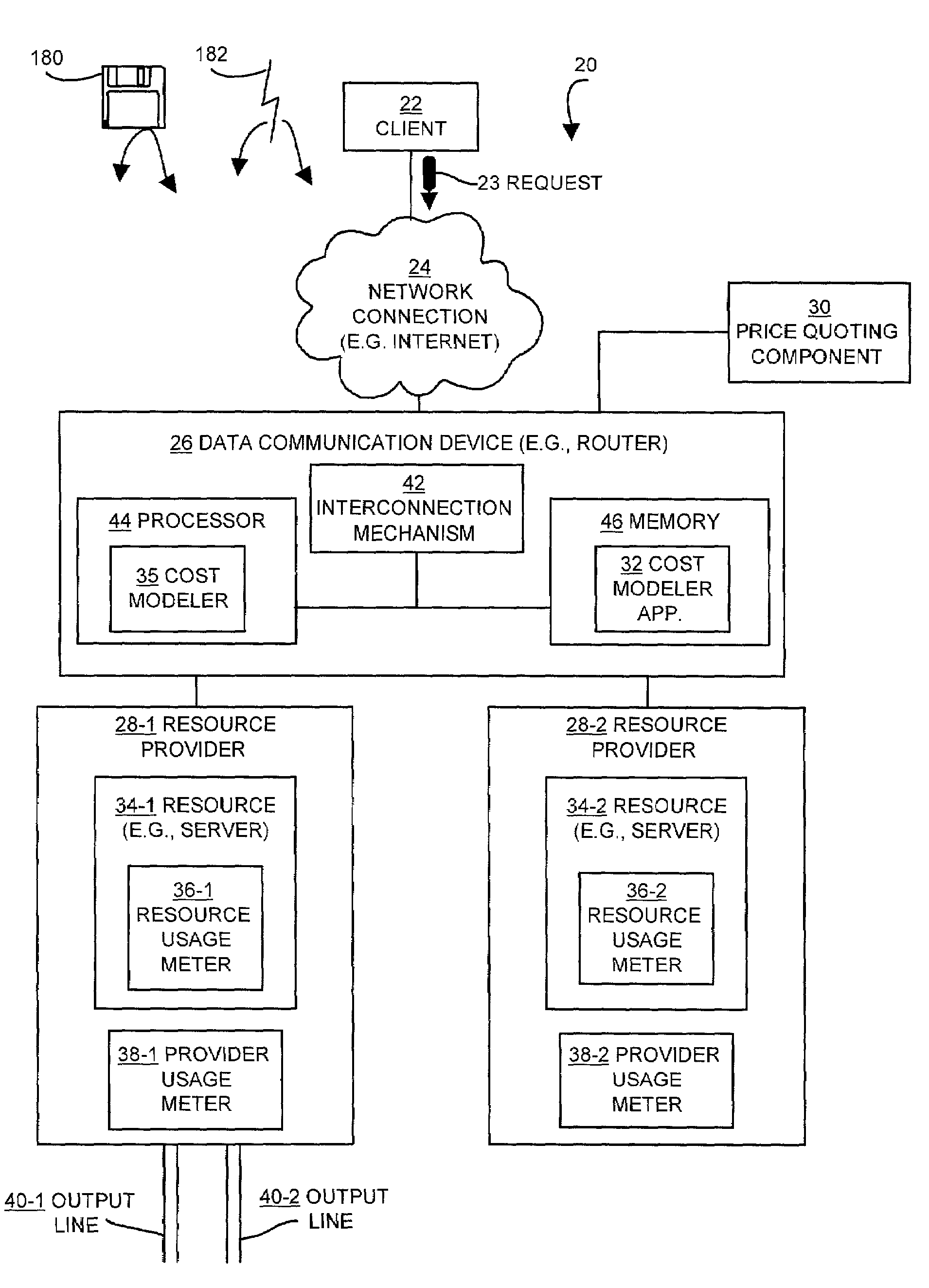
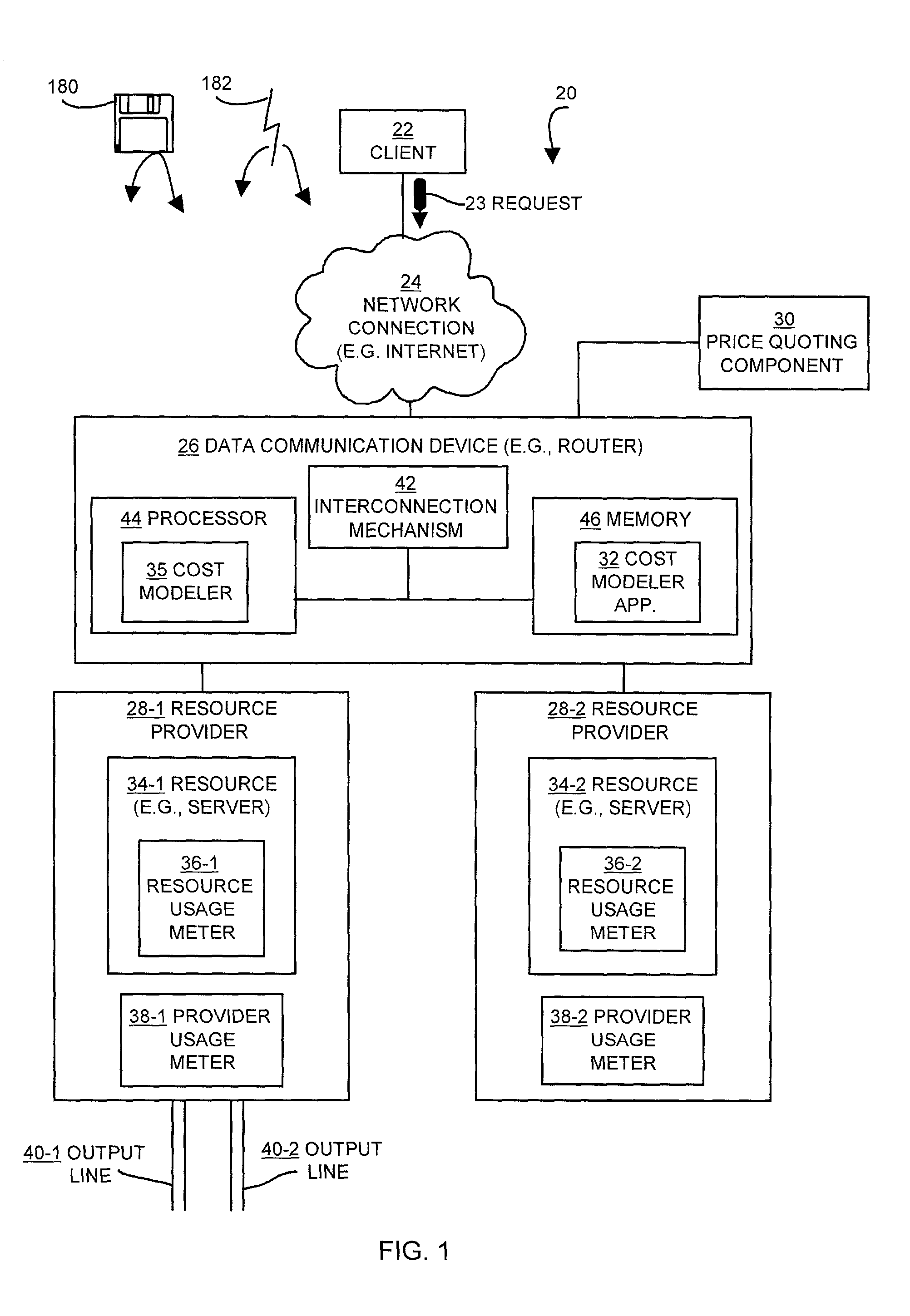
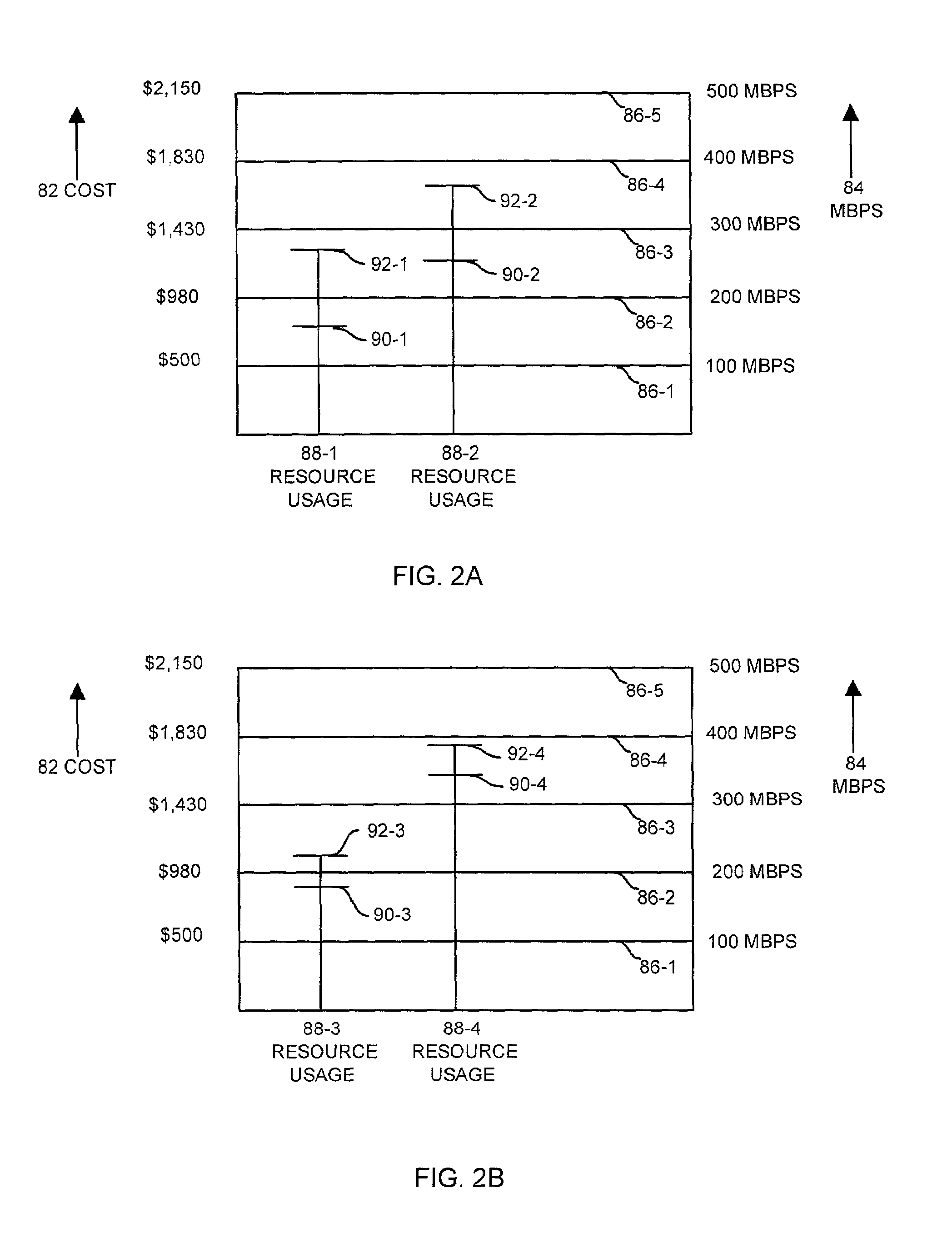
Methods and apparatus for selecting a server to process a request
InactiveUS7320131B1Cost incrementLow costMultiprogramming arrangementsComputer security arrangementsPeak valueClient-side
The invention is directed to techniques for selecting a resource from several resources to process a request from a client. A client sends the request to a data communications device (e.g., network device or switch), which measures usage information from usage meters associated with each resource (e.g., server). The data communications device then makes a usage estimate for each server of the increase in usage required for that server to process the request from the client. Then the data communications device selects one of the servers depending on the usage estimates required to respond to the client's request. The data communications device can consider other factors such as the current level of usage, past usage, and the increased cost of responding to the request. In addition, the data communications device can consider the peak usage level of each resource already established in a current billing period.
Owner:CISCO TECH INC
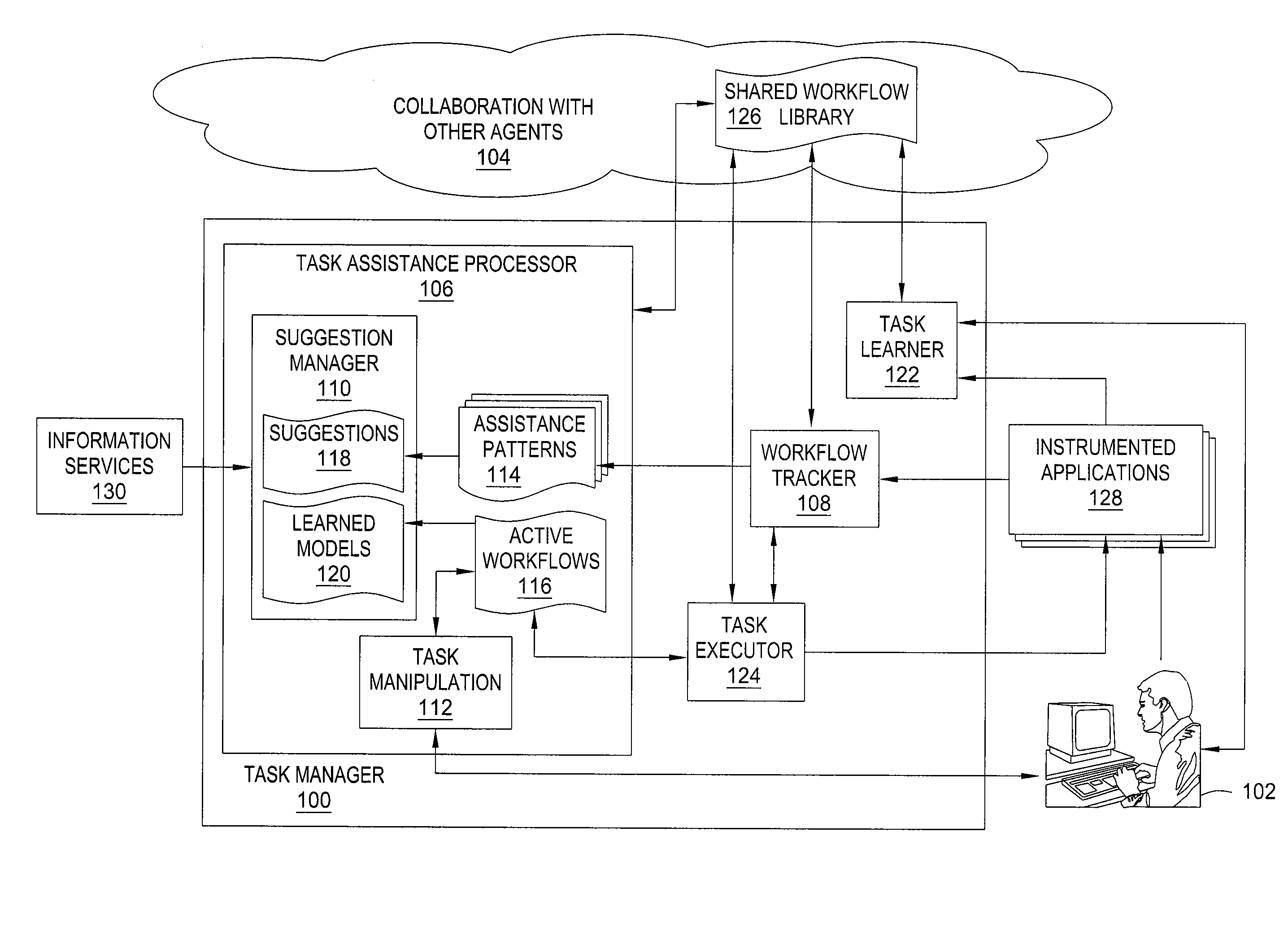
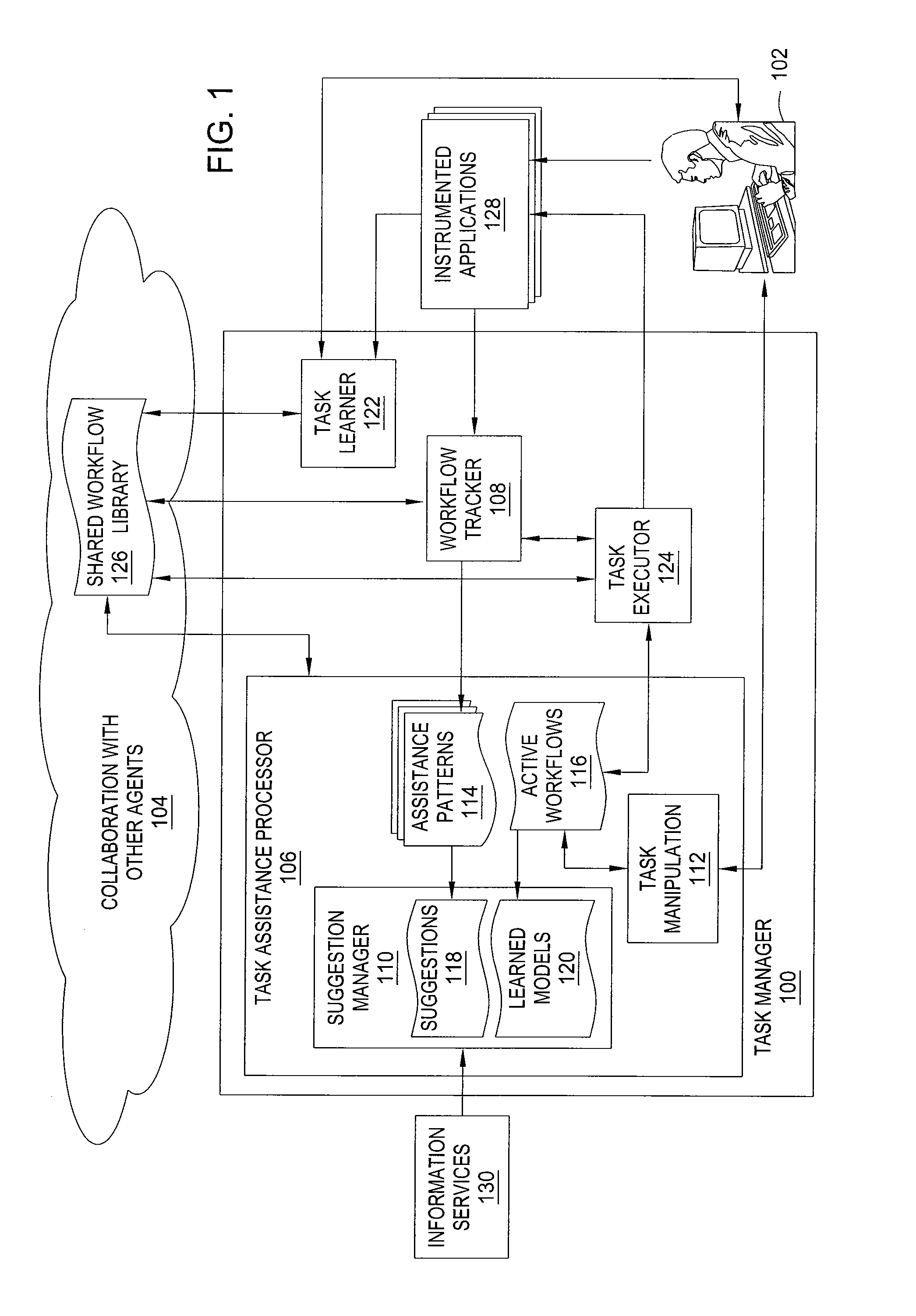
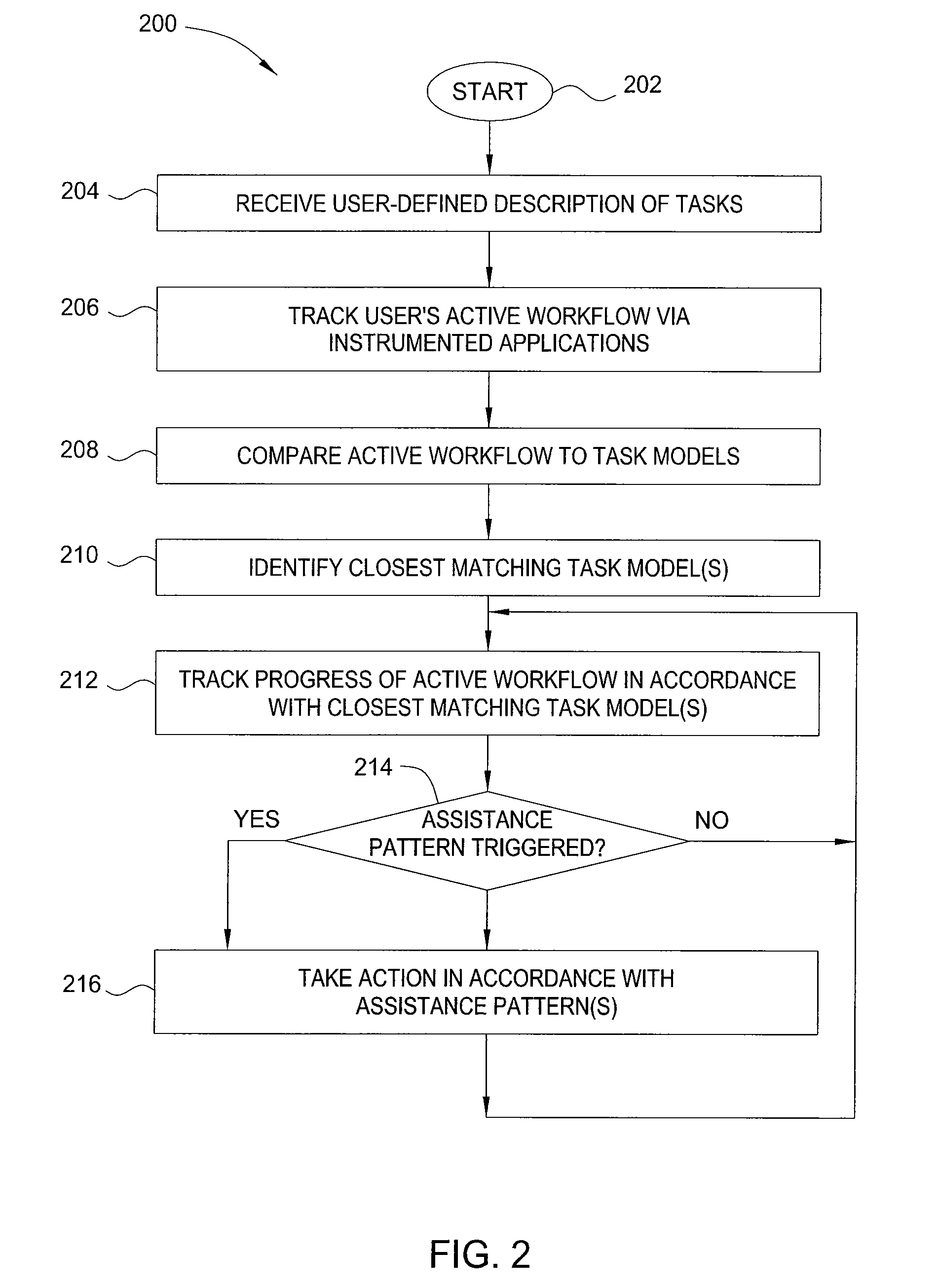
Method and apparatus for automated assistance with task management
ActiveUS20090307162A1Digital computer detailsMultiprogramming arrangementsCoprocessorApplication software
The present invention relates to a method and apparatus for assisting with automated task management. In one embodiment, an apparatus for assisting a user in the execution of a task, where the task includes one or more workflows required to accomplish a goal defined by the user, includes a task learner for creating new workflows from user demonstrations, a workflow tracker for identifying and tracking the progress of a current workflow executing on a machine used by the user, a task assistance processor coupled to the workflow tracker, for generating a suggestion based on the progress of the current workflow, and a task executor coupled to the task assistance processor, for manipulating an application on the machine used by the user to carry out the suggestion.
Owner:SRI INTERNATIONAL
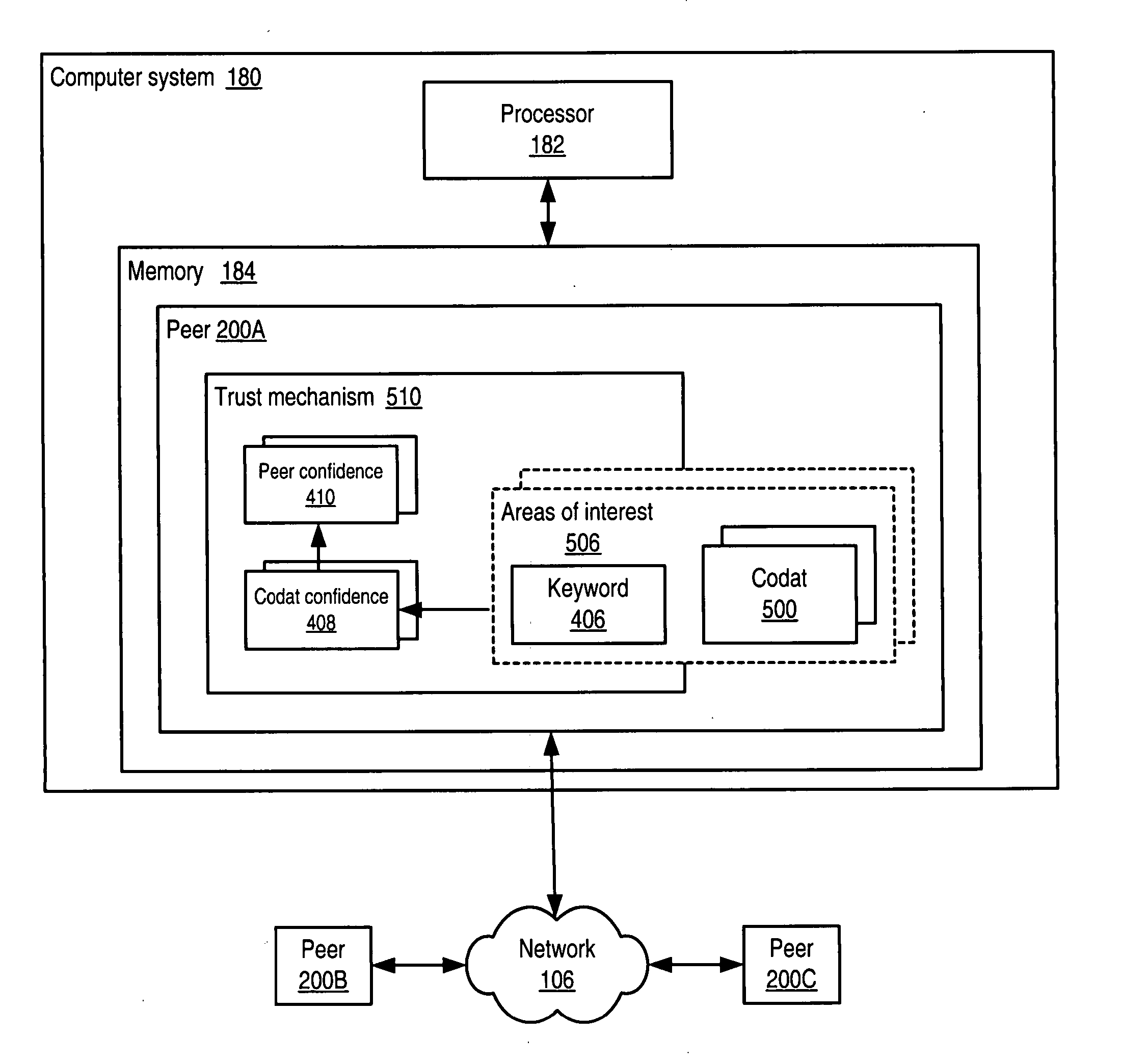
Trust mechanism for a peer-to-peer network computing platform
ActiveUS20050086300A1Generate and confidenceMultiprogramming arrangementsMultiple digital computer combinationsTrust relationshipDatabase
Owner:ORACLE INT CORP
Mobile device client
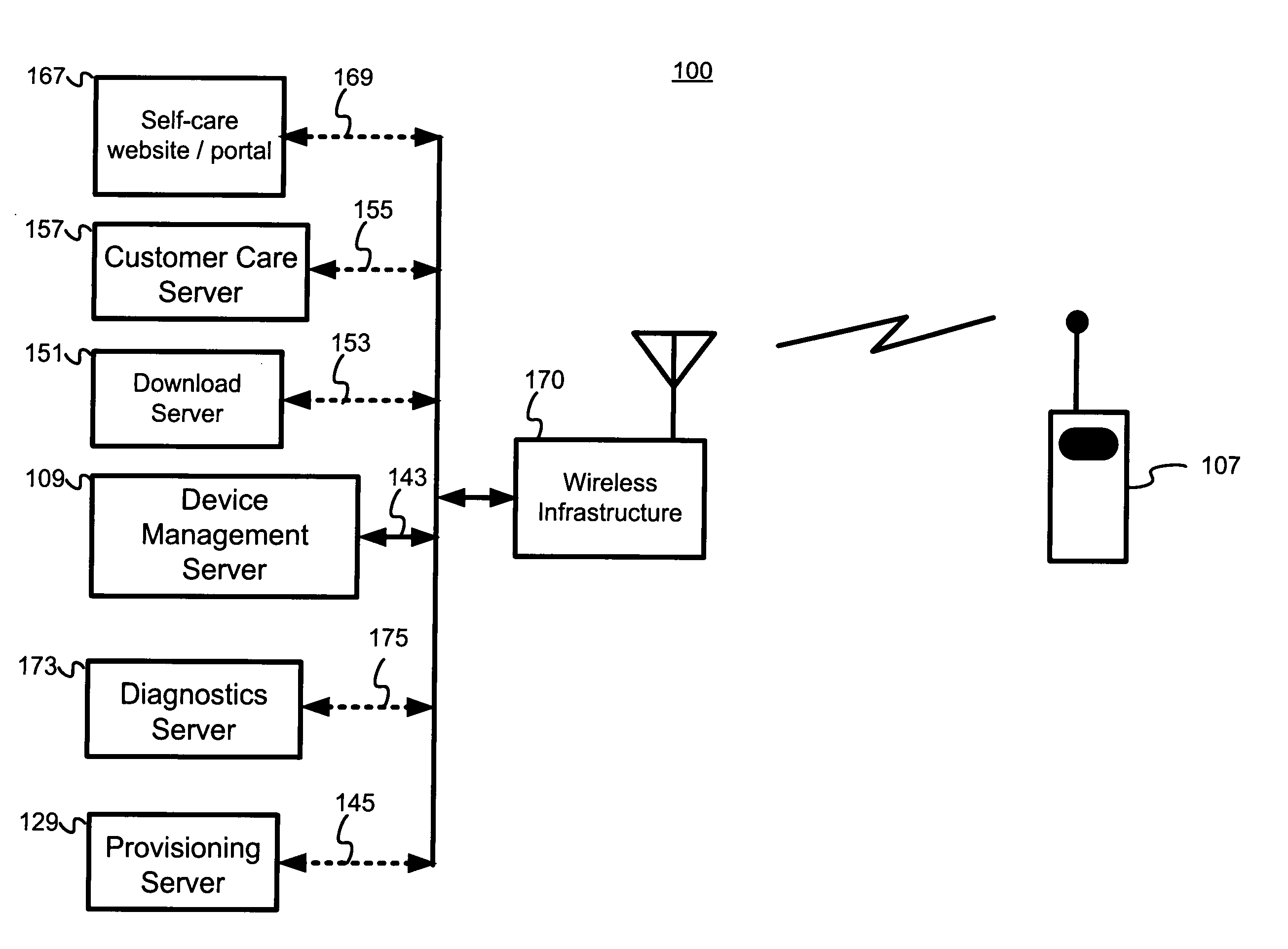
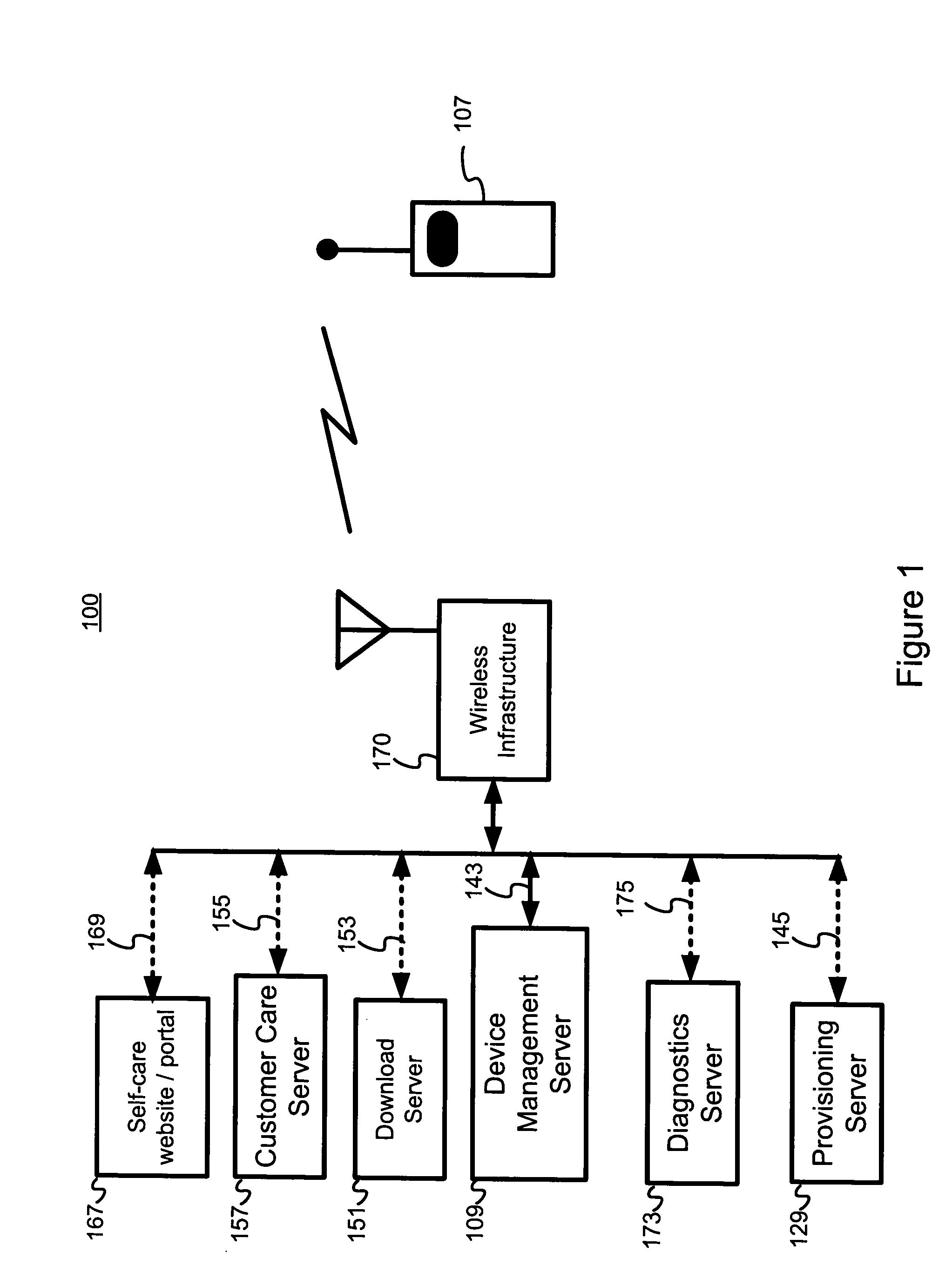
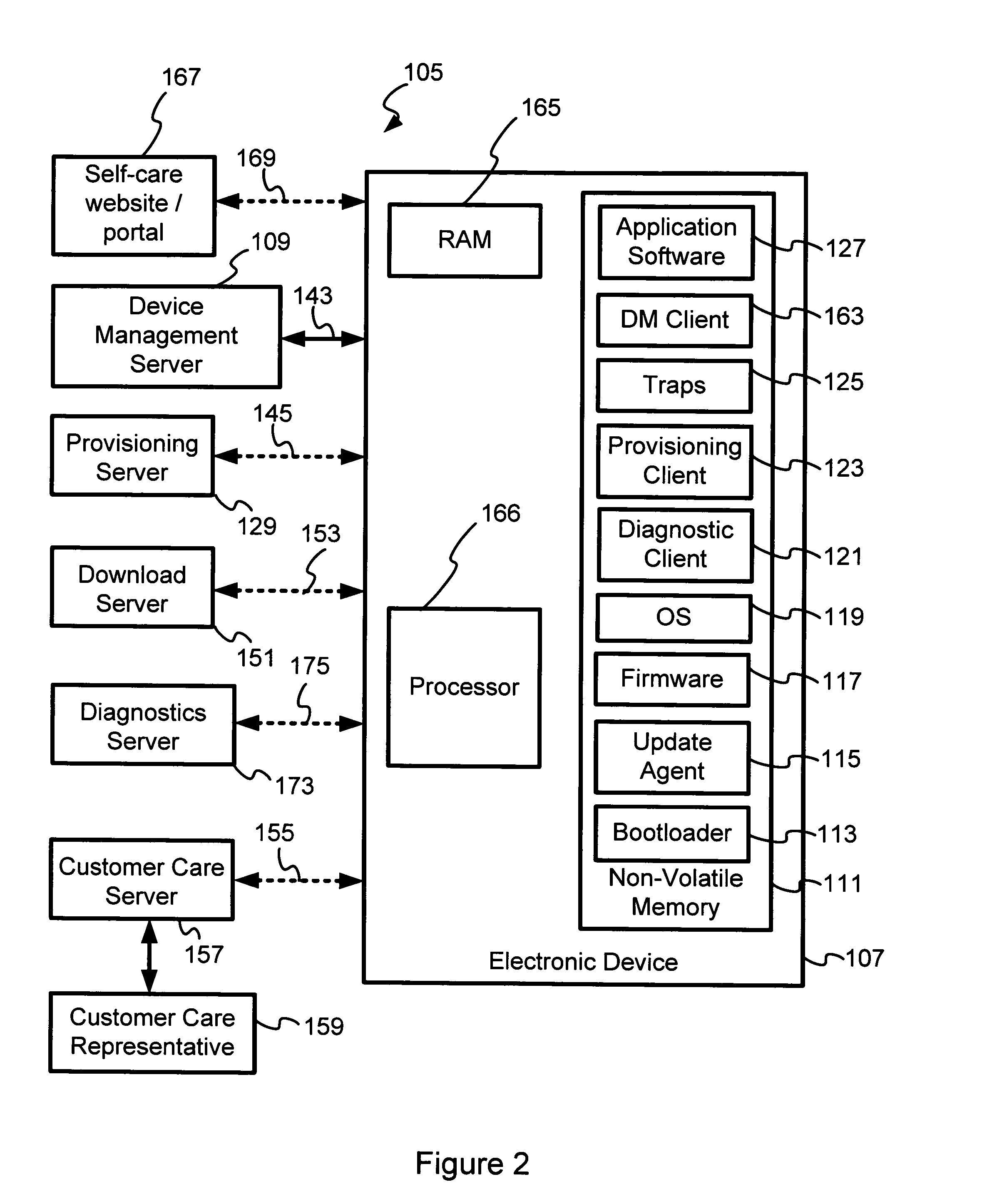
A device client that supports customer care and distribution of update packages to electronic devices makes it possible to efficiently manage and update firmware and software in electronic devices. A terminal management / device management server employs extensions to an industry standard device management protocol to update configuration information, to provision the electronic device, and to manage the electronic device, for example. The electronic device may receive update packages, and update agent(s) in the electronic device may update the firmware and / or software of the electronic device. A diagnostic client in the electronic device facilitates remote diagnosis and a traps client facilitates setting traps and retrieving collected information. A terminal management server may remotely invoke control actions within the electronic device using management objects not supported by the industry standard device management protocol. A user of the electronic device may use a self-care portal to administer self-care and to conduct diagnostics. A subsequent customer-care call may use such information collected during self-care.
Owner:QUALCOMM INC
Back-end decoupled management model and management system utilizing same
InactiveUS6871346B1Easy to manageDigital data processing detailsMultiprogramming arrangementsWeb-Based Enterprise ManagementWindows management instrumentation
Presented is a web-based enterprise management compliant management framework whose back end components are decoupled from the various user interfaces available for accessing the management system. In the Windows environment, the management system of the instant invention is also compliant with the Windows management instrumentation (WMI) requirements. This management system includes WMI providers which implement standard interfaces which decouple all semantic and syntactic checks from the user interface and which provide common error strings, help, etc. to a user regardless of the user interface being used. The providers of the management system of the instant invention store and access data in the active directory. As such, these providers present a customizable user interface which may be based on a user's expertise level and which may be dynamically localized to the user's preferred language. Transaction support is also provided which prevents multiple users from changing the same attributes at the same time through different user interfaces.
Owner:MICROSOFT TECH LICENSING LLC
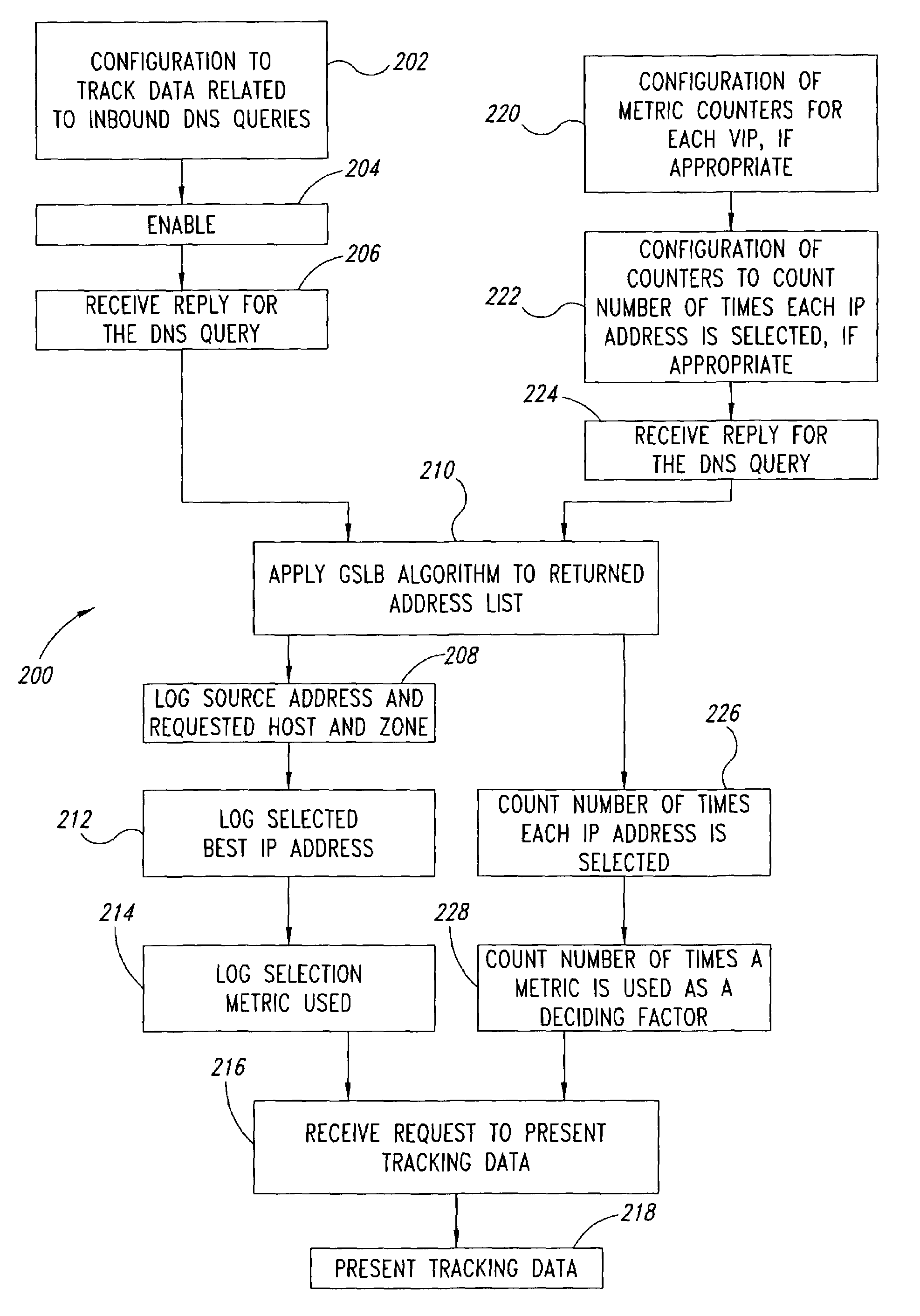
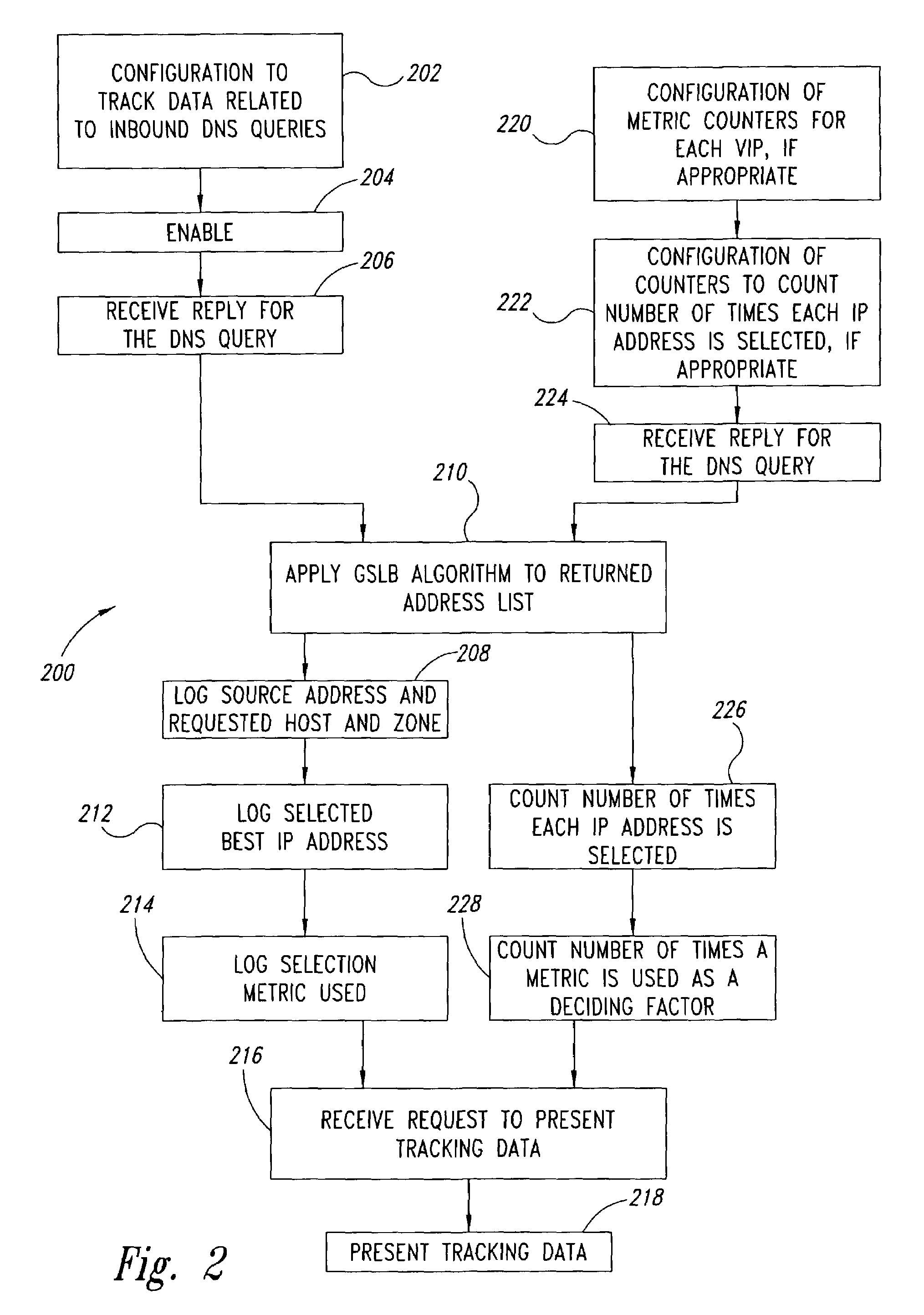
Statistical tracking of global server load balancing for selecting the best network address from ordered list of network addresses based on a set of performance metrics
ActiveUS7086061B1Multiprogramming arrangementsMultiple digital computer combinationsPolicy decisionIp address
Server load-balancing operation-related data, such as data associated with a system configured for global server load balancing (GSLB) that orders IP addresses into a list based on a set of performance metrics, is tracked. Such operation-related data includes inbound source IP addresses (e.g., the address of the originator of a DNS request), the requested host and zone, identification of the selected “best” IP addresses resulting from application of a GSLB algorithm and the selection metric used to decide on an IP address as the “best” one. Furthermore, the data includes a count of the selected “best” IP addresses selected via application of the GSLB algorithm, and for each of these IP addresses, the list of deciding performance metrics, along with a count of the number of times each of these metrics in the list was used as a deciding factor in selection of this IP address as the best one. This tracking feature allows better understanding of GSLB policy decisions (such as those associated with performance, maintenance, and troubleshooting) and intelligent deployment of large-scale resilient GSLB networks.
Owner:AVAGO TECH INT SALES PTE LTD
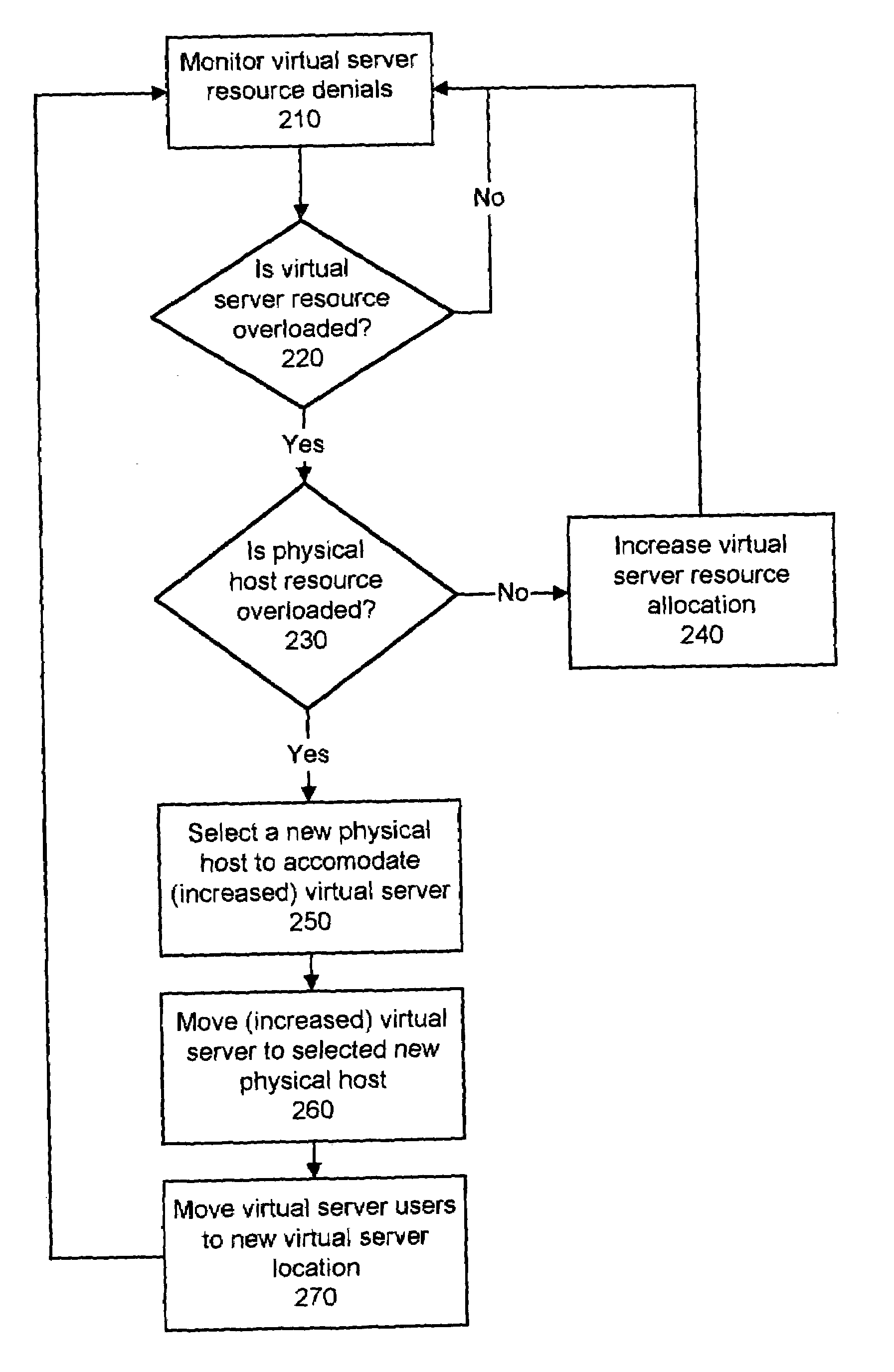
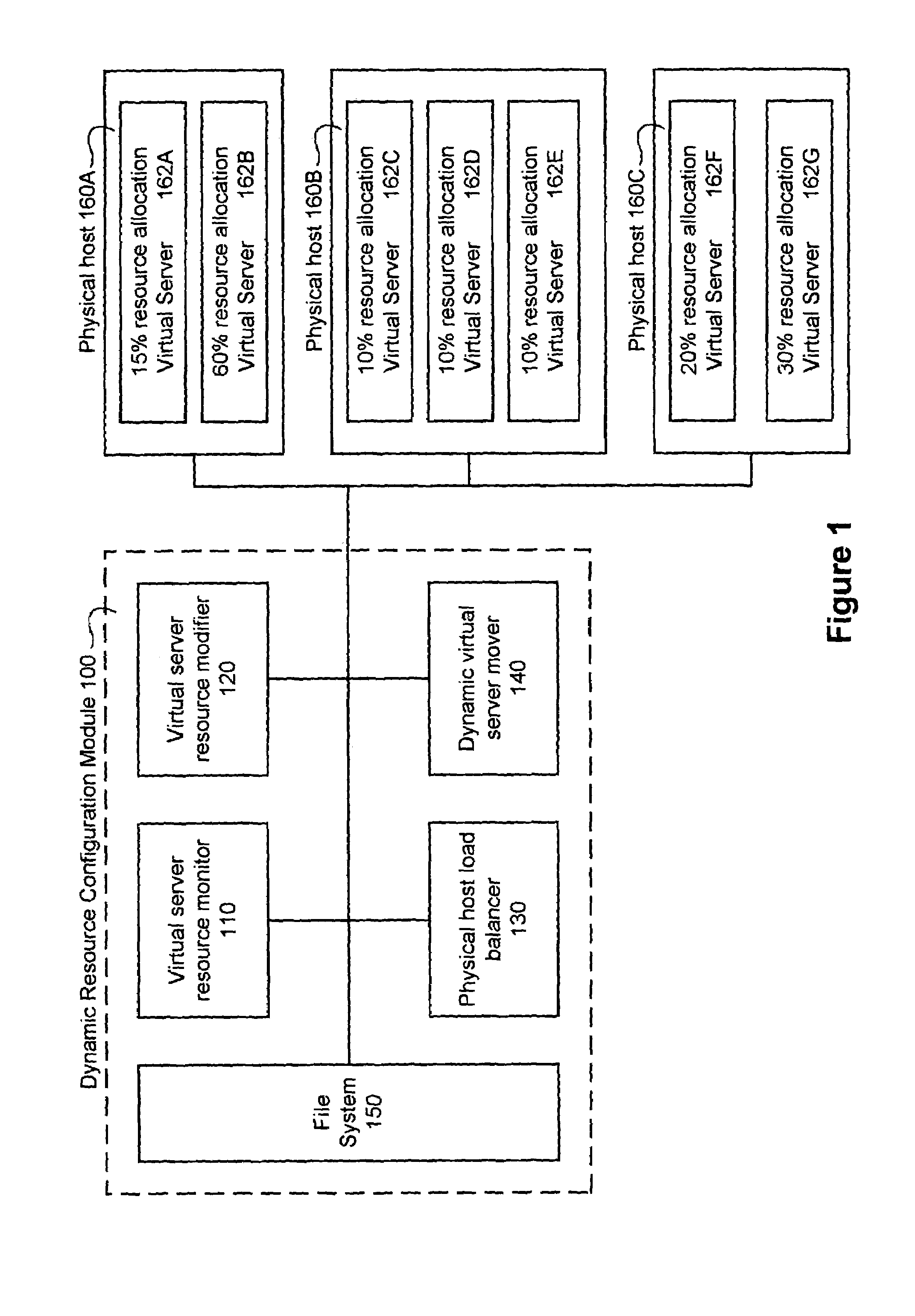
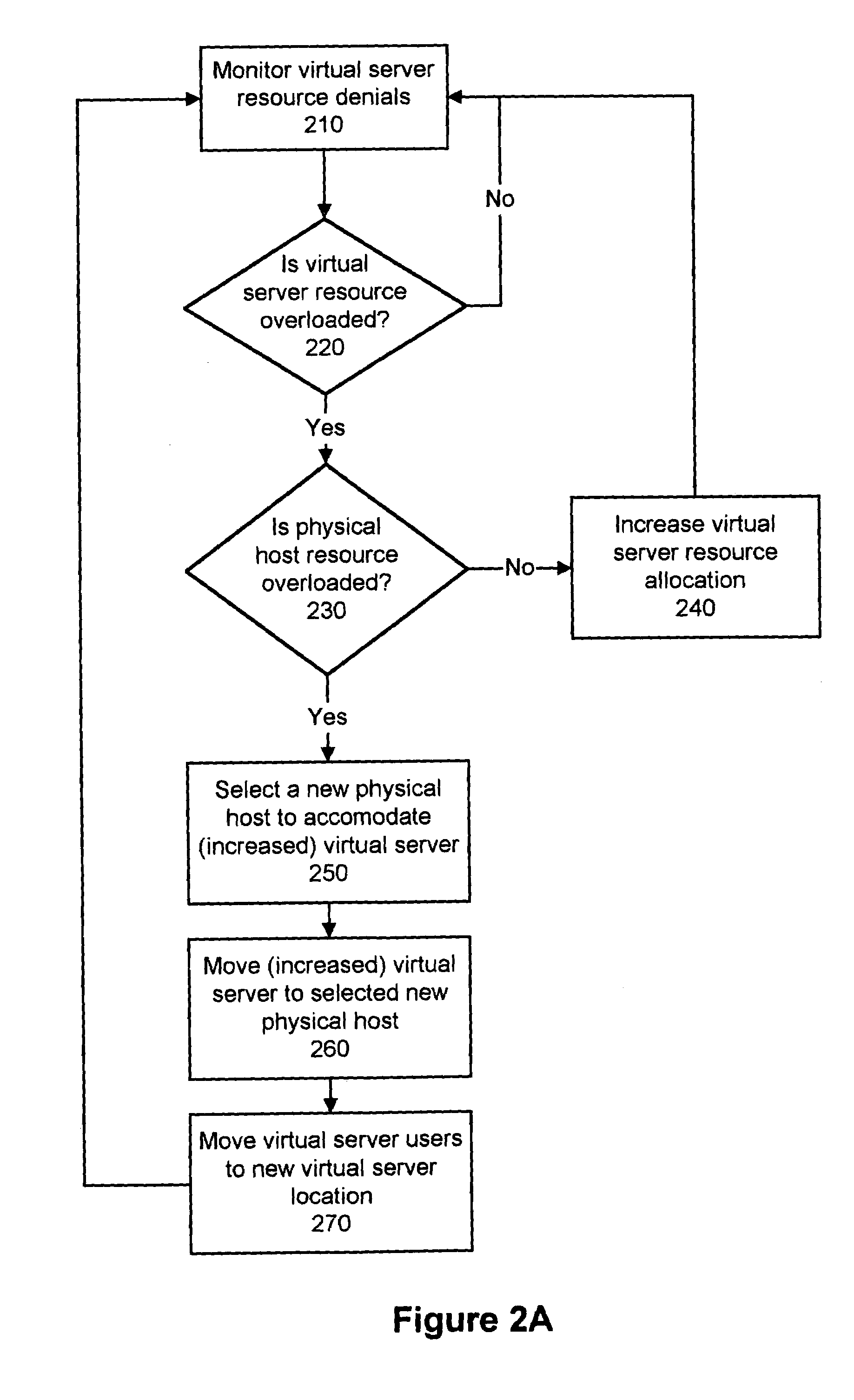
Dynamically modifying the resources of a virtual server
InactiveUS6985937B1Guaranteed service qualityError preventionFrequency-division multiplex detailsQuality of serviceResource based
A system and a method dynamically adjusts the quality of service guarantees for virtual servers based upon the resource demands experienced by the virtual servers. Virtual server resource denials are monitored to determine if a virtual server is overloaded based upon the resource denials. Virtual server resources are modified dynamically to respond to the changing resource requirements of each virtual server. Occasionally, a physical host housing a virtual server may not have additional resources to allocate to a virtual server requiring increased resources. In this instance, a virtual server hosted by the overloaded physical host is transferred to another physical host with sufficient resources.
Owner:INTELLECTUAL VENTURES I LLC
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com